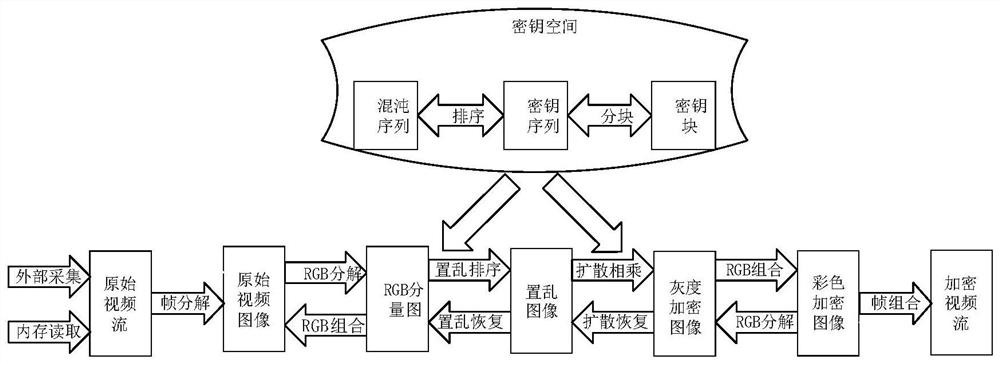
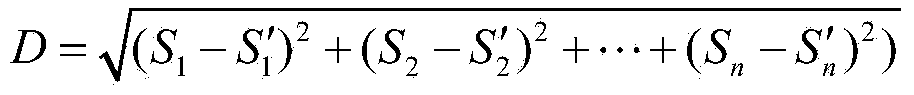Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
46results about How to "Expand the key space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
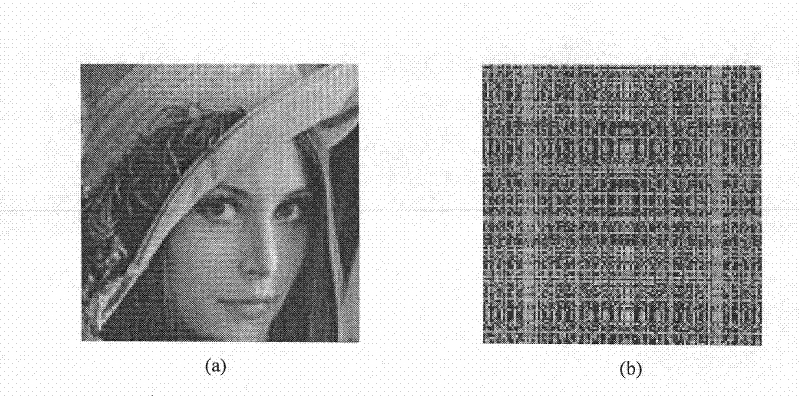
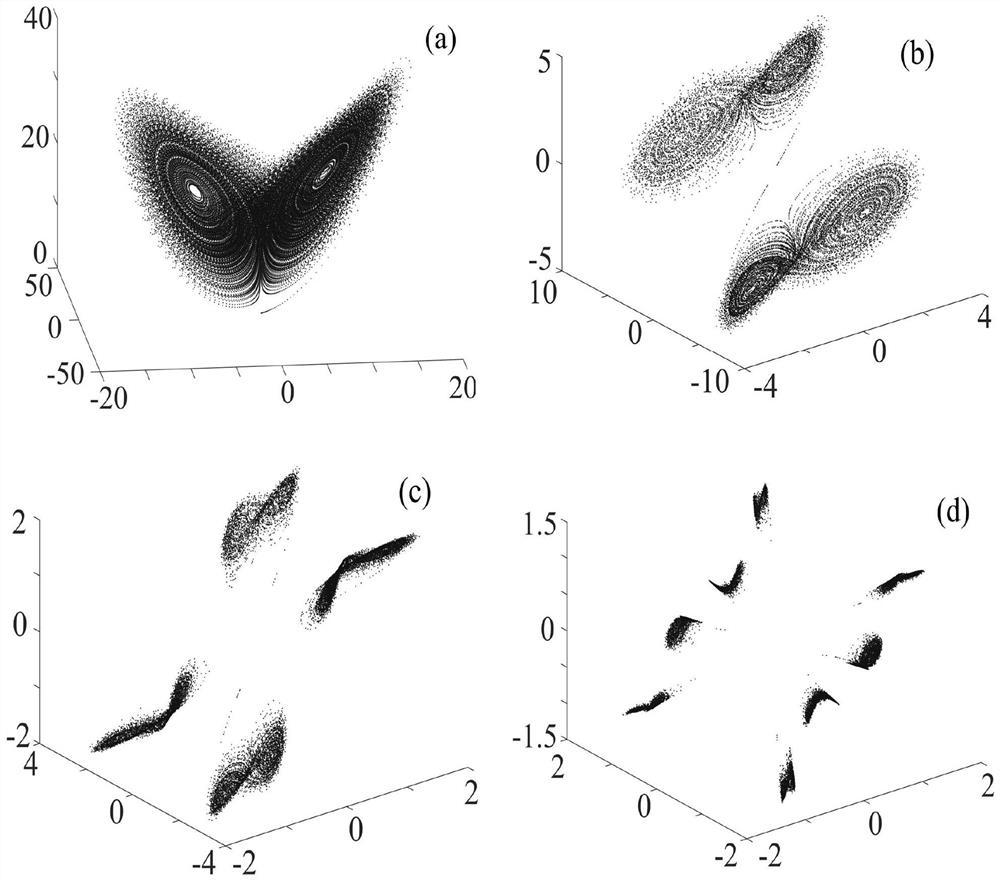
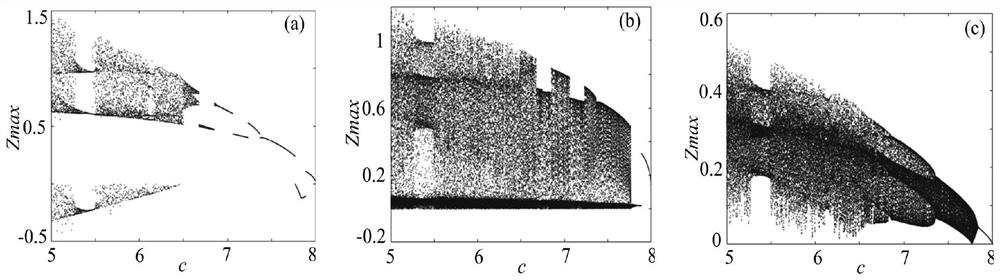
Color image encryption and decryption method based on multiple-fractional-order chaotic systems
ActiveCN102982499ARich Dynamic BehaviorBig Key SensitivityImage data processing detailsKey spaceAlgorithm
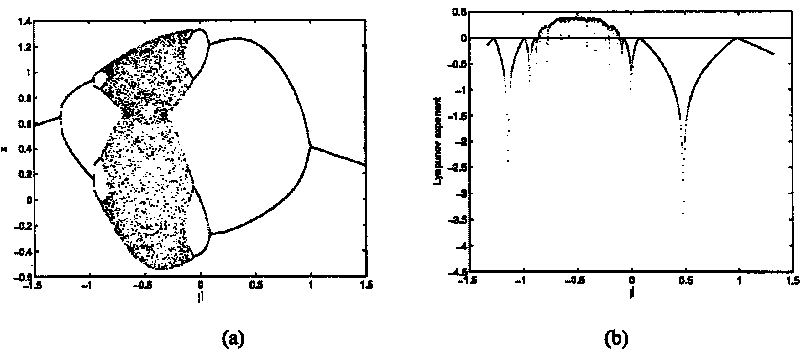
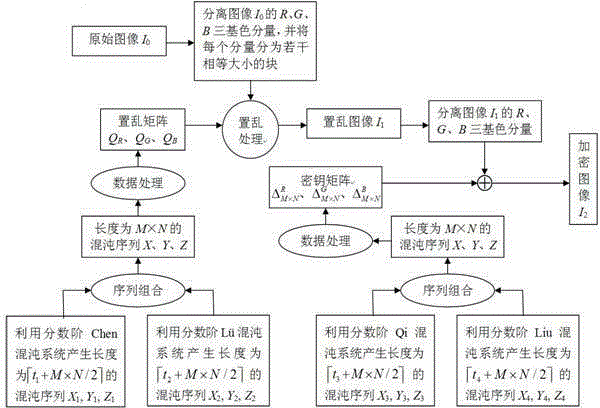
The invention discloses a color image encryption and decryption method based on multiple-fractional-order chaotic systems. An encryption algorithm comprises an original image scrambling stage and a scrambling image encryption stage. Firstly, two different fractional-order chaotic systems are utilize to generate three scrambling arrays and respectively process R, G and B three primary color component arrays of an original color image I0 in a scrambling mode to obtain scrambled image I1. Furthermore, another two different fractional-order chaotic systems are utilize to generate three secret key arrays and carries out exclusive OR operation on elements on the secret key arrays and pixel of the scrambled image I1 one by one to change values of all pixel points of the scrambled image I1 to obtain encrypted image I2, and the image decryption is a reversed process of the encryption. The method uses the multiple-fractional-order chaotic systems so as to greatly enhance safety. Furthermore, the algorithm secret keys are large in space, high in secret key sensitiveness and strong in impact resistance.
Owner:HENAN UNIVERSITY
Digital image encryption method based on DNA sequence and multi-chaotic mapping
ActiveCN101706946AEasy to implementEasy to controlGenetic modelsImage data processing detailsChaotic systemsDigital image
The invention discloses a novel digital image encryption method belonging to the field of DNA calculation and image encryption, and provides a digital image encryption method based on a DNA sequence and multi-chaotic mapping. The traditional encryption algorithm based on chaos has the defects that a key space is small, a chaos system is easy to analyze and forecast, and the like; and almost of the current encryption systems based on DNA need complex biological operation and are hard to realize. In order to overcome the defects, the invention provides the digital image encryption method based on a DNA sequence and multi-chaotic mapping, comprising the following steps of: firstly, scrambling the positions of pixels of images by utilizing a two-dimension chaotic sequence generated by Cubic mapping and Haar wavelet functions, and then disrobing the pixel values of the images under the action of a chaotic sequence generated by the DNA sequence and the Logistic mapping. The experimental result shows that the algorithm is easy to realize, has better encryption effect on images, large key space and high sensitivity to keys and can effectively resist exhaustive attack and statistical attack.
Owner:DALIAN UNIV
DNA dynamic coding based colored image encryption method
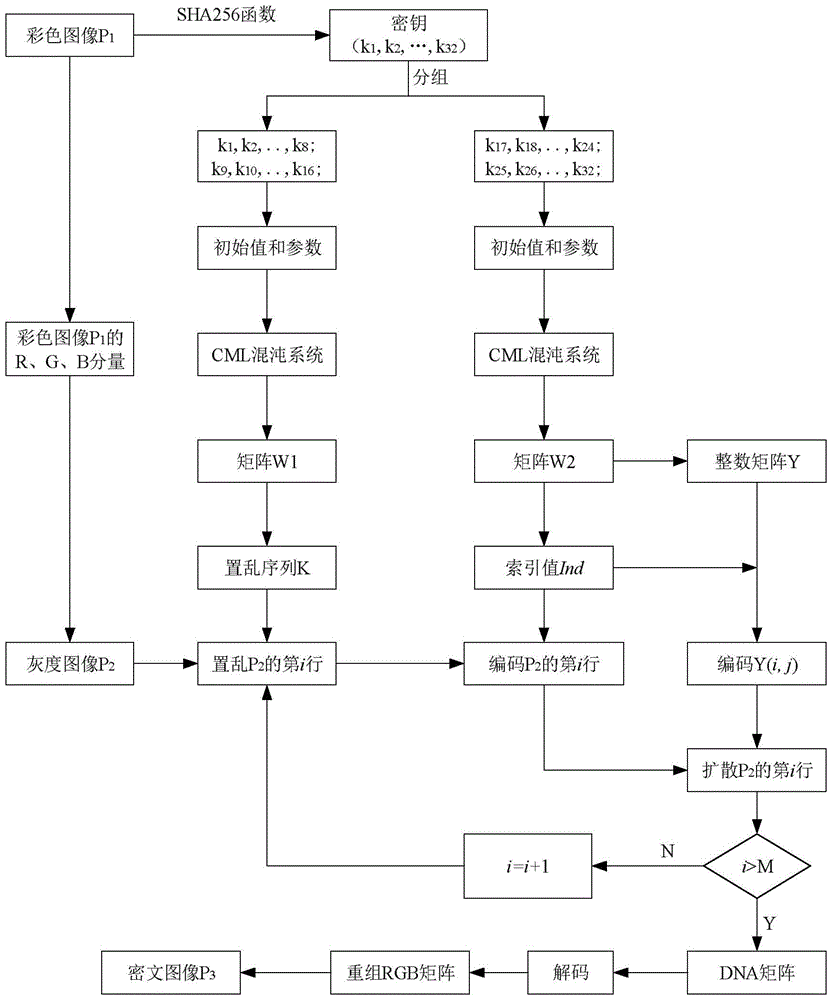
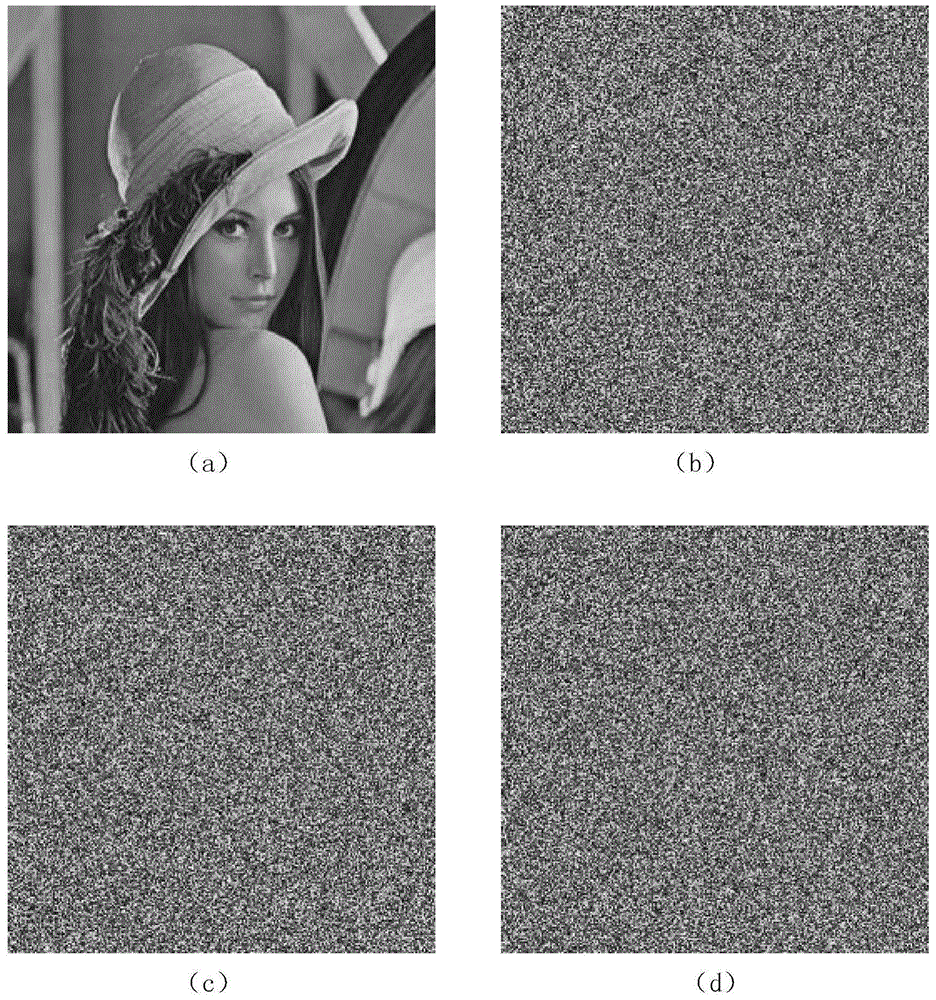
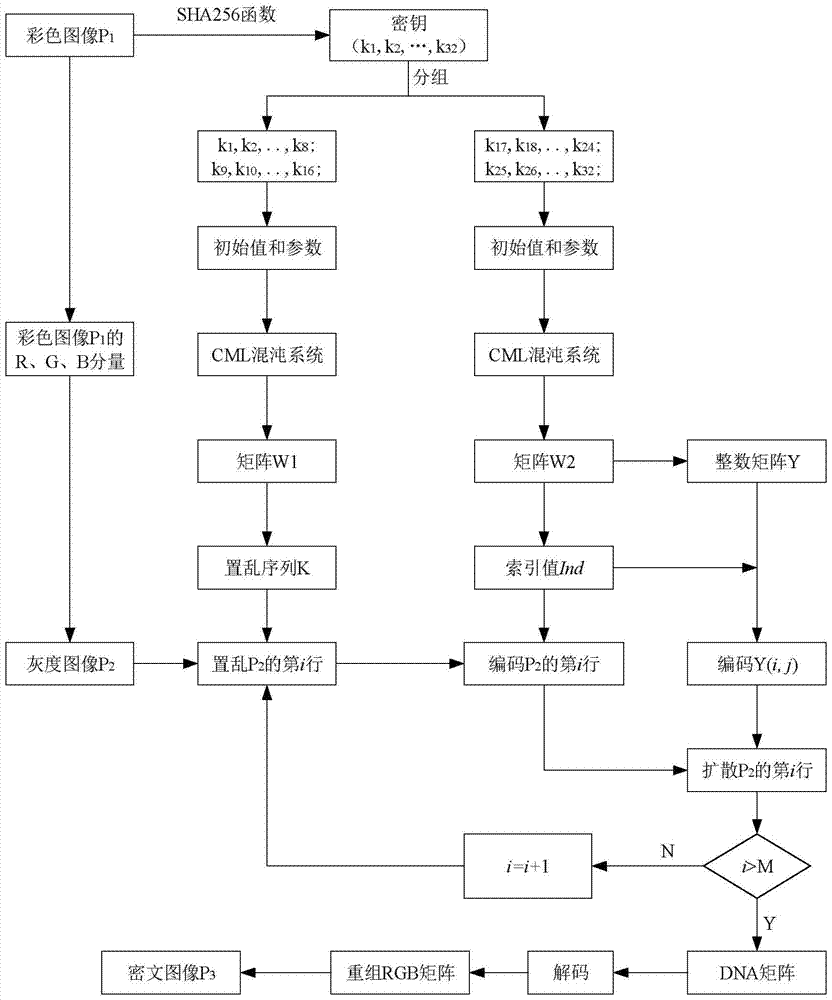
The present invention relates to a DNA dynamic coding based colored image encryption method, comprising: obtaining a key through a colored plain-text image; by the key, calculating an initial value and a parameter of a chaotic system used in scrambling and diffusion processes; substituting the initial value and the parameter to the chaotic system for iteration to obtain W1 and W2, obtaining a scrambling matrix K from W1, obtaining an integer matrix Y and an index matrix Ind from W2, and performing DNA coding on Y according to the index matrix Ind; and performing scrambling on the plain-text image row by row by using the matrix K, then performing coding and diffusion until all rows finish DNA coding, and finally performing decoding and recomposing on a DNA matrix, to obtain a final colored ciphertext image. According to the method, a function SHA256 is used to generate the key, so that the key space is expanded; the generation of the key depends on a plain-text, so that plain-text attack can be effectively resisted; chaotic characteristics are combined with DNA dynamic coding, so that the security is further improved; and meanwhile, scrambling and diffusion operations are performed according to the row of images, so that parallel computing is facilitated and the efficiency is improved.
Owner:HENAN UNIVERSITY
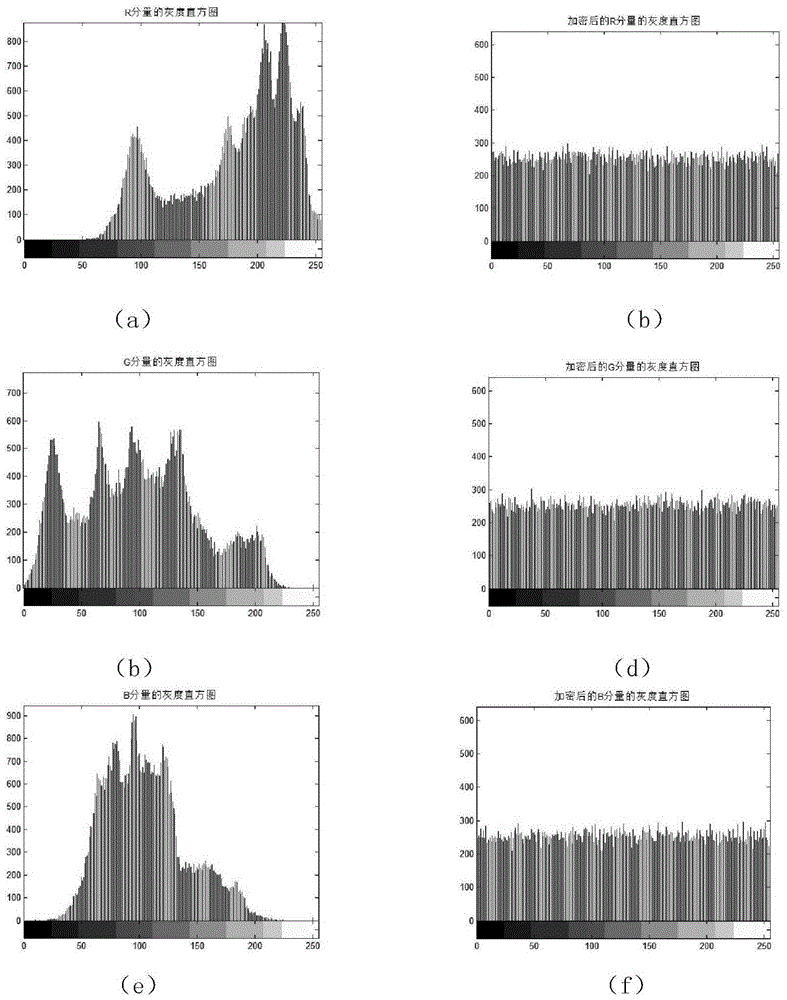
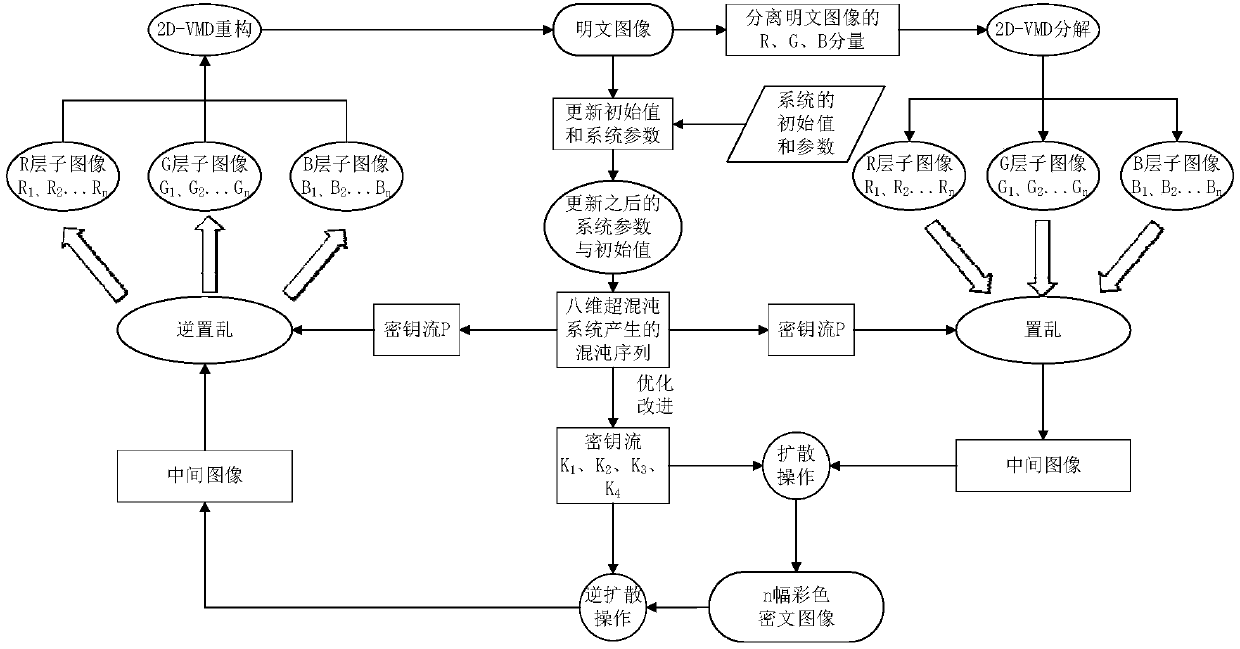
Color digital image encryption method based on 2D-VMD and eight-dimensional hyperchaotic system
ActiveCN108322622AIncreased sensitivityExpand the key spacePictoral communicationComputer visionMultiple attack
The invention provides a color digital image encryption method based on 2D-VMD and an eight-dimensional hyperchaotic system, and belongs to the technical field of information security. The problems ofpoor security, small key space and breaking easiness of the existing color digital image encryption methods are solved. The technical points are as follows: separating red, green and blue componentsof a color plaintext image; randomly selecting an initial value of the system, updating and calculating parameters and the initial value of the eight-dimensional hyperchaotic system by using the colorplaintext image, performing iteration on the hyperchaotic system to generate two key sequences with high randomness; separately decomposing the red, green and blue components by using a 2D-VMD method, separately performing pixel position scrambling and pixel value diffusion encryption on sub-images obtained by decompression, finally obtaining color ciphertext images of corresponding decompositionlayers, and decrypting the color ciphertext images. Compared with the existing encryption methods, the color image encryption algorithm provided by the invention has a significant increase in key space and can effectively resist multiple attacks.
Owner:HARBIN UNIV OF SCI & TECH
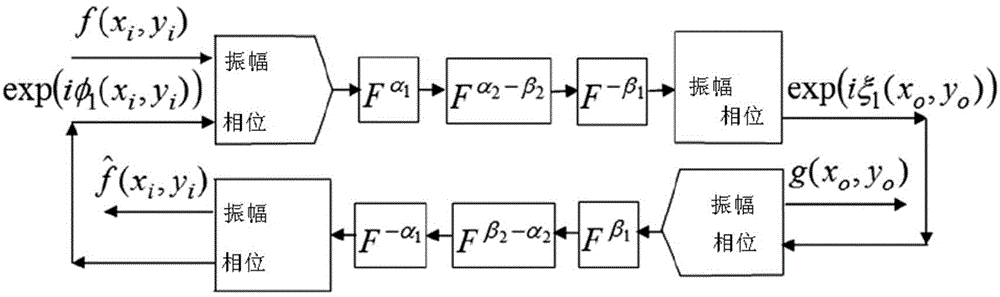
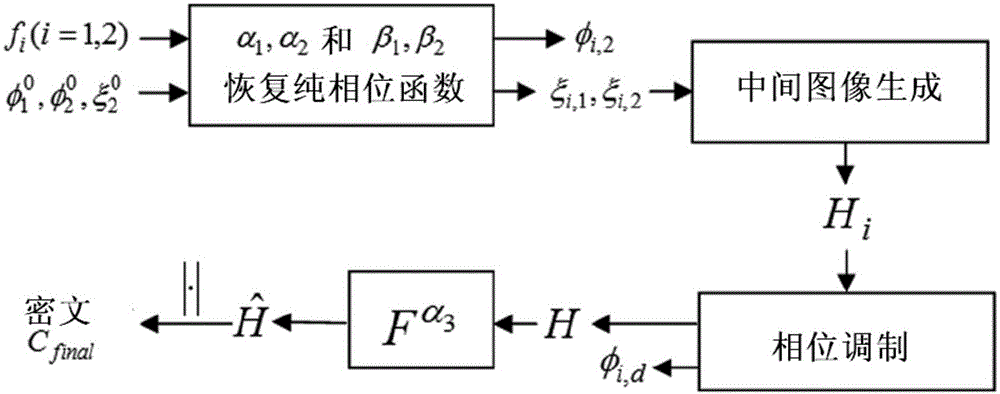
Asymmetric double-image encryption method based on fractional Fourier domain phase recovery procedure
InactiveCN103955883AImprove securityStrong resistanceImage data processing detailsFast Fourier transformNon symmetric
An asymmetric double-image encryption method based on a fractional Fourier domain phase recovery procedure comprises the steps of pure phase extraction, phase modulation and fractional Fourier transform. The asymmetric double-image encryption method based on the fractional Fourier domain phase recovery procedure is applied to double-image encryption, the encryption process is different from the decryption process, an encryption key is different from a decryption key, and the defects that a traditional symmetric encryption algorithm is easy to attack and an encryption key is the same as a decryption key are overcome. Through attack tests, it is proved that the method is high in resistance to violent attacks, noise attacks and other specific attacks. Meanwhile, key space is large, the problem that a traditional encryption algorithm is insufficient in key space is solved, the decryption process can be realized through an optical method, and a system is simple and convenient to operate.
Owner:XIAN UNIV OF TECH
Biometrics-based cryptographic key generation system and method
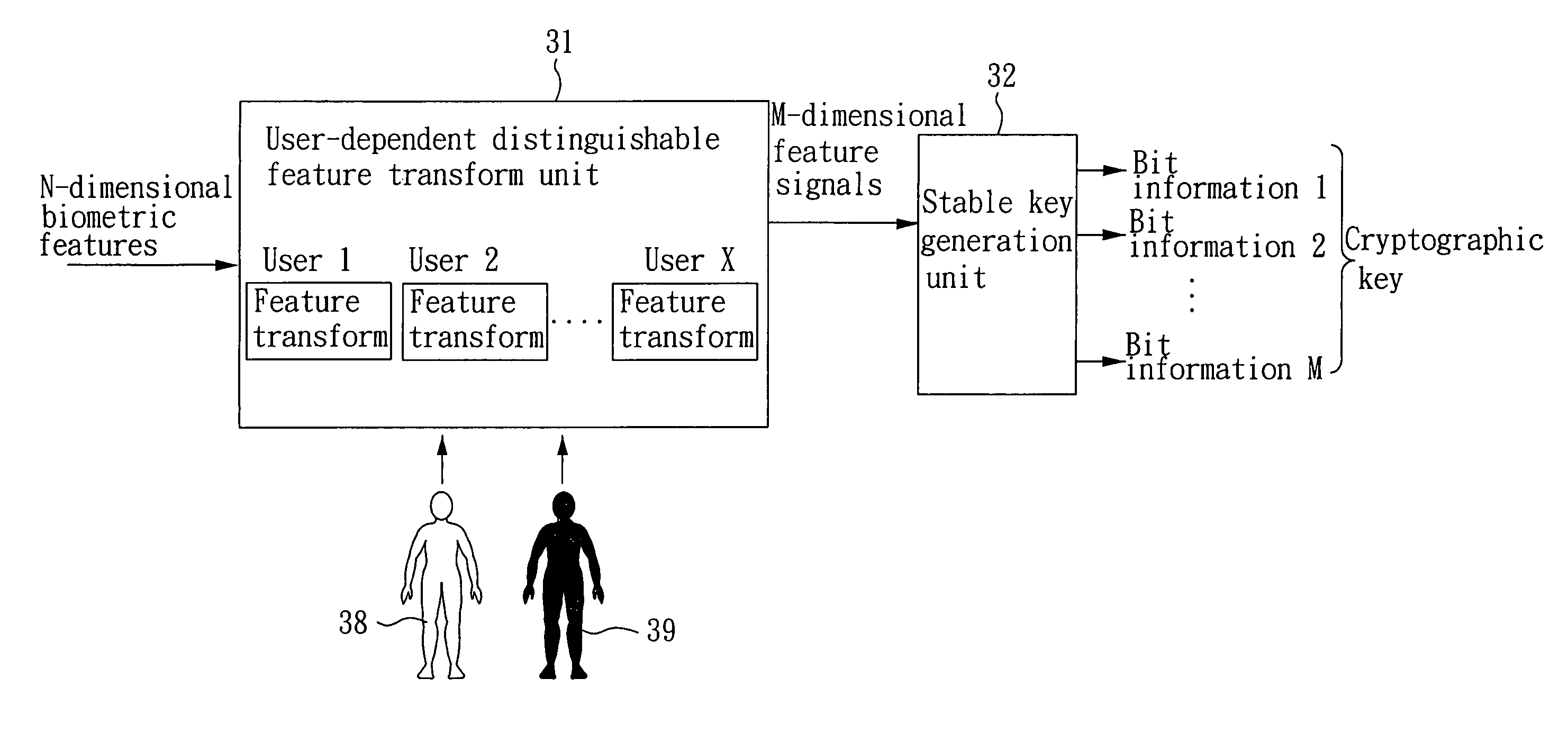
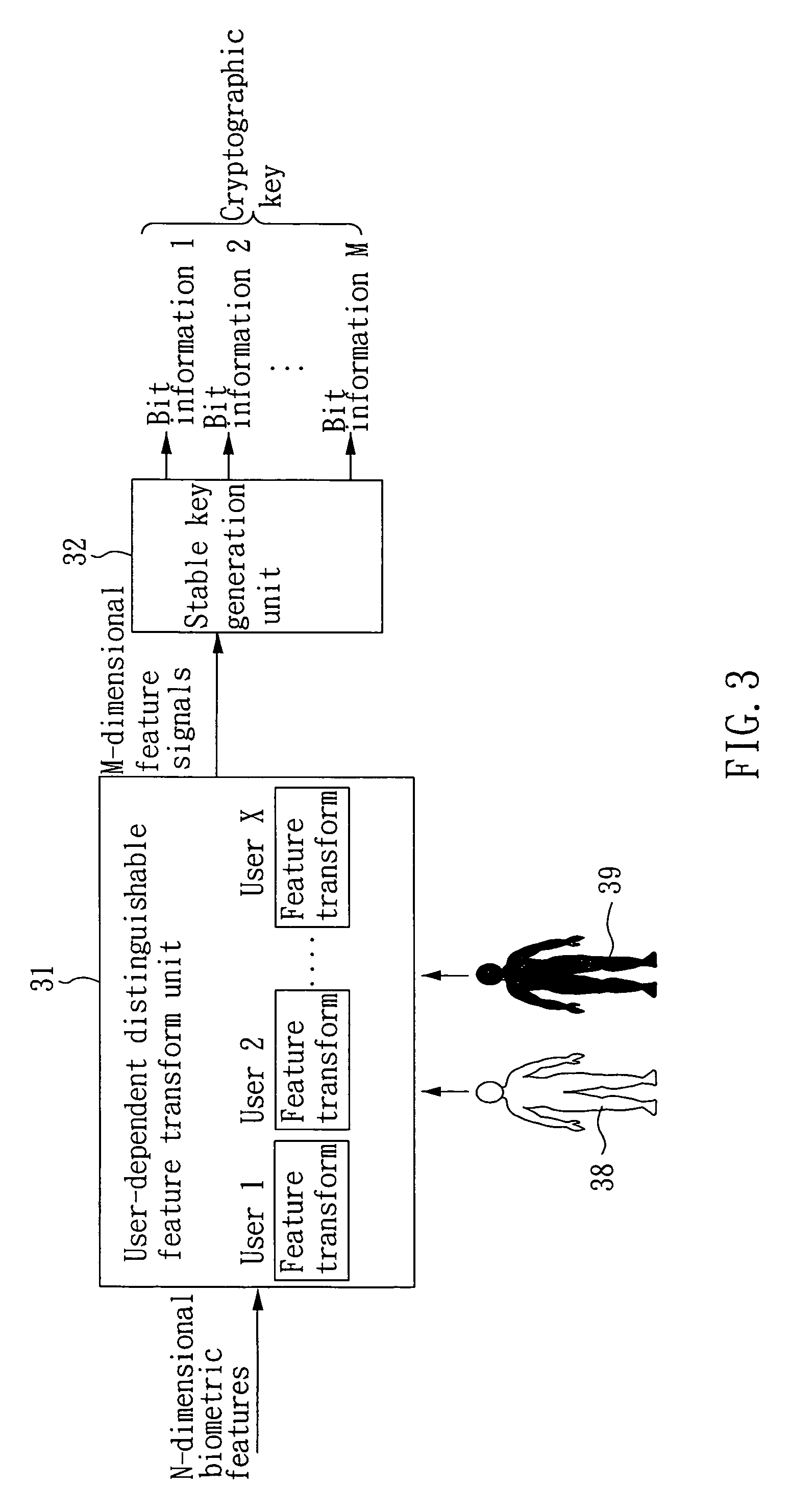
ActiveUS7804956B2Increase the lengthExpand the key spaceComputer security arrangementsSpeech recognitionCryptographic key generationCharacteristic space
The present invention provides a biometrics-based cryptographic key generation system and method. A user-dependent distinguishable feature transform unit provides a feature transformation for each authentic user, which receives N-dimensional biometric features and performs a feature transformation to produce M-dimensional feature signals, such that the transformed feature signals of the authentic user are compact in the transformed feature space while those of other users presumed as imposters are either diverse or far away from those of the authentic user. A stable key generation unit receives the transformed feature signals to produce a cryptographic key based on bit information respectively provided by the M-dimensional feature signals, wherein the length of the bit information provided by the feature signal of each dimension is proportional to the degree of distinguishability in the dimension.
Owner:A10 NETWORKS
Image encryption method based on projection synchronization of hyperchaotic system
ActiveCN106997606AHas cryptographic propertiesIncreased complexityImage codingSecuring communication by chaotic signalsChosen-plaintext attackChaotic systems
The invention discloses an image encryption method based on the projection synchronization of a hyperchaotic system. The method comprises the steps of plaintext image quantifying and ciphertext image quantifying. The first step comprises generating of a hyperchaotic sequence of a hyperchaotic driving system, image row scrambling, image column scrambling, image diffusing, circulation image row scrambling, image column scrambling, multiple rounds of image diffusing, and a ciphertext image is acquired. The second step comprises ciphertext image quantifying, generating of a hyperchaotic sequence of a hyperchaotic response system, time acquiring, column scrambling index and line scrambling index valuing, image inverse diffusing, image inverse column scrambling, image inverse row scrambling, circulation image inverse diffusing, image inverse column scrambling, multiple rounds of image inverse row scrambling, and a decrypted image is acquired. According to the invention, a feedback mechanism with the current image is introduced; the row (column) scrambling address code and the key matrix are dynamically changed in each round of encryption; experiments show that the method has the advantages of good encryption effect, high security and large key space, can resist selected plaintext attacks, known plaintext attacks and various statistical attacks.
Owner:SHAANXI NORMAL UNIV
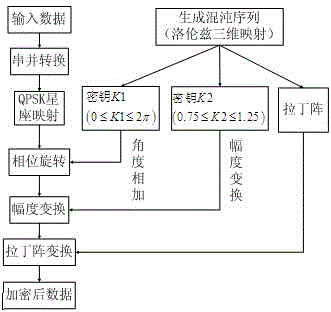
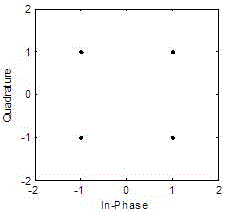
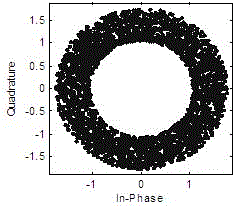
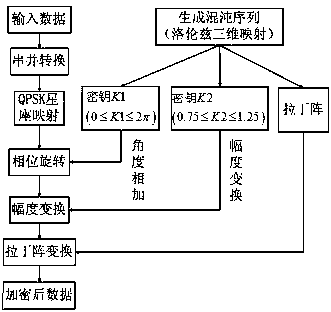
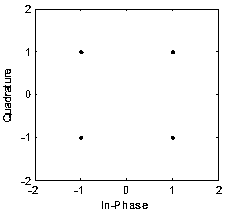
Physical layer encryption method introducing Latin array
ActiveCN105846947AImprove securityDisassociationSecret communicationSecuring communication by chaotic signalsPhysical layerChaotic systems
The invention relates to a physical layer encryption method introducing a Latin array, comprising steps of using a chaotic system and a Latin array to generate a key which is good in performance, using the key to scramble a constellation graph, making distribution of constellation points of various modulation modes on a complex plane toward uniformity, making individual characteristic parameters of various modulation modes toward consistency, achieving a goal of protecting the modulation mode and the modulation information from the physical layer, and fully utilizing the mapped complex plane information to achieve a goal of maximally expanding the key space. The physical layer encryption method introduces an Extract function, fully eliminates the relevance between the chaotic sequences, does not need to generate massive keys on the premise that the key space is guaranteed, greatly reduces the complexity of realizing hardware, performs an NIST random test on a generated key and verifies the unpredictability.
Owner:NAT UNIV OF DEFENSE TECH
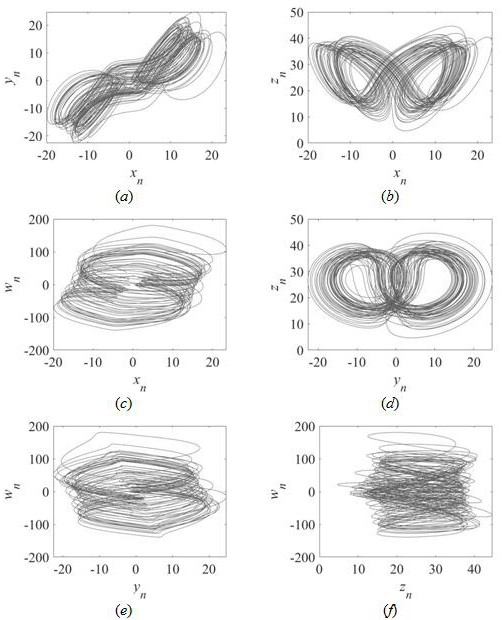
Hyper-chaotic encryption method based on Josephf traversal and bit plane reconstruction
ActiveCN112422266AImprove securityBit disorderEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsAlgorithmBit plane
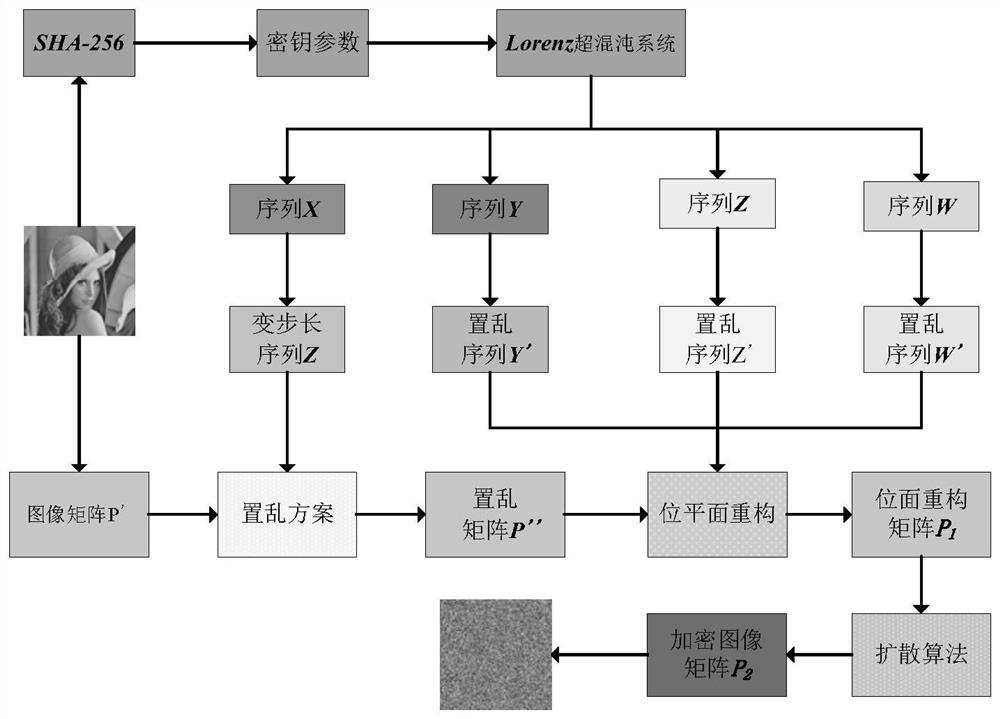
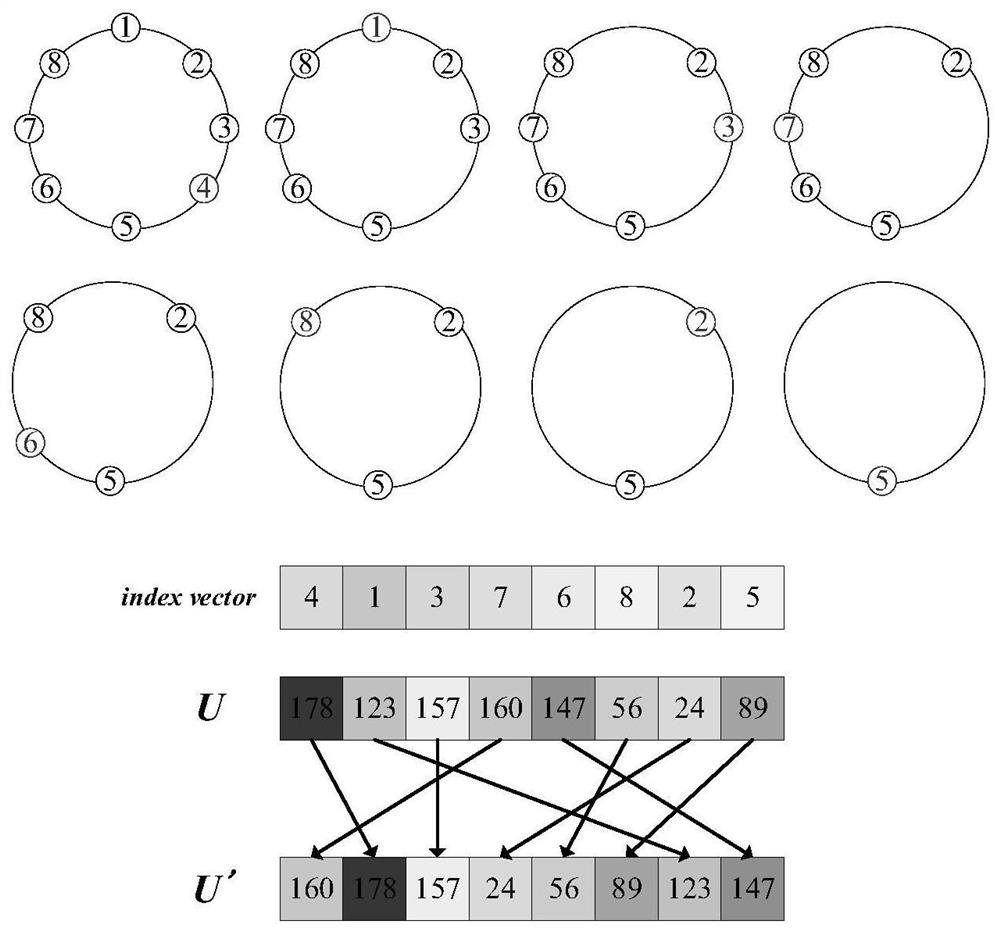
The invention provides a hyper-chaotic encryption method based on Josephf traversal and bit plane reconstruction. The hyper-chaotic encryption method comprises the following steps: converting a grayscale image into an image matrix; inputting the image matrix into an SHA-256 algorithm as a secret key, and obtaining initialization parameters according to the secret key; substituting the initialization parameters into a hyper-chaotic Lorenz system for iteration to generate four chaotic sequences, processing one chaotic sequence to serve as a variable step size sequence, performing pixel positionscrambling on a one-dimensional sequence of an image matrix by utilizing an improved Josephf traversal method, and rearranging a pixel scrambling matrix; dividing the pixel scrambling matrix into eight bit planes, and performing bit plane reconstruction on the pixel scrambling matrix by using the other three chaotic sequences and a bit plane reconstruction method to generate a bit plane reconstruction image matrix; and diffusing the bit plane reconstruction image matrix to generate a final encrypted image. According to the method, different types of images can be encrypted into uniformly distributed encrypted images, and the method has very sensitive key sensitivity and can resist various attacks.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Chaotic key distribution system and method based on dispersion keying synchronization
ActiveCN110635902AIncrease speedImprove securityKey distribution for secure communicationSecuring communication by chaotic signalsDistribution systemOptical switch
The invention belongs to the technical field of secret communication. The invention in particular relates to a chaotic key safety distribution system and method based on dispersion keying synchronization. The problems in the background technology are solved. The system comprises a first DFB laser 1, a first 1*2 optical fiber coupler 2, a CFBG chirped fiber bragg grating 3, a second 1*2 optical fiber coupler 4, a communication party A and a communication party B. Each of the communication party A and the communication party B comprises an optical fiber circulator, an optical switch, a memory,a first dispersion module, a second dispersion module, a photoelectric detector, an analog-to-digital converter and a bit filter. When the optical switch is switched, a random sequence of dispersion feedback can be directly obtained, involved key distribution is not influenced by synchronous recovery time, and the key distribution rate is improved; and, meanwhile, the chaotic light state of the first DFB laser is changed through dispersion feedback, so that the chaotic light directly emitted by the first DFB laser is not related to the chaotic light after dispersion feedback, and the securityof key distribution is enhanced by using nonlinear characteristics.
Owner:TAIYUAN UNIV OF TECH
Color image encryption and decryption method and system based on double-chaos cross diffusion
PendingCN107330338AExpand the key spaceDestroy correlationDigital data protectionImage data processing detailsNumeric ValueTablet computer
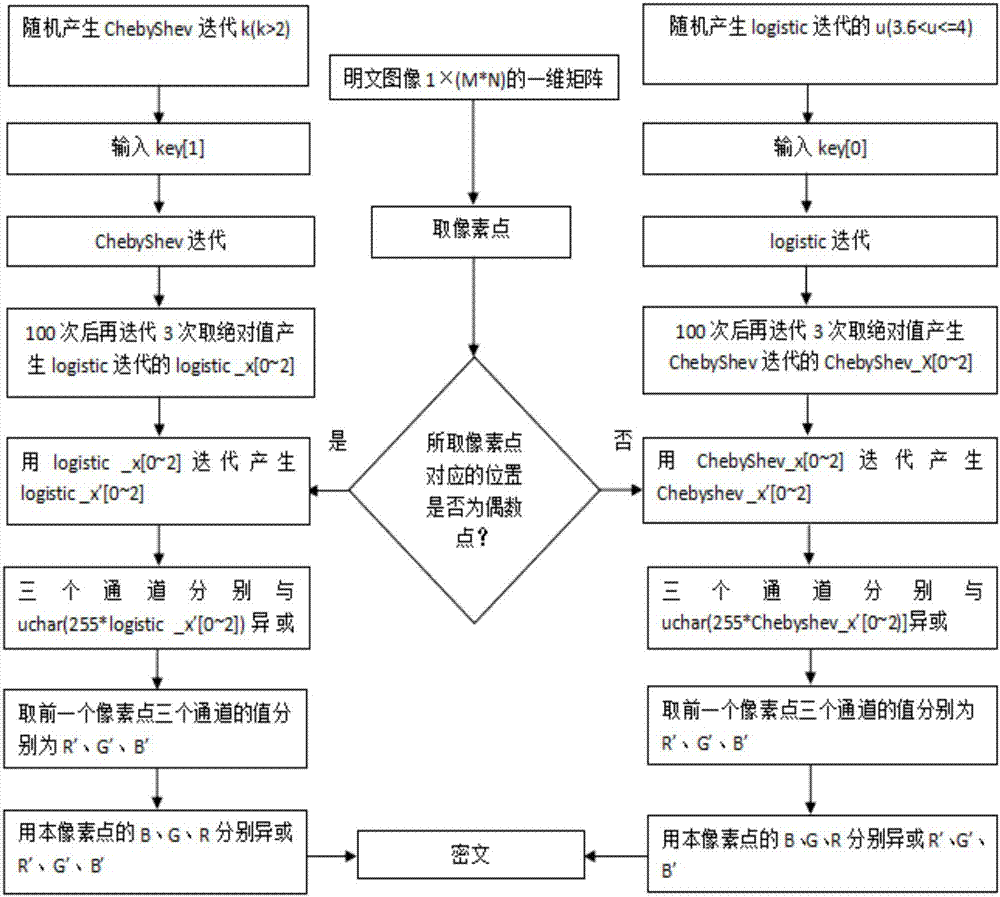
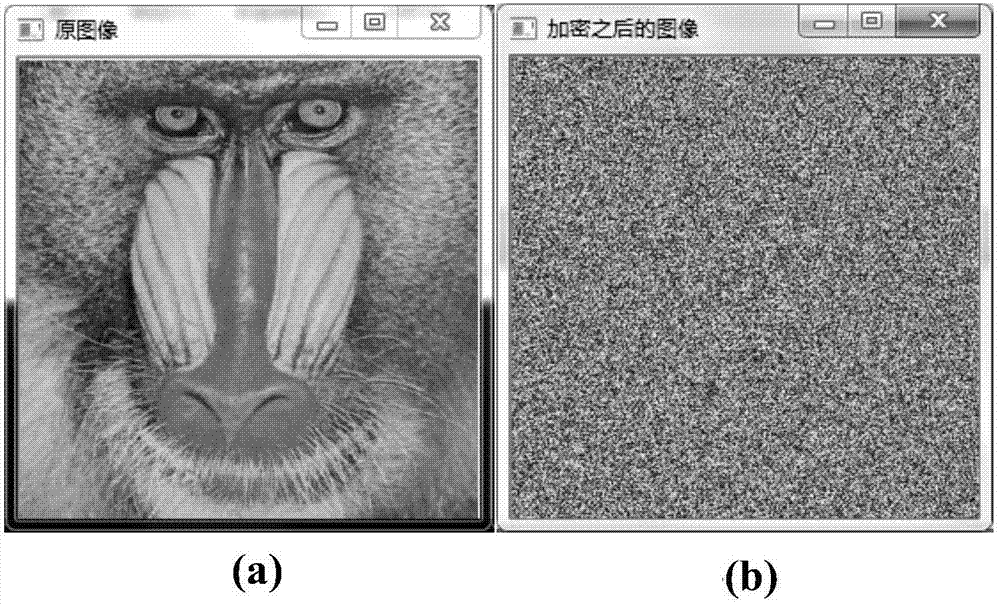
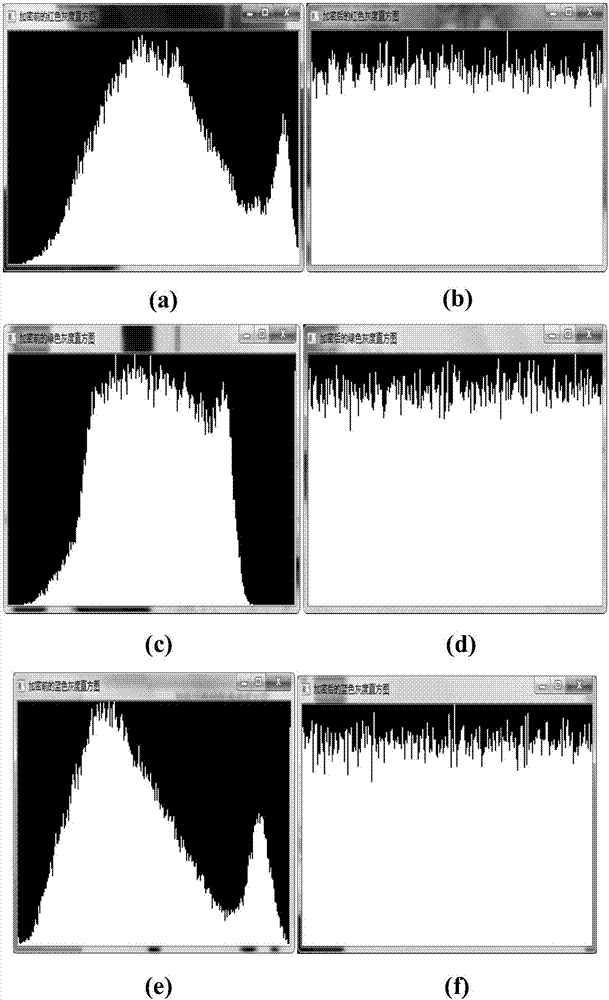
The invention discloses a color image encryption and decryption method and system based on double-chaos cross diffusion. Firstly, parameters of Logistic and ChebyShev iteration are randomly generated, initial secret keys needed by Logistic and ChebyShev iteration are input, after a transit state is eliminated through multiple times of iteration, Logistic and ChebyShev are used for carrying out iteration three times respectively, iteration results serve as initial secret keys used during encryption respectively, and therefore secret key space is actually increased. Then a pixel point in an image is taken, if the value corresponding to the position of the pixel point is an odd number, an encryption key is obtained through ChebyShev iteration, or else the encryption key is obtained through Logistic iteration, and therefore the dependency between adjacent pixel points is reduced. Then R, G and B channels of the pixel point and R', G' and B' of the former encrypted pixel point are subjected to difference or operation for diffusion. The iteration frequency is reduced on the premise of guaranteeing safety, the encryption time can be shortened, efficiency is improved, and the method and system are especially suitable for image encryption of mobile equipment such as mobile phones and tablet computers with the high real-time performance requirement.
Owner:HENGYANG NORMAL UNIV
Cellular automata and chaotic mapping-based digital image encryption method and decryption method thereof
InactiveCN106373082AHas chaotic propertiesChaotic characteristics are goodImage data processing detailsComputer visionExclusive or
The invention provides a cellular automata and chaotic mapping-based digital image encryption method and a decryption method thereof. The encryption method includes the following steps that: a 288-bit key is utilized to generate chaotic mapping parameters and cellular automaton evolution rules which are required by an encryption algorithm; pre-processing such as three-dimensional decomposition and blocking, is carried out on an original image; 3D chaotic mapping is adopted to scramble pixel positions; cross-exclusive-OR operation is performed on image blocks to be encrypted; and a 2D second-order cellular automata used for generating boundaries, which is provided by the present invention, is utilized to carry out iterative encryption on an unfolded plaintext, pixels are mixed, and iteration is repeated until an iteration requirement is satisfied; and reverse pre-processing is carried out, and blocked ciphertext images are combined into a ciphertext image.
Owner:SUN YAT SEN UNIV
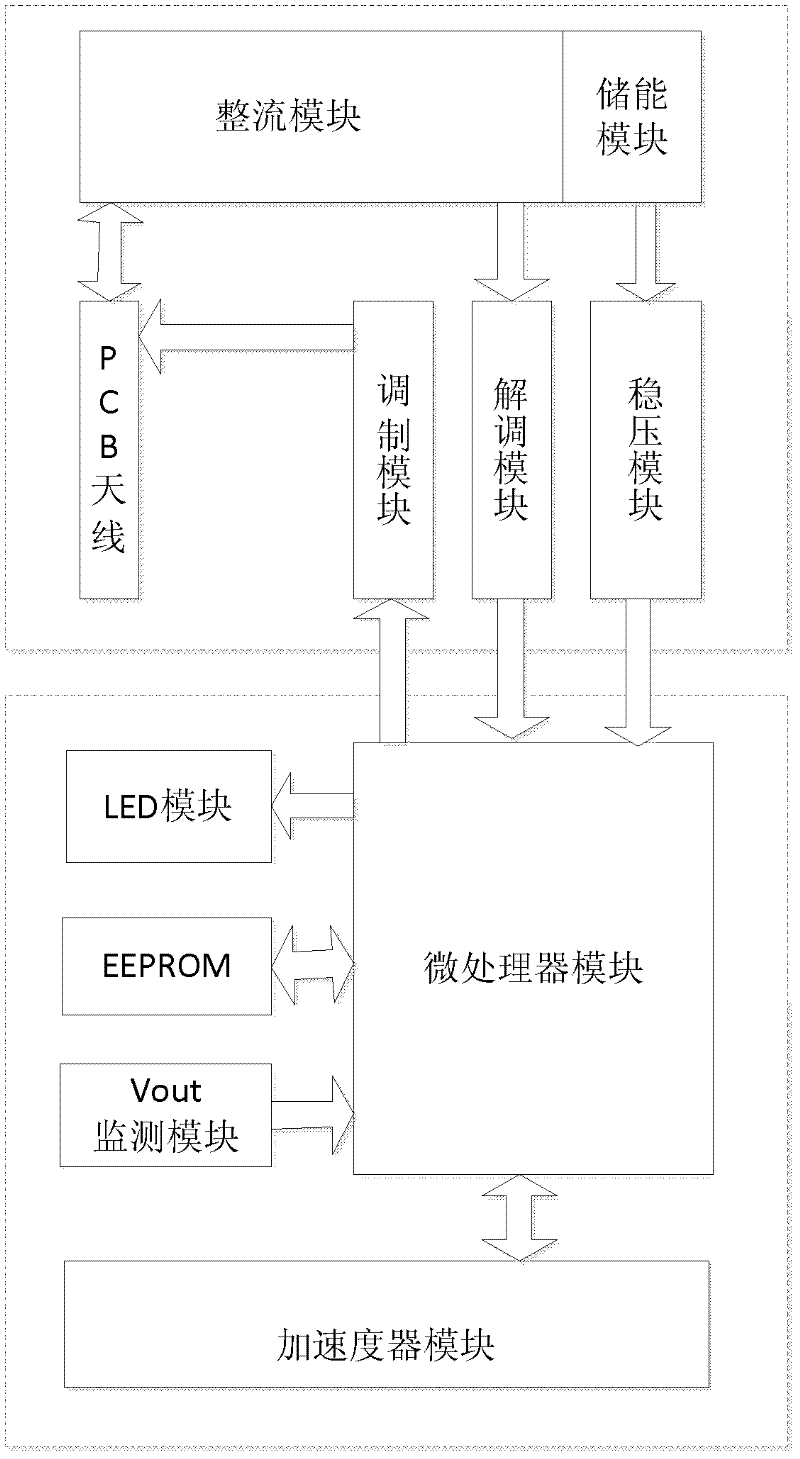
Intelligent authentication system and method based on wireless power supply sensor
ActiveCN102523091ALarge key spaceEncryption complexity adjustableEnergy efficient ICTUser identity/authority verificationComputer hardwareAuthentication system
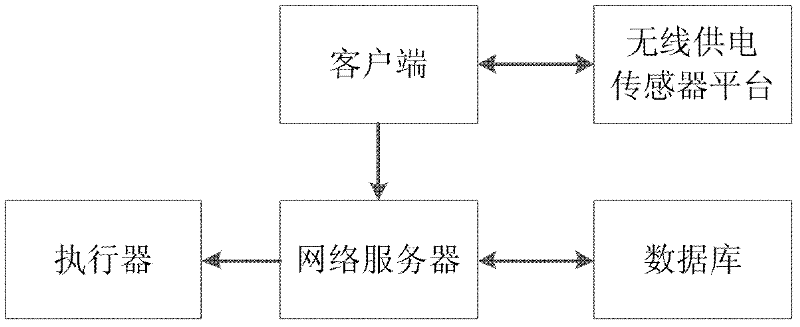
The invention discloses an intelligent authentication system and a method based on a wireless power supply sensor. The system comprises a wireless power supply sensor platform, a client, a network server, an executor and a database. The wireless power supply sensor platform acquires acceleration in a three-dimensional direction and transmits the acceleration to the client; after the client receives data, the data is transmitted to the network server; and the network server analyzes the data and converts the data into the acceleration in the three-dimensional direction for further processing. The intelligent authentication system and the method have the advantages that the hardware design of the original wireless power supply sensor is improved, the wireless power supply sensor is enabled to have a smaller volume and better communication efficiency, the defect that the traditional encryption authentication method purely depends on physical keys is overcome, the key space is very high and the encryption complexity is adjustable.
Owner:ZHEJIANG UNIV
Encryption and decryption method based on coupling and self-triggering cellular automata
InactiveCN105099654ASimple local actionIntrinsic parallelismComputing modelsSecuring communicationCellular automationCoupling
The invention discloses an encryption and decryption method based on coupling and self-triggering cellular automata. The encryption and decryption method comprises: according to the properties of the coupling and self-triggering cellular automata, adopting n interactional cellular automata as an entirety, and constructing an encryption and decryption system of coupling and self-triggering cellular automata. A simulation experiment result indicates that the algorithm greatly improves the key space and effectively prevents brute force attack; and meanwhile, when a random number is introduced in an encryption process to prevent an attacker from obtaining an exclusive plaintext and ciphertext pair, so that known plaintext attach and selective ciphertext attach are effectively prevented.
Owner:NANJING UNIV OF SCI & TECH
Method for authenticating smartphone user based on multi-image switching
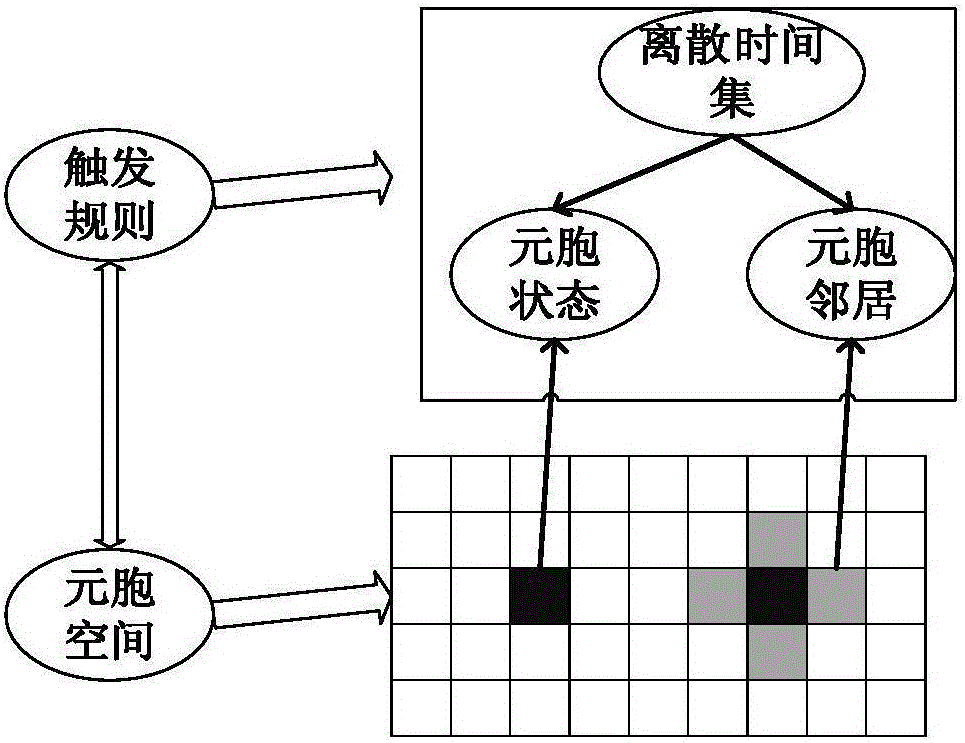
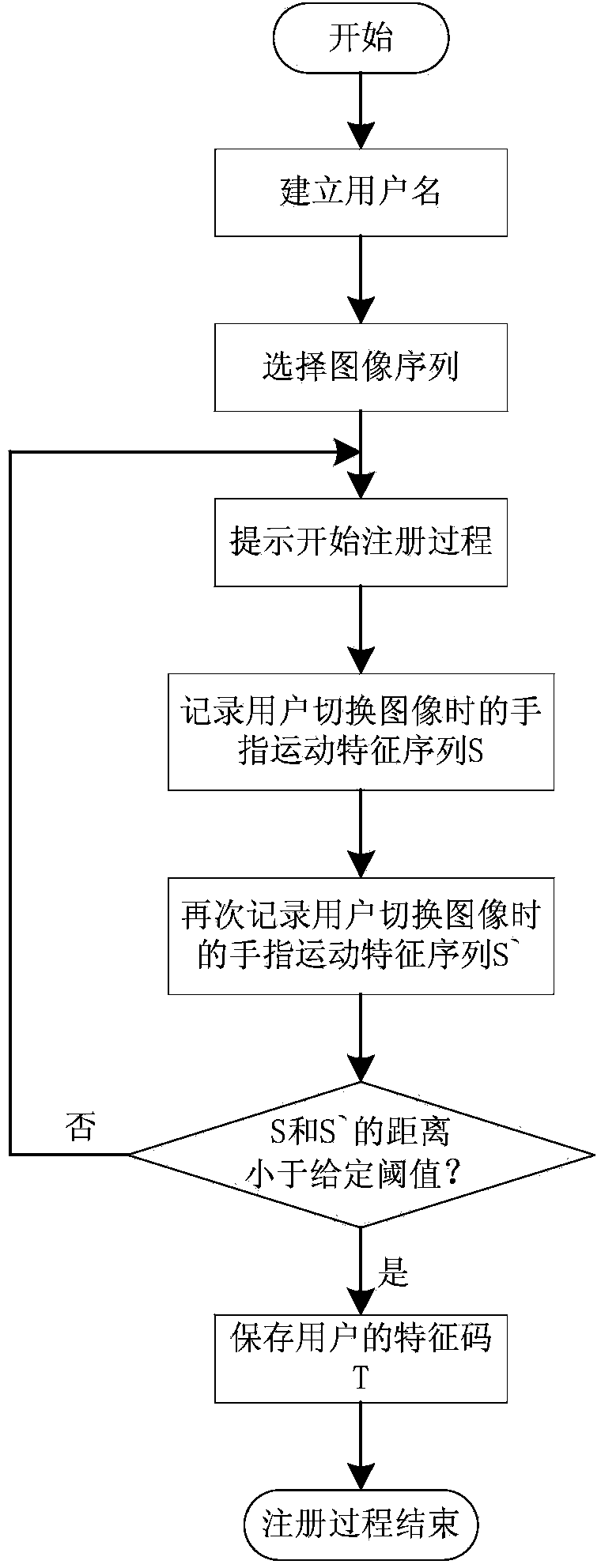
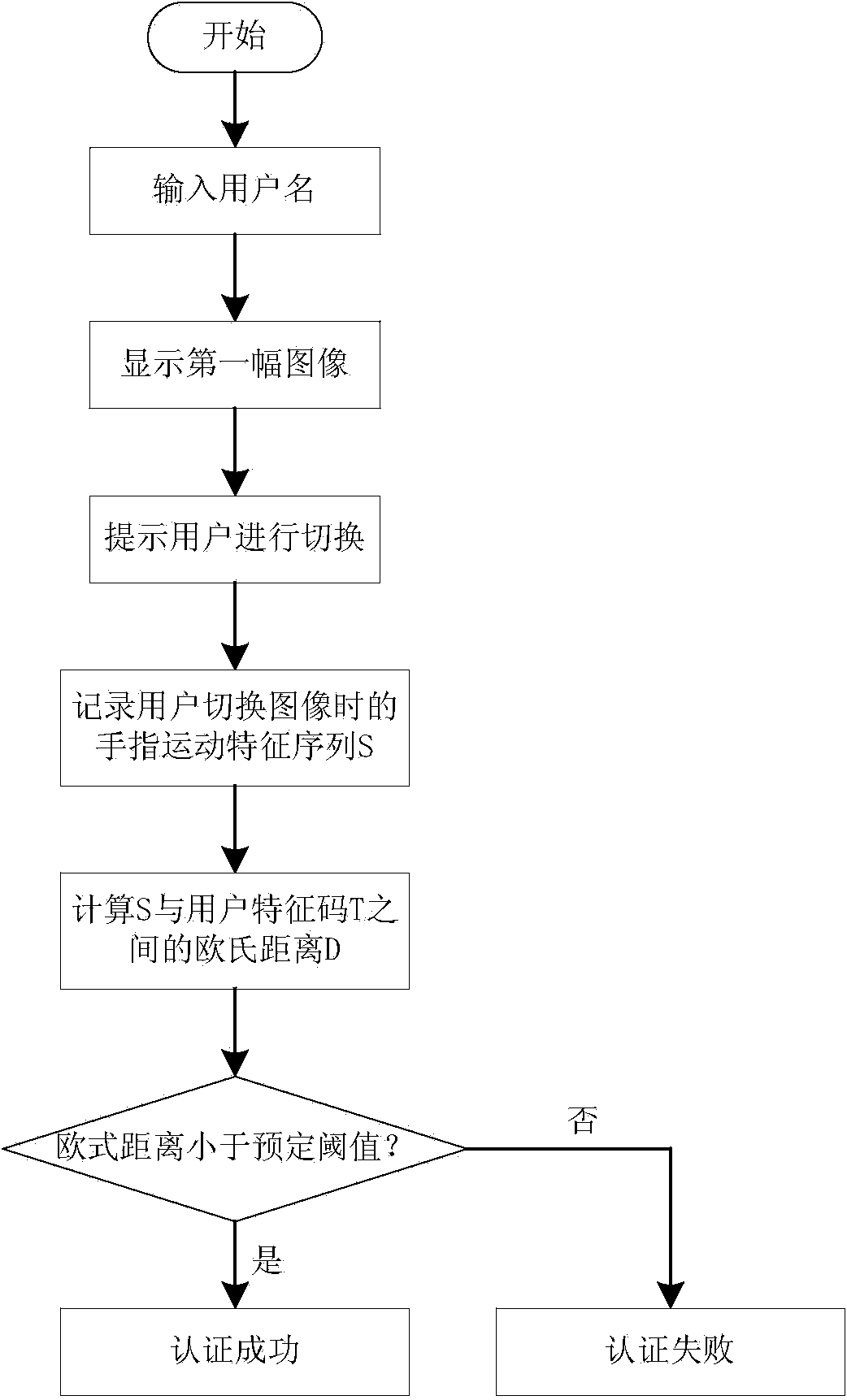
InactiveCN103530542AExpand the key spaceHigh anti-brute force attack performanceDigital data authenticationInput/output processes for data processingInternal memoryMulti-image
The invention provides a method for authenticating a smartphone user based on multi-image switching. The method comprises the steps of firstly, selecting an image sequence by the user, then, recording a motion feature sequence of fingers when the user switches images, wherein the image sequence is stored in an internal storage of a smartphone, and the motion feature sequence comprises starting point coordinates, end point coordinates, speed and the like. The feature sequence is processed and then marked as feature codes of the user, wherein the feature codes are used for distinguishing different users. Compared with PIN authentication, the method has the advantages of greatly expanding secrete key space, being convenient to use, practical and free of adding any additional device, and having the quite high recognition rate and safety.
Owner:SOUTHEAST UNIV
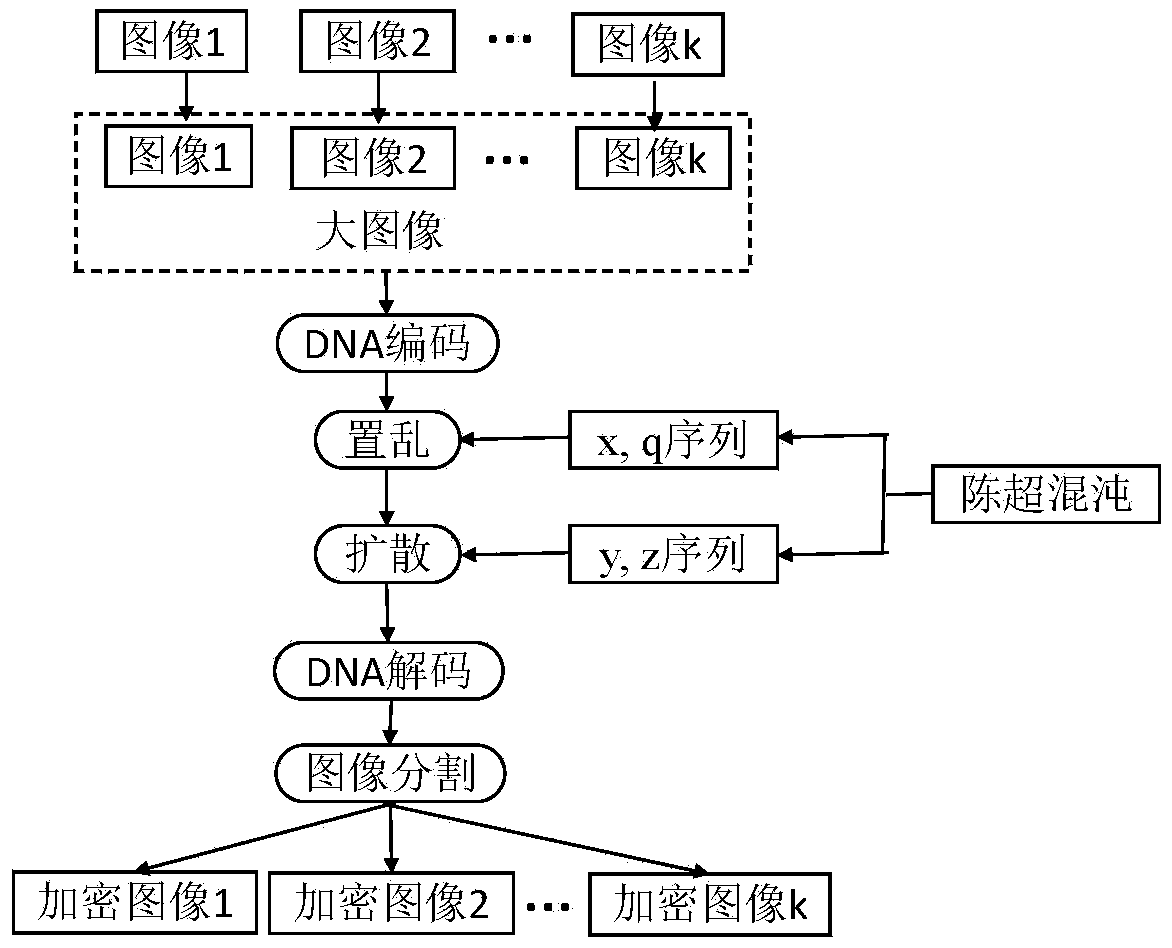
Multi-image encryption menthod based on DNA encoding and Chenchao chaos
InactiveCN108521534AImprove securityLarge key spaceSecuring communication by chaotic signalsPictoral communicationDna encodingDiffusion
The invention discloses a multi-image encryption method based on DNA encoding and Chenchao chaos, and belongs to the field of information encryption. At present, the network batch image transmission and storage become more and more often in daily life, the invention provides the multi-image encryption method based on DNA encoding and Chenchao chaos protecting the content security of multiple interacted images. The method comprises the following steps: firstly performing DNA encoding on k images, and forming a big image; secondly, scrambling the bit image by using chaos sequences produced by using the Chenchao chaos; thirdly, performing the DNA computation on the scrambled big image and the chaos sequence so as to accomplish the diffusion; and finally performing DNA decoding on a diffusionresult to obtain k encrypted images. The experiment shows that the algorithm can simultaneously encrypt multiple interacted images, the secret key space is large, the secret key sensitivity is strong,and the security is high.
Owner:CHINA UNIV OF MINING & TECH
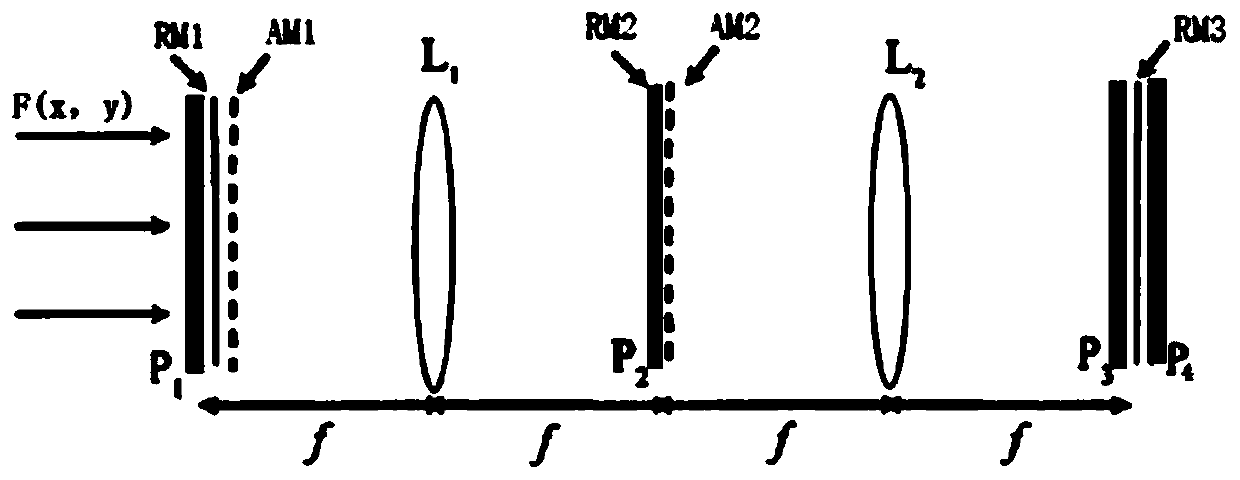
Hybrid chaotic virtual optical image encryption method
InactiveCN109981921AHigh sensitivityEvenly distributedSecuring communication by chaotic signalsPictoral communicationSpacetimeChaotic systems
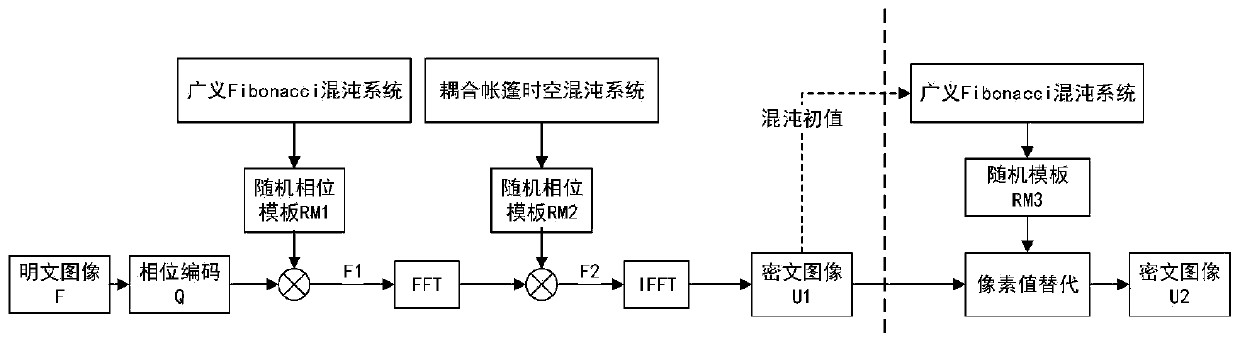
The invention discloses a hybrid chaotic virtual optical image encryption method, which comprises the following steps of: 1, assuming that the size of a plaintext image is M * N, and sequentially reading pixel values of each point of the image from left to right to obtain a pixel matrix F (x, y); step 2, performing phase encoding on the plaintext image F (x, y) to obtain Q (x, y); step 2, modulating Q (x, y) through a random phase template RM1 to obtain F1 (x, y); step 3, carrying out Fourier transform on F1 (x, y), and carrying out random phase template RM2 modulation to obtain F2 (alpha, y);step 4, carrying out inverse Fourier transform on F2 (alpha beta) to obtain a ciphertext image U1; and step 5, performing secondary encryption of pixel value substitution on U1 (x, y) to obtain a ciphertext image U2. According to the invention, a coparametric generalized Fibonacci chaotic system and a coupled tent space-time chaotic system are adopted to respectively construct random templates with good uniformity; therefore, the two chaotic systems have a linkage effect, the defect that the distribution of random template elements constructed by the Logistic chaotic system is not uniform isovercome, and the hiding property on a ciphertext and the sensitivity on a secret key are enhanced.
Owner:QIQIHAR UNIVERSITY
Color Image Encryption Method Based on DNA Dynamic Coding
The present invention relates to a DNA dynamic coding based colored image encryption method, comprising: obtaining a key through a colored plain-text image; by the key, calculating an initial value and a parameter of a chaotic system used in scrambling and diffusion processes; substituting the initial value and the parameter to the chaotic system for iteration to obtain W1 and W2, obtaining a scrambling matrix K from W1, obtaining an integer matrix Y and an index matrix Ind from W2, and performing DNA coding on Y according to the index matrix Ind; and performing scrambling on the plain-text image row by row by using the matrix K, then performing coding and diffusion until all rows finish DNA coding, and finally performing decoding and recomposing on a DNA matrix, to obtain a final colored ciphertext image. According to the method, a function SHA256 is used to generate the key, so that the key space is expanded; the generation of the key depends on a plain-text, so that plain-text attack can be effectively resisted; chaotic characteristics are combined with DNA dynamic coding, so that the security is further improved; and meanwhile, scrambling and diffusion operations are performed according to the row of images, so that parallel computing is facilitated and the efficiency is improved.
Owner:HENAN UNIVERSITY
Digital image encryption method based on DNA sequence and multi-chaotic mapping
ActiveCN101706946BEasy to implementEasy to controlGenetic modelsImage data processing detailsChaotic systemsComputer vision
The invention discloses a novel digital image encryption method belonging to the field of DNA calculation and image encryption, and provides a digital image encryption method based on a DNA sequence and multi-chaotic mapping. The traditional encryption algorithm based on chaos has the defects that a key space is small, a chaos system is easy to analyze and forecast, and the like; and almost of the current encryption systems based on DNA need complex biological operation and are hard to realize. In order to overcome the defects, the invention provides the digital image encryption method based on a DNA sequence and multi-chaotic mapping, comprising the following steps of: firstly, scrambling the positions of pixels of images by utilizing a two-dimension chaotic sequence generated by Cubic mapping and Haar wavelet functions, and then disrobing the pixel values of the images under the action of a chaotic sequence generated by the DNA sequence and the Logistic mapping. The experimental result shows that the algorithm is easy to realize, has better encryption effect on images, large key space and high sensitivity to keys and can effectively resist exhaustive attack and statistical attack.
Owner:DALIAN UNIV
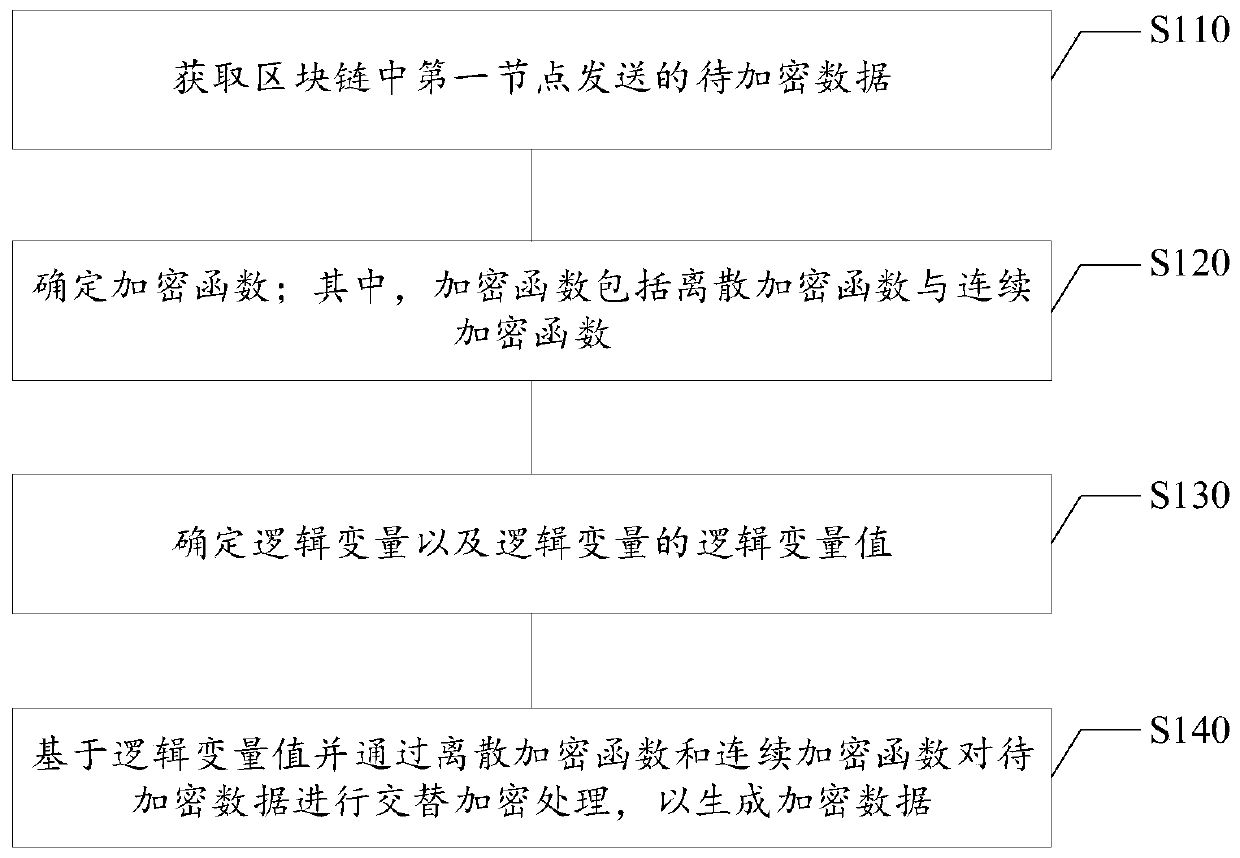
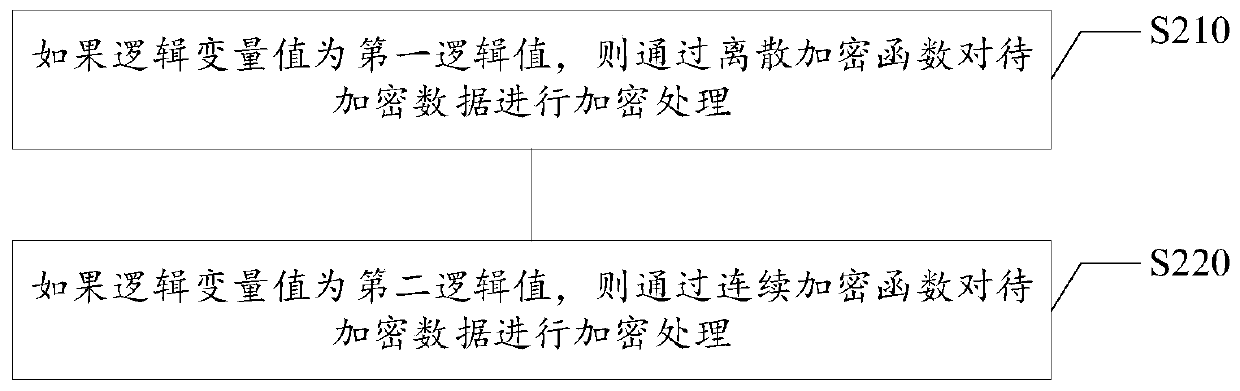
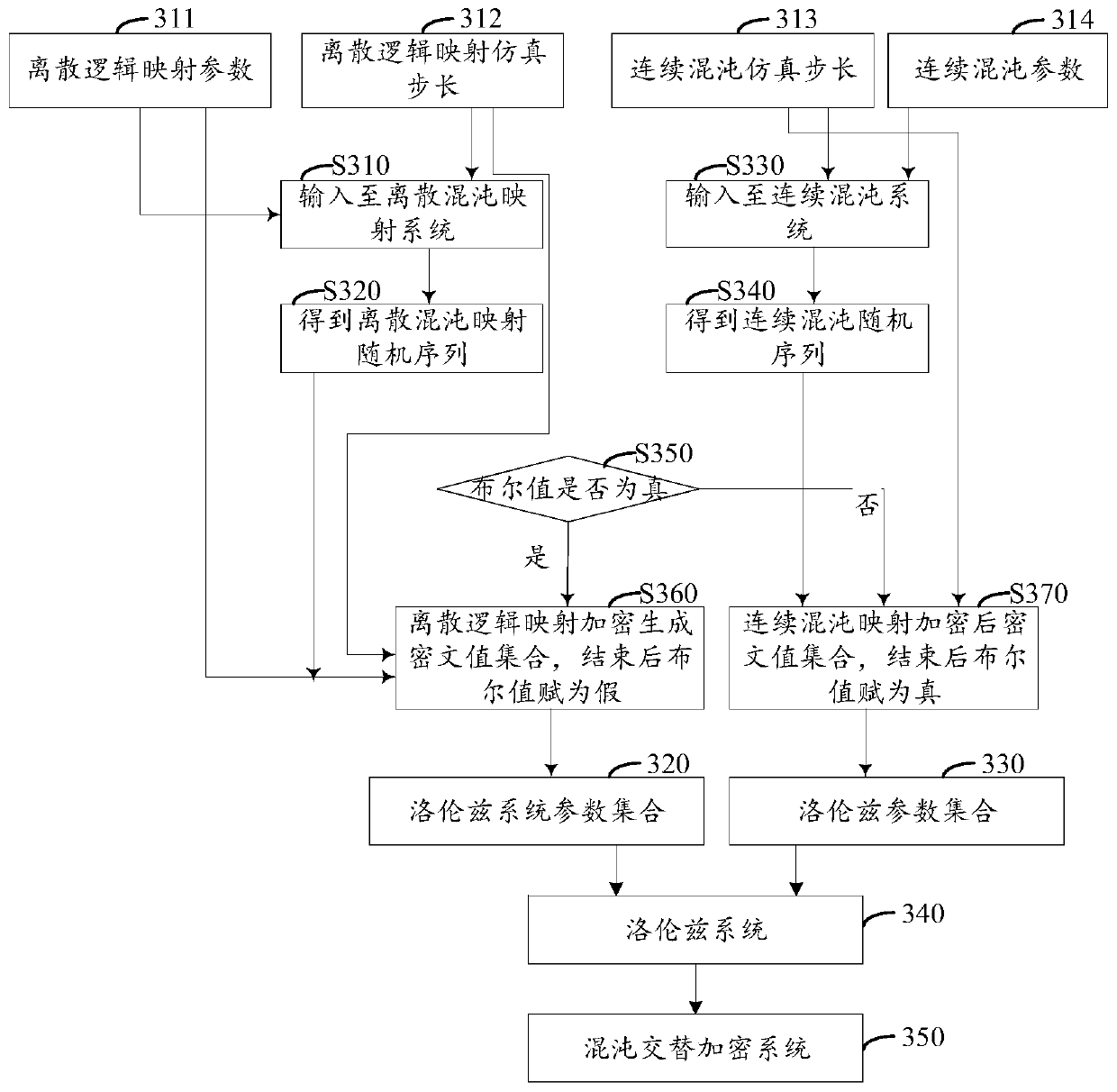
Block chain encryption method and device, electronic equipment and storage medium
InactiveCN110995749AImprove securityIncrease randomnessEncryption apparatus with shift registers/memoriesPublic key for secure communicationComputer hardwareComputer engineering
The invention relates to a blockchain encryption method and device, electronic equipment and a computer readable storage medium, relates to the technical field of blockchains, and can be applied to ascene of encrypting data in a blockchain. The blockchain encryption method comprises the steps of obtaining to-be-encrypted data sent by a first node in a blockchain; determining an encryption function; wherein the encryption function comprises a discrete encryption function and a continuous encryption function; determining a logic variable and a logic variable value of the logic variable; and performing alternate encryption processing on the to-be-encrypted data through the discrete encryption function and the continuous encryption function based on the logic variable value to generate encrypted data. According to the method and the device, the plaintext data in the block chain can be encrypted alternately by adopting Logistic mapping and sine chaotic mapping, so that the randomness of the chaotic sequence is further enhanced, the key space is expanded, and the data in the block chain is safer.
Owner:JD DIGITS HAIYI INFORMATION TECHNOLOGY CO LTD +1
Color Image Encryption and Decryption Method Based on Multiple Fractional Chaos System
ActiveCN102982499BRich Dynamic BehaviorBig Key SensitivityImage data processing detailsKey spaceAlgorithm
Owner:HENAN UNIVERSITY
Method and device for realizing Shield block cipher generated by novel secret key and readable storage medium
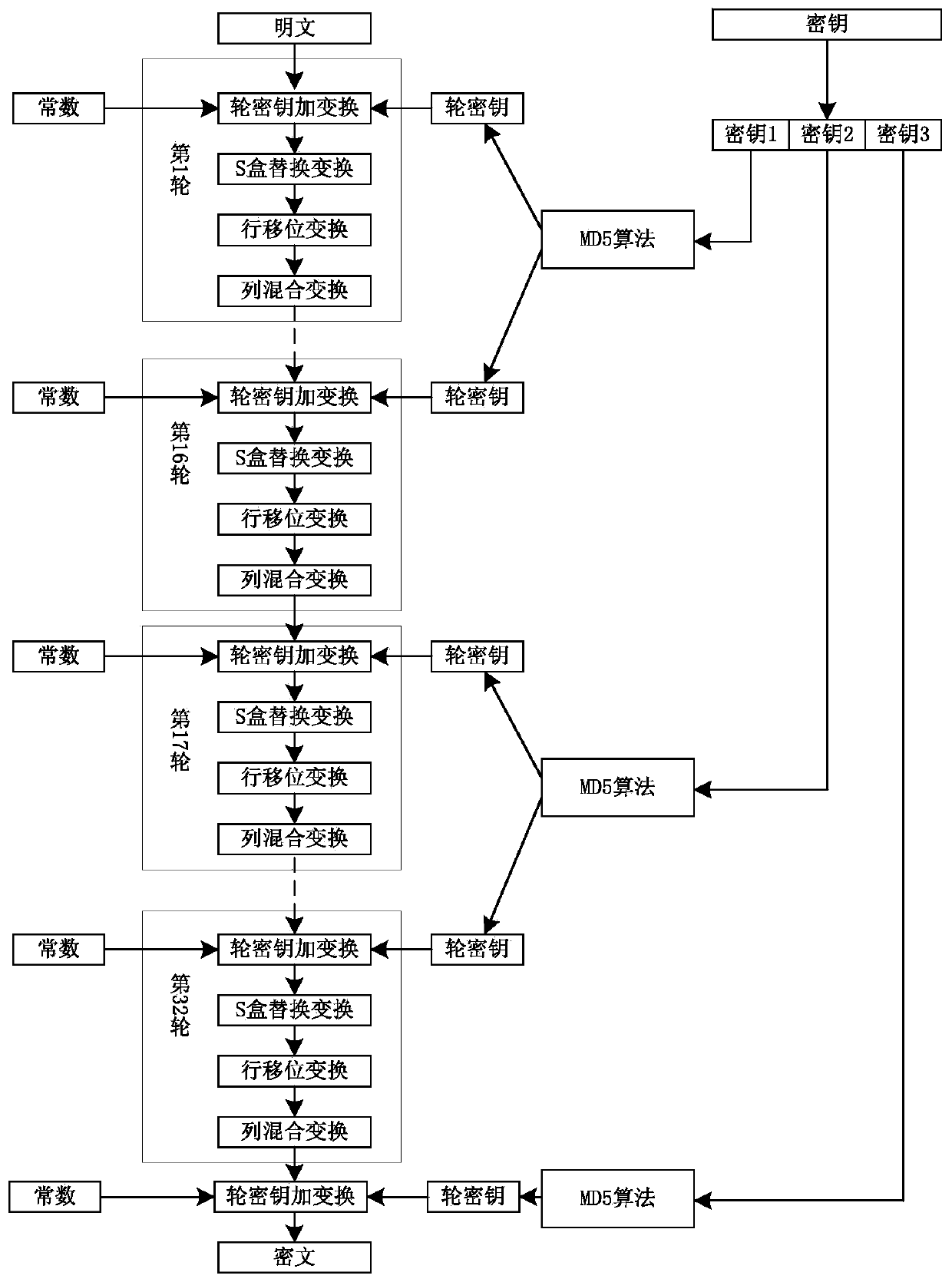
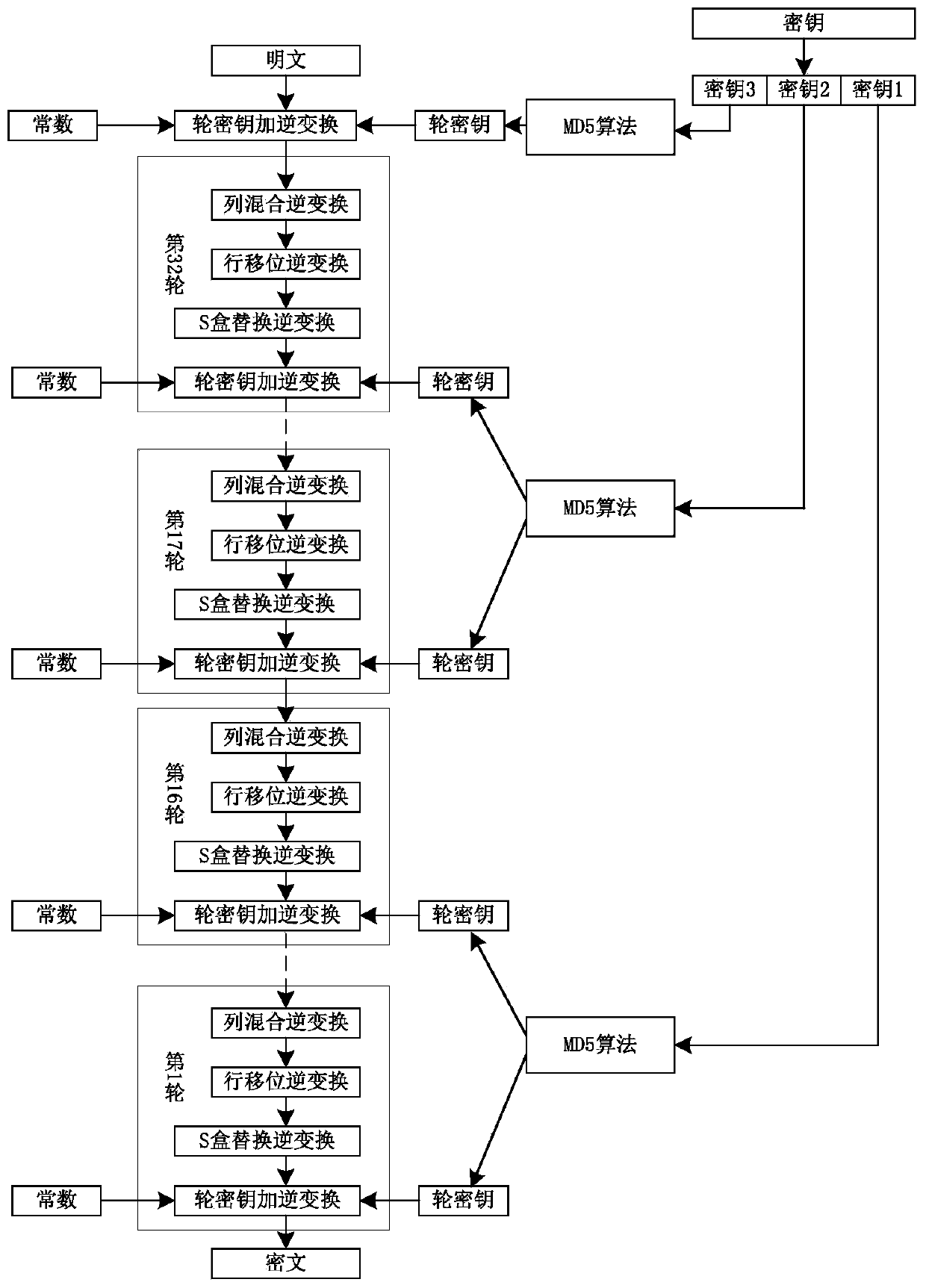
ActiveCN111262685AIncrease the difficulty of analysisLarge key spaceEncryption apparatus with shift registers/memoriesKey sizeKey space
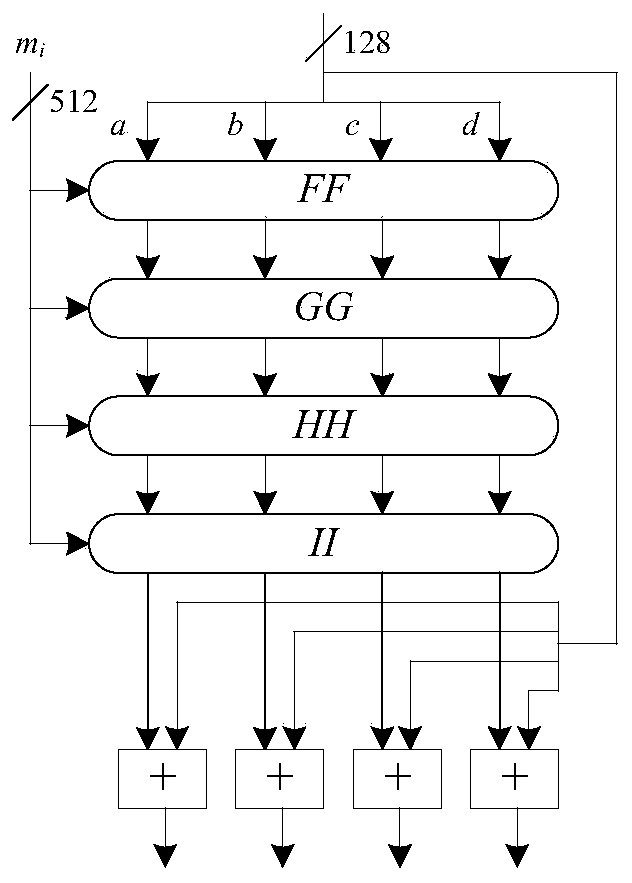
The invention discloses a method and a device for realizing a Shield block cipher generated by a novel secret key, and a readable storage medium. According to the method, the Shield grouping length isdesigned to be 128 bits, a secret key is any length, an encryption round function is based on an SPN structure, and the encryption sequence is round secret key addition, S box replacement, row shifting and column hybrid transformation in sequence. The secret key expansion function divides an original secret key into three parts, generates three round secret keys by using a hash function MD5, anduses the round secret keys in different rounds of addition operation. According to the S box replacement transformation, 128-bit data replacement transformation is carried out by adopting two 4 * 4 Sboxes; the data are divided into 32 4-bit units; and along with the change of encryption / decryption rounds, the data units respectively carry out corresponding S box increasing / decreasing replacementoperation. According to the invention, the occupied area resource of the Shield cipher is small; the storage space for storing the original secret key is reduced; and the known attack can be well resisted by increasing the length of the secret key and expanding the secret key space.
Owner:HENGYANG NORMAL UNIV
Multiple image encryption method based on pwlcm chaos
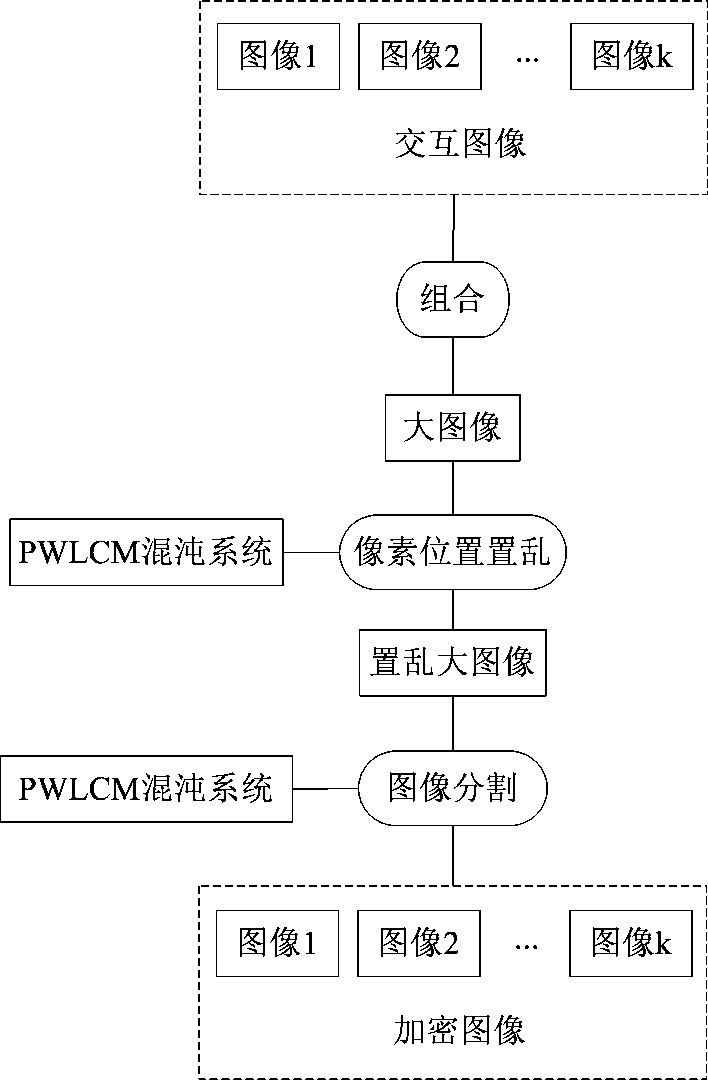
InactiveCN105450899BAchieve protectionLarge key spacePictoral communicationPattern recognitionSingle image
A multi-image encryption method based on piecewise linear chaotic map (PWLCM) belongs to the field of information encryption, and aims to solve the problems that most of the conventional image encryption methods take a single image as an encryption object, and cannot adapt to mass image encryption, and the encryption efficiency of the conventional image encryption methods is relatively low. Being different to the conventional image encryption methods, the multi-image encryption method takes multiple images as encryption objects, and adopts the steps of converting the multiple images into a single large image, encrypting the single large image, and converting the encrypted single large image into multiple encrypted images, so as to protect contents in the multiple images. The multi-image encryption method comprises the key steps of combining k interactive images into a large image, encrypting the large image according to PWLCM to obtain an encrypted large image, dividing the encrypted large image into k encrypted images, and naming the k encrypted images sequentially according to a chaotic sequence generated based on PWLCM. Test results show that the method is easy to implement, the encryption effect is favorable, the encryption efficiency and security are high, and communication security of contents of any multiple images can be protected simultaneously.
Owner:CHINA UNIV OF MINING & TECH
Video image encryption method based on cascade chaotic technology
ActiveCN112511899AImprove securityExpand the key spaceKey distribution for secure communicationDigital data protectionData informationEngineering
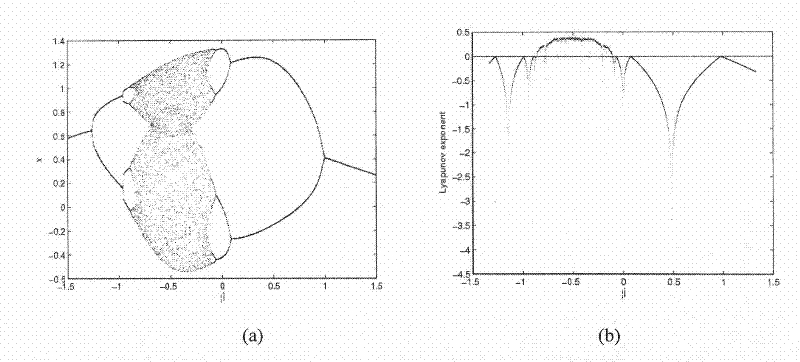
The invention relates to a video image encryption method based on a cascade chaotic technology. The method comprises a construction encryption process and a decryption process of a key space, and comprises the following steps of: firstly, constructing a cascade chaotic mapping, and generating the key space required by encryption and decryption by using the mapping; then, directly reading an existing video file in a computer disk, or calling a camera to acquire a video image, obtain an image sequence of each frame, compress an original image of each frame to obtain data information of the images, and performing encryption and decryption to obtain color images and R, G and B components before and after encryption and decryption; and therefore, the video data stream before and after final encryption and decryption can be obtained. The method has good practicability for video image encryption, and the problem that an existing chaotic encryption method is small in Lyapunov index, so that the sensitivity of a system to an initial value is not high is solved; and the chaotic mapping interval is small, so that the key space is small, and the sequence security is low.
Owner:SHANDONG UNIV OF SCI & TECH
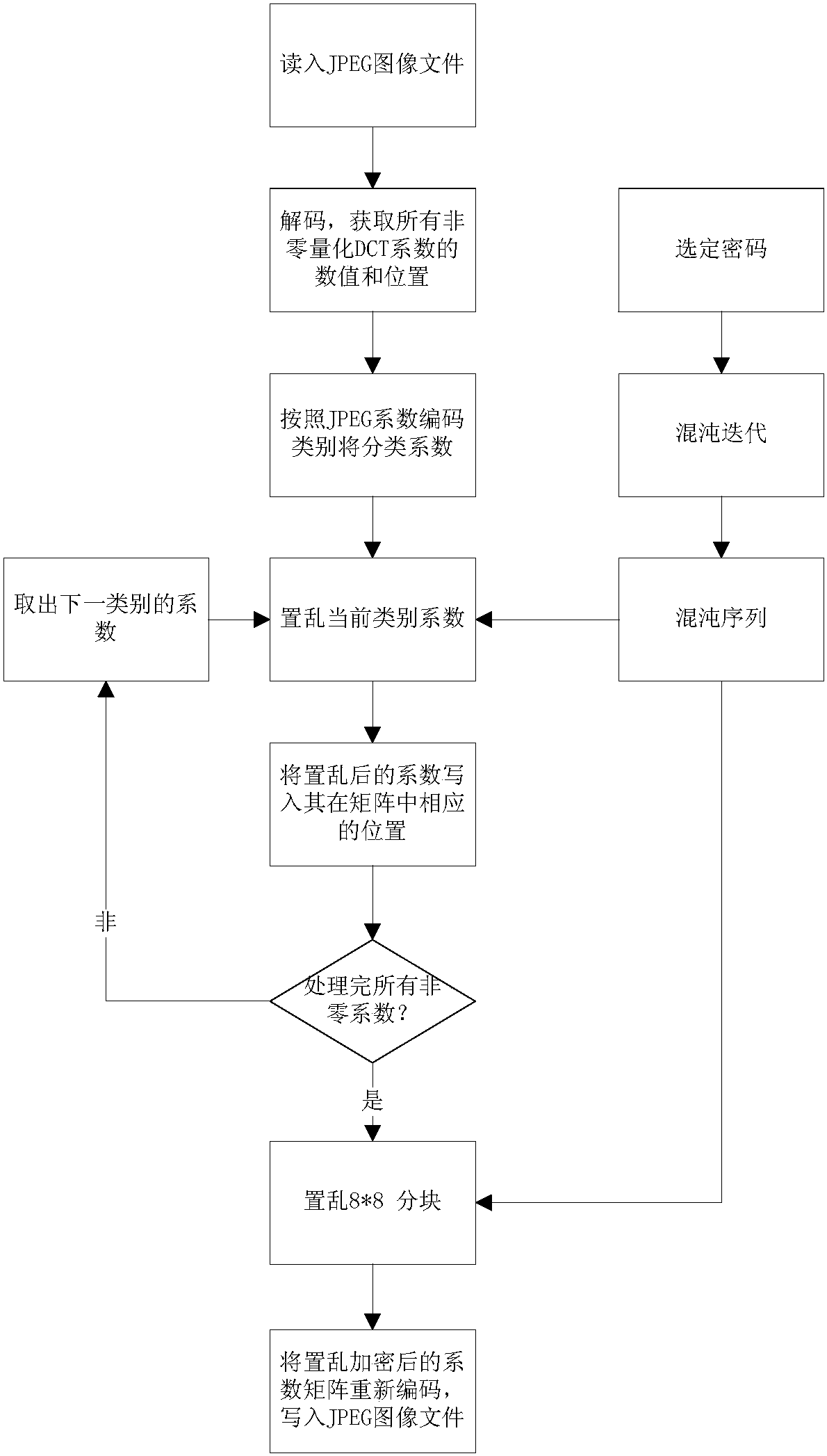
JPEG image encryption method based on similar coefficient scrambling
InactiveCN105975866BIncrease the compression ratioExpand the key spaceImage codingDigital data protectionPlaintextJPEG
The invention relates to an intra-class coefficient scrambling-based JPEG image encryption method. The method comprises the following steps: firstly reading in a JPEG image file, acquiring a Huffman coding table and image data which undergoes JPEG coding compression, carrying out decoding to acquire all the non-zero quantized DCT coefficient numerical values and positions and carrying out classification; selecting a password, carrying out chaotic iteration by utilizing the password, so as to generate a chaotic sequence, and scrambling the non-zero coefficients and 8*8 block of each class by utilizing the chaotic sequence; and carrying out entropy coding on a scrambled quantized DCT coefficient matrix, and writing the coded data into the JPEG image file so as to complete intra-class coefficient scrambling-based JPEG image encryption. According to the method disclosed in the invention, scrambling is carried out on different classes of quantized DCT coefficients through the chaotic sequence, and the quantized DC coefficients and the non-zero AC coefficients are processed by directly using one encryption scheme, so that the safety and the high efficiency are both considered; and the encrypted images are similar to clear text image files in the aspect of size, and have high compression ratios.
Owner:CHANGAN UNIV
Cryptographic system and method
ActiveUS20170346621A1Expand the key spaceCryptographic attack countermeasuresComputer hardwareCipher
A system for cryptographic processing comprises message unit (1, 7, 12) for providing a first message representation (3, 6, 11), wherein the first message representation is a representation of a message. The system comprises key unit (2) for providing a key representation (4, 9, 14), wherein the key representation is an encrypted representation of a first key of a first cryptographic algorithm and a second key of a second cryptographic algorithm, wherein the first cryptographic algorithm is different from the second cryptographic algorithm. The system comprises step unit (5, 10, 15) for performing a step of the first cryptographic algorithm and a step of the second cryptographic algorithm based on the first message representation (3, 6, 11) and the key representation, to obtain a second message representation (6, 11, 16).
Owner:KONINKLJIJKE PHILIPS NV
Construction method of unequal-order fractional order chaotic system
InactiveCN110995406ACalculation speedHigh precisionSecuring communication by chaotic signalsDigital signal processingKey space
The invention relates to a construction method of an unequal-order fractional order chaotic system. According to the invention, a new unequal-order fractional order chaotic system is defined based onCaputo, and a digital circuit is designed as a chaotic sequence generator by using a digital signal processing technology. The new four-dimensional unequal-order fractional order chaotic system has very complex dynamic characteristics, including complex phenomena of multi-attractor coexistence, attractor hiding and the like. Four variable orders are added to the unequal-order fractional order chaotic system to serve as bifurcation control parameters, the secret key space of the system is increased, and the chaotic performance of the system is improved. And based on the TMS320F28335, the fractional order chaotic system is high in implementation flexibility and high in usability, and any fractional order chaotic system can be implemented.
Owner:海特运通(浙江)科技产业发展有限公司 +1
The Construction Method of New Chaotic System Based on Fractal Algorithm
ActiveCN110098917BExpand the key spaceIncrease flexibilitySecuring communication by chaotic signalsKey spaceAlgorithm
The invention discloses a method for constructing a new chaotic system based on a fractal algorithm, which includes selecting a three-dimensional chaotic system and taking the chaotic sequence generated by it as the input sequence of the fractal algorithm; applying the obtained chaotic sequence to the ternary fractal algorithm to obtain the final A new type of fractal chaotic system. The construction method of this new type of chaotic system based on fractal algorithm provided by the present invention can construct many different chaotic systems by selecting different chaotic subsystems and increasing the number of fractals, which can not only improve the key space of the system, but also improve the applicability Strong, high flexibility.
Owner:CENT SOUTH UNIV
A Physical Layer Encryption Method Introducing Latin Matrix
ActiveCN105846947BImprove securityDisassociationSecret communicationSecuring communication by chaotic signalsKey spaceAlgorithm
Owner:NAT UNIV OF DEFENSE TECH
A large key space chaotic optical communication transceiver
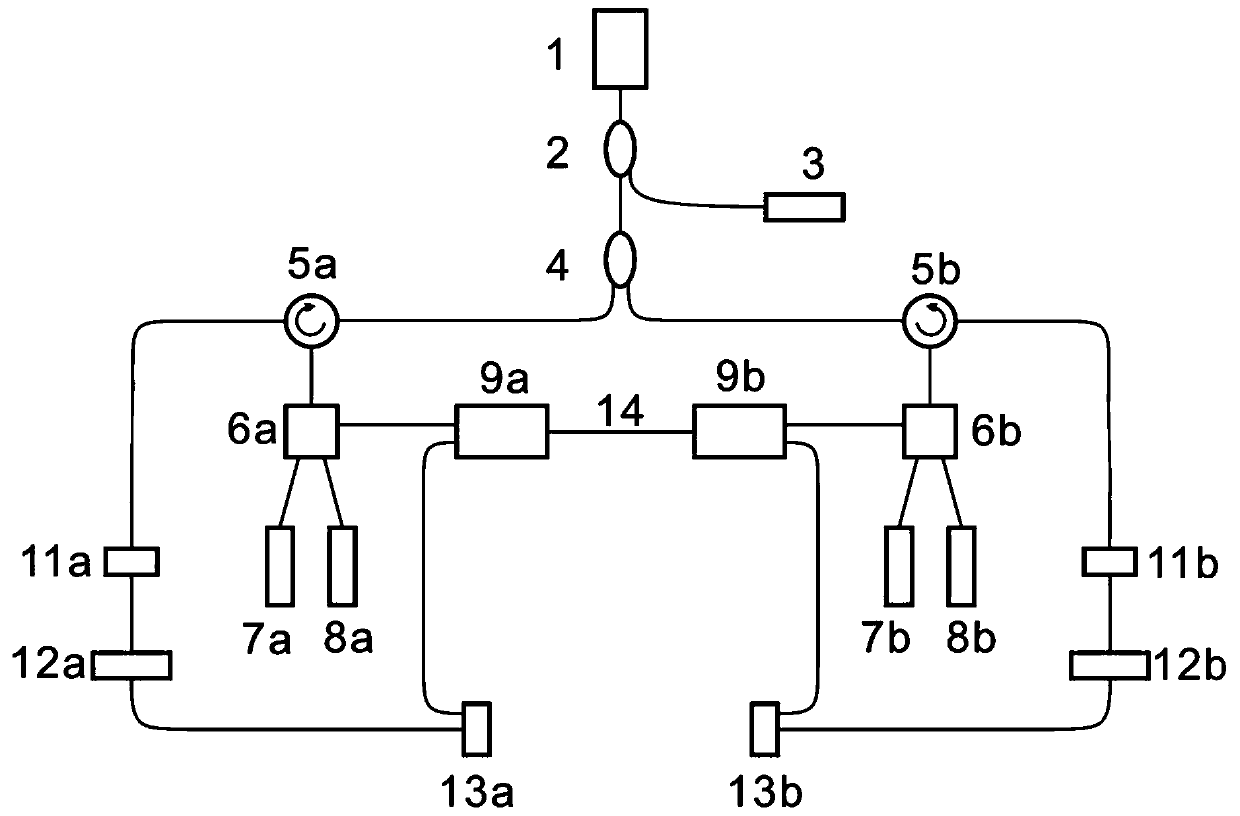
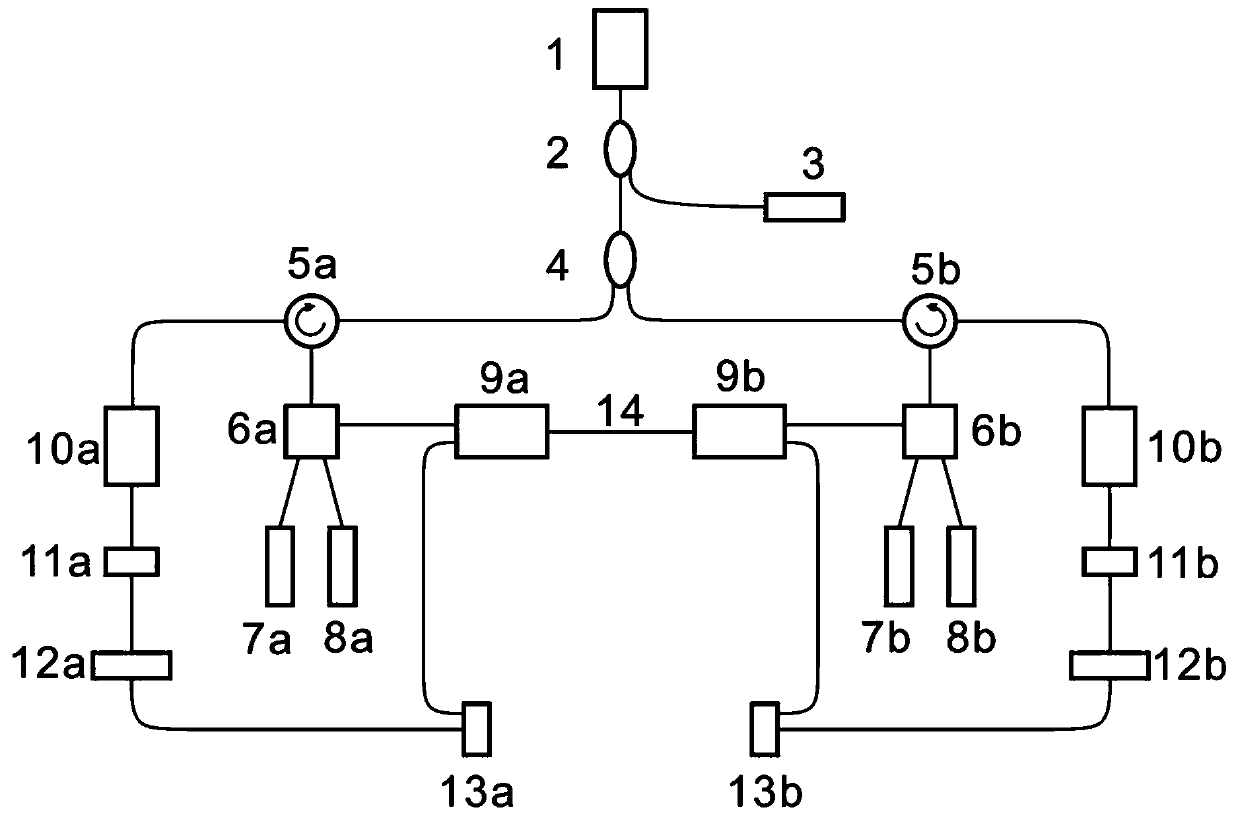
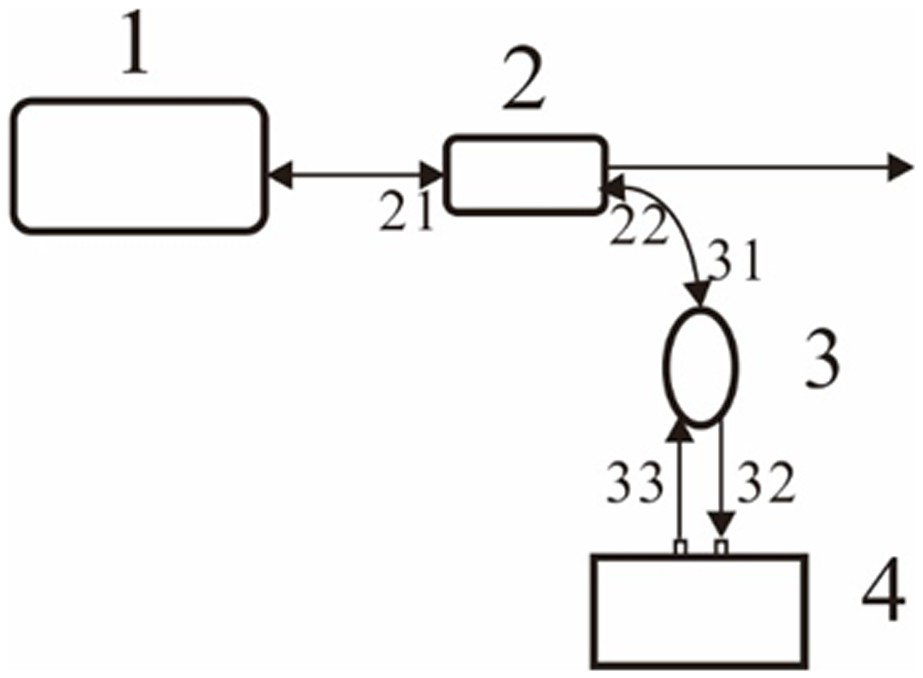
ActiveCN111147145BEnsure safetySimple structureElectromagnetic transmission optical aspectsSecuring communication by chaotic signalsKey spaceTransceiver
The present invention is a chaotic optical communication transceiver with a large key space, which belongs to the technical field of secure optical communication; the key space is increased by increasing the number of external cavities, the structure is complex, and it is susceptible to environmental interference, and the pseudo-random code modulation increases the key space and cannot play chaos The unique hardware encryption advantage of secure communication increases the complexity of the feedback loop and increases the key space, which is expensive and inconvenient for integration and large-scale production; the present invention provides a chaotic optical communication transceiver with a large key space, and the key space is DFB semiconductor The laser feedback intensity, driving current and key parameters of the random filter module are combined. The random filter module replaces the traditional feedback mirror to realize the random selection function after the optical path range is encoded to the spectrum, which greatly improves the key space of the chaotic optical communication transceiver and meets the legal requirements. The confidential communication of users increases the difficulty of stealing by illegal users, effectively hides delay characteristics, ensures hardware consistency, facilitates chaotic synchronization, and facilitates large-scale production.
Owner:TAIYUAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com