Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
48 results about "Intel HEX" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Intel HEX is a file format that conveys binary information in ASCII text form. It is commonly used for programming microcontrollers, EPROMs, and other types of programmable logic devices. In a typical application, a compiler or assembler converts a program's source code (such as in C or assembly language) to machine code and outputs it into a HEX file. Common file extensions used for the resulting files are A43 or HEX. The HEX file is then read by a programmer to write the machine code into a PROM or is transferred to the target system for loading and execution.
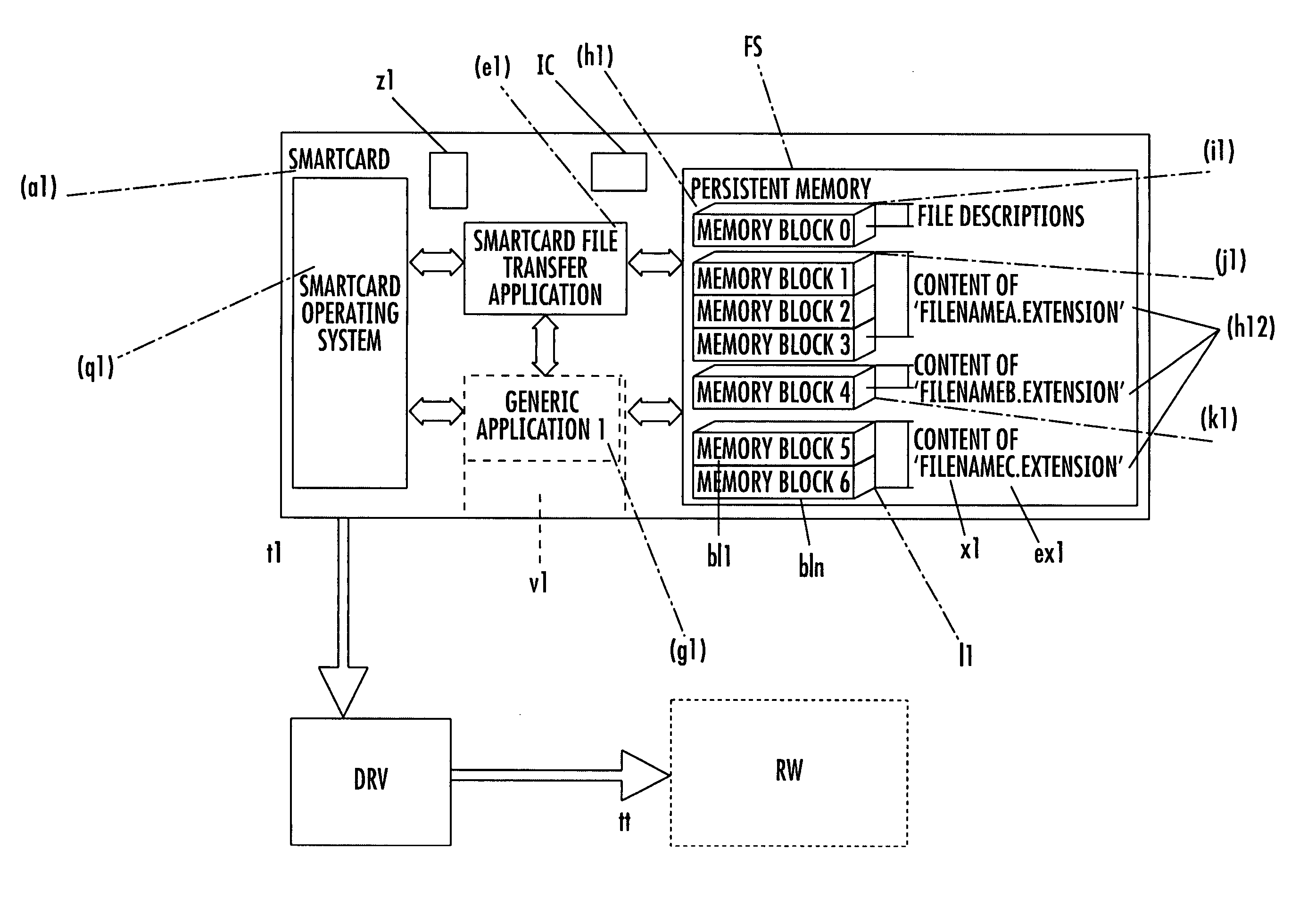
IC card file system
InactiveUS20070152070A1AccessibilityAcutation objectsDigital data information retrievalIntel HEXApplication software
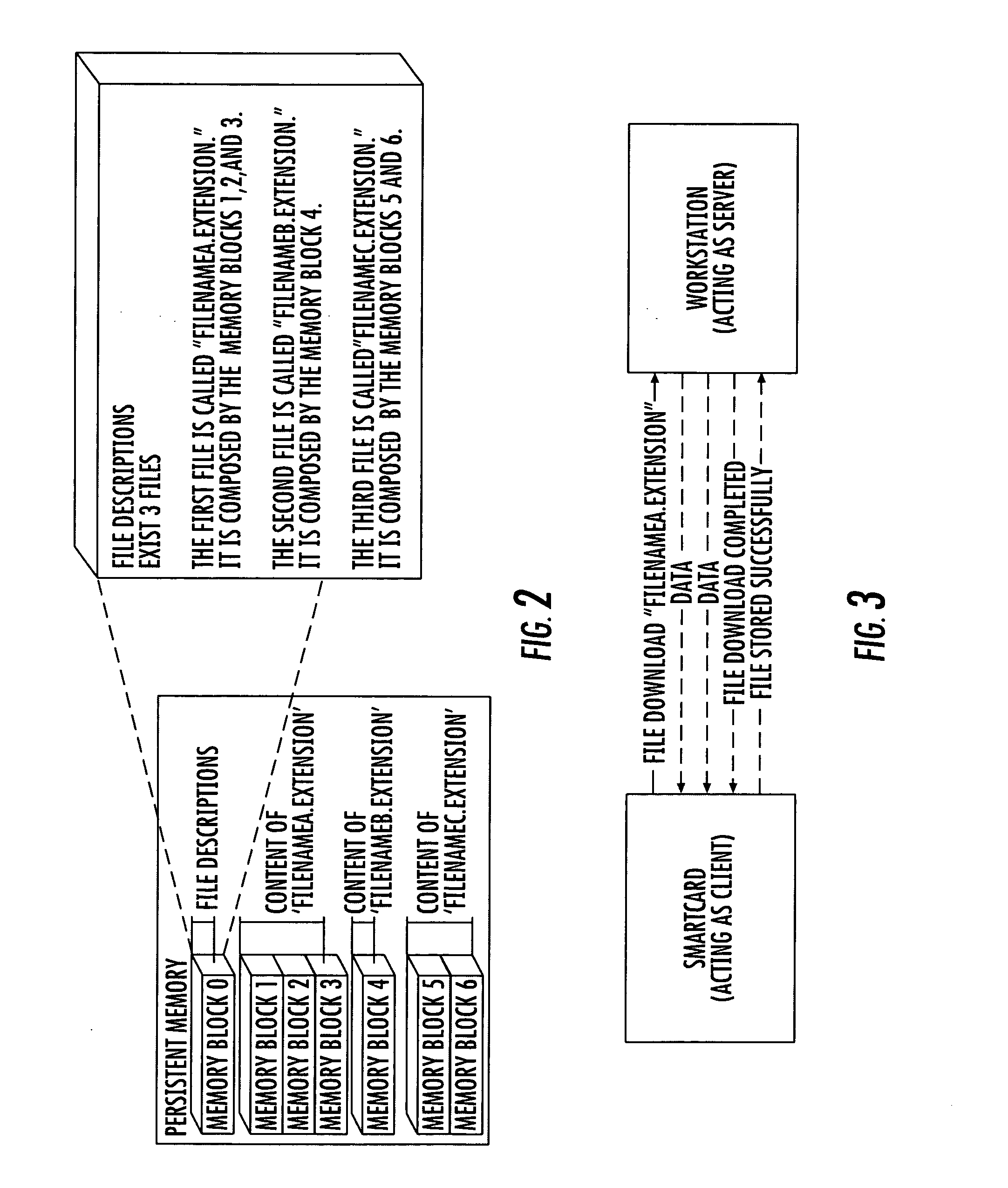
File system for IC CARD comprising an integrated circuit IC, non volatile memories ROM and / or E2PROM and at least a volatile memory RAM, for organizing files storage inside the non volatile memories and defining, through a logical structure, their accessibility by an IC Card application, stored inside one of said non volatile memories or IC or loaded in the volatile memory and in communication with an external read-write device; an interchange application, stored inside one of said non volatile memories, drives the organization of files in an additional tag-length logic structures of arbitrary length, allowing the identification of files through alphanumeric identifiers of arbitrary length and extension, and their accessibility by an external read-write device, eventually non IC card purpose, like a workstation a personal computer or a PDA interconnected to the IC Card by means of standard communication interface. The file system organizes said tag-length logic structure as individually memory blocks, each identified by an hexadecimal identification number and a block size and one of these memory blocks, more particularly one per non volatile memory, describes the content of the non volatile memory, comprising the number of files stored, their file name and extension and, for each file, the location of memory blocks composing its content.
Owner:STMICROELECTRONICS INT NV
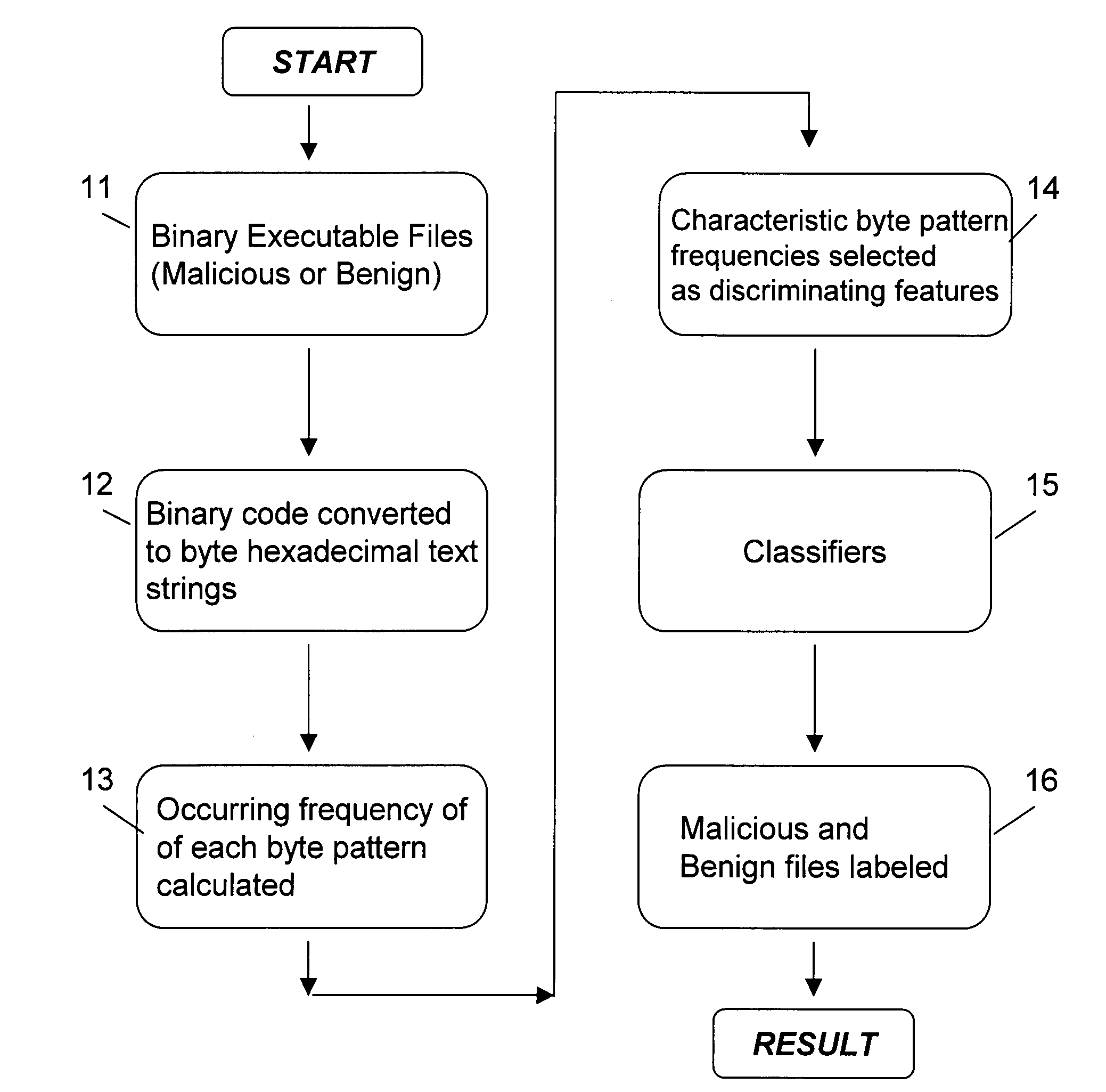
Detection of malicious computer executables
A method of detecting malicious binary executable files is accomplished by inputting a binary executable file; converting the binary executable file to byte hexadecimal text strings; calculating the frequency of each byte pattern in the byte hexadecimal text strings; selecting characteristic byte pattern frequencies as discriminating features; classifying the discriminating features as malicious or benign; labeling the binary executable file as malicious or benign; and outputting the labeled malicious or benign binary executable file.
Owner:LOS ALAMOS NATIONAL SECURITY
Virtual machine data backup
Disclosed is a method and system for efficiently backing up a virtual machine file. A virtual machine file is logically divided into a plurality of fixed-size blocks of similar size, for example, a number of 1 MB data blocks. An MD5 hash value is generated from the contents of each block. Each block is written to a file having a filename that includes a filesystem-compliant form (e.g., hexadecimal form) of the computed MD5 hash value. A backup device includes a directory hierarchy having a plurality of first-level directories corresponding to the first two bytes of the hash value, and a plurality of second-level directories corresponding to the next two bytes of the hash value. The blocks are uniquely stored in the directory corresponding to the byte value pairs of the hash. The present disclosure provides data integrity checking and reduces storage requirements for duplicative, redundant, or null data.
Owner:PHD VIRTUAL TECH
Detection of malicious computer executables
A method of detecting malicious binary executable files is accomplished by inputting a binary executable file; converting the binary executable file to byte hexadecimal text strings; calculating the frequency of each byte pattern in the byte hexadecimal text strings; selecting characteristic byte pattern frequencies as discriminating features; classifying the discriminating features as malicious or benign; labeling the binary executable file as malicious or benign; and outputting the labeled malicious or benign binary executable file.
Owner:LOS ALAMOS NATIONAL SECURITY
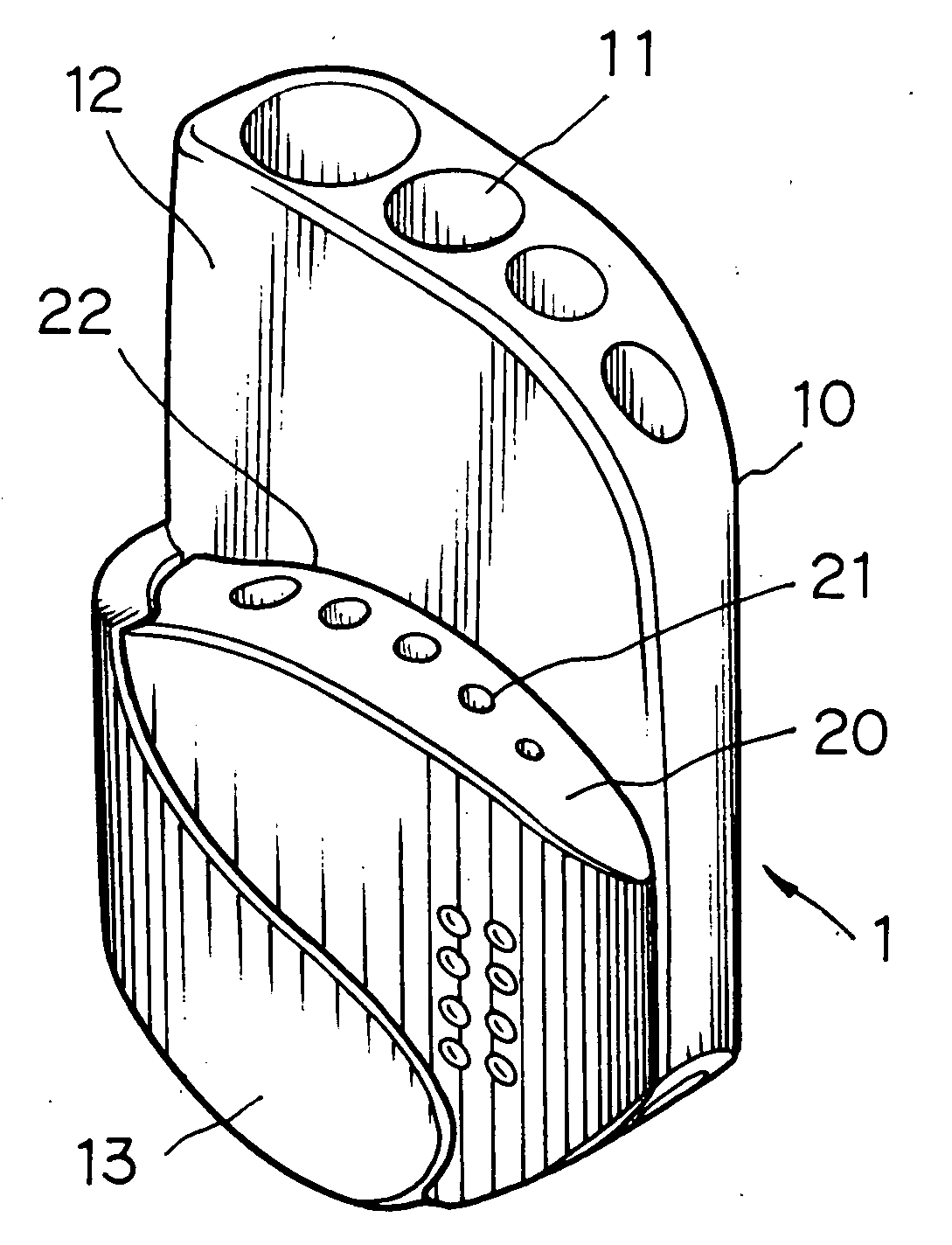
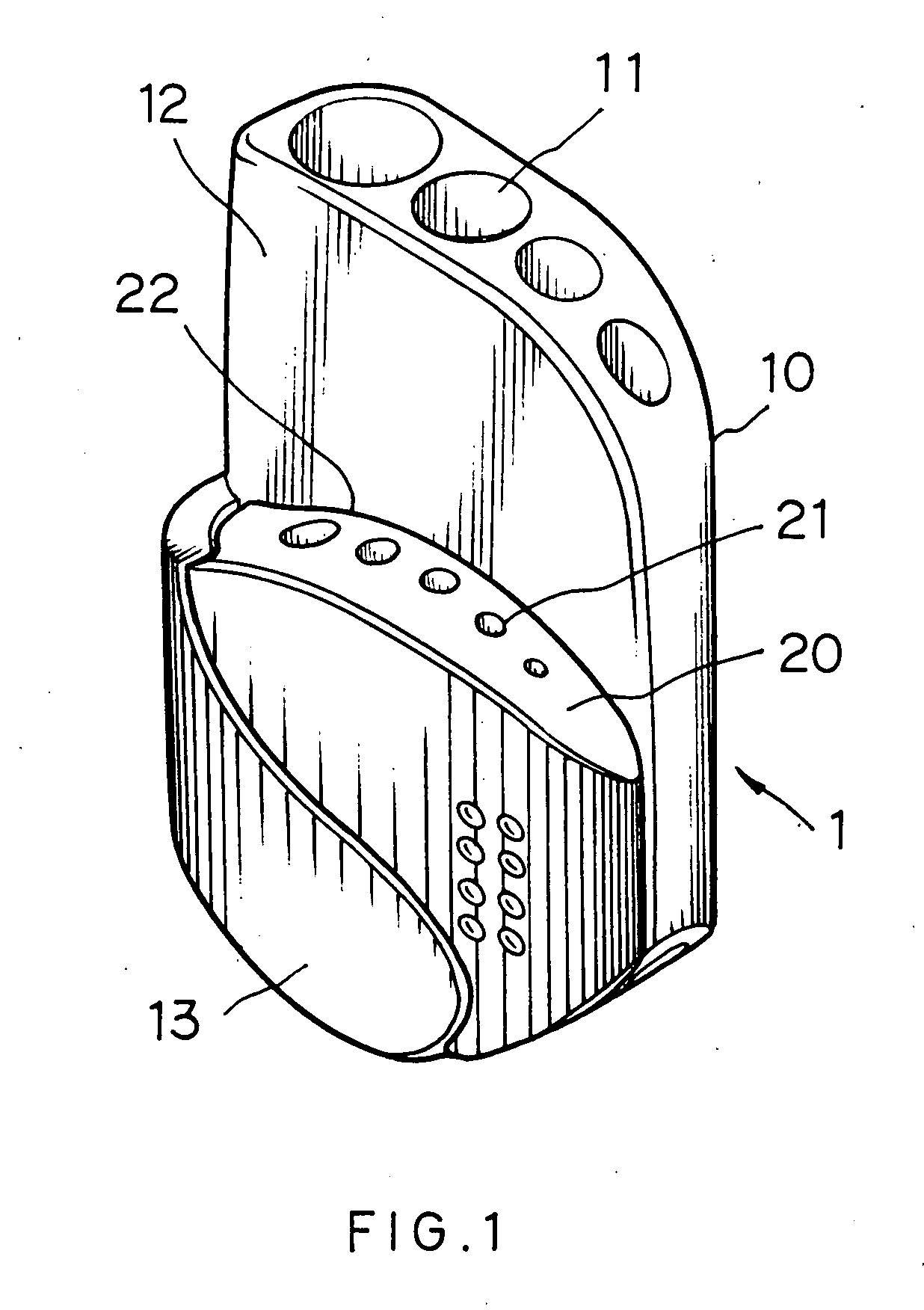
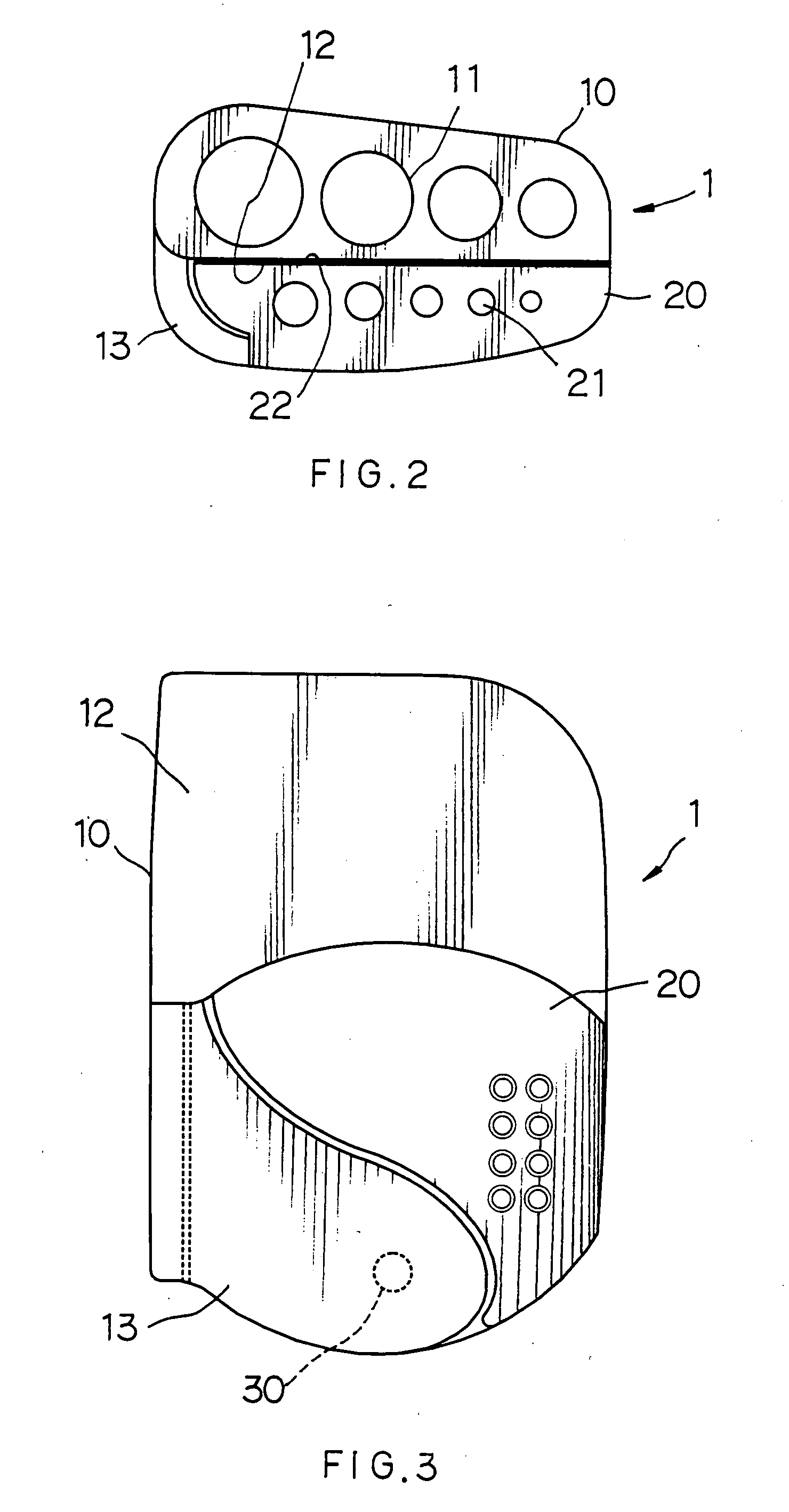
Hex key holder with mechanism for pivotably securing a smaller block to a larger block for facilitating access to hex keys in the smaller block
A hex key holder in one embodiment includes a larger block including a plurality of penetrating channels of circular section for retaining a plurality of first hex keys, and a curved arm extending forwardly from one side of the larger block, a smaller block including a plurality of penetrating channels of circular section for retaining a plurality of second hex keys smaller than the first hex keys, and a pivot for pivotably securing the smaller block between the larger block and the arm. The invention can facilitate access to the second hex keys by tilting the smaller block.
Owner:JACO INT CORP
System and method for filtering message
ActiveUS7725550B2Multiple digital computer combinationsData switching networksIntel HEXComputer hardware
A system and method for message filtering are disclosed. A conversion target letter table is generated which stores information on letters that may be used to elude filtering, the table storing the hex code information of each letter that may be used for eluding filtering and the conversion letter information regarding the conversion letter to which each letter is to be converted. A hex code of a message text inputted by a user is compared with the hex codes of the table, and when a conversion target letter is included, it is converted to the conversion letter stored in the conversion target table associated with the letter. When the conversion is completed, it is determined whether or not pre-configured prohibited words are included in the converted message; and message filtering is performed.
Owner:NHN CORP
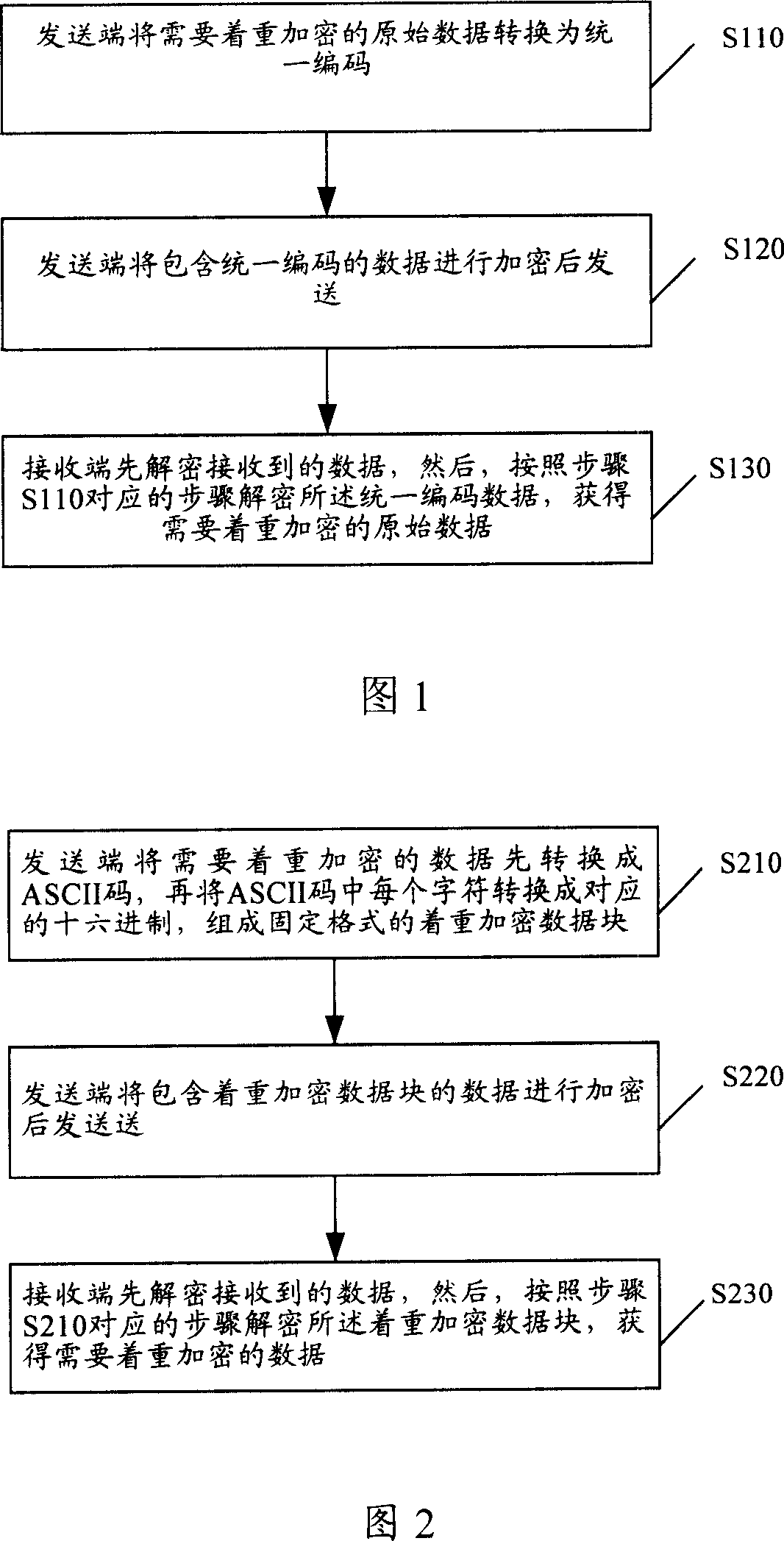
Data safety transmission method
InactiveCN1988441AImprove securityGuaranteed reliabilitySecuring communicationIntel HEXComputer hardware
This invention relates to a method for transmitting data safely including: 1, a transmission end codes the original data necessary to be encrypted uniformly, 2, the transmission end ciphers the contained code data then transmits them, 3, the receiving end de-ciphers the received data then decodes said code data in terms of step 1 to get the encrypted original data, which are coded as follows: converting the necessary ciphered original data to ASCII code, then converts every character in the ASCII code to a corresponding hexadecimal system to form an emphasized ciphered data block of fixed format, or first of all converts the necessary emphasized encrypted data to the hexadecimal to form the data block with fixed format.
Owner:CHINA UNIONPAY
Method and system for selectively recording system information
Owner:L3 TECH INC
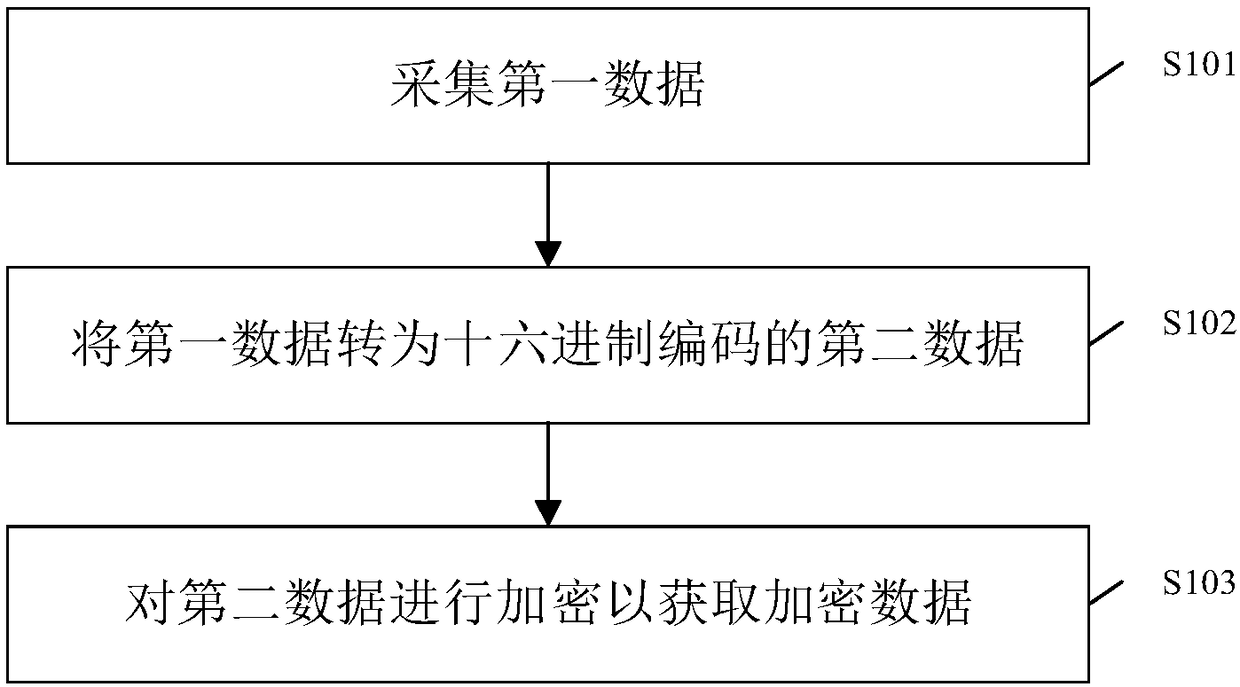
Data encryption method
InactiveCN108429735AEnsure safetyIncrease the difficultyKey distribution for secure communicationMultiple keys/algorithms usageIntel HEXComputer hardware
The invention provides a data encryption method. The data encryption method comprises the following steps that first data is acquired, wherein the first data is fingerprint data, identity card data, adigital cipher and / or MF card data; the first data is converted into hexadecimal coded second data; and the second data is subjected to a hardware encryption mechanism and a software encryption mechanism to acquire encrypted data. According to the data encryption method, by means of the process that the first data is acquired and converted into the hexadecimal coded second data, and then the second data is encrypted to acquire the encrypted data, the security of the data can be guaranteed.
Owner:陈柱
Method and apparatus for converting between different digital data representation formats
InactiveUS6263353B1Digital computer detailsHandling data according to predetermined rulesIntel HEXDigital data
A method and apparatus for converting digital data representations, such as network addresses of different computer networks. Input data, which in one embodiment includes a hexadecimal network address, contains a plurality of bytes, with each byte having a plurality of digits arranged in positions. A first set of digits from the bytes is selected having a first digit position. The digits in the first set are shifted to a second digit position to generate a first resultant. A second set of digits is selected having a third digit position. The digits in the second set are shifted to a fourth digit position to generate a second resultant. The first and second resultants are summed to generate a converted output network address.
Owner:ADVANCED MICRO DEVICES INC
System and Method for Filtering Message
ActiveUS20080263159A1Multiple digital computer combinationsData switching networksIntel HEXComputer hardware
A system and method for message filtering are disclosed. A conversion target letter table is generated which stores information on letters that may be used to elude filtering, the table storing the hex code information of each letter that may be used for eluding filtering and the conversion letter information regarding the conversion letter to which each letter is to be converted. A hex code of a message text inputted by a user is compared with the hex codes of the table, and when a conversion target letter is included, it is converted to the conversion letter stored in the conversion target table associated with the letter. When the conversion is completed, it is determined whether or not pre-configured prohibited words are included in the converted message; and message filtering is performed.
Owner:NHN CORP
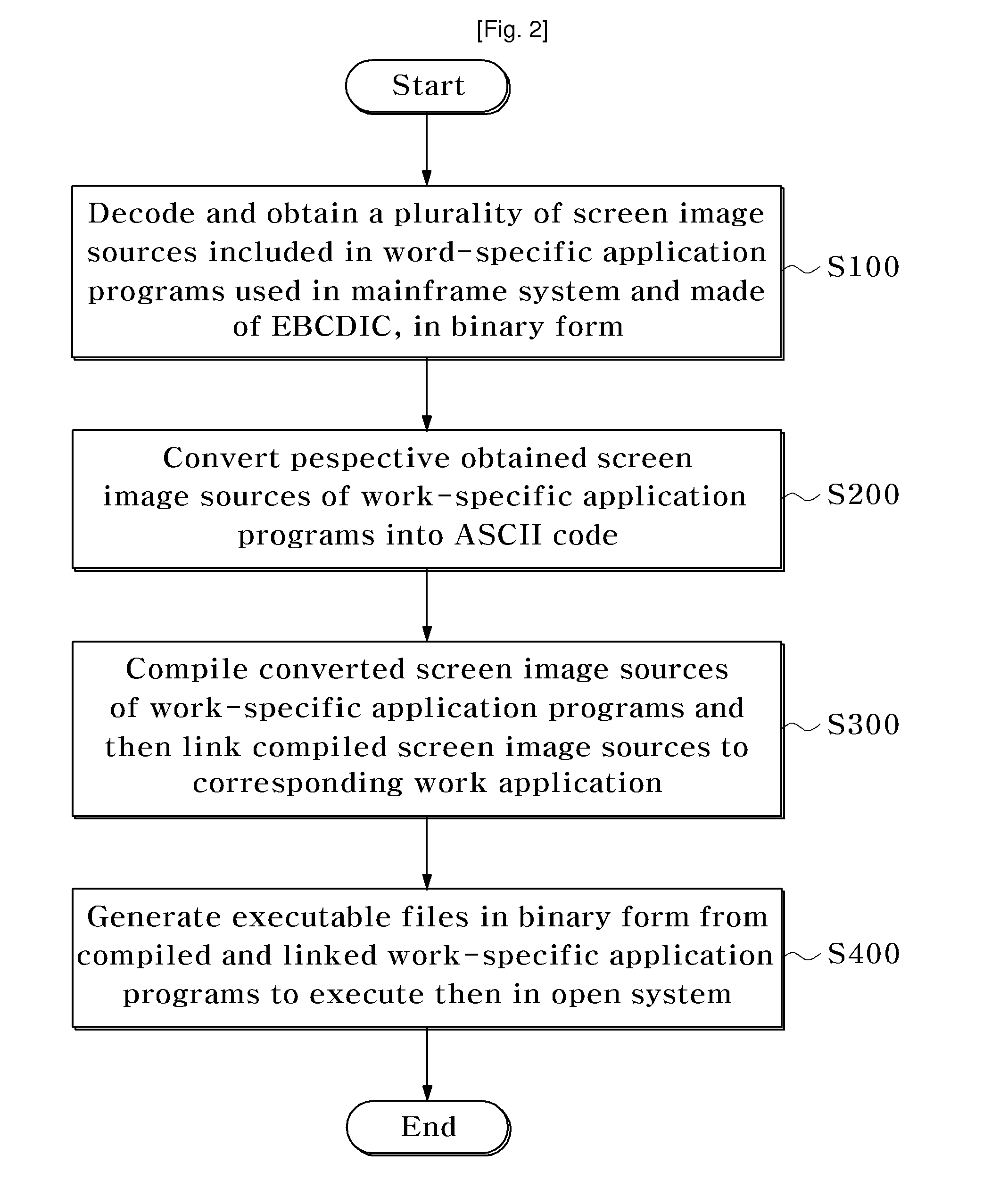
Migration apparatus which convert application program of mainframe system into application program of open system and method for thereof
InactiveCN101553779AReduce errorsEfficient reuseProgram code adaptionProgram loading/initiatingIntel HEXEBCDIC
The invention provides a migration apparatus and method for converting an application program of a mainframe system into an appropriate application program for an open system. The migration apparatus includes: a source obtaining module connected with the mainframe system, and decoding and obtaining sources of work-specific application programs made of Extended Binary Coded Decimal Interchange Code(EBCDIC) in binary form; a code conversion module converting the respective sources of the work-specific application programs obtained by the source obtaining module into American Standard Code for Information Interchange (ASCII) code, hexadecimal characters being converted to correspond to ASCII code using a previously set hexadecimal code conversion table; a compiling and link processing module compiling the sources of the work-specific application programs converted by the code conversion module and then bundling the compiled sources of the work-specific application programs with corresponding work application programs; and an executable file generation module generating executable files in binary form from the work-specific application programs processed by the compiling and link processing module to execute them in an environment of the open system. The migration apparatus and method efficiently reuse a conventionally used application program via the rehosting process of converting a mainframe system into an open system.
Owner:SAMSUNG SDS CO LTD
Adaptive Transaction Message Format Display Interface for Use in a Message Data Exchange System
ActiveUS20080016244A1Multiple digital computer combinationsOffice automationIntel HEXData transformation
A system provides an integration engine debugging and trace function that adaptively captures and displays trace information and promotes easier and more efficient troubleshooting. A system adaptively displays transaction message data for use with a data exchange system for exchanging data between different computer systems using different data formats. The system includes a repository of data comprising transaction messages communicated between different computer systems using different data formats. A data converter converts transaction message data into Hex and non-Hex representations. A display processor provides data representing a first display image including data representing a single transaction message in both Hex and non-Hex data format and enabling a user to initiate generation of a second display image for presenting the transaction message exclusively in a non-Hex representation.
Owner:CERNER INNOVATION
Data compression method for supporting virtual memory management in a demand paging system
InactiveCN101356509AMemory architecture accessing/allocationMemory adressing/allocation/relocationData compressionIntel HEX
A virtual memory management unit ( 306 ) includes a redundancy insertion module ( 307 ) which is used for inserting redundancy into an encoded data stream to be compressed, such that after being compressed each logical data block fits into a different one from a set of equal-sized physical data blocks of a given size. For example, said redundancy may be given by no-operation (NOP) instructions represented by a number of dummy sequences of a given length (L) into an encoded data stream to be compressed, each dummy sequence being composed of a number of identical binary or hexadecimal fill-in values.
Owner:SONY ERICSSON MOBILE COMM AB
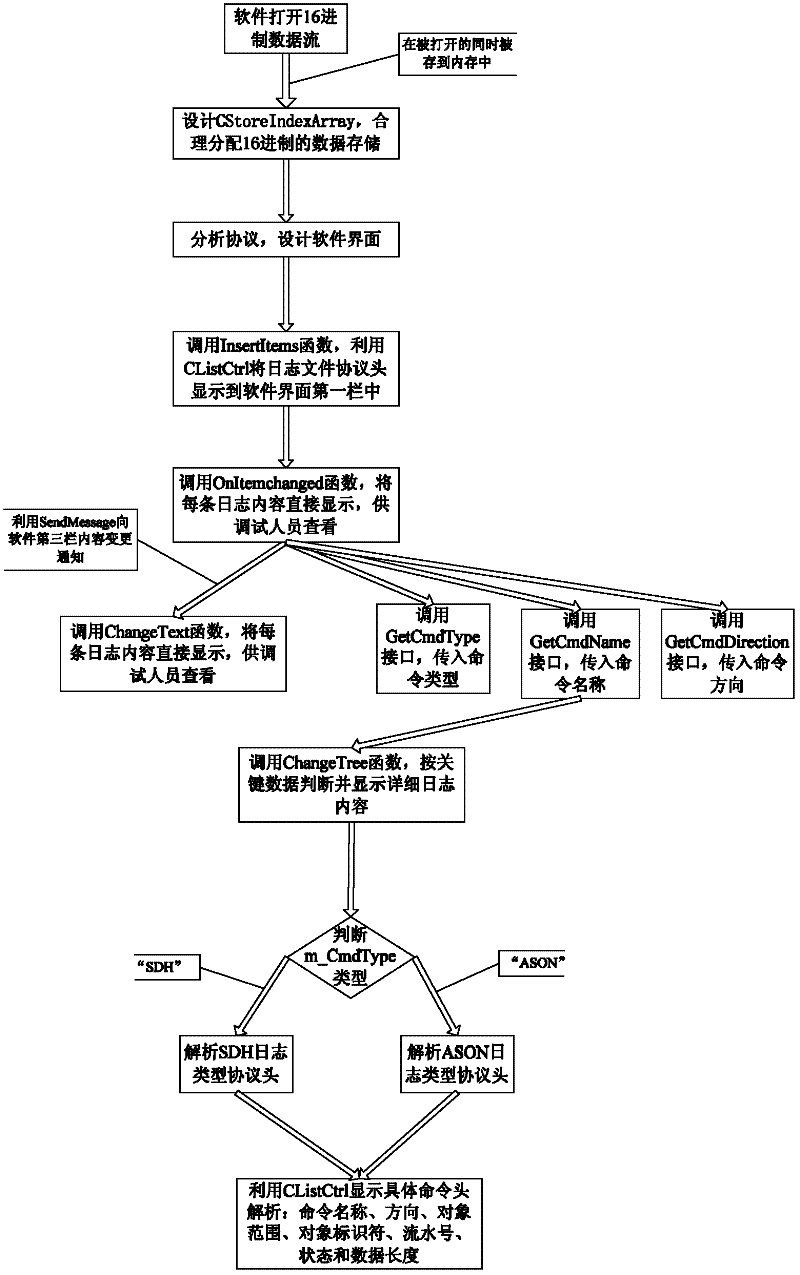
Method for analyzing and managing log file with hexadecimal data
The invention relates to a method for analyzing and managing a log file with hexadecimal data, which comprises the following steps: obtaining the content of a log file with hexadecimal data, which is recorded in a form of the hexadecimal data, in the process of opening the log file with the hexadecimal data, and loading the obtained hexadecimal data by using a multi-dimensional array; and combining the hexadecimal data in the multi-dimensional array and a relevant communication protocol together for analyzing by row division and byte division, reading the content in the hexadecimal data into information which can be directly read and also displaying the information on a man-machine interactive interface, wherein a multi-layer display mode is adopted for the man-machine interactive interface, and the relevant communication protocol is a private communication protocol corresponding to the log file. According to the method disclosed by the invention, the content of a log file with hexadecimal data generated by communication software can be analyzed; and moreover, by combining the relevant communication protocol, the content of the log file, which is recorded by the hexadecimal data, is read into the information which can be directly read, and the information is also displayed by changing the protocol. The method for analyzing and managing the log file with the hexadecimal data can be used for conveniently managing and analyzing the log file with the hexadecimal data.
Owner:FENGHUO COMM SCI & TECH CO LTD
Data interface protocol for two-way radio communication systems
InactiveUS7099680B2Improve abilitiesBackward compatibility is assuredNetwork topologiesRadio transmissionIntel HEXCommunications system
A method and system is disclosed that allows for the designation of over 1,000,000 individual users in a communication system, such as an EDACS system, using the existing five-digit portion of command message utilized for specifying the destination address. This is accomplished by using an Extended Addressing Digital Interface (EADI) protocol using hexadecimal characters in the command message rather than decimal characters, thereby creating an “extended addressing” (EA) capability. The largest five-digit hexadecimal number, FFFFF, corresponds to the decimal number 1,048,575, thereby realizing the ability to exceed one million users, without having to change the size (number of digits) in the command message. Backward compatibility is assured by adding new mode commands that identify a particular command message as being generated by EA compatible equipment.
Owner:PINE VALLEY INVESTMENTS INC
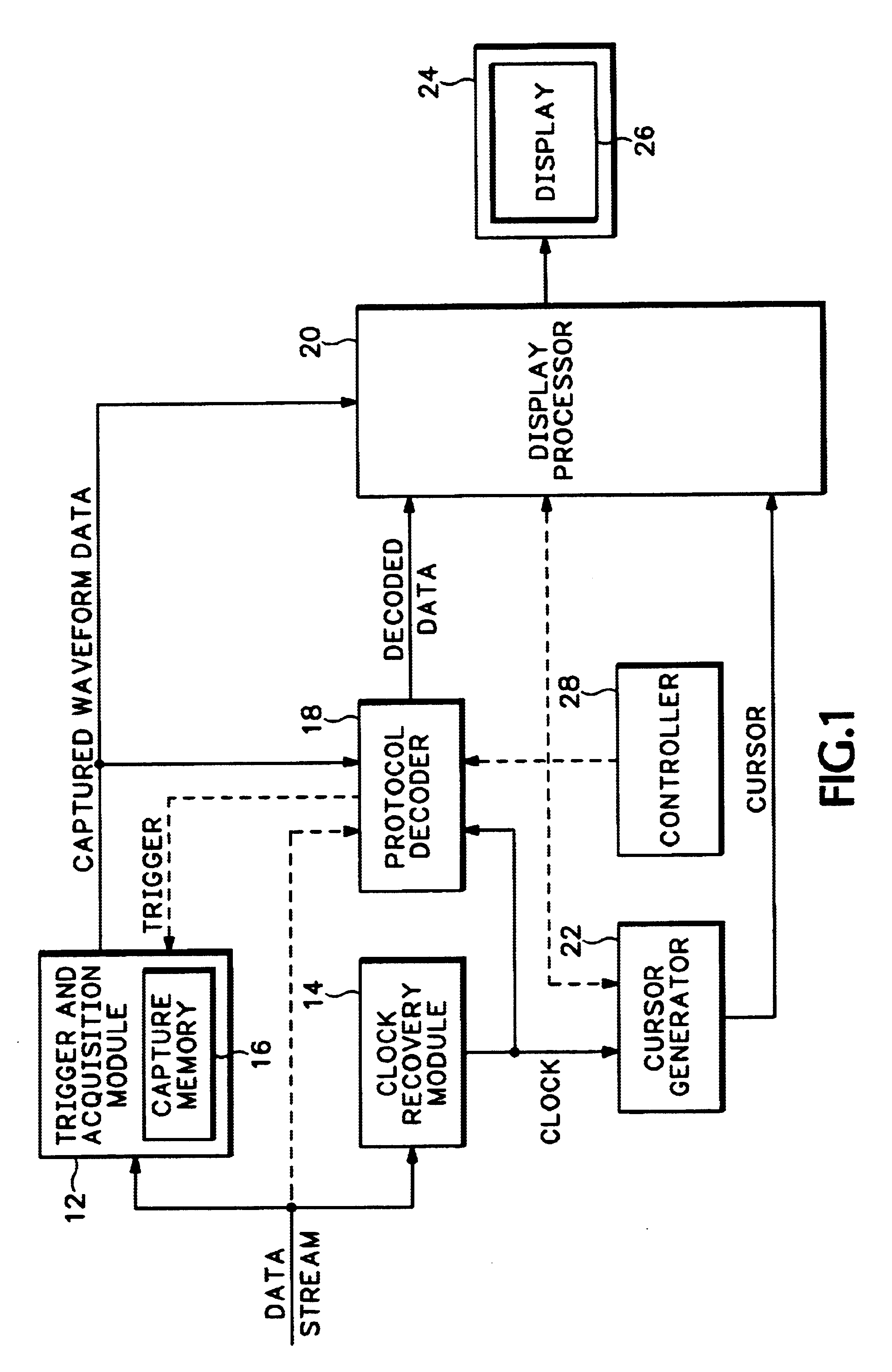
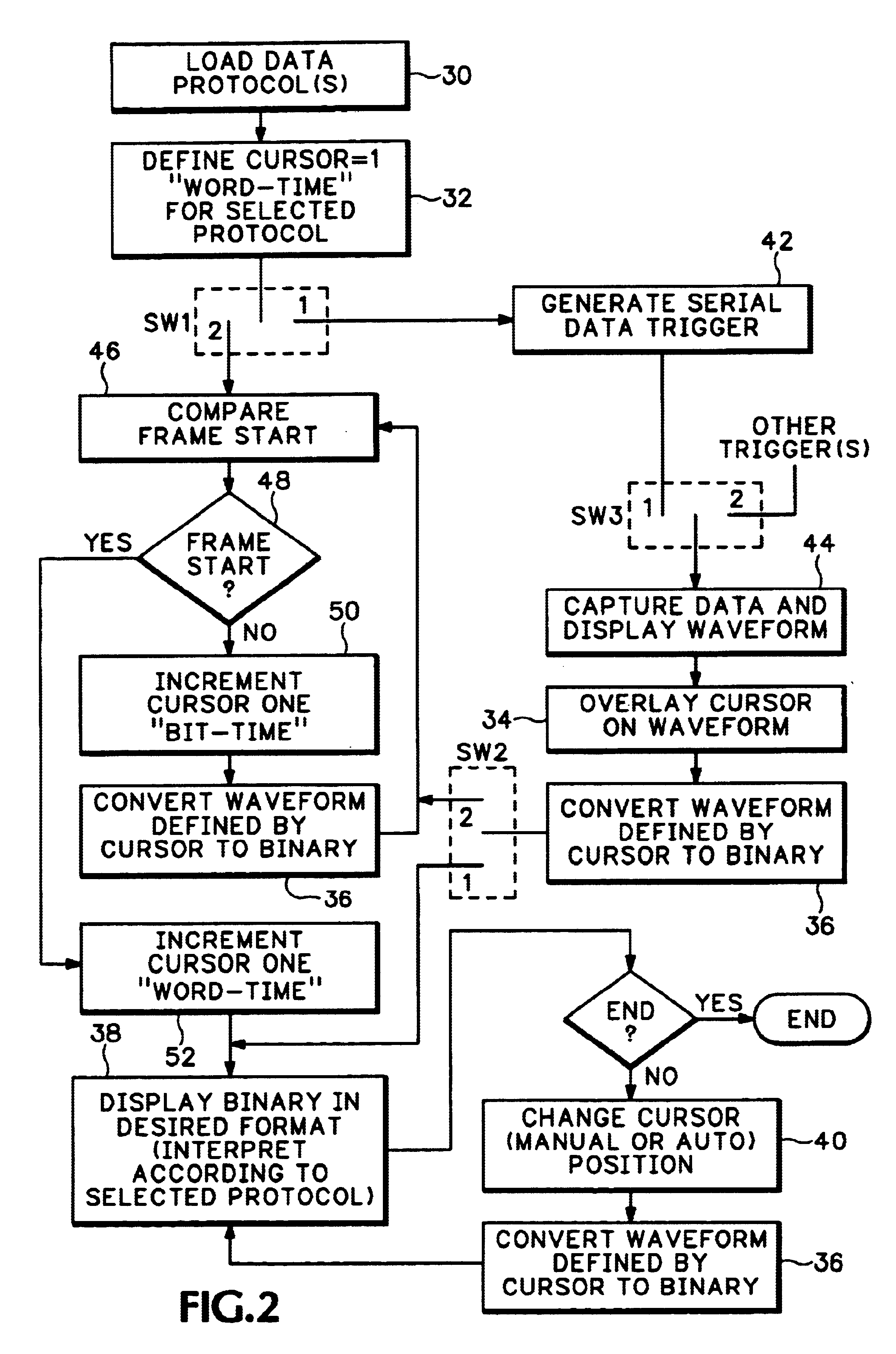
Serial data cursor
InactiveUS6847349B2Cathode-ray tube indicatorsInput/output processes for data processingDigital dataIntel HEX
A serial data cursor for extracting content from an analog waveform representing a serial digital data stream has a horizontal length equal to a “word-time” as determined by parameters of a protocol for the serial digital data stream and a clock recovered from the serial digital data stream. The serial data cursor delimits a portion of the analog waveform, which is then decoded into human readable form, such as binary, octal, hexadecimal, alpha-numeric or the like. A trigger may be generated from a specific parameter of the protocol, such as a frame start, so that the serial data cursor initially highlights a first data word of a frame of the serial digital data stream. Alternatively the decoded portion of the analog waveform may be compared to the specific parameter, and the serial data cursor incremented by a “bit-time” until the specific parameter is found in the serial digital data stream.
Owner:TEKTRONIX INC
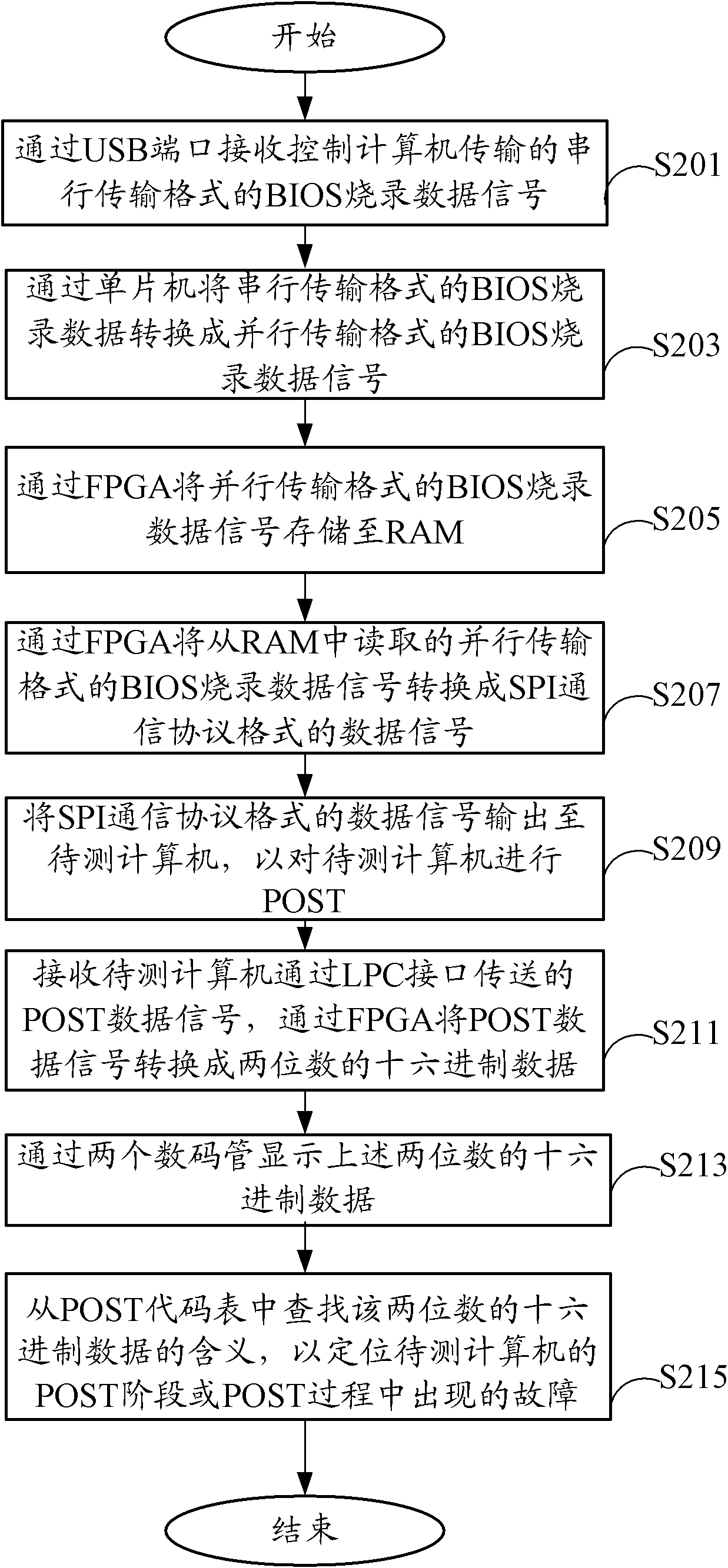
BIOS (Basic Input Output System) debugger and debugging method
InactiveCN102385545AReduce testing costsHigh speedDetecting faulty computer hardwareIntel HEXSerial transfer
The invention relates to a BIOS (basic input output system) debugger and a BIOS debugging method. The BIOS debugging method comprises a single chip microcomputer, an FPGA (field programmable gate array) chip, an RAM (random access memory) and two seven-segment digital tubes, wherein the FPGA chip is connected with the single chip microcomputer, the RAM and the two seven-segment digital tubes. BIOS burning data signals in a series transmission format output by a control computer is converted into the BIOS burning data signals in a parallel transmission format to be output to the FPGA chip by the single chip microcomputer. The BIOS burning data signals in the parallel transmission format is stored into the RAM by the FPGA chip, the BIOS burning data signals read in RAM 30 are converted into data signals in an SPI (serial peripheral interface) communication protocol format and then are output to a computer to be tested, so that the POST (power on self test) of the computer to be tested is conducted. The POST data signals output by the computer to be tested are also converted into two-digit hexadecimal data to be output to the two seven-segment digital tubes for displaying.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Method and system for recording system information
ActiveUS20050005065A1Vehicle testingRegistering/indicating working of vehiclesIntel HEXDocument handling
A method and apparatus for recording data concerning a system is provided. The apparatus comprises a memory card, such as a COMPACTFLASH card, and a processor unit, such as a T2CAS processor unit. The memory card includes a supplemental file that contains instructions as to what data is to be recorded and when the recording should start and stop. To conserve space the supplemental file is written as a sequence of hexadecimal characters whose position in the sequence and binary bit value indicates which data is to be recorded and when. A lookup table can be used to interpret the supplemental file. The processor unit includes or is coupled to a memory card reader / writer.
Owner:L3 TECH INC
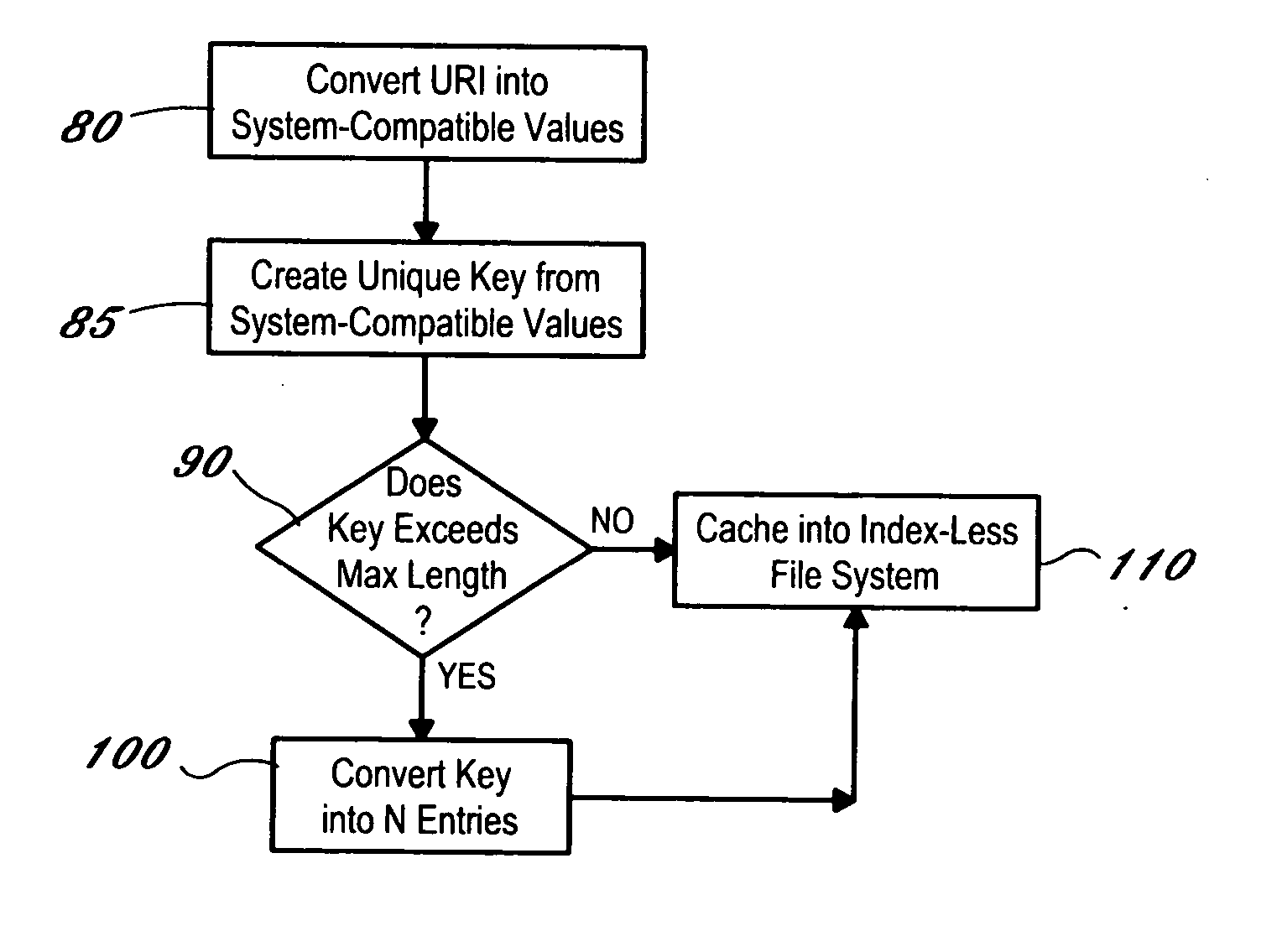
System and method for generating a unique, file system independent key from a URI (Universal Resource Identifier) for use in an index-less VoiceXML browser caching mechanism
InactiveUS20050125372A1Digital data processing detailsMultiple digital computer combinationsIntel HEXWeb browser
A method and system of storing and accessing documents on a computer file system utilizing a file system-independent key for use in an index-less browser caching mechanism. The present invention is a method and system for storing a resource such as a document or group of documents on a computer file system using a Universal Resource Indicator (URI) as the file name by generating a unique system-independent key from the URI for use in an index-less browser caching system. The invention takes into account the various file entry length limitations enforced by each unique file system by converting the specified URI into a key containing hexadecimal values of the key's characteristics. In this fashion, an index-less browser caching system such as a Web browser of a VoiceXML browser is created that is file system-independent.
Owner:IBM CORP
Method for automatically generating check code of development program of embedded system
InactiveCN102023884ARealize automatic generationUniqueProgram controlRedundant data error correctionIntel HEXSystem development
The invention relates to a method for automatically generating a check code of a development program of an embedded system, which comprises the following steps of: (1) compiling a CommA for calculating the check code and automatically calculating the check code command according to an output file of a compiler; (2) compiling a CommB which adds and writes the check code generated by the CommA to a generated hexadecimal or binary file; (3) after compiling and generating the hexadecimal or binary source file, automatically operating the check code command of the calculation program according to an open interface provided in the compiling development environment of the embedded system; and (4) executing the compiling process again and burning the code with automatically added check code to a device; The check code is generated automatically after compiling the code and unique check code is automatically generated and added according to change of the generated hexadecimal or binary source file; meanwhile the check code of the program can be automatically generated without manual operation so that the check code of the program is more unique and reliable.
Owner:SHENZHEN CLOU ELECTRONICS
Migration Apparatus Which Convert Application Program of Mainframe System into Application Program of Open System and Method for Thereof
InactiveUS20100095283A1Error minimizationQuick conversionProgram code adaptionProgram loading/initiatingIntel HEXEBCDIC
Provided are a migration apparatus and method for converting an application program of a mainframe system into an appropriate application program for an open system. The migration apparatus includes: a source obtaining module connected with the mainframe system, and decoding and obtaining sources of work-specific application programs made of Extended Binary Coded Decimal Interchange Code (EBCDIC) in binary form; a code conversion module converting the respective sources of the work-specific application programs obtained by the source obtaining module into American Standard Code for Information Interchange (ASCII) code, hexadecimal characters being converted to correspond to ASCII code using a previously set hexadecimal code conversion table; a compiling and link processing module compiling the sources of the work-specific application programs converted by the code conversion module and then bundling the compiled sources of the work-specific application programs with corresponding work application programs; and an executable file generation module generating executable files in binary form from the work-specific application programs processed by the compiling and link processing module to execute them in an environment of the open system. The migration apparatus and method efficiently reuse a conventionally used application program via the rehosting process of converting a mainframe system into an open system.
Owner:SAMSUNG SDS CO LTD
Watermark processing method and system
ActiveCN104134023AImplement watermarkingIncrease watermark capacityProgram/content distribution protectionIntel HEXRelationship extraction
The invention provides a watermark processing method and system. Watermark character string information are coded into quinary bitstreams, quinary check beginning information and quinary check ending information are added in the quinary bitstreams, and therefore quinary embedded information is acquired; pdf files are loaded, the pdf files are unified on a standard blank character in a hexadecimal mode, a preset mapping relation between the pdf files is represented according to the quinary content and the hexadecimal of the standard blank character, and the content of the standard blank character is modified to embed the quinary embedded information into the pdf files; the pdf files are analyzed to acquire the content of the stand blank character, the quinary embedded information is extracted according to the preset mapping relation, the quinary bitstreams are extracted from the quinary embedded information according to the quinary check beginning information and the quinary check ending information, and the quinary bitstreams are decoded into the watermark character string information.
Owner:BEIJING UNIV OF POSTS & TELECOMM
System and method for generating a unique, file system independent key from a URI (universal resource indentifier) for use in an index-less voicexml browser caching mechanism
Owner:INT BUSINESS MASCH CORP
On-the-fly reordering of 32-bit per component texture images in a multi-cycle data transfer
ActiveUS7522171B1Efficiently reorganizing and processingDigital data processing detailsDigital computer detailsIntel HEXGraphics
A system of processing data in a graphics processing unit having a core configured to process data in hexadecimal form and other graphics modules configured to process data in quads includes a transpose buffer with a crossbar to reorganize incoming data, several memory banks to store the reorganized data over a period of several clock cycles, and a second crossbar for reorganizing the stored data after it is read from the bank of memories in one clock cycle. The method for converting between data in hexadecimal form and data in quads includes providing data in hexadecimal form, reorganizing the data provided in hexadecimal form, storing the reorganized data in several memories, and reading several of the memory locations, which contain all of the elements of the quad, in one clock cycle.
Owner:NVIDIA CORP
ROM structure and method for writing in INTEL HEX file
InactiveCN101324861ASave resourcesImprove work efficiencyMemory adressing/allocation/relocationIntel HEXData filling
The invention discloses an ROM structure and a method for writing an INTEL HEX file. The ROM is composed of n groups of RAMs, each group comprises eight dual-channel RAMs, each dual-channel RAM comprises an A channel and a B channel, and an identical address is respectively set for the address signals addrA and addrB of the A channel and the B channel of each RAM in each group; the address signals addrA and addrB input to the RAMs in each group are determined according to the address signals input to the ROM; the RAMs in each group respectively output data with two bytes; the n groups of the RAMs output data with 2*n bytes. The method for writing the INTEL HEX file by using the ROM structure is as follows: encoding and data padding are performed to the INTEL HEX file; and then data mapping is performed. By adopting the ROM structure and the method, a plurality of continuous data can be output after one address signal is input, and the ROM structure and the method are suitable for the single-chip microcomputer of the RISC architecture.
Owner:EAST CHINA NORMAL UNIV
Method and system for managing the contents of an event log stored within a computer
ActiveUS7188220B2Large memory capacitySignificant time delayMemory loss protectionMultiprogramming arrangementsIntel HEXEvent data
Methods and systems for utilizing and recording, writing, or logging data regarding system events occurring within a computer are provided. These systems and methods define a unique erased value, such as the hexadecimal value 0FFh, that identifies unused memory records in an event log. When the computer system receives notification that an event has occurred, it searches for the next memory record containing the erased value in a memory record field designated as a search byte field. Once the unused record is found, the event data concerning the event that occurred is stored in the identified memory record, without updating a pointer to the next unused record. A power event method is provided to update the pointer. A utility application is also provides functions for reading, displaying, erasing, and compiling and displaying statistics concerning the event data in the event log independent of a next unused memory record pointer.
Owner:AMERICAN MEGATRENDS
Hexadecimal file fast decompression method
A computer implemented method of selectively accesses a set of subdivisions of a compressed file, wherein the compressed file is a hex dump file. A request to access a first data byte string is received. The first data byte string has a first address from within the compressed file. The compressed file comprises a plurality of subdivisions. Each of the plurality of subdivisions is provided with an address range to indicate the addresses of byte strings contained therein. The address range for each of the plurality of subdivisions is the file name for each of the plurality of subdivisions. A set of subdivisions from the plurality of subdivisions is identified that contains a first data byte string. The step of identifying the set of subdivisions comprises comparing the first address to the address range for the plurality of subdivisions. Only the set of subdivisions which contains the first data byte string is extracted.
Owner:IBM CORP
Language processing system
InactiveUS20080120317A1Natural language data processingSpecial data processing applicationsIntel HEXNatural language processing
A language processing system is provided, including at least one computer-readable medium having stored thereon instructions for performing a method. The method may include retrieving a first body of alphanumeric character-based text from a first database. The method may also include converting the first body of alphanumeric character-based text into a multi-bit character encoding. In addition, the method may include writing the multi-bit encoded text to a non-formatted text file and storing the multi-bit encoded text from the text file in a second database. Further, the method may include converting the multi-bit encoded text in the second database to a set of hexidecimal codes and creating, from the set of hexidecimal codes, a web-based report that reproduces the first body of alphanumeric character-based text.
Owner:CATERPILLAR INC
Content preloading method in mobile terminal apparatus
InactiveCN1794173AReduce production processReduce the failure rateSubstation equipmentProgram loading/initiatingIntel HEXFile system
The present invention relates to a method for saving various content to be installed as a file system image installed in a mobile terminal in advance, and then downloading it to the flash memory of the mobile terminal, which is characterized in that it contains in sequence: Download the application software and template content of the mobile terminal successively, convert the template content into a hexadecimal image file and save it in the flash memory system, read the hexadecimal image of the application software into decimal, and insert the hexadecimal image file of the above template content. Hexadecimal image file and then synthesize it with the image file of the application software to generate a hexadecimal image file, and download the finally generated hexadecimal image file to the mobile terminal. The invention can be installed in the terminal machine without additional manufacturing engineering, and reduces the failure rate that may occur when downloading or installing by manual operation in the manufacturing engineering of the mobile terminal machine.
Owner:LG ELECTRONICS (CHINA) R&D CENT CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com