Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
286results about How to "Efficient addition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
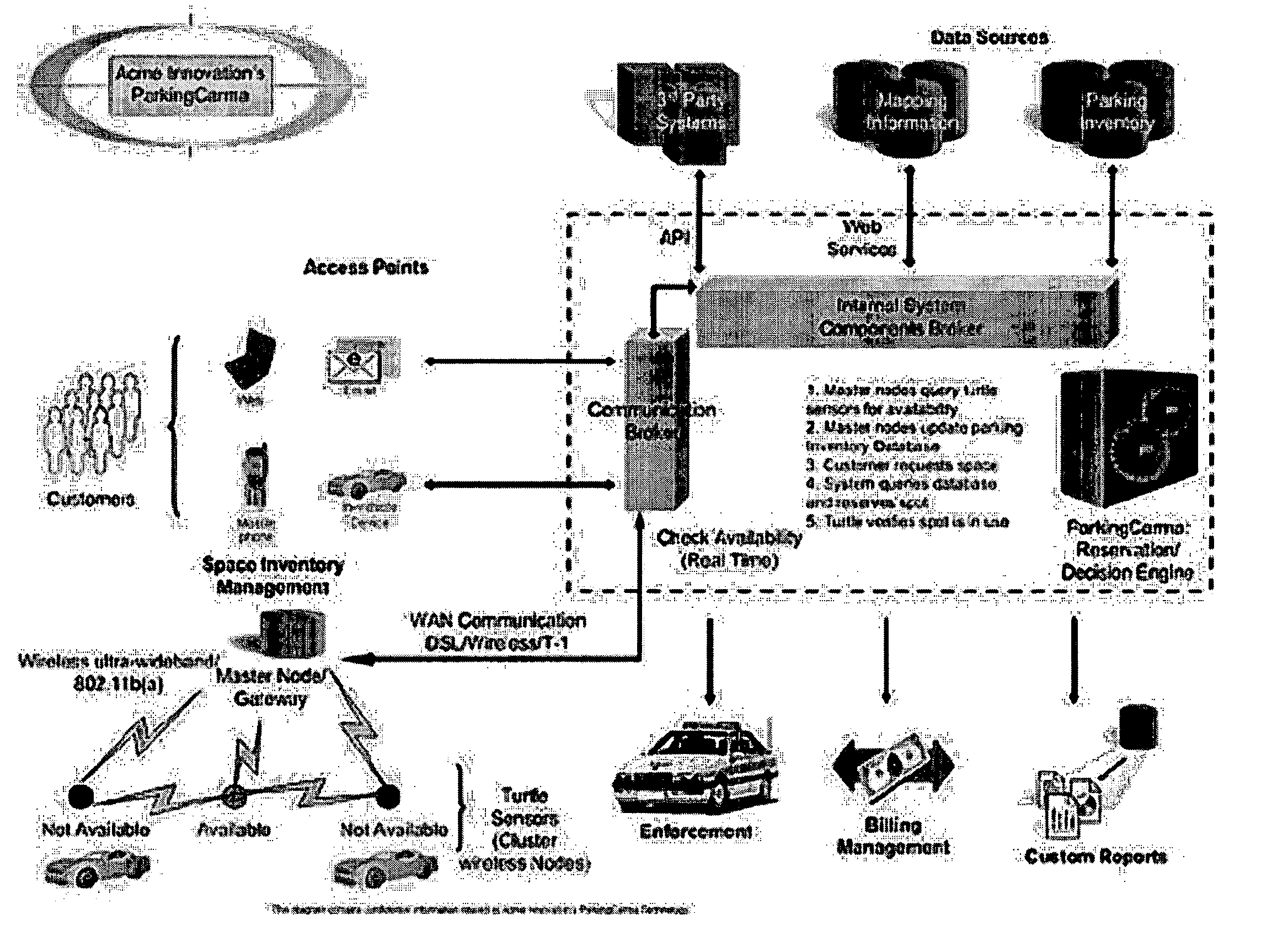
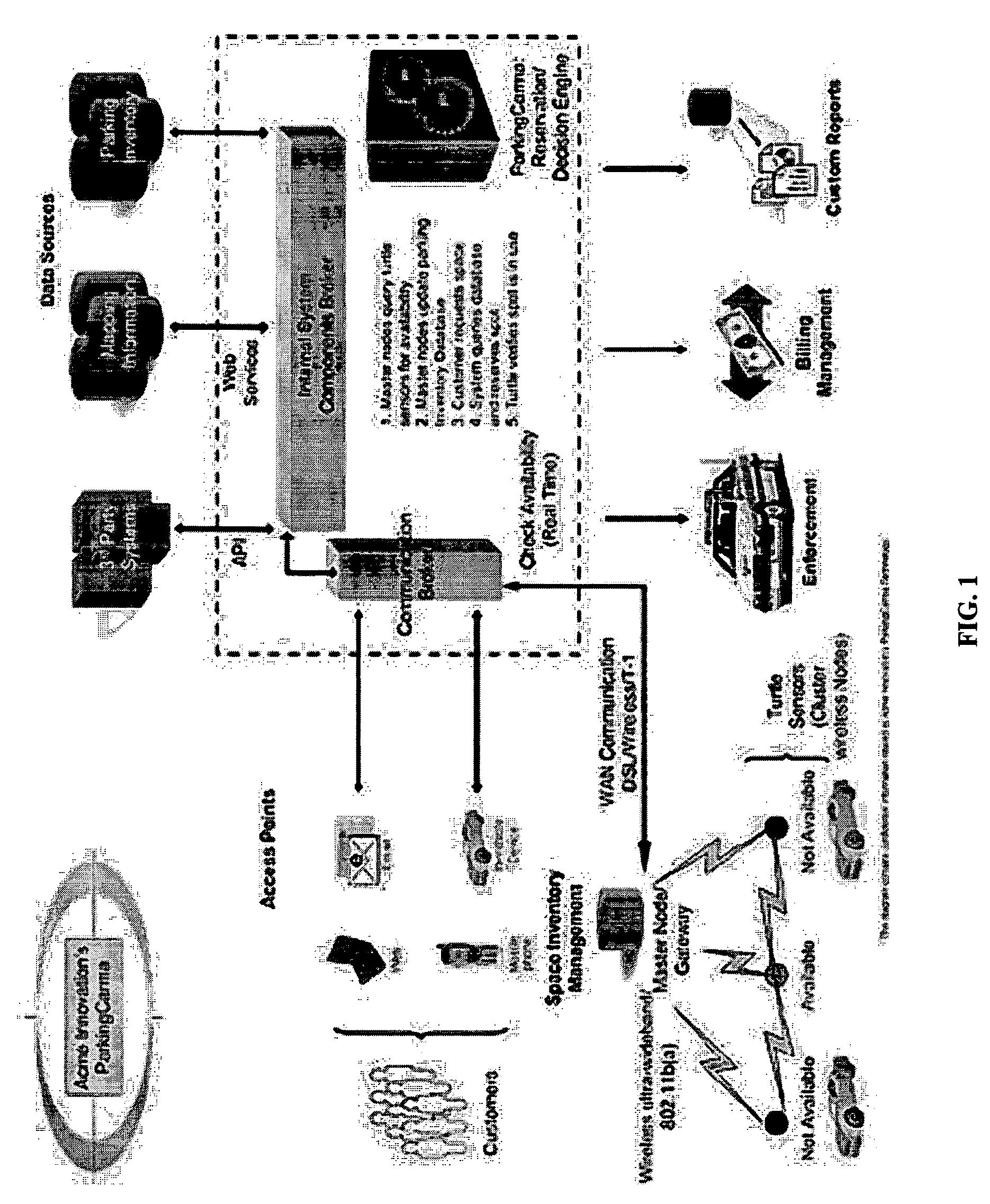
Mathods & apparatus dynamically managing parking
InactiveUS20050280555A1Efficient additionTicket-issuing apparatusIndication of parksing free spacesTransceiverWireless mesh network
A dynamic parking management system and method includes use of an intelligent software engine that, in some embodiments, interfaces with a wireless mesh network and multi-channel communication devices that, as a system, increases customer convenience which maximizes return on parking resources. The present invention uses a parking transceiver mesh network node located proximate to one or more parking spaces to provide accurate and current data to a database of available parking assets. Parking availability algorithms are used to analyze this data to select optimal parking spaces for subscribers / drivers and predict future availability of parking spaces. Additional functionality comes from the parking transceiver's ability to recognize specific vehicles and specific customers with predefined requirements.
Owner:WARNER FREDERICK MALTBY IV
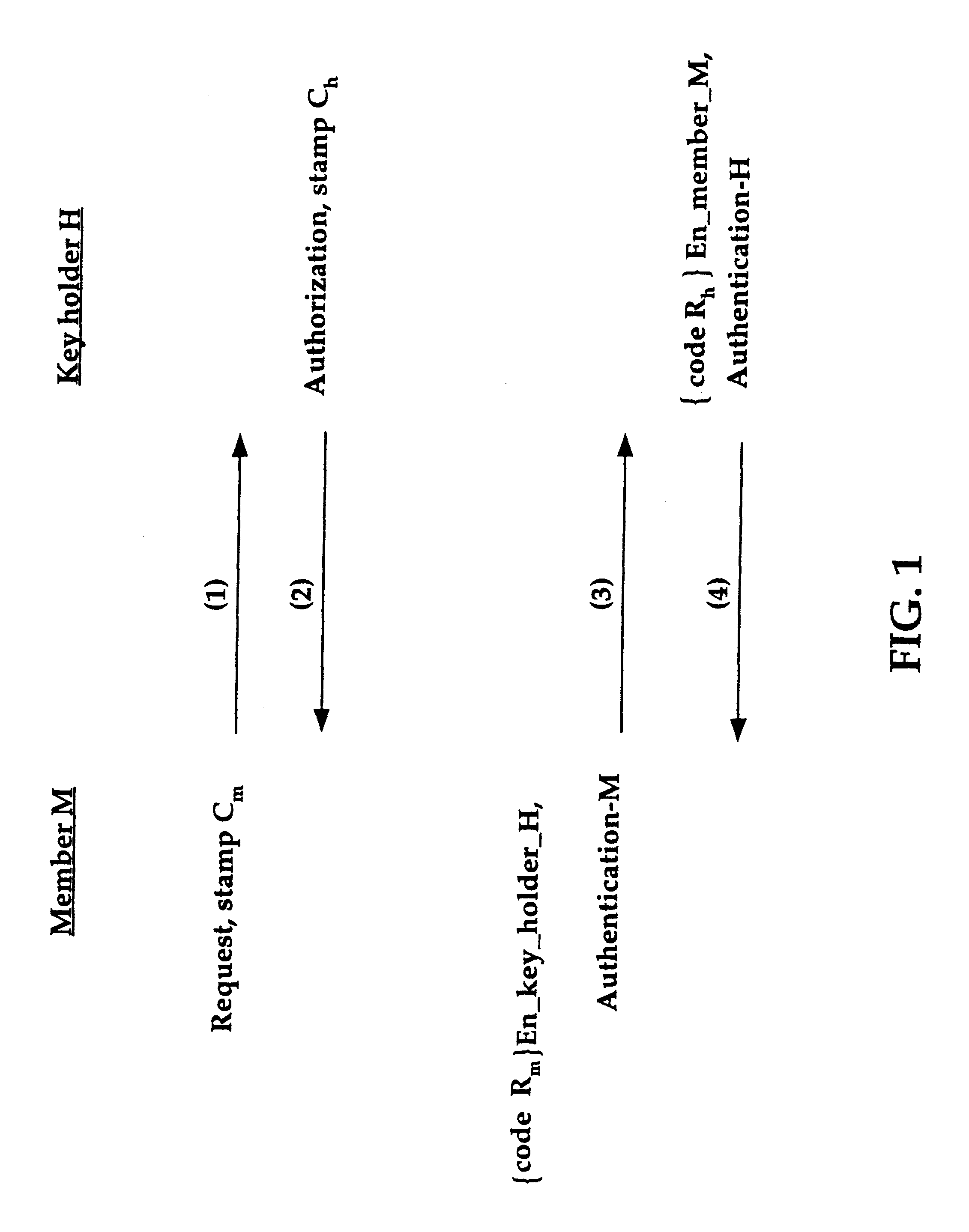
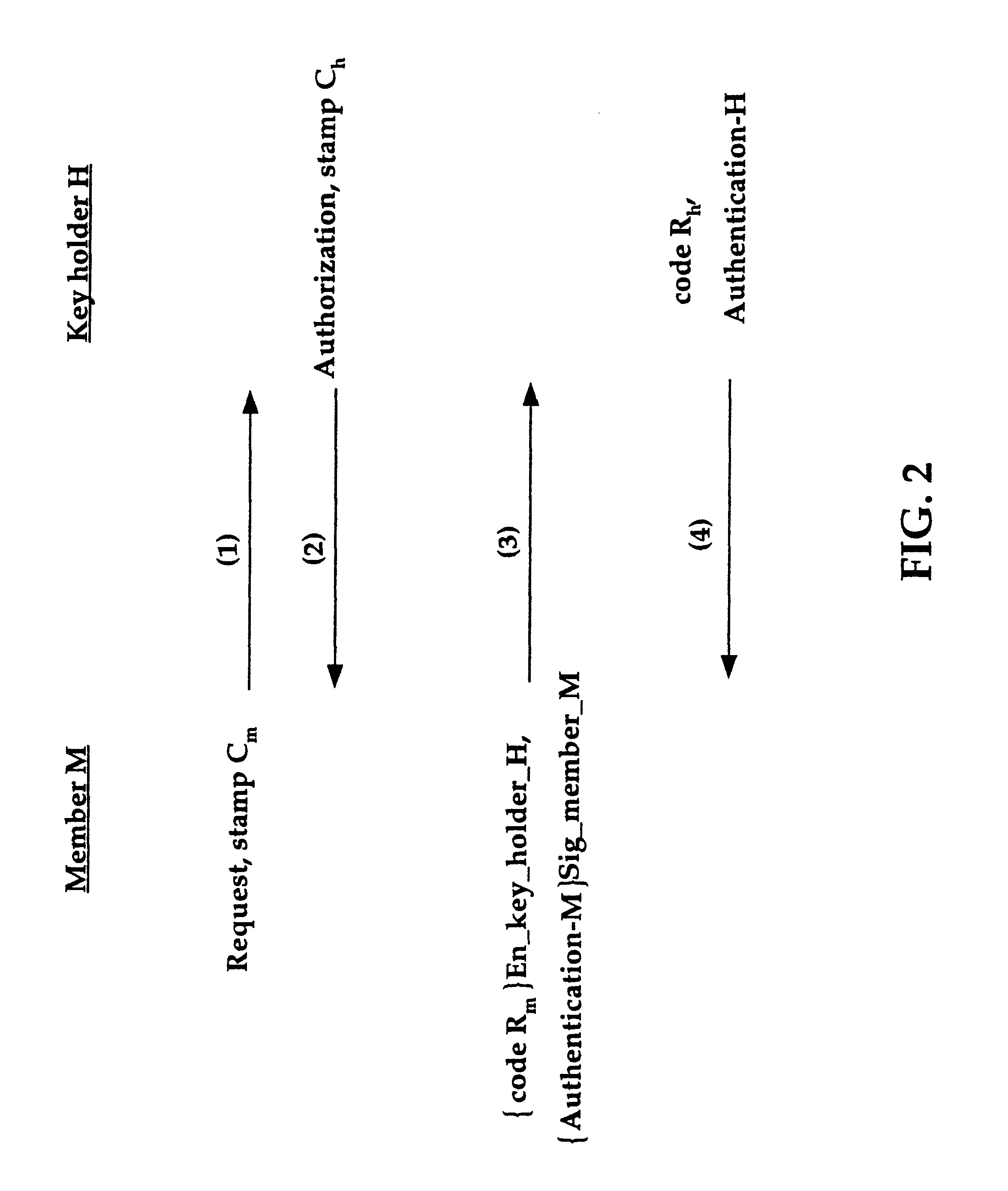
Group key distribution
InactiveUS6038322AEfficient additionLow costKey distribution for secure communicationPublic key for secure communicationTimestampNetwork addressing
A method for distributing a secret key from a key holder H to intended group members M. The method assumes that during the distribution process each party, a group member M and the key holder H, can decrypt and encrypt exchanged information such that the encrypter knows that the decrypter will be the intended party. The method preferably uses a public key / private key encryption technique in which, for example, a trusted Certificate Authority in a public key infrastructure signs the certificates to provide the public keys involved in the encryption. Alternatively, the method, together with a symmetric cipher, uses a shared secret, established in an authenticated mechanism that is outside the information exchanges of the invention. Additionally, the method uses a strong mixing function that takes several items of data as input and produces a pseudo-random authentication (or digest). Inputs to the mixing function include identity stamps that are generated by each member M and key holder H. These inputs can be the identity of the stamp generator, such as a network address, port, or protocol, a timestamp, and / or a secret value that is known only to the stamp generator. The stamps include information to bind member M if generated by key holder H, and to bind key holder H if generated by member M. Consequently, the invention authenticates each communication exchange between member M and key holder H.
Owner:CISCO TECH INC
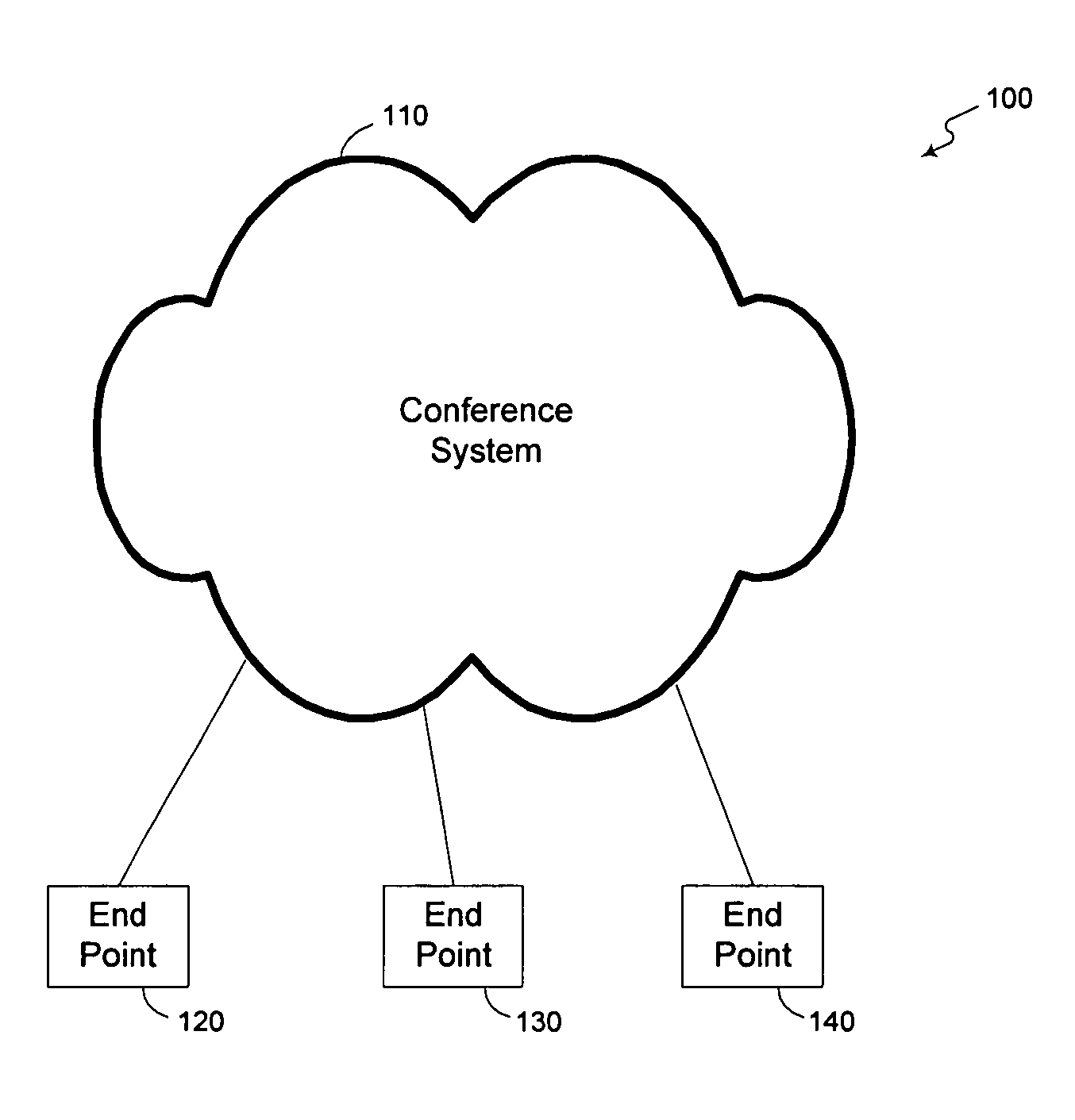
Methods and apparatus for automatically adding a media component to an established multimedia collaboration session
ActiveUS20050004982A1Improve efficiencyFacilitates free-flowingTelevision conference systemsMultiple digital computer combinationsClient-sideFree flow
A multimedia collaboration system that facilitates more efficient, free-flowing collaboration sessions. In order to make addition of new participants, media components, and or network access device to a collaboration session more efficient, client devices associated with each participant can store endpoint address information that can be automatically obtained by the multimedia collaboration system. The endpoint address information can then be used to add the new participants, media components, and or network access device.
Owner:IBM CORP
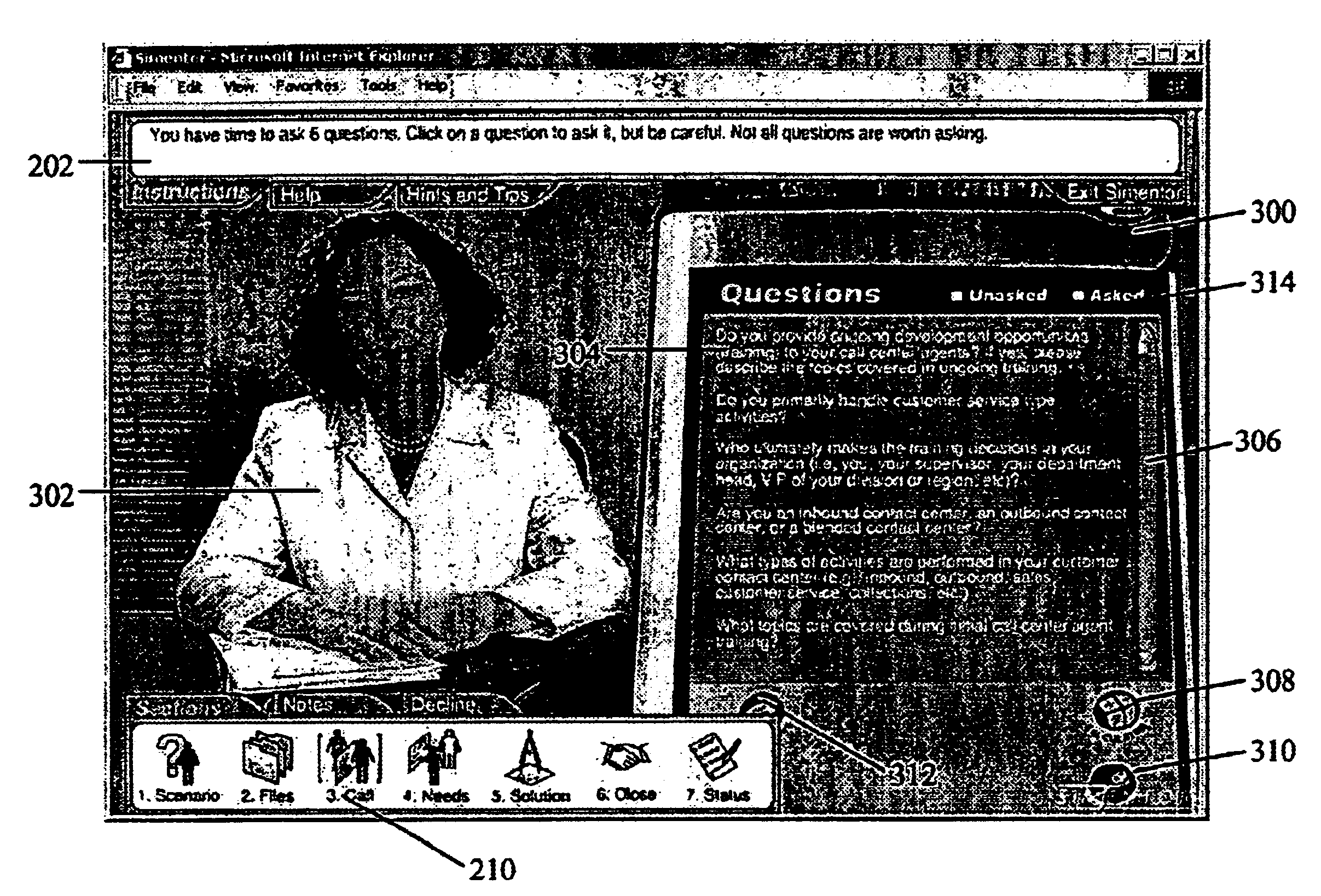
Interactive training system and method
InactiveUS6755659B2Efficient creation and implementation and utilizationFacilitate creation and implementation and utilizationElectrical appliancesSpecial data processing applicationsAugmentation systemComputer based simulation
The present disclosure relates to a system and method for facilitating personnel education and training, and more particularly to a system and method that allows efficient creation, implementation and utilization of interactive training modules and / or scenarios. The disclosed system and method facilitate creation, implementation and utilization of computer-based simulations by personnel involved in a wide range of educational, professional and / or business pursuits, and include administrative functionalities that greatly enhance system / method efficiency, flexibility and the ease and speed with which educational / training modules and scenarios may be customized and / or implemented.
Owner:ACCESS TECH
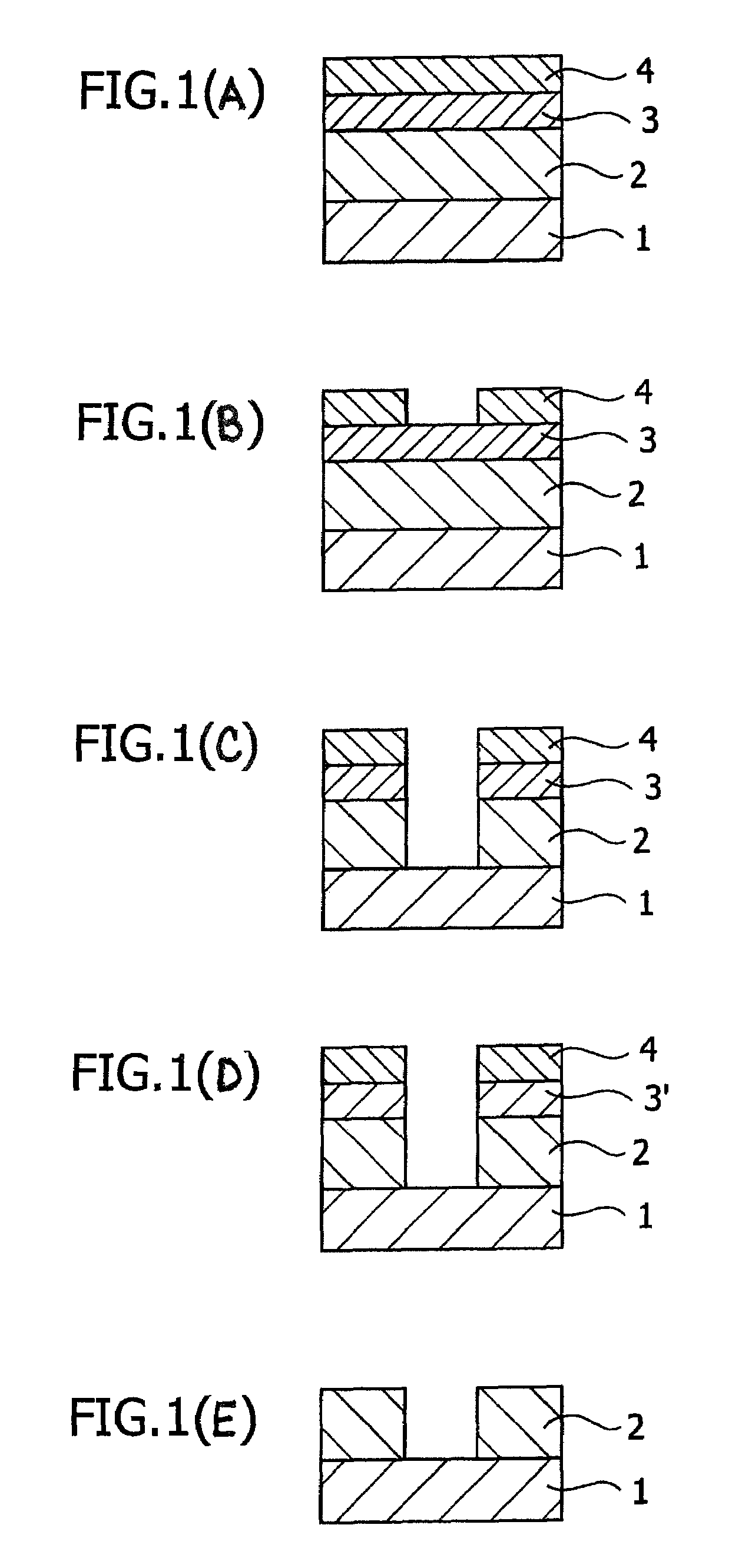
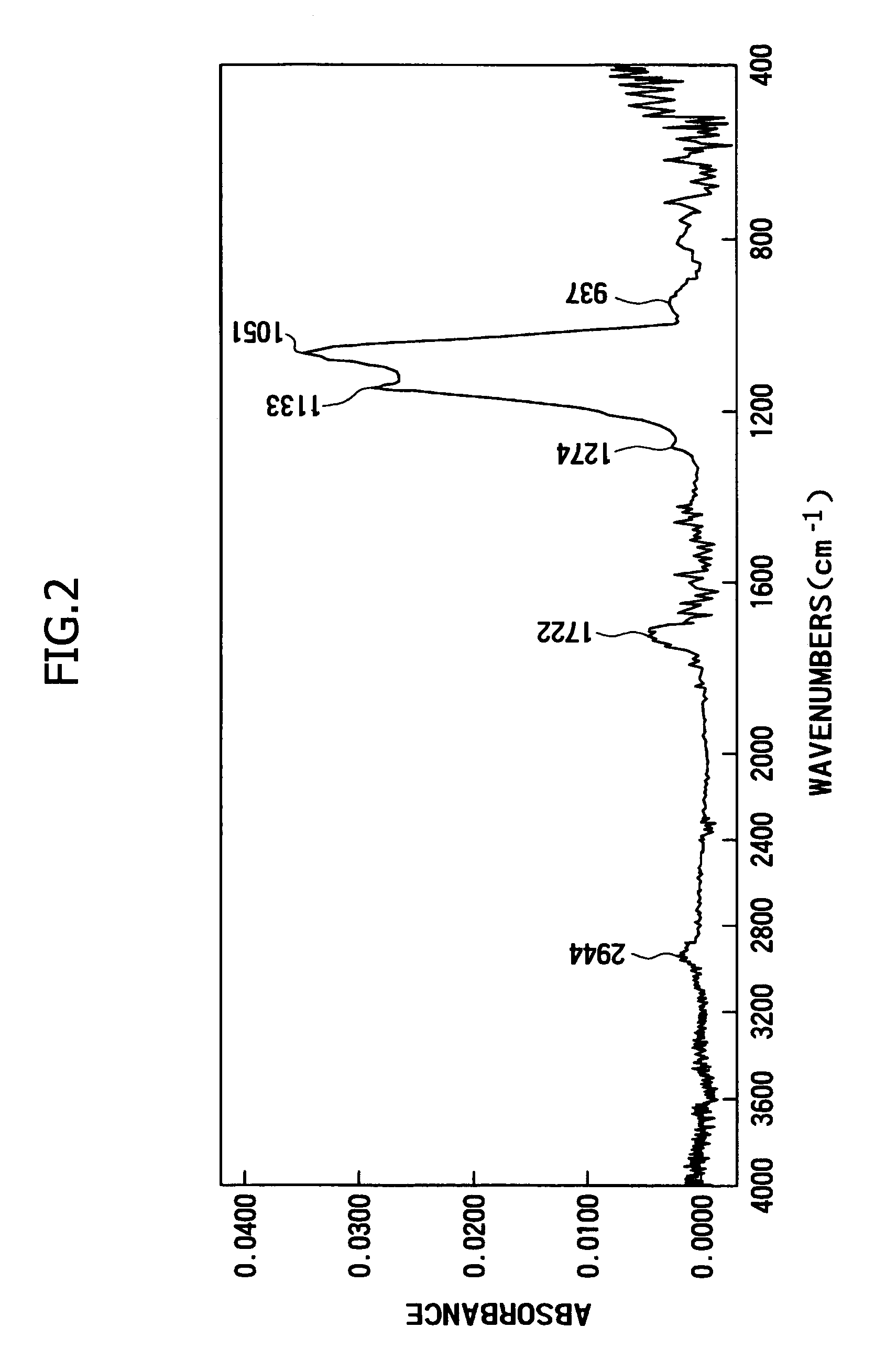
Antireflective film-forming composition, method for manufacturing the same, and antireflective film and pattern formation method using the same
ActiveUS20050277058A1Improve etch selectivityEtching speed is fastSemiconductor/solid-state device manufacturingSilver halide emulsionsCross-linkResist
The present invention provides a material for an antireflective film characterized by high etching selectivity with respect to a resist, that is, which has a fast etching speed when compared to the resist, and in addition, can be removed without damage to a film which is to be processed. The present invention also provides a pattern formation method for forming an antireflective film layer on a substrate using this antireflective film-forming composition, and a pattern formation method that uses this antireflective film as a hard mask, and a pattern formation method that uses this antireflective film as a hard mask for processing the substrate. The present invention provides an antireflective film-forming composition comprising an organic solvent, a cross linking agent, and a polymer comprising a light absorbing group obtained by hydrolyzing and condensing more than one type of silicon compound, a crosslinking group and a non-crosslinking group.
Owner:SHIN ETSU CHEM IND CO LTD +1
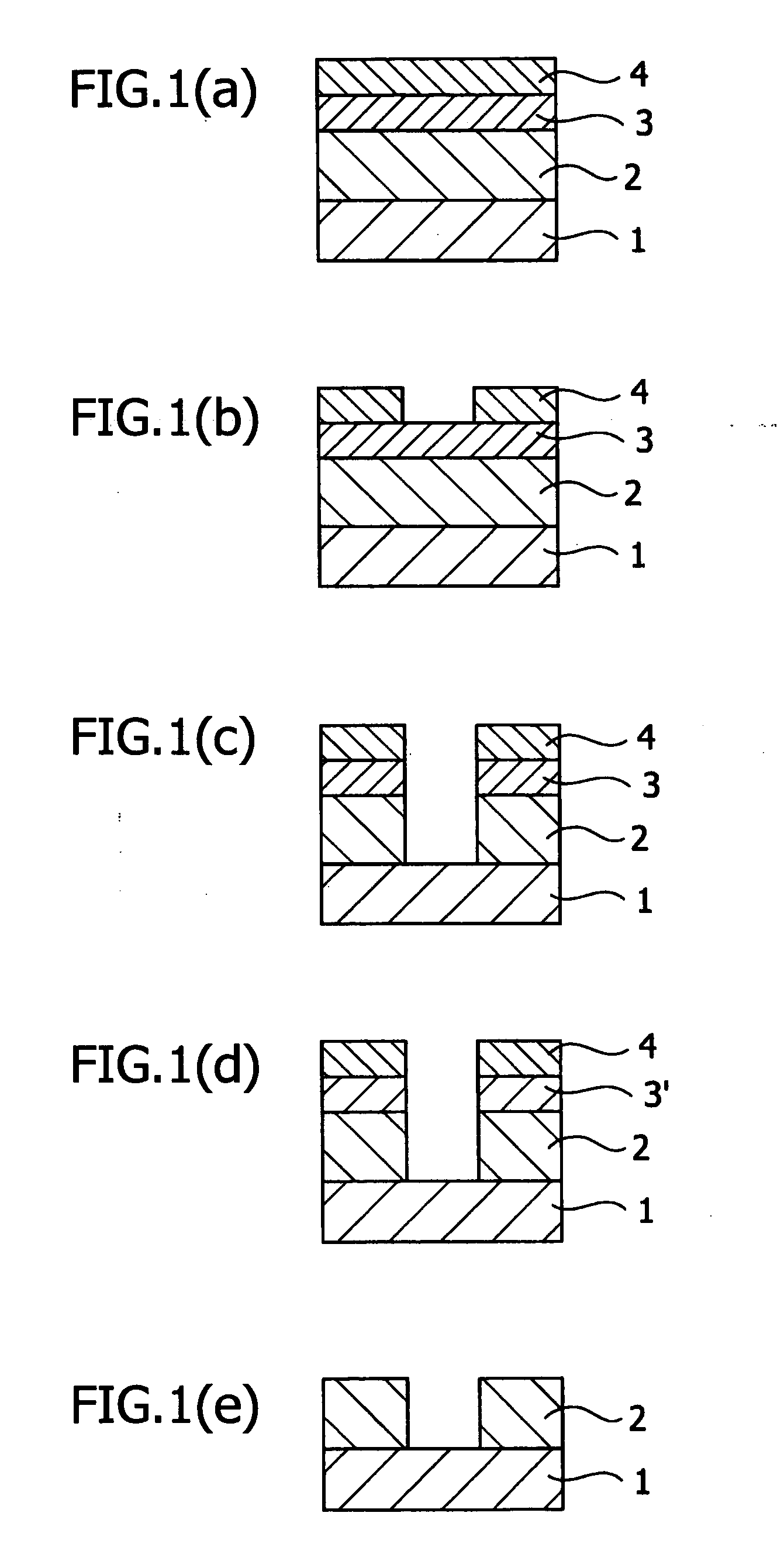
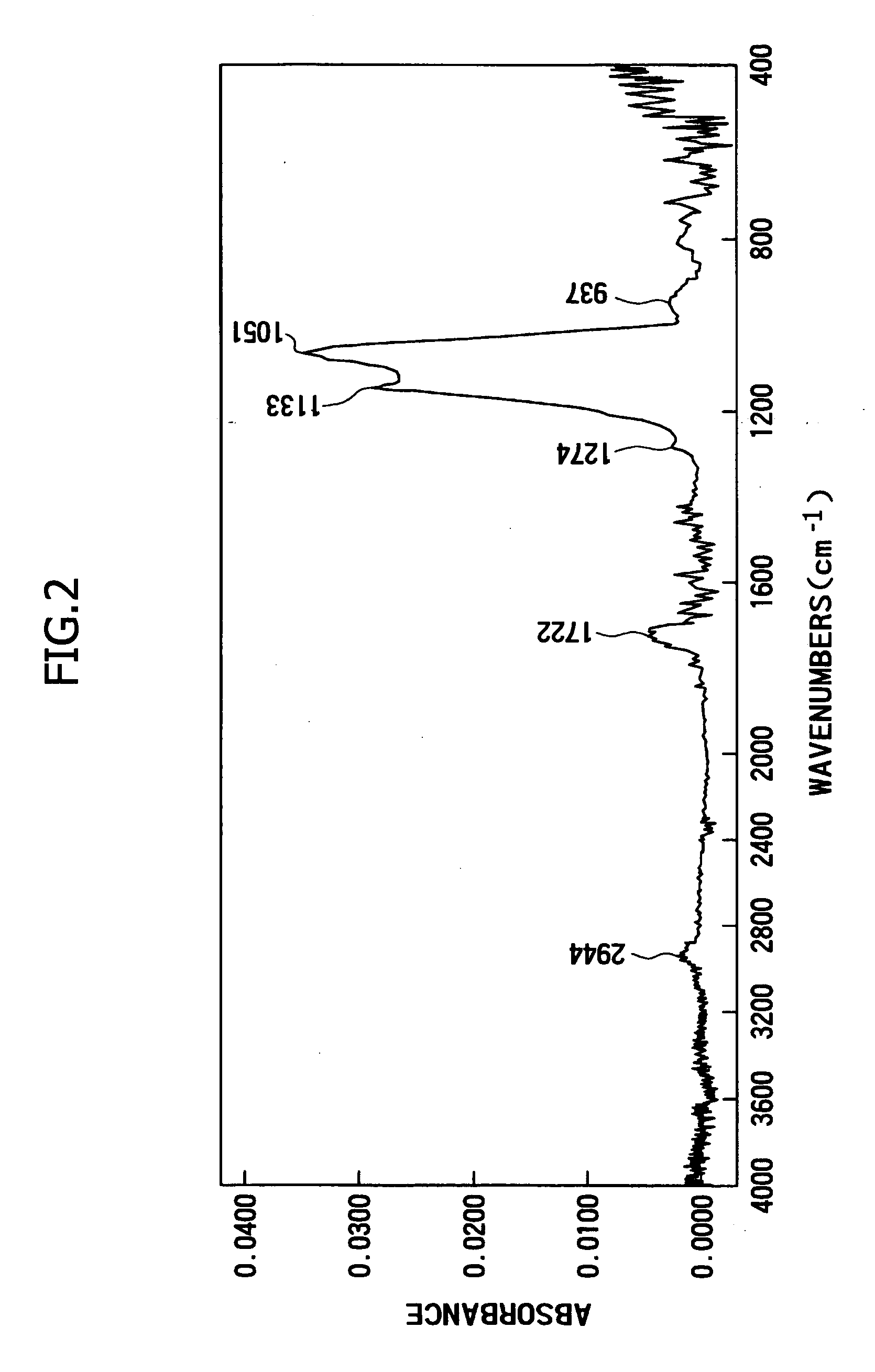
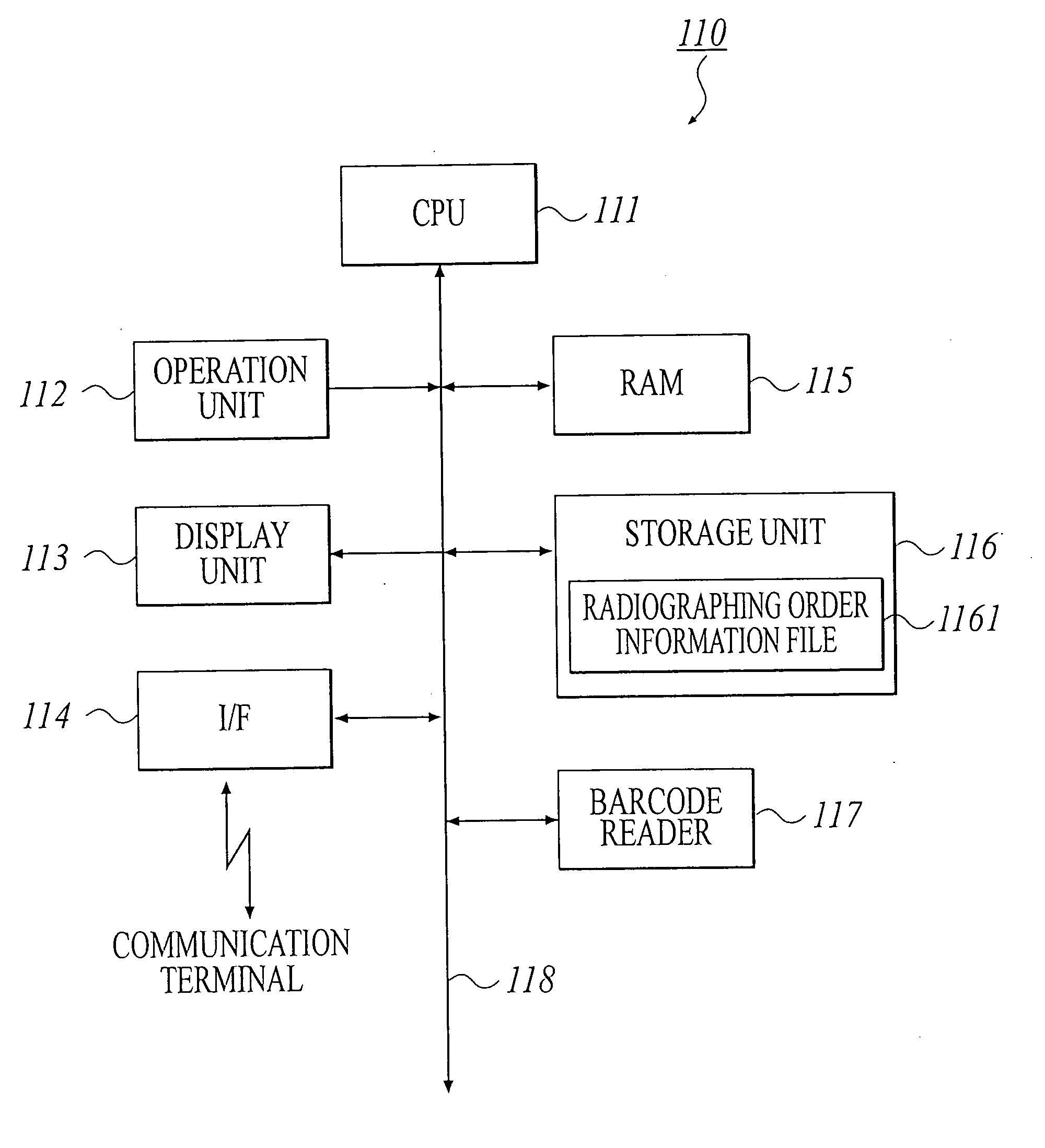
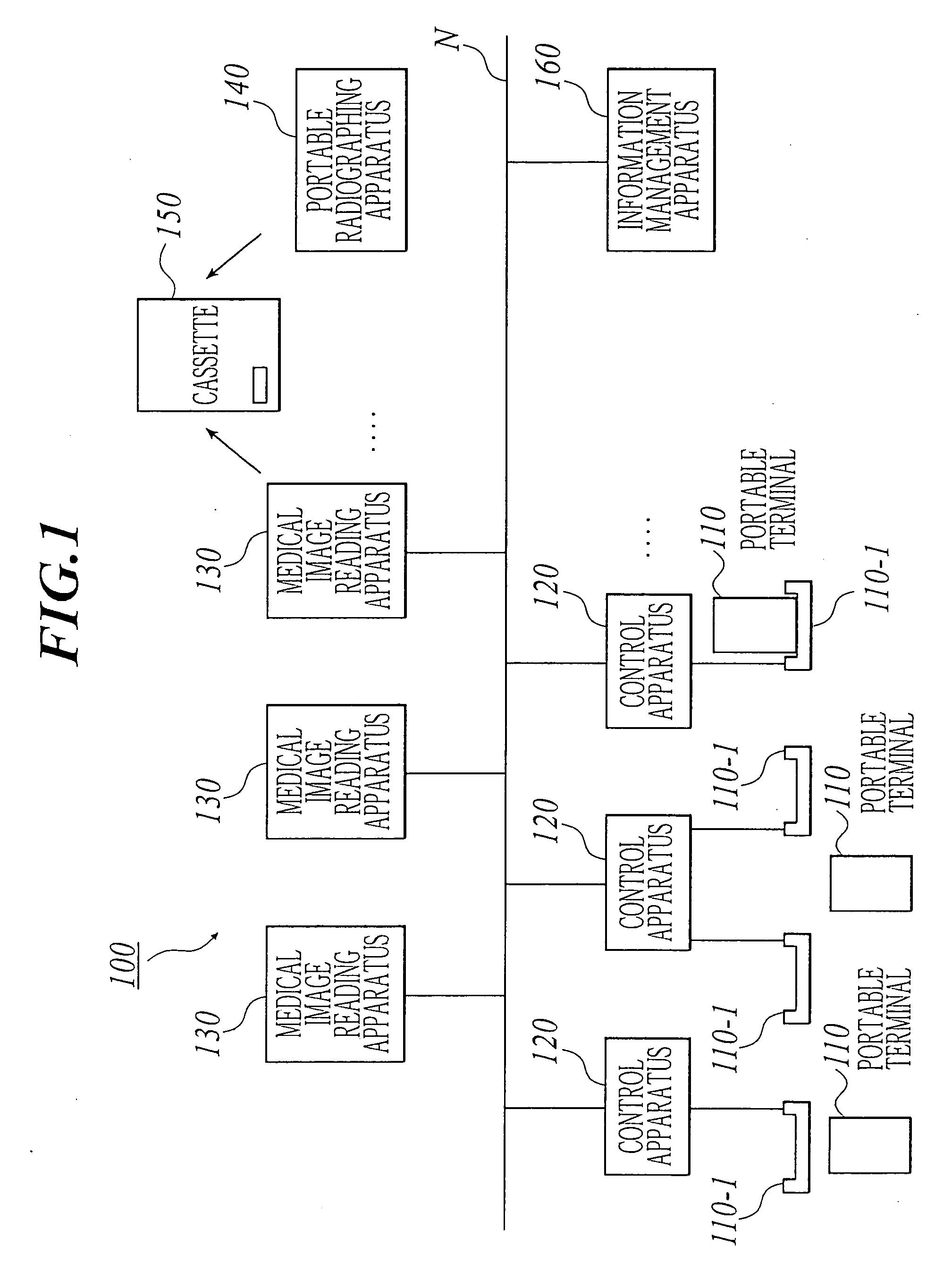
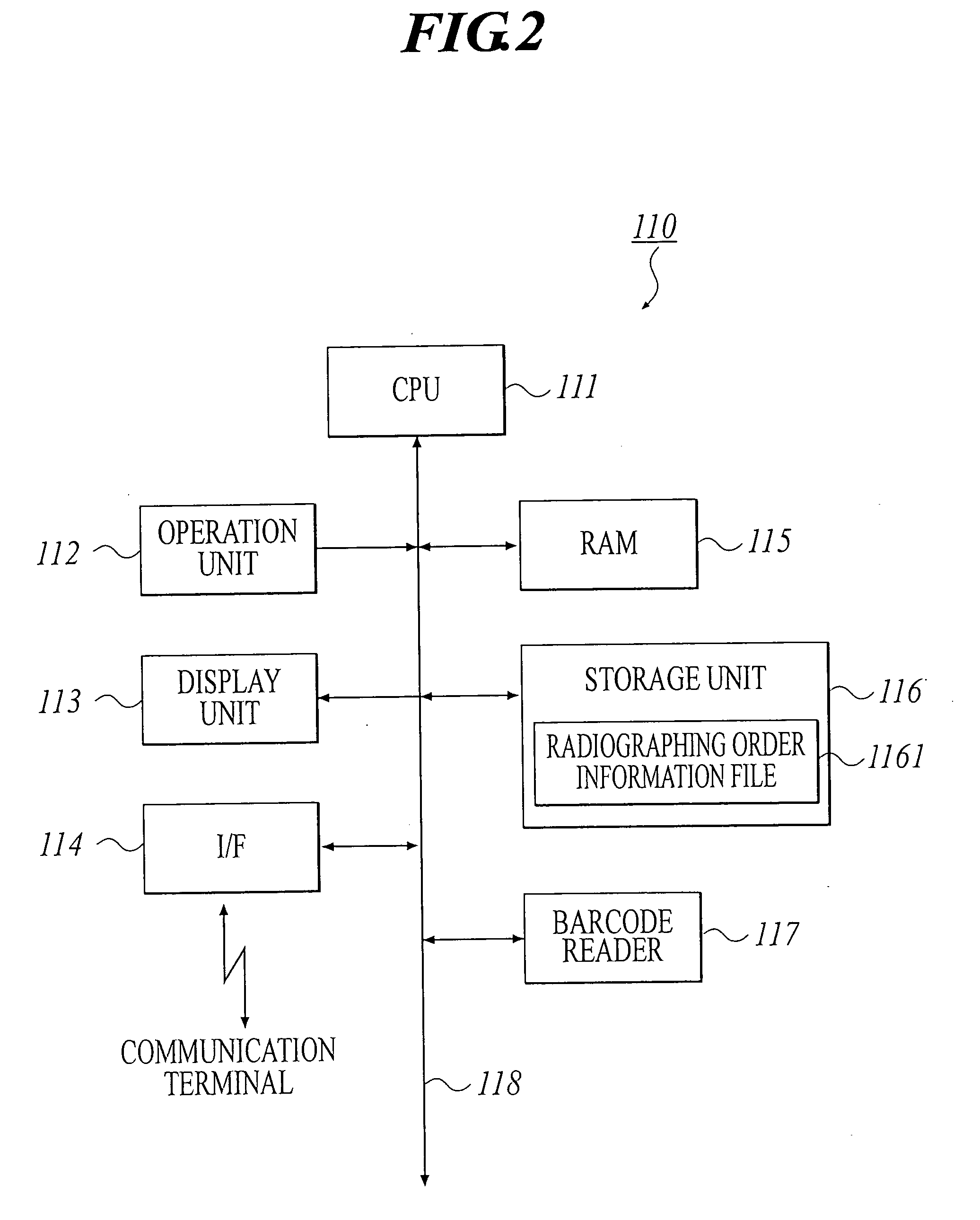
Medical image radiographing system, medical image management method and portable terminal
InactiveUS20040086163A1Efficient additionAccurate acquisitionData processing applicationsLocal control/monitoringComputer terminalData mining
a medical image radiograping system capable of modifying radiographing order information suitably. In the system, a control apparatus has: an obtaining section for obtaining identification information of a cassette; a storage for storing the identification information related to radiographing order information, and storing the radiographing order information renewed according to radiographing; and a communication section for transmitting the radiographing order information and the identification information, and the control apparatus has: a storage for storing radiographing order information; a communication section for receiving the radiographing order information and the identification information; a determination section for determining whether the radiographing order information received agrees with the radiographing order information stored or not; and a management section for controlling both the radiographing order information stored and the radiographing order information received and the identification information of the cassete, according to a result determined by the determination section.
Owner:KONICA MINOLTA INC
Group key distribution
InactiveUS6215878B1Efficient additionLow costKey distribution for secure communicationPublic key for secure communicationTimestampNetwork addressing
Owner:CISCO TECH INC
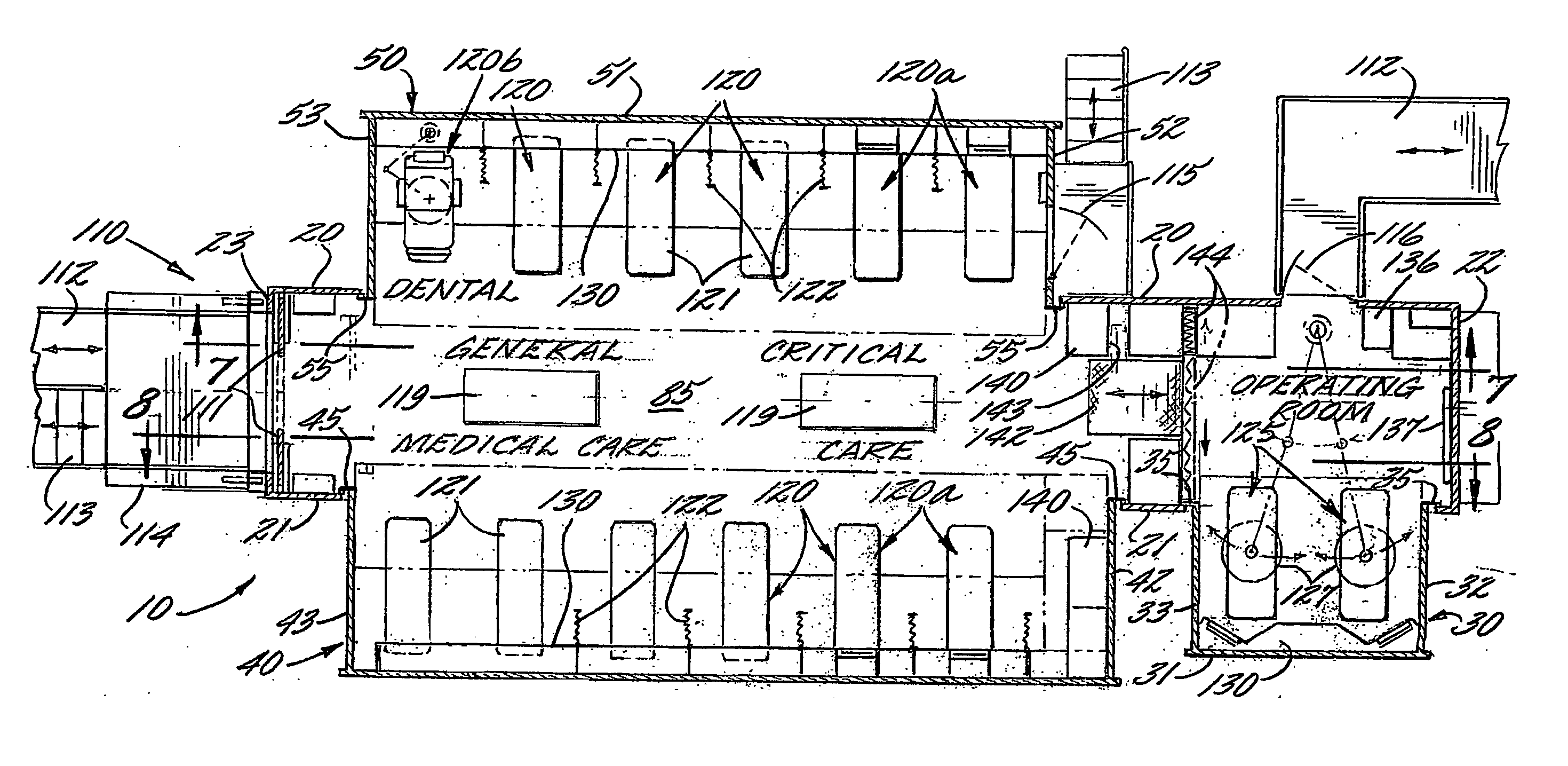
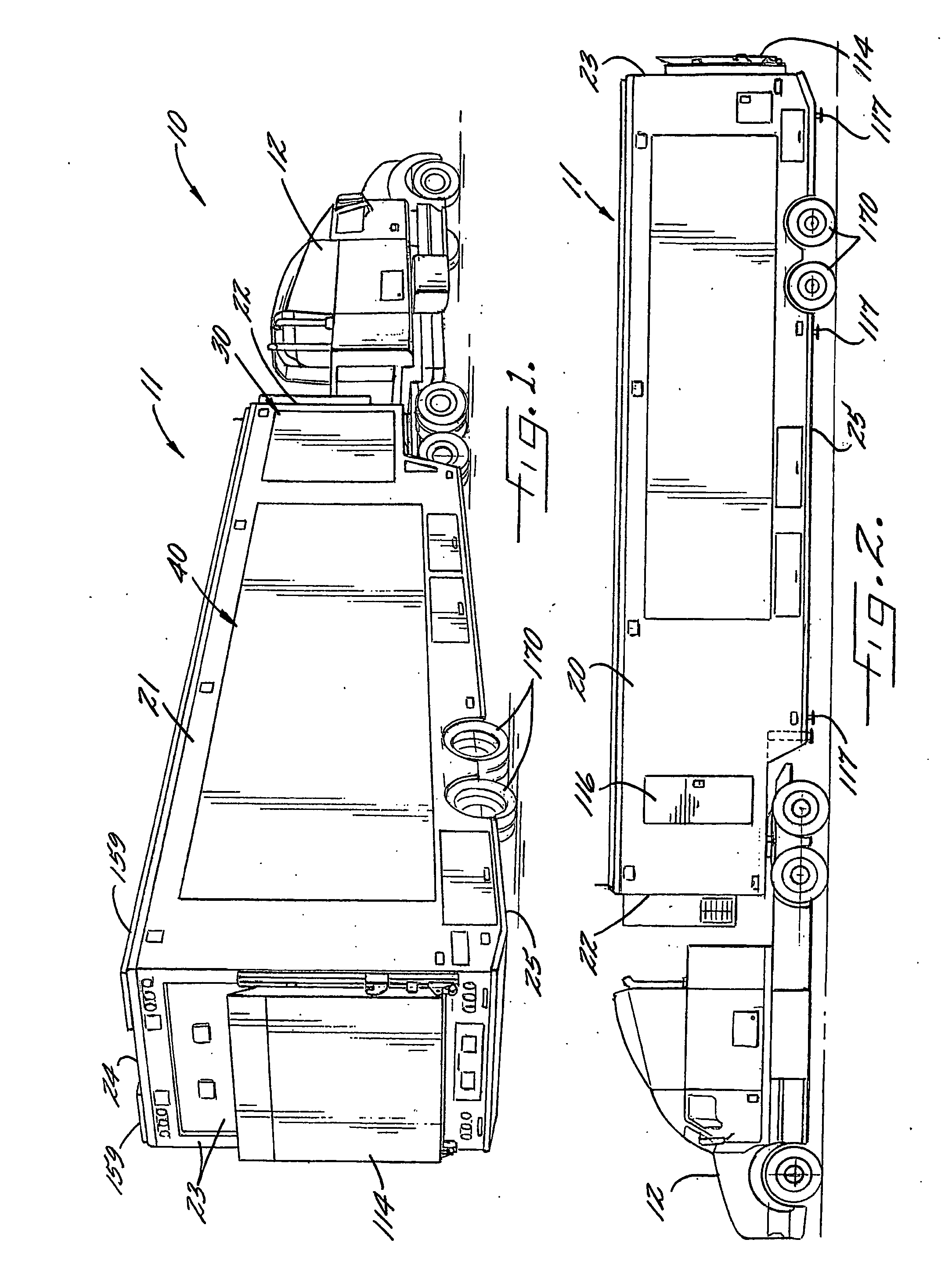
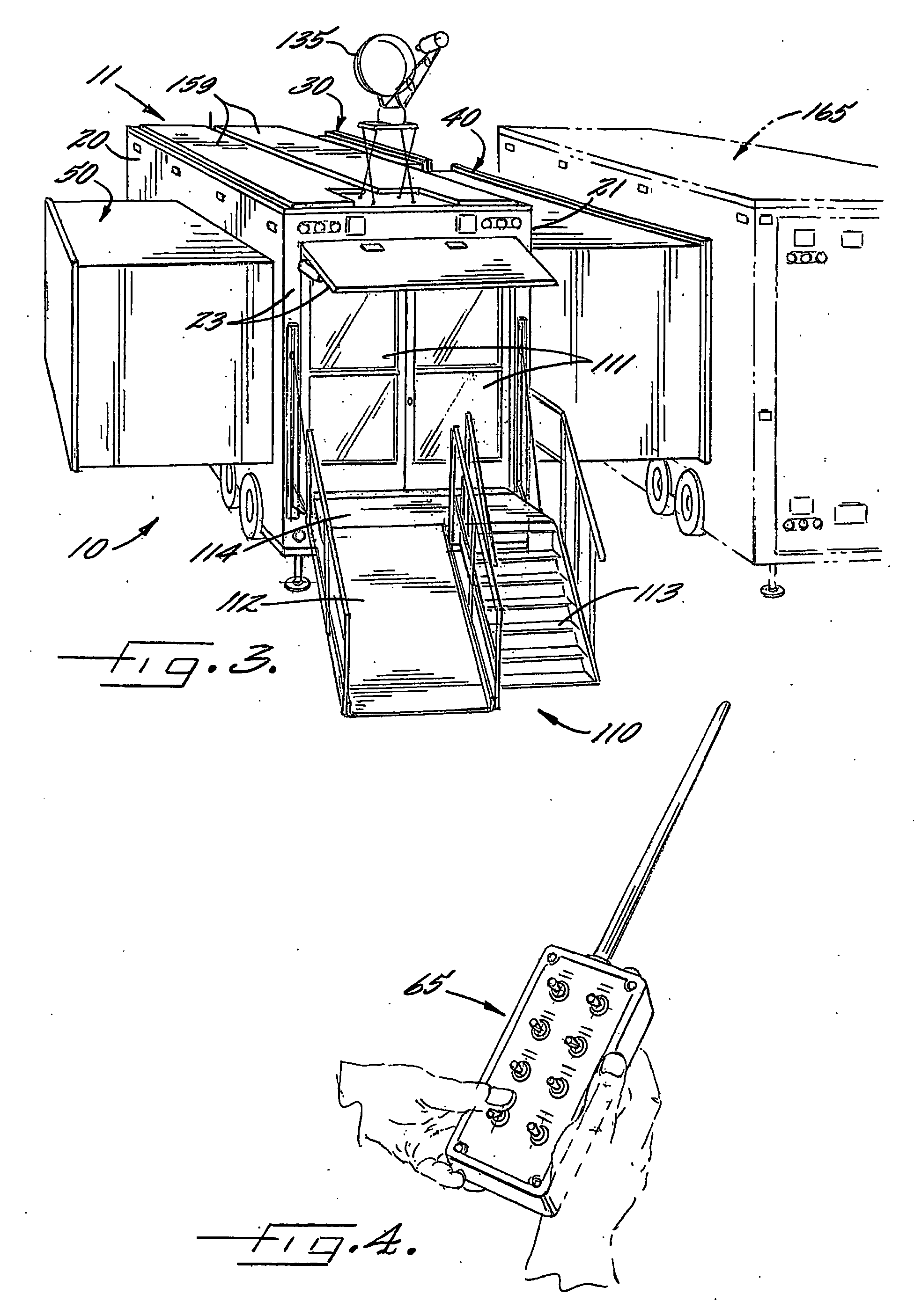
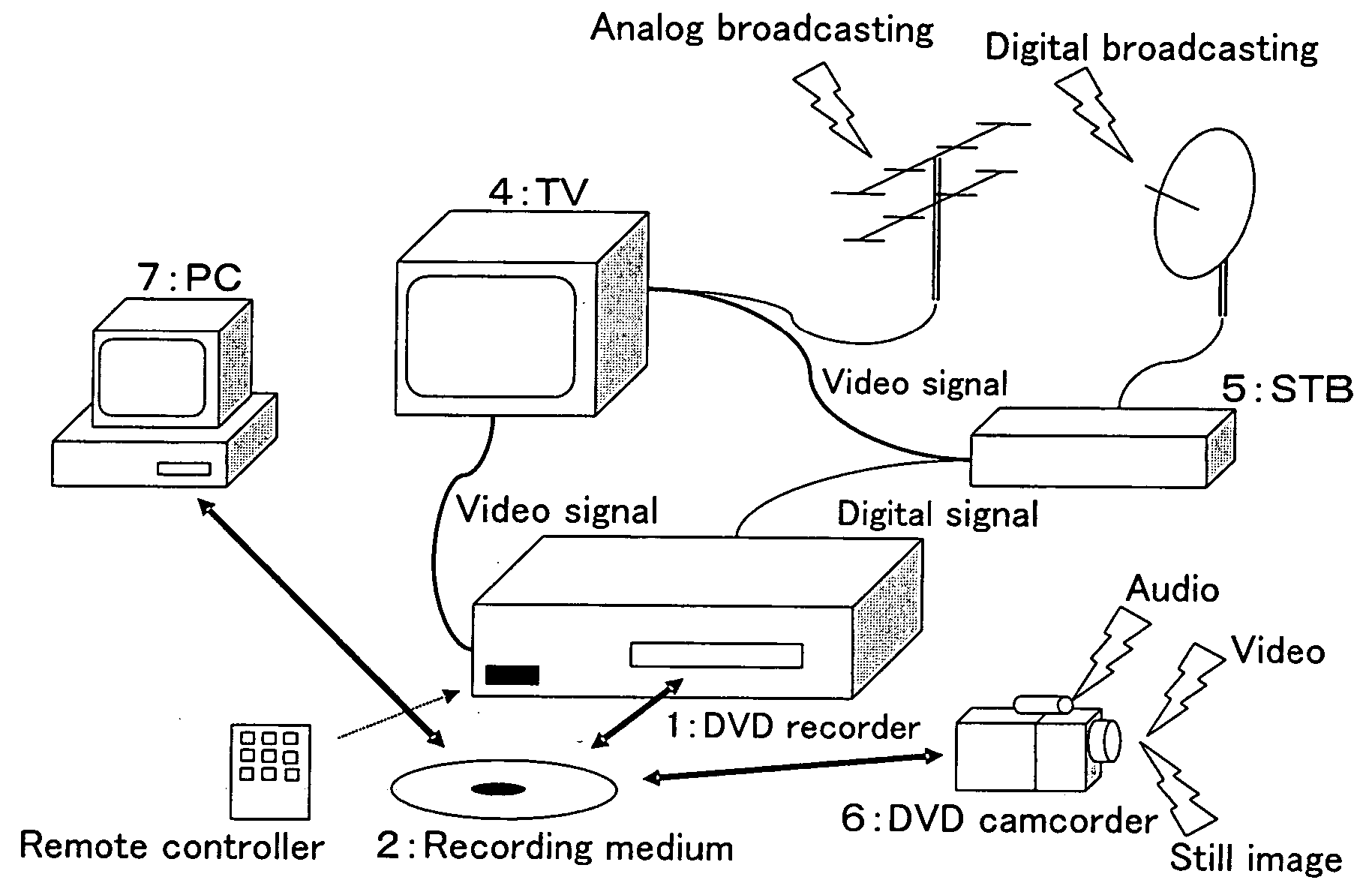
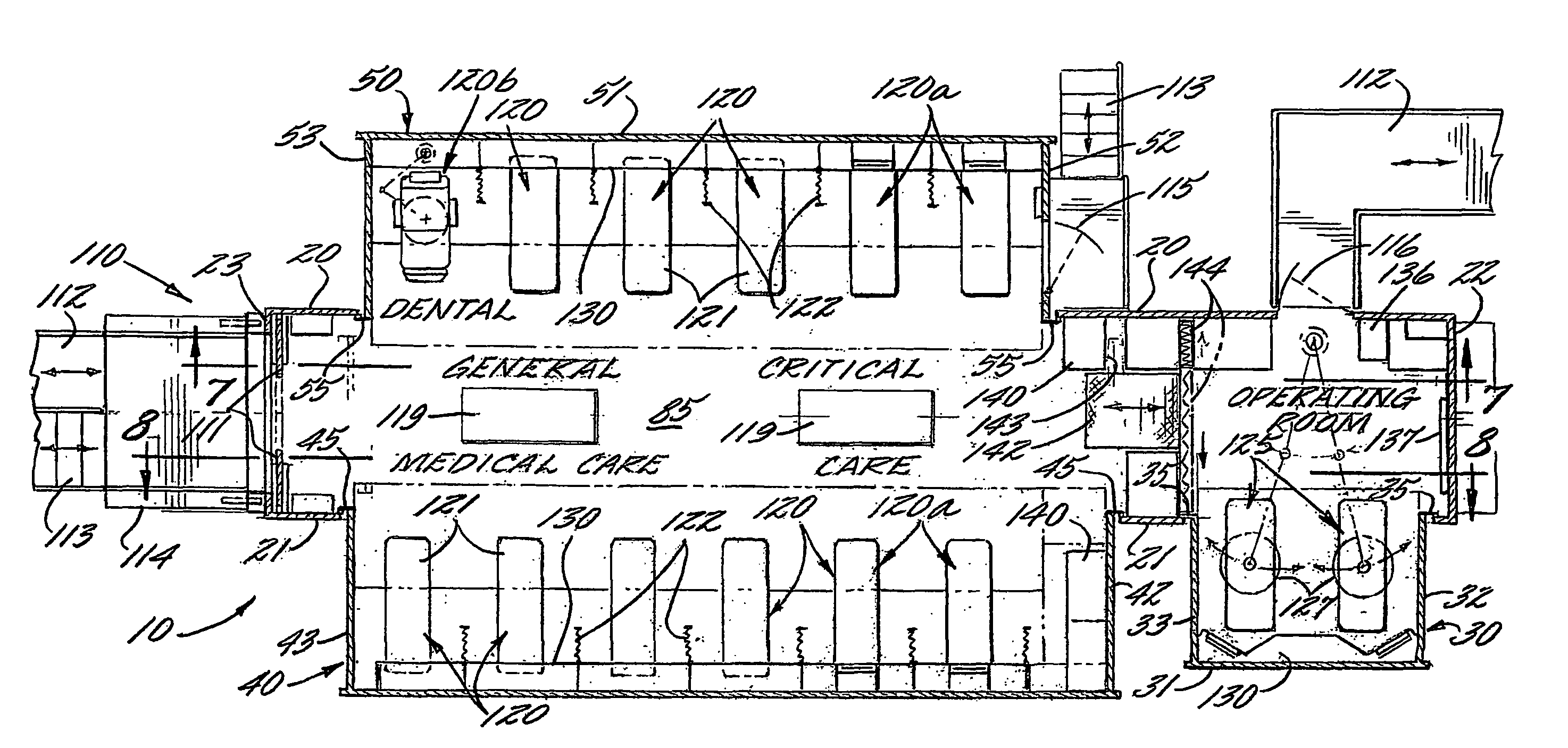
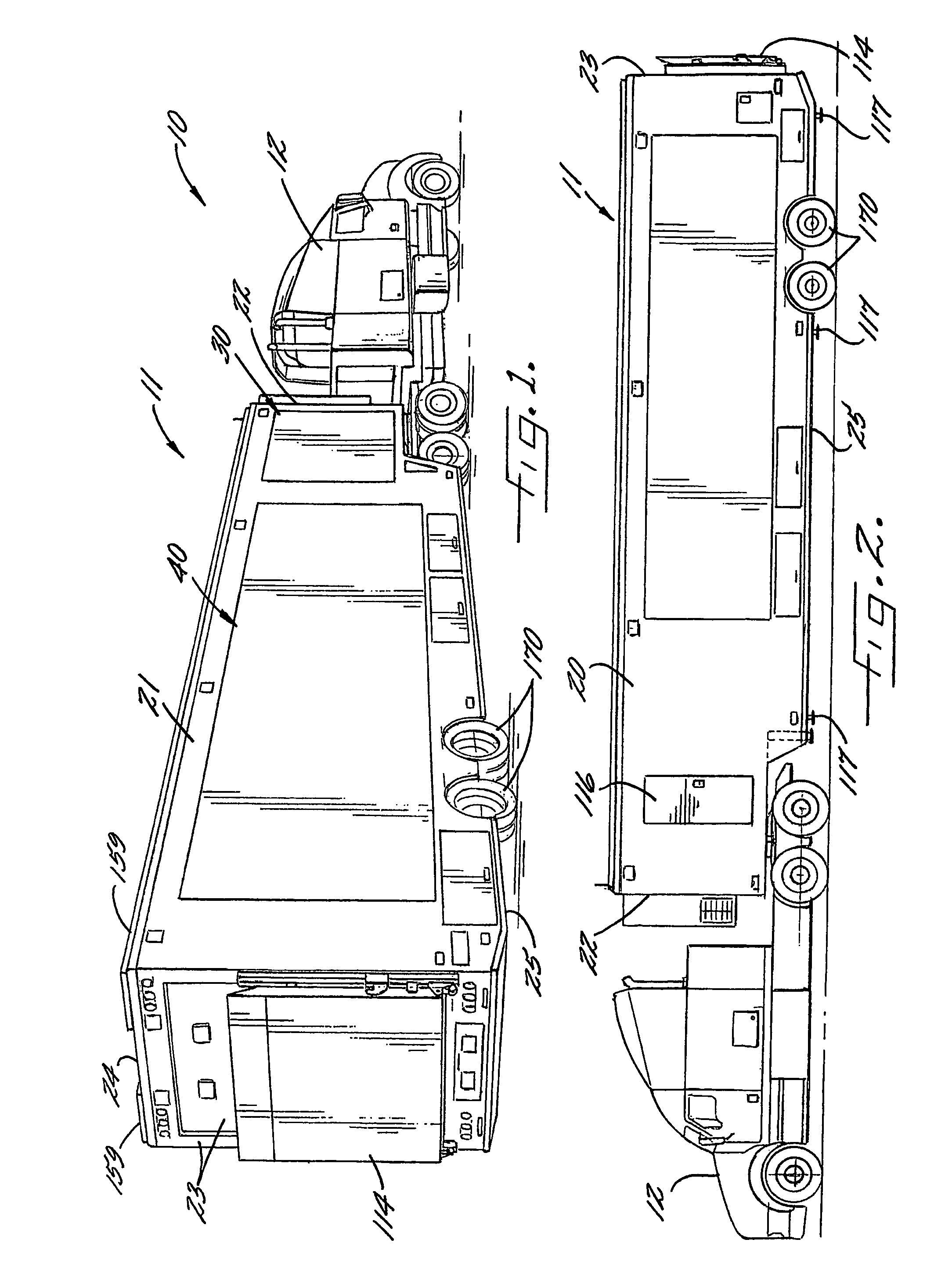
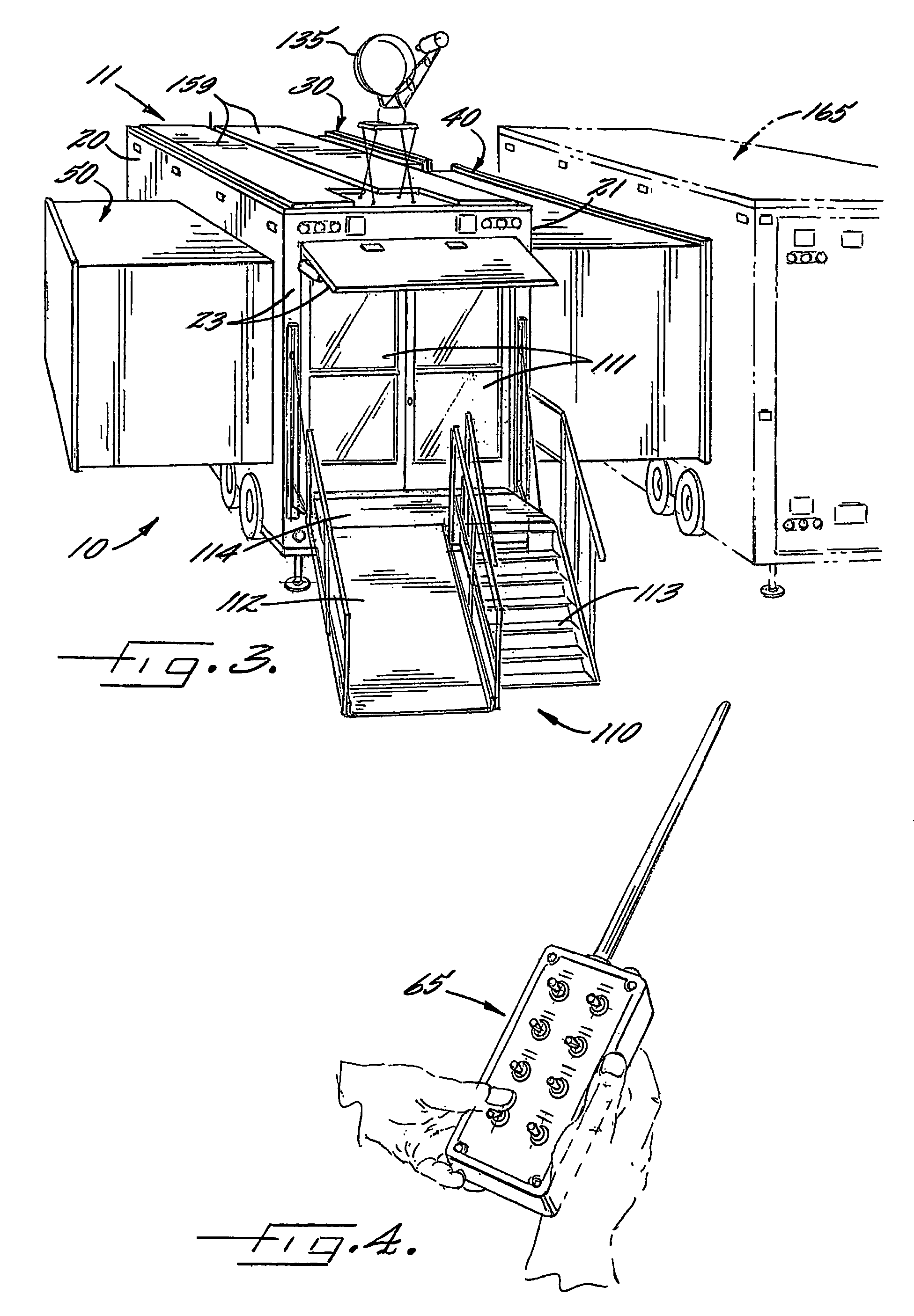
Mobile medical facility
ActiveUS20070102946A1Easy to transportReduce the burden onHospitalsVehicle with living accommodationEngineeringMedical treatment
Owner:CHARLOTTE MECKLENBURG HOSPITAL AUTHORITY
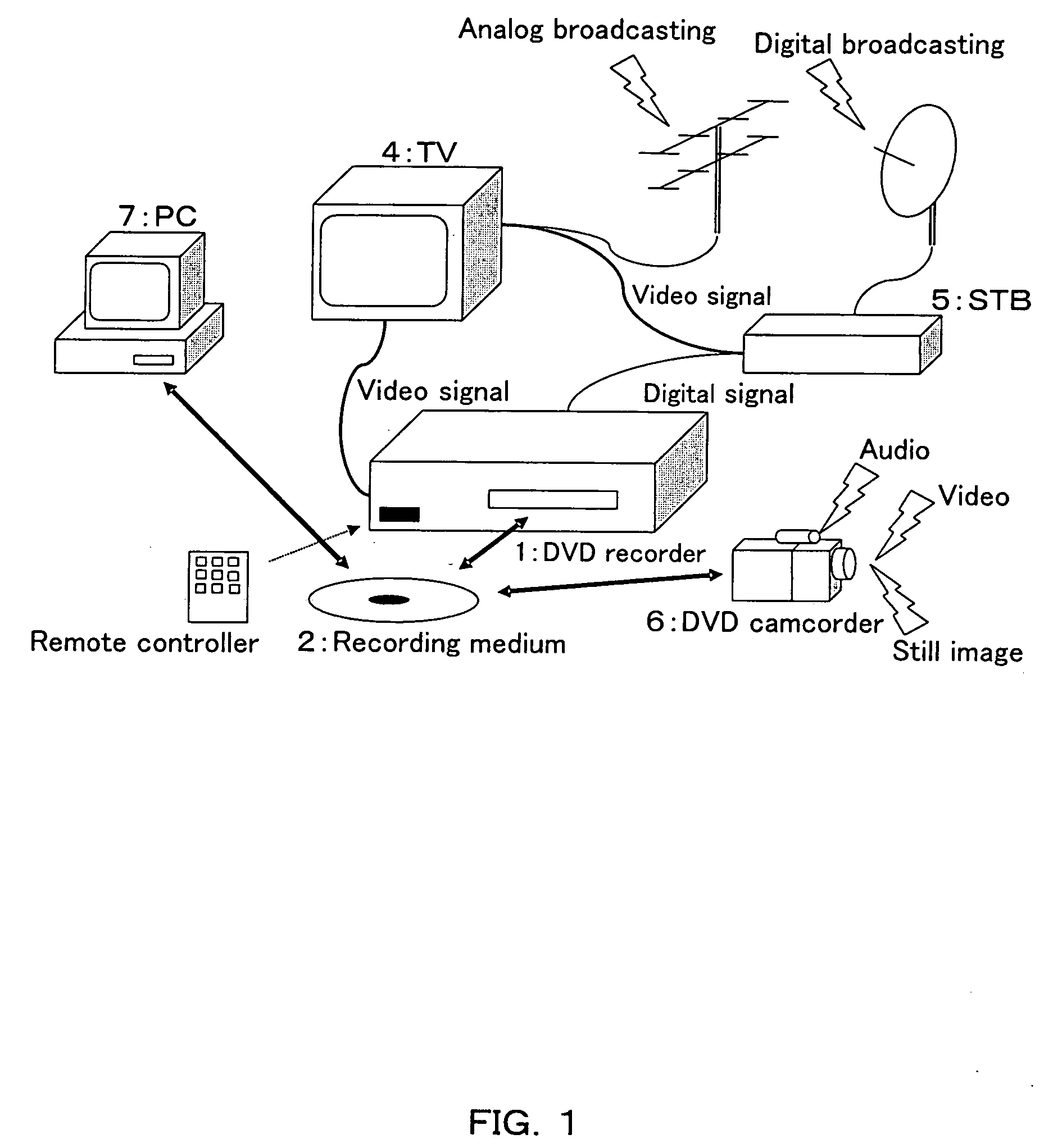
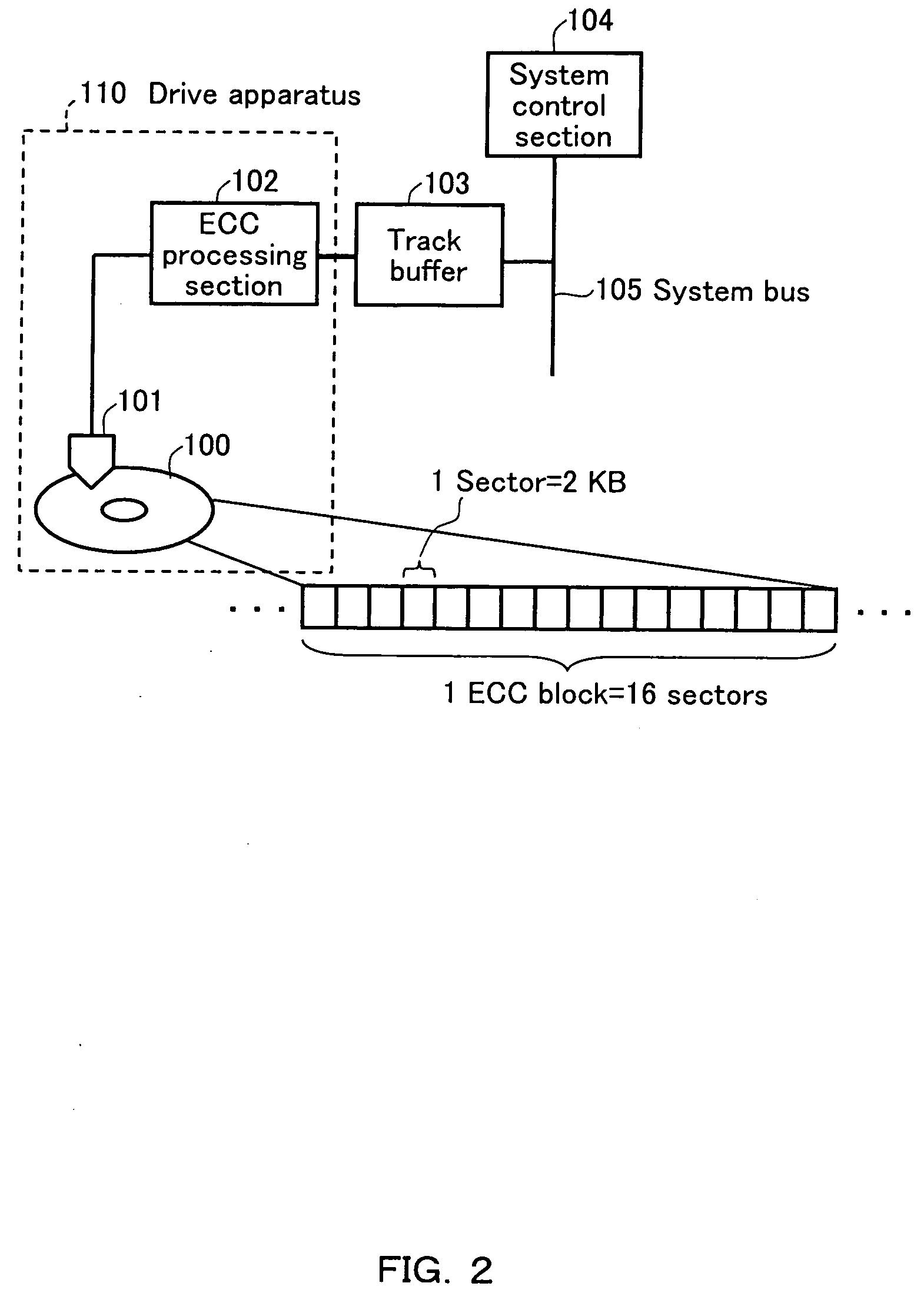
Recording medium, recording device usint the same, and reproduction device
InactiveUS20060133223A1Efficient executionEfficient additionTelevision system detailsData buffering arrangementsInformation processingFile system
A recording apparatus is provided that includes a recording section for recording information onto a recording medium, a file system processing section for managing the information as a file using file system information having a directory hierarchy structure capable of being referenced using a path name, a contents management information processing section for managing the directory and the file using contents management information, and an extension information processing section for managing extension information with respect to the directory and the file. The contents management information includes media object management information for referencing the directory and the file using object reference information obtained by converting the path name, and extended object management information for managing the extension information. The directory and the file are associated with the extension information via the object reference information.
Owner:PANASONIC CORP
Mobile medical facility
ActiveUS7794001B2Easy to transportReduce the burden onHospitalsVehicle with living accommodationEngineeringMedical treatment
Owner:CHARLOTTE MECKLENBURG HOSPITAL AUTHORITY
Common interconnection network content keyword interactive system
InactiveCN1932817APromote innovationIncrease initiativeSpecial data processing applicationsClient-sideArray data structure
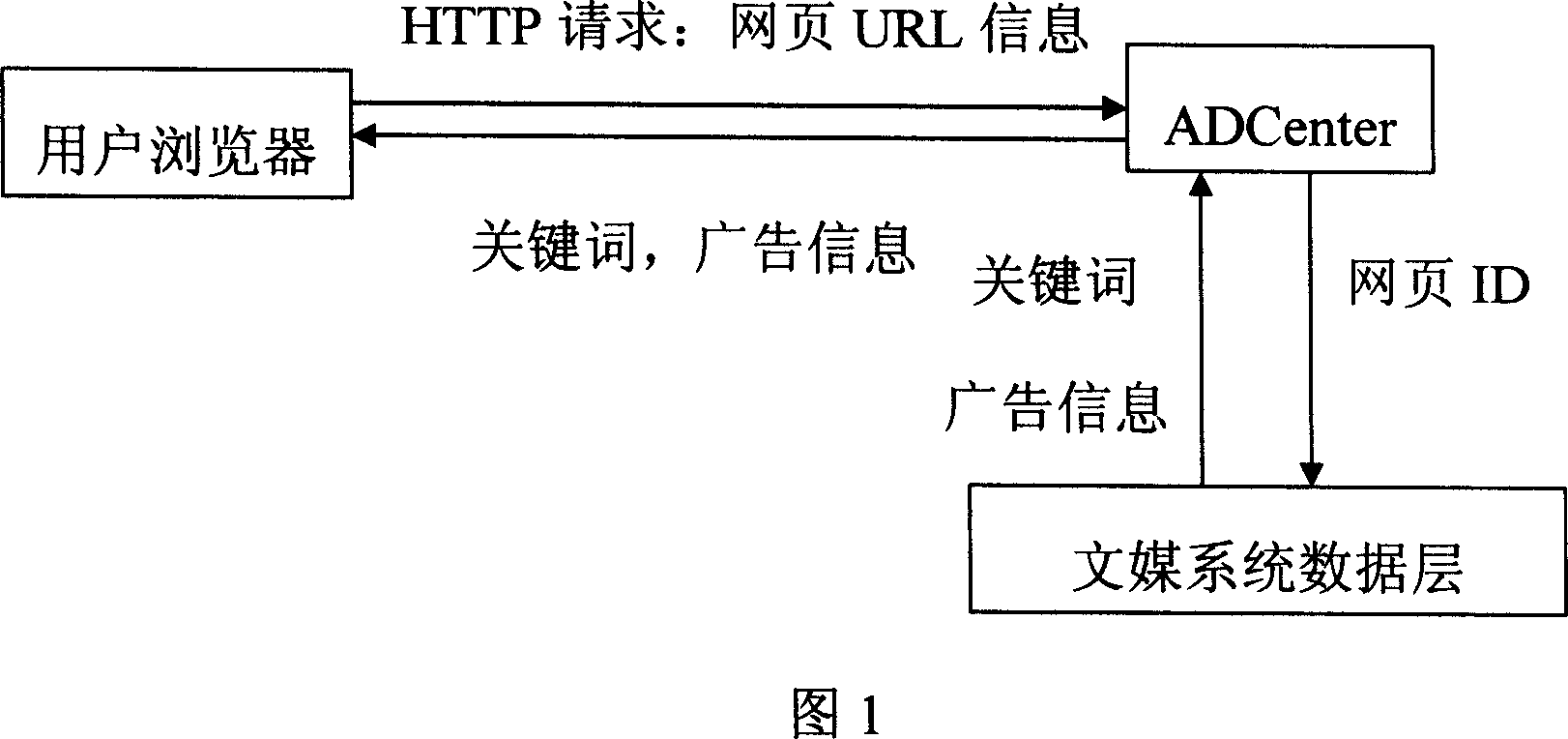
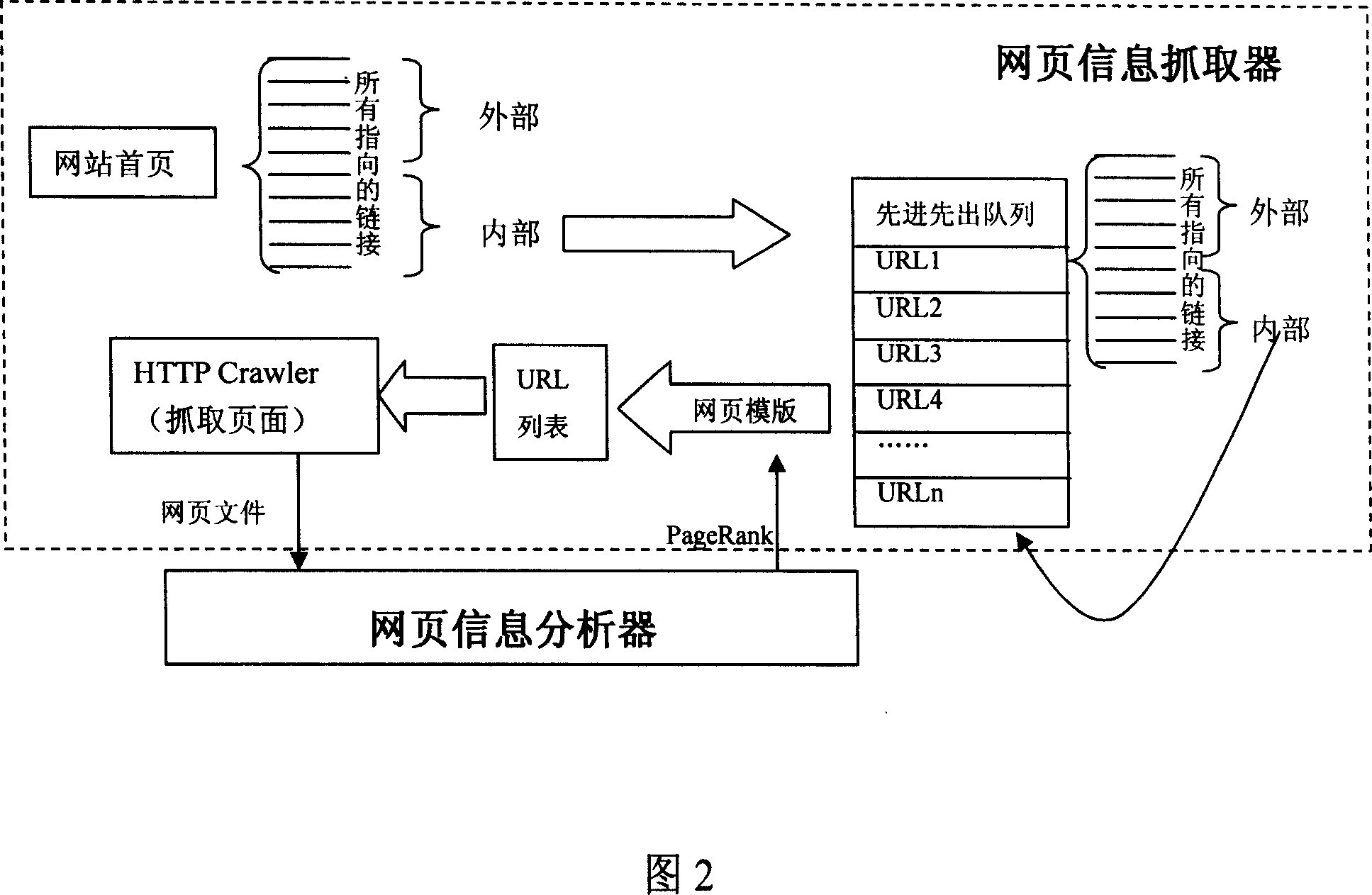
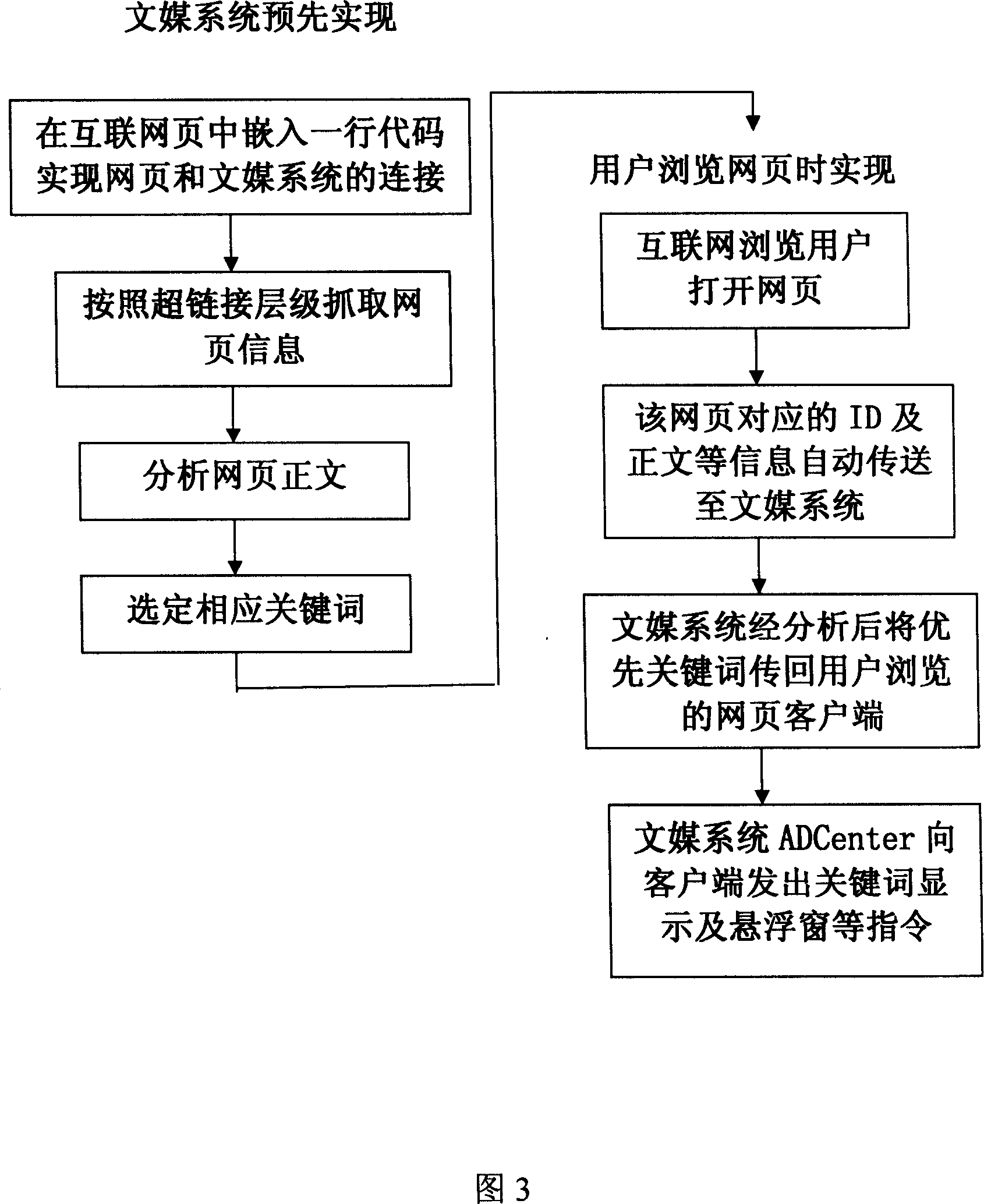
Mutual universal network content keyword mutual system with true matching keyword and simply and rapidly adding keyword at real time. It relates to web page information grasp-organ, web page information analyzer to analyze the grasped page text, keyword index module to count matrix of web page and keyword. It also owns keyword demand module to find out keyword array which corresponds to the ID of web pages of keyword filtrating needed in the said web page, keyword matrix and JavaScript code interface. Then calculate the intersection about advertisement keyword bank to get a series of keywords and to classify and screen out the front keywords according to web page and advertisement keyword and advertisement keyword bank. Its AD Center module incepts HTTP demand sent by JavaScript code, calculates web pages ID corresponding URL, sends ID demand to keyword demand module, incepts the feedback keyword and the corresponding mutual advertisement information and adds them to the web page user ending by alternating with JavaScript code interface.
Owner:陈远
Magnetic recording medium
InactiveUS20030017365A1High running durabilityGuaranteed uptimeMagnetic materials for record carriersRecord information storageParticulatesHigh density
Provided is a particulate magnetic recording medium having good processing properties and being inexpensive to produce, similar to prior recording media, wherein by controlling the magnetic clusters that appear due to recording at short wavelengths and thinning of the magnetic layer, good high-density characteristics are achieved in combination with MR heads. The magnetic recording medium comprising an essentially nonmagnetic lower layer and a magnetic layer comprising a ferromagnetic powder and a binder in this order, wherein the magnetic layer has a thickness ranging from 0.01 to 0.15 mum and a coercivity equal to or higher than 159 kA / m, ferromagnetic particles contained in the ferromagnetic powder have a size less than ½ of the minimum recording wavelength, and an average size of magnetic cluster at DC erase is equal to or higher than 0.5x104 nm2 and less than 5.5x104 nm2.
Owner:FUJIFILM CORP
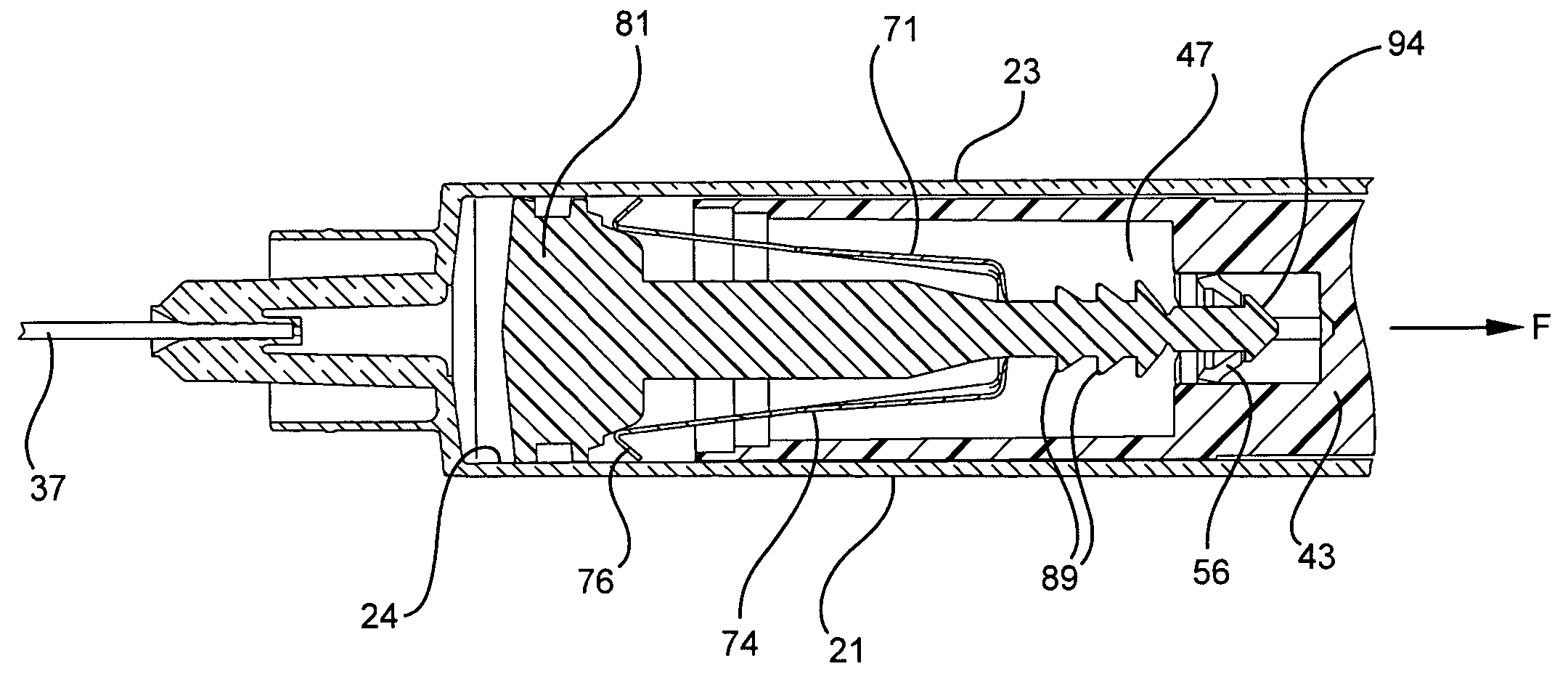
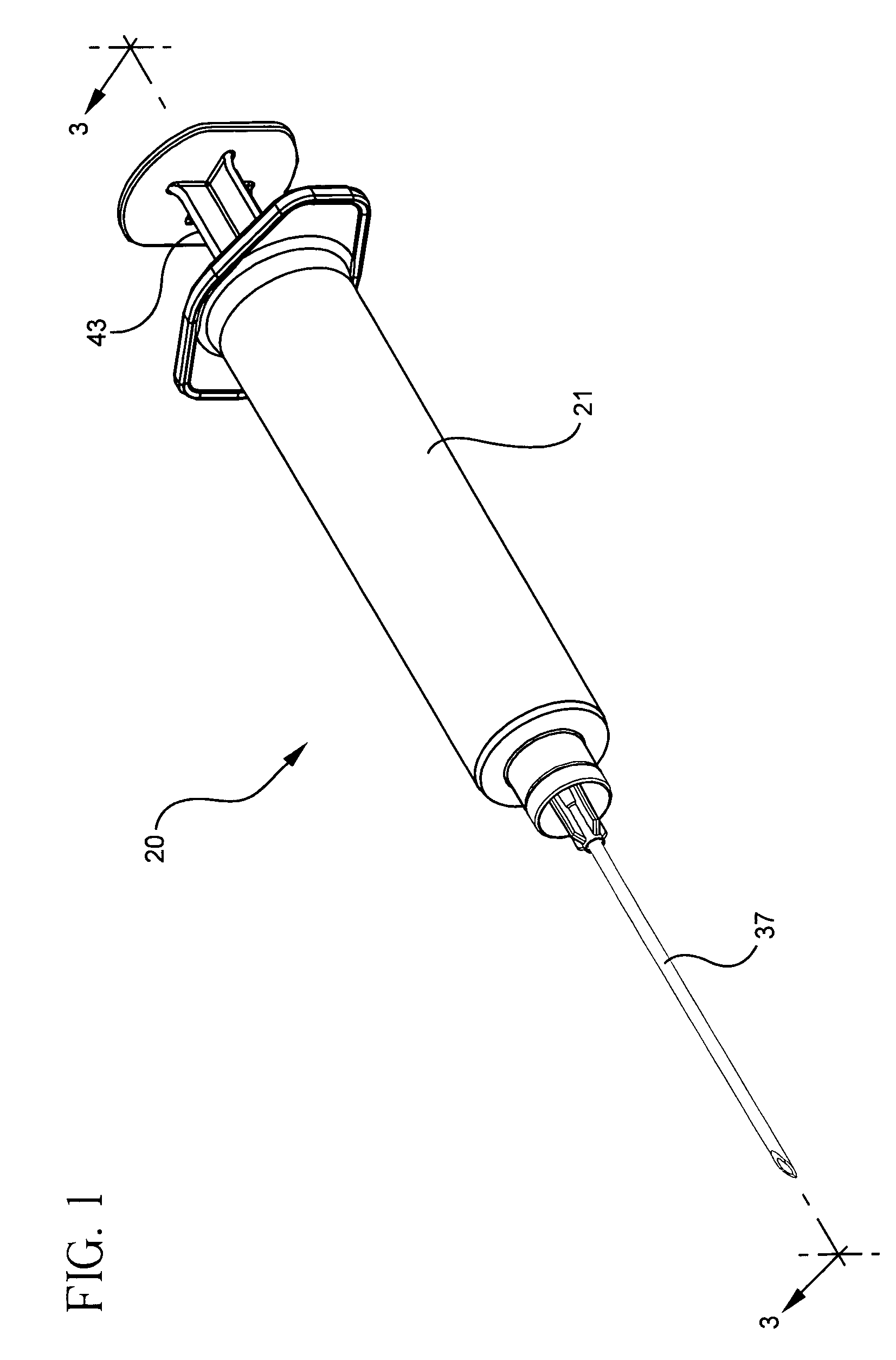
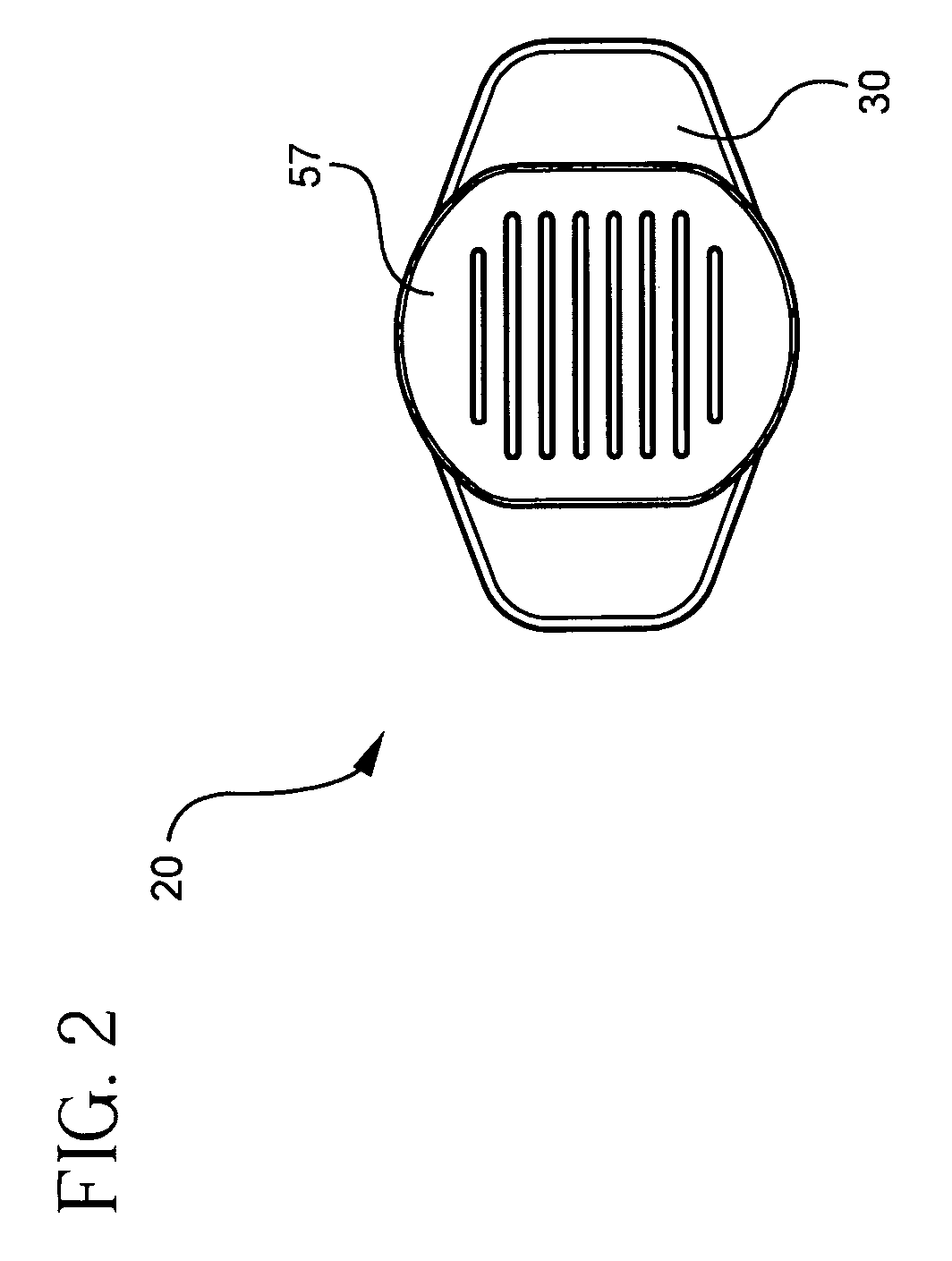
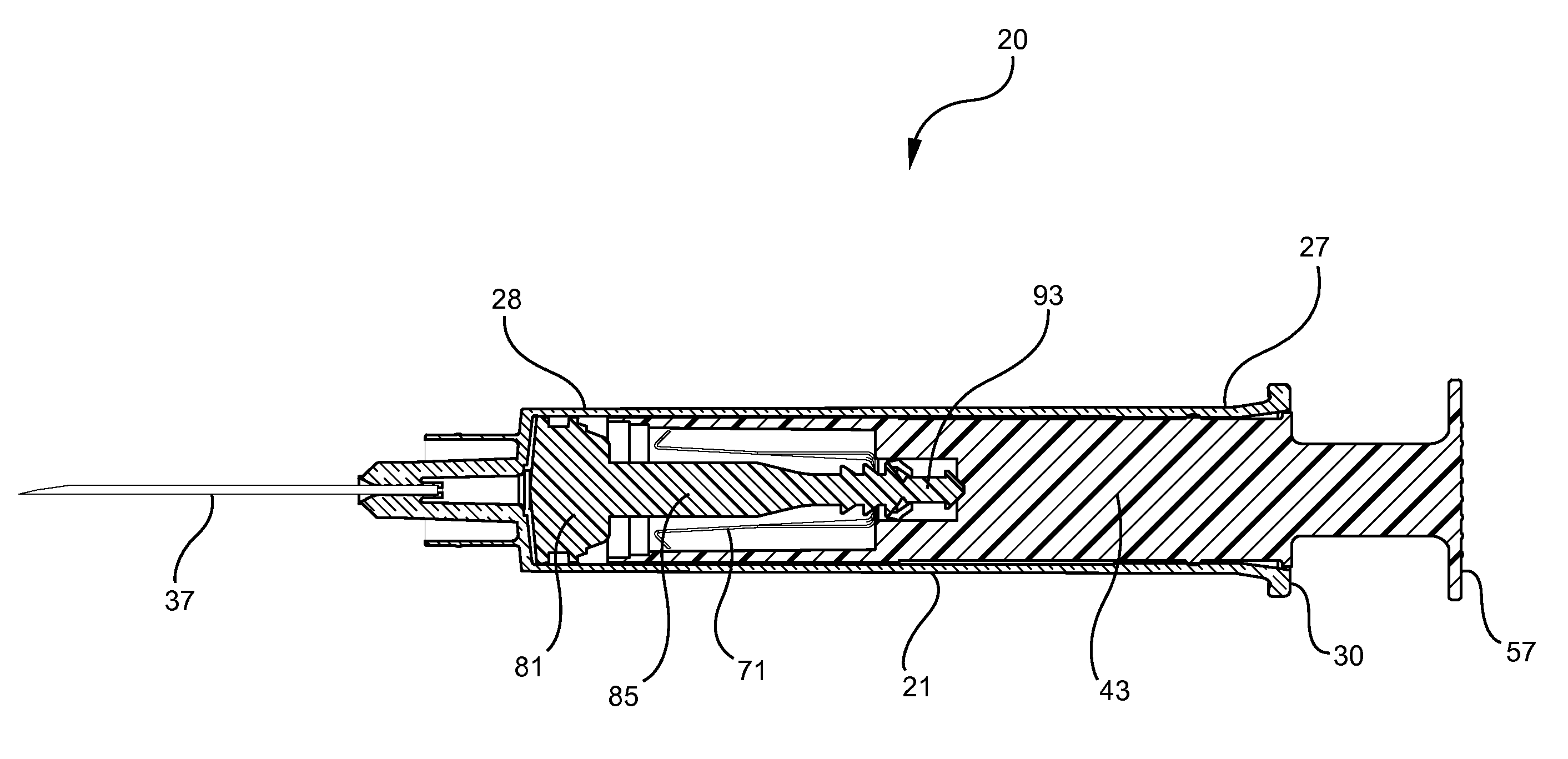
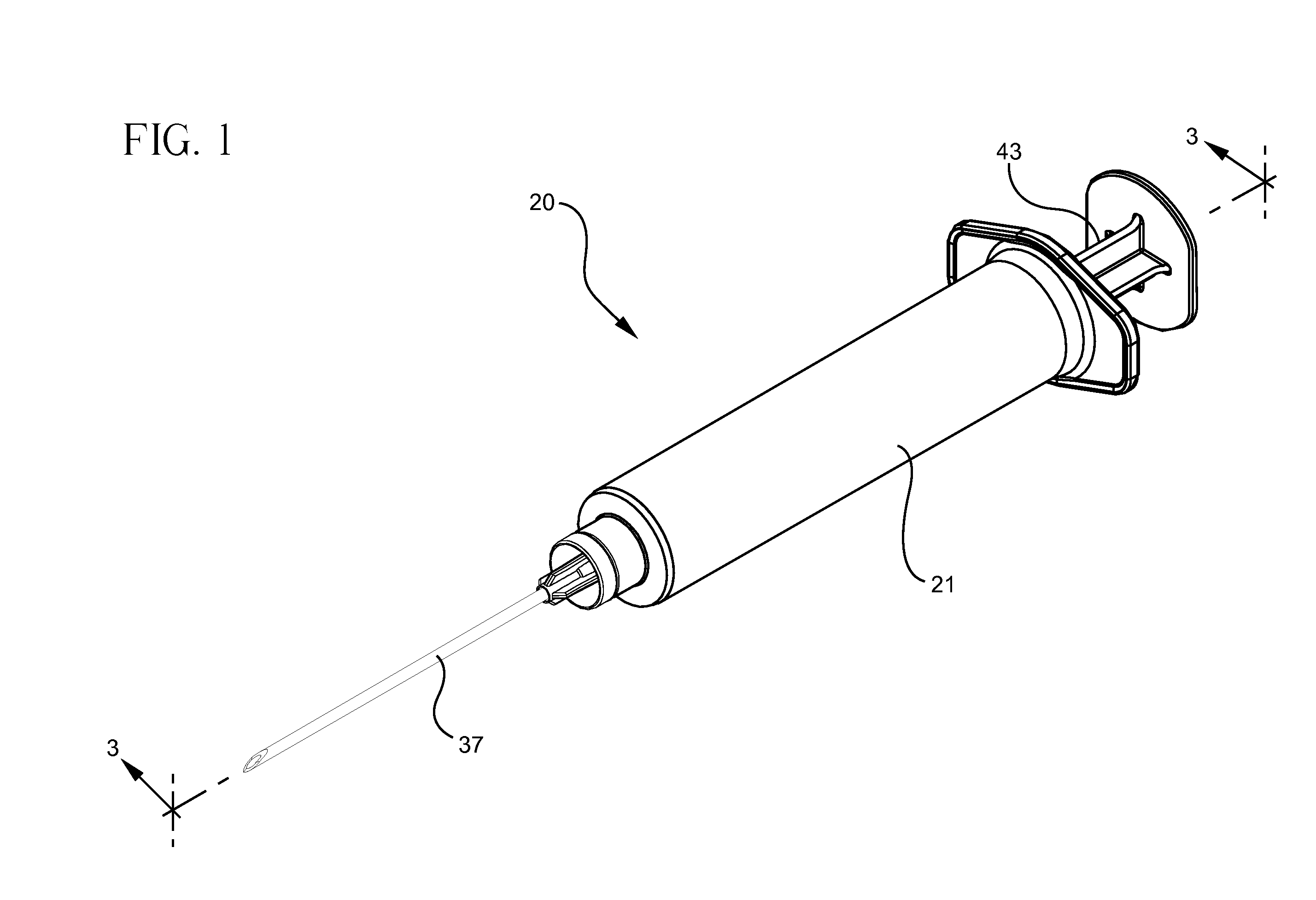
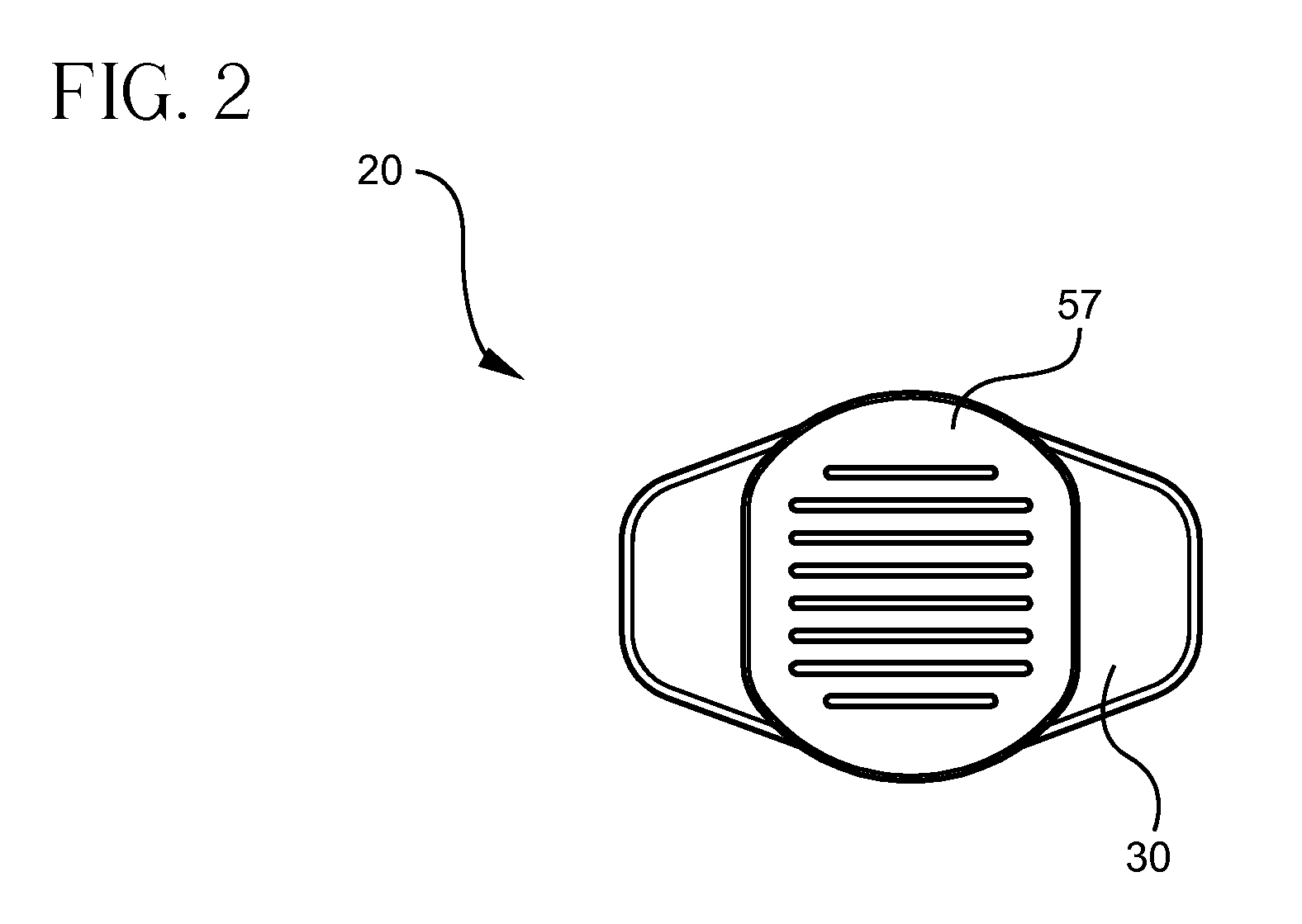
Syringe assembly having disabling mechanism
ActiveUS7331935B2Easy to operateEfficient additionInfusion syringesIntravenous devicesLocking mechanismDetent
A syringe assembly having passive disabling structure includes a barrel and a plunger rod assembly. The plunger rod assembly includes a plunger rod and a stopper connected by an indexing locking element. The number of strokes of the syringe plunger before the stopper is locked into the barrel rendering the syringe assembly unusable is determined by the number of detents on the plunger rod and stopper which engage the locking mechanism. Upon completion of the final delivery stroke, any attempt to withdraw the plunger rod from the barrel will cause the locking element to engage the barrel and trap the stopper in the barrel preventing further use of the syringe.
Owner:BECTON DICKINSON & CO
Antireflective film-forming composition, method for manufacturing the same, and antireflective film and pattern formation method using the same
ActiveUS7541134B2Improve etch selectivityEtching speed is fastSemiconductor/solid-state device manufacturingSilver halide emulsionsResistCross-link
The present invention provides a material for an antireflective film characterized by high etching selectivity with respect to a resist, that is, which has a fast etching speed when compared to the resist, and in addition, can be removed without damage to a film which is to be processed. The present invention also provides a pattern formation method for forming an antireflective film layer on a substrate using this antireflective film-forming composition, and a pattern formation method that uses this antireflective film as a hard mask, and a pattern formation method that uses this antireflective film as a hard mask for processing the substrate. The present invention also provides an antireflective film-forming composition comprising an organic solvent, a cross linking agent, and a polymer comprising a light absorbing group obtained by hydrolyzing and condensing more than one type of silicon compound, a crosslinking group and a non-crosslinking group.
Owner:SHIN ETSU CHEM CO LTD +1
Positive resist composition and patterning process
ActiveUS20120220112A1Improve adhesionExpand coveragePhotosensitive materialsSemiconductor/solid-state device manufacturingResistImage resolution
A positive resist composition based on a polymer comprising recurring units of (meth)acrylate having a cyclic acid labile group and a dihydroxynaphthalene novolak resin, and containing a photoacid generator is improved in resolution, step coverage and adhesion on a highly reflective stepped substrate, has high resolution, and forms a pattern of good profile and minimal edge roughness through exposure and development.
Owner:SHIN ETSU CHEM IND CO LTD
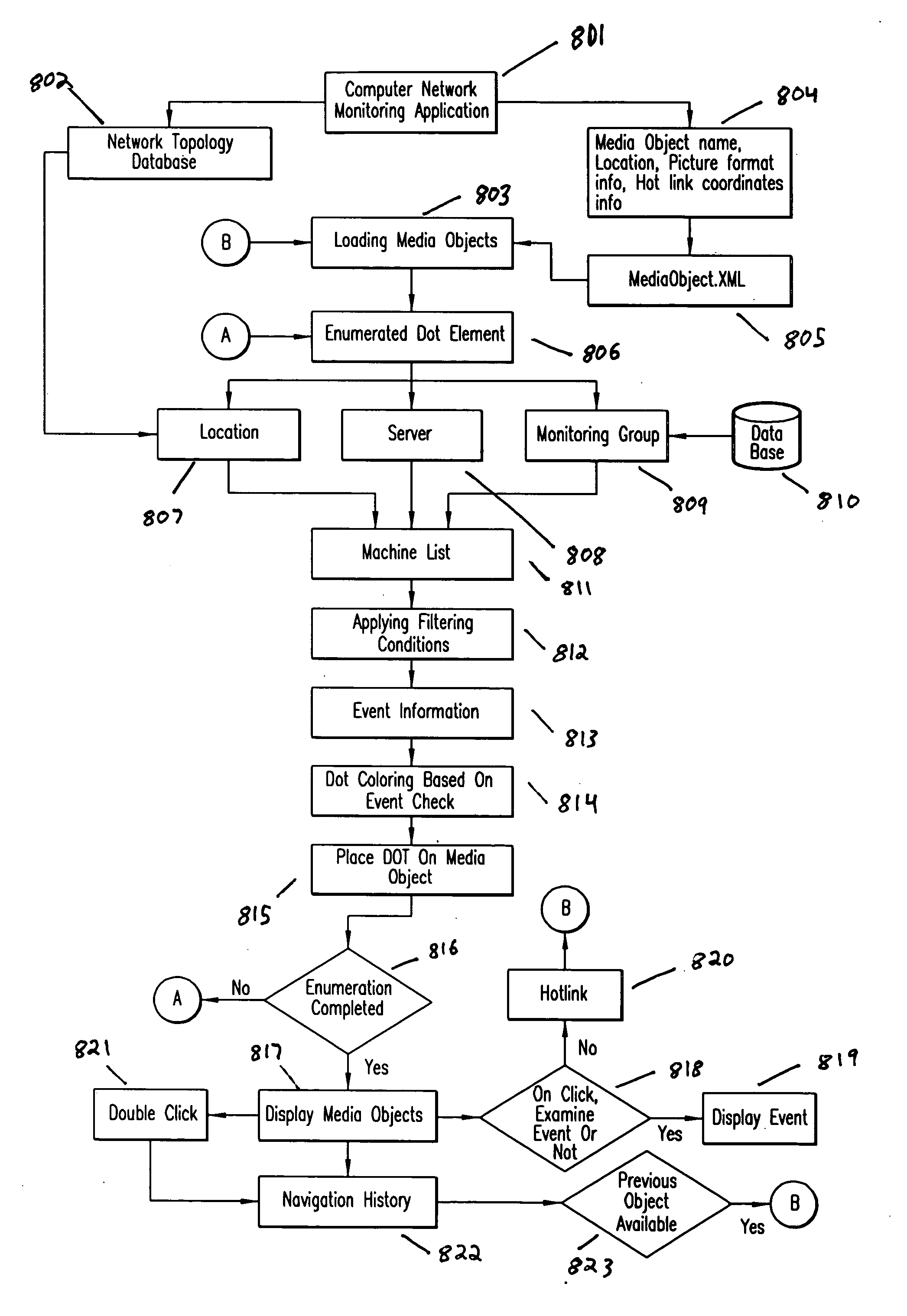
Method and system for defining media objects for computer network monitoring
ActiveUS20060294231A1Much timeMuch effortError detection/correctionDigital computer detailsReal-time computingNetwork monitoring
Owner:ARB INTPROP HLDG HK
Printed Temperature Sensor
InactiveUS20130203201A1Efficient additionImprove the immunityThermoelectric device manufacture/treatmentPrinted electric component incorporationElectrical resistance and conductanceHeat sensitive
A method of producing a temperature sensing device is provided. The method includes forming at least one silicon layer and at least one electrode or contact to define a thermistor structure. At least the silicon layer is formed by printing, and at least one of the silicon layer and the electrode or contact is supported by a substrate during printing thereof. Preferably, the electrodes or contacts are formed by printing, using an ink comprising silicon particles having a size in the range 10 nanometres to 100 micrometres, and a liquid vehicle composed of a binder and a suitable solvent. In some embodiments the substrate is an object the temperature of which is to be measured. Instead, the substrate may be a template, may be sacrificial, or may be a flexible or rigid material. Various device geometries are disclosed.
Owner:PST SENSORS
Shape follow-up support deformation control method for selective laser melting forming of thin-walled part
ActiveCN108372298AEfficient additionAvoid complex and hard-to-remove problemsAdditive manufacturing apparatusIncreasing energy efficiencySelective laser meltingDeformation control
The invention relates to a shape follow-up support deformation control method for selective laser melting forming of a thin-walled part. On the basis of existing selective laser melting forming support adding, the stress deformation behavior of the large thin-walled structural part in the forming process is analyzed and predicted, according to the molded surface structural characteristics, a design method that different shape follow-up supports are added at different positions is adopted, the problems such as cracking and deformation at the different positions such as the bottom in the selective laser melting forming process are solved through the method of supporting structure shape follow-up adding, the stability in the forming process is effectively improved, and the reliability of thequality of the formed structure part is guaranteed.
Owner:AVIC BEIJING AERONAUTICAL MFG TECH RES INST
Agricultural fibre fuel pellets
A method of preparing fuel pellets includes the steps of providing a feedstock in the form of agricultural hull fibres having a moisture content of about 10 to about 16%; and compressing and extruding the agricultural fibre feedstock through a die to obtain fuel pellets in the form of small cylinders having a diameter of about ⅜ inch to ¾ inch or more, said pellets having an ash content of about 1.1% to about 20% by weight and a calorific value of about 7,000 BTUs per pound of fuel on a dry basis. The agricultural hull fibres may be derived from all whole grains and seeds. For example, are comprised of at least one of corn bran fibre, rye bran fibre; oat bran fibre, rice bran fibre, soy bran fibre, canola bran fibre and wheat bran fibre. The method may include the step of pre-treating the agricultural whole grain and seed hull fibre feedstock with high temperature steam before being formed into pellets at a sufficient temperature and sufficient time to activate hemicellulose within the fibre as a binding agent. The method may include the step of mixing the agricultural whole grain and seed hull fibre feedstock with a sequestering agent before being formed into pellets for sequestering alkali metal vapors and raising the fusion point of the inorganic elements during combustion of the pellets. The sequestering agent may be calcium carbonate added in amounts up to about 0.5% by weight. The pellets contain additives comprised of ammonium nitrate, calcium, manganese, magnesium, aluminum, barium, iron, potassium and amorphous silicate, which sequester potassium and chlorides and alter the fusion point of the inorganic elements present in the fuel.
Owner:EVERGREEN BIOFUELS
Syringe assembly having disabling mechanism
A syringe assembly having passive disabling structure includes a barrel and a plunger rod assembly. The plunger rod assembly includes a plunger rod and a stopper connected by an indexing locking element. The number of strokes of the syringe plunger before the stopper is locked into the barrel rendering the syringe assembly unusable is determined by the number of detents on the plunger rod and stopper which engage the locking mechanism. Upon completion of the final delivery stroke, any attempt to withdraw the plunger rod from the barrel will cause the locking element to engage the barrel and trap the stopper in the barrel preventing further use of the syringe.
Owner:BECTON DICKINSON & CO
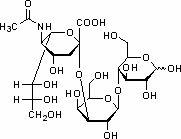
Preparation method of 3'-sialic acid lactose
InactiveCN102154163AChange the status quo of less ingredientsEfficient additionBacteriaMicroorganism based processesEscherichia coliSialic acid
The invention provides a preparation method of 3'-sialic acid lactose, belonging to the technical field of biological engineering. The preparation method comprises the following steps of: taking colibacillus CCTCC (colibacillus China center for type culture collection) NO: M208088 as a starting strain, adding a fermentation medium into a fermentation tank, fermenting for 2-6h, then adding a fed batch culture medium, and adding lactose in a flowing way at the mid-later period of the fermentation; and centrifuging the fermentation liquid to obtain liquid supernatant 1 and a thallus, diluting the centrifuged thallus by adding water and splitting in a heating way, recentrifuging to obtain liquid supernatant 2, merging the liquid supernatant 1 and the liquid supernatant 2, and absorbing, desorbing and vacuum drying by ion exchange resin to obtain the 3'-sialic acid lactose. A mass of the 3'-sialic acid lactose can be prepared by the CCTCC NO: M208088. The 3'-sialic acid lactose can change the current situation that the sialyloligosaccharide component is less in exogenous adding substances in conventional baby milk, and can provide the guarantee to add more efficient sialic acid trophic factors into the baby milk.
Owner:朱莉
Methods and apparatus for automatically adding a media component to an established multimedia collaboration session
ActiveUS8775511B2Improve efficiencyFacilitates free-flowingTelevision conference systemsMultiple digital computer combinationsClient-sideFree flow
A multimedia collaboration system that facilitates more efficient, free-flowing collaboration sessions. In order to make addition of new participants, media components, and or network access device to a collaboration session more efficient, client devices associated with each participant can store endpoint address information that can be automatically obtained by the multimedia collaboration system. The endpoint address information can then be used to add the new participants, media components, and or network access device.
Owner:INT BUSINESS MASCH CORP
Adsorption Heat Pump, Adsorption Refrigerator and Adsorber Elements Therefor
InactiveUS20090217691A1Efficiently dissipatedProne to feverDomestic cooling apparatusBoiler absorbersHeat conductingEngineering
The invention relates to an adsorber element for a heat exchanger and an adsorption heat pump or adsorption refrigerator that contains at least one such adsorber element. The adsorber element includes a heat-conducting solid body and a sorption material for a vaporous adsorbate arranged on the surface of this solid body. A fluid-tight foil composite is arranged on the outer surface of the open-pore solid body, at least in the areas in which a contact with a heat transfer fluid is provided, wherein this adsorber element is embodied such that the heat exchange between the open-pore solid body and the heat transfer fluid can take place via the fluid-tight foil composite.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Fully biodegradable and multi-functional plastic mulch
ActiveCN103289134AFully biodegradableCreate pollutionClimate change adaptationPlant protective coveringsEcological environmentAdditive ingredient
The present invention provides fully biodegradable and multi-functional plastic mulch. The plastic mulch comprises, by weight percent: natural biopolymers of starch or derivatives thereof, biodegradable synthetic polymers, an interfacial reinforcer, a compound plasticizer with urea as a main ingredient, a nitrogen phosphorus and potassium compound fertilizer, pesticides, herbicides and trace fertilizers. The plastic mulch of the present invention not only has heat and moisture preservation functions, and is fully biodegradable after use, eliminating the contamination to soil causes by residual plastic mulch debris; and functional additives of fertilizers and nutrients, pesticides, herbicides etc. in the plastic mulch are sustainedly released as the plastic munch degrading, so the plastic mulch has long lasting effects of weed controlling, pest killing, and sustainedly released fertilizing, significantly reducing the use amount of fertilizers and pesticides, decreasing costs, and protecting the ecological environment. The invention also provides a method for preparing the multi-functional plastic mulch.
Owner:ANHUI XUELANG BIOTECHNOLOGY CO LTD
Organic light emitting diode display
InactiveUS20120267660A1Increased durabilityImproves vapor transmission resistanceElectroluminescent light sourcesSolid-state devicesDisplay deviceSealant
An organic light emitting diode (OLED) display includes: a display substrate; an organic light emitting element formed over the display substrate; a thin film encapsulation layer formed over the display substrate to cover the organic light emitting element; an encapsulation member facing the display substrate with the organic light emitting element and the thin film encapsulation layer therebetween; a sealant surrounding the organic light emitting element and the thin film encapsulation layer disposed between the display substrate and the encapsulation member, and bonding the display substrate and the encapsulation member; and a light control member disposed between the encapsulation member and the thin film encapsulation layer.
Owner:SAMSUNG DISPLAY CO LTD
Multi Passage Fuel Manifold and Methods of Construction
ActiveUS20100051726A1Minimize the numberSmall sizeContinuous combustion chamberTurbine/propulsion fuel flow conduitsEngineeringGas turbines
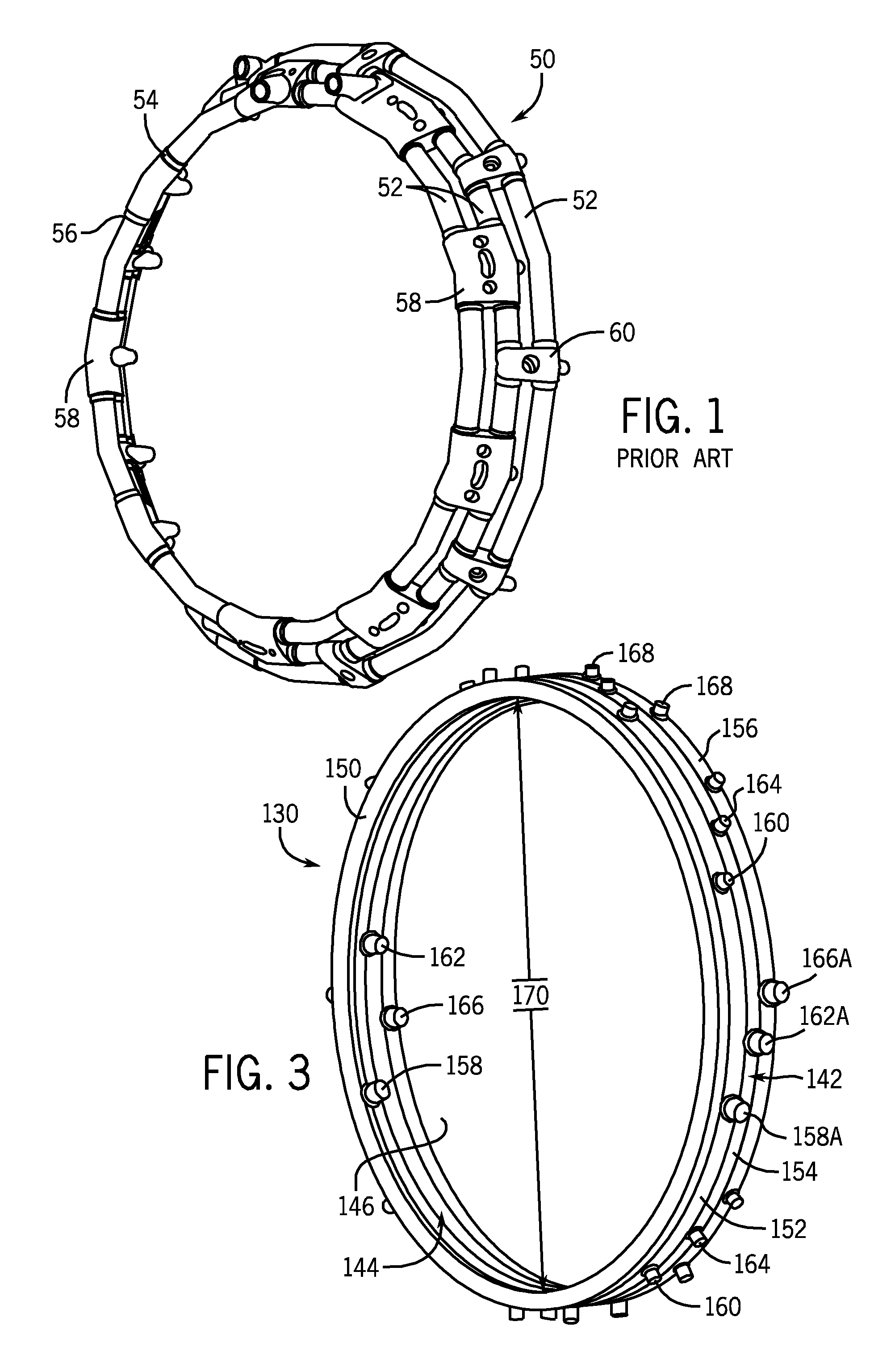
Integrally formed, multi zone fuel manifolds for gas turbine engines and methods of construction are provided. The fuel manifold includes a plurality of annular channel members positioned adjacent each other, aligned and coupled together at the inner and outer peripheral sides thereof, with each pair of channel members defining a separate fluid conduit or passage within the manifold assembly. The fuel manifold can be constructed of any number of stacked and secured channel members to provide a compact multi zone fuel manifold having the desired number of fluid conduits or passages with a minimum number of sealed joints.
Owner:WOODWARD GOVERNOR CO
Positioning apparatus
InactiveUS7152331B2Low stiffnessIncrease stiffnessSemiconductor/solid-state device manufacturingUsing electrical meansBall screwLocation Equipment
A positioning apparatus has a stage, guide elements provided on both ends of the stage, and drive elements which are provided at one of both ends of the stage and move the stage along the guide elements. Like linear guide rails 61A, 61B and linear guide bearings 23A, 23B, two guide elements are provided in an area where a ball screw shaft 52 serving as a drive element is placed. One guide element is provided in an area where a non-drive element is provided.
Owner:NSK LTD
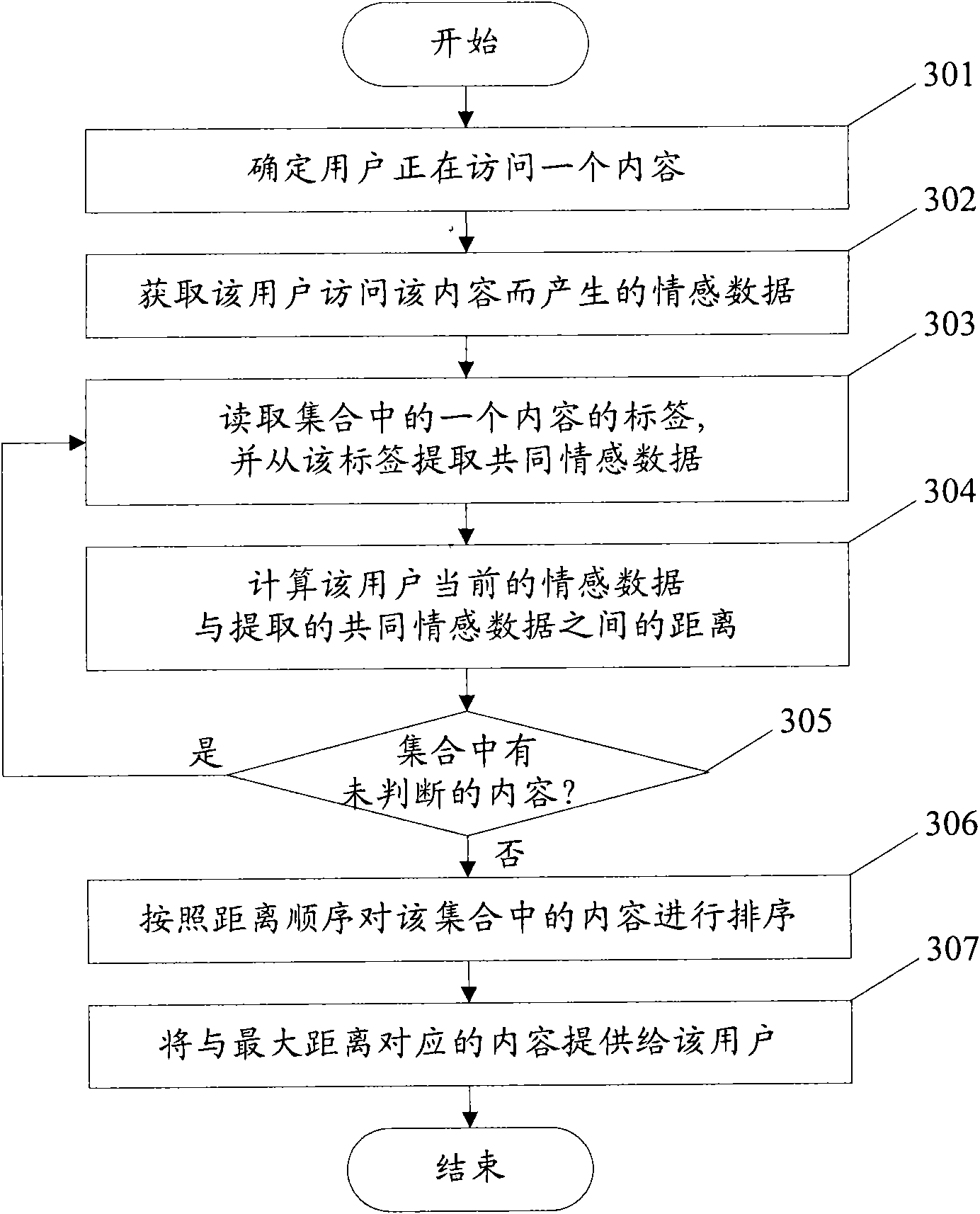
Methods and device for adding and processing label with emotional data
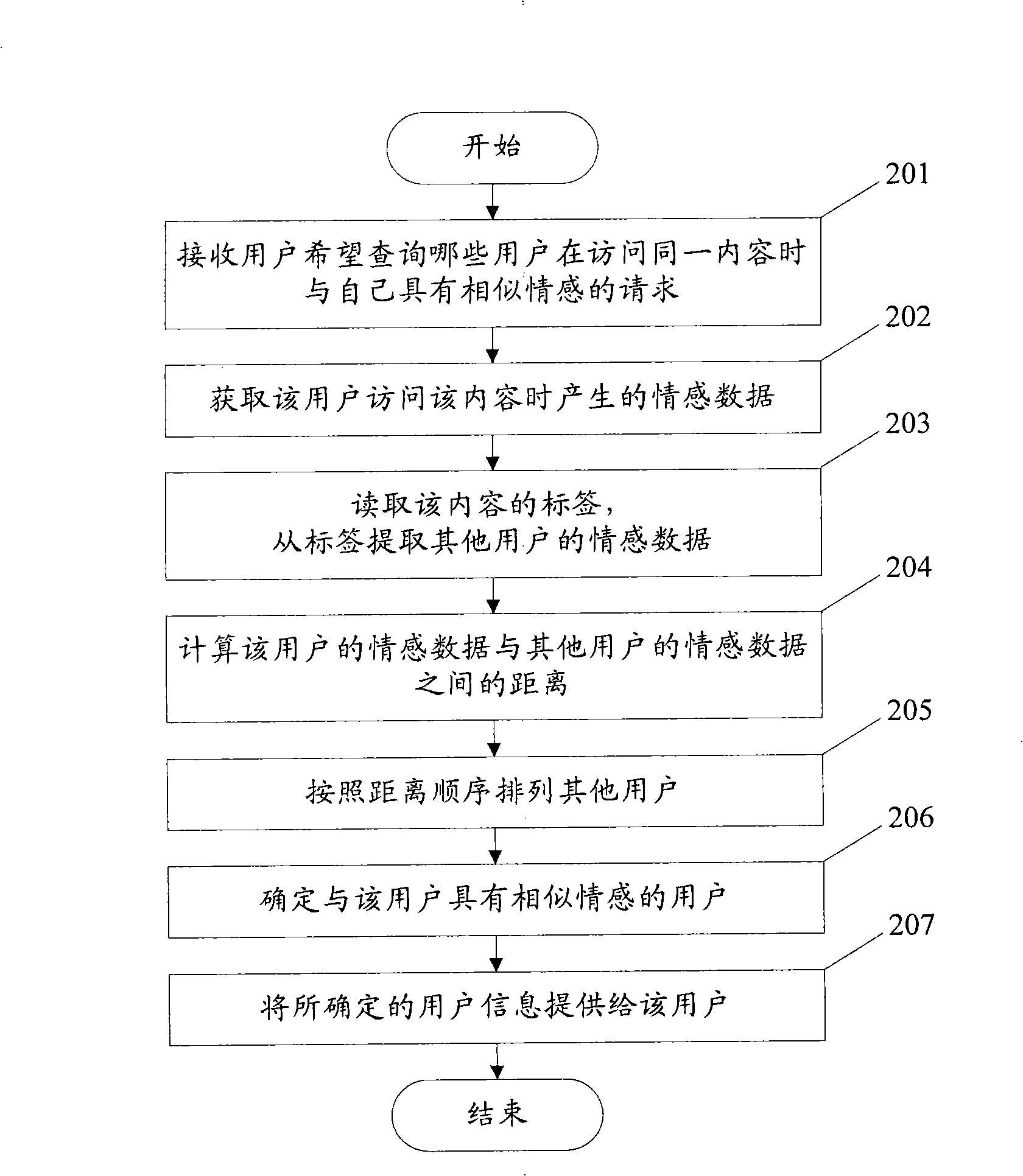
InactiveCN101853259AEasy to addQuick addMarketingSpecial data processing applicationsComputer science
The invention discloses a method and a device for adding and processing a label with emotional data. The method for adding the label with emotional data comprises the following steps: receiving emotional data generated when a user visits the content, wherein the emotional data is obtained according to measurable physiological parameters reflecting the emotions of the user; and based on the emotional data, adding the label with the emotional data to the content. The method for processing the label with the emotional data comprises the following steps: extracting the emotional data from the label with the emotional data, wherein the label corresponds to one content; and providing services by utilizing the emotional data. By using the methods and the device, the label with the emotional data into the content can be conveniently, quickly and efficiently added, and the user experience can be improved.
Owner:INT BUSINESS MASCH CORP
Shimless aligner
InactiveUS7905465B1Cost effectiveMinimal downtimePortable framesLifting devicesVertical alignmentEngineering
A shimless aligner for insertion between a machine foot and base to align the foot relative to the base, which foot and base are secured together by a hold-down bolt extending between the foot and base. The aligner includes, a top plate having a slanted bottom surface, a taper wedge having a slanted top surface slidably engaging the slanted bottom surface of the top plate and further having a vertical alignment rod extending substantially laterally, a bottom plate below the taper wedge, and a back plate attached substantially perpendicularly at one end of the bottom plate. For receiving the hold-down bolt, the top and bottom plates have a corresponding hole, while the taper wedge has a slot. Said back plate has a hole for the vertical alignment rod to slidably engage the hole thereby preventing rotation of the taper wedge during vertical alignment operations and preserving bent foot corrections.
Owner:SOFTWAY INDAL SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com