Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
249results about How to "Ensure protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
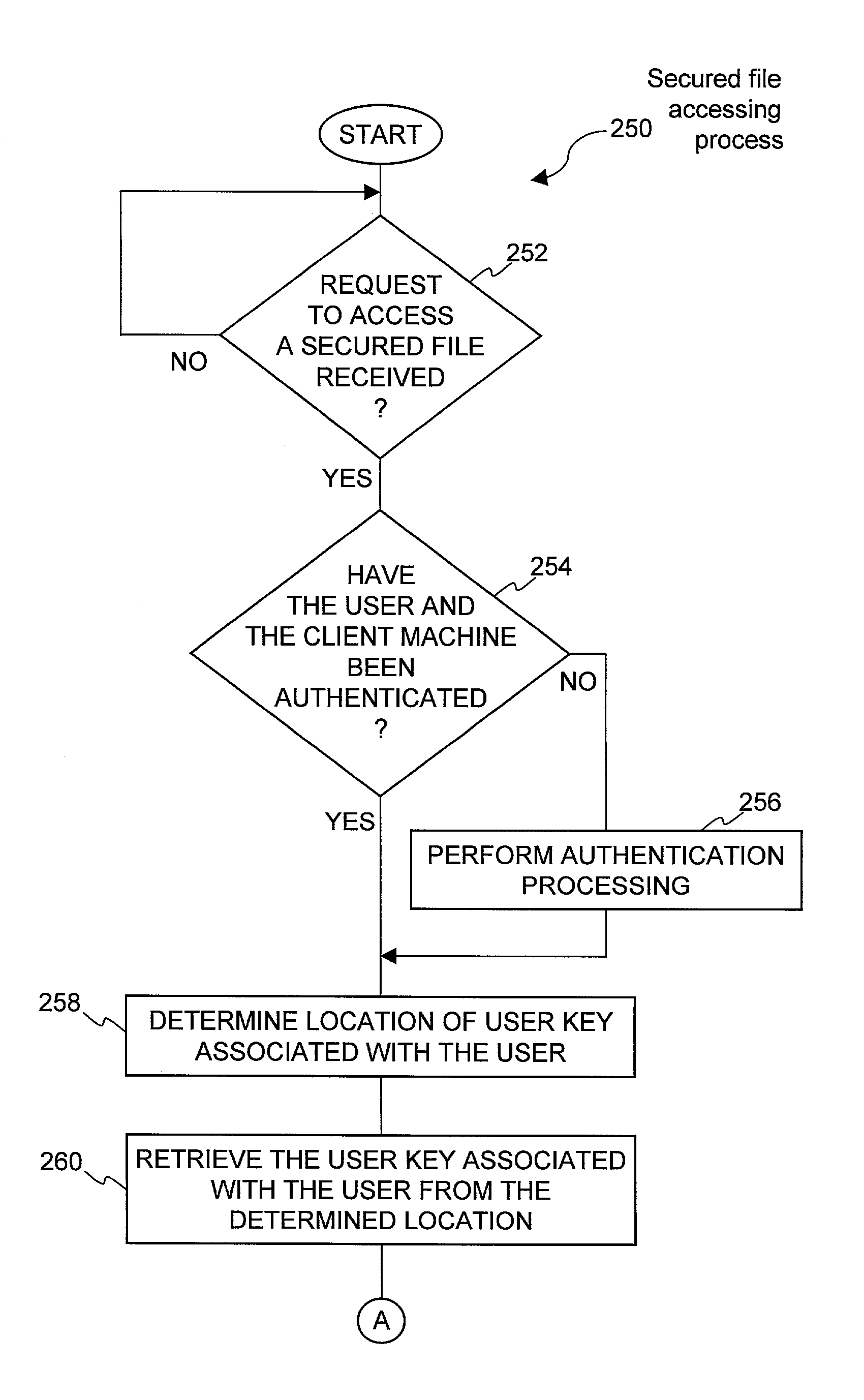
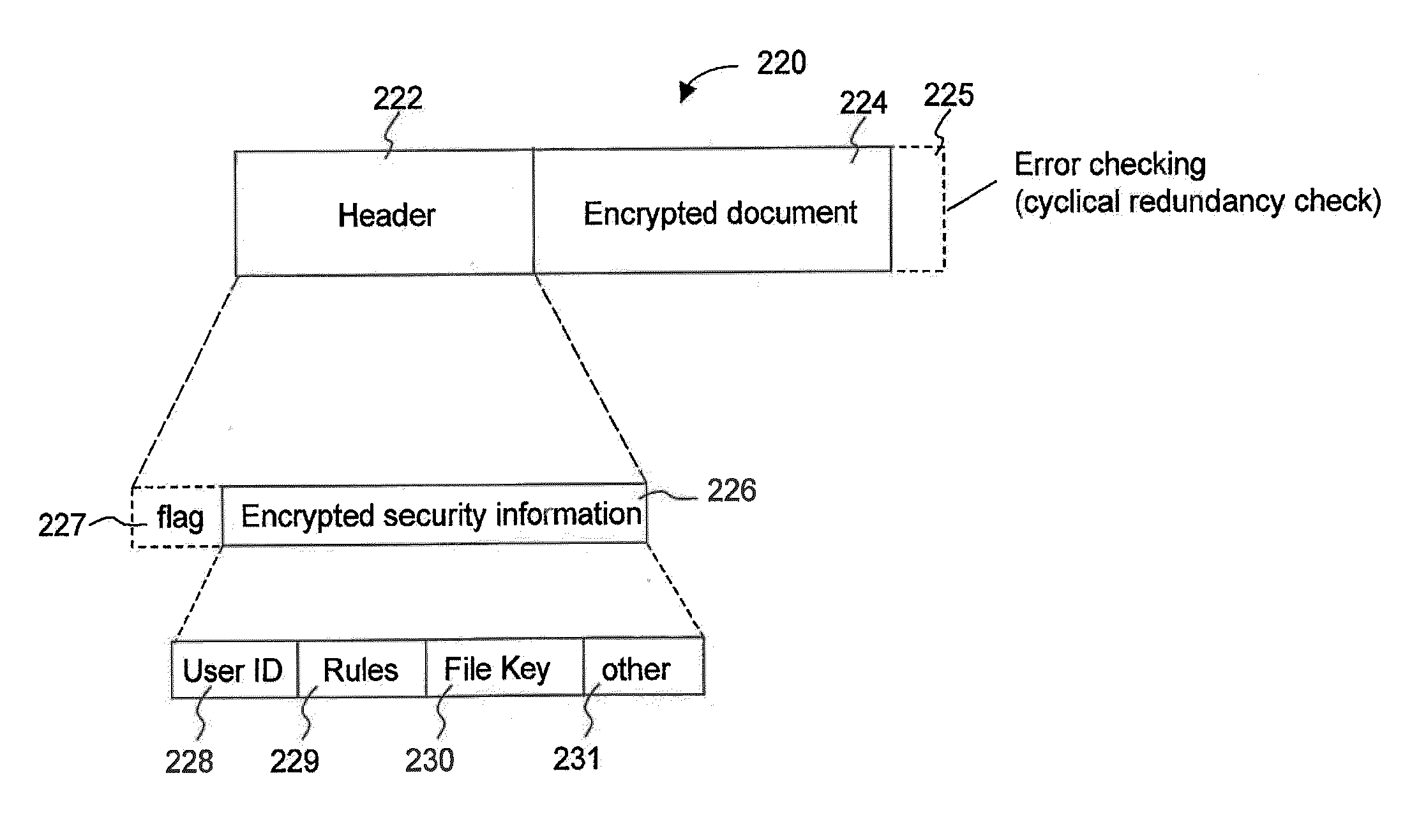
System and method for providing different levels of key security for controlling access to secured items
With files secured by encryption techniques, keys are often required to gain access to the secured files. Techniques for providing and using multiple levels of keystores for securing the keys are disclosed. The keystores store keys that are needed by users in order to access secured files. The different levels of keystores offer compromises between security and flexibility / ease of use.
Owner:INTELLECTUAL VENTURES I LLC
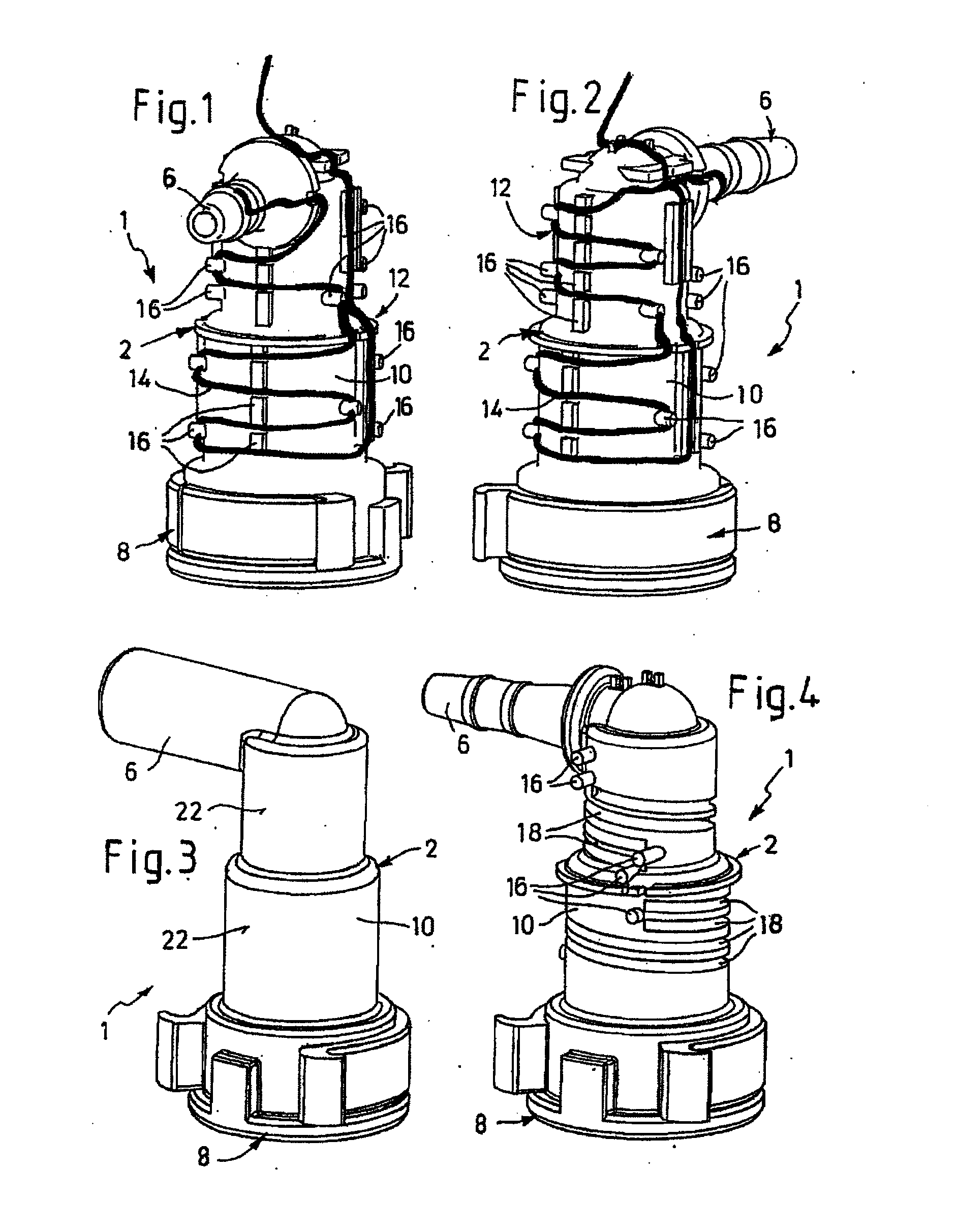
Line connector for media lines
ActiveUS20100290764A1Improve heat transfer performanceImprove mechanical propertiesValve members for heating/coolingPipe heating/coolingLine tubingElectrical conductor
The present invention relates to a line connector for media lines, consisting of a connector piece with at least one junction portion for junction connection to a media line or to an assembly and with a transitional portion contiguous to the junction portion and having a flow duct. In this case, at least in the region of the transitional portion, electrical heating means are provided in an arrangement at least partially surrounding the flow duct. Furthermore, the invention relates to a ready-made media line consisting of a pipeline with a heating conductor arranged on the circumference and with a heatable line connector fastened at least to one pipeline end of the media line.
Owner:VOSS AUTOMOTIVE
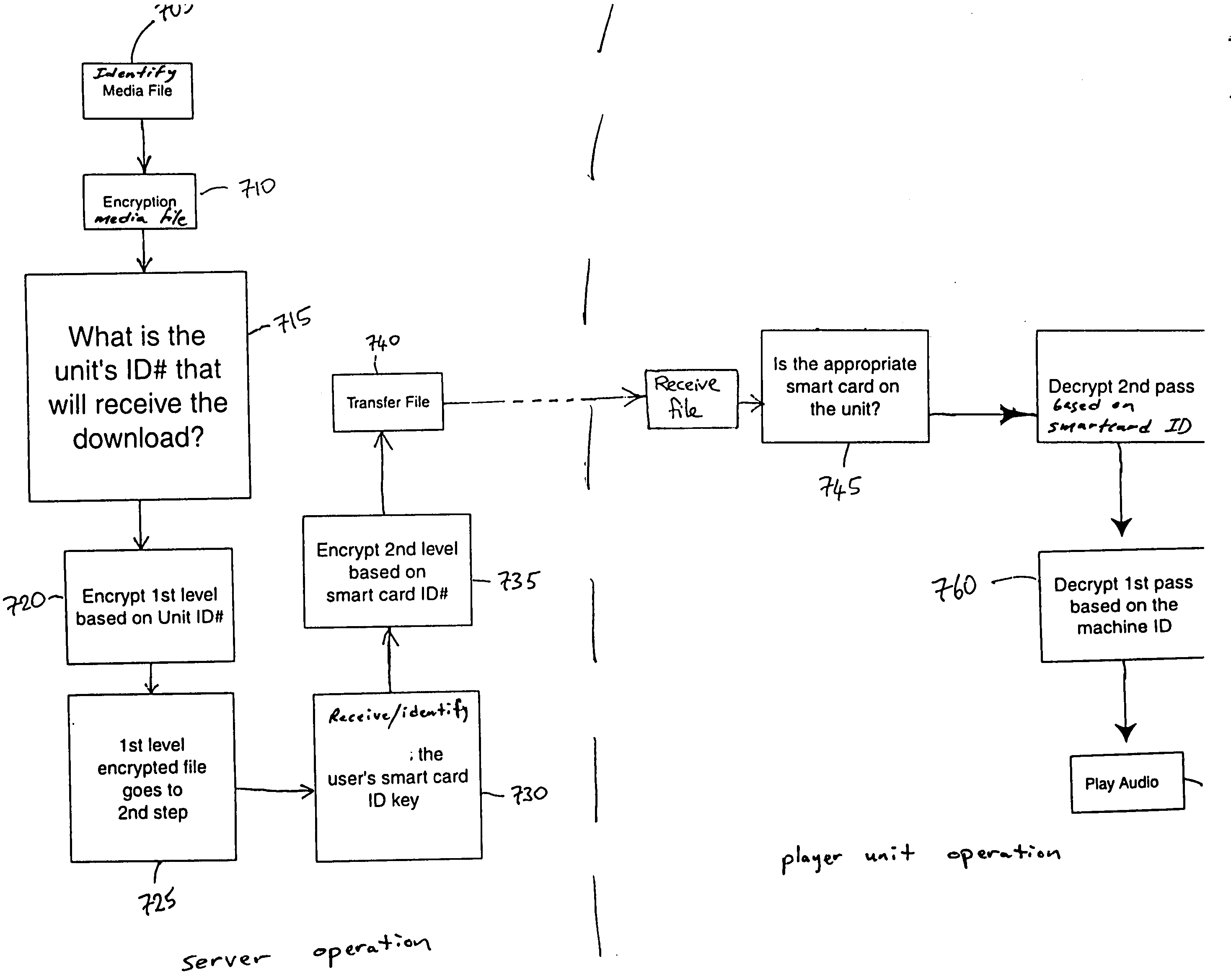
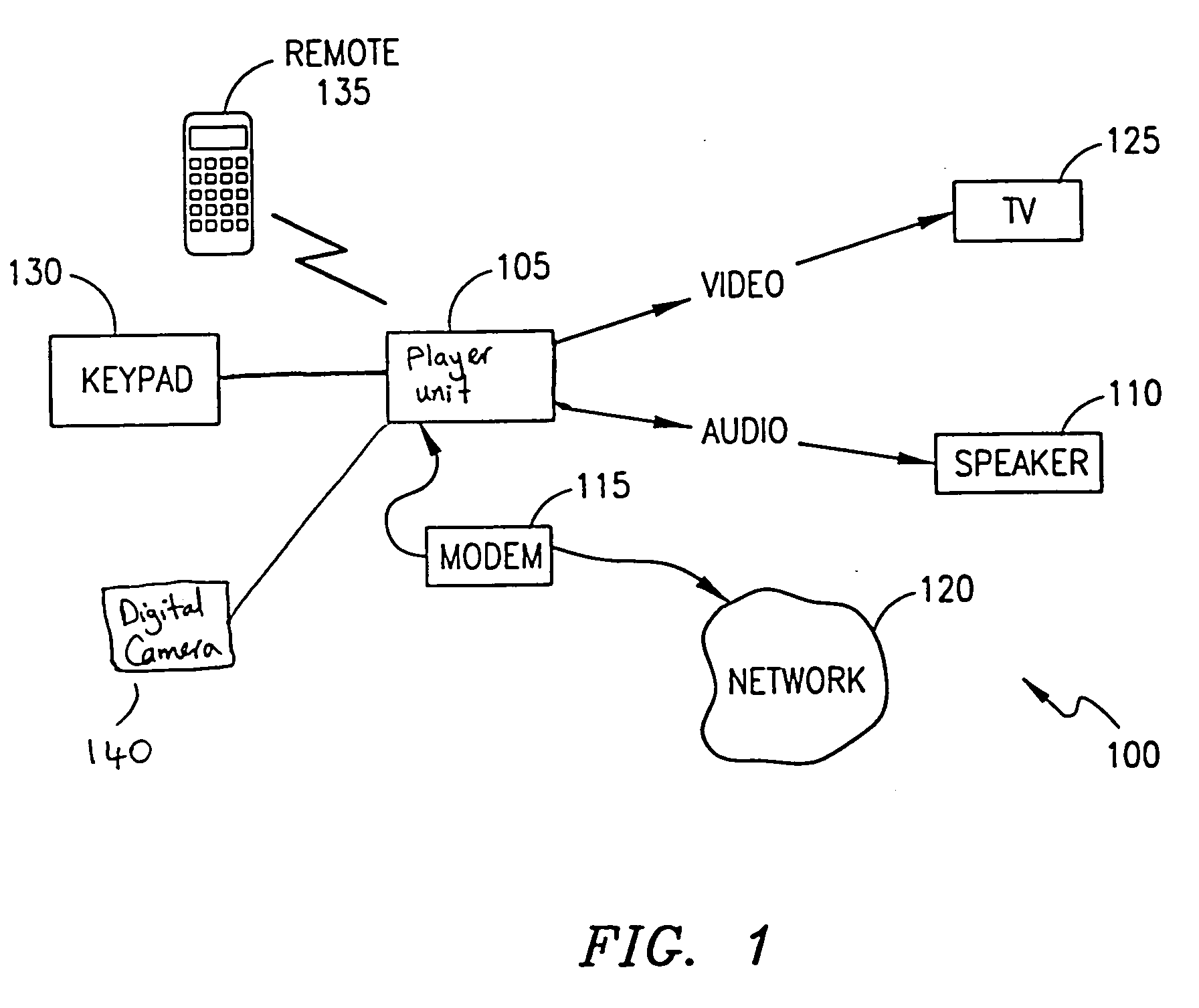
System, method and apparatus for controlling the dissemination of digital works
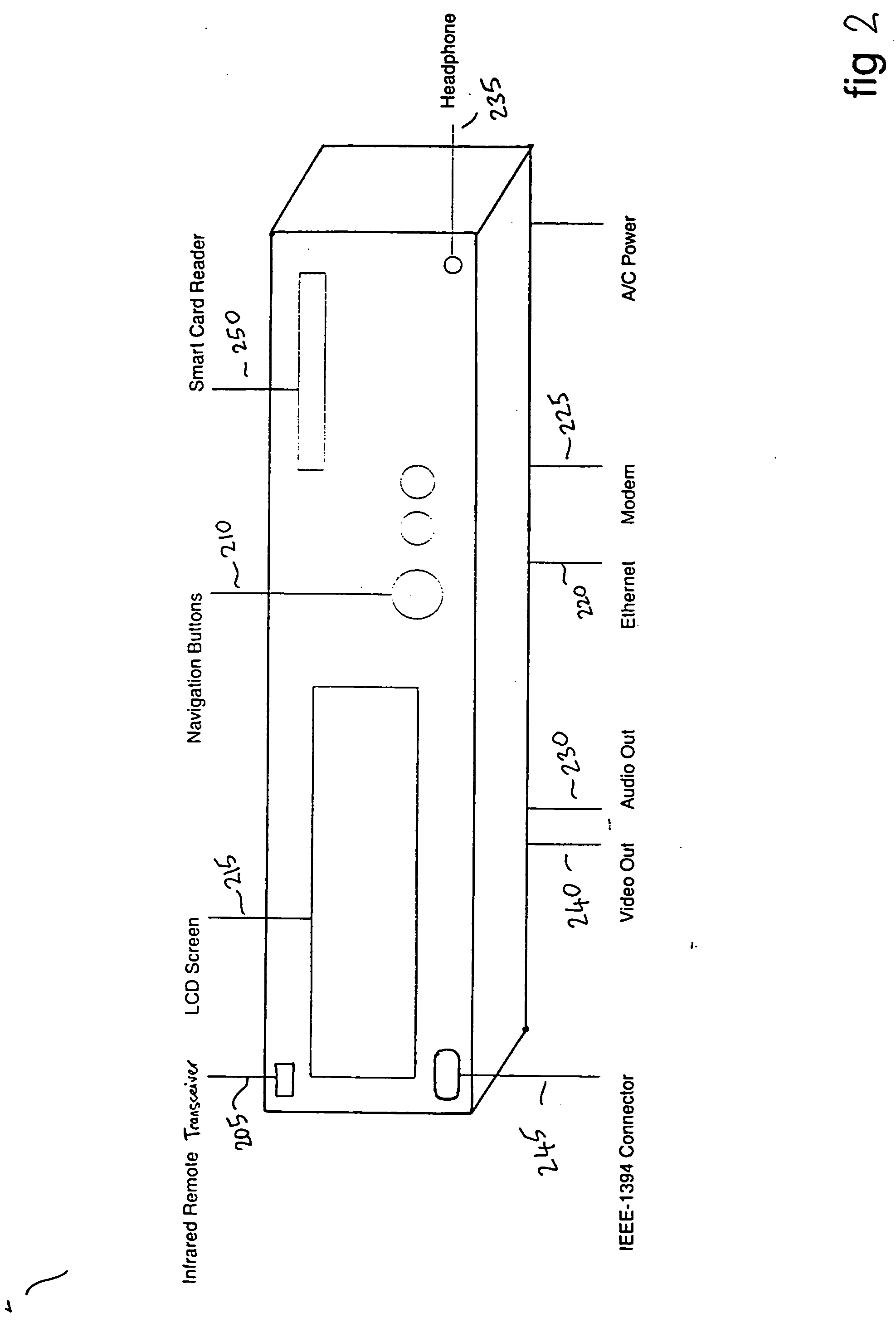
InactiveUS20060080741A1Ensure protectionTelevision system detailsDigital data processing detailsPersonalizationCommunication unit
A system, business methodology and apparatus for facilitating controlled dissemination of digital works is disclosed. An audio and video organizer, entertainment, and communication unit that plays back audio and video media content received from a central storage server. The unit relies on a smartcard, which has a personalized key that unlocks encrypted content. Using the unit, a user can purchase music or other types of media using a appropriate ordering method. The central storage server then transmits a double-encrypted, compressed audio file to the unit, where it is decrypted based on the smartcard key, and available for listening.
Owner:NAIR MARK
Information management system
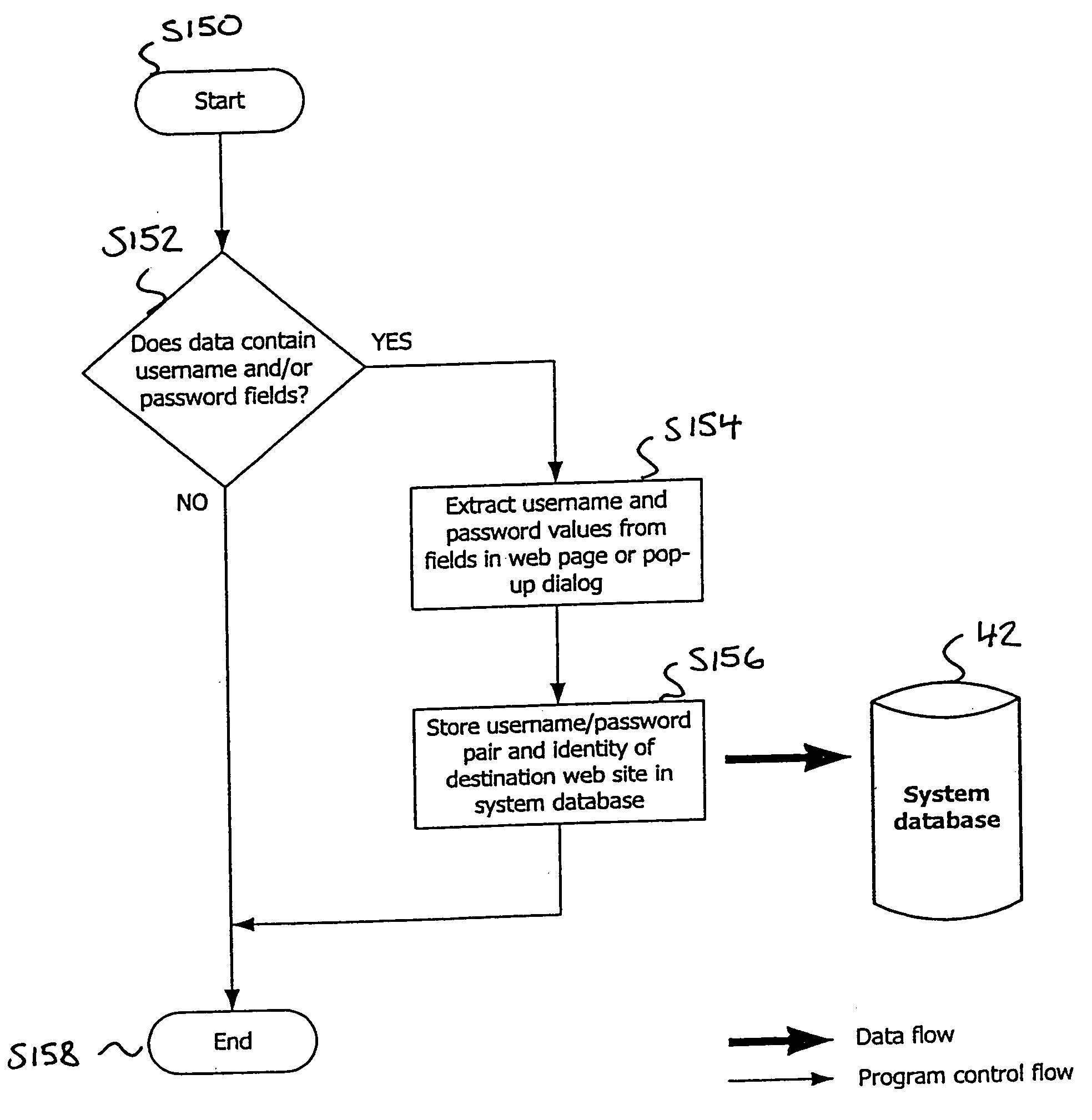
ActiveUS20050203855A1Check is unnecessaryEnsure protectionUnauthorized memory use protectionHardware monitoringThe InternetWorkstation
An information management system is described comprising one or more workstations running applications to allow a user of the workstation to connect to a network, such as the Internet. Each application has an analyzer, which monitors transmission data that the application is about to transmit to the network or about to receive from the network and which determines an appropriate action to take regarding that transmission data. Such actions may be extracting data from the transmission data, such as passwords and usernames, digital certificates or eCommerce transaction details for storage in a database; ensuring that the transmission data is transmitted at an encryption strength appropriate to the contents of the transmission data; determining whether a check needs to be made as to whether a digital certificate received in transmission data is in force, and determining whether a transaction about to be made by a user of one of the workstations needs third party approval before it is made. The analyzer may consult a policy data containing a policy to govern the workstations in order to make its determination. The information management system provides many advantages in the eCommerce environment to on-line trading companies, who may benefit by being able to regulate the transactions made by their staff according to their instructions in a policy data, automatically maintain records of passwords and business conducted on-line, avoid paying for unnecessary checks on the validity of digital certificates and ensure that transmissions of data made by their staff are always protected at an agreed strength of encryption.
Owner:COMP ASSOC THINK INC
Information management system
InactiveUS20050216771A1Ensure protectionDigital data processing detailsDigital data protectionThe InternetWorkstation
An information management system is described comprising one or more workstations running applications to allow a user of the workstation to connect to a network, such as the Internet. Each application has an analyser, which monitors transmission data that the application is about to transmit to the network or about to receive from the network and which determines an appropriate action to take regarding that transmission data. Such actions may be extracting data from the transmission data, such as passwords and usernames, digital certificates or eCommerce transaction details for storage in a database; ensuring that the transmission data is transmitted at an encryption strength appropriate to the contents of the transmission data; determining whether a check needs to be made as to whether a digital certificate received in transmission data is in force, and determining whether a transaction about to be made by a user of one of the workstations needs third party approval before it is made. The analyser may consult a policy data containing a policy to govern the workstations in order to make its determination. The information management system provides many advantages in the eCommerce environment to on-line trading companies, who may benefit by being able to regulate the transactions made by their staff according to their instructions in a policy data, automatically maintain records of passwords and business conducted on-line, avoid paying for unnecessary checks on the validity of digital certificates and ensure that transmissions of data made by their staff are always protected at an agreed strength of encryption.
Owner:COMP ASSOC THINK INC
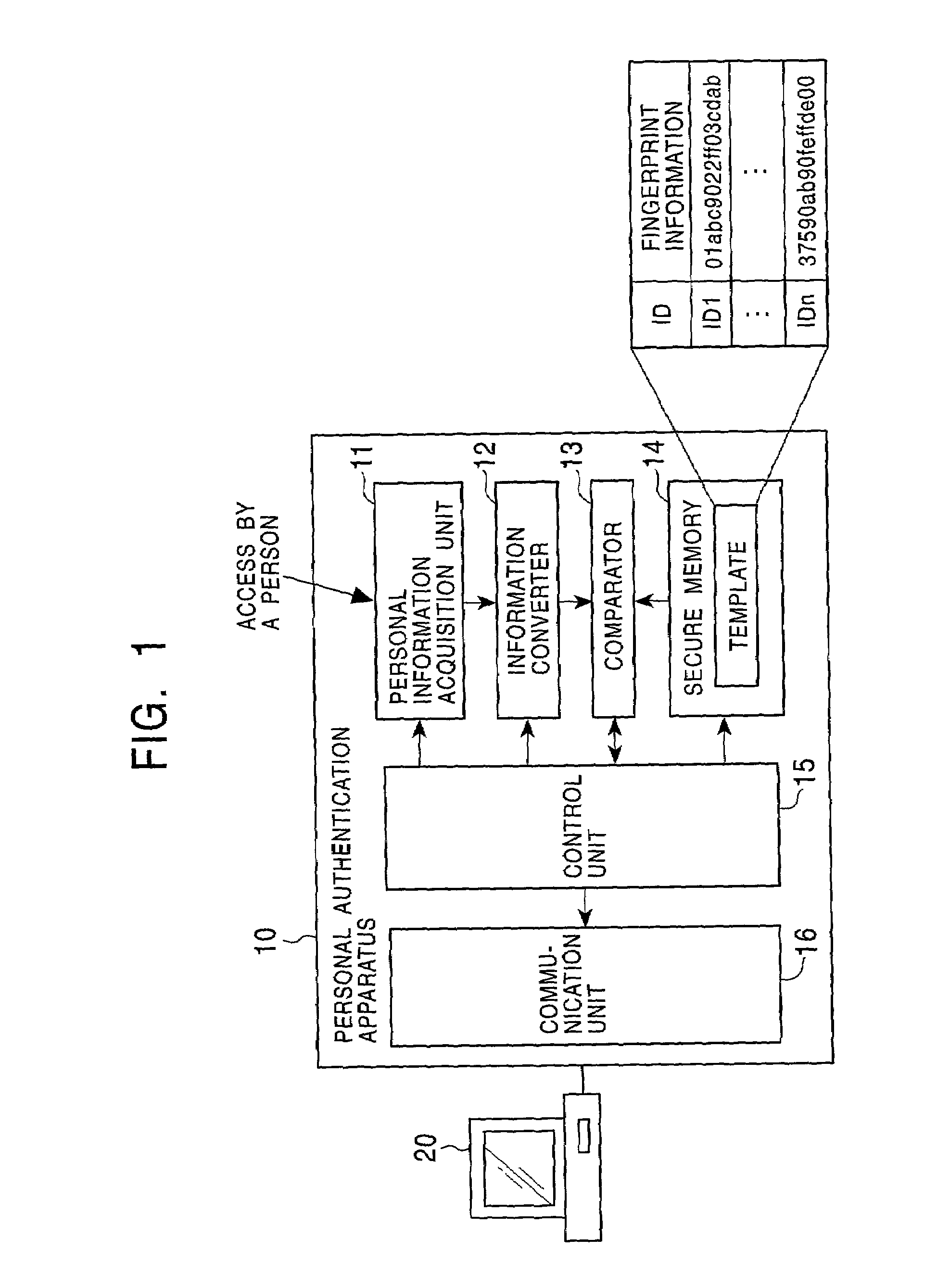
Person authentication system, person authentication method, information processing apparatus, and program providing medium
InactiveUS7287158B2Data efficientEnsure protectionData processing applicationsDigital data processing detailsInformation processingThird party
A person authentication system capable of performing personal authentication by comparing templates that is personal identification data with sampling information input by a user is disclosed. For example, a service provider (SP) or a user device (UD) acquires the templates from a person identification certificate (IDC) generated by a personal identification certificate authority that is a third party to thereby perform personal authentication. The IDC stores data, such as a certificate identifier and a user identifier, in accordance with a format, and also stores encrypted templates in a manner that the data can be decrypted by an entity that performs authentication. This arrangement achieves efficient template retrieval and a personal authentication process, as well as effective prevention of the templates from being leaking out.
Owner:SONY CORP
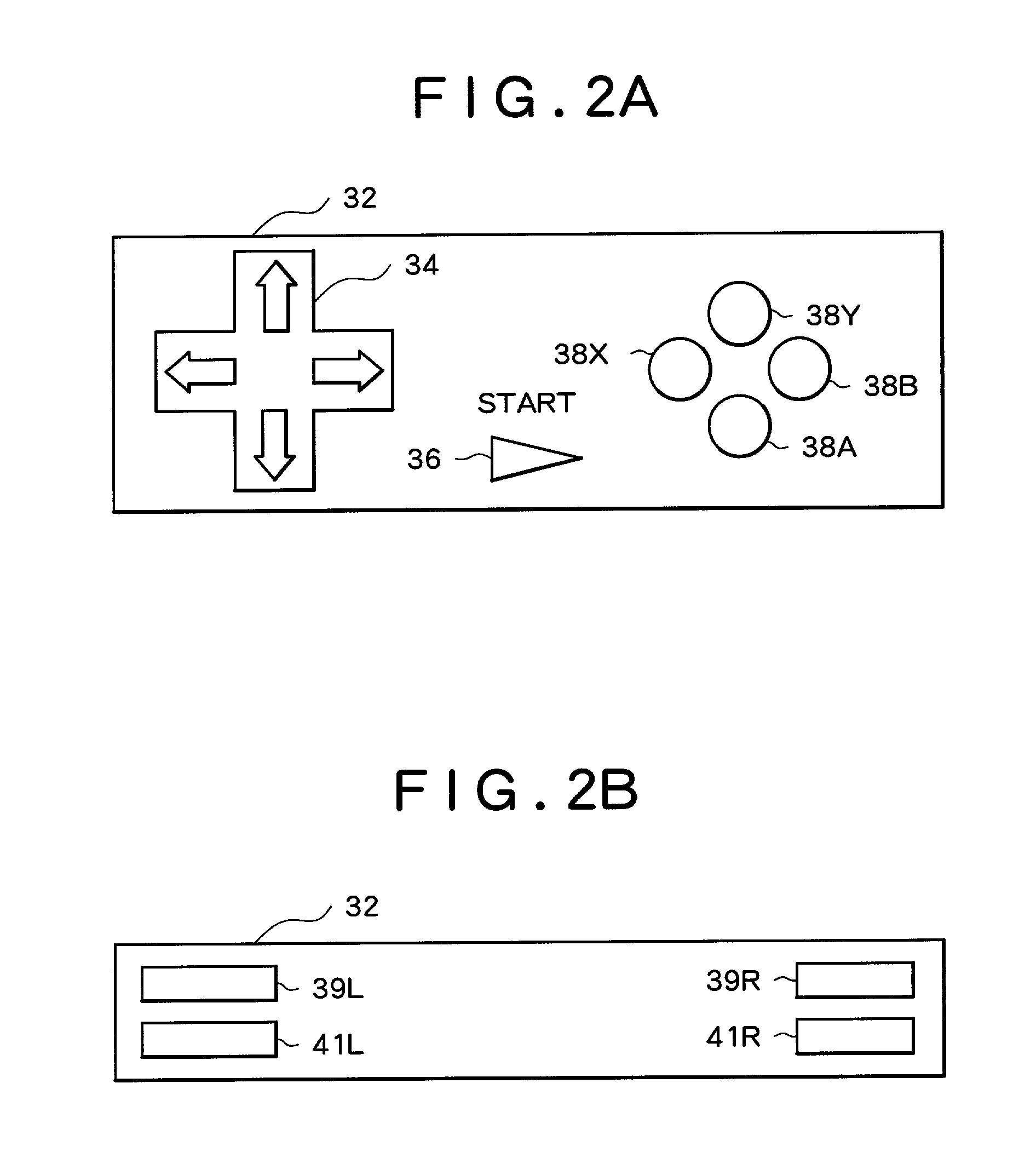
Game device, method of controlling game machine, information storage medium, and program distribution device and method
InactiveUS20020006823A1Avoid excessive forceEnsure protectionVideo gamesSpecial data processing applicationsEngineeringPressure sensitive
A player is prevented from applying an excessive force to a button on a pressure sensitive controller. For a game device comprising a controller 32 for supplying one of digital values in a predetermined range in accordance with the force pressing a button, the predetermined range includes a response range in which at least some of the digital values smaller than a predetermined threshold fall, and a response limit range in which the digital value at said predetermined threshold or greater falls. When a digital value supplied from the controller 32 falls in the response range, a response image changing in accordance with a change in the digital value is displayed. On the other hand, when the value falls in the response limit range, a response limit image whose change in accordance with the digital value is limited is displayed.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
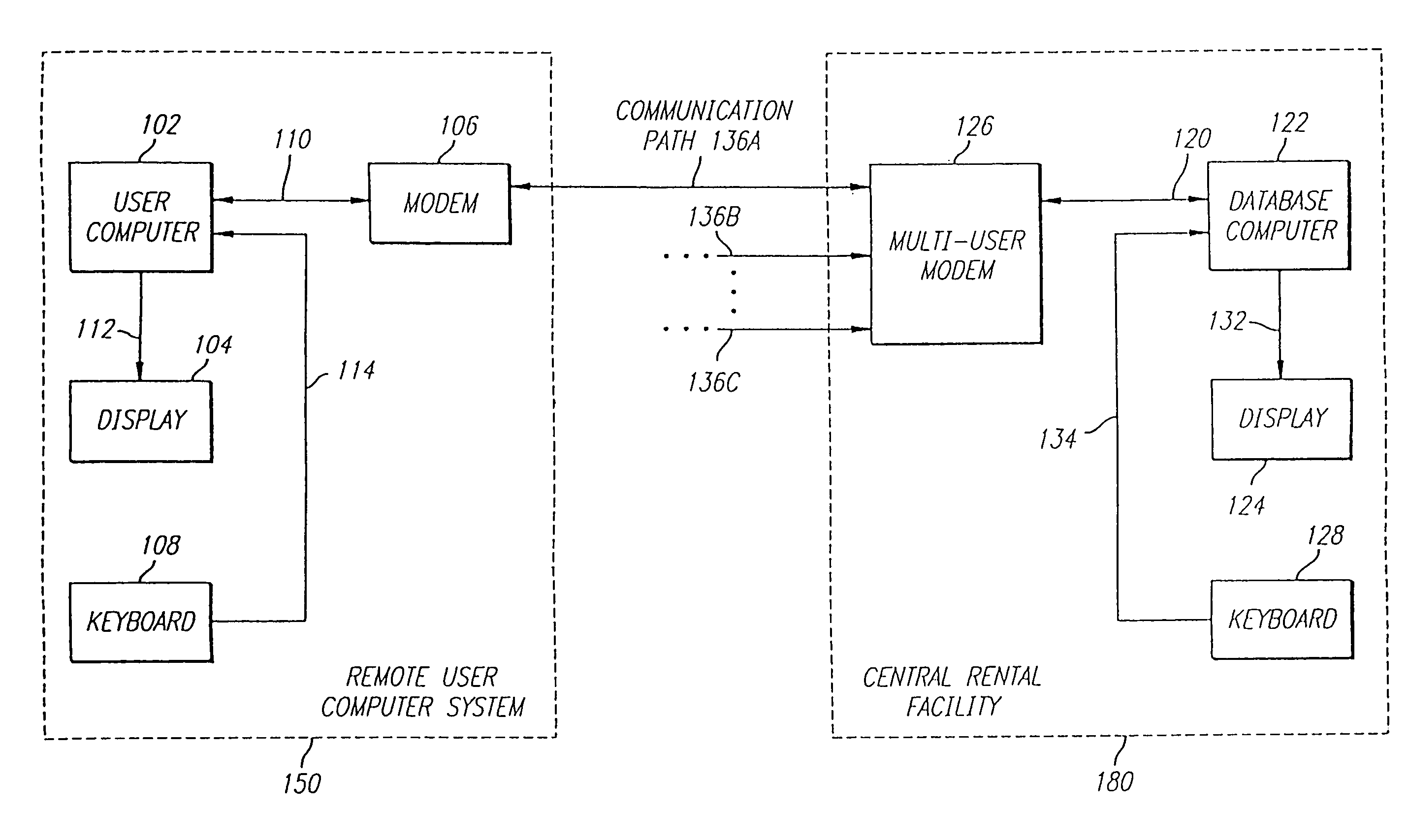
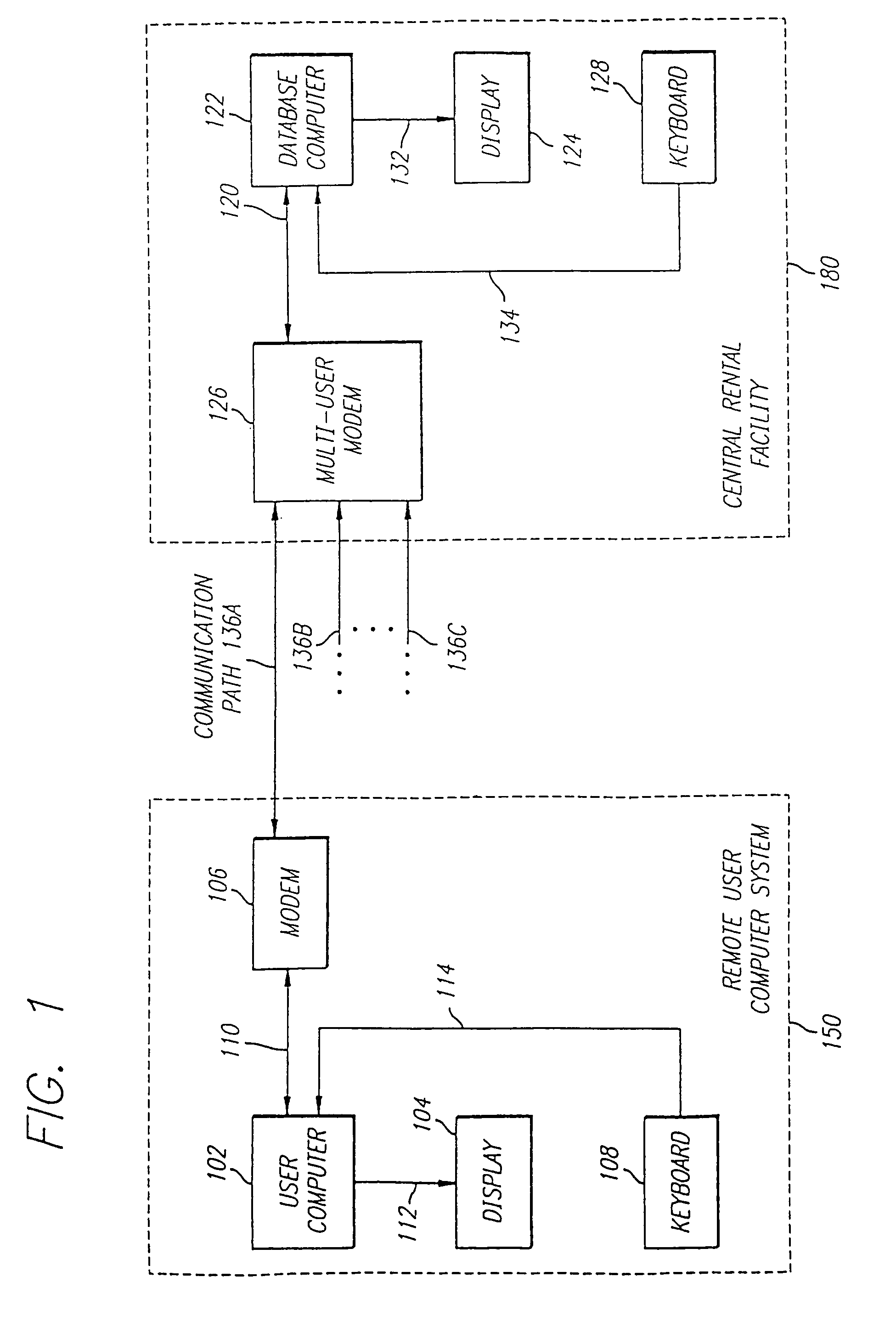
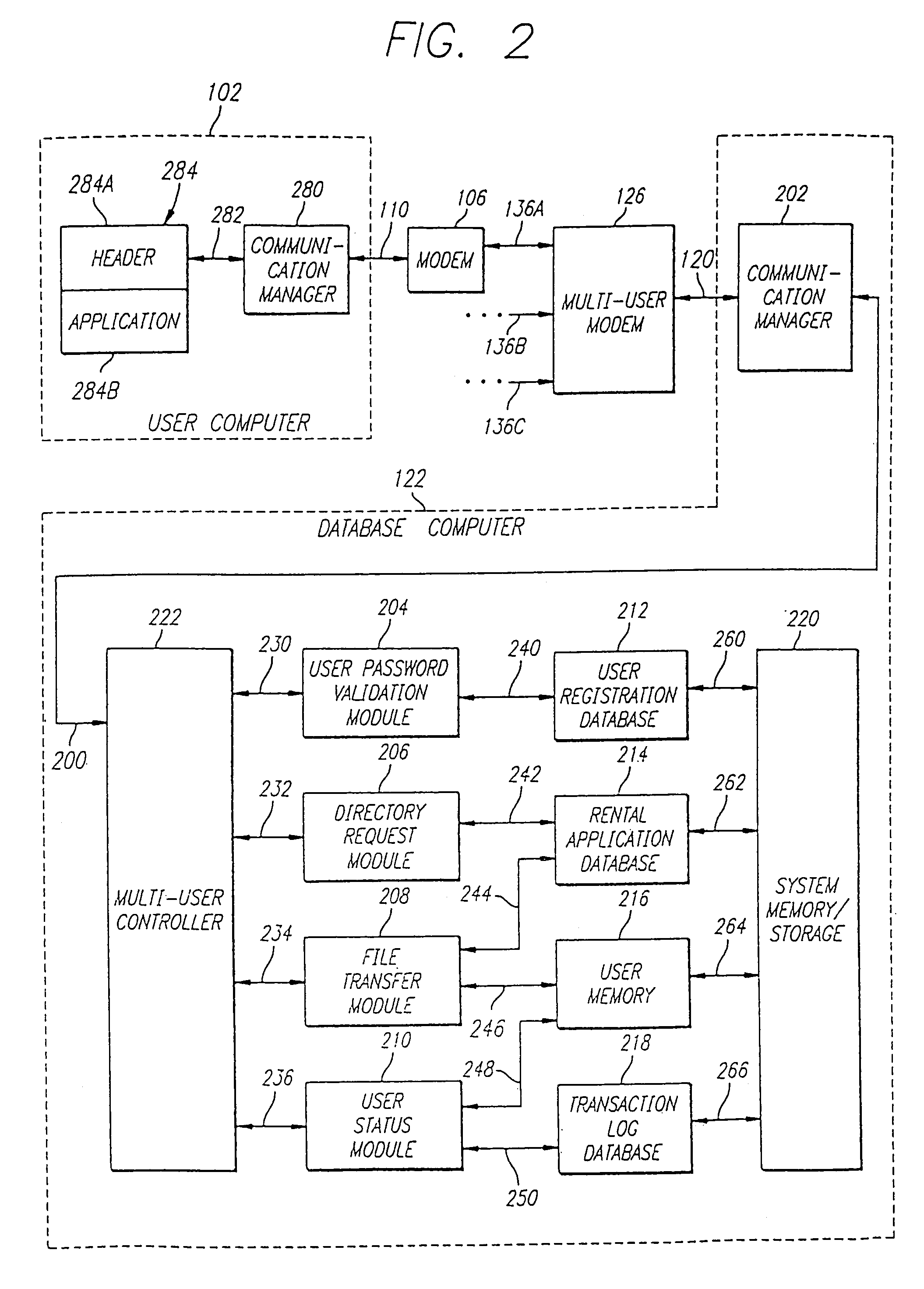
System and method for transferring items having value
InactiveUS7778924B1Ensure protectionComputer security arrangementsFranking apparatusRelevant informationDigital signature
The present invention is directed to a system for providing secured access to a software rental or a postage metering system. The virtual postage meter software of this invention enables a user to print postage indicia on documents, envelopes or labels. To generate valid postage indicia the virtual meter software is executed on a first computer while it is in communication with the remotely located second computer. All communication between the first computer and the second computer utilize data encryption algorithms to preserve the security and integrity of the data transferred. In one embodiment, the second computer is a collection of one or more computers with virtual postage meter enabling software capable of communicating simultaneously to a number of user computers that are concurrently executing the virtual postage meter software. The second computer is connected to one or more US FIPS 140-1 security level 3 or better certified cryptographic devices identified as Postal Security Devices (PSD). The printed postage indicia appears as a two-dimensional barcode that includes digital signature, amount of postage, ZIP code and other relevant information.
Owner:STAMPS COM
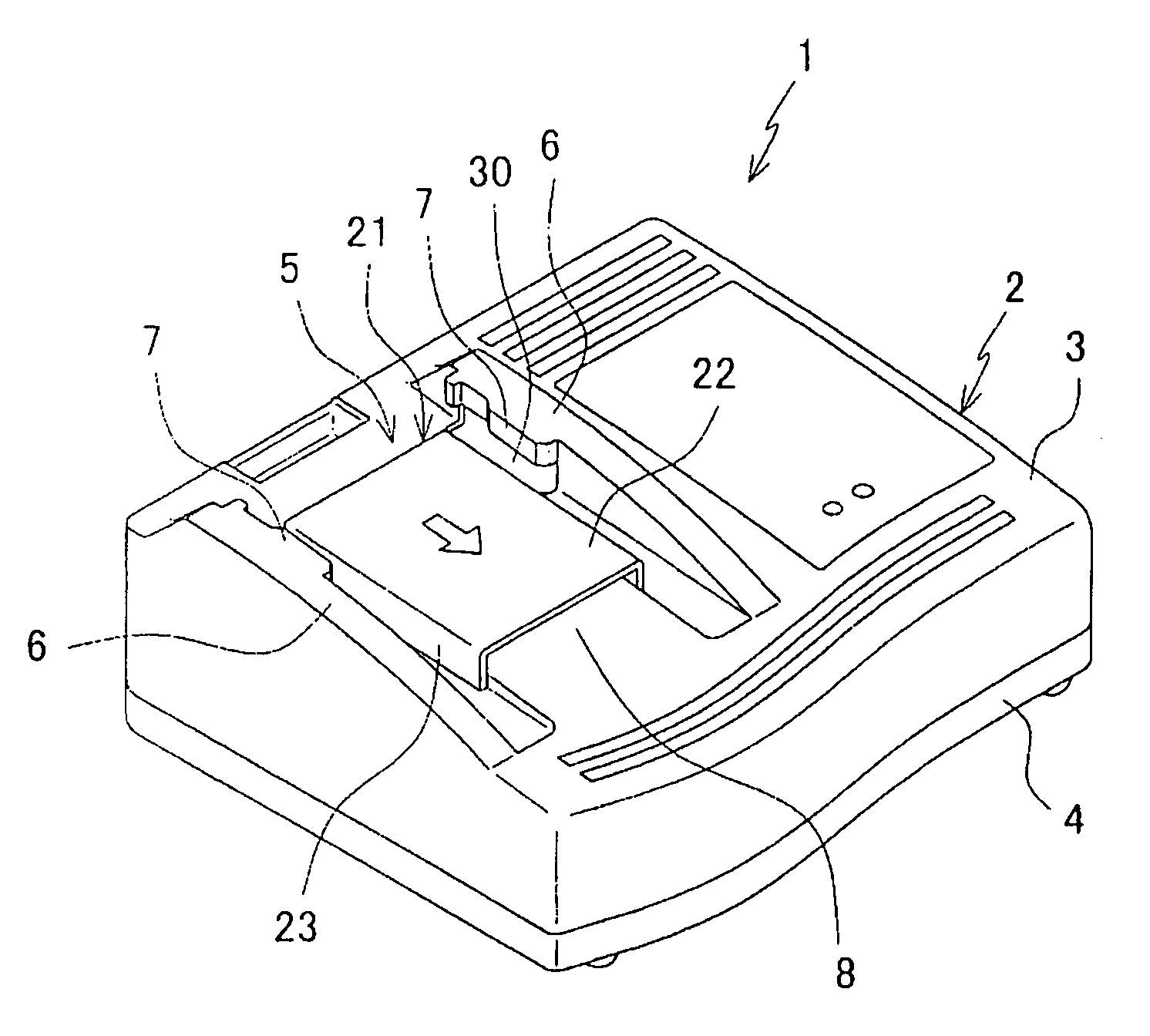
Battery charger with improved terminal protection
ActiveUS7064519B2High dustproofingHigh waterproofingBatteries circuit arrangementsSecondary cells charging/dischargingEngineeringBattery pack
A charger (1) includes a connecting portion (5) provided in an upper case (3) of the charger. The connection portion (5) includes a pair of guide rails (6) to which a battery pack (40) is slidably attached. The charger further includes between the guide rails (6) a terminal block having various terminals (12–14) as well as a slide cover (21) linearly slidable in parallel with the direction in which the battery pack slides on the charger. Under normal operating conditions, the slide cover (21) is biased to a rear position in which the cover (21) is located over and protects a terminal block (11). When the battery pack (40) is set on the charger, the battery pack abuts and slides the slide cover to a forward position in which the terminal block (11) is exposed.
Owner:MAKITA CORP
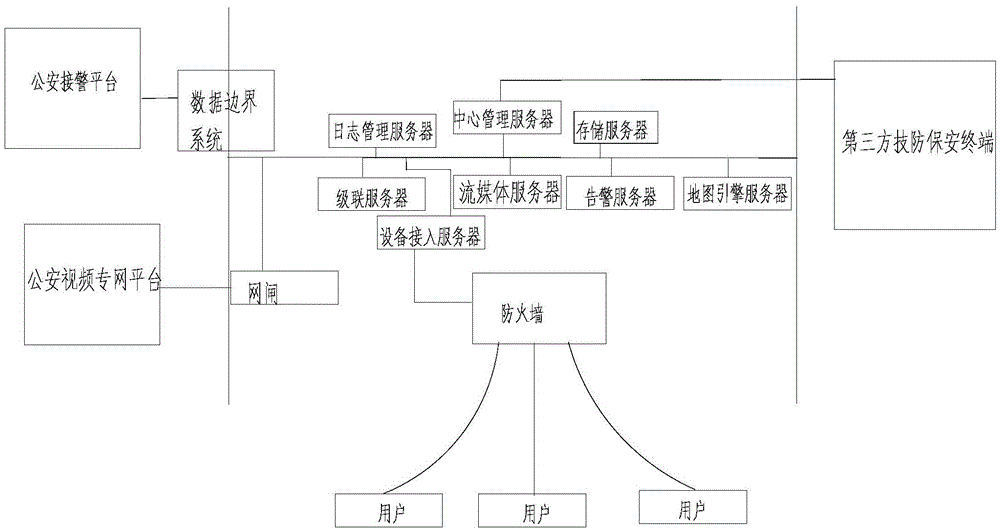
Social security protection video monitoring cloud platform and monitoring method
InactiveCN105491066AFast internetEasy to manageClosed circuit television systemsTransmissionVideo monitoringThird party
The invention belongs to the security prevention technical field and relates to a social security protection video monitoring cloud platform and monitoring method. The monitoring method includes the following steps that: a monitoring cloud platform is established; resources to be monitored are connected into the monitoring cloud platform; the cloud platform is docked with a public security alarm answering platform through a data boundary system; the cloud platform is docked with a public security video private network platform through a gatekeeper; and a third party safety technical prevention security protection terminal is docked with the cloud platform, and user alarm information which is authorized to the third party safety technical prevention security protection terminal is pushed to the third party safety technical prevention security protection terminal, and alarm information confirmed by the third party safety technical prevention security protection terminal is transmitted to the public security alarm answering platform through the cloud platform. With the social security protection video monitoring cloud platform and monitoring method adopted, a traditional video monitoring system which can record monitoring images, operate independently, is used for post-event verification, and cannot realize a networking function and a prevention function can be improved; and the management and intelligent life level of customers can be improved.
Owner:丁美华
Water-based environment-friendly finishing paint and preparation method thereof
InactiveCN101712833AGood anti-corrosion decoration effectHigh hardnessEpoxy resin coatingsWater basedEpoxy
The invention discloses a water-based environment-friendly finishing paint, which is prepared from the following compositions in part by weight: 20 to 70 parts of water borne acrylic resin solution of which the solid content is 30 to 80 percent and / or 20 to 70 parts of water borne epoxy resin solution of which the solid content is 30 to 80 percent, 4 to 10 parts of water borne amino resin solution of which the solid content is 60 to 98 percent; 1 to 5 parts of organic amine, 0.2 to 2 parts of wetting and leveling agent, 0.2 to 2 parts of thickener, 0.1 to 0.8 part of defoaming agent, 1 to 5 parts of adhesion promoter, 0.2 to 5 parts of catalyst, 10 to 30 parts of alcohol diluting solvent and / or 1 to 5 parts of nontoxic ether diluting solvent, and 20 to 50 parts of deionized water, wherein the catalyst is one or more of ammonias, alcohols and benzenesulfonic acids. The water-based environment-friendly finishing paint has the advantages of wide applicable range, high hardness, good flexibility, strong adhesion, good scratchproof performance, and environmental protection. Simultaneously, the invention also discloses a method for preparing the water-based environment-friendly finishing paint.
Owner:重庆亢石新材料科技有限公司
Pressure compensation device for a housing of an electrochemical device
InactiveUS20130032219A1Reliable pressure compensationSimple structureLighting and heating apparatusEqualizing valvesInternal pressureEngineering
A pressure compensation device for compensating an internal pressure in a housing of an electrochemical device is provided, including at least one gas through-opening and at least one membrane element with a gas-permeable membrane, which is deformable depending on a change in the internal pressure and by which the gas through-opening is blocked, and a protective degassing element, which is configured and arranged in such a way that when a critical deformation of the membrane is reached, it damages the membrane in such a way that the membrane at least partially opens the gas through-opening for protective degassing of the housing. The pressure compensation device allows both reliable pressure compensation between the interior of the housing and the exterior of the housing of an electrochemical device during normal operation of the electrochemical device and also ensures reliable bursting protection in the event of excess internal pressure in the housing.
Owner:ELRINGKLINGER AG
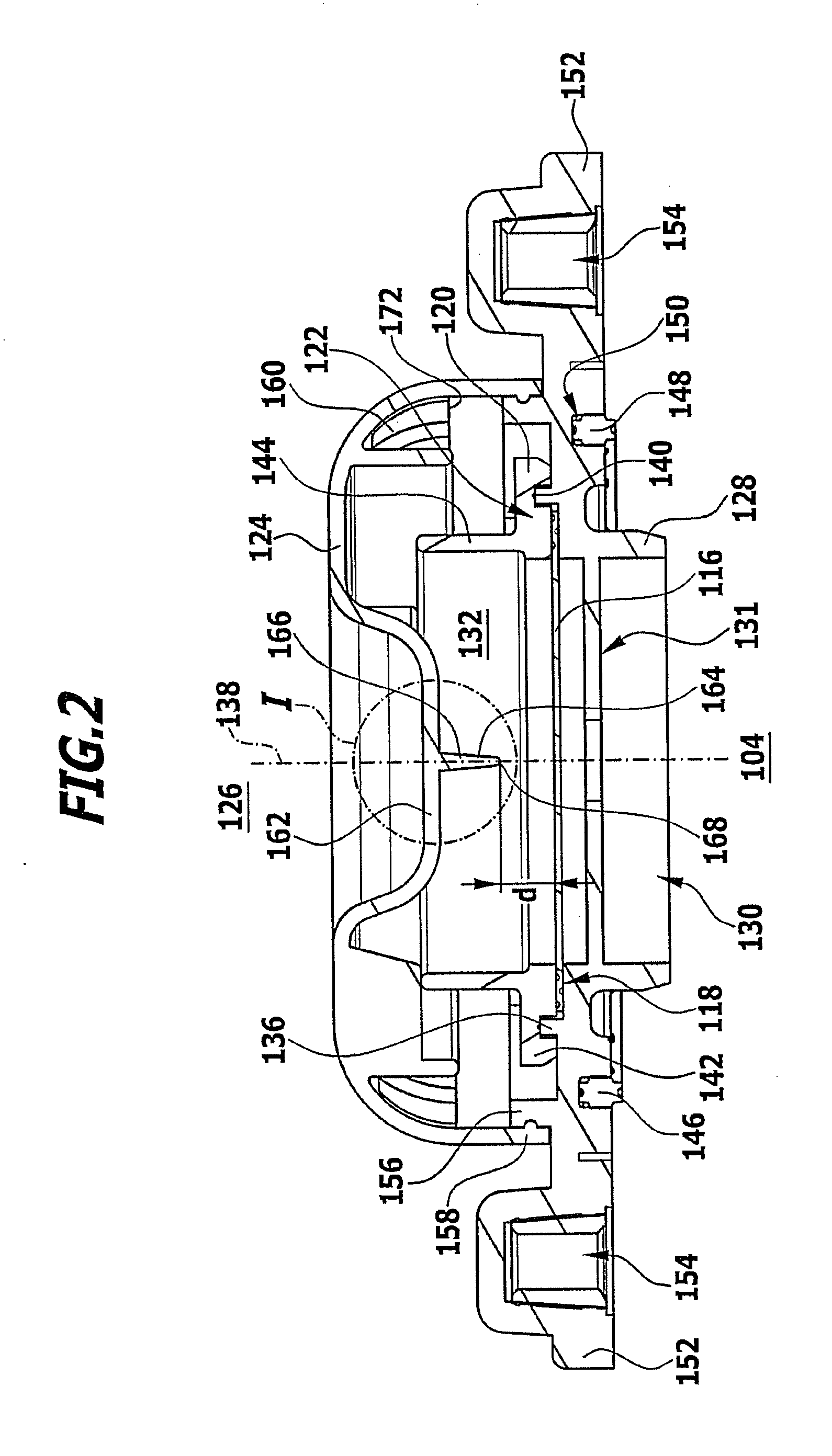
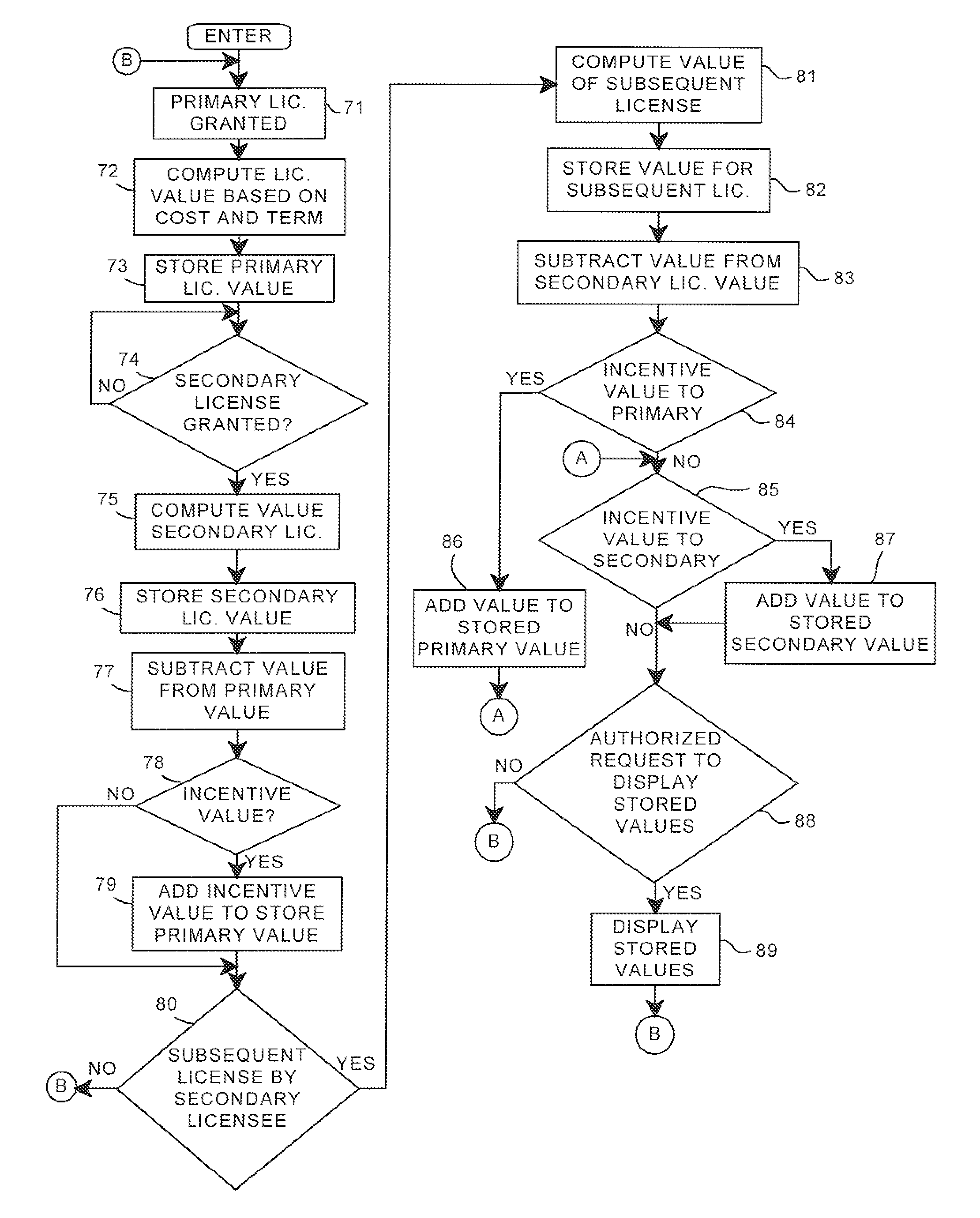
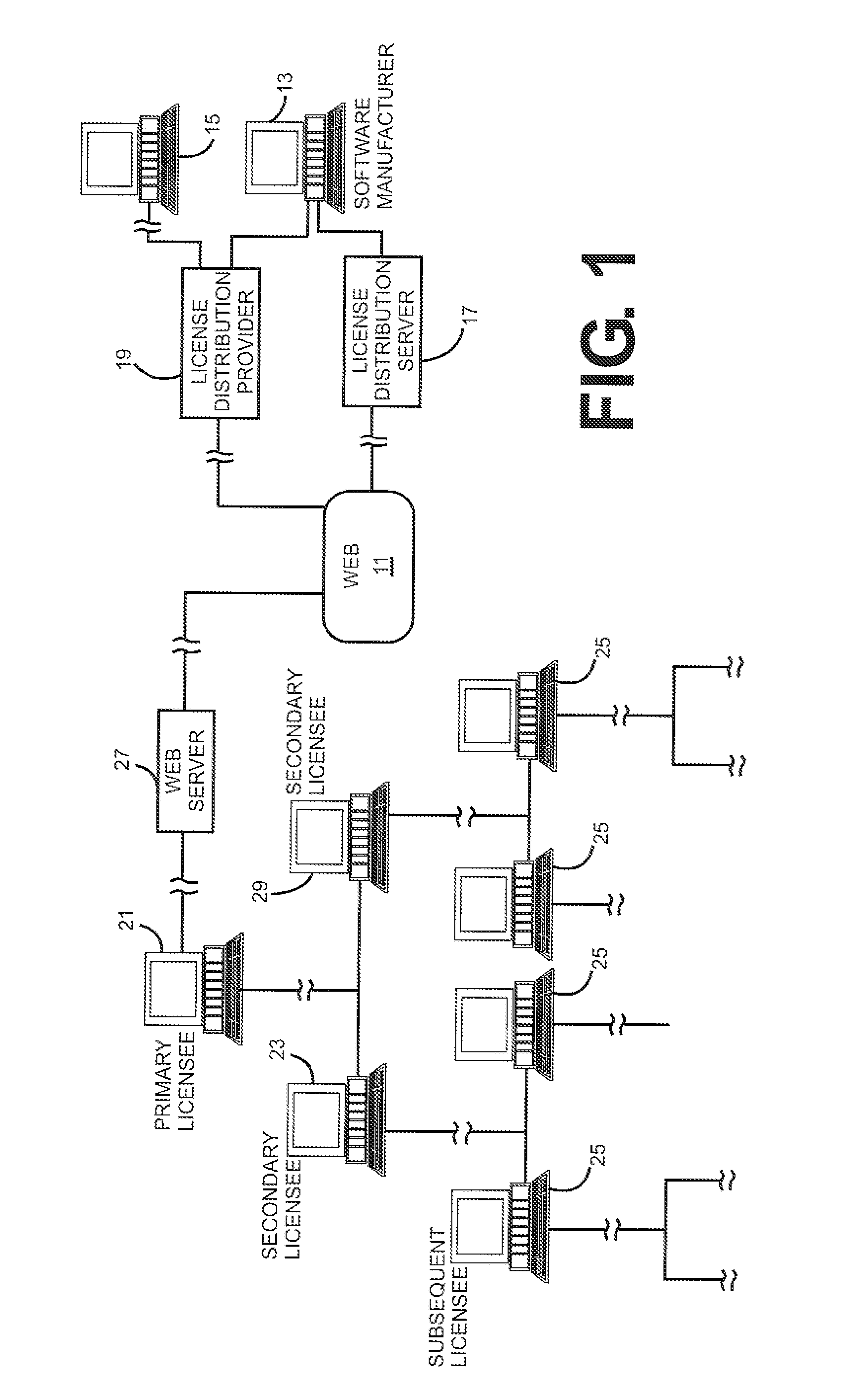
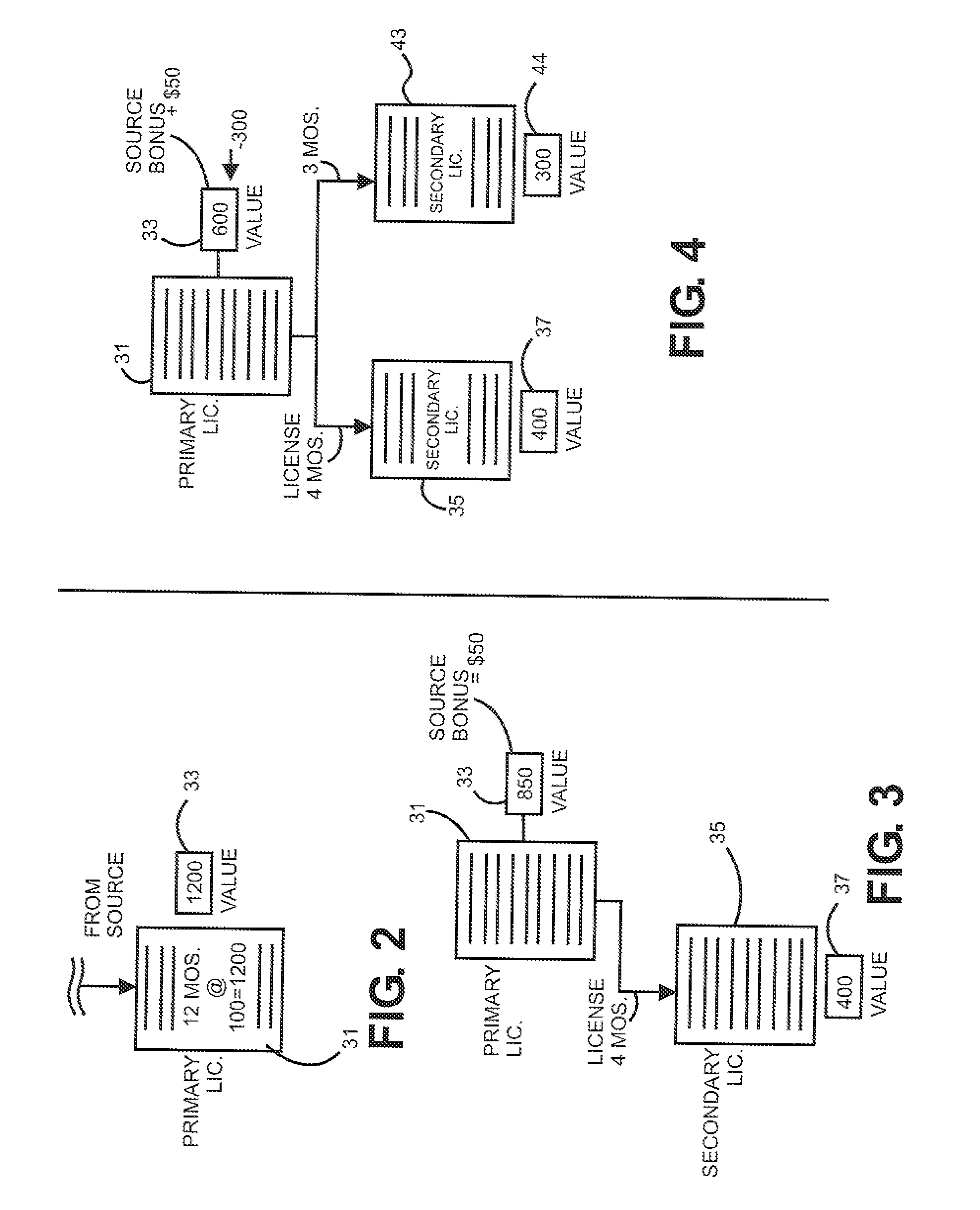
Tracking, distribution and management of apportionable licenses granted for distributed software products
InactiveUS20080162360A1Conveniently implementedMaximize flexibilityCryptography processingUser identity/authority verificationSoftware engineeringLicense
A computer controlled implementation for distributing portions of a license to use software entities, granted by a licensor to a primary licensee, to subsequent secondary licensees comprising determining a dividable value for the primary license to use a software entity, enabling the primary licensee to grant a portion of the dividable value of the primary license to use the software entity to a secondary licensee, enabling the licensor, the licensee and the secondary licensee to add value to said values of the licenses and tracking said value of the license and of the portion granted to said secondary licensee.
Owner:KYNDRYL INC
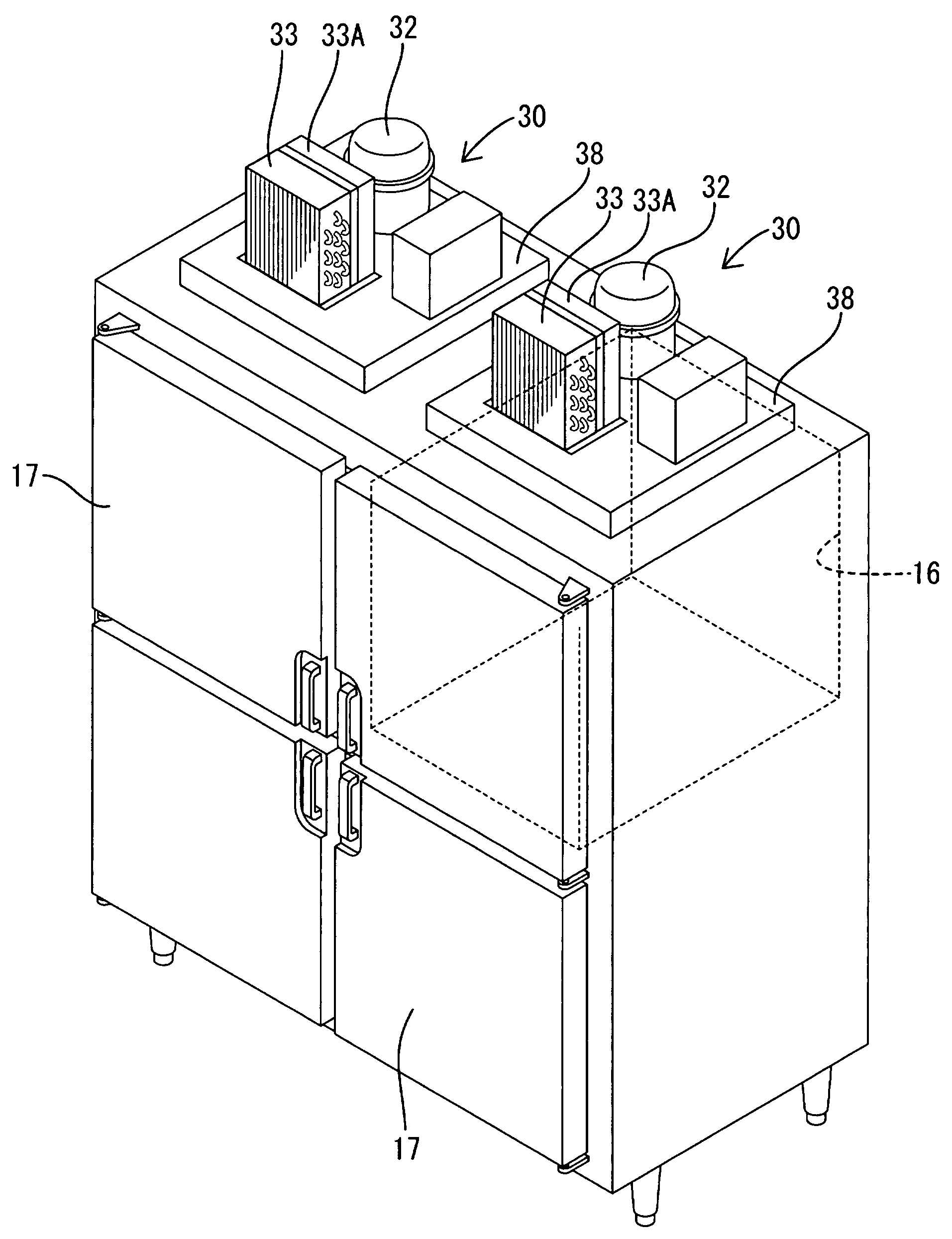
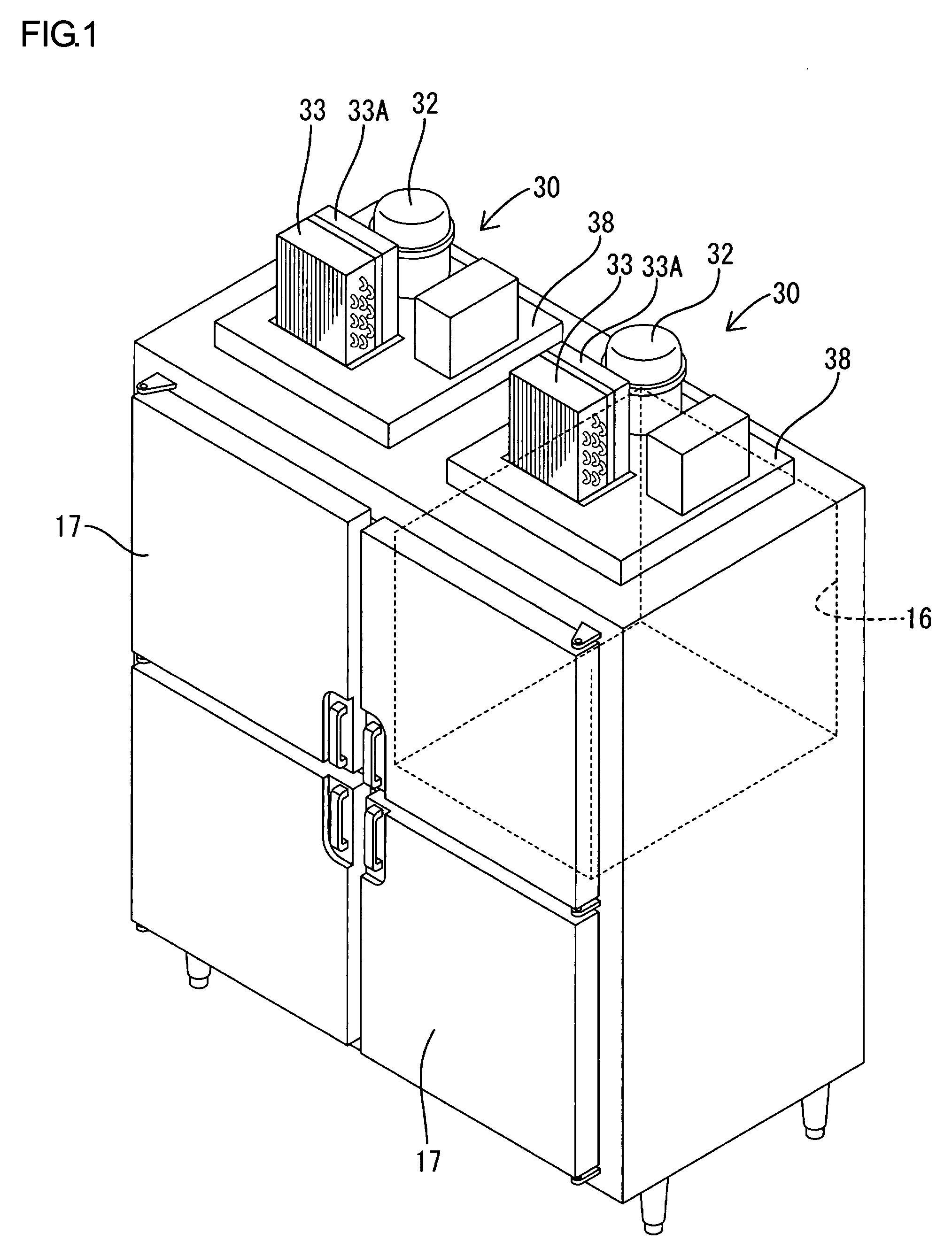
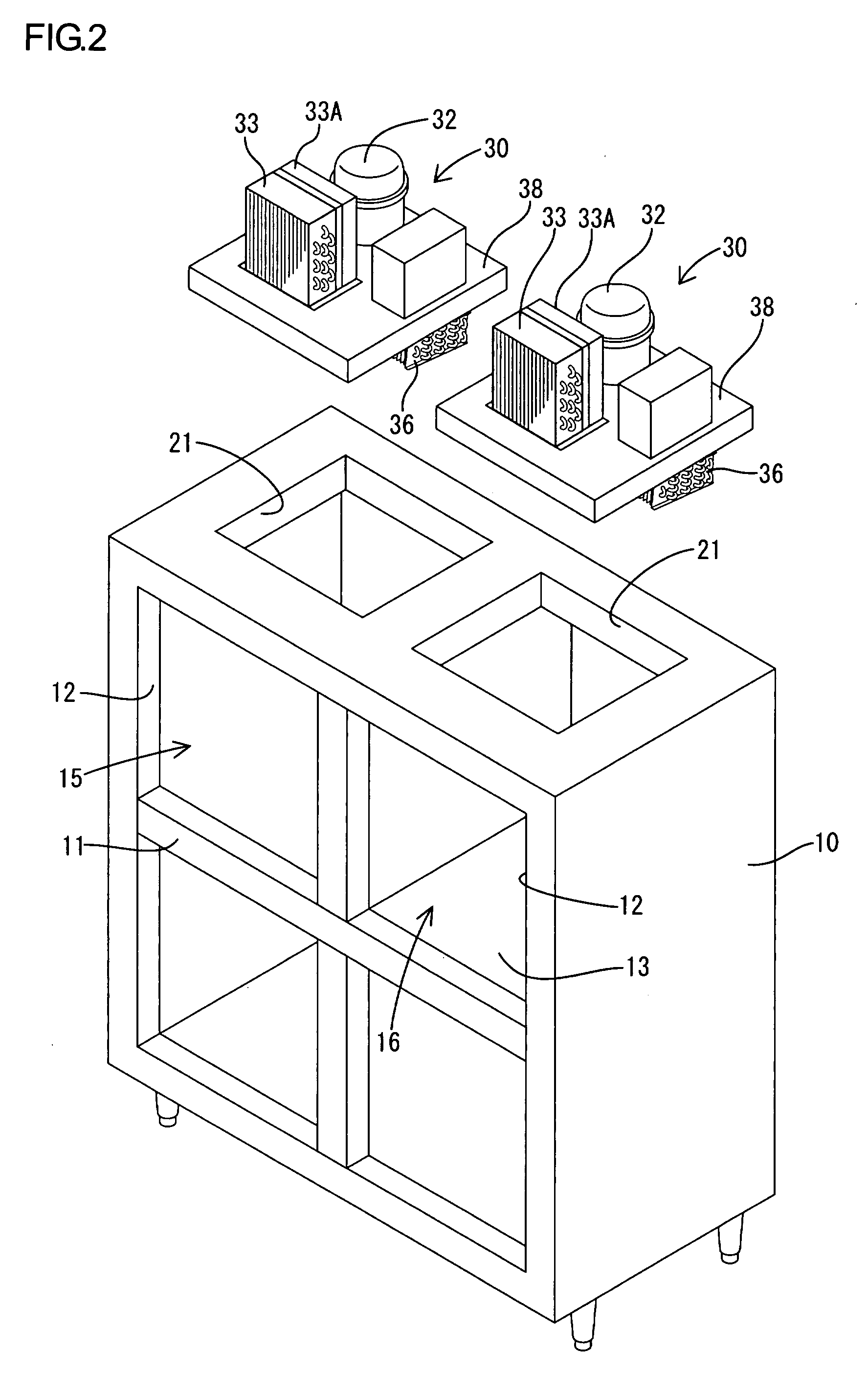
Refrigeration unit
InactiveUS20090001866A1Performance of compressor is loweredAvoid temperature riseCompression machines with non-reversible cycleFurniture partsHigh pressureRefrigerant
In a refrigeration unit including a variable performance compressor driven by an inverter motor, a sensor is configured to detect a physical amount corresponding to a refrigerant pressure on the high-pressure side of a refrigerant circuit. A measured value of the physical amount is compared with a first reference value corresponding to a first predetermined pressure of the refrigerant and a second reference value corresponding to a second predetermined pressure lower than the first predetermined pressure. A protective operation can start if the comparison result indicates that an actual refrigerant pressure is higher than the first predetermined pressure. The performance of the compressor can be gradually lowered if the comparison result indicates that an actual refrigerant pressure is between the first predetermined pressure and the second predetermined pressure.
Owner:HOSHIZAKI ELECTRIC CO LTD
Microporous polymer membrane modified by aqueous polymer, manufacturing method and use thereof
ActiveUS20110229768A1Low costImprove performanceRadiation applicationsDouble layer capacitorsHydrophilic monomerPolyolefin
Microporous polyolefin membrane modified by aqueous polymer of the invention is obtained by the following steps: copolymerizing 100 parts of a water-soluble polymer, 30-500 parts of a hydrophobic monomer, 0-200 parts of a hydrophilic monomer and 1-5 parts of an initiator into polymeric colloid emulsion; adding 0-100% of an inorganic filler and 20-100% of a plasticizer based on 100% solid content of the polymeric colloid emulsion to obtain slurry; and coating the slurry on one or two surfaces of the surface modified microporous polyolefin membrane and then drying. The microporous polyolefin membrane modified by aqueous polymer has thermal shutdown effect and little thermal shrinkage, and improves the main problem of shrinkage of the microporous polyolefin membrane at high temperature.
Owner:SICHUAN INDIGO TECH CO LTD
Aqueous environment-friendly packaging steel drum paint and preparation method thereof
InactiveCN101735703AGood anti-corrosion decoration effectHigh hardnessAnti-corrosive paintsEpoxy resin coatingsEpoxyAcrylic resin
The invention relates to an aqueous environment-friendly packaging steel drum paint, which is prepared by mixing the following compositions in part by weight: 20 to 70 parts of aqueous solution of acrylic resin with a solid content of 30 to 80 percent and / or aqueous solution of epoxy resin with the solid content of 30 to 80 percent, 4 to 10 parts of aqueous solution of amino resin with the solid content of 60 to 98 percent, 1 to 5 parts of organic amine, 1 to 50 parts of filling materials with the granularity of more than 2,000 meshes, 0.5 to 10 parts of color paste, 0.2 to 2 parts of wetting levelling agent, 0.2 to 2 parts of thickening agent, 0.1 to 0.8 part of antifoaming agent, 1 to 5 parts of adhesive force accelerant, 0.2 to 5 parts of catalyst, 0 to 30 parts of alcohol diluting solvent and / or 0 to 5 parts of non-toxic ether diluting solvent, and 20 to 50 parts of deionized water. The aqueous environment-friendly packaging steel drum paint has the advantages of wide application range, high rigidity, good flexibility, strong adhesive force and good anti-scraping and anti-collision properties and environmental protection; and meanwhile, the invention discloses a preparation method for the aqueous environment-friendly packaging steel drum paint.
Owner:重庆亢石新材料科技有限公司
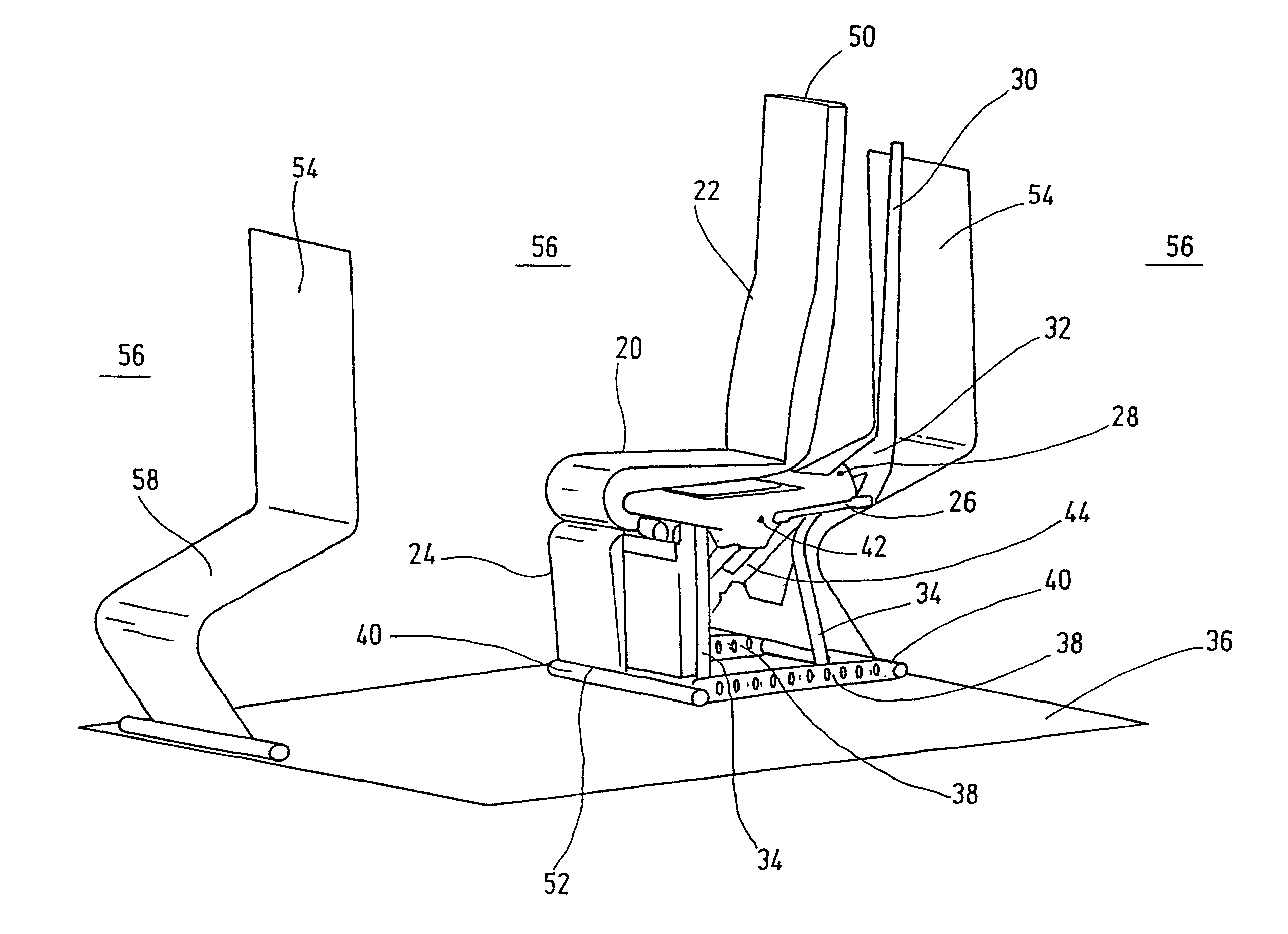
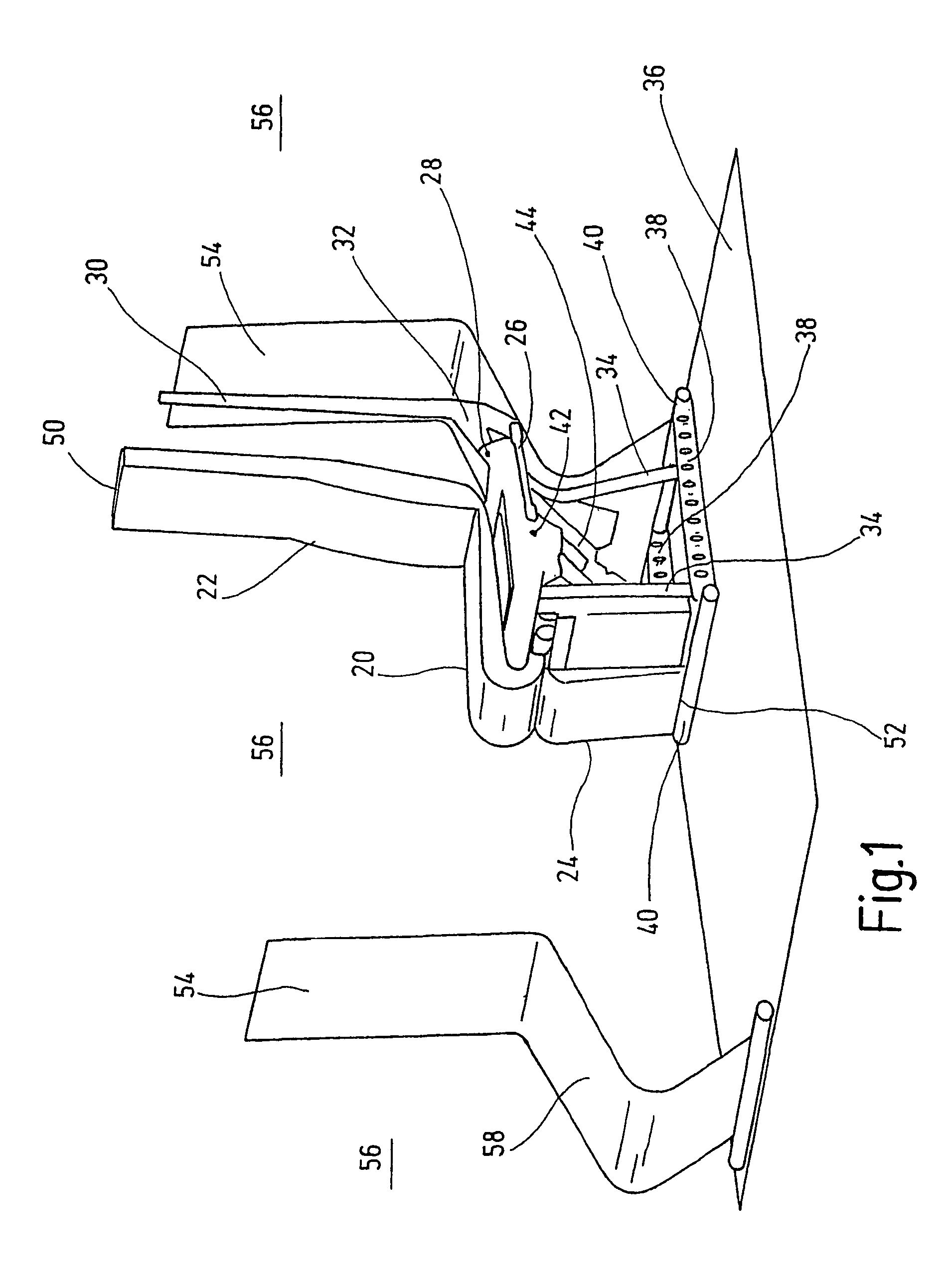
Vehicle seat with seating components adjustable within a spatial constraint
InactiveUS7427102B2Avoids damaging collisionImprove ergonomicsVehicle seatsPedestrian/occupant safety arrangementDevice MonitorEngineering
A vehicle seat has seating components, such as a seat piece (20), a backrest (22) and a leg-rest (24), which are adjustable as to their positions, particularly in their relative inclination, by at least one operating device (26, 44). A monitoring device monitors all the boundary geometries (50, 52) of the moving seat components which may cause collisions and which have given spatial constraints (54). The monitoring device controls the operating devices (26, 44) at all points to guarantee a collision-free movement of all seat components within the spatial constraints. The vehicle seat considered as a total system can undergo adjustment processes without a damaging collision occurring.
Owner:RECARO AIRCRAFT SEATING GMBH & CO KG
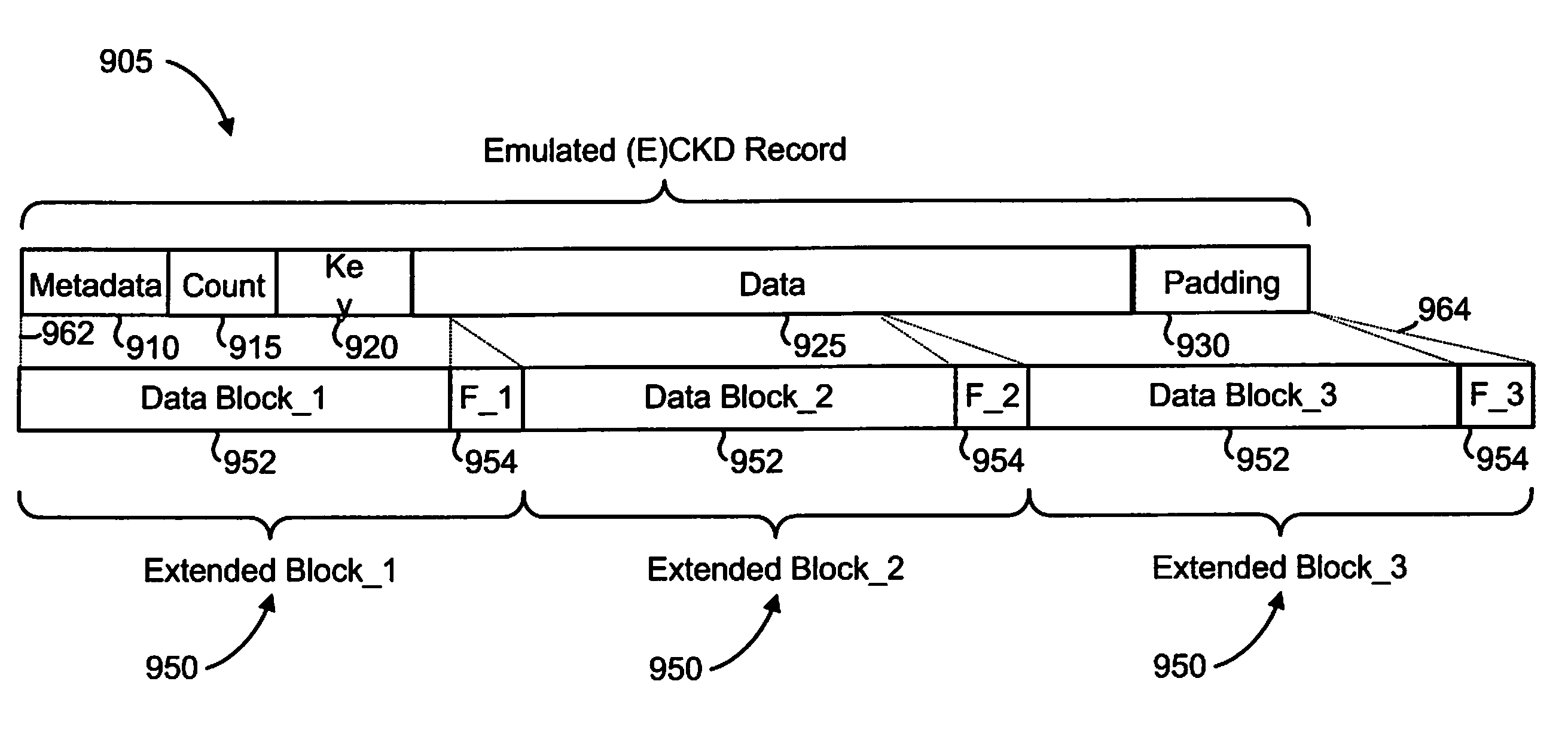
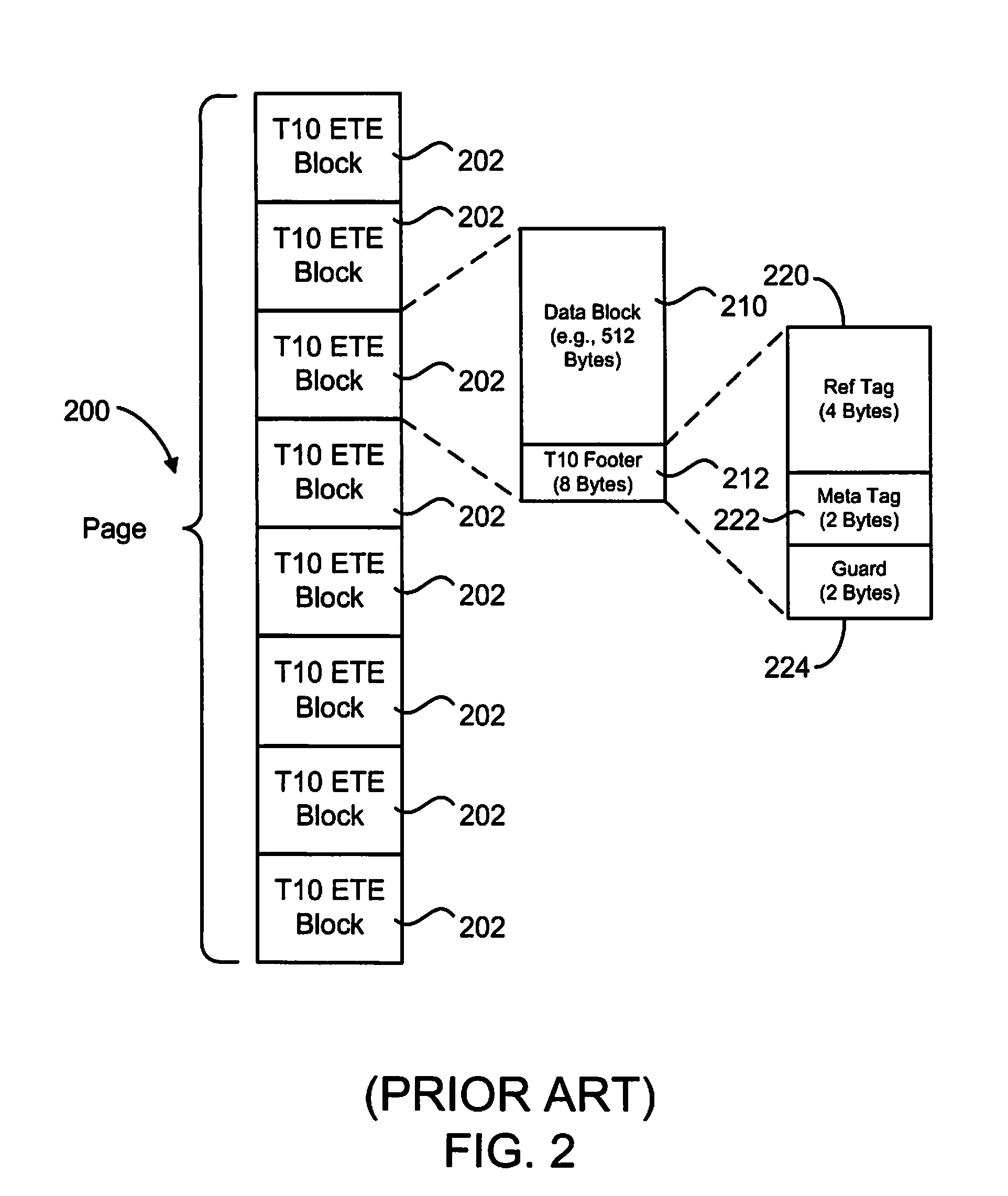
Data Protection Method for Variable Length Records by Utilizing High Performance Block Storage Metadata
ActiveUS20090259924A1Ensure protectionVerify integrityCode conversionRecord information storageVariable-length codeChecksum
An enhanced mechanism for providing data protection for variable length records utilizes high performance block storage metadata. In an embodiment, an emulated record that emulates a variable length record, such as a Count-Key-Data (CKD) record or an Extended-Count-Key-Data (ECKD) record, is generated by a Host Bus Adapter (HBA) of a mainframe system. The emulated record comprises a sequence of extended fixed-length blocks, each of which includes a data block and a footer. A confluence of the footers defines a high performance block storage metadata unit associated with the emulated record and includes a checksum that covers all data blocks and all footers of the entire emulated record. In one embodiment, the checksum is checked during transit of the emulated record between a HBA and a storage subsystem (e.g., by the HBA when the emulated record is received from the storage subsystem, and / or by a switch in the data transfer path), during a hardening step when writing the emulated record to a disk, and / or during a verification step when reading the emulated record from the disk.
Owner:IBM CORP
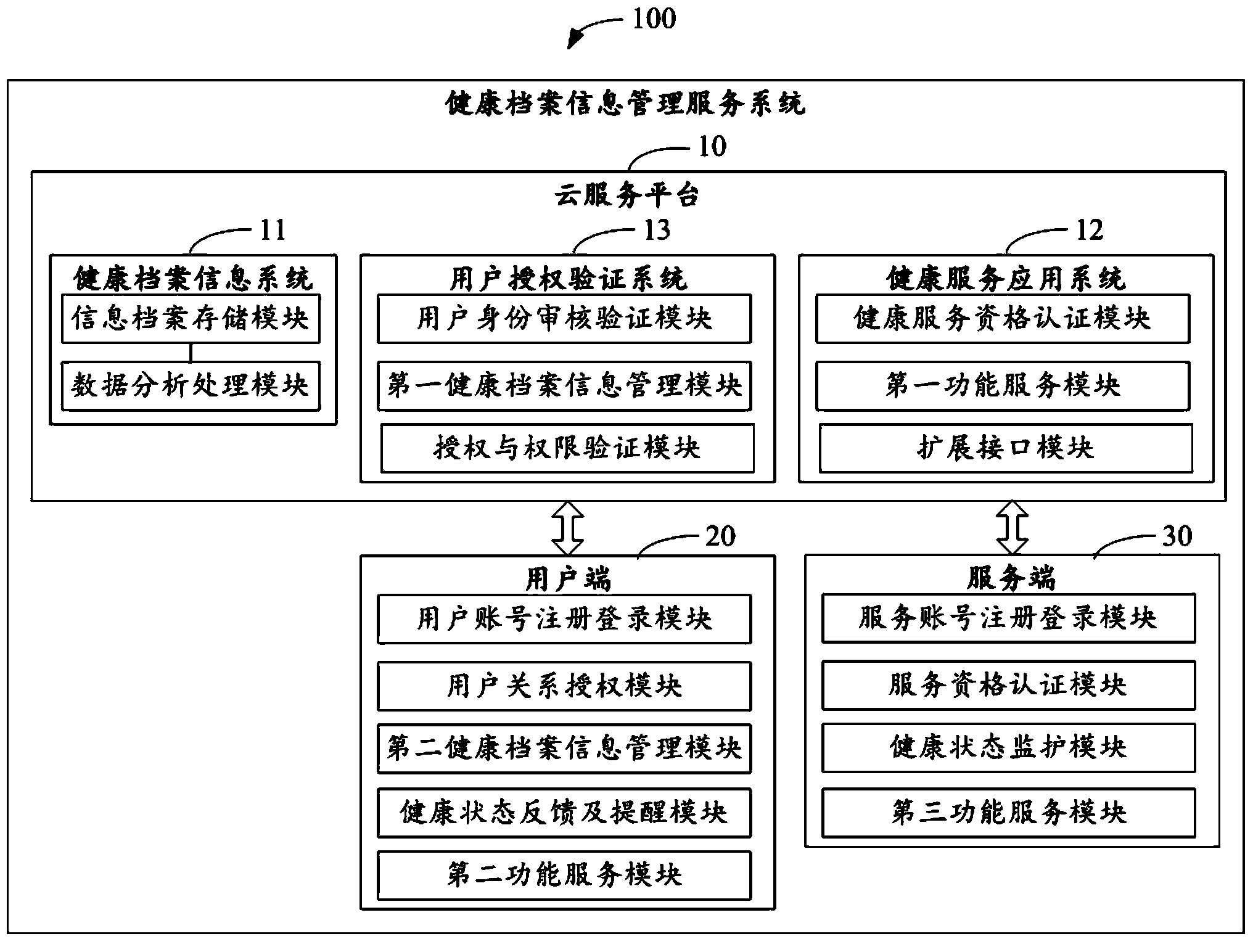
Health archive information management service system and method
InactiveCN103886529AEnsure safetyEnsure protectionData processing applicationsPatient-specific dataData analysisService system
The invention discloses a health archive information management service system and a method, which are applied to a health archive information management service center. The health archive information management service method comprises that: a cloud service platform stores health archive information, generates or updates the health archive under a user account according to the stored health archive information, performs data analysis processing on the health archive information to obtain health analysis result and determines matching service items from the service items provided by a service terminal according to the health result; and the cloud service platform pushes the matching service items to the corresponding client according to the service request transmitted from the client and realizes the function services corresponding to the service items chosen by the client. The invention discloses a health archive information management service system.
Owner:SHENZHEN AIKANG INFORMATION TECH
System and Method for Providing Different Levels of Key Security for Controlling Access to Secured Items
InactiveUS20110258438A1Efficient accessEnsure protectionKey distribution for secure communicationUnauthorized memory use protectionEase of AccessEncryption
With files secured by encryption techniques, keys are often required to gain access to the secured files. Techniques for providing and using multiple levels of keystores for securing the keys are disclosed. The keystores store keys that are needed by users in order to access secured files. The different levels of keystores offer compromises between security and flexibility / ease of use.
Owner:INTELLECTUAL VENTURES I LLC
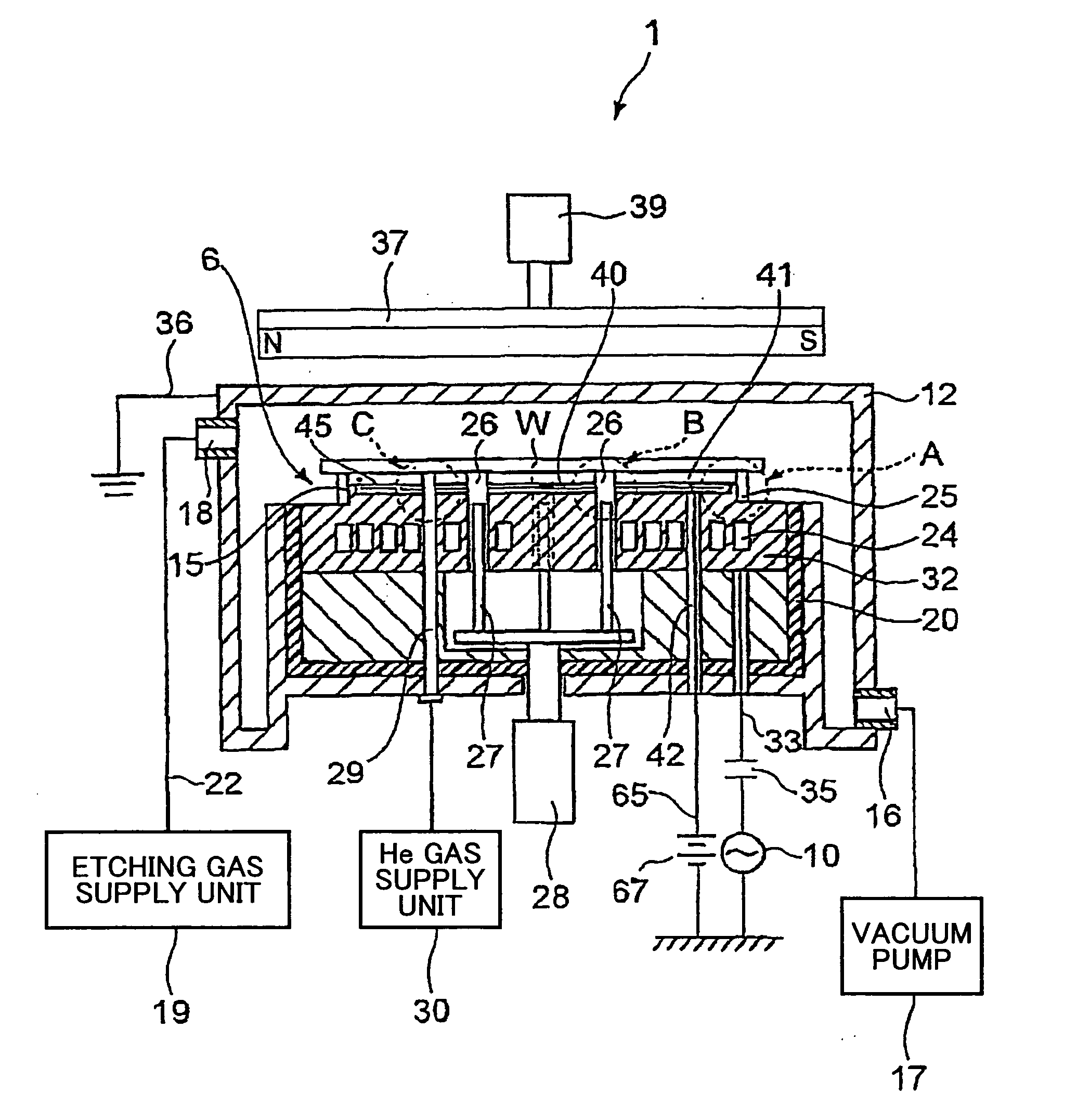
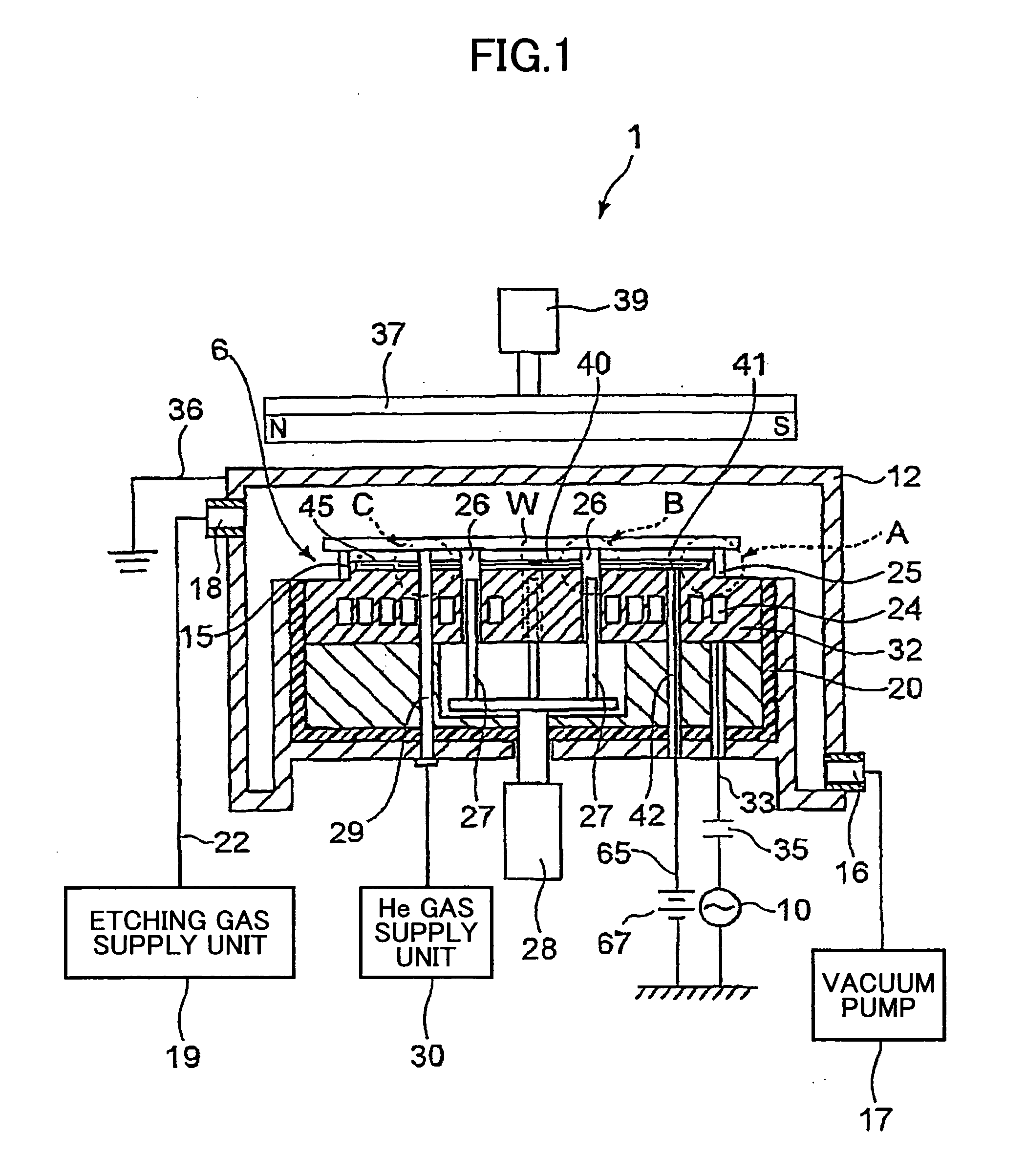
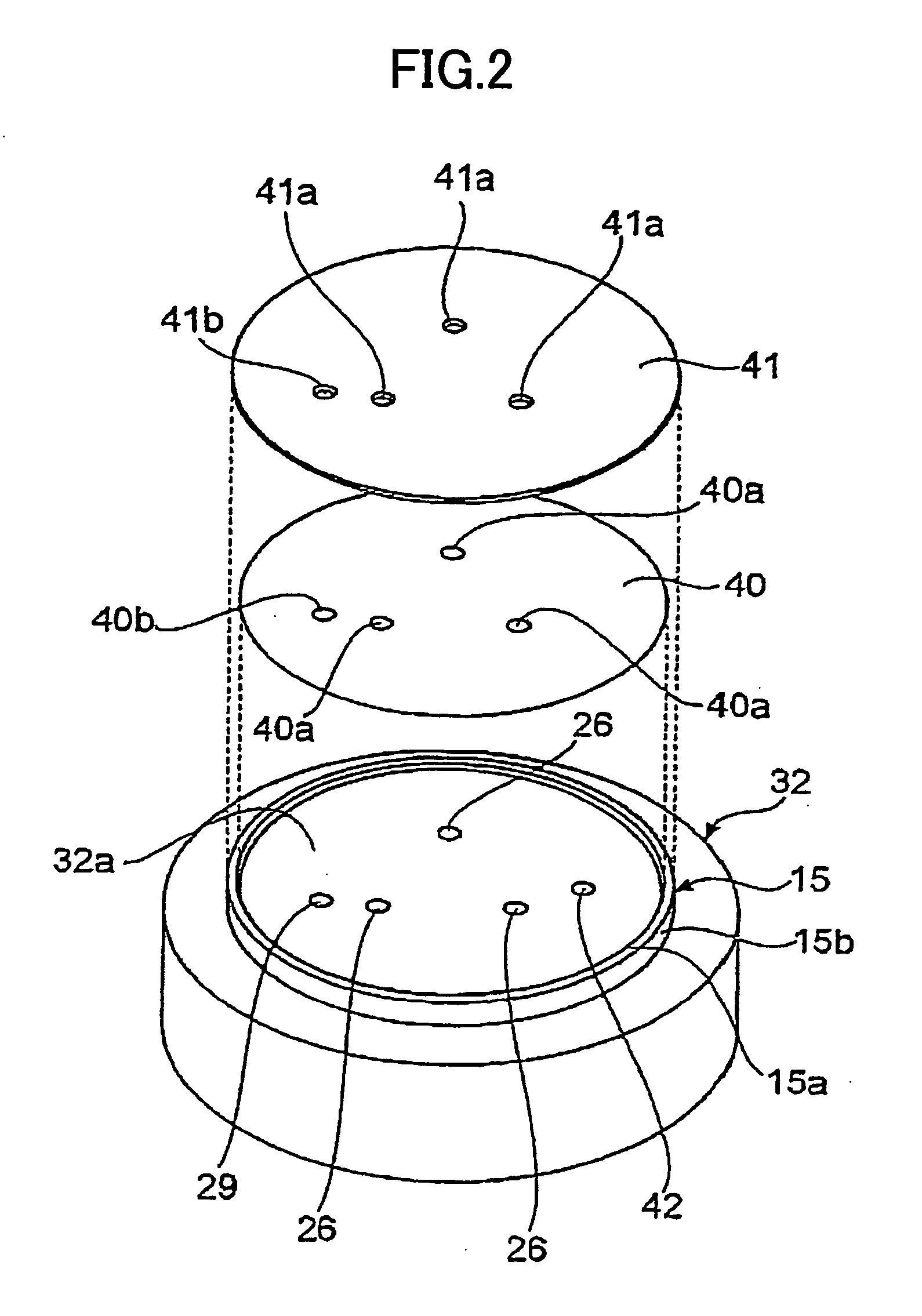
Substrate holding mechanism using electrostaic chuck and method of manufacturing the same
InactiveUS20060175772A1Avoid layeringExtended service lifeSleeve/socket jointsLamination ancillary operationsEngineeringMechanical engineering
A substrate holding apparatus includes a stage configured to support a substrate to be processed, the stage including a surface, and a continuous convex portion surrounding a predetermined region of the surface which convex portion includes a periphery surface and an upper surface that is positioned higher than the surface of the stage; an electrostatic attraction sheet configured to attract a substrate with electrostatic force, the electrostatic attraction sheet being arranged on the surface of the stage within the region surrounded by the convex portion; a first protection member configured to protect the electrostatic attraction sheet, the first protection member being arranged on the electrostatic attraction sheet and including a side surface and a portion that is arranged to face opposite the upper surface of the convex portion; an adhesive layer that is arranged at least between the electrostatic attraction sheet and the first protection member and is configured to bond the electrostatic attraction sheet and the first protection member; and a second protection member that covers at least the outer peripheral surface of the convex portion and the side surface of the first protection member to conceal at least the adhesive layer.
Owner:TOKYO ELECTRON LTD
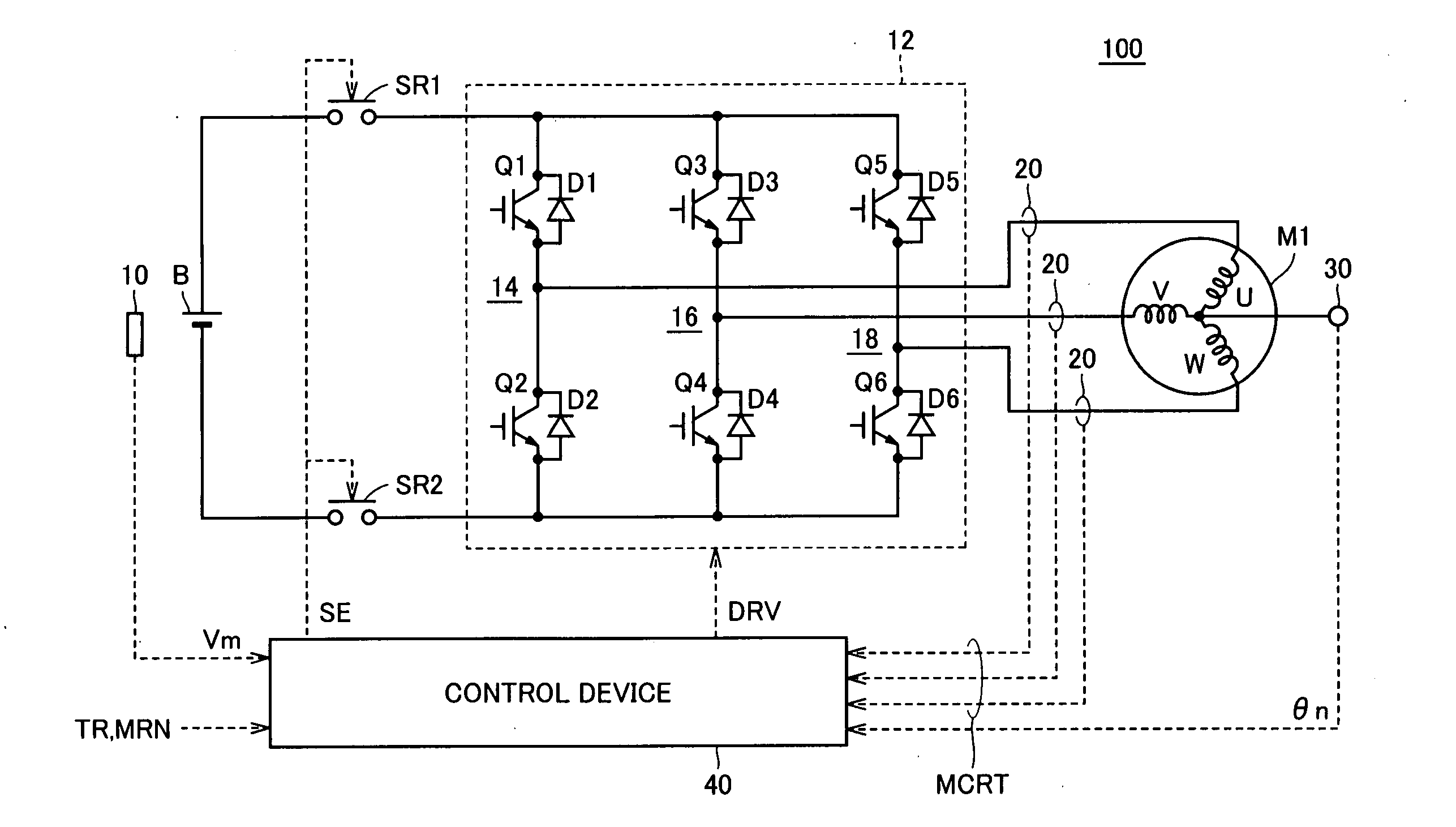
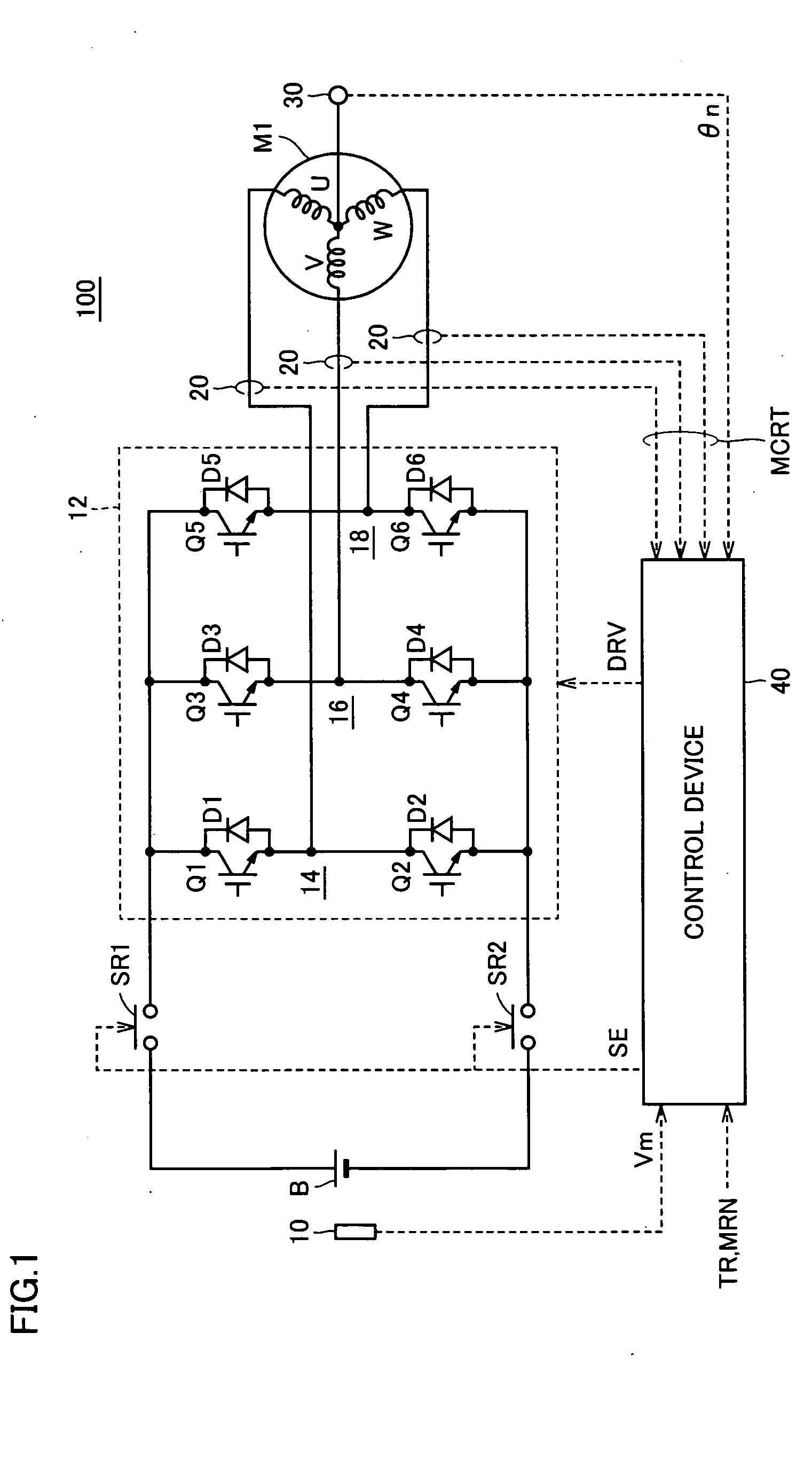
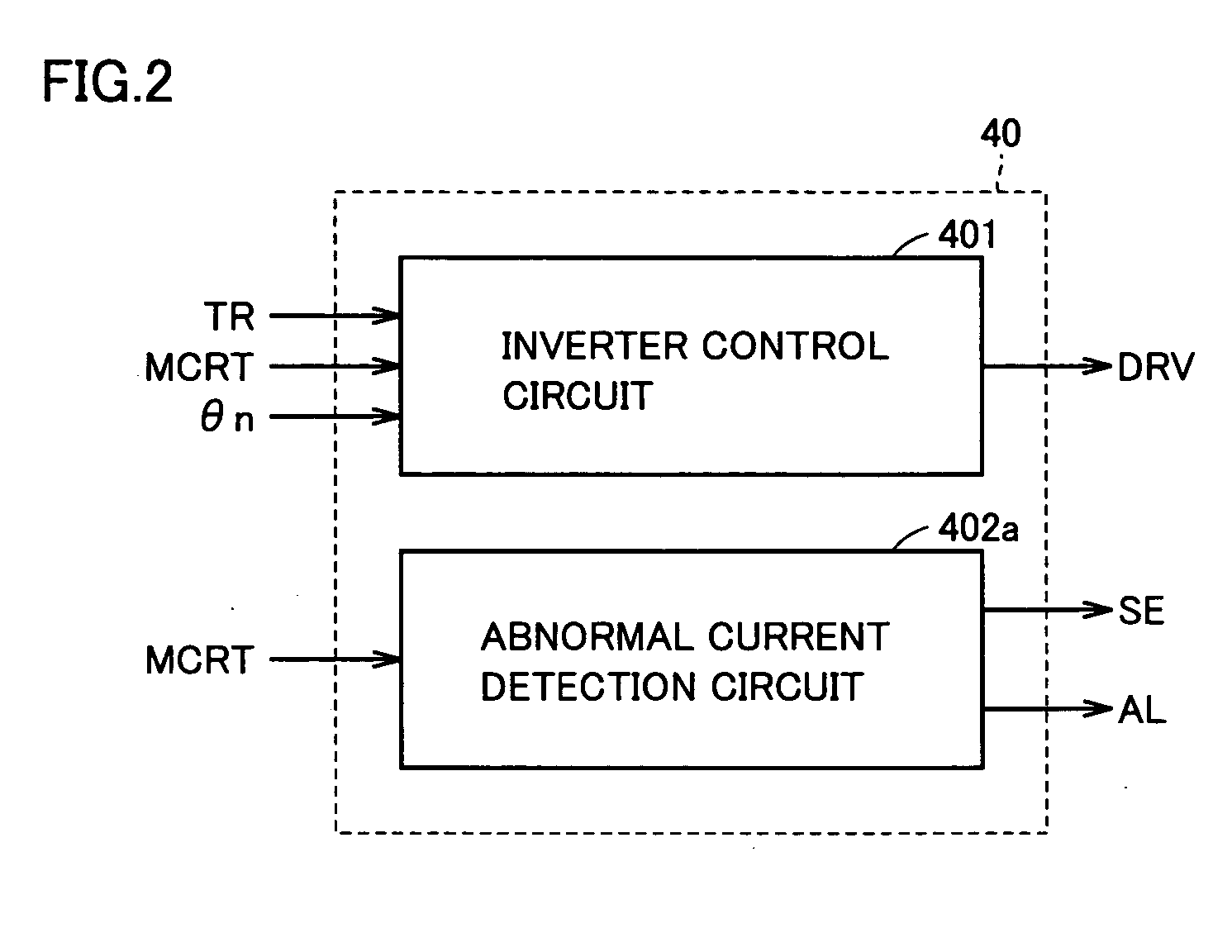
Power supply apparatus capable of detecting abnormality of current flowing through drive circuit
ActiveUS20060007615A1Improve accuracyEnsure protectionHybrid vehiclesAC motor controlEngineeringElectrical current
A current detection unit starts sampling of a motor current at the timing when the motor current has exceeded a threshold value, and holds a maximum motor current value for each prescribed operation cycle. An abnormality determination unit determines whether the maximum motor current value is greater than the threshold value, and counts the number of times that the maximum motor current value continuously exceeds the threshold value. When the count value has reached at least 3, the abnormality determination unit generates and outputs a detection signal indicating abnormality in the motor current to a relay drive unit and a notification unit. The relay drive unit in receipt of the detection signal generates a signal to turn off the system relays. The notification unit generates and outputs a signal AL to display means outside the power supply apparatus.
Owner:DENSO CORP
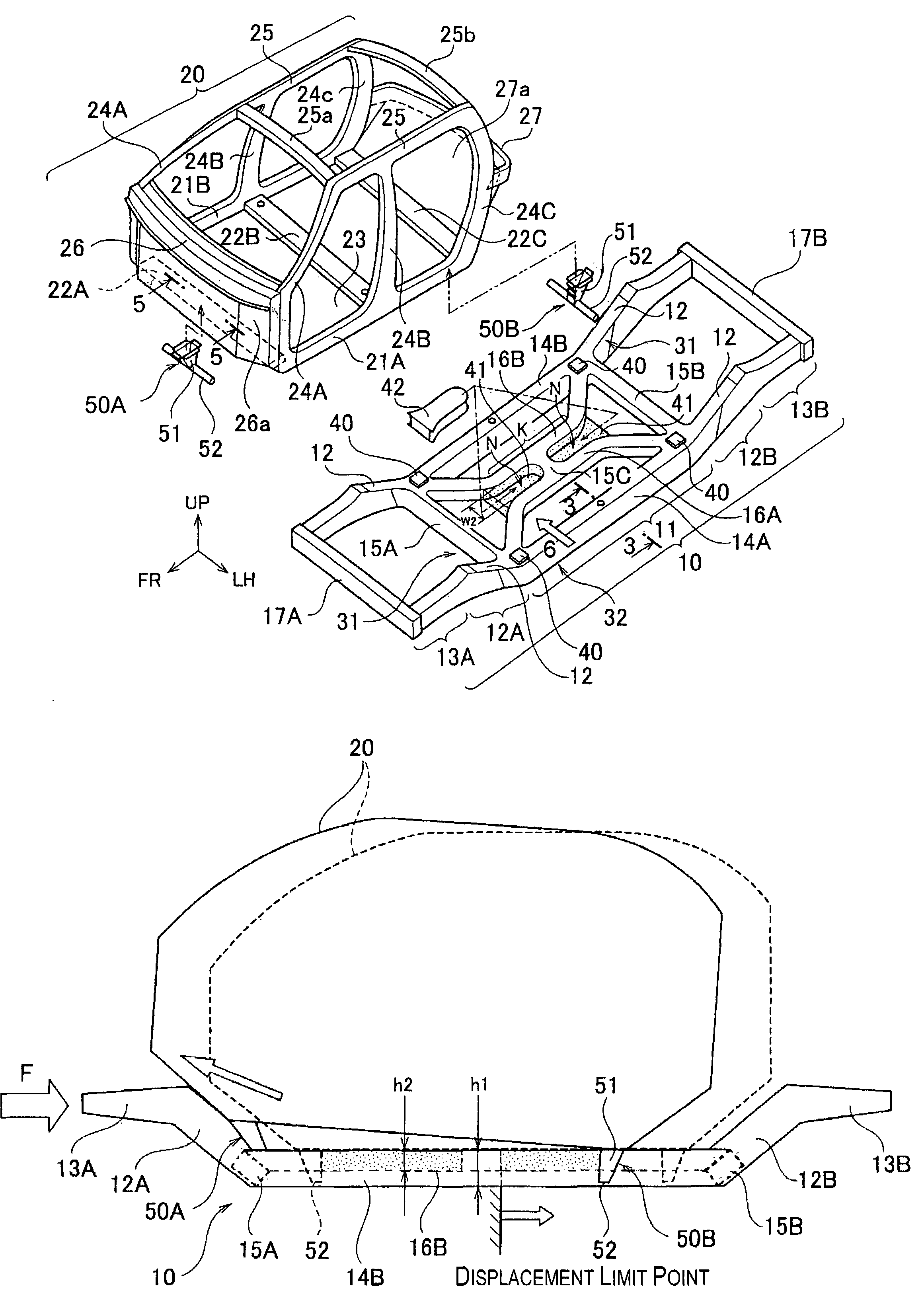
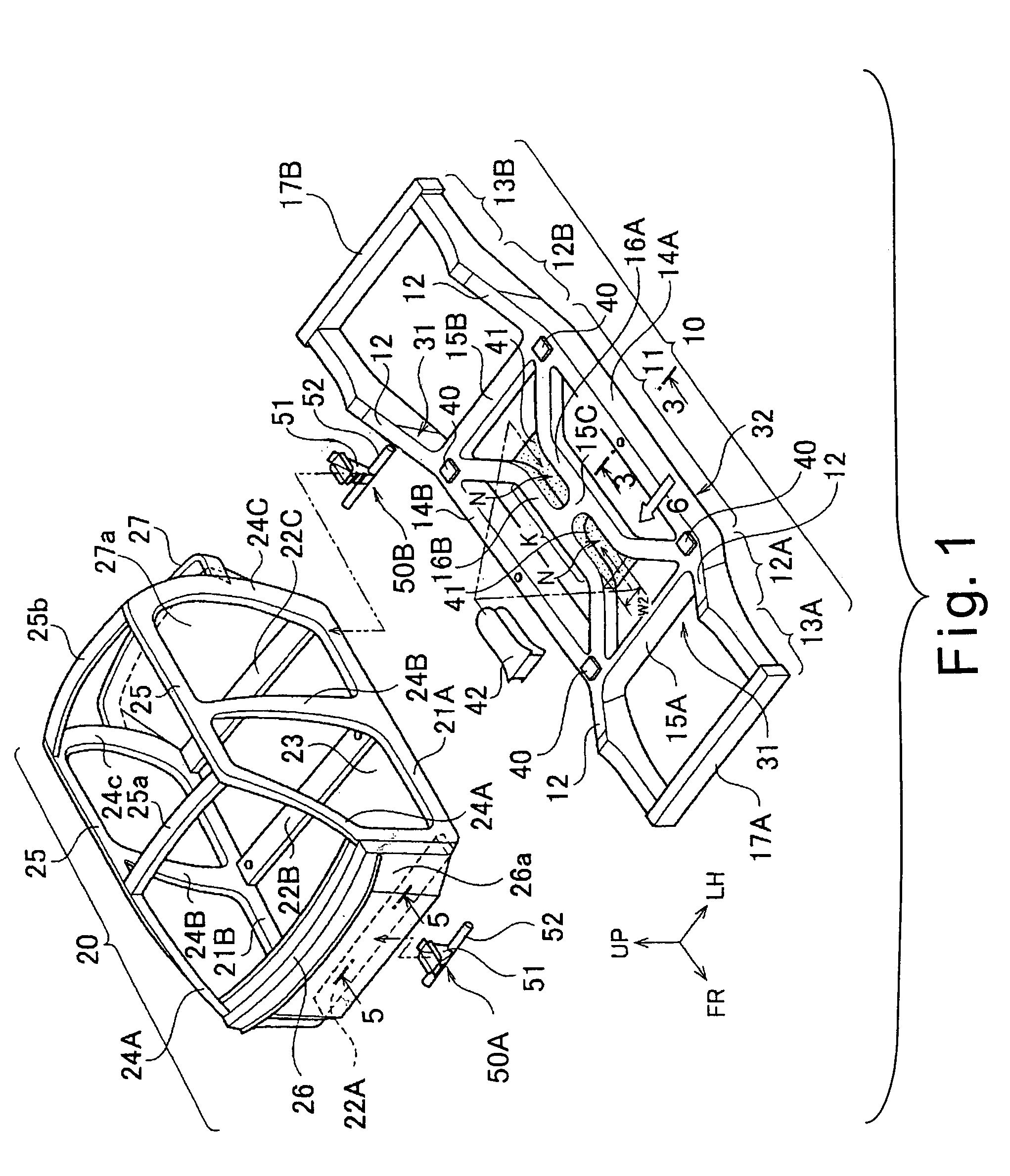
Vehicle body structure
InactiveUS7185934B2High strengthHigh impact energy absorption capacityVehicle body-frame connectionsElectric propulsion mountingVehicle frameEngineering
A vehicle body structure is configured that enables a cabin section and a chassis frame to move relative to each other and enables both strength of the vehicle body and the safety of the occupants during a collision to be ensured with good efficiency. The cabin section serves as the space in which the passengers reside. The chassis frame and cabin section are separate, independent structures connected through a displacement mechanism in such a manner that the chassis frame and cabin section can move separately relative to each other, when a collision occurs. As a result, transmission of the collision impact to the cabin section is alleviated in an effective manner and the strength of the cabin section and chassis frame can be increased.
Owner:NISSAN MOTOR CO LTD
Method of laying data cables and the like in underground pipes and pipe-cable combinations
InactiveUS6572306B2Ensure protectionLabelling non-rigid containersUnderground chambersSewageEngineering
One or more electric and / or data transmitting cables are confined in an elongated strip-shaped body containing a hardenable resin or the like, and the body is placed against a portion of the internal surface of an underground sewage, water or other pipe. An expandible tubular liner is thereupon introduced into the pipe and is expanded to press the body against the pipe. The body is caused to set, by conveying a hot fluid through the liner and / or by electrically heating the cable or cables, and to adhere to the internal surface of the pipe. The liner can remain in the pipe and can be bonded to the strip-shaped body and / or to the remaining portion of the internal surface of the pipe. Alternatively, the liner is caused to collapse and is withdrawn from the pipe once the strip-shaped body is bonded to the internal surface of the pipe.
Owner:PRUSAK MARTIN
Integrated circuit device
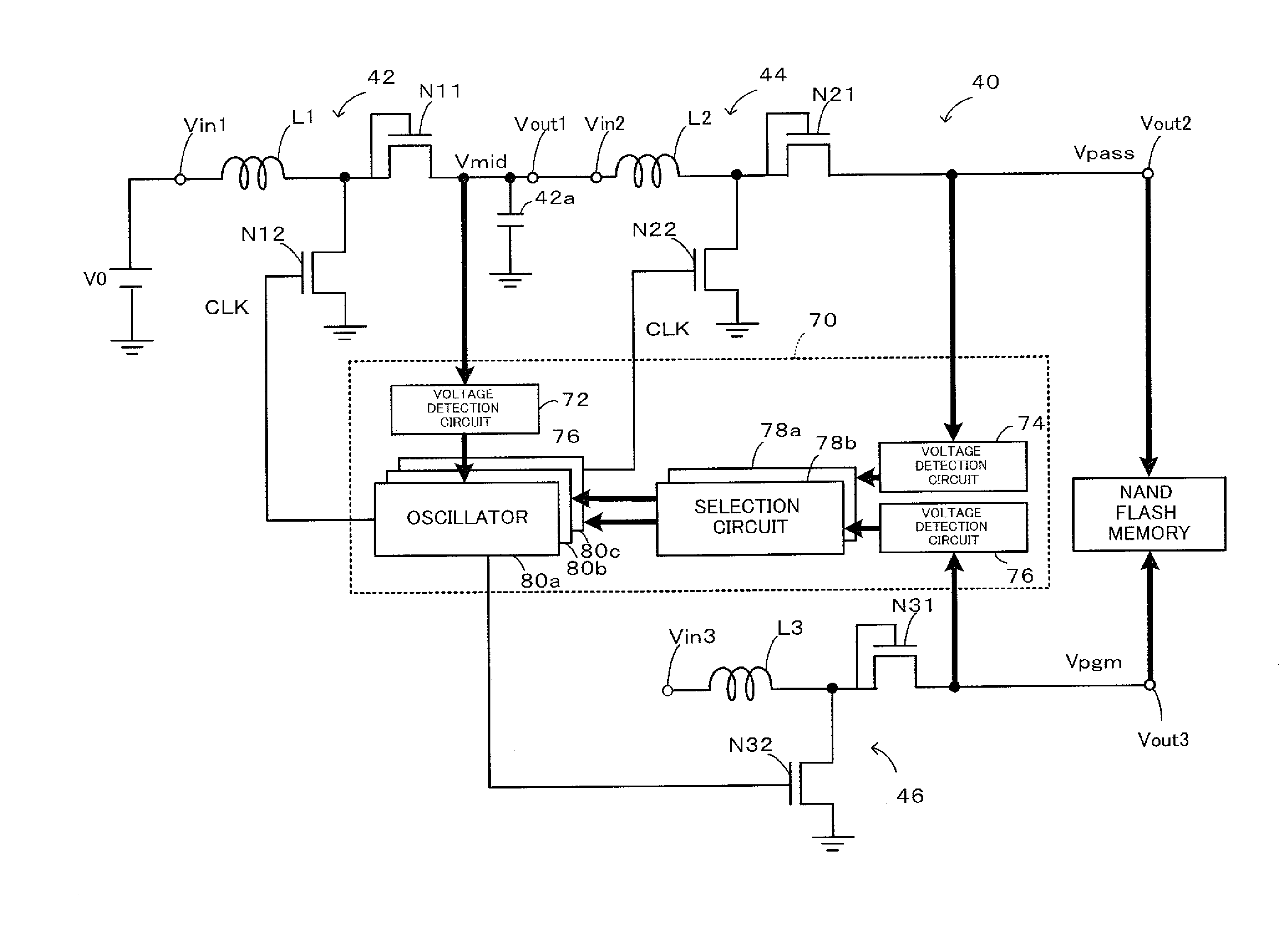
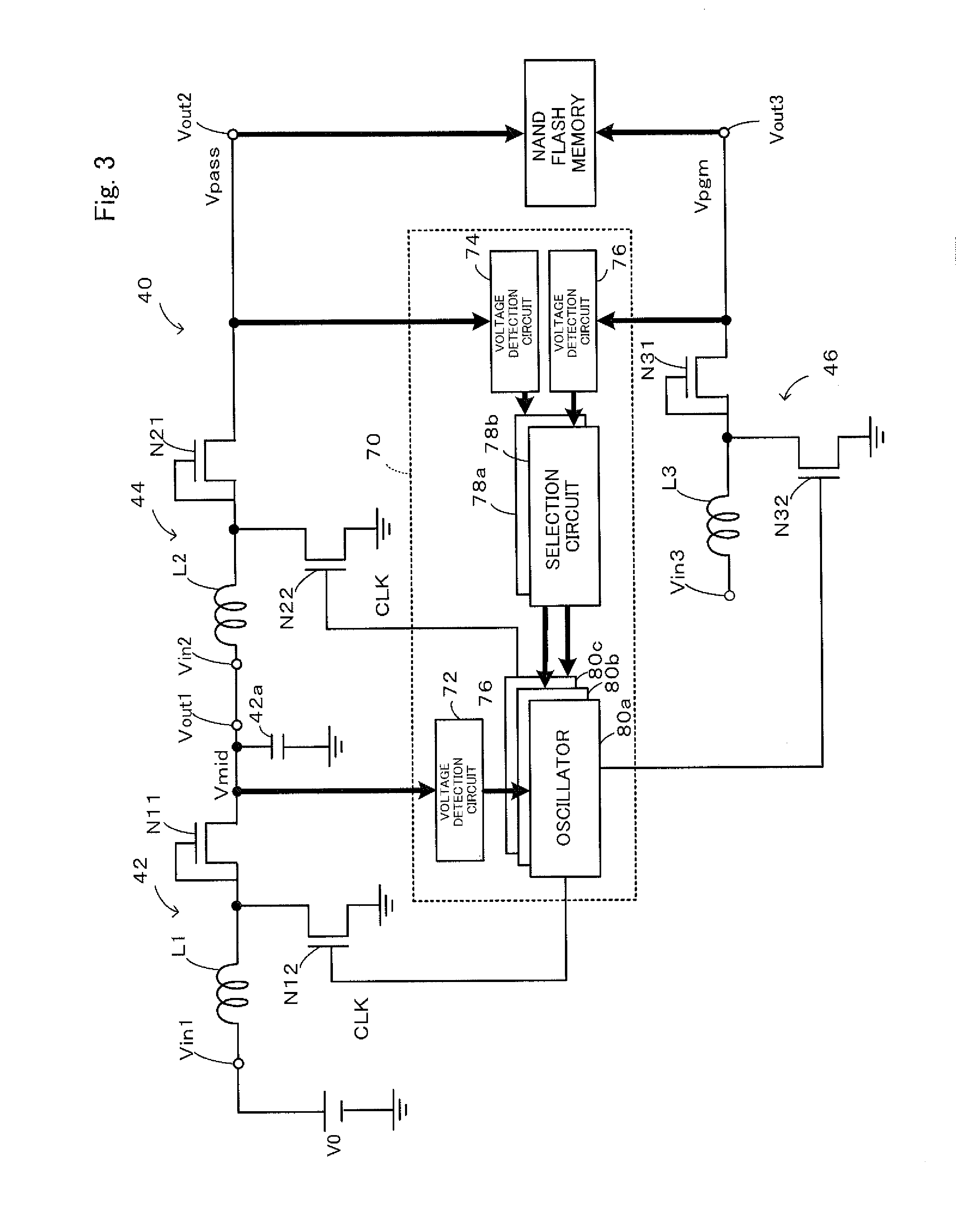
InactiveUS20140104952A1Protection deviceEnsure protectionDc-dc conversionRead-only memoriesEngineeringBoost converter
A booster circuit is configured, such that: in response to a reading request for reading data from a flash memory, when a voltage of an output terminal detected by a voltage detection circuit is not higher than a voltage, an oscillator outputs a control clock signal of predetermined on time and off time to a transistor of a boost converter to perform switching control of the transistor; and when the voltage detection circuit detects that the voltage of the output terminal reaches a voltage, an oscillator outputs a control clock signal of an on time and an off time input from a selection circuit to a transistor of a boost converter to perform switching control of the transistor.
Owner:THE UNIV OF TOKYO
Flip-down footrests for an all-terrain vehicle
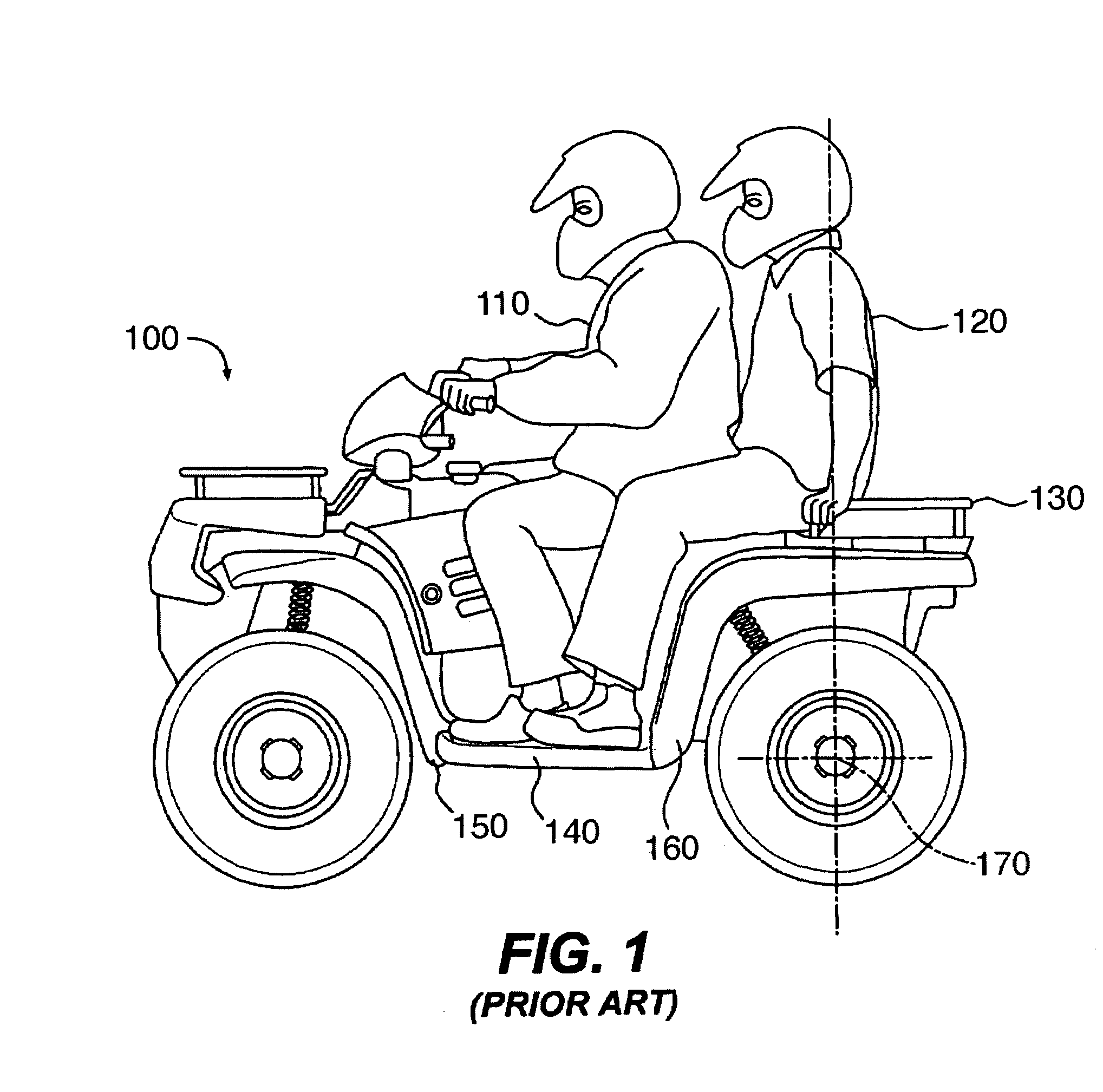
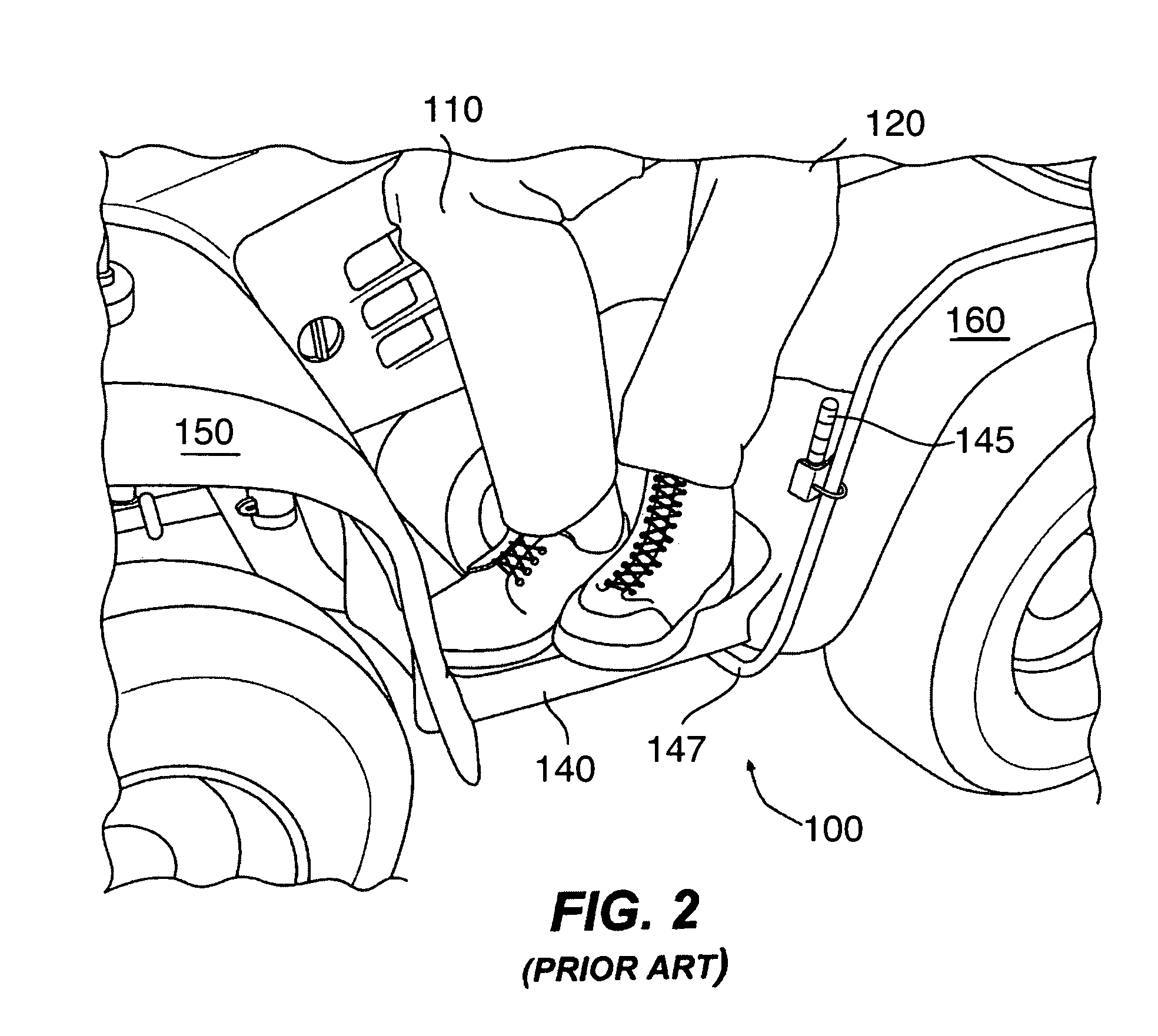
A two-seater all-terrain vehicle (ATV) has straddle-type driver and rear passenger seats, and a pair of movable rear footrests to support the feet of a rear passenger. The rear footrests pivot from a stowed non-supporting position to a supporting position. When folded into the non-supporting position, the rear footrests become substantially flush with side paneling of the vehicle. The all-terrain vehicle may further include a pair of vertical and horizontal adjustment mechanisms for independently vertically adjusting each of the rear passenger footrests so that passengers of varying height can be comfortably accommodated on the rear seat. A cargo space is provided under the passenger's footrest, the cargo space being enlarged when the passenger's footrests are in the stowed position. Restraints and other holding mechanisms are also provided. The flip-down adjustable rear footrests may be used on other types of straddle-type recreational vehicles.
Owner:BOMBARDIER RECREATIONAL PROD INC
Method/system to speed up antivirus scans using a journal file system
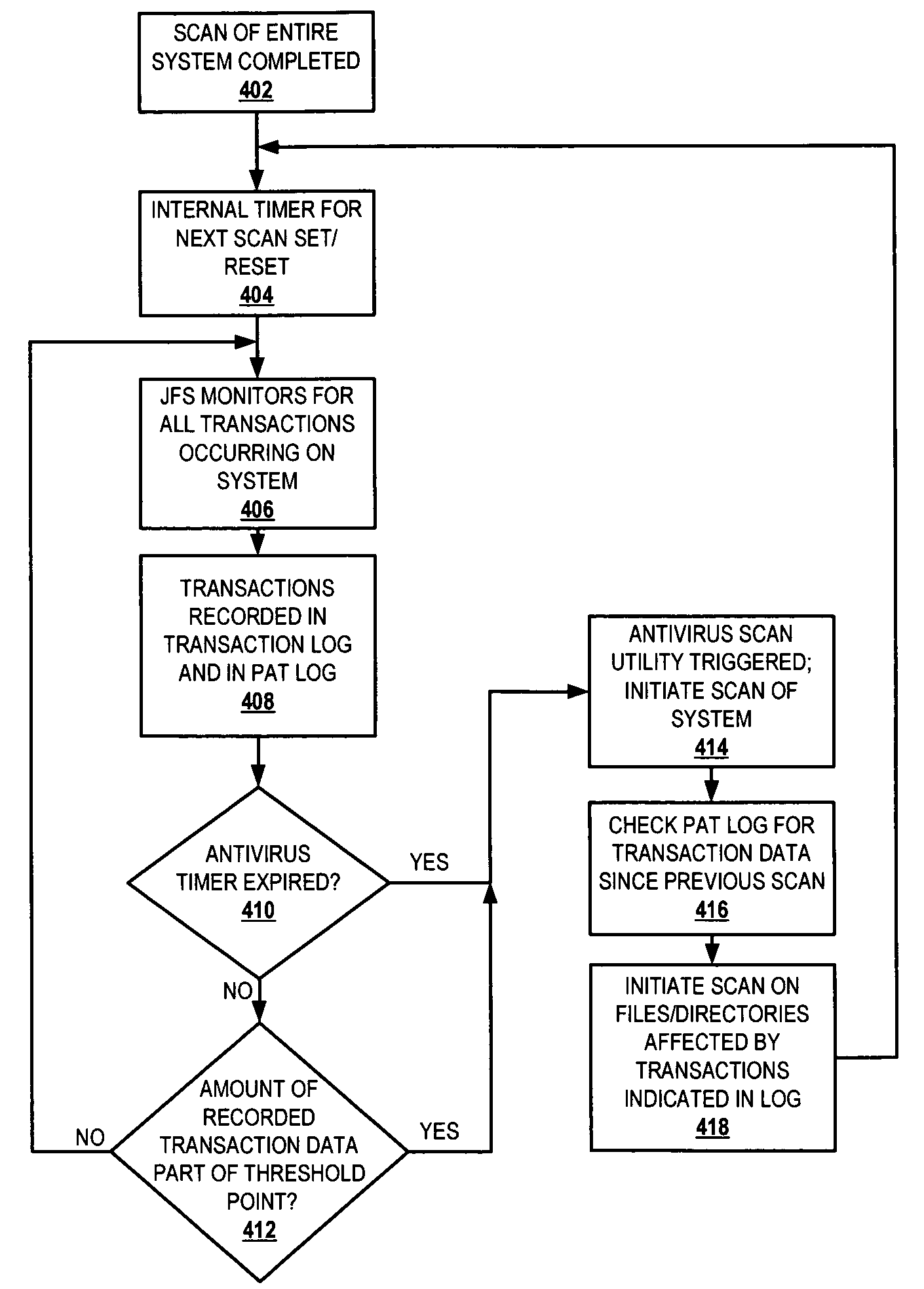
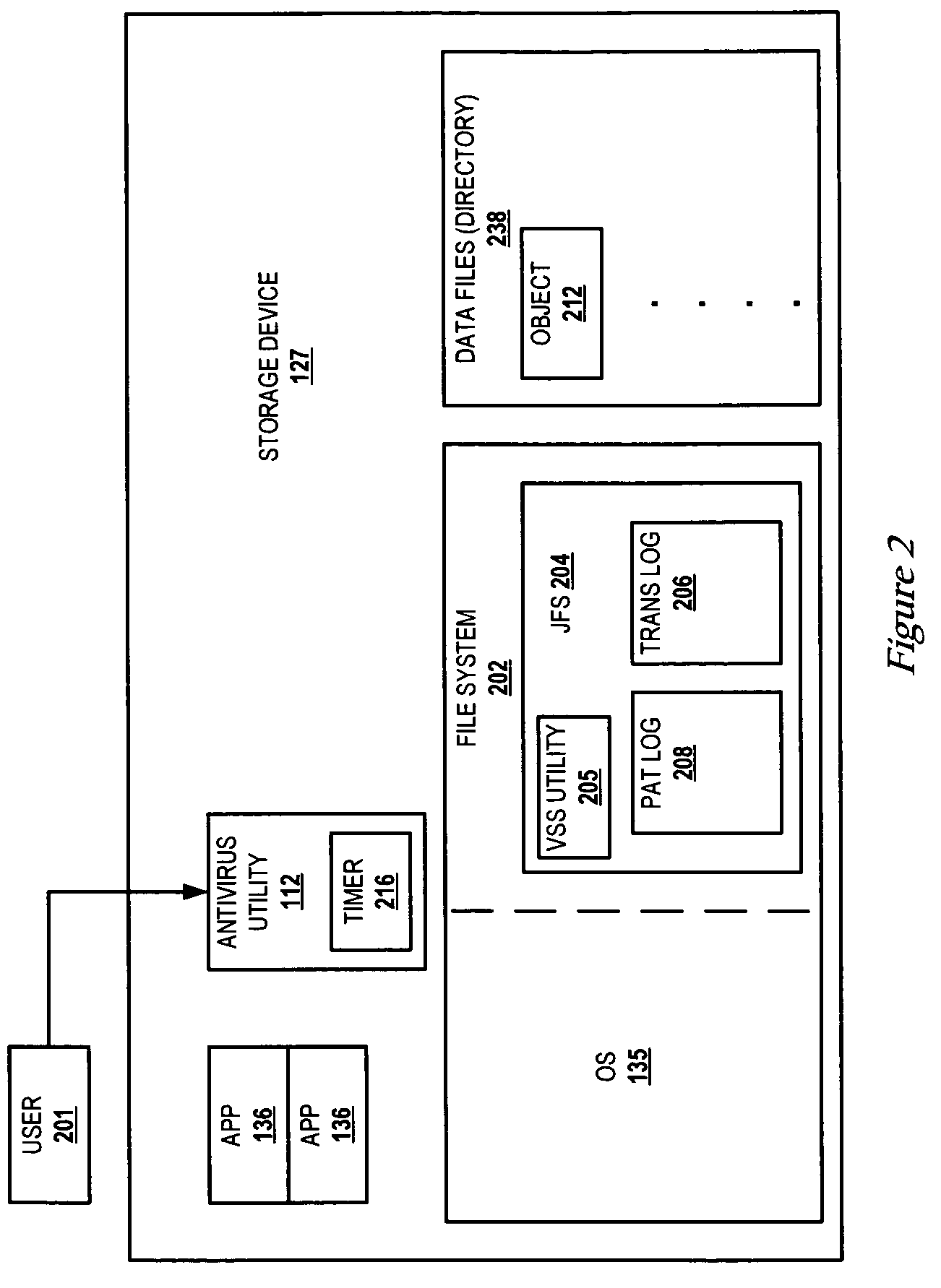
InactiveUS7540027B2Shorten the length of timeFunction increaseMemory loss protectionUnauthorized memory use protectionTimestampFile system
A method and system that reduces the length of time required to complete antivirus scans. An enhanced journal file system (JFS) includes an antivirus utility function, which utilizes a low level log of the JFS to store a history of transactions that occur since a previous scan operation. The log is immune from normal purge operations by the JFS and cannot be circumvented without driver level access. Thus, a virus that changes the timestamp on the file or otherwise attempts to hide its viral activity does not affect the log. When the antivirus scanning utility initiates an antivirus scan of the system, the antivirus scanning utility obtains the history since the last scan from the persistent log. The antivirus scanning utility “replays” the log and carries out the antivirus scan on all files, directories, etc. associated with any transactions that occurred since the last scan.
Owner:INT BUSINESS MASCH CORP
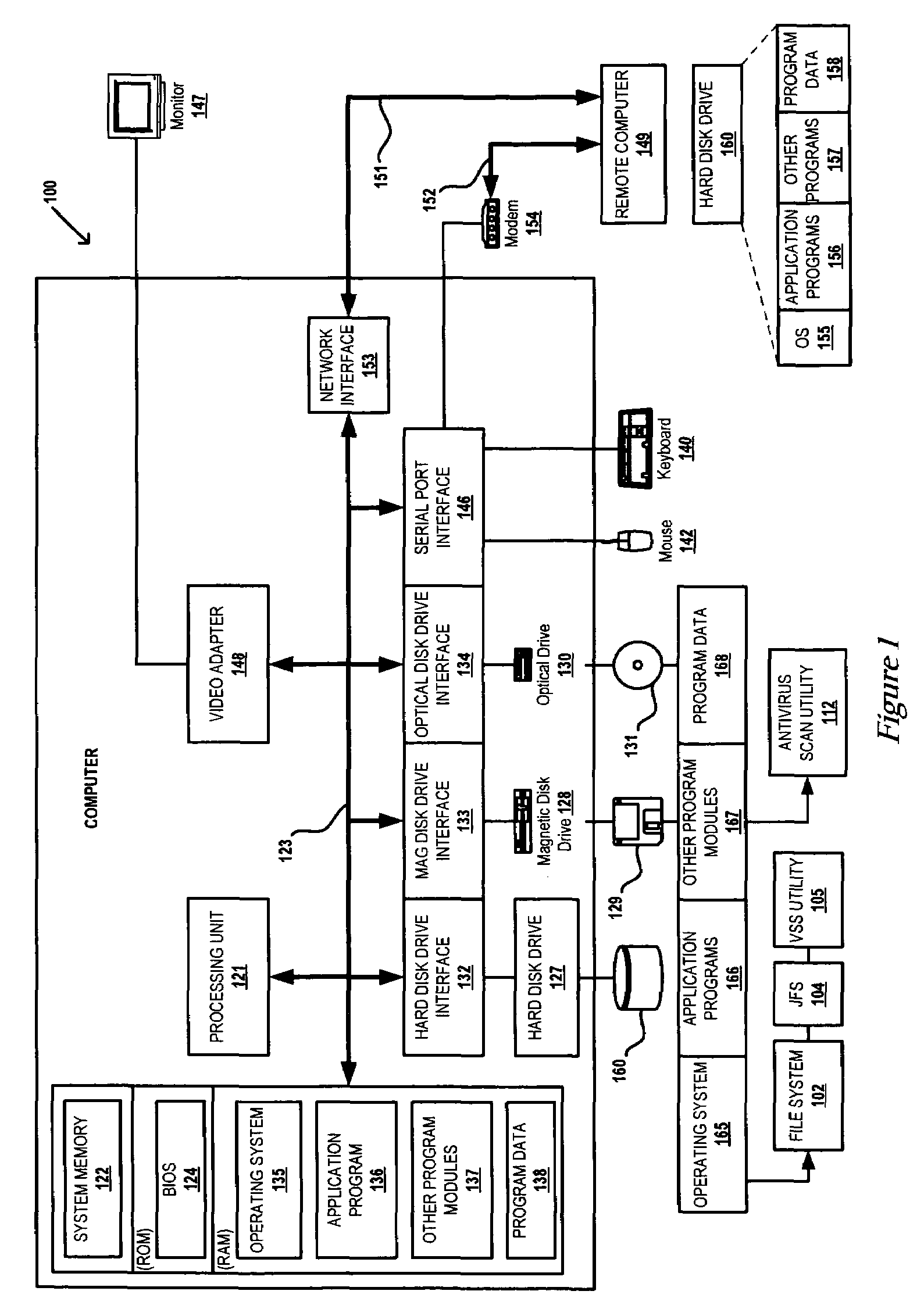
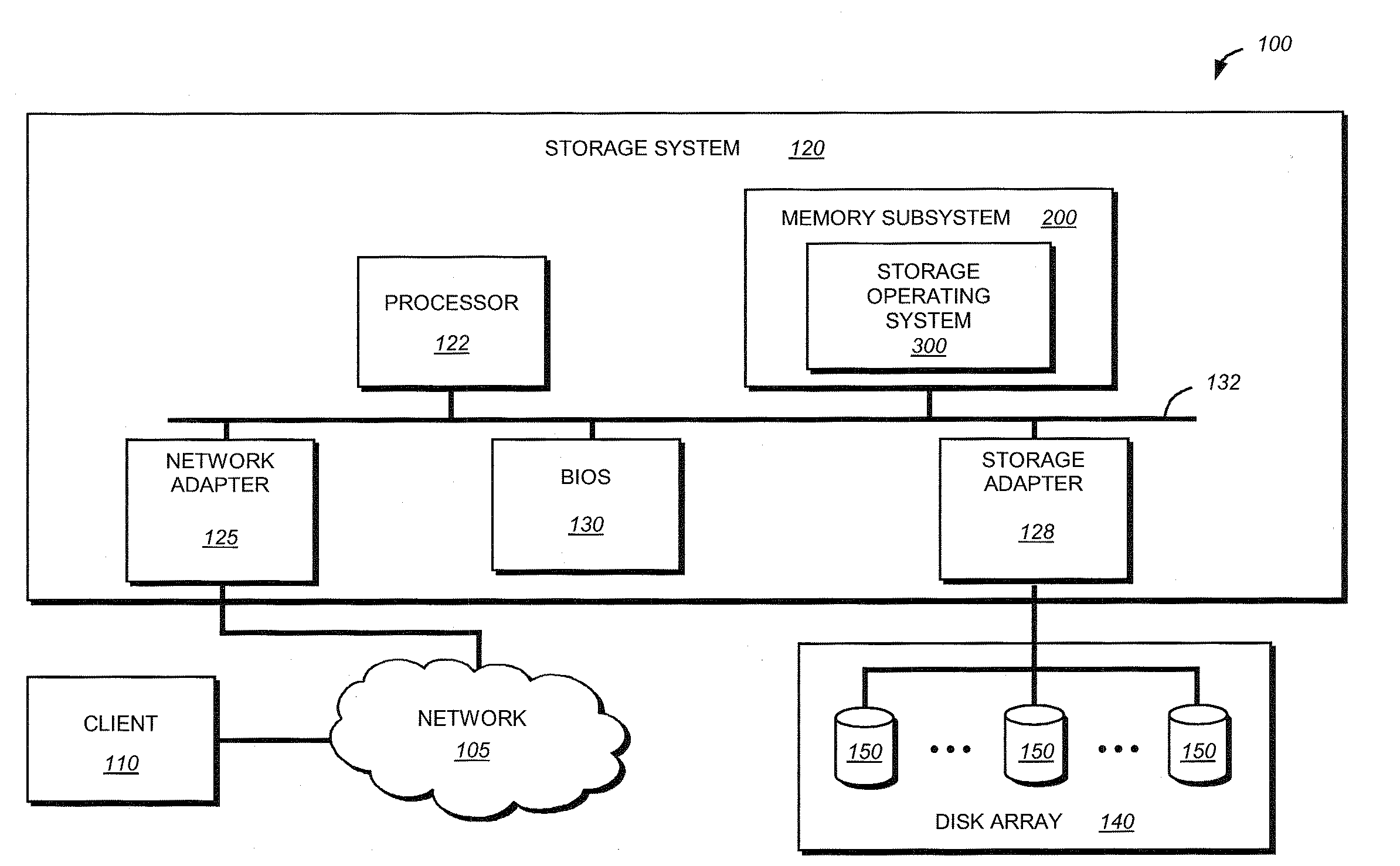
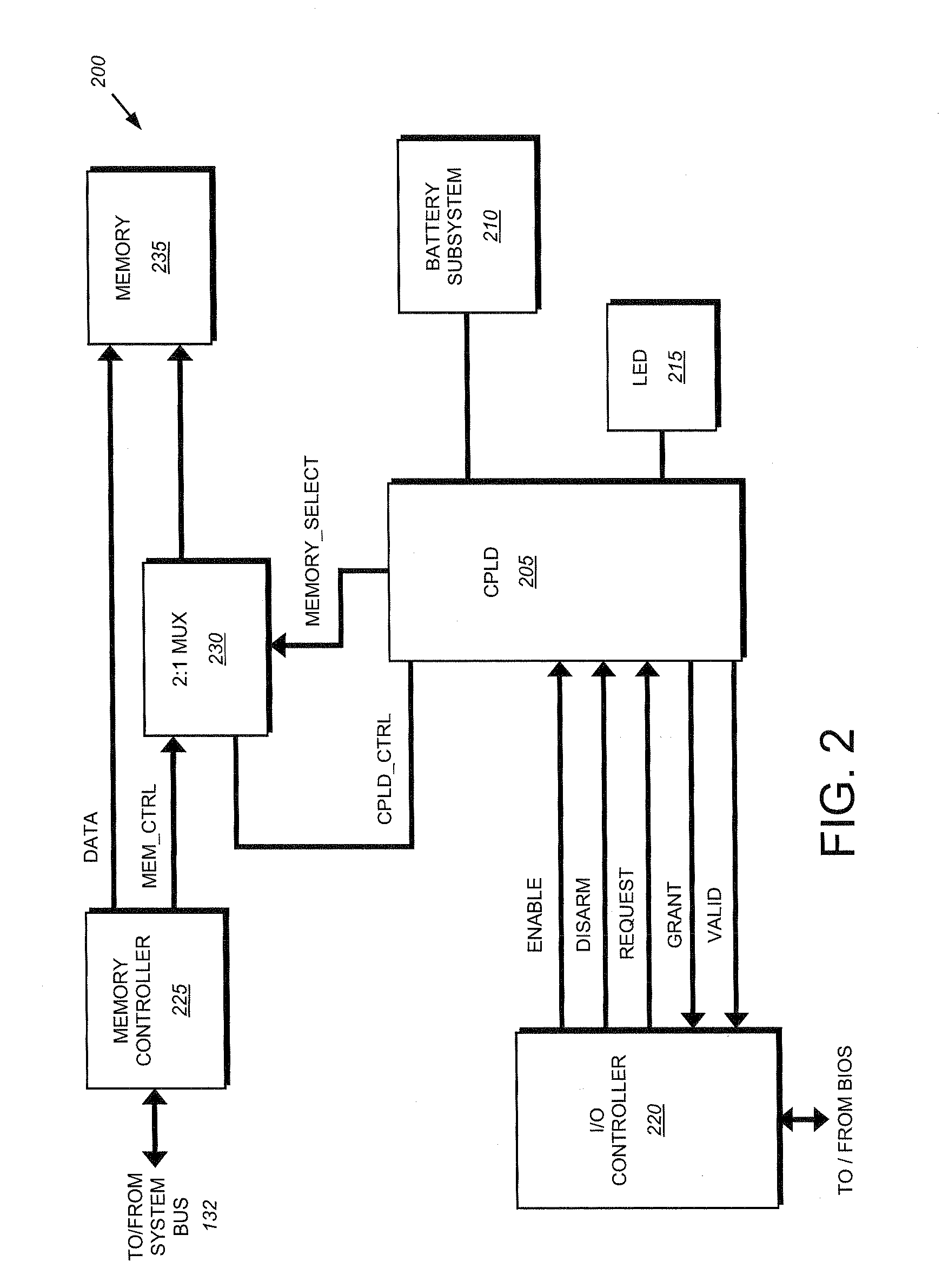
System and method for protecting memory during system initialization
ActiveUS20080270776A1Extend battery lifeOvercome disadvantagesError detection/correctionDigital computer detailsMultiplexerProgrammable logic device
A system and method for protecting memory during system initialization is provided. A complex programmable logic device (CPLD) is operatively interconnected with a multiplexer to enable control of a memory to be switched between a memory controller and the CPLD in response to error conditions. If an error condition is identified, the CPLD assumes control of the memory and activates a battery subsystem to provide memory refreshes until system re-initialization. Upon system bring-up, interactions between the BIOS and CPLD assure that protected memory is fully recovered by the system. The contents of memory will remain protected from any further faults that may occur during the bring-up sequence.
Owner:NETWORK APPLIANCE INC
Information management system
ActiveUS20050204172A1Check is unnecessaryEnsure protectionDigital data processing detailsUser identity/authority verificationThe InternetWorkstation
An information management system is described comprising one or more workstations running applications to allow a user of the workstation to connect to a network, such as the Internet. Each application has an analyser, which monitors transmission data that the application is about to transmit to the network or about to receive from the network and which determines an appropriate action to take regarding that transmission data. Such actions may be extracting data from the transmission data, such as passwords and usernames, digital certificates or eCommerce transaction details for storage in a database; ensuring that the transmission data is transmitted at an encryption strength appropriate to the contents of the transmission data; determining whether a check needs to be made as to whether a digital certificate received in transmission data is in force, and determining whether a transaction about to be made by a user of one of the workstations needs third party approval before it is made. The analyser may consult a policy data containing a policy to govern the workstations in order to make its determination. The information management system provides many advantages in the eCommerce environment to on-line trading companies, who may benefit by being able to regulate the transactions made by their staff according to their instructions in a policy data, automatically maintain records of passwords and business conducted on-line, avoid paying for unnecessary checks on the validity of digital certificates and ensure that transmissions of data made by their staff are always protected at an agreed strength of encryption.
Owner:COMP ASSOC THINK INC
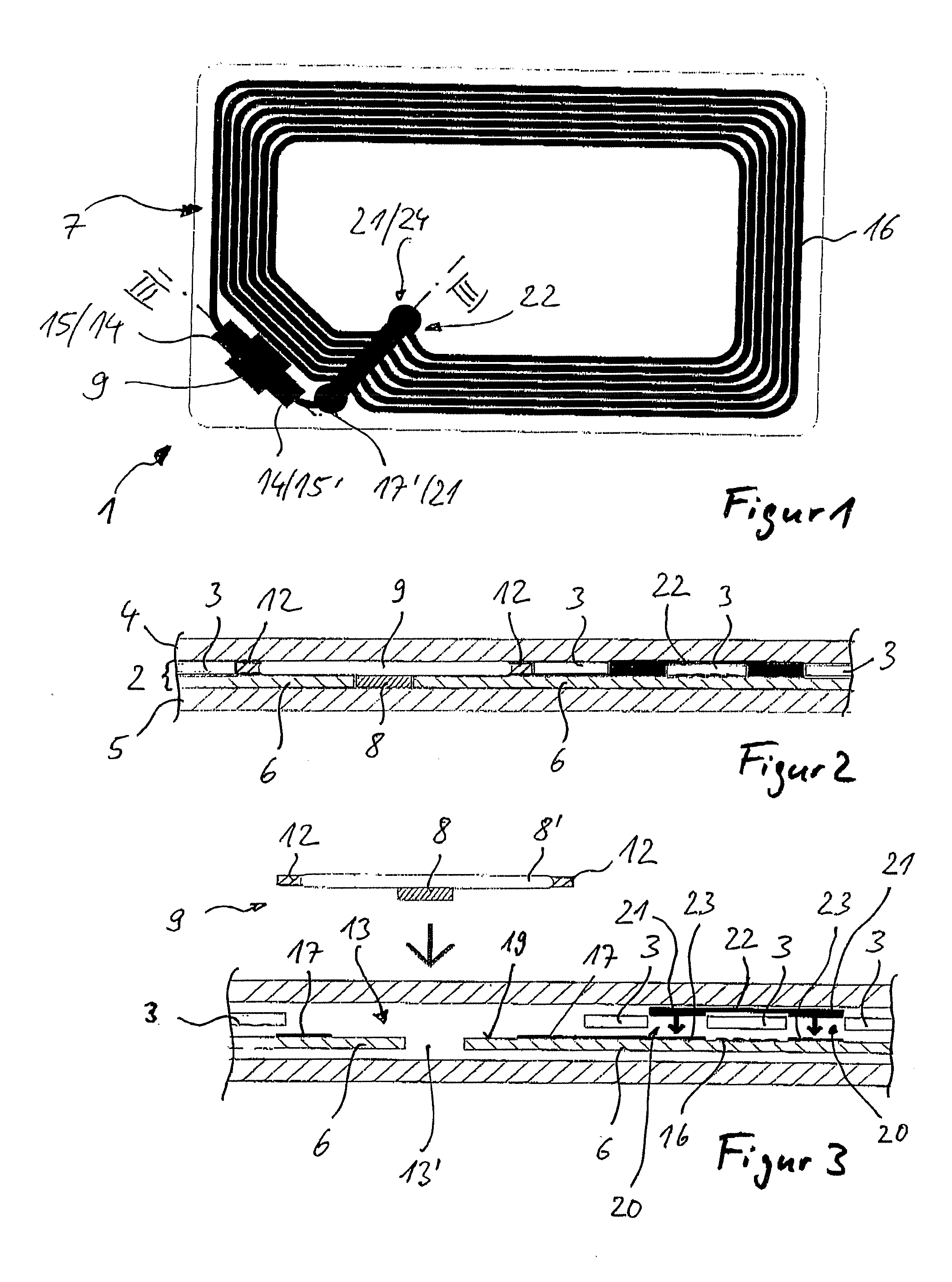
Card and Manufacturing Method
InactiveUS20070176273A1Simplifies electrical contactPrevents undesirable tearingSemiconductor/solid-state device detailsSolid-state devicesConductor CoilElectrical and Electronics engineering
The invention relates to a card for contactless data and / or energy transmission by means of external devices, containing a multilayer card body which has a substrate layer for accommodating an antenna coil having exposed coil connections on a top side of the substrate layer which are connected in an electrically conductive manner to connections for a chip module containing a chip, the chip being enclosed in a recess in the substrate layer; the windings of the antenna coil extend on the top side of the substrate layer, and a compensation layer extends on the top side of the substrate layer; the compensation layer has a chip module opening for placing the chip module on the substrate layer, and has a bridge opening for the contacting of connections of an antenna bridge which extends transverse to the windings.
Owner:ASSA ABLOY AB
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com