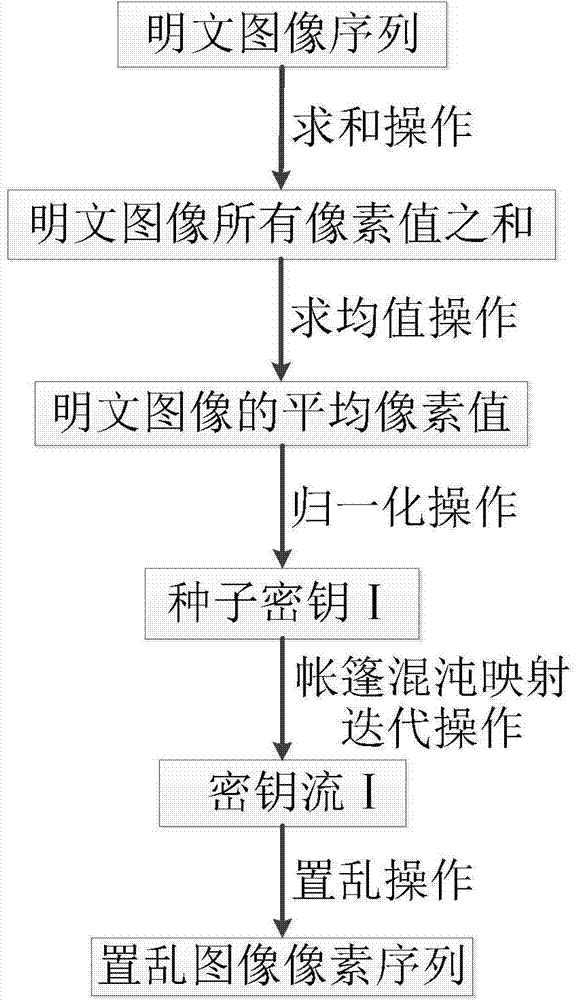
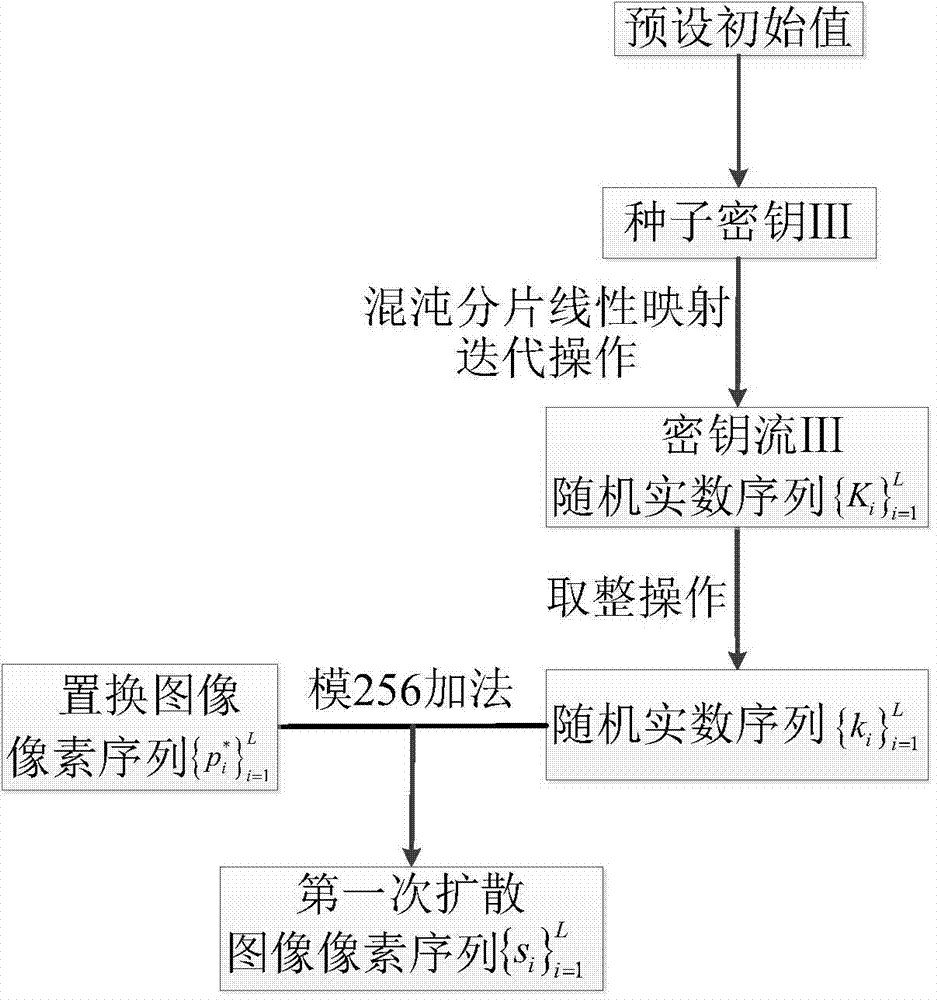
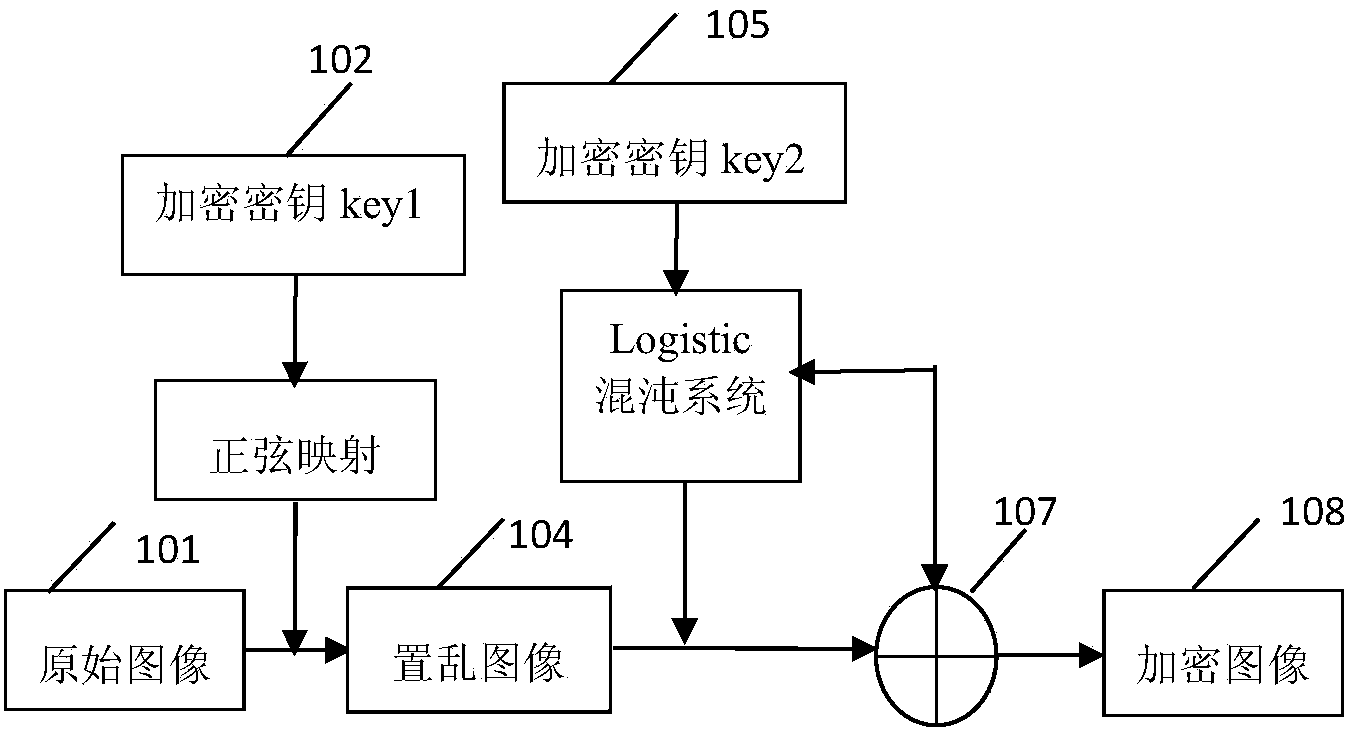
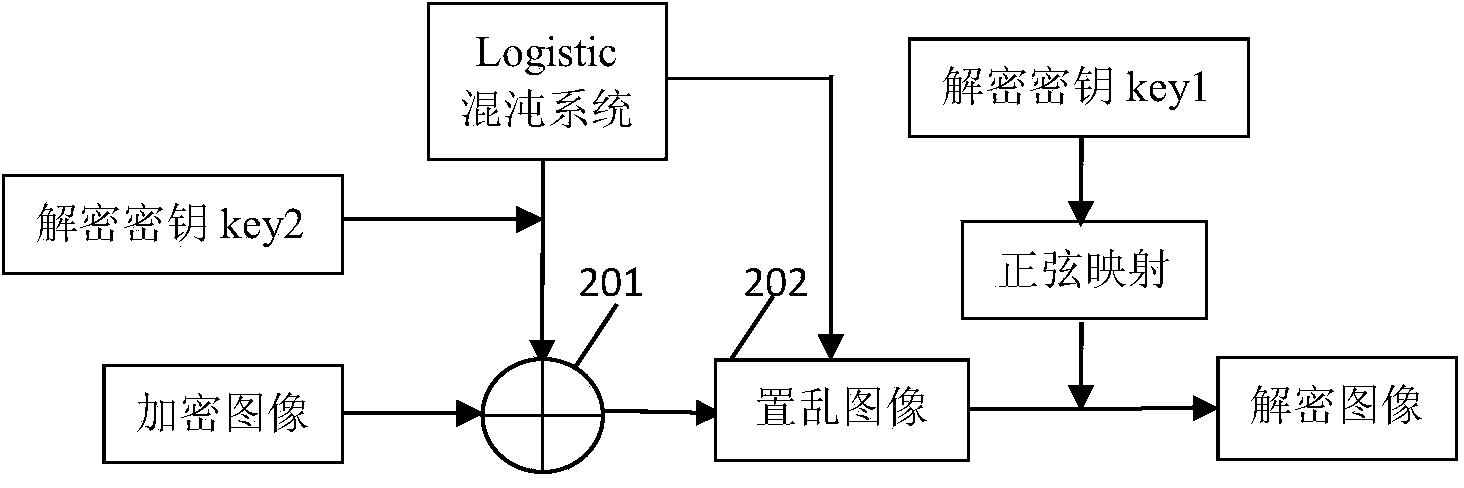
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
283results about How to "Large key space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
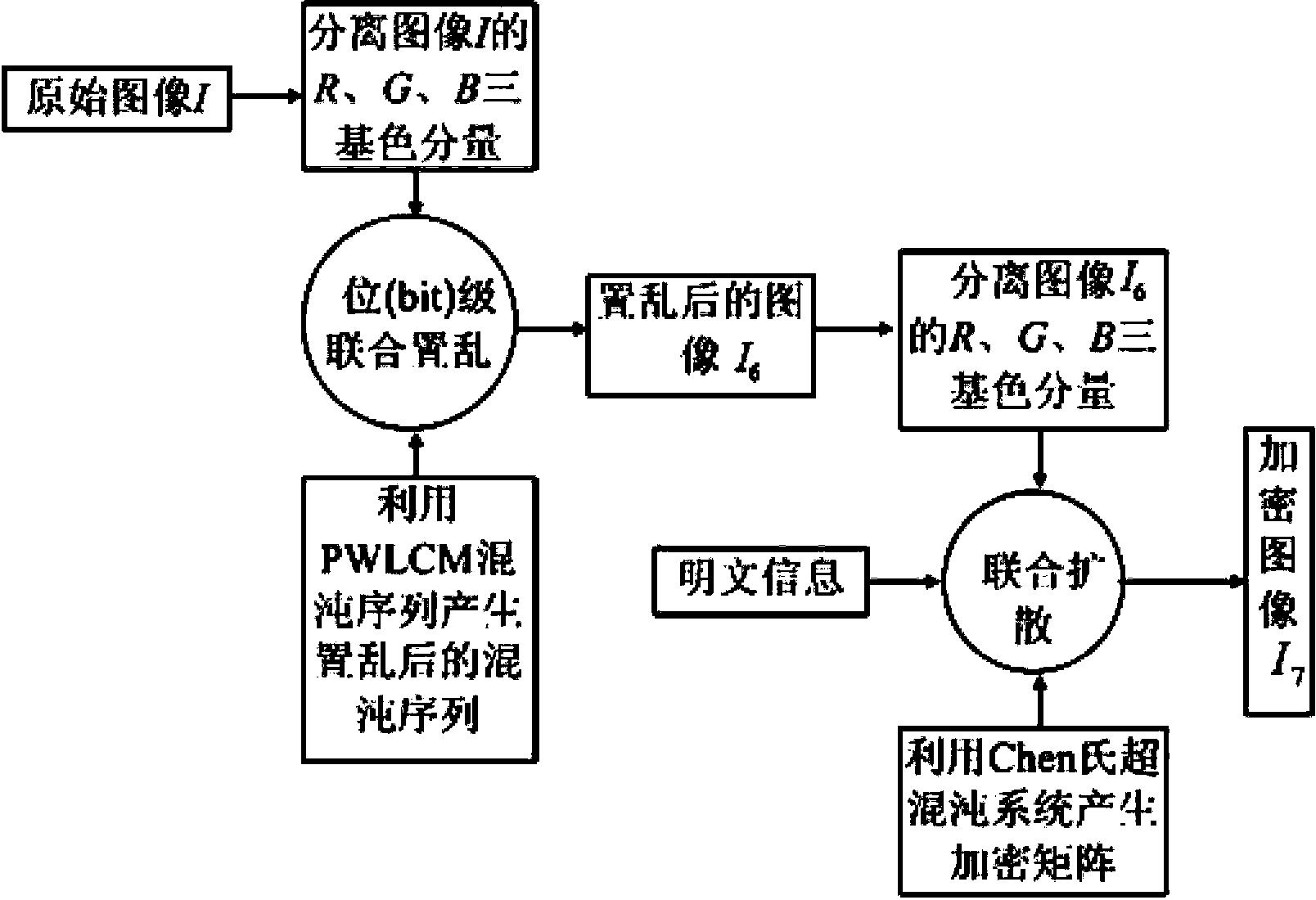
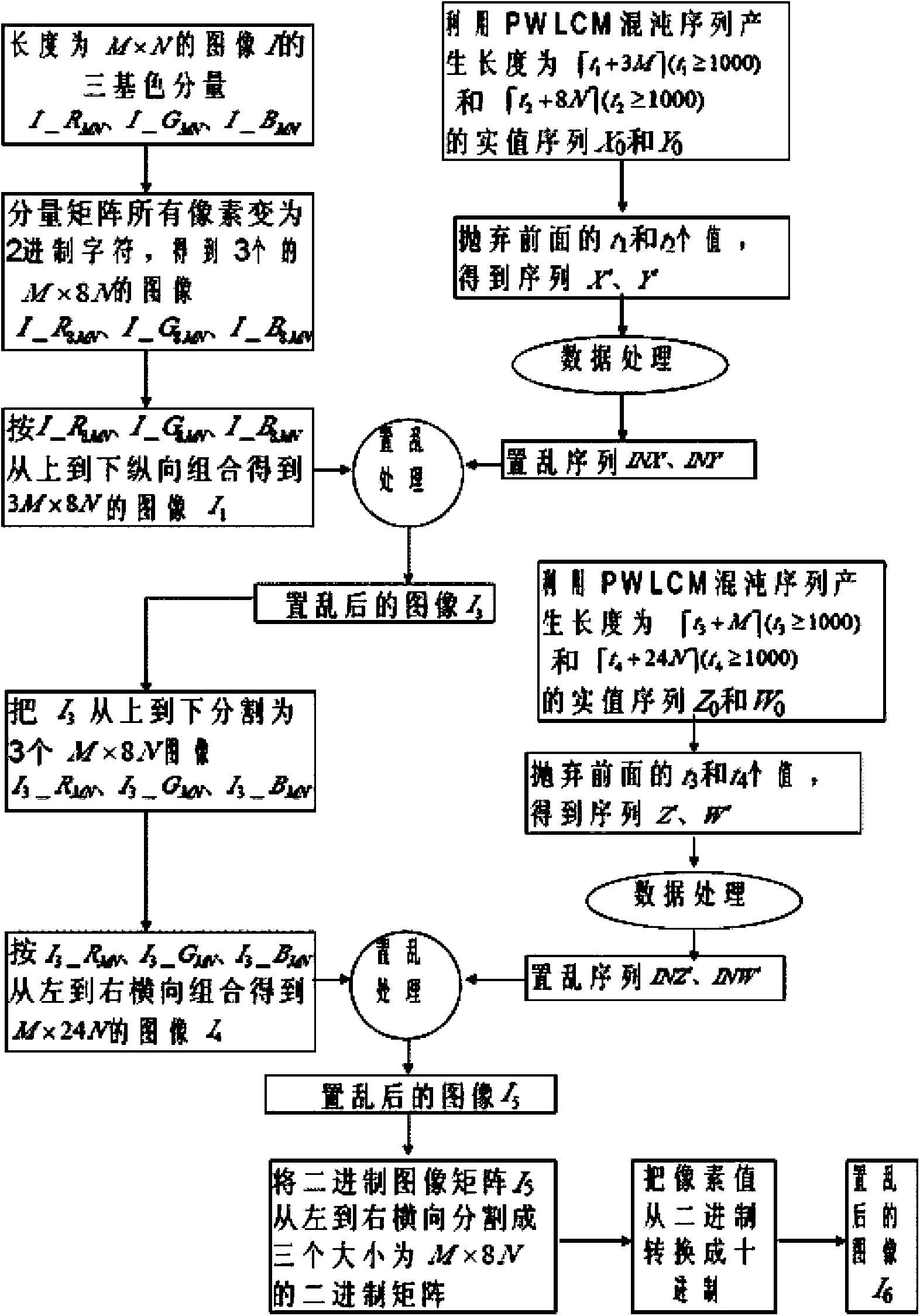
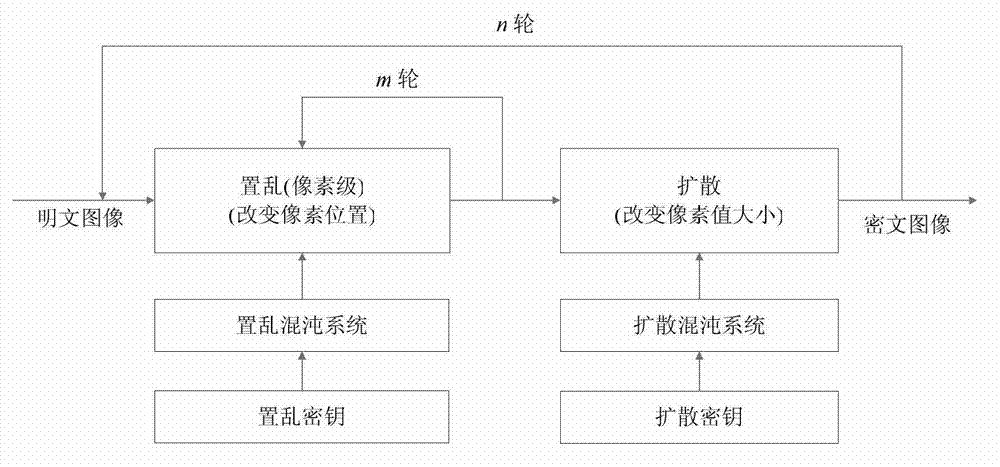
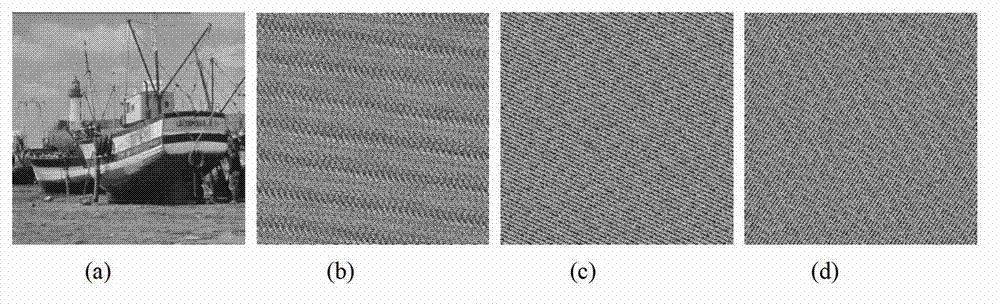
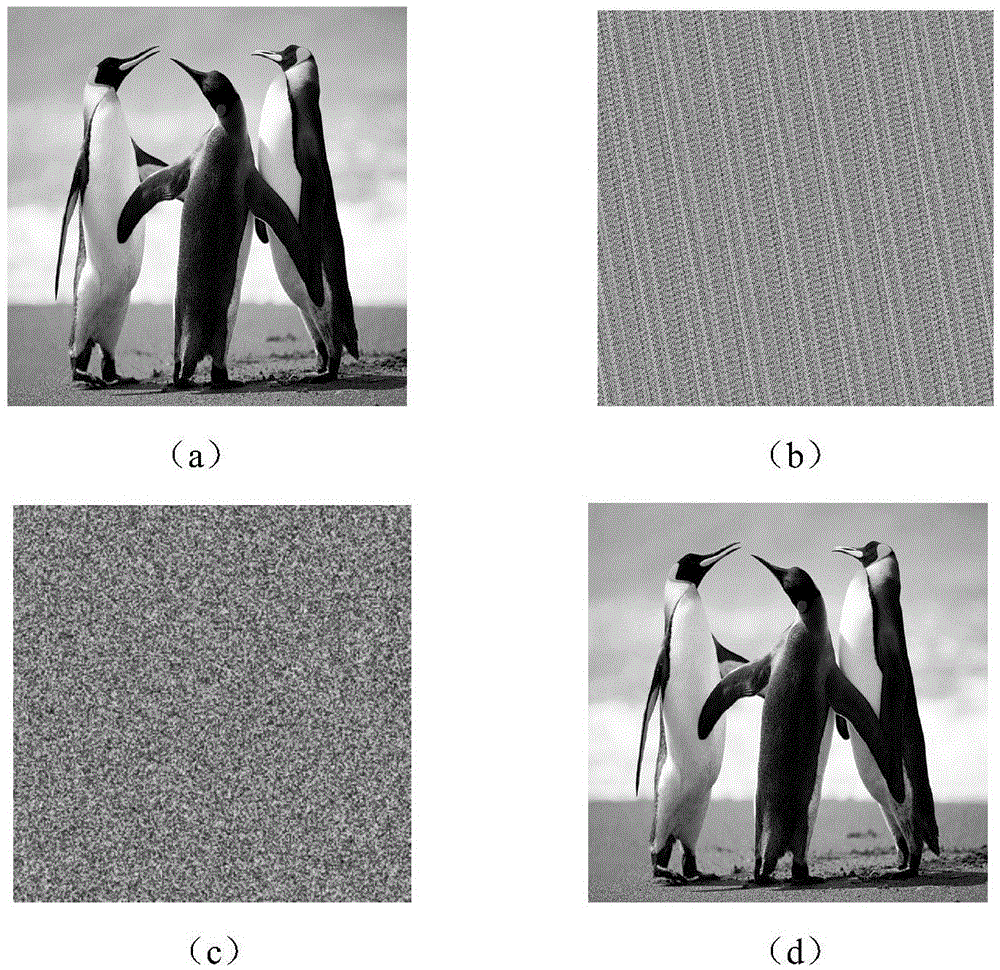
Color image encryption method based on chaos sequence and hyper-chaos system
InactiveCN103489151AImprove securityLarge key spaceImage data processing detailsChaotic systemsDiffusion
The invention relates to a color image encryption method based on a chaos sequence and a hyper-chaos system. The color image encryption method mainly comprises the following steps: an original color image is subjected to bit level united scrambling to obtain a scrambled image; the scrambled image is decomposed into three primary color components, that is R, G and B, and the hyper-chaos system is used for generating an encryption matrix which is used for encrypting the scrambled image; all pixel values of the three primary color components of the scrambled image are changed by utilizing the encryption matrix in combination with plaintext information and information of the three primary color components, united diffusion is conducted to obtain the three primary color components of the image after the united diffusion, and therefore a final encrypted image is obtained. By means of the color image encryption method, a secret key space is greatly enlarged, the safety, the encryption effect and the sensitivity of a secret key are higher, the anti-attack ability is stronger, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
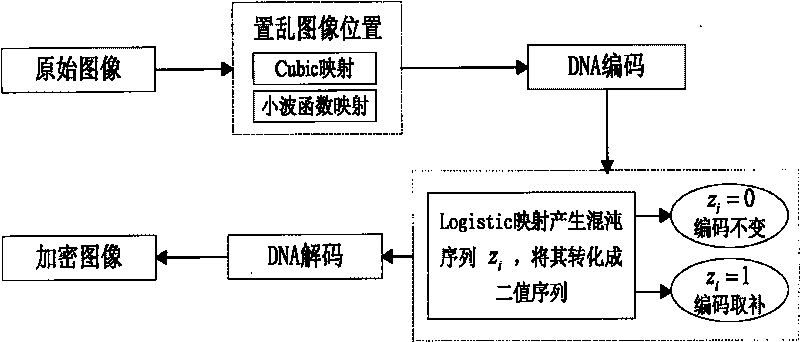
Digital image encryption method based on DNA sequence and multi-chaotic mapping
ActiveCN101706946AEasy to implementEasy to controlGenetic modelsImage data processing detailsChaotic systemsDigital image
The invention discloses a novel digital image encryption method belonging to the field of DNA calculation and image encryption, and provides a digital image encryption method based on a DNA sequence and multi-chaotic mapping. The traditional encryption algorithm based on chaos has the defects that a key space is small, a chaos system is easy to analyze and forecast, and the like; and almost of the current encryption systems based on DNA need complex biological operation and are hard to realize. In order to overcome the defects, the invention provides the digital image encryption method based on a DNA sequence and multi-chaotic mapping, comprising the following steps of: firstly, scrambling the positions of pixels of images by utilizing a two-dimension chaotic sequence generated by Cubic mapping and Haar wavelet functions, and then disrobing the pixel values of the images under the action of a chaotic sequence generated by the DNA sequence and the Logistic mapping. The experimental result shows that the algorithm is easy to realize, has better encryption effect on images, large key space and high sensitivity to keys and can effectively resist exhaustive attack and statistical attack.
Owner:DALIAN UNIV
Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
ActiveCN104008520AImprove securityLarge key spaceImage data processing detailsComputer hardwareDiffusion
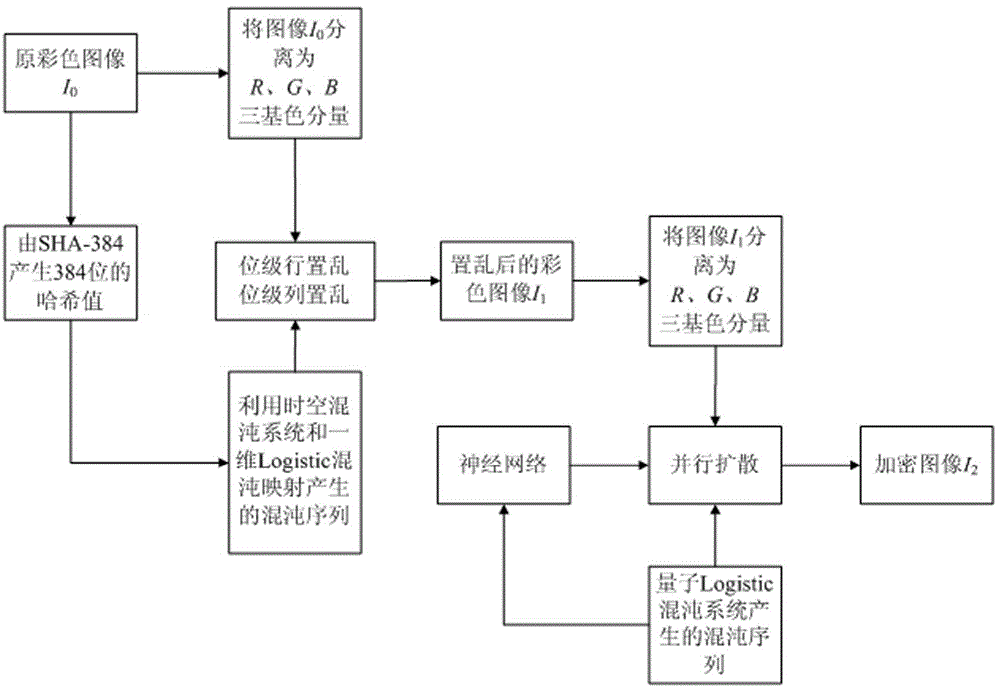
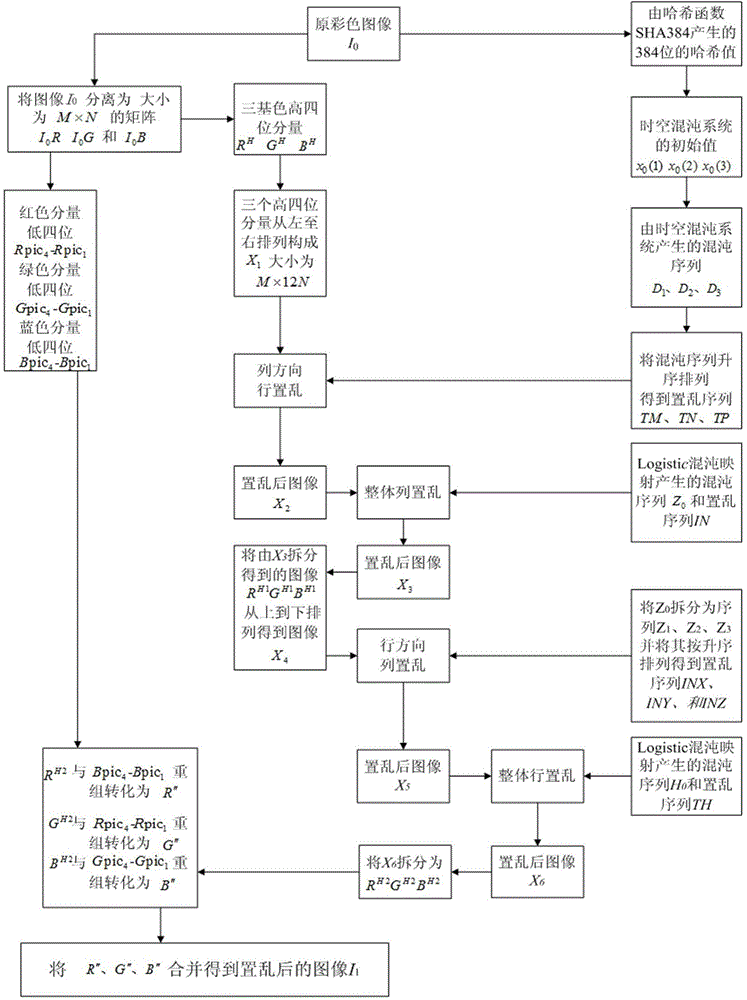
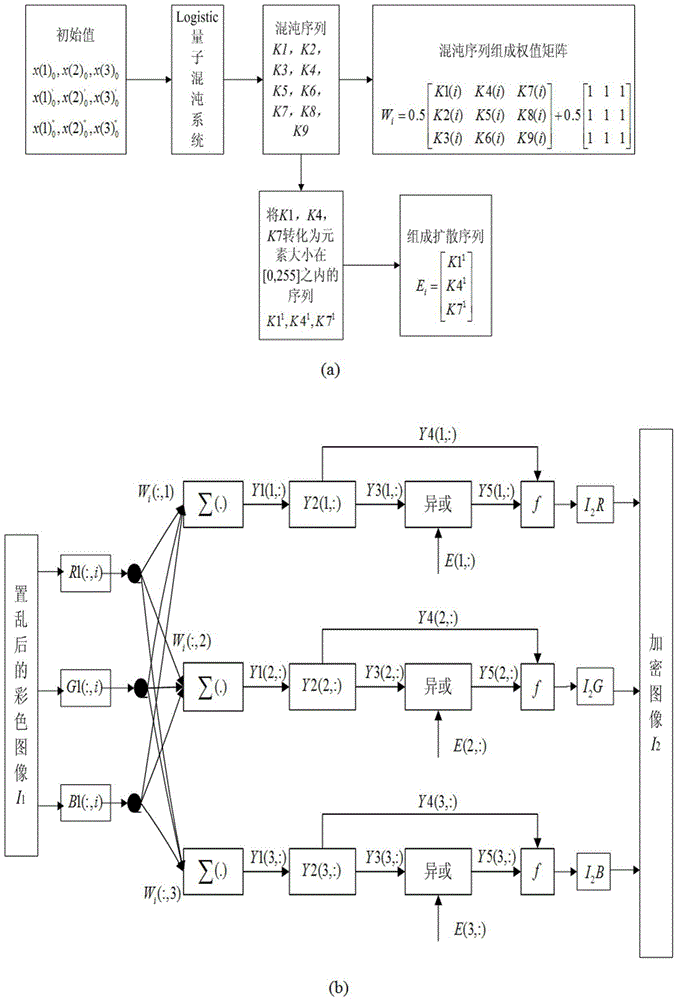
The invention relates to a color image encryption method based on an SHA-384 function, a spatiotemporal chaotic system, a quantum chaotic system and a neural network. The method includes the steps that an original color image I0 is calculated through the SHA-384 function, a Hash value is obtained as a secret key, the Hash value, a CML and one-dimension Logistic chaotic mapping are utilized for generating a chaos sequence, bit-level line-column scrambling is carried out on high four-digit images of components of three primary colors of the I0 through the chaos sequence, and a scrambled image I1 is obtained; the Logistic quantum chaotic system is utilized for generating a chaos sequence for encrypting the scrambled image, and is combined with the neural network to carry out parallel diffusion processing on all pixel values of components of three primary colors of the I1, and a final encrypted image I2 is obtained. By the method, the space of the secret key is greatly enlarged, the safety, encryption effect and secret key sensibility are higher, the attack resistance capacity is higher, the scrambling process and the encryption time are shorter, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
Image fusion encryption method based on DNA sequences and multiple chaotic mappings
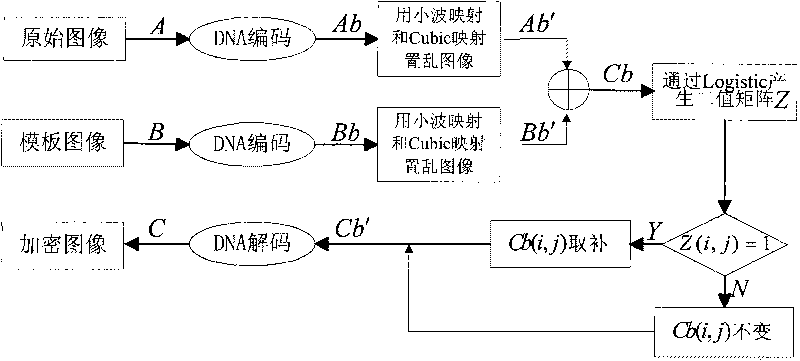
ActiveCN101706947AGood encryptionLarge key spaceGenetic modelsChaos modelsChaotic systemsImage fusion
The invention discloses an image fusion encryption algorithm based on DNA sequences and multiple chaotic mappings, belonging to the field of DNA computation and image encryption. The traditional chaos-based encryption algorithm has the defects that the key space is small, the chaotic system is easy to be analyzed and predicted, and the like, and the existing image fusion based encryption method features difficult control of fusion parameters and low safety. To overcome the above defects, the invention first utilizes the two-dimensional chaotic sequence based scrambled coded original image and the template image which are generated by the Cubic mapping and the wavelet function to obtain two DNA sequence matrices, then carries out addition operation on the two scrambled DNA sequence matrices and finally utilizes the chaotic sequence generated by Logistic mapping and the DNA sequence matrices obtained by addition operation to interact to obtain the encrypted image. The experimental results show that the algorithm can effectively encrypt the digital images and has higher safety.
Owner:DALIAN UNIV
DNA dynamic coding based colored image encryption method
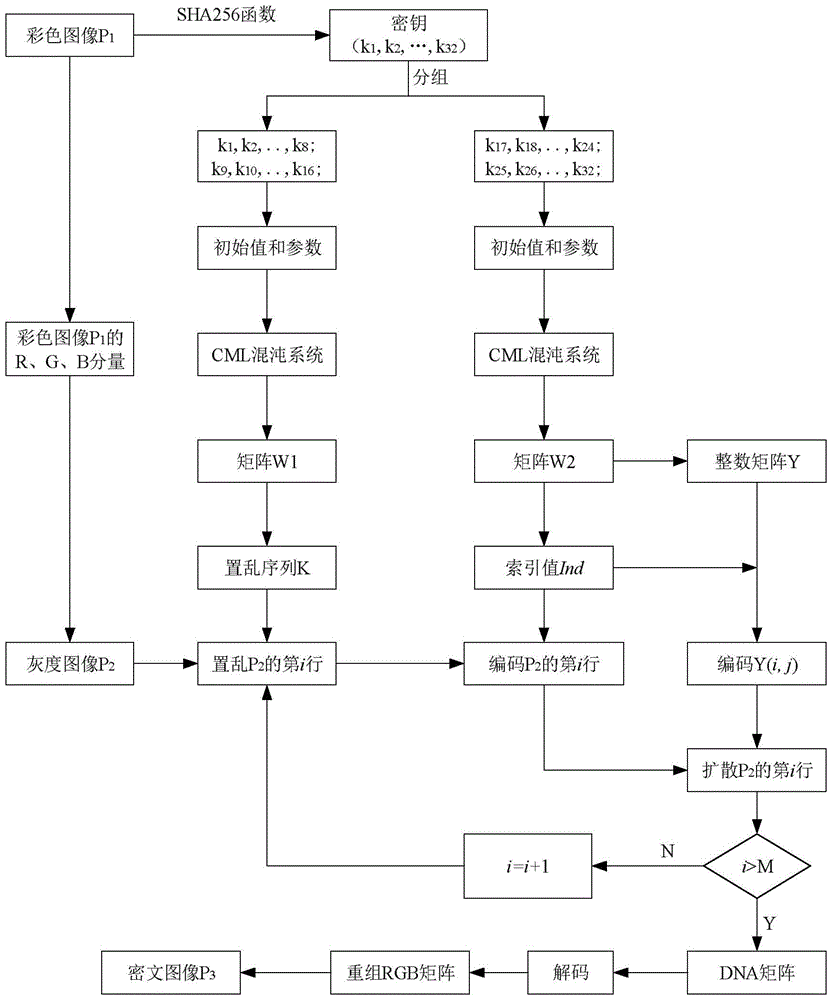
The present invention relates to a DNA dynamic coding based colored image encryption method, comprising: obtaining a key through a colored plain-text image; by the key, calculating an initial value and a parameter of a chaotic system used in scrambling and diffusion processes; substituting the initial value and the parameter to the chaotic system for iteration to obtain W1 and W2, obtaining a scrambling matrix K from W1, obtaining an integer matrix Y and an index matrix Ind from W2, and performing DNA coding on Y according to the index matrix Ind; and performing scrambling on the plain-text image row by row by using the matrix K, then performing coding and diffusion until all rows finish DNA coding, and finally performing decoding and recomposing on a DNA matrix, to obtain a final colored ciphertext image. According to the method, a function SHA256 is used to generate the key, so that the key space is expanded; the generation of the key depends on a plain-text, so that plain-text attack can be effectively resisted; chaotic characteristics are combined with DNA dynamic coding, so that the security is further improved; and meanwhile, scrambling and diffusion operations are performed according to the row of images, so that parallel computing is facilitated and the efficiency is improved.
Owner:HENAN UNIVERSITY
Image encryption method based on DNA sub-sequence operation
ActiveCN101702240AGood encryptionLarge key spaceGenetic modelsImage codingComputer visionDigital image
The invention discloses a novel digital image encryption method, which belongs to the field of DNA calculation and image encryption, in particular an image encryption method based on DNA sub-sequence operation. Current encryption systems based on DNA mostly need complex biological operations that are difficult to realize. Compared with traditional encryption methods based on DNA, the method of the invention abandons the complex biological operations, combines the DNA sub-sequence operations including extending, cutting, deleting and transposition and Logistic chaotic mapping to scramble pixel positions and pixel values of images. The experimental results indicate that the method has the advantages of easy realization, good encryption effect for images, large key space and strong sensibility to key and effective resistance to savage attacks and statistical attacks.
Owner:DALIAN UNIV
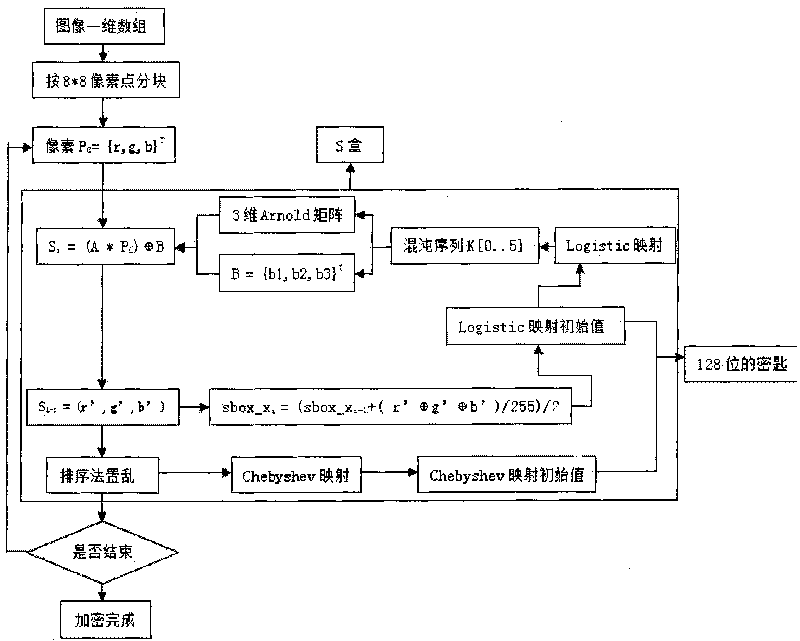
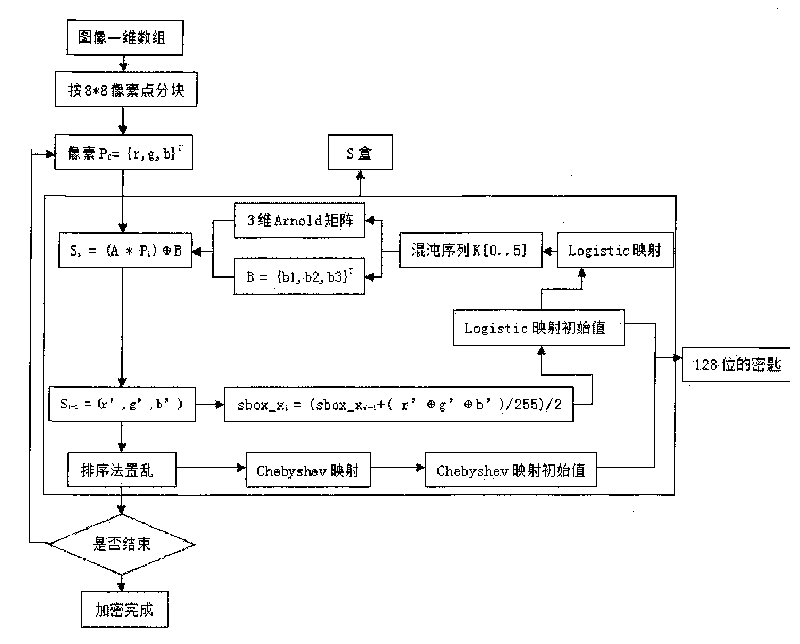
Three-dimensional Arnold mapping-based image grouping encryption method
InactiveCN101739695AIncreased sensitivityHigh sensitivityImage codingChaos modelsGraphicsChebyshev map
The invention relates to a three-dimensional Arnold mapping-based image grouping encryption method, which is characterized by comprising the following steps: firstly, adopting an Amold mapping extended to three dimensions to construct an S box; then, performing sorting scrambling on a chaotic sequence generated by a Chebyshev mapping; and finishing the encryption operation through multi-iteration. The theoretical analysis and experimental result prove that the three-dimensional Arnold mapping-based image grouping encryption method has the advantages of large key space, high sensitivity, high speed, excellent safety, strong attack resistance, and the like. Compared with other similar methods, the three-dimensional Arnold mapping-based image grouping encryption method guarantees the safety and has higher speed, and is more applicable for graphic data encryption. The main superiority of the method is that: the method has enough key space to resist an exhaustive attack, and the change of a key at any bit can completely change an initial value and the parameters of the chaotic sequence. Therefore, the sensitivity of the key is greatly improved; any useful information cannot be exposed by the statistical property; and the relativity of adjacent pixels of an intensity diagram is small and the attack resistance is strong.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
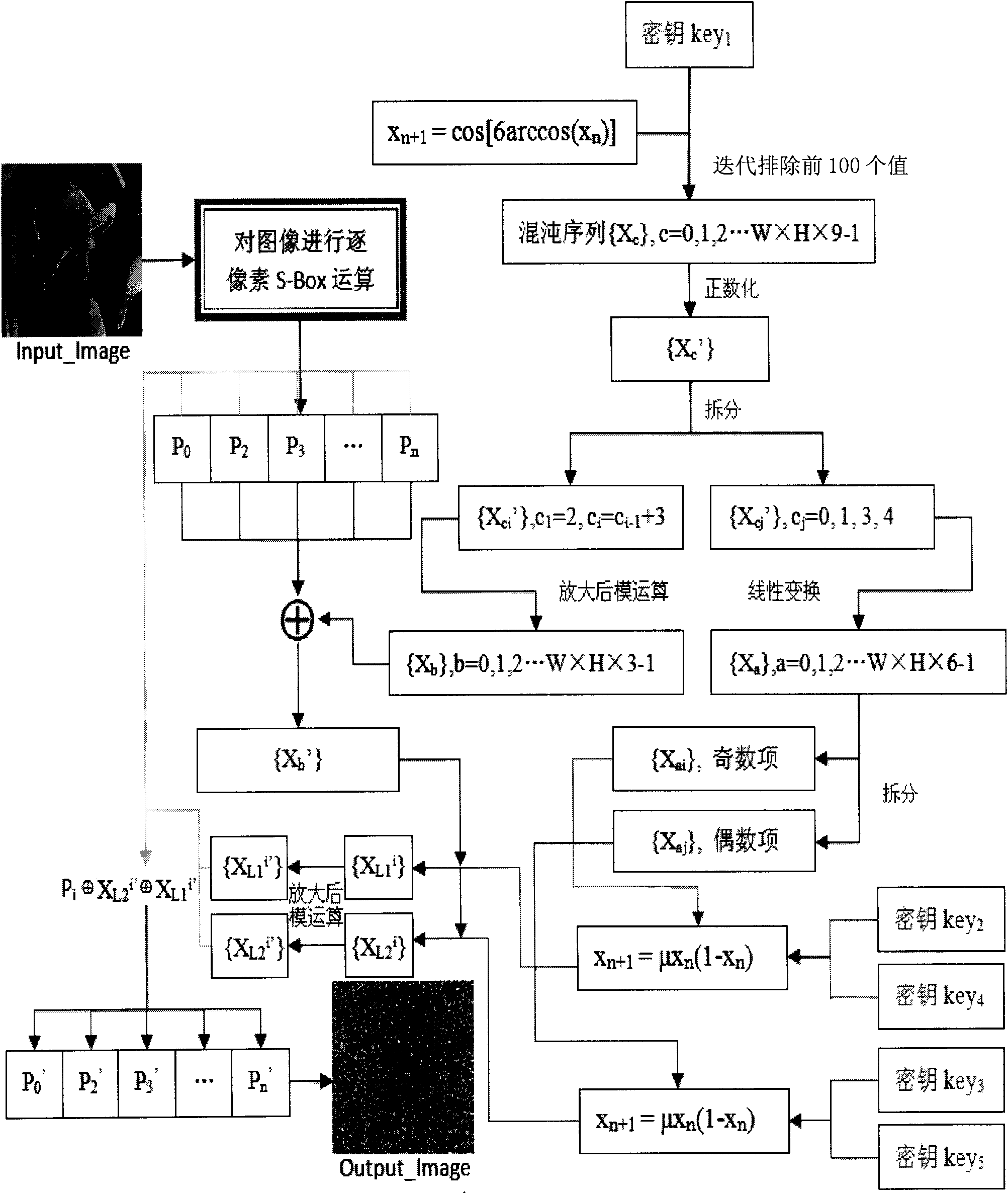
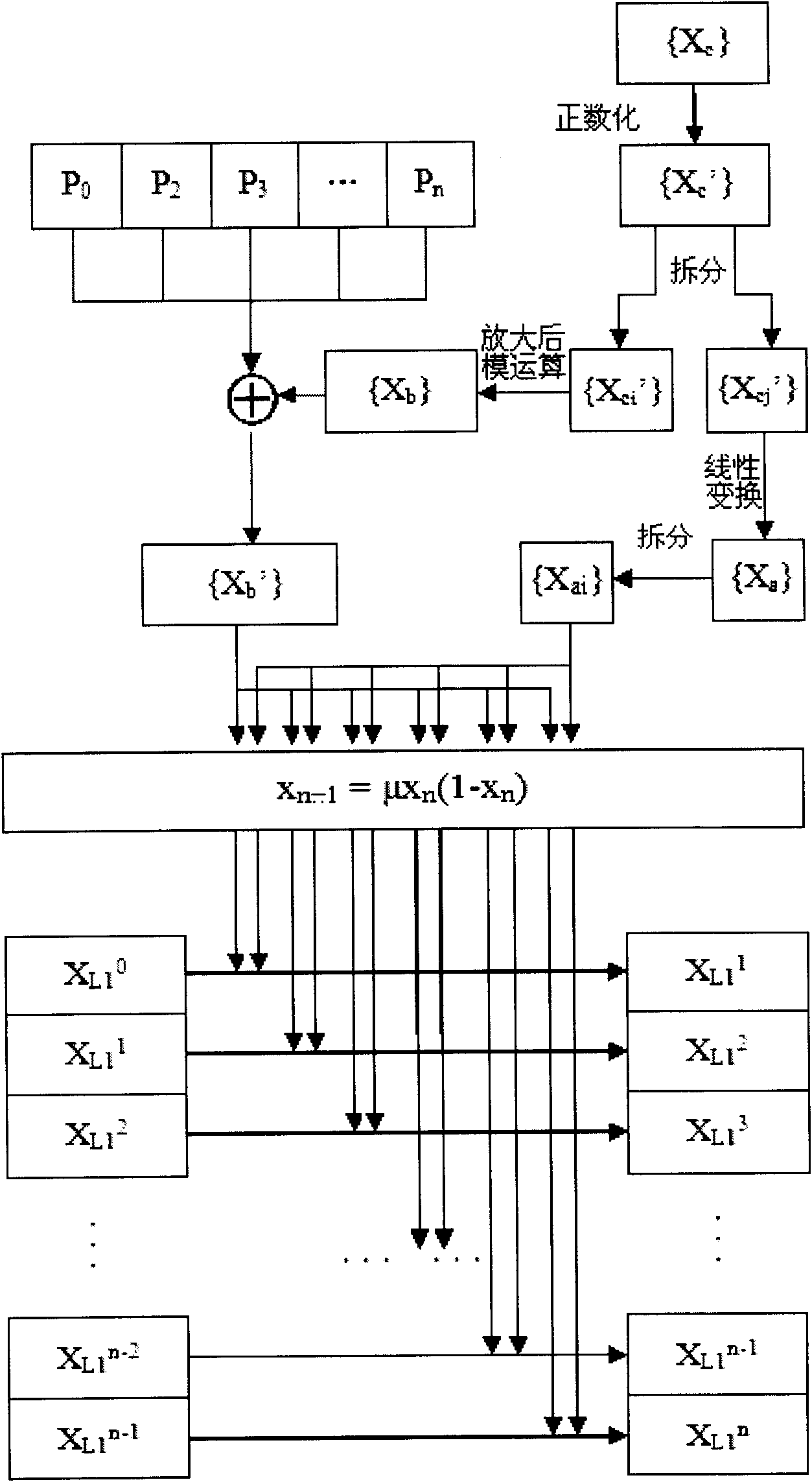
Color image encrypting method based on multi-chaos system
InactiveCN101604439AResist attackLarge key spaceImage data processing detailsArray data structureChaotic systems
The invention relates to a color image encrypting method based on a multi-chaos system, which is technically characterized in that the gray value of each pixel of an Input-image is recorded as a two-dimensional matrix P(x,y), S box transformation is performed to the P(x,y), and a transformation result is transformed into a pile of pixel groups P(h*x+y), i.e. P0, P1, P2, P3, to Pn, and the pixel groups are recorded as a sequence Pi; XOR operation is performed to each value of {XL1'} and {XL2'} and each pixel in Pi, i.e. Pi'=Pi +XL2'+XL1', thereby finishing the encrypting process. The invention has the advantages of large key space, high key sensitivity, good security and strong anti-attack ability. The security of the method can be completely independent of the attribute of an image and is especially suitable for the condition with higher security requirement.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Image encryption method based on Feistel network and dynamic DNA encoding
ActiveCN108365947AStrong randomnessStrong resistance to attackKey distribution for secure communicationSecuring communication by chaotic signalsPlaintextCiphertext
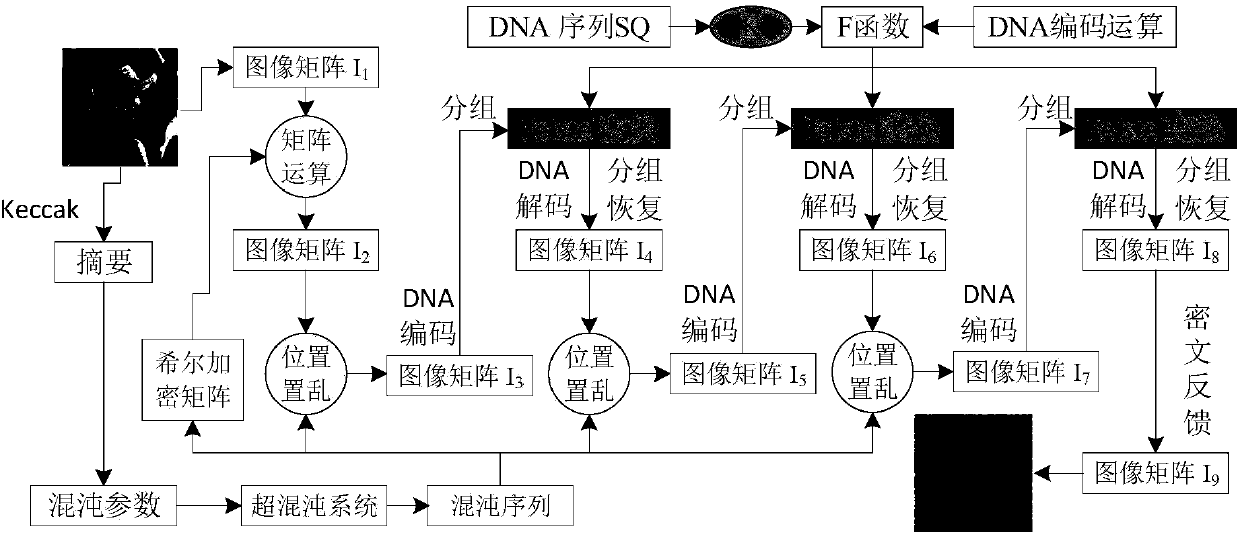
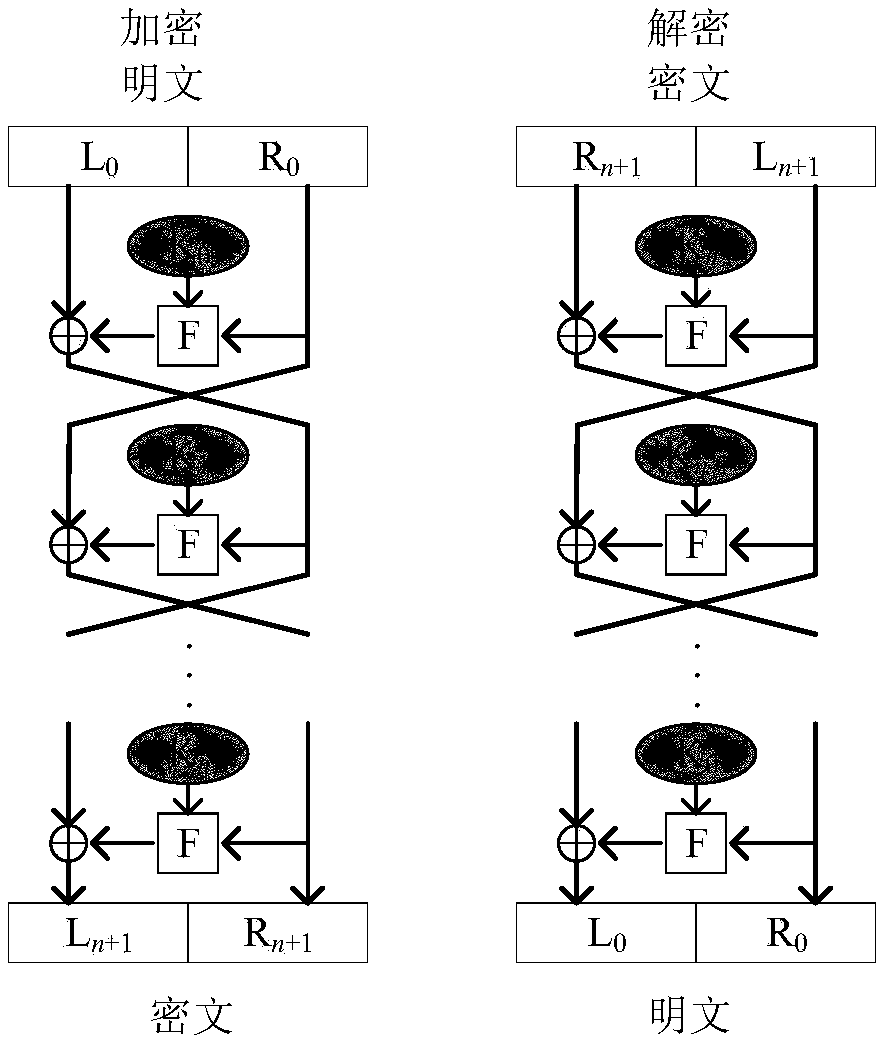
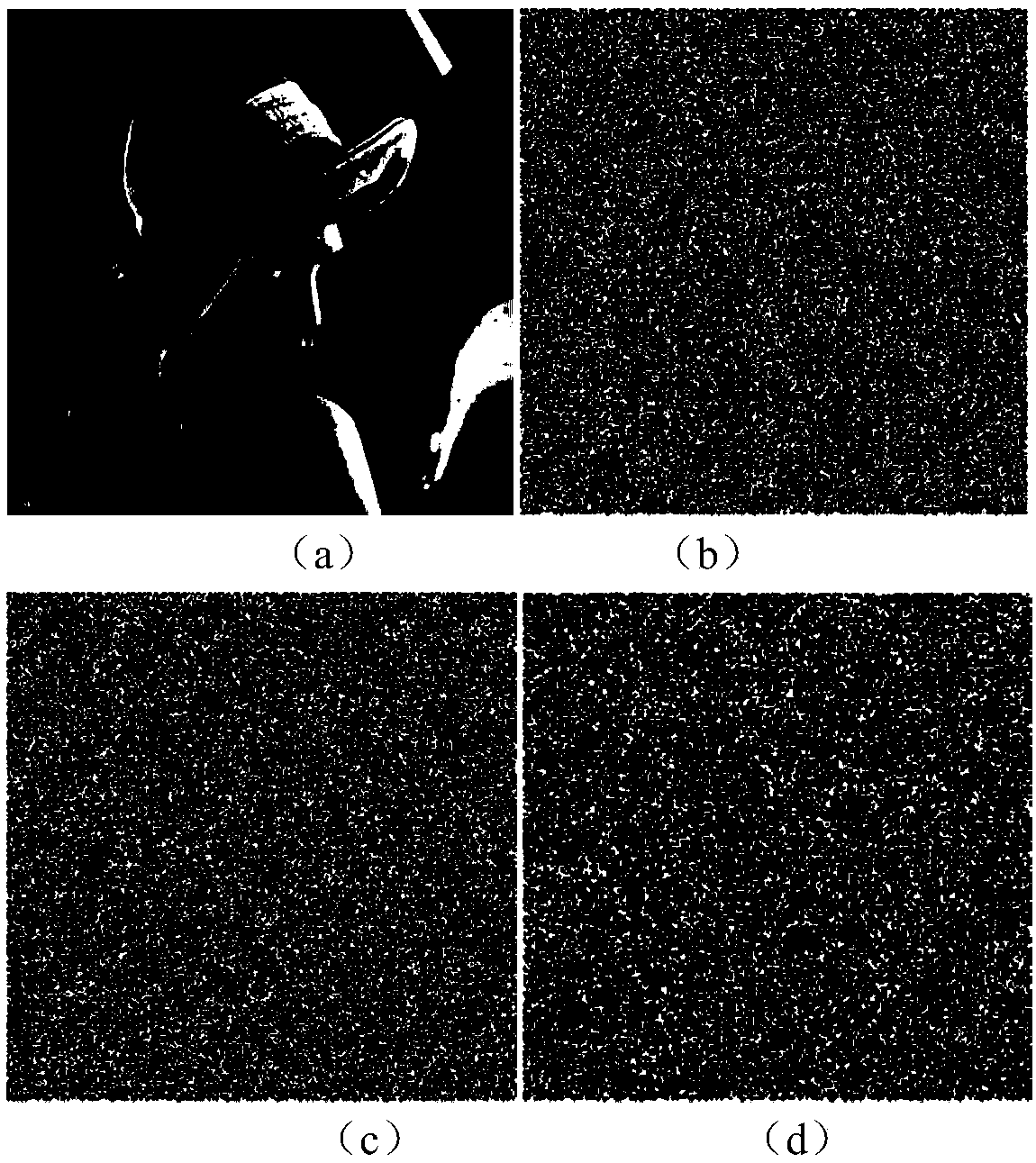
The invention provides an image encryption method based on a Feistel network and dynamic DNA encoding. The method comprises the following steps: computing a Hash value of an original plaintext image by using a Keccak algorithm, and taking the Hash value as an initial value of a hyper-chaotic Chen system, generating a Hill encryption matrix by using a chaotic sequence generated by the hyper-chaoticChen system so as to replace pixels of an original image; realizing image pixel value diffusion by using the DNA encoding operation as a F function of the Feistel network, and a DNA sequence base asa key of the Feistel network; and performing further diffusion through ciphertext feedback. Through three turns of chaotic scrambling-DNA encoding-Feistel conversion-DNA decoding, the ciphertext randomness and attack resistance are stronger, the scrambling conversion of the image pixel location and the diffusion of the pixel value are realized, and the encryption turn is reduced due to repeated scrambling and DNA encoding and decoding. Through the image encryption method provided by the invention, the image can be effectively encrypted, the plaintext sensitivity is strong, the plaintext attack, the differential attack and the statistical attack can be effectively resisted
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
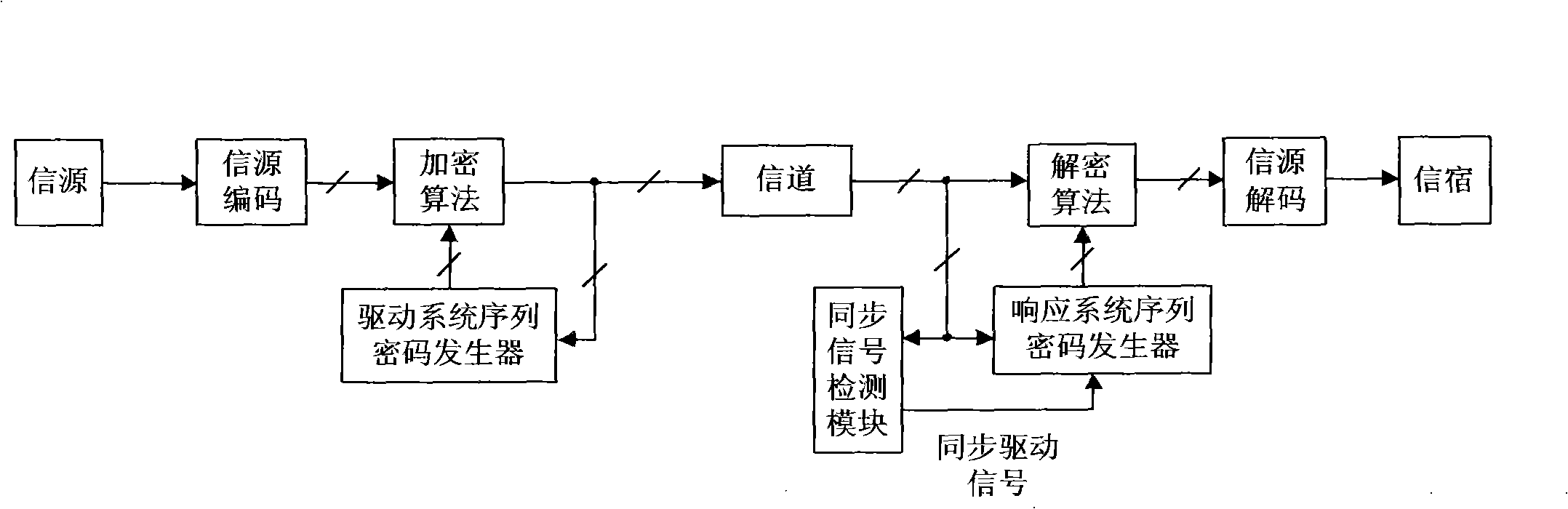
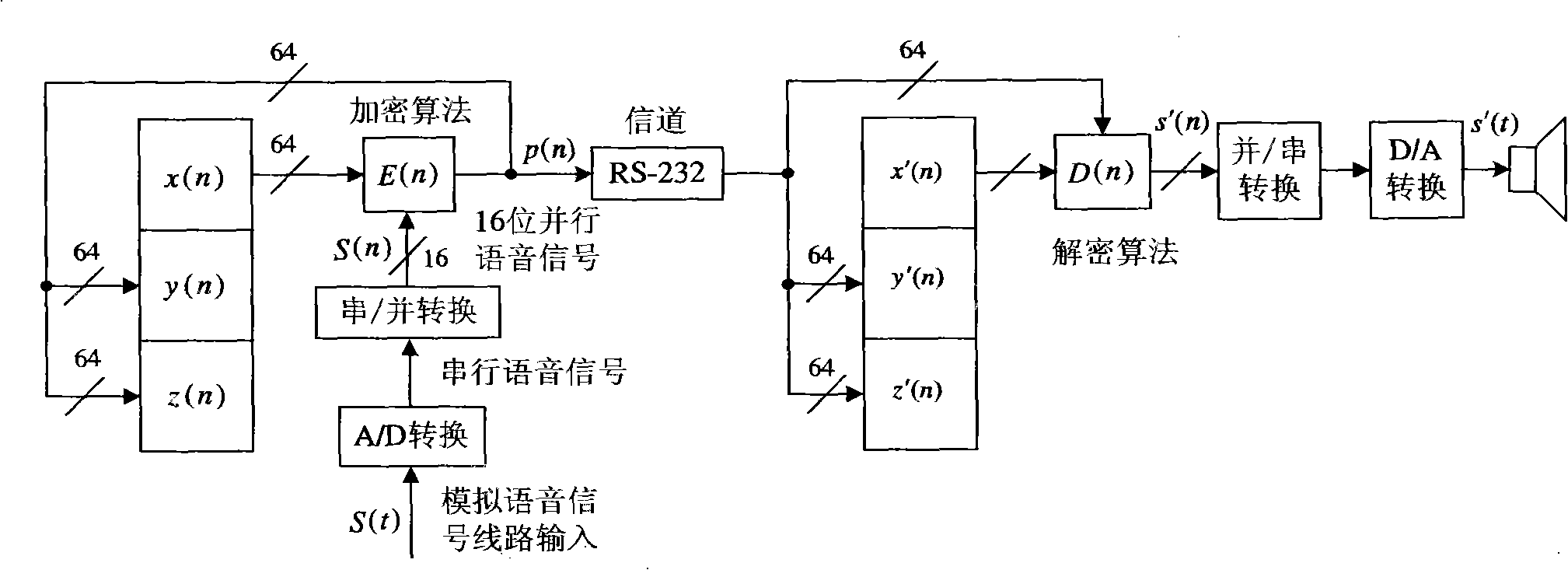
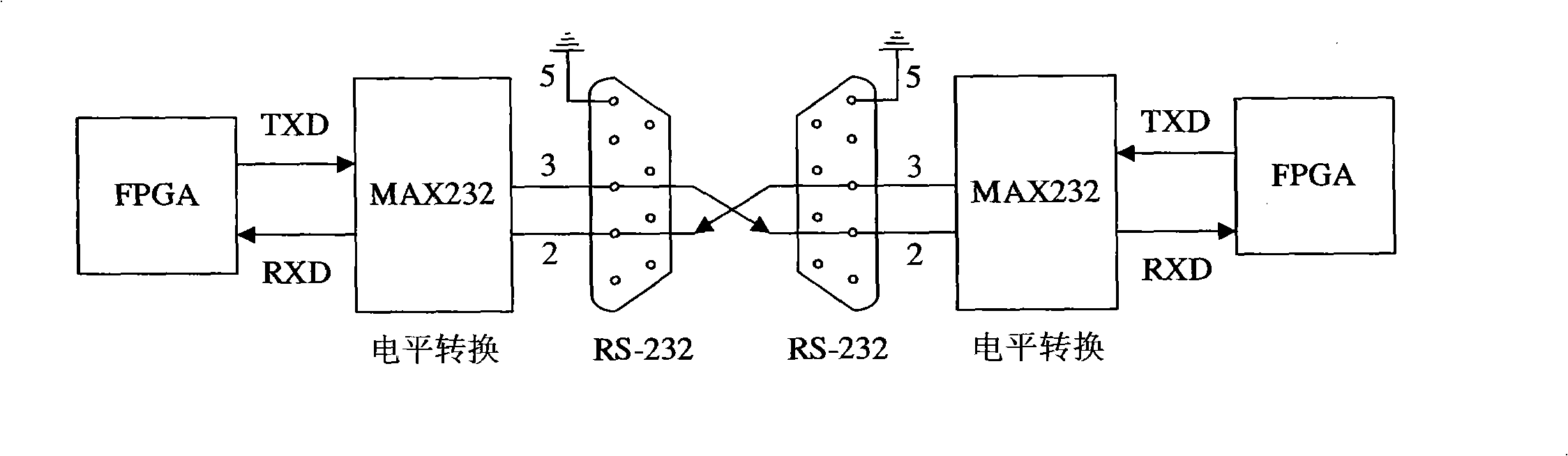
Design method for chaos digital secret communication system based on FPGA
InactiveCN101345615AIncreased complexityImprove real-time performanceSecuring communicationComputer architectureCommunications system
The invention relates to design method for FPGA based chaos digital secure communication system comprising following steps: executing discrete process for continuous chaos system by FPGA hardware, designing chaos discrete system by FPGA hardware and make it produce digital chaos sequence in a certain accuracy, adopting the digital chaos sequence as key, designing drive response type synchronous secure communication system based on choas discrete system, constructing a closed loop with interior signal, accomplishing two block FPGA development board finite digital voice communication using lattice type Cai chaos and real time voice secure communication system design based on lattice type Cai chaos. The invention is highly secure and accomplishes combination of chaos encryption system and traditional cipher system. The inventive secure communication system not only serve voice secure communication, but transmit confidential binary file. As long as data can be represented as binary data, it can execute secure communication. The inventive system can employ graph encryption / decryption and transmit over Ethernet.
Owner:GUANGDONG UNIV OF TECH
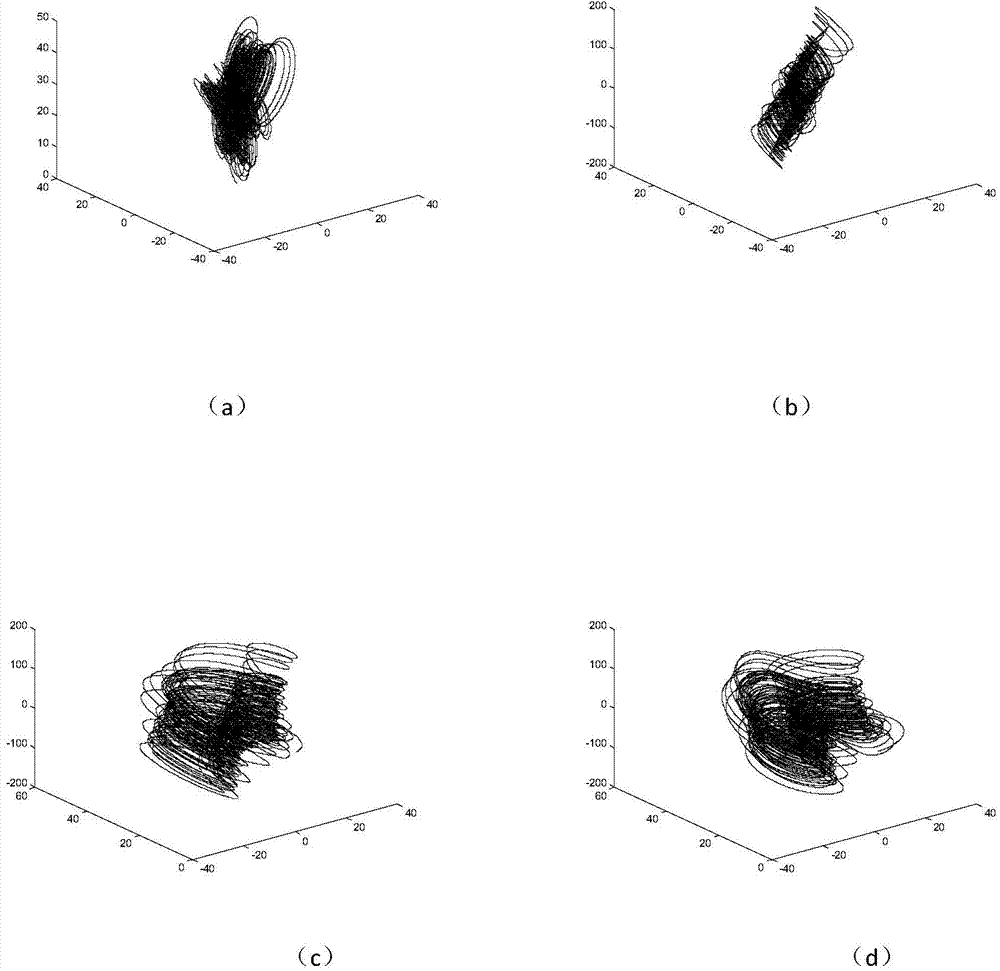
Digital image encryption method based on Cat mapping and hyper-chaos Lorenz system
InactiveCN103167213ASimple structureHigh speedSecuring communicationPictoral communicationKey sizeChosen-plaintext attack
The invention discloses a digital image encryption method based on a Cat mapping and hyper-chaos Lorenz system, and belongs to the field of image encryption. According to the digital image encryption method, a key length of an image encryption system is 247 digits and is higher than classical cryptography algorithms of the data encryption standard (DES, 56 digits), the advanced encryption standard (AES, the basic standard is 128 digits) and the international data encryption algorithm (IDEA, 128 digits). By introducing a secret key stream generative mechanism related to plaintexts, secret key streams are enabled to be related to both secret keys and the plaintexts, and even when the same diffusion secret keys are used to encrypt different plaintext images, the generated secret key streams are different. Therefore, the known-resistant / plaintext-selective attack capacity of the encryption system is obviously improved.
Owner:NORTHEASTERN UNIV
Highly precise safe palm recognition method encrypted based on phase characteristic of Log-Gabor mixed filtering
InactiveCN101308542AAvoid the effects of identificationHigh expressionCharacter and pattern recognitionComputation complexityPrivacy protection
The invention discloses a high-precision security palmprint identification method based on 2D Log-Gabor mixed-phase characteristic encryption. The method adopts a 4-directional mixed 2D Log-Gabor mixed filter to filter the preprocessed palmprint images; then the method adopts a phase encoding way to extract the phase characteristics from the filtering result, and then carries out encryption operation to the extracted mixed-phase characteristics by a cipher sequence through XOR processing; finally, the two encrypted palmprint mixed-phase characteristics obtained after the encryption operation are matched through Hamming distance matching algorithm to obtain a matching result. The algorithm is less affected by acquisition light conditions; the encryption operation to the palmprint mixed-phase characteristics by a cipher sequence through XOR processing can increase the distance between classes without changing the inner-class distance, so as to improve the palmprint identification accuracy and reduce the computational complexity; besides, the user can protect the privacy protection by changing the cipher, so the system has high security.
Owner:SOUTHWEST JIAOTONG UNIV
Multi-chaos system based method of encrypting images related to plaintext
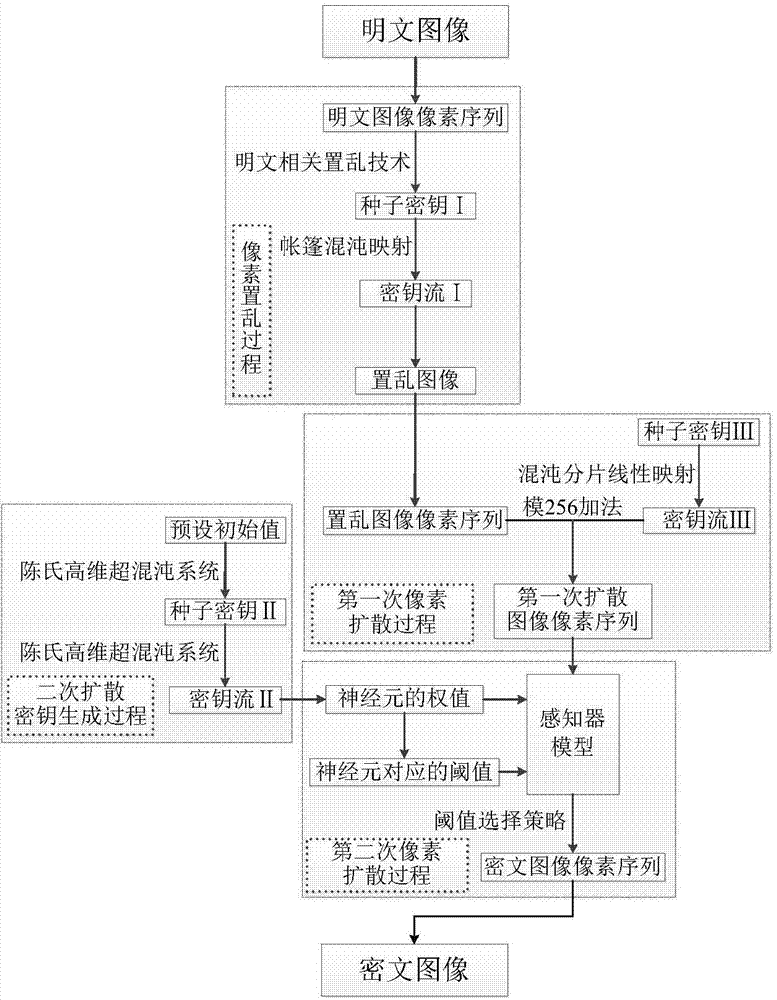
ActiveCN104751403AReduce correlationEnsure safetyImage data processing detailsPlaintextInformation processing
The invention provides a multi-chaos system based method of encrypting images related to plaintext and belongs to the field of information security. The method combining the plaintext-related scrambling technique, the multi-chaos system and a sensor model includes: scrambling plaintext images by means of the plaintext related scrambling technique based on tent chaotic mapping, subjecting the images to primary diffusion by means of chaotic piecewise linear mapping, and performing secondary diffusion by the combination of a Chen's high-dimensional hyper-chaotic system and the sensor model to finally generate ciphertext images. The algorithm structure of scrambling, diffusion and diffusion is used, relevance between the plaintext and keys is established, key space is enlarged, scrambling effect is better, diffusion degree is higher, and the ability to resist common attacks, such as exhaustive attack, statistical attach and differential attach is achieved. The method is applicable to image information processing and implementation of encryption techniques of other multimedia messages and also applicable to hardware static encryption and industrial productions, such as computer receiving or transmitting ports.
Owner:BEIHANG UNIV
Image encryption method based on sine mapping and Logistic chaos sequence
InactiveCN103530571ALarge key spaceGood against plaintext attackDigital data protectionPictoral communicationComputer visionPixel matrix
The invention relates to an image encryption method based on sine mapping and a Logistic chaos sequence. The image encryption method is technically characterized by including the steps of recording gray values of all pixel points of an original image as a two-dimensional matrix Q(x,y), obtaining a numerical value c by conducting the bitwise XOR on the gray value of each pixel point of the image, obtaining the chaos sequence through sine mapping, conducting scrambling c times on the original image in a certain mode, obtaining a scrambled image pixel matrix Q1(x,y), conducting bitwise XOR calculation bit by bit through the chaos sequence produced by a Logistic chaos system and the matrix Q1(x,y), and completing the encryption process. Due to the fact that the image is encrypted through two types of chaos mapping, the image encryption method has the advantages of being high in imperceptibility, high in secret key sensitivity, good in safety, strong in anti-attack capacity, particularly high in anti-plaintext-attack capacity, and suitable for being used for image secret communication.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Image encryption method based on chaotic mapping and bit-level replacement
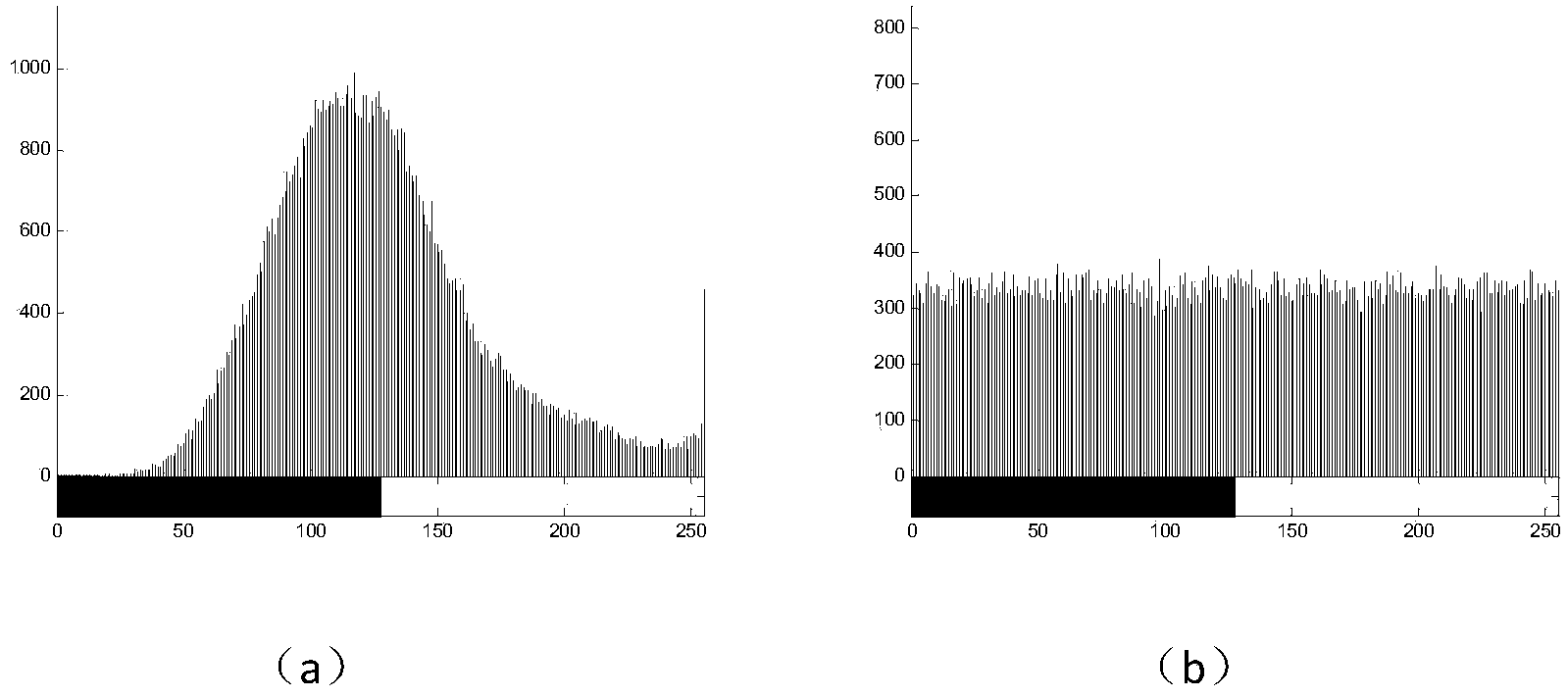
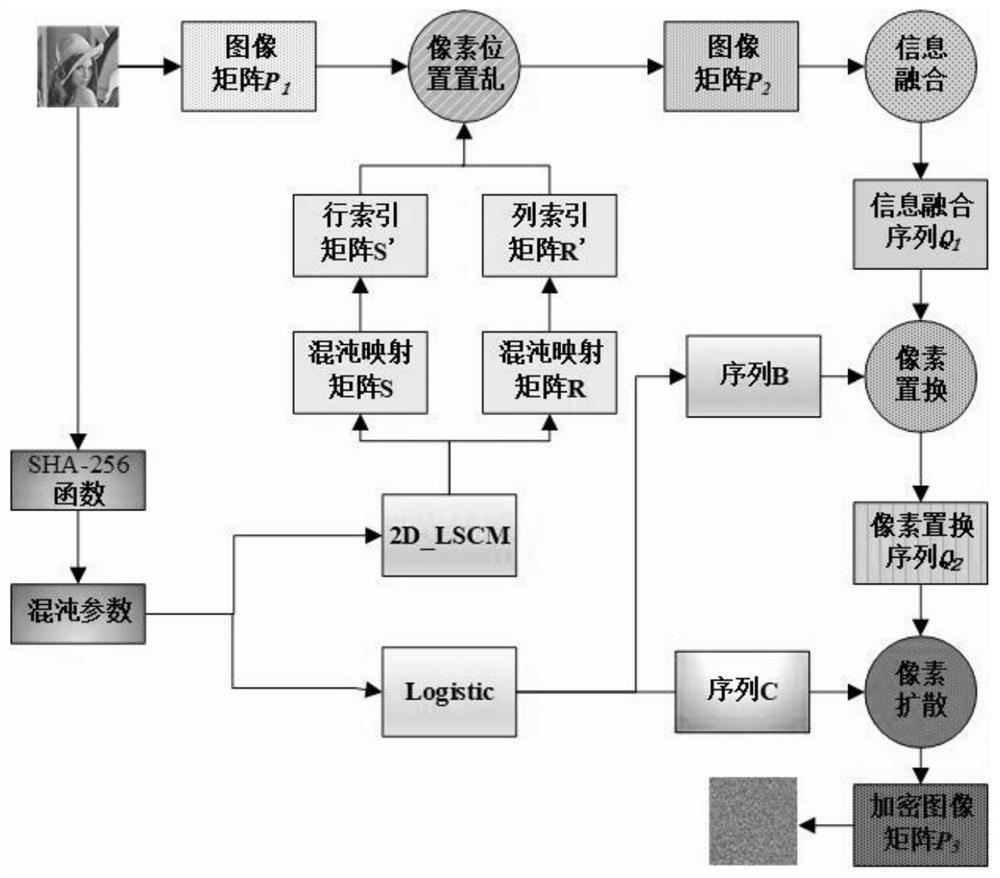
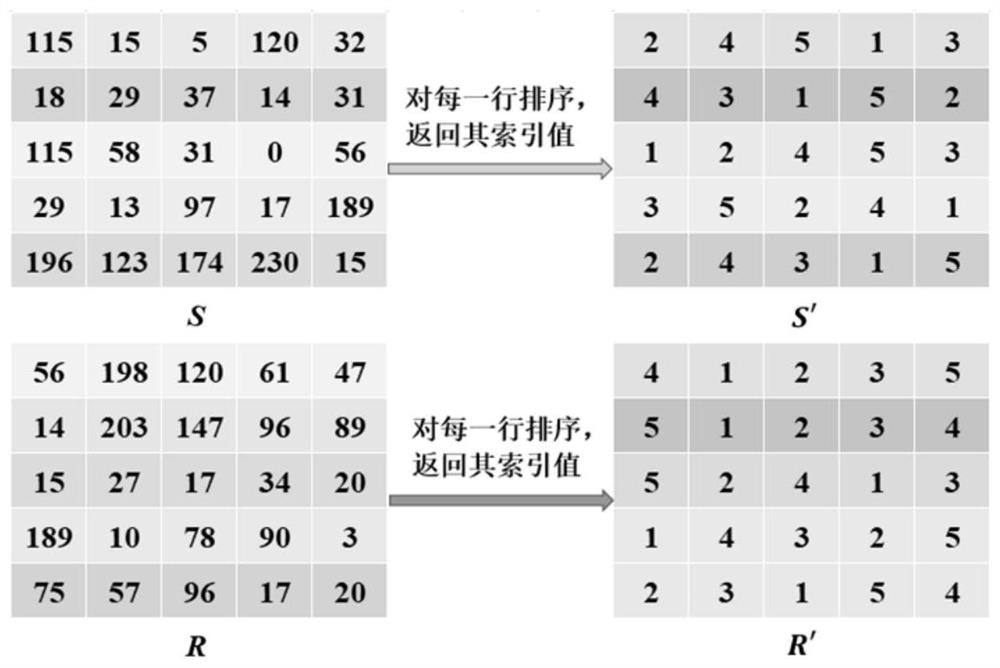
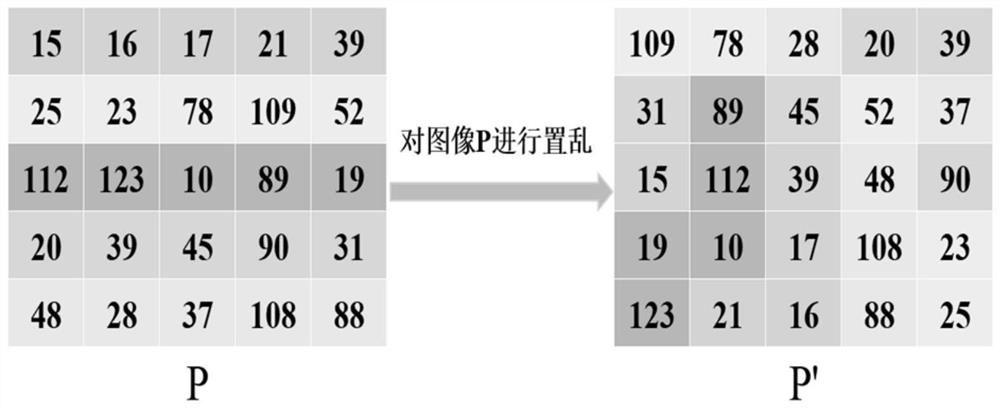
ActiveCN112084517ALarge key spaceImprove securityDigital data protectionSecuring communication by chaotic signalsKey spaceAlgorithm
The invention provides an image encryption method based on chaotic mapping and bit-level replacement. The method comprises the following steps: converting a grayscale image into an image matrix; iterating 2D-LSCM mapping to generate a chaotic sequence and mapping the chaotic sequence into a matrix, and returning a position index to perform pixel position exchange on the image matrix after descending sorting of each row; sequentially exchanging the lowest three bits in every two pixel bits to obtain an information fusion sequence of the image; performing iteration on the Logistic mapping to generate a chaotic sequence, and performing operation on the information fusion sequence and the chaotic sequence to obtain a pixel replacement column of the image; and performing pixel diffusion on thepixel replacement sequence of the image by using a chaotic sequence and a ciphertext diffusion technology to obtain an encrypted image. The chaotic mapping and scrambled images are used for replacement operation, the differential attack resistance is enhanced through bit information fusion operation and an image pixel-based diffusion method, the secret key space is large enough, violent attack canbe better resisted, and good safety is achieved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Image encryption method based on multidimensional chaotic system and Josephf scrambling
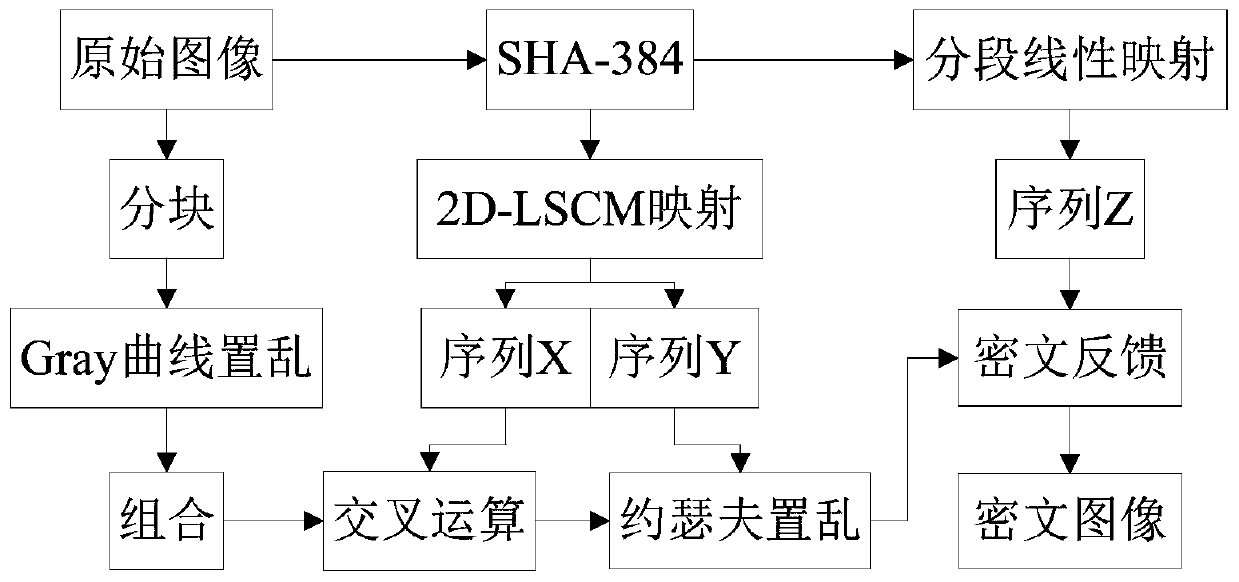
ActiveCN111105339AAchieve diffusionIncreased sensitivityImage data processing detailsKey spaceAlgorithm
The invention provides an image encryption method based on a multi-dimensional chaotic system and Josephf scrambling, and the method comprises the steps: carrying out the initialization of PWLCM mapping and 2D-LSCM mapping, and obtaining a sequence X, a sequence Y and a sequence Z; uniformly dividing the original image into sub-matrixes according to indexes, carrying out Gray curve scrambling on pixels in the sub-matrixes, and carrying out sequential recombination to obtain a recombined image matrix; taking out elements in the sequence X as a crossover operator, and performing bit crossover operation on the recombined image matrix to obtain an image matrix; taking out a pseudo-random value in the sequence Y as the step value of fixed-step Josephh scrambling, and performing Josephh scrambling operation on the image matrix to obtain a matrix; and taking out the pseudo-random value in the sequence Z and the element pixel value in the matrix to carry out XOR ciphertext feedback to obtain afinal encrypted image. The method can effectively encrypt the image, has a large key space, has high sensitivity to the to-be-encrypted image and the initial key, and has good defense capability whenresisting various attack modes.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Image two-grade encrypting method based on double-chaos system
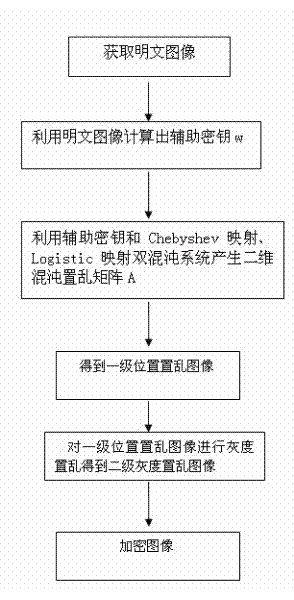
InactiveCN102693523ALarge key spaceEnhanced ability to resist known plaintext attacksImage data processing detailsKnown-plaintext attackComputer vision
The invention discloses an image two-grade encrypting method based on a double-chaos system, relating to the field of image encrypting systems. The adopted method comprises the steps of creating an auxiliary key by a plaintext image firstly; creating a two-dimension chaos scrambling matrix by the auxiliary key combined with the double-chaos system of the Chebyshev mapping and Logistic mapping to dually scramble the position and grey level of the pixels of plaintext image so as to realize the encryption of images. According to the image two-grade encrypting method, the auxiliary key based on the plaintext image is introduced to expand key space and correlate the key with the plaintext, so that the ability of the image encryption system for resisting attack of the known plaintext is enhanced; and meanwhile, the complicated characteristics of dynamics of the double-chaos system is utilized to dually scramble the position and grey level of the plaintext image, with good encryption effect and high security.
Owner:SOUTH CHINA UNIV OF TECH
Image compression sensing and image encrypting method based on sparse matrix control
InactiveCN104463765AImprove scrambling effectImprove securityImage data processing detailsImage transferCiphertext
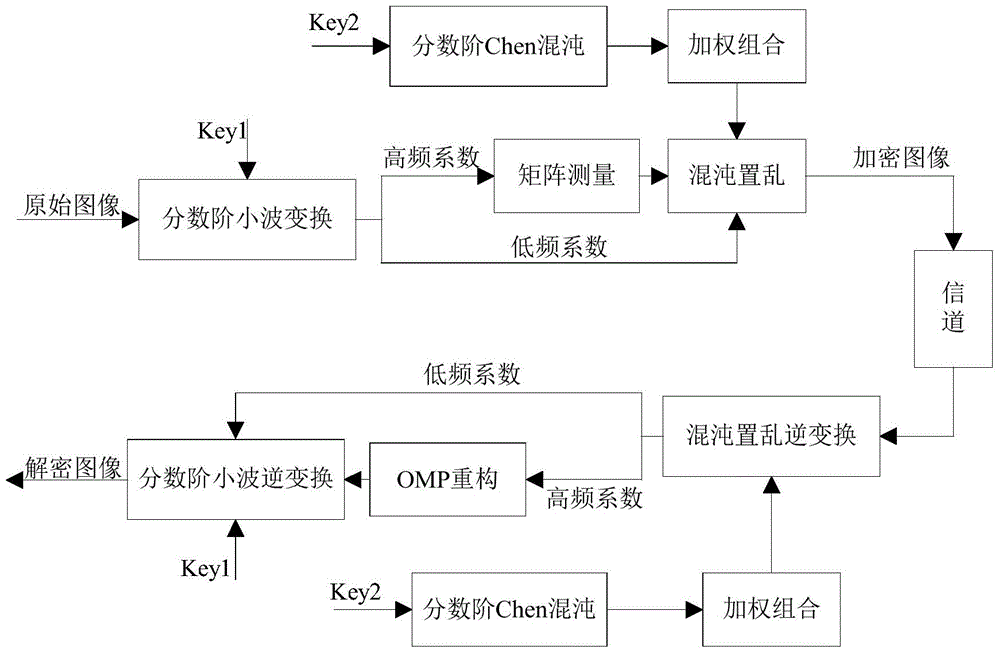
The invention provides an image compression sensing and image encrypting method based on sparse matrix control. An order is used as a secret key for controlling generation of a fraction wavelet transformation sparse matrix, and then the sparse matrix is used for carrying out sparse expression for an image to obtain a low-frequency coefficient matrix and a high-frequency coefficient matrix of the image; measurement matrixes of the number of corresponding measurement times are constructed according to the sparseness of the coefficient matrixes, and sparse coefficients are measured to obtain a compressed and encrypted image. In order to improve the safety of an encryption algorithm, fraction Chen chaos sequences of a weighted array are used for scrambling measurement values to obtain a ciphertext. The fraction wavelet transformation and fraction Chen chaos scrambling are combined, and the non-linear characteristic of the fraction order property and the fraction chaos sequences is fully utilized. The image is encrypted while being compressed, the difficulty of the large data size when the image is transmitted can be effectively overcome, and image information leakage is prevented.
Owner:NANCHANG UNIV
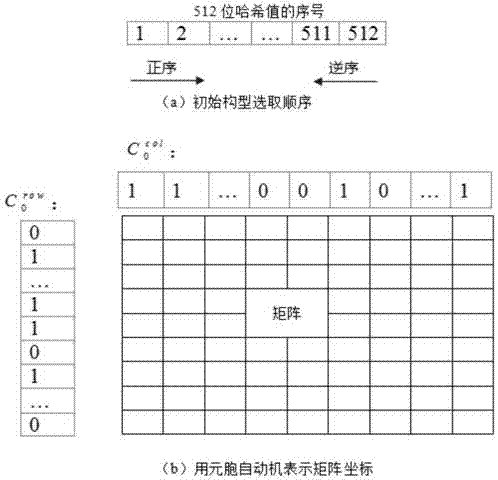
Image encryption algorithm based on memoristor hyper-chaotic system, cellular automaton and DNA calculation
ActiveCN106023052AImprove securityEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackCellular automation
The invention relates to an image encryption algorithm based on memoristor hyper-chaotic system, cellular automaton and DNA calculation. First of all, a four-dimensional memoristor hyper-chaotic system based on a Chua circuit is employed, at the same time, a secret key is generated by enabling a plaintext image on an SHA256 function; a pseudo random sequence generated by the chaos system is taken as a basis of DNA dynamic encoding, rules of cellular dynamic evolution are determined according to a DNA matrix after diffusion, and in an encryption process, partitioning processing is performed on the image; and finally, the image is encrypted through a pseudo DNA calculation method, and diffusion operation is carried out while the image is scrambled. According to the invention, on one hand, secret key space is increased and the capability of the algorithm in fending off violent attacks is enhanced; and on the other hand, the secret key is enabled to be generated through close reliance on a plaintext, the capability of the algorithm in fending off plaintext attacks is improved, the capability of fending off exhausive attacks is higher, parallel calculation is facilitated, the operation efficiency is further improved, and the security of the algorithm is improved.
Owner:HENAN UNIVERSITY
Chaotic secret optical communication system based on dual-drive Mach-Zehnder modulator
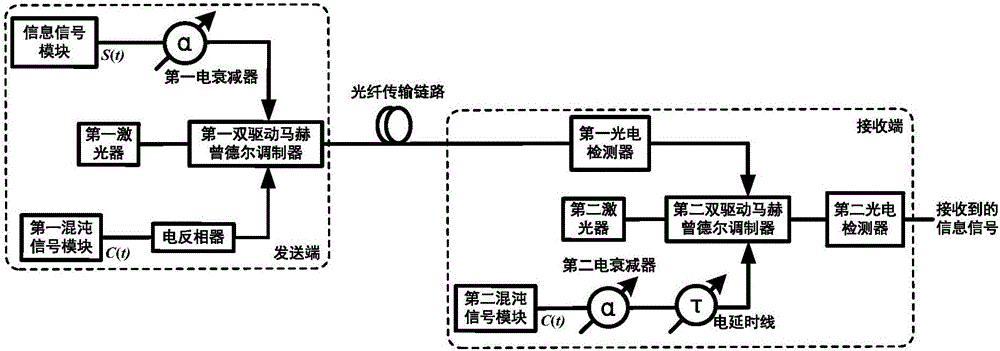
InactiveCN106169951ALarge key spaceImprove concealmentSecuring communication by chaotic signalsElectromagnetic transmission optical aspectsCommunications systemOptical communication
The invention provides a chaotic secret optical communication system based on a dual-drive Mach-Zehnder modulator. The system comprises a sending end, a fiber transmission link and a receiving end, wherein the sending end sends signals to the receiving end through the fiber transmission link; and the sending end is used for sending information signals and chaotic signals, and the receiving end is used for decrypting received signals. According to the invention, based on the dual-drive Mach-Zehnder modulator, the information signals are hidden in electric chaotic signals, and since the synchronization feature of the electric chaotic signals is superior to that of optical chaotic signals, synchronization of the secret communication system can be easily realized; and through integrated utilization of an electric time-delay line, electric attenuators and the like, the secret key space of the secret optical communication system is increased, the invisibility of the information signals is improved, and the anti-decryption performance of the system is enhanced. Besides, the system has high universality and is applied to information signals in various modulation formats.
Owner:SHANGHAI JIAO TONG UNIV
Novel chaos-based image lossless compression encryption joint algorithm
ActiveCN105704500AEnsure safetyLarge key spaceTelevision systemsSecuring communication by chaotic signalsLossless compression algorithmData compression ratio
The invention discloses an image lossless compression encryption joint algorithm based on multiple kinds of chaos, which belongs to the technical field of multimedia information safety. In view of high safety requirements of the image lossless compression algorithm SPIHT, an image lossless compression encryption joint algorithm based on multiple kinds of chaos is designed. The algorithm is designed to generate an encryption pseudo random sequence which is safer and is not easy to be broken, a wavelet transform coefficient matrix is encrypted in a mode of design local diffusion and overall scrambling, and during an SPIHT coding process, and multiple turns of encryption are carried out on a sorting scanning part. Theoretical analysis and experimental results show that the algorithm of the invention has the advantages that the encryption speed is quick; the safety is high; influences on a compression ratio are few; an image file can be kept to be lossless; and the application prospect and the practical value are wide.
Owner:HARBIN INST OF TECH AT WEIHAI
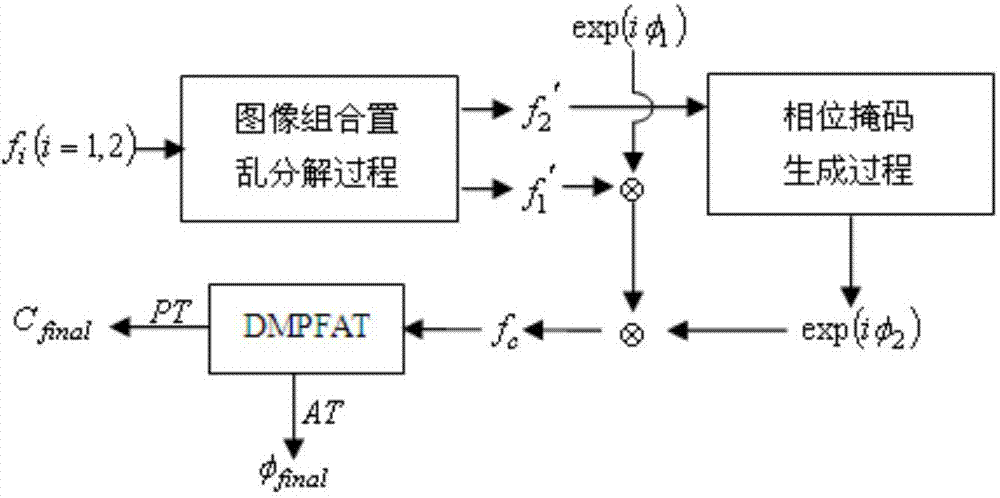
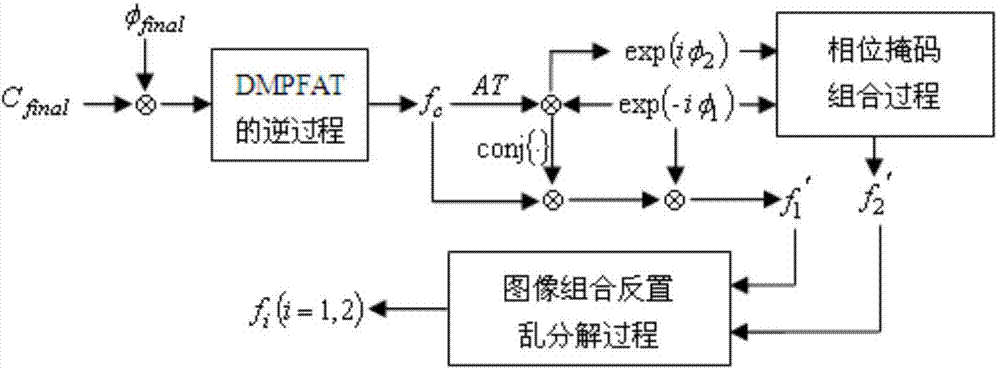
Double-image encryption and decryption method
InactiveCN104778652AAdd nonlinearityIncrease disorderImage codingImage data processing detailsCiphertextDecomposition
The invention discloses a double-image encryption and decryption method which comprises: an image combination step of combing original images; a chaotic scrambling step of scrambling and expanding a combined image by using Logistic chaotic mapping; an image decomposition step of decomposing the chaotically-scrambled image; a modulation phase mask generating step of generating a phase mask based on a chaotic random sequence generated by the chaotic mapping and the decomposed image; a temporary image generating step of generating a temporary image according to the image obtained by decomposition and the phase mask; multi-parameter discrete fraction angle transformation steps of performing two-dimensional DMPFAT transformation on the temporary image and truncating a transformed phase part to obtain a final ciphertext image; an initial value of the chaotic mapping in chaotic scrambling and / or a parameter value of multi-parameter discrete fraction angle transformation are used as private secrete keys. The method disclosed by the invention is convenient for the storage, the transmission and the management of the secrete keys; the secret key space of a cryptographic system is enlarged, and the safety and the effectiveness of the method are improved.
Owner:GUANGDONG RIZHENG IND
Quantum chaotic image encryption method based on bit scrambling
ActiveCN105631796ASimple physical structureResolve Loss of PrecisionImage data processing detailsComputer hardwareChaotic systems
The invention discloses a quantum chaotic image encryption method based on bit scrambling. The method comprises steps: a Logistic quantum chaotic system is used for generating a chaotic sequence, bit scrambling is carried out on R, G and B three-primary color component pixel values of an original image p, and a middle scrambling image I is obtained; and then, encryption operation is carried out on the middle scrambling image I, and a final encryption image q is obtained. The encryption method of the invention greatly increases the secret key space, the safety, the encryption effect and the secret key sensitivity are higher, the anti-attack ability is stronger, and the deciphering difficulty is greatly improved.
Owner:GUANGDONG UNIV OF TECH
Multiple uncertainty encryption system with misleading function
The invention discloses a multiple uncertainty encryption system with a misleading function, which aims at attacks such as rubber-hose attacks, key stealing, brute force attacks and the like. Multiple encryption is performed, and an algorithm and encryption multiplicity are uncertain, so the system has multiple uncertainty, a password analyzer cannot perform analysis, and even though the brute force attacks are adopted, a plaintext obtained only by incomplete single decryption is meaningless. The encryption multiplicity of the algorithm, encryption algorithms of each layer and keys of each layer are all uncertain, and are all included in a structural master key. The multiple uncertainty makes securer the algorithm. The system is required to comprise an improved one-time pad mechanism, and one-time pad has high reversibility, so the encryption system can obtain pseudo keys in two ways to mislead and confuse the password analyzer, and has high value in military affairs and special occasions.
Owner:桂林轻鸿科技有限公司
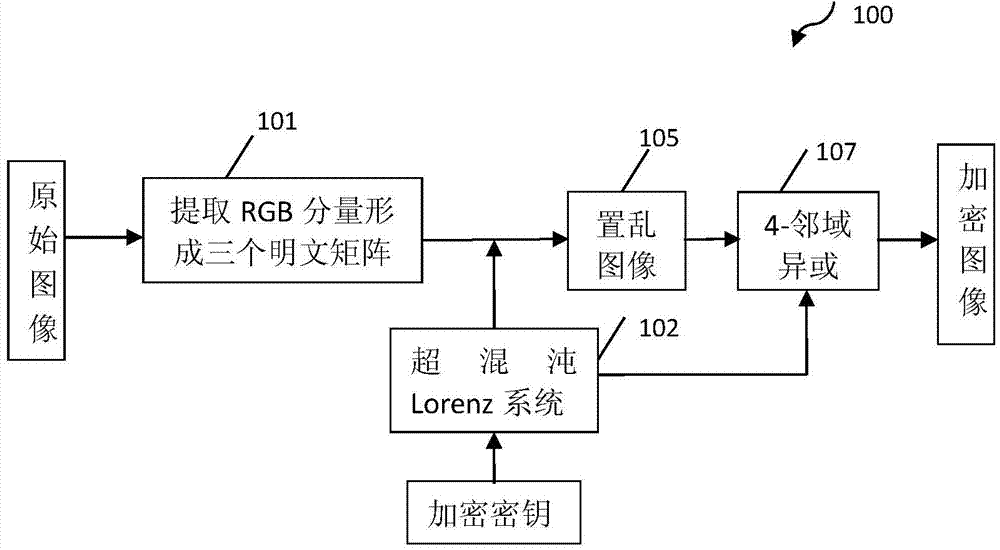
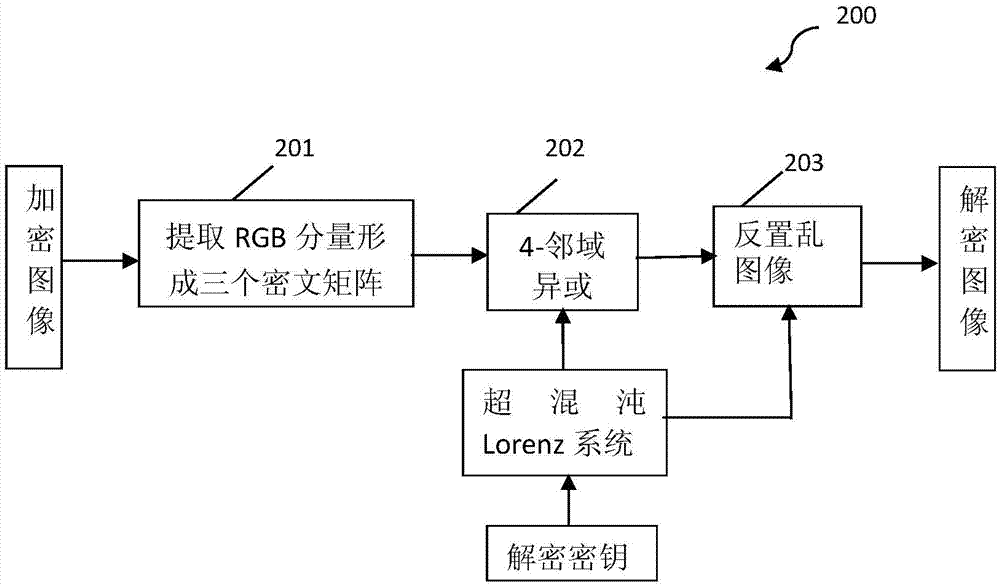
4-neighborhood exclusive or image encryption method based on hyper-chaos lorenz system
InactiveCN103491279ALarge key spaceImprove securitySecuring communicationPictoral communicationPattern recognitionColor image
The invention relates to a 4-neighborhood exclusive or image encryption method based on a hyper-chaos Lorenz system. The method is characterized in that RGE three components of an original color image are extracted, the grey levels of all pixel points in the RGE three components are recorded as a two-dimensional matrix PR, a two-dimensional matrix PG and a two-dimensional matrix PB, scrambling is carried out on the matrix PR, the matrix PG and the matrix PB respectively by means of chaos sequences generated by the hyper-chaos Lorenz to obtain an image pixel matrix PR1, an image pixel matrix PG1 and an image pixel matrix PB1 after scrambling, and 4-neighborhood exclusive or encryption is carried out on the matrix PR1 through reusing of the processed chaos sequences of the Lorenz, the matrix PG1 and the matrix PB1 respectively, so the encryption process is completed. The scrambling and 4-neighborhood exclusive or encryption are carried out on the color image through the hyper-chaos Lorenz system, so the method has the advantages of being large in secret key space, good in safety and strong in plaintext attack resistance and is suitable for image secret communication.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
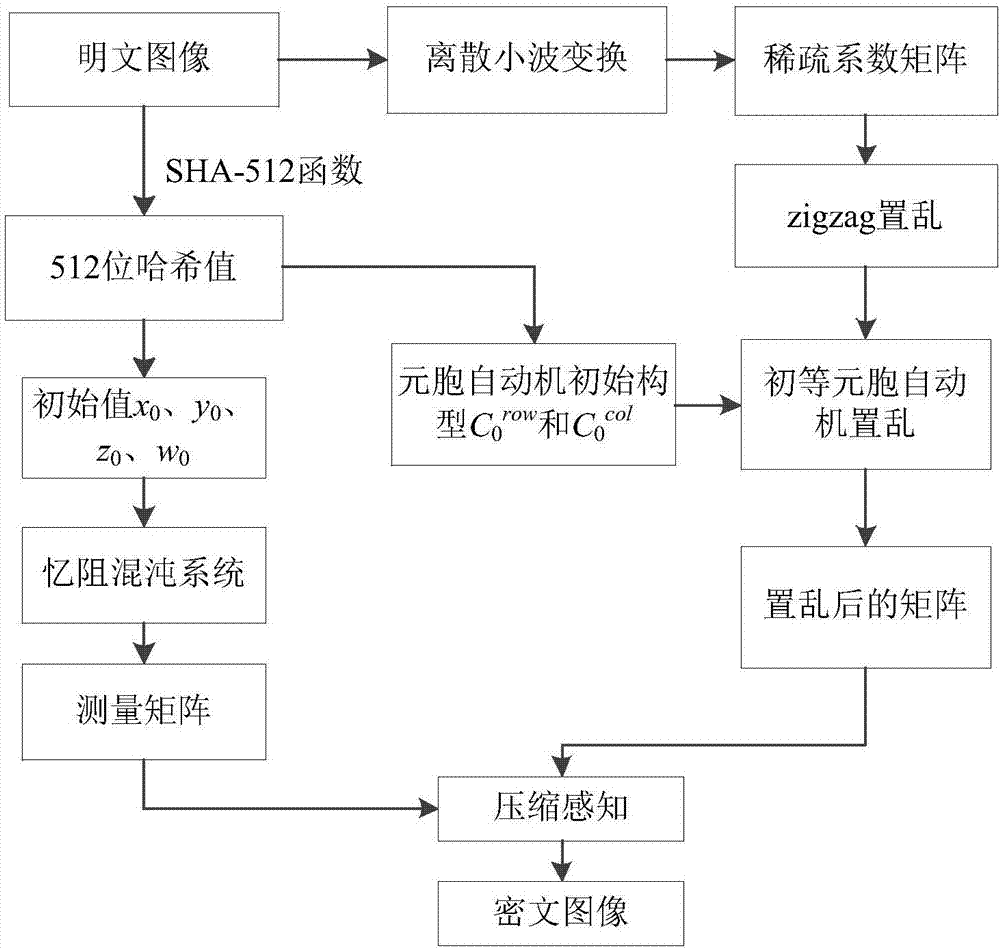
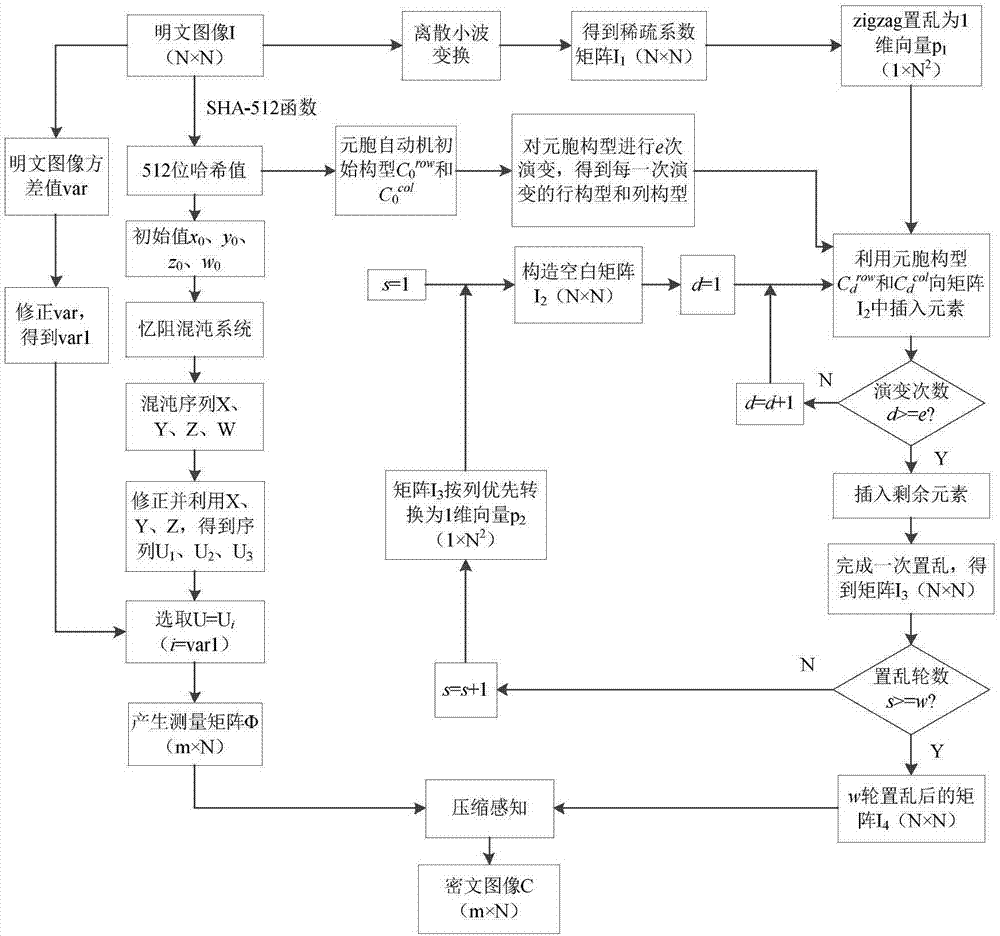
Image encryption method based on memristive chaotic system, elementary cellular automaton (ECA) and compression perception
ActiveCN107492064AIncrease scramblingLarge key spaceImage data processing detailsCellular automationCiphertext
The invention belongs to the field of image encryption, and particularly relates to an image encryption method based on a memristive chaotic system, an elementary cellular automaton (ECA) and compression perception. The method includes: firstly, carrying out discrete wavelet transform on an image, and then obtaining a sparse coefficient matrix; then adopting a zigzag scrambling method to carry out scrambling on the sparse coefficient matrix, and then utilizing the elementary cellular automaton for scrambling operation; and finally, using a measurement matrix, which is generated by the memristive chaotic system, to carry out compression perception on the image after scrambling to obtain a final ciphertext image. The plaintext image generates initial values of the chaotic system and an initial configuration of the cellular automaton through being applied to SHA-512 functions, and correlation between an algorithm and the plaintext image is enhanced. According to the method, image encryption technology of combining the elementary cellular automaton and compression perception is adopted , the elementary cellular automaton is utilized to carry out scrambling on the image, the image is encrypted while image compression is realized through compression perception, the amount of transmitted data is reduced, and image information leakage is prevented. The method has higher safety performance.
Owner:HENAN UNIVERSITY
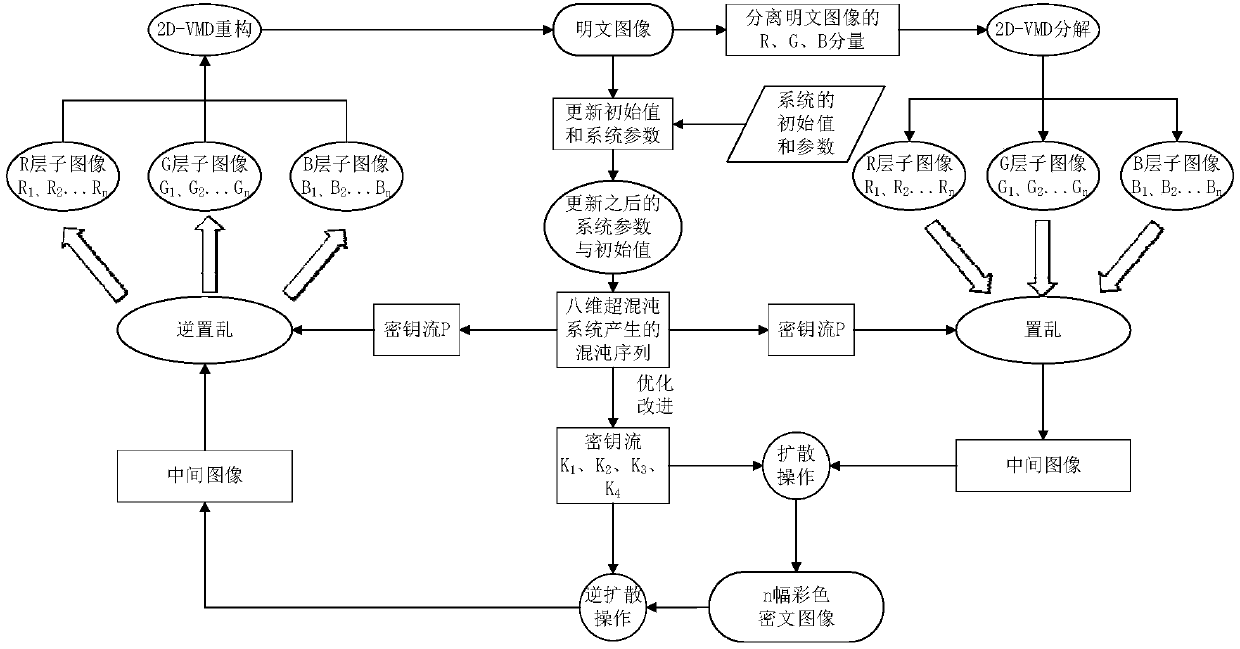
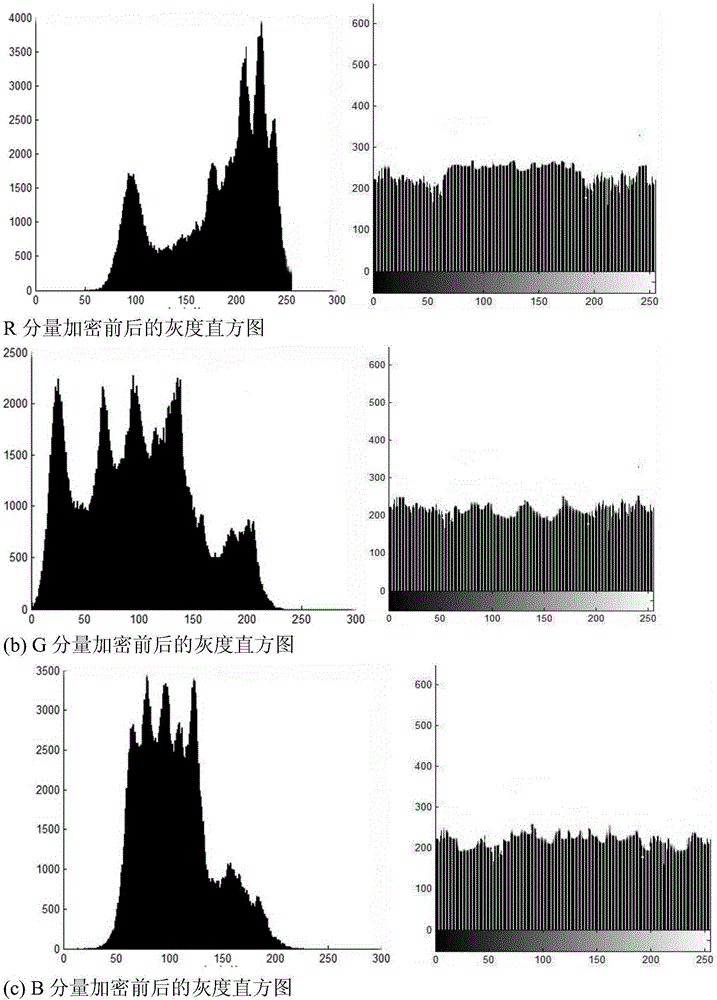
Color digital image encryption method based on 2D-VMD and eight-dimensional hyperchaotic system
ActiveCN108322622AIncreased sensitivityExpand the key spacePictoral communicationComputer visionMultiple attack
The invention provides a color digital image encryption method based on 2D-VMD and an eight-dimensional hyperchaotic system, and belongs to the technical field of information security. The problems ofpoor security, small key space and breaking easiness of the existing color digital image encryption methods are solved. The technical points are as follows: separating red, green and blue componentsof a color plaintext image; randomly selecting an initial value of the system, updating and calculating parameters and the initial value of the eight-dimensional hyperchaotic system by using the colorplaintext image, performing iteration on the hyperchaotic system to generate two key sequences with high randomness; separately decomposing the red, green and blue components by using a 2D-VMD method, separately performing pixel position scrambling and pixel value diffusion encryption on sub-images obtained by decompression, finally obtaining color ciphertext images of corresponding decompositionlayers, and decrypting the color ciphertext images. Compared with the existing encryption methods, the color image encryption algorithm provided by the invention has a significant increase in key space and can effectively resist multiple attacks.
Owner:HARBIN UNIV OF SCI & TECH
Image encryption method based on compressed sensing and three-dimensional cat mapping
ActiveCN109360141AEnsure safetyCiphertext Image DiscoveryDigital data protectionImage data processing detailsChaotic systemsCompressed sensing
Owner:HENAN UNIVERSITY
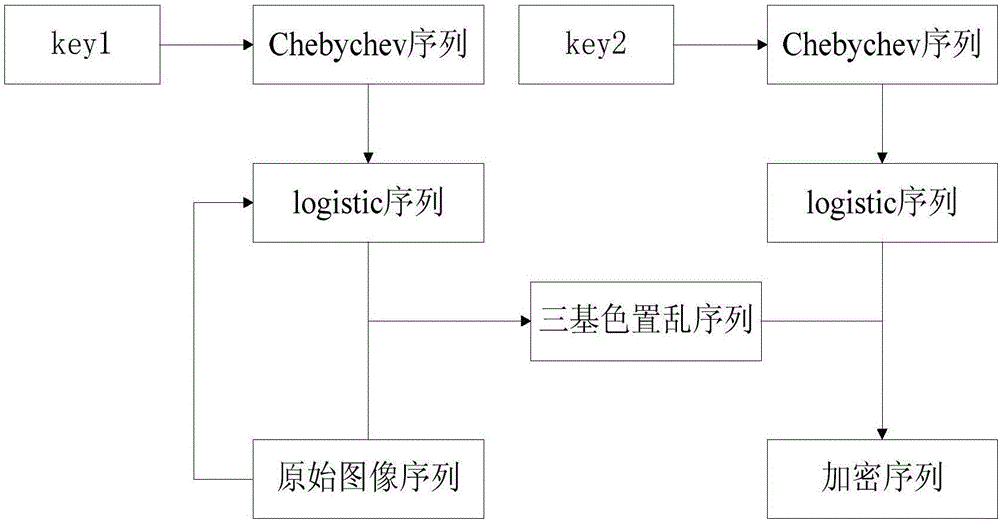
Plaintext feature-based double-chaos image encryption method
The invention discloses a plaintext feature-based double-chaos image encryption method. According to the method, Logistic mapping and Chebyshev mapping are combined; a key is generated by means of the balance of the Chebyshev mapping; the parameters of the Logistic mapping are controlled, so that a plurality of different Logistic sequences can be generated to carry out overall scrambling on color components in an image; and diffusion operation is performed scrambled image pixels, so that plaintext information can be better hidden. As indicated by an experimental simulation result, the method can not only resist statistical characteristic analysis and differential attack, but also can resist selective plaintext (ciphertext) attack, and has the advantages of good encryption effect, large key space and the like.
Owner:GUANGDONG UNIV OF TECH
Image encryption and decryption method based on improved Joseph traversal and generalized Henon mapping
ActiveCN103929563AIncrease the number of replacements generatedEnsure safetySecuring communicationPictoral communicationComputer hardwareCoupling
The invention provides an image encryption and decryption method based on improved Joseph traversal and generalized Henon mapping. An SHA-1 value of an image to be encrypted and encryption parameters selected by a user are combined to serve as a secret key, generalized Henon mapping is driven to randomly disturb the initial position, the counting-off interval and the counting-off direction of Joseph traversal mapping used for position point permutation, so that different encryption images and encryption parameters correspond to different position point permutation processes in essence; coupling of all the encryption steps is enhanced, different encryption processes are started according to different images to be encrypted, so that selective plain text attacks are effectively resisted, and the image encryption and decryption method has large secret key space and is easy to implement and low in cost.
Owner:江苏瀚洋精工科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com