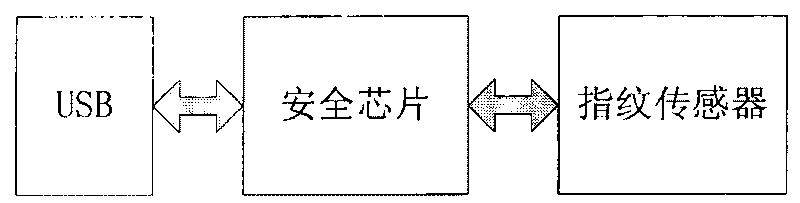
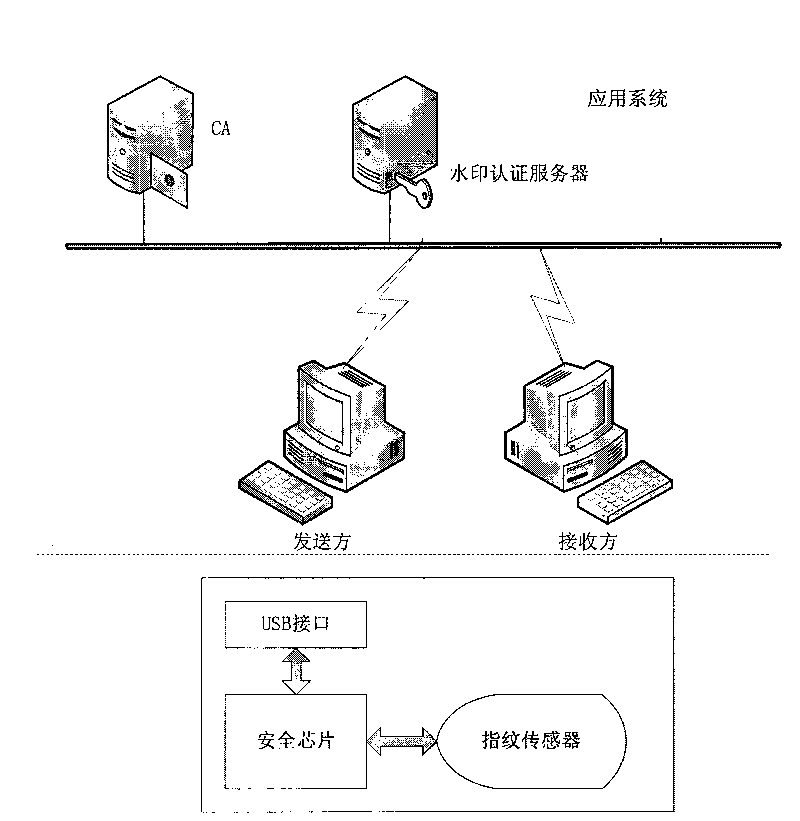
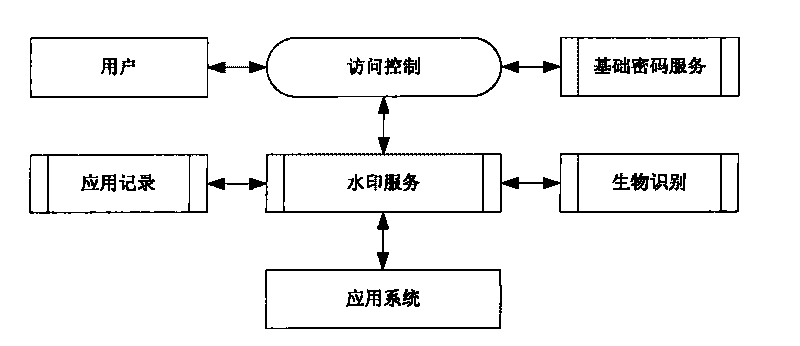
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
544 results about "Key Holder" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
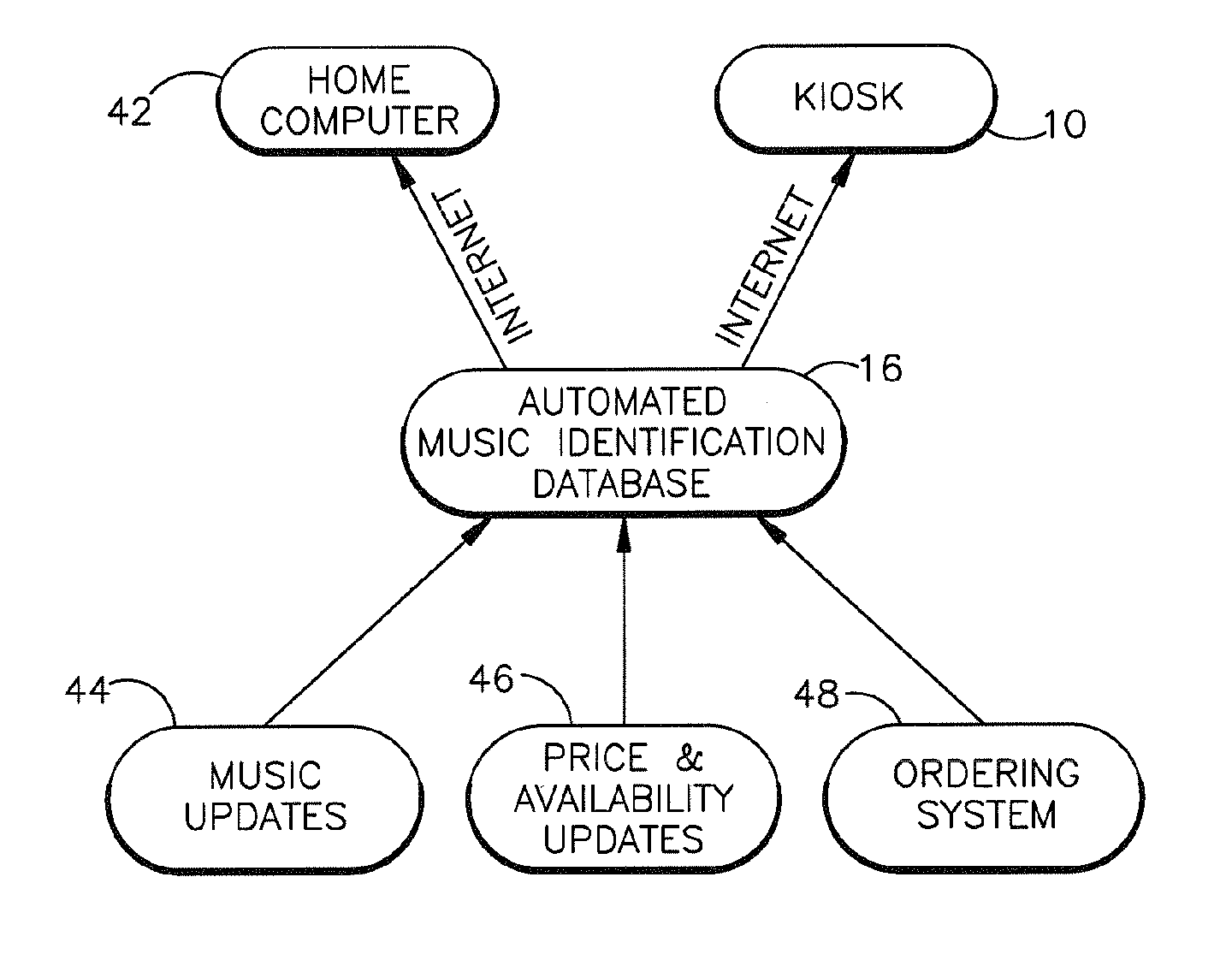
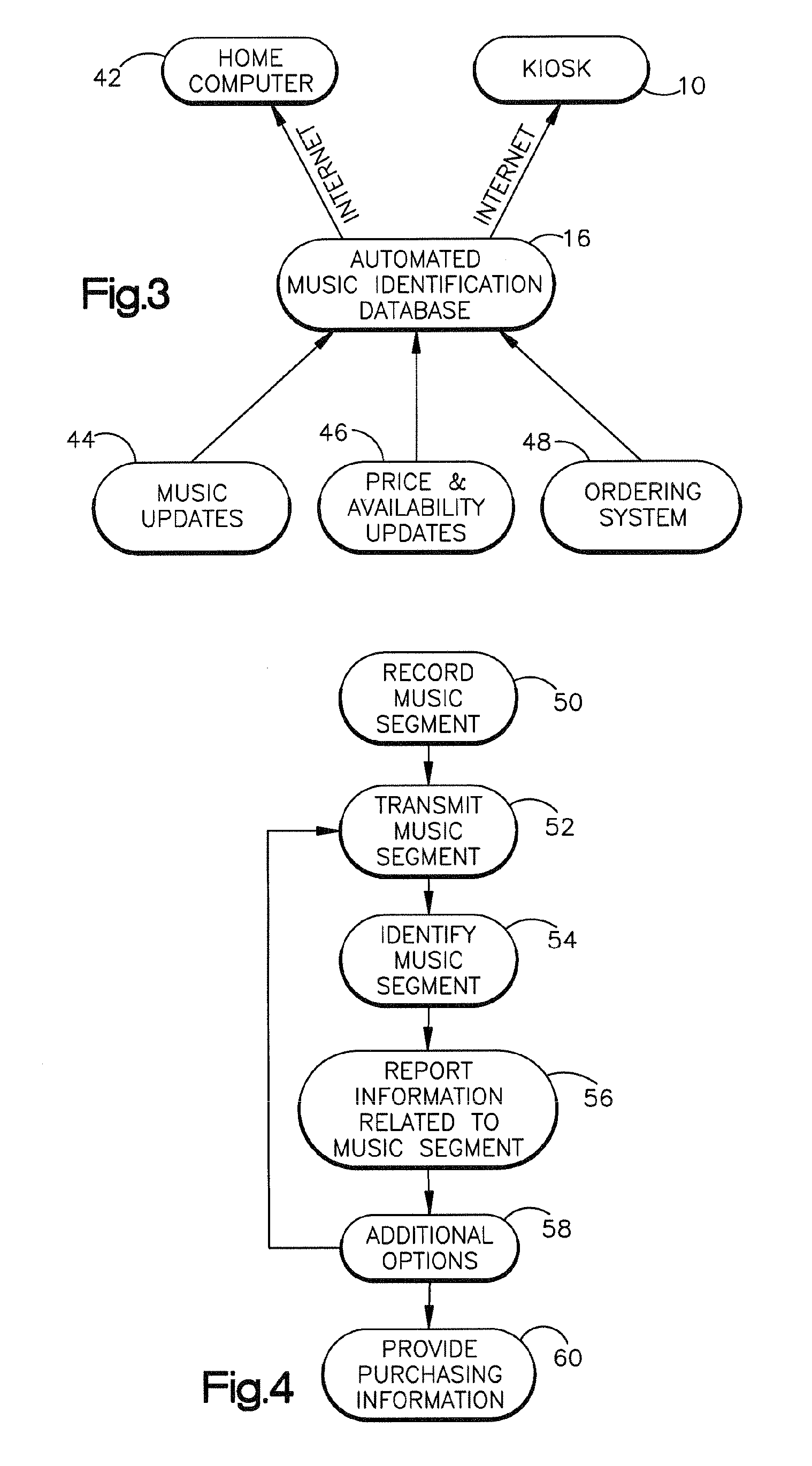
Music identification system
InactiveUS6941275B1Provide informationMetadata audio data retrievalSpecific information broadcast systemsPaymentThe Internet
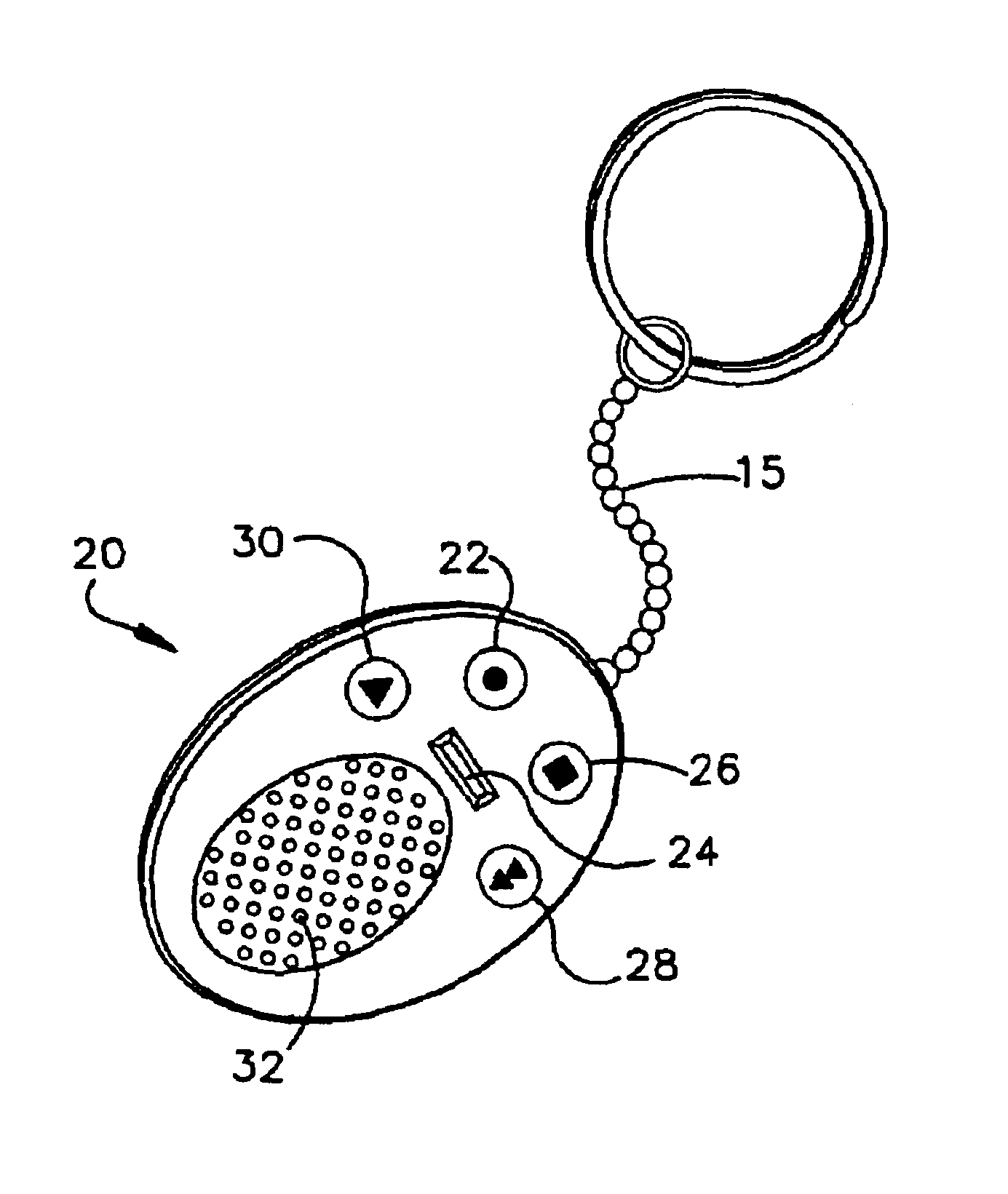
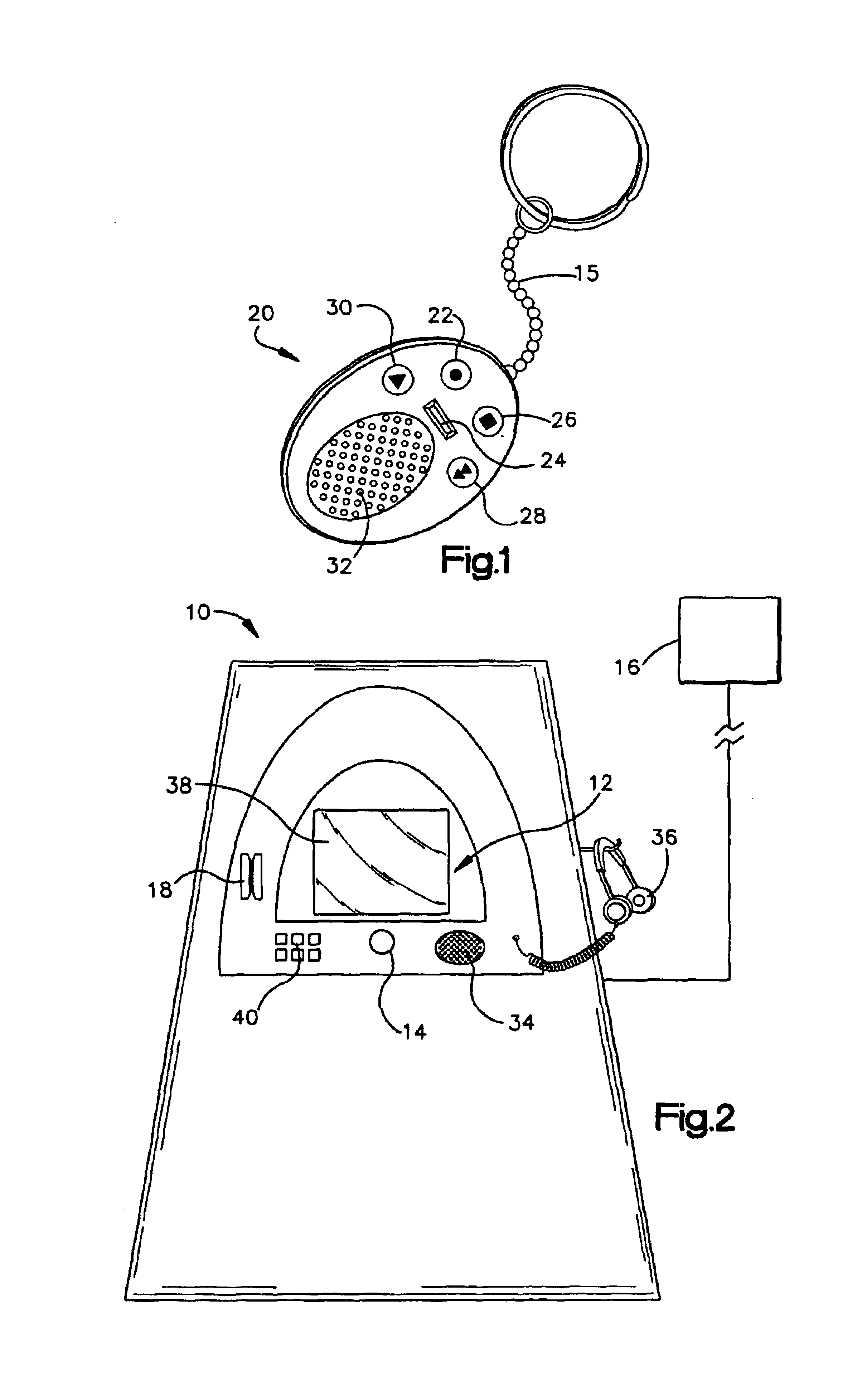
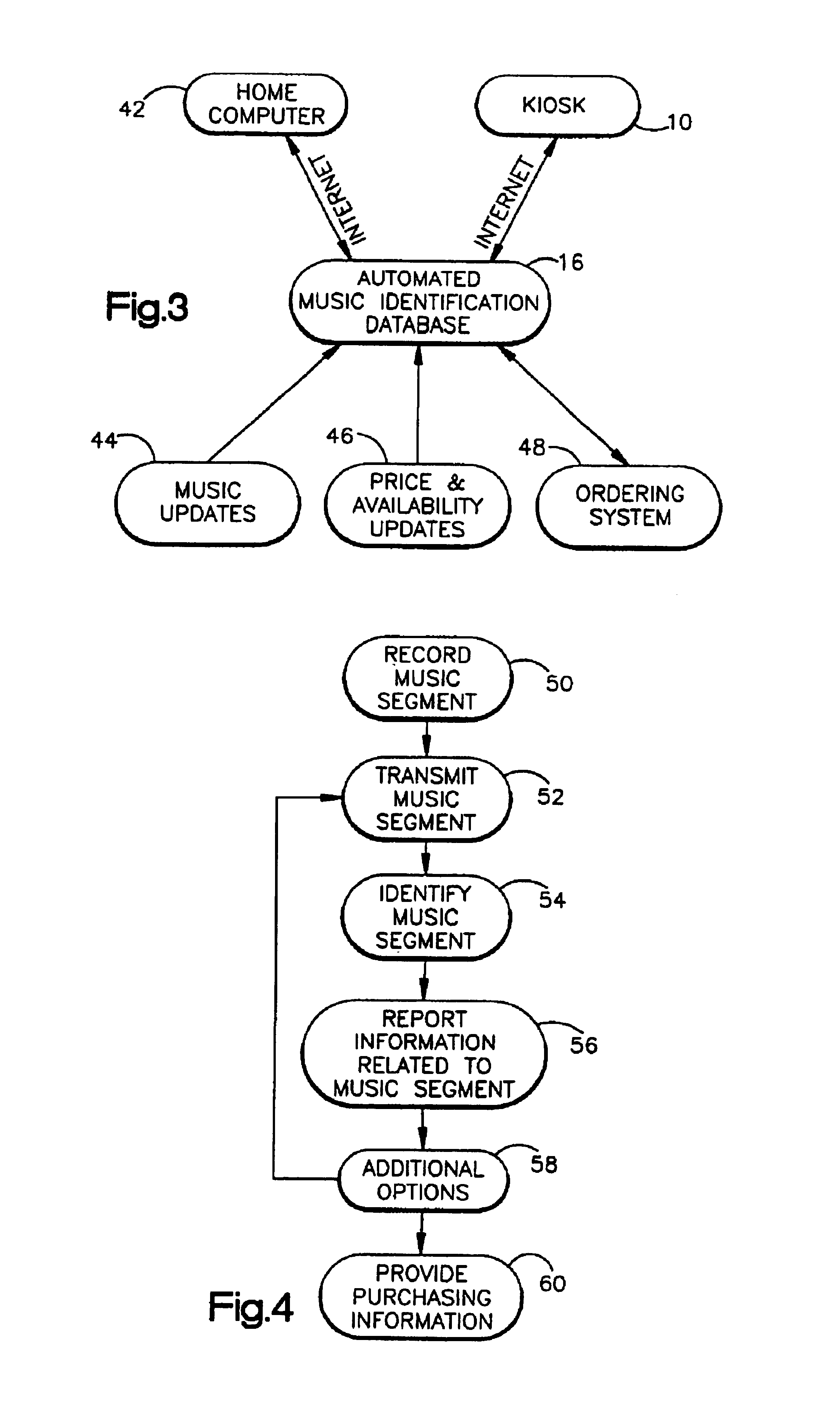
The present invention relates to a music identification / purchasing system, specifically to a method for marking the time and the name of the radio station in portable device such as a key holder, watch, cellular phone, beeper or the like which will allow the user to learn via internet or regular telephone the name of the song, artist and / or music company by matching the stored data with broadcast archive. The system will allow for purchase of the full length of the identified music item or related music. An alternate embodiment provides the listener with convenient means to record a segment of the music in which he / she is interested. The recorded music segment is played back into an apparatus which can identify the song based on the play back and provide the user with information on the identified song such as title, singer or artist, composer, producer, etc., and provide related purchasing information. The user can make selections and provide payment data to the music identification / purchasing system which will result in the selections being delivered to the user by mail.
Owner:TUNE HUNTER
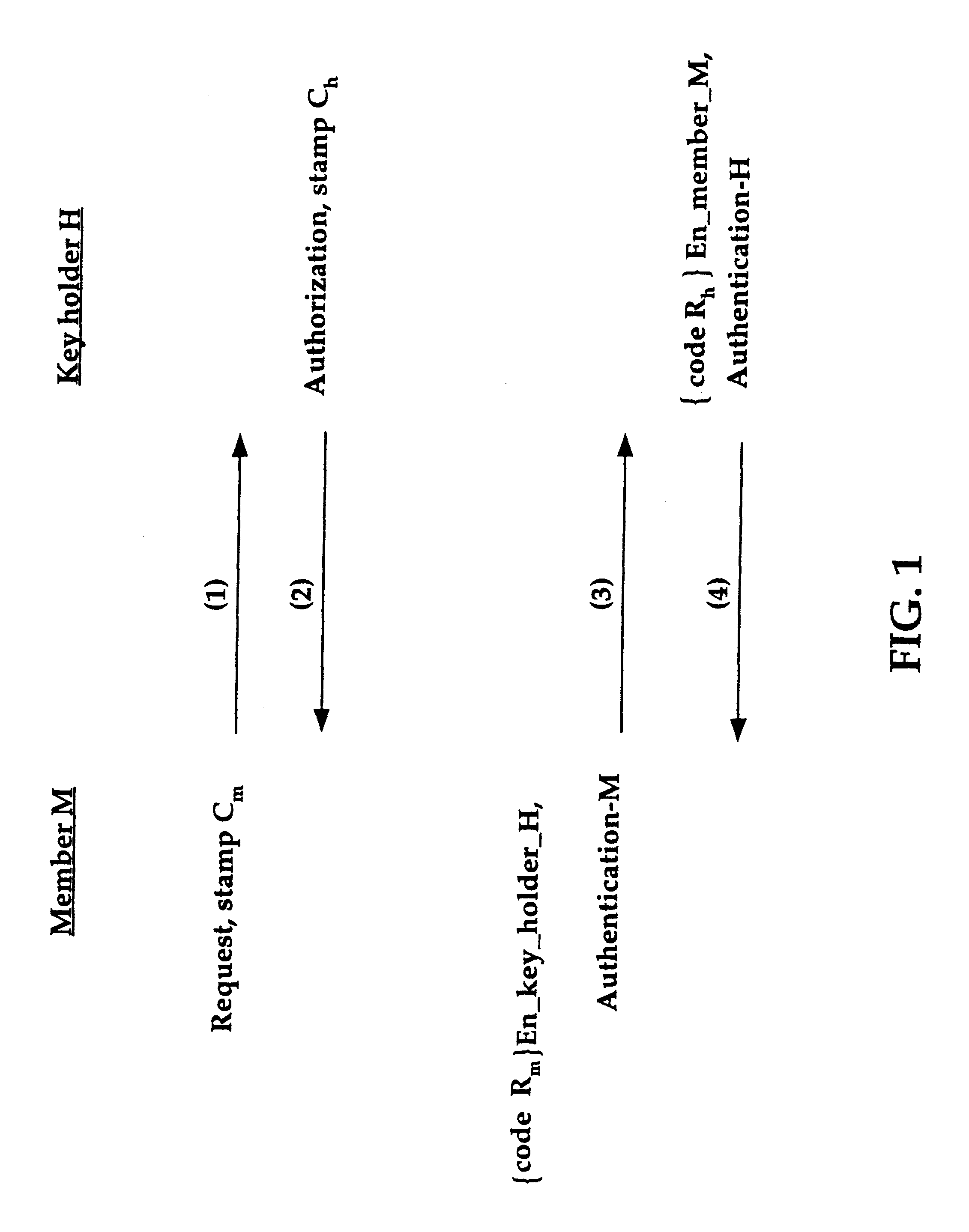
Group key distribution
InactiveUS6038322AEfficient additionLow costKey distribution for secure communicationPublic key for secure communicationTimestampNetwork addressing
A method for distributing a secret key from a key holder H to intended group members M. The method assumes that during the distribution process each party, a group member M and the key holder H, can decrypt and encrypt exchanged information such that the encrypter knows that the decrypter will be the intended party. The method preferably uses a public key / private key encryption technique in which, for example, a trusted Certificate Authority in a public key infrastructure signs the certificates to provide the public keys involved in the encryption. Alternatively, the method, together with a symmetric cipher, uses a shared secret, established in an authenticated mechanism that is outside the information exchanges of the invention. Additionally, the method uses a strong mixing function that takes several items of data as input and produces a pseudo-random authentication (or digest). Inputs to the mixing function include identity stamps that are generated by each member M and key holder H. These inputs can be the identity of the stamp generator, such as a network address, port, or protocol, a timestamp, and / or a secret value that is known only to the stamp generator. The stamps include information to bind member M if generated by key holder H, and to bind key holder H if generated by member M. Consequently, the invention authenticates each communication exchange between member M and key holder H.
Owner:CISCO TECH INC
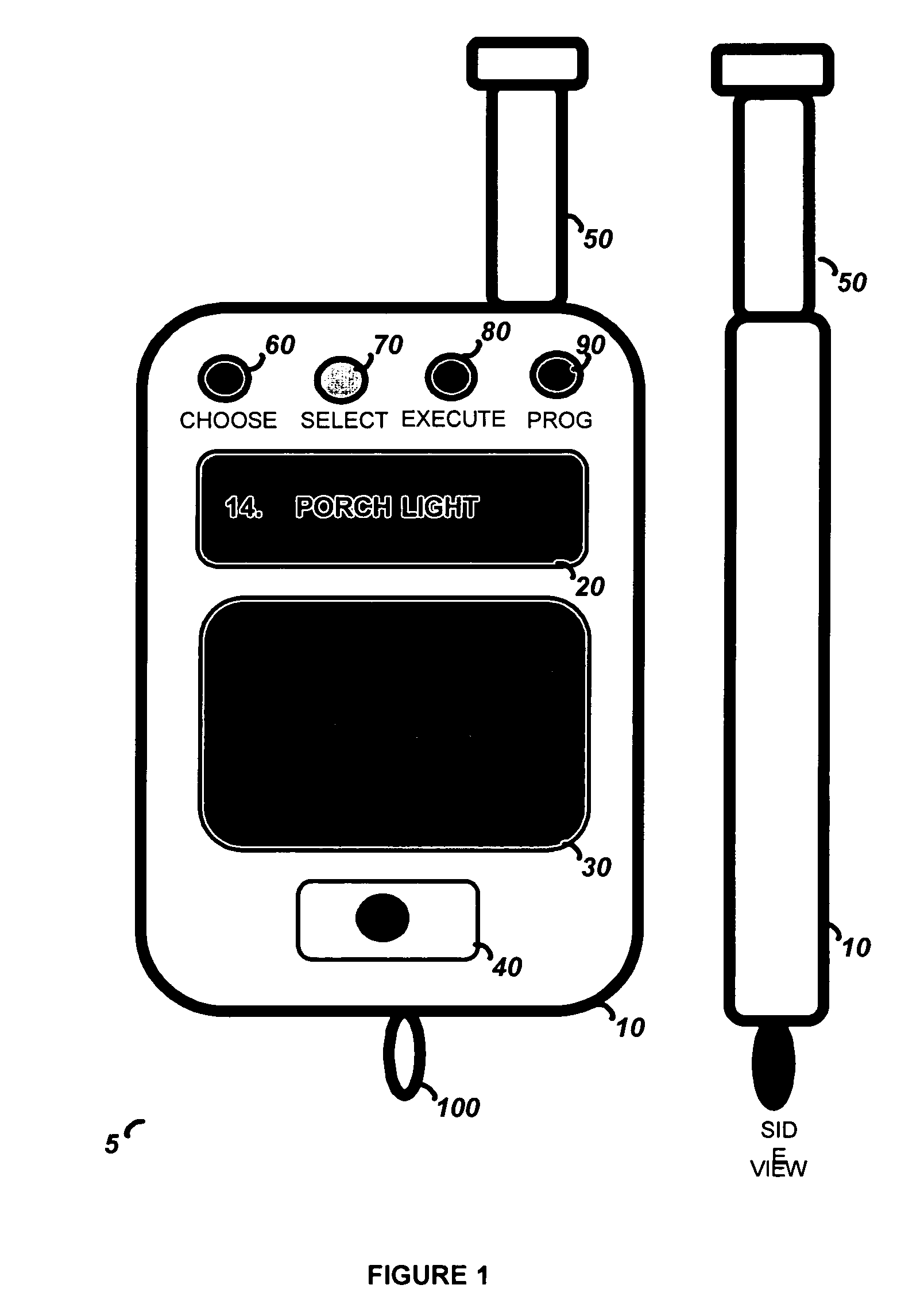
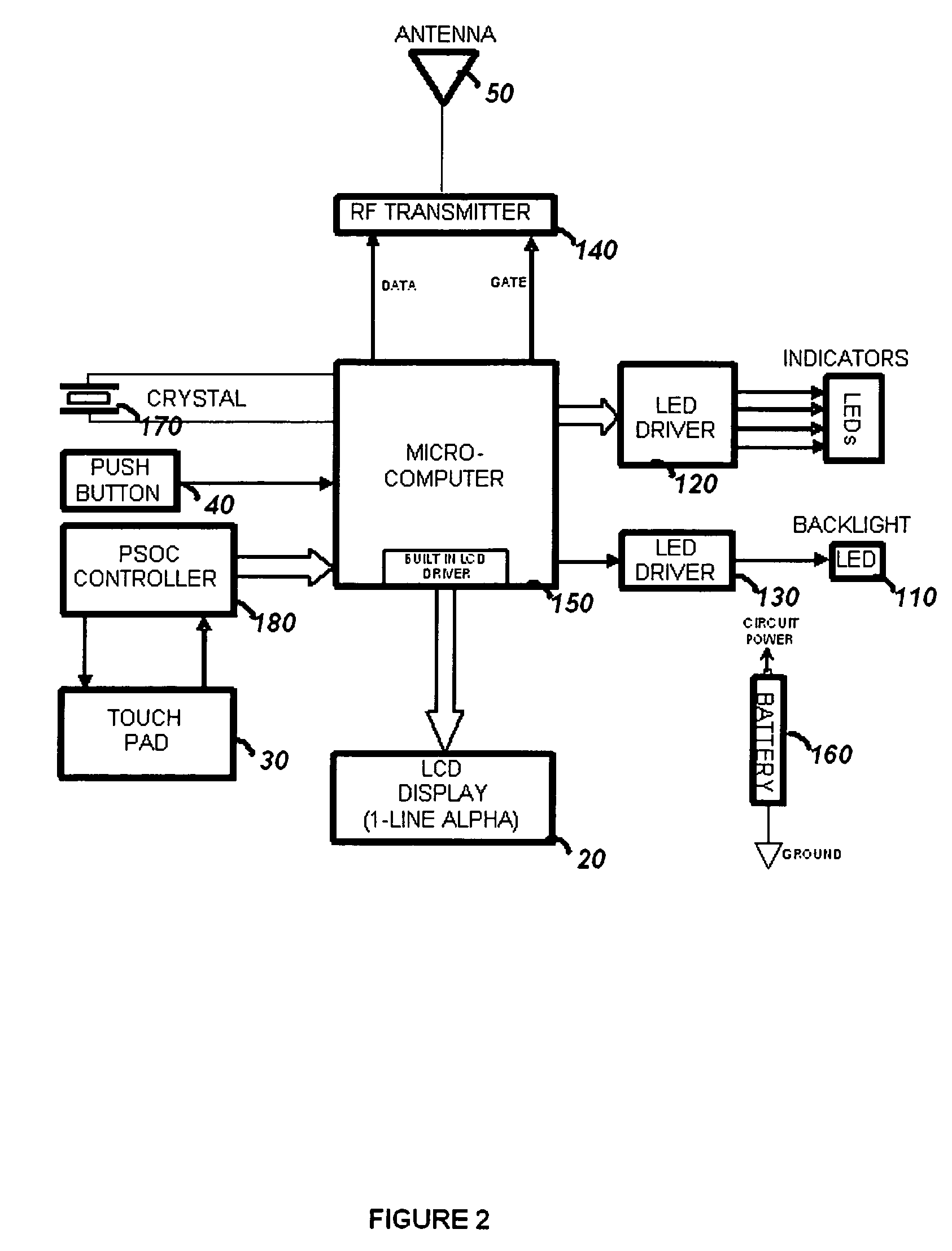
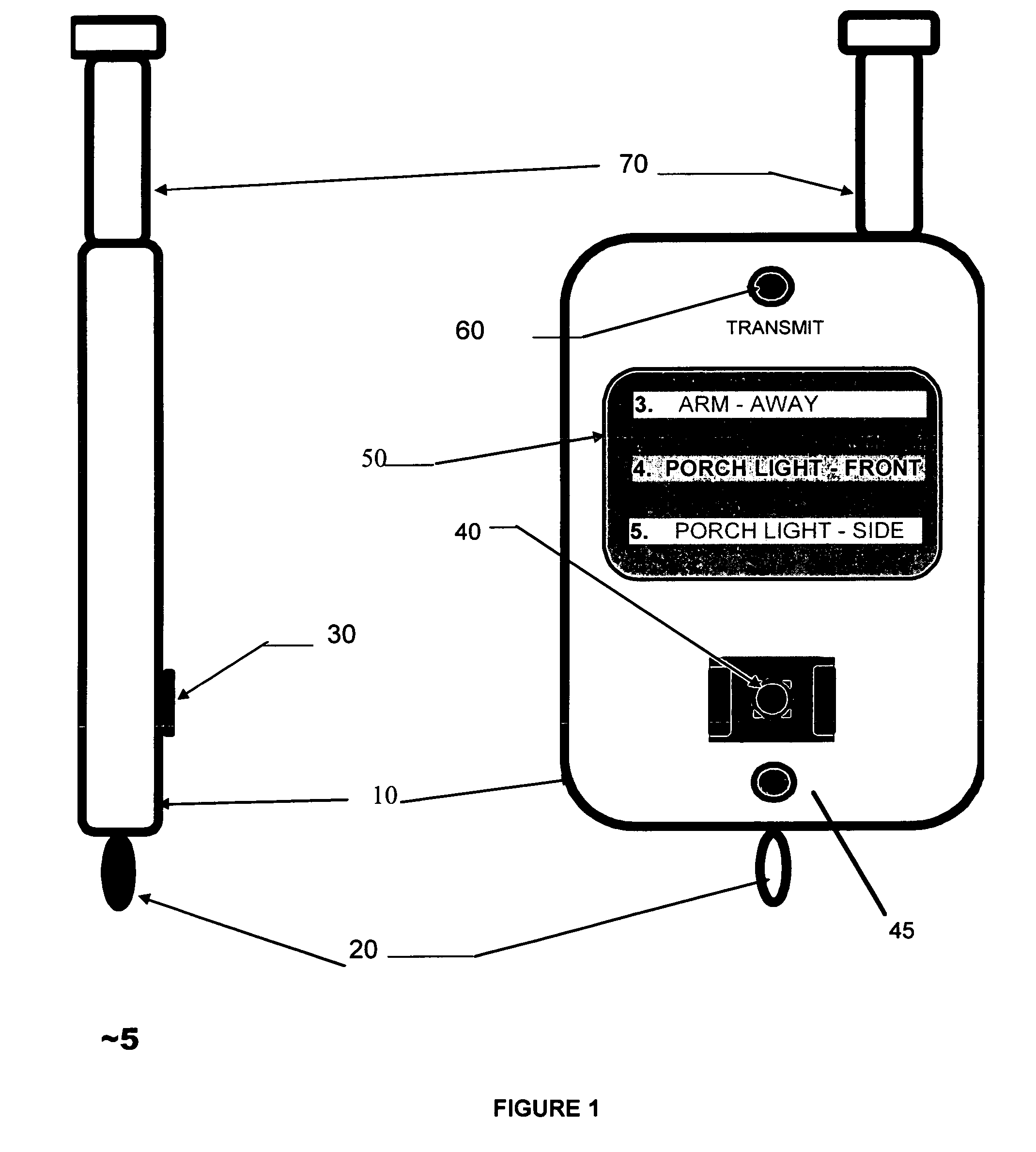
Touchscreen device for controlling a security system
The present invention is a hand held portable remote such as a key fob that allows a user to interact with the security system using a flat panel touch-pad. The touch-pad input allows a user to rapidly select and control a large number of security functions, such as Arm, Disarm, Panic, garage door open, lamp on / off, and lamp dimming control, etc. The security device comprises a housing, a wireless communication port for interface with the security system, a touch-pad input device, and processing circuitry. In order to operate the security device, the user generates a user input by creating a contact motion on the touch-pad input device with a fingertip. The contact motion may consist of a swiping motion, a tapping, or a circular motion. In order to distinguish the contact motion clearly, when the fingertip contact comprises a wider than normal contact, it causes the processing circuitry to not generate an output signal. The security device also comprises an LCD display for displaying alpha numeric control options to a user and LED indicators for indicating the modes of the processing circuitry.
Owner:ADEMCO INC
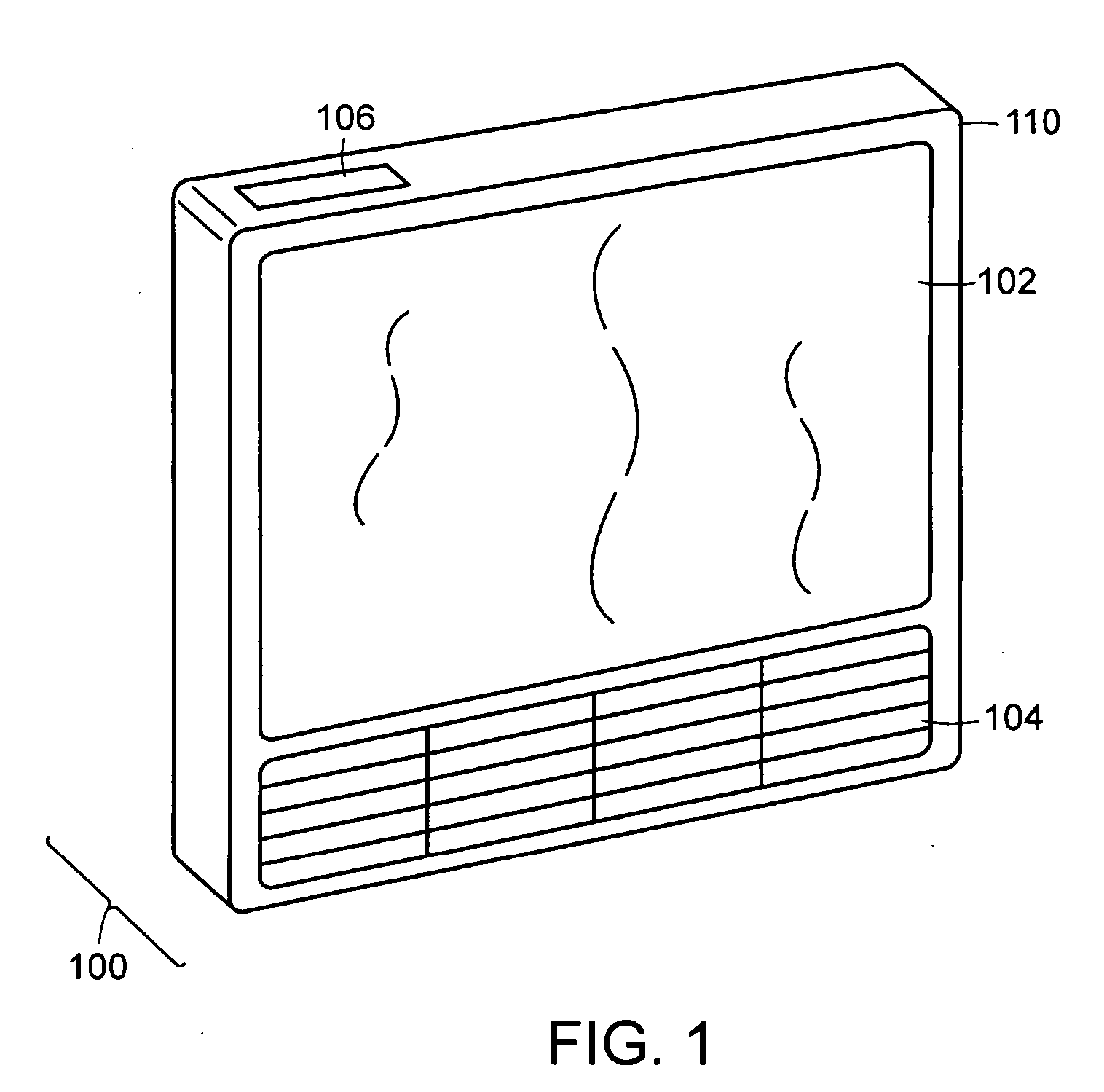
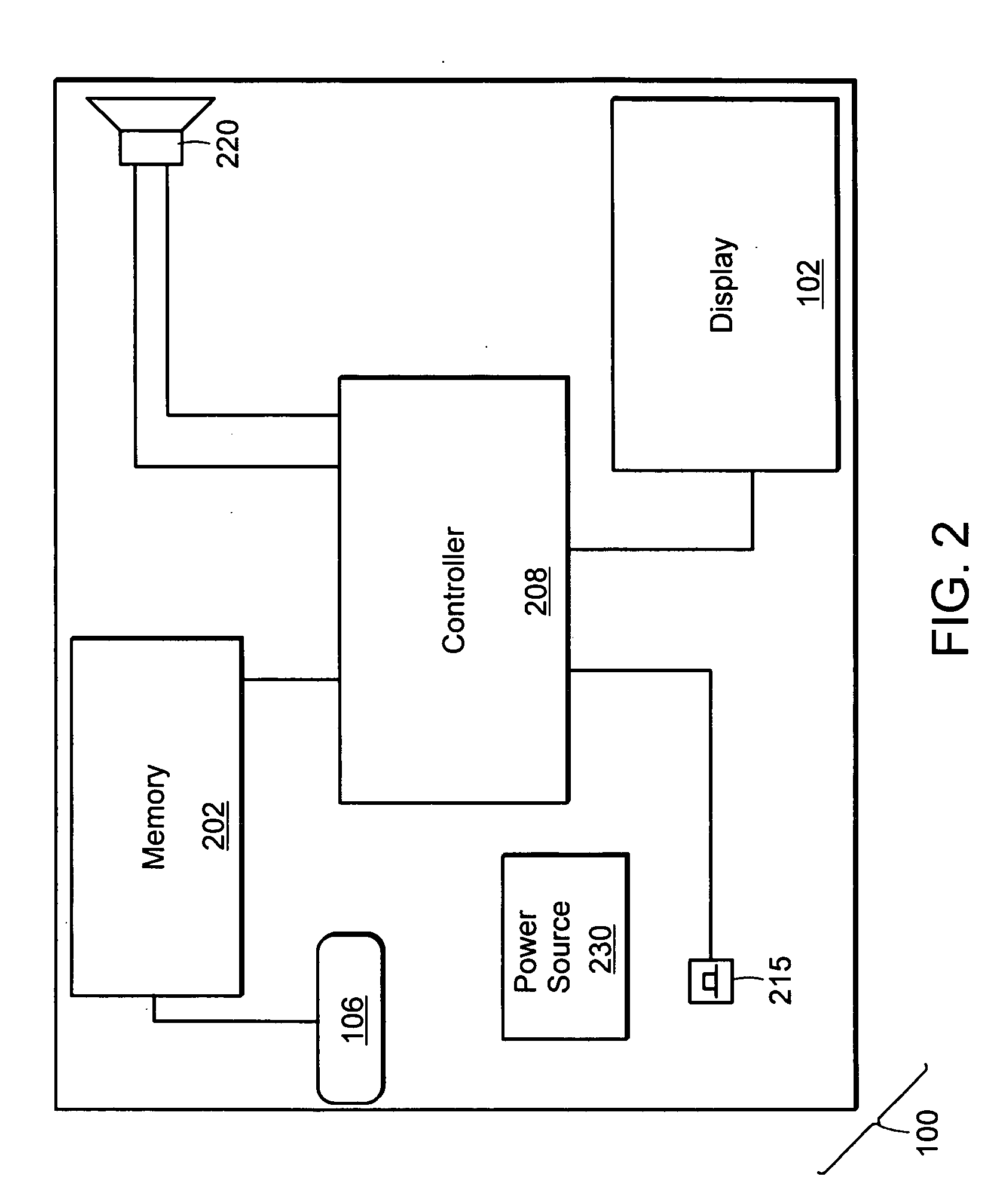
Key Fob and System for Indicating the Lock Status of a Door Lock
The present invention provides a system that records, at a remote location, the current status of a door lock. This invention provides a key fob device, which records the current status of a door look. The key fob indicates to the user the current lock status of the given door(s) in question. The key fob is a small key chain attached device, which records the state of the door locks, or other devices or appliances, as one departs from the door. The system of the present invention comprises a sensor at the door that detects the current lock status of a door and transmits this lock to the key fob. Also incorporated into the key fob is circuitry that receives and records this received lock status. A display component in the key fob displays this current lock status when prompted by the user.
Owner:IBM CORP
Music identification system
InactiveUS20060004640A1Metadata audio data retrievalSpecific information broadcast systemsPaymentThe Internet
The present invention relates to a music identification / purchasing system, specifically to a method for marking the time and the name of the radio station in portable device such as a key holder, watch, cellular phone, beeper or the like which will allow the user to learn via internet or regular telephone the name of the song, artist and / or music company by matching the stored data with broadcast archive. The system will allow for purchase of the full length of the identified music item or related music. An alternate embodiment provides the listener with convenient means to record a segment of the music in which he / she is interested. The recorded music segment is played back into an apparatus which can identify the song based on the play back and provide the user with information on the identified song such as title, singer or artist, composer, producer, etc., and provide related purchasing information. The user can make selections and provide payment data to the music identification / purchasing system which will result in the selections being delivered to the user by mail.
Owner:SWIERCZEK REMI
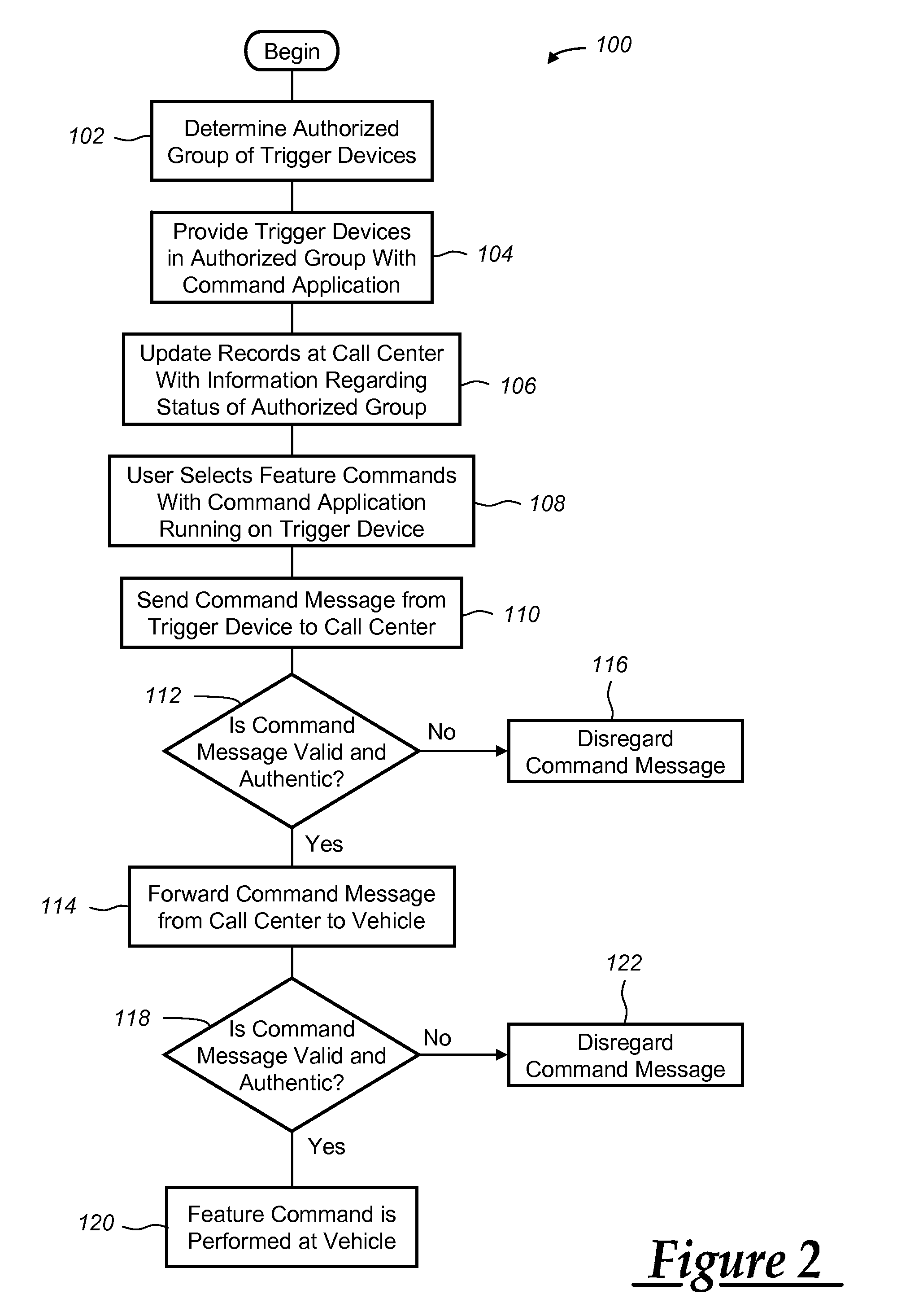
Method for remotely controlling vehicle features
A method and system that enables users to remotely control or manage certain vehicle features, such as emergency flashers or a remote engine start, through the use of a trigger device other than a conventional vehicle key fob. For example, a trigger device like a mobile phone, a personal digital assistant (PDA), or a computer can be used to remotely control or activate select vehicle features. In one embodiment, short message service (SMS) messages are used to send feature commands either directly from the trigger device to the vehicle or via a call center or other message processing entity.
Owner:GENERA MOTORS LLC
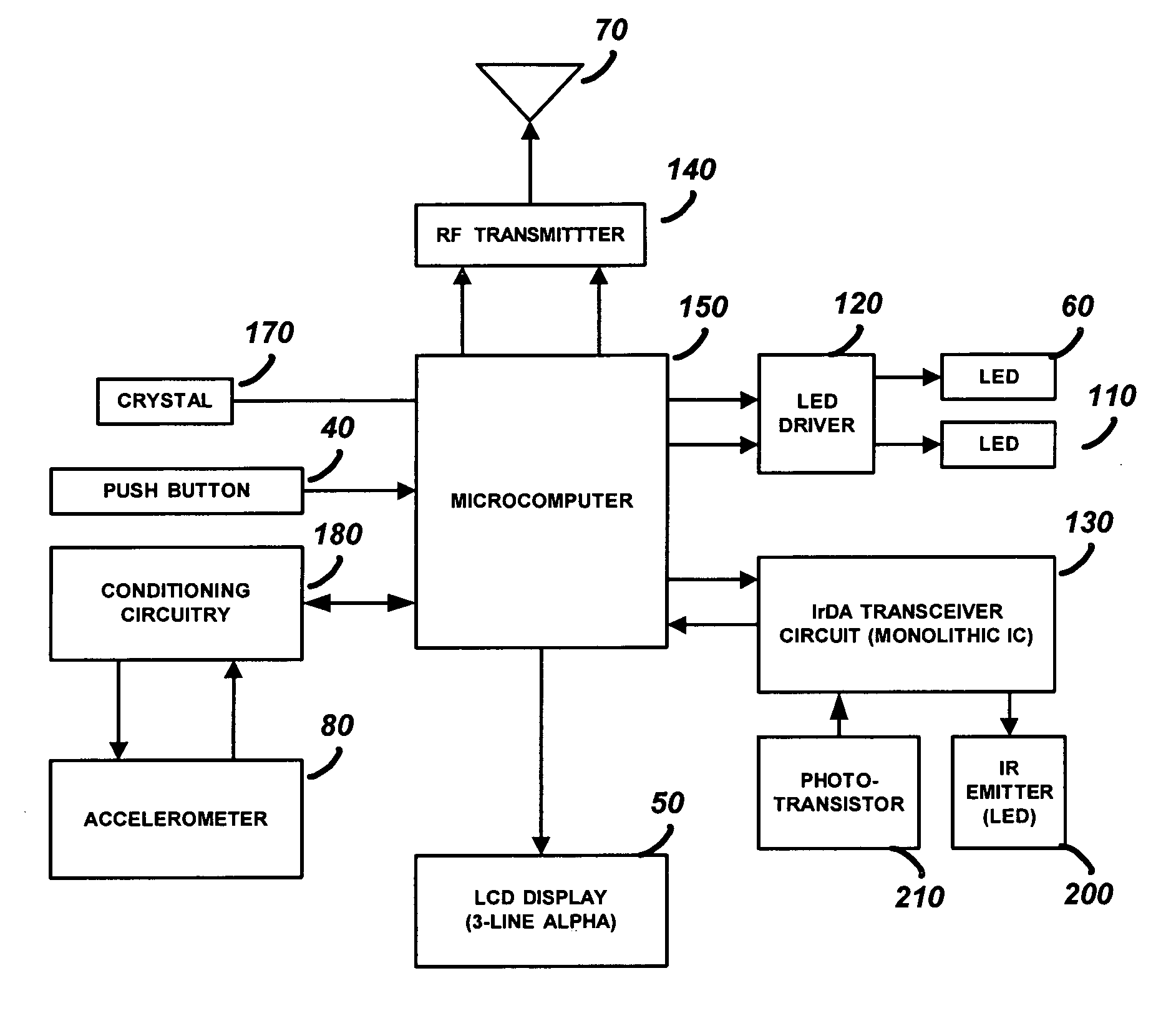
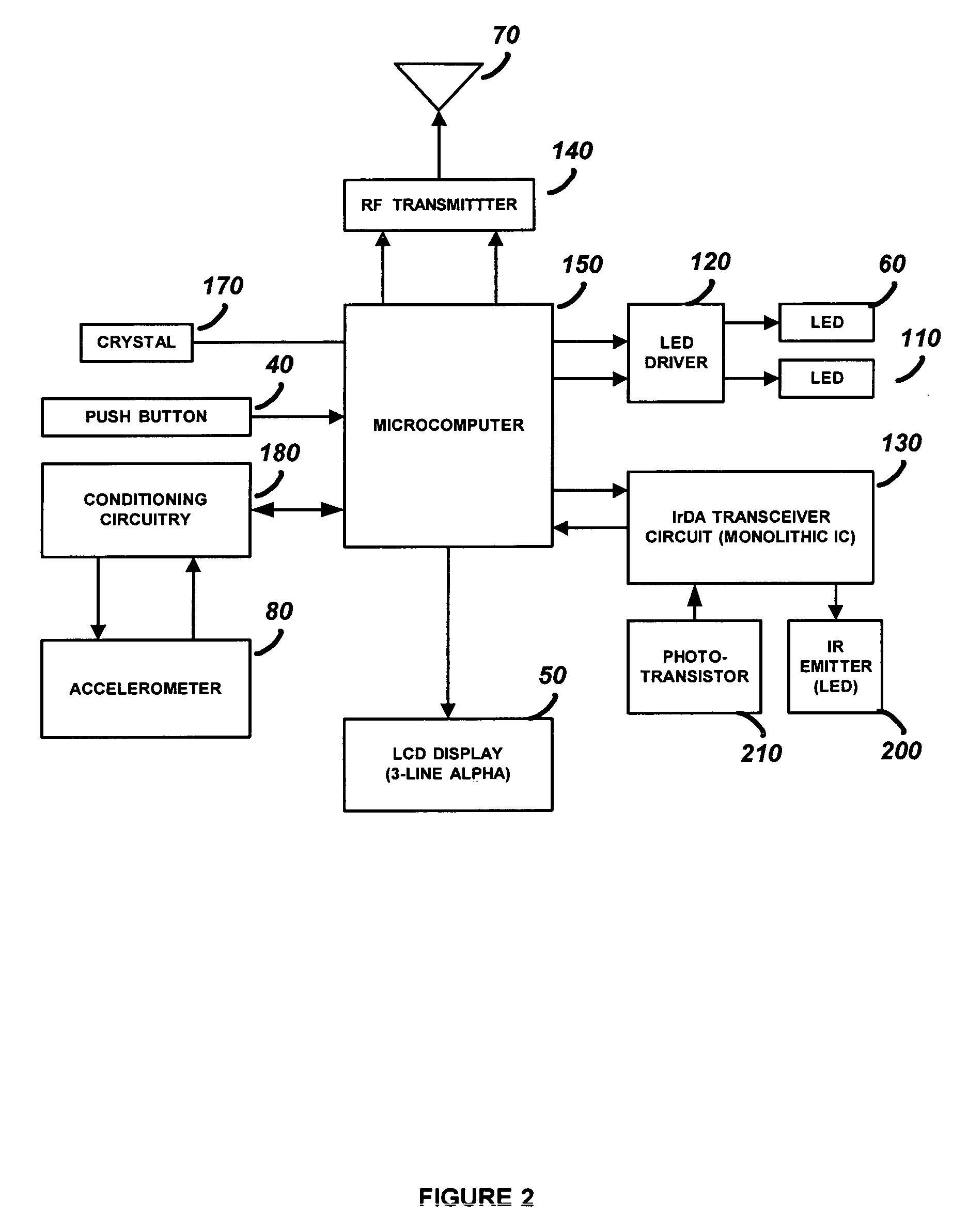
One button multifunction key fob for controlling a security system
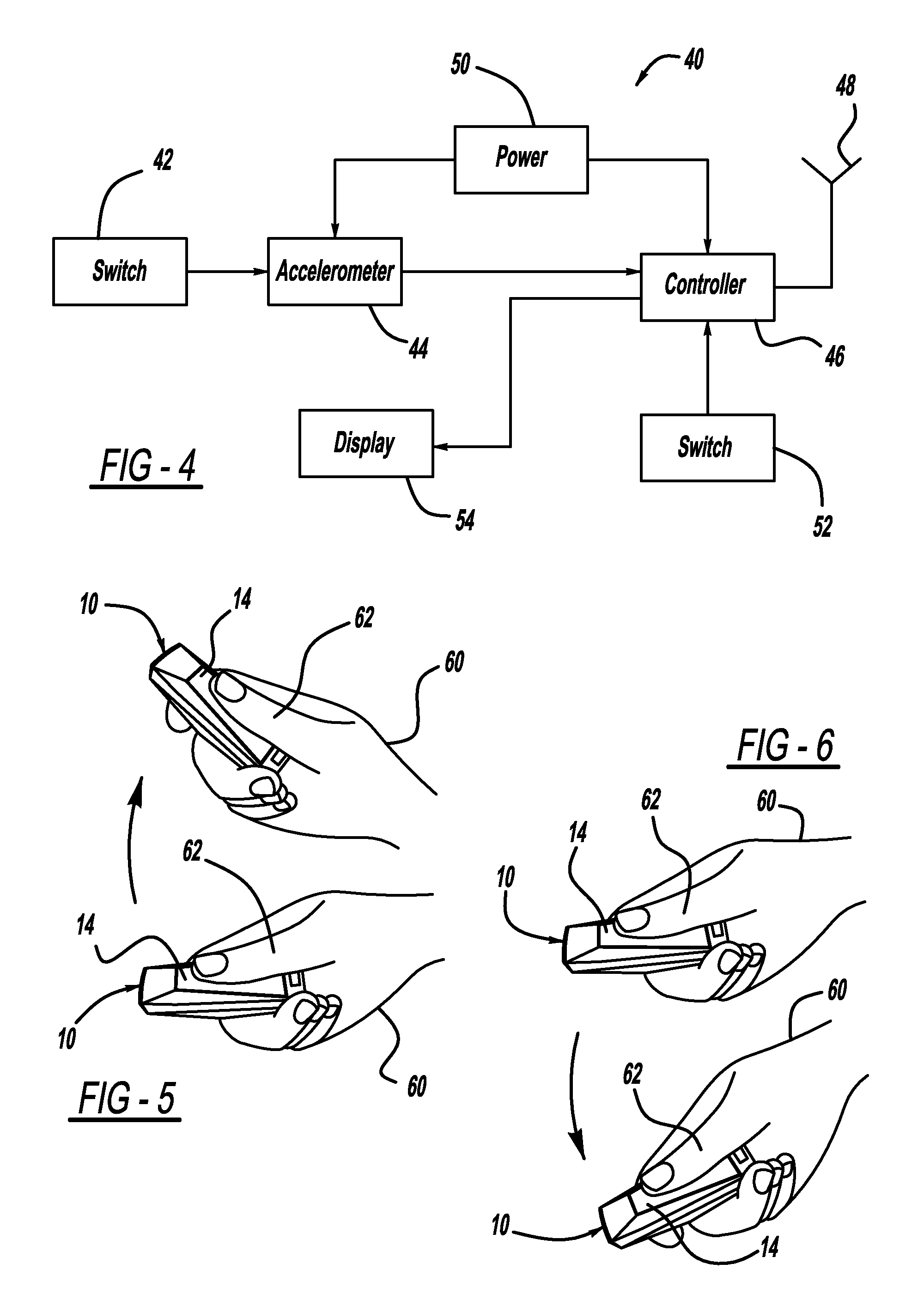
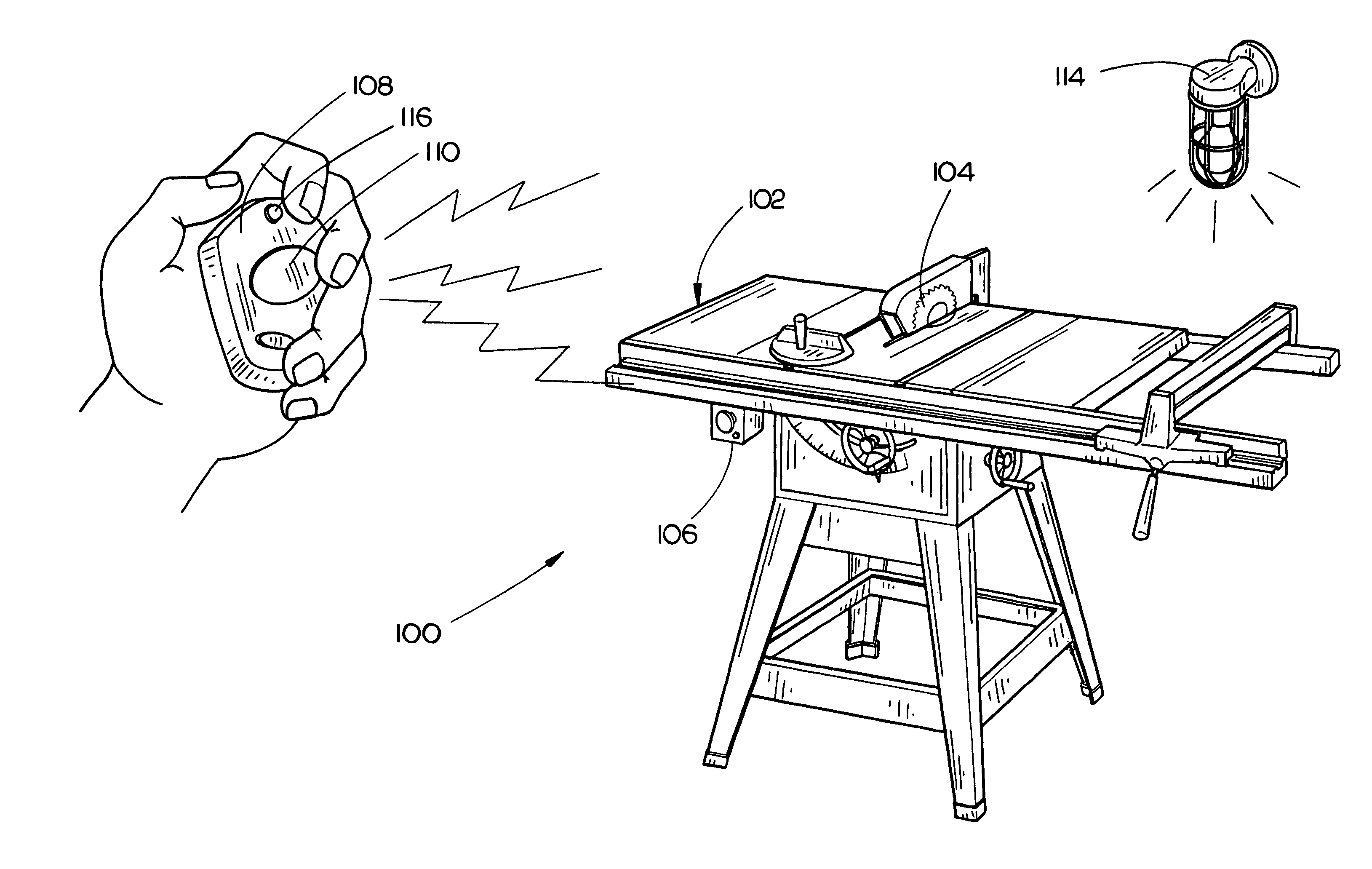
ActiveUS7796052B2Electric signal transmission systemsNon-electrical signal transmission systemsAccelerometerControl signal
A security device which is a hand held portable remote device such as a key fob that allows a user to interact with a security system using a single button. The security system functions such as arming, disarming, panic, garage door open, lamp on / off, and lamp dimming control will be displayed by the security device as control options and will be selected by a user using a forward, backward, left or right tilting motion and depressing the power on / select button. Once a control option has been selected, the security device will transmit the control option to the security system. The security device has a portable housing, a wireless communication port for interface with a security system, a display panel, an accelerometer device, and processing circuitry. The accelerometer device is used to determine the tilt of the security device and provide a control signal related to the tilt. The security device also has an infrared communication port for downloading control options, and single push button, for turning the security device on and for initiating the transmission of the output signal.
Owner:ADEMCO INC
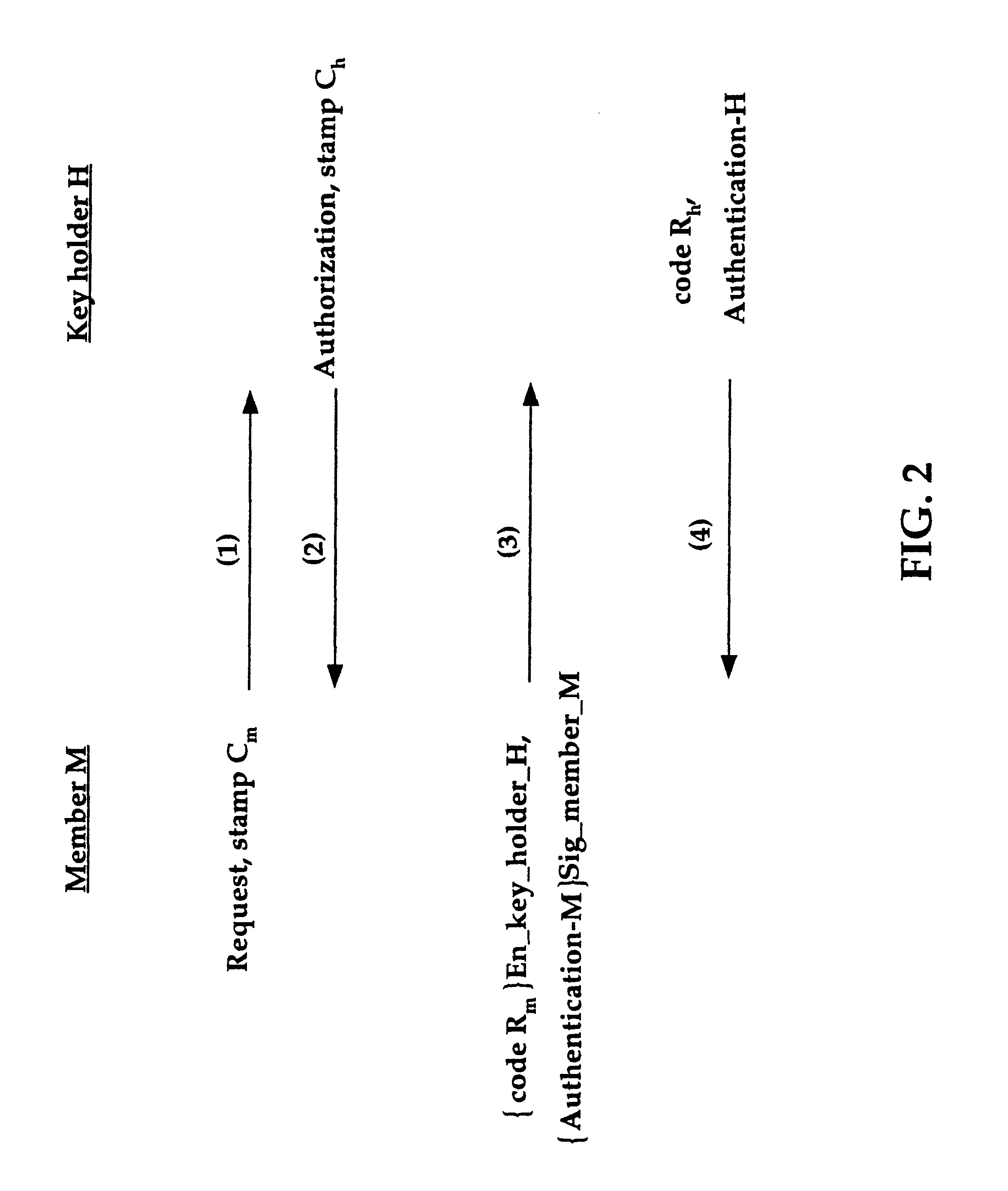
Group key distribution
InactiveUS6215878B1Efficient additionLow costKey distribution for secure communicationPublic key for secure communicationTimestampNetwork addressing
Owner:CISCO TECH INC
Key fob device and method
A device and method for a key fob. The key fob device can include a housing, a lid defining one or more apertures, a circuit board including one or more switches, and a flexible film coupled to the housing and / or the lid. The flexible film can include one or more contact surfaces and stylized graphics.
Owner:STRATTEC SECURITY +1
Source identification for unauthorized copies of content
ActiveUS8739308B1Digital data processing detailsAnalogue secracy/subscription systemsKey HolderAuthentication
Systems and methods for authentication generate keys from secret credentials shared between authenticating parties and authenticators. Generation of the keys may involve utilizing specialized information in the form of parameters that are used to specialize keys. Keys and / or information derived from keys held by multiple authorities may be used to generate other keys such that signatures requiring such keys and / or information can be verified without access to the keys. Keys may also be derived to form a hierarchy of keys that are distributed such that a key holder's ability to decrypt data depends on the key's position in the hierarchy relative to the position of a key used to encrypt the data. Key hierarchies may also be used to distribute key sets to content processing devices to enable the devices to decrypt content such that sources or potential sources of unauthorized content are identifiable from the decrypted content.
Owner:AMAZON TECH INC
Object-proximity monitoring and alarm system
InactiveUS20050030188A1Efficient manufacturingEffective installationElectric devicesPedestrian/occupant safety arrangementTransceiverEngineering
A weight-sensitive mat or other sensor determines whether a child seat in a vehicle is occupied, a transmitter is proximate to the sensor, and a keychain fob or other portable unit includes a receiver and an alarm. Generally, if the child seat is occupied and the keychain fob is removed from proximity to the transmitter, the transmitter communicates this to the keychain fob receiver and the alarm is activated. Exemplary embodiments include an add-on kit including a base unit with a transceiver for use with existing car seats having a base and a detachable shell, an add-on kit without the base unit for use with existing unitary car seats, a car seat with the child sensor, transmitter, and / or base unit built into it, and an automatic checklist feature for diaper bags, strollers, etc.
Owner:SEATSIGNAL
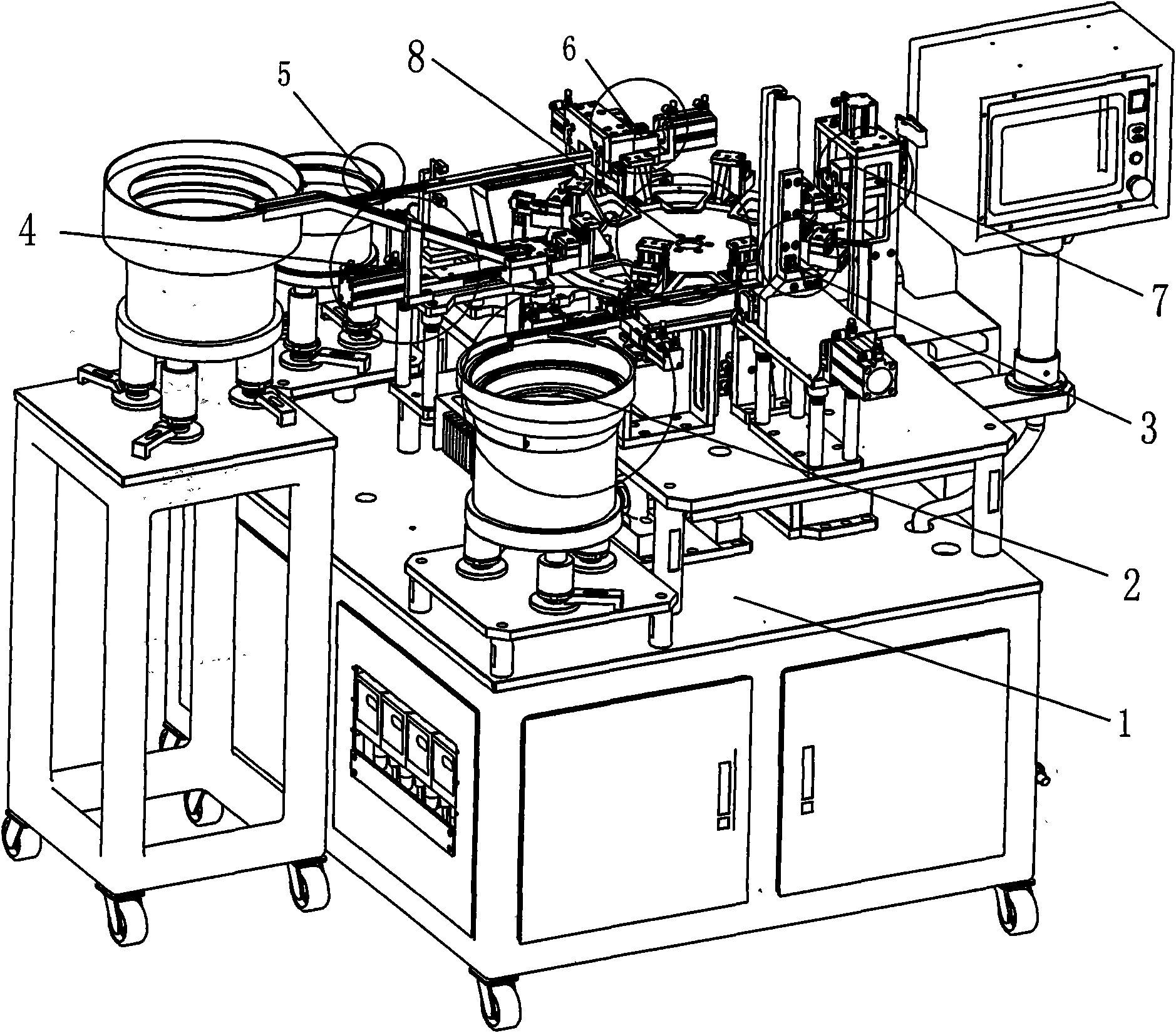
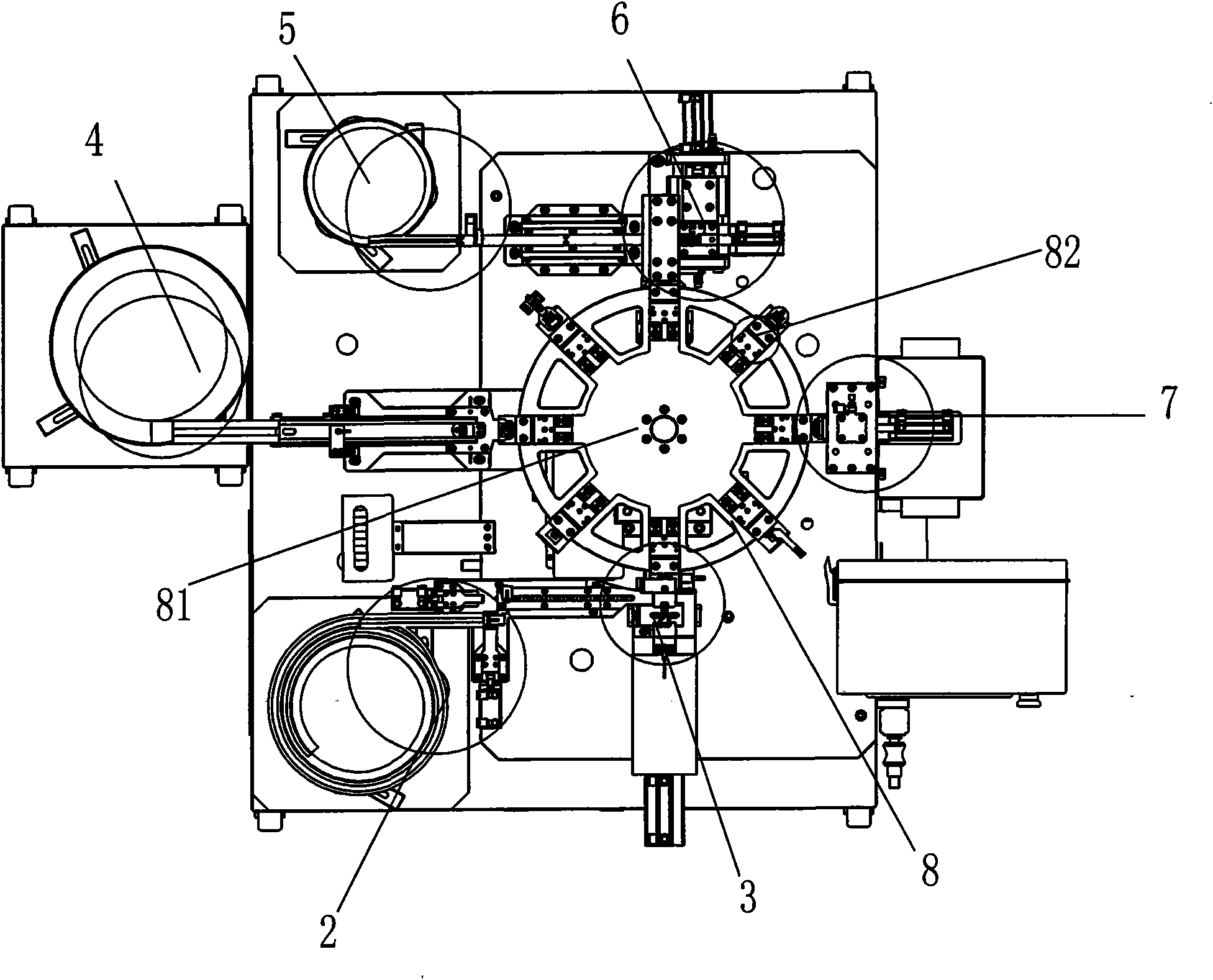
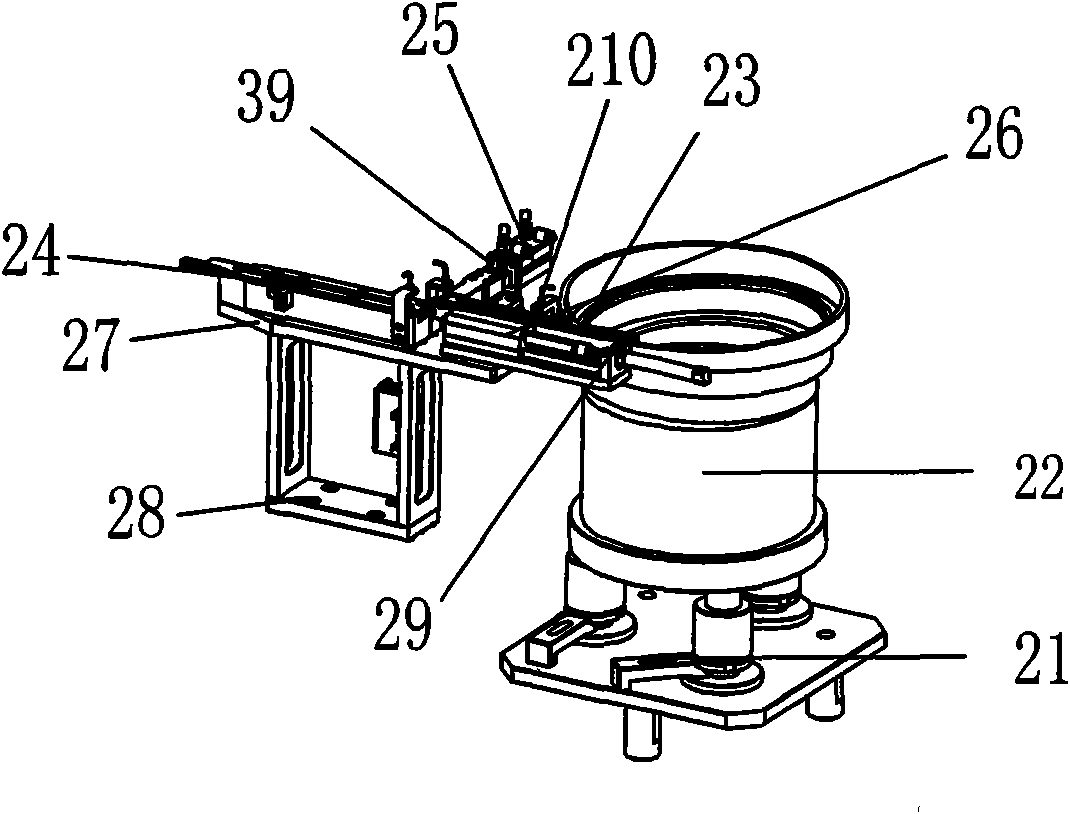
Folding key assembling machine
InactiveCN101972932ARealize automatic feedingRealize the assemblyAssembly machinesSemi automaticControl circuit
The invention relates to a folding key assembling machine, which comprises a worktable, and a plastic head feeding mechanism, a hardware press-in mechanism, a key handle feeding mechanism, a pin feeding mechanism, a pin pressing mechanism, a loading mechanism and an assembling and conveying mechanism which are arranged on the worktable, wherein the assembling and conveying mechanism is provided with a key holder; the hardware press-in mechanism, the key handle feeding mechanism and the pin pressing mechanism are connected with the assembling and conveying mechanism in turn; the output end of the plastic head feeding mechanism is connected with the hardware press-in mechanism; the output end of the pin feeding mechanism is connected with the pin pressing mechanism; and the mechanisms are connected with the main control circuit electrically. In the invention, the automatic feeding mechanism and the automatic assembling mechanism are combined scientifically; the operation mechanicals form a continuous operation streamline for automatically feeding and assembling folding keys in place of the manual and semi-automatic ways of assembling the folding keys; thus, the production efficiency of the folding keys is improved obviously, assembly quality is improved, production cost is saved and labor intensity is lowered.
Owner:周俊雄
System and method for protecting data files by periodically refreshing a decryption key
InactiveUS6937726B1Eliminate disadvantagesImprove efficiencyKey distribution for secure communicationPublic key for secure communicationData fileDocumentation
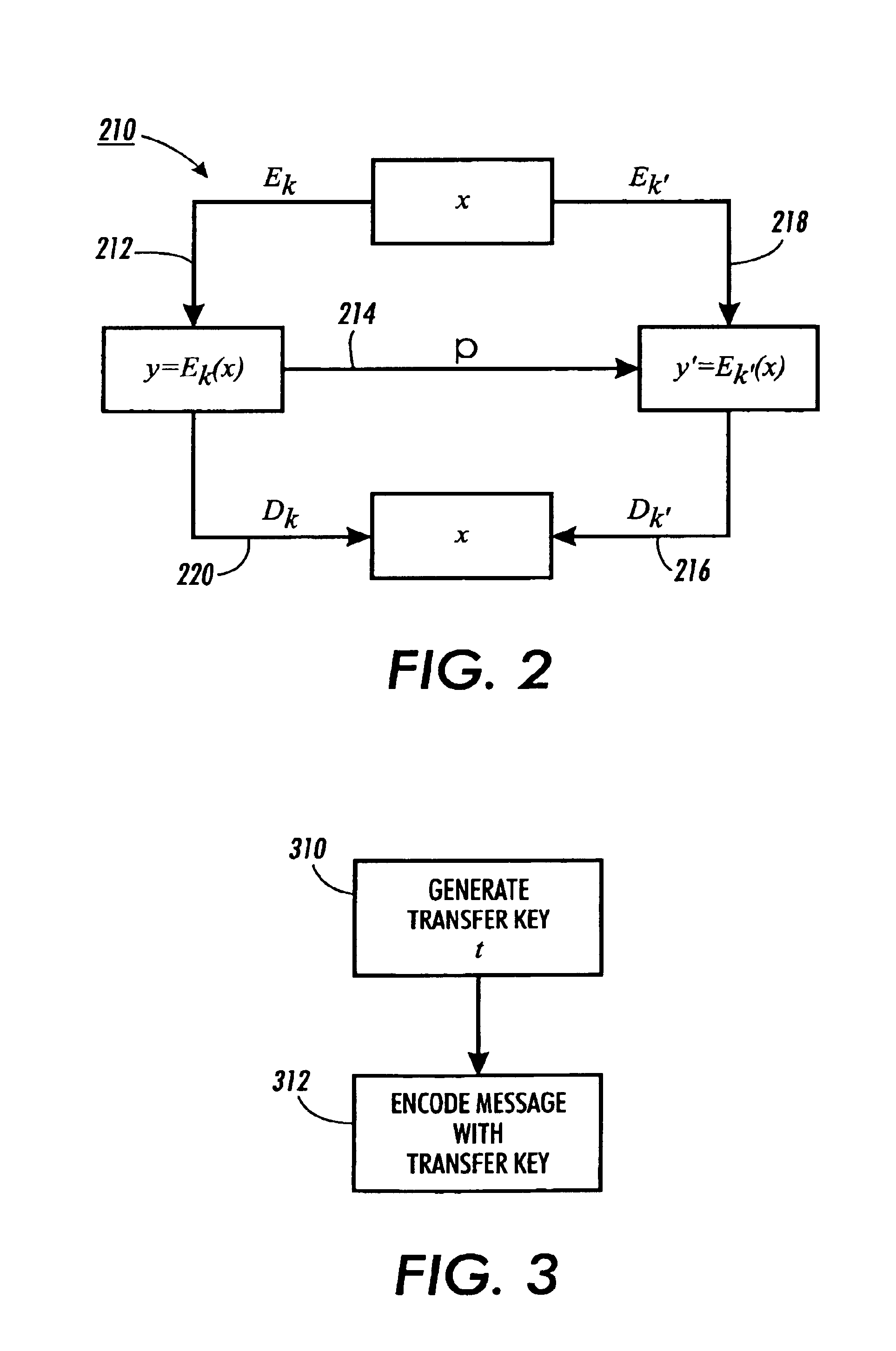
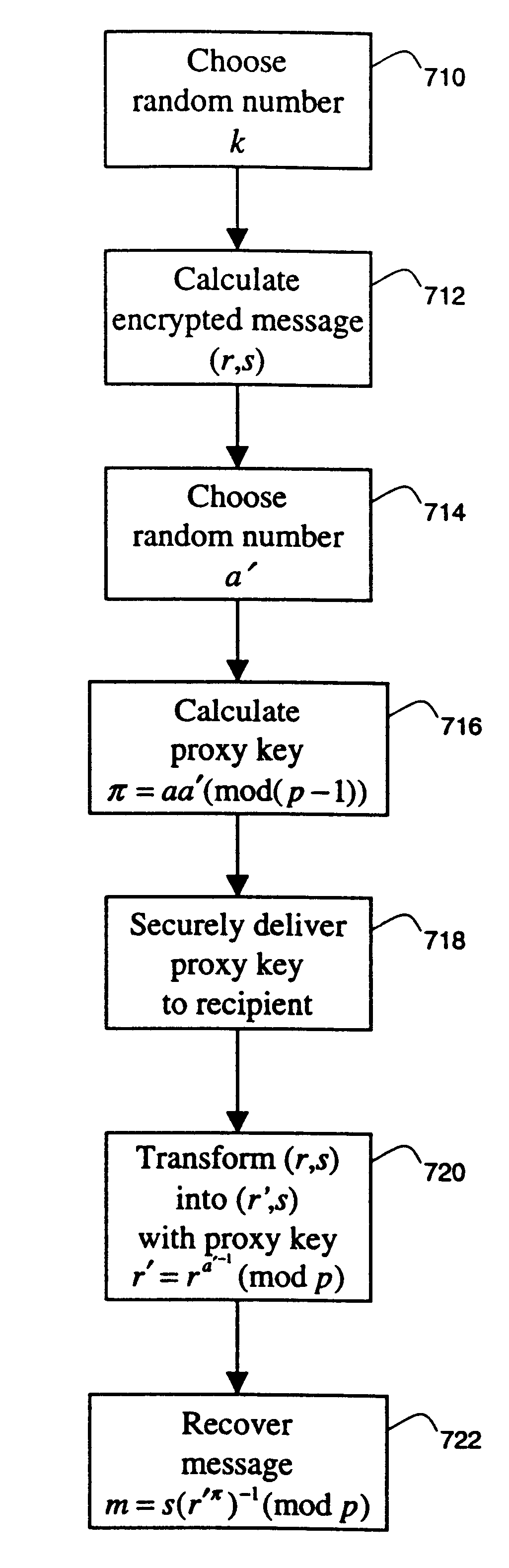
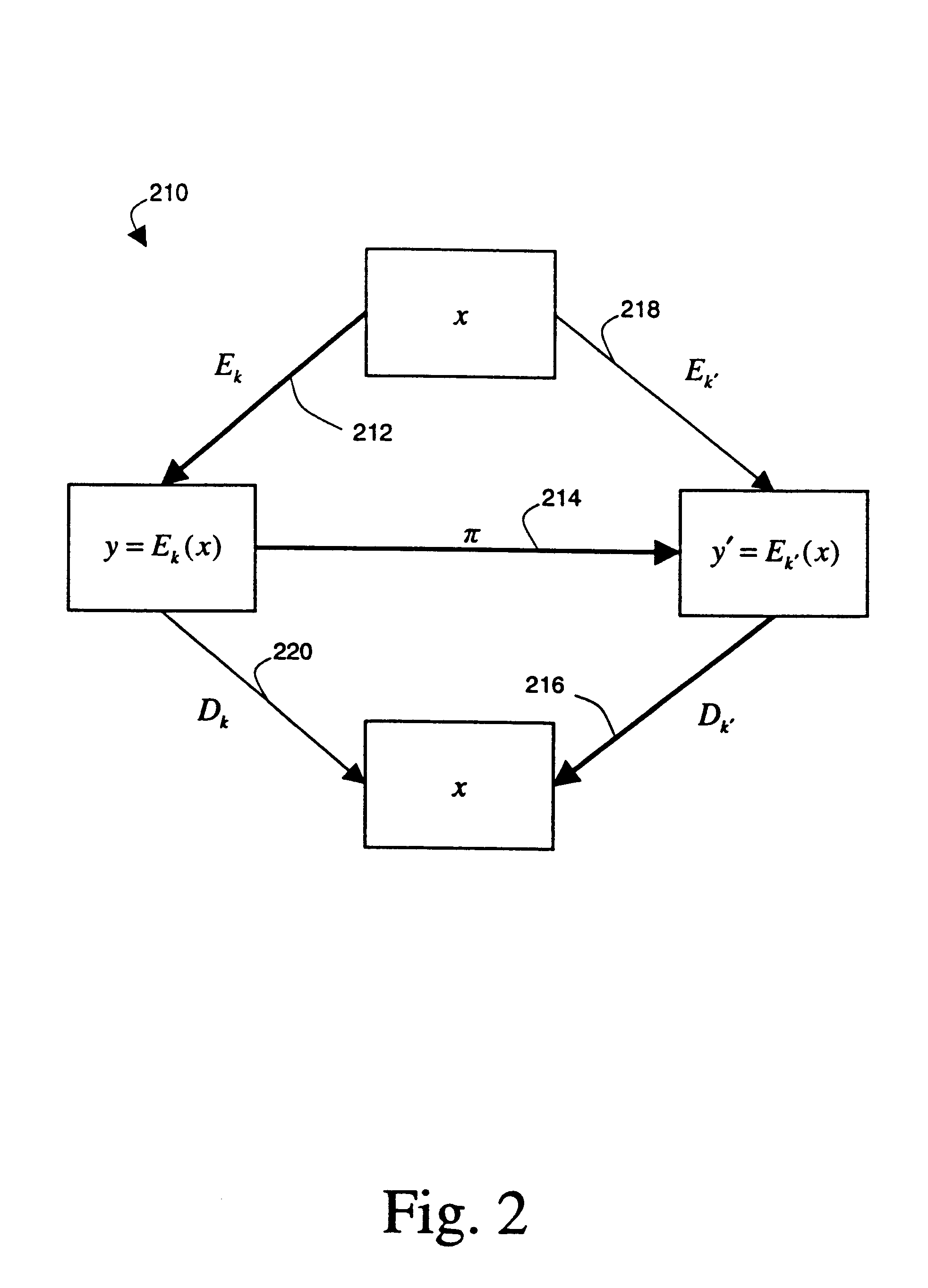
Methods for transferring among key holders in encoding and cryptographic systems the right to decode and decrypt messages in a way that does not explicitly reveal decoding and decrypting keys used and the original messages. Such methods are more secure and more efficient than typical re-encoding and re-encryption schemes, and are useful in developing such applications as document distribution and long-term file protection.
Owner:CONTENTGUARD HLDG
Gesture control key fob
A key fob for a vehicle that provides a certain vehicle function depending on the motion applied to the key fob. The key fob includes a switch that is pressed when the vehicle operator wishes to transmit a command. Pressing the switch causes a device, such as a camera or accelerometer, to be put in a motion detecting mode, where a subsequent motion of the key fob causes the key fob to transmit a command associated with that motion. For example, the vehicle operator can press the switch on the key fob and make an upward motion, which will cause the vehicle door locks to unlock. Likewise, pressing the switch on the key fob and making a downward motion may cause the door locks to lock.
Owner:GM GLOBAL TECH OPERATIONS LLC
Power tool with remote stop
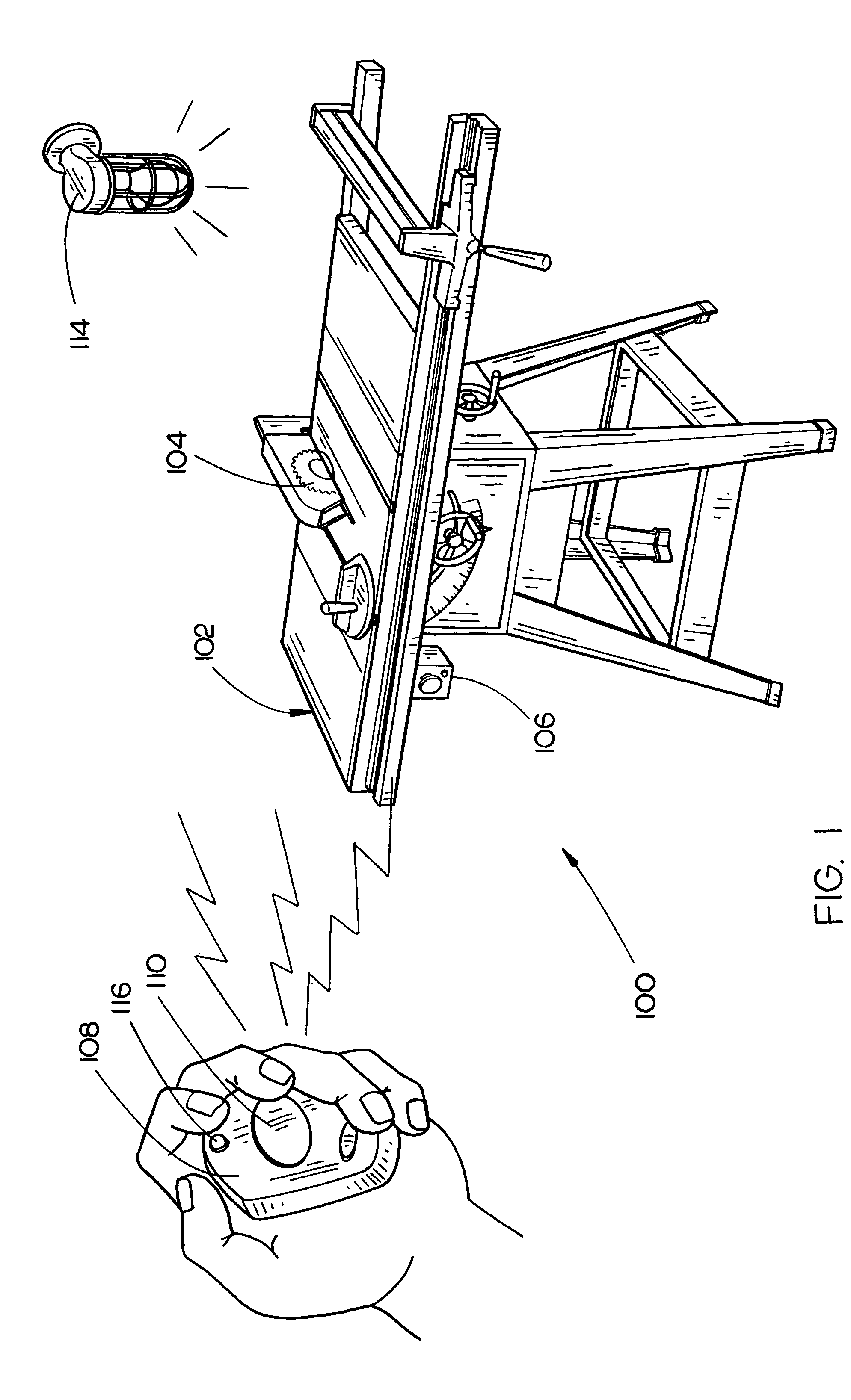
InactiveUS7064502B2DC motor speed/torque controlNon-electrical signal transmission systemsElectricityHand held
The present invention is directed to a power tool including a wireless remote stop for terminating the flow of electricity to an electric motor. The electric motor is configured for operating a working element assembly of a power tool, such as an arbor / circular saw blade included a table saw. In an embodiment, a remote stop is a hand-held fob, having a housing and a button. Alternatively, the remote stop may be implemented as a foot pedal apparatus, for being disposed on a shop floor.
Owner:BLACK & DECKER INC
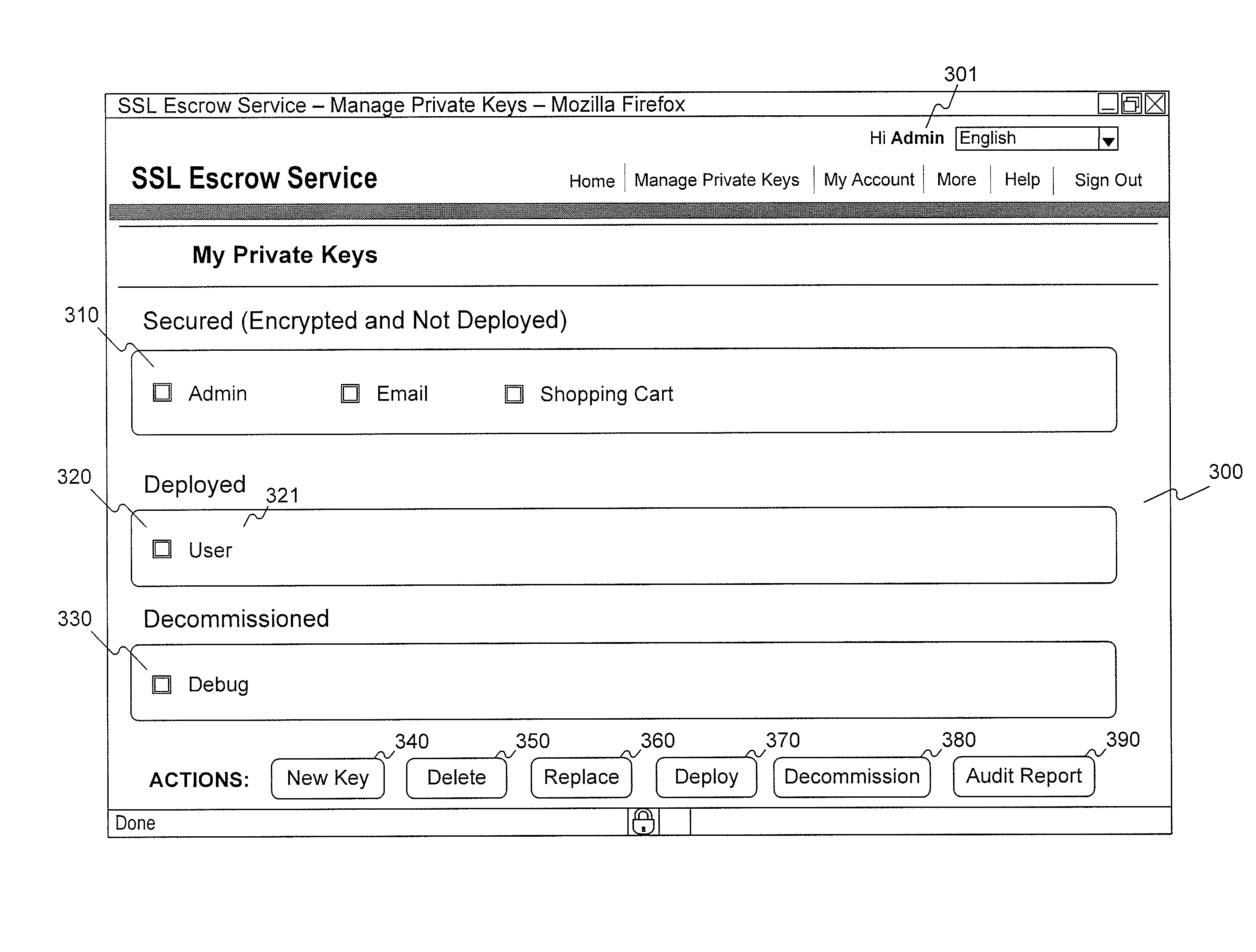
Management of ssl certificate escrow
ActiveUS20120170753A1Key distribution for secure communicationComputer security arrangementsInternet privacyKey escrow
Methods and systems for providing a secure SSL certificate escrow service comprise: providing a secure upload webpage for a private key holder to upload an encrypted copy of a private key; receiving the encrypted copy of the private key from the private key holder via the secure upload webpage; storing the encrypted copy of the private key in memory; providing a secure decryption webpage for the private key holder to enable the private key escrow service to decrypt the private key; receiving an instruction to decrypt the private key from the private key holder through the secure decryption webpage; and decrypting the private key in response to the instruction to decrypt the private key.
Owner:VERISIGN
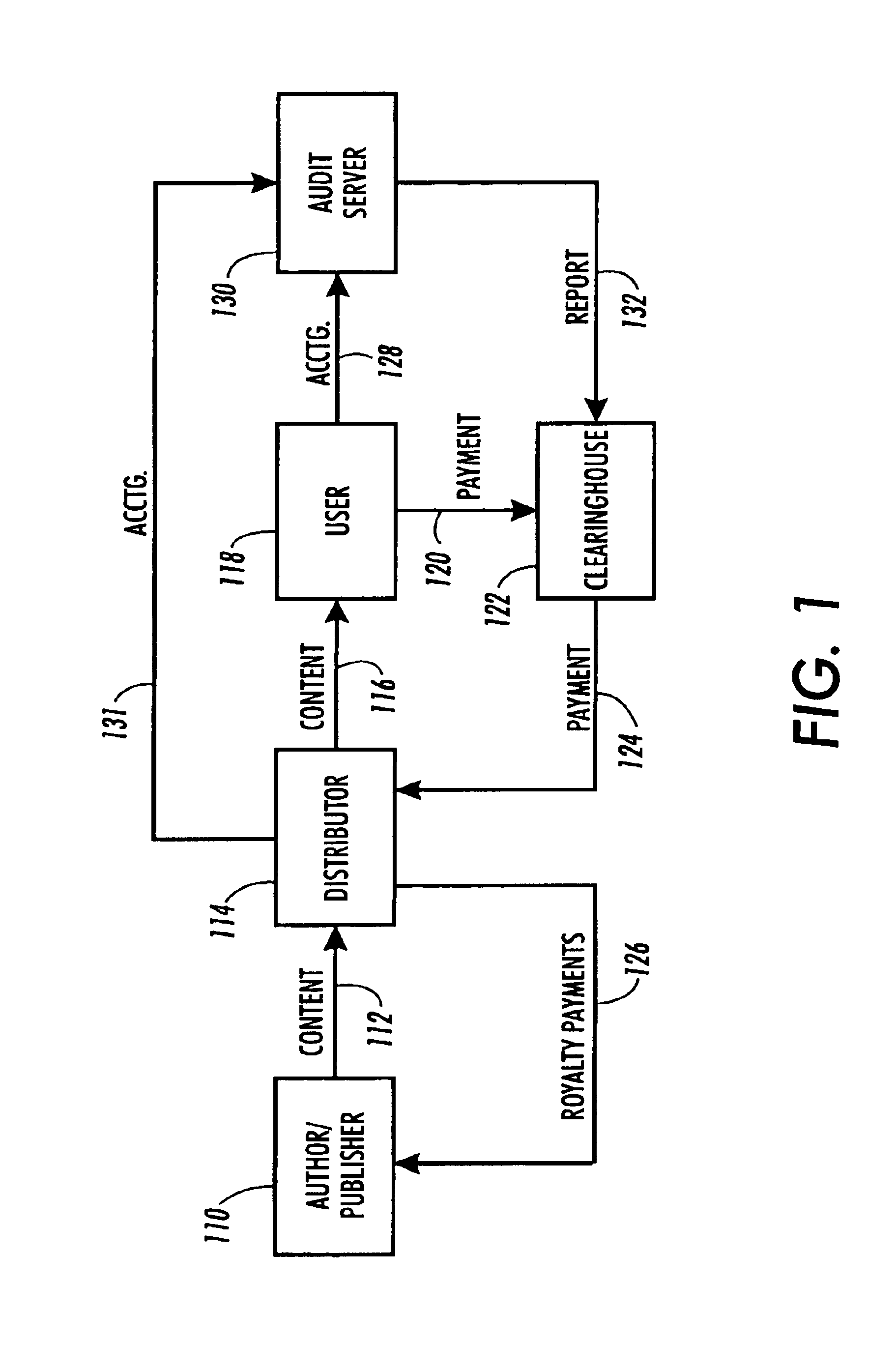
System and method for document distribution
InactiveUS7356688B1Eliminate disadvantagesImprove efficiencyKey distribution for secure communicationPublic key for secure communicationDistribution methodDocumentation
Methods for transferring among key holders in encoding and cryptographic systems the right to decode and decrypt messages in a way that does not explicitly reveal decoding and decrypting keys used and the original messages. Such methods are more secure and more efficient than typical re-encoding and re-encryption schemes, and are useful in developing such applications as document distribution and long-term file protection.
Owner:CONTENTGUARD HLDG
Automatic pet trainer
InactiveUS7263953B2Improve behaviorKeep the pet entertained/busyAnimal feeding devicesAnimal housingRemote controlEngineering
Owner:SUNDARARAJAN KRISHNAMURTHY
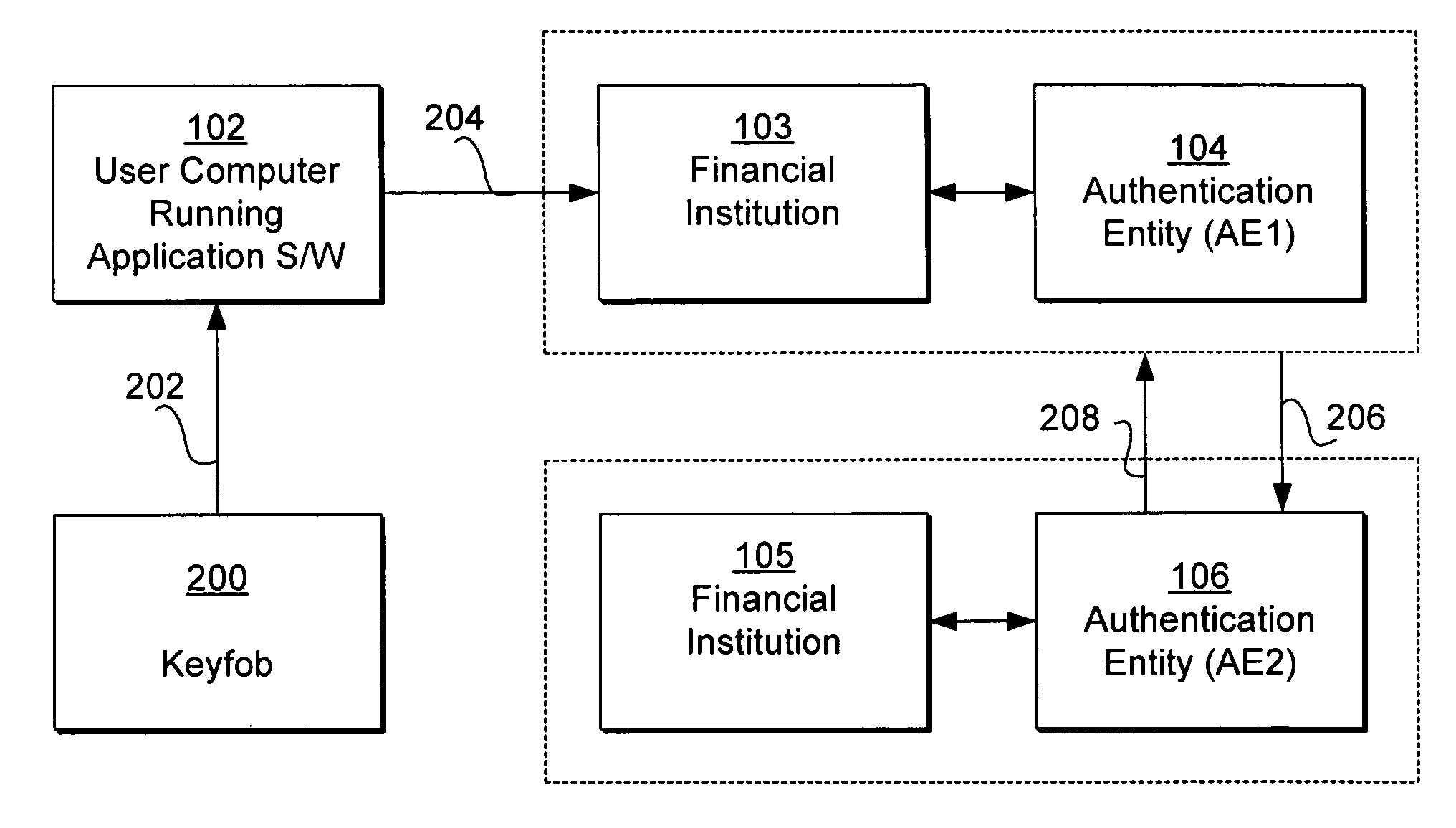
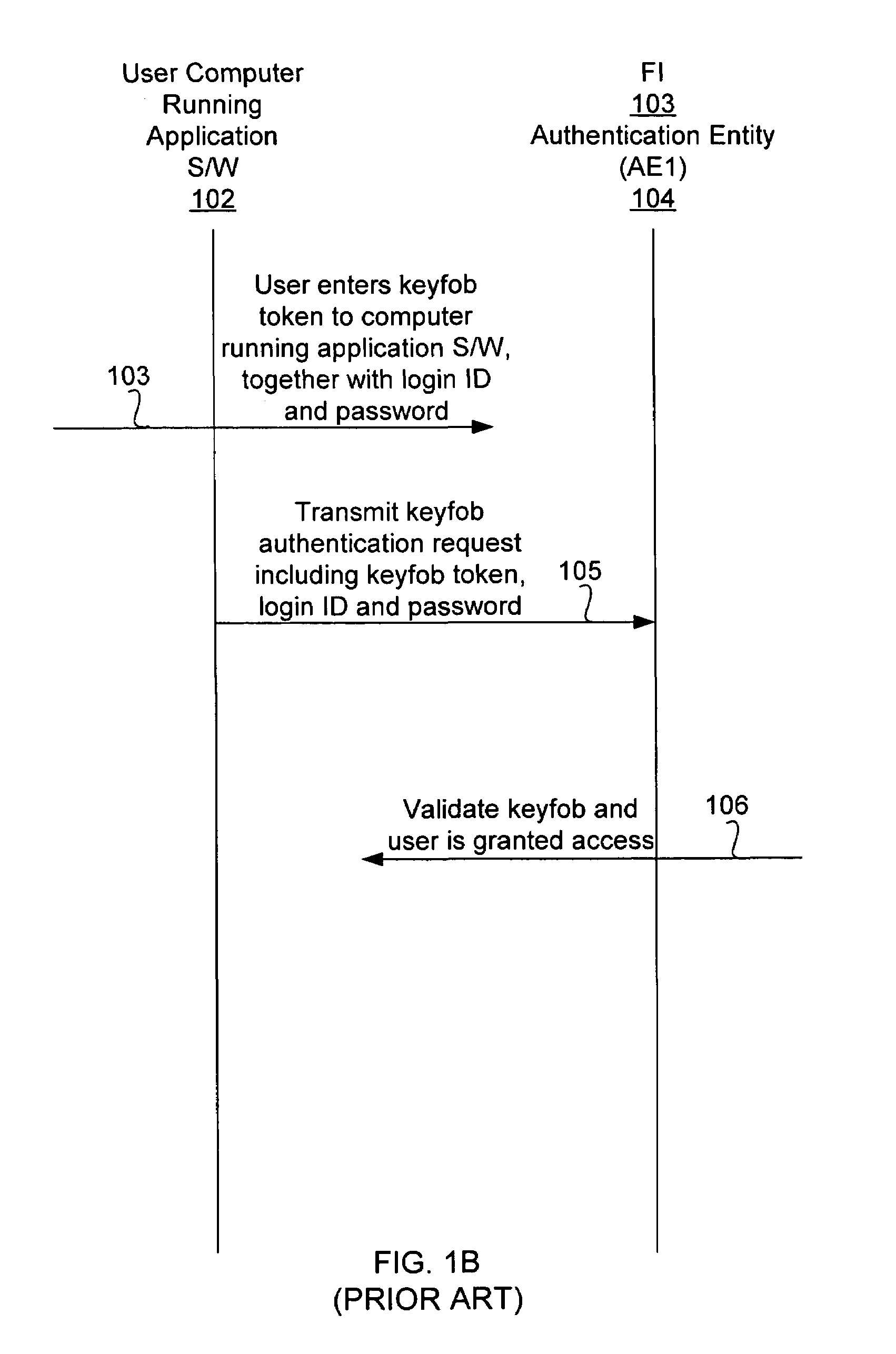
Keyfob for use with multiple authentication entities
ActiveUS7624433B1Digital data processing detailsMultiple digital computer combinationsInternet privacyAuthentication
A token generator such as a keyfob is used to access the computer of an authentication entity different from the authentication entity that issued the token generator. The token generator stores authentication entity identification information identifying the authentication entity that issued the token generator. The token generator causes a user computer to transmit an authentication request including such authentication entity identification information together with a token generated in synchronization with the authentication entity issuing the token generator, so that the authentication request can be routed to the appropriate authentication entity that issued the keyfob for validation. The authentication request can be sent directly to the authentication entity that issued the token generator. The authentication request can also be sent to the authentication entity that issued the token generator via another authentication entity to which the user computer attempts to access.
Owner:INTUIT INC
Dual key fob
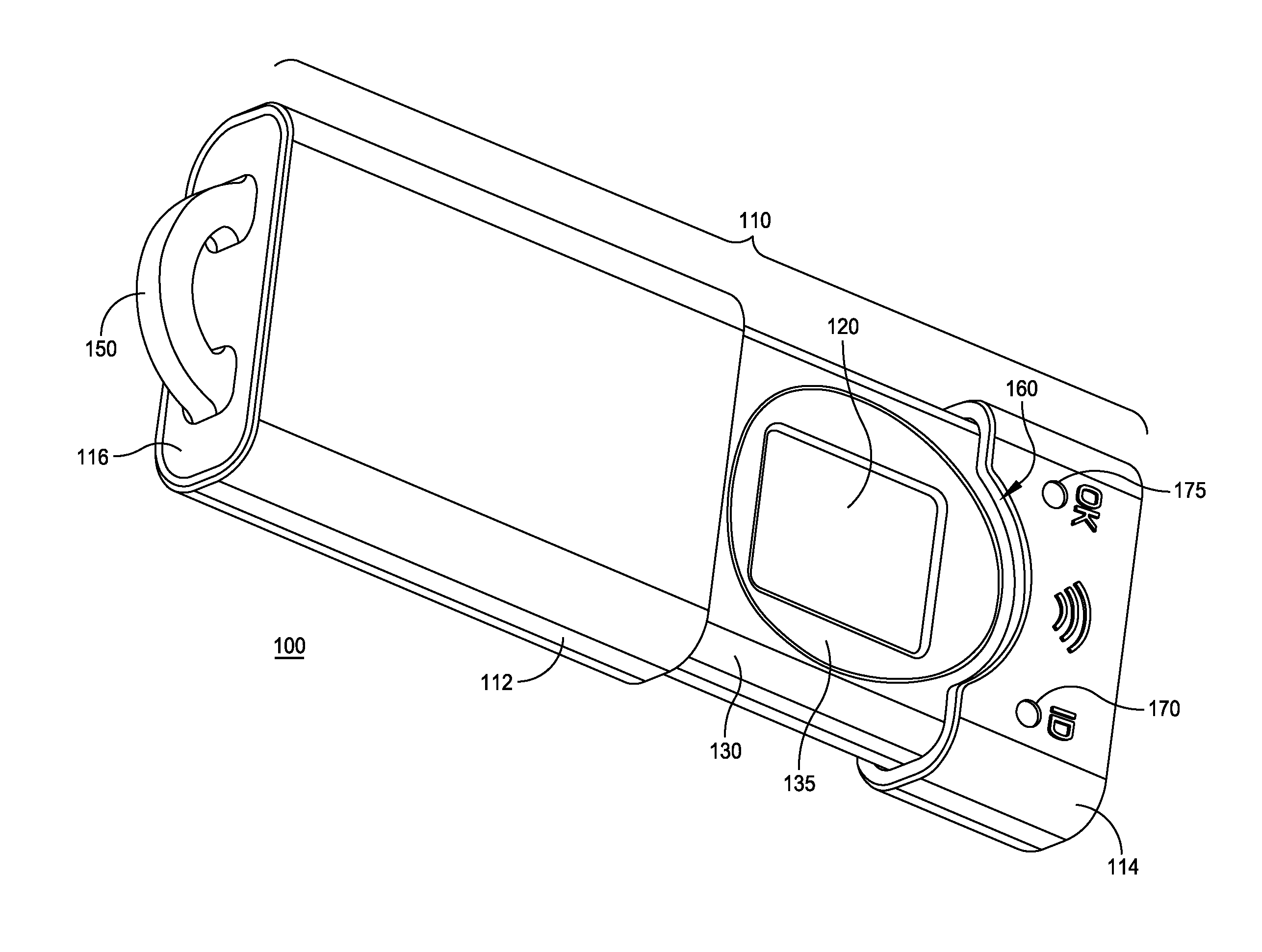
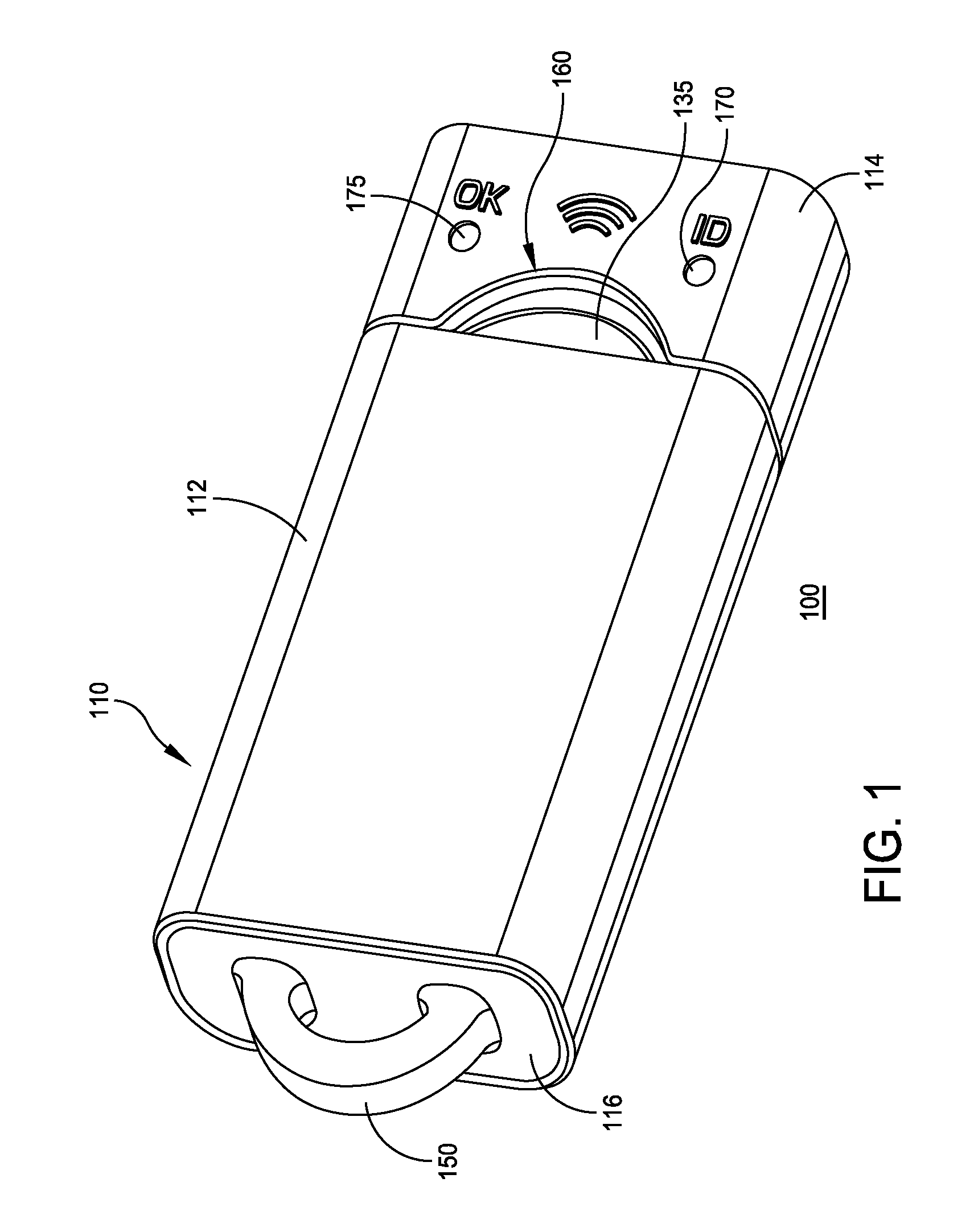
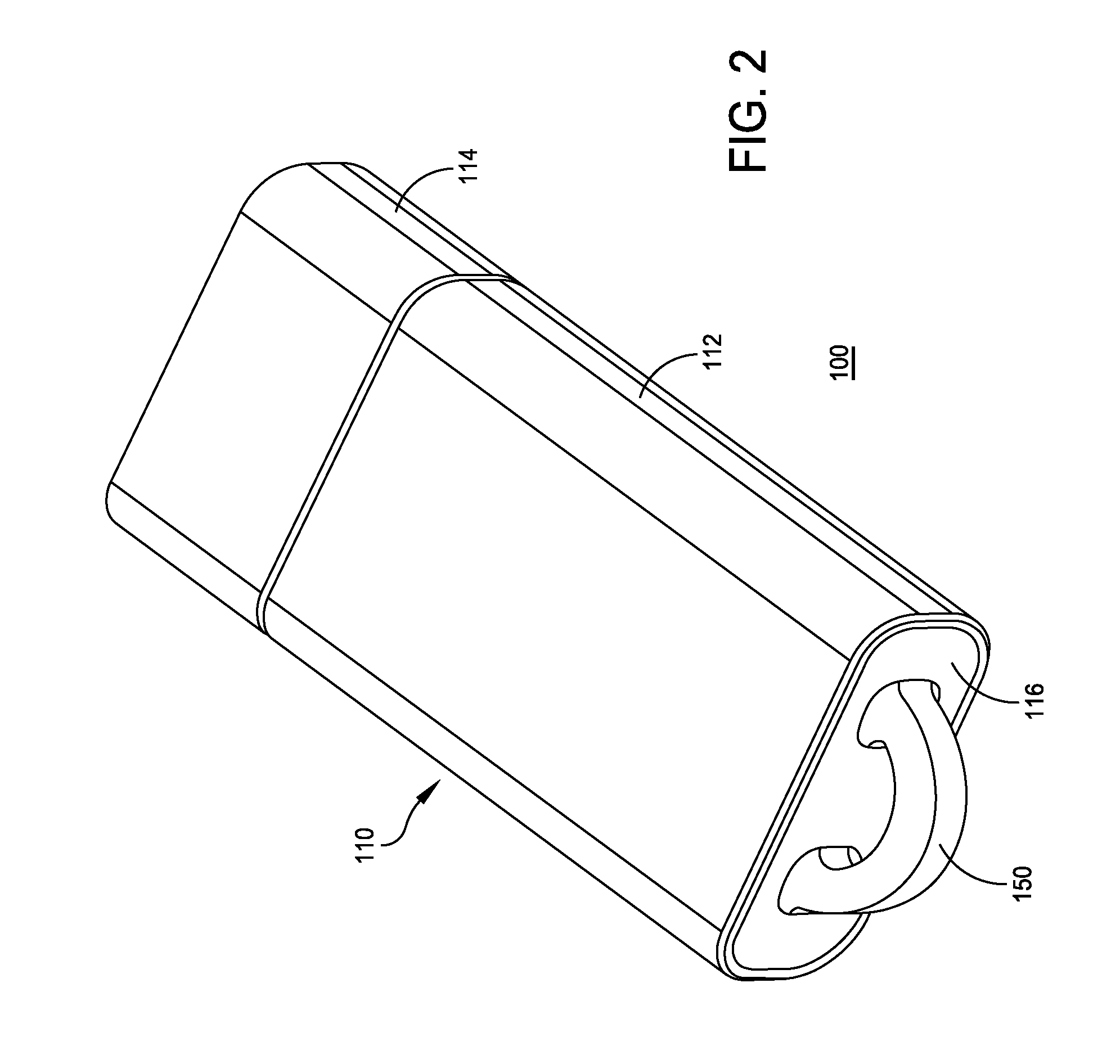
InactiveUS7463134B1Electric signal transmission systemsDigital data processing detailsEngineeringKey Holder
A dual key fob adapted for employing the wireless printed circuit boards of two other wireless entry key fobs. A top and bottom cover of the composite key fob houses the two wireless printed circuit boards together with a battery holder, power transfer interfaces for coupling battery power to the wireless printed circuit boards, and two elastomeric key shorting members with push buttons accessible through openings in the top and bottom covers for allowing a person to operated the respective circuits of either wireless printed circuit board.
Owner:STILLEY RUSSELL L
System and method for transferring the right to decode messages in a symmetric encoding scheme
InactiveUS6859533B1Eliminate disadvantagesImprove efficiencyMultiple keys/algorithms usagePublic key for secure communicationDocumentationKey Holder
Methods for transferring among key holders in encoding and cryptographic systems the right to decode and decrypt messages in a way that does not explicitly reveal decoding and decrypting keys used and the original messages. Such methods are more secure and more efficient than typical re-encoding and re-encryption schemes, and are useful in developing such applications as document distribution and long-term file protection.
Owner:CONTENTGUARD HLDG
Methods and systems for secure keyless entry for vehicle fleet management
InactiveUS20090015373A1Programme controlElectric signal transmission systemsFleet managementPersonalization
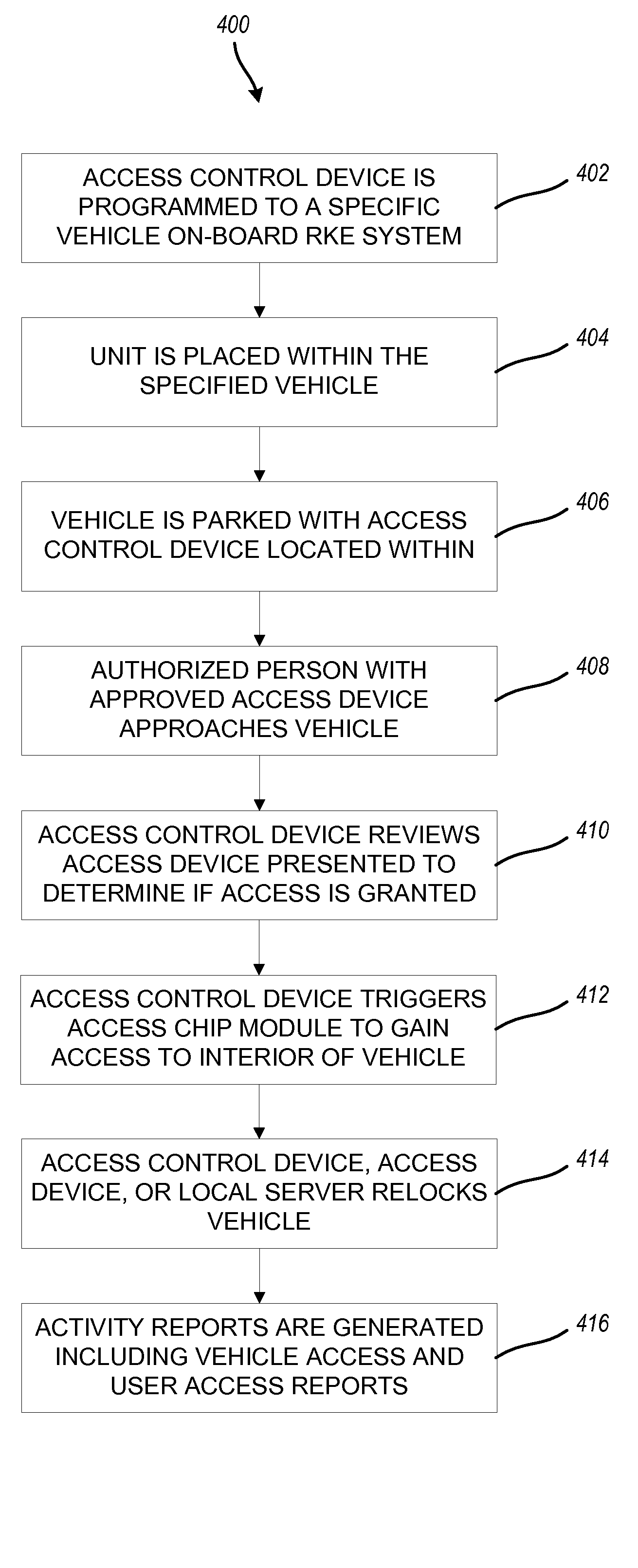
The technology described herein provides a keyless entry system and associated method for fleet vehicle management. Secure keyless entry is provided to a user for a vehicle in the fleet vehicle management environment without the user having possession of a vehicle key or a vehicle key fob to gain entry to the vehicle. Additionally, in various embodiments, this technology provides a personalized, programmable access device carried by a user desiring access to a particular locked vehicle in a fleet vehicle management environment, an access control device configured to access electronically an on-board vehicle keyless entry system, and an access chip module electronically attached to the access control device and configured to activate the on-board vehicle keyless entry system and thereby unlock the particular locked vehicle. Furthermore, this technology provides a system with local management, reporting, audit trails, wireless connectivity to each access control device, and self-testing.
Owner:KELLY MICHAEL P +2
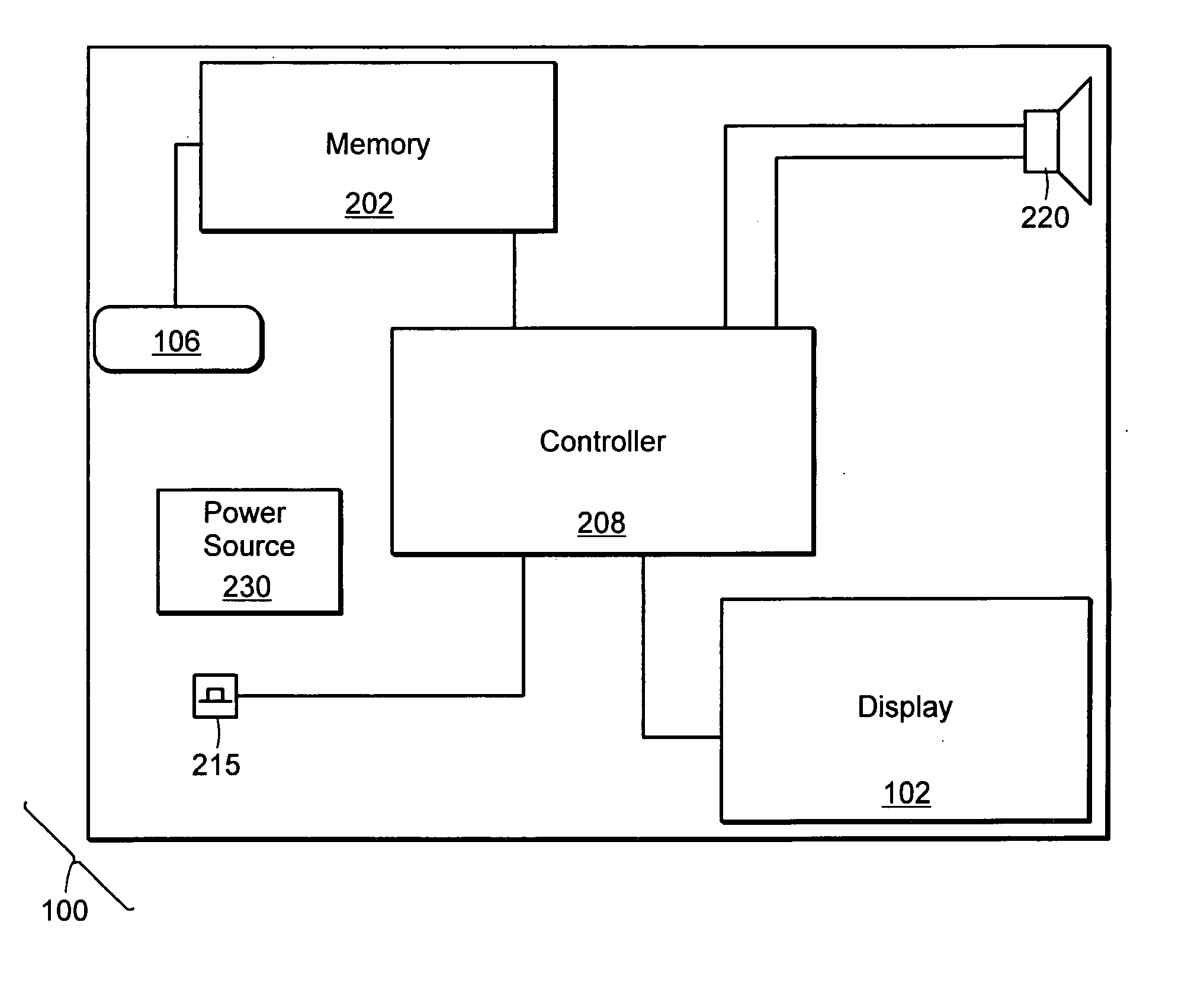
Video message device
A video display device. The video display device includes a display device, a display, and a memory device for storing video data. A controller controls the display and the memory device so as to display a video sequence as a function of the video data stored in the memory device. The video display device may be adapted to be a trophy, a plaque, lapel pin, sports equipment, sports memorabilia, a trading card, a board game piece, a book marker, a key fob, a business card, a desk accessory, a promotional give-away item, a direct mail item, a refrigerator magnet or a souvenir.
Owner:VISICHIP
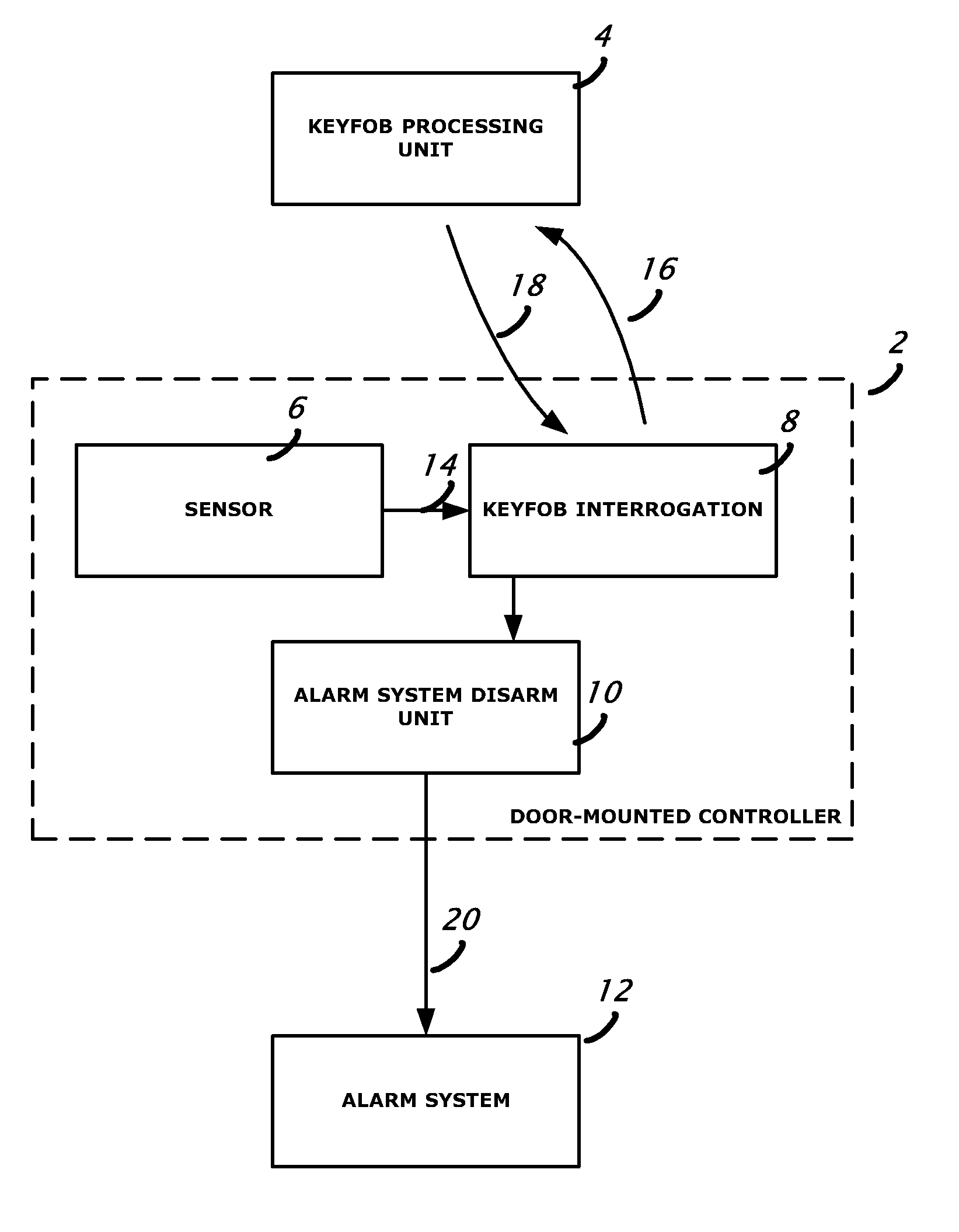
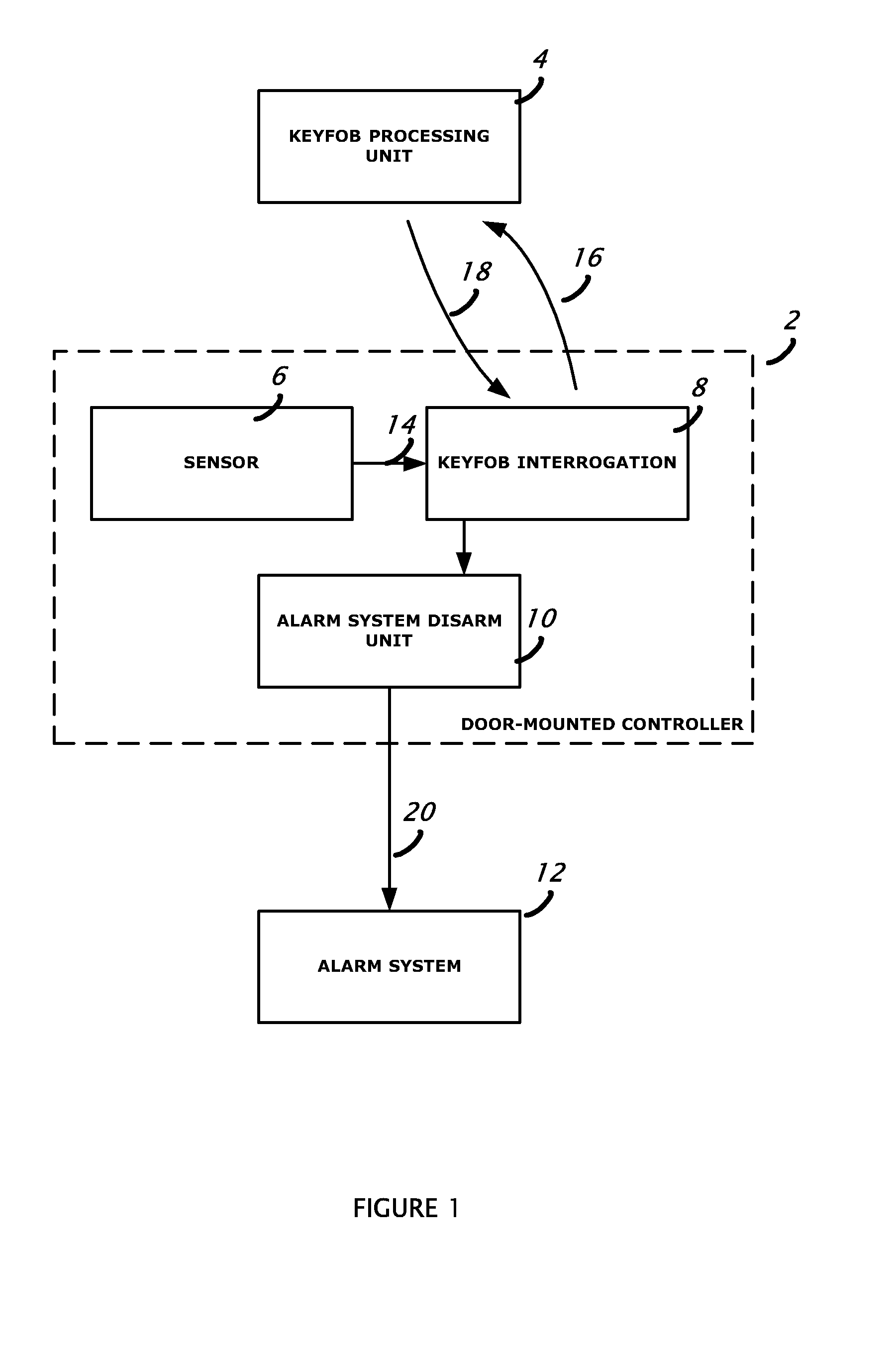
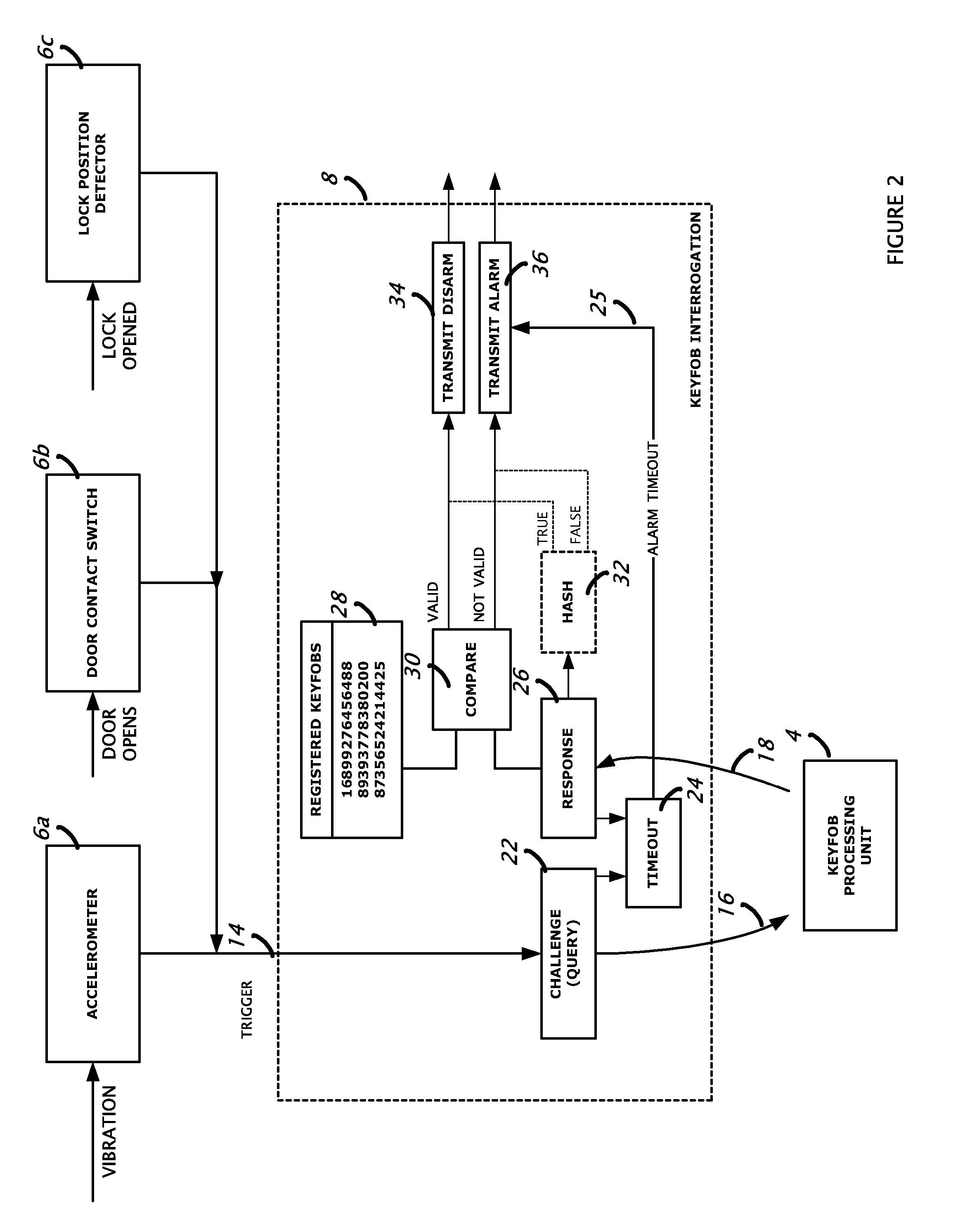
Passive disarming transceiver for security systems
A method of disarming an alarm system in a premises by detecting motion of at least part of a door in the premises to trigger generation of a challenge signal; transmitting the challenge signal; receiving a response signal from an associated disarm device such as a keyfob; determining if the response signal is valid as having been generated by an authorized disarm device; and if the response signal is valid, then transmitting a disarm message effective to cause the alarm system to become disarmed.
Owner:HONEYWELL INT INC
Location device and wireless mulitfuntion key-fob system
The present invention comprises a key-fob device including portable remote units with Radio Frequency (RF) receivers or transceivers capable of receiving command transmissions from a high power wireless network and / or RF tower or low power wireless system and / or handheld device. Upon receiving a user's activation signal from the wireless network, the key-fob will then emit an audible sound, activate a flashing light and / or activate various vehicle functions.
Owner:PICONE STEPHEN J +1
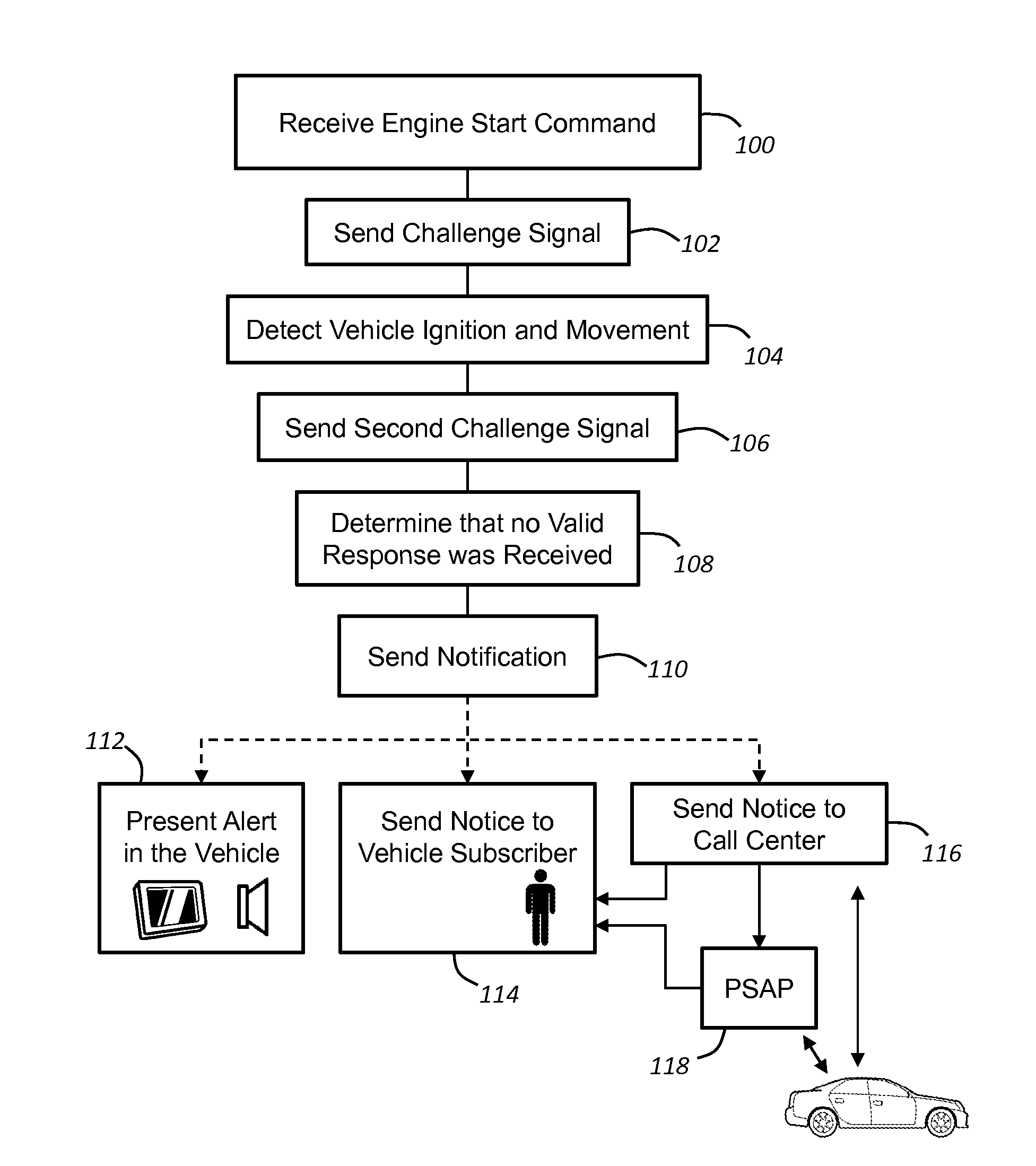
Keyfob proximity theft notification
A method of providing a notification following a passive, keyless start of a vehicle when a keyfob for the vehicle is not within a passenger compartment of the vehicle. Where a motor is started using a passive keyless start (PKS) system having a keyfob transceiver within the keyfob and a vehicle transceiver (VT) within the vehicle, the absence of the keyfob may be determined by the failure to receive an accurate response signal from the keyfob transceiver following the transmission of a vehicle challenge signal from the vehicle transceiver. Upon this determination, a notification may be provided directly or indirectly to the vehicle user via a wireless carrier system.
Owner:GM GLOBAL TECH OPERATIONS LLC
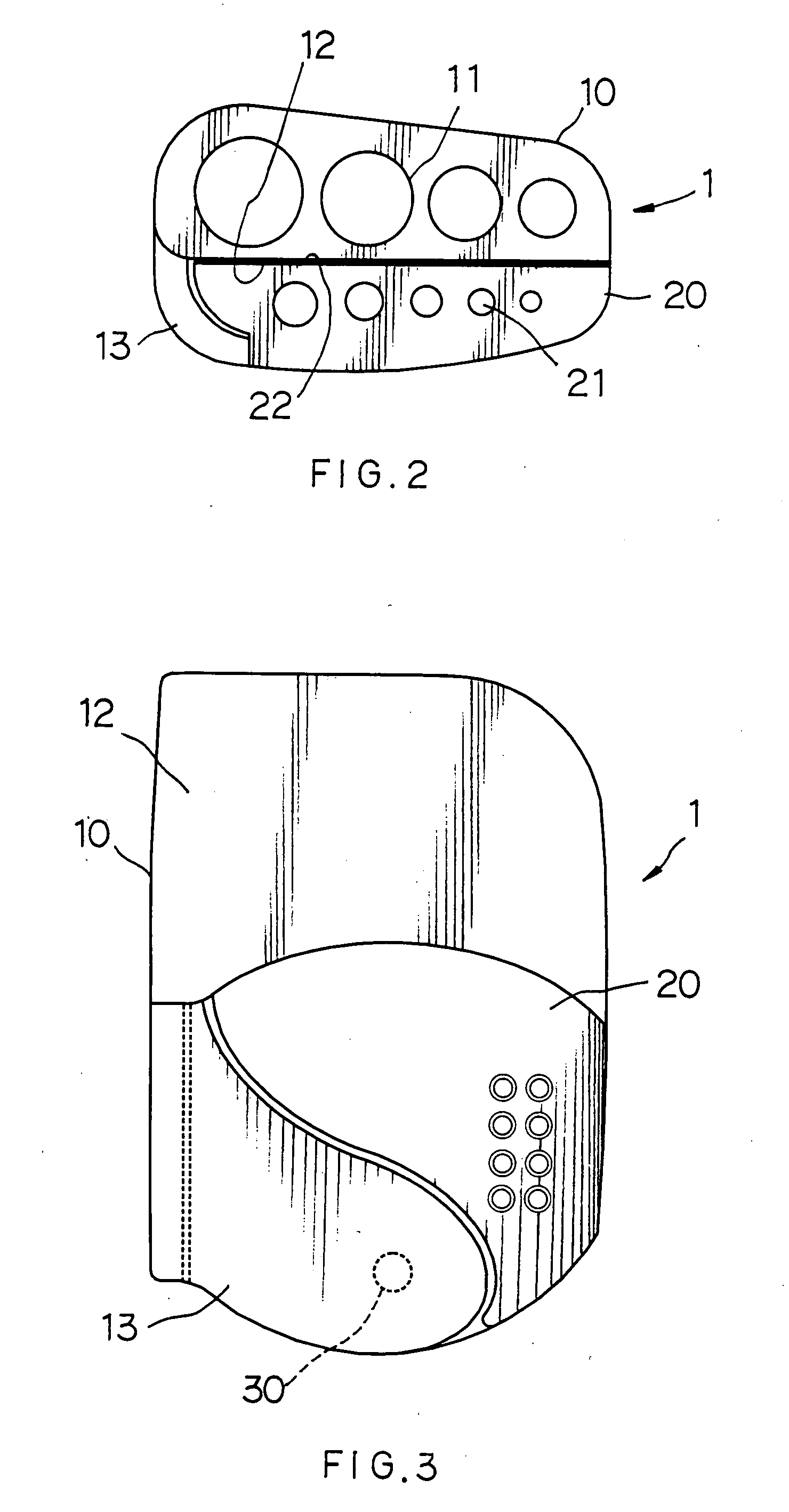
Hex key holder with mechanism for pivotably securing a smaller block to a larger block for facilitating access to hex keys in the smaller block
A hex key holder in one embodiment includes a larger block including a plurality of penetrating channels of circular section for retaining a plurality of first hex keys, and a curved arm extending forwardly from one side of the larger block, a smaller block including a plurality of penetrating channels of circular section for retaining a plurality of second hex keys smaller than the first hex keys, and a pivot for pivotably securing the smaller block between the larger block and the arm. The invention can facilitate access to the second hex keys by tilting the smaller block.
Owner:JACO INT CORP
Key fob with protected biometric sensor
ActiveUS20120212322A1Selective exposure of the fingerprint area sensorImage analysisLock applicationsKey HolderTransmitter
A key fob includes a biometric sensor including a fingerprint area sensor having a surface for receiving a finger, and a controller includes at least one processor configured to authenticate a user of the key fob based on biometric information obtained with the biometric sensor and stored biometric information for an individual. The key fob includes a RF transmitter for communicating stored transaction information to a reader upon authentication of the user and a housing. The housing includes a base for supporting the biometric sensor and a cover sleeve slidably engaged with the base to allow for extension from and retraction into the sleeve by the base, thereby permitting selective exposure of the fingerprint area sensor under user actuation.
Owner:IDSOE TORE ETHOLM
Security certificate method based on fingerprint, cryptographic technology and fragile digital watermark
ActiveCN101729256AAuthenticityAvoid the risk of being stolenUser identity/authority verificationImage data processing detailsDigital signatureSecure authentication
The invention discloses a security certificate method based on fingerprint, cryptographic technology and fragile digital watermark, comprising the following steps: a sender collects a fingerprint image, calculates summary information of the fingerprint image and inserts the summary information, a secret key and digital information which is digitally signed and encrypted into the fingerprint image as a watermark; the fingerprint of the sender is collected, the fingerprint image inserted with the watermark is sent to a receiver after the fingerprint of the sender is qualified; after receiving information, the receiver firstly detects and verifies whether the fingerprint image is inserted with the digital watermark and whether the digital watermark is right or not so as to indentify identity authenticity; digital watermark information is extracted from the received image; the summary information of the fingerprint image from which the watermark is extracted is calculated; and the summary information is compared with the summary information of the fingerprint image recorded in the watermark information to approve information authenticity. The invention can effectively overcome the defects that the existing digital signature security certificate can not approve the legal KEY holder and the fingerprint in the fingerprint certificate is easy to clone and embezzle.
Owner:SHENZHEN POKA ELECTRONICS EQUIP +1
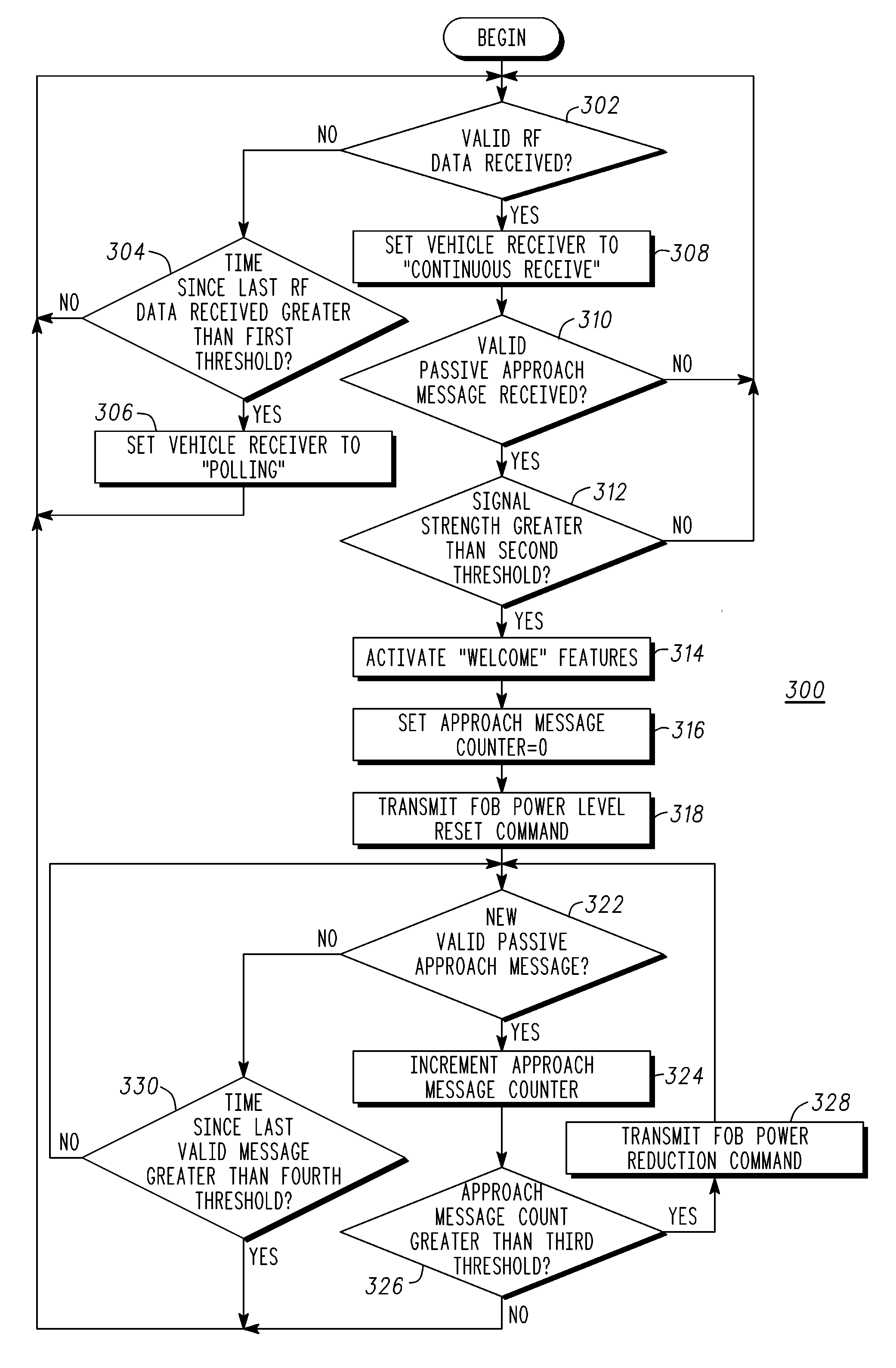
Method of passively detecting an approach to a vehicle
InactiveUS20100304690A1Reduced powerElectric signal transmission systemsMultiple keys/algorithms usageEngineeringPassive detection
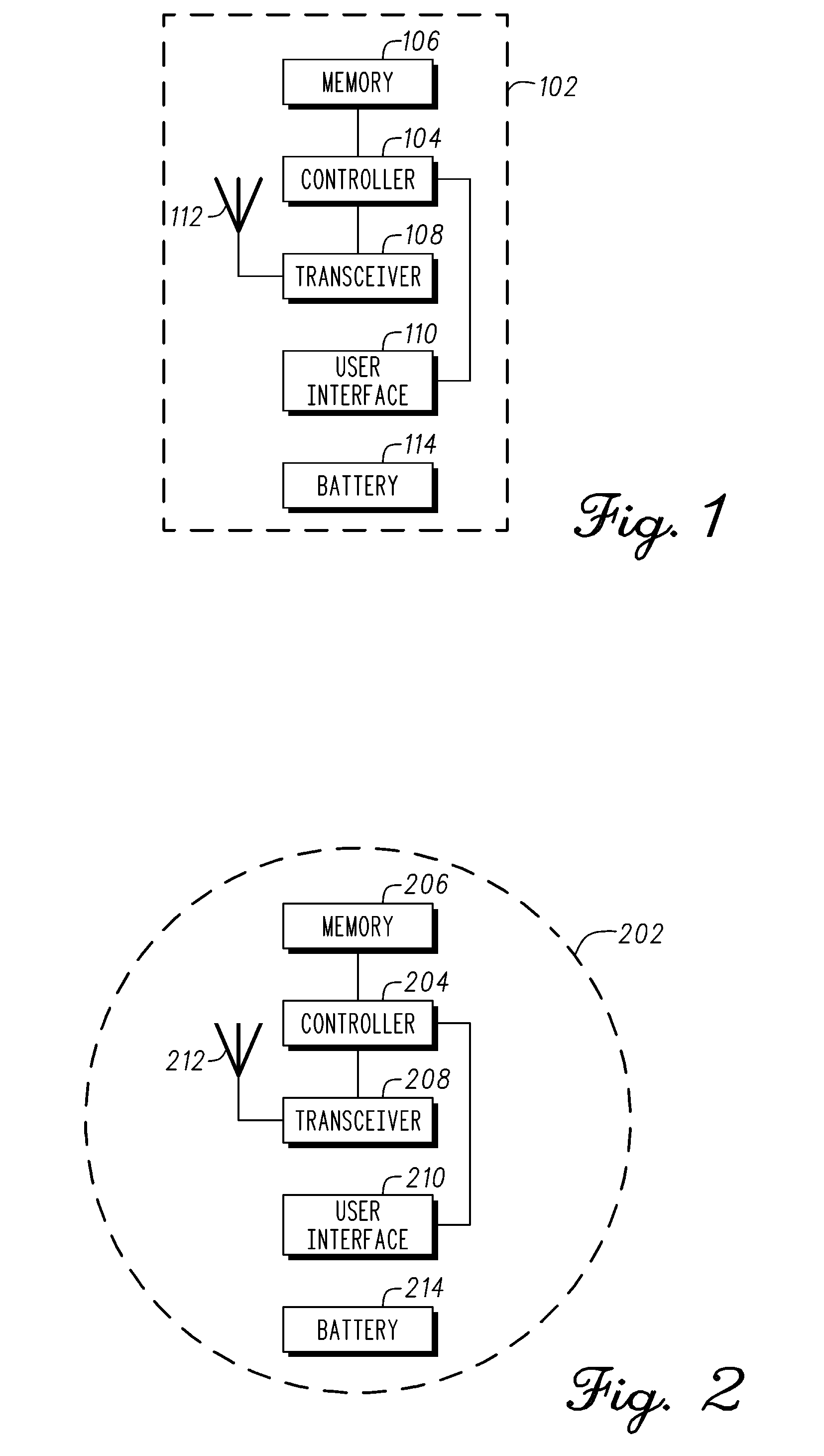
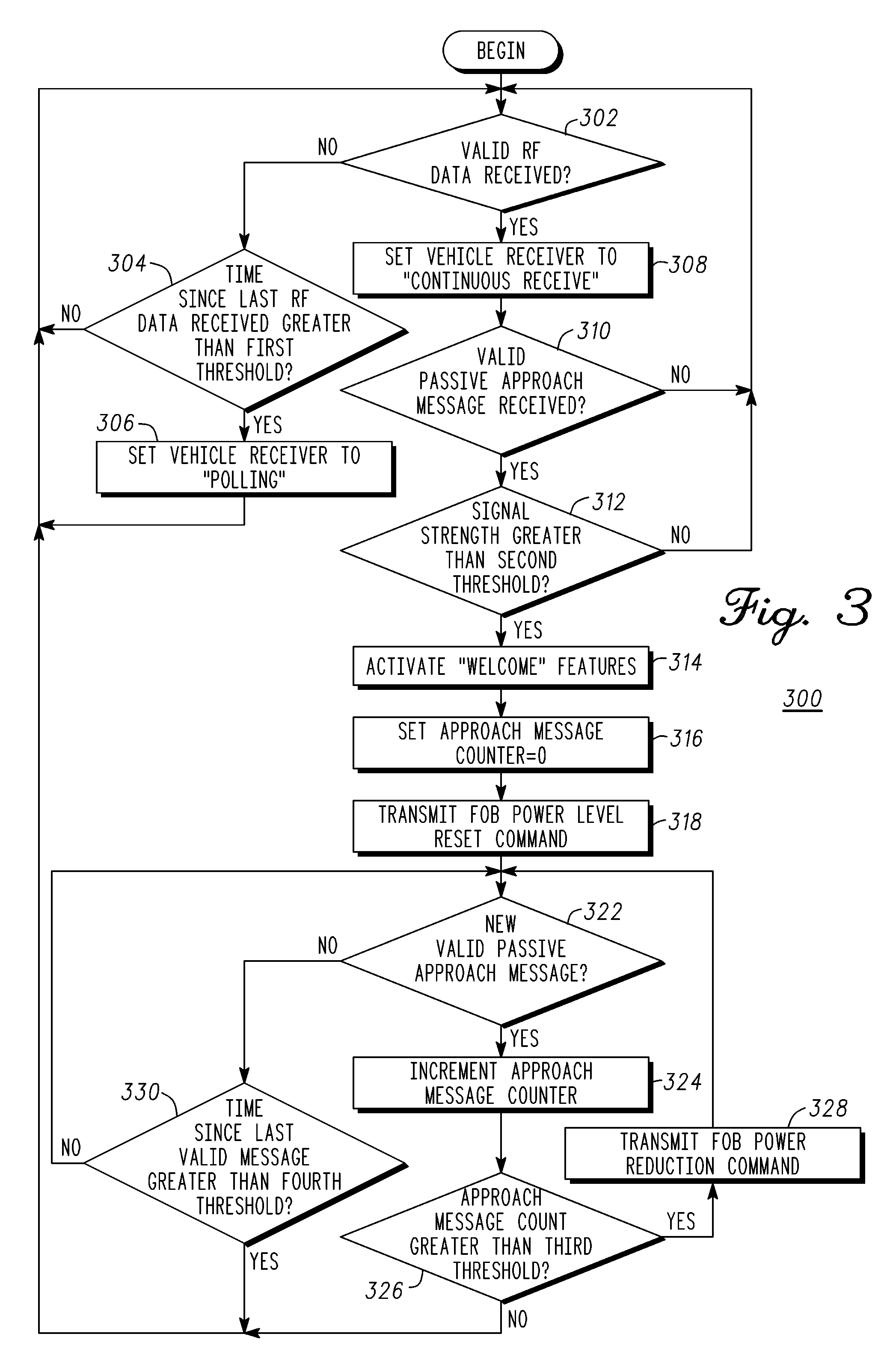
A method for activating vehicle features when approaching a vehicle includes receiving (302) a message by a vehicle system (102) from a key fob (202), determining (312) if the key fob (202) is approaching the vehicle, activating (314) selected vehicle features if approaching the vehicle, and instructing (328) the key fob (202), if not approaching the vehicle, to reduce power until the message is no longer received by the vehicle system (102).
Owner:GM GLOBAL TECH OPERATIONS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com