Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37results about How to "Reduce data overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
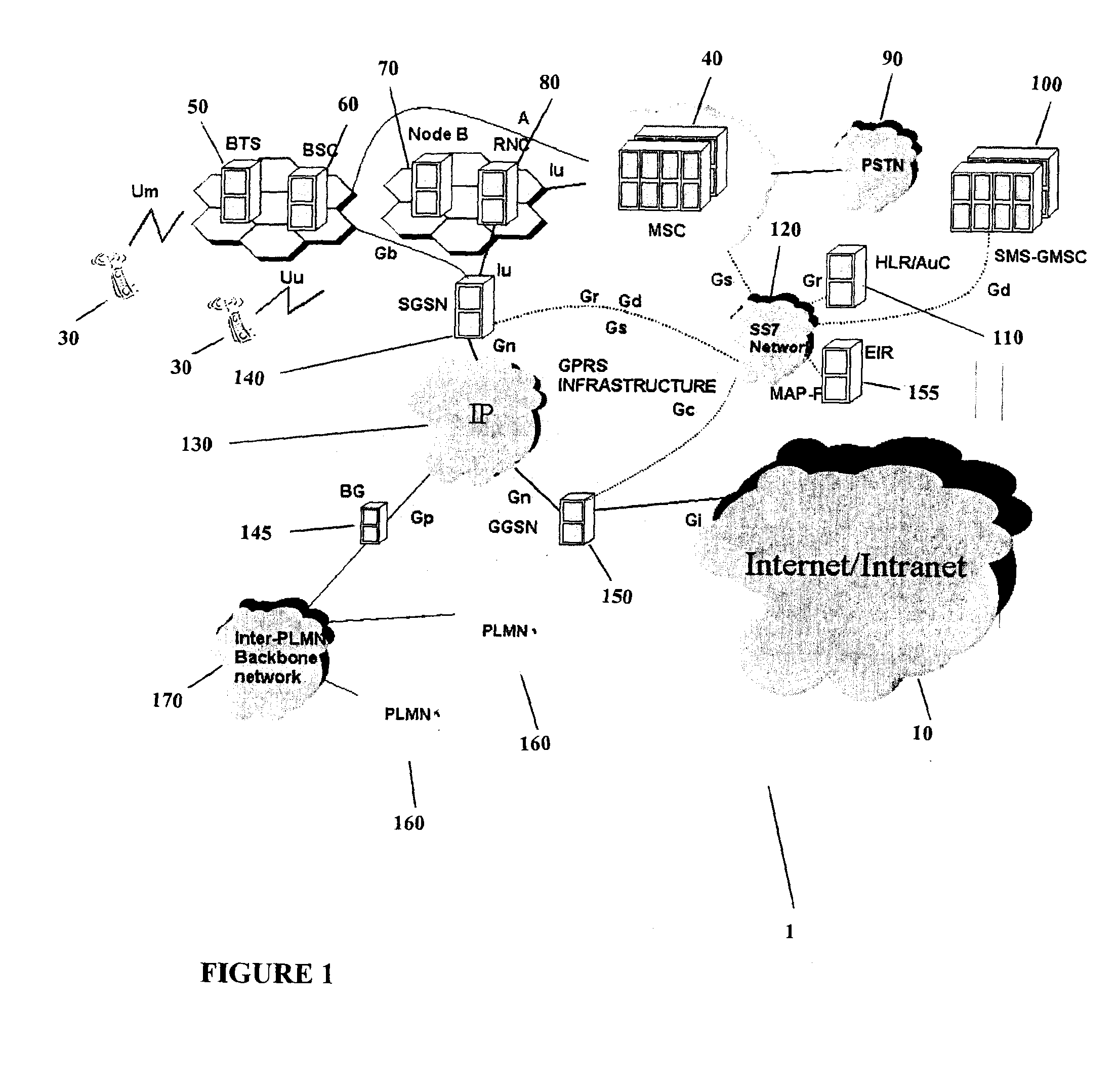
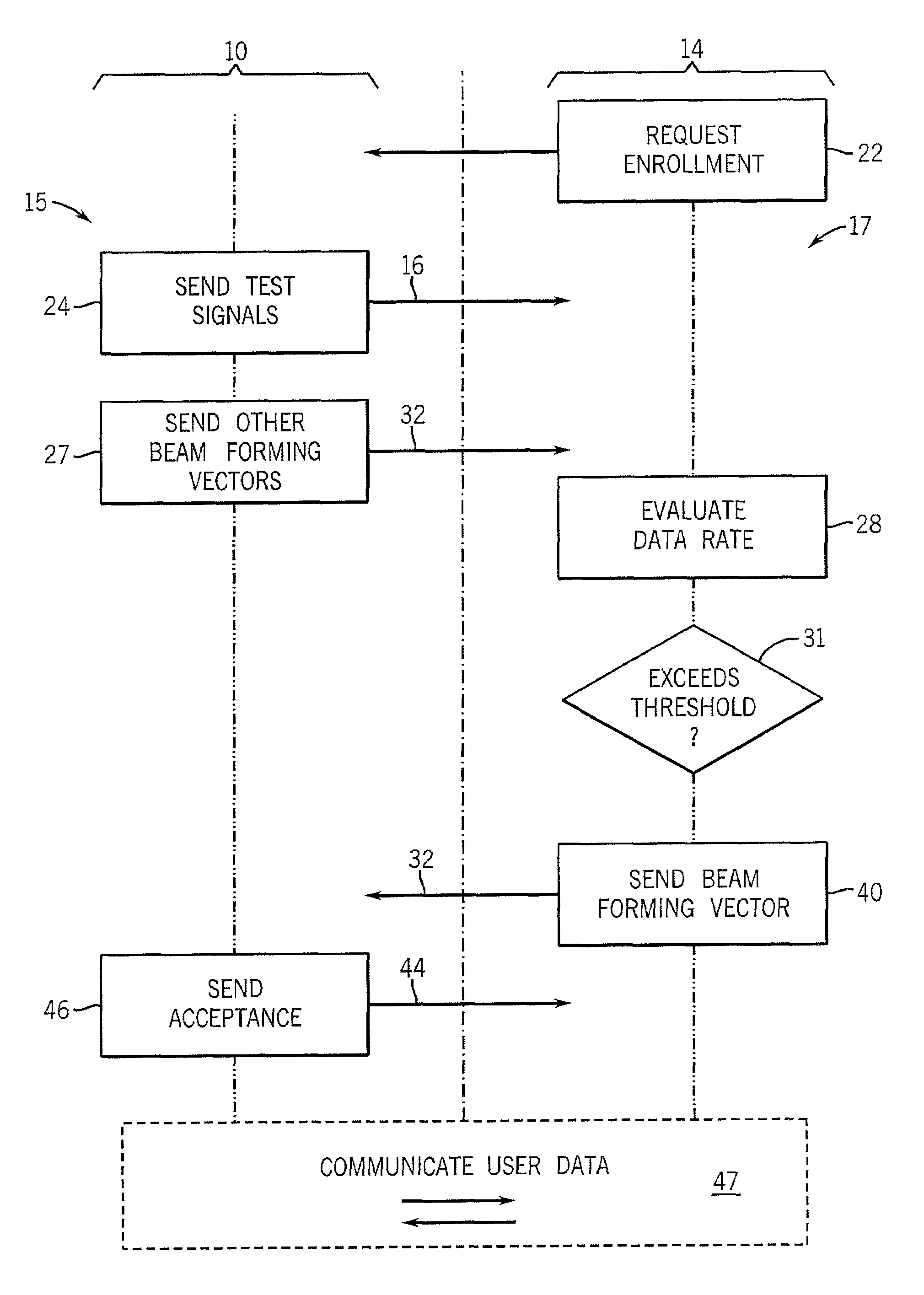
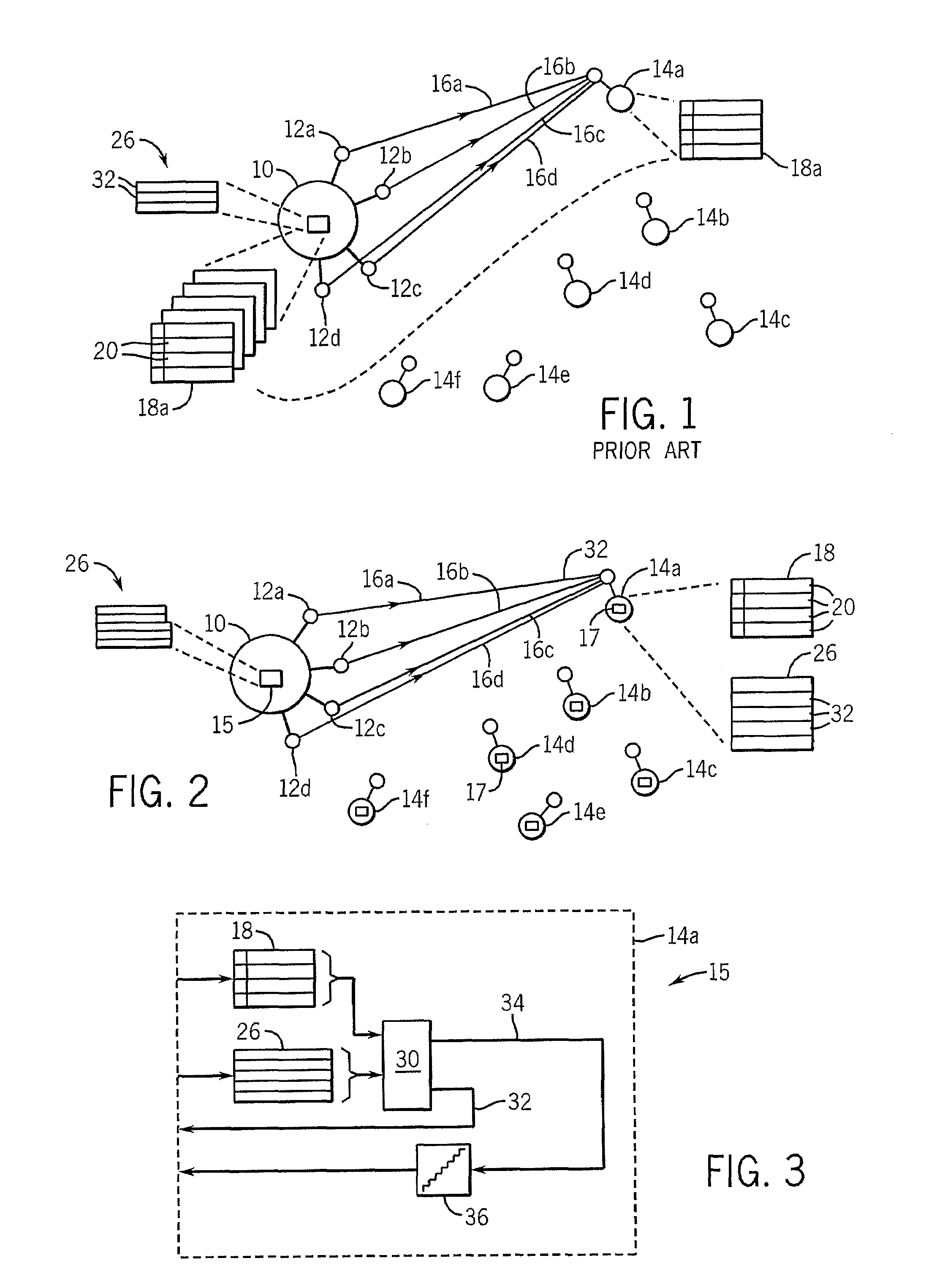
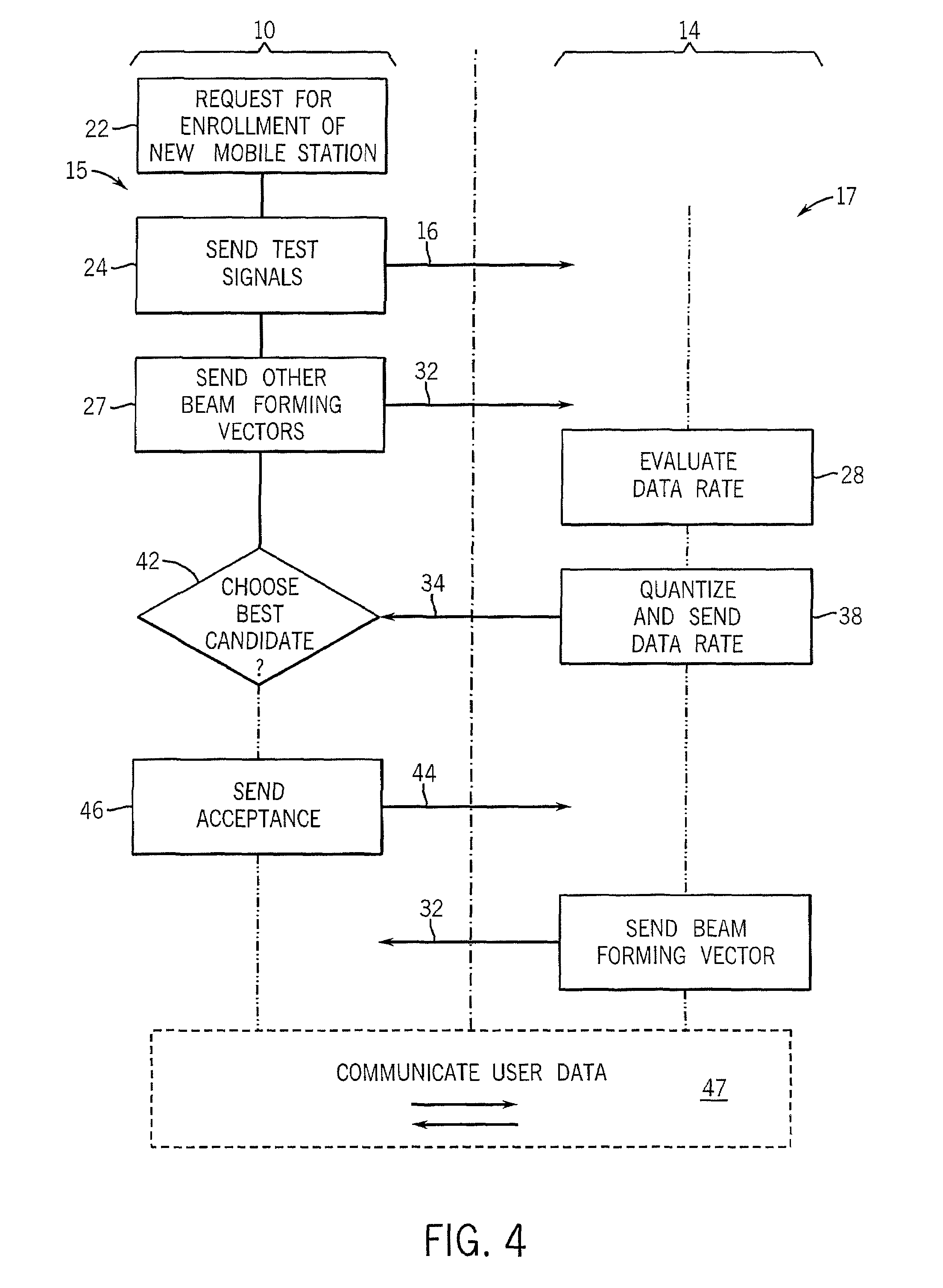
System and Method of Traffic Management Over Mixed Networks
InactiveUS20080279216A1Efficiently decideReduce overheadNetwork traffic/resource managementTime-division multiplexTraffic capacityMix network
A method and apparatus is provided of handling modified packets containing additional information regarding source and data type for efficient processing within a mixed network. Incoming and outgoing packets are sent via a dynamic protocol which adapts to circumstances, including the type of network being used, the type of packet being transmitted and the network guidelines.
Owner:MOBIDIA INC
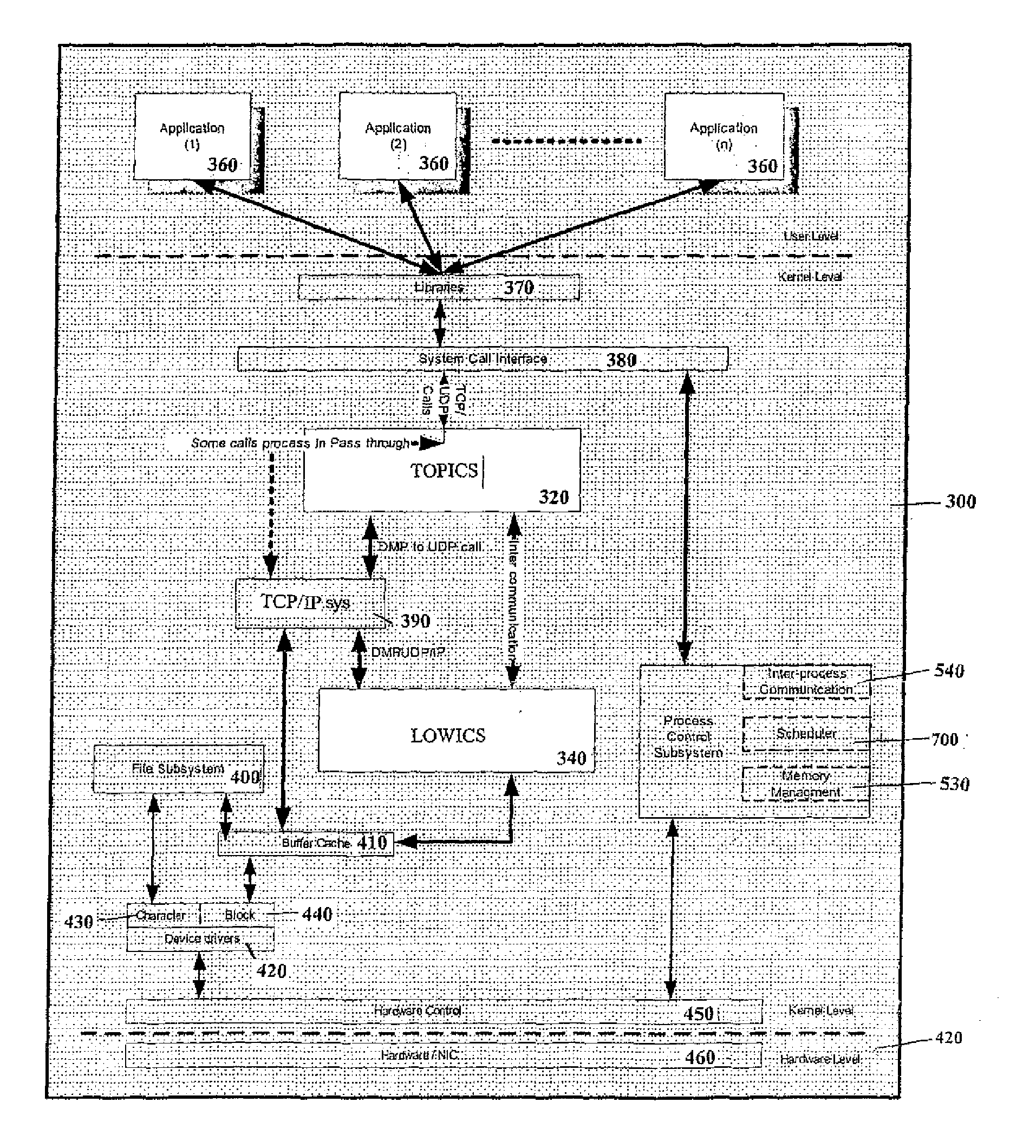
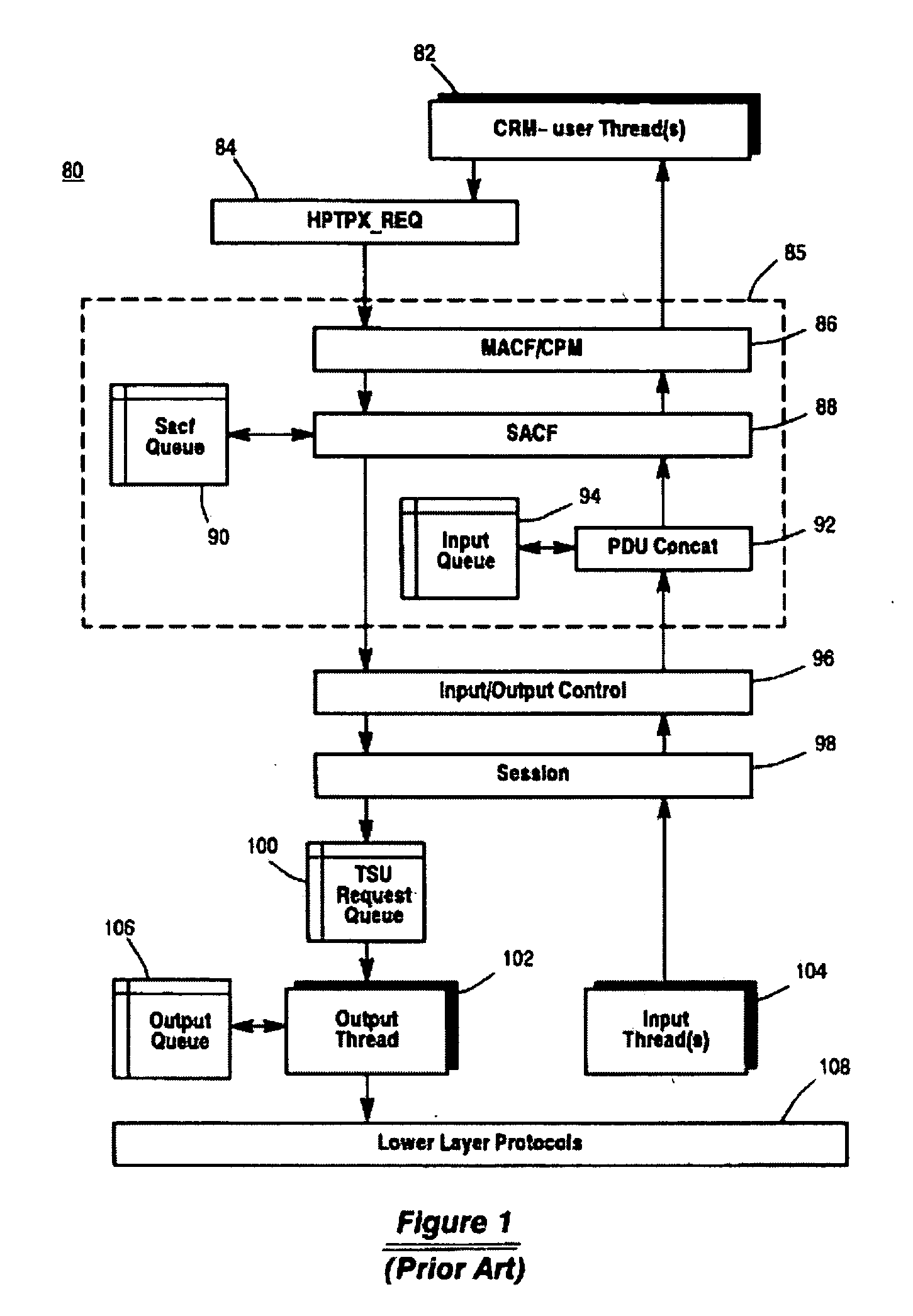
Message transfer using multiplexed connections in an open system interconnection transaction processing environment
InactiveUS20050193056A1Less complexSimpler connection creationMultiple digital computer combinationsSecuring communicationMessage lengthMultiplexing
Novel message formats for use in a distributed transaction environment are disclosed. Each message includes a message type field, a message length field, and a data field, typically in the foregoing order, and each field in the message has a fixed number of bytes. The message type and data length fields may be comprised of a single header. The data field may include novel groups of OSI TP PDUs where each grouping characterizes the content of the data in the PDU. A novel apparatus for use in a distributed transaction environment also is disclosed. The apparatus may include a peer processing machine and a multiplexed TCP / IP connection for exchanging messages with other peer processing machines in the distributed transaction environment.
Owner:UNISYS CORP
System and Method of Registering with an Access Point
InactiveUS20080293413A1Efficiently decideReduce overheadNetwork traffic/resource managementRadio/inductive link selection arrangementsTelecommunicationsMobile device
A method of registering a mobile device with an access point, is provided in which the mobile device preregisters with access points nearby in order to accelerate the registration process when roaming is initiated. Roaming may be initiated when the SNR is increasing relative to the current access point and decreasing relative to another access point.
Owner:MOBIDIA INC
Method and apparatus for processing video
ActiveUS20170013269A1Inhibit decrease in bandwidth efficiencyEffective alignmentProcessor architectures/configurationDigital video signal modificationVideo bitstreamComputer graphics (images)
The present invention relates to a method for processing a video, comprising: a step in which a video central processing unit communicates with a host, receives a bitstream, parses header information, and generates a plurality of tasks for parallel processing; a step in which free scan information is generated by a free scan of a video bitstream inputted from the host according to the control of the video central processing unit; and a step in which a plurality of video processing units process the plurality of tasks on the basis of the free scan information and the parsed header information by receiving the control of the video central processing unit.
Owner:CHIPS&MEDIA
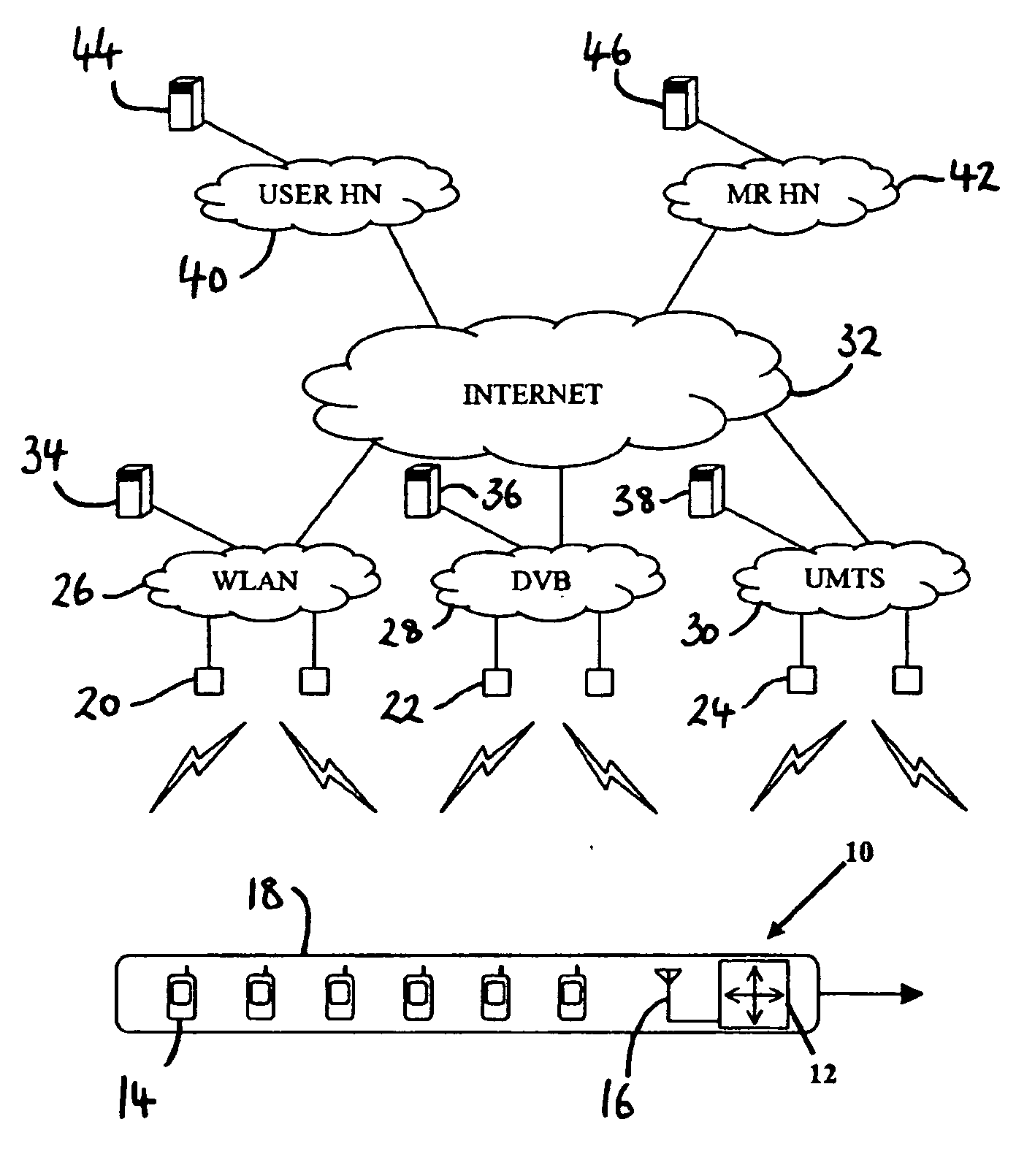
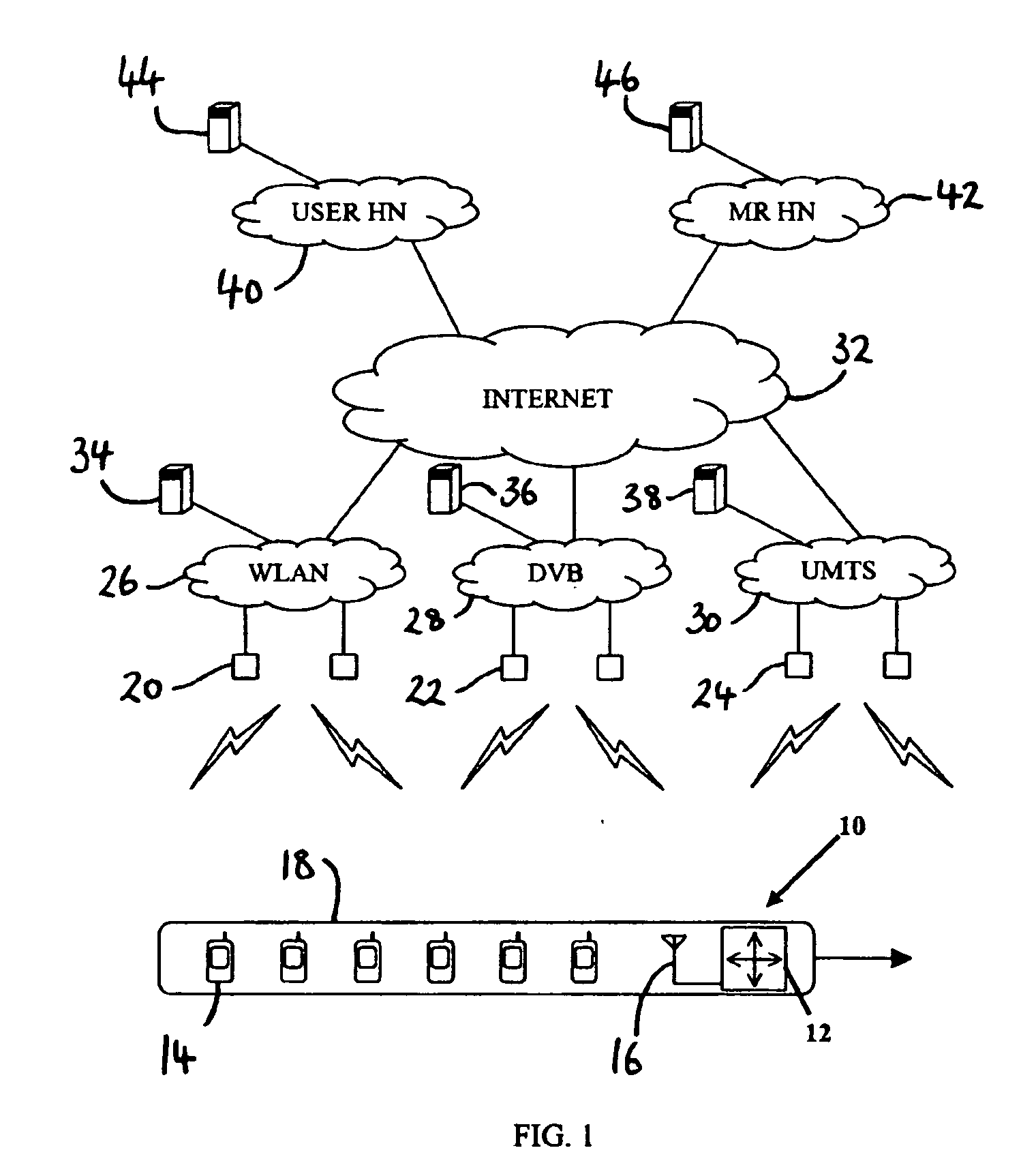
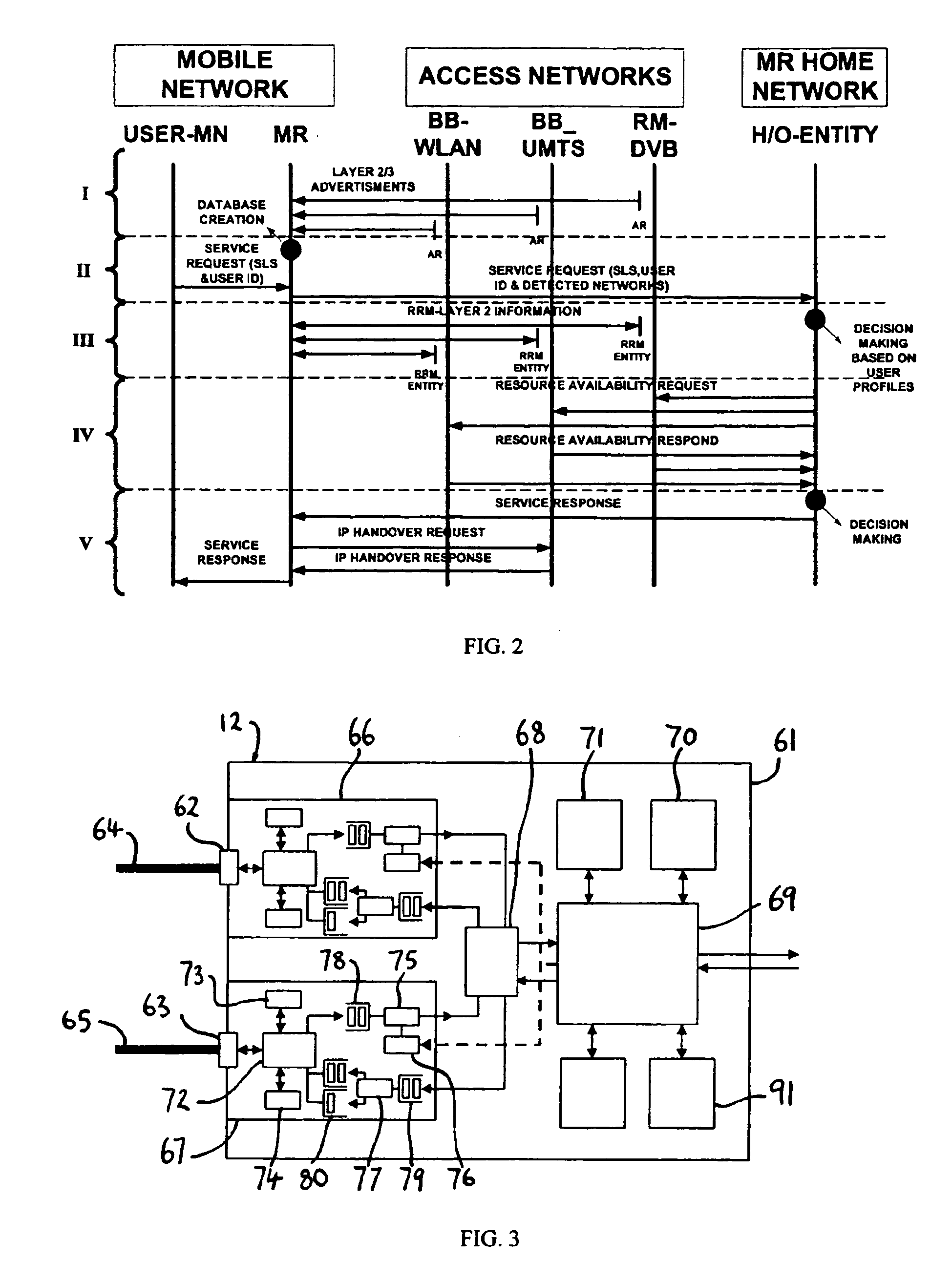
Access router selection method
InactiveUS20070147320A1Reduce data overheadNetwork traffic/resource managementNetwork topologiesMobile WebHeterogeneous network
In a heterogeneous network environment a method of selecting an access router (20) among a number of available access routers (20, 22, 24) for a group of mobile network nodes (14) attached to a mobile router (12), each access router (20, 22, 24) providing access to packet-switched resources in a respective network domain (26, 28, 30) and each mobile network node (14) having a desired QoS level at the network layer, which method comprises the steps of: (a) determining a group QoS level acceptable to substantially all mobile network nodes (14) in said group; (b) using said group QoS level to query at least one of said number of respective network domains (26, 28, 30) to determine whether or not it can meet said group QoS level; and (c) using a response from said at least one network domain (26, 28, 30) to decide whether or not to perform a network layer handover of said group of mobile network nodes (14) to one of said number of available access routers (20, 22, 24).
Owner:KING'S COLLEGE LONDON
System And Method Of Providing Service Information To A Carrier
InactiveUS20090122712A1Efficiently decideReduce overheadError preventionTransmission systemsService informationMobile device
A method of providing service performance information to a carrier for an application over a network is provided, wherein parameters relating to the application are transmitted to a mobile device, and the mobile device stores information relating to packets transmitted for the application. Should the information stored exceed the parameters, an alert is sent to the network.
Owner:MOBIDIA INC
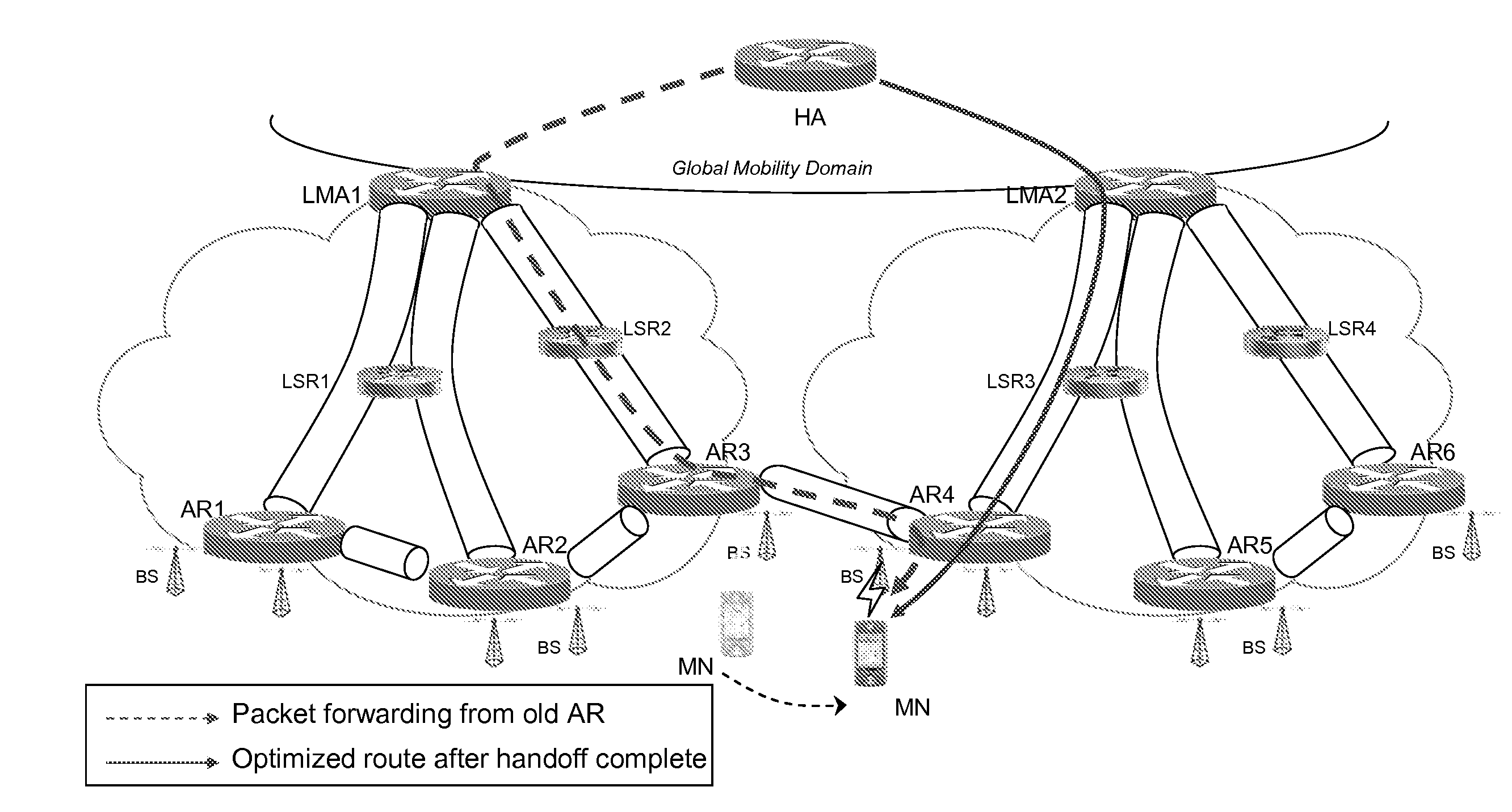
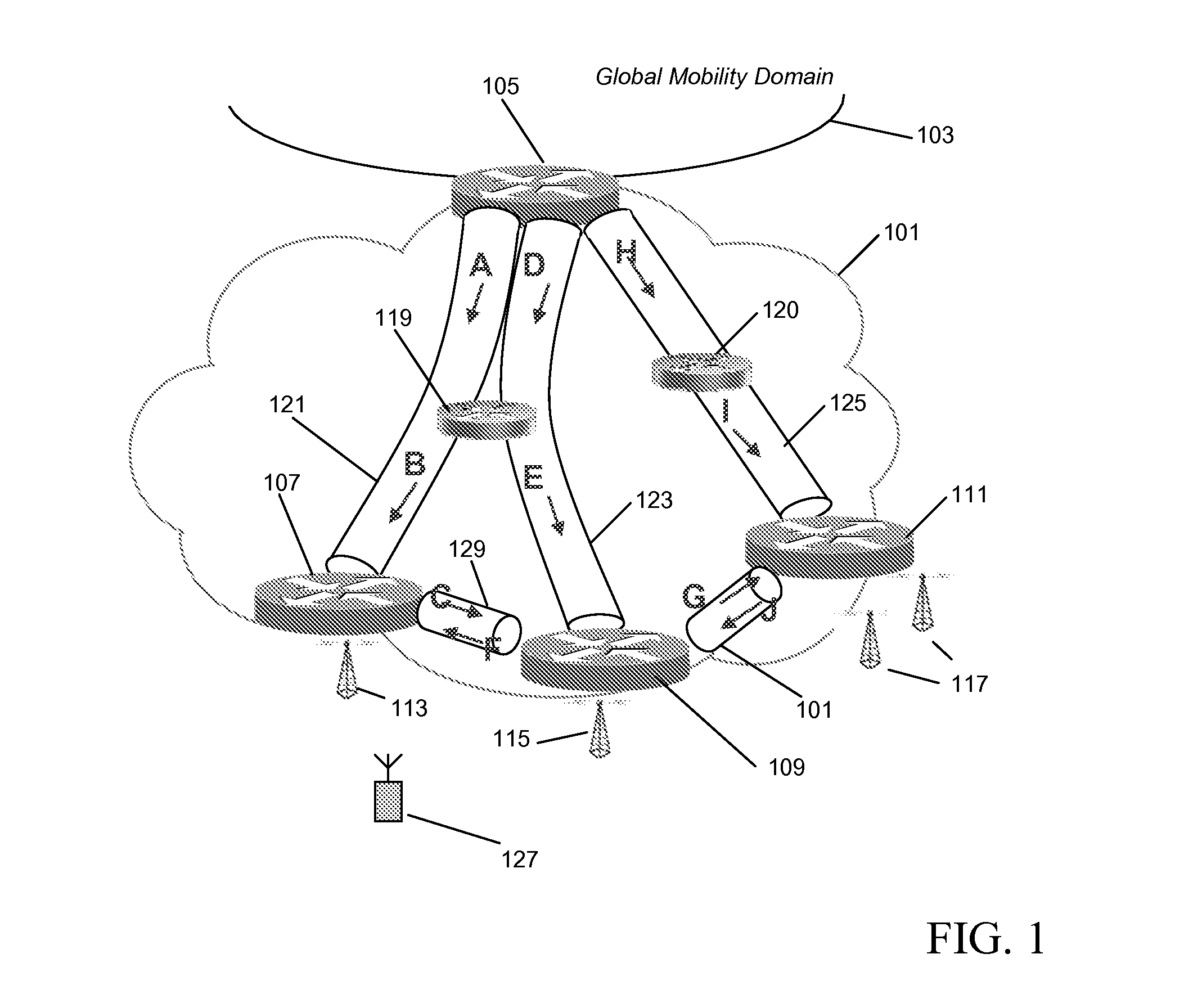
Handover in a mobile network domain
InactiveUS20080130571A1Easy to moveGood switching effectWireless network protocolsRadio/inductive link selection arrangementsNetwork packetMulti protocol
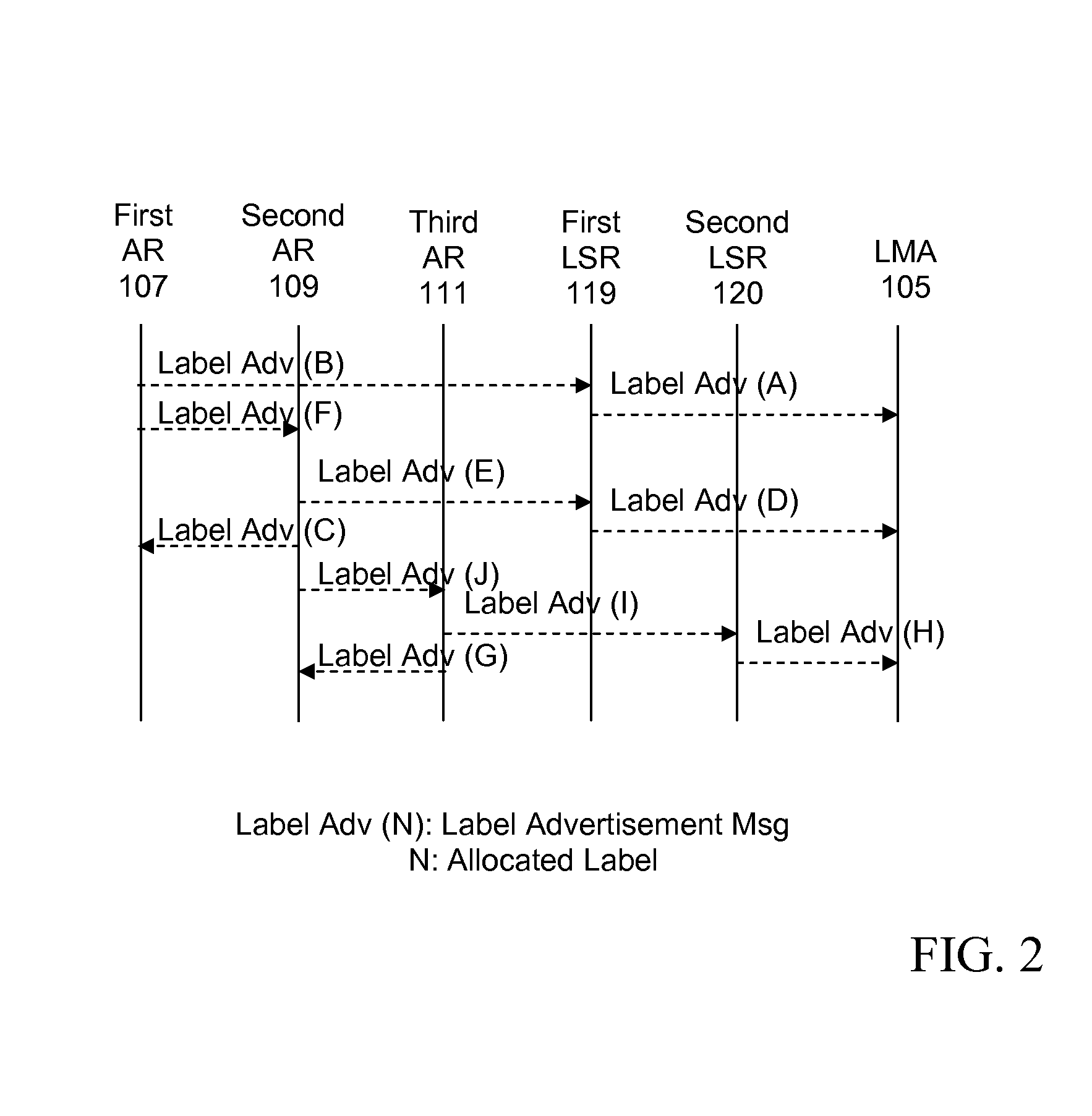
A mobile network domain (101) comprises a mobility anchor node (105) providing a non-mobile network attachment and at least a first and second access router (107, 109) supporting access by mobile nodes (127). The nodes of the mobile network domain (101) support label encapsulated tunneling. Label switching paths (121, 129) are established between the mobility anchor node (105) and the access routers (107, 109) as well as between the access routers (107, 109) themselves. When a handover of a mobile node (127) from the first access router (107) to the second access router (109) is detected, the first access router (107) forwards data packets for the mobile node (127) received via a first label switching path (121) to the second access router (109) via a direct label switching path (129) between the access routers (107, 109). The forwarded data packets are label encapsulated tunneling data packets. The invention may for example combine NetLMM (Network based Local Mobility Management) and MPLS (Multi-Protocol Label Switching) techniques to provide better performance and handover.
Owner:MOTOROLA INC
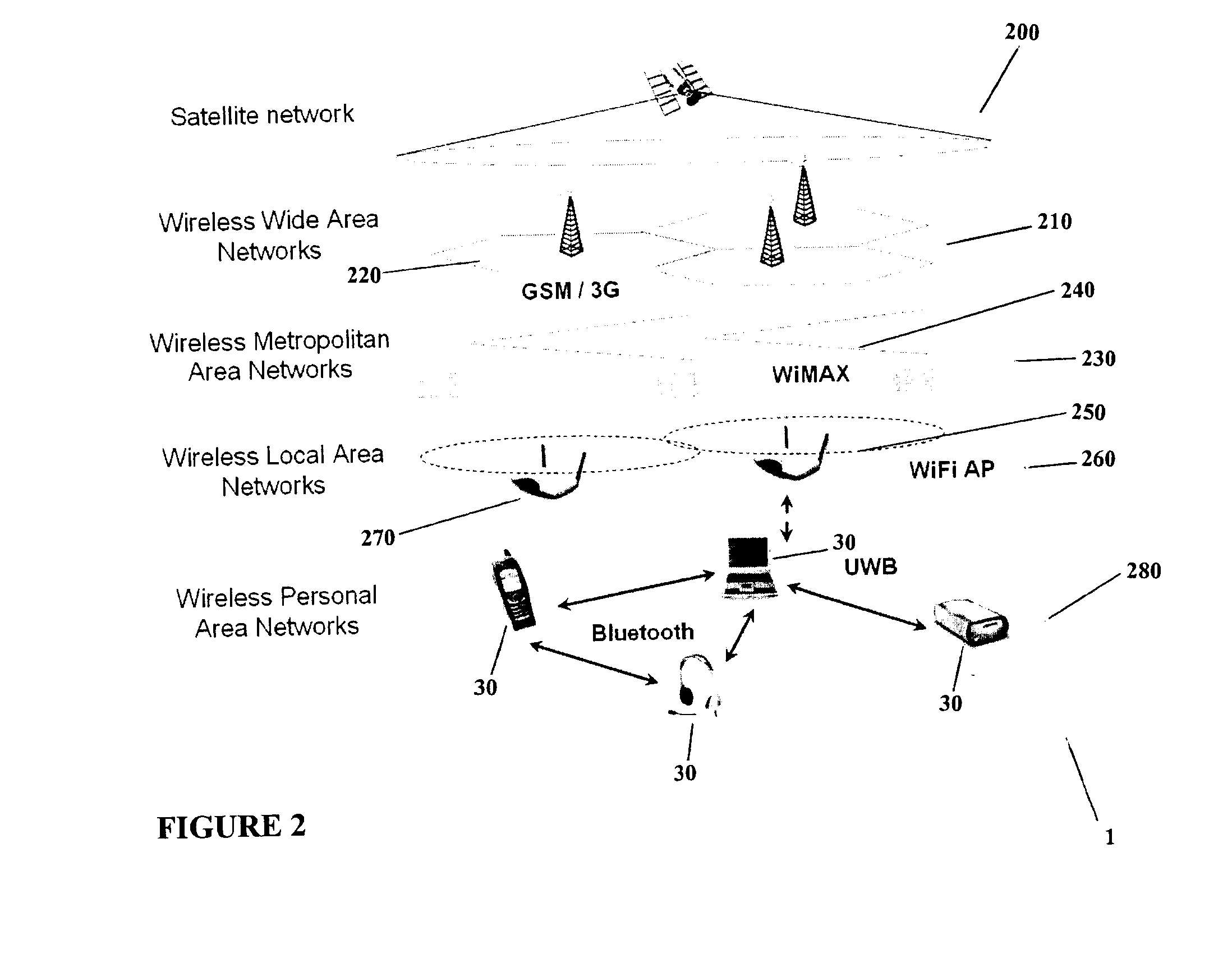
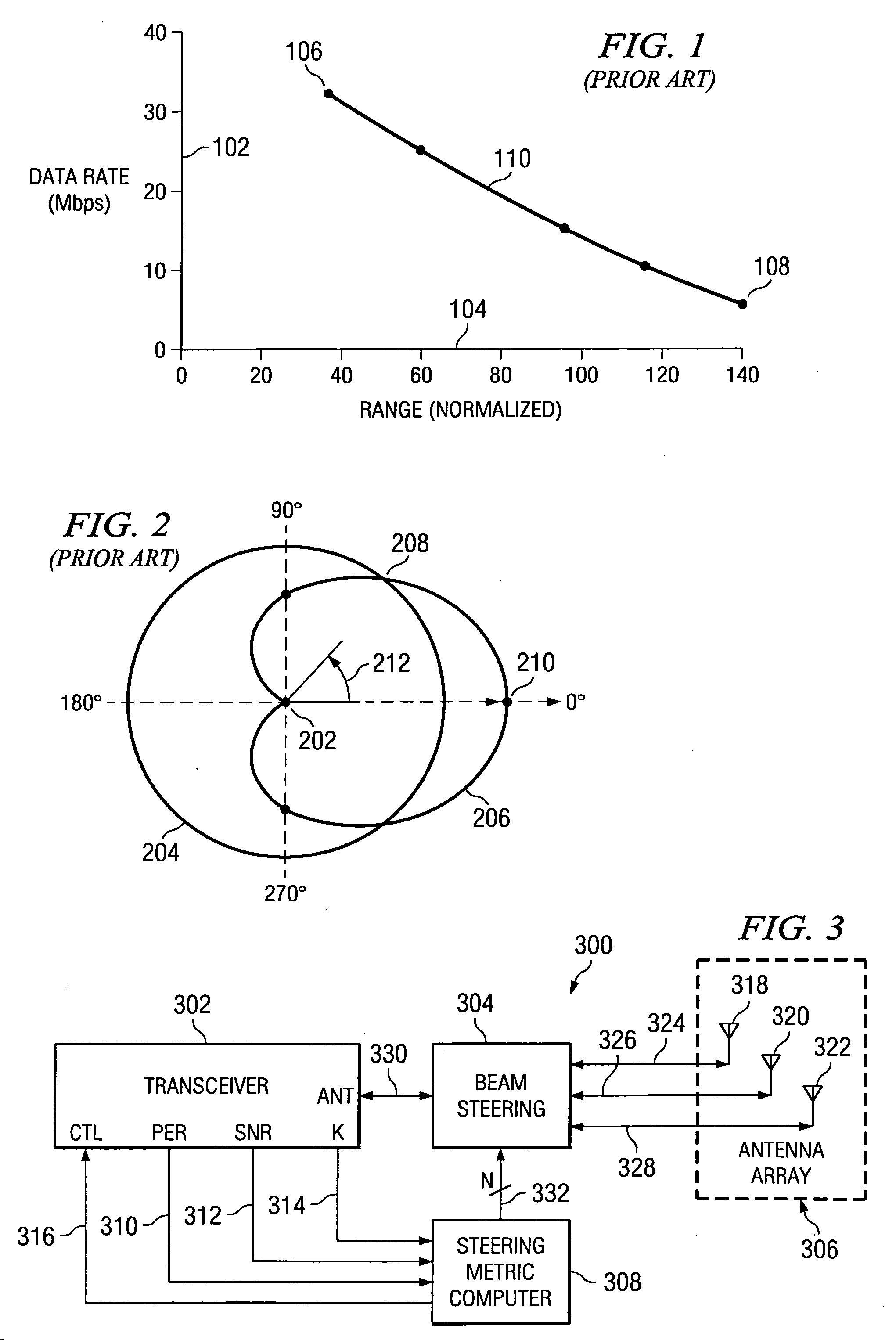
System and method for steering directional antenna for wireless communications
ActiveUS7120468B1Improve optimizationReduce data overheadMultiplex communicationSubstation equipmentWireless communication systemsCommunications system
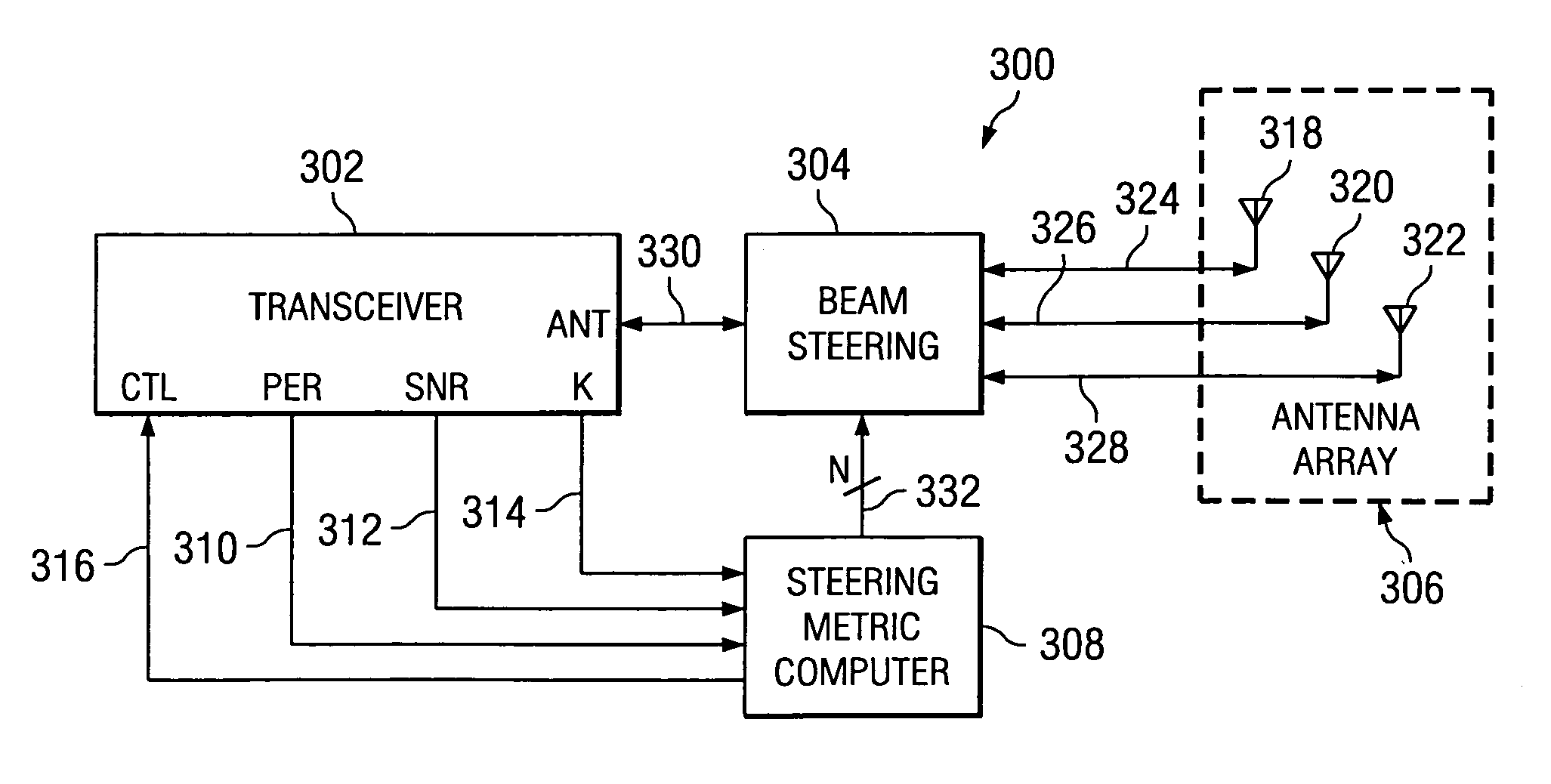
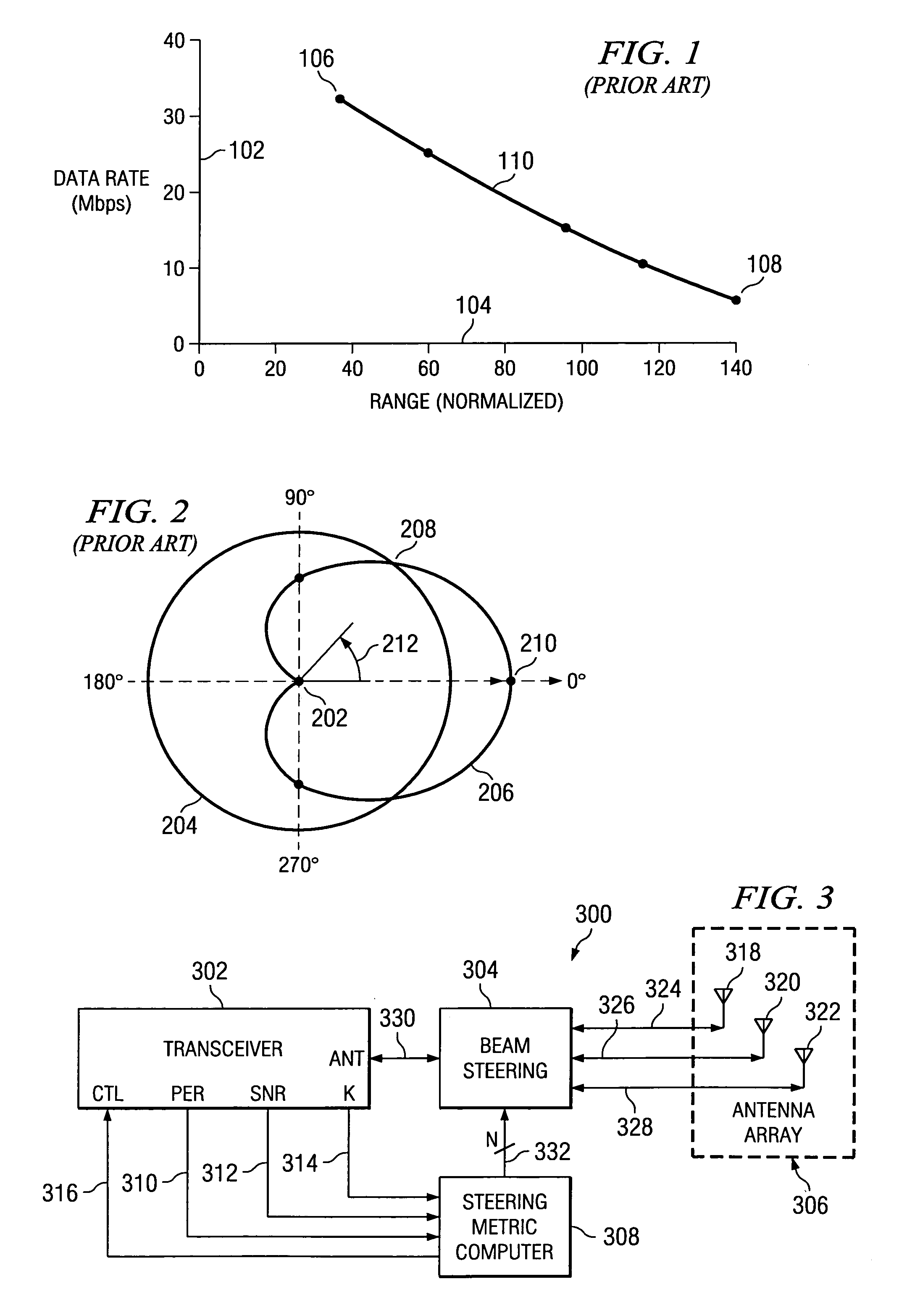
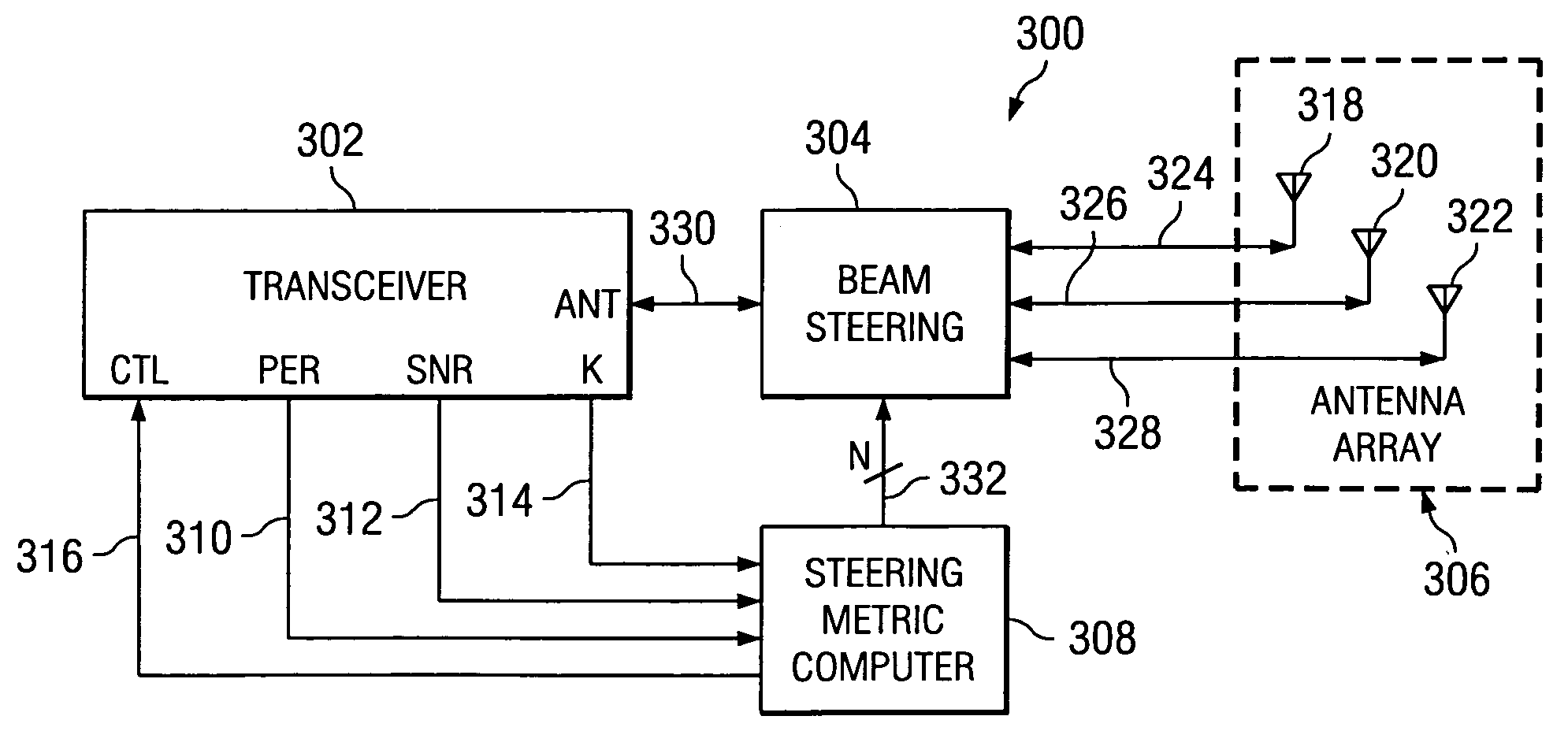
A system and method for determining an optimal antenna position of a directional antenna in a wireless communication system are described. The optimal antenna position is determined by calculating a steering metric value for possible antenna positions and the antenna position with the highest steering metric value is selected as the optimal antenna position.
Owner:TEXAS INSTR INC
System and method for steering directional antenna for wireless communications
ActiveUS20060234663A1Easy to optimizeReduce data overheadMultiplex communicationSubstation equipmentCommunications systemDirectional antenna
A system and method for determining an optimal antenna position of a directional antenna in a wireless communication system are described. The optimal antenna position is determined by calculating a steering metric value for possible antenna positions and the antenna position with the highest steering metric value is selected as the optimal antenna position.
Owner:TEXAS INSTR INC
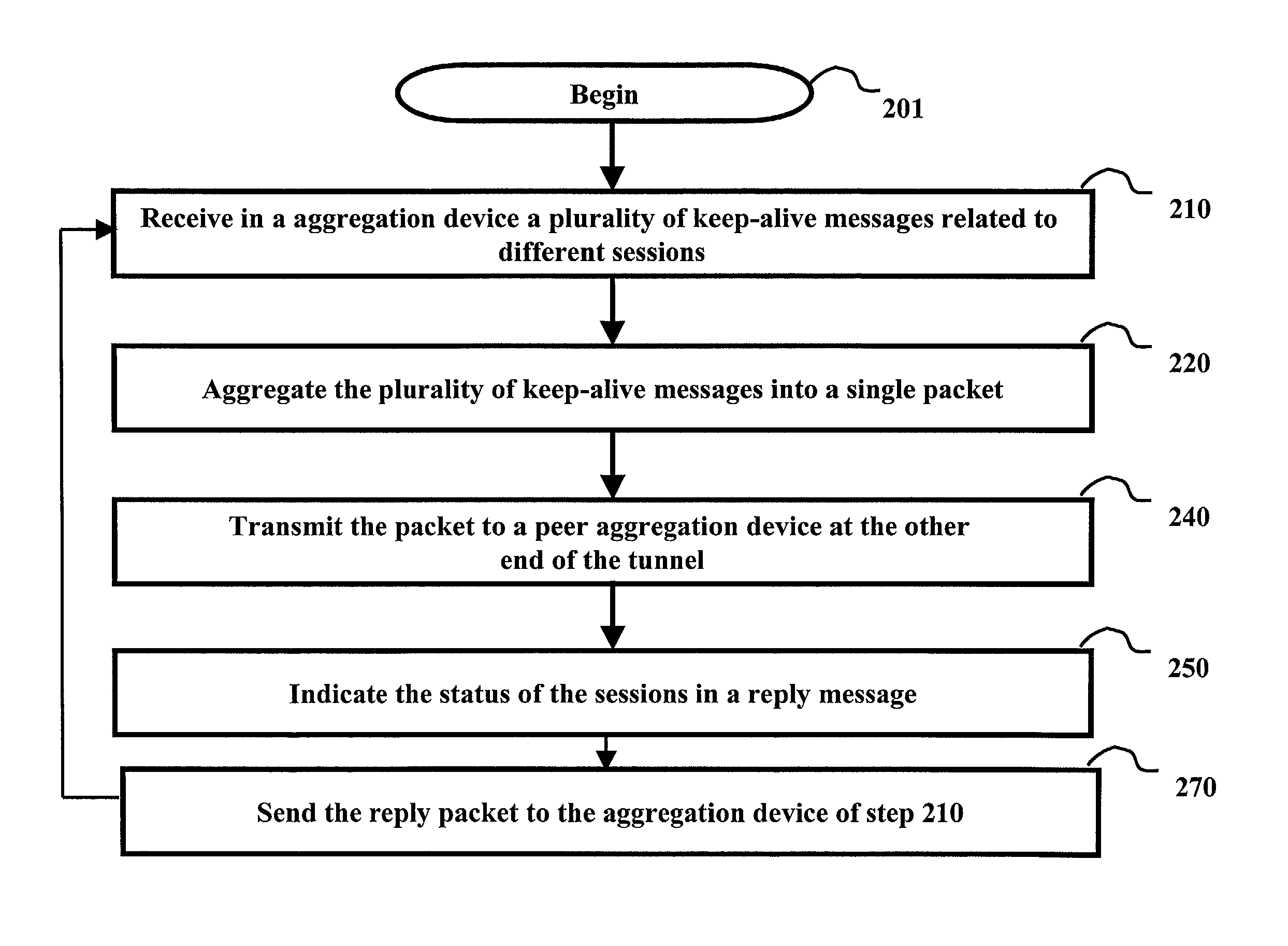
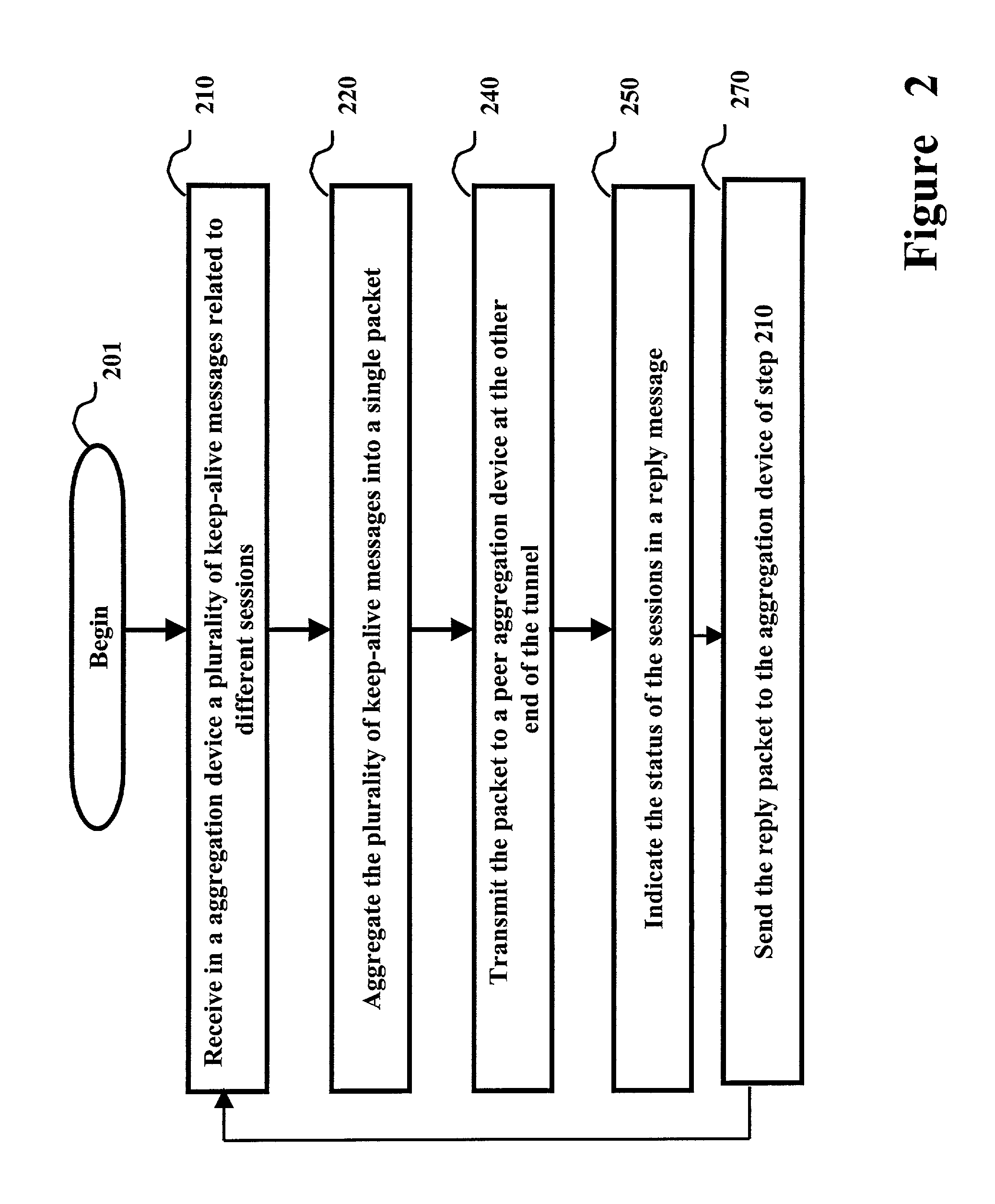
Aggregation devices processing keep-alive messages of point-to-point sessions
ActiveUS8156209B1Minimize overheadReduce data overheadMultiple digital computer combinationsElectric digital data processingNetwork access serverTraffic capacity
Several keep-alive messages of point to point (PPP) sessions received from a remote system are aggregated into a single packet in an aggregation device (e.g., network access server). The aggregated packet is sent to a peer aggregation device (e.g., home gateway) at the other end of the PPP session. The peer aggregation device may send the status of the sessions in a single packet. As a result, the data traffic on a communication backbone due to keep-alive status checks may be reduced. Without waiting for the peer aggregation device to provide the status information, a proxy reply may be generated from the aggregation device.
Owner:CISCO TECH INC
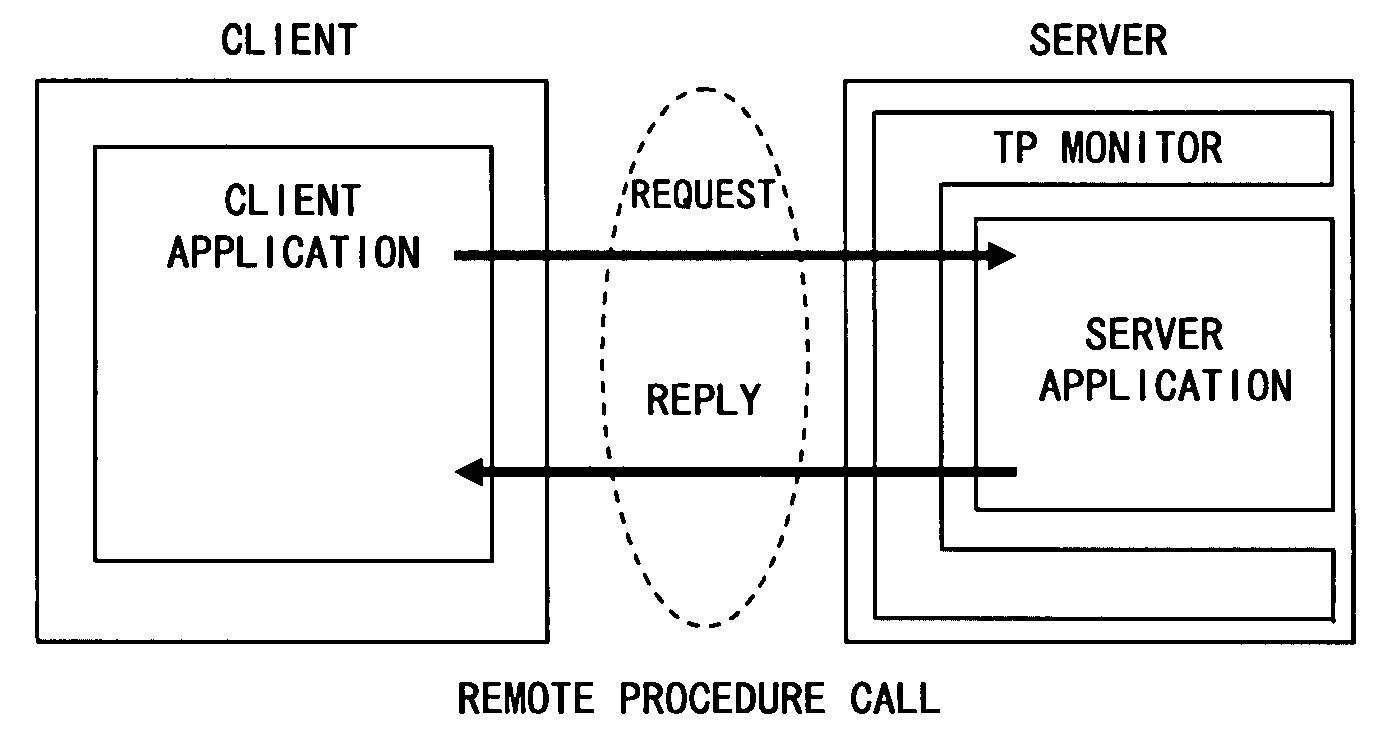
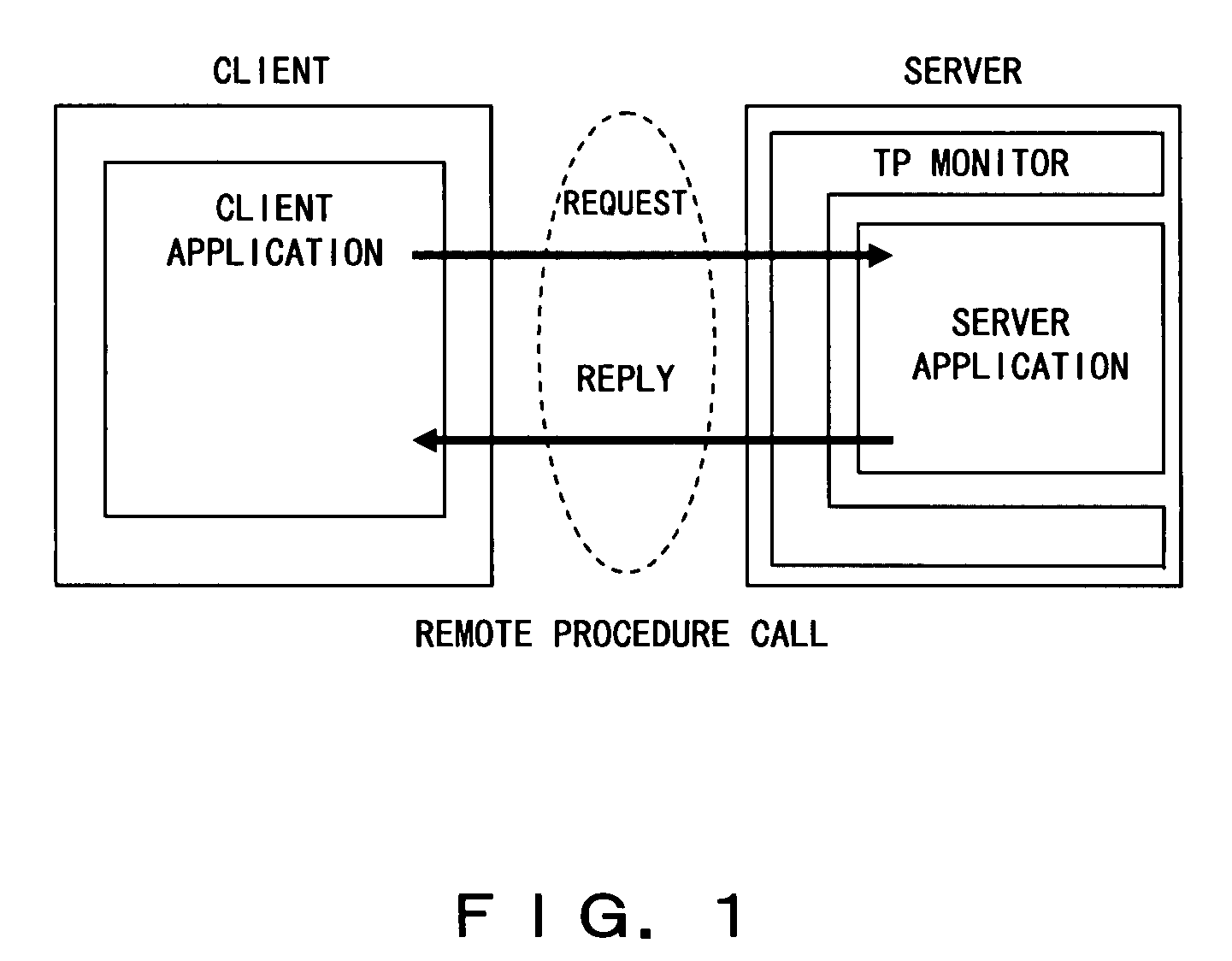
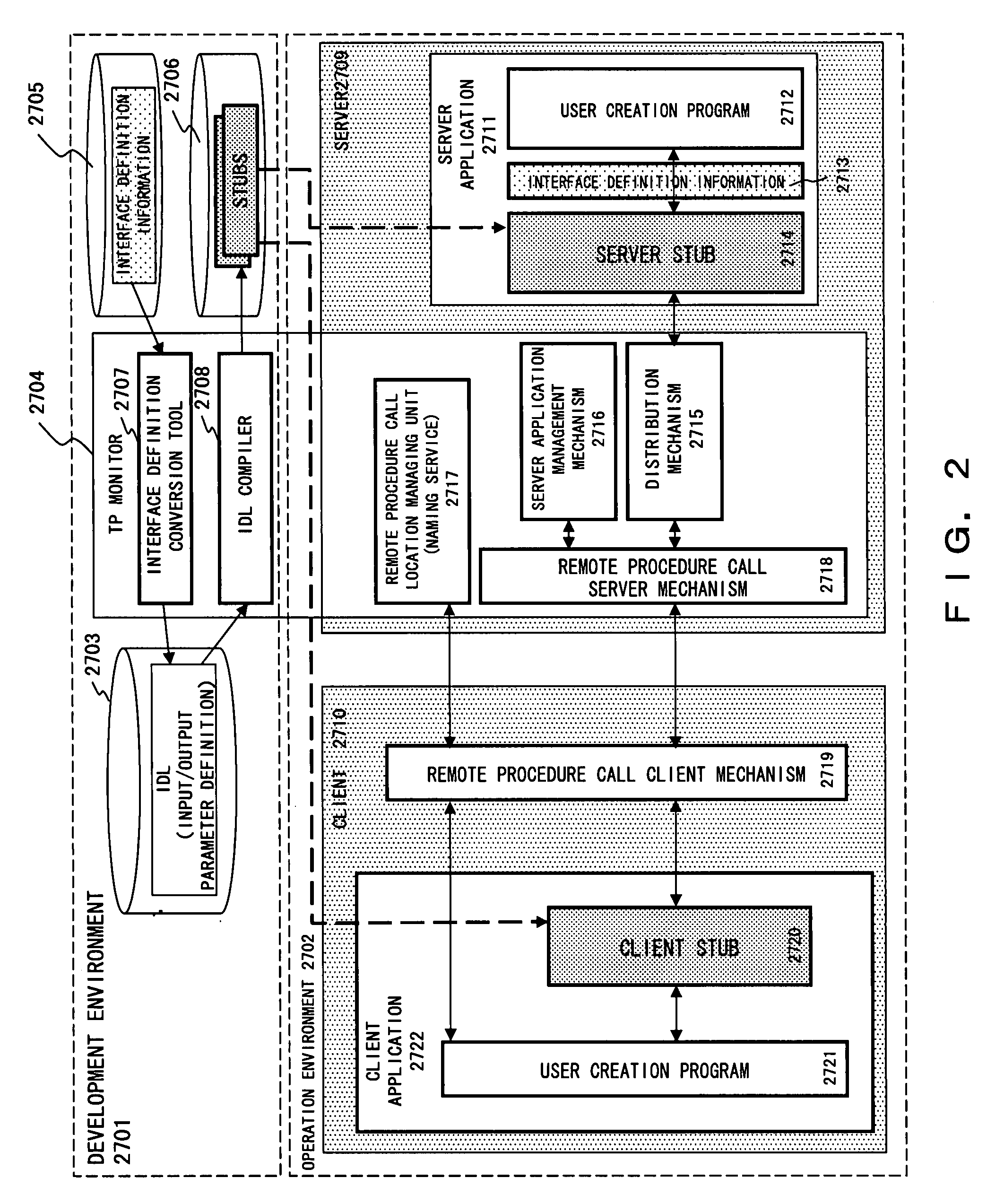
Remote procedure call system, remote procedure call method, program for implementing remote procedure call system
InactiveUS20080163269A1Reduce overheadImprove performanceFinanceInterprogram communicationData classApplication software
Input / output data classes defined based on an interface between a server and a client are embedded in a client application, and input / output data objects, which are instances of the input / output data classes, are generated when the client application calls a server application with a remote procedure call. When the client receives a reply message from the server, a data conversion for output parameters is not performed, and the output parameters are transferred unchanged to the data region of the output data object. Thereafter, when the client application references an output parameter, an obtainment process for the corresponding parameter of the output data object is called, the data conversion is performed only for the output parameter required for the obtainment process, and the value of the output parameter referenced by the client application is returned.
Owner:FUJITSU LTD
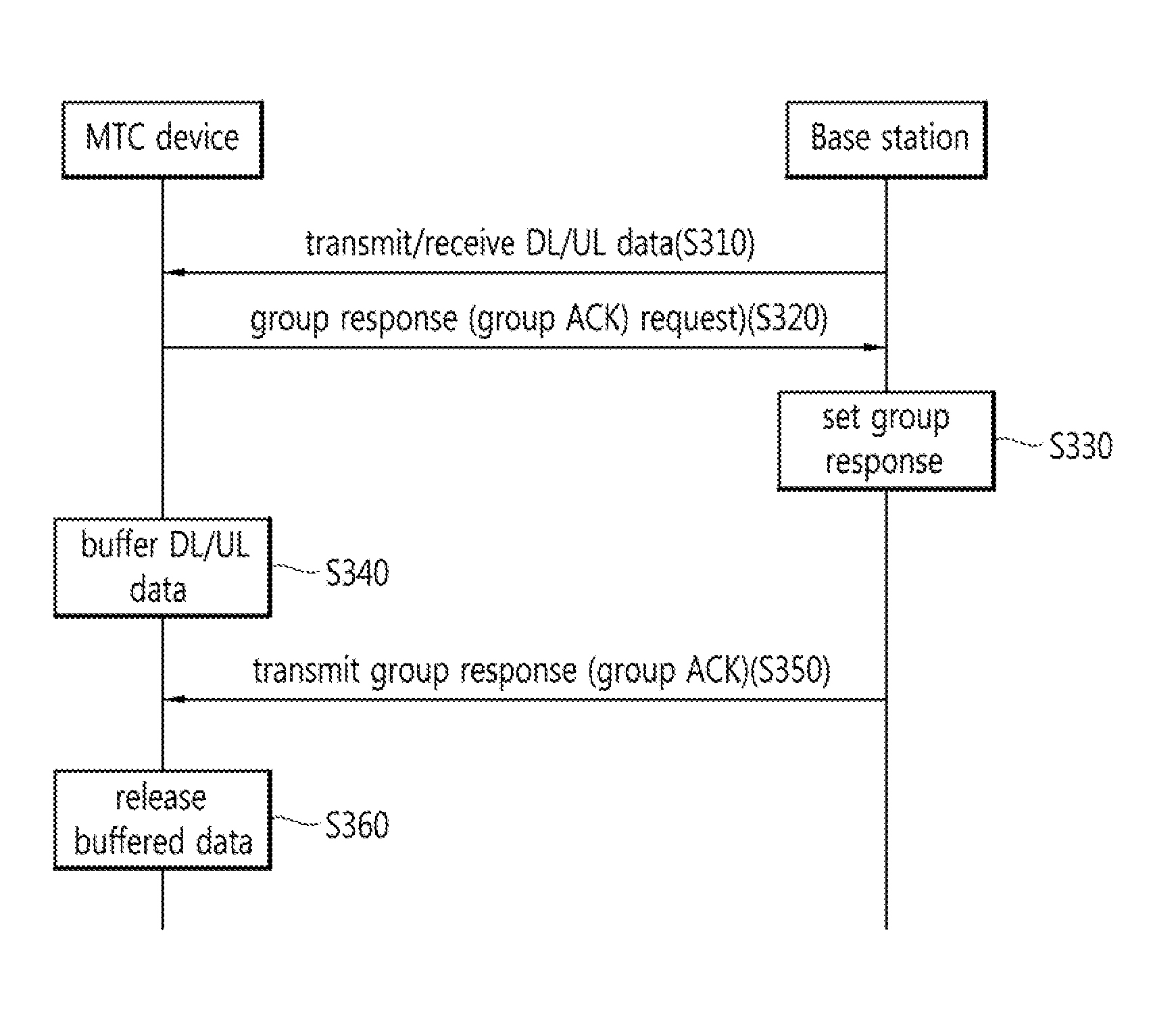
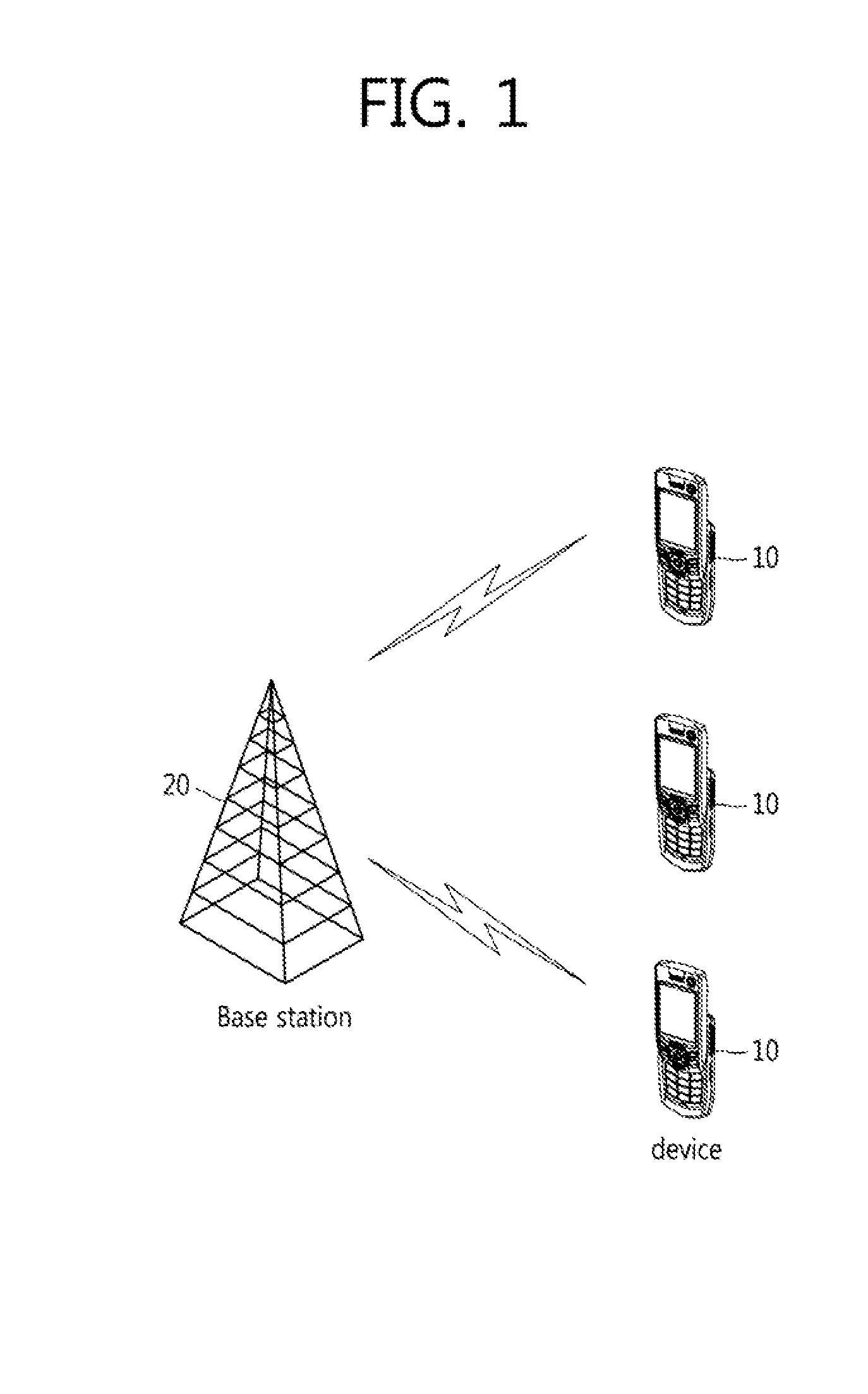
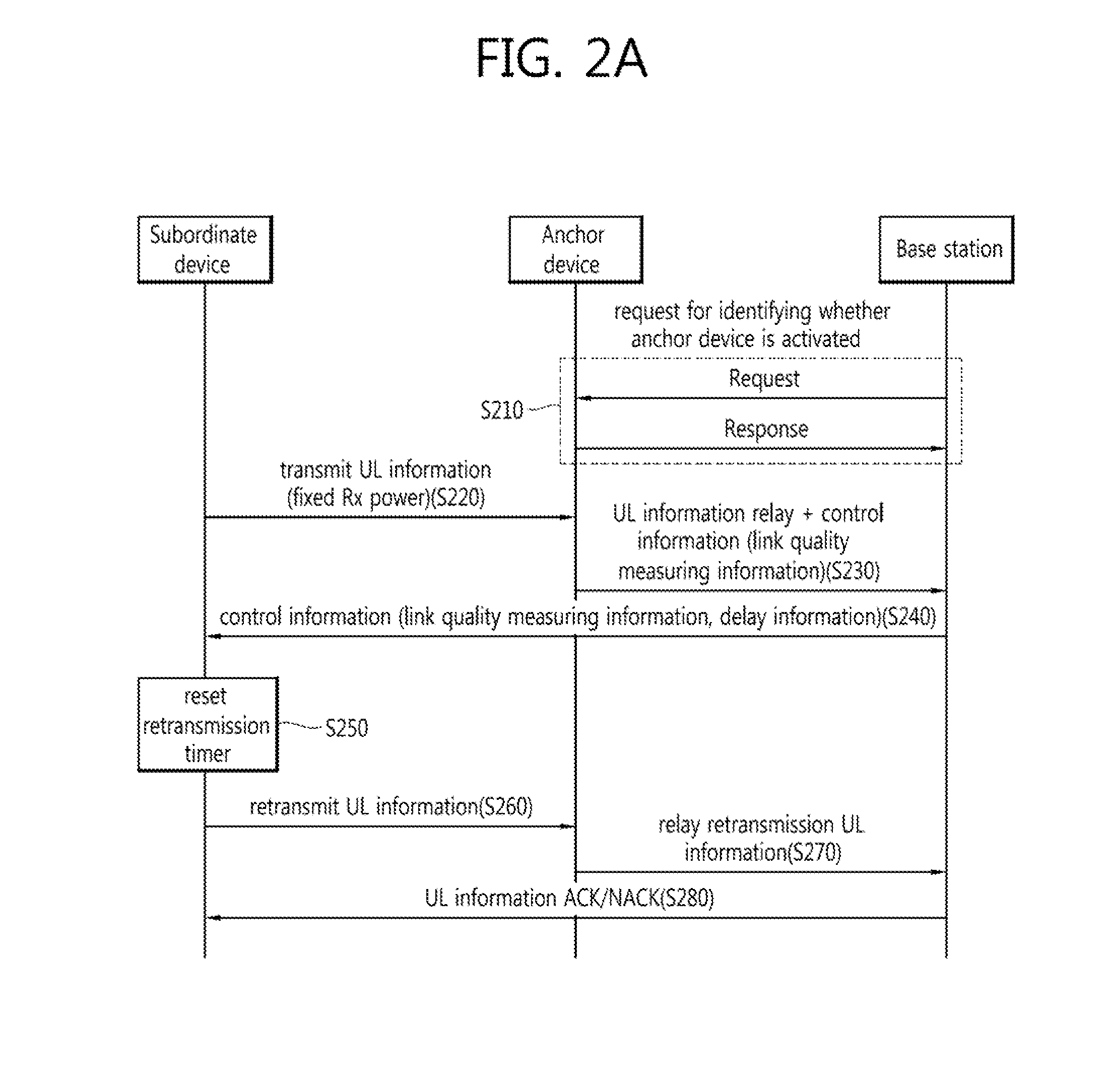
Method and apparatus for transceiving control information and/or data to/from a base station via an anchor terminal in a wireless access system supporting machine-type communication
InactiveUS20130121296A1Reduce data overheadReduce overheadConnection managementSignalling characterisationElectrical and Electronics engineeringReal-time computing
The present description relates to a method in which a first terminal communicates with a base station via a second terminal in a wireless access system supporting machine-type communication (MTC). The method comprises the following steps: transmitting, to the second terminal, uplink data to be transmitted to the base station; receiving, from the base station, control information corresponding to the quality of a link between the first terminal and the second terminal; and retransmitting the uplink data to the second terminal in accordance with the received control information, wherein the control information includes information on the delay between the second terminal and the base station, and information on the measured quality of the link between the first terminal and the second terminal
Owner:LG ELECTRONICS INC
Ecn-enabled multicast protocol for wireless communication systems under blockage
ActiveUS20140126357A1Increase data rateNetwork capacity useError preventionNetwork traffic/resource managementPacket lossEngineering
A system and method are provided for implementing performance improvements in a multicast protocol for networks that support incipient congestion indications via packet marking in instances of packet loss in the network during time-correlated blockages by providing indications in the physical (PHY) layer. A receiver rate calculation is adjusted so that a loss due to blockage is ignored completely and only packets marked using an Explicit Congestion Notification (ECN) packet marking protocol are treated as losses. Receiver rates are modified based on ECN principles to ignore losses. A NORM receiver rate equation may remain substantially unchanged while a sender is enabled to keep sending at a higher data rate, even in instances of blockage in support of higher system throughputs without defining a completely new receiver rate equation. Time-correlated blockages are not treated as losses.
Owner:LOCKHEED MARTIN CORP
Virtualized Wireless Communication System and Establishing Method thereof
InactiveUS20130272162A1Enhance real-time behaviorIncrease flexibilityData switching by path configurationNetwork planningVirtualizationCommunications system
The present application discloses a virtualized wireless communication network and an establishing method thereof. The virtualized wireless communication network system includes a plurality of virtual nodes, the plurality of virtual nodes being divided into multiple virtual node cliques according to interference relations among the plurality of virtual nodes, wherein, each virtual node represents a wireless communication node; and a plurality of clique communication management modules that are one-to-one associated with the multiple virtual node cliques, wherein, each clique communication management module is configured to manage data exchange between an associated virtual node clique and other virtual node cliques, so as to emulate communication behavior of the wireless communication node. The present invention has many advantages such as high flexibility, good scalability, low cost and the like. Compared with a centralized virtualization solution, this solution can significantly reduce management data overhead and thus enhance the real-time behavior of the whole system.
Owner:IBM CORP
Communicating with a machine to machine device
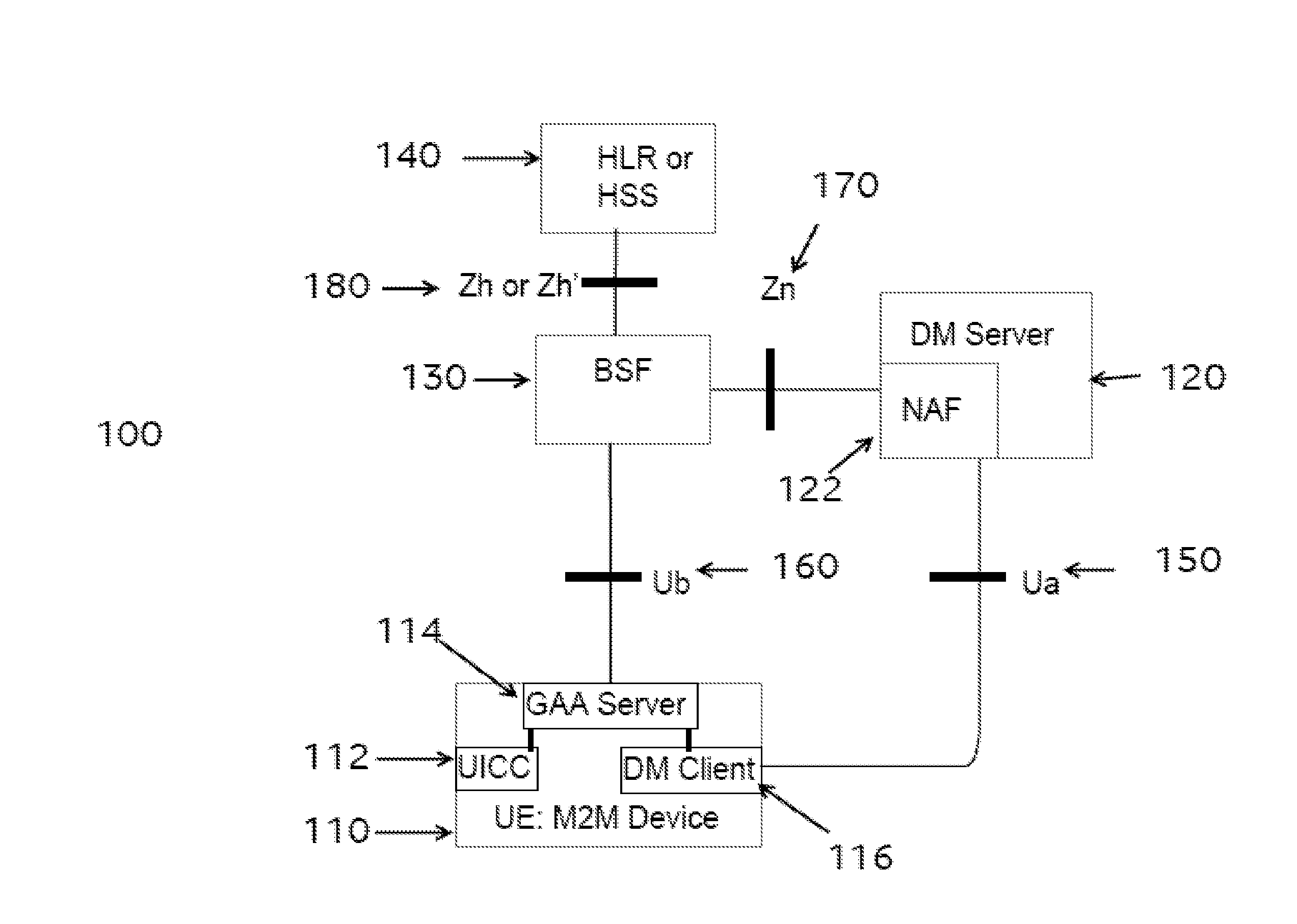
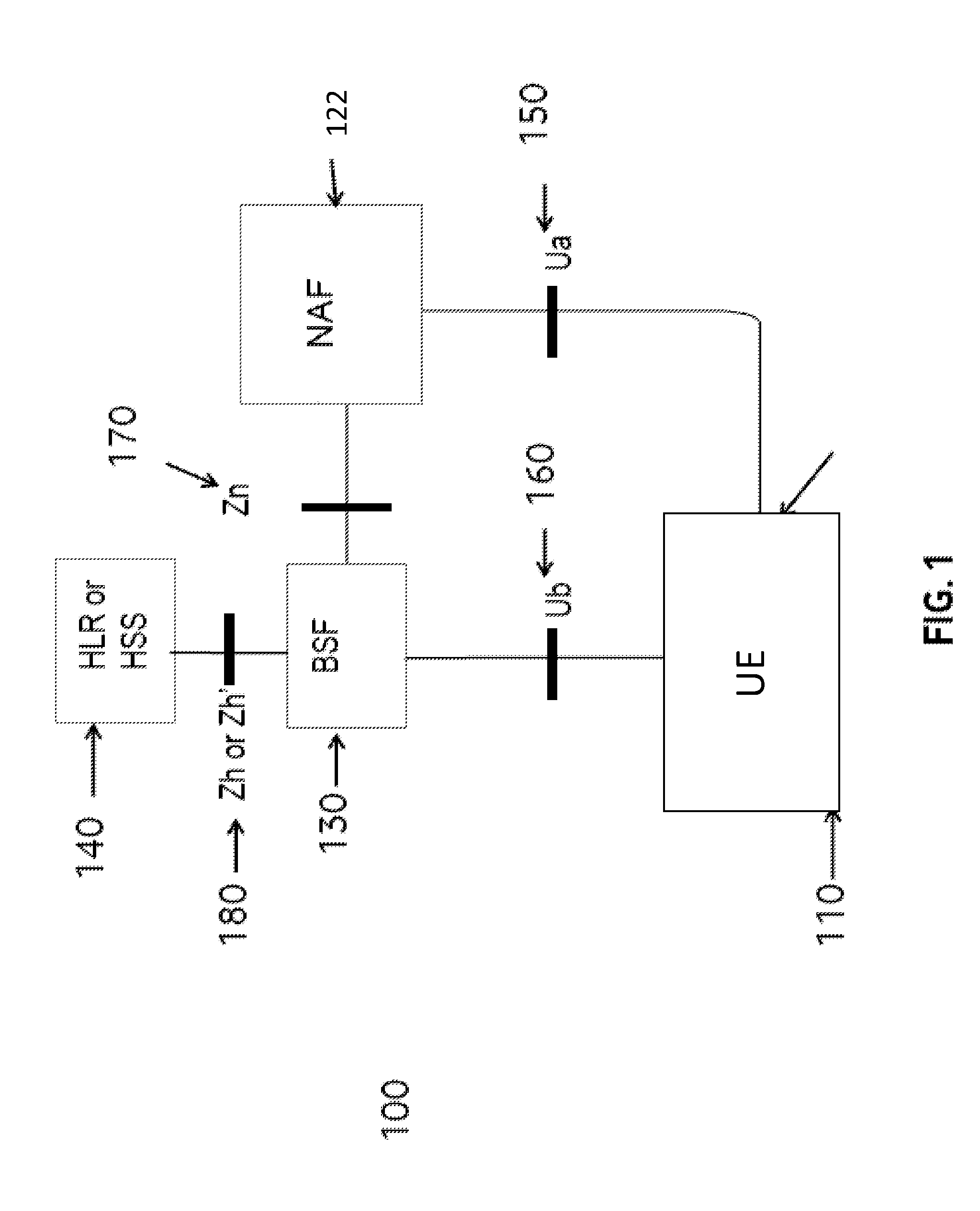
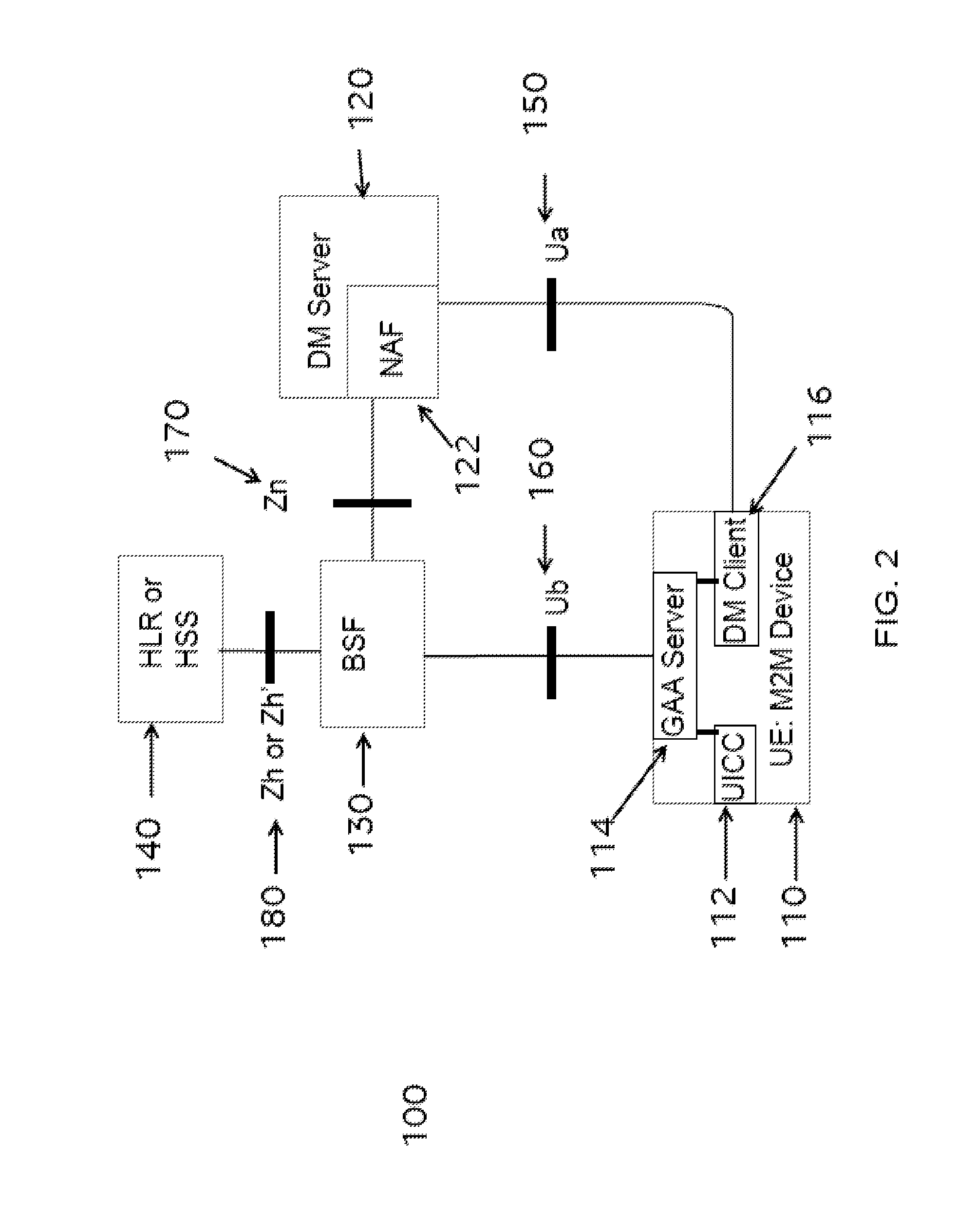
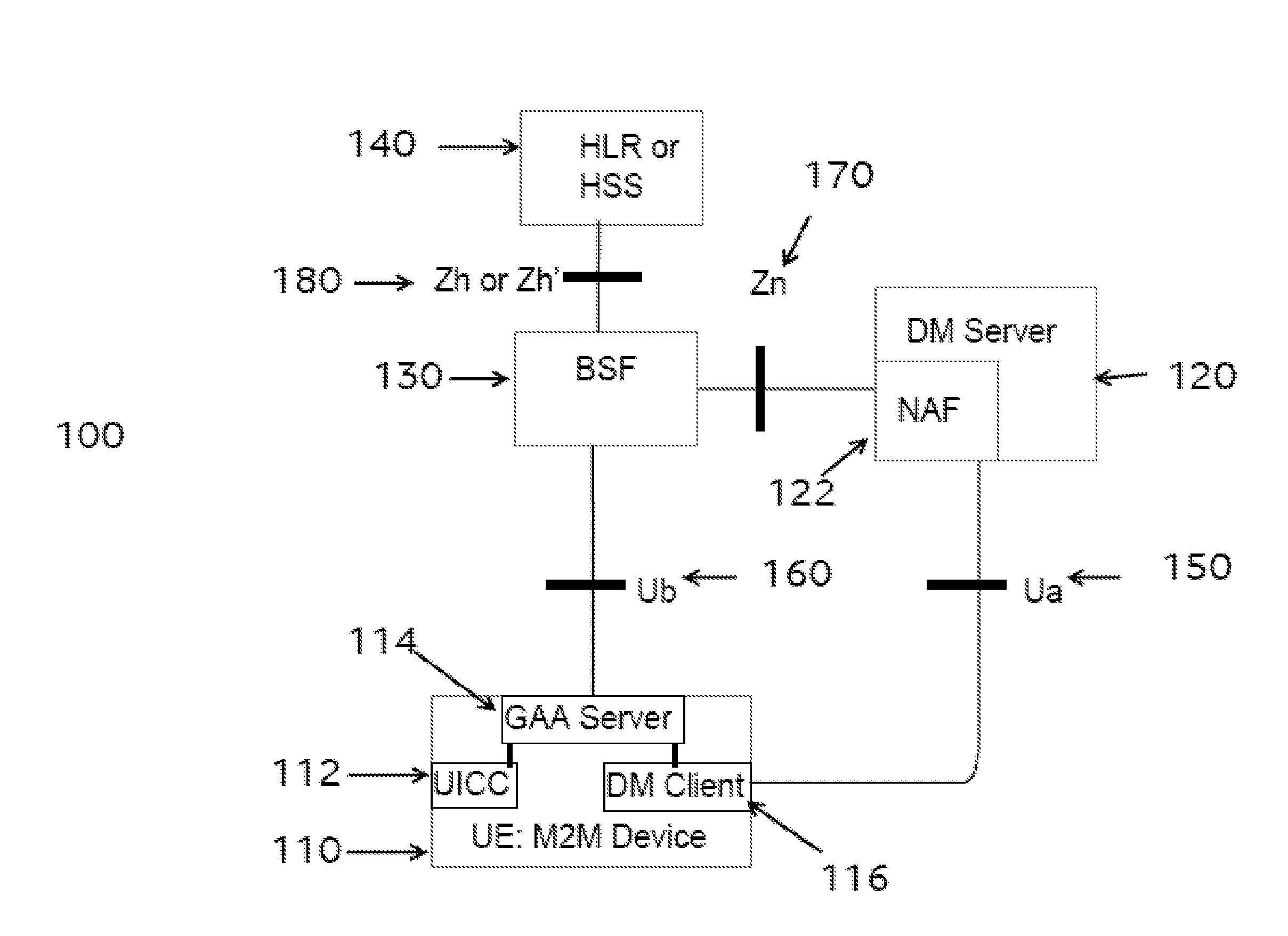
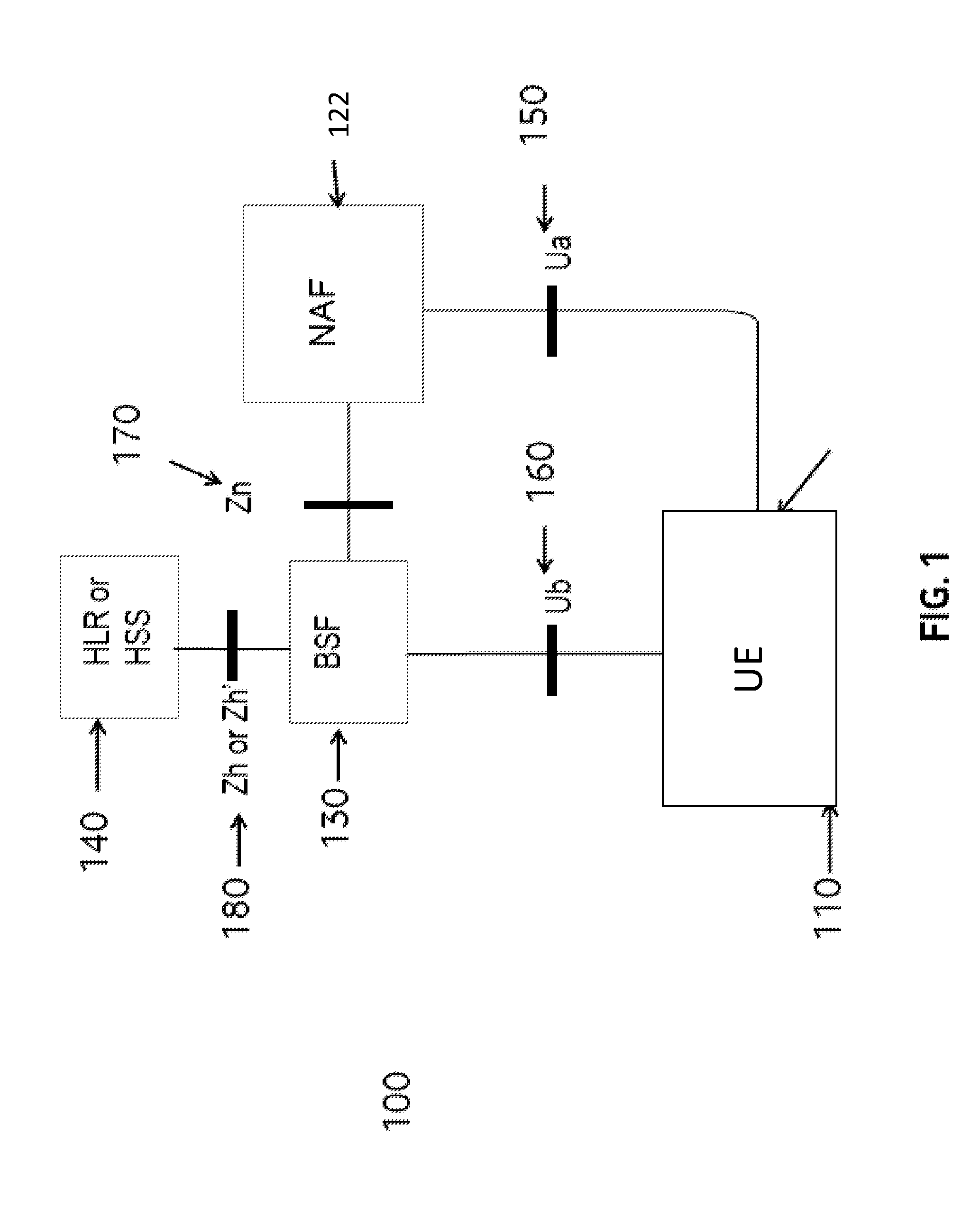
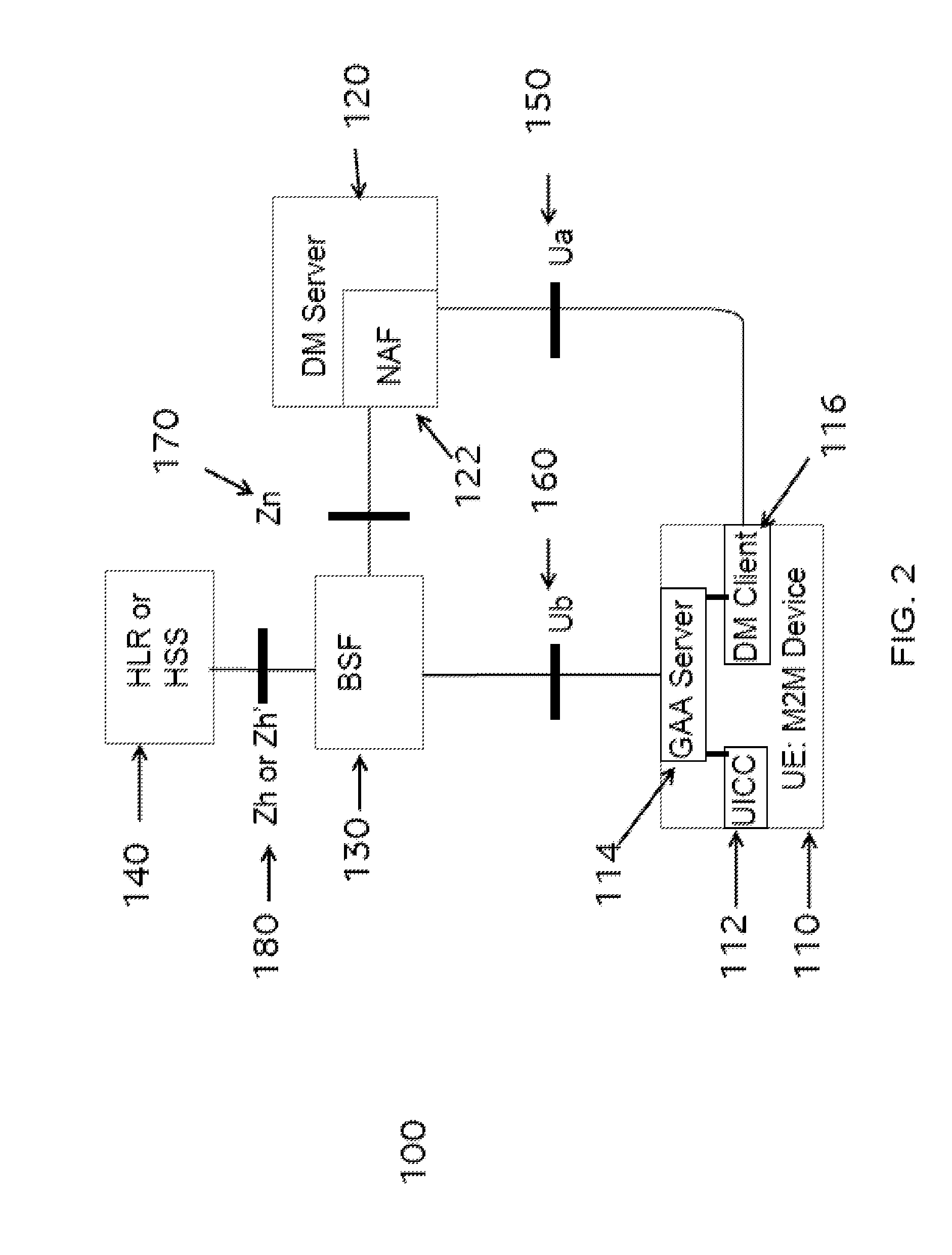
ActiveUS20160234255A1Reduce data overheadUnnecessary data transferInternal/peripheral component protectionWireless commuication servicesSecure communicationSecurity information
Owner:VODAFONE IP LICENSING
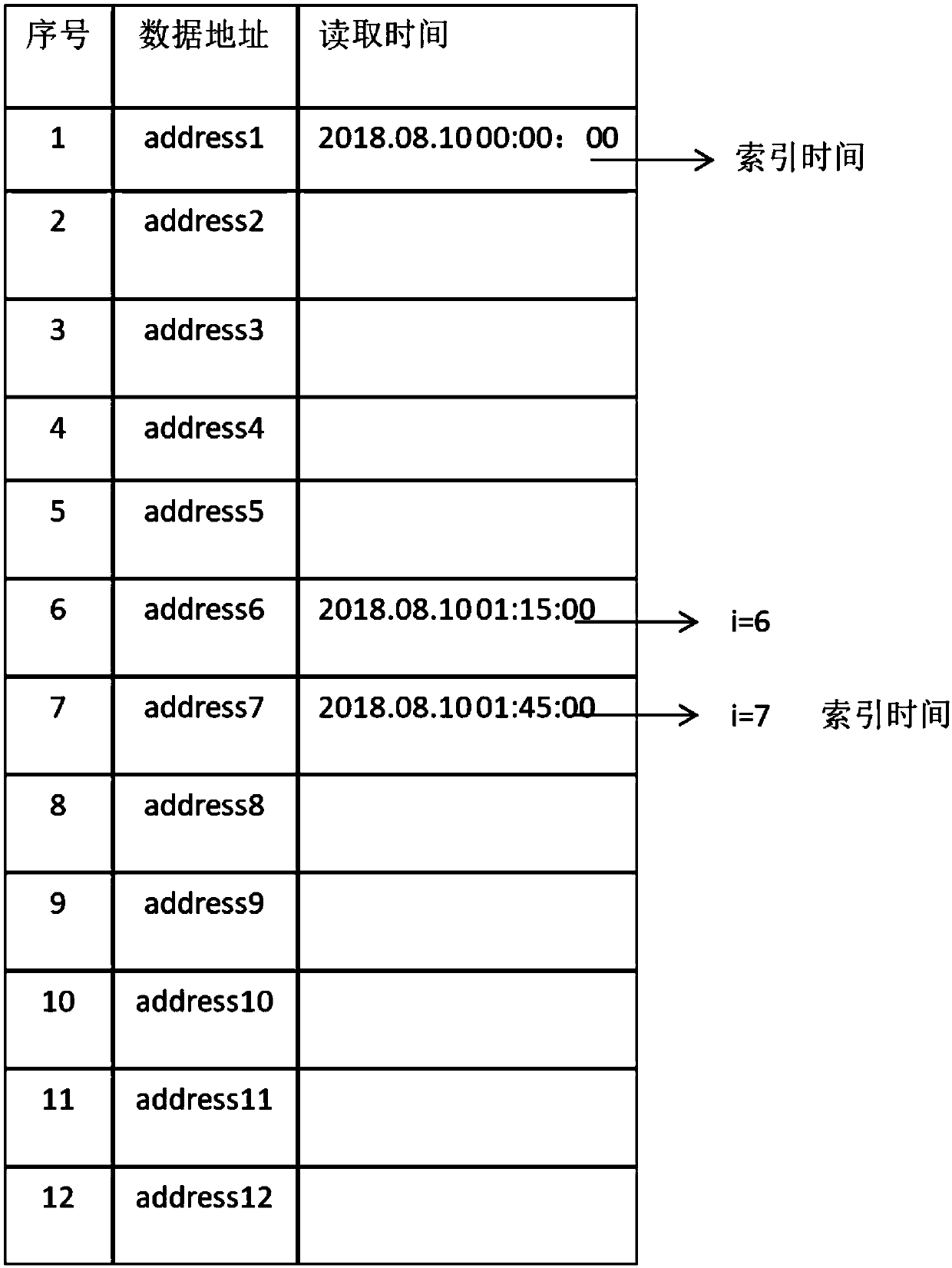
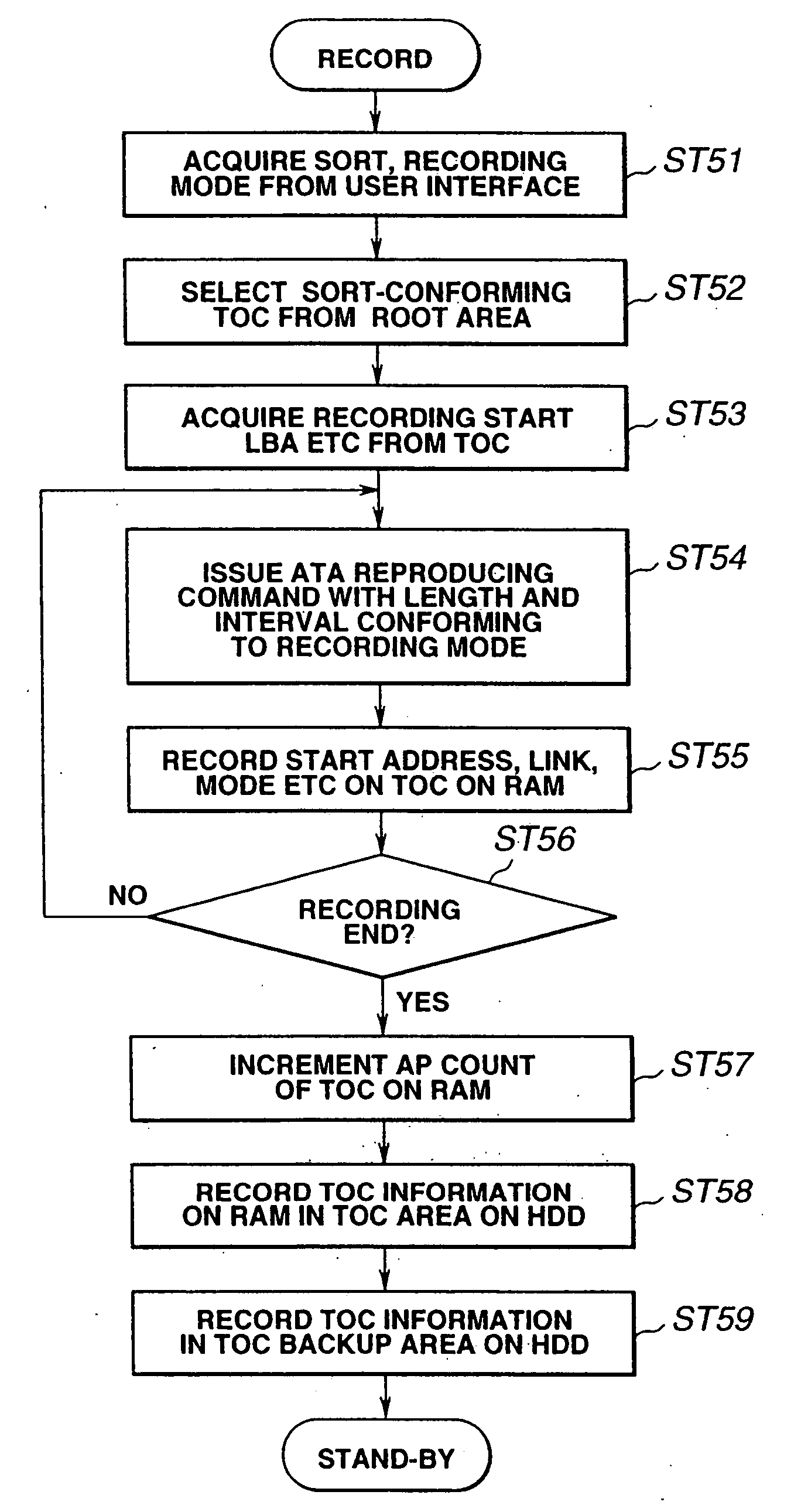
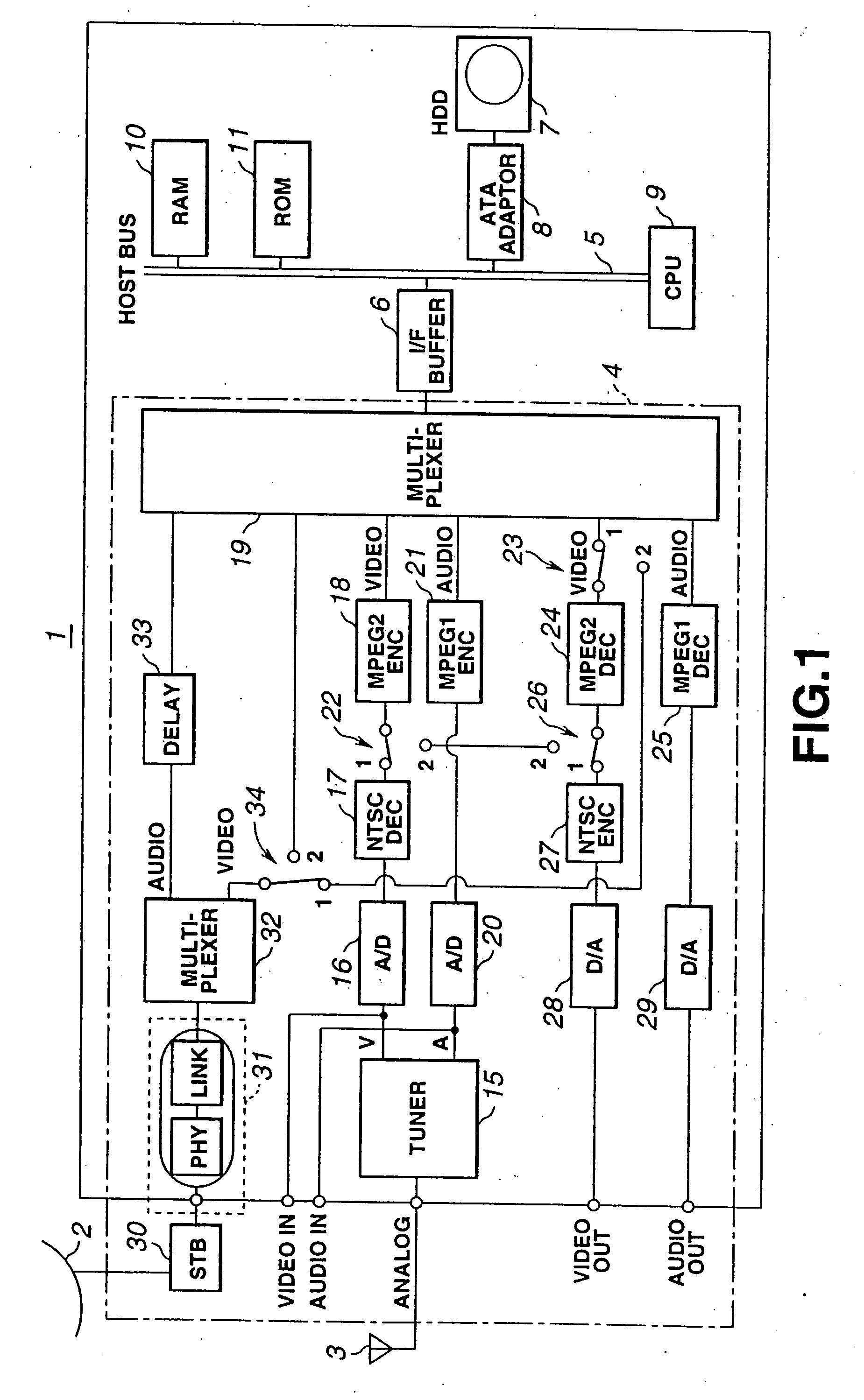
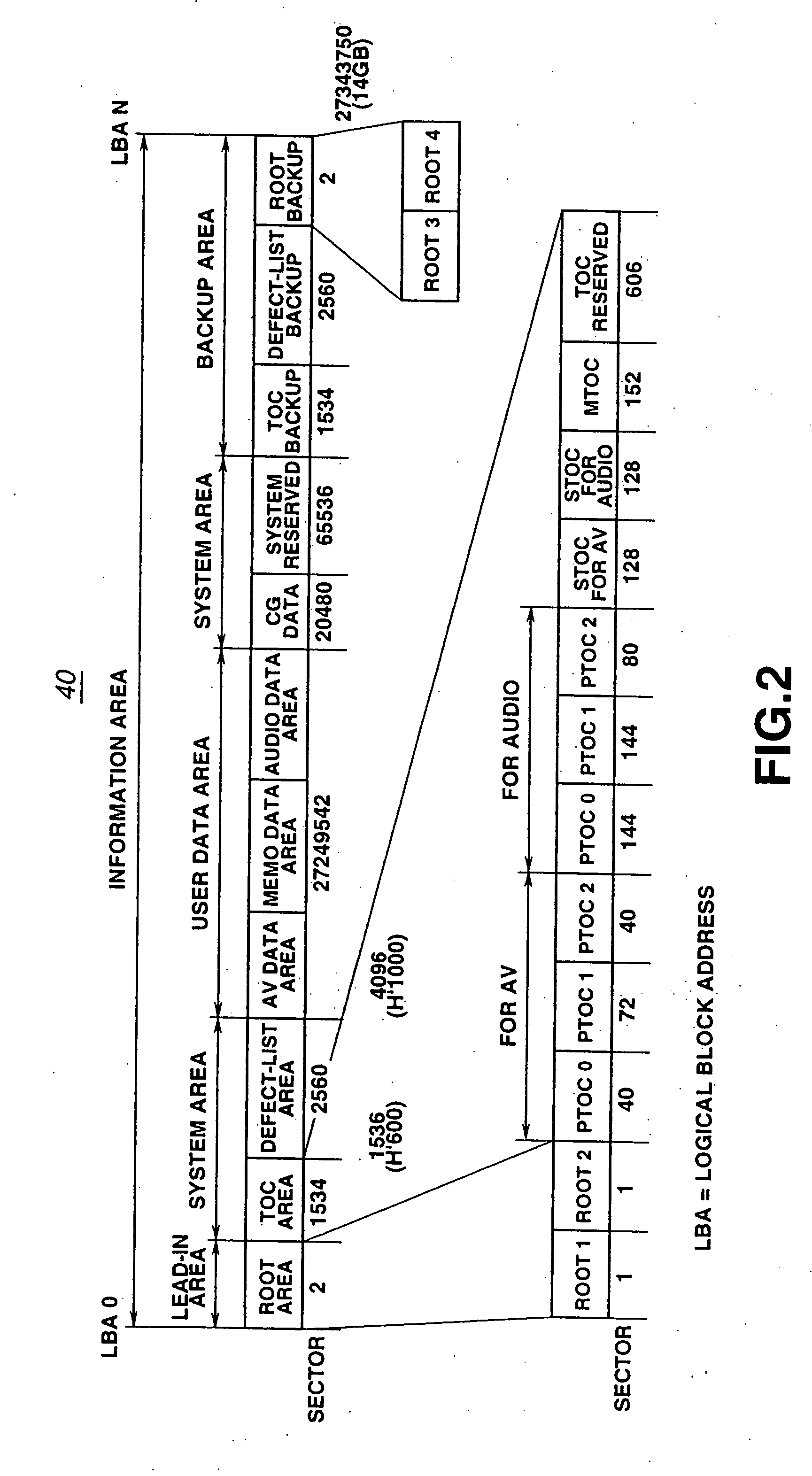
Information recording method and apparatus, information reproducing method and apparatus
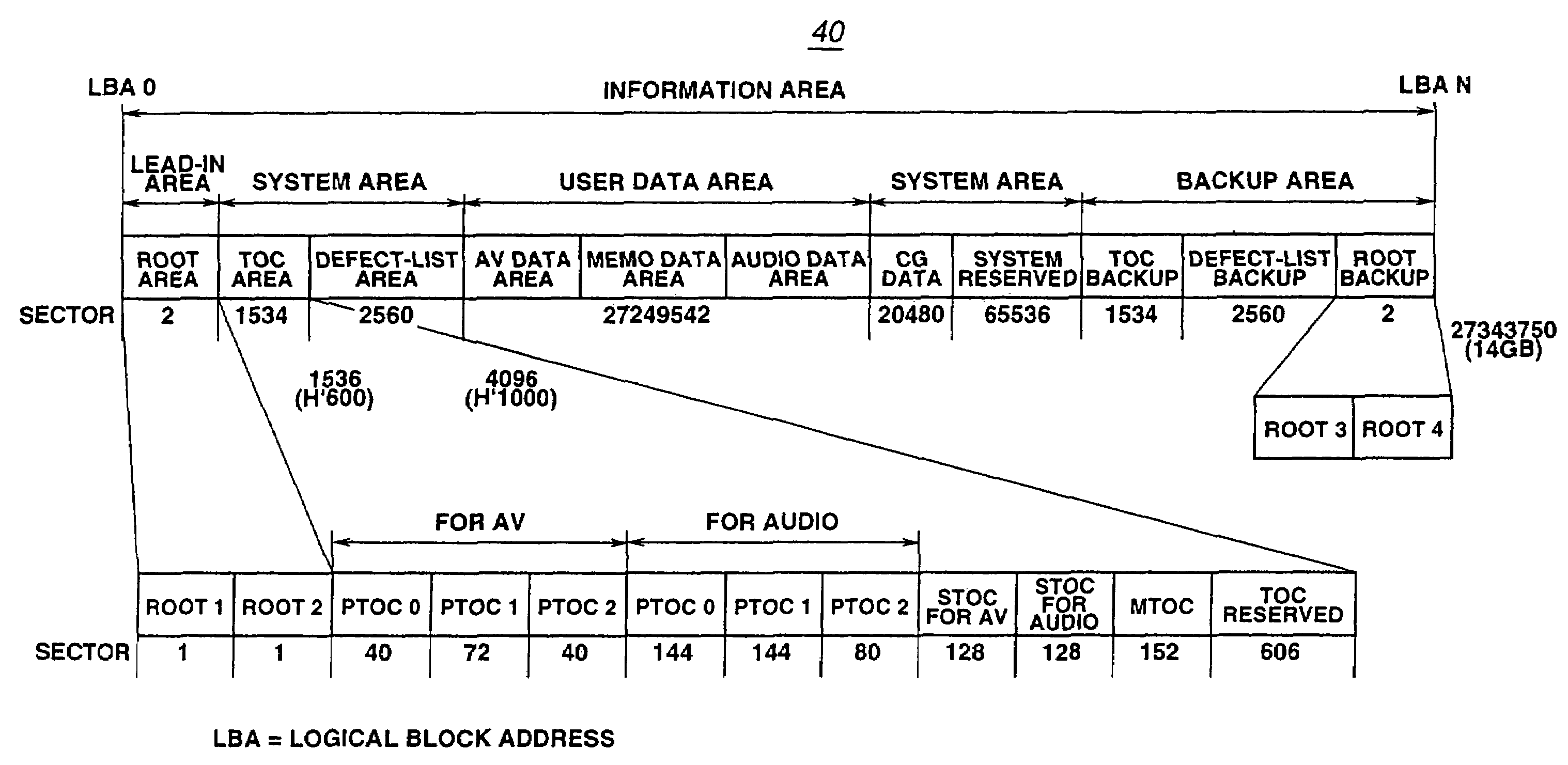
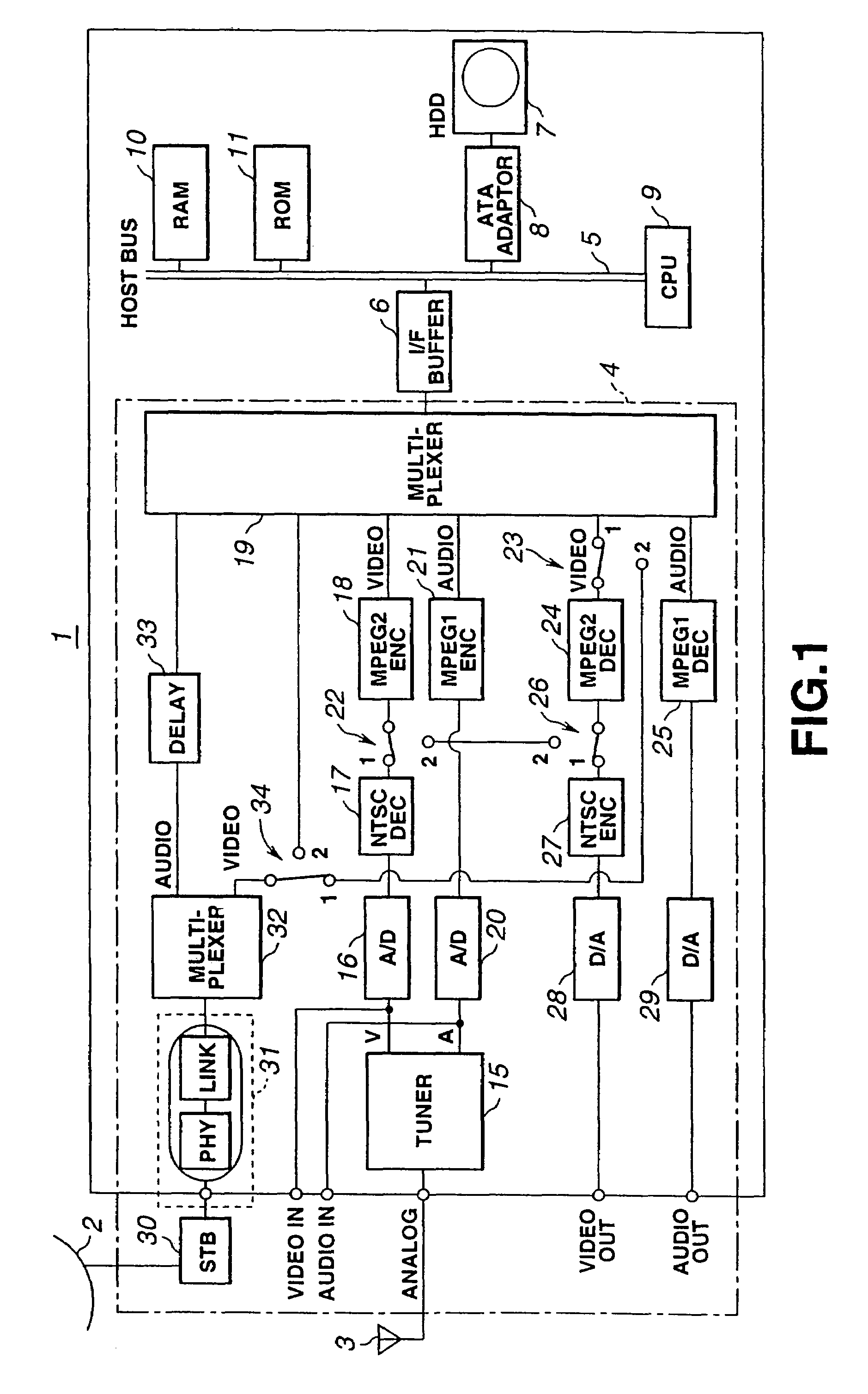
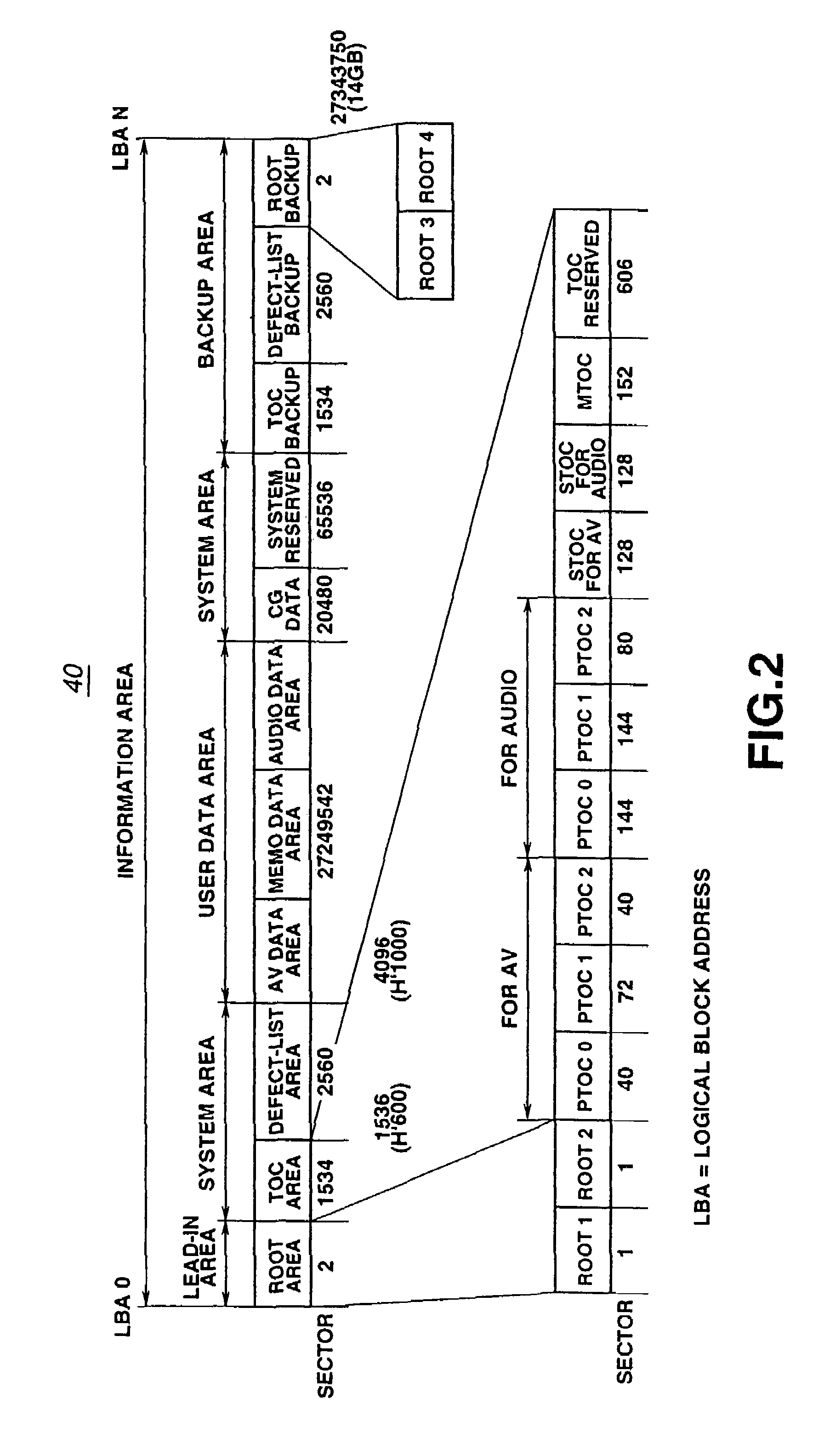
InactiveUS7426615B2No risk of fragmentationContinuity is assuredDisc-shaped record carriersInput/output to record carriersComputer hardwareContinuous recording
Owner:SONY CORP
Optimizing message forwarding in a wireless mesh network
ActiveUS20170181053A1Ensure data reliabilityReduce data overheadNetwork traffic/resource managementNetwork topologiesData transmissionMesh networking
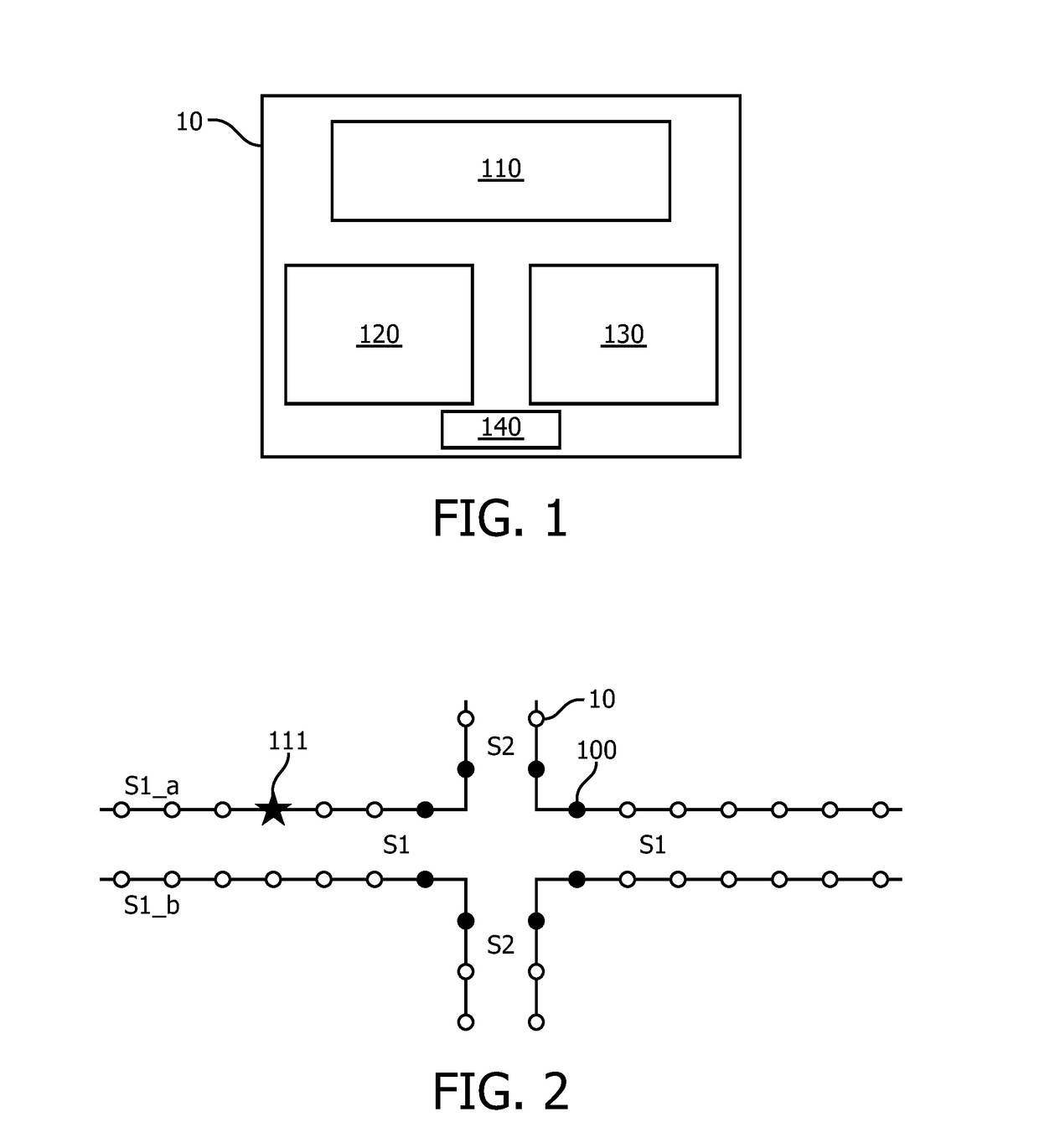
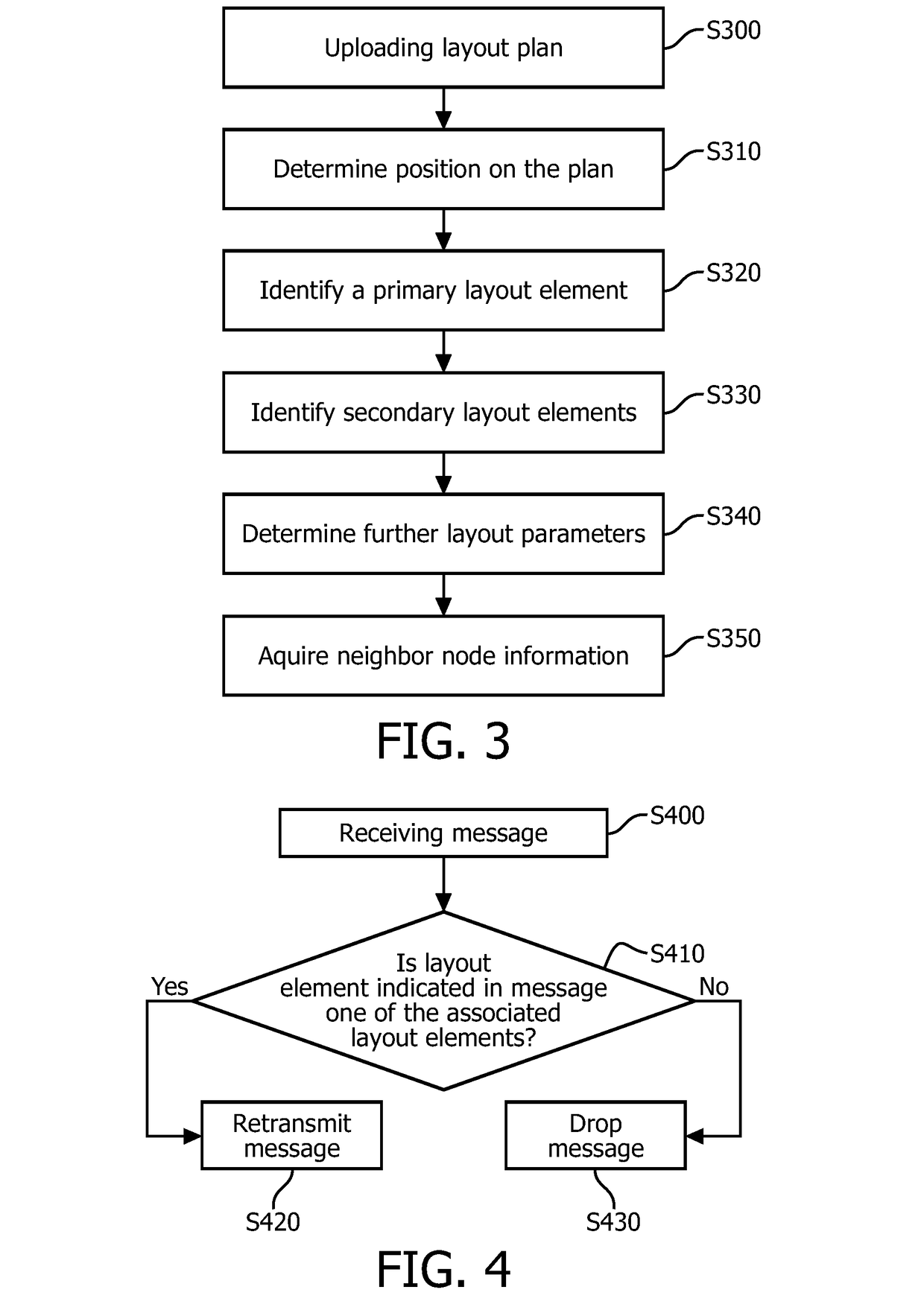
For ensuring reliability of data transmission in a wireless mesh network, while reducing the data overhead of the transmissions, a node for a wireless mesh network and a method of controlling the same are provided, wherein the node is configured to decide about retransmission of a message received from a transmitting node, based on whether the transmitting node has at least one layout element of a layout plan in common with the node, at least one of the layout elements of the layout plan being associated with the node.
Owner:SIGNIFY HLDG BV
Virtualized Wireless Communication System and Establishing Method Thereof
InactiveUS20150230101A1Enhance real-time behaviorIncrease flexibilityNetworks interconnectionNetwork planningExtensibilityVirtualization
Owner:INT BUSINESS MASCH CORP
Safe data transmission method, device and system
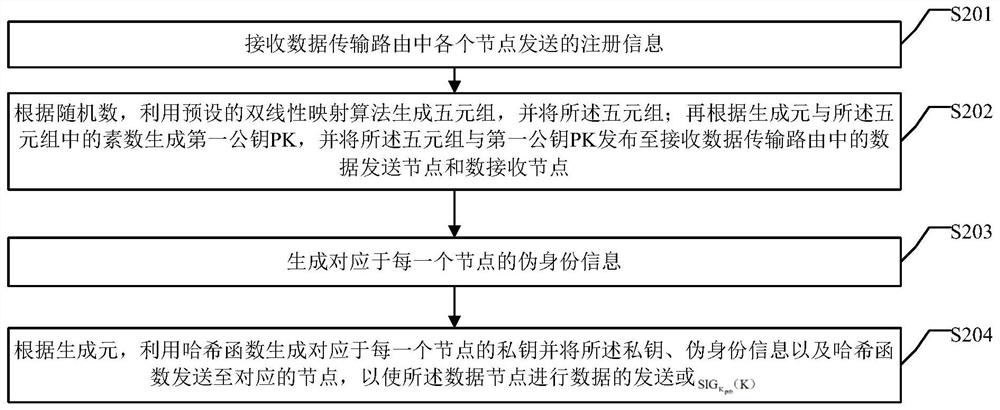
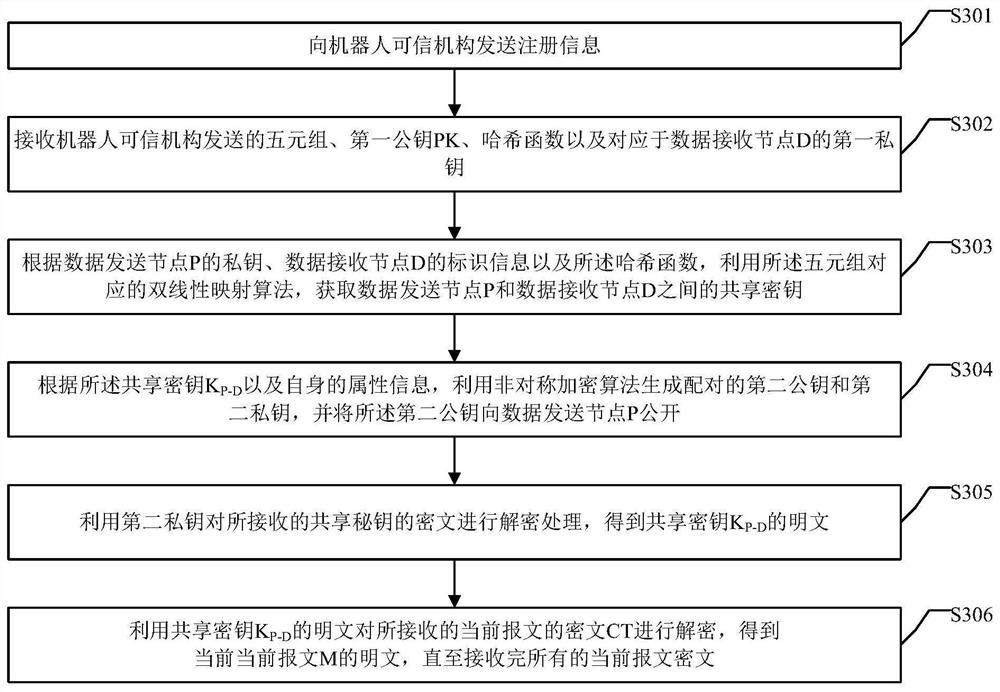
ActiveCN111726346AReduce overheadImprove data encryption efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionCiphertext
The invention provides a safe data transmission method, device and system. The method comprises the steps that registration information is sent to a robot trusted mechanism; a quintuple, a first public key PK, a hash function and a first private key corresponding to the data sending node P sent by the robot trusted mechanism are received; a shared key between the data sending node P and the data receiving node D is obtained; signature encryption processing is carried out on the shared key KP-D to obtain an encrypted ciphertext of the shared key shown in the specification; 15) the data sendingnode P uses the shared key KP-D and uses an AES encryption algorithm to encrypt the current message M to obtain a ciphertext CT=Encrypt(PK,M,T) of the current message; and 16) the data sending node Psends the ciphertext CT of the current message and the encrypted ciphertext of the shared key shown in the specification to the data receiving node D. By applying the embodiment of the invention, thedata overhead can be reduced.
Owner:HEFEI HRG XUANYUAN INTELLIGENT TECH CO LTD
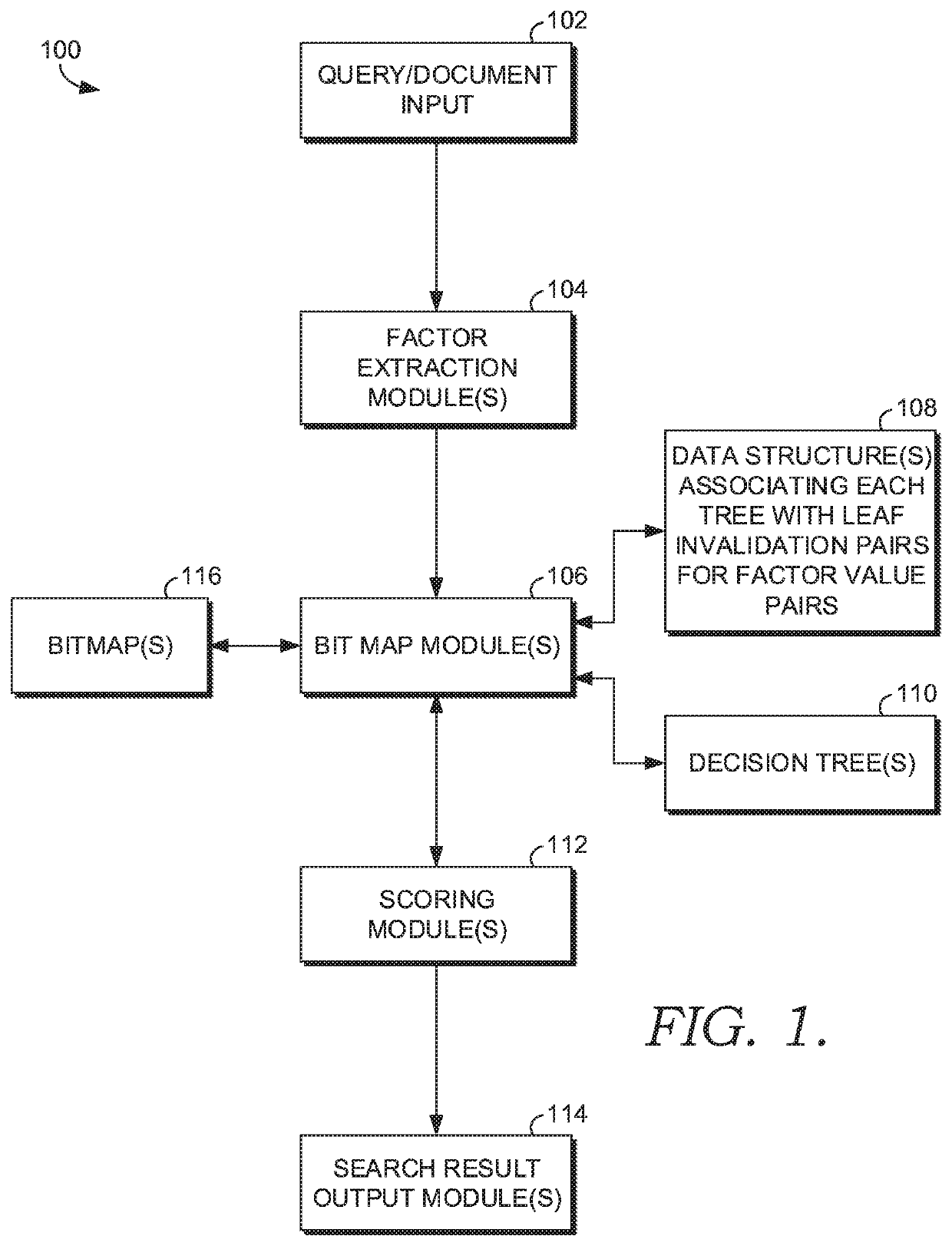
Efficient leaf invalidation for query execution
InactiveUS20200065395A1Reduce chanceTechnology is expensiveSpecial data processing applicationsTheoretical computer scienceData science
One or more factors of a query and one or more search result candidates are identified. A plurality of decision trees are associated, via a data structure, with one or more leaf invalidation pairs for at least a first value of the one or more factors. The one or more search result candidates are scored based at least in part on the associating of the plurality of decision trees with one or more leaf invalidation pairs for at least the first value of the one or more factors within the data structure.
Owner:EBAY INC
Communicating with a machine to machine device
InactiveUS20160234183A1Reduce data overheadUnnecessary data transferInternal/peripheral component protectionWireless commuication servicesSecure communicationNetwork application
The present disclosure provides methods and apparatus for administering an interface between a machine-to-machine, M2M, device and a network application function, NAF, for secure communication between the M2M device and the NAF. In one method, the M2M device administers the interface by transmitting administration data to the NAF, wherein the administration data comprises a name for the M2M device, and wherein the name for the M2M device is equal to, or derived at least in part from, or otherwise linked to, at least part of data that are shared between the M2M device and a boot-strapping server.
Owner:VODAFONE IP LICENSING
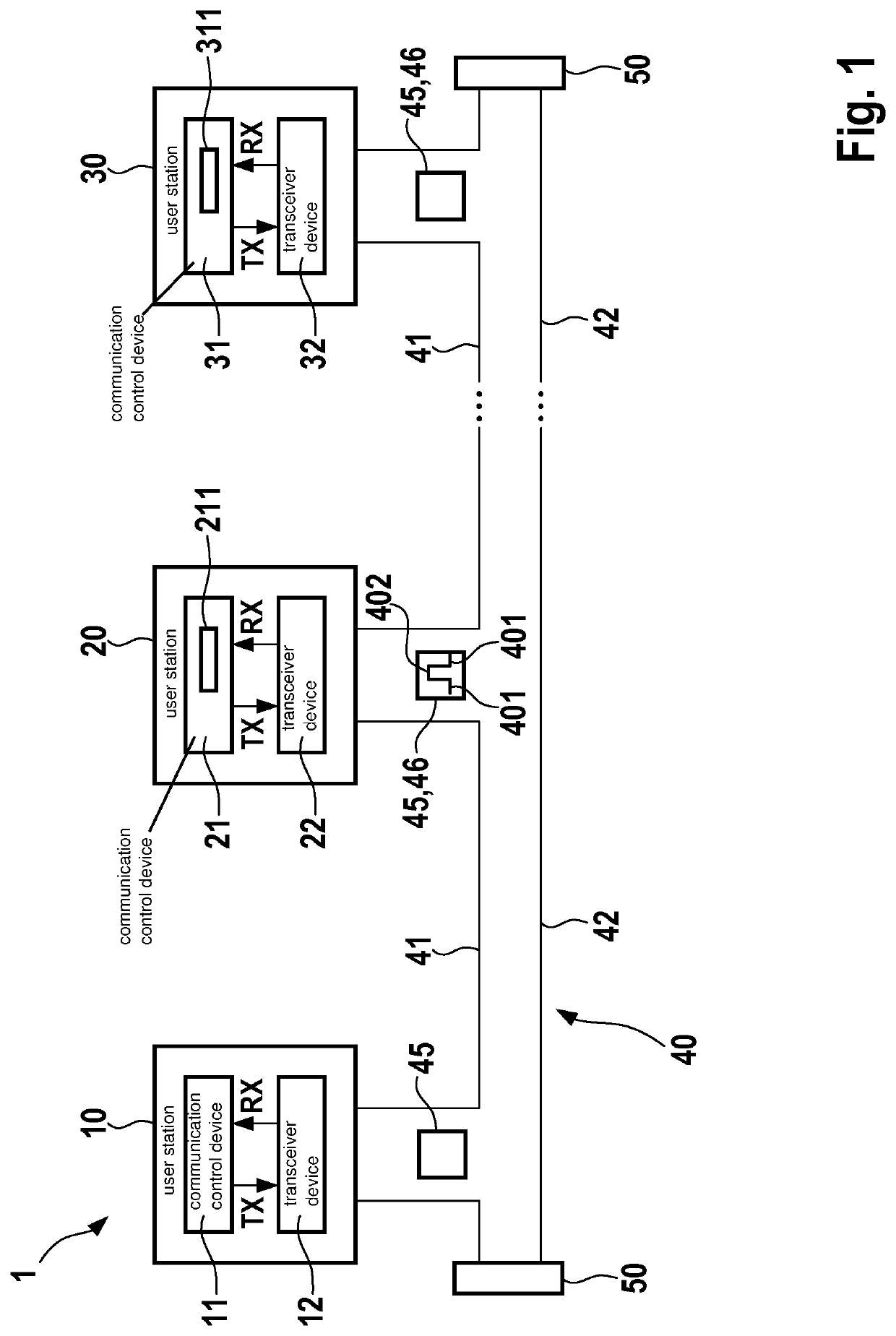
User station for a serial bus system, and method for transmitting a message in a serial bus system
ActiveUS20210406213A1Increase the number ofHigh rateElectric digital data processingHigh level techniquesCommunication controlEmbedded system
A user station for a serial bus system and a method for transmitting a message in a serial bus system. The user station includes a communication control device for transmitting messages to a bus of the bus system and / or for receiving messages from the bus of the bus system, and a bit rate switchover unit for switching over a bit rate of the messages from a first bit rate in a first communication phase to a second bit rate for a second communication phase. The bit rate switching unit is designed to switch the bit rate from the first bit rate over to the second bit rate, due to an edge of a predetermined bit sequence that includes one bit of the first communication phase and one bit of the second communication phase.
Owner:ROBERT BOSCH GMBH
Radio resource management system and radio resource management method
ActiveUS20170118763A1Reduce data overheadAssess restrictionConnection managementTelecommunicationsSystems management
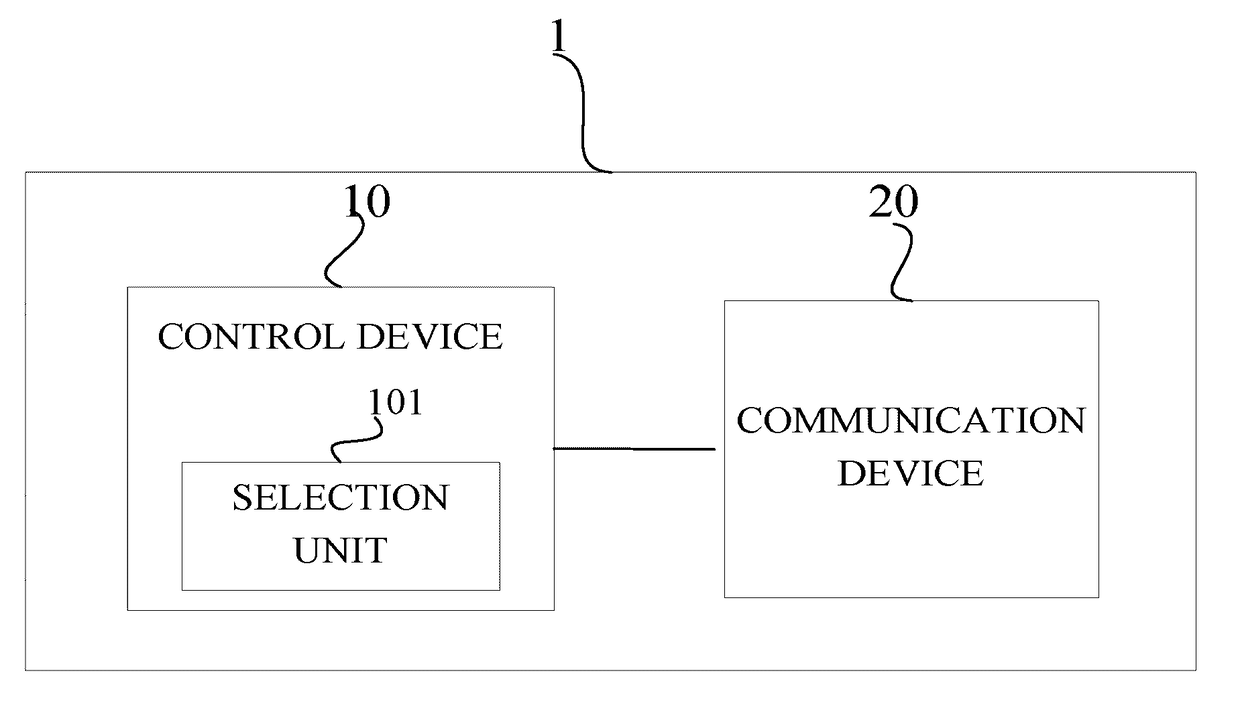
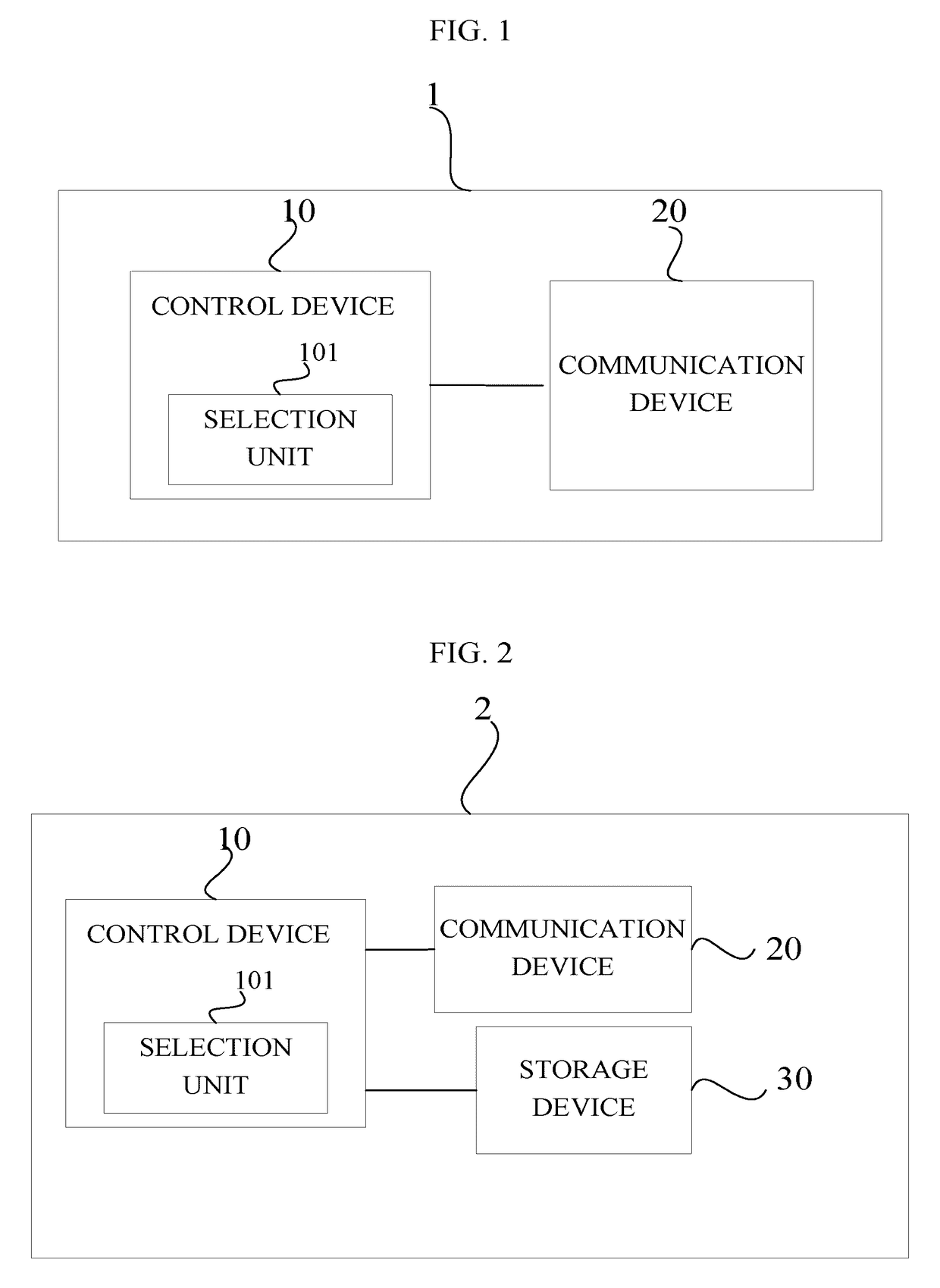
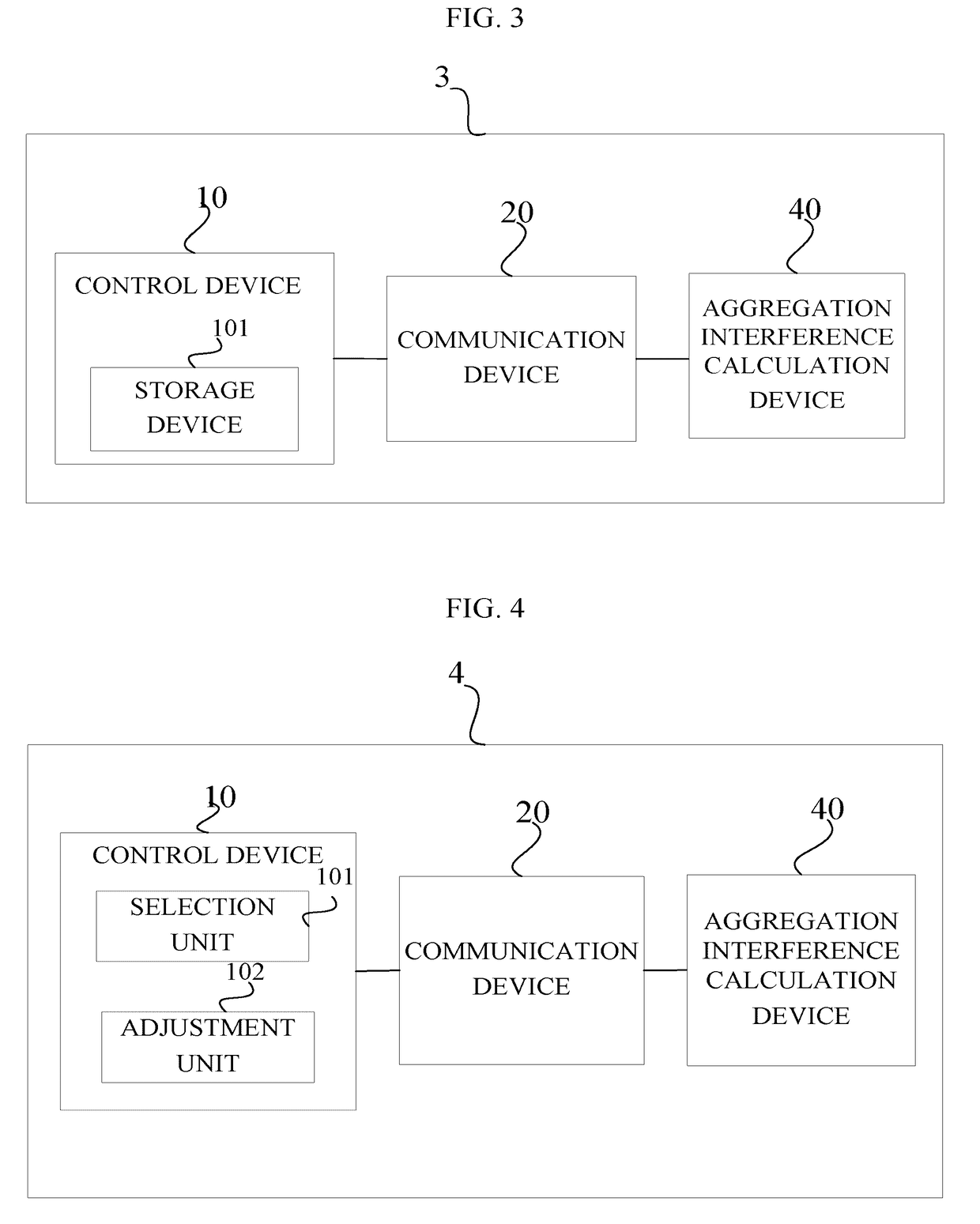
The present disclosure provides a radio resource management system and method. The radio resource management system includes a control device for determining, based on geographical location information of at least one secondary system and at least one primary system managed by the radio resource management system, a radio resource available to the at least one secondary system among licensed radio resources of the at least one primary system when the primary system is not interfered with, the control device including a selection unit for selecting at least one object liable to be interfered with by the secondary system managed by another radio resource management system from the at least one primary system, from the at least one secondary system, or from the at least one primary system and the at least one secondary system based on the geographical location information; and a communication device for transmitting the geographical location information of the at least one object selected by the selection unit to the another radio resource management system. The present disclosure can reduce an information interaction between radio resource management systems.
Owner:SONY CORP
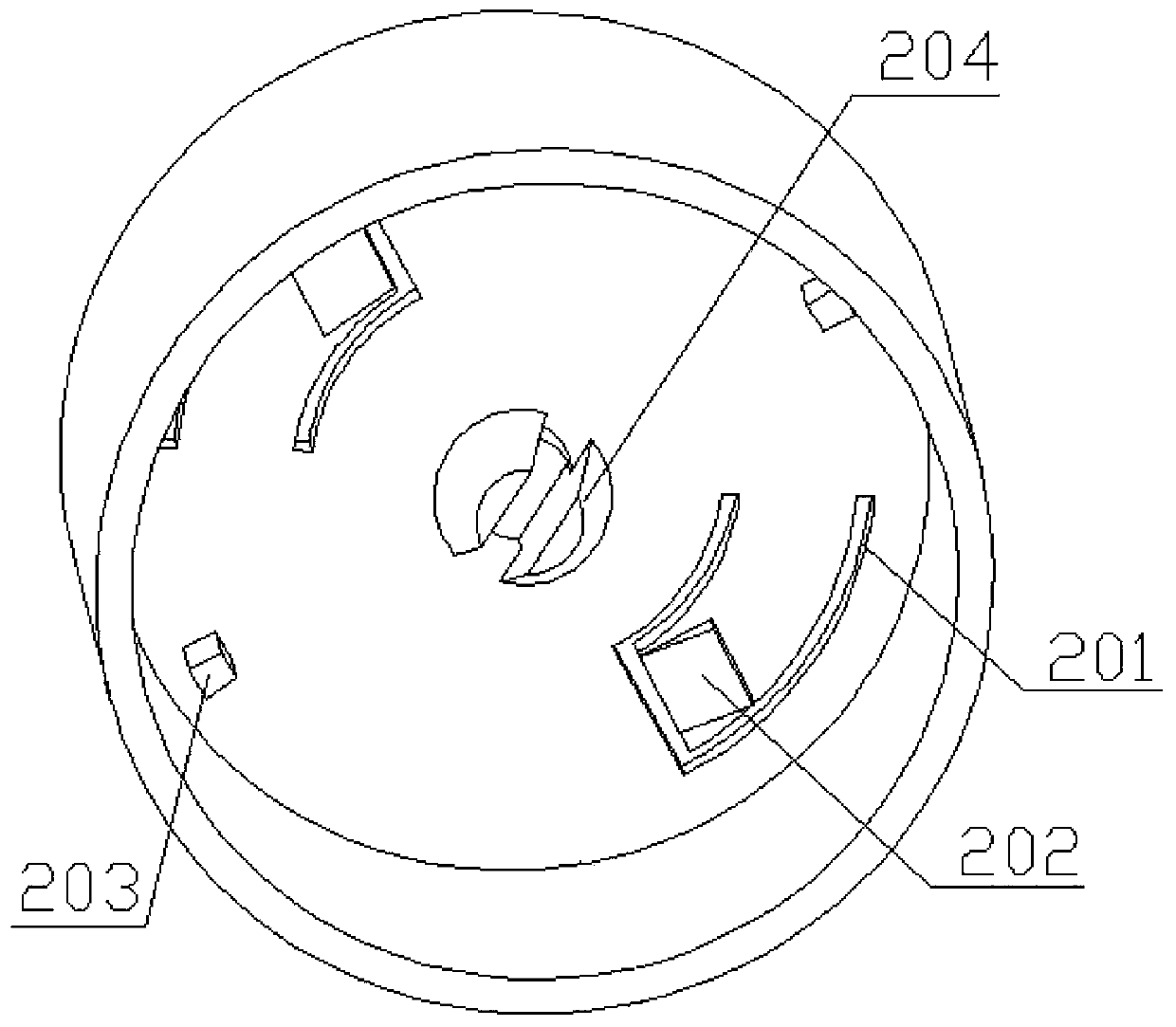
Anti-counterfeiting bottle cap based on security chip cryptographic algorithm and bottle cap activation and anti-counterfeiting method
InactiveCN111047337ARich functionalityReduce design sizeContainer decorationsLevel indicationsAlgorithmEngineering
The invention relates to an anti-counterfeiting bottle cap based on a security chip cryptographic algorithm and an activation and anti-counterfeiting method. The bottle cap comprises a middle cap sleeving a bottom cap, a security NFC label and a switching value acquisition circuit connected with a port of the security NFC label are arranged in the bottom cap, label state marking parameters are stored in the security NFC label, and a cut-off mechanism is arranged on the middle cap; before the bottle cap is opened, an input circuit of the switching value acquisition circuit is intact, the middlecap can rotate relative to the bottom cap, and at the moment, the label state marking parameter is recorded as a state I and information corresponding to the state I is readable; in the process of rotating the middle cover, the cut-off mechanism causes irreversible damage to an input circuit, the security NFC label immediately modifies a label state marking parameter into a state II until the security NFC label cannot receive a switching value input signal any more, and information corresponding to the state II is enabled to be readable. According to the invention, anti-counterfeiting and bottle opening verification before and after cover opening are supported, the anti-counterfeiting performance is improved by adopting a complex security algorithm, and copying and playback are prevented.
Owner:绍兴心越科技有限公司
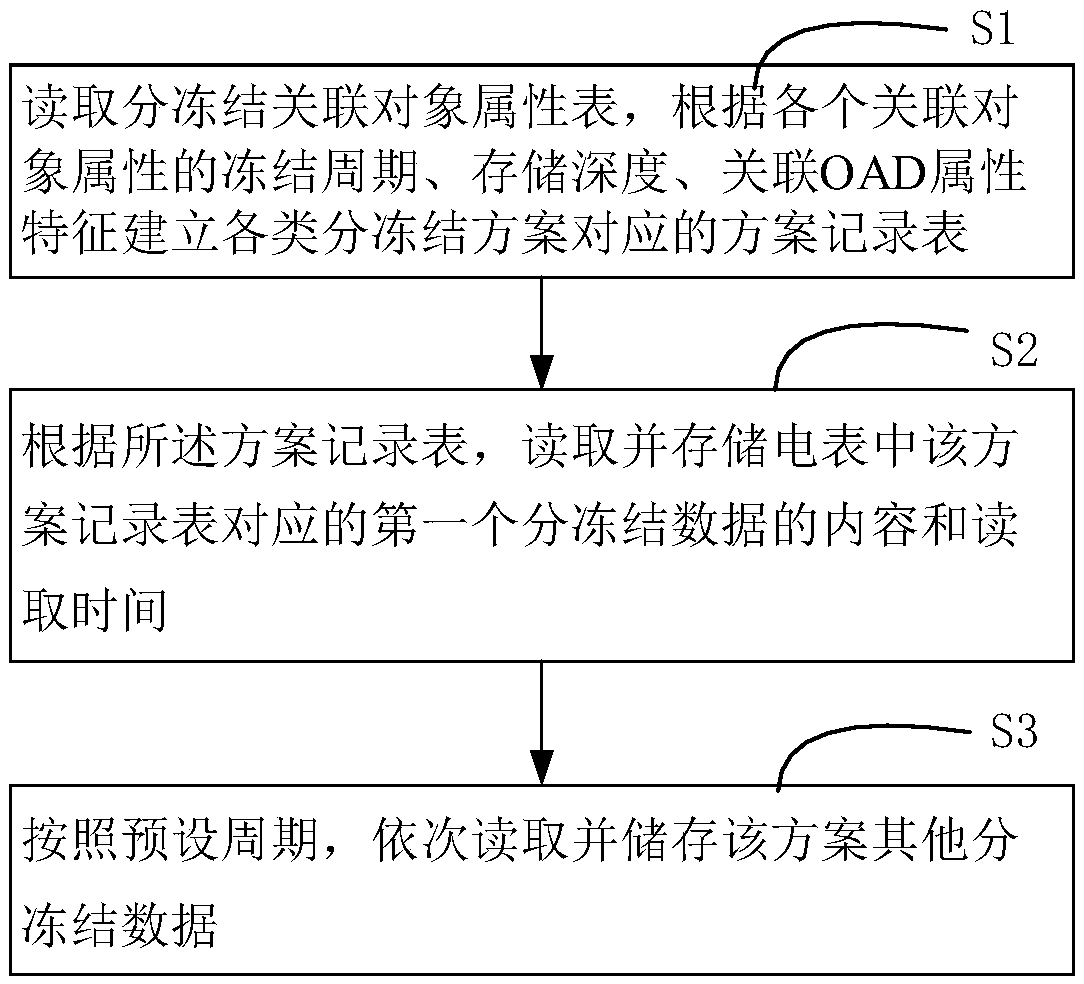
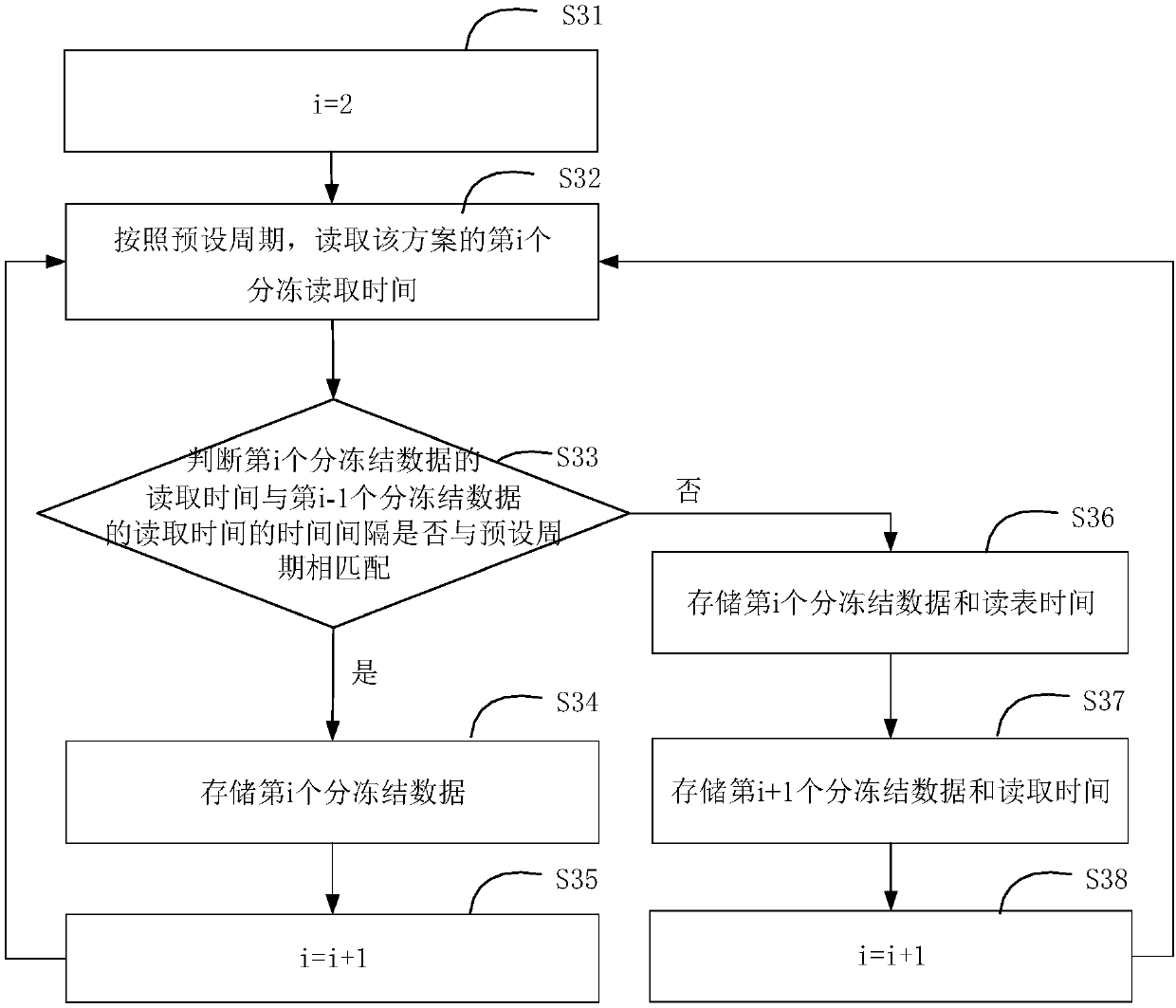
Intelligent electric meter segmented freezing data storage method and device and intelligent electric meter segmented freezing data query method and device
InactiveCN109614447AReduce data overheadIncrease the number ofSpecial data processing applicationsDatabase modelsData queryData needs
The invention discloses an intelligent electric meter segmented freezing data storage method and device and an intelligent electric meter segmented freezing data query method and device. The method comprises the following steps: S1, reading a segmented freezing associated object attribute table, and establishing a scheme record table corresponding to each segmented freezing scheme according to thefreezing period, the storage depth and the associated OAD attribute characteristics of each associated object attribute; S2, according to the scheme record table, reading and storing the content andreading time of first segmented freezing data corresponding to the scheme record table in the electric meter, and; and S3, sequentially reading and storing other segmented freezing data of the schemeaccording to a preset period. According to the invention, the technical problem that in an existing scheme, the reading time data of each piece of segmented freezing data needs to be stored, and the occupied storage space is large is solved, the data expenditure is reduced, and the quantity of segmented freezing data capable of being stored is increased.
Owner:AKSU POWER SUPPLY COMPANY STATE GRID XINJIANG ELECTRIC POWER +1
Information recording method and apparatus, information reproducing method and apparatus
InactiveUS20070245078A1No risk of fragmentationContinuity is assuredDisc-shaped record carriersInput/output to record carriersComputer hardwareStorage cell
Owner:SONY CORP
Distributed scheduling method for multi-antenna wireless system
ActiveUS8179843B2Improve computing powerImprove scalabilityMultiplex communicationData switching by path configurationData rateRate change
A channel allocation system for a beam-forming wireless network selects receivers to enroll in communication from a pool of candidate receivers, by off-loading a determination of the effects of adding each candidate receiver to the candidate receiver itself. In one embodiment, the candidate receivers nominate themselves for enrollment based on their determination of aggregate data rate changes resulting from their enrollment and the comparison of this aggregate data rate change against an estimate of the aggregate data rate changes of other candidate receivers.
Owner:WISCONSIN ALUMNI RES FOUND
Method and apparatus for implementing a block chain node device
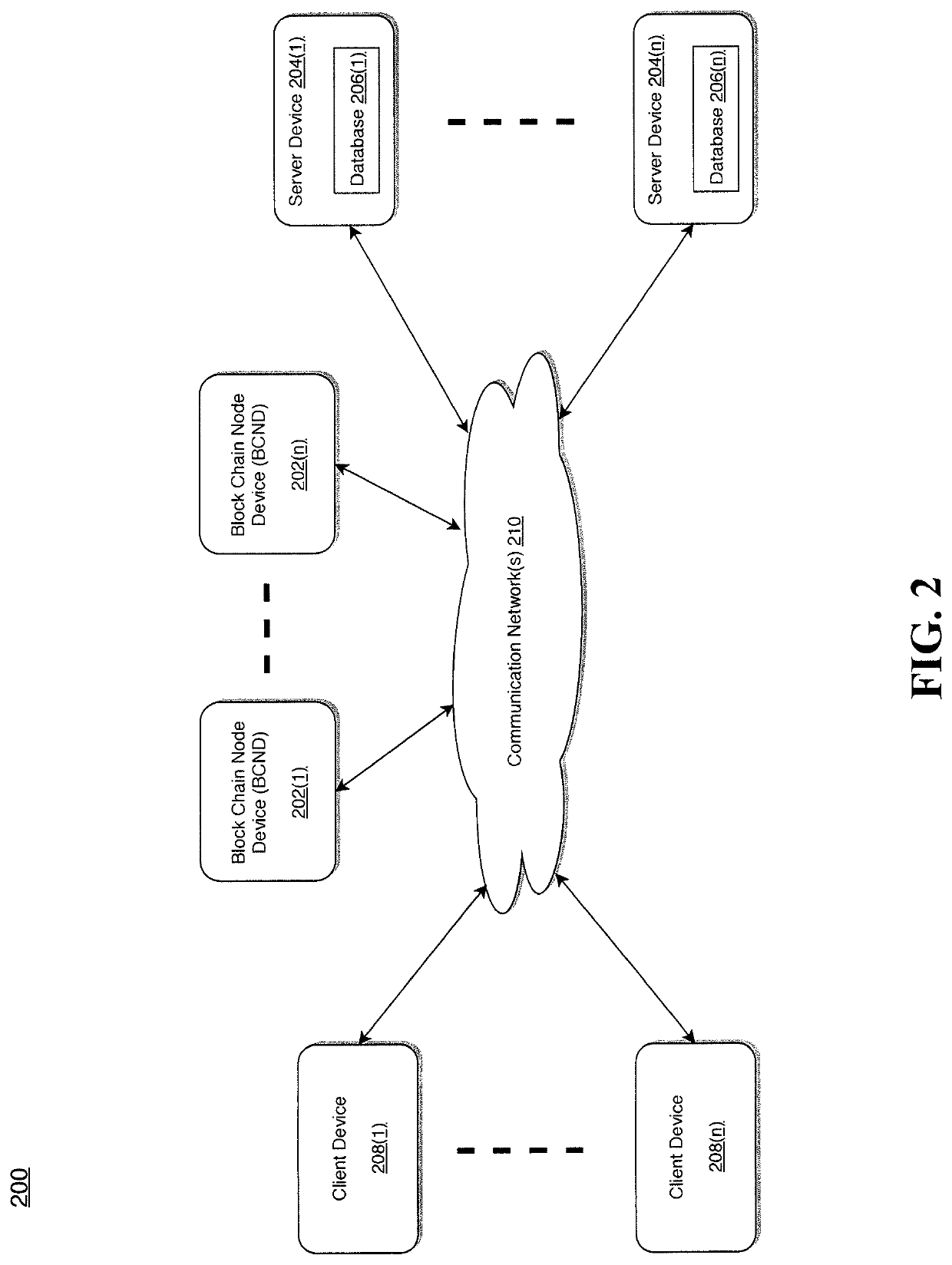
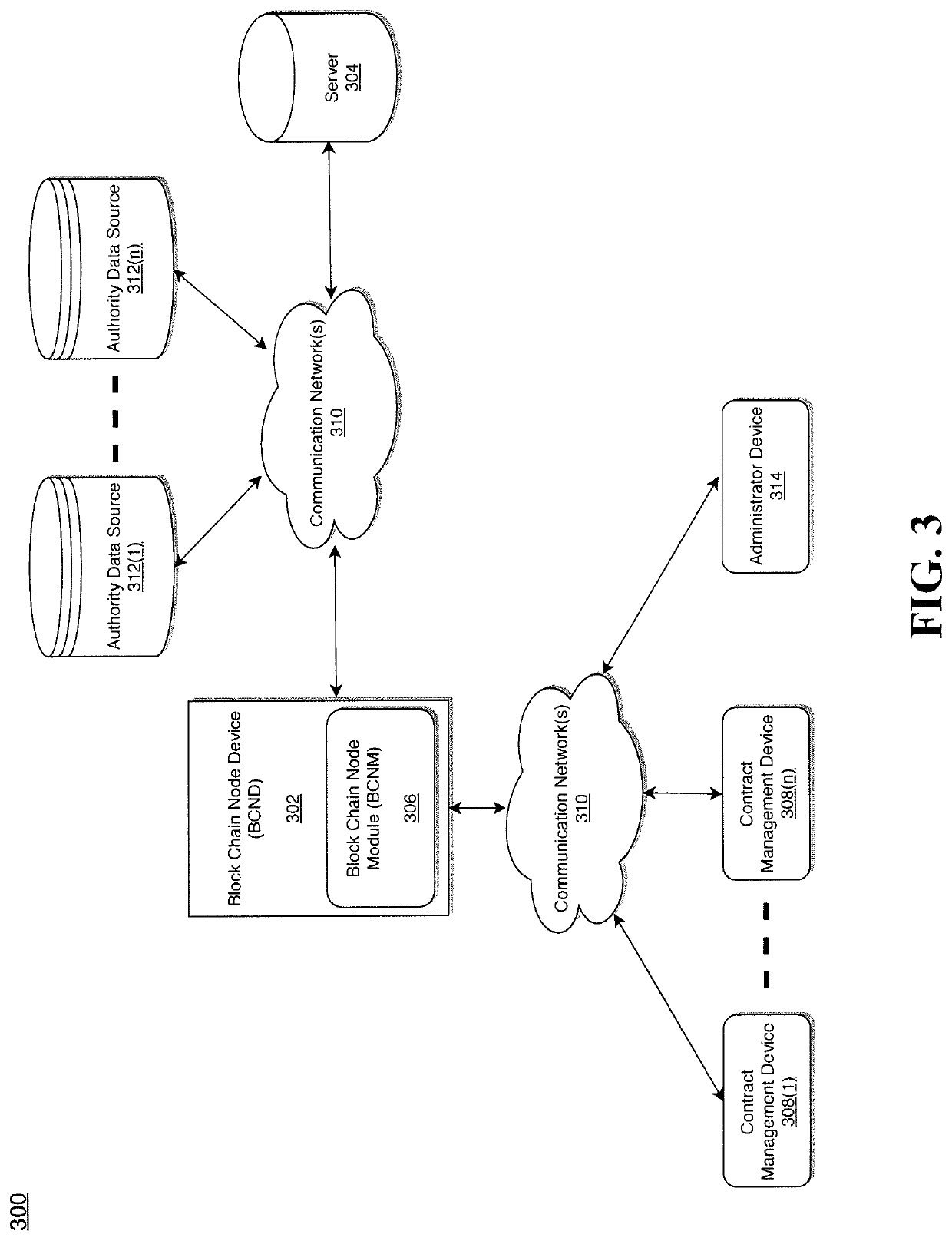
ActiveUS11443327B2Reduce utilizationReduce data overheadDatabase updatingCryptography processingComputer networkGraphical user interface
Various methods, apparatuses / systems, and media for implementing a block chain node device are disclosed. A processor allows hosting a received smart contract on a block chain ledger. The smart contract includes a digital model of a contract that describes base policy between an organization and a client. A receiver receives a side car contract from an external database. The side car contract includes a digital addendum to the smart contract and one or more modifications to one or more terms of the contract according to one or more regulatory provisions. The processor attaches the side car contract to the smart contract, and causes a graphical user interface (GUI) to report the one or more terms of the contract according to the one or more modifications in the side car contract in response to one or more received requests to thereby facilitate compliance with the regulatory provisions.
Owner:JPMORGAN CHASE BANK NA
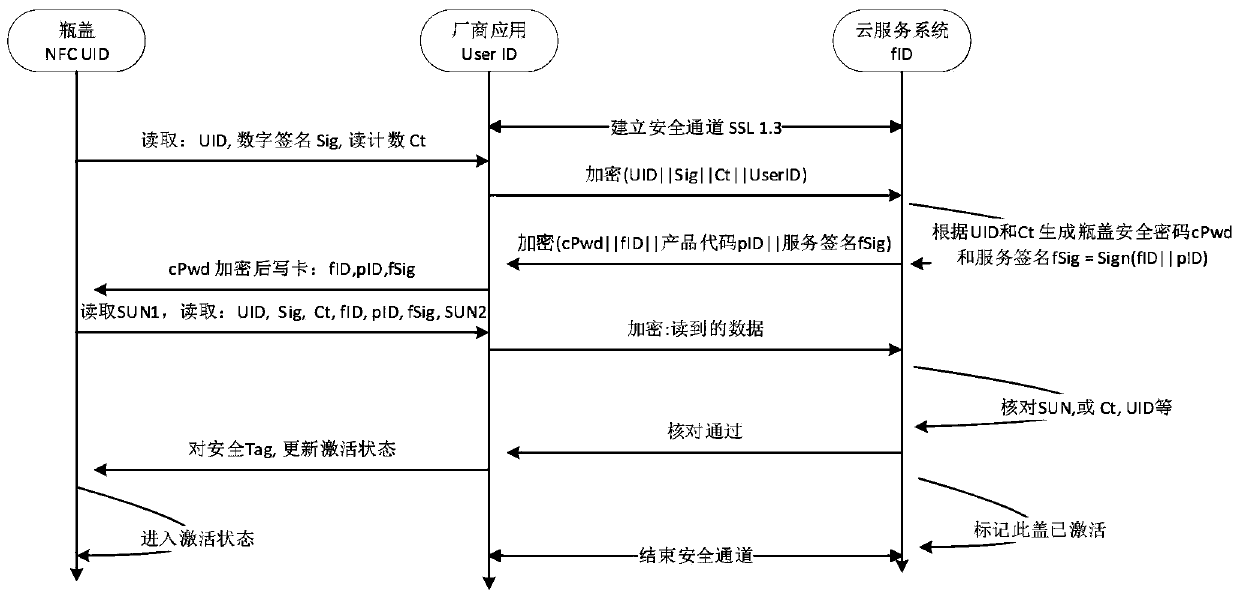
Product circulation authenticity verification method
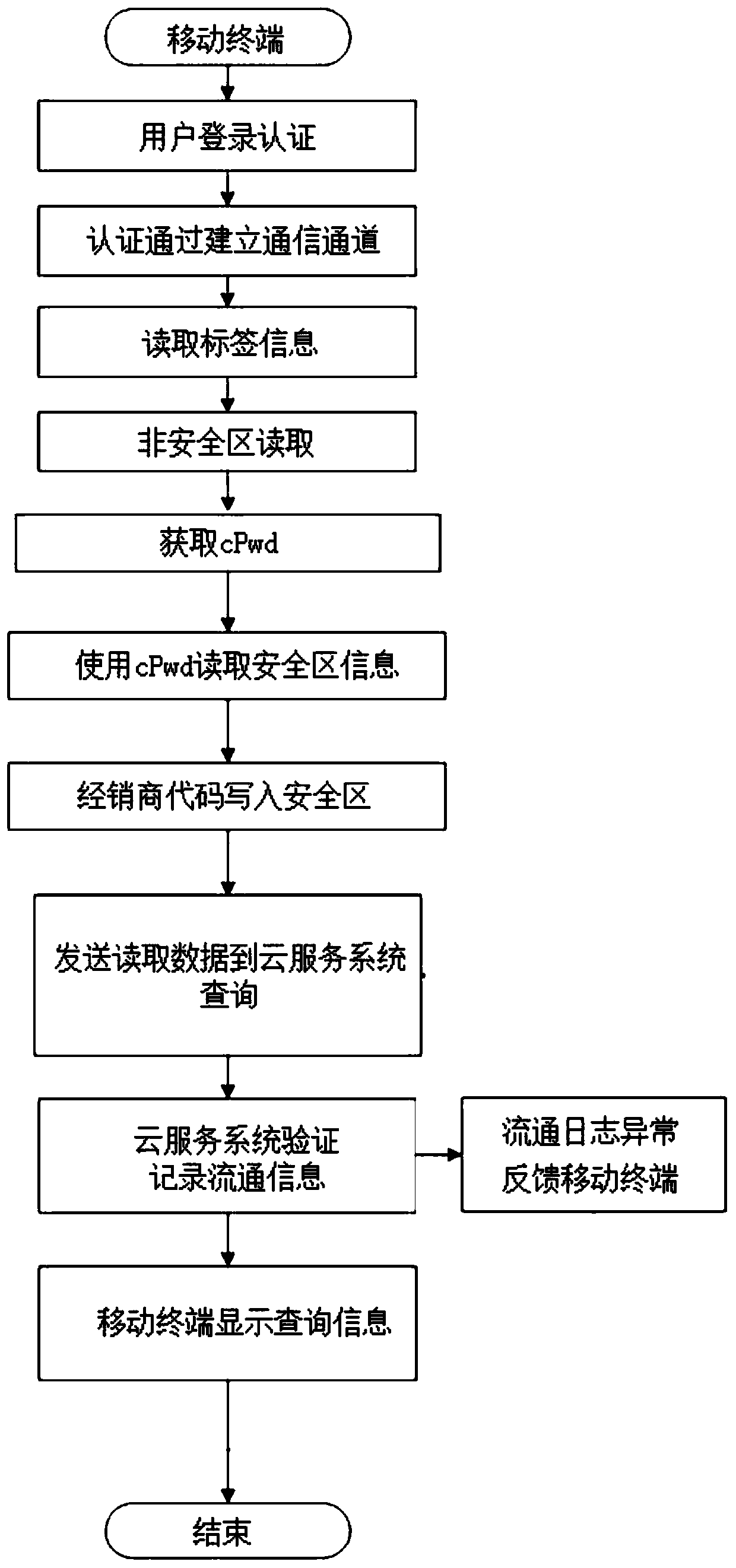
InactiveCN111210229AImprove accuracyReduce data overheadUser identity/authority verificationCo-operative working arrangementsLogistics managementDigital signature
The invention relates to a product circulation authenticity verification method. A mobile terminal reads the information stored in the non-safe area of an anti-counterfeiting label, obtains the safe reading password from a cloud service system and then reads the safe area storage information and the dynamic safety certification number in the label, the mobile terminal encrypts the read informationand feeds back the encrypted information to the cloud service system, and the dealer code is written into the safe area of the label; the cloud service system decrypts the received data and recalculates the dynamic authentication number; checking and verifying the received data; the verification content comprises dynamic authentication number verification, digital signature verification, countervalue verification and log analysis confirmation. Through the comprehensive anti-counterfeiting verification means, the anti-counterfeiting label is prevented from being copied and played back, dynamic encryption calculation is adopted for information interaction, the safety of receiving and inquiring feedback information is guaranteed, whether product circulation records are abnormal or not can be monitored, the authenticity and accuracy of logistics information are guaranteed, and the anti-counterfeiting safety in the product process is comprehensively improved.
Owner:绍兴心越科技有限公司
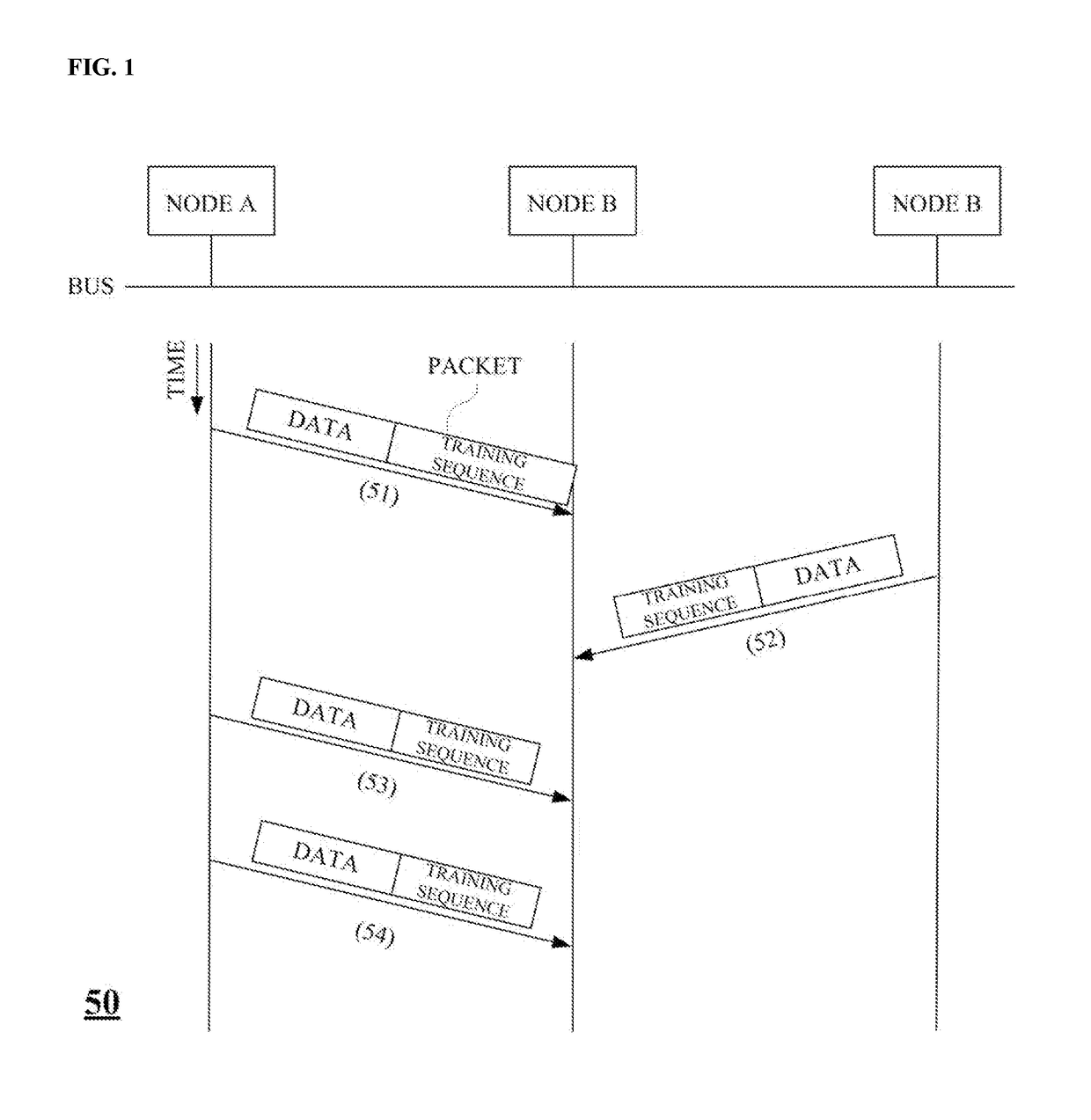
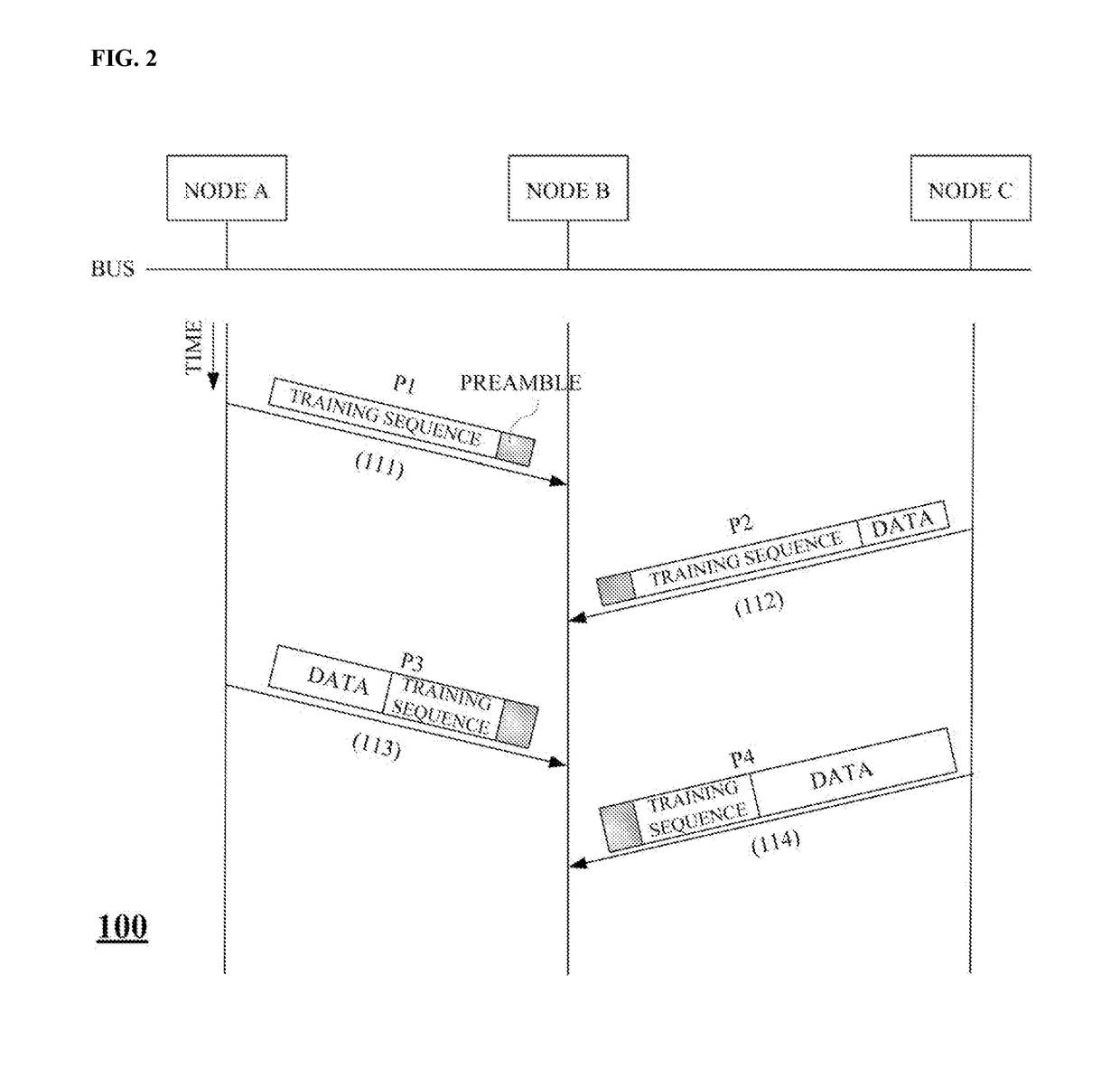
Method for high speed equalization of packet data received from bus topology network, method for transmitting and receiving packet data in bus topology network, and receiver of bus topology network
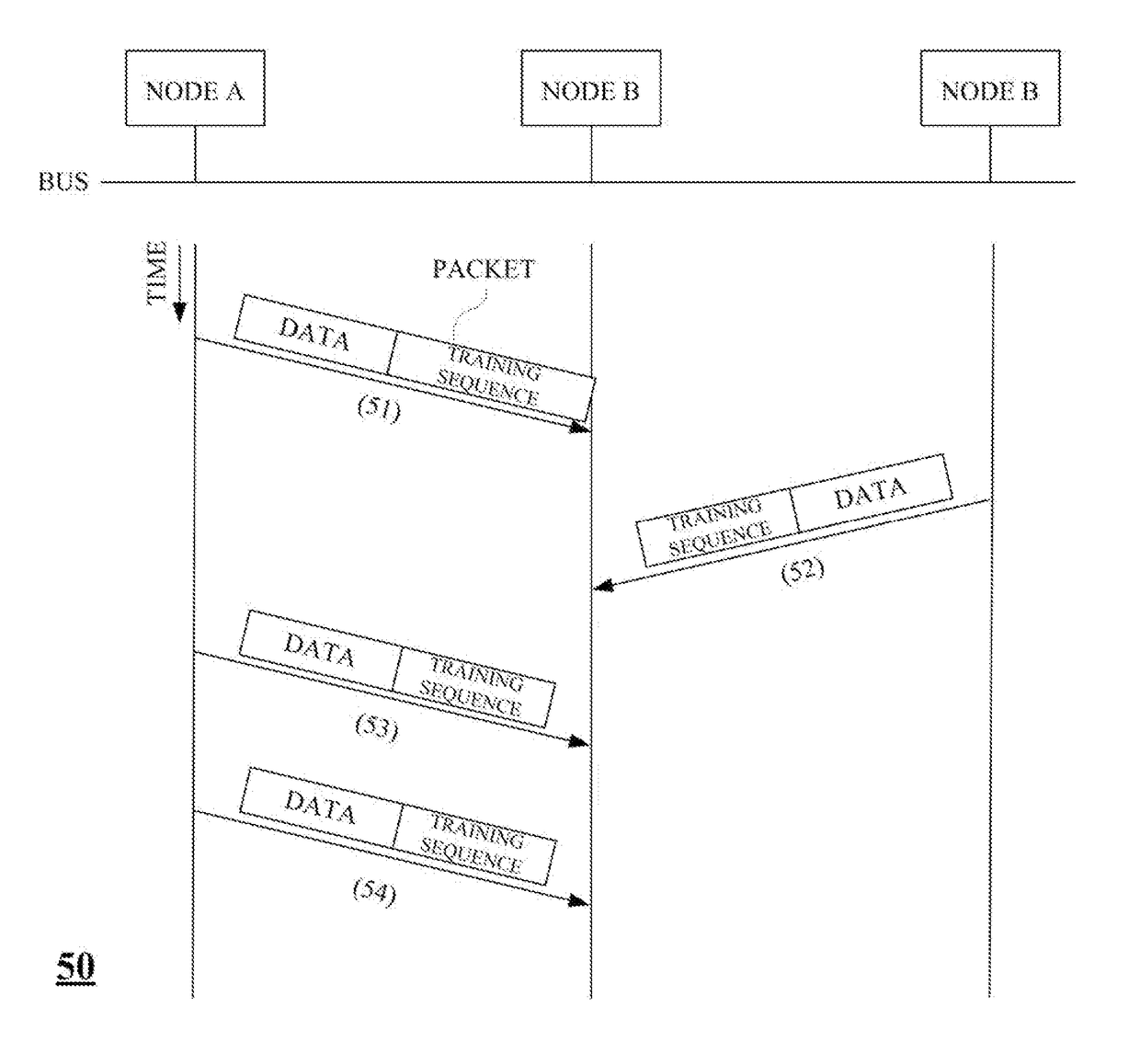
ActiveUS20180013577A1Reduce data overheadSystem throughput be maximizeTransmitter/receiver shaping networksBus networksBus networkReal-time computing
A method of equalizing received packet data in a bus topology network, including: receiving, by a receiver of a second node, a first packet from a first node in a bus topology network in which two or more nodes are connected via a bus; setting, by the receiver, an equalizer coefficient of an equalizer using a first training sequence of the first packet and storing the set equalizer coefficient; receiving, by the receiver, a second packet including a second training sequence shorter than the first training sequence from the first node; and equalizing, by the receiver, the second packet using the stored equalizer coefficient.
Owner:VSI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com