Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "CVSS" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
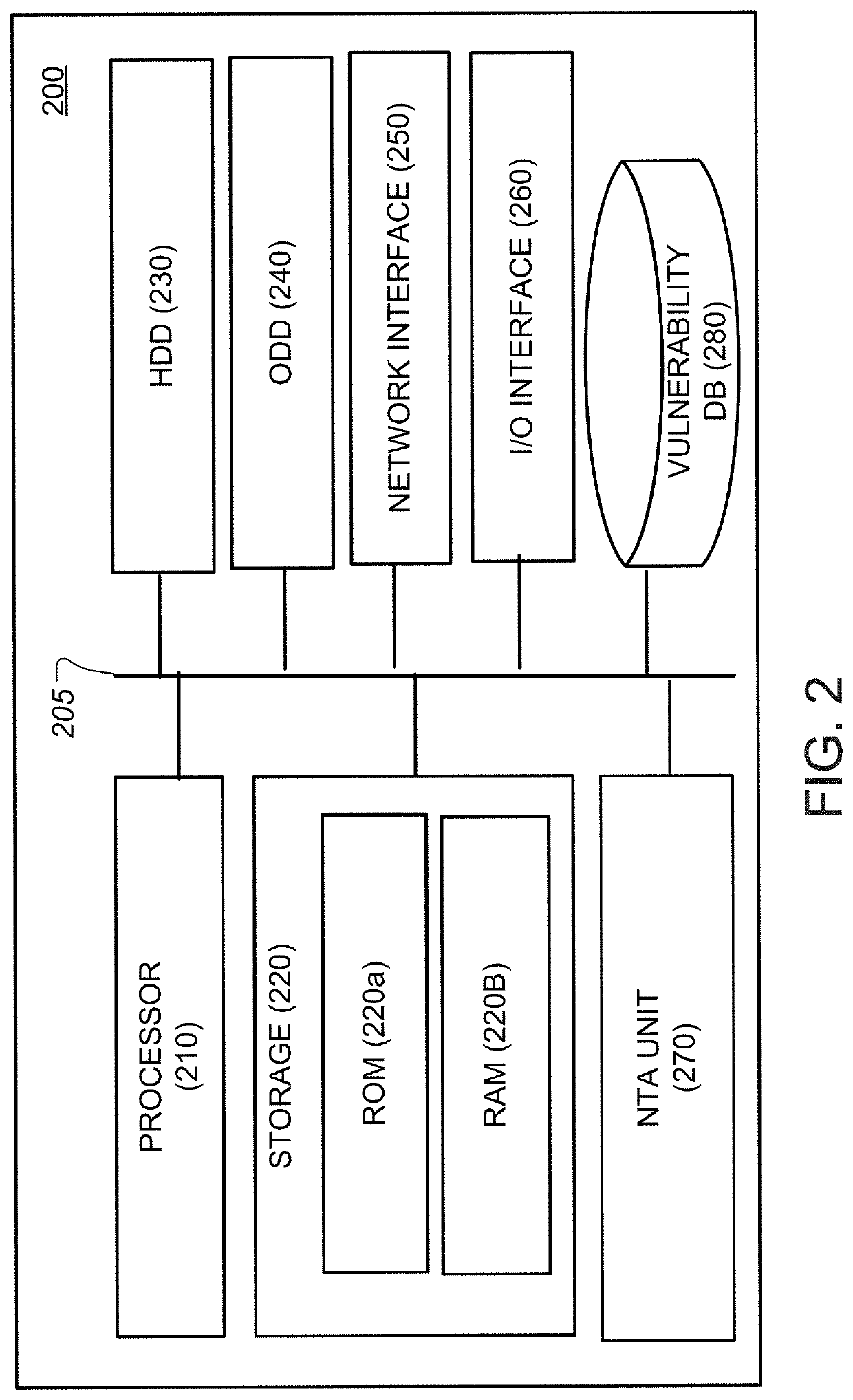
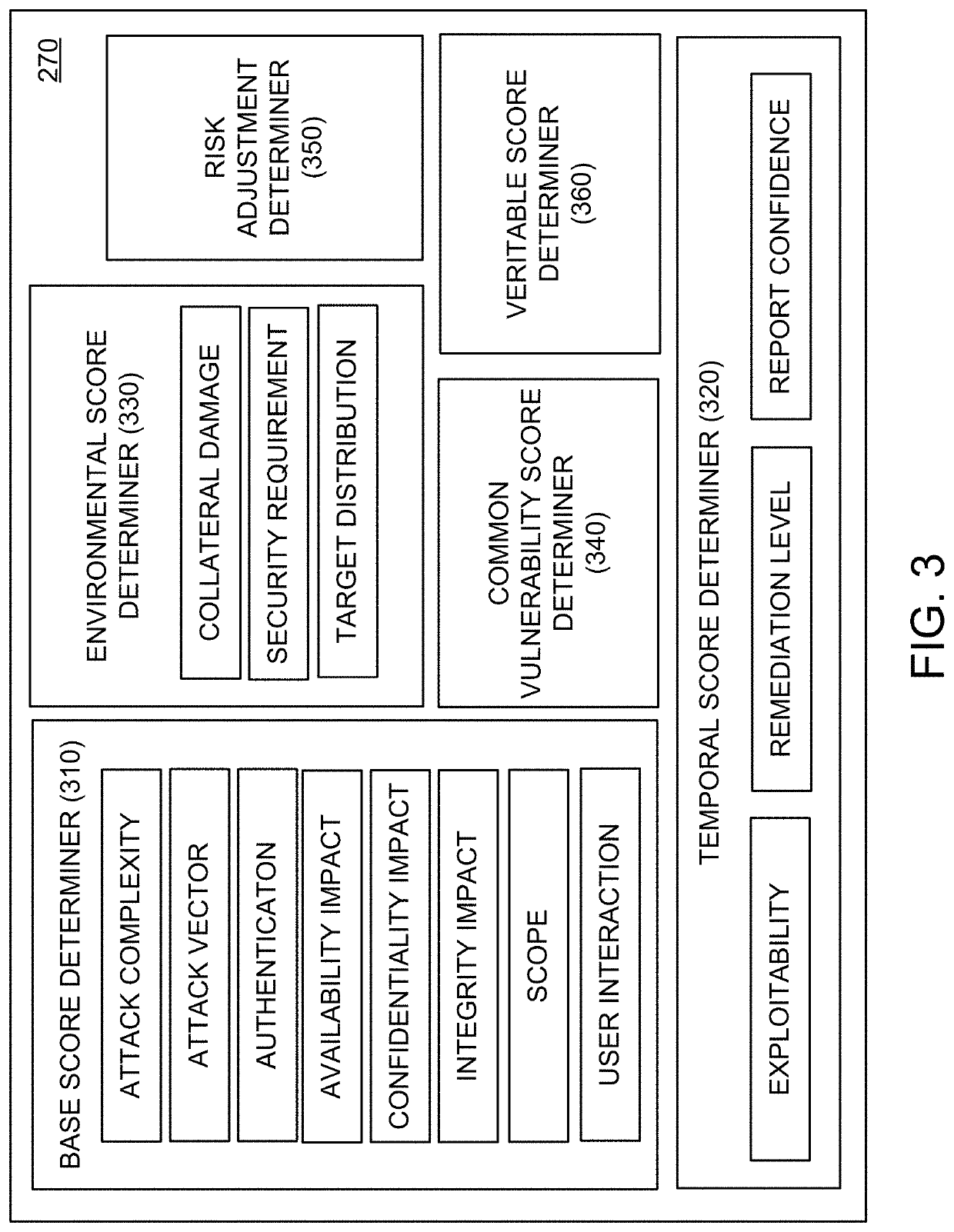
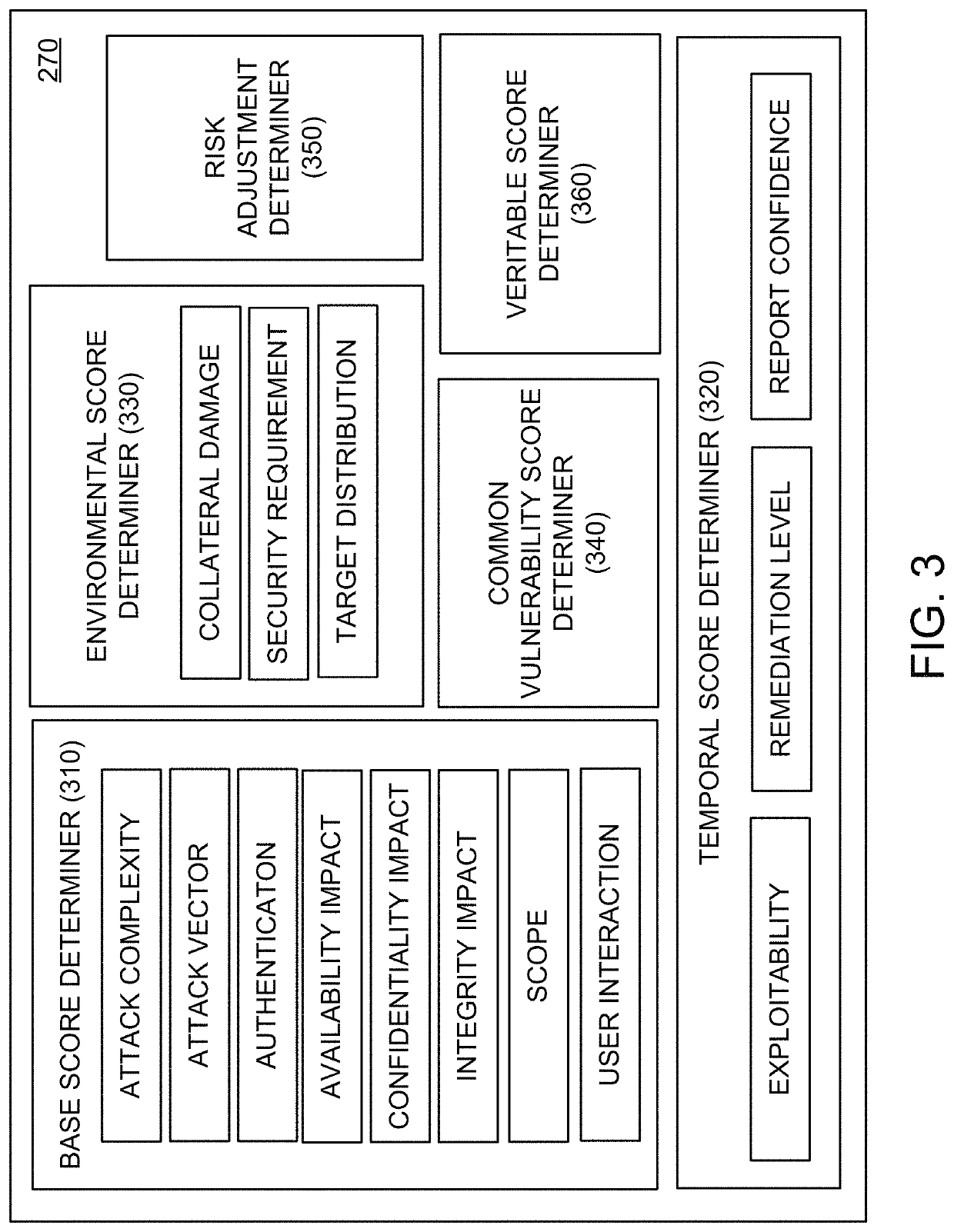
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. Scores are calculated based on a formula that depends on several metrics that approximate ease of exploit and the impact of exploit. Scores range from 0 to 10, with 10 being the most severe. While many utilize only the CVSS Base score for determining severity, temporal and environmental scores also exist, to factor in availability of mitigations and how widespread vulnerable systems are within an organization, respectively.
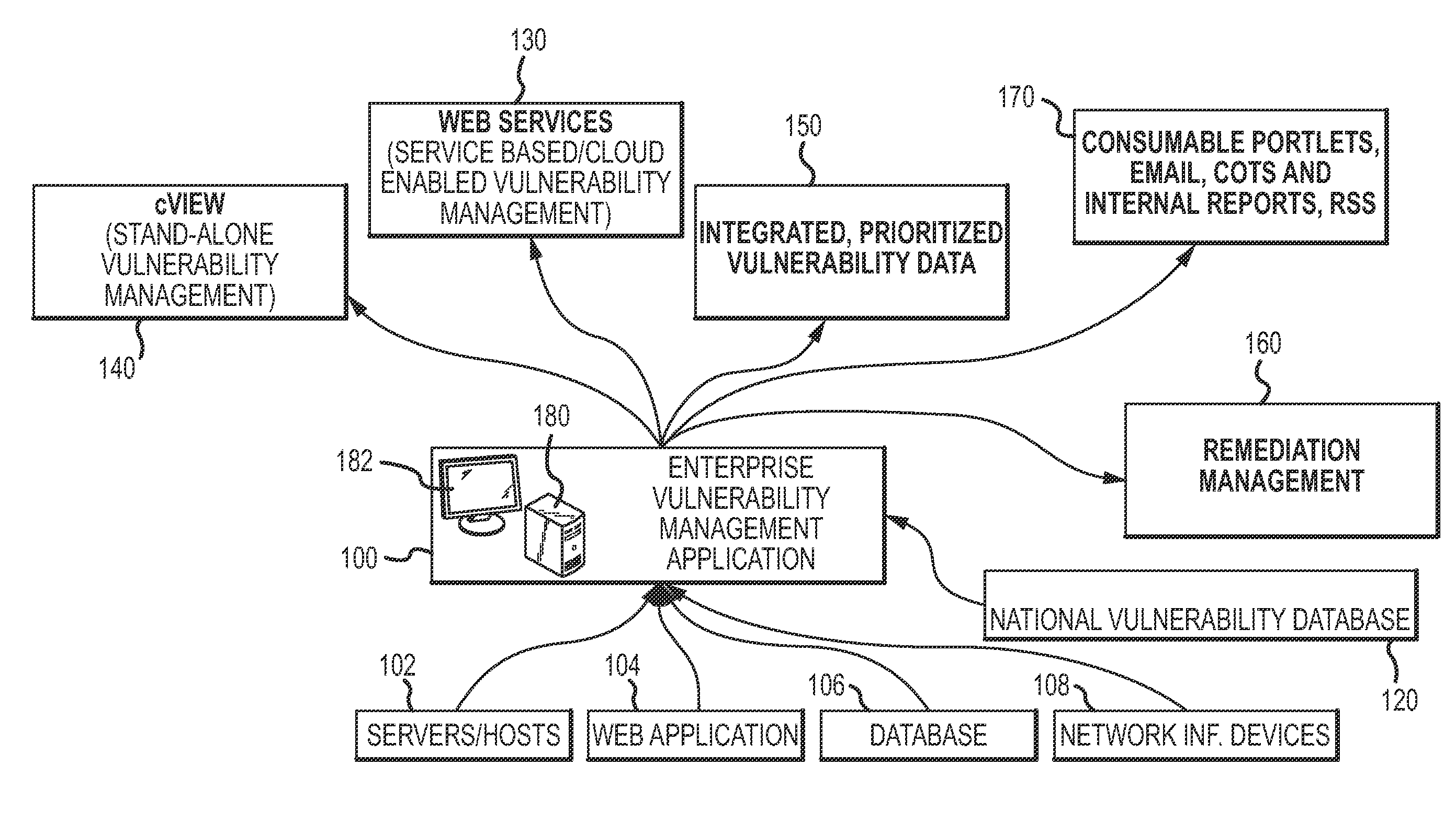
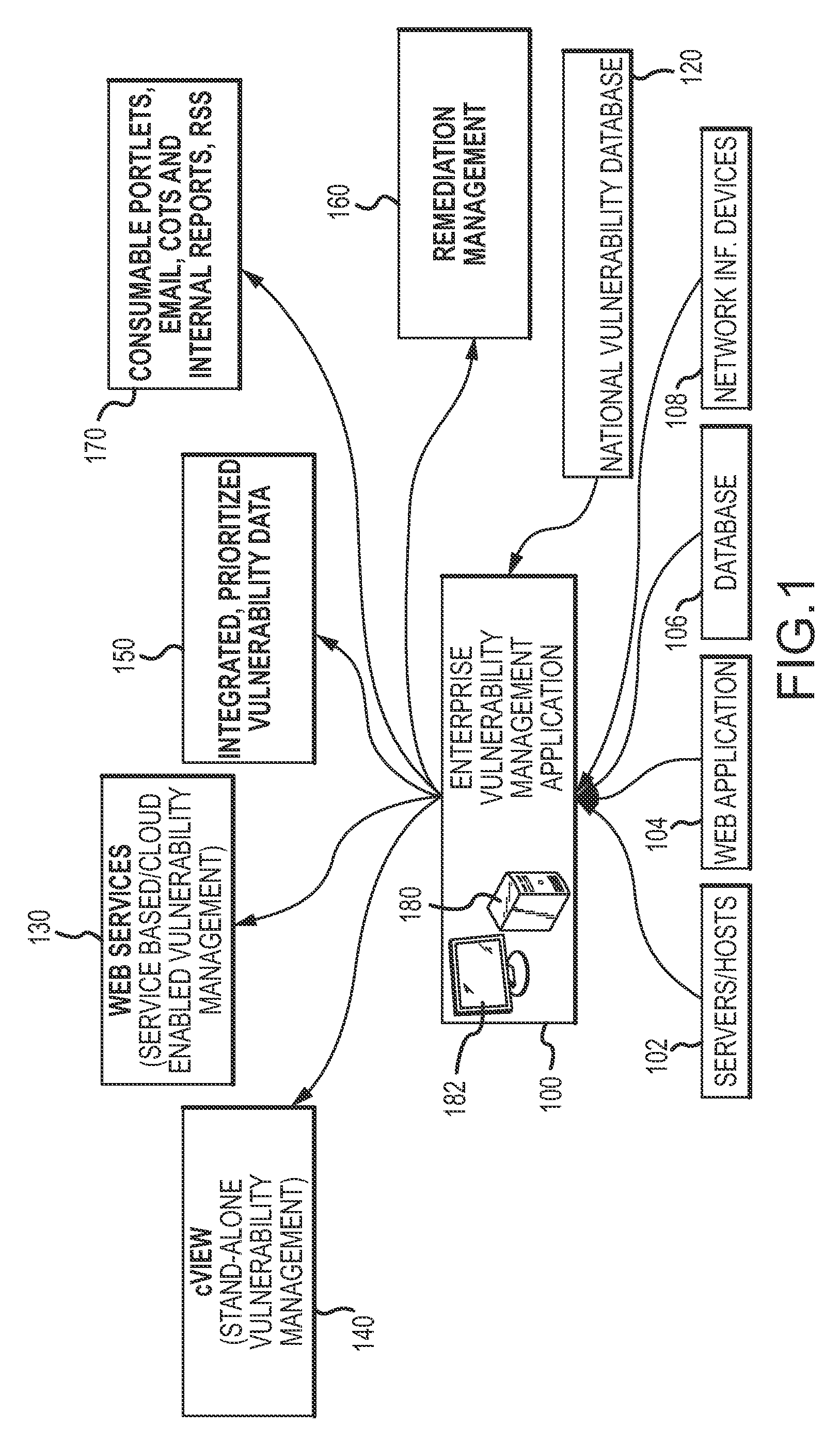
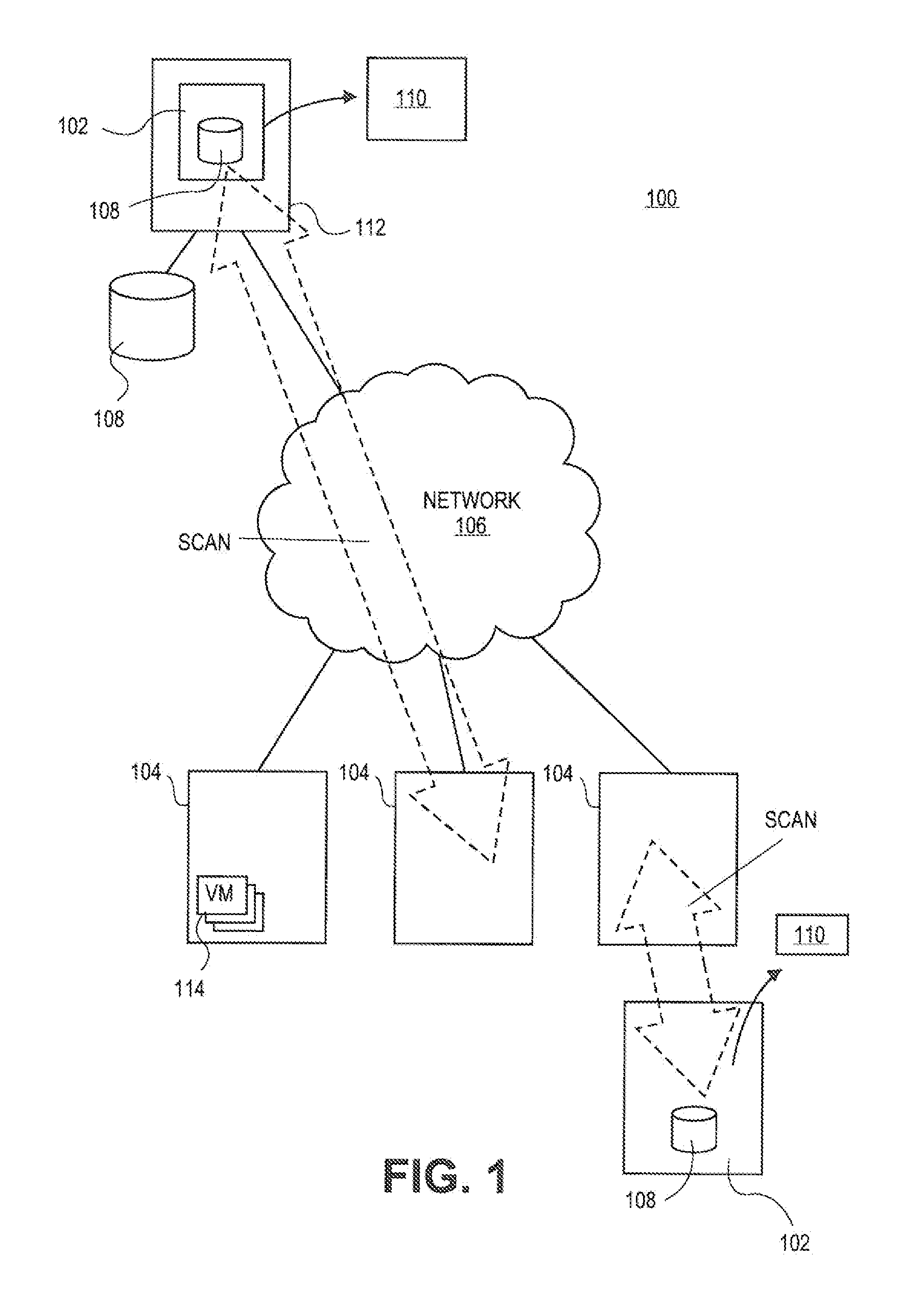
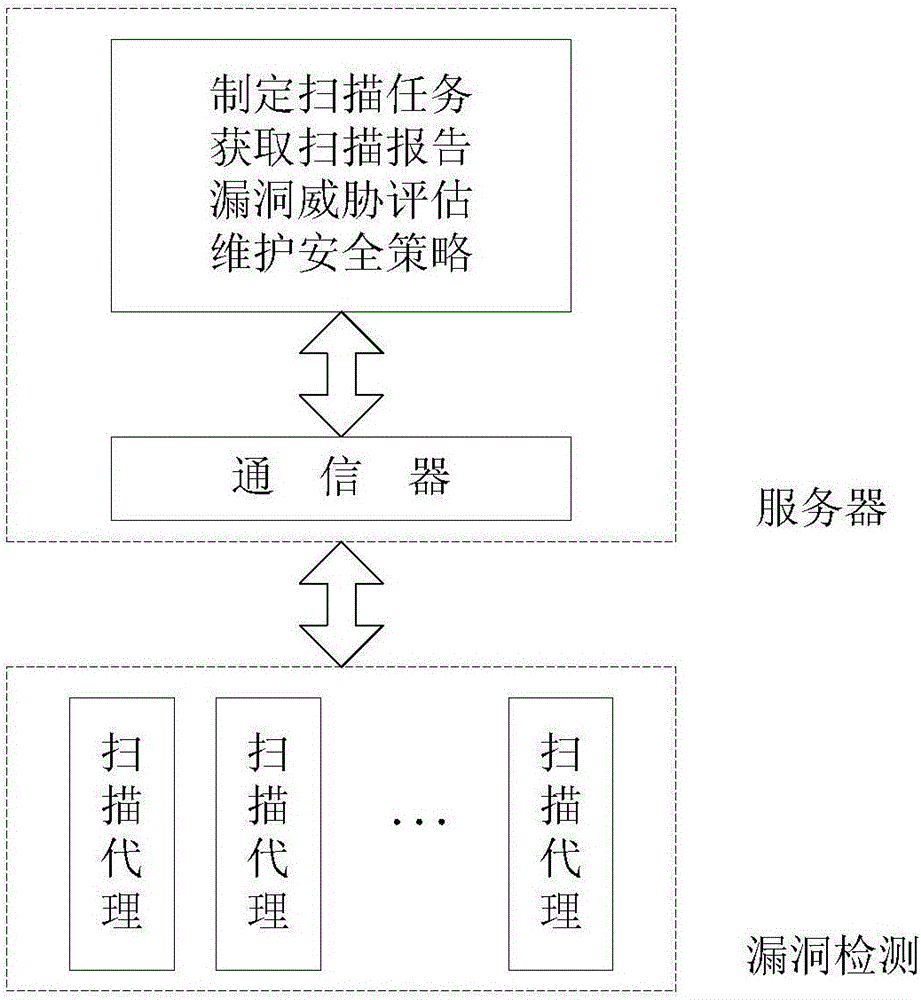
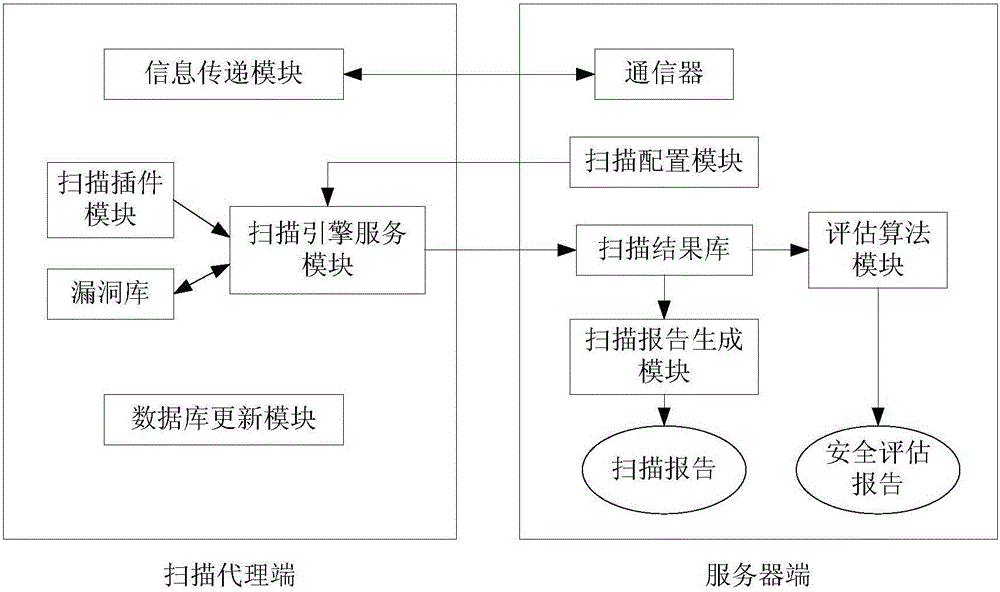
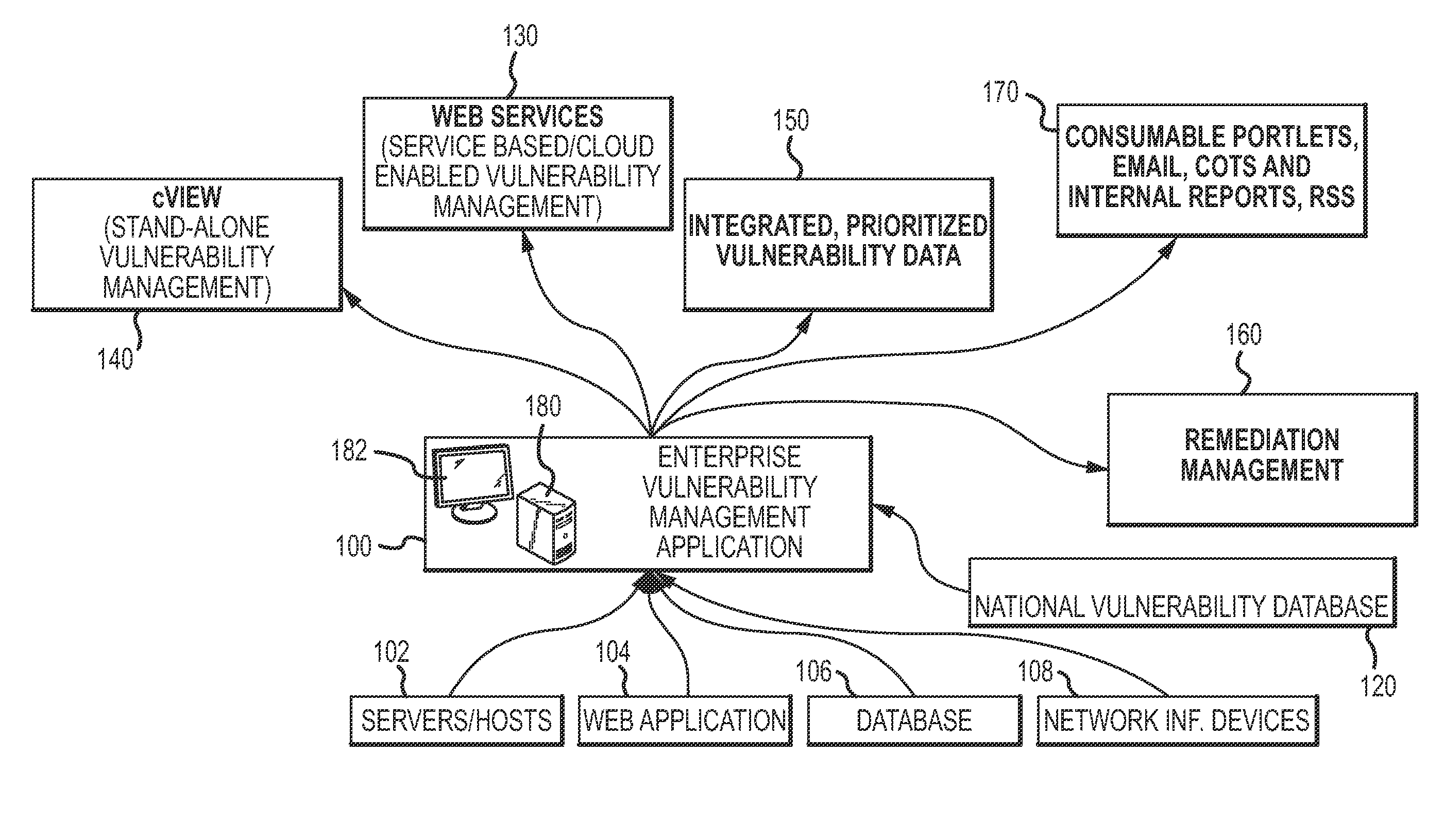
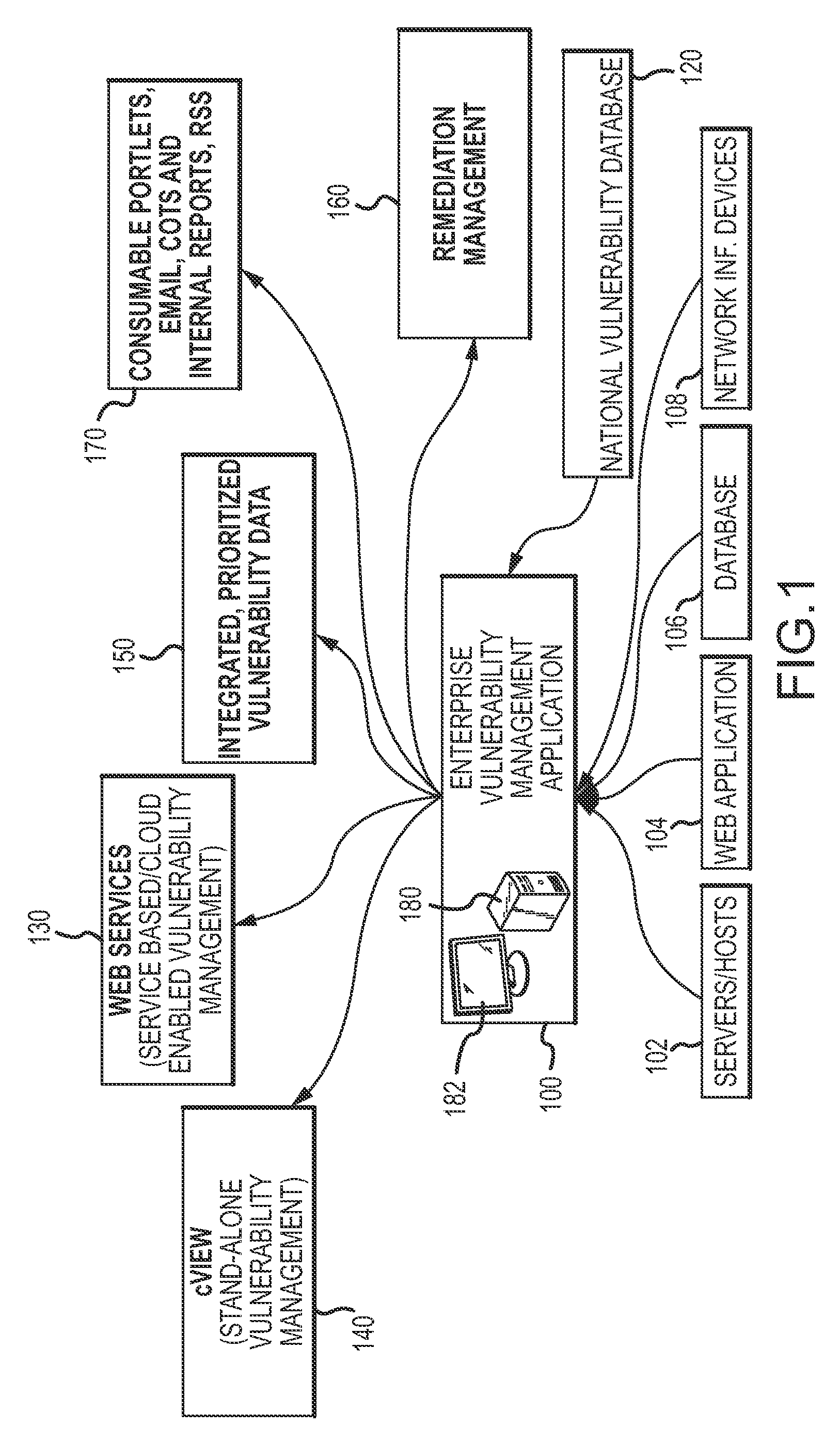
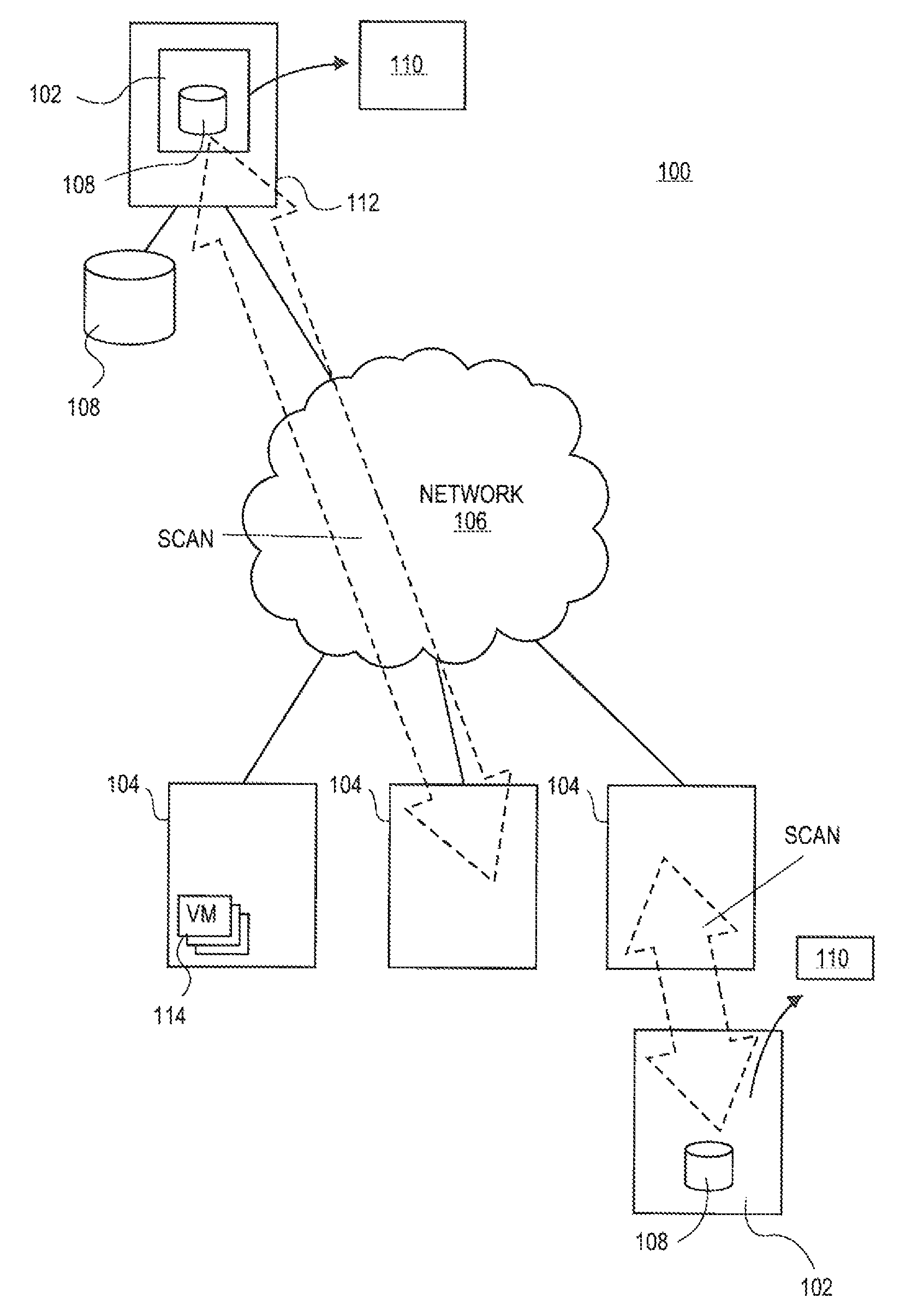
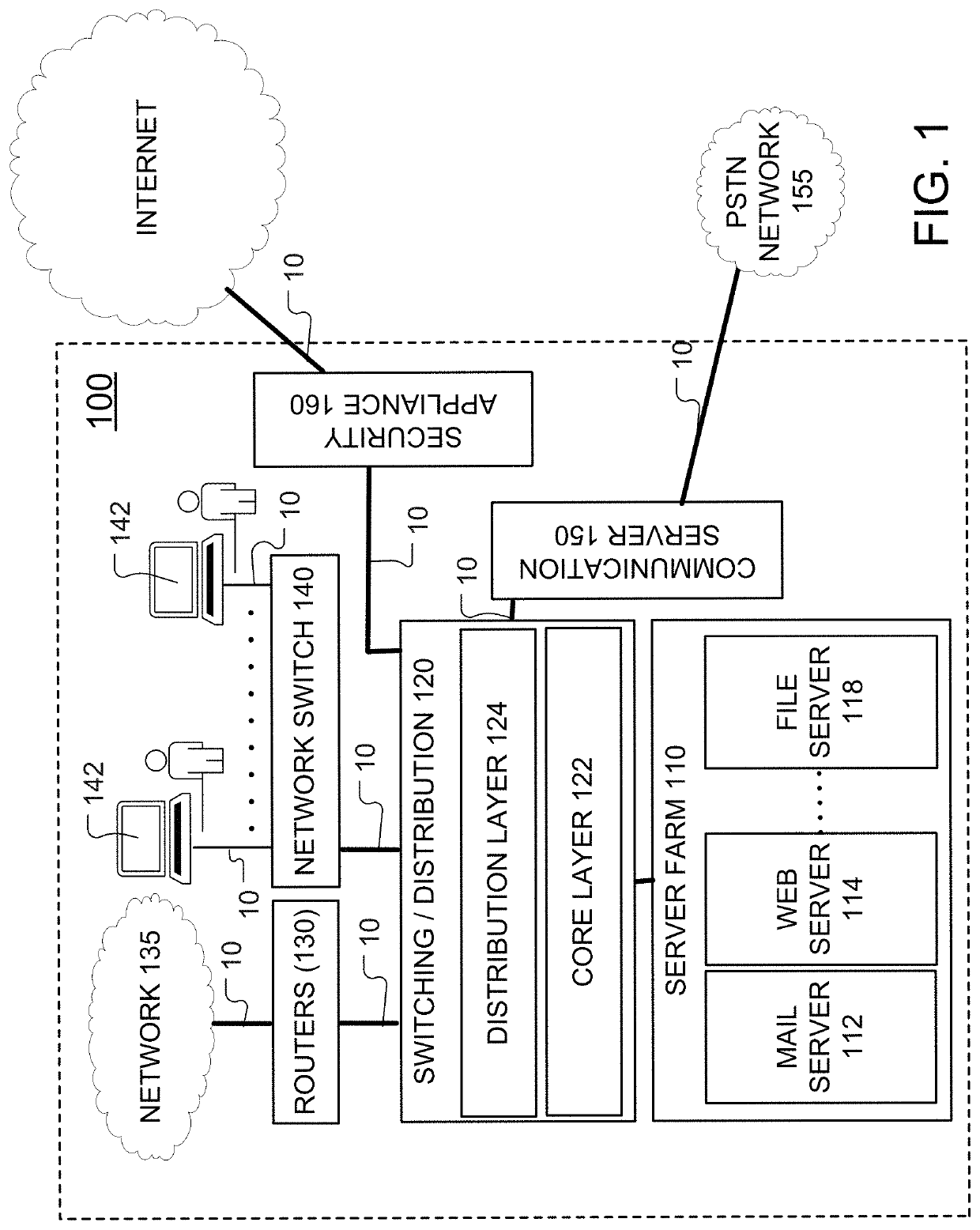
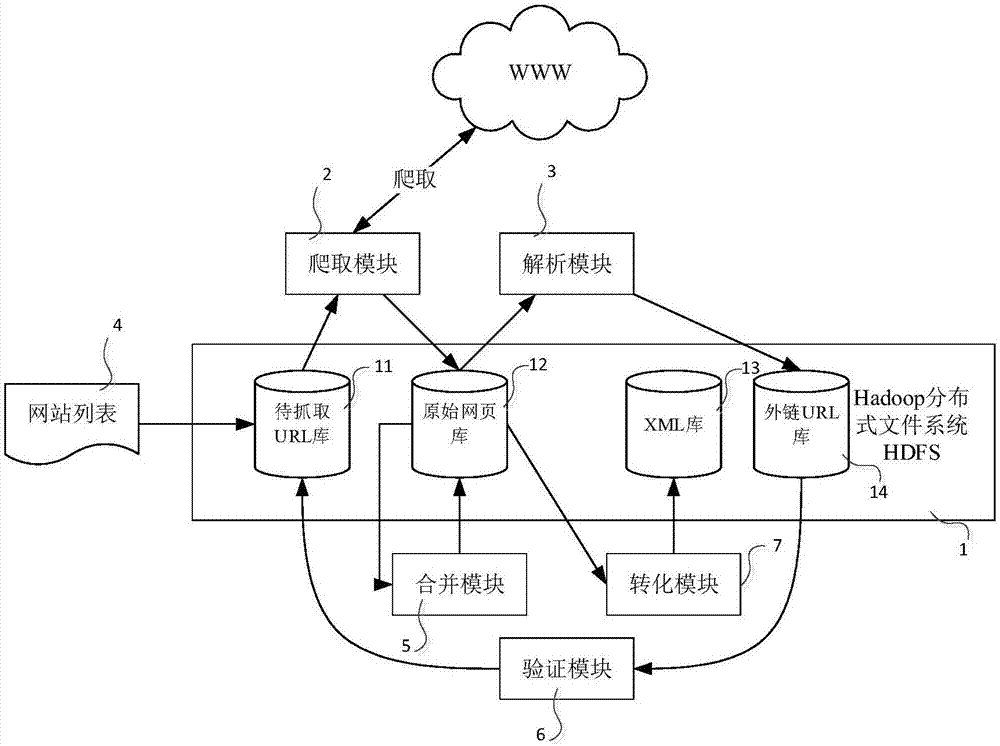
Enterprise vulnerability management
ActiveUS20120304300A1Fast data analysisEasy to addMemory loss protectionError detection/correctionVulnerability managementRemedial action
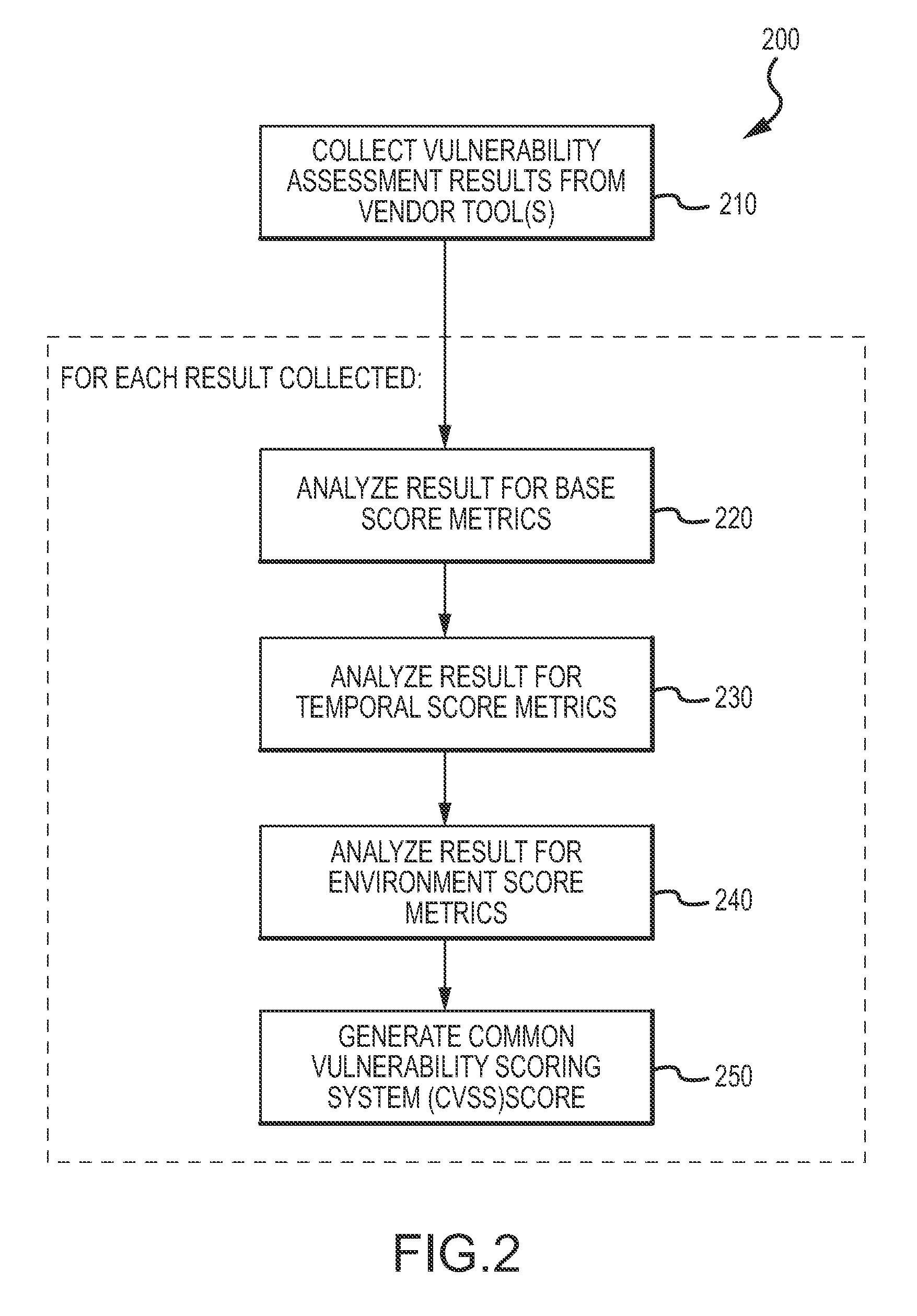
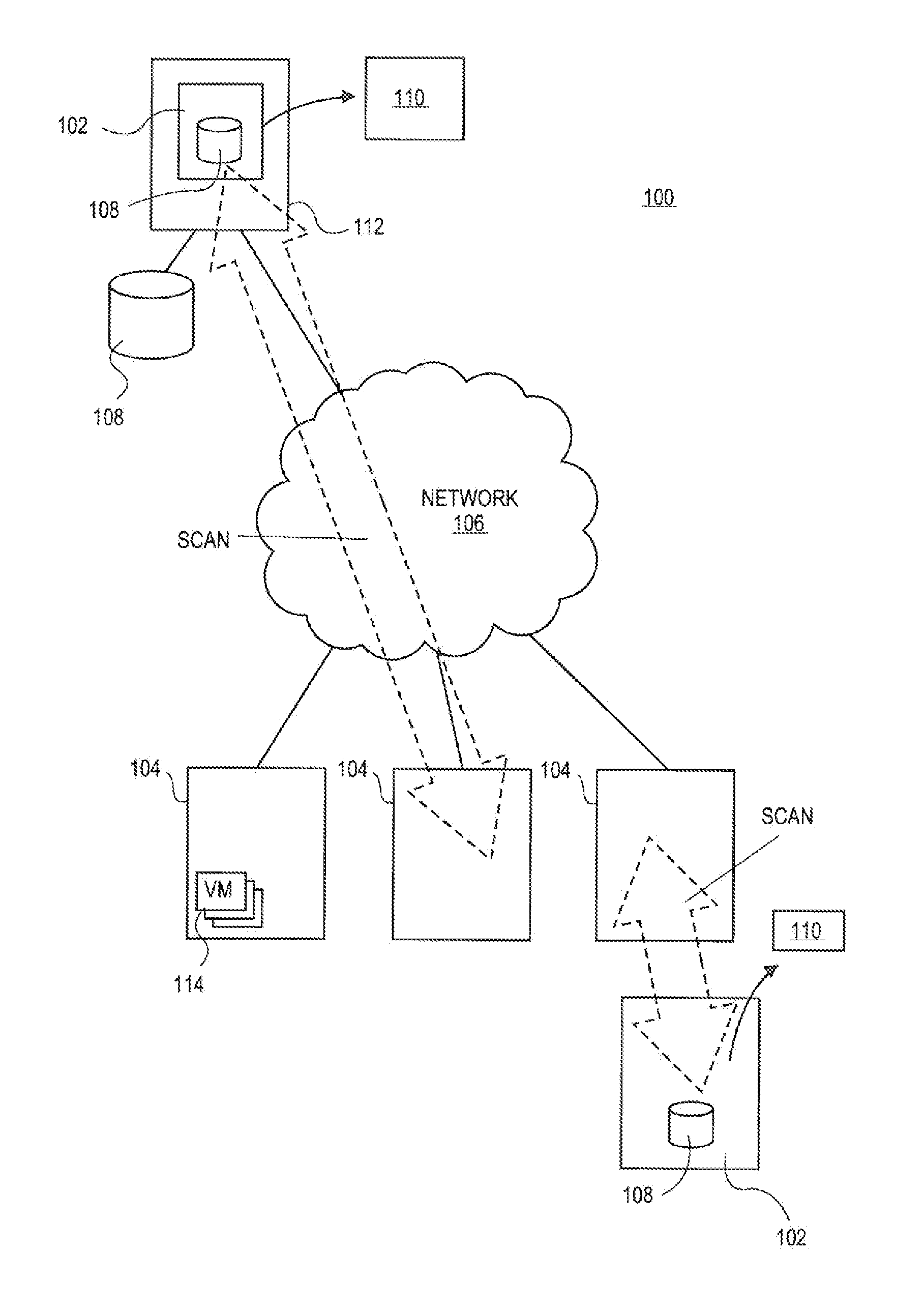
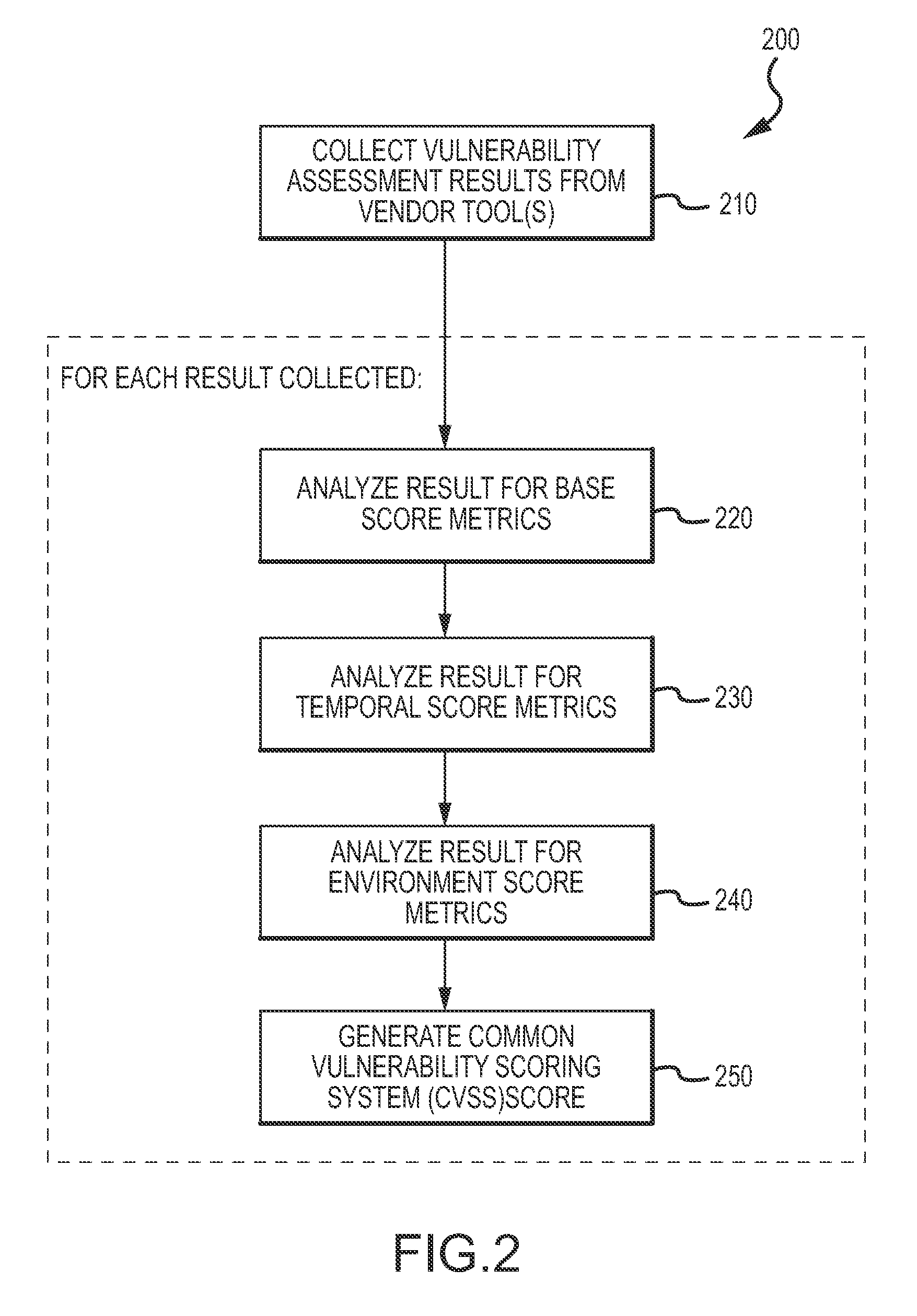
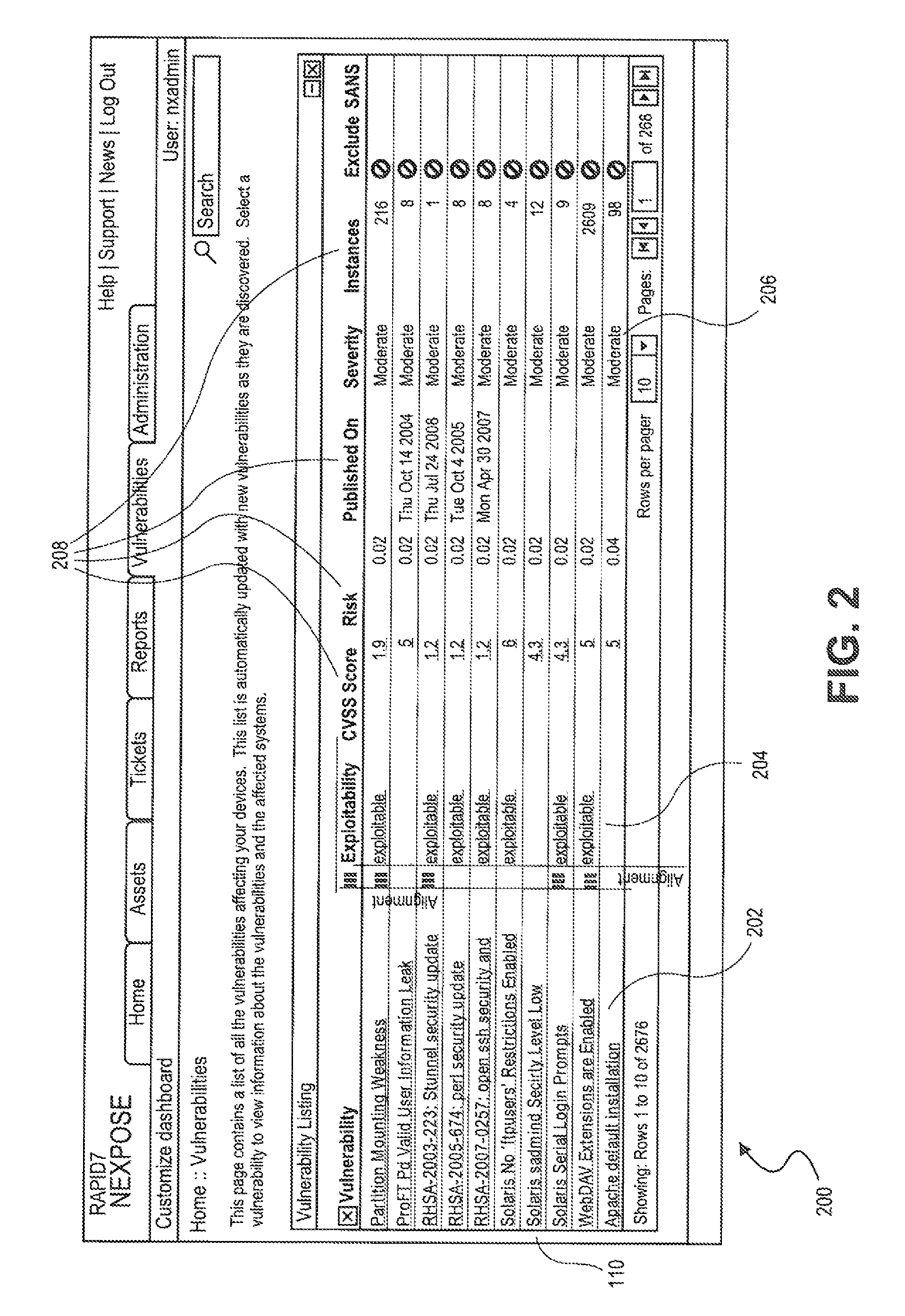
An enterprise vulnerability management application (EVMA), enterprise vulnerability management process (EVMP) and system. In one embodiment, the EVMP may include executing computer software code on at least one computer hardware platform to receive login information from a user, inventory current information technology assets of the enterprise, conduct vulnerability scanning of the inventoried information technology assets, analyze vulnerability correlation and prioritization of the information technology assets, remediate one or more vulnerabilities of the information technology assets, and report to the user about the vulnerabilities and remediation undertaken. As part of the analysis, one or more vulnerability scores such as, for example, Common Vulnerability Scoring System (CVSS) scores, may be generated from base score metrics, temporal score metrics and environment score metrics.
Owner:LEIDOS INNOVATIONS TECH INC
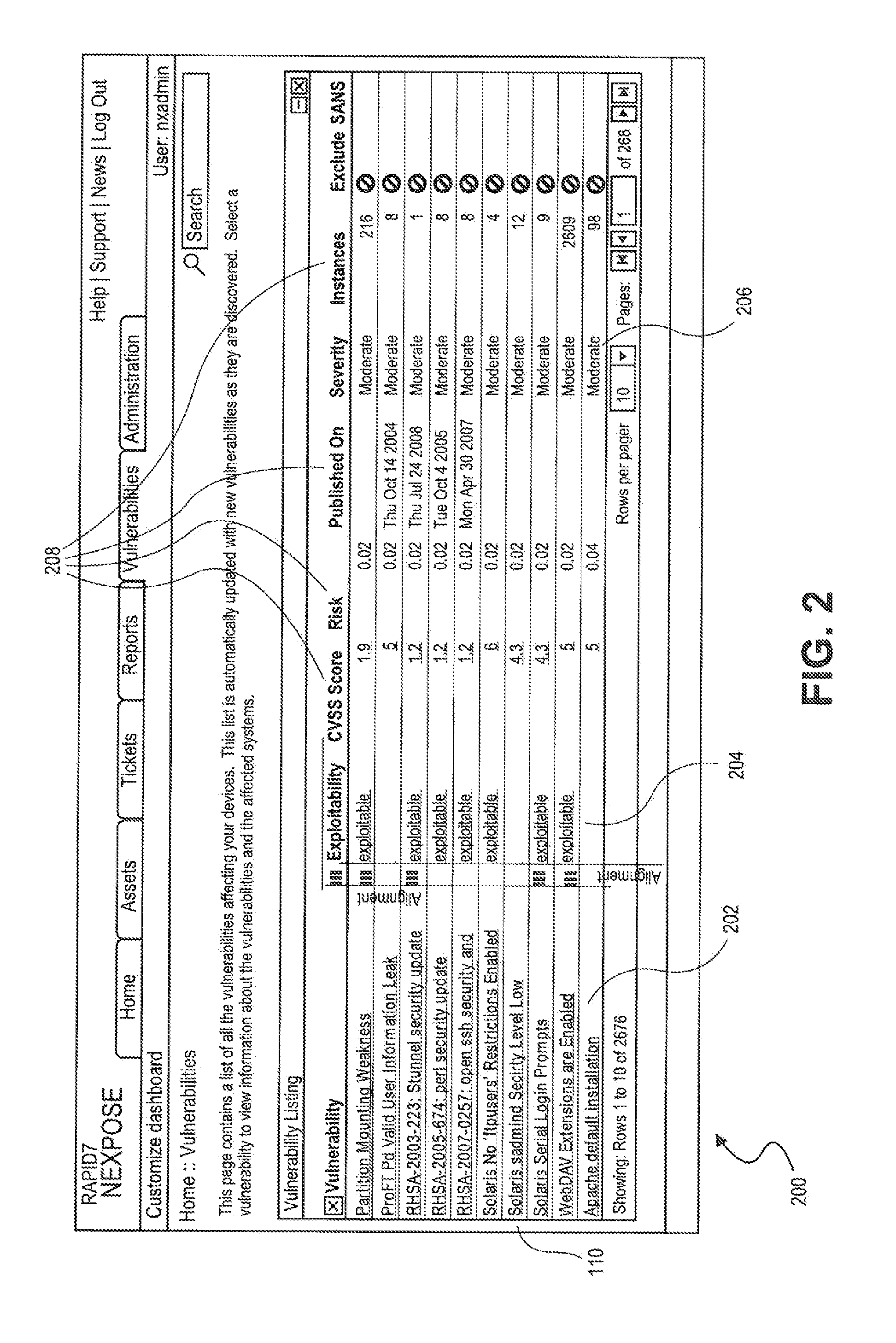
Methods and systems for improved risk scoring of vulnerabilities
A security tool can identify vulnerabilities in a computing system and determine a risk level of the vulnerabilities based on base and optional CVSS vectors and additional factors that represent the evolving nature of vulnerabilities. Likewise, the security tool can determine an overall risk for vulnerabilities, an asset, and / or a collection of assets that encompasses a global view of an asset's risk and / or collection of assets' risk, business considerations of an entity that own and controls the asset and / or the collection of assets, and the entity's associations.
Owner:RAPID7
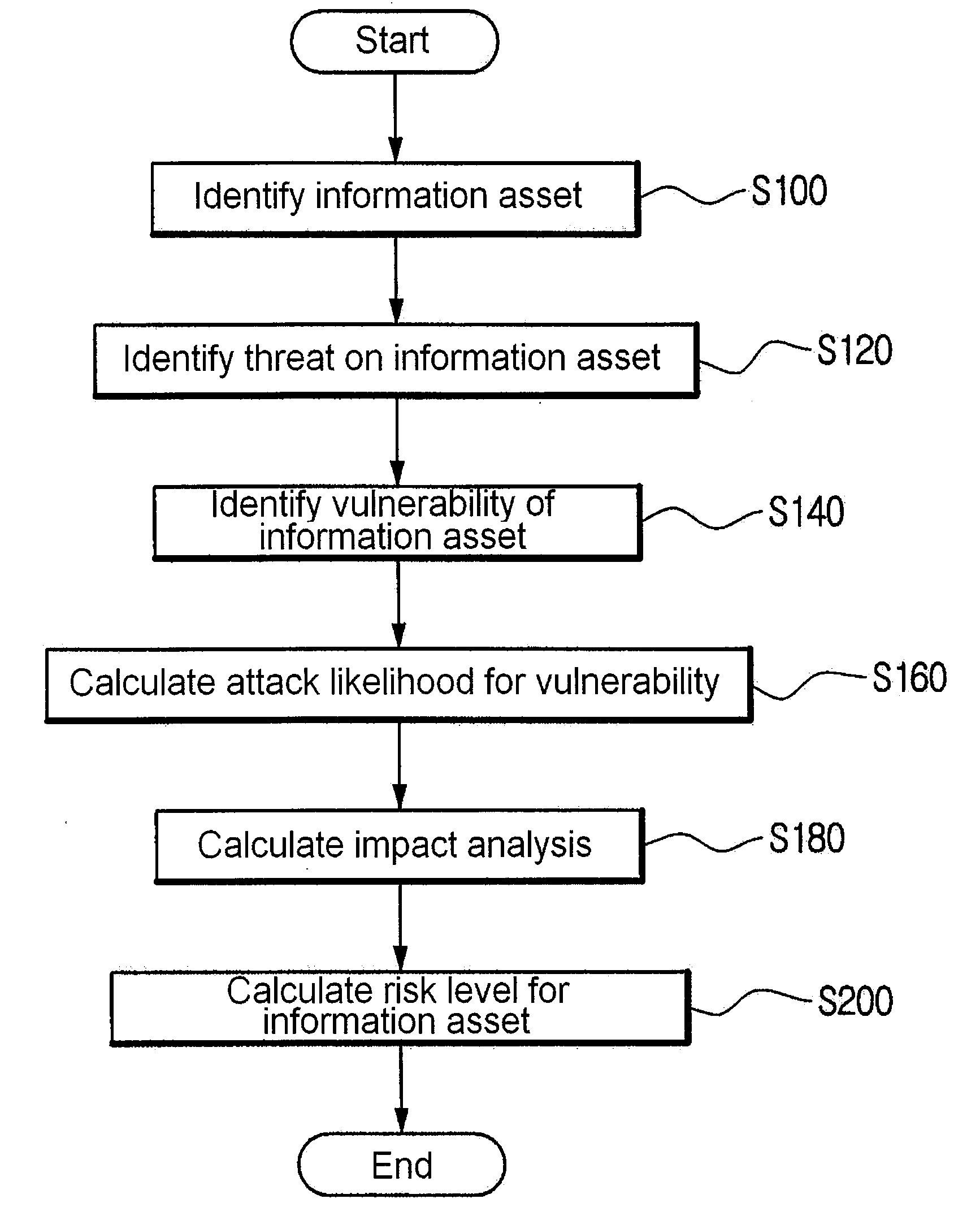
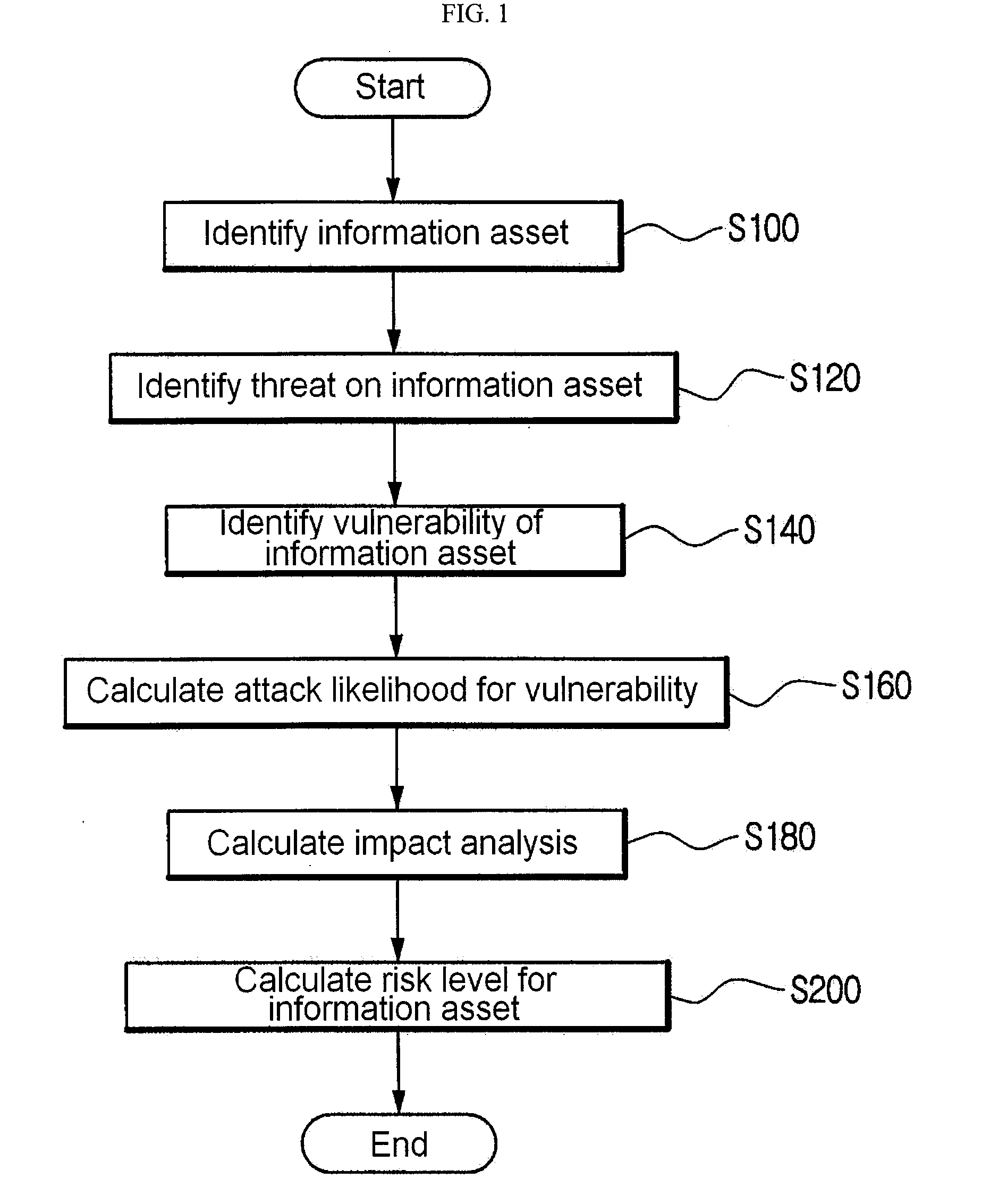
Method for risk analysis using information asset modelling
InactiveUS20090099885A1Minimizing interventionMemory loss protectionError detection/correctionRisk levelNetwork service
A method for risk analysis using information asset modeling. The method has the steps of: (a) identifying an information asset which uses or provides a network service; (b) identifying a threat on the information asset through a computer network; (c) identifying a vulnerability of the information asset; (d) calculating an AL (attack likelihood) by using a CVSS (Common Vulnerability Scoring System) score obtained by converting a severity caused by a success of an attack on the vulnerability into a standardized value; (e) computing the value of the information asset so as to calculate an IM (impact analysis); and (f) multiplying the calculated AL and IM so as to determine an RL (risk level) for the information asset.
Owner:KOREA INTERNET & SECURITY AGENCY
Electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and evaluation system based on the model
ActiveCN105763562AImprove accuracyImprove timelinessPlatform integrity maintainanceTransmissionDistributed structureStructure of Management Information
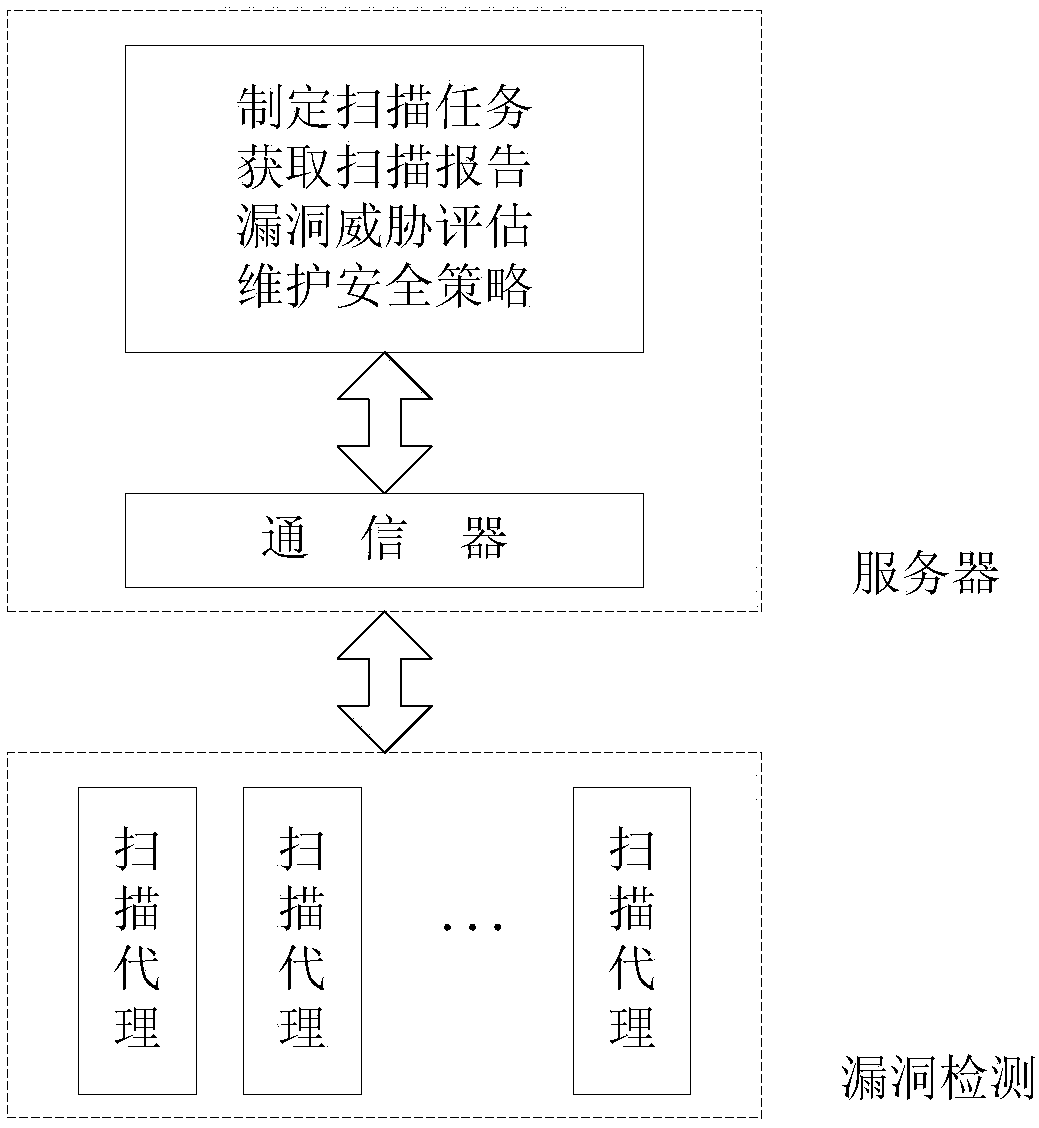
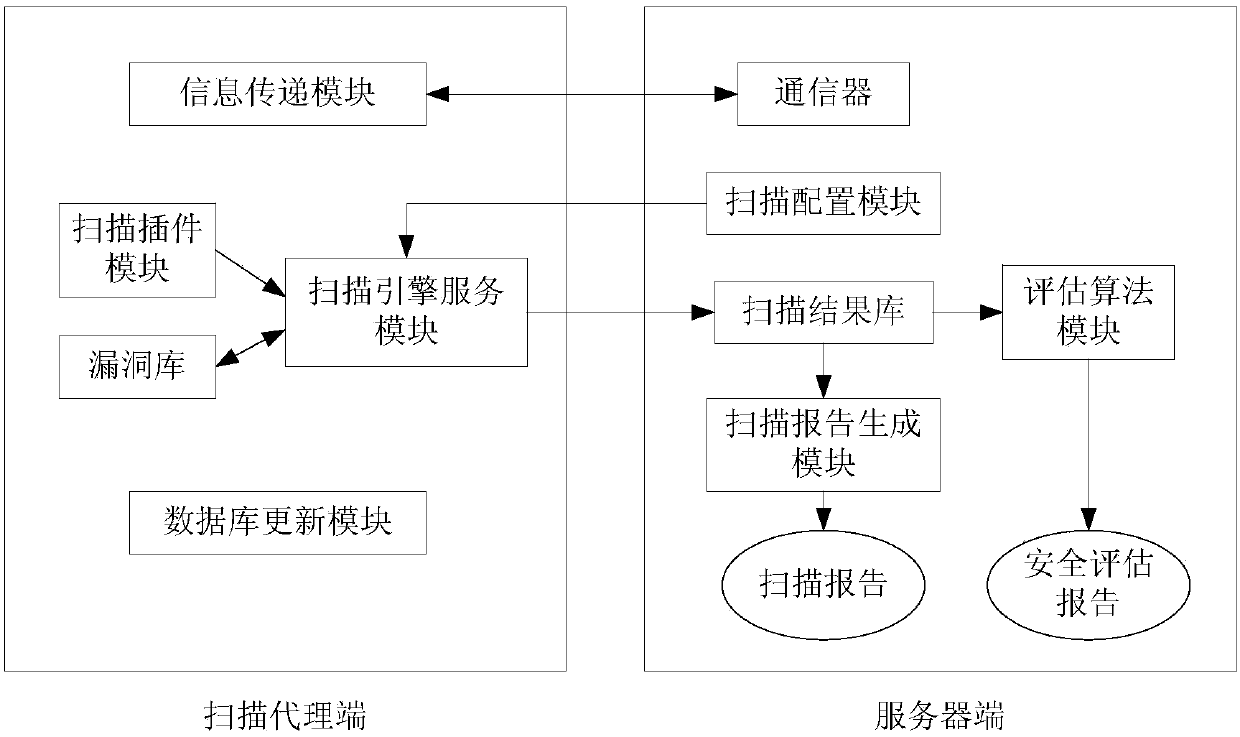
The invention discloses an electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and an evaluation system based on the model, the model selects three groups of security vulnerability evaluation factors including vulnerability distribution threat degree, access approach and utilization complexity; an analytic hierarchy process is adopted to establish a vulnerability threat degree evaluation model, and a parameter construction method is provided; on the basis of quantitative evaluation, the evaluation result defines a vulnerability threat level, and the objectivity of quantitative evaluation and visibility of qualitative evaluation are considered; and the system related to the invention comprises a vulnerability detection part and a server part which adopt distributed structure. According to the invention, a vulnerability scanning system and a security area of the electric power information network are combined, an electric power information network vulnerability threat evaluation algorithm based on CVSS and analytic hierarchy process is adopted to perform vulnerability threat evaluation, so that the system can be safer and more accurate for performing vulnerability scanning and safety evaluation on the electric power information network.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Enterprise vulnerability management
ActiveUS8789192B2Easy to addIncrease capacityMemory loss protectionError detection/correctionVulnerability managementRemedial action
Owner:LEIDOS INNOVATIONS TECH INC
Matrix visualization method based on state transition graph
InactiveCN106549950AIntuitive descriptionClear descriptionData switching networksTheoretical computer scienceNetwork topology
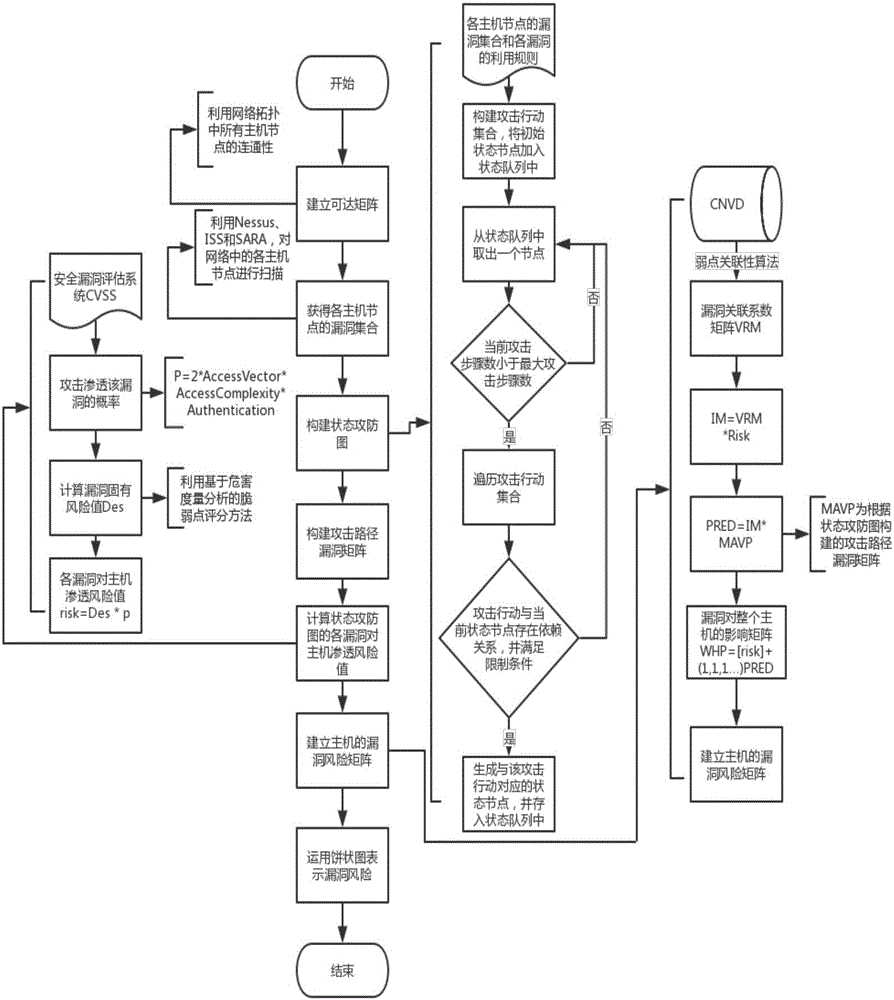
The invention discloses a matrix visualization method based on a state transition graph. The method comprises the following steps: establishing a reachable matrix according to the connectivity of all host nodes in a network topology; scanning the host nodes in a network through vulnerability scanning tools (Nessus, ISS and SARA), so that a vulnerability set for each host node is obtained; constructing the state transition graph according to the vulnerability sets of the host nodes and exploitation rules of vulnerabilities; constructing an attack path vulnerability matrix according to the state transition graph; calculating host penetration risk values of the vulnerabilities in the state transition graph based on a common vulnerability scoring system (CVSS); calculating a host vulnerability risk matrix of the state transition graph through matrix operation; and representing host vulnerability risks through a pie chart, so that a network security administrator can search for a host with the highest risk value and carry out maintenance. The method provided by the invention has the advantages that vulnerability risk information of hosts in the network can be visually and clearly described, so that a new thread of thought is provided for the visualization of risk results of the state transition graph.
Owner:NANJING UNIV OF SCI & TECH
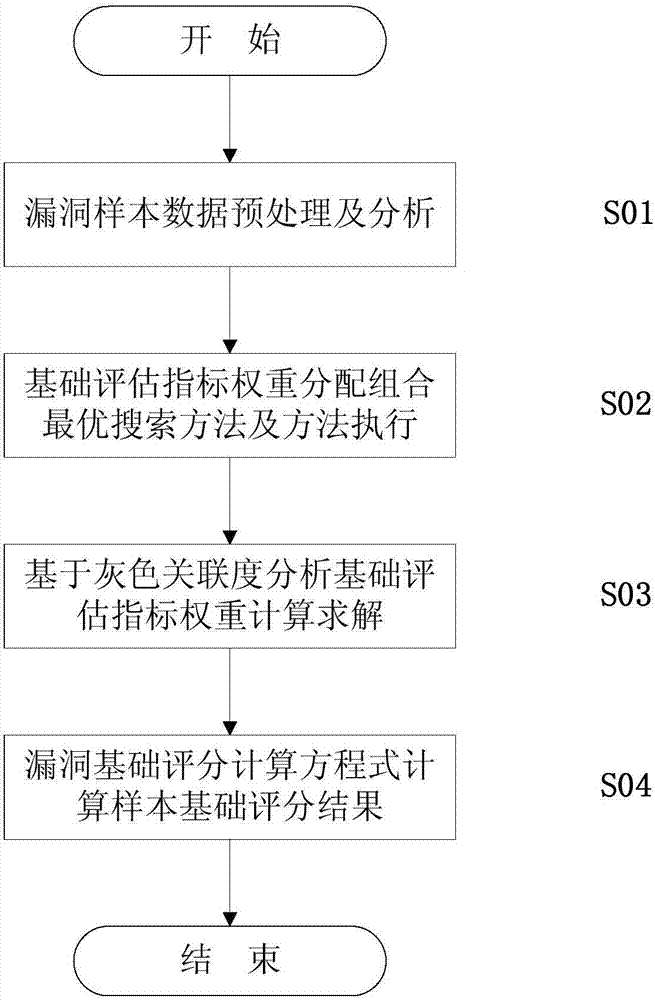
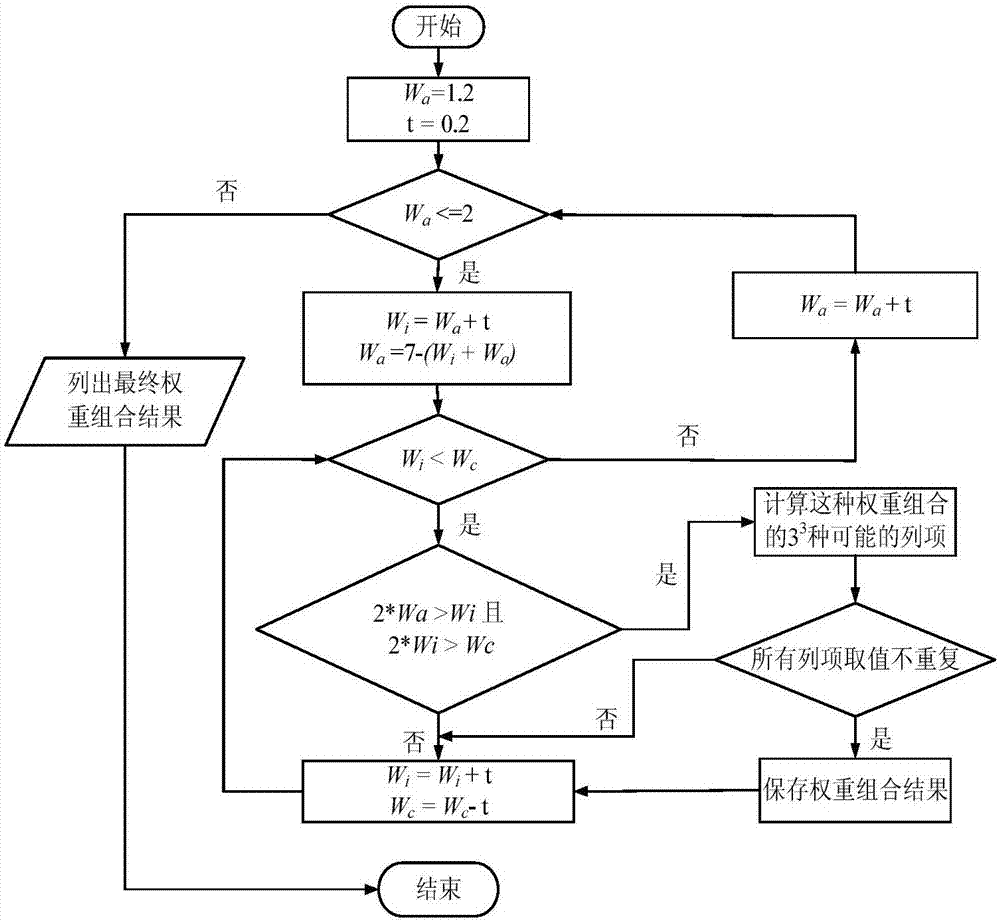
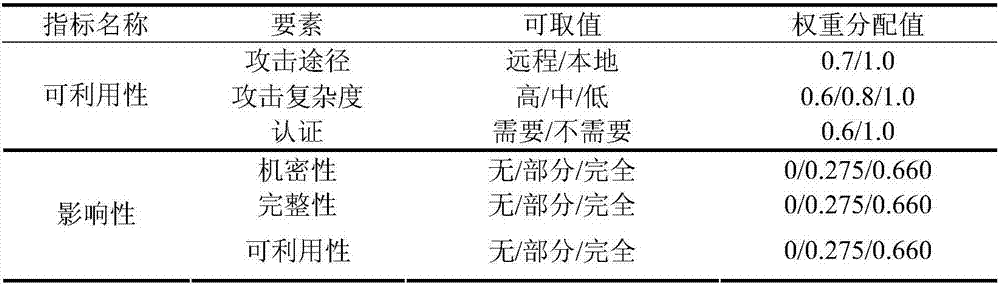
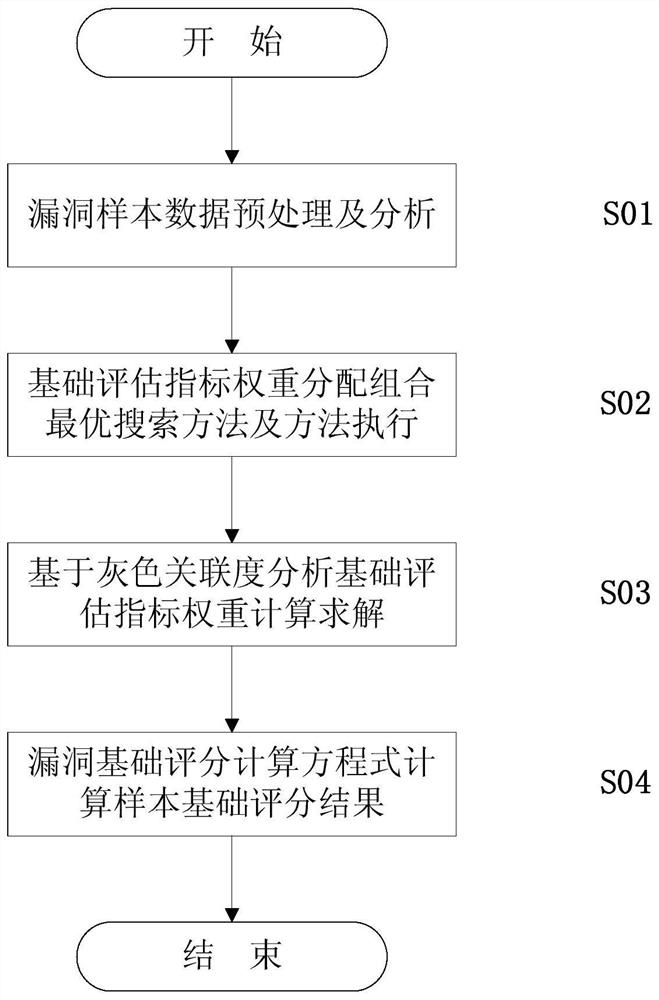
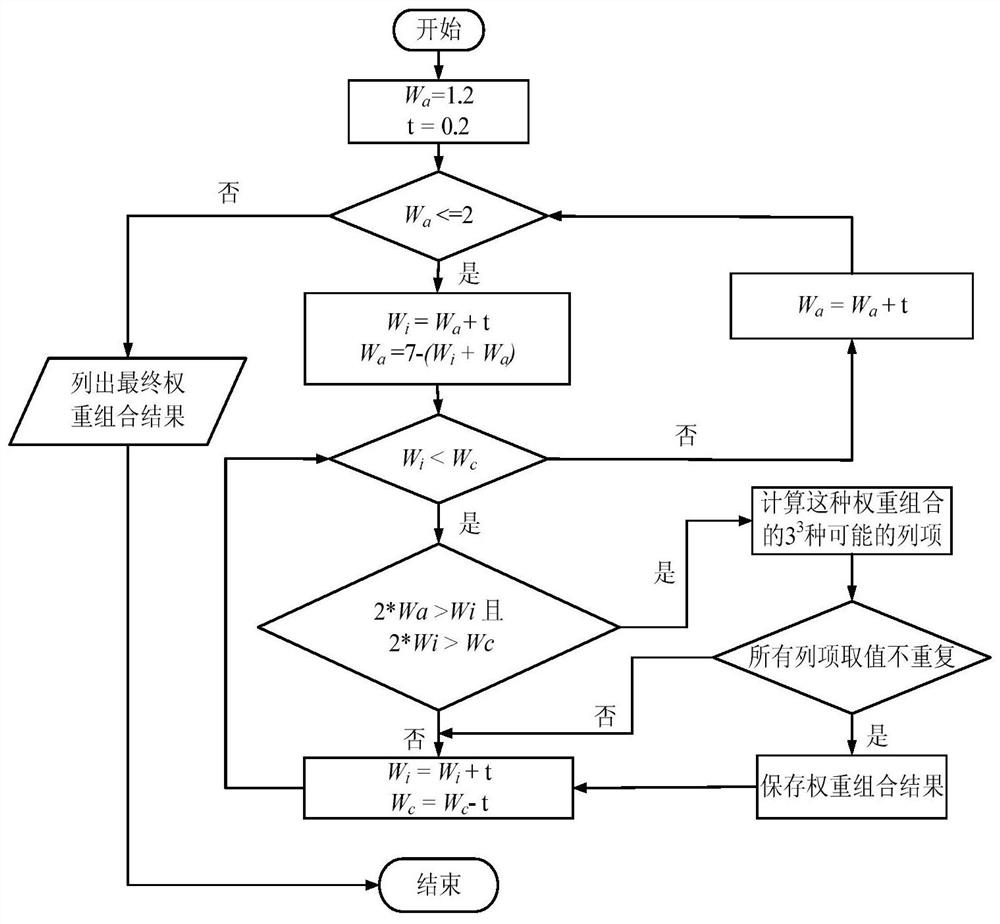
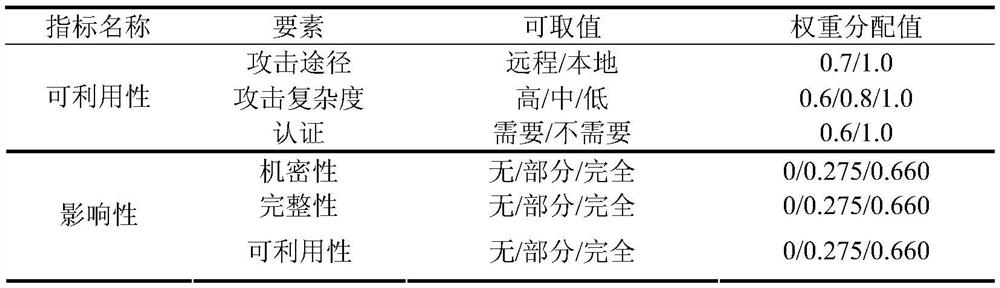
Loophole risk basic evaluation method based on CVSS
The invention provides a loophole risk basic evaluation method based on a CVSS. The method comprises the steps of S01, preprocessing data; S02, determining weights of the three basic evaluation indexes, and conducting optimization; S03, solving the weights of the basic evaluation indexes; S04, calculating a basic evaluation estimation value of every loophole threat. Compared with the prior art, according to the loophole risk basic evaluation method based on the CVSS, on the basis of CVSS evaluation, a basic evaluation estimation index weight distribution method is redesigned, according to the relative importance of the basic evaluation indexes, the weights of the basic evaluation indexes are optimized and distributed, a grey correlation degree index weight solving method is combined with the basic evaluation estimation index weight distribution method, so that the evaluation result is more objective, the diversity of the evaluation result is improved, and the loophole threat is conveniently and visually distinguished.
Owner:CIVIL AVIATION UNIV OF CHINA
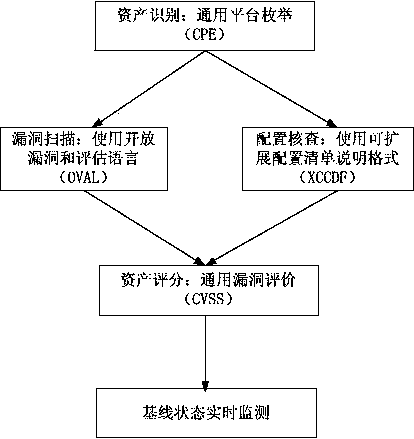
Security baseline assessment method based on SCAP
InactiveCN103927491AQuick extractionRepair in timePlatform integrity maintainanceSecurity levelBaselining
The invention discloses a security baseline assessment method based on a SCAP. The security baseline assessment method based on the SCAP comprises the first step of asset identification, wherein rules are named through CPE for an assessed object, and the basic management foundation is provided for each assessment item, the second step of CVE, wherein CVE is carried out on the target object whose asset is assessed by using OVAL; the third step of CCE, wherein the security configuration of the asset is inspected by using an XCCDF, the fourth step of security scoring, wherein the security level of the asset is scored through a CVSS, and the fifth step of state baseline monitoring, wherein state baseline monitoring is carried out on the assessed target object reaching an established security baseline. By means of the security baseline assessment method based on the SCAP, the work of CVE, patch management and the like can be combined, and state baseline monitoring can be carried out on the assessed target object.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
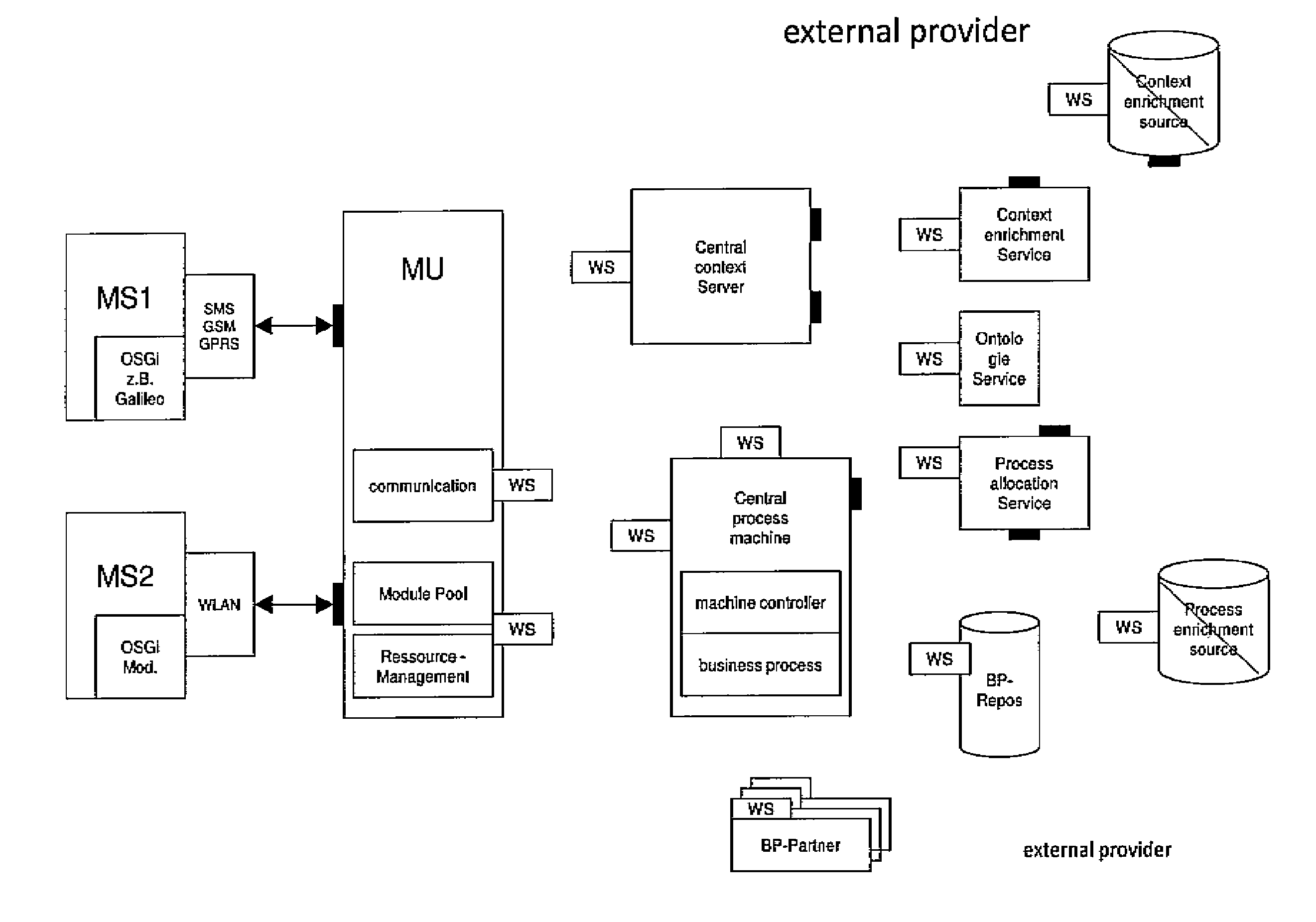
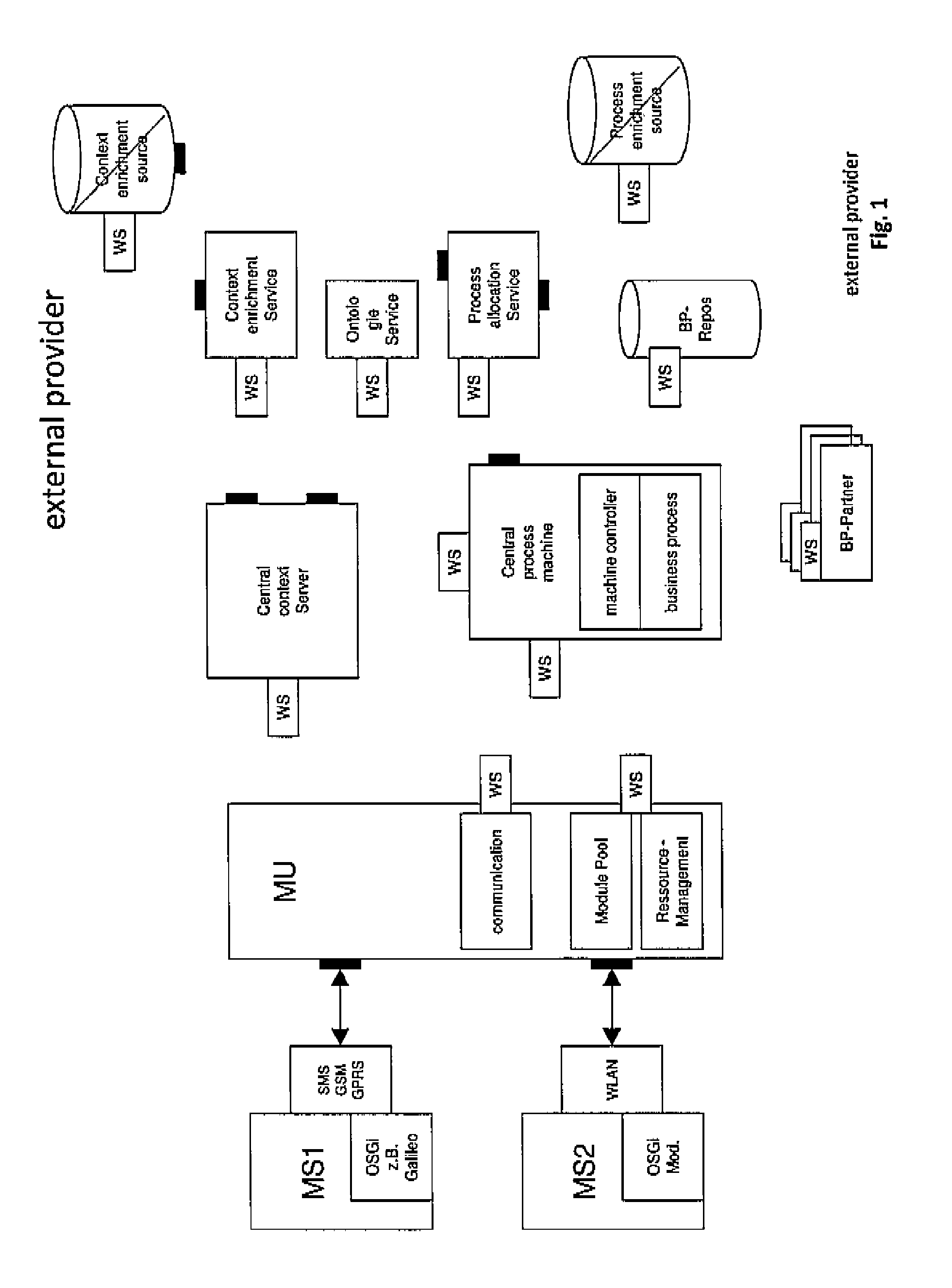
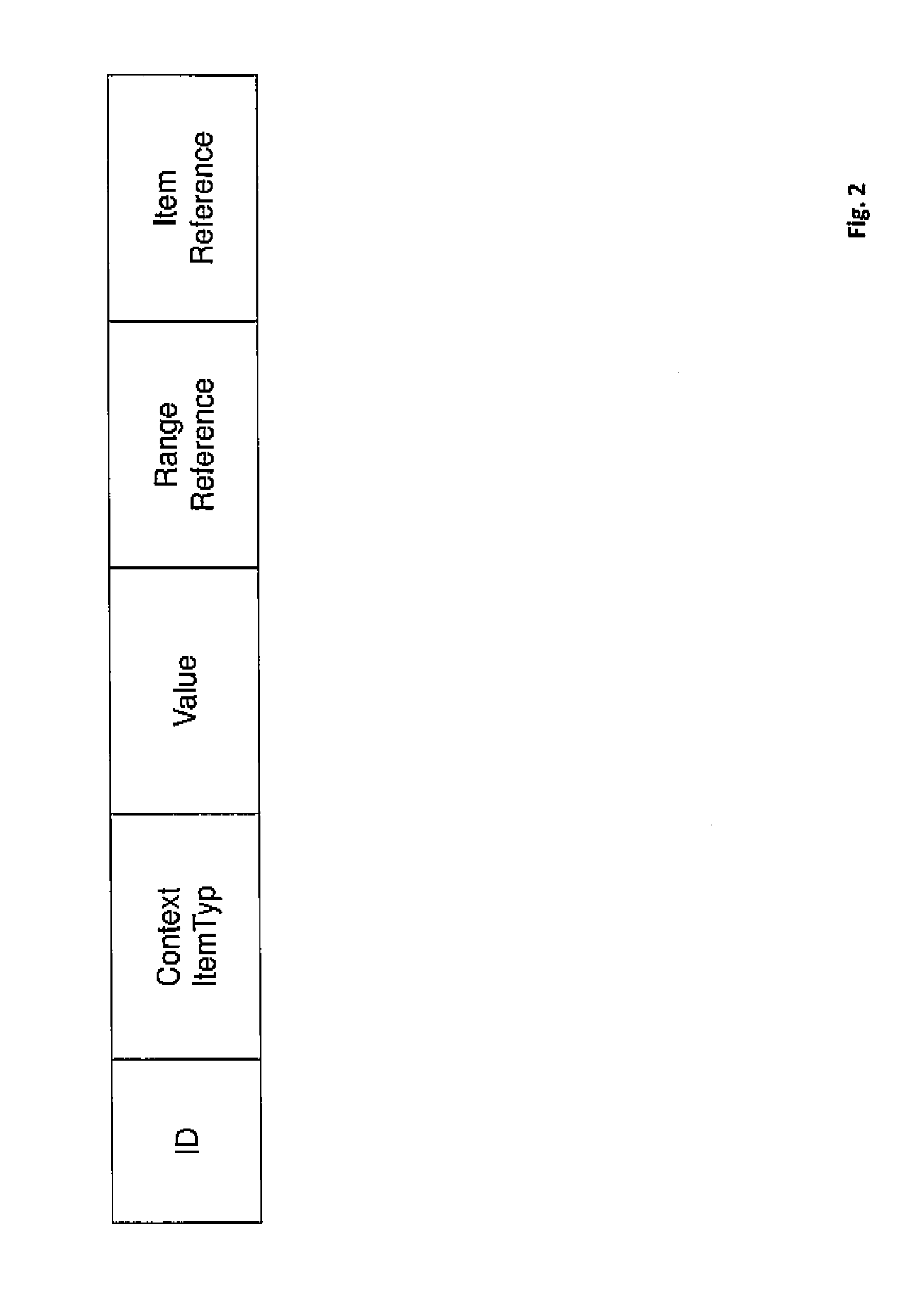
Method and device for the context-driven integration of context-variable systems into process sequences
InactiveUS8996660B2Digital data information retrievalDigital data processing detailsManagement unitDatabase
Method for the context-driven integration of context-variable systems (CVSs), in particular but not exclusively in the form of mobile systems (MSs), into processes, which system can collect sensor data, comprising an infrastructure system which is connected to the MS via a network, wherein the infrastructure system comprises a central enrichment service (CES) and process retrieval service (PRS), there also being provided a central process engine (CPE) on which the sequence of the processes is controlled, a management unit (MU) functioning as a proxy between the CPS and MU, including the steps:a) booting up the MS and determining the initial context, i.e. context information which is directly accessible to the system;b) transmitting the (initial) context to the CES via the network and enriching the context there;c) selecting the appropriate process for the MS based on the context information with the aid of the PRS, and filing the context information in the process;d) transferring the context information to the MS via the MU, so that the MU can determine the MS based on the context information;e) carrying-out of the process by the CPE which sends queries to the MS only via the MU, the queries comprising the context information, so that the MU dynamically forwards an allocation of the query to an MS based on the context information;f) returning the responses from the MS to the processes on the CPE via the MU.
Owner:FACHHOCHSCHULE DER WIRTSCHAFT +1
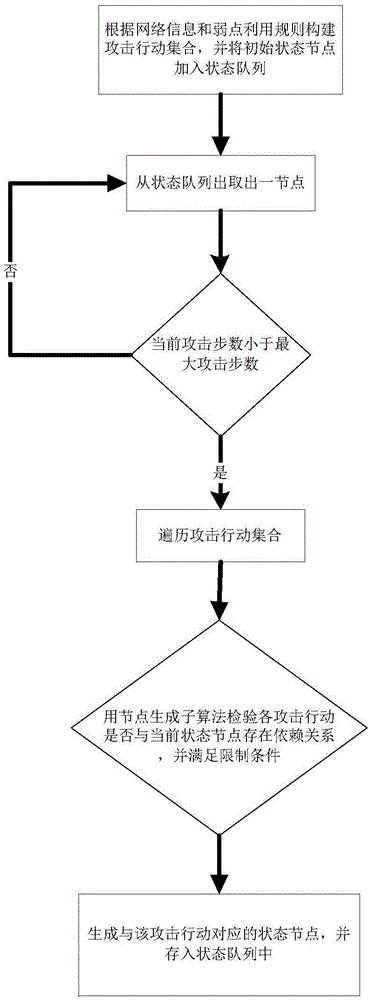
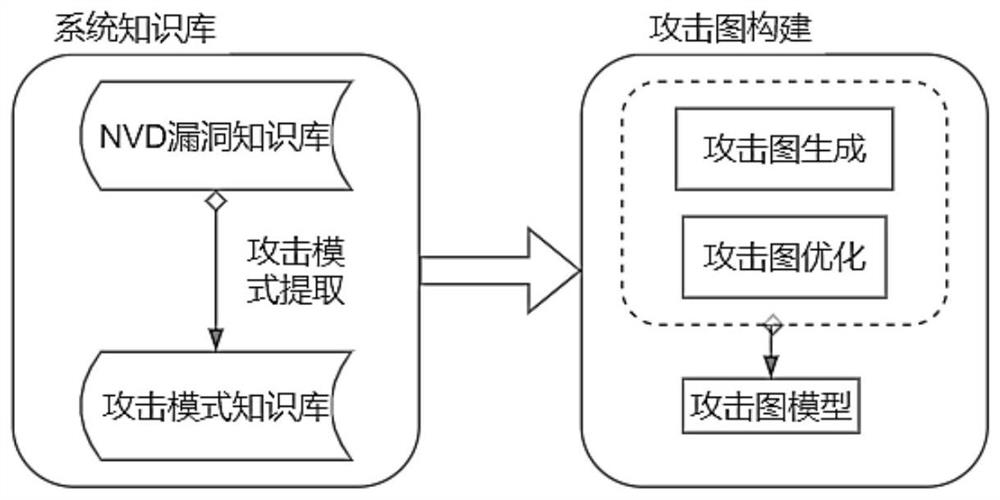
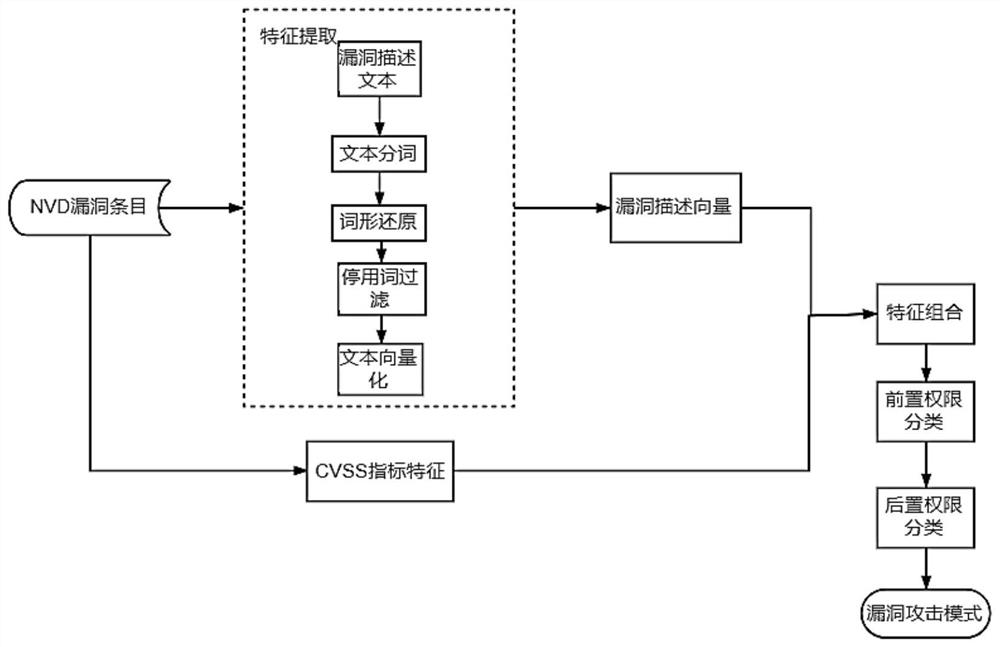
Method for generating attack path and attack graph based on multiple dimensions
The invention discloses a method for generating an attack path and an attack graph based on multiple dimensions, and belongs to the technical field of network security. According to the method, vulnerability entry samples are collected, a vulnerability knowledge base is established, and a front permission and a rear permission are marked for each vulnerability entry sample; features, including vulnerability description text features and CVSS index features, of each vulnerability entry sample in the vulnerability knowledge base are extracted; text preprocessing is performed on the vulnerabilitydescription text features; an attack mode is defined by using a triple < the prepositive authority, the postpositive authority and the vulnerability entry >; an attack mode knowledge base is constructed; for the target industrial control network, an attack graph is generated by adopting a breadth-first forward attack graph generation algorithm based on an attack graph optimization strategy. The multi-dimensional attack paths and the high-dimensional attack graphs corresponding to various attack modes are generated by analyzing the environment attributes of different terminals, the attack graph generation process is optimized, and the attack graph generation efficiency is improved.
Owner:JILIN PROVINCE ELECTRIC POWER RES INST OF JILIN ELECTRIC POWER CO LTD +5
Methods and systems for improved risk scoring of vulnerabilities
A security tool can identify vulnerabilities in a computing system and determine a risk level of the vulnerabilities based on base and optional CVSS vectors and additional factors that represent the evolving nature of vulnerabilities. Likewise, the security tool can determine an overall risk for vulnerabilities, an asset, and / or a collection of assets that encompasses a global view of an asset's risk and / or collection of assets' risk, business considerations of an entity that own and controls the asset and / or the collection of assets, and the entity's associations.
Owner:RAPID7
Cybersecurity vulnerability classification and remediation based on network utilization
ActiveUS20200162498A1Accurately vulnerabilityComputer security arrangementsData switching networksCyber-attackInternet traffic
A technology solution for remediating a cyberattack risk in a computing resource asset in a network system. The technology solution includes monitoring data traffic directed to the computing resource asset in the network system along with data traffic to one or more additional computing resource assets in the network system, generating network utilization data based on the monitored data traffic to the computing resource asset and the monitored data traffic to the one or more additional computing resource assets in the network system, receiving a common vulnerability score (CVSS) for a vulnerability in the computing resource asset, determining a network traffic adjustment (NTA) value for the common vulnerability score (CVSS) based on the network utilization data, adjusting the common vulnerability score (CVSS) by the network traffic adjustment (NTA) value to generate a prioritized common vulnerability score (PCVSS) for the computing resource asset, and remediating the computing resource asset to resolve the vulnerability based on the prioritized common vulnerability (PCVSS) score.
Owner:SAUDI ARABIAN OIL CO
Method and system for establishing electric power information network model for electric cps risk assessment
ActiveCN105763562BImprove accuracyImprove timelinessPlatform integrity maintainanceTransmissionDistributed structureInformation networks
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
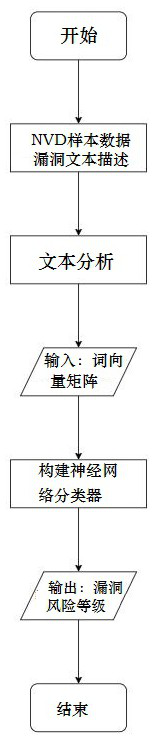
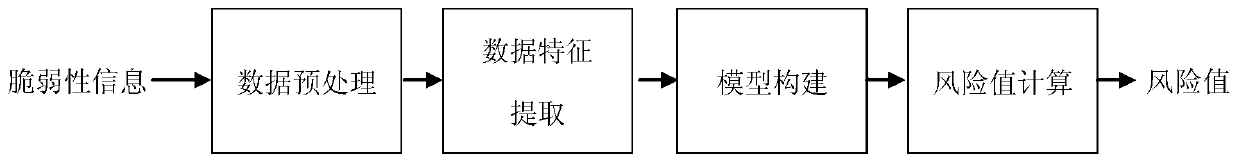
Unknown vulnerability risk assessment method based on text analysis
InactiveCN112035846ADetermine severityHigh degree of automationCharacter and pattern recognitionNatural language data processingRisk levelComputer users
The invention relates to an unknown vulnerability risk assessment method based on text analysis, and belongs to the technical field of network unknown vulnerability risk assessment, and the method comprises the steps: taking an American national vulnerability database and an NVD as sample data sources, and obtaining an existing vulnerability text description; performing text analysis on the samplevulnerability text description, and extracting a vector matrix; establishing a classification model by utilizing the extracted vector matrix and the corresponding CVSS score; and when risk assessmentis carried out on any vulnerability which is not scored, carrying out the step 2 firstly to obtain a corresponding vector matrix, and then inputting the corresponding vector matrix into the classification model obtained in the step 3 to obtain a vulnerability risk level. For vulnerabilities which do not exist in an existing vulnerability library, the risk levels of the vulnerabilities are automatically evaluated according to the vulnerability text description of the vulnerabilities, and the method is not limited to vulnerability library data any more. The automatic risk level assessment is helpful for the computer user to determine the severity of the vulnerability according to the vulnerability description, and provides a basis for the processing and sorting of the user.
Owner:江苏开博科技有限公司
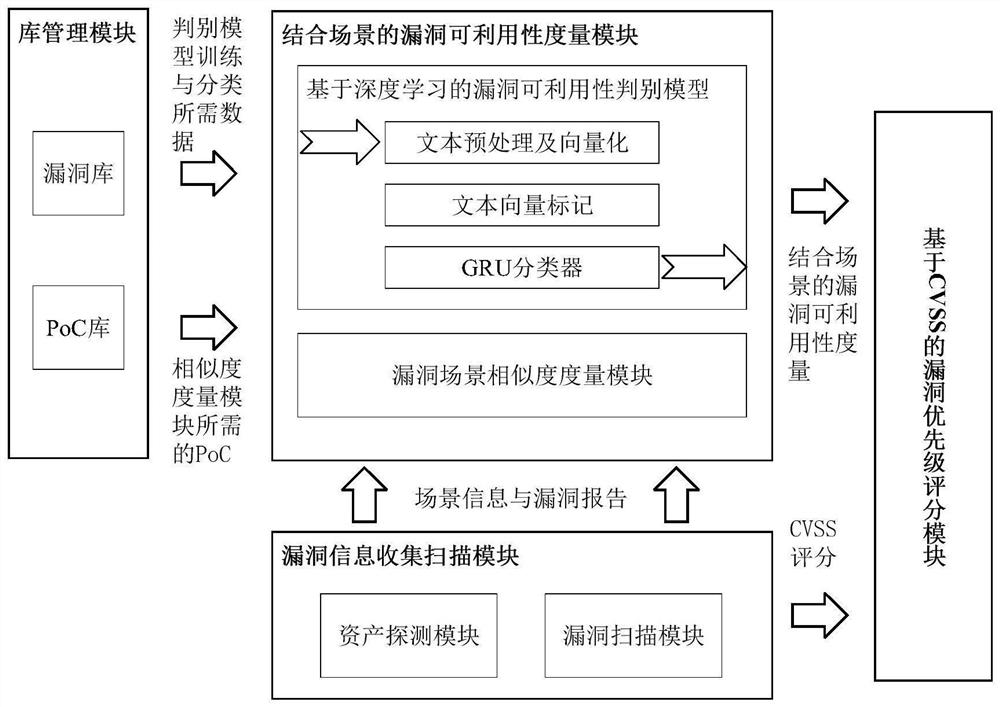
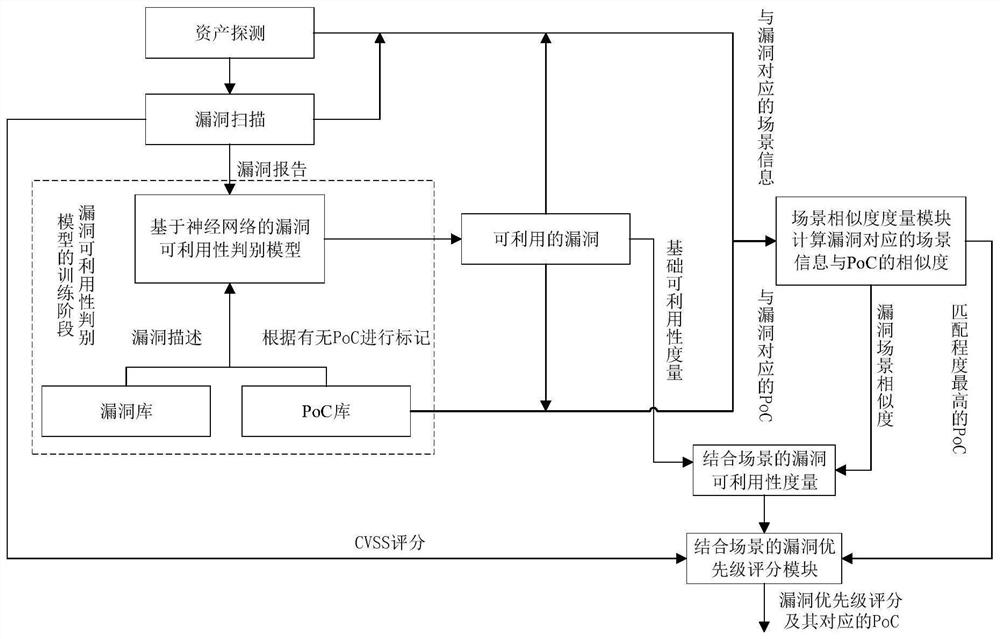
Vulnerability priority analysis method, system and device for industrial control system and storage medium
ActiveCN112818351AMitigating biasRelieve stressPlatform integrity maintainanceNeural architecturesComputer scienceIndustrial control system
The invention relates to an industrial control system-oriented vulnerability priority analysis method, system and device and a storage medium, which are characterized in that scene and vulnerability information obtained by detecting and scanning is combined with a PoC to give a scene-combined vulnerability availability measure, and then based on a CVSS framework, the measure value is combined with a CVSS score in a vulnerability report to give a vulnerability priority score. According to the method, the deviation caused by the fact that only attributes of vulnerabilities are considered in the CVSS scoring in the industrial control system is relieved. According to the system, the pressure of vulnerability verification under the industrial control system is effectively relieved, the vulnerability priority score under the scene where the vulnerability is located is efficiently and automatically given based on the CVSS, and meanwhile, the recommended PoC is provided to facilitate next verification.
Owner:HARBIN INST OF TECH AT WEIHAI +1
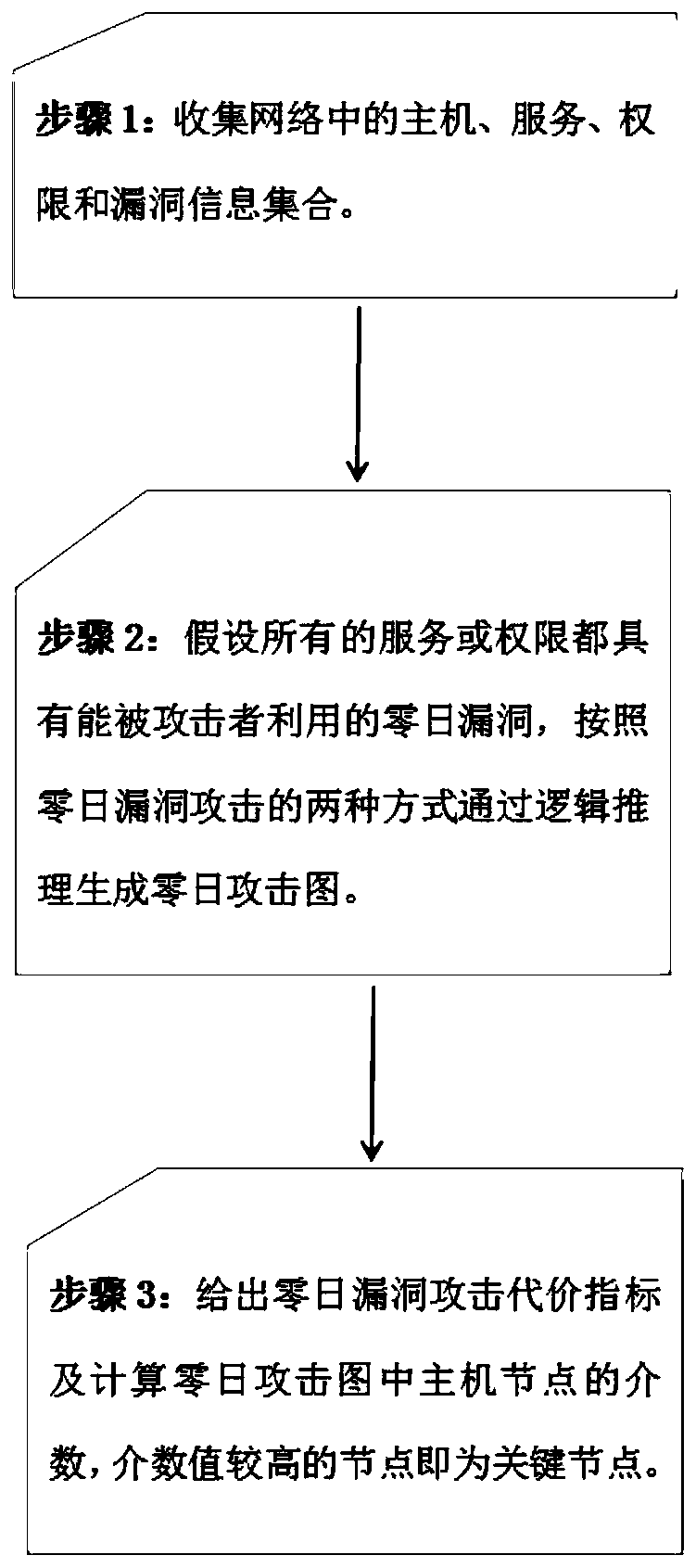
Network vulnerability assessment method based on zero-day attack graph
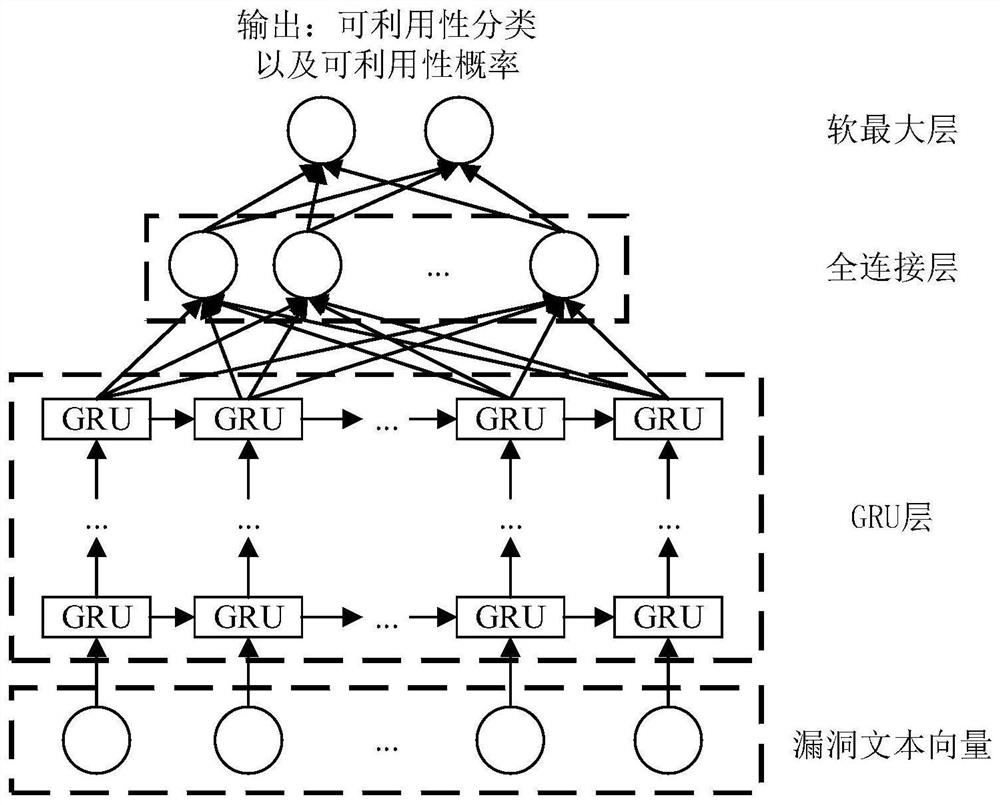
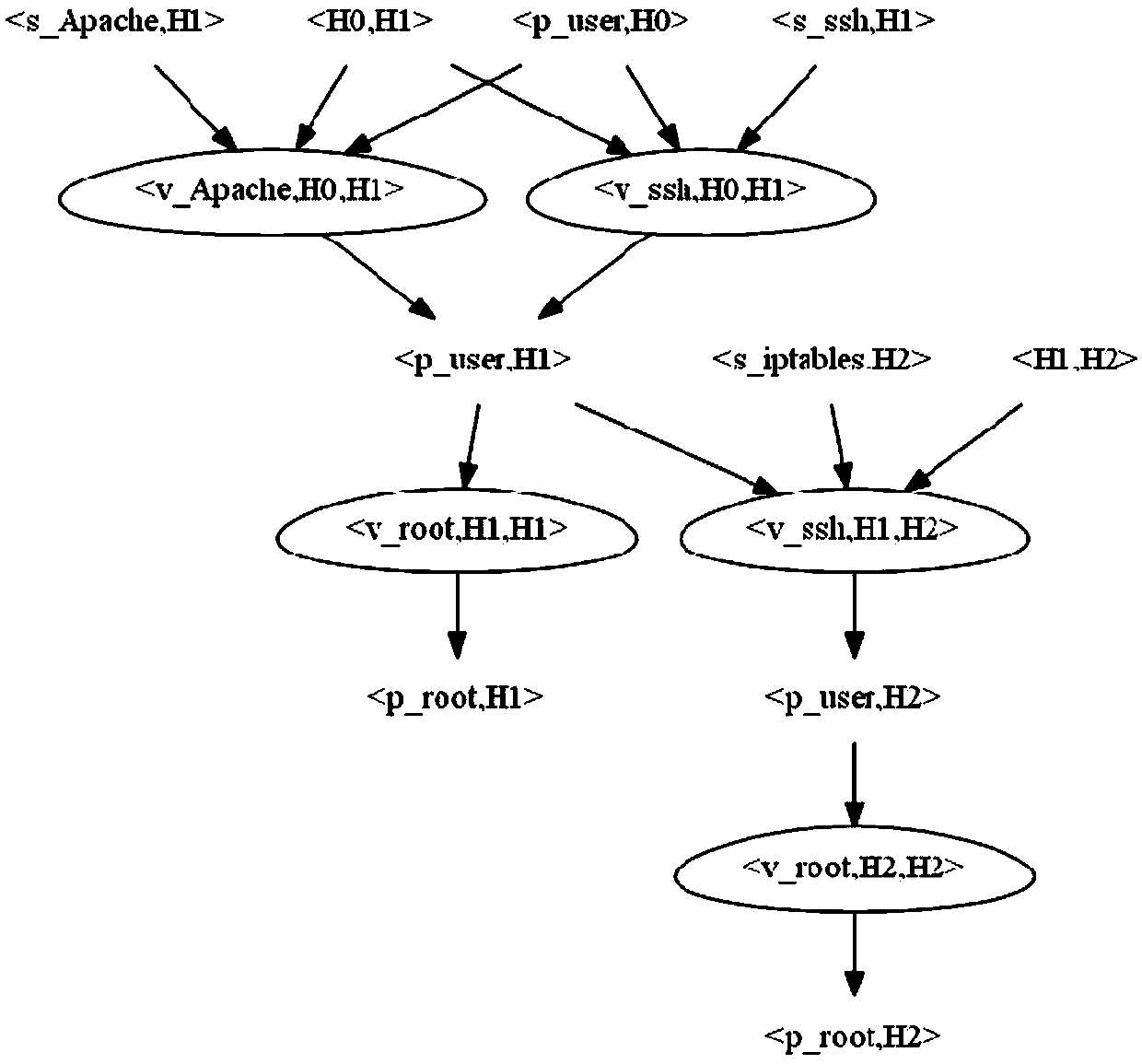
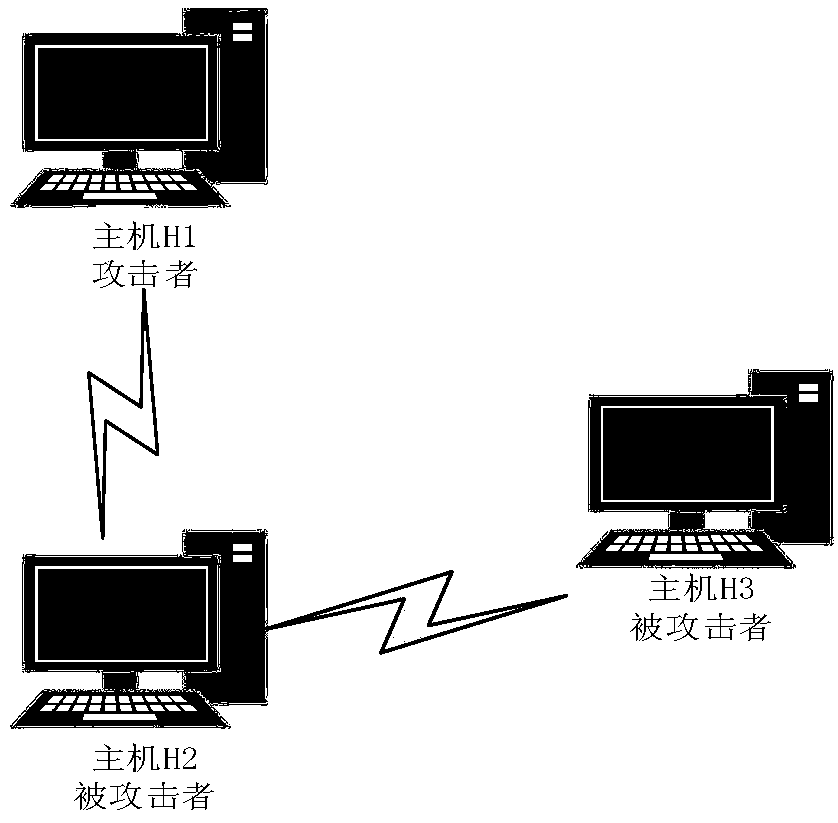
The invention discloses a network vulnerability assessment method based on zero-day attack graph. First it is assumed that all services on a host in a network contain a zero-day vulnerability, a zero-day attack graph is generated through logical reasoning of a given pattern, and then the attack cost for utilizing the zero-day vulnerability to attack is quantified based on a vulnerability scanningtechnology and CVSS vulnerability scoring system, and finally, a network centrality theory is utilized to make an analysis to obtain the key vulnerabilities in the network. All possible unknown vulnerabilities in the network are fully considered while known vulnerabilities are dealt with, so that the assessment method has the capability of dealing with unknown vulnerabilities, can discover potential network vulnerabilities through logical reasoning, and assess the security of the current network, thereby providing a reference basis for further network security protection, and improving the security, reliability and availability of the network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Multilayer impact factor-based security vulnerability threat quantification method
ActiveCN107292178ATightly boundPrevent deviationPlatform integrity maintainanceQuantification methodsComputer science
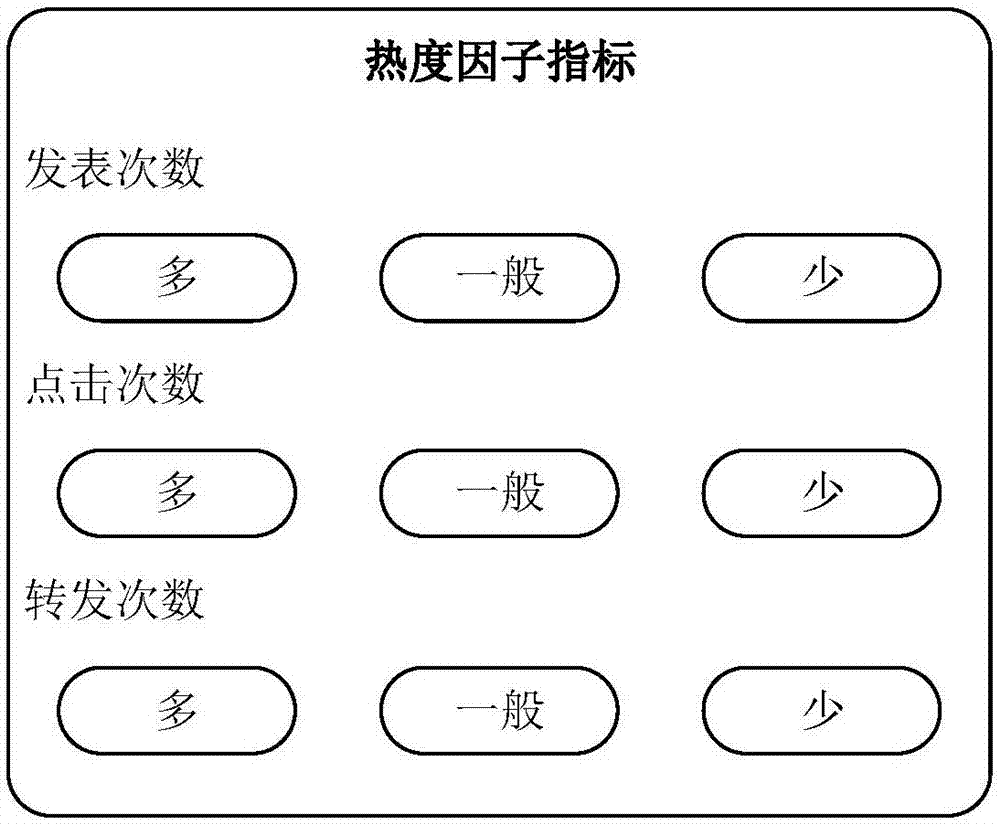
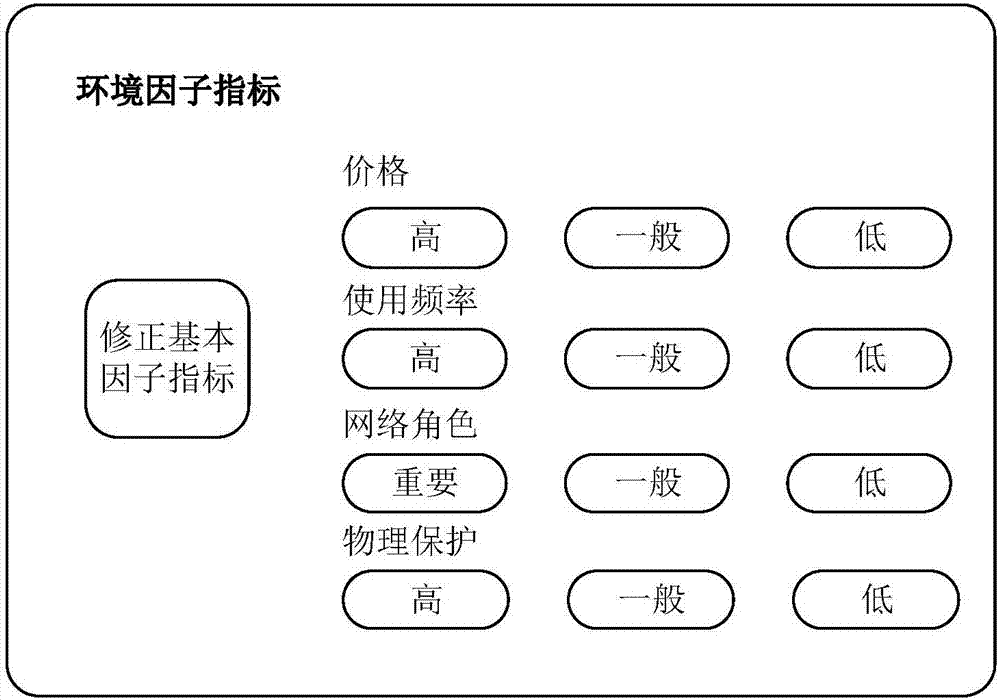
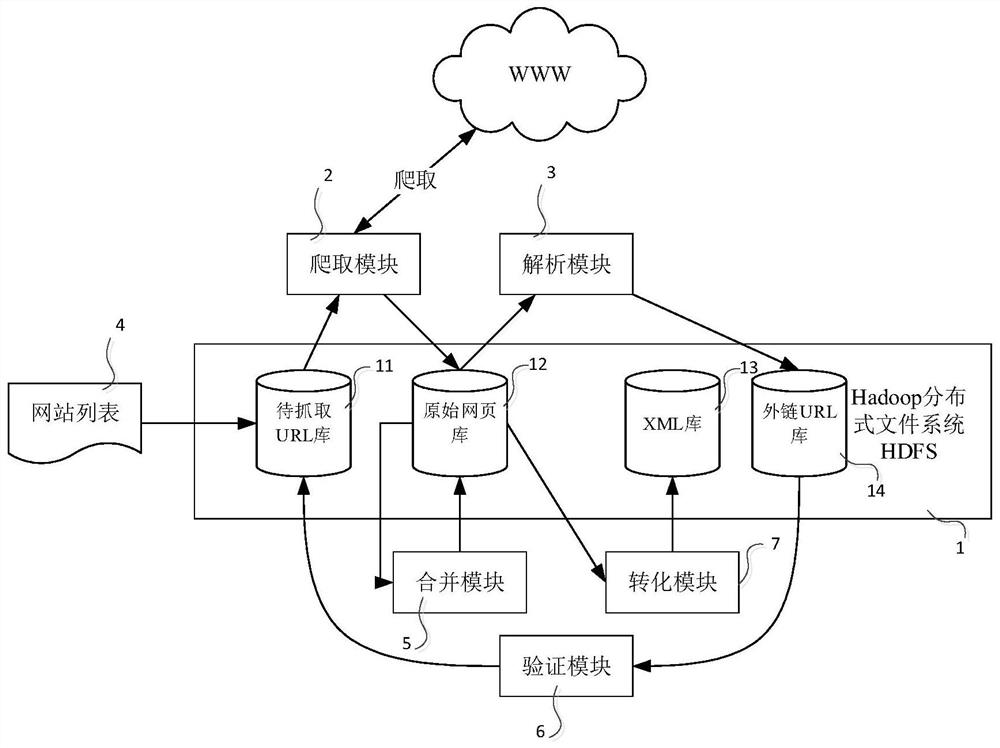
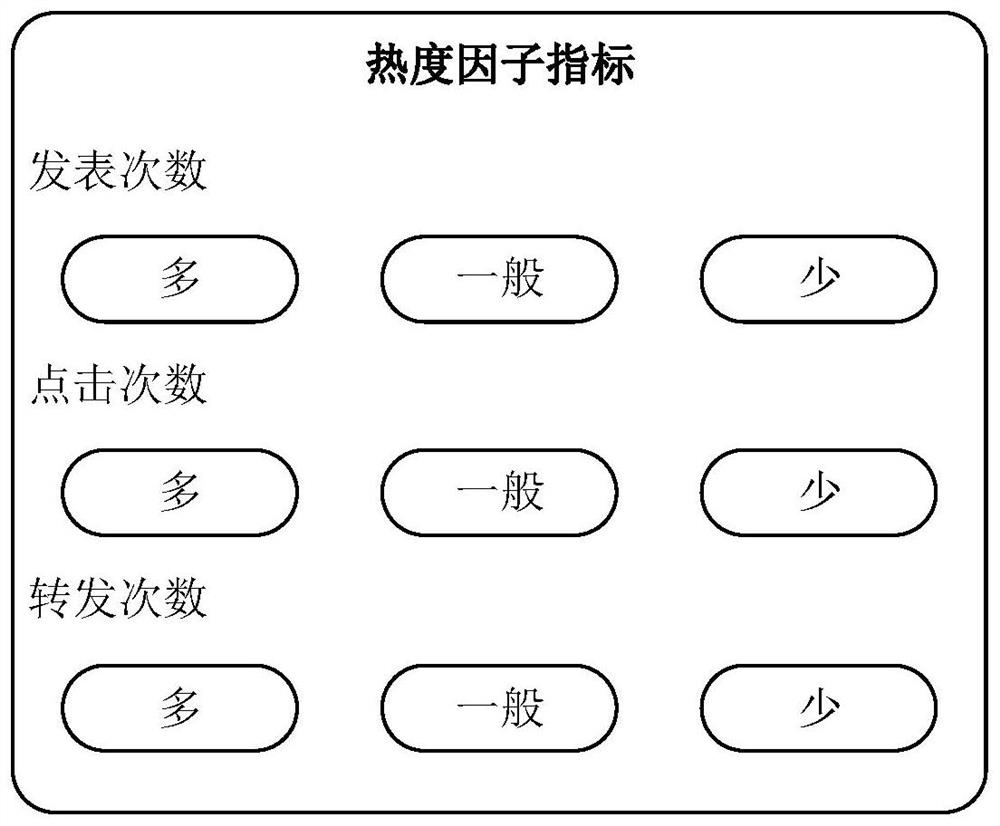
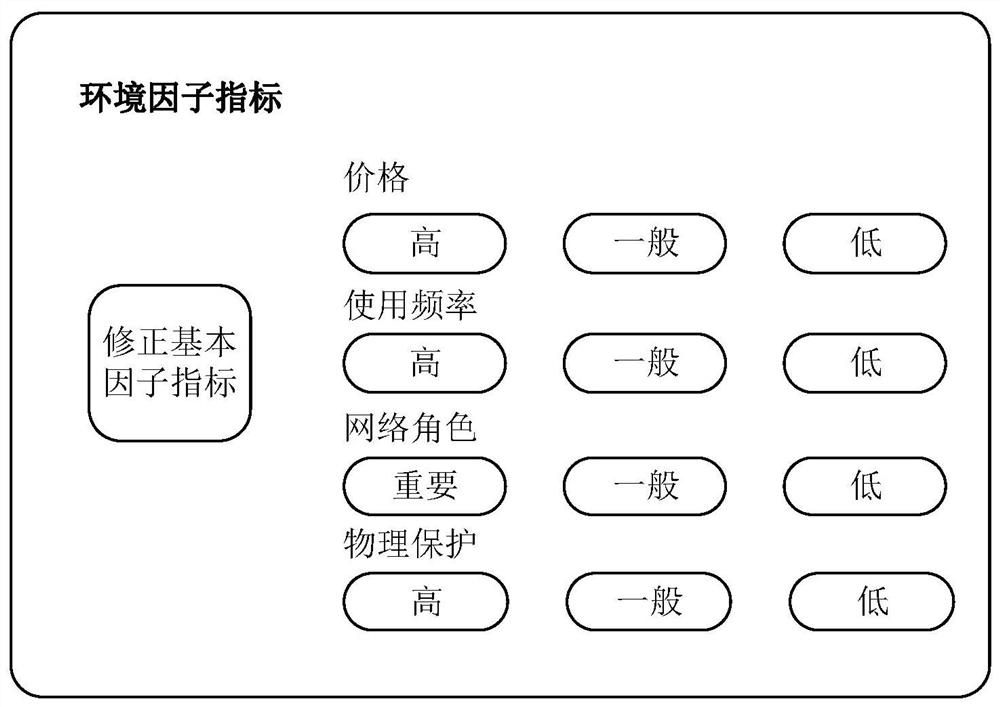
The invention discloses a multilayer impact factor-based security vulnerability threat quantification method. The method comprises the following steps of: 1, determining a website to be crawled, crawling website data and processing the website data to obtain content related to heat assessment; 2, processing the crawled website data, carrying out heat assessment and correcting the score of a CVSS basic factor through a formula 1: ScoreBase=min [(ScoreBasc+ScoreConcerned), 8] (Formula 1), ScoreSconcerned=5*Publish*Click*Transmit (Formula2), wherein ScoreConcerned is a heat score, ScoreBasc is a basic score, Publish is a publish frequency, Click is a click frequency and Transmit is a transmit frequency; 3, carrying out asset assessment; and 4, fusing an asset assessment result obtained in the step 3 with a CVSS basic score by referring to a CVSS algorithm so as to obtain a final hole score, and substituting the final hole score into a CVSS assessment algorithm to obtain a final hole score.
Owner:BEIJING INST OF COMP TECH & APPL
Automatic vulnerability quantitative evaluation method and system
ActiveCN110808947AReduce the impactSimplify scoring stepsCharacter and pattern recognitionMachine learningEvaluation resultRisk quantification
The invention provides an automatic vulnerability quantitative evaluation method and system. According to the risk evaluation method, existing risk evaluation information is researched, key features are extracted, automatic risk quantitative analysis is carried out in combination with an artificial intelligence related algorithm, the influence degree of vulnerability is objectively reflected, scoring factors are simplified, and the influence on risk evaluation along with time changes is avoided. The method has the advantages that the CVSS score is learned and combined with the objective resultof network search, the vulnerability evaluation value is automatically obtained, the scoring step is simplified, and the influence of subjective factors on the evaluation result is reduced.
Owner:NANJING NARI GROUP CORP +4
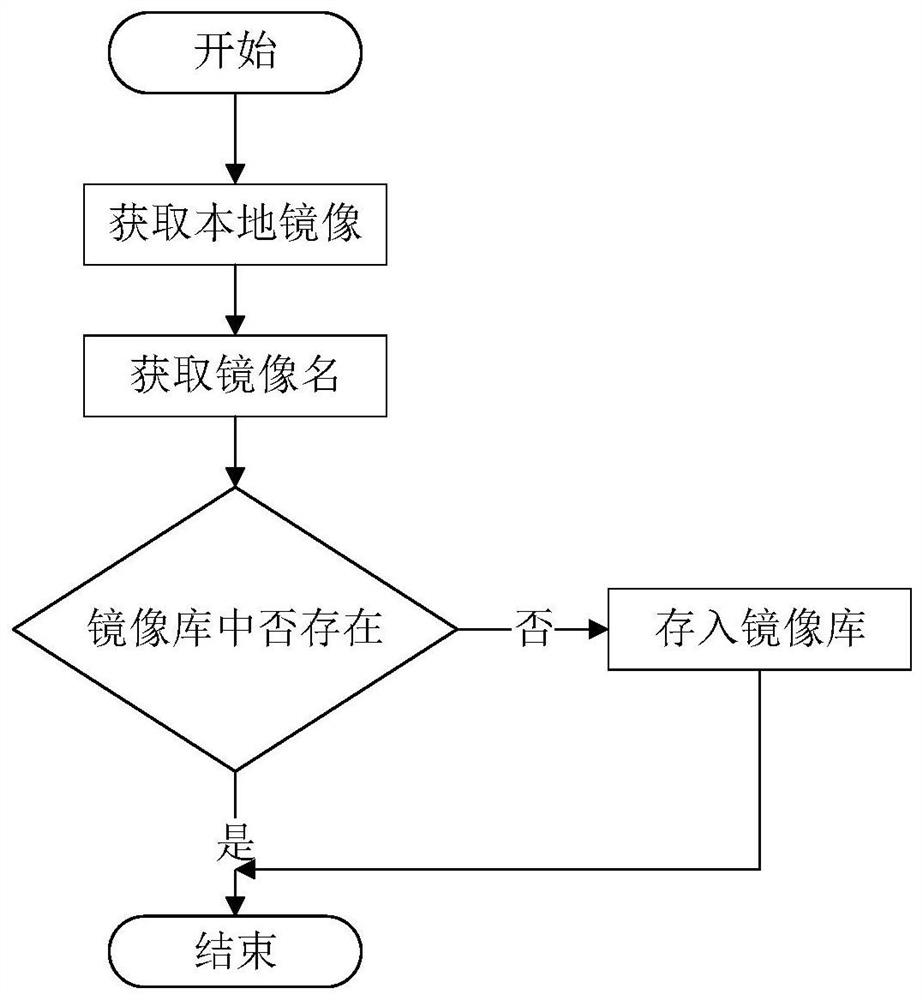
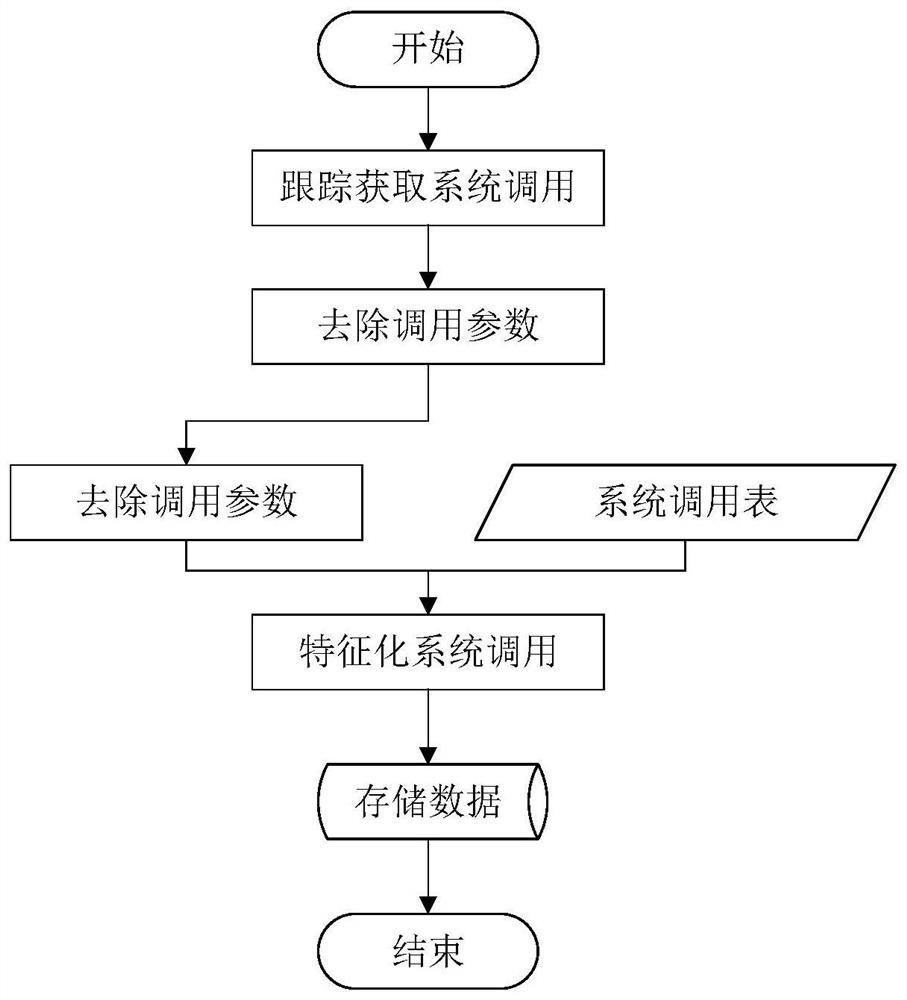
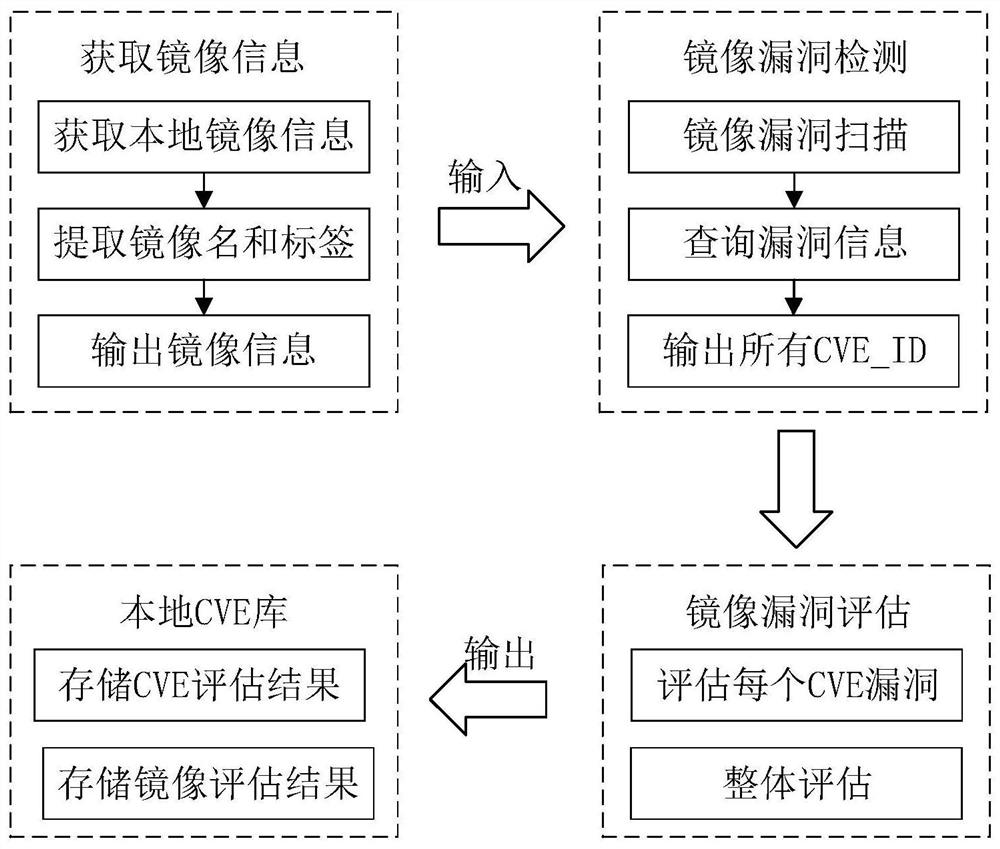
Container safety detection method based on machine learning
InactiveCN112882797AReduce security risksTimely detection of intrusionsPlatform integrity maintainanceMachine learningPattern recognitionAlgorithm
The invention discloses a container security detection method based on machine learning. The method comprises the following steps: collecting local mirror image information and running container information through a script; scanning mirror image vulnerability information through a tool Anchore; evaluating the vulnerability severity score by using CVSS; realizing the mirror image security evaluation according to all vulnerability scoring results of the mirror image; collecting system calls generated by the container in operation through a tool Strace; generating a system call mapping file in combination with the system call table; characterizing the system call mapping file in combination with a sliding window method; calculating a TF-IDF value of each word in the feature file by using an optimized machine learning method TF-IDF; performing training or detecting by using the features; and updating local data, so the intrusion detection rate is improved. Vulnerability detection and evaluation of the container mirror image and intrusion detection of the container in operation are fused, and safety detection of the container in the whole life cycle from mirror image downloading to operation ending is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Cybersecurity vulnerability classification and remediation based on network utilization
ActiveUS11277429B2Accurately vulnerabilityComputer security arrangementsTransmissionCyber-attackInternet traffic
A technology solution for remediating a cyberattack risk in a computing resource asset in a network system. The technology solution includes monitoring data traffic directed to the computing resource asset in the network system along with data traffic to one or more additional computing resource assets in the network system, generating network utilization data based on the monitored data traffic to the computing resource asset and the monitored data traffic to the one or more additional computing resource assets in the network system, receiving a common vulnerability score (CVSS) for a vulnerability in the computing resource asset, determining a network traffic adjustment (NTA) value for the common vulnerability score (CVSS) based on the network utilization data, adjusting the common vulnerability score (CVSS) by the network traffic adjustment (NTA) value to generate a prioritized common vulnerability score (PCVSS) for the computing resource asset, and remediating the computing resource asset to resolve the vulnerability based on the prioritized common vulnerability (PCVSS) score.
Owner:SAUDI ARABIAN OIL CO
Risk-based vulnerability threat degree dynamic calculation method
InactiveCN112464252AGet rid of high, mediumDegree of freedomCharacter and pattern recognitionPlatform integrity maintainanceHazardCalculation methods
The invention discloses a risk-based vulnerability threat degree dynamic calculation method which specifically comprises the following steps: S1, directionally collecting vulnerability data in an NVDand CVE vulnerability database by adopting a crawler engine, carrying out timed incremental updating, taking the vulnerability data as a basic vulnerability database, and carrying out dissociation processing by taking a utilization mode and a CVSS score of the basic vulnerability database as classification directions to obtain a dissociated vulnerability database. The invention relates to the technical field of vulnerability risk level evaluation. Compared with a vulnerability rating standard in a general vulnerability scoring system, the risk-based vulnerability threat degree dynamic calculation method has the advantages that the RTS scoring mode judges the threat degree of the vulnerability according to the standard of 0-3000 scores, so that the threat degree of each vulnerability can bejudged more meticulously; The traditional high, medium and low levels are no longer used as the unique measurement standard of the vulnerability hazard degree.
Owner:山东泽鹿安全技术有限公司
Multi-dimensional software security risk assessment method based on CVSS
InactiveCN114065223AGuaranteed discretizationDiversity guaranteedPlatform integrity maintainanceEvaluation resultData set
The invention discloses a multi-dimensional software security risk assessment method based on CVSS. The problem that a CVSS measurement assessment standard cannot accurately and comprehensively evaluate vulnerability risk levels is solved. The method comprises the following implementation steps: acquiring software vulnerability data; analyzing vulnerability data and integrating into a data set; readjusting the weight of the relative importance measurement index; optimizing a distribution scheme of the measurement indexes in the influence; adding vulnerability type measurement indexes; adding utilization time probability measurement in the risk score; obtaining a risk assessment result by using the risk assessment formula. Relative importance weight distribution is carried out on measurement indexes in influence, vulnerability measurement indexes are added in availability measurement, and time utilization probabilities are added in risk scores. Compared with a traditional evaluation method, the method has more accurate scoring standards, more comprehensive evaluation factors and more dimensional evaluation results. The method is used for risk assessment of software vulnerabilities.
Owner:XIAN TECHNOLOGICAL UNIV
A security vulnerability threat quantification method based on multi-level impact factors
The invention discloses a multilayer impact factor-based security vulnerability threat quantification method. The method comprises the following steps of: 1, determining a website to be crawled, crawling website data and processing the website data to obtain content related to heat assessment; 2, processing the crawled website data, carrying out heat assessment and correcting the score of a CVSS basic factor through a formula 1: ScoreBase=min [(ScoreBasc+ScoreConcerned), 8] (Formula 1), ScoreSconcerned=5*Publish*Click*Transmit (Formula2), wherein ScoreConcerned is a heat score, ScoreBasc is a basic score, Publish is a publish frequency, Click is a click frequency and Transmit is a transmit frequency; 3, carrying out asset assessment; and 4, fusing an asset assessment result obtained in the step 3 with a CVSS basic score by referring to a CVSS algorithm so as to obtain a final hole score, and substituting the final hole score into a CVSS assessment algorithm to obtain a final hole score.
Owner:BEIJING INST OF COMP TECH & APPL
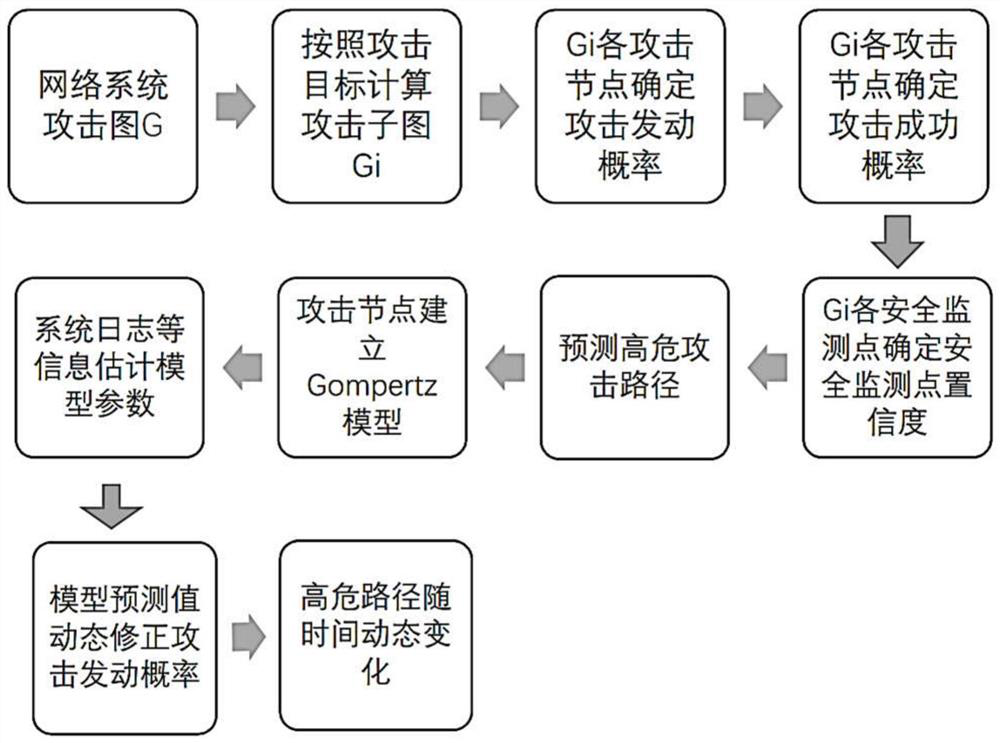
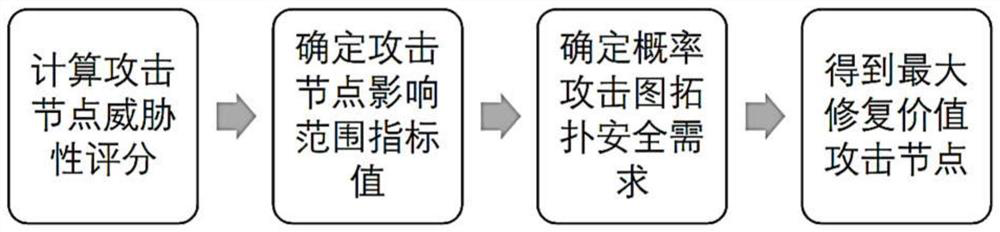
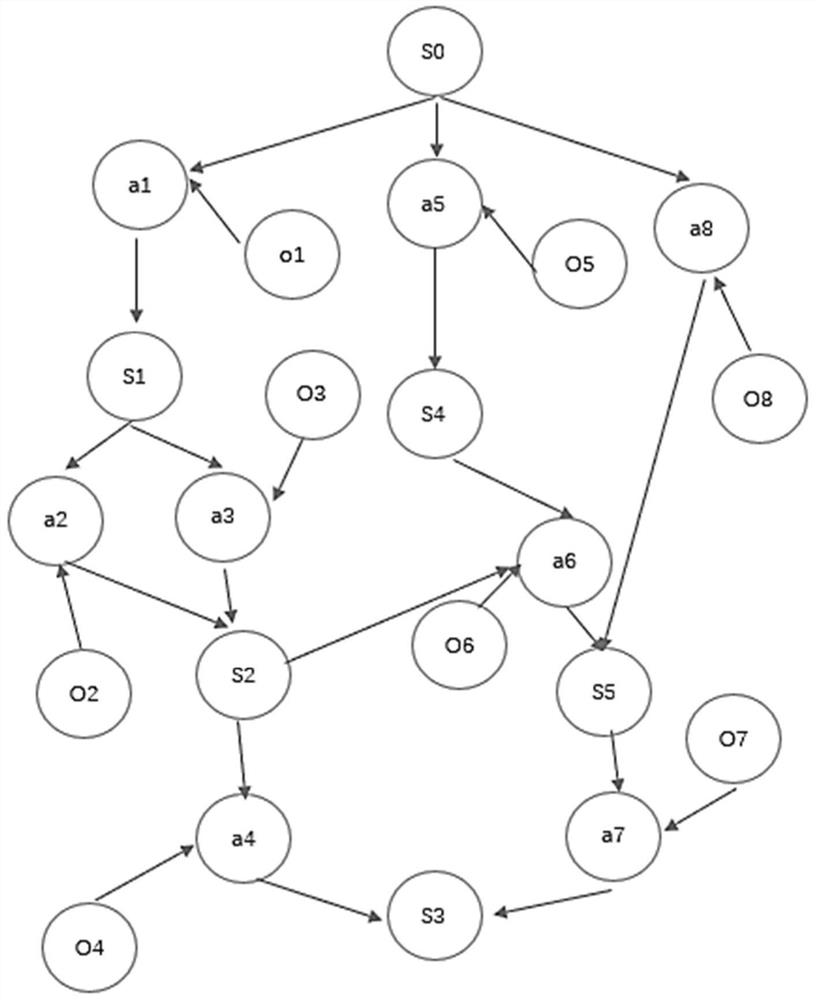
A high-risk attack path dynamic prediction and repair system and method
ActiveCN111683080BHigh precisionImprove referenceData switching networksComplex mathematical operationsPrediction algorithmsMathematical model
A system and method for dynamic prediction and repair of high-risk attack paths. The high-risk attack path prediction module uses an attack subgraph generation algorithm to generate an attack subgraph according to the attack target, and then uses the improved CVSS scoring strategy and expert knowledge base to estimate the attack launch of each attack node. probability, attack success probability, and confidence of security monitoring points to obtain a probability attack graph, and finally obtain a high-risk attack path through the maximum probability attack path prediction algorithm. The high-risk attack path dynamic correction module uses the system log and security monitoring point alarm information as the data source to establish the Gompertz mathematical model, which dynamically reflects the characteristics of each attack and the utilization probability of the path it is located in over time. The repair strategy module evaluates the objective impact scope of the attack, the objective threat, and the security requirements brought about by the topological position of the attack through the attack comprehensive impact assessment algorithm, and reveals the maximum value repair point. The invention has high prediction accuracy and higher reference degree.
Owner:XIDIAN UNIV
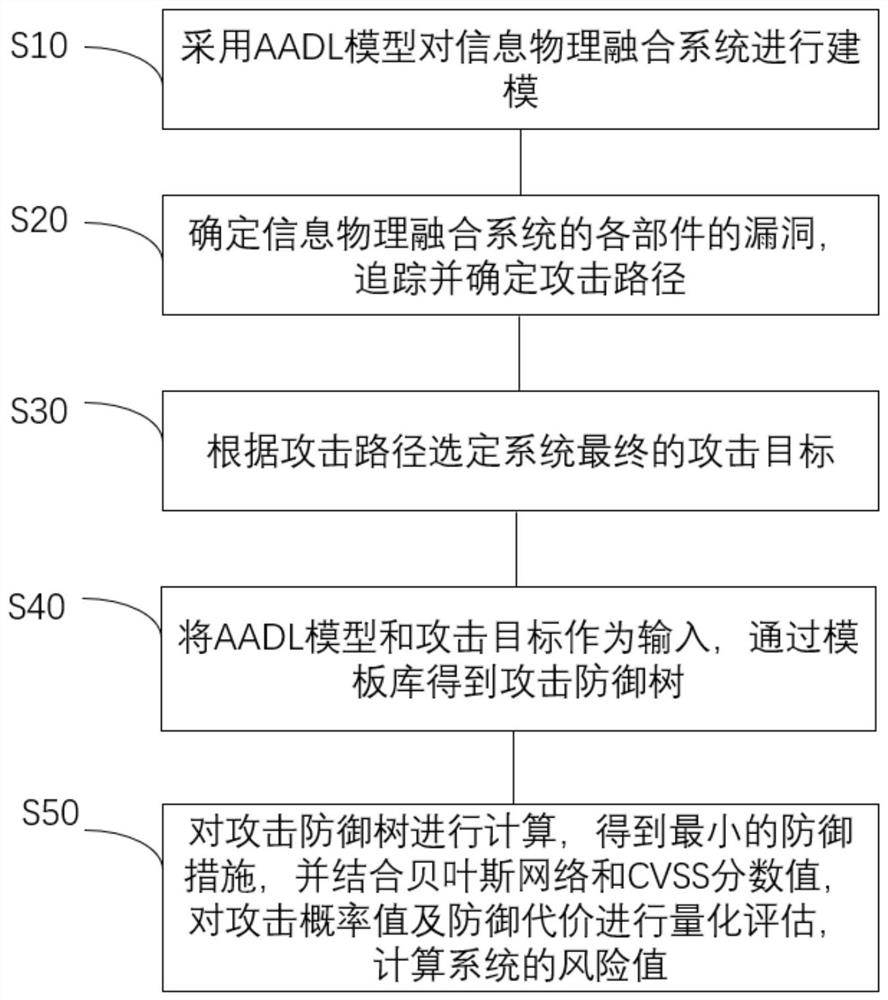
AADL-based automatic generation method of attack defense tree
The invention discloses an AADL-based automatic generation method of an attack defense tree. The method comprises the following steps: modeling an information physical fusion system by adopting an AADL model; determining vulnerabilities of each component of the cyber-physical fusion system, and tracking and determining an attack path; selecting a final attack target of the system according to the attack path; taking the AADL model and an attack target as input, and obtaining an attack defense tree through a template library; and calculating the attack defense tree to obtain a minimum defense measure, performing quantitative evaluation on an attack probability value and a defense cost by combining a Bayesian network and a CVSS score value, and calculating a risk value of the system. The problems that a complex system is difficult to model, and risk vulnerabilities in the system are difficult to determine, track and solve, including the influence of network attacks on a physical system and an information system, are solved.
Owner:NANJING FORESTRY UNIV
Vulnerability risk assessment method based on cvss
The invention provides a loophole risk basic evaluation method based on a CVSS. The method comprises the steps of S01, preprocessing data; S02, determining weights of the three basic evaluation indexes, and conducting optimization; S03, solving the weights of the basic evaluation indexes; S04, calculating a basic evaluation estimation value of every loophole threat. Compared with the prior art, according to the loophole risk basic evaluation method based on the CVSS, on the basis of CVSS evaluation, a basic evaluation estimation index weight distribution method is redesigned, according to the relative importance of the basic evaluation indexes, the weights of the basic evaluation indexes are optimized and distributed, a grey correlation degree index weight solving method is combined with the basic evaluation estimation index weight distribution method, so that the evaluation result is more objective, the diversity of the evaluation result is improved, and the loophole threat is conveniently and visually distinguished.
Owner:CIVIL AVIATION UNIV OF CHINA
A network vulnerability assessment method based on zero-day attack graph
The invention discloses a network vulnerability assessment method based on zero-day attack graph. First it is assumed that all services on a host in a network contain a zero-day vulnerability, a zero-day attack graph is generated through logical reasoning of a given pattern, and then the attack cost for utilizing the zero-day vulnerability to attack is quantified based on a vulnerability scanningtechnology and CVSS vulnerability scoring system, and finally, a network centrality theory is utilized to make an analysis to obtain the key vulnerabilities in the network. All possible unknown vulnerabilities in the network are fully considered while known vulnerabilities are dealt with, so that the assessment method has the capability of dealing with unknown vulnerabilities, can discover potential network vulnerabilities through logical reasoning, and assess the security of the current network, thereby providing a reference basis for further network security protection, and improving the security, reliability and availability of the network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
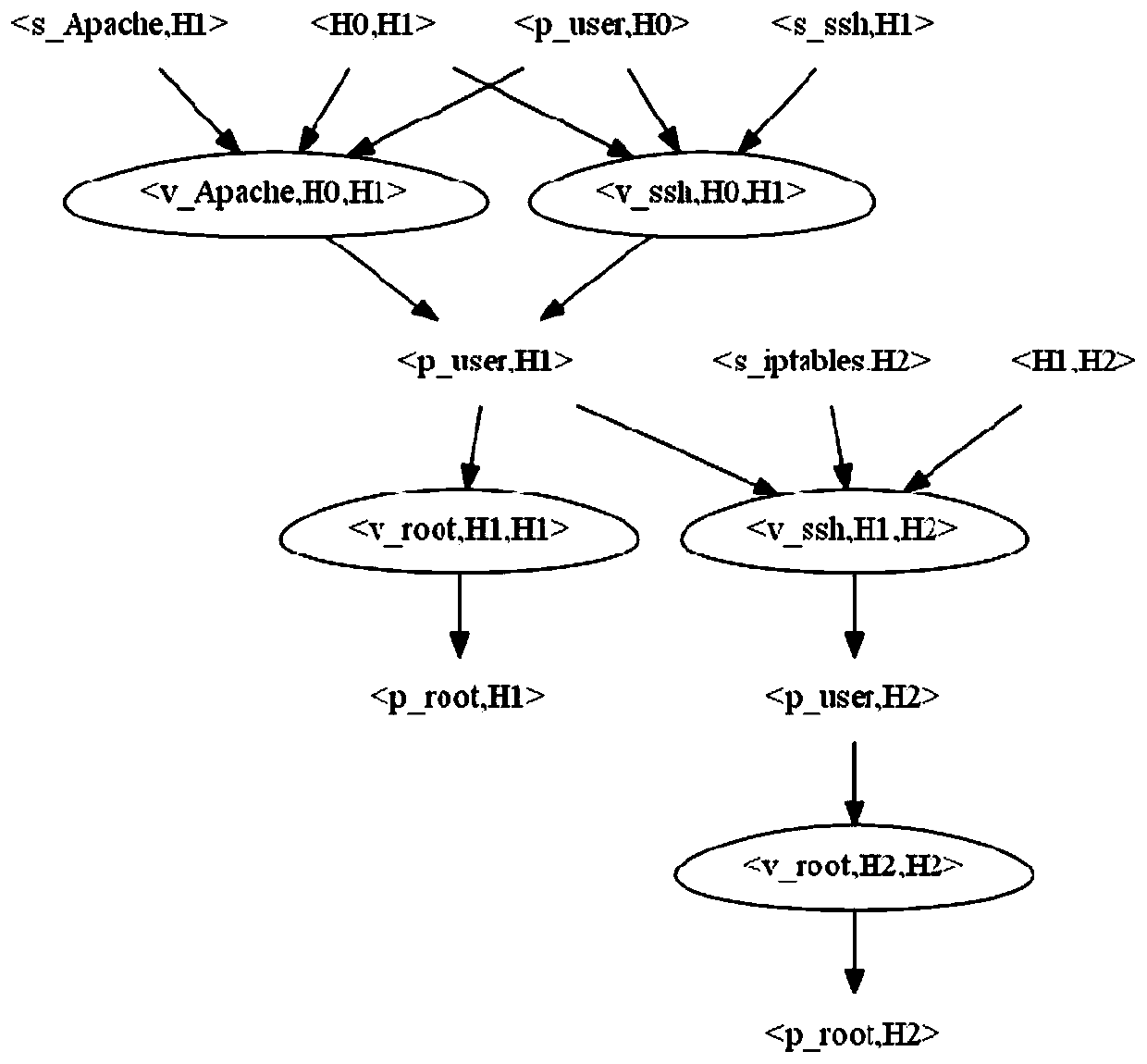
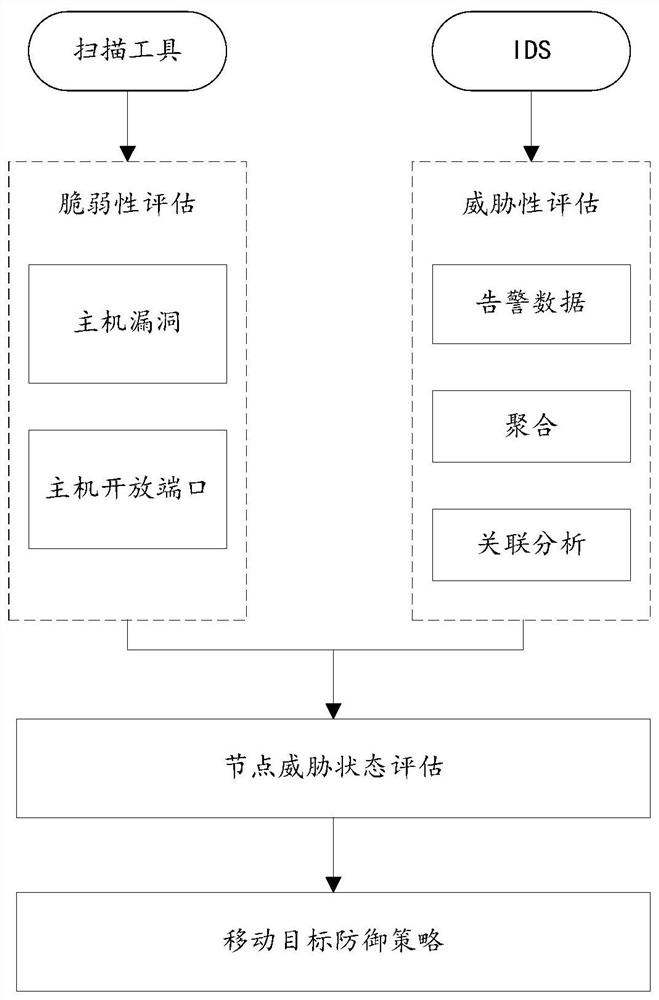
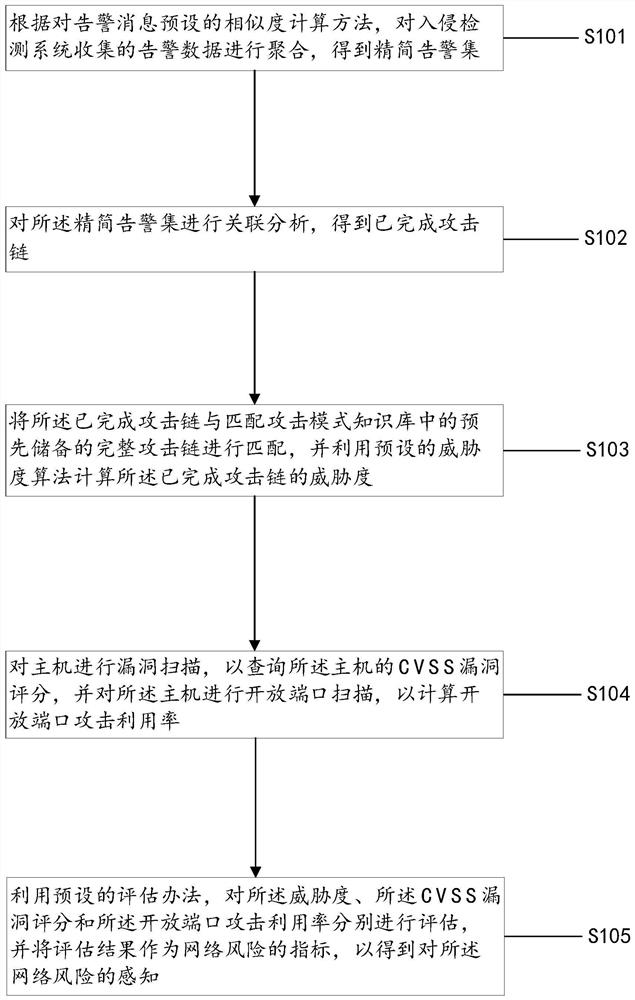
Network risk sensing method and network risk defense method
The embodiment of the invention provides a network risk sensing method and a network risk defense method. The network risk sensing method comprises the following steps: aggregating alarm data collected by an IDS to obtain a simplified alarm set; performing association analysis on the simplified alarm set to obtain a completed attack chain; matching the completed attack chain with a complete attack chain in a matching attack mode knowledge base, and calculating the threat degree of the completed attack chain; performing vulnerability scanning on a host, and querying a CVSS vulnerability score of the host; and performing open port scanning on the host, and calculating an open port attack utilization rate. The network risk defense method comprises: defending the host according to a CVSS vulnerability score in combination with the threat degree of the completed attack chain and the open port attack utilization rate. According to the method provided by the invention, multi-dimensional data is fused to carry out threat sensing, and state evaluation is carried out in combination with a scoring result, so that the accuracy of defense implementation is ensured, defense can be automatically completed, and manual decision is not needed.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
Method for generating attack scenario in mobile cloud computing scene
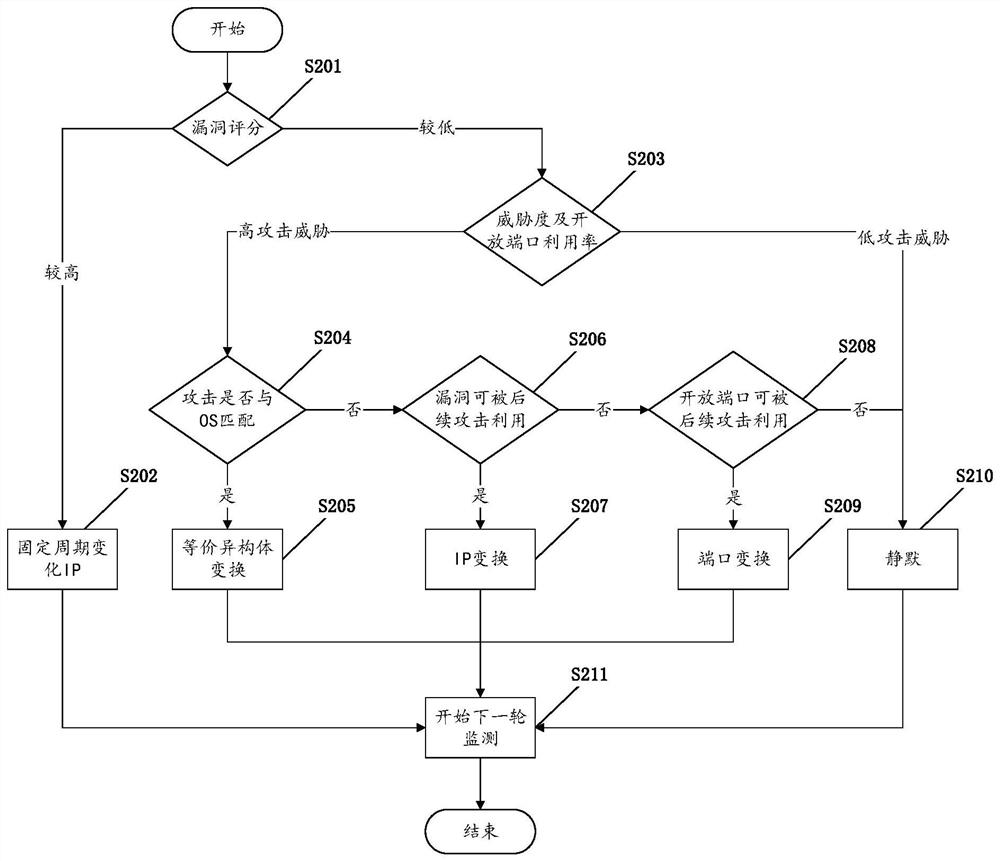
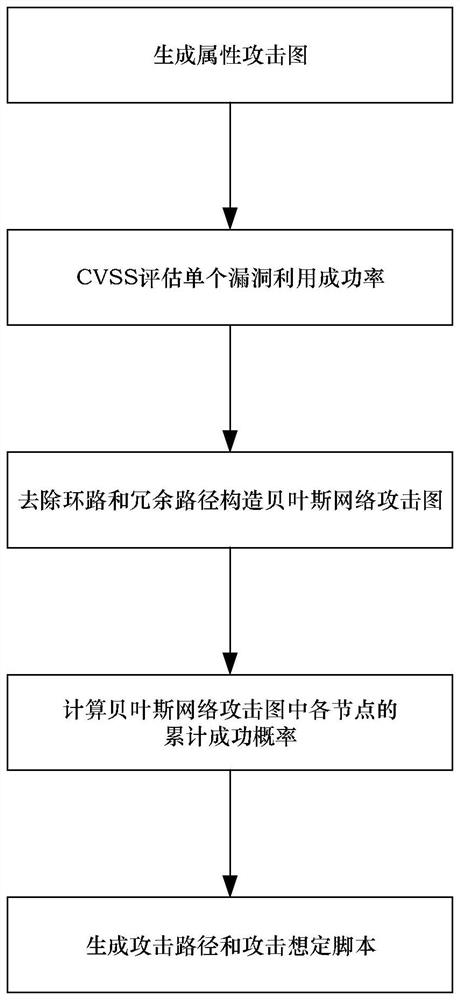
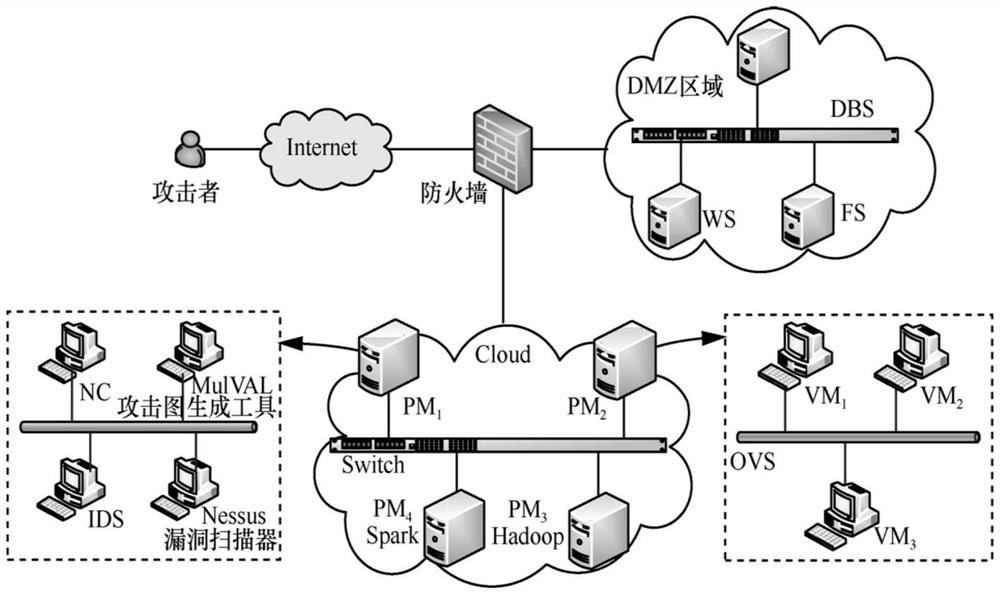
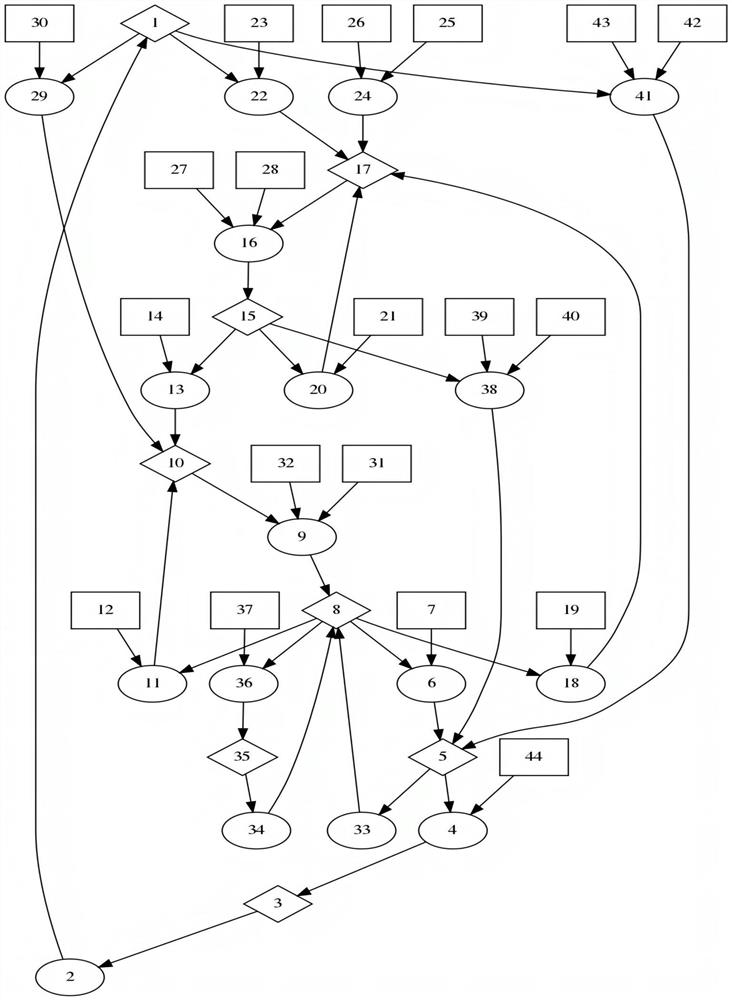
ActiveCN114095935ASmall scaleImprove accuracySecurity arrangementSecuring communicationPathPingAlgorithm
The invention discloses a method for generating an attack scenario in a mobile cloud computing scene, and relates to the field of network security. According to the method, firstly, a MulVAL tool is used for generating an attribute attack graph for the state of a target network, a CVSS is used for evaluating the utilization success rate of a single vulnerability, then a loop removal and redundant path algorithm is used for constructing a Bayesian network attack graph, and an improved node probability calculation algorithm is used for evaluating the cumulative success probability of each node of the attribute attack graph; and finally, an optimal attack path is generated by using a dynamic attack path generation algorithm, and then the attack path is described by using a network attack scenario description language to obtain an attack scenario script. According to the method, the process of obtaining the attack scenario in the mobile cloud computing scene is automated and dynamic, and the improved node probability calculation algorithm is used for processing the condition that a ring appears, so that the calculation of the accumulated success probability of each node on the attack graph is more vivid and accurate.
Owner:BEIHANG UNIV
An automated vulnerability quantitative assessment method and system
ActiveCN110808947BSimplify scoring stepsCharacter and pattern recognitionMachine learningEvaluation resultRisk quantification
The present invention provides an automated vulnerability quantitative assessment method and system, by researching existing risk assessment information, extracting key features, and combining artificial intelligence related algorithms for automated risk quantitative analysis, objectively reflecting the impact of vulnerability size, simplify scoring factors, and address the impact on risk assessment over time. The invention has the advantages of learning the CVSS scoring and combining with the objective results of the network search to automatically obtain the vulnerability evaluation value, simplifying the scoring steps and reducing the influence of subjective factors on the evaluation results.
Owner:NANJING NARI GROUP CORP +4
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com