Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5104results about "Recording signal processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
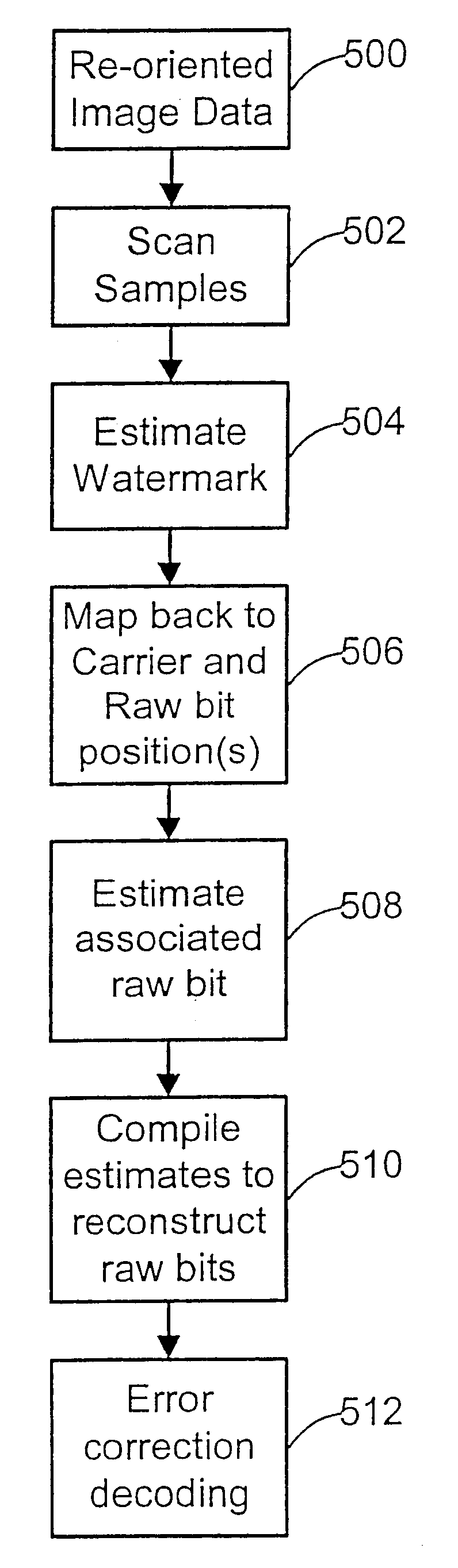
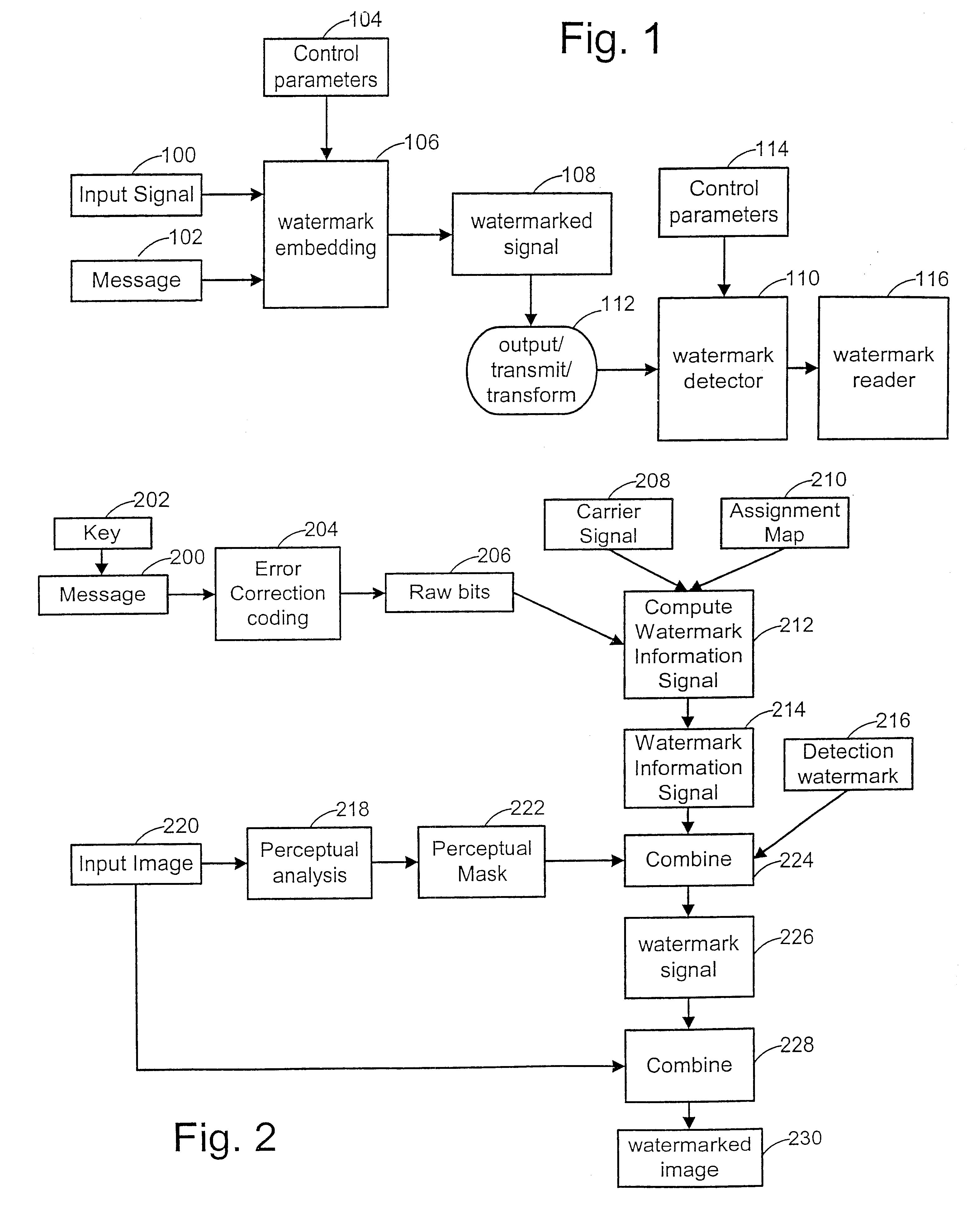
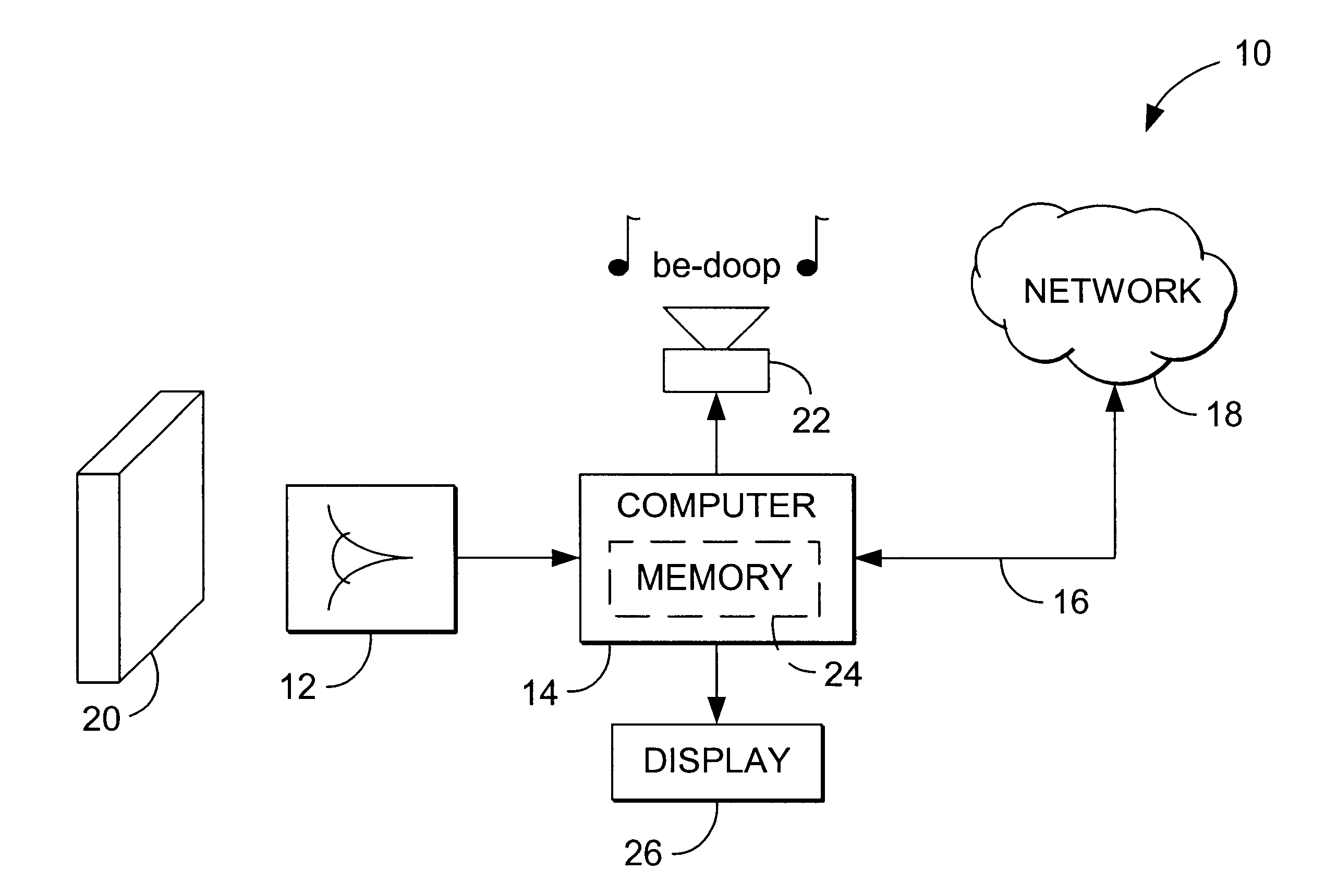
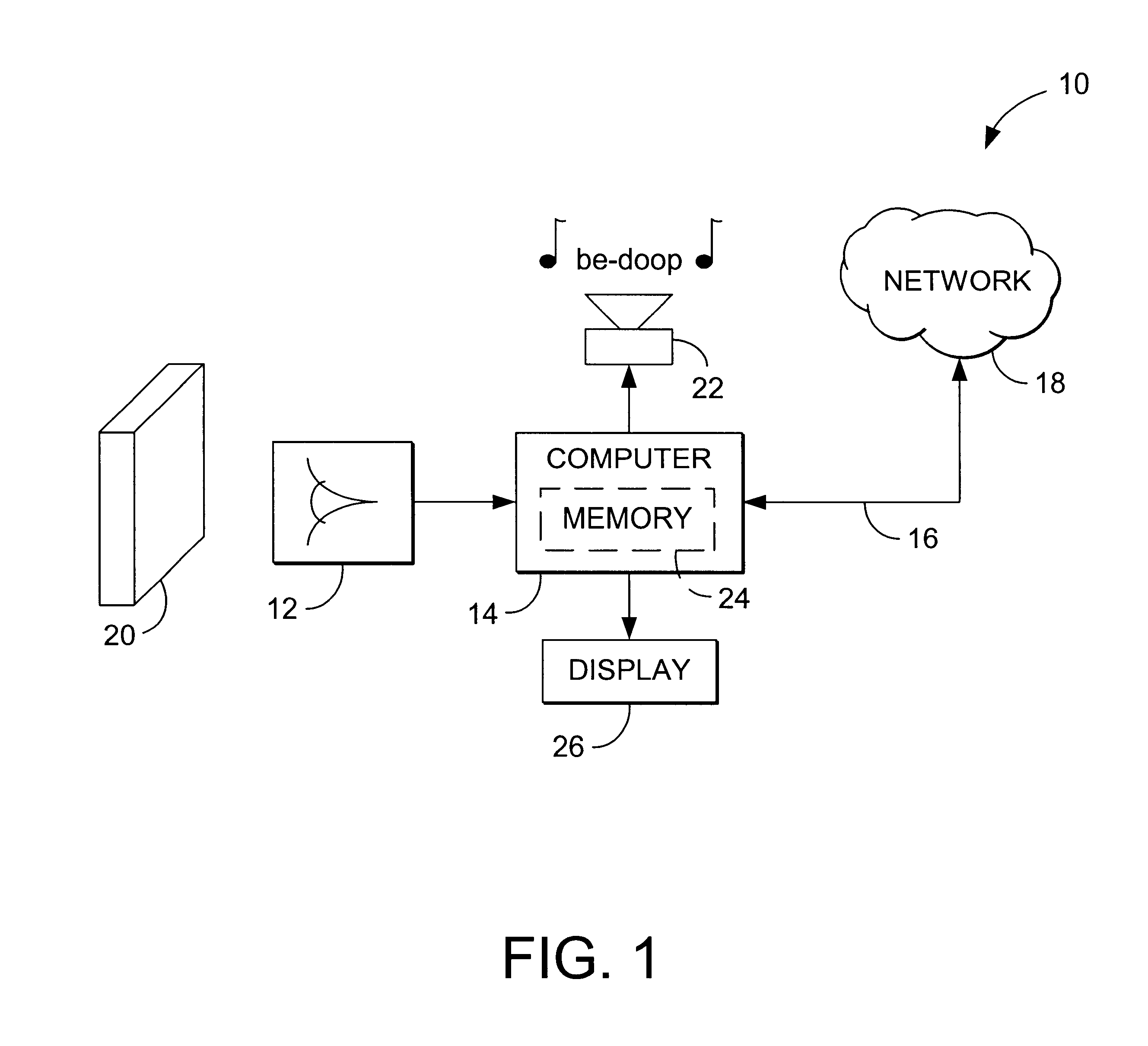
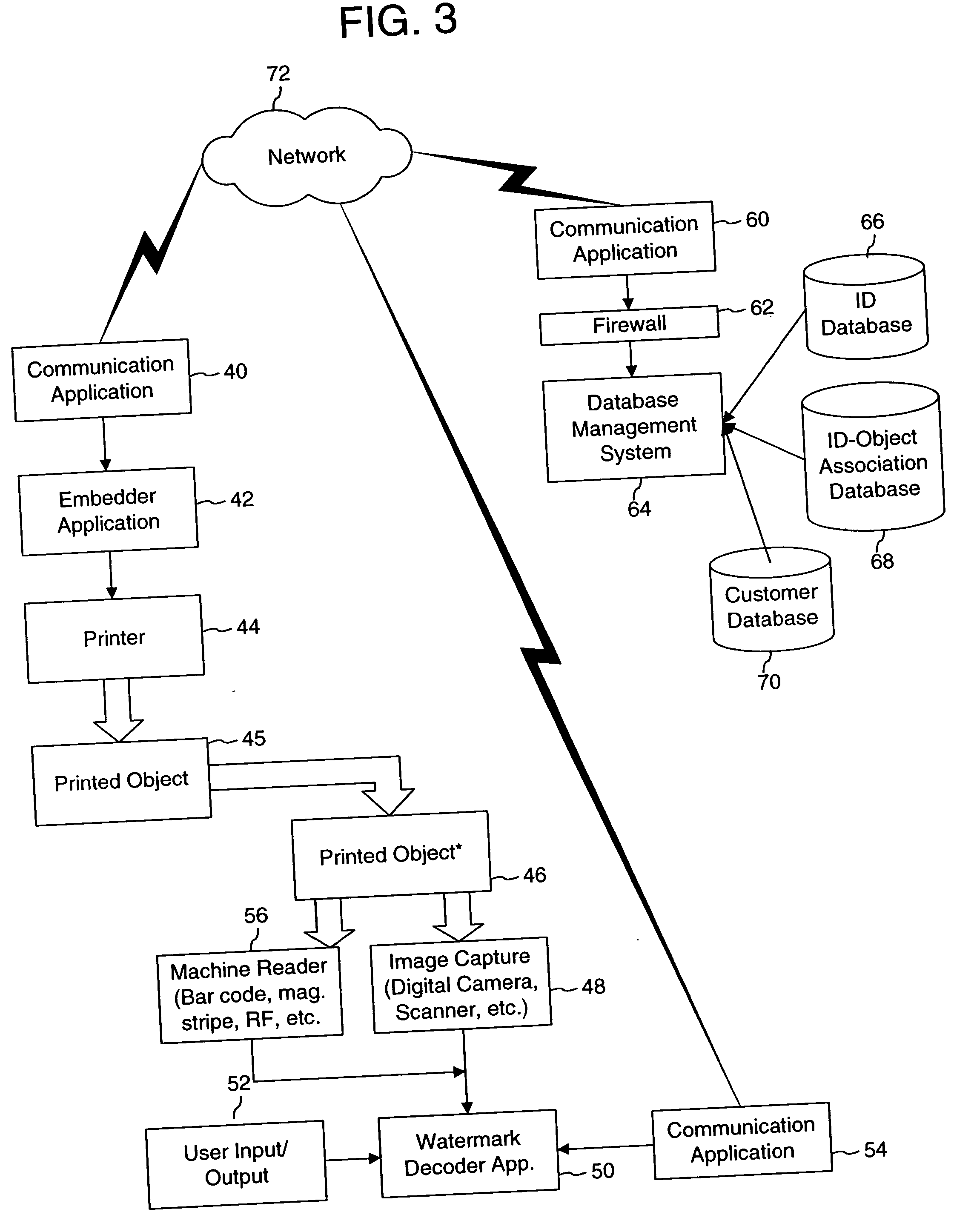
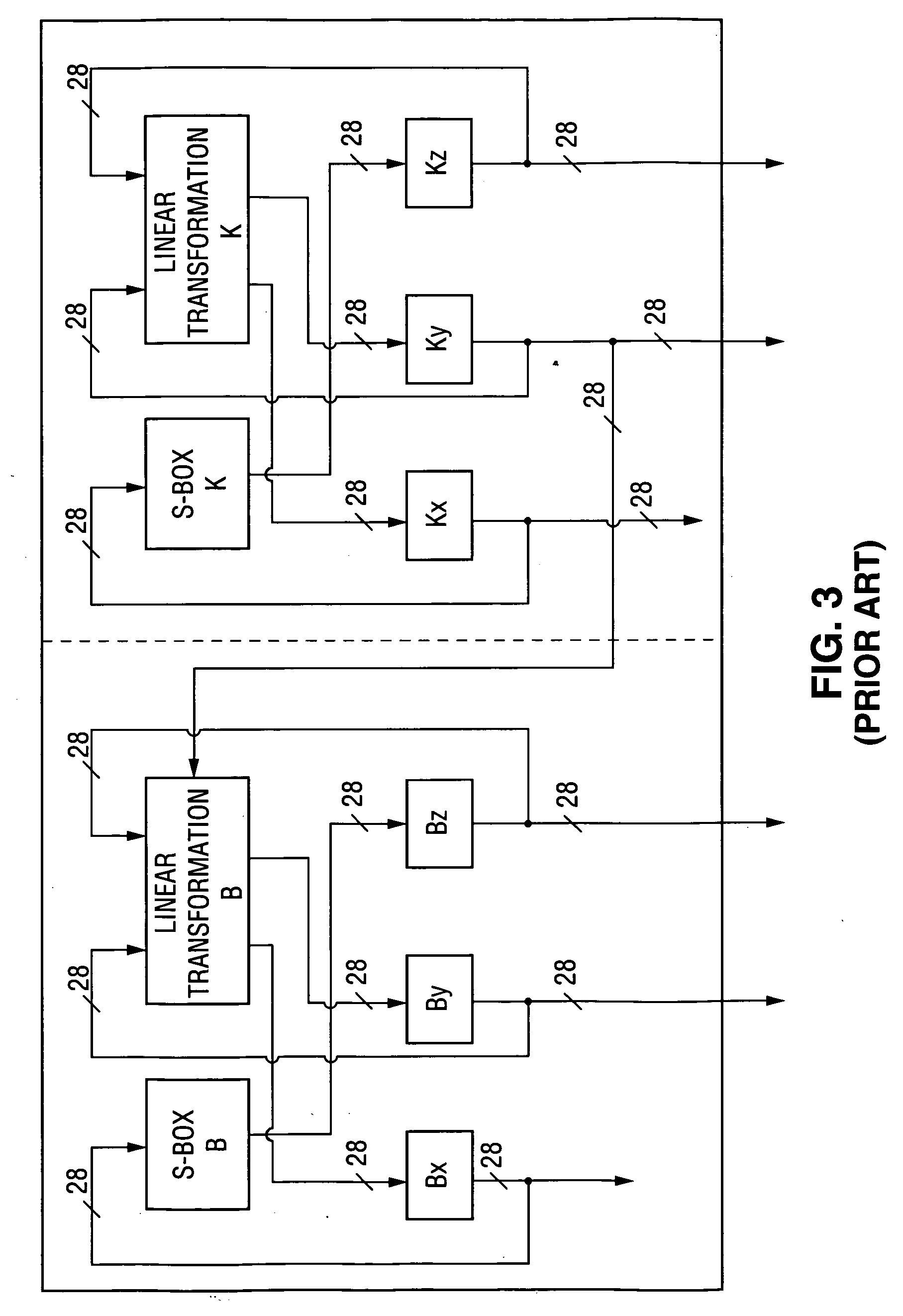
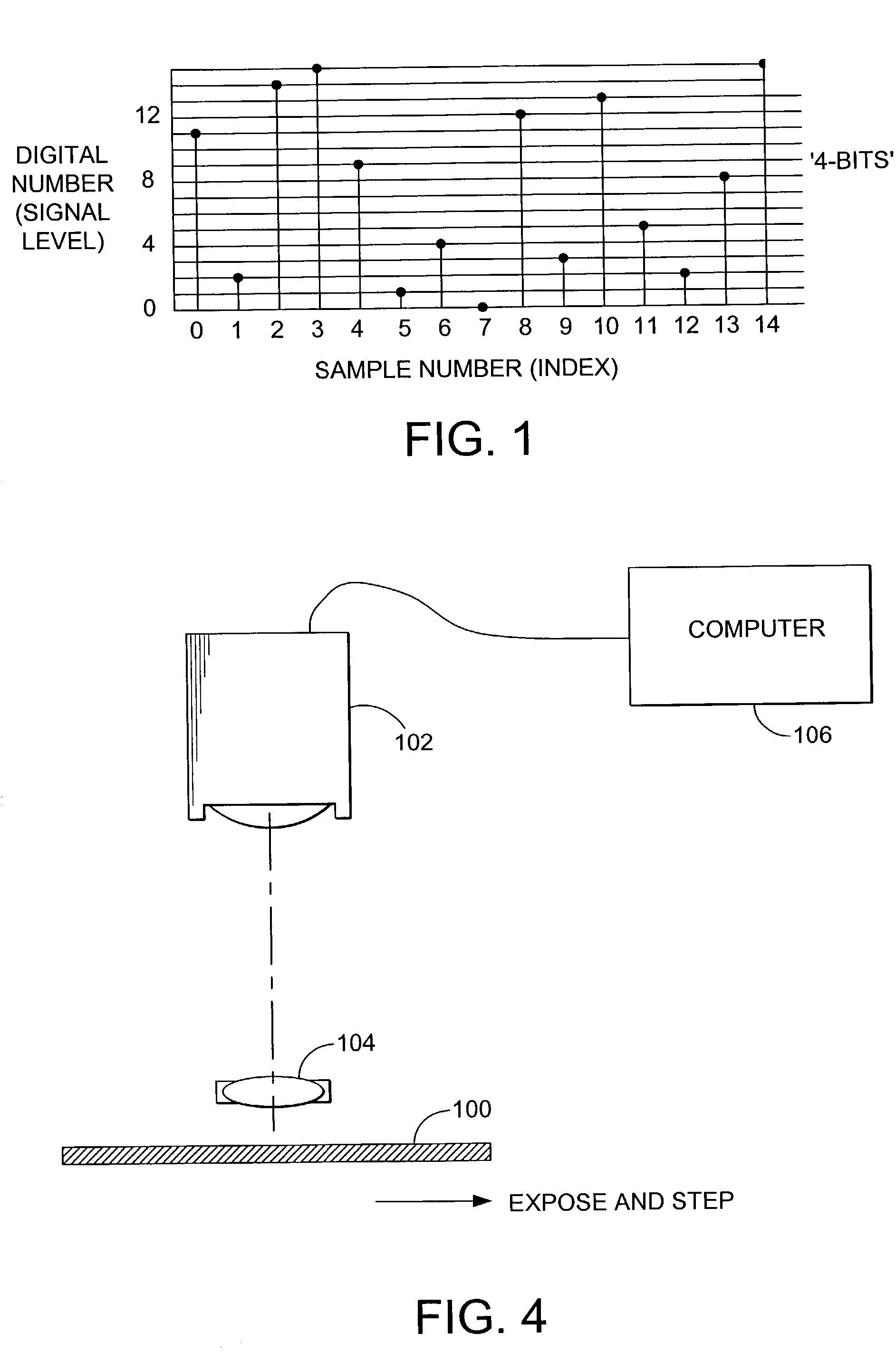
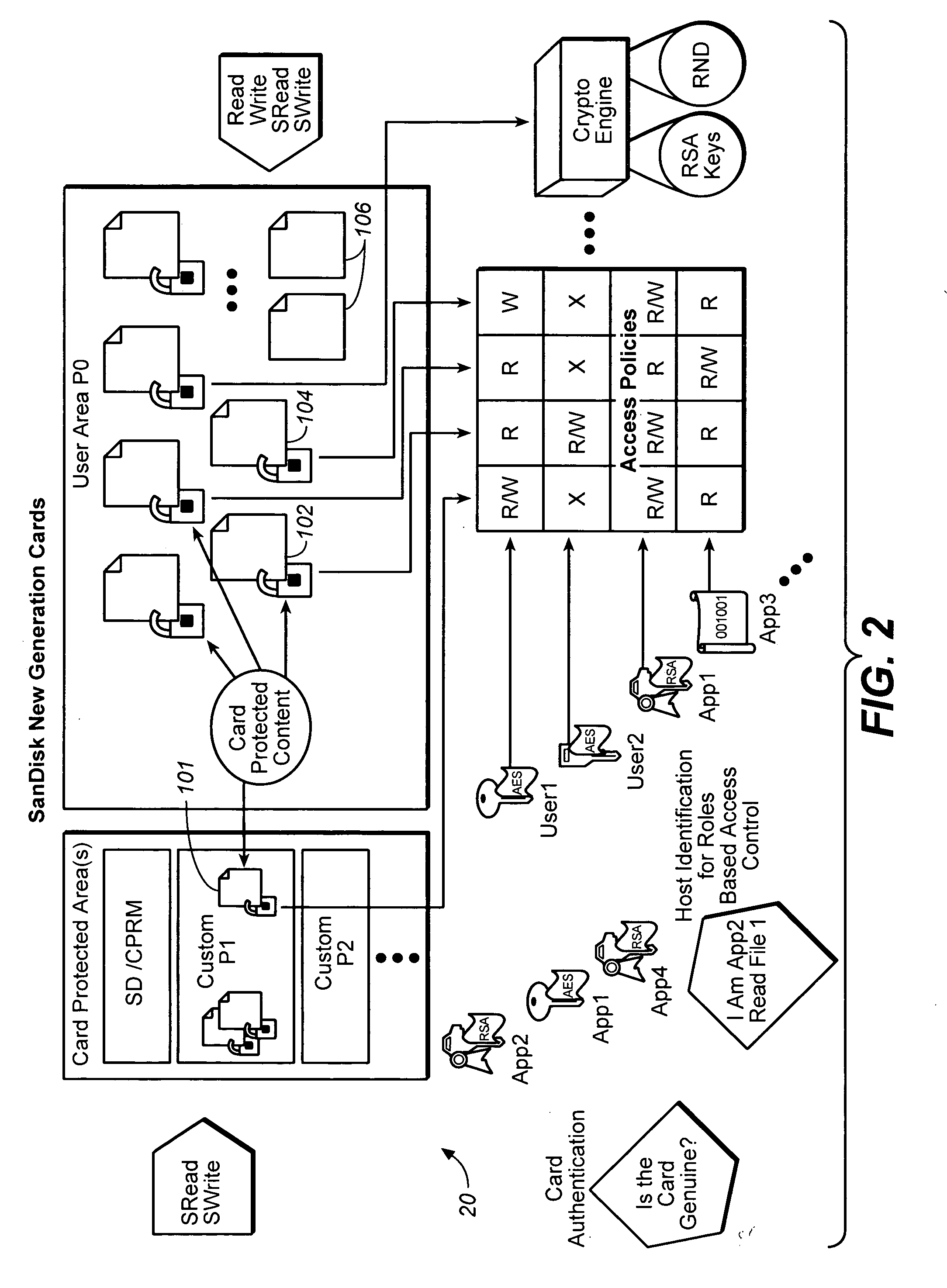
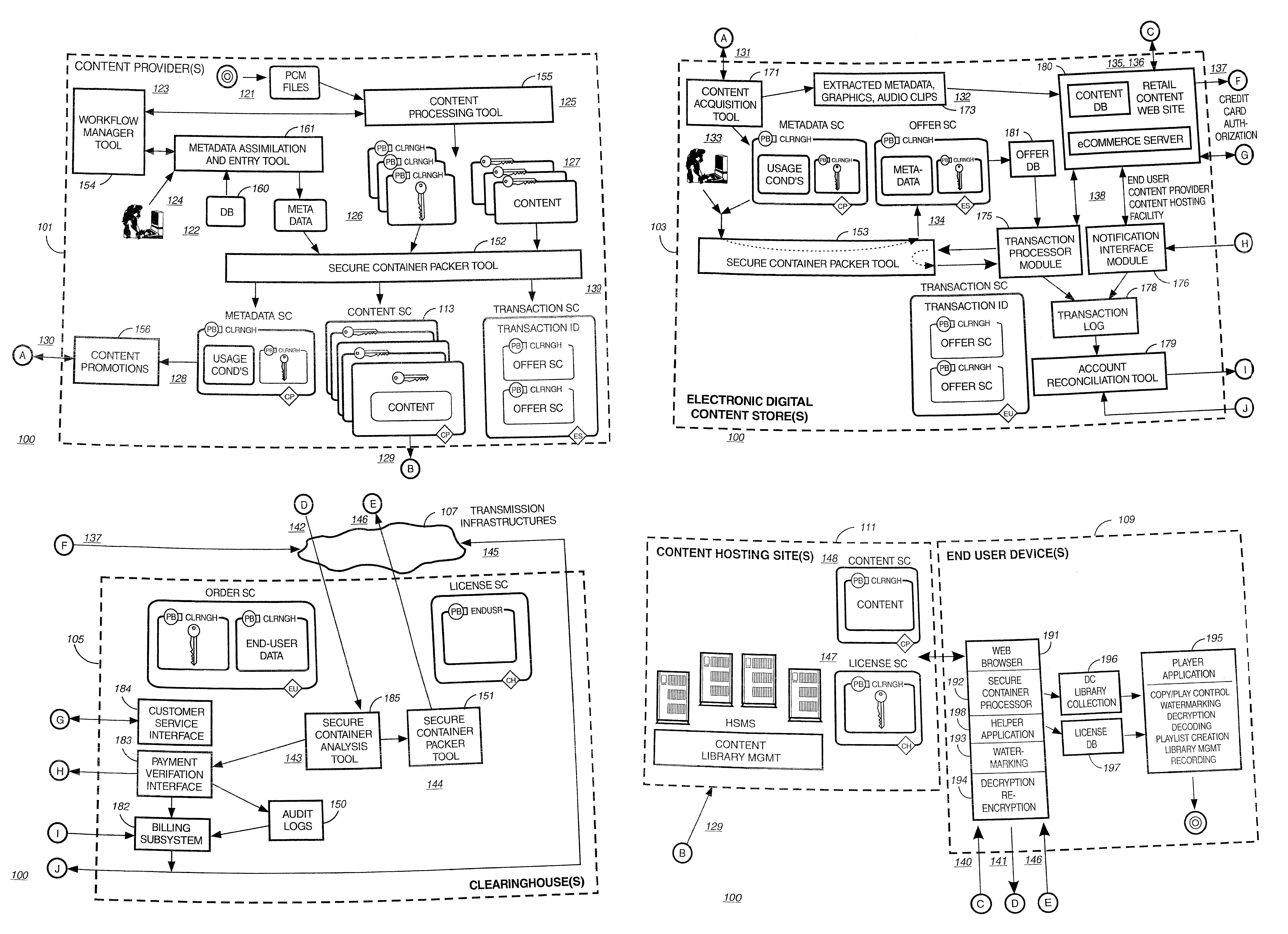
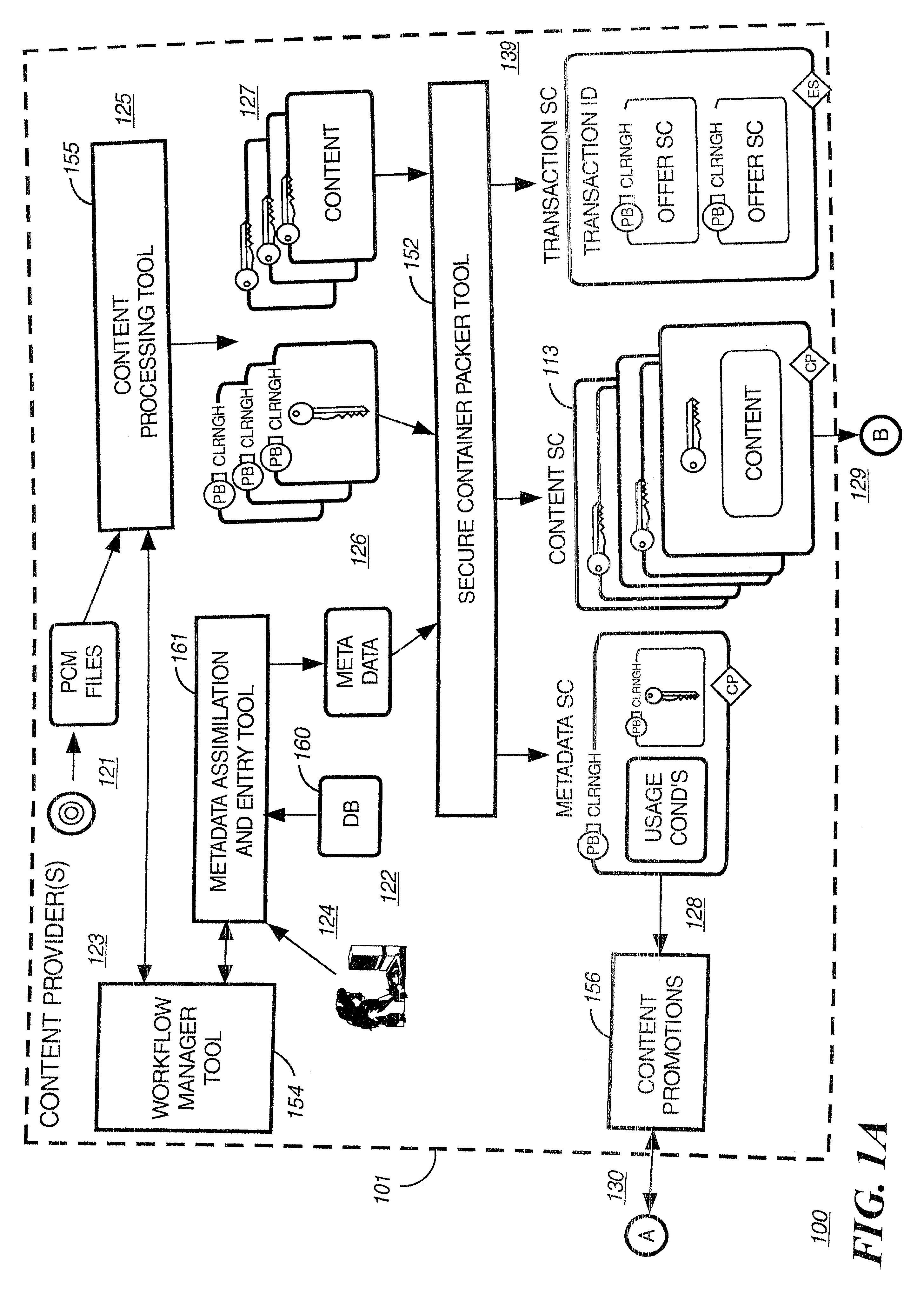
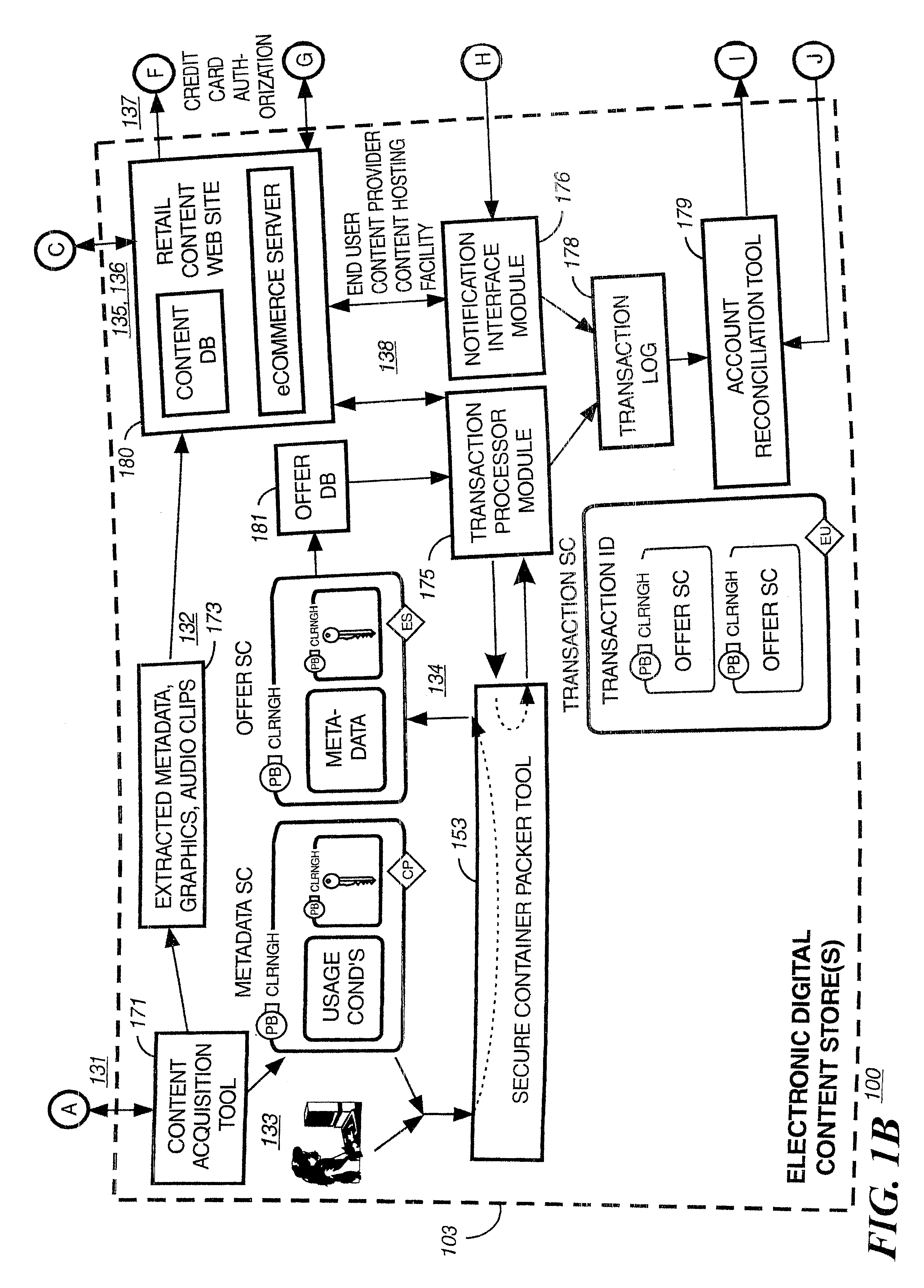
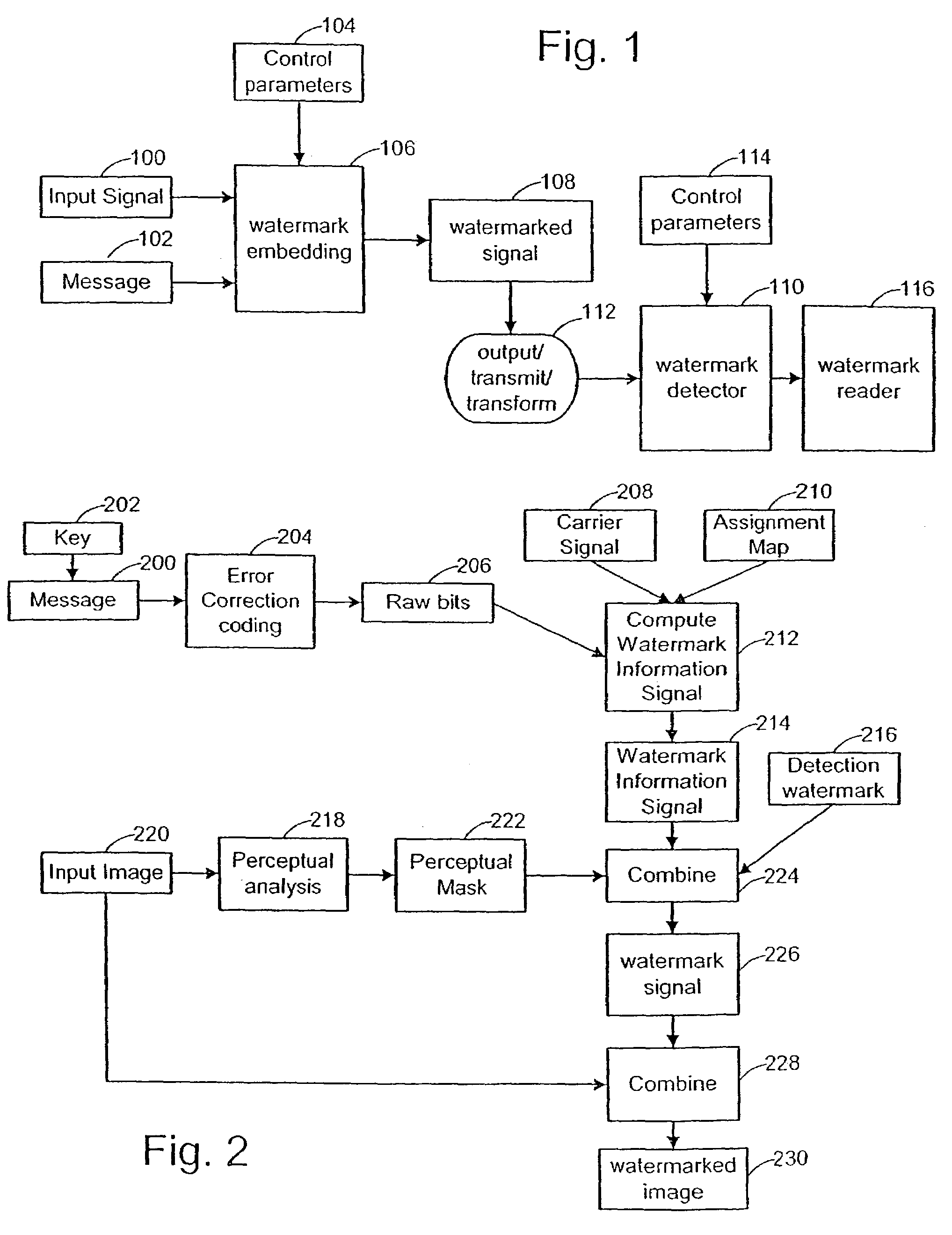
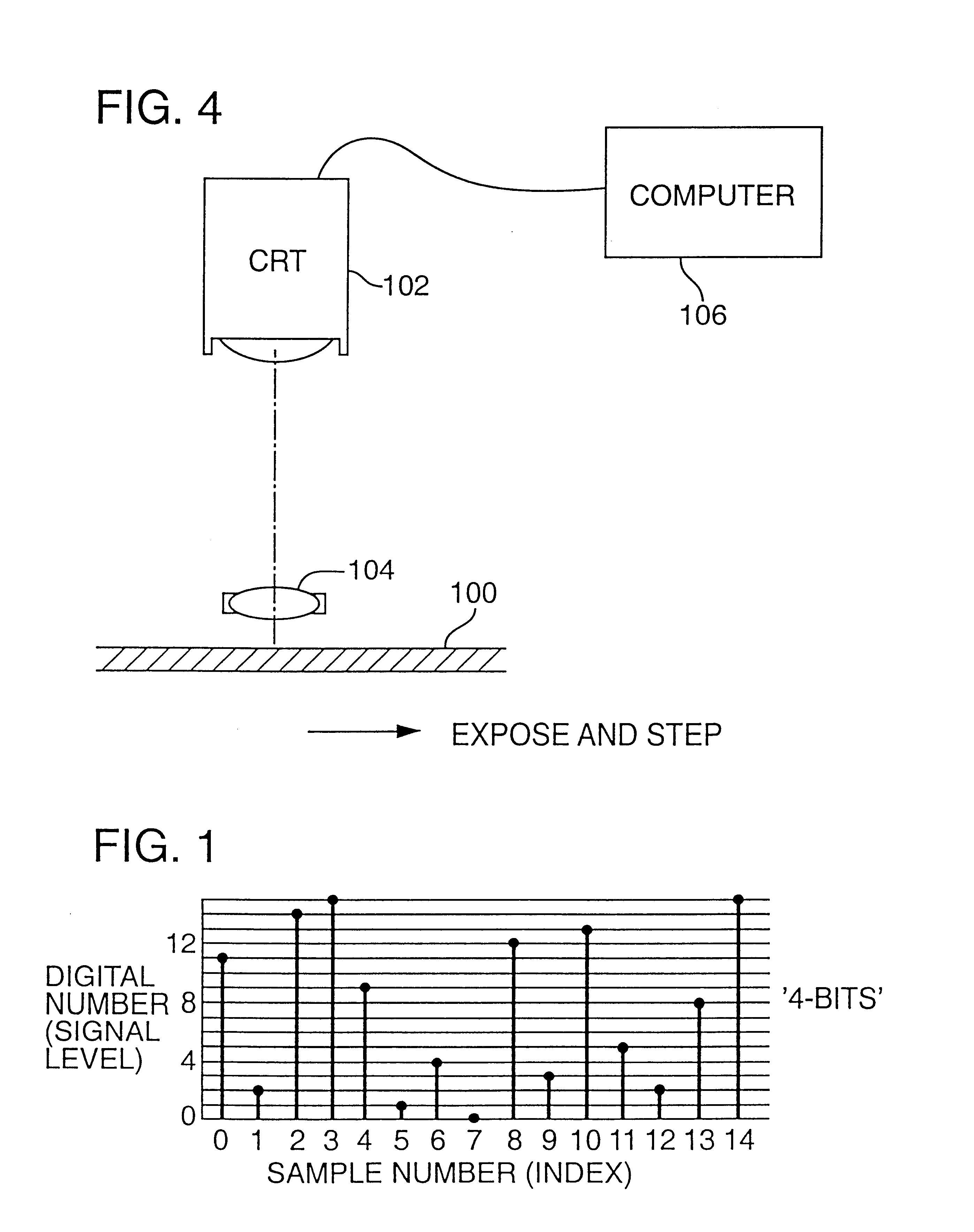
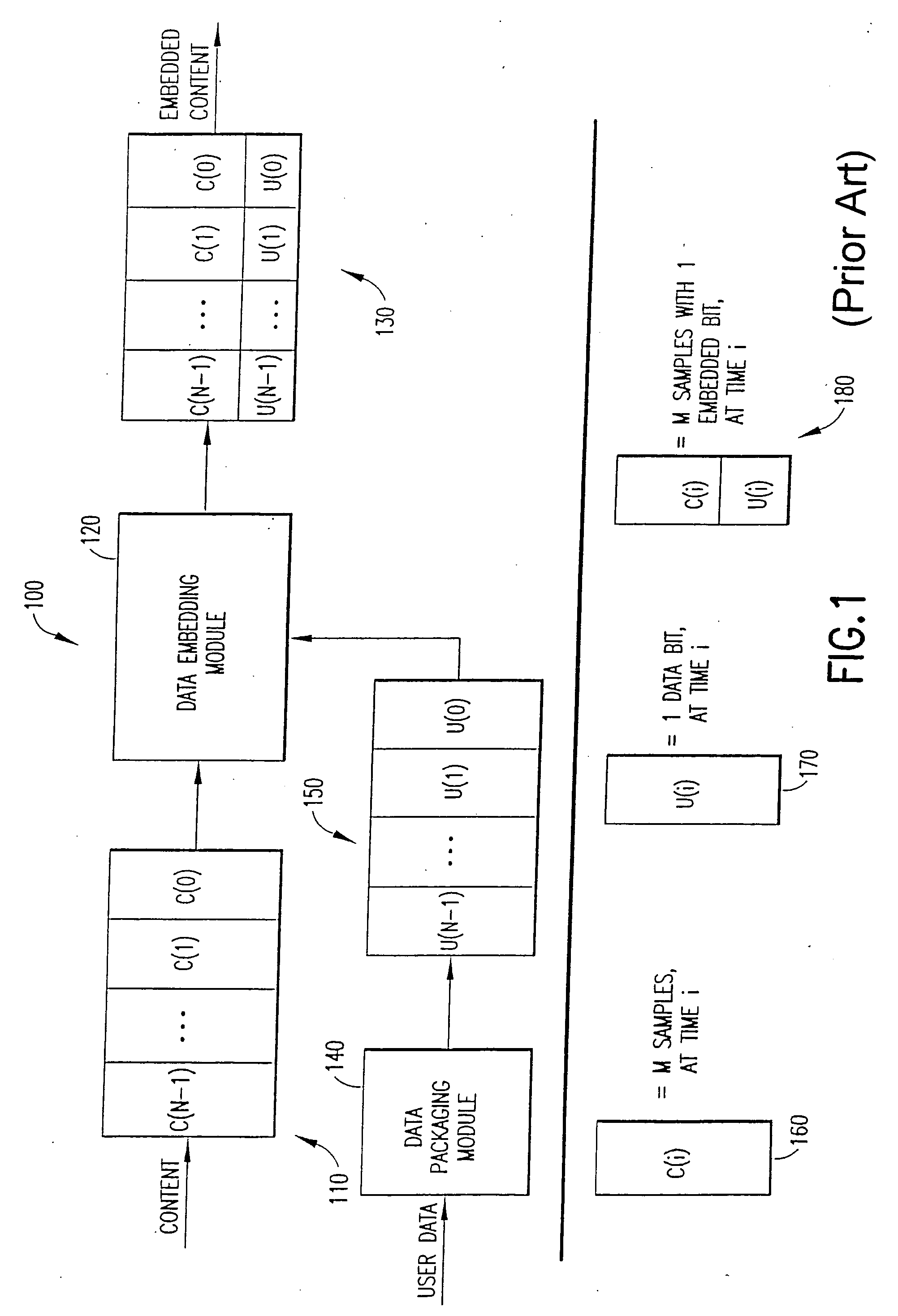
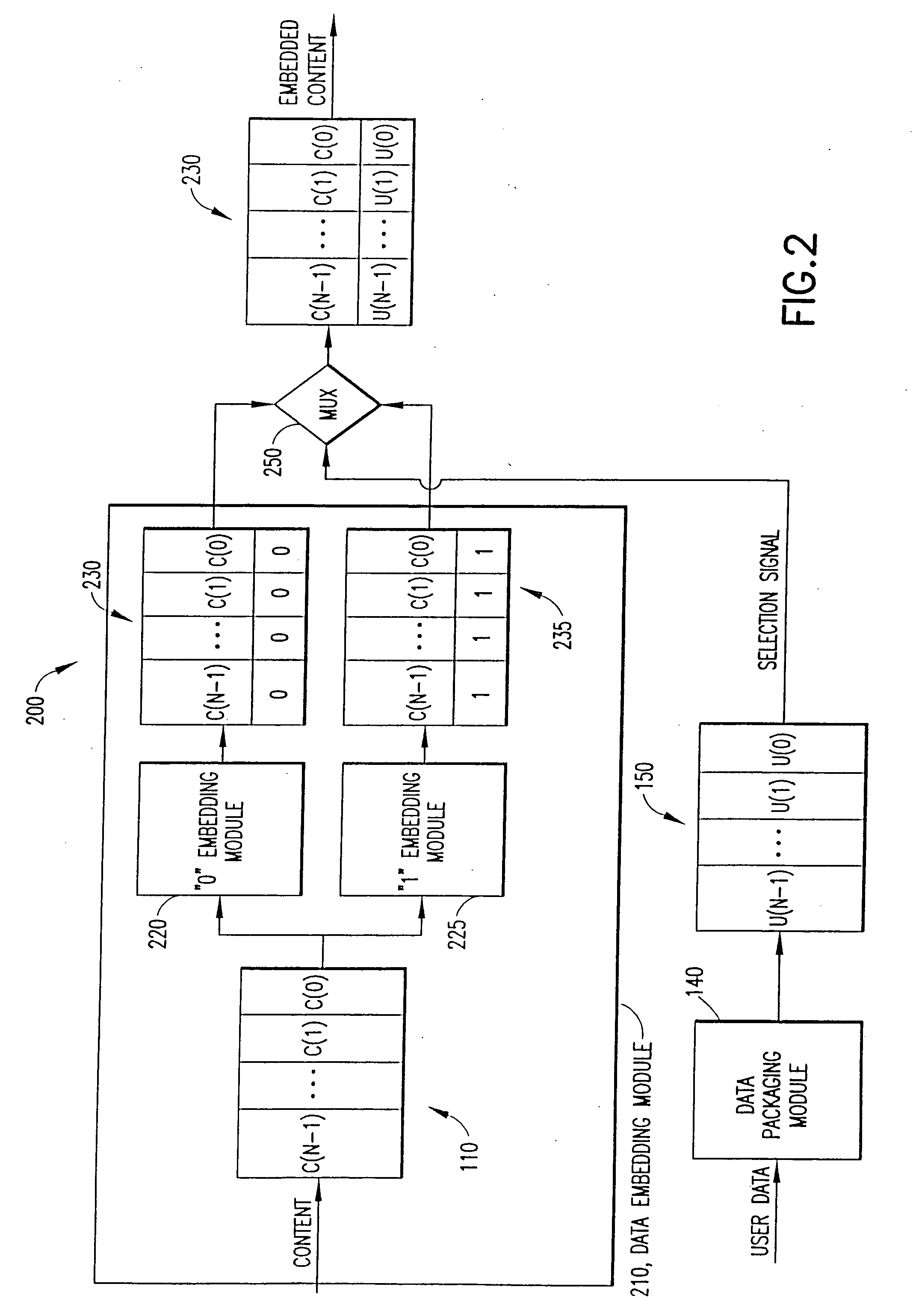
Watermark embedder and reader
InactiveUS6614914B1Mitigates effect of printingEasy to detectCoin-freed apparatusRecord information storageGraphicsComputer hardware
A watermark system includes an embedder, detector, and reader. The watermark embedder encodes a watermark signal in a host signal to create a combined signal. The detector looks for the watermark signal in a potentially corrupted version of the combined signal, and computes its orientation. Finally, a reader extracts a message in the watermark signal from the combined signal using the orientation to approximate the original state of the combined signal. While adapted for images, video and audio, the watermark system applies to other electronic and physical media. For example, it can be applied to mark graphical models, blank paper, film and other substrates, texturing objects for ID purposes, etc.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
Linking of computers based on optical sensing of digital data
InactiveUS6311214B1Reduce businessLow costCoin-freed apparatusRecord information storageDigital dataBusiness card
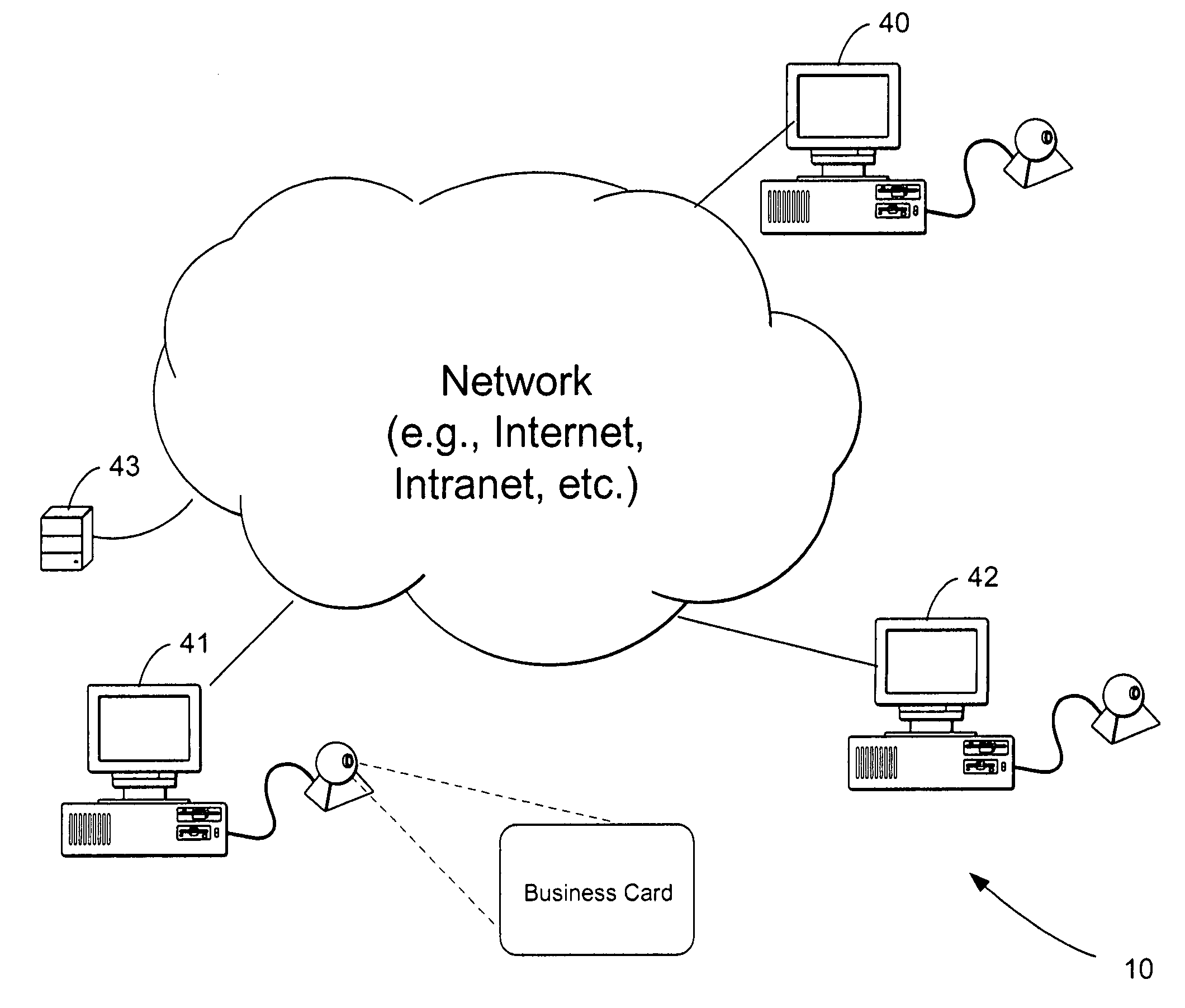
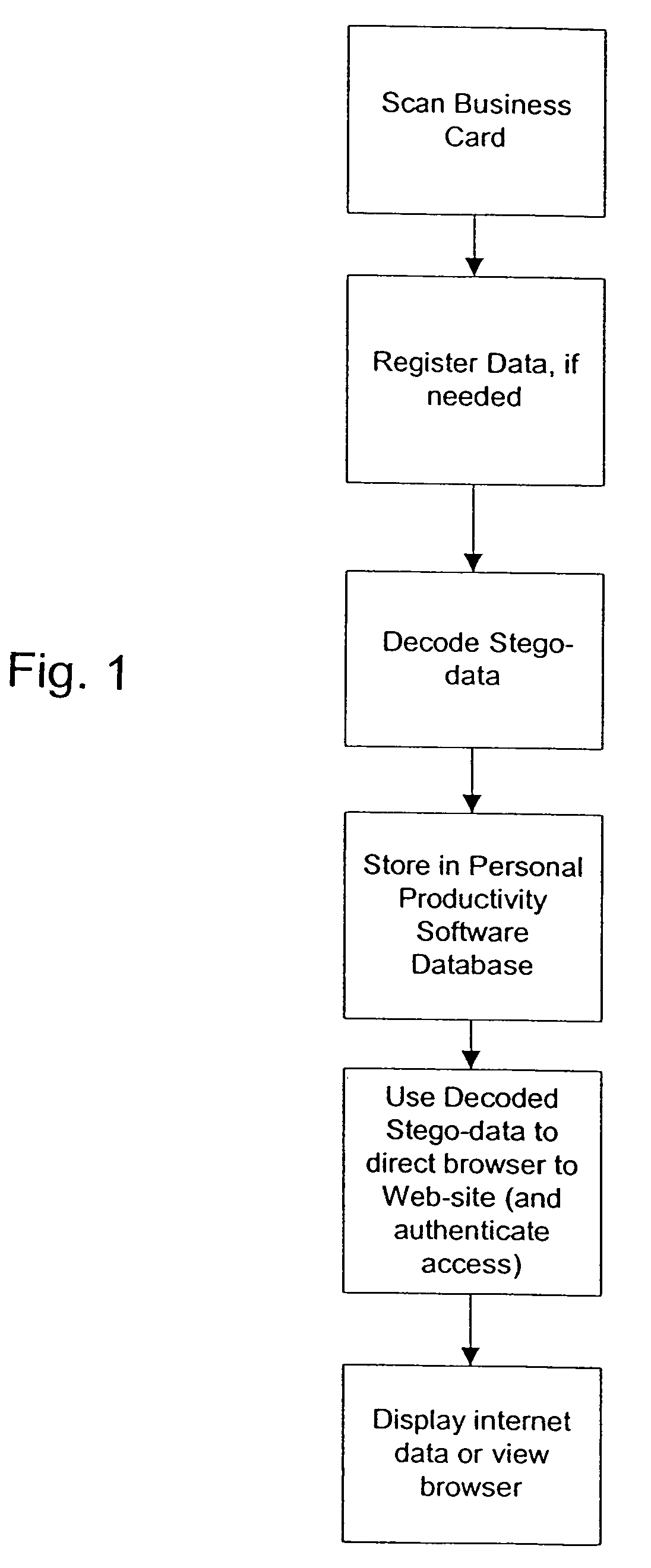
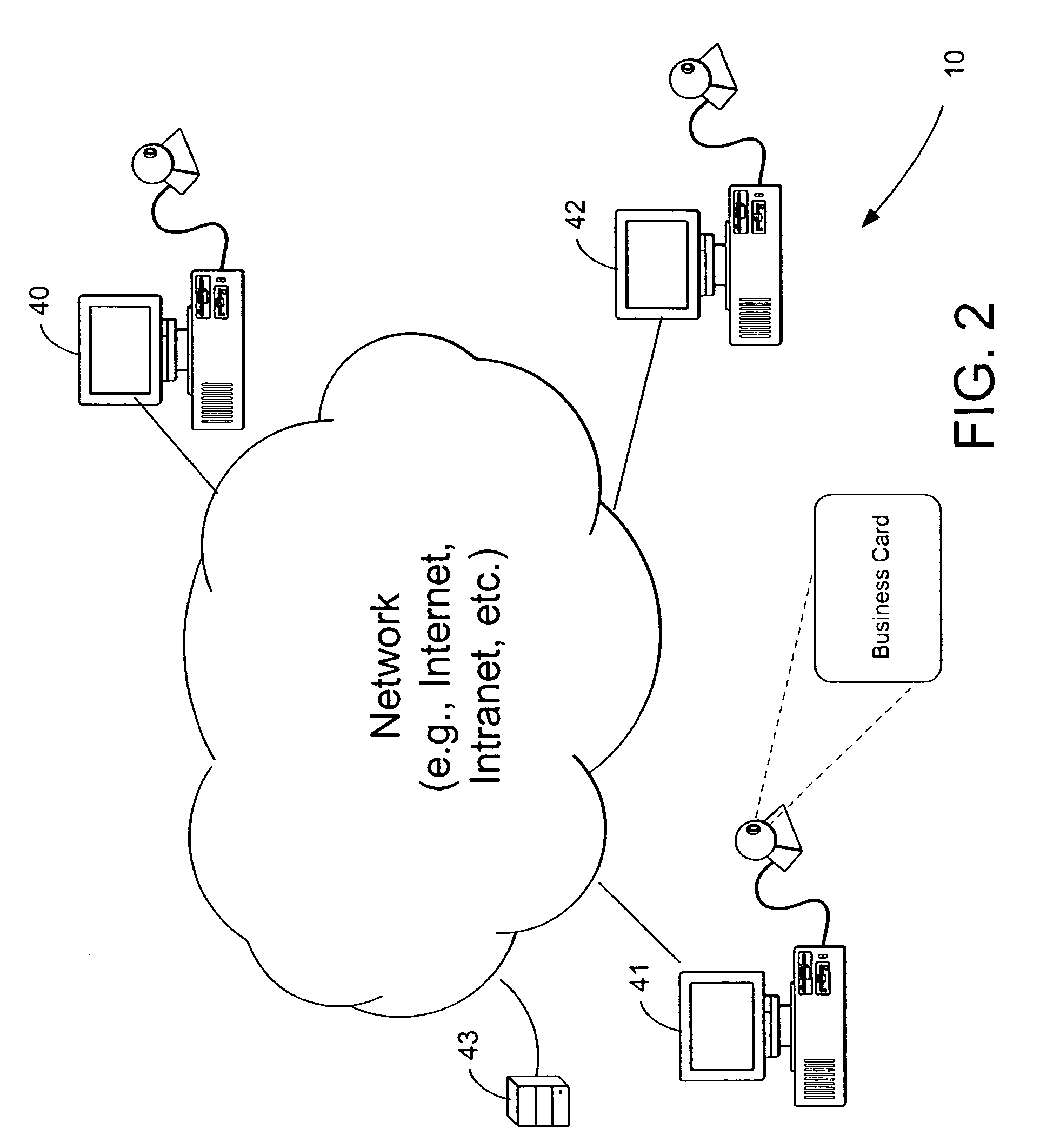
A printed object, such as an item of postal mail, a book, printed advertising, a business card, product packaging, etc., is steganographically encoded with plural-bit data. When such an object is presented to an optical sensor, the plural-bit data is decoded and used to establish a link to an internet address corresponding to that object.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
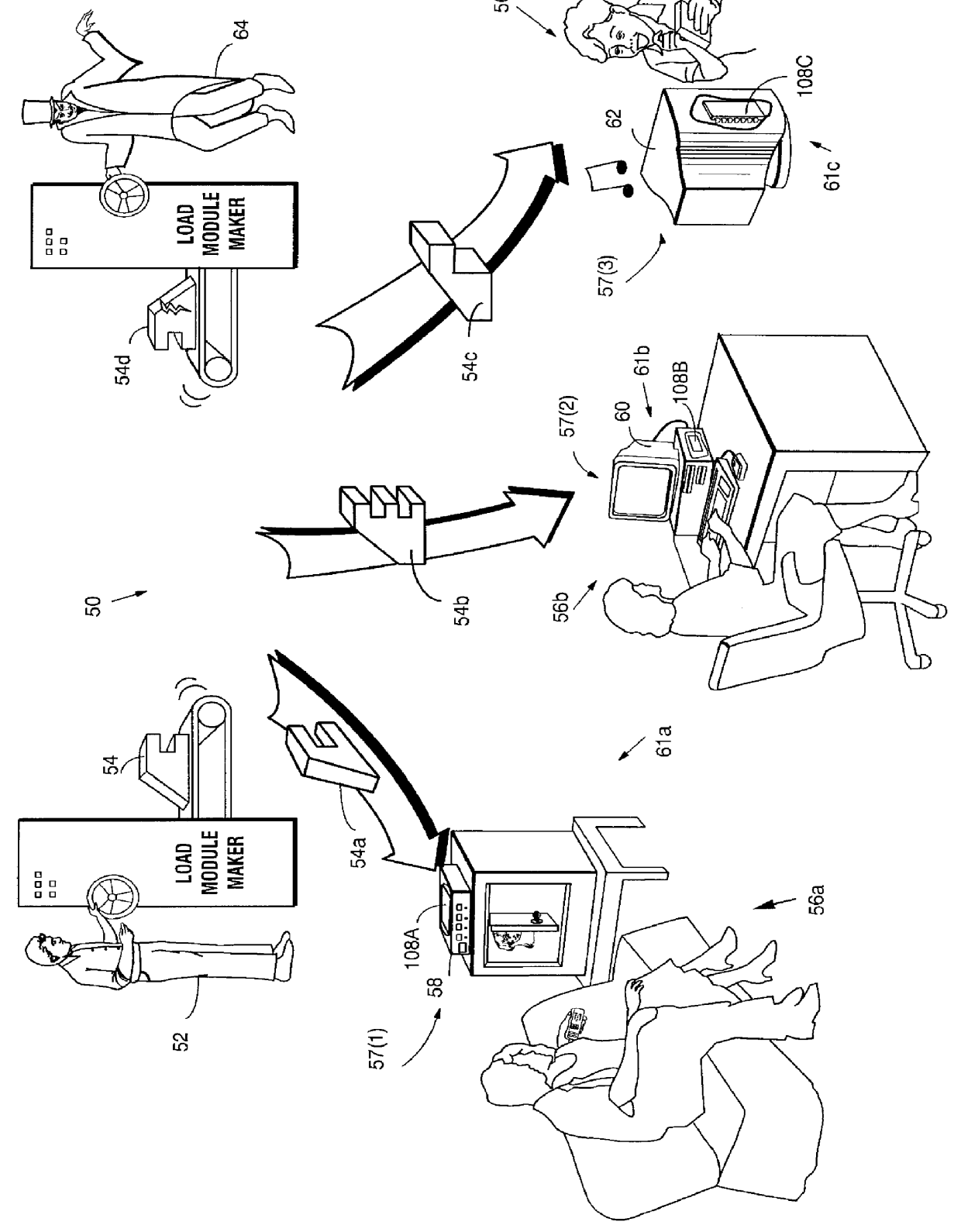
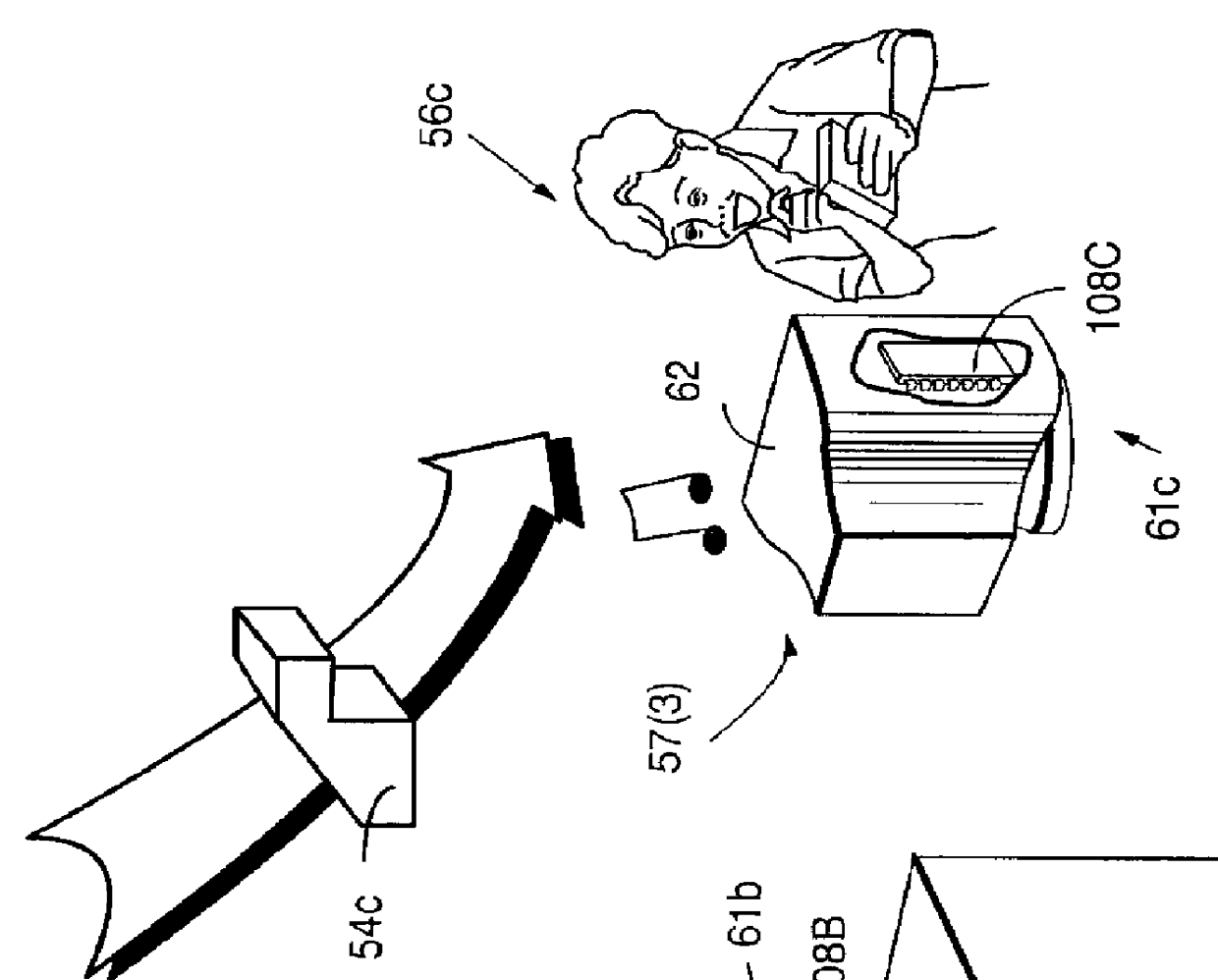
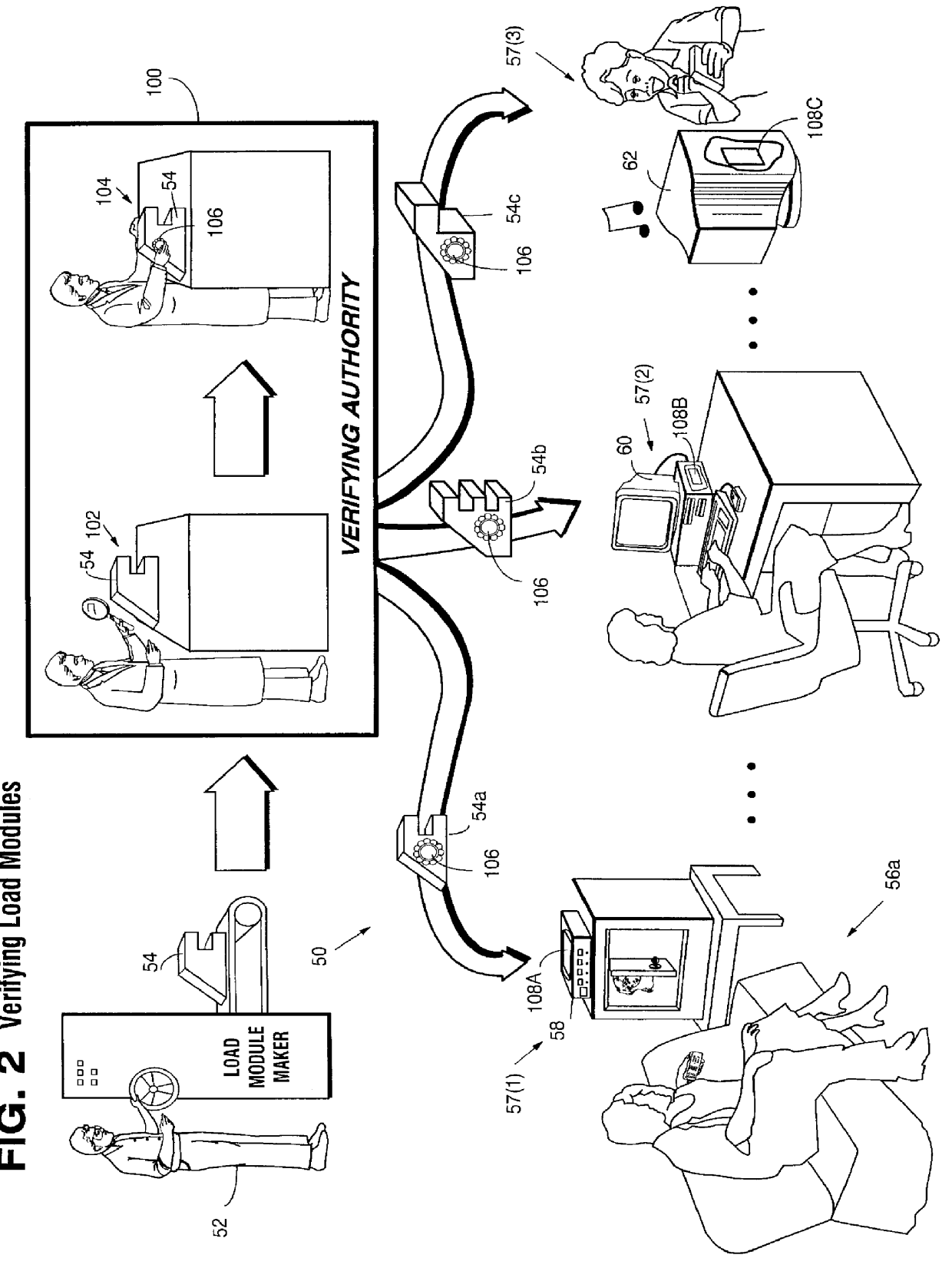
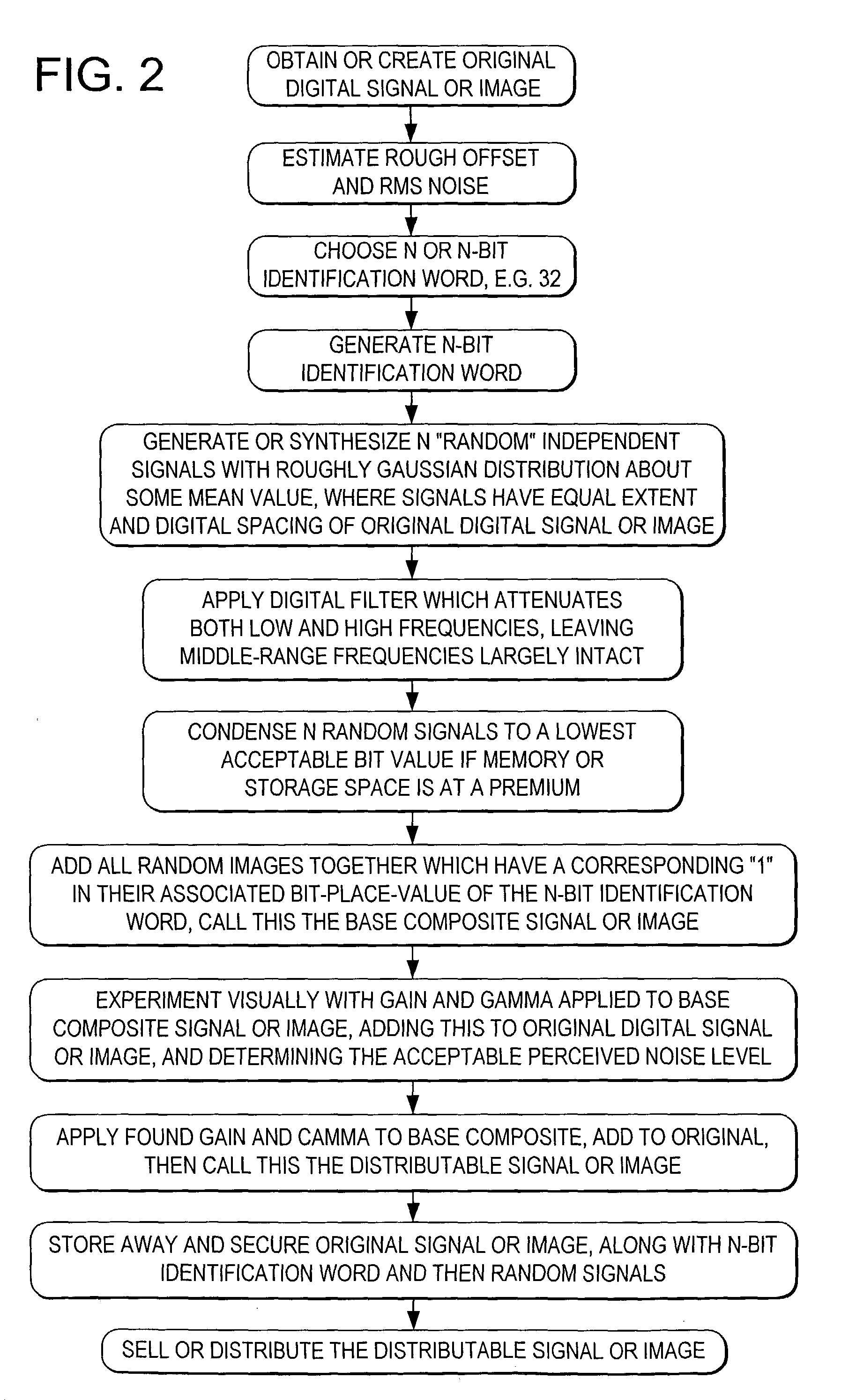
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
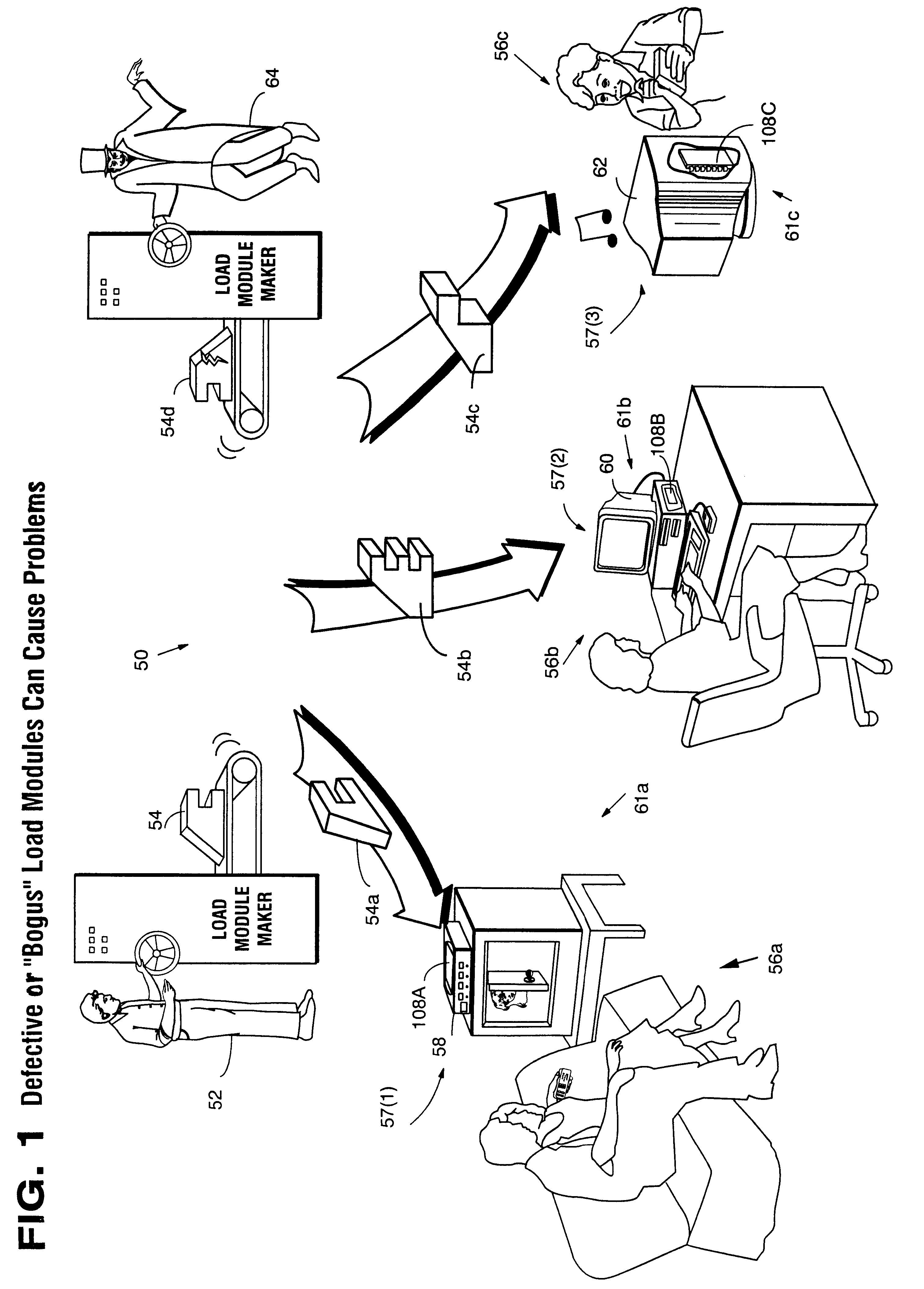
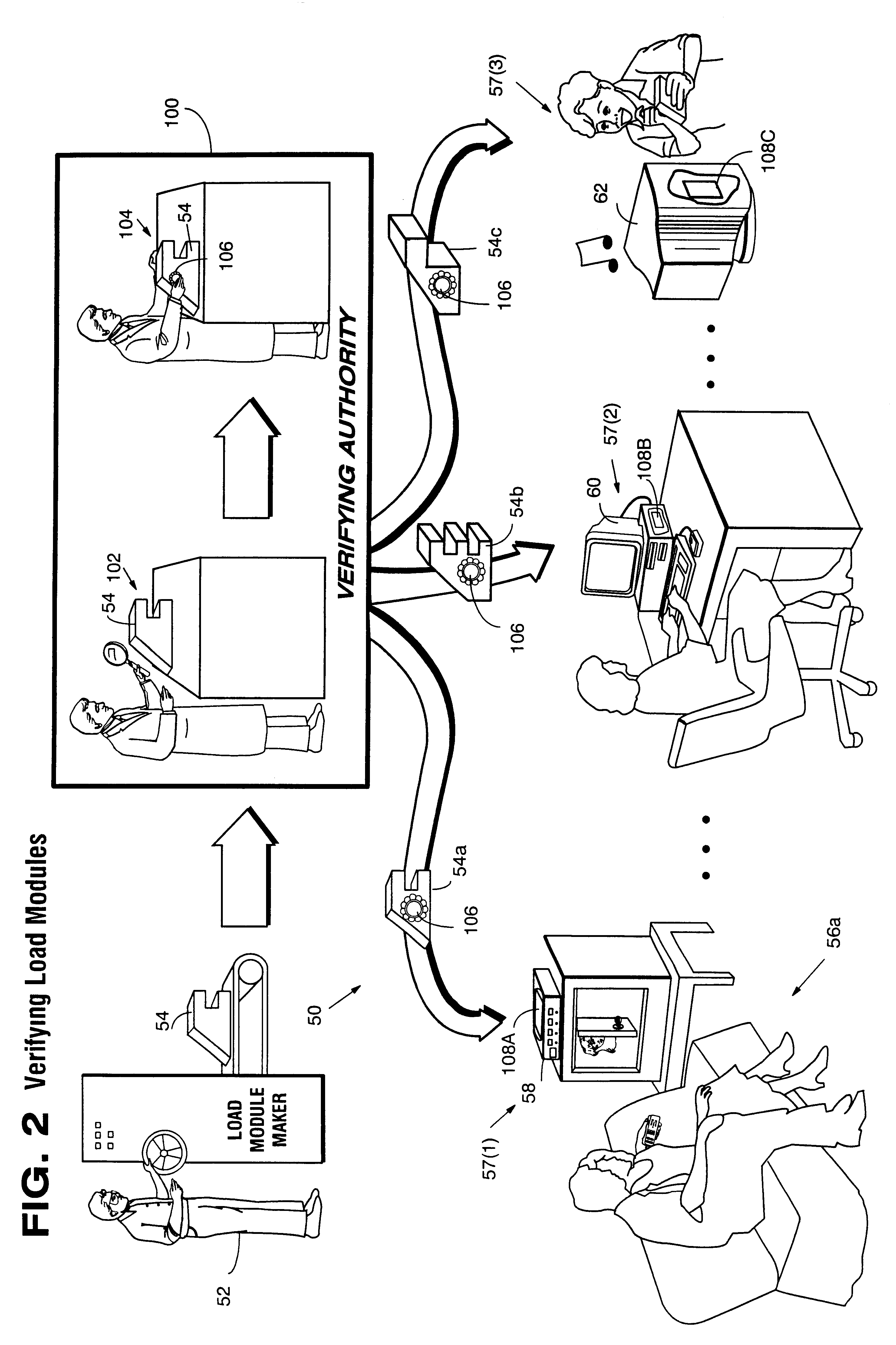
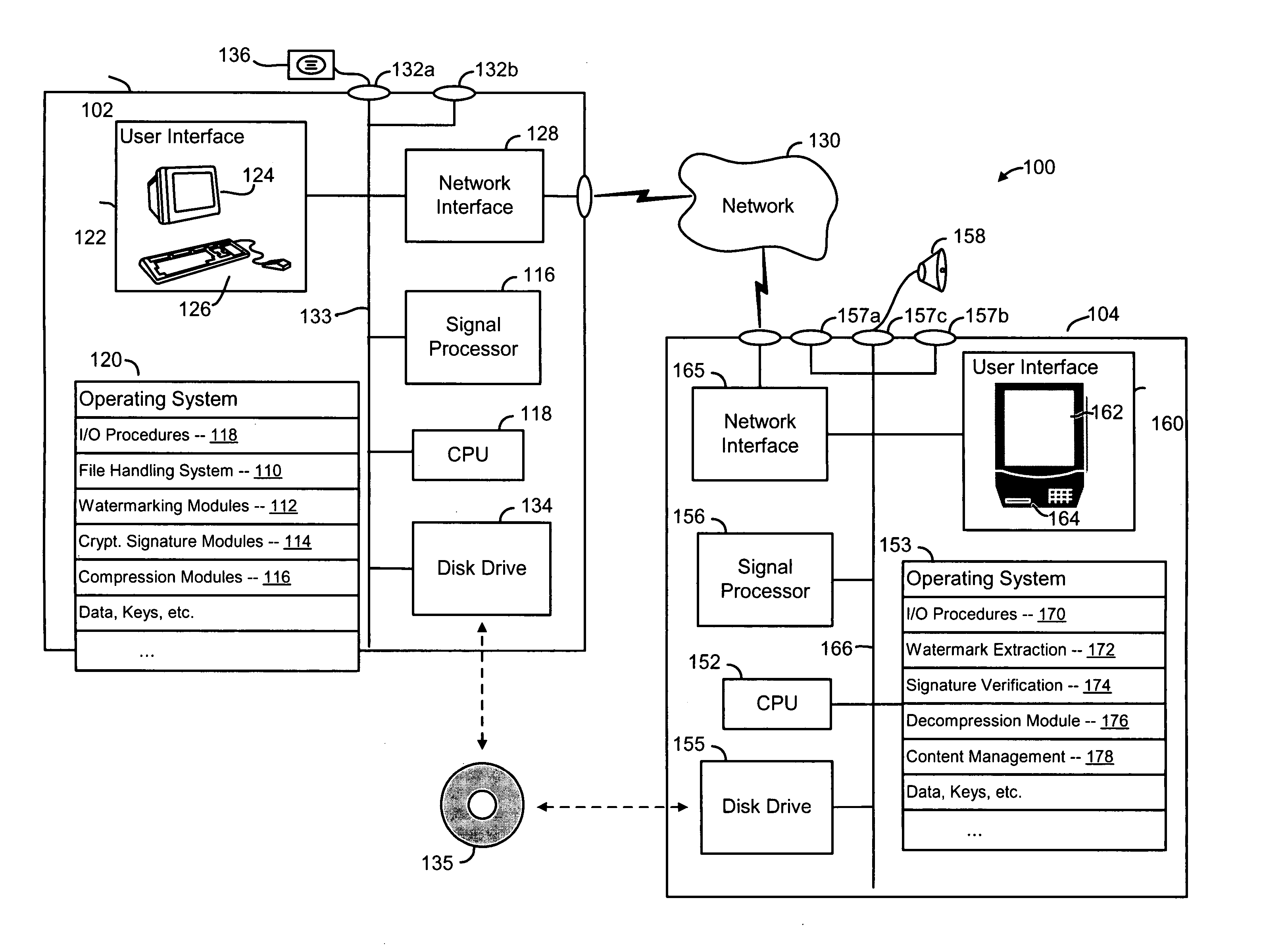
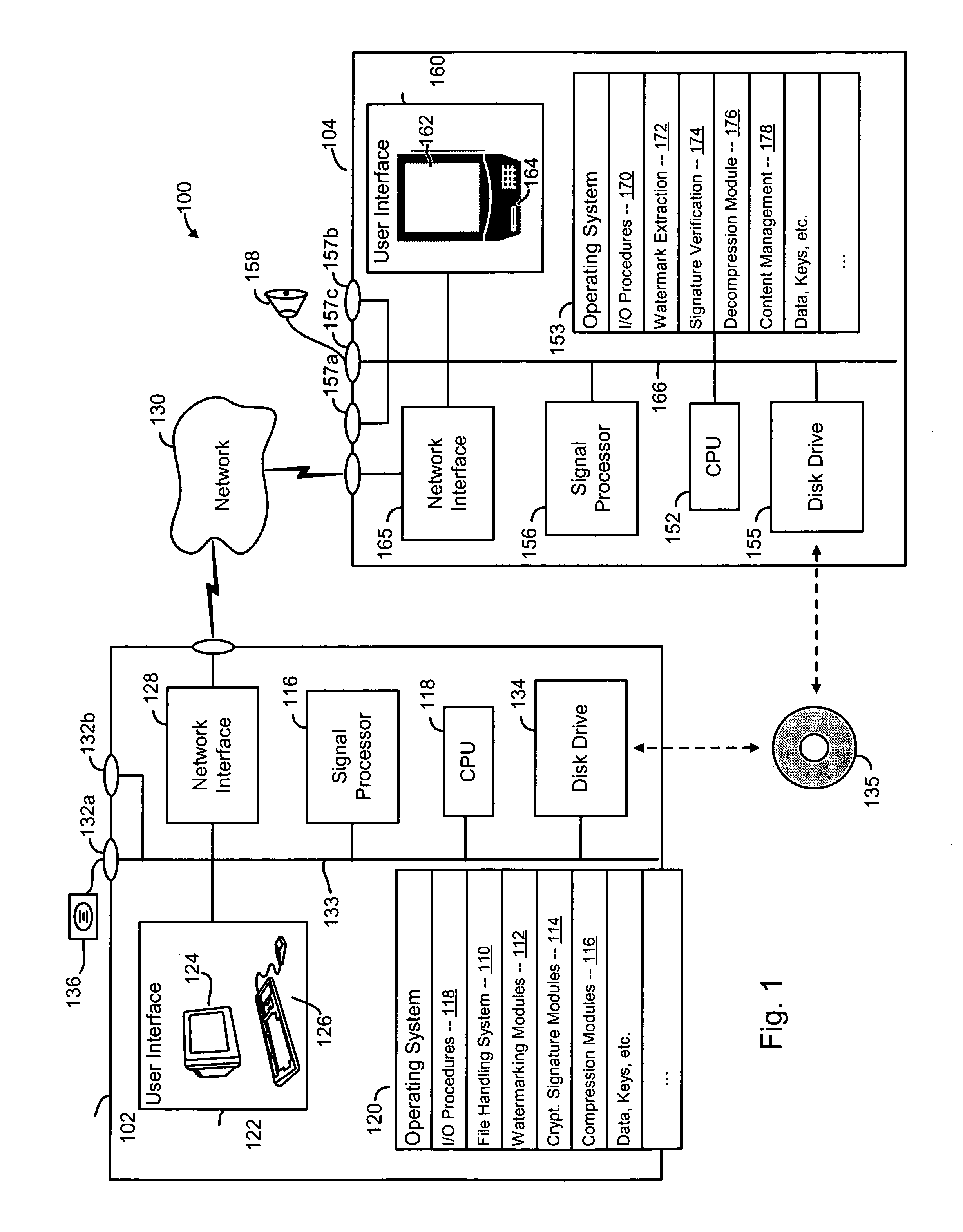
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
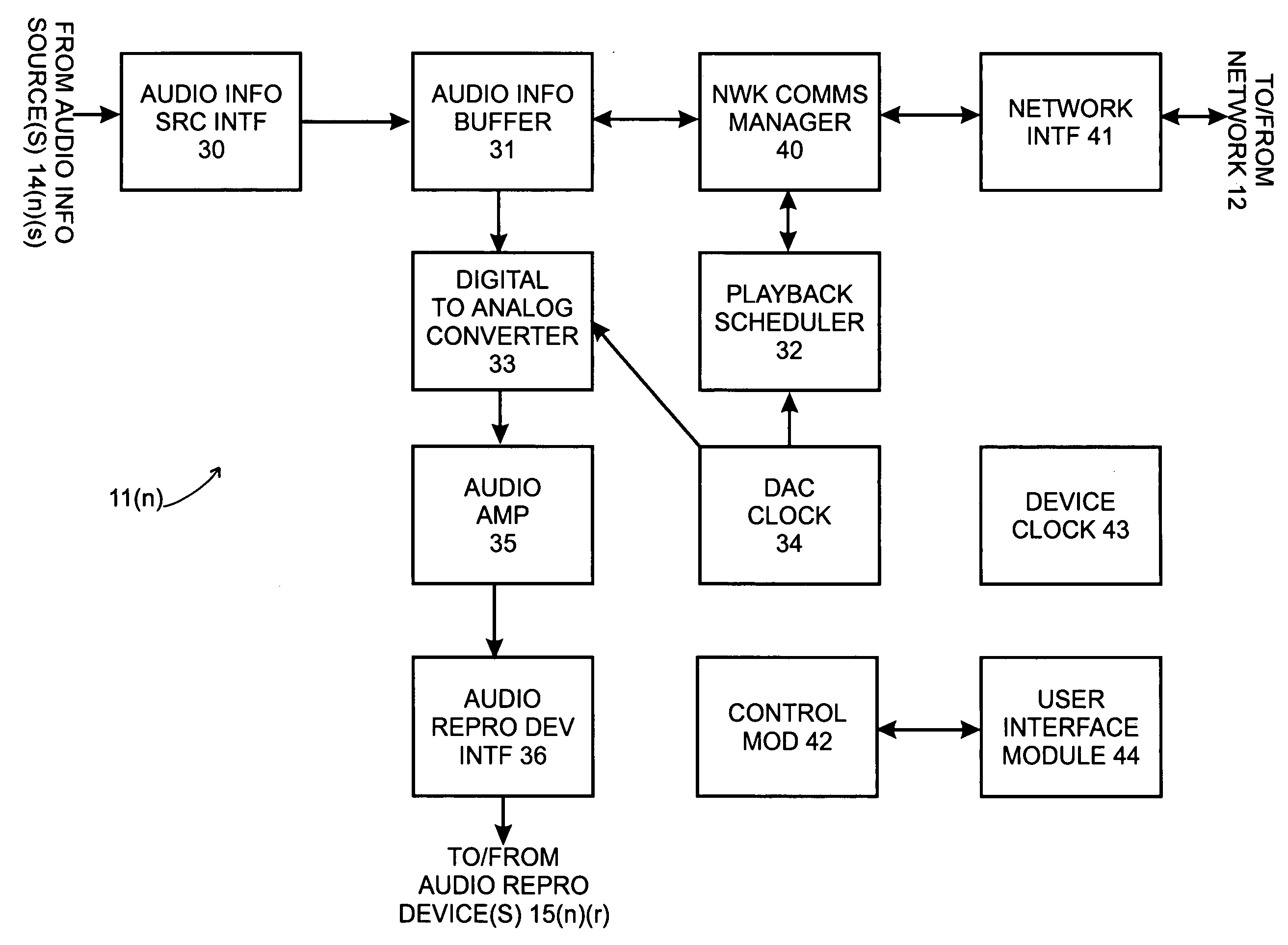
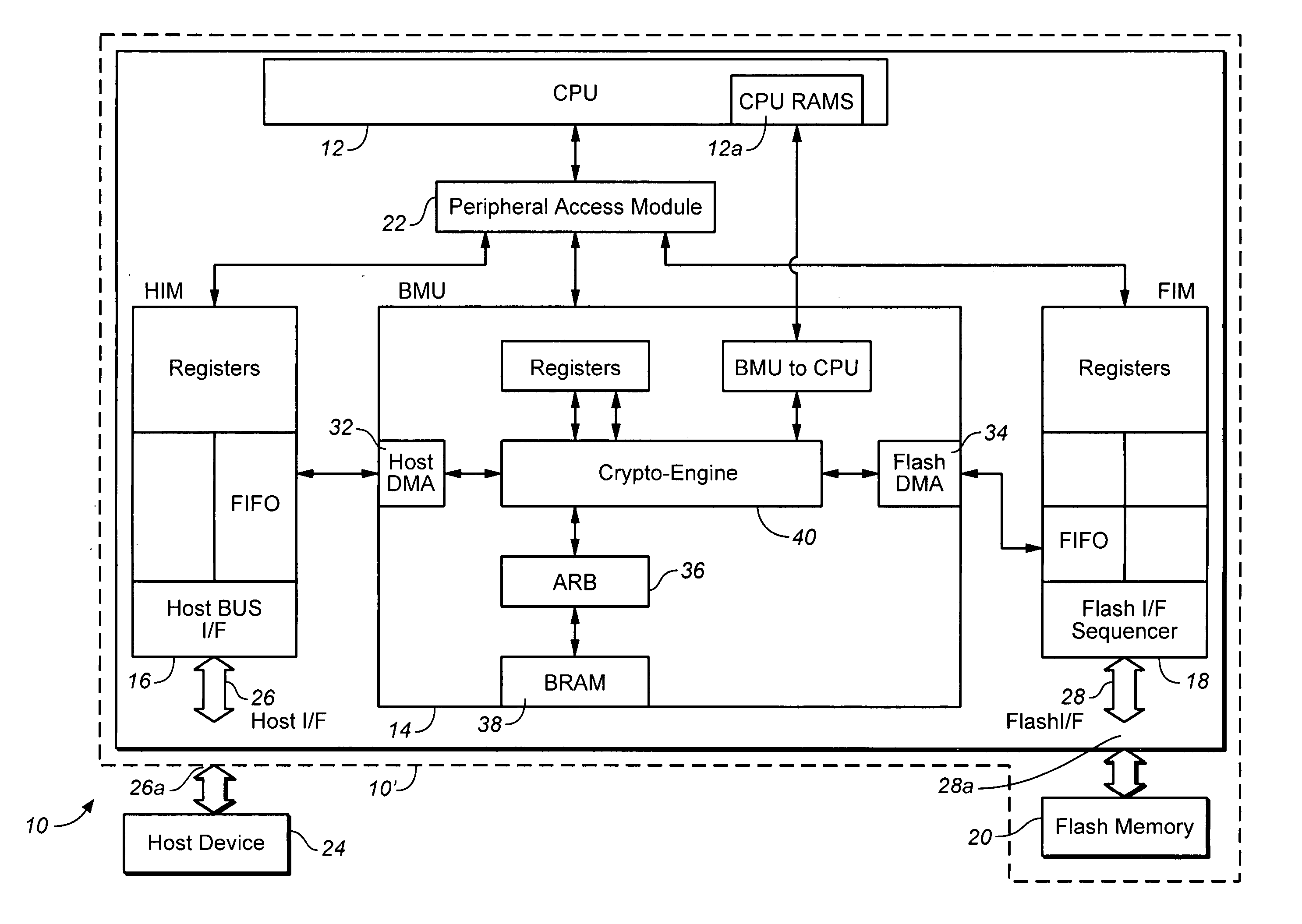
System and method for synchronizing operations among a plurality of independently clocked digital data processing devices
ActiveUS20070038999A1Maintenance operationTelevision system detailsGain controlElectronic data processingIndependent clock
A system is described for maintaining synchrony of operations among a plurality of devices that have independent clocking arrangements. The system includes a task distribution device that distributes tasks to a synchrony group comprising a plurality of devices that are to perform the tasks distributed by the task distribution device in synchrony. The task distribution device distributes each task to the members of the synchrony group over a network. Each task is associated with a time stamp that indicates a time, relative to a clock maintained by the task distribution device, at which the members of the synchrony group are to execute the task. Each member of the synchrony group periodically obtains from the task distribution device an indication of the current time indicated by its clock, determines a time differential between the task distribution device's clock and its respective clock and determines therefrom a time at which, according to its respective clock, the time stamp indicates that it is to execute the task.
Owner:SONOS
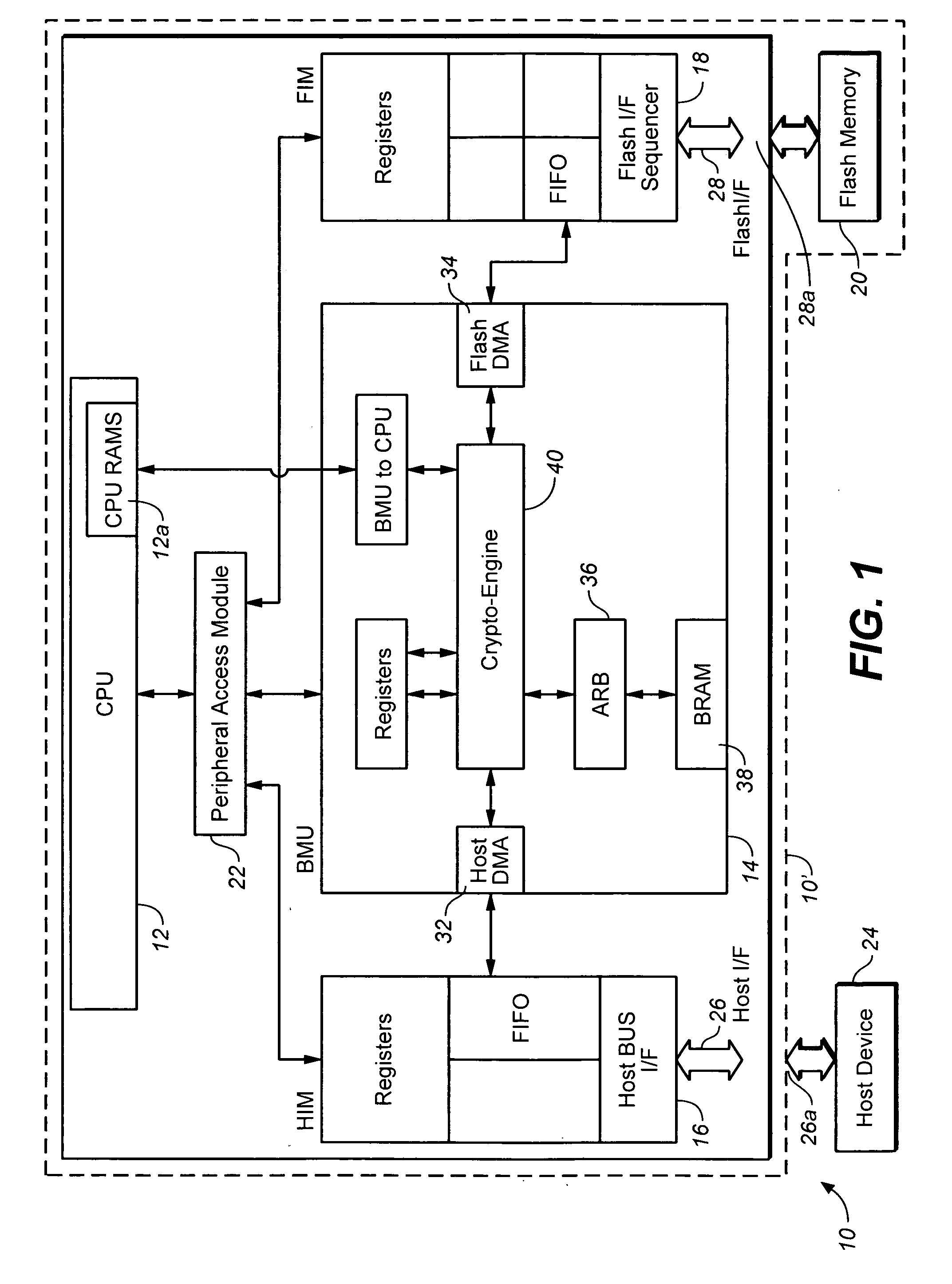
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
Digital authentication with digital and analog documents
InactiveUS20040153649A1More dataCompact formDigitally marking record carriersDigital data processing detailsAuthentication information
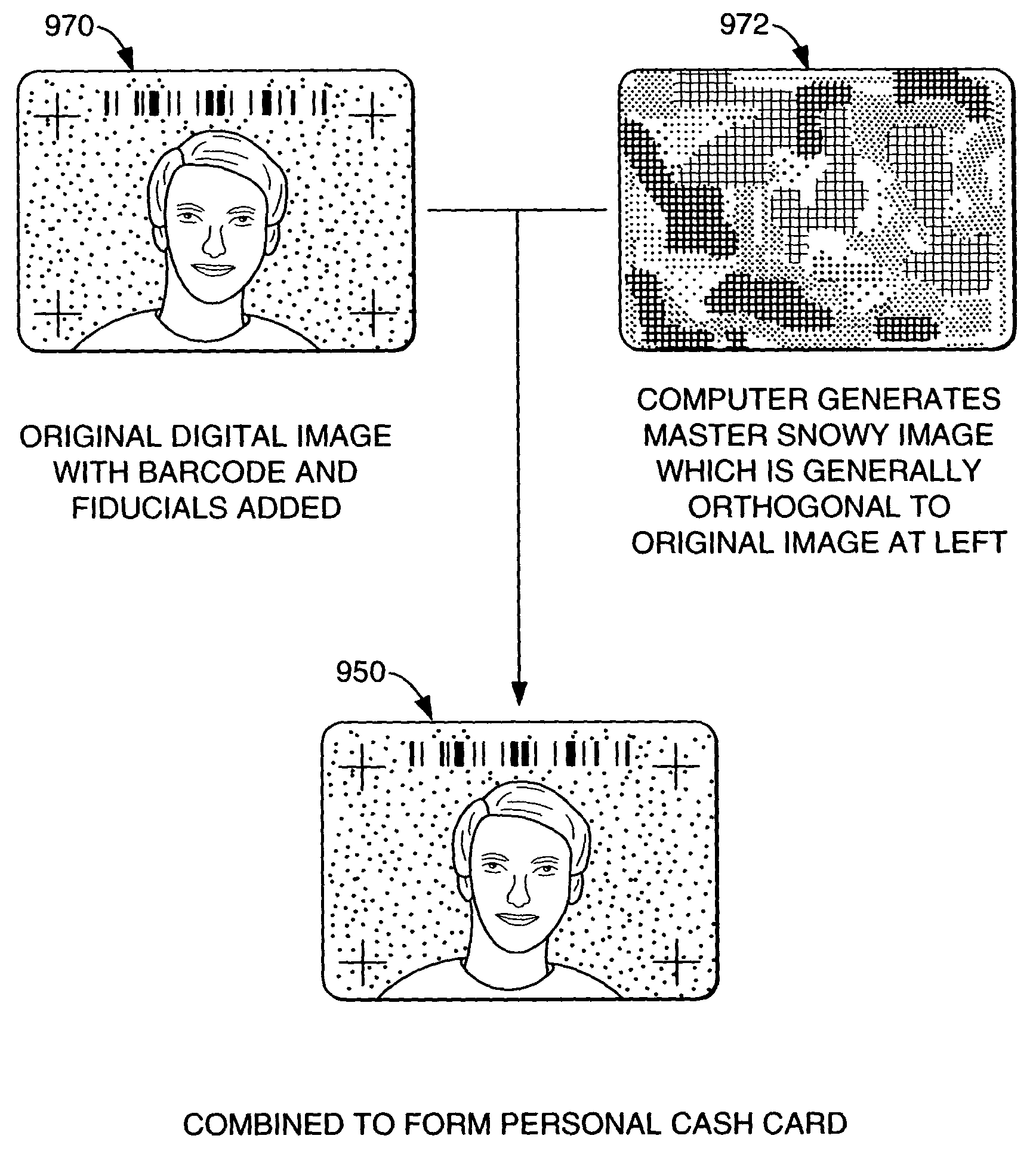
The disclosure describes systems for creating and authenticating printed objects using authentication information. Techniques for incorporating authentication information into digital representations of objects and using the authentication information to authenticate the objects are also provided.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
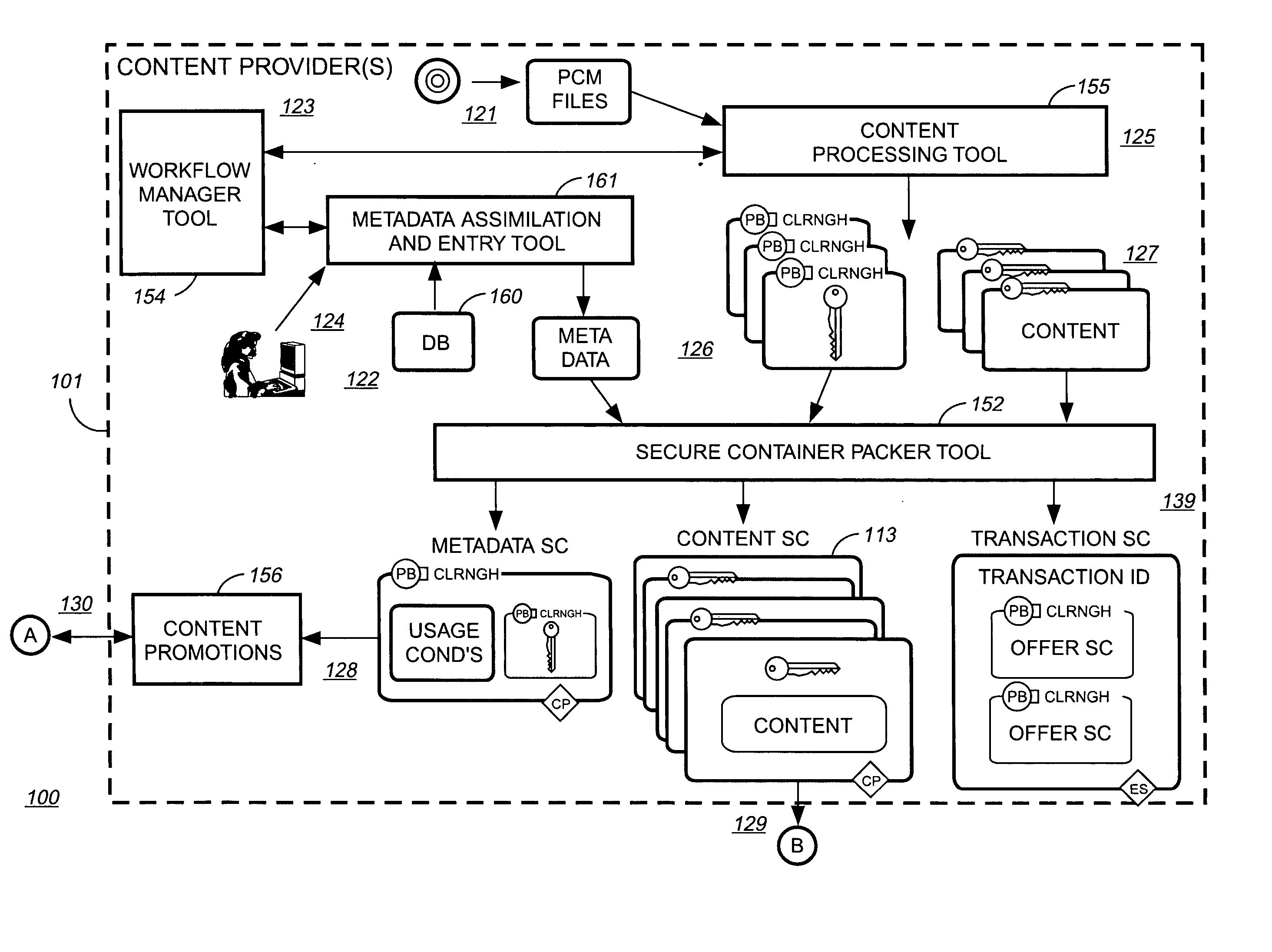
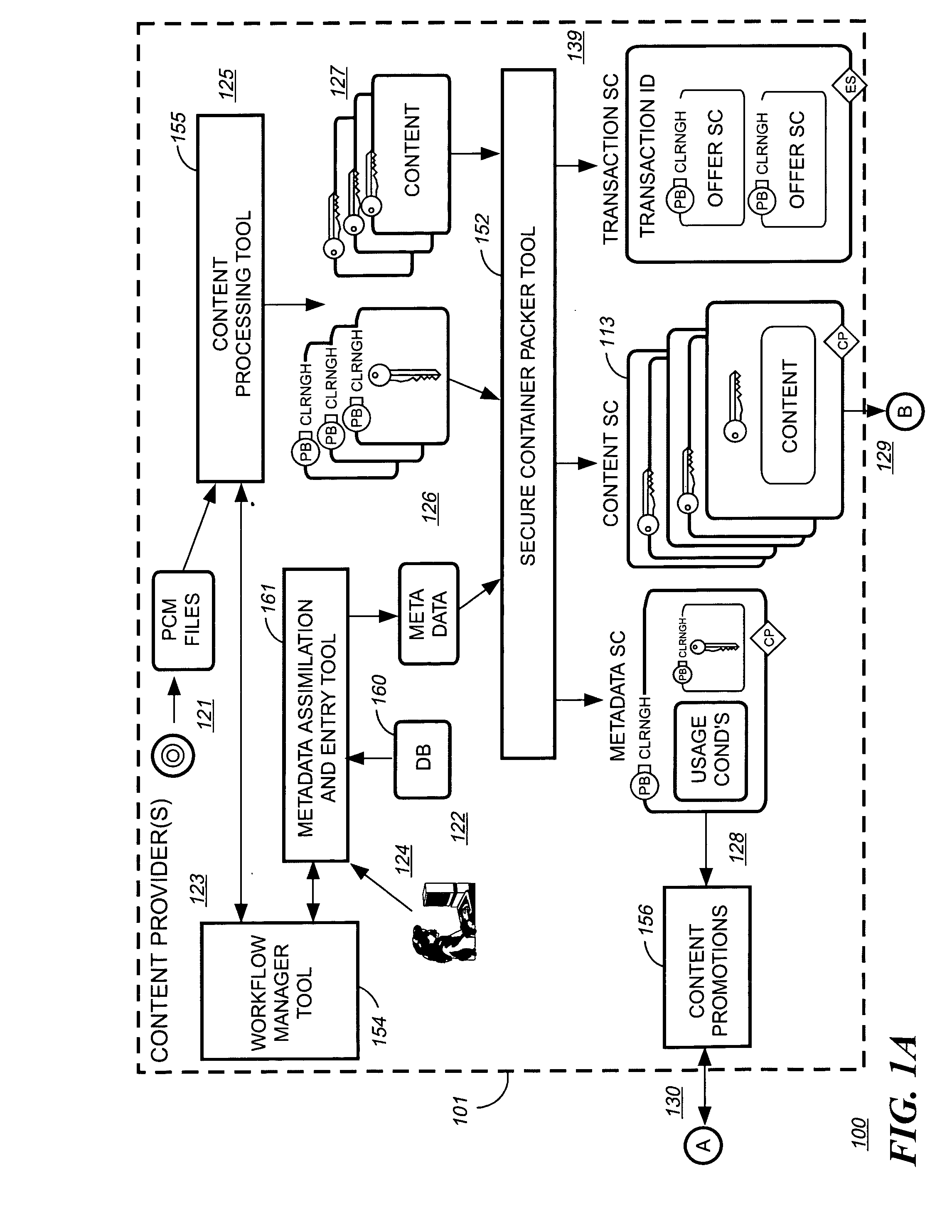
Method and system for securing local database file of local content stored on end-user system
InactiveUS20020002468A1Digital data processing detailsUnauthorized memory use protectionDatasheetDigital content
A method and system for forming a data table in memory on an end user system. The data table forming a library index of storage locations to electronic digital content in memory. The method consists of retrieving an encrypted file from storage. The file has a beginning, an end and a trailer section located just prior to the end. The file is read from the end a predetermined distance to verify if an identifier is present. Reading and decrypting the trailer section from the file read. Determining if there are any updates in the trailer section. In the case there are no updates in the trailer section then decrypting the reference table containing one or more data table location indicators for data items with the first decrypting key. Next, decrypting one or data items with the first decrypting key. Populating the data table with data items at locations specified in the reference table.
Owner:IBM CORP
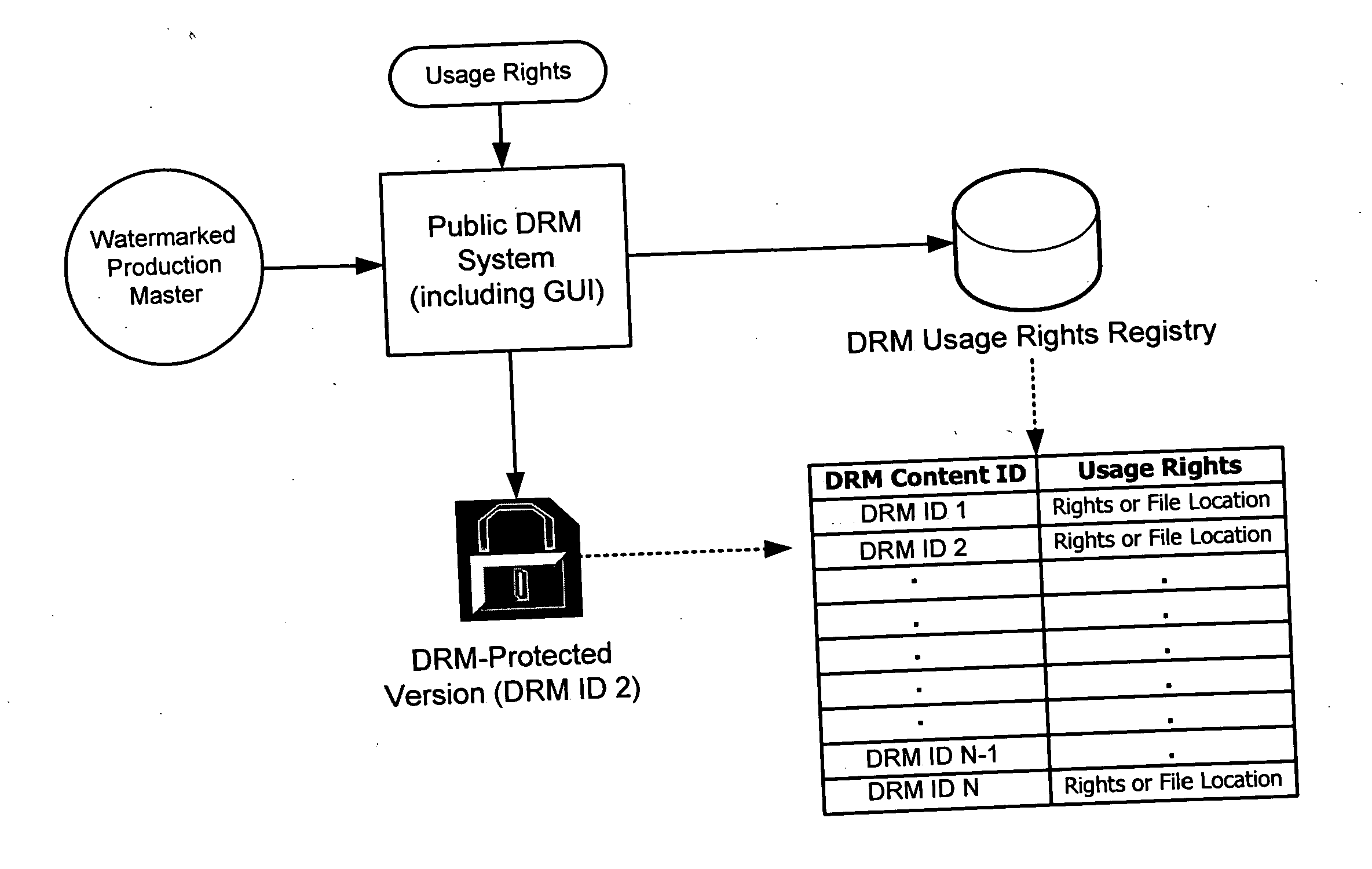
Rights management systems and methods using digital watermarking
ActiveUS20060062426A1Difficult to controlDifficult to trackUser identity/authority verificationAnalogue secracy/subscription systemsContent IdentifierRights management
A digital watermark (DWM) content identifier is steganographically embedded in content. The DWM content identifier provides a link to a rights registry storing usage rights associated with the content. In some implementations the rights registry provides an association between the DWM content identifier and a digital rights management (DRM) content identifier. The DRM content identifier is used to find associated usage rights. The DWM content identifier can also be used to transfer content from a first DRM system to a second DRM system.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Method and apparatus for content protection in a personal digital network environment
InactiveUS20050144468A1Easy to disassembleReliable lockingTelevision system detailsUser identity/authority verificationGraphicsVideo processing
In some embodiments, the invention is a personal digital network (“PDN”) including hardware (sometimes referred to as Ingress circuitry) configured to transcrypt encrypted content that enters the PDN. Typically, the transcryption (decryption followed by re-encryption) is performed in hardware within the Ingress circuitry and the re-encryption occurs before the decrypted content is accessible by hardware or software external to the Ingress circuitry. Typically, transcrypted content that leaves the Ingress circuitry remains in re-encrypted form within the PDN whenever it is transferred between integrated circuits or is otherwise easily accessible by software, until it is decrypted within hardware (sometimes referred to as Egress circuitry) for display or playback or output from the PDN. Typically, the PDN is implemented so that no secret in Ingress or Egress circuitry (for use or transfer by the Ingress or Egress circuitry) is accessible in unencrypted form to software or firmware within the PDN or to any entity external to the PDN. Other aspects of the invention are methods for protecting content in a PDN (e.g., an open computing system) and devices (e.g., multimedia graphics cards, set top boxes, or video processors) for use in a PDN.
Owner:OPTIMUM CONTENT PROTECTION
Method and system for exploring similarities
InactiveUS20060195790A1Record information storageData switching by path configurationDegree of similarityUser interface
A method and computer readable medium for exploring similar users and items of a media service. In one aspect, a user can explore for similar users iteratively. In one aspect, a user interface is generated that displays a user selectable indicia representing a similar member function for allowing a user to search a media service for at least one other user which has a degree of similarity with respect to the searching user. In another aspect, a method facilitates the search of such a similar user within a media service.
Owner:HUAWEI TECH CO LTD
Method of linking on-line data to printed documents
InactiveUS7051086B2Readily apparentRecord information storageMultiple digital computer combinationsGraphicsBusiness card
The present invention relates to linking on-line data to printed documents, such as business cards, envelopes, stickers, stationary, letterhead, résumés, etc. In one embodiment, a card-user registers with an on-line database and receives a gallery item including a steganographically-embedded unique identifier. The gallery item, such as a graphical background, text, shading, graphic, etc., is integrated and then printed with a document. The printed document can then be presented an optical-scanner, which outputs data. The output data is decoded to identify the unique identifier. The unique identifier is then used to index into the on-line database to retrieve information related to the proprietor of the document. In one embodiment, the on-line database includes features such as providing an immediate contact number, translation and / or pronunciation ability, and storage of audio / video files.
Owner:DIGIMARC CORP
Embedding auxiliary signals with multiple components into media signals
InactiveUS7113614B2Television system detailsCoin-freed apparatusDigital watermarkingComputer science
Owner:DIGIMARC CORP
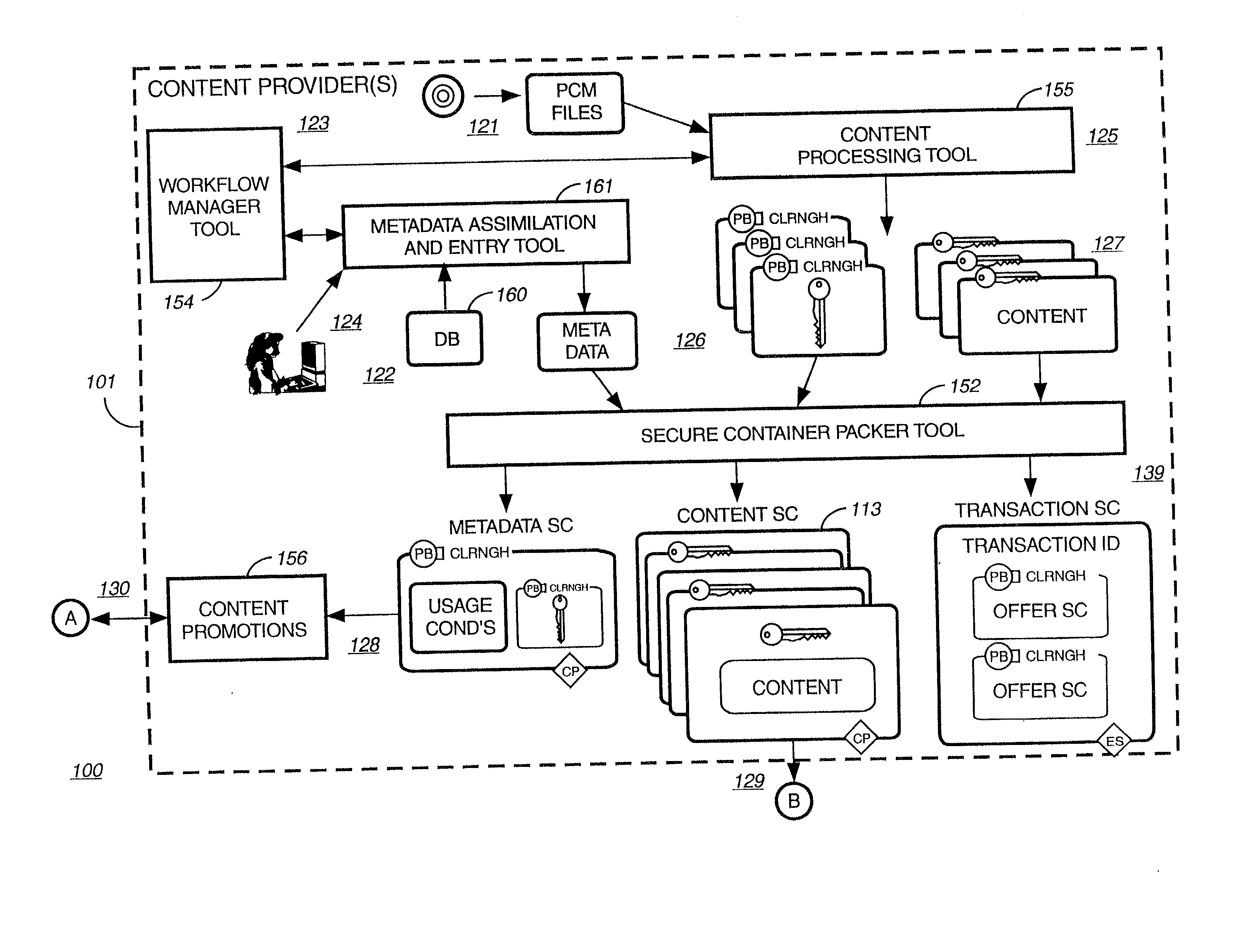
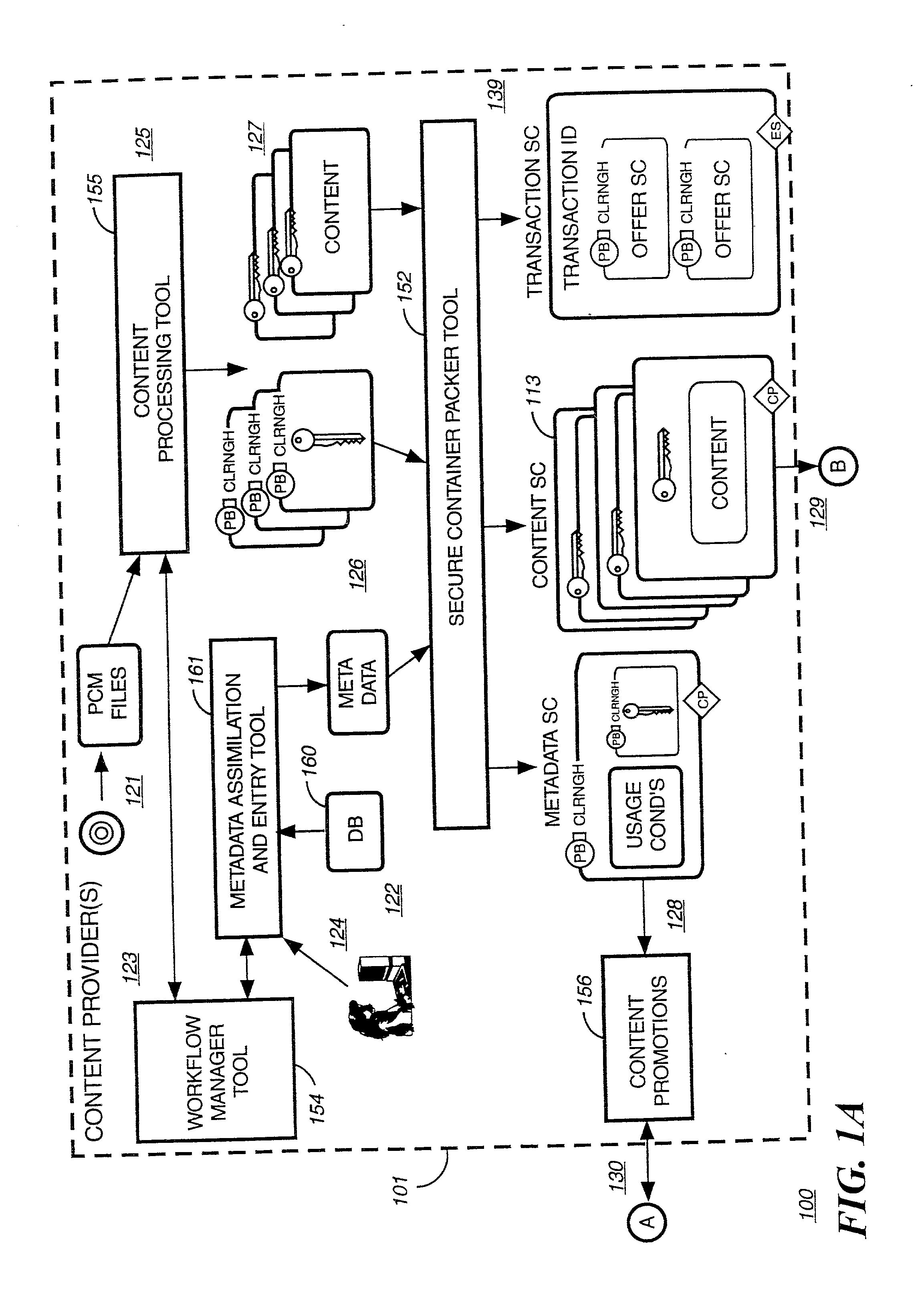
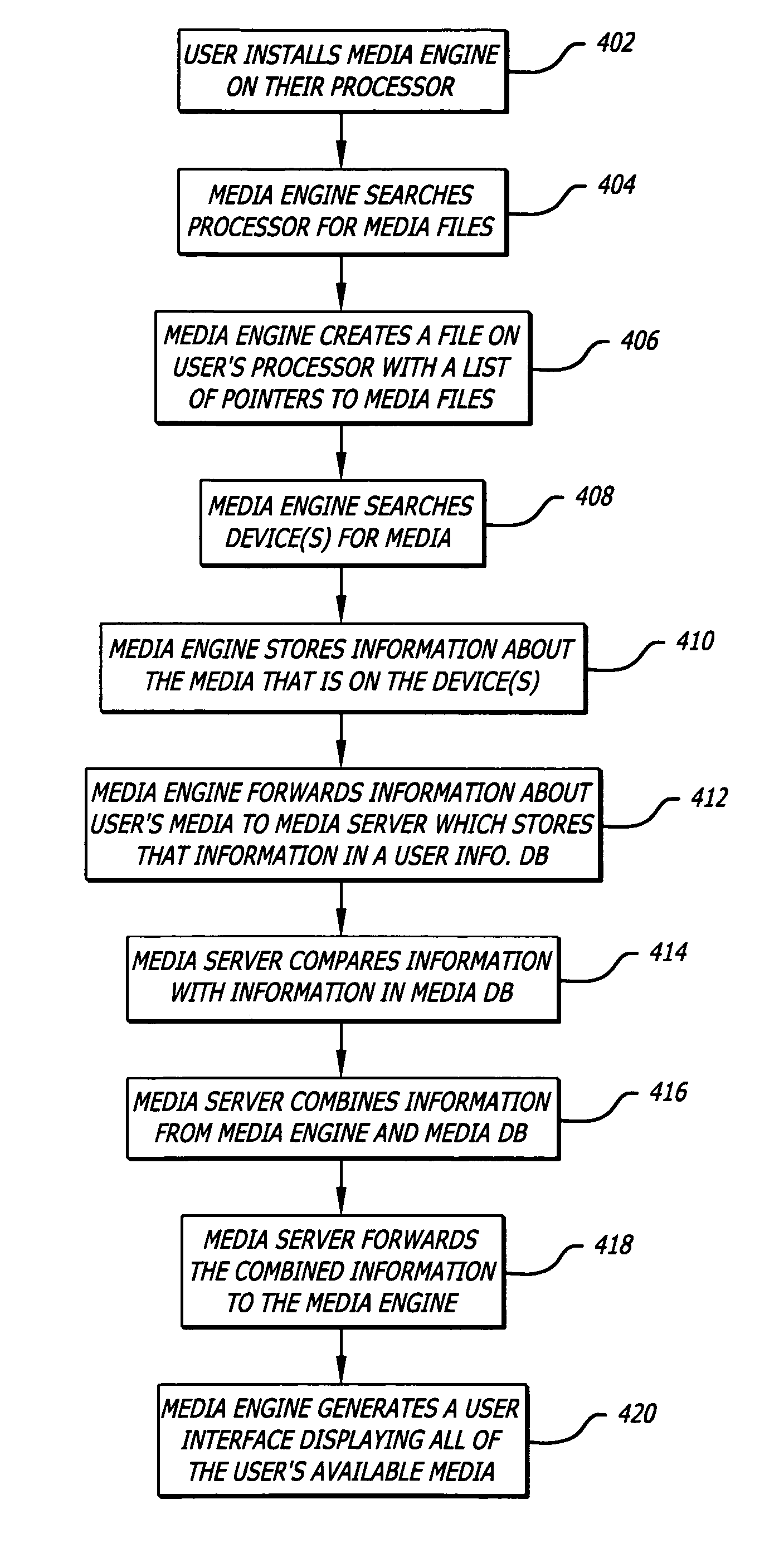
Method for secure storage and delivery of media content
InactiveUS20070043667A1Easy accessSimple manufacturing processRecord information storageInternal/peripheral component protectionContent distributionService provision
The memory device contains control structures that allow media content to be stored securely and distributed in a manner envisioned by the content owner, or service providers involved in the distribution. A wide variety of different avenues become available for distributing media content using such memory devices, such as where the devices contain one or more of the following: abridged preview media content, encrypted unabridged media content, prepaid content, rights and / or rules governing access to such content. The memory device has a type of control structures that enable a service provider (who can also be the content owner) to create a secure environment for media content distribution where end users and terminals register with the service provider, and gain access to the content in a manner controlled by the service provider. The various components to be loaded (e.g. abridged preview media content, encrypted unabridged media content, prepaid content, rights and / or rules governing access to such content) may be generated and loaded in a secure and efficient manner.
Owner:SANDISK TECH LLC
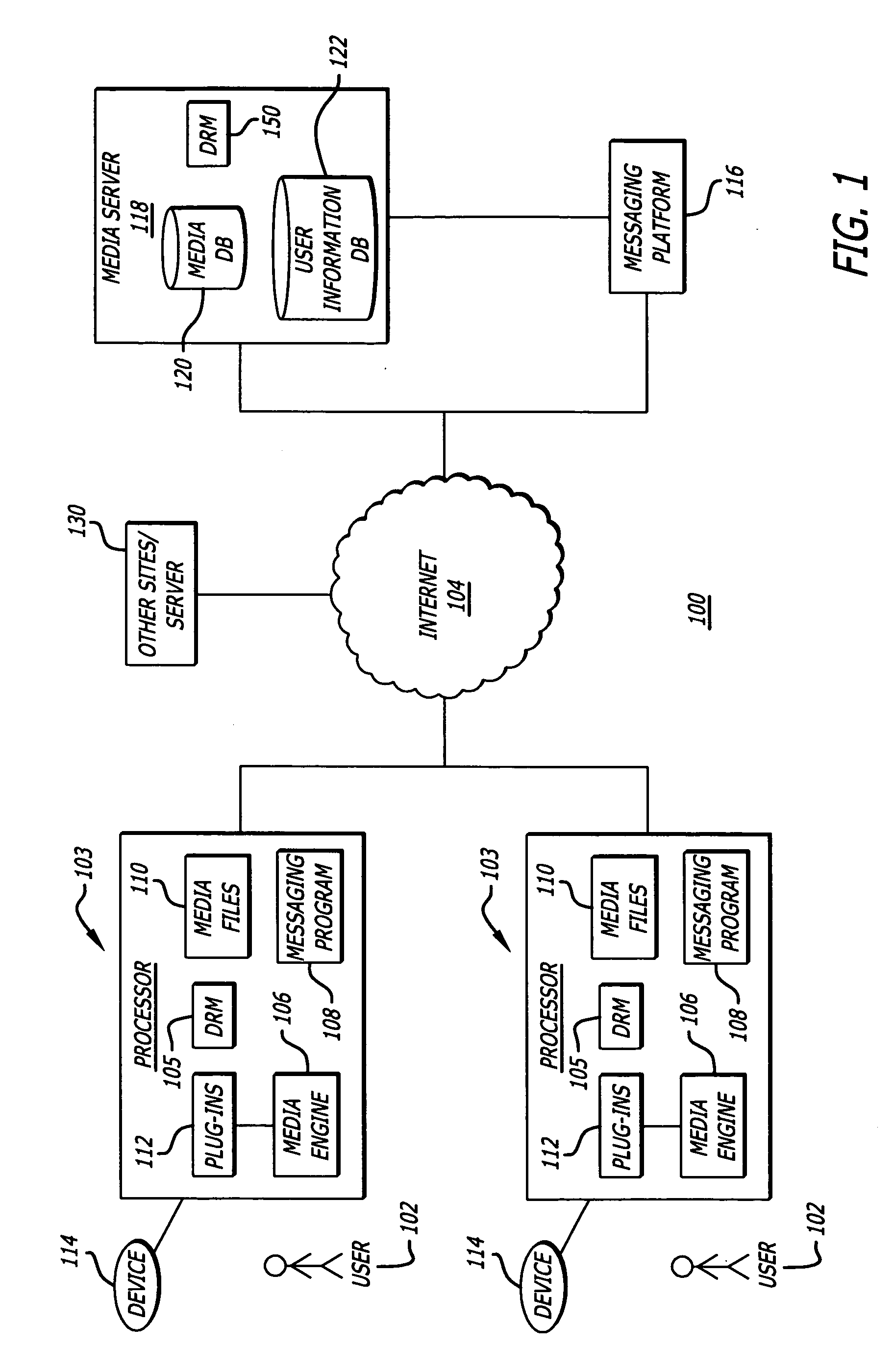
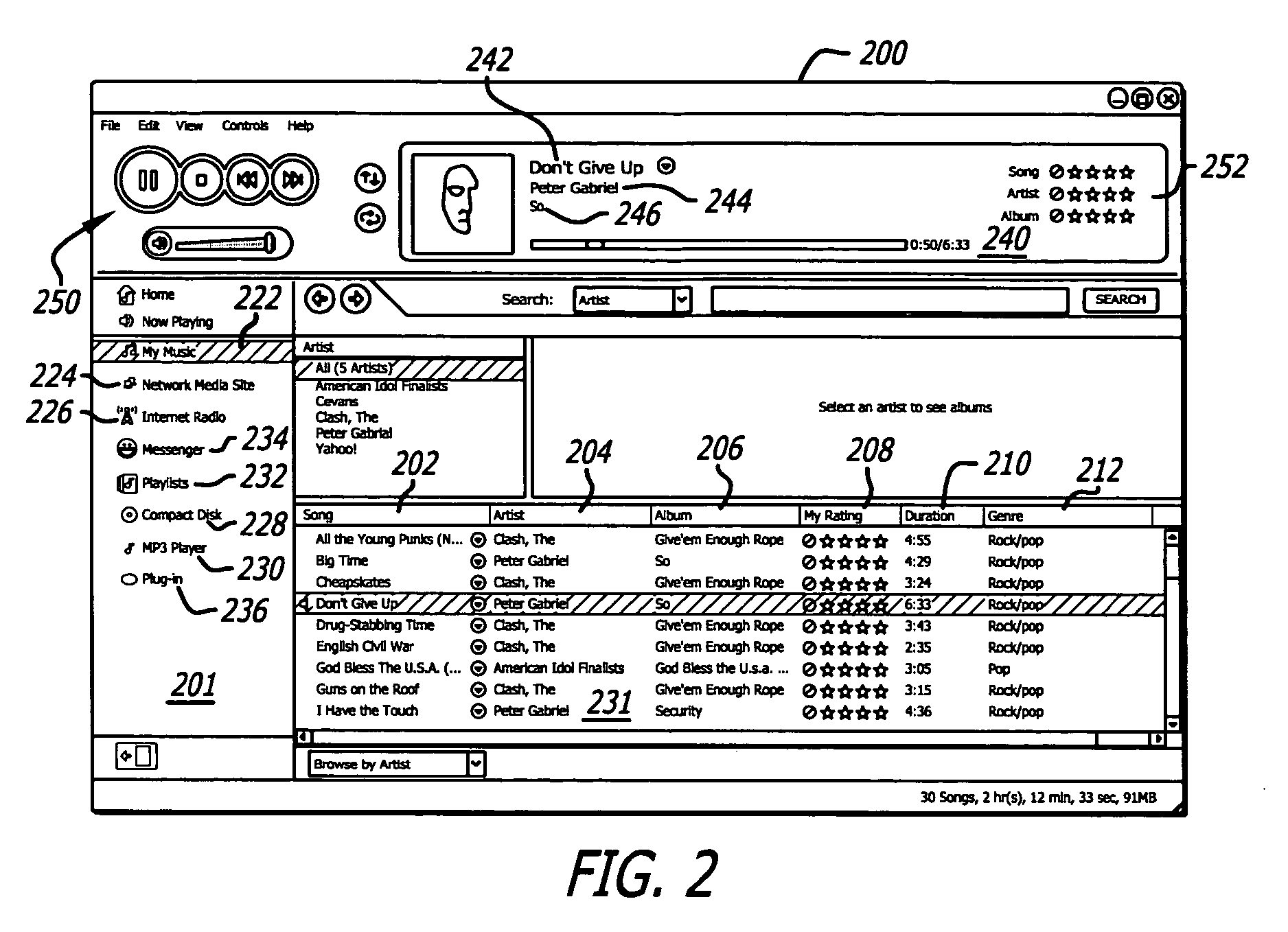
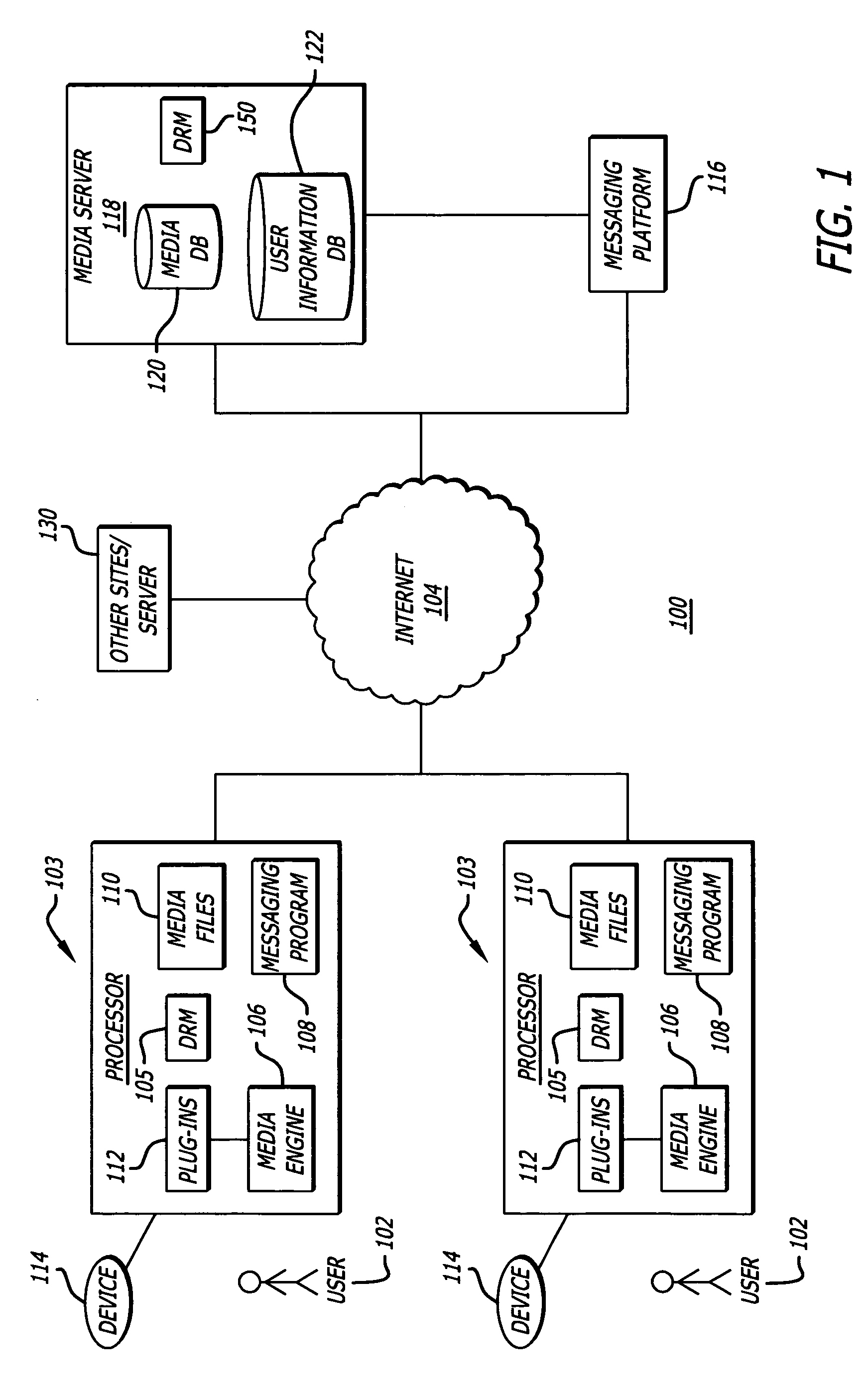
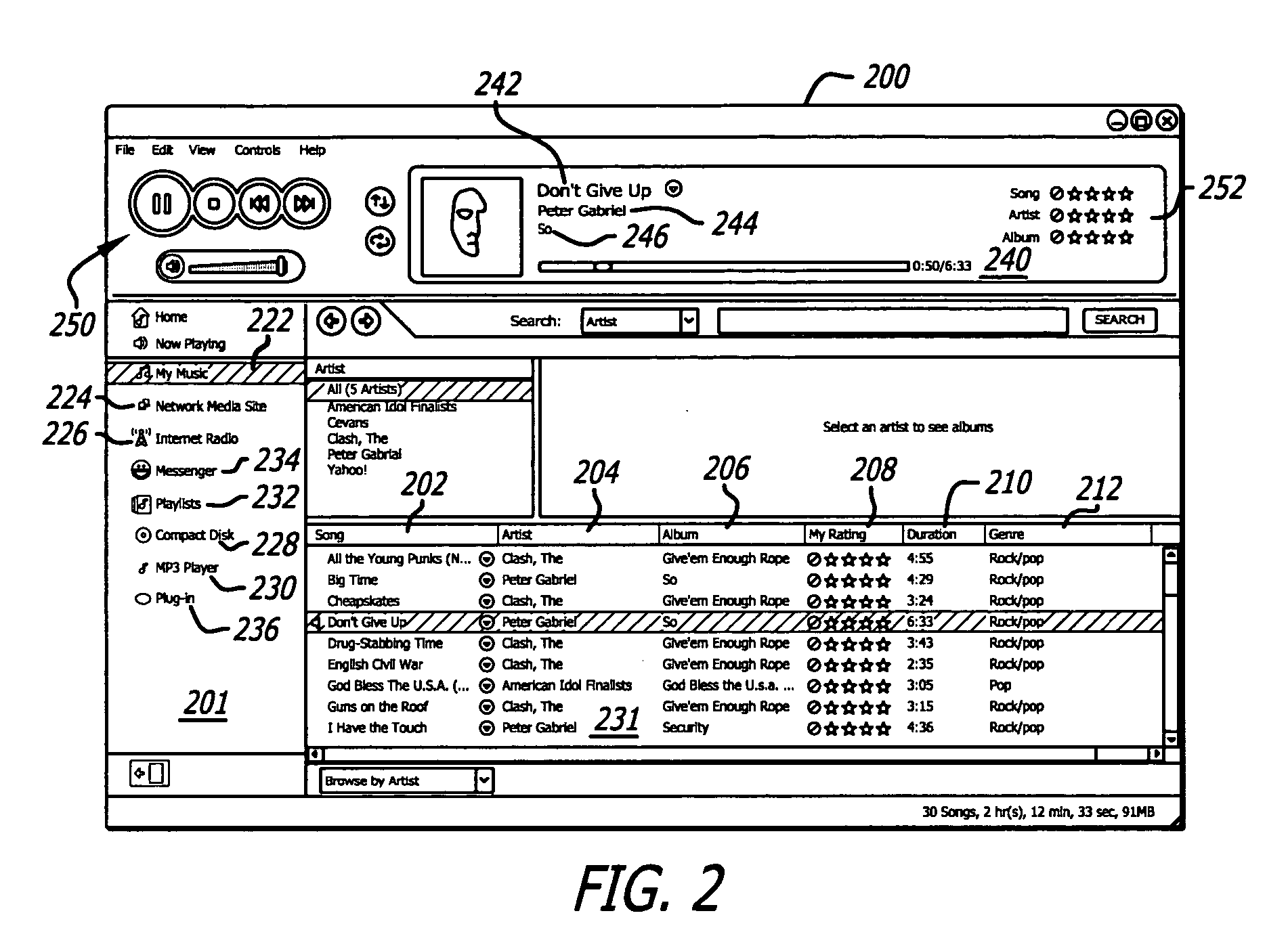
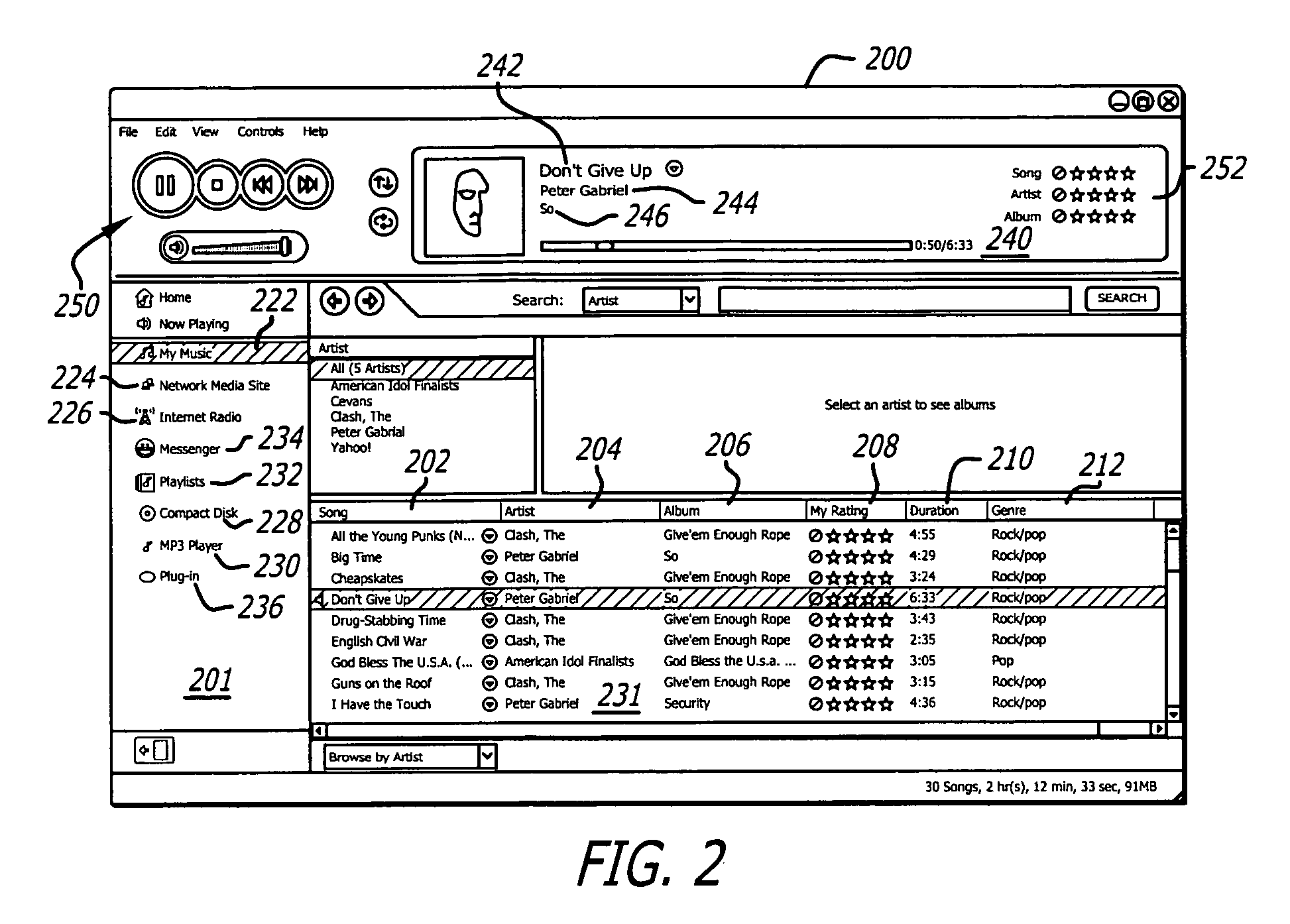
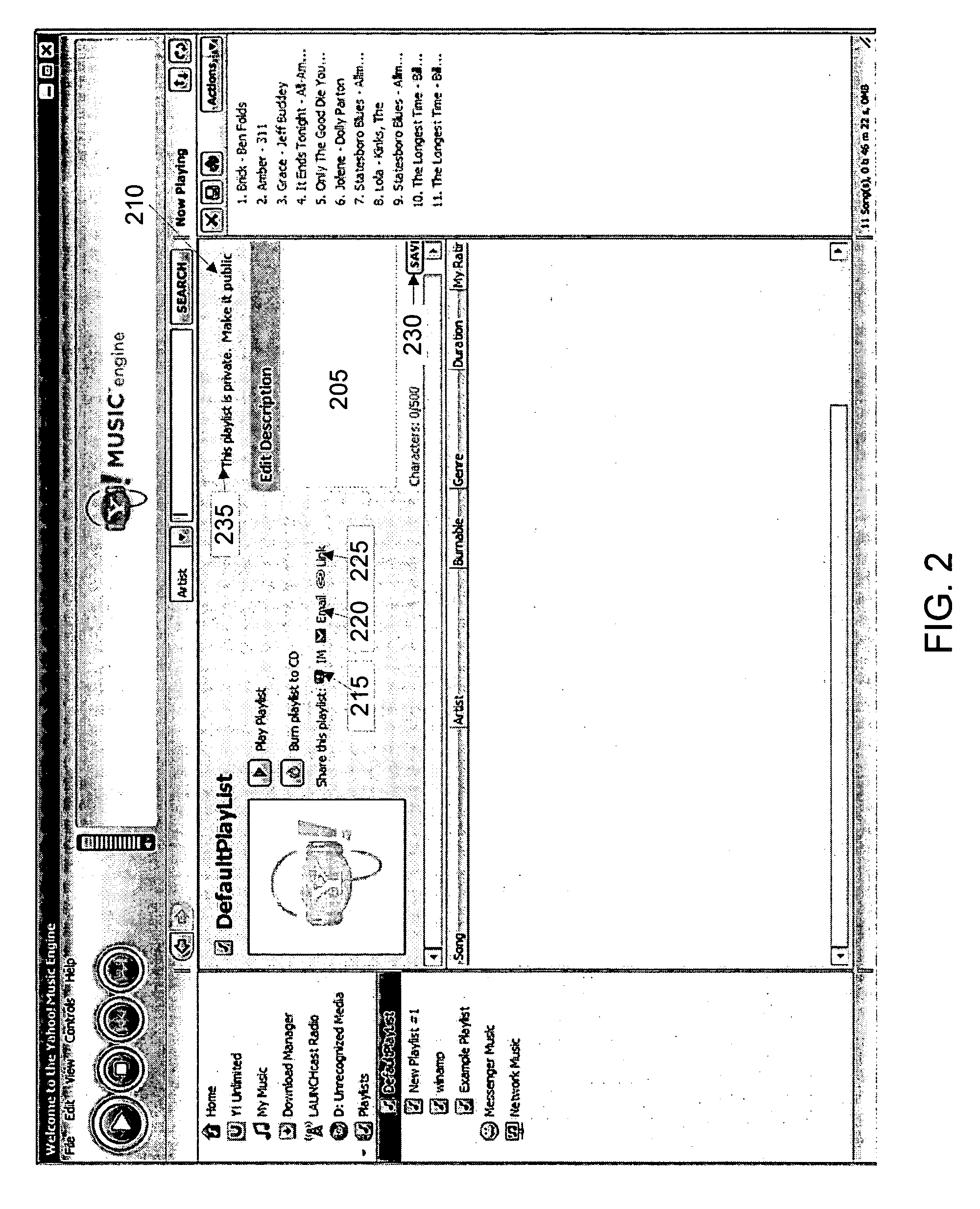
Media engine user interface
ActiveUS20060195789A1Record information storagePayment architectureApplication softwareMessage passing
A user interface and associated computer readable medium for a user interface within a media management application. In one aspect, the user interface comprises a plurality of panes displaying a list of one or more media file sources, a list of user selectable media file identifiers, selected information associated with the listed media file identifiers, instructional information as to how a user can cause one of the panes to display selected information associated with the listed media file identifiers and a media player control interface. In one aspect, the user interface comprises panes displaying an instant messaging platform as a media file source and a list of indicia representing messaging users that a user communicates with. In another aspect, selecting the indicia representing a messaging user can cause a pane to display information associated with media files found in a media library of the selected messaging user.
Owner:HUAWEI TECH CO LTD
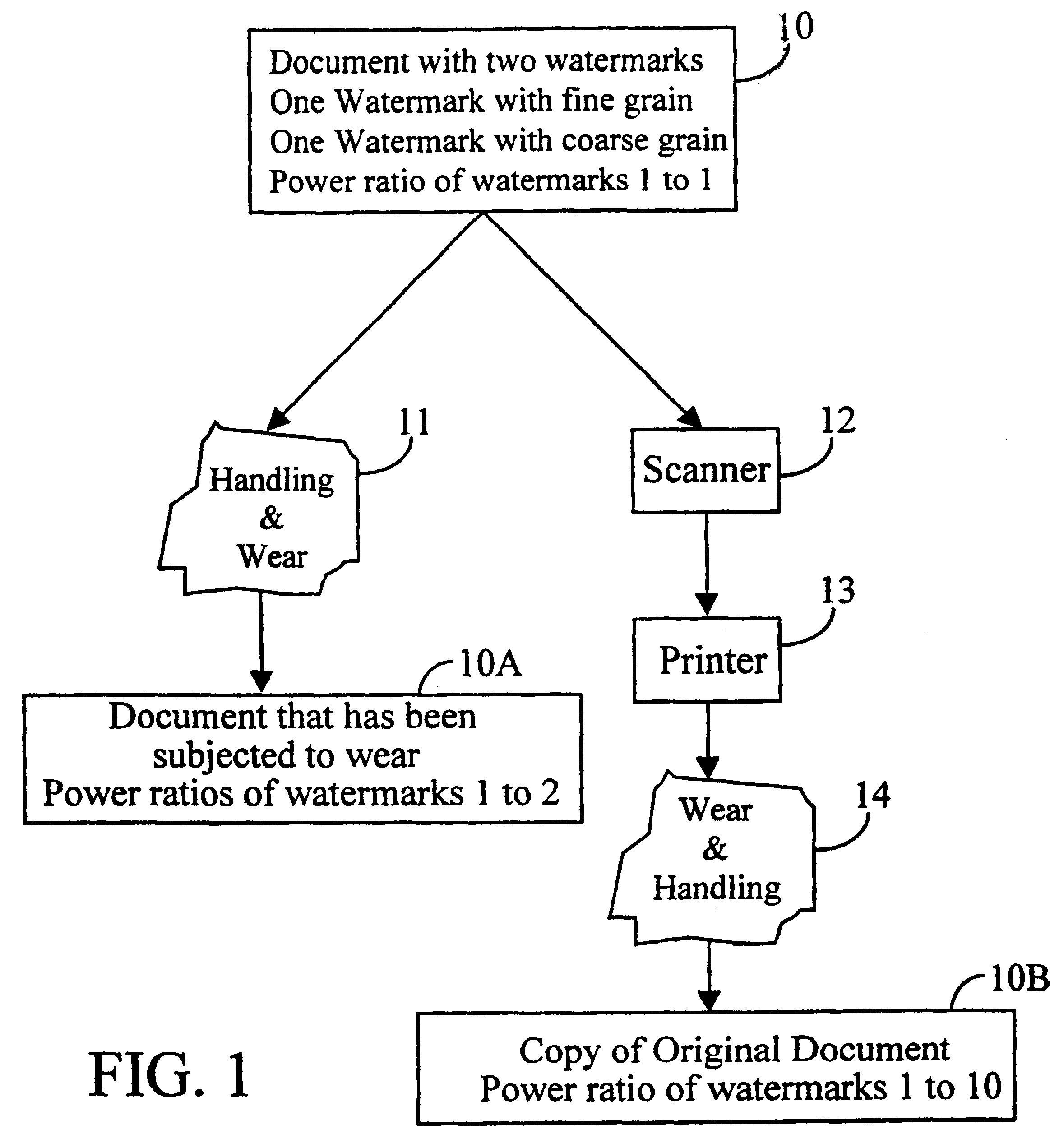
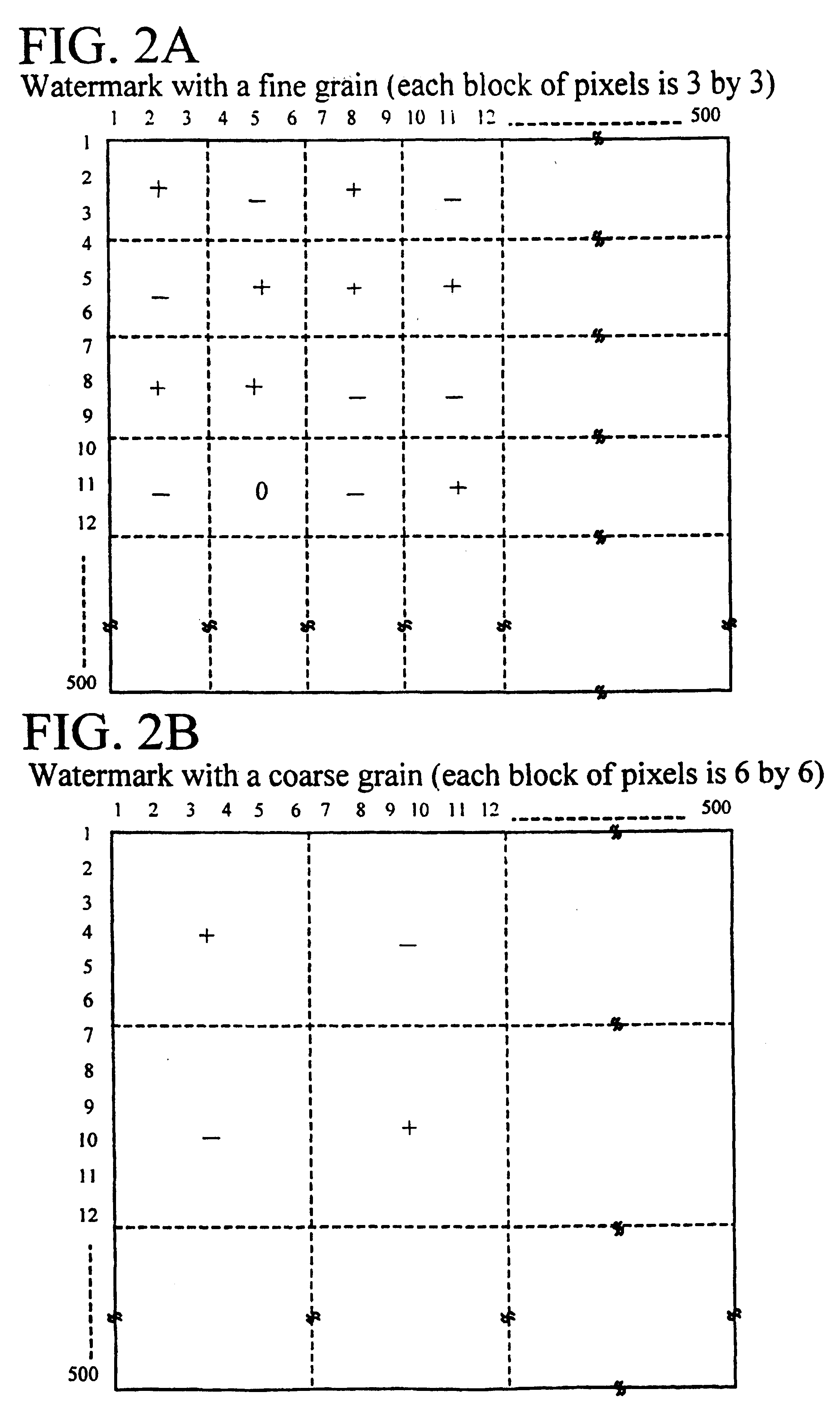
Methods and systems using multiple watermarks
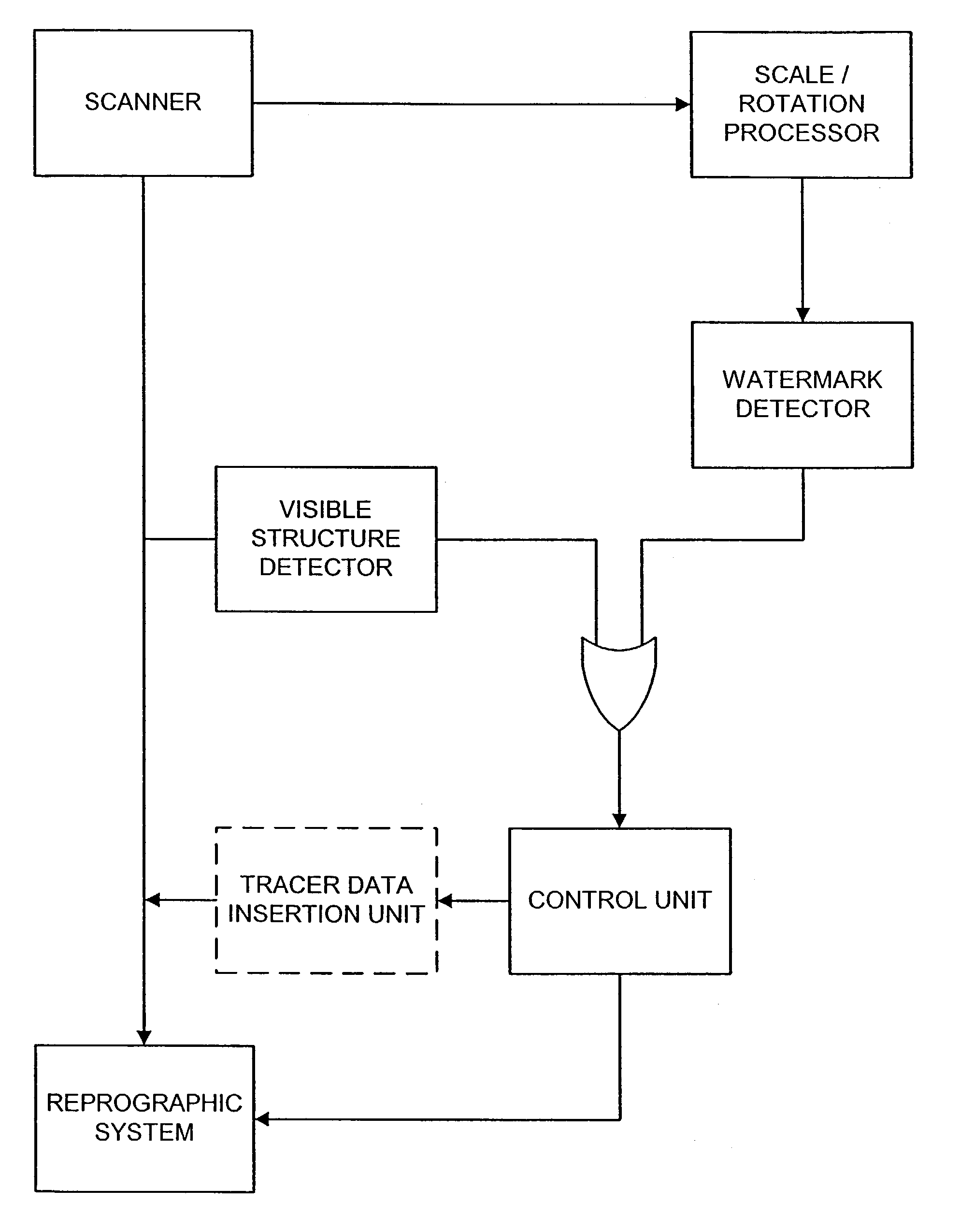
InactiveUS6636615B1Decreased energy levelImage enhancementImage analysisDocumentationDigital watermarking
Two or more digital watermarks, with different characteristics, are embedded in a document. The characteristics are chosen so that the watermarks will be affected in different manners if the document is subsequently copied or reproduced. The detection process or mechanism reads two or more of the watermarks and compares their characteristics. While wear and handling may change the characteristics of the digital watermarks in a document, the relationship between the characteristics of the multiple digital watermarks in a document will nevertheless give an indication as to whether a document is an original or a copy of an original. Document wear can be independently assessed and used as an aid in interpreting the detected watermark characteristics.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
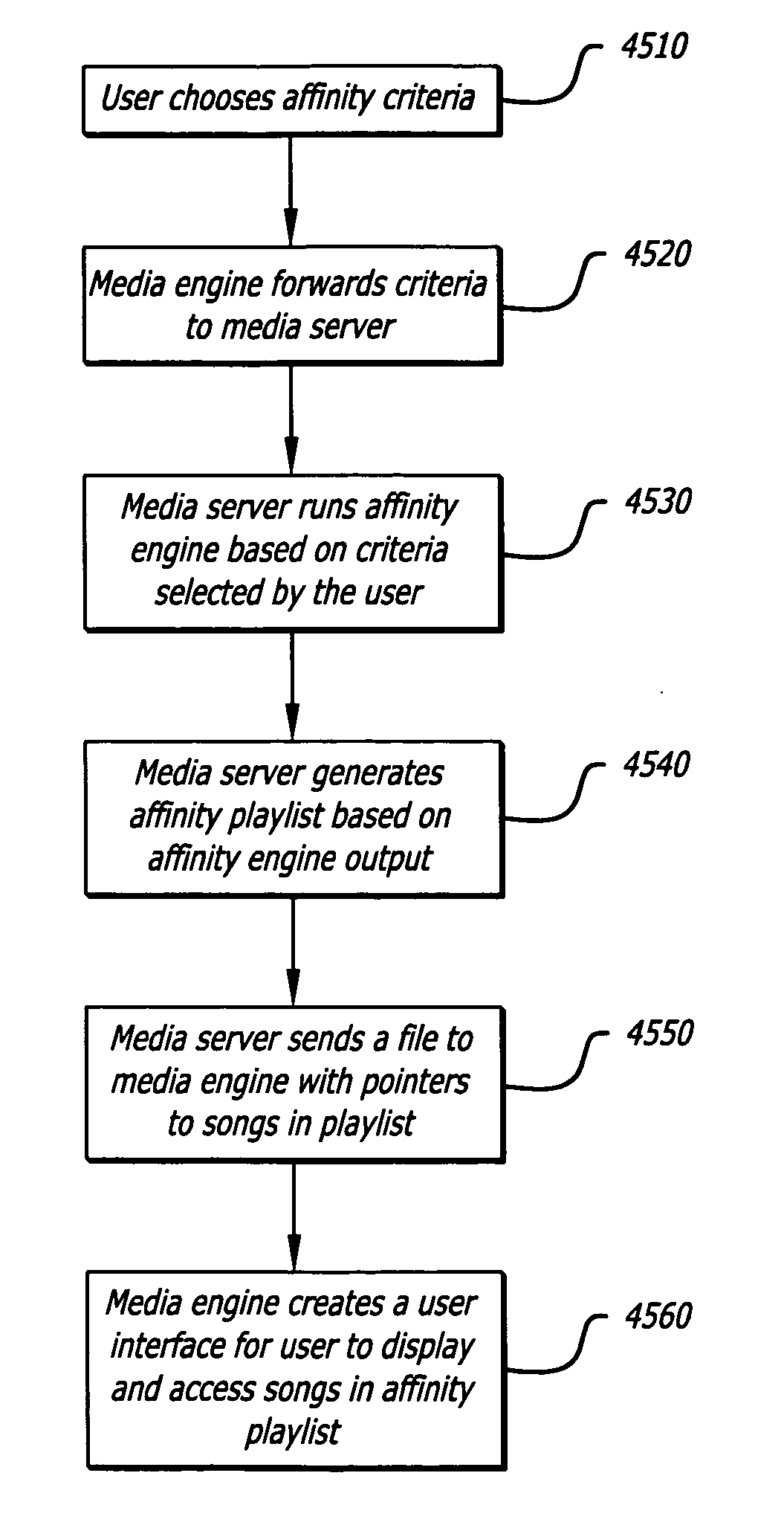
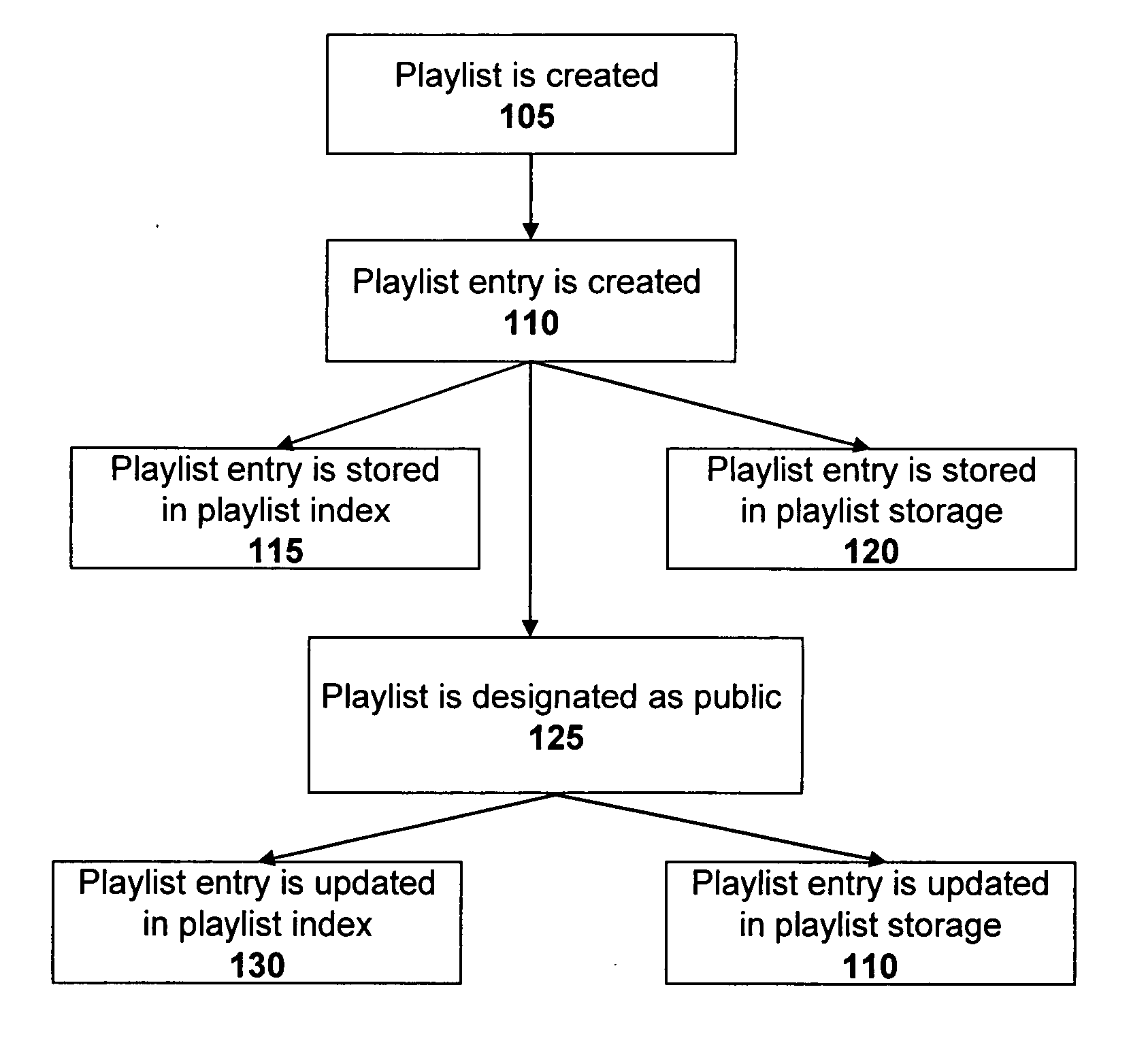
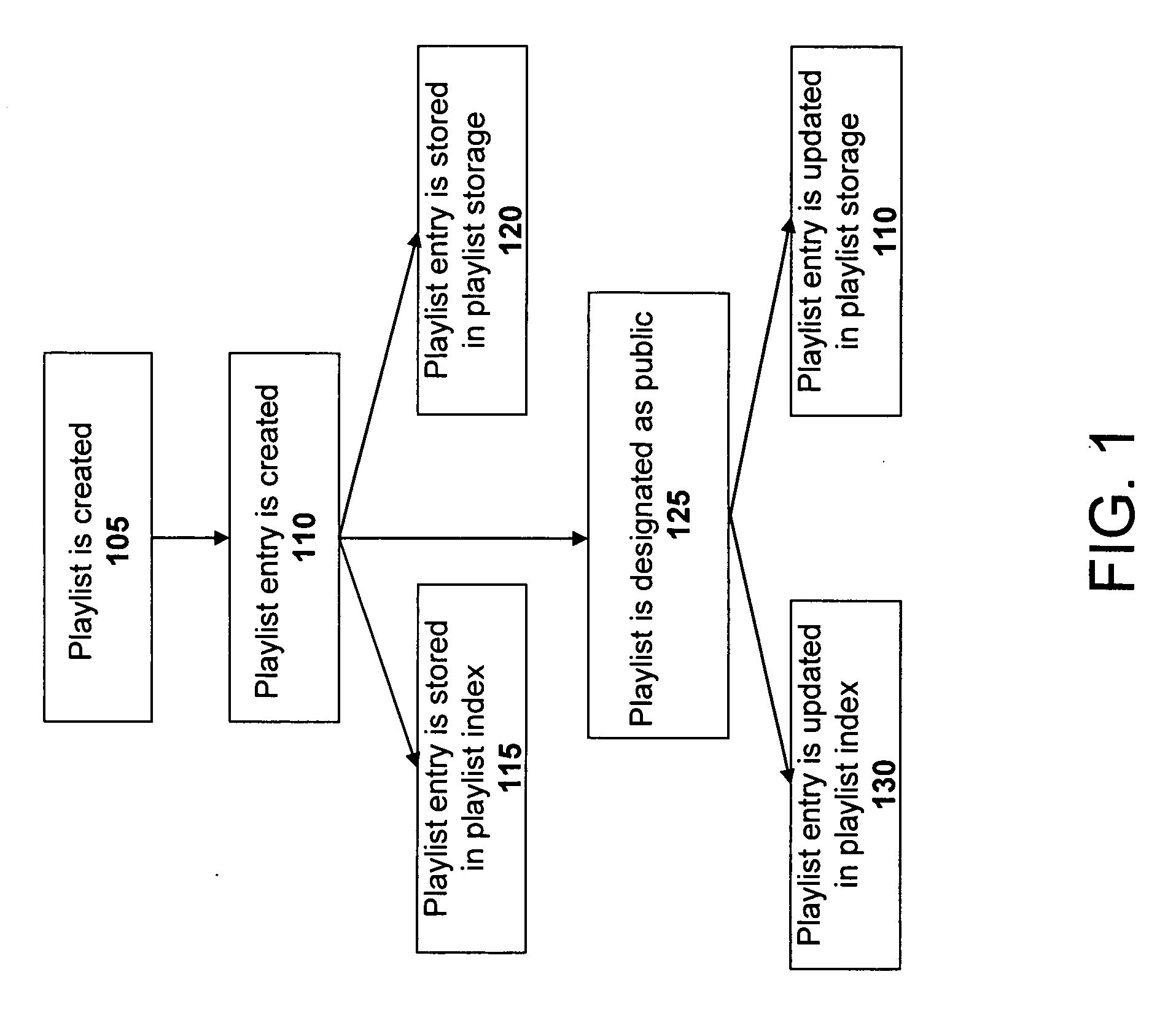
Method and system for generating affinity based playlists
ActiveUS20060195516A1Record information storageMultiple digital computer combinationsRating scoreFile attribute
A system and method of generating a playlist of affinity related media files using affinity relationship data. In one aspect the relationship affinity data is based upon a user rating score obtained from a population of user's ratings associated with media file attributes. In one aspect, a media file attribute which can include an artist, album, title, and genre information associated with a media file is received from a user, indicating the user's desire to create an affinity playlist of media files having an affinity relationship based upon the selected media file attribute.
Owner:HUAWEI TECH CO LTD
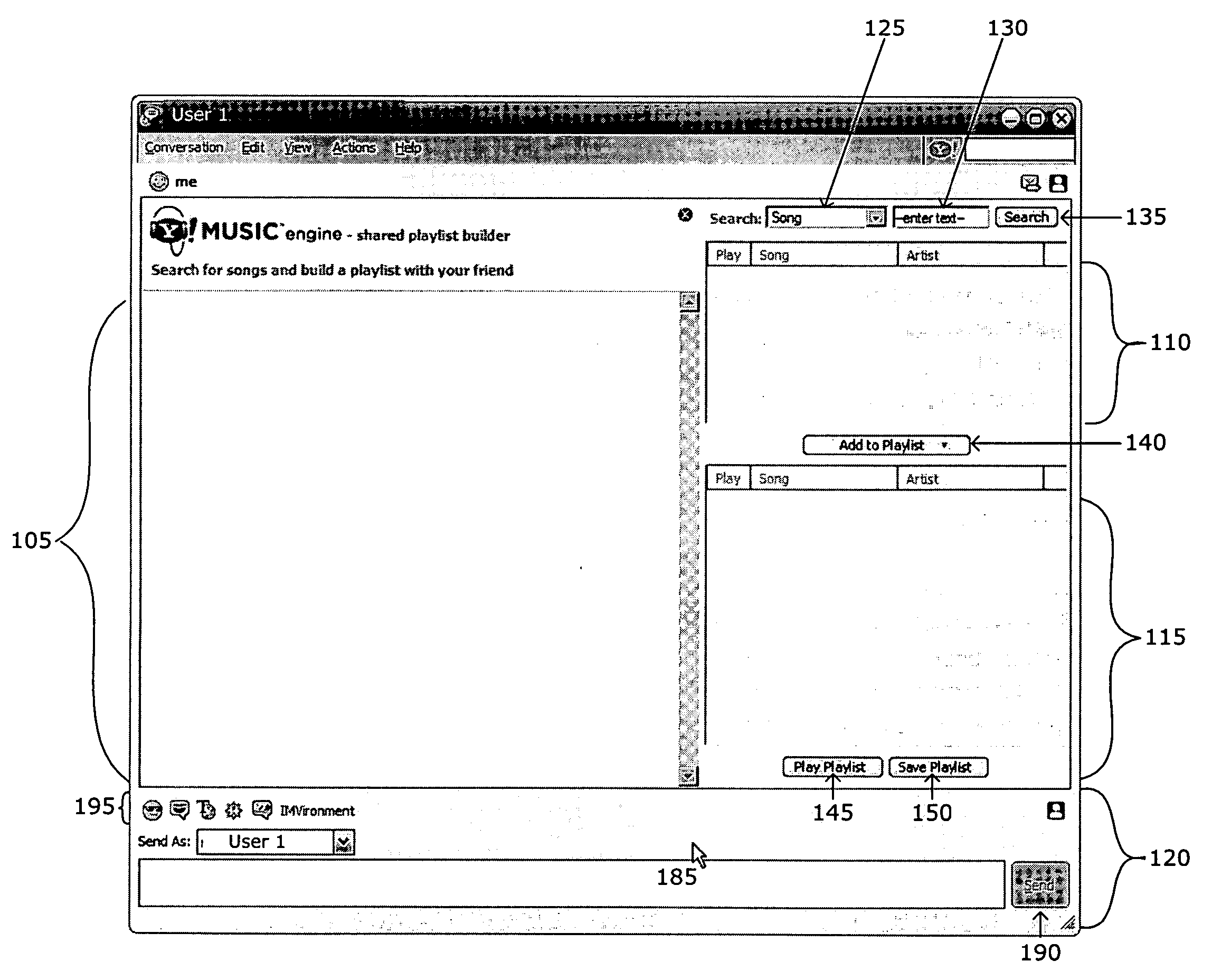
System and method for creating a collaborative playlist
ActiveUS20060195521A1Record information storageMultiple digital computer combinationsApplication softwareUser interface
A method, server, and user interface associated with creating a collaborative playlist between one or more users based on user interaction with a media program. In one embodiment, the media program is an instant messaging application.
Owner:HUAWEI TECH CO LTD
Method for determining internet users geographic region
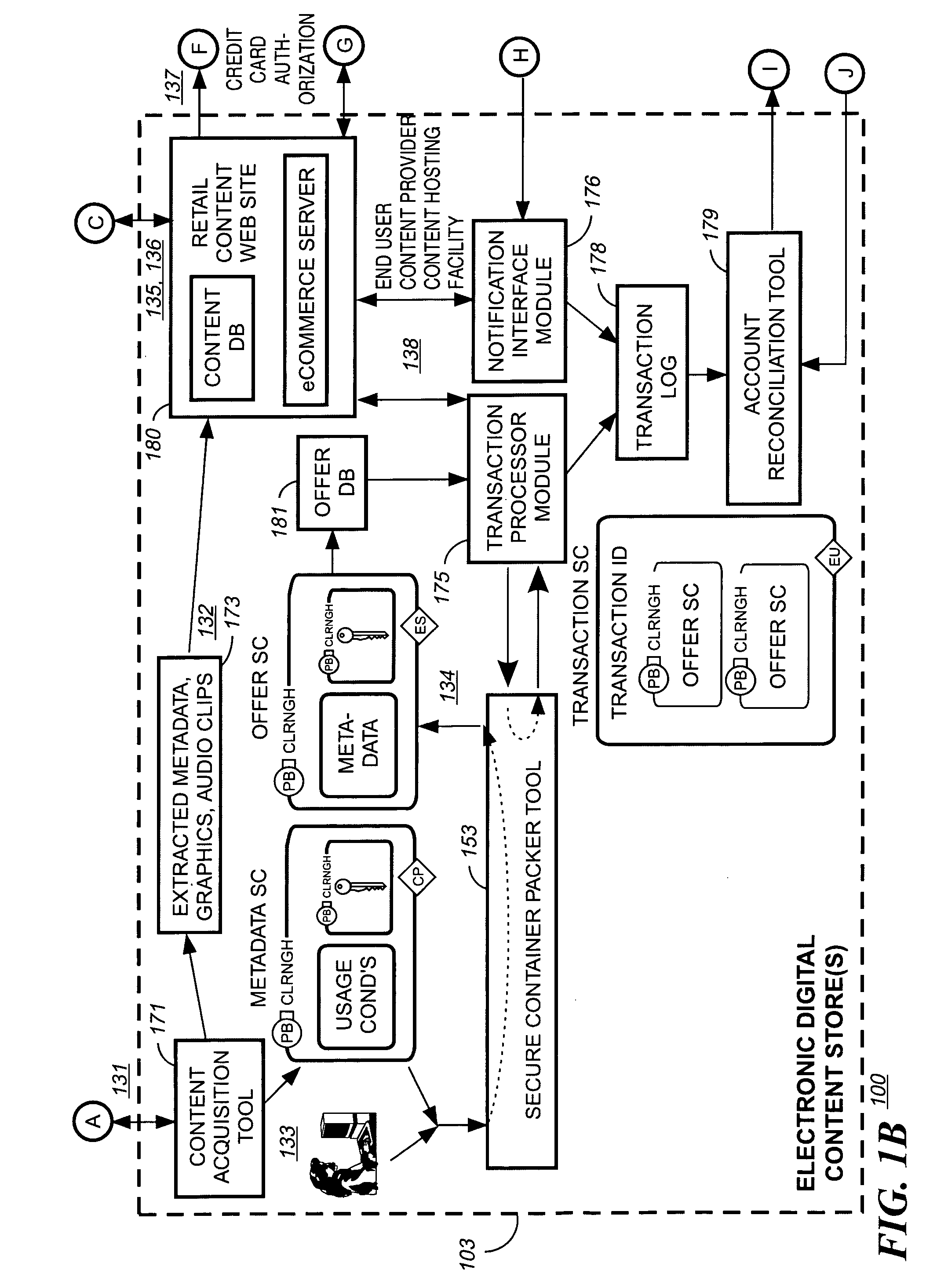
InactiveUS6859791B1Digital data processing detailsRecord information storageCredit cardGeographic regions
A method at a clearing house to verify the geographic region of an end user device for receiving encrypted digital content. In one embodiment the geographic region is a country. The method comprising three sub-methods. In the first sub-method the address is verified by determining the credit card clearing address of the end user using an address verification system. In the second sub-method the address is verified by determining the IP address of the end user device requesting delivery of the encrypted digital content. And in the third sub-method the address is verified by checking that the IP address of the end user device requesting delivery of the encrypted digital content is the identical IP address of the end user device requesting a license to use the encrypted digital content. Depending on predetermined system settings, one or more of the above combination of the three sub-methods is then checked, before authorizing the decrypting of the encrypted digital content includes decrypting the encrypted digital content if the address verification system returns an address in a predetermined geographic region and the IP address of the end user device is in a predetermined geographic region.
Owner:LEVEL 3 COMM LLC
Watermark embedder and reader
A watermark system includes an embedder, detector, and reader. The watermark embedder encodes a watermark signal in a host signal to create a combined signal. The detector looks for the watermark signal in a potentially corrupted version of the combined signal, and computes its orientation. Finally, a reader extracts a message in the watermark signal from the combined signal using the orientation to approximate the original state of the combined signal. While adapted for images, video and audio, the watermark system applies to other electronic and physical media. For example, it can be applied to mark graphical models, blank paper, film and other substrates, texturing objects for ID purposes, etc.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
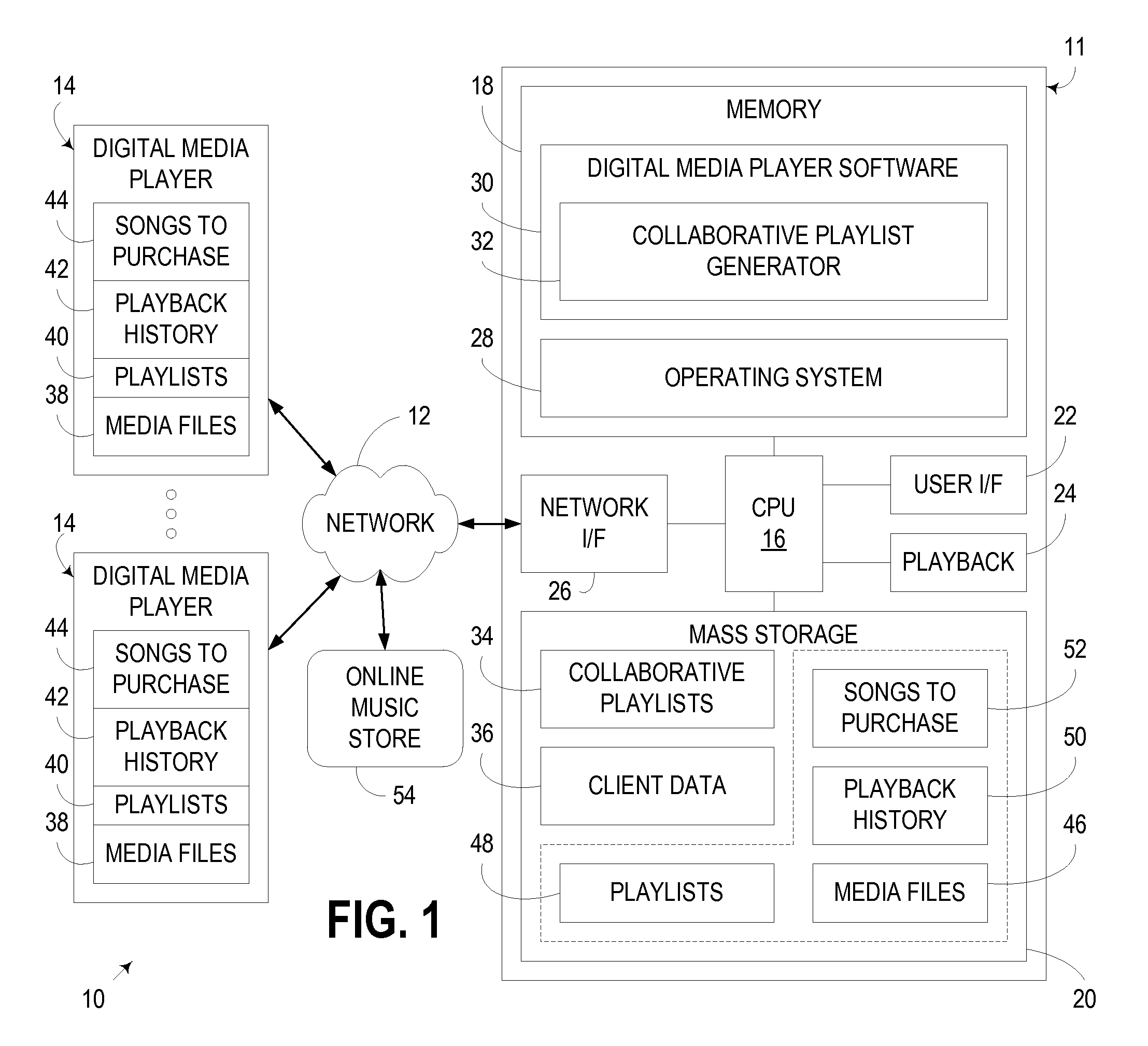
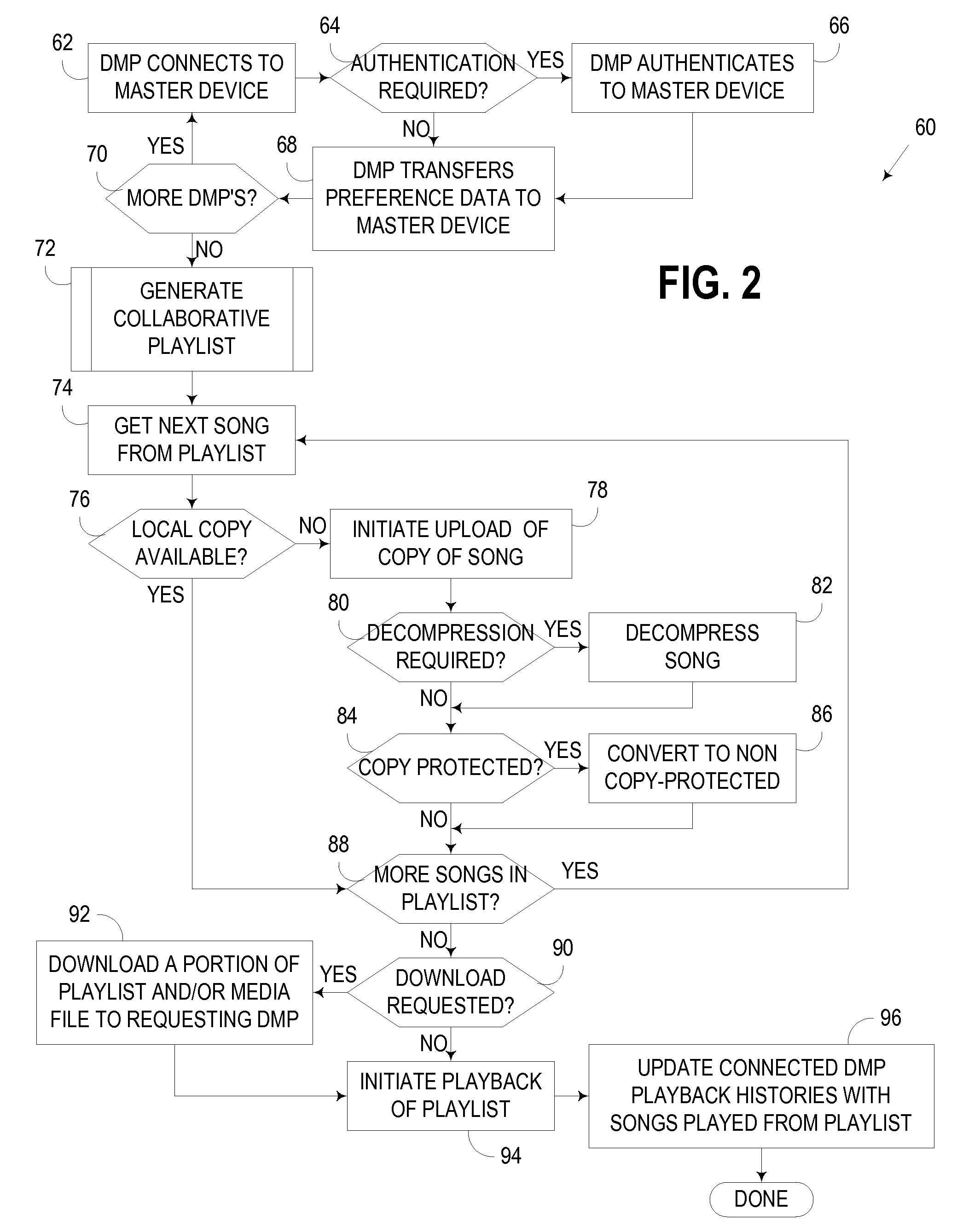
Generation of Collaborative Playlist Based Upon Musical Preference Data from Multiple Digital Media Players
InactiveUS20080091717A1Metadata audio data retrievalUsing non-detectable carrier informationPreference dataMultimedia
An apparatus, program product, and method collect musical preference data from a plurality of digital media players and generate therefrom a “collaborative” playlist of media files. The collaborative playlist may be used, for example, to identify and play back media files that most, if not all, of the users of the digital media players would likely find enjoyable.
Owner:IBM CORP
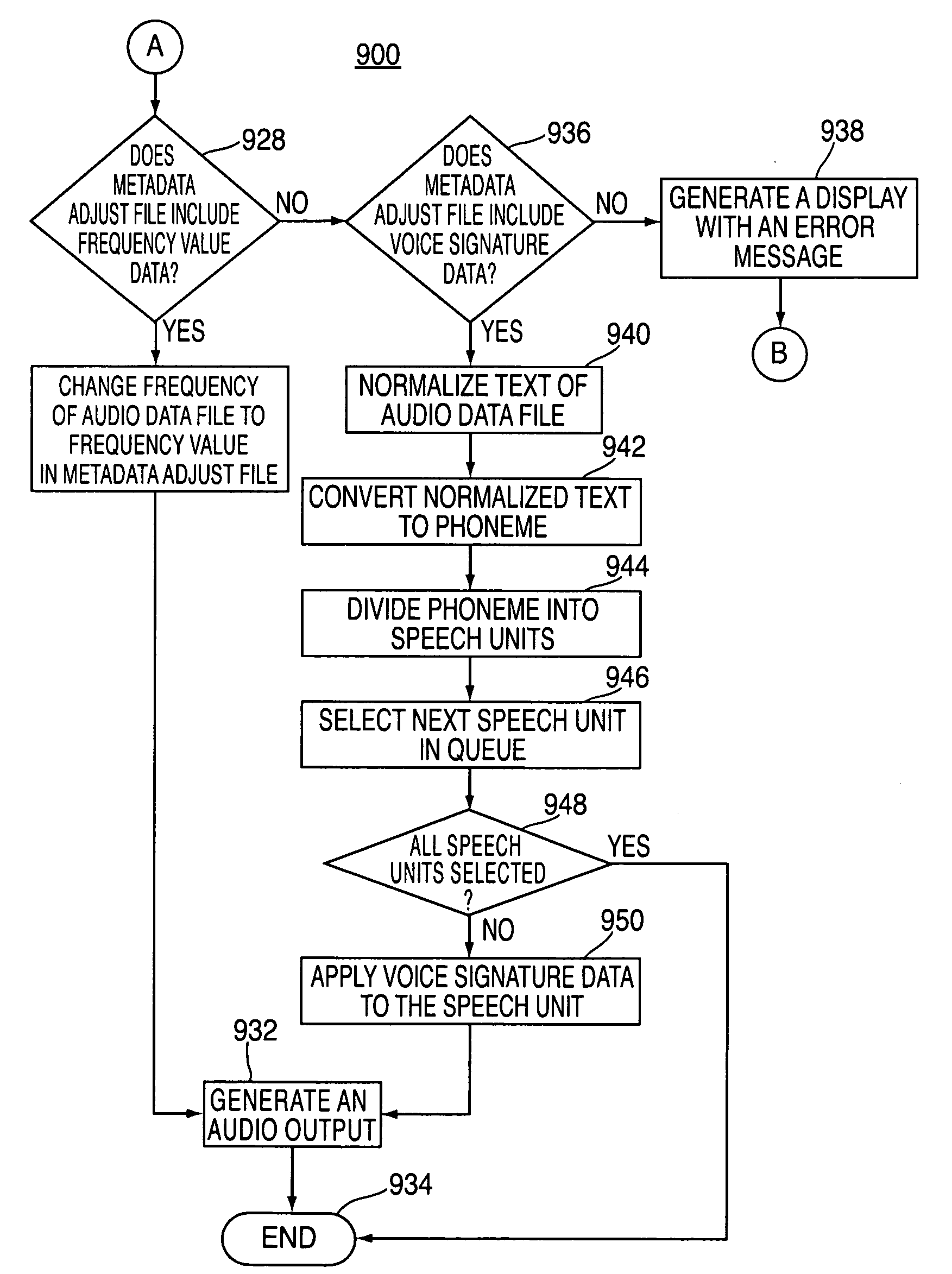
Methods and apparatus for altering audio output signals
ActiveUS20090177300A1Electronic editing digitised analogue information signalsRecord information storageData fileAudio frequency
Methods, systems and computer readable media for altering an audio output are provided. In some embodiments, the system may change the original frequency content of an audio data file to a second frequency content so that a recorded audio track will sound as if a different person had recorded it when it is played back. In other embodiments, the system may receive an audio data file and a voice signature, and it may apply the voice signature to the audio data file to alter the audio output of the audio data file. In that instance, the audio data file may be a textual representation of a recorded audio data file.
Owner:APPLE INC
Ambient sound responsive media player
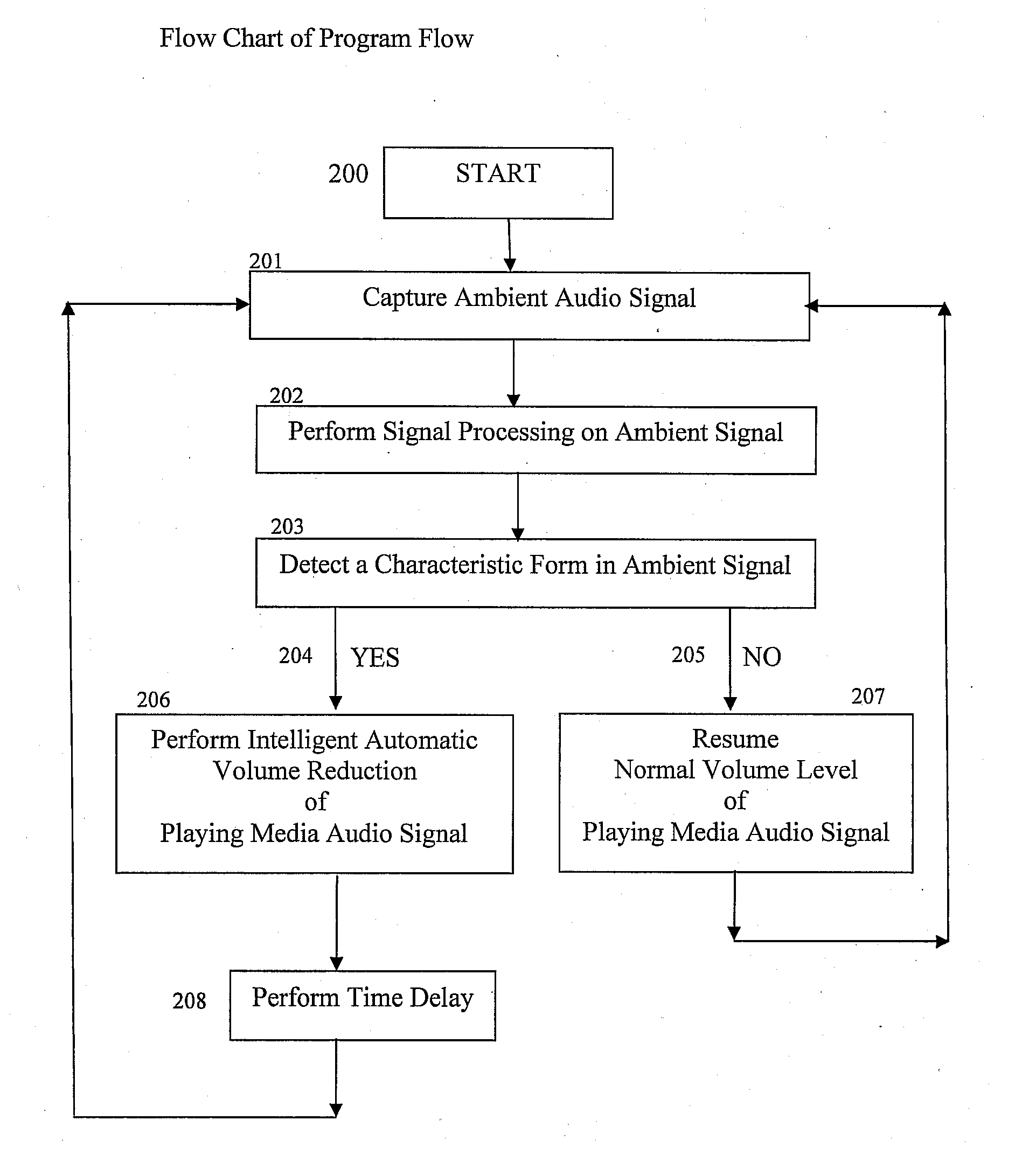
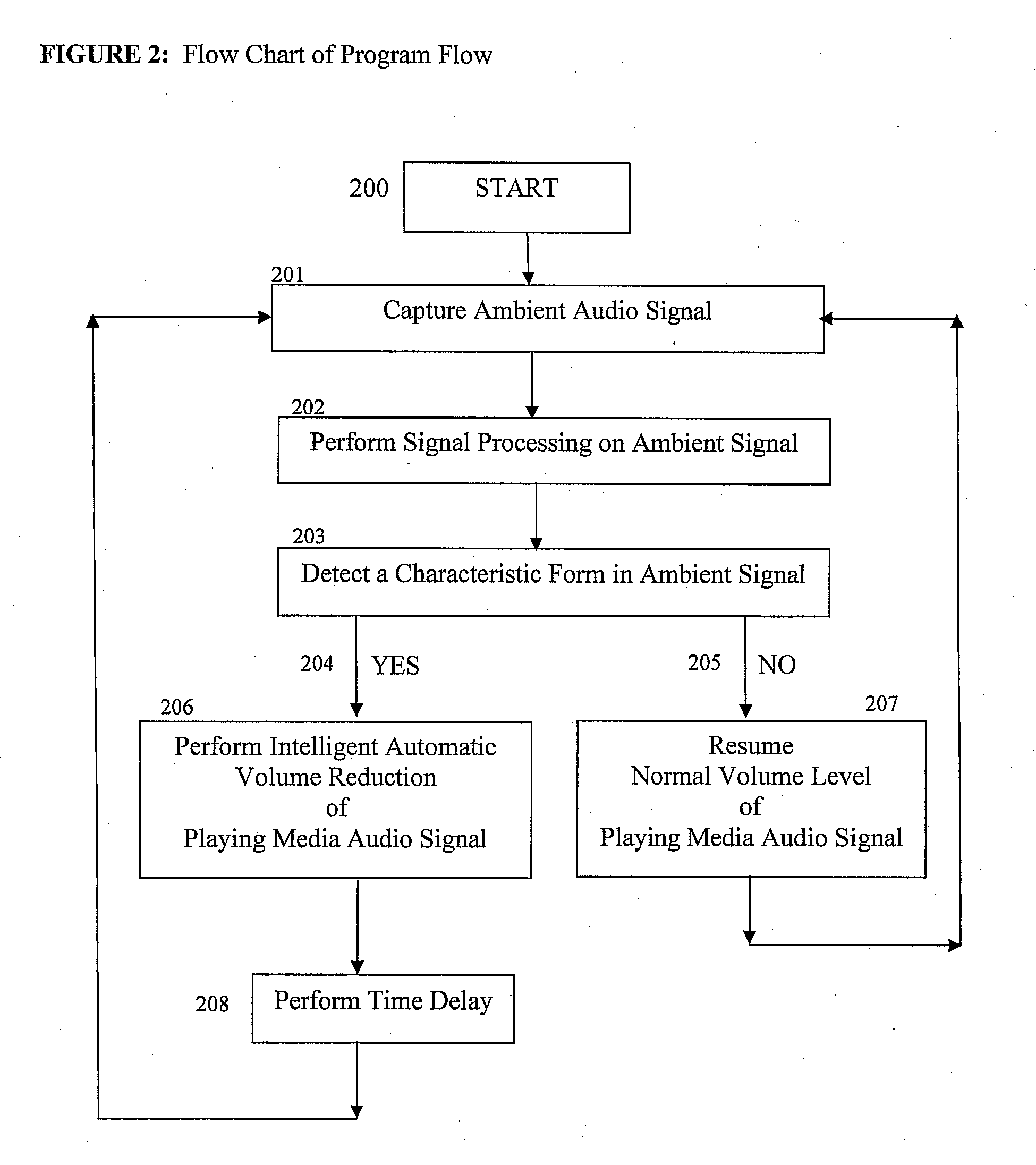
InactiveUS20070189544A1Reduce outputRecording carrier detailsGain controlComputer scienceAudio frequency
Some embodiments of the present invention provide a method of adjusting an output of a media player comprising capturing an ambient audio signal; processing the ambient audio signal to determine whether one or more characteristic forms are present within the ambient audio signal; and reducing an output of a media player from a first volume to a second volume if the one or more characteristic forms are present within the ambient audio signal. The characteristic forms may be, for example, a name or personal identifier of a user of the media player, the voice of a user of the media player, or an alarm or siren.
Owner:GOOGLE LLC
Tile-based digital watermarking techniques
InactiveUS6879701B1Television system detailsCoin-freed apparatusComputer graphics (images)Digital image
A tile-based arrangement is employed to effect watermarking of plural-bit auxiliary data into still or moving digital images. In a particular embodiment, the plural-bit auxiliary data is represented as a rectangular block of overlay data. This block is repetitively tiled, both vertically and horizontally, across the image, and combined with the image data to effect the encoding.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Method for sharing and searching playlists
ActiveUS20060195479A1Easy to displayRecord information storagePayment architectureComputer scienceUser defined
Owner:HUAWEI TECH CO LTD
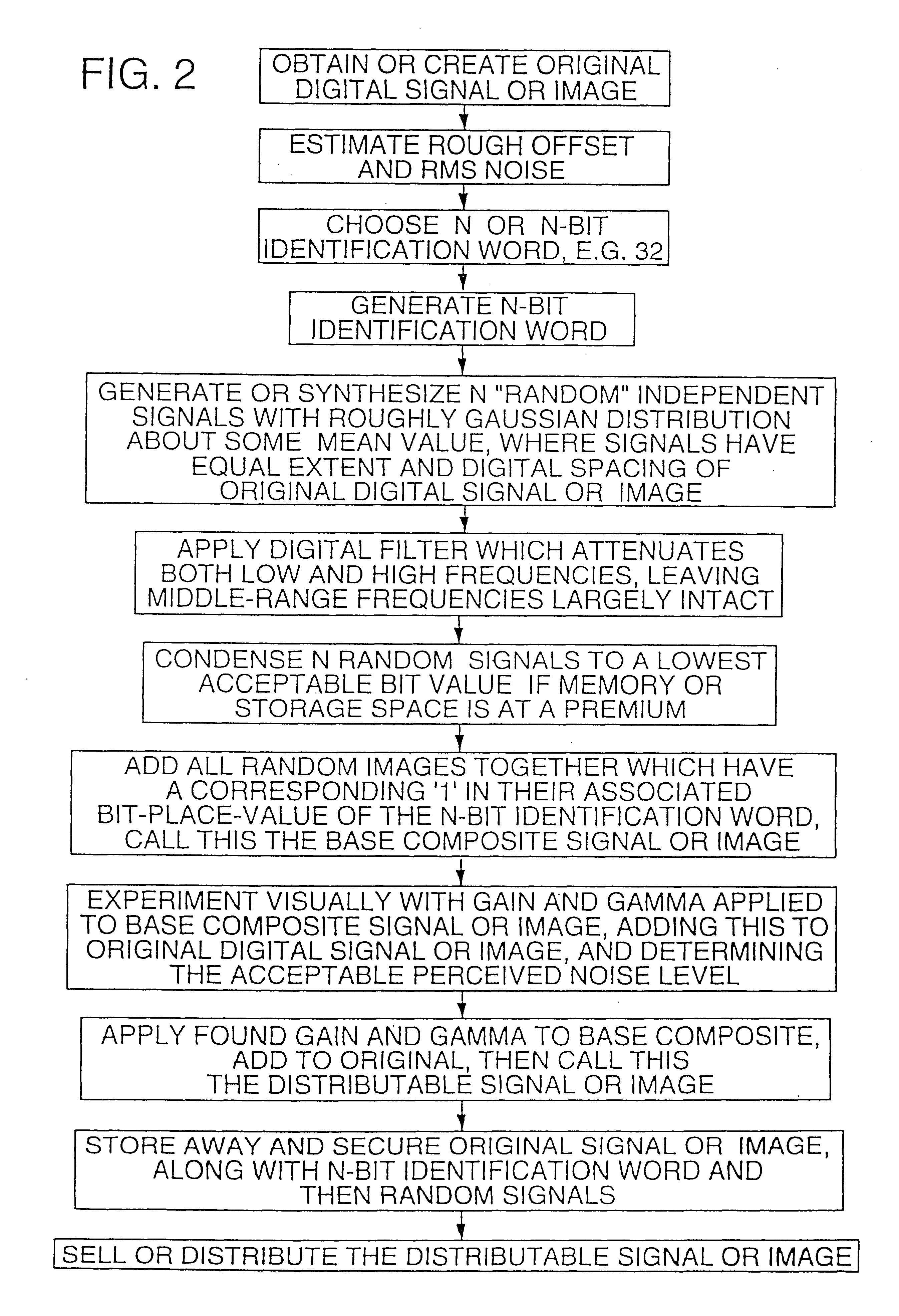
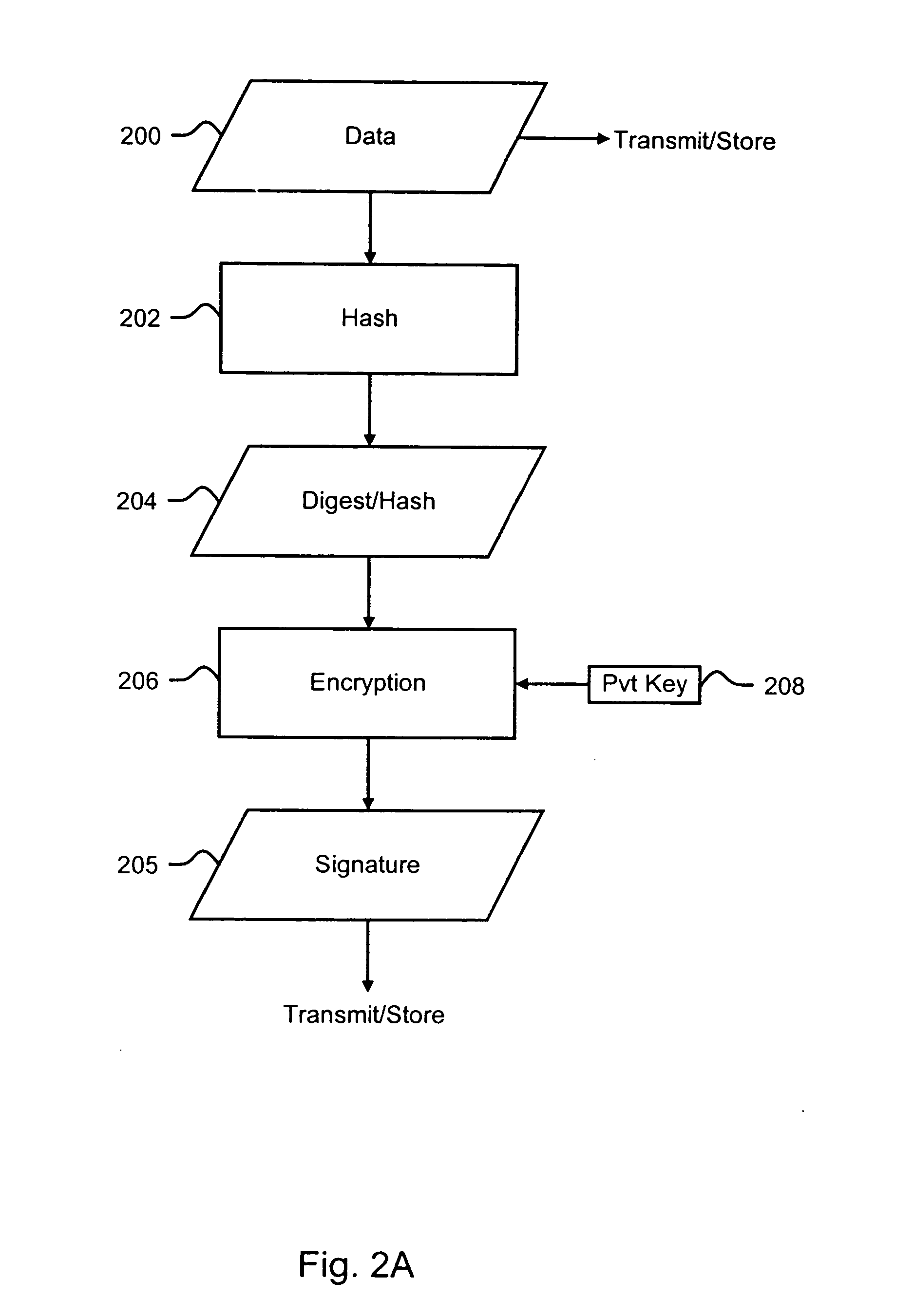
Methods and systems for encoding and protecting data using digital signature and watermarking techniques
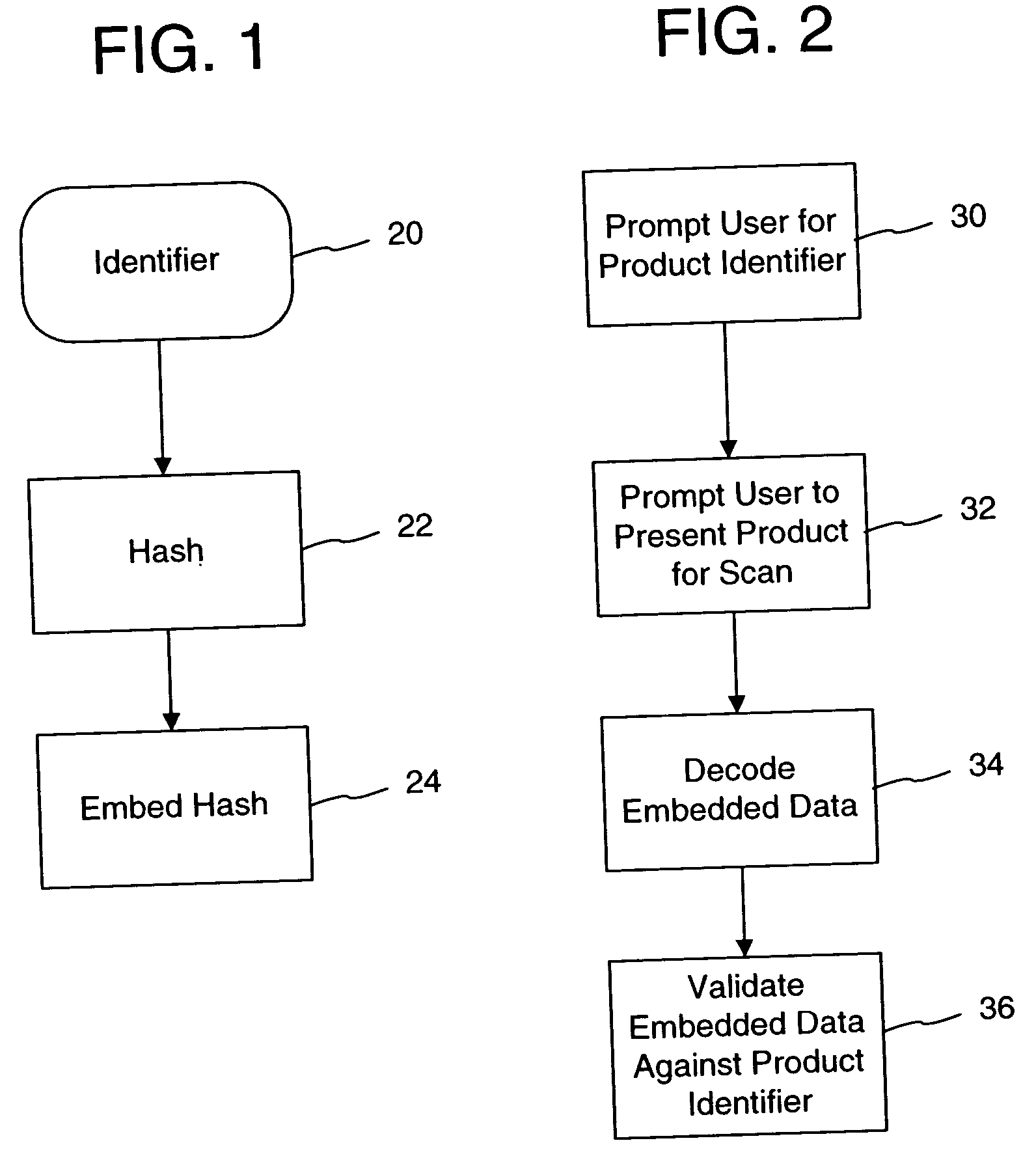
InactiveUS20050050332A1Verify authenticityTelevision system detailsUser identity/authority verificationCompact discDigital signature
Systems and methods are provided for protecting and managing electronic data signals that are registered in accordance with a predefined encoding scheme, while allowing access to unregistered data signals. In one embodiment a relatively hard-to-remove, easy-to-detect, strong watermark is inserted in a data signal. The data signal is divided into a sequence of blocks, and a digital signature for each block is embedded in the signal via a watermark. The data signal is then stored and distributed on, e.g., a compact disc, a DVD, or the like. When a user attempts to access or use a portion of the data signal, the signal is checked for the presence of a watermark containing the digital signature for the desired portion of the signal. If the watermark is found, the digital signature is extracted and used to verify the authenticity of the desired portion of the signal. If the signature-containing watermark is not found, the signal is checked for the presence of the strong watermark. If the strong watermark is found, further use of the signal is inhibited, as the presence of the strong watermark, in combination with the absence or corruption of the signature-containing watermark, provides evidence that the signal has been improperly modified. If, on the other hand, the strong mark is not found, further use of the data signal can be allowed, as the absence of the strong mark indicates that the data signal was never registered with the signature-containing watermark.
Owner:INTERTRUST TECH CORP
Updating usage conditions in lieu of download digital rights management protected content
InactiveUS20060089912A1Digital data processing detailsRecord information storageDigital rights managementEnd user
A method on an end user system for creating additional copies onto at least one computer readable medium such as CDs, DVDs, ZipDisks™, tape, Flash memory, and RAM. The method comprising the steps of: receiving encrypted content with associated usage conditions and a first hash value; receiving a selection from an end user to create at least one copy of the-encrypted content onto at least one computer readable medium; sending a request to an online electronic store of the encrypted content selected to be copied; receiving from the electronic store a description of the content selected to be copied along with a second hash value; and determining if the first hash value received is identical to the second hash value and if the first hash and the second hash value is identical authorizing the creating additional copies onto at least one computer readable medium.
Owner:IBM CORP
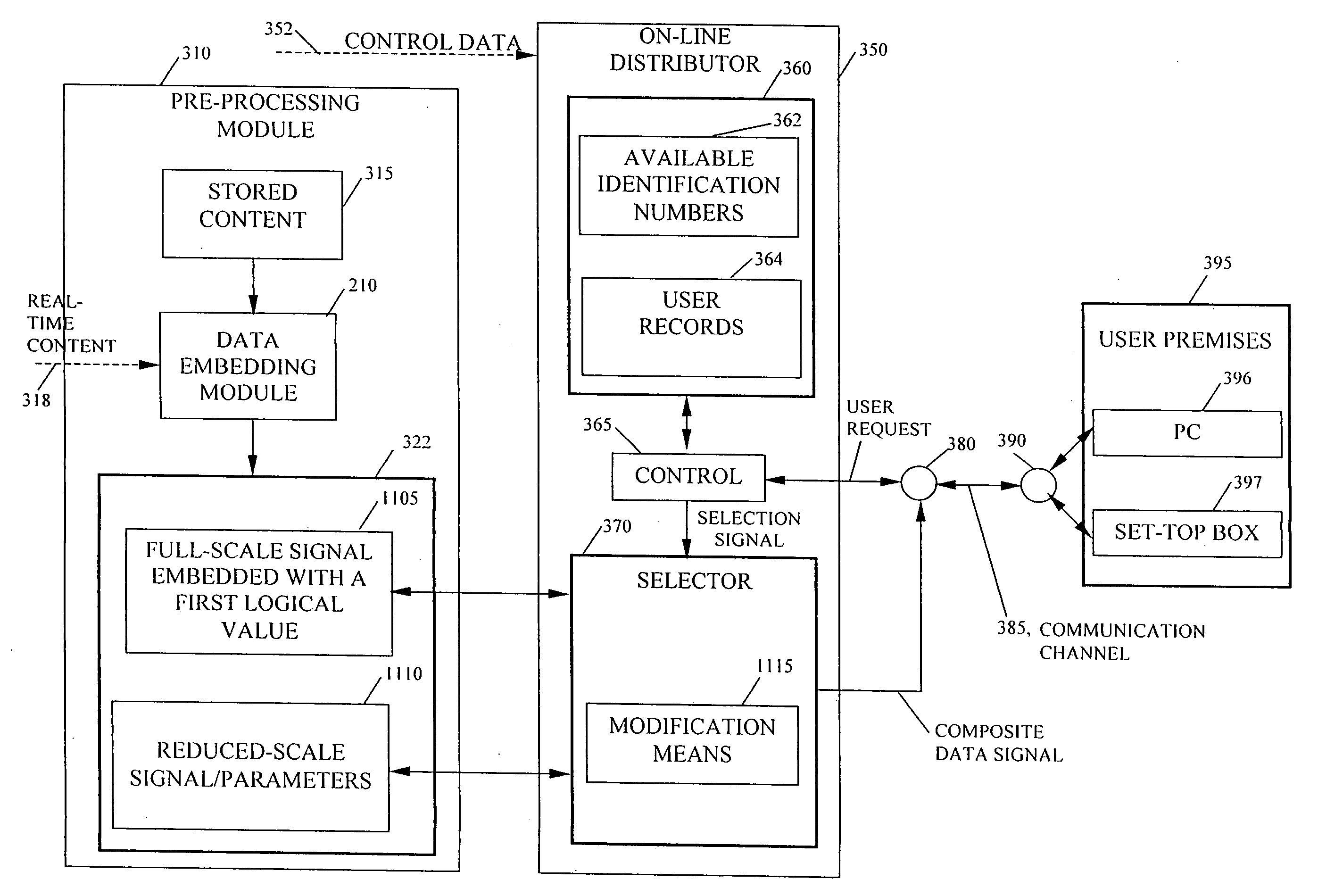
Pre-processed information embedding system
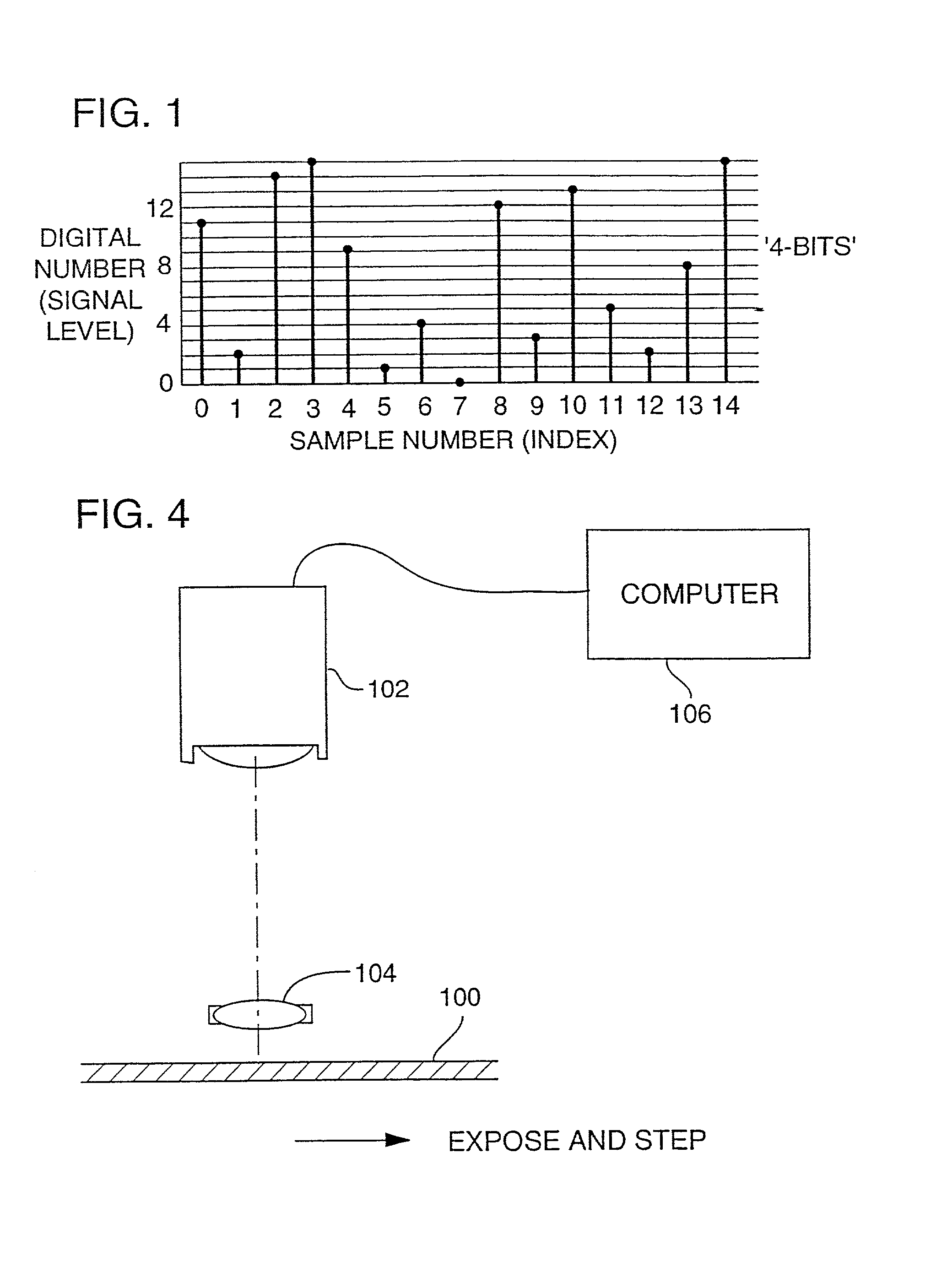
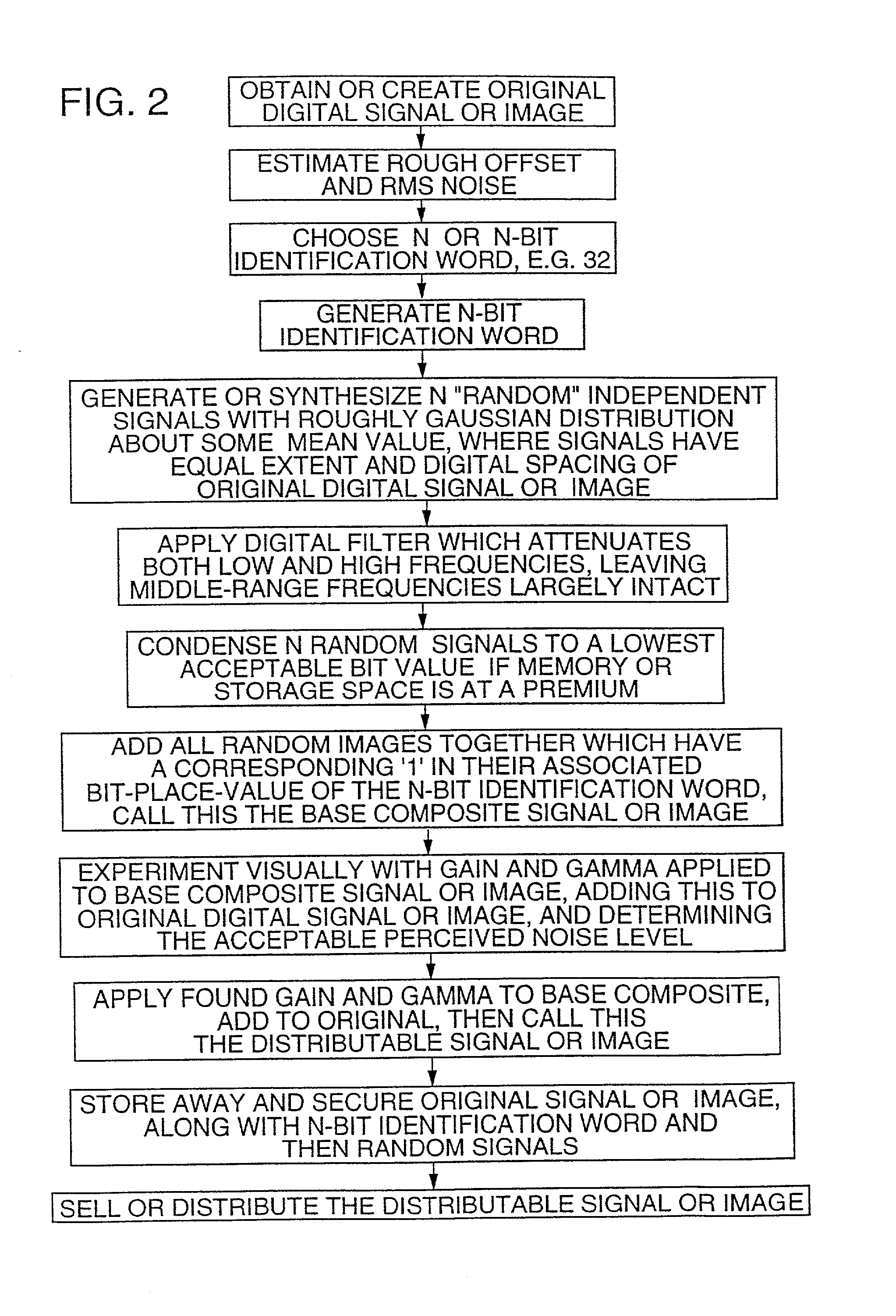
InactiveUS20060005029A1Reduce the possibilityReduce distractionsTelevision system detailsUser identity/authority verificationComputer hardwareComputation complexity
Methods are provided for embedding auxiliary information in a host content signal which reduce the memory, bandwidth and computational complexity of the embedding and transmission systems. In one embodiment, a first reduced-scale signal is produced which corresponds to the host content embedded with a first logical value and producing a second reduced-scale signal corresponding to the host content embedded with a second logical value. A first set of segments from the first reduced-scale signal may be combined with a second set of segments from the second reduced-scale signal in a pre-defined manner to produce a composite embedded host content. Thus the storage and transmission requirements of the watermarking system are reduced to having to deal with only the original content plus two reduced-scale signals.
Owner:VOBILE
Content indexing and searching using content identifiers and associated metadata
A method of indexing content for network searching comprises identifying media content signals stored at sites distributed over a distributed computer network; extracting content identifiers from the content signals; using the content identifiers to obtain metadata used to classify the media content signals; and creating a searchable index of the media content signals based on the metadata, wherein users access the searchable index on the distributed computer network to submit a search query for the searchable index to retrieve links to the media content signals.
Owner:DIGIMARC CORP
Internet linking from image content
InactiveUS7058697B2Commercial value is not compromisedMaximization of identification signal energyCoin-freed apparatusRecord information storageGraphicsThe Internet
Address information is steganographically encoded into audio or graphic data, and thereafter decoded to permit linking to the internet. The address information can be a literal URL, or may be an index to a database from which a corresponding URL can be obtained.
Owner:DIGIMARC CORP
Video image information playback method and video image information playback device
InactiveUS20140169762A1Color television signals processingRecord information storageComputer graphics (images)Video image
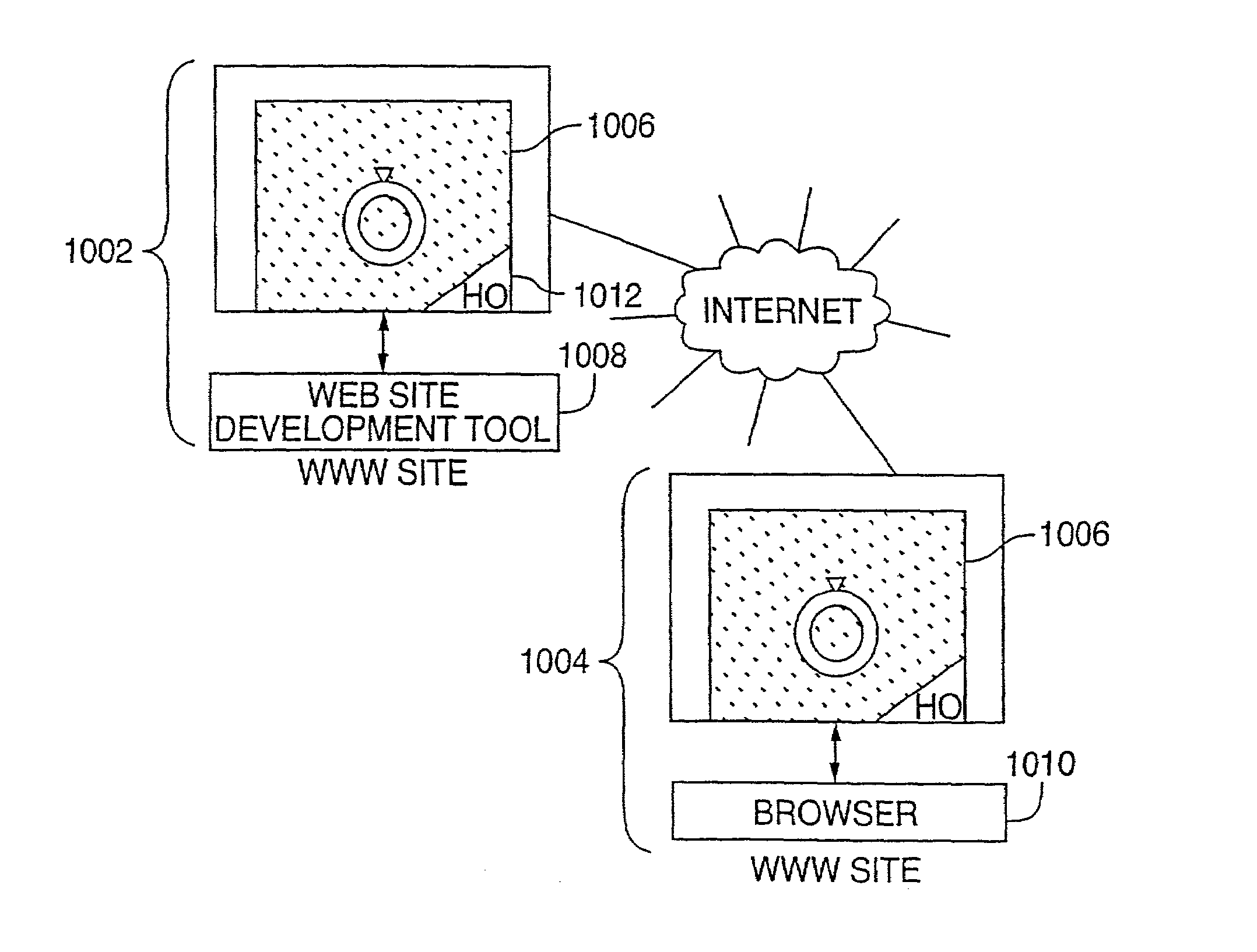
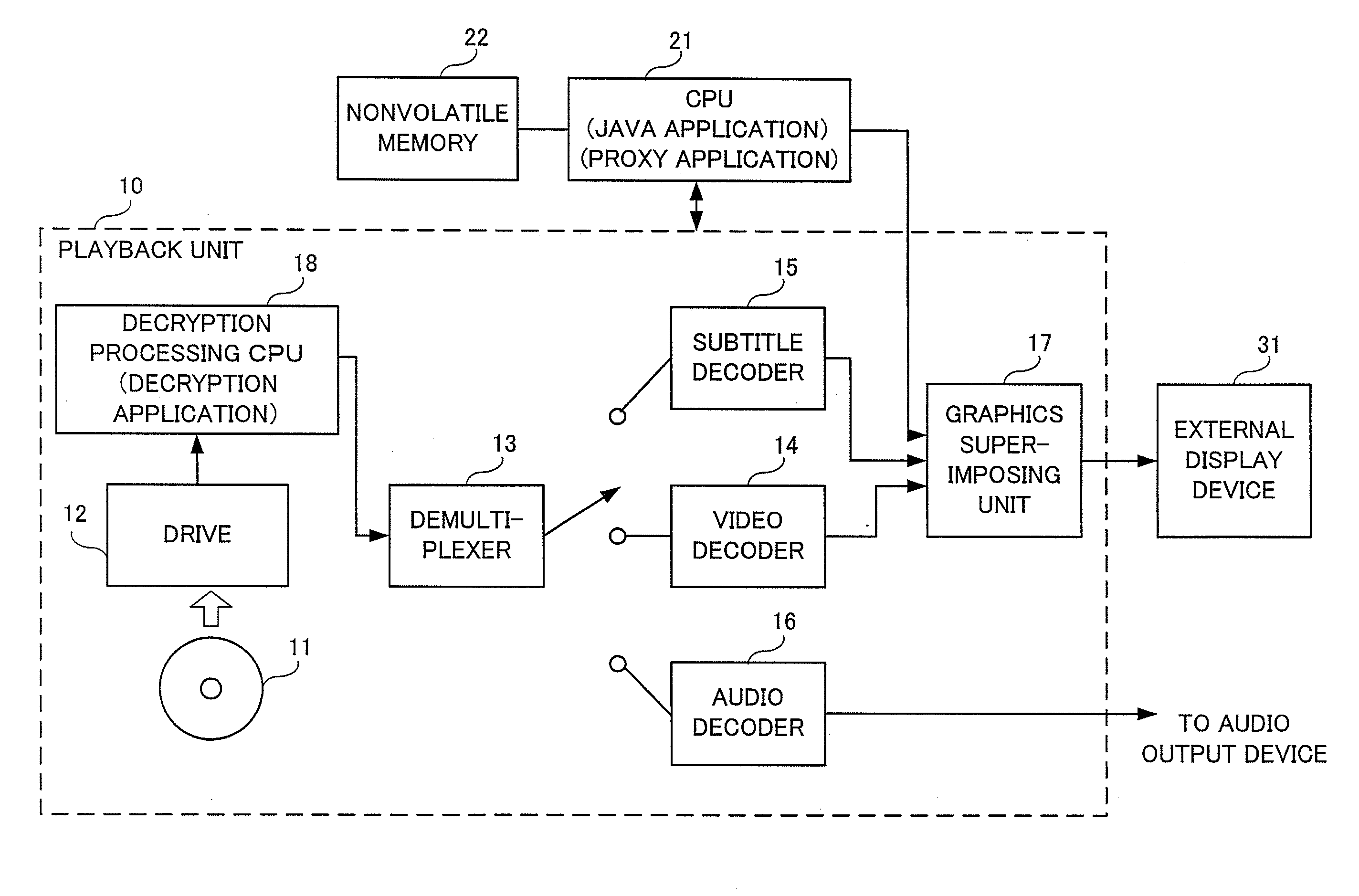
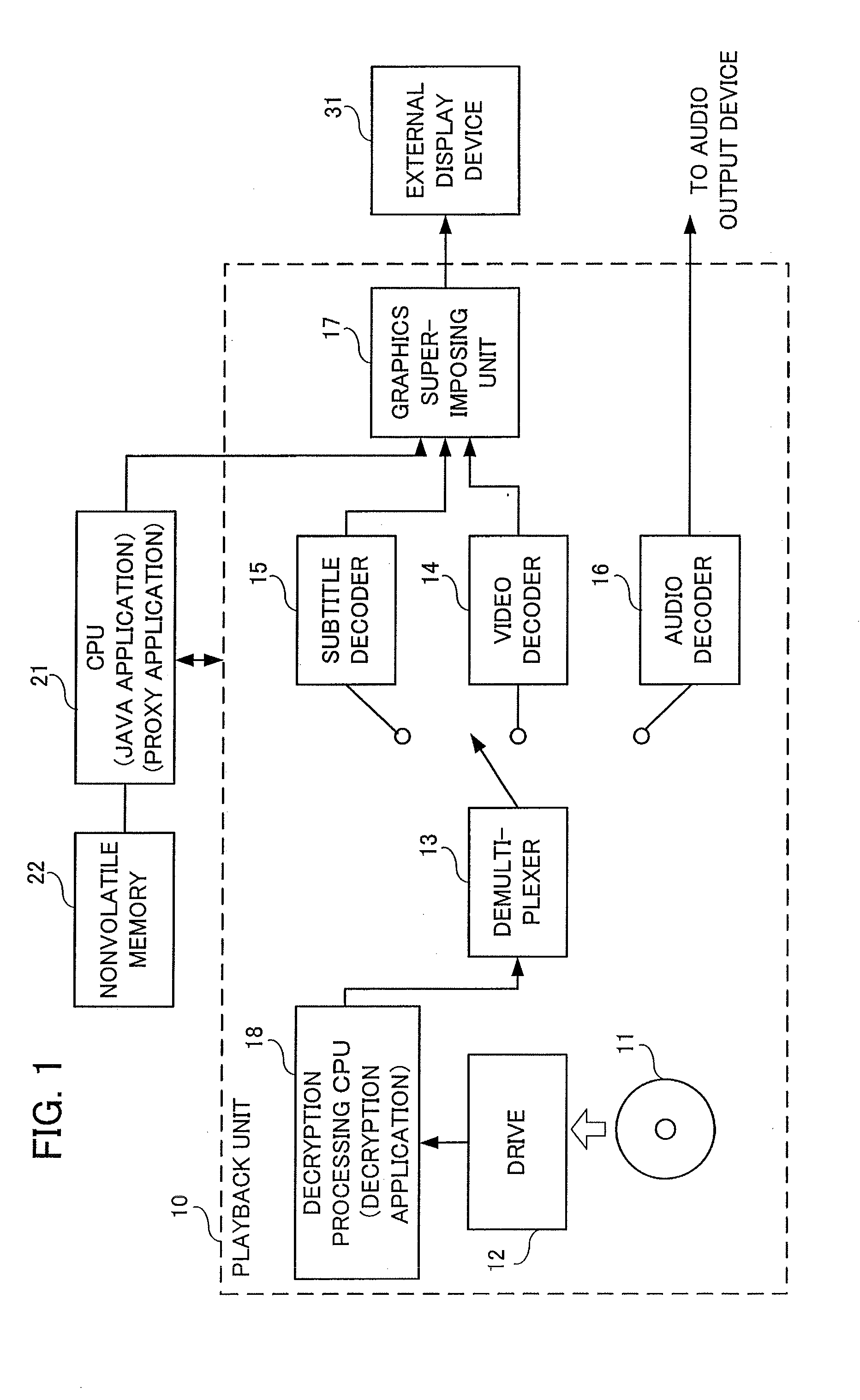
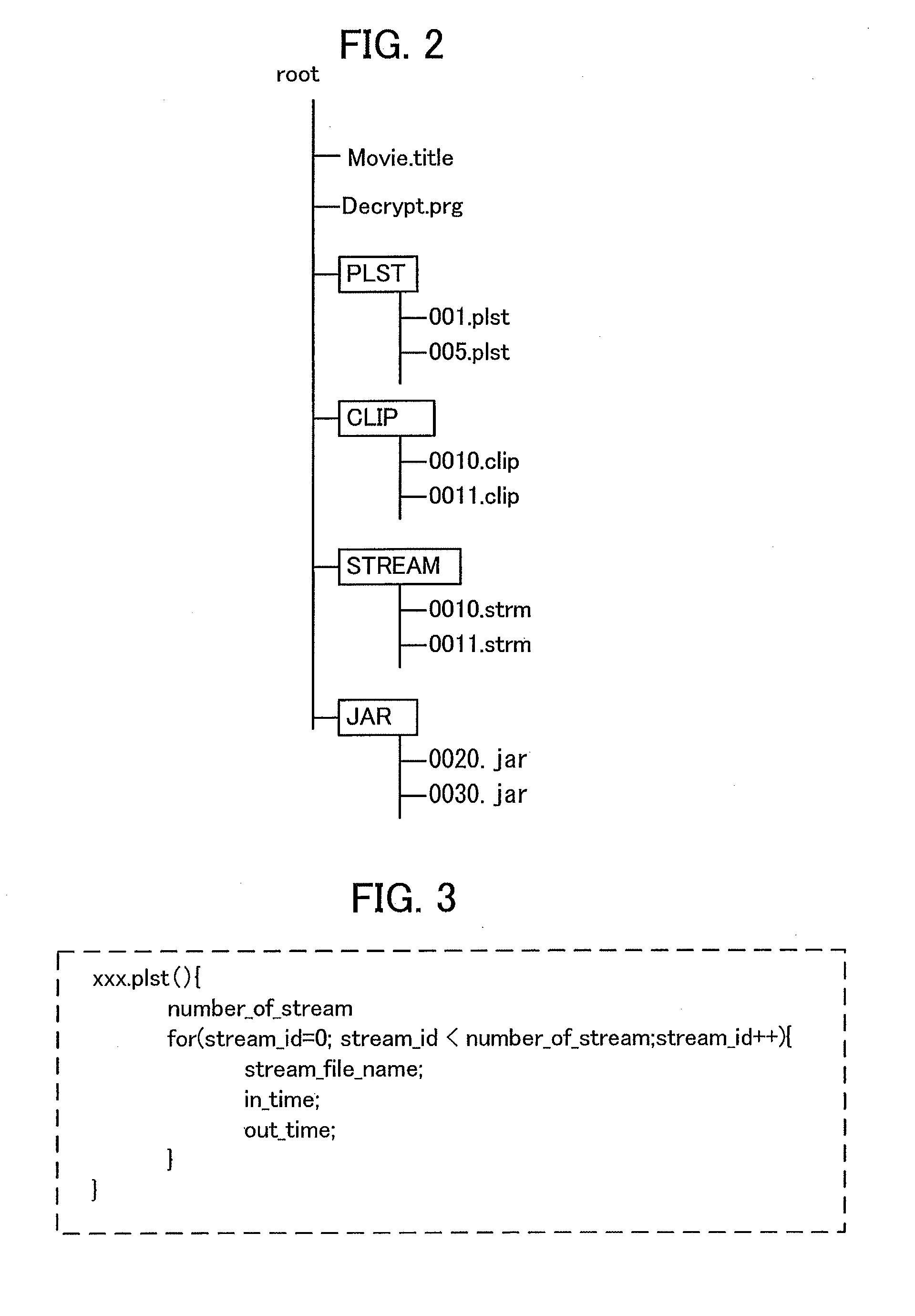
A video image information playback method and a video image information playback device with which user convenience can be obtained at the start of resume playback. The video image information playback method is a method of playback of a recording medium on which virtual-machine-based content has been recorded. During normal playback of the virtual-machine-based content, a program running on a virtual machine and a decryption program that decrypts encrypted virtual-machine-based content perform decryption processing for the virtual-machine-based content while exchanging data. After suspension of playback of the virtual-machine-based content, at the start of resume playback, which is executed following an instruction to resume playback, a proxy program is launched in place of the program that runs on the virtual machine. The proxy program and the decryption program perform playback of the video image of the virtual-machine-based content while exchanging data.
Owner:MITSUBISHI ELECTRIC CORP
Popular searches
Character and pattern recognition Plural information simultaneous broadcast Recording signal processing Sensing record carriers Special data processing applications Acutation objects Digital data information retrieval Paper-money testing devices Co-operative working arrangements Image data processing details
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com