Network vulnerability assessment method based on zero-day attack graph
An attack graph and vulnerability technology, applied in the field of network security, can solve the problems of lack of objectivity in evaluation, failure to consider zero-day vulnerabilities, lack of selection basis for Markov transfer models, etc., to achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
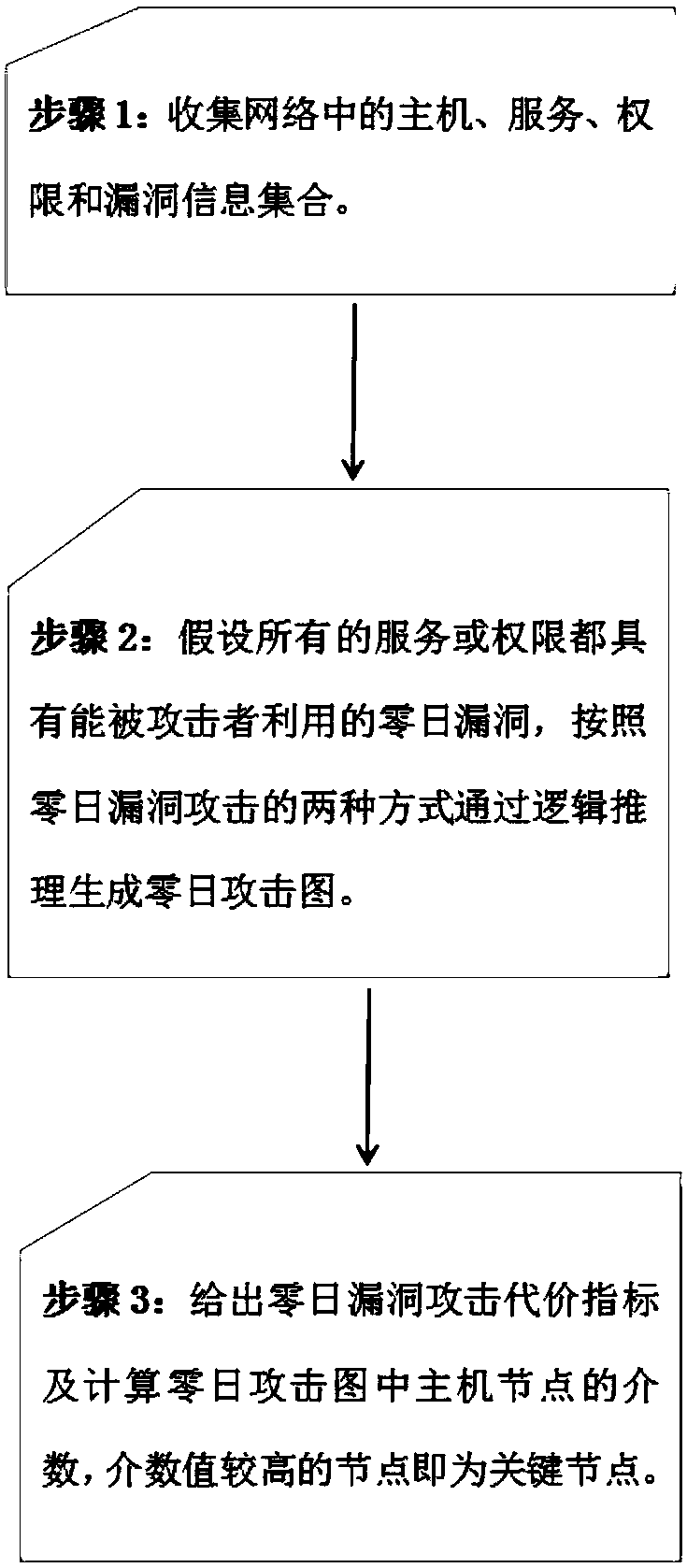
[0028] The present invention will be described in detail below with reference to the accompanying drawings and examples.
[0029] Step 1: Obtain the information of the physical network, specifically:
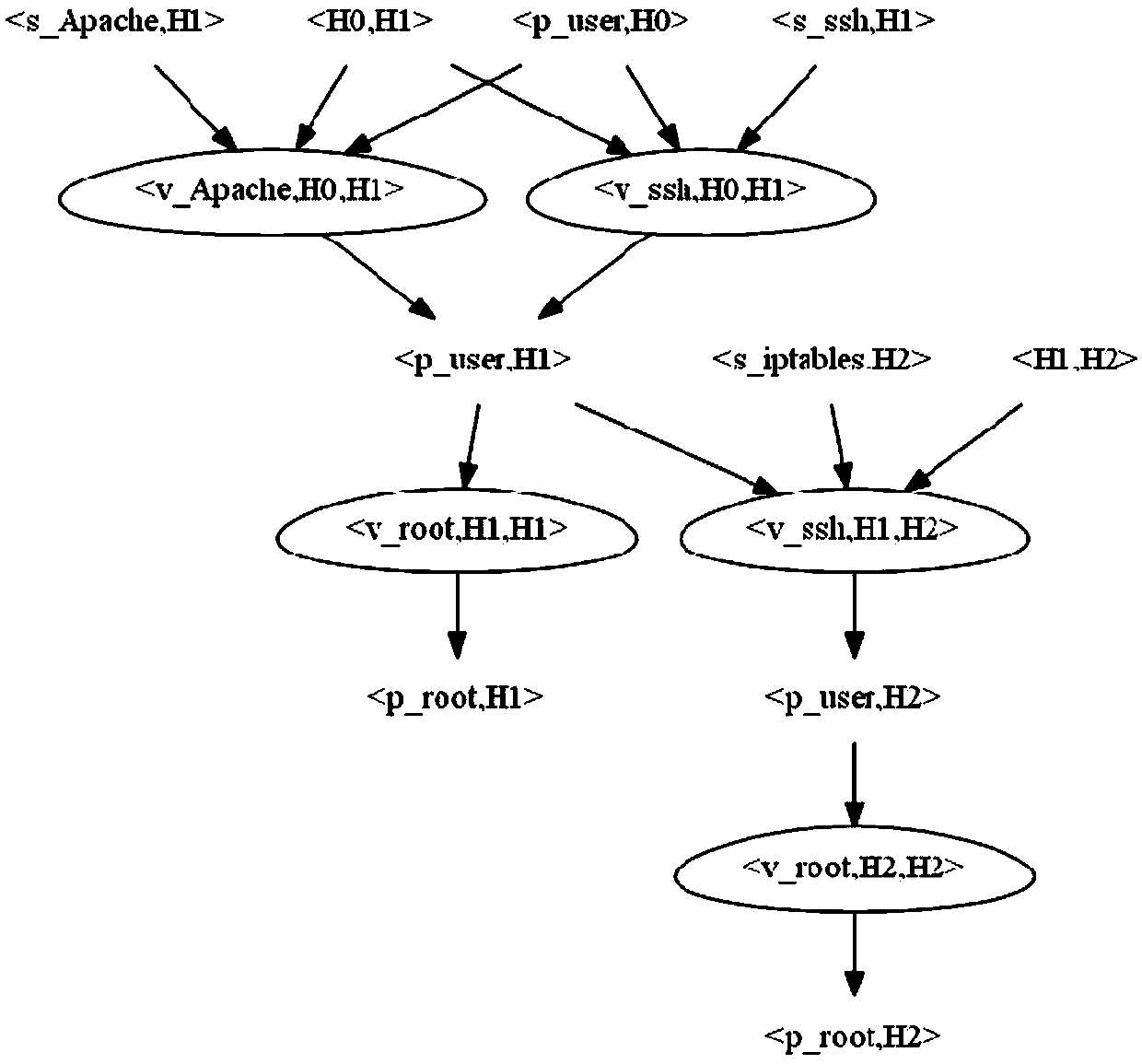
[0030] From the perspective of the attacker, we collectively refer to routers, switches, bridges, computer terminals, etc. in the network as hosts; the system or installed applications of the host are called services (or applications); the users of the host have The operation of the service is called authority; the defect or error exploited on the service is called vulnerability, which are denoted by H, S, P, and V respectively. The following mapping relationship exists among the collections:
[0031] 1. Determine the services contained in each host, that is, the mapping from the host to the service set, expressed as: serv(.)={|s_http∈S,h_h1∈H};
[0032] 2. Determine which permissions each host contains, that is, the mapping from host to permission, expressed as: priv(.)={|p_u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com