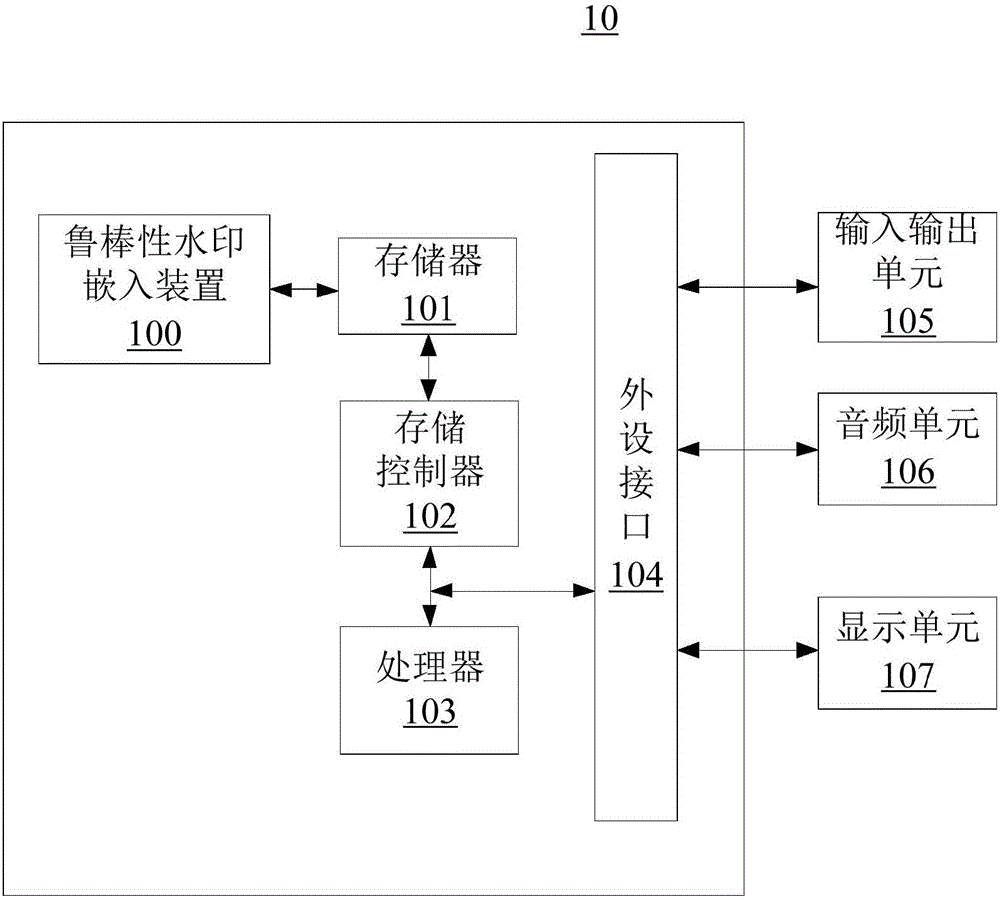
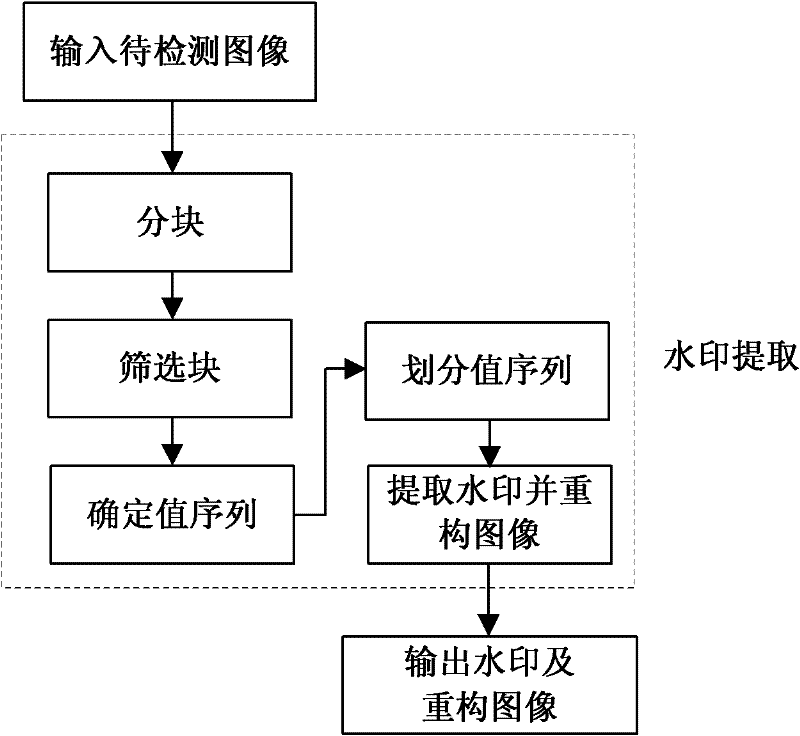
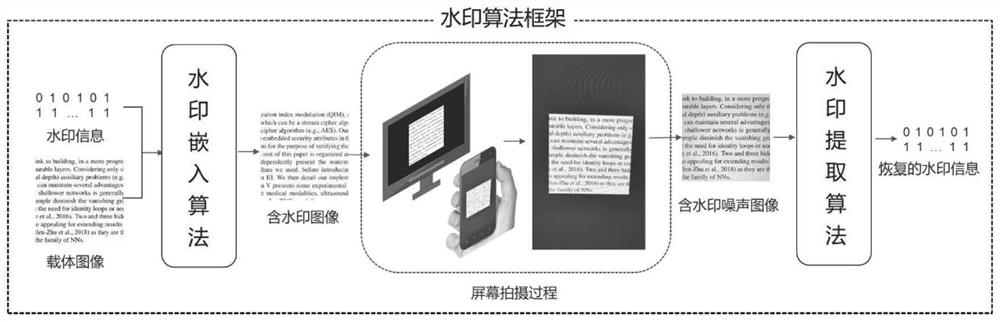
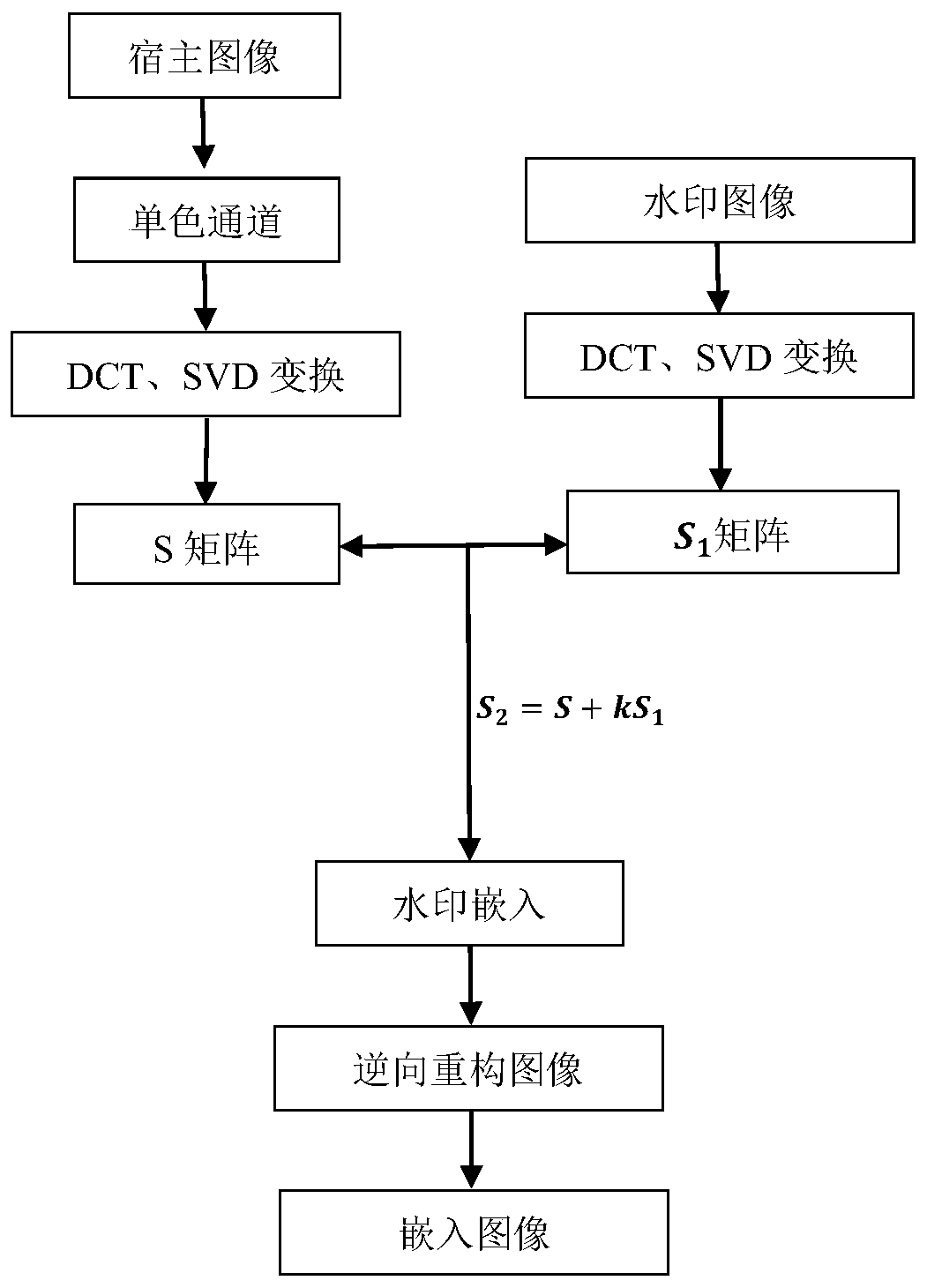
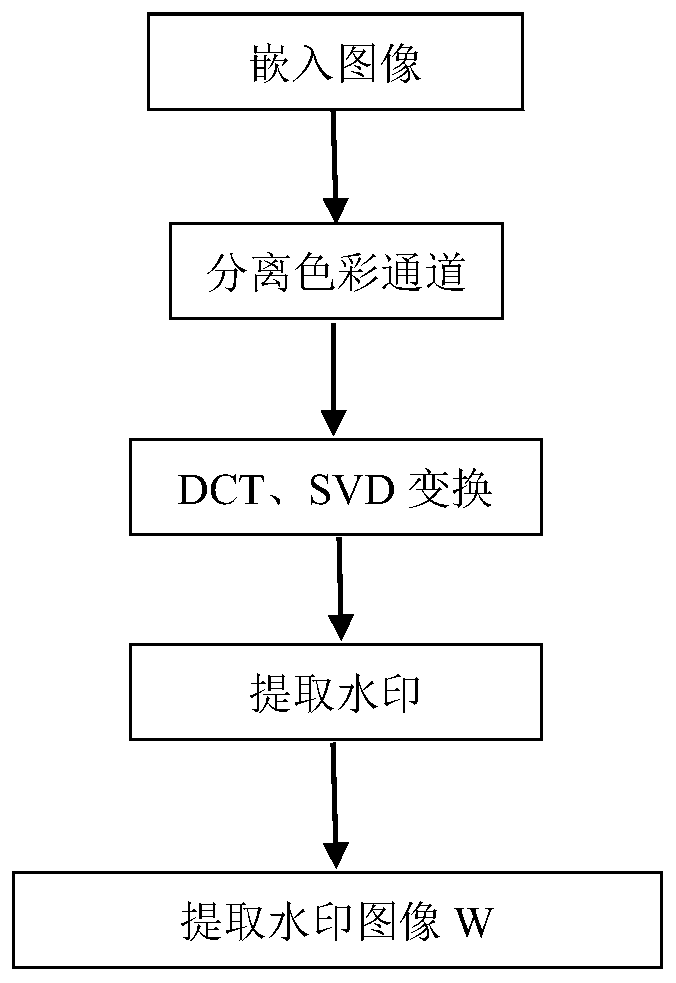
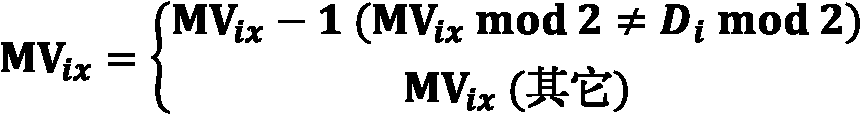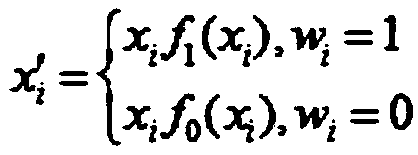Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40results about How to "Increase watermark capacity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
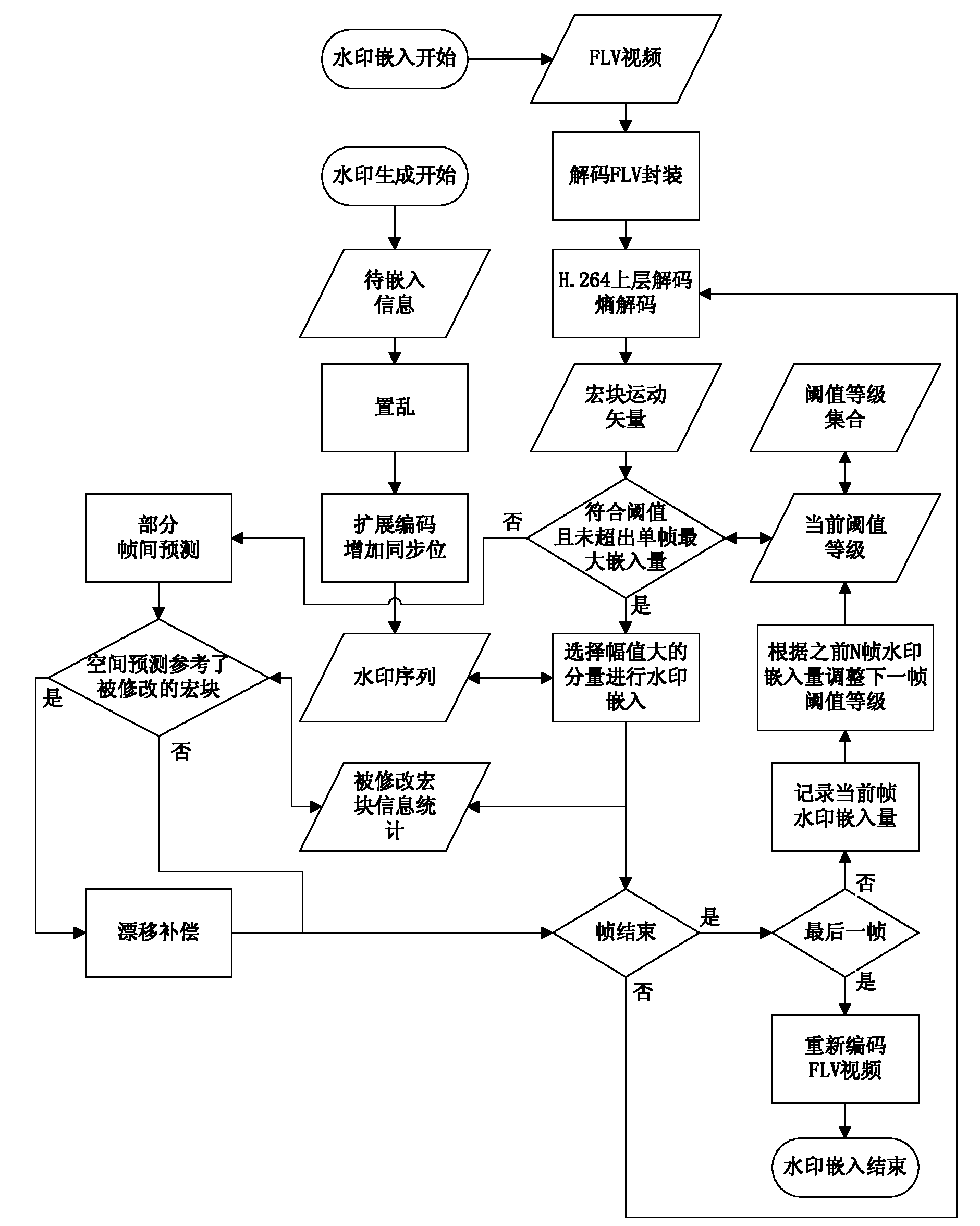
Adaptive H.264 compressed domain video watermark embedding and extracting method
ActiveCN101951520AImprove extraction efficiencyGuaranteed real-timeTelevision systemsImage data processing detailsCompensation effectMotion vector
The invention relates to an adaptive H.264 compressed domain video watermark embedding and extracting method in the technical field of information security, which can realize the real-time operation of video information hiding. The threshold value of a motion vector is adaptively adjusted according to watermark embedding amount statistical data of an adjacent frame, so that watermark capacity is ensured and the requirement of embedding a one-time watermark among a few frames is met; and error diffusion caused by modifying the motion vector is accurately positioned in a partial interframe prediction mode, so that good drift and distortion compensation effects can be achieved.
Owner:SHANGHAI JIAO TONG UNIV
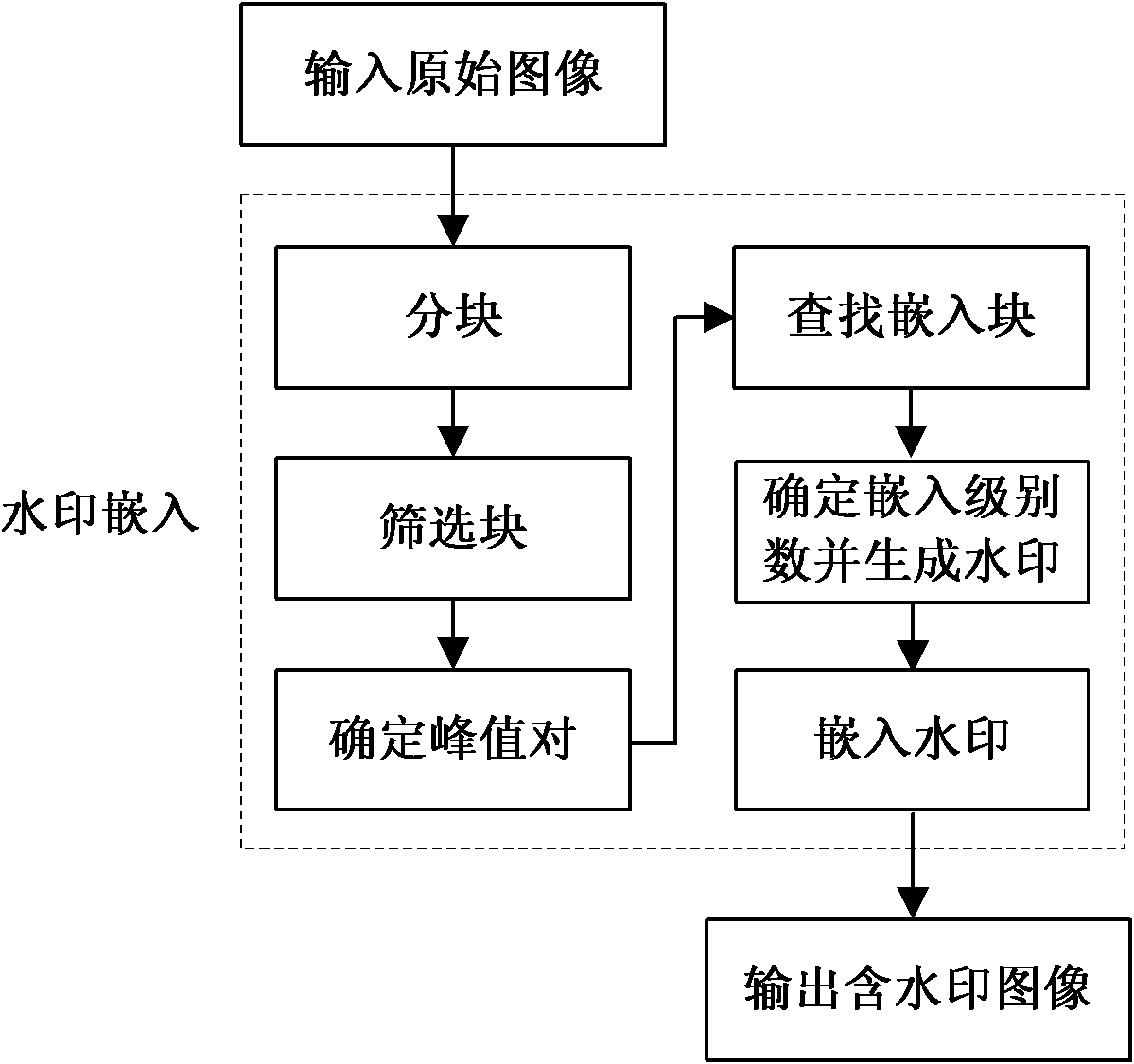
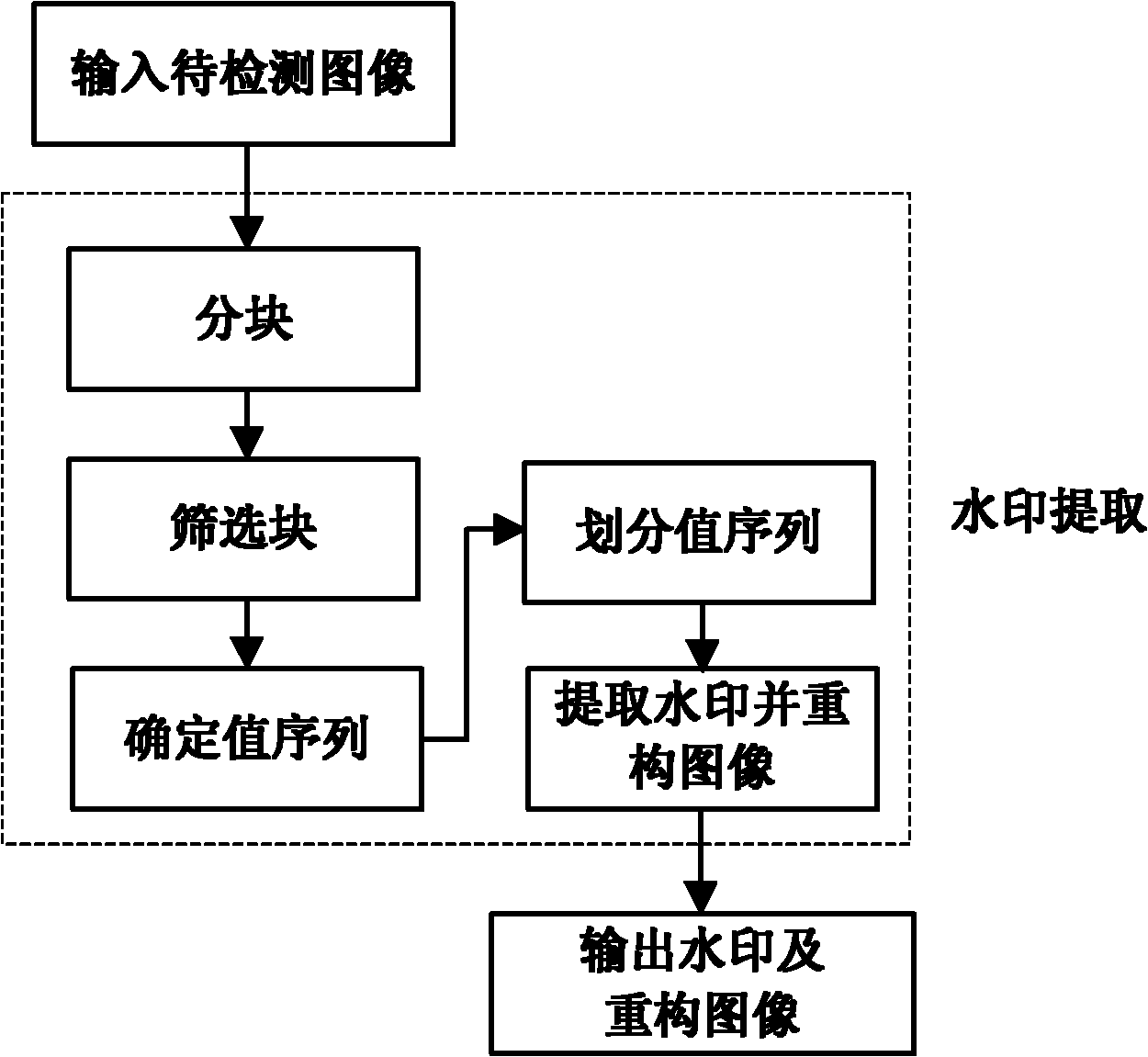
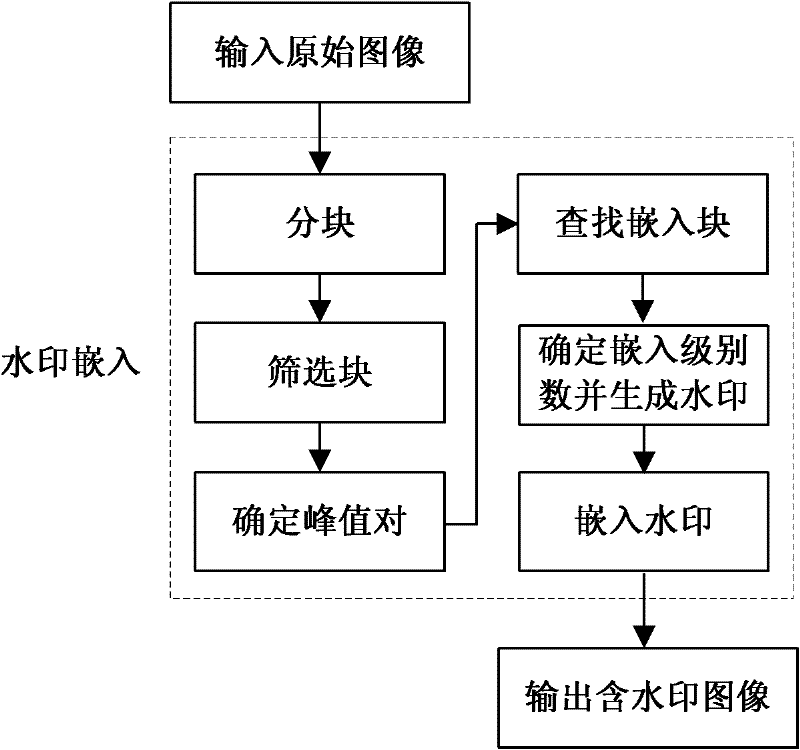
Robust reversible watermark embedding and extracting method based on histogram neighborhood
InactiveCN102156955AIncrease watermark capacityPrevent overflowImage data processing detailsCluster algorithmAlgorithm
The invention discloses a robust reversible watermark embedding and extracting method based on histogram neighborhood, mainly solves the shortage of poor comprehensive properties of the existing method. The method comprises the following steps of: firstly partitioning an original image, and screening a set of candidate blocks by means of embedding level; then calculating characteristic values of the candidate blocks, determining peak value pair, and obtaining a set of reliable embedding blocks by means of neighborhood selection of the peak value pair; finally, implementing watermark embedding by modifying the characteristic values of the embedding blocks; in the extraction process, the embedding block of an image to be detected is obtained, and the characteristic histogram value sequences of the embedding blocks are sorted by means of a clustering algorithm to obtain a set of sorted sequences, then the watermark is extracted by comparing the characteristic values of the embedding blocks with the sorted sequences, and a reconstructed image is subsequently obtained by modifying the characteristic values of the embedding blocks in the image to be detected. The embedding and extracting method has the advantages the robustness with reliable loss compression attack to JPEG (Joint Photographic Experts Group) and JPEG2000 is provided, the capacity is large, the invisibility is good, the overall performance of the method is superior to that of the similar methods, and the method can be applied to the copyright protection of a digital image.
Owner:XIDIAN UNIV
Piracy tracing watermarking method applicable to streaming media environment
ActiveCN102307320AImprove real-time performanceReduce complexityTelevision systemsDigital video signal modificationWatermark methodMotion vector
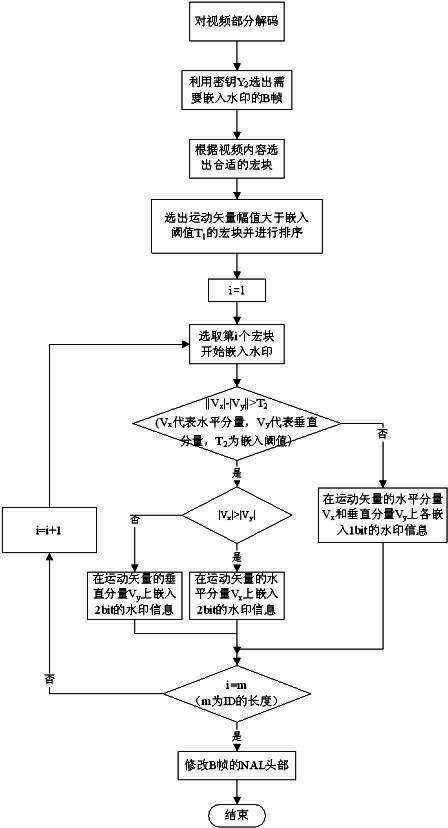
The invention relates to a piracy tracing watermarking method applicable to streaming media environment, and belongs to the multimedia information safety field. The method comprises the following steps: firstly segmenting video before the watermark embedding procedure; according to content of streaming video, selecting macroblocks meeting the conditions to be embedded with watermarks during the watermark embedding process; and determining the macroblock which is best suited for being embedding with watermark information by adopting a quicksort algorithm. In the piracy tracing watermarking method, based on difference between horizontal direction and vertical direction of motion vector of the macroblock, appropriate motion components are adaptively selected to be embedded with 2-bit watermark information, and the NAL (network abstraction layer) head of a B-frame is modified after the watermark embedding procedure so that the watermark can cope with the situations such as frame loss and the like resulting from network transmission. By adopting the piracy tracing watermarking method, the watermark information can be embedded into the streaming video in real time so as to achieve the purpose of piracy tracing.
Owner:JIANGSU YITONG HIGH TECH
H.264 standard motion vector-based method for embedding and extracting fragile watermark
InactiveCN102088611AAvoid the cumulative effect of errorsGuaranteed redundancyTelevision systemsDigital video signal modificationComputation complexityMotion vector
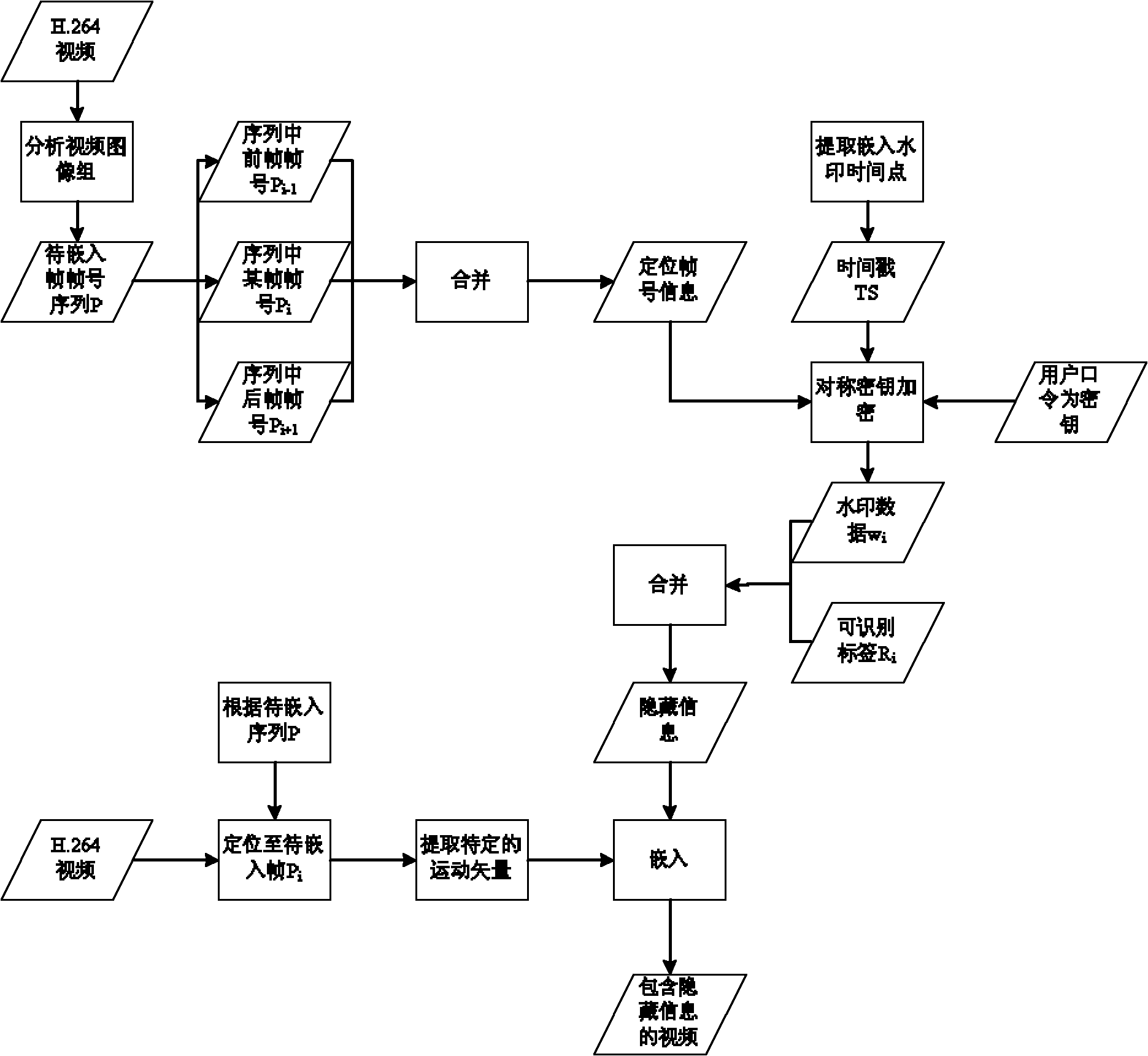
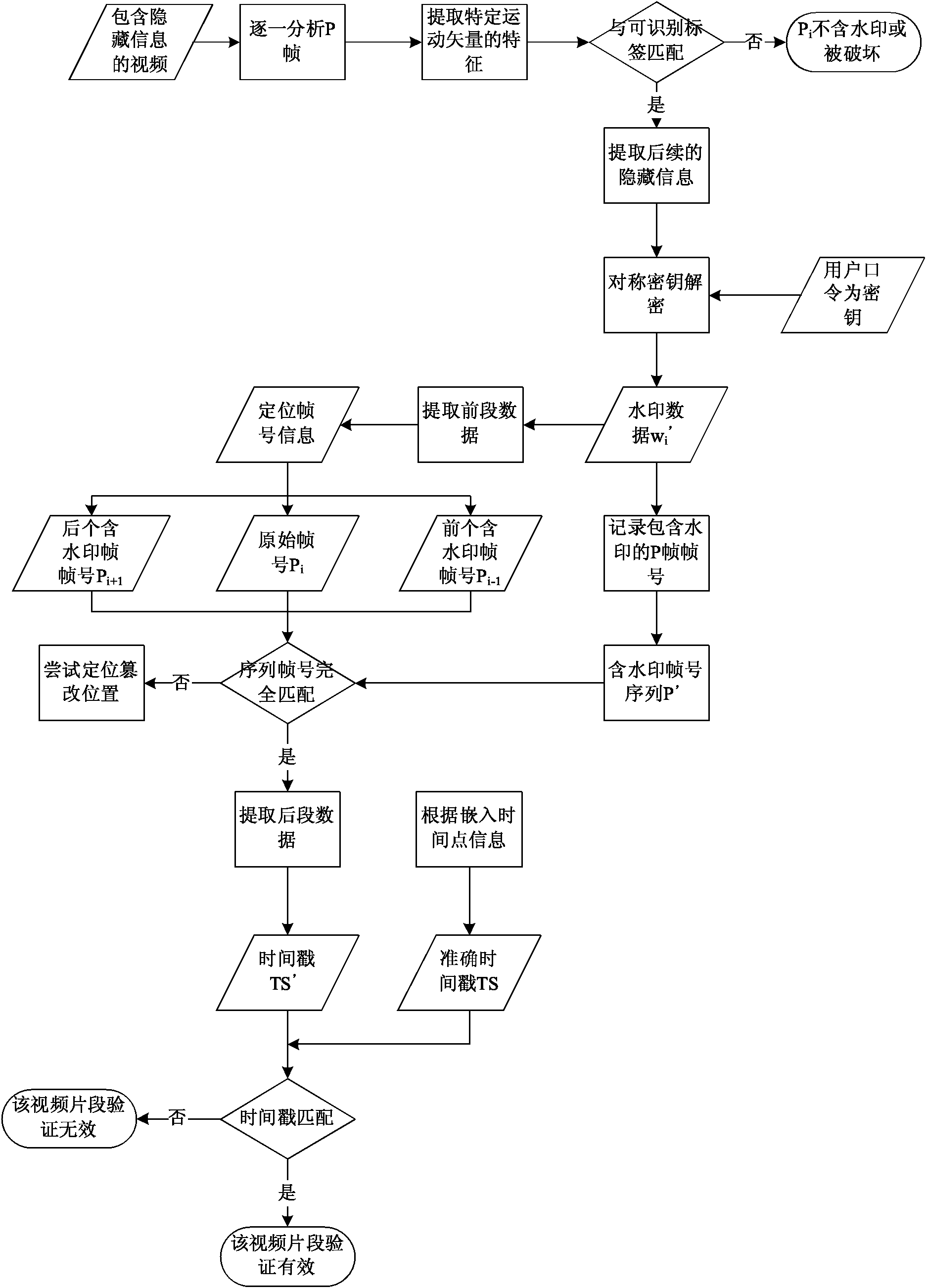
The invention discloses an H.264 standard motion vector-based method for embedding and extracting a fragile watermark, which belongs to the technical field of information security. Watermark information is selectively embedded into the motion vector of a frame P in front of a frame I, so that watermark capacity and fidelity are high; the watermark information comprises a frame number and a time stamp, and is encrypted with a symmetric cryptographic algorithm, so that the watermark information has attack resistance and video tampering can be positioned at a certain accuracy; and an implementation process is performed in a compressed domain, computation complexity is low and the influence on a video coding bit rate is low.
Owner:SHANGHAI JIAO TONG UNIV
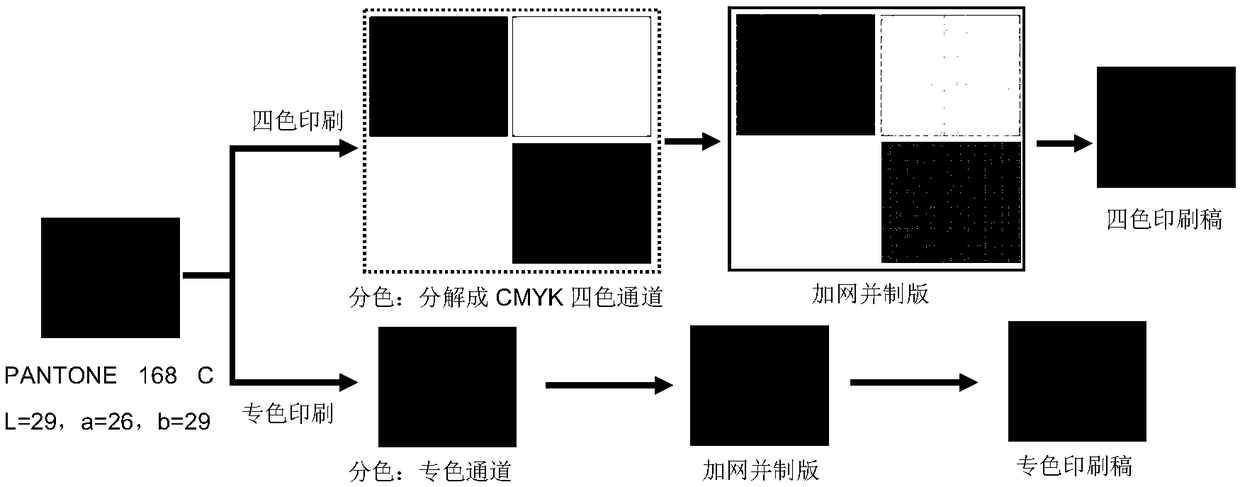
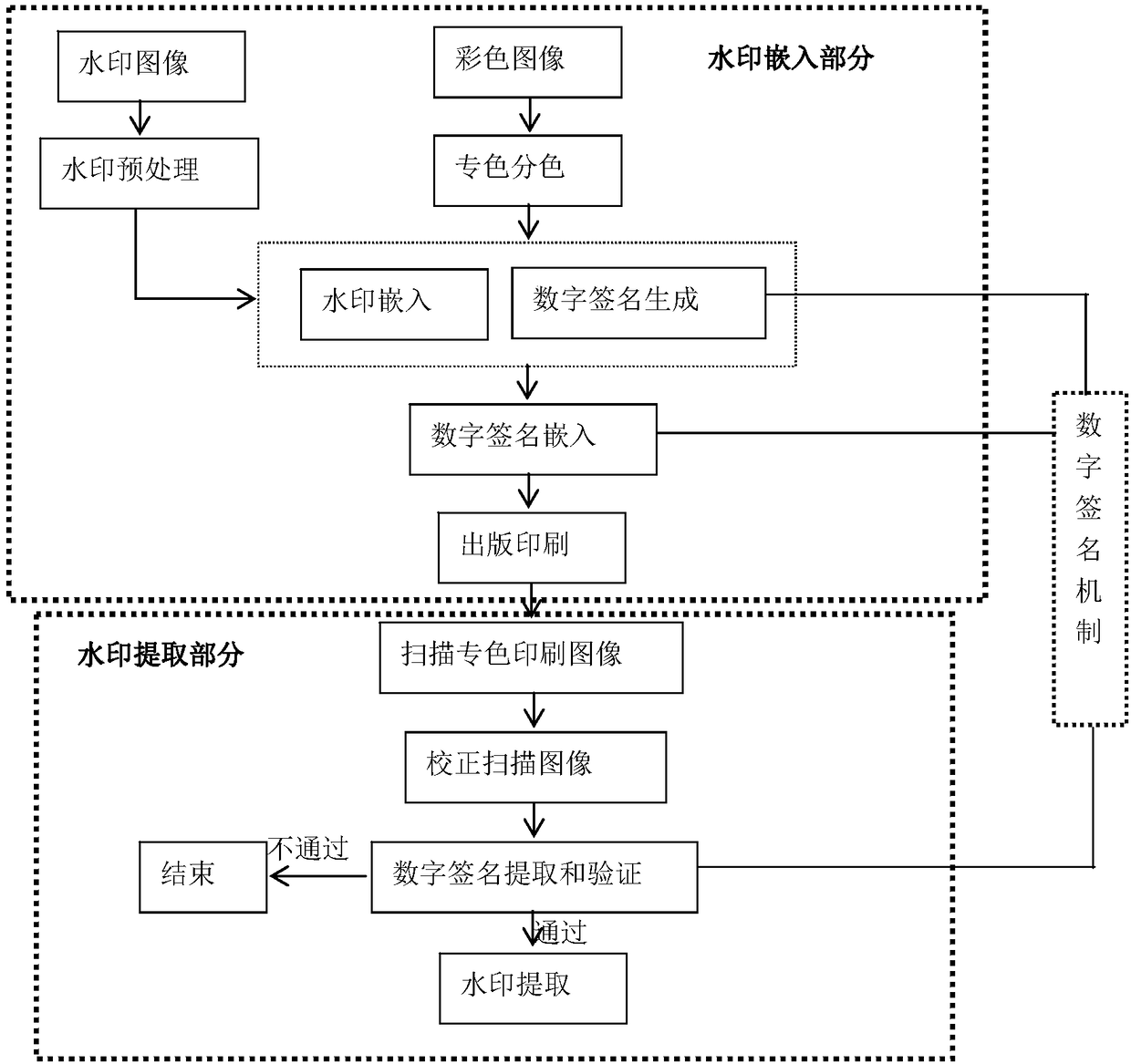
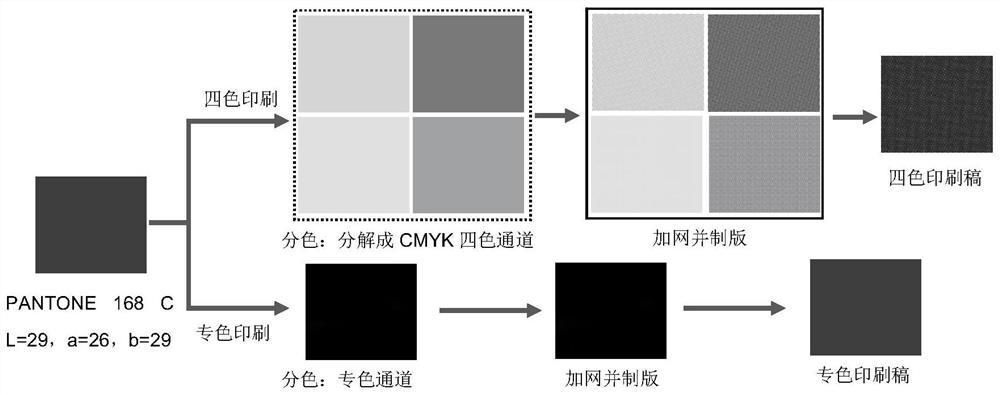
Conversion principle based on color space in special color printing
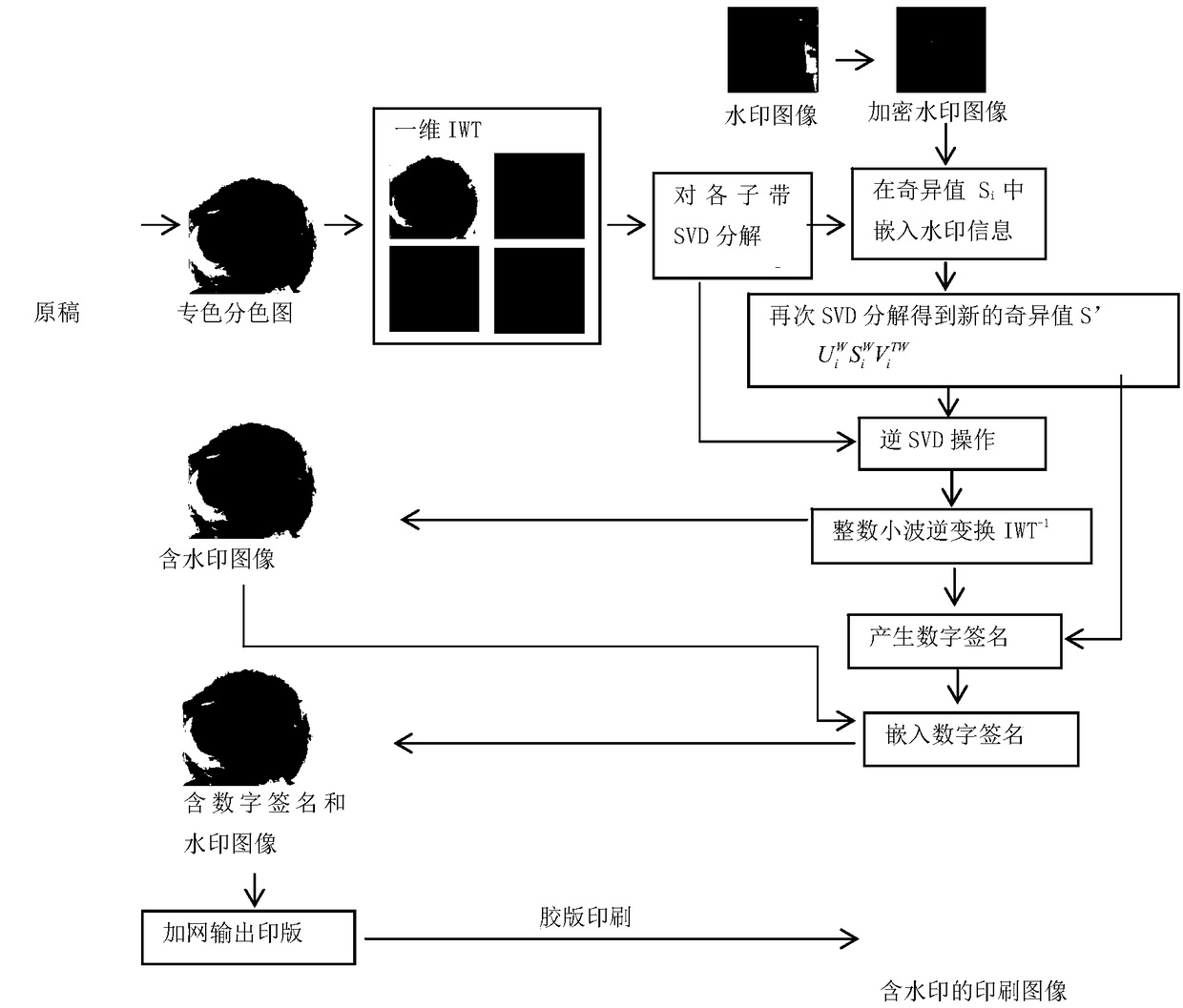
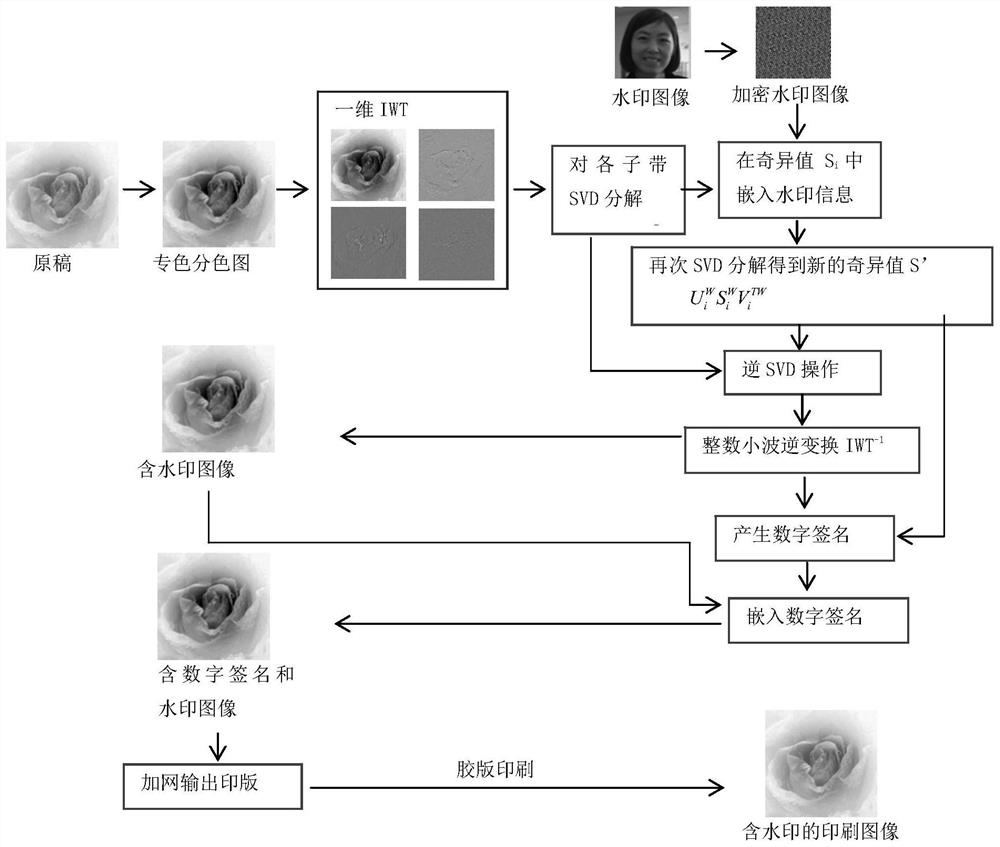
ActiveCN108460716AImprove stabilityIncrease watermark capacityImage analysisImage watermarkingColor imageColor printing
The invention provides a conversion principle based on color space in special color printing, and a special color printing image digital watermark method and system combining IWT and SVD. According tothe method and the system, a carrier image is decomposed into a special color channel, and the special color channel is subjected to IMWT conversion, then the watermark information is directly embedded into the singular value of each sub-band of the first-stage IWT. In order to improve watermark safety, Arnold scrambling encryption processing is conducted on the watermark image, and digital signature capable of resisting the printing-scanning process is embedded in the U and V of the image. In order to improve the robustness of digital signature and watermark, a step correction model for scanning a special color image is provided, and the scanned images are corrected, the digital signatures are extracted for verification, and the watermark information can be extracted if the digital signature is verified. The method has excellent performances in terms of watermark transparency, robustness and capacity, and can resist the printing-scanning process of the offset plate. The algorithm complexity is low, the execution efficiency is high, and the extraction time is not less than 1 second.
Owner:DALIAN POLYTECHNIC UNIVERSITY
Webpage link protection method based on control character coding and steganography
InactiveCN104050400AStop the spreadReduce negative impactProgram/content distribution protectionControl characterWeb page
The invention relates to a webpage link protection method based on control character coding and steganography. Watermark information can be embedded through selected control characters which are not displayed at a browser end, and thus link information in a webpage can be protected. First, the webpage is partitioned into blocks according to links, watermark information with any bit is generated according to all the characters of all the sub-blocks and coded into corresponding control characters to be embedded into the webpage, and a webpage with watermarks is generated; in detection, whether the link blocks are tampered or not is judged by comparing the relations between different bit numbers and thresholds of extracted watermarks and reconstructed watermarks corresponding to the link blocks; when tampered link blocks are detected, all attribute information including link addresses is deleted, and blocks are marked with warning mark information, so that a prompt is given to a user. Through the webpage link protection method based on control character coding and steganography, link block information in the webpage can be effectively protected; when the link blocks are tampered, the tampering can be detected out in time, and false information is prevented from being propagated, so that negative effects of tampered link blocks on images ad business of enterprise and public institutions are reduced.
Owner:SOUTHWEST JIAOTONG UNIV
Robust watermark embedding and detection method and device
ActiveCN106530205AIncrease watermark capacityImprove adaptabilityImage watermarkingComputer hardwareComputer science
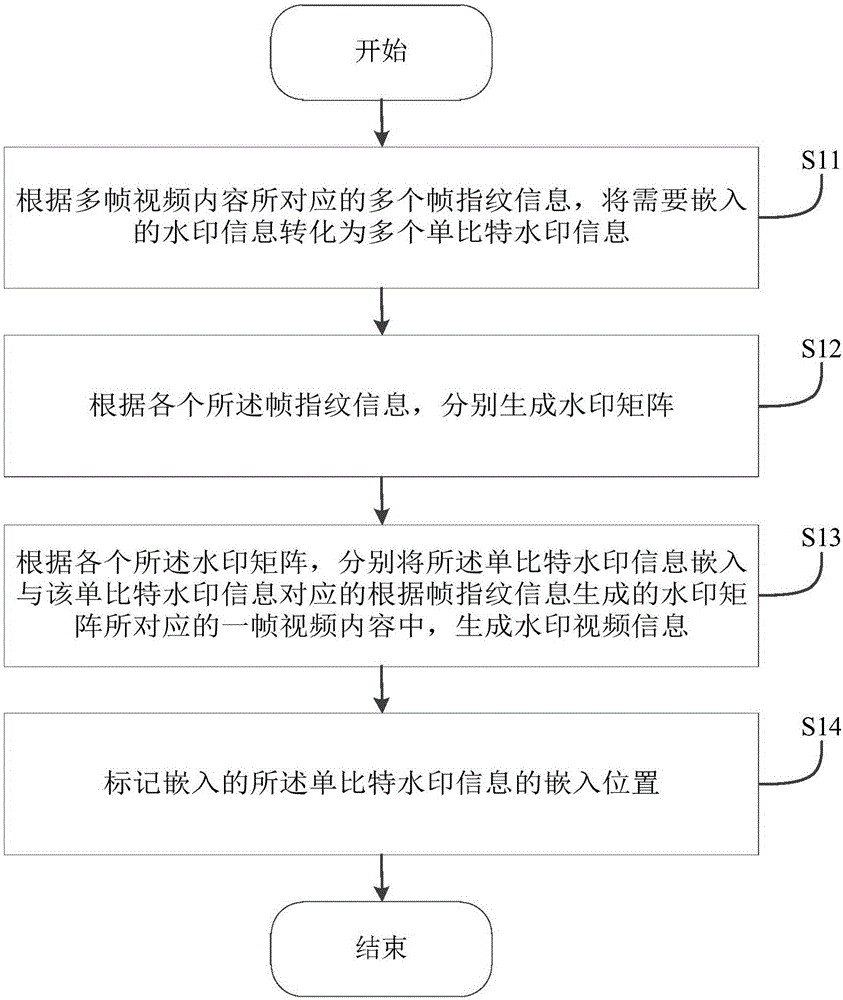
The embodiment of the invention provides a robust watermark embedding and detection method and device, and relates to the technical field of digital information content and copyright protection. The robust watermark embedding method includes the following steps: according to a plurality of pieces of frame fingerprint information corresponding to multiframe video content, converting watermark information that needs to be embedded into a plurality of pieces single-bit watermark information, the frame fingerprint information and the single-bit watermark information being in one-to-one correspondence; according to each piece of frame fingerprint information, generating a watermark matrix corresponding to each piece of single-bit watermark information; and according to each watermark matrix, embedding the single-bit watermark information in a frame of video content corresponding to the watermark matrix corresponding to the single-bit watermark information and generated according to the frame fingerprint information, and generating watermark video information. The method is employed to perform watermark embedding, robustness of watermarks can be enhanced, watermarks are guaranteed not to become invalid when a video is subjected to an analog conversion attack, and a pirate source can be searched according to the embedded watermarks.
Owner:北京鹏润鸿途科技股份有限公司
Method for embedding and extracting digital watermarks of three-dimensional point model
InactiveCN102044059AResistance to Affine Transformation AttacksStrong geometric invarianceImage data processing detailsAlgorithmProjection image
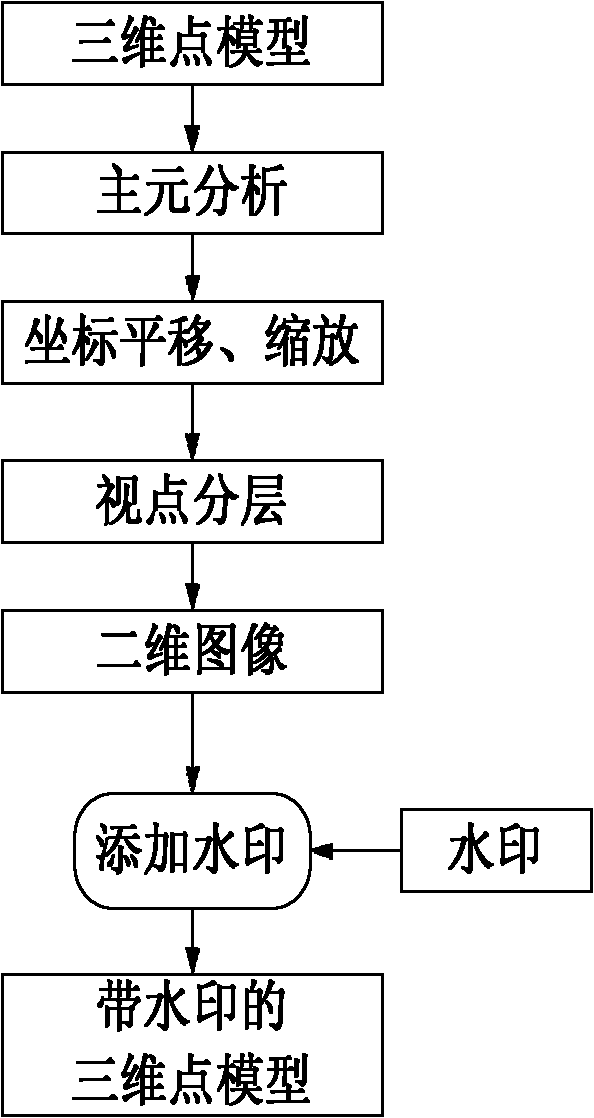
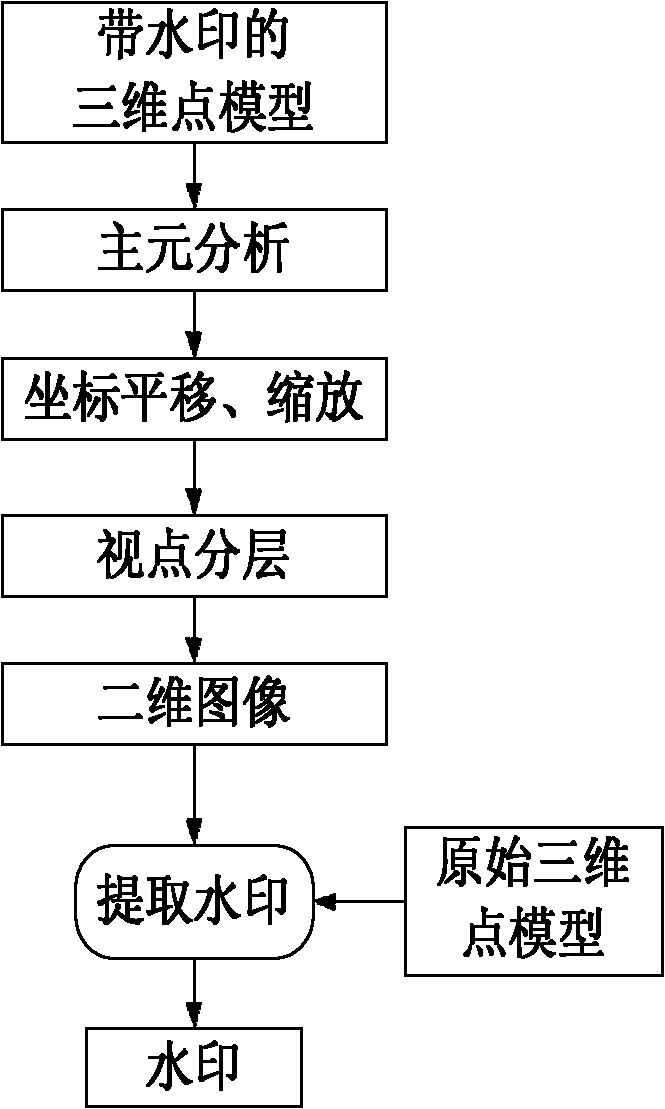
The invention discloses a method for embedding and extracting digital watermarks in specific to a three-dimensional point model, comprising the steps of: firstly, reconfiguring the coordinates of a model by adopting a principal component analysis method, then, forming a plurality of projected images inside a spherical surface with a gravity as a sphere by using a visual operator and taking the gravity center as a view point, converting a three-dimensional model into a two-dimensional image, regulating a spectrum coefficient of a low-frequency part by applying a two-dimensional frequency domain analysis method, and mapping the low-frequency part back to the three-dimensional model to realize the embedding and the extracting of the watermarks of the three-dimensional point model. In the invention, the calculated amount is moderate, the watermark capacity is large, and the method is suitable for large-scale point models and can be used for resisting various affine transformation attacks, achieving certain robustness to peak reordering, peak resampling and other various attacks, and effectively protecting the copyright of three-dimensional products.
Owner:SOUTHEAST UNIV
Watermarking embedding and authentication method of positioning PDF electronic invoice falsification
InactiveCN104899822AIncrease watermark capacityImprove securityImage data processing detailsComputer hardwareInvoice
Provided is a watermarking embedding and authentication method of positioning PDF electronic invoice falsification, comprising: A, watermarking generation based on a file reading page, concretely including blocking a reader page, parsing a code page file structure, generating authentication information, and generating watermarking in dependence on the authentication information; B, watermarking embedding based on file codes; C, updating of a cross reference and an end-of-file; and D, generation of a PDF electronic invoice file with watermarking, including performing E authentication information reconstruction, authentication information extraction and F falsification authentication on a PDF electronic file to be detected, and F falsification authentication including falsification authenticity determination and falsification positioning and marking. The method can guarantee invisibility of watermarking, and meanwhile control file increment within 1%. The method has the characteristics of high falsification detection accuracy, and low false drop rate, and can effectively resist replacing, adding, deleting, etc.
Owner:SOUTHWEST JIAOTONG UNIV
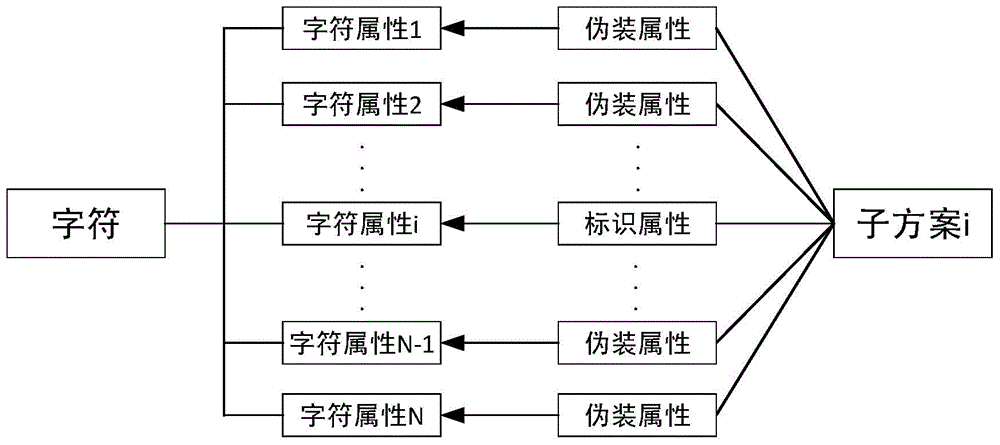
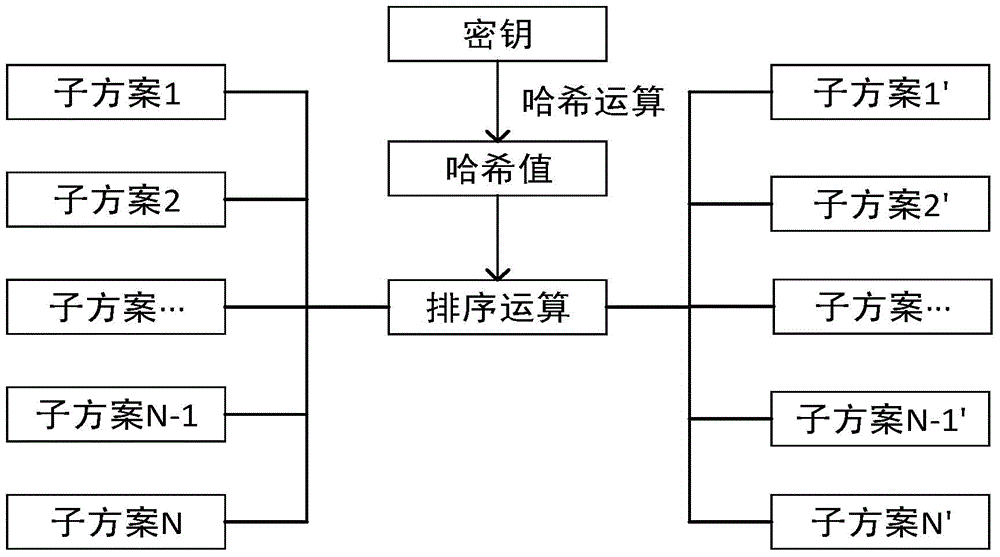
Scheme self-adaptive digital watermark embedding and extracting method based on camouflage technology
InactiveCN104376236AImprove concealmentIncrease watermark capacityNatural language data processingProgram/content distribution protectionWatermark robustnessSelf adaptive
The invention provides a scheme self-adaptive digital watermark embedding and extracting method based on the camouflage technology. The method comprises the main steps that multiple sets of subschemes of relevant operations having both the camouflage property and the identity property are built; an index number is set for each set of subschemes, and an initial scheme sequence is obtained by arraying the subschemes in an ascending order; the BKDR Hash value of secret key information is calculated, and is used for carrying out sorting operation on the initial subscheme sequence to obtain a self-adaptive scheme sequence; according to a self-adaptive scheme sequence table, watermark information is embedded in sequence in a circulation mode. The scheme self-adaptive digital watermark embedding and extracting method has the advantages that the tamper localization function is achieved, the purpose of improving the safety of formatted text document watermark robustness is achieved by means of the camouflage technology, and the problem that watermark information is likely to be illegally extracted and then cracked due to the method of embedding watermarks by adjusting formats of formatted text document watermarks is solved.
Owner:UNIV OF SHANGHAI FOR SCI & TECH +1
Watermark processing method and system
ActiveCN104134023AImplement watermarkingIncrease watermark capacityProgram/content distribution protectionIntel HEXRelationship extraction
The invention provides a watermark processing method and system. Watermark character string information are coded into quinary bitstreams, quinary check beginning information and quinary check ending information are added in the quinary bitstreams, and therefore quinary embedded information is acquired; pdf files are loaded, the pdf files are unified on a standard blank character in a hexadecimal mode, a preset mapping relation between the pdf files is represented according to the quinary content and the hexadecimal of the standard blank character, and the content of the standard blank character is modified to embed the quinary embedded information into the pdf files; the pdf files are analyzed to acquire the content of the stand blank character, the quinary embedded information is extracted according to the preset mapping relation, the quinary bitstreams are extracted from the quinary embedded information according to the quinary check beginning information and the quinary check ending information, and the quinary bitstreams are decoded into the watermark character string information.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Watermarking algorithm based on DCT domain of video frame
ActiveCN105657431AImprove visual qualityImprove robustnessDigital video signal modificationPattern recognitionVideo quality
The invention discloses a watermarking algorithm based on a DCT domain of a video frame, and comprises a video watermark embedding method and a video watermark extraction method. The watermarking algorithm has the characteristic of adaptive embedding intensity, and videos of different sizes can have appropriate intensities, thus video quality and robustness can be compromised, especially when video scale is changed, the effect is especially good, and a step of judging whether the frame is suitable for hiding watermark improves the visual quality of a video including a watermark; only suitable key frames are extracted, so that the robustness of a system is improved, and the extraction speed is accelerated; besides, the brightness, saturation adjustment, fuzzy and other attacks also have a good robustness; under the circumstance of not reducing the accuracy, a digital segmented embedding method greatly improves a watermarking capacity, and as long as the number of times that a certain number appears satisfies a certain preset condition, the number can be taken as a final result without extracting all key frames of the video, so that the operation time can be reduced.
Owner:HANGZHOU ARCVIDEO TECHNOLOGY CO LTD
Spatial domain color image blind watermarking method fused with Haar transform
ActiveCN110415155AIncrease watermark capacityStrong Watermark RobustnessImage watermarkingHadamard transformColor image
The invention discloses a spatial domain color image blind watermarking method fused with Haar transform by combining the advantages of good concealment of an airspace digital watermarking algorithm and strong robustness of a frequency domain digital watermarking algorithm. According to the method, based on the characteristic that Haar transform has correlation between space-frequency domains, themaximum energy coefficient in a matrix of an image block after Haar transform is directly obtained in a space domain. The embedding and blind extraction of digital watermarks are completed by quantizing the maximum energy coefficient. According to the method, the color image digital watermark can be embedded into the color host image. The method has the advantages of being high in robustness, good in watermark concealment, high in safety, high in execution efficiency and high in embedding amount. The method is suitable for occasions of high-concealment high-capacity color digital image rapidcopyright protection.
Owner:LUDONG UNIVERSITY
Robust reversible watermark embedding and extracting method based on histogram neighborhood
InactiveCN102156955BIncrease watermark capacityPrevent overflowImage data processing detailsCluster algorithmAlgorithm
The invention discloses a robust reversible watermark embedding and extracting method based on histogram neighborhood, mainly solves the shortage of poor comprehensive properties of the existing method. The method comprises the following steps of: firstly partitioning an original image, and screening a set of candidate blocks by means of embedding level; then calculating characteristic values of the candidate blocks, determining peak value pair, and obtaining a set of reliable embedding blocks by means of neighborhood selection of the peak value pair; finally, implementing watermark embeddingby modifying the characteristic values of the embedding blocks; in the extraction process, the embedding block of an image to be detected is obtained, and the characteristic histogram value sequencesof the embedding blocks are sorted by means of a clustering algorithm to obtain a set of sorted sequences, then the watermark is extracted by comparing the characteristic values of the embedding blocks with the sorted sequences, and a reconstructed image is subsequently obtained by modifying the characteristic values of the embedding blocks in the image to be detected. The embedding and extracting method has the advantages the robustness with reliable loss compression attack to JPEG (Joint Photographic Experts Group) and JPEG2000 is provided, the capacity is large, the invisibility is good, the overall performance of the method is superior to that of the similar methods, and the method can be applied to the copyright protection of a digital image.
Owner:XIDIAN UNIV
Color blind watermarking method based on Hamming code, eigenvalue decomposition and image correction
ActiveCN111223035AImprove robustnessWatermark is invisibleImage data processing detailsPattern recognitionColor image
The invention discloses a color blind watermarking method based on Hamming codes, eigenvalue decomposition and image correction by combining a Hamming coding theory and eigenvalue decomposition. Firstly, all characteristic values of a pixel block are obtained according to characteristics of characteristic value decomposition, and embedding and blind extraction of a digital watermark are completedby quantizing the sum of absolute values of the characteristic values; secondly, according to the geometric attributes of the image containing the watermark, the image after various geometric attackscan be corrected. According to the method, the digital watermark of the color image can be embedded into the color host image, so that the method not only has better watermark concealment and higher safety, but also has stronger robustness and larger embedding capacity, and is suitable for occasions of copyright protection of high-capacity color digital images with strong robustness.
Owner:上海瑞盛联信息科技有限公司
Watermark embedding method and detection method based on polar-harmonic-Fourier moment
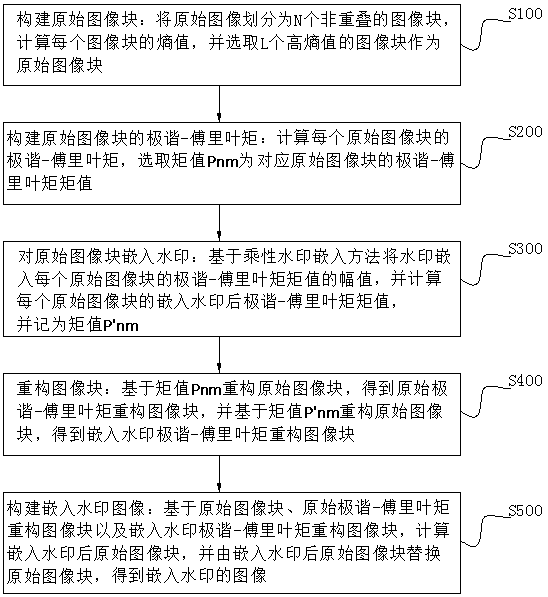
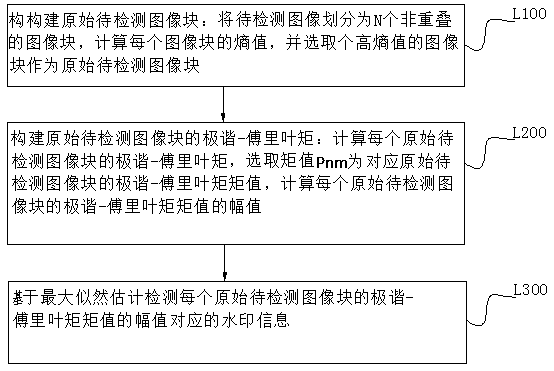
InactiveCN108876692ARobustStrong imperceptibilityImage data processing detailsAlgorithmWatermark method
The invention discloses a watermark embedding method and detection method based on polar-harmonic-Fourier moment, and belongs to the field of the watermark embedding and detection. A to-be-solved technical problems are that the irresistible geometric attack is existent in the existing watermark embedding and detection method, the watermark capacity is small, and partial algorithm is the non-blinddetection algorithm. The embedding method comprises the following steps: constructing an original image block; constructing a polar-harmonic-Fourier moment of the original image block; embedding watermark for the original image block, and computing the polar-harmonic-Fourier moment value of each original image block after embedding the watermark; reconstructing the original image block based on the moment value; and constructing the watermark-embedded image. The watermark detection method comprises the following steps: constructing the original to-be-detected image block; performing polar-harmonic-Fourier moment reconstruction on the original to-be-detected image block; detecting the watermark information corresponding to the amplitude of the polar-harmonic-Fourier moment value of each original to-be-detected image block based on the maximum likelihood estimation. The watermark method can resist the geometric attack and is large in capacity.
Owner:QILU UNIV OF TECH
Embedding method and extracting method of color image
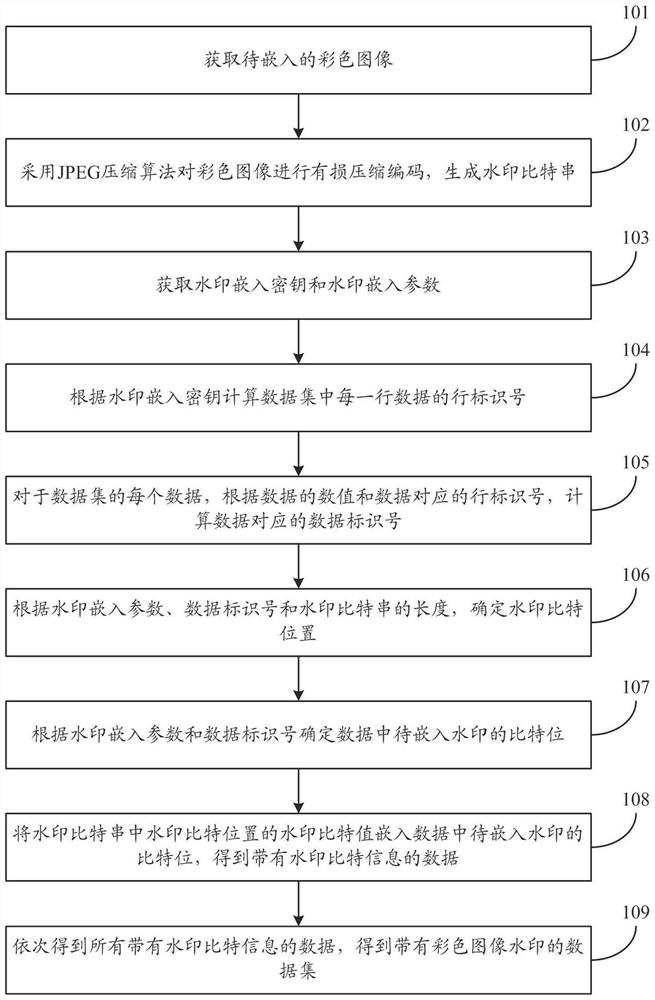
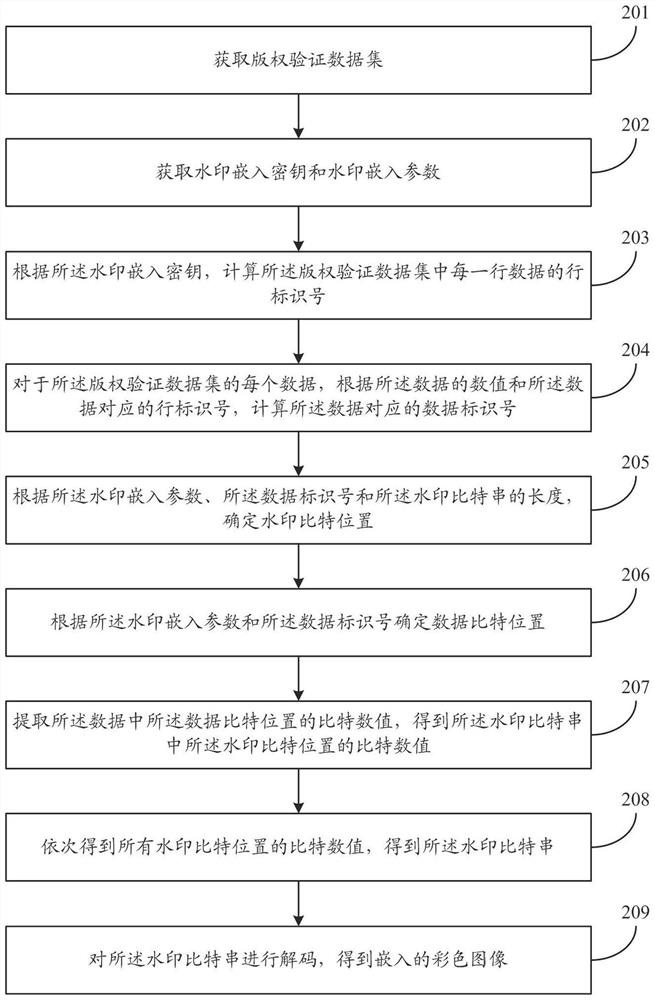
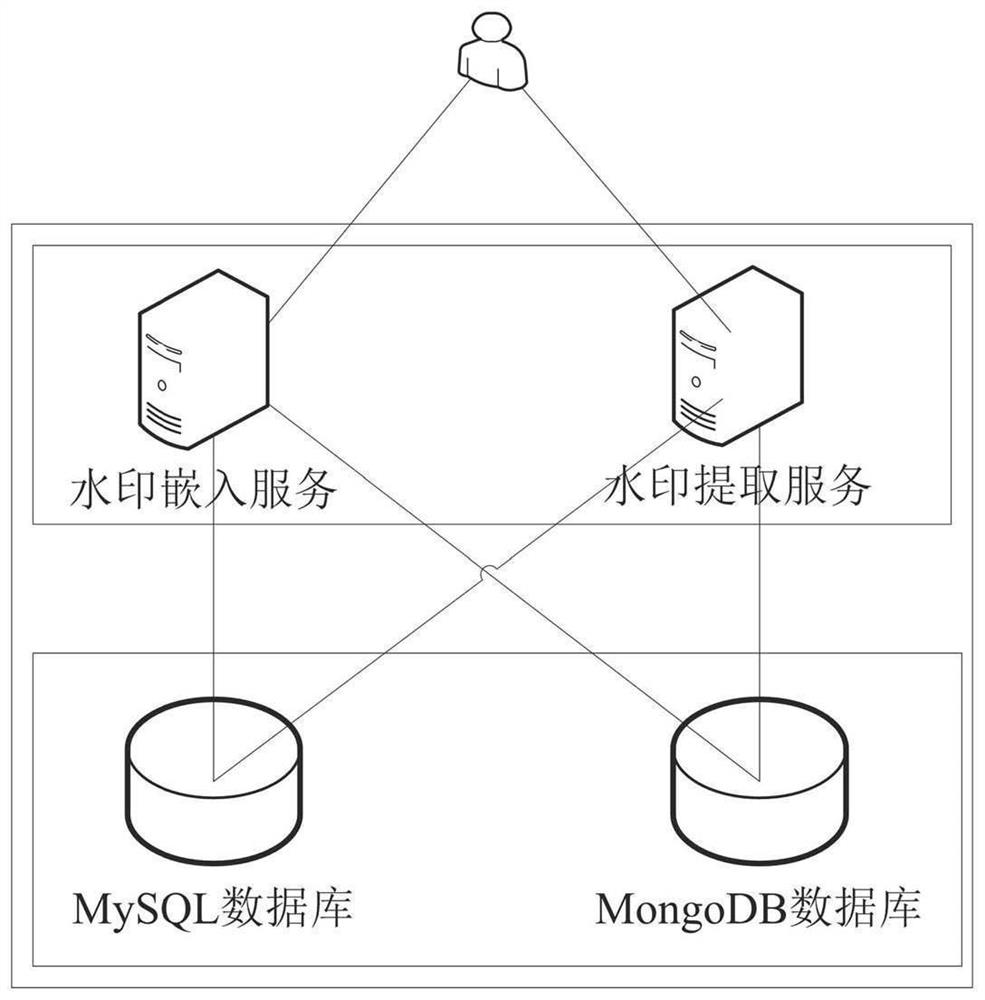
PendingCN111652789AImplement embeddingTroubleshooting Difficulty Embedding Color ImagesImage watermarkingEnergy efficient computingColor image watermarkingCalculated data
The invention relates to an embedding method and an extracting method of a color image. The embedding method comprises the following steps: carrying out lossy compression coding on a color image by adopting a JPEG compression algorithm to generate a watermark bit string; calculating a row identification number of each row of data in the data set according to the watermark embedding key; calculating a data identification number corresponding to the data in the data set according to the numerical value of the data and the row identification number corresponding to the data; determining a watermark bit position according to the watermark embedding parameter, the data identification number and the length of the watermark bit string; determining the bit of the watermark to be embedded in the data according to the watermark embedding parameter and the data identification number; embedding the watermark bit value of the watermark bit position in the watermark bit string into the bit of the watermark to be embedded in the data to obtain data with watermark bit information; and sequentially obtaining all data with watermark bit information, and obtaining a data set with color image watermarks. The method can improve the protection effect of the data copyright.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Anti-screen-shooting text image watermark embedding and extracting method based on deep learning
PendingCN114648436AIncrease watermark capacityImprove robustnessCharacter and pattern recognitionImage data processing detailsEngineeringComputer vision
The invention discloses an anti-screen-shooting text image watermark embedding and extracting method based on deep learning. The method specifically comprises the following steps: step 1, preparing a training set and a test set; 2, establishing a screen shooting text image watermark resisting model; 3, training the screen shooting text image watermark resisting model; 4, inputting the images in the test set into the screen shooting resistant text image watermark model trained in the step 3 one by one, and detecting the accuracy of the model; and step 5, inputting a carrier image which needs to be subjected to watermark embedding into the trained screen shooting resistant text image watermark model to obtain the carrier image after watermark embedding and watermark information. The method provided by the invention has the characteristics of high watermark capacity, high robustness and strong practicability. In the actual use process, the cost is lower, the detection precision is higher, and the consumed time is shorter.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Anti-print-scanning text image digital watermarking method
PendingCN112651879AOvercome the shortcoming that the ability to resist printing and scanning attacks is not strongImprove robustnessImage enhancementImage analysisWatermark methodImage correction
The invention discloses an anti-print-scanning text image digital watermarking method. The method comprises the following specific steps: (1) text line identification; (2) text character recognition; (3) watermark information preprocessing; (4) watermark embedding pretreatment; (5) watermark embedding; (6) image correction; (7) watermark extraction pretreatment; and (8) extracting the watermark. The text watermarking method solves the problems that the redundancy is low and the watermark is not strong in resistance to printing and scanning attacks when the watermark is embedded in the text watermarking method. According to the method, the advantages of an airspace text watermarking algorithm are utilized, the robustness to printing scanning attacks is high, the invisibility of watermarks is good, calculation is simple, and the watermark embedding capacity is high.
Owner:山西西电信息技术研究院有限公司
A watermarking algorithm based on dct domain of video frame
ActiveCN105657431BImprove visual qualityImprove robustnessDigital video signal modificationPattern recognitionKey frame
The invention discloses a watermarking algorithm based on a DCT domain of a video frame, and comprises a video watermark embedding method and a video watermark extraction method. The watermarking algorithm has the characteristic of adaptive embedding intensity, and videos of different sizes can have appropriate intensities, thus video quality and robustness can be compromised, especially when video scale is changed, the effect is especially good, and a step of judging whether the frame is suitable for hiding watermark improves the visual quality of a video including a watermark; only suitable key frames are extracted, so that the robustness of a system is improved, and the extraction speed is accelerated; besides, the brightness, saturation adjustment, fuzzy and other attacks also have a good robustness; under the circumstance of not reducing the accuracy, a digital segmented embedding method greatly improves a watermarking capacity, and as long as the number of times that a certain number appears satisfies a certain preset condition, the number can be taken as a final result without extracting all key frames of the video, so that the operation time can be reduced.
Owner:HANGZHOU ARCVIDEO TECHNOLOGY CO LTD
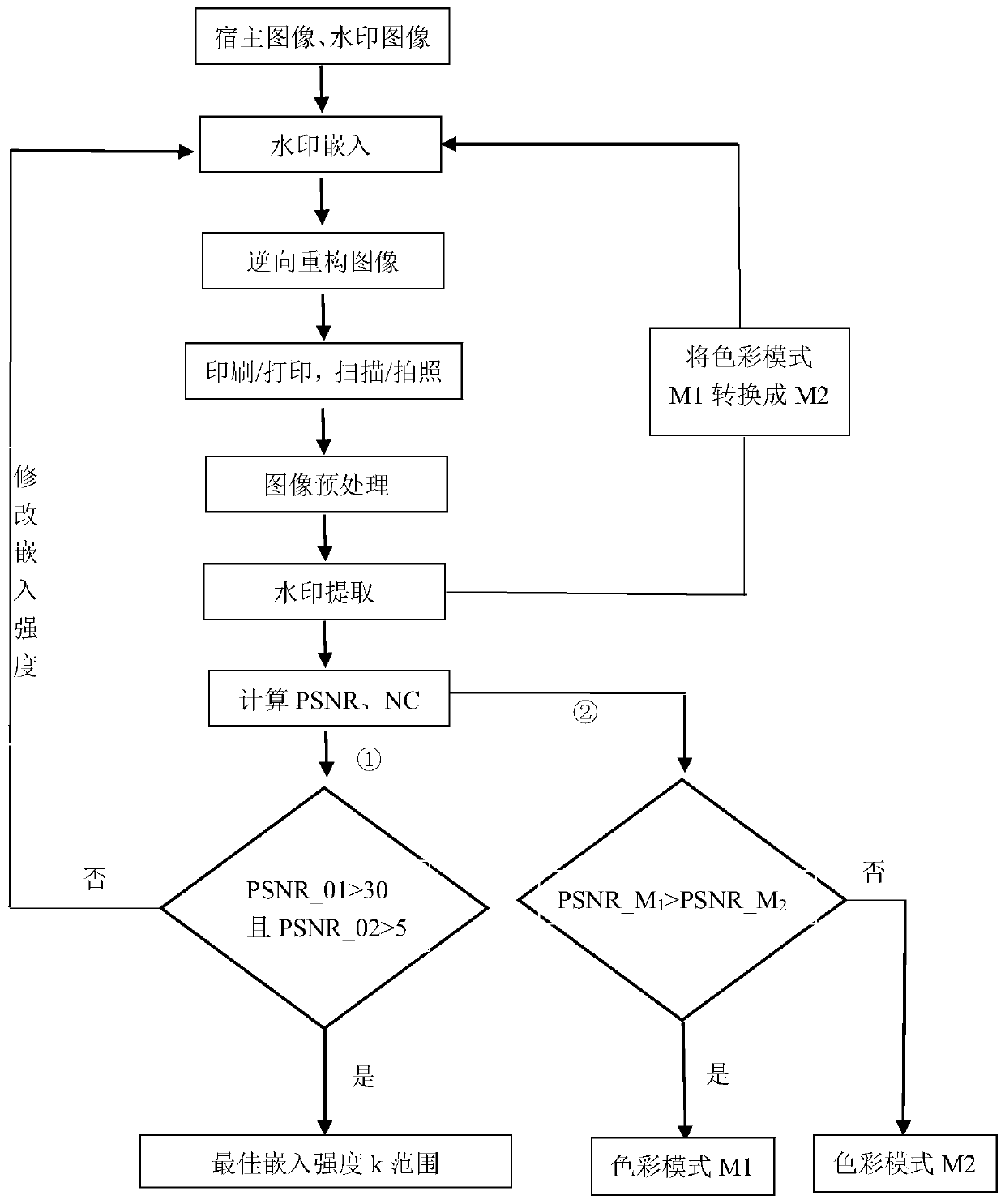
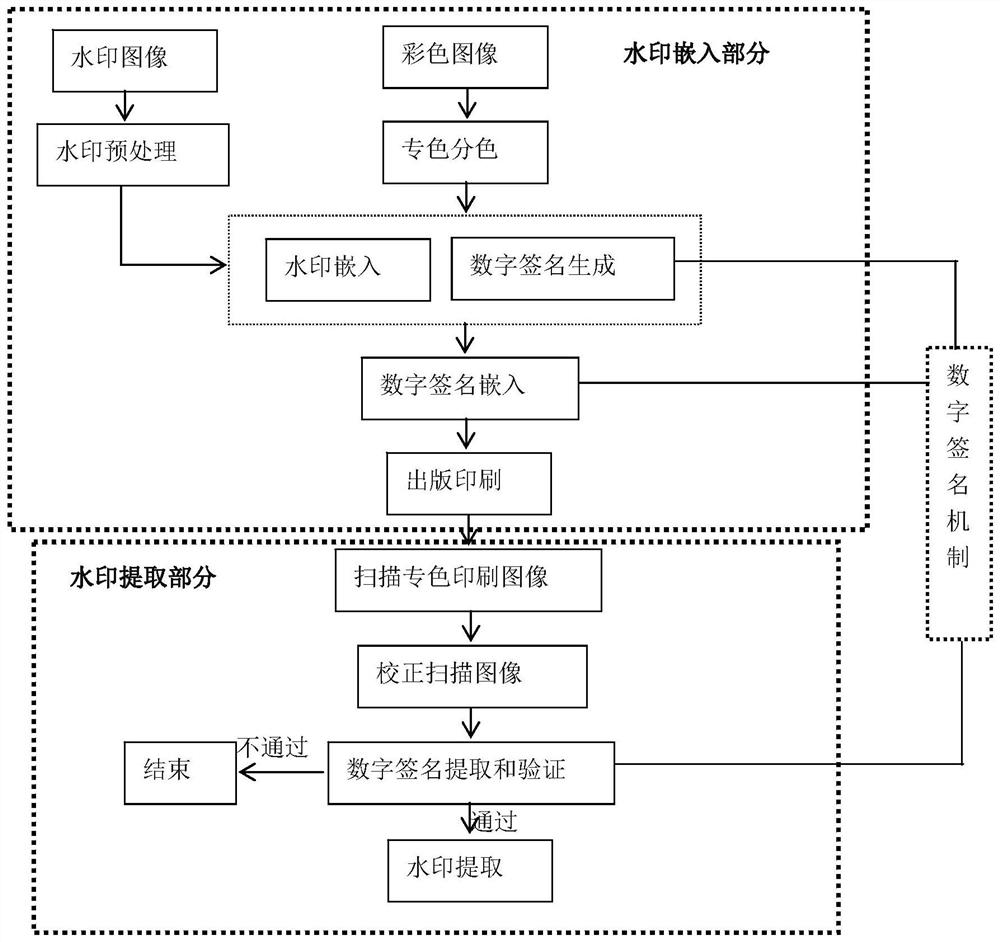
Digital watermark embedding environment determination method, device and equipment and readable storage medium
ActiveCN110992236AHigh transparencyImprove robustnessImage data processing detailsEnergy efficient computingPattern recognitionComputer graphics (images)
The invention belongs to the field of anti-counterfeiting of printed matters, and discloses a digital watermark embedding environment determination method, device and equipment and a readable storagemedium. The method comprises the steps of embedding a watermark image into a host image through a DCT-SVD method in a preset embedding strength and color mode to obtain an embedded image; printing theembedded image and performing scanning or photographing to obtain a scanned image; performing watermark extraction on the scanned image to obtain an extracted watermark image; modifying the preset embedding strength and the color mode and repeating the above steps; and comparing and evaluating the embedded image and the host image as well as the extracted watermark image and the watermark image through a PSNR image evaluation method to obtain the optimal embedding strength and the optimal embedding color mode of the watermark image. Through the method, the embedding strength range and the color mode of the digital watermark can be obtained, and the watermark capacity and the printing-scanning / photographing resistance of the digital watermark are improved.
Owner:北京奇良海德印刷股份有限公司
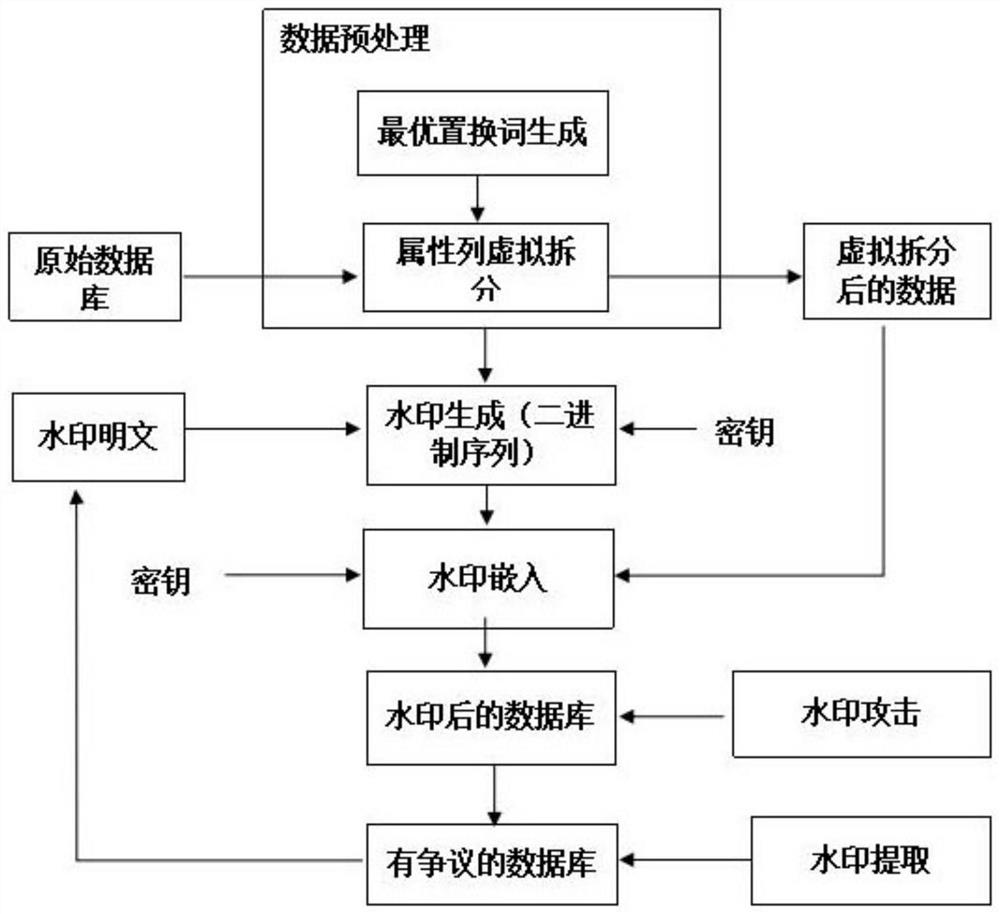
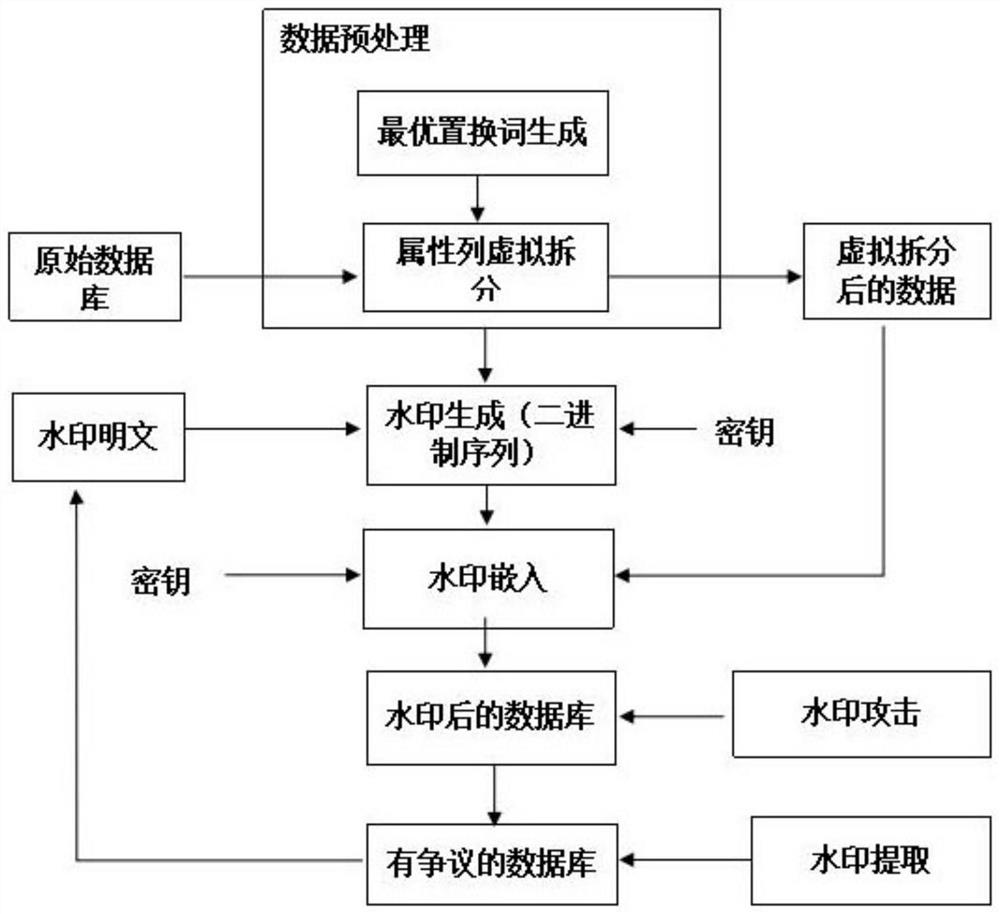
Digital watermarking algorithm of relational database
ActiveCN111797369AResistance to Common AttacksReduce distortionRelational databasesNatural language data processingDatabase securityNumeric Value
The invention relates to a digital watermarking algorithm of a relational database. The threat problems of copyright protection, confidentiality and privacy of content and authenticity and integrity of data faced by the security of the existing database are solved. The method comprises the following steps: 1, preprocessing data; 2, converting a watermark plaintext into a binary sequence by using aprivate key of a database copyright owner; 3, respectively executing a watermark embedding program by taking each attribute value as a non-numerical attribute column of the natural language as a unit; 4, publishing the database table embedded with the watermark; 5, when a copyright dispute occurs, carrying out watermark extraction work on the database table with the copyright dispute, and using the watermark as an effective proof of copyright affiliation; and 6, completing watermark extraction according to the personal private key of the database owner, the key corresponding to the attributecolumn, the existence of the virtual splitting column and the embedding process operation record involved in step 3. The method can be widely applied to copyright protection of character database security.
Owner:HARBIN INST OF TECH AT WEIHAI
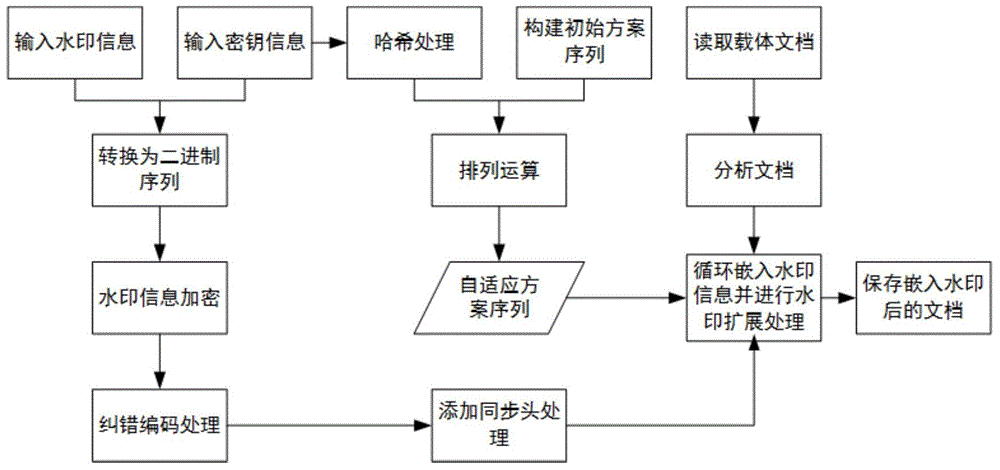
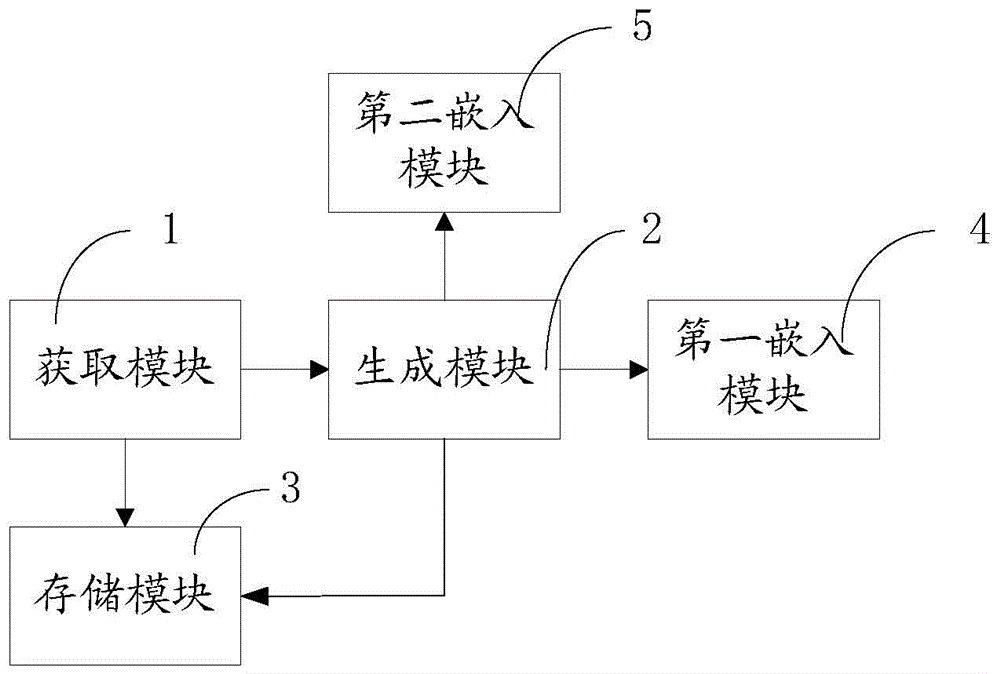
Method and device for embedding and extracting multiple digital watermarks in documents
ActiveCN103761459BImprove securityIncrease watermark capacityNatural language data processingProgram/content distribution protectionUser inputDocumentation
The invention relates to a document multiple digital watermarking insertion method and device, and a document multiple digital watermarking extraction method and device. The document multiple digital watermarking insertion method comprises the following steps of obtaining an original watermarking message, a secret key and a document to be processed, wherein the original watermarking message is input by a user; calculating a summary message in the original watermarking message, generating new watermarking messages, storing the original watermarking message and the new watermarking messages into a database as a database record together, dividing characters in the document into two layers, obtaining the number of sets of the new watermarking messages to be inserted into the first layer of the document according to the total number of the characters of the first layer of the document and the length of the digits of the new watermarking messages, inserting the multiple sets of new watermarking messages into the property digits of the first layer of the document sequentially from front to back, and inserting the multiple sets of new watermarking messages into the property digits of the second layer of the document sequentially from back to front. Based on the character property of the document of the Word format, safety is improved due to the use of the secret key, robustness is enhanced due to repeated insertion, and watermarking capacity is improved due to multiple insertions.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Piracy tracing watermarking method applicable to streaming media environment
ActiveCN102307320BImprove real-time performanceReduce complexityTelevision systemsDigital video signal modificationWatermark methodMotion vector
The invention relates to a piracy tracing watermarking method applicable to streaming media environment, and belongs to the multimedia information safety field. The method comprises the following steps: firstly segmenting video before the watermark embedding procedure; according to content of streaming video, selecting macroblocks meeting the conditions to be embedded with watermarks during the watermark embedding process; and determining the macroblock which is best suited for being embedding with watermark information by adopting a quicksort algorithm. In the piracy tracing watermarking method, based on difference between horizontal direction and vertical direction of motion vector of the macroblock, appropriate motion components are adaptively selected to be embedded with 2-bit watermark information, and the NAL (network abstraction layer) head of a B-frame is modified after the watermark embedding procedure so that the watermark can cope with the situations such as frame loss and the like resulting from network transmission. By adopting the piracy tracing watermarking method, the watermark information can be embedded into the streaming video in real time so as to achieve the purpose of piracy tracing.
Owner:JIANGSU YITONG HIGH TECH
Color-blind Watermarking Method Based on Hamming Code, Eigenvalue Decomposition and Image Correction
ActiveCN111223035BImprove robustnessWatermark is invisibleImage data processing detailsPattern recognitionColor image
The invention combines Hamming code theory and eigenvalue decomposition, and discloses a color-blind watermark method based on Hamming code, eigenvalue decomposition and image correction. First, according to the characteristics of eigenvalue decomposition, the present invention obtains all the eigenvalues of the pixel block, and completes the embedding and blind extraction of the digital watermark by quantifying the sum of the absolute values of the eigenvalues; Geometry attribute, rectifies images after various geometric attacks. The invention can embed the color image digital watermark into the color host image, which not only has good watermark concealment and high security, but also has strong robustness and large embedding capacity, and is suitable for strong robust Occasions for copyright protection of large-capacity color digital images.
Owner:上海瑞盛联信息科技有限公司
Spot color printing image digital watermarking method and system
ActiveCN108460716BImprove stabilityIncrease watermark capacityImage analysisImage watermarkingPattern recognitionDigital signature
Based on the conversion principle of color space in spot color printing, the invention combines IWT and SVD to propose a digital watermarking method and system for spot color printing images. The method and system decompose the carrier image into spot color channels, perform IWT conversion on the spot color channels, and then directly embed the watermark information into the singular values of each subband of the first-level IWT; in order to improve the security of the watermark, the watermark image is Arnold configured Random encryption processing, and embed a digital signature that can resist the printing-scanning process in the U and V of the embedded watermark image; in order to improve the robustness of digital signature and watermark, a tone correction model for scanning spot color images is proposed , correct the scanned image, then extract the digital signature for verification, and extract the watermark information if the verification is passed. The invention has excellent performance in watermark transparency, robustness and capacity, can resist offset printing-scanning process, has low algorithm complexity, high execution efficiency, and the extraction time is less than 1 second.
Owner:DALIAN POLYTECHNIC UNIVERSITY
A Digital Watermarking Method for Relational Database
ActiveCN111797369BResistance to Common AttacksReduce distortionRelational databasesNatural language data processingPlaintextRelational database
The invention relates to a digital watermarking algorithm of a relational database, which solves the threat problems of copyright protection, content confidentiality and privacy, and data authenticity and integrity faced by the existing database security. Processing; use the private key of the copyright owner of the database to convert the watermark plaintext into a binary sequence; execute the watermark embedding program in units of non-numeric attribute columns with each attribute value in natural language; publish the database table after embedding the watermark; When a copyright dispute occurs, it is necessary to extract the watermark from the database tables involved in copyright disputes, and use this as an effective proof of copyright ownership; according to the database owner’s personal private key, the key corresponding to the attribute column There are virtual split columns and embedding process operation records to complete watermark extraction. The present invention can be widely applied to the copyright protection of character database safety.
Owner:HARBIN INST OF TECH AT WEIHAI
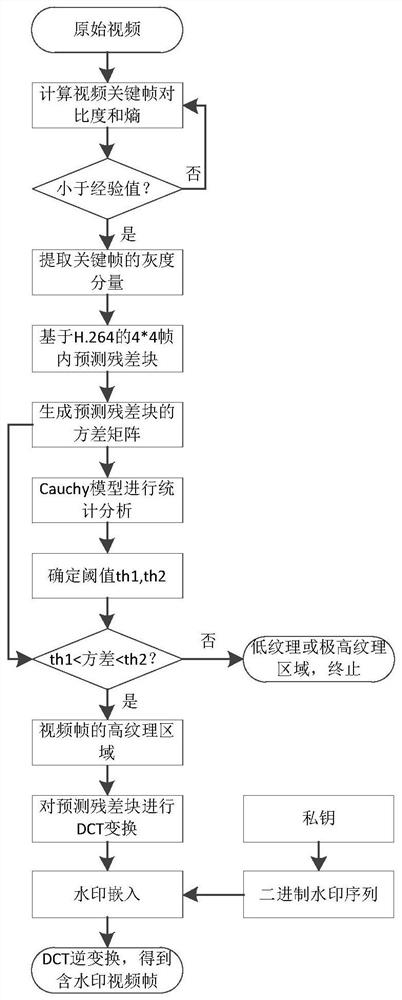
An Adaptive Video Watermark Embedding and Extraction Method Based on ANOVA
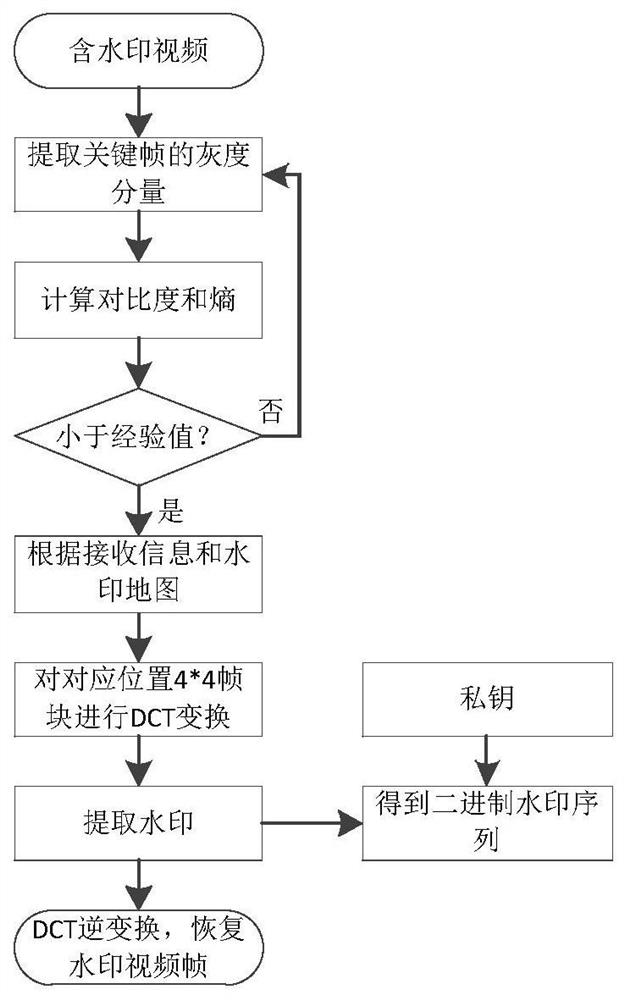
ActiveCN110191343BHigh transparencyIncrease watermark capacityDigital video signal modificationGradationKey frame
The present invention relates to an adaptive video watermark embedding method based on variance analysis, which comprises the following steps of calculating contrast and entropy for received video key frames, and discarding the frame if both the contrast and entropy are lower than a preset threshold; If it meets the requirements, go to the next step; extract the grayscale component of the key frame; perform 4*4 intra-frame prediction based on H.264 on the extracted grayscale image, and calculate the prediction residual matrix; calculate the variance of the prediction residual matrix, And generate the variance matrix of the video frame; according to the threshold th 1 and th 2 , divide the texture complexity of the video frame into low-texture regions S 0 , the highly textured region S 1 and higher texture regions S 2 ; Perform DCT transformation on the 4*4 video frame block in the high texture area, and embed the watermark information on the DC coefficient of the DCT. The embedding method adaptively embeds the watermark information in the high texture area of the video frame, and transforms the invisibility and robustness of the domain watermark.
Owner:HOHAI UNIV
A watermark embedding and authentication method that can locate the tampering of pdf electronic invoices
InactiveCN104899822BIncrease watermark capacityImprove securityImage data processing detailsInvoiceFalse detection
A watermark embedding and authentication method capable of locating tampering of PDF electronic invoices, including A generating watermarks based on document reading pages, specifically including reader page segmentation, parsing code page file structures; generating authentication information, and generating watermarks based on the authentication information; B Watermark embedding based on file code; C. Update of cross index table and file tail; D. Generation of watermarked PDF electronic invoice file; Tamper authenticity judgment and tamper positioning and marking. In this method, while ensuring that the watermark is invisible, the file increment is small and controlled within 1%. It has high detection accuracy for tampering, low false detection rate, and can effectively resist tampering such as replacement, addition and deletion.
Owner:SOUTHWEST JIAOTONG UNIV
Spatial domain adaptive color image blind watermarking method based on Slant transform
ActiveCN111882478AIncrease watermark capacityWatermark is invisibleImage data processing detailsPattern recognitionColor image
The invention discloses a spatial domain adaptive color image blind watermarking method based on Slant transform by combining a Slant transform theory and an integer pairing theory. Firstly, the maximum energy coefficient of a coefficient matrix obtained after Slant transformation is directly solved in an airspace according to watermark capacity, a self-adaptive watermark coding mode and Slant transformation characteristics, the coefficient is quantized to complete embedding of the color watermark, and the method has good concealment and large watermark capacity; Secondly, the step length canbe adaptively quantified according to the size of the image, the geometric attributes of the attacked image can also be utilized to correct the images of various attacks, and the robustness of geometric attack resistance is high. A plurality of integer keys can be encrypted into a large integer and steganographically written into the file structure of the image, so that the security is relativelyhigh. The invention is suitable for occasions of efficient color digital image copyright protection with high safety, good concealment, strong robustness and large watermark capacity.
Owner:上海瑞盛联信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com