Vulnerability risk assessment method based on cvss
A vulnerability and basic technology, applied in the field of vulnerability risk basic assessment based on CVSS, can solve the problems of not considering relative importance, duplication of resources, waste, etc., to achieve the effect of more objective assessment results and improved diversity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but the following embodiments in no way limit the present invention.
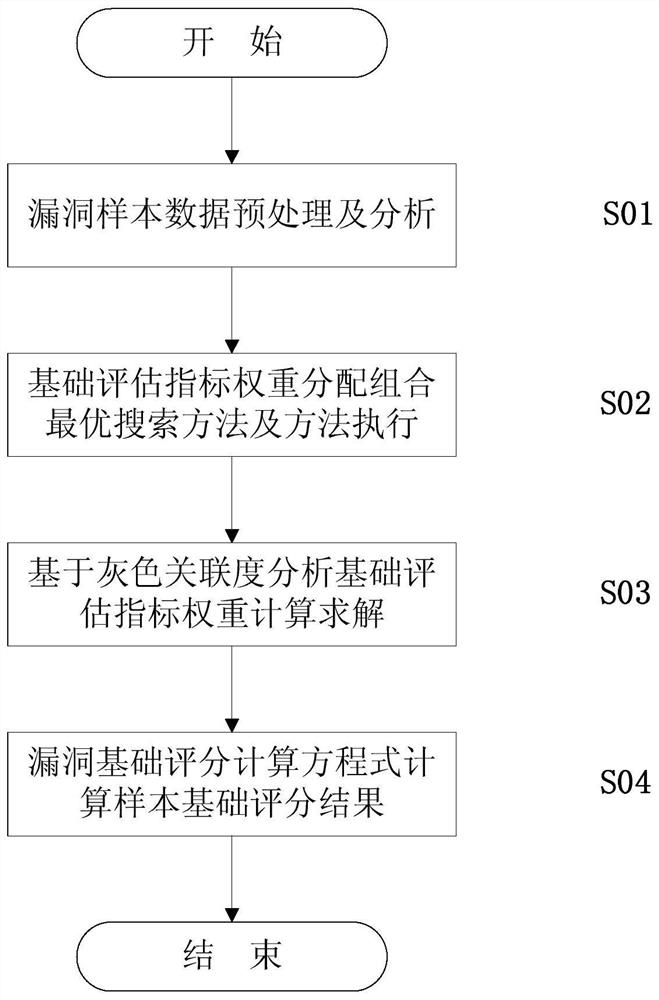
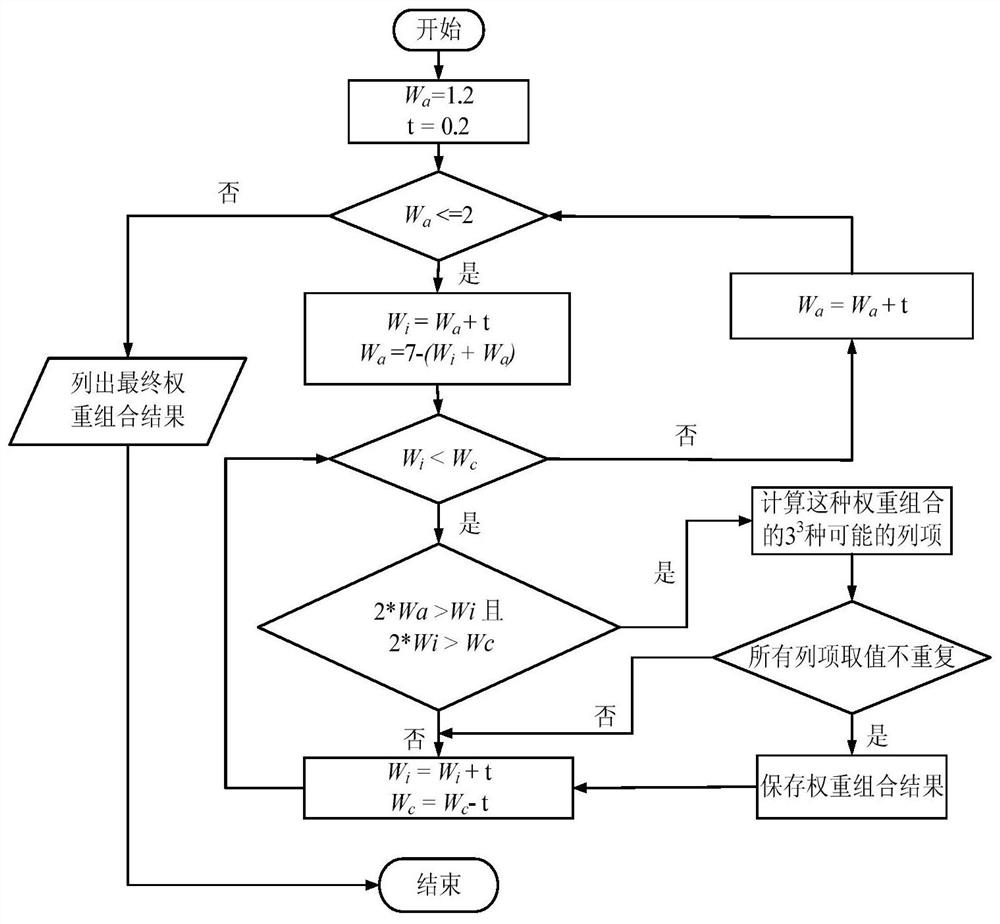
[0030] Such as figure 1 As shown, the CVSS-based vulnerability risk assessment method provided by the present invention comprises the following steps carried out in order:
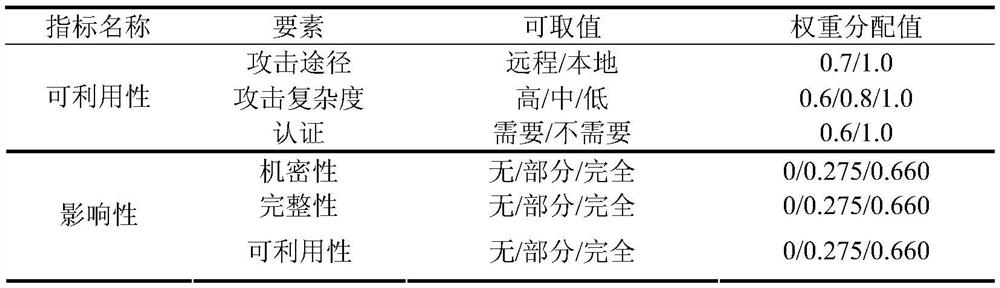
[0031]1) Stage S01 of collecting vulnerability data in the system and preprocessing the data: Randomly select a number of vulnerability data from the vulnerabilities recorded in the NVD vulnerability database in the past three years as data samples, and then according to the confidentiality impact, integrity impact and reliability Utilize the attributes of the three basic evaluation indicators of impact to divide the data of each of the above vulnerabilities into three categories, and calculate the respective proportions and categories of the data of the three attributes of full impact, partial impact, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com