Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
143results about How to "Fast internet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
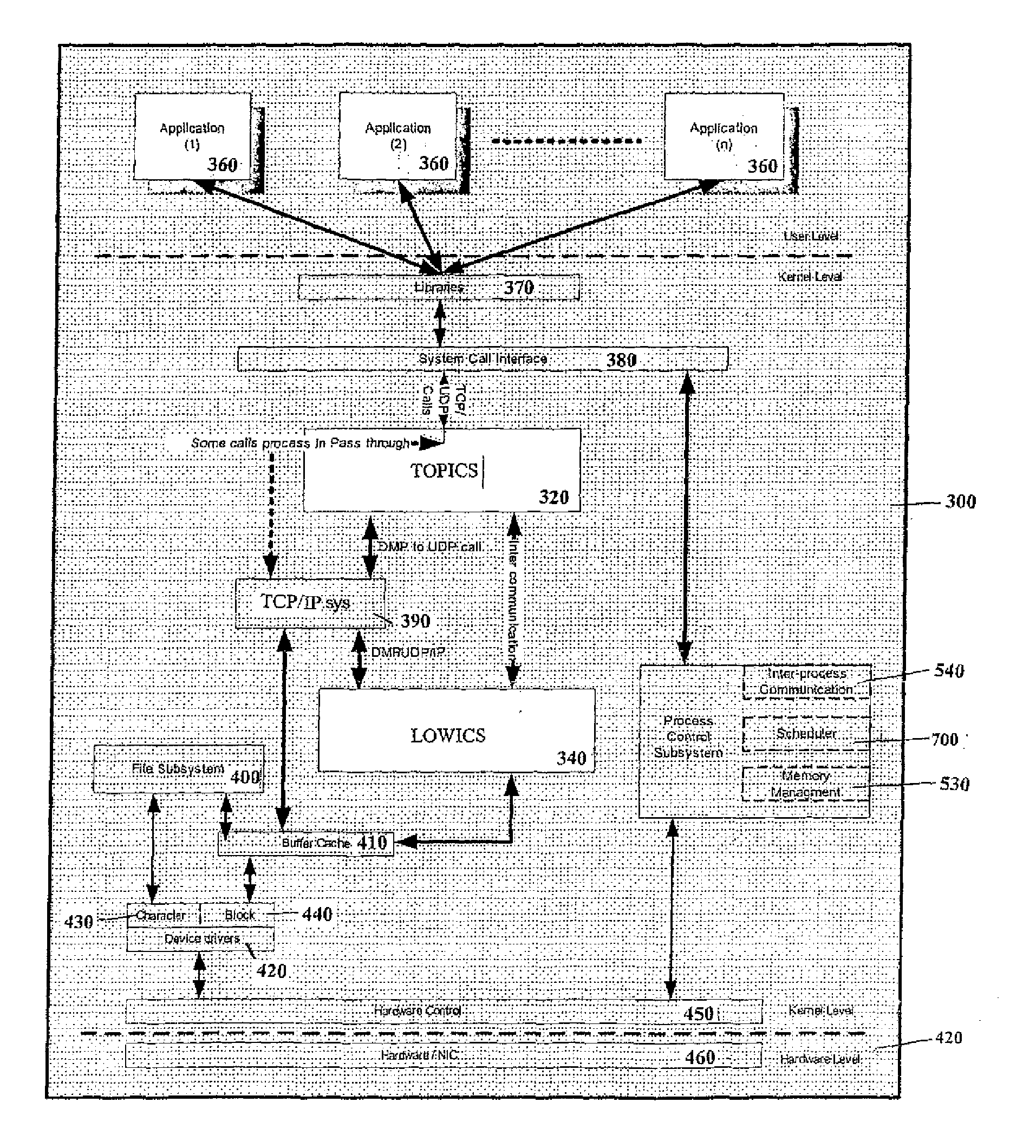
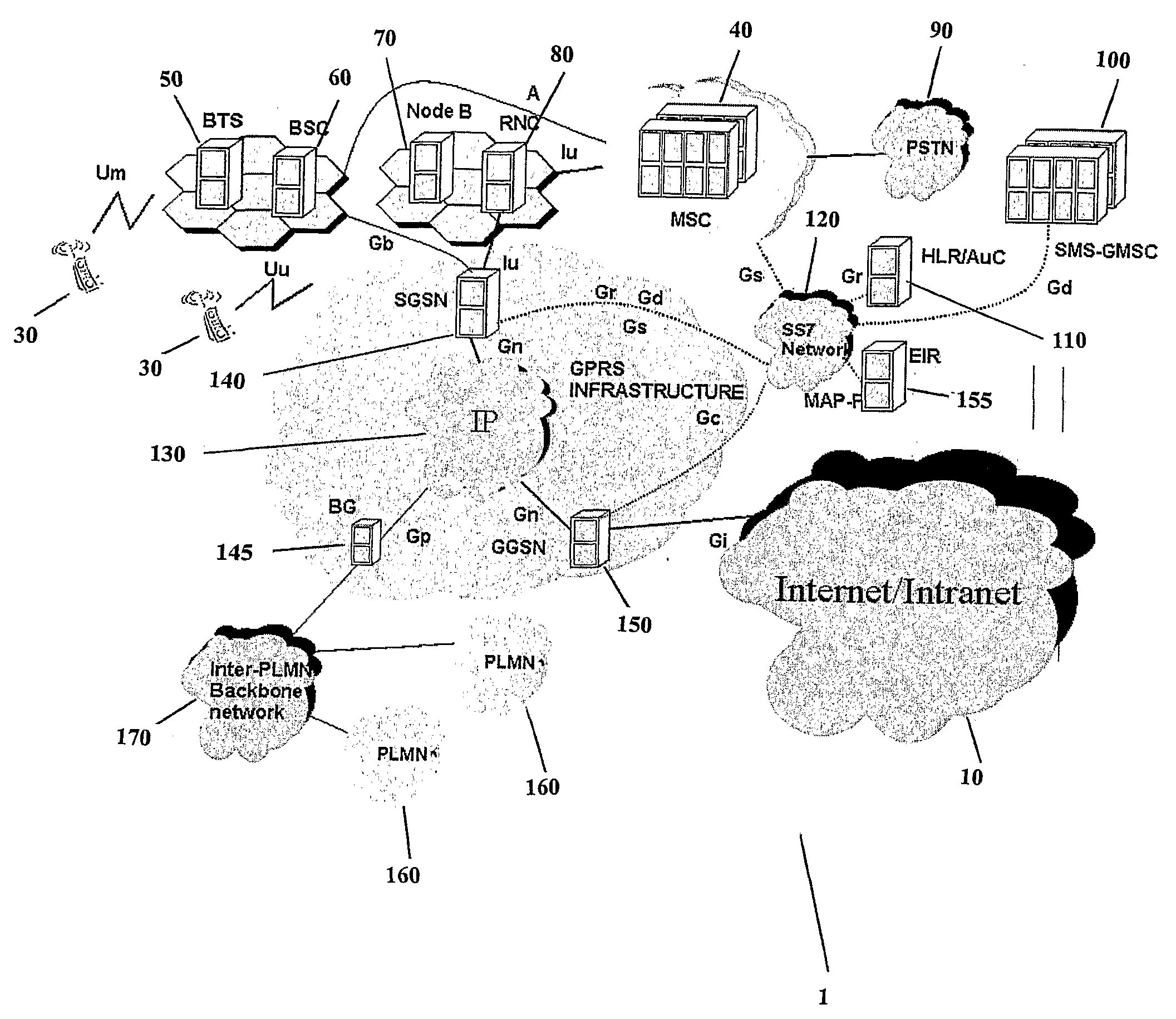
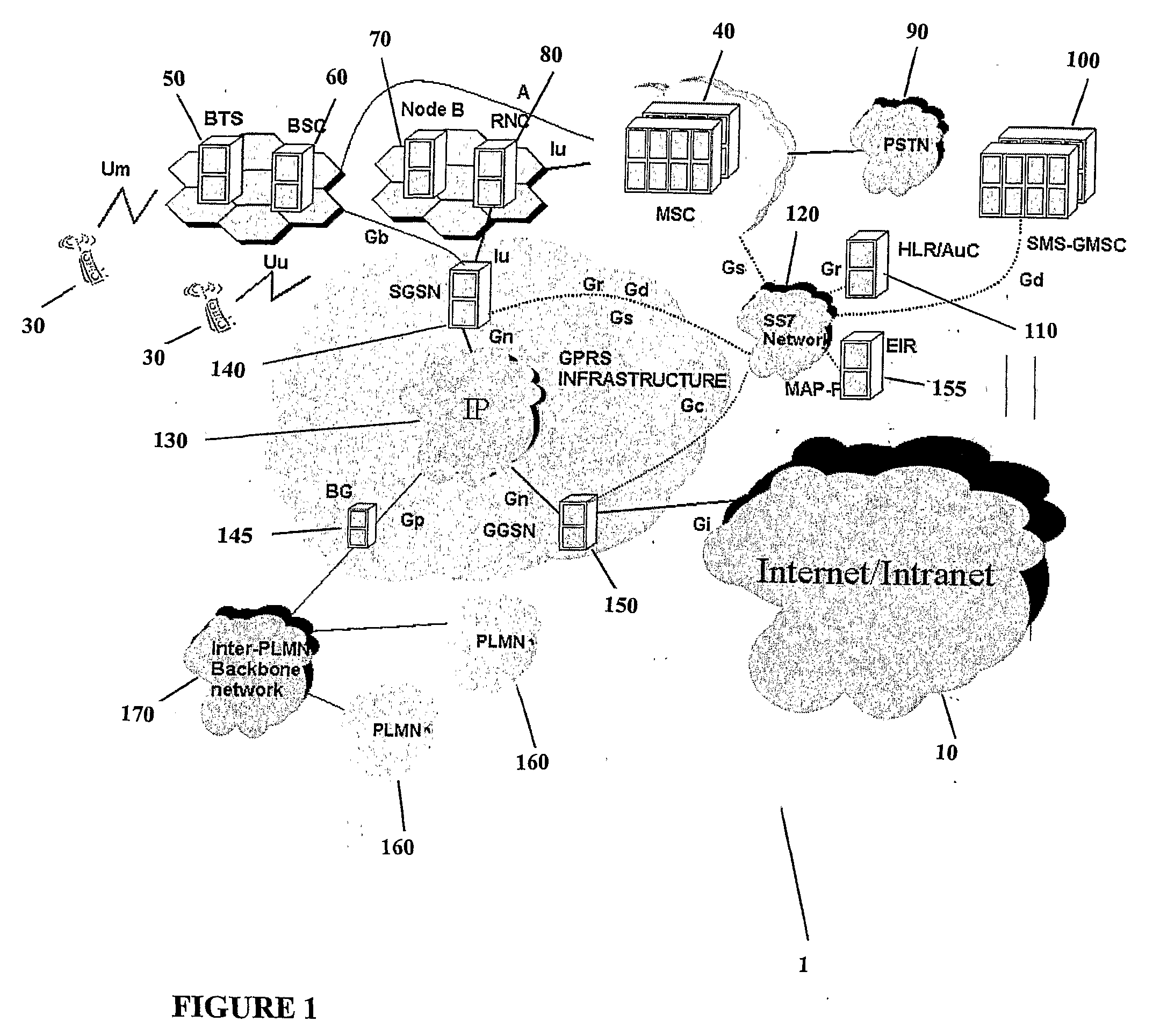
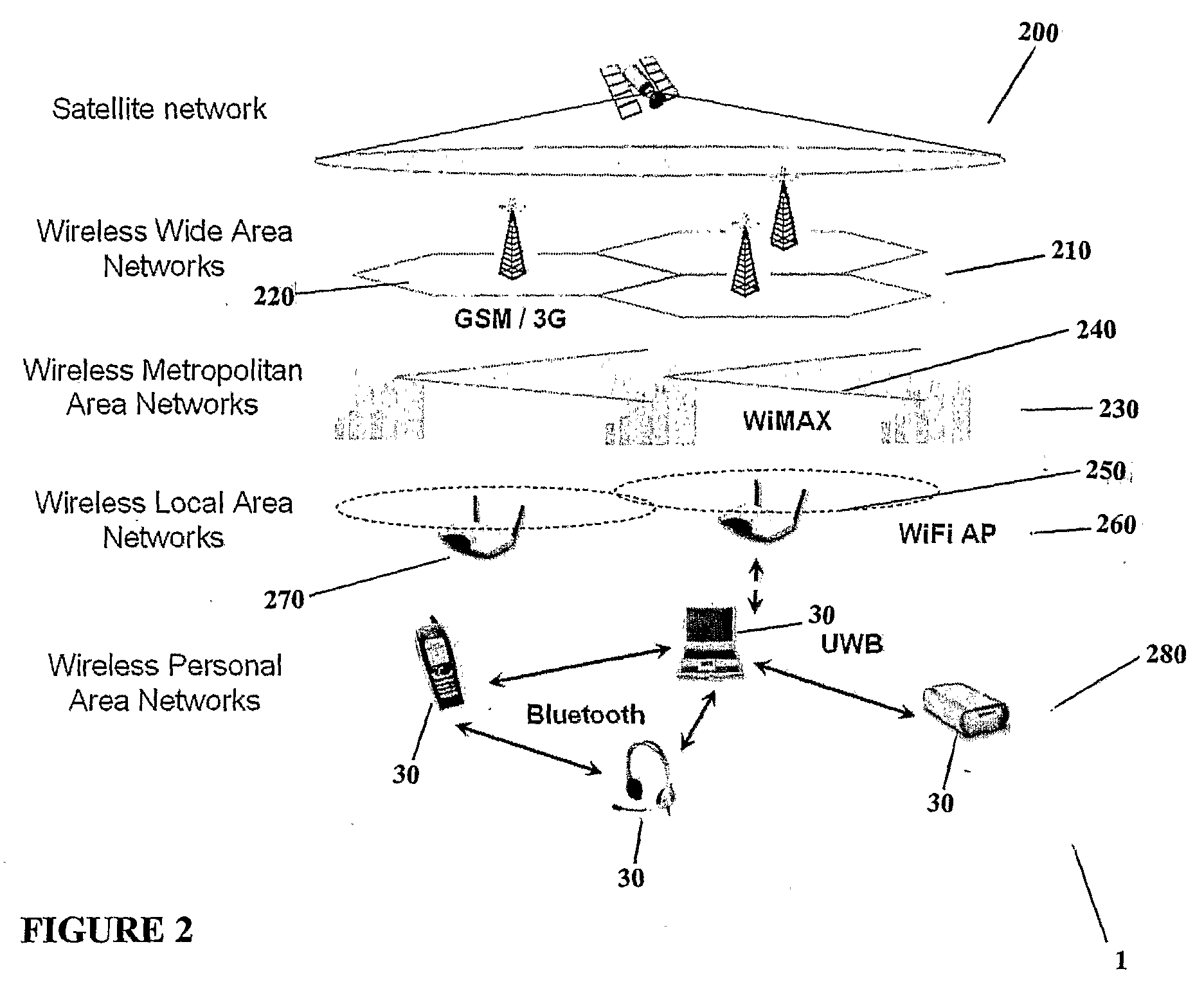
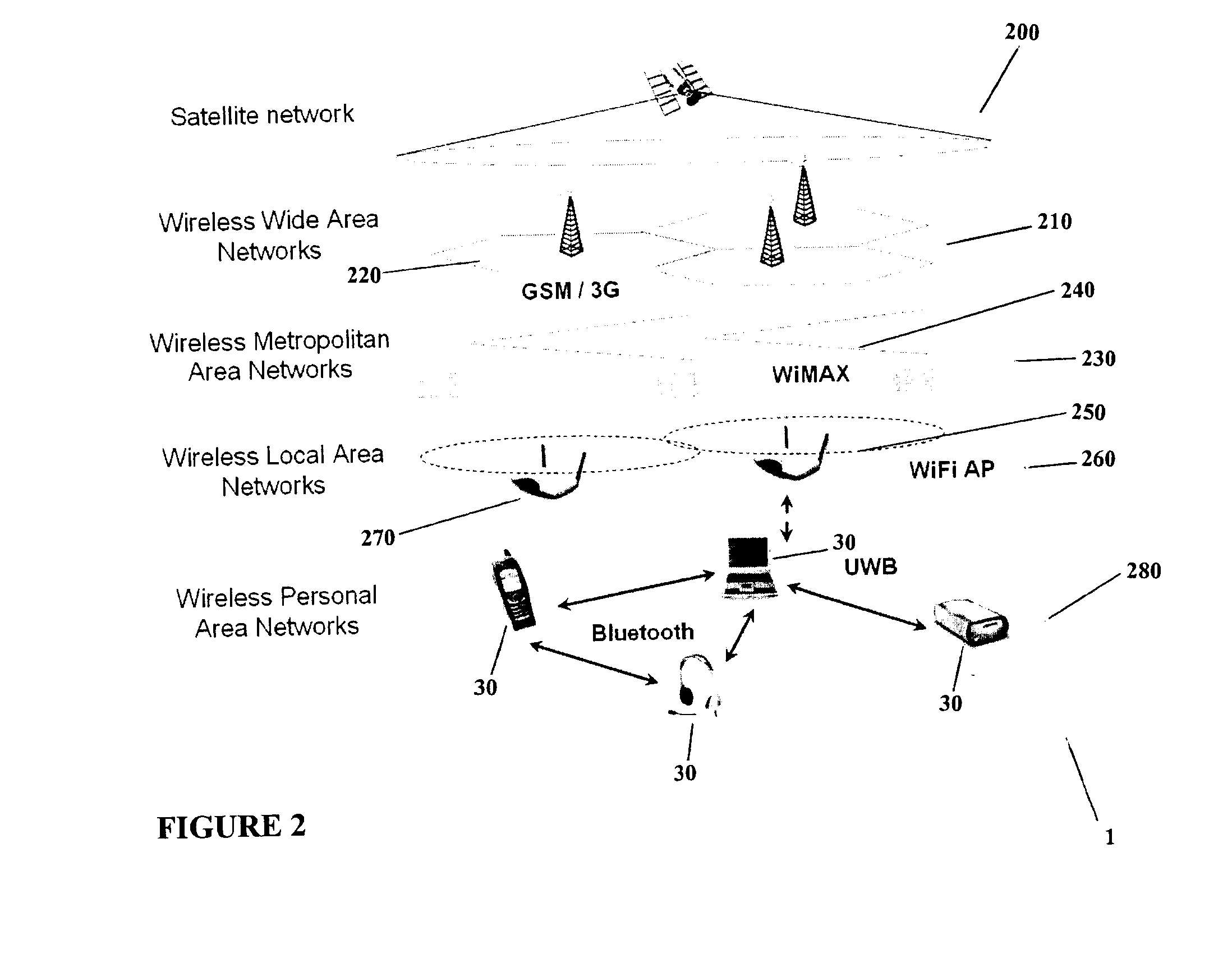
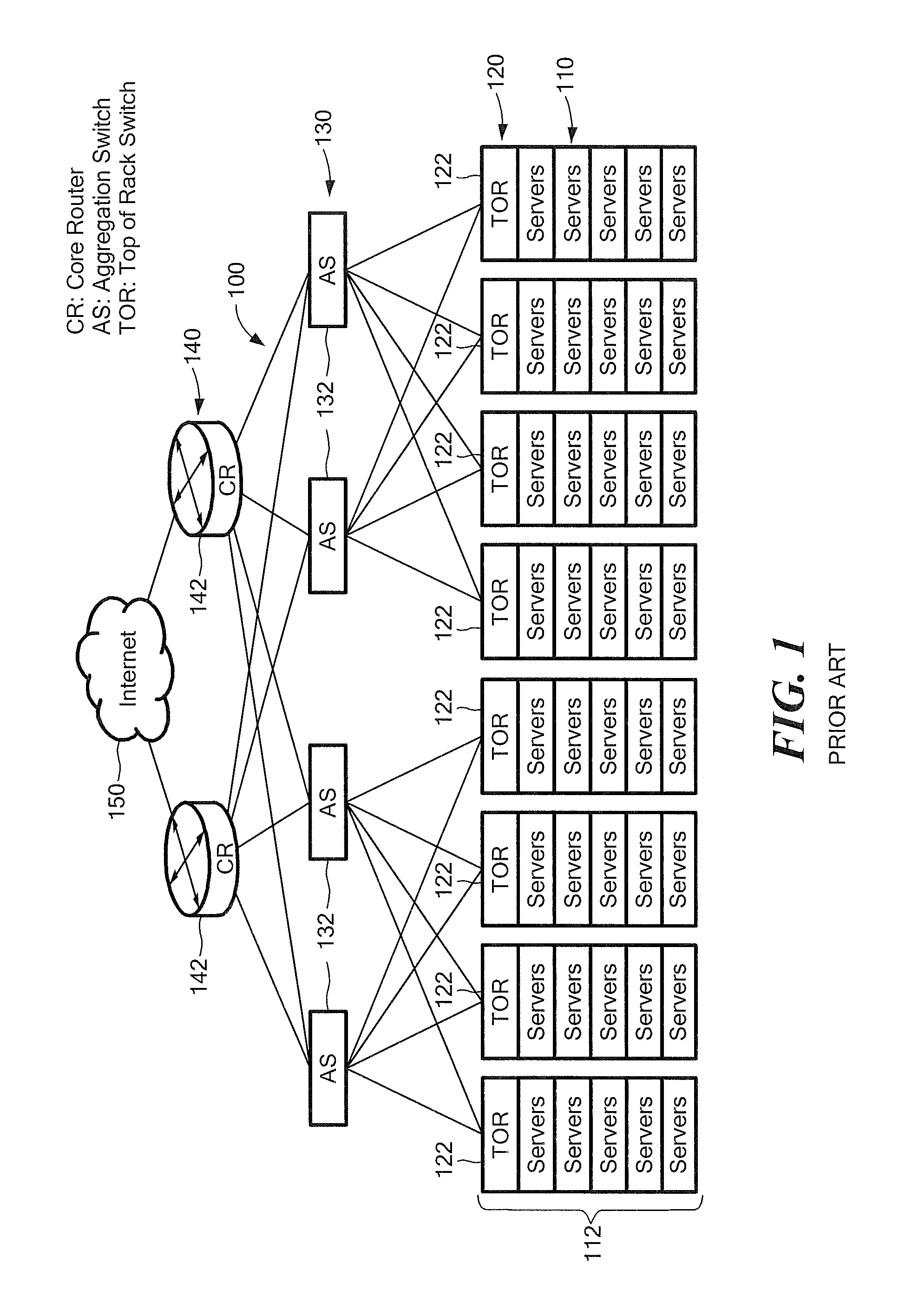
System and Method of Traffic Management Over Mixed Networks
InactiveUS20080279216A1Efficiently decideReduce overheadNetwork traffic/resource managementTime-division multiplexTraffic capacityMix network
A method and apparatus is provided of handling modified packets containing additional information regarding source and data type for efficient processing within a mixed network. Incoming and outgoing packets are sent via a dynamic protocol which adapts to circumstances, including the type of network being used, the type of packet being transmitted and the network guidelines.
Owner:MOBIDIA INC
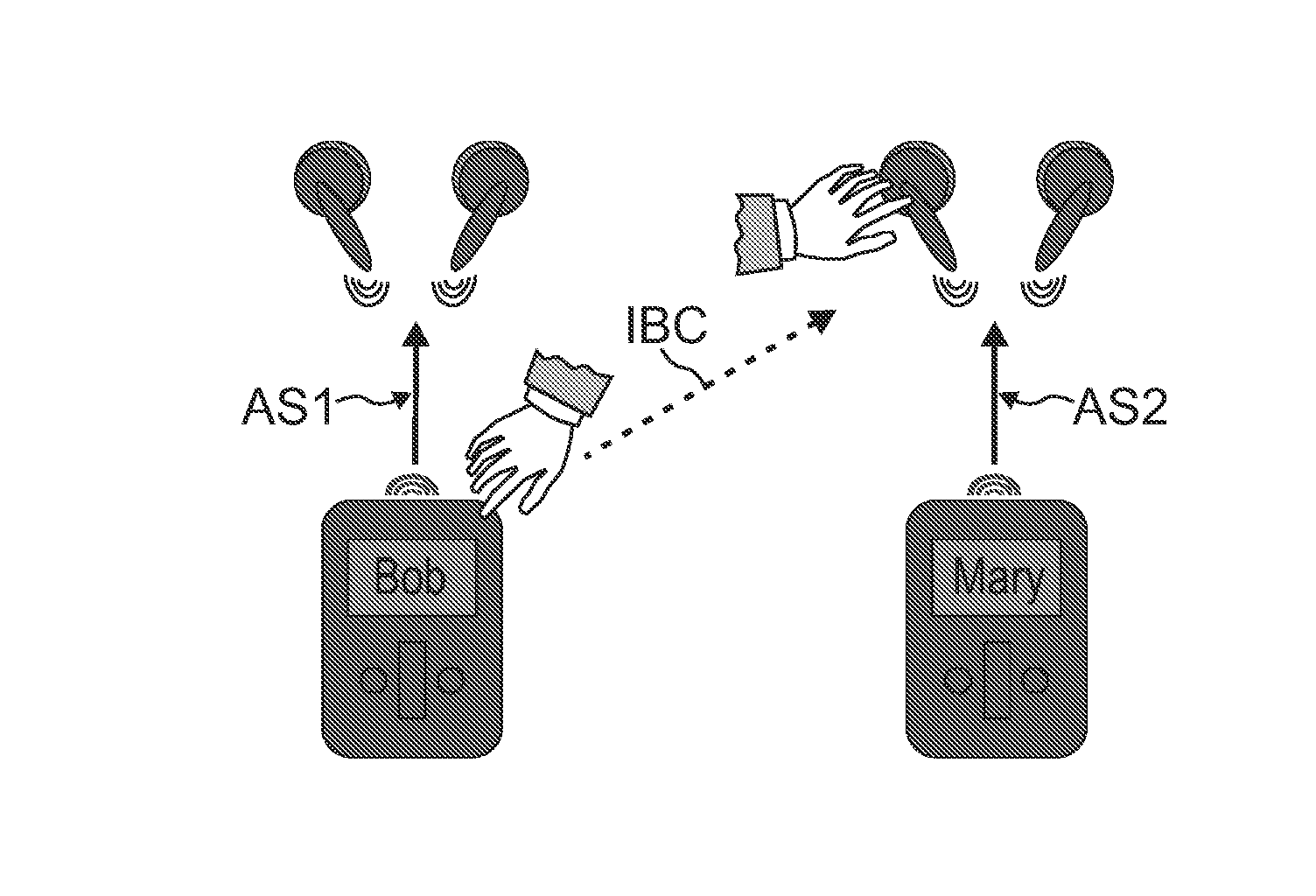
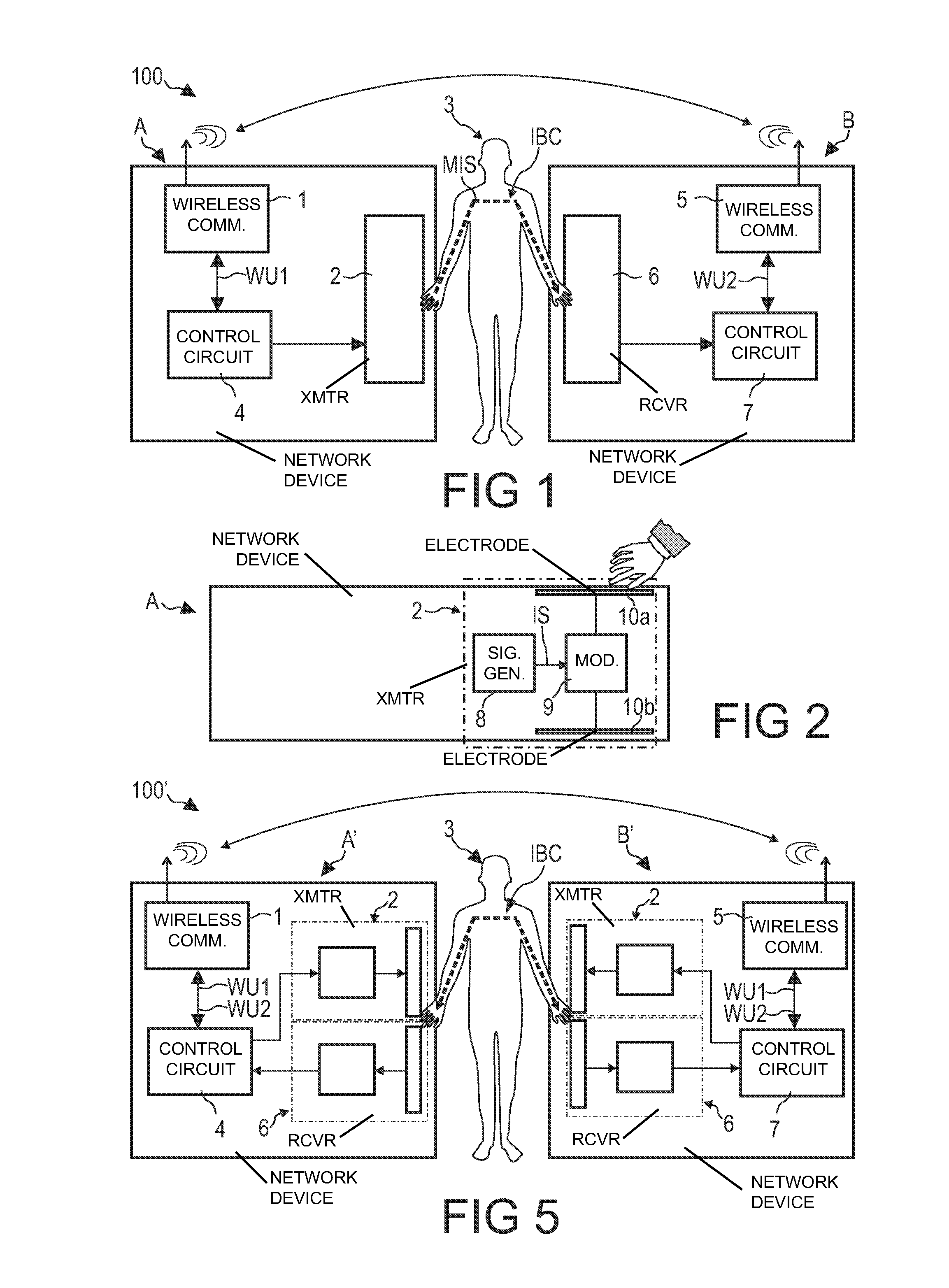
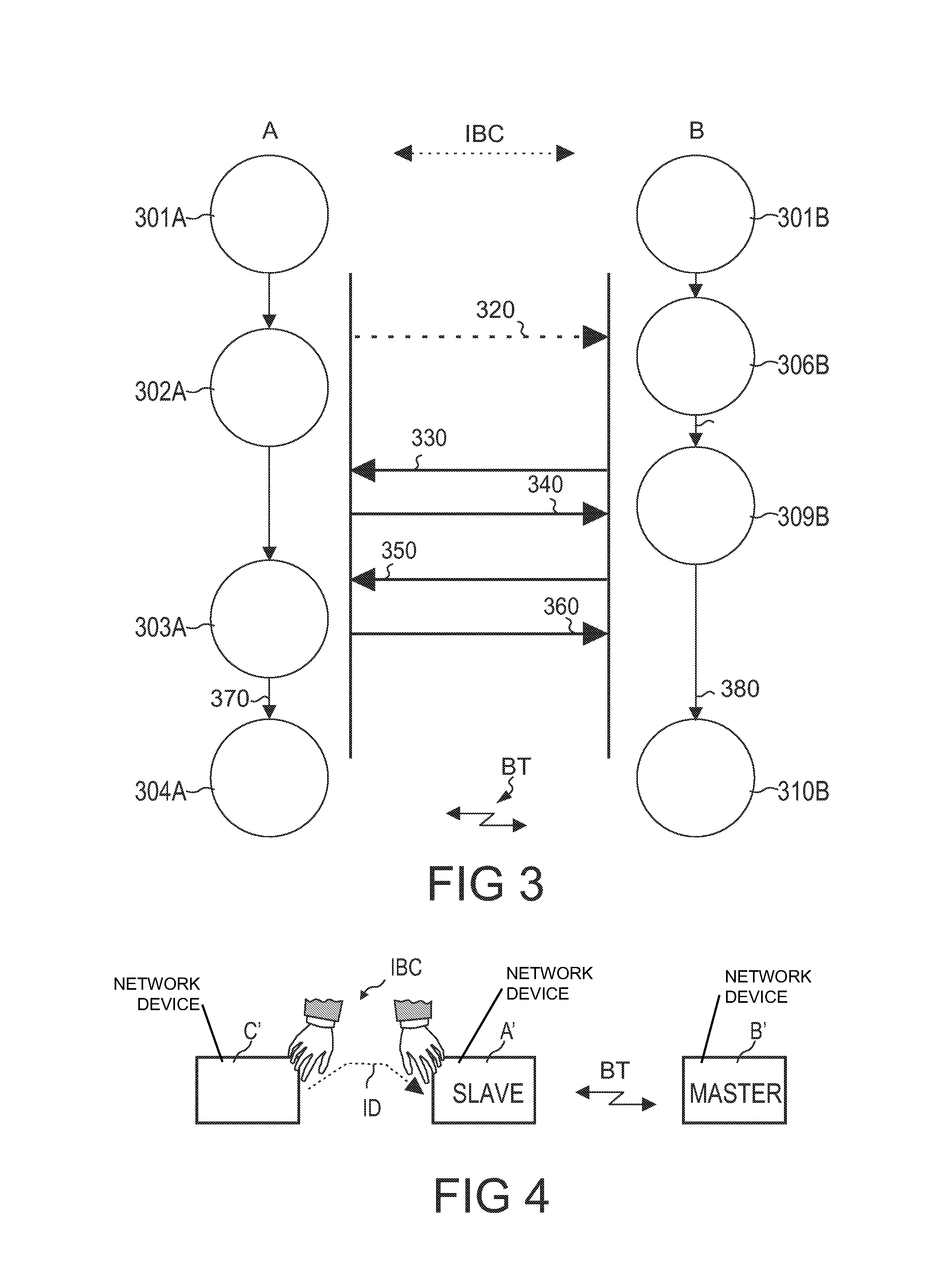
Device Capable of Being Operated Within a Network, Network System, Method of Operating a Device Within a Network, Program Element, and Computer-Readable Medium
InactiveUS20080259043A1Easily instructMisuse is securely avoidedTransmissionSelective content distributionCommunication unitHuman–computer interaction
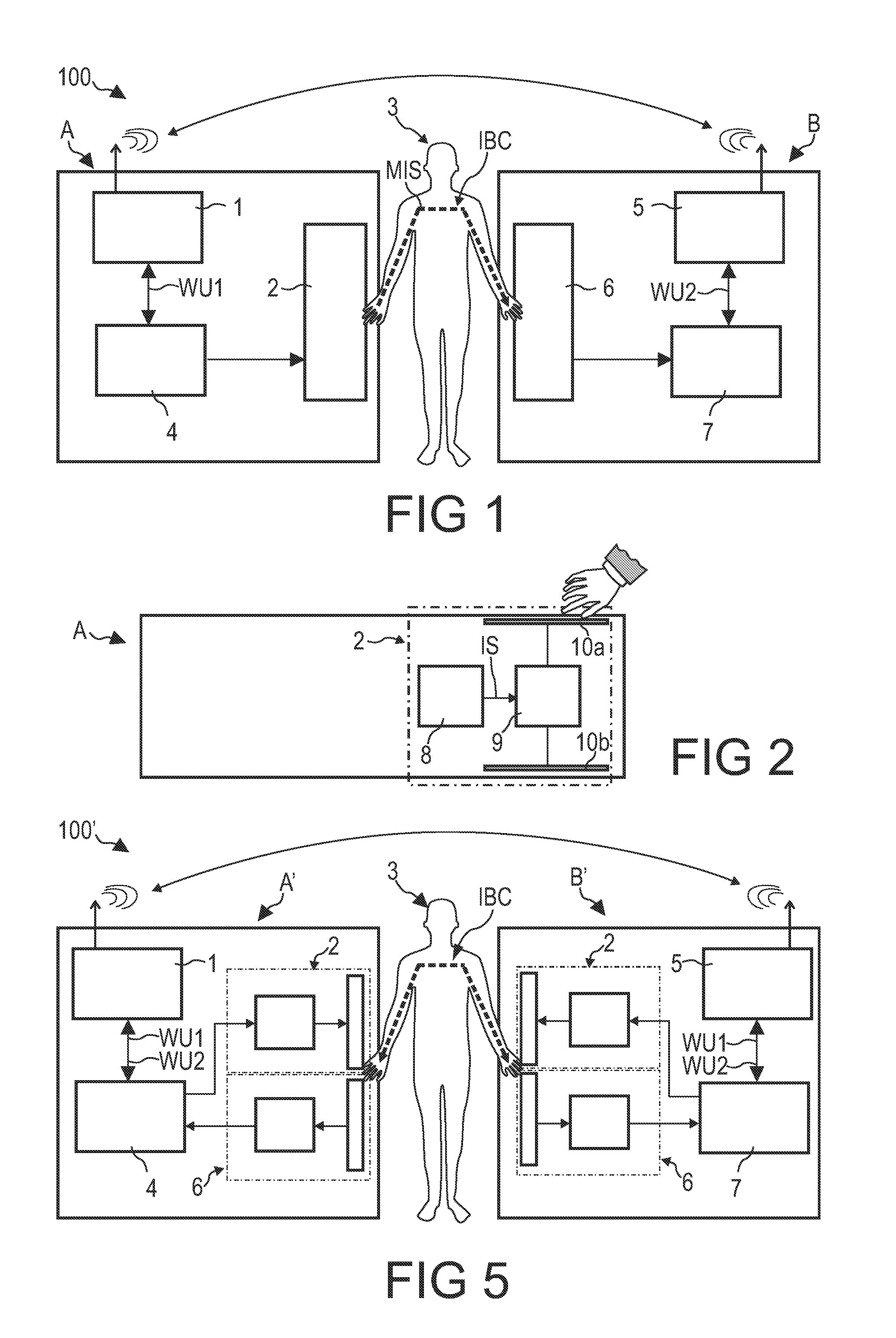
A device (A) is described, which is capable of being operated within a network comprising a touch interface (2) which is adapted to detect that a user (3) touches the touch interface (2) and simultaneously touches a touch interface (6) of another device (B) capable of being operated within a network, and a communication unit (1) adapted to communicate with a communication unit (5) of the other device (B) via a communication network established between the device (A) and the other device (B) when detecting that the user touches the touch interface (2) of the device (A) and simultaneously touches the touch interlace (6) of the other device (B).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
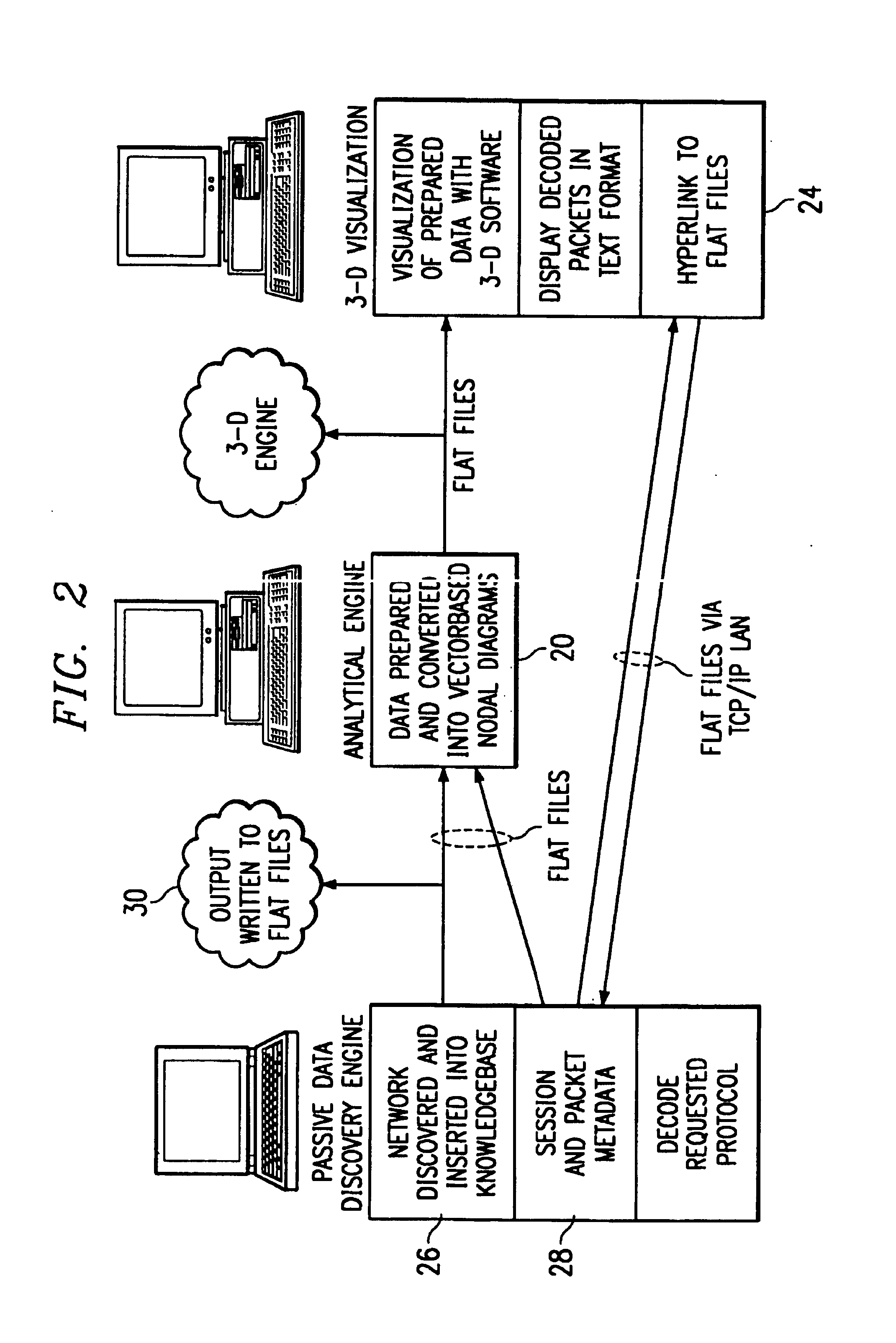
Information security analysis system
InactiveUS7047423B1Reduce bandwidth usageTraffic bottleneckDigital data processing detailsDigital computer detailsDigital dataOperational system
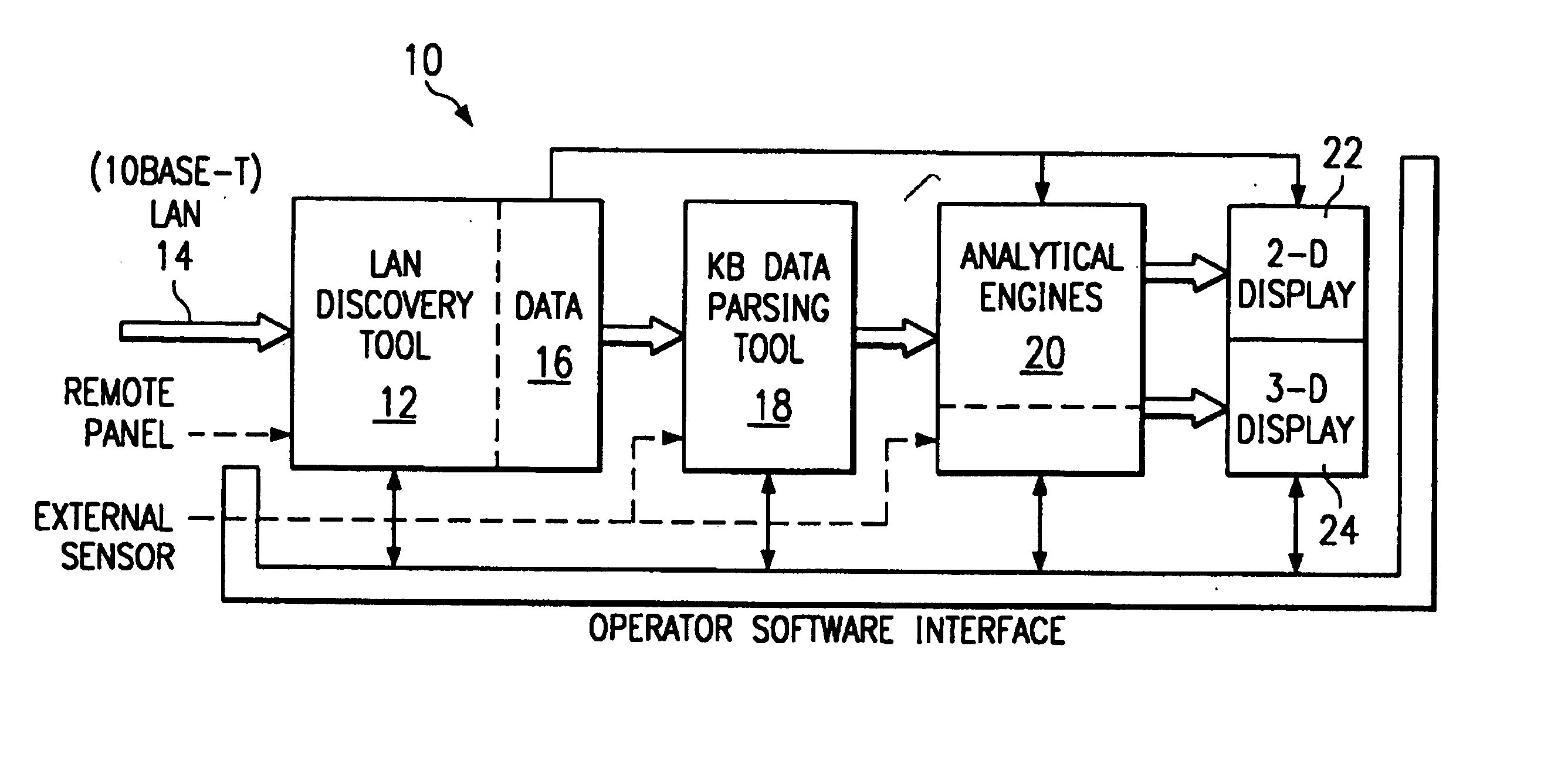
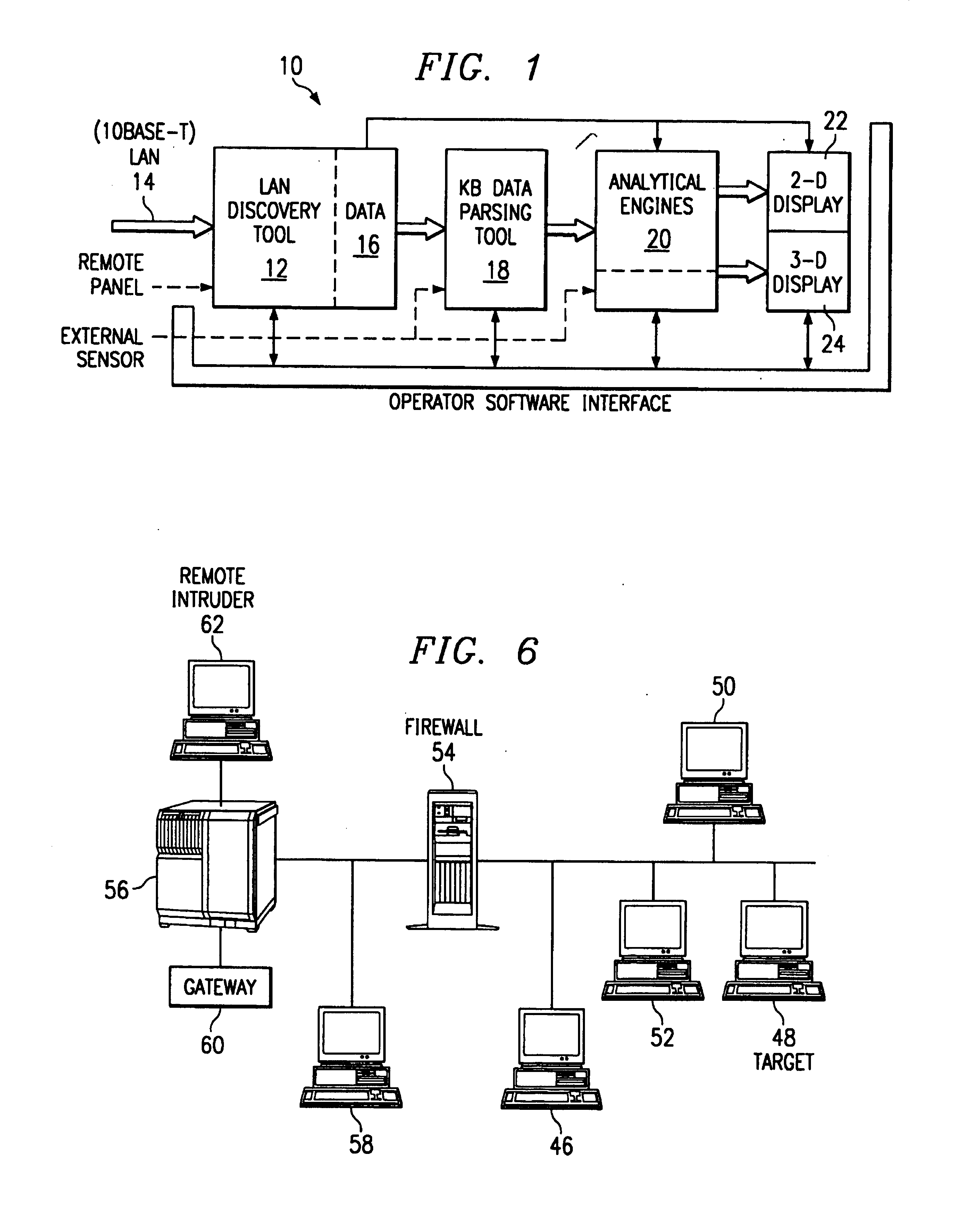
The analysis system is a collection, configuration and integration of software programs that reside on multiple interconnected computer platforms. The software, less computer operating systems, is a combination of sensor, analysis, data conversion, and visualization programs. The hardware platforms consist of several different types of interconnected computers, which share the software programs, data files, and visualization programs via a Local Area Network (LAN). This collection and integration of software and the migration to a single computer platform results in an approach to LAN / WAN monitoring in either a passive and / or active mode. The architecture permits digital data input from external sensors for analysis, display and correlation with data and displays derived from four major software concept groups. These are: Virus Computer Code Detection; Analysis of Computer Source and Executable Code; Dynamic Monitoring of Data Communication Networks; 3-D Visualization and Animation of Data.
Owner:COMP ASSOC THINK INC
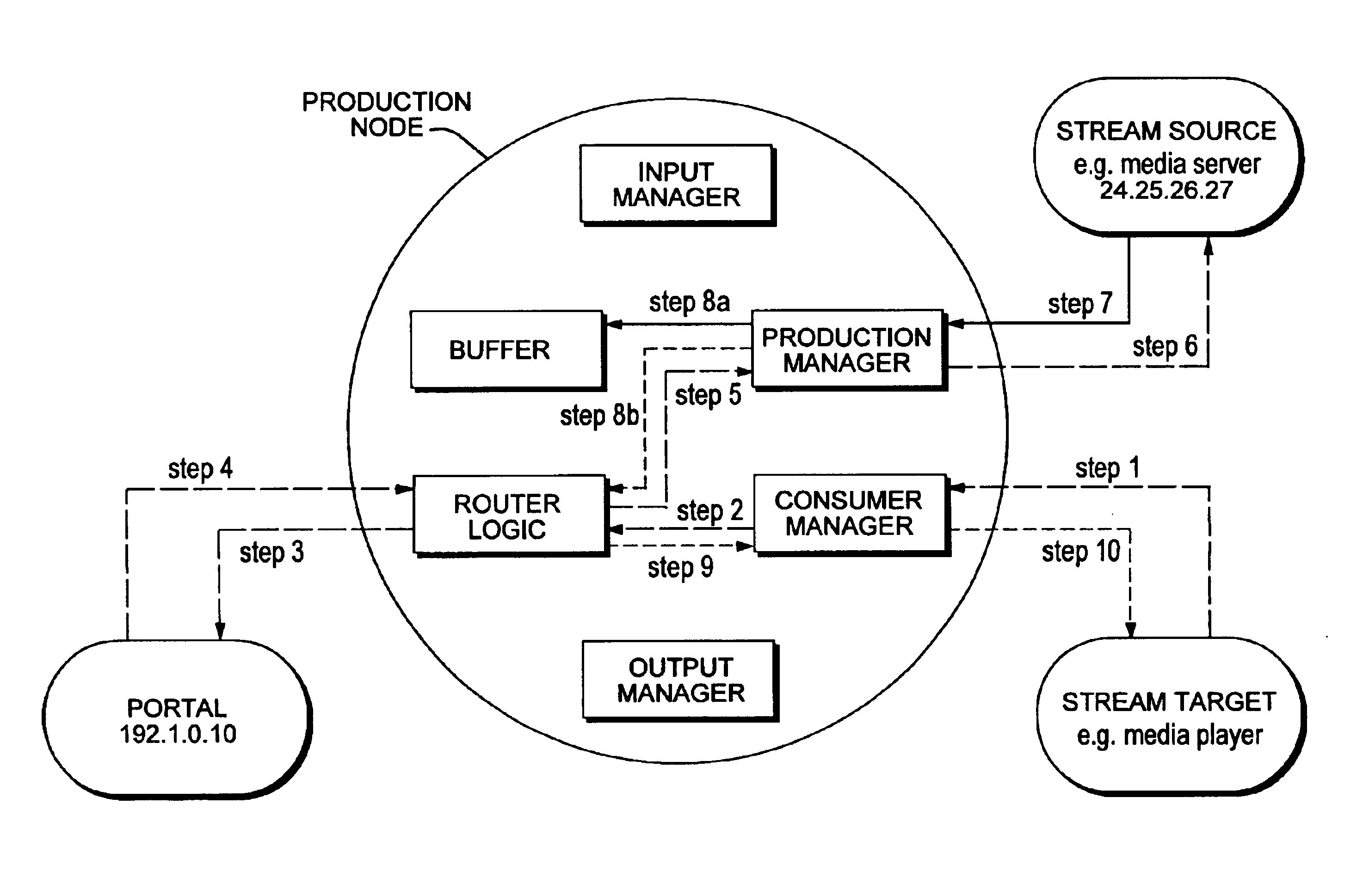
Organic data network having a dynamic topology
InactiveUS7065548B2Reduce failureReduced flexibilityRoad vehicles traffic controlMultiple digital computer combinationsThe InternetMobile phone
The invention relates to a method and system of growing a network and distributing data using the network including one or more production nodes that send data and a plurality of consumer nodes that receive data from one or more production nodes or at least one other consumer node. The first software resides on each of the consumer nodes and the second software resides on each of the production nodes wherein a data request is not relayed and routed through several intermediate nodes in a path way but only is made to a logically adjacent node and where the logically adjacent nodes take no action to retrieve data from another node if the logically adjacent node is unable to fulfill the request itself. The invention can be implemented for mobile phones, streaming internet applications and cable television.
Owner:NONEND INVENTIONS NV
System and Method of Registering with an Access Point
InactiveUS20080293413A1Efficiently decideReduce overheadNetwork traffic/resource managementRadio/inductive link selection arrangementsTelecommunicationsMobile device
A method of registering a mobile device with an access point, is provided in which the mobile device preregisters with access points nearby in order to accelerate the registration process when roaming is initiated. Roaming may be initiated when the SNR is increasing relative to the current access point and decreasing relative to another access point.
Owner:MOBIDIA INC
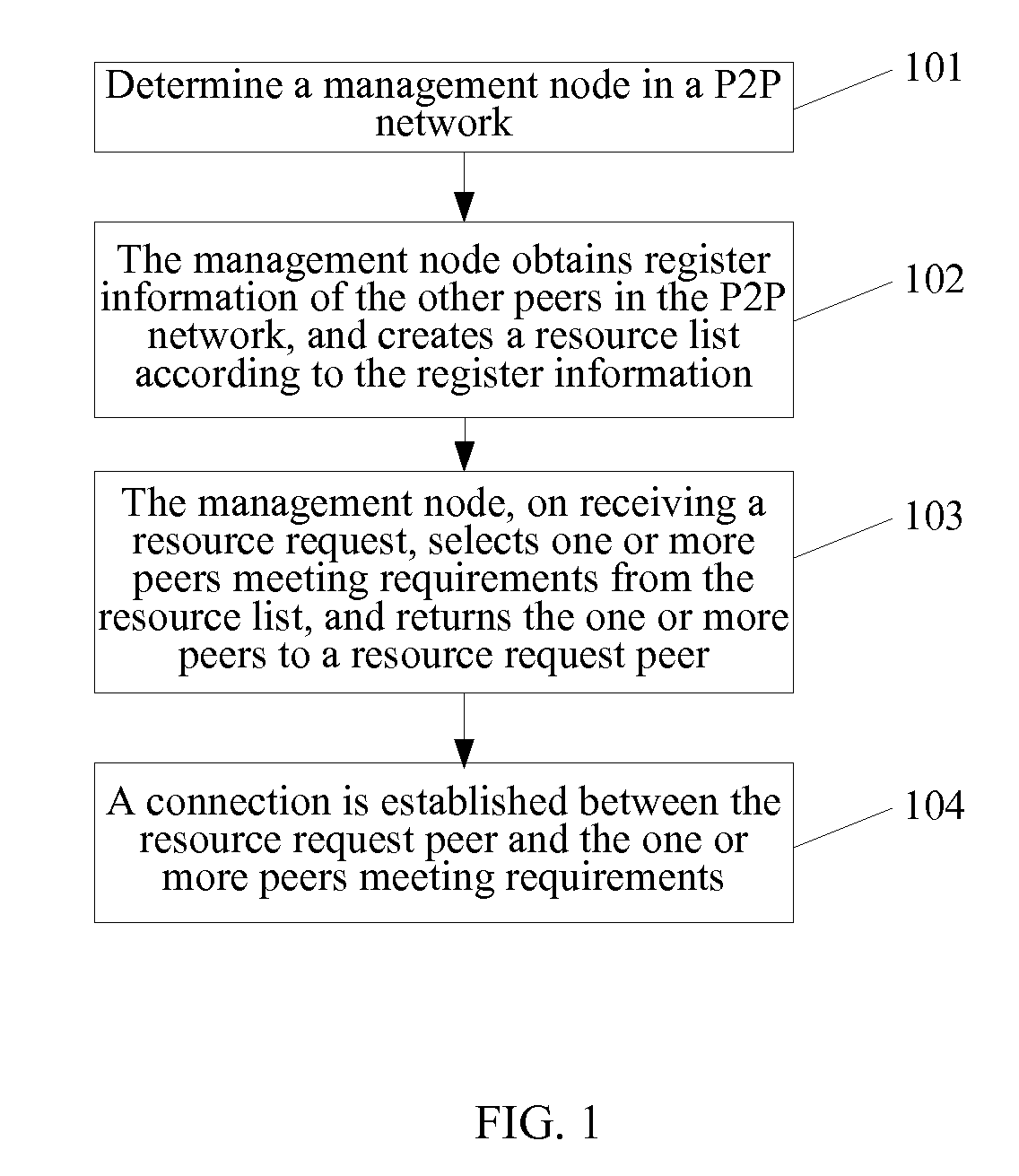
Method, system and device for establishing a peer to peer connection in a p2p network
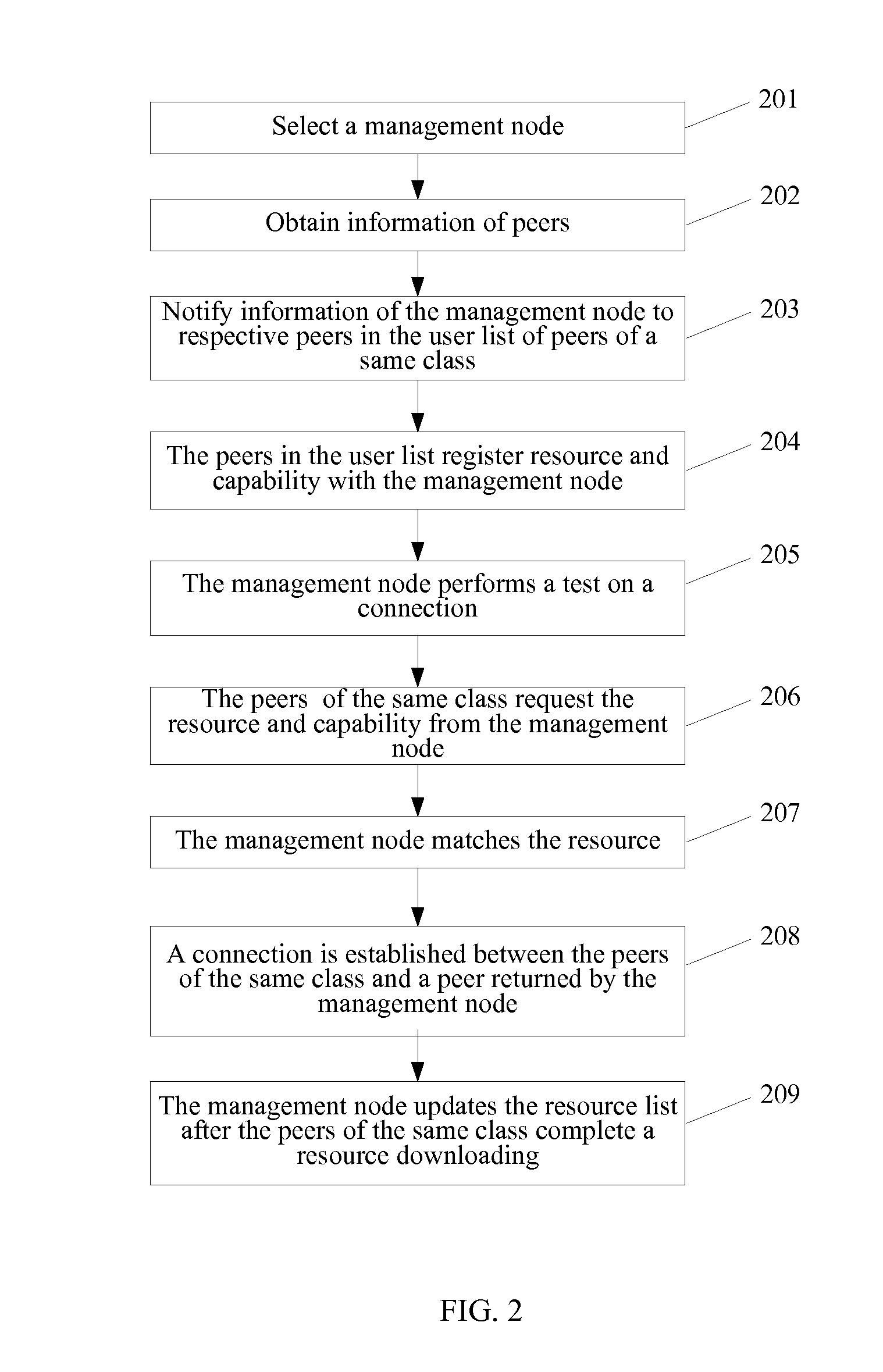
ActiveUS20090177772A1Improve manageabilityReduce occupancyMultiple digital computer combinationsTransmissionDistributed computingPeer-to-peer
A method and system for establishing a peer to peer connection in a P2P network and a peer device in the P2P network, wherein the method comprises of the following: (1) a management node in the P2P network receives a resource request; (2) the management node selects one or more peers which meet the demand from a resource list established previously according to the logon information of the other peers in the P2P network to return it to a resource request peer; (3) the connection is established between the said resource request peer and the said peers which meet the demand.
Owner:HUAWEI TECH CO LTD
Computing system for providing software components on demand to a mobile device
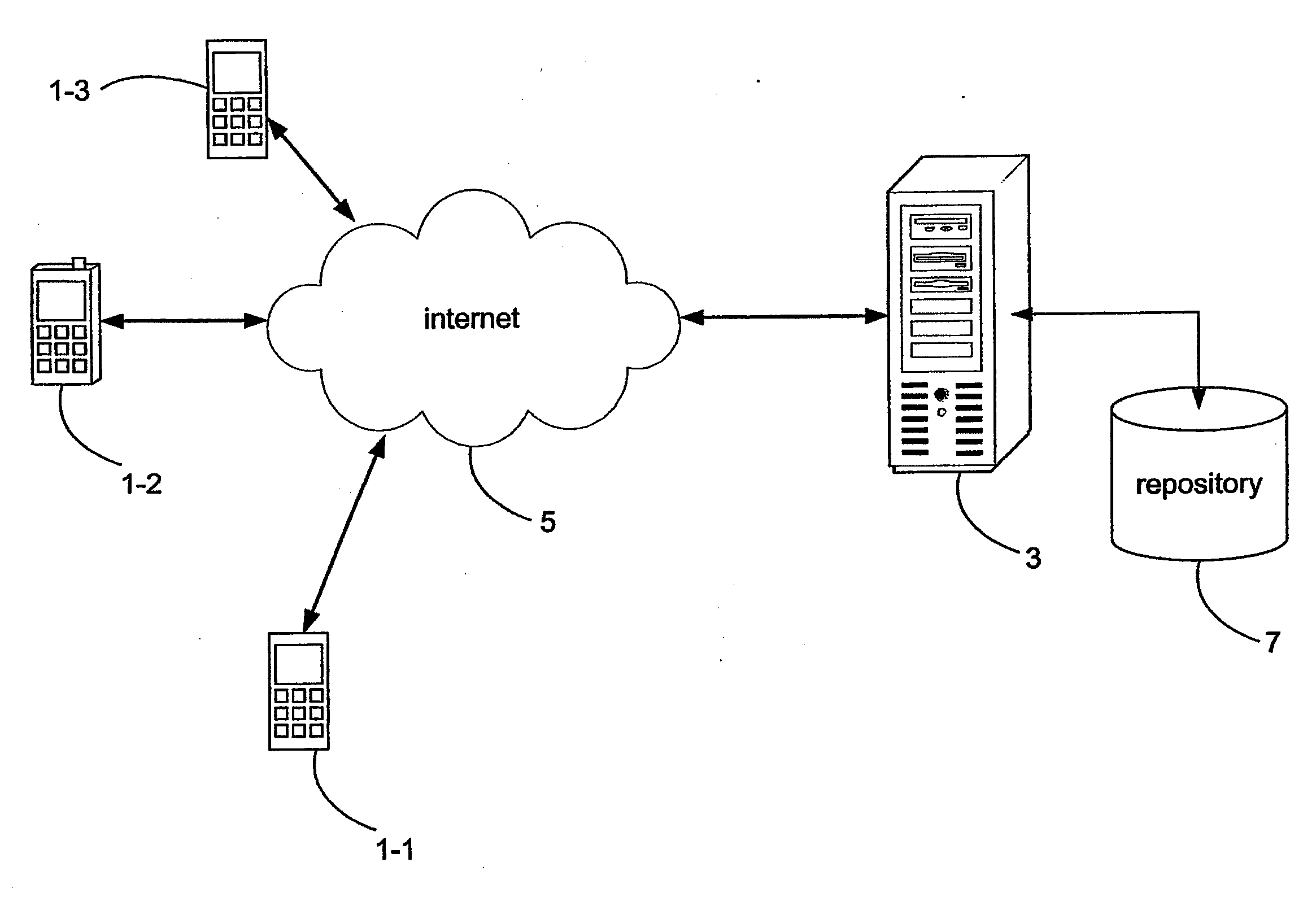
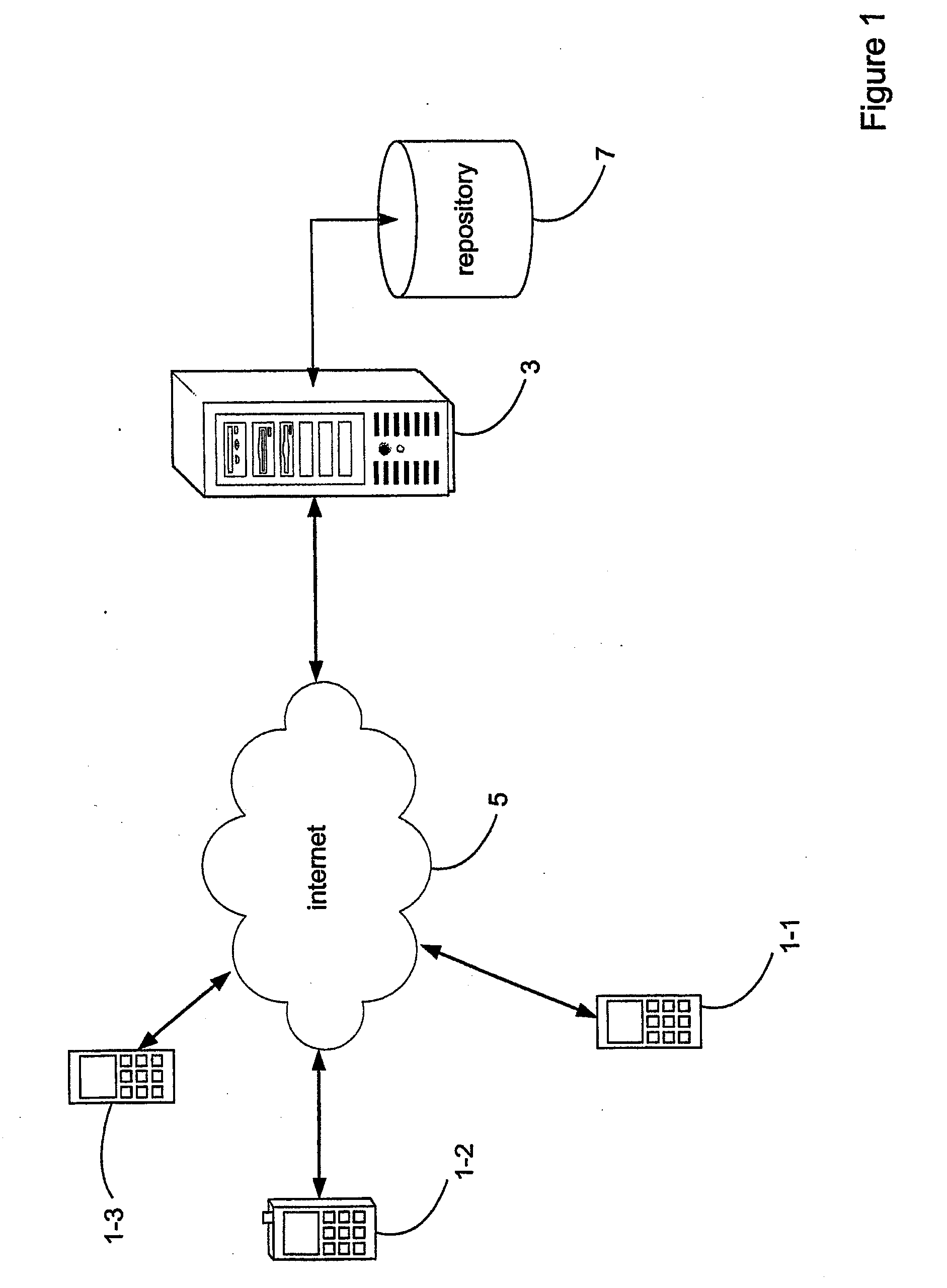
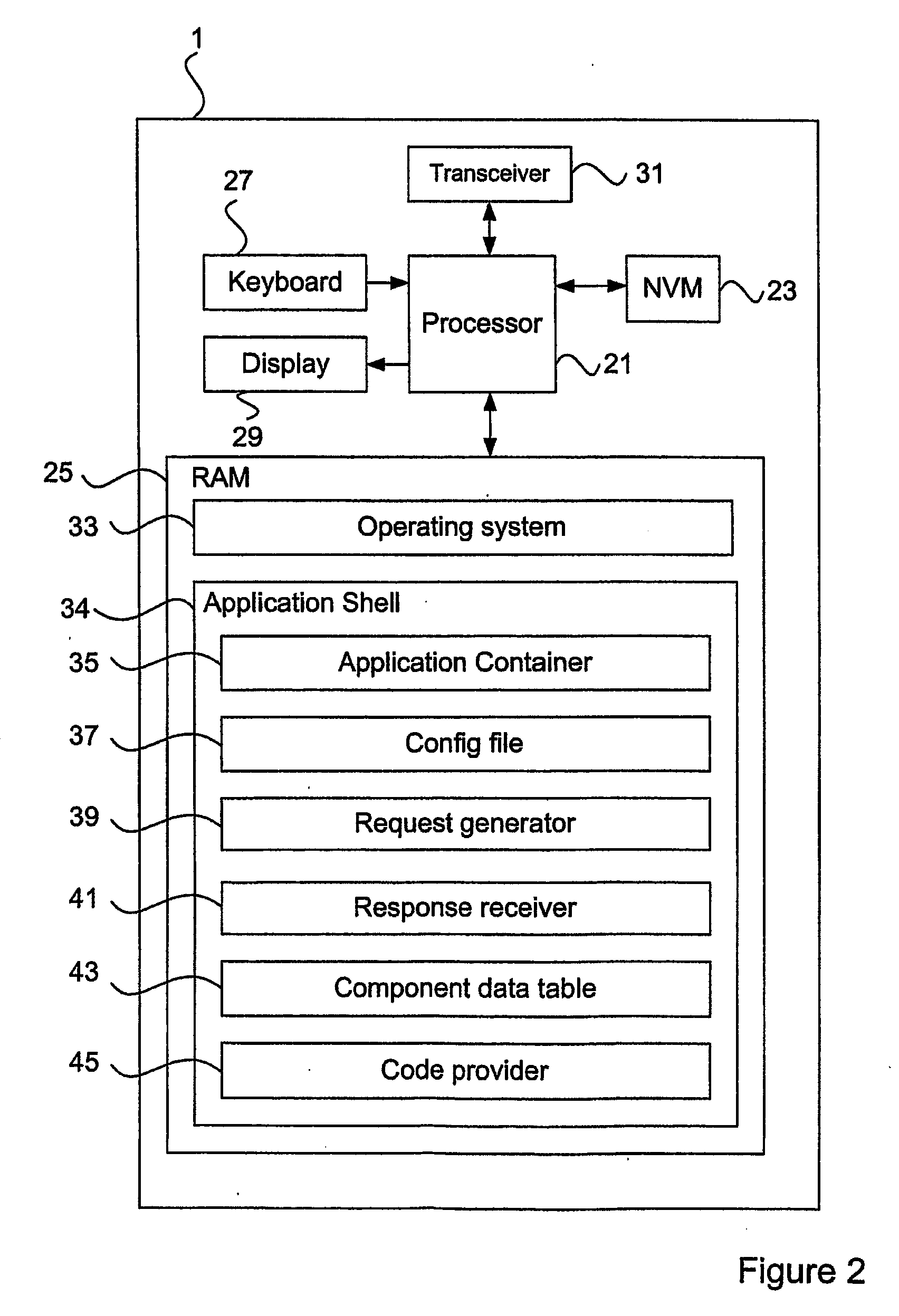
ActiveUS20090282403A1Reduce delaysReduce development costsProgram loading/initiatingTransmissionClient-sideLocation data
A computing system includes a computer network, a server connected thereto, and a client device for communicating with the server over the computer network. The client device runs an application shell software module providing a dynamically configurable application in a piecemeal manner by individually downloading and running a plurality of software components that are individually stored on the computer network and downloaded / run when needed. The server receives a request for available software components from the application shell software module, controls a search of an index for available software components and transmits a response to the application shell software module providing details of available software components. The application shell software module receives details of available software components from the server, retrieves a selected software component from the location identified by location data for the selected software component, and starts and stops the selected software component within the application shell software module in accordance with received data.
Owner:UNIVIRTUA IRELAND
Methods and apparatus for efficient multi-tasking
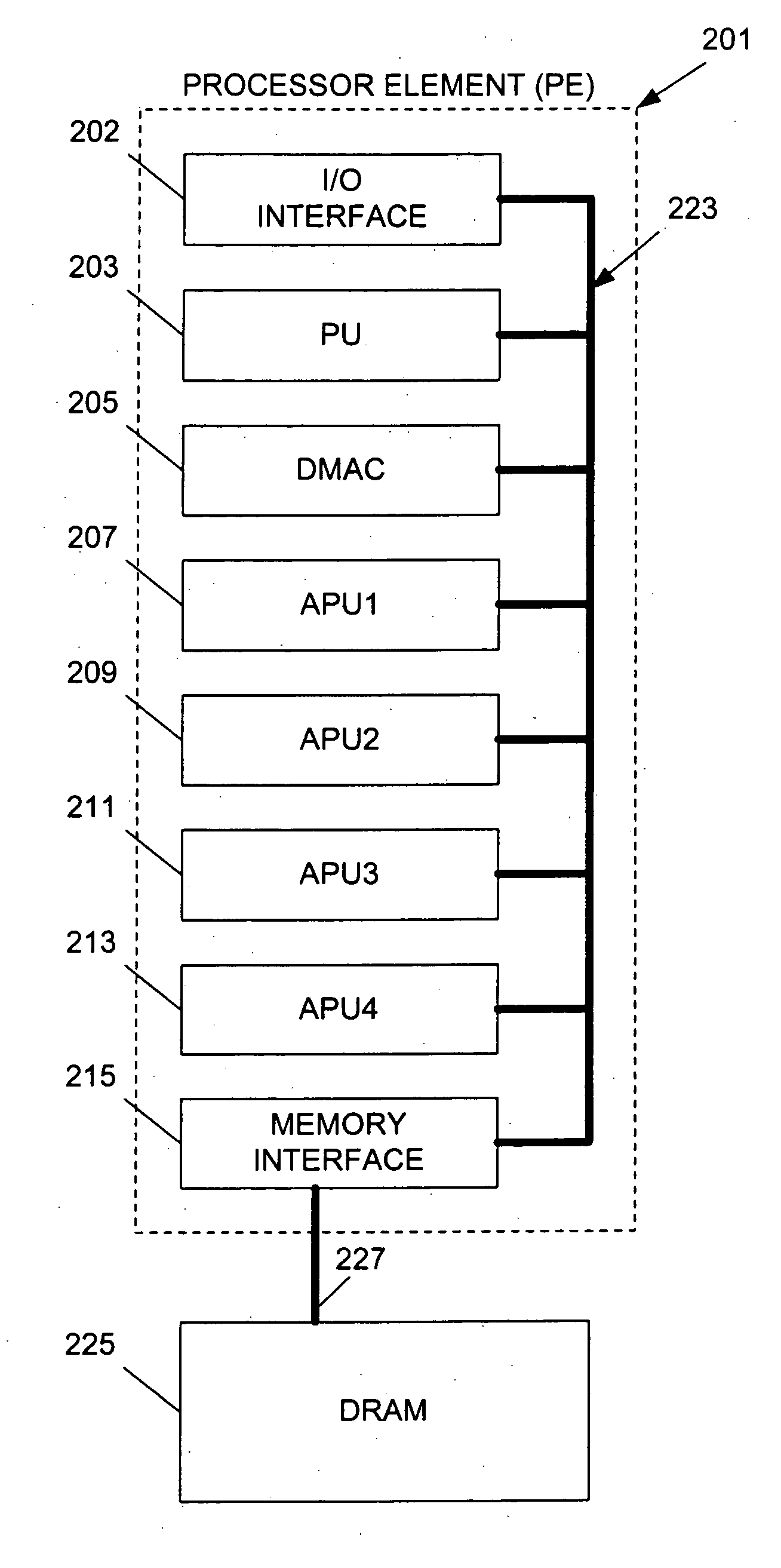
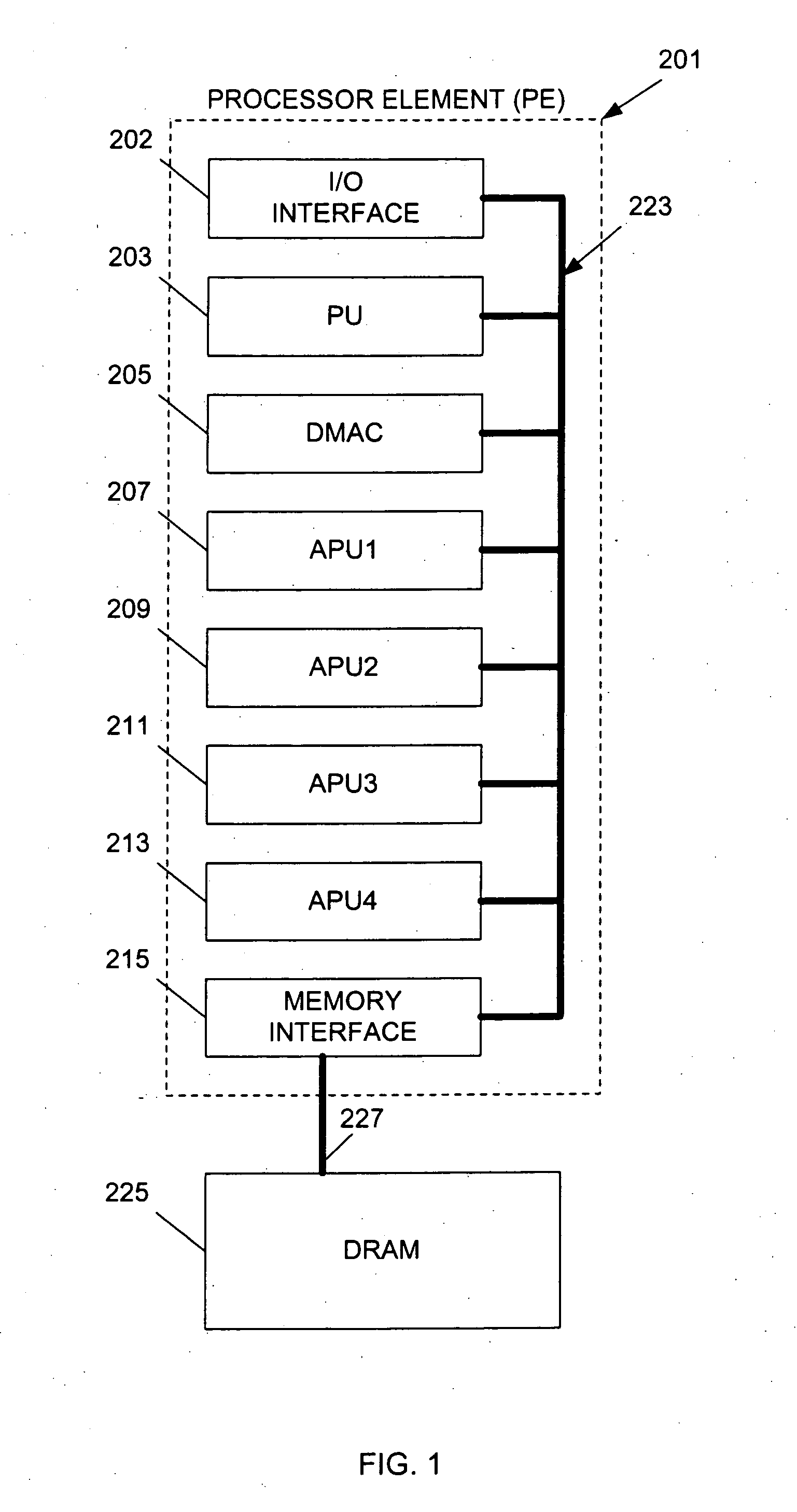
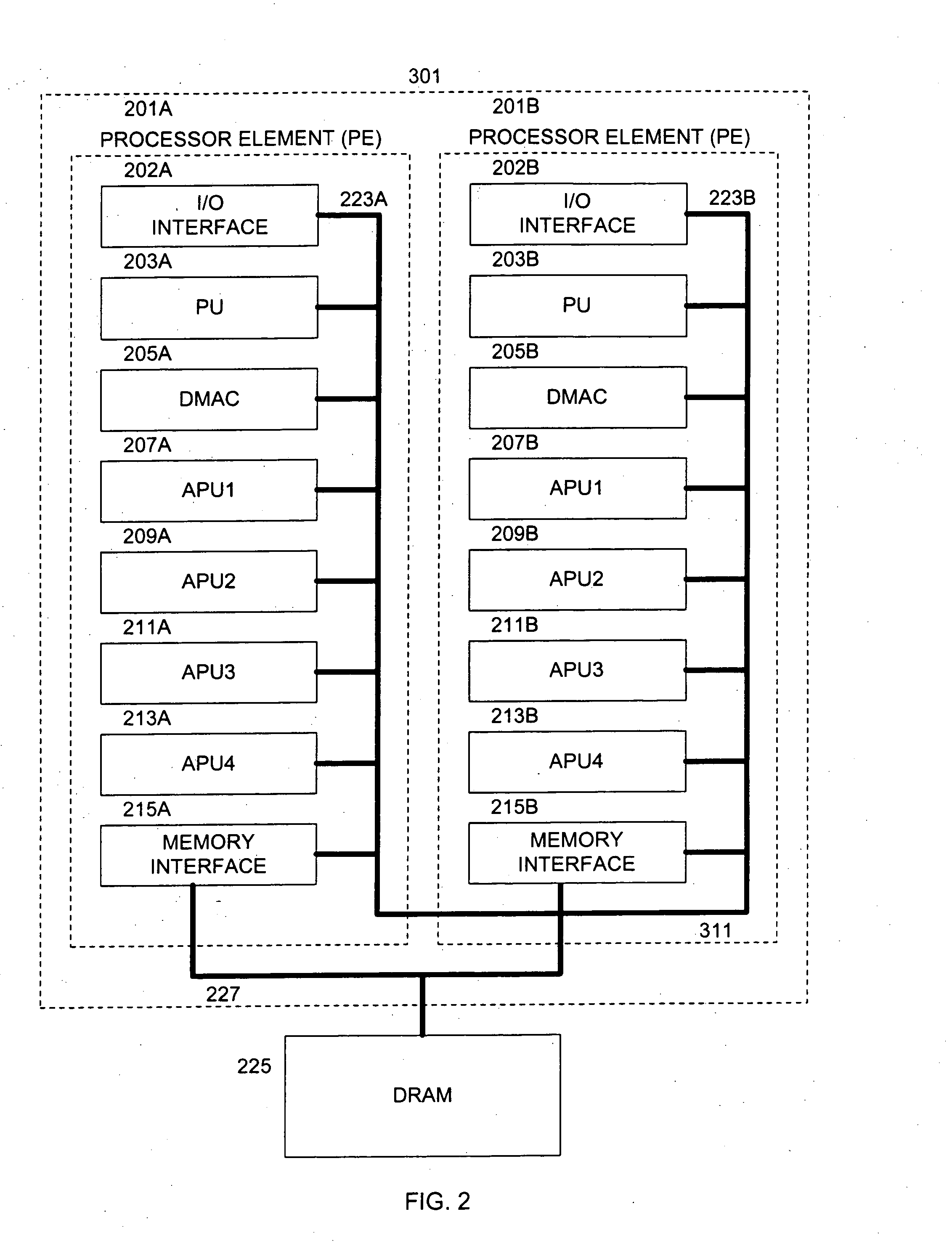
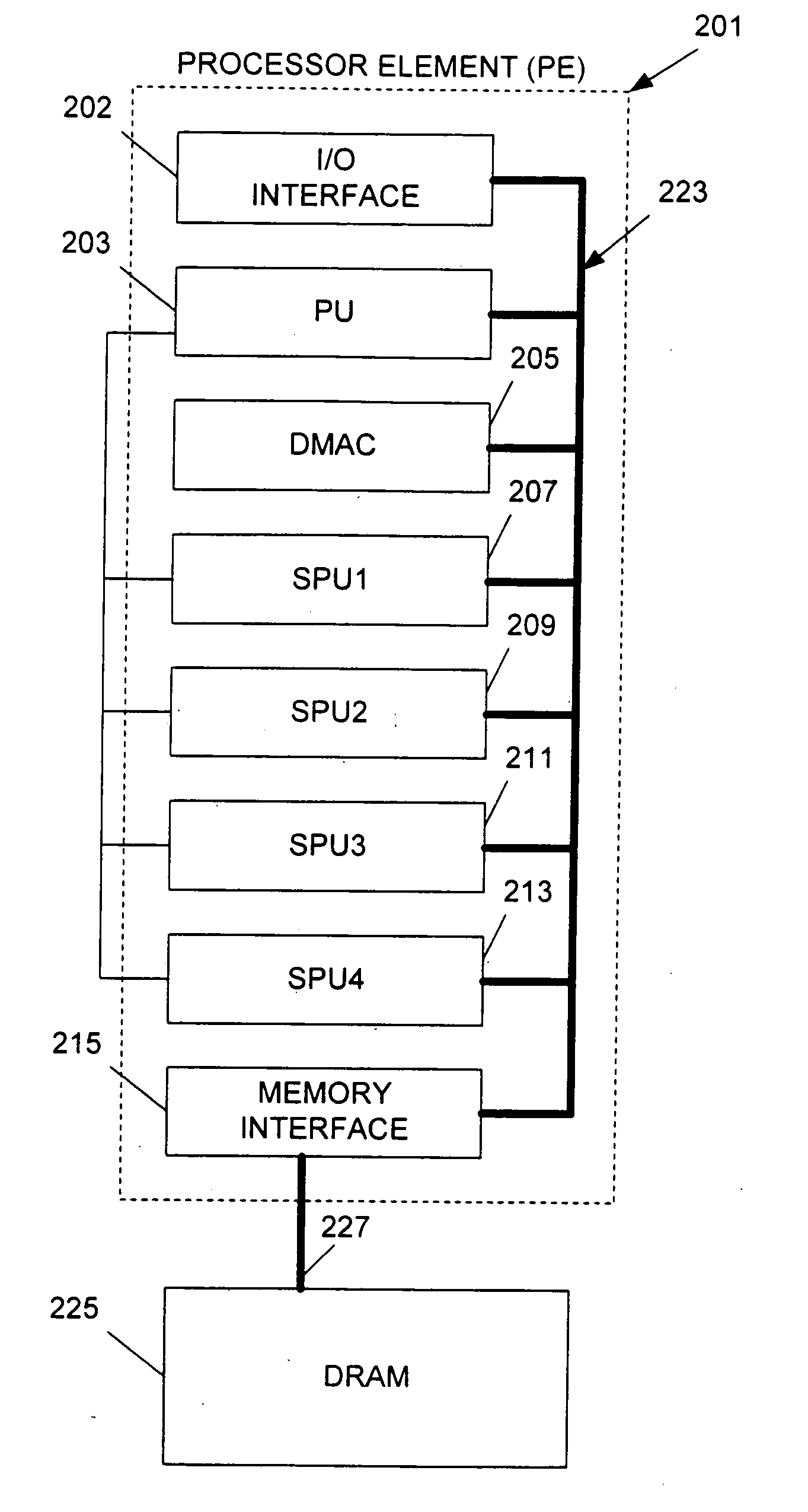
InactiveUS20050120185A1Efficient high speed processingEasy to buildMemory loss protectionProgram synchronisationMemory interfaceData store
A system includes a shared memory; a memory interface unit coupled to the shared memory and operable to retrieve data from the shared memory at requested addresses, and to write data to the shared memory at requested addresses; and a plurality of processing units in communication with the memory interface and operable to (i) instruct the memory interface unit that data be loaded with reservation from the shared memory at a specified address such that any operations may be performed on the data, and (ii) instruct the memory interface unit that the data be stored in the shared memory at the specified address, wherein at least one of the processing units includes a status register having one or more bits indicating whether a reservation was lost: whether the data at the specified address in shared memory was modified.
Owner:IBM CORP +1
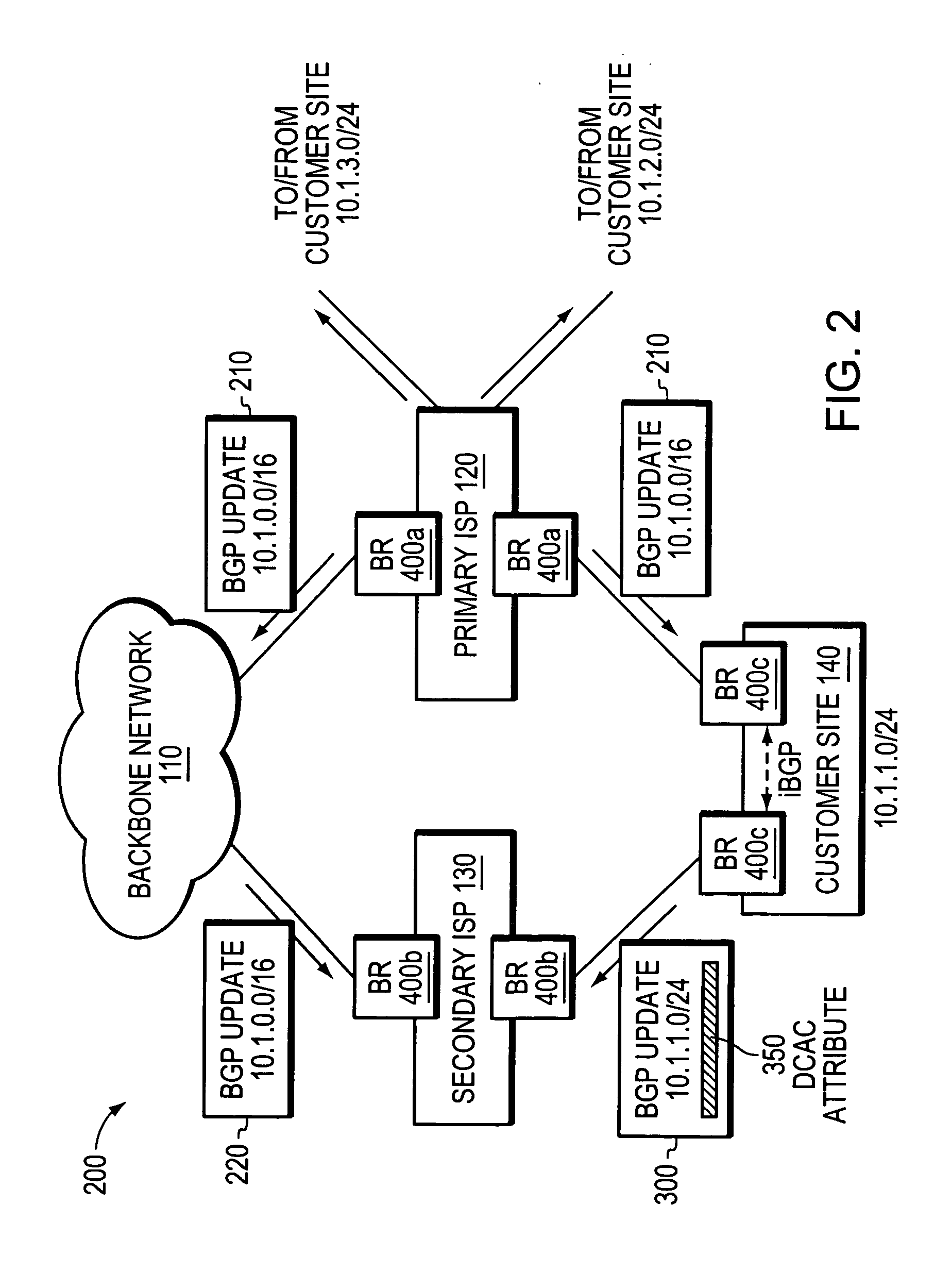
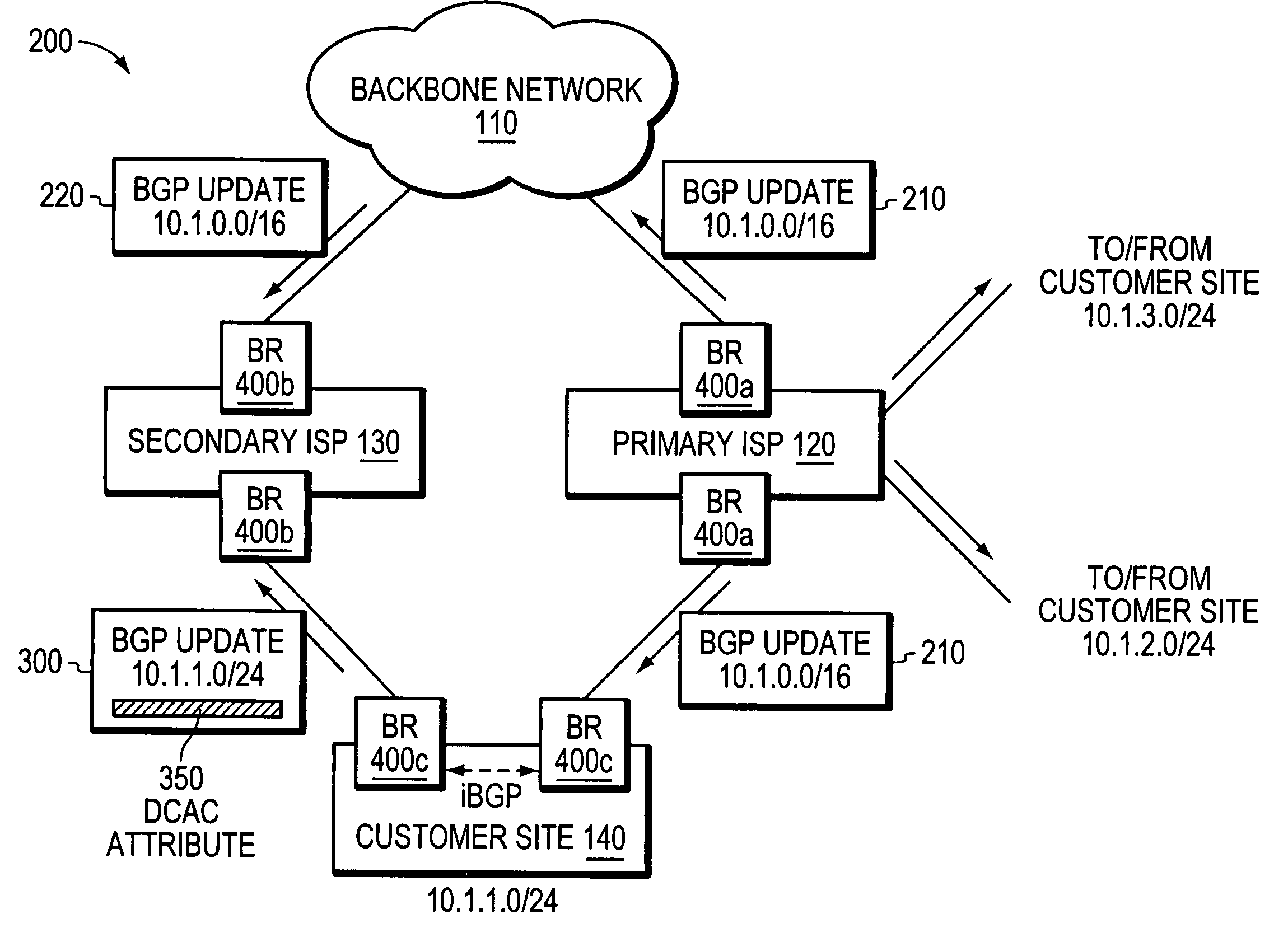
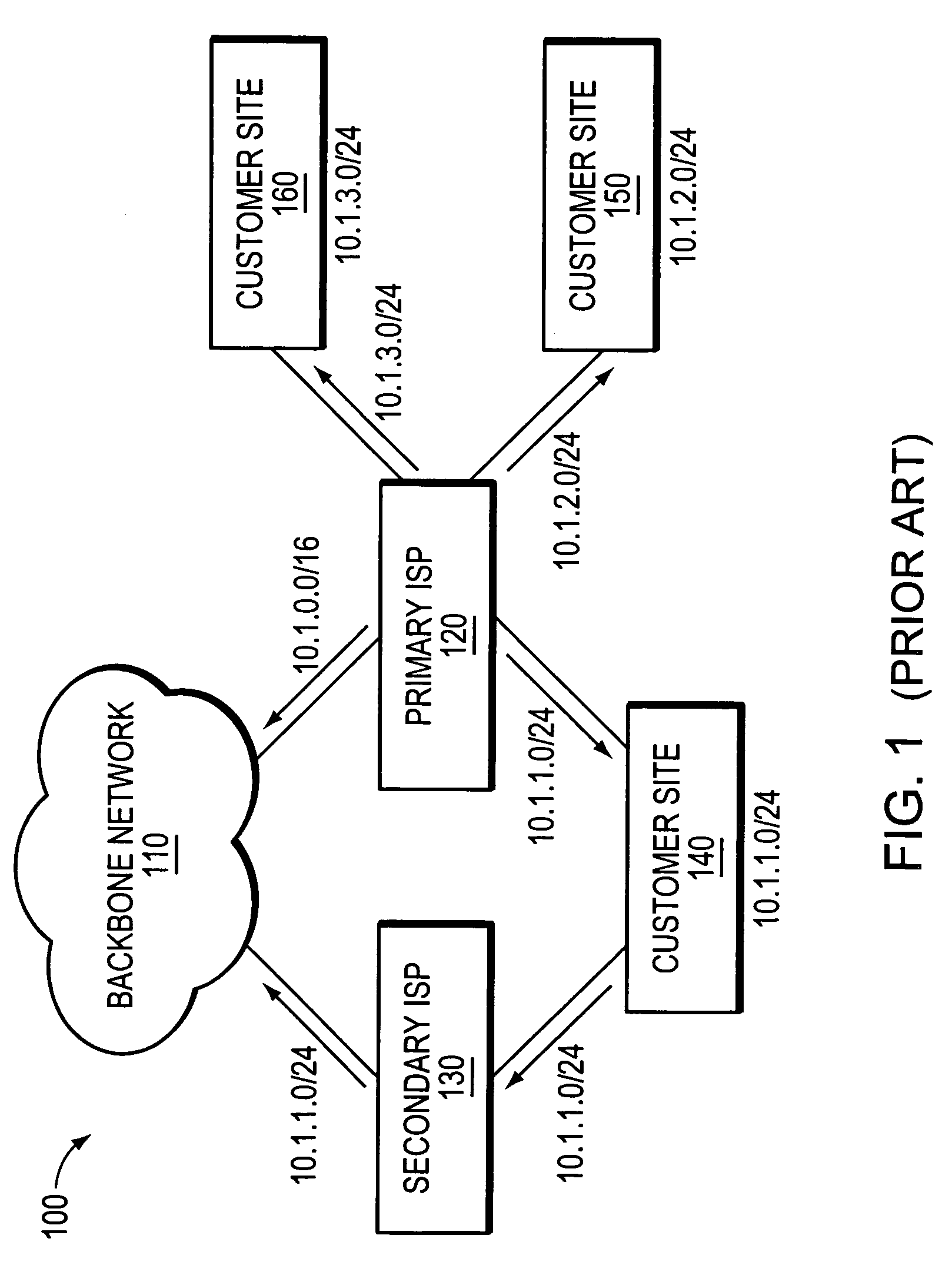
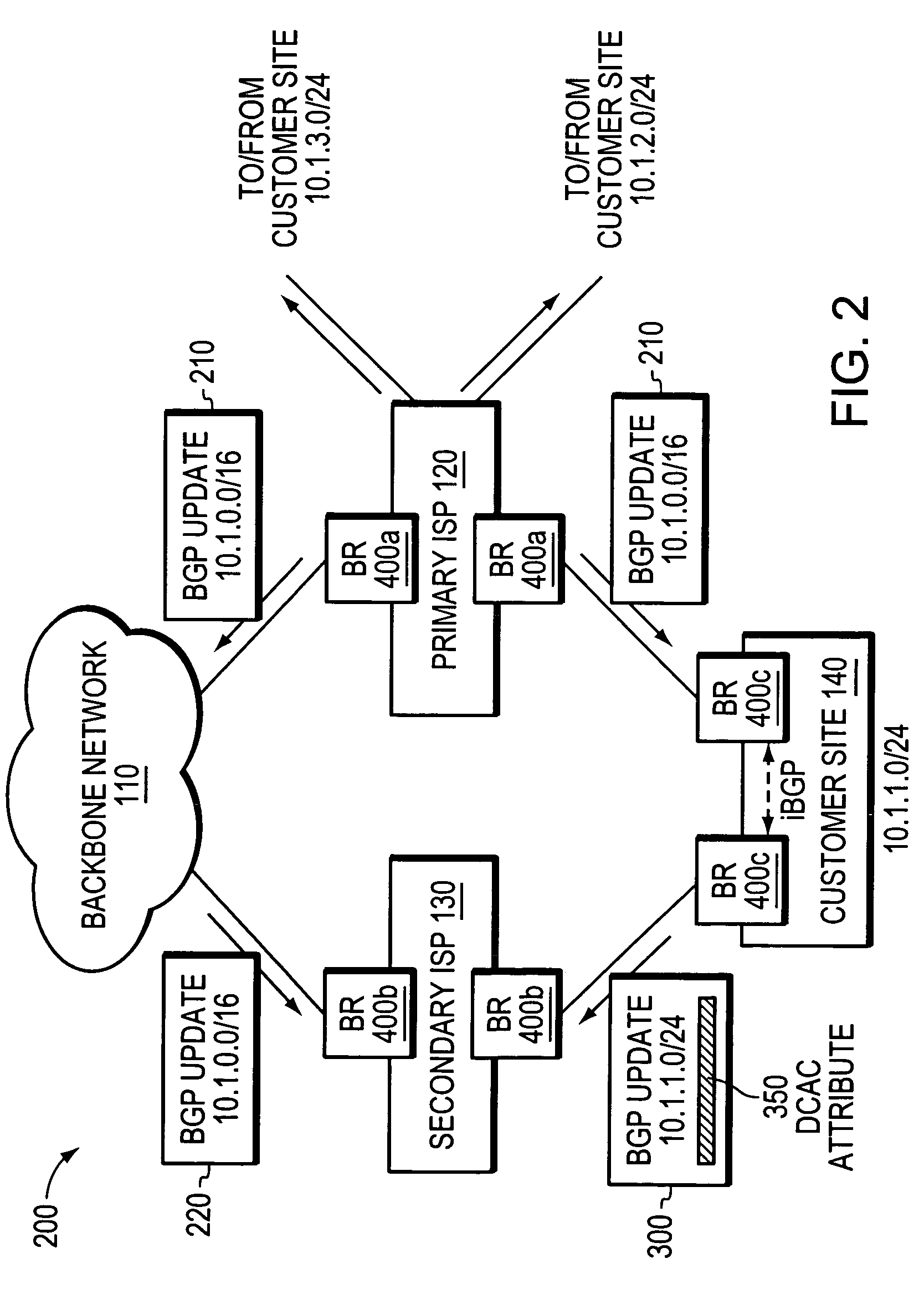
Multi-homing using controlled route leakage at a backup service provider
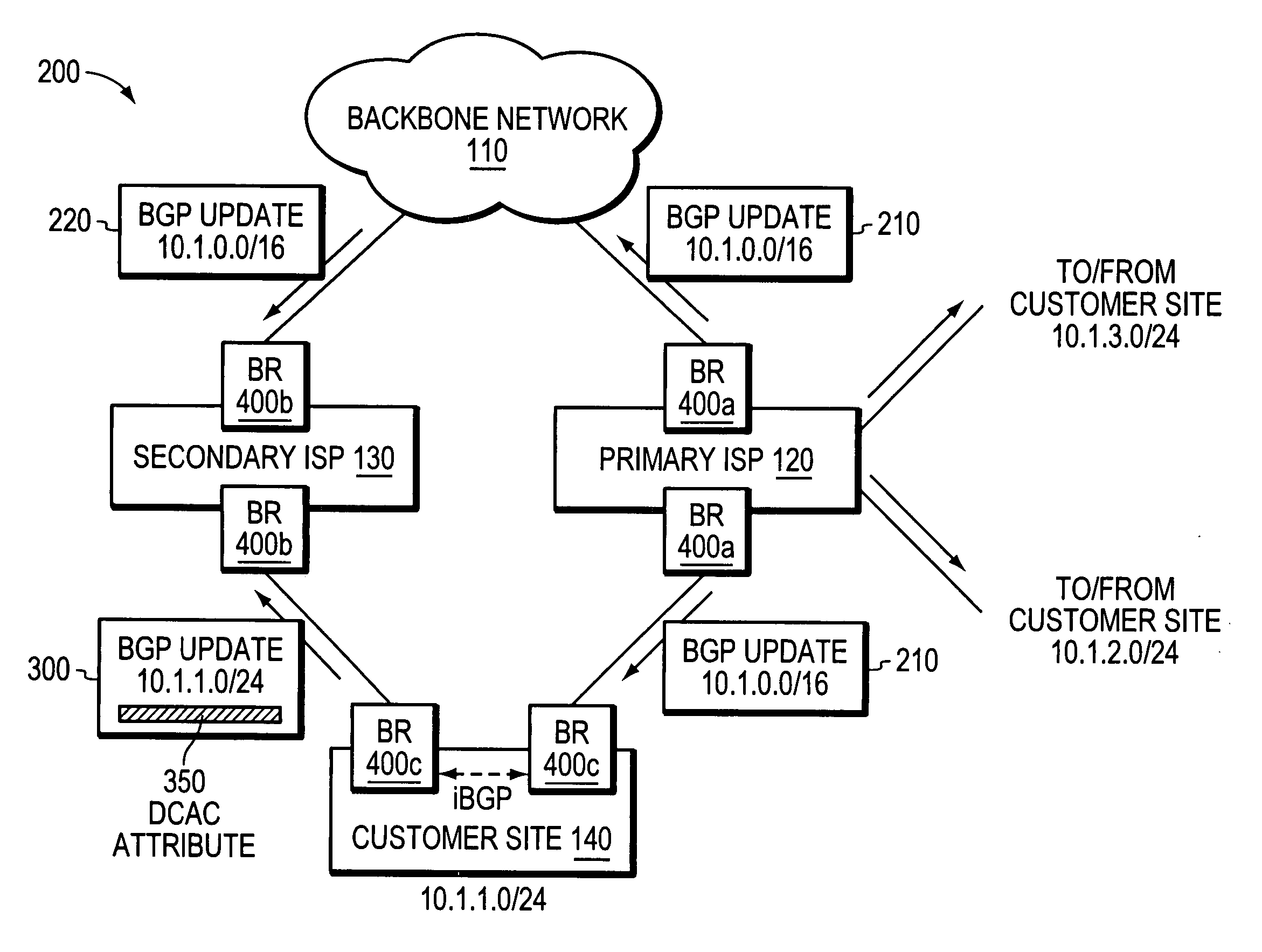
ActiveUS20060268681A1Faster network convergenceBetter bandwidth utilizationError preventionFrequency-division multiplex detailsNetwork addressingNetwork address
A technique is provided for implementing route aggregation in a computer network containing a multi-homed customer site connected to primary and second networks, which in turn are both connected to a common “backbone” network. According to the technique, the primary network allocates a block of network addresses for the customer site, and the customer site notifies the secondary network of its allocated addresses. The secondary network first determines whether the primary network has already advertised an aggregated route which incorporates the customer site's route. If so, the secondary network “suppresses” (i.e., does not advertise) the customer site's route. The secondary network only “unsuppresses” the customer site's route if it detects that the primary network has lost connectivity to the customer site and / or the backbone network.
Owner:CISCO TECH INC
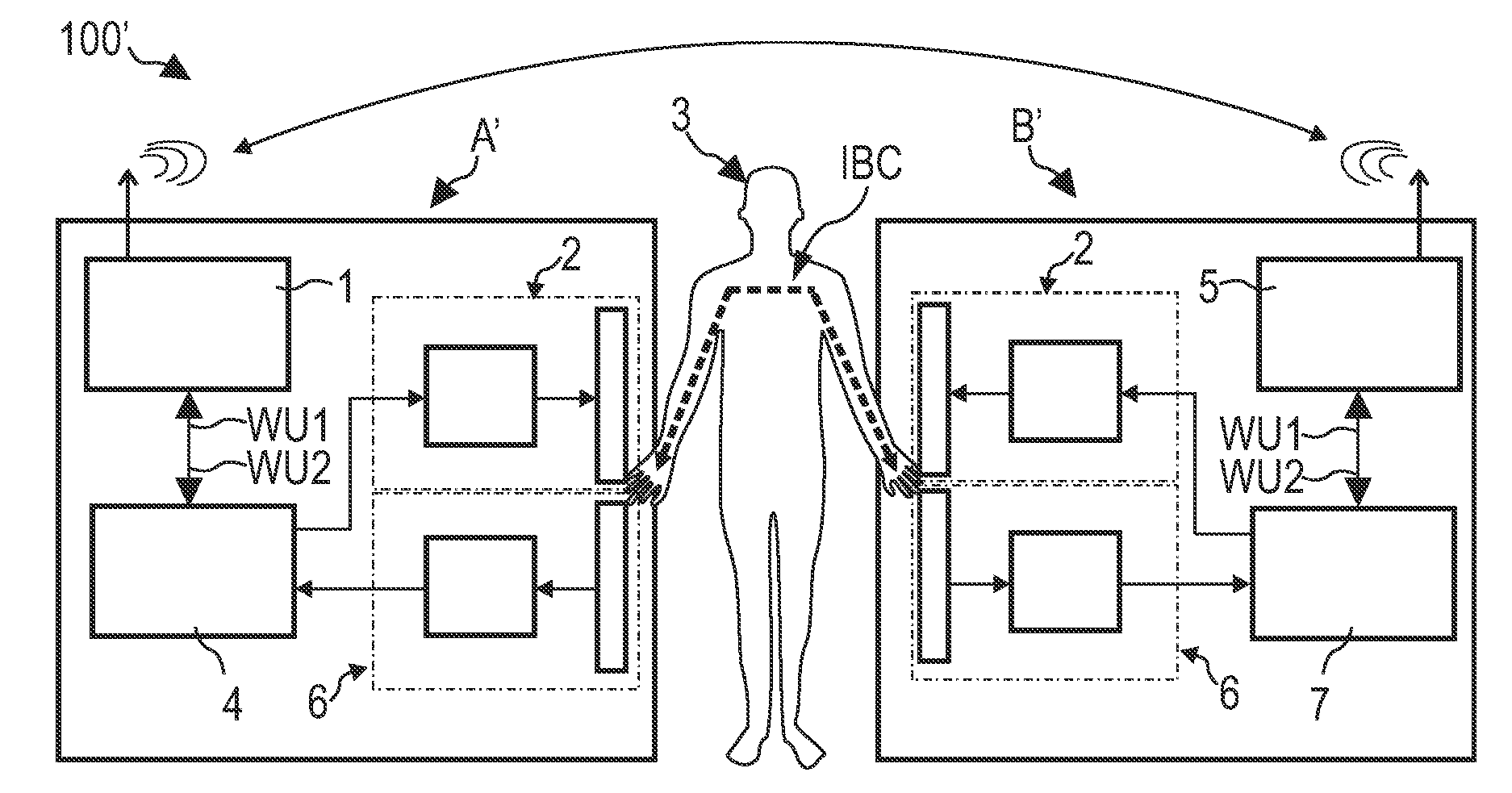
Device capable of being operated within a network, network system, method of operating a device within a network, program element, and computer-readable medium
InactiveUS8253693B2Easily instructMisuse is securely avoidedInput/output for user-computer interactionCathode-ray tube indicatorsCommunication unitHuman–computer interaction
A device (A) is described, which is capable of being operated within a network comprising a touch interface (2) which is adapted to detect that a user (3) touches the touch interface (2) and simultaneously touches a touch interface (6) of another device (B) capable of being operated within a network, and a communication unit (1) adapted to communicate with a communication unit (5) of the other device (B) via a communication network established between the device (A) and the other device (B) when detecting that the user touches the touch interface (2) of the device (A) and simultaneously touches the touch interlace (6) of the other device (B).
Owner:KONINK PHILIPS ELECTRONICS NV
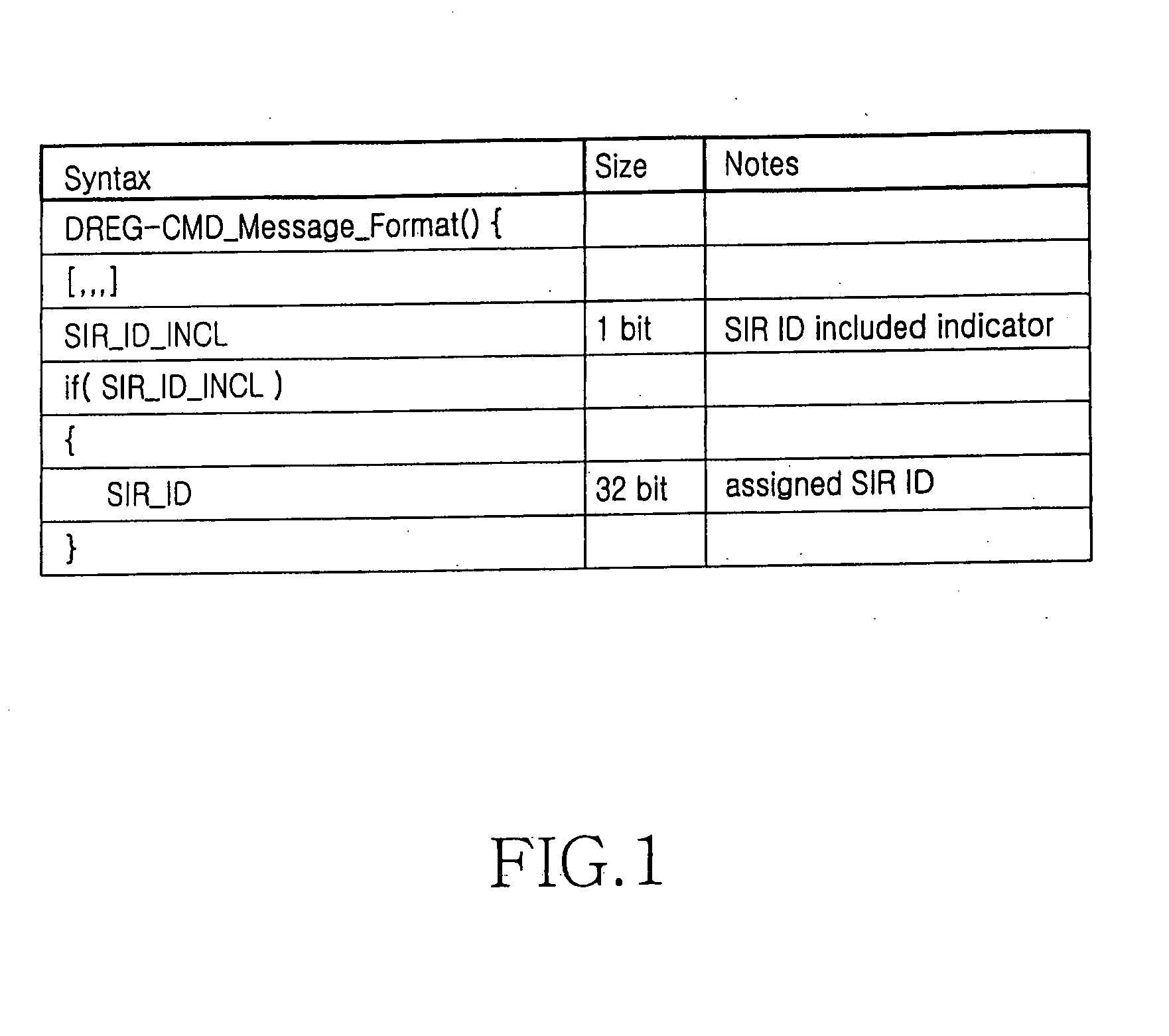
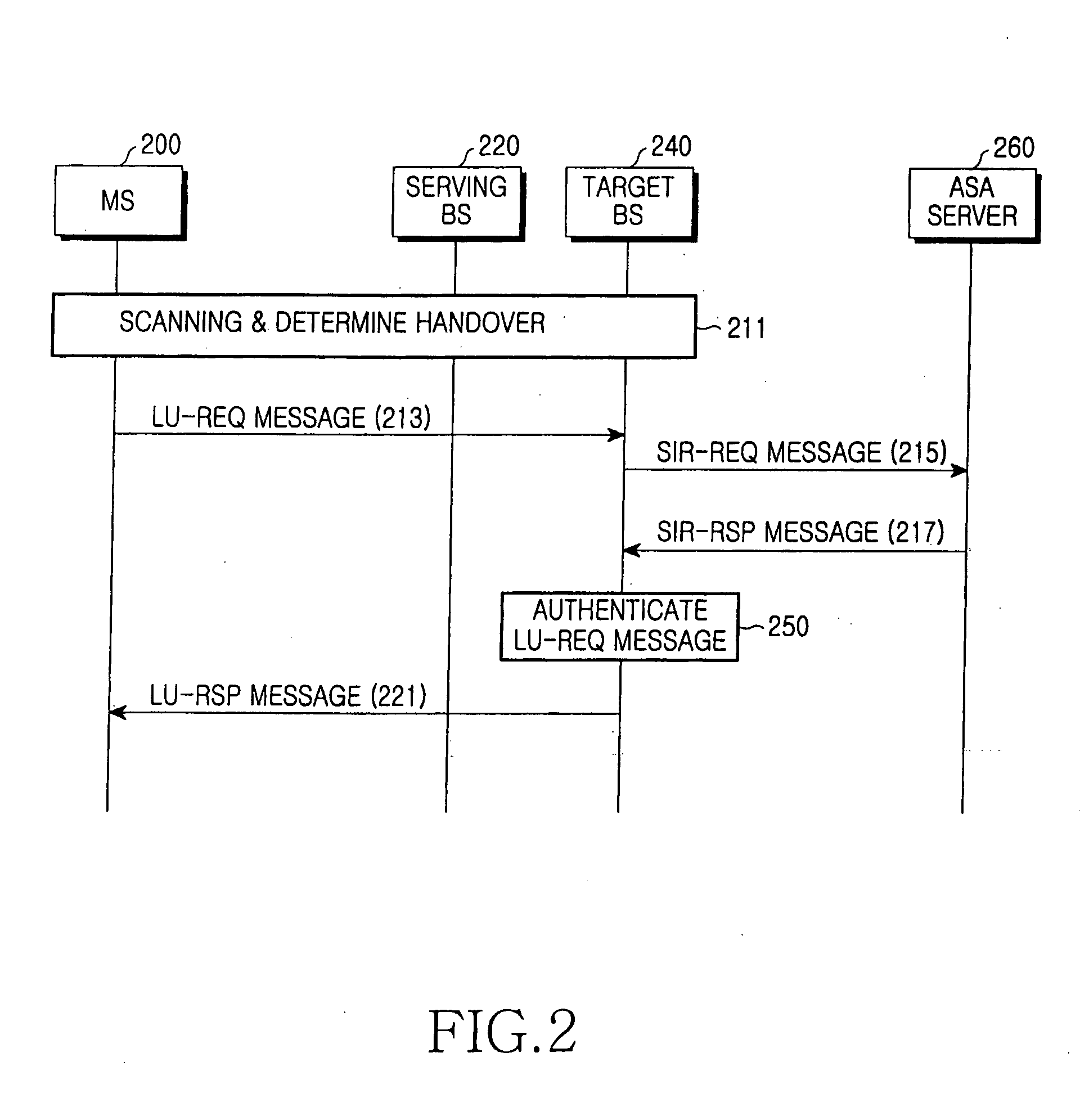
System and method for fast network re-entry in a broadband wireless access communication system
ActiveUS20050277417A1Fast internetRadio/inductive link selection arrangementsSecurity arrangementRe entryCommunications system
A system and method for fast network re-entry in a broadband wireless access communication system. A mobile station transmits a first message requiring fast network re-entry to a base station and performs the fast network re-entry together with the base station when receiving a second message approving the fast network re-entry from the base station. The base station receives the first message, authenticates the first message using final session information of the mobile station that is previously stored in the base station, transmits the second message to the mobile station when succeeding in authentication of the first message, and performs the fast network re-entry together with the mobile station.
Owner:NOKIA TECHNOLOGLES OY
System And Method Of Providing Service Information To A Carrier
InactiveUS20090122712A1Efficiently decideReduce overheadError preventionTransmission systemsService informationMobile device
A method of providing service performance information to a carrier for an application over a network is provided, wherein parameters relating to the application are transmitted to a mobile device, and the mobile device stores information relating to packets transmitted for the application. Should the information stored exceed the parameters, an alert is sent to the network.
Owner:MOBIDIA INC
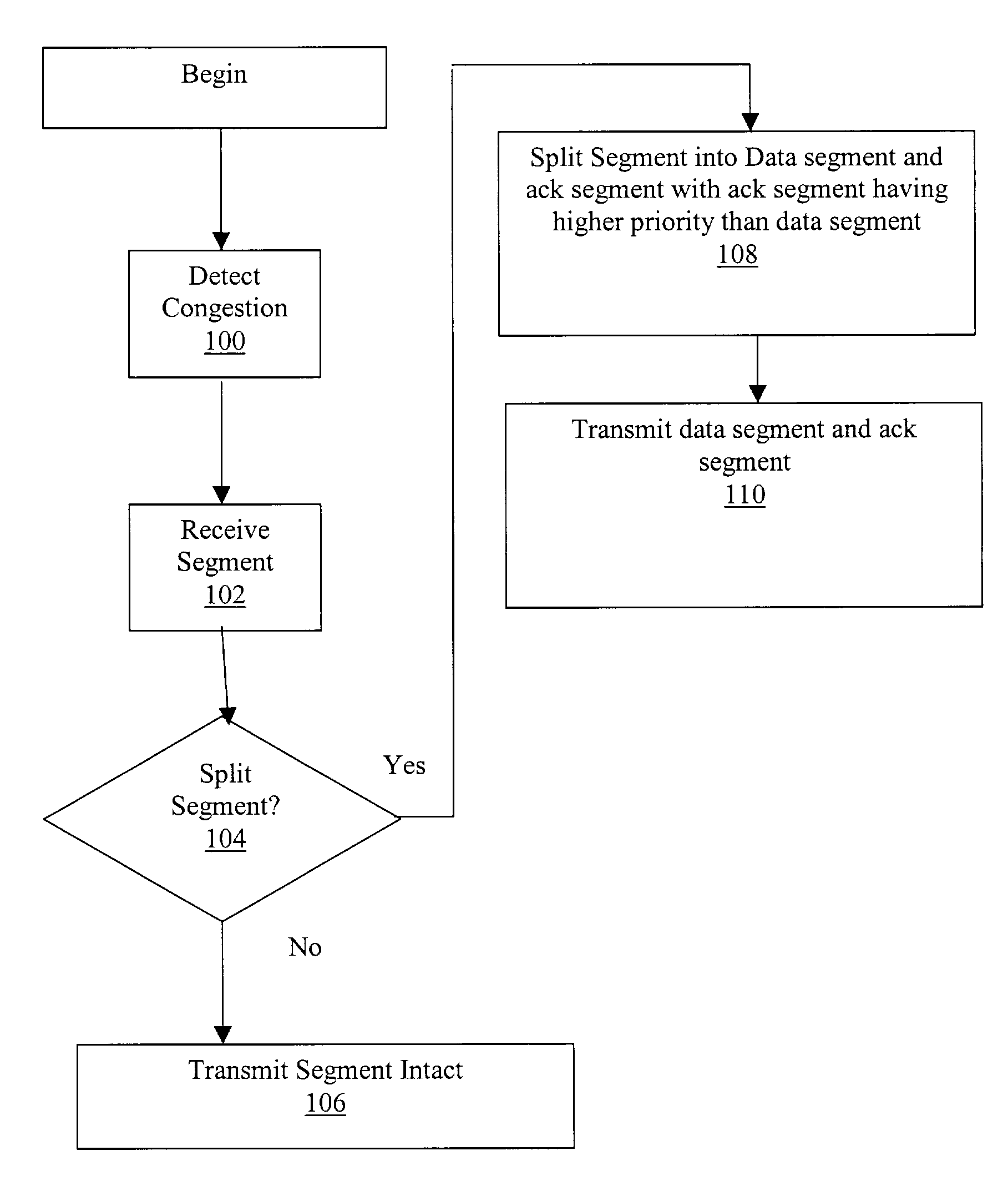
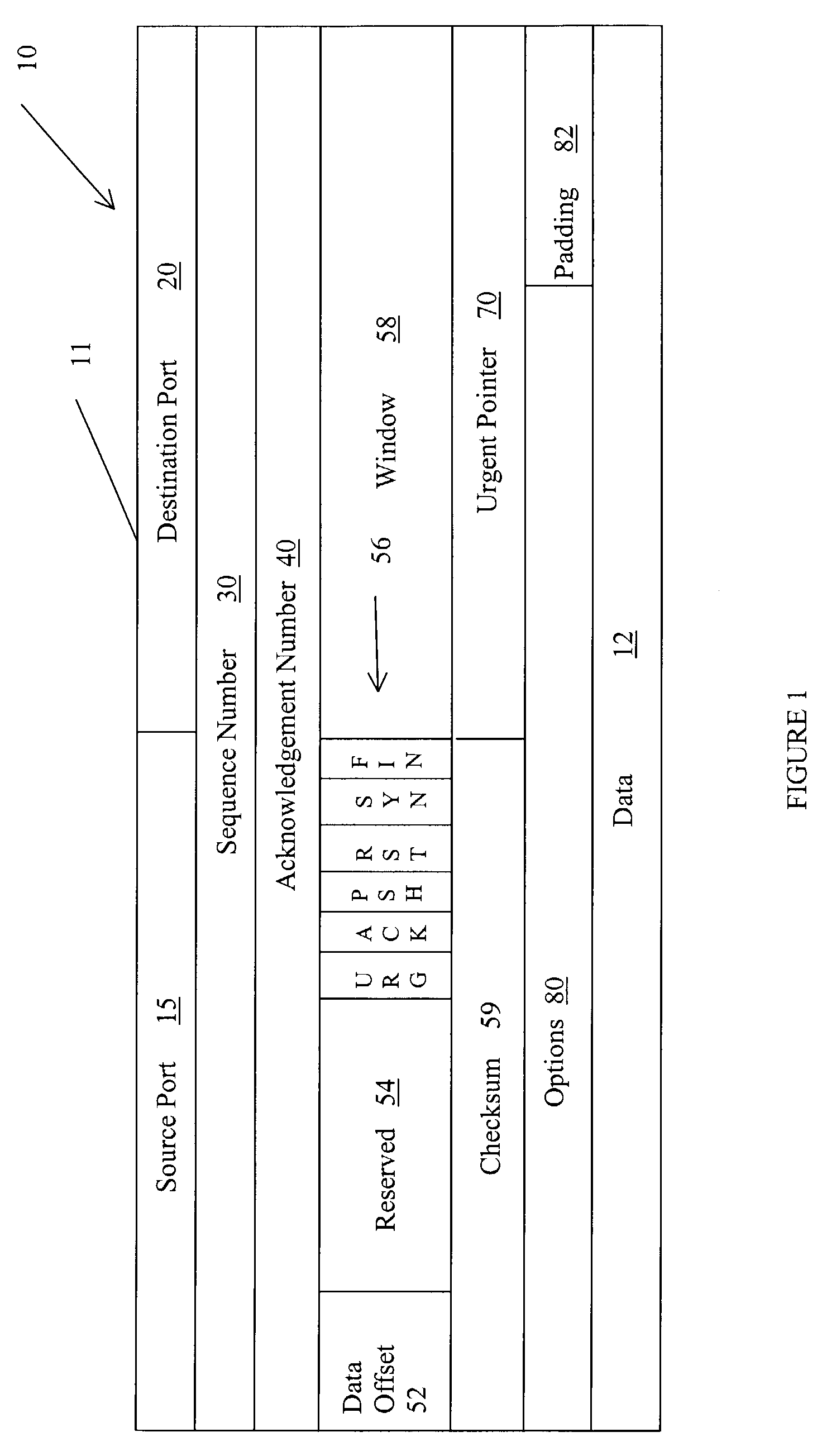
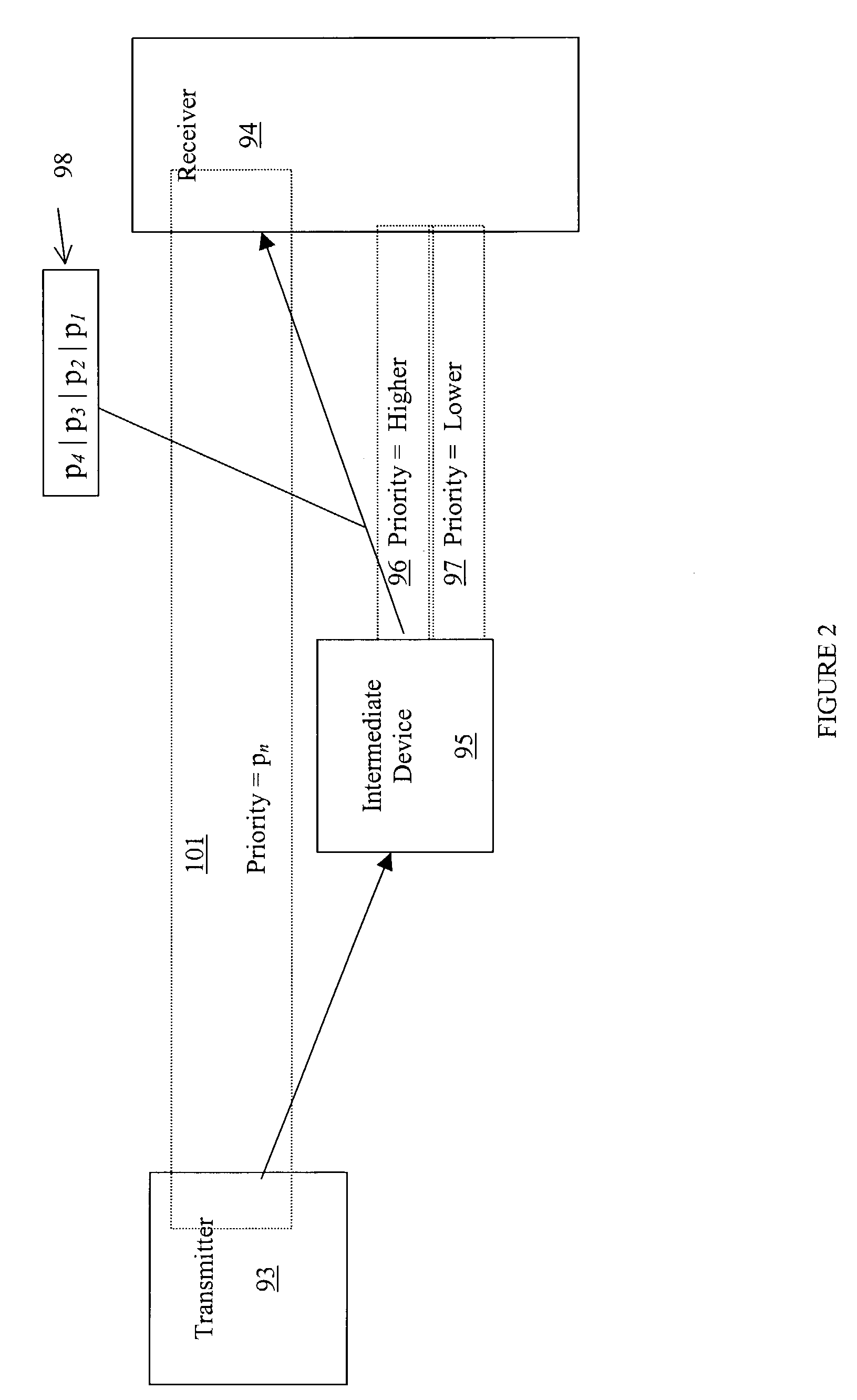
Method for splitting data and acknowledgements in a TCP session
InactiveUS7359326B1Increased data speedFast internetFrequency-division multiplex detailsTransmission systemsQuality of serviceData segment
In a Quality of Service system, segments in a TCP session are assigned a priority level. A segment may contain an acknowledgement and data. The system determines if network congestion is detected or anticipated in the segment's priority band or in a higher priority band. When the TCP segment arrives at a network point, the segment is split into an acknowledgement segment and a data segment. The acknowledgement segment is scheduled at a higher QoS priority than the data segment.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Setting timers of a router
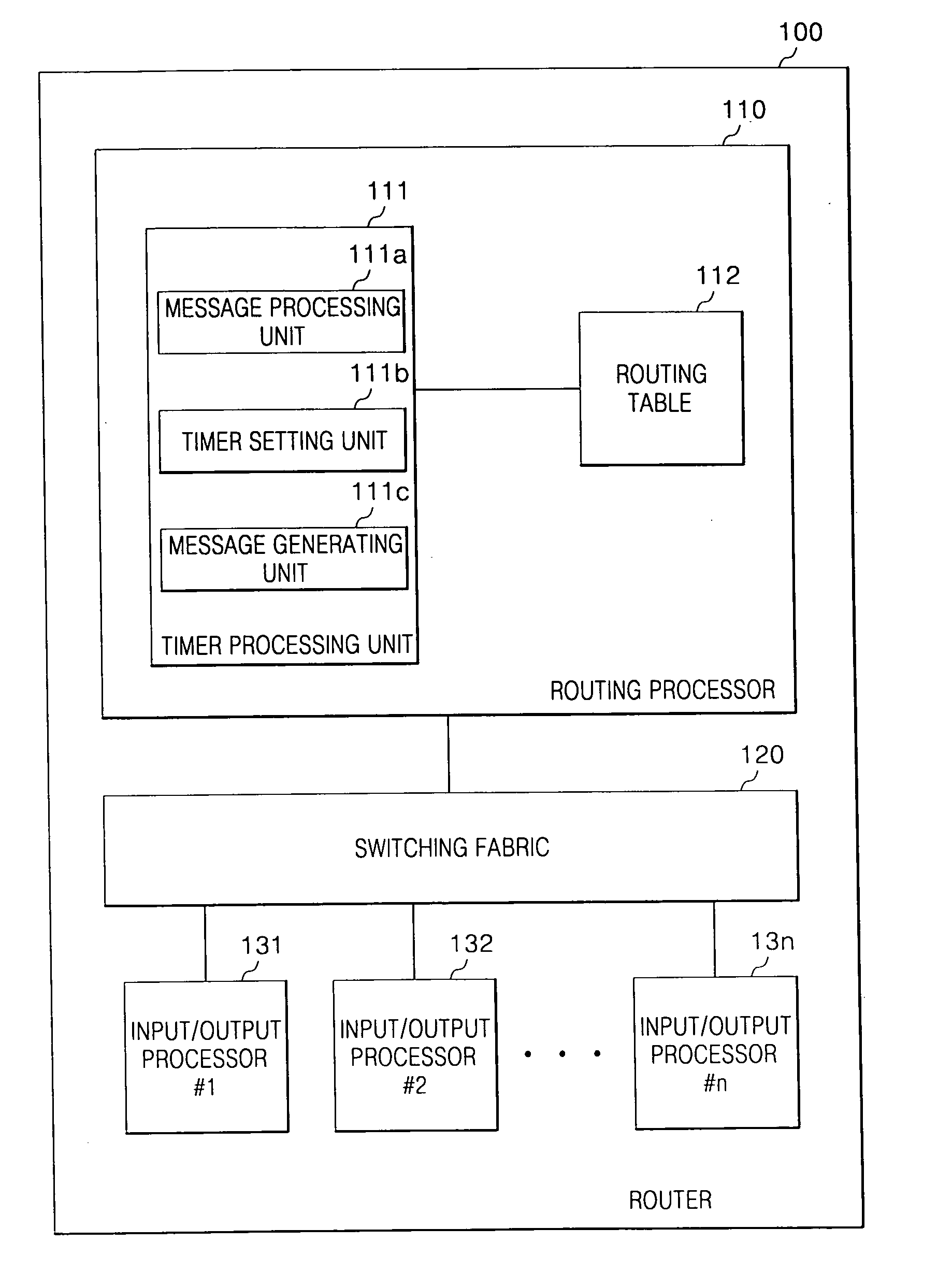
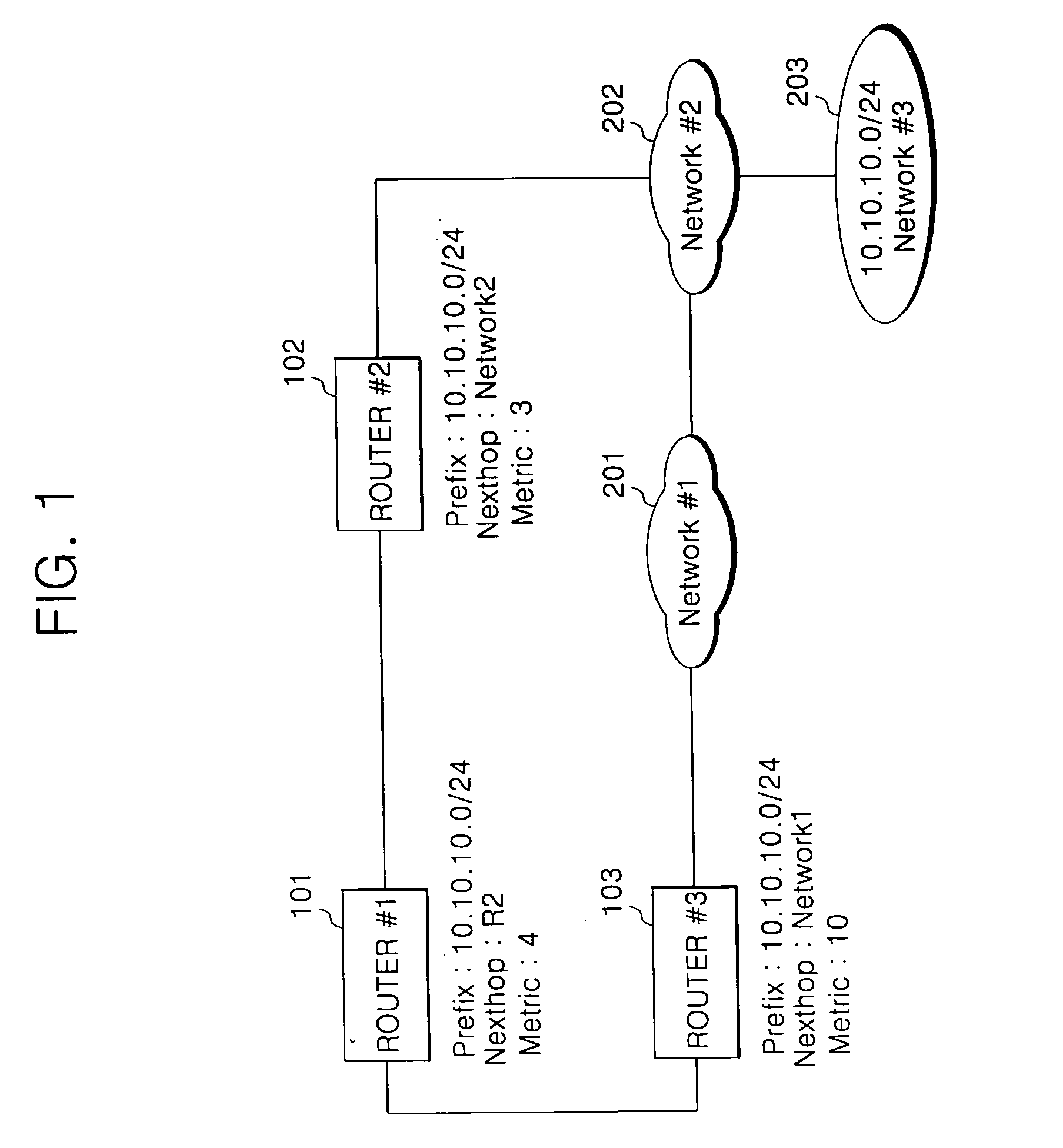
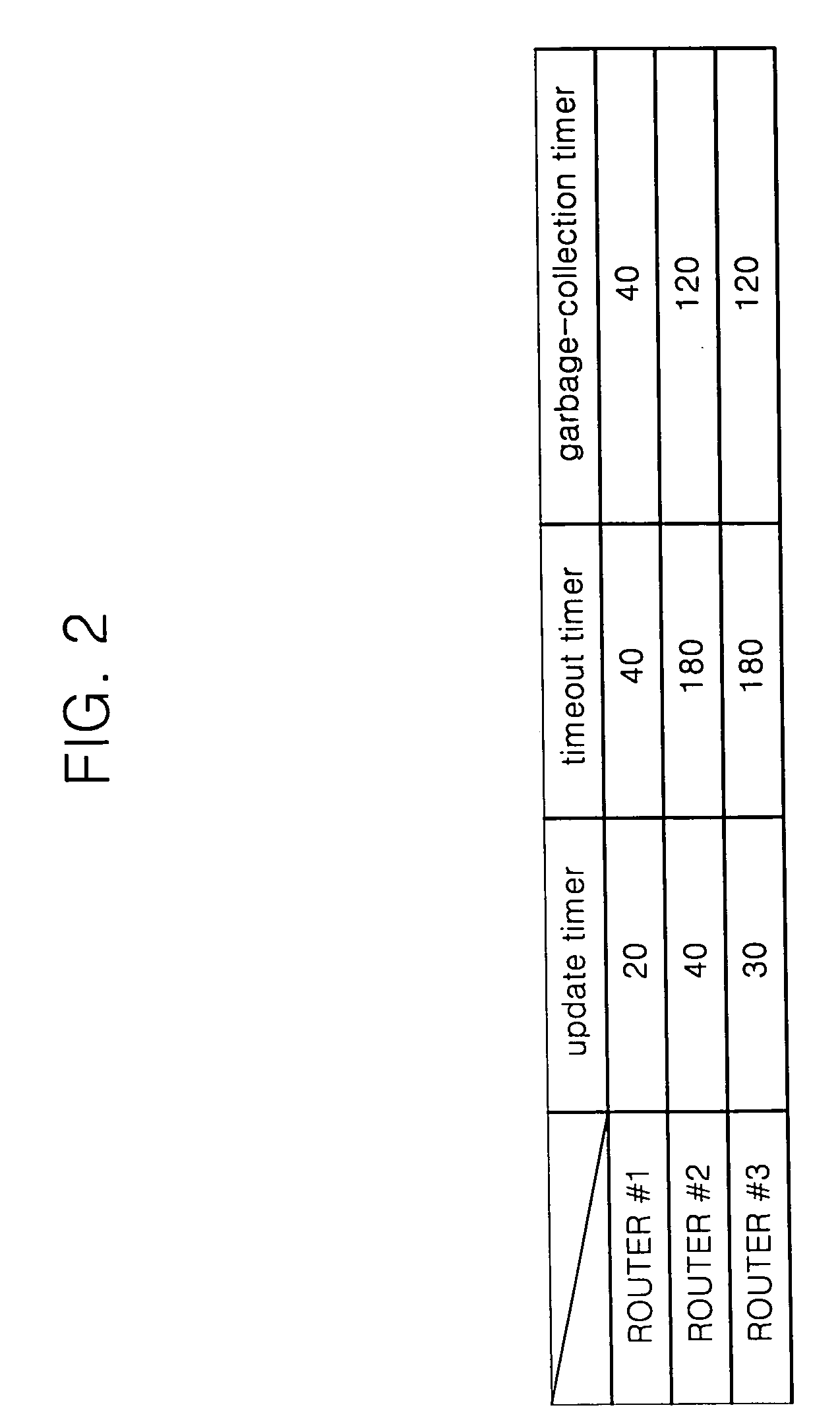
InactiveUS20050180438A1Avoid slappingFast internetData switching by path configurationTimerRouting protocol
A method and apparatus and a program storage device, readable by a machine, tangibly embodying a program of instructions executable by the machine performs a method including: receiving an update message at a router, the update message including a timer value from at least one other router according to a routing protocol; extracting the timer value from the update message received from the at least one other router; and resetting the timer value in response to a difference between the extracted timer value of the at least one other router and the set timer value.
Owner:SAMSUNG ELECTRONICS CO LTD
Devices and methods for beacon communication in ad-hoc networks
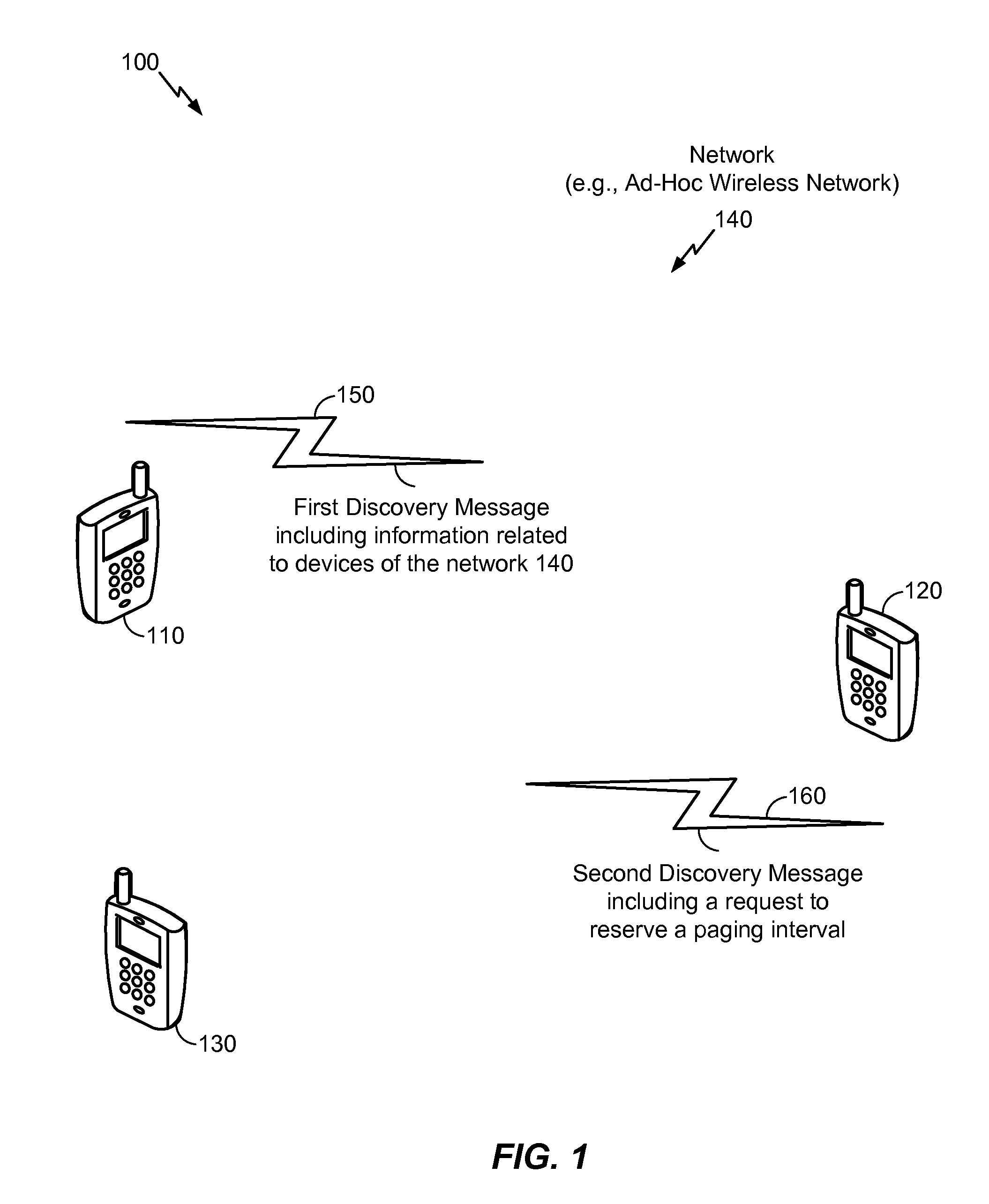
InactiveUS20130265906A1Quick checkFast and reliable operationNetwork topologiesData switching by path configurationTelecommunicationsWireless network
A method includes receiving discovery messages from respective devices of an ad-hoc wireless network. The messages are received by a first device in the ad-hoc wireless network prior to a particular discovery interval. The discovery messages include information identifying the respective devices. The method further includes caching the information identifying the respective devices. During the particular discovery interval, a first discovery message is sent. The first discovery message includes a request to reserve a paging interval during the particular discovery interval. The first discovery message further includes an indication of the information.
Owner:QUALCOMM INC
System and method for optimizing contiguous channel operation with cellular reuse
InactiveUS20050053047A1Alleviation of interferenceReduce morbidityPower managementElectric signal transmission systemsPopulationAutomatic meter reading
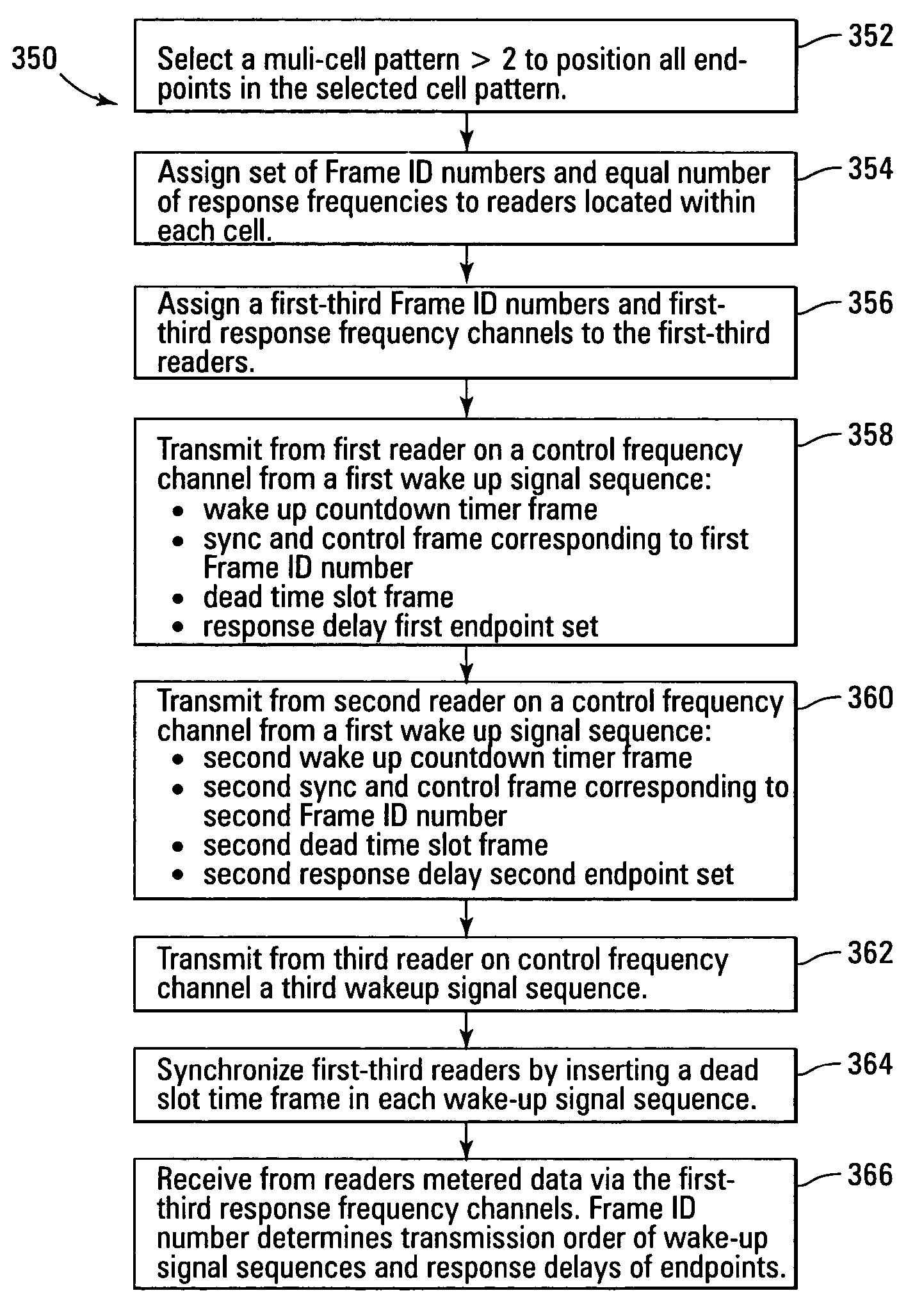
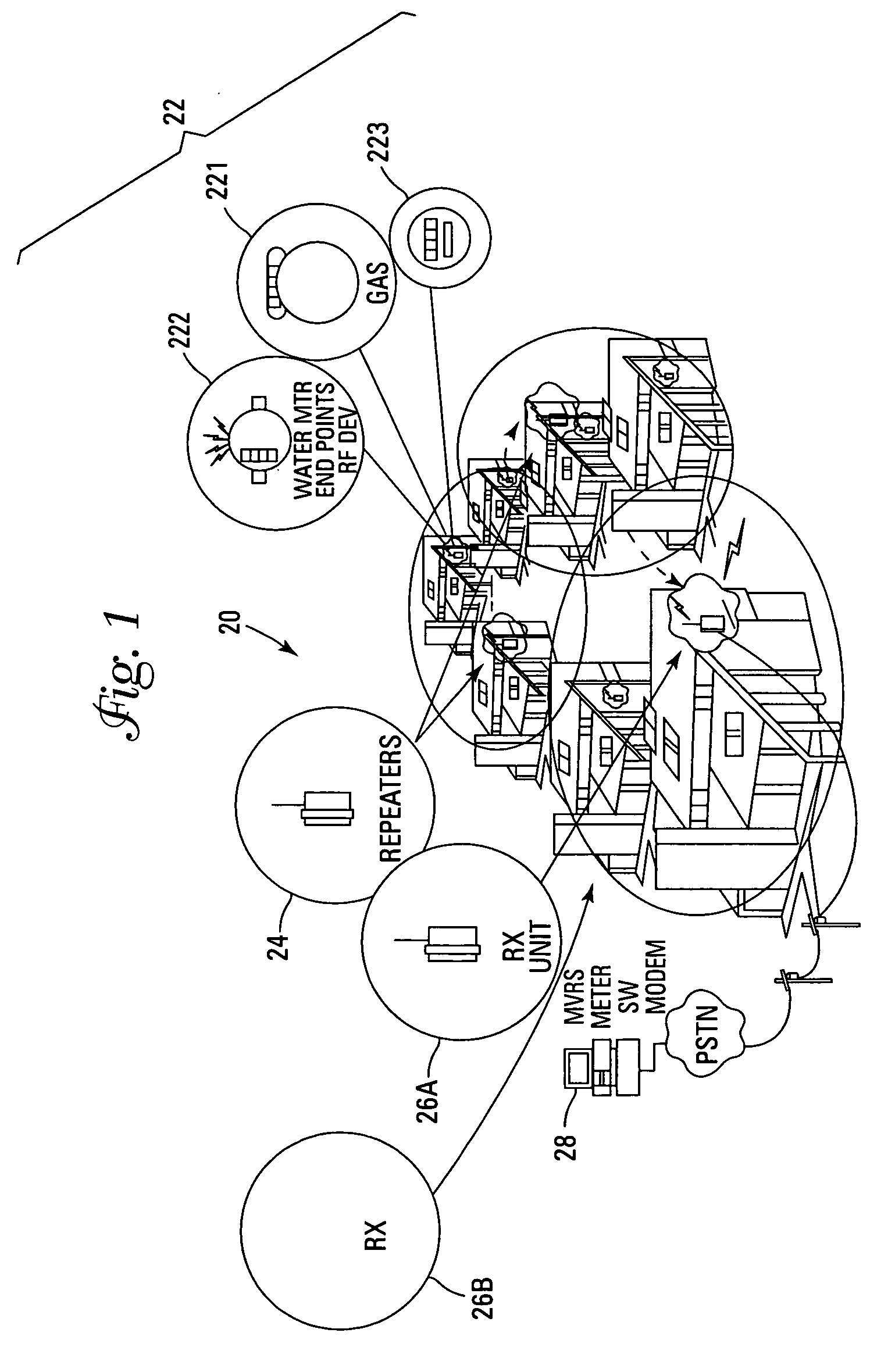
A method for communicating with automatic meter reading (AMR) endpoints in adjacent cells, when the endpoints are arranged in a cell pattern similar to a cellular telephone system, is disclosed that substantially reduces the likelihood of signal interference. A Frame ID is identified as corresponding to a particular receive frequency that a system reader (receiver / collector) uses when listening for endpoint responses. In this example embodiment of the AMR network model, all endpoints in the network listen on the same control frequency to receive commands sent out from the readers. To allow for a relatively fast network read cycle, cells that are spaced far enough away from each other as to not interfere with each other are allowed to transmit at the same time. Cells with the same Frame ID are configured to be spaced a safe distance from each other so as not to interfere with each other's endpoint population.
Owner:ITRON
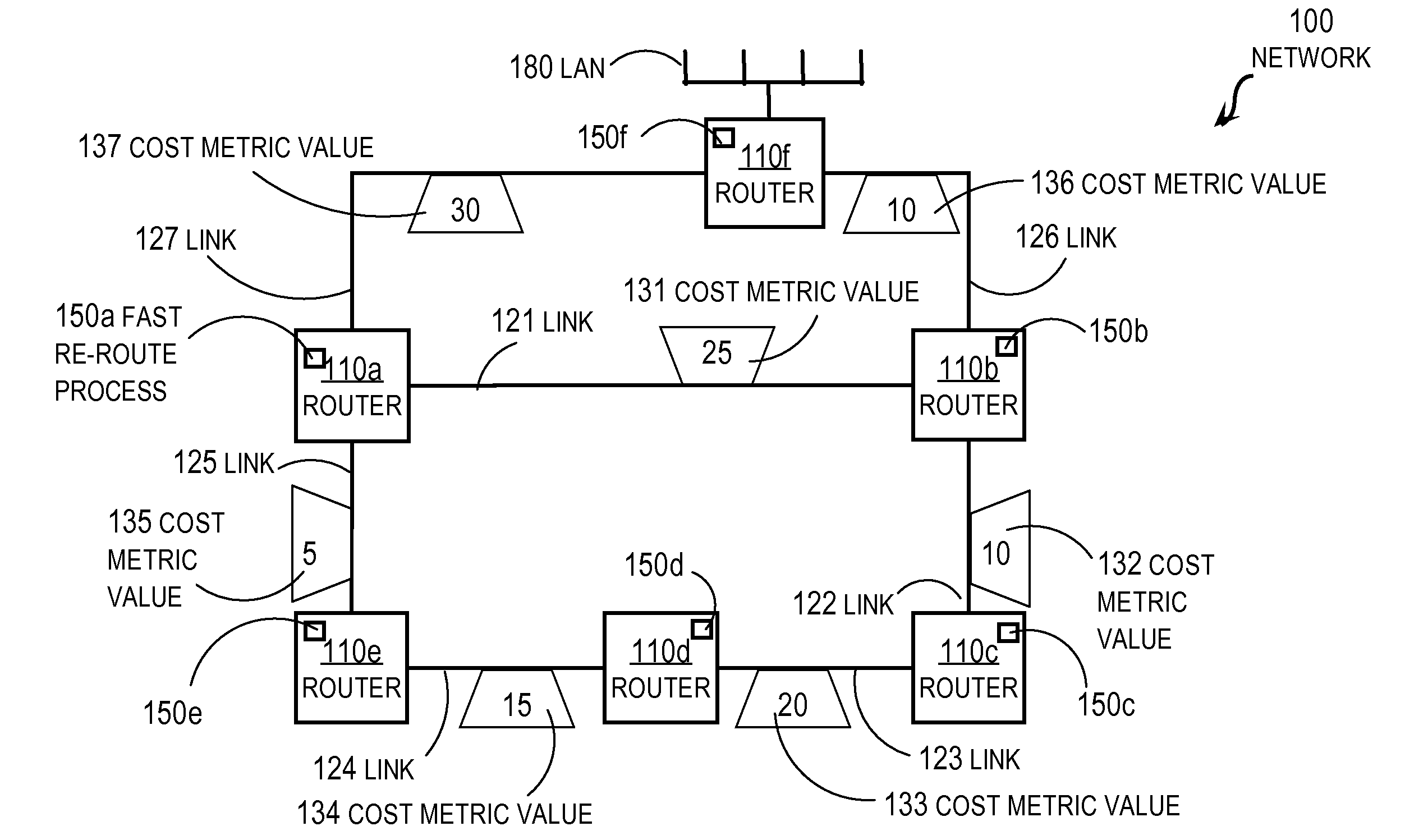
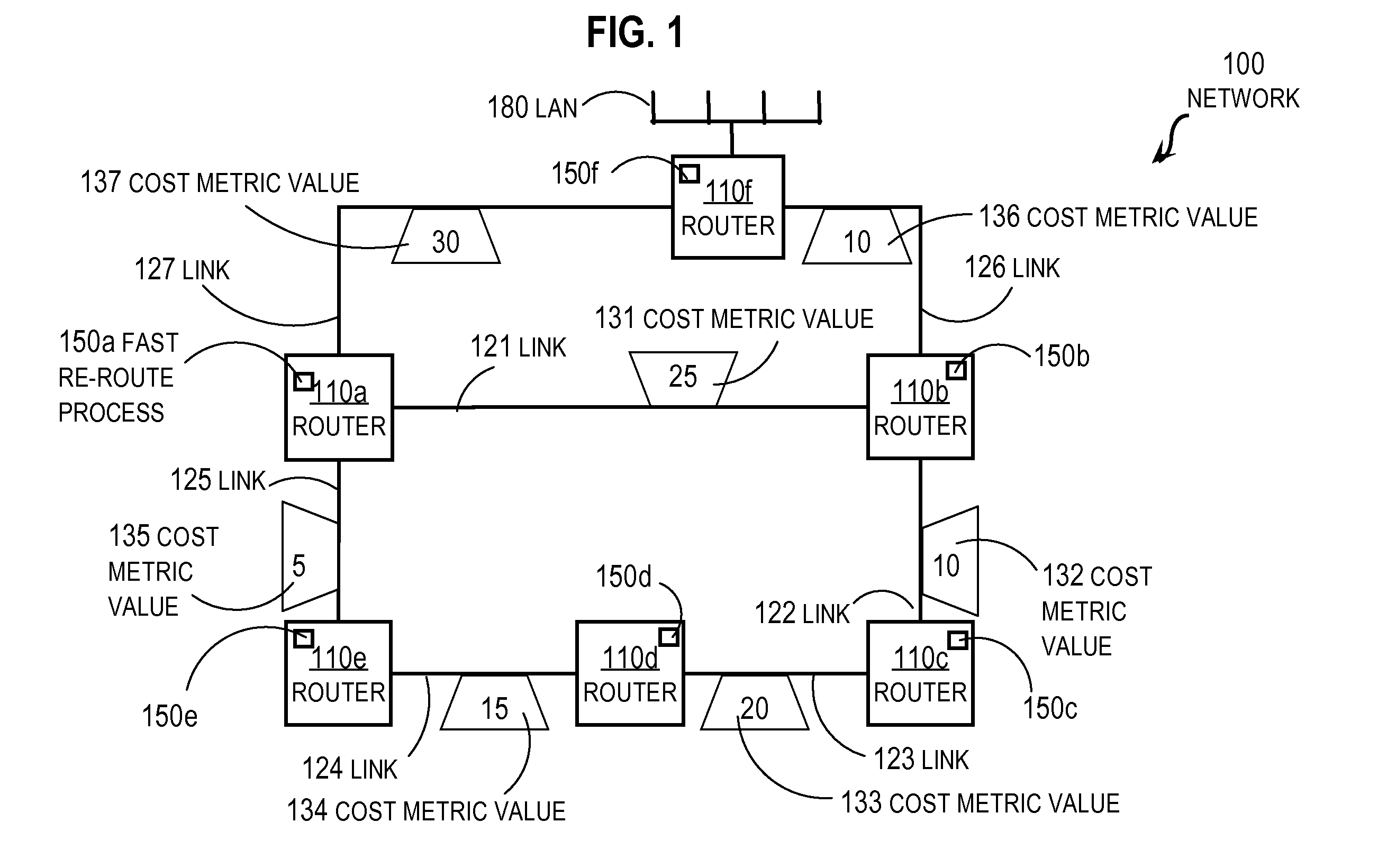
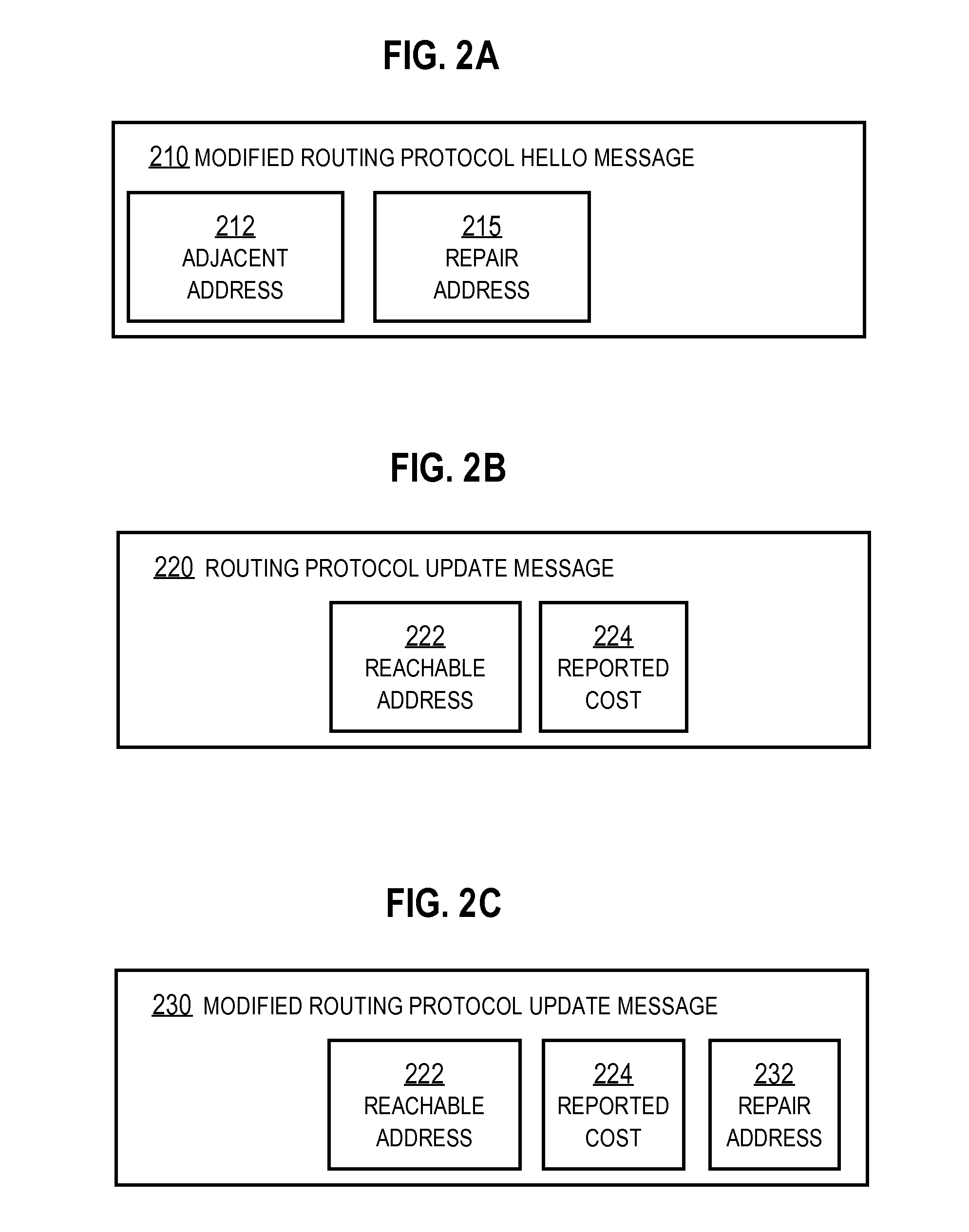
Fast Re-routing in Distance Vector Routing Protocol Networks
ActiveUS20080310433A1Promote recoveryFast internetData switching by path configurationDistance-vector routing protocolReachability
In one embodiment, a method includes sending an adjacency discovery message 1 from a local router over a direct link to a first neighbor router. An adjacency discovery message is not forwarded and includes a repair address. The repair address indicates the local router but is not advertised as reachable over the direct link. An outbound routing update message is sent to a different second neighbor router. The outbound routing update message is forwarded and includes reachability data that indicates the repair address is reachable. A payload of an inbound tunneled packet received at the local router and directed to the repair address is forwarded based on a destination indicated in the payload.
Owner:CISCO TECH INC
Method and system for synchronization in communication system
ActiveUS20080318567A1Improve detection rateMore system resourceSynchronisation arrangementModulated-carrier systemsTransceiverCommunications system
A method for uplink synchronization of a first transceiver and a second transceiver in a multi-user cellular communication system having communication resources divided into communication channels. The method includes the following steps. A first signature sequence is transmitted from the second transceiver to the first transceiver, where the signature sequence is selected from a first set of signature sequences. In the first transceiver, the received signal is correlated with at least one signature sequence from a second set of signature sequences to estimate the time of arrival of the signature sequence to synchronize transmission between the second transceiver and the first transceiver. In transmitting the first signature sequence from the second transceiver to the first transceiver, the first signature sequence constitutes at least part of a zero-correlation zone sequence.
Owner:HUAWEI TECH CO LTD
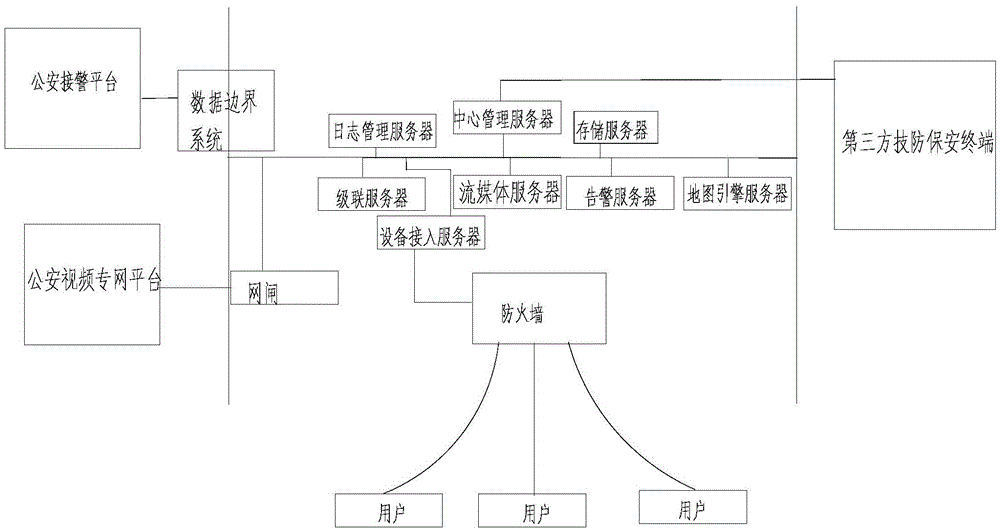
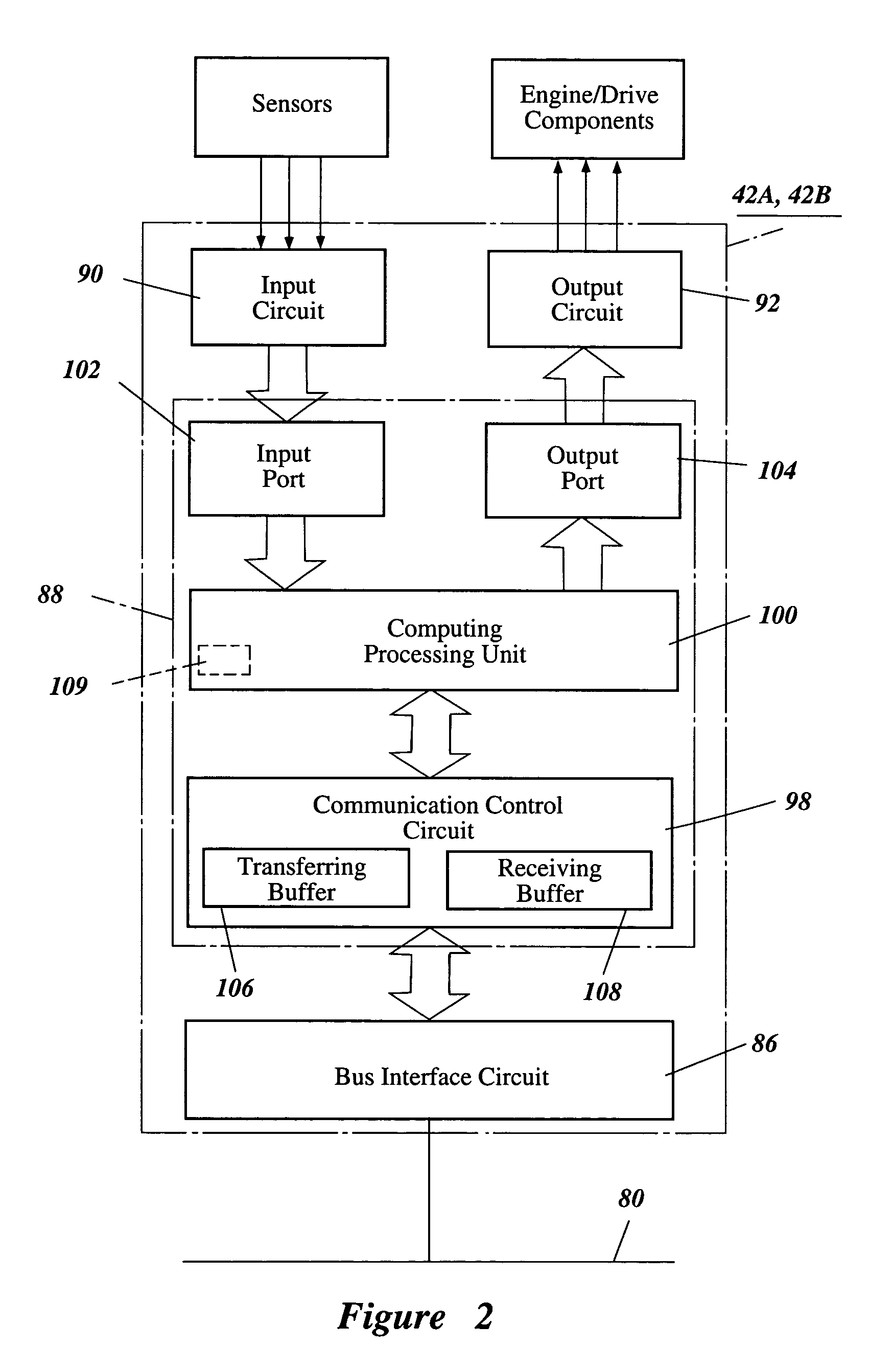
Social security protection video monitoring cloud platform and monitoring method
InactiveCN105491066AFast internetEasy to manageClosed circuit television systemsTransmissionVideo monitoringThird party
The invention belongs to the security prevention technical field and relates to a social security protection video monitoring cloud platform and monitoring method. The monitoring method includes the following steps that: a monitoring cloud platform is established; resources to be monitored are connected into the monitoring cloud platform; the cloud platform is docked with a public security alarm answering platform through a data boundary system; the cloud platform is docked with a public security video private network platform through a gatekeeper; and a third party safety technical prevention security protection terminal is docked with the cloud platform, and user alarm information which is authorized to the third party safety technical prevention security protection terminal is pushed to the third party safety technical prevention security protection terminal, and alarm information confirmed by the third party safety technical prevention security protection terminal is transmitted to the public security alarm answering platform through the cloud platform. With the social security protection video monitoring cloud platform and monitoring method adopted, a traditional video monitoring system which can record monitoring images, operate independently, is used for post-event verification, and cannot realize a networking function and a prevention function can be improved; and the management and intelligent life level of customers can be improved.
Owner:丁美华
Methods and apparatus for reducing power dissipation in a multi-processor system
InactiveUS20050228967A1Reduce power consumptionEfficient high speed processingEnergy efficient ICTResource allocationMain processing unitMulti processor
Methods and apparatus for monitoring processor tasks and associated processor loads therefor that are allocated to be performed by respective sub-processing units associated with a main processing unit; re-allocating at least some of the tasks based on their associated processor loads such that at least one of the sub-processing units is not scheduled to perform any tasks; and commanding the sub-processing units that are not scheduled to perform any tasks into a low power consumption state.
Owner:SONY COMPUTER ENTERTAINMENT INC
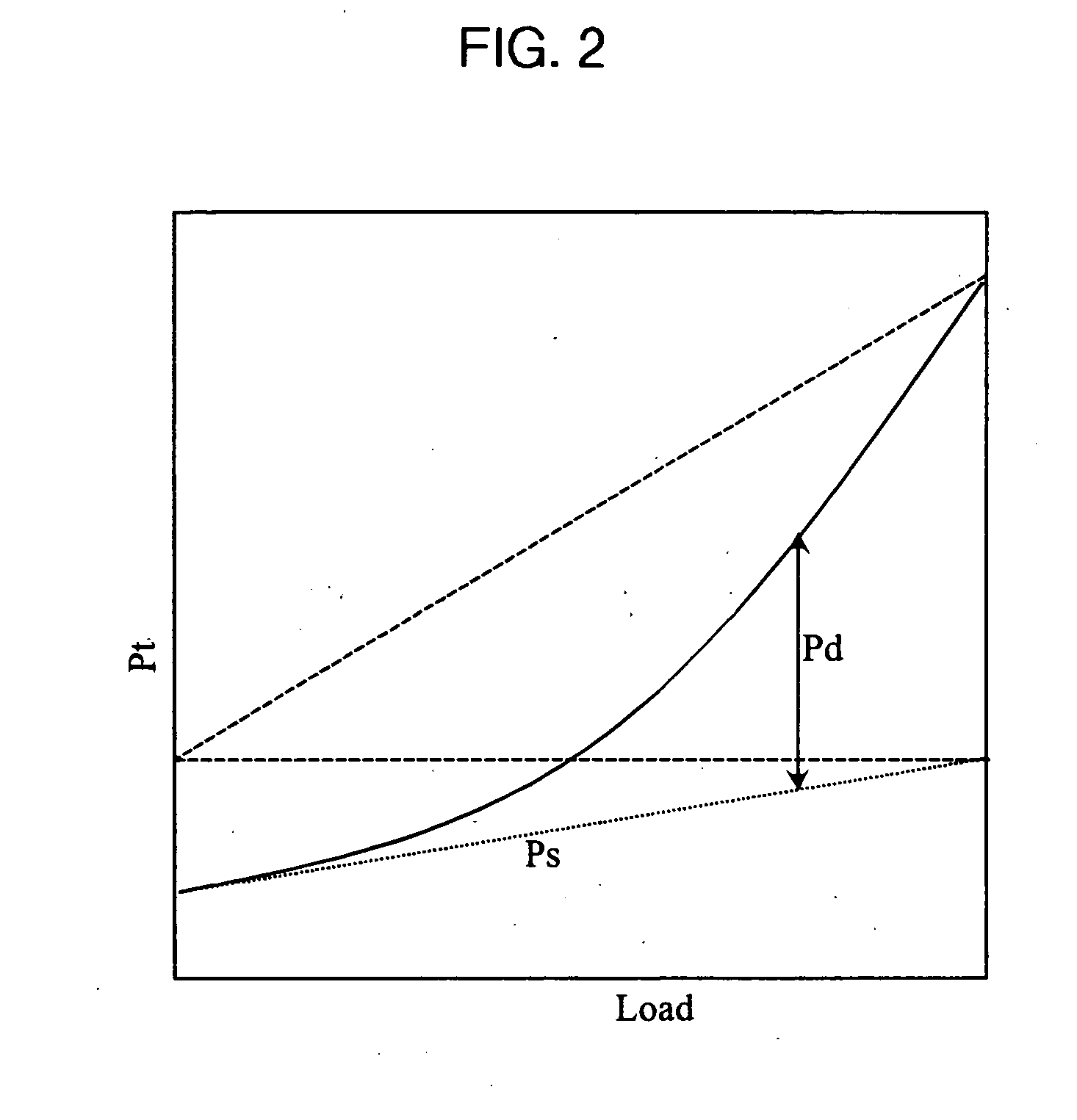
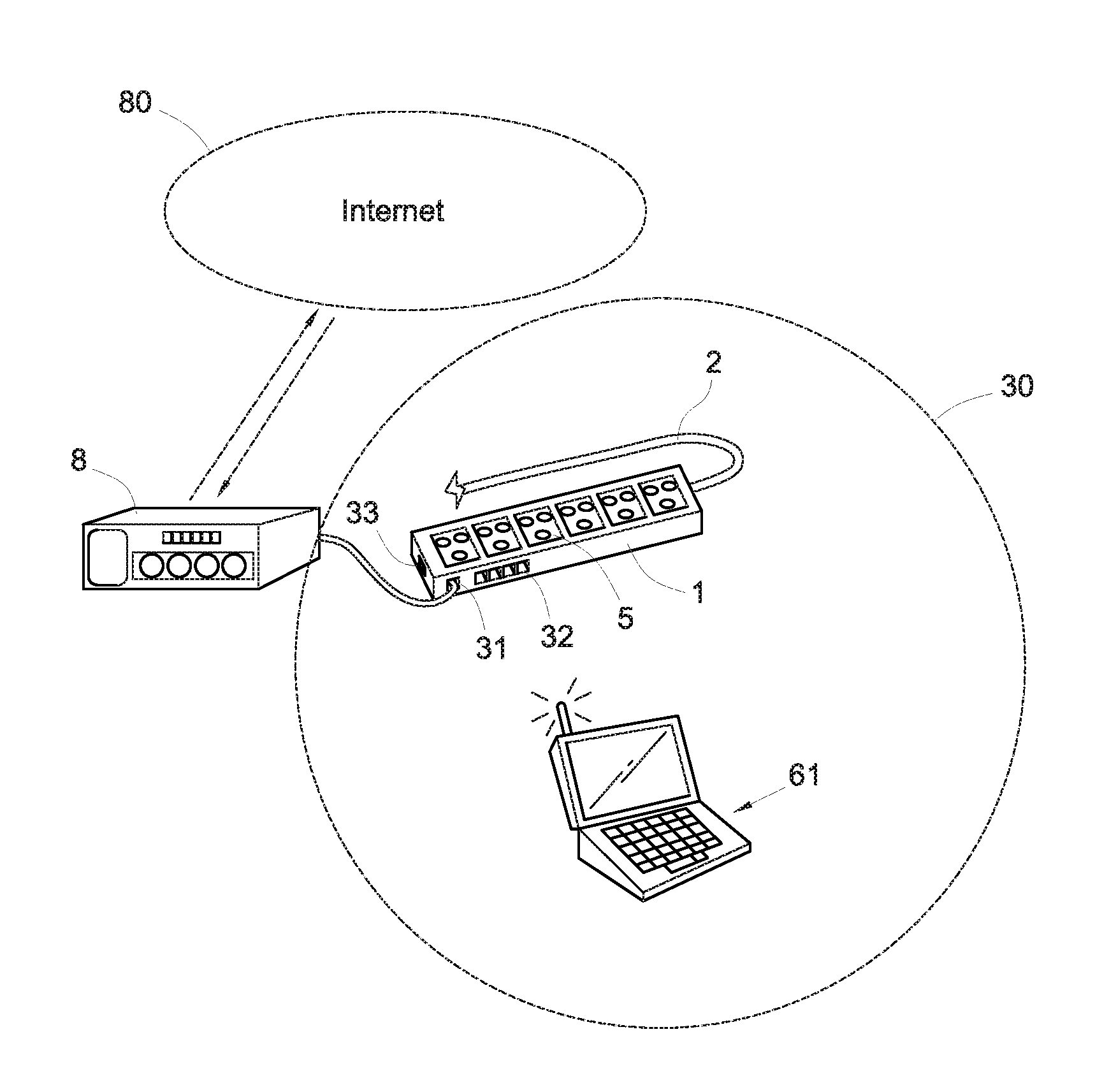
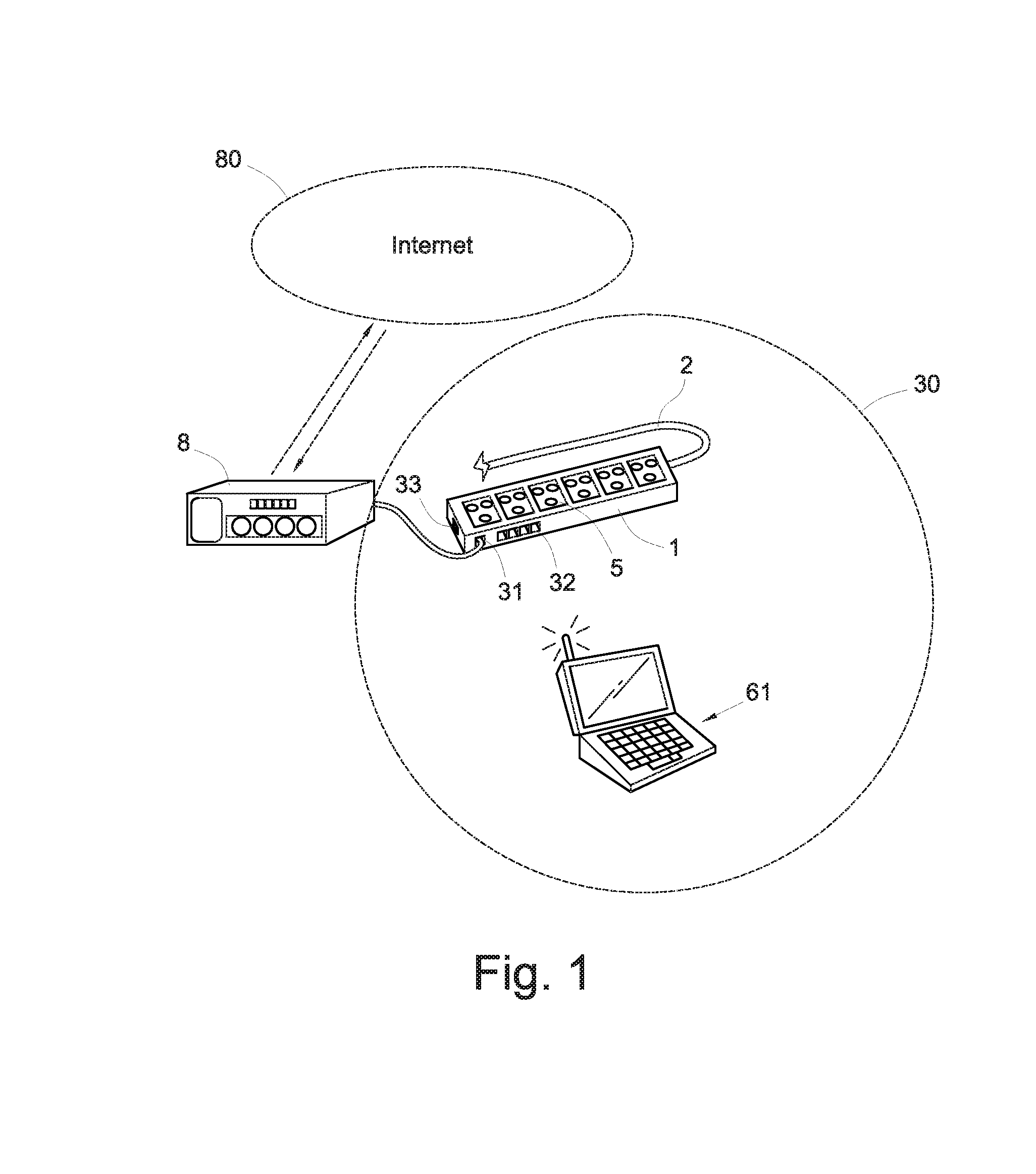
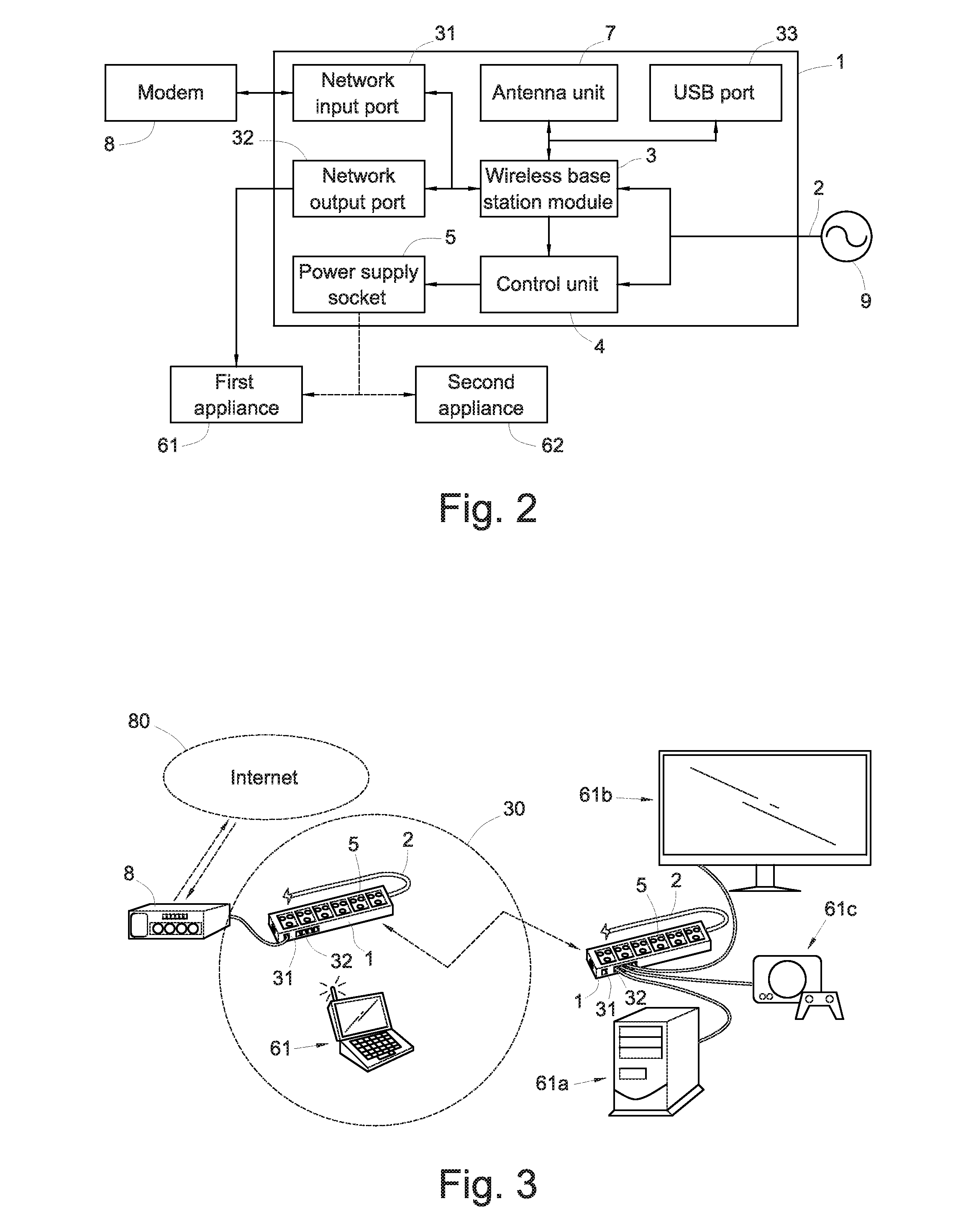
Power supply dock with wireless network and power management functions
InactiveUS20130339766A1Coverage of be quickly enlargeLow deployment costVolume/mass flow measurementPower supply for data processingElectricityEngineering
A power supply dock with wireless network and power management functions, comprising an enclosure, a wireless base station module and a control unit disposed in the enclosure, and a plurality of power supply sockets disposed on the enclosure. The wireless base station module communicates with an external first electric appliance via a wireless network. The power supply sockets are electrically connected to and supply power to the first electric appliance or an external second electric appliance. The power supply dock is connected with the utility power to power the wireless base station module so that the wireless network can be deployed quickly, and the coverage of the wireless network can be quickly enlarged through disposition of a plurality of such power supply docks.
Owner:CHEN JIANN JYH +1
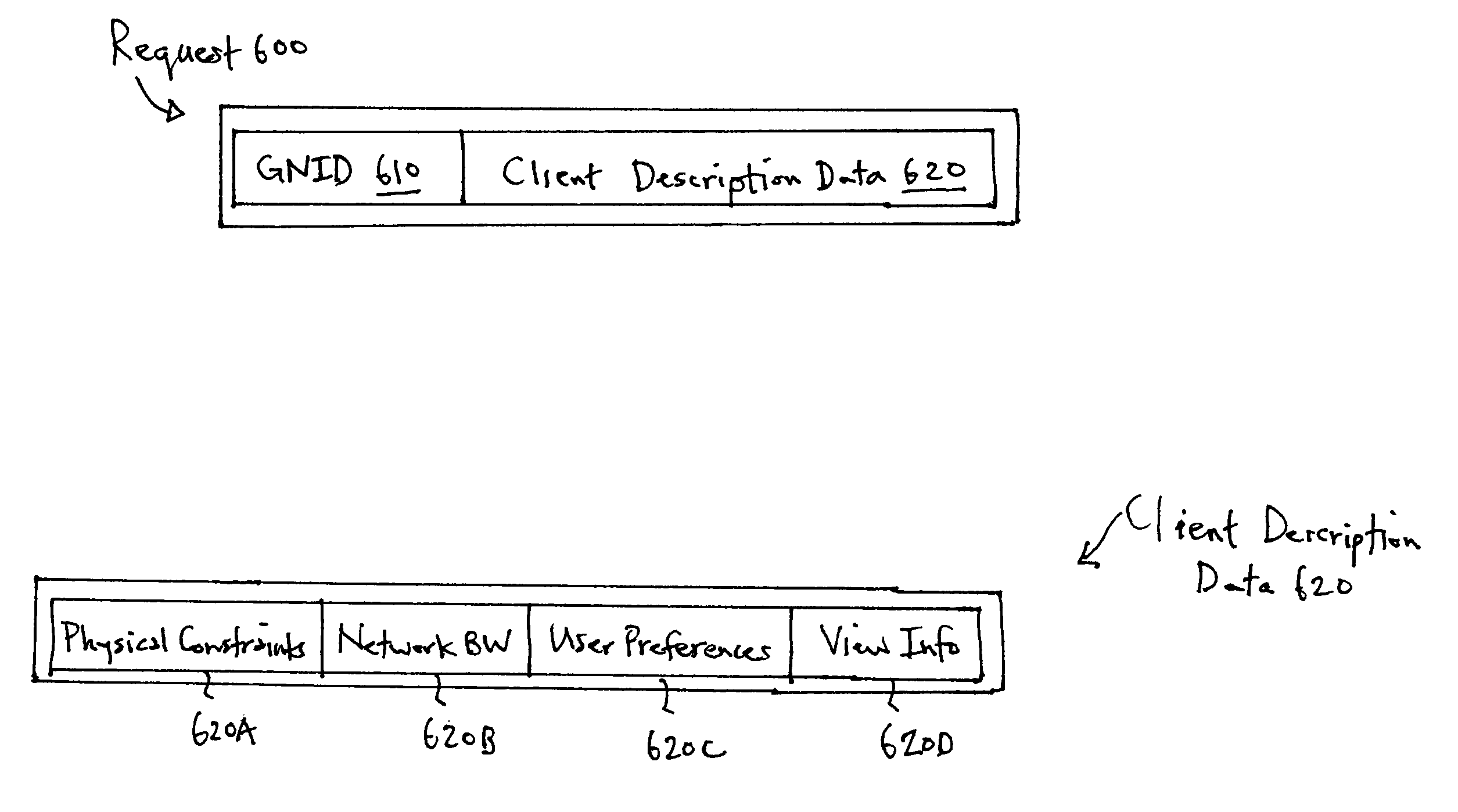
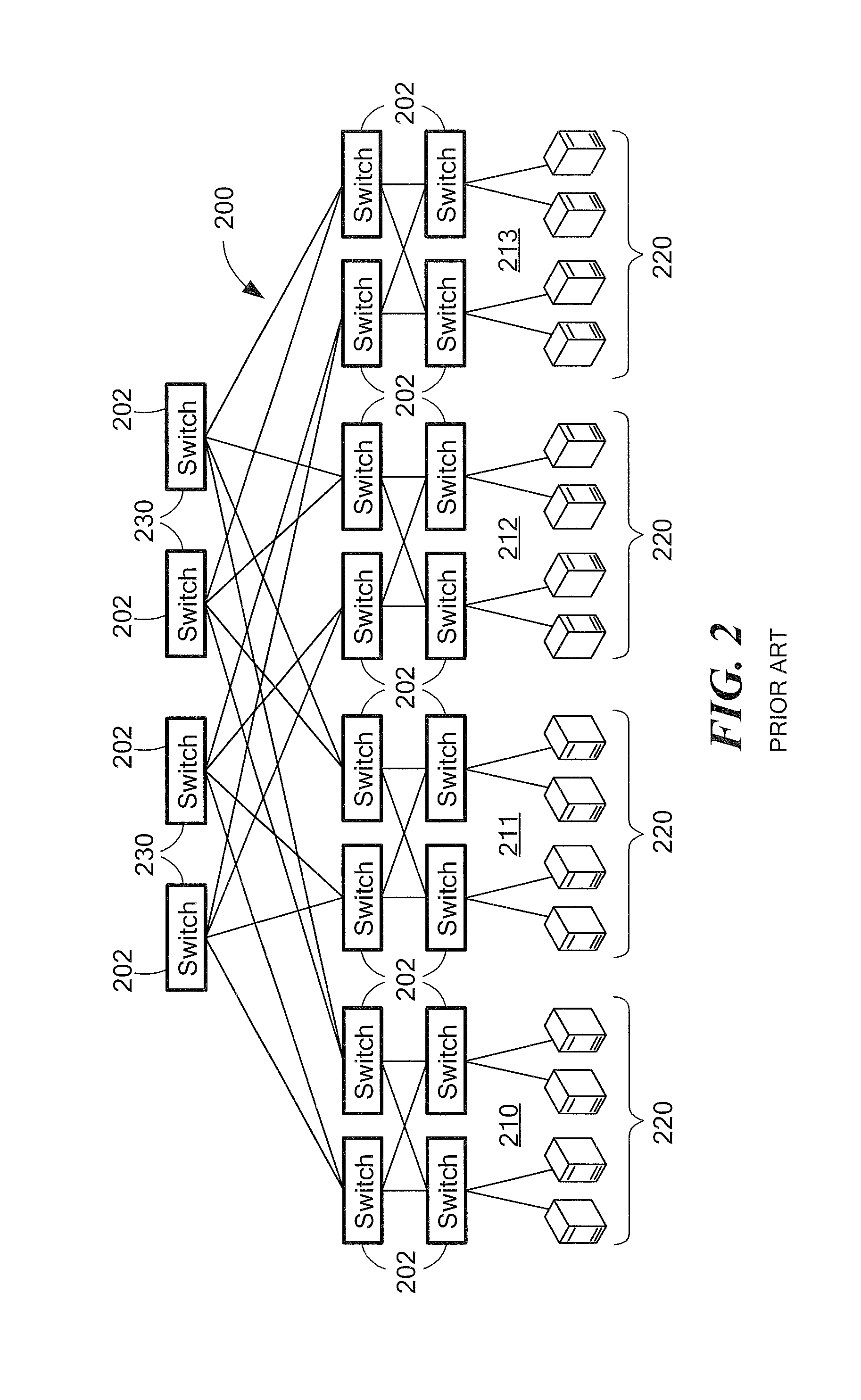
Software system for efficient data transport across a distributed system for interactive viewing
ActiveUS8035636B1Small sizeFast internetImage data processing detailsAnimationGraphicsSoftware system
A server receives a graphics data request from a client system through a network. The request includes client description data describing capabilities of the client system. The server accesses the requested graphics data from an augmented scene graph. The server determines which one or more operations from a set of operations are to be performed on the graphics data based on the client description data. The set of operations includes:(a) compiling the graphics data; and(b) removing nodes from the compiled graphics data that are not visible to a user to obtain view-limited compiled graphics data.(c) culling the view-limited compiled graphics data with a view frustum to obtain state-sorted graphics data and(d) rendering the state-sorted graphics data to obtain images.The server performs the one or more operations on the graphics data to obtain resultant graphics data, and, transmits the resultant graphics data to the client system.
Owner:ORACLE INT CORP
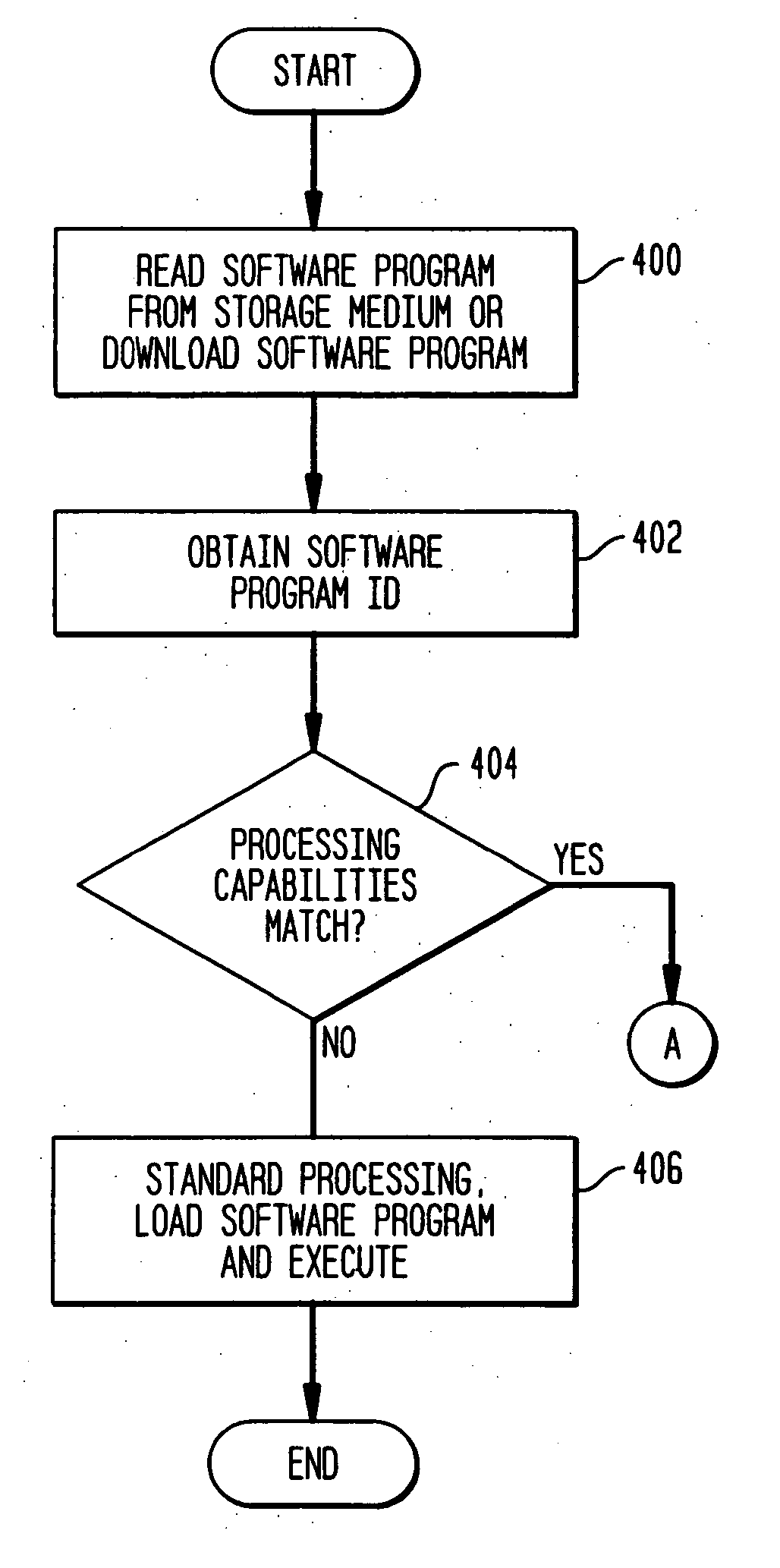
Methods and apparatus for distributing software applications
ActiveUS20060075397A1Efficient high speed processingEasy to buildProgram/content distribution protectionSpecific program execution arrangementsSoftware engineeringSoftware
Methods and apparatus for enabling execution of software programs permit: obtaining identification information that is indicative of a version of a software program; determining whether processing capabilities of a processor on which the software program is to be executed are incompatible with proper execution of the version of the software program; and at least partially modifying the version of the software program to obtain a more suitable version of the software program that will execute properly on the processor.
Owner:DROPBOX +1
Multi-homing using controlled route leakage at a backup service provider
ActiveUS7630392B2Fast internetImprove utilizationBroadcast transmission systemsTime-division multiplexNetwork addressingNetwork address
A technique for implementing route aggregation in a computer network containing a multi-homed customer site connected to primary and second networks, which in turn are both connected to a common “backbone” network. According to the technique, the primary network allocates a block of network addresses for the customer site, and the customer site notifies the secondary network of its allocated addresses. The secondary network first determines whether the primary network has already advertised an aggregated route which incorporates the customer site's route. If so, the secondary network “suppresses” (i.e., does not advertise) the customer site's route. The secondary network only “unsuppresses” the customer site's route if it detects that the primary network has lost connectivity to the customer site and / or the backbone network.
Owner:CISCO TECH INC
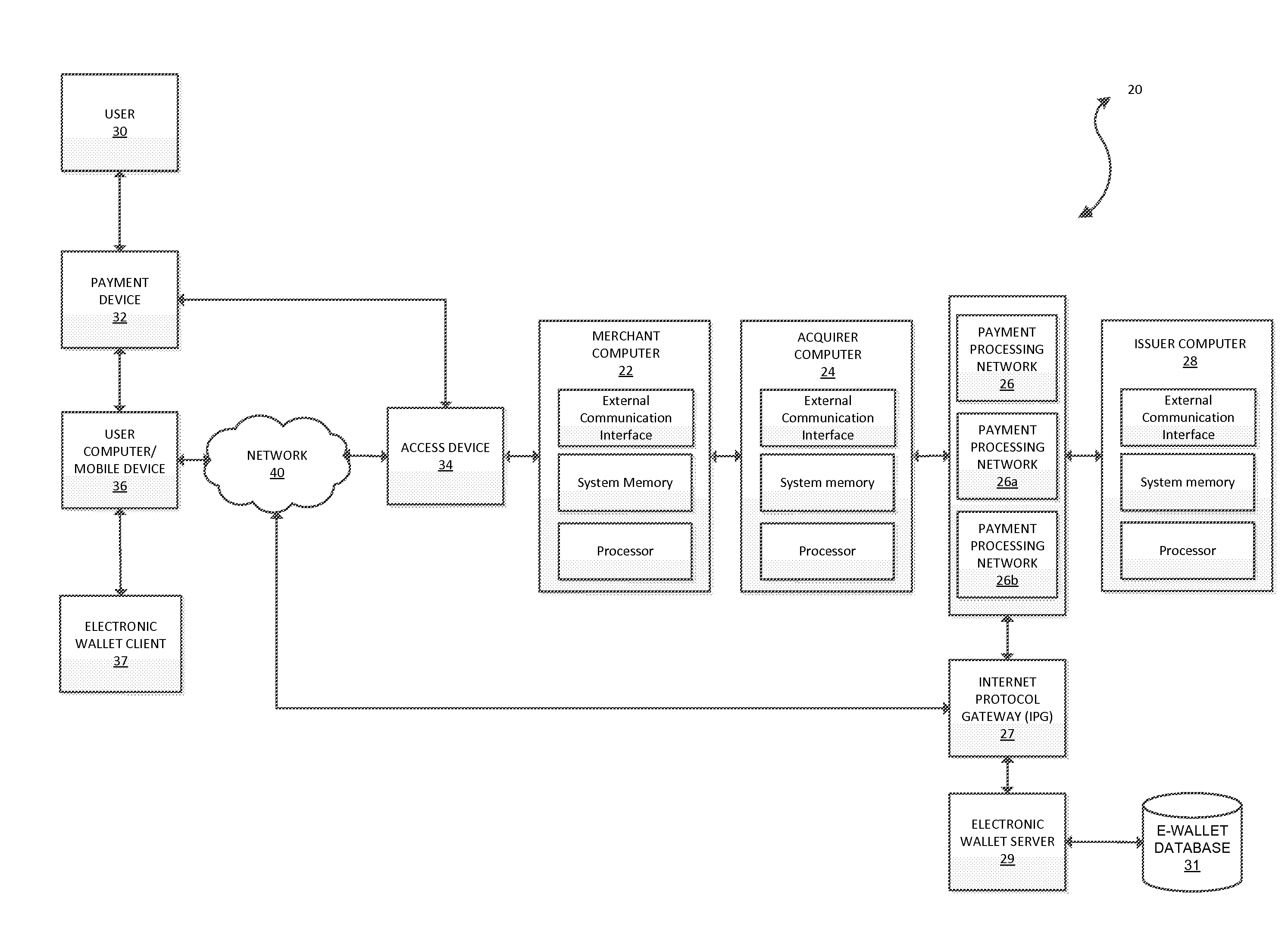
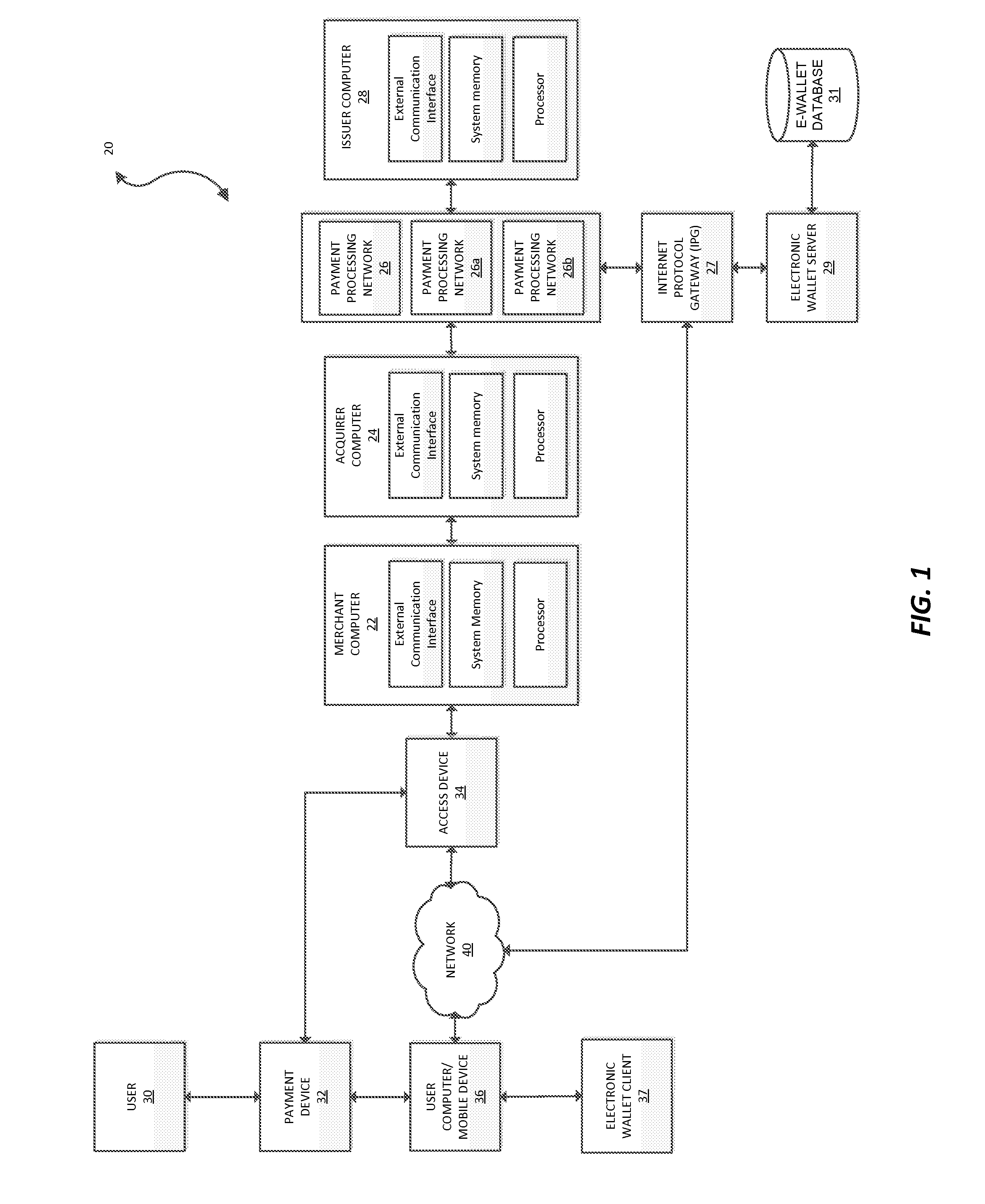
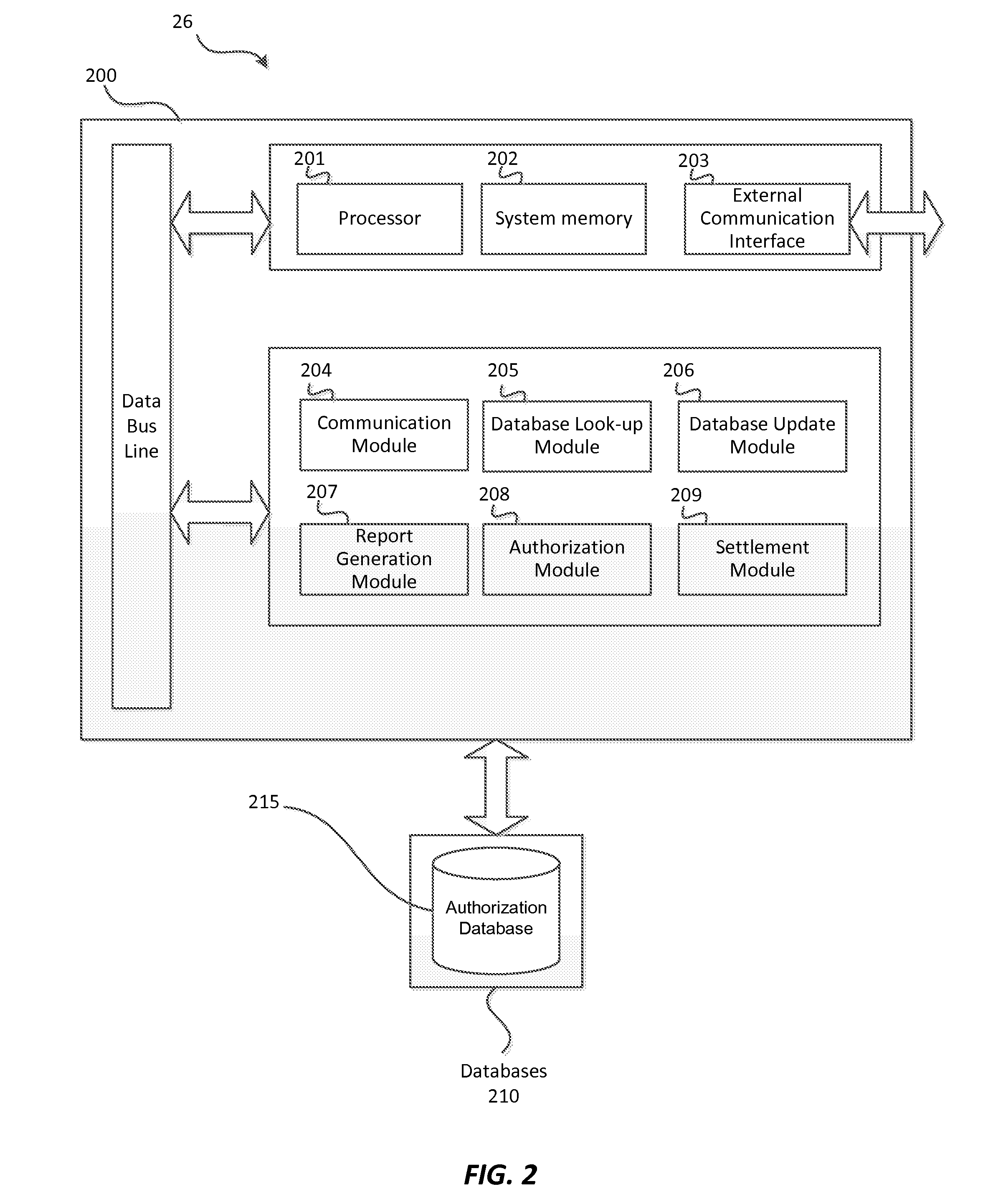
Payment system pre-selection environment processing
InactiveUS20140025567A1Easy to carryImprove performanceFinanceDebit schemesApplication IdentifierComputer science
Systems and methods for payment system pre-selection environment processing are provided. One such method comprises receiving payment information from a payment device from a consumer. The method further comprises executing a pre-selection phase to determine a preferred application identifier (AID) and routing option based on the payment information. The method also comprises completing a transaction using the preferred AID and routing option.
Owner:VISA INT SERVICE ASSOC
Network node connection configuration
ActiveUS20150078746A1Firmly connectedLow costMultiplex system selection arrangementsData switching by path configurationInterconnectionComputer science
A system and method for connectivity configuration of a network node permits an optical signal to be passed through the node and shifted from a first connector position to a second connector position that is offset from the first connector position. The shifted optical signal permits a number of distant nodes in the network to be reached with a direct optical connection, which can be configured to be bidirectional. The disclosed connectivity configuration reduces the cabling requirements for the network and simplifies the interconnections.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
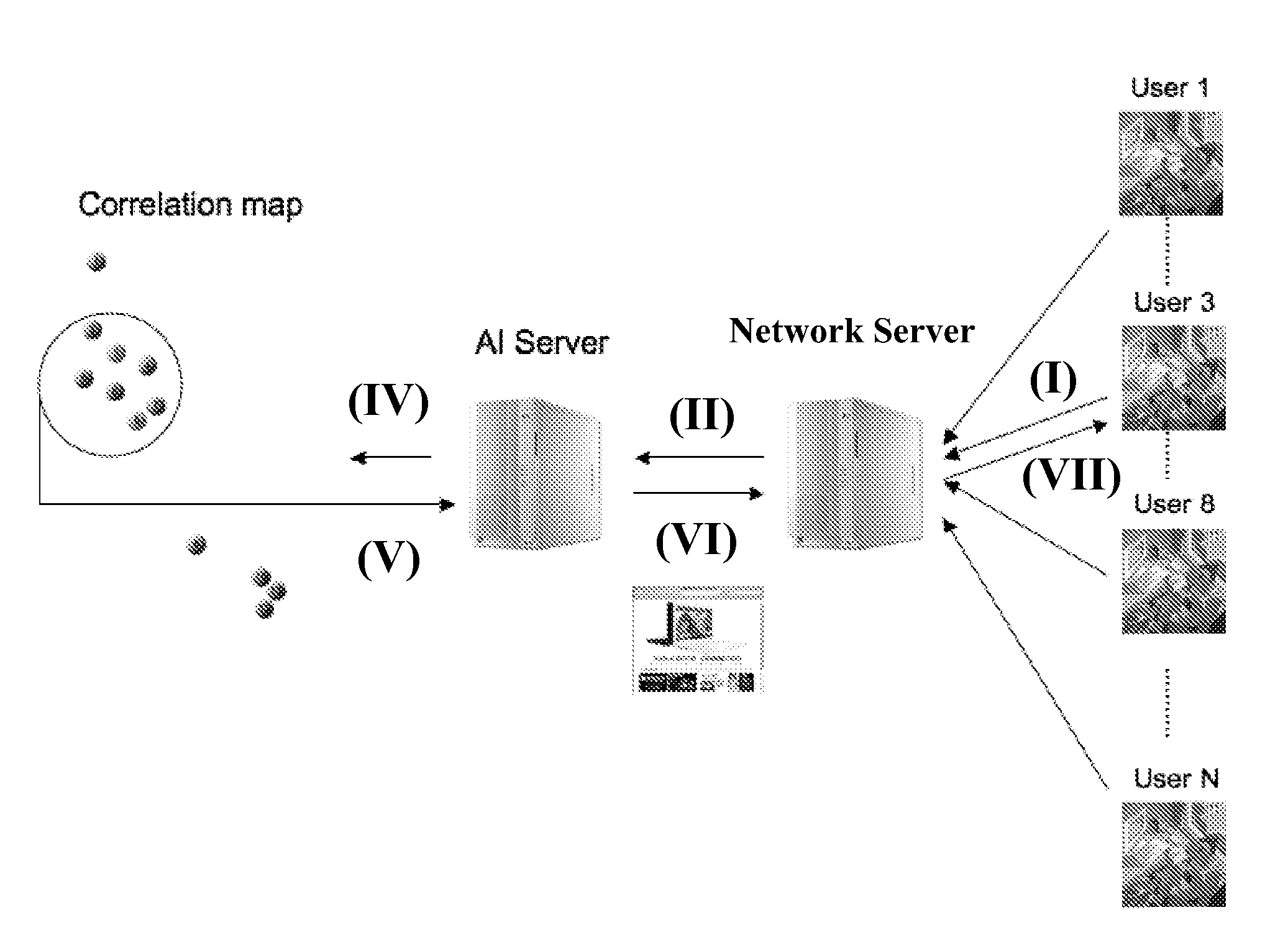
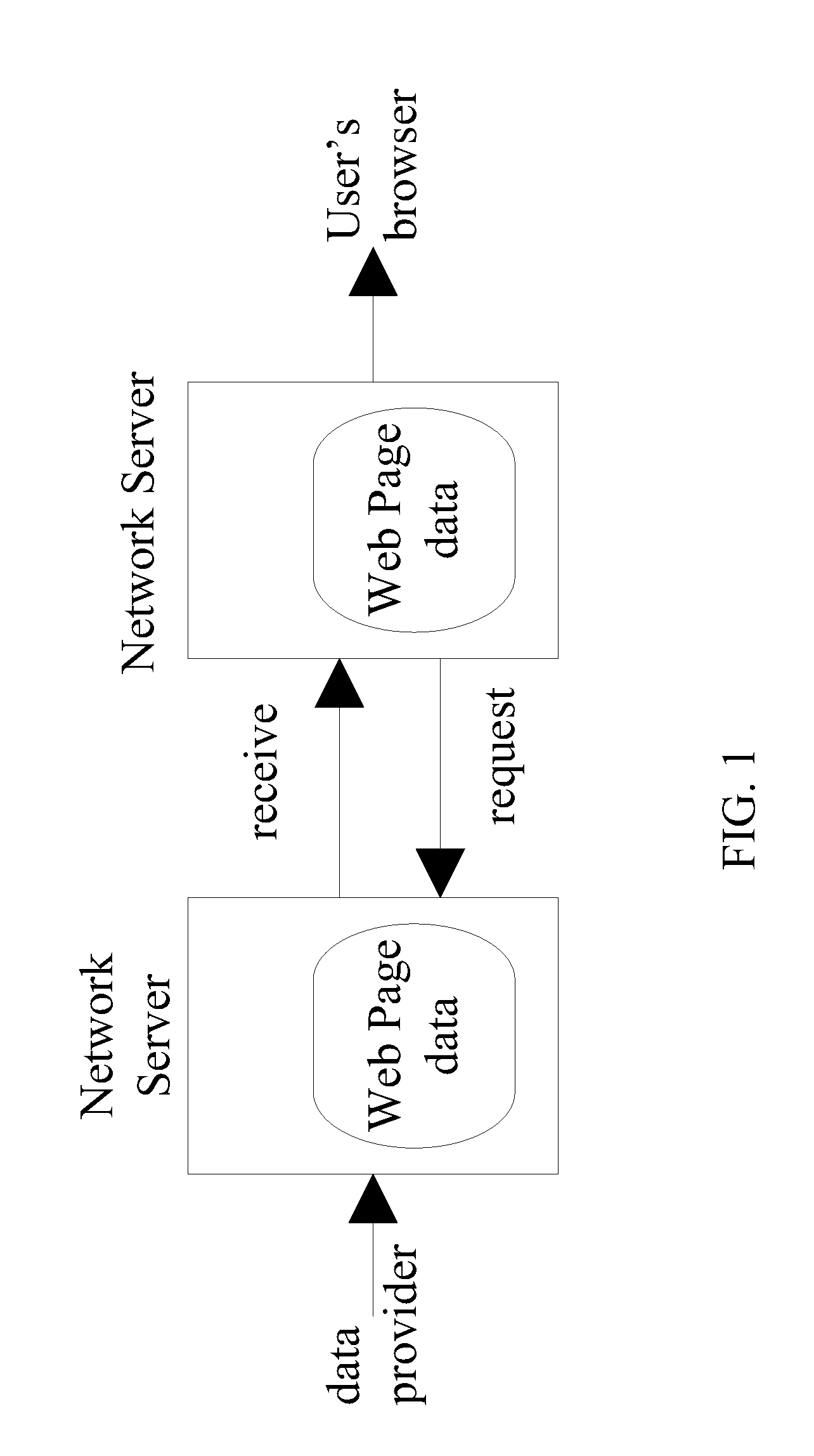
System and method for automatic generation of user-oriented homepage
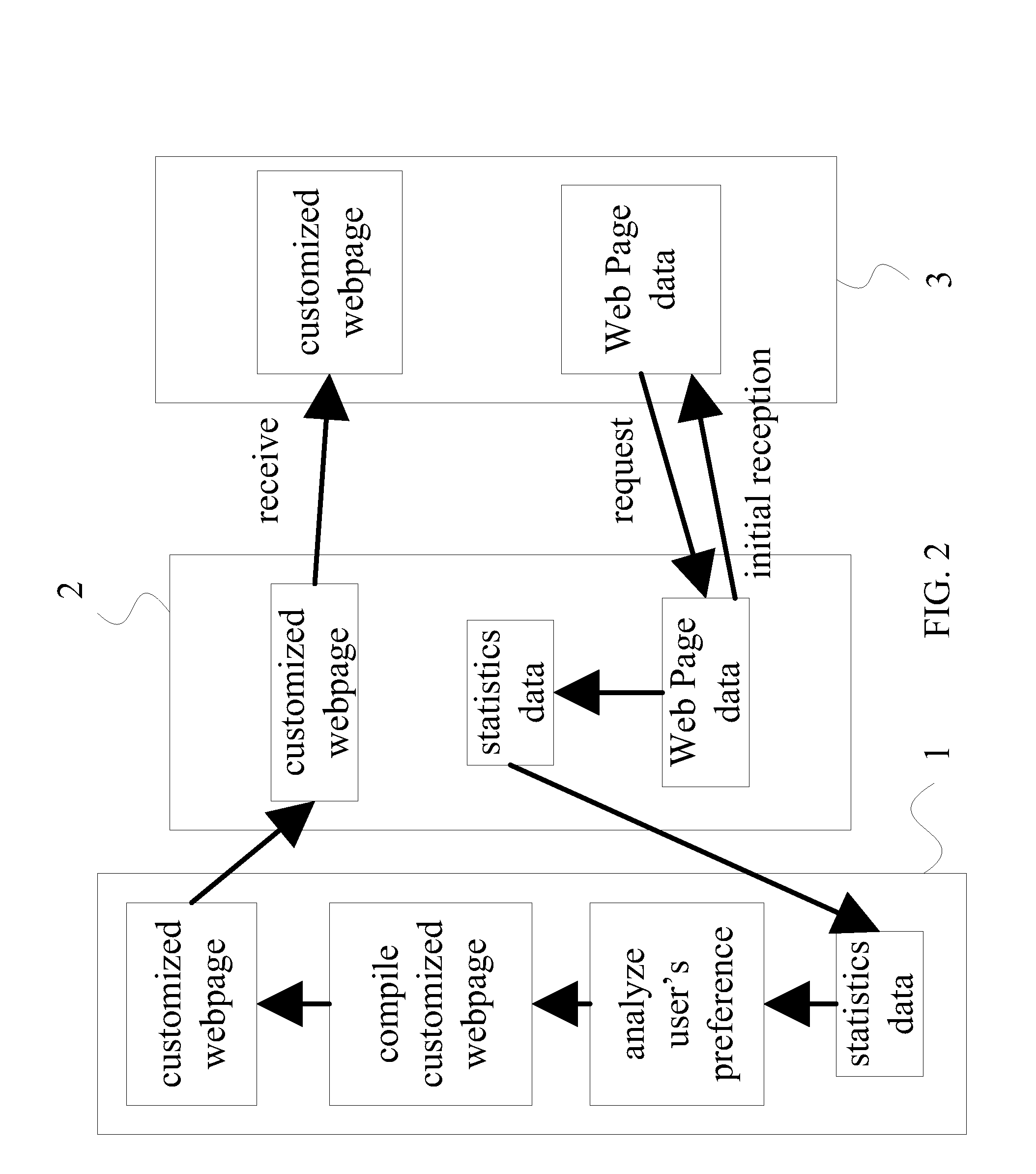
InactiveUS20090099995A1Calculation speedThe analysis result is accurateWebsite content managementKnowledge representationUniform resource locatorData mining
The present invention discloses a system and a method for automatic generation of a user-oriented homepage, said system comprises an active real-time artificial intelligence network server working with a traditional network server and a fast relational data processing method to track and determine from a webpage browsing log server a user behavior for webpage browsing, and then to compile user browsing characteristics to design the webpage automatically into a user-oriented homepage. Therefore, every time when a user connects to a same URL, said user-oriented homepage presents information that said user requires or prefers.
Owner:SENALYTIX INC +1
Method for adaptively modifying the observed collective behavior of individual sensor nodes based on broadcasting of parameters
InactiveUS20080209026A1Adapt quicklyFast processingPower managementNetwork topologiesData processing systemSensor node
A method for continually controlling the collective behavior of a set of computing devices in a distributed data processing system. A gateway node disseminates a specification request comprising a set of parameters to a set of computing devices. The gateway node may be unaware of the number and identity of individual computing devices. Each computing node receiving the request determines whether its attributes satisfy the predicates expressed in the specification request. If so, the node processes the parameters in the specification request and modifies its own behavior based on the values in the parameters of the specification request. Subsequently, the gateway node may also observe the quality of information (QoI) values communicated from the set of computing devices. The gateway node iteratively modifies the parameters disseminated in subsequent specification requests based on a divergence between a computed quality of information value and a desired quality of information value.
Owner:IBM CORP
Multiple node network and communication method within the network
ActiveUS7408950B2Start fastFast internetError prevention/detection by using return channelPropulsion power plantsData fieldDelayed time
A multiple node network includes a plurality of terminal nodes. A management node manages the terminal nodes. A bus connects the respective terminal nodes and the management node to one another. The respective terminal nodes and the management node communicate with each other using a frame that includes at least an identifier field and a data field. The data field has a discriminative number. Each terminal node transfers the frame to the management node. A contention between the terminal nodes is arbitrated by comparing the respective identifier fields of the terminal nodes. When the arbitration fails, each terminal node repeatedly transfers the frame to the management node after a delay time that is unique for the particular terminal node and that is calculated based upon the discriminative number in the data field.
Owner:YAMAHA MARINE KK
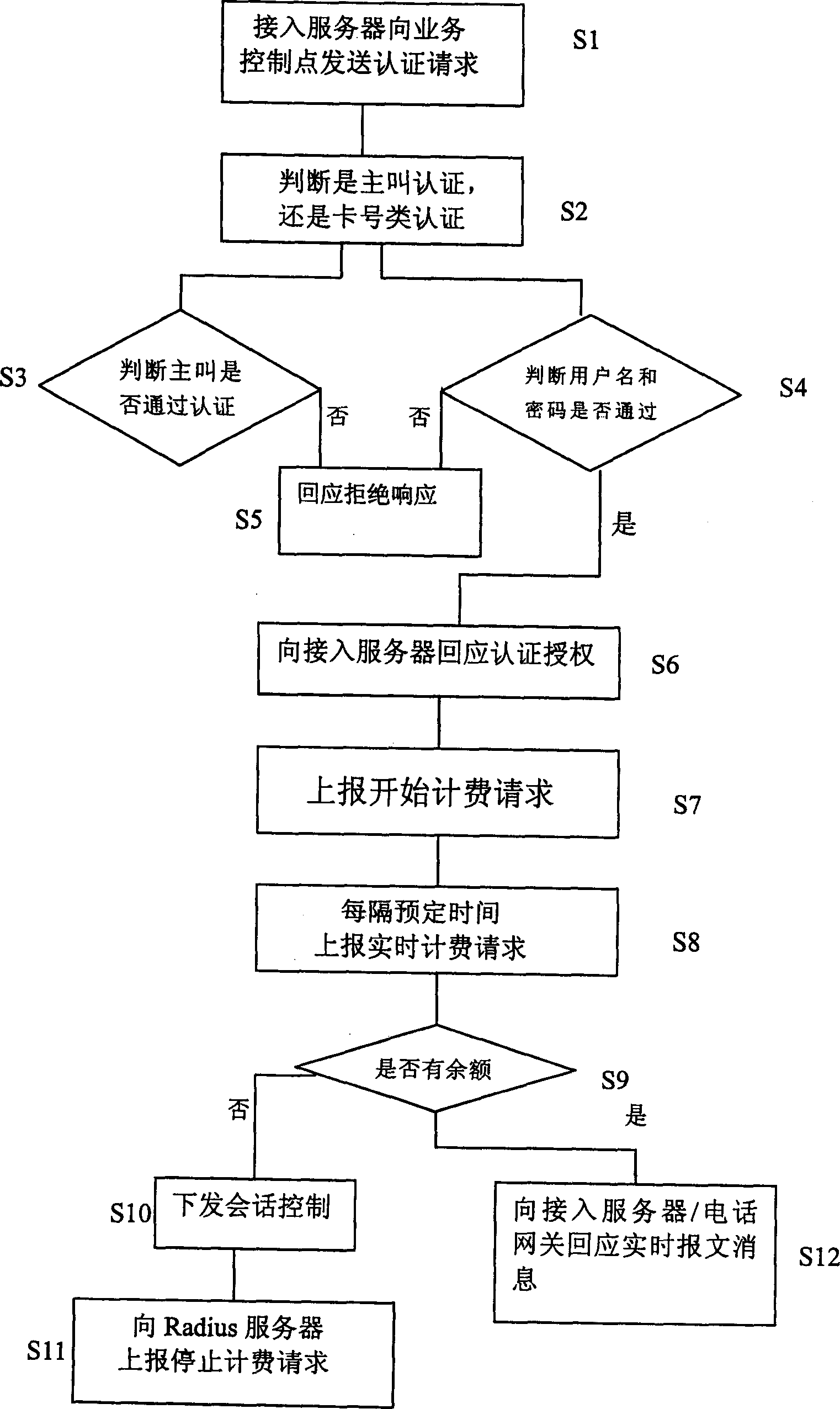
Method for switching in intelligence net by using prepaid cards
InactiveCN1447579ASpeed dialFast internetSpecial service for subscribersReal-time chargingSession control
A method allowing multiple persons and operations to log and run on network as well as dial up ID phone includes following steps. The switch in server sends the authentication request to the operation control point. With the request being passed, the operation control point responds the authentication authorization and calculates the maximum time allowed for the to the prepaid card. With the authorization being received, the server switches the call and reports the request for starting charging. The operation control point makes response to the server at the time when receiving the request. The server reports such request every preset time interval. Once the said request being received, the optical control point judges whether the balance on the card is enough.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com