Method for authenticating smartphone user based on multi-image switching
A user authentication and smart phone technology, applied in digital data authentication, computer security devices, data processing input/output process, etc., can solve problems such as large amount of calculation, large amount of processed data, complex algorithm, etc., and achieve high recognition rate and security, high resistance to brute force attack performance, and the effect of key space expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The specific implementation manner of the present invention will be described below in conjunction with the accompanying drawings.
[0016] The implementation of the present invention is divided into 2 steps, namely:
[0017] The first step is the user registration process;
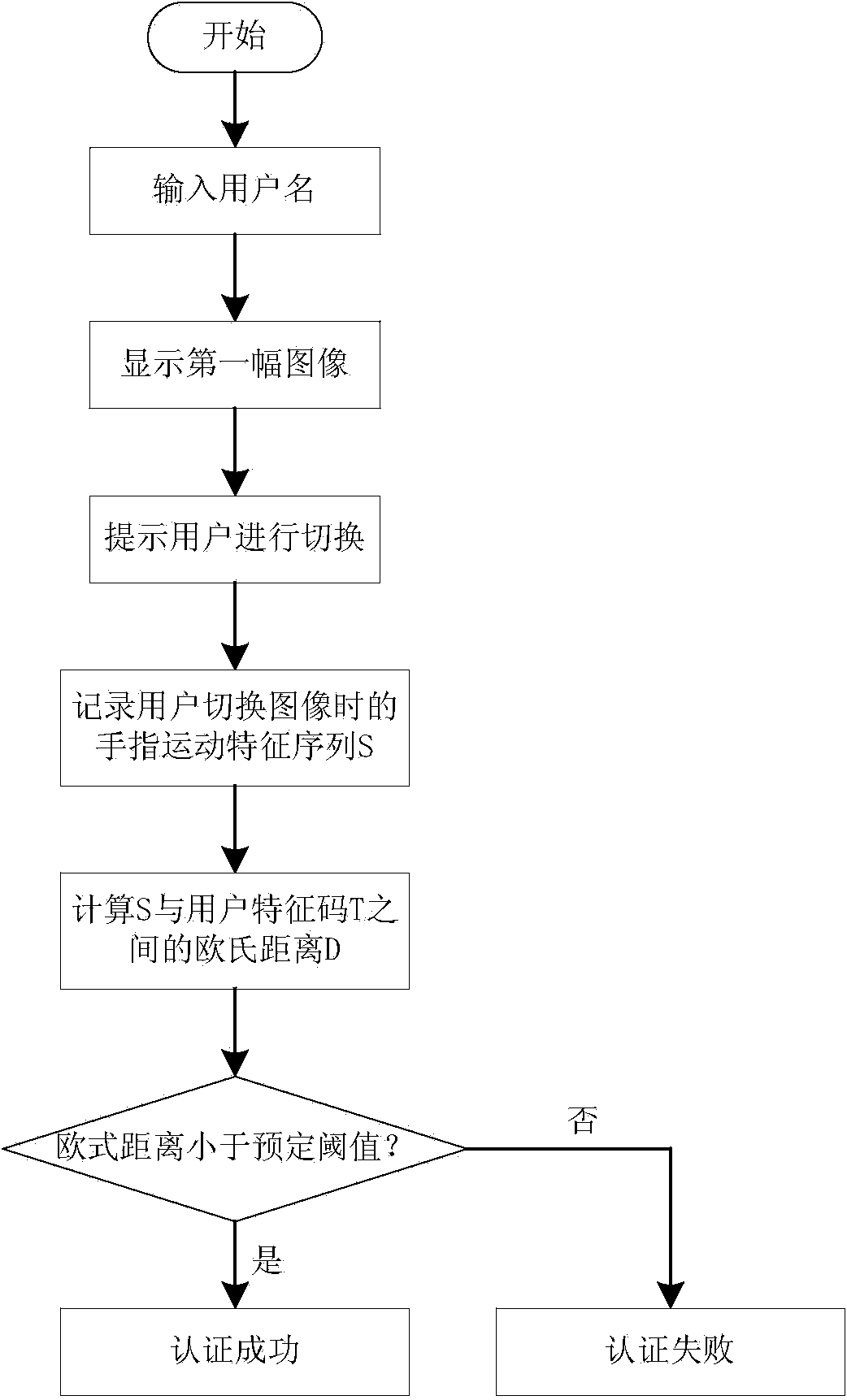
[0018] The second step is the user authentication process.
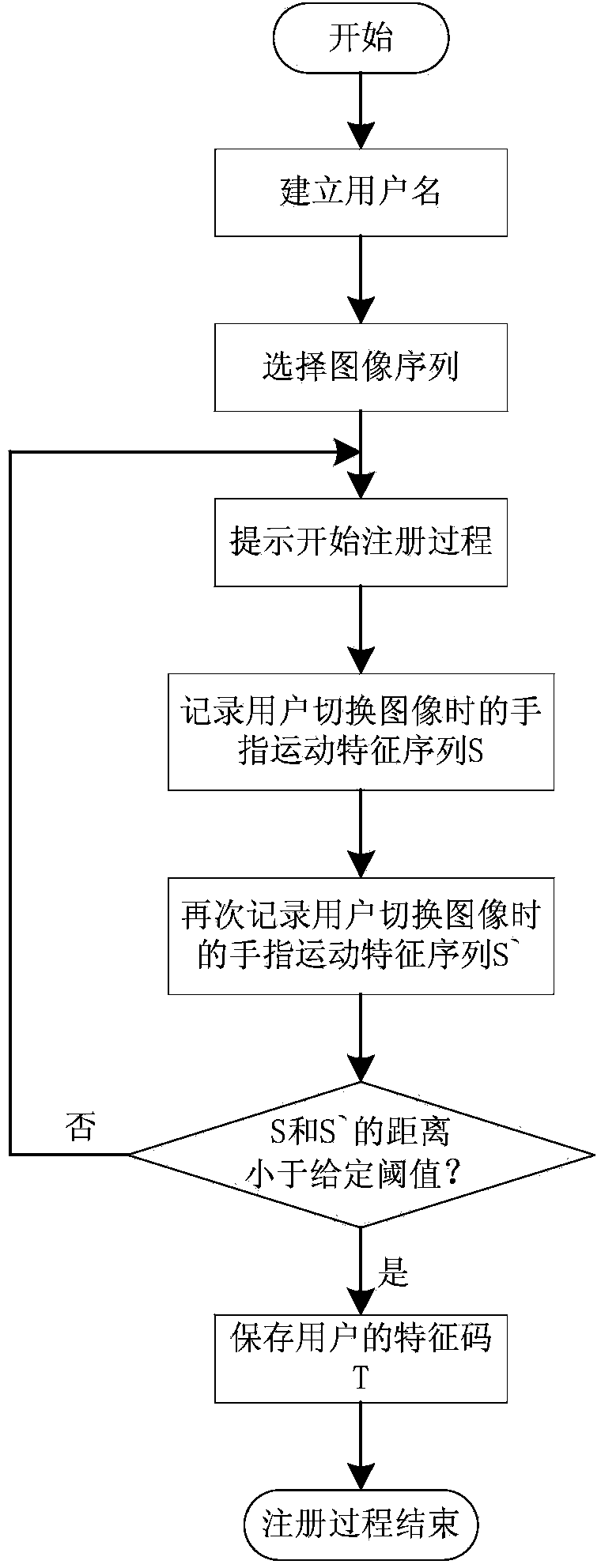
[0019] The user registration process is as follows figure 1 As shown, the specific steps are described in detail as follows:
[0020] (1) Create a user name;
[0021] The user name consists of 6 to 20 alphanumeric characters, such as "zhangsan2013", "wangguihua" and so on.
[0022] (2), select the image sequence;
[0023] List an image collection for the user to select multiple images, for example 5, to form an image sequence. For safety reasons, the image sequence should be saved in the internal memory card of the smart phone instead of an external memory card such as an SD card. The image format is not limited, and JPG files are g...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com