Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
70results about How to "Increase imperceptibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Audio spread-spectrum watermark processing method for protecting audio data
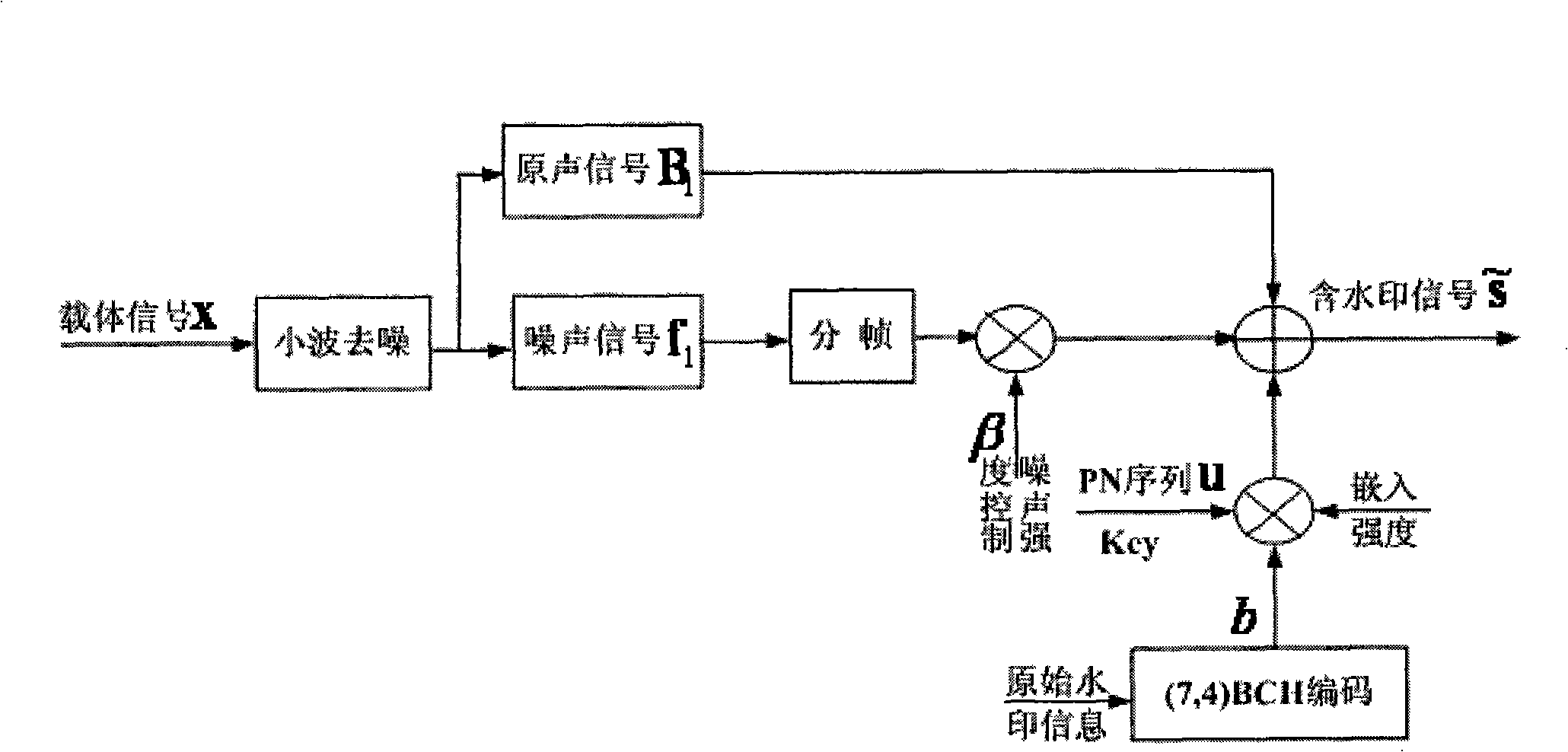
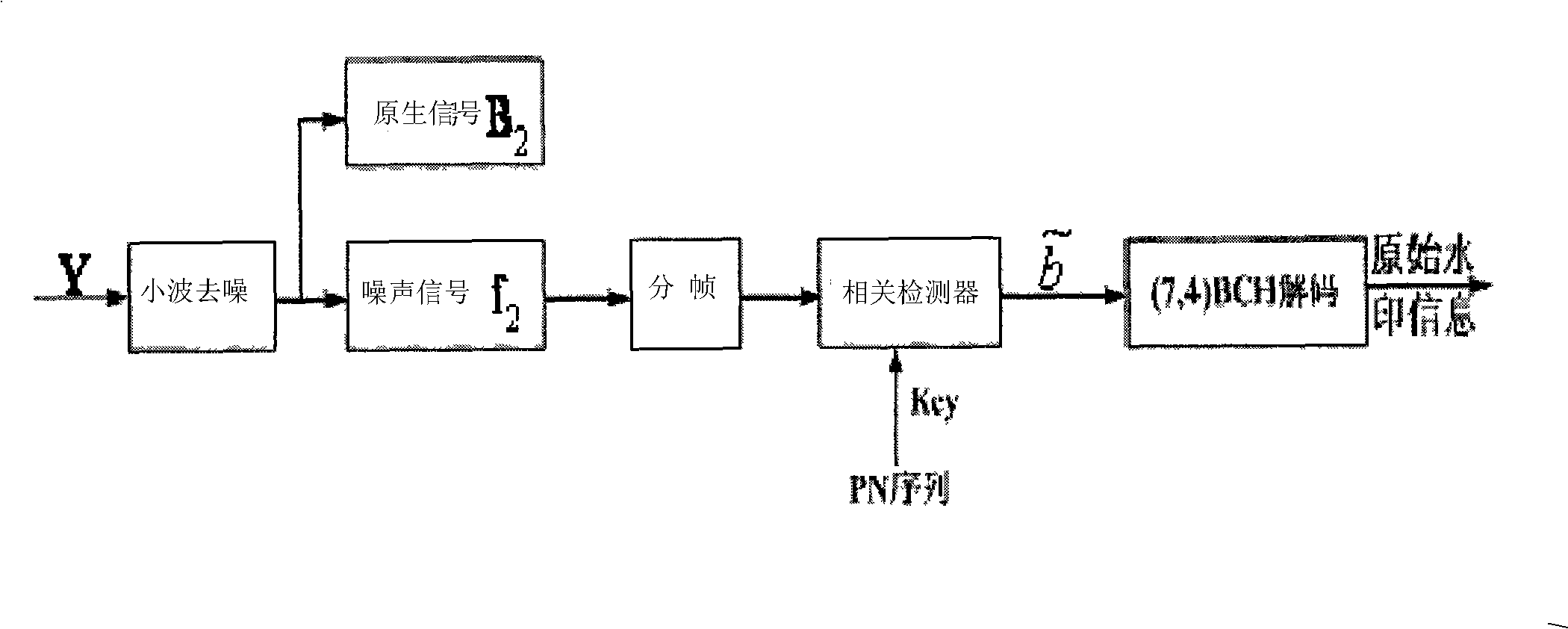
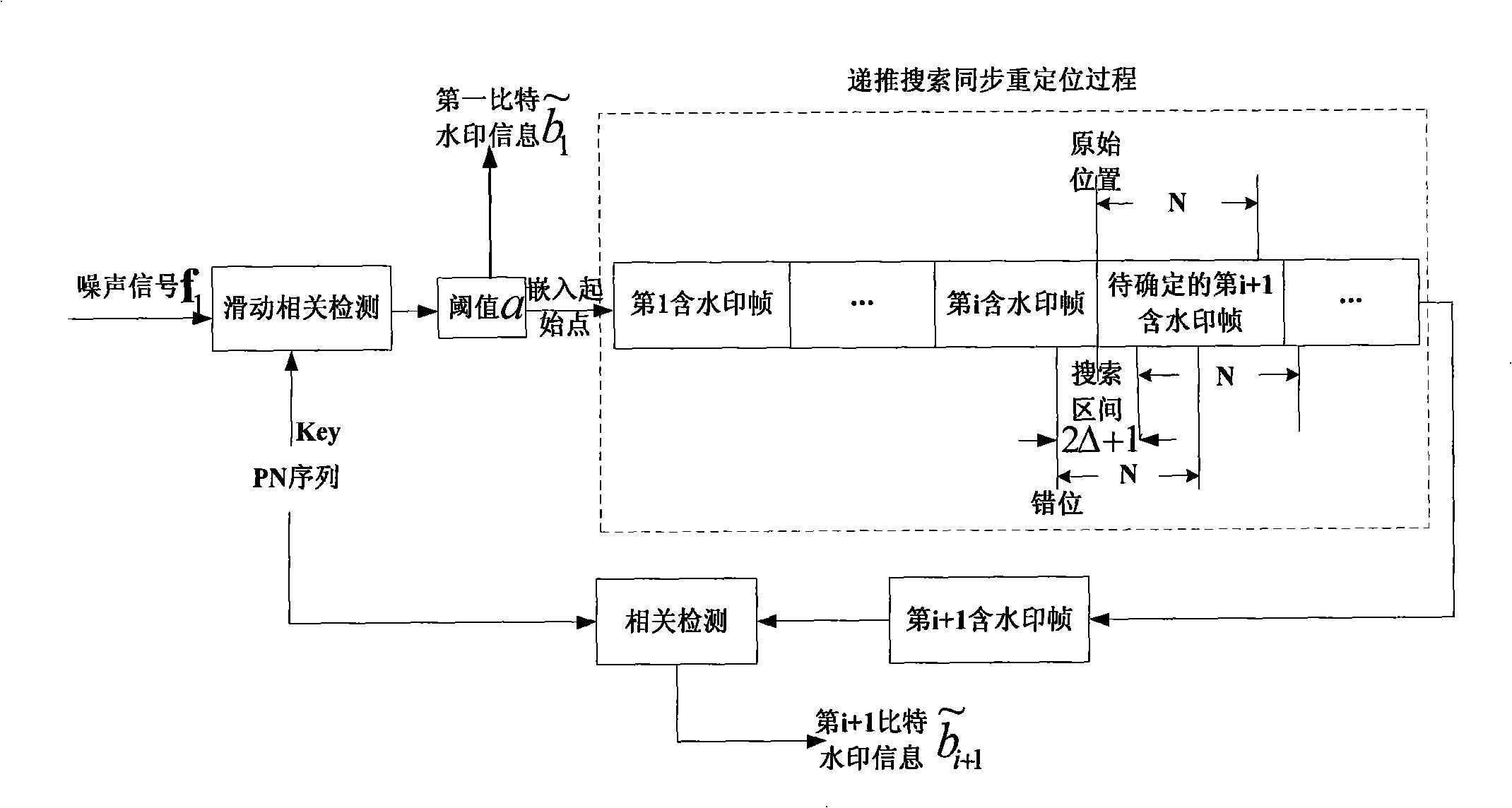
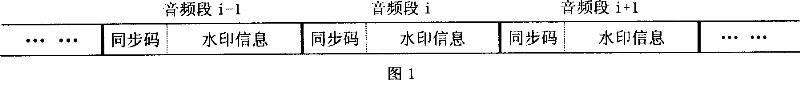
The invention discloses an audio spread spectrum watermark processing method for protecting the audio data, comprising two processes: a watermark embedding process and a watermark extraction process; in the embedding process, a wavelet de-noising technique is used for separating the noise of the signal and noise intensity control factor is used for reducing the noise signal intensity, and the effect of the noise of the signal on the detector performance is reduced; in order to improve the performance of the detector, the wavelet de-noising technique is also used in the water extraction process; in order to overcome the problem of excessively large correlation sliding detection calculation quantity in the corresponding detection, a synchronous positioning mechanism is designed. The algorithm is applicable to music and speech, which can effectively resist the attack of normal signal processing, more particularly, the attack of DA / AD conversion, thus being applied to the fields such as audio copyright protection, temper-proofing, certification, etc.
Owner:CHONGQING TELECOMMUNICATION INSTITUTE
Image watermarking embedding and extracting method based on singular value decomposition and principal component analysis
InactiveCN104599225AAchieve initial hidingImprove robustnessImage data processing detailsSingular value decompositionKernel principal component analysis
The invention discloses an image watermarking embedding method based on singular value decomposition and principal component analysis. The method includes: S1a, conducting scrambling processing on the original watermarking image W and obtaining the scrambled watermarking image W' ; S2a, conducting blocking on an original carrier image I, dividing the original carrier image I into an image block C of 8X8 and further obtaining original carrier image blocks; S3a, conducting the singular value decomposition on the original carrier image blocks C and obtaining the singular value of each image block; S4a, taking the singular value of each image block as the eigenvalue of the principal component analysis, conducting the principal component analysis on the singular value, extracting the component Y of the principal component whose the contribution rate reaches above 99.99%; and S5a, embedding watermarks in the component Y of the principal component, obtaining the component Y' of the principal component embedded with the watermarking image information, conducting inverse transformations of the principal component analysis and the singular value decomposition on Y', and obtaining the carrier image I' embedded with the watermarking.
Owner:HENAN NORMAL UNIV
Machine learning-based color image watermark embedding and detecting method
InactiveCN104680473AImprove practicalityIncrease imperceptibilityImage data processing detailsFeature vectorLearning based
The invention discloses a machine learning-based color image watermark embedding and detecting method. The method comprises the following steps of firstly, using a matrix-based image normalizing technology to map a carrier image to a geometric invariant space, and combining a invariant centroid theory to determine an important area in a normalized color image; secondly, performing non-subsample Contourlet conversion on the important area of the G-component normalized color image; finally, according to a G-component visual mask model, adaptively determining embedding intensity, so that an image watermark is embedded in a low-frequency area, and the embedded watermark is guaranteed to have very good transparency and very high robustness; during watermark detection, by using the height relativity among color image components, selecting a stable feature vector training SVR (Support Vector Regression) model, and using the SVR training model to extract digital watermark information.
Owner:LIAONING NORMAL UNIVERSITY
Novel method of digital watermarking for protecting literary property of music works
InactiveCN101038771AImprove practicalityIncrease imperceptibilityRecord information storageRecording signal processingComputer hardwareData segment
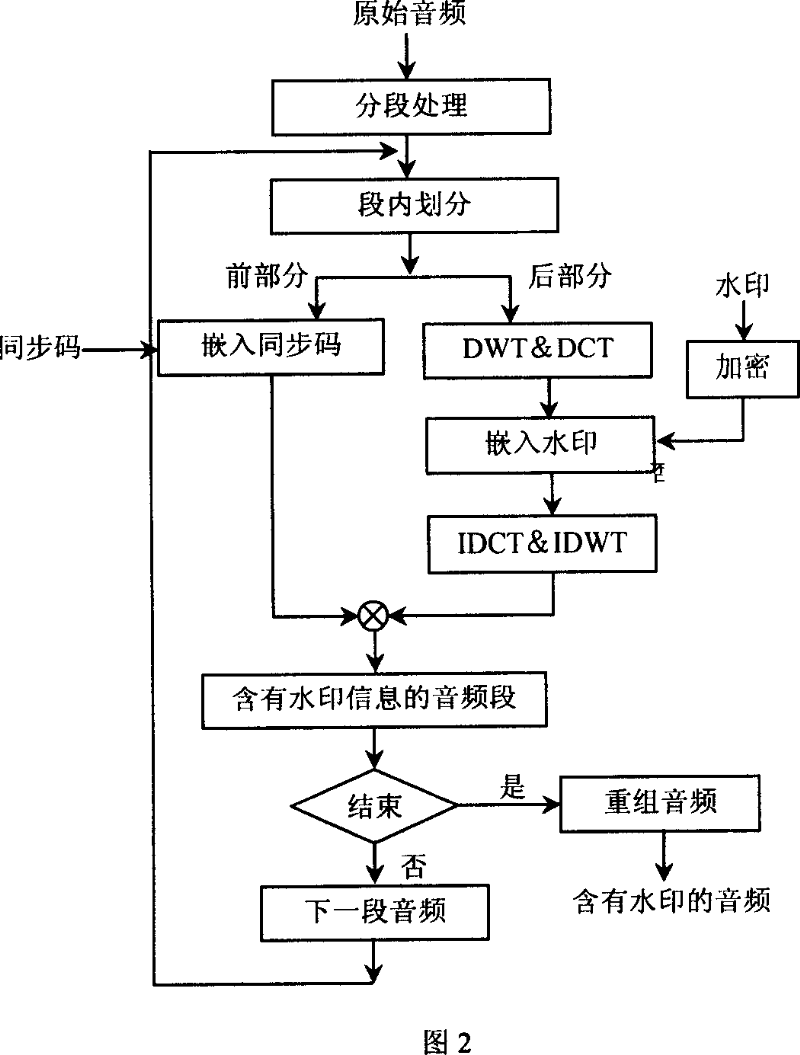
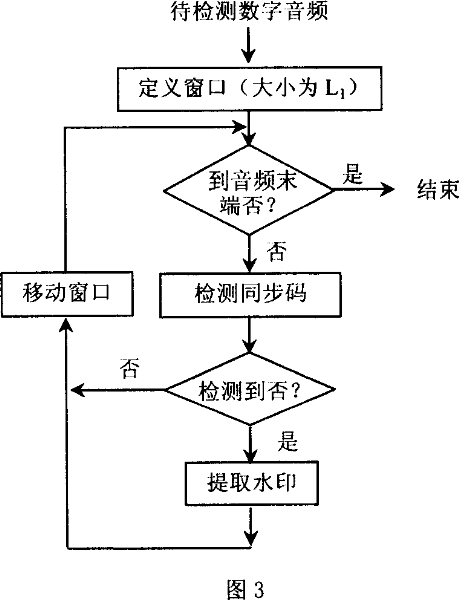
The invention belongs to an information safety, multimedia information processing field, in particular, the invention is a new digital watermark method for protecting copyright of a music production, mainly comprises a synchronization code, a watermark embedding and detecting. At first, the invention performs information embedding by segmenting the music production and dividing each music data segment into two front and rear portions. The synchronization code is embeded into the front portion by modifying a statistical average value of a plurality of sampled values, and the rear portion is used for embedding watermark information, the embedding process comprises: performing DWT on the music data segments, then performing DCT on low-frequency coefficients in a wavelet field, embedding the encrypted watermark information in the low / middle frequency coefficients of the DCT field by a self-adaptive quantization method, finally obtaining the digital music production with embeded watermark information by a reverse converting process and re-combining the music data segments. Detecting the digital watermark is a reverse process of the embedding process. The invention can be used in music productions of different types independent of adjustment of a threshold value.
Owner:LIAONING NORMAL UNIVERSITY
H264 video watermarking method based on regional DCT (discrete cosine transform) coefficients
InactiveCN103237209AImprove robustnessLight in massTelevision systemsPattern recognitionVideo encoding
The invention discloses an H264 video watermarking method based on regional DCT (discrete cosine transform) coefficients, and belongs to the technical field of multimedia information security. The method includes dividing video frame I into regions, calculating energy of each region, selecting proper video regional DCT coefficients to embed watermarks and embedding the watermarks into a plurality of macro blocks dispersedly; and robustness of the watermarks is improved. Dynamic quantifying step sizes are adopted for updating the video regional DCT coefficients, and imperceptibility of the watermarks is improved. Watermark embedding is performed with video coding compression, and affections of the watermark embedding on video code rate are reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
Radar data protection method based on combination of information hiding and encryption techniques
ActiveCN104993923AImprove securityImprove confidentialitySecuring communicationFilename extensionRadar
The invention provides a radar data protection method based on the combination of information hiding and encryption techniques. The radar data protection method comprises the steps of hiding the encrypted radar data information in a digital image, and modifying the filename extension to further hide the file with the hidden radar data. According to the method, three barriers for protecting the radar data are established, and therefore, the probability that the confidential radar information is cracked can be effectively reduced and the security of the radar data can be protected better.
Owner:WUHAN UNIV
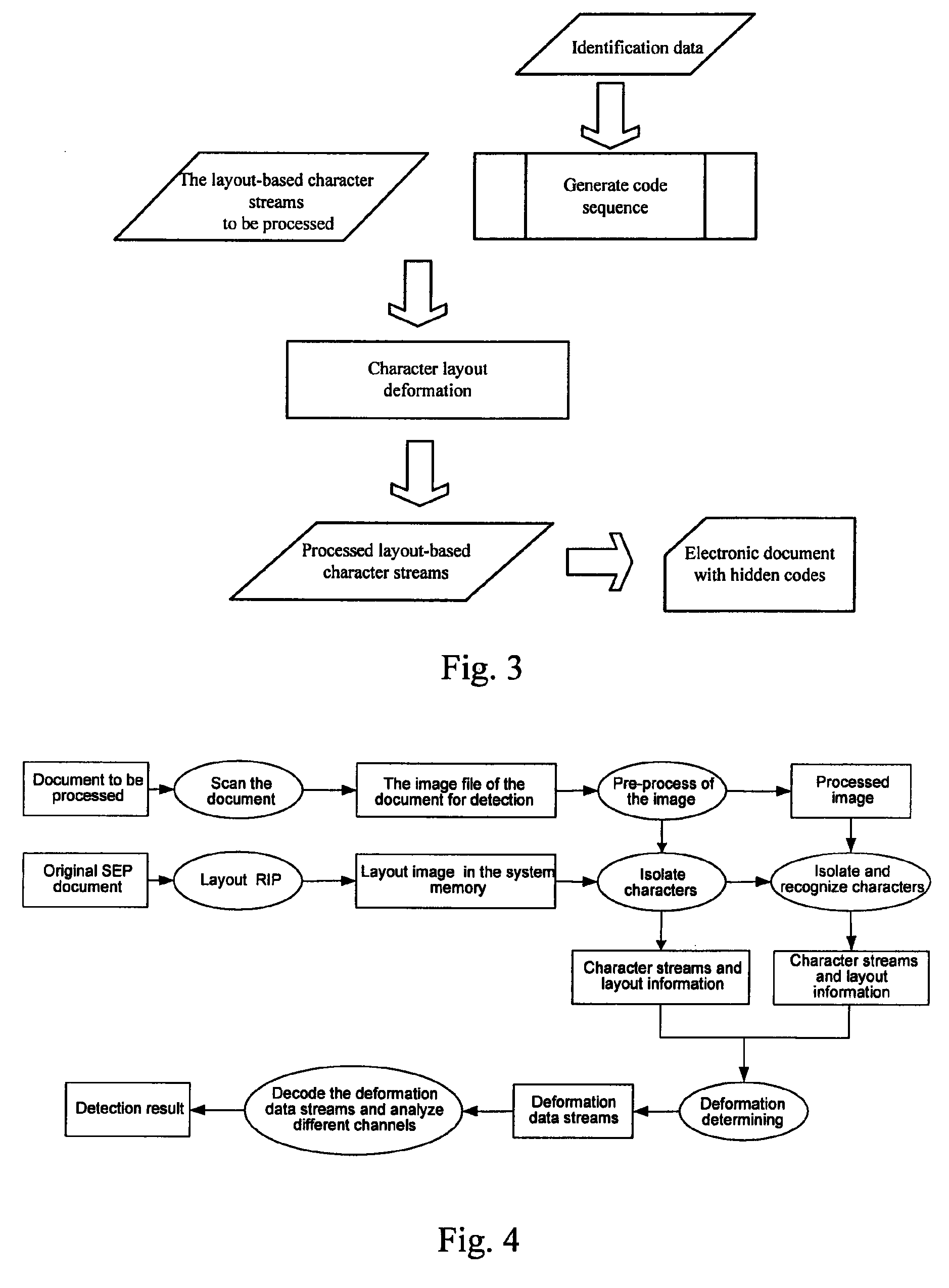
Embedding and detecting hidden information
ActiveUS8311265B2Improve balanceSmoothly embeds the hidden information into a documentCharacter and pattern recognitionImage data processing detailsAlgorithm
A novel method is disclosed for embedding hidden information in a document comprising characters, including: determining hidden information to be embedded in each class of layout transformation respectively; acquiring a code sequence for each class of layout transformation by coding the hidden information to be embedded in the class of layout transformation; performing layout transformation on characters from the document according to the acquired code sequence for each class of layout transformation respectively.
Owner:BEIJING SURSEN INT TECH CO LTD
Robust digital audio watermark embedding and detection method based on polar harmonic transform
InactiveCN105632506AGood frequency domain localization featuresImprove numerical stabilitySpeech analysisNumerical stabilityDecomposition
The invention discloses a robust digital audio watermark embedding and detection method based on polar harmonic transform. Advantages of great frequency domain localization features, multi-scale, redundancy and translation invariance, the features of non-stationary of greatly describing signals and maintaining the shape of the signals and the same length of audio frequency of each sub-band after decomposition with that of the original audio frequency of nonsubsampled wavelet transform are utilized; then great numerical stability of polar harmonic transform is also utilized, and watermarks are embedded in stable torque values to resist the normal signal attack; and then the synchronization code technology is combined. The experimental results indicate that normal signal processing can be resisted and the desynchronization attack can also be effectively resisted so that the method has great imperceptibility and robustness. Besides, the method also has advantages of being simple in design and easy to realize.
Owner:LIAONING NORMAL UNIVERSITY
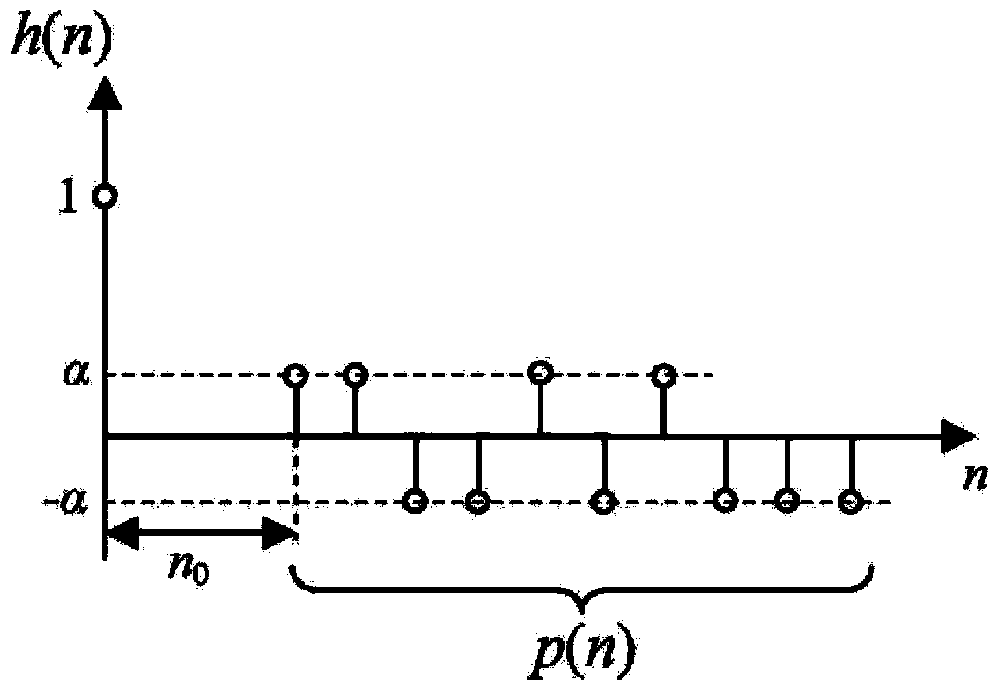
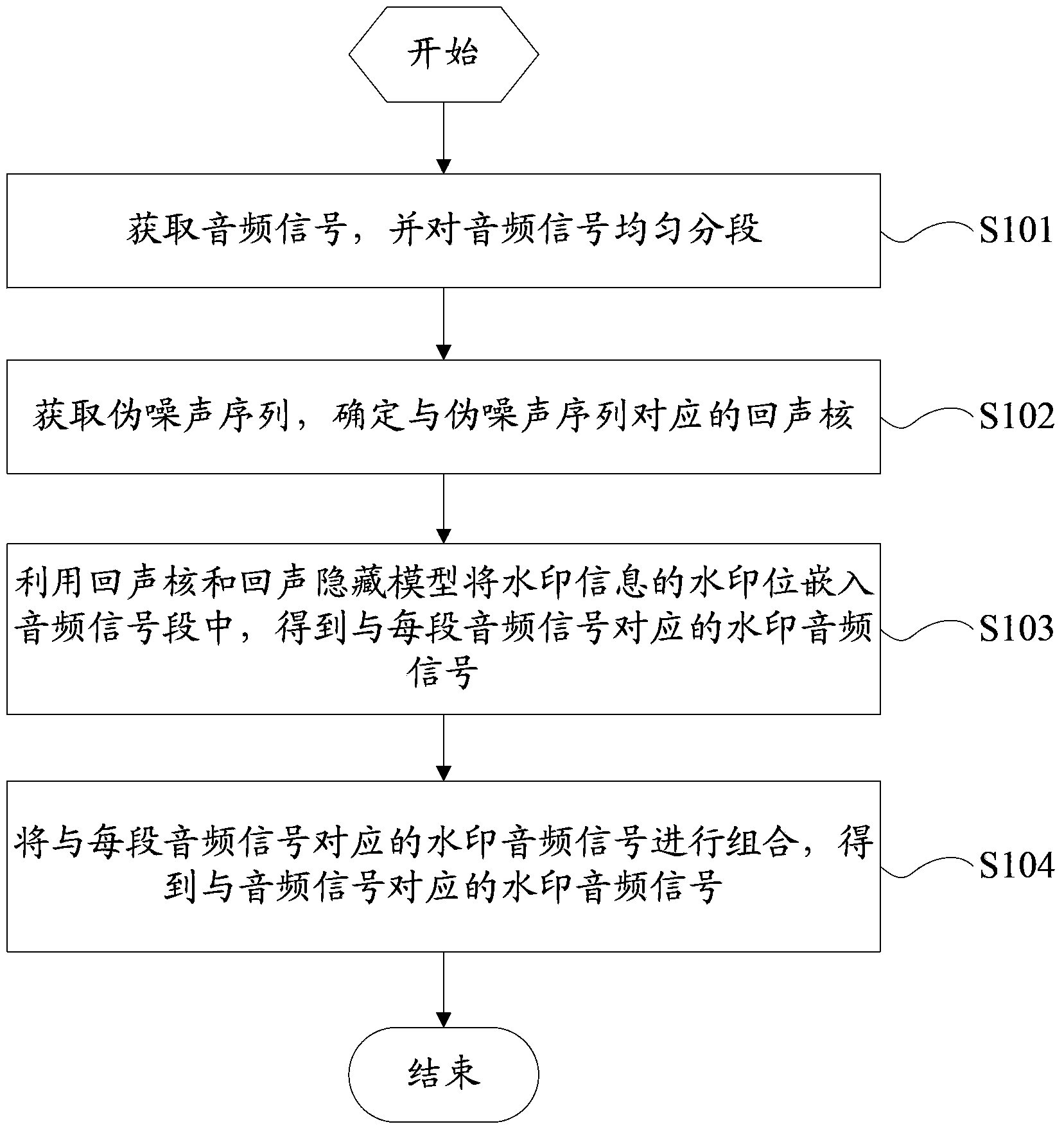
Audio watermark embedding and extracting method and device
InactiveCN103413552AImprove robustnessIncrease imperceptibilitySpeech analysisAudio watermarkAudio signal
The invention provides an audio watermark embedding and extracting method and device. The embedding method includes the steps of obtaining an audio signal, uniformly segmenting the audio signal, obtaining a pseudo noise sequence, determining an echo kernel corresponding to the pseudo noise sequence, embedding a watermark bit in audio signal segments through the echo kernel and an echo hiding model, obtaining watermark audio signals corresponding to the audio signal segments, combining the watermark audio signals corresponding to the audio signal segments, and obtaining a watermark audio signal corresponding to the audio signal. Compared with an existing sequence p(n), the pseudo noise sequence q(n) has little energy in a human ear sensitive area, so that imperceptibility of watermark information is greatly improved. Besides, according to characteristics of the pseudo noise sequence q(n) used in the watermark embedding method, the invention further provides a novel decoding function which is used for extracting watermarks from the watermark audio signal, and the audio watermark extracting method based on the decoding function is high in robustness.
Owner:SICHUAN UNIV
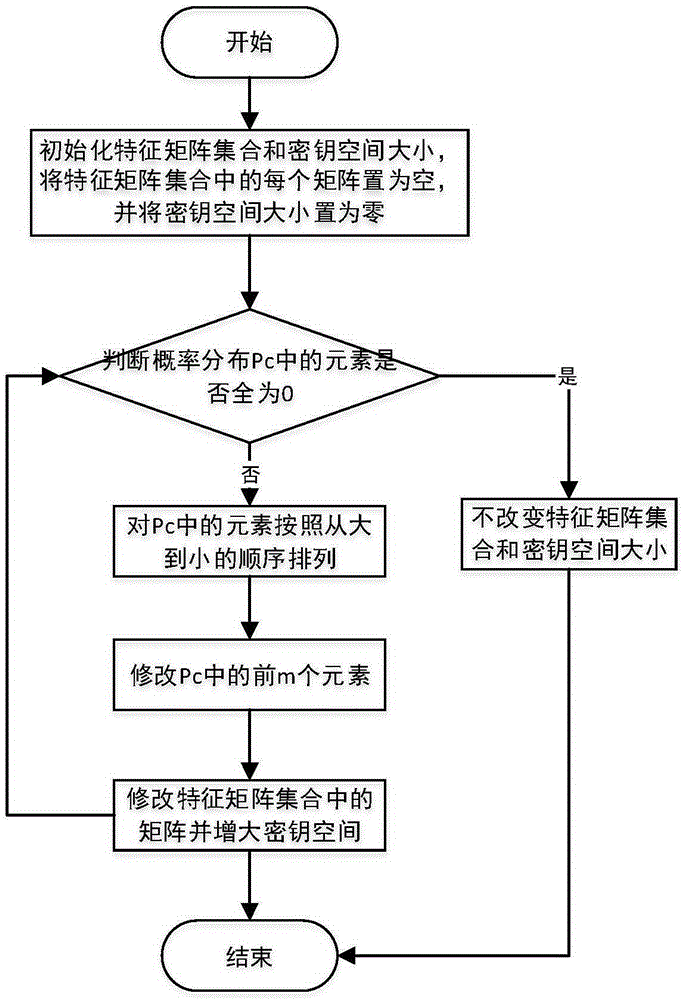
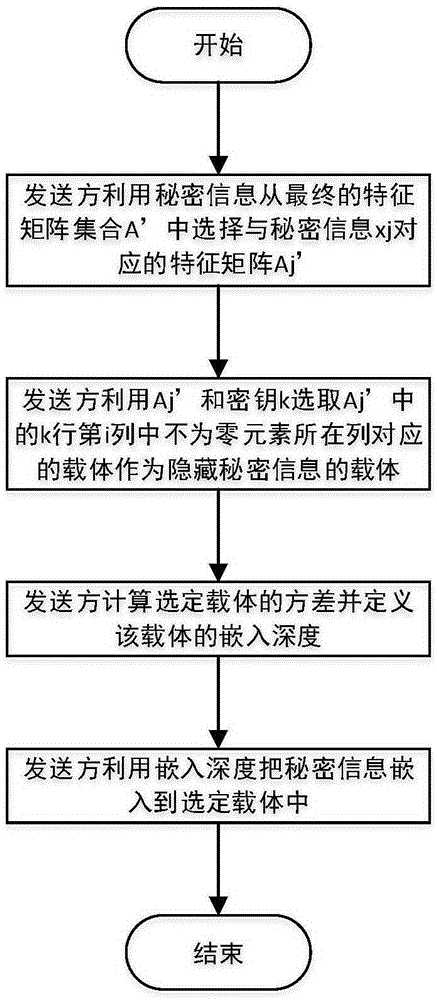
Method for hiding secret information in images
ActiveCN105389517AImprove securityEasy to solveKey distribution for secure communicationDigital data protectionCharacteristic matrixPseudorandom number generator
The invention discloses a method for hiding secret information in images, and mainly aims to solve the problem that consideration cannot be given to both robustness and security in the prior art. The method comprises the following steps: 1) a sender selects carrier images from a carrier image library via a shared key, conducts block segmentation on the selected carrier images, and selects a pseudorandom number generator for each block, so as to acquire the probability distribution of candidate hiding carriers; 2) the sender creates a characteristic matrix of the carrier images; 3) the sender acquires a final characteristic matrix set and the key space size; 4) the sender hides the secret information in carriers via the final characteristic matrix set and the key space size; 5) the sender sends an obtained carrier set in which the secret information is embedded to a receiver; and 6) the receiver acquires the secret information. The method can improve the security of a hiding system while guaranteeing the robustness of the hiding system, and can be used for changing the hiding position of the secret information in an image in real time when the contents of the image are changed.
Owner:西安纳容电子通讯有限公司
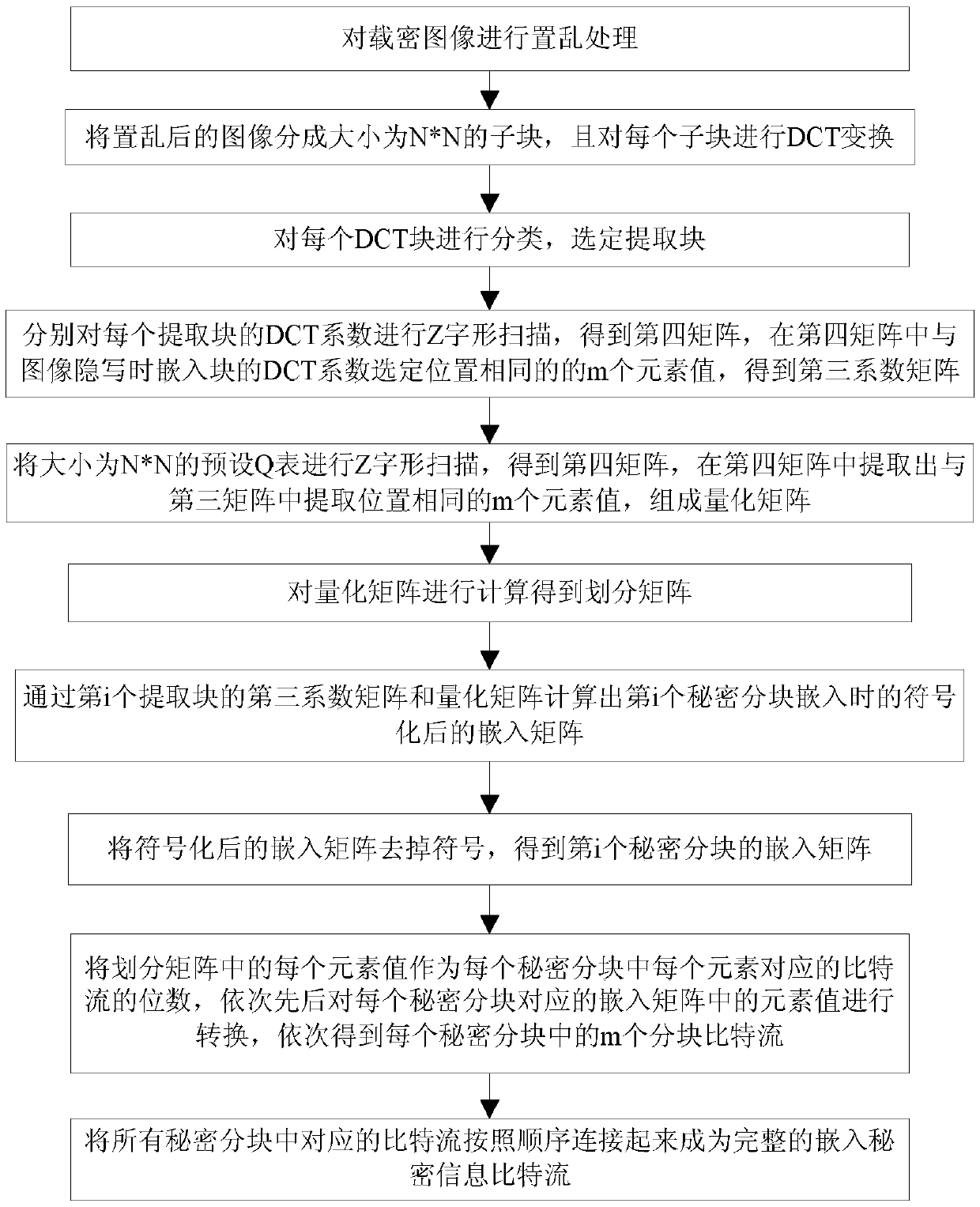
High-capacity image steganography method and a secret information extraction method
ActiveCN109658322AIncreased complexityImprove securityImage enhancementImage data processing detailsQuantization matrixInverse operation
The invention discloses a high-capacity image steganography method. The method comprises the following steps: carrying out scrambling processing on a carrier image; Dividing the scrambled image into N* N sub-blocks and carrying out DCT (Discrete Cosine Transform); Classifying each DCT block, and selecting an embedded block; Element values at selected positions are extracted from a matrix obtainedafter the DCT coefficient of each embedded block is scanned in a Z shape, and a coefficient matrix is obtained; Extracting element values which are the same as the element values at the selected positions from a matrix obtained after Z-shaped scanning of the Q table to form a quantization matrix; Calculating a division matrix and block capacity through the quantization matrix; Dividing the bit stream of the secret information according to the block capacity; Calculating an embedded matrix for the divided bit stream; Calculating a new coefficient matrix; Replacing the DCT coefficient with theelement value in the new coefficient matrix, and carrying out inverse operation of Z-shaped scanning to obtain a new DCT coefficient; And carrying out DCT inverse transformation on each sub-block andthen carrying out inverse scrambling processing. The invention also discloses a secret message extraction method. And the image complexity is high and the embedding capacity is large.
Owner:NINGBO UNIV
Shear wave domain audio watermark embedding and detecting method based on robust QR decomposition
InactiveCN105608661AImprove numerical stabilityIncrease imperceptibilityImage watermarkingQR decompositionNumerical stability
The present invention discloses a shear wave domain audio watermark embedding and detecting method based on robust QR decomposition. By using the good frequency domain localization features of non-downsampling shear wave transform, multi-directional property, translation invariance and near optimal sparse representation ability, each subband audio and an original audio have the same length after decomposition, added with the good numerical stability of QR decomposition, an R matrix obtained by decomposition is an upper triangle stable matrix, a watermark is embedded into the upper triangle of the R matrix, and then the synchronous code technology is combined. A test result shows that: according to the method, conventional signal processing can be resisted and a desynchronization attack can be effectively resisted, and the method has good imperceptibility and robustness. In addition, the method has the advantages of simple design and easy implementation.
Owner:LIAONING NORMAL UNIVERSITY
Digital watermark embedding and protection methods for database
ActiveCN108614961AImprove robustnessIncrease imperceptibilityProgram/content distribution protectionThe InternetBinary tree
The invention discloses a digital watermark embedding method for a database. The method comprises the steps of scoring an attribute column of the target database, and according to a scoring result, selecting an attribute of performing embedding; by using a tuple selection algorithm and a binary tree-based histogram shifting algorithm, marking a tuple embedded with a digital watermark, and storingthe position of a mark through a mapping matrix; and according to the mapping matrix, embedding the digital watermark in the target database for multiple times repeatedly by using a watermarking algorithm of the binary tree-based histogram shifting algorithm. The invention furthermore discloses a protection method for the database and a watermark generation and embedding method for the internet car database. Compared with other methods, the method has the advantages that the robustness and imperceptibility of the digital watermark are improved through the algorithm; the attack resistance capability is stronger; the quantity of information which can be used for authentication is higher; and the effect of the digital watermark during specific application is enhanced.
Owner:DONGFENG PEUGEOT CITROEN AUTOMOBILE
Digital image steganography method and secret information extraction method
ActiveCN109785221AIncrease imperceptibilityImprove securityImage data processing detailsMean squareThree-dimensional space
The invention relates to a digital image steganography method which is used for embedding a binary secret message S into an original carrier image Gc with the size of M x N. The digital image steganography method is characterized by comprising the following steps of: firstly calculating a steganography system B of the secret message; Dividing the original carrier image Gc into three continuous pixel group sequences Q which are not overlapped with one another; Converting the binary secret message S into a B-system secret message SB; Taking out a group of data from the three-pixel group sequenceQ according to a sequence; Taking out a bit of secret data dB from the B-system secret message SB according to a sequence; Determining a candidate pixel value field set [phi]B (x, y, z) of the three-dimensional space point (x, y, z), and parameters k1 and k2: searching the candidate pixel value field set [phi]B (x, y, z) to find out (x ', y', z '), and satisfying f (x', y ', z') = dB; Replacing (x, y, z) in the three-pixel-group sequence Q by using (x ', y', z ') to complete steganography embedding of the secret data dB; Compared with the prior art, the method has the advantages that a smaller mean square error can be obtained, and the non-perceptibility and safety of the steganographic image can be effectively improved.
Owner:NINGBO UNIV
High-capacity reversible image watermarking algorithm with improved difference expansion
ActiveCN110490790ALarge capacityGuaranteed visual qualityImage data processing detailsImaging processingAlgorithm
The invention relates to image processing, the invention relates to the technical field of digital watermarking, and discloses a high-capacity reversible image watermarking algorithm with improved difference expansion. The algorithm comprises the steps of watermark embedding and watermark extraction, watermark embedding of an original image and watermark extraction of an image containing watermarks through cat face scrambling, a generalized difference expansion method, improved gray scale overflow processing and a difference quantification method. Compared with the prior art, the algorithm hasthe advantages that the pixel mean value before and after watermark embedding through a generalized difference expansion method is invariant, so that the smoothness value before and after watermark embedding is invariant, and watermark extraction is facilitated; an improved gray overflow processing method is used, on the premise that certain visual quality is guaranteed, watermark embedding can be conducted multiple times, and the watermark embedding capacity is increased; auxiliary information is embedded through a difference quantization algorithm, so that the method has relatively good imperceptibility and relatively high effective load capacity; and after the watermark is extracted, the original image can be completely recovered, the similarity between the extracted watermark and theoriginal watermark is extremely high, and the error is small.
Owner:HUAIYIN INSTITUTE OF TECHNOLOGY
High-security steganography method for voice over IP
ActiveCN107886962AReduce distortionIncrease imperceptibilitySpeech analysisEmbedding rateVoice over IP
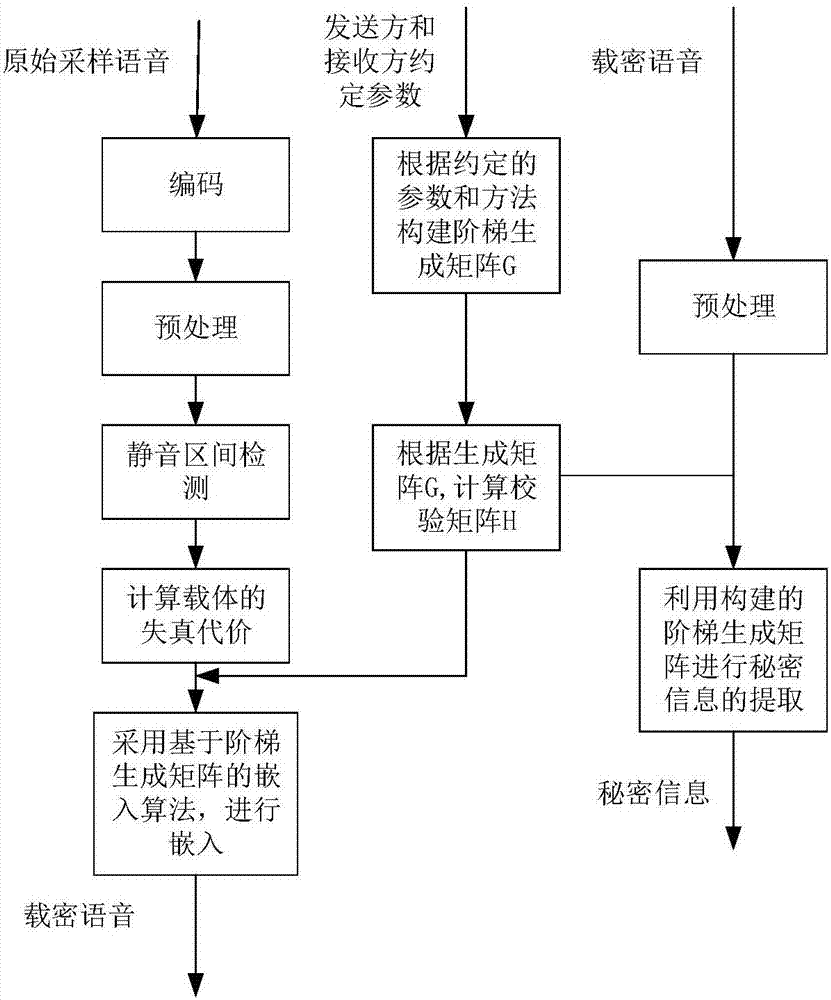
The invention discloses a high-security steganography method for voice over IP, which includes the following steps: a sender reads original sampled voice, and compresses and encodes the original sampled voice to get a carrier voice sequence; the sender extracts an intensity sequence and an amplitude sequence of the carrier voice sequence, divides the carrier voice sequence into a silent interval and a non-salient interval, and defines the distortion costs for different carrier voice intervals; the sender constructs a ladder generation matrix according to the length and embedding rate of the carrier voice sequence; the sender embeds secret information according to the distortion costs and the generation matrix, calculates out a modification vector minimizing carrier distortion, and modifiesthe carrier voice sequence according to the modification vector obtained to get a secret information carrying voice sequence; and after receiving the secret information carrying voice sequence, a receiver recovers a secret information sequence according to the ladder generation matrix. Stable embedding capacity is maintained. The amount of distortion introduced during carrier modification is reduced. The security of information hiding is improved.
Owner:NANJING UNIV OF SCI & TECH
Robust digital audio watermarking algorithm in view of time-frequency analysis
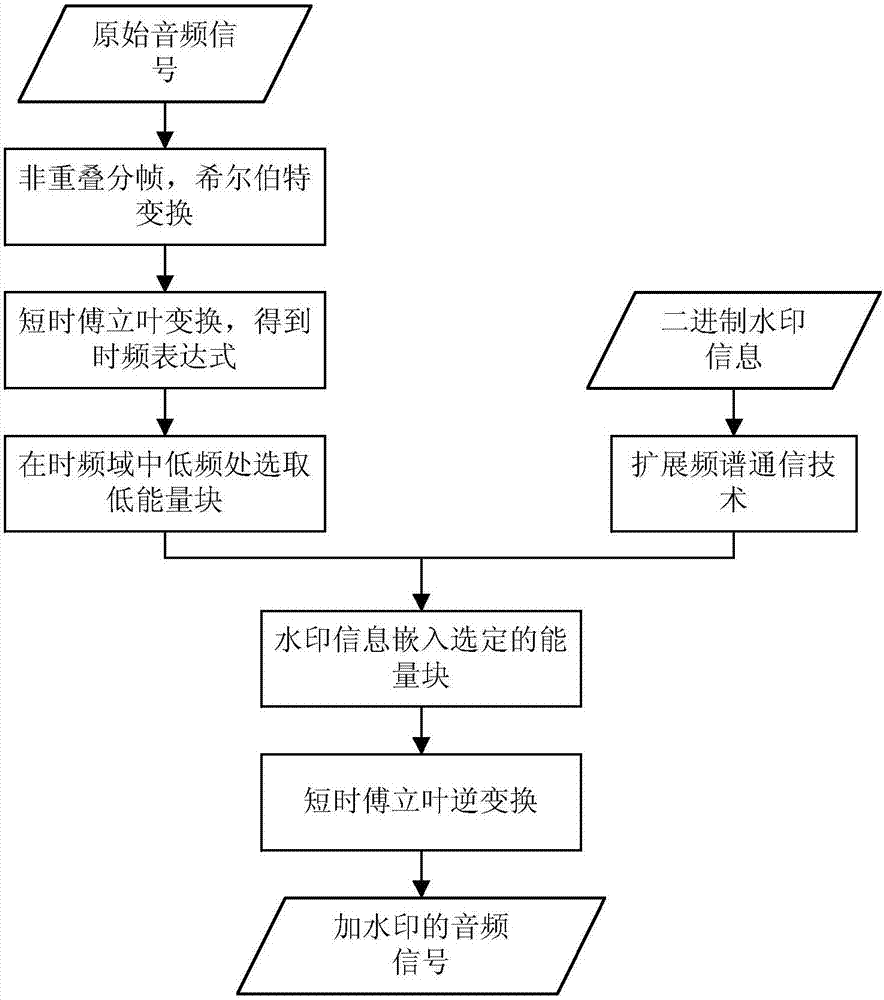
ActiveCN106898358AFully consider time-varying characteristicsIncrease imperceptibilitySpeech analysisTransmissionFrequency domainFourier transform
The invention provides a robust digital audio watermarking algorithm in view of time-frequency analysis. The algorithm comprises steps of: first subjecting a selected audio segment to non-overlapping short-time Fourier transform to obtain a time-frequency distribution map of an audio signal, performing windowing and blocking in the low and medium frequency range of the time-frequency distribution map, and randomly selecting a characteristic energy block with low energy as a specific position for embedding a watermark; embedding generated binary watermark bits into the corresponding characteristic energy blocks by means of an extended code by using an improved spread spectrum watermark embedding method; after the watermark embedding, obtaining the characteristic energy blocks with embedded watermark by means of a watermark embedding position conveyed by a watermark embedder, and recovering a watermark sequence by using a watermarked characteristic energy block vector and the plus or minus characteristic of spread code inner product. The algorithm can guarantee the quality of a main signal by embedding the watermark into the low-frequency and low-energy position of the frequency domain, and can still recover the watermark after the watermarked signal is subjected to quantification, noise, amplitude zooming, AAC coding compression and low-pass filtering.
Owner:WUHAN UNIV
Blind audio watermark implementing method based on logarithmic quantization index modulation
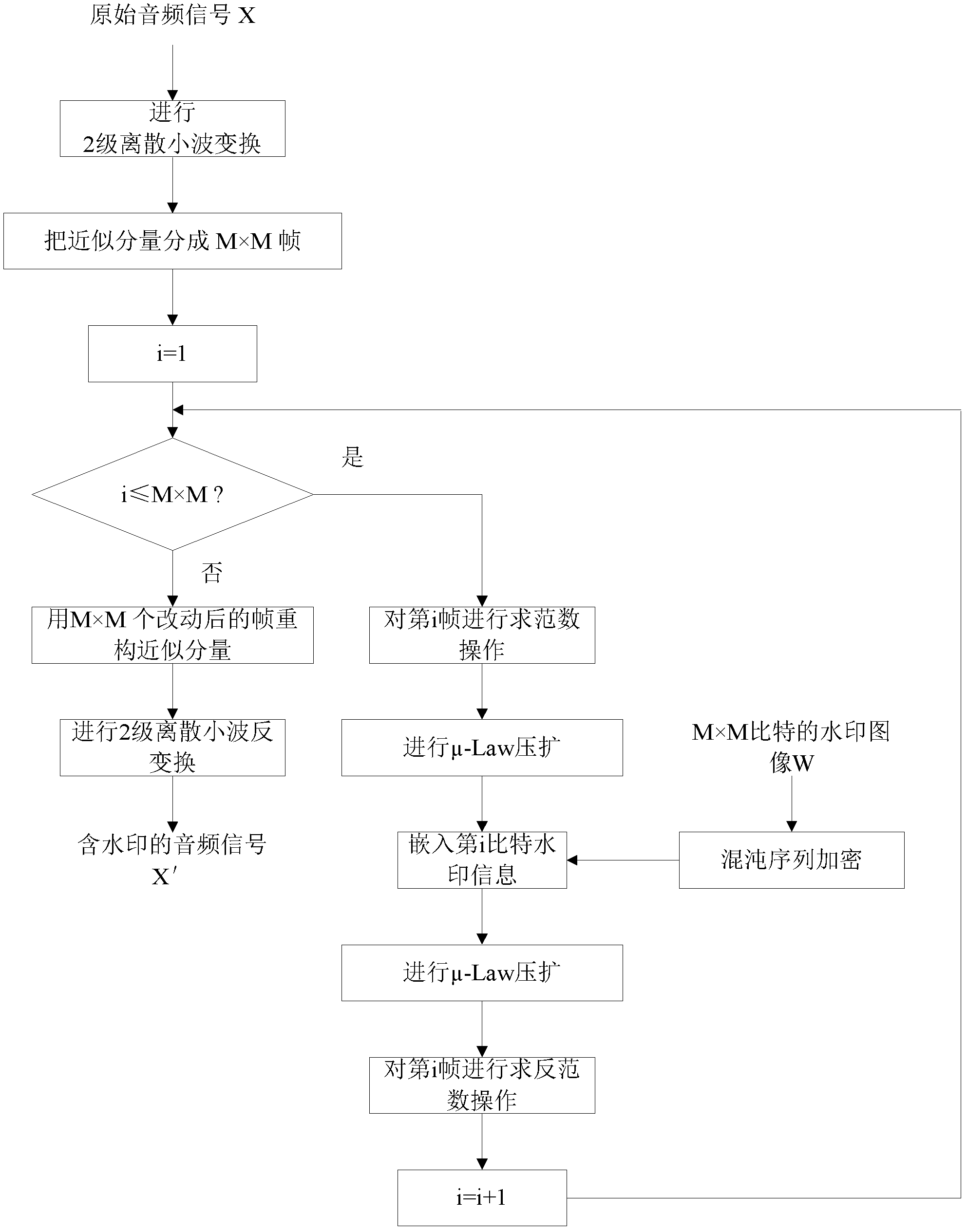
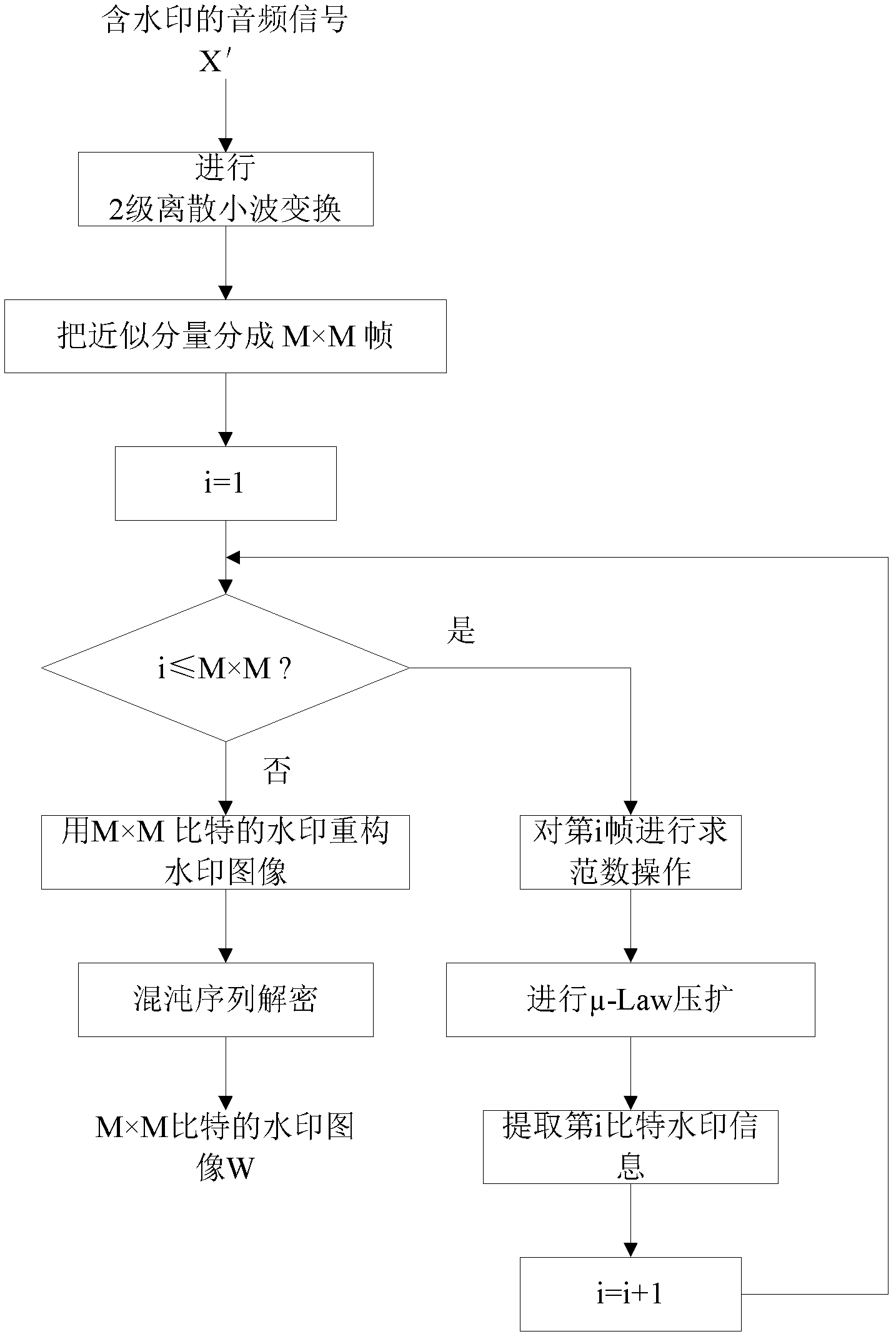
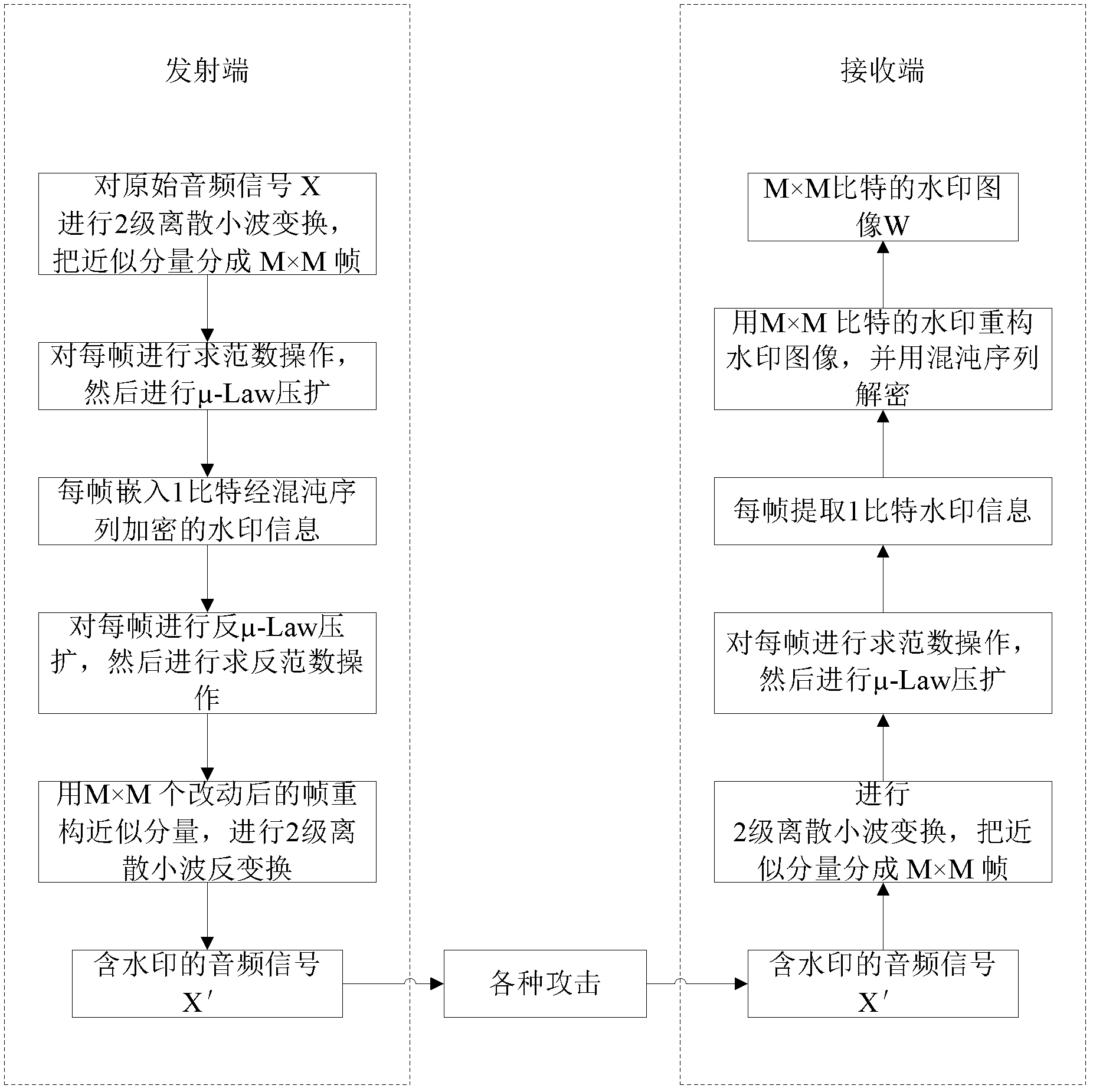
InactiveCN102664014AImprove sound qualityReduce complexitySpeech analysisComputer hardwareAudio watermark
The invention discloses a blind audio watermark implementing method based on logarithmic quantization index modulation, and belongs to the technical field of audio watermarks. The blind audio watermark implementing method is characterized by including sufficiently utilizing robustness of vector norms and imperceptibility of the logarithmic quantization index modulation based on mu-law companding; improving safety and robustness of a watermark by the aid of a chaos sequence encryption watermark image; converting the sectioned vector norms of wavelet approximate components into a transform domain via the mu-law companding; then embedding an encryption binary watermark image; and extracting the binary watermark image after the watermark is attacked. The audio watermark algorithm has the advantages of high volume, fine tone, imperceptibility and robustness and low complexity, the watermark still can be correctly extracted by the aid of the method under various watermark attack conditions, and accordingly amplitude attack can be effectively resisted by the method.
Owner:TSINGHUA UNIV
Information steganography algorithm of binary image double disturbance scoring based on STC coding
ActiveCN109963159ALow embedding distortionGood visual quality of imagesDigital video signal modificationAlgorithmImaging quality
The invention provides a binary image double disturbance scoring information steganography algorithm based on STC coding. According to the algorithm, disturbance scoring is conducted on an image through an improved crmiLTP distortion measurement method, the influence of pixel point overturning before steganography and pixel point overturning after steganography on a disturbance mapping graph is considered, secret information is embedded through efficient STC coding on the basis of block hiding, and finally the steganography algorithm small in visual distortion and high in safety is designed. According to the invention, the carrier image property is considered; a double disturbance scoring criterion is set, bidirectional evaluation analysis is carried out on reversible points of an image edge area, and STC coding is combined, so that the algorithm has high image quality, small visual distortion and certain anti-steganography analysis and detection performance, and has a very large effect on secure secret communication.
Owner:SUN YAT SEN UNIV
Robust image watermarking method and system based on deep learning and attention network
ActiveCN113989096AIncrease imperceptibilityImprove robustnessImage data processing detailsNeural architecturesPattern recognitionAttention model
The invention belongs to the technical field of digital image watermarking, and provides a robust image watermarking method and system based on deep learning and an attention network, and the method comprises the following steps: obtaining an original image tensor; obtaining an attention image tensor according to the obtained original image tensor and an attention model; generating a watermark-containing image based on the obtained attention image tensor and a watermark embedding model; generating an attacked image according to the generated watermark-containing image and the constructed attack network model; and extracting an image watermark according to the attacked image, the attention model and the deep learning model. Attention weights are deduced along two dimensions of a channel and a space by utilizing the perception capability of a human visual system to different regions and the anti-attack capability of different pixel points, and regions which have small influence on human visual perception and are good in robustness are searched for watermark embedding.
Owner:SHANDONG UNIV
Gray scale video watermarking algorithm based on core tensor
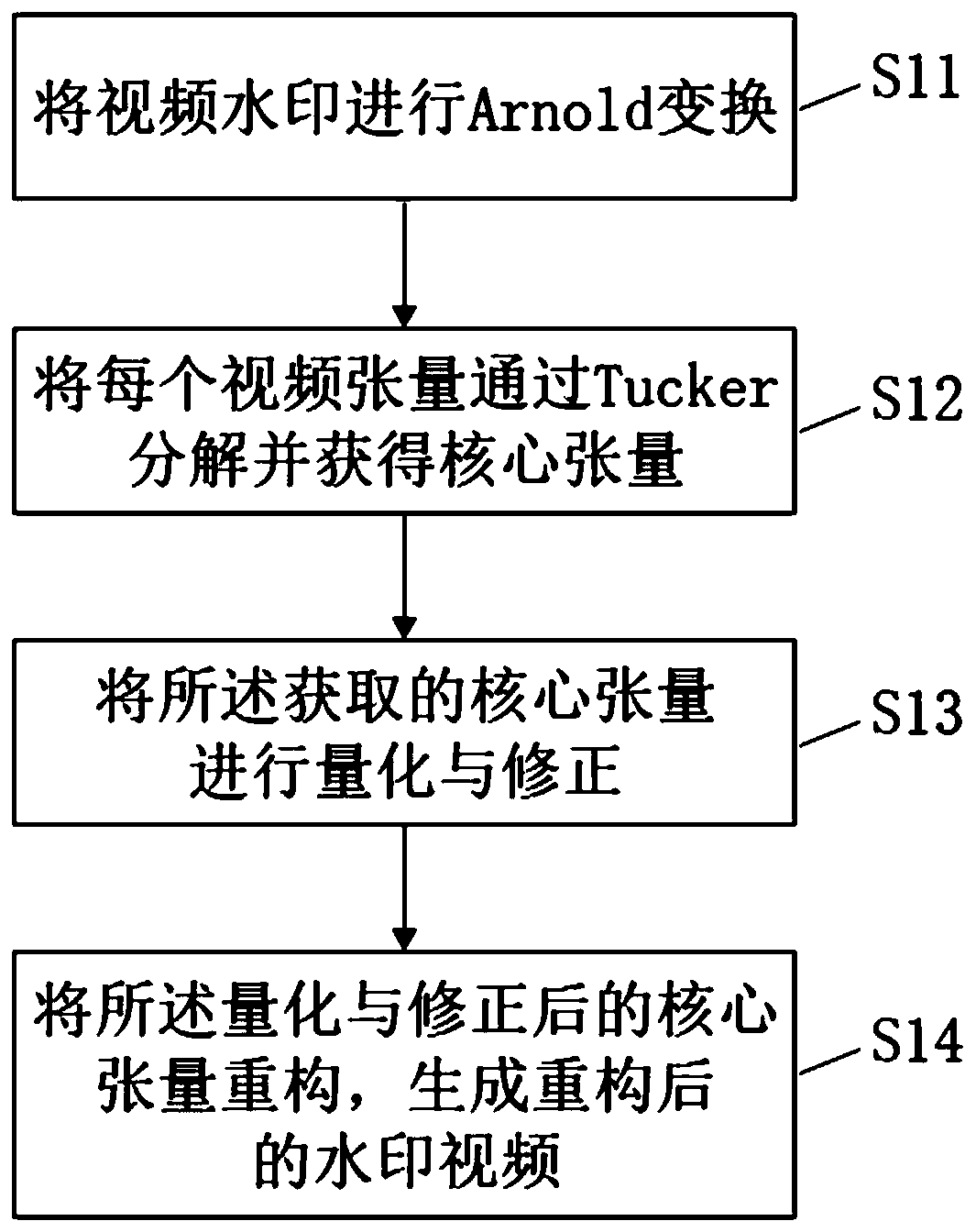
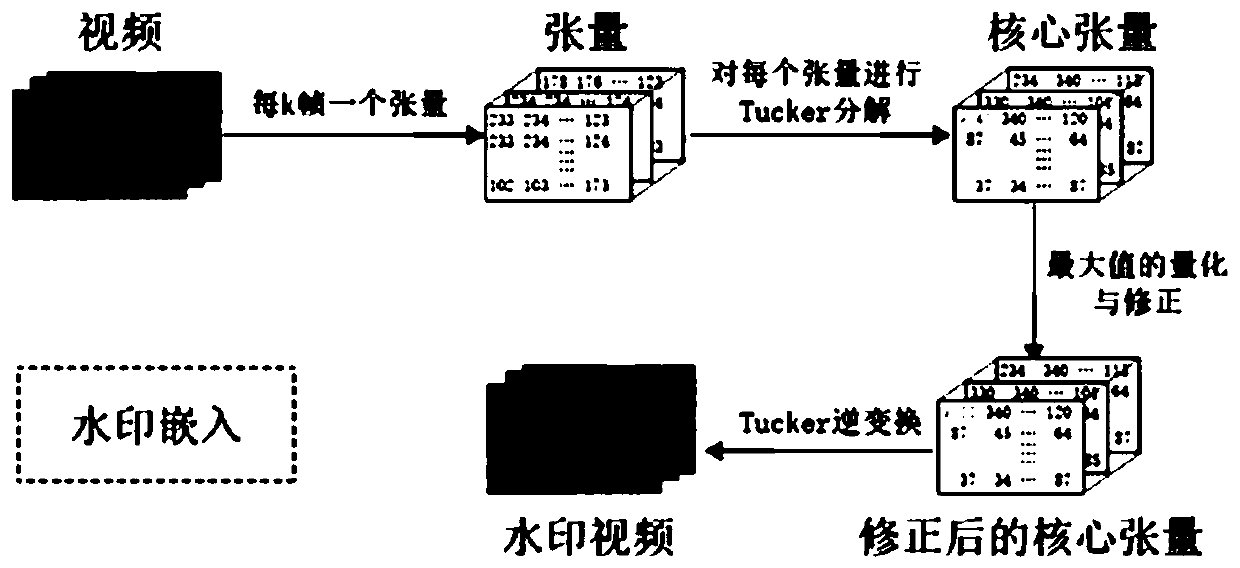
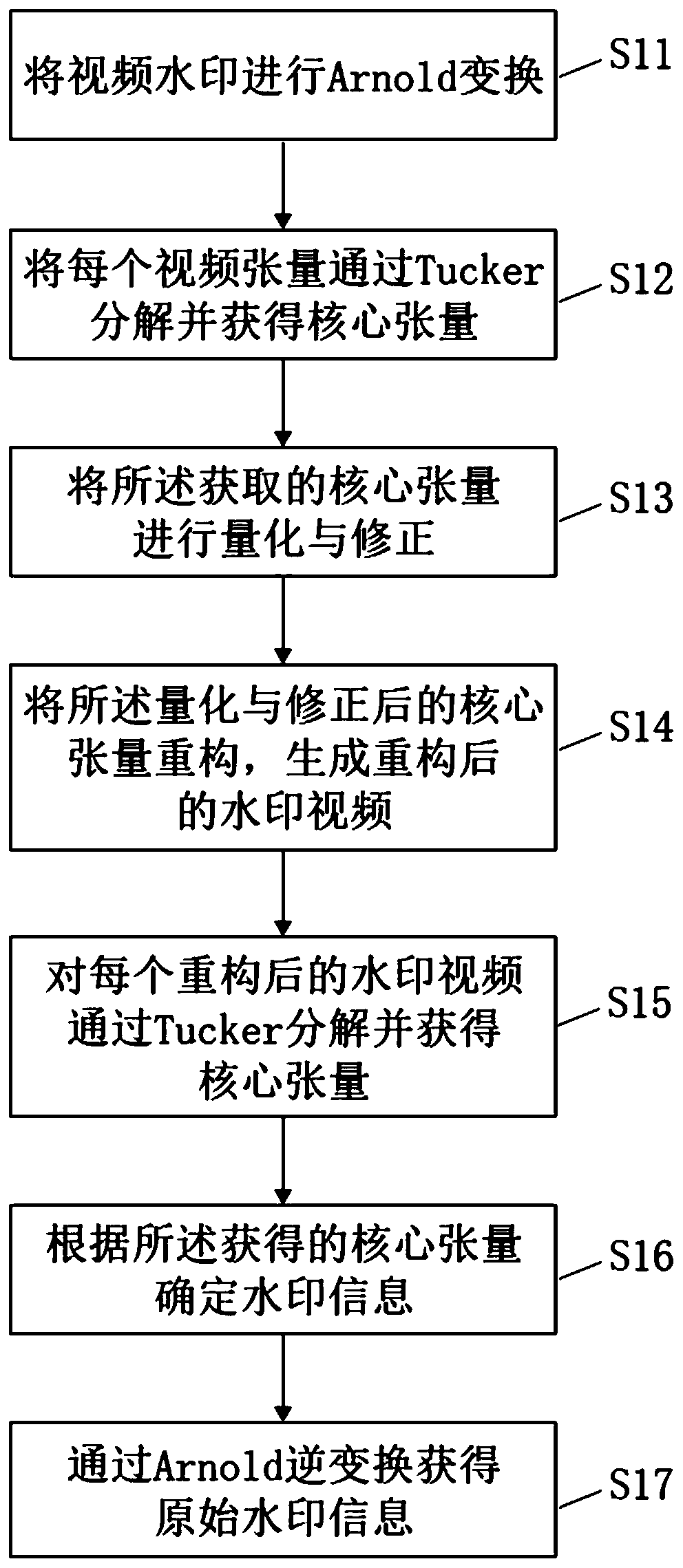
PendingCN110111232AIncrease imperceptibilityFully consider the relevanceDigital data protectionImage watermarkingArnold transformationTucker decomposition
The invention discloses a gray scale video watermarking algorithm based on core tensor. The gray scale video watermarking algorithm comprises the following steps: S11, carrying out Arnold transformation on a video watermark; S12, decomposing each video tensor through Tucker and obtaining a core tensor; S13, quantifying and correcting the obtained core tensor; and S14, reconstructing the quantizedand corrected core tensor to generate a reconstructed watermark video. According to the invention, the grayscale video is represented by three orders as tensors, and the correlation between adjacent frames of the video is fully considered. By quantifying the core tensor, the watermark information is uniformly dispersed into each frame of the video, so that the non-perceptibility of the algorithm and the common video attack are improved.
Owner:绍兴聚量数据技术有限公司 +1
Digital watermark treatment method for copyright protection
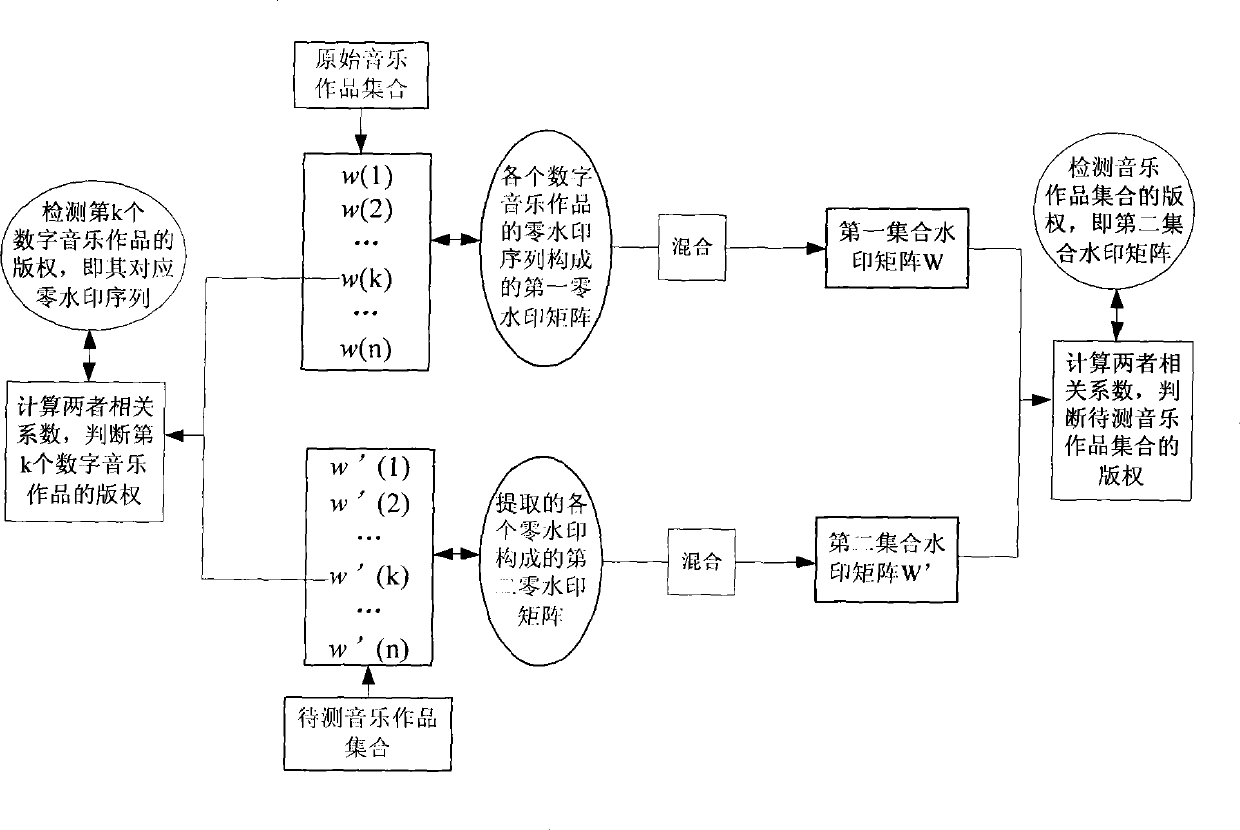
InactiveCN101504850AAchieve copyright protectionReduce computational complexityRecord information storageRecording signal processingWorking setComputer science
The invention discloses a digital watermark processing method for copyright protection, which comprises the following steps: by calculating related coefficients of a first set watermark matrix and a second set watermark matrix, judging whether the acquired related coefficients are more than a first set threshold value, and realizing the detection of the copyright protection for all digital musical works in a whole musical work set; and simultaneously, by calculating related coefficients of a first zero watermark sequence of each primary digital musical work and a second zero watermark sequence of the corresponding digital musical work to be detected, judging whether each acquired related coefficient is more than a second set threshold value, and realizing the detection of the copyright protection for a single digital musical work. Compared with the prior watermark processing method which uses the single digital musical work as a carrier, the method of the invention also can integrally protect the broadly existent musical work set in a form of set according to the characteristic that each digital musical work in the musical work set has the same copyright, and at the same time protects the single digital musical work.
Owner:NINGBO UNIV
Watermark embedding method and device, watermark detection method and device and electronic equipment
ActiveCN112241929AIncrease imperceptibilityImprove accuracyImage data processing detailsComputer visionEngineering
The invention discloses a watermark embedding method and a watermark detection method. The watermark embedding method comprises the steps of obtaining a noise template needing to be embedded into a to-be-embedded image; obtaining a gradient characteristic value of a pixel of the image to be embedded, and generating a zero setting mask according to the gradient characteristic value; determining a weight template according to the zero setting mask; obtaining watermark information according to the weight template and the noise template; embedding the watermark information into the image to be embedded. The watermark detection method comprises the steps of obtaining a high-frequency component of a to-be-detected image; performing first autocorrelation processing on the high-frequency componentto obtain a first autocorrelation result; performing second autocorrelation processing on the first autocorrelation result to obtain a second autocorrelation result; judging whether the to-be-detected image contains a watermark template or not according to the second autocorrelation result. By adopting the method, the digital image embedded with the watermark can resist attacks such as puzzle, matting, bottom changing and the like for the digital image.
Owner:ALIBABA GRP HLDG LTD
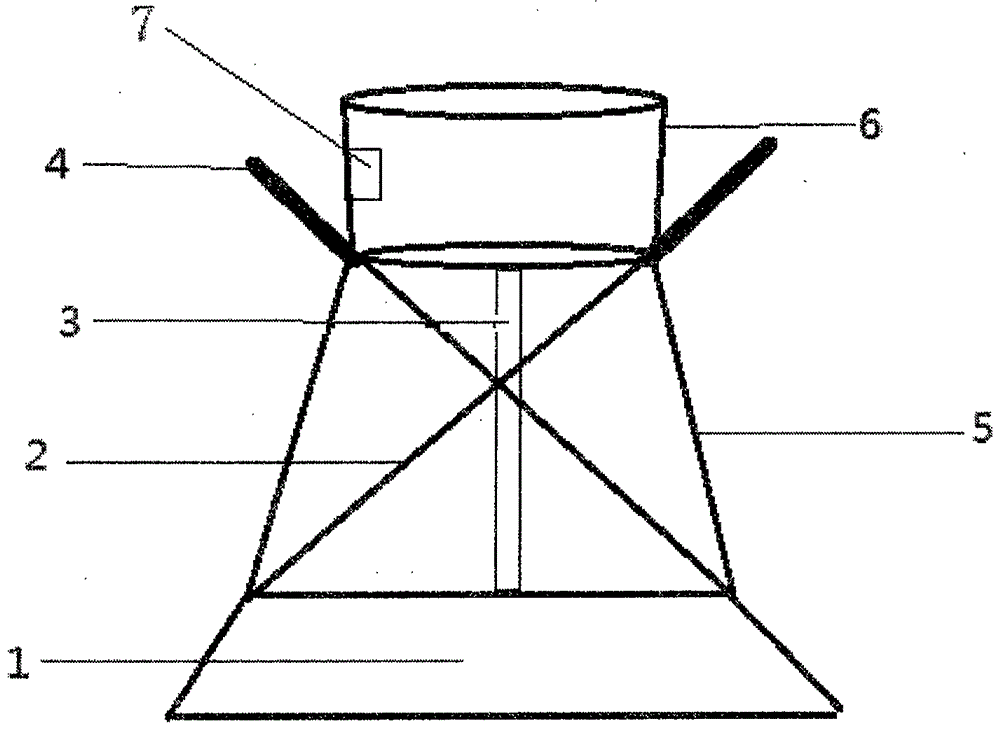
Thoracic tumor radiotherapy facilitating combined type positioning rack device
InactiveCN106823150AFulfil requirementsEasy to operateRadiation therapyPlastic materialsConformal radiation therapy
The invention discloses a thoracic tumor radiotherapy facilitating combined type positioning rack device. According to the upper portion of the thoracic tumor radiotherapy facilitating combined type positioning rack device, a support plate and armrests are arranged at the top; two side baffles are connected to both sides of an inclined plate; a pillow box is arranged in the middle of the inclined plate, the lower edges of the pillow box and the inclined plate are aligned; a soft plastic material base is arranged at the bottom. The thoracic tumor radiotherapy facilitating combined type positioning rack device can avoid random deviation of skin markers and ensure high repeatability and consistency of the skin positioning marker and is applied to limiting and fixing the thoracic position of a thoracic tumor patient during radiotherapy.
Owner:SHANDONG RES INST OF TUMOUR PREVENTION TREATMENT
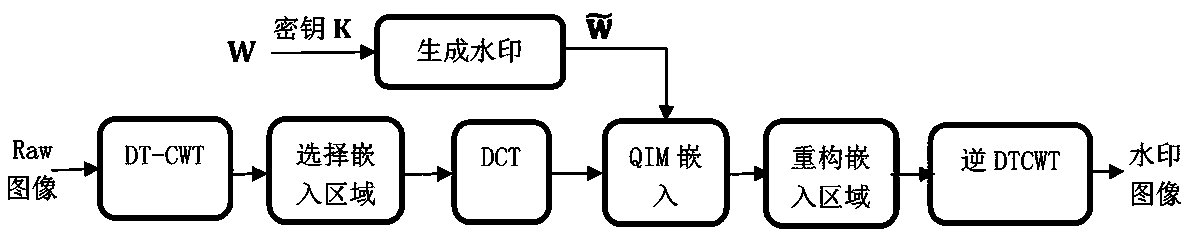
CWT-QIM digital blind watermarking algorithm for RAW format image
ActiveCN109544434AImprove robustnessGuaranteed robustnessImage watermarkingHigh level techniquesDigital contentDct transform
The invention discloses a CWT-QIM digital blind watermarking algorithm, which includes the embedding process and the extracting process of watermark. The embedding process of watermark includes the generation of watermark image, selection of an embedded area, DCT transform and vector quantization modulation-based embedding; the watermark extraction process is basically the inverse operation of thewatermark embedding process; the algorithm of the invention has excellent robustness and transparency, can effectively resist JPEG image compression, Gaussian noise, median filter, salt and pepper noise, scaling, rotation, cropping and other image attacks, improve the performance of digital watermarking algorithm, quantization and embedding watermark information, and can be extracted blindly without the original carrier image, can be easily and effectively applied to digital content authentication or digital copyright protection and other fields.
Owner:江苏水印科技有限公司
Sparse adversarial attack method based on weighted gradient hash activation thermodynamic diagram
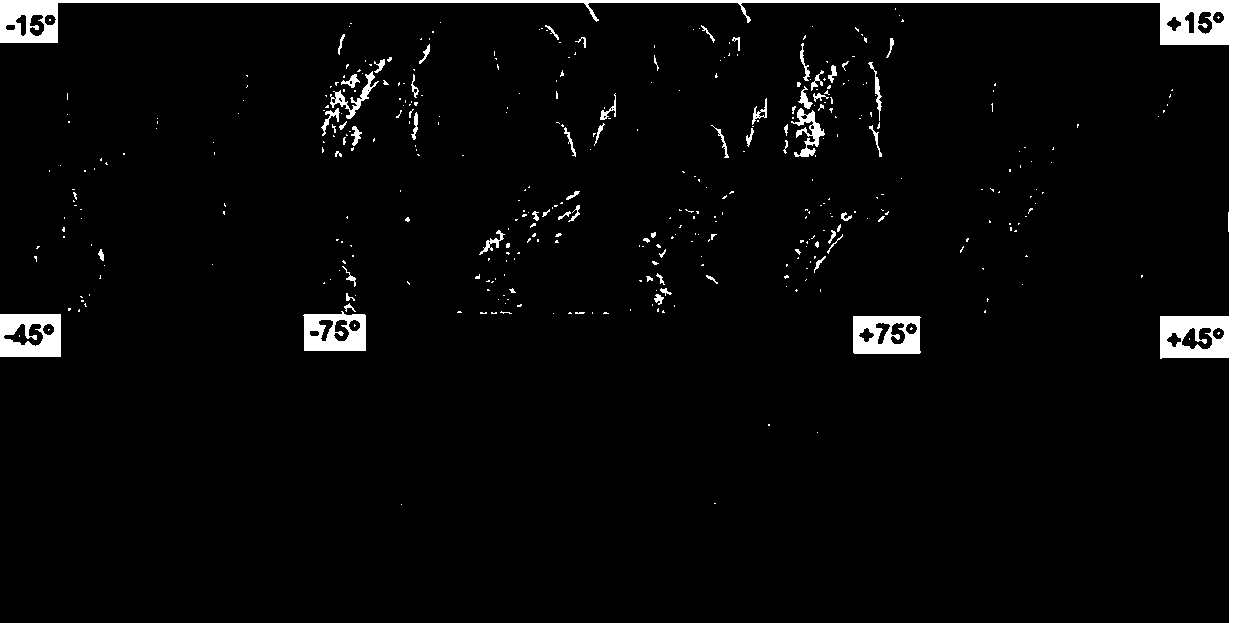
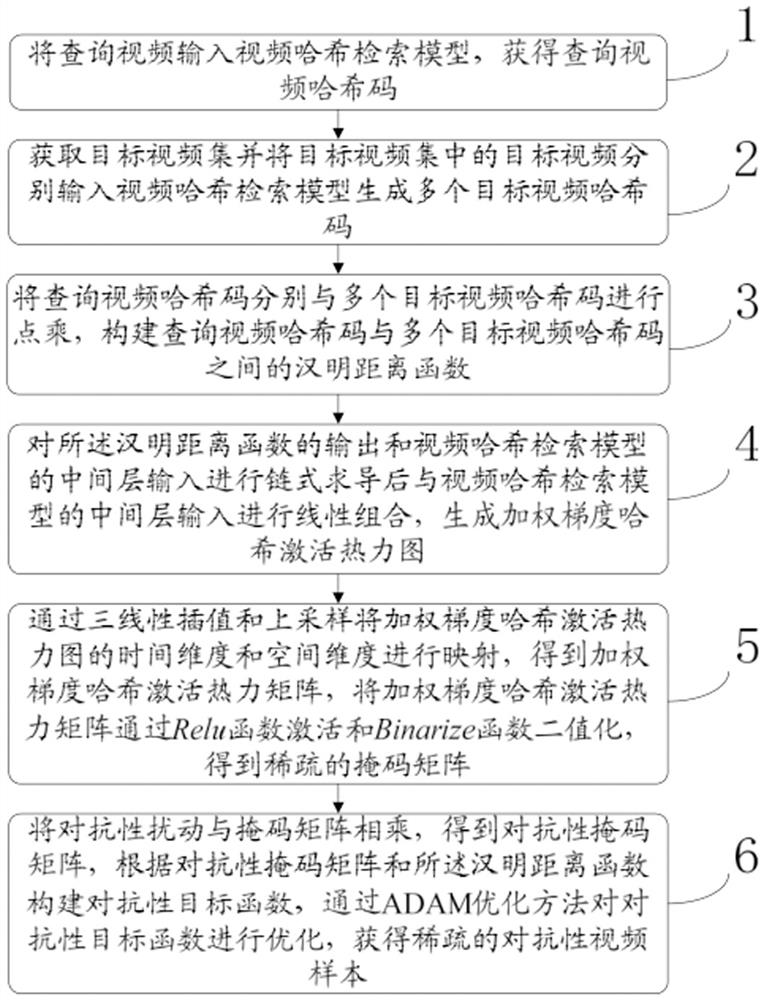
ActiveCN113343025AIncrease imperceptibilityReduce pixel costVideo data indexingSpecial data processing applicationsTheoretical computer scienceHamming distance
The invention provides a sparse adversarial attack method based on a weighted gradient Hash activation thermodynamic diagram, which comprises the following steps of: 1, inputting a query video into a video Hash retrieval model to obtain a query video Hash code; 2, acquiring a target video set and respectively inputting target videos in the target video set into the video hash retrieval model to generate a plurality of target video hash codes; and 3, performing point multiplication on the query video hash code and the plurality of target video hash codes, and constructing a Hamming distance function between the query video hash code and the plurality of target video hash codes. According to the sparse adversarial attack method based on the weighted gradient hash activation thermodynamic diagram, the position and the sensitive area of the sparse adversarial attack are determined by using the accuracy of the sensitivity of the weighted gradient hash activation thermodynamic diagram, the pixel cost of the adversarial attack is reduced, and the accuracy and efficiency of sparse adversarial attacks and the imperceptibility of adversarial samples are improved.
Owner:CENT SOUTH UNIV
MDCT quantization coefficient small value region-based advanced audio coding (AAC) audio steganography and extraction method
ActiveCN104867496AReduce computational complexityIncrease imperceptibilitySpeech analysisSteganalysisComputation complexity
The invention discloses an MDCT quantization coefficient small value region-based advanced audio coding (AAC) audio steganography and extraction method. The method includes the following steps that: 1, a mapping table containing index pairs and code length is established according to an AAC audio codebook; steganography rules are established according to the mapping table; and 3, insertion and extraction of secret information can be realized through utilizing the mapping table and the steganography rules. With the method of the invention adopted, computational complexity in steganography and extraction processes can be decreased, and imperceptibility and anti-steganalysis of steganography can be improved, and therefore, information can be hidden in and extracted from AAC audios safely and efficiently.
Owner:合肥庐阳科技创新集团有限公司
Method for hiding information and method for obtaining information
InactiveCN108768581AIncrease imperceptibilityImprove concealmentSecret communicationTransmissionTime domainCovert communication
The application relates to a method for hiding information and a method for obtaining information. The method for hiding the information comprises the following steps: obtaining a bit sequence at a predetermined position of a source bit-stream of public information, and initializing a complex Gauss random sequence generator by means of the bit sequence to generate a complex Gauss random sequence;performing spread spectrum modulation on secret information according to the complex Gauss random sequence to obtain a Gauss spread spectrum signal; and superimposing the Gauss spread spectrum signalon a conventional spread spectrum signal of public information to obtain a mixed signal. By means of the method for hiding the information, through pseudo-gaussianizing the communication signal of thesecret information, the mixed signal embedded in the secret information tends to be the same as the signal sent without embedding the secret information in terms of time-domain characteristic components, frequency-domain characteristic components or demodulation results; therefore, the information receiving end can recover the secret information and the public information normally, the imperceptibility of the secret information is improved, and the concealment of covert communication process is improved.
Owner:GUANGZHOU HAIGE COMM GRP INC
Stereoscopic video robust watermarking method based on tensor decomposition
PendingCN110838082AGuaranteed relevanceImprove robustnessImage watermarkingPattern recognitionStereoscopic video
The invention discloses a stereoscopic video robust watermarking method based on tensor decomposition. A watermark is embedded into the watermark embedding end, the brightness components of the left viewpoint color video and the right viewpoint color video are converted into third-order tensors; tensor decomposition is carried out on the third-order tensor; the two-dimensional matrix representations of the two feature maps containing the main energy are synthesized into a three-dimensional matrix in sequence; the three-dimensional matrix is converted into a three-order tensor; tensor decomposition is carried out on the third-order tensor; non-overlapping sub-image block processing is carried out on the obtained feature map containing the main energy, to-be-embedded blocks are determined,a coefficient in a left singular matrix of each to-be-embedded block is modified according to each bit in an original binary watermark sequence to obtain a corresponding watermark-containing block, and inverse operation is carried out on the watermark-containing block to finally obtain a watermark-containing three-dimensional video; at a watermark extraction end, image block processing is performed in the same way, to-be-extracted blocks are determined according to the to-be-embedded blocks, and watermark information are extracted from each to-be-extracted block. The method has the advantages of being good in robustness and imperceptibility.
Owner:COLLEGE OF SCI & TECH NINGBO UNIV
High-capacity reversible image watermarking algorithm based on multi-scale decomposition and interpolation expansion
ActiveCN110738592AImprove homogeneityIncrease embedded valueImage data processing detailsMultiscale decompositionImaging processing
The invention relates to the technical field of image processing, and discloses a high-capacity reversible image watermarking algorithm based on a multi-scale decomposition and interpolation algorithm, which comprises a watermark embedding part and a watermark extracting part, and is characterized in that the watermark embedding capacity is further increased through multi-scale decomposition and interpolation expansion before watermark embedding; watermark information is embedded through a generalized interpolation expansion method, pixel value overflow of overflowing corresponding image pixelpoints is avoided through gray scale overflow processing, then the embedding capacity is further increased, and watermark extraction is an inverse process of watermark embedding. Compared with the prior art, the method has the advantages that when equivalent watermark information is embedded, good watermark-containing image visual quality is kept, and better invisibility and payload capacity areachieved.
Owner:HUAIYIN INSTITUTE OF TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com