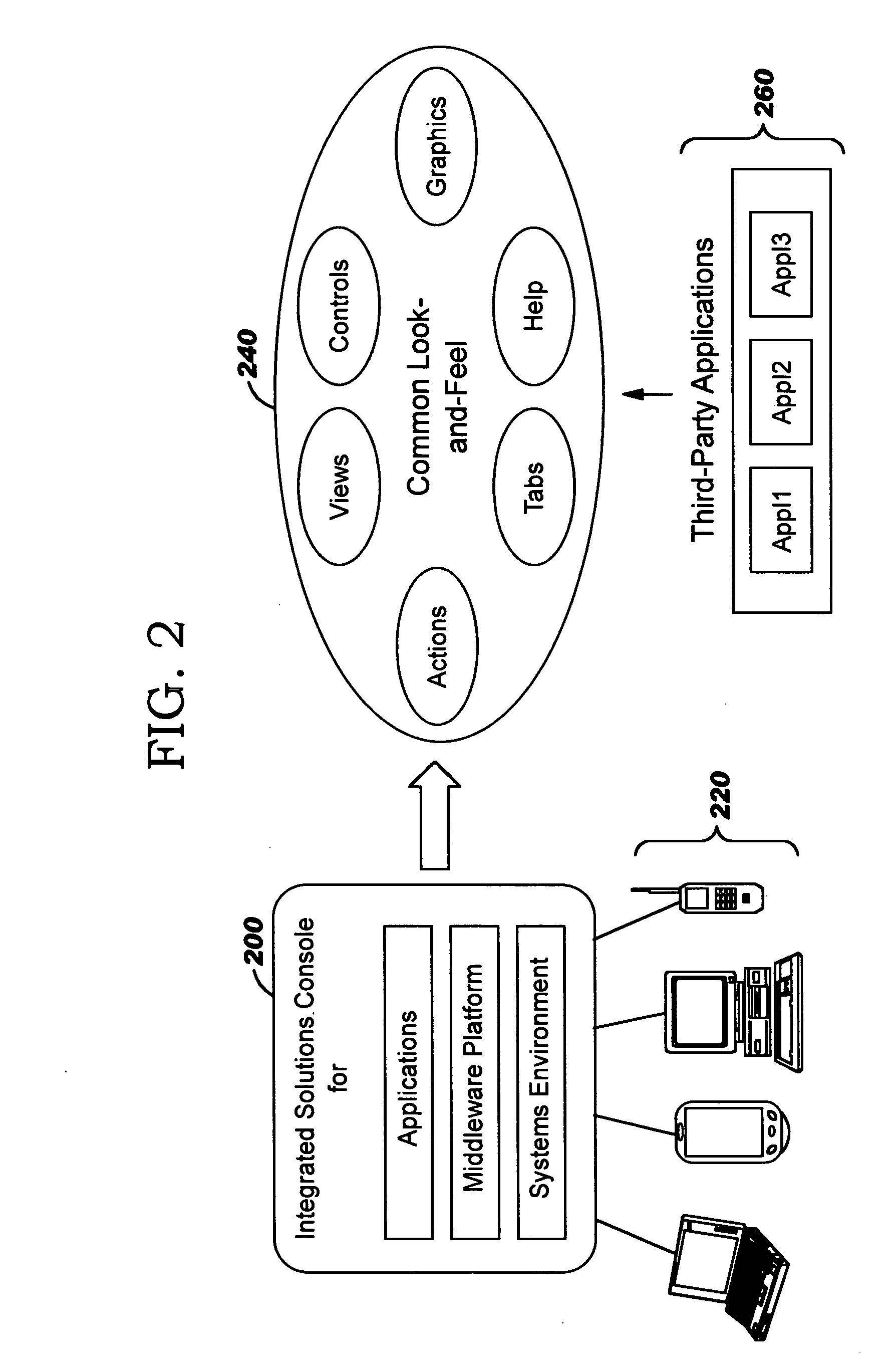
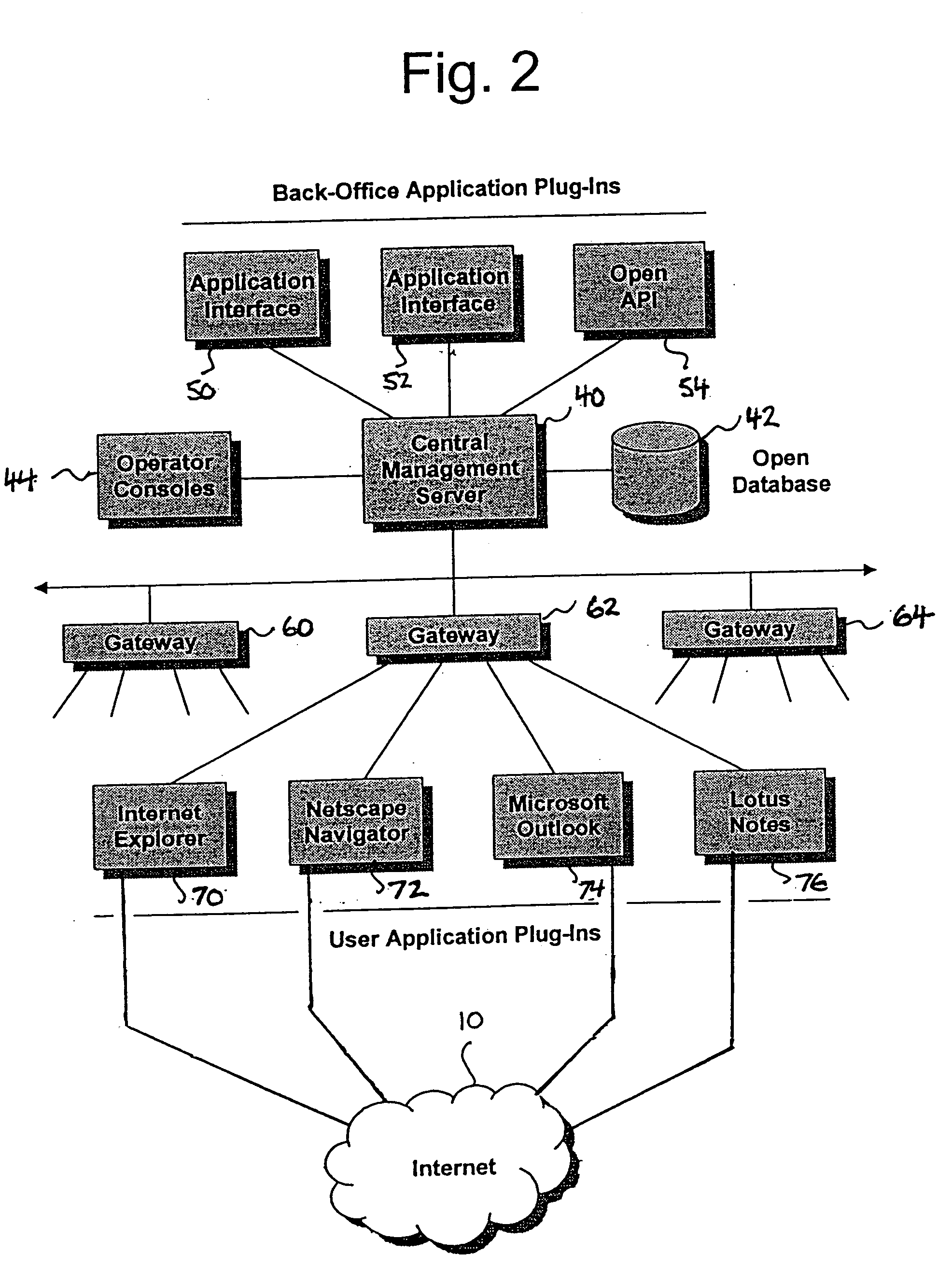
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
385 results about "Information technology management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
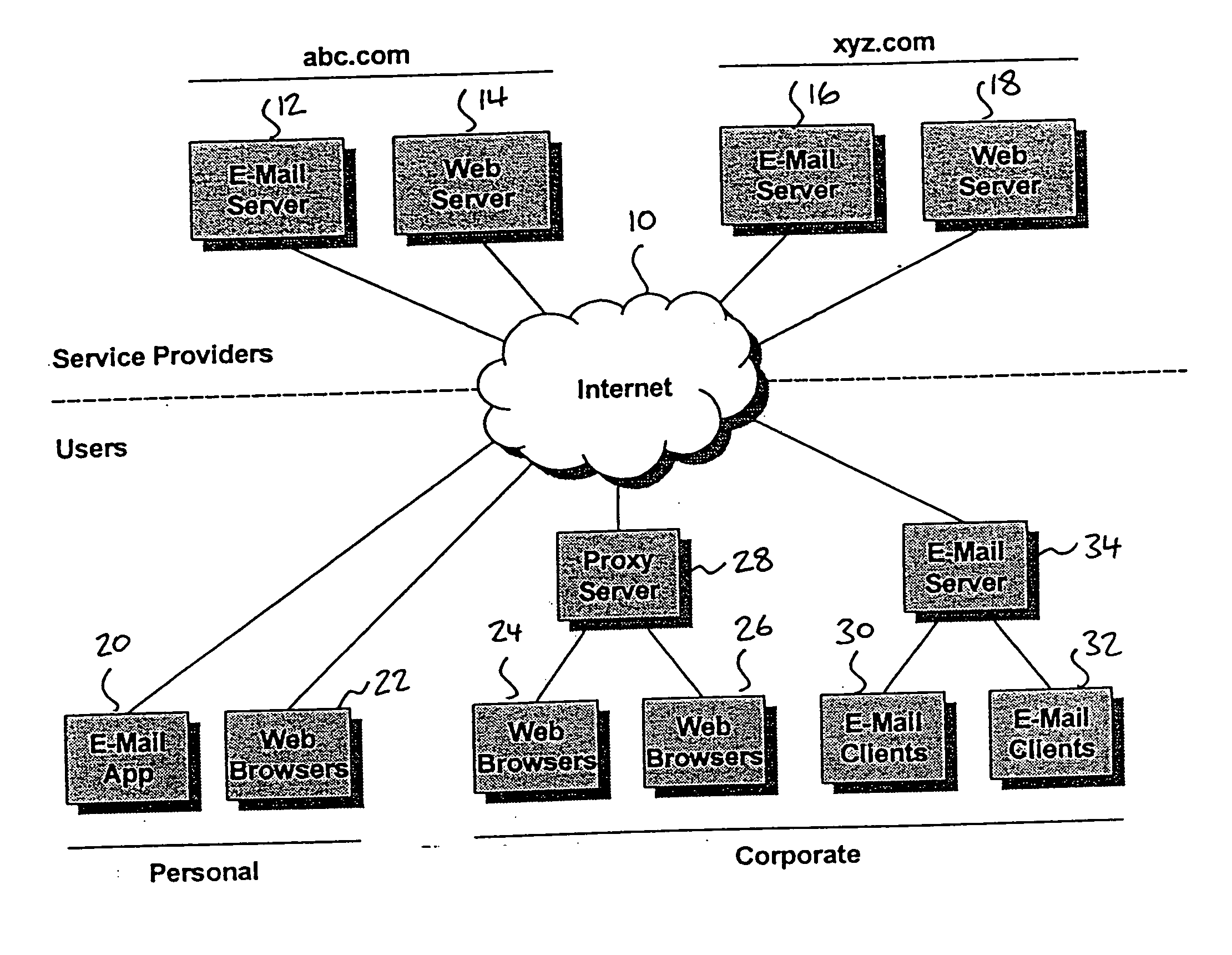
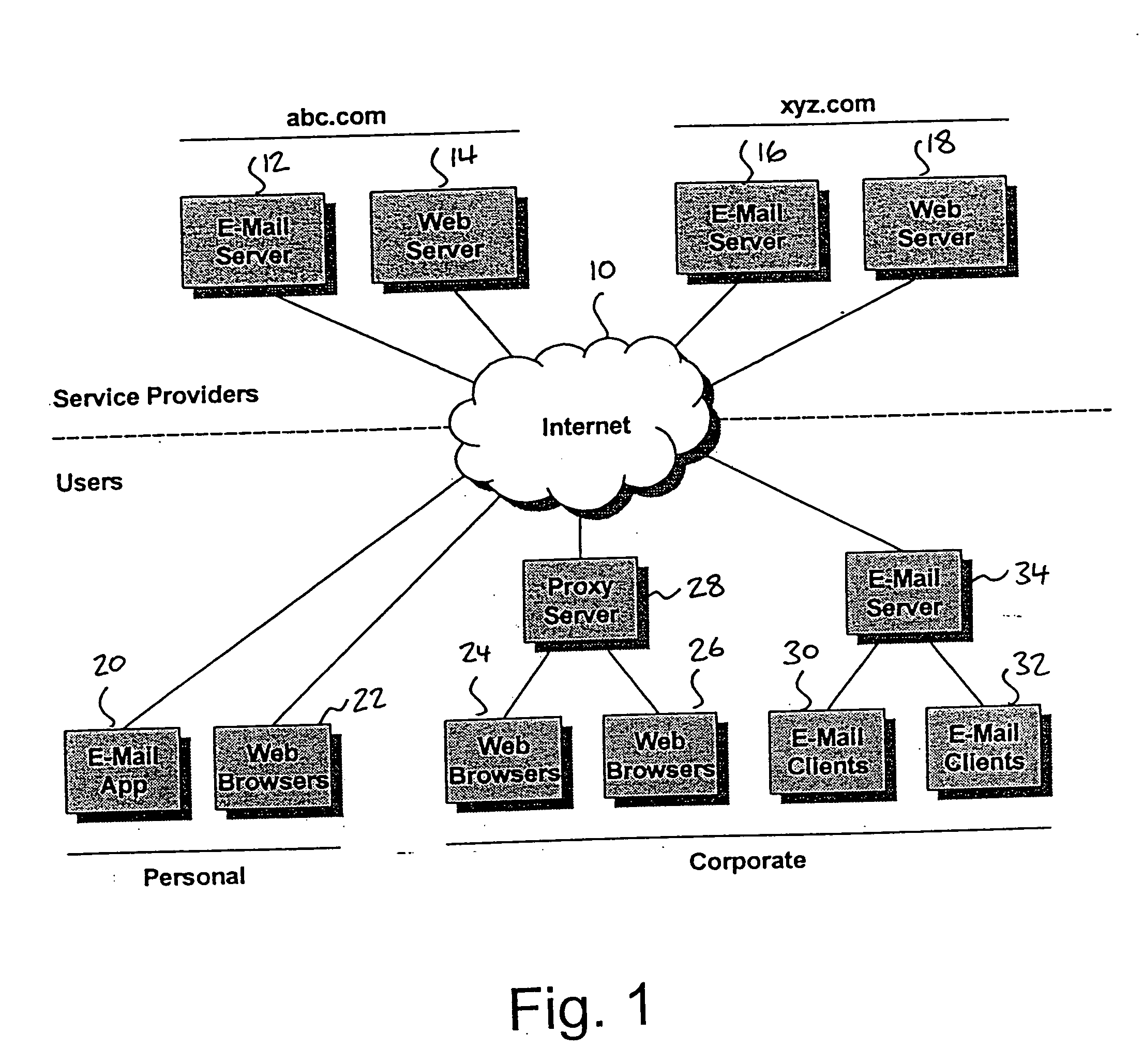
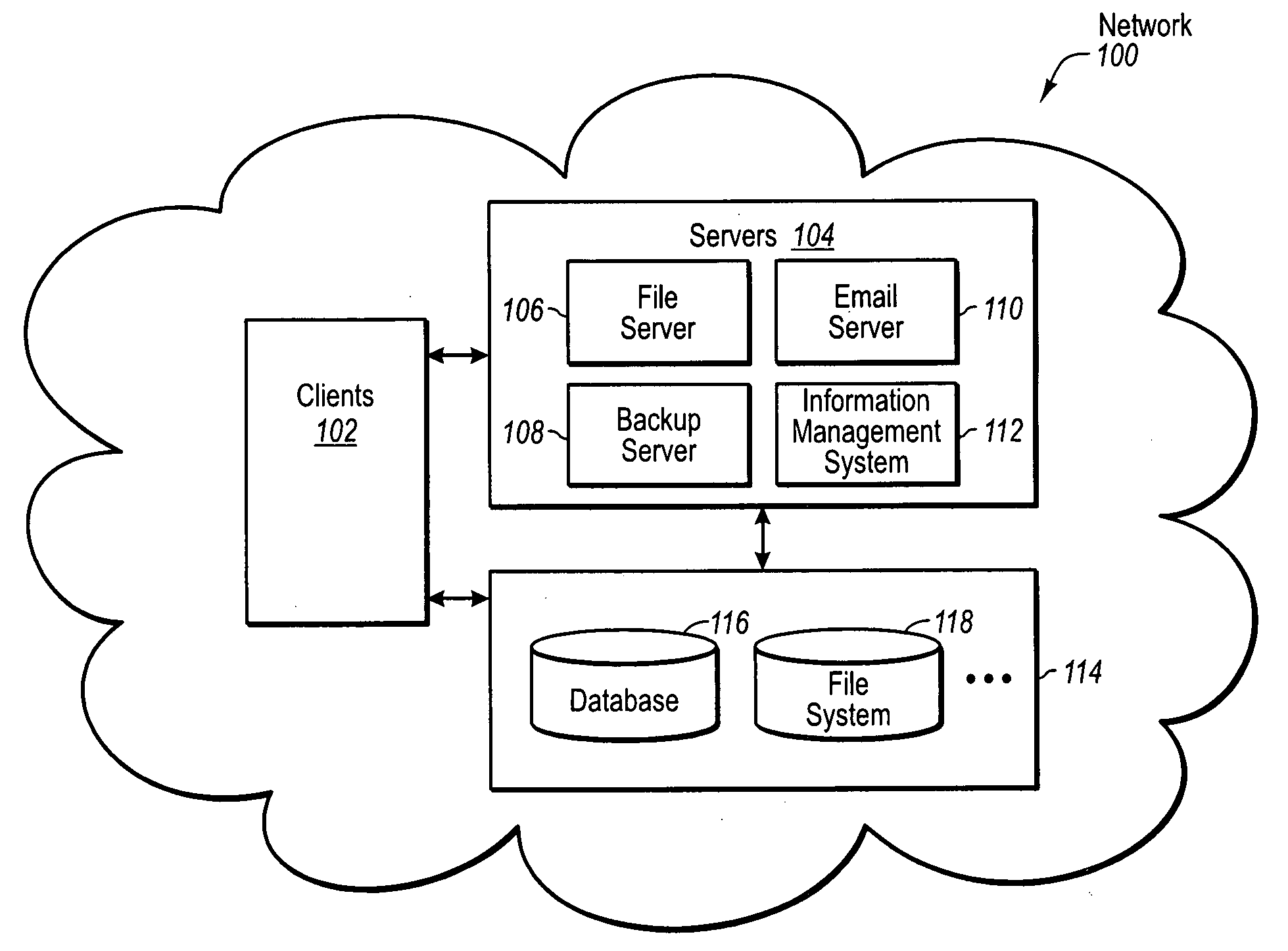
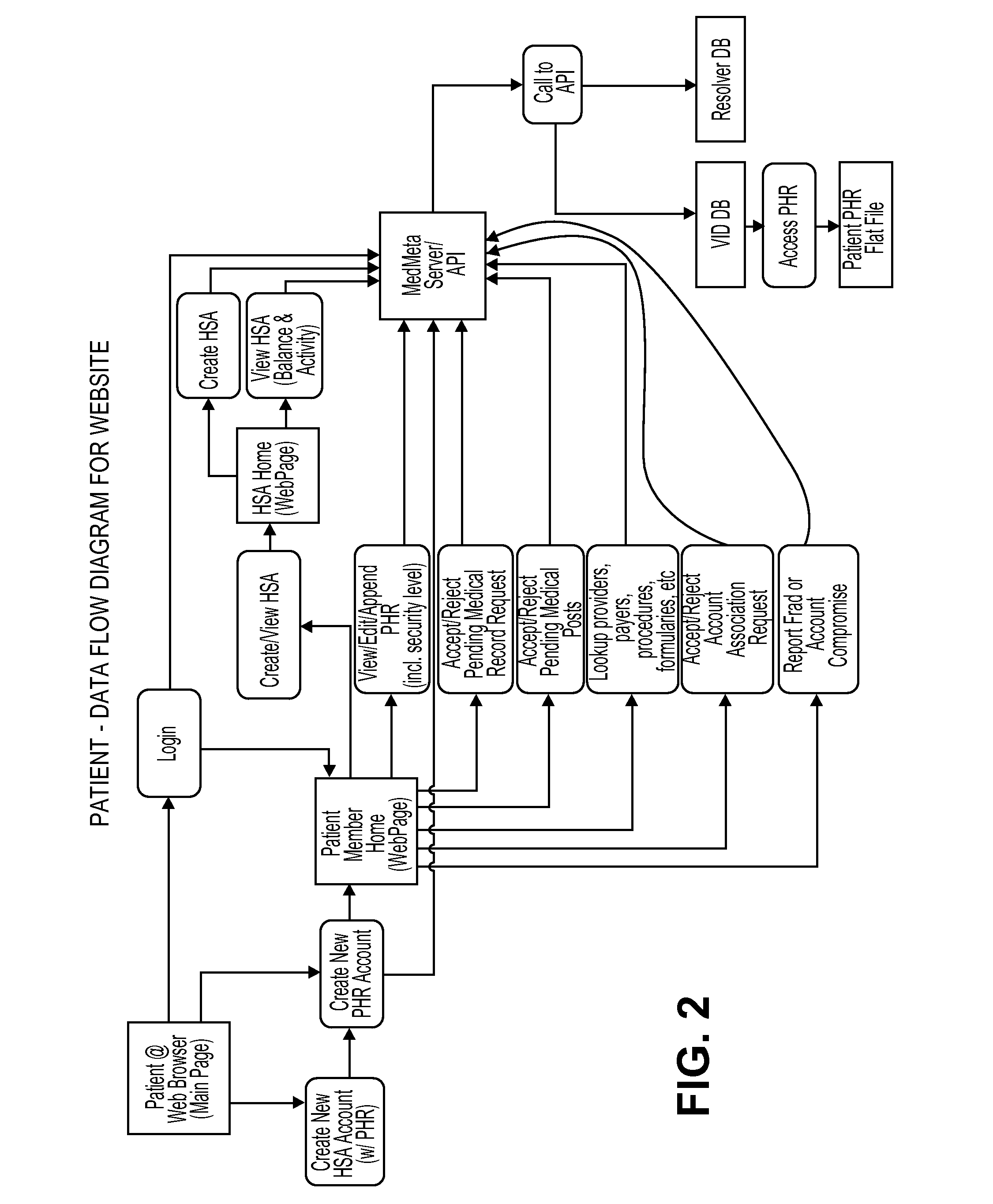
IT management is the discipline whereby all of the information technology resources of a firm are managed in accordance with its needs and priorities. These resources may include tangible investments like computer hardware, software, data, networks and data centre facilities, as well as the staff who are hired to maintain them.
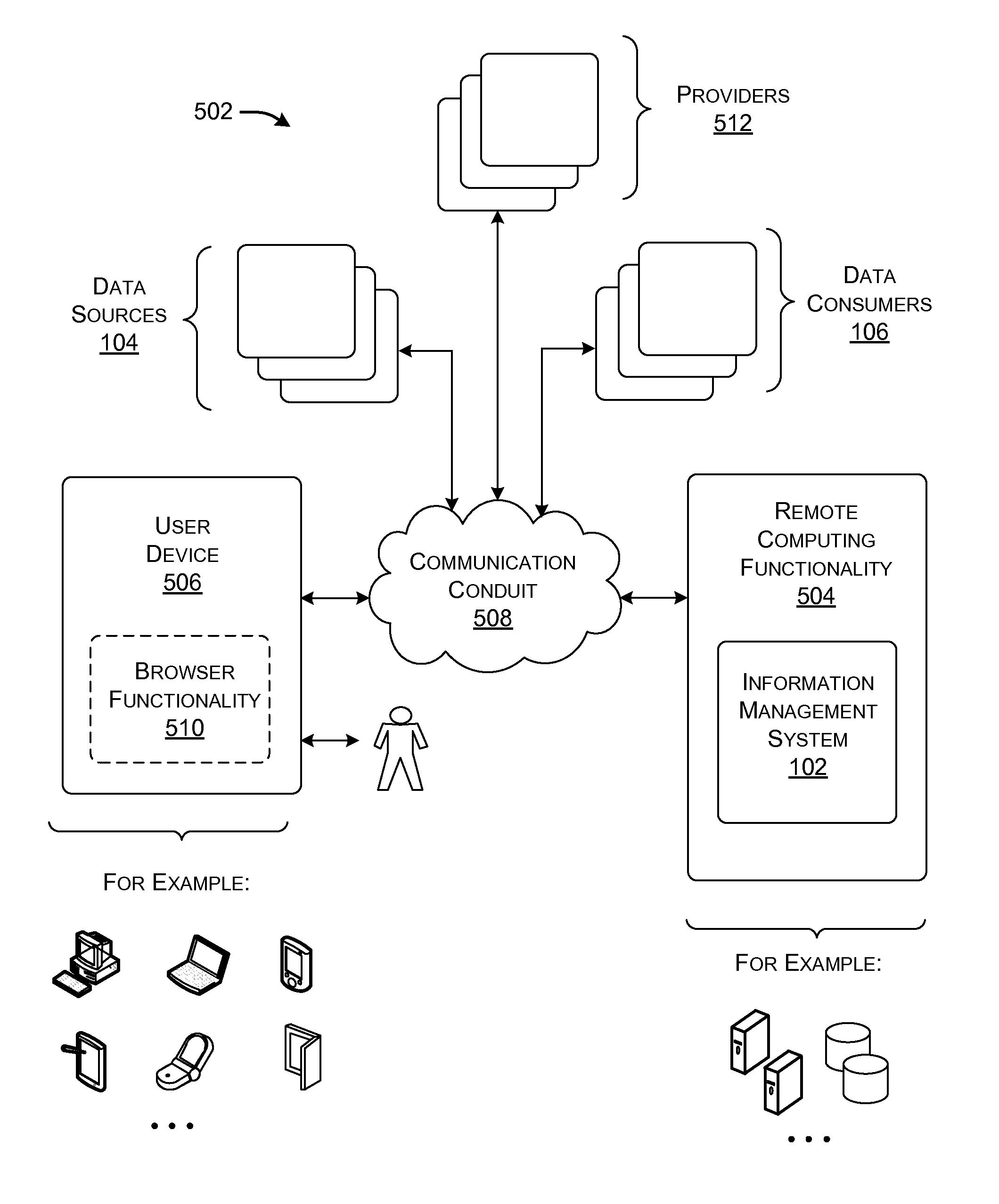
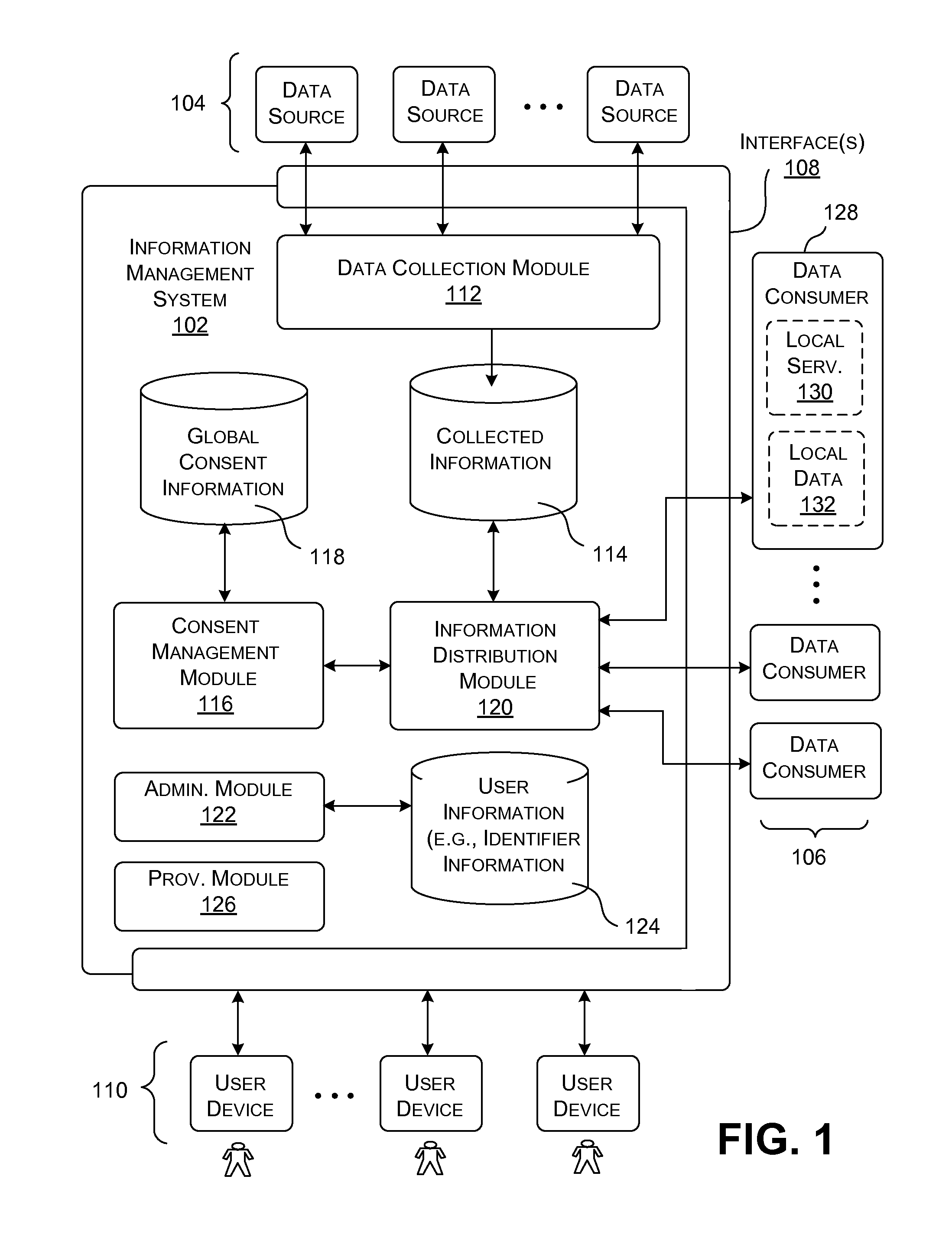
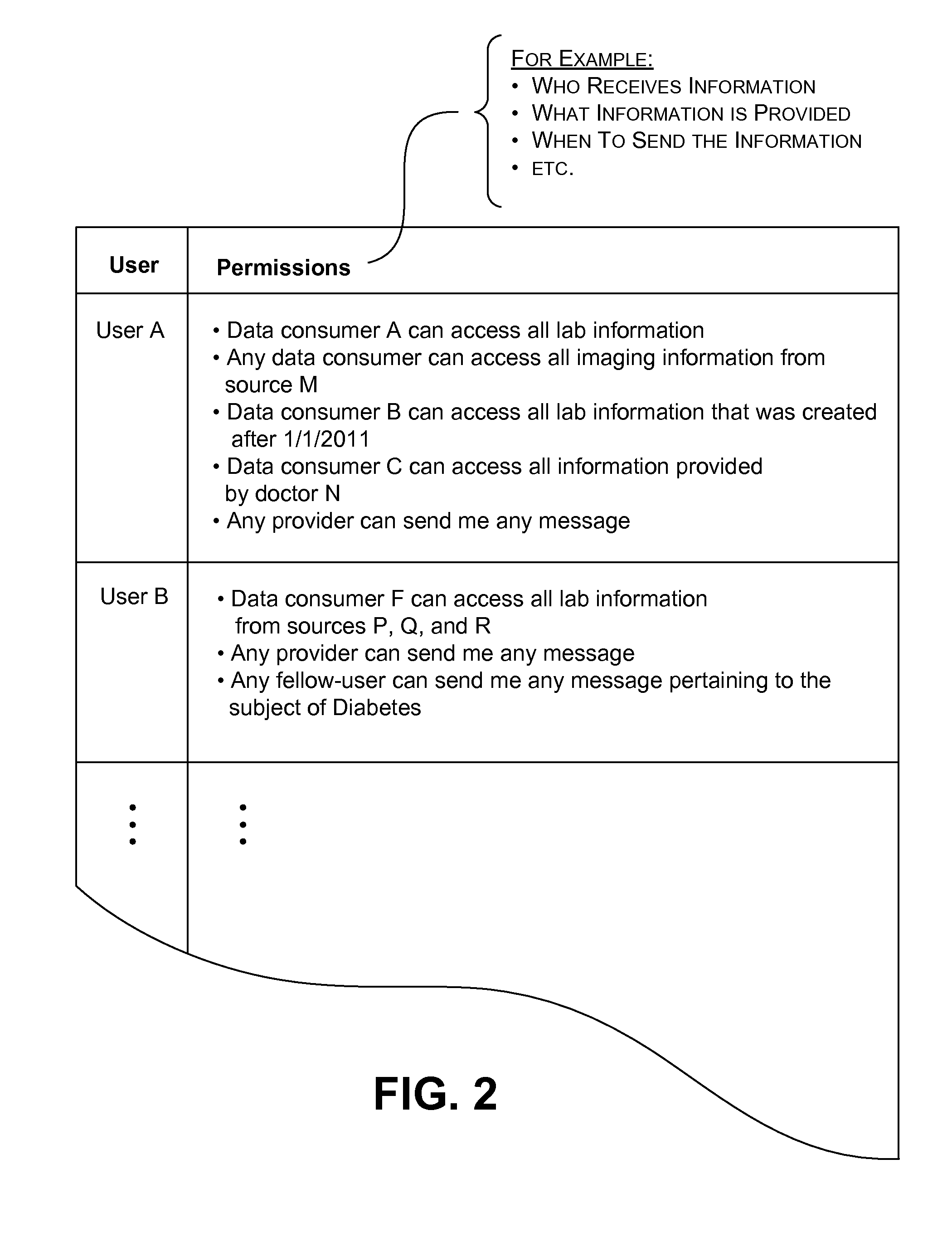
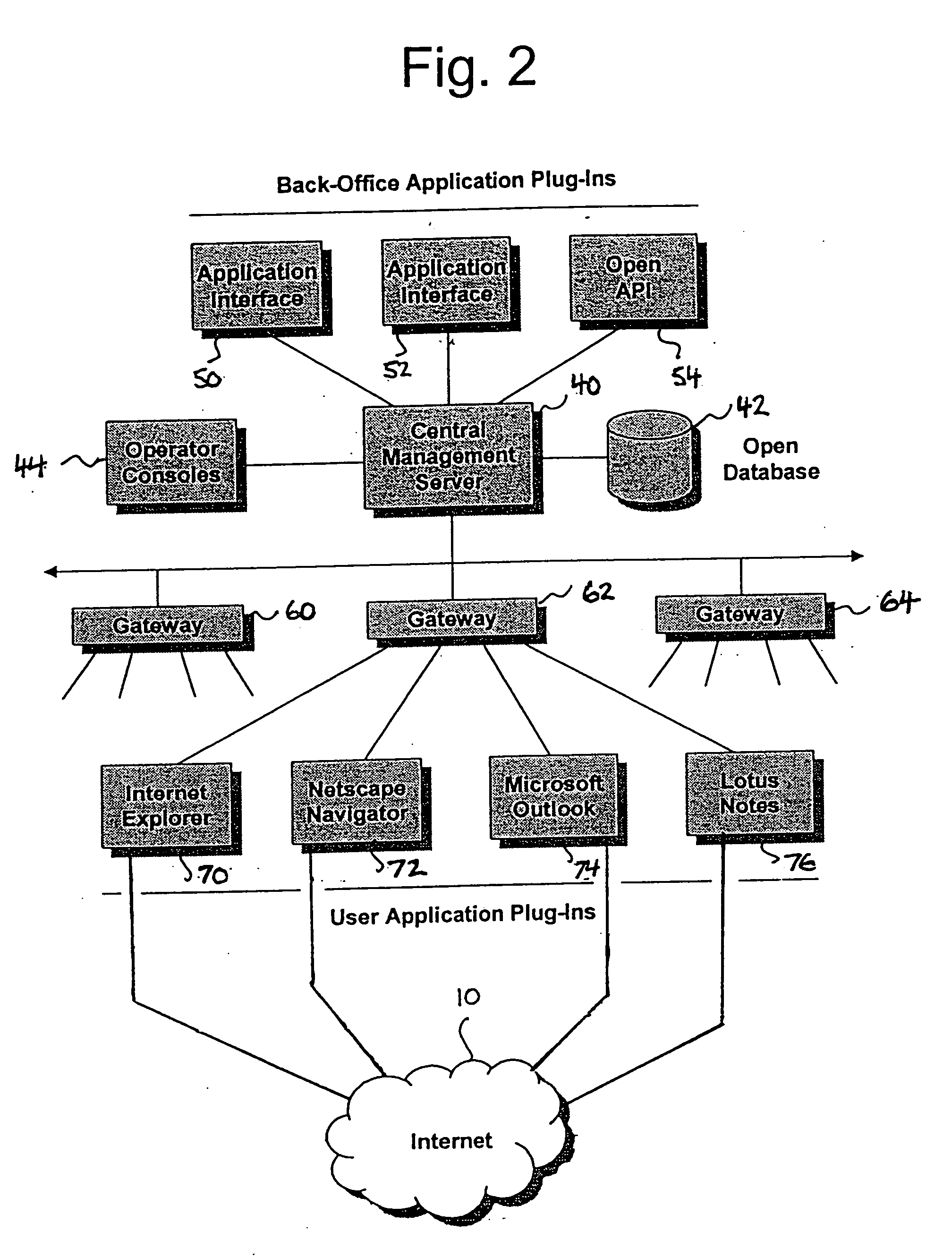
Distributing collected information to data consumers based on global user consent information
InactiveUS20120254320A1Well formedTelemedicineMultiple digital computer combinationsInformation functionDatasource
An information management system is described herein which maintains collected information that pertains to users, received from one or more data sources. The information management system also maintains a store of consent information. The consent information describes, for each user, at least one permission rule (established by the user) which enables at least one data consumer to receive at least part of the collected information for that user. Upon the occurrence of a triggering event, an information distribution module operates by distributing identified part(s) of the collected information to appropriate data consumer(s), as governed by the consent information. In this manner of operation, the consent information functions as global metadata which, from a centralized platform, governs the dissemination of the collected information to any data consumer in an application-agnostic manner.
Owner:MICROSOFT TECH LICENSING LLC
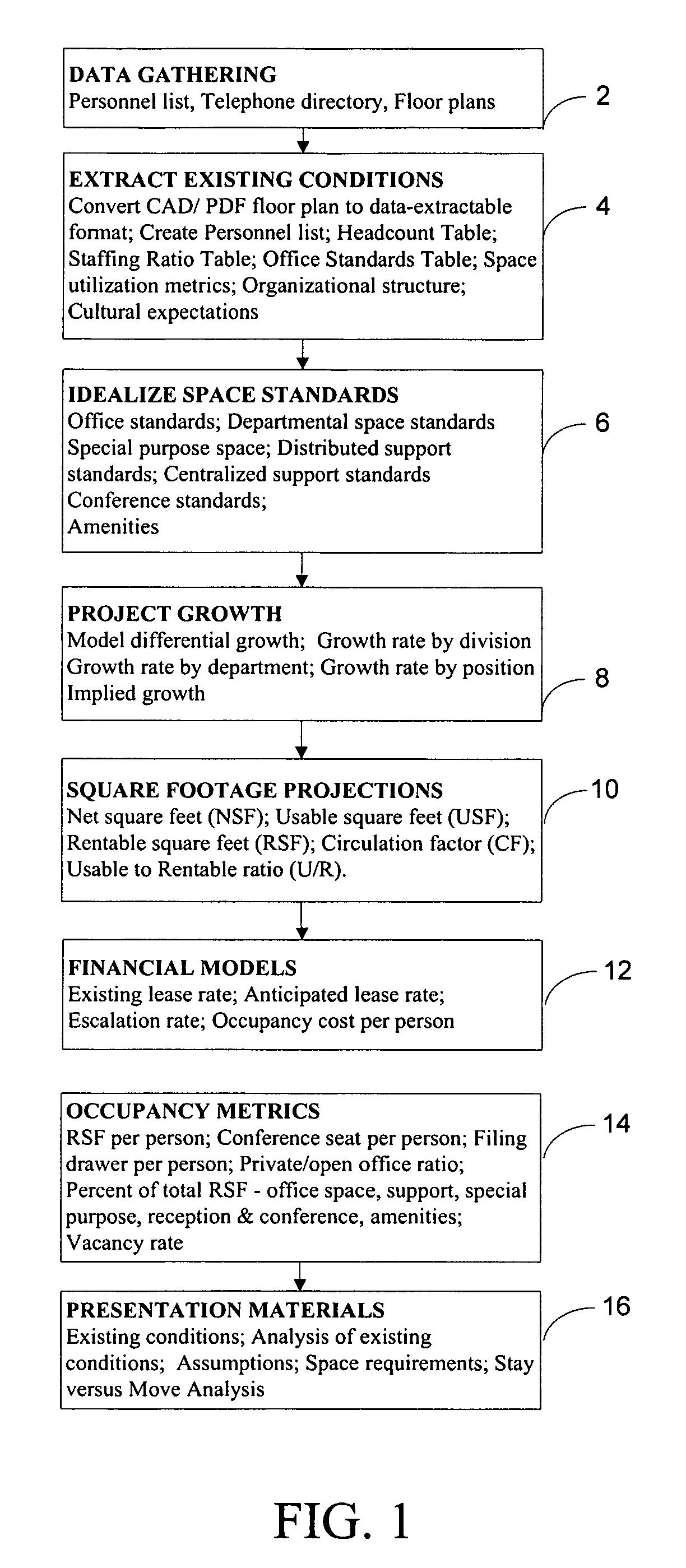
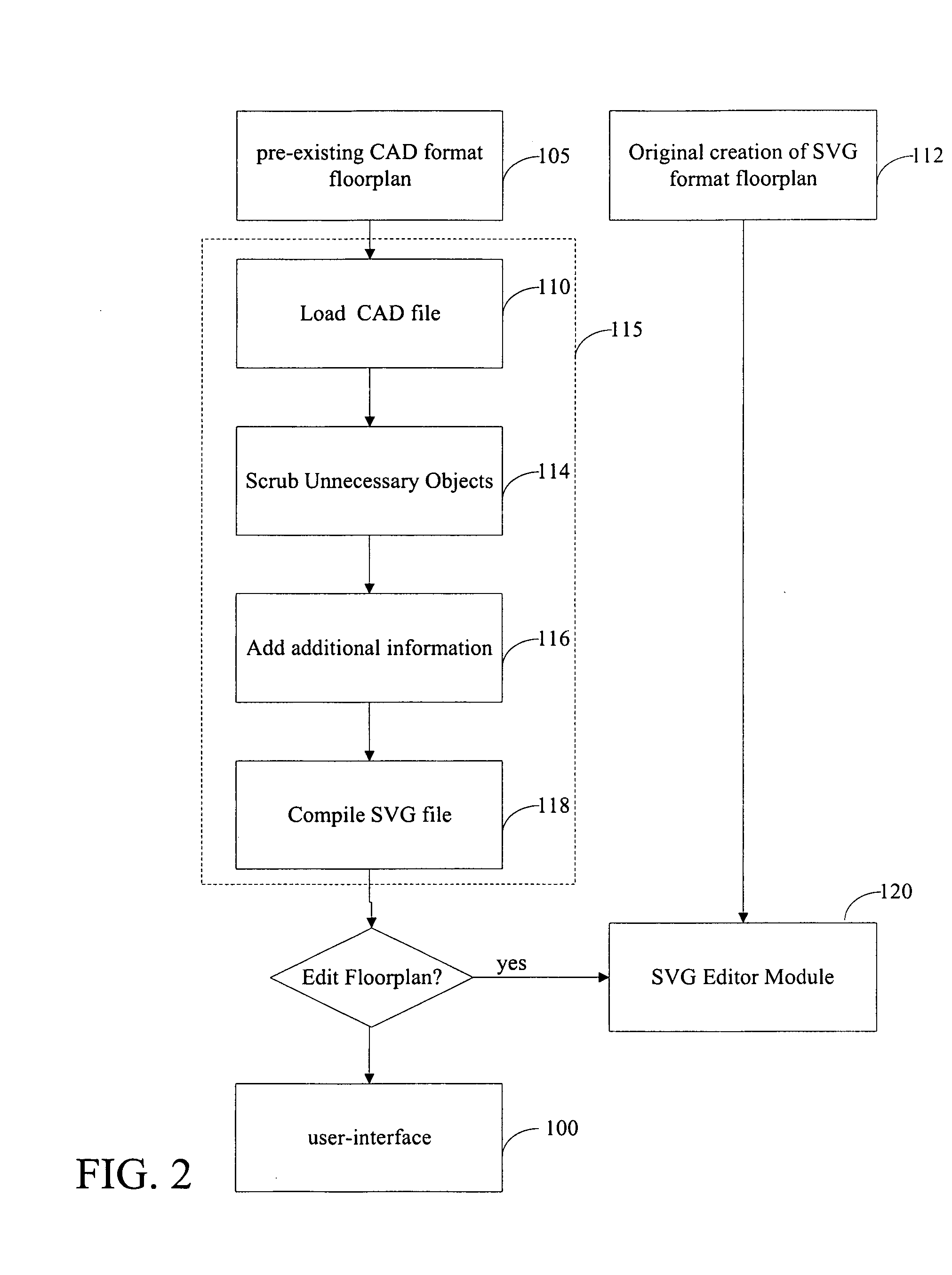
Office management solution
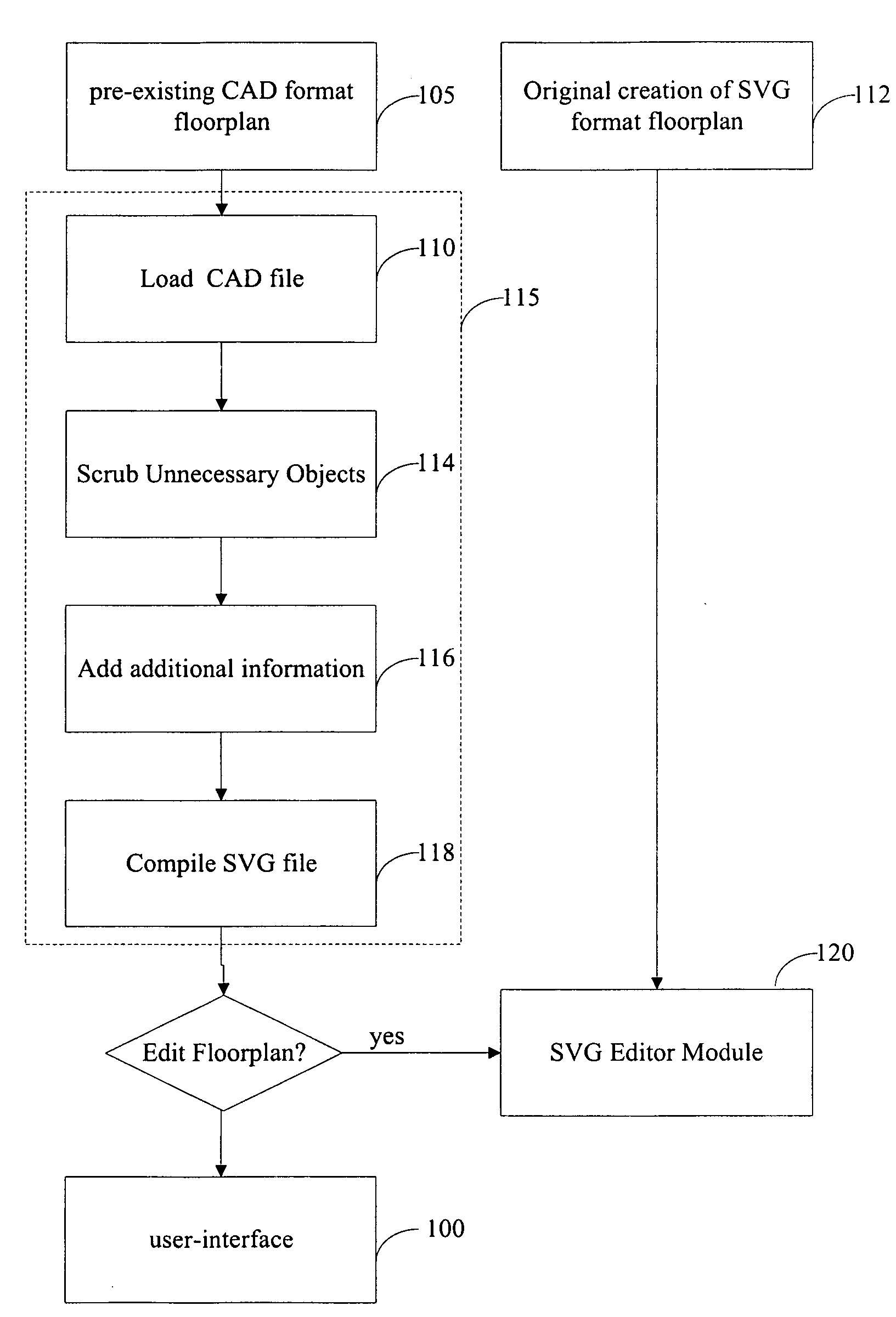
InactiveUS20080183483A1Special trainingGeometric CADSpecial data processing applicationsDrag and dropRelational database
A spatial database interface for generally managing assets in a graphical user environment is disclosed, in the particular context of a CAOM office management software solution for managing office facilities inclusive of office layouts (equipment, furniture, information technology assets and other assets) and basic human resources within a physically-defined office space. The software is a web-based custom map application that links a relational database to an SVG or browser rendering format layout map that shows physical locations and relationships among people, rooms and other assets. It imposes a graphical user interface for point-and-click identification of the assets, reporting and reconfiguration (for “what-if” scenarios), and drag-and-drop manipulation of the assets. The software is resident on a web-enabled server hosted by an application service provider. The assets are associated with asset data stored in a web-enabled database and are linked to corresponding visual icons represented on the layout map by embedded HTML elements such as IFrames. All asset data is stored in the database, and robust searching, analysis and reporting capabilities are provided to employ the data.
Owner:HART MARCIA A
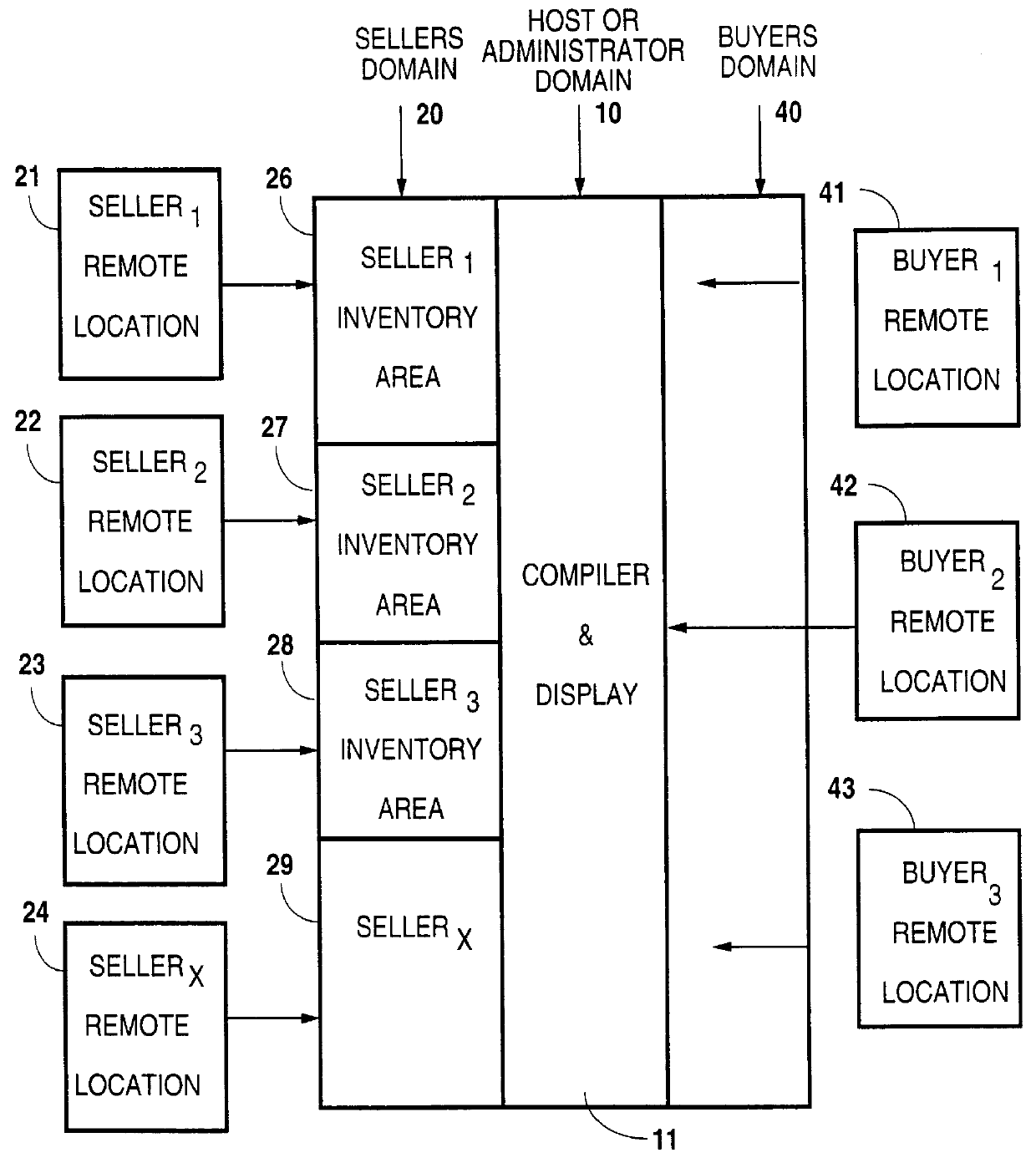
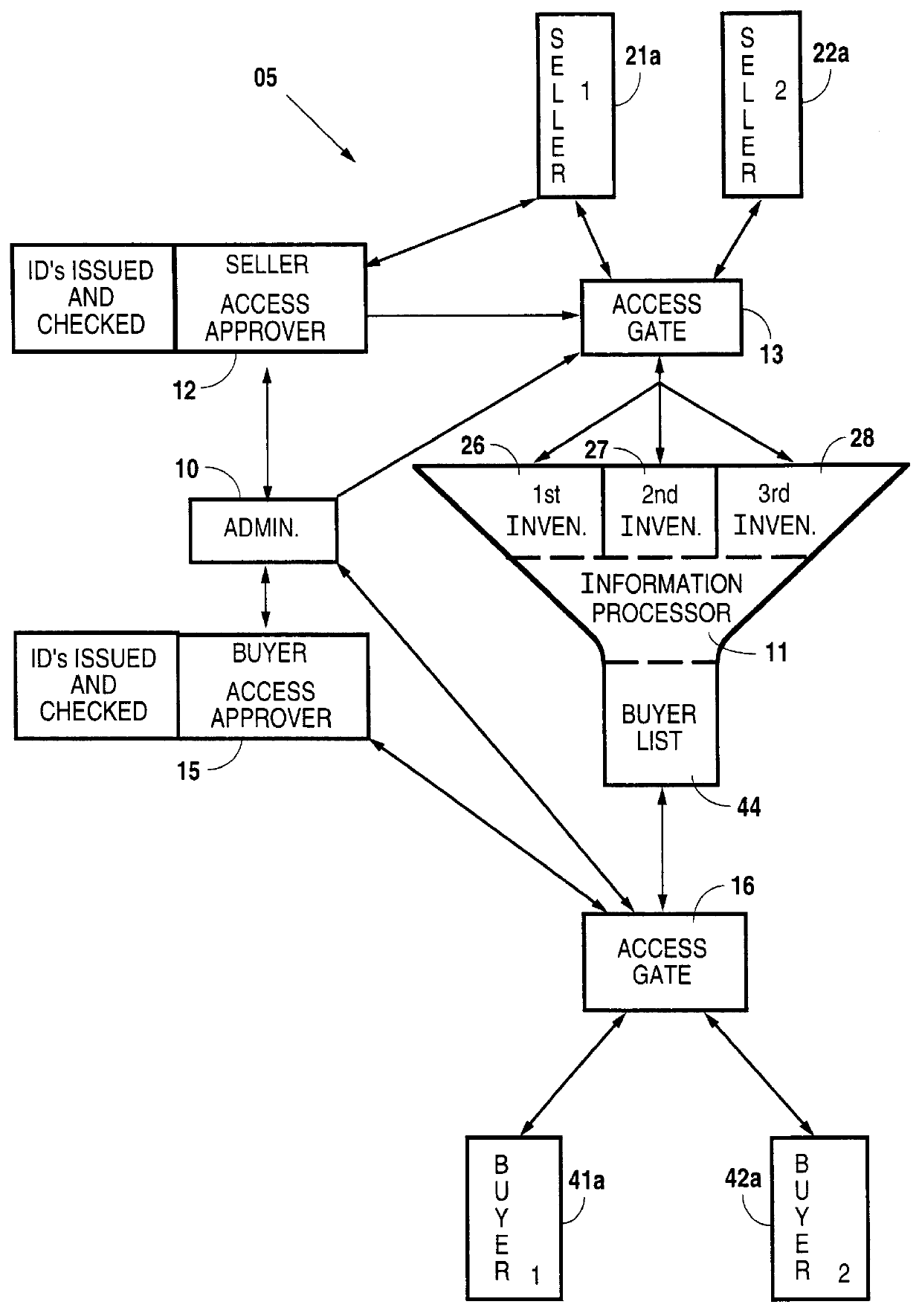
Automated and independently accessible inventory information exchange system
A method for exchanging information between providers and users of products and services in which an information management system is established that is computer based and has information processing and storage capabilities. The system also has electronic communication connections that permit buyers and sellers to electronically connect with the information management system for information exchange. Limited electronic access to the information management system is granted to approved sellers of products and services. After approval, each such seller is enabled to access inventory information of that seller for amendment purposes. Similarly, limited electronic access to the information management system is granted to approved buyers of products and services and are provided a searching capability to search a compilation of a plurality of seller's inventory information using criteria specified by that approved buyer. Last, a buyer's listing of products and services is compiled from the compilation of the seller's inventory information for that buyer based on that buyer's search criteria and in which duplicate inventory items are removed therefrom.
Owner:CXT SYST INC
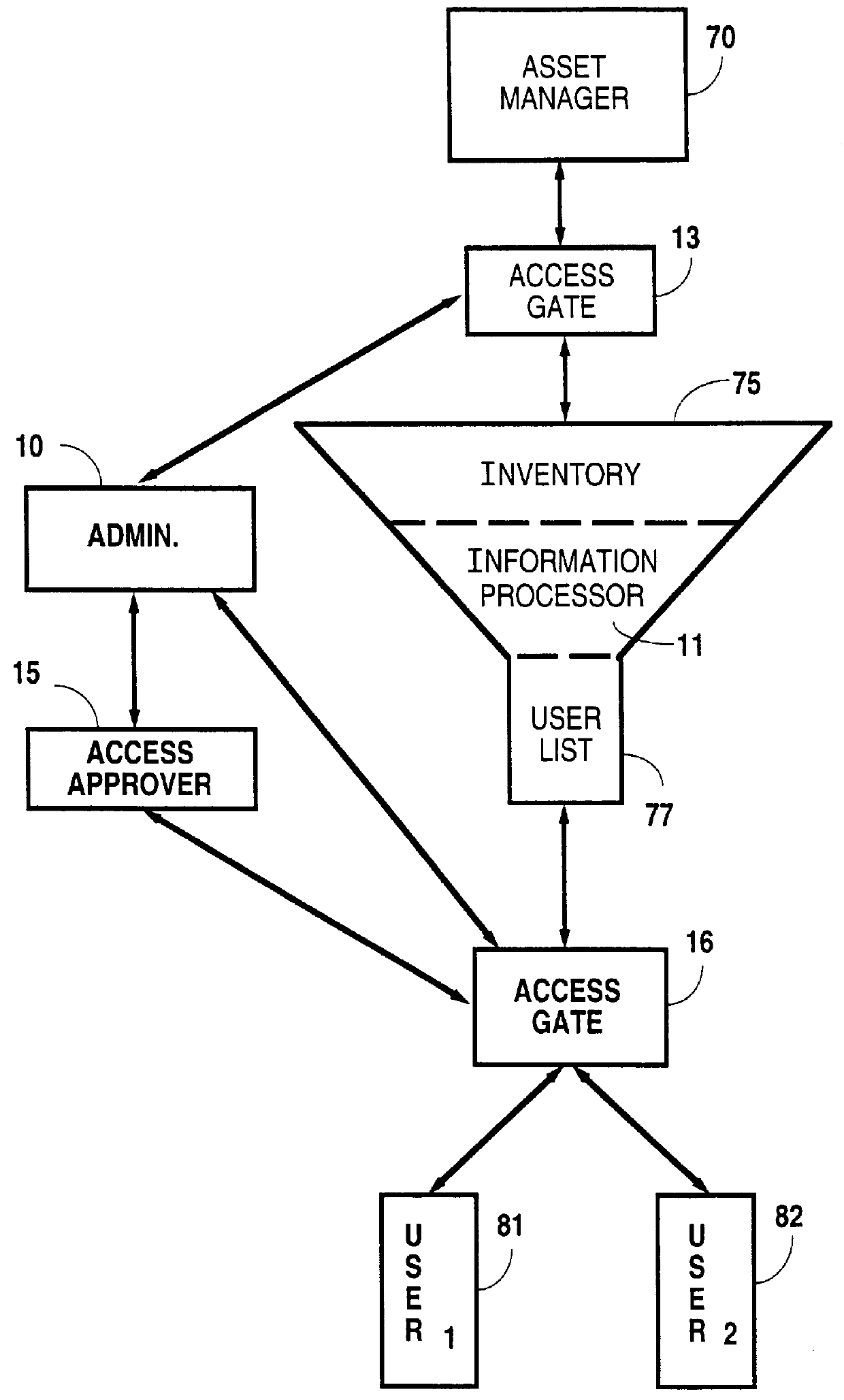
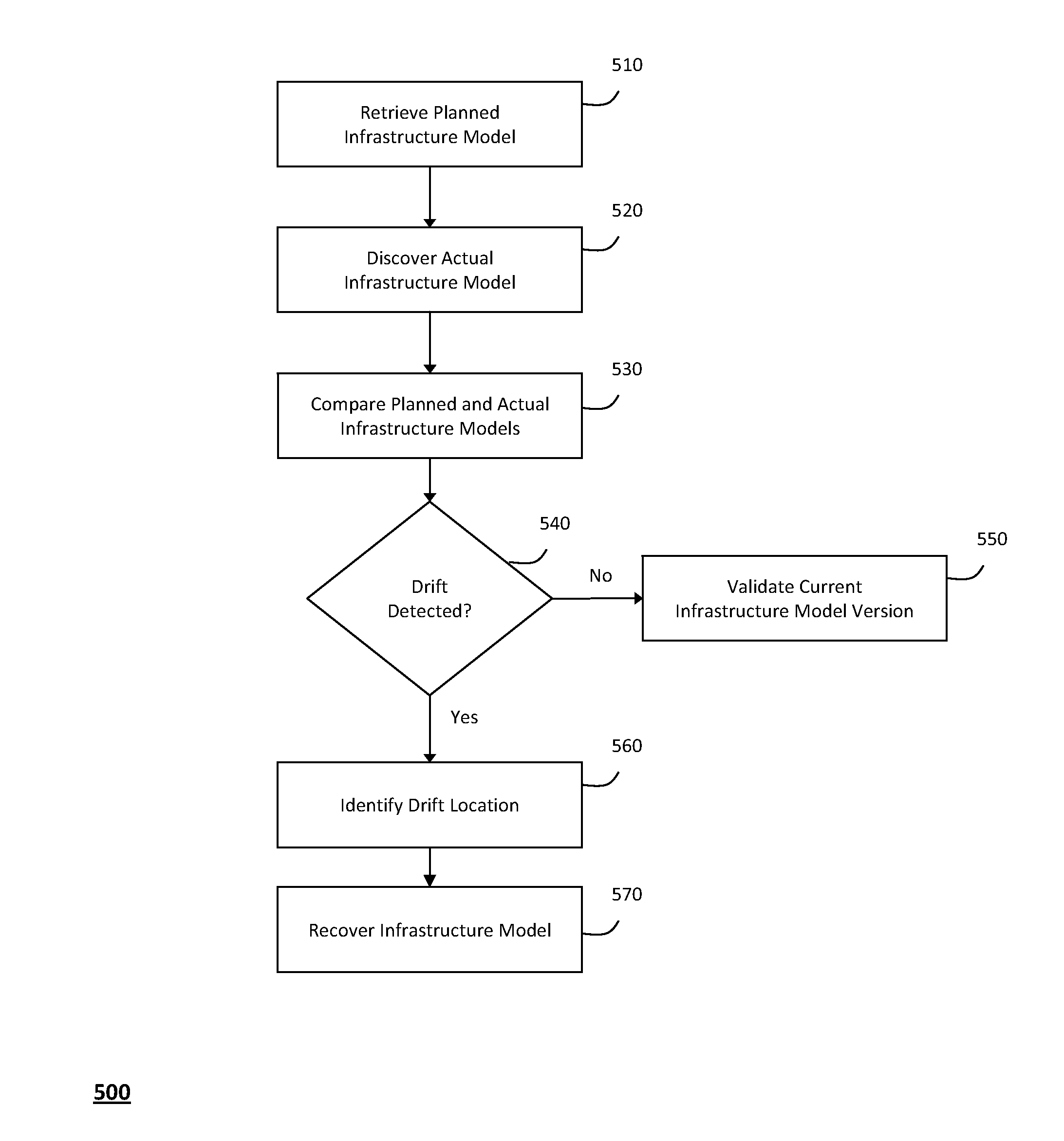
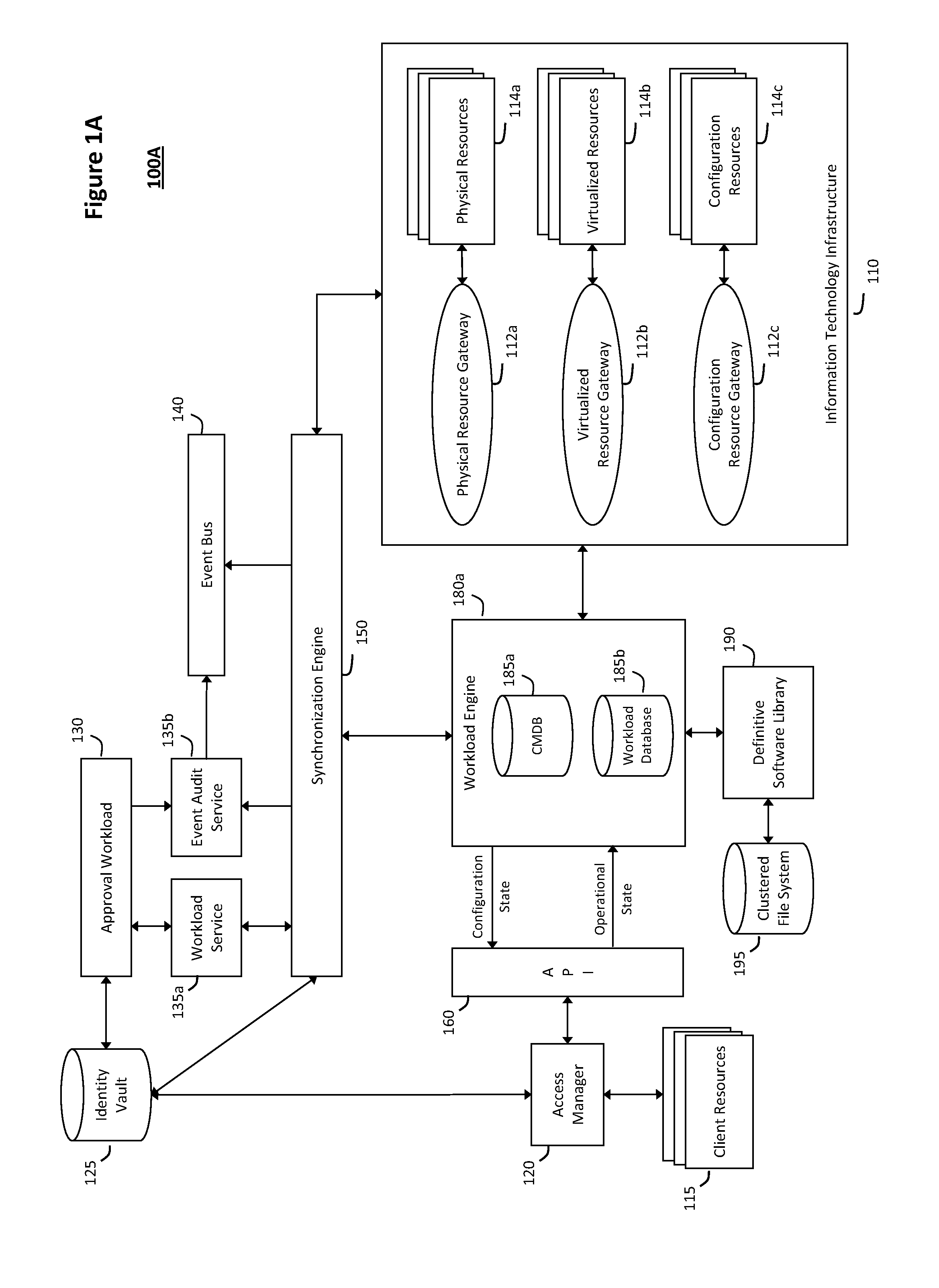
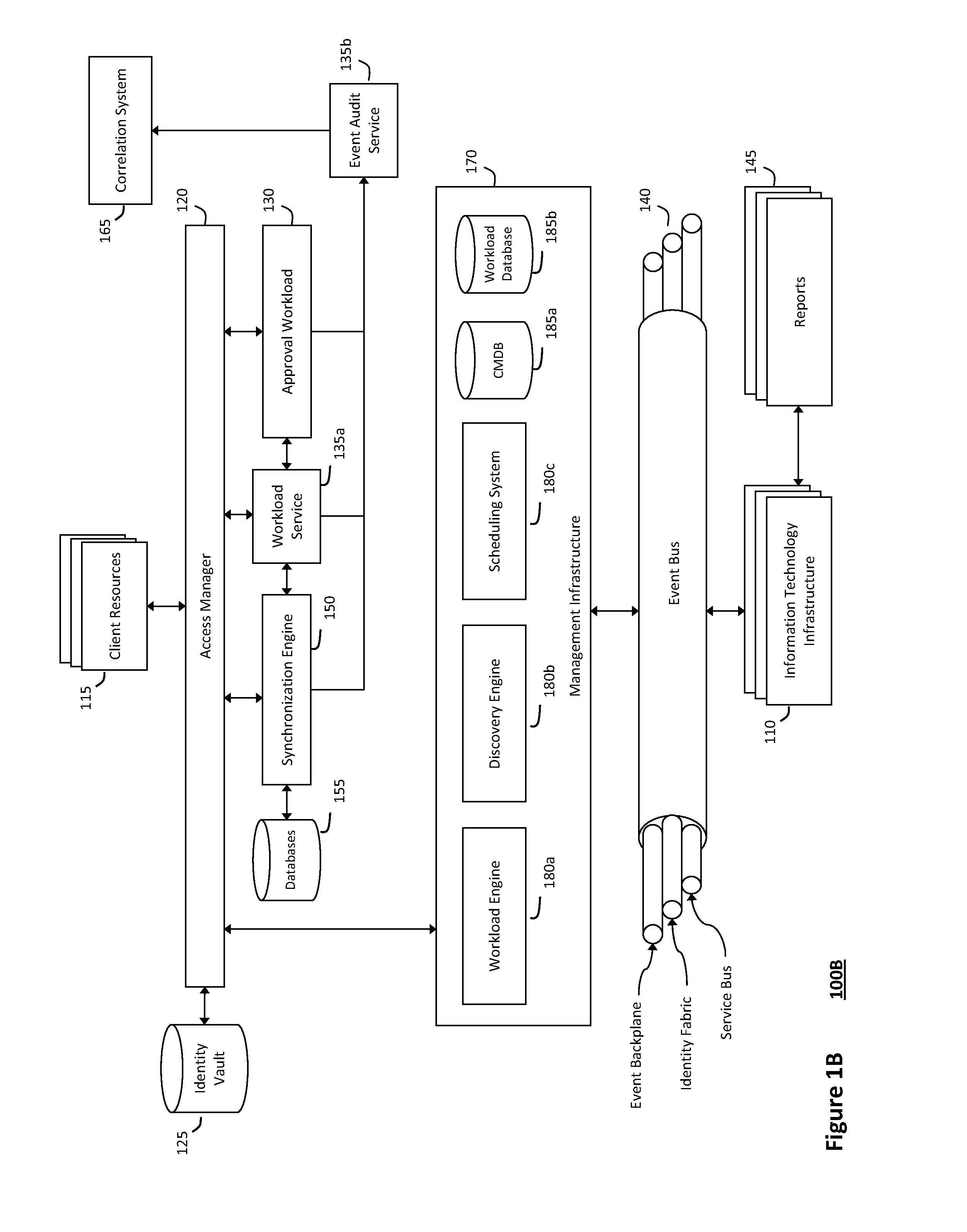
System and method for managing information technology models in an intelligent workload management system
ActiveUS20110126047A1Free computational resourceAgile and flexible managementFault responseDigital computer detailsPlanned changeService-oriented architecture
The system and method described herein for managing information technology models in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing planned changes and recovery processes for version-controlled snapshots of the information technology models. For example, a discovery engine may enrich models of an infrastructure with identity information obtained from an identity vault and the infrastructure itself, and a management infrastructure may then manage planned changes to the infrastructure model. In particular, the management infrastructure may construct implementation plans that coordinate interaction between managed entities to implement the planned changes, and may further detect drifts between operational states and planned states for the infrastructure models.
Owner:MICRO FOCUS SOFTWARE INC
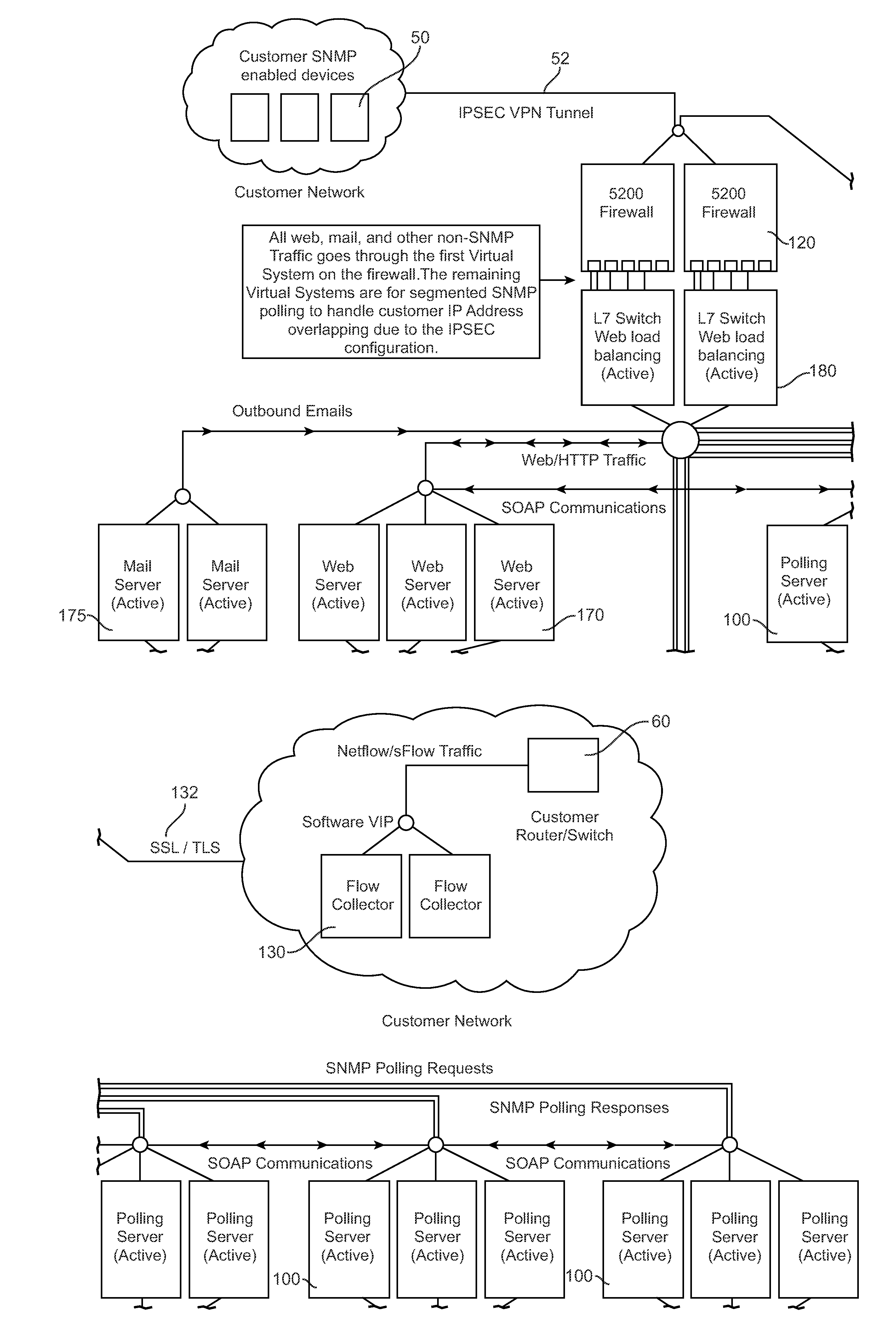
System and interface for monitoring information technology assets
ActiveUS7752301B1Retain controlStandardize the interfaceDigital computer detailsTransmissionApplication service providerRelevance analysis
An application service provider (ASP)-based interface and system for analyzing performance and costs of respective enterprise information technology assets from the correlation of metrics data of enterprise SNMP-enabled devices.
Owner:DYNATRACE
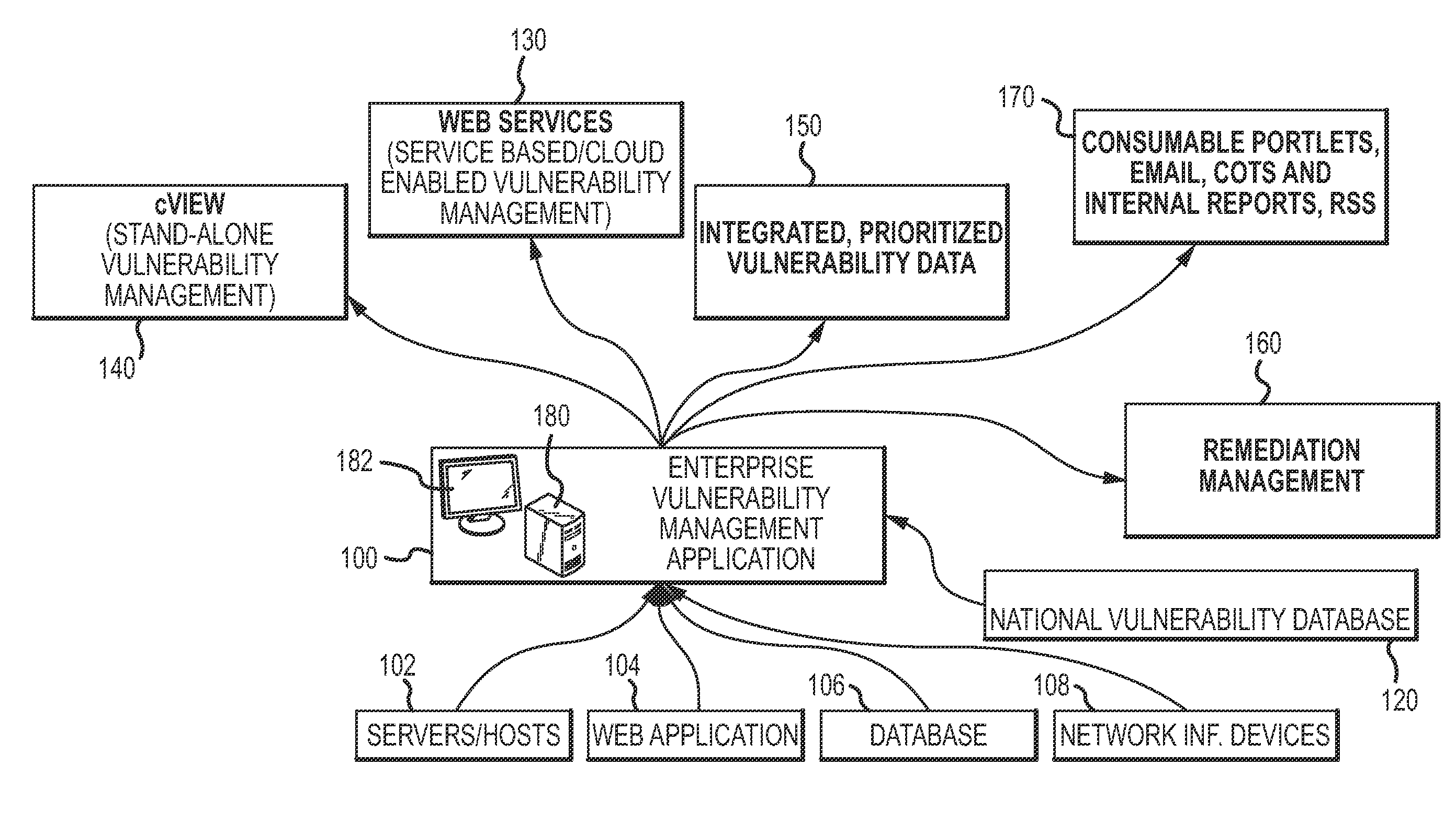
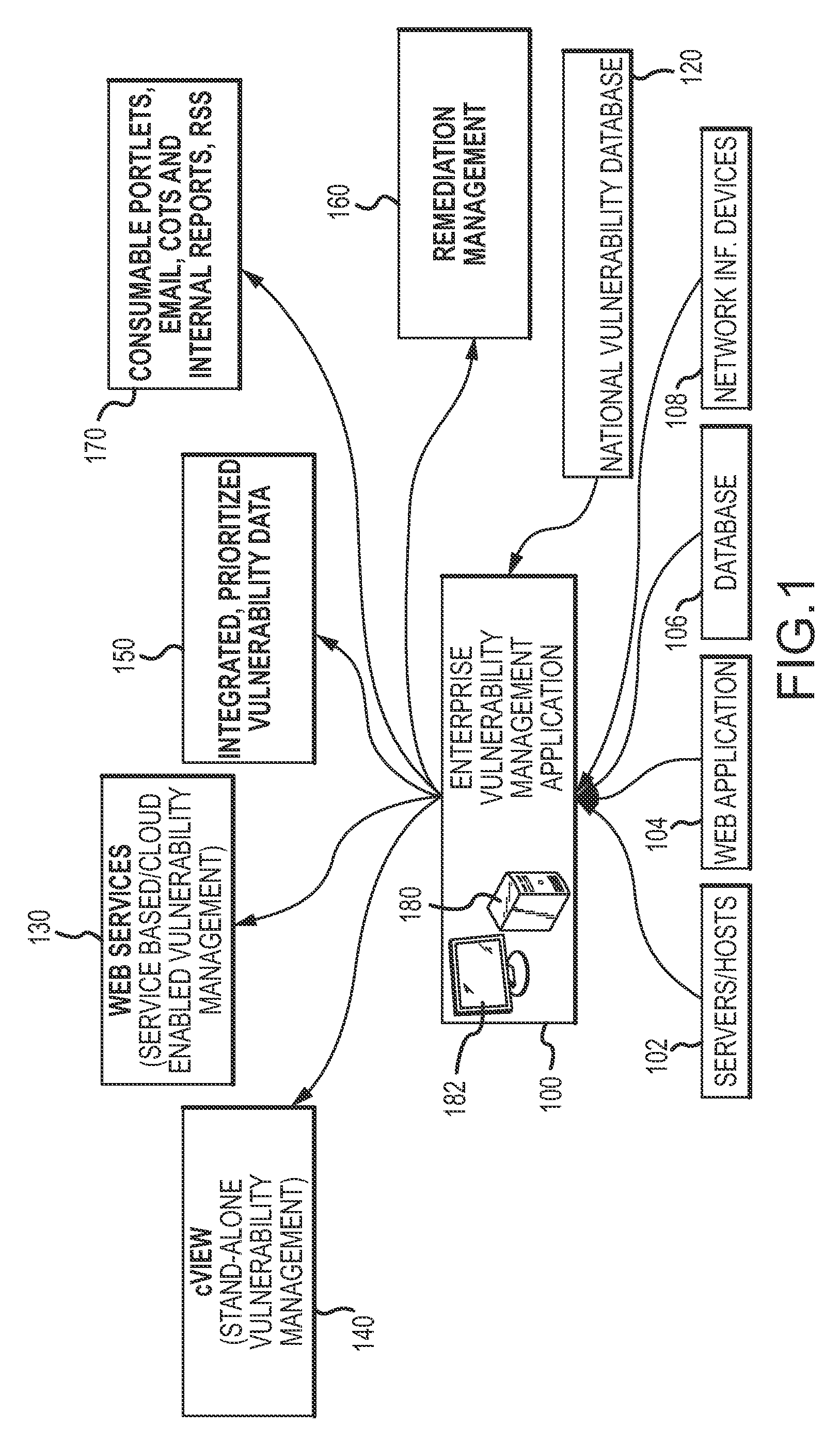
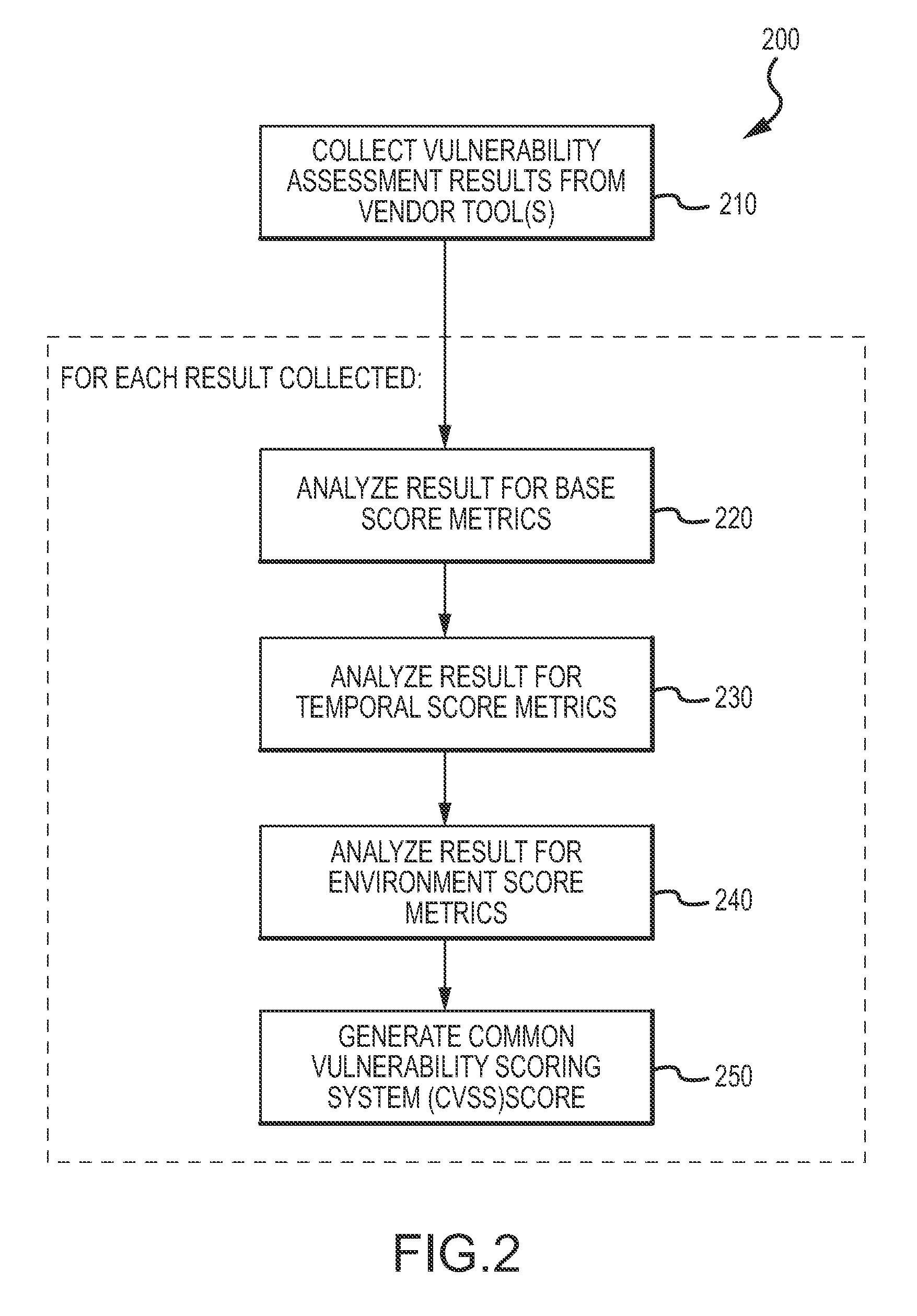
Enterprise vulnerability management
ActiveUS20120304300A1Fast data analysisEasy to addMemory loss protectionError detection/correctionVulnerability managementRemedial action
An enterprise vulnerability management application (EVMA), enterprise vulnerability management process (EVMP) and system. In one embodiment, the EVMP may include executing computer software code on at least one computer hardware platform to receive login information from a user, inventory current information technology assets of the enterprise, conduct vulnerability scanning of the inventoried information technology assets, analyze vulnerability correlation and prioritization of the information technology assets, remediate one or more vulnerabilities of the information technology assets, and report to the user about the vulnerabilities and remediation undertaken. As part of the analysis, one or more vulnerability scores such as, for example, Common Vulnerability Scoring System (CVSS) scores, may be generated from base score metrics, temporal score metrics and environment score metrics.
Owner:LEIDOS INNOVATIONS TECH INC
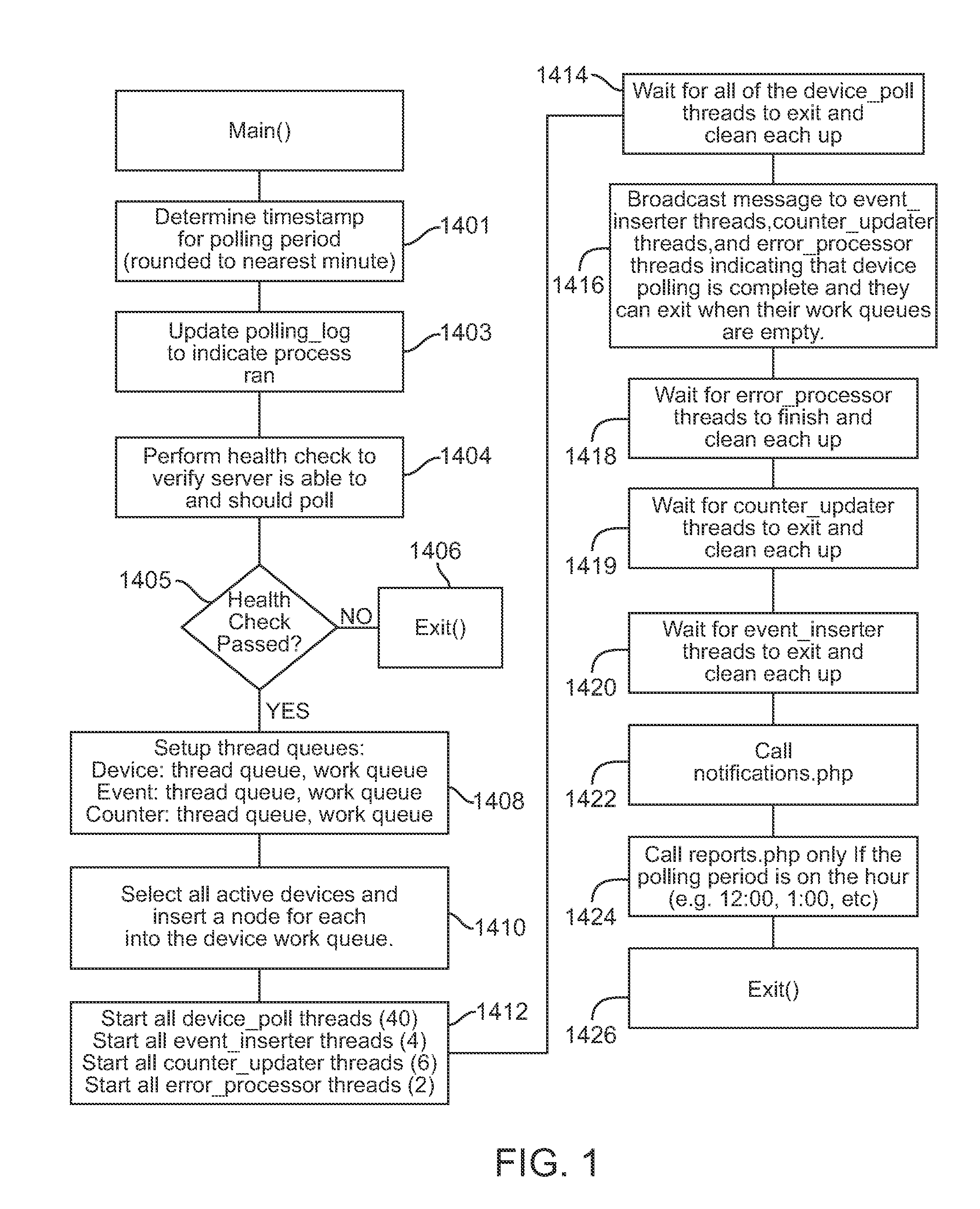
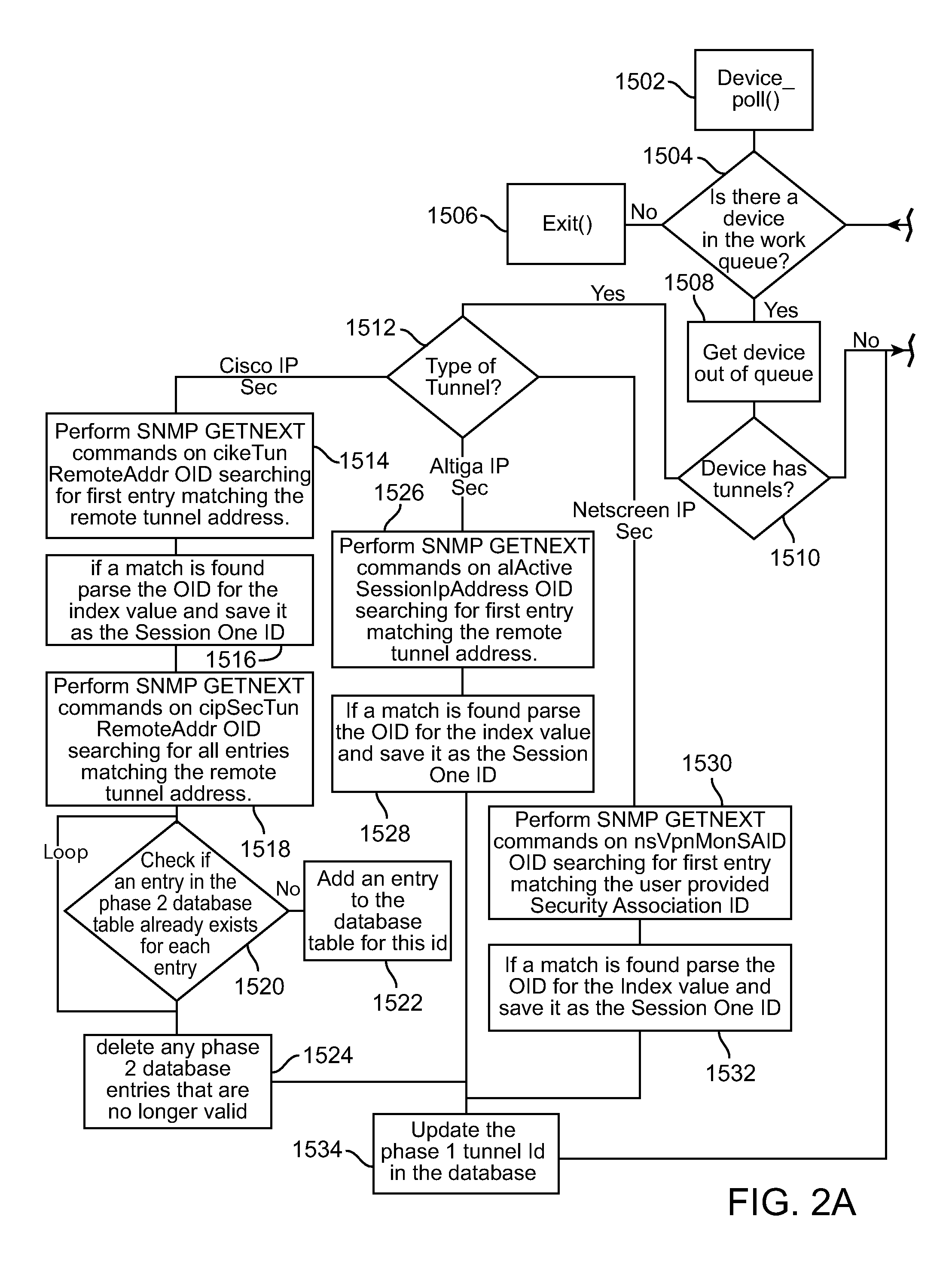
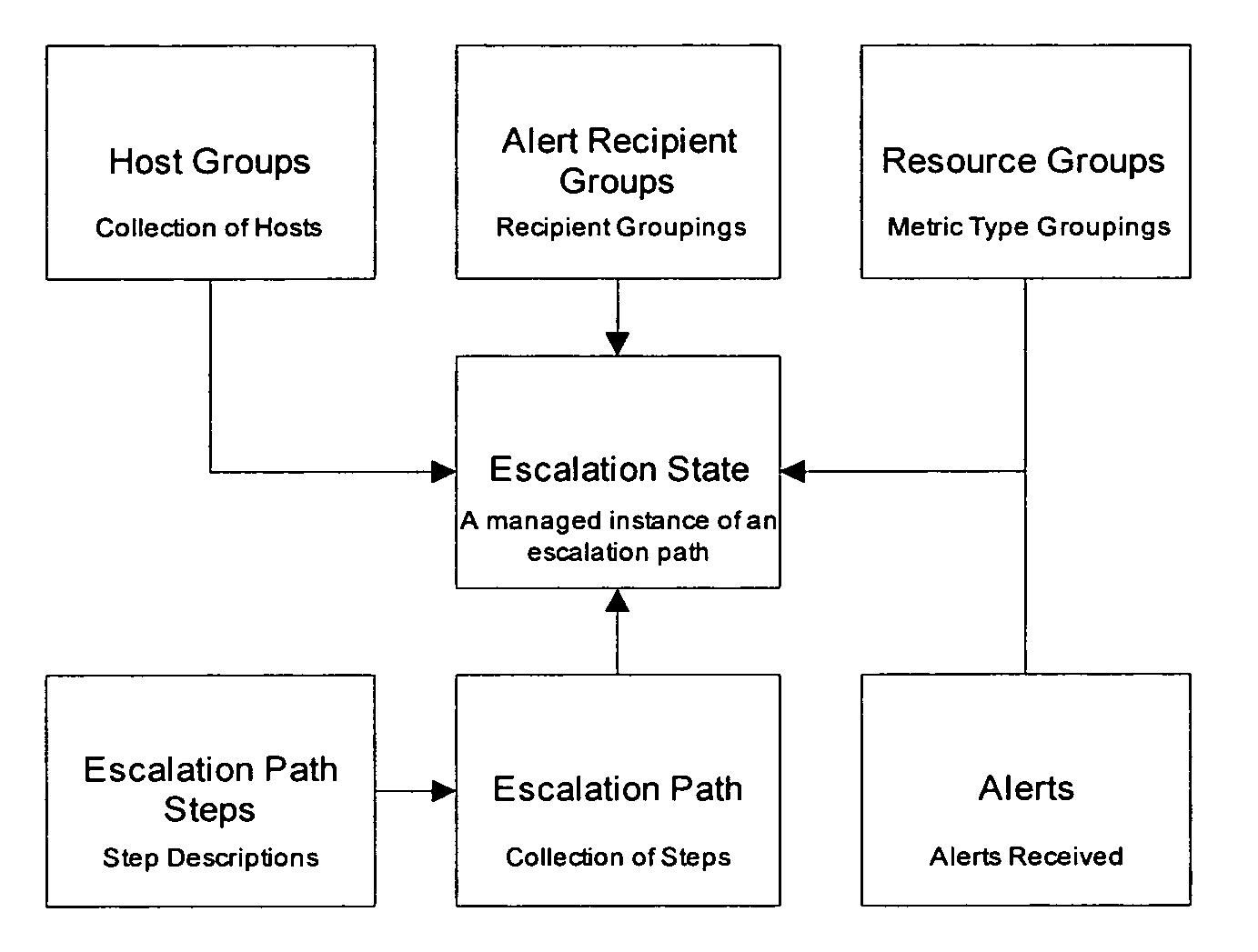
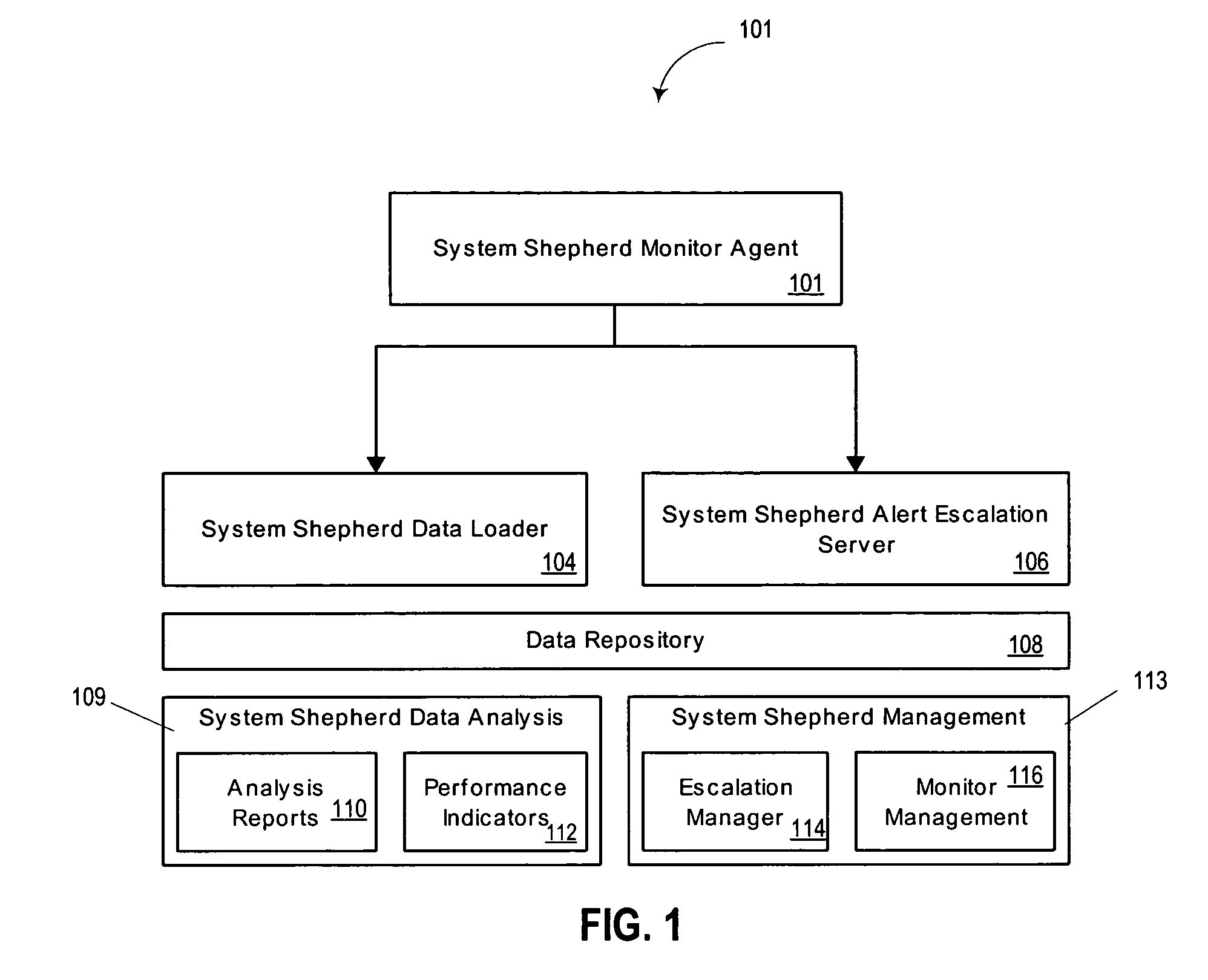
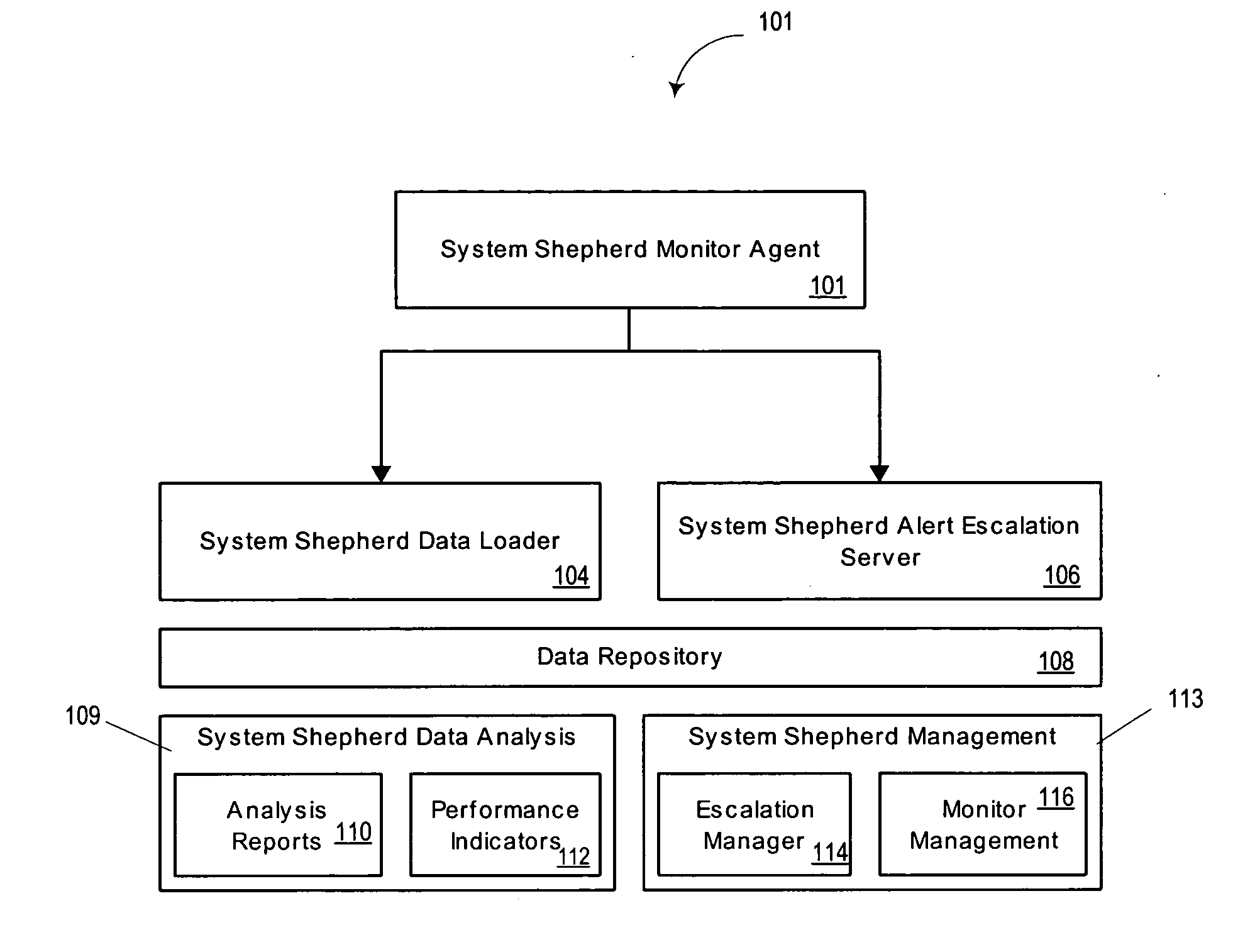
System and method for monitoring processes of an information technology system
ActiveUS7079010B2Easy to detectEasy to predictError detection/correctionElectric testing/monitoringOperational systemAnalysis tools
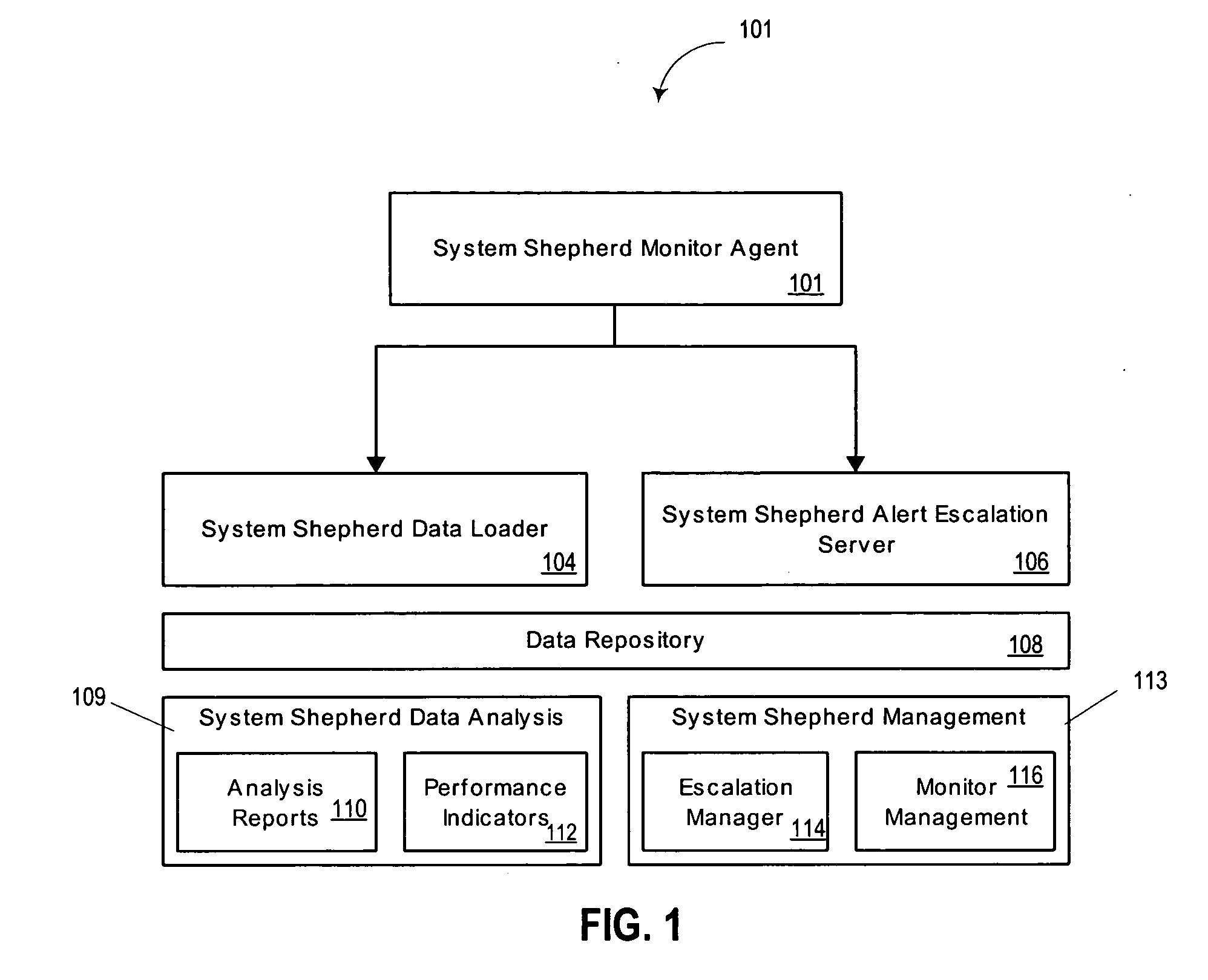
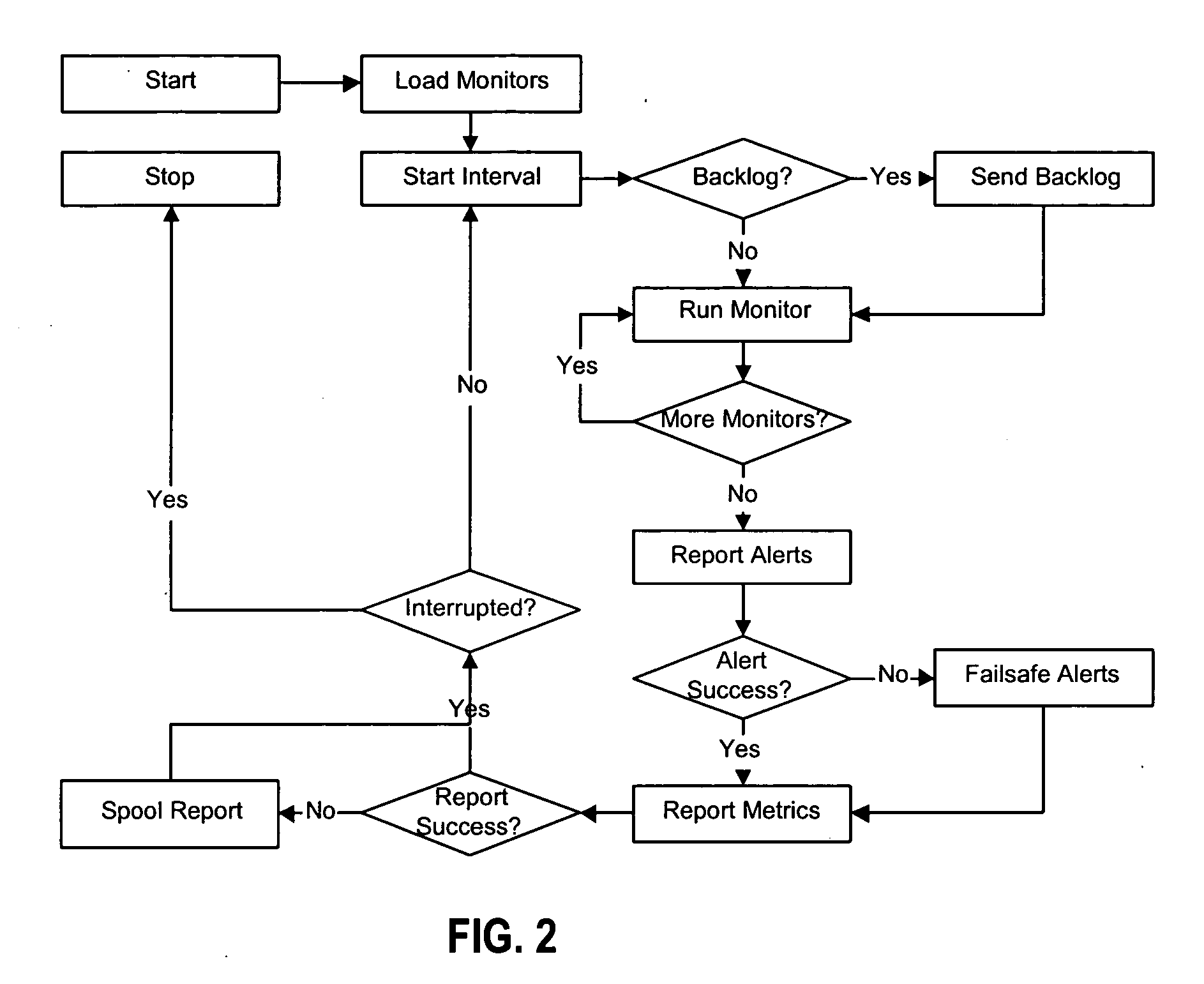
A system and method are provided for monitoring processes of an information technology (IT) system. In one example, the system comprises a monitor agent configured to collect performance and availability metrics associated with a host machine, a network, an operating system, a database or an application; a data loader, wherein the monitor agent is further configured to transmit the metrics to the data loader; an escalation server configured to receive and manage alerts generated by the monitor agent, and further configured to group an alert entering the escalation server into a resource group; and an analysis tool including an analysis tool application configured to assist a system manager in visualizing and understanding the performance of the information technology system through the use of a visual graph, a performance report, a real-time operating status or a system health report.
Owner:ABSOLUTE PERFORMANCE INC
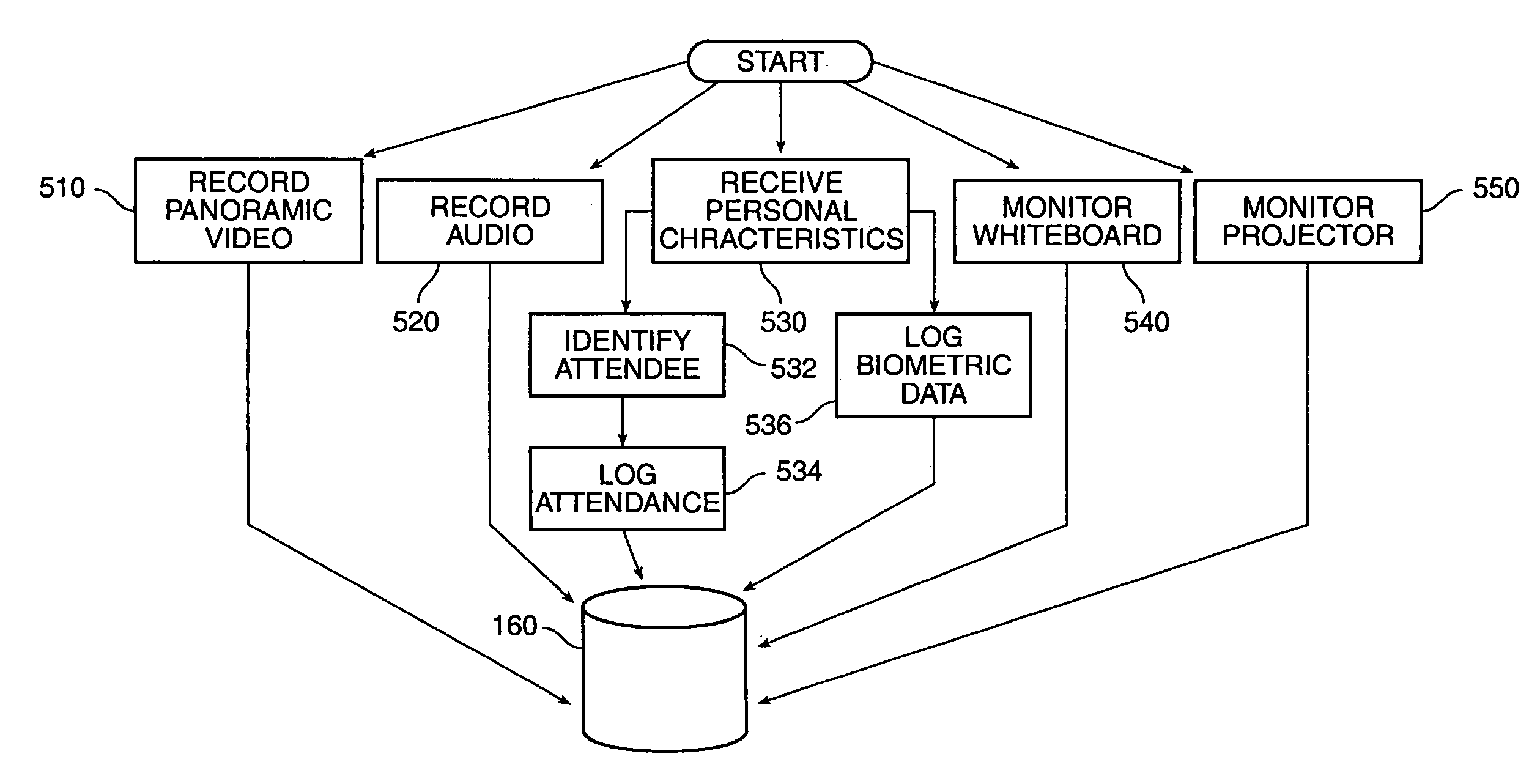
Method and system for information management to facilitate the exchange of ideas during a collaborative effort
InactiveUS7299405B1Easy to optimizeTelevision system detailsTelevision conference systemsDocumentationExchange of information
A unique combination of components is disclosed to facilitate information management during a collaborative effort. Interaction during a meeting is supported by the use of devices in a manner that allows attendees to quickly retrieve and display documents on-command or automatically. The information includes previously recorded meetings among other things. The disclosed method and system, thus, facilitates the exchange of information during meetings.
Owner:RICOH KK
System and method for monitoring processes of an information technology system
ActiveUS20050228880A1Easy to detectEasy to predictError detection/correctionDigital computer detailsOperational systemAnalysis tools
A system and method are provided for monitoring processes of an information technology (IT) system. In one example, the system comprises a monitor agent configured to collect performance and availability metrics associated with a host machine, a network, an operating system, a database or an application; a data loader, wherein the monitor agent is further configured to transmit the metrics to the data loader; an escalation server configured to receive and manage alerts generated by the monitor agent, and further configured to group an alert entering the escalation server into a resource group; and an analysis tool including an analysis tool application configured to assist a system manager in visualizing and understanding the performance of the information technology system through the use of a visual graph, a performance report, a real-time operating status or a system health report.
Owner:ABSOLUTE PERFORMANCE INC
Method and system for managing information technology data
InactiveUS20060200477A1Increase awarenessLow costDigital data processing detailsRelational databasesIntegrated databaseDatabase schema
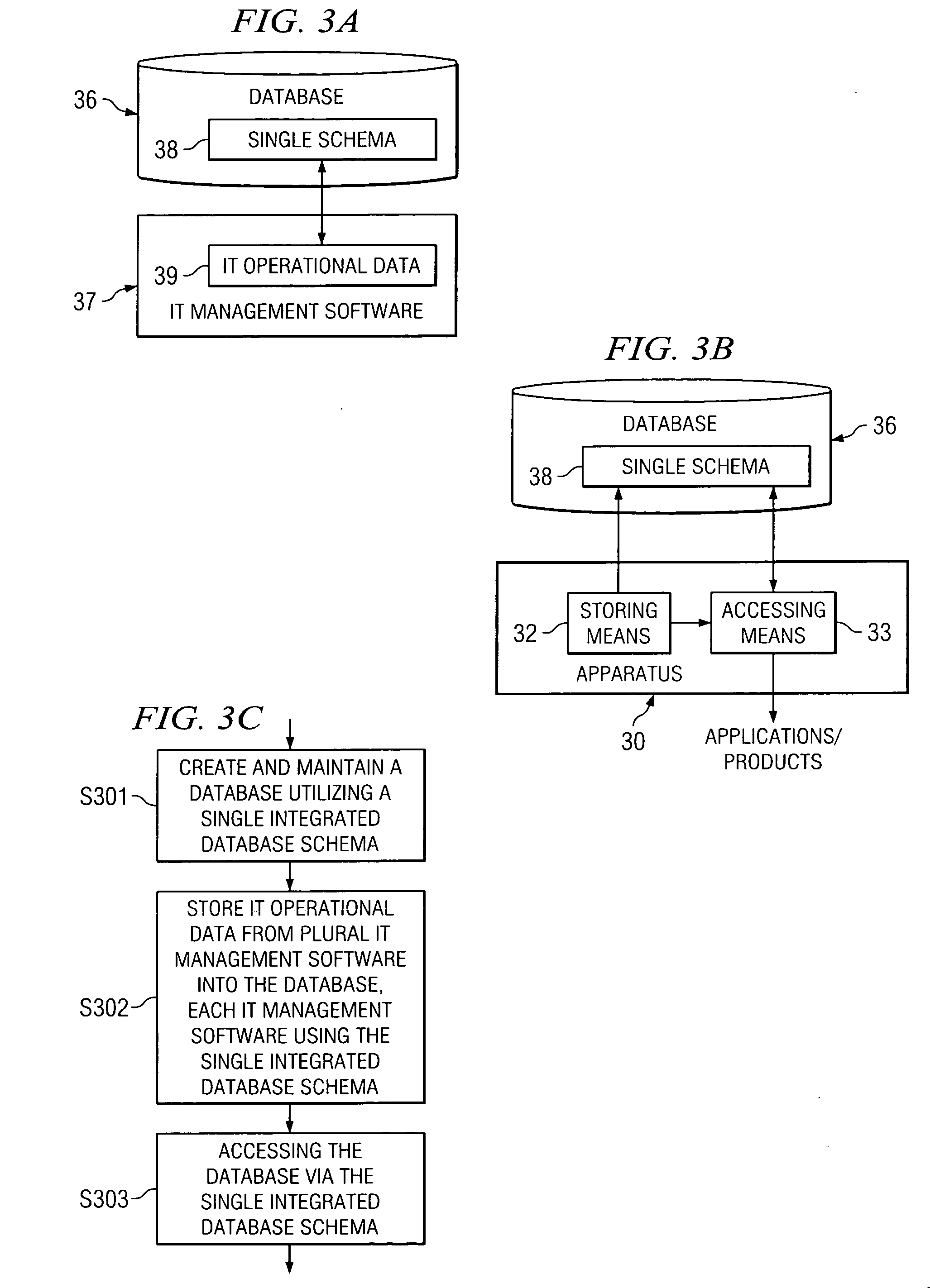
Database system for storing information technology (IT) management operational data and a method and apparatus for managing IT data are provided. The database utilizes an integrated database schema. IT operational data is stored into the database using the integrated database schema and the database is accessed by plural applications and / or products using the integrated database schema.
Owner:COMP ASSOC THINK INC
Intelligent bookmarks and information management system based on same
ActiveUS7899829B1Ability to manageDigital data information retrievalDigital data processing detailsDocumentation procedureUser input
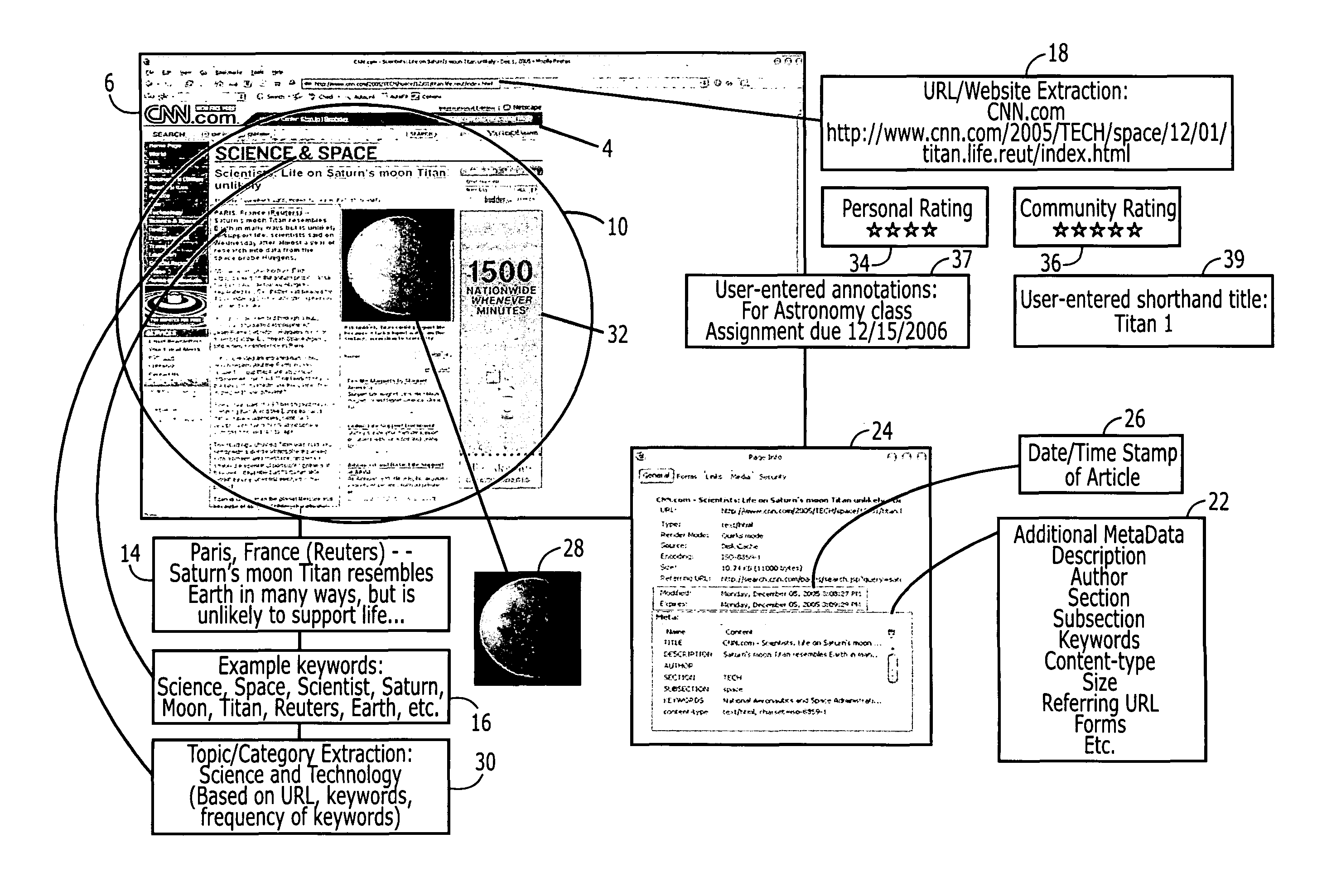
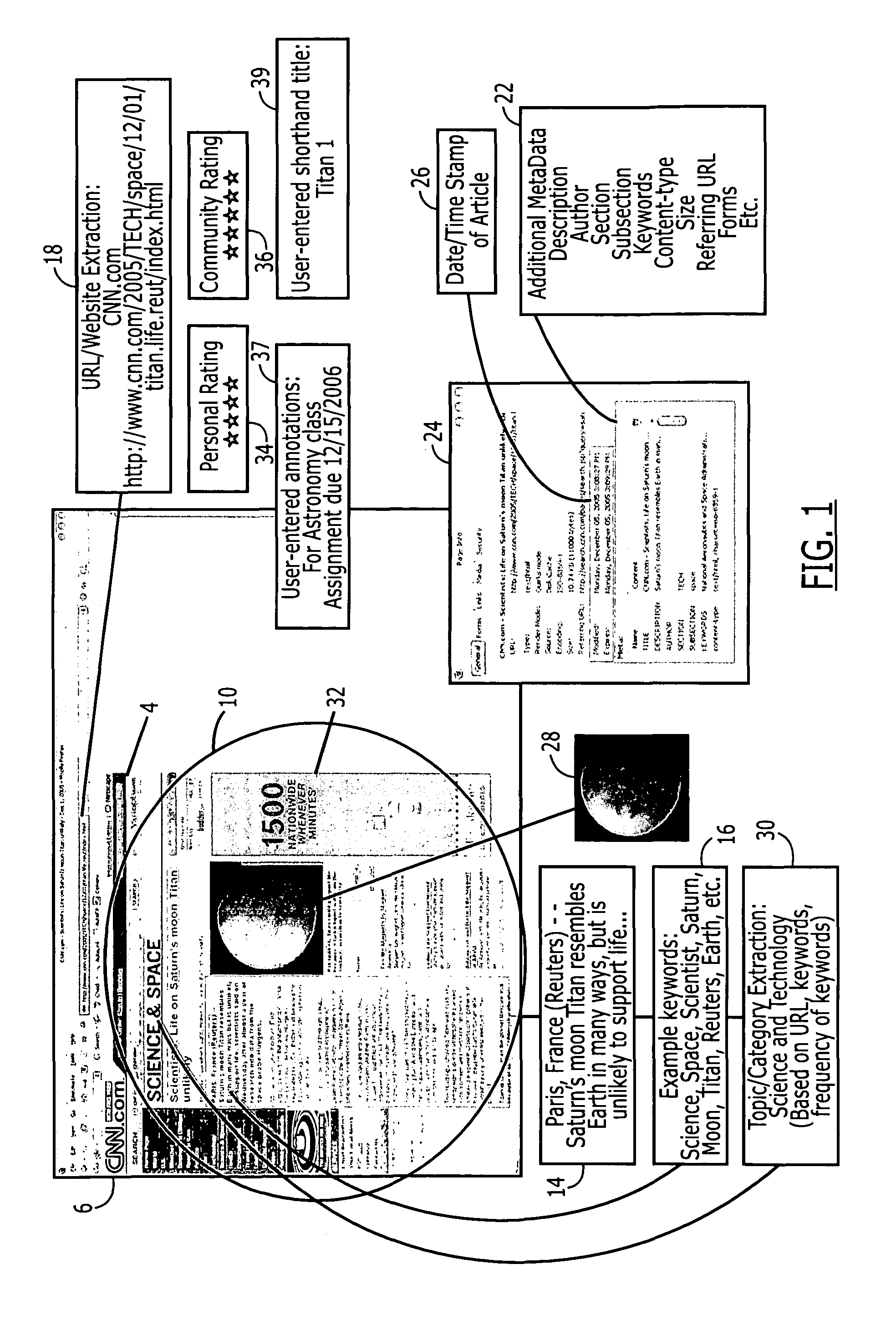
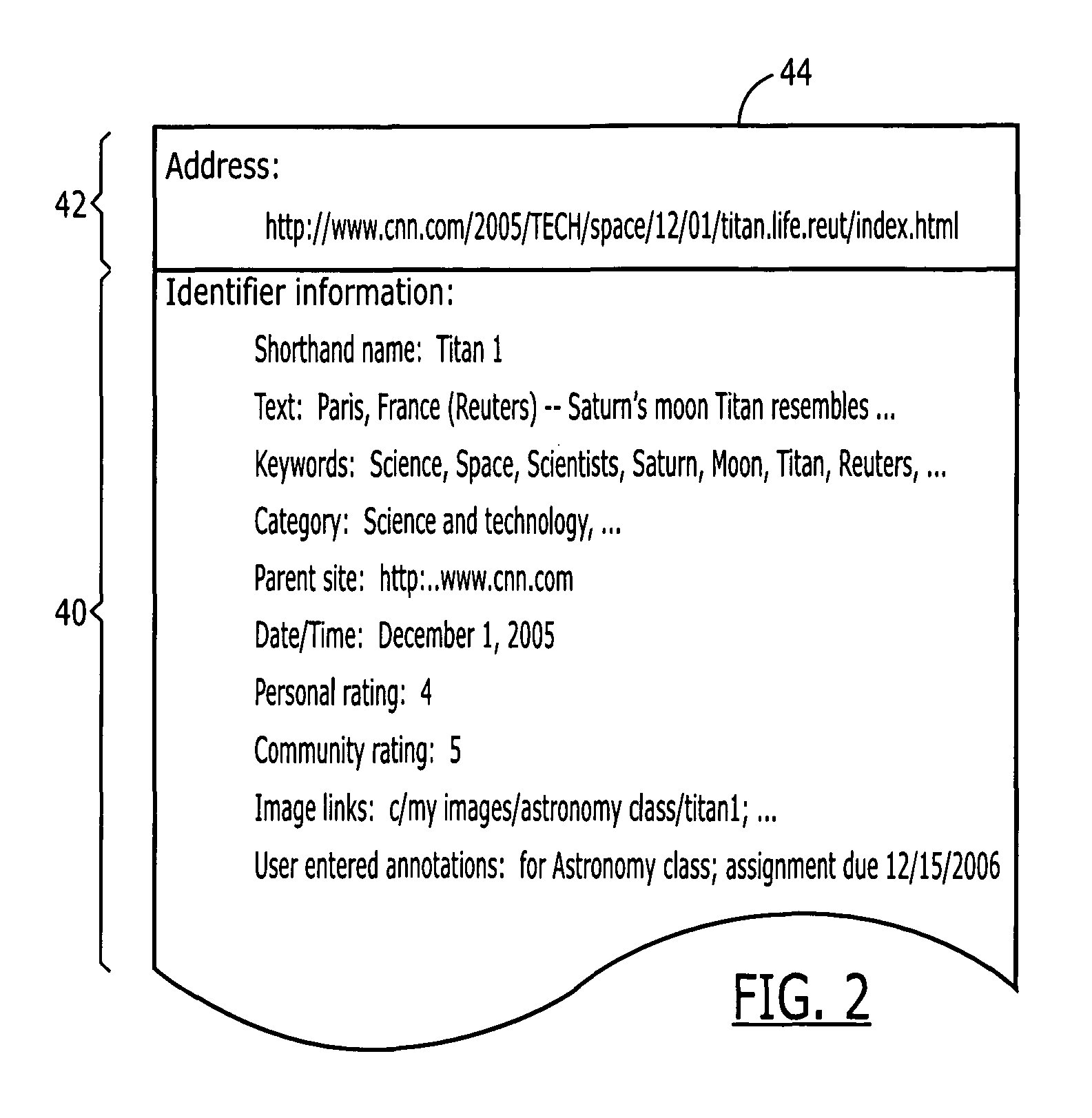
An intelligent bookmark is a collection of information, including an address (e.g., a URL) for a document (e.g., web page) or other hyper-media enabled item bundled together with selected other information. The selected other information may be manually or automatically obtained from the document, the browser history leading up to the display of the document, user entered annotations, etc. A collection of intelligent bookmarks may be sorted and searched using the selected other information. Intelligent bookmarks may be exchanged between users, and users may edit the bookmark content or in layers above the bookmark. Users may rate the bookmarks. A complete system provides for creating, storing, accessing, editing, grouping, exchanging, and searching intelligent bookmarks locally and / or remotely via a server.
Owner:IP3 2021 SERIES 600 OF ALLIED SECURITY TRUST I
Automated information lifecycle management system for network data storage
ActiveUS7693877B1Digital data information retrievalDigital data processing detailsNetwork dataData store
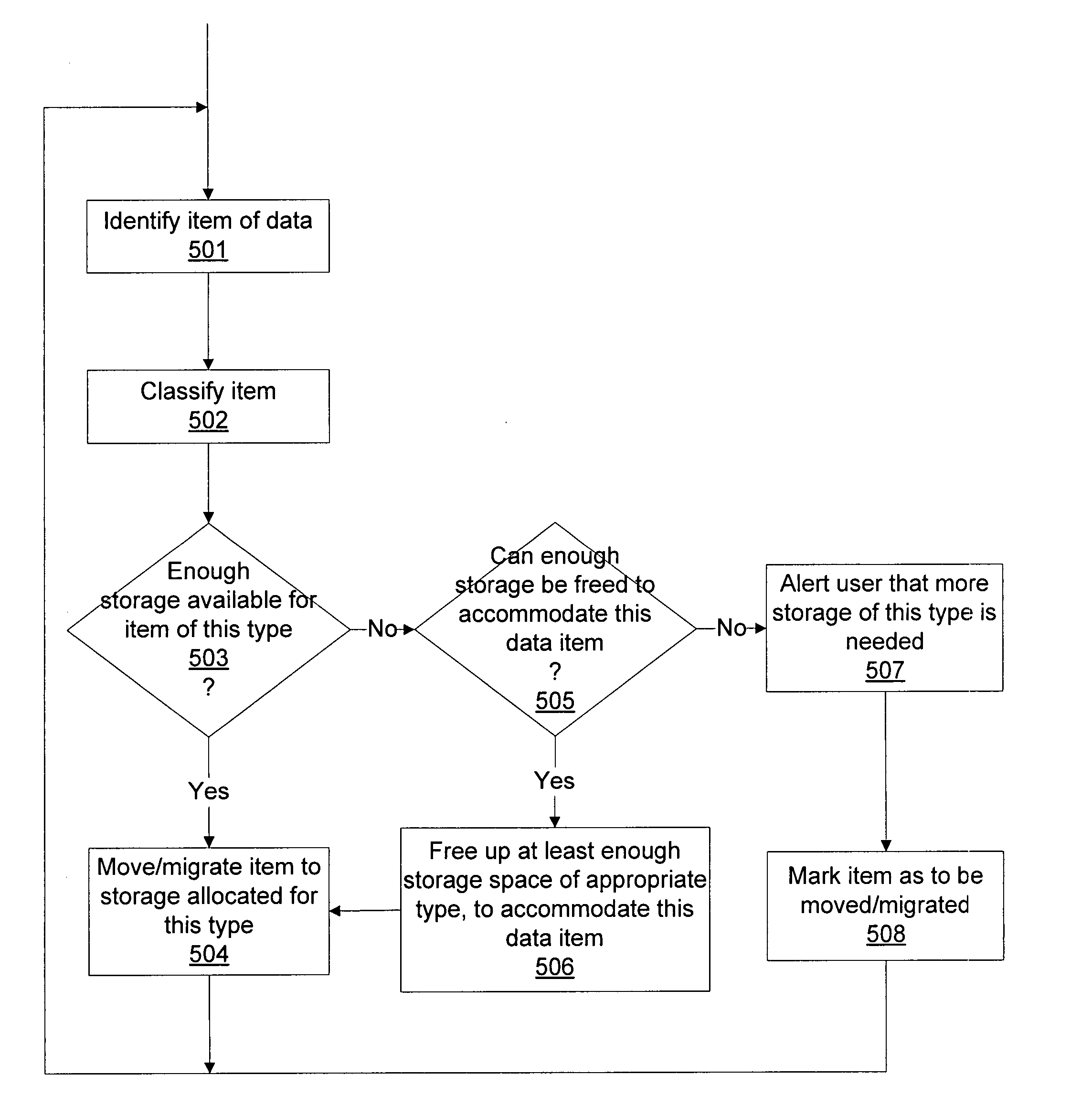
An automated information lifecycle management (ILM) system for network storage automatically searches a network storage system to identify data items stored therein. The network storage system includes multiple data storage facilities of different types coupled to a network. The ILM system automatically classifies each of the data items into a category of multiple data categories, and automatically optimizes each of the data items to a particular data storage facility of the multiple data storage facilities, according to the category into which the data item was classified. The ILM system may also automatically discover and detect storage devices added to the network and assign them to the proper storage class, for storing data of the corresponding category. The ILM system further may automatically determine or predict when additional storage capacity is needed for any particular class of storage and may alert a user accordingly and / or free up additional storage capacity.
Owner:NETWORK APPLIANCE INC
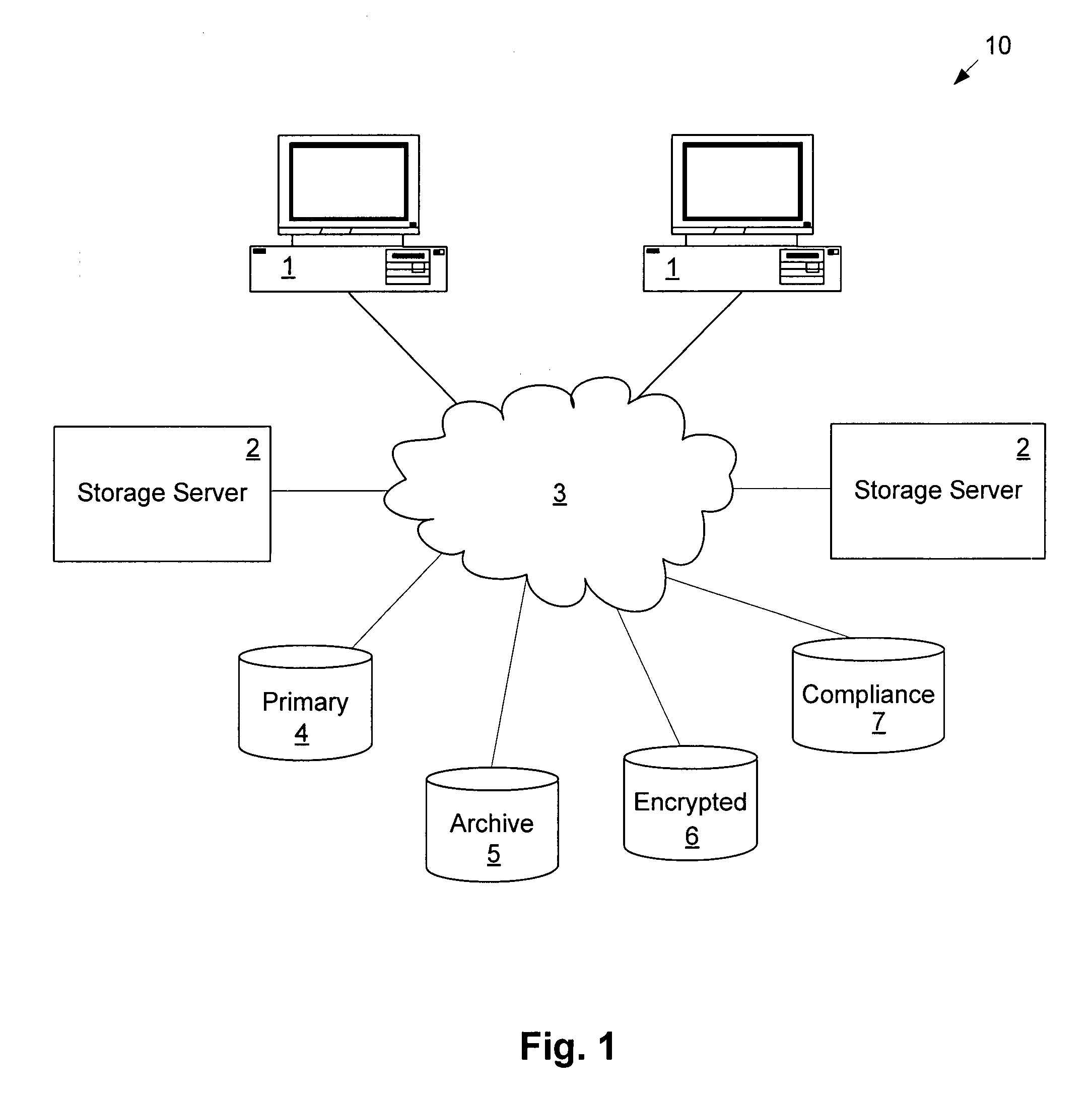
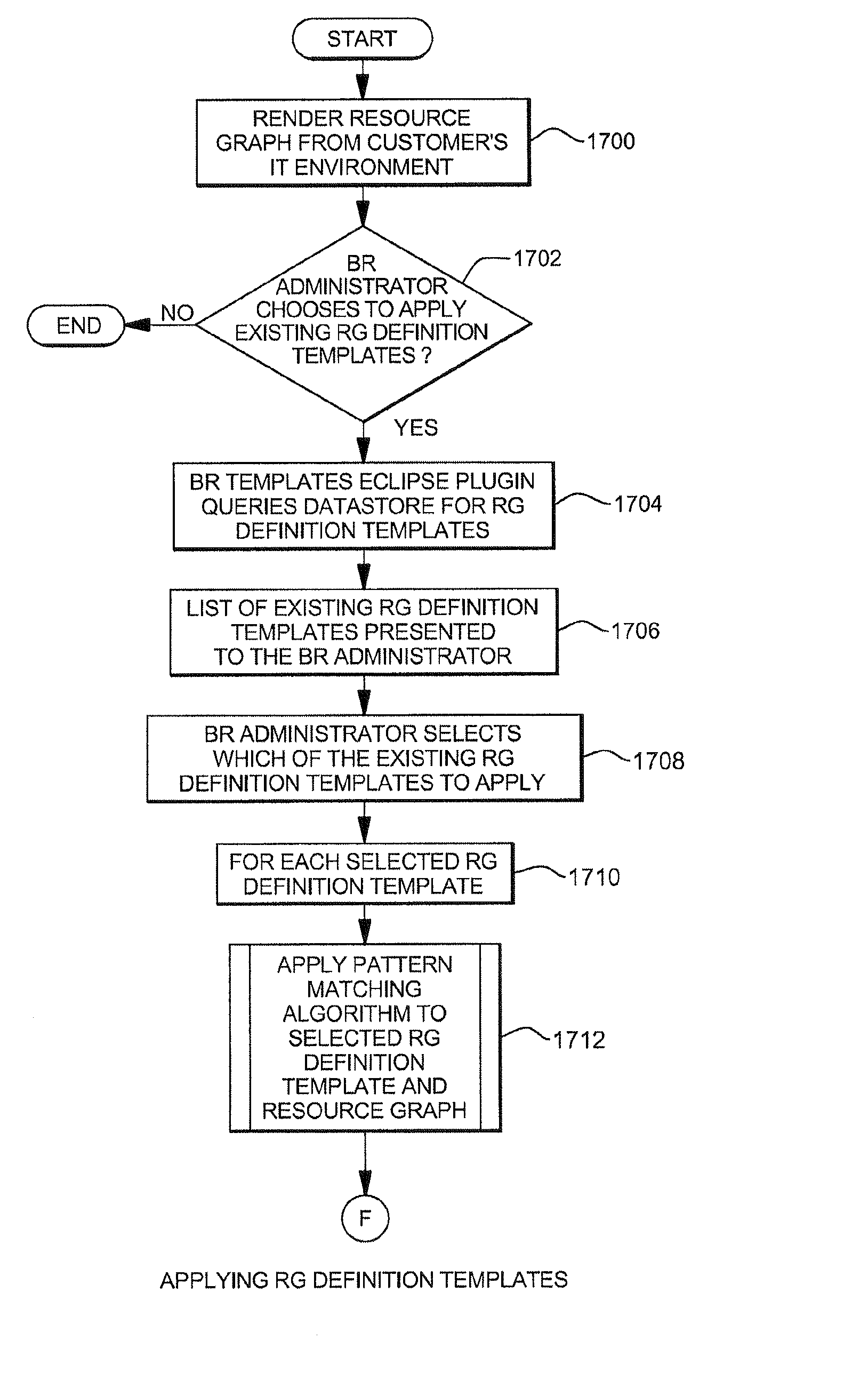
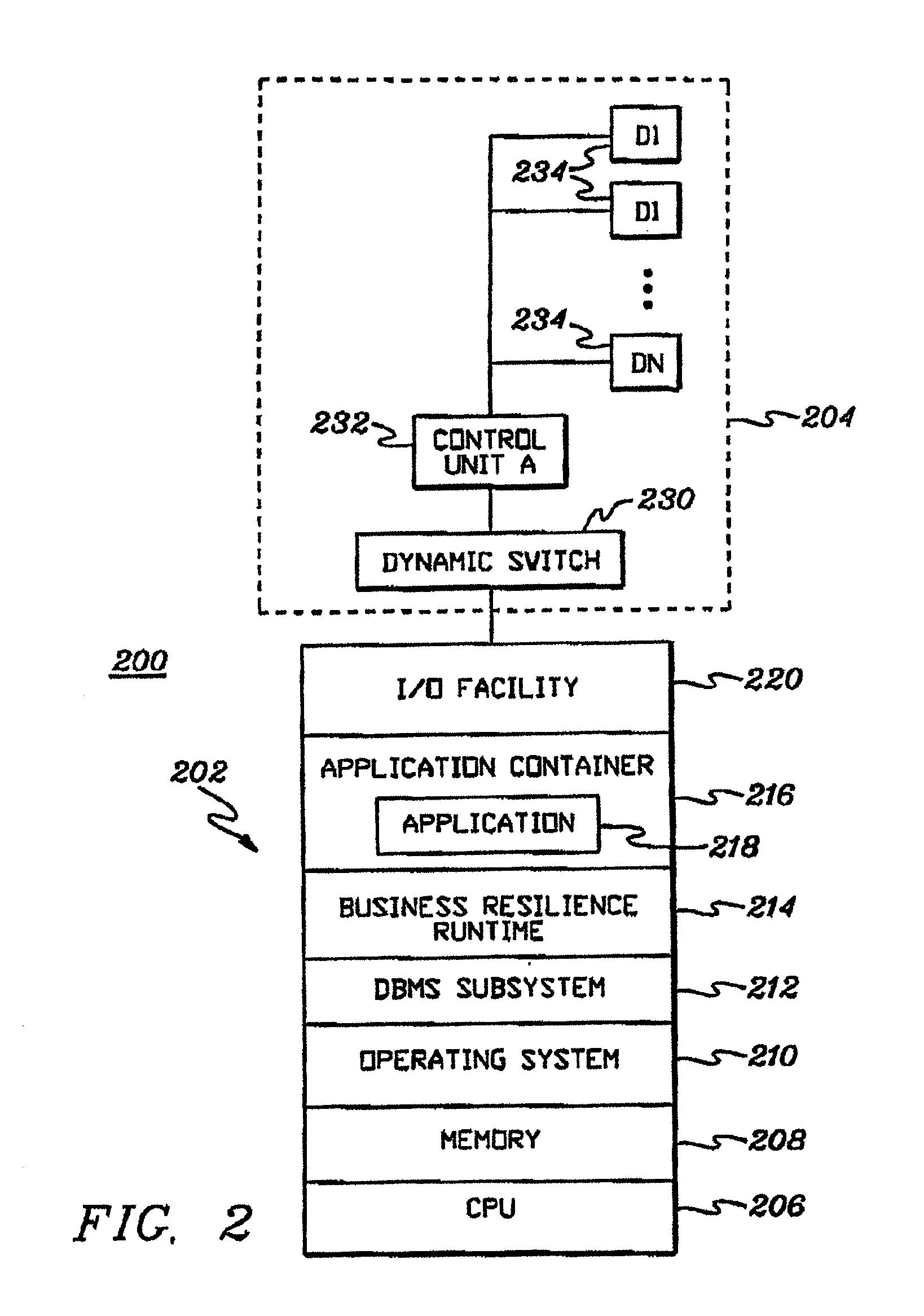
Defining and using templates in configuring information technology environments
InactiveUS20090171705A1Easy to manageOptimizationPayment architectureResourcesData storeComputer science
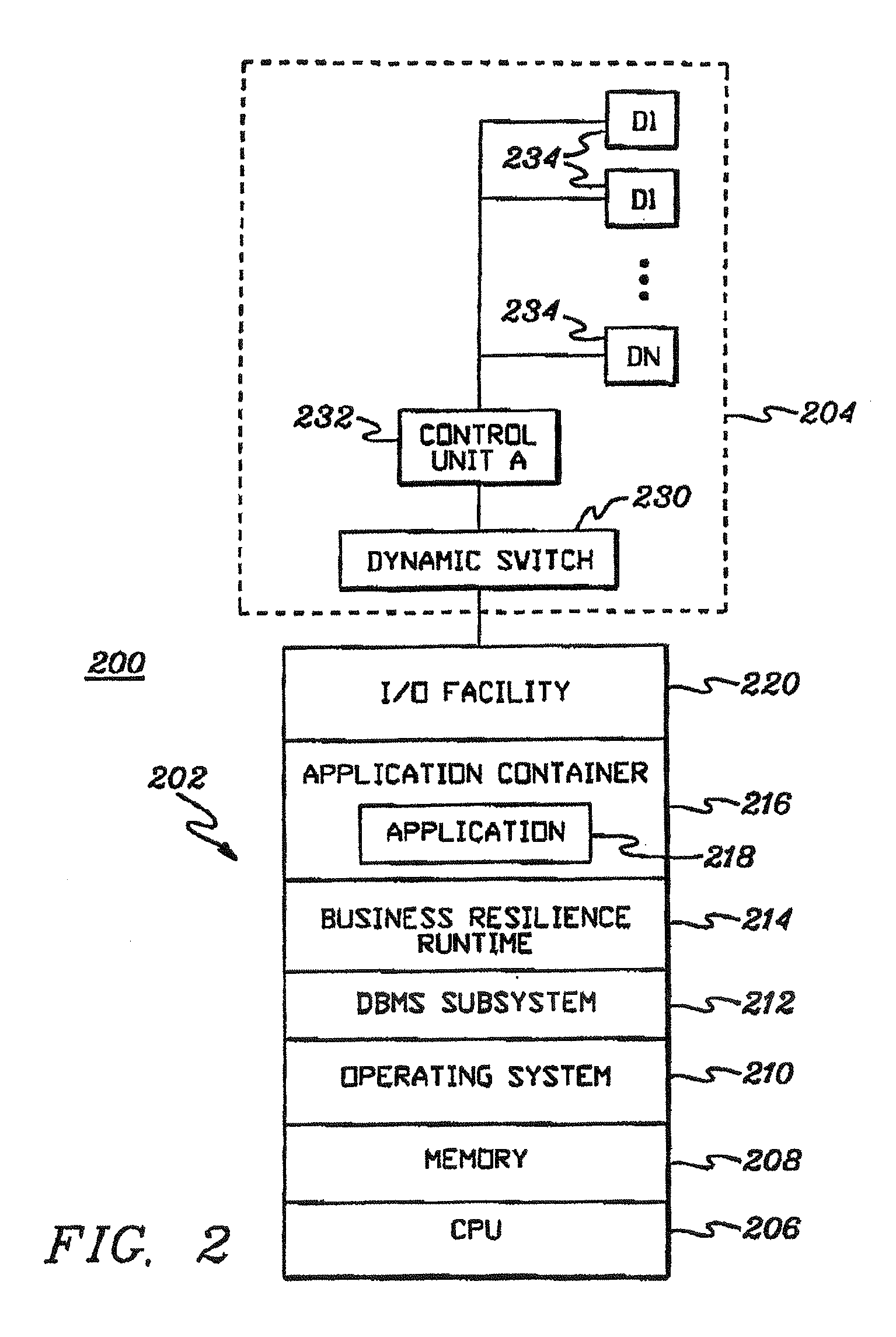
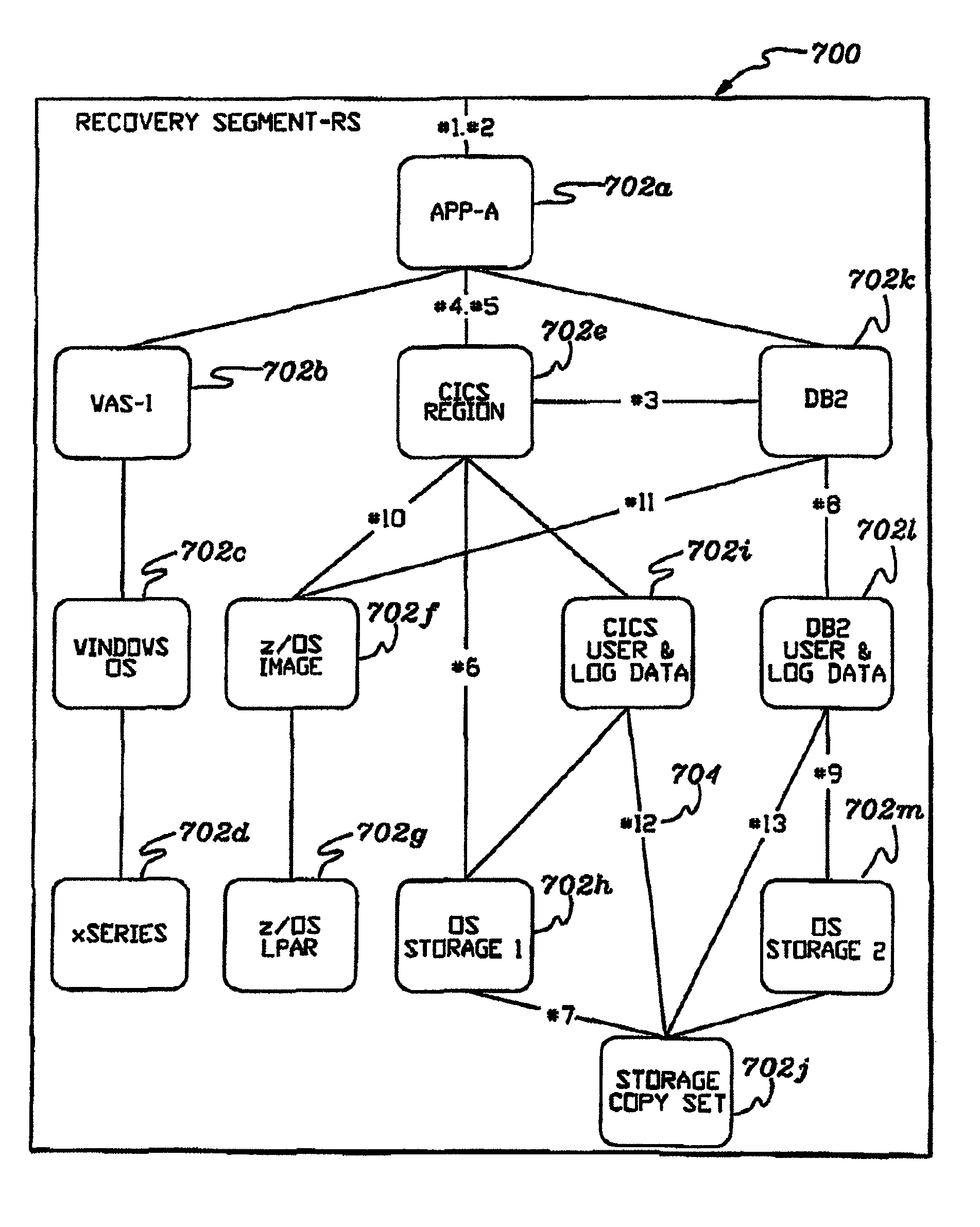
Templates are provided and used in an Information Technology (IT) environment. A template represents a pattern of resources and resource relationships of the IT environment. Templates are applied to automatically generate recommendations of programmatic representations of artifacts of the IT environment. The artifacts include Recovery Segments, Redundancy Groups, Business Resilience Manager deployment configurations and / or resource pairing represented by relationship data stores, as examples.
Owner:IBM CORP
System and method for information management
InactiveUS20080141247A1Same speedEasy to manageMultiprogramming arrangementsMemory systemsMessage boardComputer science
The vast majority of today's busy families with computers, personal digital assistants (PDAs), and cell phones (all modern computing devices classified generally as computers), still use wall calendars, sticky notes, and kitchen message boards to coordinate their everyday activities. The complexity of family schedules and household information, ease of use, ease of access, and portability have remained powerful barriers to adoption of electronic solutions. This invention features computer-based input methods for use in group calendaring such that in the shortest possible amount of time, and with the least amount of effort, notations can be made of one or more events or tasks pertaining to one or more people using computers in one or more computer networks.
Owner:SARAVANAN THIAGARAJAN
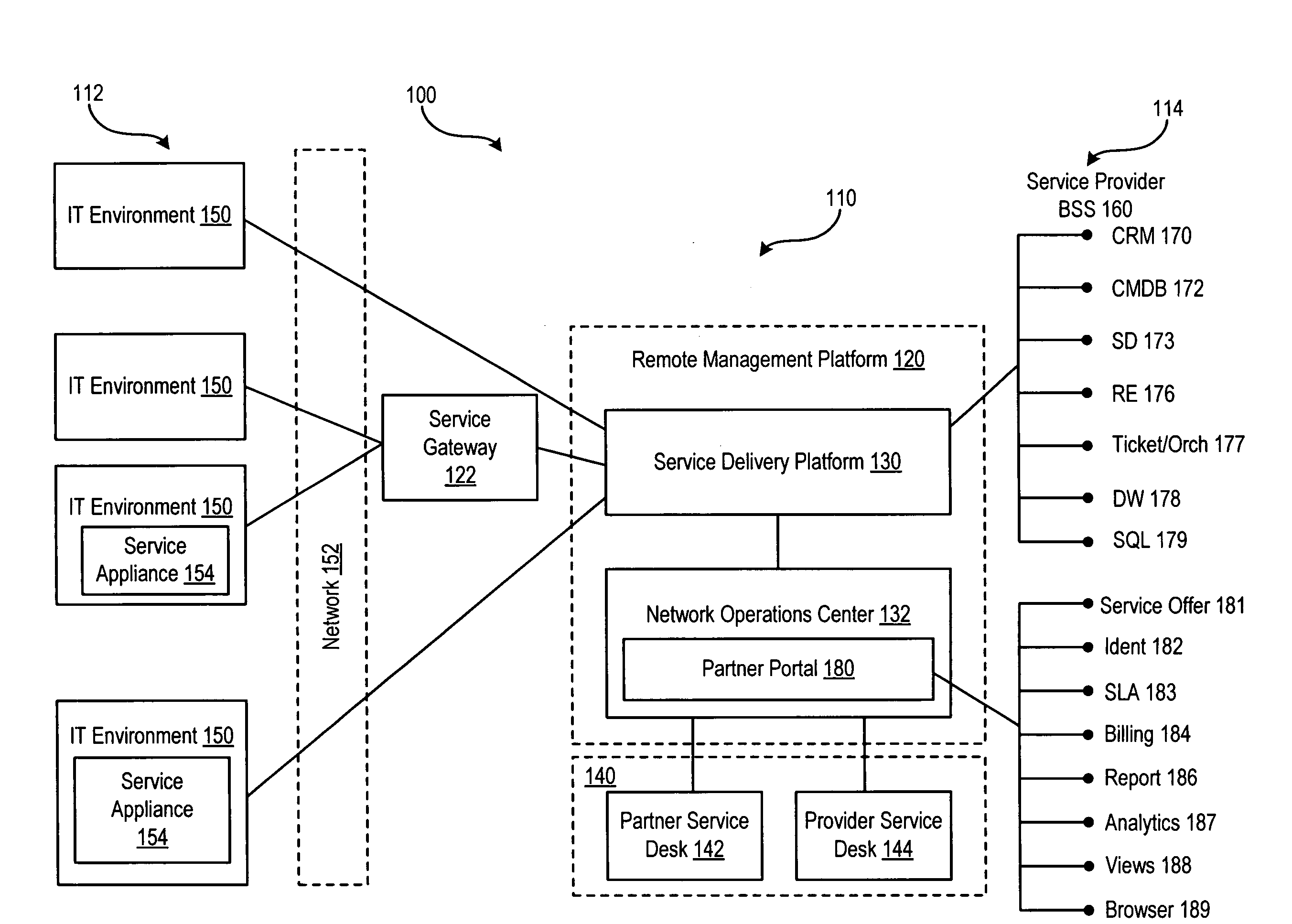
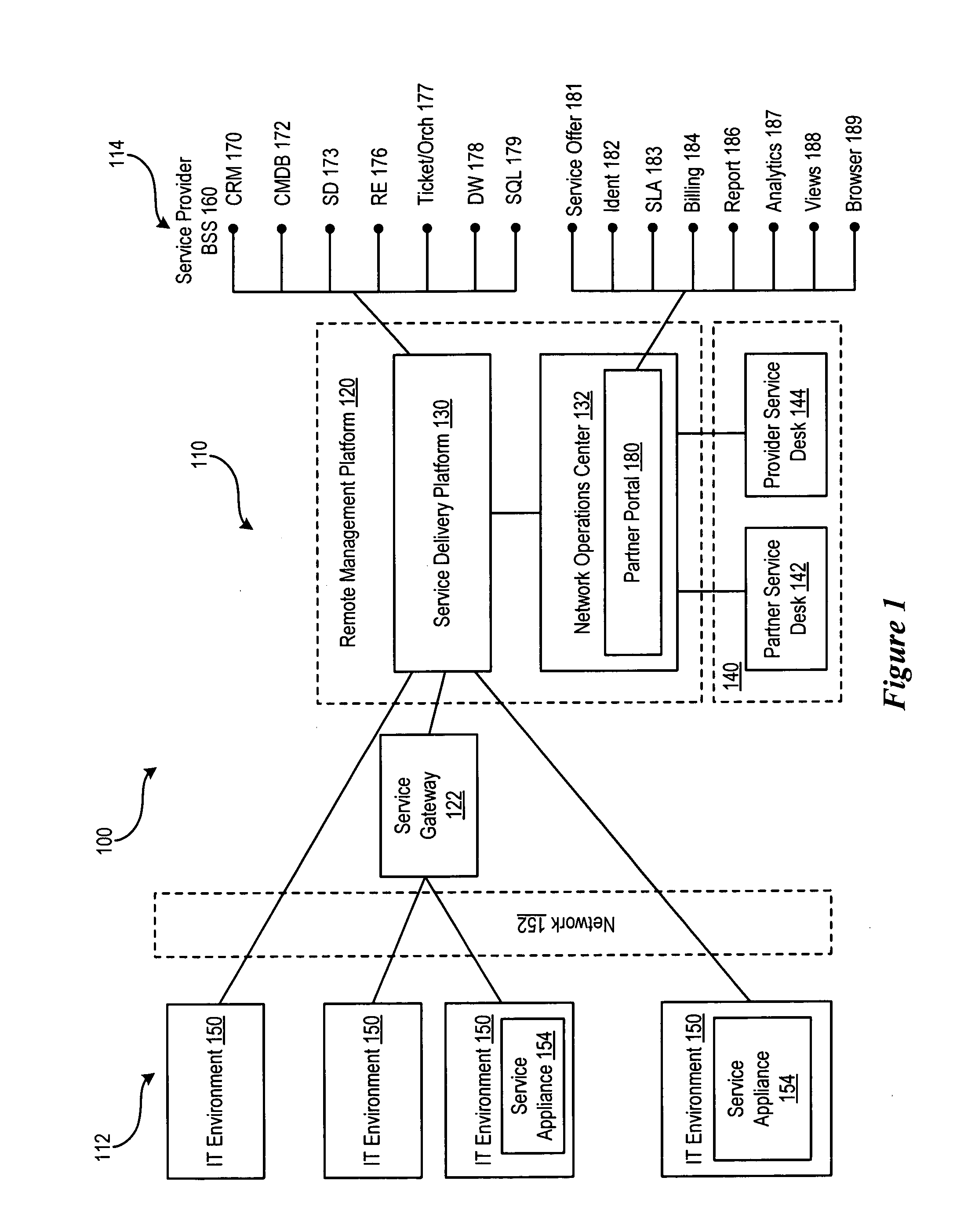
Service delivery platform for automated and remote information technology management
An apparatus for providing remote services to an integrated information technology environment. The information technology environment comprises a services appliance. The services appliance provides agent-less monitoring of information handling systems within the information technology environment. The apparatus comprises a remote management platform. The remote management platform comprises a service delivery platform and a network operations center. The service delivery platform receives services information from the services appliance, analyzes the services information and determines a response based upon the services information. The service delivery platform provides the response to the network operations center. The network operation center proactively initiates the response based upon the services information.
Owner:DELL PROD LP
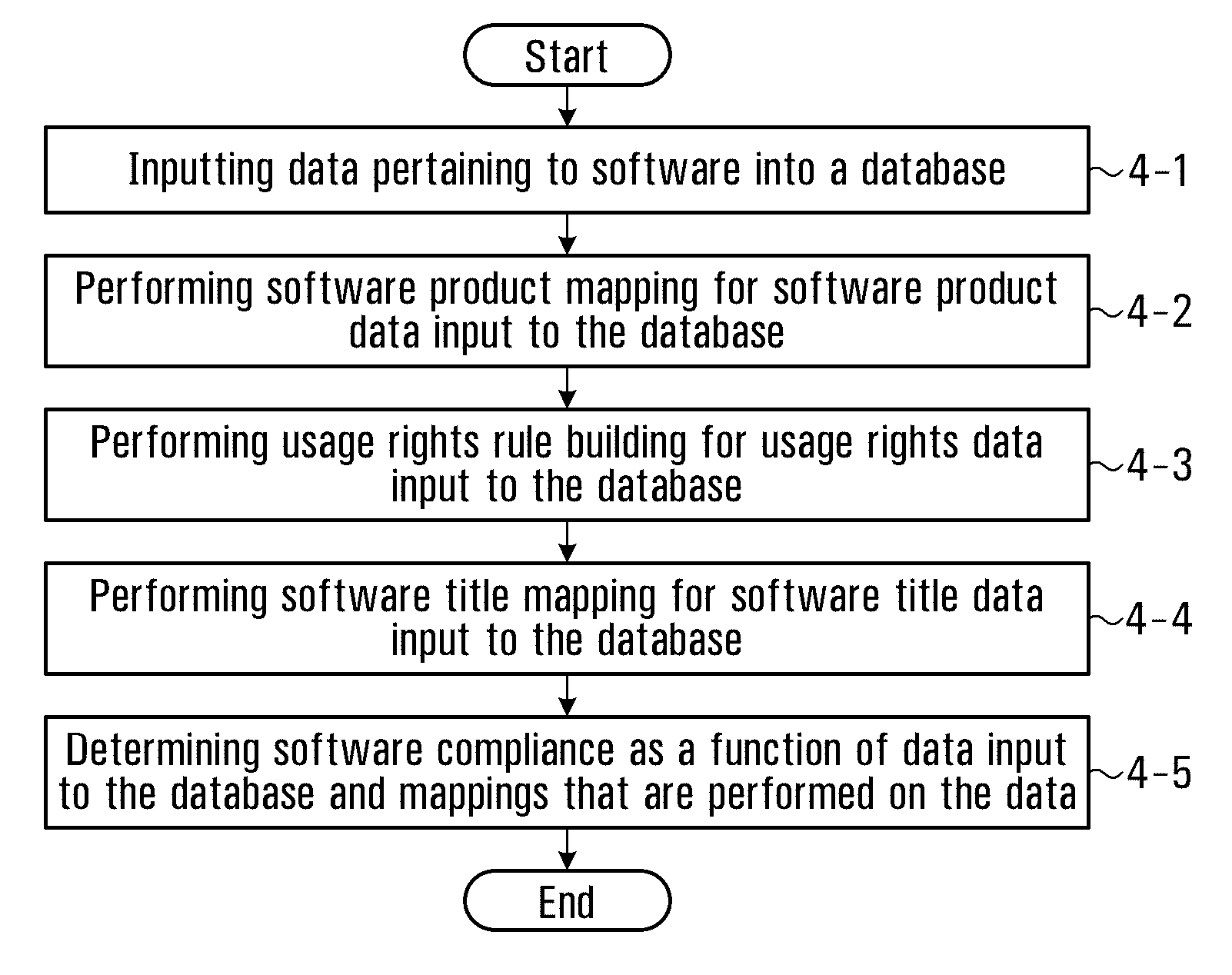
Method and system for information technology asset management
InactiveUS20120304248A1Computer security arrangementsBuying/selling/leasing transactionsSoftware asset managementIT service management
As aspects of the present invention provides a manner of software asset management involving inputting data pertaining to software into a database; performing software product mapping for software product data input to the database; performing usage rights rule building for usage rights data input to the database; performing software title mapping for software title data input to the database; and determining software compliance as a function of data input to the database and mappings that are performed on the data. Another aspect of the present invention includes method of inputting or importing data into a database m an IT service management system involving: the system importing the data into temporary storage m the database; the system applying validation rules; the system applying the transformation rules; the user reviewing the processed data; the user modifying the processed data; the user requests that the processed data be committed to the database; the system committing the processed data to records in the database.
Owner:PROVANCE TECH
Using content aggregation to build administration consoles
InactiveUS20050198201A1Flexibly updateableMultiple digital computer combinationsHybrid transportPortletEnd user
Content aggregation is used to build administration consoles. Preferred embodiments enable providing a solution-based approach to information technology (“IT”) administration, whereby content can be flexibly arranged to provide a content view that is adapted for the IT solution deployed in a particular IT environment. In preferred embodiments, portal technology is used for the aggregation framework, and portlets are used for creating content. Alternatively, other approaches such as struts and tiles may be used. Preferred embodiments deploy an administration console as a Web-accessible application, and this console consolidates the administration interfaces for an arbitrary set of management operations, including administration of an arbitrary collection of hardware and / or software resources. Roles / permissions may be used when rendering content for the console, thereby customizing a view to individual end users (or user groups).
Owner:IBM CORP
Information management system
ActiveUS20050203855A1Check is unnecessaryEnsure protectionUnauthorized memory use protectionHardware monitoringThe InternetWorkstation
An information management system is described comprising one or more workstations running applications to allow a user of the workstation to connect to a network, such as the Internet. Each application has an analyzer, which monitors transmission data that the application is about to transmit to the network or about to receive from the network and which determines an appropriate action to take regarding that transmission data. Such actions may be extracting data from the transmission data, such as passwords and usernames, digital certificates or eCommerce transaction details for storage in a database; ensuring that the transmission data is transmitted at an encryption strength appropriate to the contents of the transmission data; determining whether a check needs to be made as to whether a digital certificate received in transmission data is in force, and determining whether a transaction about to be made by a user of one of the workstations needs third party approval before it is made. The analyzer may consult a policy data containing a policy to govern the workstations in order to make its determination. The information management system provides many advantages in the eCommerce environment to on-line trading companies, who may benefit by being able to regulate the transactions made by their staff according to their instructions in a policy data, automatically maintain records of passwords and business conducted on-line, avoid paying for unnecessary checks on the validity of digital certificates and ensure that transmissions of data made by their staff are always protected at an agreed strength of encryption.
Owner:COMP ASSOC THINK INC
On demand data center service end-to-end service provisioning and management
InactiveUS20060031813A1Specific program execution arrangementsMemory systemsOn demandData center services
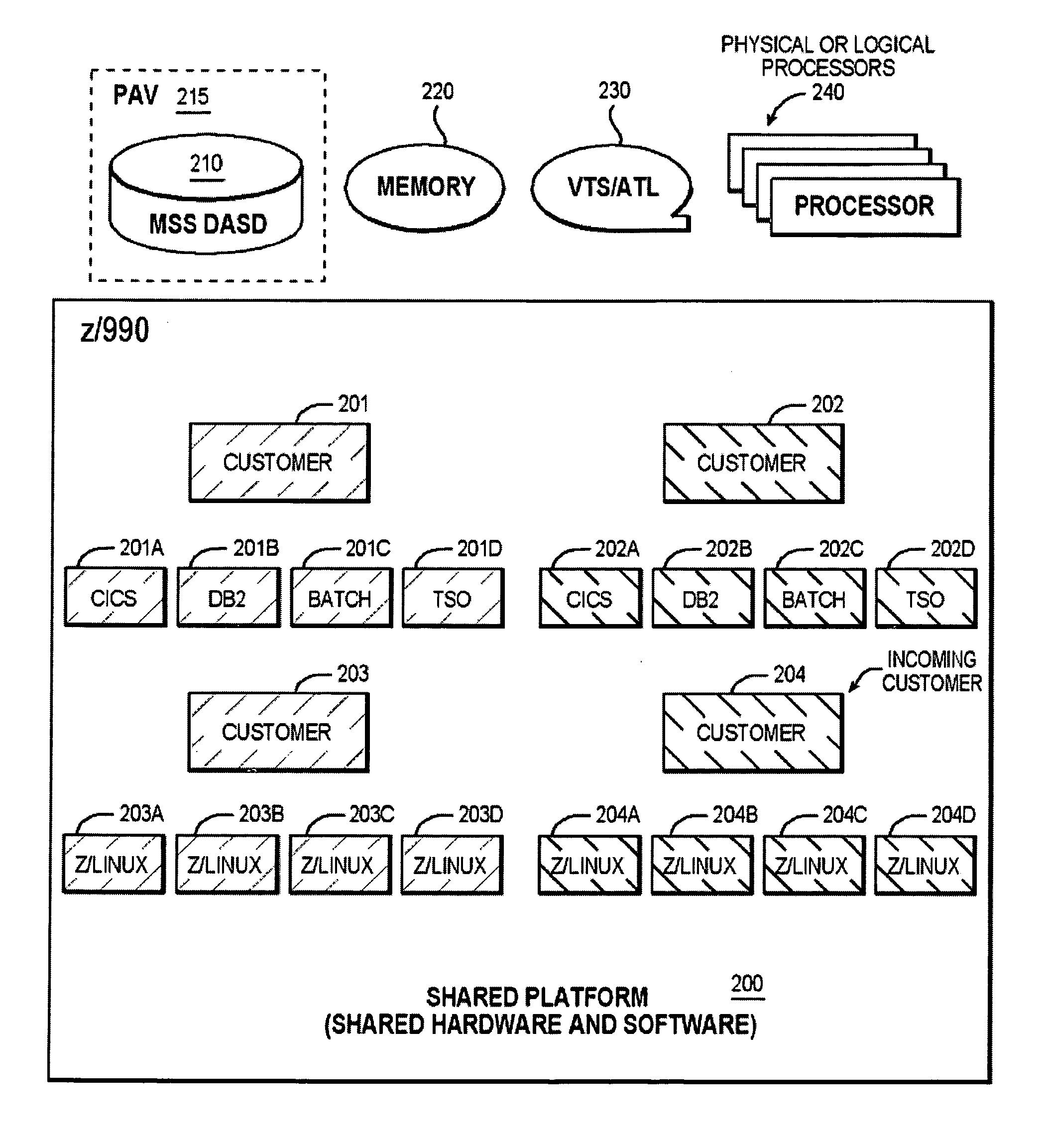
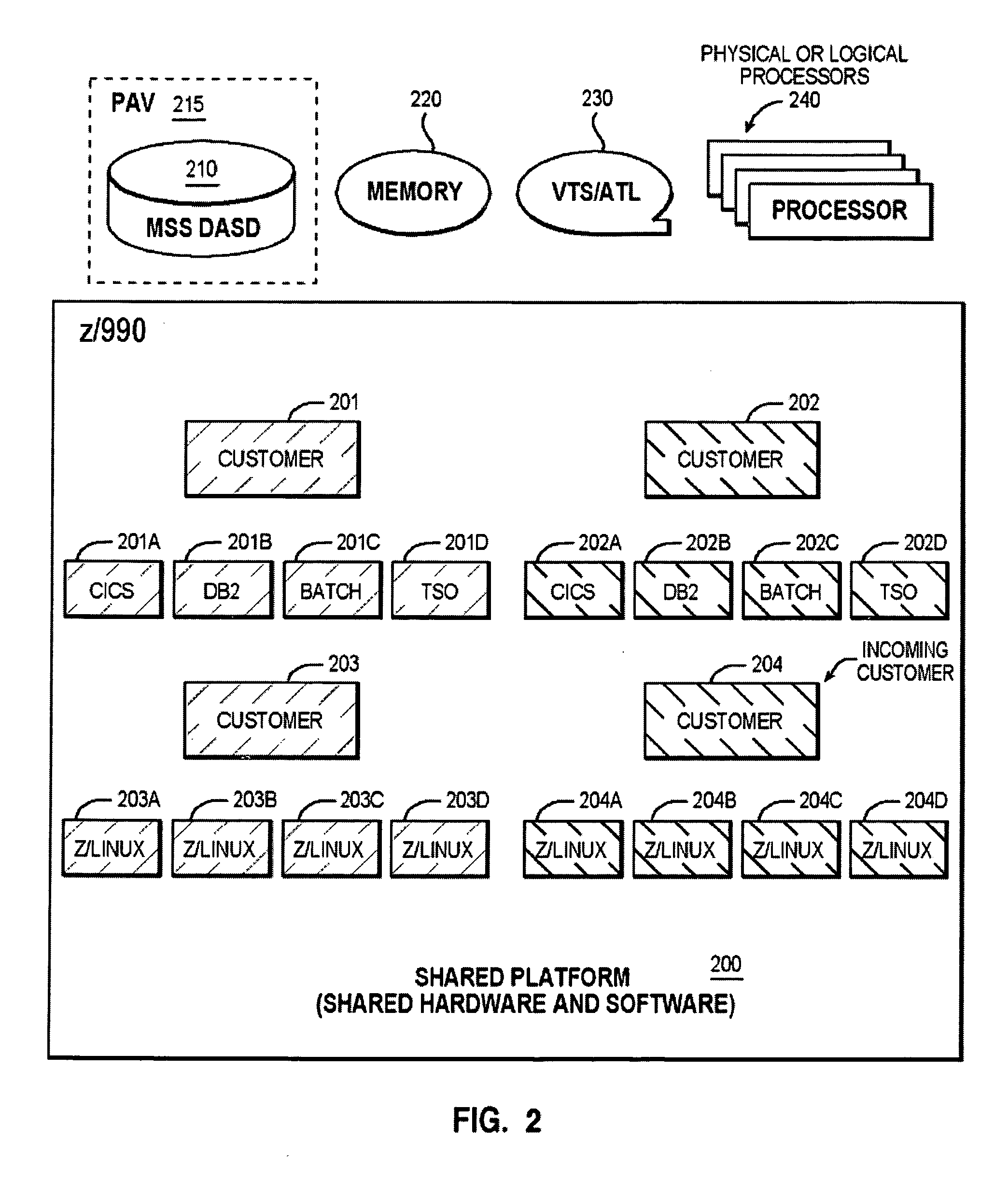
An example of a solution provided here comprises: providing a shared platform that is prepared to accept an incoming customer; for the incoming customer, (a) utilizing at least one information technology management control point; and (b) porting the incoming customer's application, or boarding the incoming customer's application, or both; accepting the incoming customer, among multiple customers, on the shared platform; and sharing hardware and software, among the multiple customers.
Owner:IBM CORP
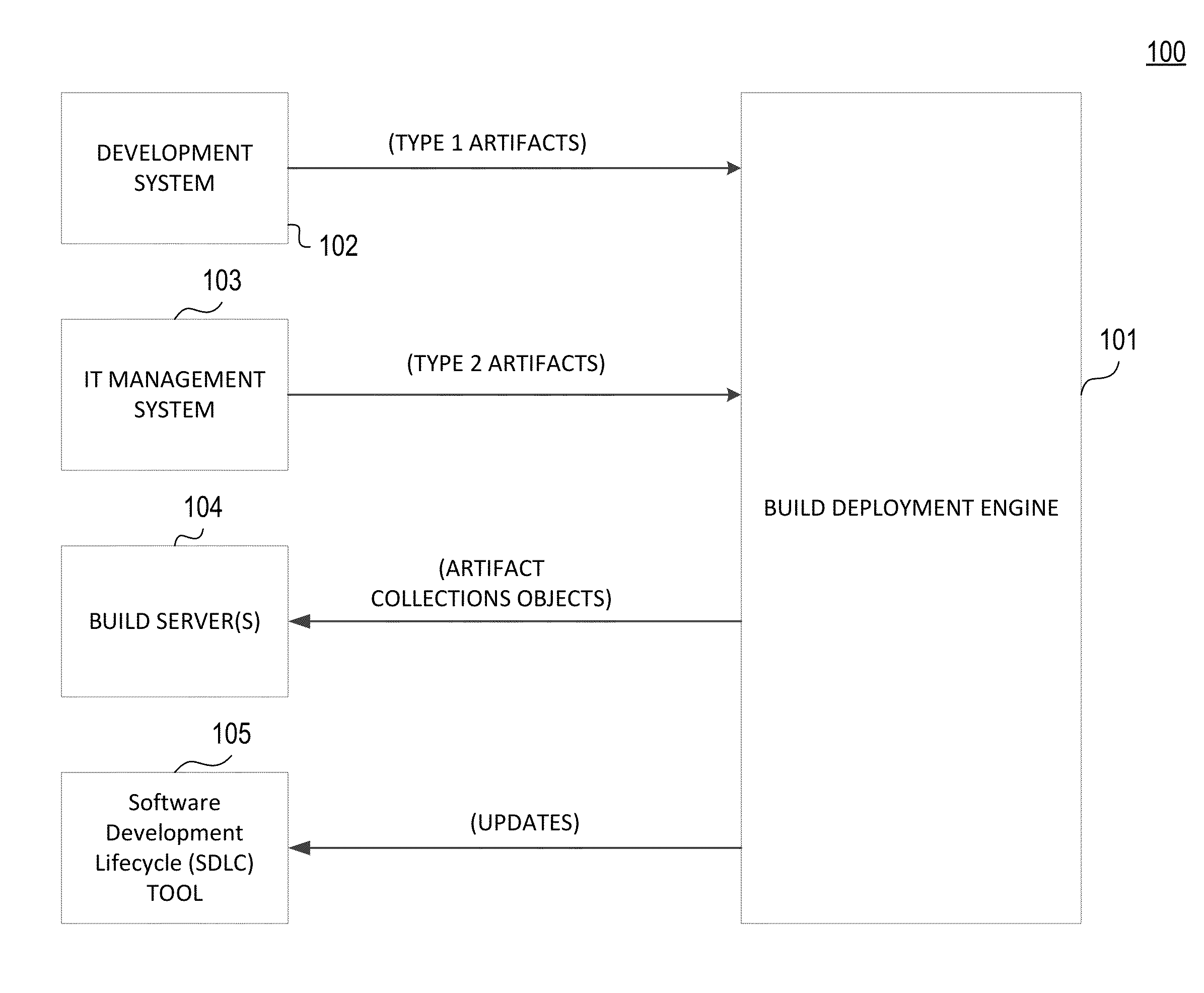
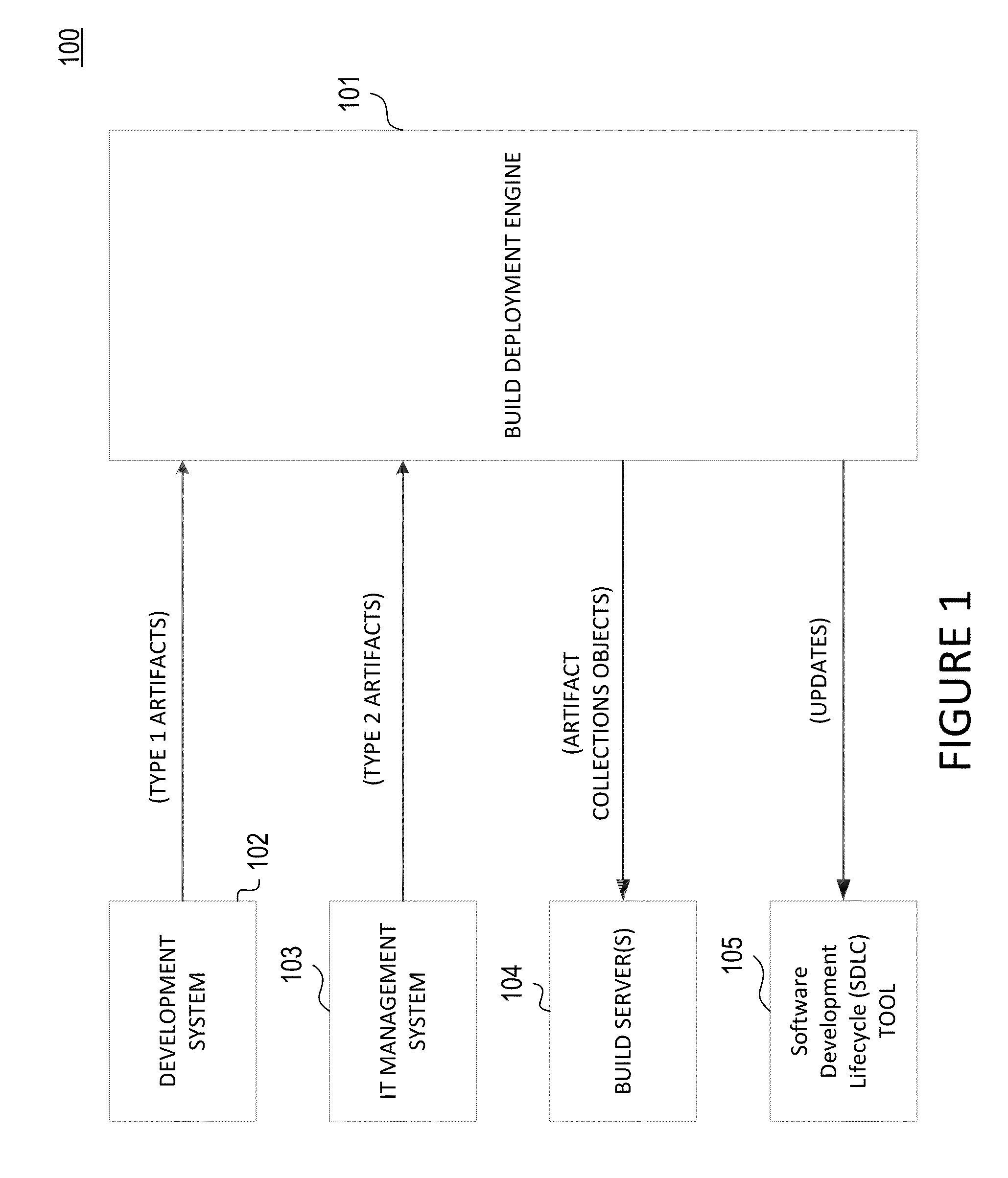
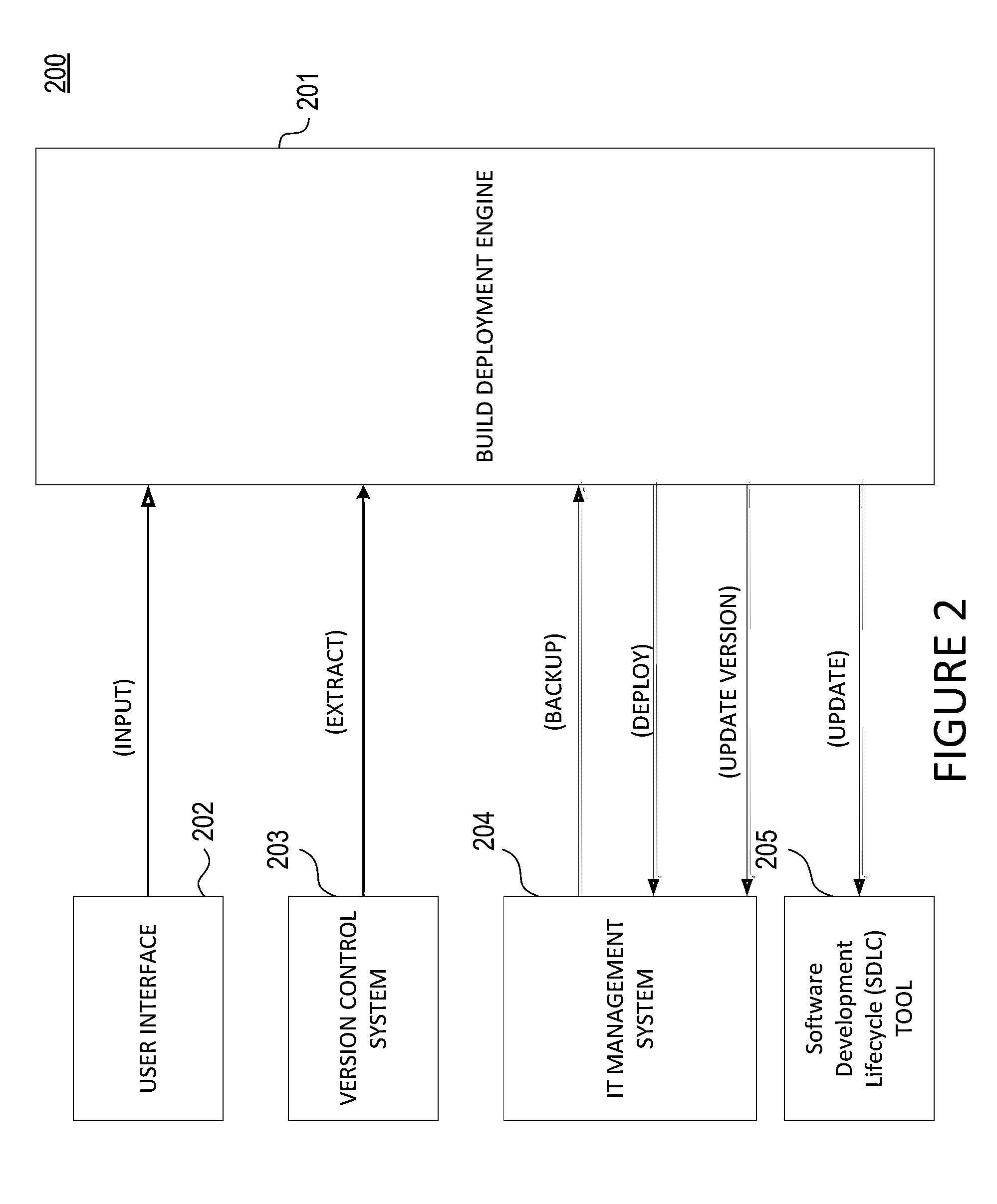
Build Deployment Automation for Information Technology Management
ActiveUS20150248280A1Reduce the burden onVersion controlProgram loading/initiatingAutomationWeb server
A computer-executable mechanism captures code modifications for a computer-executable process from a development environment into build packages that may be deployed onto specified target environments with trace, audit, code compliance and rollback options from one single web portal. The mechanism supports build package code changes from different sources, automated test of the resulting build packages, and phantom source control of all packaged code base to reduce the burden on developers to manually source control code. The computer-executable mechanism supports a portal web server for building and deploying build packages to render user responses to configurable actions that may be passed on to a job sequencer to execute a series of jobs. A computer-executable roll-back mechanism takes a snapshot of the target environment prior to deployment of a build package so that a complete release rollback or an incremental release rollback may occur as needed.
Owner:BANK OF AMERICA CORP
Information management system
InactiveUS20050216771A1Ensure protectionDigital data processing detailsDigital data protectionThe InternetWorkstation
An information management system is described comprising one or more workstations running applications to allow a user of the workstation to connect to a network, such as the Internet. Each application has an analyser, which monitors transmission data that the application is about to transmit to the network or about to receive from the network and which determines an appropriate action to take regarding that transmission data. Such actions may be extracting data from the transmission data, such as passwords and usernames, digital certificates or eCommerce transaction details for storage in a database; ensuring that the transmission data is transmitted at an encryption strength appropriate to the contents of the transmission data; determining whether a check needs to be made as to whether a digital certificate received in transmission data is in force, and determining whether a transaction about to be made by a user of one of the workstations needs third party approval before it is made. The analyser may consult a policy data containing a policy to govern the workstations in order to make its determination. The information management system provides many advantages in the eCommerce environment to on-line trading companies, who may benefit by being able to regulate the transactions made by their staff according to their instructions in a policy data, automatically maintain records of passwords and business conducted on-line, avoid paying for unnecessary checks on the validity of digital certificates and ensure that transmissions of data made by their staff are always protected at an agreed strength of encryption.
Owner:COMP ASSOC THINK INC
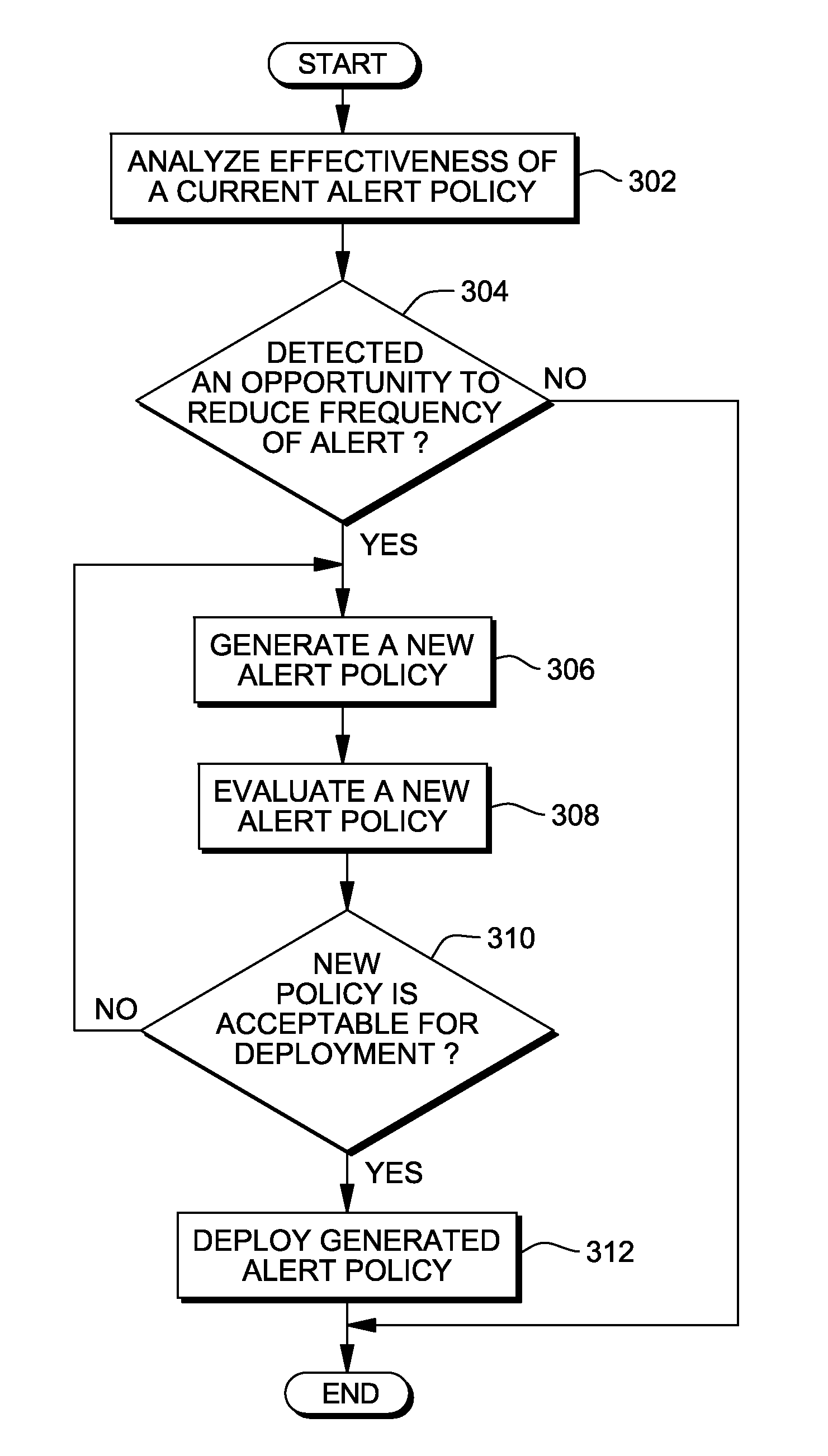
Reduction of alerts in information technology systems
InactiveUS8380838B2Multiple digital computer combinationsNon-redundant fault processingService-level agreementStructure of Management Information
Aspects of the present invention dynamically reduce a frequency at which IT infrastructure automatically generates alerts. Historical data across a plurality of data sources in the IT infrastructure is analyzed. An opportunity to reduce the frequency at which the IT infrastructure automatically generates the alerts is identified. A new alert policy addressing the opportunity to reduce alert frequency is generated. An impact of the new alert policy on a set of predefined service level objectives (SLOs) and service level agreements (SLAs) is evaluated. The new alert policy is deployed in the IT infrastructure.
Owner:GLOBALFOUNDRIES INC
Conditional computer runtime control of an information technology environment based on pairing constructs
ActiveUS20090172668A1Digital computer detailsMultiprogramming arrangementsTime informationResource based
Management of an Information Technology (IT) environment is conditionally controlled based on runtime analysis of resource pairing constructs. Resource pairings are provided, and evaluated based on the current state of the environment. This real-time information is then used in performing managerial tasks, the results of which are effected by the runtime conditions.
Owner:IBM CORP
Programmatic validation in an information technology environment
InactiveUS20090172769A1User identity/authority verificationComputer security arrangementsProgram validationApplication software
Programmatically validating service level policies established for business applications of an Information Technology environment. The programmatic validation predicts whether the policies are achievable within the environment. Examples of service level policies include quantitative goals, redundancy levels and resource use.
Owner:IBM CORP
Information management
ActiveUS20080071908A1Optimize dataReceive serviceData processing applicationsDigital computer detailsService level objectivePersonal information management
Providing information management in a networked environment. Information management provides services such as data protection, backup, retention, compliance, etc., by classifying the objects and / or infrastructure of an entity according to its value to the entity. Information management begins by discovering the data in a network and by discovering the servers and services operating in a network. Next, the data is classified according to rules that can be set by the entity, by the line of business within the entity, by regulation, and the like. Often, classification includes the collection and / or generation of metadata. After the data is classified, service level objectives can be identified and mapped to service levels. After service levels are selected, the corresponding actions can be orchestrated such that the objects of the entity received the selected services in the service level.
Owner:EMC IP HLDG CO LLC
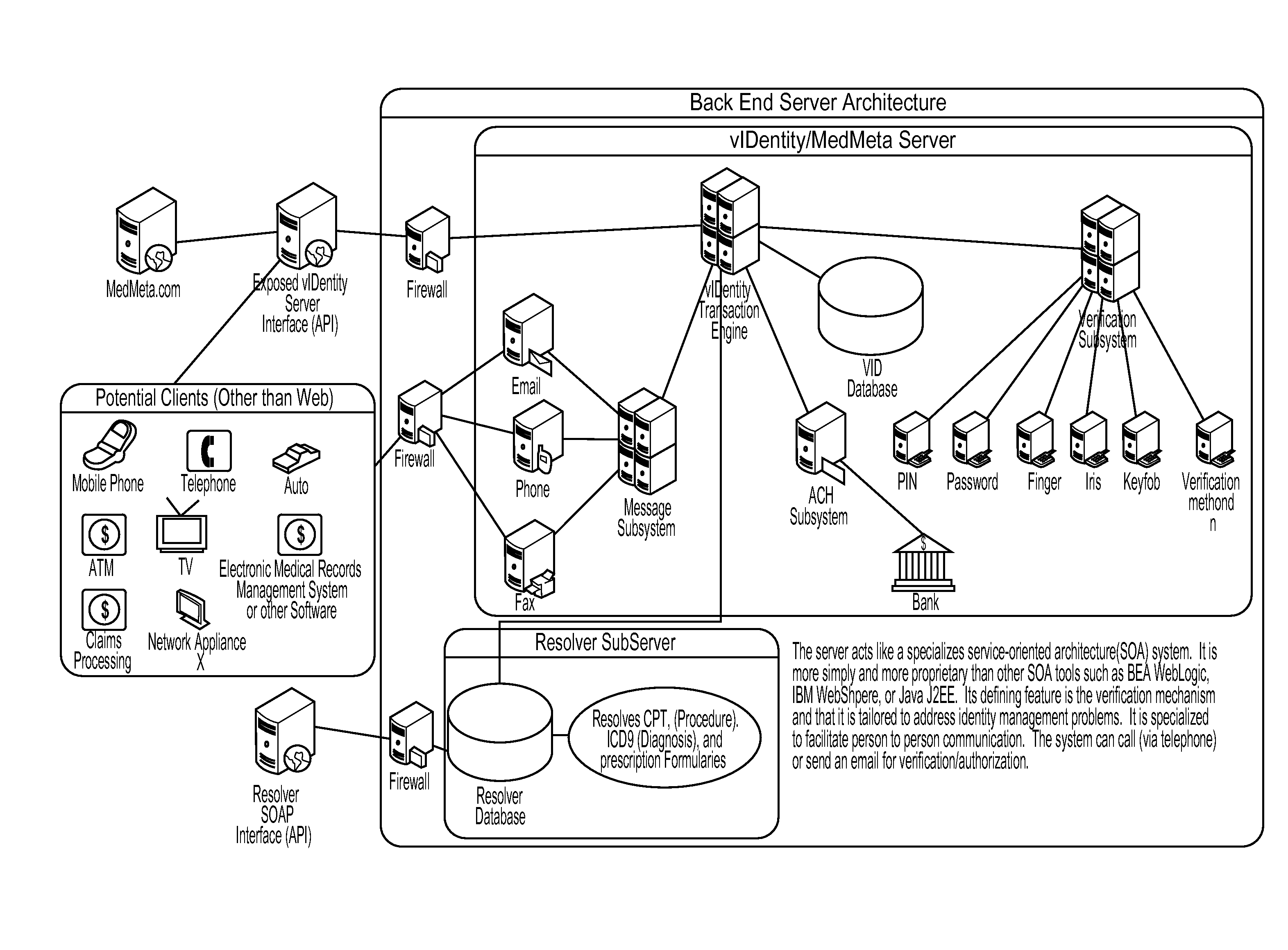
Identity verification and information management
InactiveUS20110047628A1Efficient and secure and verified information exchangeEfficient, secure and verified information exchangeDigital data processing detailsAnalogue secracy/subscription systemsClient-sideData format
The present invention provides an efficient, secure and verified information exchange using an identity verification platform and common interface data formats, whereby an individual can set different levels of access for different clients and further set different levels of access for different files. Therefore, the present invention provides a multi-layer access to records particular to an individual.
Owner:VIDENTITY SYST
Information technology portfolio management
Techniques are disclosed for managing an information technology portfolio using assessments that are based on a set of criteria. Each of the criteria may have one or more attributes, and may be different in priority from one another. The criteria are preferably directed toward evaluating, ensuring, and / or improving acceptance of the products in the portfolio by their target marketplace or market segment. Assessments are performed, using the criteria and attributes, and results of these assessments may be used when making various decisions regarding the products in the portfolio.
Owner:IBM CORP
Systems and methods for transaction and information management
ActiveUS7640190B1Improve customer satisfactionImprove accuracyAutomatic exchangesBuying/selling/leasing transactionsPaymentVisibility
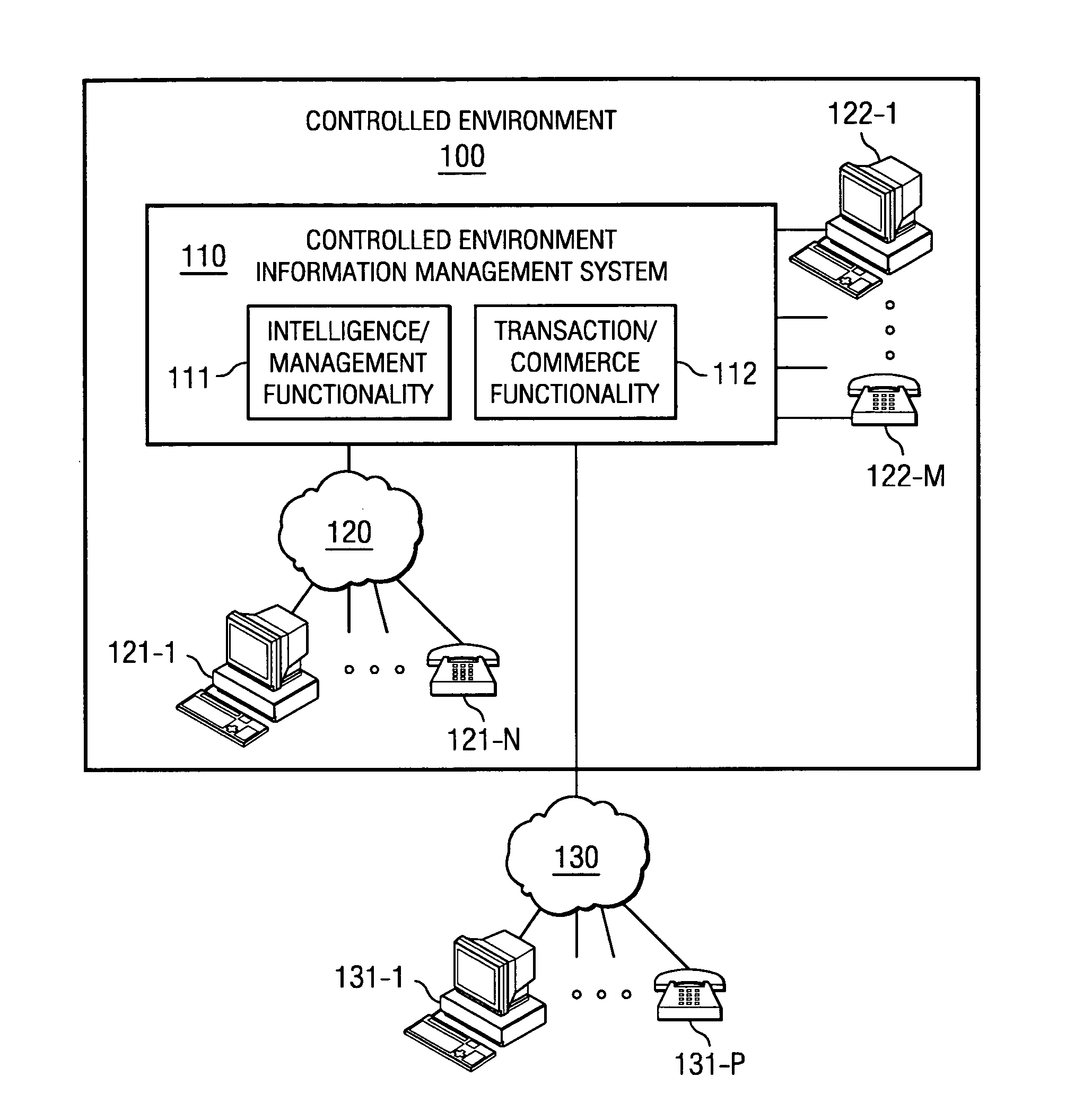
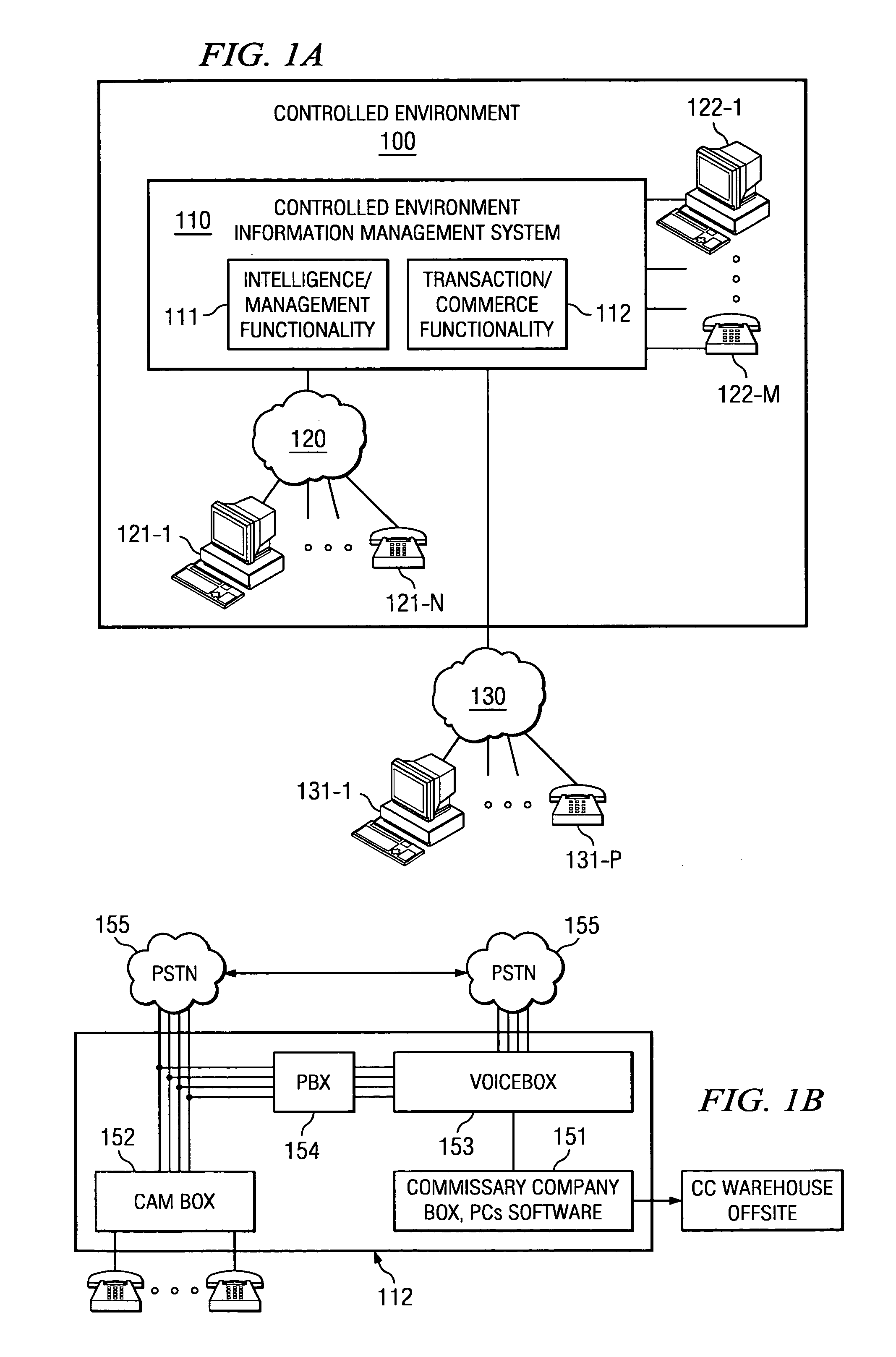
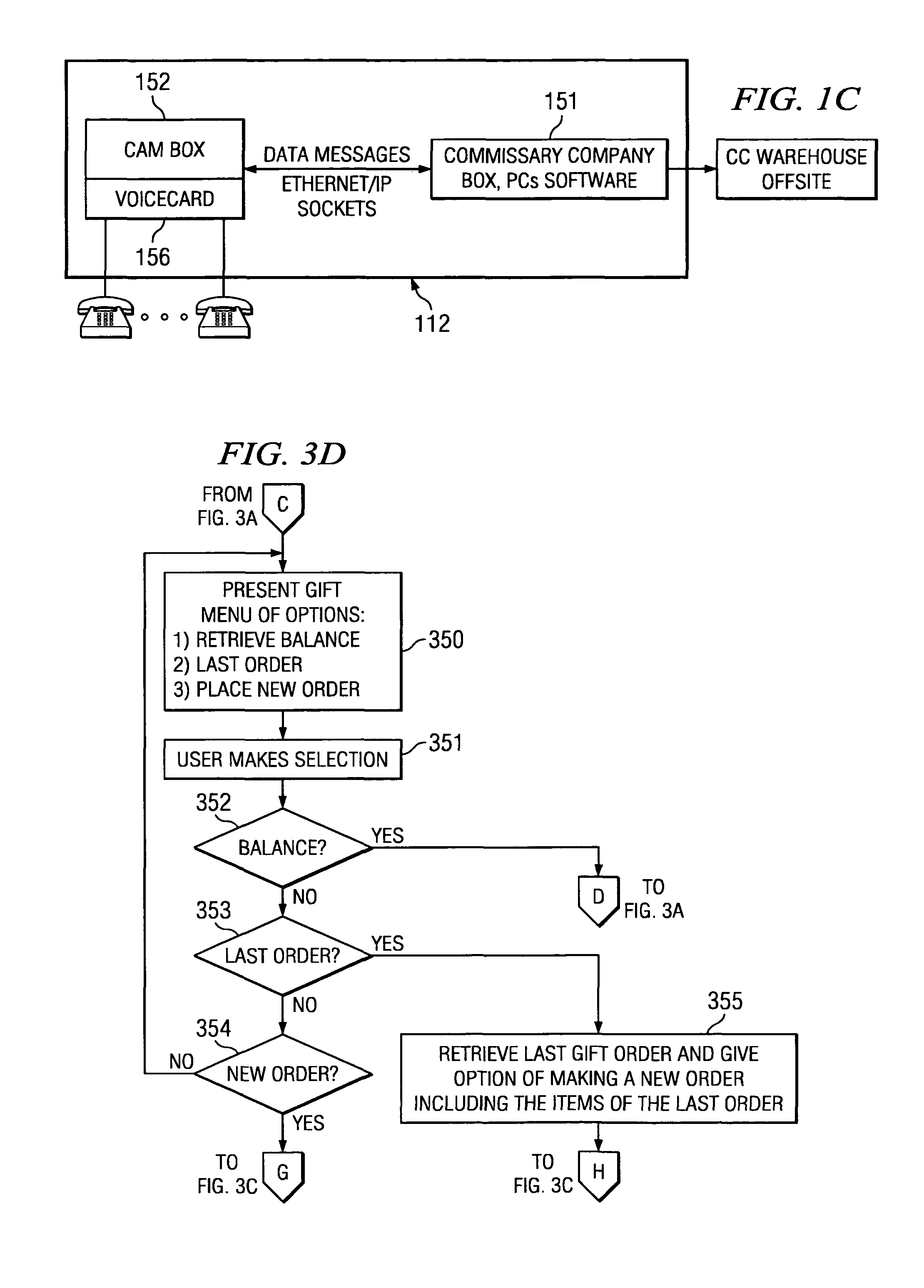
Disclosed are systems and methods which utilize information communication systems for transaction and information management. According to embodiments, an automated information management engine is provided enabling and facilitating the purchase of goods and services through various payment options resulting in increased profitability and visibility safely, securely and conveniently. Embodiments utilize a telephony system, and / or other information communication system, having access terminals disposed within a controlled environment facility for use by residents thereof to conduct transactions or other desirable exchanges of information, goods, services, etcetera. Embodiments provide integration across various aspects of transaction and information management, such as prepaid account management, collect calling services, and commissary services, to thereby facilitate seamless user interaction for account deposit, account status inquiry, commissary ordering, and collect calling. Interactive systems of embodiments operate intelligently to facilitate and / or optimize use thereof, such as to identify low account status and implement interaction to solicit deposit of funds.
Owner:SECURUS TECH HLDG
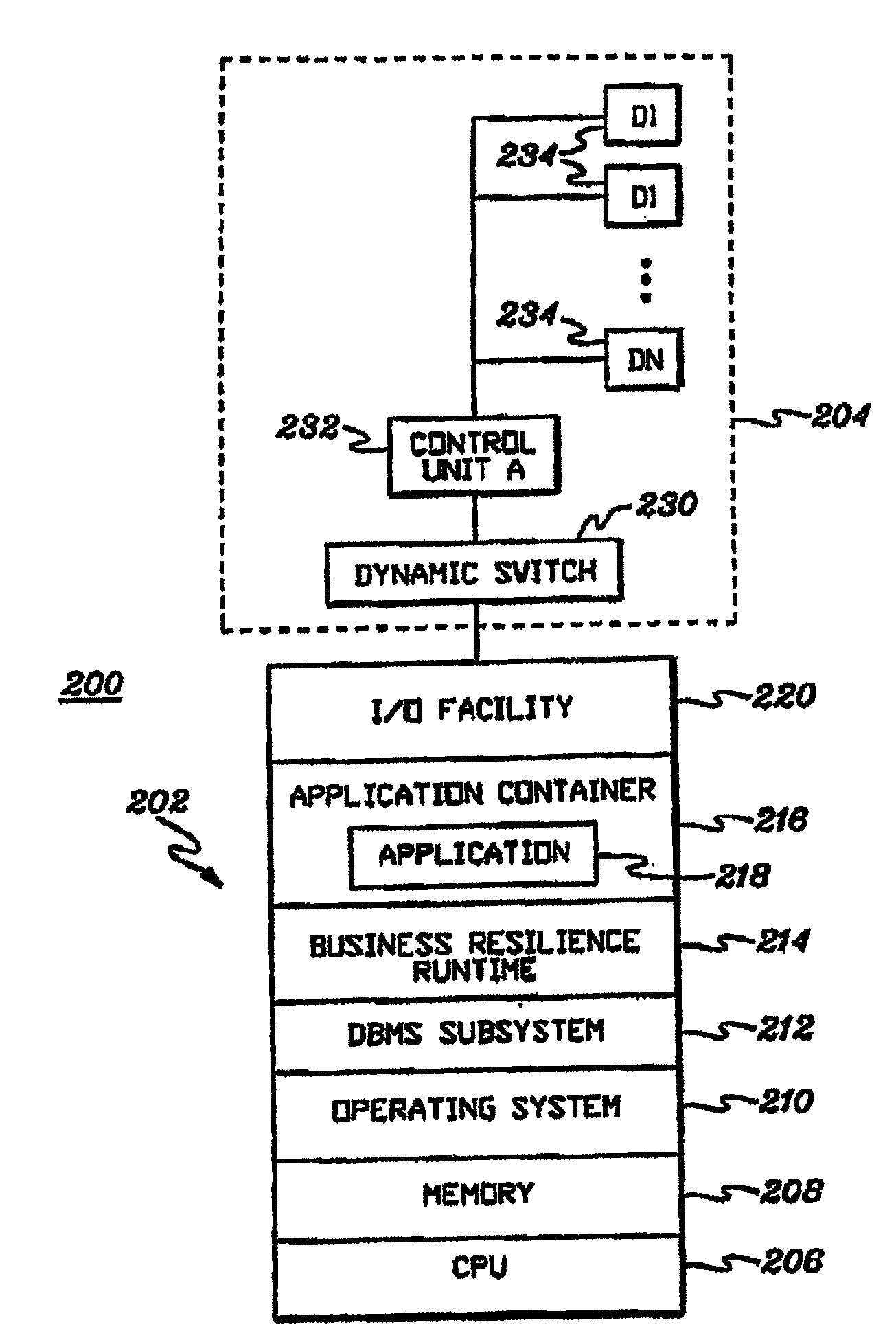
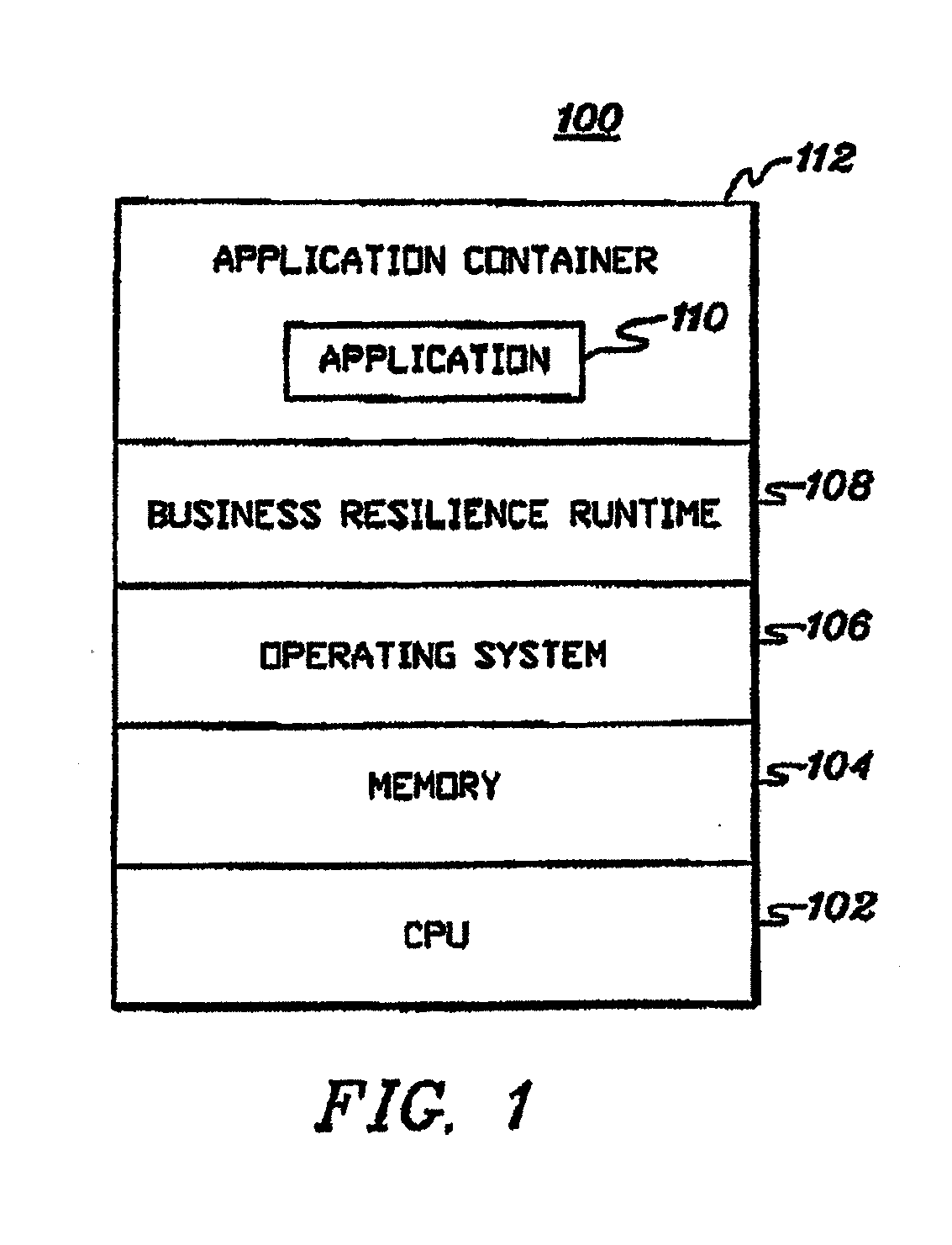
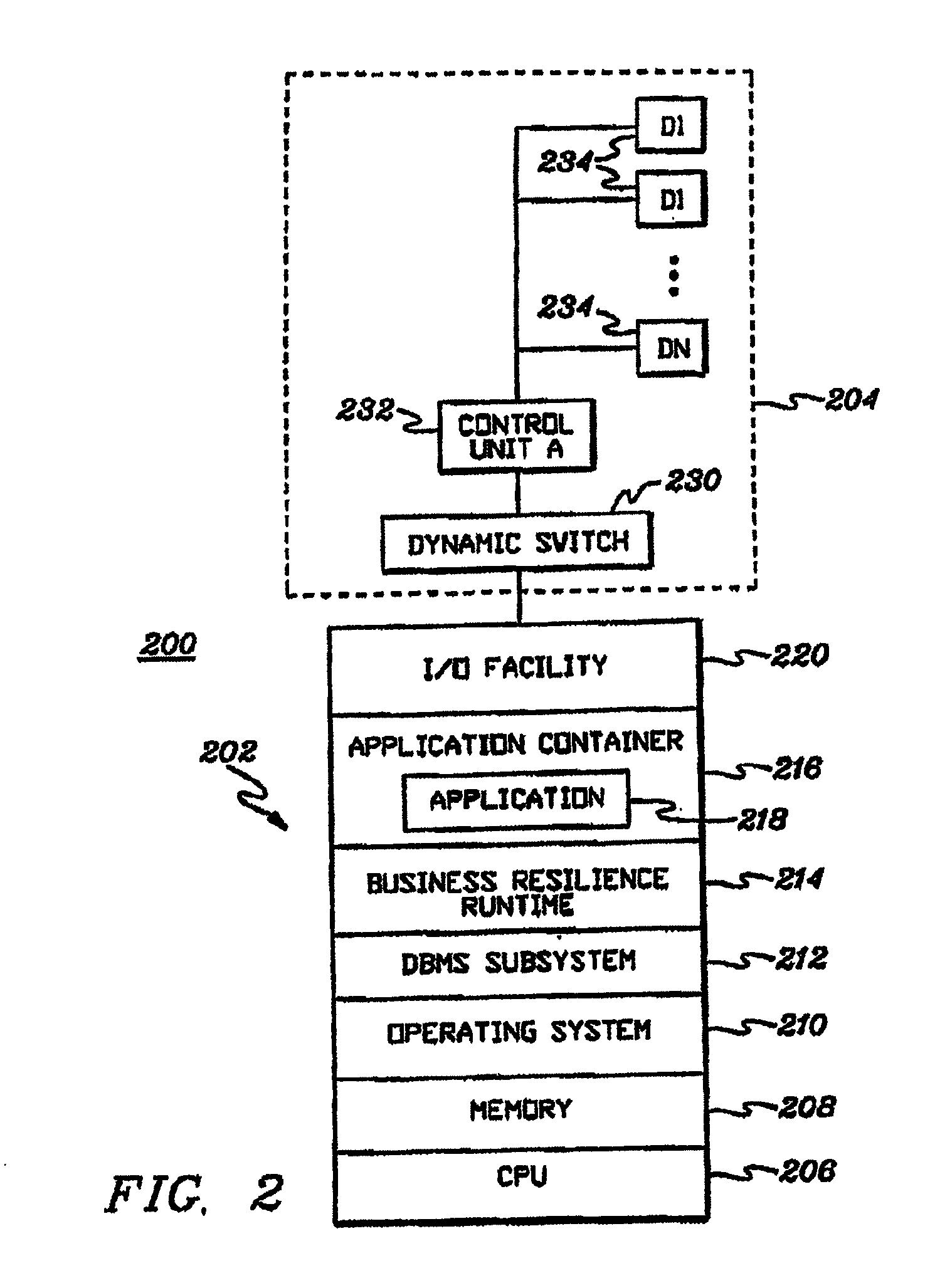
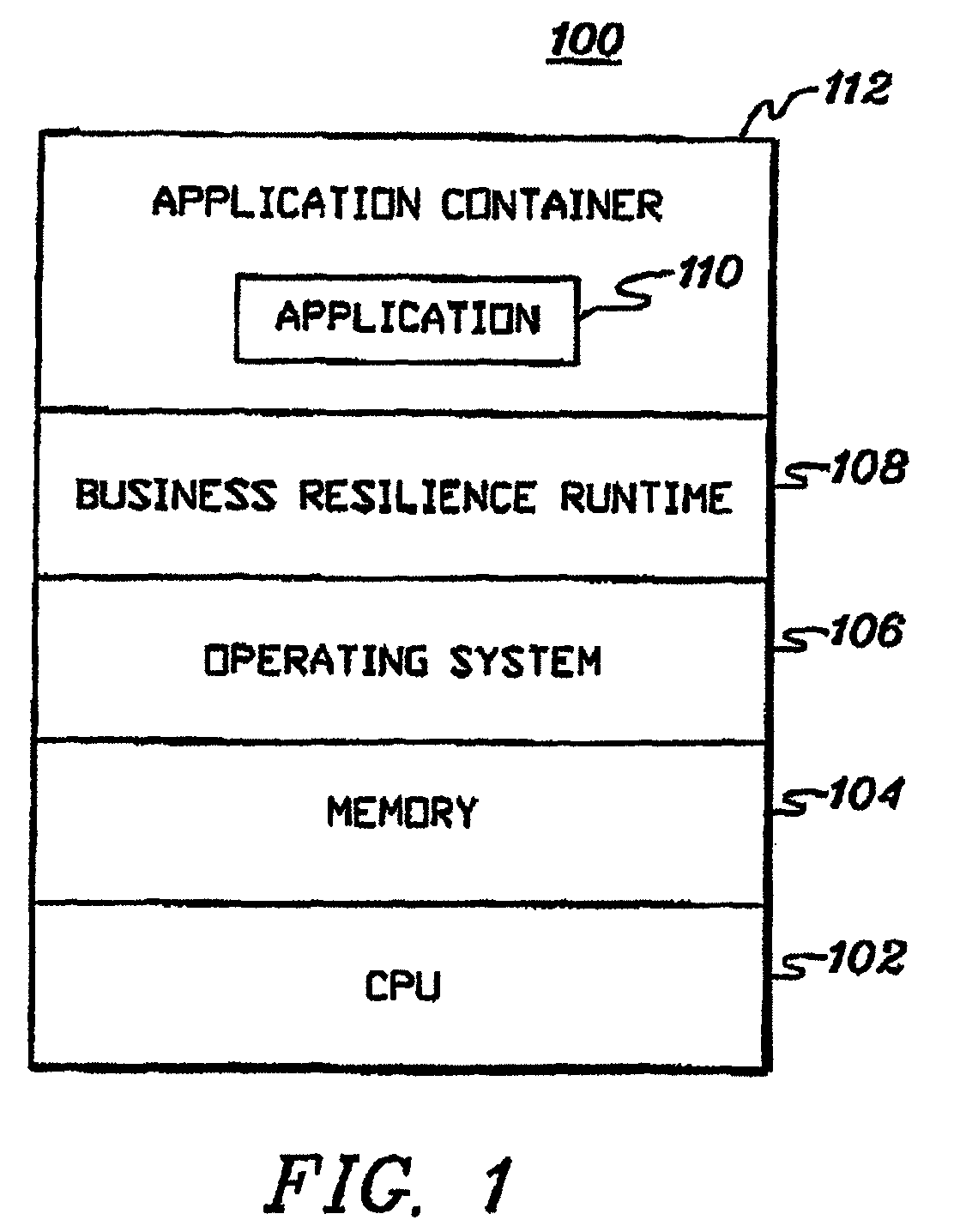
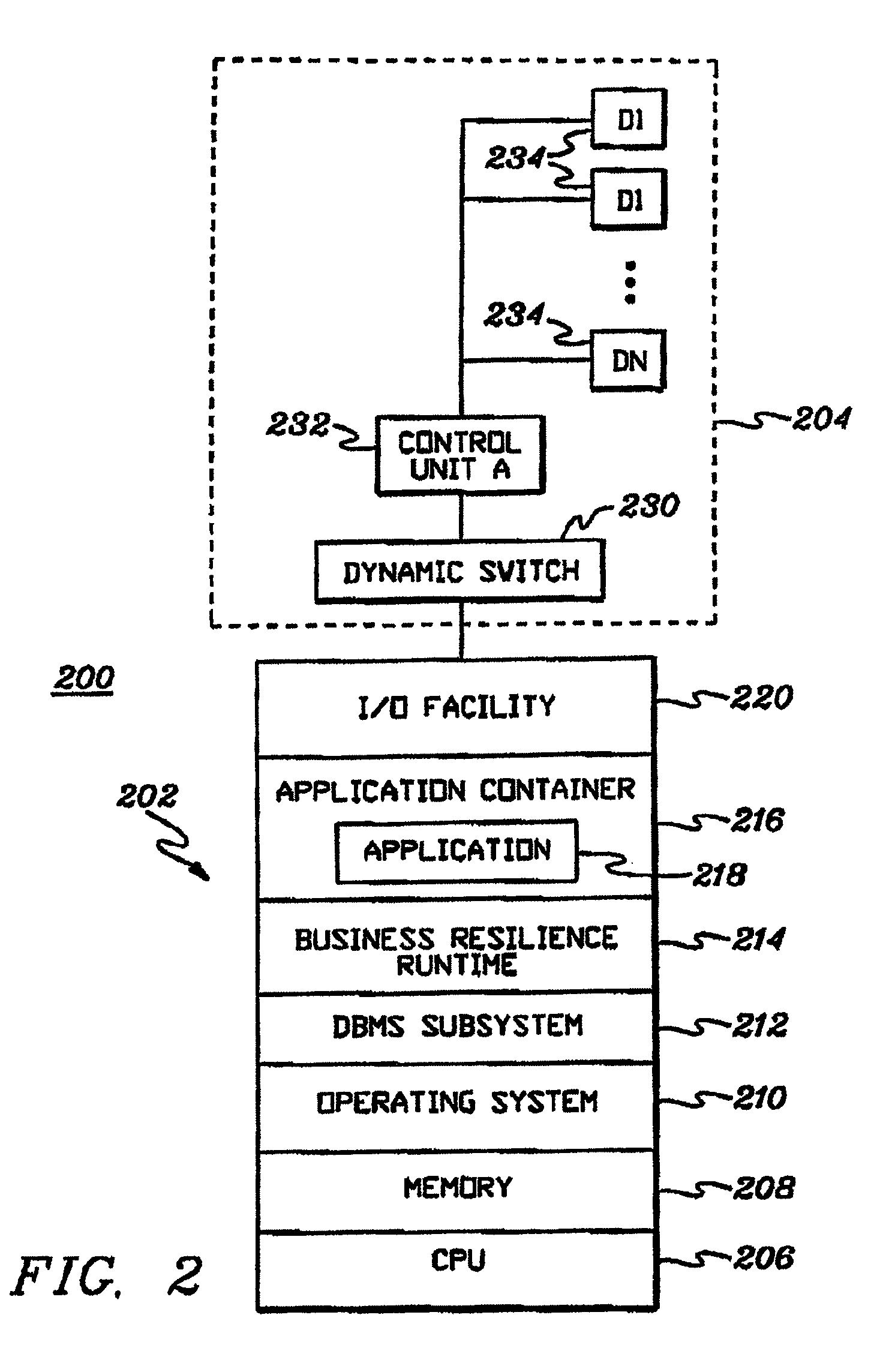
Adaptive business resiliency computer system for information technology environments
ActiveUS8447859B2Error detection/correctionDigital computer detailsApplication softwareSelf adaptive
Programmatically adapting an Information Technology (IT) environment to changes associated with business applications of the IT environment. The programmatically adapting is performed in the context of the business application. The changes can reflect changes in the IT environment, changes to the business application, changes to the business environment and / or failures within the environment, as examples.
Owner:IBM CORP
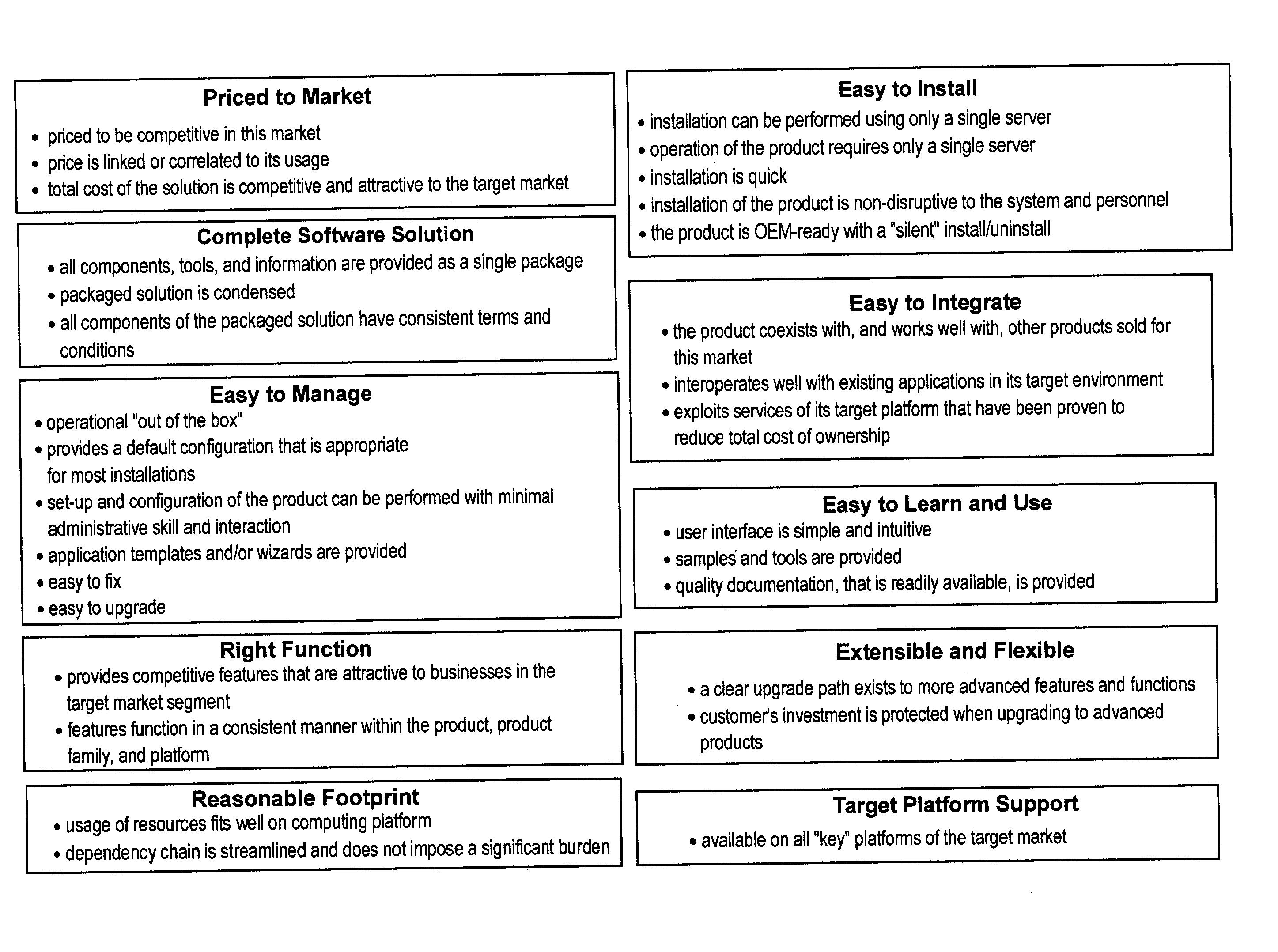
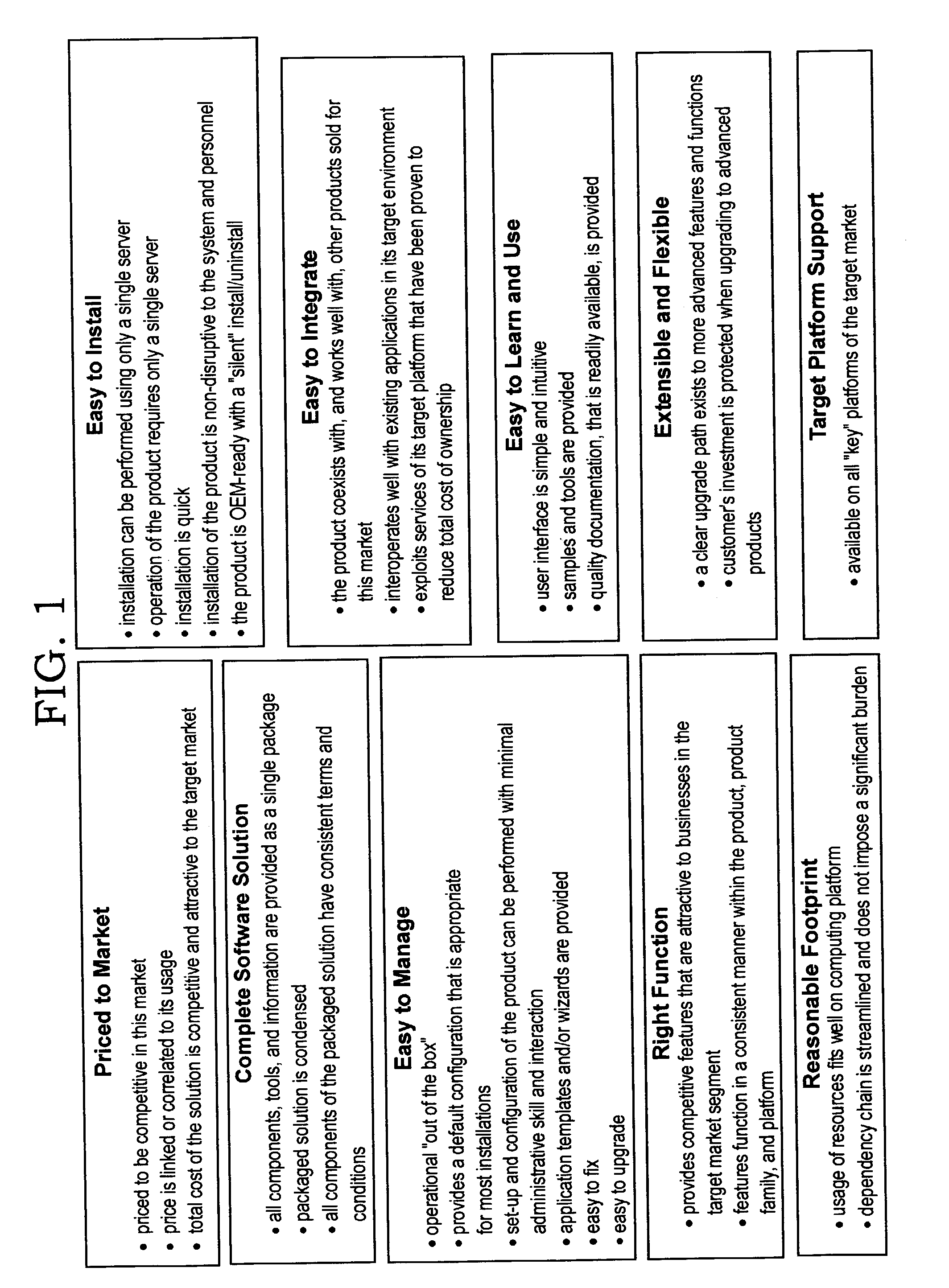
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com