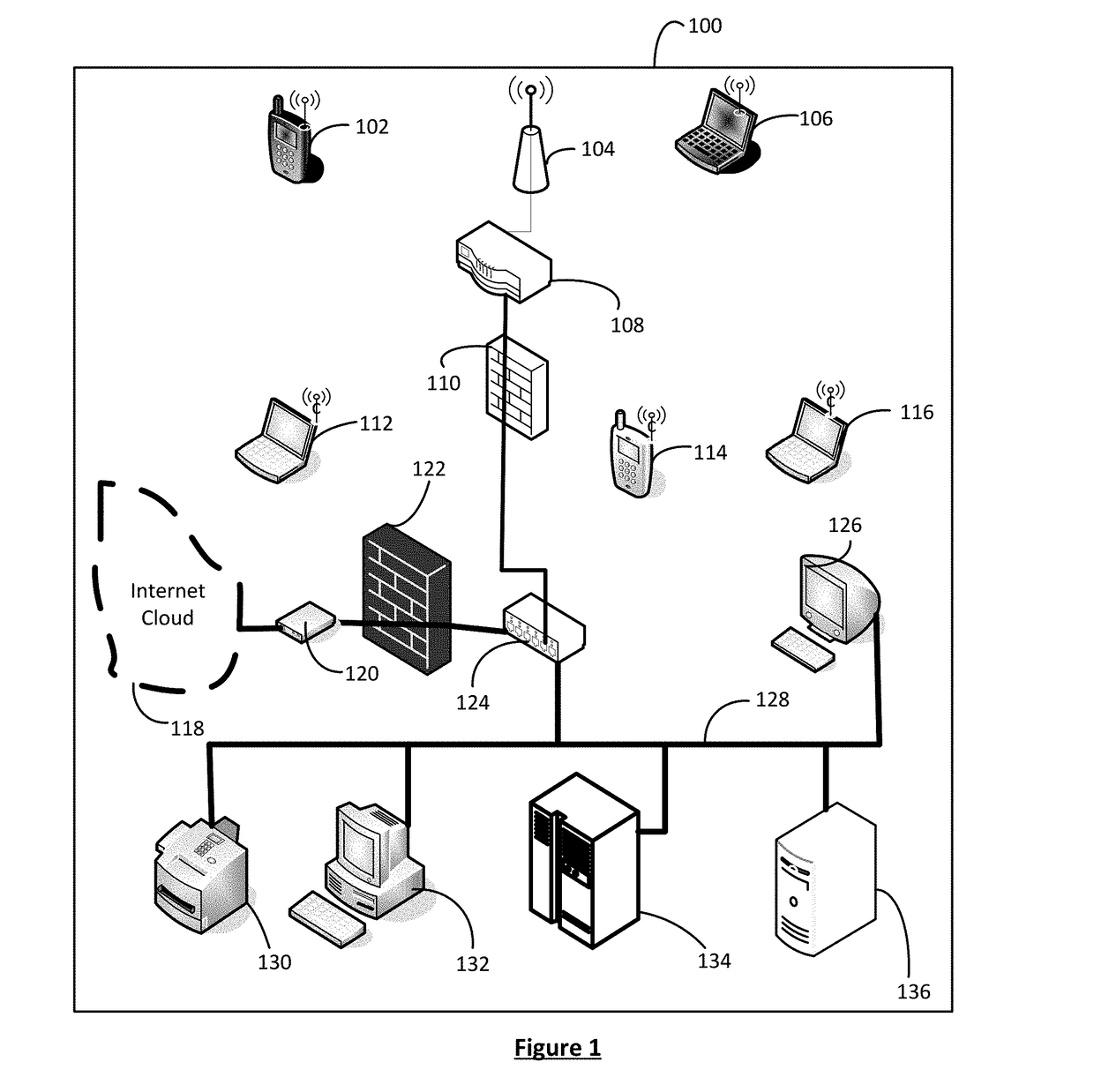
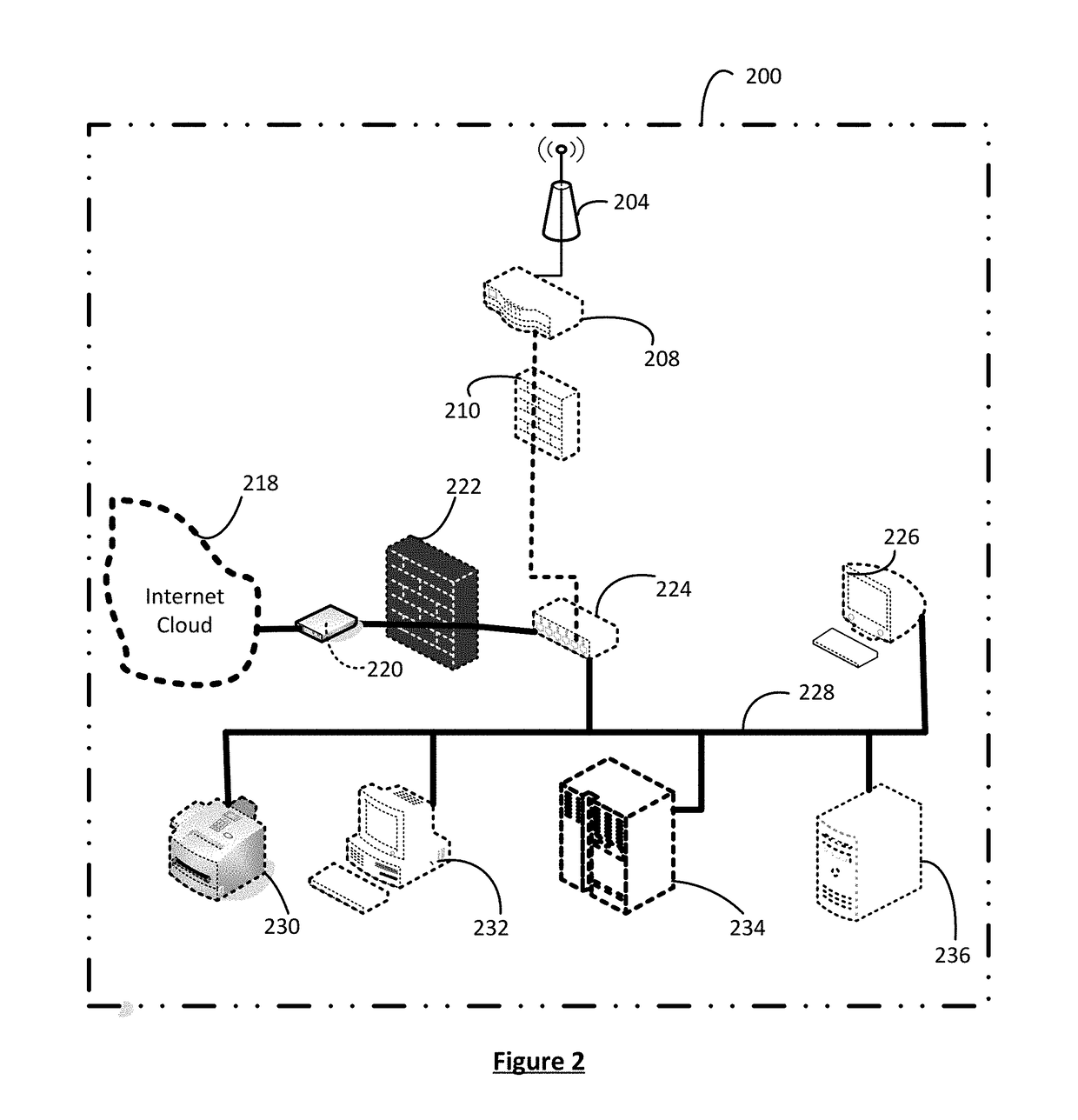
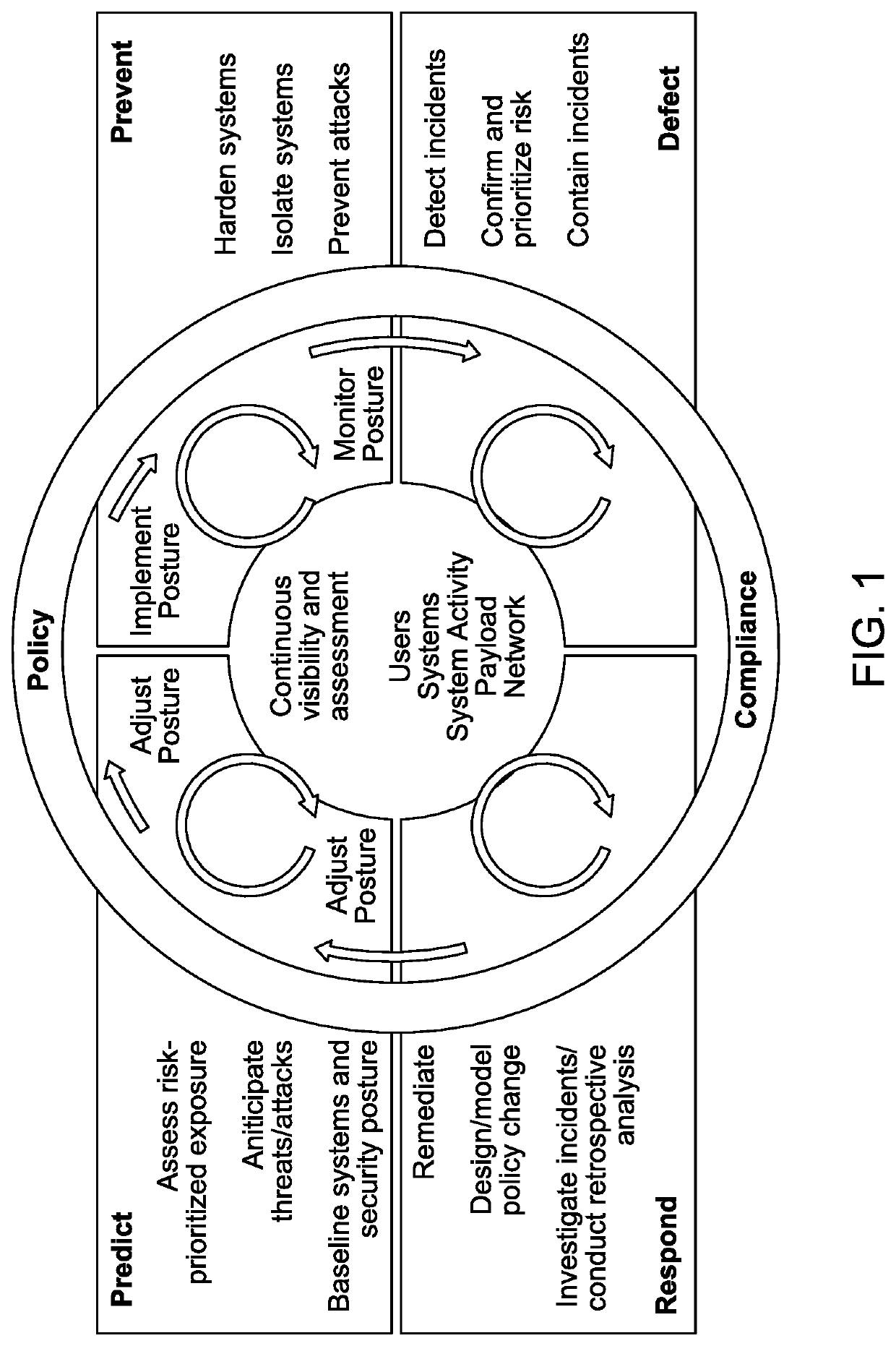
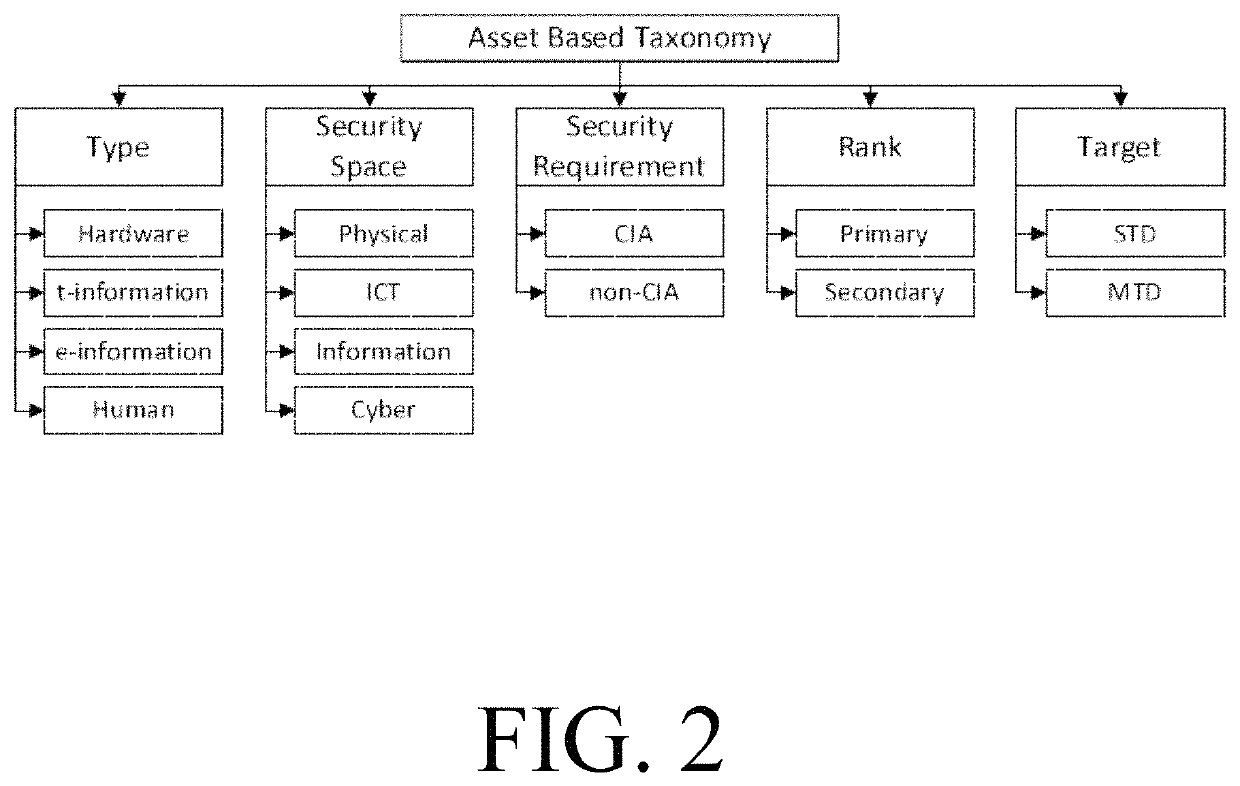
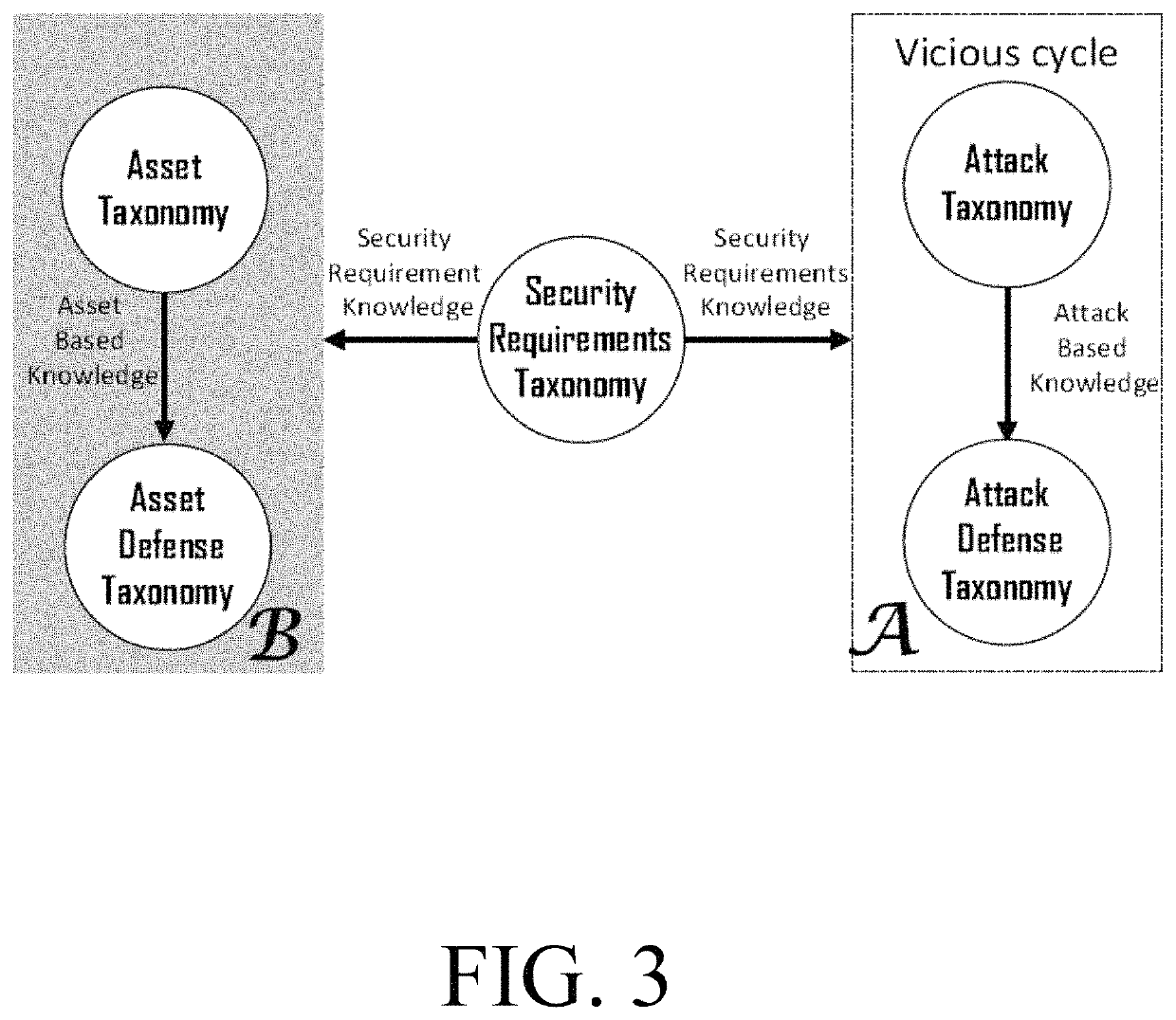
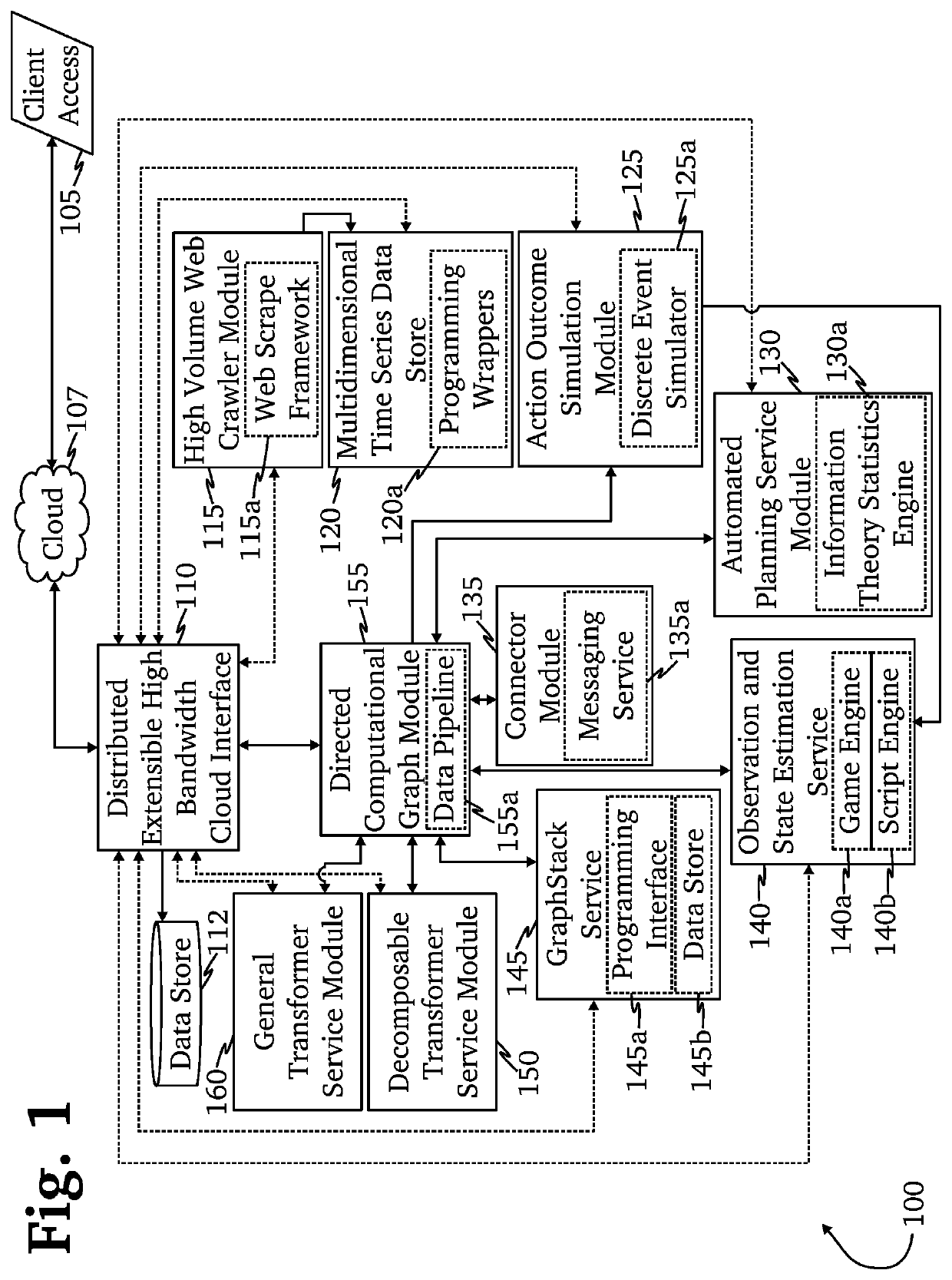
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "Zero-day attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A zero-day (also known as 0-day) vulnerability is a computer-software vulnerability that is unknown to, or unaddressed by, those who should be interested in mitigating the vulnerability (including the vendor of the target software). Until the vulnerability is mitigated, hackers can exploit it to adversely affect computer programs, data, additional computers or a network. An exploit directed at a zero-day is called a zero-day exploit, or zero-day attack.
Zero-day discovery system
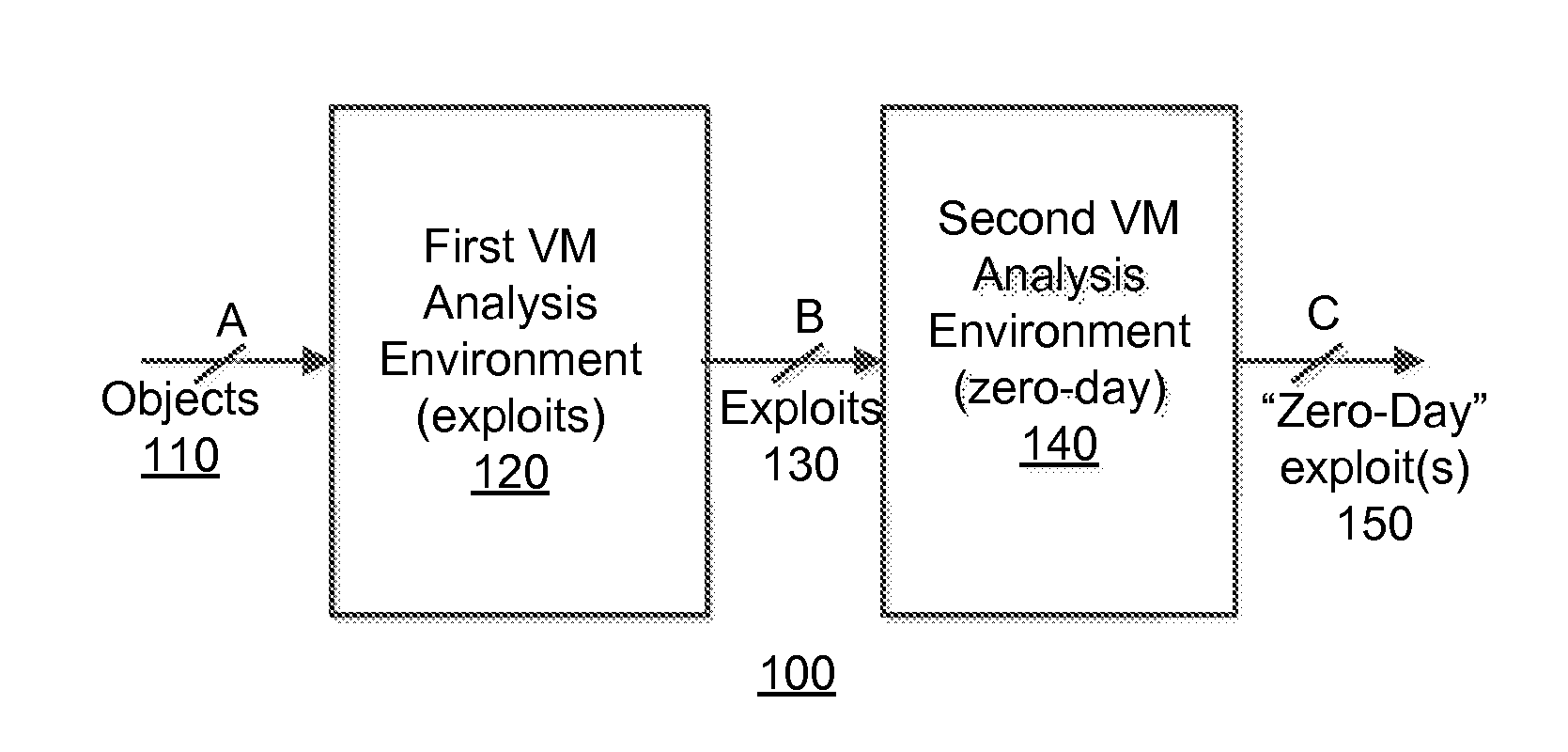
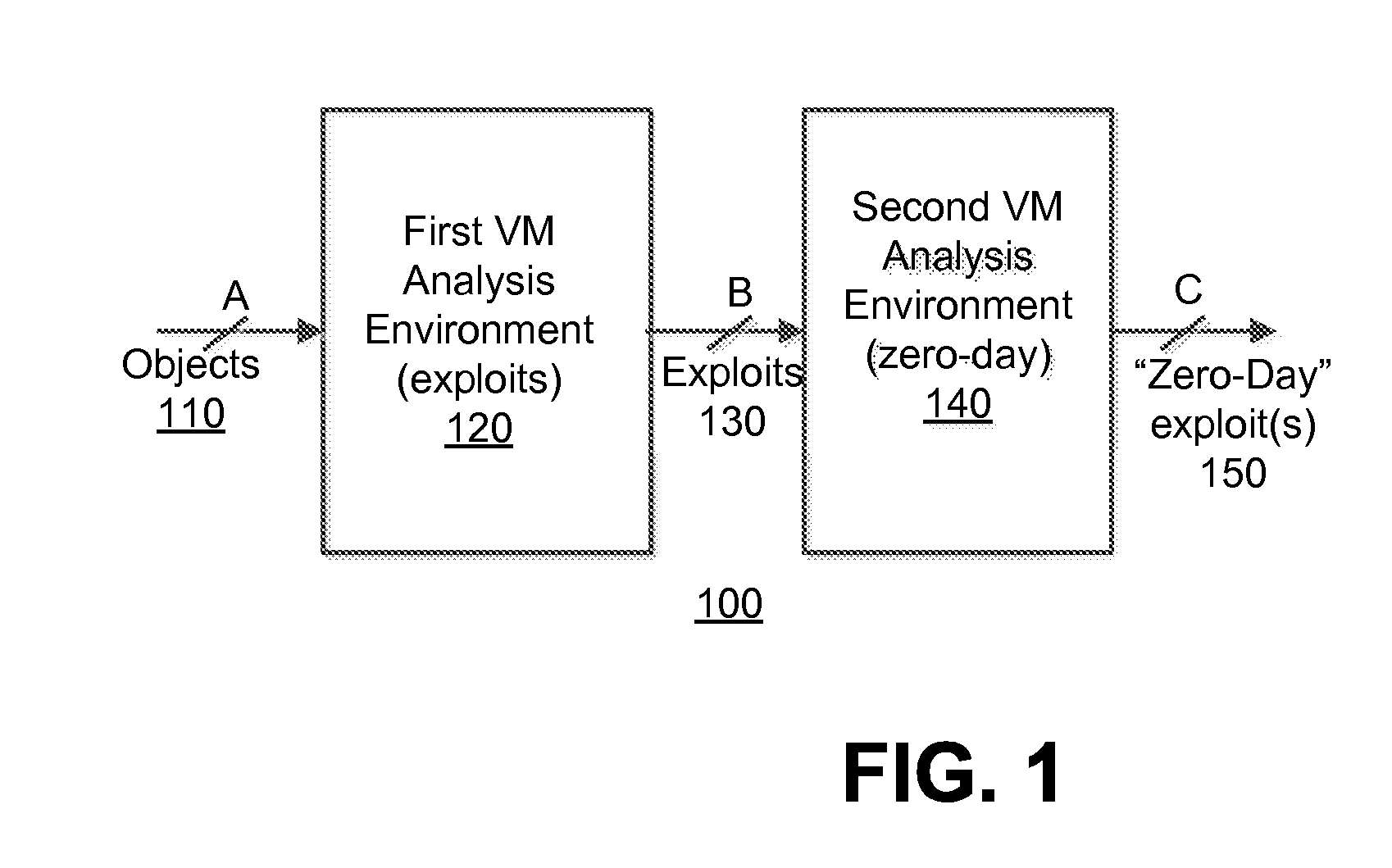
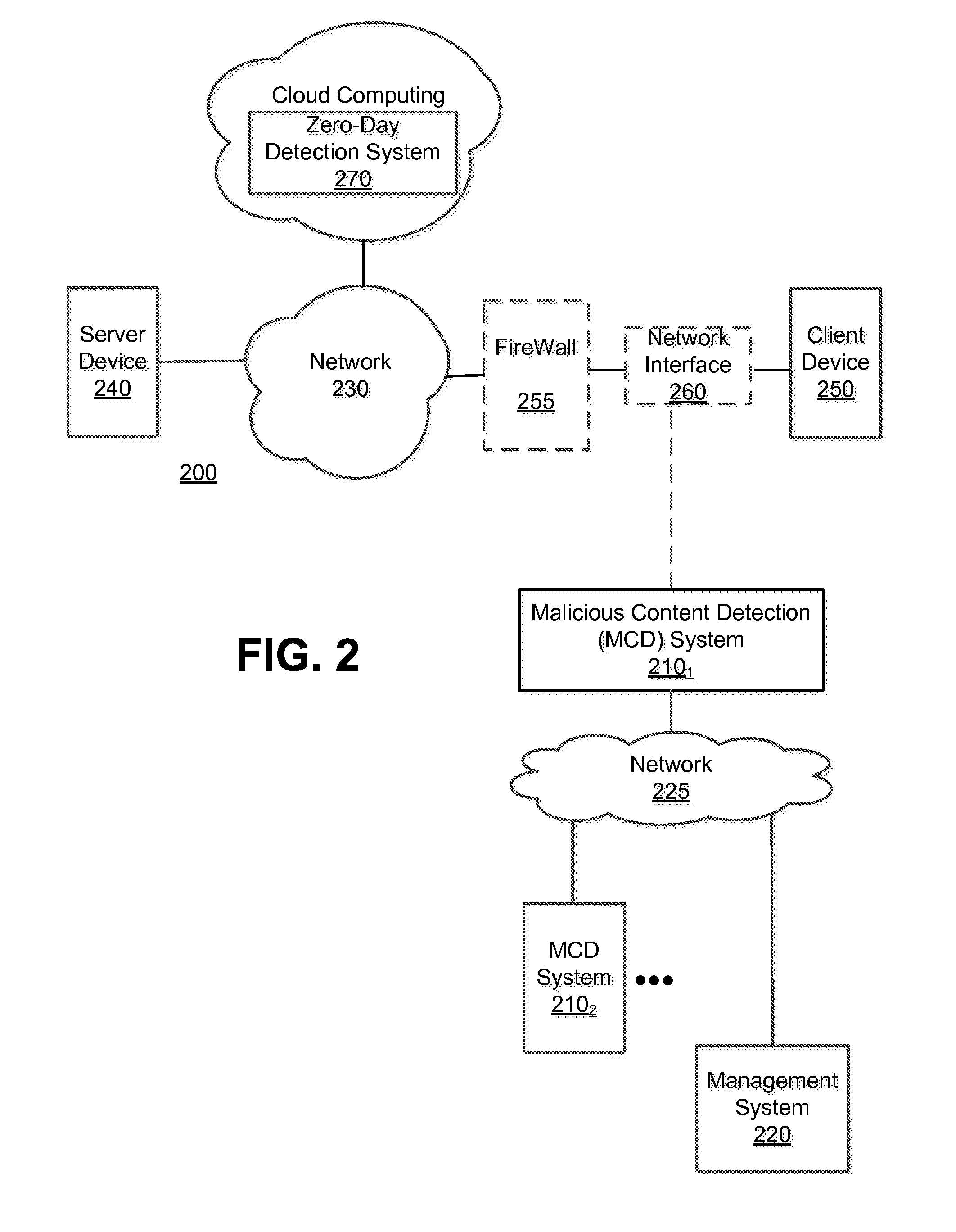
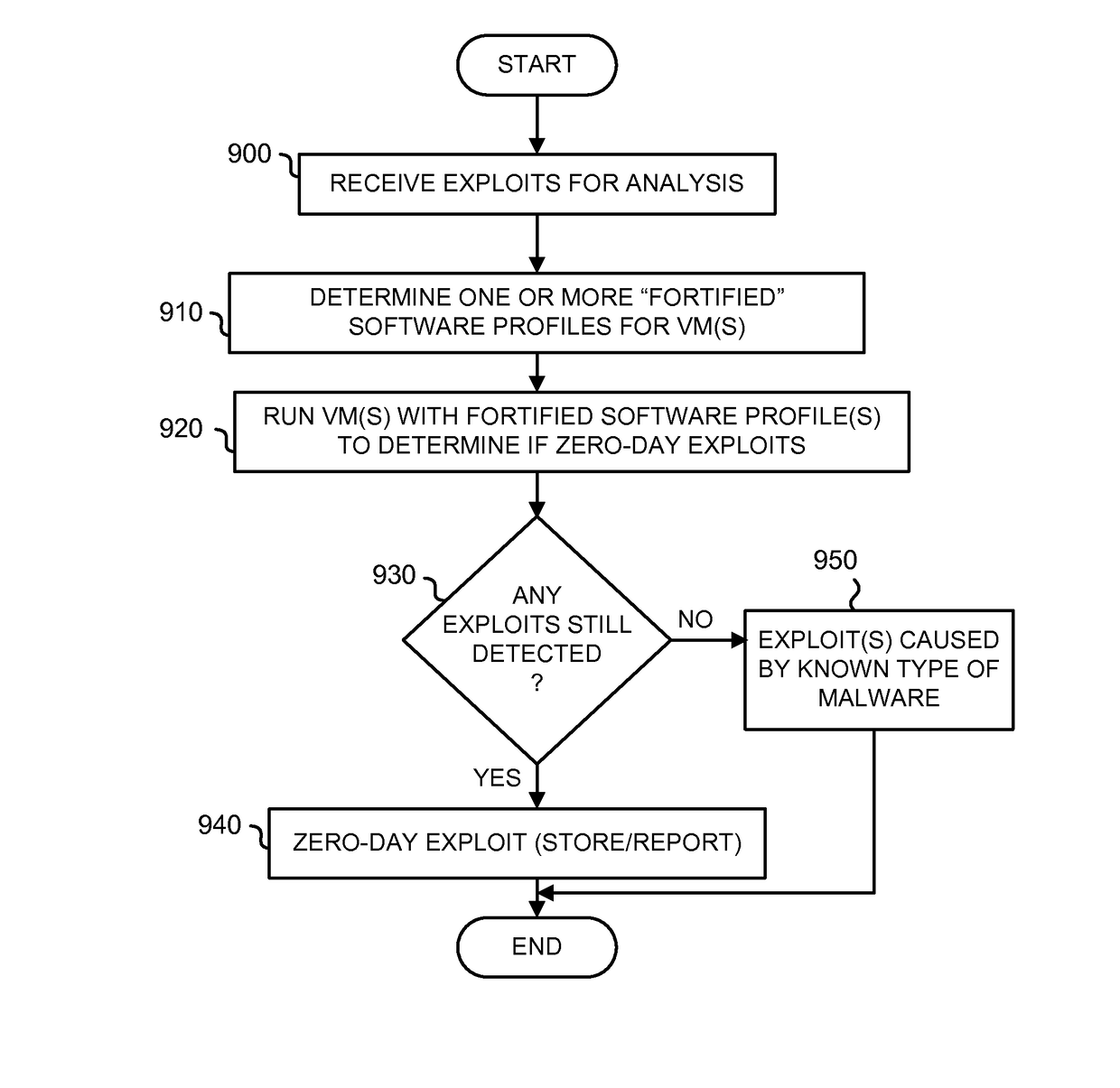
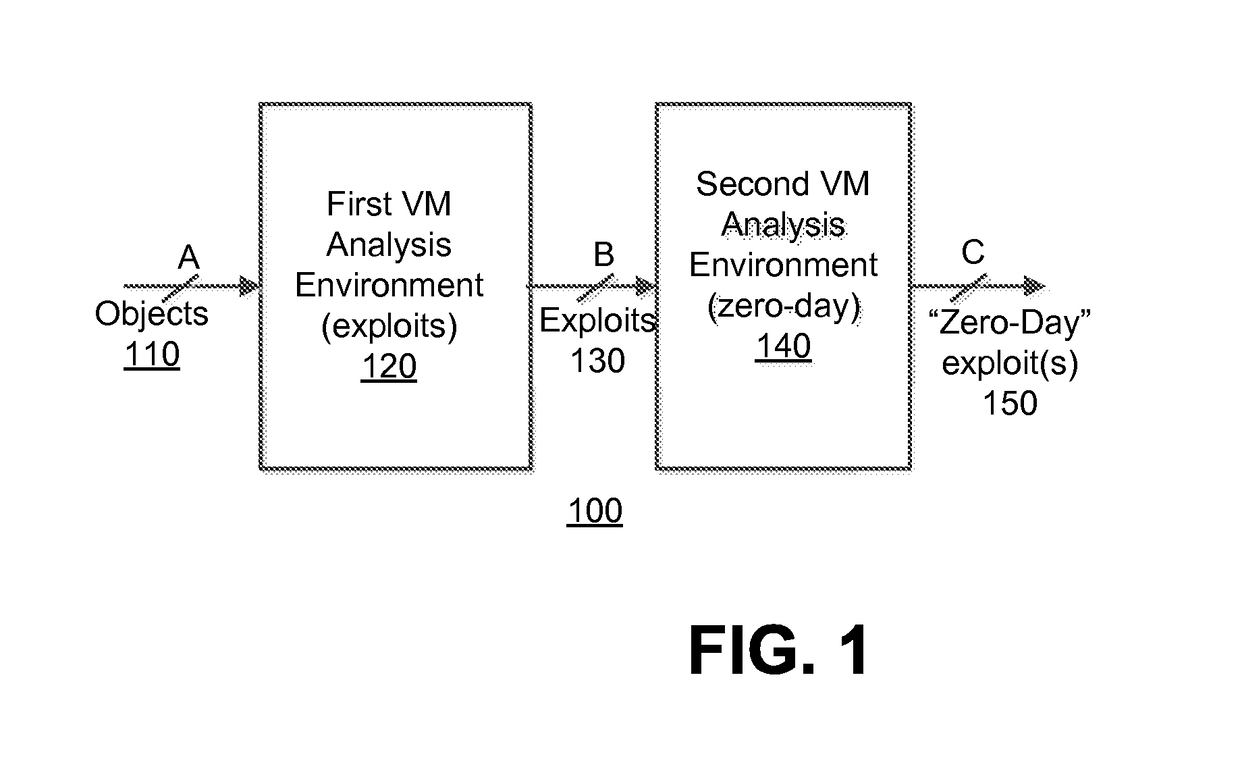
A method for determining a zero-day attack by an electronic device is described. According to one embodiment, the method comprises instantiating, by the electronic device, at least one virtual machine, the at least one virtual machine being based on a fortified software profile. The method further comprises executing content capable of behaving as an exploit on the at least one virtual machine, and determining that the exploit is associated with zero-day exploit when the exploit, upon execution of the content on the at least one virtual machine, performs an undesired behavior.
Owner:FIREEYE SECURITY HLDG US LLC
Zero-day discovery system
A method for determining a zero-day attack by an electronic device is described. According to one embodiment, the method comprises instantiating, by the electronic device, at least one virtual machine, the at least one virtual machine being based on a fortified software profile. The method further comprises executing content capable of behaving as an exploit on the at least one virtual machine, and determining that the exploit is associated with zero-day exploit when the exploit, upon execution of the content on the at least one virtual machine, performs an undesired behavior.
Owner:FIREEYE SECURITY HLDG US LLC
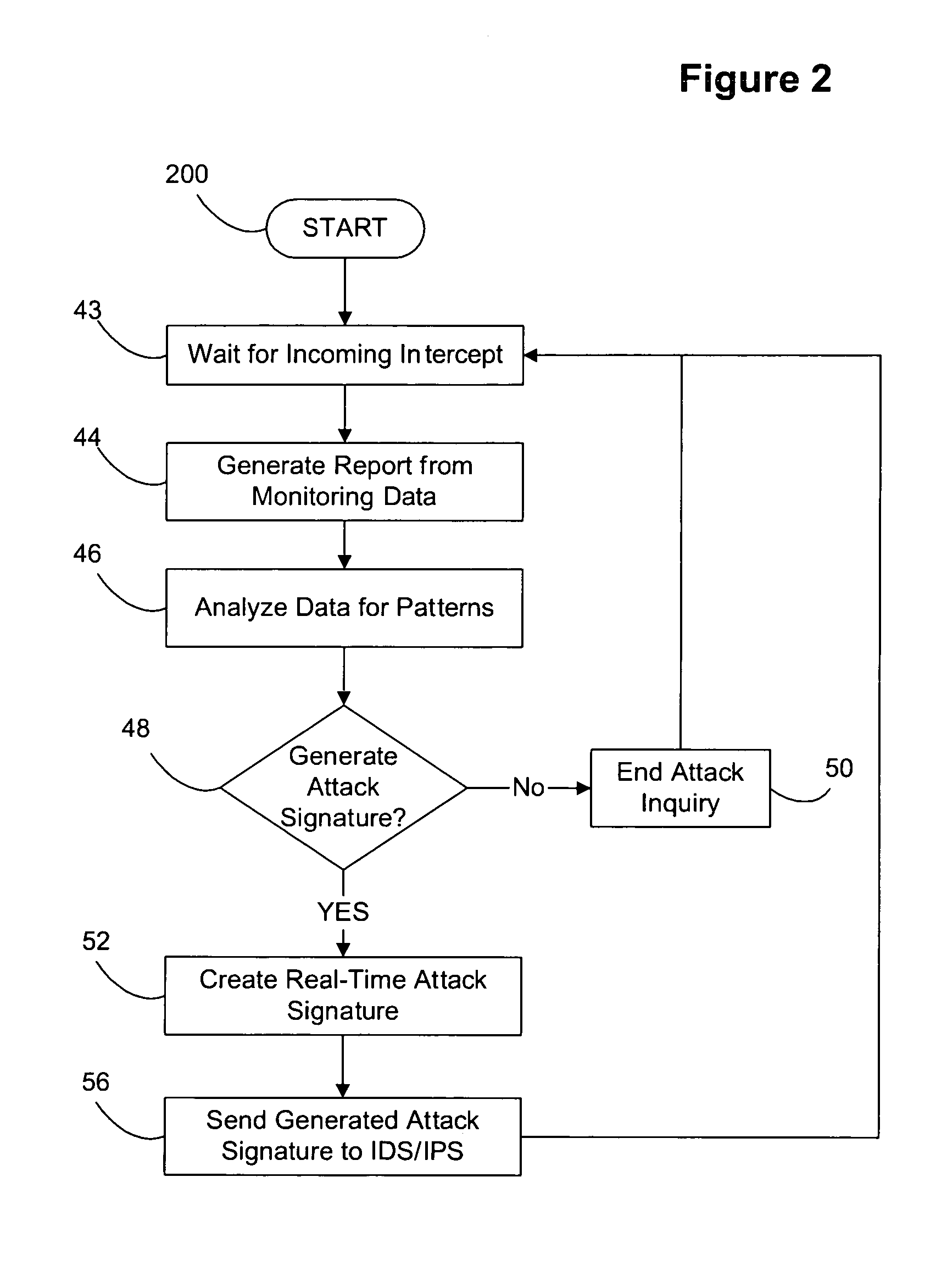
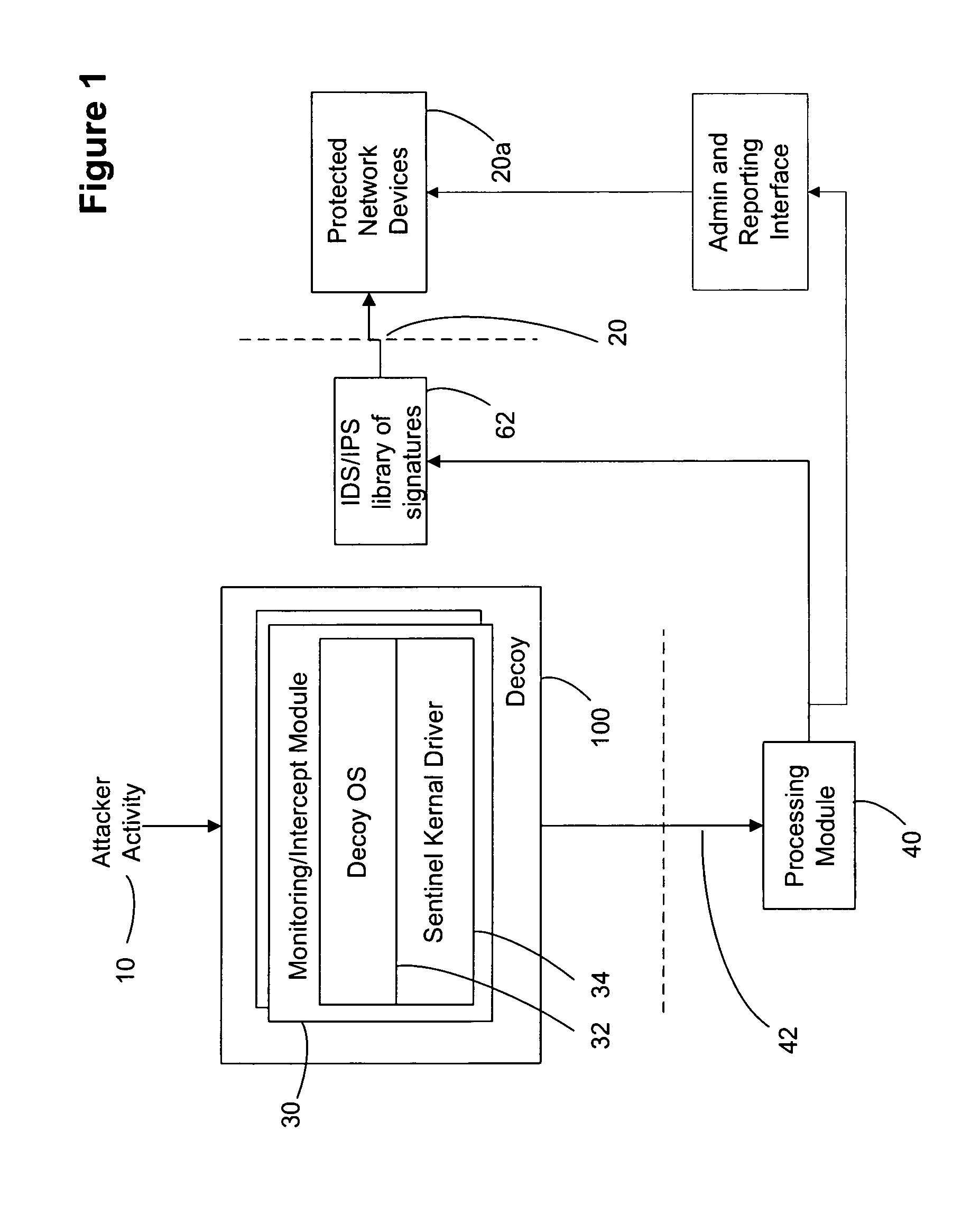
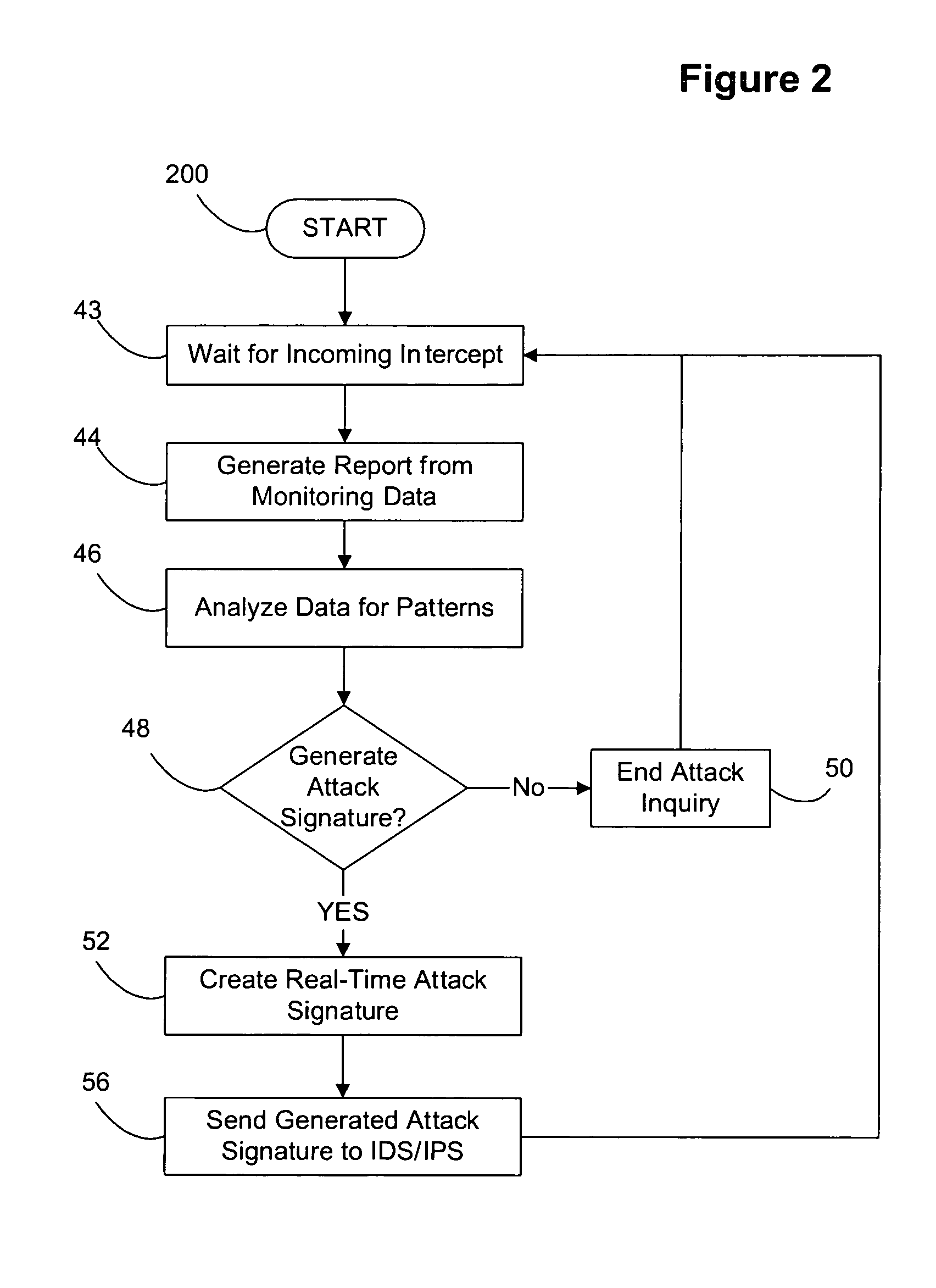
Decoy network technology with automatic signature generation for intrusion detection and intrusion prevention systems
ActiveUS20070271614A1Unauthorised/fraudulent call preventionDigital data processing detailsOperational systemDecoy
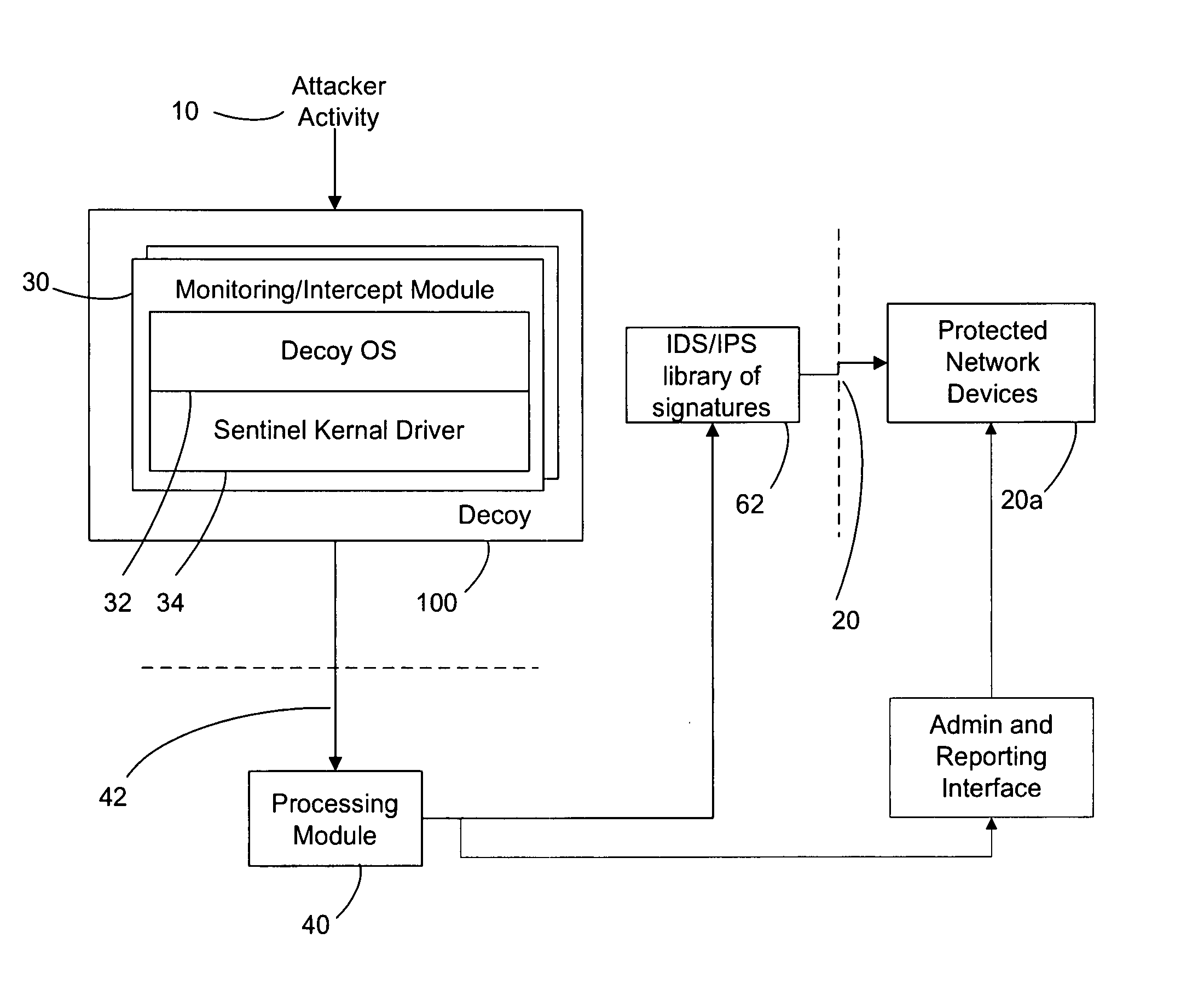
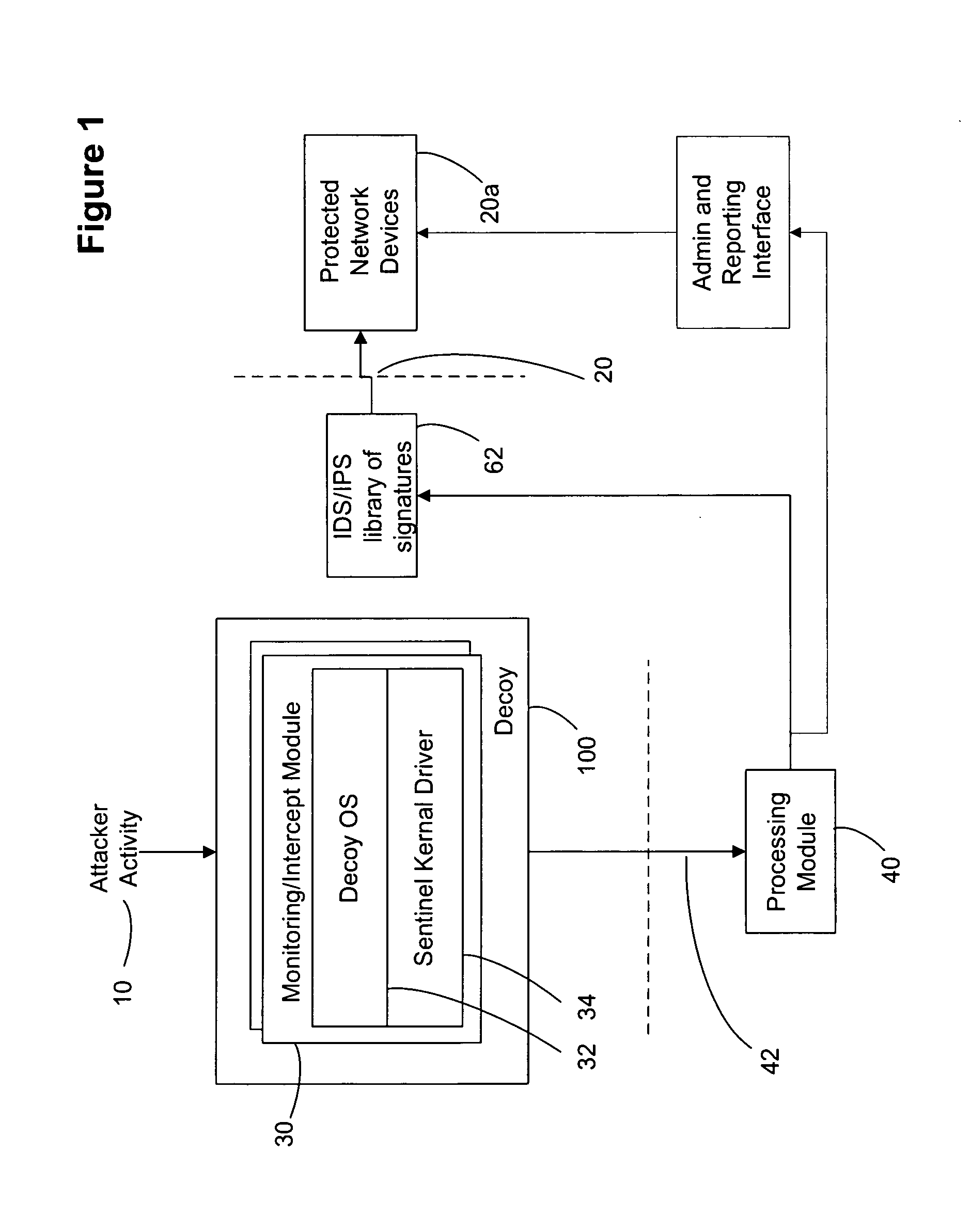
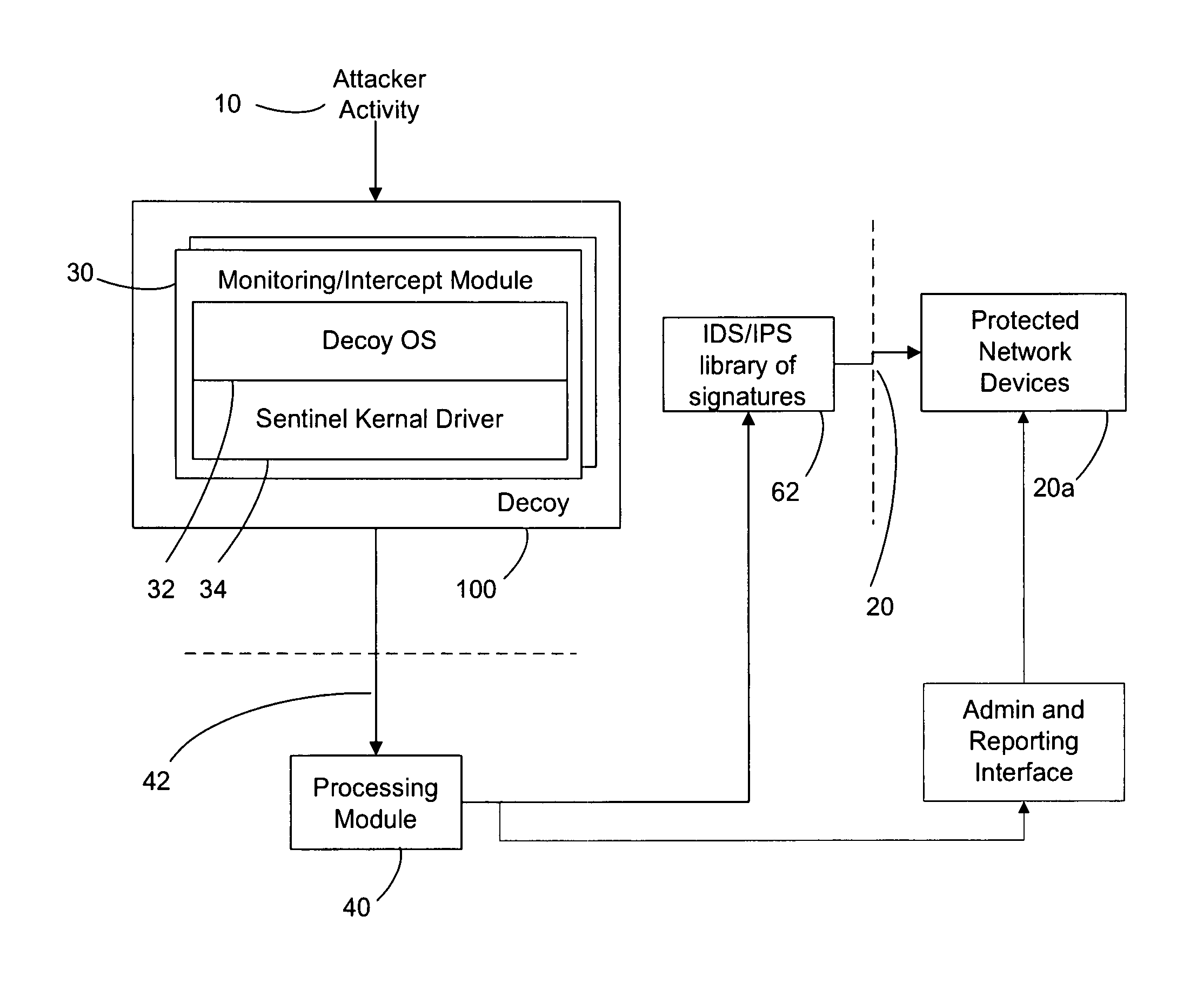
Improved methods and systems for decoy networks with automatic signature generation for intrusion detection and intrusion prevention systems. A modular decoy network with front-end monitor / intercept module(s) with a processing back-end that is separate from the protected network. The front-end presents a standard fully functional operating system that is a decoy so that the instigator of an attack is lead to believe a connection has been made to the protected network. The front-end includes a hidden sentinel kernal driver that monitors connections to the system and captures attack-identifying information. The captured information is sent to the processing module for report generation, data analysis and generation of an attack signature. The generated attack signature can then be applied to the library of signatures of the intrusion detection system or intrusion prevention system of the protected network to defend against network based attacks including zero-day attacks.
Owner:COUNTERTACK
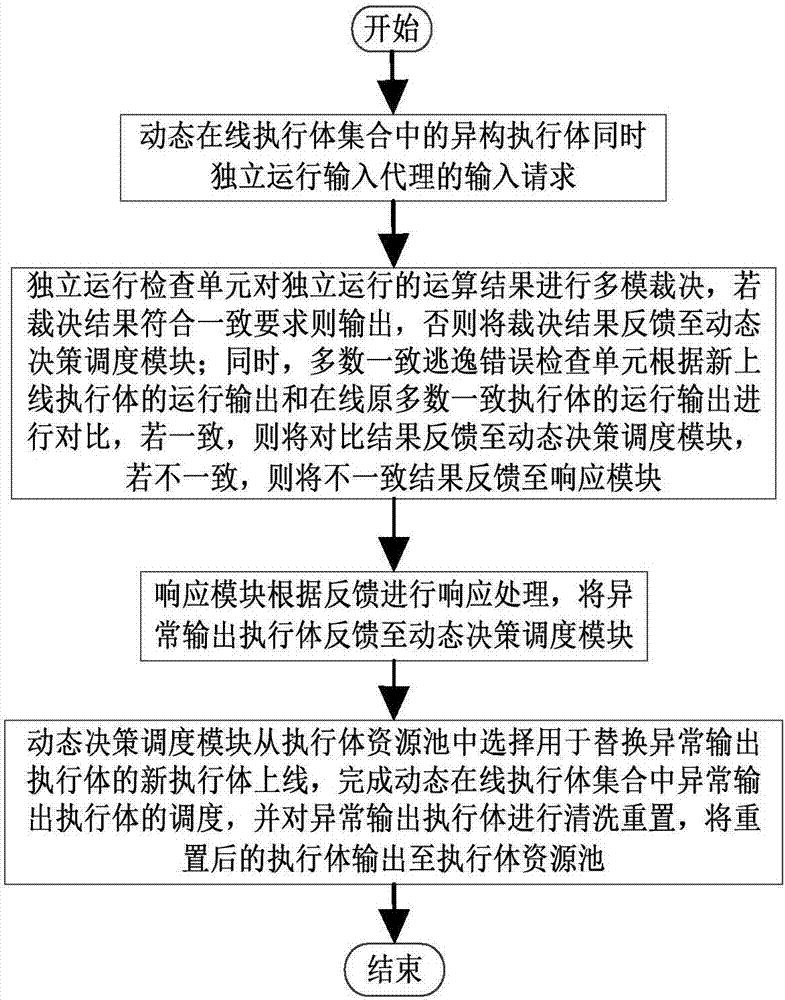
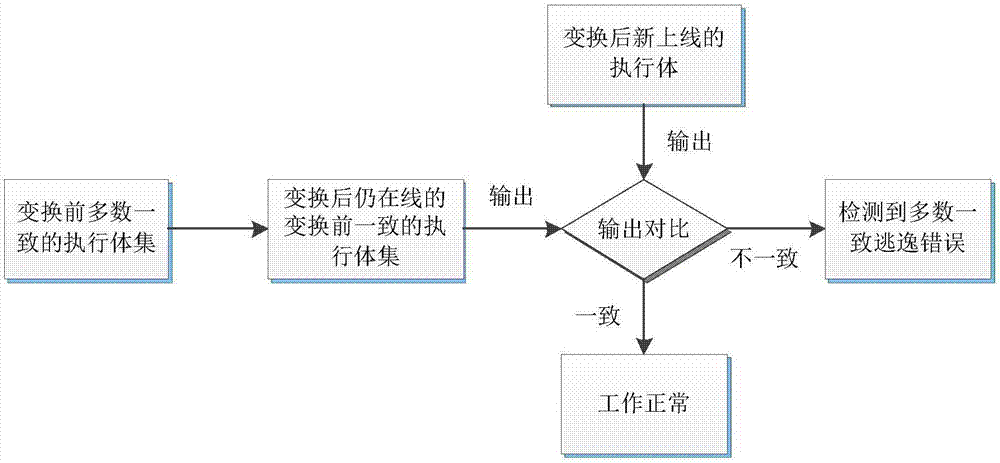
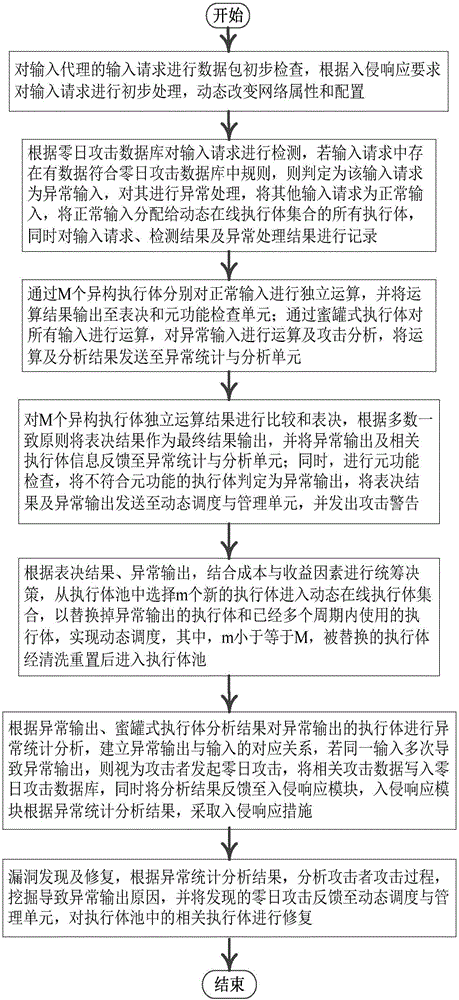
Majority consistent escape error processing device based on mimicry security defense zero-day attack and method thereof
ActiveCN106874755AGuaranteed robustnessGuaranteed survivabilityPlatform integrity maintainanceResource poolError processing
The invention relates to a majority consistent escape error processing device based on mimicry security defense zero-day attack and a method thereof. The method comprises: a heterogeneous executive in a dynamic online executive assembly independently operating an input request; performing multimode adjudication on an operation result, if an adjudication result meets a consistency requirement, outputting the adjudication result, if not, feeding back the adjudication result to a dynamic decision dispatching module; comparing new online executive operation output with online original majority consistent executive operation output, respectively feeding back results to the dynamic decision dispatching module and a responding module; the responding module processing the response according to feedback, and feeding back abnormal output executive to the dynamic decision dispatching module; and the dynamic decision dispatching module selecting new executive to be online from an executive resource pool, and cleaning and resetting offline executives. The method is used to provide means of detection and response when majority of mimicry defense online executives are attacked, and solves security threat a mimicry defense system faces, so as to enhance robustness of the mimicry system.
Owner:THE PLA INFORMATION ENG UNIV
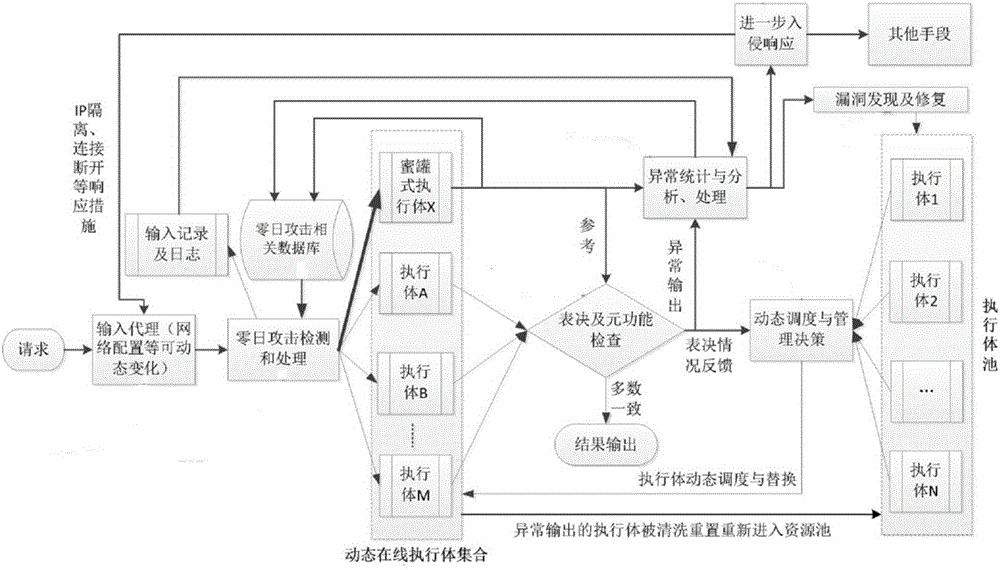
Mimicry defense architecture based zero-day attack detection, analysis and response system and method thereof
The invention relates to a mimicry defense architecture based zero-day attack detection, analysis and response system and a method thereof. The method comprises the steps of performing attack detection and processing on the input, cheating and inducing an attacker through honeypot type executing bodies, and performing meta-function inspection on the output of each executing body; performing statistical analysis on abnormal output by combining abnormal information, updating a zero-day attack database, feeding back an analysis result to an intrusion response module, and preventing persistent attacks of the attacker; performing dynamic adjustment and management on an online executing body by combining voting conditions, executing body dispatching, the executing body with abnormal output and the like, and selecting executing bodies from an executing body resource pool to get into a dynamic online executing body set; and analyzing a zero-day vulnerability in the executing body with abnormal output according to an anomaly statistical analysis result, and repairing the related executing bodies in the executing body pool. According to the invention, functions and the flexibility of mimicry defense architecture are enhanced, values of the abnormal output are sufficiently utilized, and the threat and the defense cost of zero-day attacks are reduced.
Owner:THE PLA INFORMATION ENG UNIV
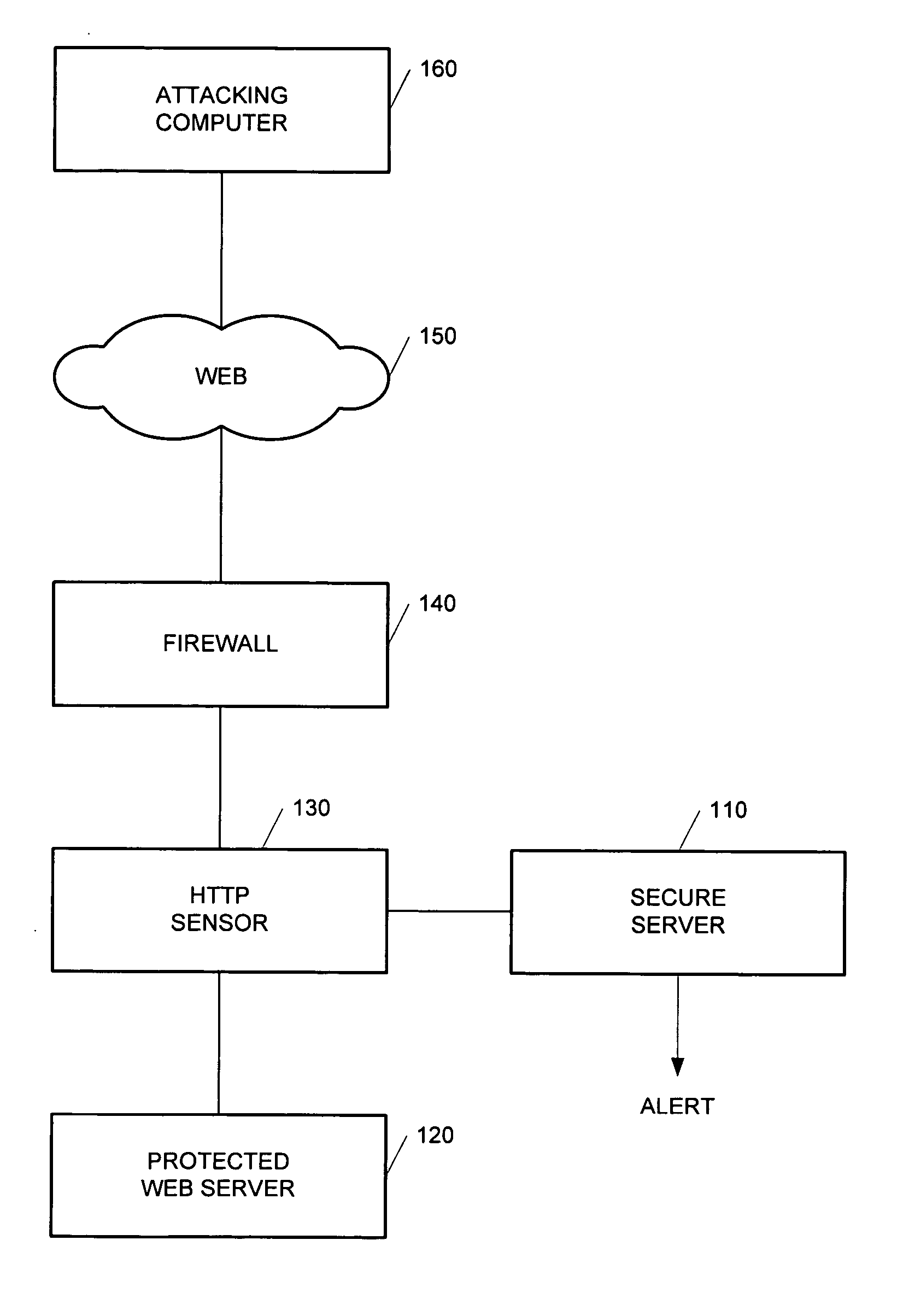
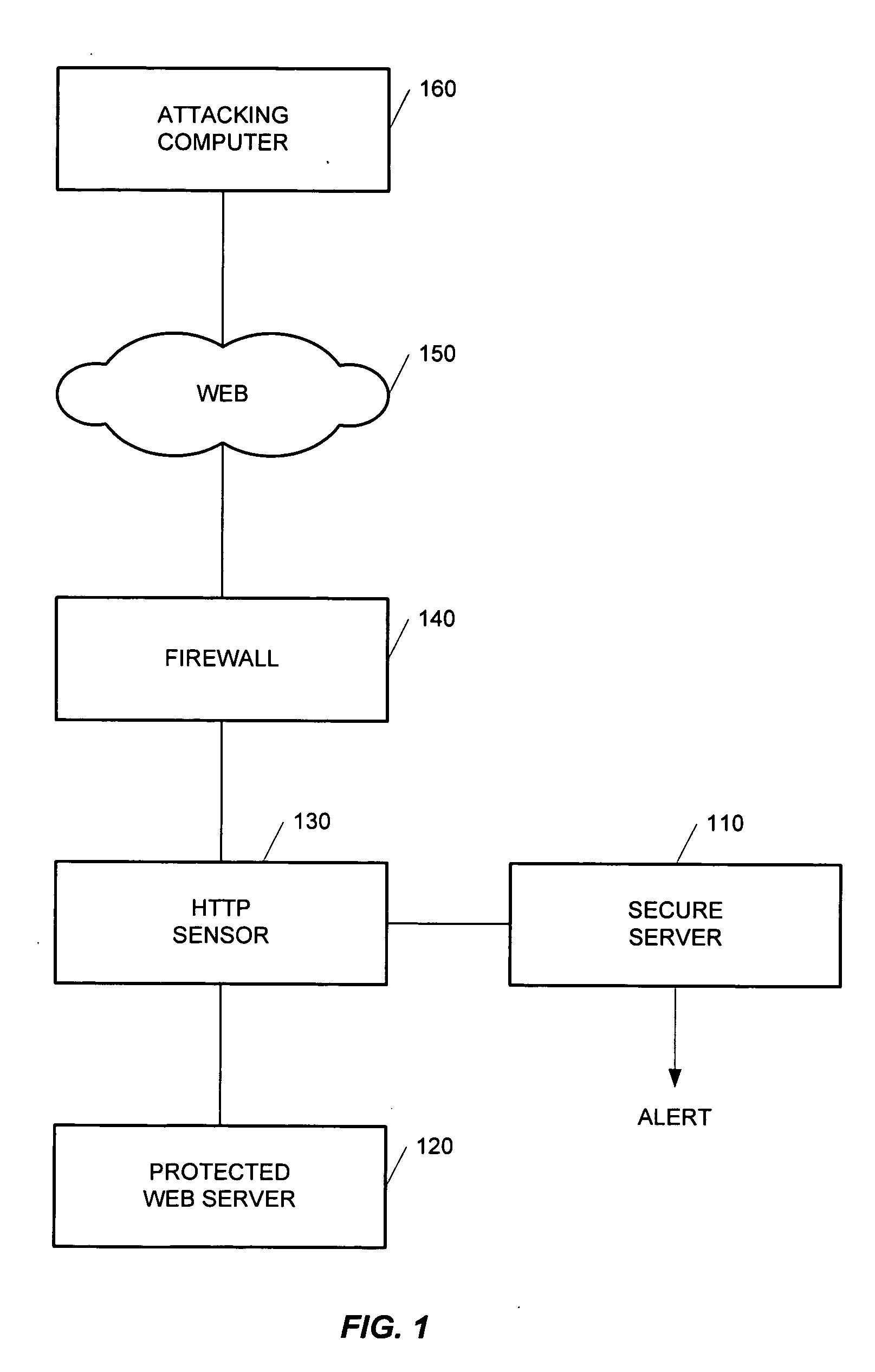
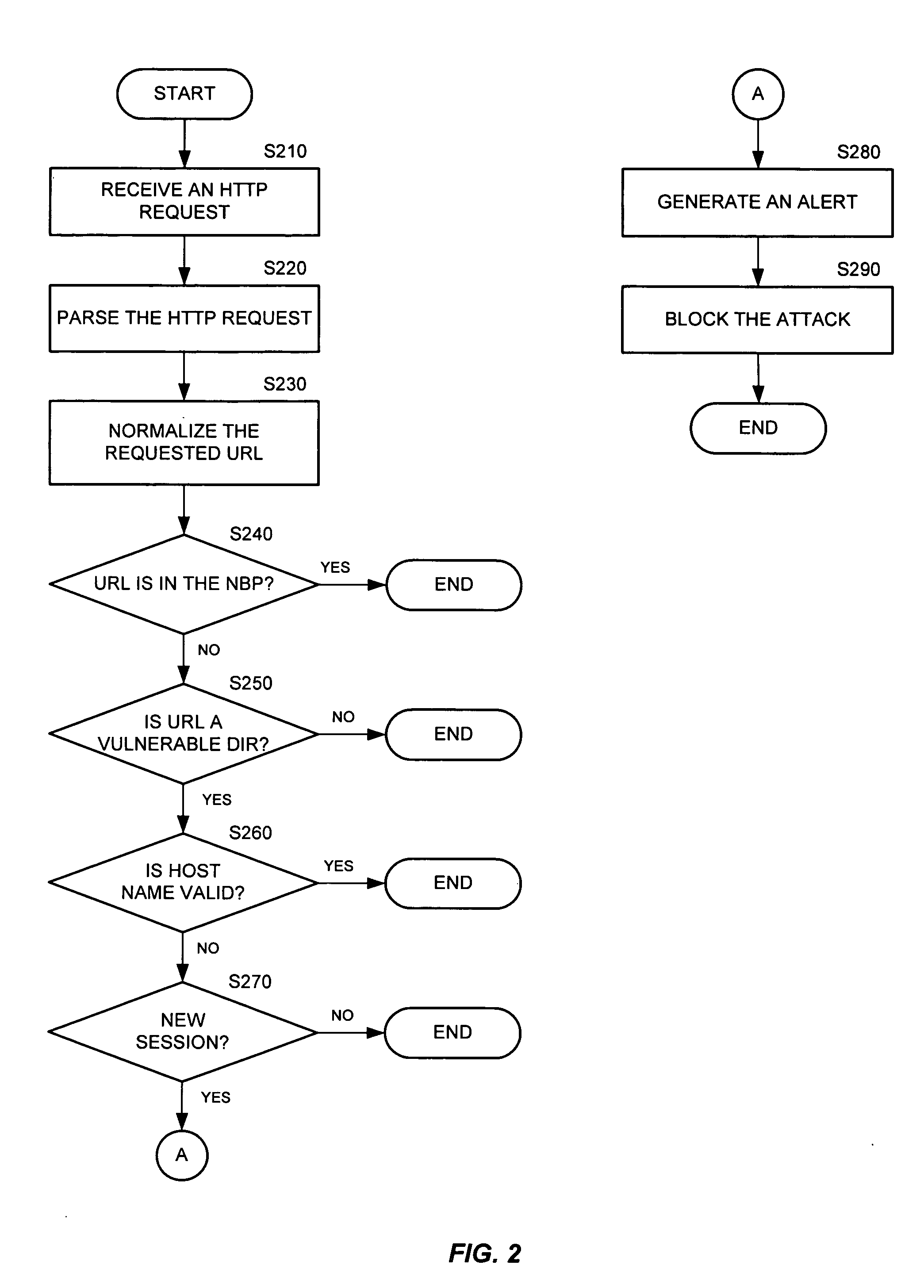
Method and apparatus for high-speed detection and blocking of zero day worm attacks
ActiveUS20050188215A1Memory loss protectionUser identity/authority verificationWeb applicationNetwork packet
A method for detection and blocking of zero day worm attacks is disclosed. A zero day worm attack is the initial appearance of a new or revised Web worm. The method compares a hypertext transfer protocol (HTTP) request sent from an attacking computer (or server) to a predefined behavior profile of a protected Web application in order to detect a worm attack. A zero day worm attack based on the first data packet of an HTTP request can be detected.
Owner:IMPERVA
Open flow table security enhancement method and device
ActiveCN103095701AEasy to carry outProtect against zero-day attacksTransmissionVirtualizationPrivate network
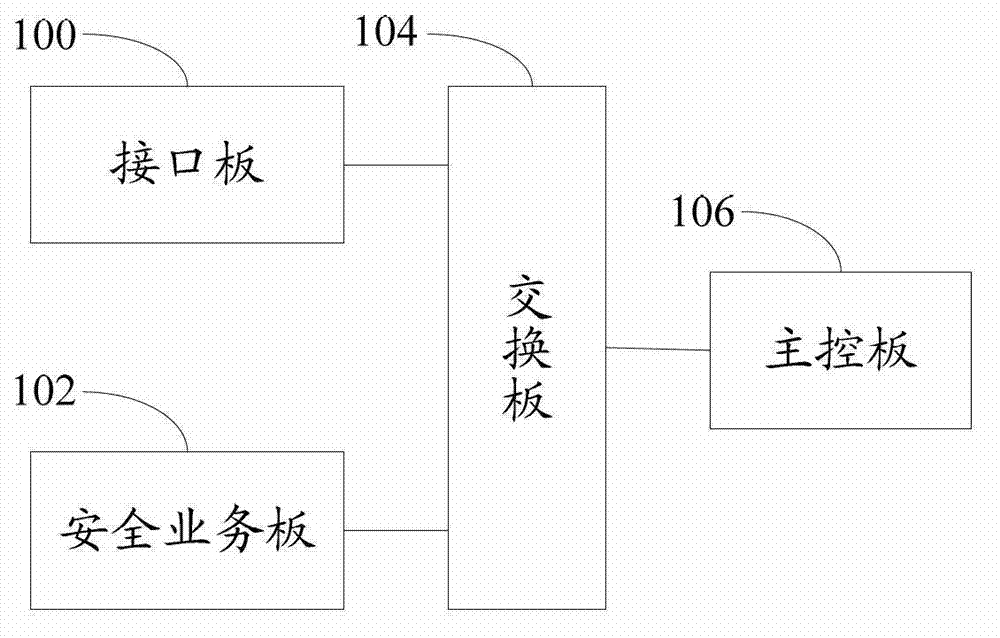
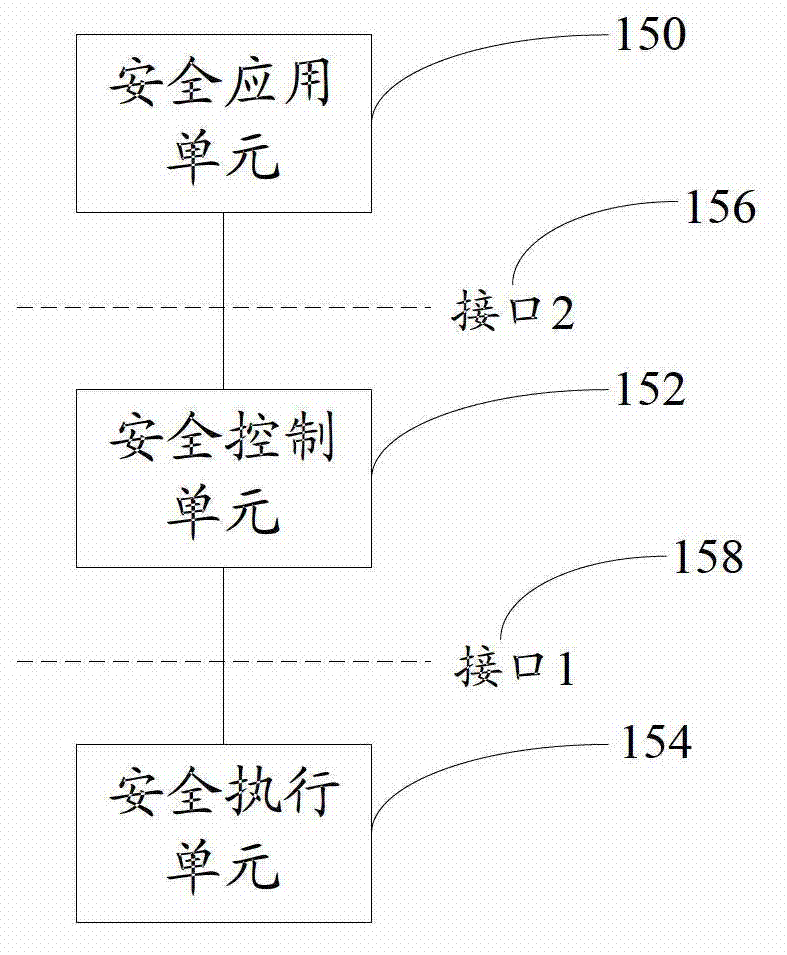
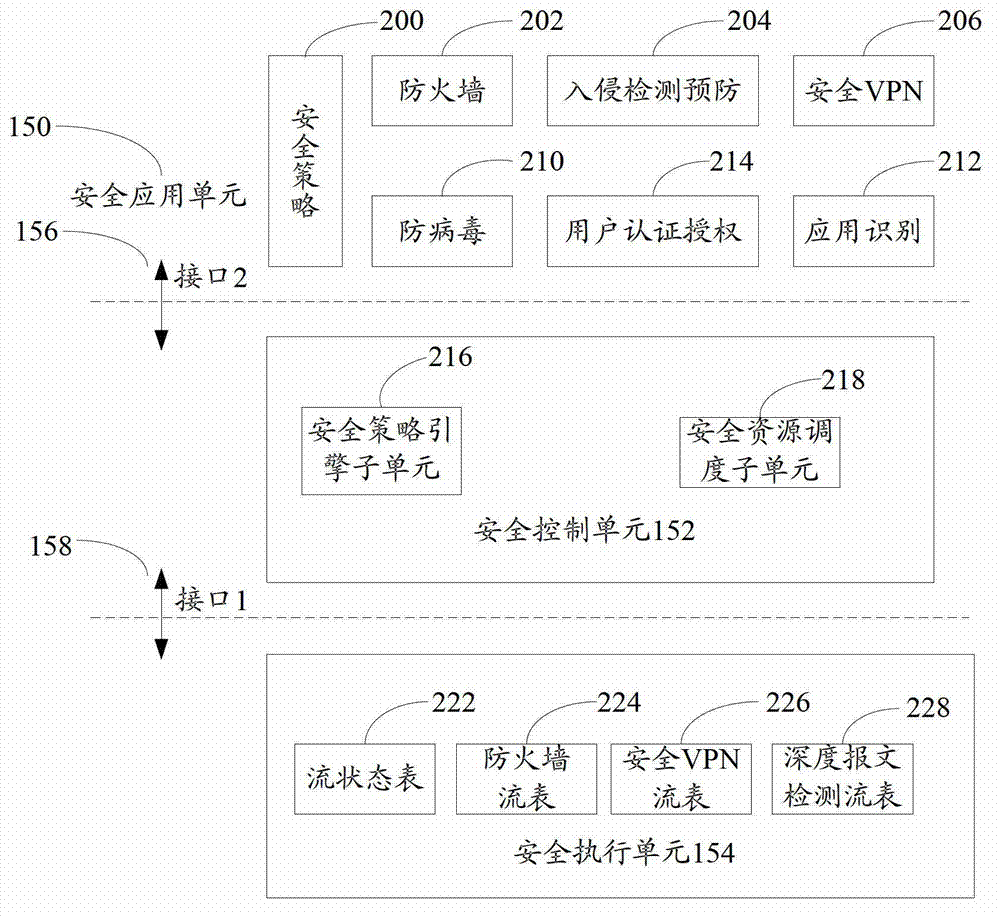
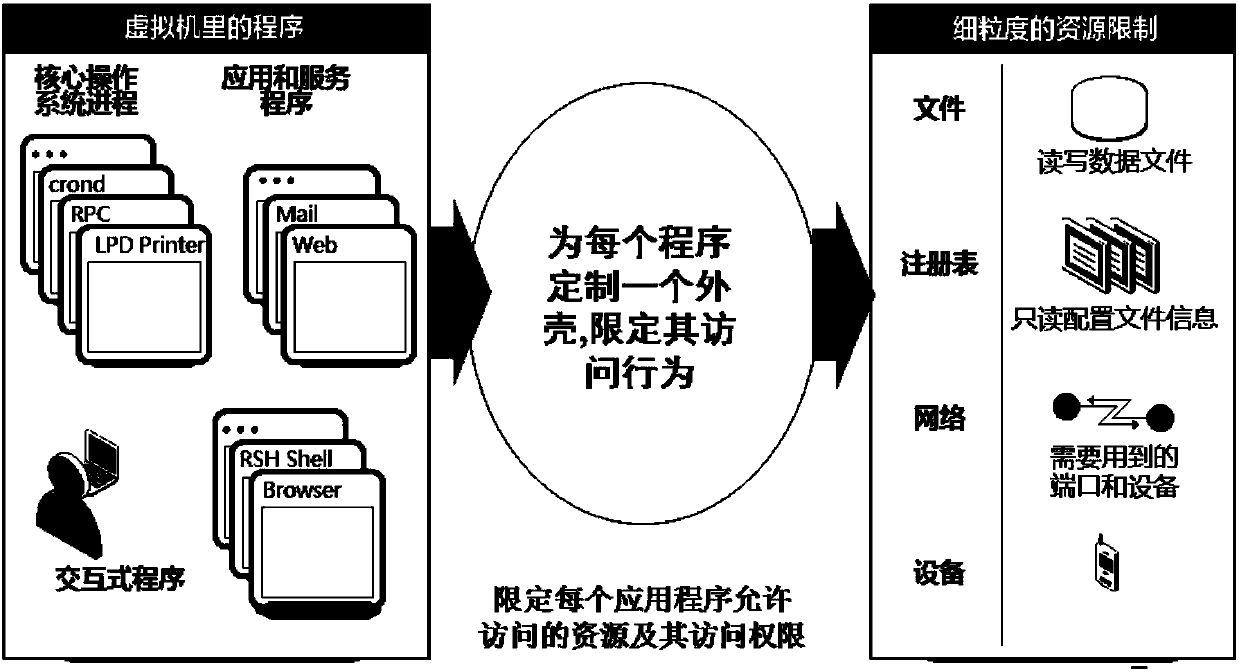
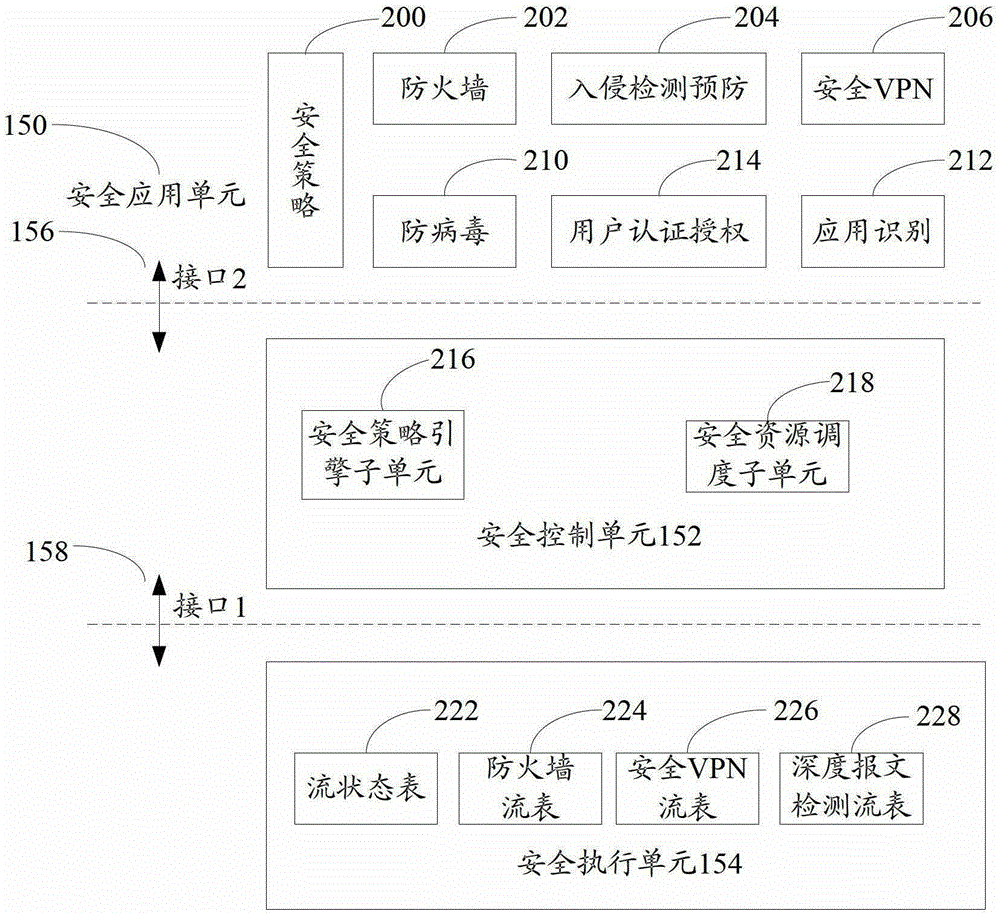
The invention discloses an open flow table security enhancement method which can enable a security control function to be separated from a security executive function. The method includes the steps of obtaining security application corresponding to each security service, extracting security strategies, security protocols and feature libraries corresponding to the various security services from the security application, analyzing the security strategies of the security services to generate a security flow table, and creating a matching rule in the security flow table, and carrying out access control to messages and inspection for a state firewall, a security virtual private network (VPN) and deep messages according to the matching rule in the security flow table. The invention simultaneously discloses an open flow table security enhancement device. The open flow table security enhancement method and the open flow table security enhancement device can enable the security execution and the security application to be independently evolved and upgraded, and bring convenience to development of new security services, and can intensively carry out security management, resist zero-day attack, and relieve distributed denial of service attack according to the security strategies, and also support a virtualization multi-tenant security mode.
Owner:ZTE CORP
White list based realization method for active defense of cloud host
ActiveCN105138901APrecise managementStop runningPlatform integrity maintainanceMalwareZero-day attack
The invention discloses a white list based realization method for active defense of a cloud host. The method involves a centralized management platform of a server and a client, and the client is mounted on each cloud host needed to be protected. The specific realization process is as follows: all binary files in the protected cloud host are scanned through server software; a cloud security center identifies out trust ratings of the scanned files and adds a graded file list library into a white list library, a black list library and a gray list library separately; and at the client, only trusted application programs in a white list are allowed to run for preventing loading of a dynamic-link library file in a kernel. Compared with the prior art, the white list based realization method for active defense of the cloud host can completely prevent potential unwanted application programs and codes and prevent advanced threats, is free of feature code update, and can consistently enable known good software, prevent known or unknown bad software, correctly manage new software and effectively prevent unknown malicious software and zero-day attacks.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
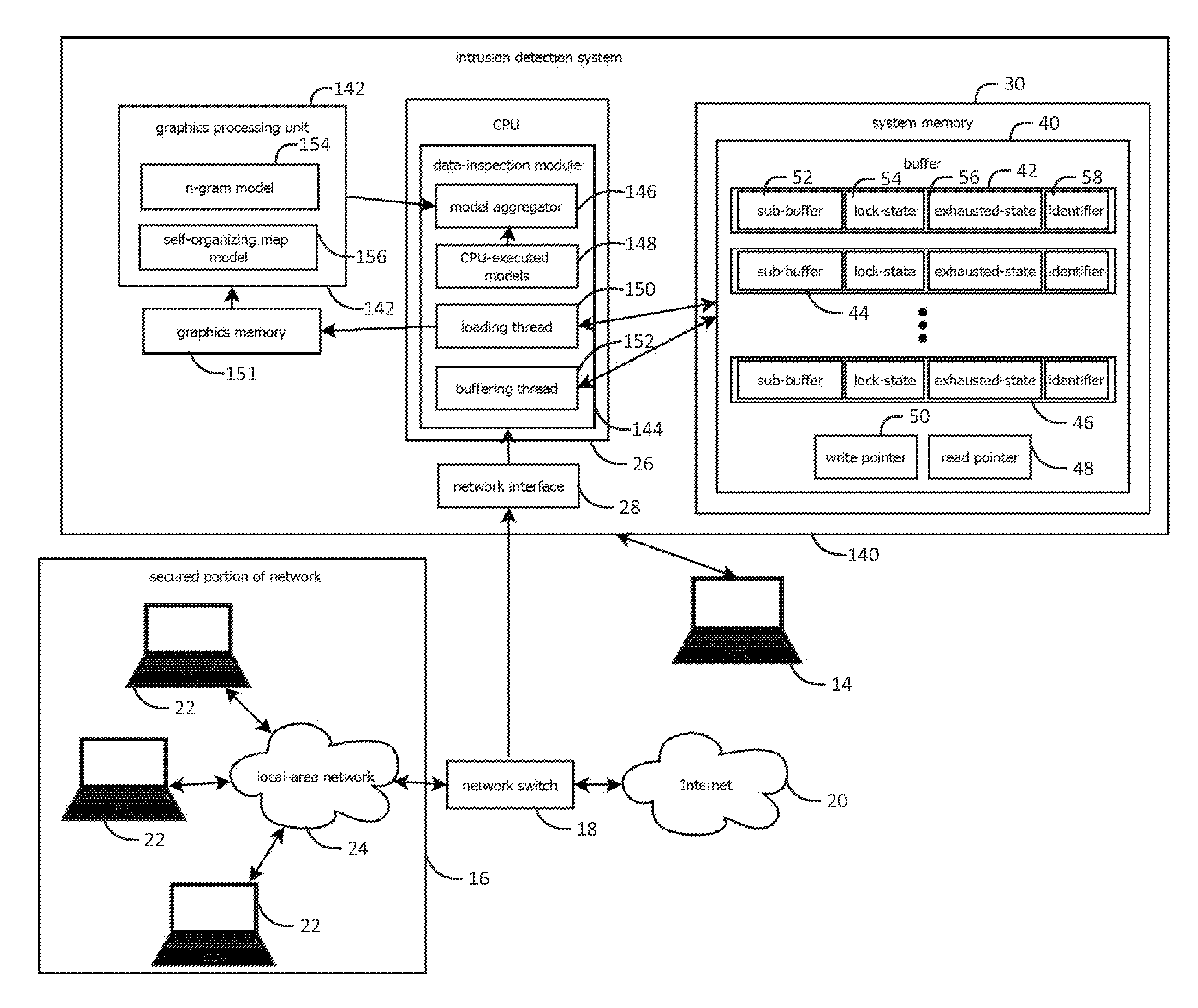
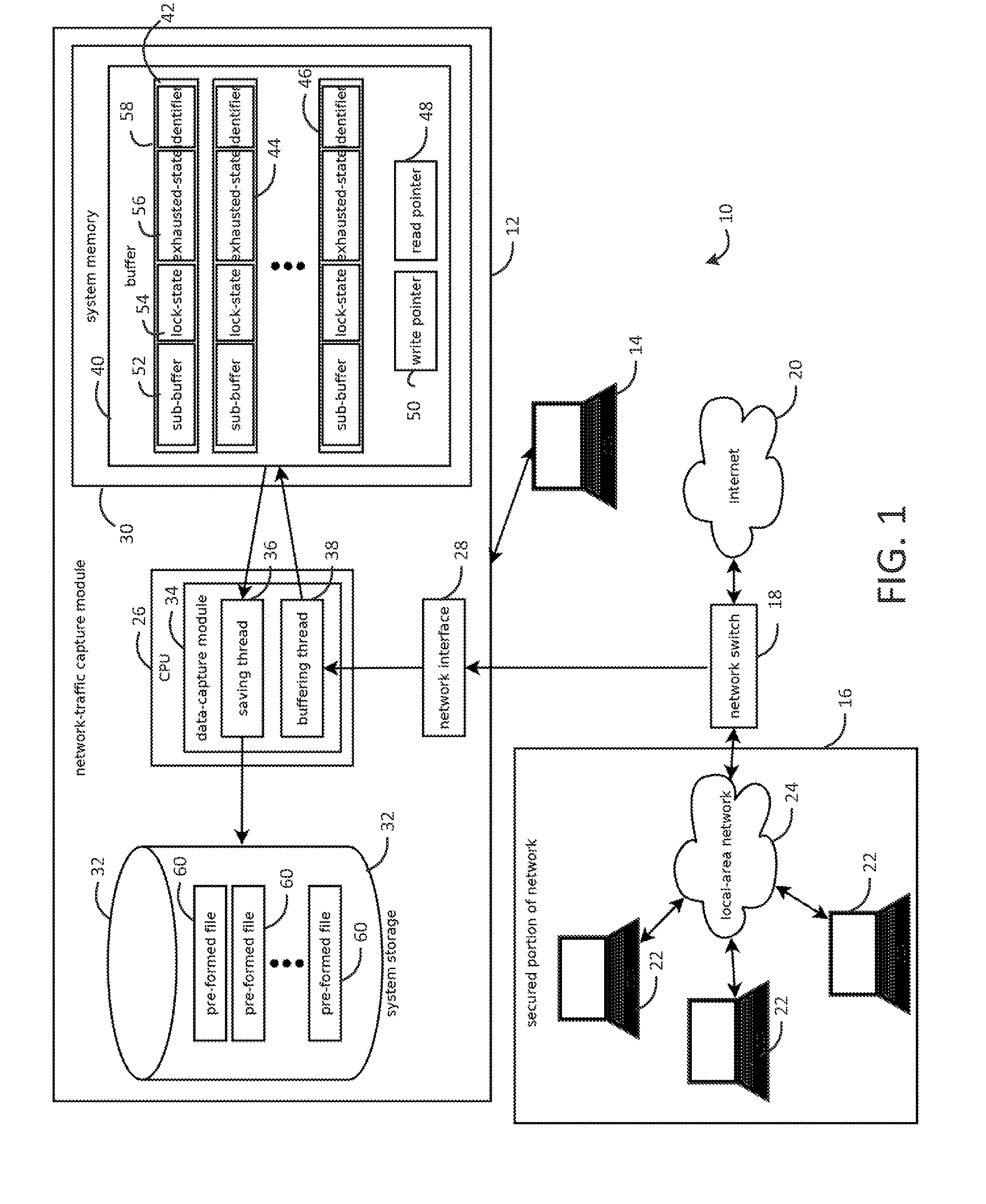
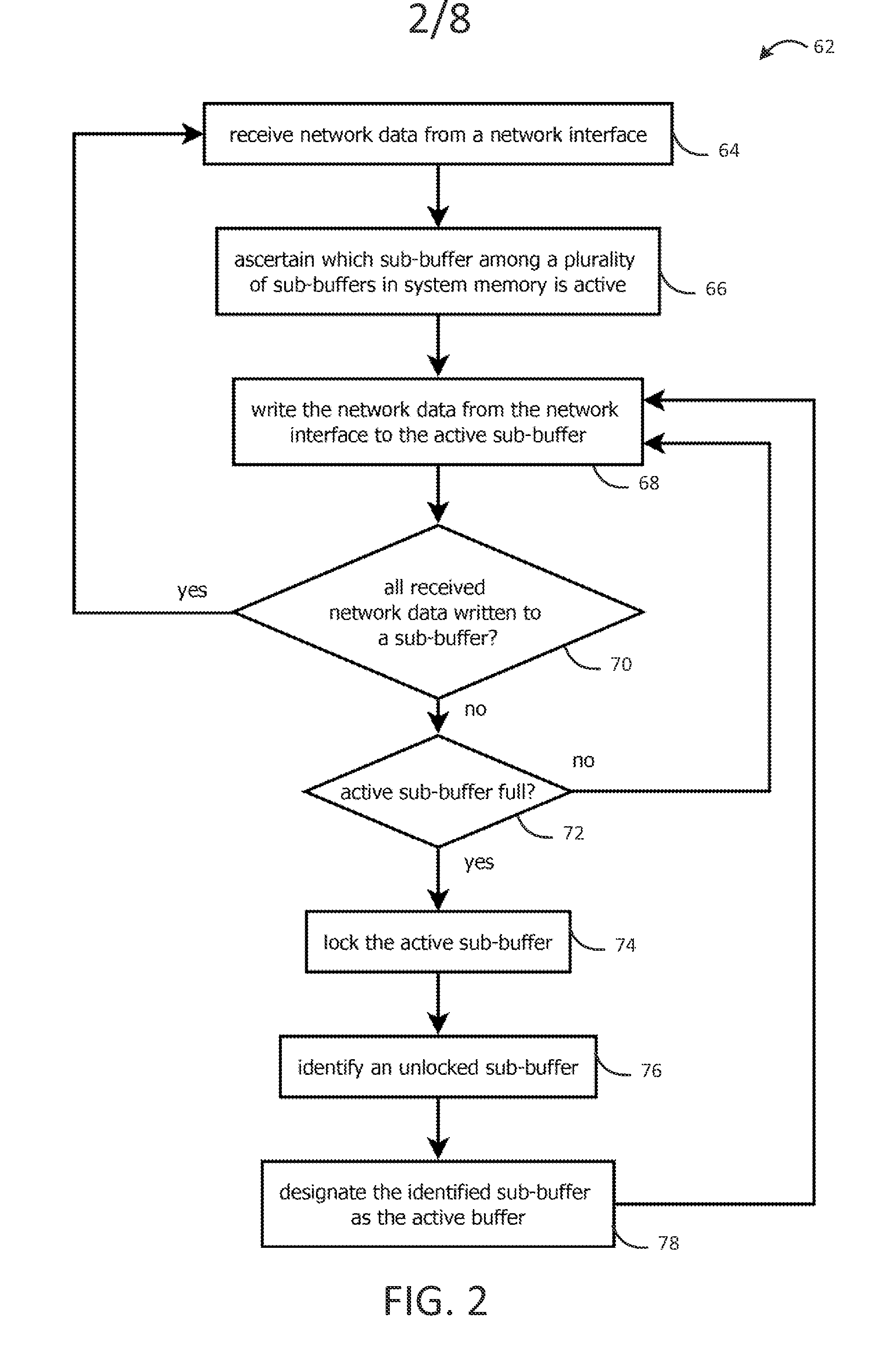
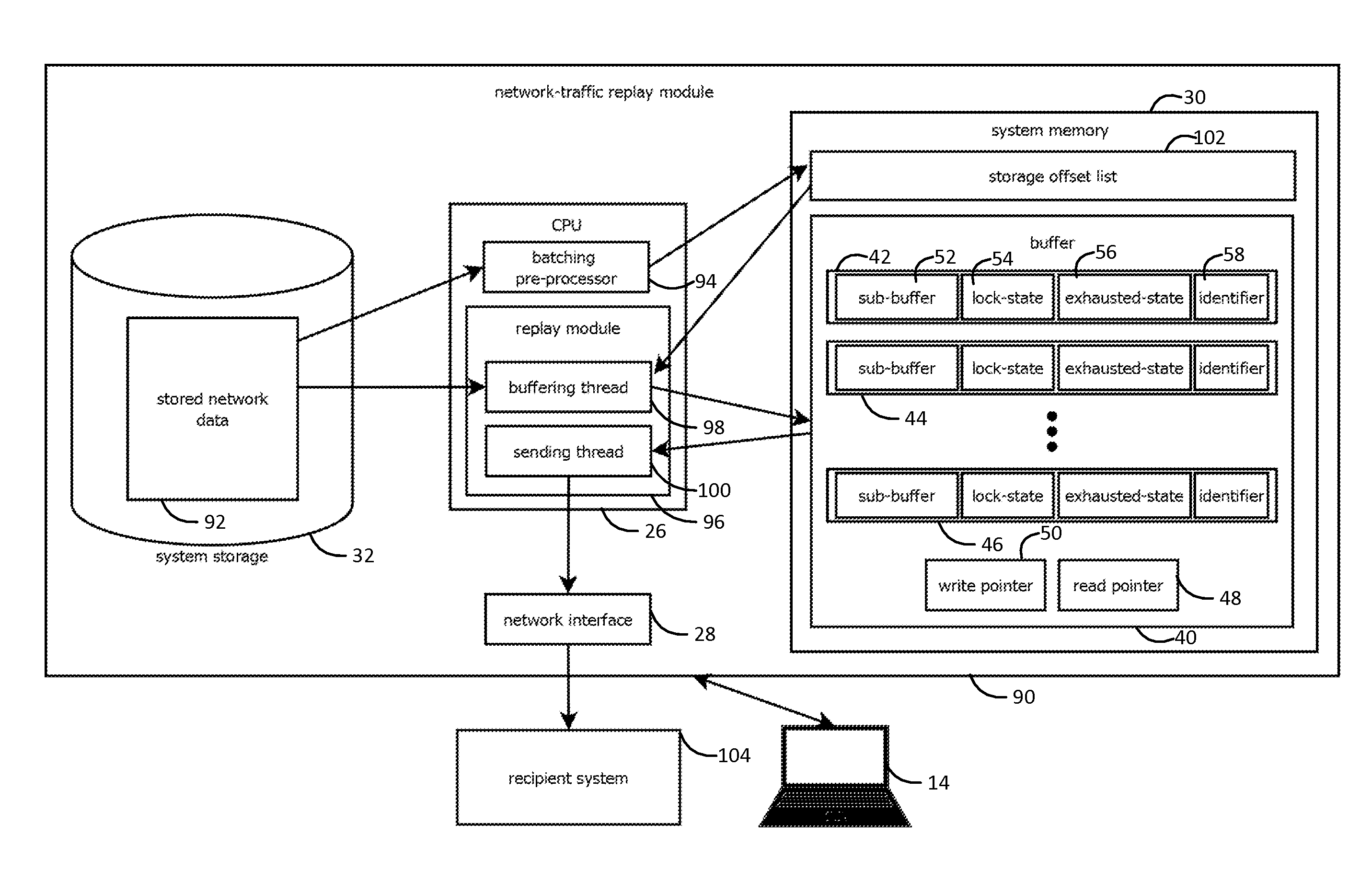
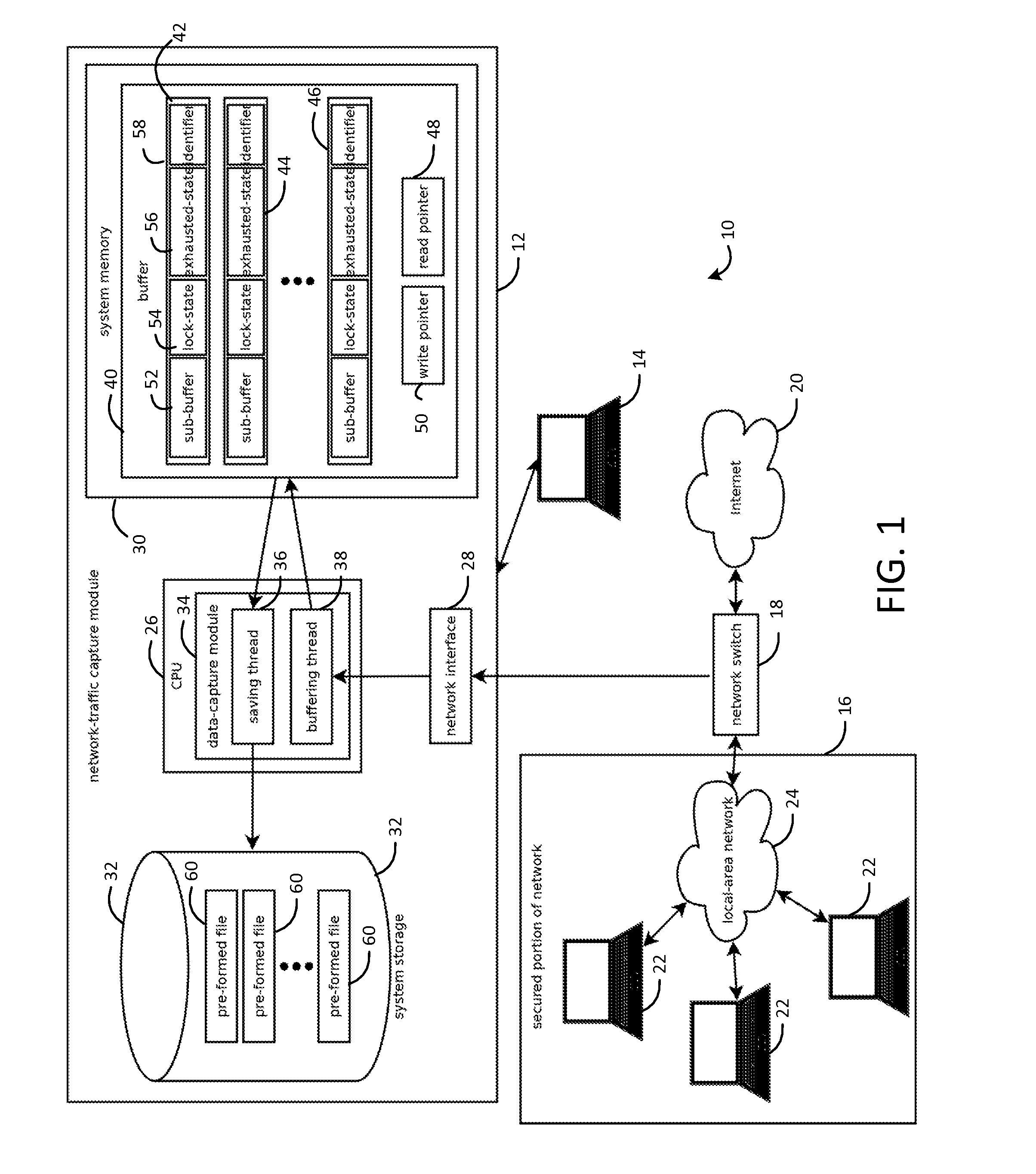
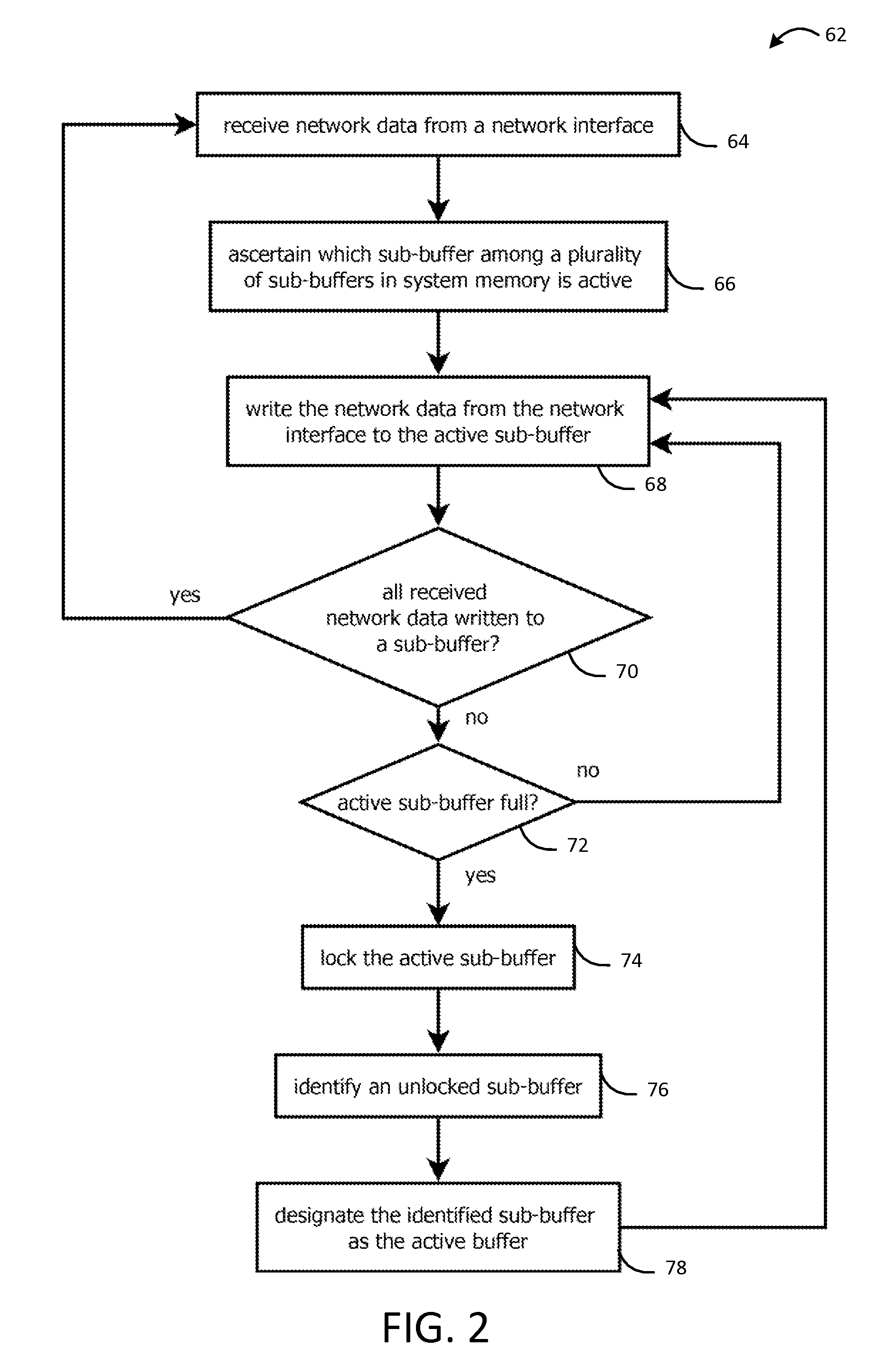
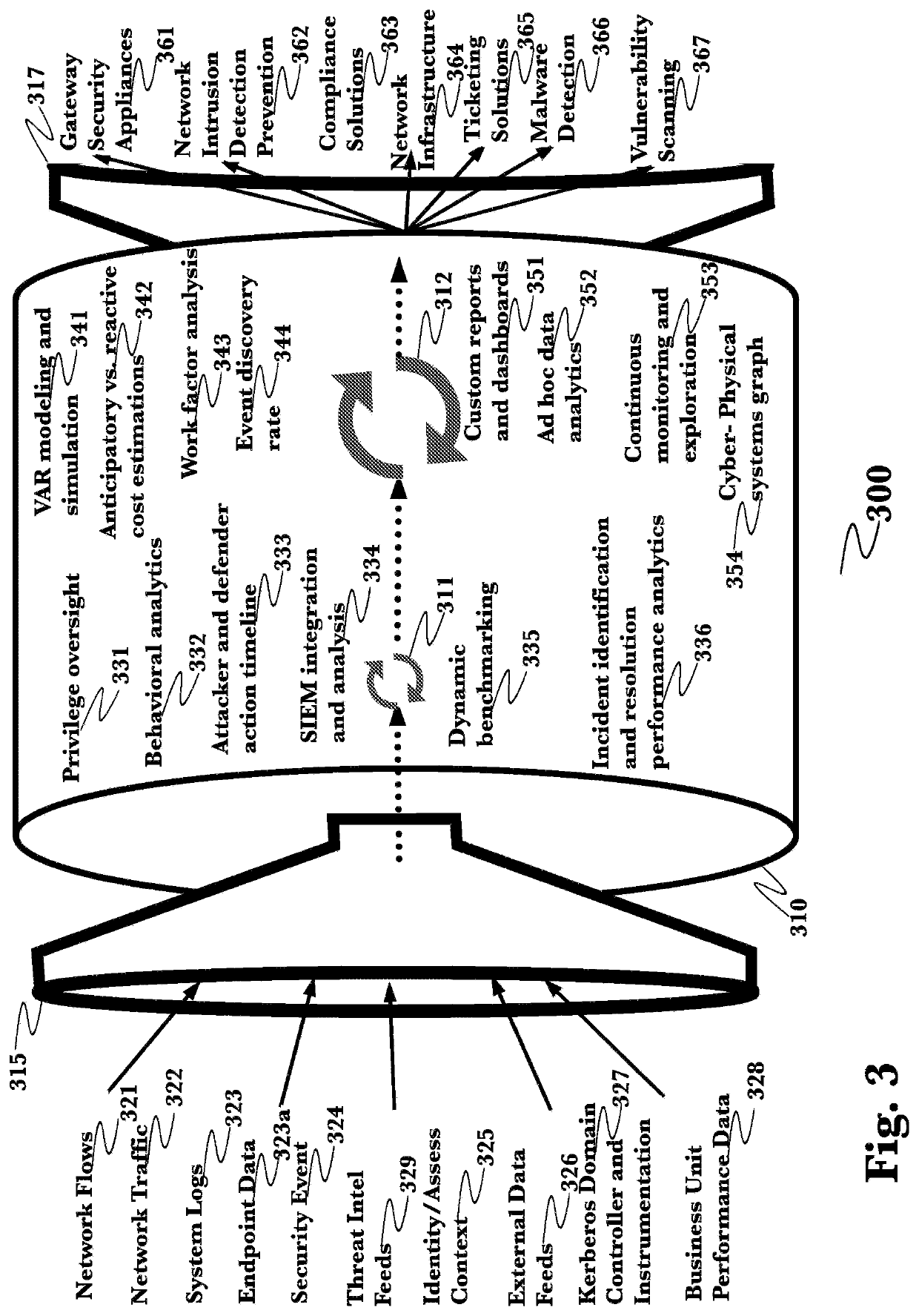
Systems and methods for capturing, replaying, or analyzing time-series data
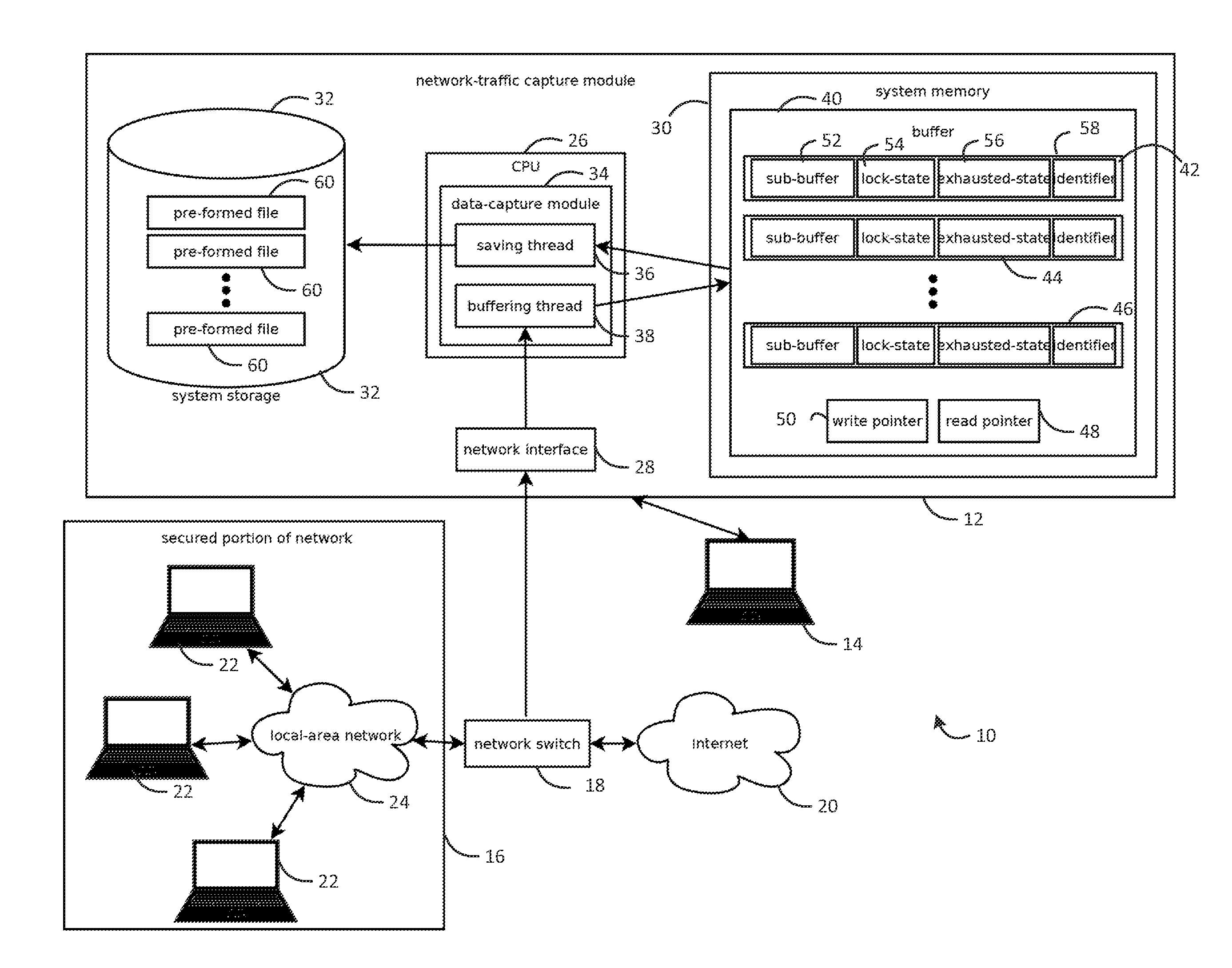
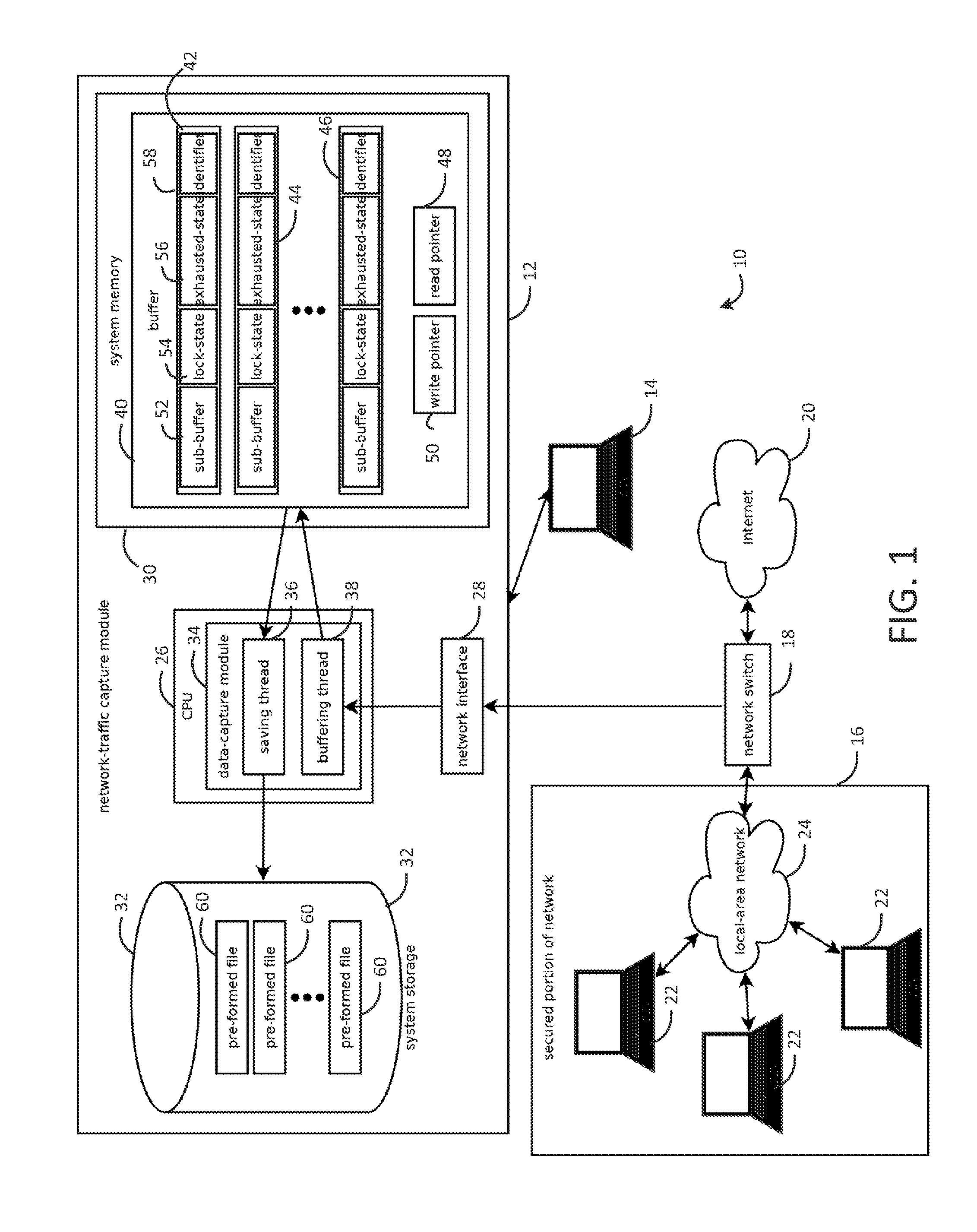
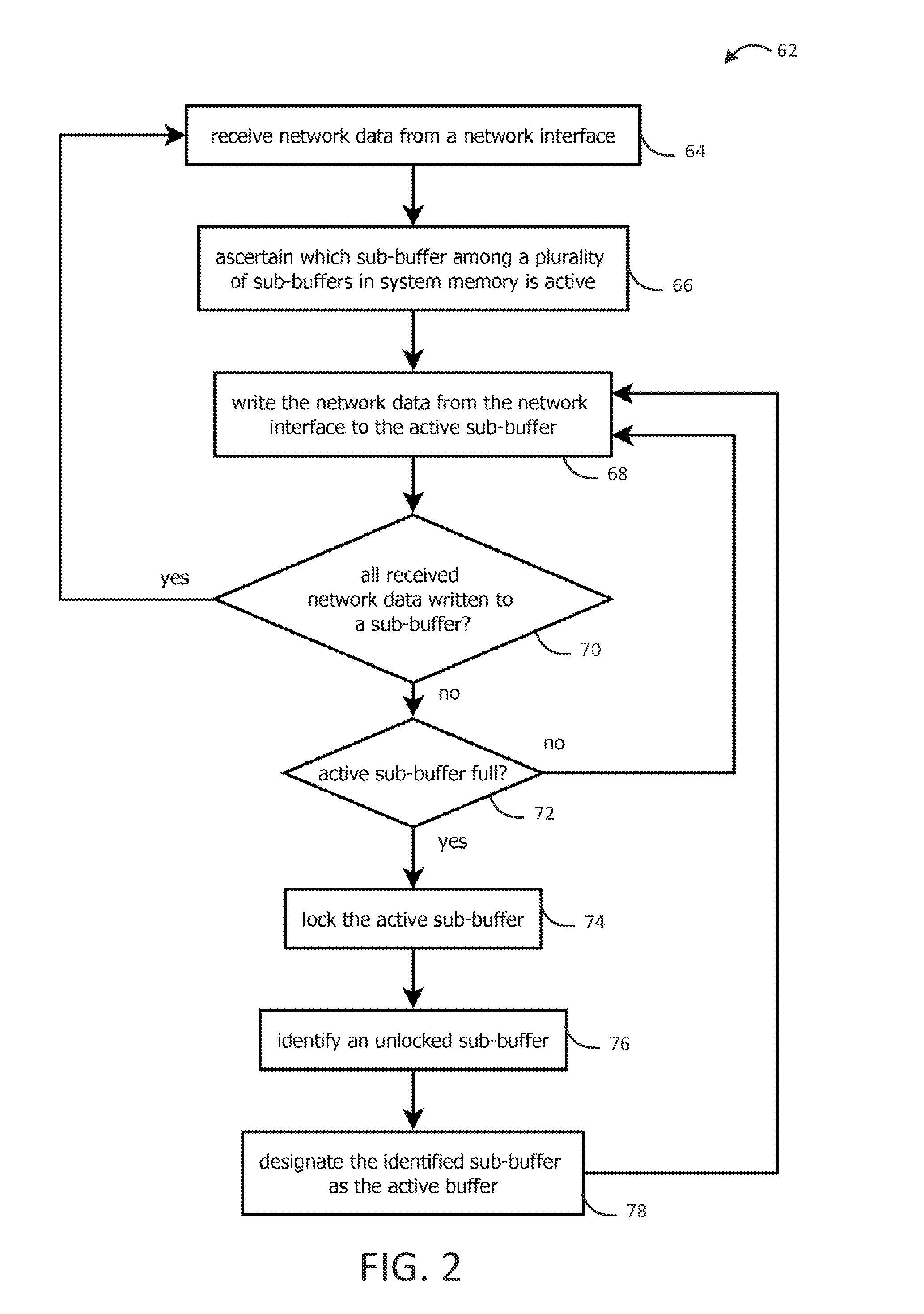
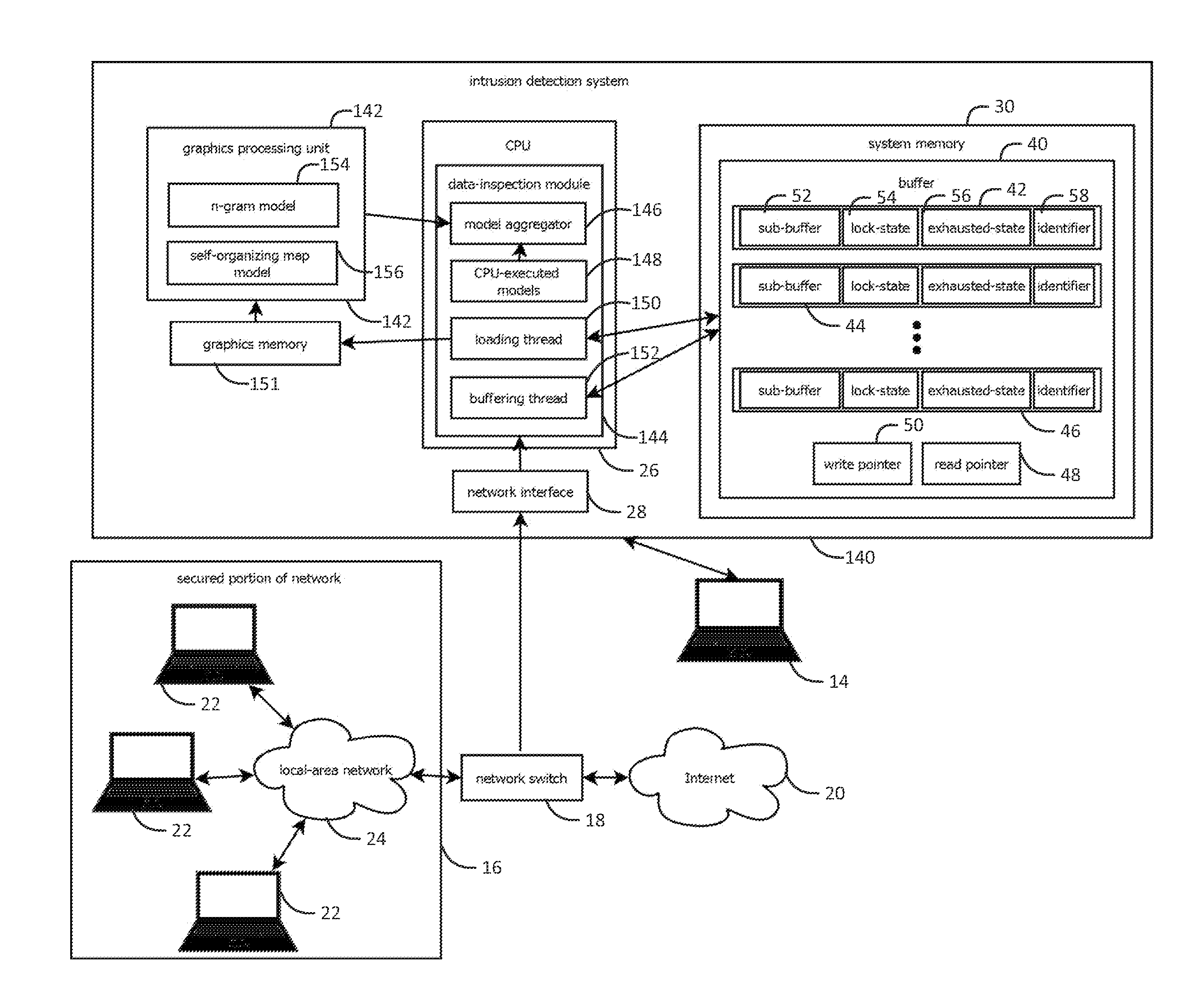
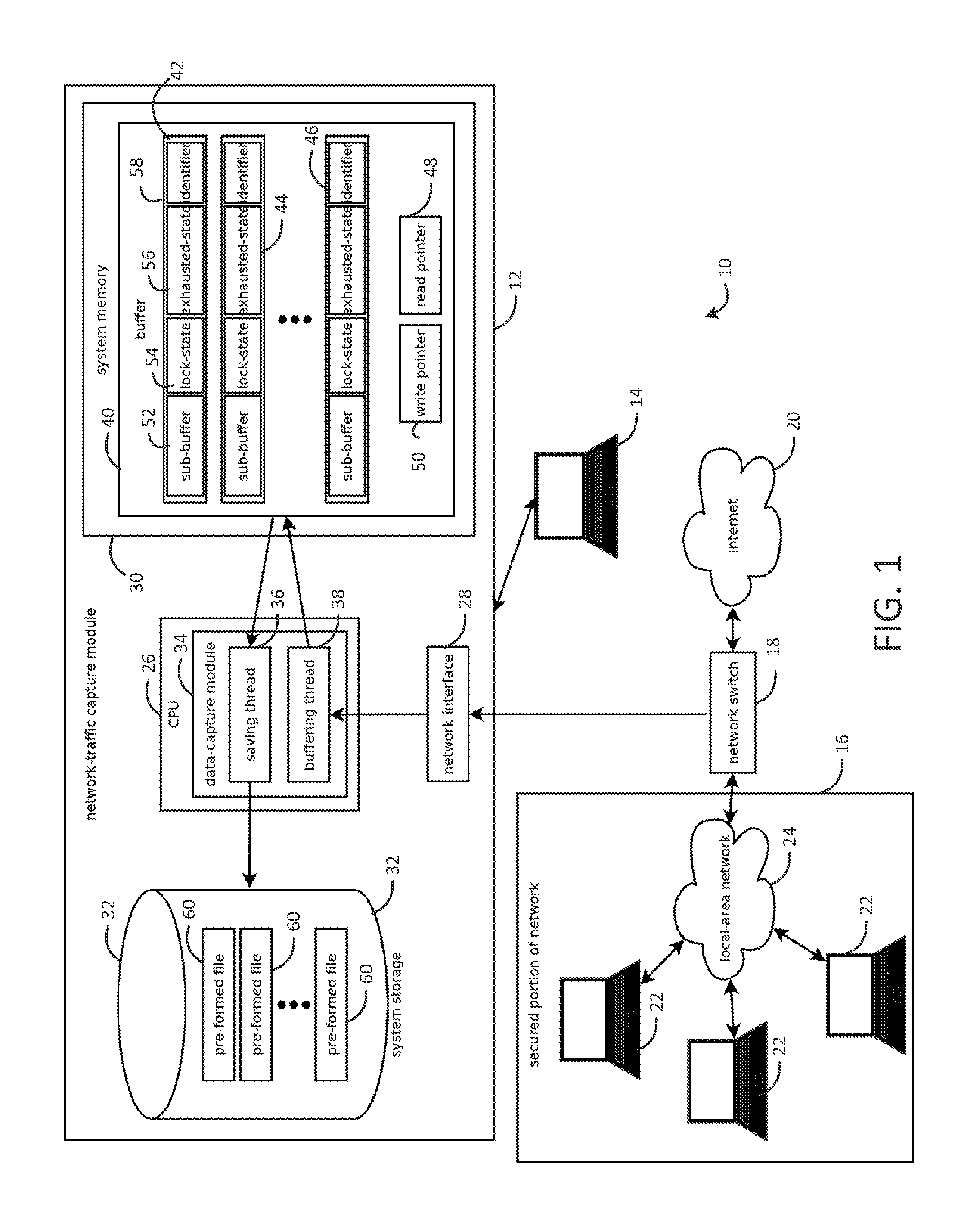
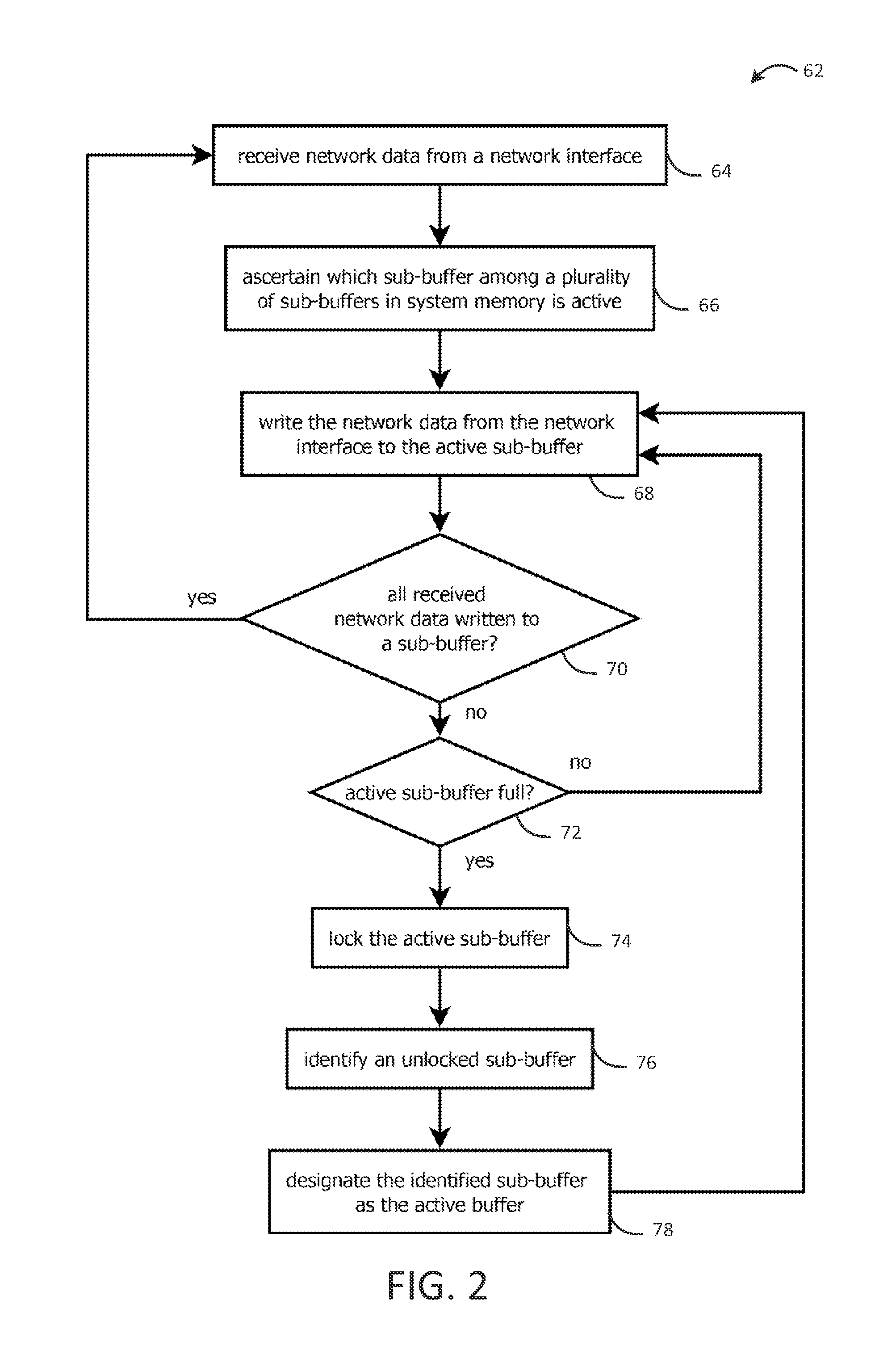
Provided is an intrusion detection system configured to detect anomalies indicative of a zero-day attack by statistically analyzing substantially all traffic on a network in real-time. The intrusion detection system, in some aspects, includes a network interface; one or more processors communicatively coupled to the network interface; system memory communicatively coupled to the processors. The system memory, in some aspects, stores instructions that when executed by the processors cause the processors to perform steps including: buffering network data from the network interface in the system memory; retrieving the network data buffered in the system memory; applying each of a plurality of statistical or machine-learning intrusion-detection models to the retrieved network data; aggregating intrusion-likelihood scores from each of the intrusion-detection models in an aggregate score, and upon the aggregate score exceeding a threshold, outputting an alert.
Owner:VECTRA NETWORKS
Method and system for data breach and malware detection
Detecting cyber threat and malware, particularly zero-day malware is a major challenge for the security community. Signature-based methods of cyber threat and malware detection are unable to detect zero-day malware. In order to detect zero-day malware and cyber threat which may have more severe impacts, a system called Compromised Detection System (CDS) and a method thereof is disclosed. The CDS uses a sophisticated approach and method based on Machine Learning to detect anomalies on the network behaviour. By such approach, CDS is able to detect unknown cyber threat and malware (aka zero day)since they will present a deviation from the normal behaviour in the network.
Owner:EFFICIENT PROTECTIONS INC
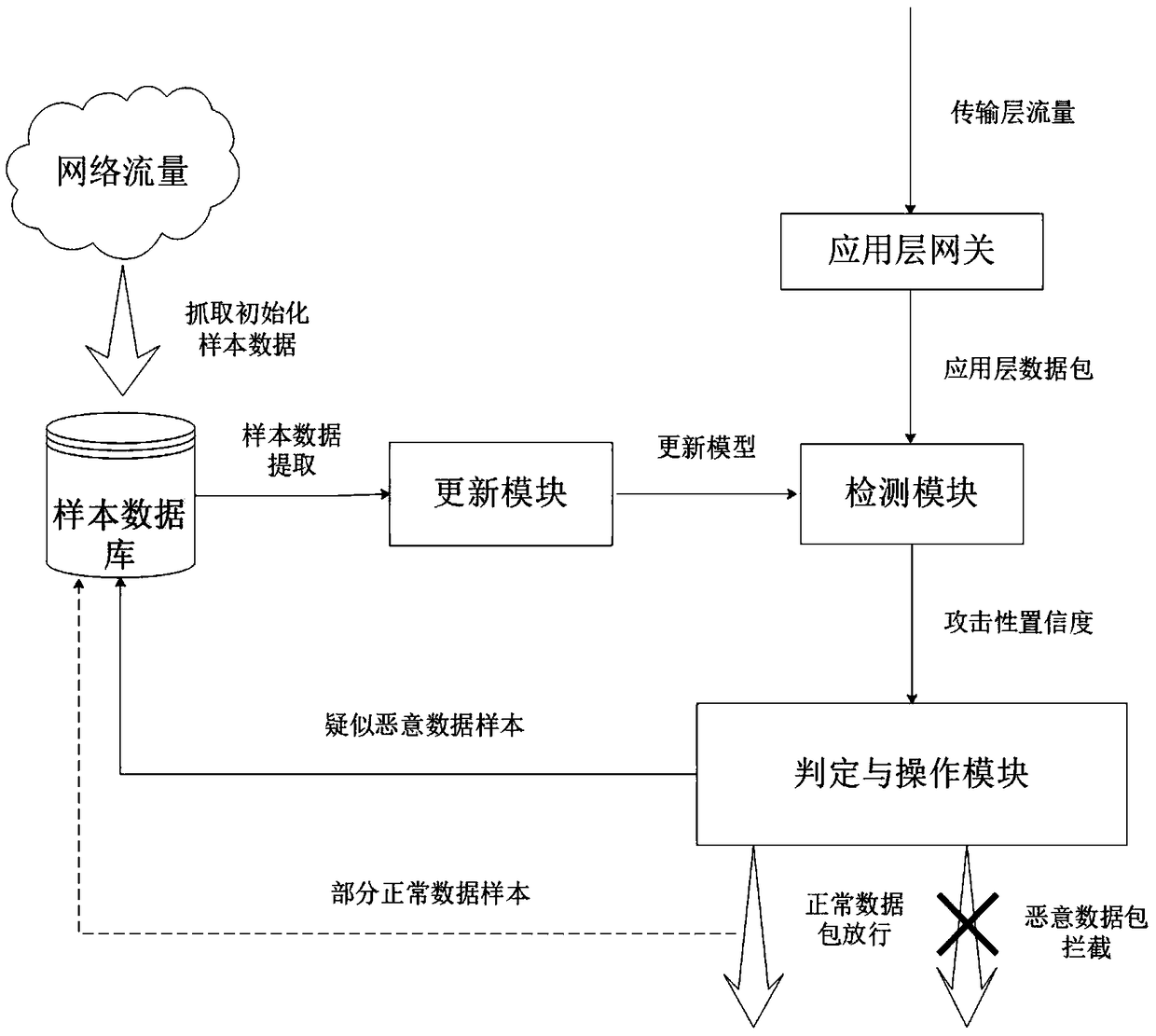
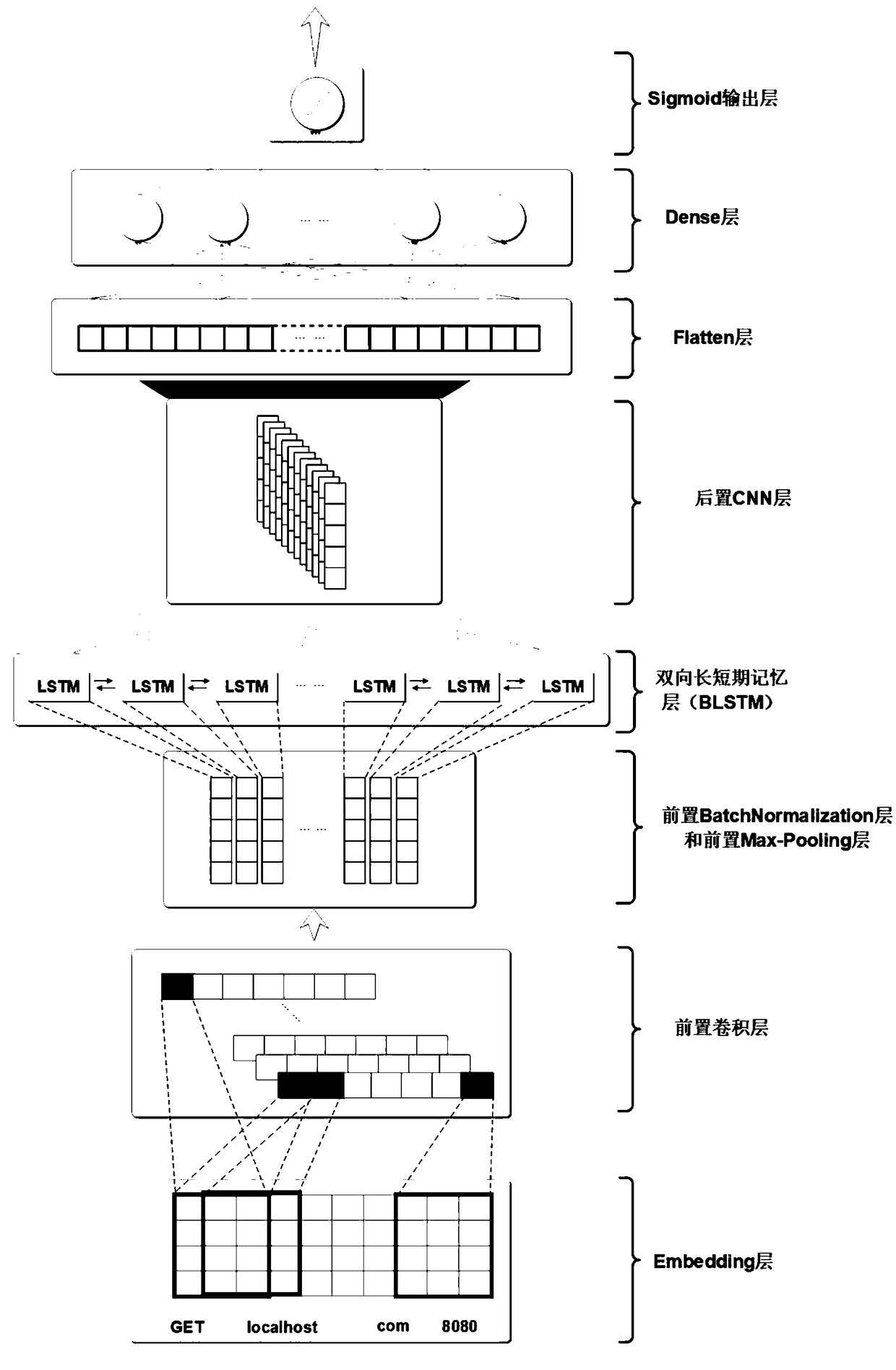
Application layer dynamic intrusion detection system and detection method based on artificial intelligence
ActiveCN108898015AImprove detection accuracyFast convergencePlatform integrity maintainanceNeural architecturesApplications of artificial intelligenceShort-term memory
The invention discloses an application layer dynamic intrusion detection system and detection method based on artificial intelligence, wherein the detection system comprises an application layer gateway, a detection module, a judgment and operation module, a sample database and an updating module, the detection module comprises a detection model mixed with a convolutional neural network and a bidirectional long and short term memory neural network. The detection module after initialization is used for making an attack judgment on an application layer data packet, filtering the data packet above the threshold value and putting the data packet into a malicious sample database, and meanwhile, the data packet under the threshold value is not processed. The updating module is used for traininga new model by using the malicious samples and normal samples with a certain proportion in the sample database and updating the detection model in the detection module in real time. According to the invention, a universal detection method is used for the attack method of the application layer, the method has the advantages of high detection rate and low misjudgment rate. Meanwhile, the intrusion detection system has the advantage of dynamic updating model, and has good filtering effect on unknown zero-day attack.
Owner:JINAN UNIVERSITY
Systems and methods for capturing or replaying time-series data
Provided is an intrusion detection system configured to detect anomalies indicative of a zero-day attack by statistically analyzing substantially all traffic on a network in real-time. The intrusion detection system, in some aspects, includes a network interface; one or more processors communicatively coupled to the network interface; system memory communicatively coupled to the processors. The system memory, in some aspects, stores instructions that when executed by the processors cause the processors to perform steps including: buffering network data from the network interface in the system memory; retrieving the network data buffered in the system memory; applying each of a plurality of statistical or machine-learning intrusion-detection models to the retrieved network data; aggregating intrusion-likelihood scores from each of the intrusion-detection models in an aggregate score, and upon the aggregate score exceeding a threshold, outputting an alert.
Owner:VECTRA NETWORKS
System and method for prevention of malware attacks on data
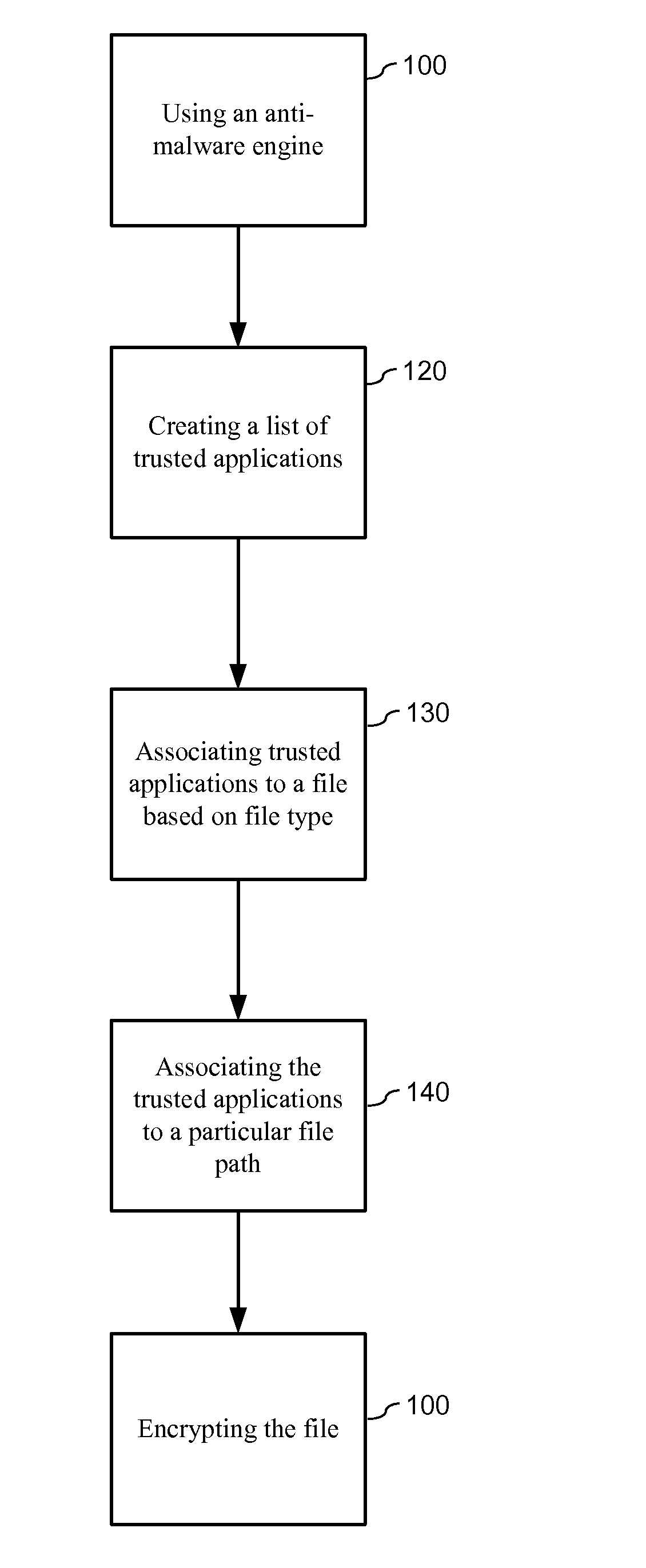
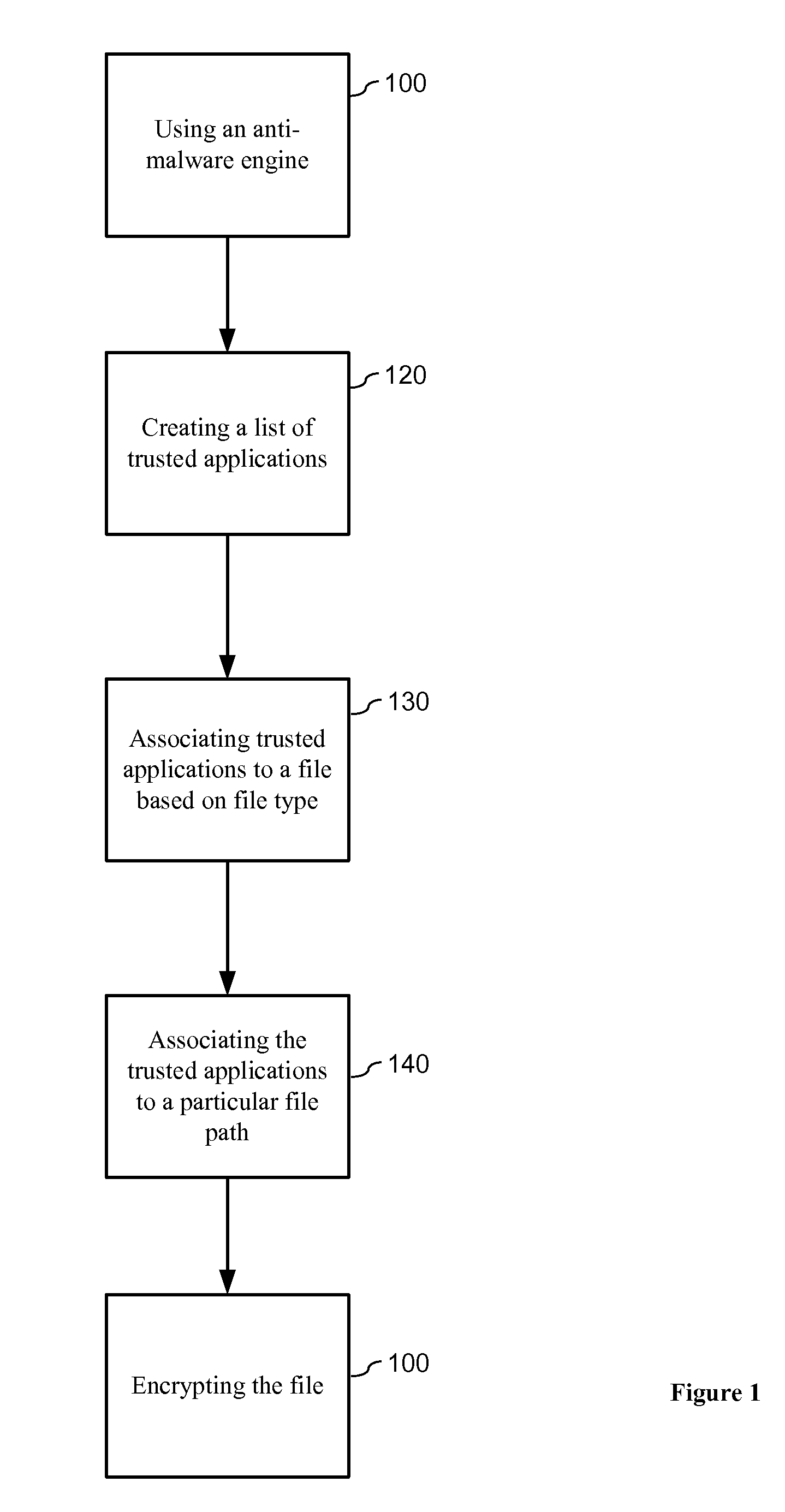
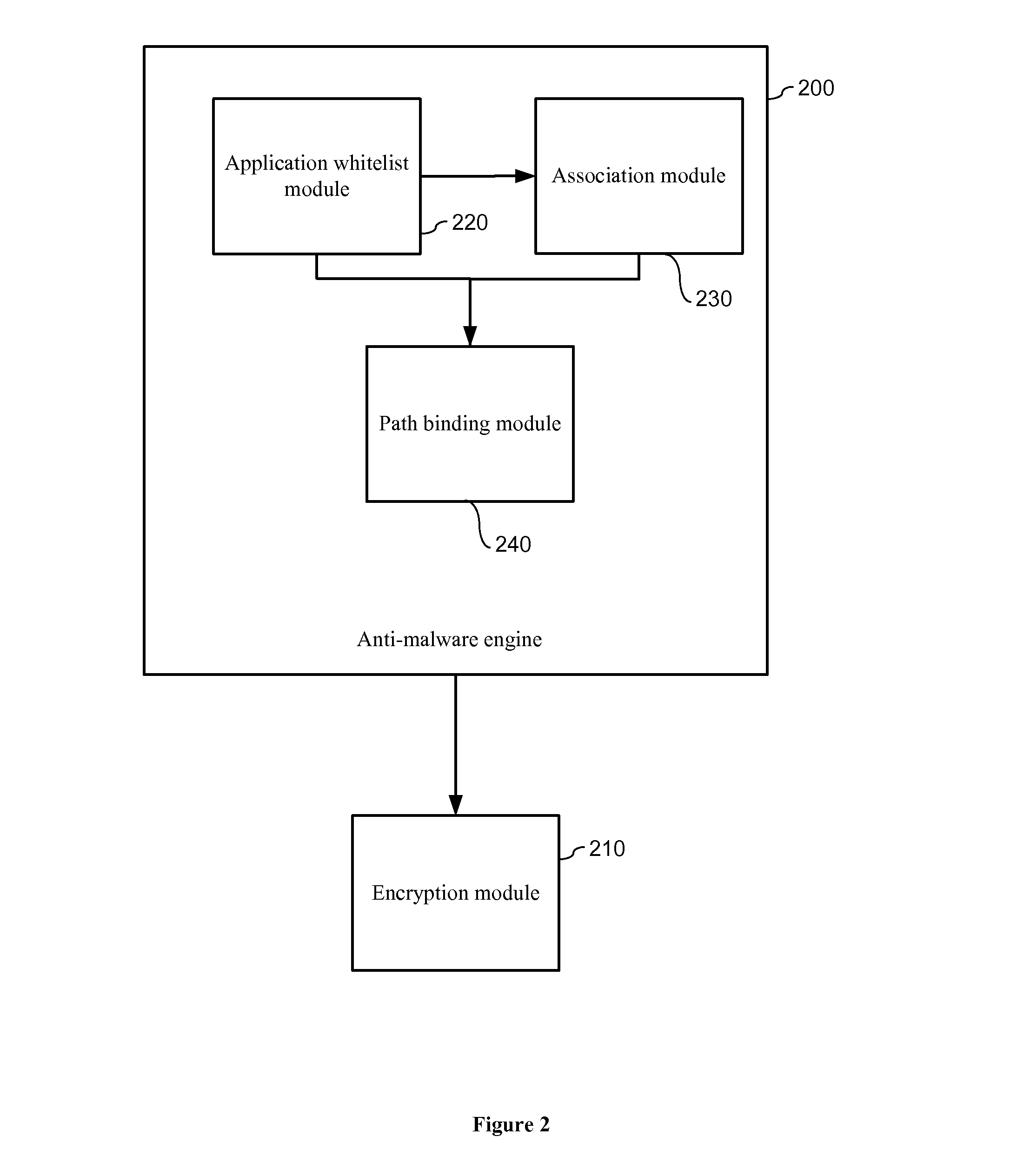
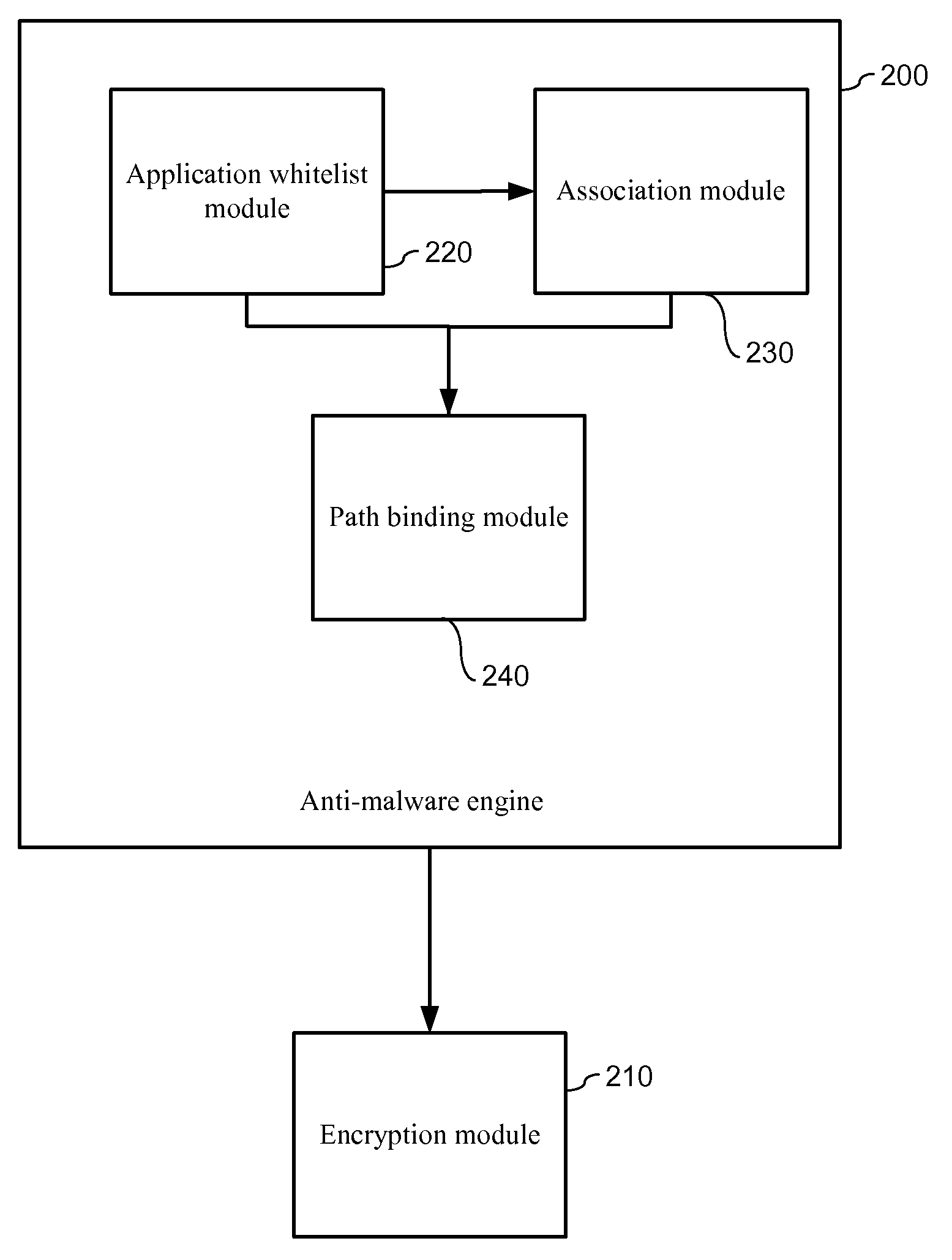
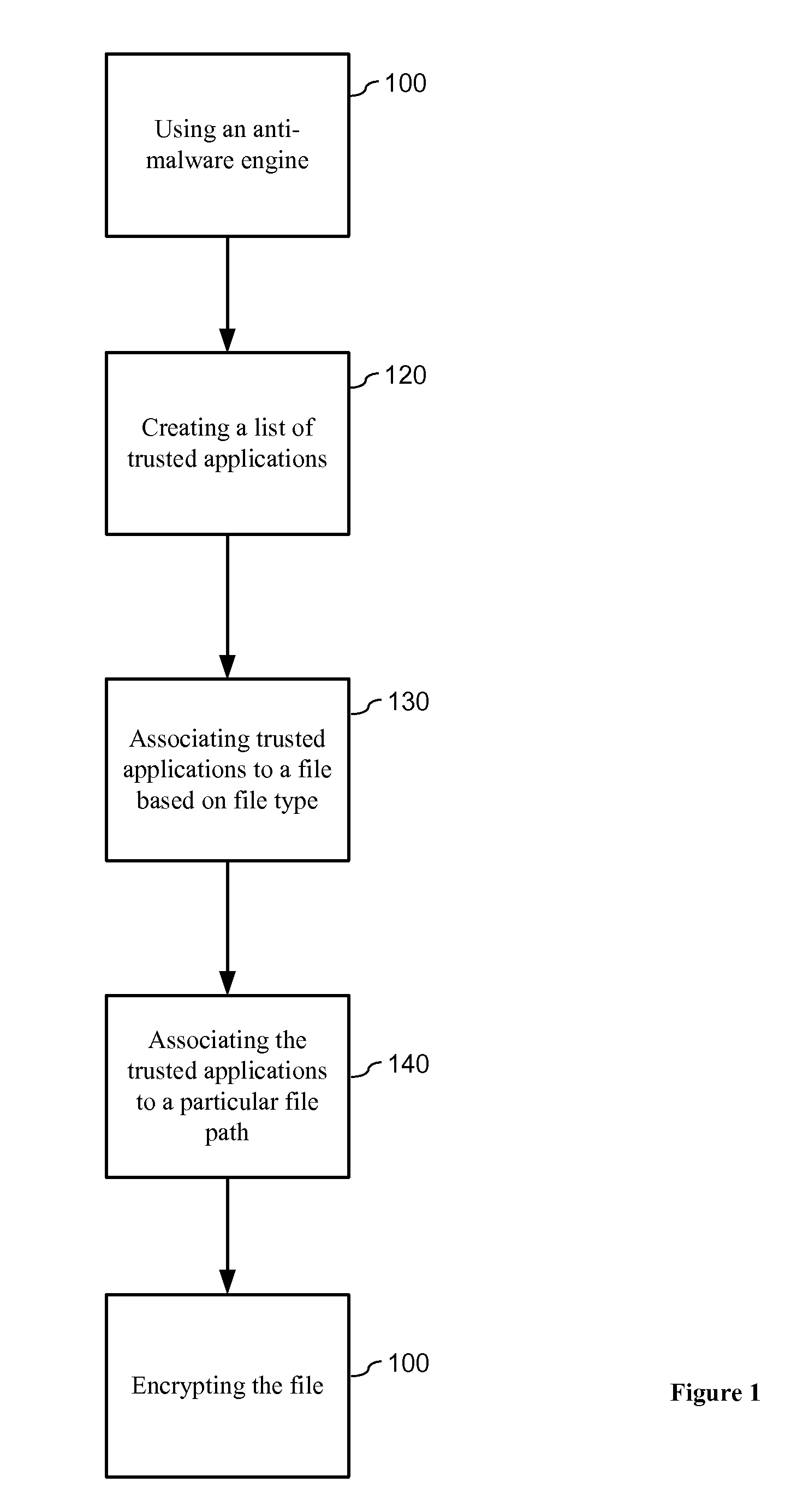
ActiveUS20140007228A1Protection attackImprove protectionMemory loss protectionError detection/correctionData fileZero-day attack
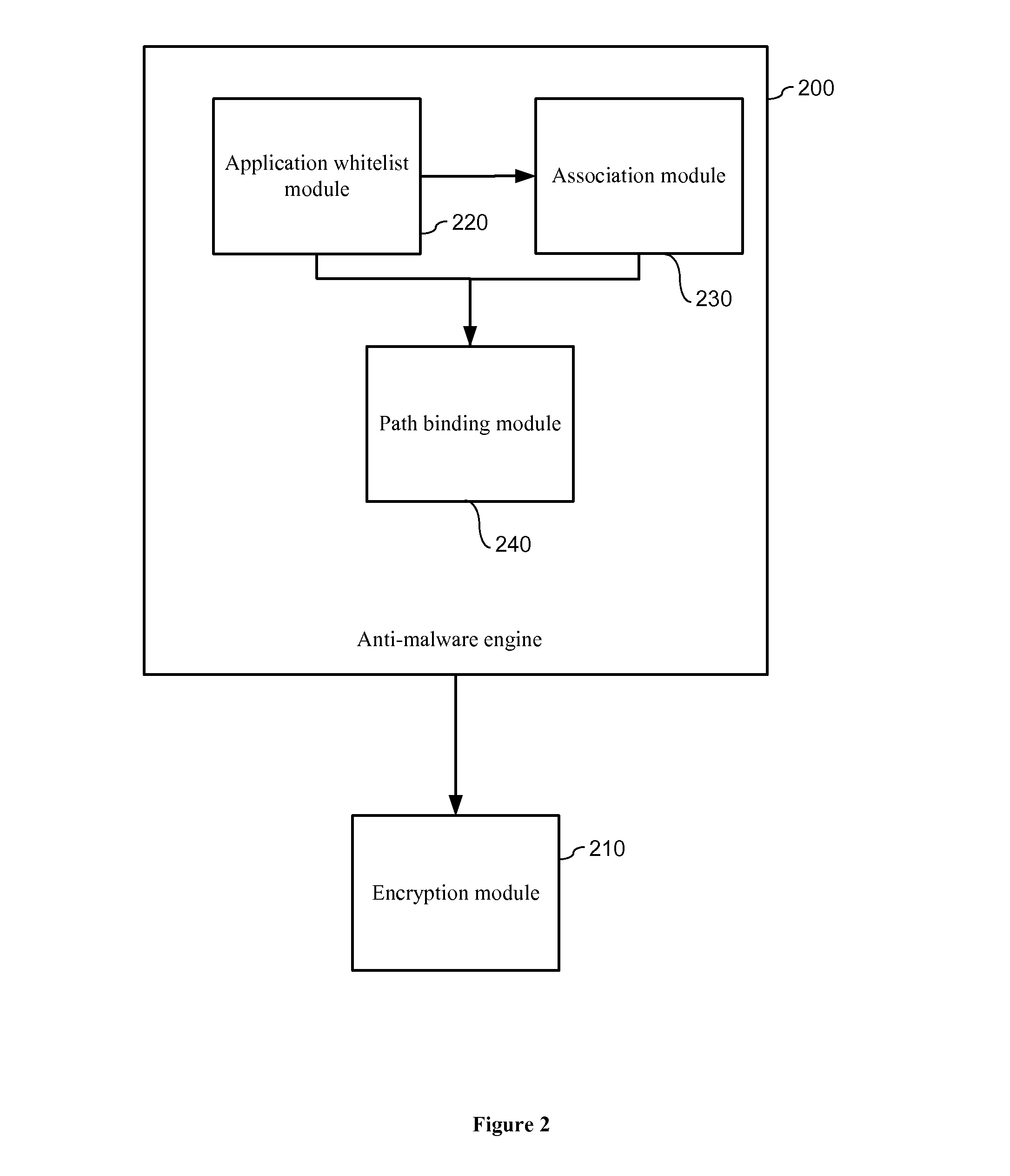
The present invention relates to data encryption and more particularly to data encryption for prevention of malware attacks designed to access user data. The present invention protects user data against regular malware and advance malware like rootkit attacks, zero day attacks and anti-malware disabler attacks. In one embodiment, the present invention uses encryption, application whitelisting, and application binding to prevent malware from accessing a victim's data files. In another embodiment, the present invention uses application path binding to further contain the malware from accessing the victim's data.
Owner:SECUREAGE TECH
Implementing a security solution using a layering system
A security solution can be implemented using a layering system. By using a layering system, any changes that are made to a computing system can be isolated within a separate write layer. Due to this isolation, the changes, which may even be malicious, can be evaluated without fear that the resources in other layers will be negatively affected. In this way, even security threats that are still unknown to antivirus solutions (so-called zero-day attacks) can be prevented from harming the system.
Owner:DELL MARKETING CORP
Systems and methods for capturing or analyzing time-series data
InactiveUS20140101762A1Memory loss protectionError detection/correctionStatistical analysisZero-day attack
Provided is an intrusion detection system configured to detect anomalies indicative of a zero-day attack by statistically analyzing substantially all traffic on a network in real-time. The intrusion detection system, in some aspects, includes a network interface; one or more processors communicatively coupled to the network interface; system memory communicatively coupled to the processors. The system memory, in some aspects, stores instructions that when executed by the processors cause the processors to perform steps including: buffering network data from the network interface in the system memory; retrieving the network data buffered in the system memory; applying each of a plurality of statistical or machine-learning intrusion-detection models to the retrieved network data; aggregating intrusion-likelihood scores from each of the intrusion-detection models in an aggregate score, and upon the aggregate score exceeding a threshold, outputting an alert.
Owner:VECTRA NETWORKS
Decoy network technology with automatic signature generation for intrusion detection and intrusion prevention systems
ActiveUS8429746B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsOperational systemDecoy
Improved methods and systems for decoy networks with automatic signature generation for intrusion detection and intrusion prevention systems. A modular decoy network with front-end monitor / intercept module(s) with a processing back-end that is separate from the protected network. The front-end presents a standard fully functional operating system that is a decoy so that the instigator of an attack is lead to believe a connection has been made to the protected network. The front-end includes a hidden sentinel kernal driver that monitors connections to the system and captures attack-identifying information. The captured information is sent to the processing module for report generation, data analysis and generation of an attack signature. The generated attack signature can then be applied to the library of signatures of the intrusion detection system or intrusion prevention system of the protected network to defend against network based attacks including zero-day attacks.
Owner:GOSECURE INC
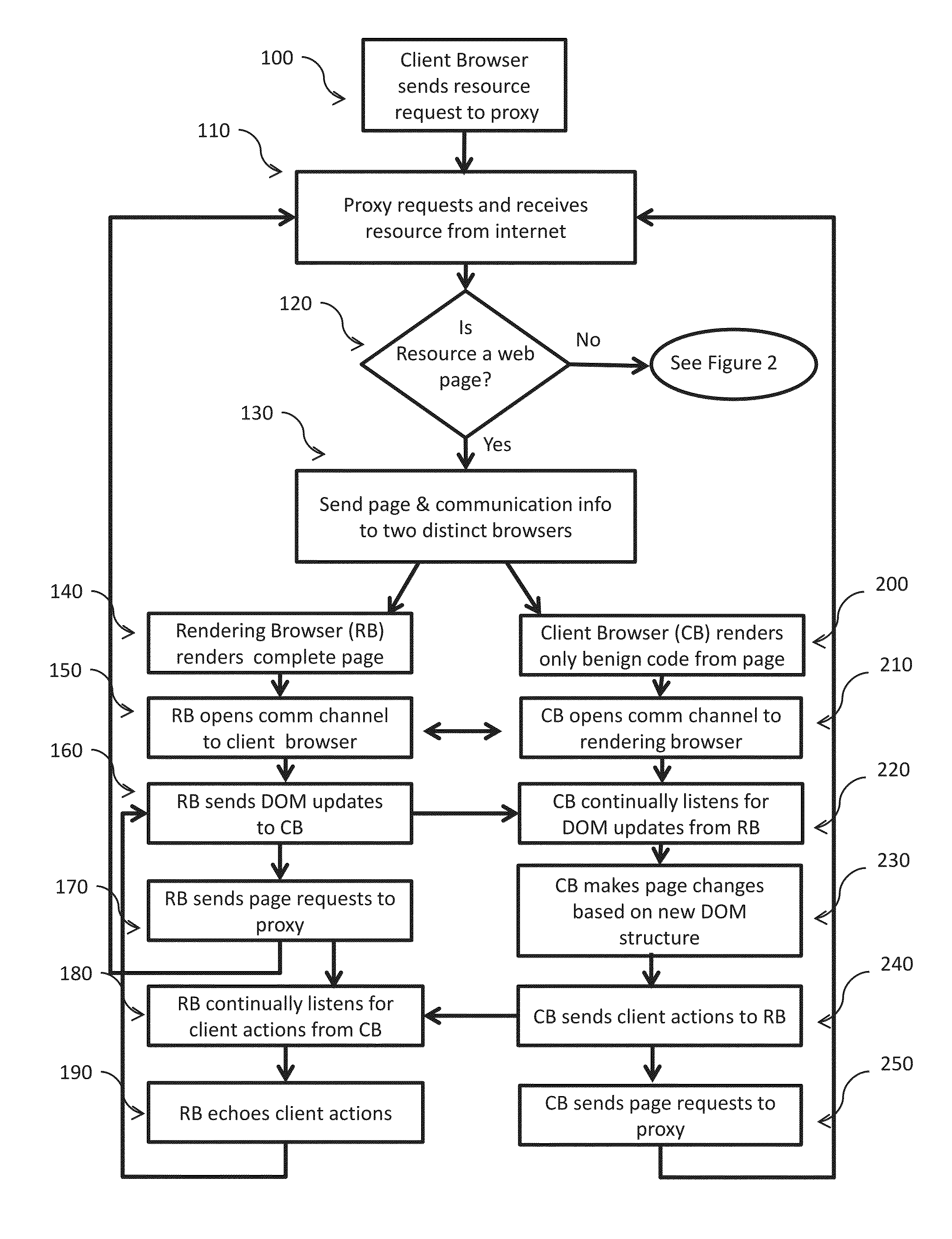
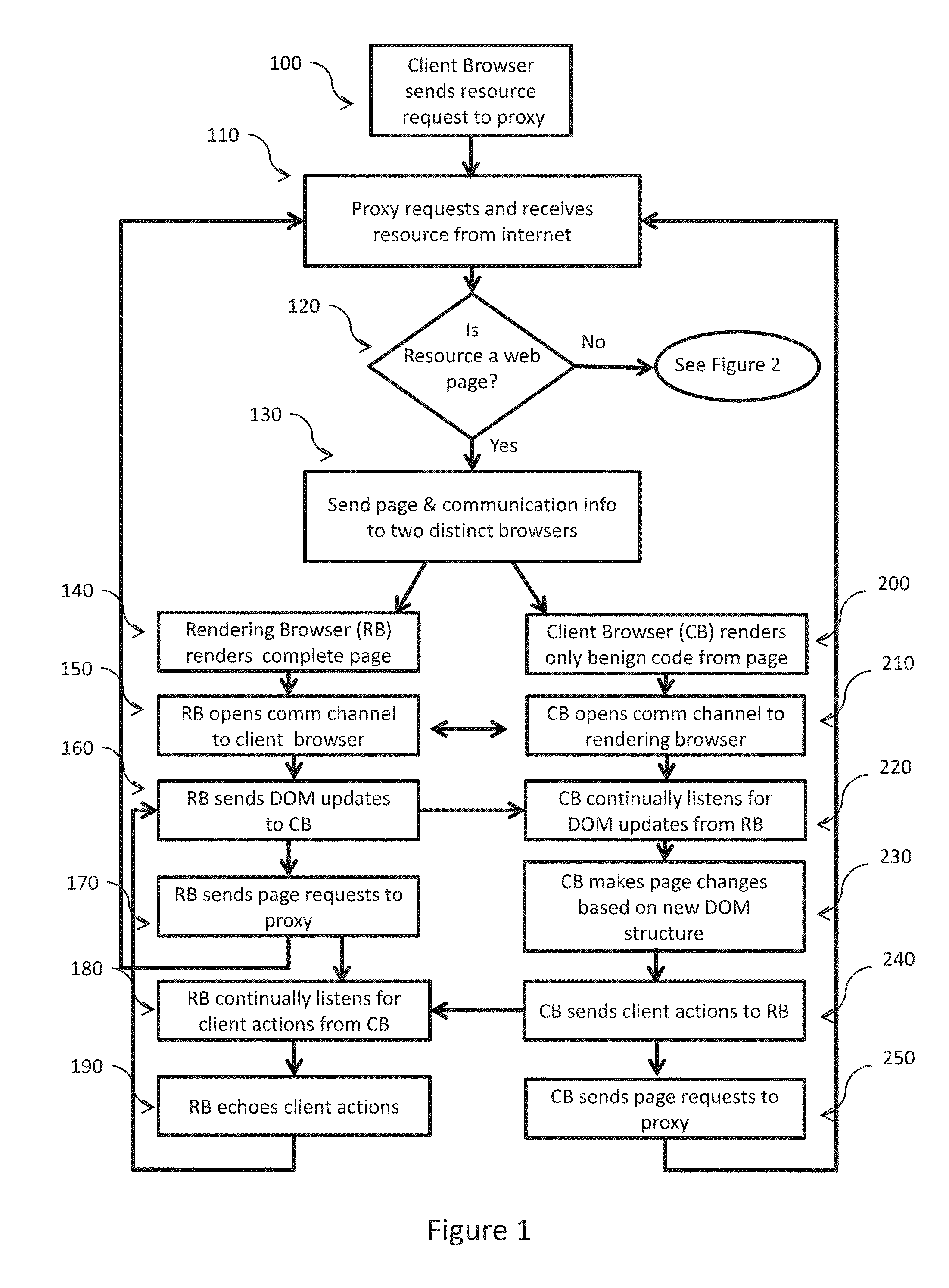
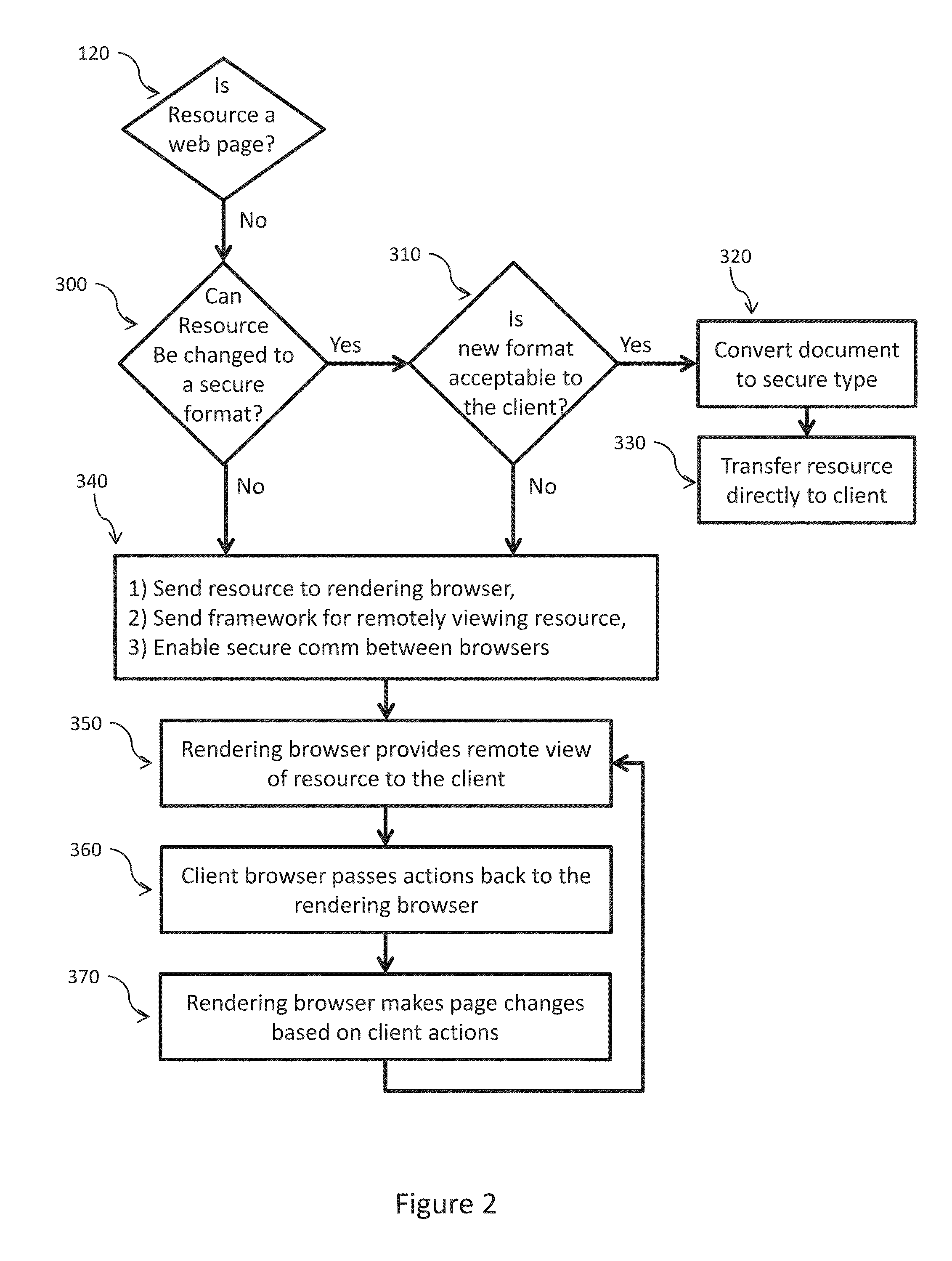
Web malware blocking through parallel resource rendering
ActiveUS20150347754A1Overcome limitationsReserved functionMemory loss protectionError detection/correctionSoftware engineeringZero-day attack
Apparatus and method for transforming Web resources into safe versions such that malicious code on the resources cannot attack the client viewing the resources. The invention separates the processing of insecure code from the processing of benign code. For Web pages, the benign code is displayed immediately to the client while insecure code is processed on a separate machine. Once insecure code is processed, benign outputs of that code are passed to the client for display. The invention safeguards the client against known and zero day exploits without requiring a catalog of malware / virus signatures, heavyweight code checkers, complete page re-writing or highly restrictive access policies. The invention provides the client with complete malware blocking while retaining most of the original functionality of the Web resource.
Owner:THE UNITED STATES OF AMERICA AS REPRESETNED BY THE SEC OF THE AIR FORCE
Systems and methods for capturing, replaying, or analyzing time-series data
ActiveUS20150082433A1Input/output to record carriersMemory loss protectionStatistical analysisZero-day attack
Provided is an intrusion detection system configured to detect anomalies indicative of a zero-day attack by statistically analyzing substantially all traffic on a network in real-time. The intrusion detection system, in some aspects, includes a network interface; one or more processors communicatively coupled to the network interface; system memory communicatively coupled to the processors. The system memory, in some aspects, stores instructions that when executed by the processors cause the processors to perform steps including: buffering network data from the network interface in the system memory; retrieving the network data buffered in the system memory; applying each of a plurality of statistical or machine-learning intrusion-detection models to the retrieved network data; aggregating intrusion-likelihood scores from each of the intrusion-detection models in an aggregate score, and upon the aggregate score exceeding a threshold, outputting an alert.
Owner:VECTRA NETWORKS
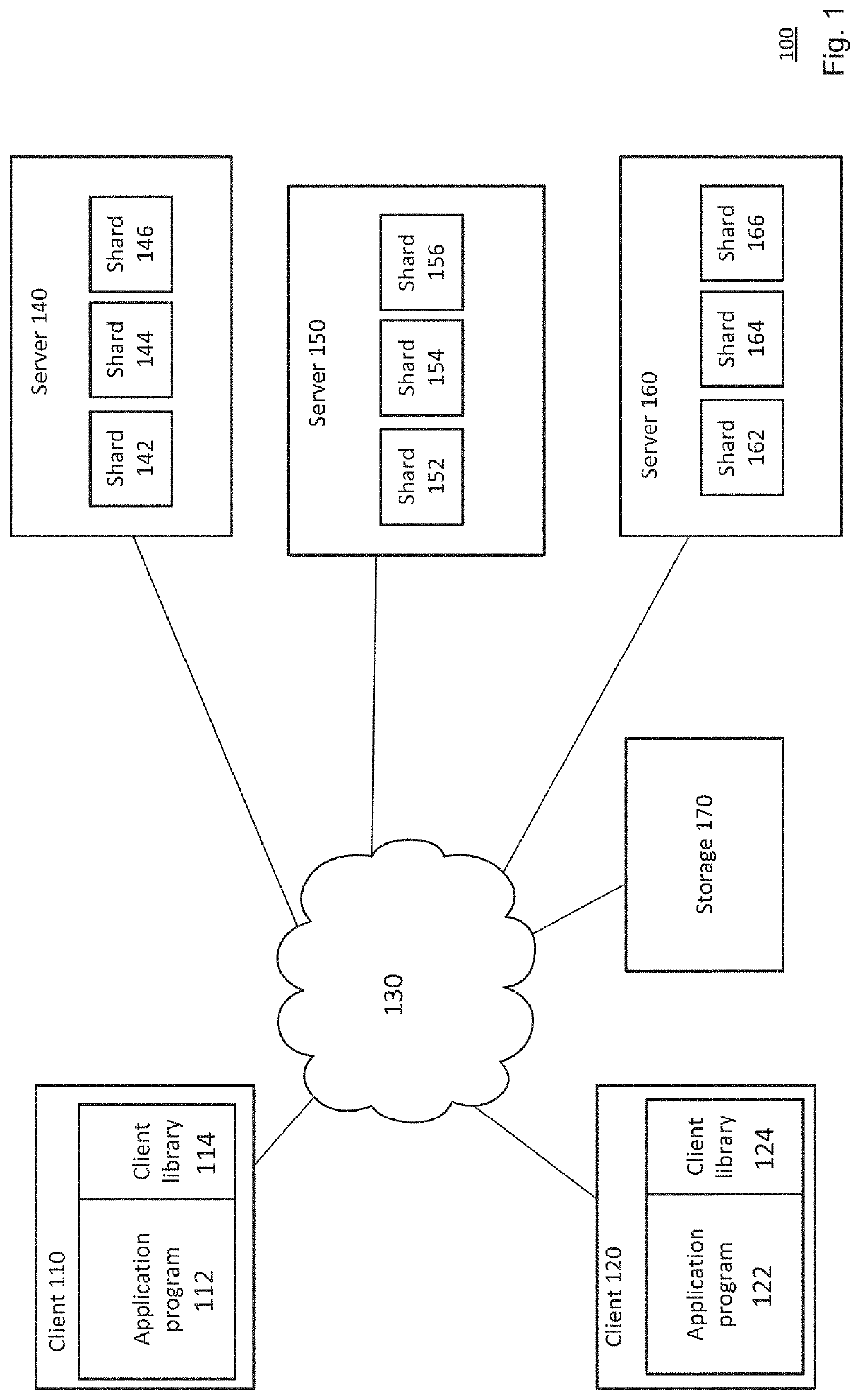
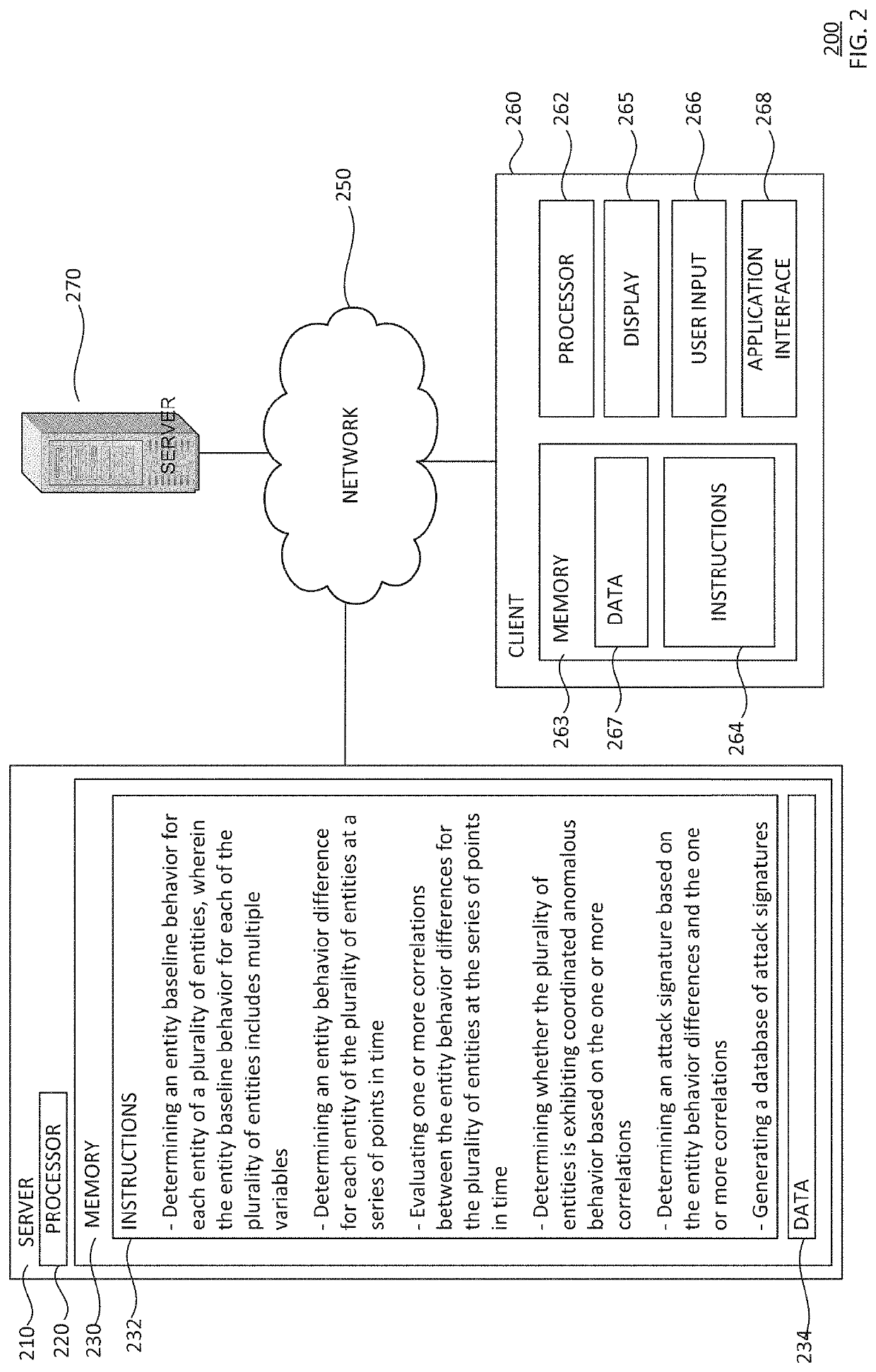
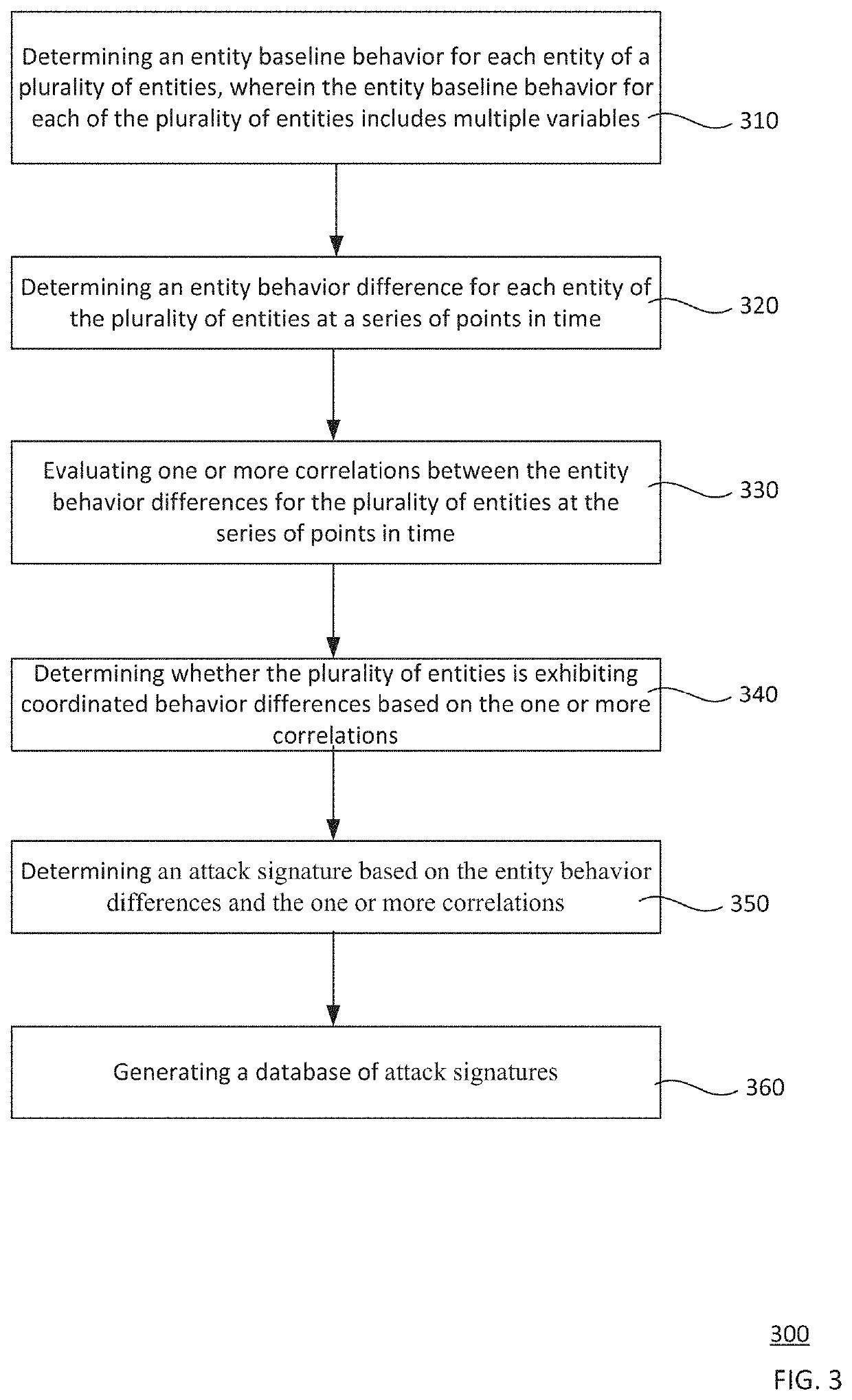
Detecting zero-day attacks with unknown signatures via mining correlation in behavioral change of entities over time
Zero-day attacks with unknown attack signatures are detected by correlating behavior differences of a plurality of entities. An entity baseline behavior for each entity of the plurality of entities is determined 310, the entity baseline behavior includes multiple variables. An entity behavior difference for each entity is determined at a series of points in time 320. Correlations between the entity behavior differences for the plurality of entities are determined at the series of points in time 330. Based on these correlations, it is determined whether the plurality of entities is exhibiting coordinated behavior differences 340. An attack signature is determined based on the entity behavior differences and the correlations 350. A database of attack signatures is generated 360.
Owner:GOOGLE LLC
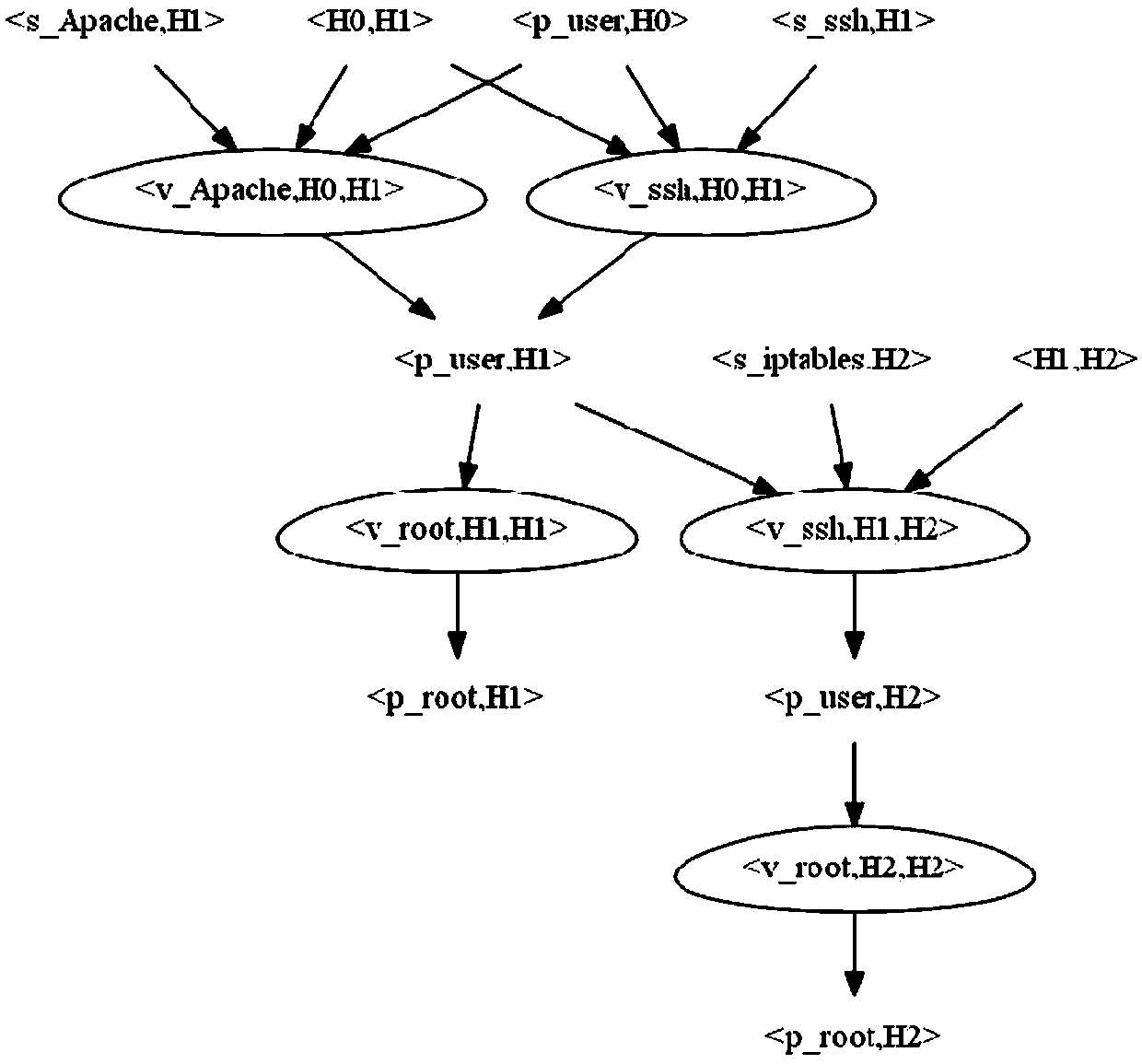
Network vulnerability assessment method based on zero-day attack graph
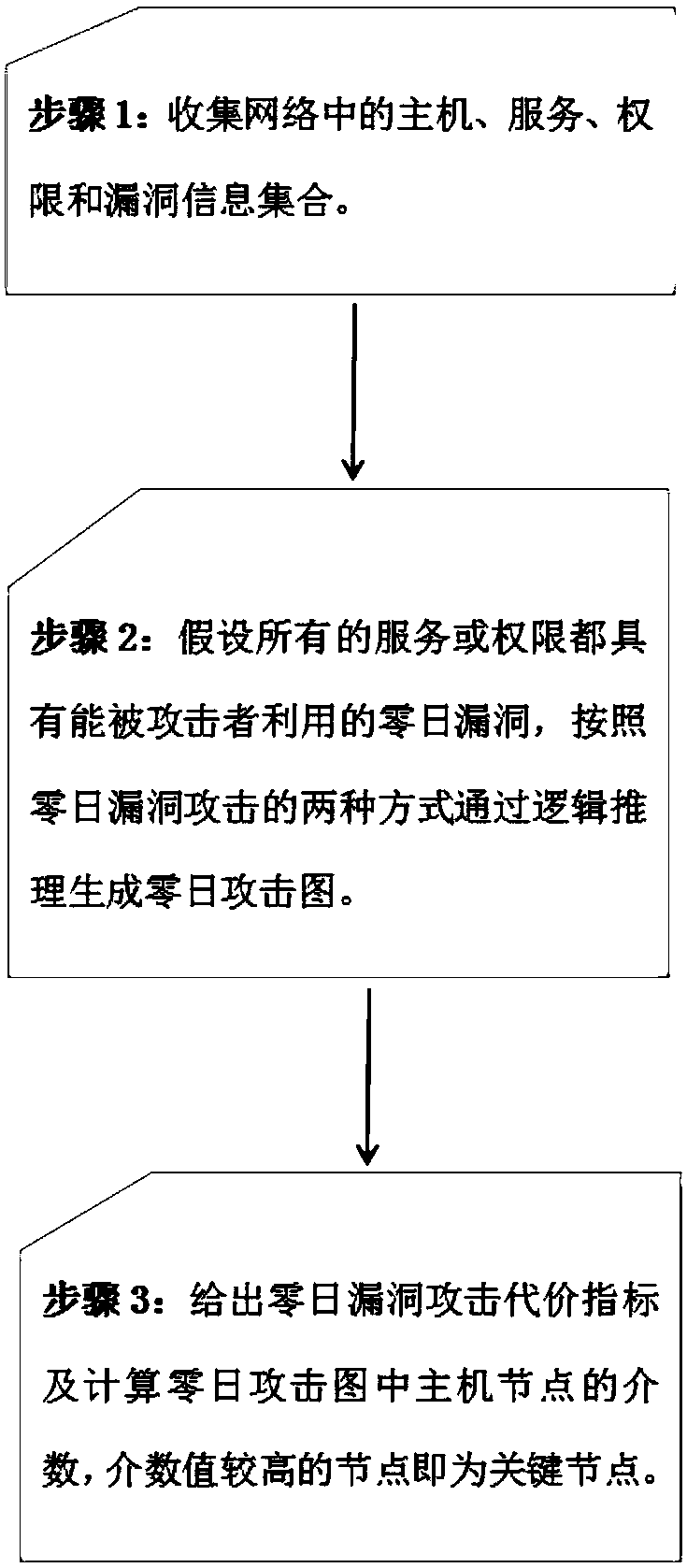
The invention discloses a network vulnerability assessment method based on zero-day attack graph. First it is assumed that all services on a host in a network contain a zero-day vulnerability, a zero-day attack graph is generated through logical reasoning of a given pattern, and then the attack cost for utilizing the zero-day vulnerability to attack is quantified based on a vulnerability scanningtechnology and CVSS vulnerability scoring system, and finally, a network centrality theory is utilized to make an analysis to obtain the key vulnerabilities in the network. All possible unknown vulnerabilities in the network are fully considered while known vulnerabilities are dealt with, so that the assessment method has the capability of dealing with unknown vulnerabilities, can discover potential network vulnerabilities through logical reasoning, and assess the security of the current network, thereby providing a reference basis for further network security protection, and improving the security, reliability and availability of the network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
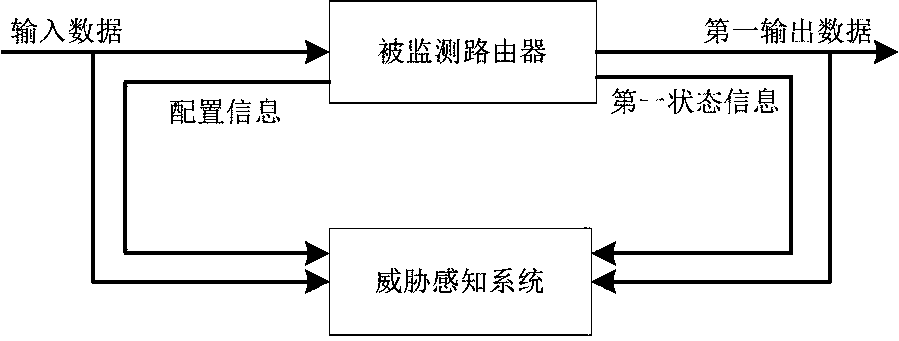
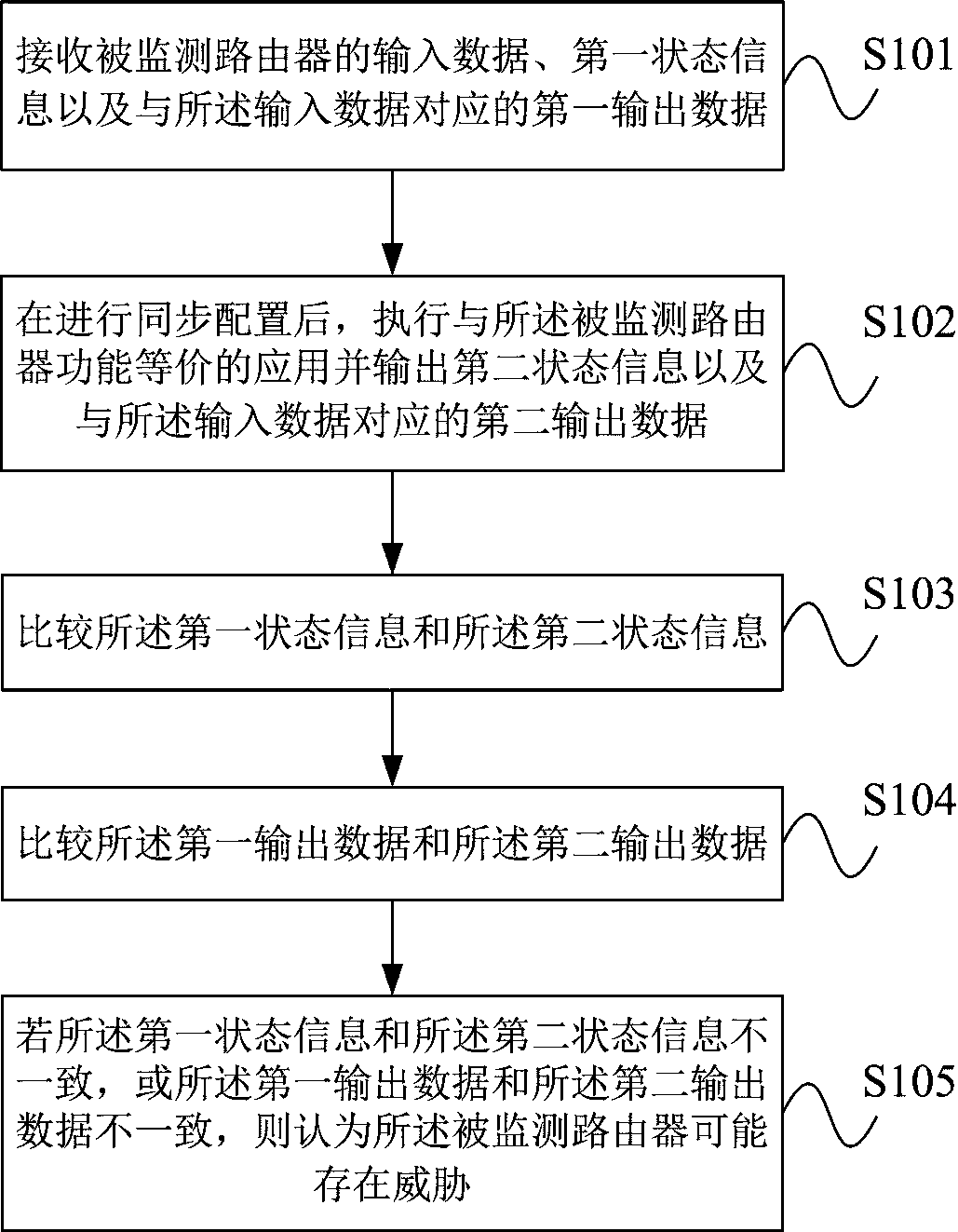
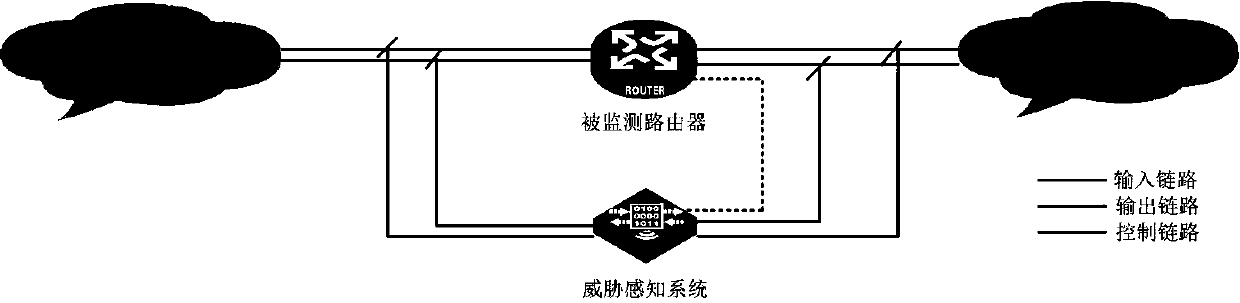
Router threat perception method and system
The invention provides a router threat perception method and system. The method comprises the following steps that: the threat perception system is consistent with the input of a monitored router; theoutput data of the monitored router is sent to the threat perception system at the same time; wherein the configuration information of the monitored router needs to be synchronously configured to thethreat perception system; and the state information of the monitored router needs to be timely collected to the threat perception system. The output data and state of the monitored router are compared with the output data and state of the threat sensing system, if the output data or state of the monitored router is inconsistent with the output data or state of the threat sensing system, the monitored router may have a threat, and alarm information is sent to a management system. The threat perception system comprises an input processing unit, a function equivalent actuator unit, a state comparison unit, an output comparison unit and an analysis alarm unit. According to the method, the problem of high difficulty in judging router threats caused by various vulnerability and attack technicalmeans can be solved, and unknown vulnerabilities and zero-day attacks can be perceived.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
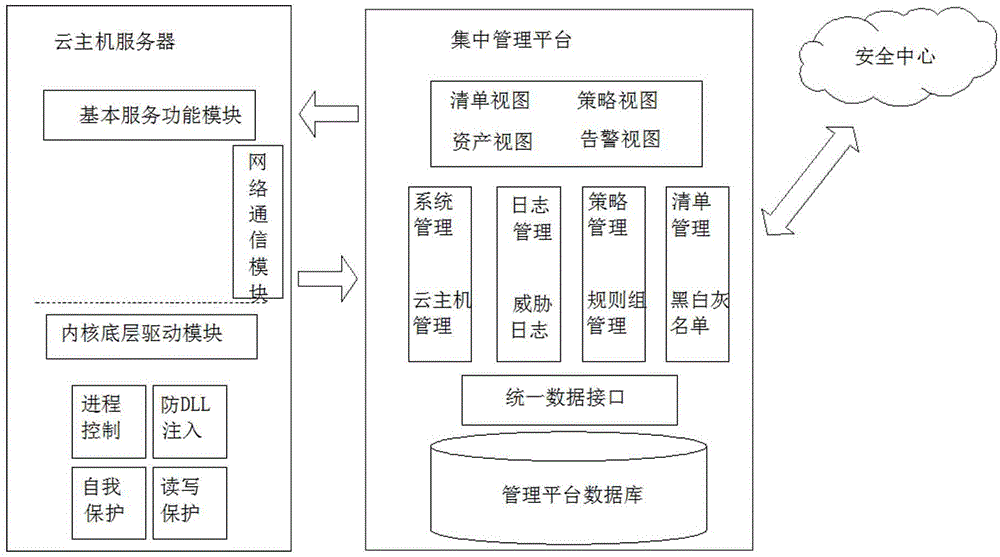
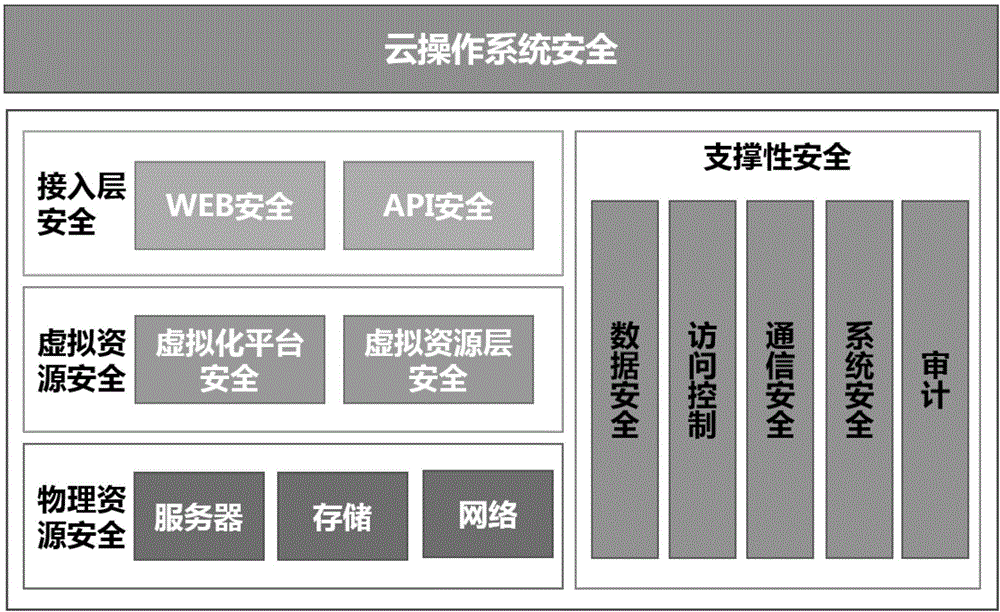
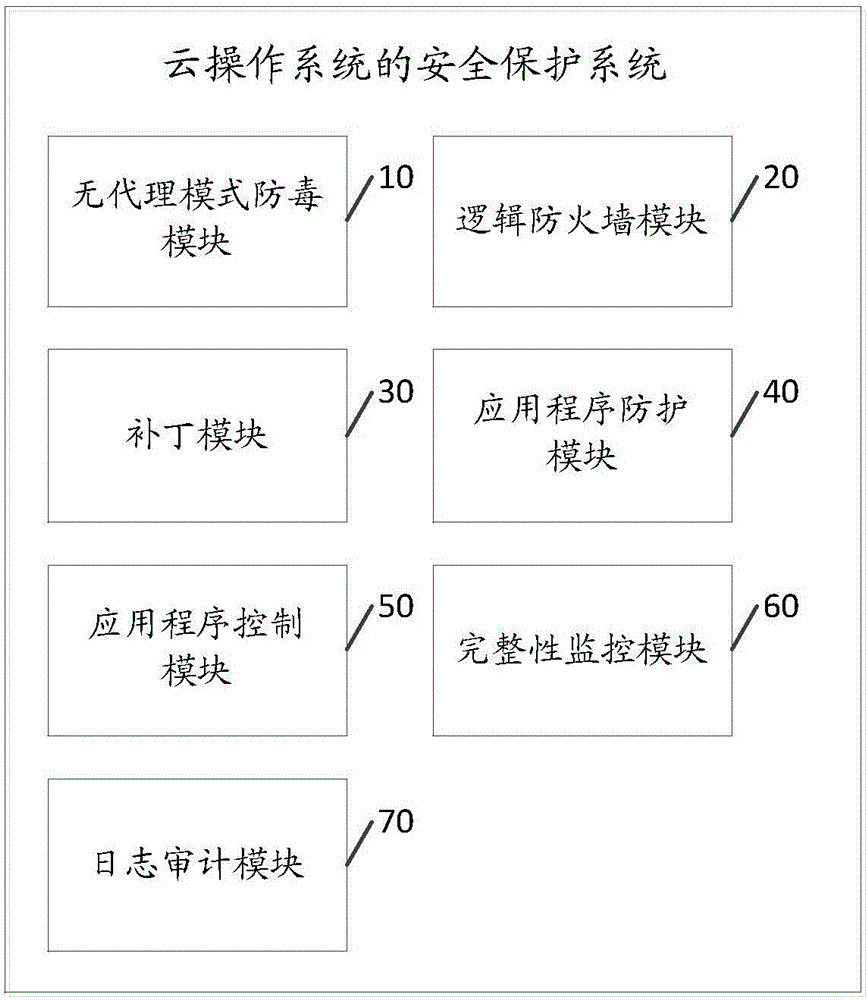
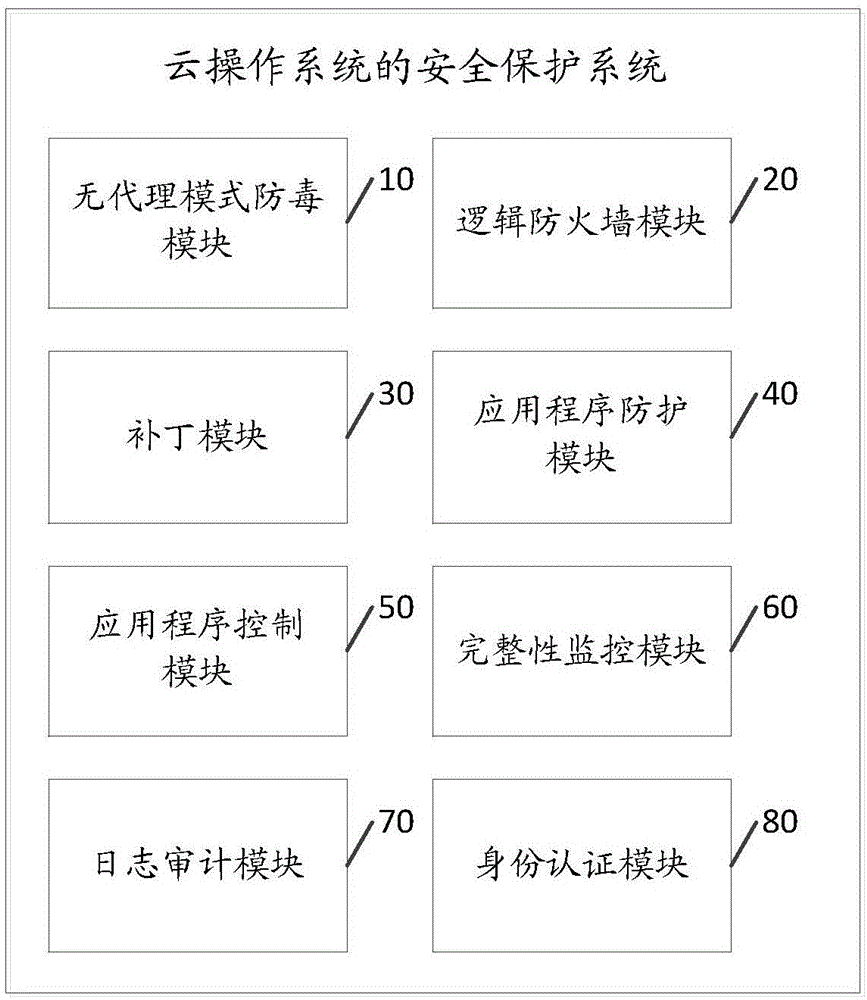
Safety protection system of cloud operation system
The invention discloses a safety protection system of a cloud operation system. The safety protection system of the cloud operation system comprises a non-proxy mode anti-virus module for scanning each application server virtual machine in the cloud operation system in the time-sharing mode, and managing the safety protection of each virtual machine under the virtualization environment; a logic firewall module for executing the network security protection to each application server virtual machine; a patch module for detecting or preventing the known attack or zero-day attack of the cloud operation system loophole; an application program protection module for detecting or preventing the known attack or zero-day attack based on the application program loophole; an application program control module for monitoring each application server virtual machine in the cloud operation system; an integrity monitoring module for detecting or preventing the unauthorized or malevolent modification in allusion to a catalogue, a file and a key value; and a log audit module for executing the audit to an safety event of each application server virtual machine. The system is capable of executing the multi-dimensional safety protection to the cloud operation system through the above-mentioned modules, and guaranteeing the safety of the cloud operation system.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Identifying and trapping wireless based attacks on networks using deceptive network emulation
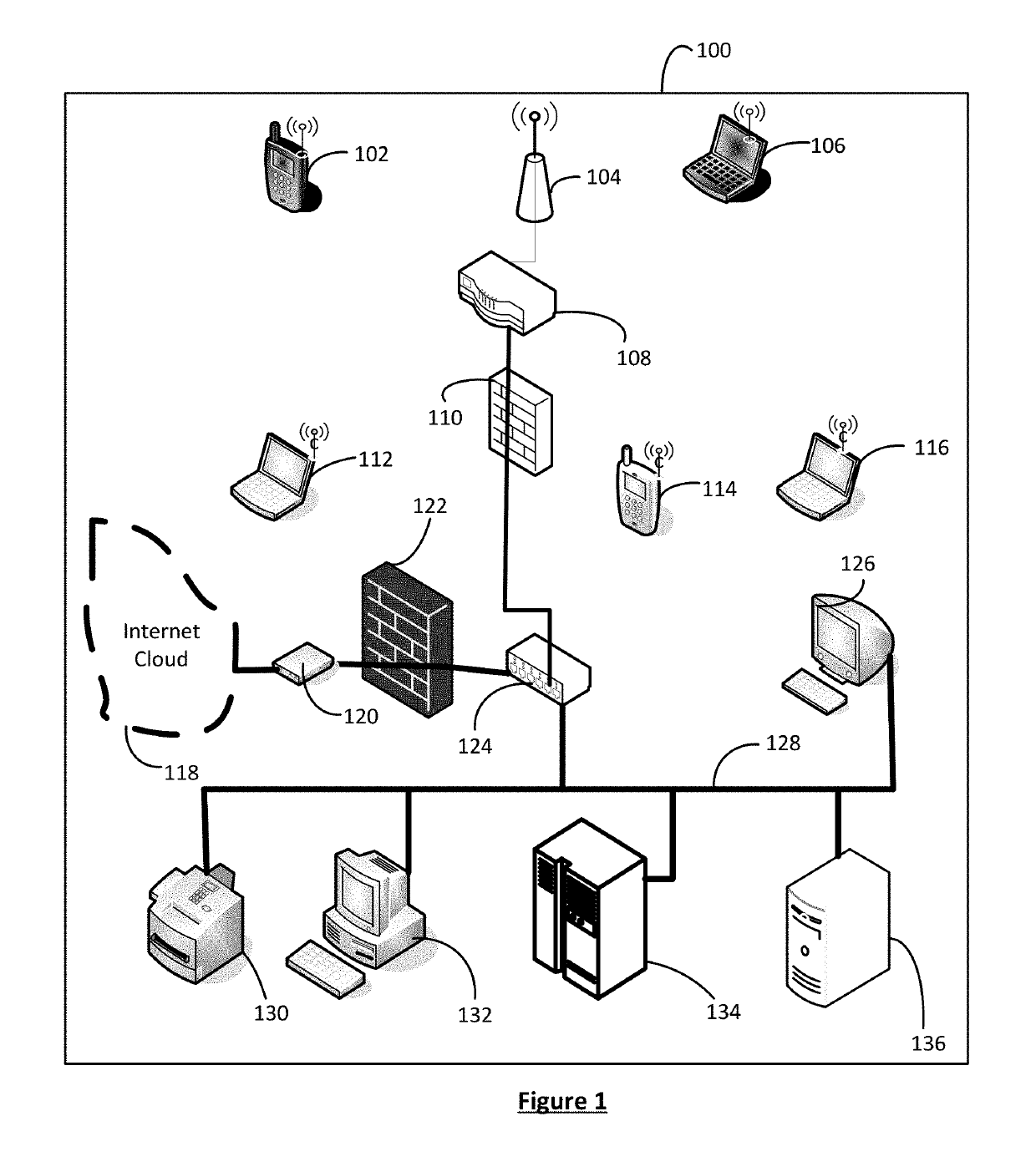
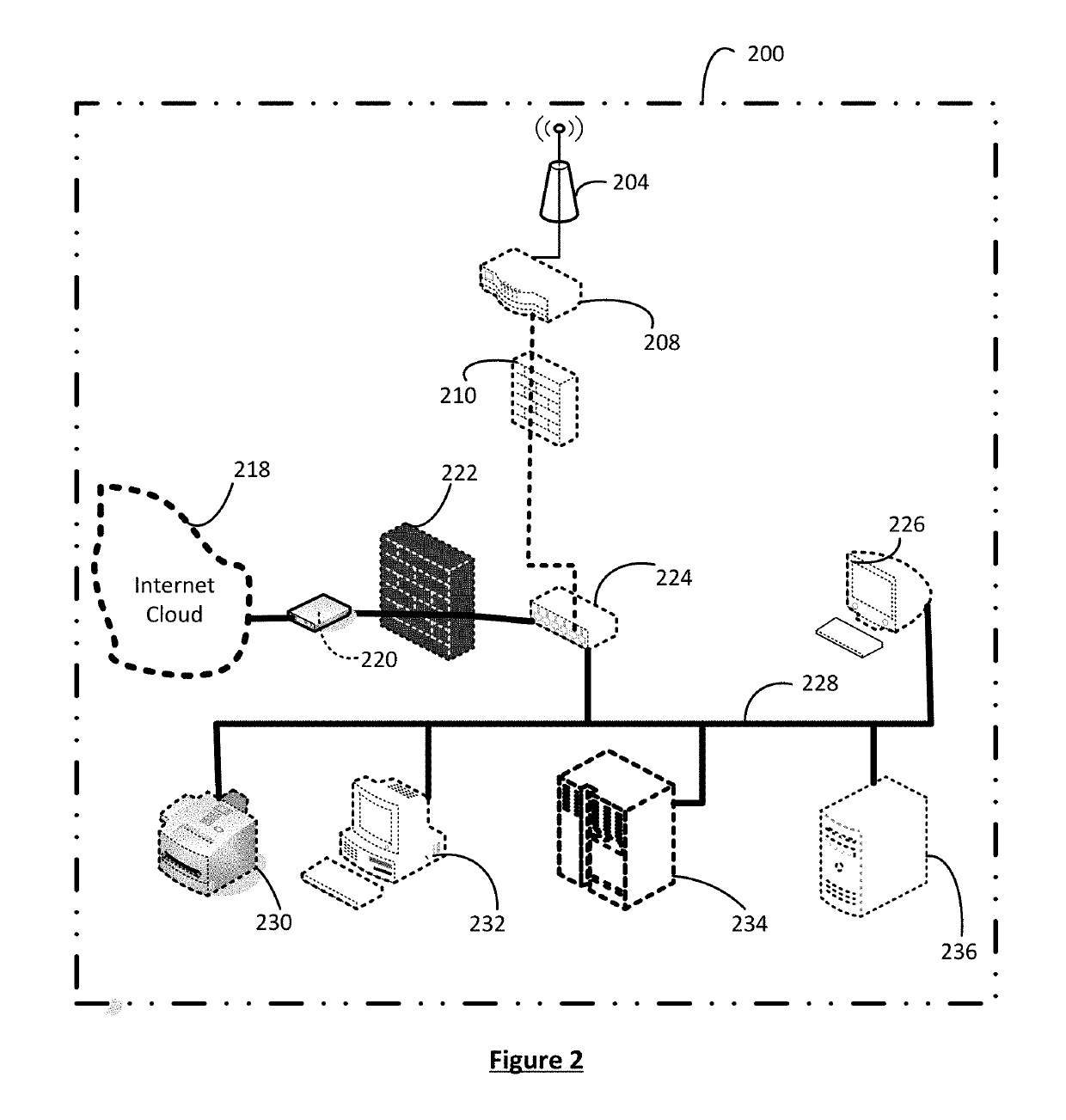
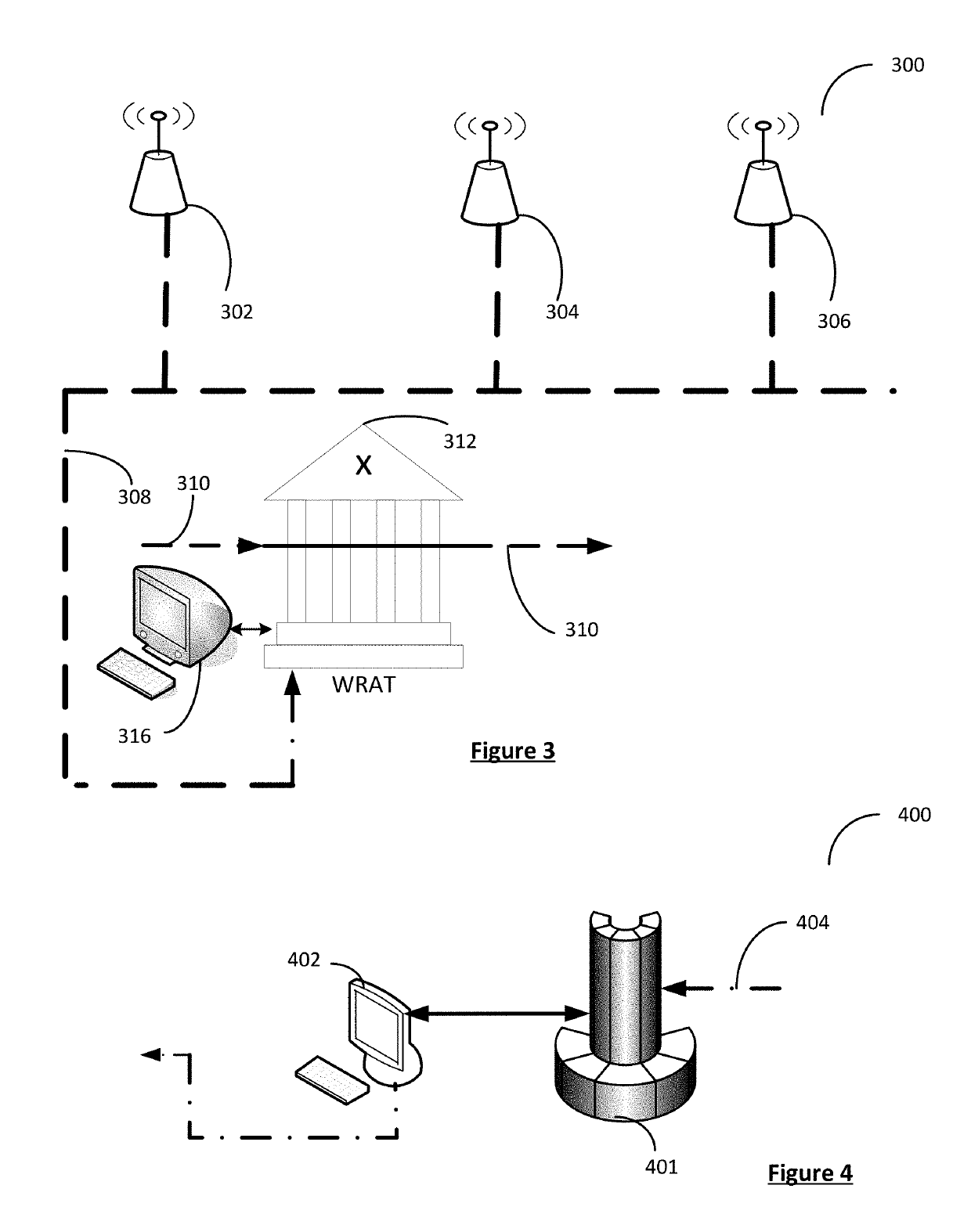
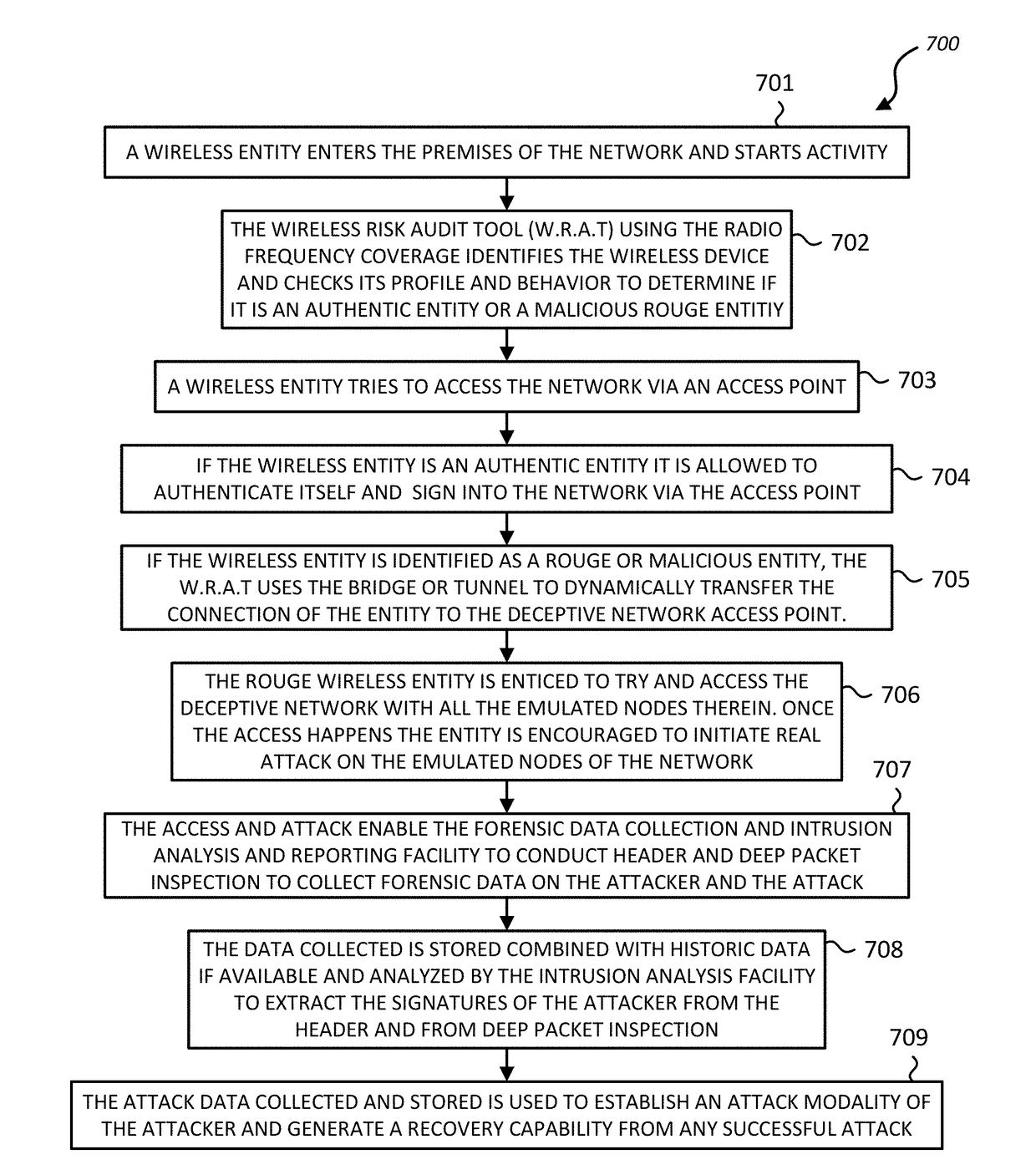
A system and method are provided that enable identifying and trapping cyber security attacks via wireless connectivity on enterprise and corporate networks. A deceptive network emulation of a specific customer network is used to invite and draw in possible attackers. The attacker is also enticed to initiate attack on the emulated deceptive network. Packet header inspection and deep packet evaluation of the attack are used for generating possible signatures of the attacker and the attack. The information from deep packet inspection combined with the understanding of attack modality derived from enablement of attack on the deceptive network are used to generate detailed defensive methodologies, response capabilities and attack signatures, so that various types of cyber attacks including zero-day attacks from the attacker can be identified, prevented or addressed and responded to.
Owner:802 SECURE INC
Identifying and Trapping Wireless Based Attacks on Networks Using Deceptive Network Emulation
A system and method are provided that enable identifying and trapping cyber security attacks via wireless connectivity on enterprise and corporate networks. A deceptive network emulation of a specific customer network is used to invite and draw in possible attackers. The attacker is also enticed to initiate attack on the emulated deceptive network. Packet header inspection and deep packet evaluation of the attack are used for generating possible signatures of the attacker and the attack. The information from deep packet inspection combined with the understanding of attack modality derived from enablement of attack on the deceptive network are used to generate detailed defensive methodologies, response capabilities and attack signatures, so that various types of cyber attacks including zero-day attacks from the attacker can be identified, prevented or addressed and responded to.
Owner:802 SECURE INC
Virtual host program security control method and device, equipment and medium
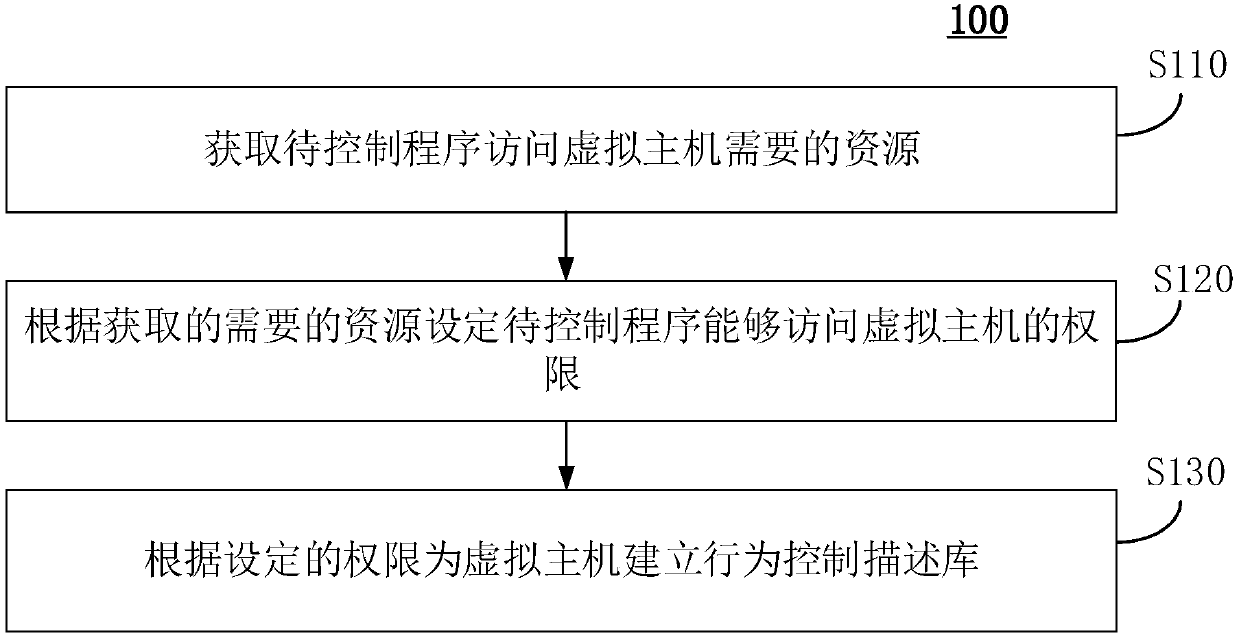
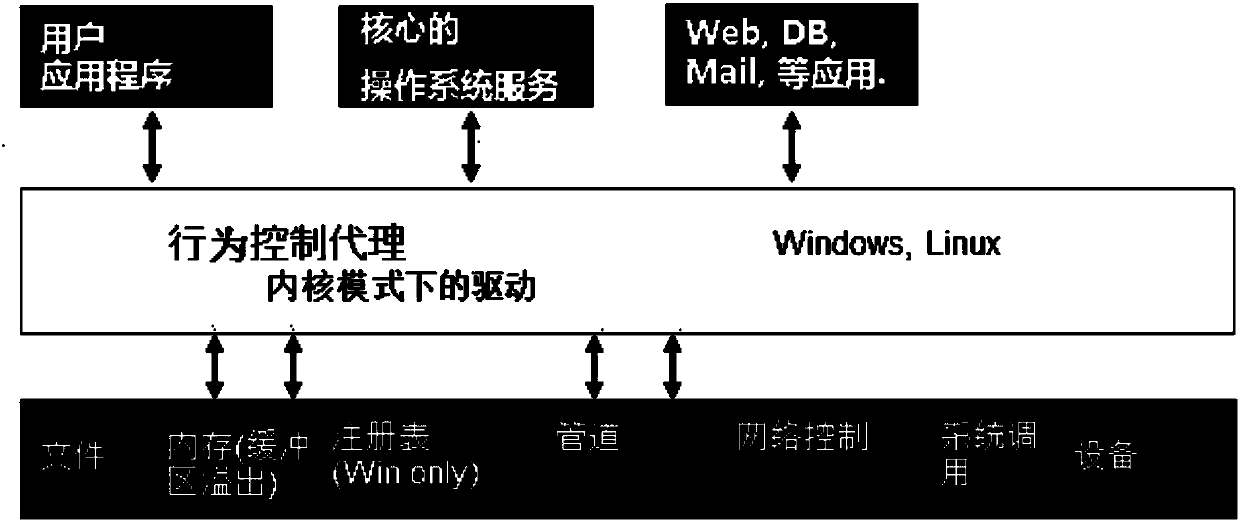
InactiveCN109992351AImplement permission monitoringDigital data authenticationSoftware simulation/interpretation/emulationProgram securityVirtual hosting
The invention discloses a virtual host program security control method and device, equipment and a medium. The method comprises the following steps: obtaining resources required by a to-be-controlledprogram to access a virtual host; setting the authority of the to-be-controlled program to access the virtual host according to the obtained required resources; and establishing a behavior control description library for the virtual host according to the set authority. The embodiment of the invention provides a virtual host program security control method. An authority is set and a behavior control description library is established; according to the method and the device, the monitoring of the to-be-controlled program of the virtual host does not depend on the existing characteristic-based strategy, and further, the to-be-controlled program can be read regularly through the preset time so as to prevent the unknown program from accessing the virtual host and actively protect the virtual host, so that the zero-day attack is effectively resisted, and the virtual host is protected from other attacks.
Owner:ZUNYI BRANCH OF CHINA MOBILE GRP GUIZHOU COMPANY +1
Open flow meter security enhancement method and device
ActiveCN103095701BEasy to carry outProtect against zero-day attacksTransmissionVirtualizationPrivate network
The invention discloses an open flow table security enhancement method which can enable a security control function to be separated from a security executive function. The method includes the steps of obtaining security application corresponding to each security service, extracting security strategies, security protocols and feature libraries corresponding to the various security services from the security application, analyzing the security strategies of the security services to generate a security flow table, and creating a matching rule in the security flow table, and carrying out access control to messages and inspection for a state firewall, a security virtual private network (VPN) and deep messages according to the matching rule in the security flow table. The invention simultaneously discloses an open flow table security enhancement device. The open flow table security enhancement method and the open flow table security enhancement device can enable the security execution and the security application to be independently evolved and upgraded, and bring convenience to development of new security services, and can intensively carry out security management, resist zero-day attack, and relieve distributed denial of service attack according to the security strategies, and also support a virtualization multi-tenant security mode.
Owner:ZTE CORP
Asset-based security systems and methods
ActiveUS11347843B2Platform integrity maintainanceSoftware simulation/interpretation/emulationAttackReachability
Methods, systems, and computer readable media for asset-based security are described. Some implementations relate to a system for asset-based detection of zero-day attacks or other attacks. The system can monitor critical assets for a violation of one or more security requirements and raise an alarm when a violation of one or more of the critical assets is detected. Further, the system can perform an information collection phase in which (a) information about the critical assets corresponding to the one or more security requirement are captured, and (b) generating a reachability graph representing one or more interrelationships between one or more of the critical assets and one or more other objects in the system.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Event-triggered reauthentication of at-risk and compromised systems and accounts
PendingUS20220255926A1Detects and mitigates zero-day exploitDetects and mitigates and other vulnerabilityDigital data authenticationSecuring communicationEvent triggerZero-day attack
Owner:QPX LLC
Majority consistent escape error processing device and method
ActiveCN106874755BGuaranteed robustnessGuaranteed survivabilityPlatform integrity maintainanceResource poolError processing
The invention relates to a majority consistent escape error processing device based on mimicry security defense zero-day attack and a method thereof. The method comprises: a heterogeneous executive in a dynamic online executive assembly independently operating an input request; performing multimode adjudication on an operation result, if an adjudication result meets a consistency requirement, outputting the adjudication result, if not, feeding back the adjudication result to a dynamic decision dispatching module; comparing new online executive operation output with online original majority consistent executive operation output, respectively feeding back results to the dynamic decision dispatching module and a responding module; the responding module processing the response according to feedback, and feeding back abnormal output executive to the dynamic decision dispatching module; and the dynamic decision dispatching module selecting new executive to be online from an executive resource pool, and cleaning and resetting offline executives. The method is used to provide means of detection and response when majority of mimicry defense online executives are attacked, and solves security threat a mimicry defense system faces, so as to enhance robustness of the mimicry system.
Owner:THE PLA INFORMATION ENG UNIV
System and method for prevention of malware attacks on data
ActiveUS8990932B2Improve protectionMemory loss protectionUnauthorized memory use protectionData fileMalware
The present invention relates to data encryption and more particularly to data encryption for prevention of malware attacks designed to access user data. The present invention protects user data against regular malware and advance malware like rootkit attacks, zero day attacks and anti-malware disabler attacks. In one embodiment, the present invention uses encryption, application whitelisting, and application binding to prevent malware from accessing a victim's data files. In another embodiment, the present invention uses application path binding to further contain the malware from accessing the victim's data.
Owner:SECUREAGE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com