Security baseline assessment method based on SCAP
A security baseline and baseline technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as spending a lot of time, delaying vulnerability repair time, and lack of interoperability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
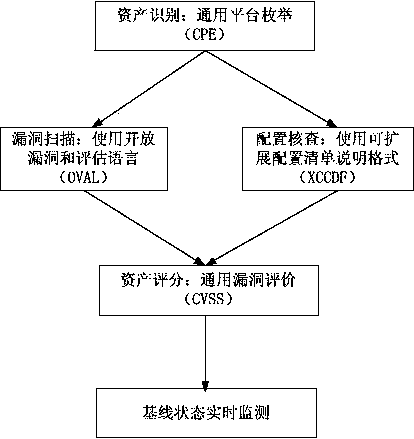
[0048] Such as figure 1 As shown, the SCAP-based security baseline assessment method includes the following steps:
[0049] S1: Asset identification: For the evaluated object, use the unified naming rules of common platform enumeration CPE to name, and build a bridge for common information compatibility and generality. For example, a 64-bit vista system can be named: cpe:2.3:o :microsoft:windows_vista:6.0:sp1:-:-:home_premium:-:x64:-.
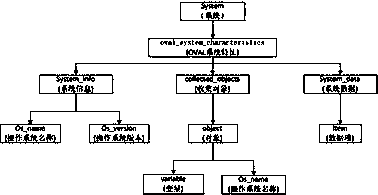
[0050]S2: CVE vulnerability scanning: The content of the vulnerability scanning result of OVAL consists of two parts: the vulnerability definition of OVAL and the user's system characteristic information. OVAL's vulnerability definition mainly includes two elements: definitions and tests. OVAL system char...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com