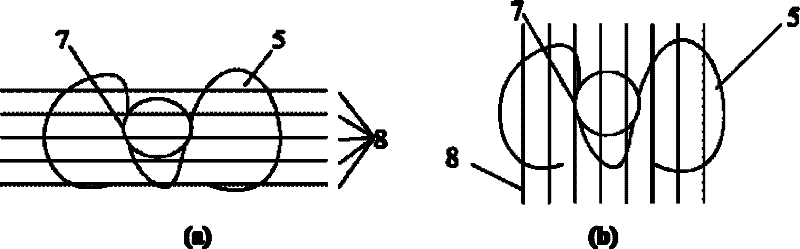Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
145results about How to "Little information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
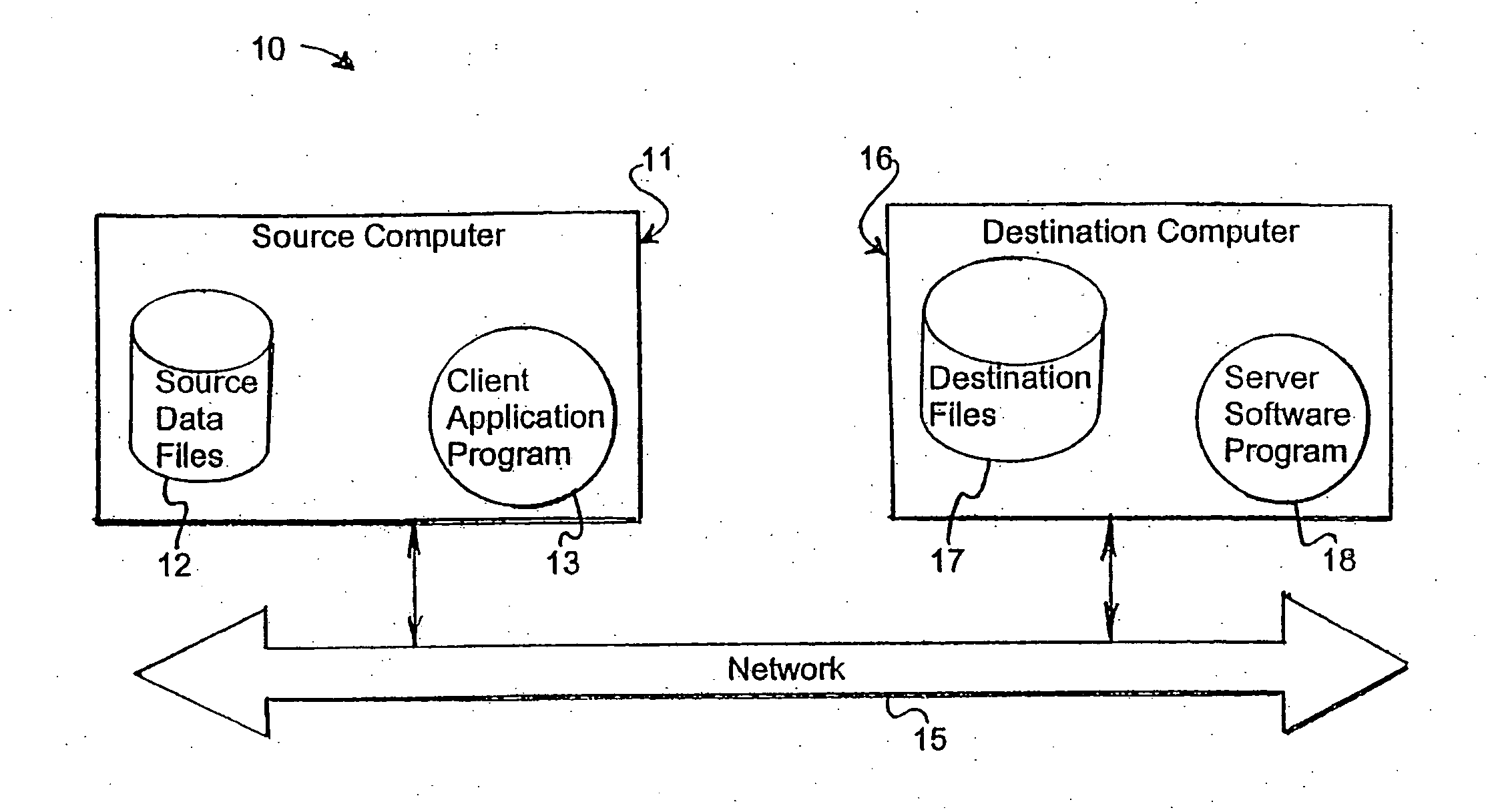
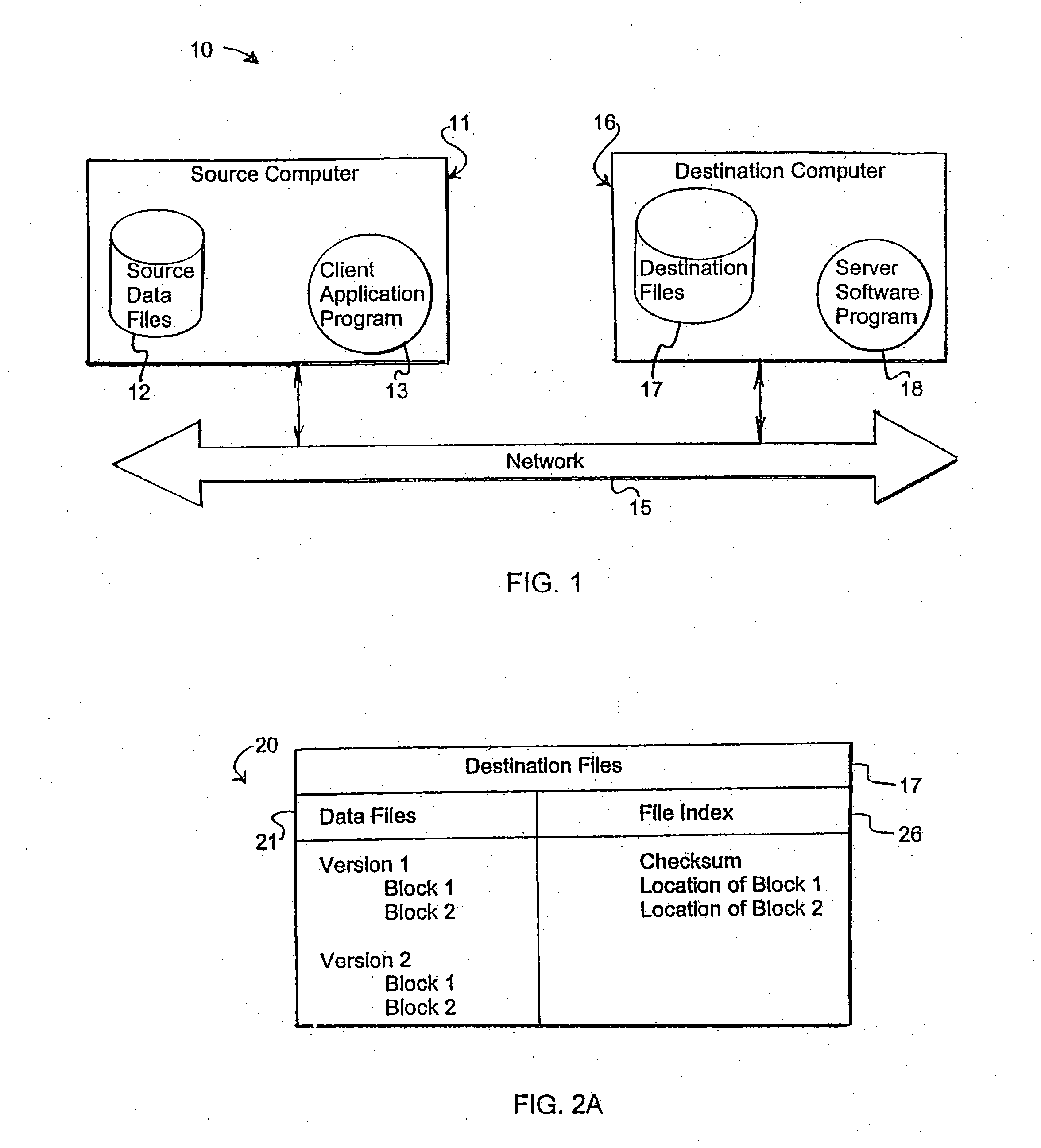
Storing and retrieving computer data files using an encrypted network drive file system
ActiveUS20060206547A1Easy to storeEasy retrievalData processing applicationsError detection/correctionHard disc driveData file
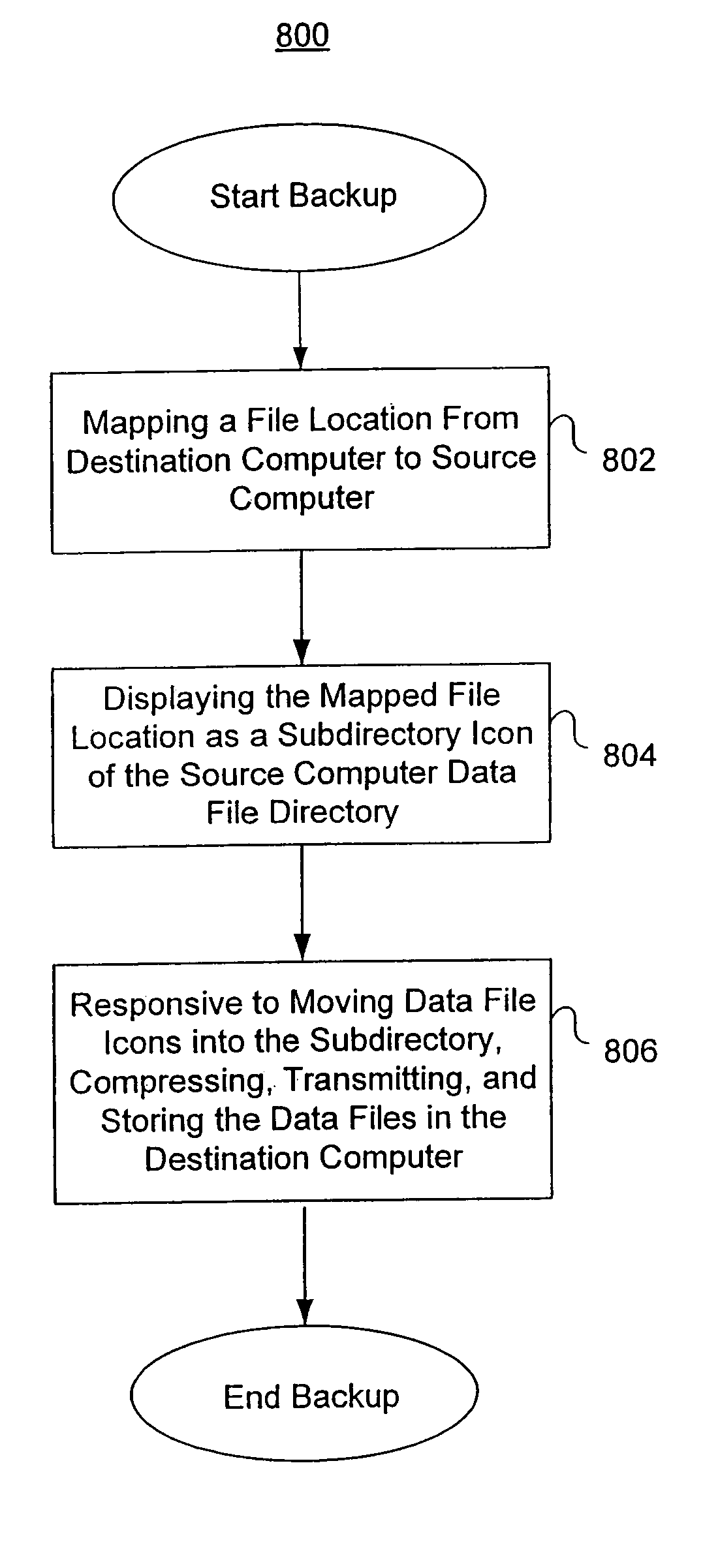
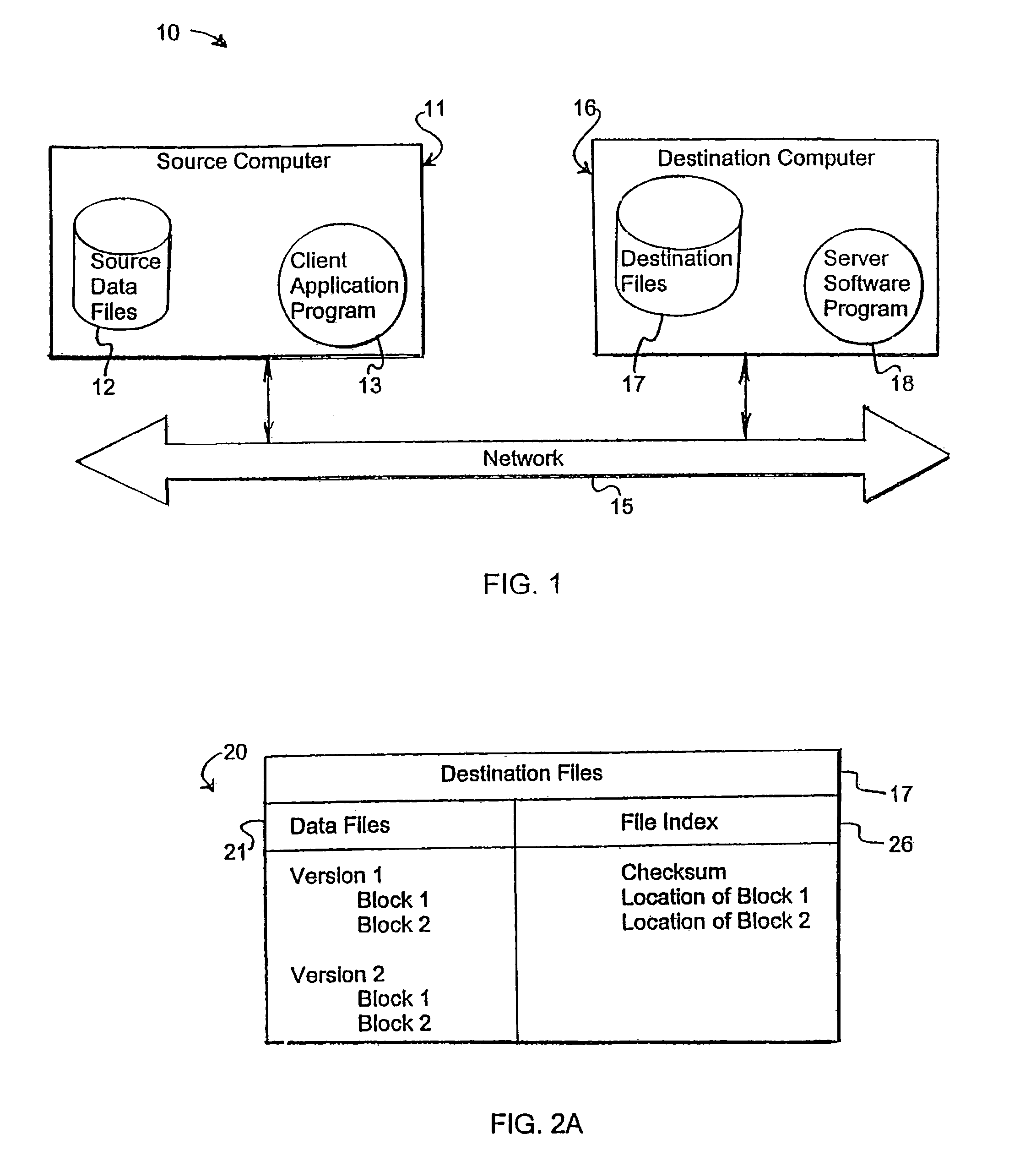
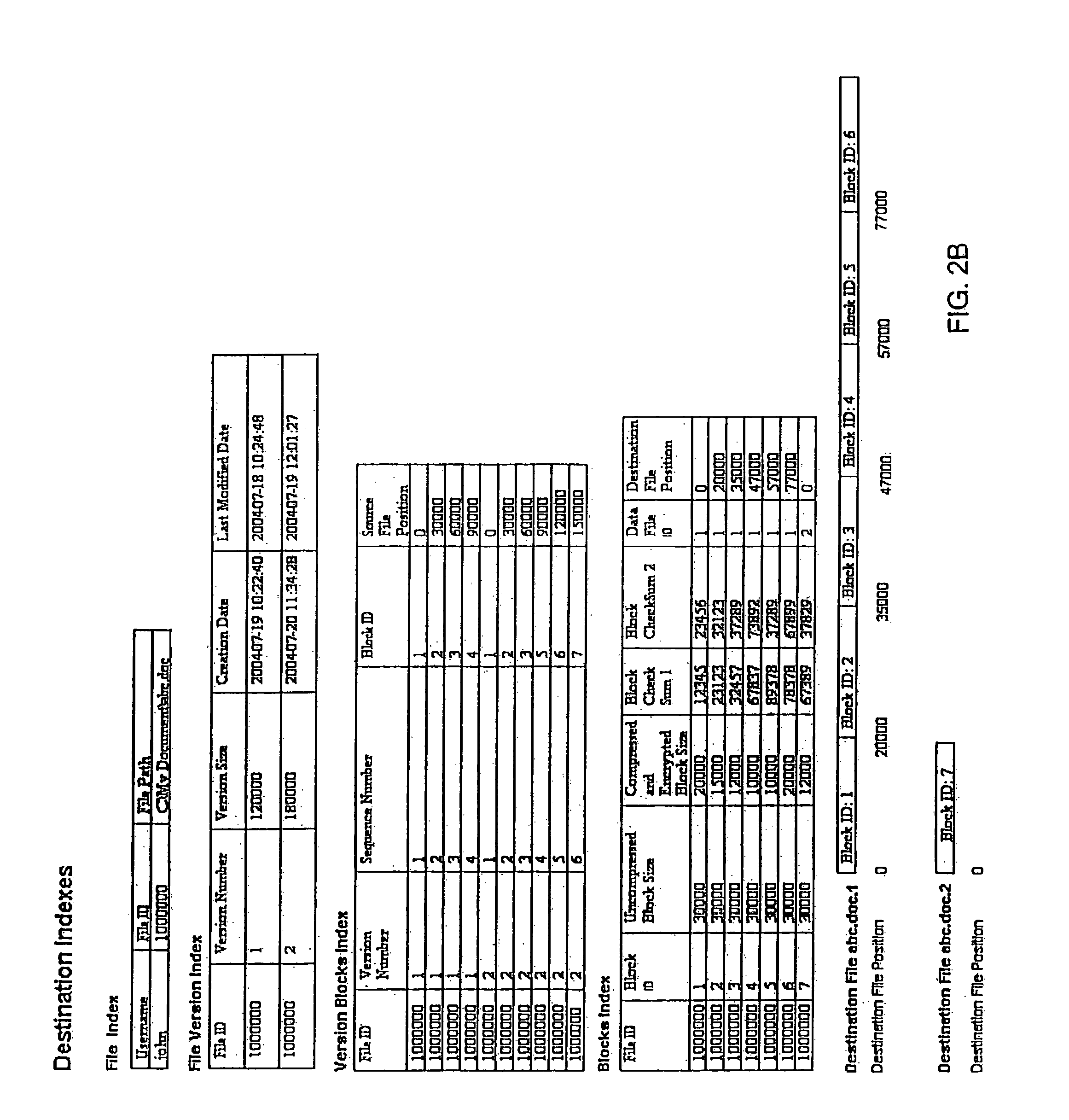
A system and method for storing computer files in a destination file is described, which may be an incremental backup system. File headers related to the files may be stored in a file index separate from a data file, or subsequent versions may be stored in the same data file while maintaining earlier versions. File headers may include locations of files, checksums, metadata about individual blocks corresponding to the data files. A system may include a client application program stored on a client computer, a network, and a server software program on a destination computer. Embodiments may include compression, encryption, or both, performed by the client application program. Files may be divided into blocks, and metadata may include locations of blocks. Files may be restored from the destination computer to the source computer. Files storage locations on the destination computer may be mapped to the client computer to appear as a virtual hard drive for convenient access by a user.
Owner:IDRIVE INC
Methods, apparatuses and computer program products for providing a constant level of information in augmented reality
InactiveUS20120001938A1Expand viewing rangeEasy to displayServices signallingCathode-ray tube indicatorsSimulationField of view
An apparatus for providing a constant level of information in an augmented reality environment may include a processor and memory storing executable computer program code that cause the apparatus to at least perform operations including determining a first number of points of interest associated with a first set of real world objects of a current location(s). The first set of real world objects is currently displayed. The computer program code may further cause the apparatus to determine whether the first number is below a predetermined threshold and may increase a view range of a device to display a second set of real world objects. The view range may be increased in order to increase the first number to a second number of points of interest that corresponds to the threshold, based on determining that the first number is below the threshold. Corresponding methods and computer program products are also provided.
Owner:NOKIA TECHNOLOGLES OY
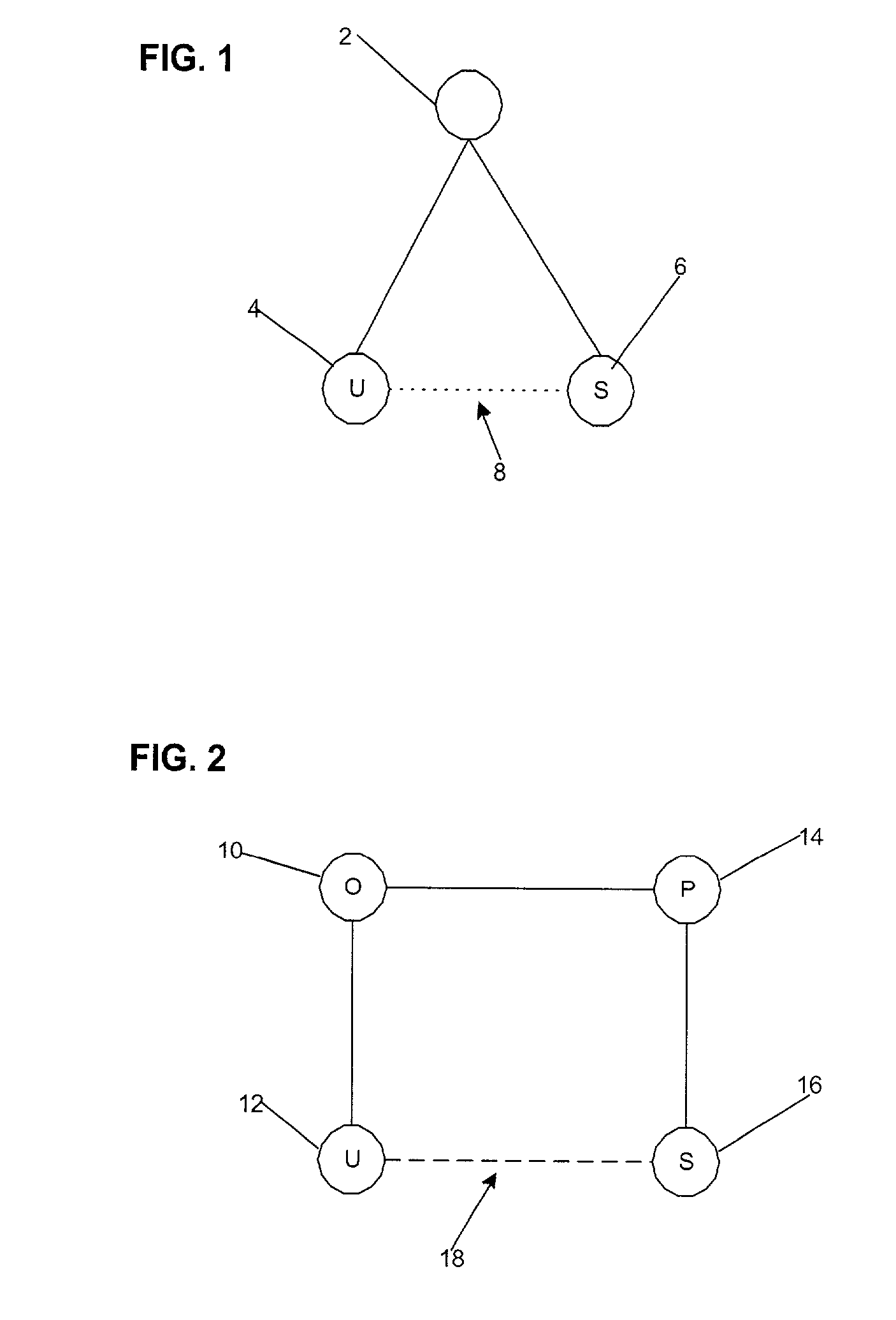
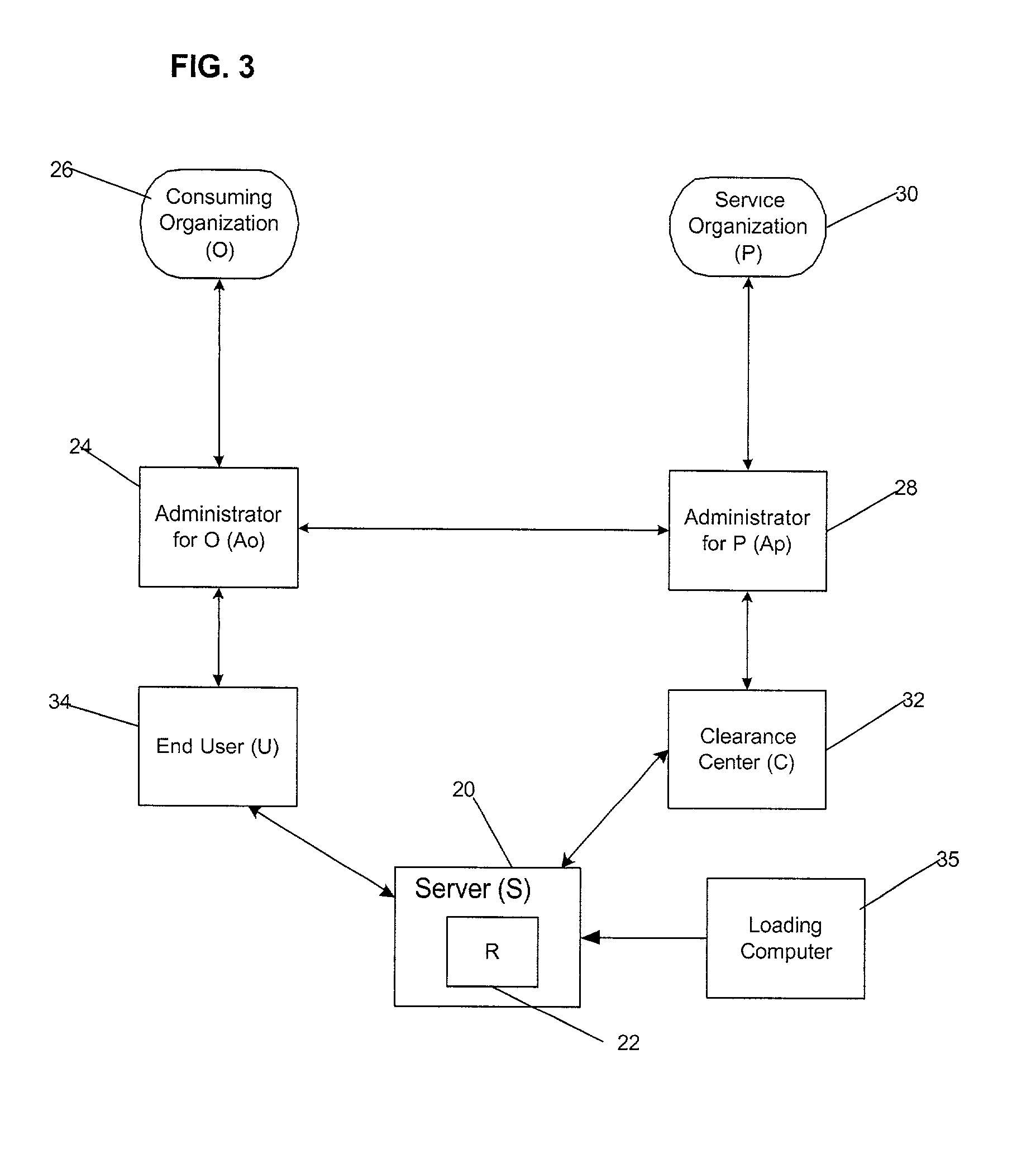
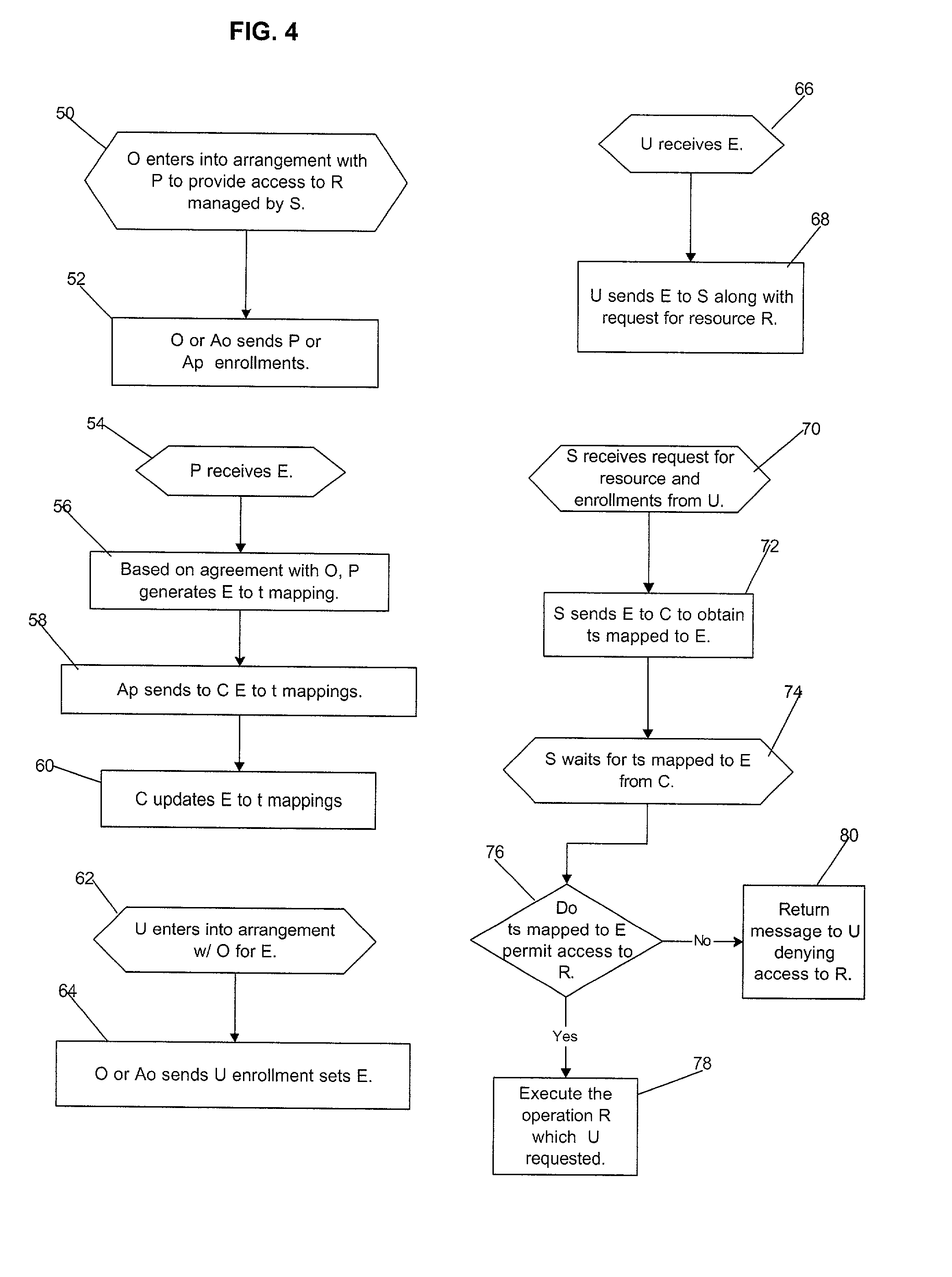
Umethod, system and program for managing relationships among entities to exchange encryption keys for use in providing access and authorization to resources
InactiveUS20010020228A1Strong level of assuranceMaintain privacyKey distribution for secure communicationUser identity/authority verificationAuthorizationComputer science
Provided is a method, system, and program for managing access to resources. Encryption keys are exchanged among a first entity, second entity, third entity, and a fourth entity. Each entity has one relationship with one other entity and the encryption keys are exchanged pursuant to the relationships. Electronic messages are encrypted with the encryption keys concerning digital enrollments to provide to the first entity. The digital enrollment is associated with at least one digital ticket that authorizes access to a resource managed by the fourth entity. Presentation of the digital enrollment causes the presentation of one digital ticket associated with the digital enrollment to authorize the first entity to access the resource.
Owner:IBM CORP
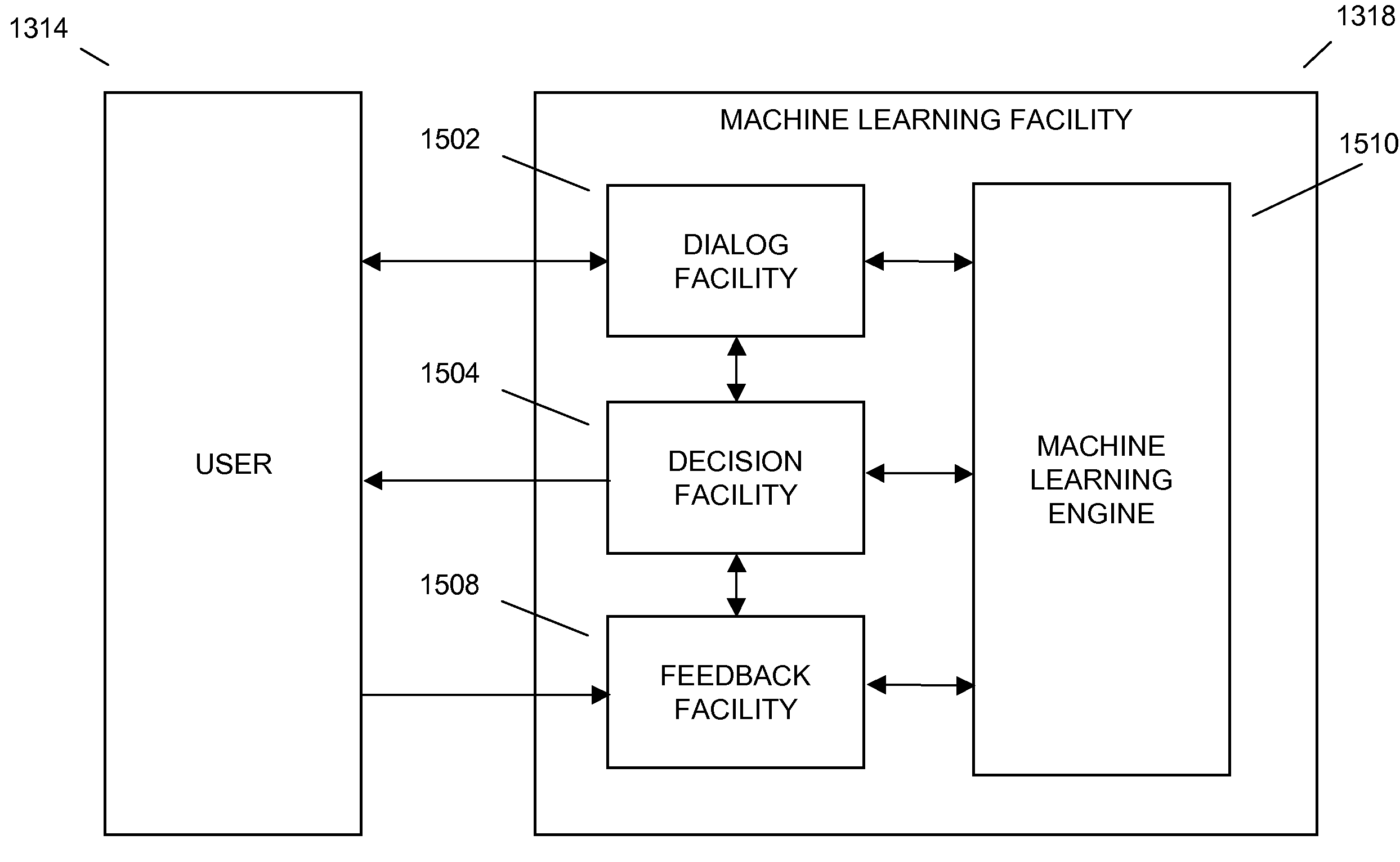
Interactive machine learning advice facility
InactiveUS20090119234A1Improve future questionImprove decisionDigital computer detailsMachine learningHuman–computer interactionArtificial intelligence
In embodiments of the present invention improved capabilities are described for helping a user make a decision through the use of a machine learning facility. The process may begin with an initial question being received by the machine learning facility from the user. The user may then be provided with a dialog consisting of questions from the machine learning facility and answers provided by the user. The machine learning facility may then provide a decision to the user based on the dialog and pertaining to the initial question, such as a recommendation, a diagnosis, a conclusion, advice, and the like. In embodiments, future questions and decisions provided by the machine learning facility may be improved through feedback provided by the user.
Owner:EBAY INC
Information search and retrieval system
InactiveUS20020087526A1The process is fast and efficientMove quicklyDigital data information retrievalDigital data processing detailsThe InternetInformation searching
Improved systems and methods are described for accessing information over a distributed network, including the World Wide Web of the Internet and local area networks. The system and methods provide users a quick, efficient, and effective way to gather information of interest to them. Notably, the invention permits the gathering of information using not just entered queries, but also the characteristics of the user and the user's real-time opinion of the search results as they are displayed. In doing so, the user is given information that is tailored to that individual, and which reflects the individual's specific opinion of the relevancy of the search results.
Owner:INTERFINANCE
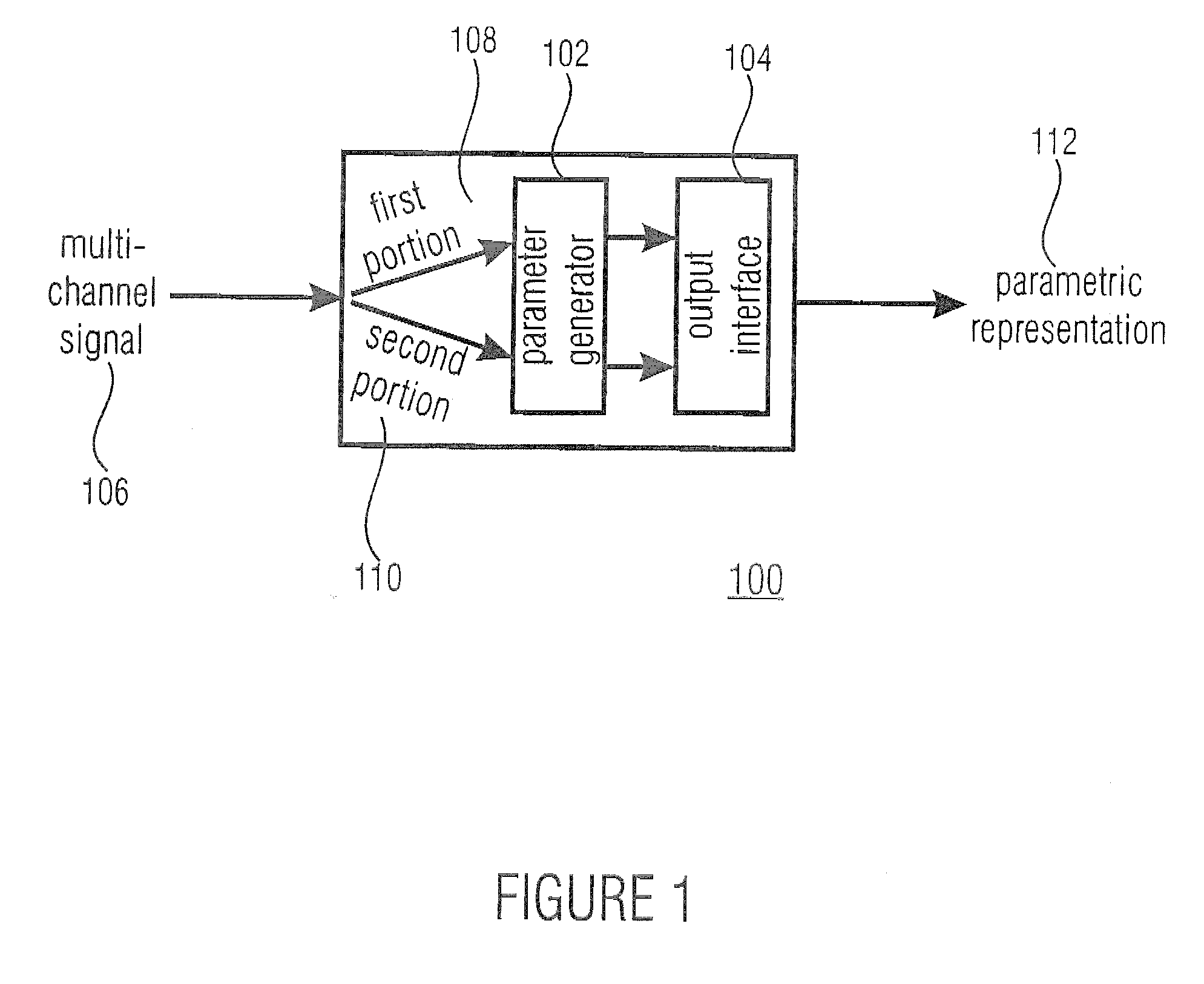
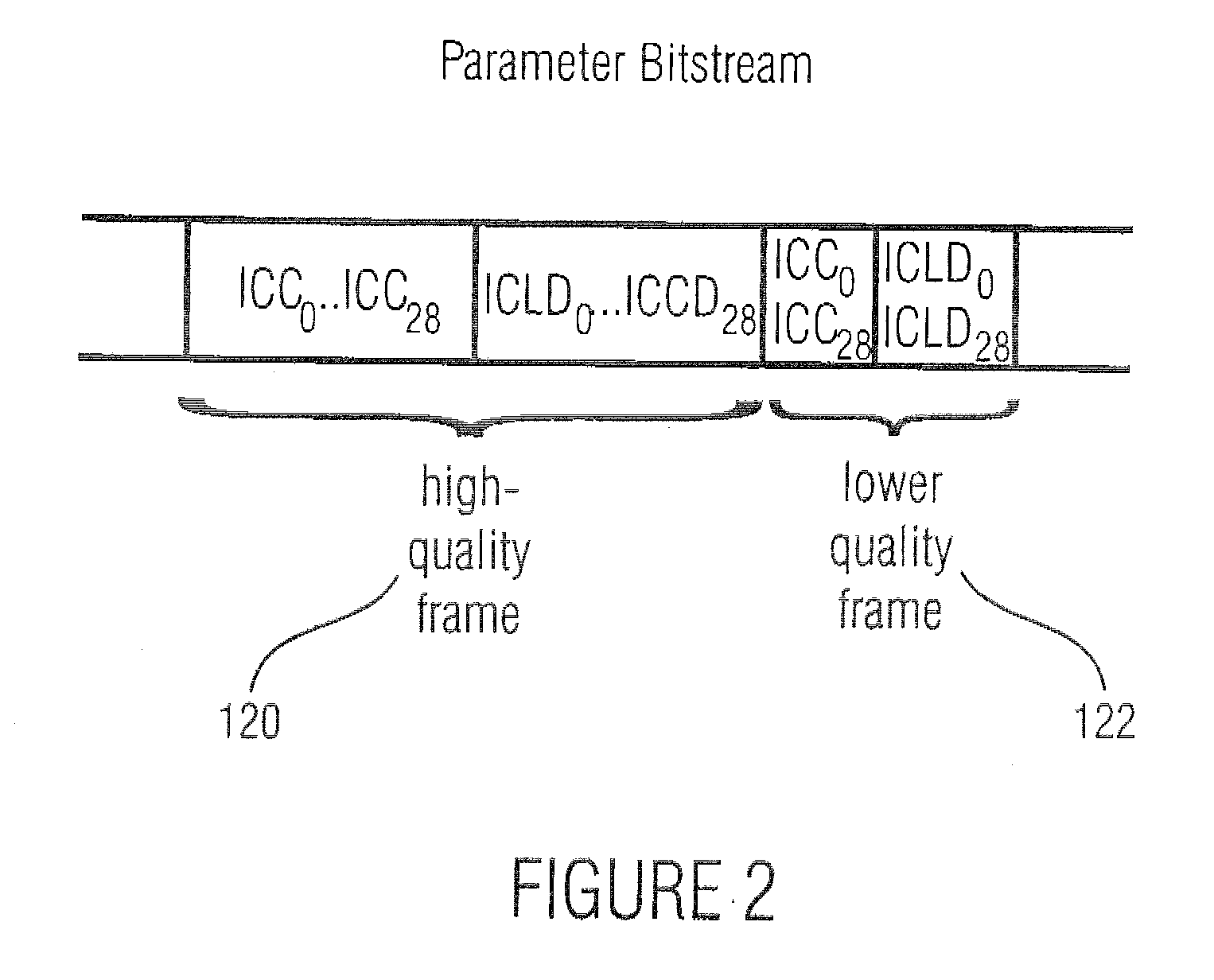
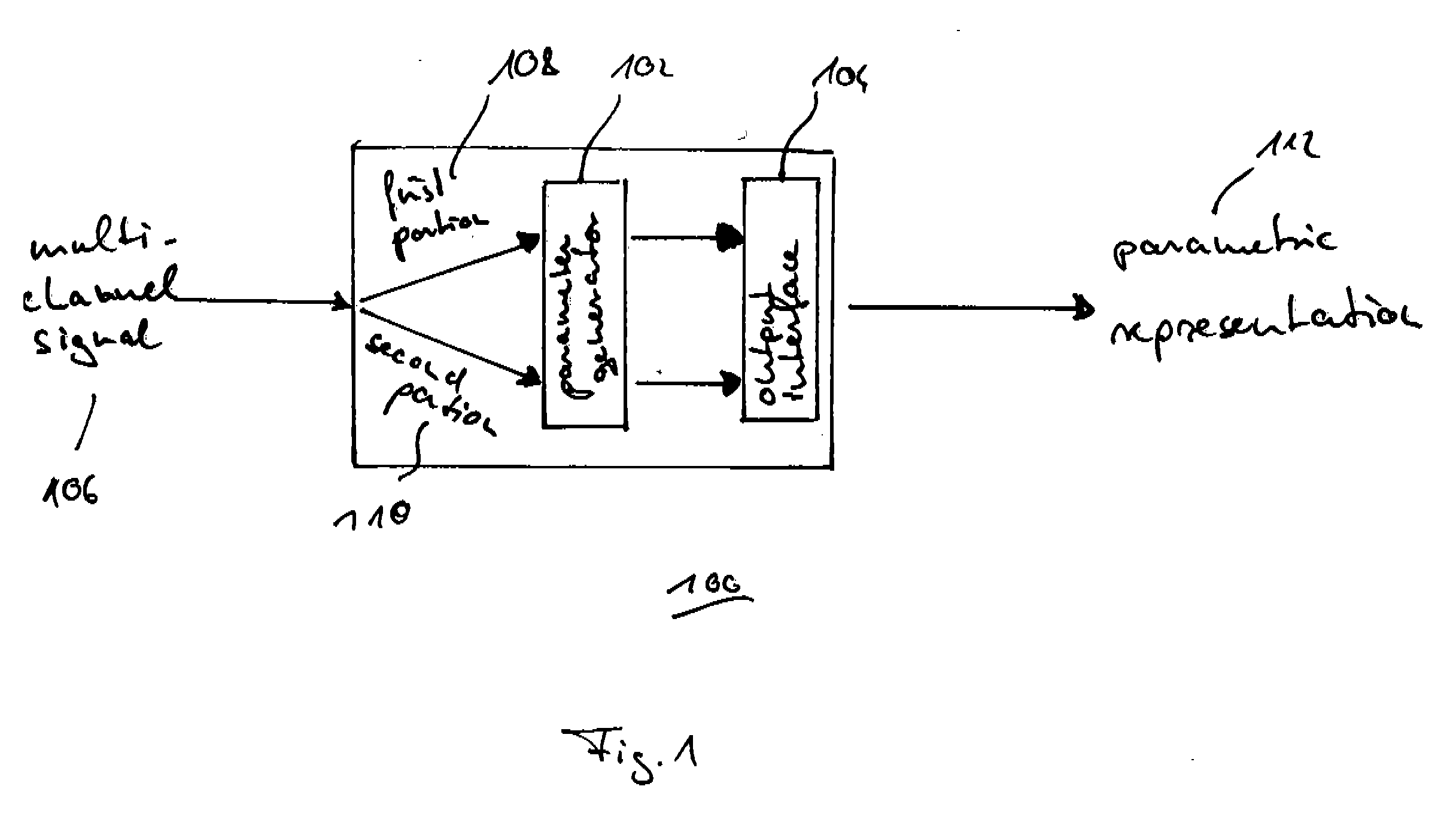
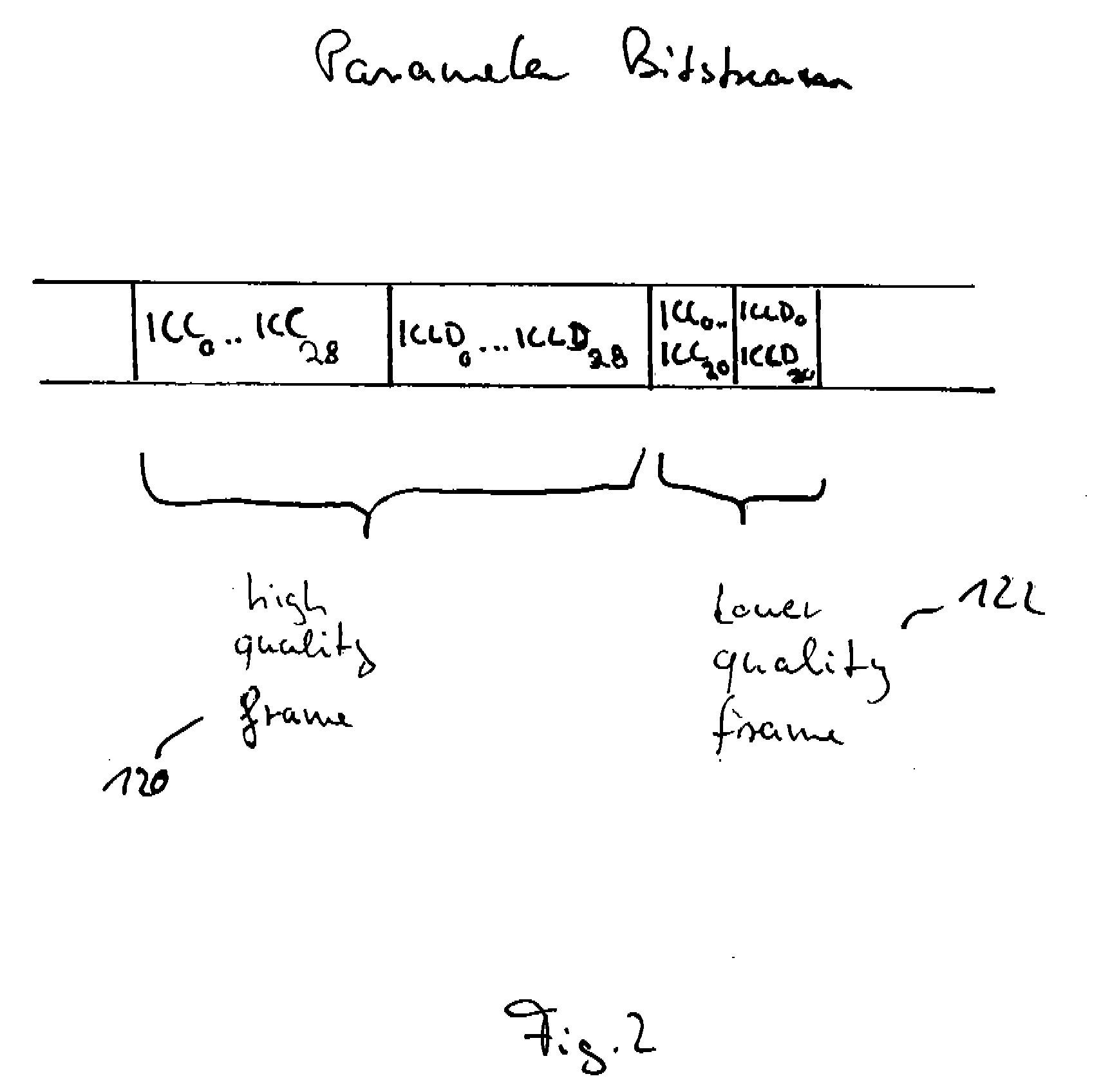
Scheme for Generating a Parametric Representation for Low-Bit Rate Applications
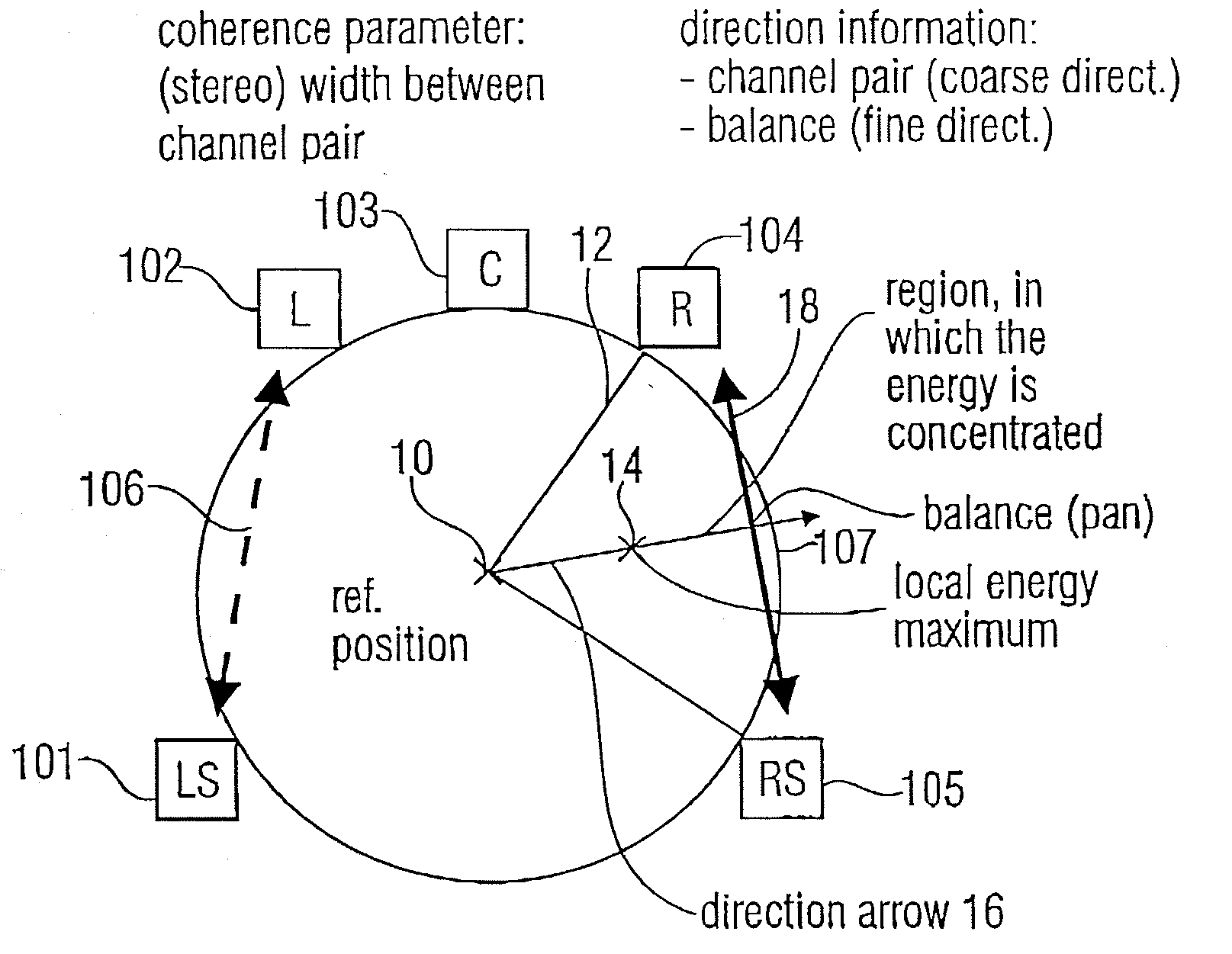
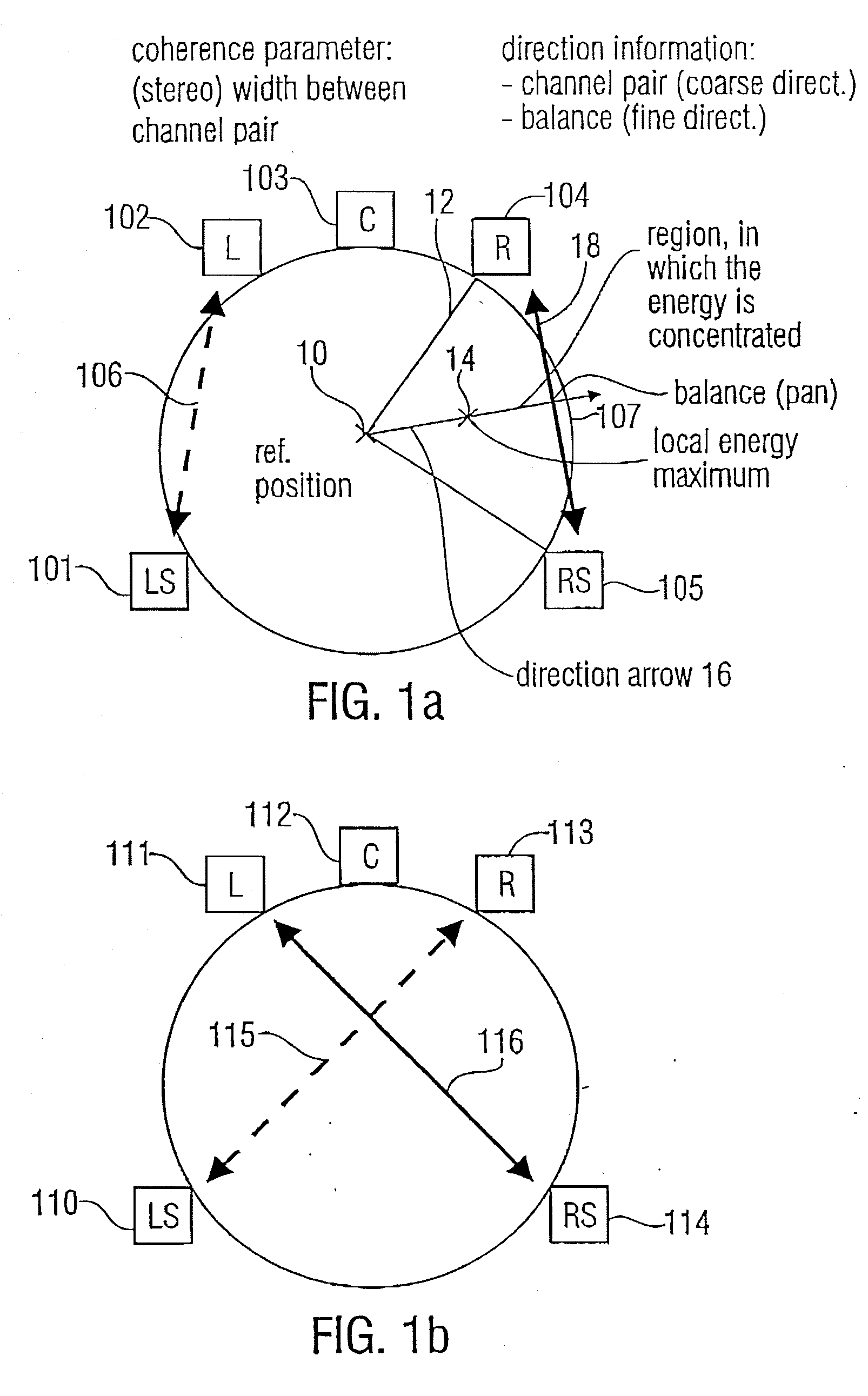
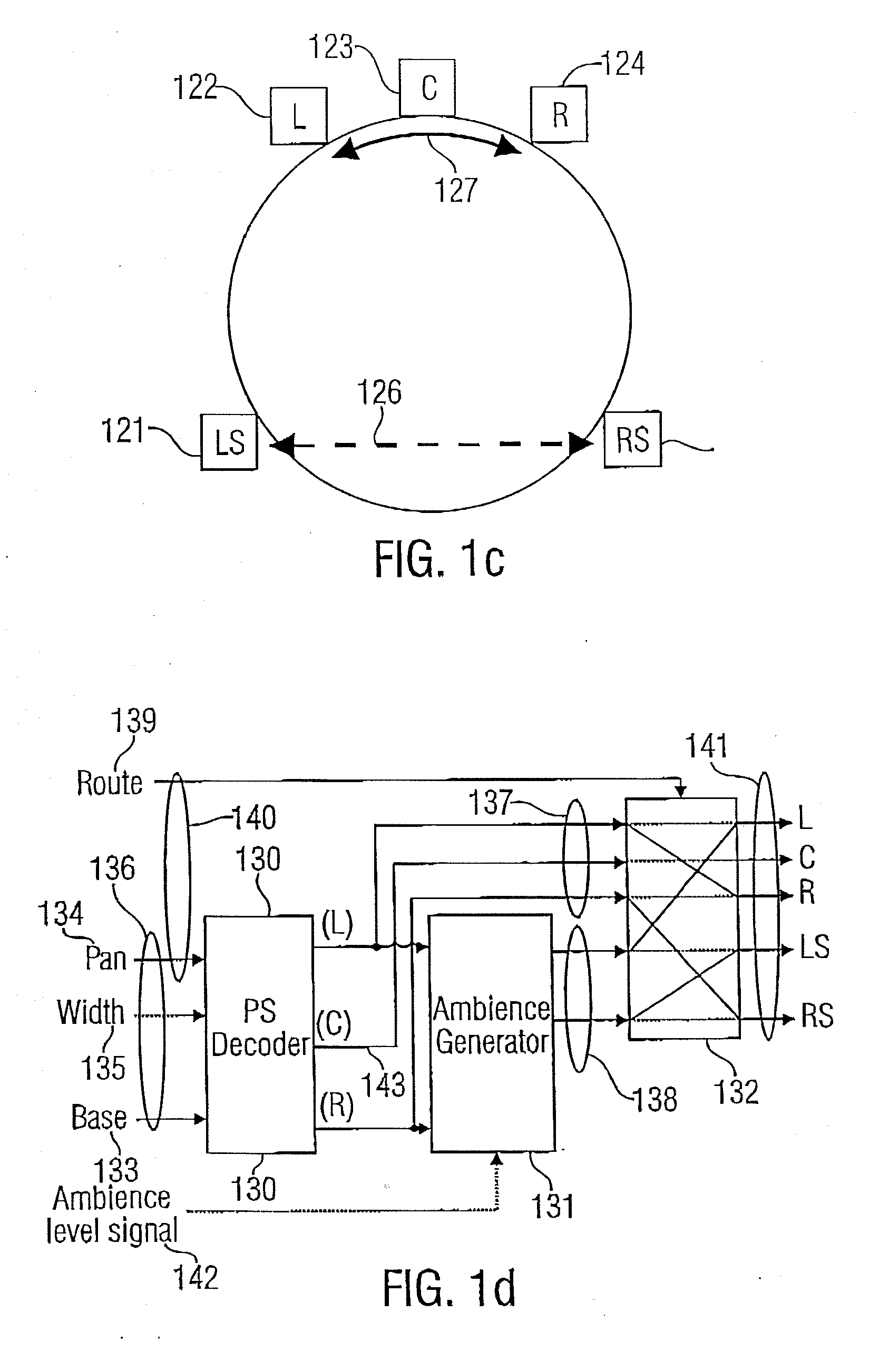
ActiveUS20070127733A1Little informationSpeech analysisBroadcast circuit arrangementsSound energyComputer science
For generating a parametric representation of a multi-channel signal especially suitable for low-bit rate applications, only the location of the maximum of the sound energy within a replay setup is encoded and transmitted using direction parameter information. For multi-channel reconstruction, the energy distribution of the output channels identified by the direction parameter information is controlled by the direction parameter information, while the energy distribution in the remaining ambience channels is not controlled by the direction parameter information.
Owner:DOLBY INT AB
Spatial position sharing system, data sharing system, network game system, and network game client
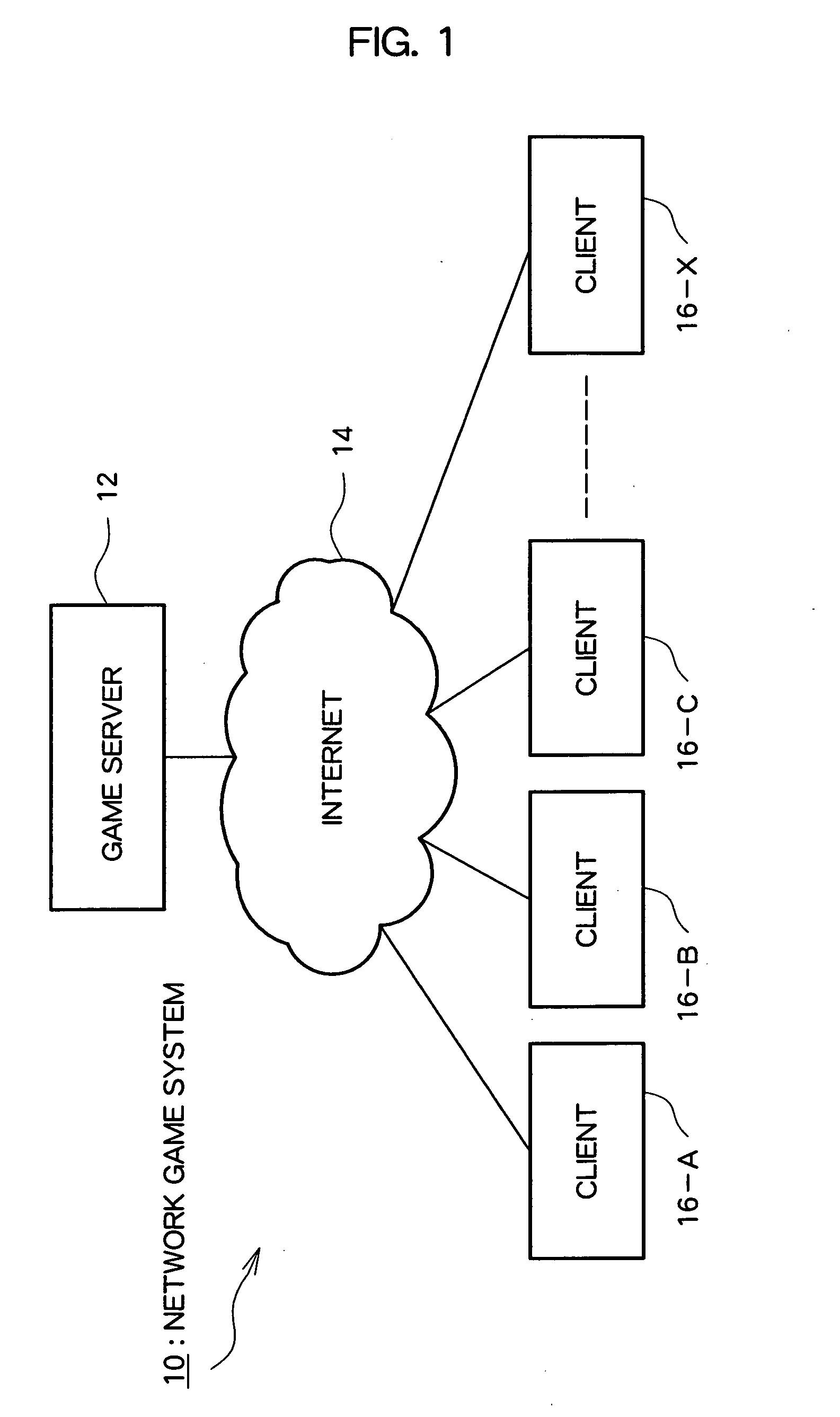
InactiveUS20060154713A1Suppress mutationImprove accuracyData processing applicationsVideo gamesVirtual spaceClient-side
In a client (16), current position information and predicted future position information for an object that have been generated in another client (16) are received, and estimated current position information for the same object in virtual space are sequentially generated based on these items of information. A game server (12) controls transfer of position information received from non-specified clients to specified clients. Further, at the client (16), in a message input mode, current position information for an object is generated automatically or semi-automatically, and that current position information is transmitted to the game server (12).
Owner:GENKI
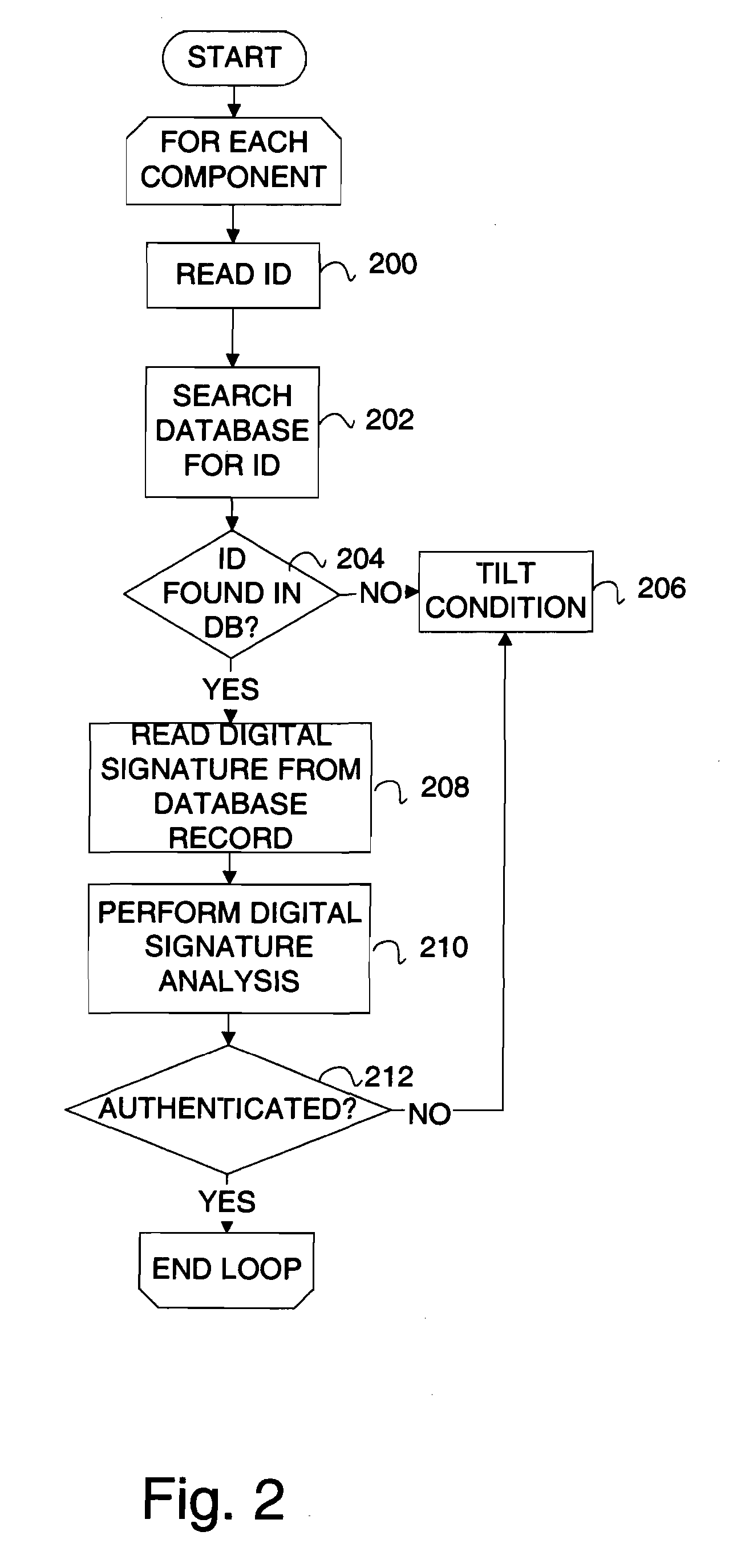
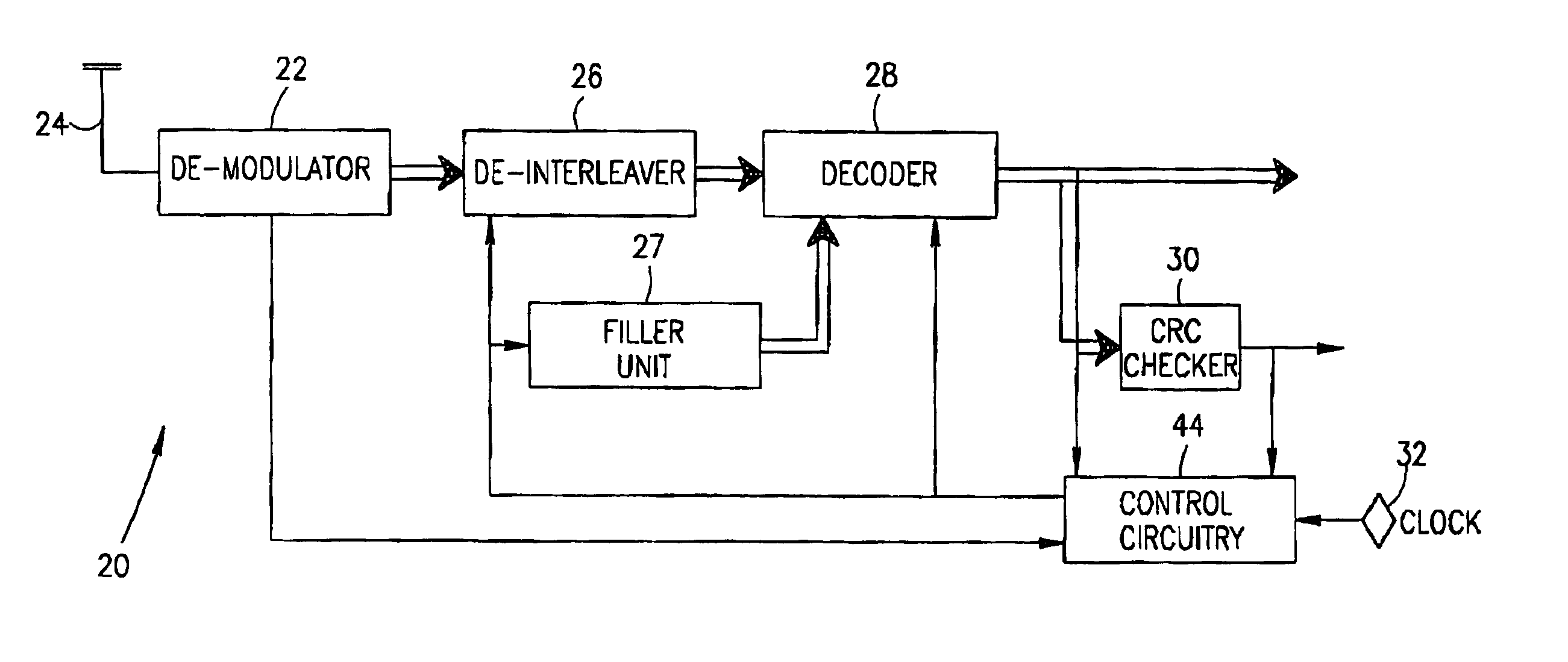
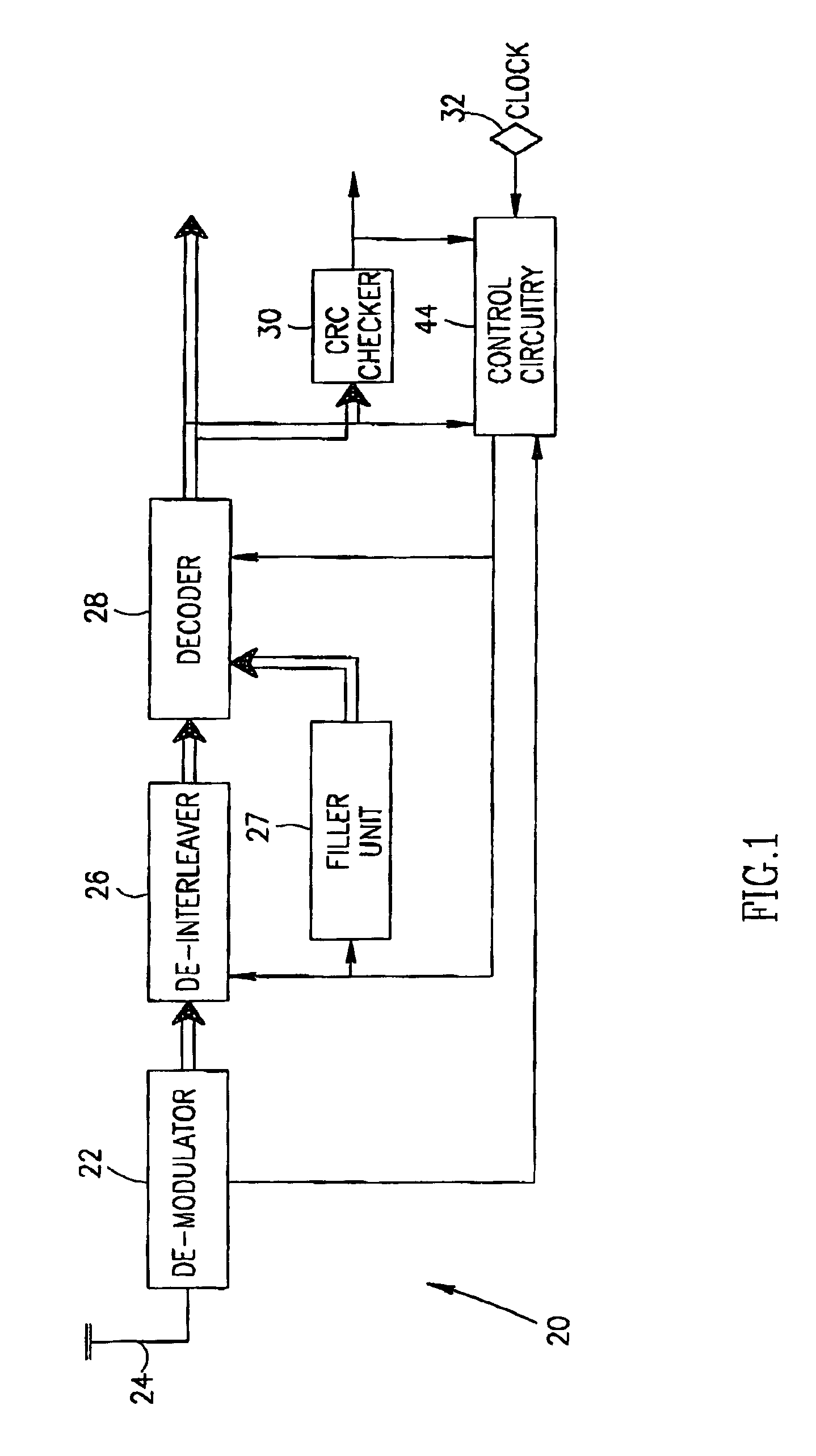
Device verification system and method
InactiveUS20070006329A1Little informationImprove securityDetecting faulty hardware by configuration testDetecting faulty hardware by remote testFile allocationOperational system
There is provided a method and system for verifying a device, having components. Identification numbers of the components are read and then verified. The process of verifying comprises matching each identification number in a database to determine whether each identification number is valid. In one embodiment, the database is remote from the device, wherein verification is performed over a network connecting a database server containing the database with the device. The device transmits the identification numbers for each of the components to the database server for verification. A file allocation structure reader may be located in a basic input / output system of the device for reading and verifying data files from a persistent storage media without loading an operating system. The device may comprise a gaming machine that contains a monitor for monitoring one or more system events being processed by the gaming machine. The monitor monitors routine and non-routine events. A detector is included for detecting selected system events so that they may be recorded.
Owner:BALLY GAMING INC
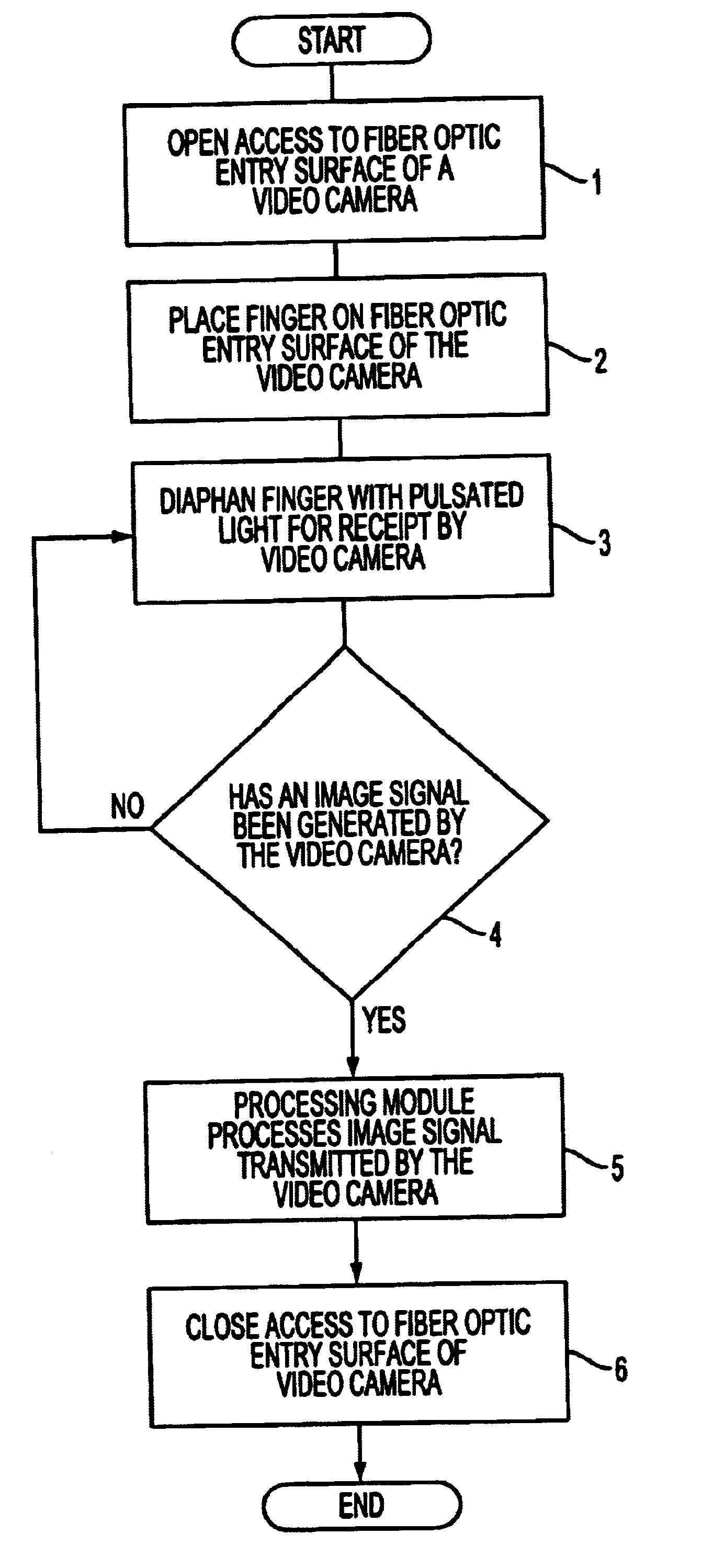
Method and apparatus for user identification using pulsating light source
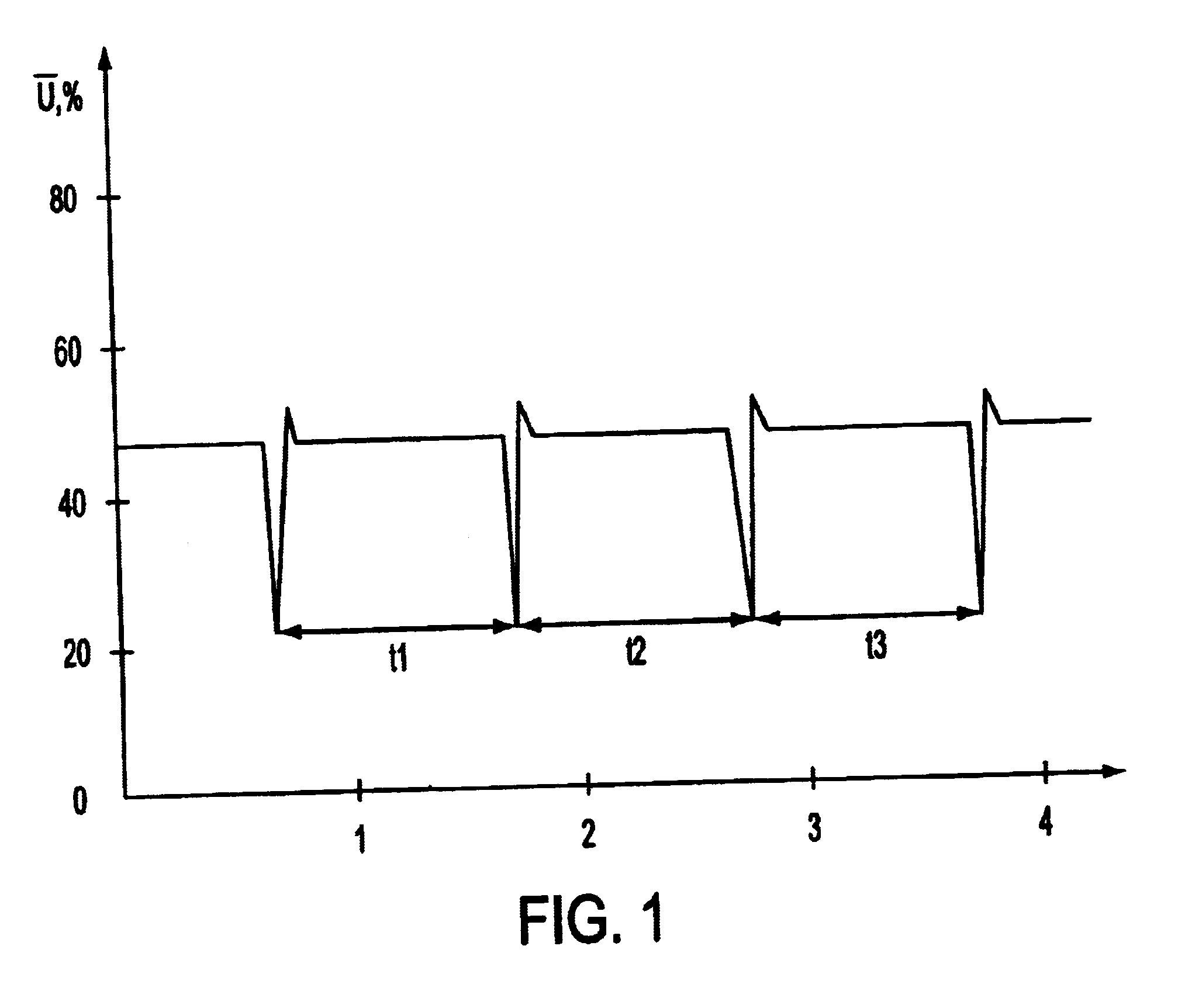
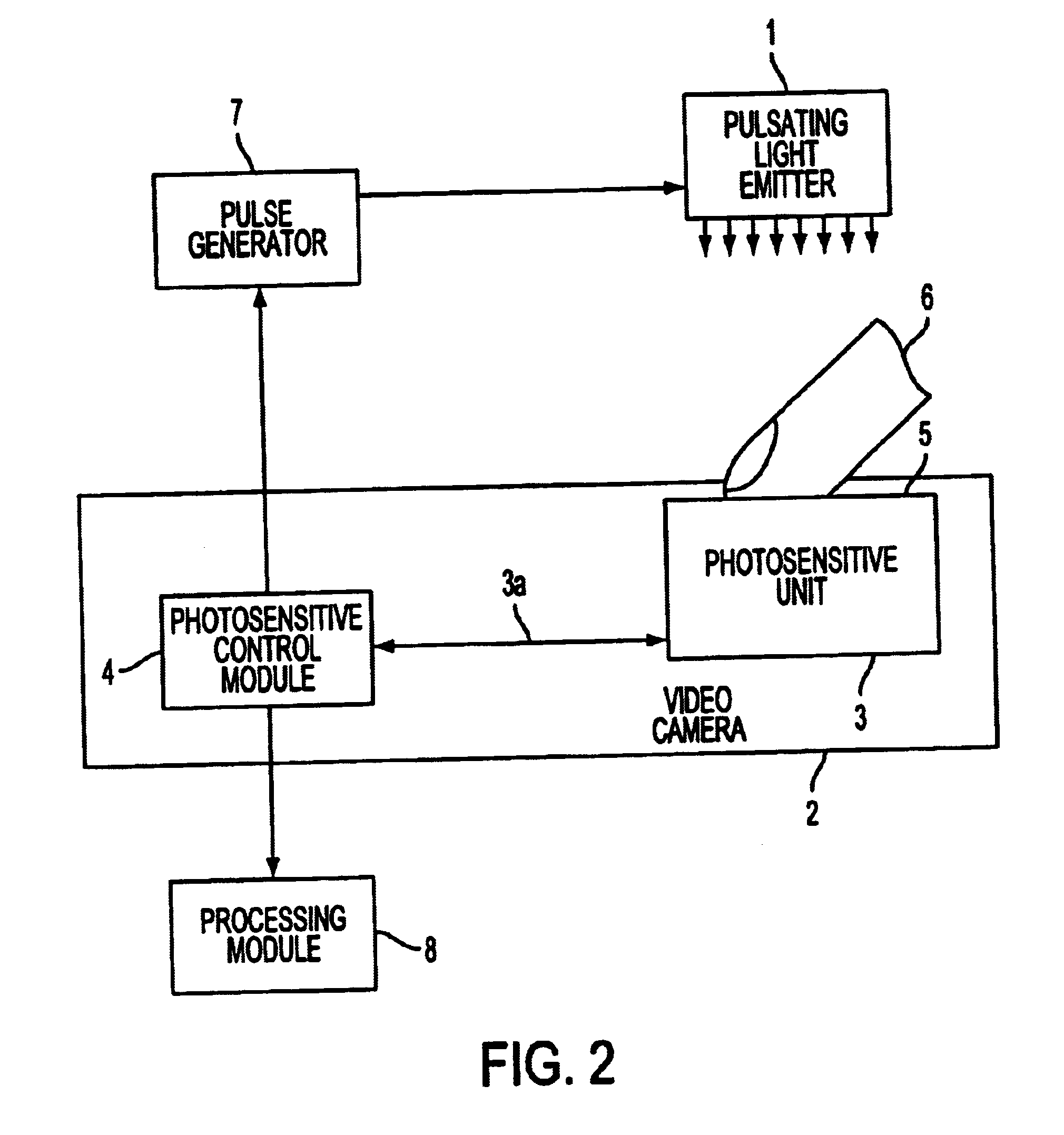
InactiveUS6668071B1Reduce probabilityReduce instabilityPrint image acquisitionDetecting live finger characterShort durationLight source
Pulsating light is used to penetrate a user's finger placed an input surface (which can be a fiber optic surface) of a video camera to avoid the effects of bloodflow from a normal human pulse on the quality of the image which would otherwise change the contrast of the image. The use of pulsating light of shorter durations than a typical human pulse provides an accurate image of a portion of a finger for identification. A retractable cover blocks the fiber optic input surface during a non-working mode, and allows access for identification during a working mode. A light source having a plurality of light emitting diodes provides light that diaphans a portion of the finger. Several successive frames of image signals allow for biometric detection and verification of a human pulse to ensure the finger is not a counterfeit.
Owner:MINKIN VIKTOR ALBERTOVICH +4
Systems and techniques for aggregation, display, and sharing of data
ActiveUS20170169800A1Less informationLess contextMemory architecture accessing/allocationData processing applicationsGraphicsNetwork packet
Systems and techniques for aggregation, display, and sharing of data. Graphic items representing data objects identified by a data package may be displayed on timelines. Each timeline may be associated with a respective class of data, and each graphic item displayed on a respective timeline may represent one or more of the data objects in the class associated with the respective timeline. A prediction may be made regarding which data will be displayed in the near future. A pre-fetch request may be generated, and the predicted data may be retrieved from a remote server and stored in a local data cache before the user requests that the predicted data be displayed.
Owner:SYNTHRO INC
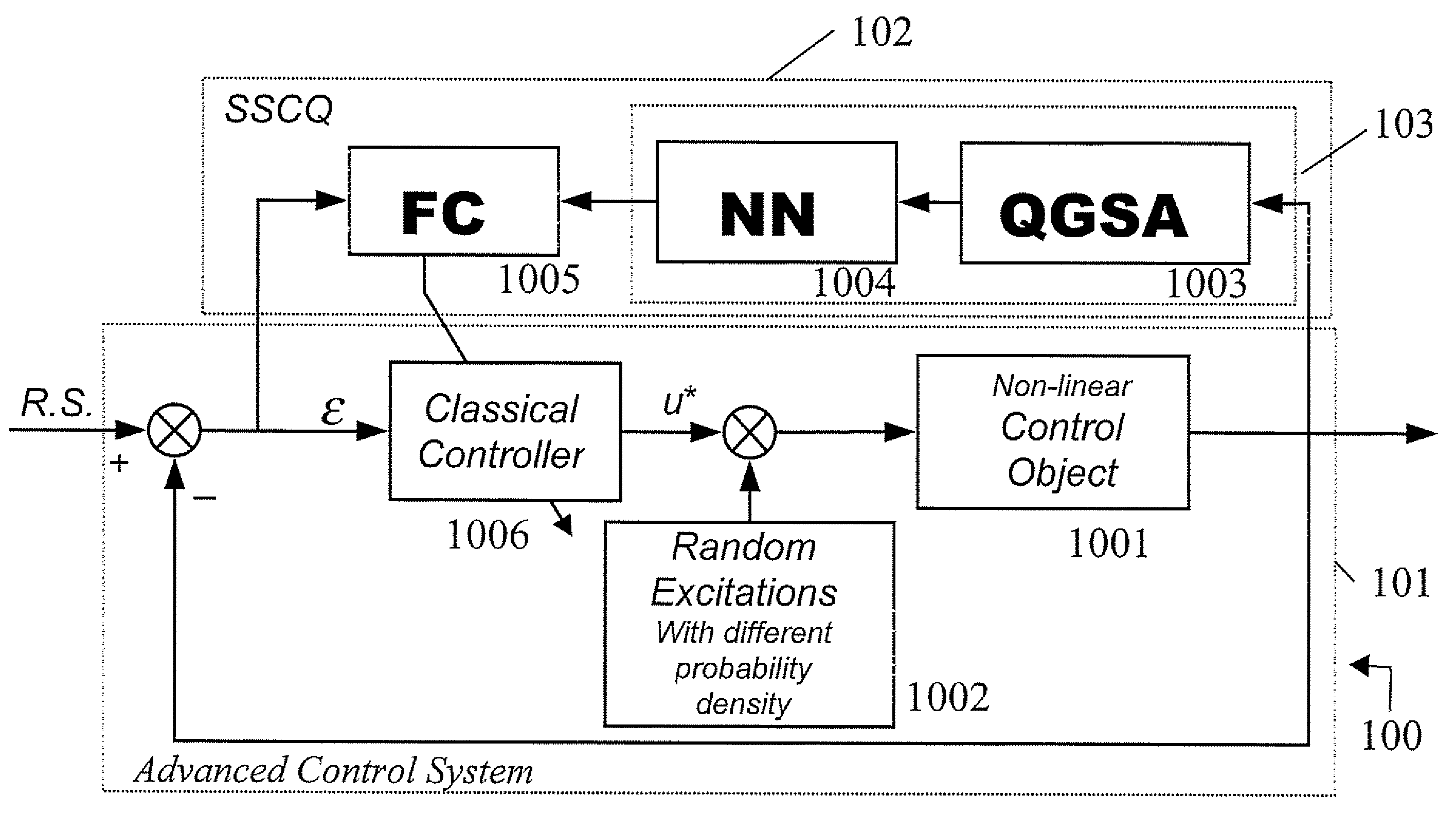
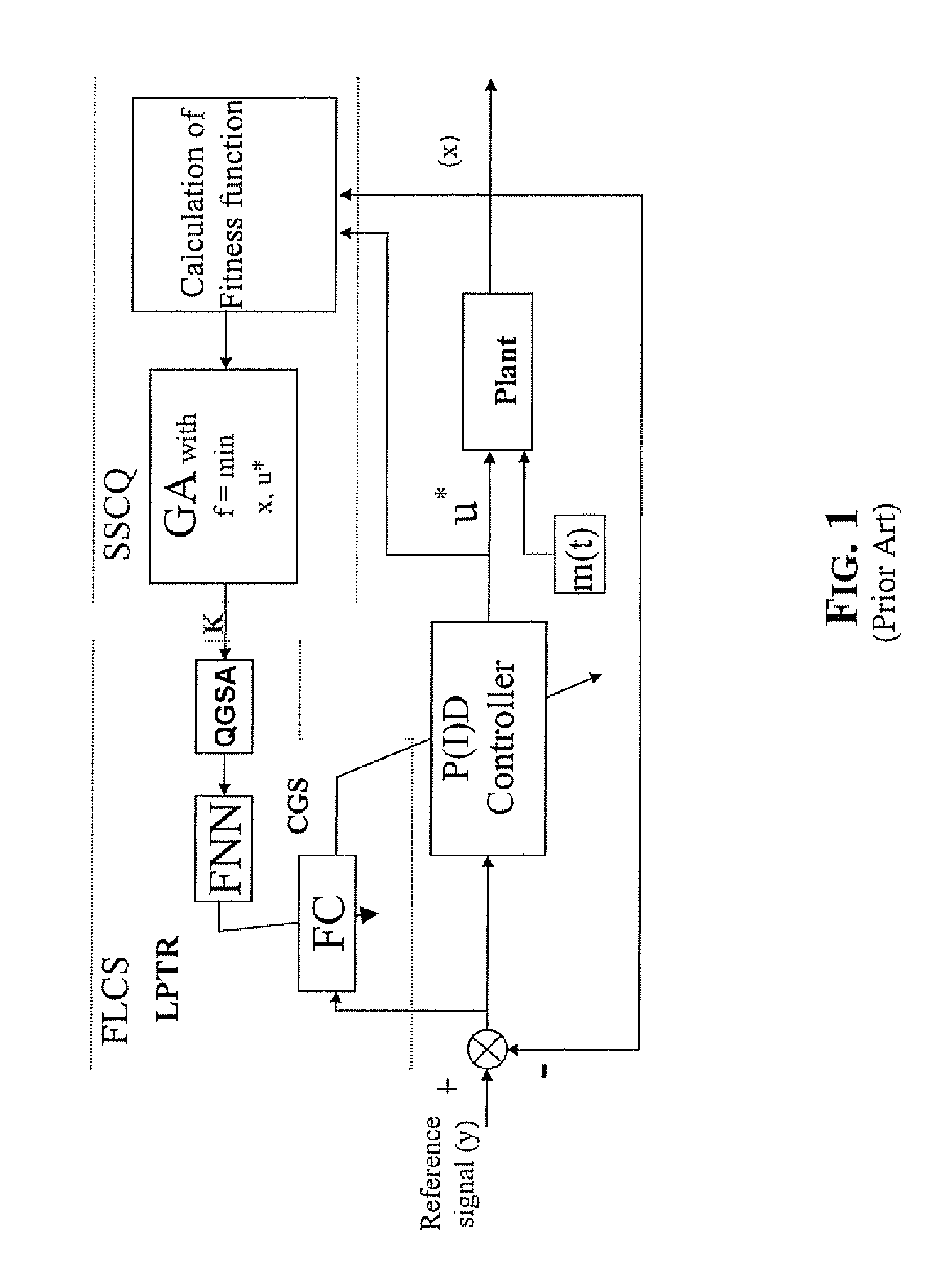
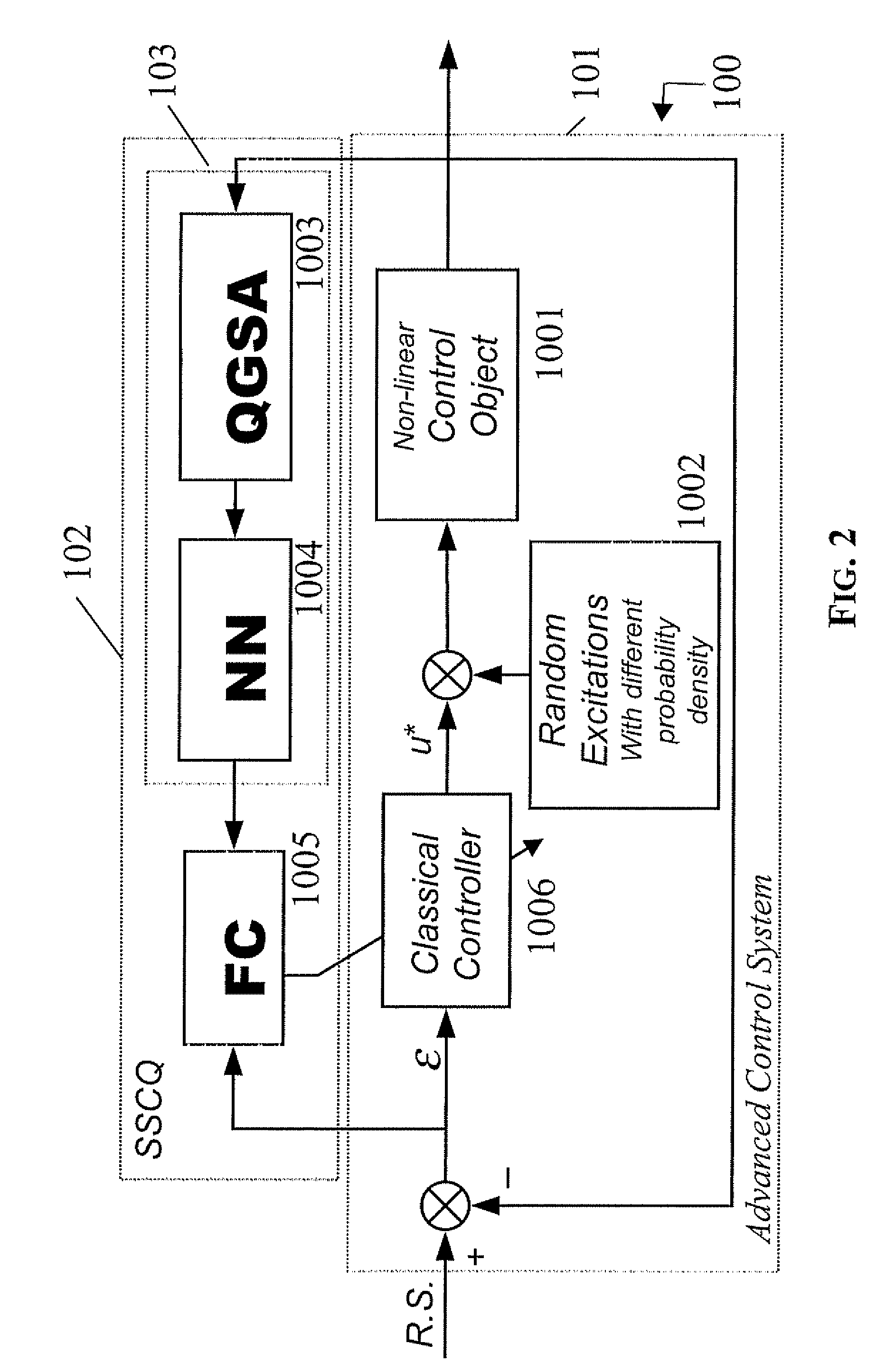
Method and device for performing a quantum algorithm to simulate a genetic algorithm
InactiveUS20080140749A1Increase diversityEasy searchQuantum computersNanoinformaticsAlgorithmQuantum algorithm
A method and device for performing a quantum algorithm where the superposition, entanglement with interference operators determined for performing selection, crossover, and mutation operations based upon a genetic algorithm. Moreover, entanglement vectors generated by the entanglement operator of the quantum algorithm may be processed by a wise controller implementing a genetic algorithm before being input to the interference operator. This algorithm may be implemented with a hardware quantum gate or with a software computer program running on a computer. Further, the algorithm can be used in a method for controlling a process and a relative control device of a process which is more robust, requires very little initial information about dynamic behavior of control objects in the design process of an intelligent control system, or random noise insensitive (invariant) in a measurement system and in a control feedback loop.
Owner:STMICROELECTRONICS SRL +1
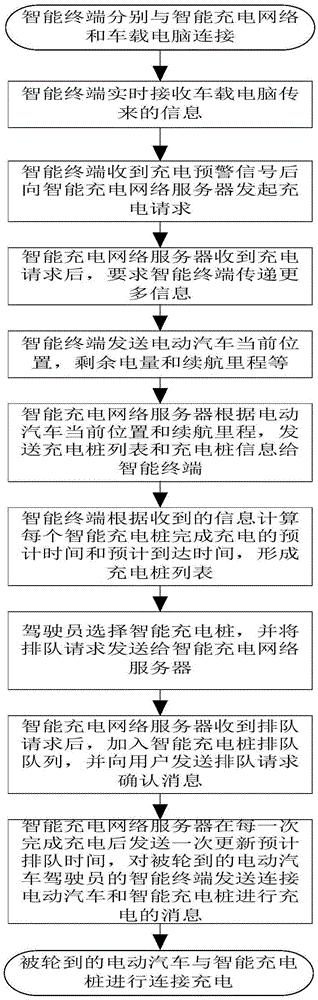
Electric vehicle intelligent queuing method capable of improving charging efficiency
InactiveCN105398347AReduce loadBalance and Utilize LoadCharging stationsElectric vehicle charging technologyElectricityDriver/operator
The invention provides an electric vehicle intelligent queuing method capable of improving charging efficiency. The method is characterized by comprising the following steps that firstly, an electric vehicle driver is in connection with an intelligent charging network and a vehicle-mounted computer of an electric vehicle through an intelligent terminal; secondly, the intelligent terminal receives electric vehicle information transmitted by the vehicle-mounted computer in real time, wherein the electric vehicle information comprises electric vehicle serial numbers, residual electricity quantity, driving mileage and charging early-warning signals; thirdly, after the intelligent terminal receives the charging early-warning signals, the intelligent terminal is in communication with the intelligent charging network server and issues a charging request to the intelligent charging network server, ..., and eleventh, the turned electric vehicle is connected with an intelligent charging pile to be charged. According to the method, through a smart phone, the charging pile can be looked for, and through the residual electricity quantity of the electric vehicle, waiting time and predicated charging time required by charging several closest charging piles can be accurately predicated, the queuing efficiency is improved, and the queuing time is shortened.
Owner:BEIJING FLASH CHARGE NETWORK TECH CO LTD
Storing and retrieving computer data files using an encrypted network drive file system
ActiveUS7506010B2Promote recoveryFast and efficientData processing applicationsError detection/correctionHard disc driveData file
Owner:IDRIVE INC
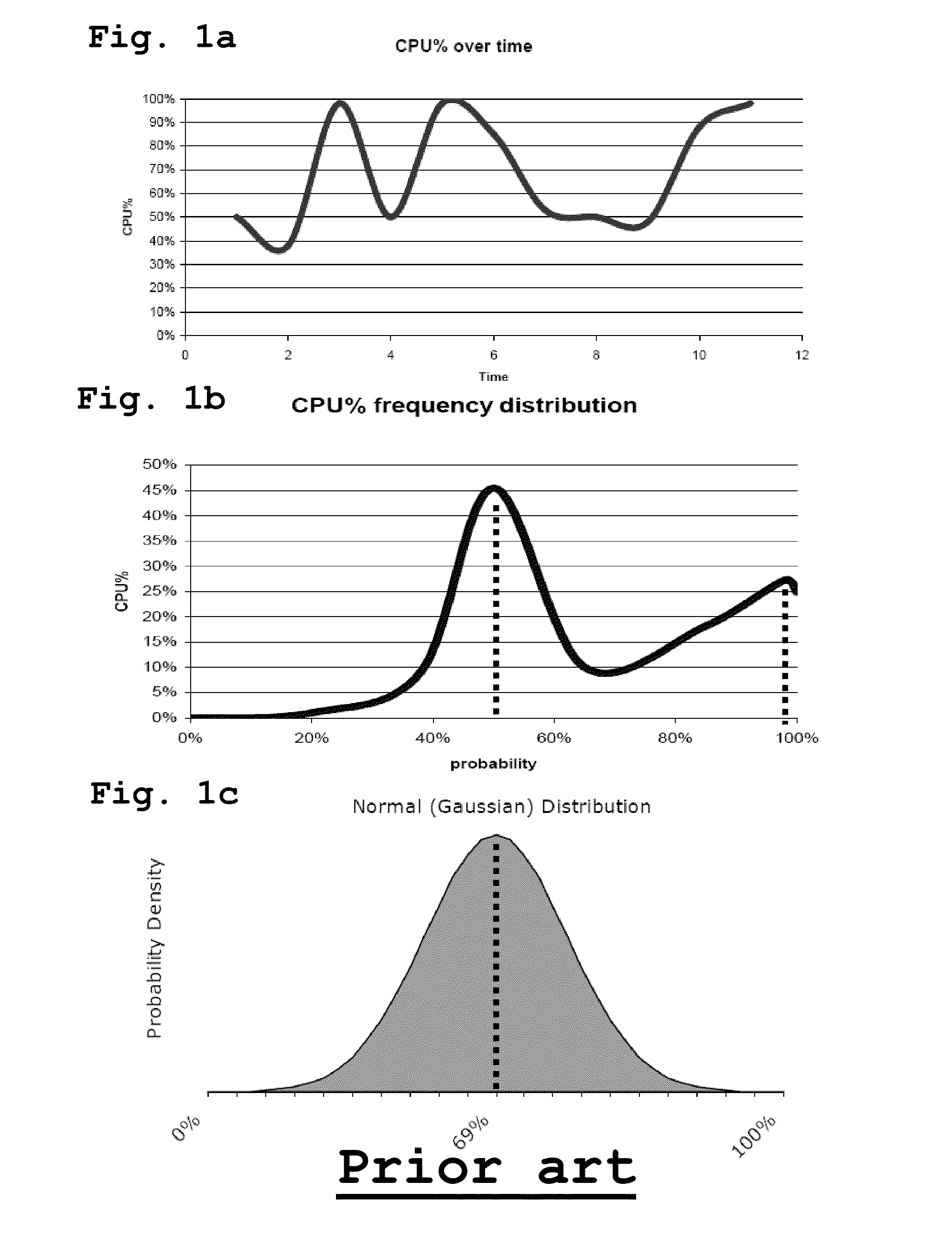
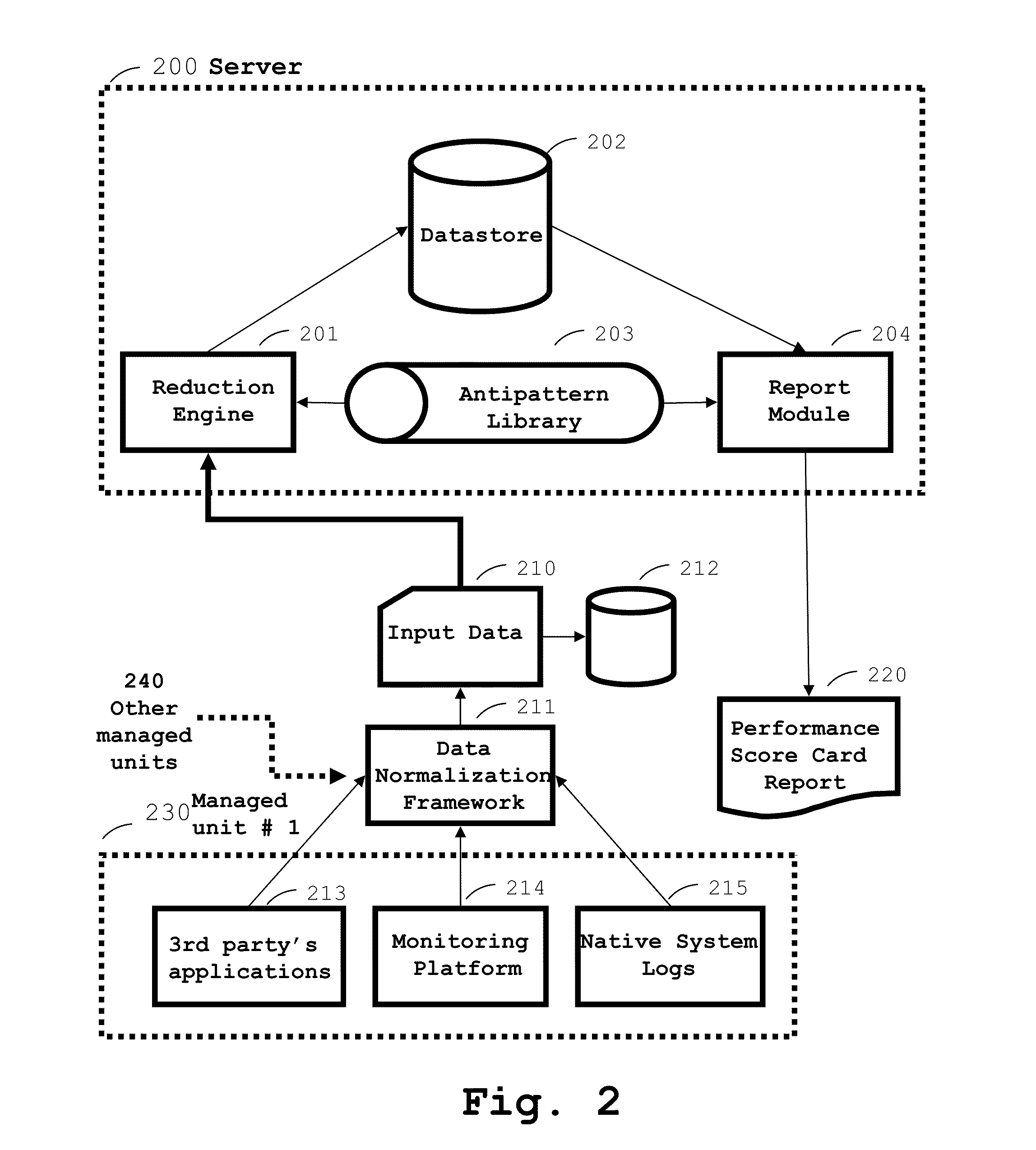
Method and system for it resources performance analysis
ActiveUS20110078106A1Reduce analysisComputationally efficientError detection/correctionKnowledge representationComputer scienceDistribution function
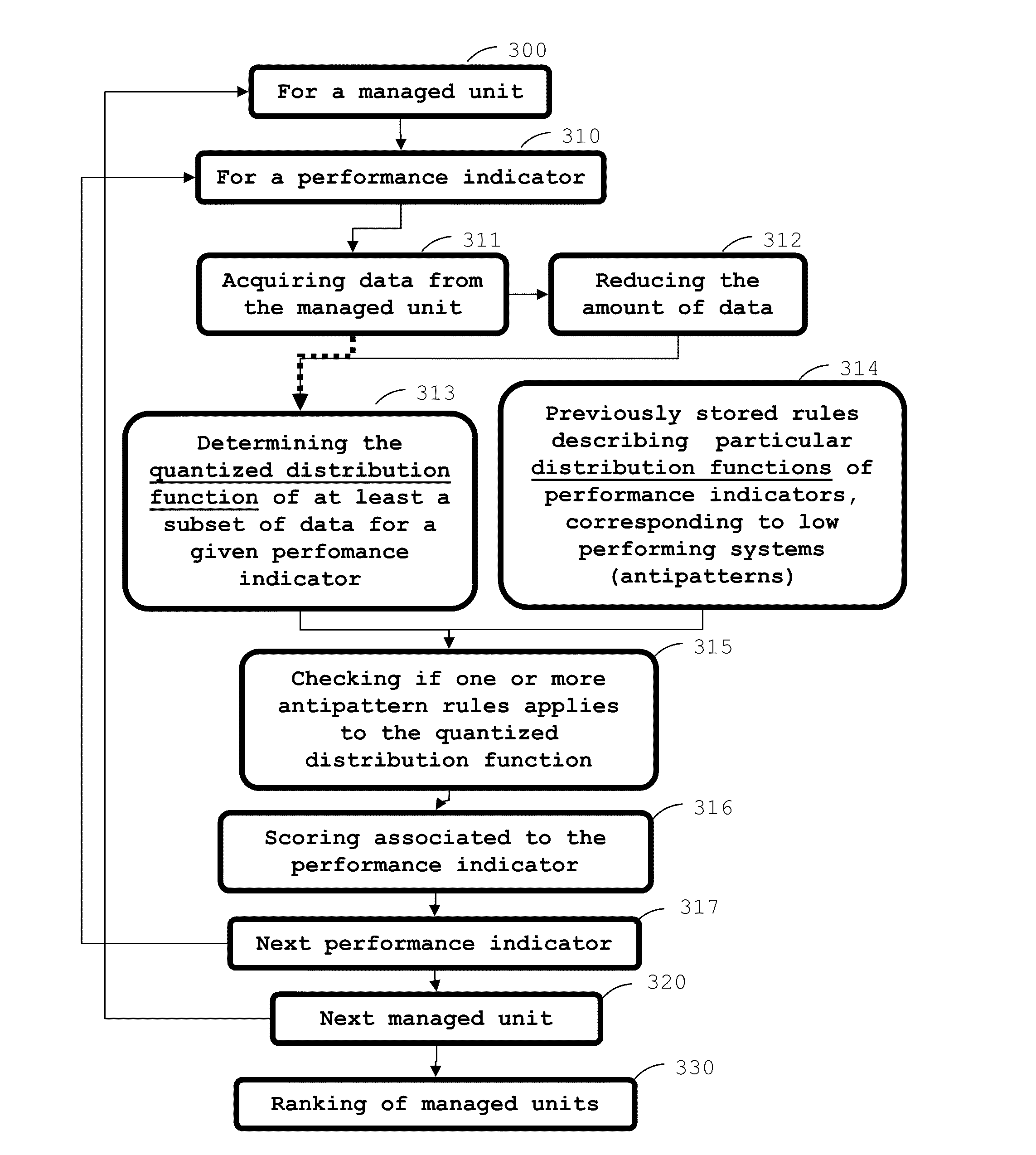
There is disclosed a method of monitoring an infrastructure comprising managed units, the method comprising the steps of: acquiring data associated with a first performance indicator from a first managed unit; determining a first quantized distribution function of at least a subset of pieces of data of the acquired data of the first managed unit; determining if the first quantized distribution function verifies one or a plurality of predefined rules describing particular distribution functions of performance indicators.
Owner:KYNDRYL INC
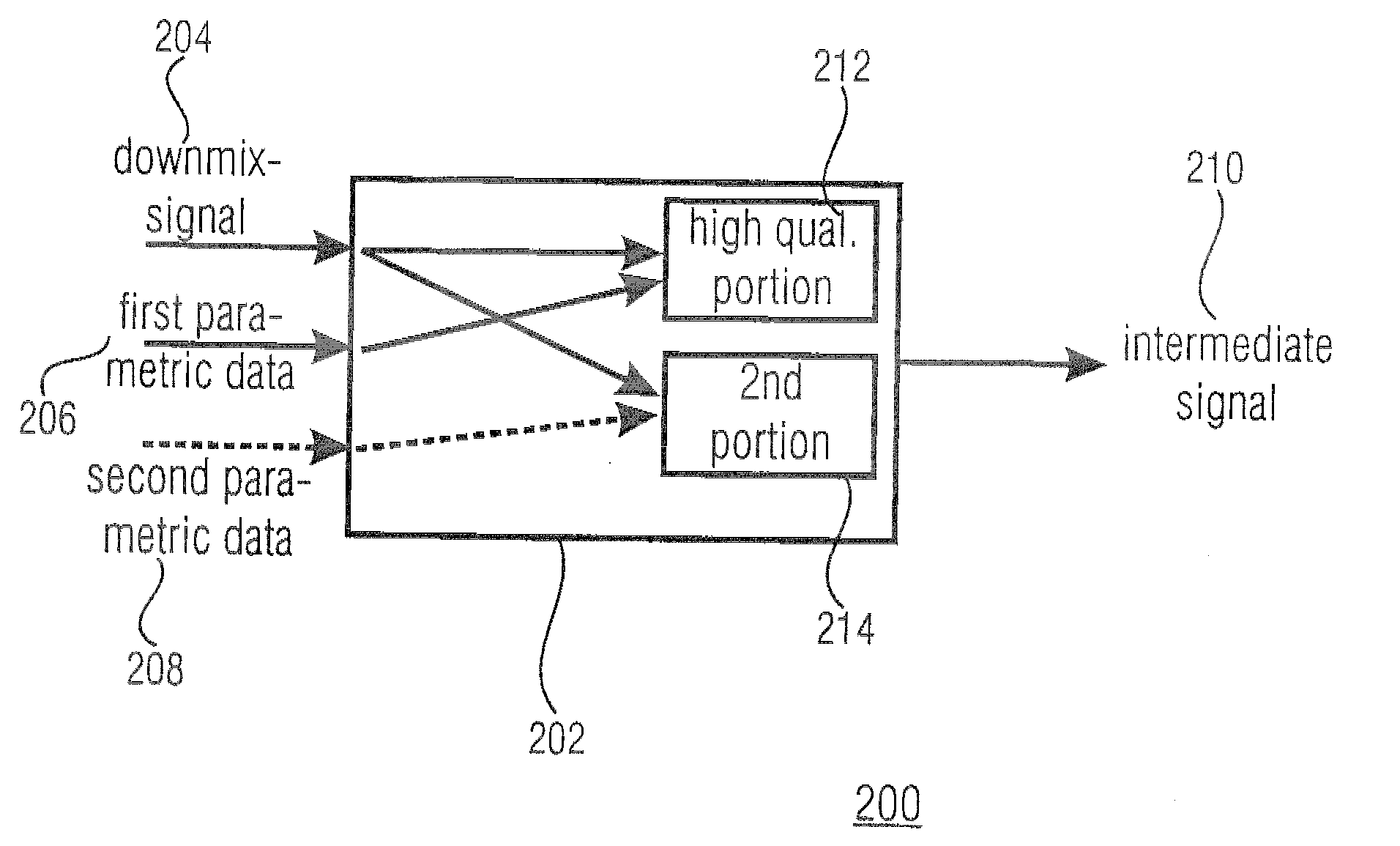
Concept for bridging the gap between parametric multi-channel audio coding and matrixed-surround multi-channel coding
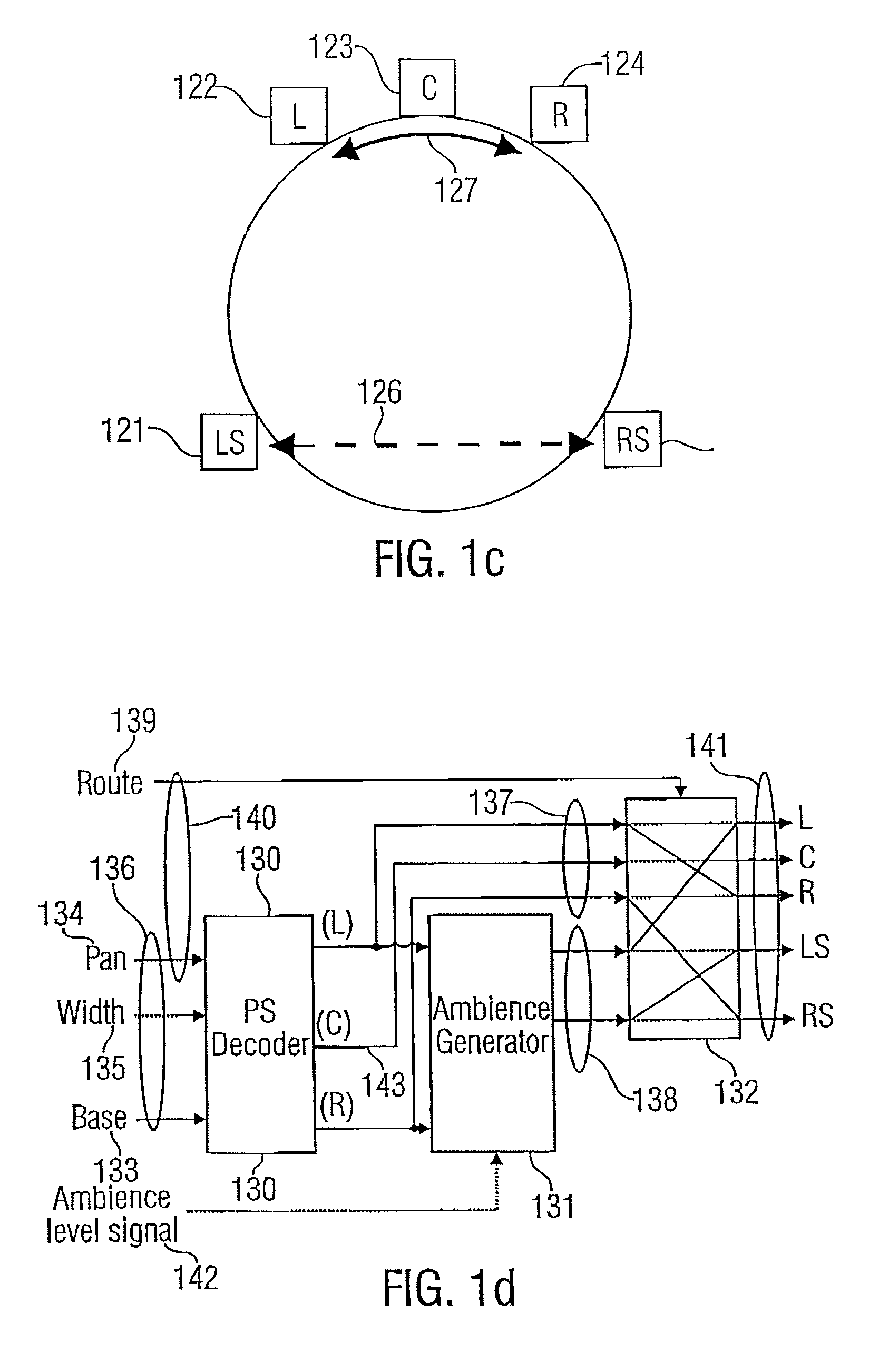
ActiveUS20070019813A1Efficient representationLittle informationSpeech analysisStereophonic systemsTelecommunicationsAudio frequency
The purpose of the invention is to bridge the gap between parametric multi-channel audio coding and matrixed-surround multi-channel coding by gradually improving the sound of an up-mix signal while raising the bit-rate consumed by the side-information starting from 0 up to the bit-rates of the parametric methods. More specifically, it provides a method of flexibly choosing an “operating point” somewhere between matrixed-surround (no side-information, limited audio quality) and fully parametric reconstruction (full side-information rate required, good quality). This operating point can be chosen dynamically (i.e. varying over time) and in response to the permissible side-information rate, as it is dictated by the individual application.
Owner:DOLBY LAB LICENSING CORP +1
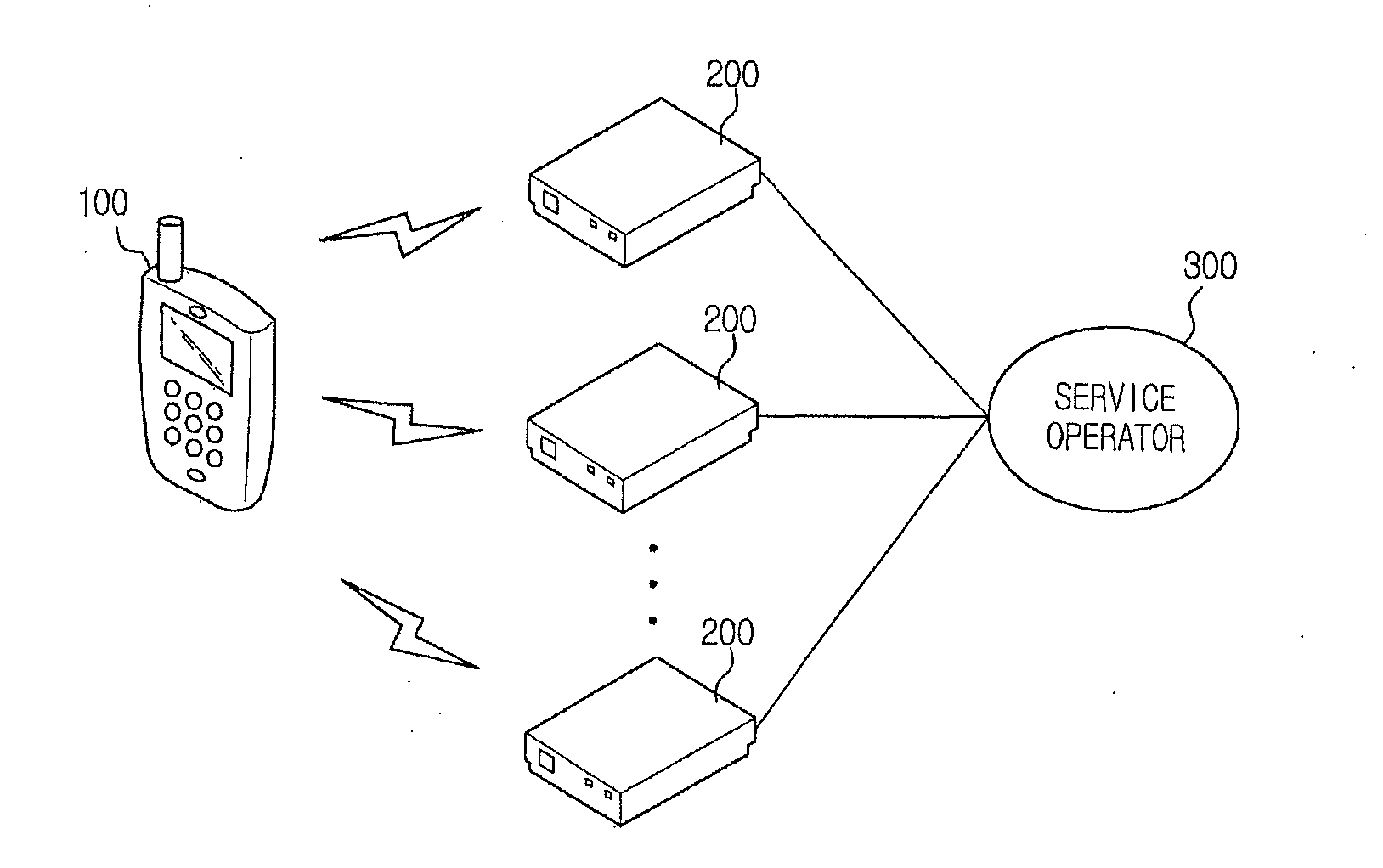
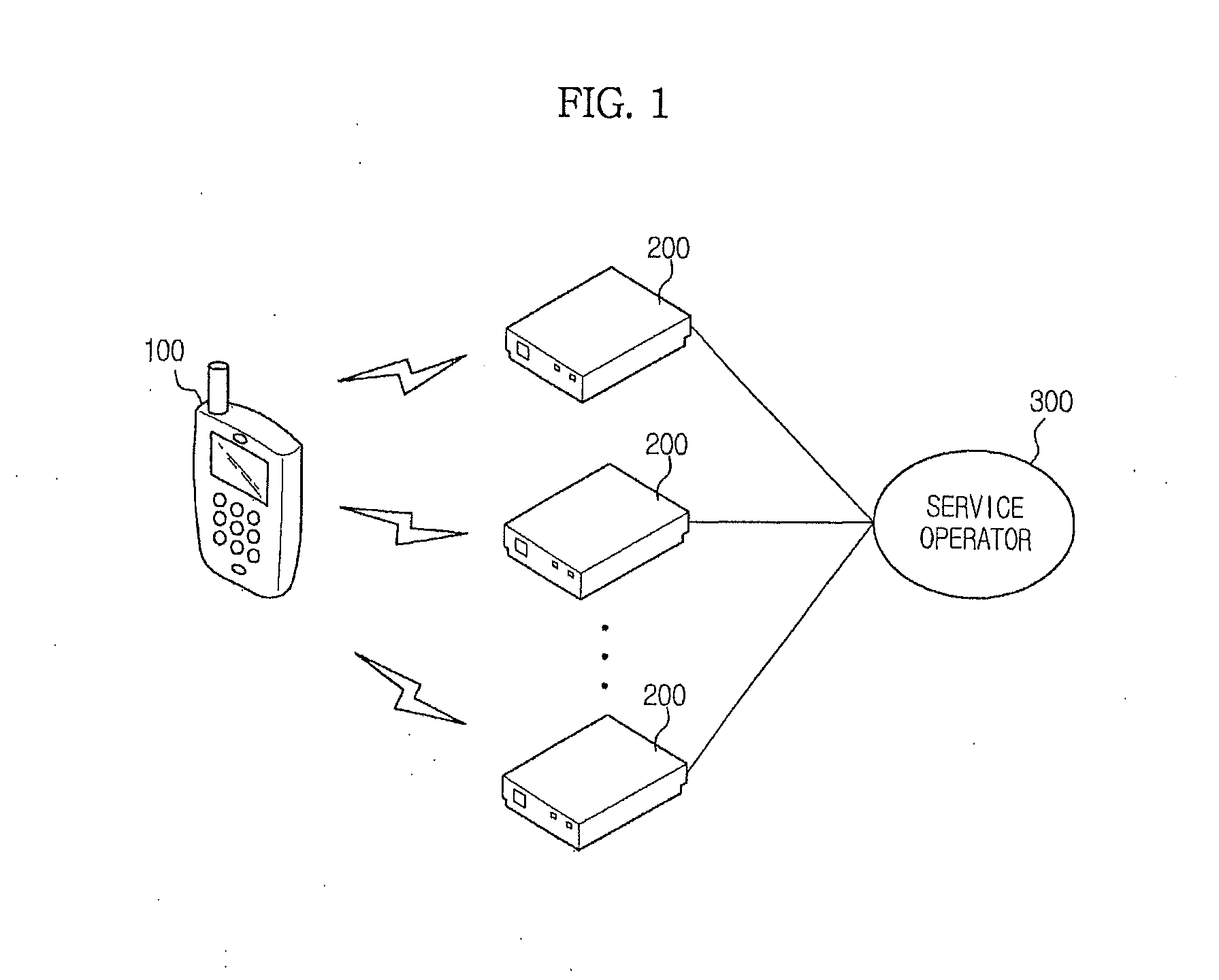
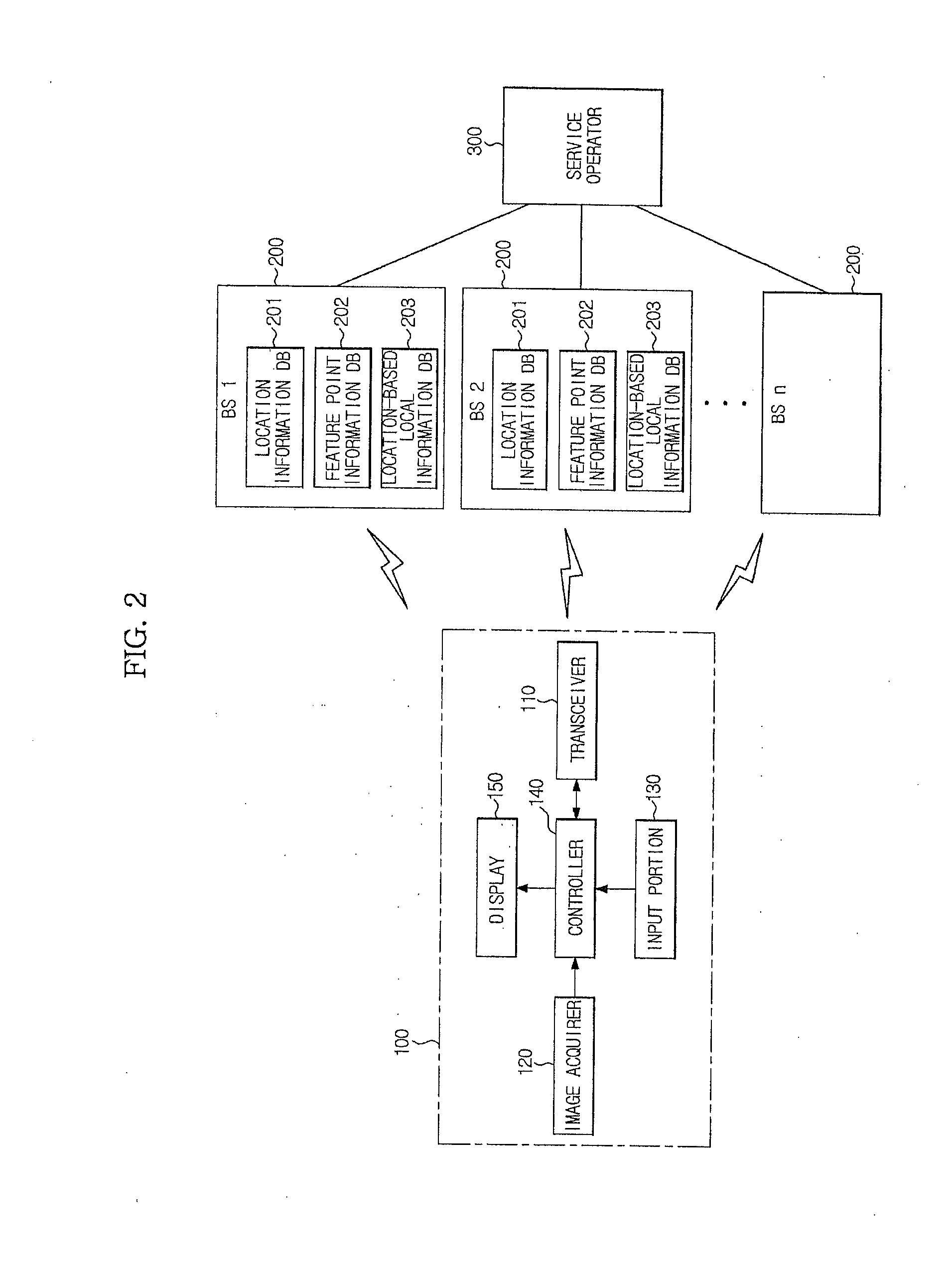
Apparatus to provide augmented reality service using location-based information and computer-readable medium and method of the same
ActiveUS20110165893A1Little informationImage enhancementImage analysisService controlLocation based information
An augmented reality (AR) service apparatus includes a camera to capture an actual image, a controller to receive feature point information about the captured image from at least one of a plurality of base stations (BSs), detect a location of the camera by matching data of feature points with data of the image, and provide location-based information in a same direction as the captured image according to the location of the camera, and a display to realize an AR service by combining the captured image with the location-based information under control of the controller.
Owner:SAMSUNG ELECTRONICS CO LTD
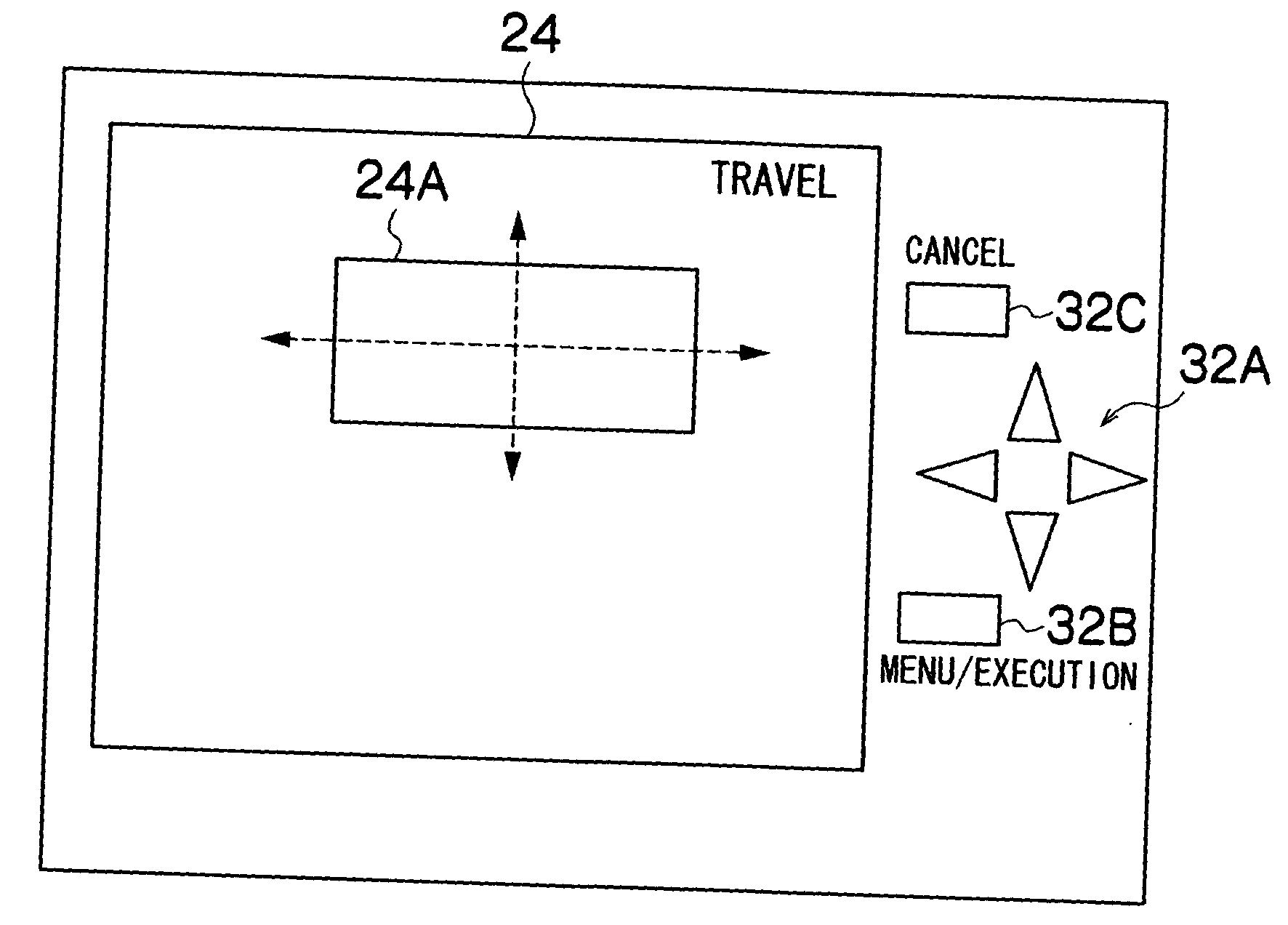
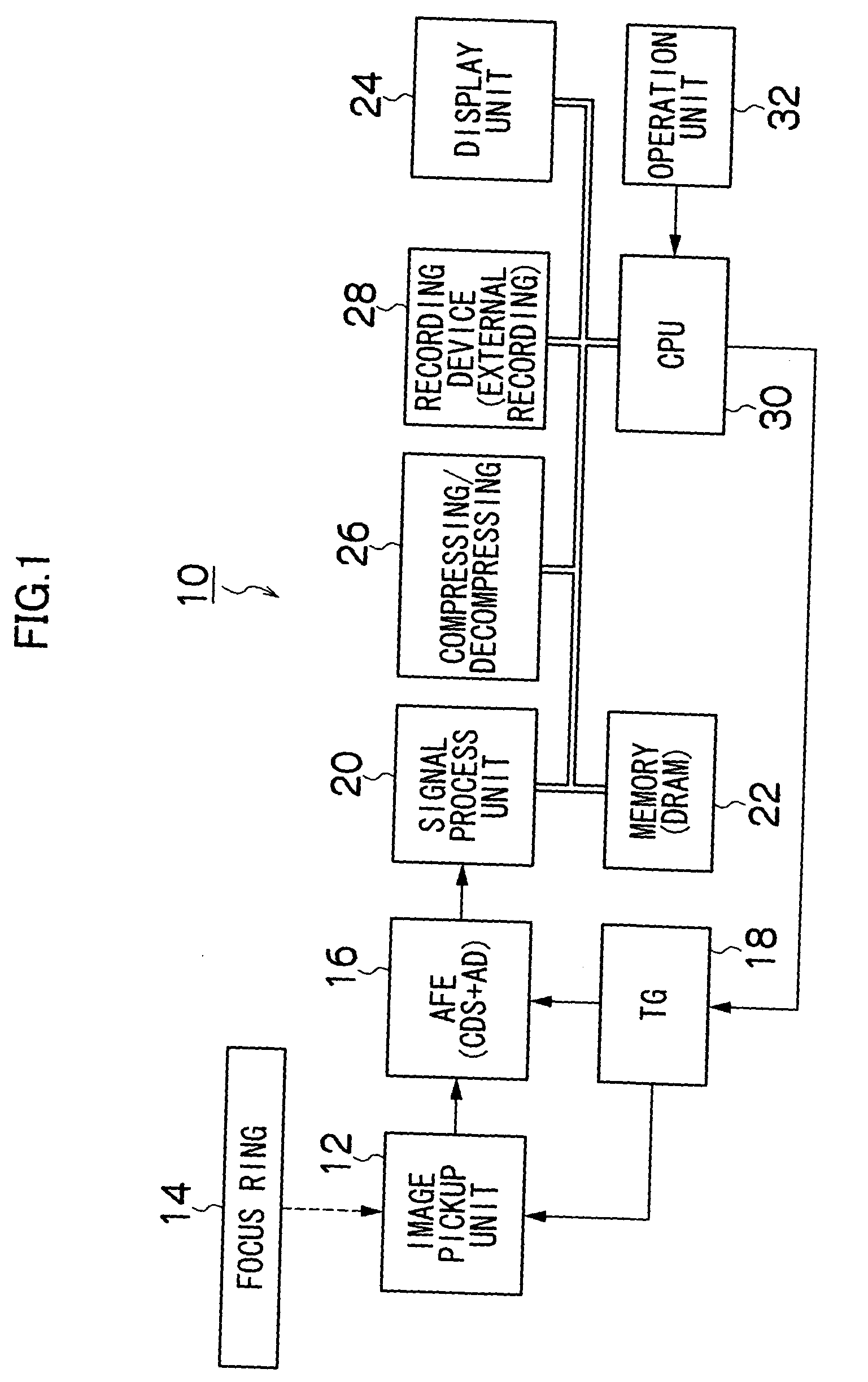
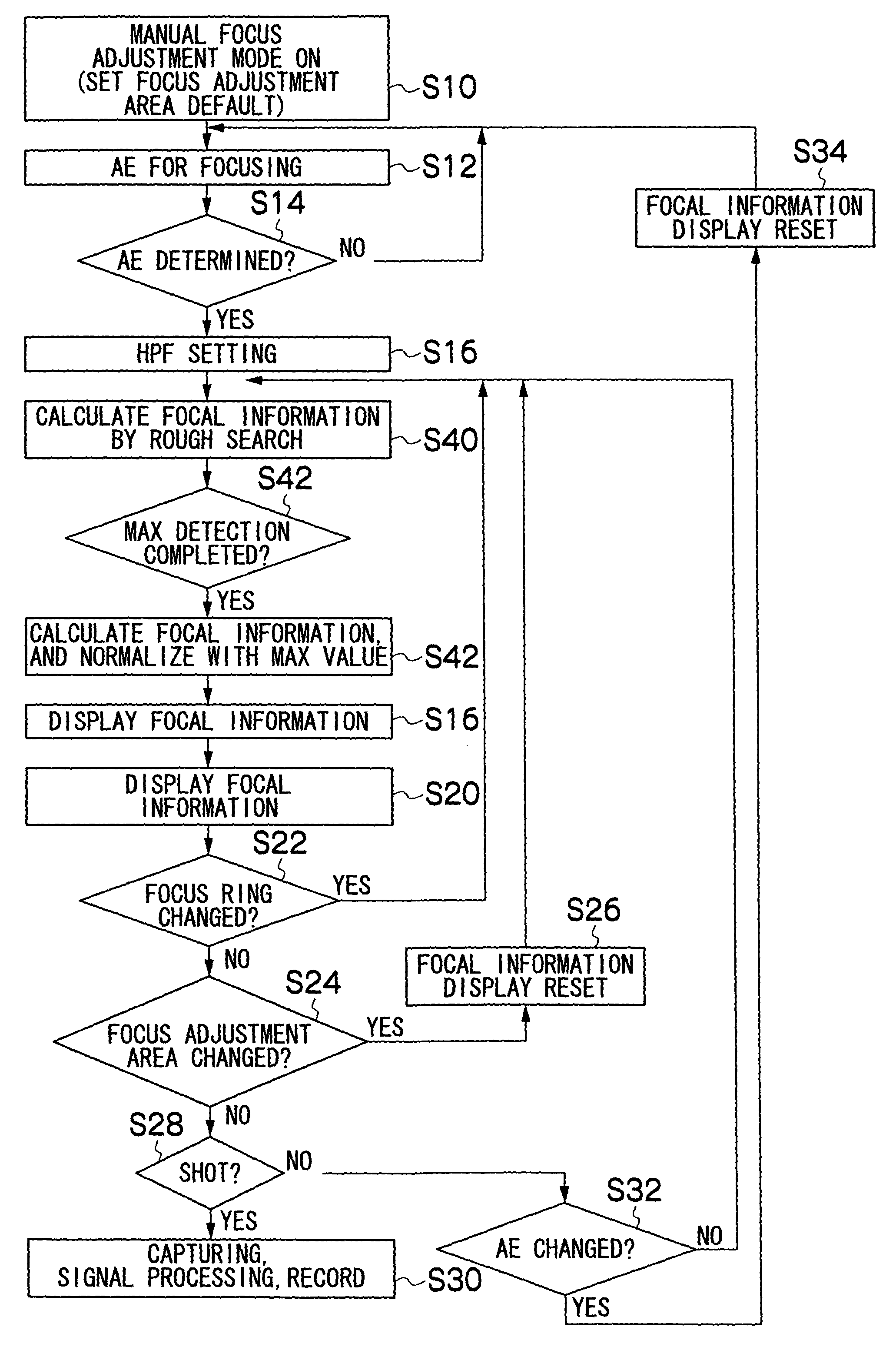
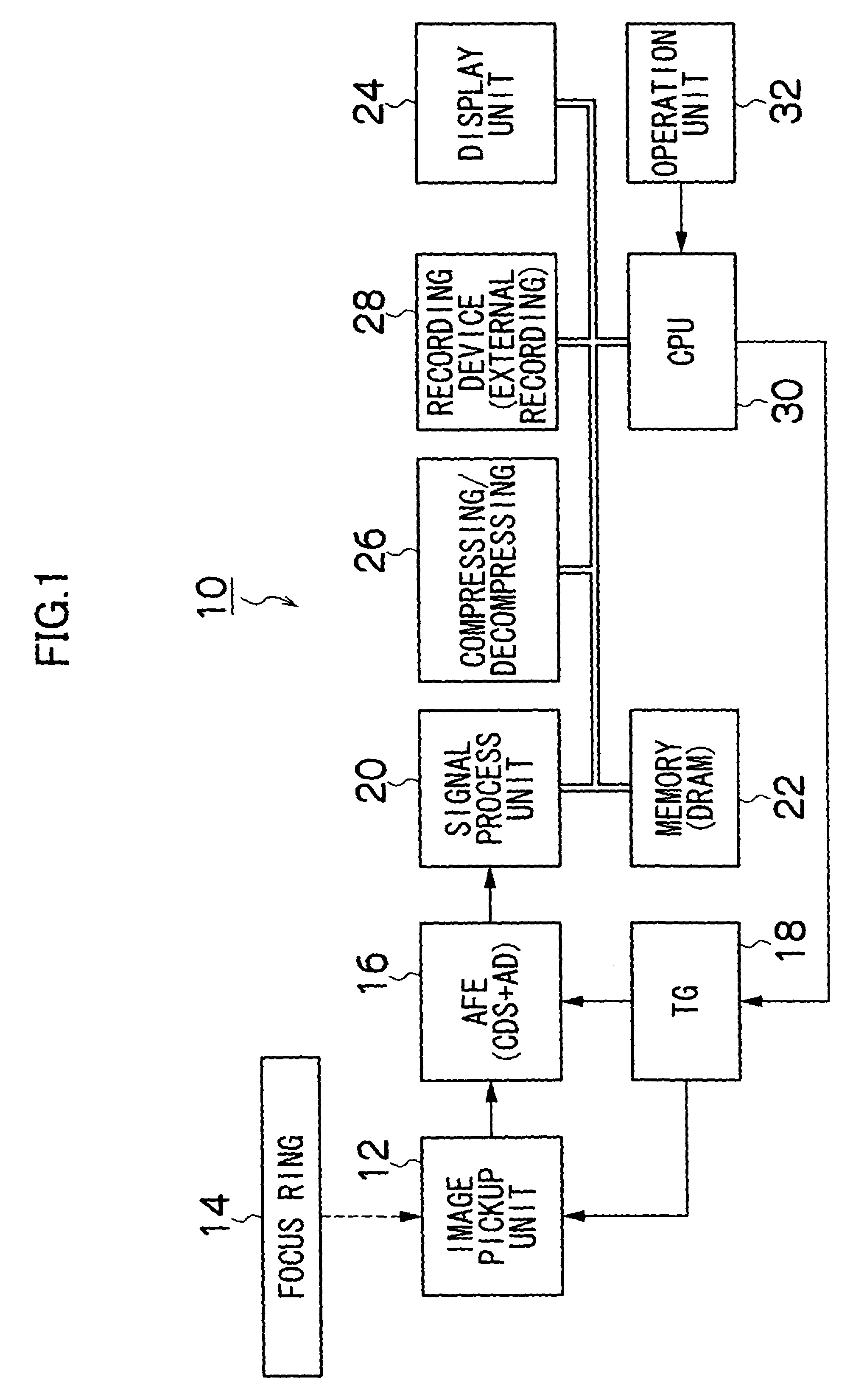
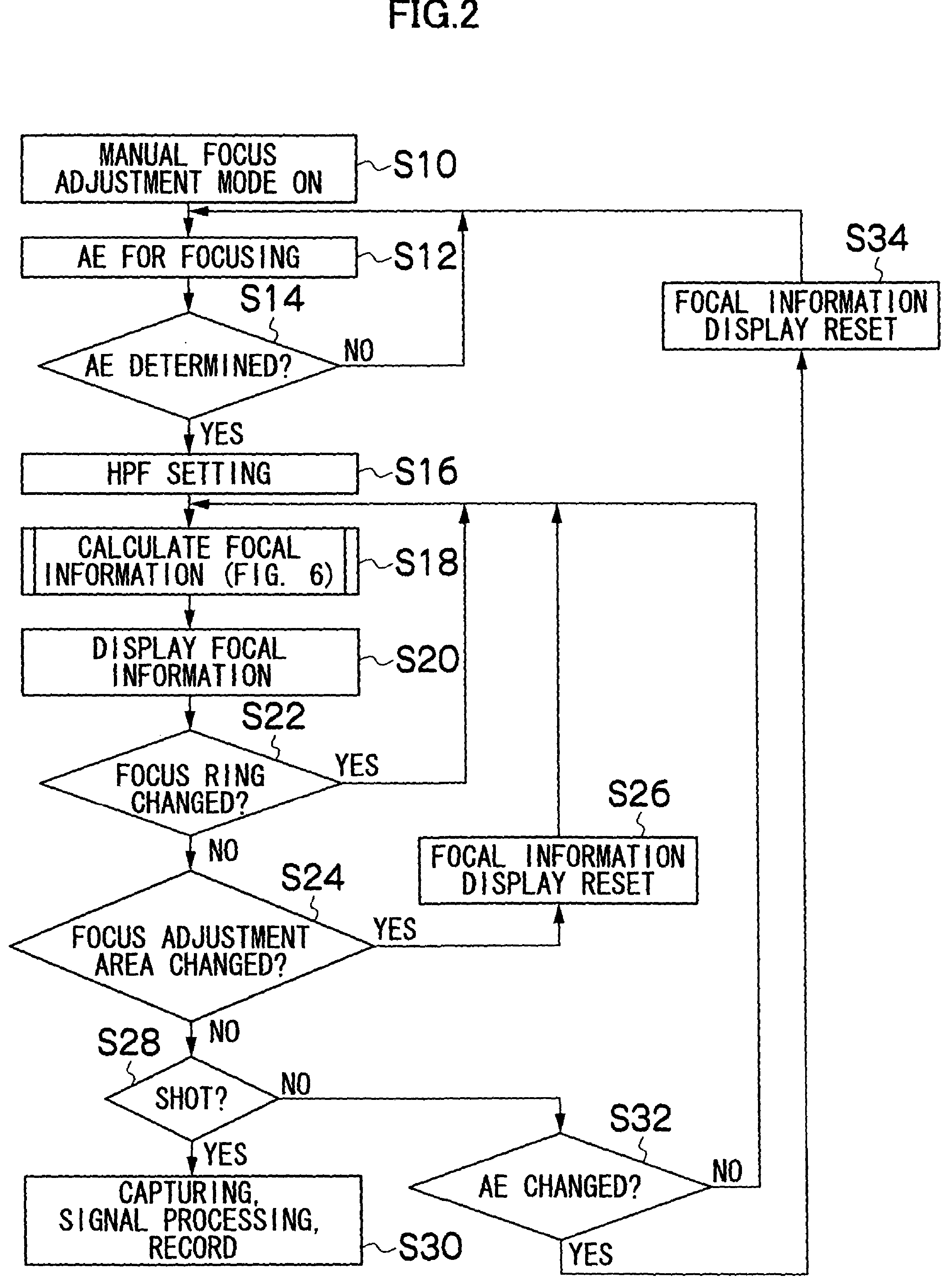
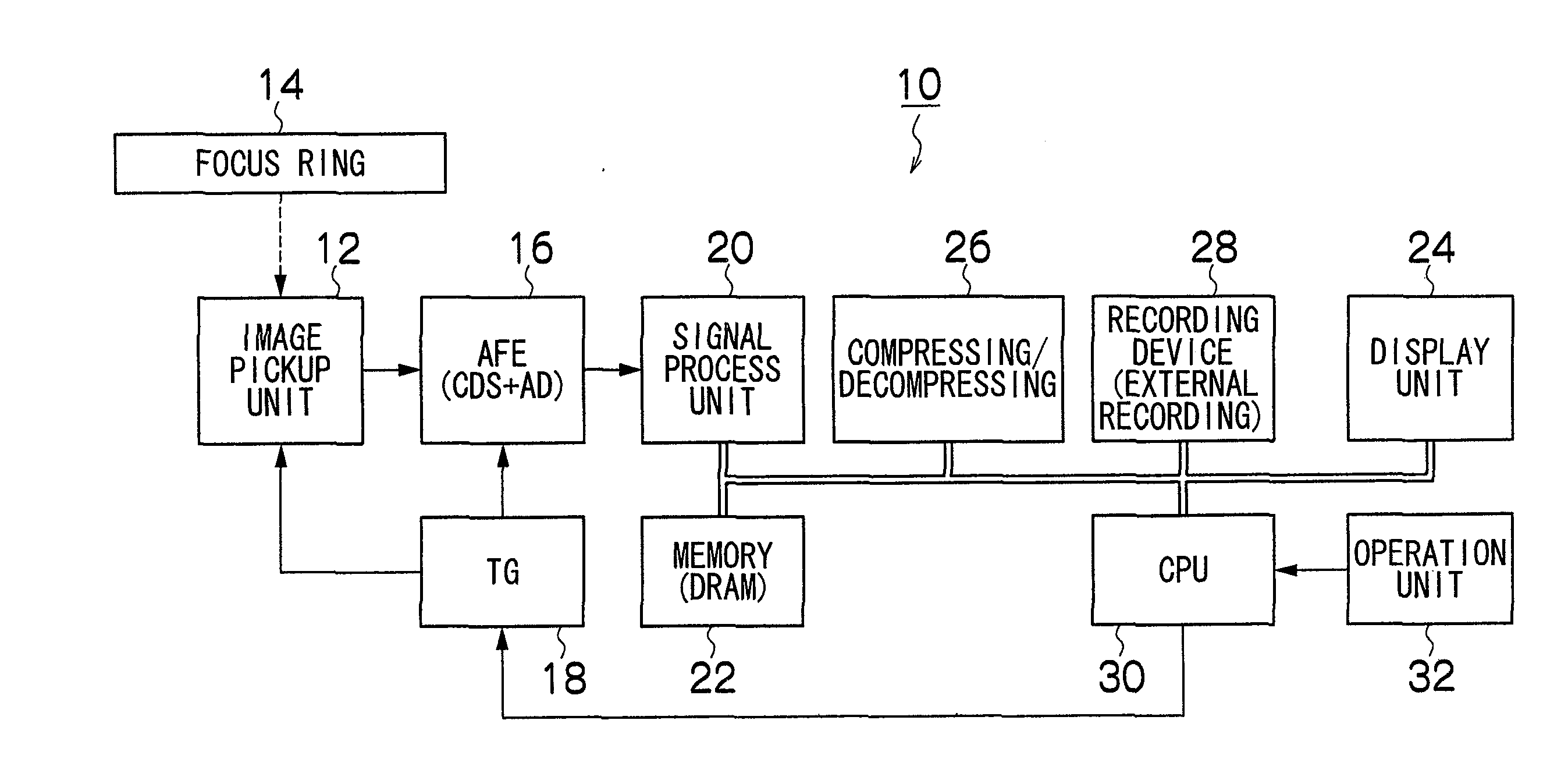
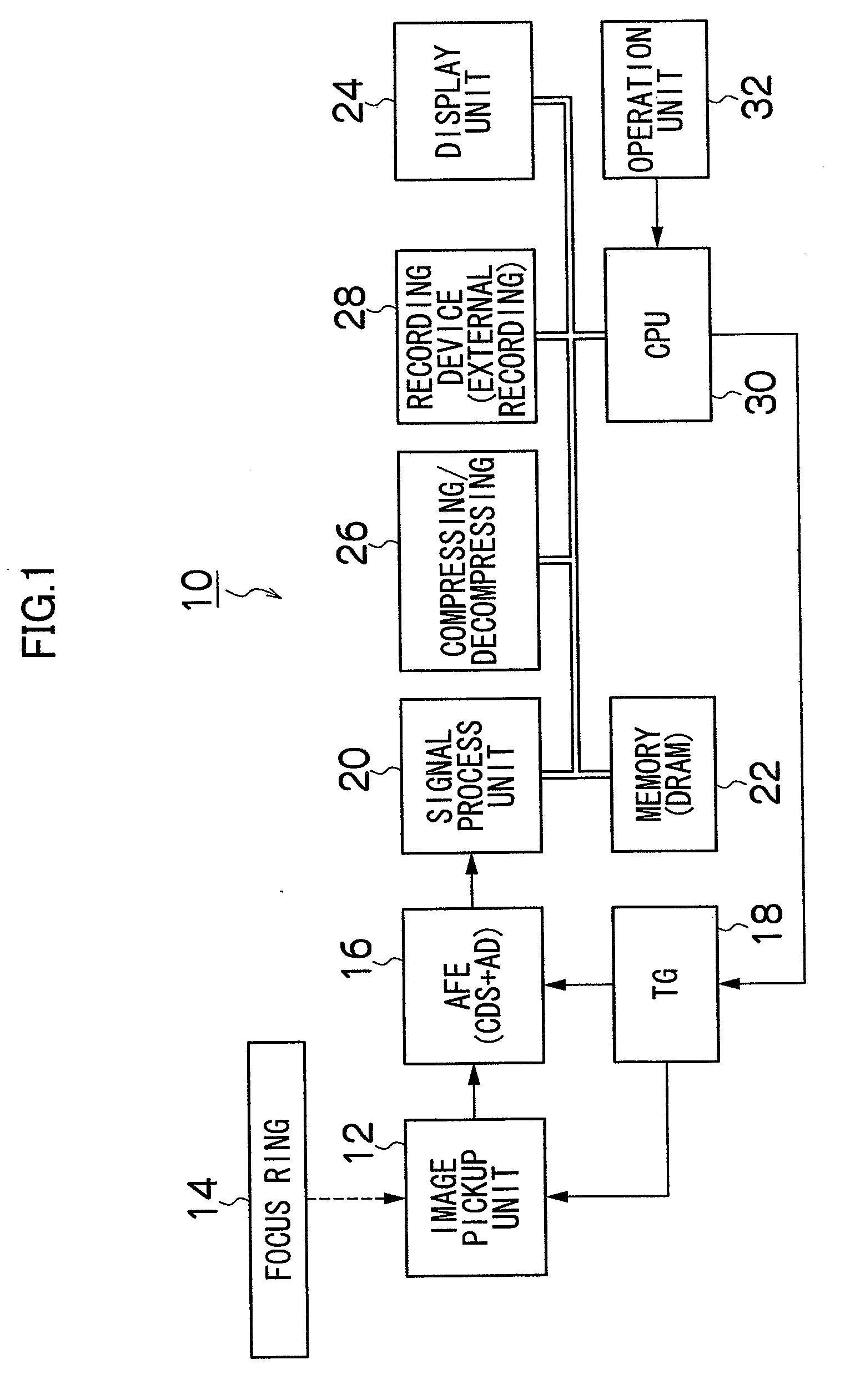
Manual focus adjustment apparatus and focus assisting program
InactiveUS20050219403A1Easy to operatePeak of the focal information becomes acuteTelevision system detailsProjector focusing arrangementCamera lensPeak value
Owner:FUJIFILM CORP
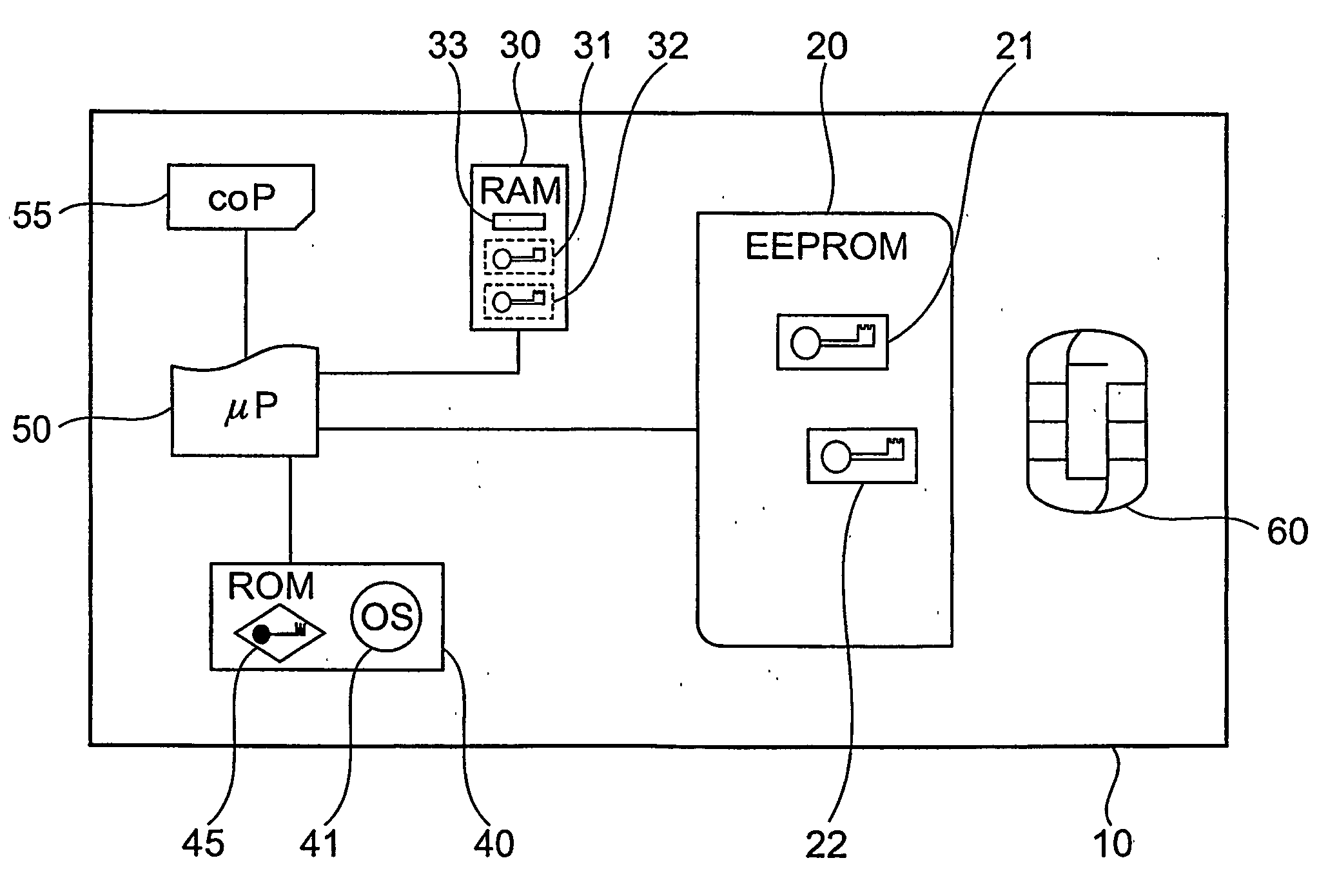
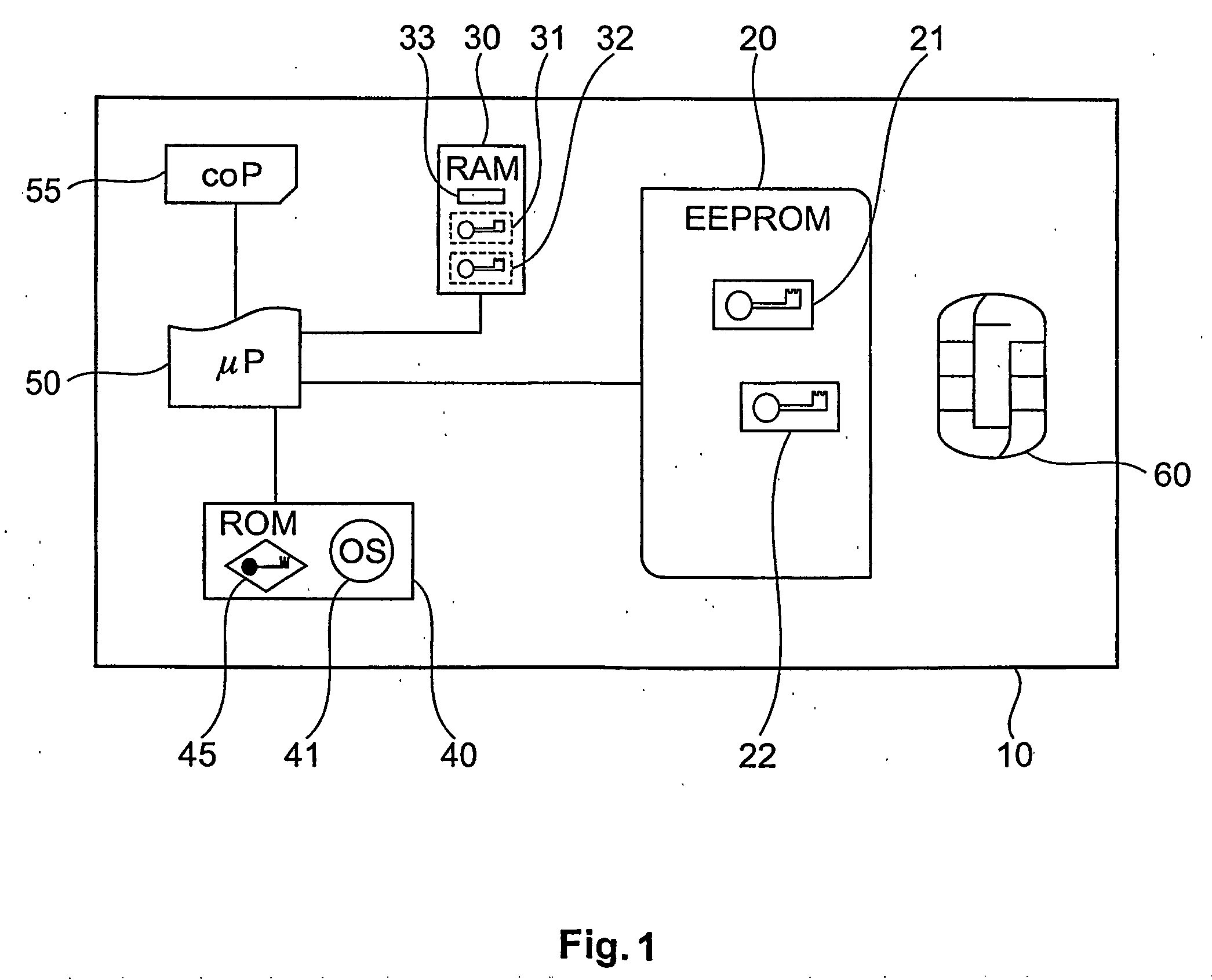
Device and method with reduced information leakage
InactiveUS20060090081A1Low level of information leakageLess-proneKey distribution for secure communicationDigital data processing detailsComputer hardwareData processing system
The invention is directed to a data-processing system comprising a processor and first encrypted information in a first persistent memory whose level of information leakage is higher than that of a second persistent memory. In the second persistent memory is stored a first cryptographic key for decrypting the first encrypted information, thereby generating therefrom first unencrypted information that is usable by the processor for executing an operation. The same cryptographic key may also be used for encrypting the first unencrypted information, thereby generating the first encrypted information. It is also directed to a method of processing such a data-processing system with an operating system, comprising a writing step for writing first unencrypted information into the first persistent memory, an encryption step for encrypting the first unencrypted information under use of the first cryptographic key, creating therefrom first encrypted information in the first persistent memory, and an access-limitation step for setting the data-processing system to a state in which writing into the first persistent memory is controlled by the operating system. It also relates to a method of executing an operation on such a data-processing system comprising a decryption step for decrypting the first encrypted information under use of the first cryptographic key, thereby generating therefrom first unencrypted information and an execution step for executing an operation by the processor, using the first unencrypted information.
Owner:IBM CORP
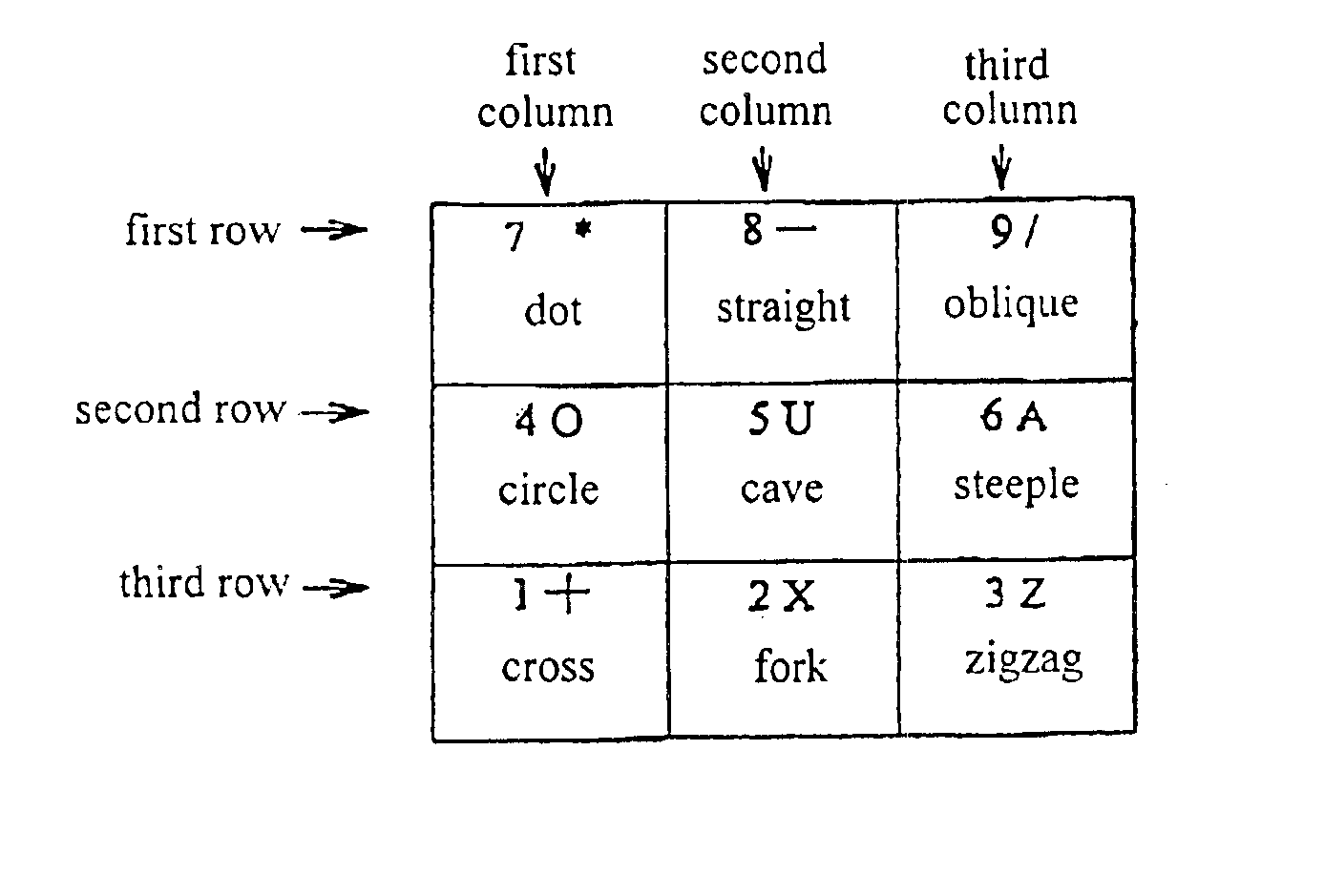
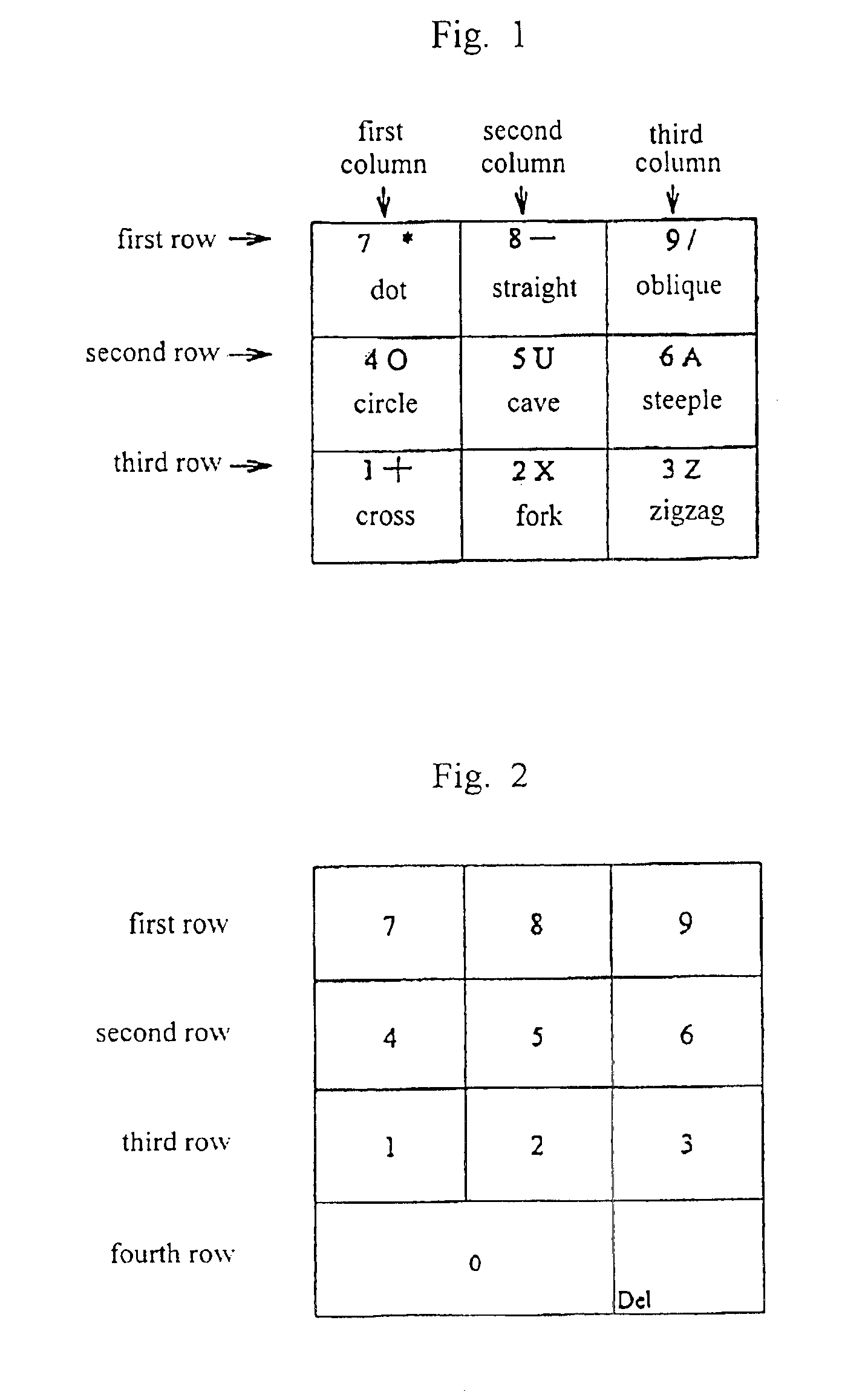
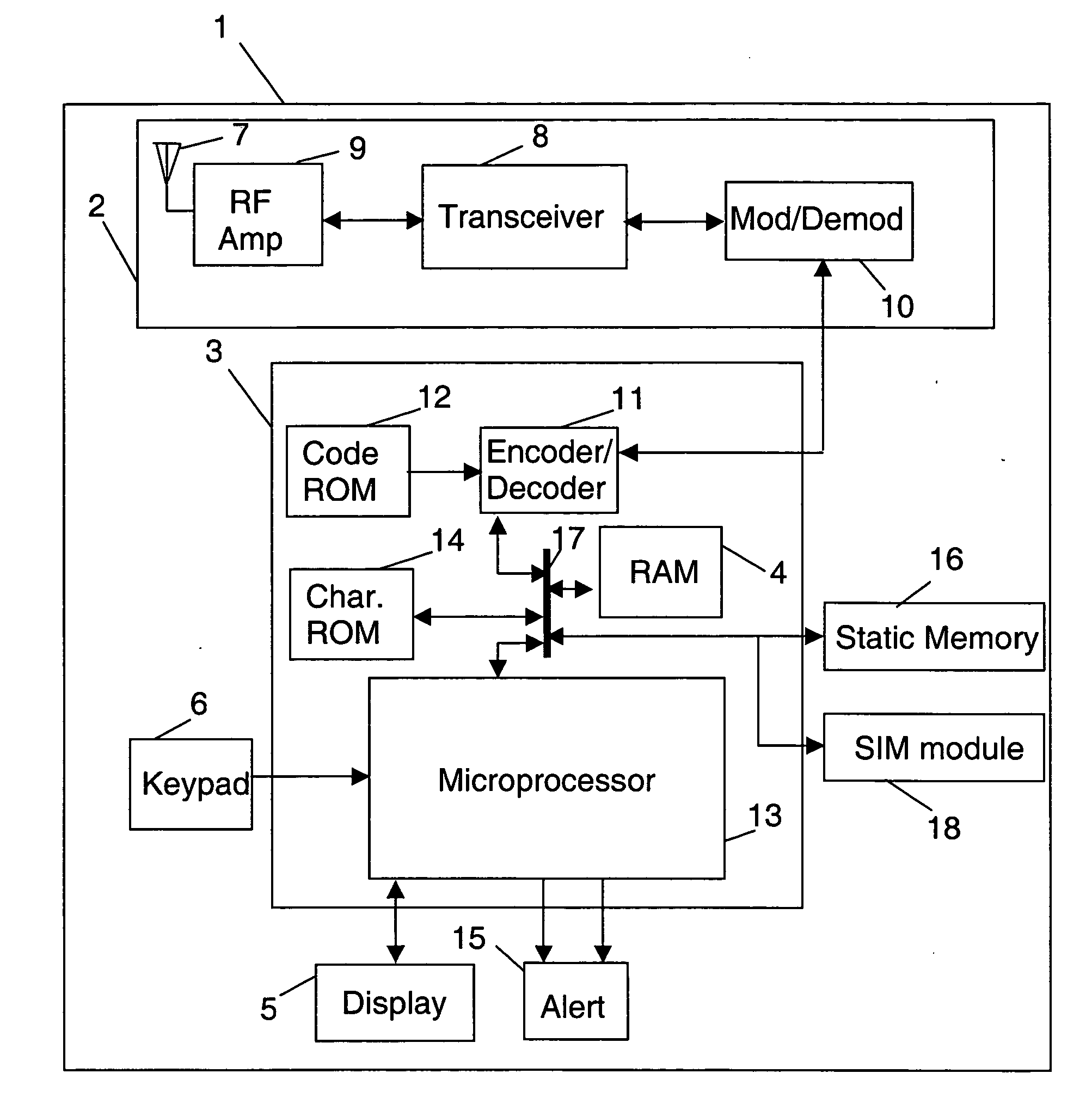
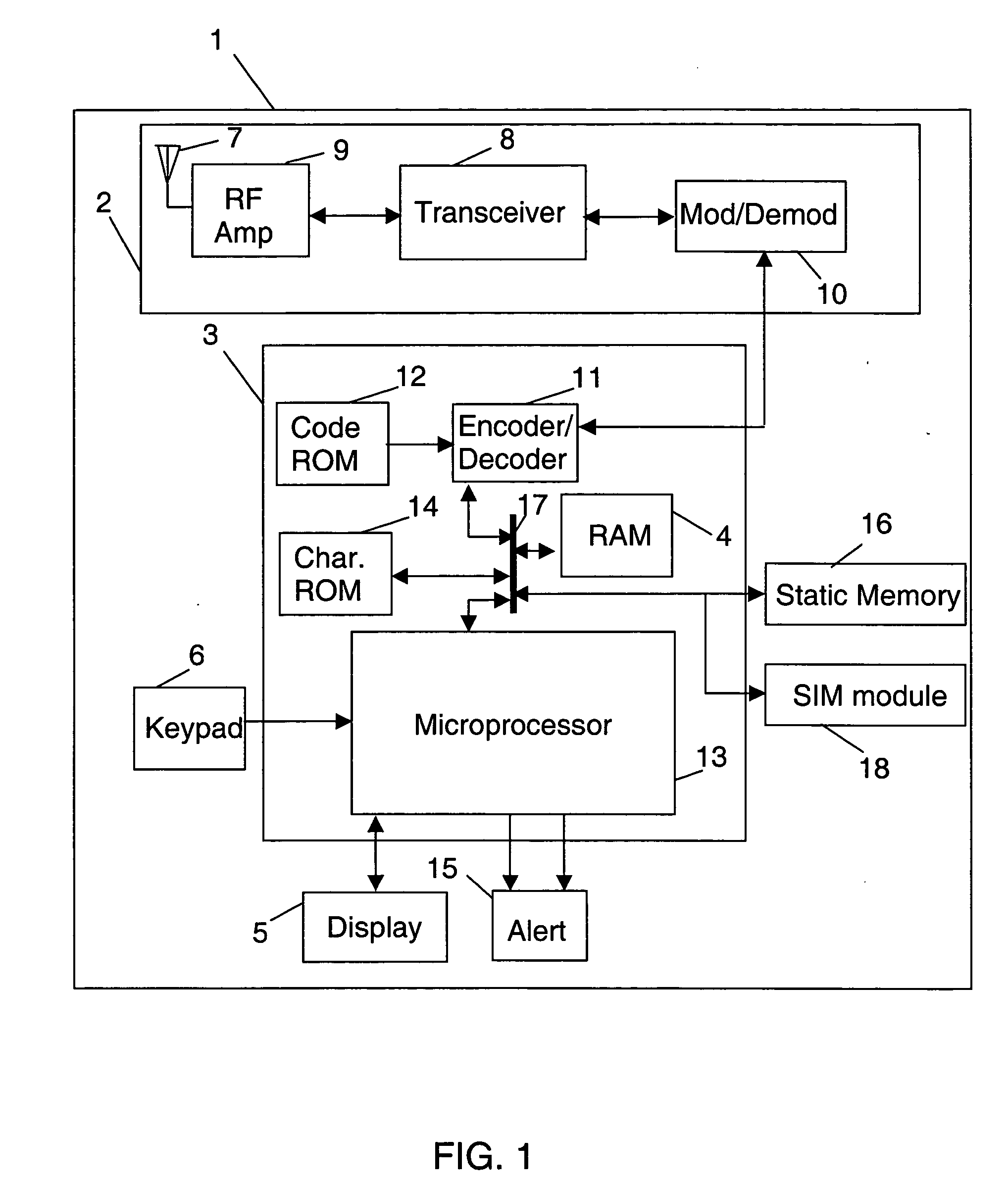
Chinese character encoding input method and its input apparatus
InactiveUS6922811B1Less key touchEasy to rememberInput/output for user-computer interactionAlphabetical characters enteringChinese character encodingMobile telephony
Disclosed are a method which is used in a computer or a communicative mobile telephone to achieve the JiuGong input of Chinese characters and a Chinese language computer or mobile telephone thereof, in which Chinese characters are divided into two classes, that is, monolithic character and transverse character, the character fonts of starting strokes are divided into nine classes, each of which respectively corresponds to the number keys 1-9 to input, 81 radicals in nine groups are used, the JiuGong pattern introduction method is adopted, and the number keys 1-9 are used to input, so that two or three keys are enough to carry out the input of a character to be inputted. The method of this invention is easy to study and could be grasped within two minutes or three without learning by rote, even an inputter who is a tyro could in short time make the input speed up to above 30 words per minute.
Owner:OCODE INFORMATION TECH +1
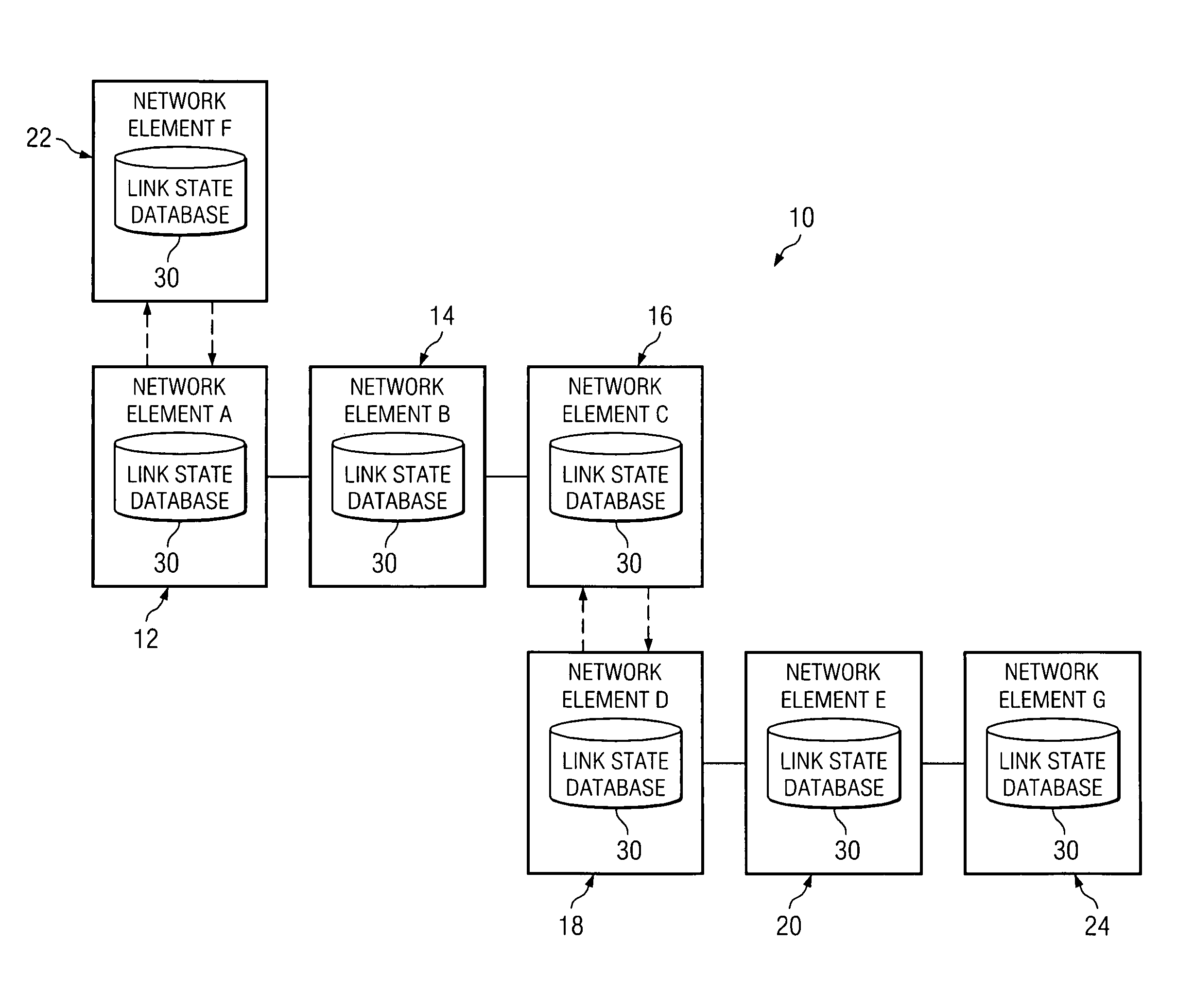
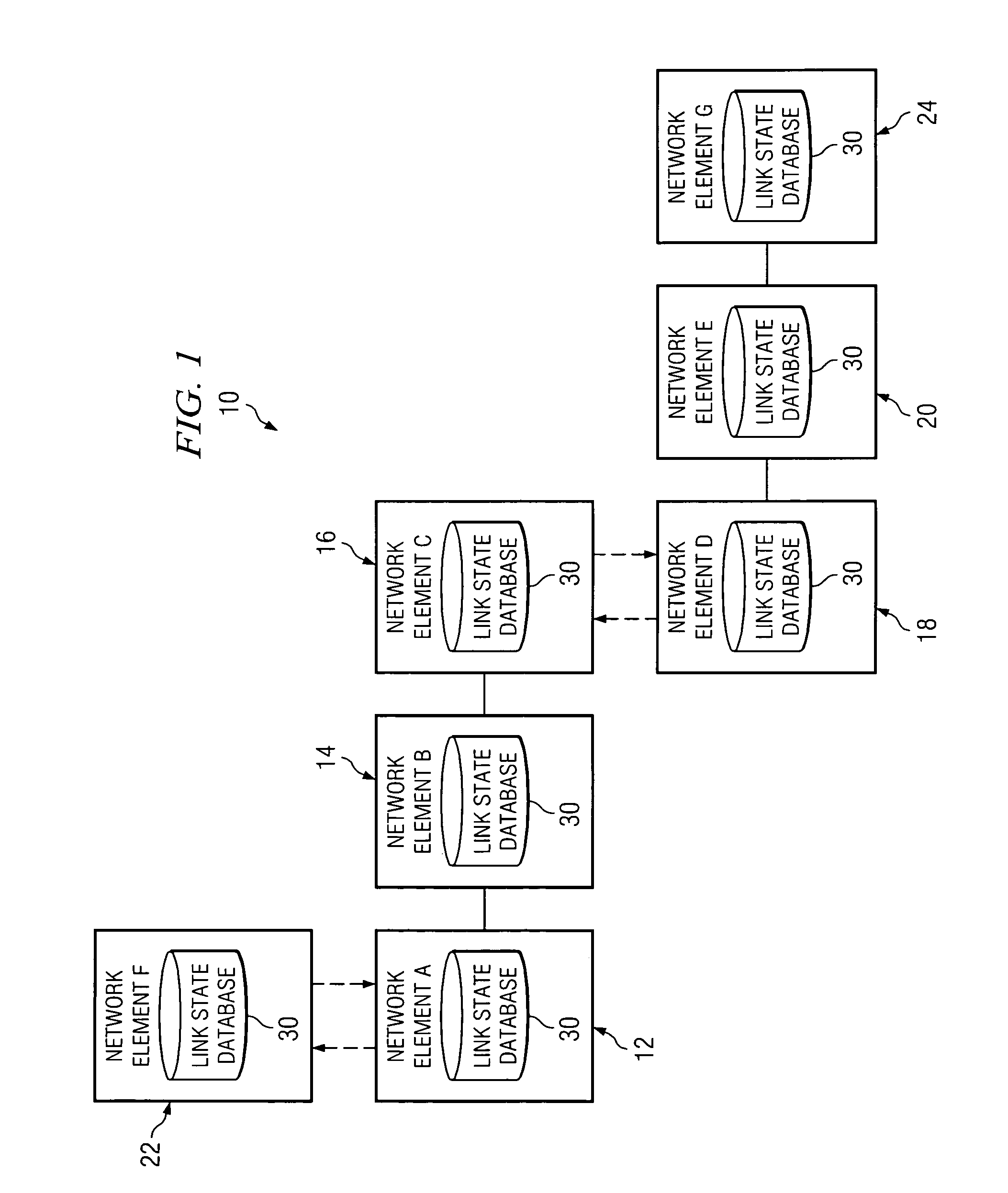
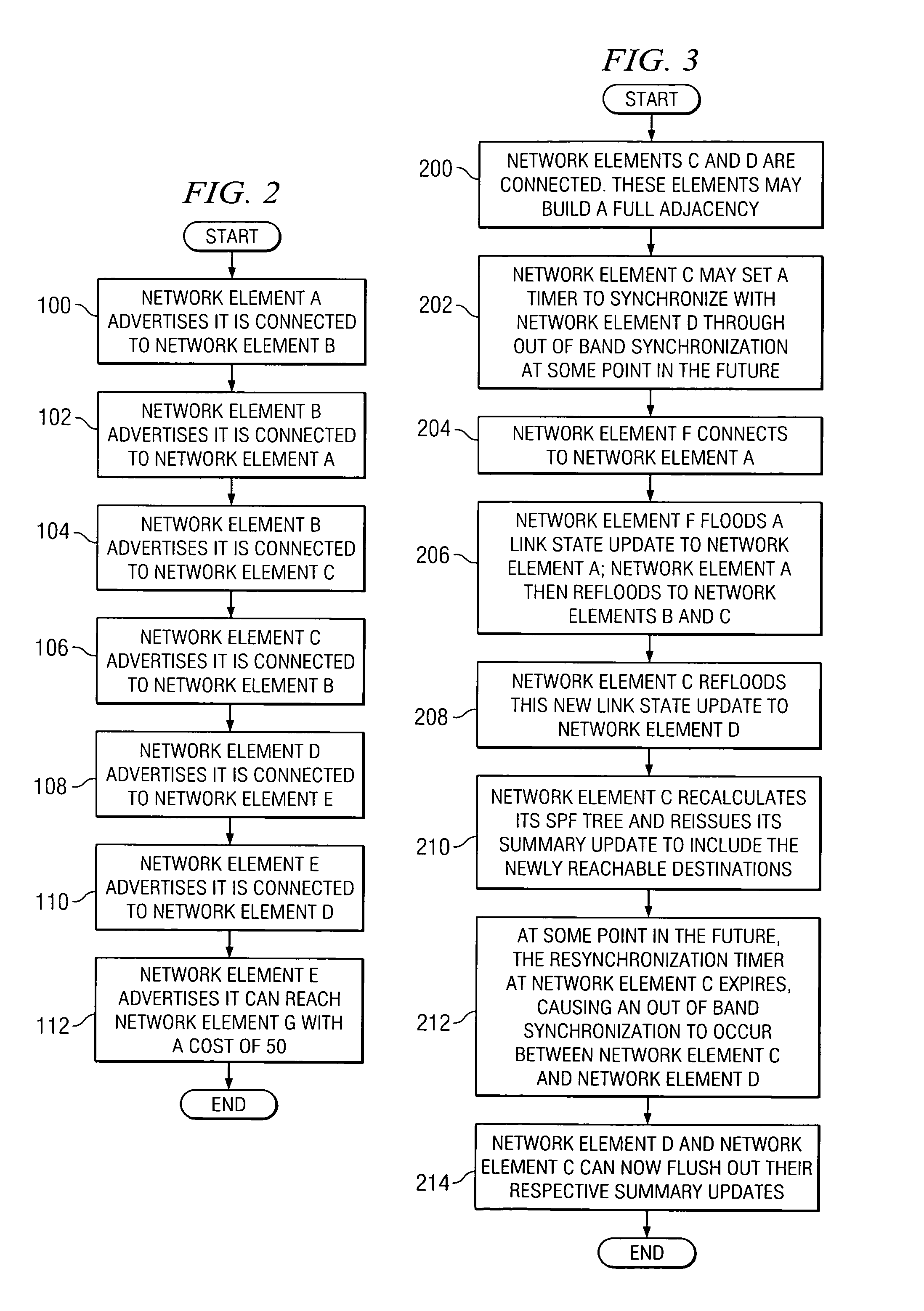
System and method for synchronizing link state databases in a network environment
ActiveUS7391730B1Avoid modificationRealize the operationError preventionTransmission systemsDistributed computingWeb environment
A method for communicating packets in a network environment is provided that includes communicating, by a first network element, a first summary update to a second network element. The method further includes receiving a second summary update from the second network element. The exchange of the first and second summary updates achieves adjacency between the first and second network elements. The first and second summary updates include, at least, locally generated state information and a single link state.
Owner:CISCO TECH INC
Concept for bridging the gap between parametric multi-channel audio coding and matrixed-surround multi-channel coding
InactiveUS20070055510A1Efficient representationLittle informationSpeech analysisStereophonic systemsOperating pointSide information
The purpose of the invention is to bridge the gap between parametric multi-channel audio coding and matrixed-surround multi-channel coding by gradually improving the sound of an up-mix signal while raising the bit-rate consumed by the side-information starting from 0 up to the bit-rates of the parametric methods. More specifically, it provides a method of flexibly choosing an “operating point” somewhere between matrixed-surround (no side-information, limited audio quality) and fully parametric reconstruction (full side-information rate required, good quality). This operating point can be chosen dynamically (i.e. varying over time) and in response to the permissible side-information rate, as it is dictated by the individual application.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Power saving in communication terminals
InactiveUS6870890B1Total current dropShorten receiving timeEnergy efficient ICTPower managementComputer hardwarePower saving
A method of receiving messages by a communication terminal. The method includes receiving symbols of a frame of a transmitted encoded message, and decoding the frame based on fewer received symbols than the number of symbols in the frame.
Owner:INTEL CORP
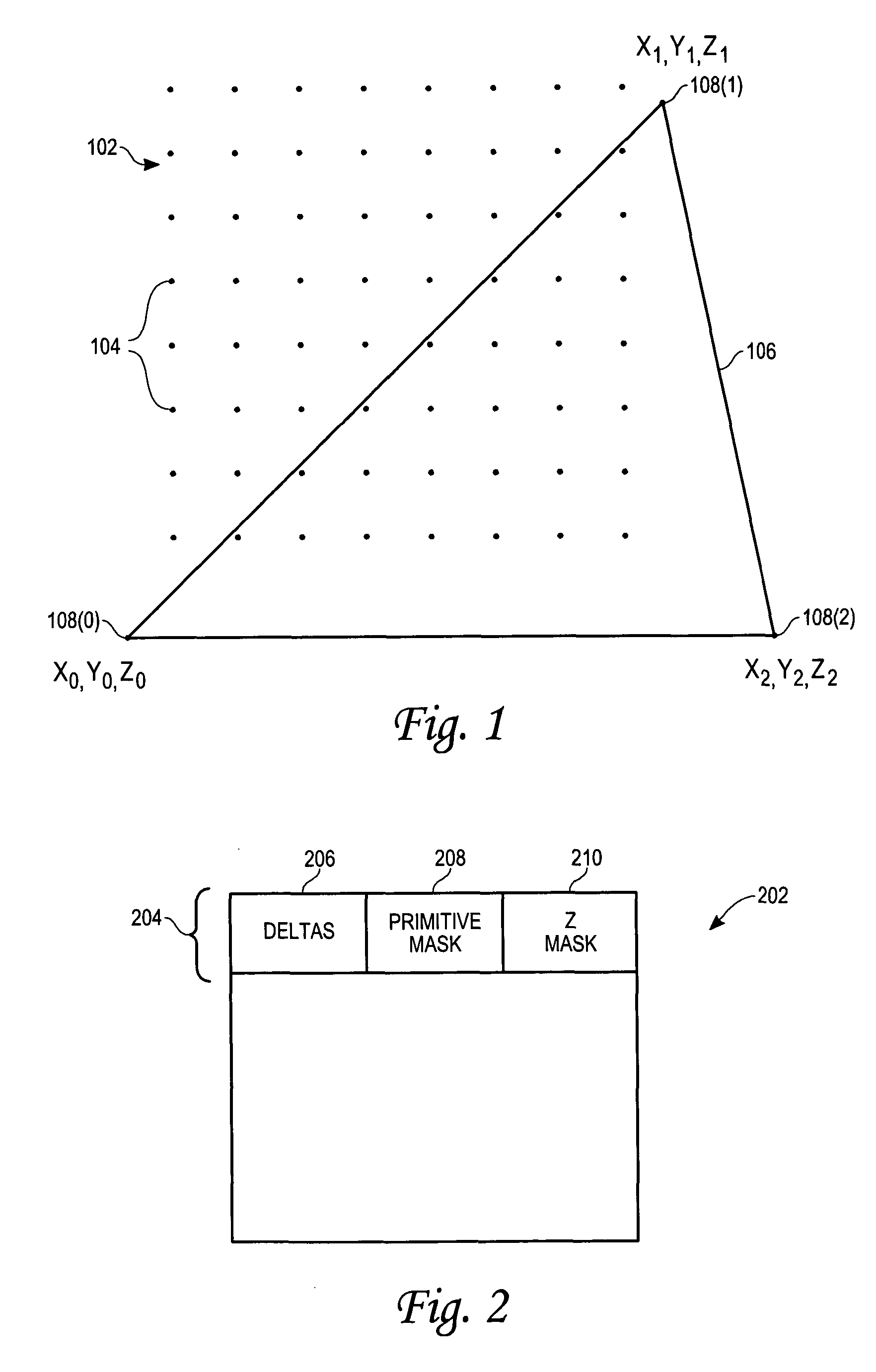
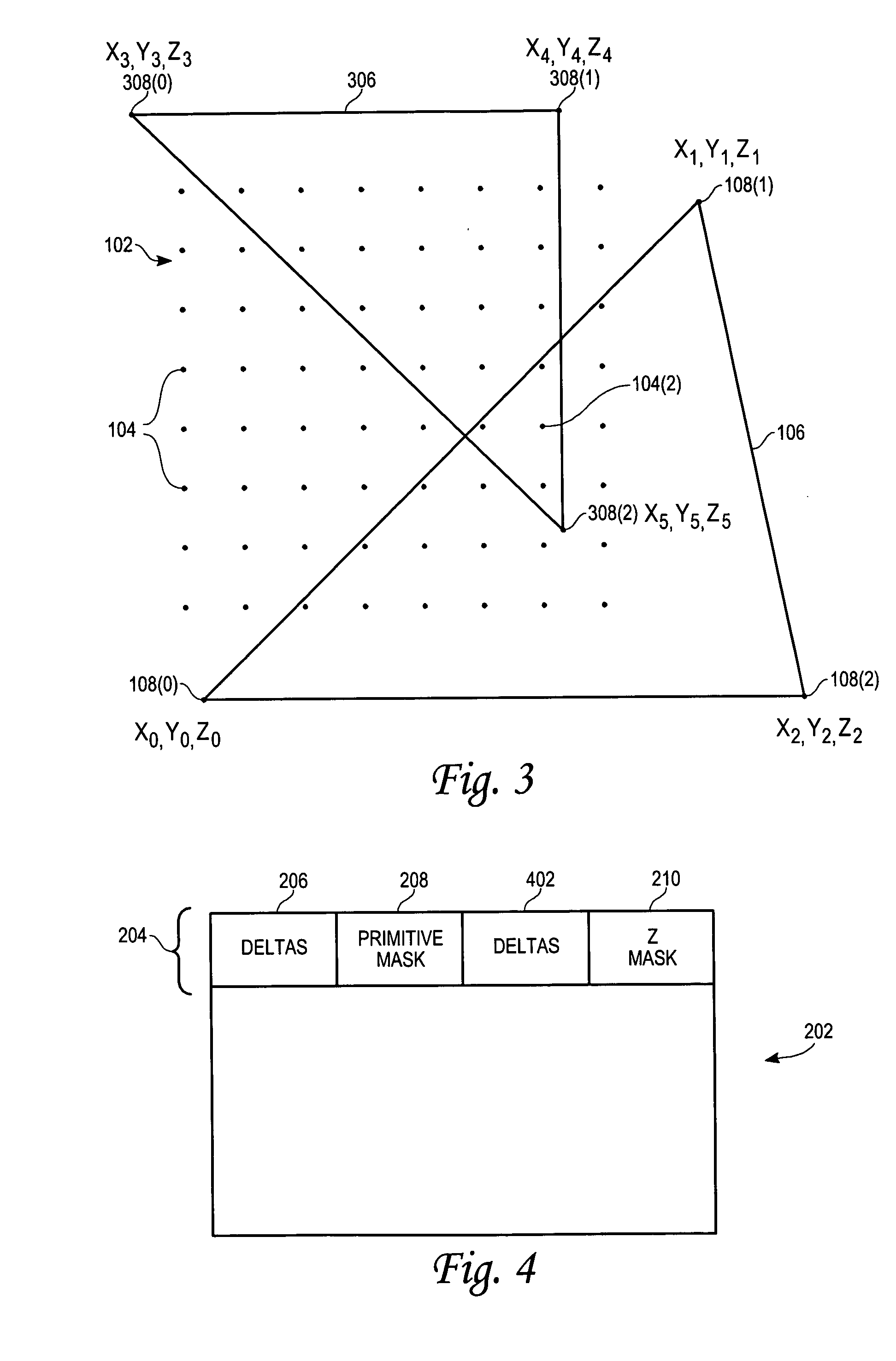
Mechanism for reducing Z buffer traffic in three-dimensional graphics processing
ActiveUS20050057564A1Reduce amountLittle informationDigital computer detailsCharacter and pattern recognitionThree dimensional graphics
Z buffer traffic experienced during graphics processing is reduced by using a compression mechanism to reduce the amount of information stored in the z buffer. The compression mechanism may be a delta-based z compression mechanism, which stores deltas in the z buffer rather than actual z values. These deltas may be used at a later time to compute the z values. By storing deltas instead of actual z values, the compression mechanism makes it possible to store significantly less information in the z buffer. By reducing the amount of information stored in the z buffer, less information will be read from and written to the z buffer, which in turn, reduces z buffer traffic. To further reduce z buffer traffic, selected deltas may be stored not in the z buffer but rather in a storage local to a graphics processing mechanism (GPM). Storing selected deltas in local storage obviates the need to read from or write to the z buffer for those deltas. As a result, z buffer traffic is even further reduced.
Owner:VIA TECH INC
Manual focus adjustment apparatus and focus assisting program
InactiveUS7932949B2Peak of the focal information becomes acuteLittle informationTelevision system detailsProjector focusing arrangementCamera lensPeak value
Owner:FUJIFILM CORP
Vertebral body having an altered native cancellous bone volume and related treatment methods
InactiveUS20050288678A1Little informationNot strongStentsBalloon catheterFilling materialsCancellous bone
The native cancellous bone volume of a vertebral body is altered to comprise a region of cancellous bone that has been compressed to form a compressed bone region that peripherally defines a cavity and another region of substantially uncompressed cancellous bone occupying at least a portion of the remaining native cancellous bone volume. A bone filling material occupies the cavity.
Owner:ORTHOPHOENIX
Manual focus adjustment apparatus and focus assisting program
ActiveUS20110058094A1Peak of the focal information becomes acuteLittle informationTelevision system detailsProjector focusing arrangementCamera lensPeak value
Owner:FUJIFILM CORP
Selective illumination of regions of an electronic display
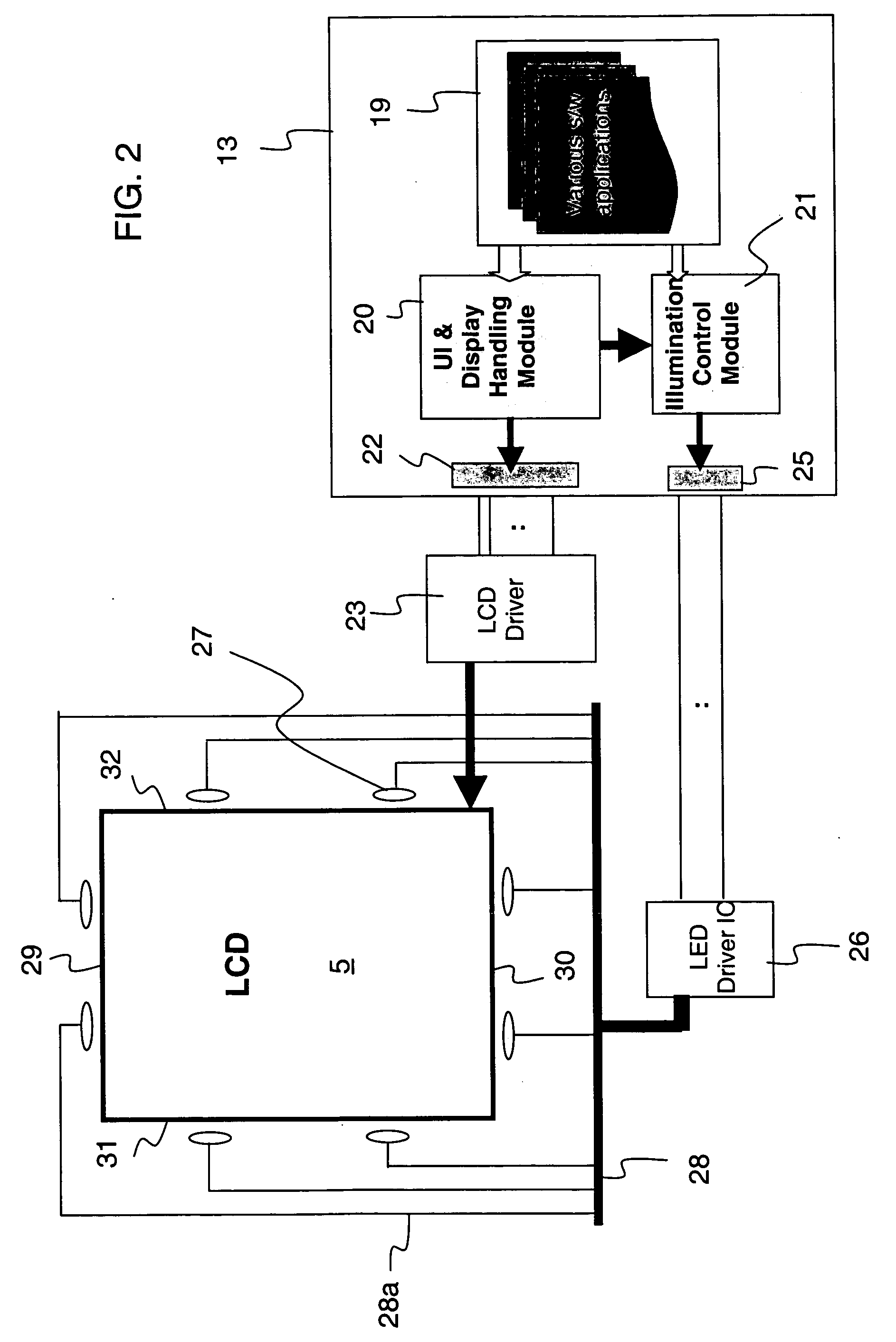
InactiveUS20050057539A1Little informationLess viewing timeCathode-ray tube indicatorsNon-linear opticsDisplay deviceEngineering
There is disclosed the selective illuminating of a display (5) for an electronic device (1) that can reduce battery power consumption. The invention provides for detecting an event that will trigger an update of the display (5) and activation of illumination elements (27) for illuminating the display and determining whether the information to be displayed will occupy a region (B-L) of the display. If so, the region of the display is selectively illuminated by one or more of the illumination elements. The predetermined illumination time period may depend on a selected combination of a size of the region, a location of said region and / or a priority associated with the event.
Owner:GOOGLE TECH HLDG LLC
Scheme for generating a parametric representation for low-bit rate applications
ActiveUS8194861B2Little informationSpeech analysisBroadcast circuit arrangementsSound energyVocal tract
Owner:DOLBY INT AB
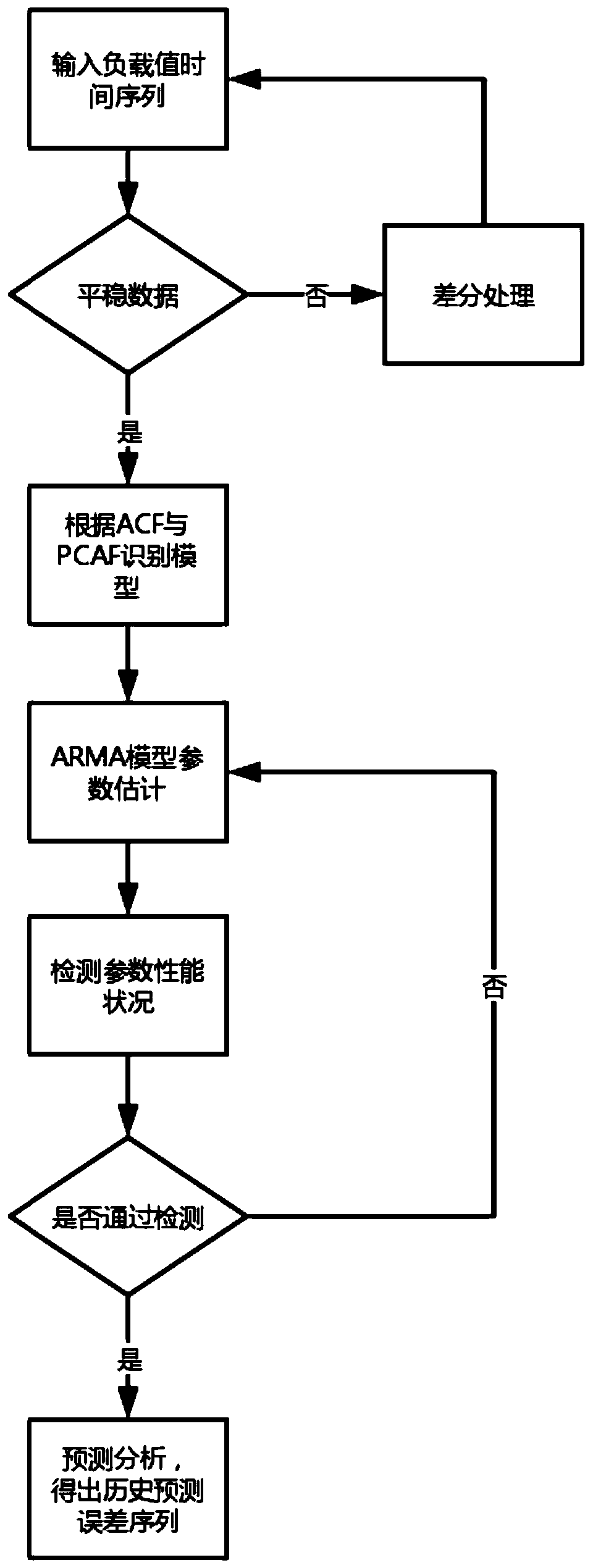
A server load prediction method and system based on a Markov chain and a time sequence model
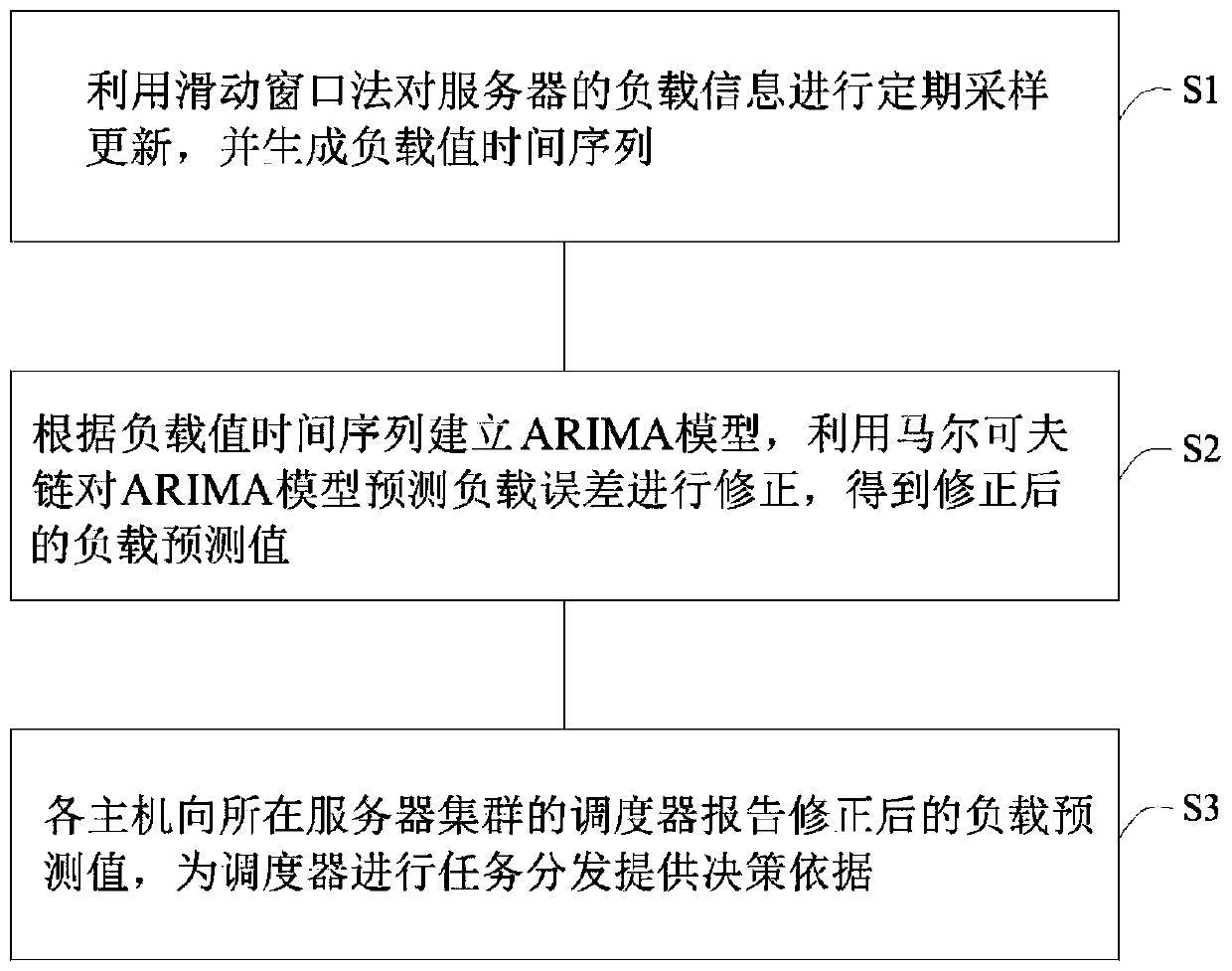
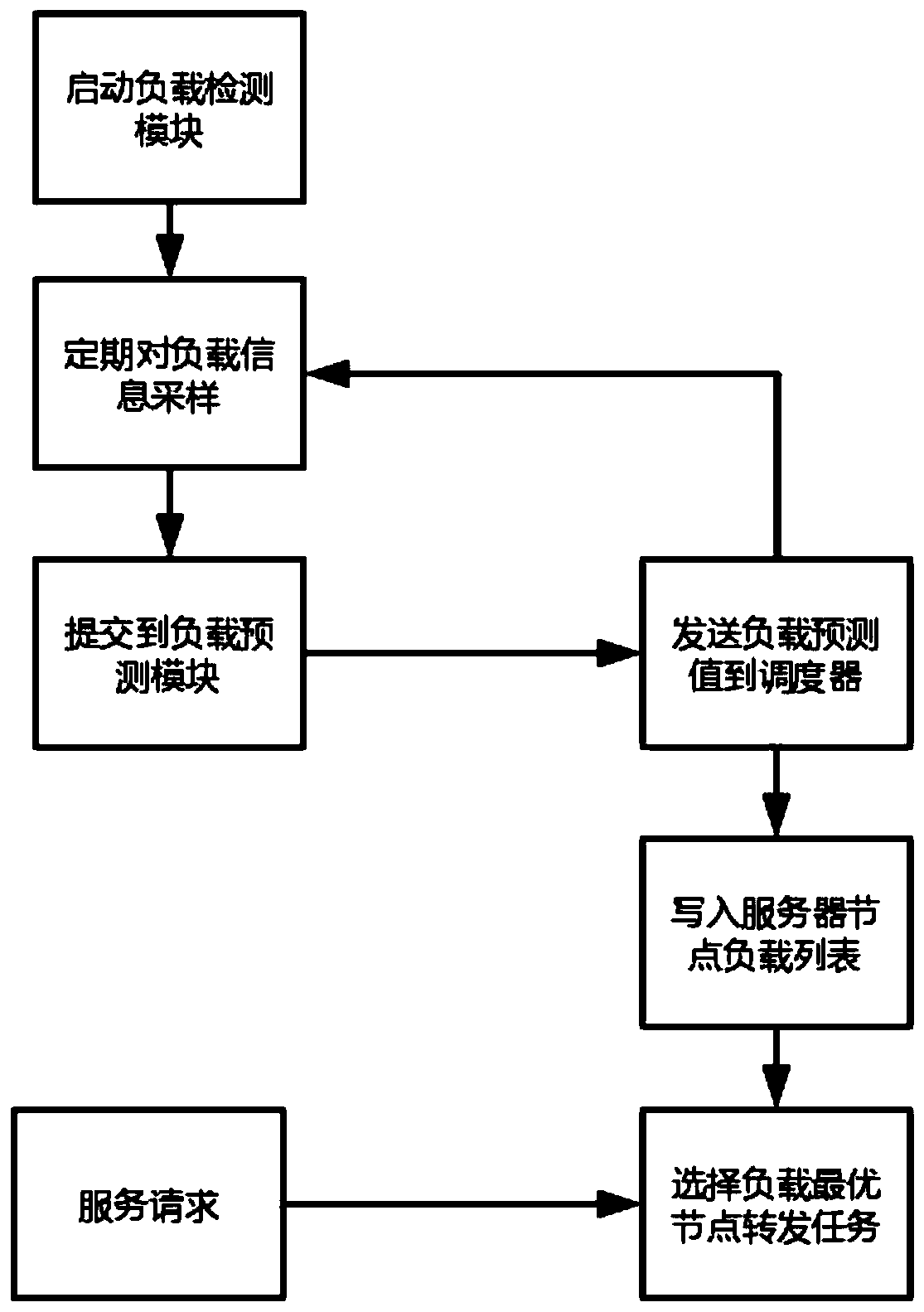
InactiveCN109787855ALittle informationEasy to operateData switching networksComplex mathematical operationsMarkov chainSlide window
The invention discloses a server load prediction method and system based on a Markov chain and a time sequence model. The method comprises the following steps: step 1, periodically sampling and updating load information of a server by utilizing a sliding window method, and generating a load value time sequence; Step 2, establishing an ARIMA model according to the load value time sequence, and correcting the predicted load error of the ARIMA model by using a Markov chain to obtain a corrected load predicted value; And step 3, each host reports the corrected load prediction value to the dispatcher of the server cluster where the host is located, and a decision basis is provided for the dispatcher to perform task distribution. The server load prediction method based on the Markov chain and the time sequence model can provide a decision basis for subsequently realizing reasonable scheduling of computing resources.
Owner:SHENZHEN INST OF ADVANCED TECH
Structured light-based high-speed detection system and method for railway fastener
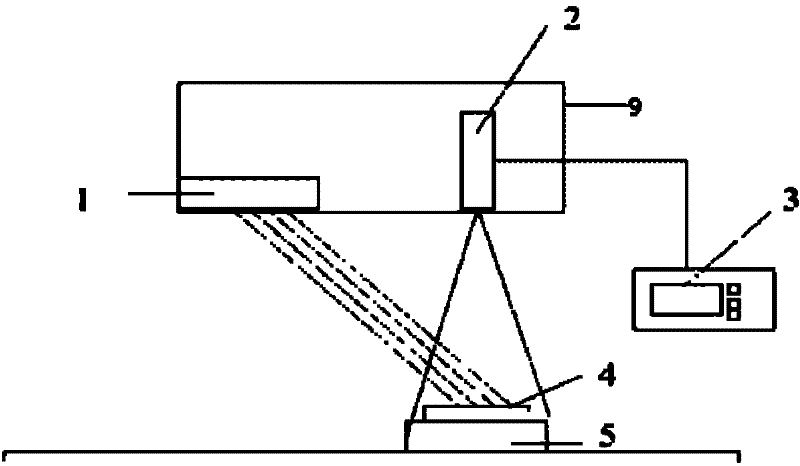
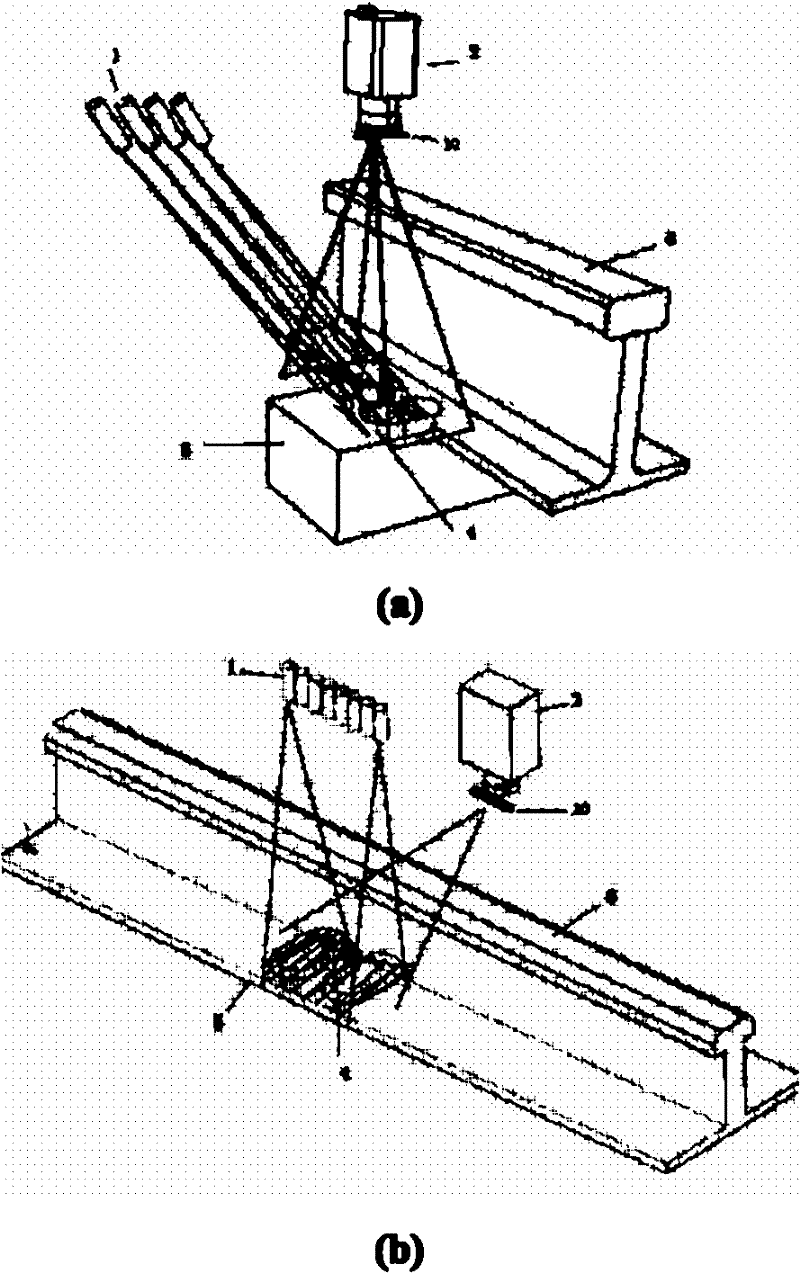
InactiveCN102221553ALittle informationHigh speedOptically investigating flaws/contaminationLaser sourceStructure based
A structured light-based high-speed detection system and a method for railway fasteners belongs to the technical field of optical detection, and the system comprises: a high-speed camera, a laser source, and a processing system, wherein the laser source and the high-speed camera are respectively disposed at the upper part of a fastener region to be detected, and emit respectively a set of structured light to the region of the fastener; the high-speed camera photographs the image of the fastener region; the high-speed camera is connected to the processing system and the image is transferred; the processing system performs image treatment and determines to obtain the detected results. The invention solves the defects of low identification speed and poor generality in the prior art, is applicable to the on-line rapid detection of railway steel rail fastener loss, and has the advantages of high identification speed, good generality, and strong adaptability.
Owner:SHANGHAI JIAO TONG UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com