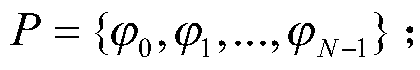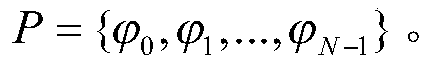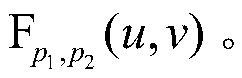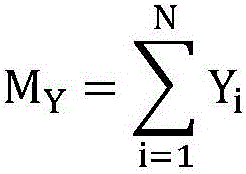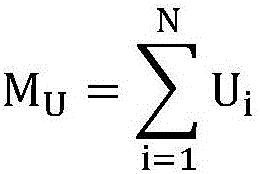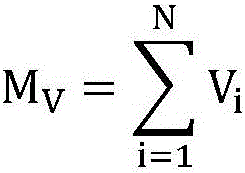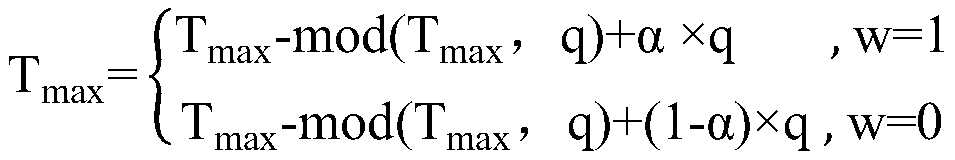Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
53 results about "Arnold transformation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Multi-chaotic mapping and DNA coding-integrated image encryption method and device
InactiveCN107610037AIncrease randomnessIncreased sensitivityImage data processing detailsSecuring communicationDna encodingArnold transformation
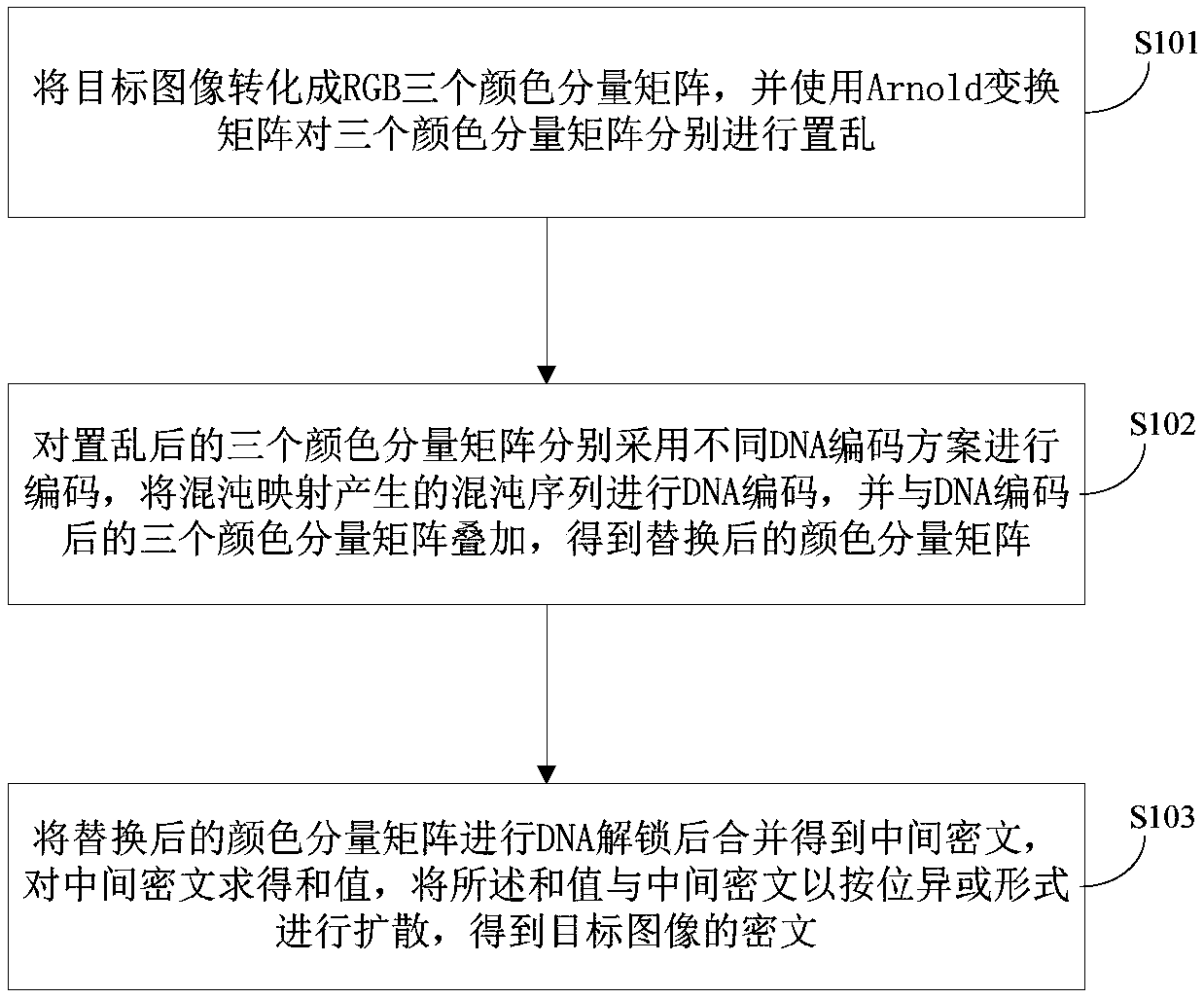
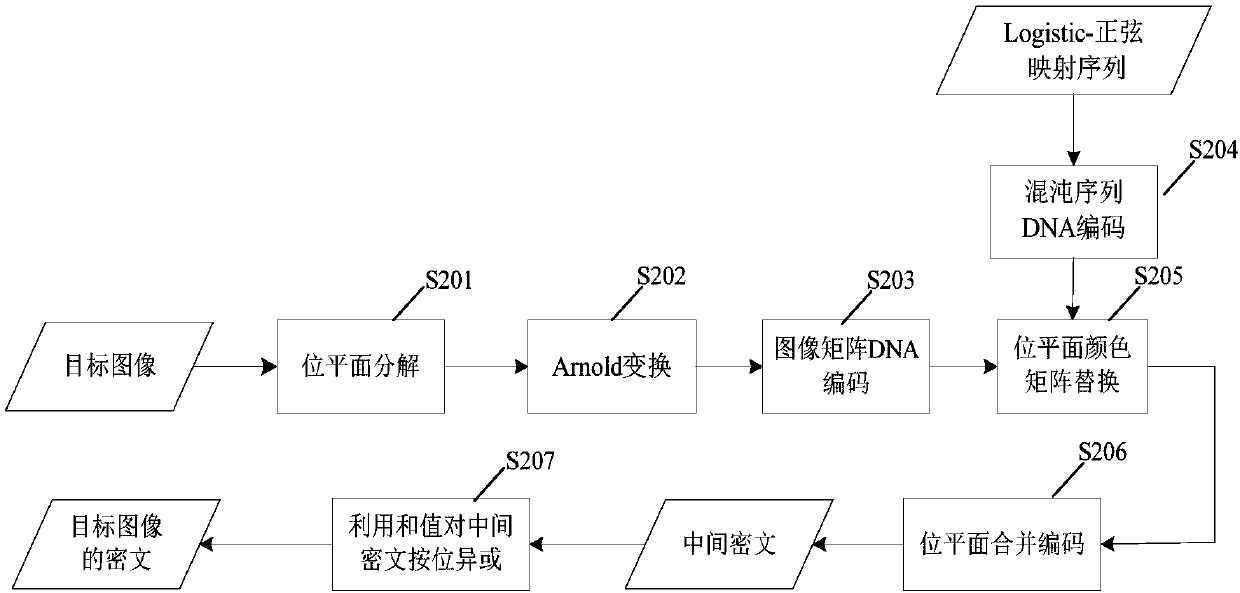
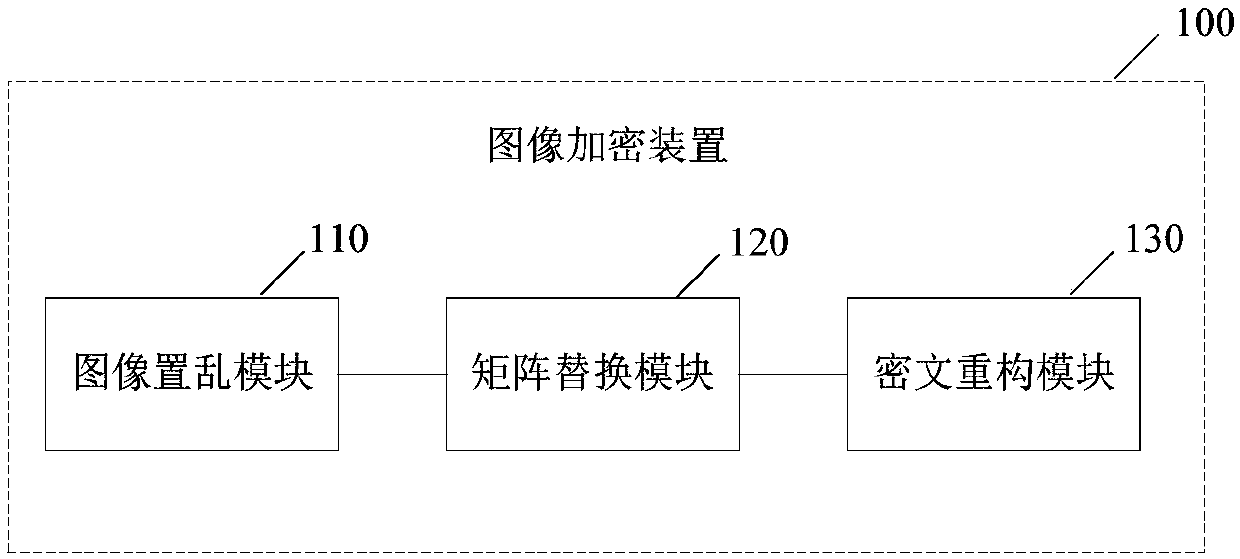
The invention provides a multi-chaotic mapping and DNA coding-integrated image encryption method and a device thereof, an image decryption method and a device thereof. The image encryption method comprises an image scrambling step used for converting a target image into RGB three color component matrixes, and respectively scrambling the three color component matrixes by adopting an Arnold transformation matrix; a matrix replacement step used for respectively carrying out coding treatment on the three color component matrixes which have been scrambled by adopting different DNA coding schemes, carrying out DNA coding treatment on a chaotic sequence generated by chaotic mapping, and overlapping the three color component matrixes after being coded with the DNA to obtain replaced color component matrixes; and a ciphertext reconstruction step used for carrying out DNA unlocking on the replaced color component matrixes, combining the obtained color component matrixes to obtain a middle ciphertext, and diffusing the middle ciphertext after a sum value is calculated and according to the bitwise XOR form. The method is high sensitivity to plaintexts and secret keys. Meanwhile, the method andthe device have a good scrambling effect and a stronger anti-statistical attack resistance.
Owner:CHONGQING UNIV OF EDUCATION
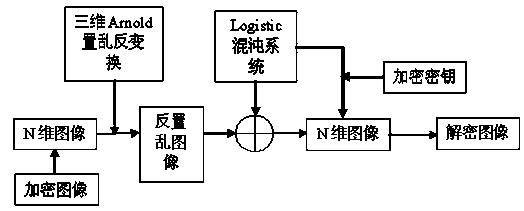
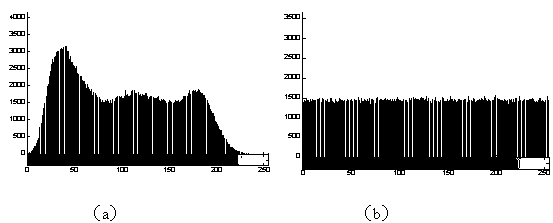
Image encryption method combining three-dimensional Arnold transformation with chaotic sequence
InactiveCN103455971AHigh degree of scramblingImprove securityImage data processing detailsPattern recognitionArnold transformation
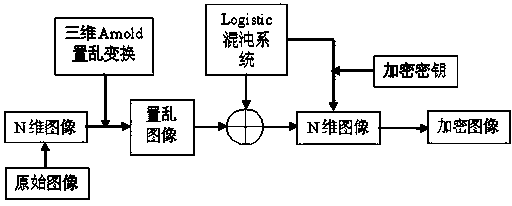
The invention relates to an image encryption method combining three-dimensional Arnold transformation with a chaotic sequence. The method includes the steps that firstly, images are processed and converted into multi-dimensional images, pixel value data matrixes of the images are acquired, multiple times of three-dimensional Arnold scrambling transformation is conducted, and then the Logistic chaotic sequence is utilized to conduct bitwise exclusive-or operation with the images to change pixel values of the images. The three-dimensional Arnold transformation is utilized to conduct pixel position scrambling on processed multi-dimensional image data, compared with an ordinary two-dimensional scrambling technology, the scrambling degree of three-dimensional Arnold transformation is higher, then, the chaotic sequence is utilized to change the pixel values, encryption is completed, and the image encryption method has the advantages of being good in safety and high in secret key sensitivity and anti-attack capacity.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Image encryption method based on Arnold transformations and Henon chaotic system
InactiveCN103442157AHigh degree of scramblingImprove securitySecuring communicationPictoral communicationPattern recognitionPlaintext
The invention relates to an image encryption method based on Arnold transformations and a Henon chaotic system. Firstly, a plurality of Arnold scrambling transformations are carried out on images, then scrambling is carried out for a second time on the images through use of a Henon chaotic sequence and then the Henon chaotic sequence is used to carry out a bit-by-bit XOR operation with images to change pixel values of the images. The two technologies are adopted to carry out pixel-value position scrambling twice so that the scrambling degree of the images is higher compared with a single scrambling technology and then the chaotic sequence is adopted to change the pixel values so that any information related to plaintext is completely hidden in the encrypted images. Therefore, the method has the advantages of being great in safety and high in anti-attack ability and the like.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
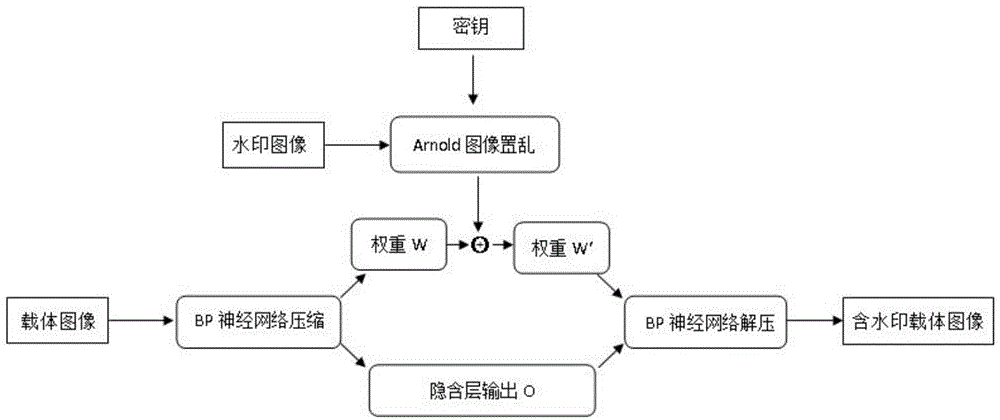
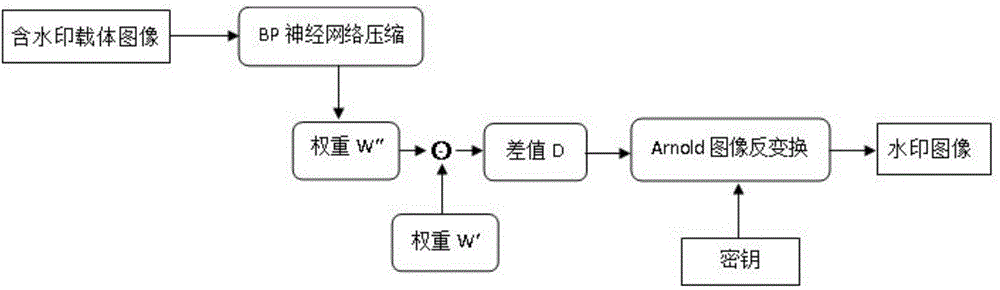
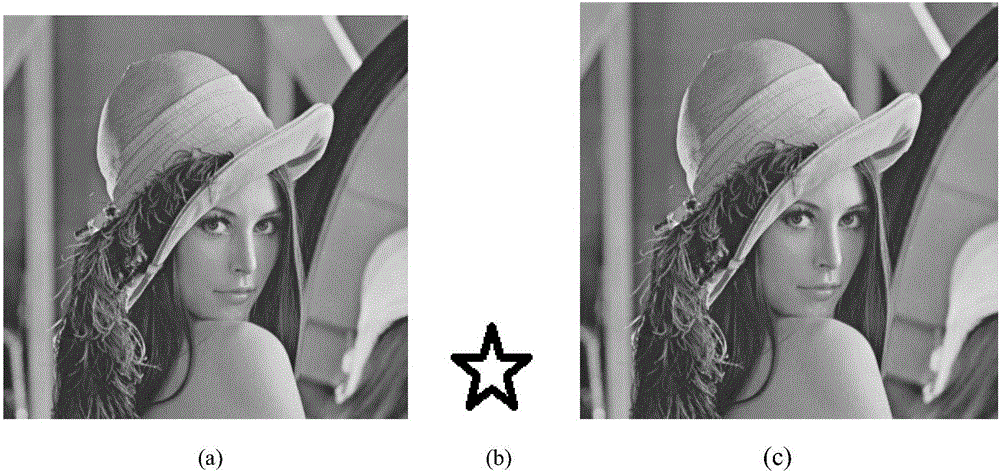
Image watermark embedding and extracting method based on back propagation (BP) neural network compressed domain
InactiveCN104616244AImprove securityAchieve complete imperceptibilityImage data processing detailsNeural learning methodsHidden layerPattern recognition
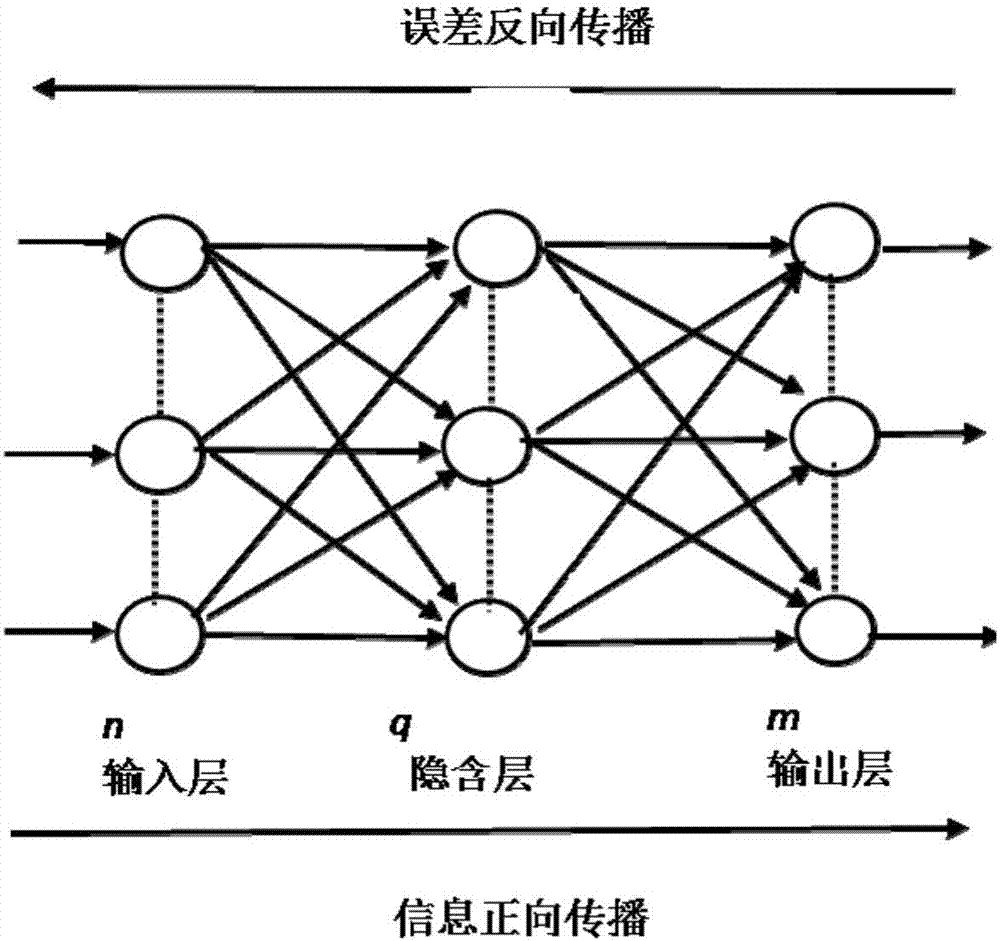
The invention discloses an image watermark embedding and extracting method based on a back propagation (BP) neural network compressed domain. The image watermark embedding and extraction method is based on Arnold transformation, to support BP neural network image compression processing, and the watermark is embedded into the neural network hidden layer to the output layer weight of the carrier image almost no effect, invisibility is very strong, and more secure. In the compressed domain that BP neural network, the carrier watermarked image even after multiple attack, is still able to remember the local relationship between pixels in order to achieve the correct detection of the watermark signal, making this embedding and extracting methods images of a variety of conventional attack has strong robustness, good balance contradictory and robust image watermarking imperceptibility between, and enables the blind to detect the watermark image.
Owner:HENAN NORMAL UNIV
Zero-watermark embedding and extracting methods and zero-watermark embedding and extracting devices based on DWT and principal component analysis (PCA) compression
InactiveCN106023056AEasy extractionMeet the requirement of invisibilityImage data processing detailsKernel principal component analysisArnold transformation
The invention relates to zero-watermarking embedding and extracting methods and zero-watermarking embedding and extracting devices based on DWT and PCA compression. When a watermark is embedded, improved Arnold transformation is used to transform an original watermark; a compression image is obtained by using wavelet transformation and PCA compression methods; and XOR operation is carried out on the compression image and a scrambled watermark image to obtain a characteristic matrix. When the watermark is extracted, discrete wavelet transformation is carried out on a carrier image with zero-watermark, the PCA compression method is used to compress a low-frequency sub-band image, XOR operation is carried out on the obtained matrix and the characteristic matrix, the scrambled watermark image is obtained, and a reverse Arnold transformation formula is used to obtain the original watermark image. According to the method and device of the invention, zero watermark is easy to construct and extract, and the safety and anti-attack capability of the watermark are improved effectively.
Owner:HENAN NORMAL UNIV
H.264/AVC compressed-domain video watermark embedding and extracting method
ActiveCN104539965AImprove robustnessImprove invisibilityDigital video signal modificationArnold transformationWatermark robustness
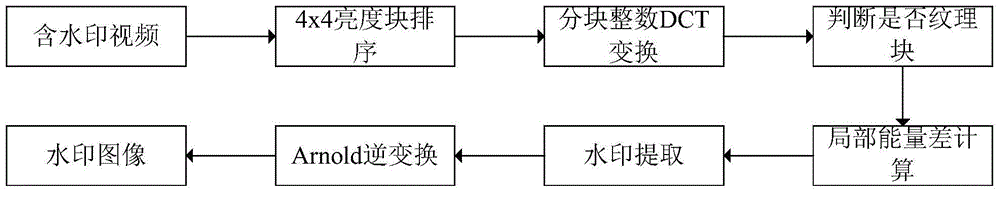
The invention discloses an H.264 / AVC compressed-domain video watermark embedding and extracting method. Binaryzation is conducted on watermark images, and binary watermark information is obtained through Arnold transformation; compressed encoding is conducted on original video by using an H.264 / AVC encoder, 16 4*4 luminance blocks of each macro block are extracted out according to the H.264 / AVC video encoding standard, and integer discrete cosine transformation is conducted on each 4*4 luminance block; according to the coefficient of each 4*4 luminance block obtained after integer discrete cosine transformation, each 4*4 luminance block is divided into a texture block body and a non-texture block body; according to the binary watermark information, the local energy difference of each macro block is modulated; entropy encoding is conducted on the 4*4 luminance blocks obtained after binary watermarks are embedded to obtain video streaming with the watermarks. According to the H.264 / AVC compressed-domain video watermark embedding and extracting method, video information (texture and energy) is fully considered, and the robustness and invisibility of the watermarks are improved; operational complexity is low, no complex parameter choice exists, and higher real-time performance is achieved; the original video is not needed in the watermark extraction, and the H.264 / AVC compressed-domain video watermark embedding and extracting method belongs to a blind watermarking method.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 38 RES INST +1
Medical image robust watermarking method based on Arnold scrambling transformation and DCT (discrete cosine transformation)
InactiveCN102930500ASolve the quickness problemImprove safety and reliabilityImage data processing detailsFeature vectorHash function
The invention discloses a medical image robust watermarking method based on Arnold scrambling transformation and DCT (discrete cosine transformation), belonging to the field of multimedia signal processing. The method comprises the following steps: firstly embedding a watermark, specifically including (1) carrying out Arnold transformation on the watermark to be embedded to implement the pretreatment, (2) carrying out overall image DCT transformation on a medical image, and extracting a vector of a feature in a transformation domain, (3) obtaining a binary logic sequence through a Hash function by using the feature vector and the pre-treated watermark; and then carrying out watermark extraction, specifically including (4) carrying out overall image DCT transformation on a medical image to be tested, and extracting a feature vector; (5) extracting the watermark by using the property of the Hash function and a binary logic sequence of a third party; and (6) obtaining the original watermark through inverse transformation of the Arnold scrambling transformation. The experiment shows that the method has a very good information hiding capability and is of great significance in protecting the information of a patient in telemedicine.
Owner:HAINAN UNIVERSITY
Watermark embedding and extraction method and device based on dynamic BP nerve network
ActiveCN107240061AImprove securityIncrease the number ofImage watermarkingHidden layerImage extraction
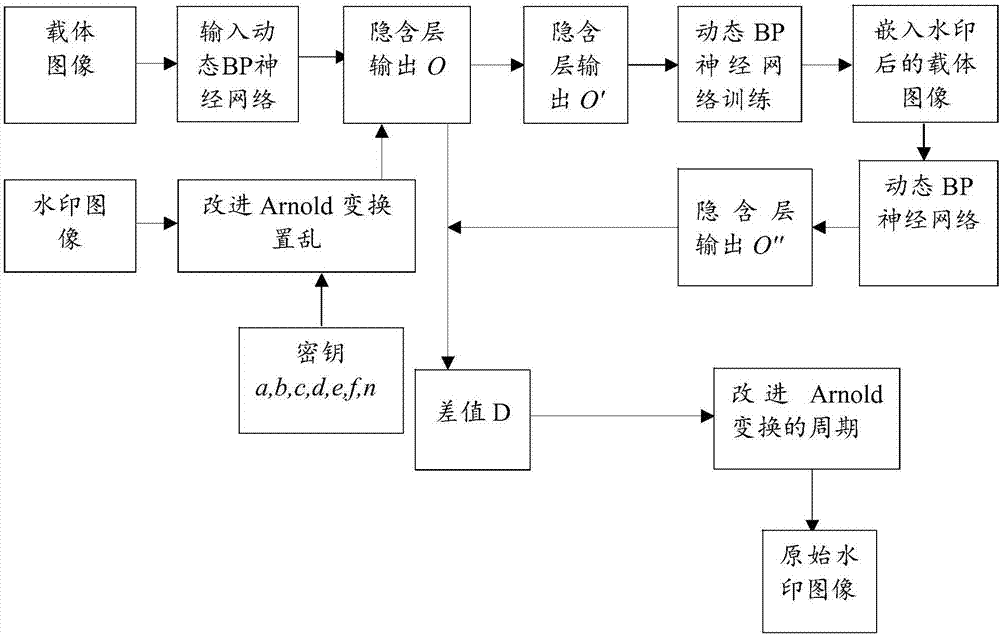
The invention relates to a watermark embedding and extraction method and device based on a dynamic BP nerve network; the method comprises the following steps: using improved Arnold transformation to scramble an original watermark image; embedding the scrambled watermark image into a dynamic BP nerve network hidden layer, and training to obtain a carrier image with an embedded watermark; the method combines the improved Arnold transformation with the dynamic BP nerve network, thus obtaining the carrier image with the watermarks; even after various attacks, the pixel sizes in the embedded positions can be still extracted, thus correctly detecting a watermark signal; in addition, the method can balance the contradictions between the image watermark robustness and imperceptibility; in addition, in a watermark image extraction process, i.e., the reverse process of the watermark embedding process, the watermark image can be finally obtained through the combination between the dynamic BP nerve network and the improved Arnold transformation.
Owner:HENAN NORMAL UNIV
Self-adaptive audio blind watermark method based on auditory model
InactiveCN106504757AEnsure safetyGuaranteed imperceptibilitySpeech analysisArnold transformationWatermark method
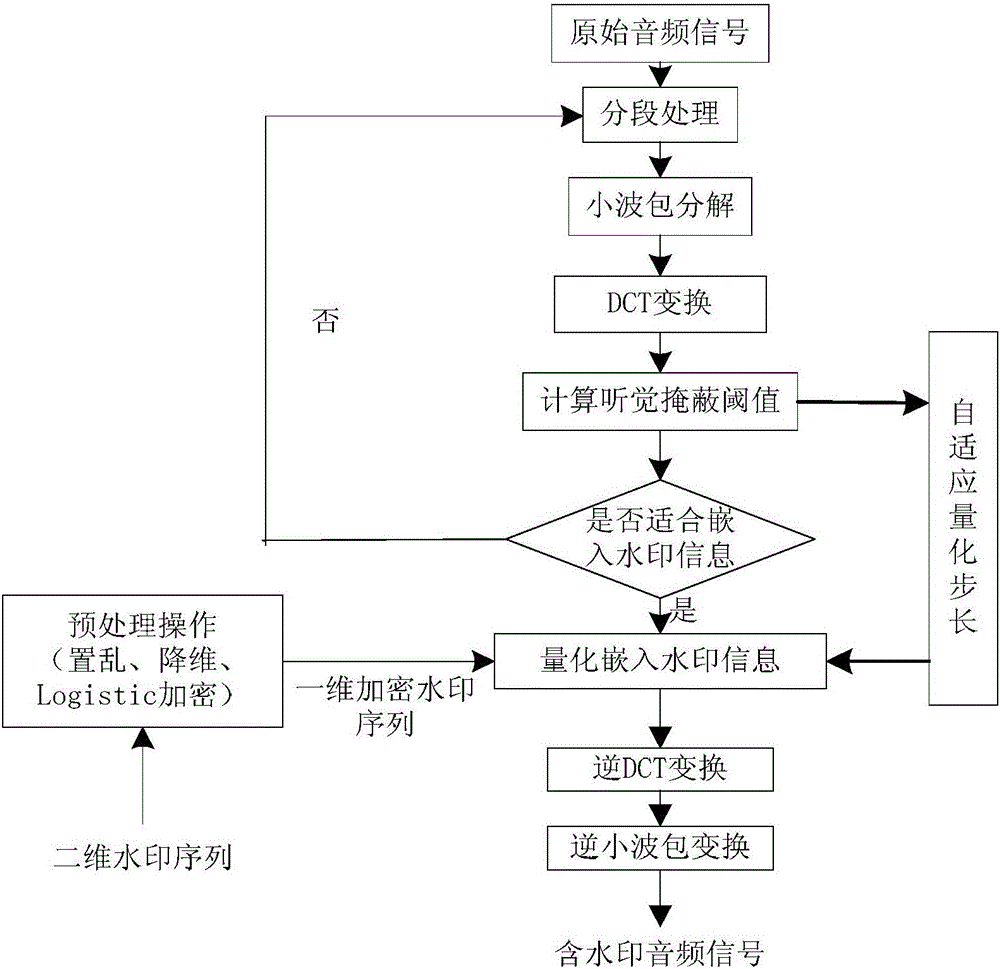
The invention provides a self-adaptive audio blind watermark method based on an auditory model. Arnold transformation, dimension reduction processing and chaotic transformation are performed on a watermark signal so that watermark information is obtained; a human ear auditory masking threshold is calculated; a watermark embedding segment and an embedding position are self-adaptively selected; embedding of a digital watermark is performed; audio segment recombination is performed, and all the audio segments without embedding of the watermark and the audio segments with embedding of the watermark are recombined so that audio signals containing all the watermarks are formed; and the digital watermark is extracted. The watermark information of large energy is embedded under the premise that the watermark signal does not influence the audio quality so that self-adaptive selection of the watermark embedding segment, the watermark embedding position and the watermark embedding strength can be realized, the imperceptibility of the algorithm can be guaranteed and the watermark robustness and the watermark embedding capacity can be enhanced. The human ear auditory characteristic can be utilized in a more detailed way so that the method has better hiding performance, the security of the watermark can be further guaranteed and the attack of common signal processing can be effectively resisted.
Owner:TIANJIN UNIV
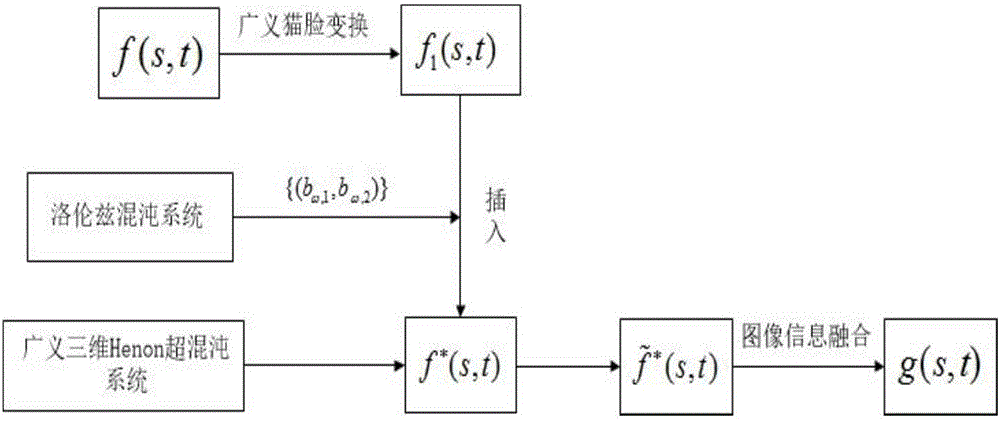
Cat mapping and chaos based image information fusion and encryption method
ActiveCN106709854AReduce correlationIncrease randomnessImage enhancementImage data processing detailsPattern recognitionArnold transformation
The invention discloses a cat mapping and chaos based image information fusion and encryption method, which mainly solves a problem that an existing technology of performing encryption on an image by using a chaotic system is insufficient in scrambling and relative poor in safety. Implementation of the method comprises the steps of 1, performing generalized Arnold transformation on an image to acquire a preliminary scrambling image; 2, acquiring a chaos generation image matrix with the length and width being four times of those of the image to be encrypted by using a generalized three-dimensional Henon hyper-chaotic system; 3, acquiring a binary substring sequence for scrambling by using Lorentz chaos; 4, inserting the preliminary scrambling image into the chaos generation image matrix by using the binary substring sequence to acquire an image matrix after insertion; and 5, reducing the image matrix after insertion by using an image information fusion technology so as to acquire a final encrypted image. The method disclosed by the invention is high in scrambling degree and high in sensitivity, improves the safety of image encryption and can be applied to information security.
Owner:XIDIAN UNIV
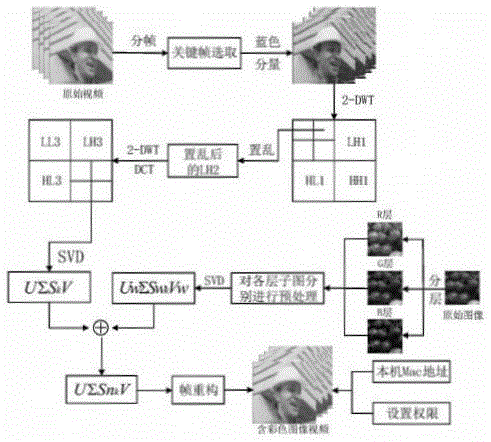
An image hiding method based on a video carrier and under an off-line controllable mechanism
ActiveCN105118018AAchieve effectivenessAchieve controllabilityImage data processing detailsProgram/content distribution protectionColor imageSingular value decomposition
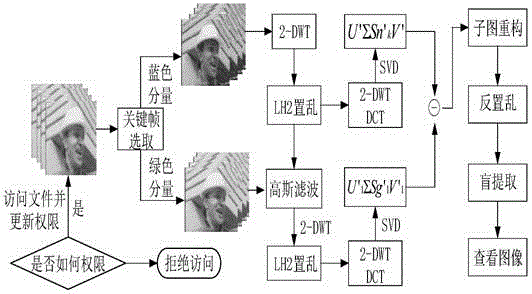
The invention discloses an image hiding method based on a video carrier and under an off-line controllable mechanism. A key frame of a video is firstly subjected to 2-DWT transformation; then Arnold transformation is carried out on sub-bands; through characteristics of singular value decomposition and multi-resolution characteristics of wavelet transformation, images are embedded in sub-band singular values which have undergone scrambling; when the video is under different attacks, blind extraction of the image can be realized; and the blind extraction specifically comprises two steps which are color image confidential storage and color image extraction checking. As technology of embedding and extraction of the color image in the video and the technology of limited frequency checking and anti-copying in an image off-line condition, the method of the invention is the image confidential storage technology based on the video carrier and under the off-line controllable mechanism, and can solve problems of confidentiality and storage of confidential and private images, thereby reaching a purpose of protecting private and confidential information, and realizing validity and controllability access of the image in an extent of competence.
Owner:ANHUI UNIVERSITY
Image encryption and reading methods and devices
InactiveCN104063833AThe process is simple and convenientLarge key spaceGeometric image transformationImage data processing detailsComputer hardwareArnold transformation
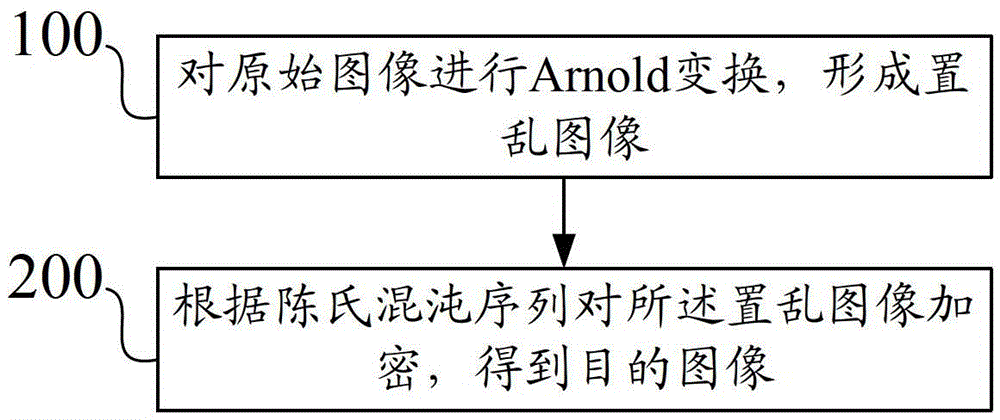
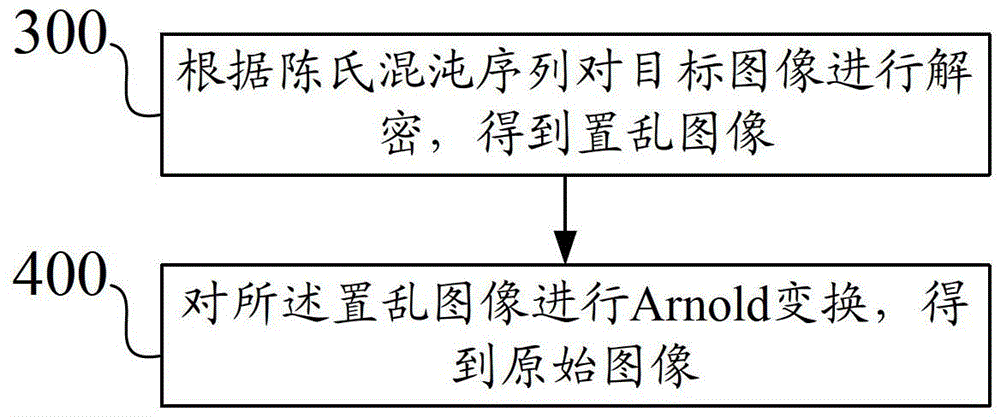
The invention provides image encryption and reading methods and devices, and relates to the field of image encryption. The image encryption method comprises: performing Arnold transformation on an original image to form a scrambling image; and according to a Chen' chaotic sequence, encrypting the scrambling image to obtain an object image. According to the methods and devices provided by the invention, first of all, an image is scrambled through the Arnold transformation, then encryption processing is carried out by use of the Chen' chaotic sequence, the whole process is simple and easily implemented, the secret key space is large, and the security is high.
Owner:CHINA INST OF WATER RESOURCES & HYDROPOWER RES
Fractional domain image encryption method based on Arnold transformation and compound chaos
InactiveCN105447396AReduce correlationImprove securityDigital data protectionPattern recognitionArnold transformation
The invention discloses a fractional domain image encryption method based on Arnold transformation and compound chaos and mainly solves the problems that the scrambling degree is low, the secret key sensitivity is low and the robustness is poor in the prior art. The method comprises the following implementation steps: (1), carrying put generalized Arnold transformation on an image so as to obtain the preliminarily scrambled image; (2), carrying out random phase encoding on the scrambled image so as to obtain the encoded image; (3), carrying out fractional Fourier transformation on the encoded image so as to obtain the transformed image; (4), generating a sequence used for scrambling by using a compound chaotic system and processing the sequence so as to obtain the processed chaos sequence; and (5), carrying out secondary scrambling on the transformed image by using the processed chaos sequence so as to obtain a final encrypted image. The method is high in scrambling degree, strong in sensibility, and good in robustness, improves image transmission security and can be applied to information security.
Owner:XIDIAN UNIV
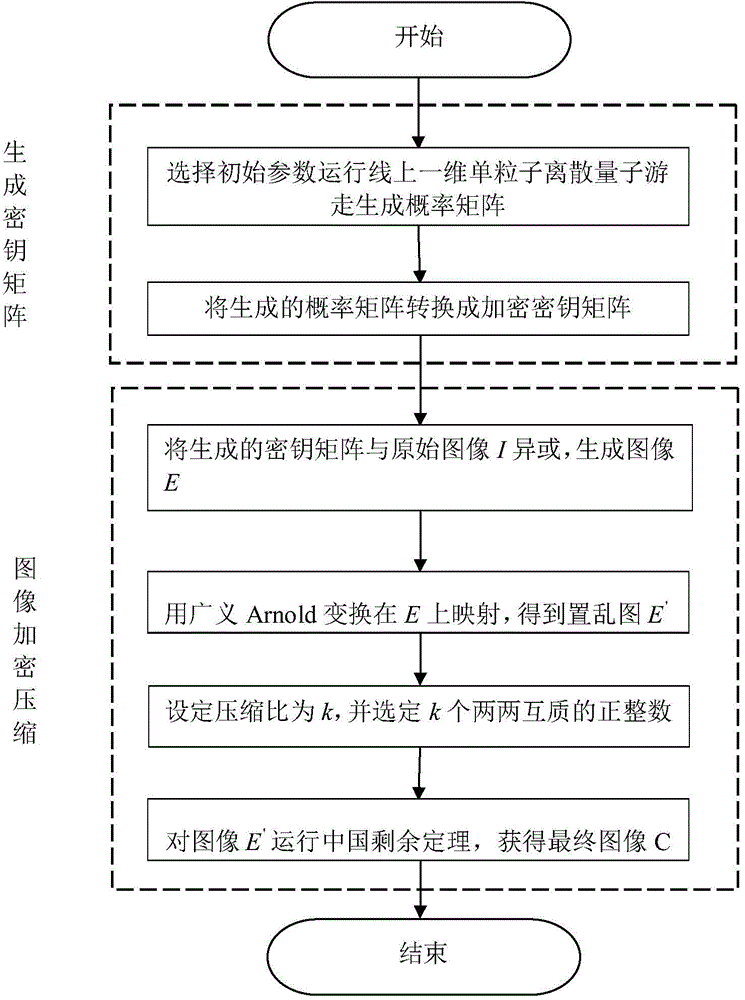
Image encryption compression method based on discrete quantum walk and Chinese remainder theorem
InactiveCN103957418ALarge key spaceCiphertext correlation is lowDigital video signal modificationKey spaceArnold transformation
The invention relates to an image encryption compression method based on a discrete quantum walk and a Chinese remainder theorem. The method comprises two phases: a secret key generation phase, i.e., generating probability distribution by use of a linear single particle one-dimensional discrete quantum random walk (QRW), and converting the probability distribution into a secret key matrix capable of encryption; and an image encryption compression phase, i.e., compressing an image by use of the generated secret key matrix and the Chinese remainder theorem. XOR operation is performed on an obtained encryption secret key and an original image, afterwards, Arnold transformation is performed on an obtained image. Diffusion and compression are carried out on a scrambling image according to a given compression ratio k by use of the Chinese remainder theorem. Compared to an image encryption compression scheme based on chaos and optics, the method provided by the invention has higher safety and better compression performance. The greatest advantage of the algorithm is that a theoretical infinite large secret key space can be generated so as to oppose a violent attack capability. Various performance comparisons indicate that the algorithm is better than prior research and can better satisfy actual demands.
Owner:BEIJING UNIV OF TECH
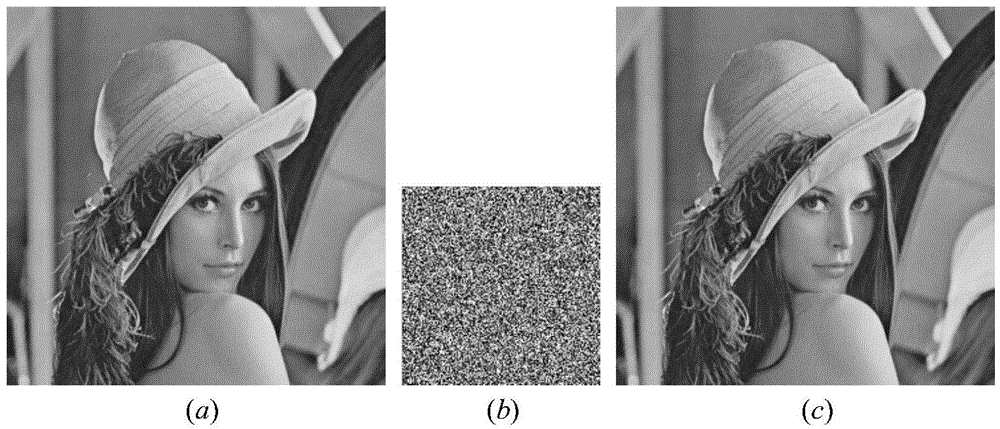
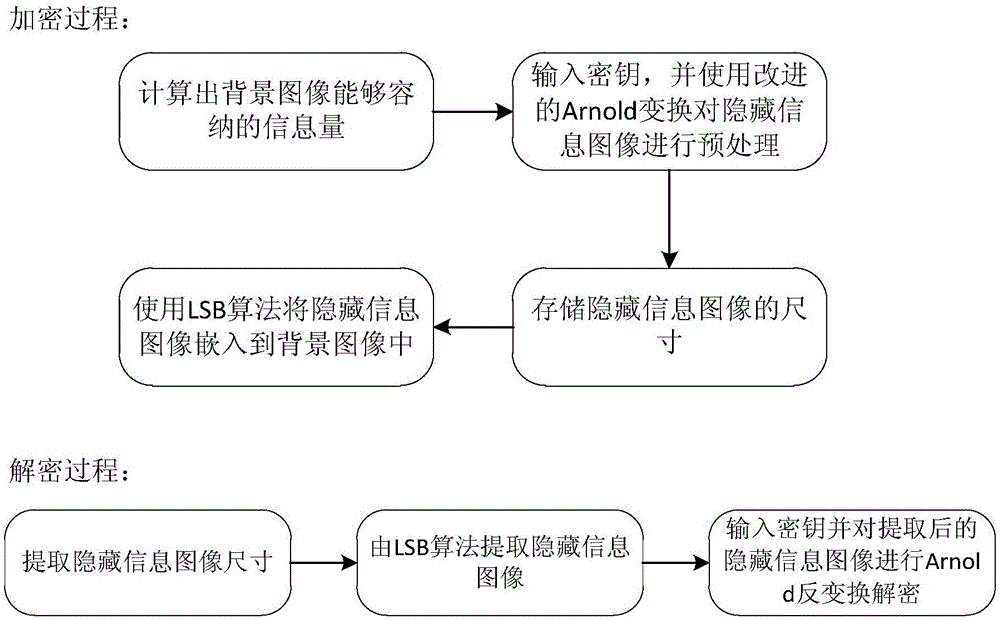
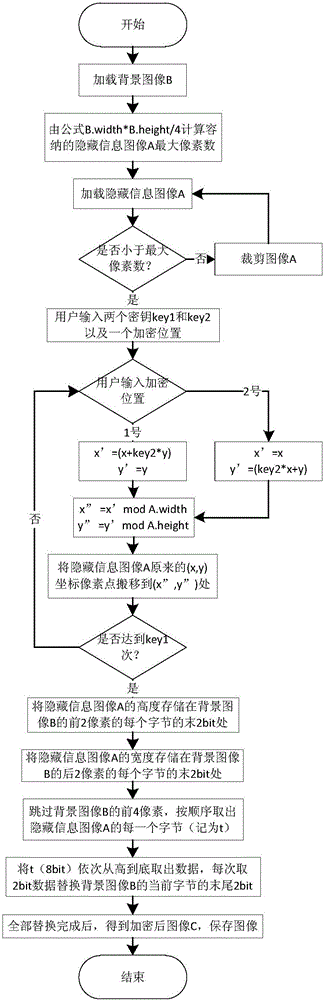
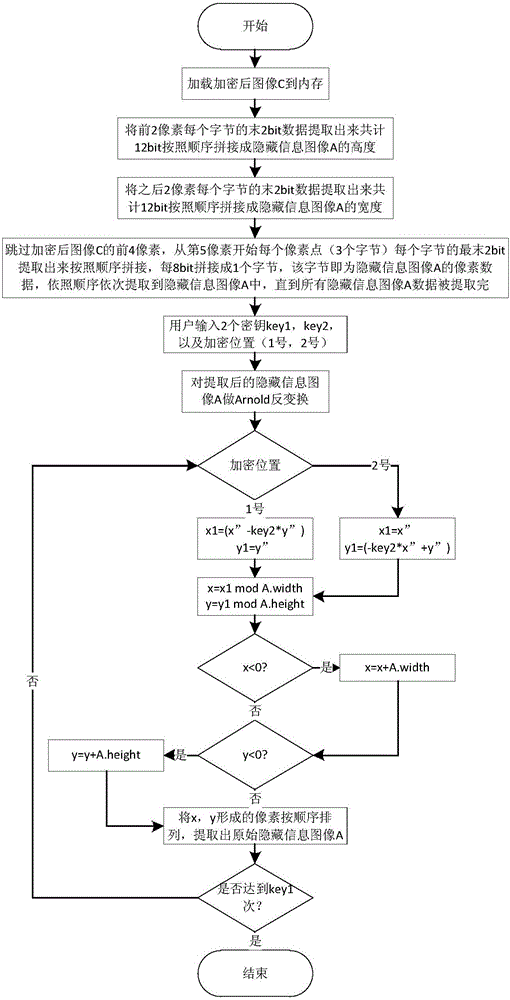
Image information encryption and decryption method based on improved Arnold transformation and LSB
ActiveCN106157231AImprove confidentialityVandal resistantImage watermarkingArnold transformationInformation quantity
The invention discloses an image information encryption and decryption method based on improved Arnold transformation and LSB. The method includes: using the improved Arnold transformation to preprocess an image, and using an LSB algorithm to embed the preprocessed image into a background image to form a new image with the encrypted image. The encryption process mainly includes: calculating the information quantity which can be contained by the background image, inputting a key, using the improved Arnold transformation to preprocess a hidden-information image, saving the size of the hidden-information image, and using the LSB algorithm to embed the hidden-information image into the background image. The decryption process mainly includes: extracting the size of the hidden-information image, using the LSB algorithm to extract the hidden-information image, inputting a key and performing reverse Arnold transformation on the extracted hidden-information image so as to achieve decryption. By the image information encryption and decryption method, information confidentiality is enhanced greatly.
Owner:NANJING UNIV OF POSTS & TELECOMM
Image encryption method based on two-dimensional Arnold transformation
InactiveCN107169911ACrypto EasyEasy to decryptImage data processing detailsArnold transformationComputer vision
The present invention provides an image encryption method based on two-dimensional Arnold transformation, and belongs to the technical field of encryption. The method comprises: expressing a two-dimensional planar image with a binary function I=f (x, y), performing two-dimensional Arnold transformation on the image f(x,y), and changing a layout of a gray value of an original image by changing pixel coordinates; and taking the original image as a matrix, wherein an image subjected to Arnold transformation is ''messy'', and due to periodicity of Arnold transformation, continuing using Arnold transformation, which can reproduce the image, so as to decrypt the image. According to the method, periodicity of Arnold transformation is used, that is, the original image can be reproduced when iteration is performed to a certain step. Compared with other encryption methods, image encryption and decryption become easier, so that image encryption efficiency is greatly increased.
Owner:黄宗美
Medical image zero-watermark embedding method based on NSCT combined transformation
ActiveCN110517182AImplement embeddingIntegrity guaranteedImage watermarkingMedical imagesFeature vectorArnold transformation
The invention discloses a medical image zero-watermark embedding method and device based on NSCT combination transformation, equipment and a readable storage medium. The scheme is implemented on the basis of hybrid transformation and Arnold transformation of NSCT, RDWT and DCT, and in the watermark embedding process, firstly, a more robust medical image feature vector is extracted in combination with the NSCT, the RDWT and the DCT so as to resist geometric attacks. Secondly, the watermark is encrypted by utilizing Arnold transformation, so that the security of watermark information is enhanced; and finally, watermark embedding is realized by using a zero watermark technology, so that the integrity, the watermark capacity and the invisibility of the medical image are ensured, the defect oforiginal image data modification caused by a traditional watermark embedding technology is avoided, and the quality of the medical image is ensured. Therefore, even if the patient information is attacked intentionally or unintentionally, the medical image and the watermark cannot be cracked as long as the unauthorized user does not know the secret key, so that the personal information of the patient is truly protected.
Owner:HAINAN UNIVERSITY
Robust watermarking method for medical images on basis of Arnold scrambling transformation and DWT (discrete wavelet transform)-DFT (discrete Fourier transform)
InactiveCN102938133ASolve the quickness problemImplement secondary encryptionImage data processing detailsThird partyFeature vector
The invention discloses a robust watermarking technology for medical images on the basis of Arnold scrambling transformation and DWT (discrete wavelet transform)-DFT (discrete Fourier transform), and belongs to the field of multimedia signal processing. The robust watermarking technology includes embedding watermarks and then extracting the watermarks, and particularly includes steps of (1), performing Arnold transformation for watermarks to be embedded; (2), performing DWT for a medical image, performing DFT for approximation sub-images of the medical image, and extracting vectors of a feature; (3), generating a binary logic sequence via a Hash function by the vectors of the feature and the preprocessed watermarks so as to complete the process for embedding the watermarks; (4), performing DWT for a medical image to be measured, performing DFT for approximation sub-images of the medical image to be measured and extracting vectors of a feature; (5), extracting watermarks by the aid of the Hash function and a binary logic sequence stored in a third party; and (6), obtaining the original watermarks via Arnold inverse transformation so as to complete the process for extracting the watermarks. The robot watermarking technology has an important significance in protecting information of patients during remote medical treatment.
Owner:HAINAN UNIVERSITY
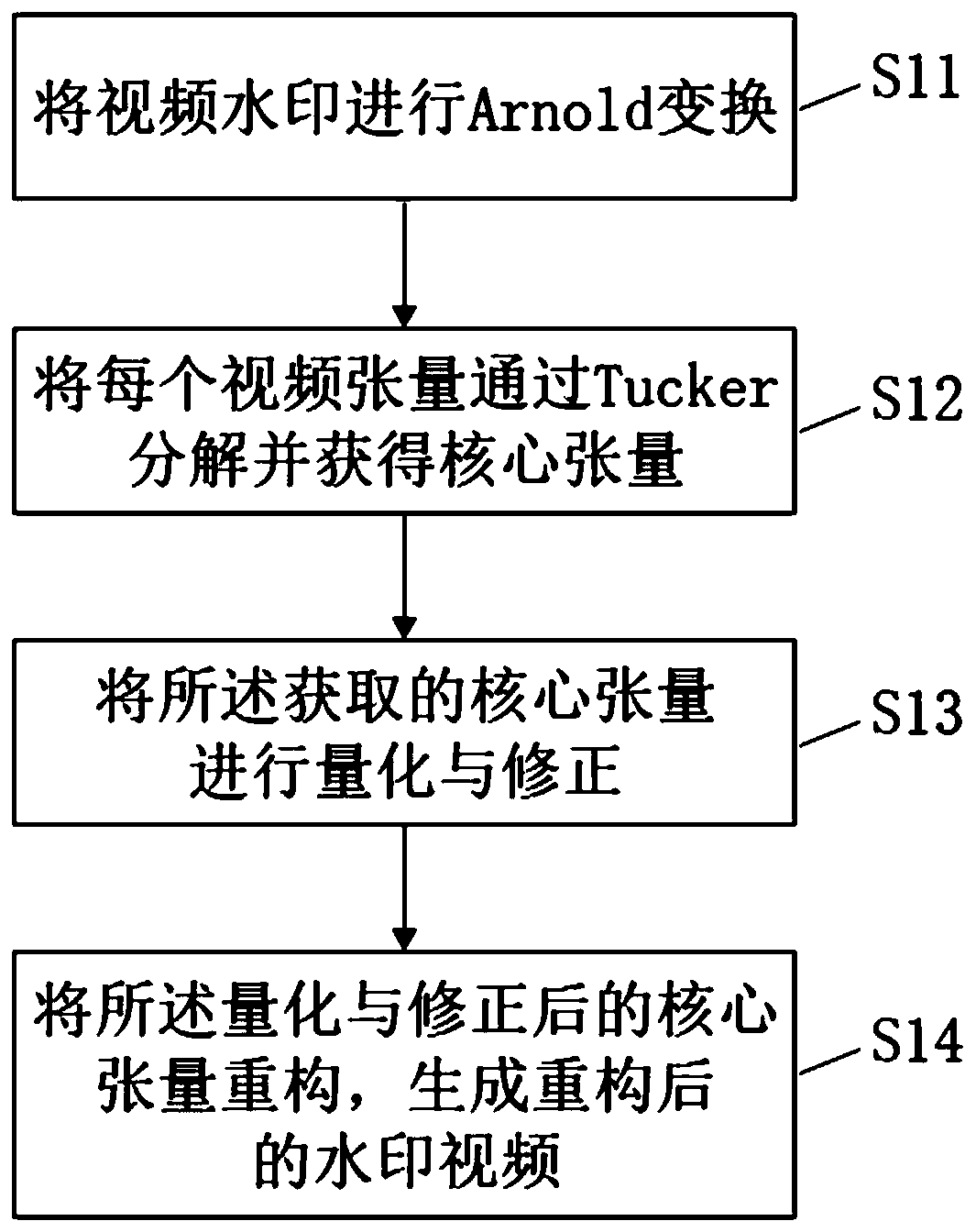
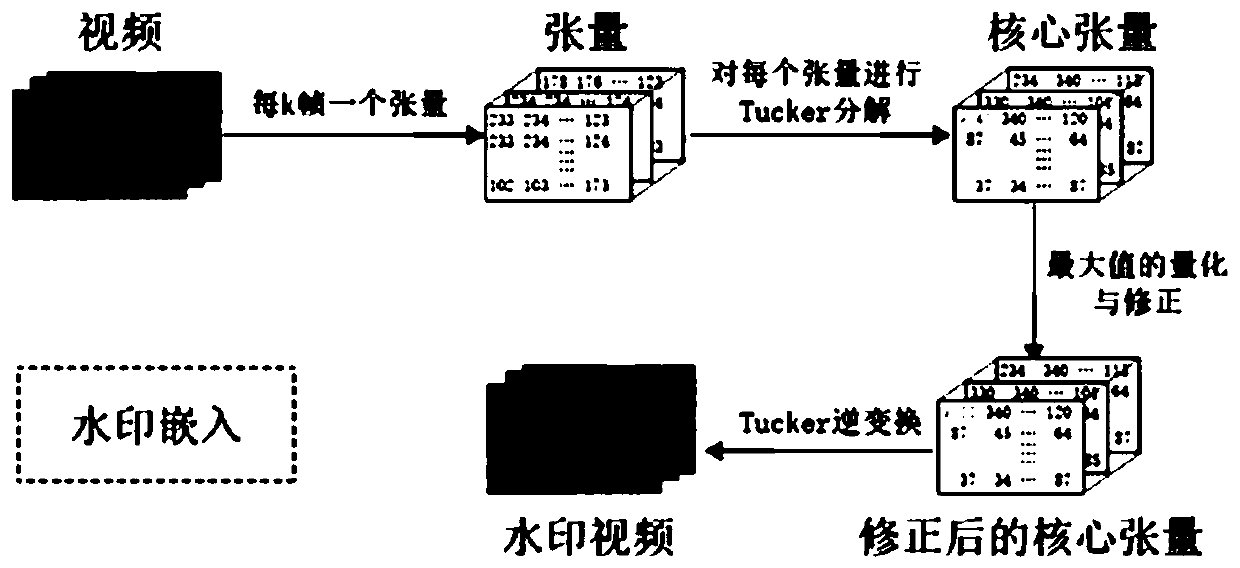
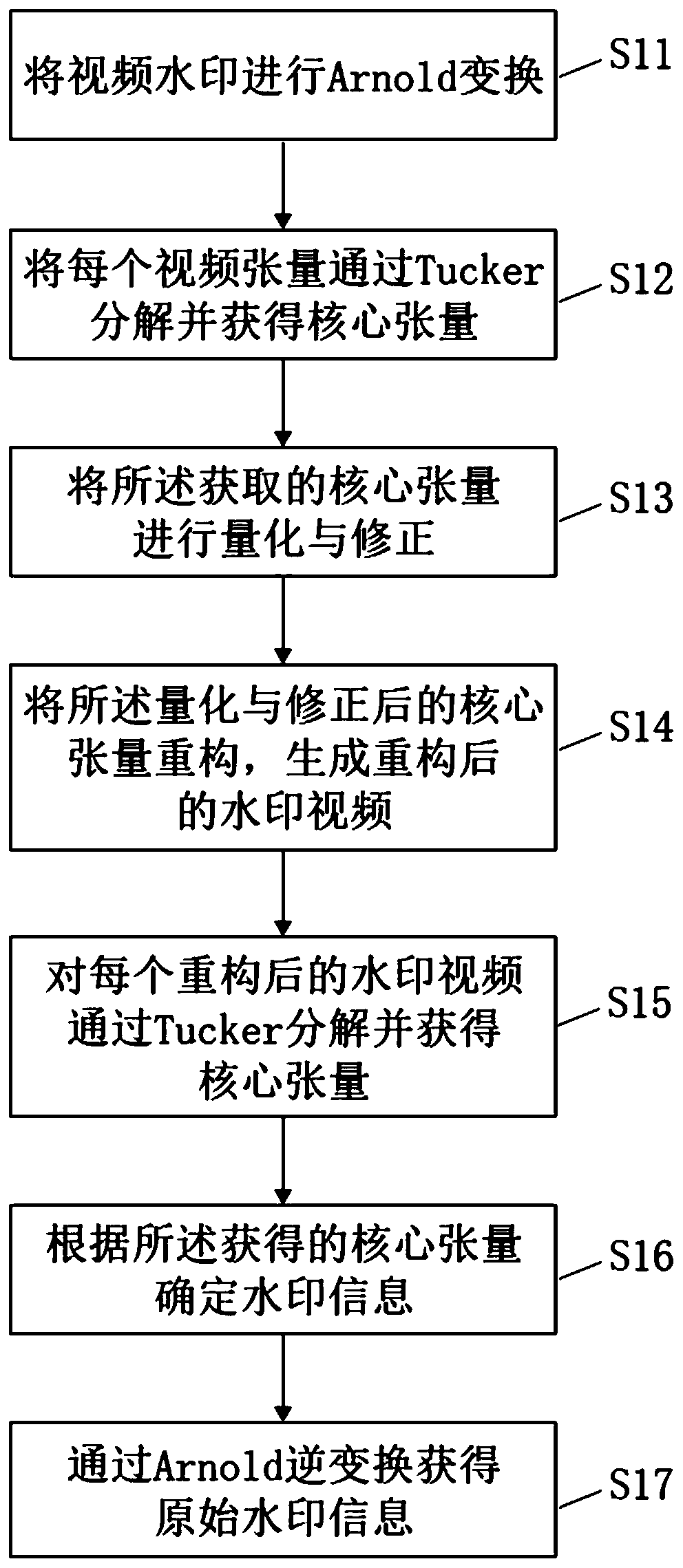
Gray scale video watermarking algorithm based on core tensor
PendingCN110111232AIncrease imperceptibilityFully consider the relevanceDigital data protectionImage watermarkingArnold transformationTucker decomposition
The invention discloses a gray scale video watermarking algorithm based on core tensor. The gray scale video watermarking algorithm comprises the following steps: S11, carrying out Arnold transformation on a video watermark; S12, decomposing each video tensor through Tucker and obtaining a core tensor; S13, quantifying and correcting the obtained core tensor; and S14, reconstructing the quantizedand corrected core tensor to generate a reconstructed watermark video. According to the invention, the grayscale video is represented by three orders as tensors, and the correlation between adjacent frames of the video is fully considered. By quantifying the core tensor, the watermark information is uniformly dispersed into each frame of the video, so that the non-perceptibility of the algorithm and the common video attack are improved.
Owner:绍兴聚量数据技术有限公司 +1
Fragile watermark embedding and detection method of MPEG-2 compressed domain video
ActiveCN105915912ADoes not affect real-timeNo impact on video qualityDigital video signal modificationSelective content distributionPattern recognitionArnold transformation
The present invention discloses a fragile watermark embedding and detection method of an MPEG-2 compressed domain video. An MPEG-2 decoder is employed to analyze the MPEG-2 video code flow according to the MPEG-2 video coding standard, the nonzero coefficient number of a brightness block Y component, a chroma block U component and a V component through DCT transformation and quantification are subjected to statistics according to the macro-block data of the I-frame video, the energy difference statistical value of the brightness block Y component is calculated according to the mapping relation; and the binary system watermarking information is generated through the Arnold transformation to embed the video code flow. The fragile watermark embedding and detection method of an MPEG-2 compressed domain video generates watermarking according to the video macro block to provide reliable watermarking embedding and detection for MPEG-2 digital products and is able perceive tiny attack; the watermarking embedding detection based on the compressed domain has no influence on the video quality, the calculation complexity is low, and the timeliness is good; and the fragile watermark embedding and the detection method of MPEG-2 compressed domain video performs watermarking detection with no need for original video and belongs to a blind watermarking method.
Owner:安徽天虹数码科技股份有限公司
A video content protection method and apparatus based on watermarks
InactiveCN106612467AImplement digital watermarkingImprove encryptionSelective content distributionComputer hardwareArnold transformation
The invention discloses a video content protection method and apparatus based on watermarks. The apparatus comprises a watermark information generation module and a watermark information embedding module. The watermark information generation module generates binary images of a check identifier and a copyright identifier according to a watermark capacity threshold, performs Arnold transformation on the binary images, generates image bit strings and encrypts the image bit strings with private keys to generate watermark information. The watermark information embedding module decodes the video images to obtain a video stream, and embeds the watermark information of the appropriate intensity in key frame transform domain intermediate frequency coefficients. According to the video content protection method and apparatus based on the watermarks, digitalal watermarks of the video content can be relatively well realized, and the digit watermarks in the invention has a relatively high encryption degree and safety degree.
Owner:上海文广互动电视有限公司
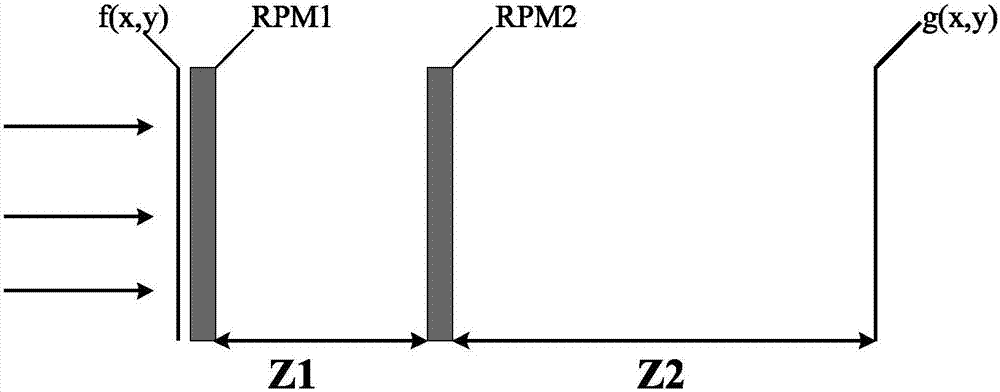
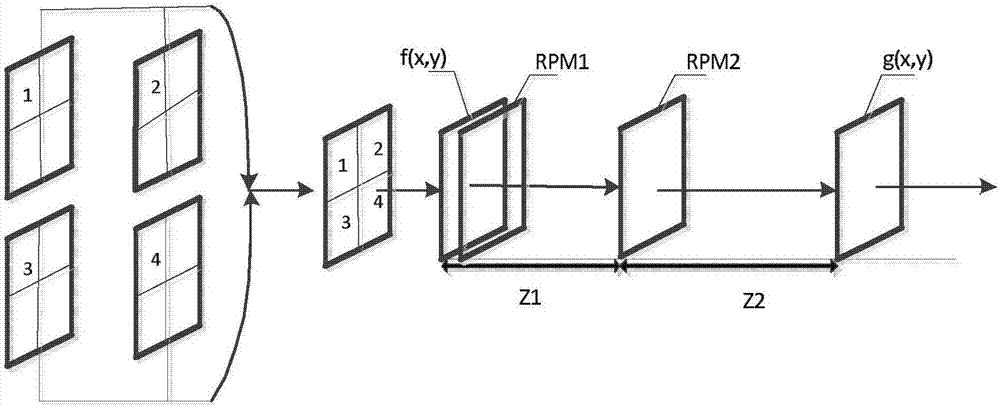
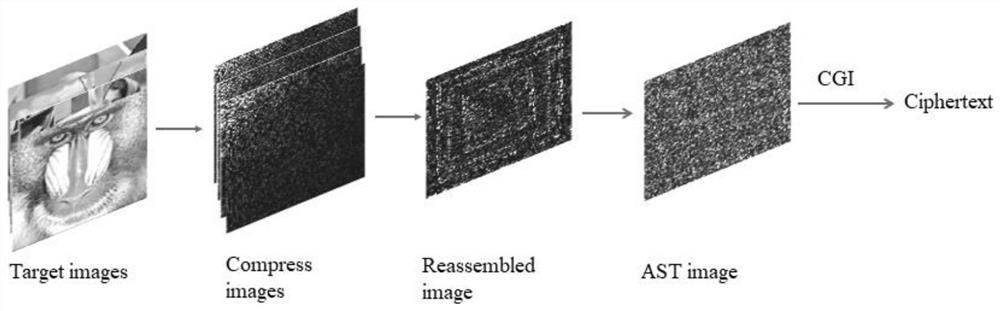
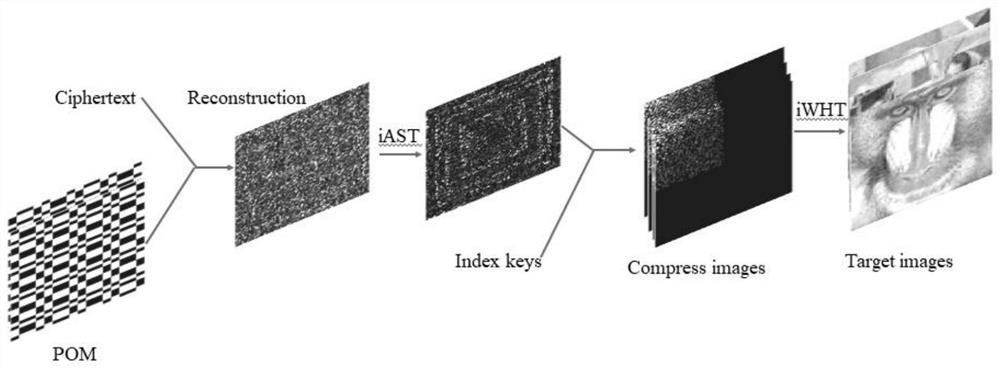
Multi-image encryption device based on computer generated hologram and multi-image encryption algorithm thereof
The invention discloses a multi-image encryption device based on a computer generated hologram and a multi-image encryption algorithm thereof. The multi-image encryption device comprises an input signal surface, a first random phase plate, a second random phase plate and an output signal surface which represent an input surface, transformation surfaces and an output surface from the left to the right. The image can be clearly displayed under the condition of ensuring information security, and the optical path is simple without transformation lens. Wavelet transformation and Fresnel double random phase encryption are used so that the design system is enabled to have high parallelism and transmission performance. Double encryption of the Arnold transformation scrambling mode is used so that the image decoding difficulty can be greatly increased and storage and transmission of the encrypted hologram are facilitated. The experiment verifies and proves that the method has great robustness and has great encryption effect.
Owner:张艳雪
JPEG (Joint Photographic Experts Group) 2000 integrated telescopic image watermarking method
InactiveCN104036449APracticalImprove robustnessImage data processing detailsSingular value decompositionArnold transformation
The invention provides a JPEG (Joint Photographic Experts Group) 2000 integrated telescopic image watermarking method. The method is characterized by comprising the watermarking embedding method and the watermarking extracting method. The watermarking embedding method comprises the following steps: 1, performing integer wavelet transformation; 2, performing Arnold transformation; 3, sequencing and layering; 4, performing H*H partitioning; 5, decomposing a singular value; 6, operating the intensity and difference value; 7, embedding an embedded watermark; 8, modifying the singular value operation; 9, decomposing and inversely operating the singular value; 10, encoding by EBCOT (Embedded Block Coding With Optimized Truncation). The watermarking extracting method comprises the following steps: 1, performing H*H blocking; 2, decomposing the singular value; 3, operating the intensity; 4, extracting information of watermarks at all levels; 5, inversely scrambling; 6, performing inverse wavelet transformation.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
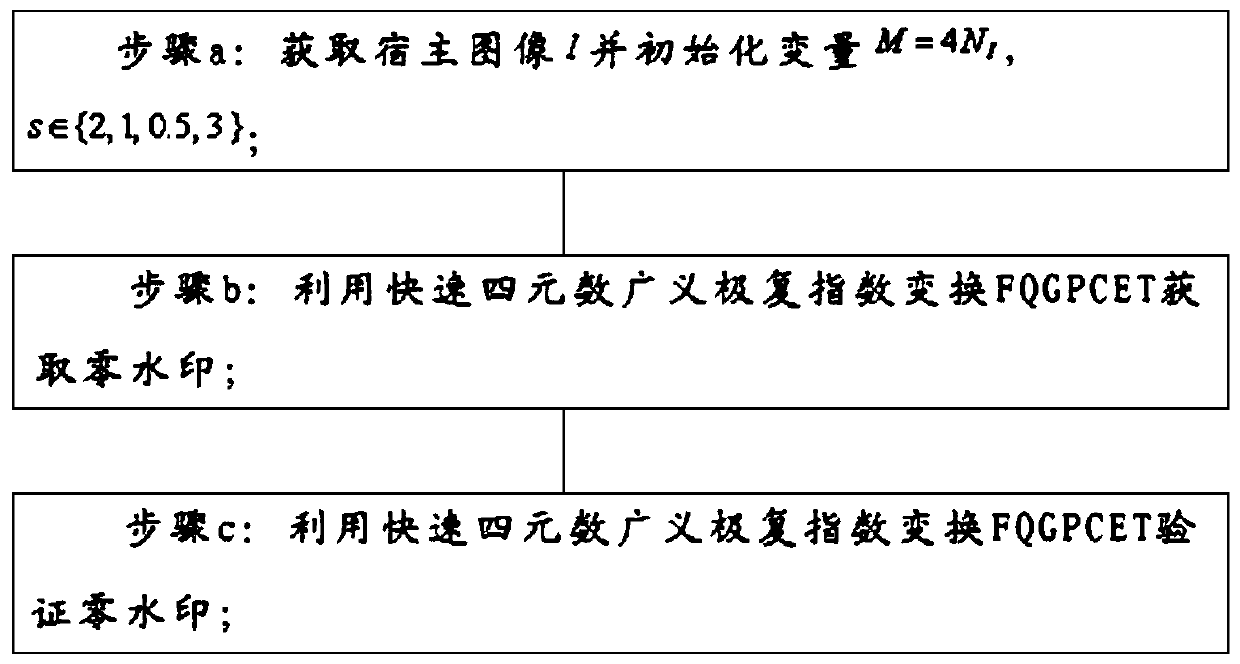
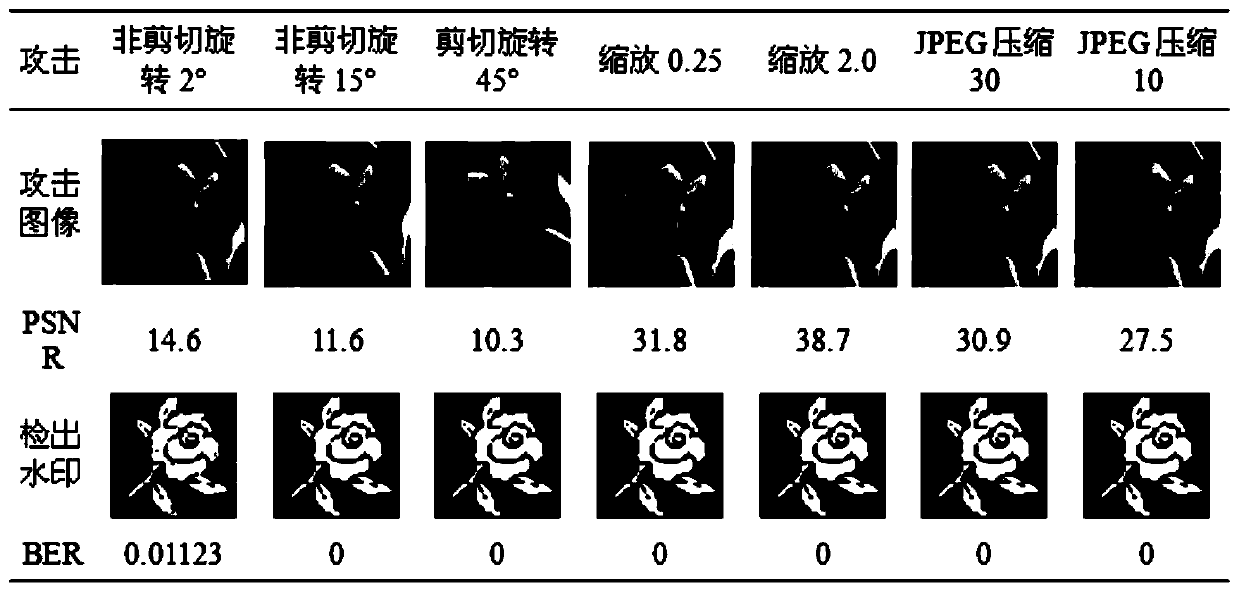
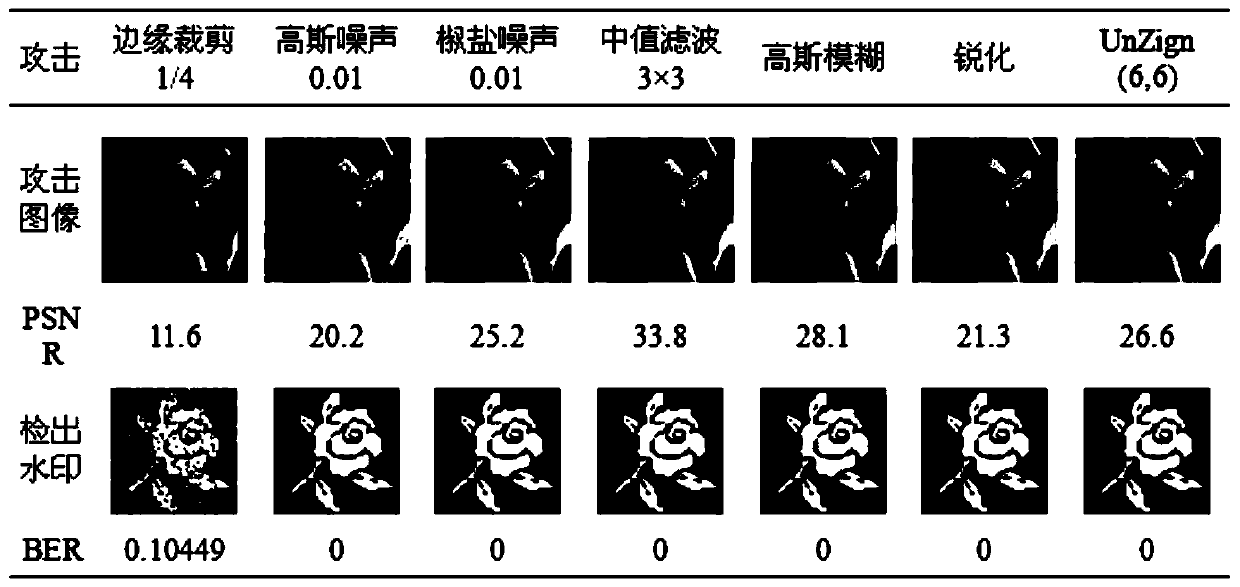
Color image zero watermarking method based on fast quaternion generalized polar complex exponential transformation
ActiveCN109919824AGood routine signal attackGood geometric attack robustnessImage data processing detailsColor imageFeature vector
The invention belongs to the technical field of digital image copyright protection, and particularly relates to a color image zero watermarking method based on rapid quaternion generalized polar complex exponential transformation. The invention provides a color image zero watermarking method based on fast quaternion generalized polar complex exponential transformation, and the method comprises thesteps: firstly, calculating the fast quaternion generalized polar complex exponential transformation FQGPCET of an original carrier image, carrying out the moment selection, and constructing a hybridlow-order moment feature with the good robustness and discrimination; secondly, utilizing asymmetric Tent mapping with good security to encrypt and convert the feature vector into a feature map; then,, scrambling the feature map and the watermark image by using generalized Arnold transformation, and taking the XOR of the scrambling results of the feature map and the watermark image to obtain a zero watermark image which can be used for copyright authentication; and finally, in order to ensure that the copyright can be publicly verified, enabling the credible mechanism to authenticate the zerowatermark, the secret key and the copyright owner identity information and adds a digital timestamp.
Owner:LIAONING NORMAL UNIVERSITY
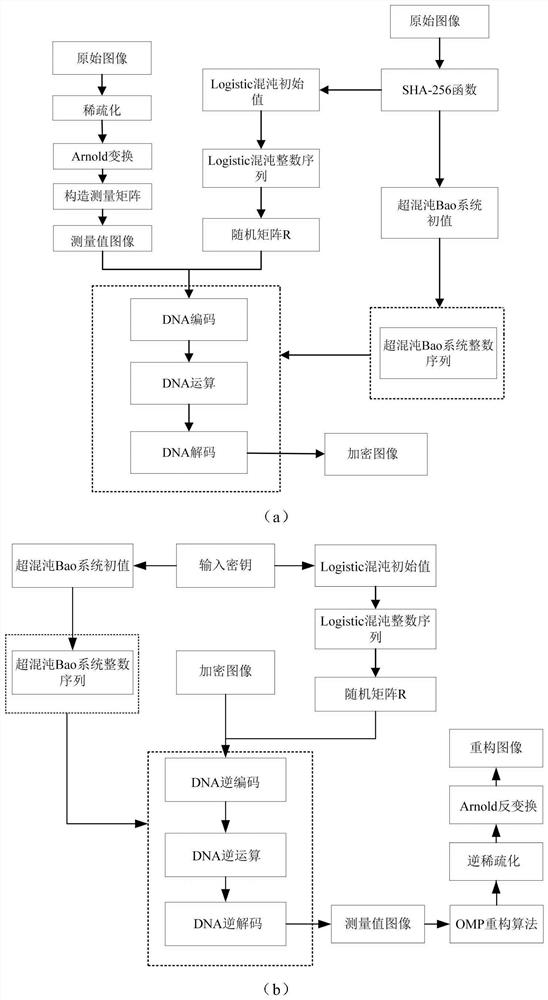
Image compression encryption and decryption method based on compressed sensing and DNA coding
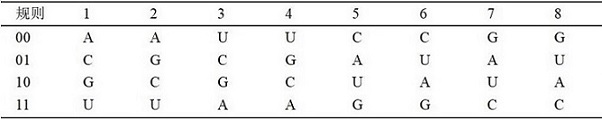
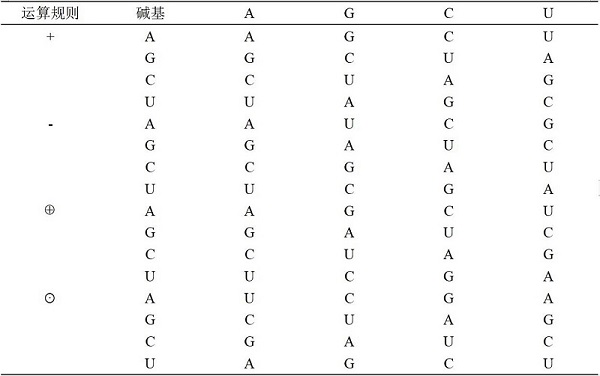
ActiveCN113297607AImprove securityReduce correlationImage codingDigital data protectionArnold transformationHash function
The invention provides an image compression encryption and decryption method based on compressed sensing and DNA coding, and the method comprises the steps: taking an original image as a parameter of an SHA-256 hash function, and obtaining a hyper-chaos Bao system integer sequence and a Logistic chaos integer sequence; converting the Logistic chaotic integer sequence into a second matrix; carrying out sparse and Arnold transformation on the original image by using wavelet transformation; constructing a Hadamard matrix as a measurement matrix based on the compression ratio; performing compression measurement on the image after sparse decomposition by using the measurement matrix to obtain a first matrix; carrying out block processing on the first matrix and the second matrix, and carrying out DNA coding, operation and decoding on each small block; dynamically controlling DNA coding, decoding and operation modes by a hyper-chaos Bao integer sequence; and combining all sub-blocks to obtain an encrypted image. The defect that traditional compressed sensing cannot resist plaintext attacks is overcome.
Owner:YANSHAN UNIV
IWT-Schur-based region-of-interest reversible watermark embedding and extracting method
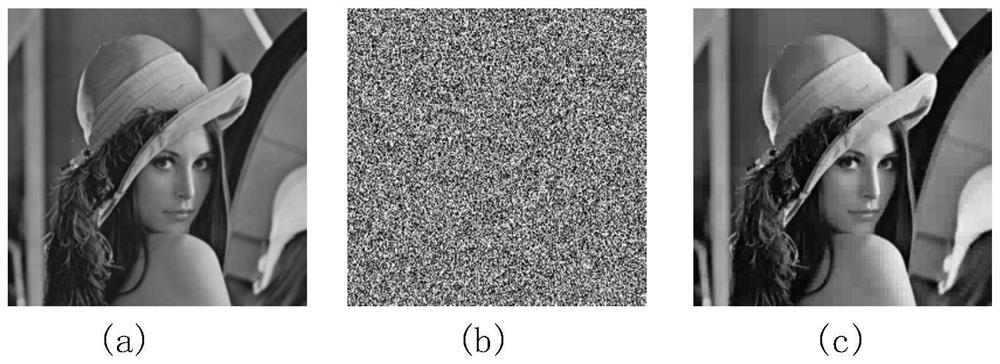
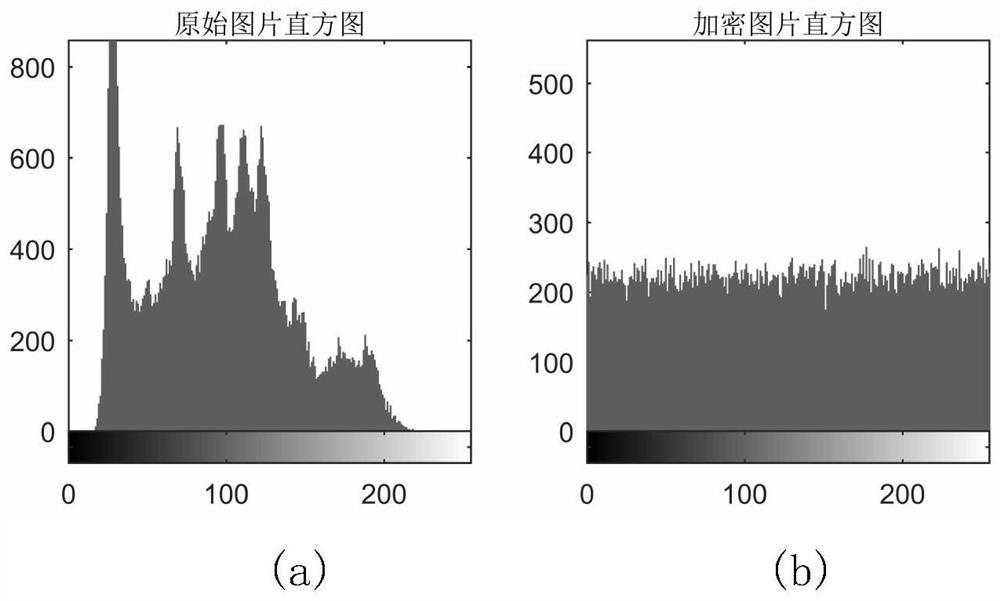
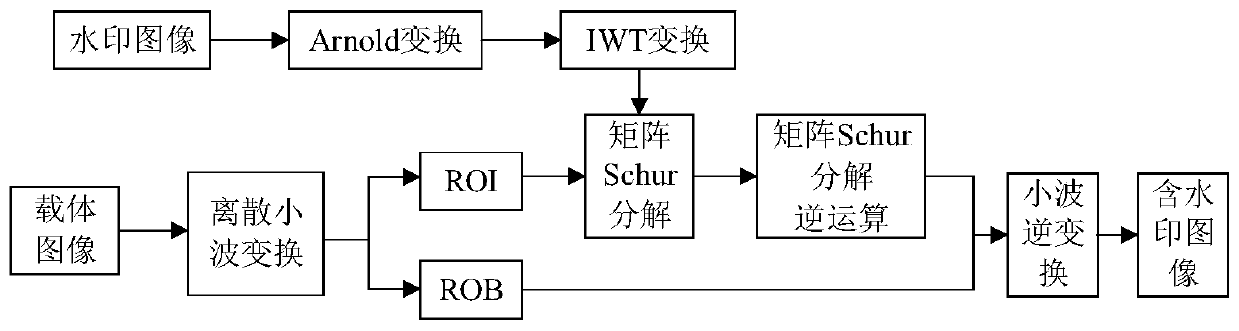
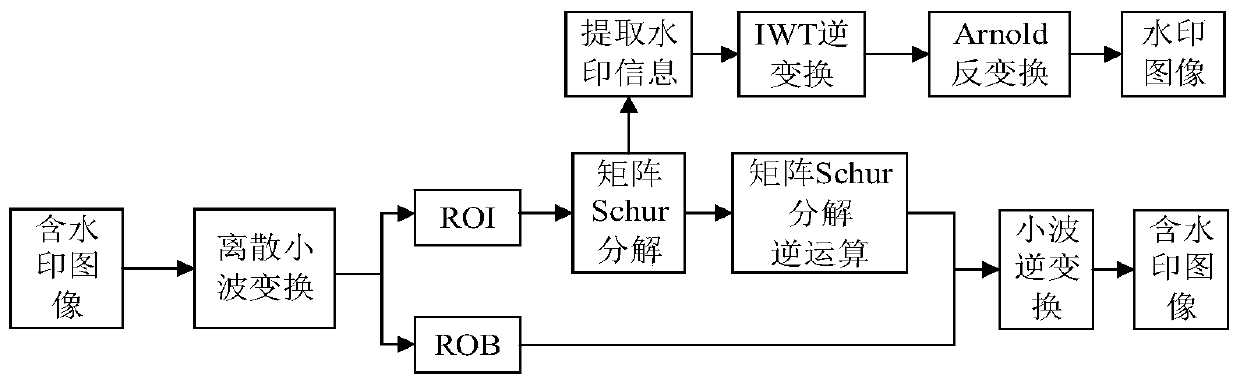
PendingCN110097490AGuaranteed Lossless RecoveryEmbedded ensureImage enhancementImage analysisPattern recognitionArnold transformation
The invention relates to an IWT-Schur-based region-of-interest reversible watermark embedding and extracting method. The method comprises steps of during watermark embedding, firstly, performing wavelet decomposition on a carrier image, screening to obtain a region-of-interest coefficient of each component, then encrypting the watermark by using Arnold transformation, carrying out integer wavelettransformation on the scrambled watermark to obtain a series of sub-bands, and finally, correspondingly embedding each sub-band of the watermark into each sub-band ROI of the carrier image by using matrix Schur decomposition. Compared with the prior art, the method has the advantages that nondestructive recovery of the region of interest is guaranteed, it is guaranteed that the watermark is completely embedded into the whole region of interest, and the watermark can better adapt to the ROI coding characteristic.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
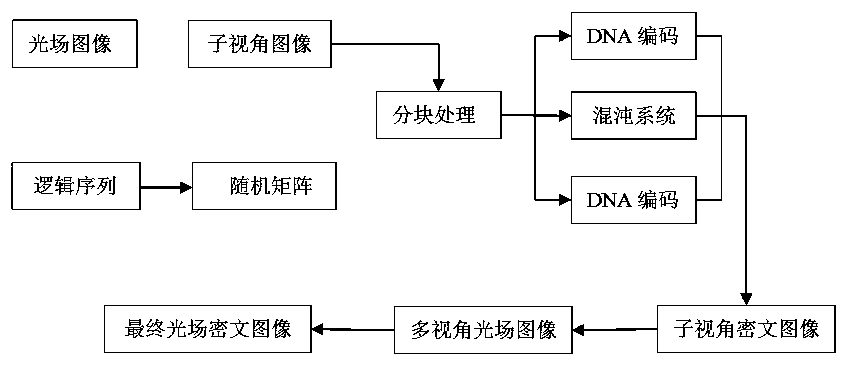
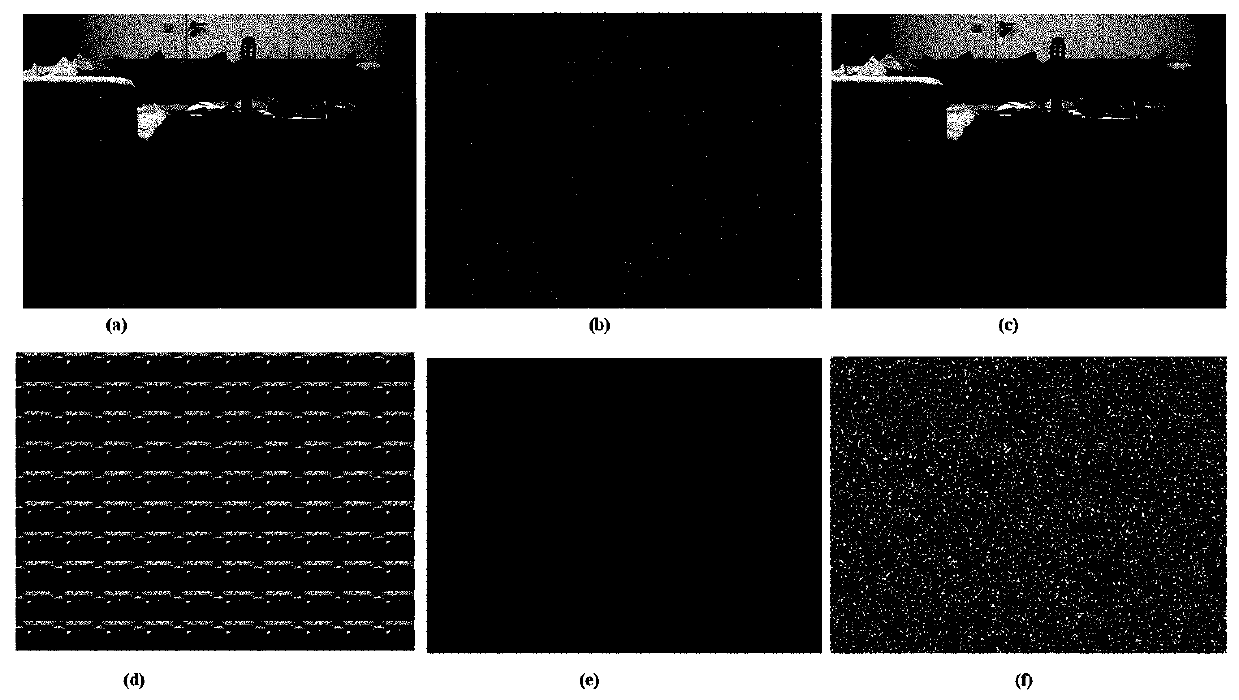
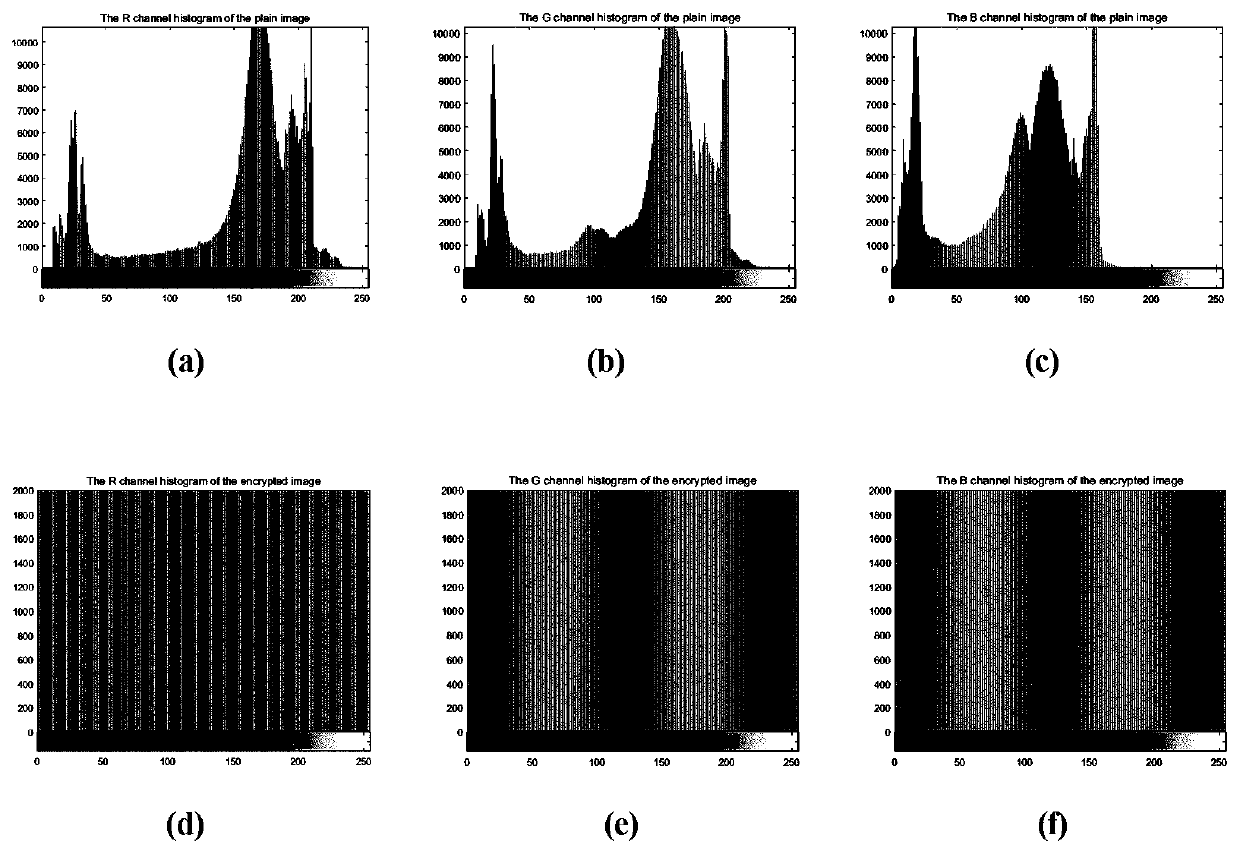
Light field image encryption method based on DNA sequence and chaotic system
The invention relates to a light field image encryption method based on a DNA sequence and a chaotic system. The light field image encryption method is characterized by comprising the following steps:firstly, carrying out two-dimensional spatial domain and angular domain representation on a four-dimensional light field image; carrying out block processing on the sub-view light field image and a random matrix generated by logic mapping; carrying out DNA coding mode selection and operation on the generated sub-blocks by utilizing the characteristics of a chaotic system; and finally, carrying out DNA decoding processing to obtain a ciphertext image of a sub-visual angle, carrying out sequential processing and angular domain removal, and carrying out Arnold transformation to obtain a final light field ciphertext image. The four-dimensional light field image can be effectively protected, and the method has the advantages of being safe, reliable and high in operation speed.
Owner:JIANGXI UNIVERSITY OF FINANCE AND ECONOMICS
Multi-image encryption and decryption method based on Walsh transform and ghost imaging calculation
ActiveCN112989371APrevent leakageSimple processDigital data protectionMulti-imageArnold transformation
The invention discloses a multi-image encryption and decryption method based on Walsh transform and ghost imaging calculation, and the method comprises the steps: encryption: carrying out Walsh-Hadamard compression transform on a plurality of plaintext images, selecting some effective pixels to carry out Arnold scrambling transform, and then loading the light intensity of an object plane to a calculation ghost imaging light path in sequence, and encrypting a target image into a ciphertext sequence; and 2, decryption: in the decryption process, sucessfully decrypting a corresponding plaintext image from a correct key set through measurement key recovery, compression algorithm reconstruction, inverse Arnold transformation and inverse Walsh-Hadamard transformation. The image encryption method provided by the invention has the advantages of simple encryption operation, high decryption efficiency and high security.
Owner:ZHEJIANG UNIVERSITY OF SCIENCE AND TECHNOLOGY
Image encryption method based on RNA and pixel depth
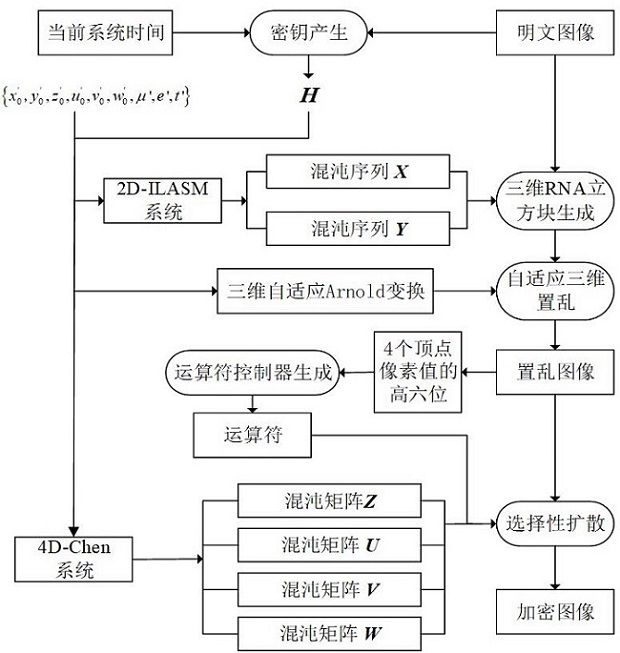
InactiveCN113612899AProtection securityImprove securityKey distribution for secure communicationSecuring communication by chaotic signalsArnold transformationReliable transmission
The invention discloses an image encryption method based on RNA and pixel depth, and belongs to the field of information encryption. At present, the network transmission security problem is increasingly severe, and in order to protect network interaction image content, the invention provides an image encryption method based on RNA and pixel depth. The method comprises the following steps: firstly layering a plaintext image and then carrying out RNA coding; secondly, scrambling the layered RNA image by using a chaos sequence, and performing three-dimensional adaptive Arnold transformation and RNA decoding on a scrambling result to obtain a scrambled image; thirdly, carrying out RNA coding on the scrambled image; using the selected RNA chaos matrix and the scrambled RNA image for diffusion through an RNA operator; and finally, performing RNA decoding on the diffusion result to obtain a final ciphertext image. Experimental results show that the method is wide in application range, good in encryption effect, high in safety and capable of guaranteeing safe and reliable transmission of images under a network platform.
Owner:CHINA UNIV OF MINING & TECH
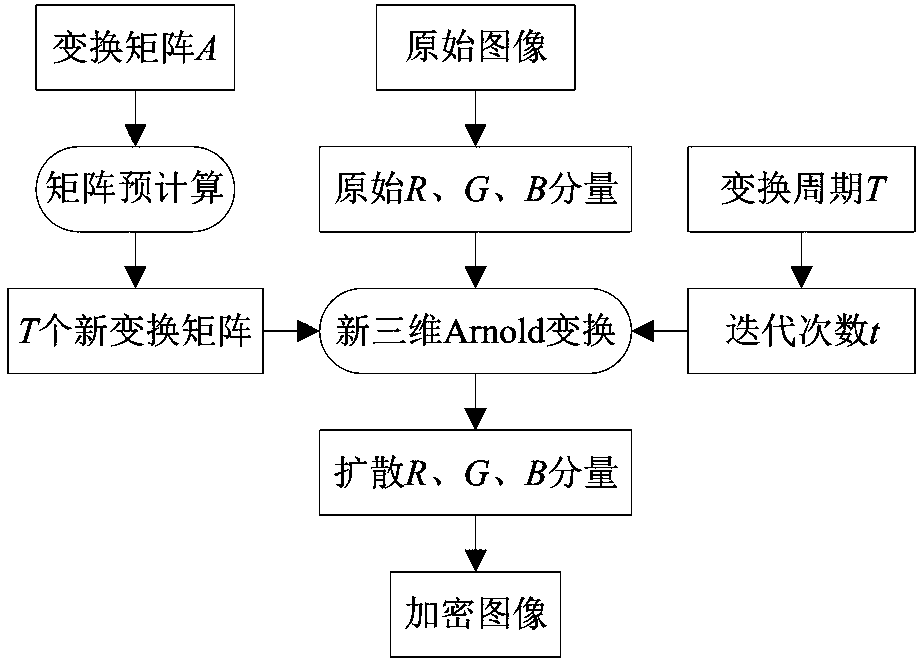
Rapid color image encryption method based on pre-storage and three-dimensional Arnold transformation
To improve the image encryption efficiency, under the inspiration of a famous external equipment on-line parallel operation (Simultaneous Peripheral Operations On-Line, Spooling) system, an idea of changing time in space is adopted to design rapid a color image rapid encryption method based on pre-storage and three-dimensional Arnold transformation. Before encryption, T new transformation matrixesin a period are pre-calculated and are respectively stored in T text files. And during encryption, reading the corresponding new transformation matrix from the t th text file (t belongs to [1, T-1]),and new three-dimensional Arnold transformation is carried out on an original image once to obtain an encrypted image. Experiments show that the method is simple to operate and easy to implement, andthe image encryption efficiency can be obviously improved.
Owner:CHINA UNIV OF MINING & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com