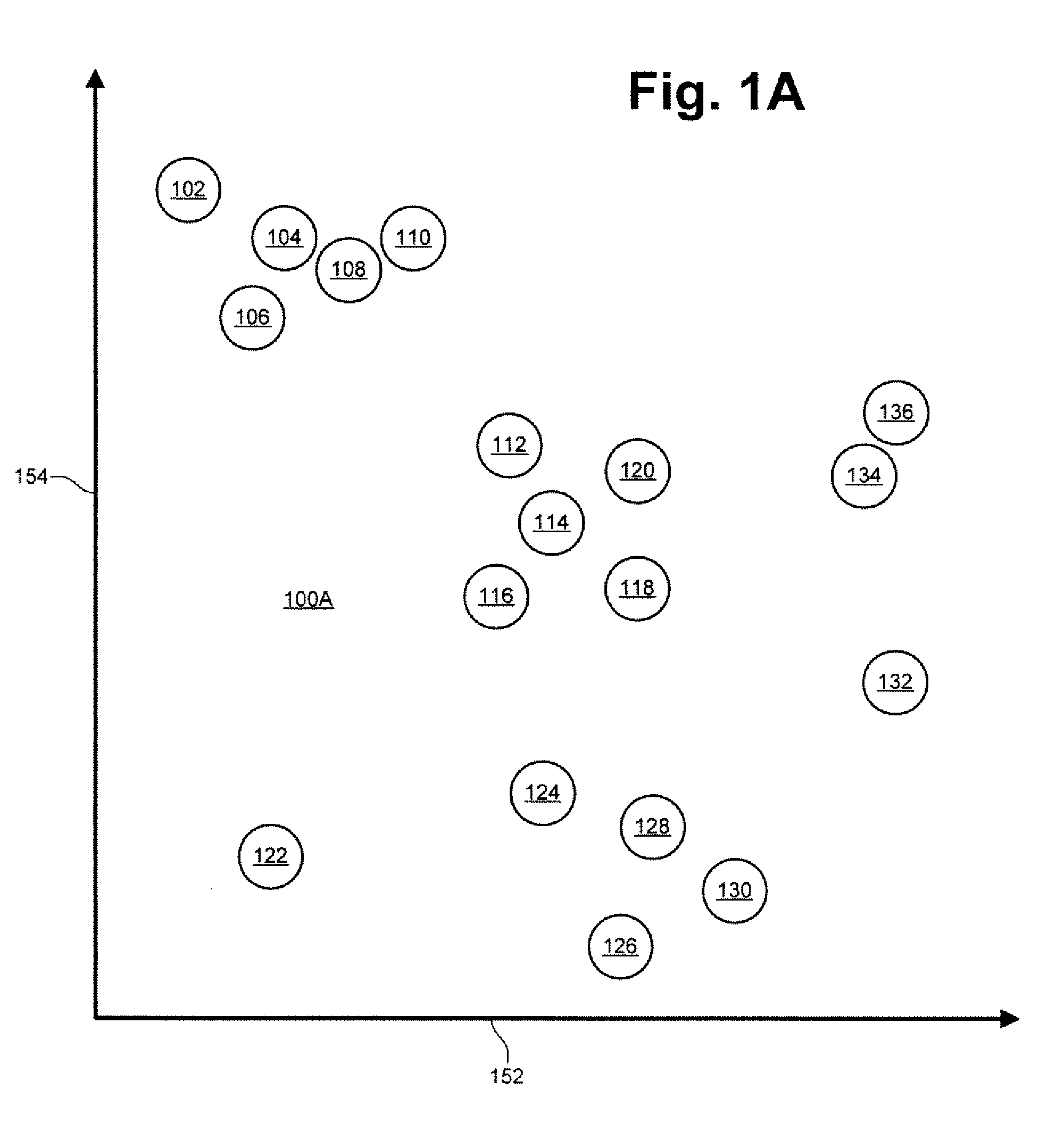
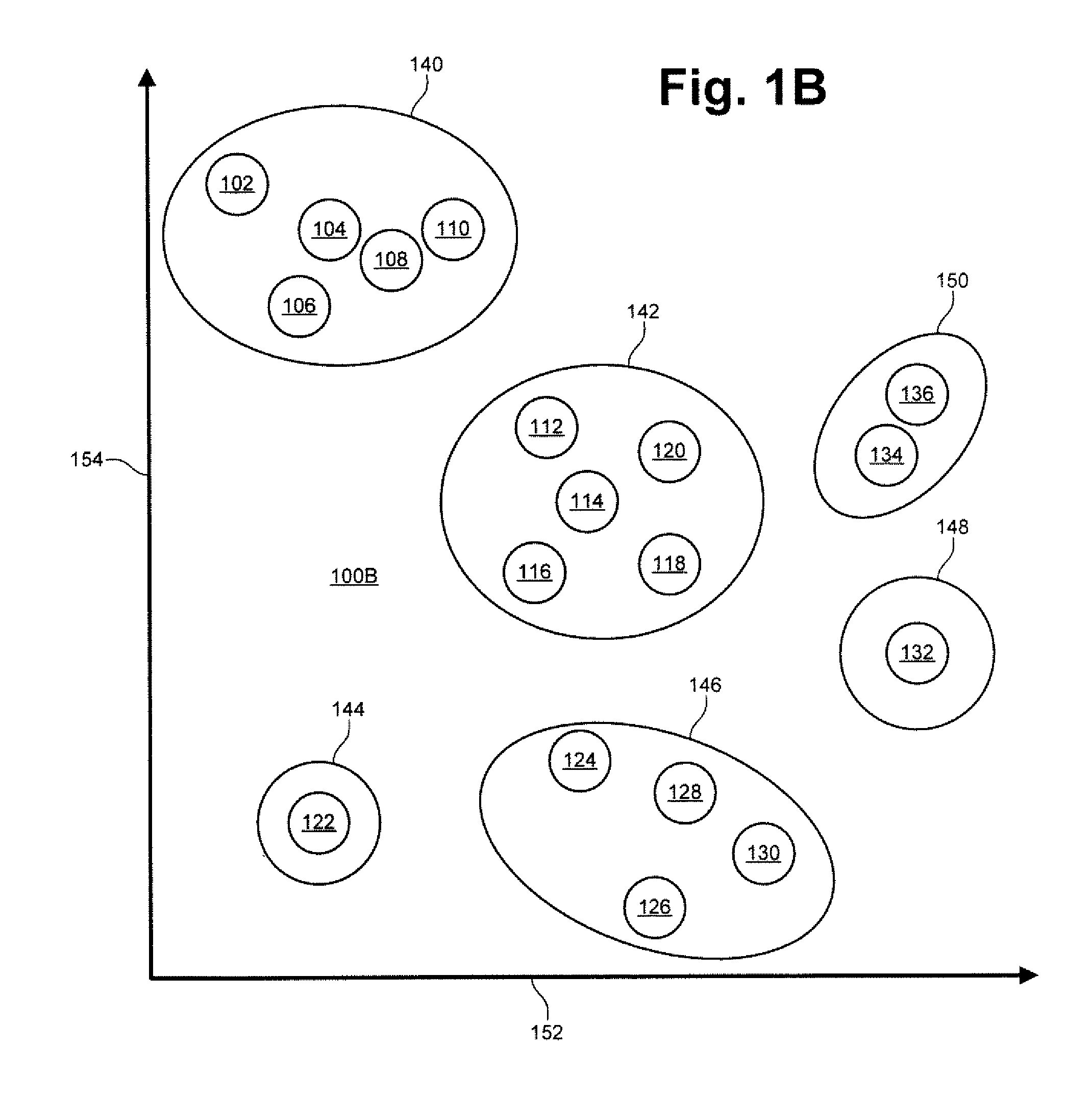
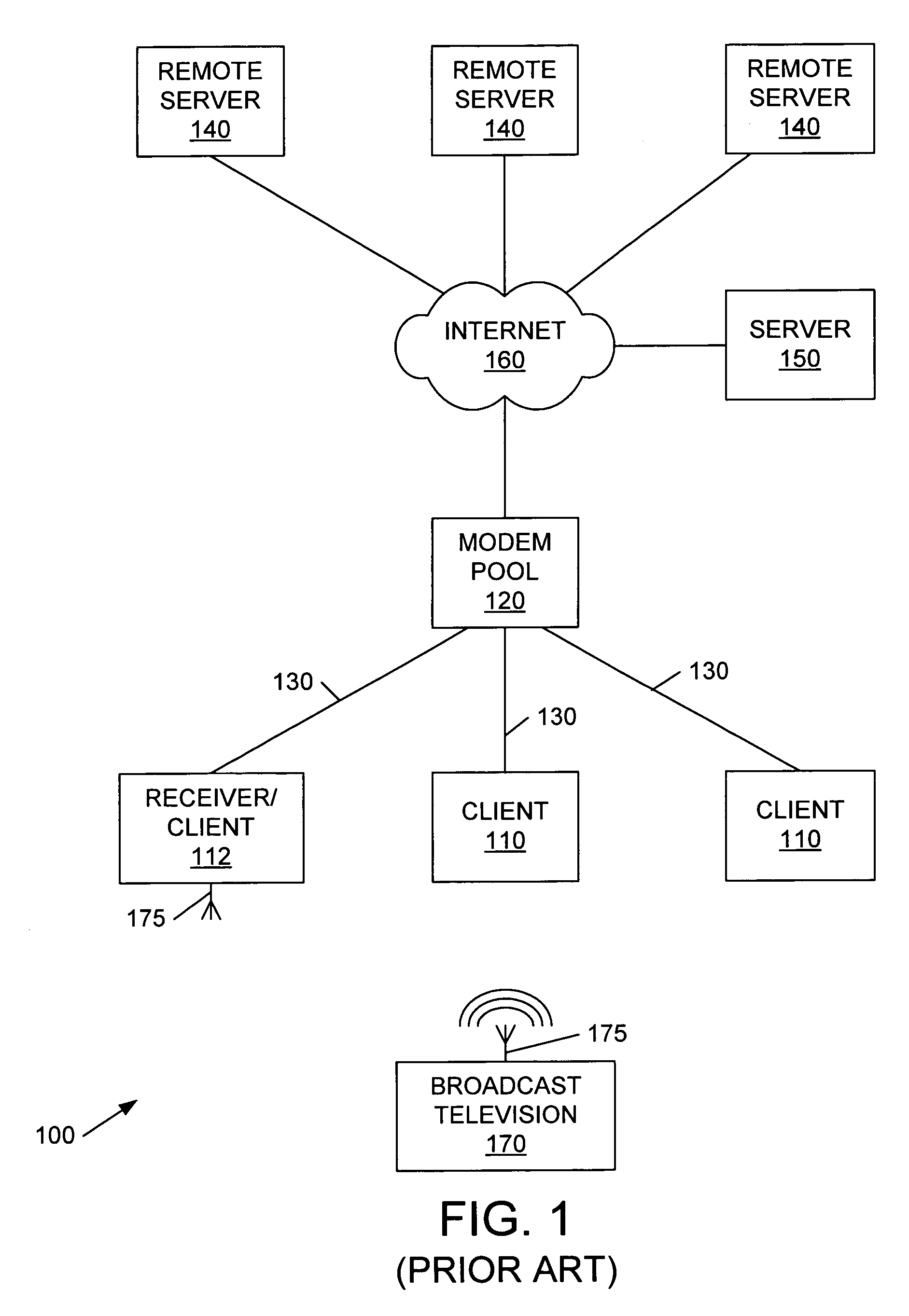
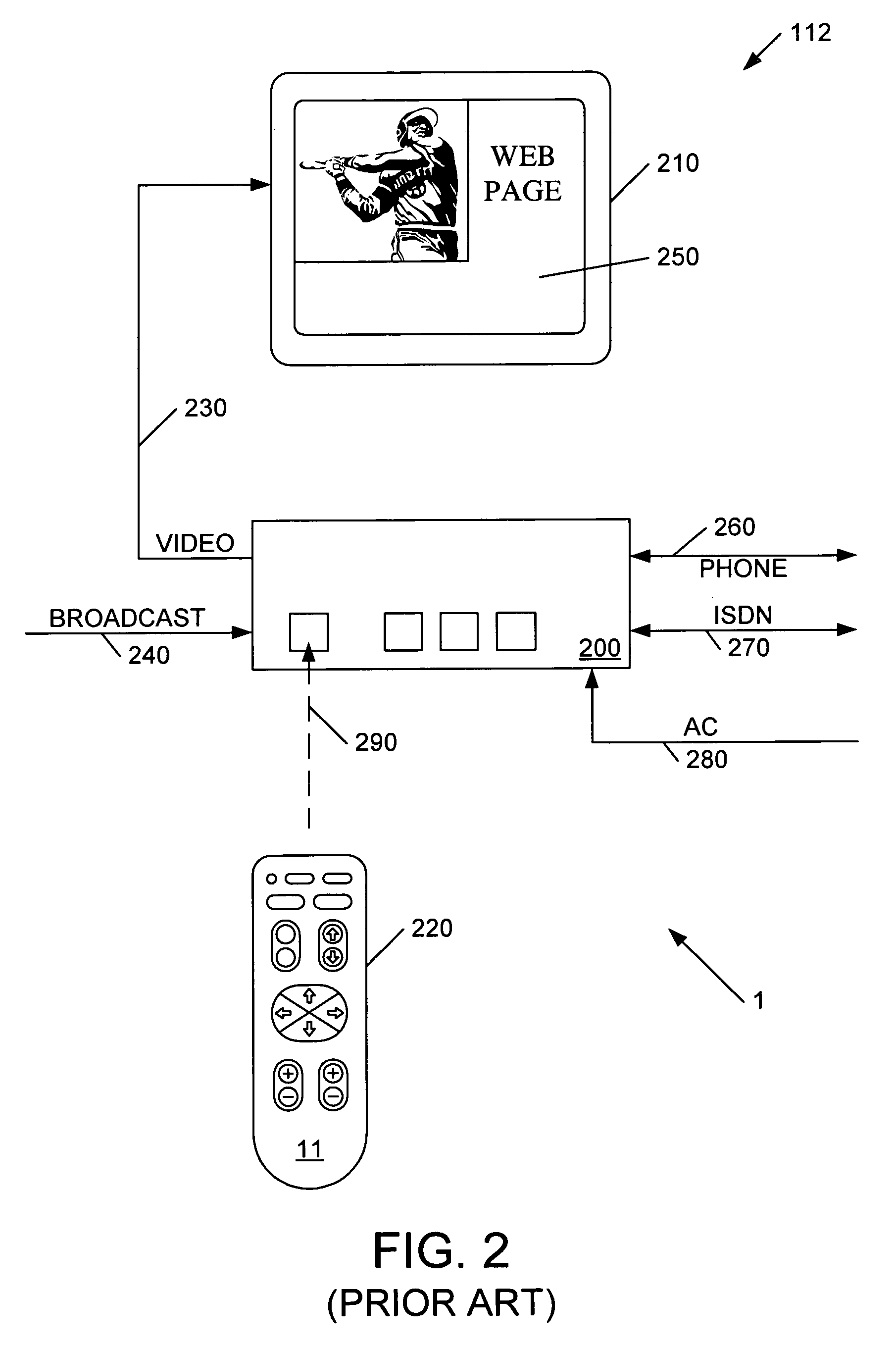
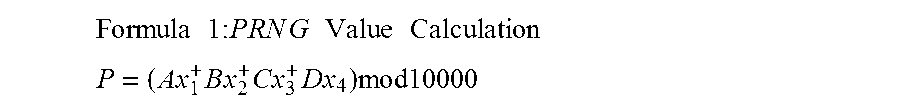Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3428 results about "Data field" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A data field is a place where you can store data. Commonly used to refer to a column in a database or a field in a data entry form or web form. The field may contain data to be entered as well as data to be displayed.
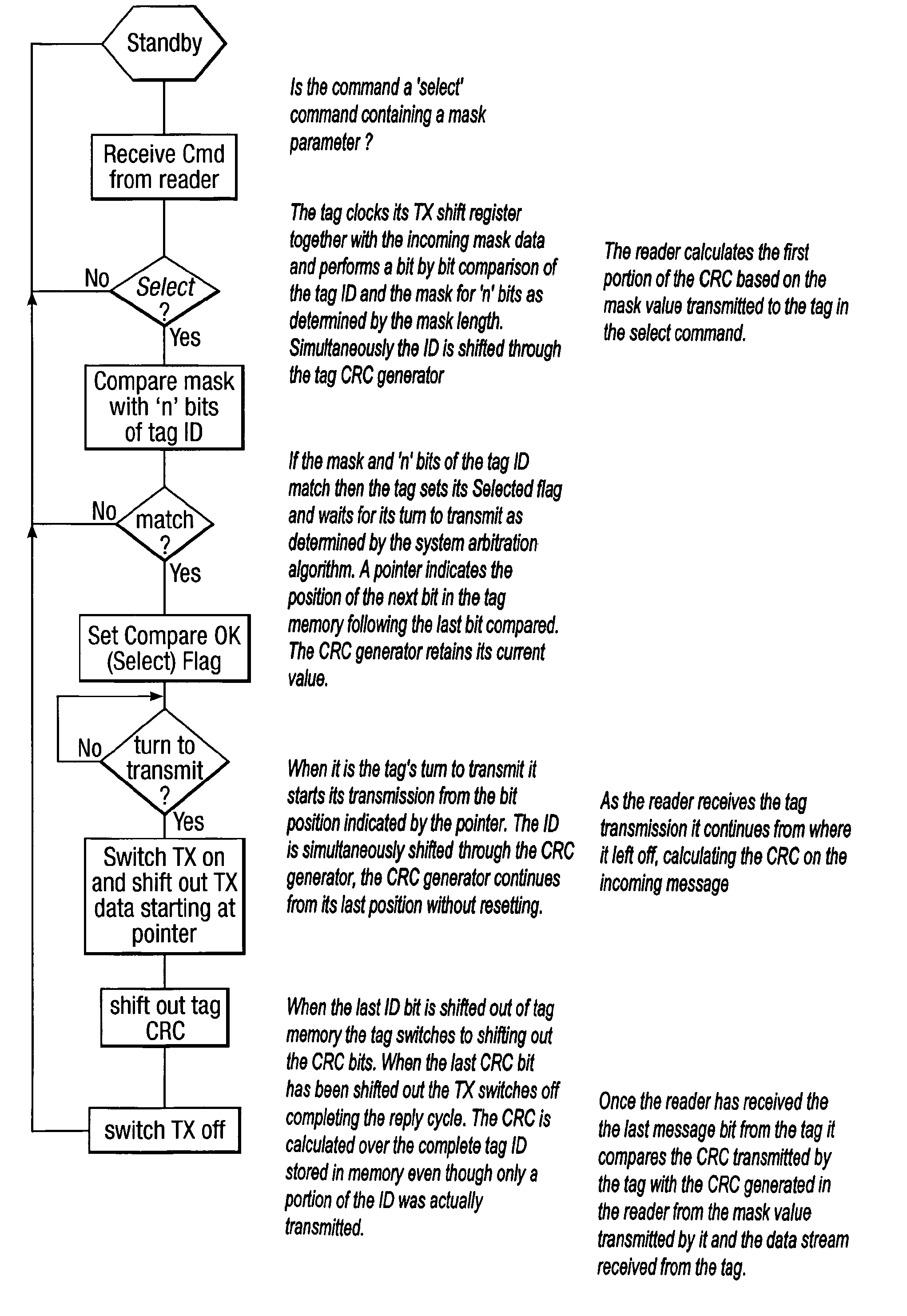
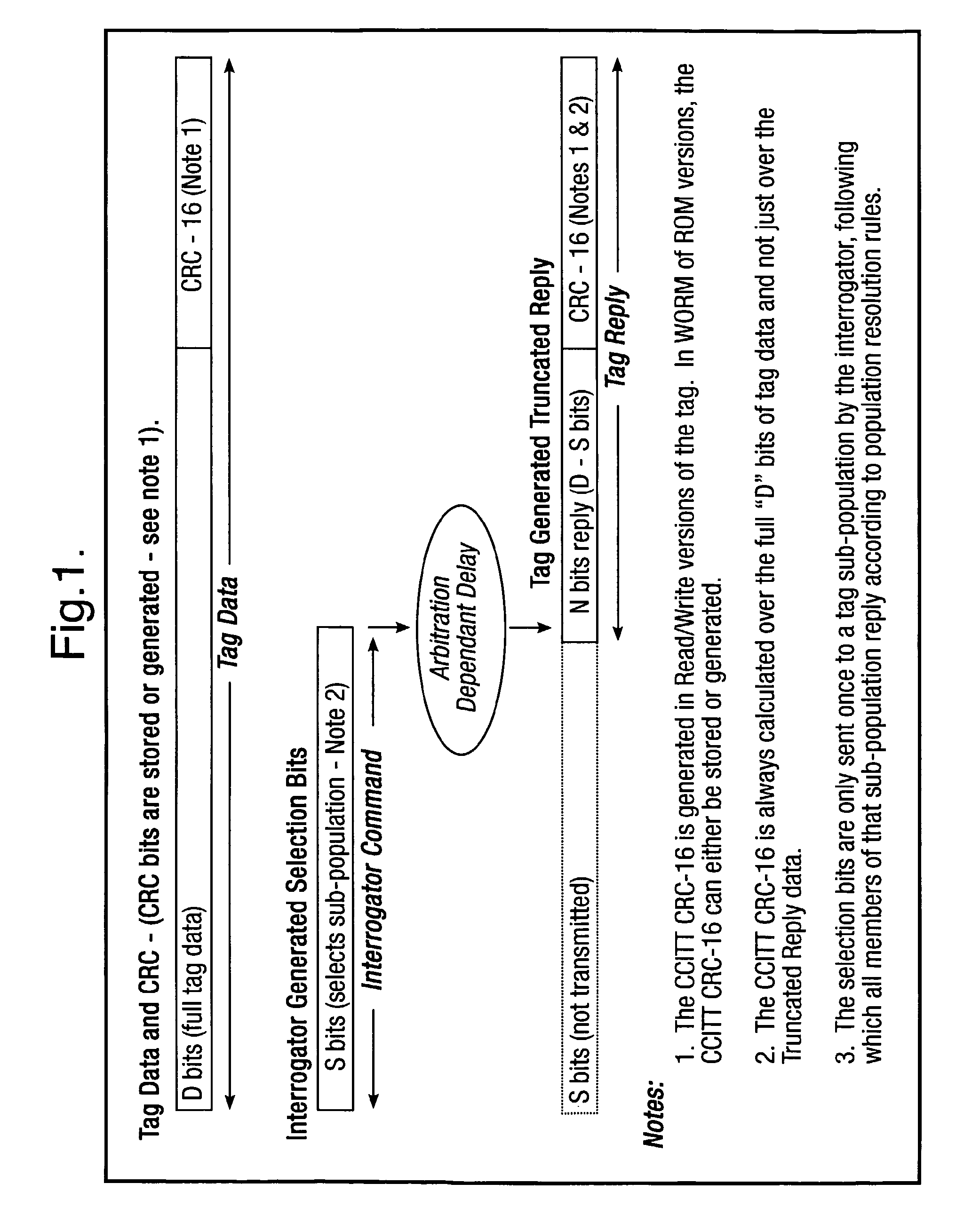
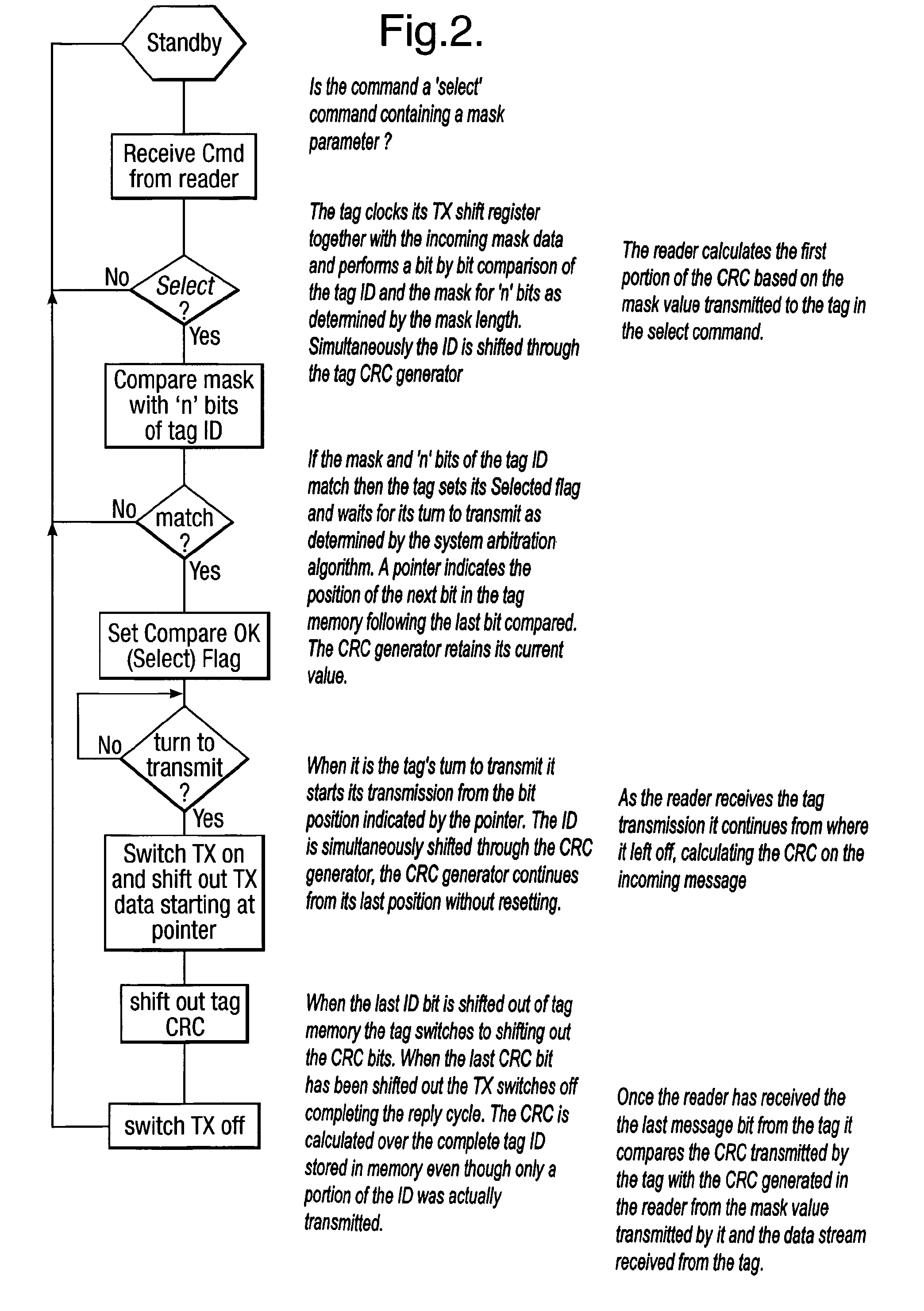
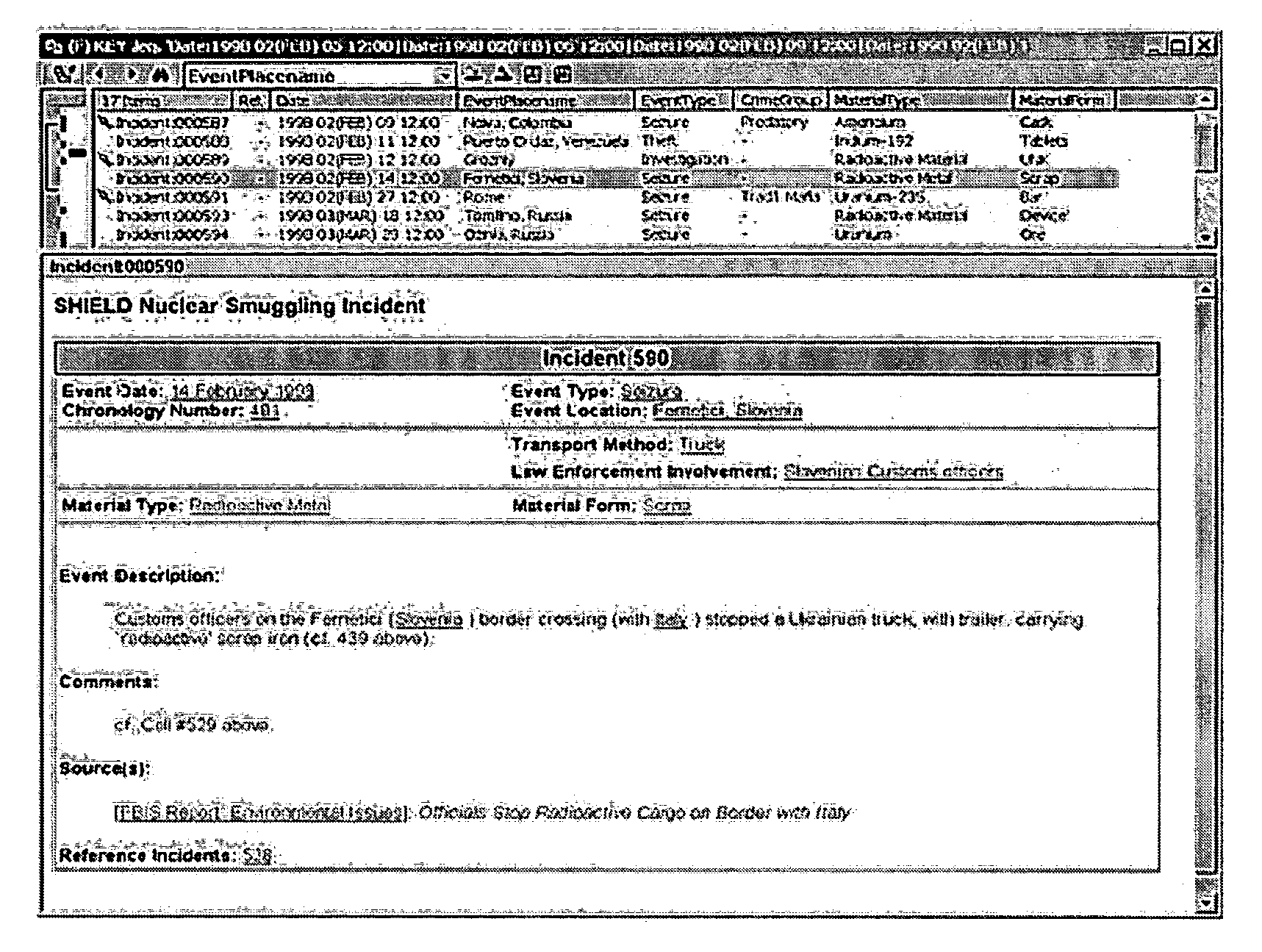
Method and system for calculating and verifying the integrity of data in a data transmission system
ActiveUS7987405B2Not having capability to accuratelyStay flexibleError preventionMemory record carrier reading problemsComputer hardwareData integrity
A method is described of calculating and verifying the integrity of data in a data communication system. The system comprises a base station and one or more remote stations, such as in an RFID system. The method includes transmitting a select instruction from the base station to the one or more remote stations, the select instruction containing a data field which matches a portion of an identity or other data field in one or more of the remote stations; transmitting from a selected remote station or stations a truncated reply containing identity data or other data of the remote station but omitting the portion transmitted by the base station; calculating in the base station a check sum or CRC from the data field originally sent and the truncated reply data received and comparing the calculated check sum or CRC with the check sum or CRC sent by the remote station.
Owner:ZEBRA TECH CORP
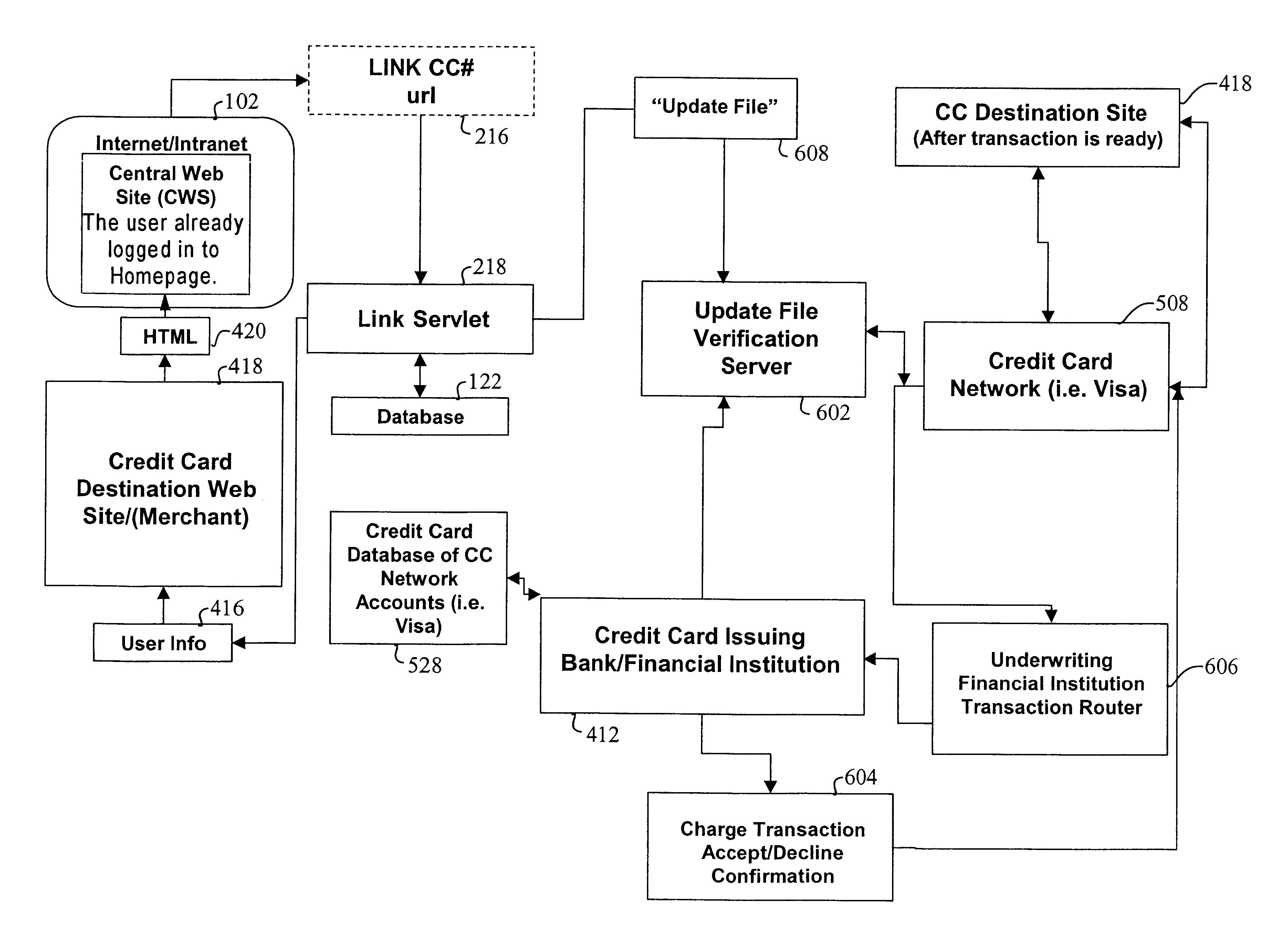
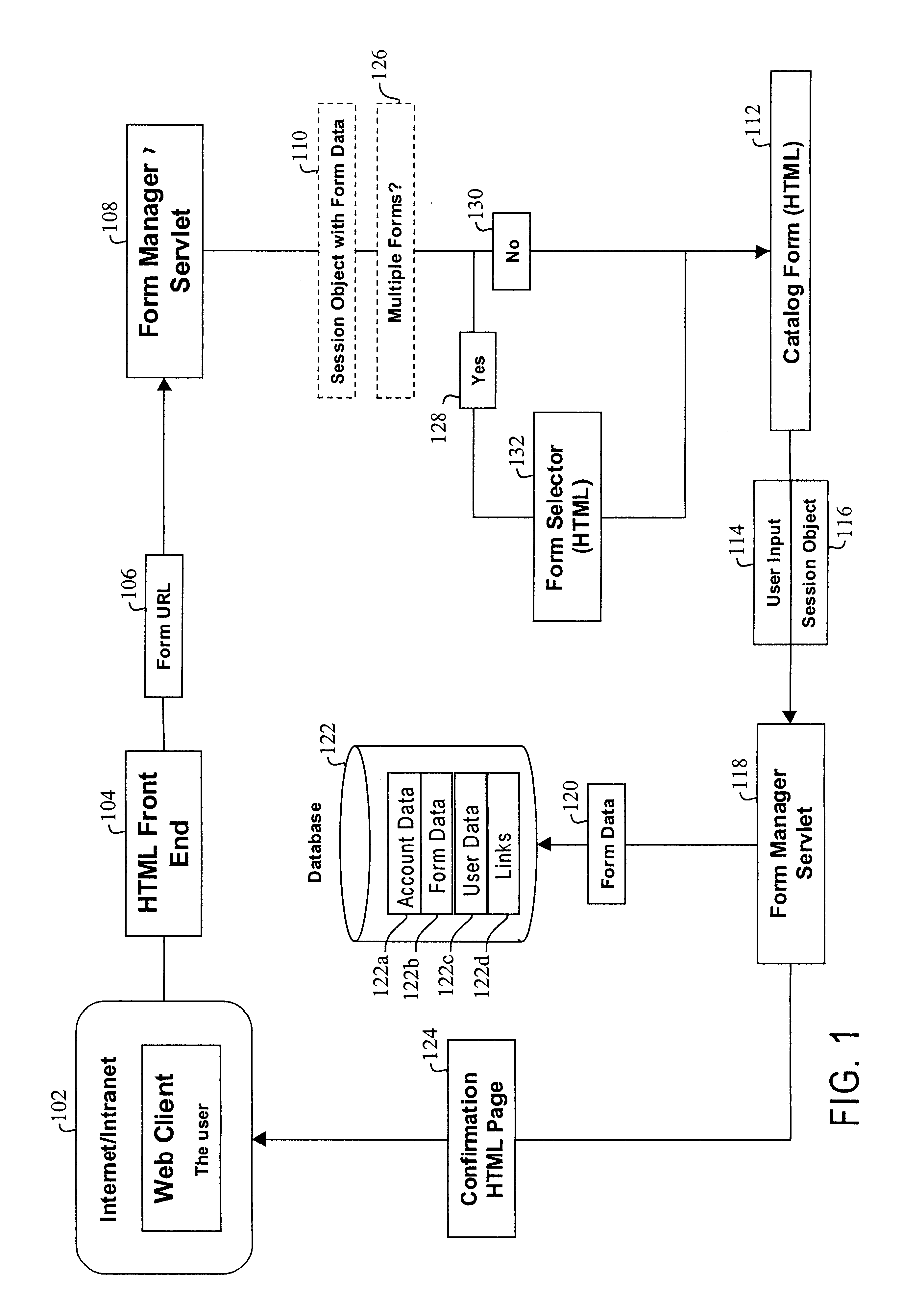
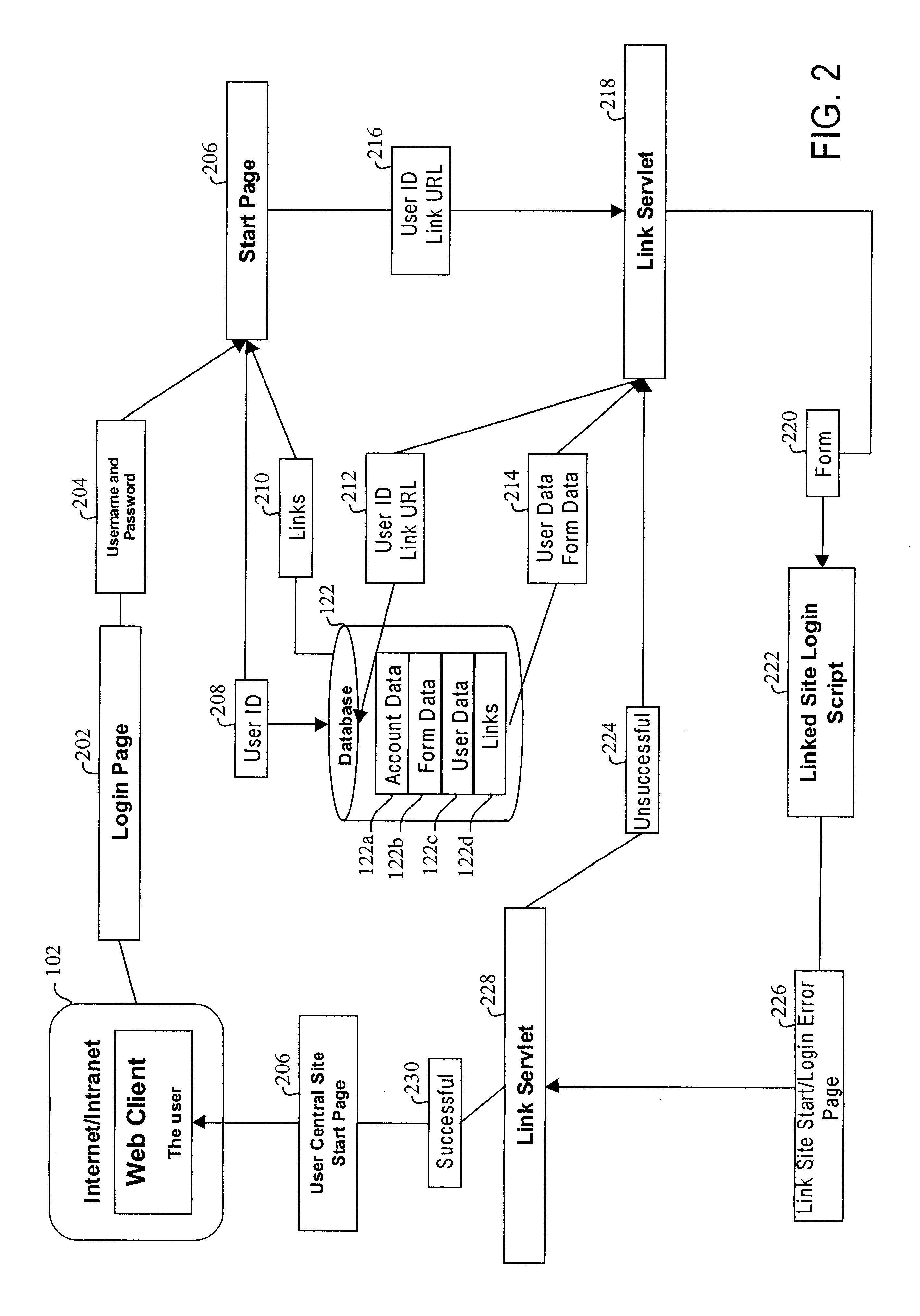
Method, system and computer readable medium for web site account and e-commerce management from a central location
InactiveUS6879965B2Minimizing activation timeMinimizing financial exposureComplete banking machinesAcutation objectsWeb siteData field
A method, system and computer readable medium for, from a central Web site, performing at least one of registering a user at a destination Web site, logging in a user at a destination Web site and managing an online financial transaction at a destination Web site, including parsing a form Web page of the destination Web site to extract form data fields therefrom; mapping form data fields of a central Web site form to corresponding extracted form data fields of the form Web page of the destination Web site; and using the mapped form data fields to perform at least one of registering a user at the destination Web site, logging in a user at the destination Web site and managing an online financial transaction of a user at the destination Web site. In another aspect, there is provided a method, system and computer readable medium for managing an online or offline financial transaction of a user, from a central Web site, including generating financial transaction account information for a user based on existing credit or debit card information; gathering from the user one or more limits that are applied to a financial transaction performed based on the financial transaction account information; receiving from a source information indicating that an online or offline financial transaction using the financial transaction account information is in progress; applying the one or more limits gathered from the user to approve or disapprove the online or offline or online financial transaction that is in progress; and transmitting an approval or disapproval signal to the source based on a result of the applying step.
Owner:SLINGSHOT TECH LLC
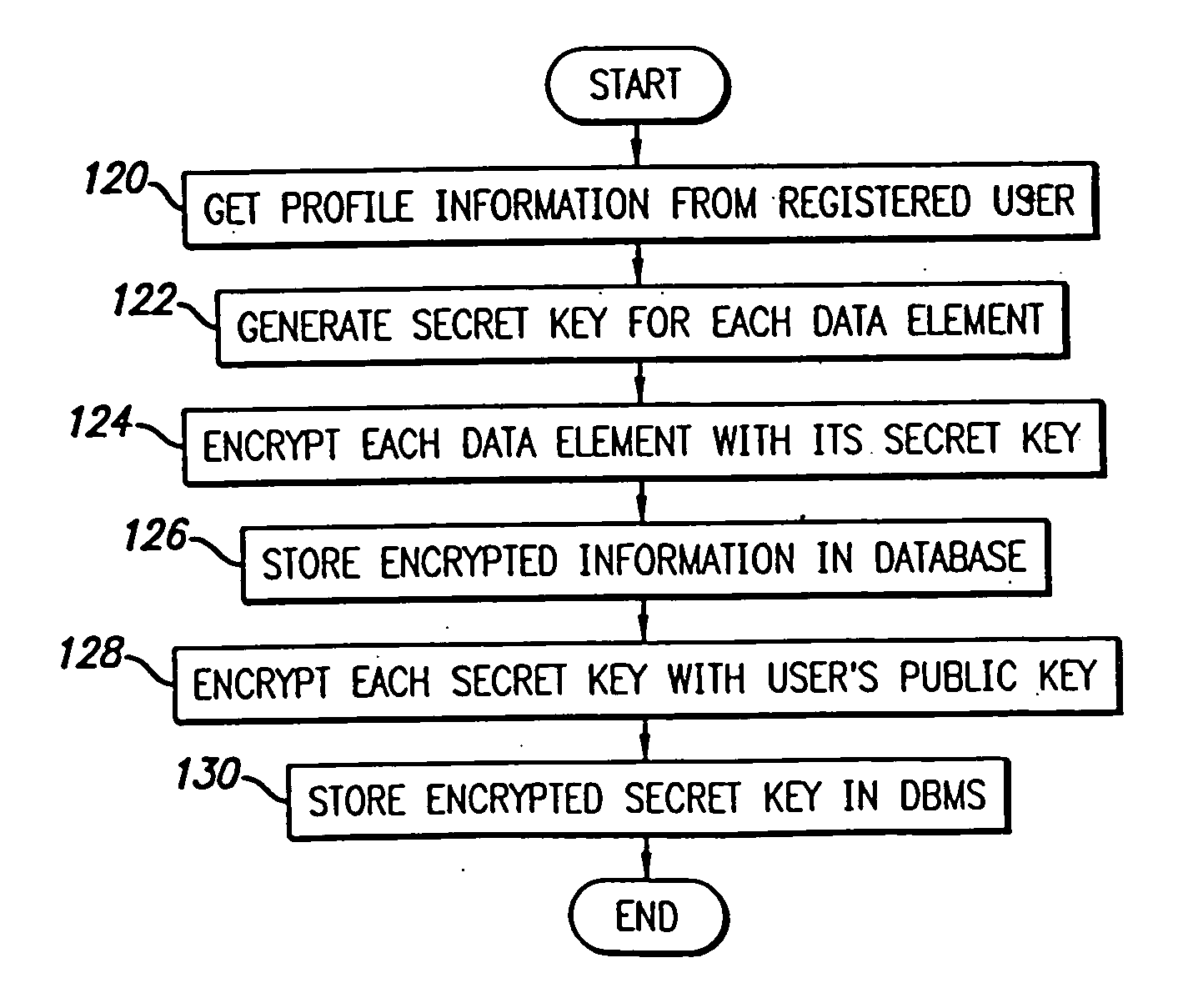
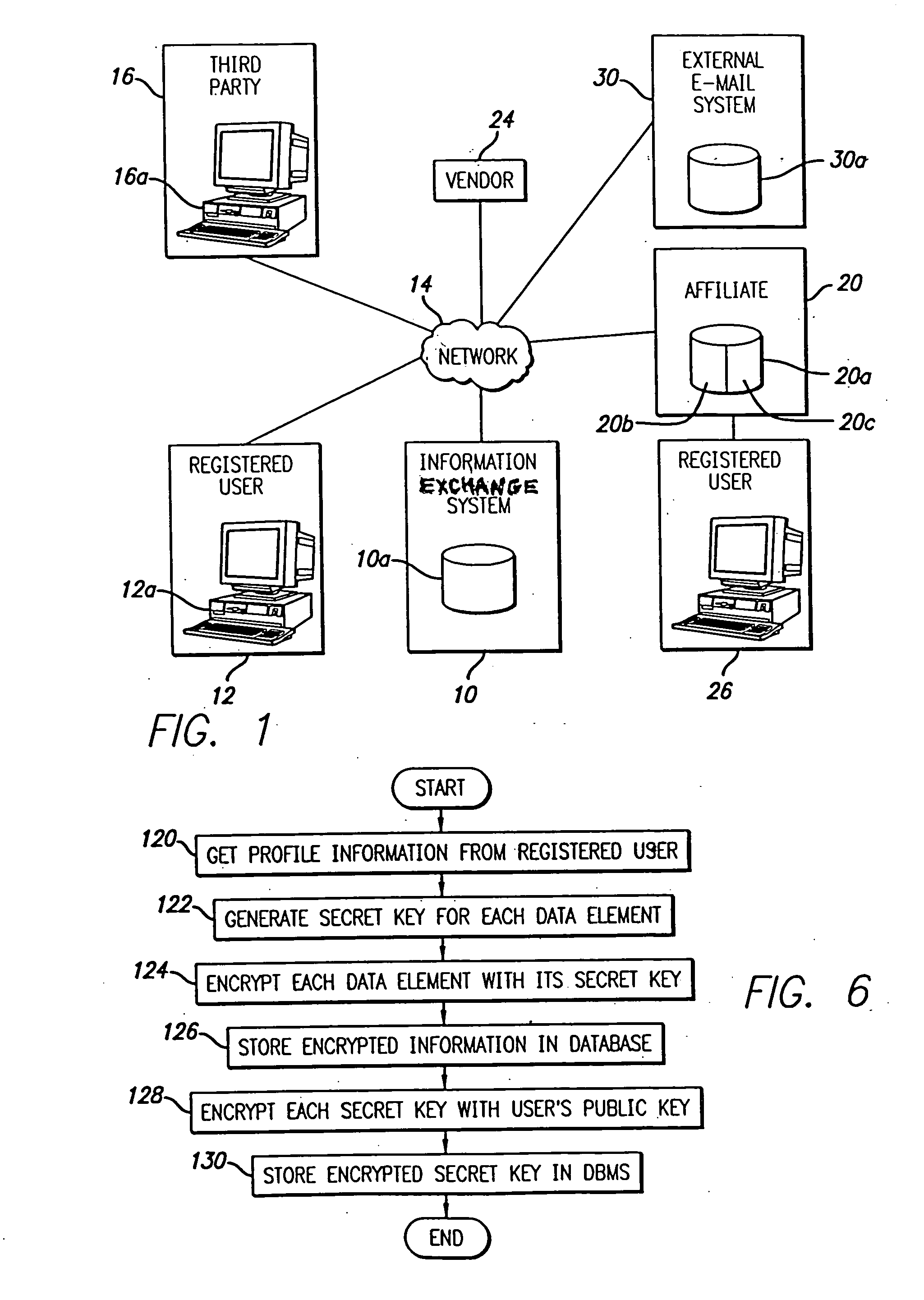
System and method for selective information exchange
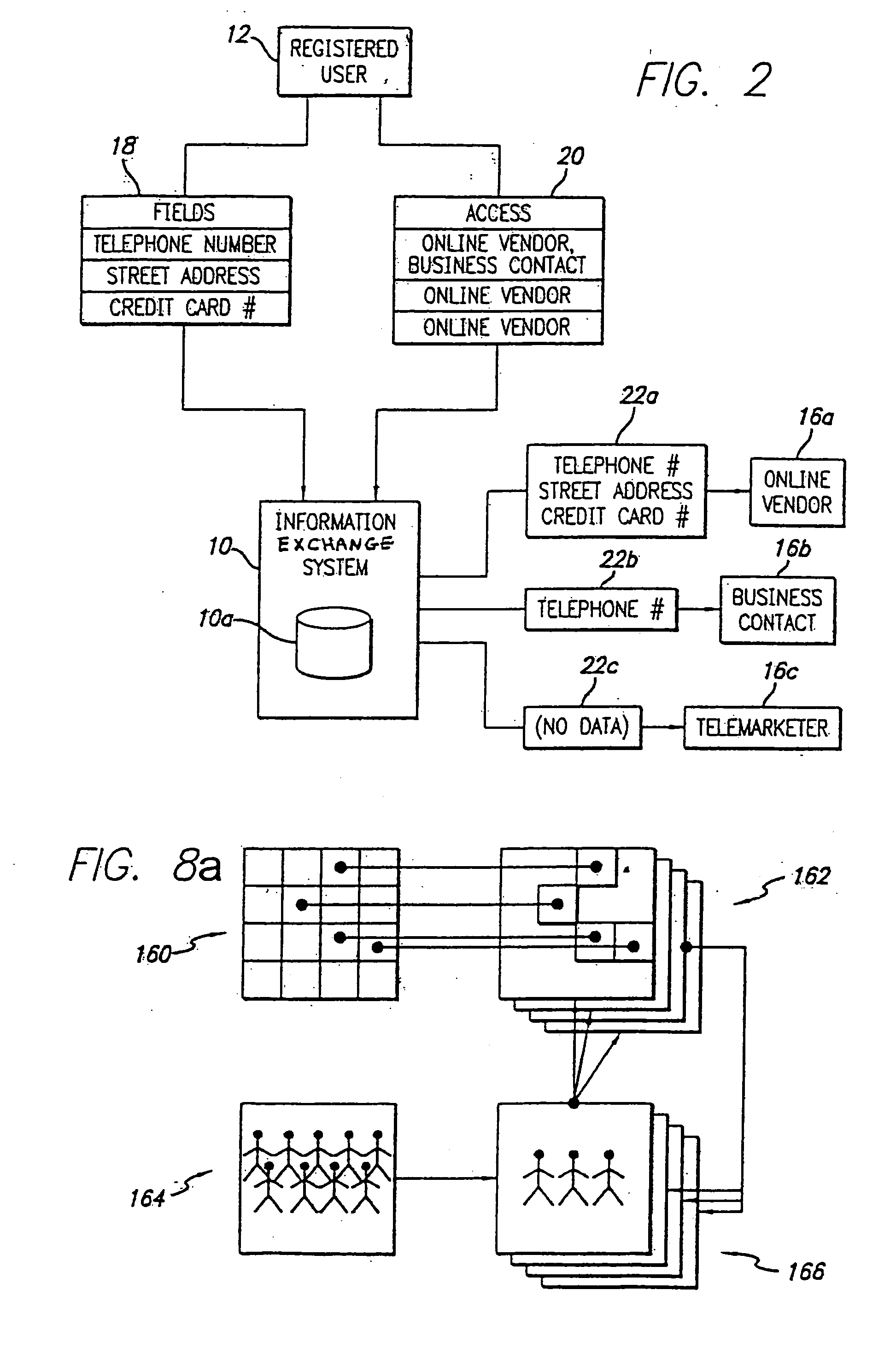
InactiveUS20050192008A1Avoid accessComputer security arrangementsRadio/inductive link selection arrangementsTime informationThe Internet
A system and method for providing users with granular control over arbitrary information that allows for selective, real-time information sharing in a communications network such as the Internet is provided. In a network including a plurality of network devices operated by a plurality of users, a real-time information exchange system for sharing user profile information between respective users includes a database management system connected to the network. The database management system, which may be distributed across the network, stores the user profile information for a plurality of registered users of the information exchange system The user profile information includes a plurality of data elements, each data element having an associated one of the plurality of registered users. Each data element has an associated group of users to whom access to the data element has been granted, and users not included in the associated group of users are denied access to the data element. Each registered user may selectively control the granting and denying of access to each of its associated data elements by other respective user, on an element-by-element, and user-by-user basis. Further, each registered user may dynamically create its own data fields.
Owner:DESAI NIMESH +5
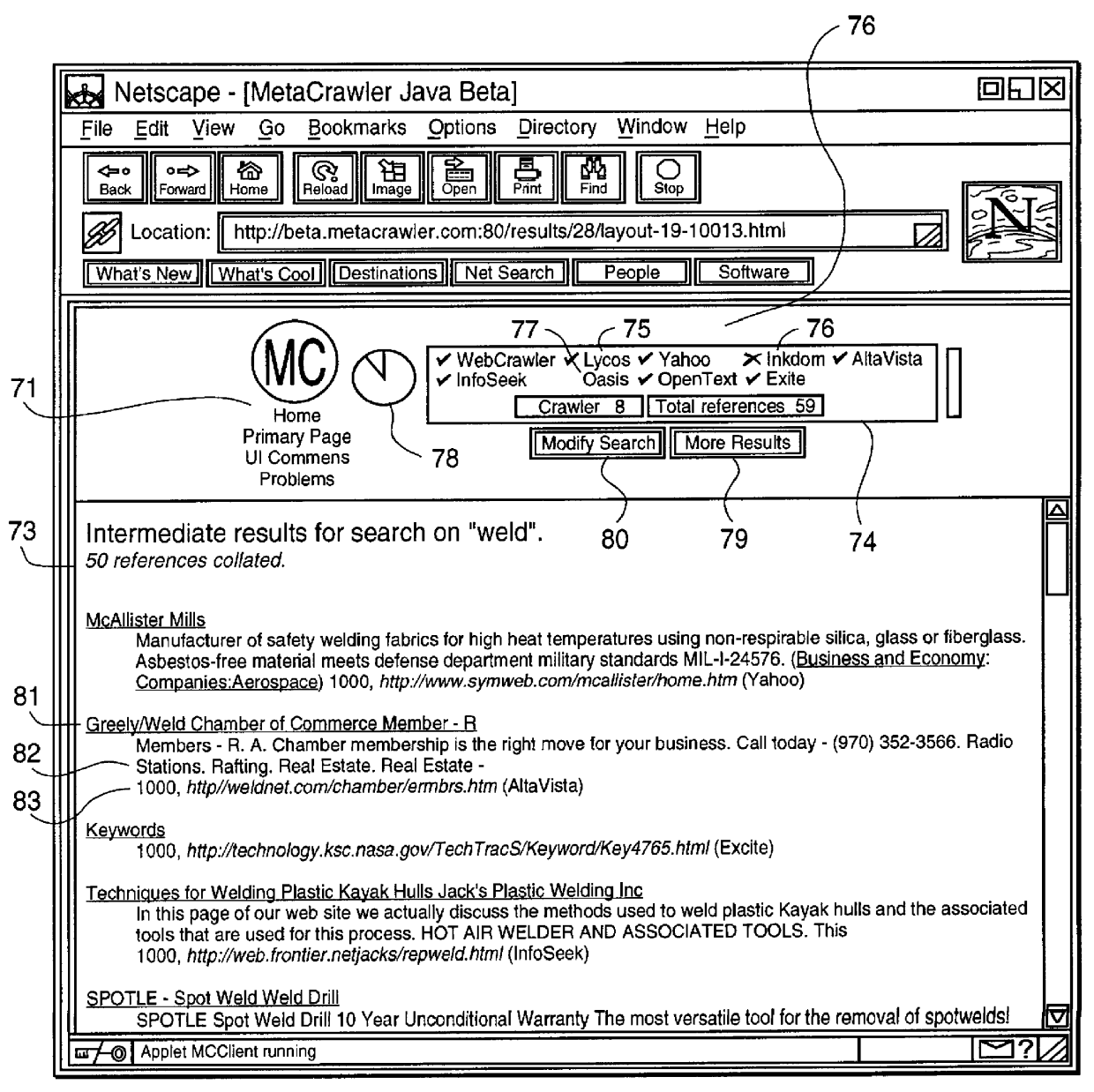
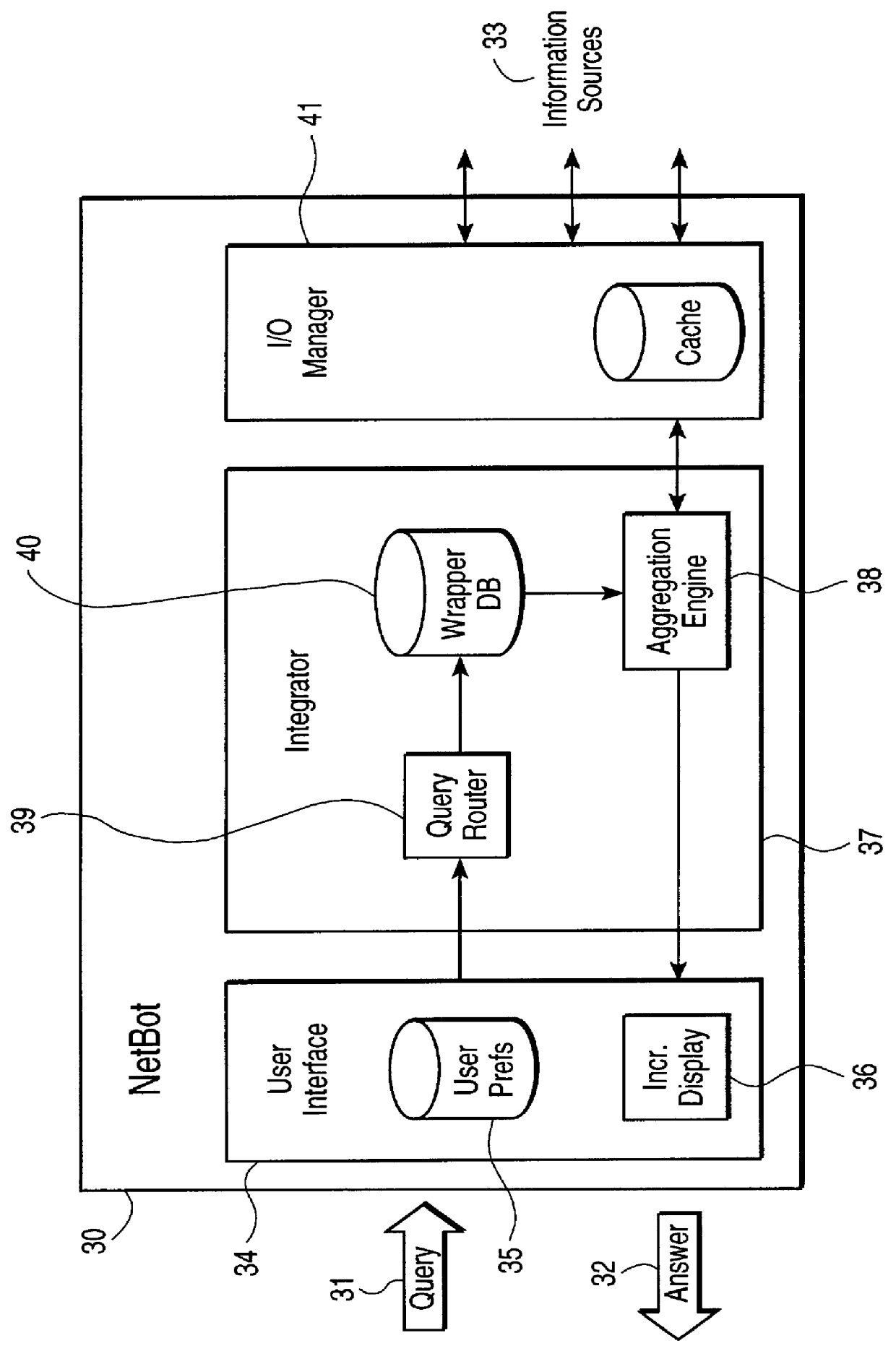
Method and system using information written in a wrapper description language to execute query on a network
InactiveUS6085186AEasy to understandEasy maintenanceData processing applicationsWeb data indexingAccess networkNetwork connection
This invention provides assistance to a user in accessing network attached information sources. In one aspect, the invention is a method for intelligently routing a user query to information sources relevant to that query, extracting relevant data fields from received responses, and intelligently presenting the extracted data in order of estimated relevance. The system of this invention implements one or more steps of the method in a centralized or distributed manner on one or more network attached computers. Further, this invention provides a novel language and implementation that facilitates easily written and maintained descriptions of information source query and response formats.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST
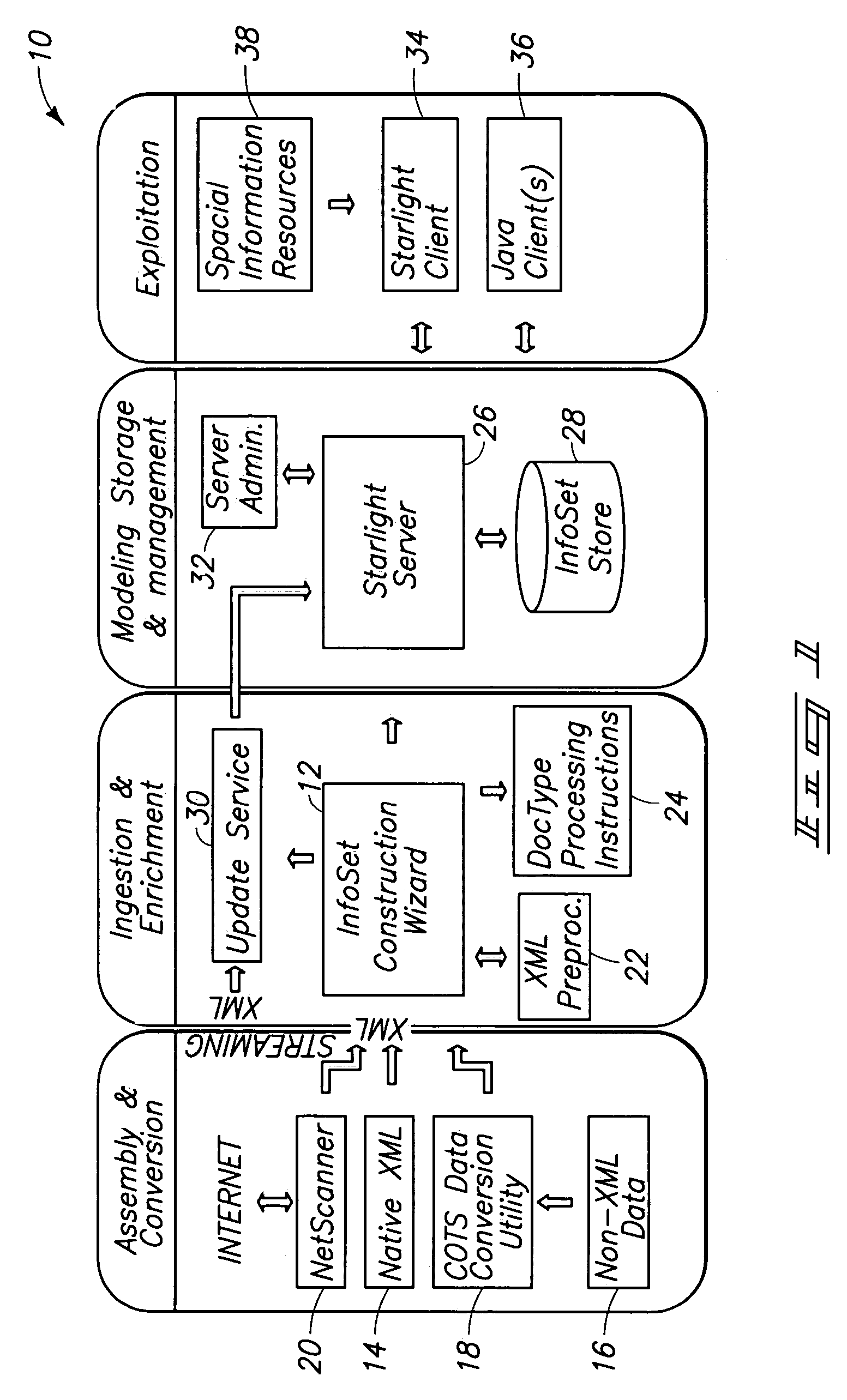
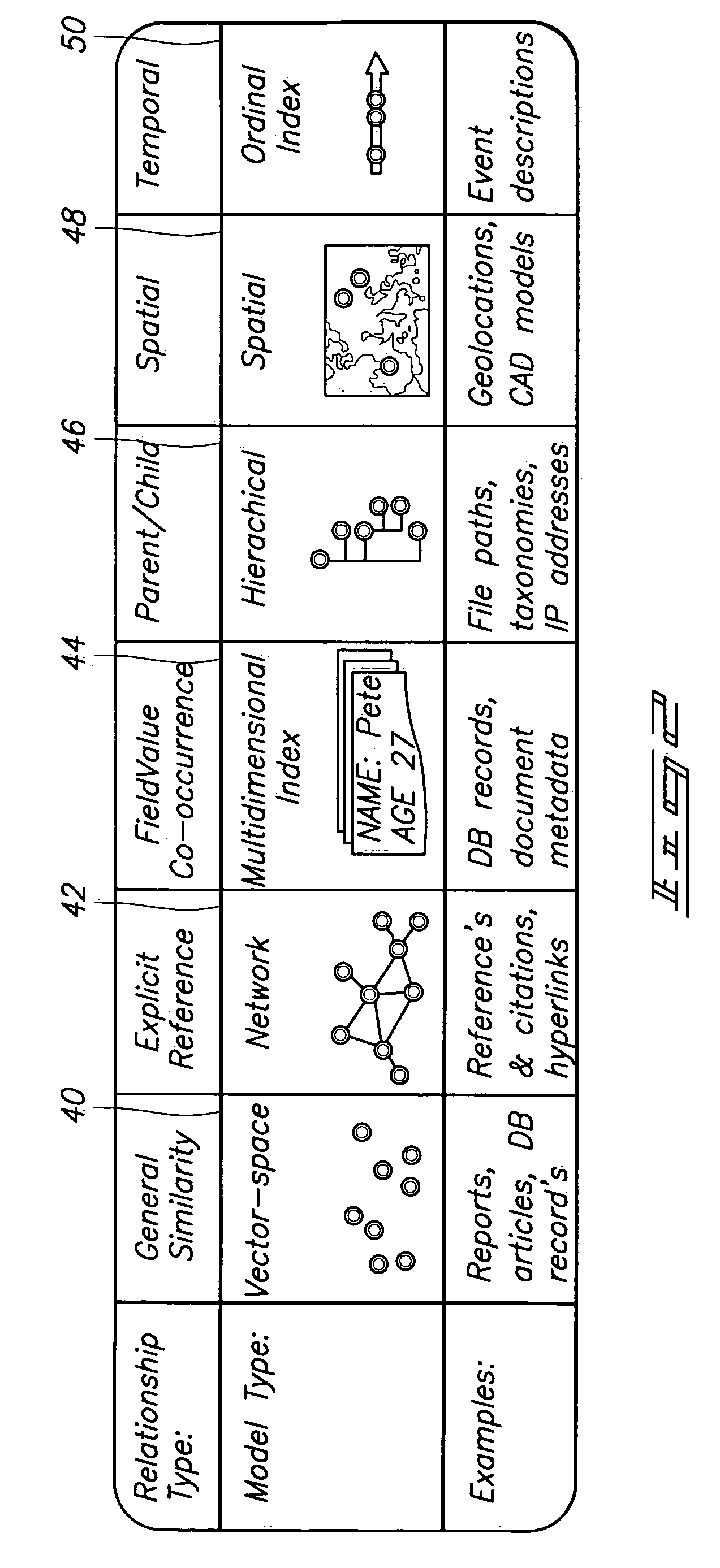
Multidimensional structured data visualization method and apparatus, text visualization method and apparatus, method and apparatus for visualizing and graphically navigating the world wide web, method and apparatus for visualizing hierarchies
A method of displaying correlations among information objects comprises receiving a query against a database; obtaining a query result set; and generating a visualization representing the components of the result set, the visualization including one of a plane and line to represent a data field, nodes representing data values, and links showing correlations among fields and values. Other visualization methods and apparatus are disclosed.
Owner:BATTELLE MEMORIAL INST
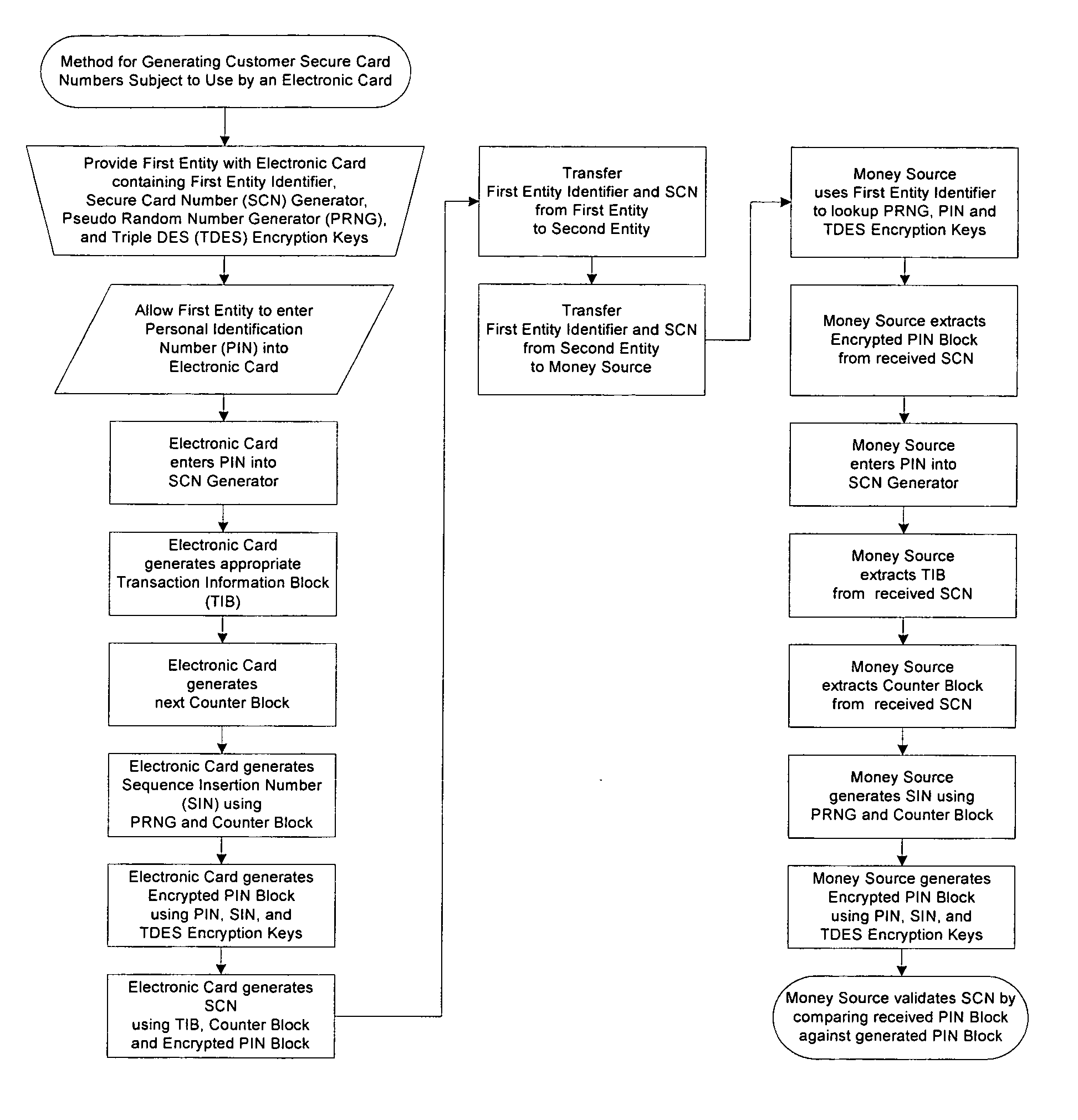
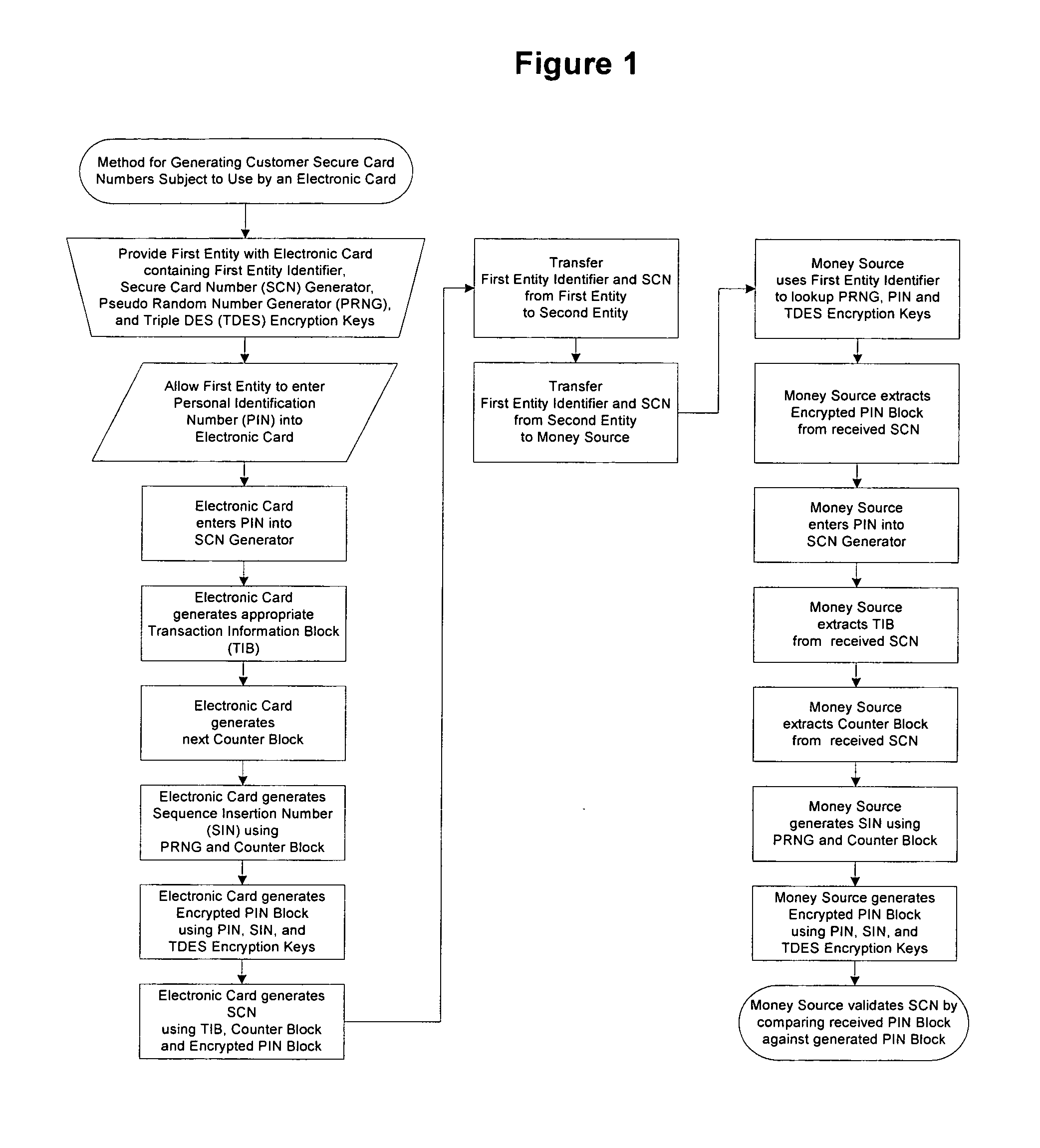
Method for generating customer secure card numbers
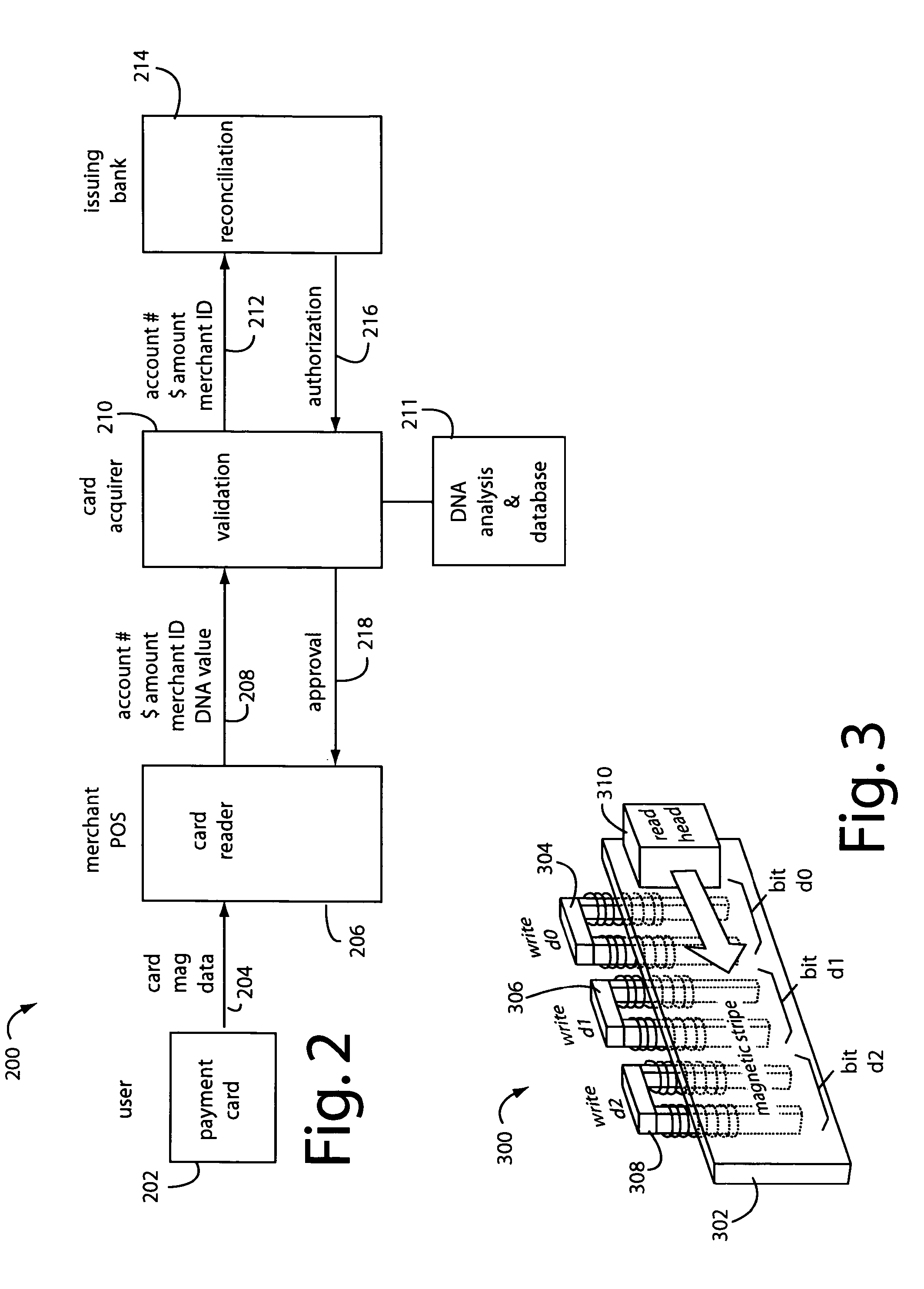
A method for providing secure transactions generates a Secure Card Number (“SCN”) for a first entity that is transferred with a first entity identifier to a second entity and then to a money source that verifies that the transaction is valid by use of the first entity identifier and the SCN. The SCN includes a 0Transaction Information Block (“TIB”), a Counter Block, and an encrypted Personal Identification Number (“PIN”) Block. The SCN is transferred to the money source in an account number or a non-account data field. The money source can use the TIB to determine whether the SCN should be used once or multiple times or to identify one of several physical devices, all of which are issued to the first entity, used to generate the SCN. The money source validates the SCN by duplicating the encryption process used to create an encrypted PIN Block and comparing the result to the encrypted PIN Block received with the transaction. A Triple Data Encryption Standard algorithm encrypts a PIN Block generated from a PIN, a Sequence Insertion Number (“SIN”) and a known starting value. The SIN can be a combination of three seed values and a random value generated by a Pseudo Random Number Generator (“PRNG”) initialized with the seed values. A Counter value is associated with the Counter Block and the seed values.
Owner:PRIVASYS
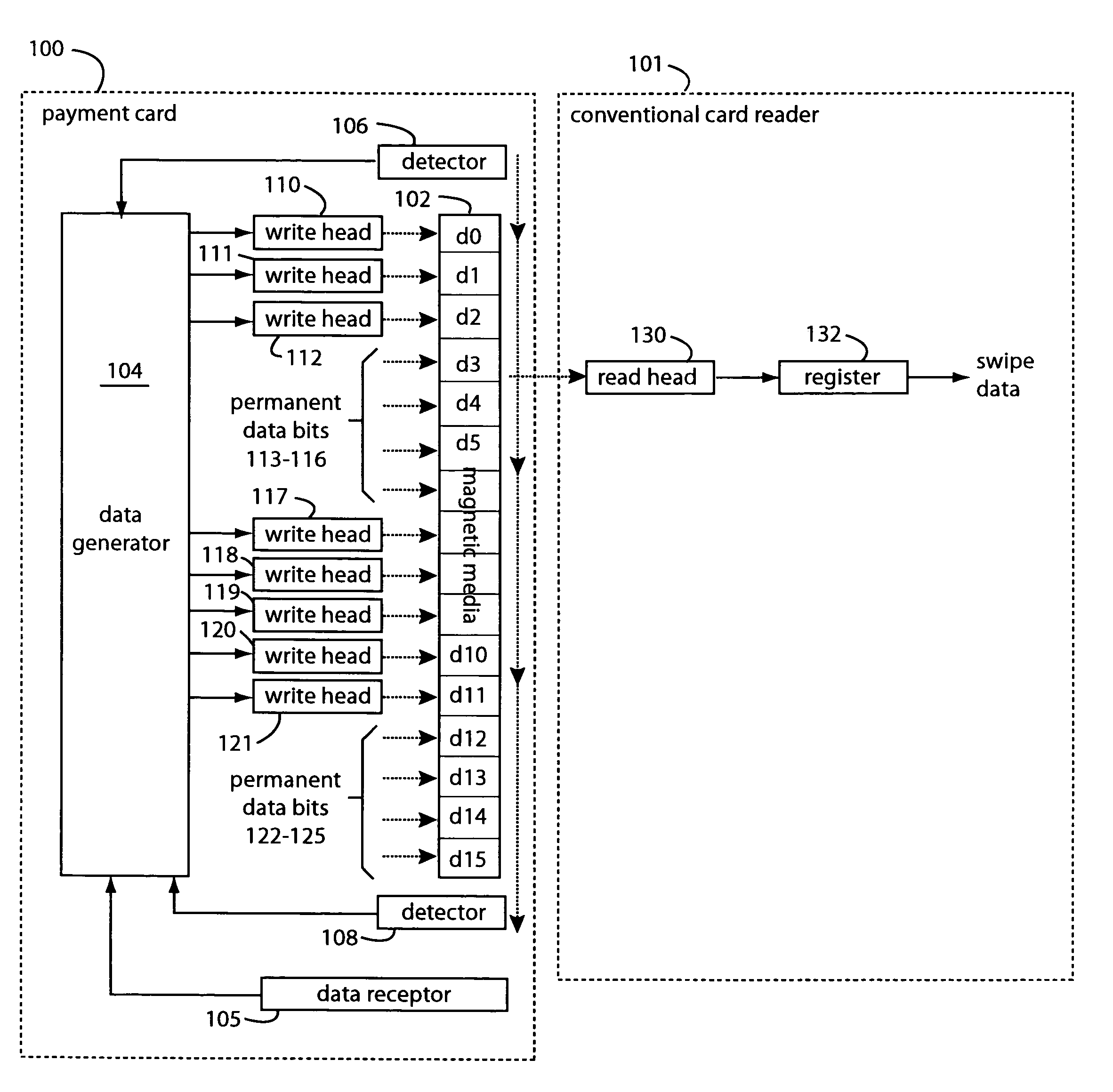
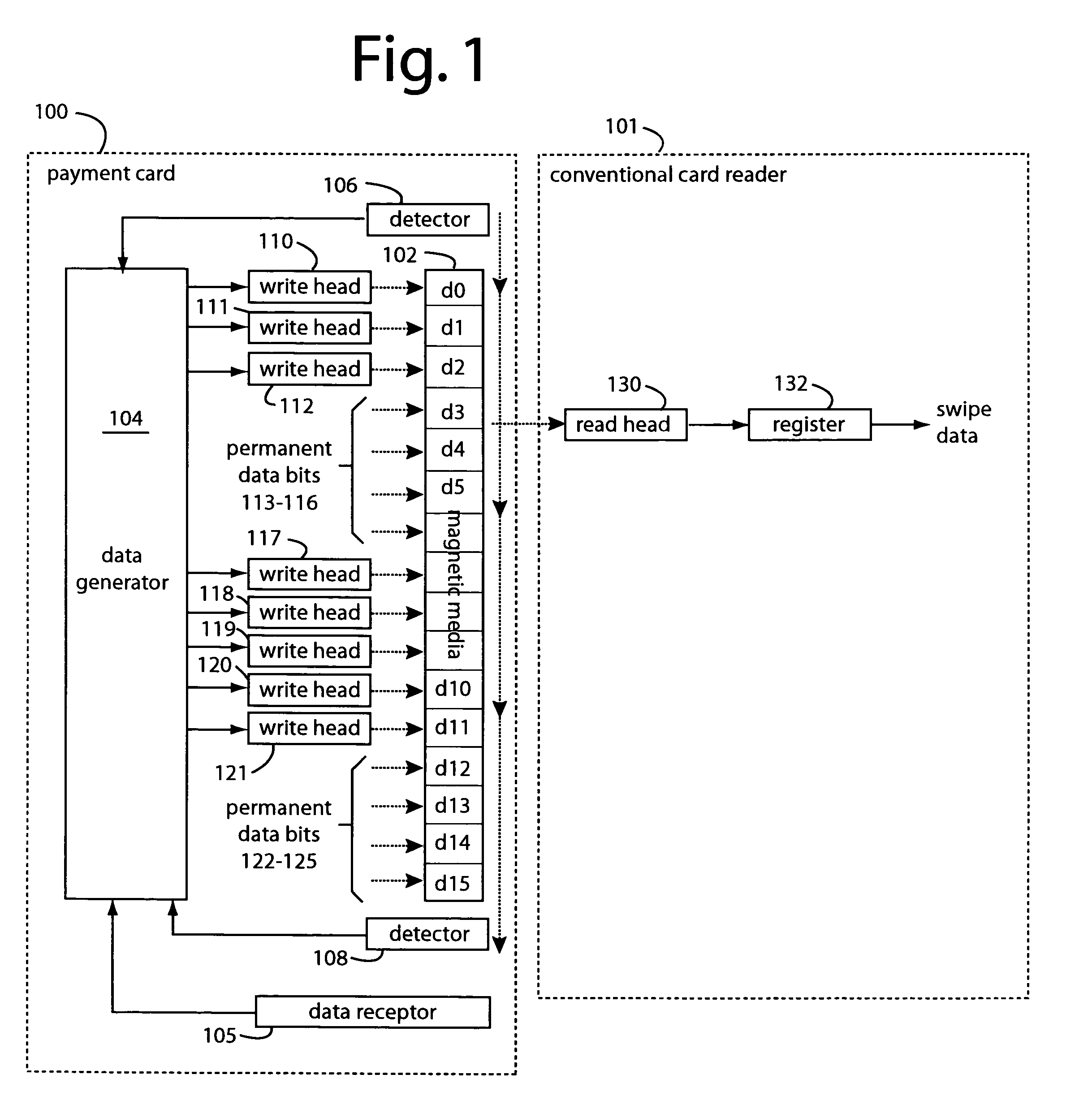
Programmable magnetic data storage card
ActiveUS7044394B2Reduce financial riskSimple and inexpensive and effectiveAcutation objectsApparatus for flat record carriersMicrocomputerComing out
A payment card comprises a plastic card with a magnetic stripe for user account data. Internal to the plastic card, and behind the magnetic stripe, a number of fixed-position magnetic write heads allow the user account data to be automatically modified. For example, a data field that counts the number of times the card has been scanned is incremented. A payment processing center keeps track of this usage-counter data field, and will not authorize transaction requests that come out of sequence. For example, as can occur from a magnetic clone of a card that has been skimmed and tried later. A card-swipe detector embedded in the plastic card detects each use in a scanner, and it signals an internal microcomputer which changes data bits sent to the write heads. Once scanned, the payment card can also disable any reading of the user account data for a short fixed period of time.
Owner:FITBIT INC
Associative database model for electronic-based informational assemblies
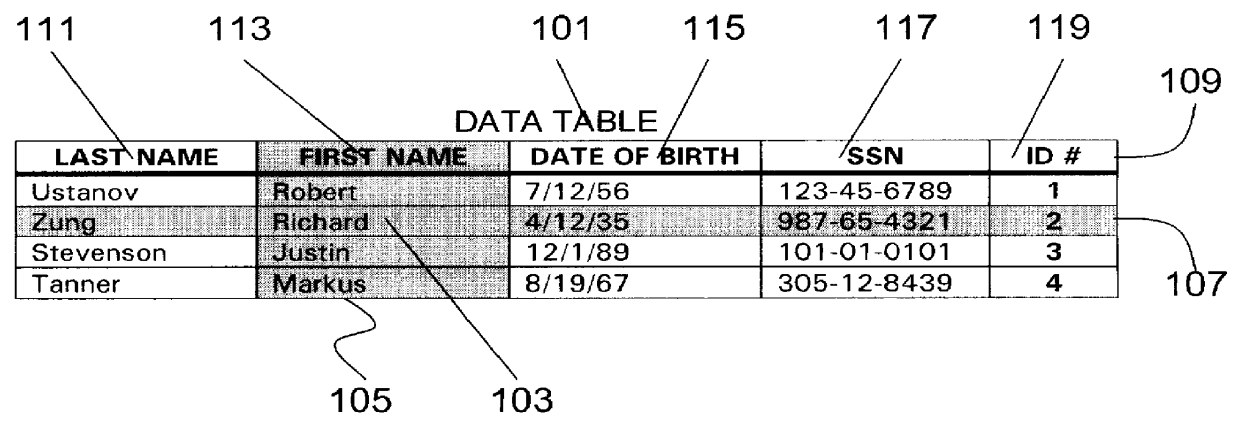
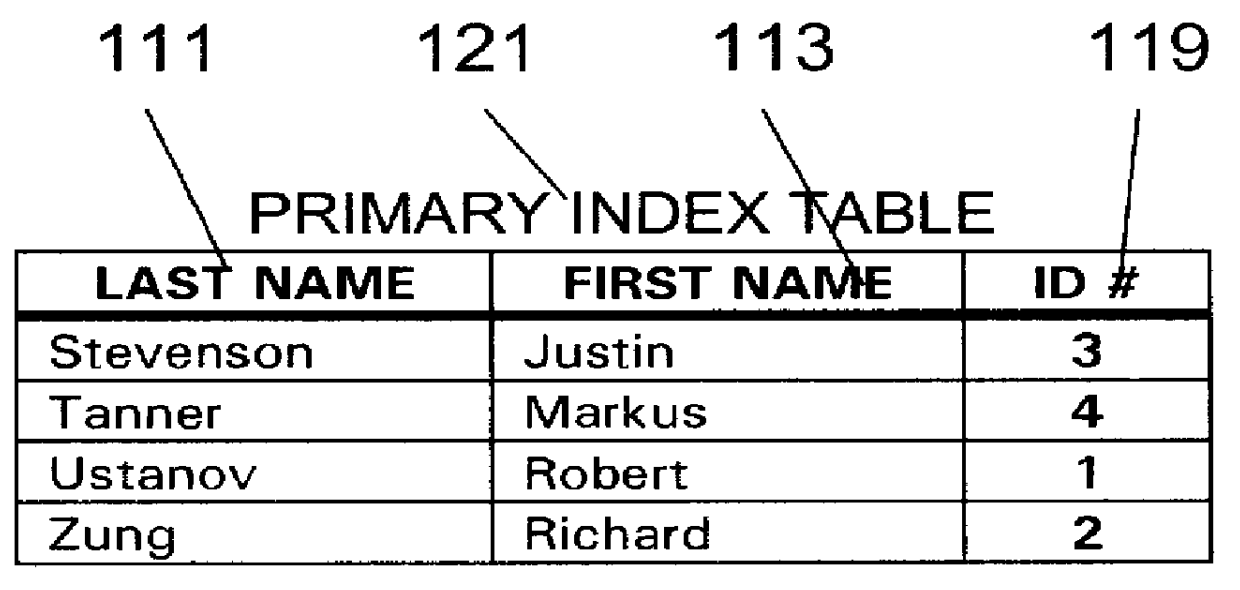
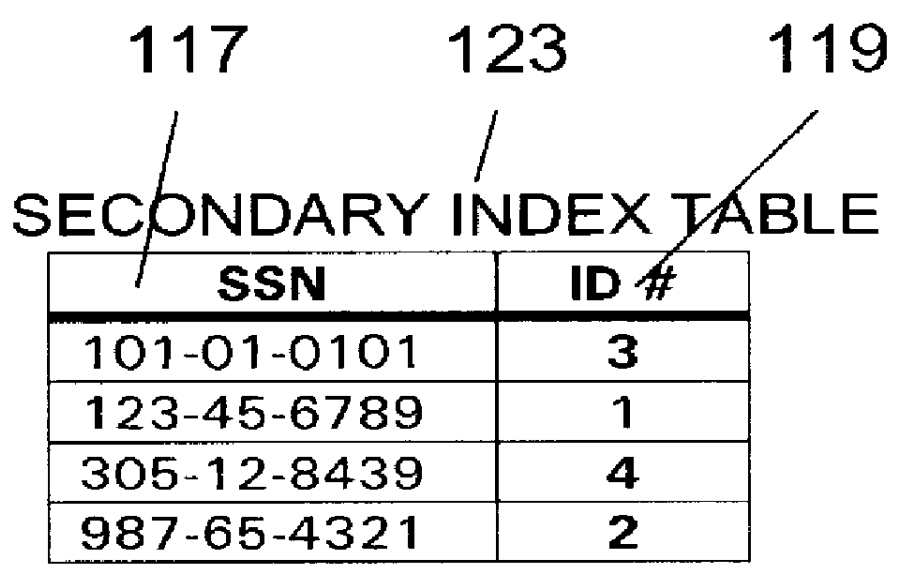
InactiveUS6112209AHigh degree of orderData processing applicationsRelational databasesData setData field
An indexing system and linking method for an assembly of electronic-based informational items stored in and ordered by a plurality of records uniquely identified over a plurality of relational data tables making up a data set wherein each table is assigned a unique domain of unique alphanumeric indicia for assignment and storage in the records. The records are ordered by the alphanumeric indicia whereby each data table acts as its own primary key. The records are bi-directionally linked to each other via a plurality of separate, central linking table indexes wherein each index record is structured with a plurality of linking fields defined to store sets of two or more alphanumeric indicia belonging to a plurality of records in the data set. Each record is further structured to include an internal set of unique indicum for each data field whereby the combination of the unique record indicum and the unique field indicum uniquely identify each record-field over the plurality of relational data tables making up the data set such that each record field may be linked to a plurality of other record-fields or records via the plurality of separate, central linking table indexes. Each central linking table indexes is further generalized to provide multiple arrays of linking indicia in a plurality of indexing fields such that a plurality of the records from a plurality of the data tables may be linked together as a data cluster. The linking values stored in the central linking table indexes may be predefined to automatically structure and link a plurality of unspecified data and changes in the data may alter the linking structure to provide further capabilities.
Owner:GUSACK MARK DAVID
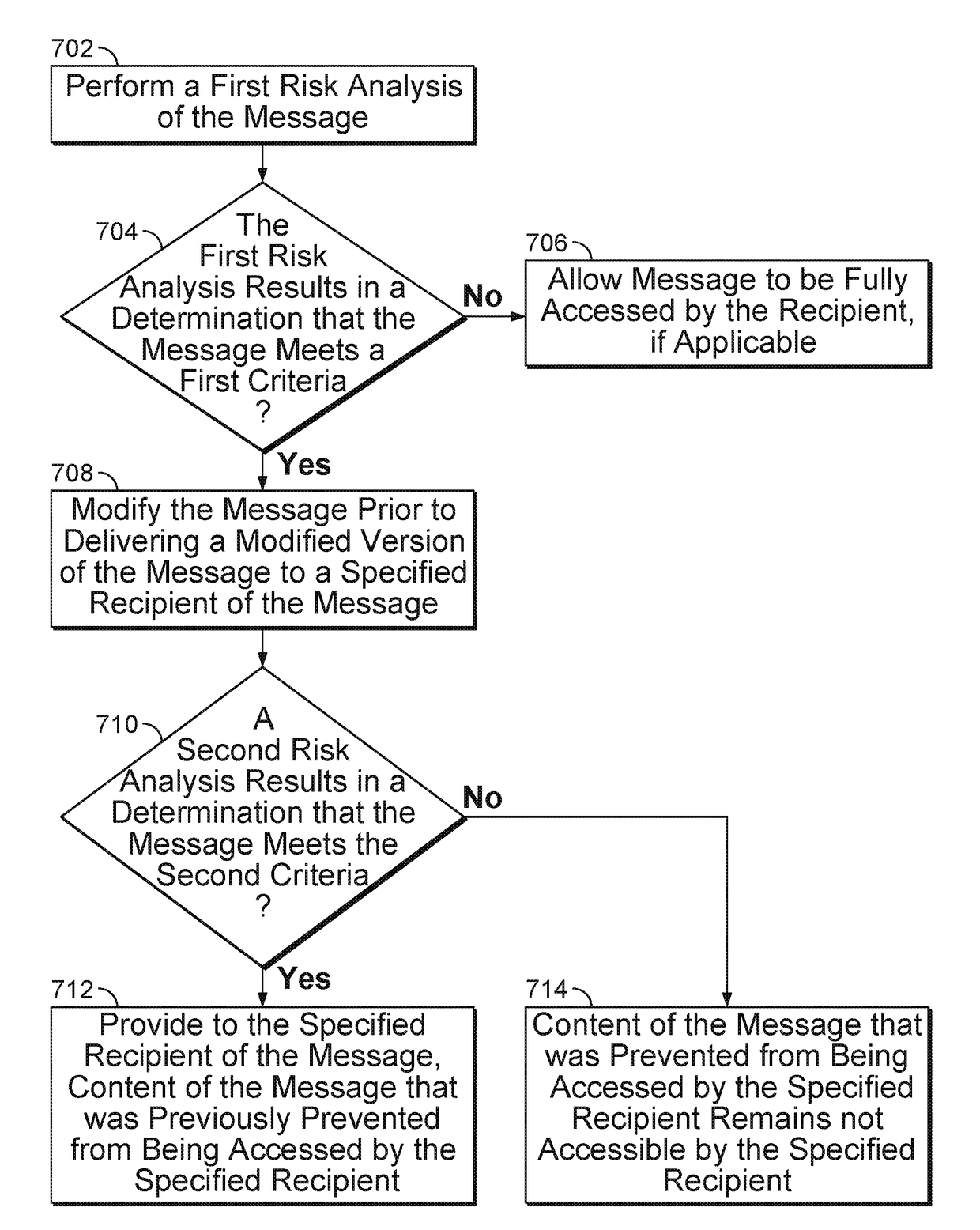
Mitigating communication risk by detecting similarity to a trusted message contact
A measure of similarity between an identifier of a sender of the message and each identifier of one or more identifiers of each trusted contact of a plurality of trusted contacts of a recipient of the message is determined. In the event the sender of the message is not any of the trusted contacts but at least one of the measure of similarity between the identifier of the sender of the message and a selected identifier of a selected trusted contact of the plurality of trusted contacts meets a threshold, the message is modified, if applicable, to alter content of a data field that includes an identification of the sender of the message. The data field is one of a plurality of data fields included in a header of the message.
Owner:AGARI DATA INC
Method and system using information written in a wrapper description language to execute query on a network
InactiveUS6102969AEasy to understandEasy maintenanceData processing applicationsWeb data indexingAccess networkNetwork connection
This invention provides assistance to a user in accessing network attached information sources. In one aspect, the invention is a method for intelligently routing a user query to information sources relevant to that query, extracting relevant data fields from received responses, and intelligently presenting the extracted data in order of estimated relevance. The system of this invention implements one or more steps of the method in a centralized or distributed manner on one or more network attached computers. Further, this invention provides a novel language and implementation that facilitates easily written and maintained descriptions of information source query and response formats.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST
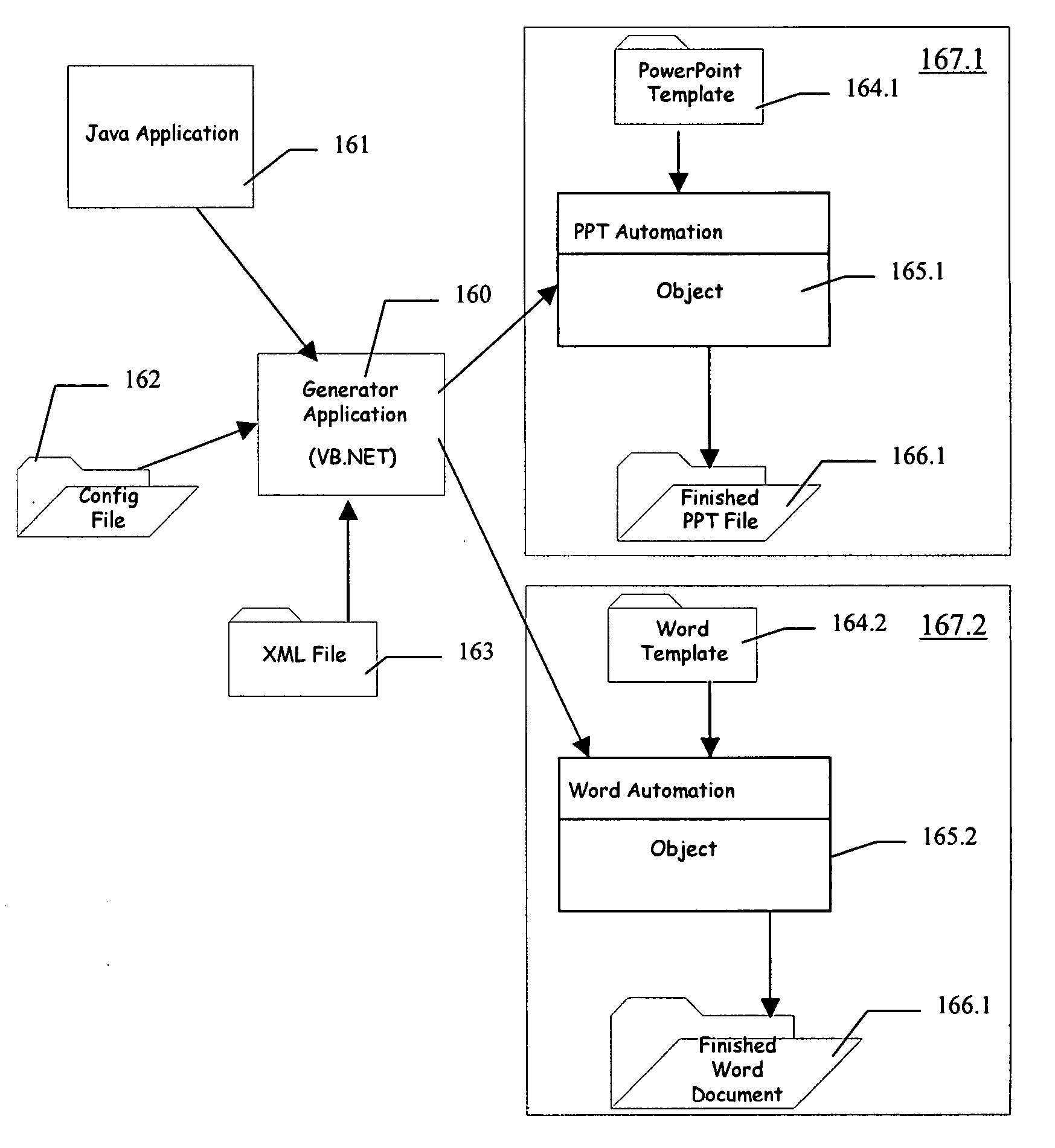
Presentation generator
A presentation generator may access one or more data sources structured into data fields. The user may create or modify a template by inserting one or more tags corresponding to data fields in the template. The template may also have one or more processing instructions for indicating the data sources and how the data sources should be queried. The processing instructions may also indicate how the data is to be grouped across various slides, pages, sections, etc. The generator may build the presentation based on the template, its tags, and its processing instructions. The resulting presentation may be accessed by a user-friendly application, such as a word processor, slide program, spreadsheet, report viewer, or other application. The user may update part or all of the presentation using information on the queries and data sources embedded in the presentation itself.
Owner:ACCENTURE GLOBAL SERVICES LTD
System and method for selectively allowing the passage of a guest through a region within a coverage area
InactiveUS6873260B2Electric signal transmission systemsMultiple keys/algorithms usageControl signalData field
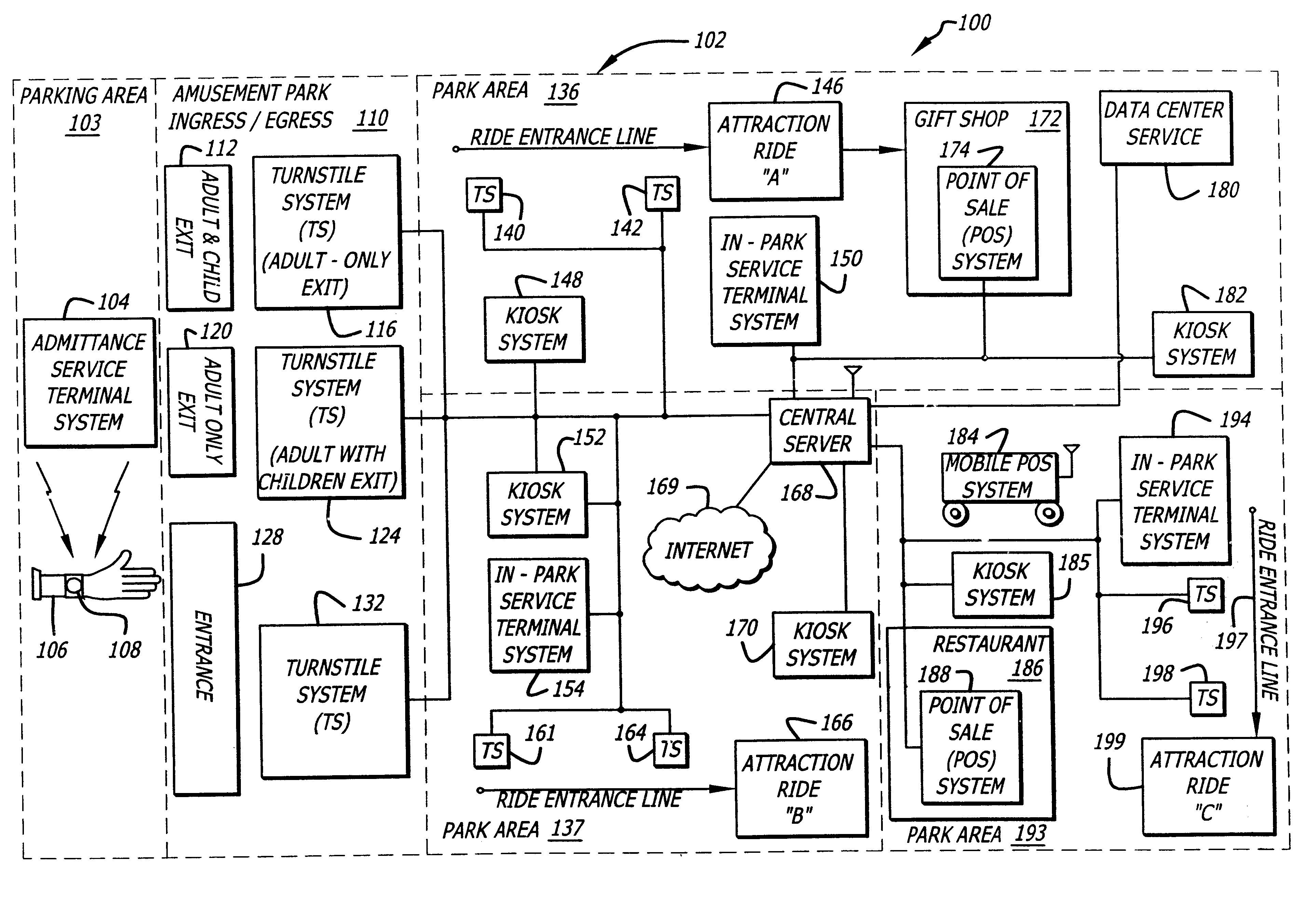
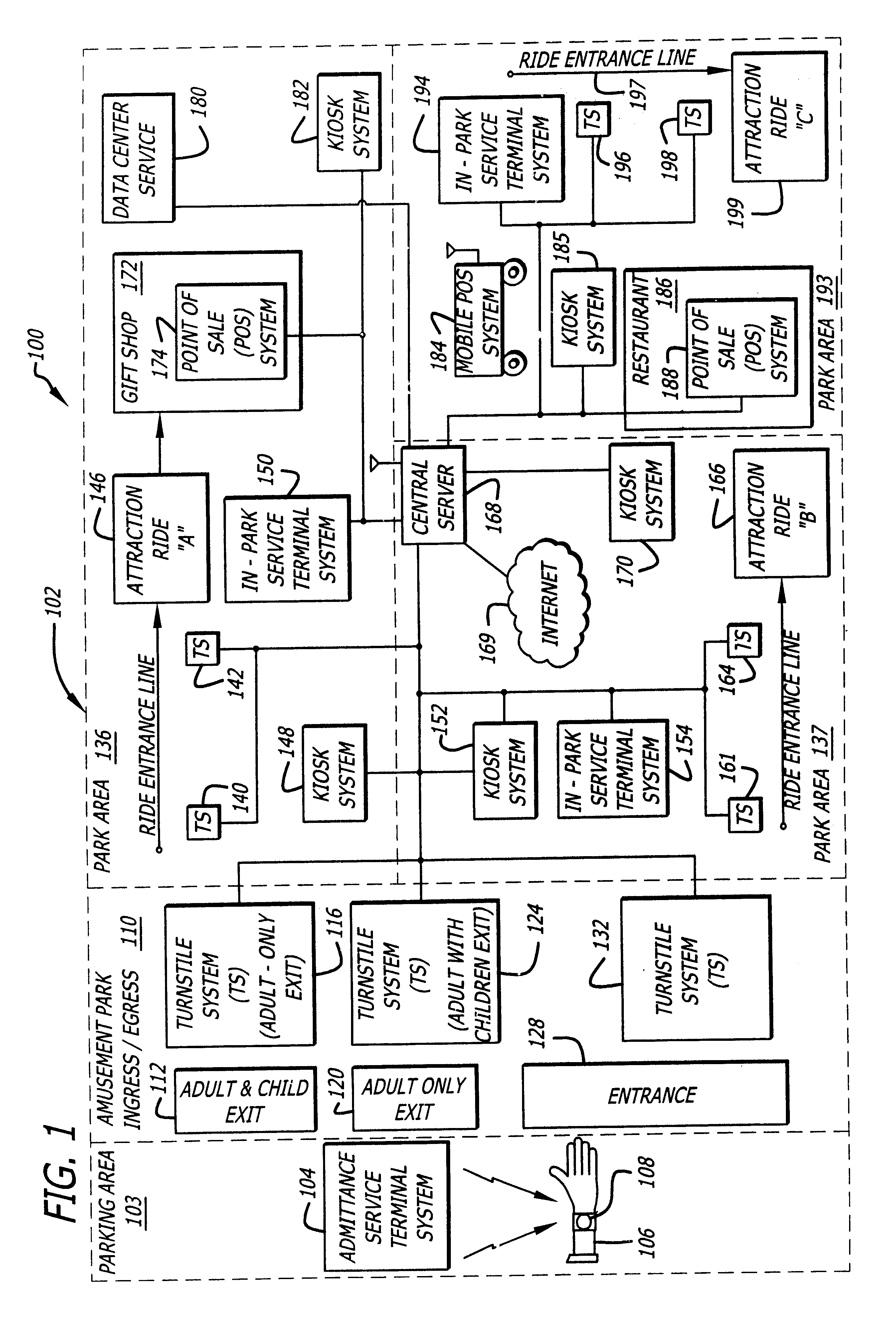
A system and method for selectively allowing the passage of a guest through a region within at a coverage area. The system includes a turnstile system having an RFID reader, a network interface, an entry mechanism and a processor, and a central server having a network interface, a non-volatile memory, and a processor. An RFID reader reads a tag identifier from an RFID tag worn by a guest. The tag identifier is transmitted from the turnstile system to the central server. The central server processor access a guest data object using the tag identifier and reads a data field containing information related to the guest. Based on this information, the central server transmits a control signal to the turnstile system to activate its entry mechanism, thereby allowing the guest to pass through. The information may relate to monetary credits of the guest, statistical information of the guest, and restrictions, disabilities, health conditions and special access of the guest.
Owner:NOBLE LINDA +1
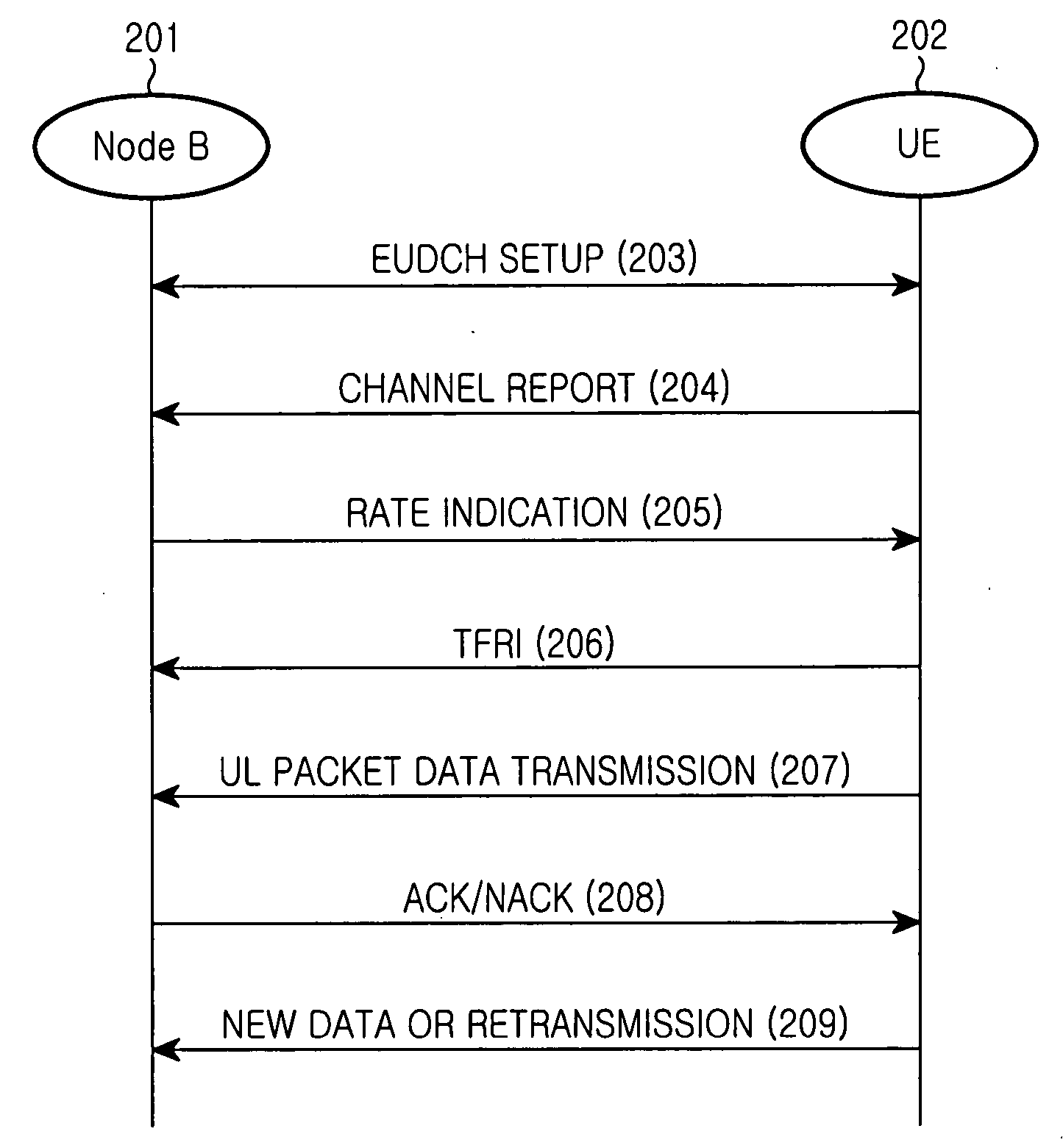
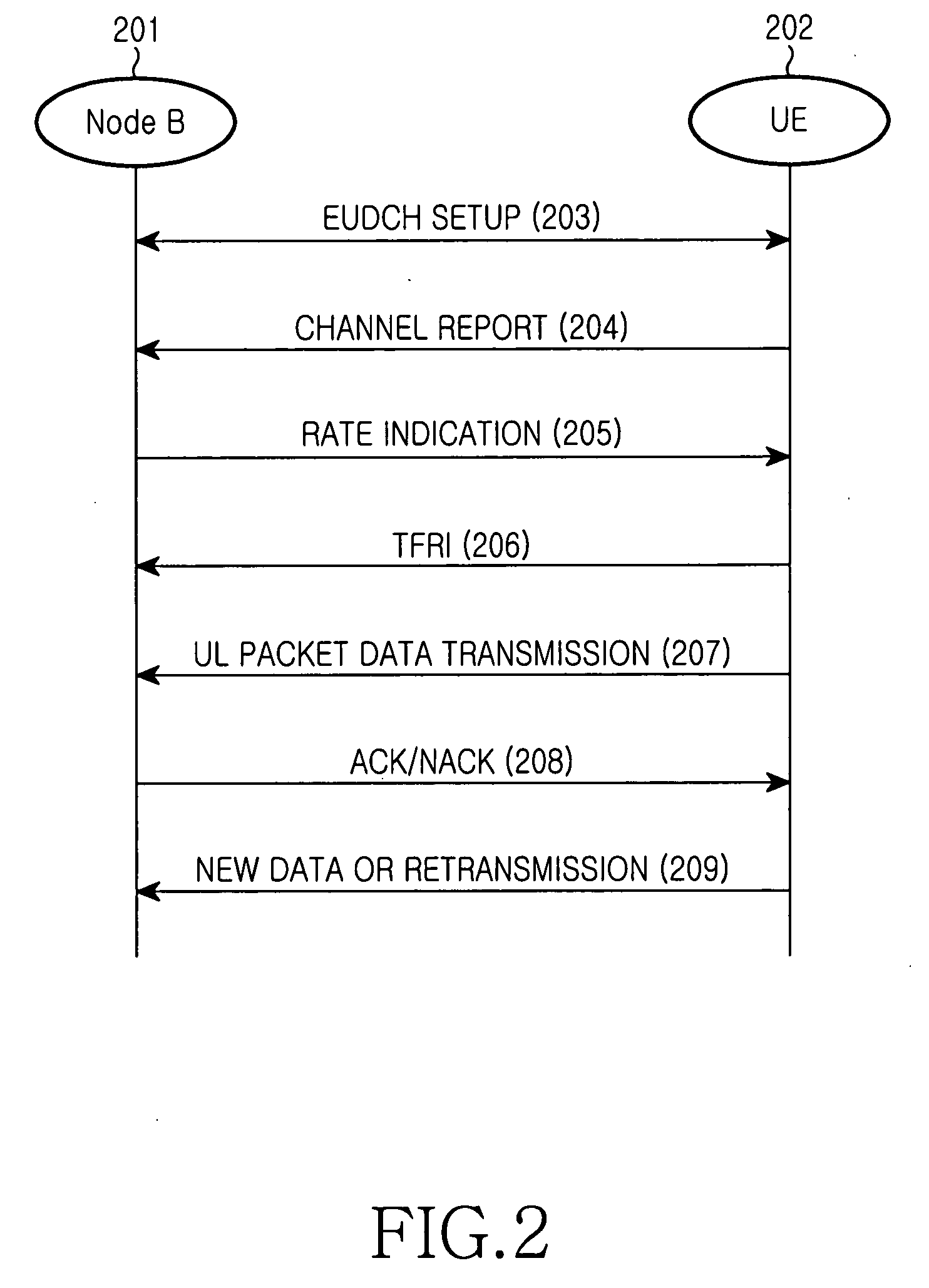
Apparatus and method for transmitting/receiving uplink data retransmission request in a CDMA communication system
InactiveUS20050013263A1Error prevention/detection by using return channelTransmission systemsCommunications systemUplink transmission
Disclosed is a code division multiple access (CDMA) communication system having a downlink dedicated physical channel (DL_DPCH) having a downlink dedicated physical control channel (DL_DPCCH) and a downlink dedicated physical data channel (DL_DPDCH). The DL_DPCCH having a transport power control (TPC) field transmitting a TPC command for controlling uplink transport power, a transport format combination indicator (TFCI) field transmitting TFCI indicating a transport format combination of a currently transmitted channel, and a pilot field transmitting a pilot. The DL_DPDCH has first and second data fields transmitting downlink data. If data is normally received over an enhanced uplink dedicated channel (EUDCH), ACK information is generated, and if data is abnormally received over the EUDCH, NACK information is generated. Bits corresponding to the ACK or NACK information are punctured at a position randomly selected from the first and second data fields of the DL_DPDCH, and the ACK or NACK information is inserted into the punctured position before being transmitted.
Owner:SAMSUNG ELECTRONICS CO LTD
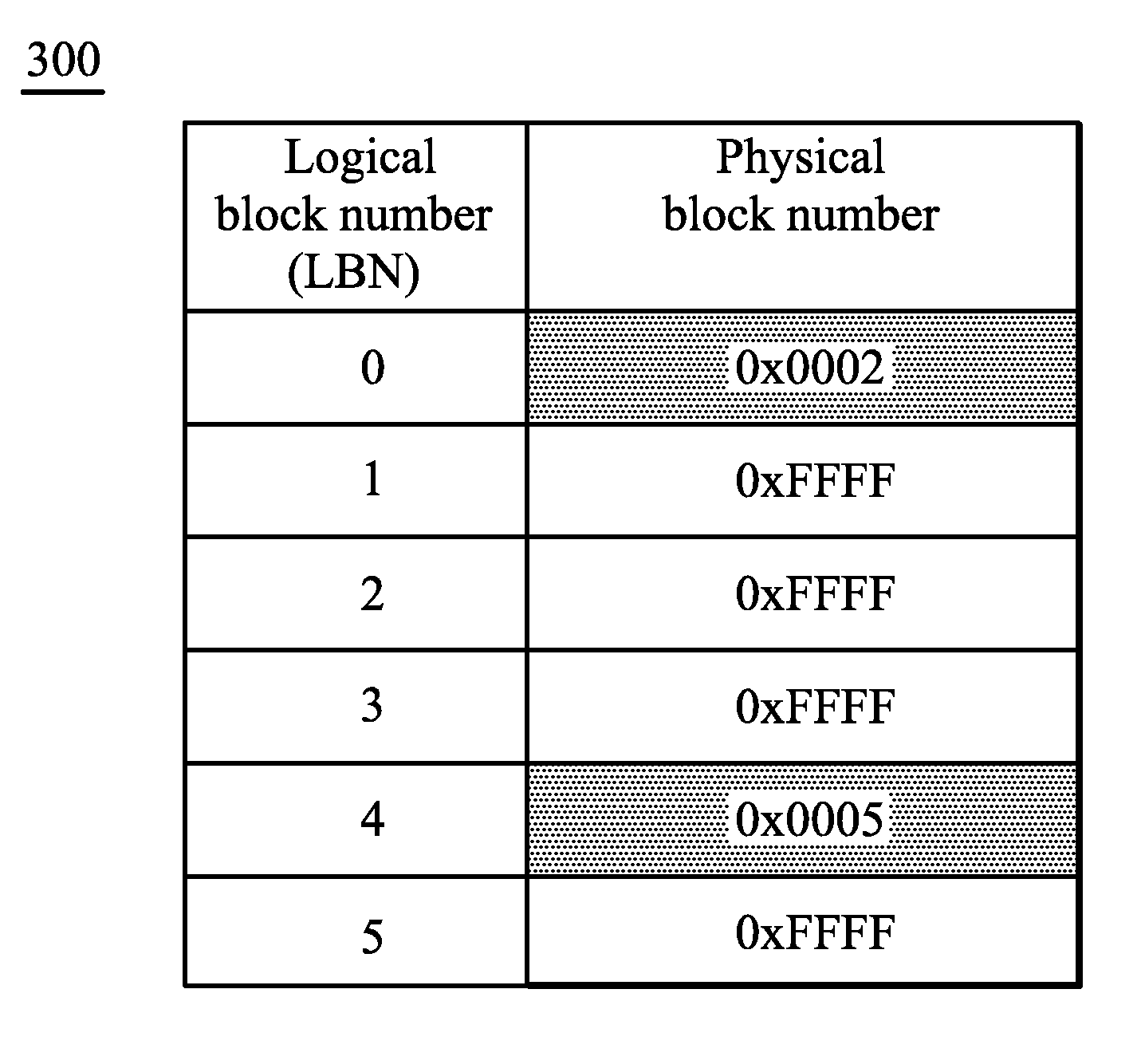
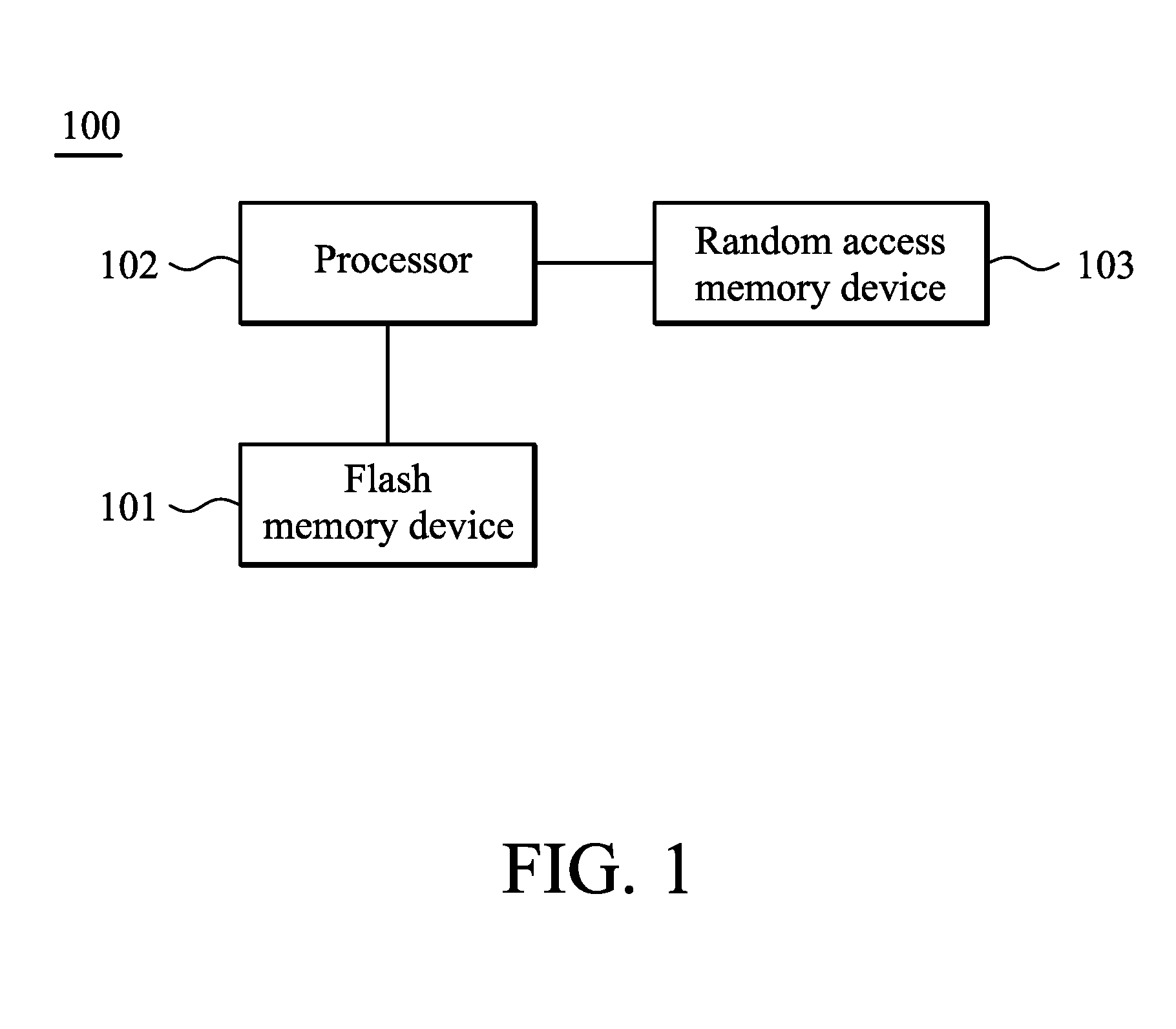
Computing systems and methods for managing flash memory device
InactiveUS20100287327A1Memory architecture accessing/allocationMemory adressing/allocation/relocationRandom access memoryData field
A computing system is provided. A flash memory device includes at least one mapping block, at least one modification block and at least one cache block. A processor is configured to perform: receiving a write command with a write logical address and predetermined data, loading content of a cache page from the cache block corresponding to the modification block according to the write logical address to a random access memory device in response to that a page of the mapping block corresponding to the write logical address has been used, the processor, reading orderly the content of the cache page stored in the random access memory device to obtain location information of an empty page of the modification block, and writing the predetermined data to the empty page according to the location information. Each cache page includes data fields to store location information corresponding to the data has been written in the pages of the modification block in order.
Owner:INTEL CORP
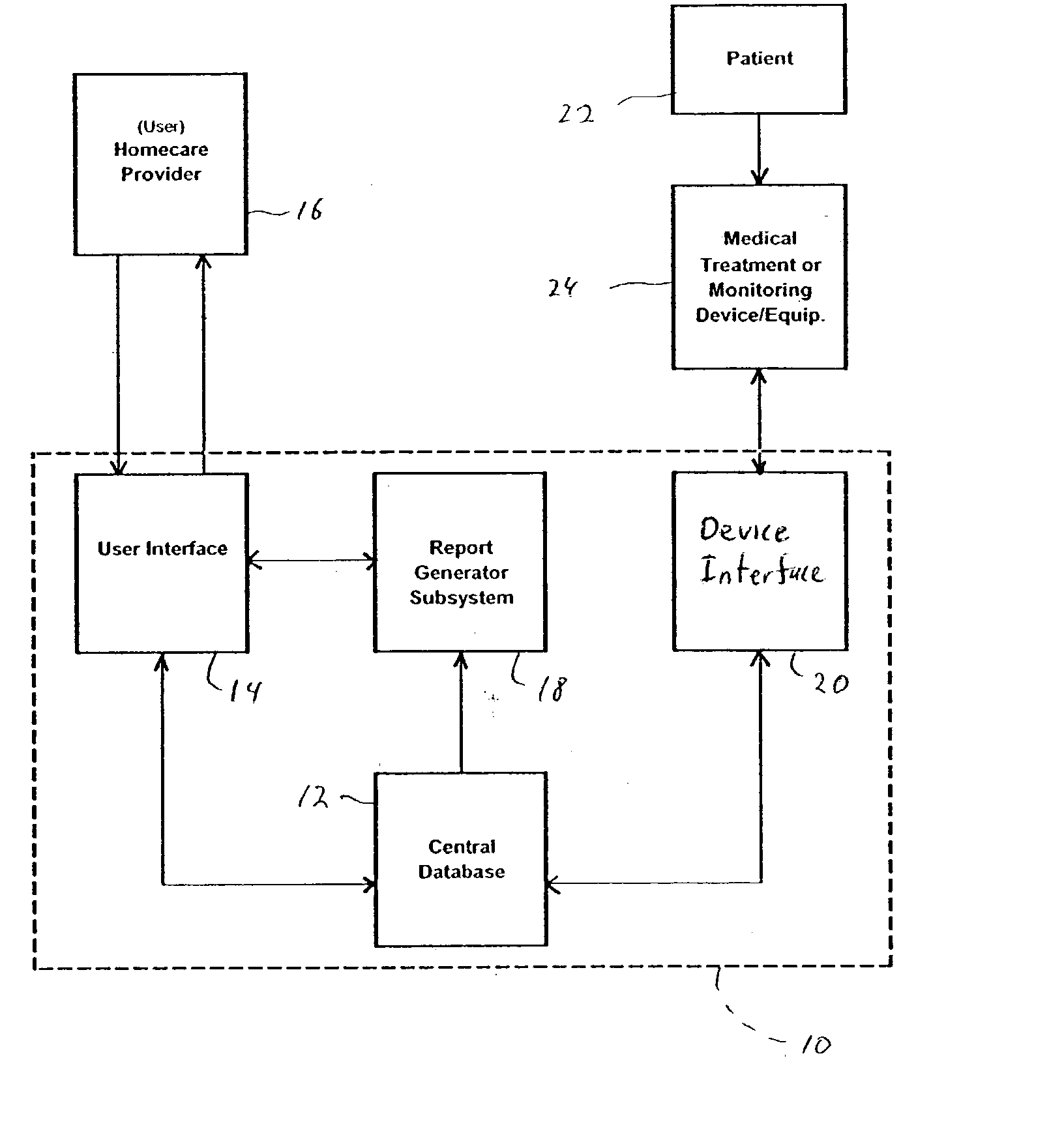
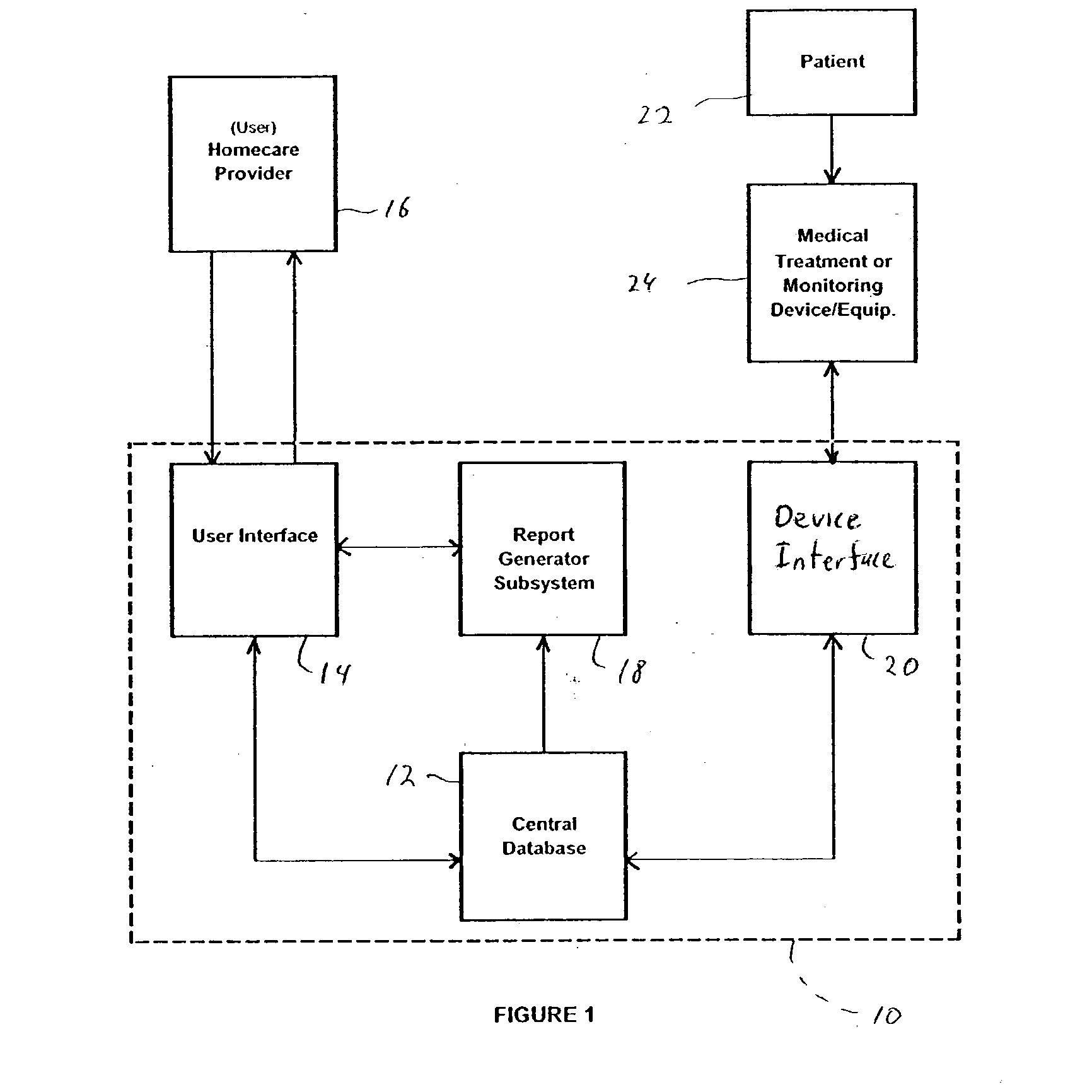
Method for managing medical information and medical information management system
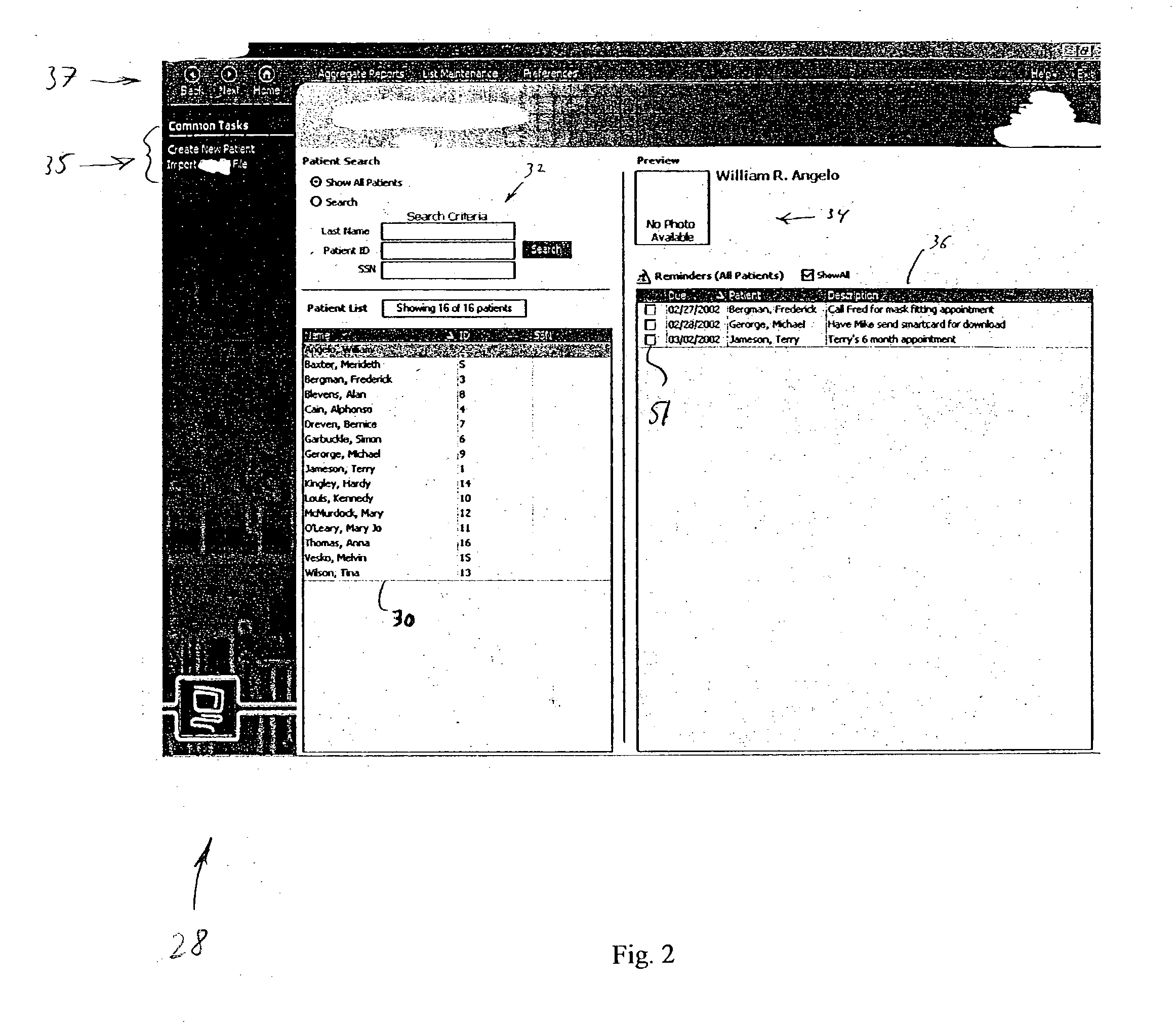
InactiveUS20030208465A1None of data is presentedEffective trackingMechanical/radiation/invasive therapiesDigital data processing detailsUser inputData field
A computer-implemented method for managing medical information that includes the steps of: providing a central database of information having disparate data fields containing data, and performing an action based upon the data in the disparate data fields. The method includes of sorting, providing warnings or reminders, searching, organizing, transmitting, and presenting data from the database. The medical information management system includes a central database resident on a computing system. The central database has multiple disparate data fields containing data pertaining to patient-related information. A user interface communicates with the central database for accepting user input and transmitting system output. A visual display also communicates with the user interface to display the disparate data fields in selected or selectable formats. The system can include a report generating module, a device interface, and a compliance calculation module, all of which are in communication with the central database.
Owner:RIC INVESTMENTS LLC
Consumer identity resolution based on transaction data
InactiveUS20140180826A1Complete banking machinesDiscounts/incentivesData processing systemTransaction data
According to an embodiment, a data processing system for facilitating consumer identity resolution comprises: a first logic module adapted to receive at least two collections of consumer records from at least two different sources; a second logic module adapted to compute first trust scores for first data fields of the first collection and second trust scores for second data fields of the second collection; a third logic module adapted to generate a master collection of consumer records comprising at least one master consumer record that is correlated to a record from the first collection and a record from the second collection, the correlation being based on at least on the trust scores; and a fourth logic module adapted to receive a set of contextual transaction data. The data processing system is adapted to identify a consumer based on the contextual transaction data and the master collection of consumer records.
Owner:QUOTIENT TECH INC
Electronic security system for monitoring and recording activity and data relating to persons
InactiveCN1833397ACo-operative working arrangementsSecuring communicationData fieldIdentification device
Owner:UNITED SECURITY APPL ID
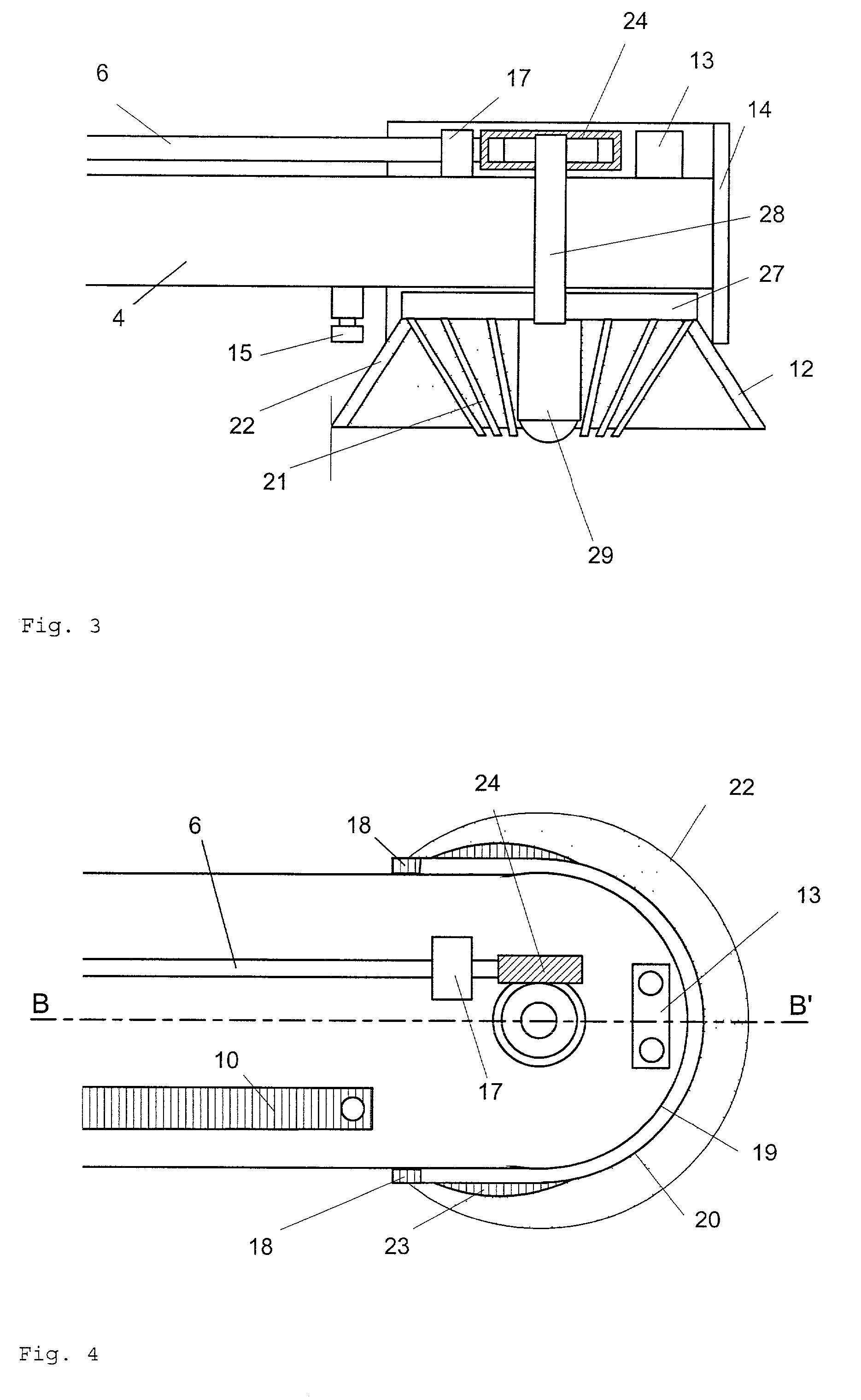
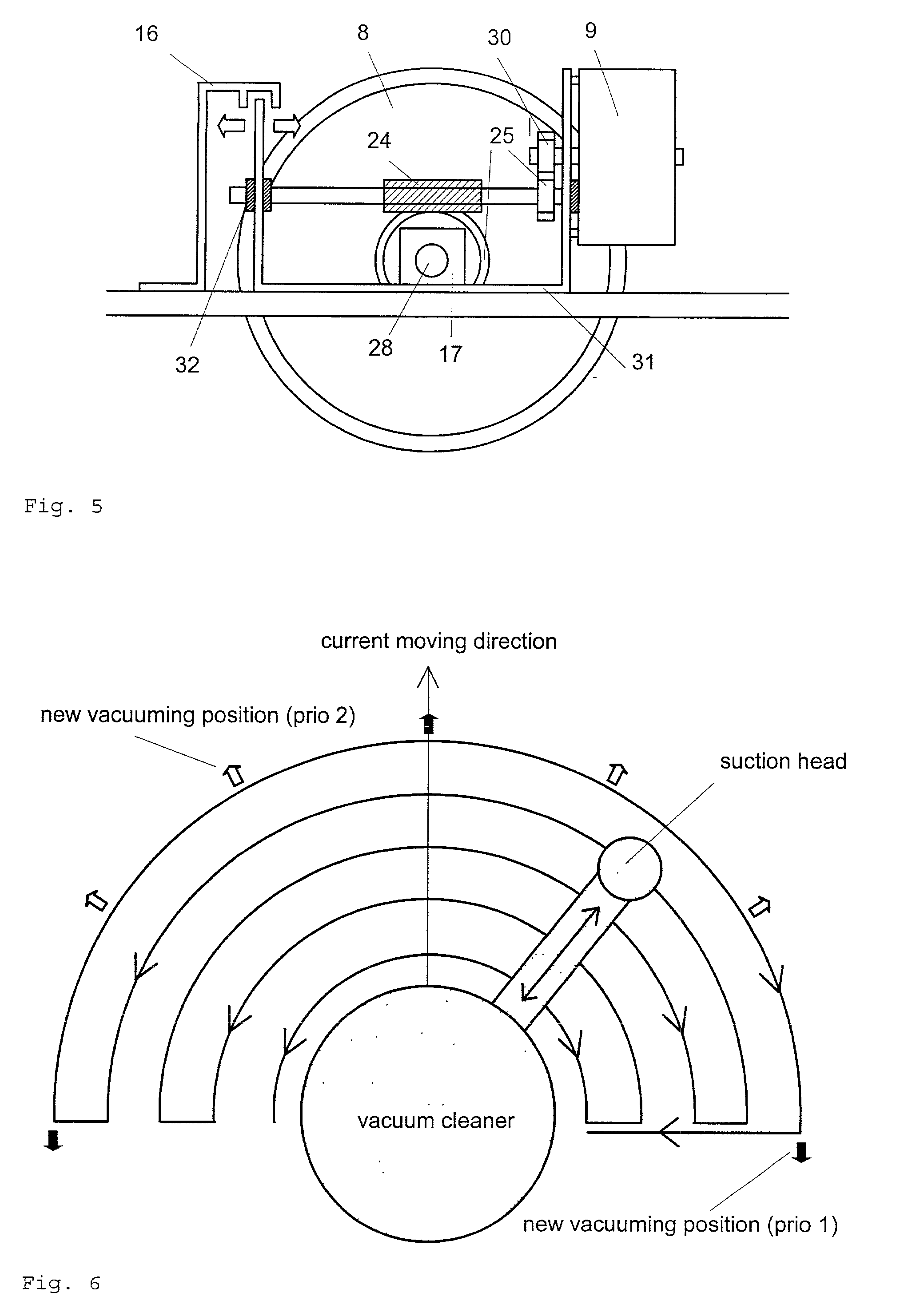
Service robot for the automatic suction of dust from floor surfaces
InactiveUS20010004719A1Automatic obstacle detectionTravelling automatic controlData fieldEngineering
The present invention is used for the complete and fully automatic examination of floor surfaces of all kind as well as for a particularly efficient suction of dust therefrom since the lower areas, the edges and the recessed can be detected. In each case, the robot is controlled so as to explore the adjacent area and to detect the potential obstacles using special sensors before storing them in a data field. The displacement towards a new location is then carried out using the stored data until the whole accessible surface has been covered. One of the main constituent members of the robot consists of an extensible arm that rests on the robot and on which contact and range sensors are arranged. When the robot is used as an automatic vacuum cleaner, an air flow is forced into the robot arm and the -cleaning effect can further be enhanced by providing one or more Circular rotary brushes at the front end of the arm. This invention can essentially be used for domestic or industrial Cleaning purposed with a view to replace traditional vacuum cleaners.
Owner:TECHN FACHHOCHSCHULE BERLIN
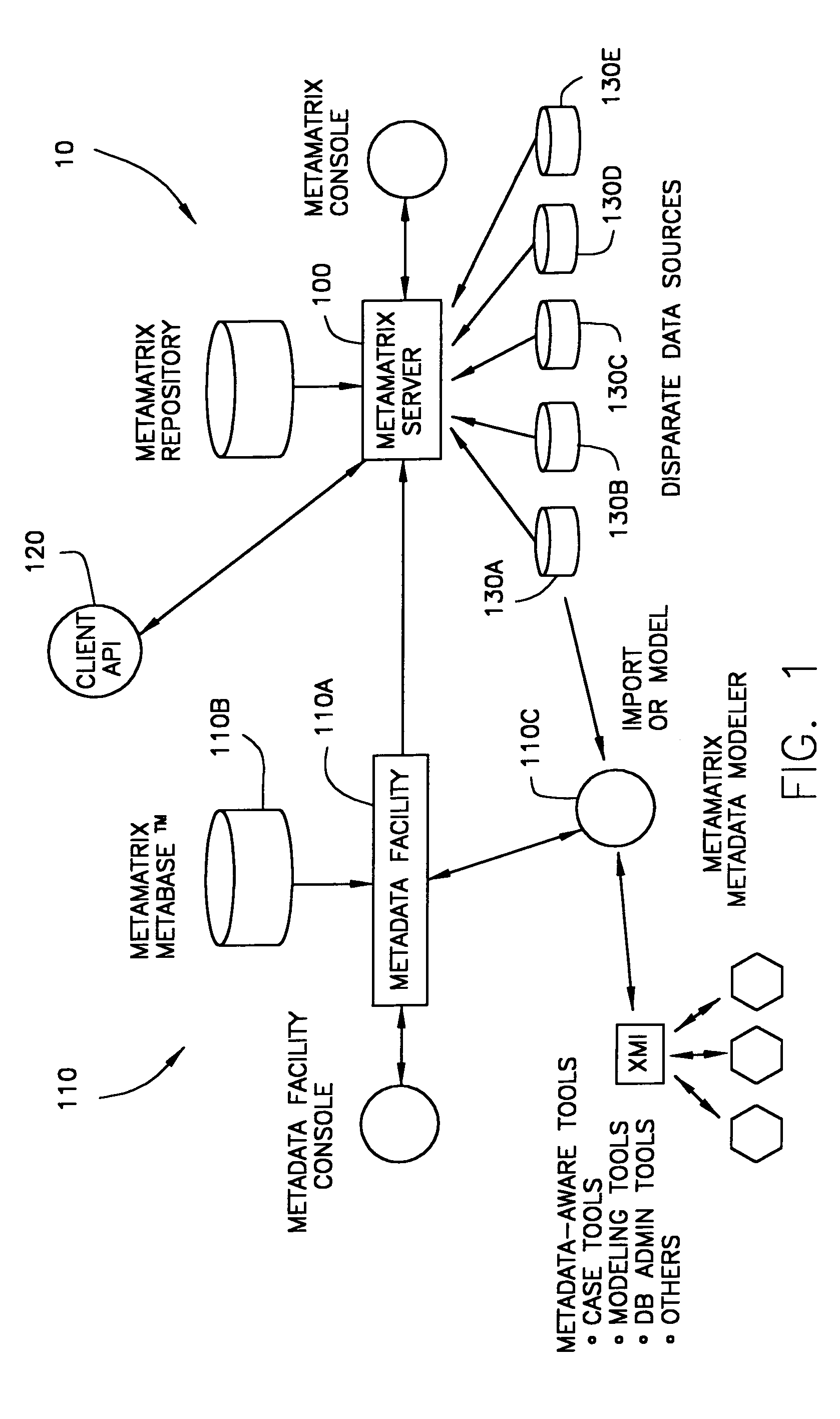
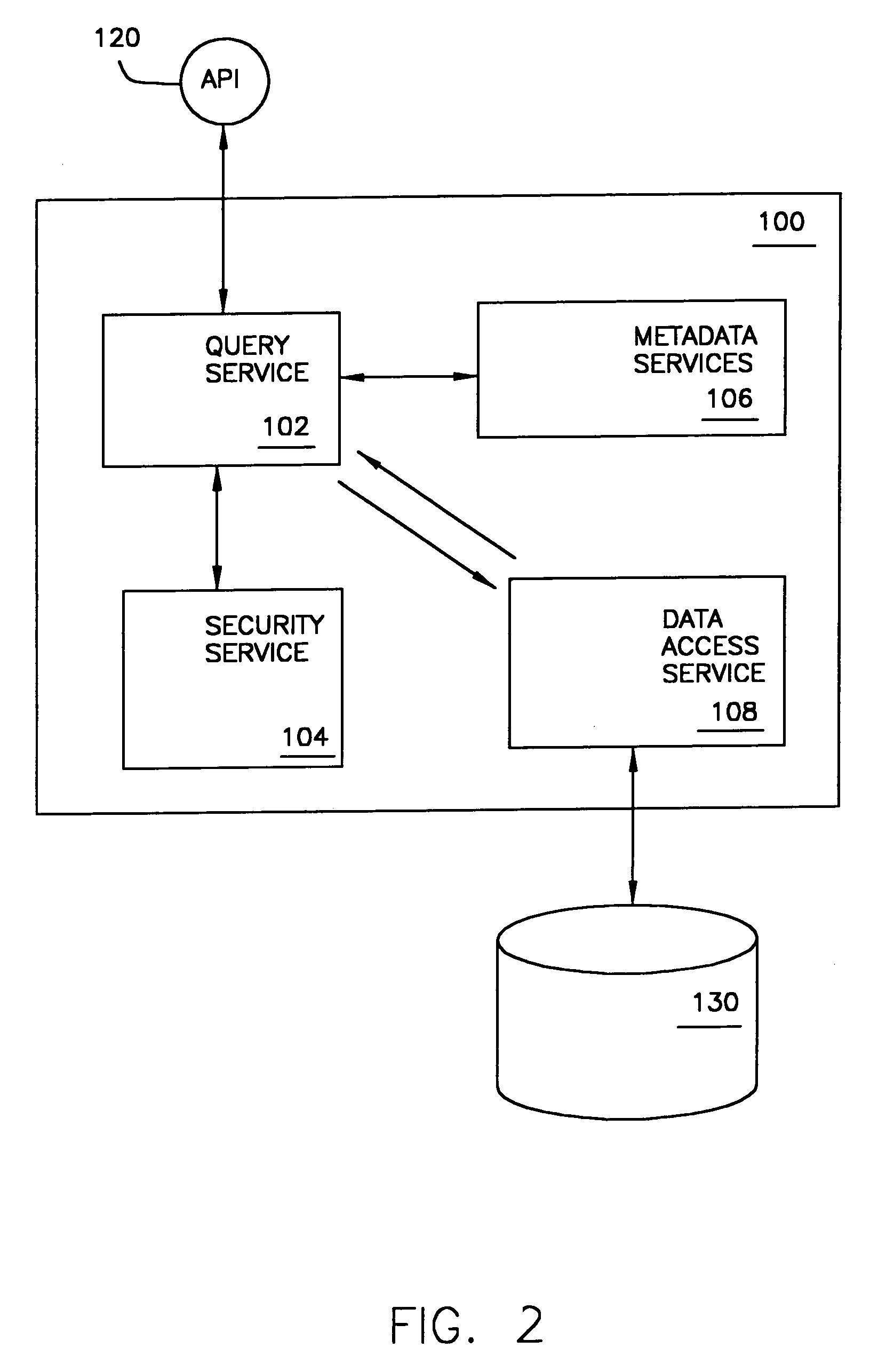
System and method for accessing data in disparate information sources
InactiveUS7668798B2Metadata text retrievalData processing applicationsRelevant informationData field
The present invention relates to a system (10) for generating and maintaining virtual and physical metadata layers in a MetaBase metadata repository (110b) in order to simplify and optimize the retrieval of data from a plurality of disparate information sources (130a-130c). The system stores in a physical metadata layer of a MetaBase metadata repository a plurality of physical metadata elements, wherein each one of the physical metadata elements corresponds to the metadata elements in the plurality of information sources. Logical metadata elements are stored in the virtual metadata layer and are linked to the physical metadata elements in order to maintain the relationships therebetween. By maintaining the relationships between the physical metadata elements, users can initiate a data query request for data corresponding to a logical metadata element, and the system is configurated to retrieve the desired data from the relevant information sources, even in the event that relevant information sources maintain the data in fields having different data field names, that the information sources employ incompatible data formats, and that the relevant information sources employ different query languages.
Owner:RED HAT
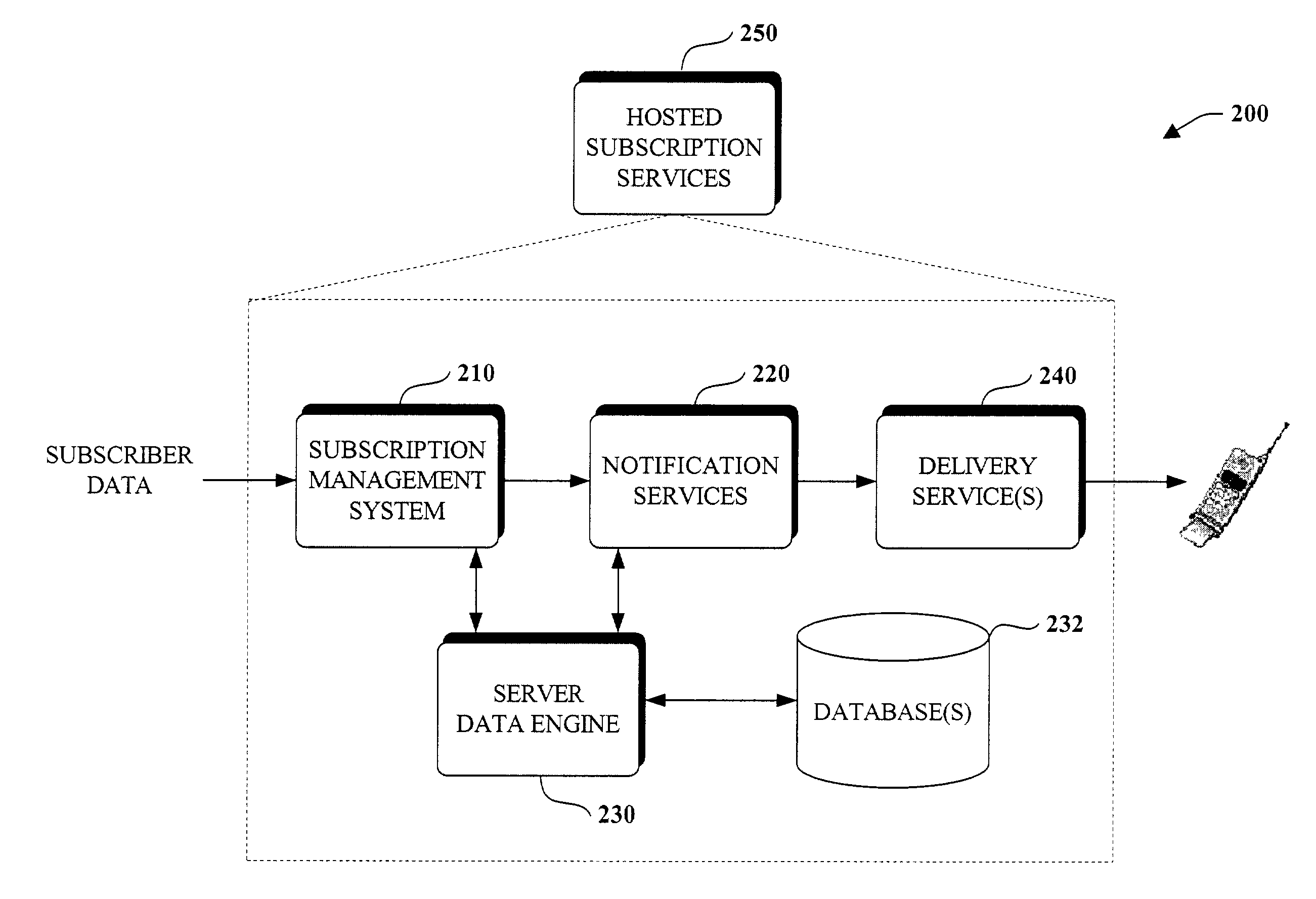
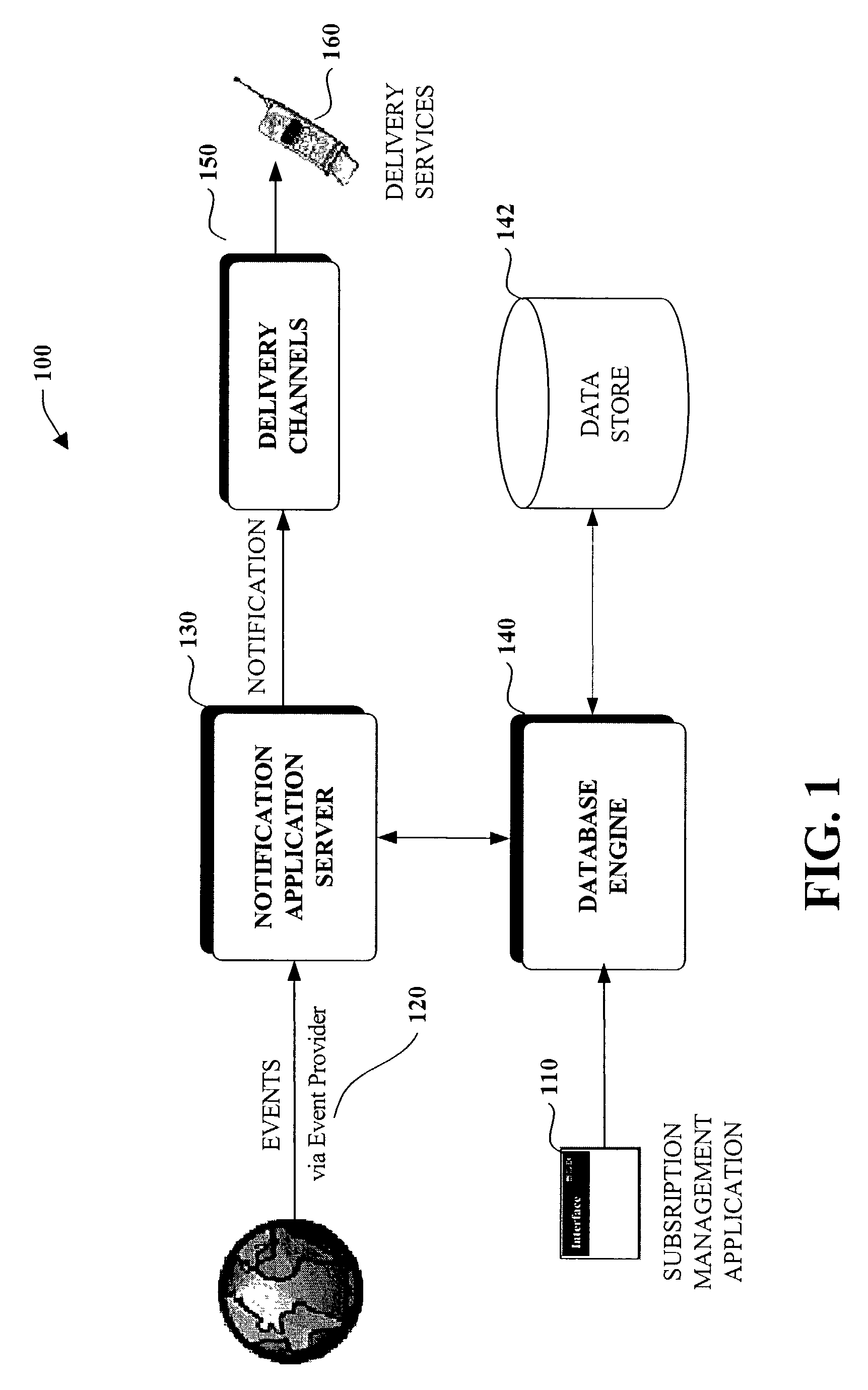
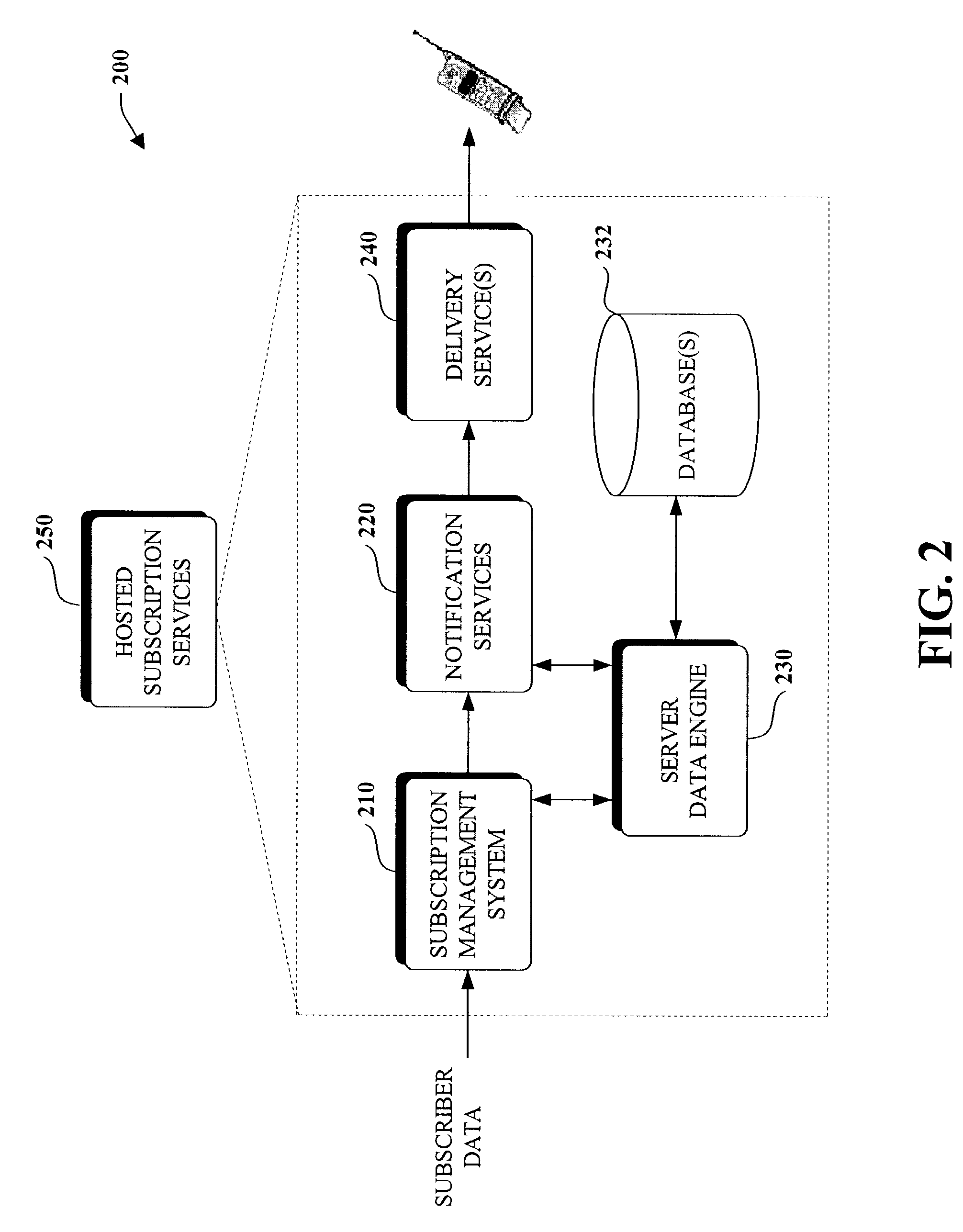
Programming model for subscription services
ActiveUS7177859B2Increase powerHigh complexityDigital data information retrievalMultiprogramming arrangementsRelevant informationData field
The present invention relates to a subscription modeling system and methodology. A query processor receives subscription query and subscriber information and transforms the query and subscriber information into data. An index component propagates at least one database with the transformed data; and a matching component that associates the transformed data with event data to generate a database of notification data that can be delivered to subscribers. The invention provides for abstracting subscription and subscriber information (as well as event information if desired) to high-level classes (e.g., data fields)—thus the invention provides for modeling such notification related information as data. Subscription applications can thus be developed at high levels wherein complex subscription queries and subscriber information can be defined as data fields for example. Databases in accordance with the data fields can be propagated with subscription / subscriber specific information. The present invention takes advantages of the processing power associated with database engines (e.g., SQL server) to generate notifications via performing a join operation on the databases (e.g., subscription database(s), subscriber database(s) and event database(s)). Accordingly, notifications are generated en masse as compared to per subscription per subscriber. Thus the present invention provides for a highly scalable and efficient notification system.
Owner:MICROSOFT TECH LICENSING LLC
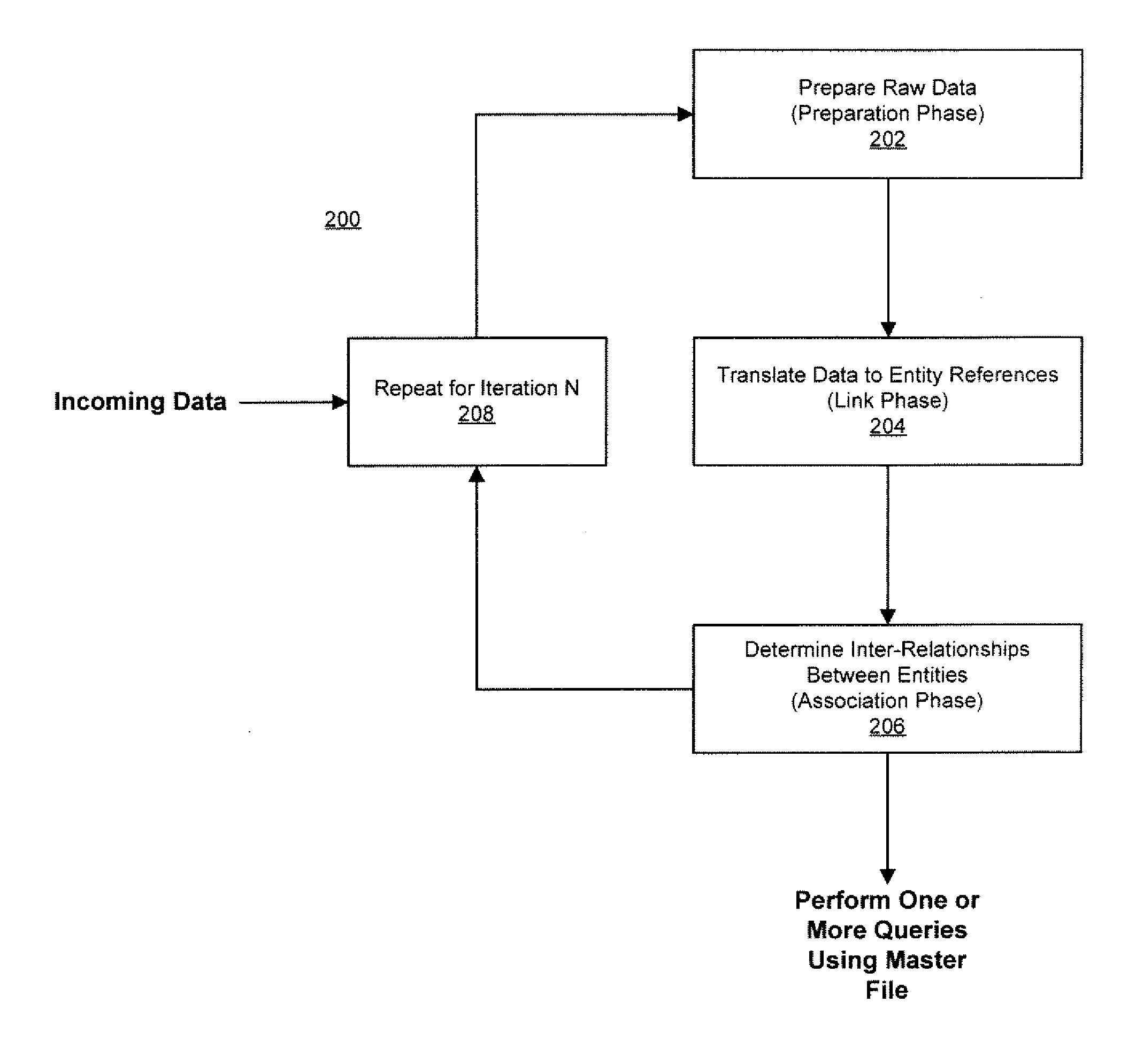
Method and system for linking and delinking data records
InactiveUS20100094910A1Reduce settingsAvoid it happening againDigital data processing detailsOffice automationData fieldData mining
Disclosed herein are various exemplary systems and methods for linking entity references to entities and identifying associations between entities. In particular, a method for delinking one or more entity references linked to a same entity is provided, where the one or more entity references having at least one common data field. The method comprises the steps of evaluating at least one actual measurement of the entity based at least in part on one or more field values of the one or more entity references, determining a difference between the at least one actual measurement and at least one predefined measurement associated with the entity and delinking the one or more entity references based at least in part on a comparison of the difference and a defined threshold.
Owner:LEXISNEXIS RISK DATA MANAGEMENT
Methods and apparatus for broadcasting interactive advertising using remote advertising templates
InactiveUS7103904B1Little informationLow bandwidthTelevision system detailsColor television detailsHyperlinkWeb site
Described are methods and apparatus for enhancing a television advertisement simultaneously displayed on a number of remote receivers. In one embodiment, one or more advertisement templates are stored in memory on each of the remote receivers. The templates include formatting information and data fields into which can be inserted predefined types of information. For example, a selected template may be adapted to receive and display an advertiser's name, product, and a hyperlink to the advertiser's web site. A content creator, (e.g., a program producer, broadcaster, affiliate, cable company or satellite provider), embeds an advertisement summary in a data service channel of a broadcast signal. The advertisement summary includes a resource identifier unique to a selected one of the advertisement templates. Upon receiving an advertisement summary directed to a resident advertisement template, the receiver combines custom advertisement information provided in the advertisement summary with formatting information provided in the advertisement template. The receiver employs the combined information to create and display a custom advertisement, which may include hyperlinks to additional produce or service information.
Owner:MICROSOFT TECH LICENSING LLC
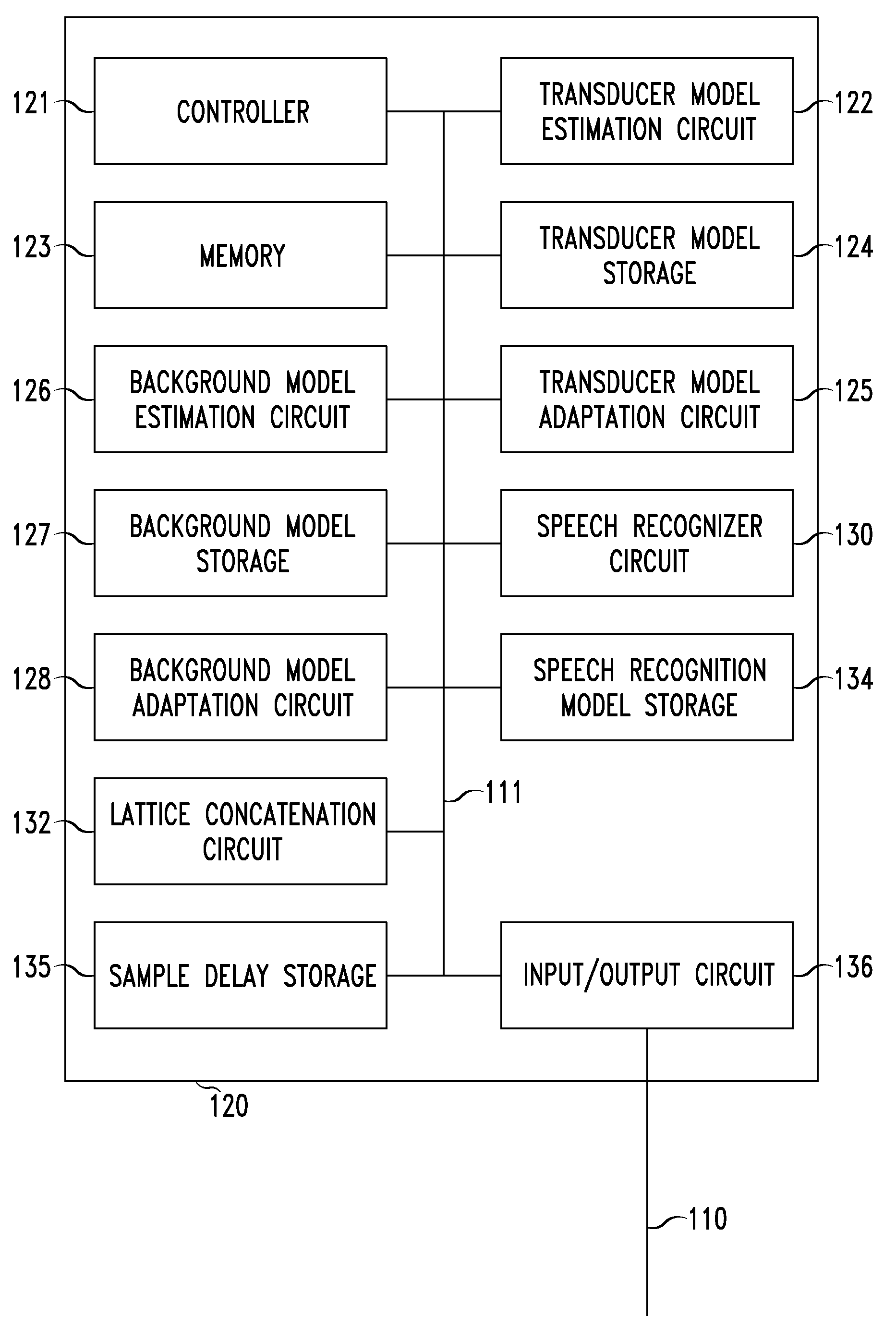
System and method of performing speech recognition based on a user identifier
InactiveUS7451081B1Natural language data processingSpeech recognitionData fieldBackground information
Owner:NUANCE COMM INC
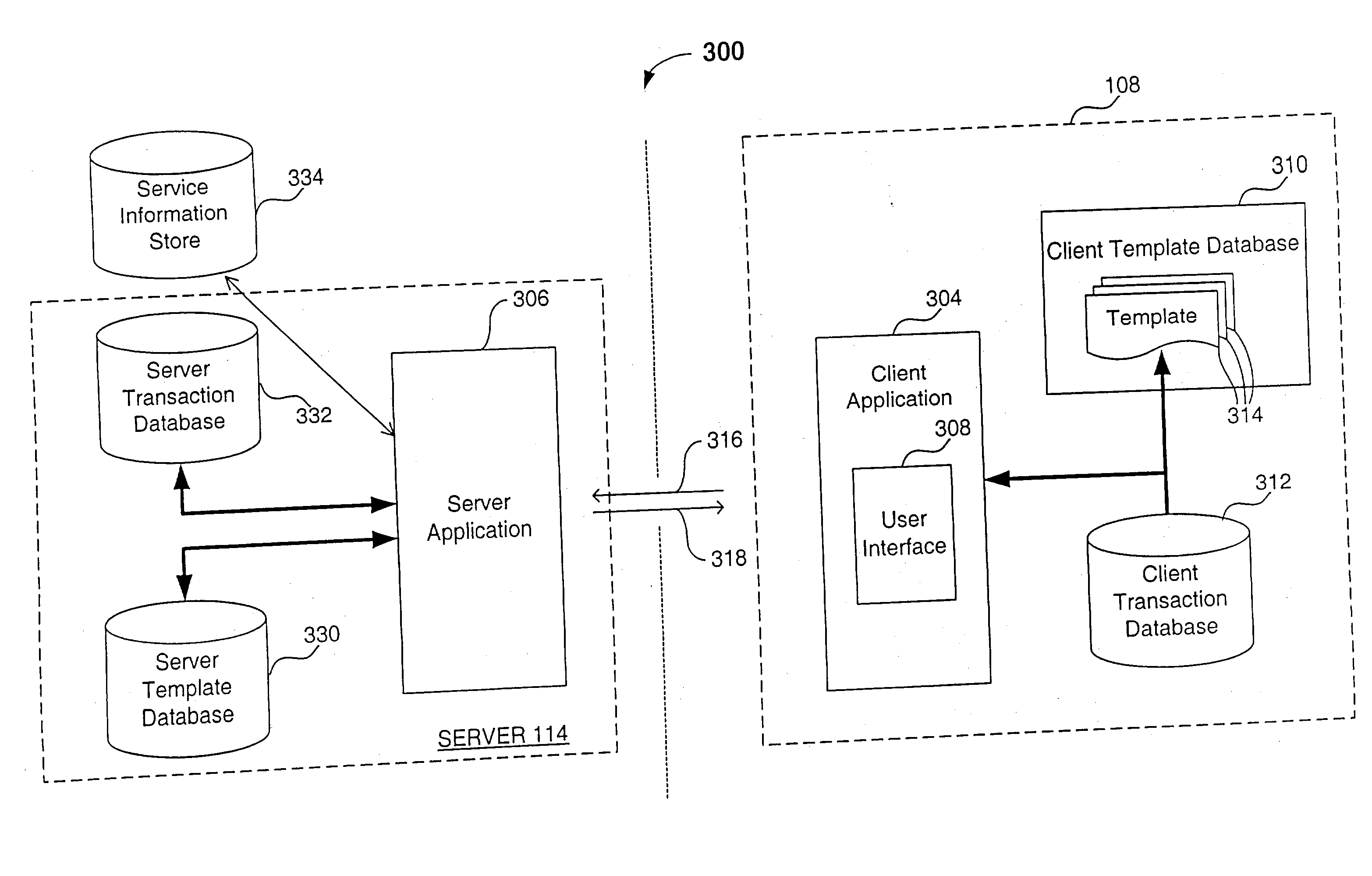
System, method and apparatus for utilizing transaction databases in a client - server environment
InactiveUS20030046291A1Data processing applicationsDigital data processing detailsData fieldTransaction data
A system, method and apparatus for utilizing transaction databases in a client-server environment. The transaction databases can be used to receive and retain multiple server responses to consecutive client requests regardless of the temporal relationship between the multiple responses and consecutive requests. One method of the invention relates to how a client device displays information. This method is for use in a client-server system including one or more servers and a client device having a client transaction database, a client template database, and a user interface adapted to enable a user to enter requests. The method includes the steps of receiving a user request from the user via the user interface and retrieving a template from the client template database based on the user request. The template includes one or more data fields. The method also includes the step of retrieving information from the client transaction database based on the template, wherein the information relates to the one or more data fields of the template. A page is then displayed based on the template and the information relating to the one or more data fields.
Owner:FASCENDA ANTHONY C
System, apparatus and method for obtaining one-time credit card numbers using a smart card
A system, apparatus and method for utilizing one-time, or temporary, “credit” card information for executing purchase transactions with a smart card or similar electronic data card device. The card is activated in an activation process with the issuer prior to receiving and utilizing temporary card information (numbers). Retrieval and submission of temporary card information is performed in an automatic process executed by application programming, such as within a web browser. By way of example, a user surfing the web commences a purchase transaction wherein their smart card communicates with the issuer of the smart card to retrieve one-time or temporary use card data which is submitted through the network for processing within the transaction. In one embodiment the programming is executed within a web browser which marks card data fields within transaction forms and automatically fills these fields with temporary card information received from the issuer.
Owner:SONY CORP +1
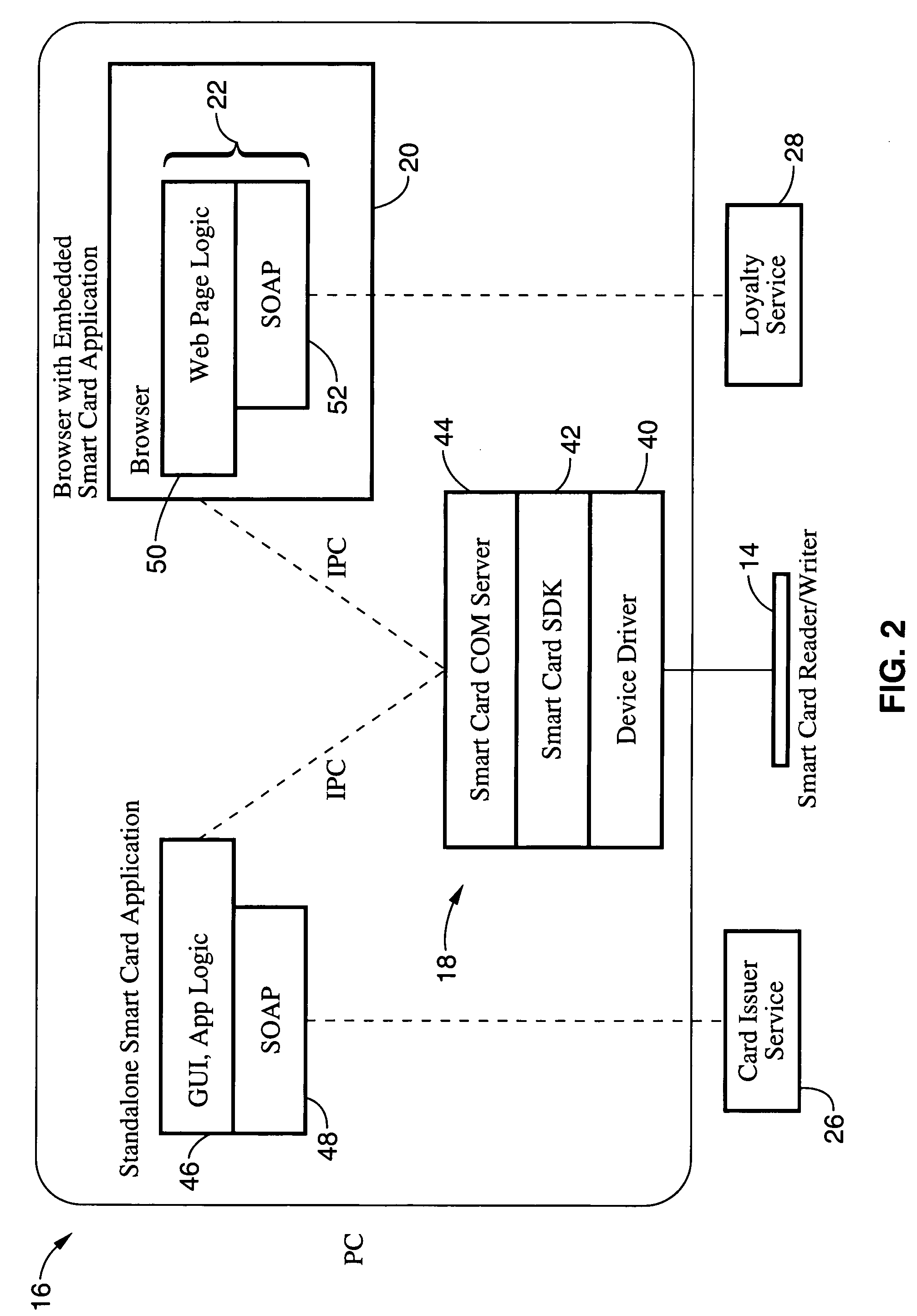
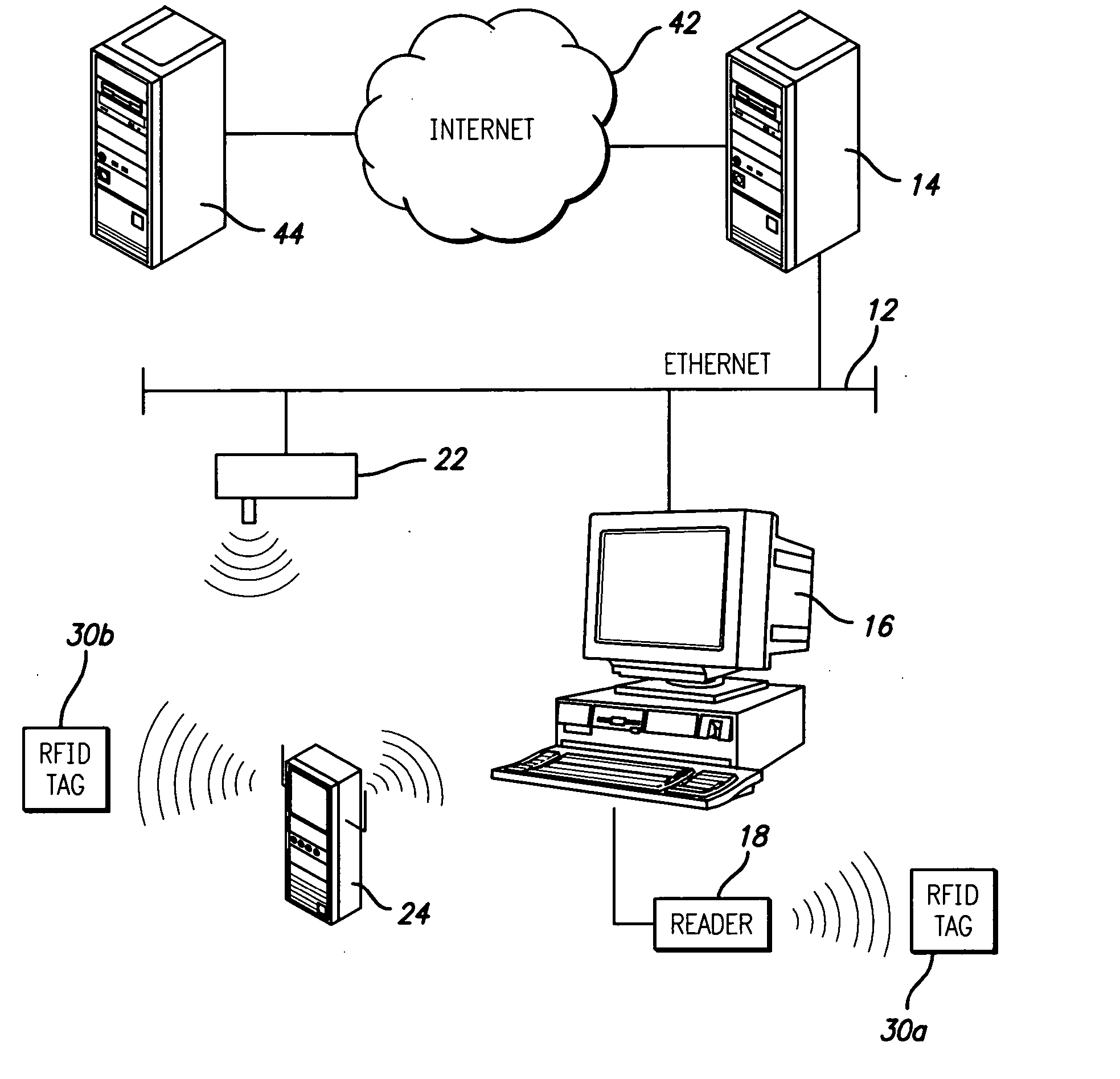
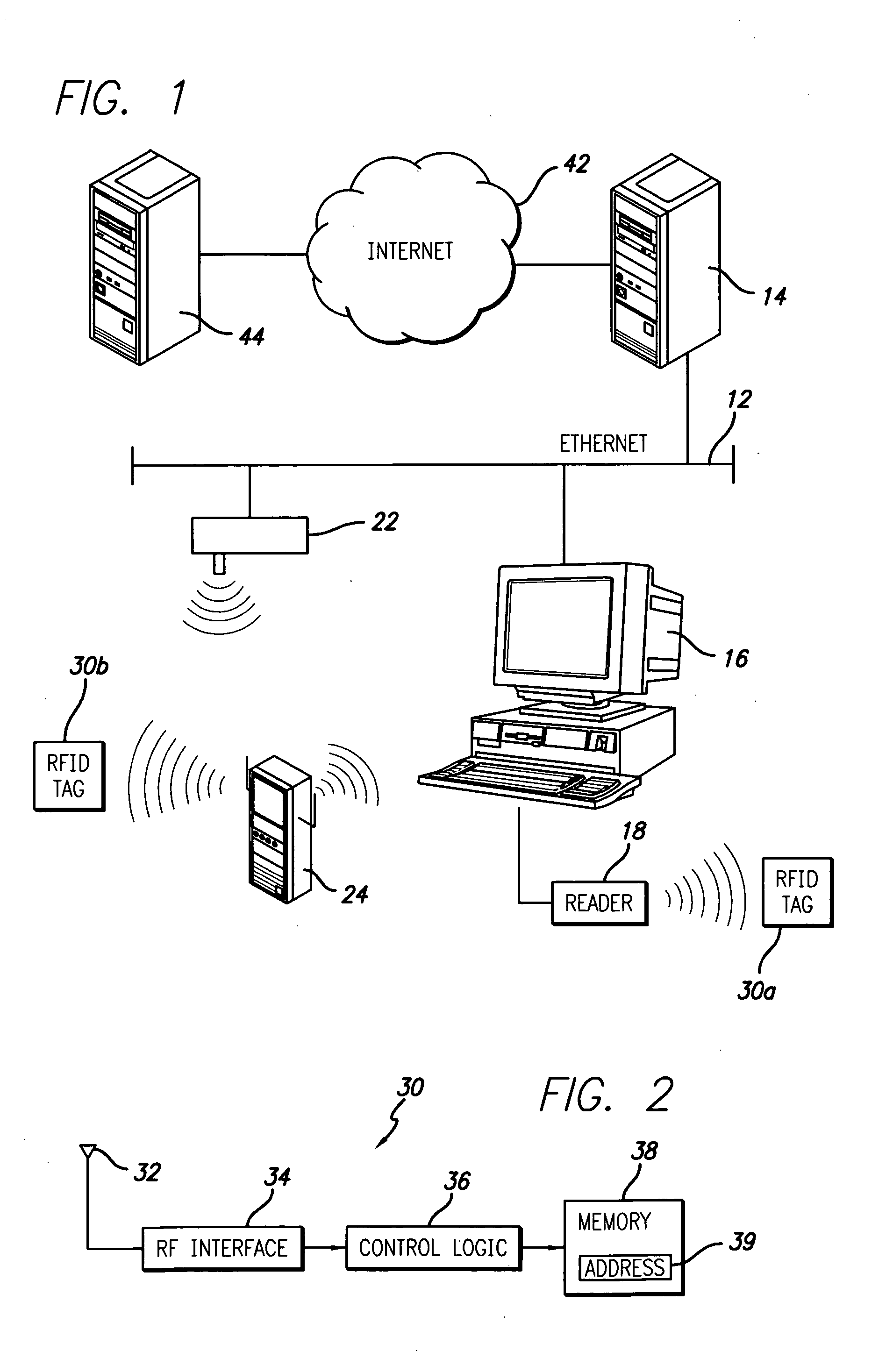
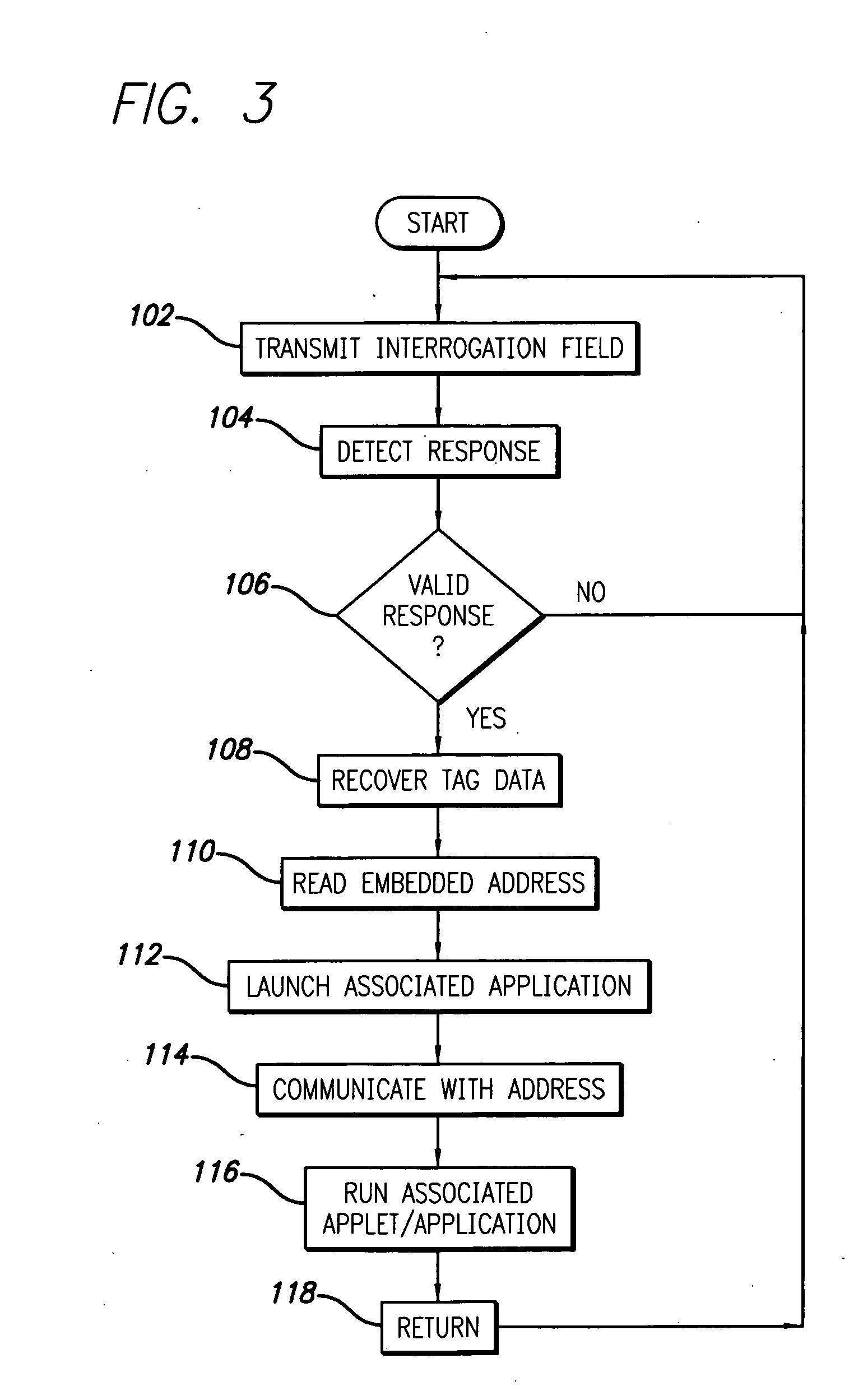
RFID tag with embedded Internet address
InactiveUS20060168644A1Easy to implementDigital data processing detailsUser identity/authority verificationEmail addressData field
A radio frequency identification (RFID) transponder comprises a memory space having a predetermined data field for storing a destination address identifying a location on the Internet corresponding to the RFID transponder. The Internet address may further comprise an e-mail address or Uniform Resource Locator (URL). In an embodiment of the invention, a computer network comprises a client computer having an application executing thereon, an RFID tag having a memory containing an Internet address corresponding to the RFID tag, and an RFID reader connected to the client computer and adapted to communicate with the RFID tag. The RFID reader recovers the Internet address from the RFID tag and provides the Internet address to the client computer. The client computer thereby communicates with the location defined by the Internet address corresponding to the RFID tag using the application. A host server is connected to the client computer, and may be further connected to the Internet. The client computer thereby can access the Internet location by operation of the application through the host server.
Owner:INTERMEC IP
Zooming controller
InactiveUS6061062ACost effectiveIncrease speedInput/output processes for data processingProportional controlImage resolution
A method and device for accessing a broad data field having a fine resolution. The user selects a scale which can be varied. The scale controls a range within the data field. By moving the range to encompass different portions of the data field, the user can scan that portion of the data field. The present invention allows the user to simultaneously select the scale while moving the range over different portions of the data field. Thus, the user can "zoom in" and "zoom out" of different portions of the data field. In one embodiment of the present invention, a particular piece of data within the broad data field can be accessed. First, the scale is selectively varied, thereby controlling a range within the data field. Then, the range is moved to encompass portions of the data field in which the piece of data resides. Next, the scale is successively decreased while, simultaneously, points successively closer to the location are kept with the range. The scale is decreased (i.e., increasing the range's resolution) and the range is moved in this manner until the piece of data is actually accessed.
Owner:APPLE INC
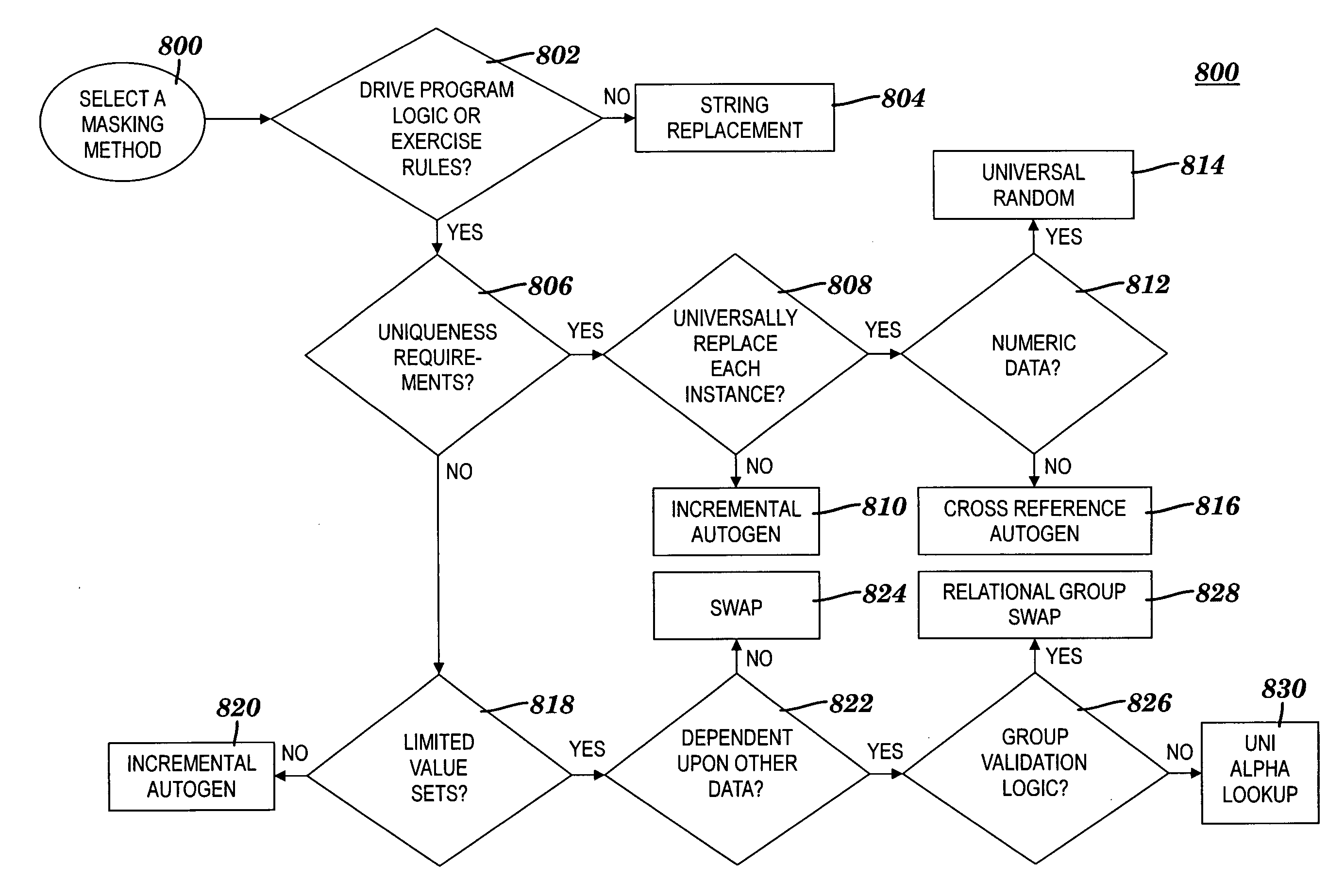
Obfuscating sensitive data while preserving data usability
InactiveUS20090132419A1Computer security arrangementsSecuring communicationConfidentialityData field
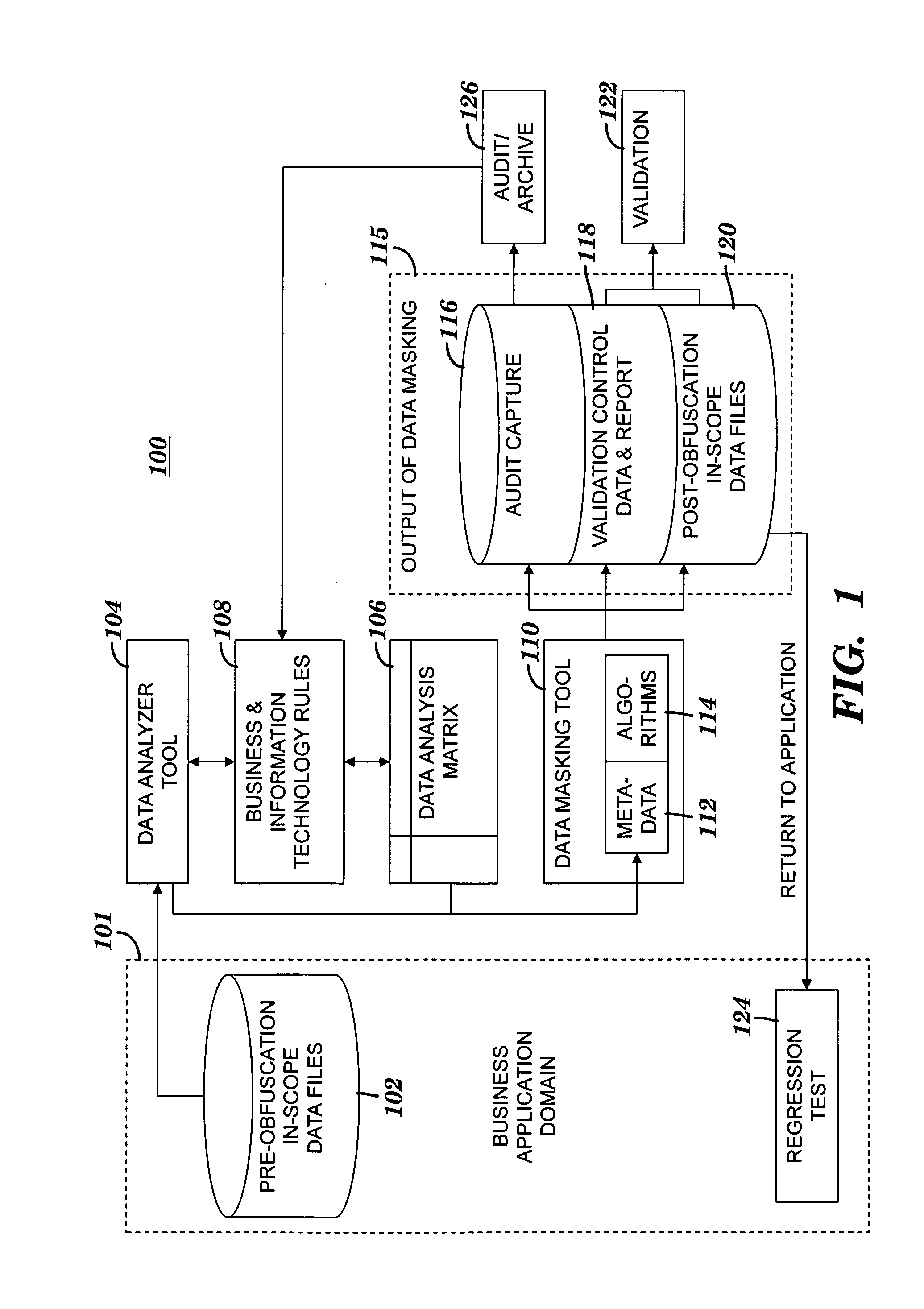
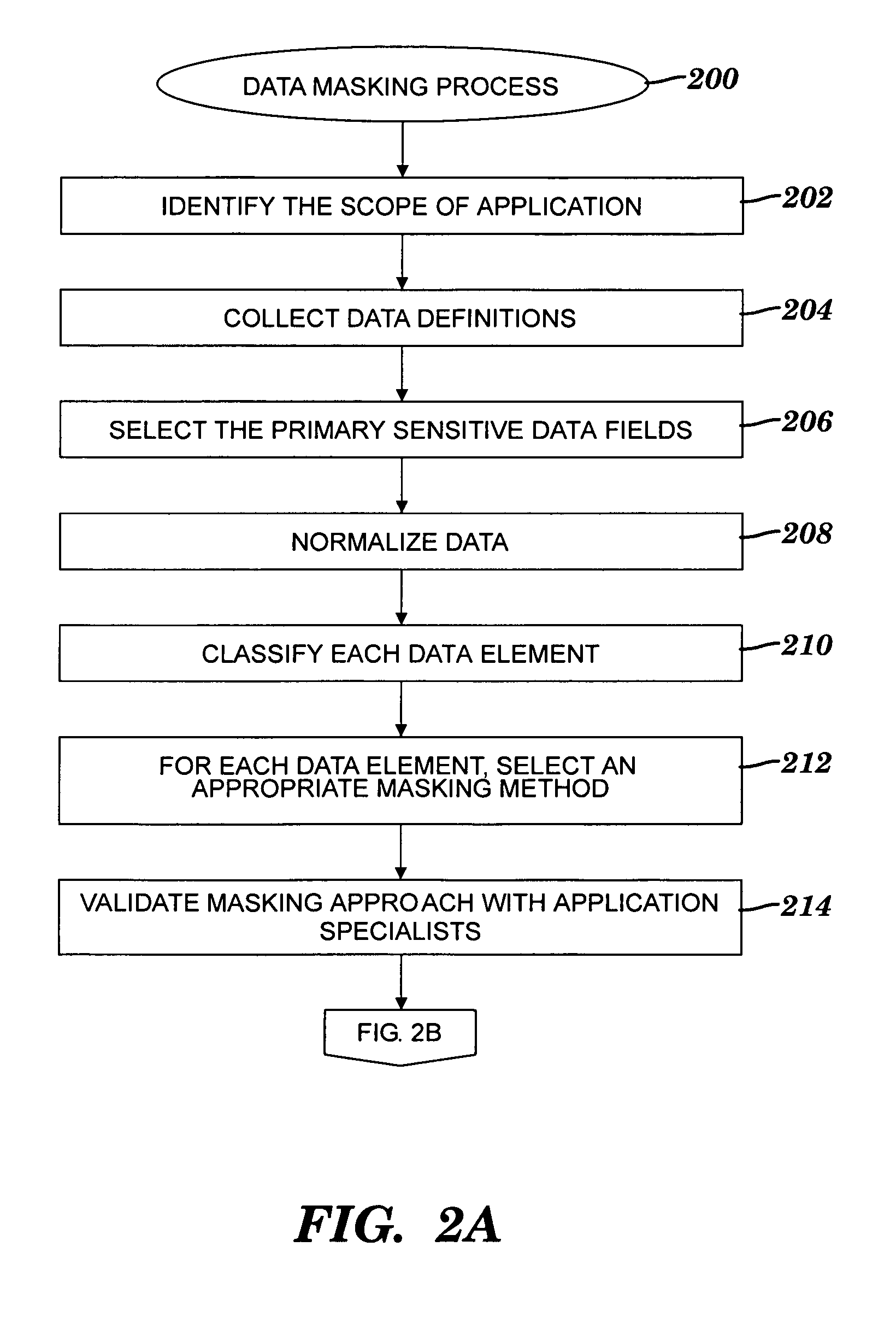
A method and system for obfuscating sensitive data while preserving data usability. The in-scope data files of an application are identified. The in-scope data files include sensitive data that must be masked to preserve its confidentiality. Data definitions are collected. Primary sensitive data fields are identified. Data names for the primary sensitive data fields are normalized. The primary sensitive data fields are classified according to sensitivity. Appropriate masking methods are selected from a pre-defined set to be applied to each data element based on rules exercised on the data. The data being masked is profiled to detect invalid data. Masking software is developed and input considerations are applied. The selected masking method is executed and operational and functional validation is performed.
Owner:IBM CORP
Method and system for customizing a mobile application using a web-based interface
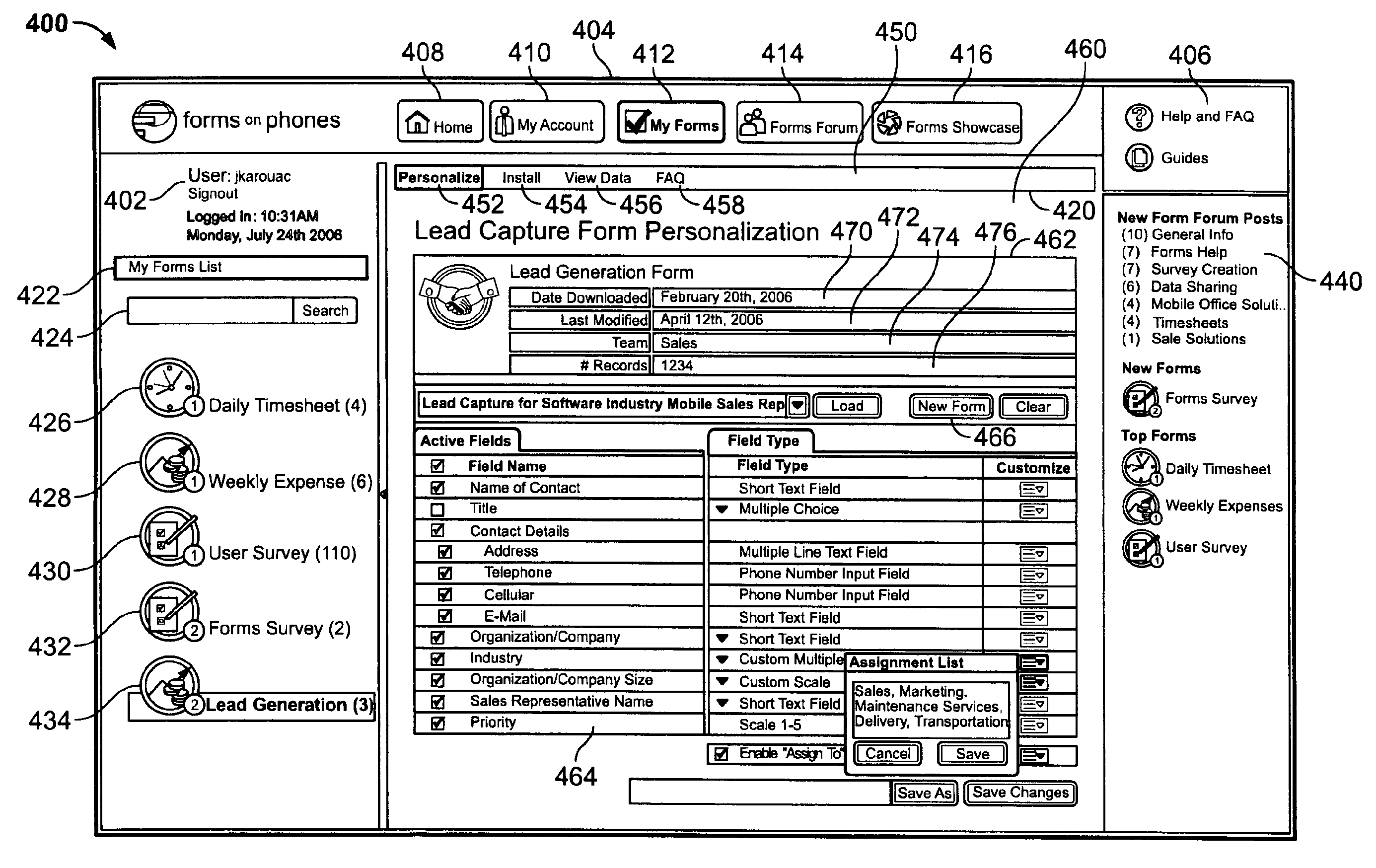
ActiveUS20100174974A1Input/output for user-computer interactionNatural language data processingData fieldApplication software
A system and method for customizing mobile-form applications via a web-based interface for distribution to a mobile device are disclosed. An example method includes providing a customizable mobile-form application template. A web-based interface is provided allowing creation of a customized mobile-form application from the customizable mobile-form application template by selecting a data field for inclusion on the customizable mobile-form application template. The customized mobile-form application may then be distributed to the mobile device.
Owner:PRONTOFORMS INC
Method and system for linking and delinking data records
ActiveUS7657540B1Reduced data setReduce settingsDigital data processing detailsOffice automationData fieldData mining
Exemplary systems and methods for linking entity references to entities and identifying associations between entities are presented. In particular, a method for delinking one or more entity references linked to a same entity is provided, where the one or more entity references have at least one common data field. The method comprises the steps of evaluating at least one actual measurement of the entity based at least in part on one or more field values of the one or more entity references, determining a difference between the at least one actual measurement and at least one predefined measurement associated with the entity and delinking the one or more entity references based at least in part on a comparison of the difference and a defined threshold.
Owner:LEXISNEXIS RISK DATA MANAGEMENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com