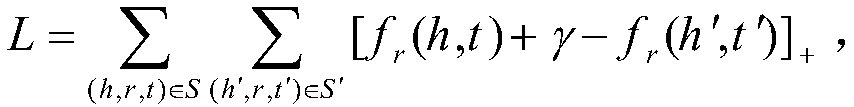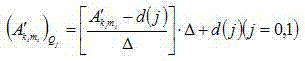Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
179results about How to "Implement embedding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
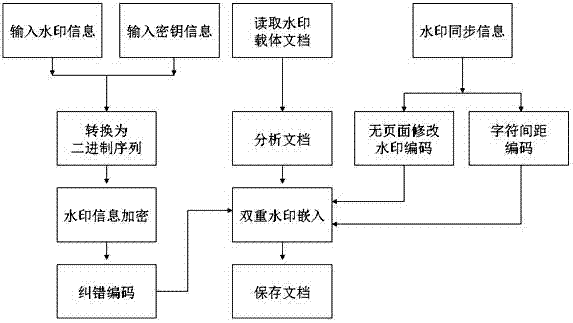
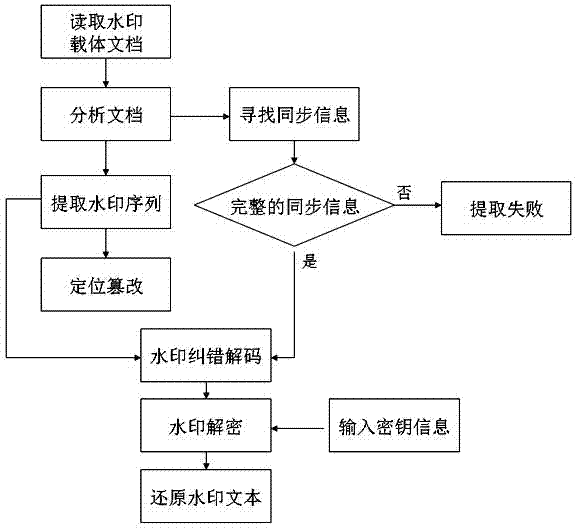
Character pitch encoding-based dual-watermark embedded text watermarking method
InactiveCN103049682AImprove robustnessRealize portabilityProgram/content distribution protectionSpecial data processing applicationsData integrityCovert communication
The invention relates to a character pitch encoding-based dual-watermark embedded text watermarking method, comprising the following steps of: converting watermark information M and a key D, which are required to be hidden, into a binary sequence, circularly executing modulus to get an encrypted binary sequence, adding error-correcting codes for the to-be-embedded watermark information, and finally embedding dual watermarks and synchronization information of the watermarks by encoding the attribute of a text object without page modification and encoding a character pitch. With the method, the text content cannot be changed, the watermark information is hidden well, and the method has the characteristics of high robustness and high capacity. By extracting the embedded watermark information, transmission and modification of a document can be controlled effectively, and whether the document is modified can be judged, and finally, the aims of digital copyright protection, data integrity authentication and safe covert communication for the text document are achieved.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
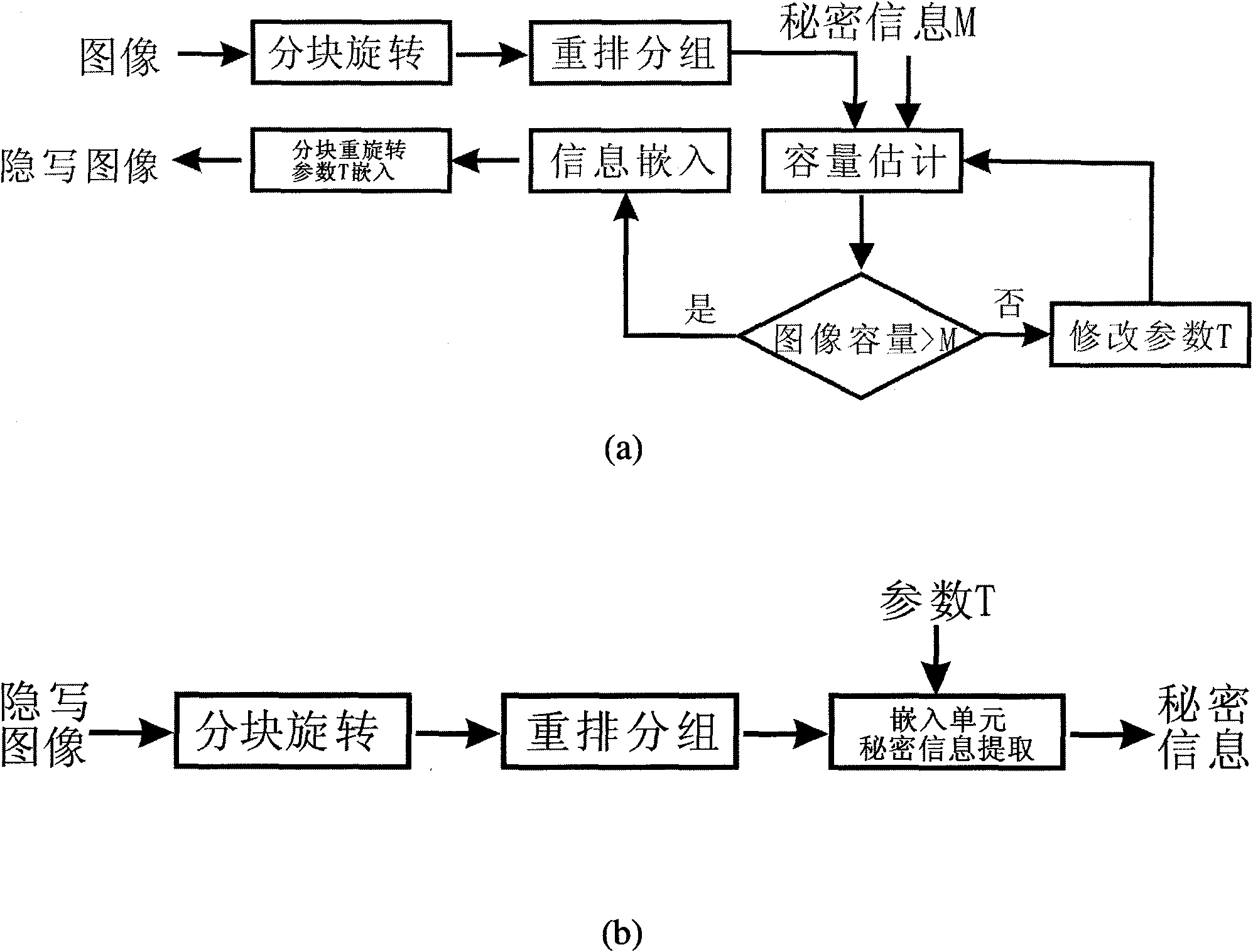
Embedding method and extracting method of reversible watermarks
InactiveCN102044061AImplement embeddingImplement extractionImage data processing detailsFlag sequenceGray level image
The invention discloses an embedding method and an extracting method of reversible watermarks, belonging to the technical field of digital watermarks. The embedding method comprises the following steps of: sequentially reading the pixel values of digital images, and establishing a position sign sequence; compressing the position sign sequence, and regulating a pixel with the pixel value of 0 or 255; calculating forecast error sequences of the digital images, and selecting internal areas and parameters T which are needed in the embedding process; and embedding the reversible watermarks according to the selected parameters. The extracting method comprises the following steps of: sequentially reading the pixel values of the digital images, and extracting various kinds of auxiliary information; uncompressing the compressed position sign sequence to obtain the uncompressed position sign sequence; carrying out inverse solution referring to the embedding parameters so as to obtain embedding information; regulating the pixel values according to the position sign sequence; and finally, sequentially substituting the sequences for least significant bits of the pixel values, wherein carrier images can be completely recovered at the time. The invention can successfully realize the embedding and the extraction of the reversible watermarks on gray level images and the recovery of original images.
Owner:PEKING UNIV
Adaptive spatial steganographic method based on adjacent pixel difference
InactiveCN101582157AImprove securityImplement embeddingImage data processing detailsPattern recognitionCovert communication
The invention provides an adaptive spatial steganographic method based on adjacent pixel difference. The method comprises the following two steps: embedding secret information and extracting the secret information. The method takes three continuous adjacent pixels in an image as an embedding unit and reaches the goal of hiding information by changing the value of the middle pixel in each unit. During information embedding, a steganographic algorithm always mains the size relationship of each pixel in the embedding unit, and adaptively adjusts the capacity of embedding information through a parameter according to the content of the image. Experiments show that the adaptive spatial steganographic method has higher safety and adaptive ability compared with the prior steganographic method based on pixel difference. Therefore, the adaptive spatial steganographic method has great practical significance to application fields such as covert communication and the like.
Owner:SUN YAT SEN UNIV
Methof for embedding and extracting watermark based on statistical model of coefficient in transform domain of digital images
InactiveCN101004831AImplement embeddingImplement extractionImage data processing detailsComputer graphics (images)Dct transform
A method for embedding and picking up digital watermark based on digital image transform coefficient statistic model includes making desired value of image sub-block DCT transform be positive or be negative by changing distribution of alternating-current coefficient on image sub-block DCT transform, enabling to embed and to pick up digital watermark before and after printing and scanning as said property can be remained still after image is printed and scanned.
Owner:PEKING UNIV +2
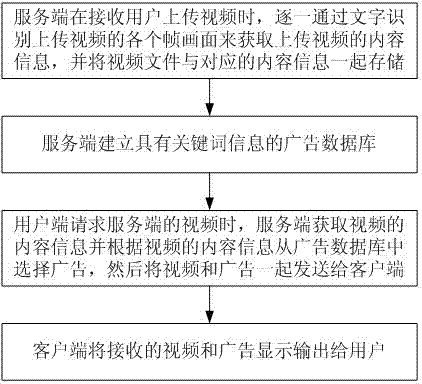
Management method of online video advertisement related to video content
InactiveCN102523533AImplement embeddingReduce operating costsSelective content distributionSpecial data processing applicationsClient-sideIndex term
The invention discloses a management method of an online video advertisement related to video content, comprising the following implementation steps of: 1) when a service end receives a video uploaded by a user, the content information of the uploaded video obtained by each frame image recognizes the gradually uploading of the video; and storing a video file and the corresponding content information together; 2) establishing an advertisement database with keyword information by the service end; 3) when a user end requests the video of the service end, obtaining the content information of the video by the service end and selecting an advertisement from the advertisement database according to the content information of the video; and then sending the video and the advertisement to a client; and 4) display output the received video and advertisement to a user by the client. The management method provided by the invention has the advantages of realization of the embedment of video advertisements, reduction of the operation cost of video services, and simplicity and convenience in use.
Owner:JIANGSU QIYIDIAN NETWORK
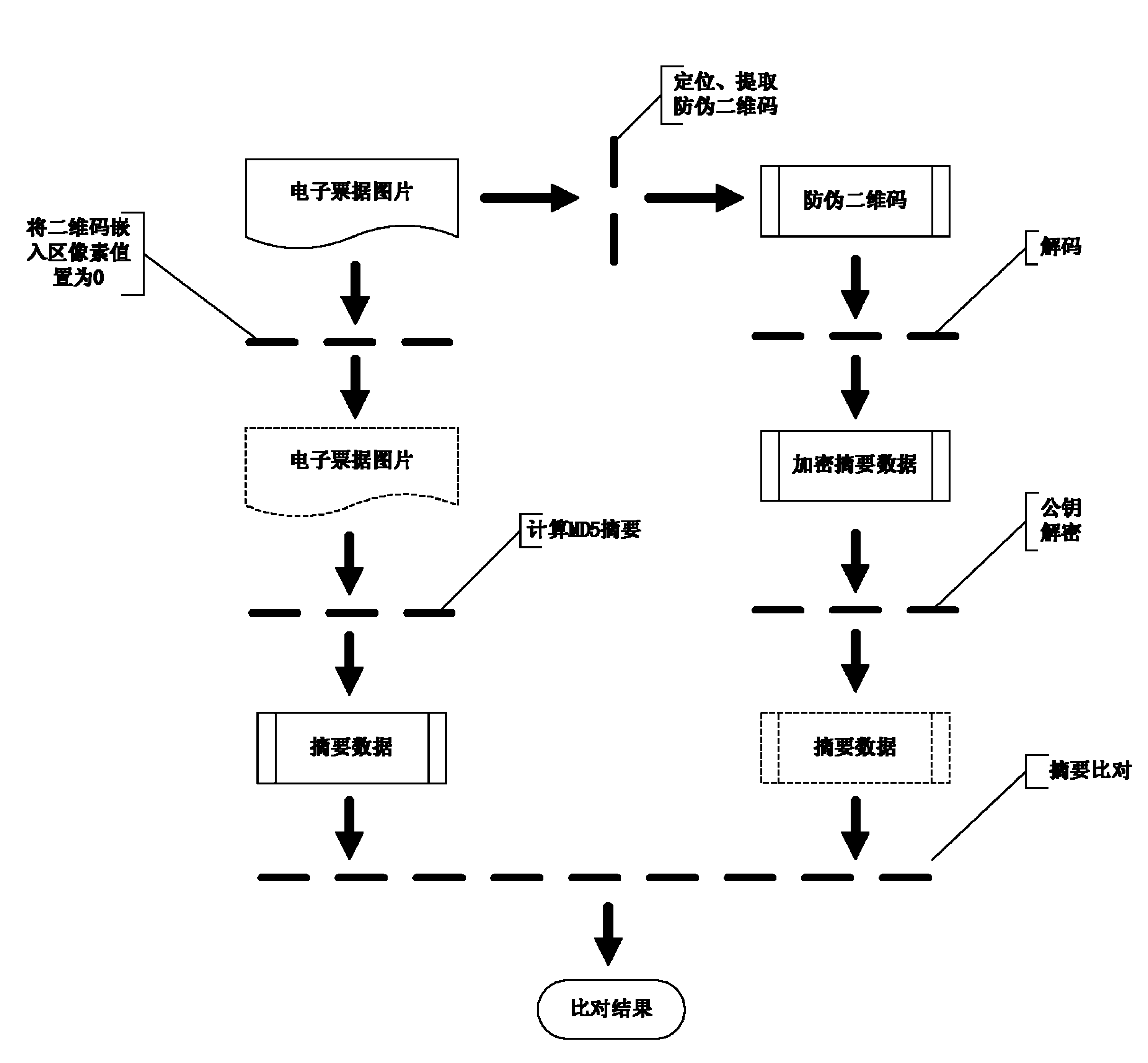
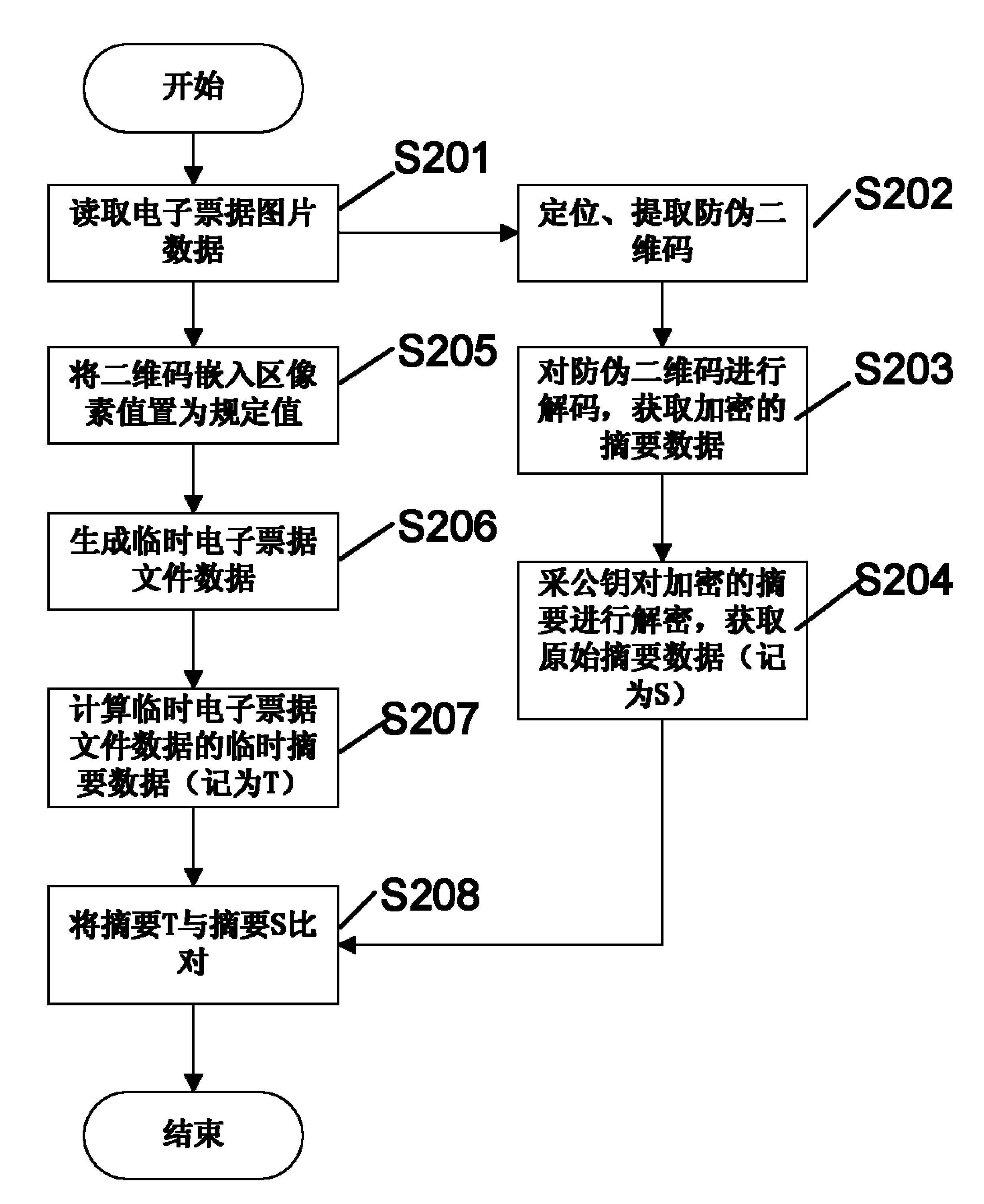
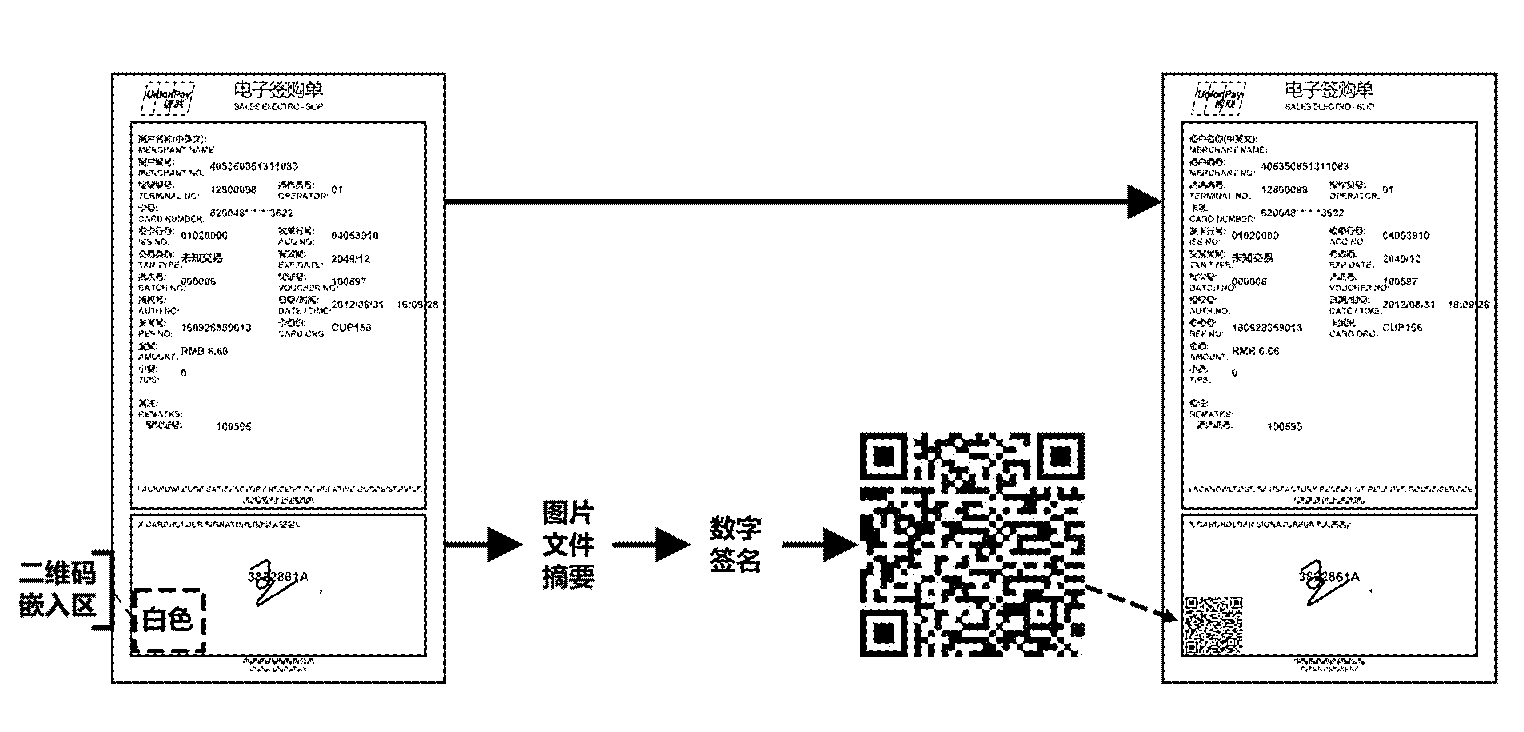
Methods and systems for generating and checking electronic note with anti-counterfeiting two-dimension code
InactiveCN104077624AImprove embedding capacity and recognition rateImprove style diversity and practicalityBilling/invoicingRecord carriers used with machinesAlgorithmTheoretical computer science
The invention relates to methods and systems for generating and checking an electronic note with an anti-counterfeiting two-dimension code. The method for generating the electronic note with the anti-counterfeiting two-dimension code comprises the following steps that: an original electronic note picture is read, and a temporary electronic note picture with a defined two-dimension code embedding region is generated; for the temporary electronic note picture, an information abstract algorithm is utilized for calculating abstract data, and in addition, the obtained abstract data is encrypted for generating the anti-counterfeiting two-dimension code; and the anti-counterfeiting two-dimension code is embedded into the two-dimension code embedding region of the original electronic note picture, and the electronic note with the anti-counterfeiting two-dimension code is obtained. The methods and the systems provided by the invention can be used for effectively preventing the tampering and the counterfeiting of the electronic note, and in addition, the diversity and the practicability of the electronic note can be greatly improved.
Owner:CHINA UNIONPAY
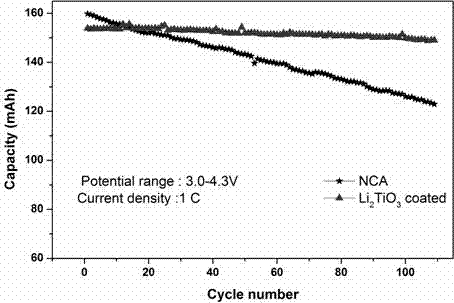
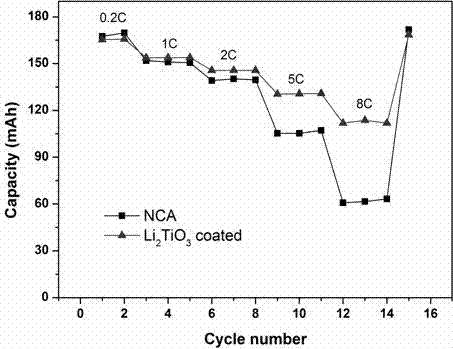
Preparation method for lithium metatitanate-coated nickel-cobalt-lithium aluminate positive electrode material
InactiveCN106910881AReduce the amount of residual alkaliImprove stabilityCell electrodesSecondary cellsAir atmosphereElectrical conductor
The invention especially discloses a preparation method for a lithium metatitanate-coated nickel-cobalt-lithium aluminate positive electrode material, belonging to the field of positive electrode materials of lithium ion batteries. The preparation method for the lithium metatitanate-coated nickel-cobalt-lithium aluminate positive electrode material is characterized by comprising the following steps: adding titanium dioxide and nickel-cobalt-lithium aluminate powder into a coating device and carrying out sufficient dispersion, adsorption and recombination so as to obtain solid powder; and putting the solid powder into a muffle furnace, carrying out heating, roasting the solid powder in an air atmosphere and then carrying out natural cooling to room temperature so as to obtain lithium metatitanate-coated nickel-cobalt-lithium aluminate. According to the invention, lithium metatitanate is used for surface coating and used as a conductor material for Li<+>, so intercalation and deintercalation of Li<+> can be better realized, and the cycle performance and rate performance of the material are improved; and through coating with lithium metatitanate, humidity sensitivity of NCA is reduced, direct contact between the electrode material and an organic electrolyte is decreased, so the structural stability of NCA is further improved and security of the material is enhanced.
Owner:SHANDONG YUHUANG NEW ENERGY TECH
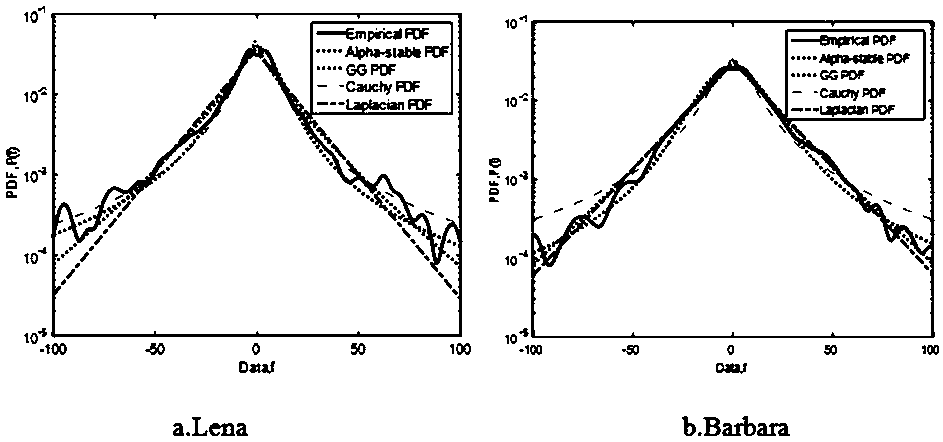
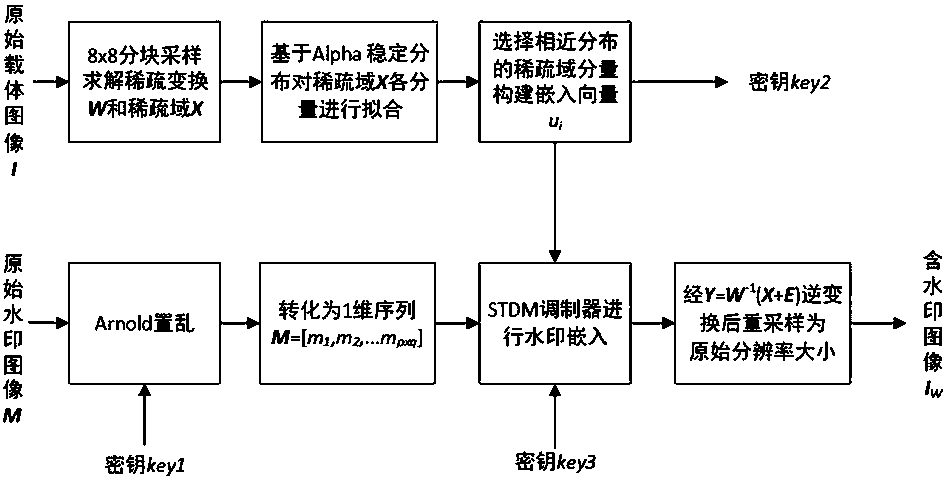
Sparse transformation-based digital blind watermark embedding and extracting method
ActiveCN108596823AImplement embeddingImplement extractionCharacter and pattern recognitionImage data processing detailsWatermark embeddingFrequency domain
The invention discloses a sparse transformation-based digital blind watermark embedding and extracting method. The method comprises the following steps of: carrying out 8*8 non-overlapped blocking onan original image; combining the segmented image blocks with a sparse transformation model; compressing an embedding range by using a sparse frequency domain space; estimating each frequency domain component coefficient on the basis of Alpha distribution; and carrying out watermark embedding by selection similarly distributed frequency domain components. During watermark extraction, original images are not required so that blind extraction is realized. Experimental results prove that the method is capable of effectively resisting the attacks of JPEG compression, noise and shearing, and has relatively good invisibility and robustness.
Owner:SUZHOU UNIV
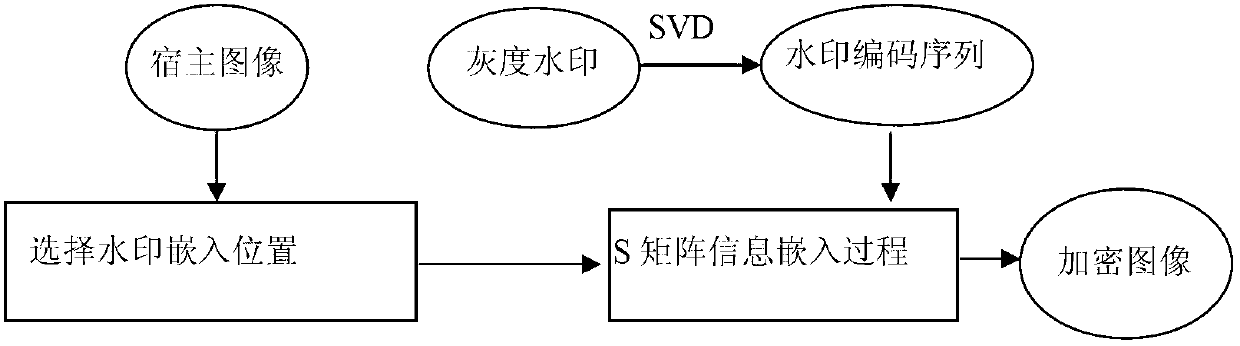
Gray image watermark embedding and extracting method based on singular value decomposition
InactiveCN103106636AInformativeIntuitive amount of informationImage data processing detailsSingular value decompositionPersonalization
The invention discloses a gray image watermark embedding and extracting method based on singular value decomposition. The gray image watermark embedding and extracting method based on singular value decomposition comprises the flowing steps: conducting singular value decomposition on an image and obtaining matrix components; conducting encoding and storage on singular values of a diagonal matrix of a singular value matrix and obtaining watermark signals; blocking a hosting image and choosing image blocks high in masking effect; conducting singular value decomposition on the image blocks and embedding the watermark signals into the image blocks; and conducting inverse transformation of the singular value decomposition on the image blocks. The gray image watermark embedding and extracting method based on singular value decomposition has the advantages that the embedding of the gray image watermark image is achieved, the watermark comprises a plurality of straight information, no using limiting exists on the size of the watermark image, and requirements of enterprises concealing personalized enterprise logos as watermarks can be met; the watermark embedding and extracting method can resist a plurality of image aggressive behaviors, and algorithm robustness is high; gray image watermark embedding and extracting method based on singular value decomposition can effectively detect watermark information content, solves the problem of image being illegally issued and the like, and is of great value for healthy and fast development of internet industries.
Owner:DALIAN NATIONALITIES UNIVERSITY
Watermarking method for medical images on basis of DFT (discrete Fourier transform) and LogisticMap
InactiveCN102938132ASolve the quickness problemImprove securityImage data processing detailsFeature vectorHash function
The invention relates to a robust watermarking method on the basis of DFT (discrete Fourier transform) and a Logistic Map, and belongs to the field of multimedia signal processing. The robust watermarking method includes preprocessing and embedding watermarks and then extracting and reducing the watermarks, and particularly includes steps of (1), generating a binary encrypted matrix by the aid of the Logistic Map; (2), obtaining encrypted watermarks; (3), performing DFT for an original image and extracting feature vectors; (4), generating a binary logic sequence by the aid of the feature vectors and the chaotically encrypted watermarks to complete the process for preprocessing and embedding the watermarks; (5), performing DFT for an image to be measured to extract vectors of a feature; (6), extracting watermarks by the aid of a Hash function and the binary logic sequence generated when the watermarks are embedded; (7), generating a binary encrypted matrix by the Logistic Map; and (8), solving the reduced watermarks so as to complete the process for extracting and reducing the watermarks. The robust watermarking technology has a high practical value in the aspect of protecting personal information of patients during remote medical treatment.
Owner:HAINAN UNIVERSITY
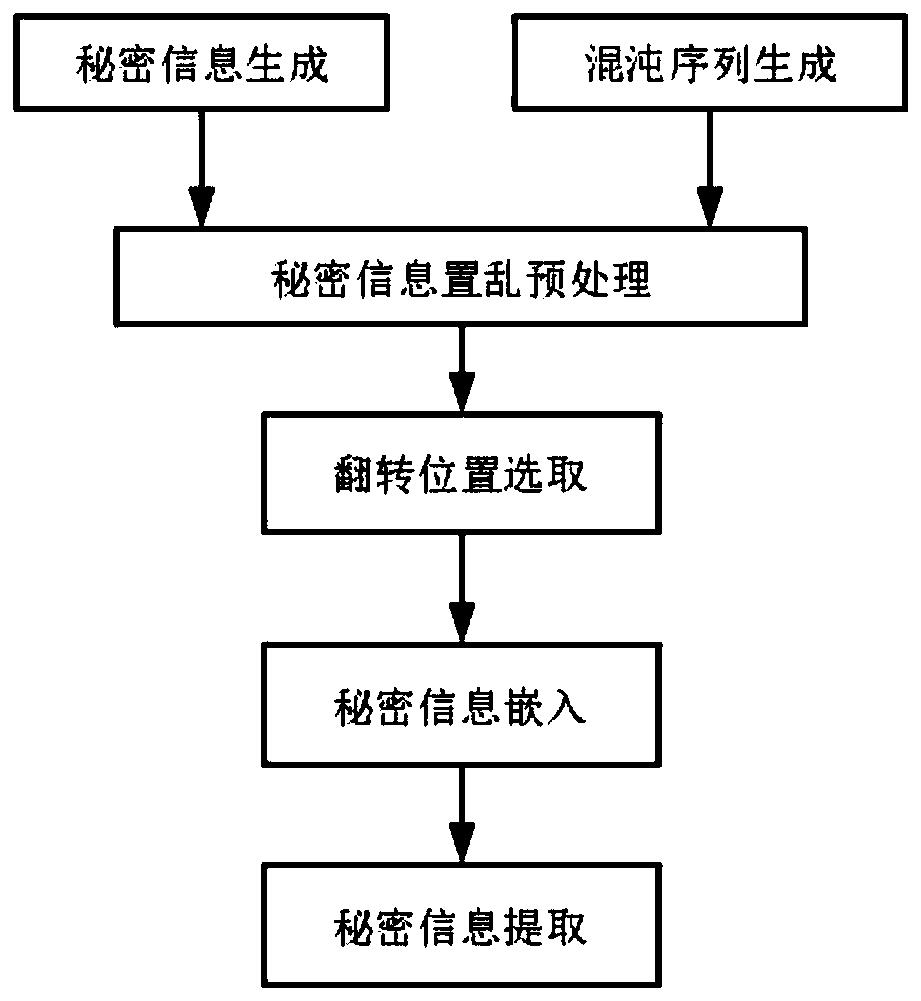
High-capacity binary image information hiding method
InactiveCN108629728AImplement embeddingImplement extractionChaos modelsNon-linear system modelsLarge capacitySide information
The invention discloses a high-capacity binary image information hiding method. In a secret information embedding part, a logistic one-dimensional chaotic system is firstly used for generating an aperiodic, non-convergent and irrelevant chaotic sequence, and the to-be-embedded information is subjected to scrambling preprocessing. After that, a scrambling secret key is stored. A secret-carrying image is segmented, and then reversible pixel blocks which conform to the visual characteristics of human eyes are determined by calculating the connectivity values of image areas before and after the pixel blocks are turned over. After that, the reversible pixel blocks are modified, and a weighted total value of non-critical pixels is adjusted by turning over the non-critical pixels. As a result, the information embedding is realized. Finally, the reversible pixel blocks are sequentially processed to complete the embedding process. In a secret information extraction part, the auxiliary information is not needed, and the secret information is extracted through the statistics of the non-critical pixel values of the reversible pixel blocks. In this way, a chaotic sequence is obtained through asecret key. The real secret information is obtained through calculation. According to the method, on the basis of guaranteeing the high invisibility, the higher embedding capacity and the better safety are realized.
Owner:BEIJING UNIV OF TECH
Lithium sulphur battery and manufacturing method thereof
InactiveCN102694196AImplement embeddingFinal product manufactureLi-accumulatorsLithium–sulfur batteryCopper foil
The invention discloses a lithium sulphur battery taking a lithium intercalated carbon material as a negative electrode in the field of an electrochemical battery and a manufacturing method thereof. The lithium sulphur battery comprises a positive electrode, a negative electrode, electrolyte, a diaphragm and an enclosure and is characterized in that the negative electrode is a lithium intercalated carbon material, rather a normal metal lithium plate. The manufacturing method for the battery comprises the following steps: (1). coating sulfur-containing positive material on an aluminium foil, and coating carbon negative material on a copper foil; (2). winding or stacking the positive electrode, the diaphragm and the negative electrode together, wherein the outermost layer is the negative electrode; (3). separating the outermost carbon negative electrode by the diaphragm, and then winding or stacking with the metal lithium plate pressed on a copper plate; (4). connecting all positive electrodes through electrode lugs, and connecting all negative electrodes with the metal lithium plate through the electrode lugs; and (5). adding lithium-ion electrolyte and keeping the mixture for 10-20 days. According to the lithium sulphur battery and the manufacturing method thereof, lithium is intercalated in the carbon negative electrode by an electrochemical method in advance, so that the condition that high-activity metal lithium appears is avoided during a using process of the traditional lithium sulphur battery, and the safety and cycling performance of the lithium sulphur battery are improved; besides, the manufacturing cost is low, the process is simple, and the application value is great.
Owner:DALIAN LICHANG NEW MATERIAL CO LTD
DWT-DCT (Discrete Wavelet Transform-Discrete Cosine Transform) and Logistic Map-based medical image robust watermarking method
InactiveCN102945543AStrong resistance to conventional attacksStrong ability to resist geometric attacksImage data processing detailsThird partyFeature vector
The invention relates to a DWT-DCT (Discrete Wavelet Transform-Discrete Cosine Transform) and Logistic Map-based medical image robust watermarking method, which belongs to the field of multimedia signal processing. The method comprises preprocessing of a watermark and embedding of the watermark, wherein the preprocessing of the watermark and embedding of the watermark comprise the following steps of: (1) obtaining an encryption matrix by using a Logistic Map; (2) obtaining an encrypted watermark; (3) performing DWT on an original image, performing DCT on an approximation sub-image and extracting the vector of a characteristic; (4) obtaining a corresponding two-valued logic sequence by using the characteristic vector and chaotically encrypted watermark, storing the two-valued sequence at a third party, and then extracting and reducing the watermark, wherein the extraction and the reduction of the watermark comprise the following steps of: (5) performing operation similar to the step (3) on an image to be tested to solve one characteristic vector; (6) extracting the encrypted watermark; (7) generating a two-valued encryption matrix by using the Logistic Map; and (8) solving the reduced watermark. According to the method, the secrecy of information of a patient can be protected.
Owner:HAINAN UNIVERSITY
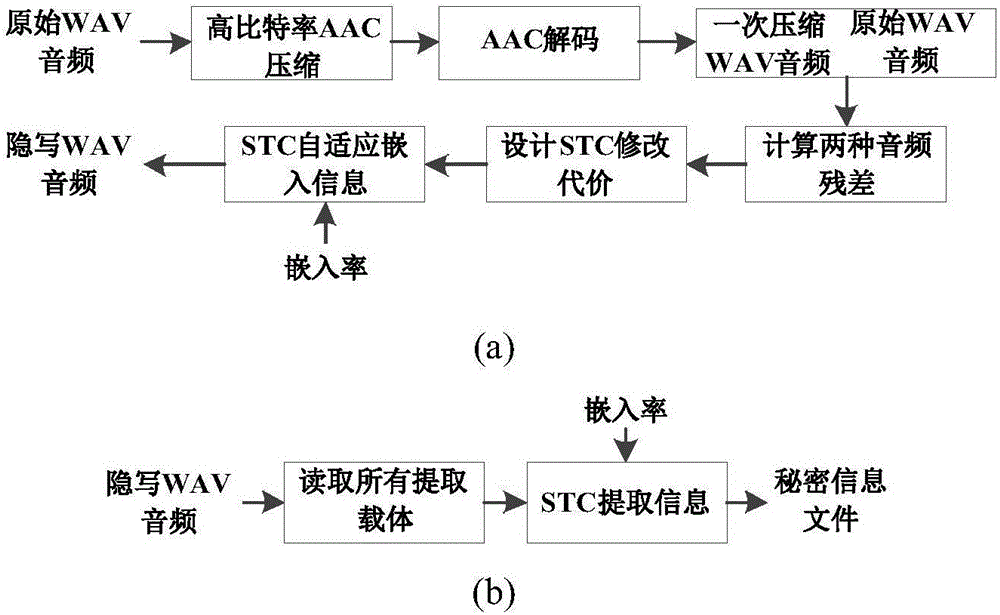
Self-adapting audio frequency spatial domain steganography method
ActiveCN106448686AAvoid randomnessProtecting Sensitive Audience LocationsSpeech analysisVIT signalsSelf adaptive
The invention relates to the multimedia information safety field, to be specific, relates to a self-adapting audio frequency spatial domain steganography method comprising embedding of secret information and extracting of secret information. A WAV audio signal single sample is used as an embedded unit, and a modification cost of every embedded unit is designed according to a signal difference between an original WAV audio signal and the WAV audio signal after once Advanced Audio Coding (AAC) high bit rate compression decompression, and an information coding tool Syndrome Trellis Codes (STC) is used to be adapted to the embedded information automatically to realize correct extracting. According to a lot of experiments, by comparing with a spatial domain steganography method based on LSB matching, the steganography method provided by the invention is advantageous in that higher audio frequency quality and safety of audio frequency after the steganography processing are provided, and therefore an important meaning is provided for covert communication and other application fields.
Owner:SUN YAT SEN UNIV
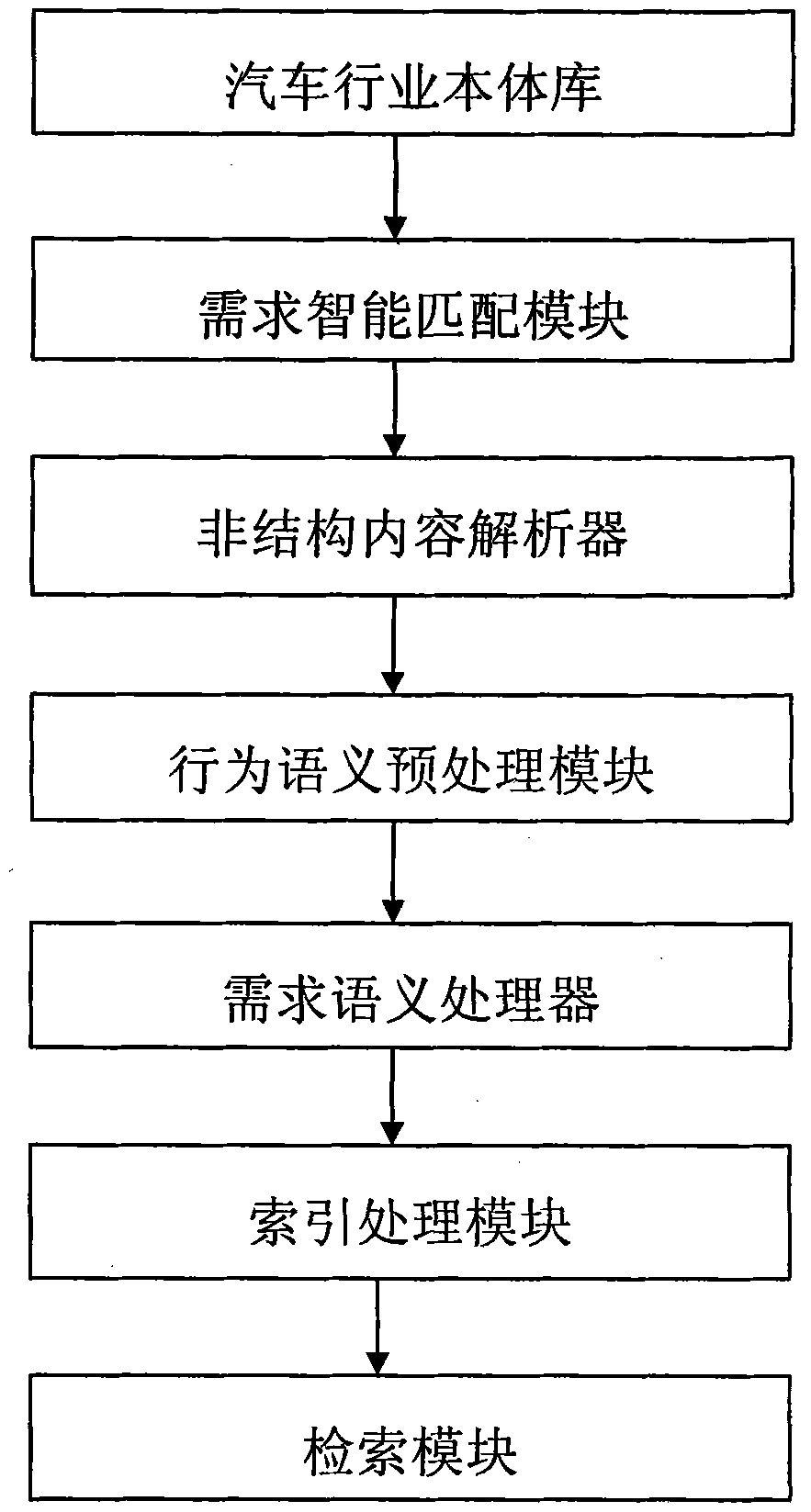
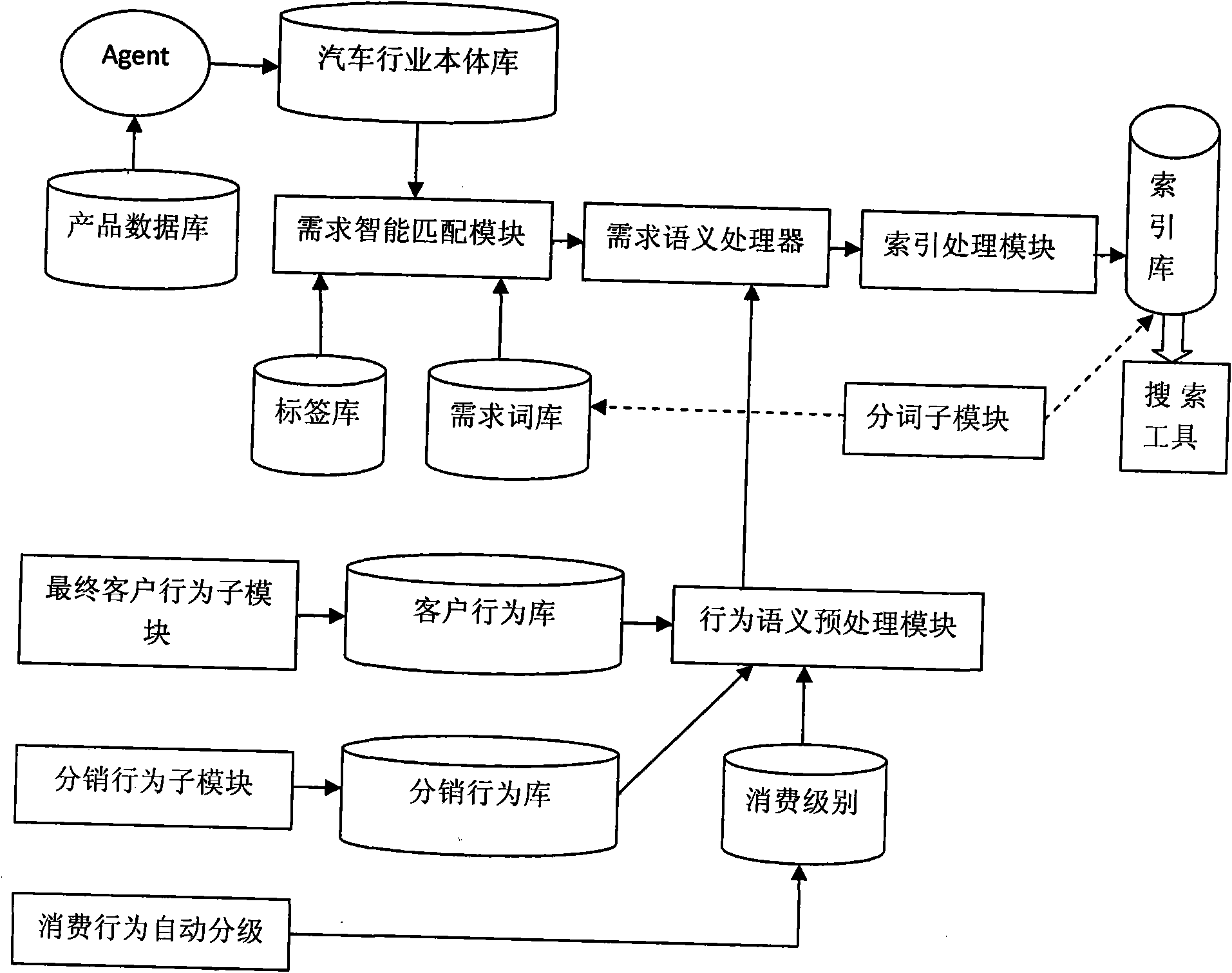
Semantic search system for automobile information analysis and service
InactiveCN102253933AImplement embeddingAchieve deliveryCommerceSpecial data processing applicationsInformation analysisData transformation
The invention relates to the technical field of semantic search and provides a semantic search system for automobile information analysis and service to solve the problems of loss, dislocation and blurring of an original latent semantic meaning in the conventional semantic processing mode. The system comprises an automobile industry ontology base, a demand intelligent matching module, a non-structure and content analyzer, a behavioral semantic meaning preprocessing module, a demand semantic processor, an index processing module and a retrieving module, wherein the automobile industry ontology base is used for supplying automobile industry domain knowledge to the demand intelligent matching module and the demand semantic processor; the demand intelligent matching module is used for matching and recombining data which is in accordance with a standard describing way according to the automobile industry domain knowledge supplied by the ontology base; the non-structure and content analyzer is used for eliminating labels of non-structures and contents to generate an abstract; the behavioral semantic meaning preprocessing module is used for preprocessing semantic information; the demand semantic processor is used for converting data into a relational data format (RDF) and finding a latent relationship between data information by using a reasoning rule; the index processing module is used for collecting, sorting and indexing information resources; and the retrieving module comprises a user interface and a searcher.
Owner:BEIJING NAITE YONGTONG TECH
An image hiding method based on a video carrier and under an off-line controllable mechanism
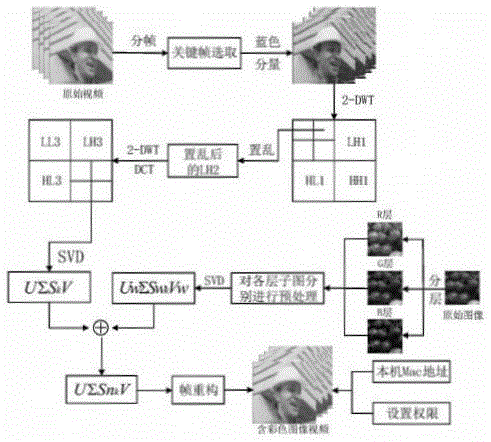
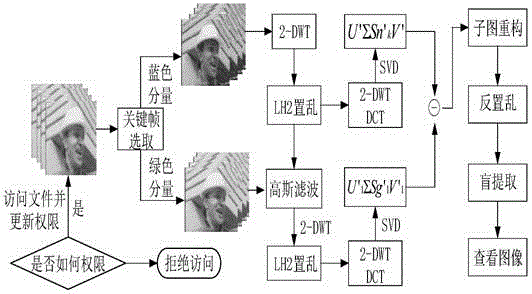
ActiveCN105118018AAchieve effectivenessAchieve controllabilityImage data processing detailsProgram/content distribution protectionColor imageSingular value decomposition
The invention discloses an image hiding method based on a video carrier and under an off-line controllable mechanism. A key frame of a video is firstly subjected to 2-DWT transformation; then Arnold transformation is carried out on sub-bands; through characteristics of singular value decomposition and multi-resolution characteristics of wavelet transformation, images are embedded in sub-band singular values which have undergone scrambling; when the video is under different attacks, blind extraction of the image can be realized; and the blind extraction specifically comprises two steps which are color image confidential storage and color image extraction checking. As technology of embedding and extraction of the color image in the video and the technology of limited frequency checking and anti-copying in an image off-line condition, the method of the invention is the image confidential storage technology based on the video carrier and under the off-line controllable mechanism, and can solve problems of confidentiality and storage of confidential and private images, thereby reaching a purpose of protecting private and confidential information, and realizing validity and controllability access of the image in an extent of competence.
Owner:ANHUI UNIVERSITY
Parallel construction method limiting Delaunay triangulation network
InactiveCN106485766AImplement the buildImplement embeddingDrawing from basic elementsParallel programming modelOperand
The invention discloses a parallel construction method limiting a Delaunay triangulation network. Work in aspects including construction of the Delaunay triangulation network, embedding of constraint conditions and parallel calculation of constraint embedding is carried out. The Delaunay triangulation network is constructed via a pointwise insertion method, construction of a convex hull uses a Graham scanning method, constraint embedding uses a method in which a polygon is subdivided into parts, a possible endless loop of an edge switching algorithm is avoided, a constraint embedded non-common influence domain is parallelized in parallel calculating, and time of constraint embedding is shortened greatly. Parallel programming needs to be combined with practical conditions to realize parallel calculating in serial codes which are large in data bulk and operand and can be parallelized, the system cost for developing multiple threads is much lower than benefit from improvement of parallel calculating due to proper task decomposition, effective data conflict processing and correct selection of parallel strategies, and advantages of parallel calculating are made obvious.
Owner:SOUTHWEST UNIVERSITY
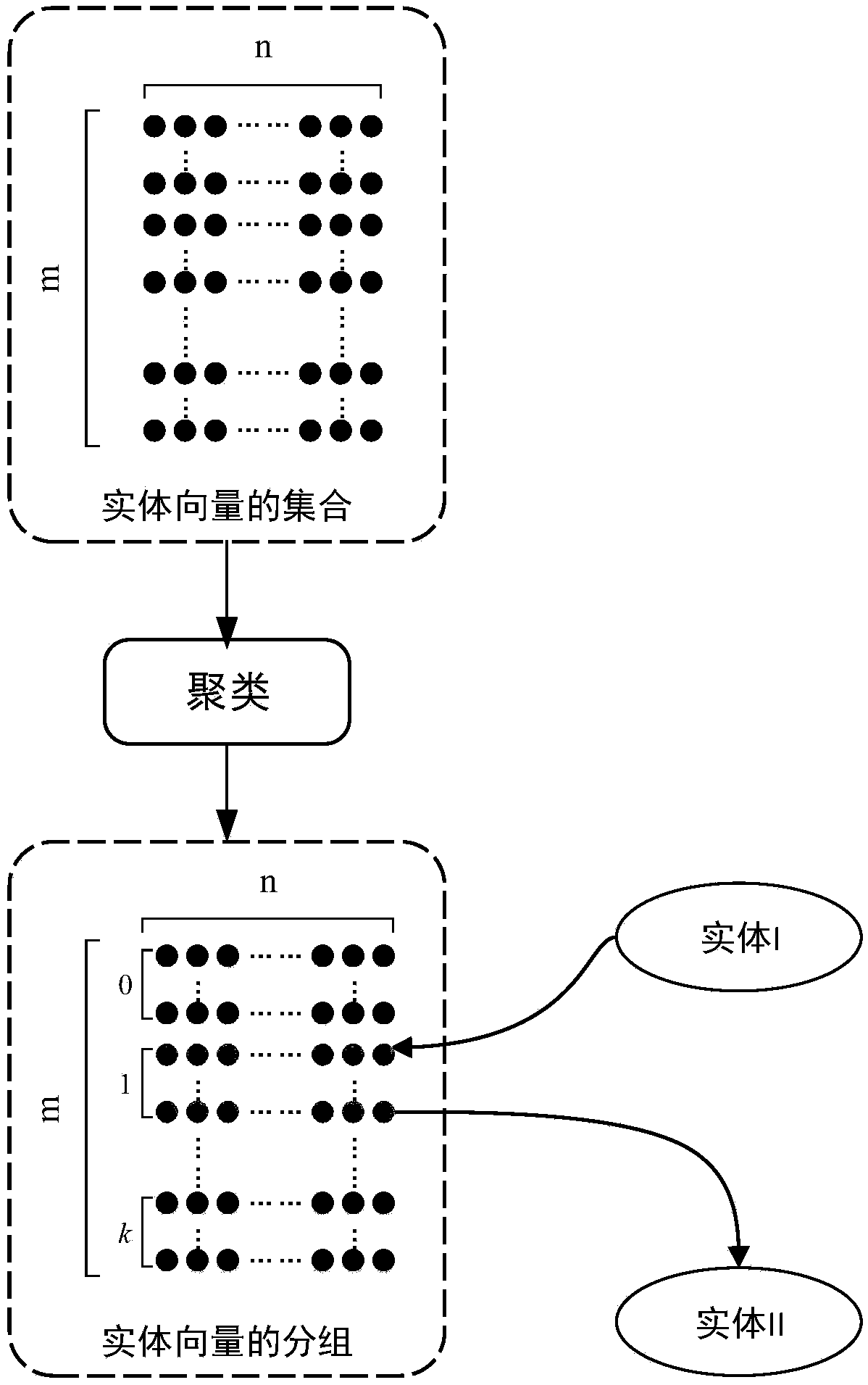
A knowledge map embedding method based on adaptive negative sampling
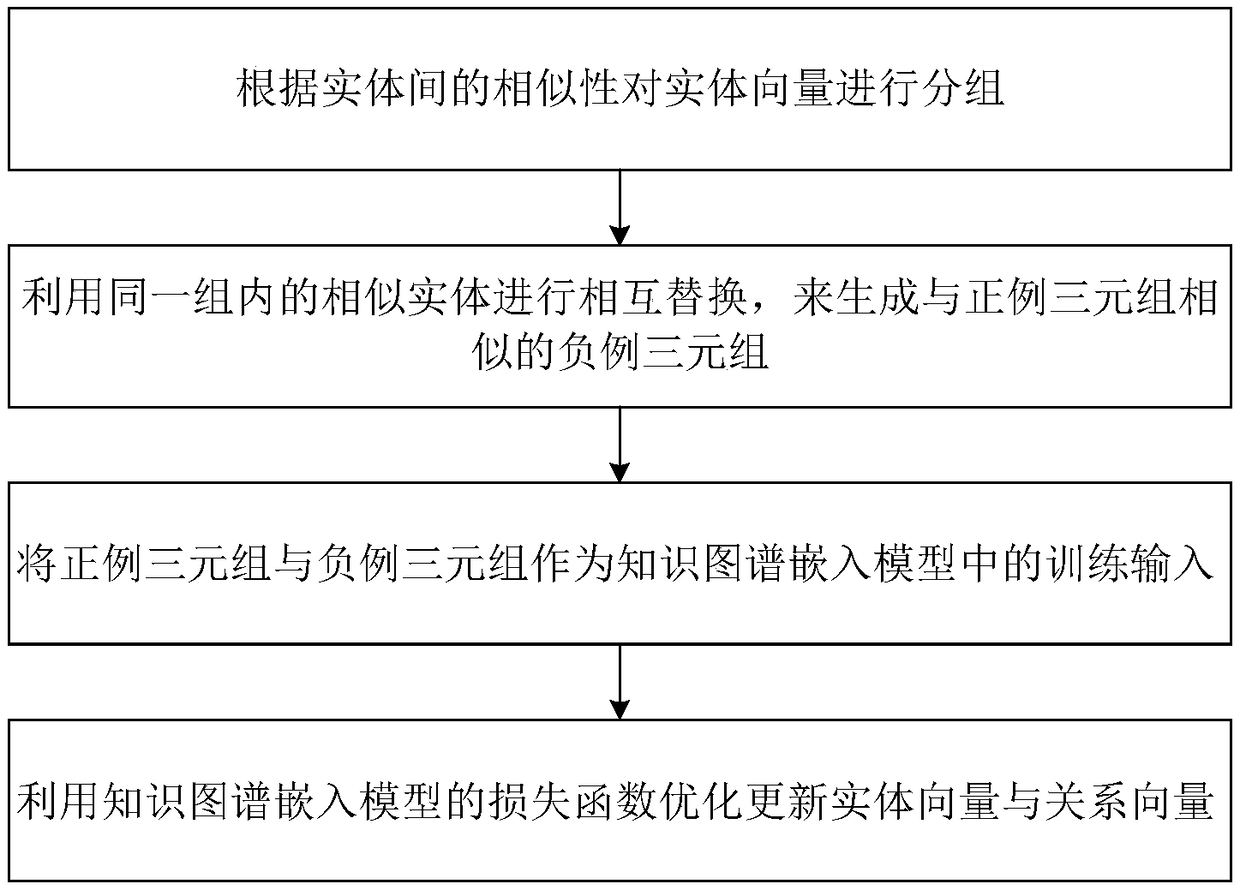
ActiveCN109376249AHigh similarityQuality improvementNatural language data processingSpecial data processing applicationsGroup entityEuclidean vector
The invention provides a knowledge map embedding method based on adaptive negative sampling, which comprises the following steps: step 1, grouping entity vectors according to similarity between entities; 2, utilizing similar entities in the same grouping to replace each other and generate negative case triple similar to positive case triple; 3, taking that positive example triple group and the negative example triple group as the training input of the knowledge map embed in the model; 4, utilizing that loss function of the knowledge map embed model to optimally update the entity vector and therelation vector. The invention improves the similarity between the substituted entity and the substituted entity, thereby improving the quality of the negative example triple. According to the frequency of entities appearing in the knowledge map, the entities are used to improve the training times of high-frequency entities. By improving the quality of negative case triple, the entity and relationship embedding in knowledge map is realized effectively.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Preparing device and method of thermoplastic resin matrix prepreg reinforced by continuous carbon fibers
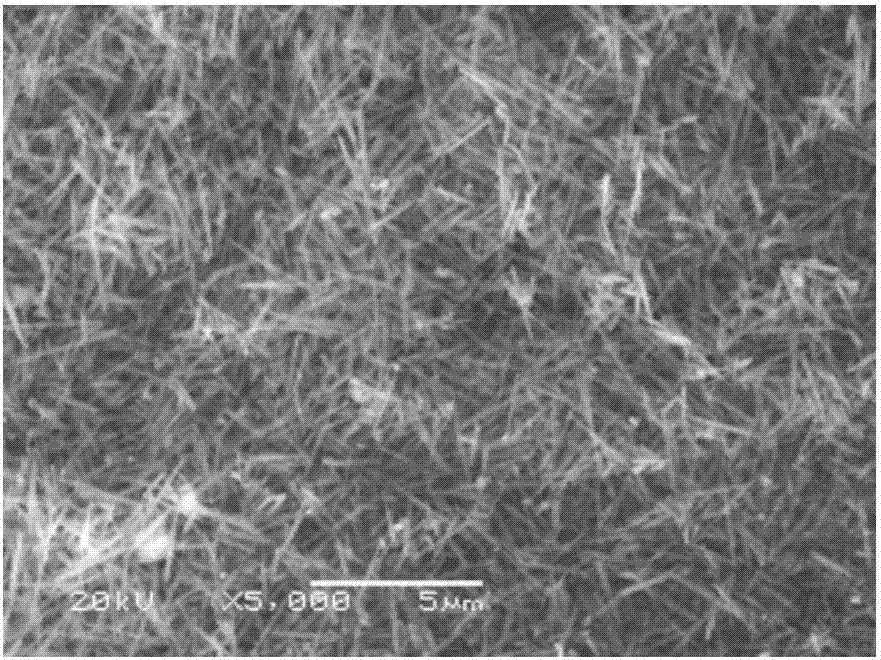
The invention discloses preparing device and method of a thermoplastic resin matrix prepreg reinforced by continuous carbon fibers and belongs to the field of composites. Left and right wedge-shaped swaying blocks are separately matched with first left and right elastic tension rollers so as to realize the bundle loosening, splitting and tensioning of the carbon fibers. Through a rapid pressing function which is performed after the left and right wedge-shaped swaying blocks are separately in contact with second left and right elastic tension rollers, tensioned carbon fiber bundles carry out rapid vertical downward cutting on a fused matrix resin film and are buried in the fused matrix resin film, and the embedding and burying of the carbon fiber bundles in the thermoplastic matrix resin are realized. Then, through the following secondary compaction of compression rollers, a thermoplastic pregreg tape with one-directional continuous carbon fibers is prepared. Through secondary spinning or weaving, various kinds of prepreg cloth or fabric reinforced by one-directional, two-directional, diagonal and three-directional continuous carbon fibers are prepared. The problems that the thermoplastic resin matrix has large viscosity and is poor at permeating and infiltrating the carbon fiber bundles, and the content of the resin is hard to precisely control are solved. The preparing device and method are also suitable for the preparation of thermosetting carbon fiber prepreg tapes.
Owner:JIANGSU UNIV
High-fidelity reversible information hiding method and device based on prediction error value sorting
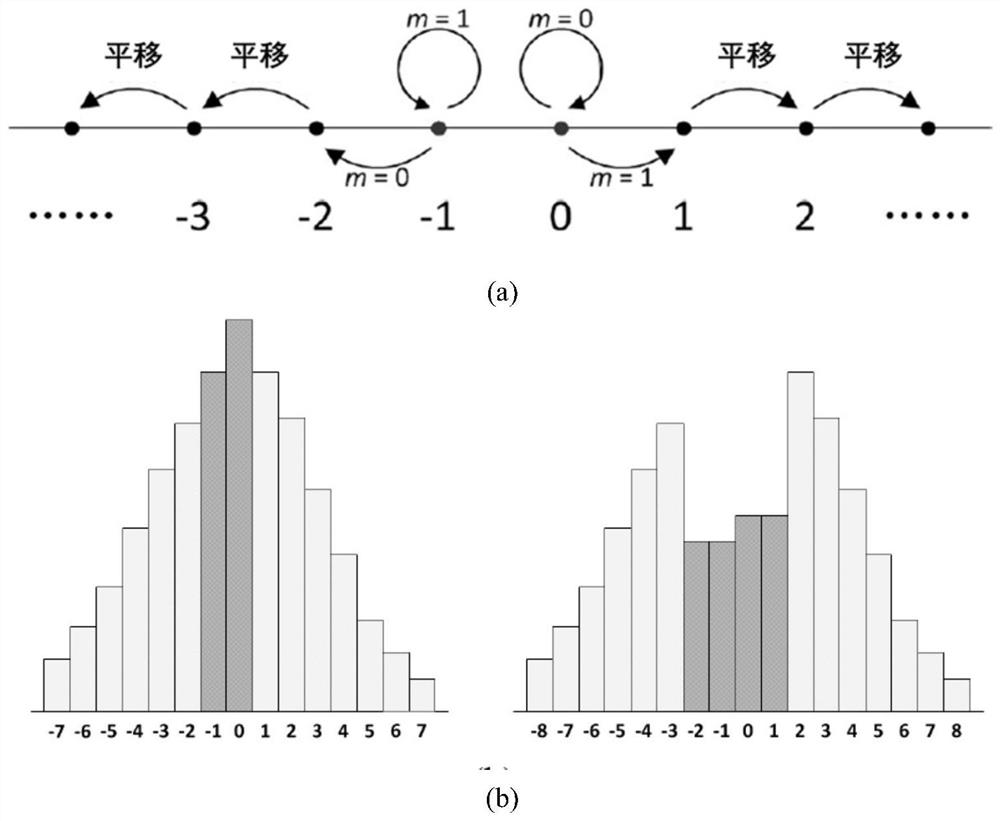
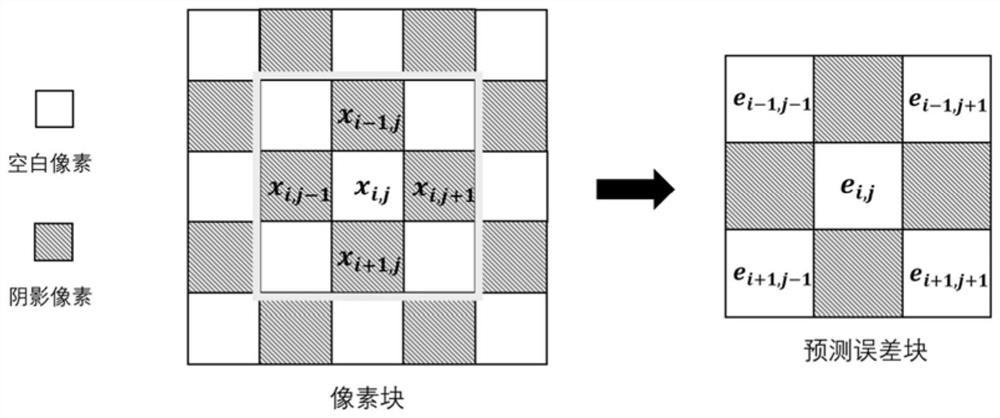
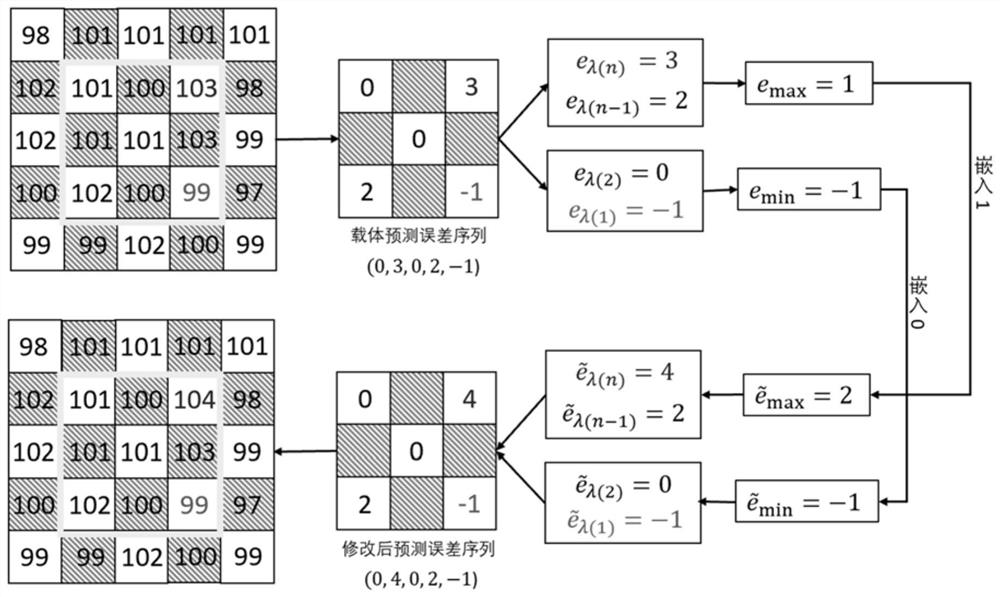
InactiveCN111898136AImplement embeddingImplement extractionDigital data protectionImage watermarkingPattern recognitionAlgorithm
The invention relates to a high-fidelity reversible information hiding method and device based on prediction error value sorting. According to the method, a method based on prediction error extensionand a method based on pixel value sorting are combined, and the defect that prediction error correlation is not utilized in a traditional method is overcome. According to the method, a carrier image is divided into non-overlapping image blocks with the same size, and local correlation between prediction errors in the blocks is considered; for each image block, prediction errors are sorted first, and then the maximum value and the minimum value therein are predicted and modified to embed secret information. According to the method, image redundancy is better utilized, good embedding performanceis achieved, embedding and extraction of secret information in the grayscale image can be achieved, an original image is recovered in a lossless mode, and the method is a high-fidelity reversible information hiding algorithm with good performance and can be used in the fields of secret communication, copyright protection and the like.
Owner:PEKING UNIV
Digital picture watermark embedding and detecting method and device
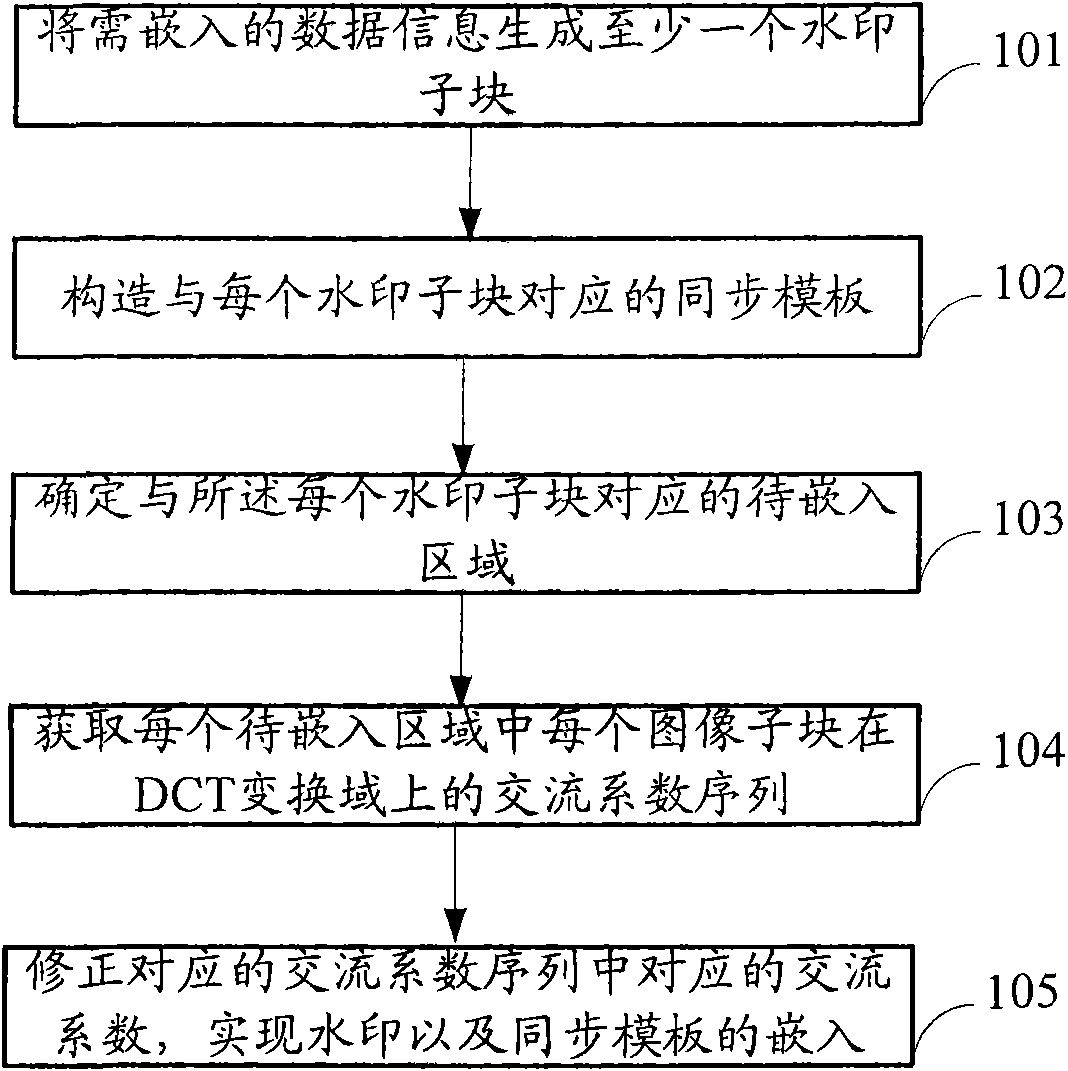
ActiveCN102117474AImplement embeddingDoes not affect extractionImage data processing detailsComputer graphics (images)Transfer procedure
The invention discloses a digital picture watermark embedding and detecting method and a device thereof for improving the capacity of a digital picture for resisting geometric attacks in the transmission process. The digital picture watermark embedding method comprises the steps that data information needing to be embedded is generated into at least one watermark sub-block, and synchronous templates corresponding to the watermark sub-blocks are constructed; areas to be embedded corresponding to the watermark sub-blocks are determined in the digital picture; the alternating-current coefficientsequence of each image sub-block in each embedded area on a discrete cosine transformation (DCT) domain is obtained; and according to the information in each watermark sub-block and the information of the corresponding position in the corresponding synchronous template, the corresponding alternating-current coefficient in the corresponding alternating-current coefficient sequence is revised so asto realize the embedding of the watermark and the synchronous template.
Owner:NEW FOUNDER HLDG DEV LLC +2
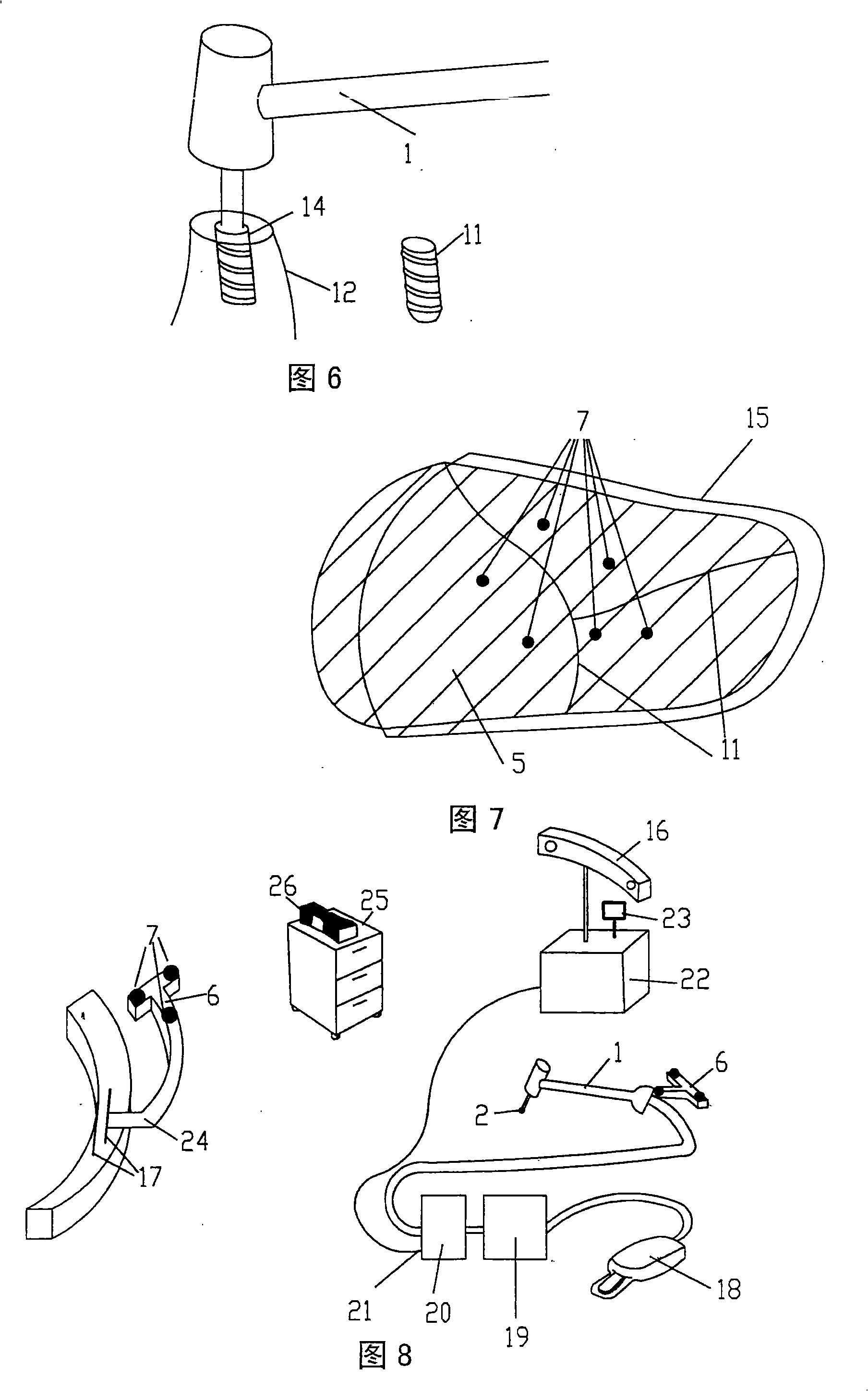
Method and device system for removing material or for working material
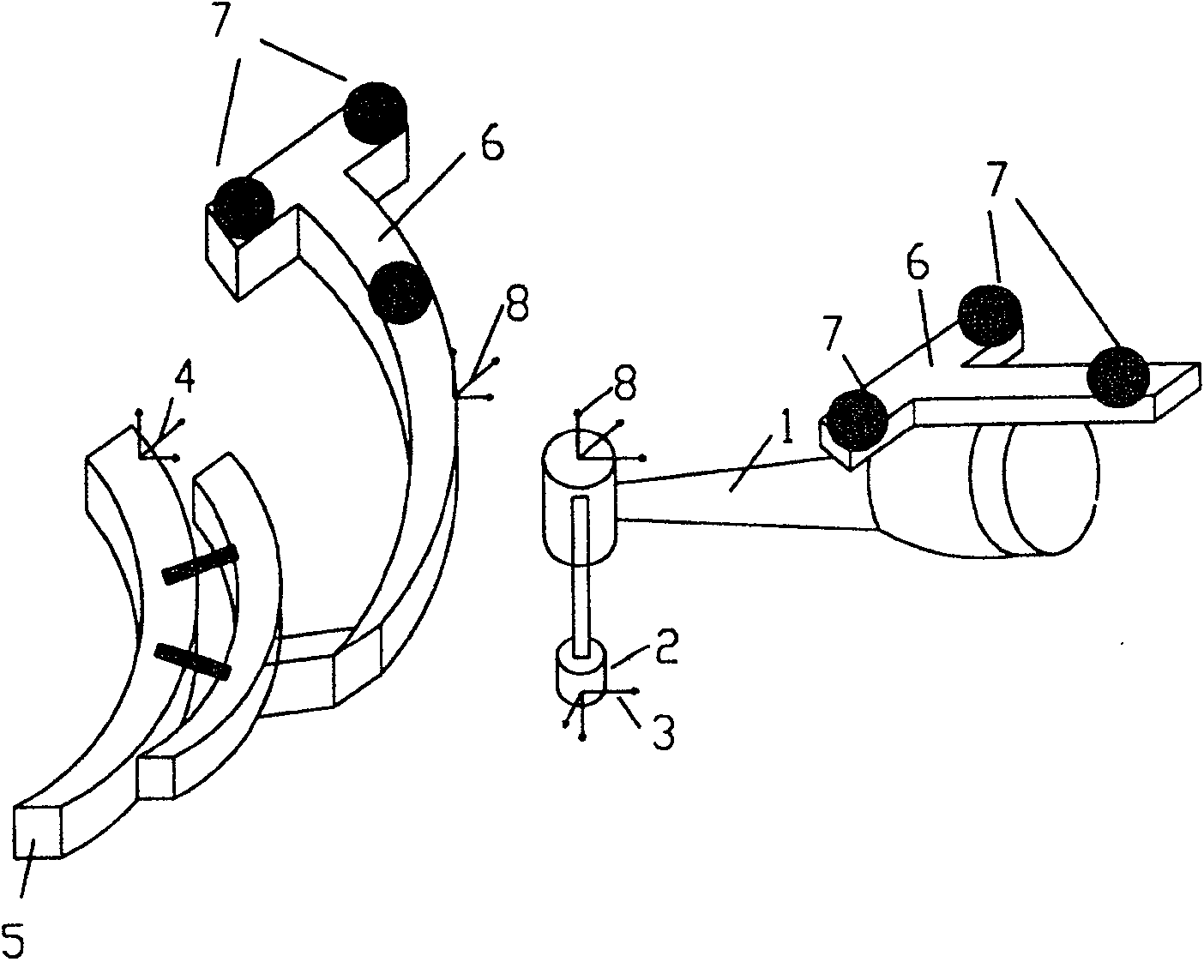
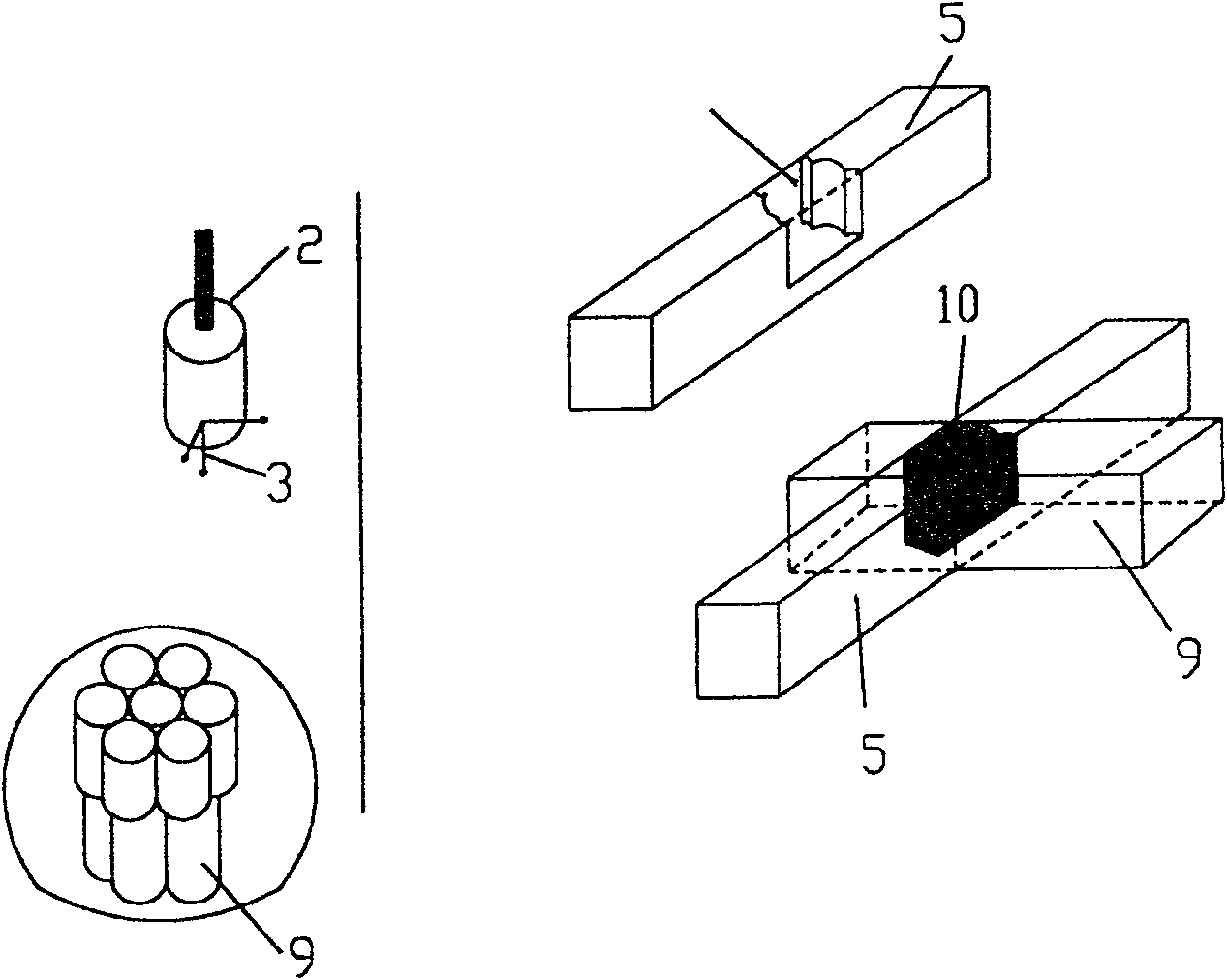
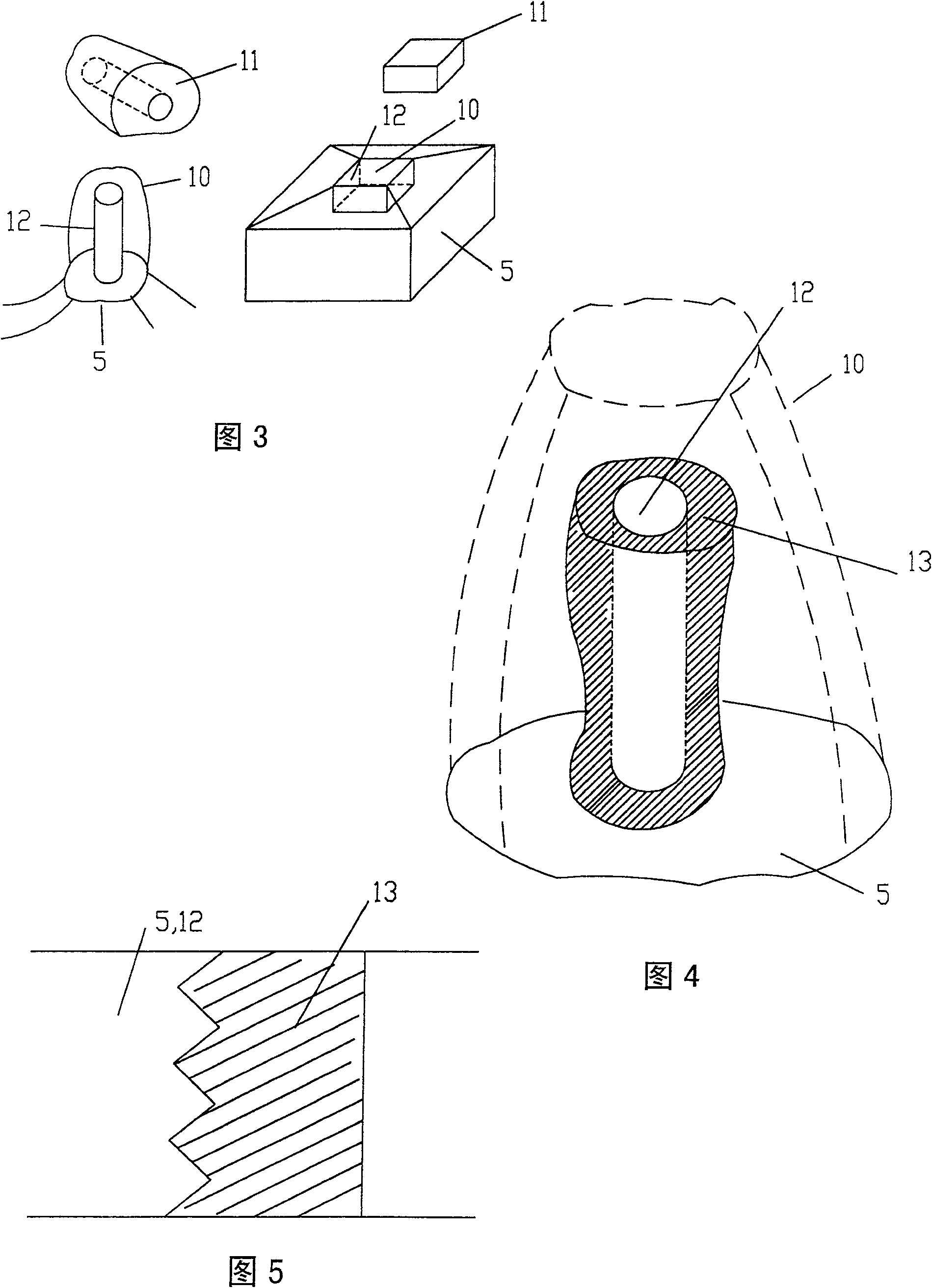
InactiveCN101259028APrecise resectionLow costDiagnosticsSurgical instrument detailsMaterial removalMaterials processing
The invention relates to a method and device system, which are provided for removing material or tissue or for working material or tissue and which can be used in the fields of medicine and dentistry as well as for the most varied types of material working in different areas of application and model working. The invention is particularly advantageous in that an exact removal of material or a highly precise, reproducible material working can be realized within the shortest amount of time by acquiring, storing and computer processing data pertaining to position and / or orientation of the effector and their changes relative to the position of at least one reference body. In addition, commands for controlling and / or regulating are initiated in such a manner that, according to a predetermined working volume and / or material removal volume and / or material remaining volume, the effector is switched into an on / off function or, in the on function, is controlled and / or regulated with regard to its power and / or parameterization.
Owner:ALL OF INNOVATION MBH
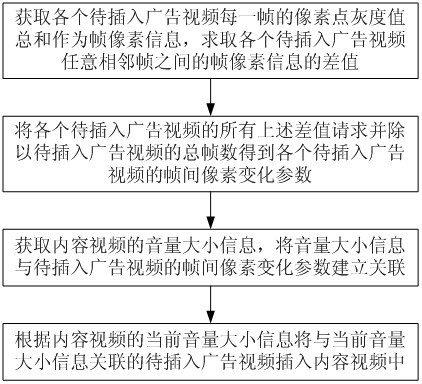
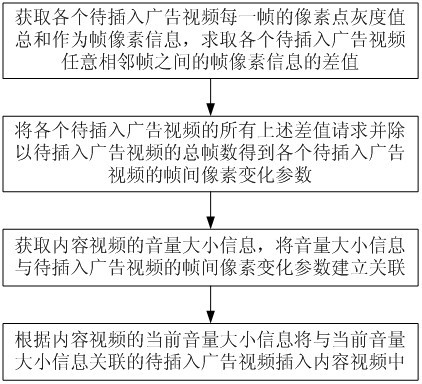
Video information synthesizing method based on audio feature information
ActiveCN102497580AReduce service operating costsImplement embeddingSelective content distributionInformation synthesisInter frame
The invention discloses a video information synthesizing method based on audio feature information. The video information synthesizing method includes the following steps of 1) acquiring total pixel point gray value of each frame of each to-be-inserted advertisement video as frame pixel information and computing difference of the frame pixel information of optional adjacent frames of each to-be-inserted advertisement video; 2) summing all the differences of each to-be-inserted advertisement video and dividing the total frames of the to-be-inserted advertisement video so that interframe pixel running parameters of each to-be-inserted advertisement video are obtained; 3) acquiring volume information of content videos and building association between the volume information and the interframe pixel running parameters of the to-be-inserted advertisement videos; and 4) inserting the to-be-inserted advertisement videos in association with the current volume information into the content video according to the volume information of the content video. The video information synthesizing method has the advantages that insertion of advertisement videos can be realized, running cost of video service can be reduced, better relativity between the inserted advertisement video and the content video is achieved and simplicity and convenience in use is realized.
Owner:广州格芬电子科技有限公司
Robustness digital water mark embedding and detection method based on local content features
InactiveCN104504643AImplement embeddingImprove robustnessImage data processing detailsPoint setImaging Feature
The invention discloses a robustness digital water mark embedding and detection method based on local content features. In the local feature region construction process, an original gray level image is subjected to feature point extraction to obtain an original image feature point set, in addition, the original image feature point is used as the center, an autocorrelation matrix is used for construction to obtain a series of oval feature regions, the PHT of the oval feature regions is calculated, in addition, the stable PHT is selected, and the water mark signal embedding is realized by adopting a quantization PHT amplitude value modulation method. A quantization formula identical to the embedding process is adopted, and the detection on the water mark information of each local feature region is reached. The PHT and the oval feature region construction theory are adopted, so that the method has the advantages that good resistance on the conventional attack and the de-synchronized attack can be realized, the digital water mark robustness can be effectively improved, and meanwhile, the imperceptibility and the water mark information amount of the digital water mark are ensured.
Owner:LIAONING NORMAL UNIVERSITY
RBF neural network-based image watermark embedding and extraction method and device
InactiveCN105205778AImplement embeddingImplement extractionImage data processing detailsNeural learning methodsPattern recognitionExtraction methods
The invention relates to an RBF neural network-based image watermark embedding and extraction method and device. According to the method, an original watermark image is encrypted, a carrier image is trained by using an optimized RBF neural network, and the encrypted watermark image is embedded into the original watermark image, wherein the optimal learning rate is set in an RBF neural network algorithm to realize self-adapting adjustment of a weight of the algorithm. The encrypted watermark image embedded in the carrier image is extracted through the optimized RBF neural network algorithm and a margin calculation, and the encrypted watermark image is subjected to recovery to obtain the original watermark image. The device comprises a scrambling module, an embedding module and an extraction module. Through the adoption of the method and the device, a contradiction between imperceptibility and robustness of the watermark image is balanced.
Owner:HENAN NORMAL UNIV
Method and device system for removing material or for working material
InactiveCN100556370CPrecise resectionLow costProgramme controlProgramme-controlled manipulatorBiomedical engineeringOrthodontics
Owner:ALL OF INNOVATION MBH
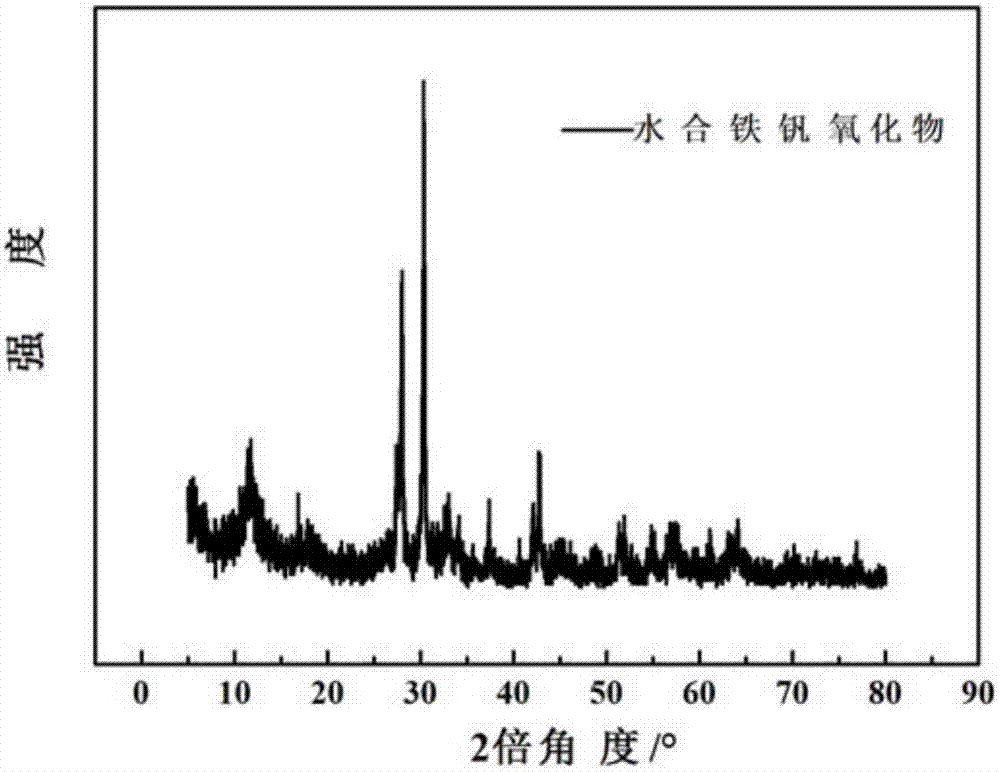
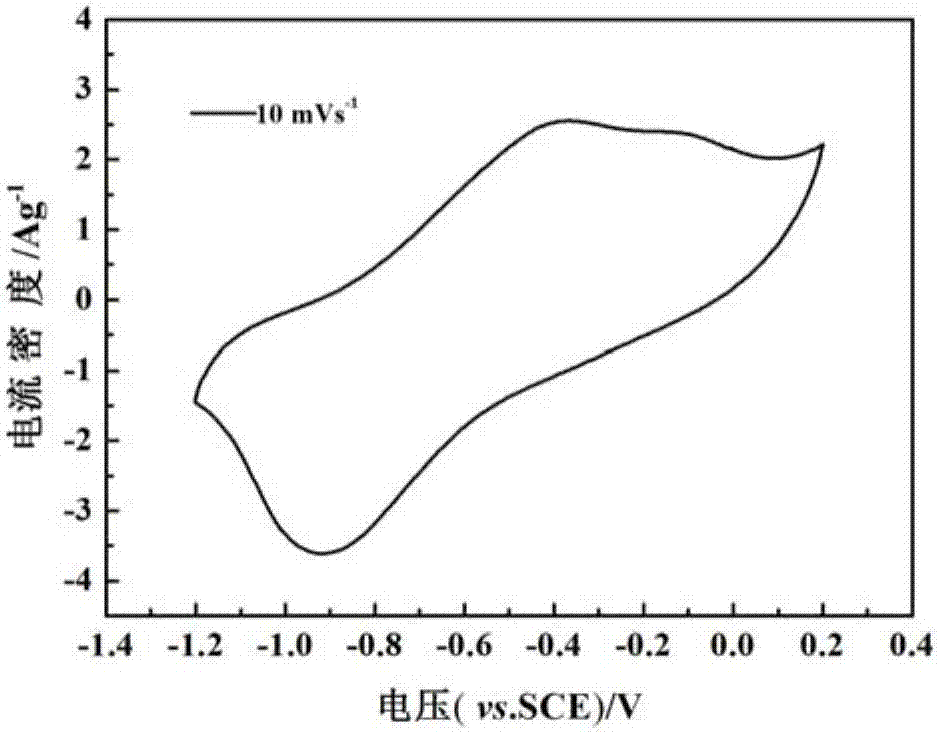
Preparation and application methods of hydrous ferrovanadium oxide as aqueous magnesium ion battery cathode material
ActiveCN107082453AImplement embeddingTo achieve prolapseCell electrodesSecondary cellsMagnesium saltAmmonium metavanadate
The invention provides preparation and application methods of hydrous ferrovanadium oxide as an aqueous magnesium ion battery cathode material. The preparation method comprises the following steps: dropwise adding an ammonium metavanadate solution into a ferric salt solution, stirring the mixed solution at room temperature for 2h; transferring the mixed solution into a reaction vessel and carrying out a hydrothermal reaction, and filtering, washing and drying sediment to obtain linear hydrous ferrovanadium oxide; mixing at the mass ratio of acetylene black to polyvinylidene fluoride to linear hydrous ferrovanadium oxide being 10%: 10%: 80% to prepare an electrode paste, and coating carbon cloth with the paste and drying at 80-100 DEG C to obtain an aqueous magnesium ion battery cathode pole piece. Cheap transition metal salt is used as a raw material, the cost is low, and sources are wide. By using rich reserves of water resources and cheap magnesium salt as an electrolyte, cost is greatly reduced, and the defect that an organic electrolyte is flammable and combustible and pollutes the environment is avoided. The green and environmental-protection requirement is achieved, and safety factor during the production and application process is raised.
Owner:HARBIN ENG UNIV
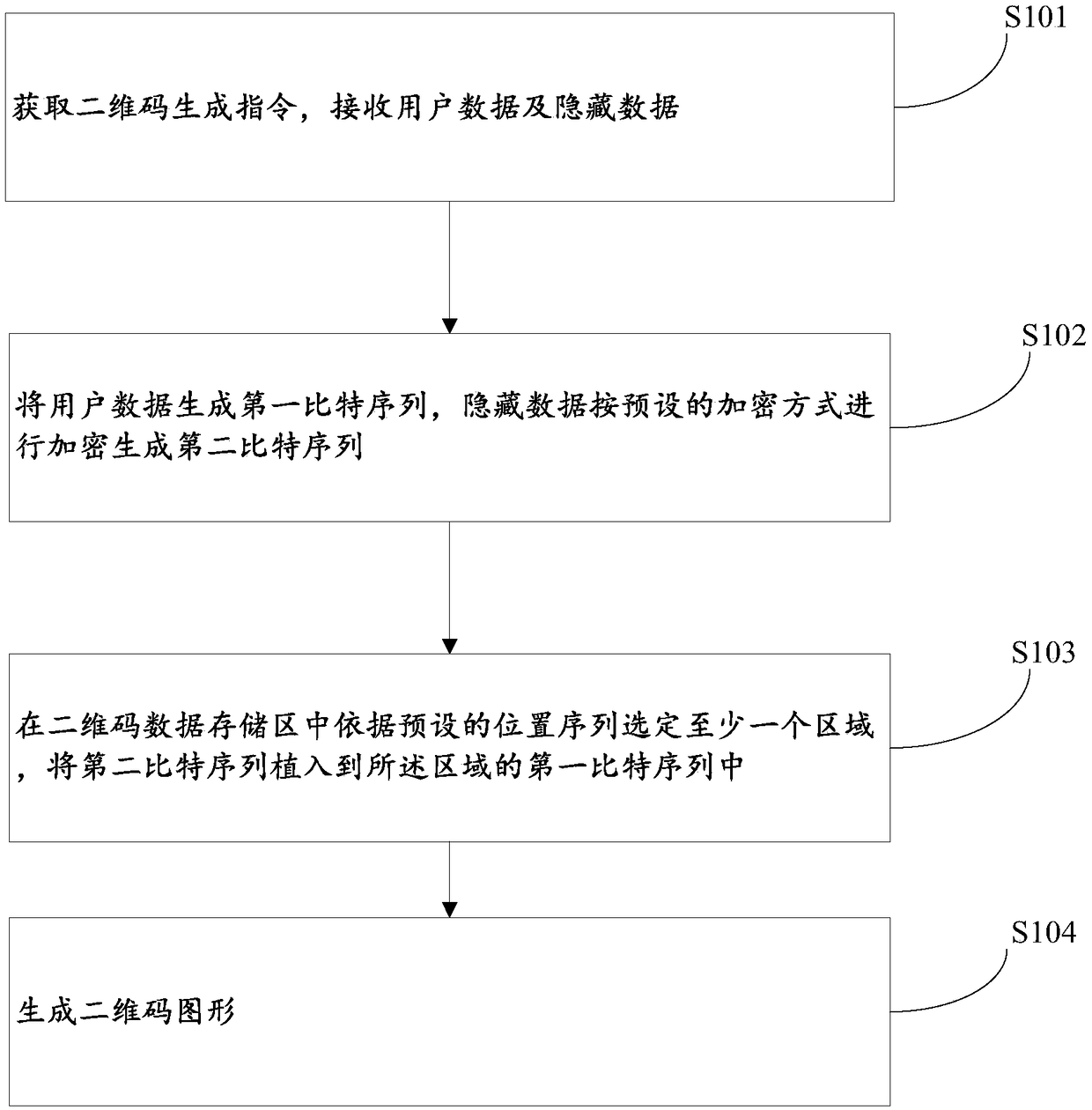
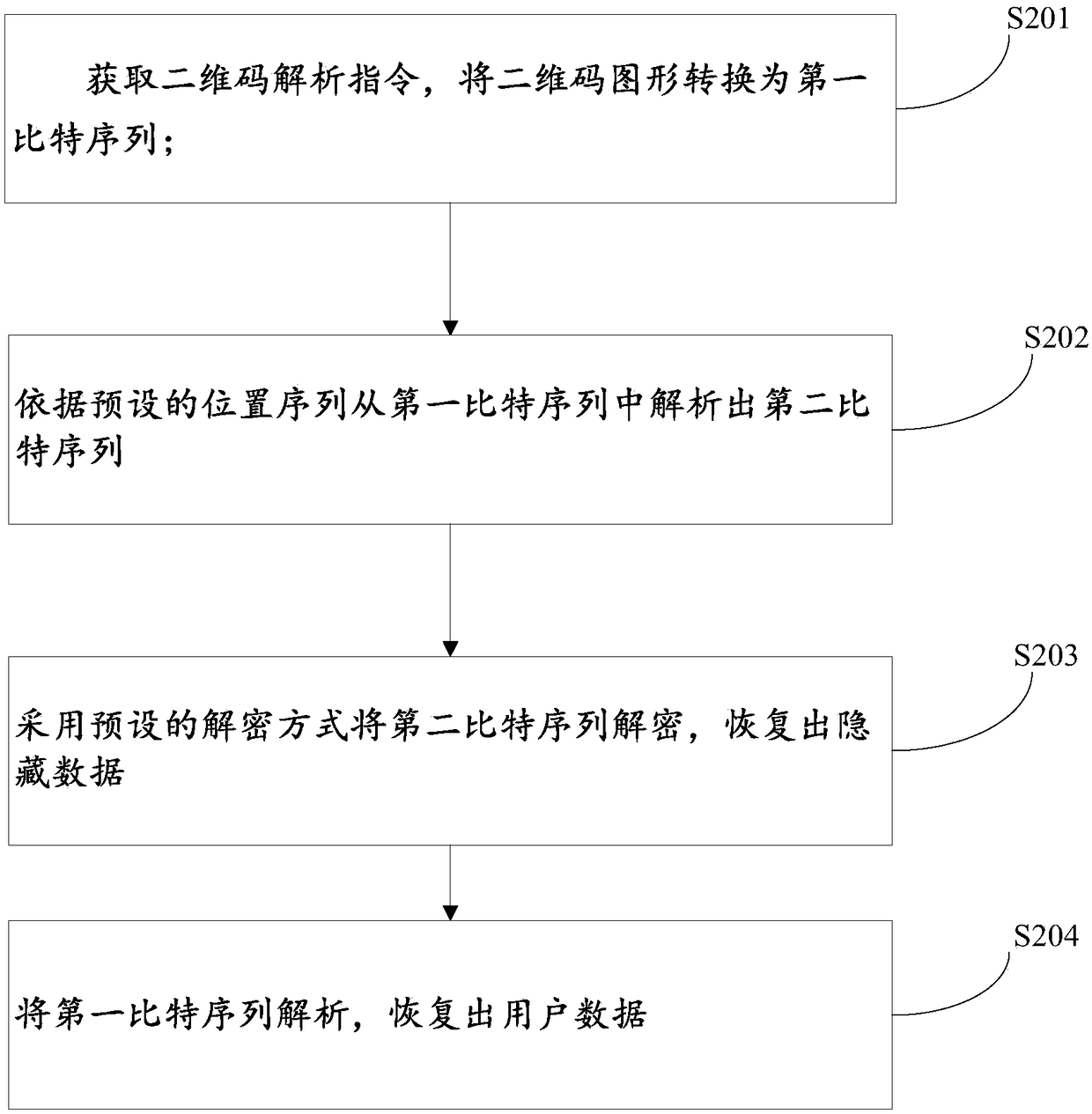
Two-dimensional code data hiding method, data extraction method and device
PendingCN108549920ADoes not affect appearanceDoes not affect the structureRecord carriers used with machinesData ingestionComputer hardware
The invention discloses a two-dimensional code data hiding method. The two-dimensional code data hiding method comprises the following steps: acquiring a two-dimensional code generation instruction, and receiving user data and hiding data; generating a first bit sequence from the user data, and encrypting the hidden data according to a preset encryption mode to generate a second bit sequence; selecting at least one region according to a preset position sequence in a two-dimensional code data storage region, and implanting the second bit sequence into the first bit sequence of the region; and generating a two-dimensional code pattern. Based on the error correction function of two-dimensional codes and the principle that the damage of the two-dimensional code pattern can be tolerated to a certain degree, the hidden data can be embedded and extracted under the condition that the appearance, the structure, the function and the data of the two-dimensional code are not influenced completely.
Owner:NEWLAND DIGITAL TECH CO LTD
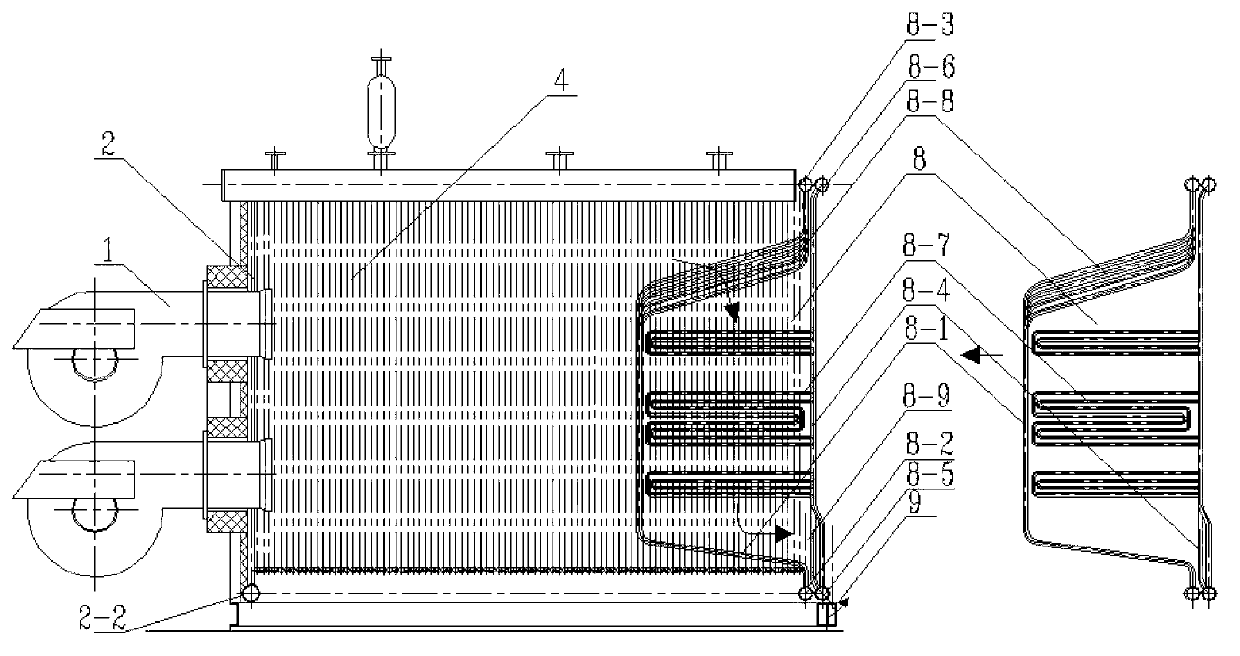
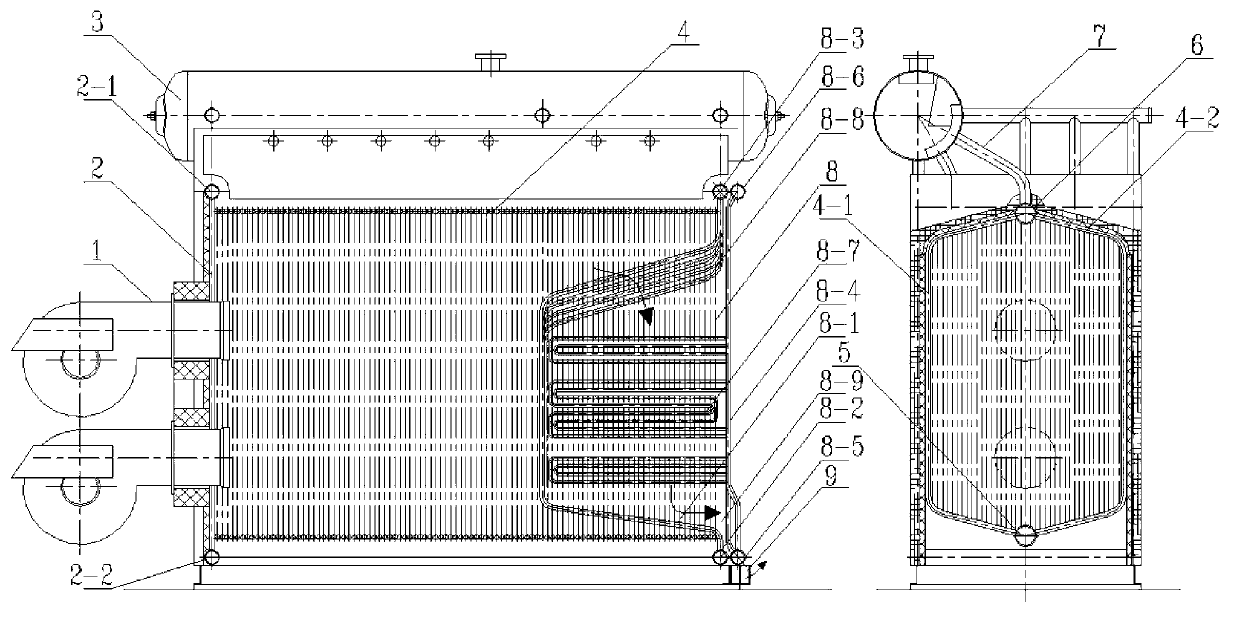
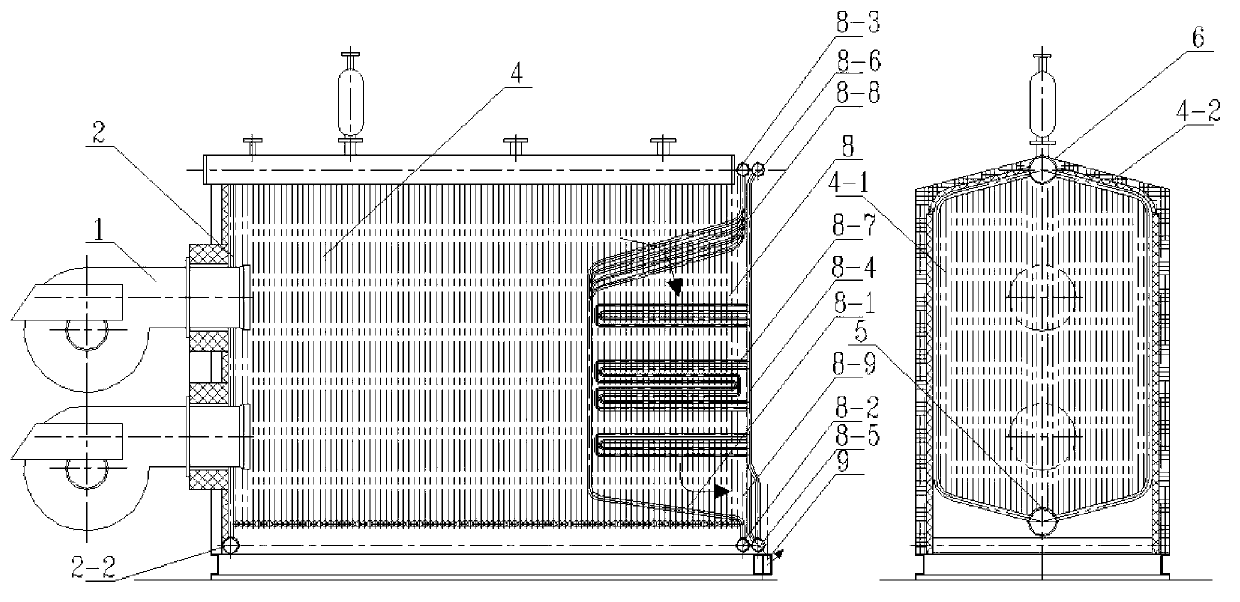
Embedded modularized assembly water pipe fuel oil and fuel gas boiler
ActiveCN103277781AReduce welding workloadShorten the installation cycleWater heatersSteam boilersButt jointEngineering
The invention relates to an embedded modularized assembly water pipe fuel oil and fuel gas boiler which comprises a radiating heated face module and a convection heated face module embedded in the radiating heated face module. The radiating heated face module comprises a radiating heated face front wall, a left wall and a right wall. A structure with an O-shaped section is composed of the left wall, the right wall, a side wall lower header and a side wall upper header. The convection heated face module comprises a convection heated face front wall and a convection heated face rear wall. The convection heated face front wall is used as a radiating heated face rear wall at the same time. A U-shaped pipe-bundle-type flag-type heated face is arranged on the convection heated face rear wall. When the boiler is a boiler with a small capacity or a medium capacity, rapid assembly can be fully achieved. When the boil is a boil with a medium capacity or a large capacity, the boiler is divided into a radiating heated face segment and a convection heated face segment for isolated transportation and embedded integral assembly is carried out on spot. Modularized butt joint can be achieved without any welding, an installation period is short and operation and maintenance are simple, convenient and easy to achieve. Moreover, whole sealing performance of the whole boiler is good, heat loss is obviously reduced and heat efficiency of the boiler is effectively improved.
Owner:XI AN JIAOTONG UNIV
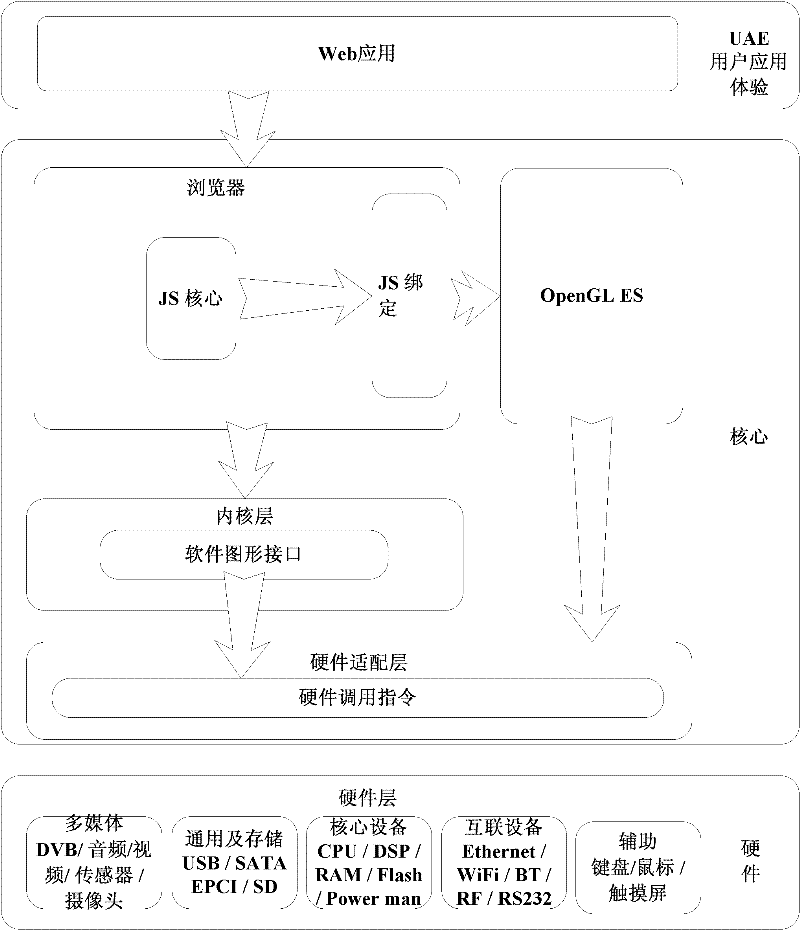
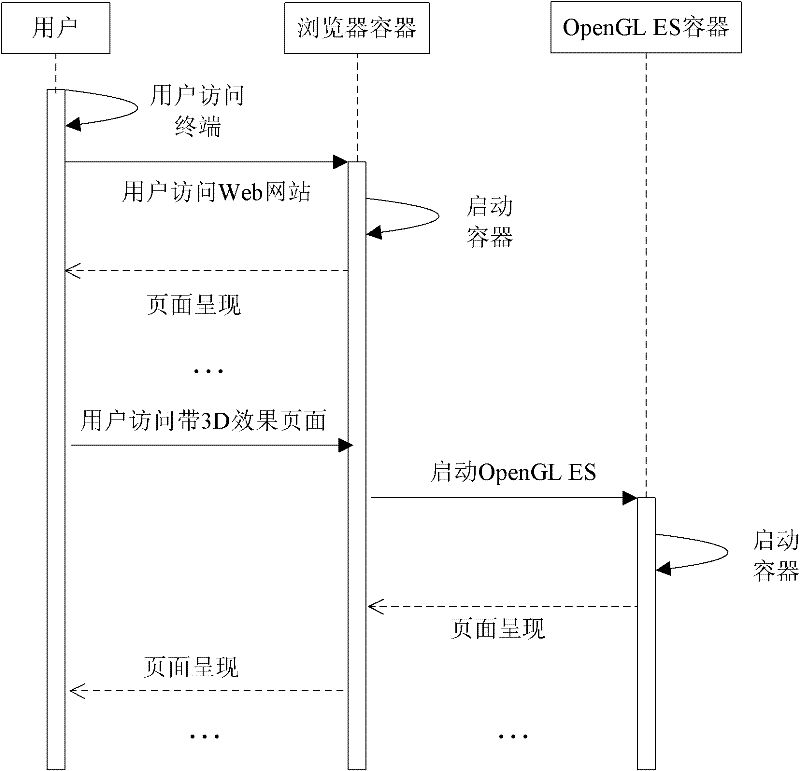
Method for embedding OpenGL ES (Open Graphics Library for Embedded System) into browser in embedded terminal
InactiveCN102253831AContainer changes reduceImplement embeddingSpecific program execution arrangementsGraphics libraryGraphics
The invention relates to a method for embedding an OpenGL ES (Open Graphics Library for Embedded System) into a browser in an embedded terminal. The method comprises the steps of: responding to a website visiting instruction of a user, and starting a browser container; when a page presents an effect irrelevant to a three-dimensional effect, running the browser container only; and when the page presents an effect relevant to the three-dimensional effect, starting an OpenGL ES container, and simultaneously running the browser container and the OpenGL ES container to realize the page presentation of the three-dimensional effect by the browser container by invoking the OpenGL ES container.
Owner:SHANGHAI ACOUSTICS LAB CHINESE ACADEMY OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com