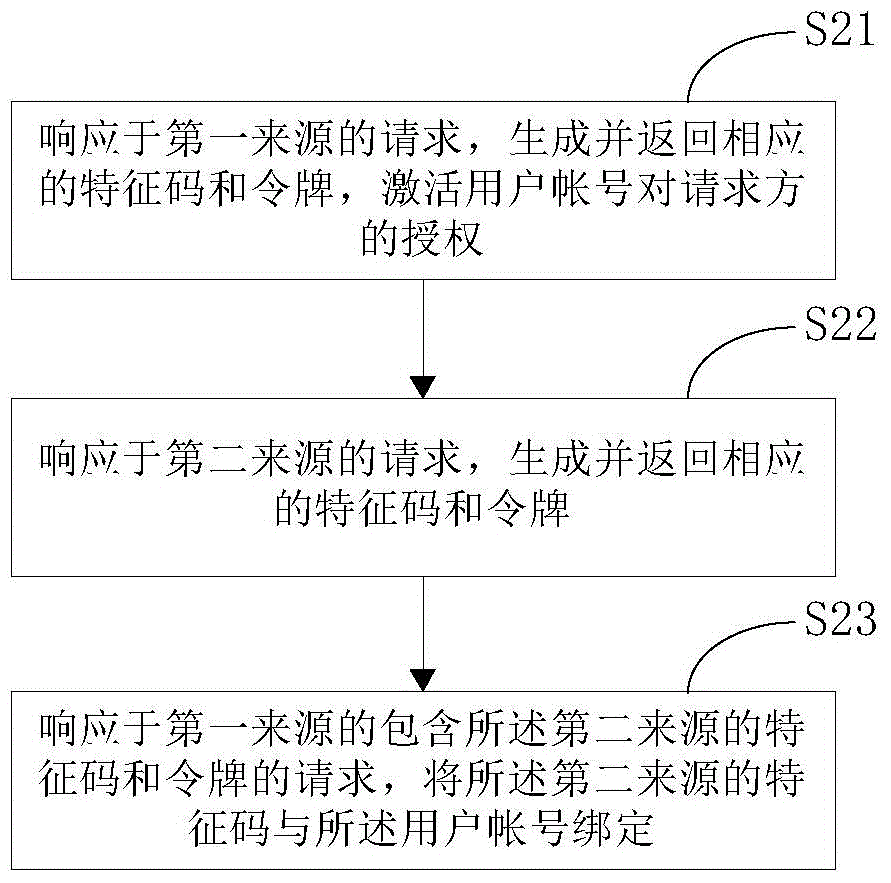
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2113 results about "Feature code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
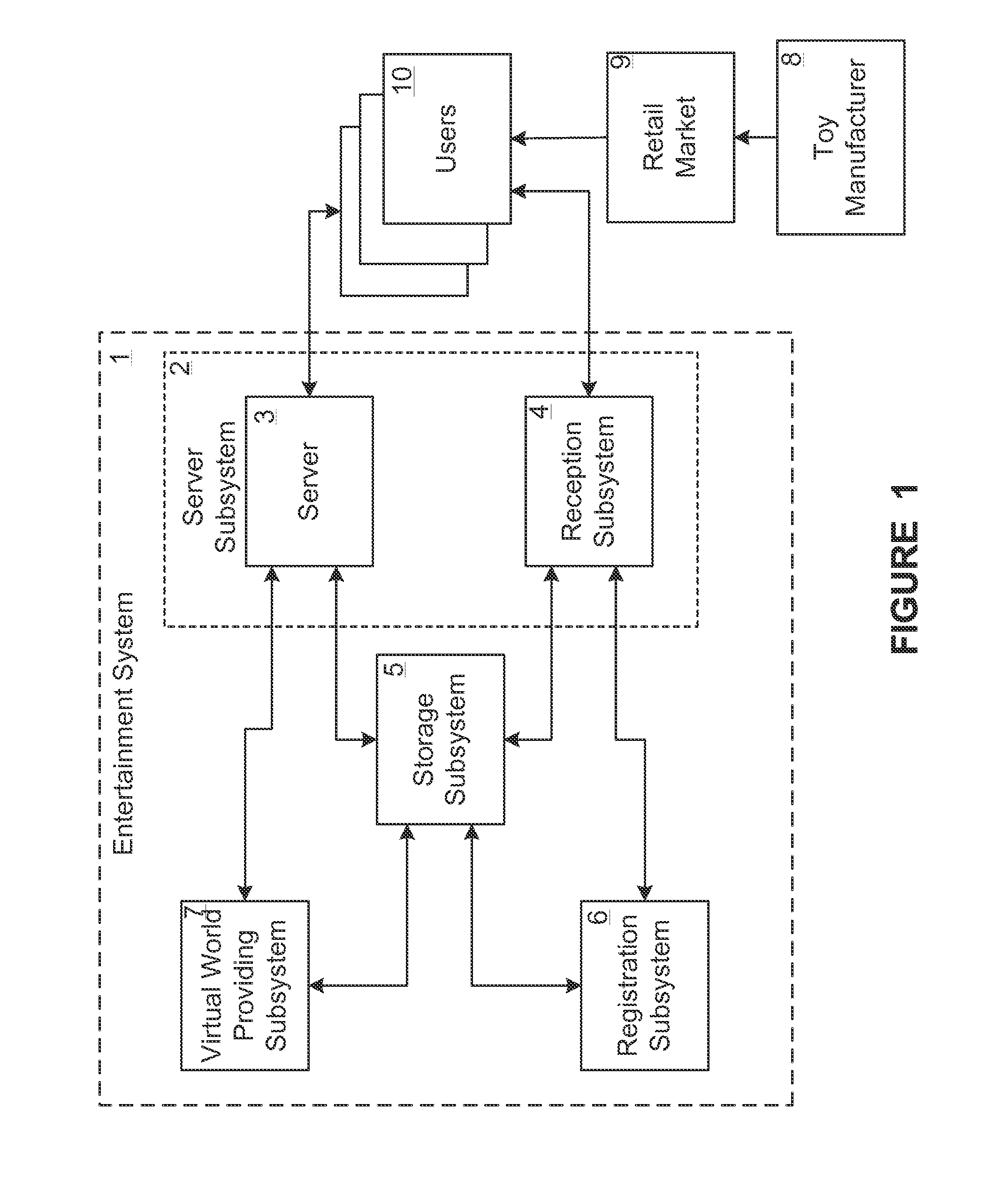
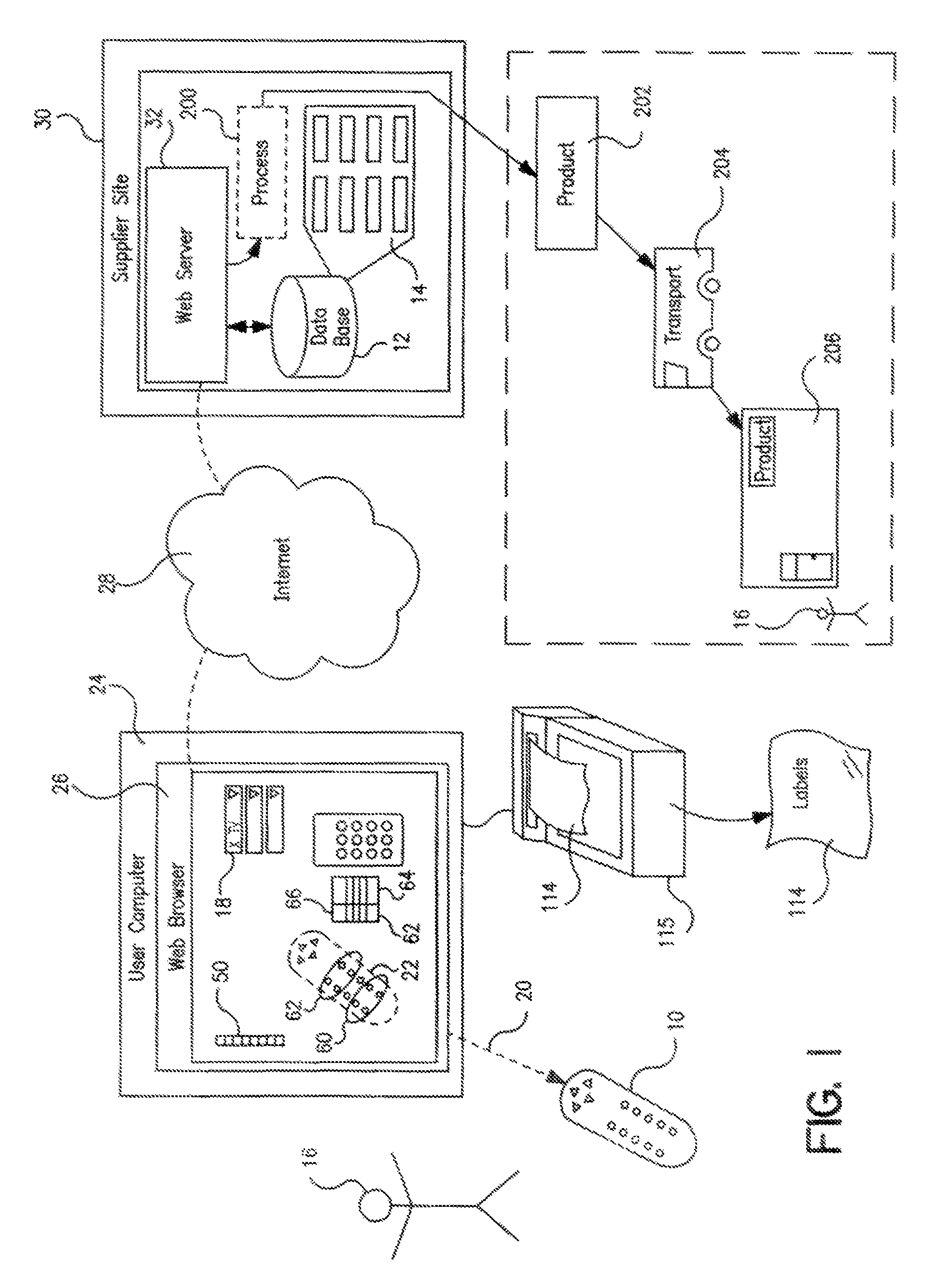
System and method for product marketing using feature codes
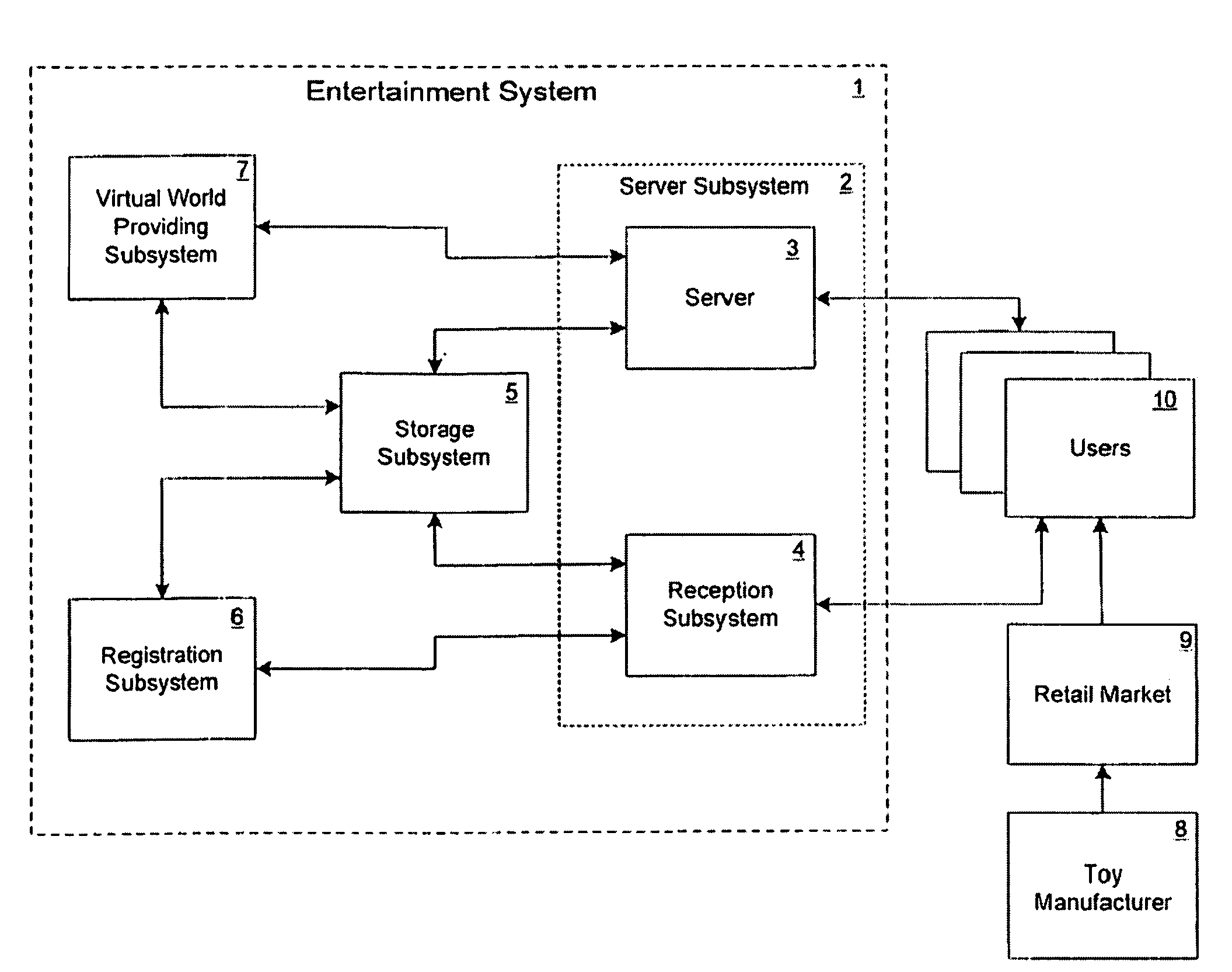
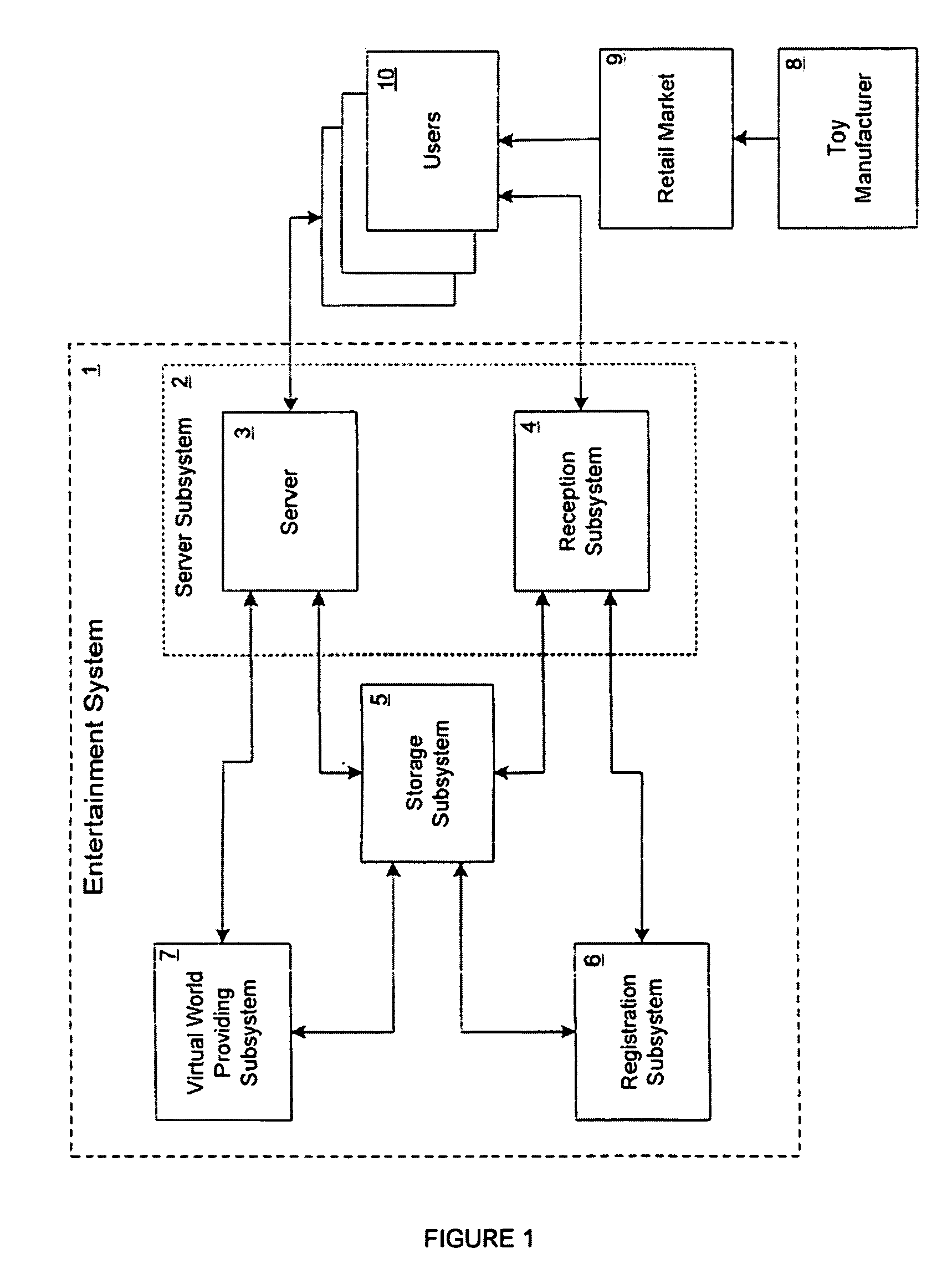
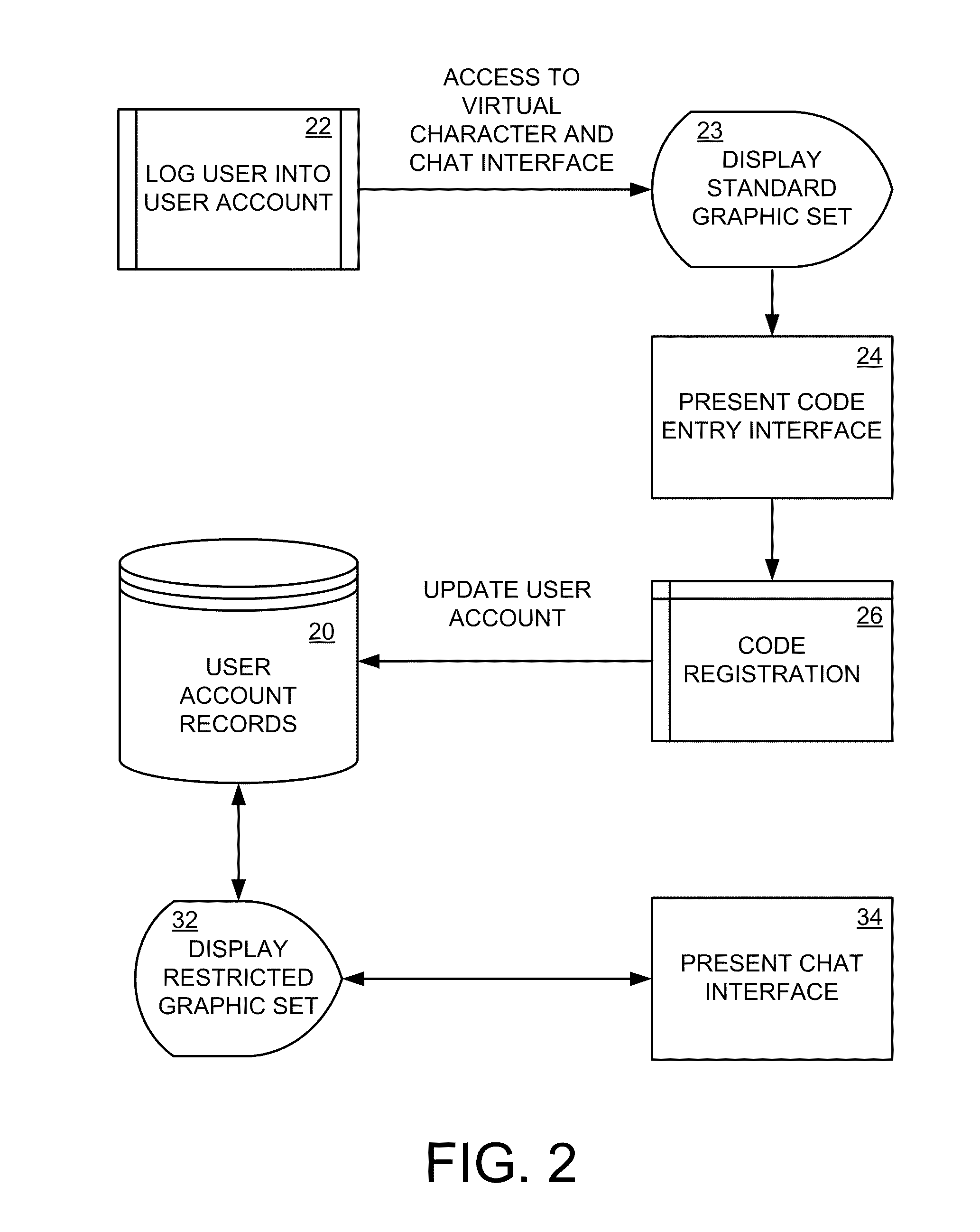
An Entertainment System including a website, in combination with a commercially purchased product, wherein the system allows a product user to register a primary product online using a registration code, allowing the user access to various activities and scenarios in a “virtual world” including a virtual representation of the product, via a computer connected to the Internet. Additional ancillary products are also provided that may be related to the primary product or the virtual world, with these ancillary products also being provided with one or more codes to provide additional content, bonus items, and / or bonus access in the virtual world.
Owner:GANZ AN ONTARIO PARTNERSHIP CONSISTING OF S H GANZ HLDG INC & 816877 ONTARIO
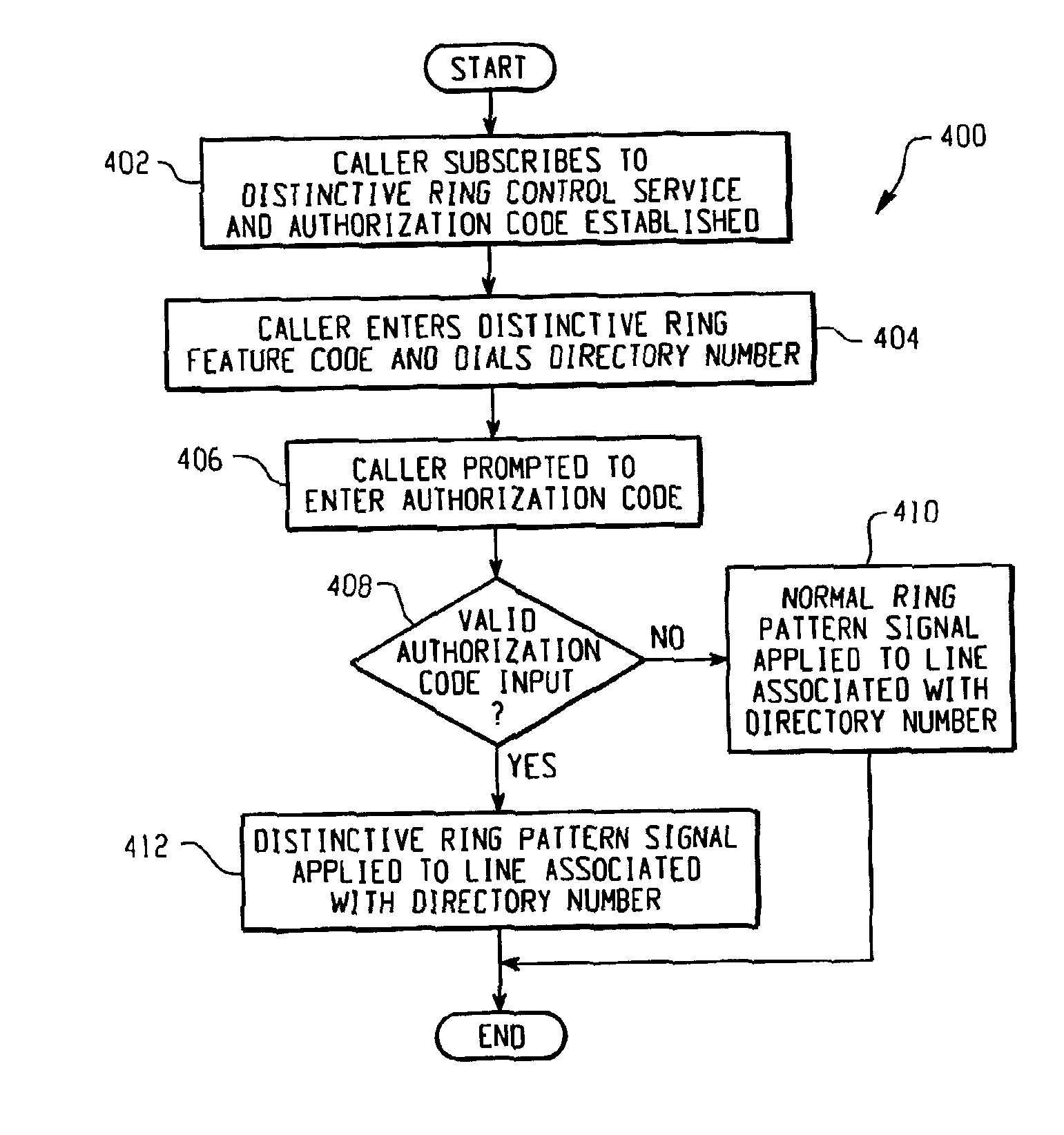
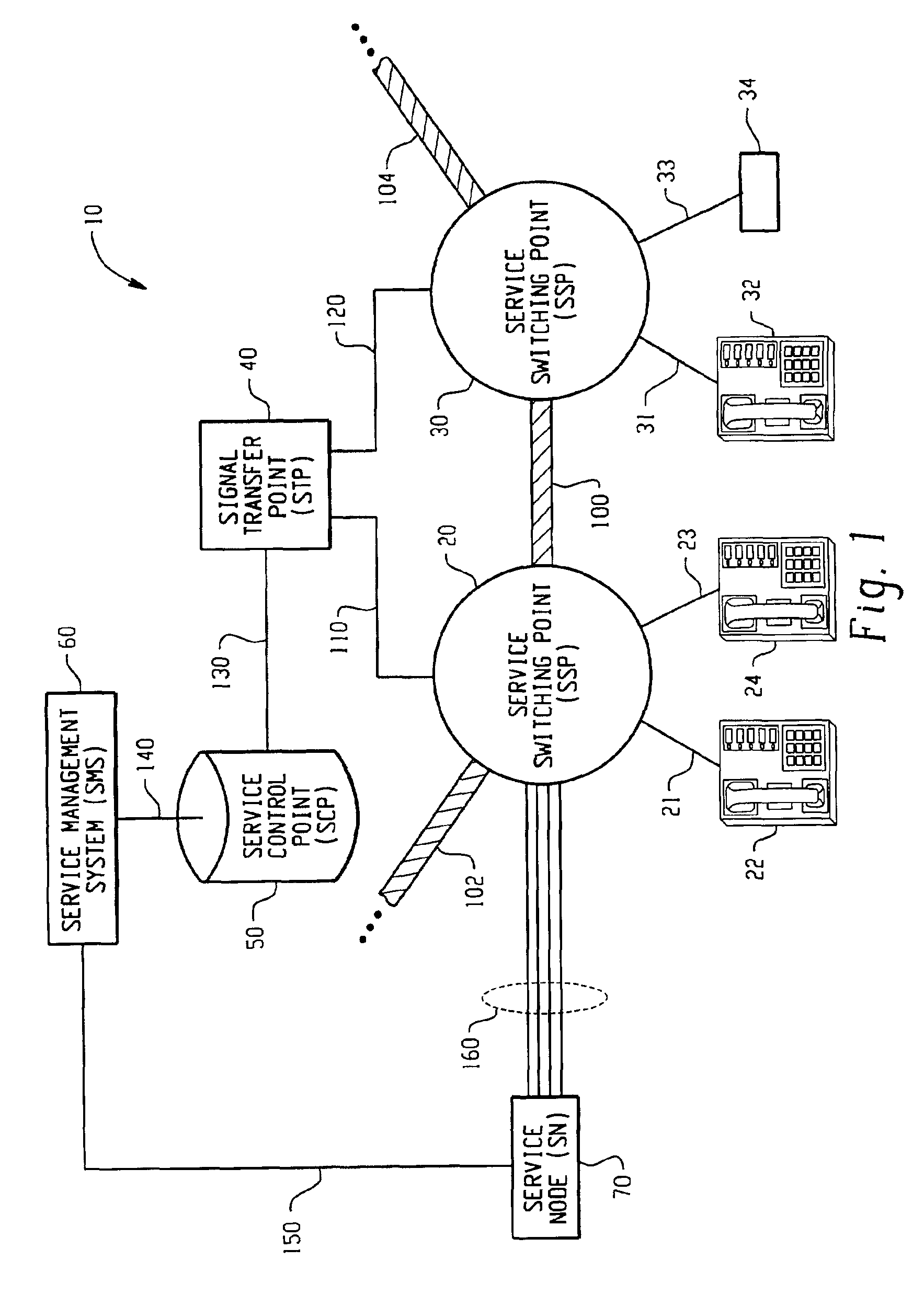
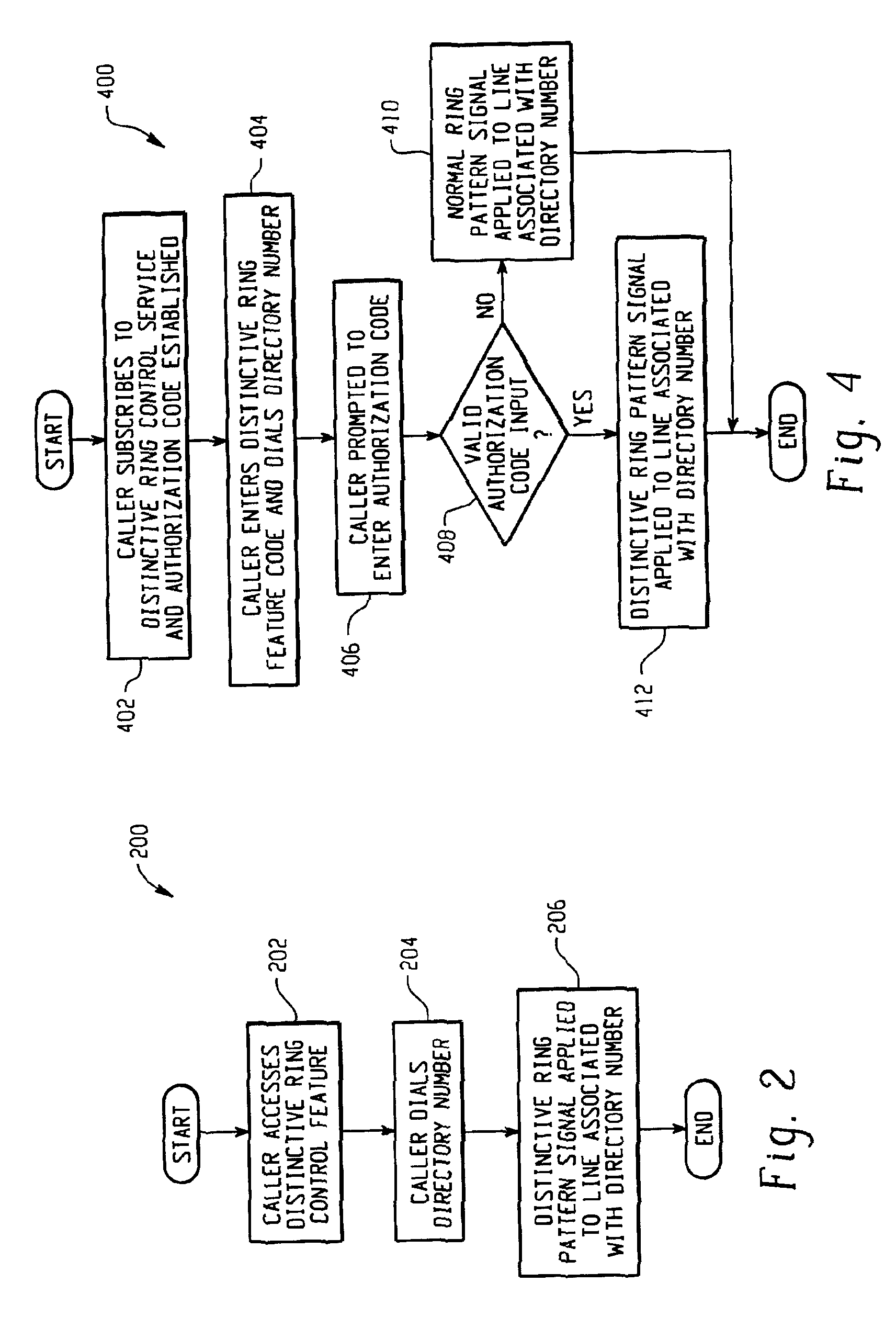
System and method for caller control of a distinctive ring
InactiveUS7106846B2Special service for subscribersCurrent supply arrangementsService controlDirectory number
Owner:BELLSOUTH INTPROP COR
Feature codes and bonuses in virtual worlds
An Entertainment System including a website, in combination with a commercially purchased product, wherein the system allows a product user to register a primary product online using a registration code, allowing the user access to various activities and scenarios in a “virtual world” including a virtual representation of the product, via a computer connected to the Internet. Additional ancillary products are also provided that may be related to the primary product or the virtual world, with these ancillary products also being provided with one or more codes to provide additional content, bonus items, and / or bonus access in the virtual world.
Owner:GANZ
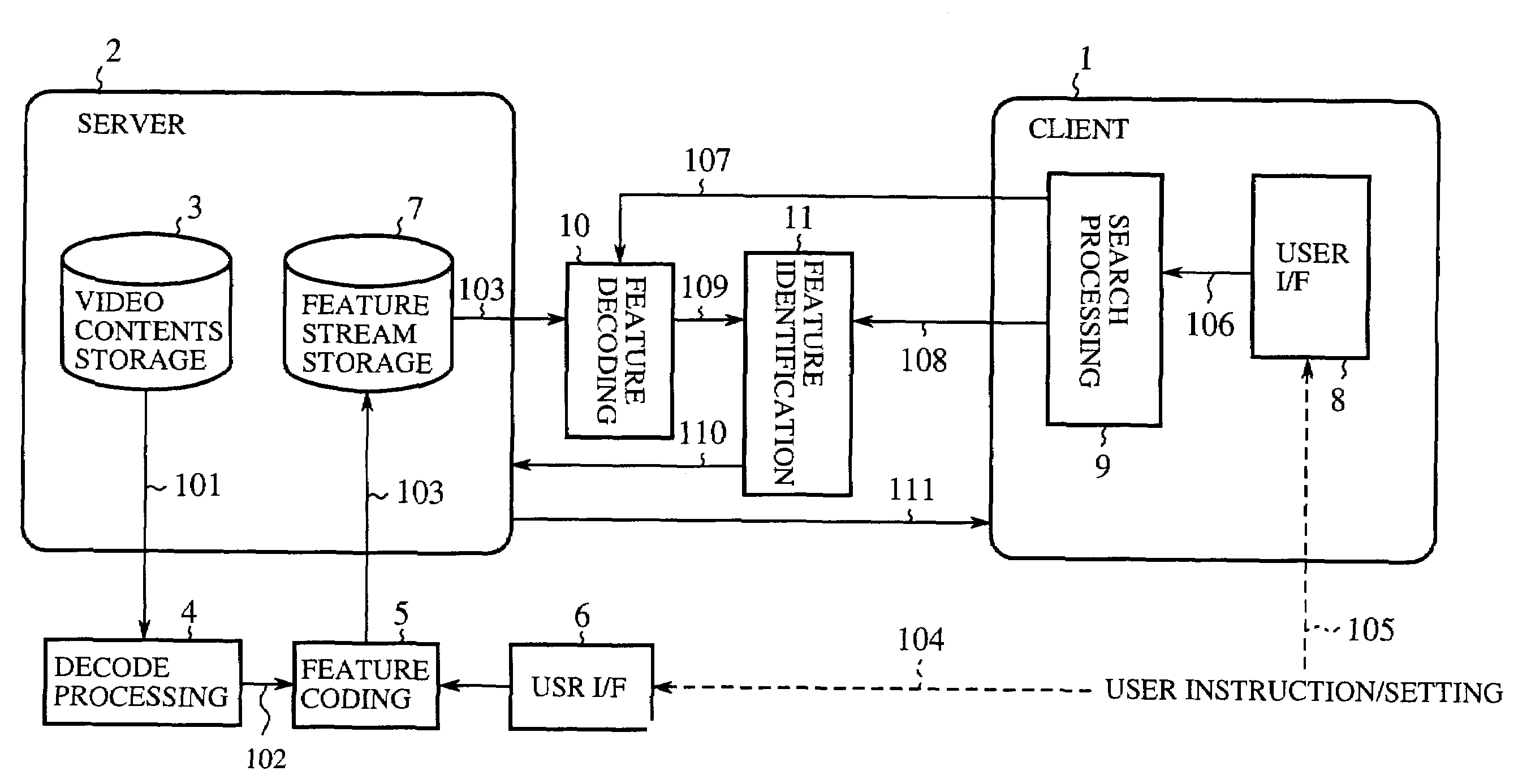
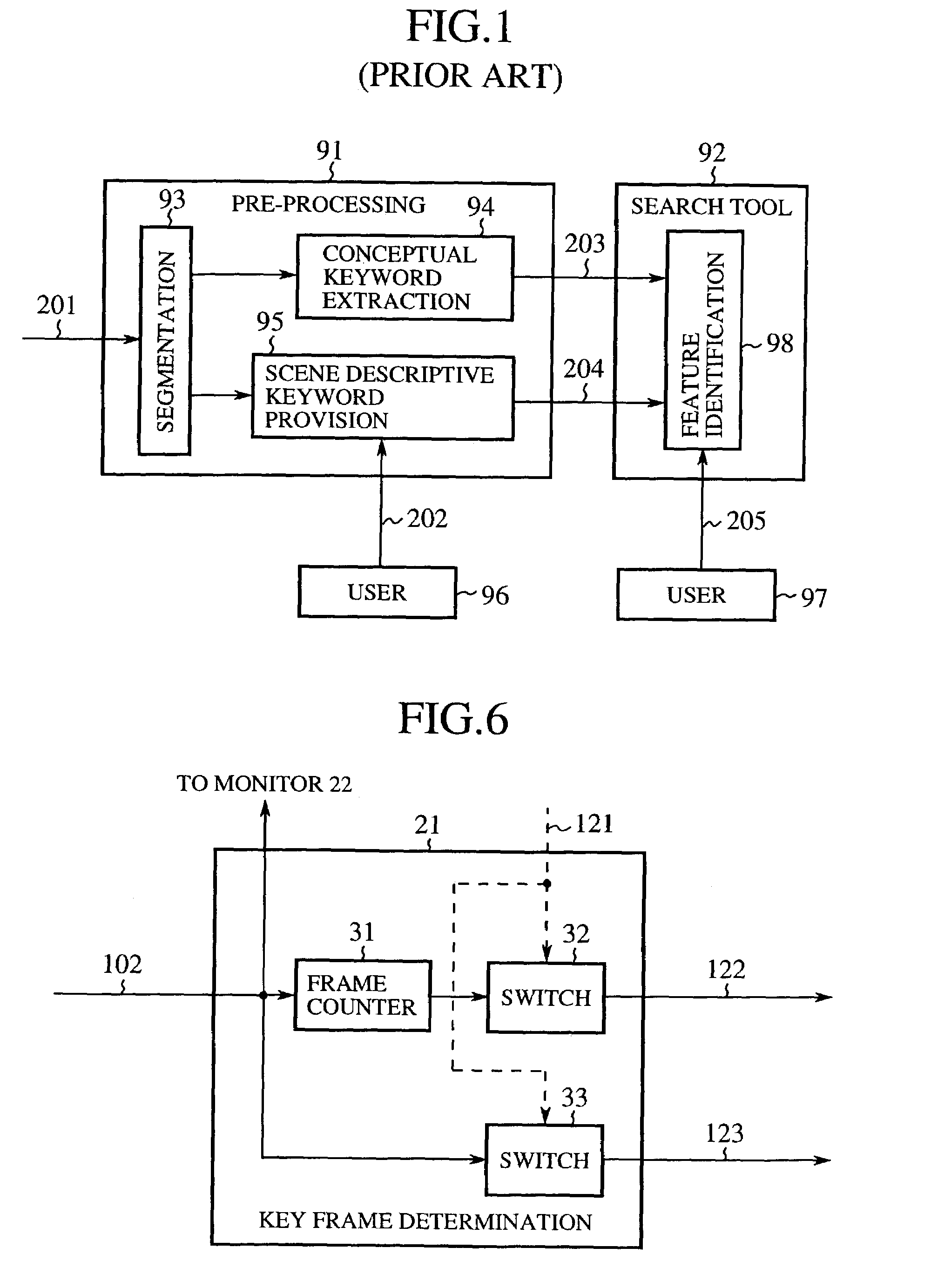
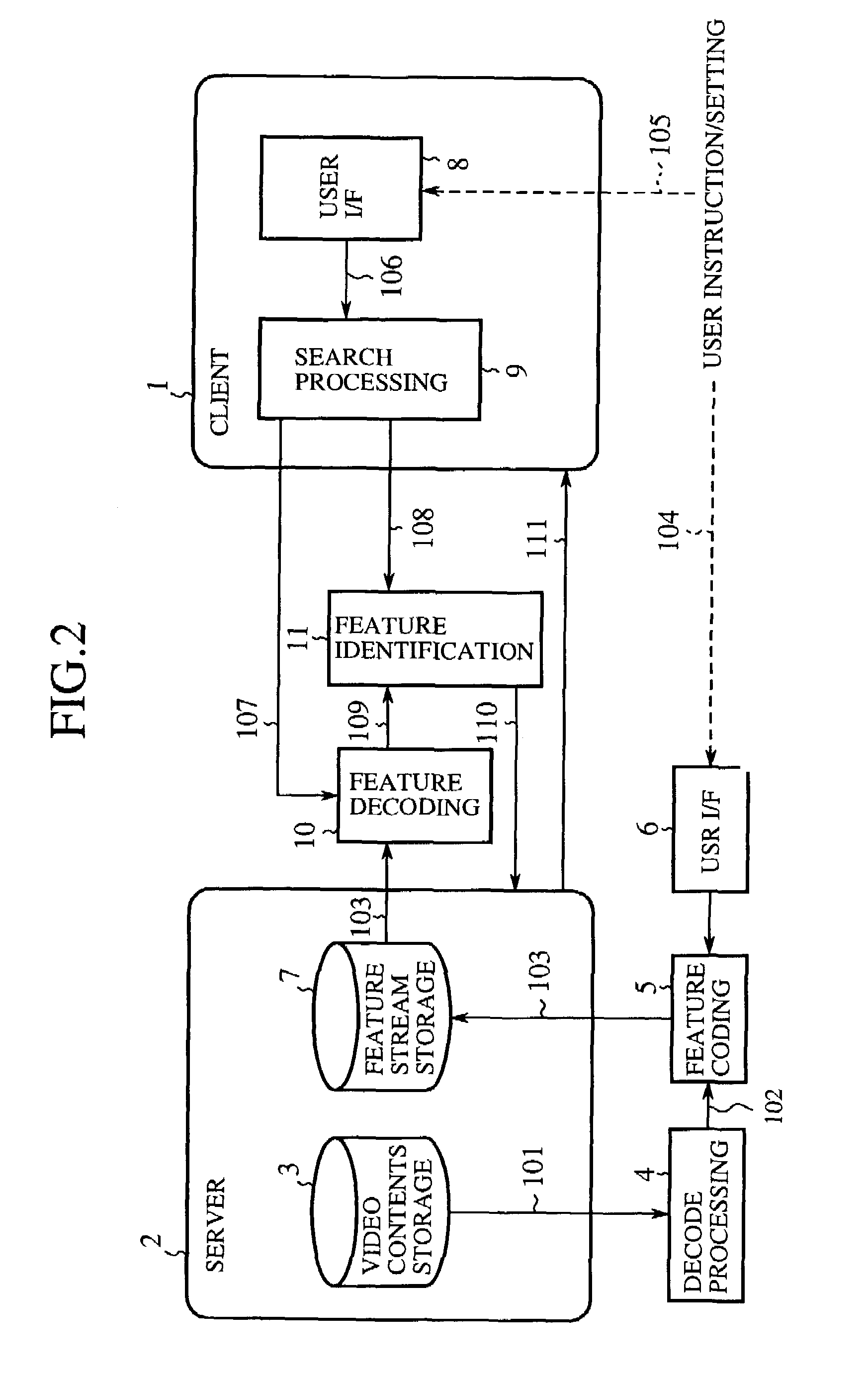
Method of image feature coding and method of image search
A feature coding unit extracts and encodes a feature of a video signal so as to generate a feature stream. A feature identifying unit checks a decoded feature obtained as a result of decoding the feature stream against a search key from a user for a match so that a video content requested by the user is retrieved.
Owner:MITSUBISHI ELECTRIC CORP
Method and apparatus for performing antivirus tasks in a mobile wireless device
InactiveUS20060161985A1Loading and unloadingRestore accuratelyMemory loss protectionUnauthorized memory use protectionOperational systemApplication programming interface
Disclosed are techniques for performing an antivirus task in a mobile wireless device running an embedded operating system. In one embodiment, calls intended for an application programming interface (API) function code is redirected to an antivirus function code. The redirection to the antivirus function code may be performed by modifying a kernel structure to point to a modified entry list instead of an API entry list. The redirection to the antivirus function code may also be performed by modifying the API function code to allow the antivirus function code to execute before the API function code. The kernel structure or the API function code may be properly restored back to its original form. Software implementations of these techniques may be readily loaded and unloaded, and may not require re-installation of the embedded operating system.
Owner:TREND MICRO INC
Customizable and upgradable devices and methods related thereto
InactiveUS8098140B1Effective distributionInvolvement of intermediate distributors is minimizedInput/output for user-computer interactionTelevision system detailsProgramming languageRemote control
A remote control is configured by a user specifying a type and brand of a consumer electronic device. A plurality of function code sets that have been identified as being candidates for commanding operations of the specified type and brand of consumer electronic device are selected and at least a subset of each of the plurality of selected function code sets is made available such that a user may determine by experimentation which one of the plurality of function code sets is appropriate for commanding operations of the specified type and brand of consumer electronic device.
Owner:UNIVERSAL ELECTRONICS INC
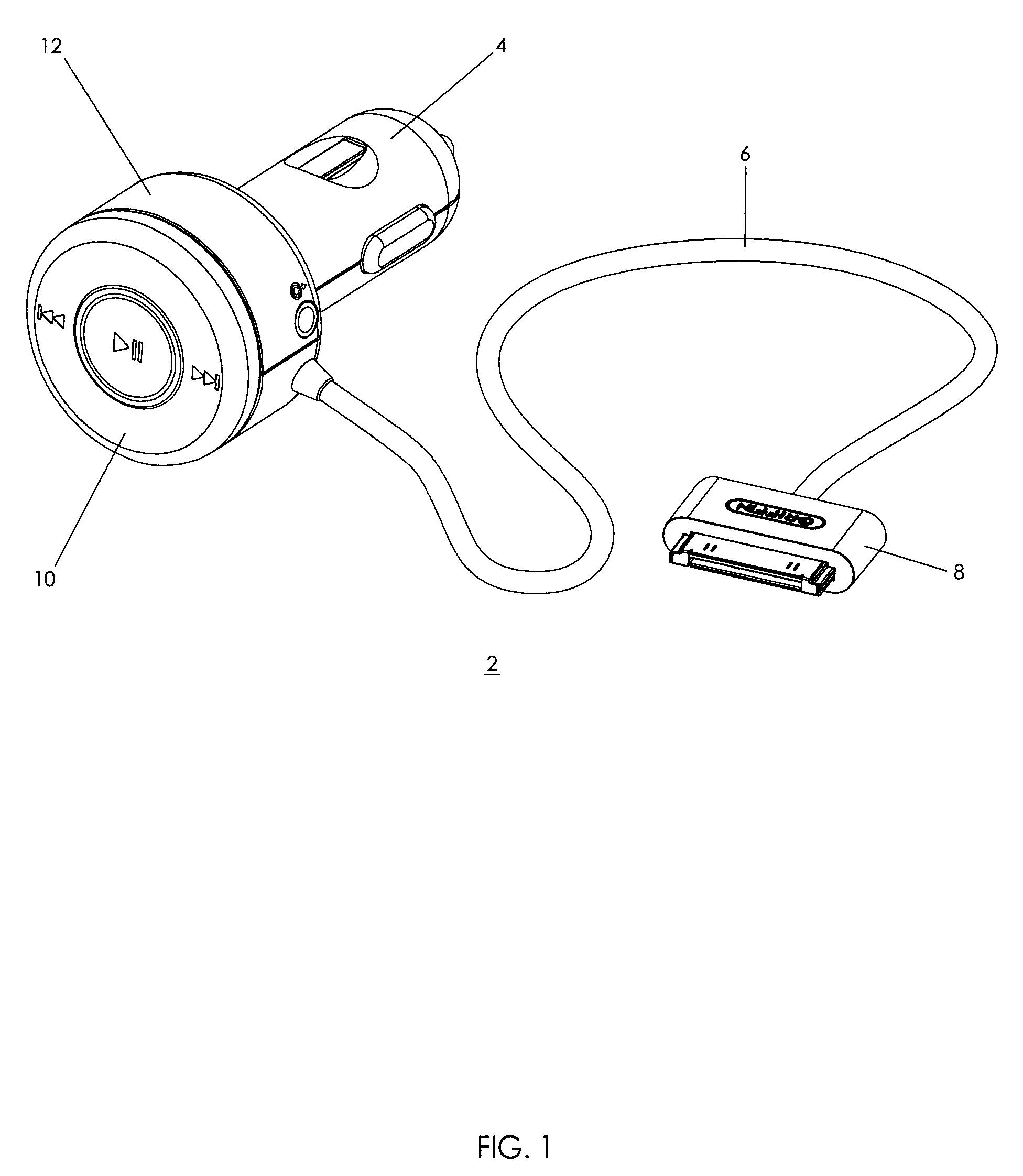
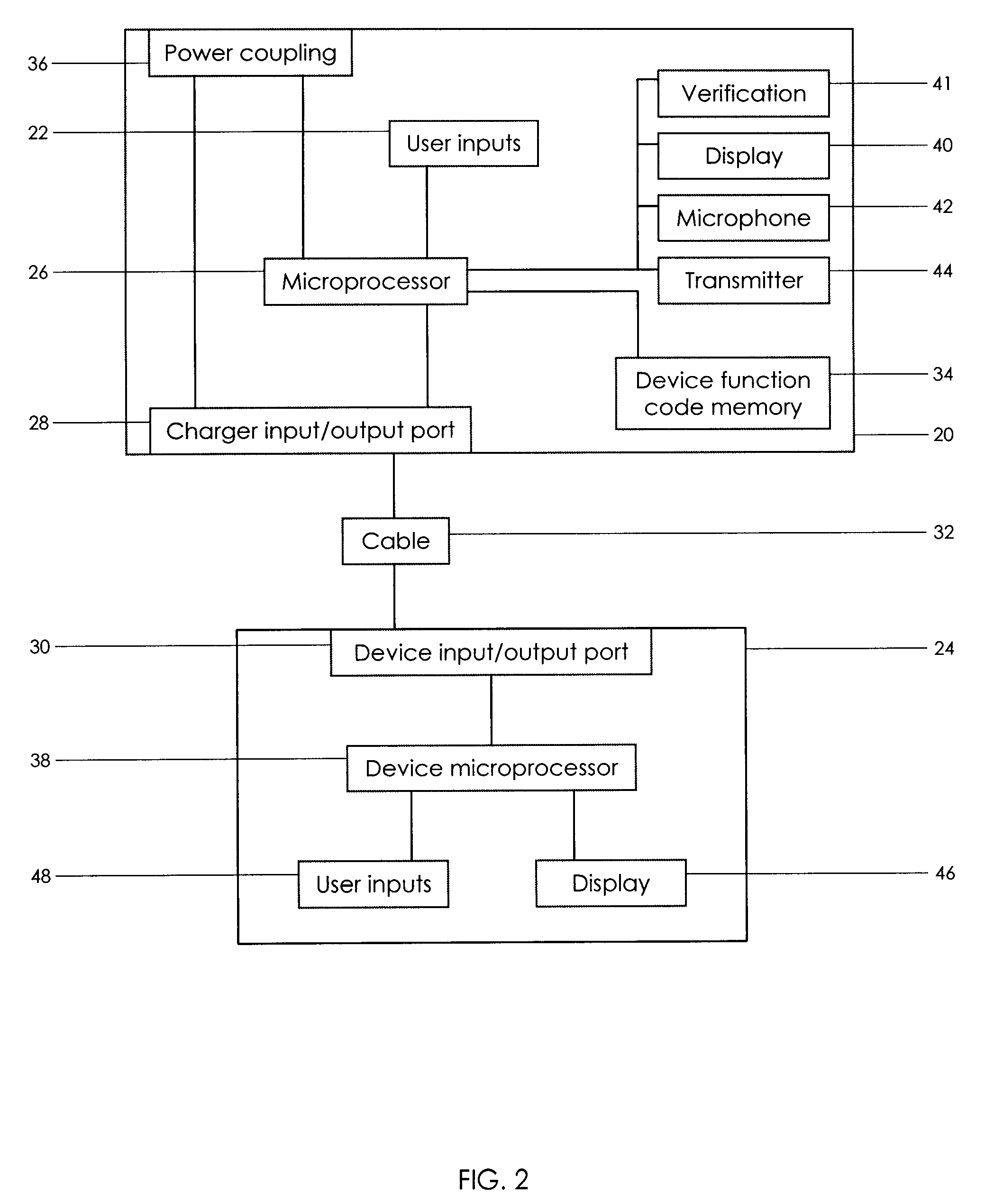
Auxiliary power adapter having device controls
InactiveUS20080015717A1Control functionBatteries circuit arrangementsWith electric batteriesMusic playerVerification system
An accessory for a portable electronic device, such as a digital music player, includes a set of device controls for controlling the portable electronic device. The accessory includes a microprocessor and a memory that contains function codes corresponding to the functions selected by the controls. Preferably, the accessory is a charger is adapted to be inserted into for a 12-volt car auxiliary power outlet and the protruding face of the charger body is a click wheel controller that rotates. The accessory may also include a FM transmitter for transmitting an audio signal received from the portable electronic device to the car stereo and a verification system for insuring the charger is produced by an authorized supplier.
Owner:VINCI BRANDS LLC
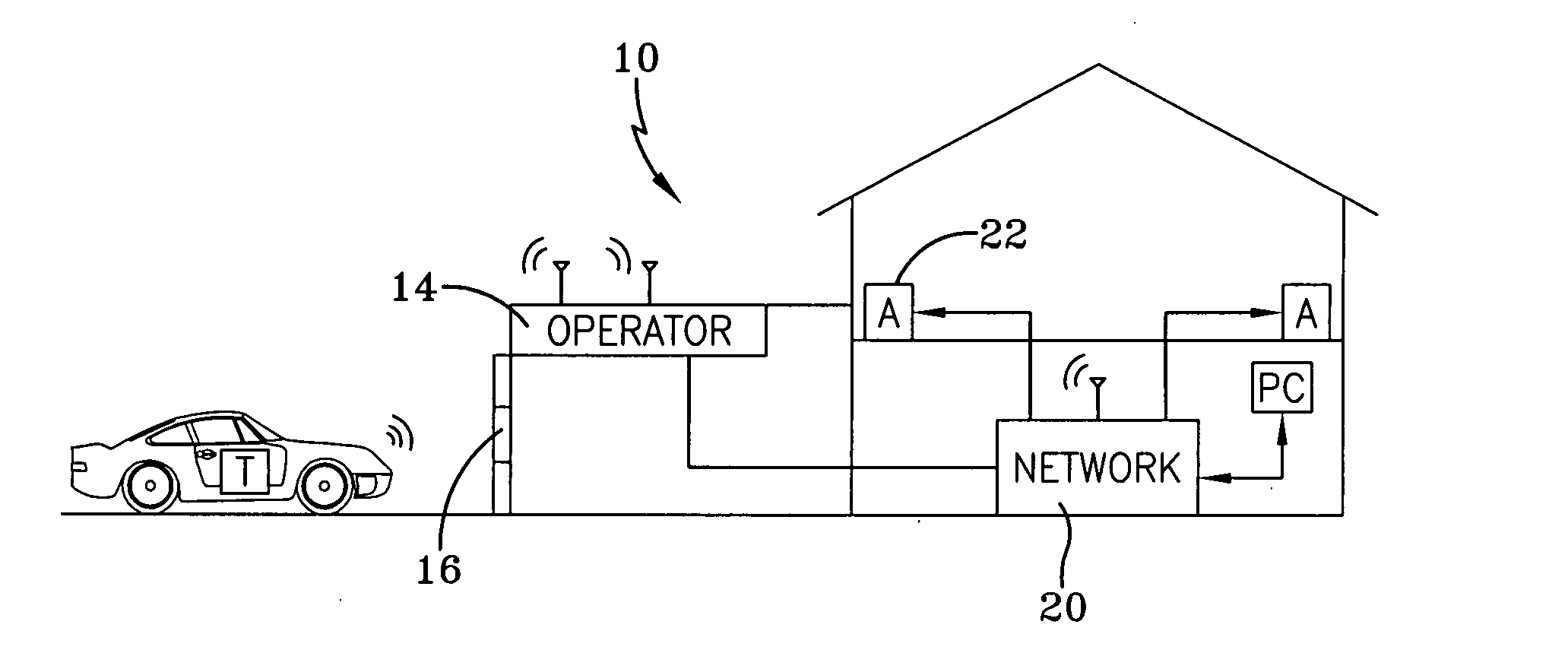
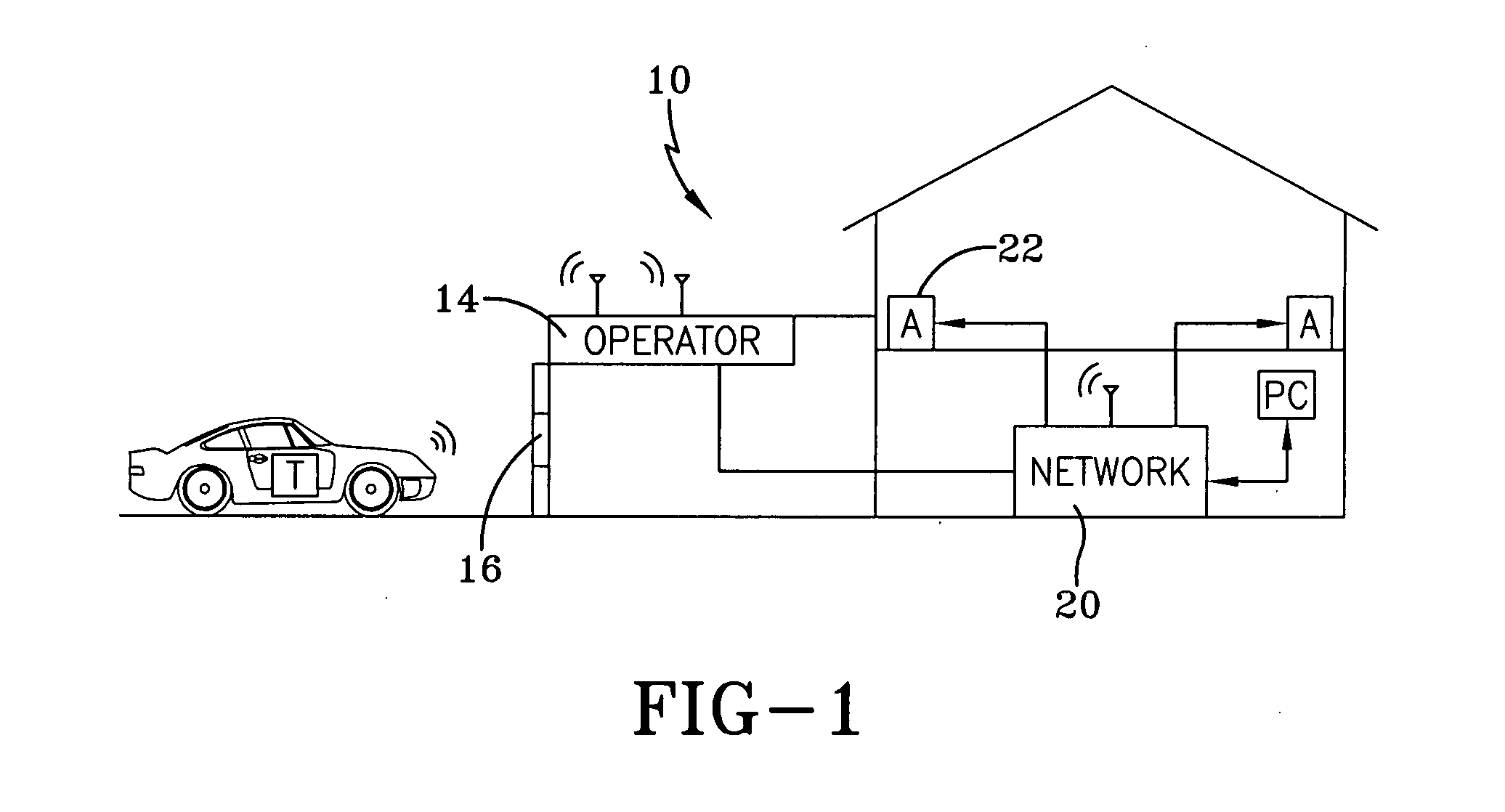
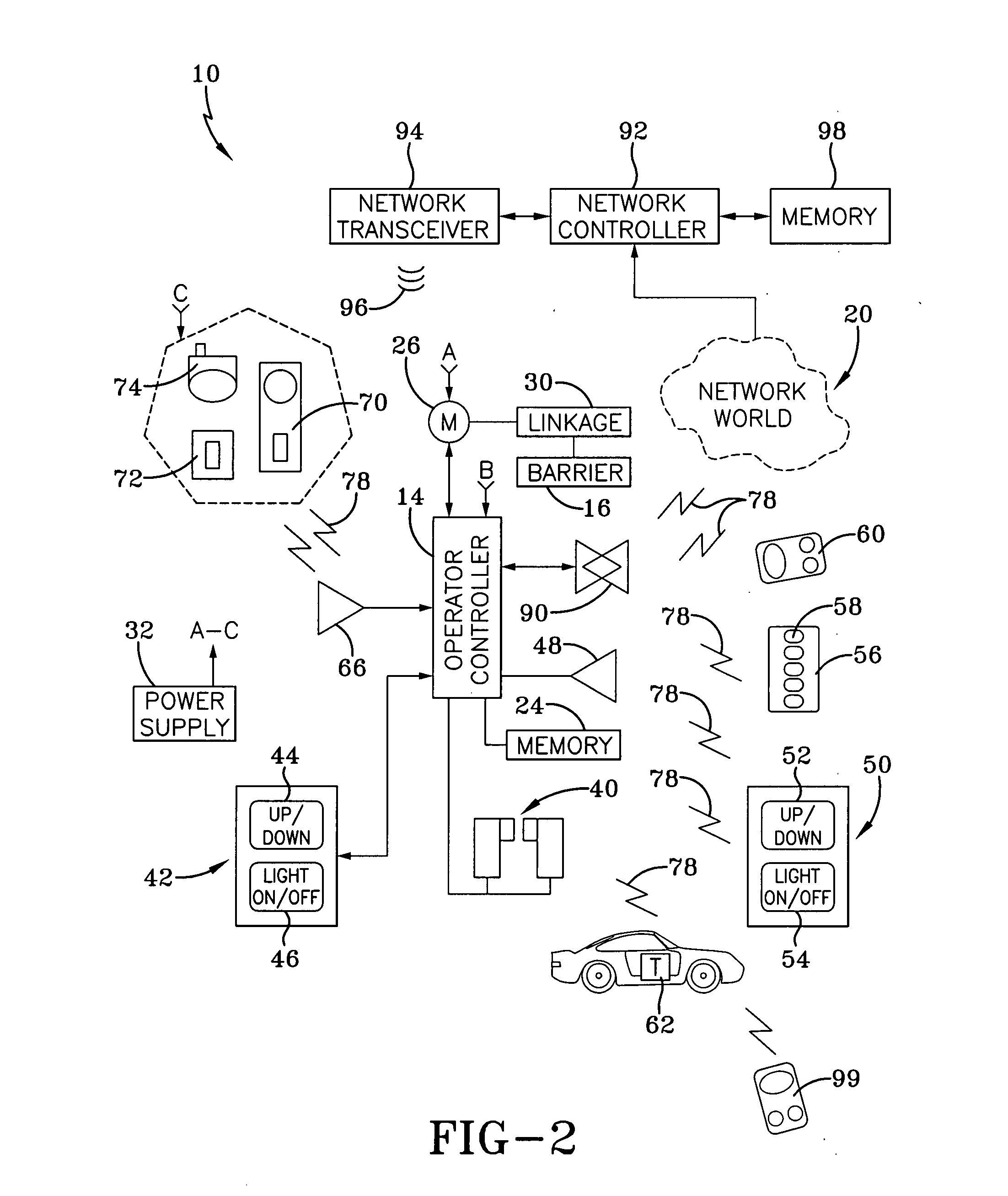
Networked movable barrier operator system
InactiveUS20070146118A1Electric signal transmission systemsDigital data processing detailsMicrocontrollerTransceiver
A network operator radio module (NORM) configured to be removably attached to a barrier operator comprises a transmitting antenna, a receiving antenna, a transceiver antenna, and a microcontroller. The module communicates with a communication network that comprises various nodes configured by a network controller module and a network communication module. Each node may be associated with a network appliance, and may be remotely controlled by sending a suitable function code to the module via local command signals. Furthermore, various local remote transmitters and keyless entry transmitters are configured to transmit function codes to control the module and the associated various network appliances.
Owner:QMOTION
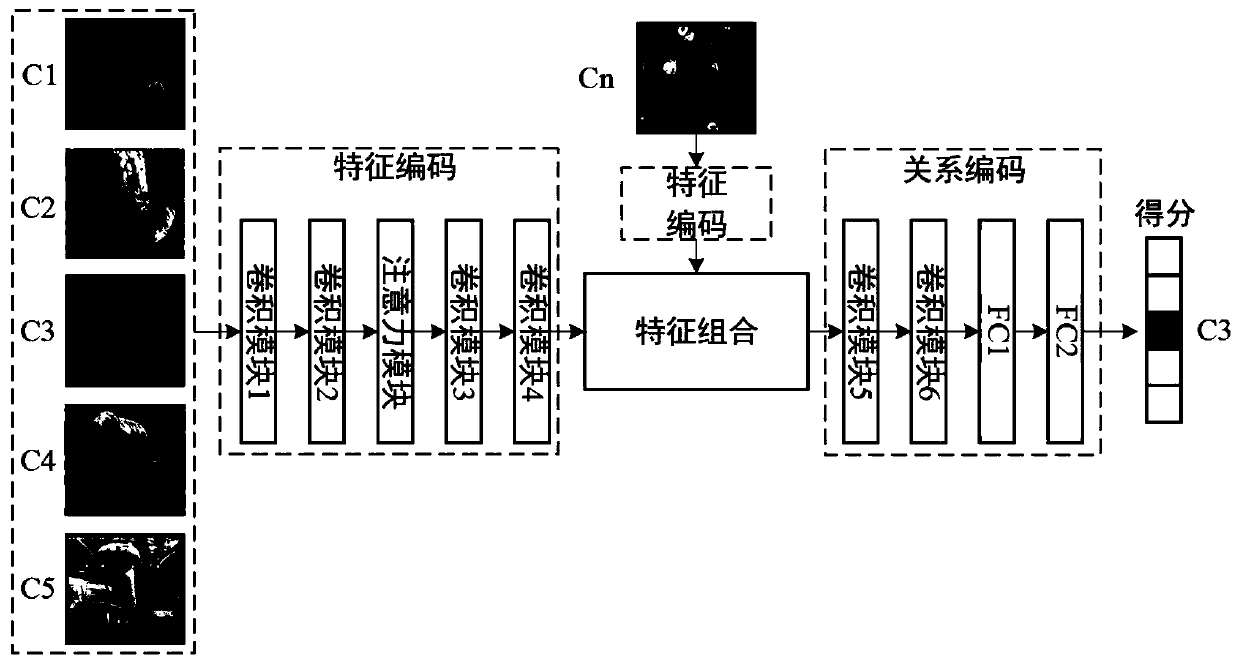
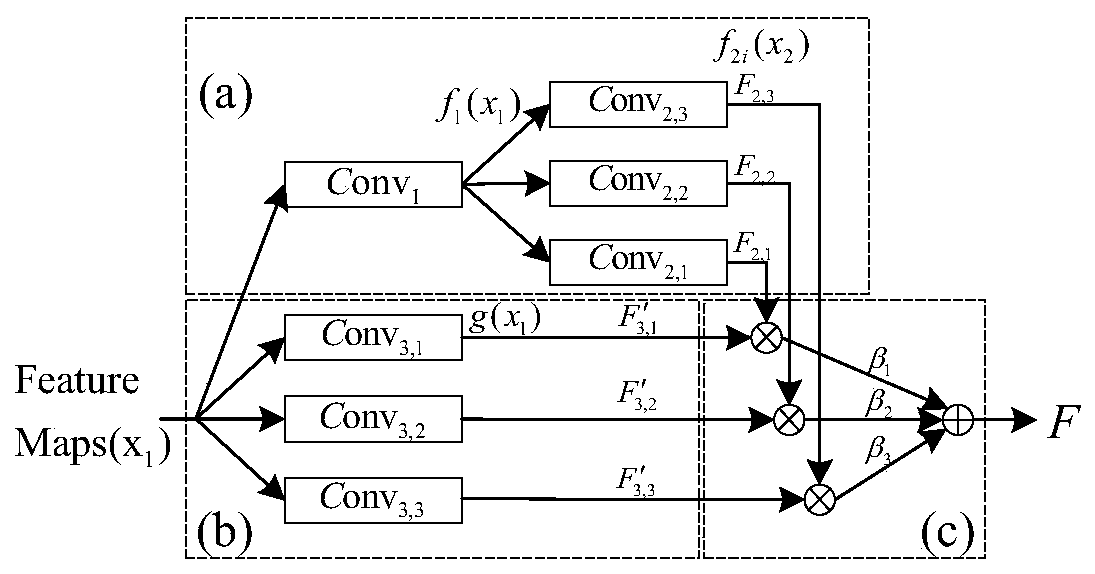
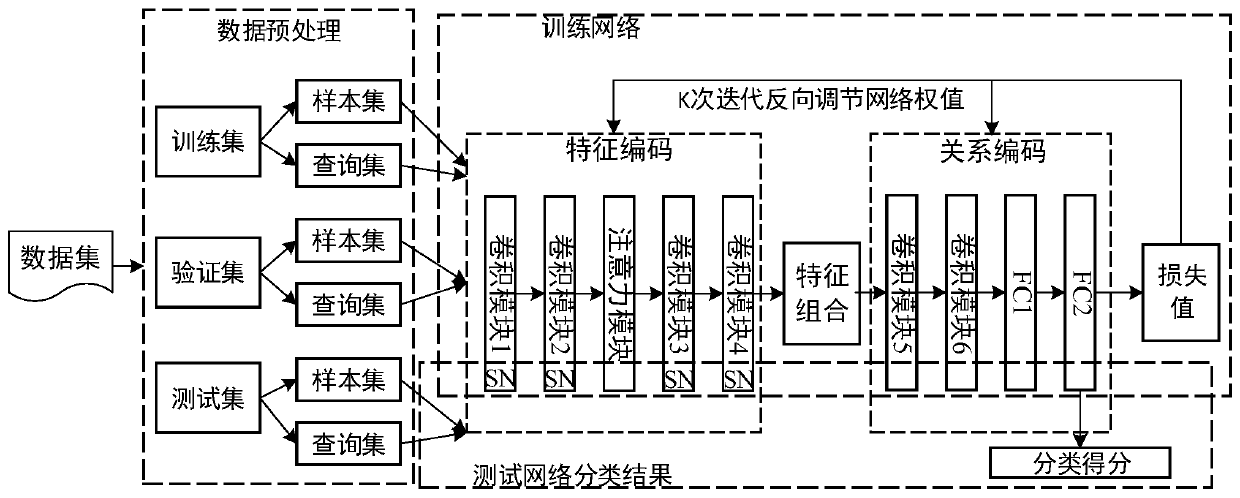
Attention mechanism relationship comparison network model method based on small sample learning
ActiveCN110020682AImprove classification accuracyImprove stabilityCharacter and pattern recognitionNeural architecturesModel methodSmall sample
The invention discloses an attention mechanism relationship comparison network model method. An attention relationship comparison network model for small sample learning under a small amount of labeled sample data is constructed. Based on a relational network architecture, the model is divided into a feature coding part, a feature combination part and a relational coding part, the feature coding module is used for extracting image feature information, and the feature combination part is used for recombining the extracted query image feature information with the training image feature information of each group to form a new combined feature map. The relation encoding module performs nonlinear metric learning of the network; by introducing an attention mechanism and a spectrum normalizationmethod into an end-to-end deep convolutional neural network model, the model has higher classification accuracy under the condition of small sample learning, the stability of a final training result of the model is improved, and the image classification accuracy of an existing model in small sample learning is improved.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY +1
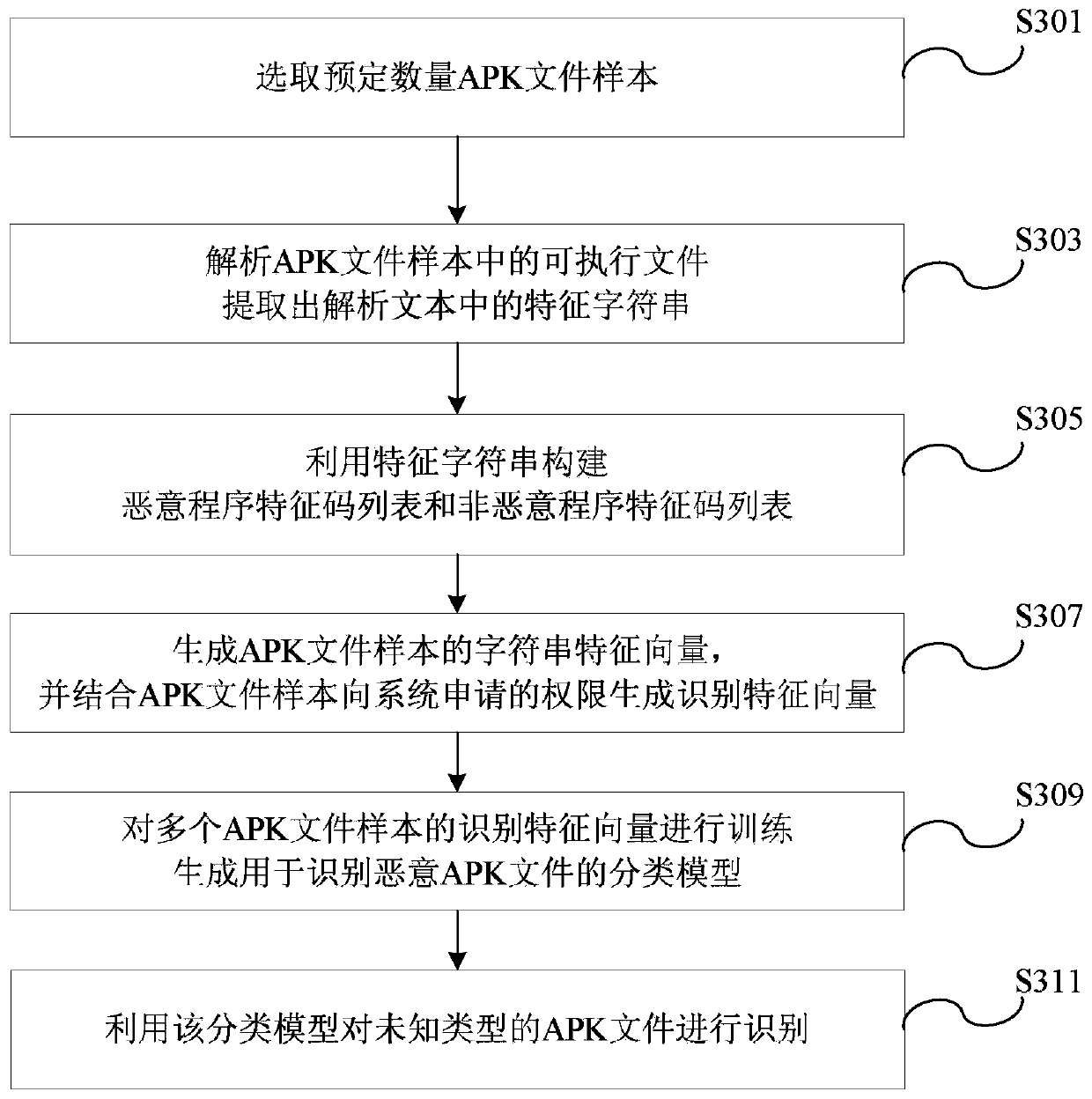
Method and device of recognizing malicious APK files
The invention discloses a method and a device of recognizing malicious APK files. The method includes the steps of selecting a predetermined amount of APK file samples; analyzing executable files in the APK file samples and extracting feature strings in the analyzed files; establishing a list of malware feature codes and a list of non-malware feature codes through the feature strings; comparing the feature strings of the APK file samples to the list of malware feature codes and the list of non-malware feature codes so as to obtain string feature vectors of the APK file samples, generating recognition feature vectors of the APK files for permissions applied by a system according to the string feature vectors and the APK file samples; training the recognition feature vectors of the APK file samples, and generating a classification model for recognizing malicious APK files; recognizing the APK files of unknown types by the classification models. The method and device has the advantages that recognition accuracy is high and unknown viruses can be predicted.
Owner:BEIJING QIHOO TECH CO LTD
Convolutional variational auto-encoder neural network-based finger vein identification method and system
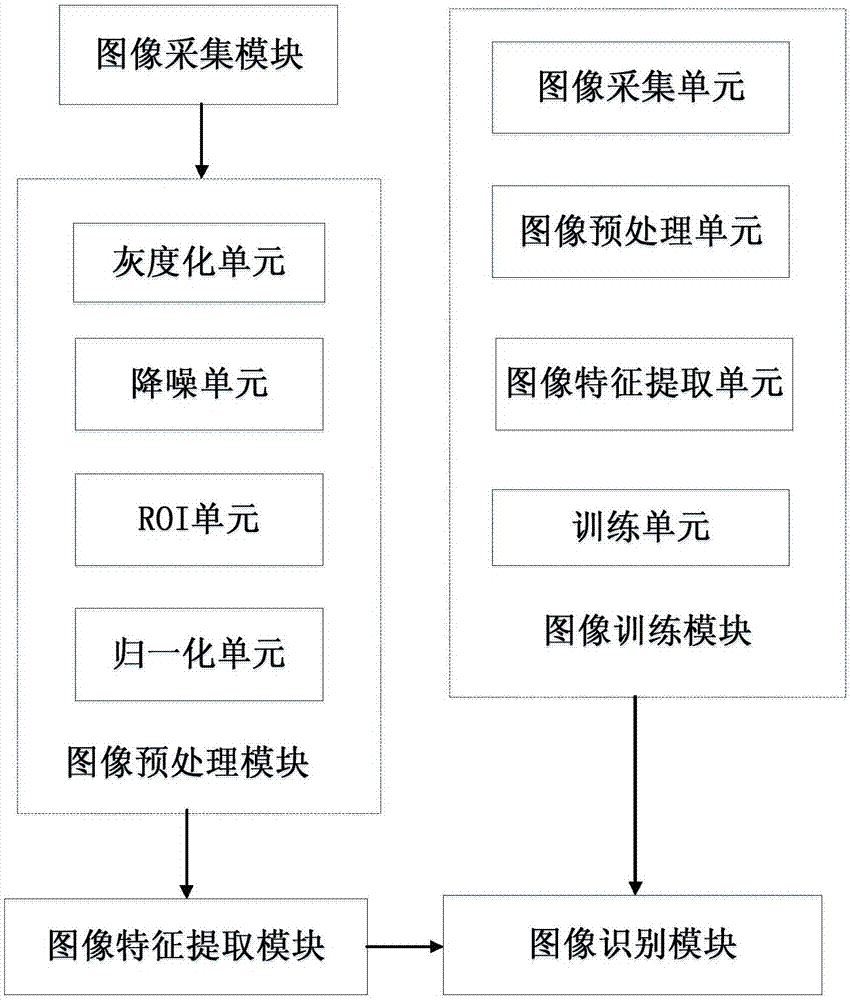
ActiveCN108009520ASolve the problem of changing lightIncrease redundancyImage enhancementImage analysisFinger vein recognitionAutoencoder
The invention discloses a convolutional variational auto-encoder neural network-based finger vein identification method and system. The system comprises an image collection module, an image preprocessing module, an image feature extraction module, an image training module and an image identification module. The identification method comprises the steps of obtaining a finger vein image of a to-be-identified user; performing image preprocessing on finger vein image information, and extracting a finger vein region-of-interest (ROI) image; extracting finger vein feature codes in a finger vein ROIthrough the convolutional variational auto-encoder neural network; and inputting the feature codes to a full connection network for performing identification processing, thereby identifying identity information of the to-be-identified user. The finger vein features can be effectively extracted; the noise redundancy is improved; and the identification precision of the finger vein identification system is remarkably improved.
Owner:西安格威西联科技有限公司
Unlocking emoticons using feature codes
ActiveUS20100293473A1Avoid inclusionsWell formedData switching networksInput/output processes for data processingGraphicsComputer science
Owner:GANZ
Method for matching finger print image based on finger print structure feature and veins analysis
ActiveCN101408932ALarge amount of informationNoise resistanceCharacter and pattern recognitionFeature codeFingerprint
The invention discloses a fingerprint image matching method based on fingerprint structural features and texture analysis. The method comprises the following steps: (1) processing the feature minutiae and the adjacent minutiae of a fingerprint image to generate structural feature vectors; (2) matching the structural feature vectors, considering the minutiae matching is successful if the vectors fall in a bounding box, representing and the fingerprint matching degree with the number of the successfully matched minutiae; (3) performing Gabor filtering on the incomplete fingerprint containing proper amount of information or the fingerprint image without central part, and dividing the fingerprint into several regions by circular grids to extract the texture features respectively; (4) representing the matching degree with the feature difference among the fingerprint images by taking the gray-scale standard deviation of each region as a feature code, and ; and (5) finding out the most matched fingerprint image by the structural features and the texture features of a BP neural network. The method is independent of translation and rotation of the fingerprint, has strong anti-noise performance, and can solve the problem of non-linear deformation in a certain range.
Owner:朱信忠
Wireless network location-based reference information
InactiveUS20050020287A1Radio/inductive link selection arrangementsMessaging/mailboxes/announcementsComputer scienceWireless network
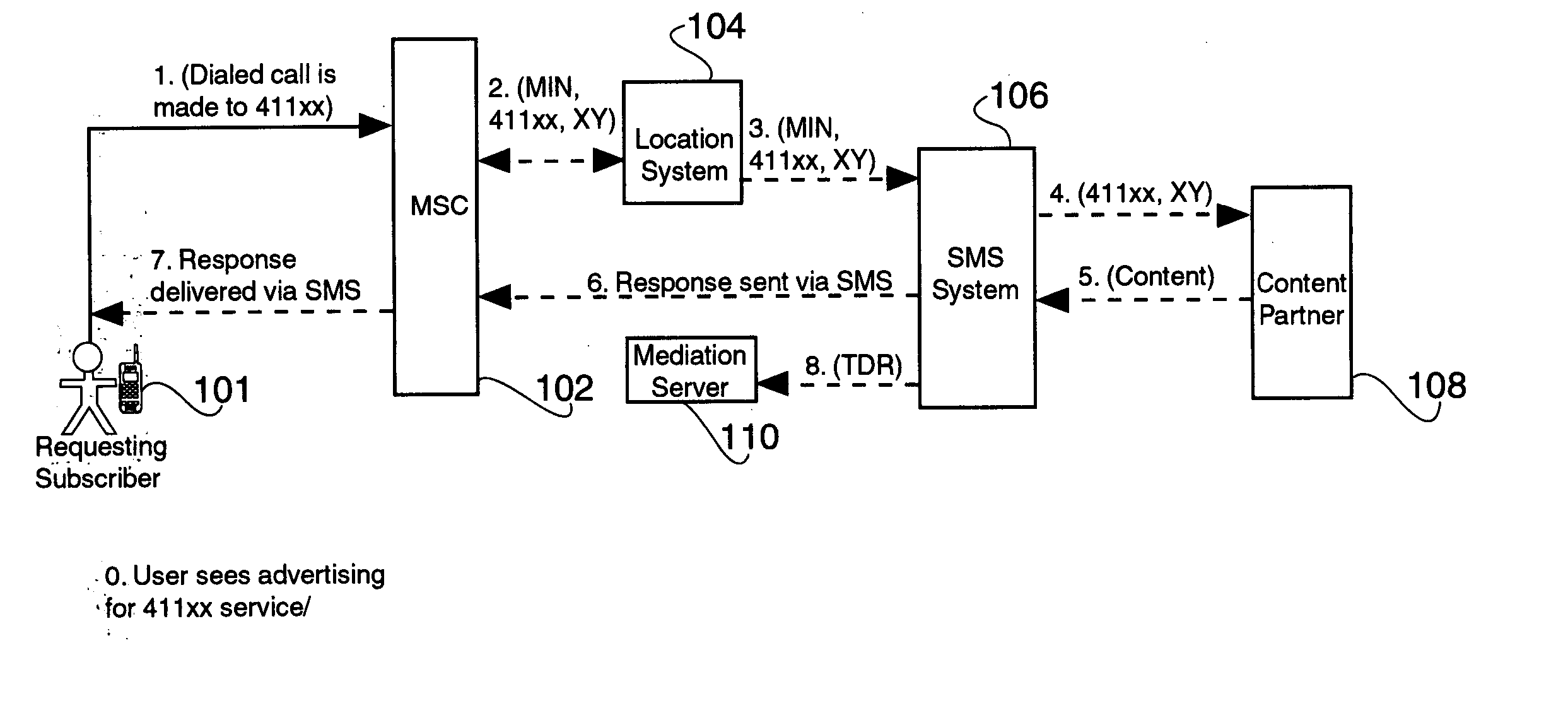
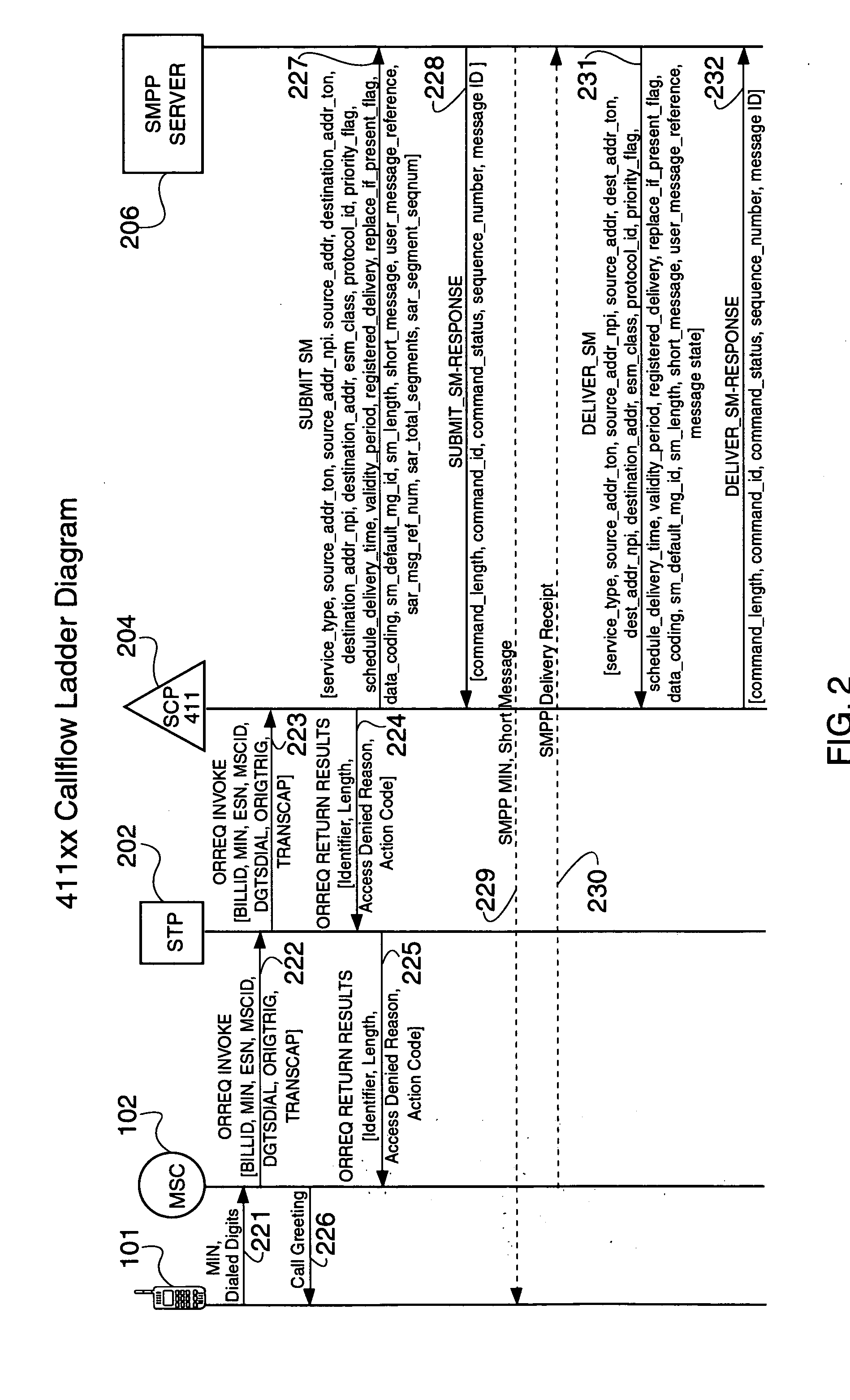
The present invention provides a ‘411xx’ value added service to wireless users. The disclosed ‘411xx’ service allows a mobile user who may be unfamiliar with their current geographic location to nevertheless obtain quick, accurate, and current information relating to the geographic area, e.g., different services in their current location, stores, libraries, gas stations, etc., via a mobile terminated (MT) short message system (SMS) message. In addition to the traditional ‘4-1-1’ dialed digits, a mobile user would also dial a number (or numbers) representing a feature code for a particular service, e.g., nearby ATMs, or traffic information. Upon receiving a 411xx call, the MSC generates an ORREQ / TCAP trigger based on a translation of the requested service represented by the extra ‘xx’ digits. The 411xx call is terminated on the MSC after an audible whisper notice plays to the caller, e.g., “thank you for calling, your requested information will be sent momentarily”.
Owner:TELECOMM INC
Dual range vehicle remote
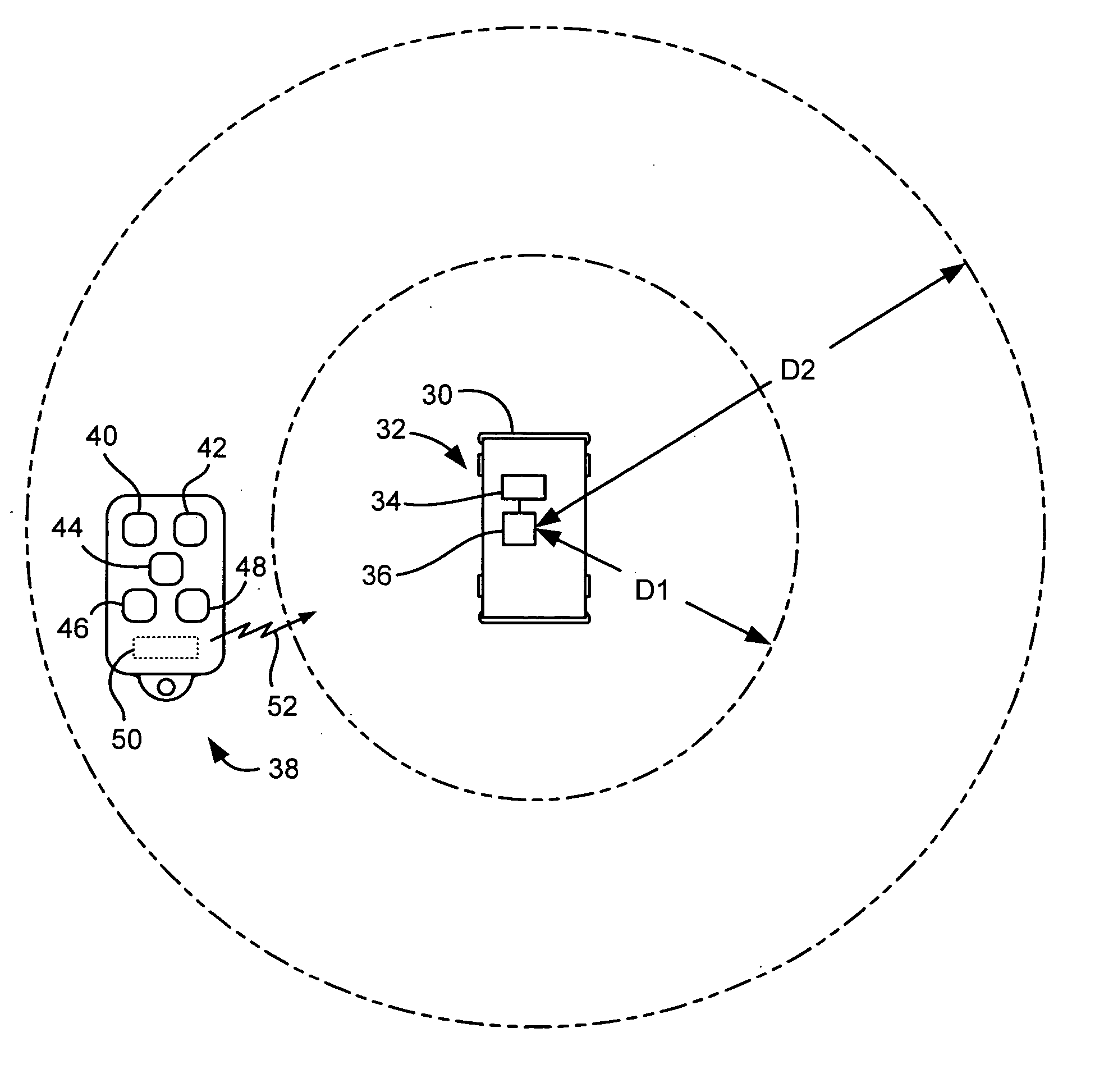
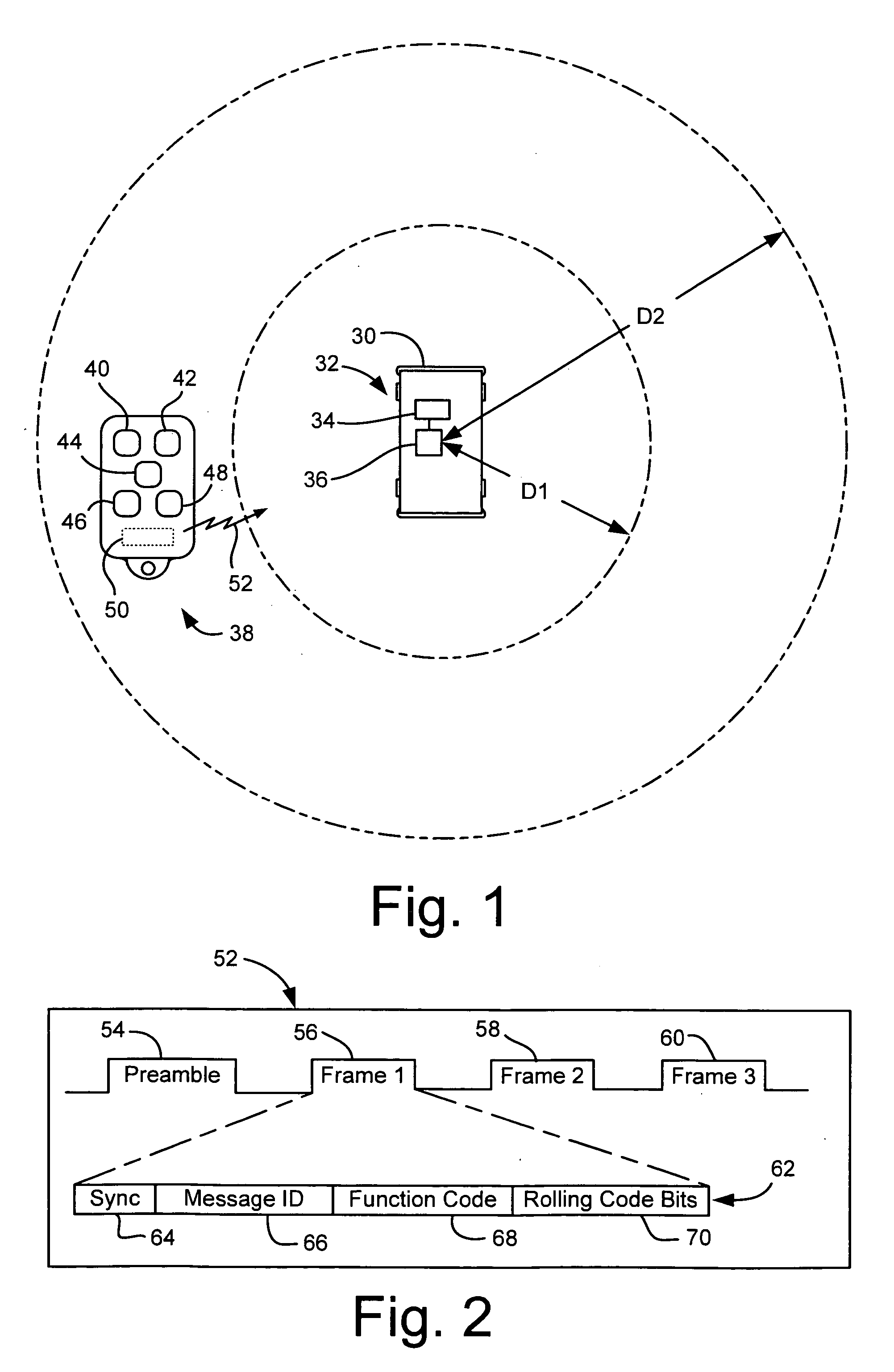
InactiveUS20060145811A1Avoid accidental activationProgramme controlElectric signal transmission systemsShortest distanceRadio frequency signal
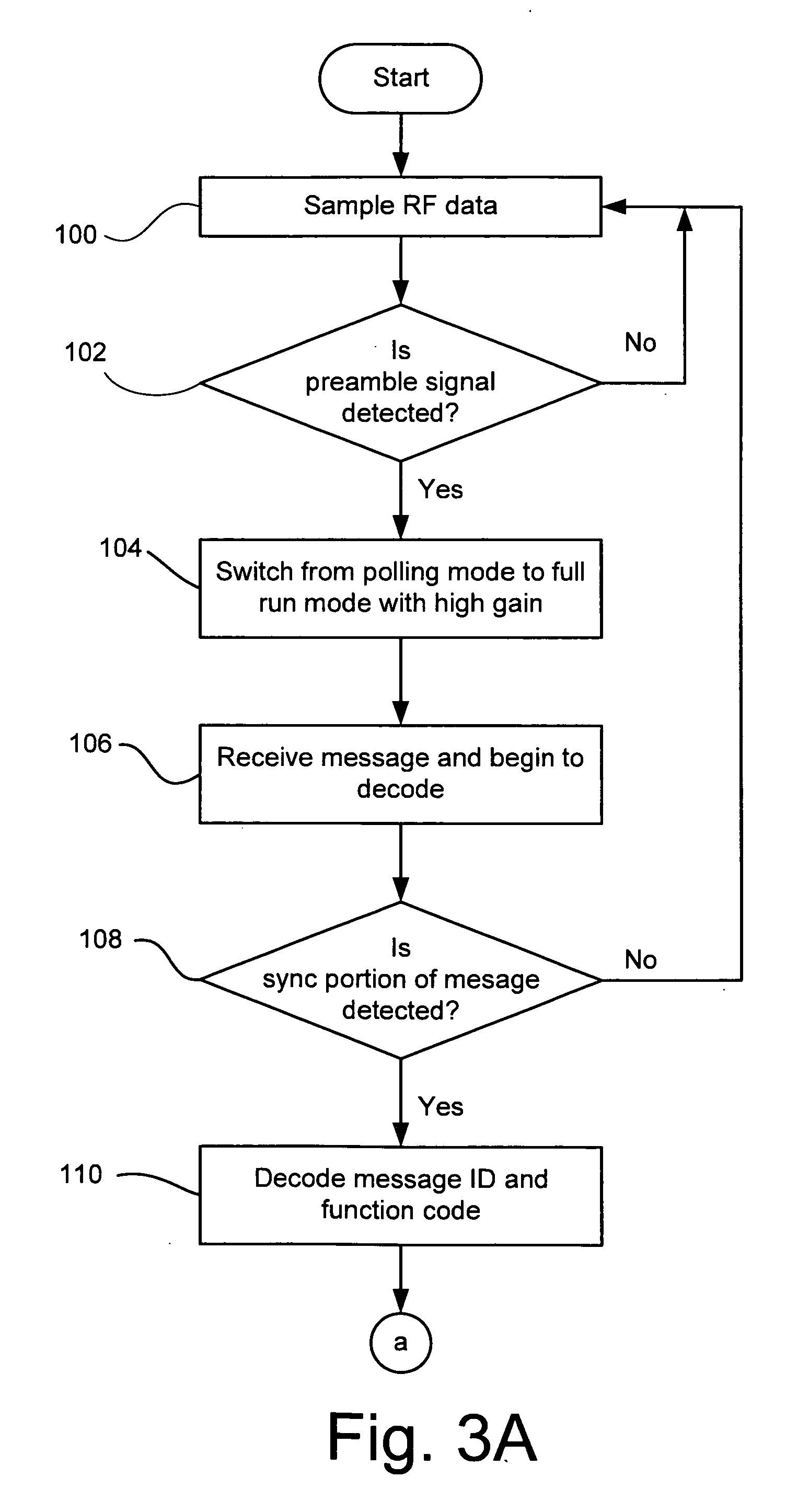
A method and system are disclosed for operating a controller of and a RKE system to provide for short distance functions that are actuatable from a key fob at a shorter distance from the vehicle than other long distance functions. This may include receiving a desired type of radio frequency signal; actuating a high gain mode of a receiver of the controller; detecting a message from an acceptable remote keyless entry transmitter; decoding a function code portion of the message; changing the receiver from the high gain mode to a lower gain mode if the function code is not a long distance function; decoding a remaining portion of the message; determining if the remaining portion of the message was decoded properly; and performing the requested function if the remaining portion of the message was decoded properly.
Owner:LEAR CORP
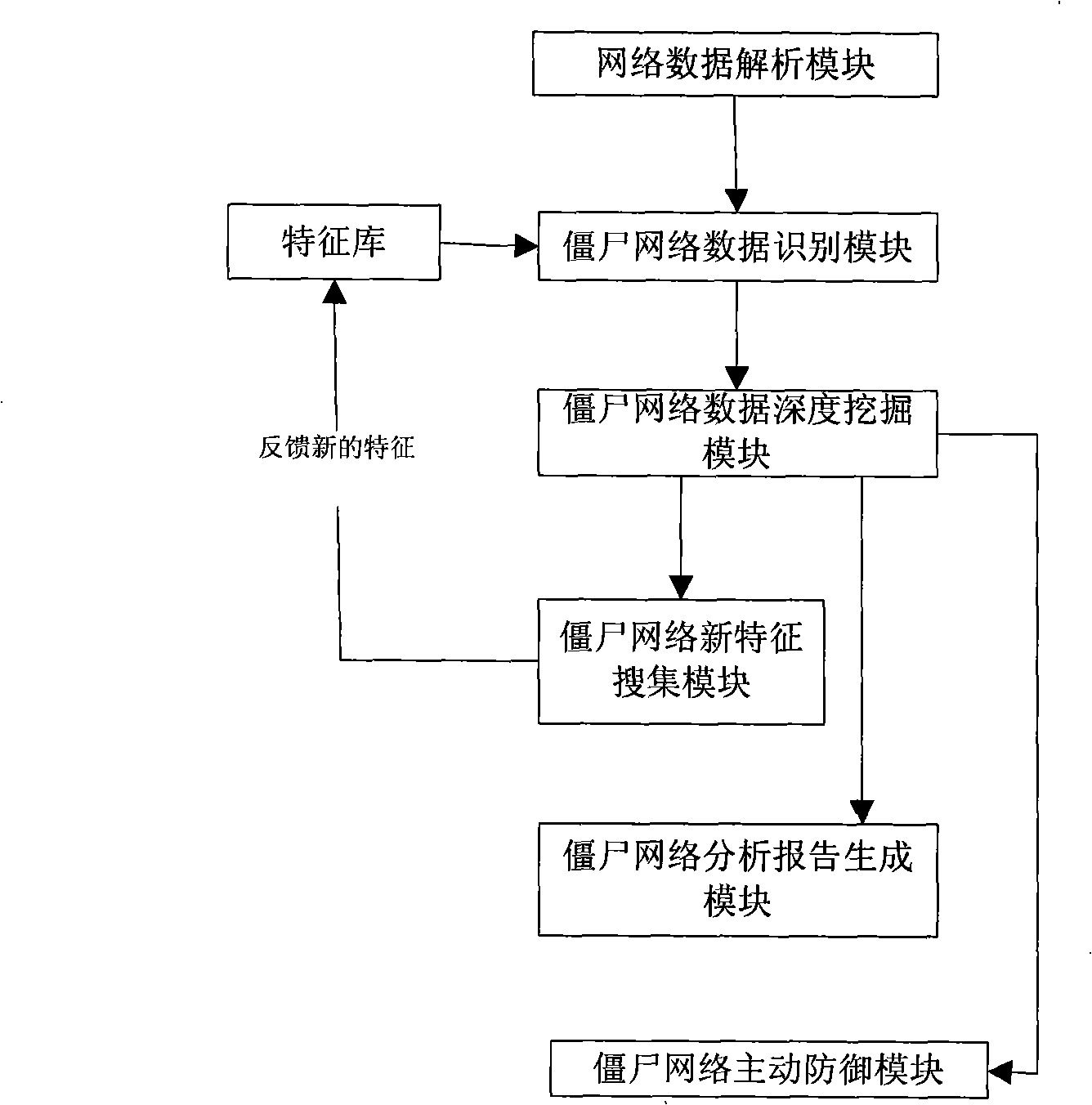
Method and system for detecting bot network
InactiveCN101404658AImprove defenseWide range of defenseData switching networksSpecial data processing applicationsNetwork packetNetwork control
The invention discloses a method for detecting a bot network and a system thereof, which belong to the field of computer security. The method comprises the following steps: first, extracting IRC protocol data from a network data packet; then, matching the protocol data with feature codes in a data feature bank to acquire a bot network data packet; dividing the bot network data packet, and linking the bot network data packets from the same bot network; finally, determining a control server, a bot computer and a bot network control computer from the same bot network according to the divided bot network data packets, thereby describing the topology of the bot network. The system comprises a network data analysis module, a bot network data identification module and a bot network data deep dig module. Compared with the prior art, the invention can analyze and defense the whole bot network integrally, and has the advantages of better defense effect, wider defense range, higher efficiency and better traceability.
Owner:RUN TECH CO LTD BEIJING
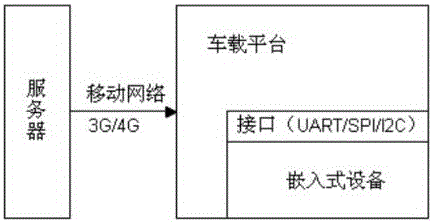
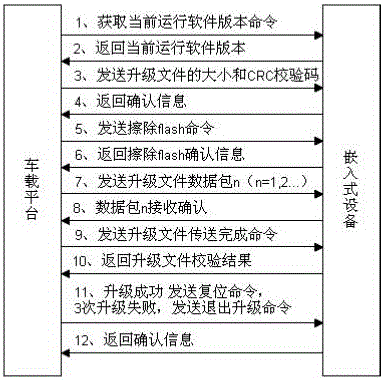
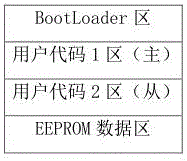
Method for realizing IAP remote upgrade through vehicle-mounted system based on mobile network
ActiveCN106569847AImprove portabilityIncrease costProgram loading/initiatingTransmissionMobile WebEmbedded system
The invention provides a method for realizing IAP remote upgrade through a vehicle-mounted system based on a mobile network. A vehicle-mounted platform downloads an upgrade file to the local from a far-end server through the mobile network, and then the vehicle-mounted platform transmits the upgrade file to a to-be-upgraded embedded device through an interface to realize the remote upgrade of the embedded device; by use of the upgrade method, the vehicle-mounted platform is used as a transmission relay of the upgrade file so as to realize an IAP remote upgrade function from the far-end server to the local embedded device; meanwhile, an upgrade function code is embedded into a user function code in the embedded device internal upgrade realization, the received upgrade file is temporarily stored at one region of the flash without covering a user program in operating, the upgrade file is copied to a user program region after verifying that the upgrade is successful; therefore, the normal operation of the user program can be guaranteed even if the upgrade is failed, and the risk that the upgrade is failed caused by accident in the upgrade process is lowered.
Owner:SOYEA TECH
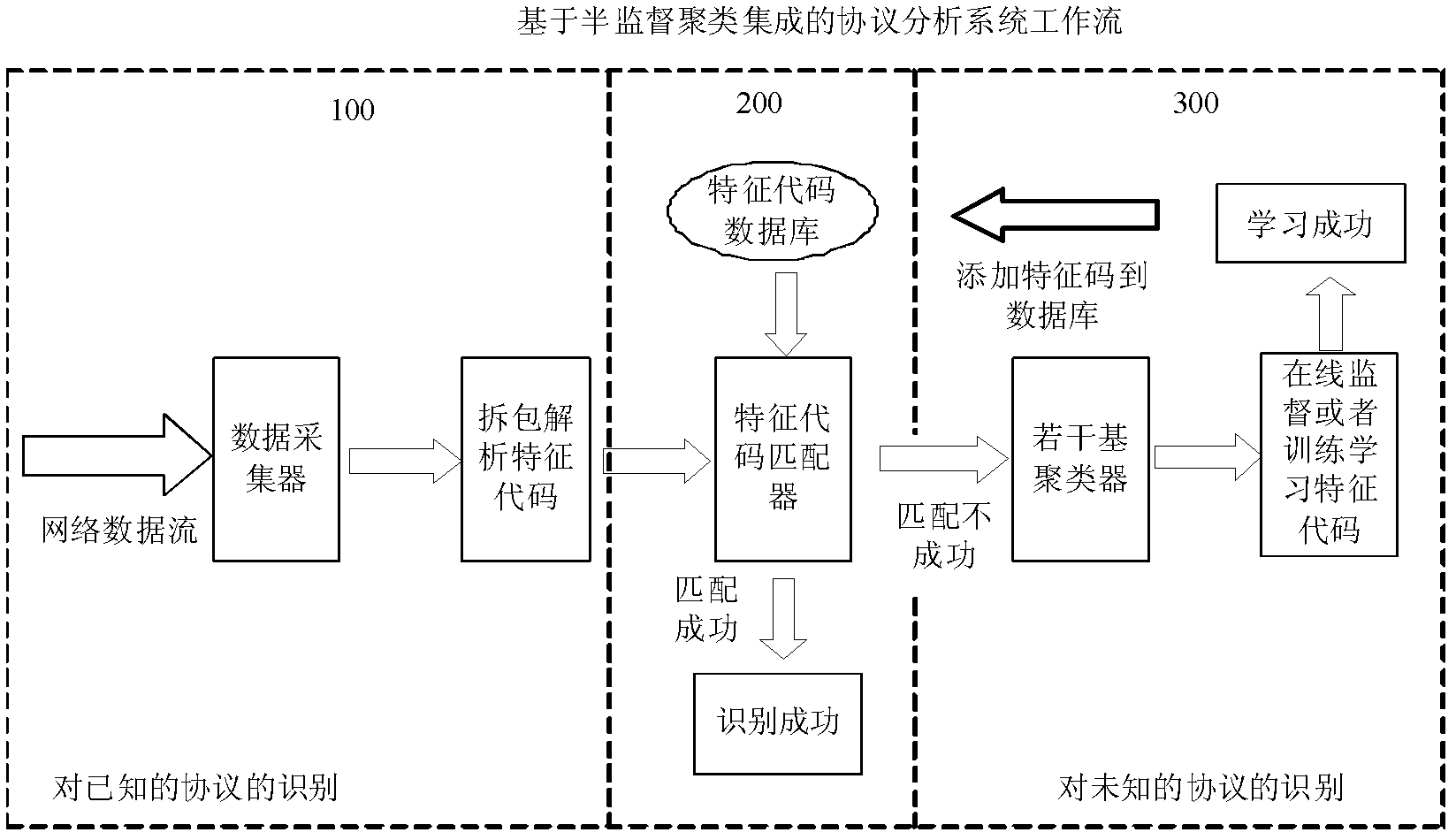
Semi-supervised clustering integrated protocol identification system
InactiveCN102546625AImprove recognition rateImprove efficiencyData switching networksNetwork packetStatistical learning
The invention discloses a semi-supervised clustering integrated protocol identification method. The method comprises the following steps: various data packets in a network are acquired; received network data is analyzed, and each field of the data packets is extracted and counted; feature code of network data obtained after the network data is analyzed is matched with various feature codes preset in a data base, if the match is successful, the data packets are corresponding protocols; data not successfully matched is subject to cluster analysis, a plurality of base clustering devices are used to cluster the data packets, and the result is fed back, and a priori label value is modified; and a semi-supervised statistical learning is carried out for the result of the clustering of the network data packets and each known protocol, and a discriminant learner is trained. According to the invention, the terminal protocol identification rate is improved, and the amount of calculation is moderate, so that the efficiency is high; one time of dialog generate less flow, inaccurate identification is not easy; and besides, the method integrates a plurality of identification methods, so as to achieve multi-dimension identification. The invention also discloses a corresponding semi-supervised clustering integrated protocol identification system.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
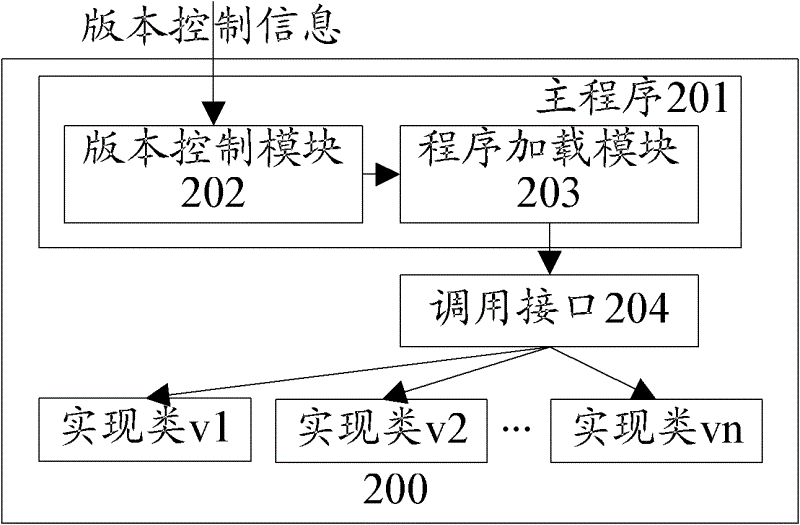
Software upgrading method and software upgrading device
ActiveCN102622241AReduce occupancyAchieve the purpose of silent updateProgram loading/initiatingTraffic capacitySoftware update
The invention discloses a software upgrading method and a software upgrading device which are used for solving the problems that update of application software of a mobile terminal occupies large network flow and is complex and inconvenient. Function codes finishing concrete program functions in a main program are extracted and packaged to form an implementation class, a call interface is abstracted, and the main program calls the implementation class through the call interface so as to finish the concrete program functions. When the function codes need updating, the main program acquires an implementation class of a new version, and the implementation class of an old version is replaced with the implementation class of the new version. When the software is updated, users only need to download code files of part of logic from a server so as to replace original code logic, and because updated content is only a subset of overall program codes, the occupied network flow is small. Under a silent update mode, the software automatically finishes an upgrading process during the software using process of the users, and accordingly the aim of silent update is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
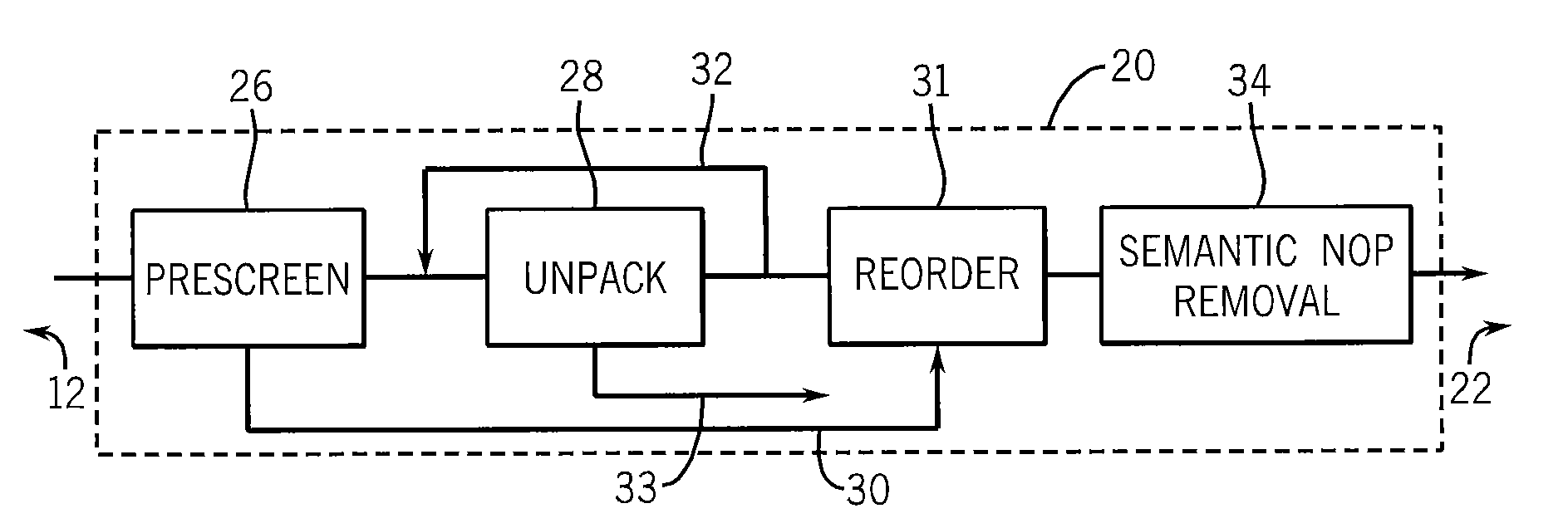
System for malware normalization and detection
InactiveUS20100011441A1Simple methodSimple taskMemory loss protectionUnauthorized memory use protectionObfuscationStandard form
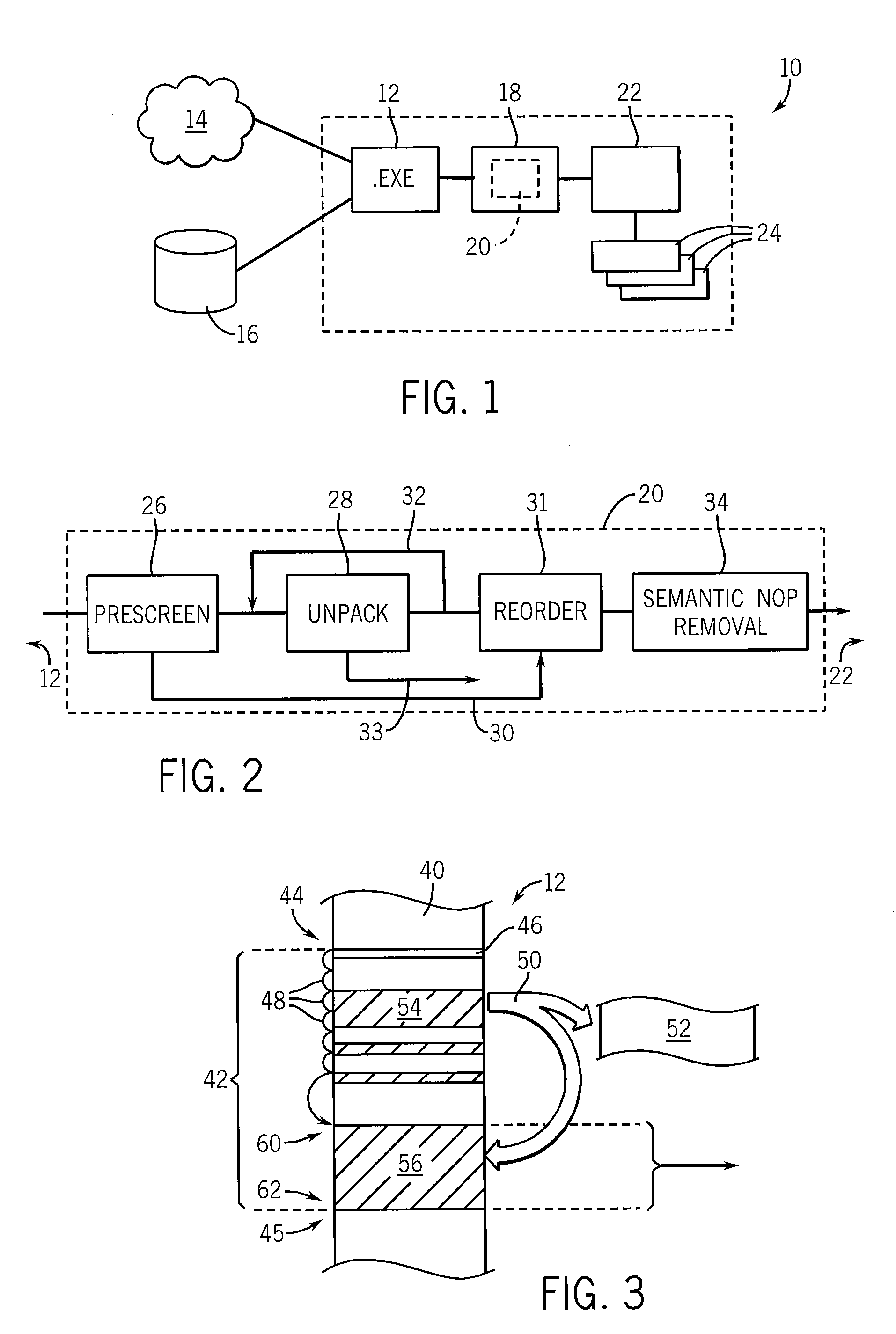
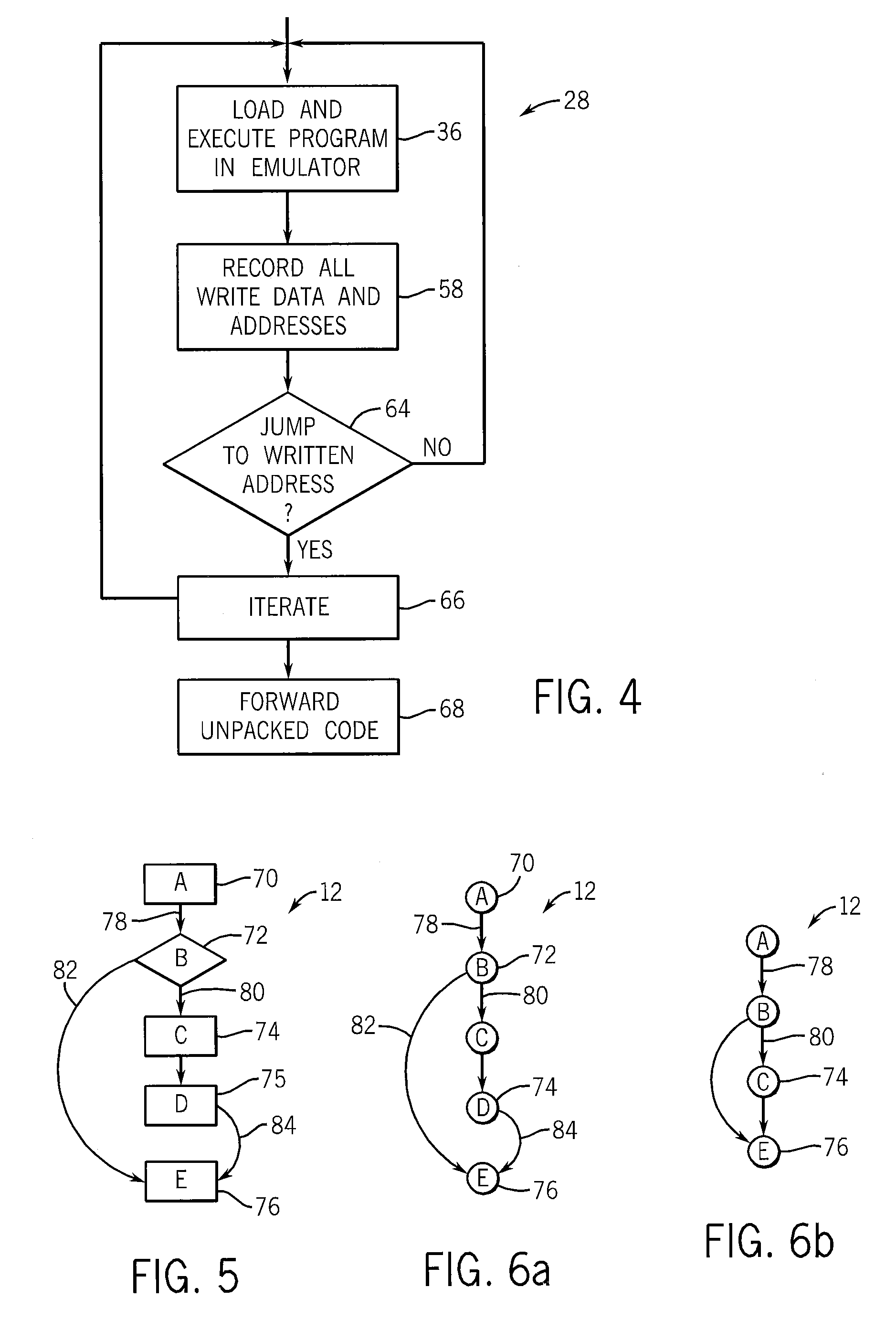
Computer programs are preprocessed to produce normalized or standard versions to remove obfuscation that might prevent the detection of embedded malware through comparison with standard malware signatures. The normalization process can provide an unpacking of compressed or encrypted malware, a reordering of the malware into a standard form, and the detection and removal of semantically identified nonfunctional code added to disguise the malware.
Owner:CHRISTODORESCU MIHAI +4
Cell phone terminal, server and account-device linking control and executing method
ActiveCN104994073AEfficient processRealize centralized managementTransmissionSmart deviceCloud server
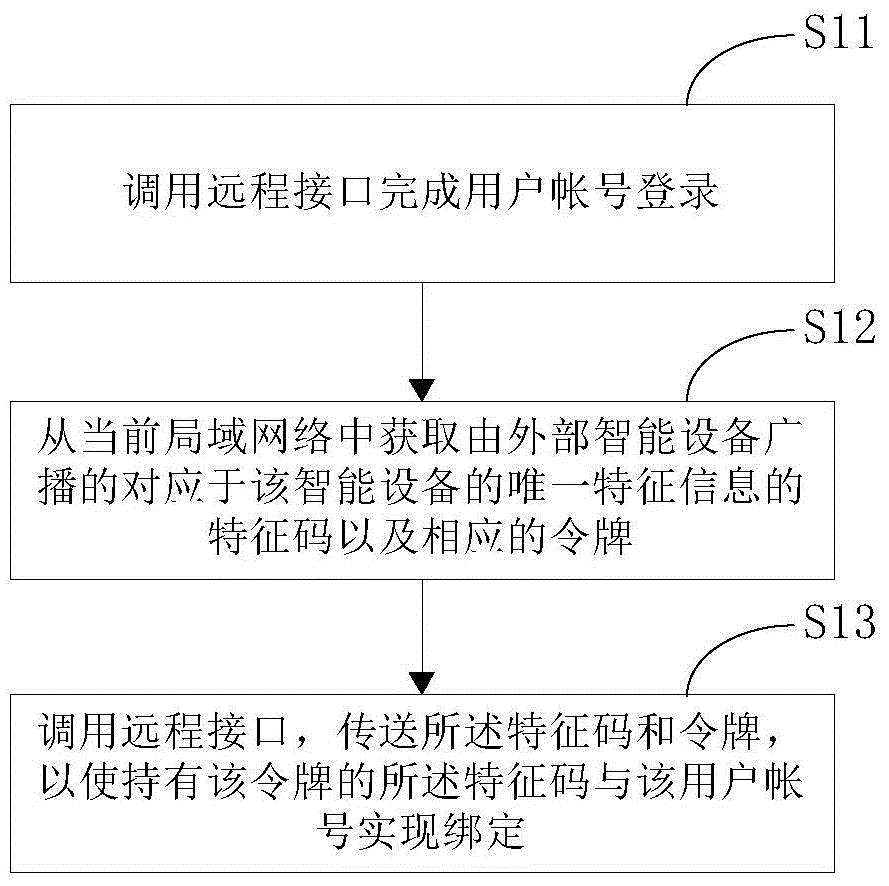
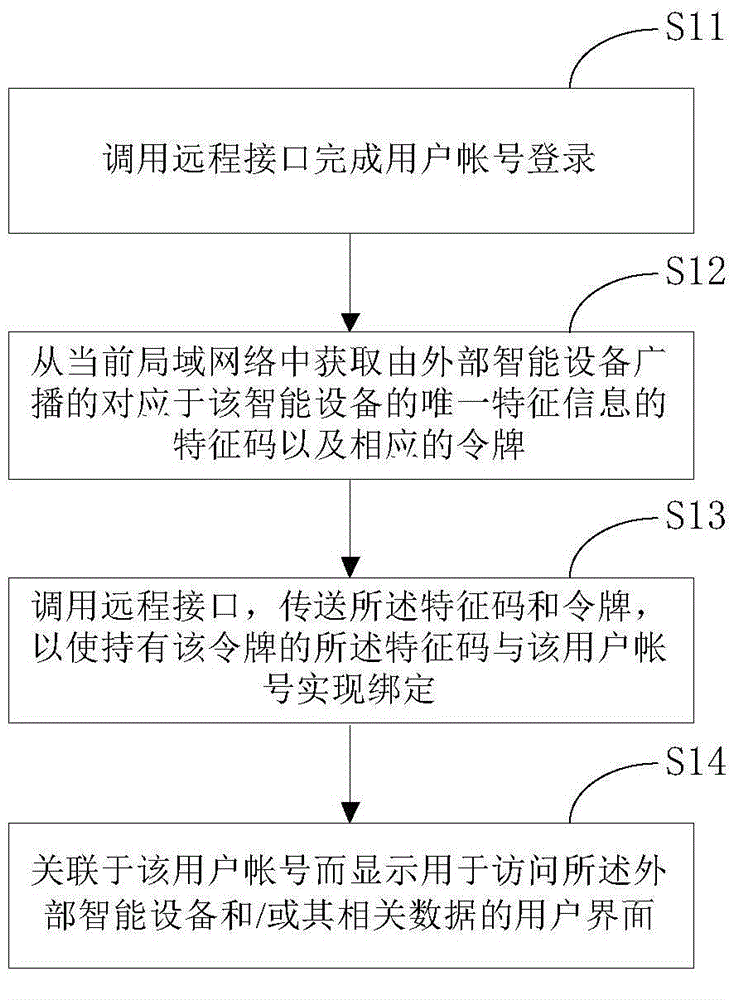
The invention discloses an account-device linking control method for a cell phone terminal. The method includes steps of calling a remote interface for user account login; obtaining a feature code corresponding to unique feature information of a smart device and broadcasted by the external smart device and a corresponding token from a current local network, wherein the token is used for verifying the authority limit of communication performed based on the feature code; calling the remote interface for transmitting the feature code and the token so as to enable the feature code with the token to be linked to the user account. Besides, the invention also discloses an adaptive cloud server and an accounting-device linking executing method adopted by the cloud server. The implementation of the invention makes the account-device linking process more convenient, efficient, safe and reliable.
Owner:BEIJING QIHOO TECH CO LTD
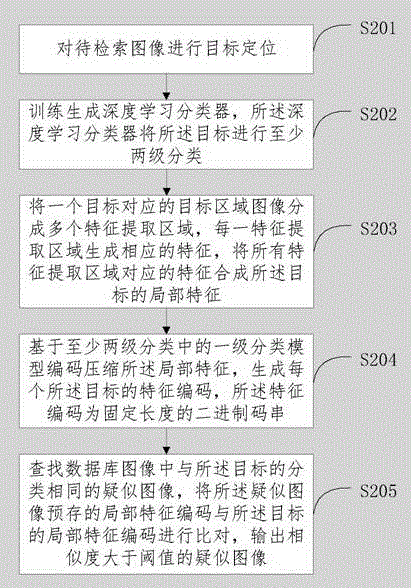
Image target searching method and device
InactiveCN106354735AImprove retrieval accuracyImprove retrieval efficiencyRelational databasesStill image data indexingPattern recognitionComputer science
The invention discloses an image target searching method and device. The searching method includes: targeting and locating the to-be-searched image; classifying and extracting local features of the target, to generate the local feature codes for the local features; searching for similar images in the database that belong to the same class with the aforementioned target; comparing the saved local feature codes of the similar images with the codes of the target local features, then outputting similar images with similarity greater than the threshold. Through targeting and locating the to-be-searched image, classifying the target into at least two classes, and generating the local feature codes for the targets. When searching, search according to the search target classifications and order according to the similarities. Through target classifications, the searched target is matched using a model under the same target classification, thus increasing the search accuracy and efficiency.
Owner:HANGZHOU HIKVISION DIGITAL TECH
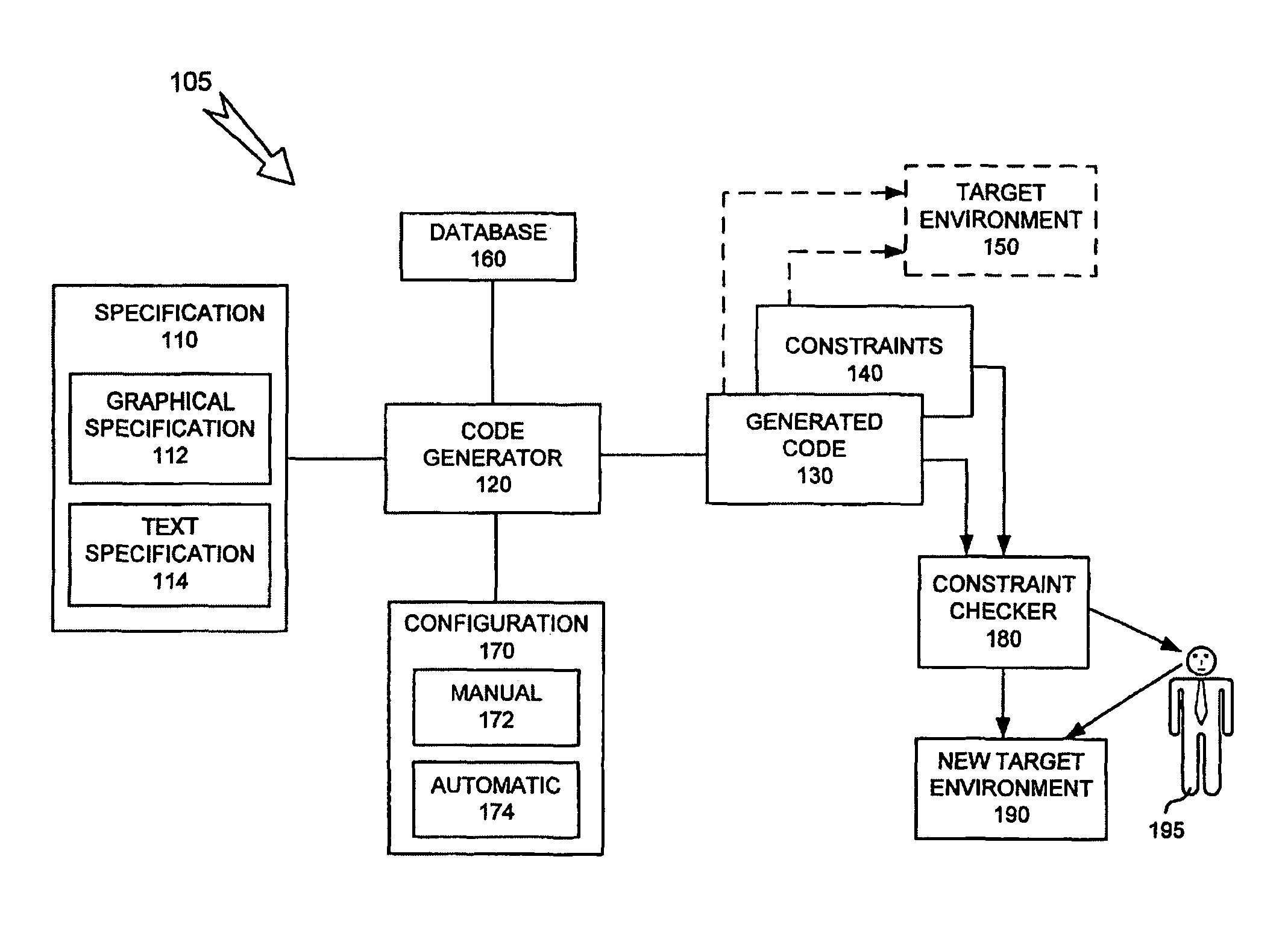
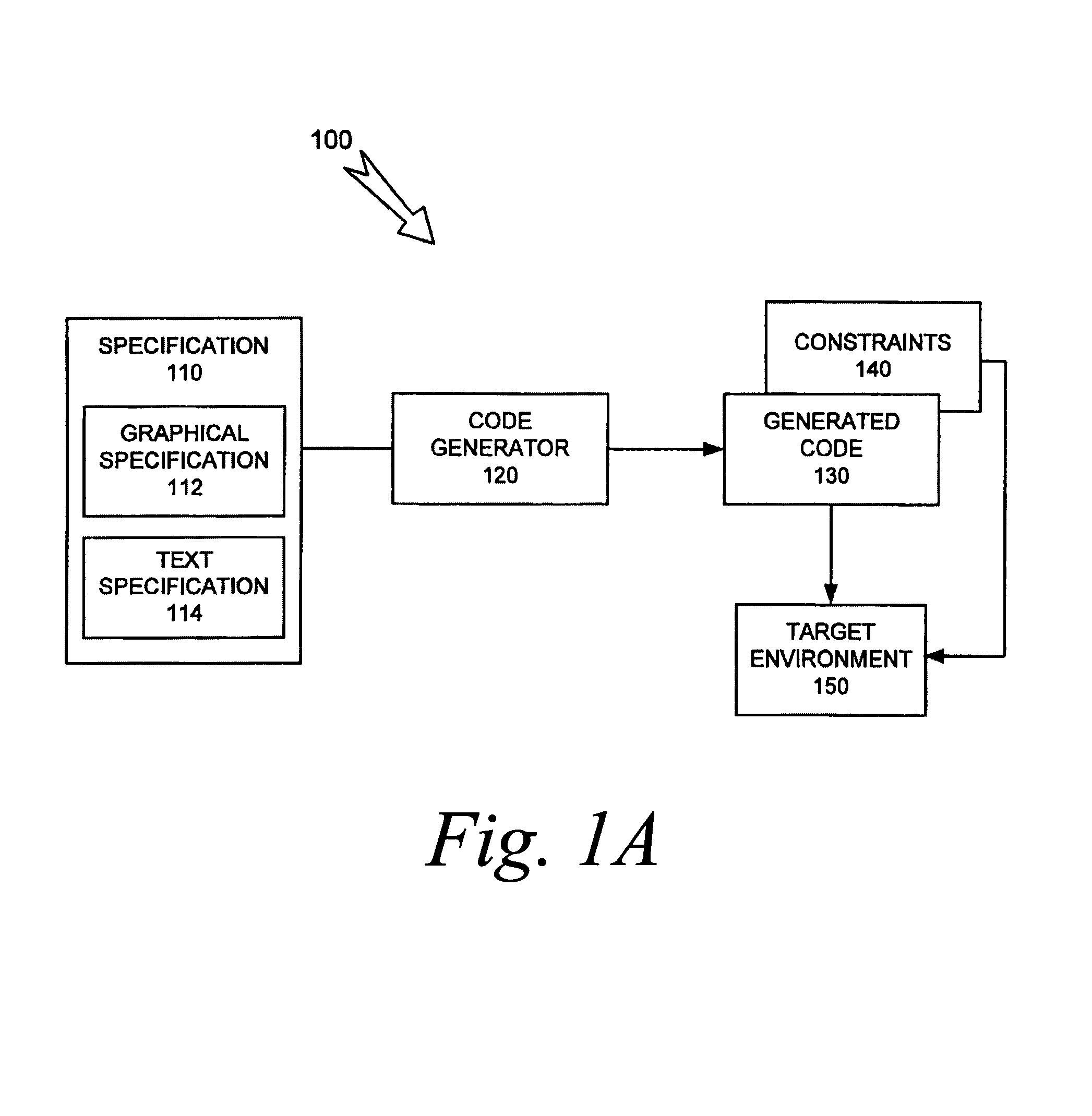
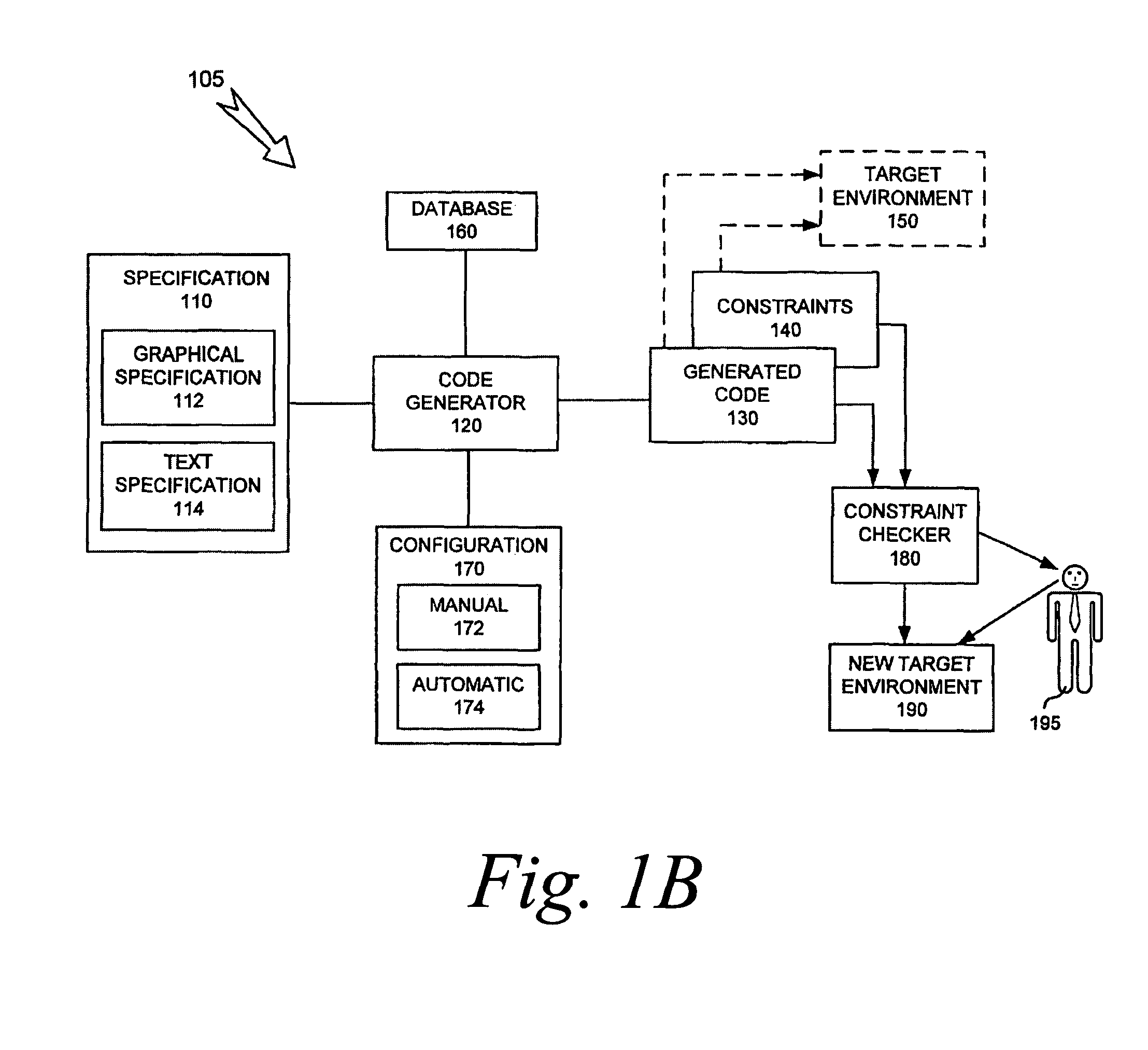
Auto-generated code validation
ActiveUS8448130B1Software engineeringSpecific program execution arrangementsTheoretical computer sciencePartial verification
A technique for generating an executable document that includes information for validating generated code is provided. The technique can include mapping an assumption to a portion of generated code, the portion containing functional code that is related to implementing the assumption, the mapping allowing at least the portion to be validated with respect to the assumption. The technique can include generating the executable document, where the executable document includes the mapping, and where the generated document validates the at least the portion of the generated code, where validating the at least the portion of the generated code validates the generated code.
Owner:THE MATHWORKS INC
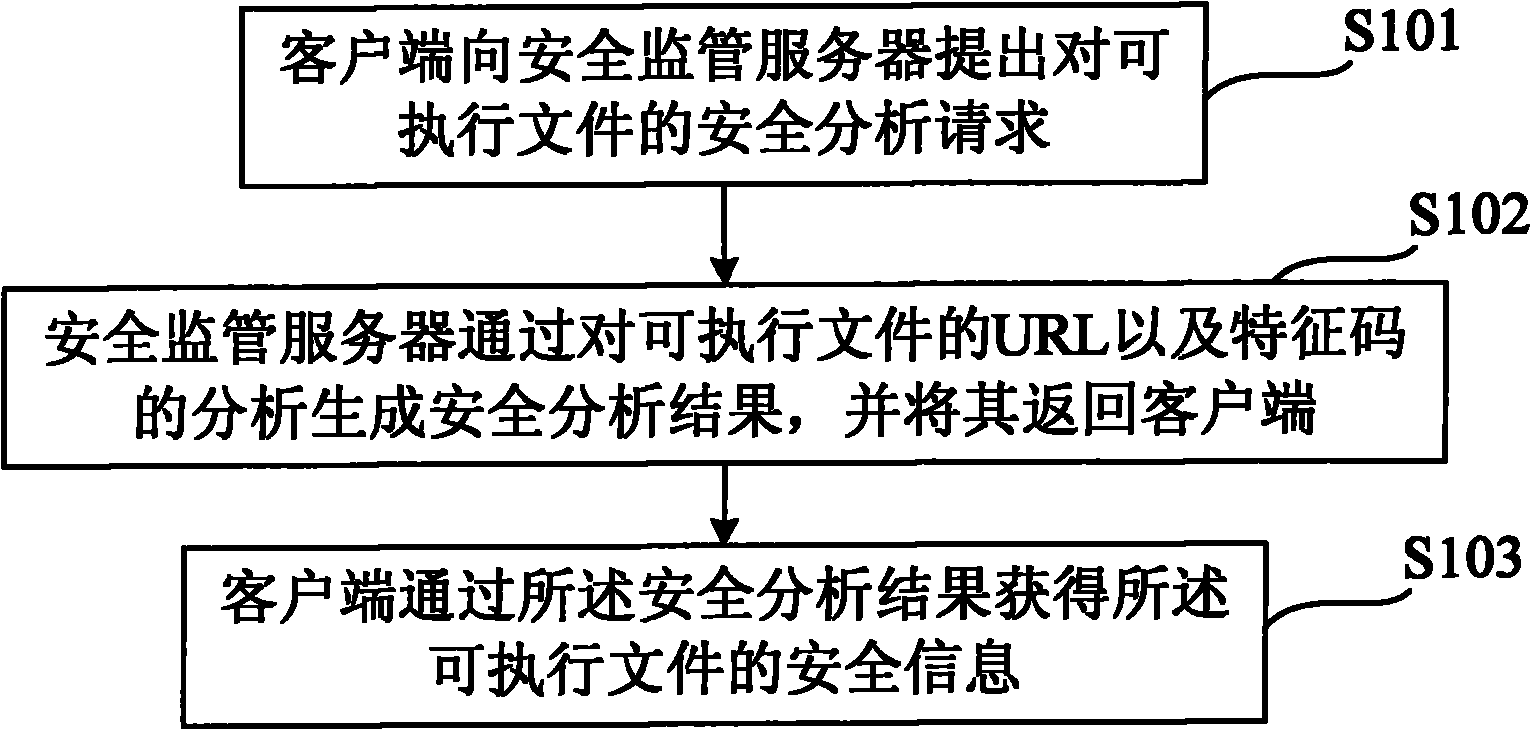
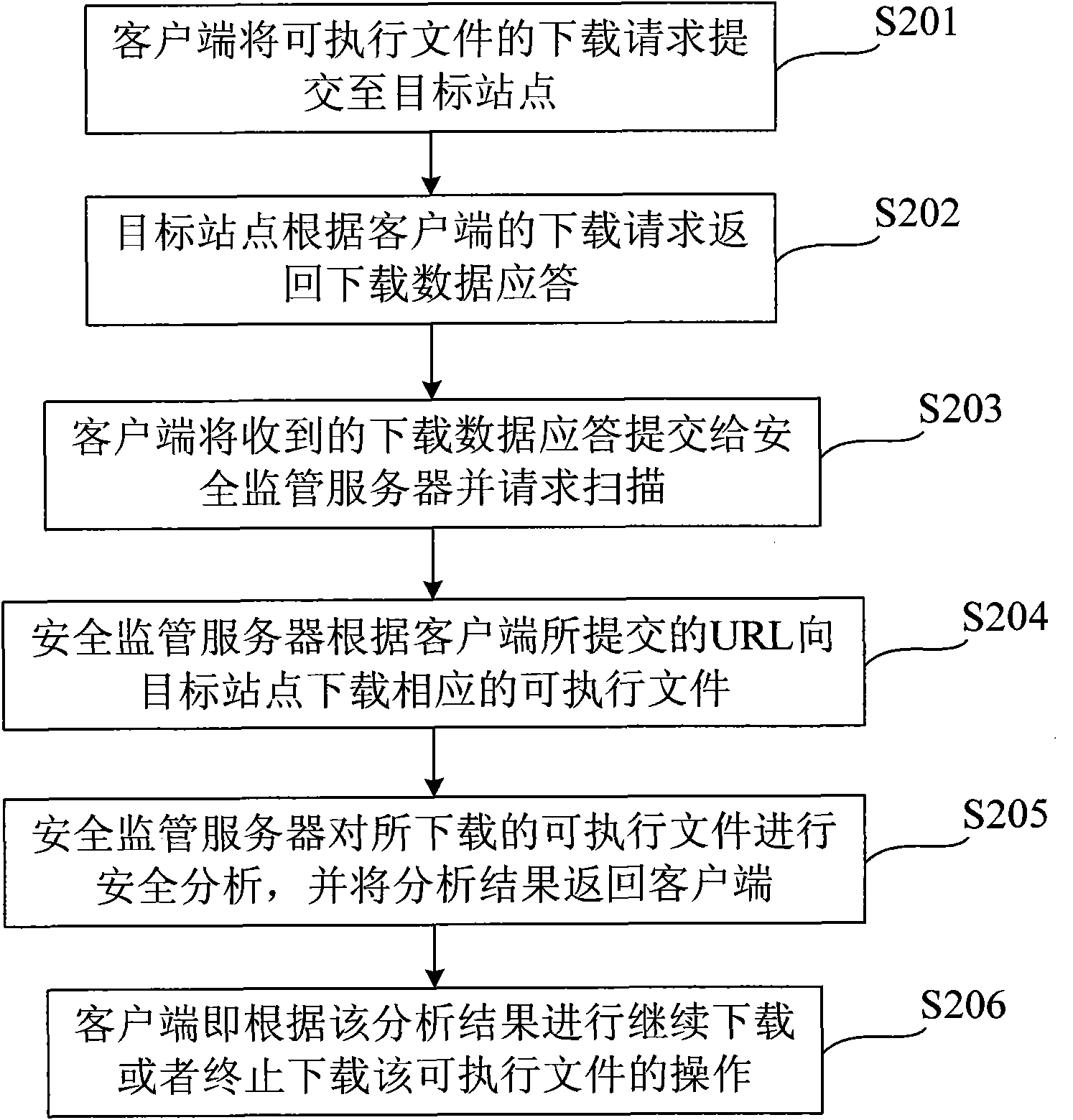
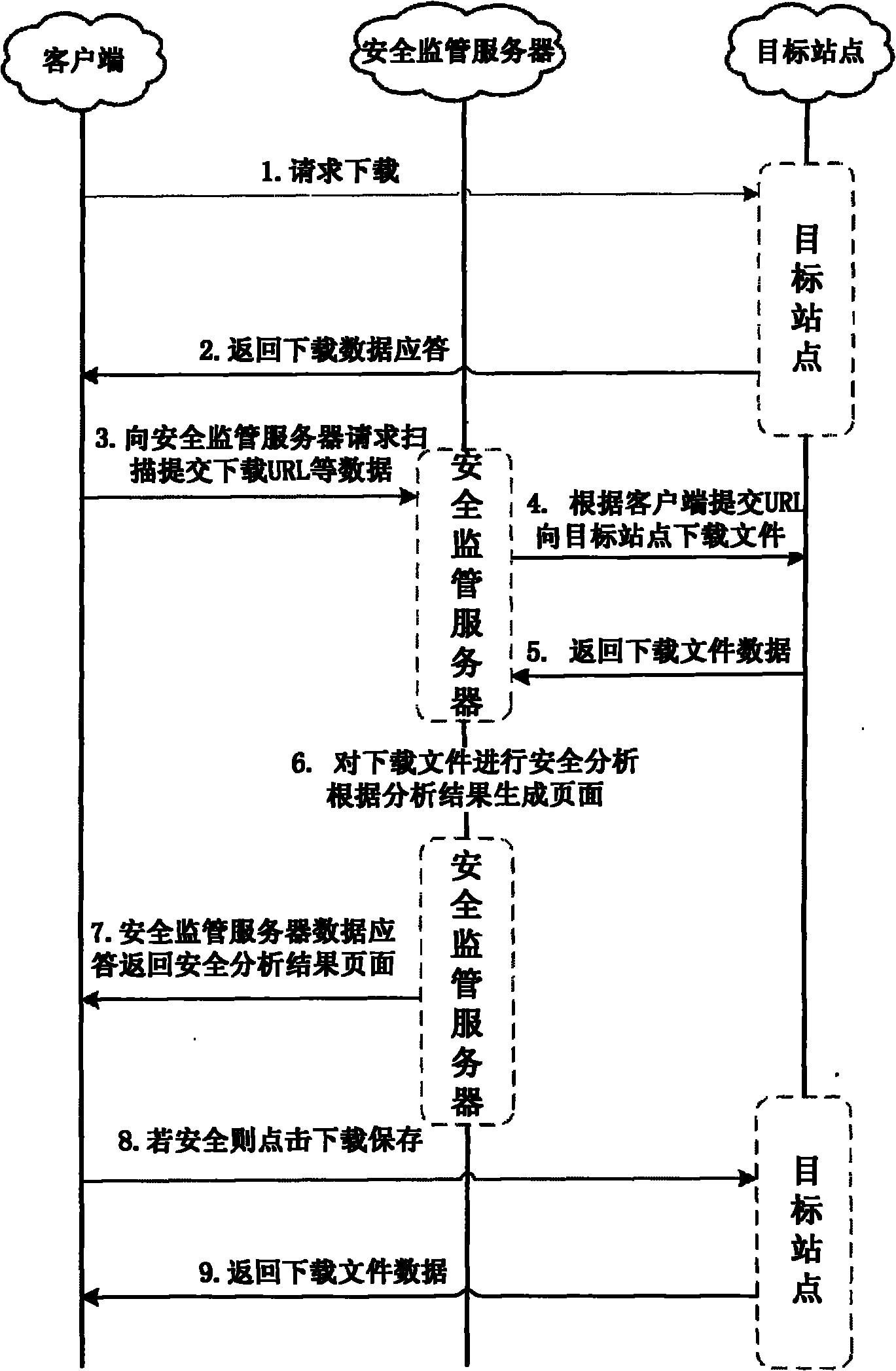
Method and system for downloading executable file securely
The invention provides a method and a system for downloading an executable file securely. The method comprises the following steps that: a client makes a security analysis request on the executable file to a security supervision server; the security supervision server performs security analysis on the executable file by using a uniform resource locator (URL) and a feature code of the executable file to generate a security analysis result and returns the security analysis result to the client; and the client acquires security information of the executable file according to the security analysis result. By the method, a user can learn security threat and hidden danger of the file before downloading or installing the executable file so as to avoid risk in advance, and compared with the method that the downloaded software is securely scanned by mobile phone security software, the method of the invention avoids the downloading of the executable file with security danger and saves terminal traffic and cost.
Owner:ALIBABA (CHINA) CO LTD
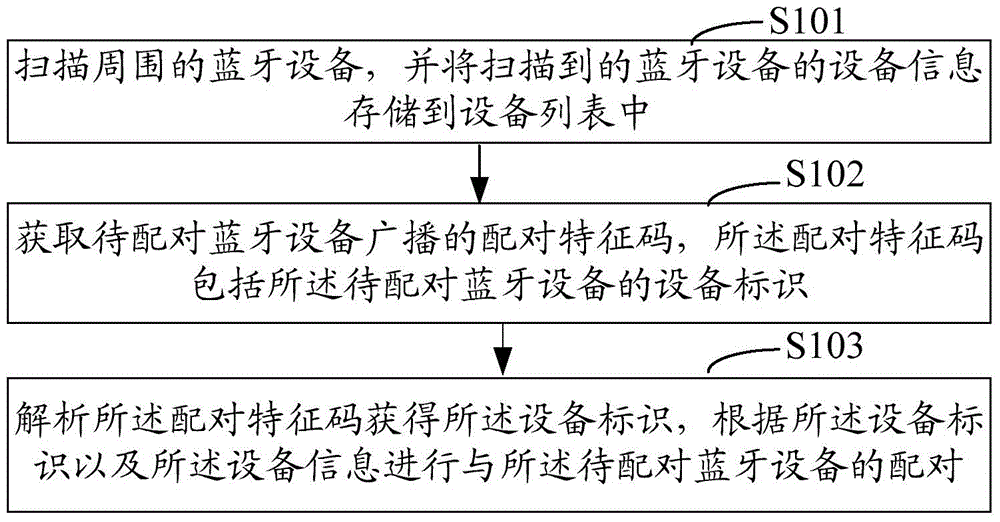
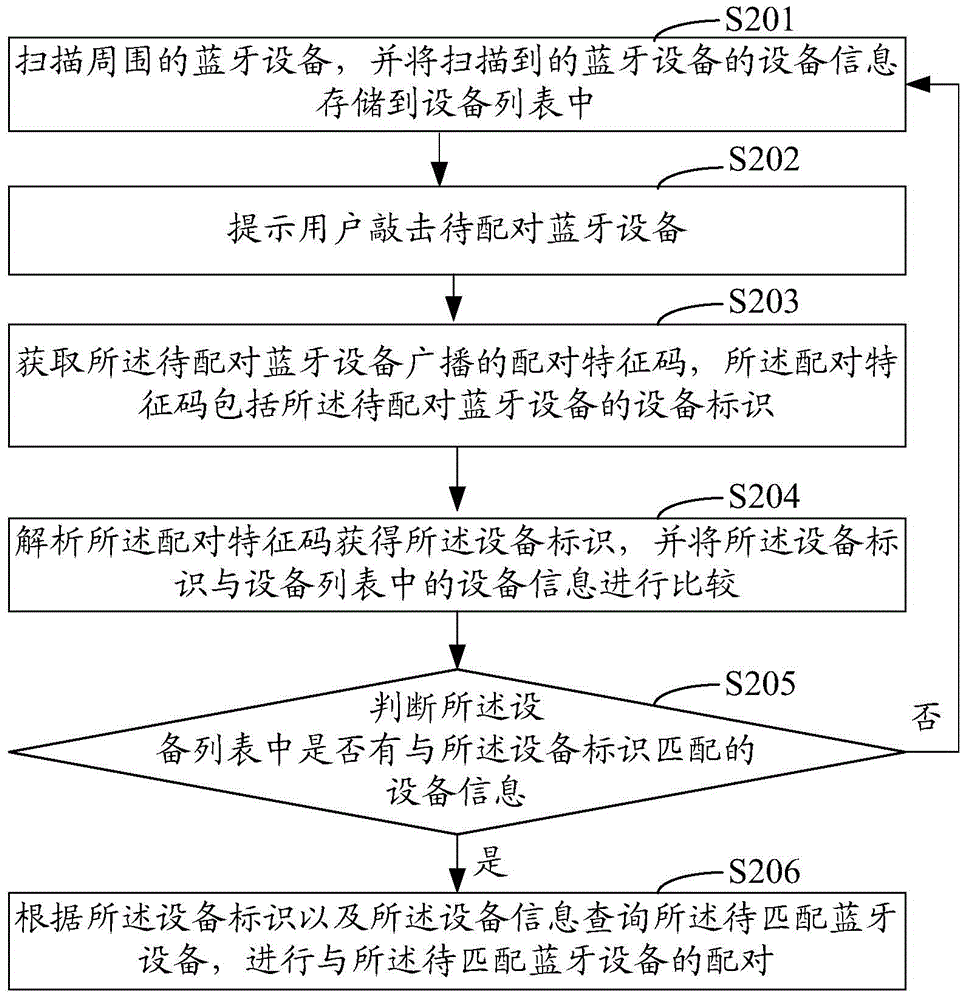
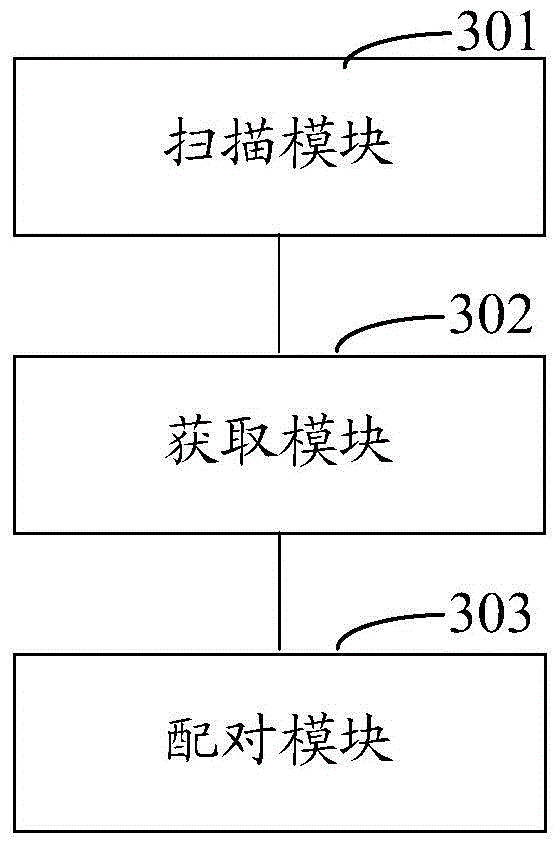
Bluetooth device matching method and system
ActiveCN104540190AEasy to useImprove experienceAssess restrictionConnection managementComputer terminalBluetooth
The invention provides a Bluetooth device matching method and system. The method includes the steps that a Bluetooth device in the surrounding environment is scanned, the device information of the scanned Bluetooth device is stored in a device list; a matching feature code broadcasted by the Bluetooth device to be matched is obtained, and the matching feature code comprises device identification of the Bluetooth device to be matched; the matching feature code is parsed, the device identification is obtained, matching with the Bluetooth device to be matched is conducted according to the device identification and the device information. By means of the scheme, matching of a mobile terminal and the Bluetooth device can be finished conveniently and fast, and using is facilitated for users.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
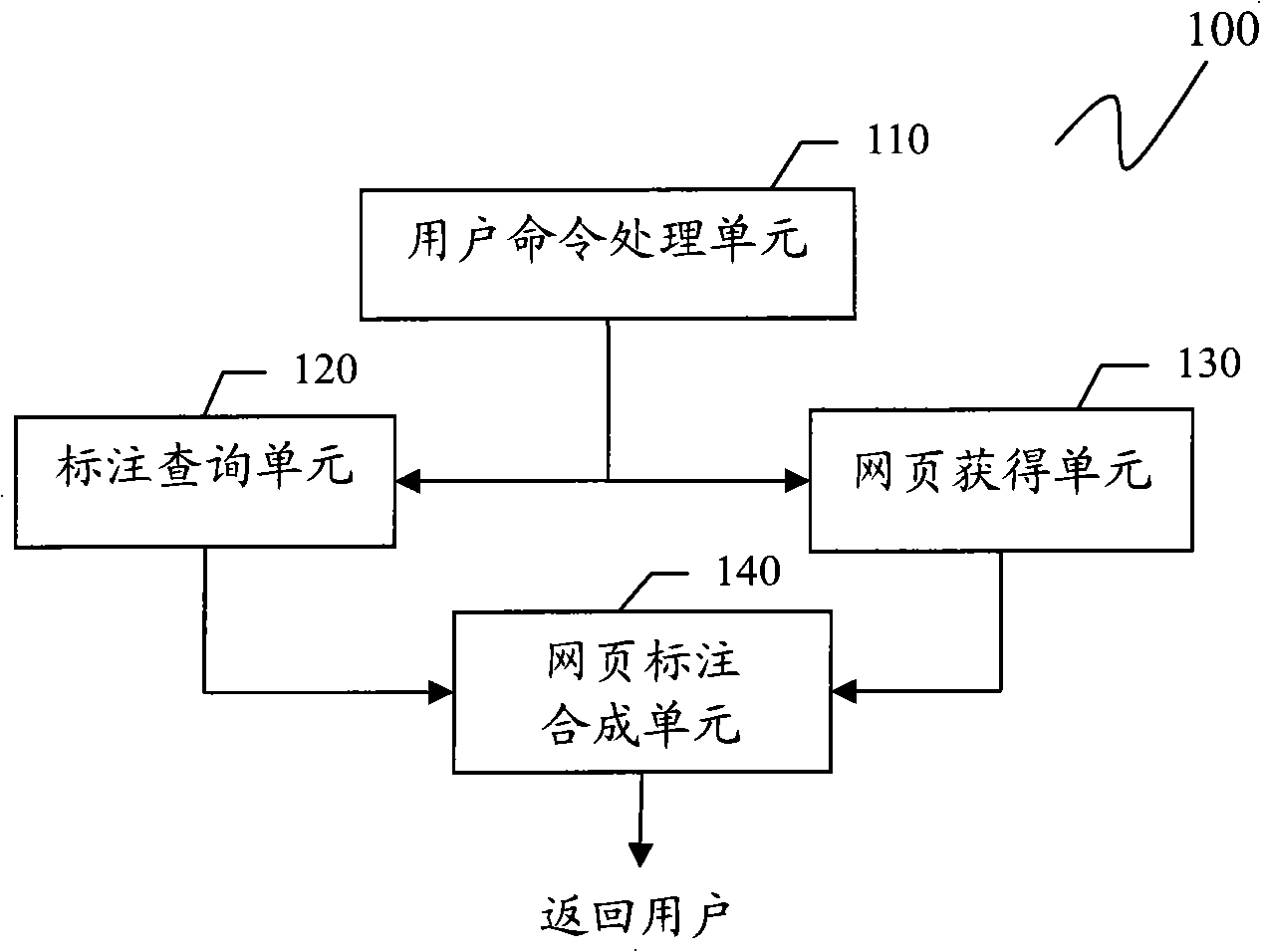
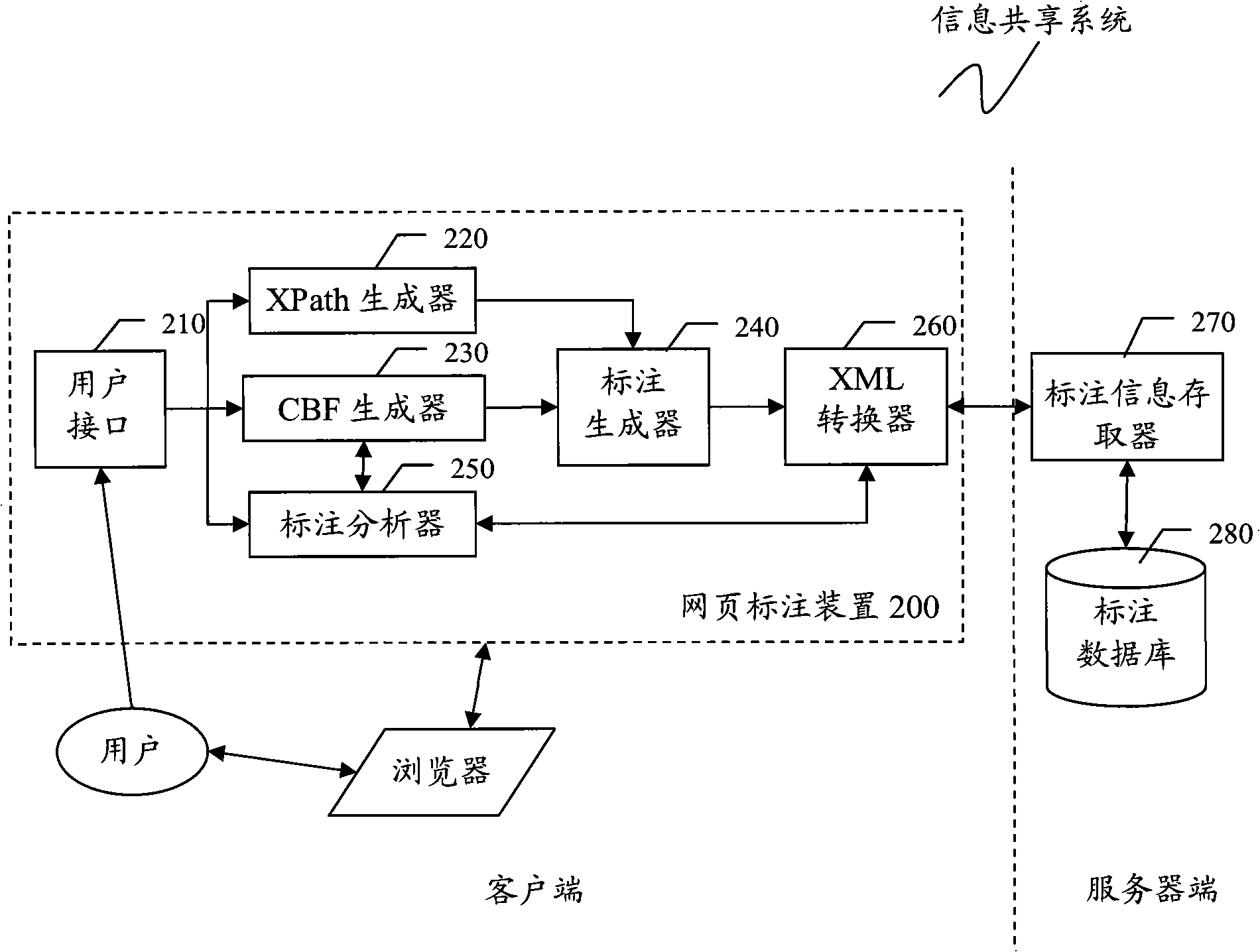
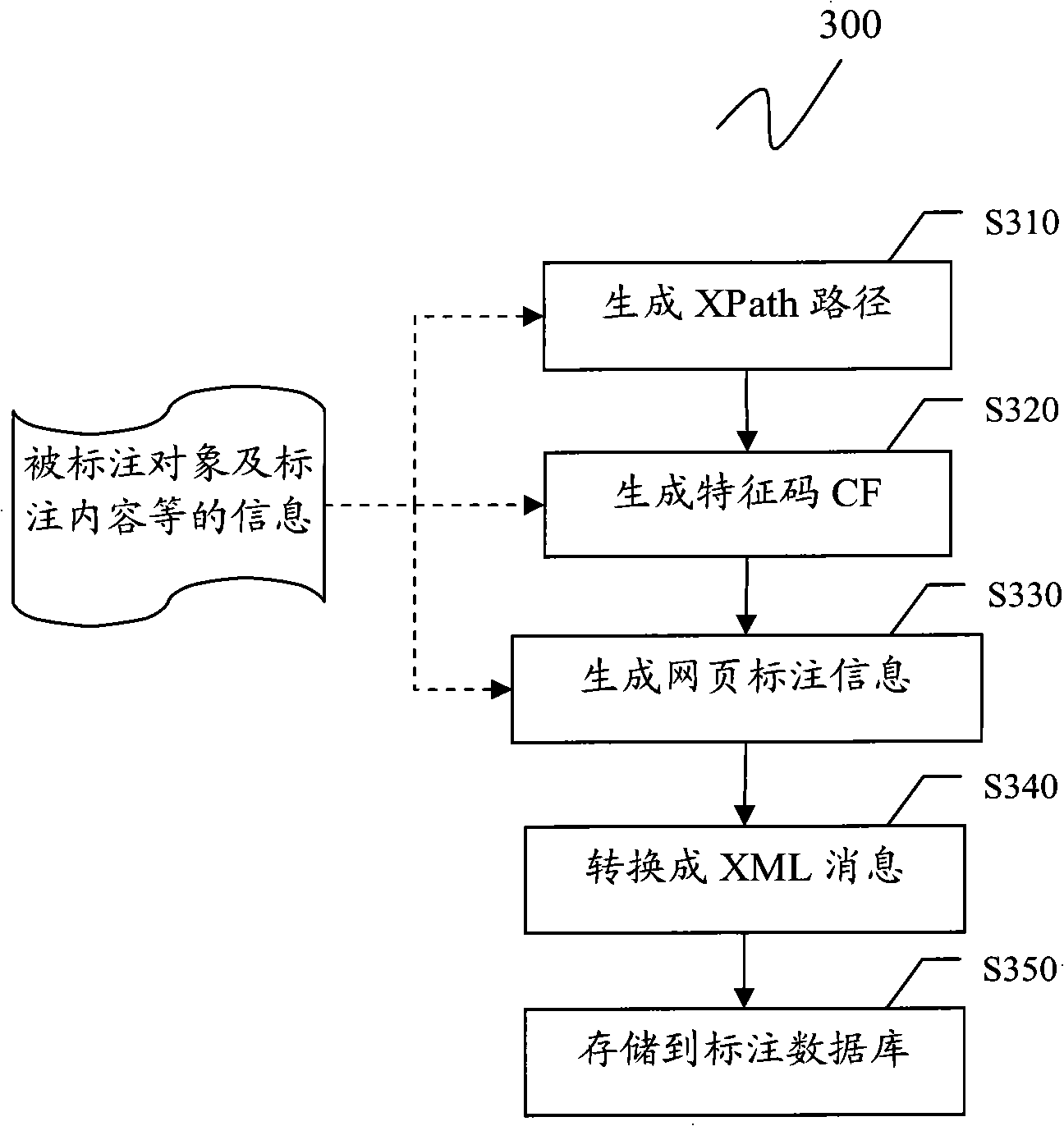
Method and device for generating or displaying webpage label and information sharing system
InactiveCN101866342ARealize dynamic trackingSpecial data processing applicationsWeb browserEngineering
The invention discloses a method and a device for generating or displaying a webpage label and an information sharing system based on the webpage label. The method for generating webpage label information comprises the following steps: responding to a user to select a target webpage element on a current webpage loaded on a client Web browser as a labelled object and extracting an XPath path of the labelled object in a document object model (DOM) tree of the current webpage; based on the labelled object and contents of context webpage elements next to the front and back parts of the labelled object in the current webpage, generating a feature code CF of the labelled object; and based on the XPath path and the feature code CF of the labelled object and a label input by the user, generating the webpage label information, wherein the webpage label information is stored in a label database of a remote label server and the feature code CF of the labelled object consists of a content-based feature (CBF) of the labelled object and the CBFs of the context webpage elements of the labelled object.
Owner:FUJITSU LTD
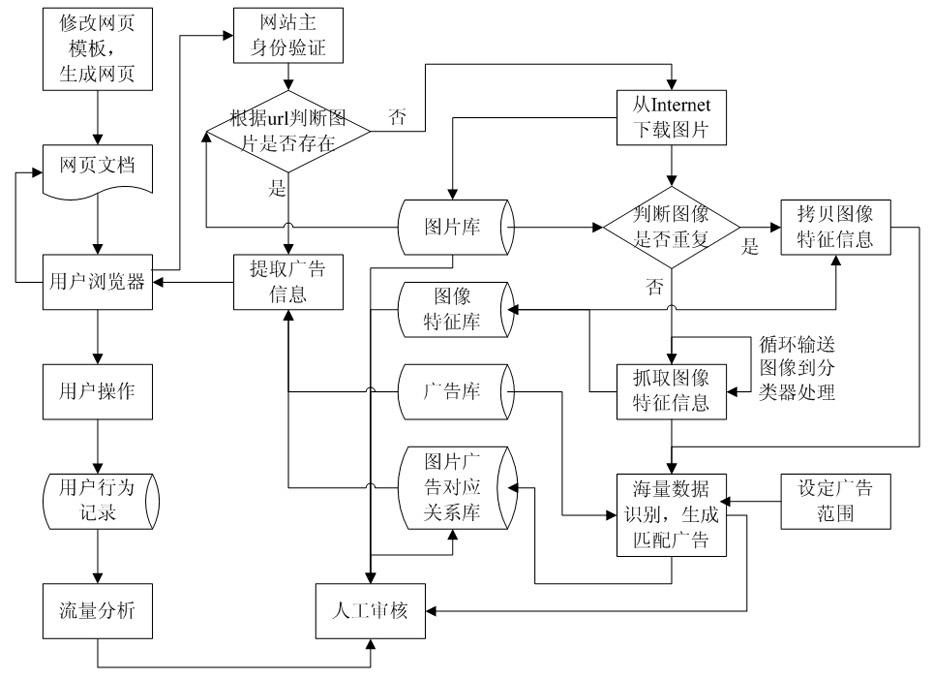
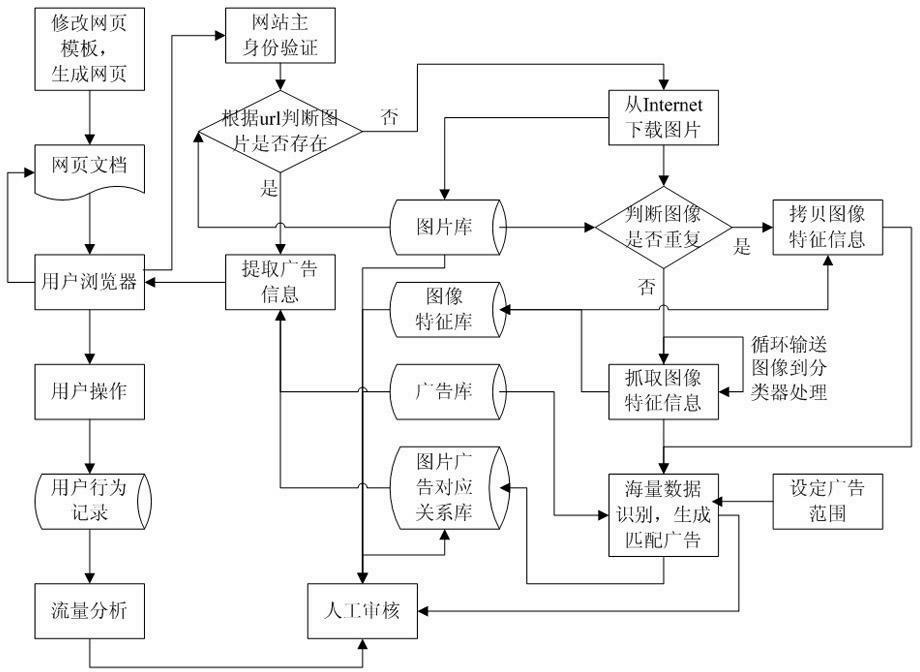
Active advertisement generation method based on Internet picture
The invention discloses an active advertisement generation method based on Internet pictures, belonging to the fields of image identification and computer software system integration. The generation method comprises a first step of setting a picture database, an advertisement database, an image feature database, and a picture-advertisement correspondence database, and sending to a background server feature codes, webpage URL information and picture URL information exclusive to the website when a webpage is loaded by a user browser; and a second step that the server process uses hash algorithm to judge whether the picture exists in the picture database according to the picture URL information, sending a corresponding advertisement to the browser if the picture exists in the picture database; and taking a different step to generate an advertisement for the picture if not. The generation method introduces static pictures into interactive content and makes full use of pictures already existed in various big websites, which makes social shopping based on rich media network advertisements and socialization be integrated with e-commerce with personalized recommendation, and makes advertisements extend from on-line stores to pictures of other websites.
Owner:北京明日时尚信息技术有限公司
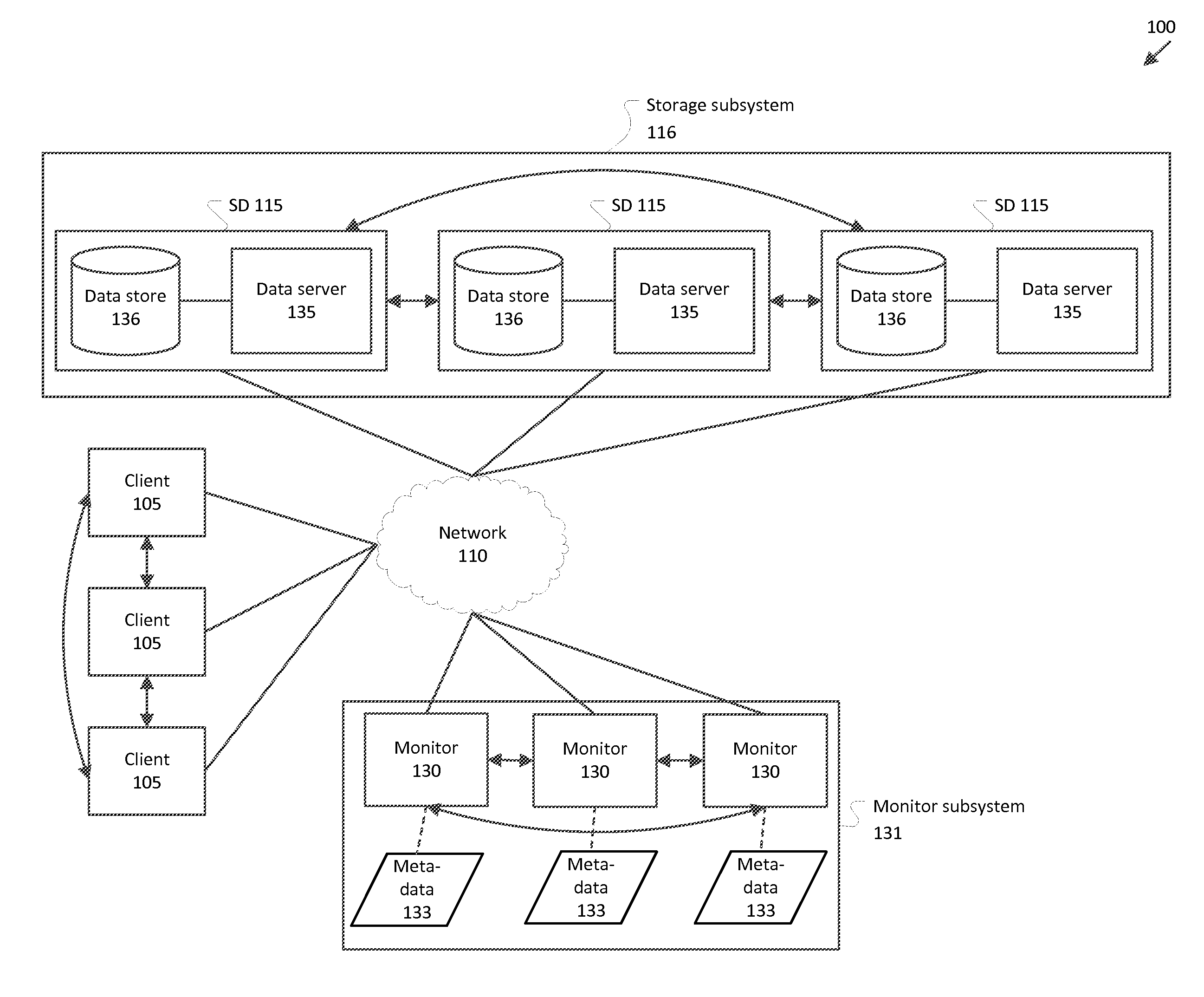
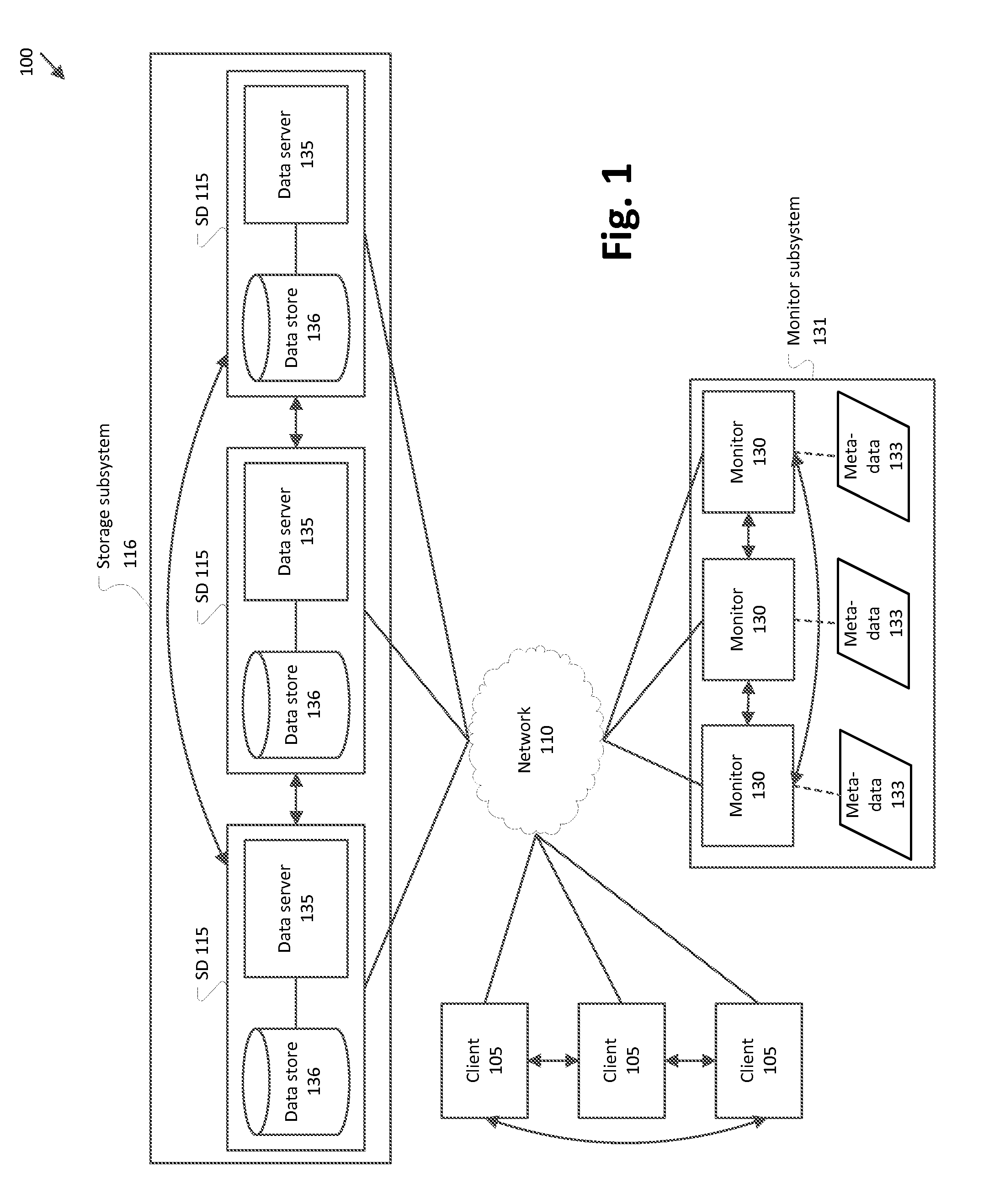
Dynamic data placement for distributed storage
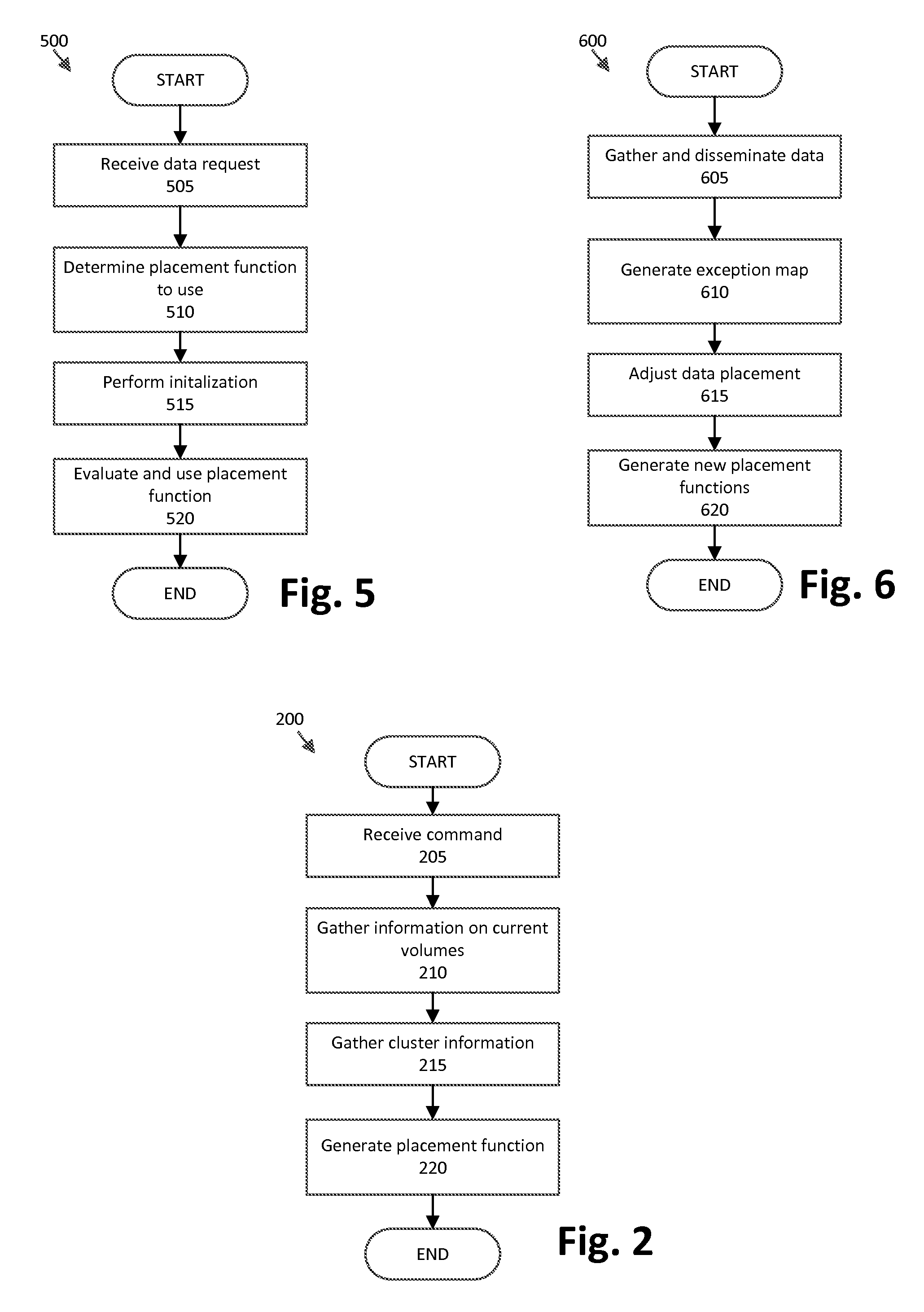
ActiveUS20120331249A1Memory loss protectionInput/output processes for data processingDynamic dataFormal description
A command is received to alter data storage in a cluster, along with parameters for executing the command. Information is obtained relating to one or more volumes in the cluster and information relating to devices in the cluster. A formal description of a placement function is generated that maps one or more object identifiers to a storage device set. Placement function code is generated by compiling the formal description of the placement function to computer-executable code.
Owner:RED HAT
White list based realization method for active defense of cloud host
ActiveCN105138901APrecise managementStop runningPlatform integrity maintainanceMalwareZero-day attack
The invention discloses a white list based realization method for active defense of a cloud host. The method involves a centralized management platform of a server and a client, and the client is mounted on each cloud host needed to be protected. The specific realization process is as follows: all binary files in the protected cloud host are scanned through server software; a cloud security center identifies out trust ratings of the scanned files and adds a graded file list library into a white list library, a black list library and a gray list library separately; and at the client, only trusted application programs in a white list are allowed to run for preventing loading of a dynamic-link library file in a kernel. Compared with the prior art, the white list based realization method for active defense of the cloud host can completely prevent potential unwanted application programs and codes and prevent advanced threats, is free of feature code update, and can consistently enable known good software, prevent known or unknown bad software, correctly manage new software and effectively prevent unknown malicious software and zero-day attacks.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Facial recognition technology-based walkman analysis method and facial recognition technology-based walkman analysis system
PendingCN110084103AImprove accuracyReduce labor intensityCharacter and pattern recognitionStill image data queryingPattern recognitionAnalysis method
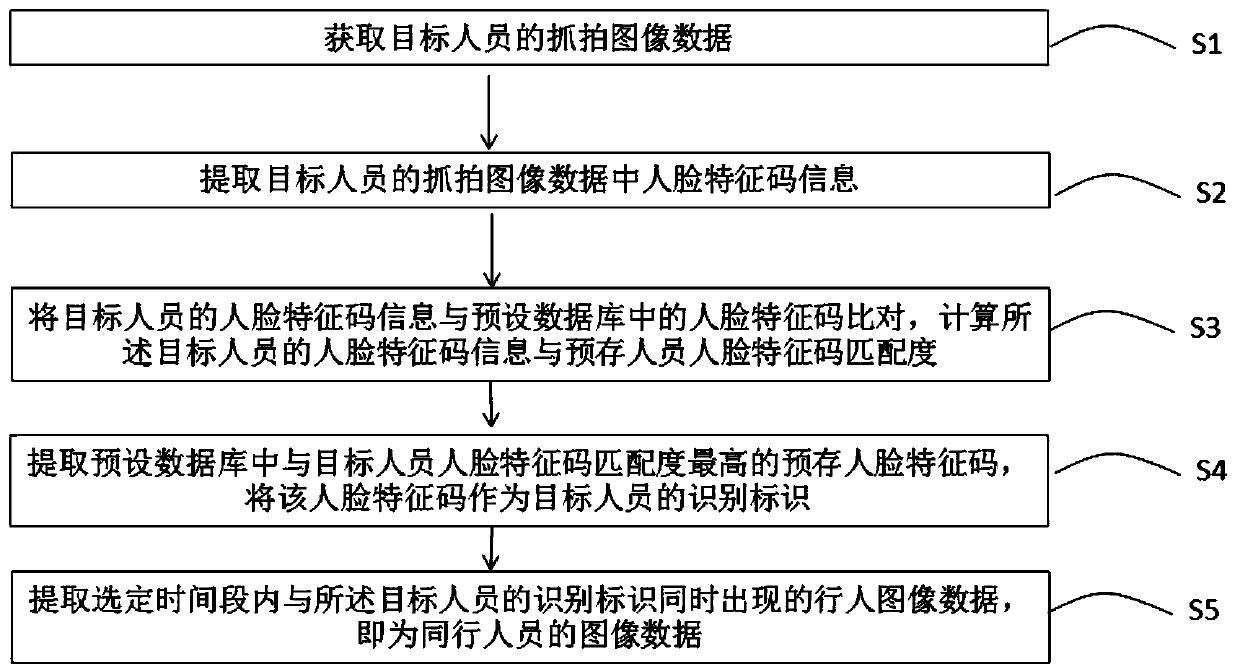
The invention belongs to the technical field of security and protection and discloses a facial recognition technology-based partner analysis method. The method comprises the following steps of carrying out intelligent analysis on captured image data through an artificial intelligence deep learning algorithm; carrying out face capture on personnel passing through a set monitoring area; abstractinga face image, extracting face feature code information, comparing the extracted face feature code information with face feature codes stored in a database; wherein the feature codes with the similarity greater than a certain threshold are classified into feature codes of the same person; taking a face feature code with the highest similarity as an identification mark of a target person; based on the identification mark and the time period, retrieving the image of the personnel to acquire namely acquiring data. The method is efficient and rapid. Through the facial recognition and big data technology, the analysis accuracy is improved, and labor intensity and the labor cost are reduced.
Owner:SHENZHEN INFINOVA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com