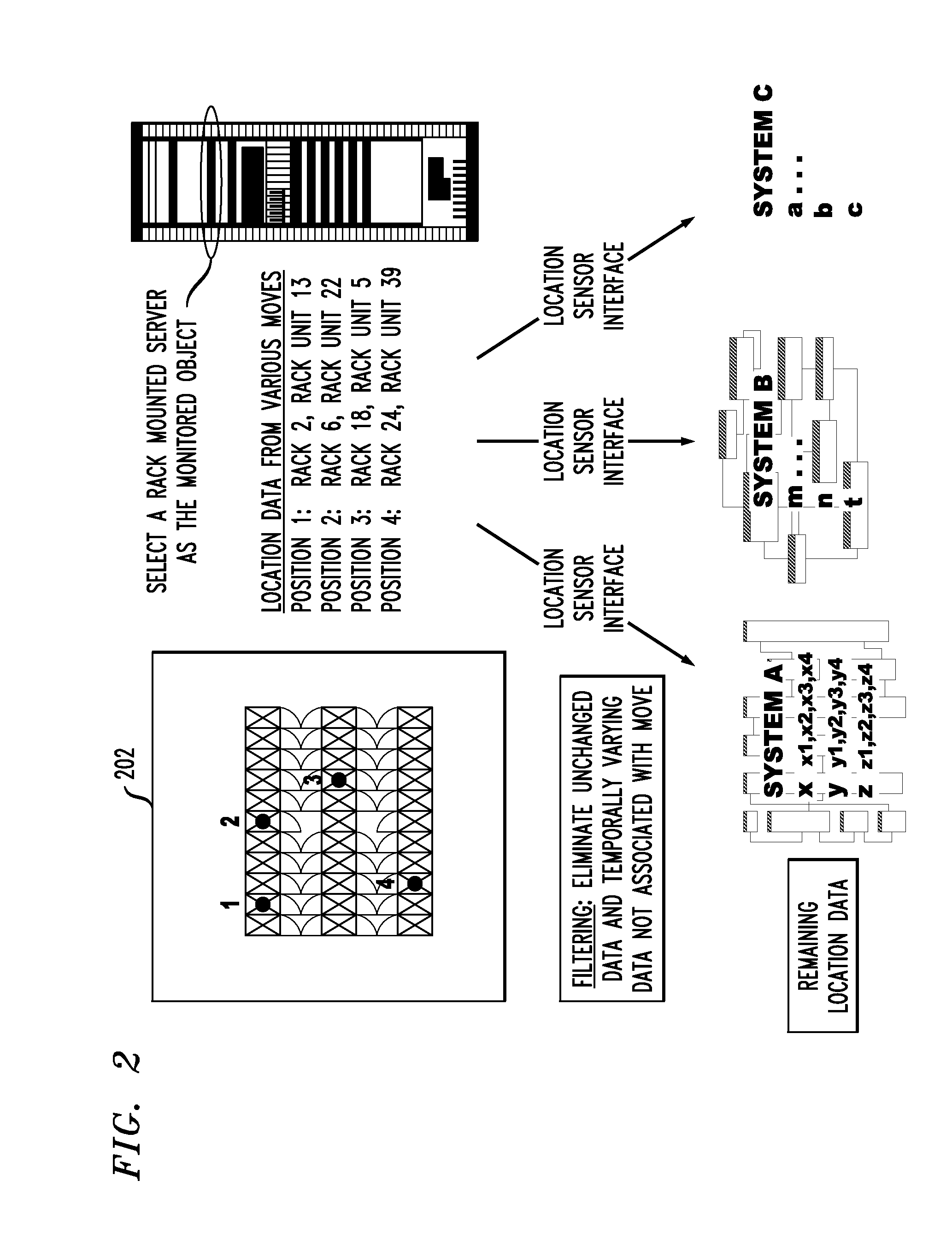
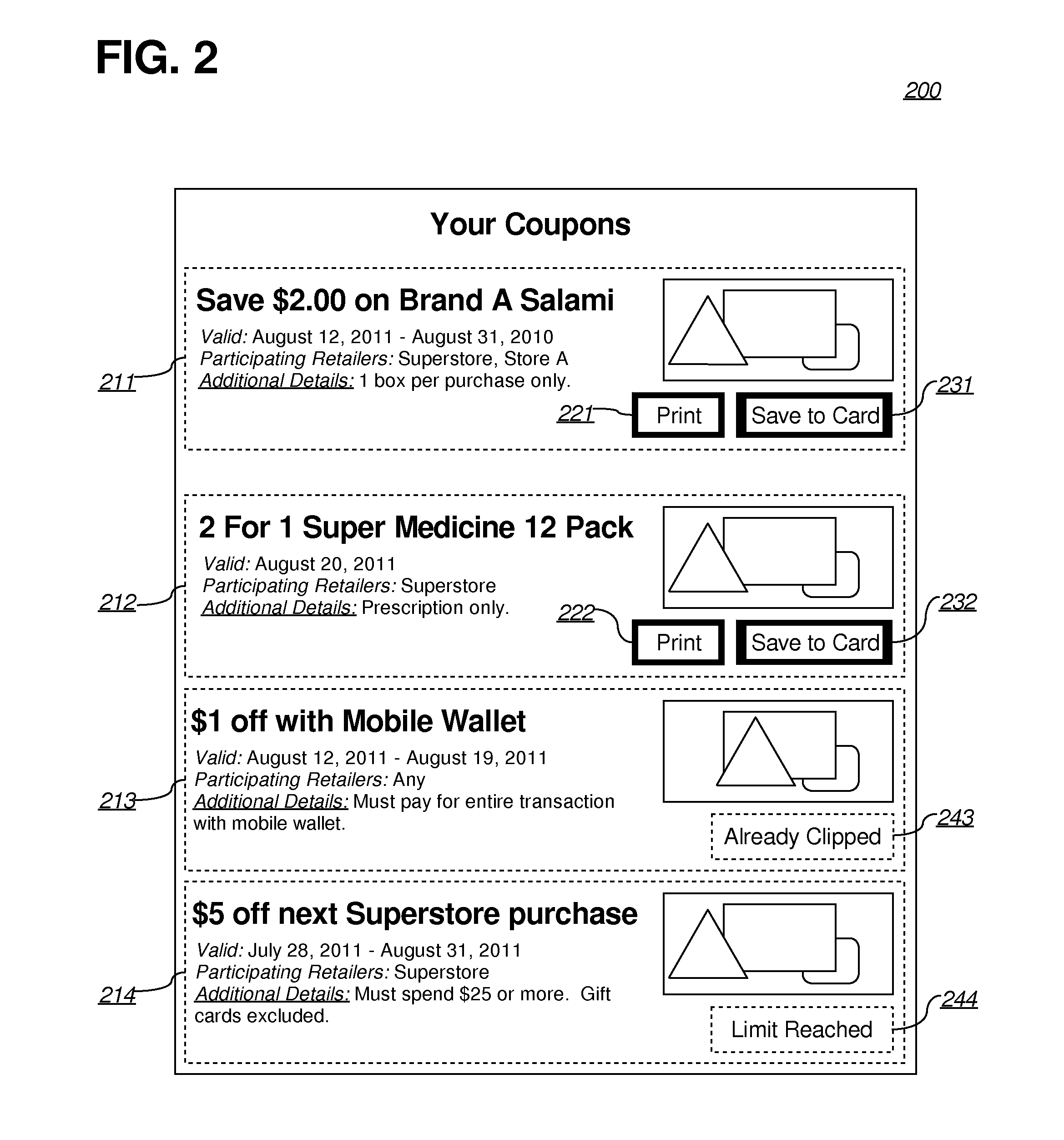
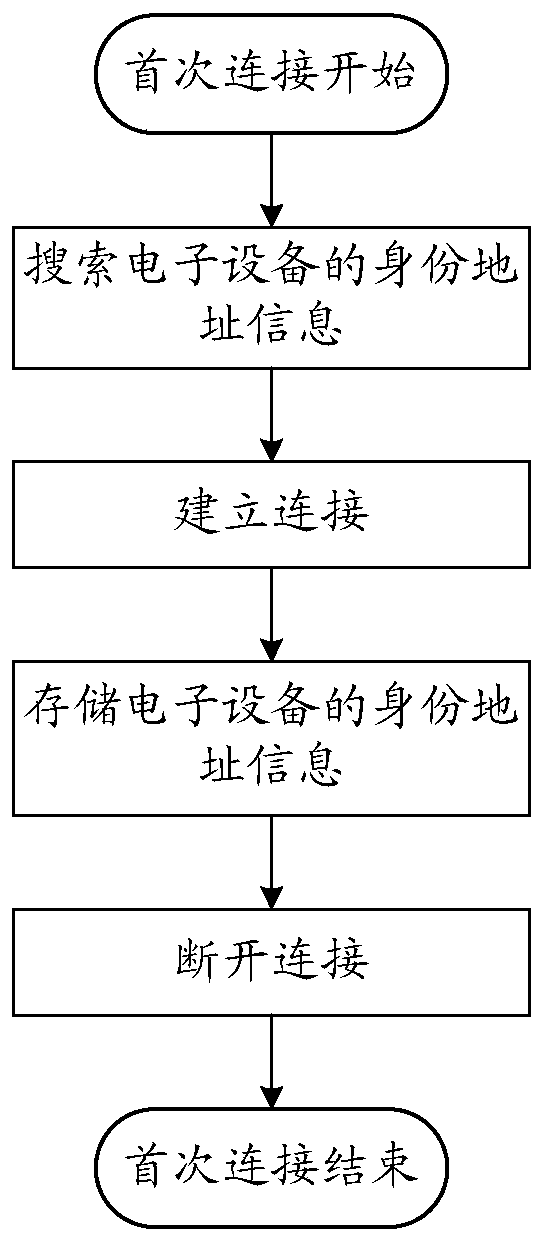
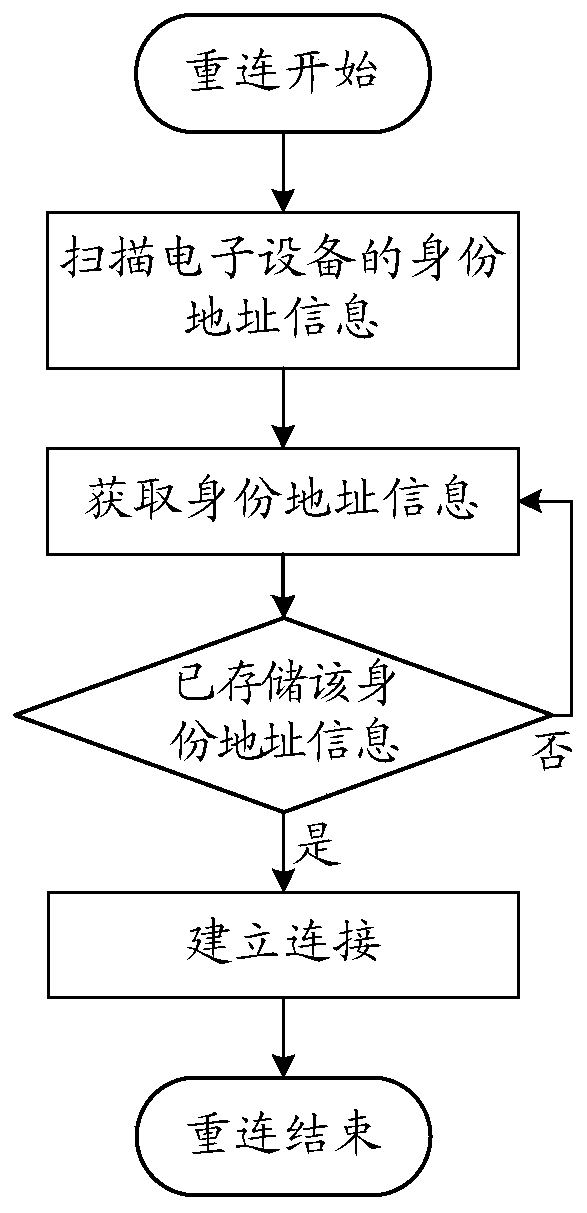
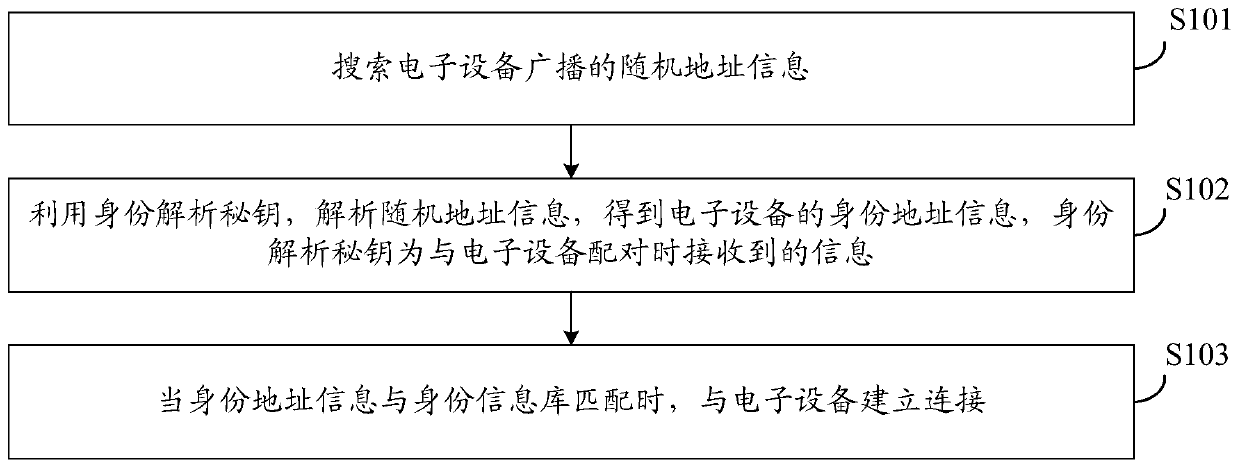
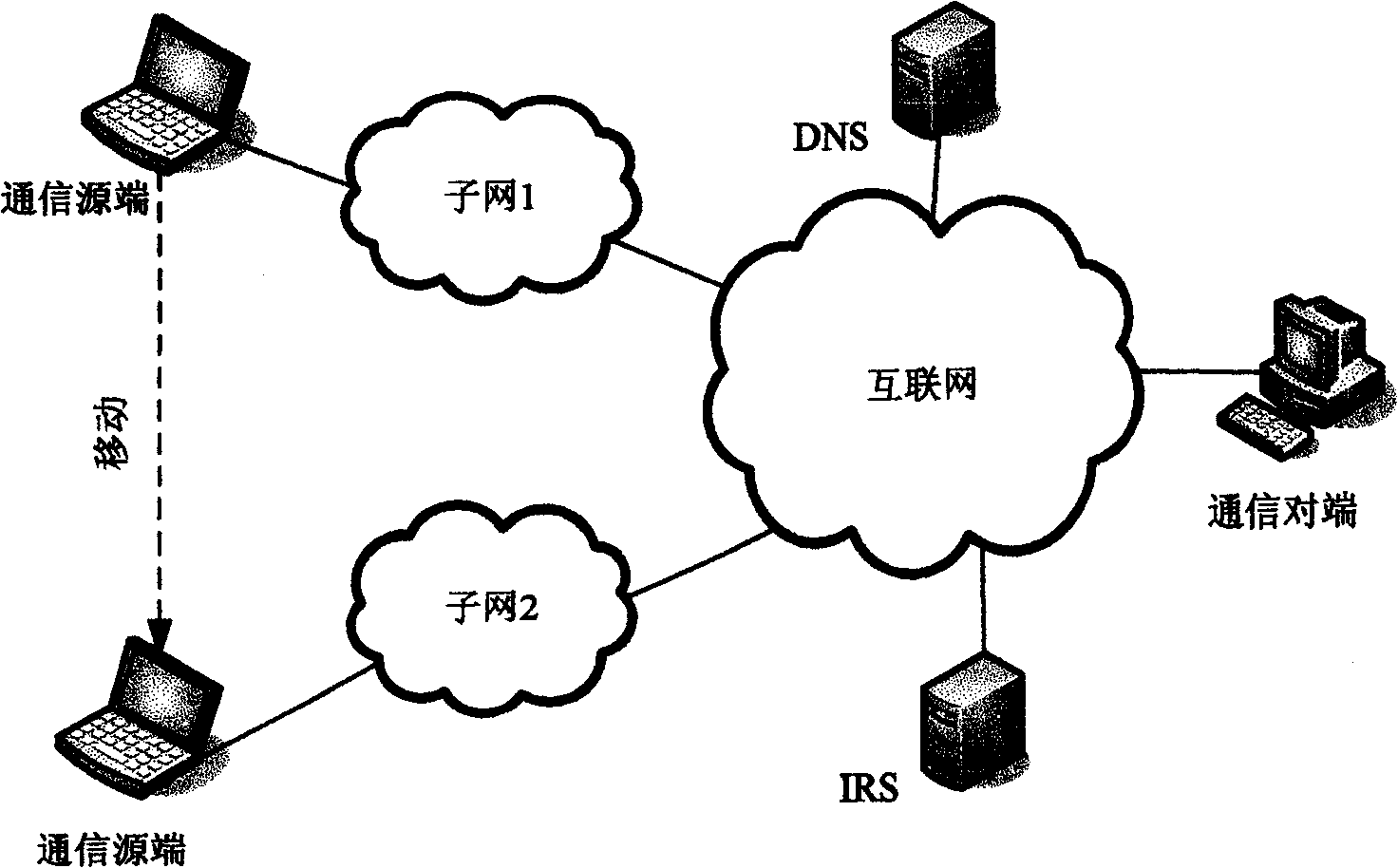
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41 results about "Identity resolution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Identity resolution is a data management process through which an identity is searched and analyzed between disparate data sets and databases to find a match and/or resolve identities.
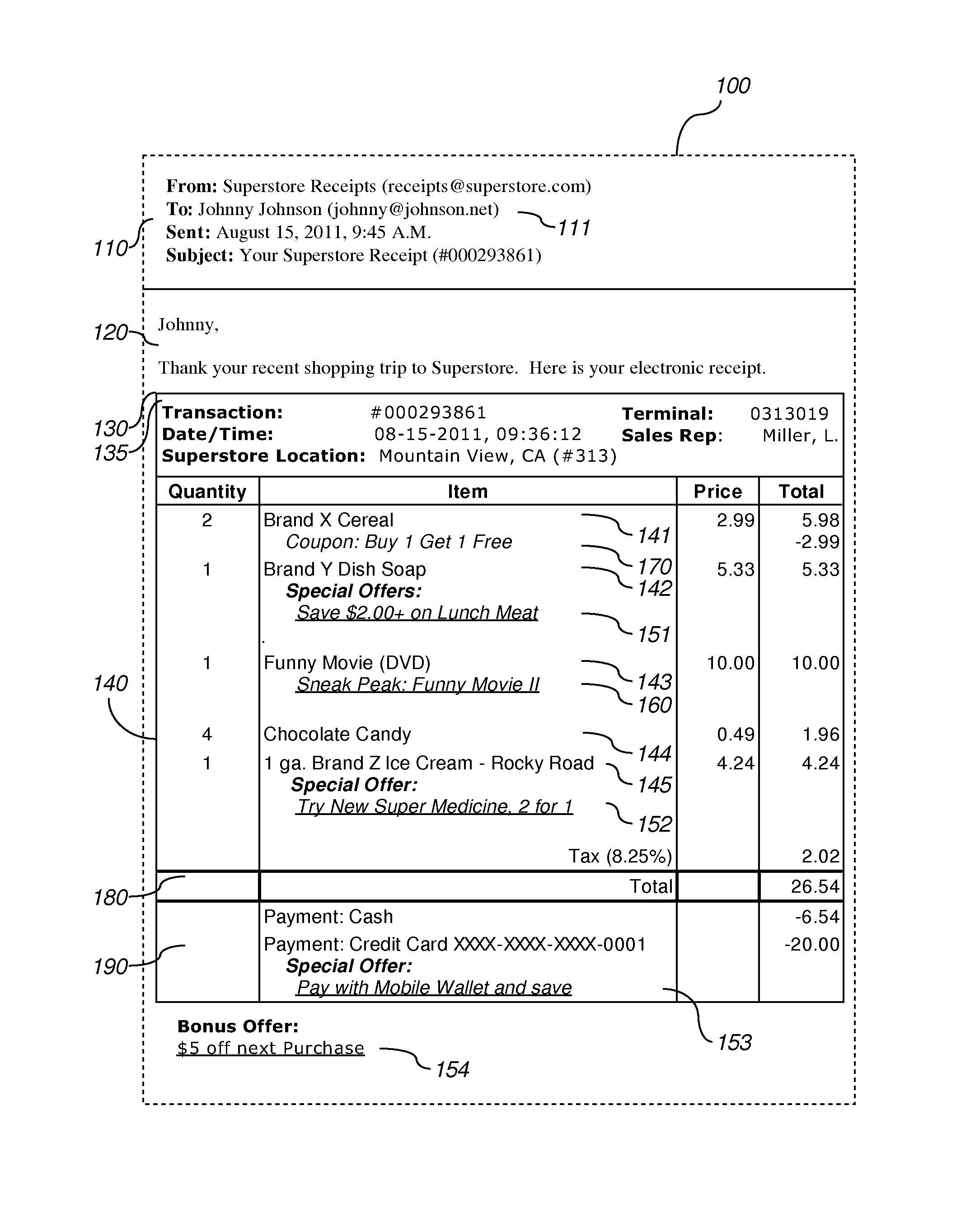
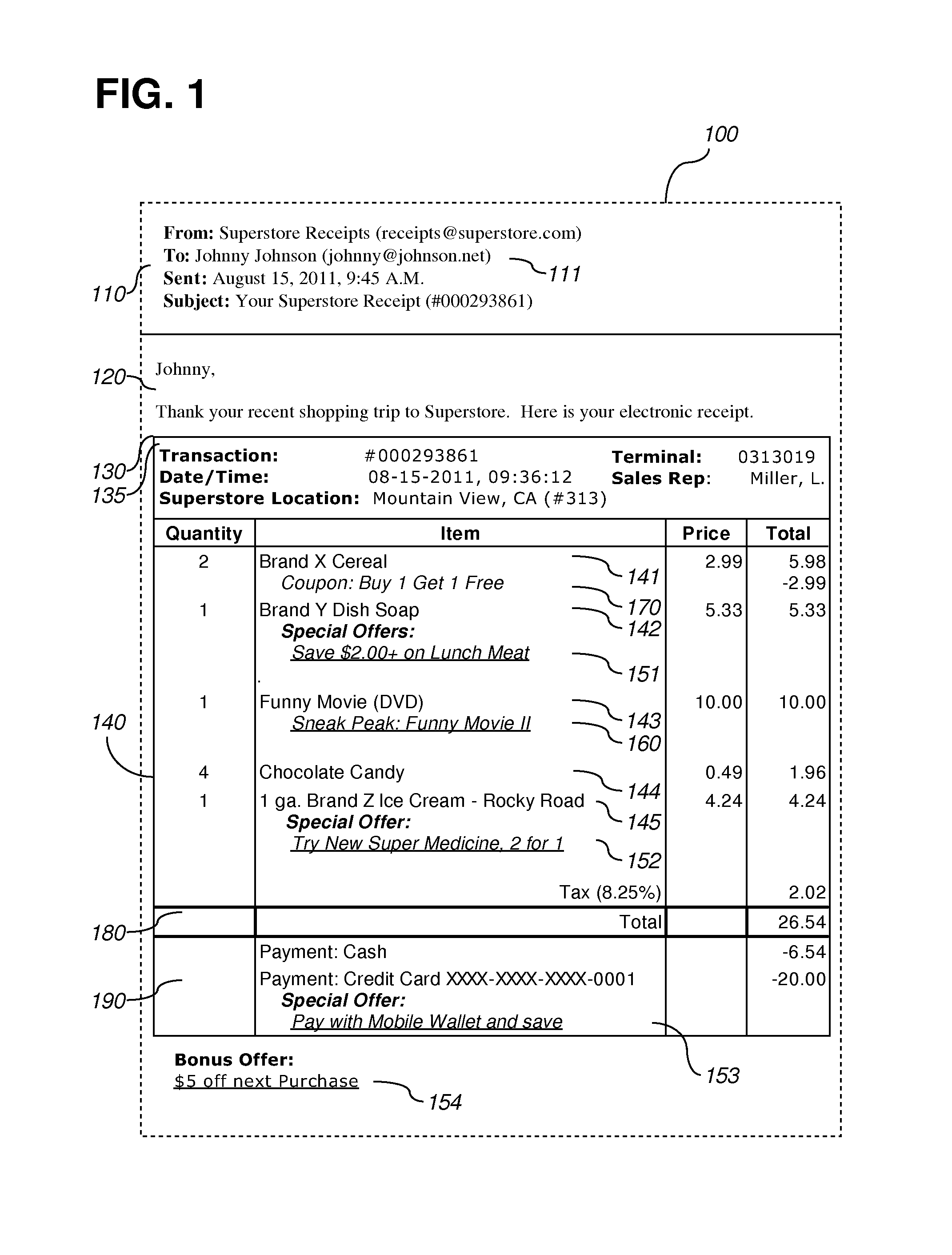
Consumer identity resolution based on transaction data
InactiveUS20140180826A1Complete banking machinesDiscounts/incentivesData processing systemTransaction data
According to an embodiment, a data processing system for facilitating consumer identity resolution comprises: a first logic module adapted to receive at least two collections of consumer records from at least two different sources; a second logic module adapted to compute first trust scores for first data fields of the first collection and second trust scores for second data fields of the second collection; a third logic module adapted to generate a master collection of consumer records comprising at least one master consumer record that is correlated to a record from the first collection and a record from the second collection, the correlation being based on at least on the trust scores; and a fourth logic module adapted to receive a set of contextual transaction data. The data processing system is adapted to identify a consumer based on the contextual transaction data and the master collection of consumer records.
Owner:QUOTIENT TECH INC
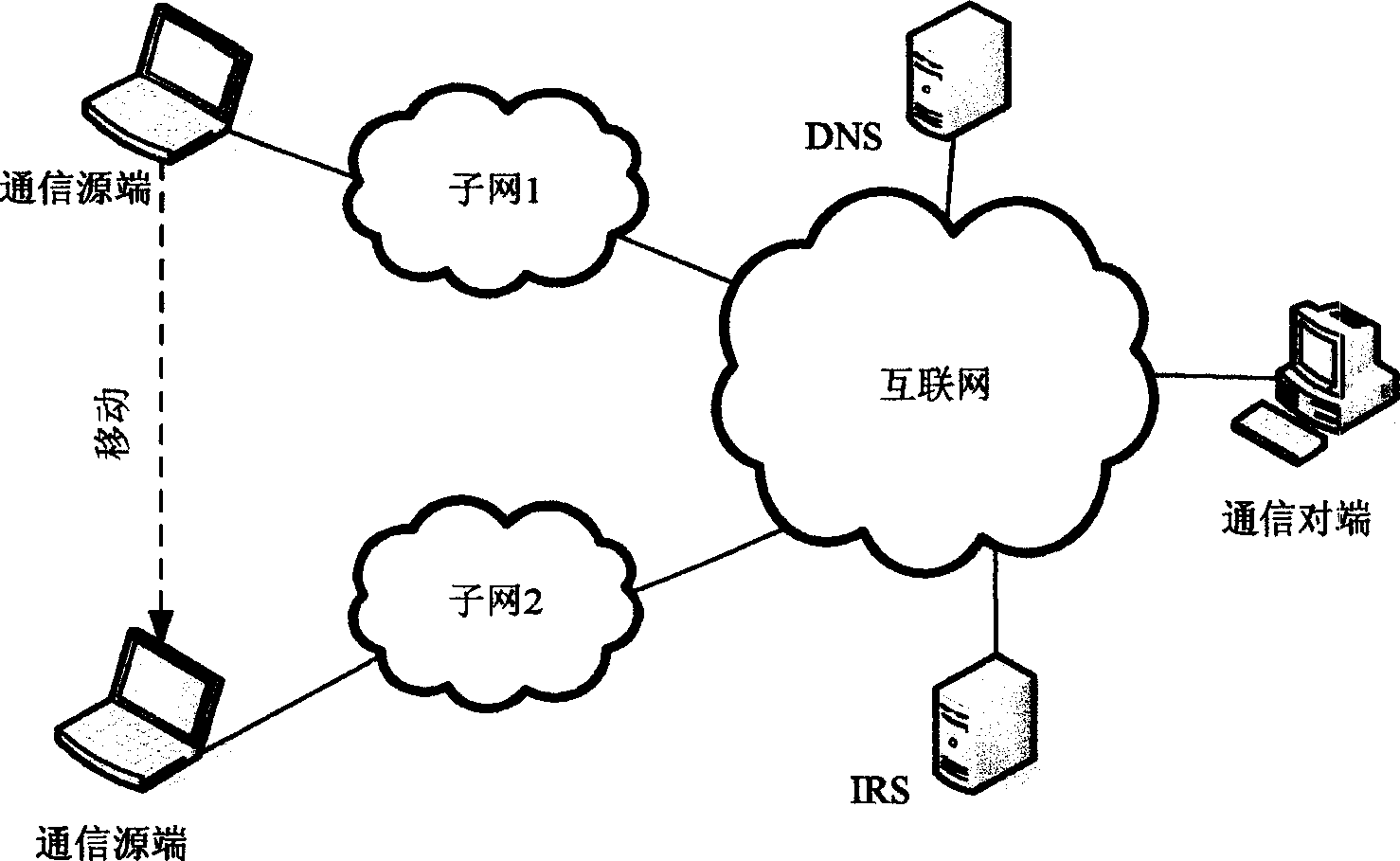
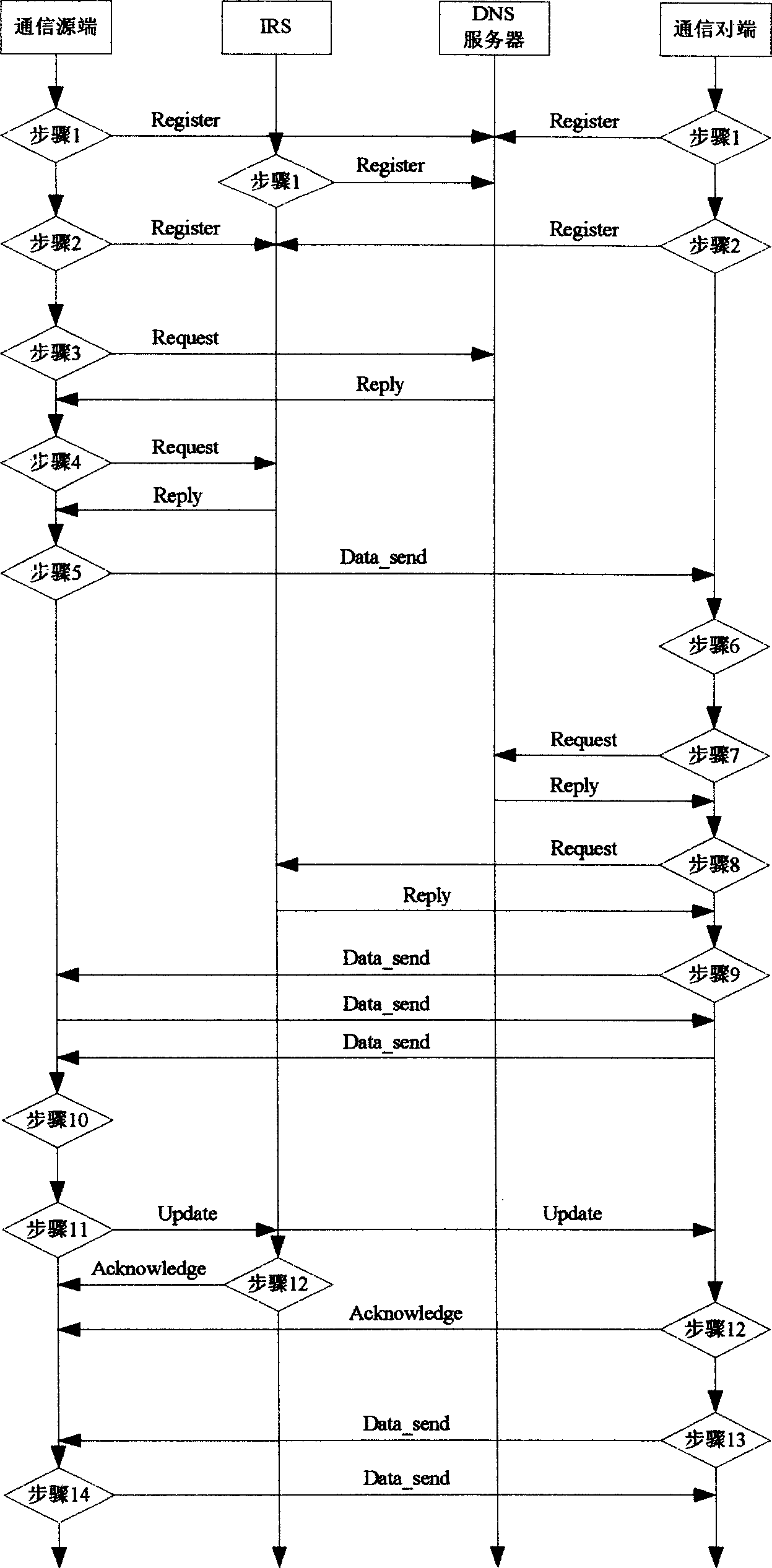
Internet access method based on identity and location separation
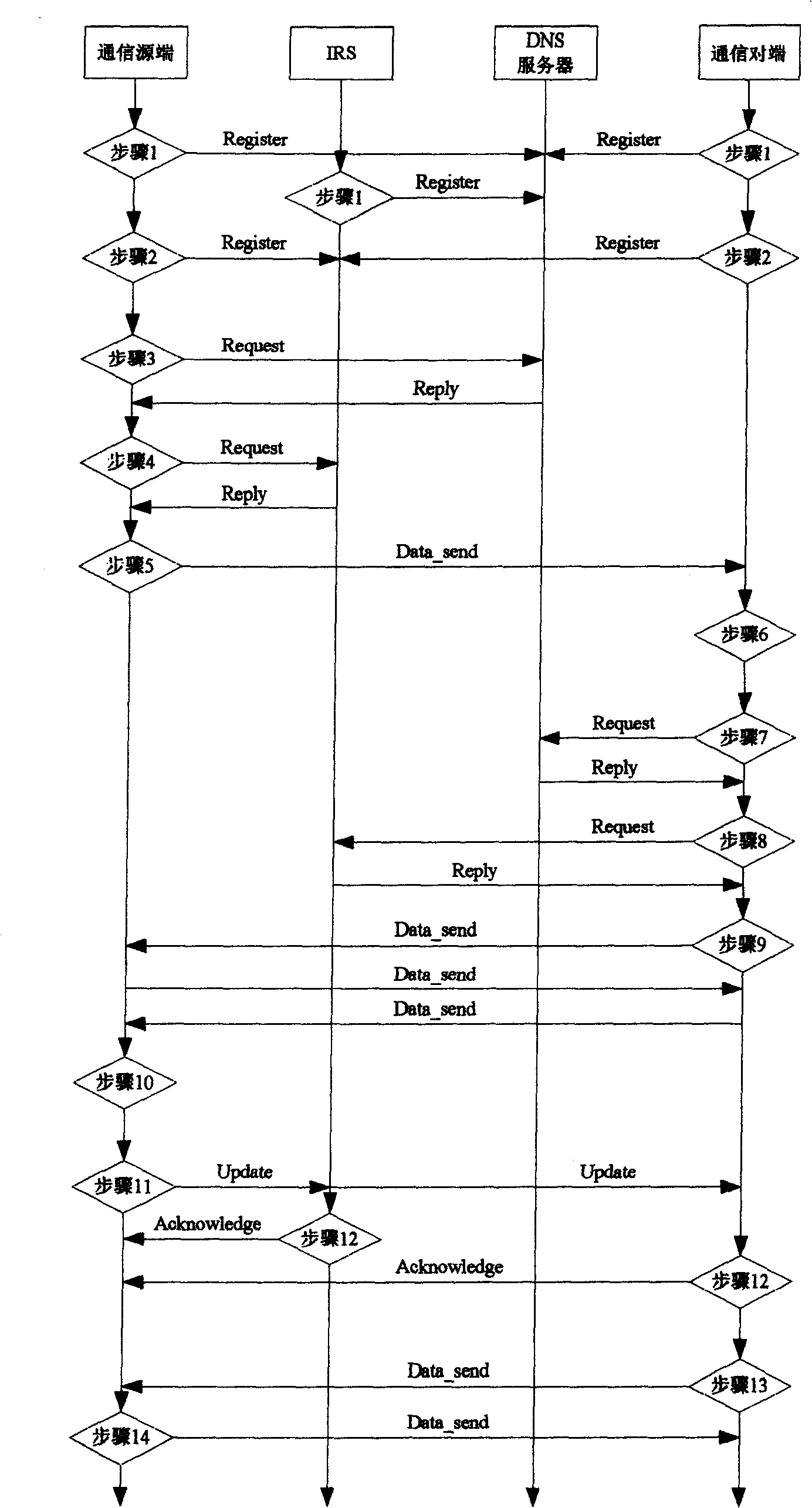
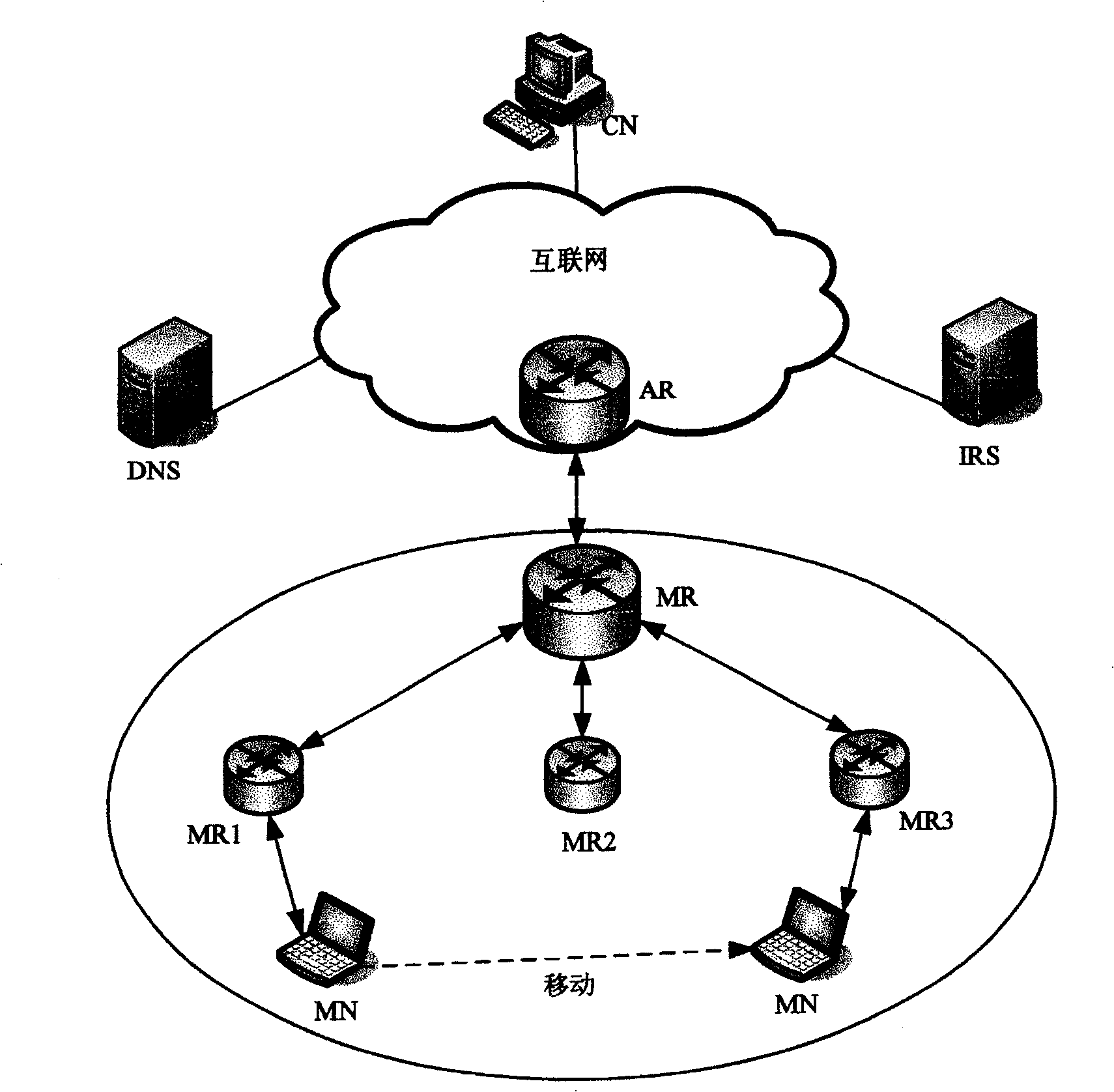
An identity and position separation based on internet mainframe accessing method separates the double function of traditional IP address, the IP address is only used as position identify of mainframe, leading-in new name-space one end mainframe identity which is used as identifiers of mainframe and terminal identifier of transmission protocol. Leading-in identity resolver for resolving map relation between mainframe and IP address and dynamically updating binding between end mainframe identifiers and IP address. DNS resolving map relation between domain name and end identifiers and recording identified resolver IP address. In communication process communication node IP address can be changed but communication node EID keeps unchanged. Said invention can make fixation termination, mobile terminal, mobile network, self-organization network etc accessing internet in unitive mode.
Owner:BEIJING JIAOTONG UNIV
Asset Identity Resolution Via Automatic Model Mapping Between Systems With Spatial Data
InactiveUS20130159351A1Digital data processing detailsSpecial data processing applicationsData scienceIdentity resolution
Owner:IBM CORP
Method and apparatus for facilitating identity resolution
InactiveUS20110125770A1Improve visual appearanceImprove abilitiesDigital data processing detailsCommerceData miningComputer program
A method, apparatus, and computer program product are therefore provided for an identity resolution application to handle identity resolution issues that arise when data regarding a persona is available from multiple sources. A method may be provided that includes receiving an indication that a first profile represents a persona of interest, searching for potential profile matches that are at least partially related to the persona of interest, and assessing a confidence level that the potential profile match belongs to the persona of interest. The method may further include providing for presentation of a potential profile match and receiving a confirmation that a potential profile match belongs to the persona of interest where the potential profile match then becomes a confirmed profile match. The first profile may comprise a plurality of data elements related to the persona of interest.
Owner:NOKIA CORP
Reverse identity profiling system with alert function
The present invention is a universal biometric monitoring system designed to locate and track terrorists, criminals, and missing or displaced persons. Via various checkpoints and a plurality of identity verification or observation ports, defining identity characteristics or biometric data is transmitted to a system that cumulatively creates a database and identity related profiles. The uses of the system are three-fold. Data is retrieved and examined in order to: Find, isolate, and restrict wanted individuals; Locate missing children; Bring order and identity resolution to groups of individuals, most specifically individuals displaced resultant to disaster situations. The system is capable of retrieving, capturing, transmitting, analyzing, and otherwise examining biometric data, cumulatively building identity profiles, and has the ability to search, match, find, trace and track identities through this system as well as set off a multiplicity of alert outputs and alarms.
Owner:OKUN SHERI LEE
Multi-dimensional digital identity authentication system based on block chain
InactiveCN112580102ASupport large-scale accessSupport for customizable identity certificatesDigital data protectionDigital data authenticationEngineeringData store
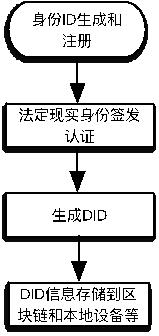
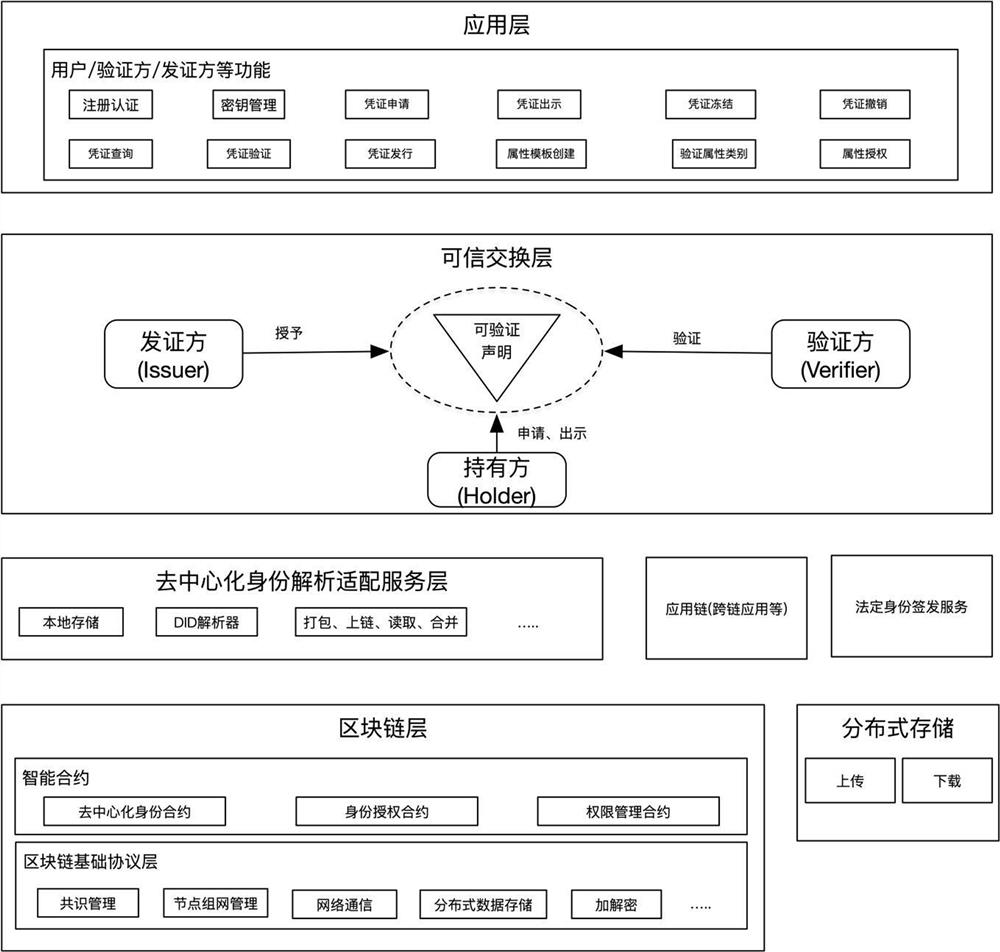
The invention discloses a multi-dimensional digital identity authentication system based on a block chain, and relates to the technical field of block chains. The system comprises: a block chain layerused for storing and anchoring a DID document and other data needing distributed storage content; a decentralized identity analysis adaptation service layer which is used for providing a unified DIDdocument analysis service for the block chain layer, and the service can be connected with other application chains at the same time to carry out cross-chain application; a trusted exchange layer which is used for obtaining a DID document through an identity on a user agent registration chain, applying for various verifiable certificates to a certificate issuer by depending on the DID document, and finally providing the DID and the verifiable certificates to a verifier to complete a verification process; and an application layer which is used for constructing a web, wherein an application of the mobile client is provided for a terminal user to use. The system supports cross-chain and cross-platform interoperation, and can be expanded in various different modes.
Owner:ZHENGZHOU UNIV
Device, system and method for implementing multicast communication
InactiveCN101222414AReduce the burden onSpecial service provision for substationAccess routeIp address
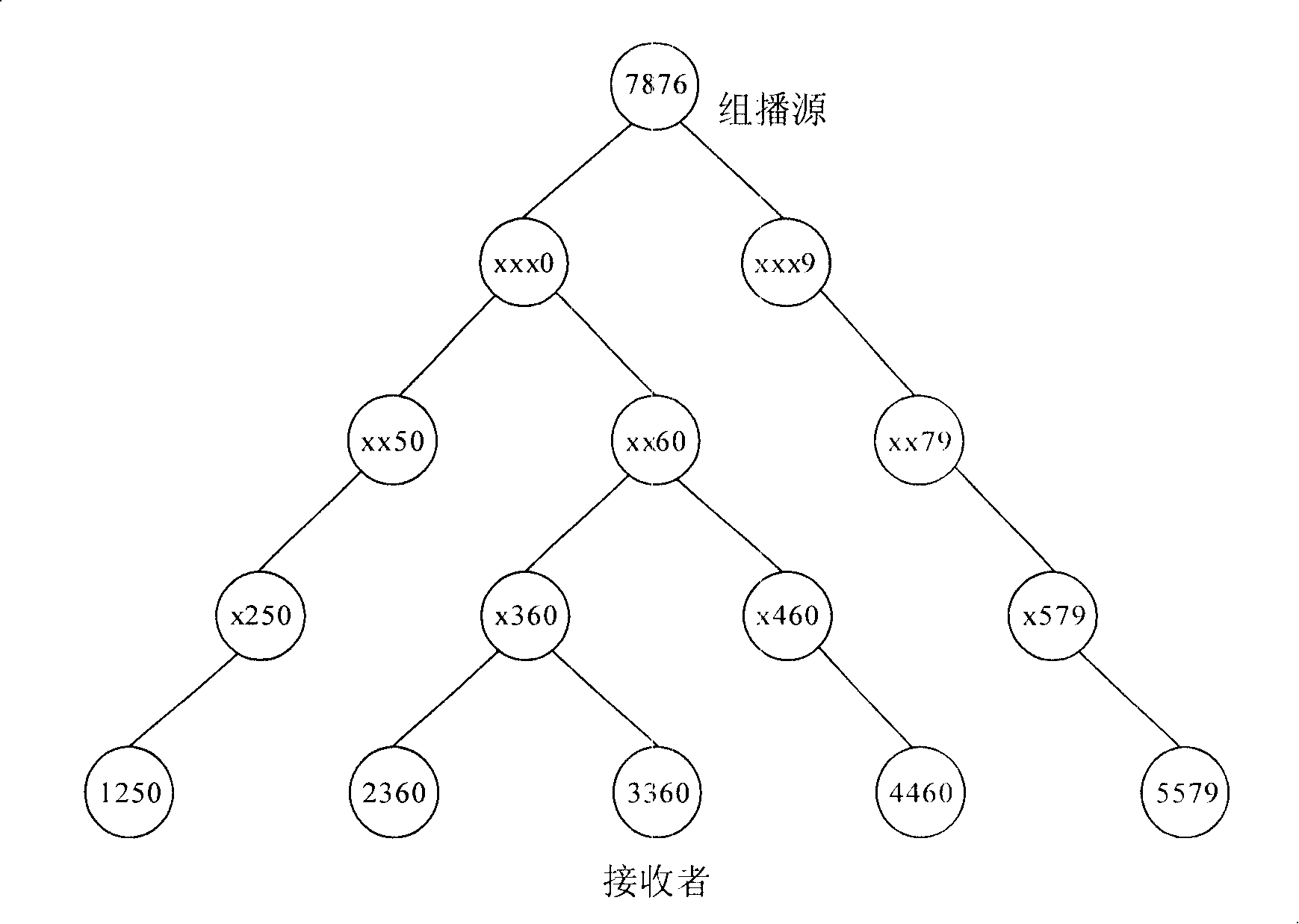
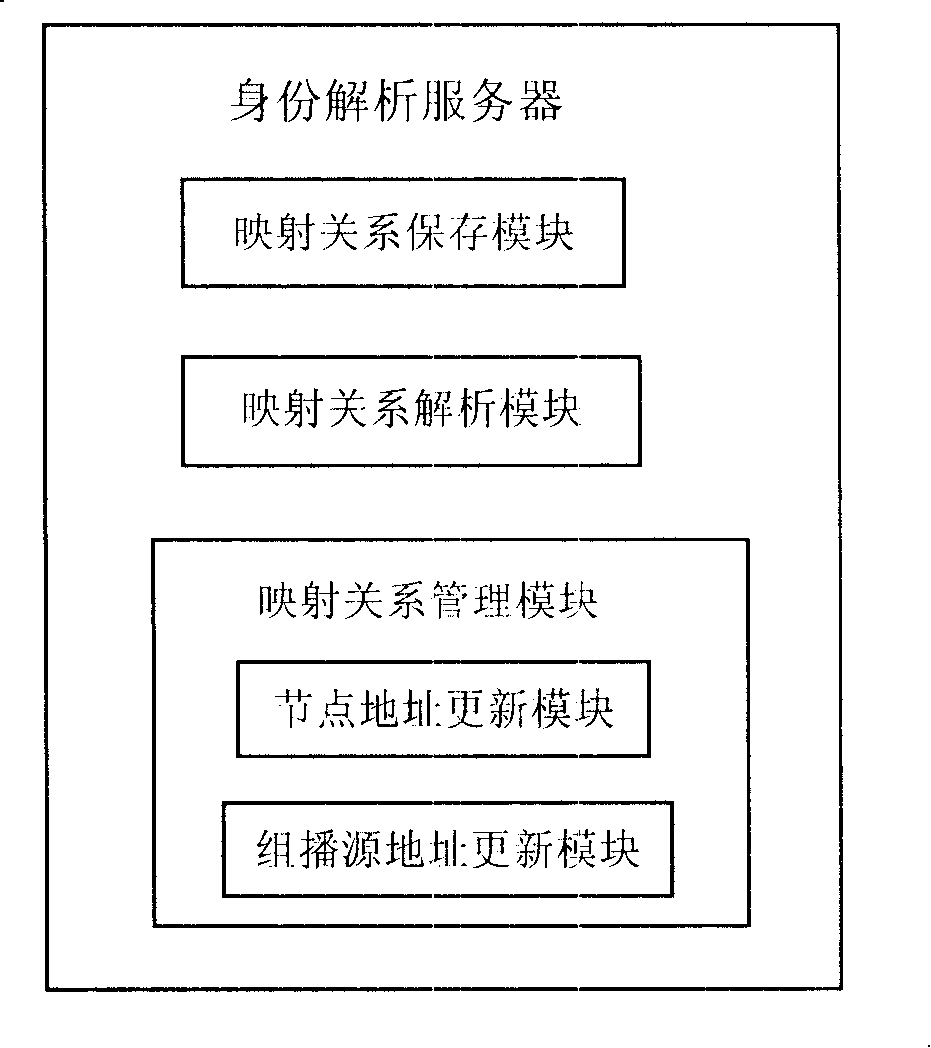
The embodiment of the invention provides a device for realizing the multicast communication, a system and a method. The device comprises an identity resolving server; the system comprises an SM, an access route, a receiver and an identity resolving server; the method mainly comprises the following steps that: the SM obtains and stores all mapping relation information between EID of all nodes and IP addresses; according to the EID information of all the nodes, a multicast tree is established and controlled; the multicast communication between the SM and the receiver is realized by the transfer of the access route according to the multicast tree and the IP address information of the nodes. The invention ensures that an intermediate node in the network takes charge of transmitting the multicast communication message without storing the state information of an application layer multicast tree or maintaining the application layer multicast tree, thereby effectively reducing the burden of a middle layer.
Owner:HUAWEI TECH CO LTD +1
Bluetooth low energy address resolving
ActiveUS20180198752A1Quick connectionNetwork topologiesSecurity arrangementAddress resolutionPrivate address
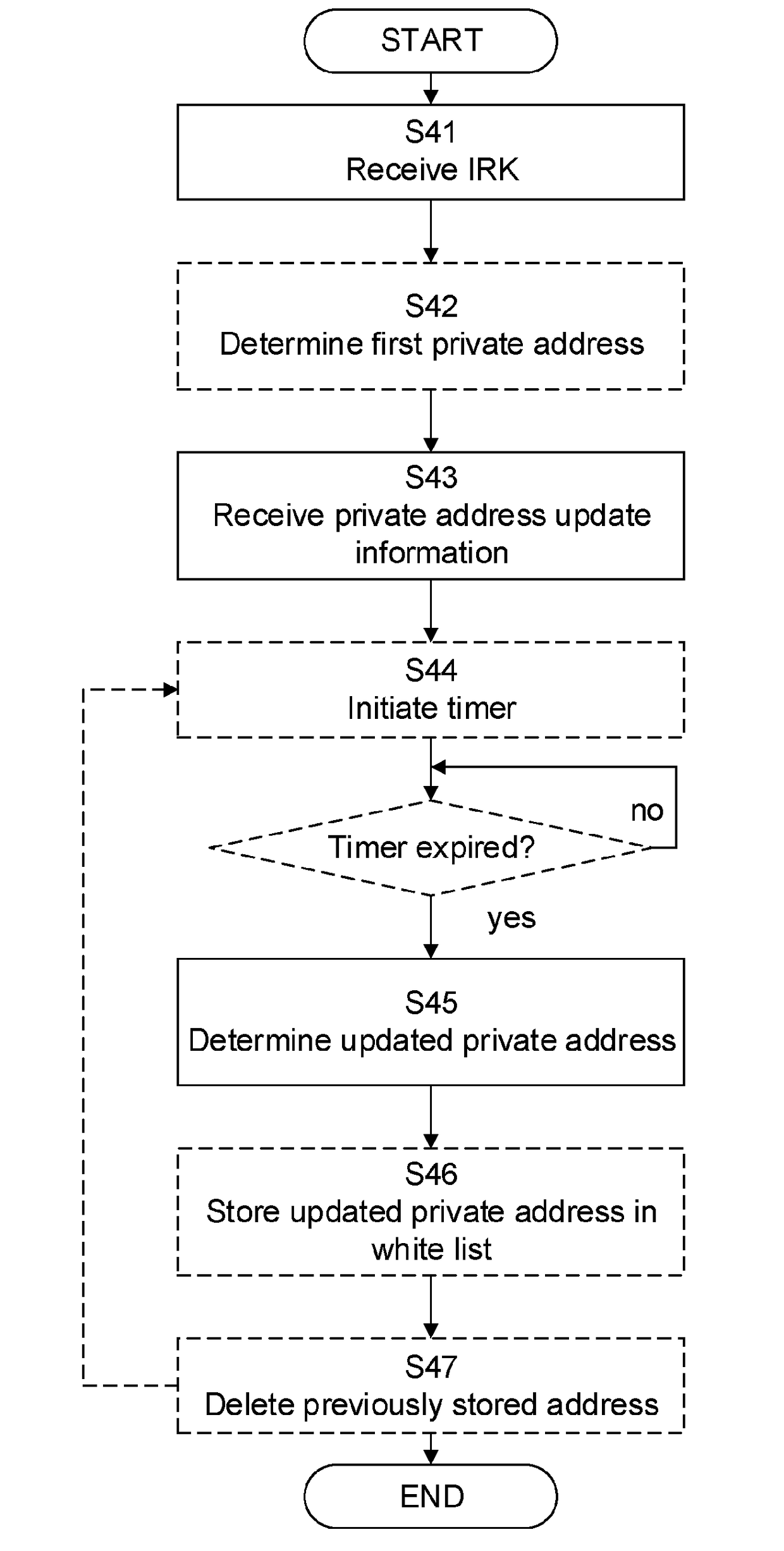
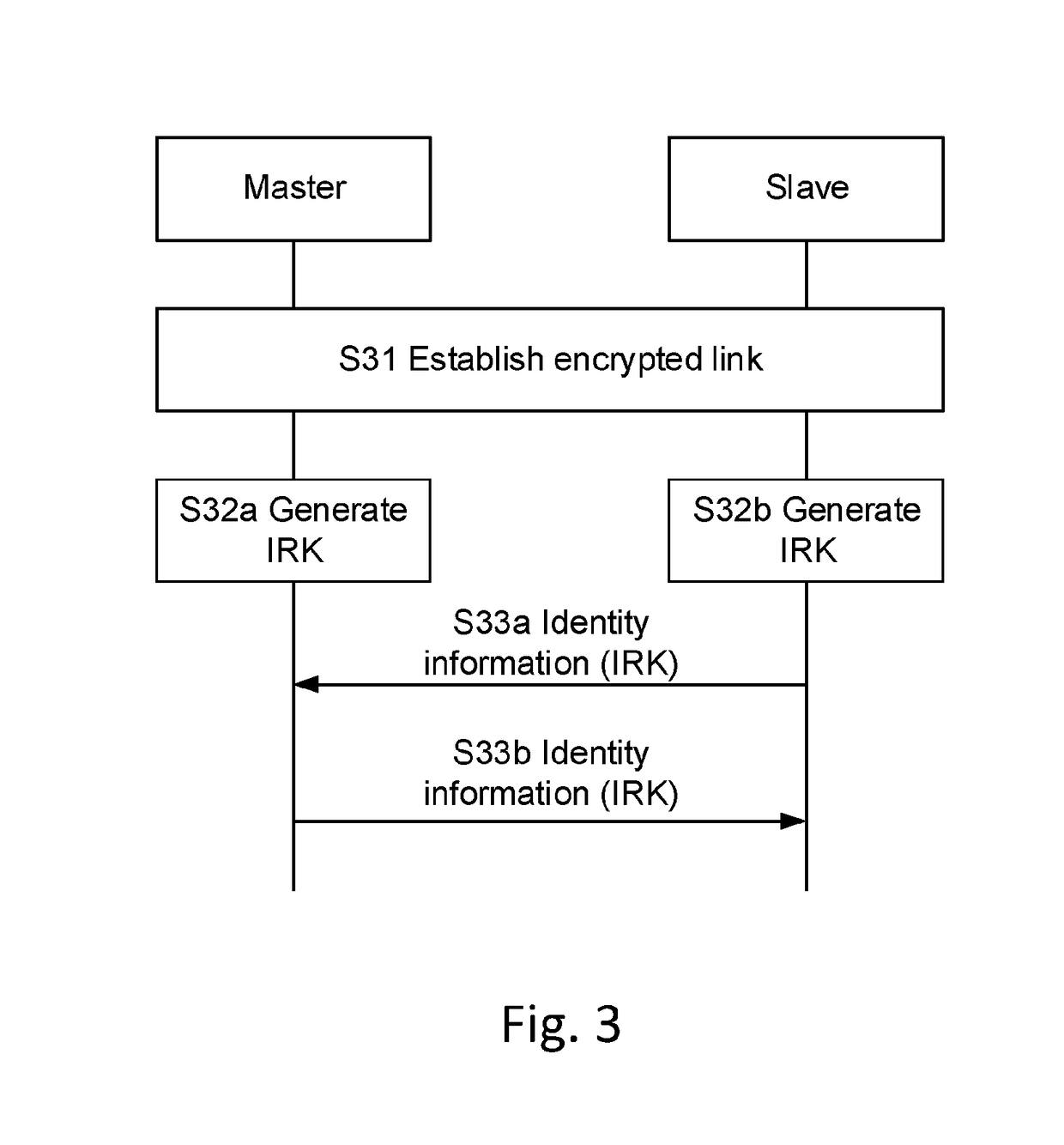
The present disclosure relates to methods and arrangements in a private address resolving node of a personal area network deploying Bluetooth low energy, BLE and in particular to methods and arrangements for proactively resolving periodically updated private addresses. When performed in a private address resolving node of a personal area network deploying Bluetooth low energy, BLE, a method comprises resolving a periodically updated private address of a private address generating node connected to the private address resolving node. The private address is used in addressing messages from the private address resolving node to the private address generating nodes. The method comprises receiving (S41), from a private address generating node in the personal area network, an Identity Resolving Key, IRK, the IRK being received over an encrypted link established between the private address resolving node and the private address generating node and receiving (S43), from the private address generating node, private address update information defining when and how to update the private address of the private address generating node. Based on the received IRK and the received private address update information, an updated private address to be used when addressing a next message to the private address generating node is determined (S45).
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and system for secured data storage and sharing over cloud based network
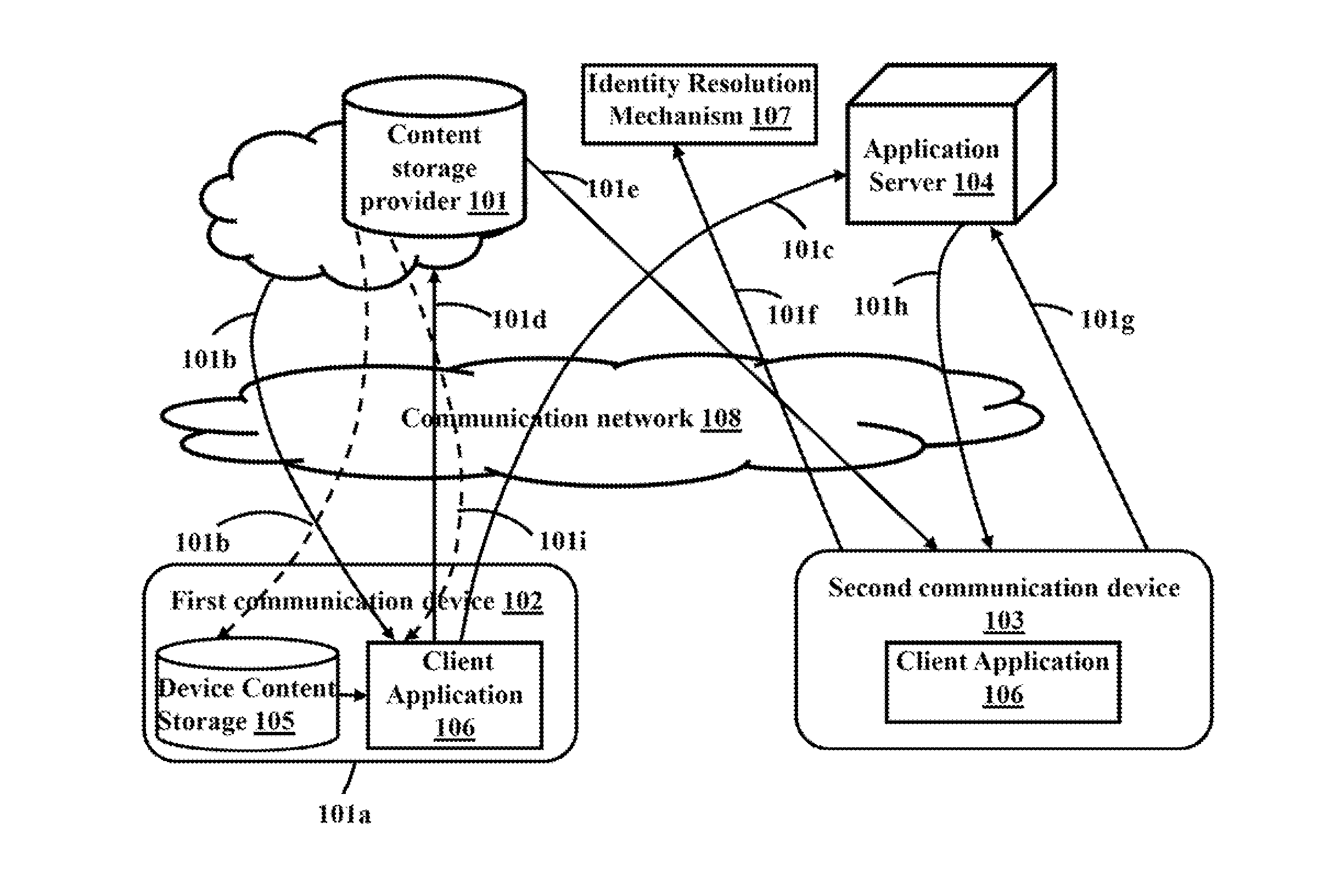
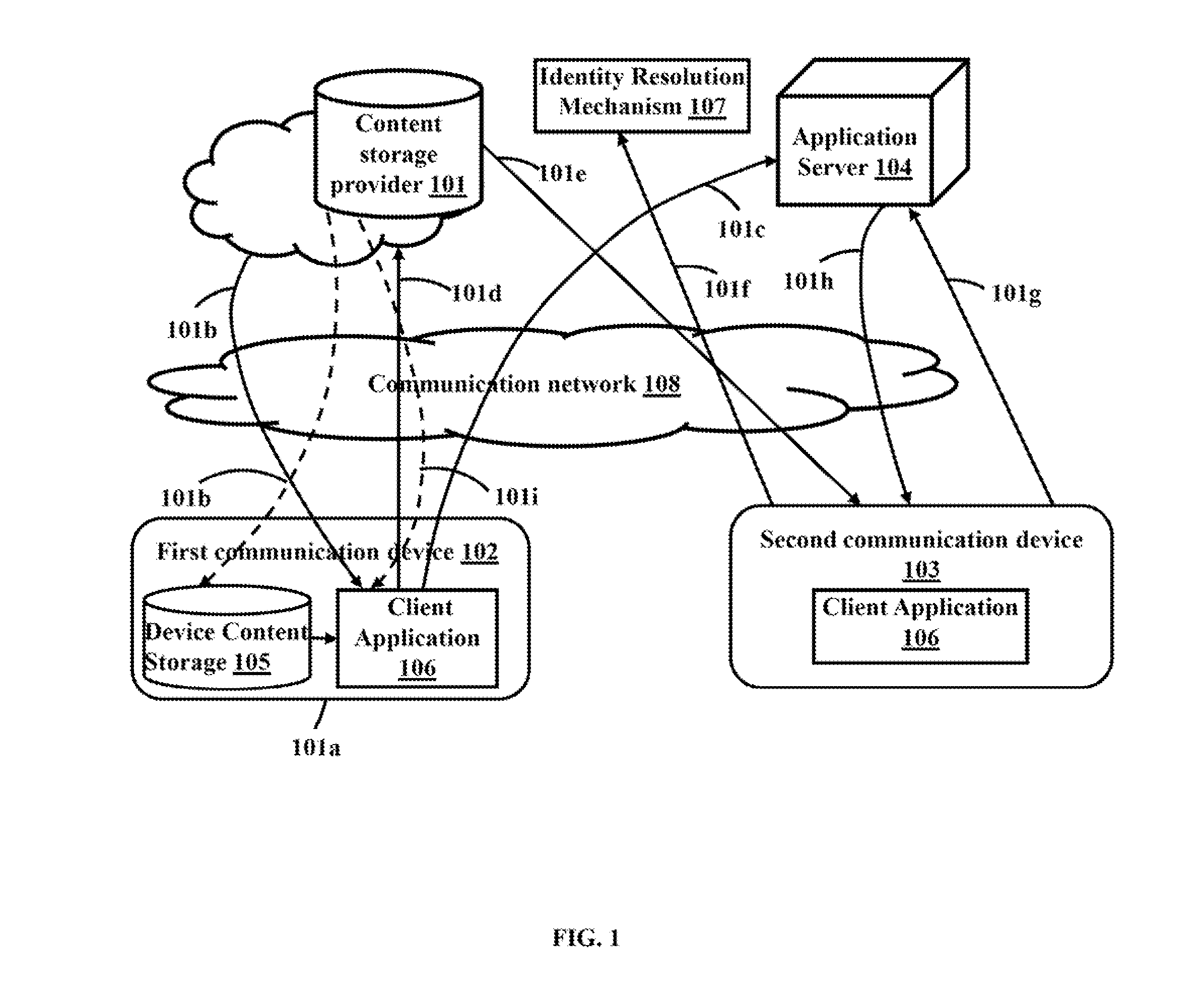
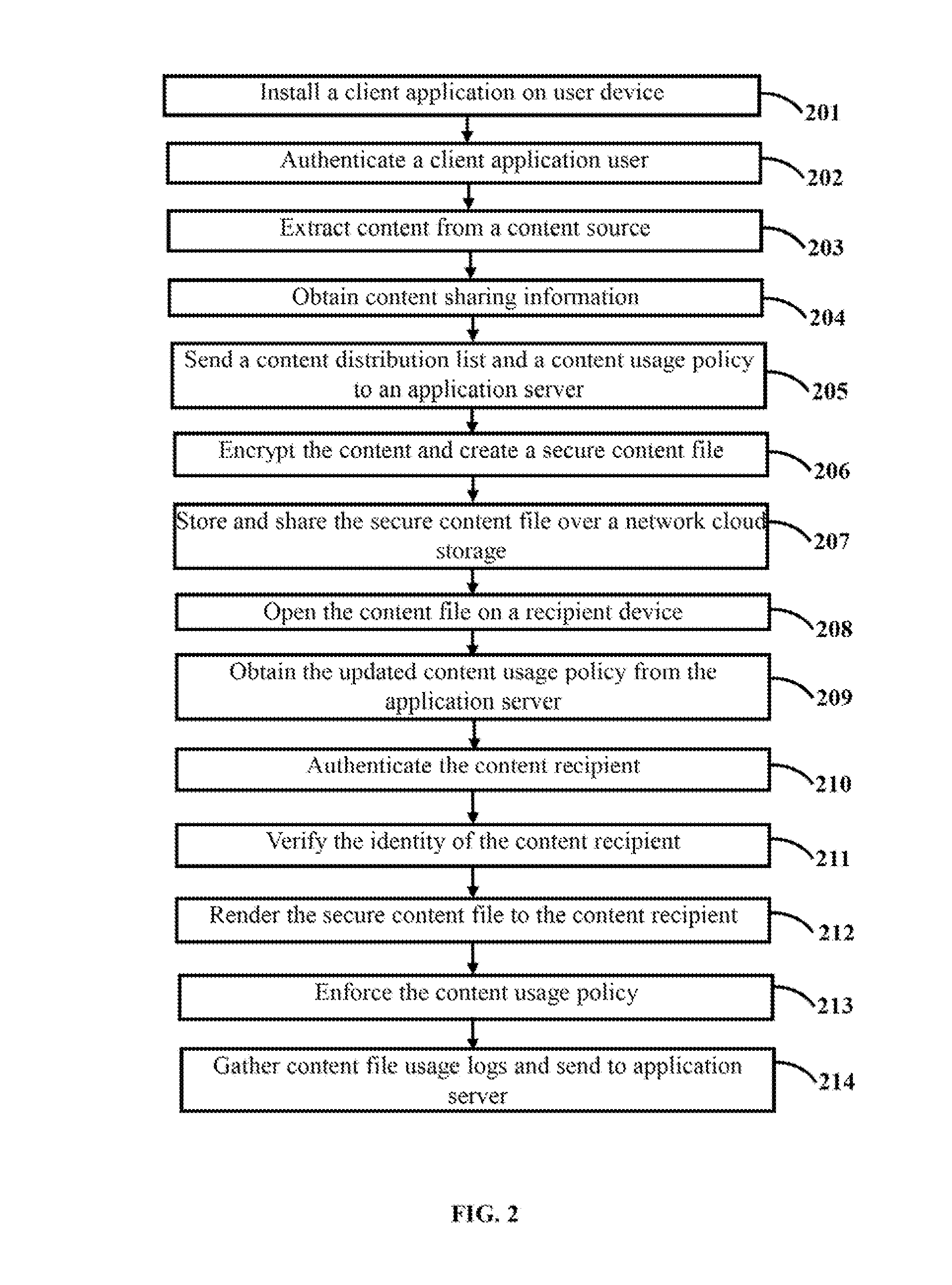
ActiveUS20140189352A1Digital data information retrievalUser identity/authority verificationContent distributionUser device
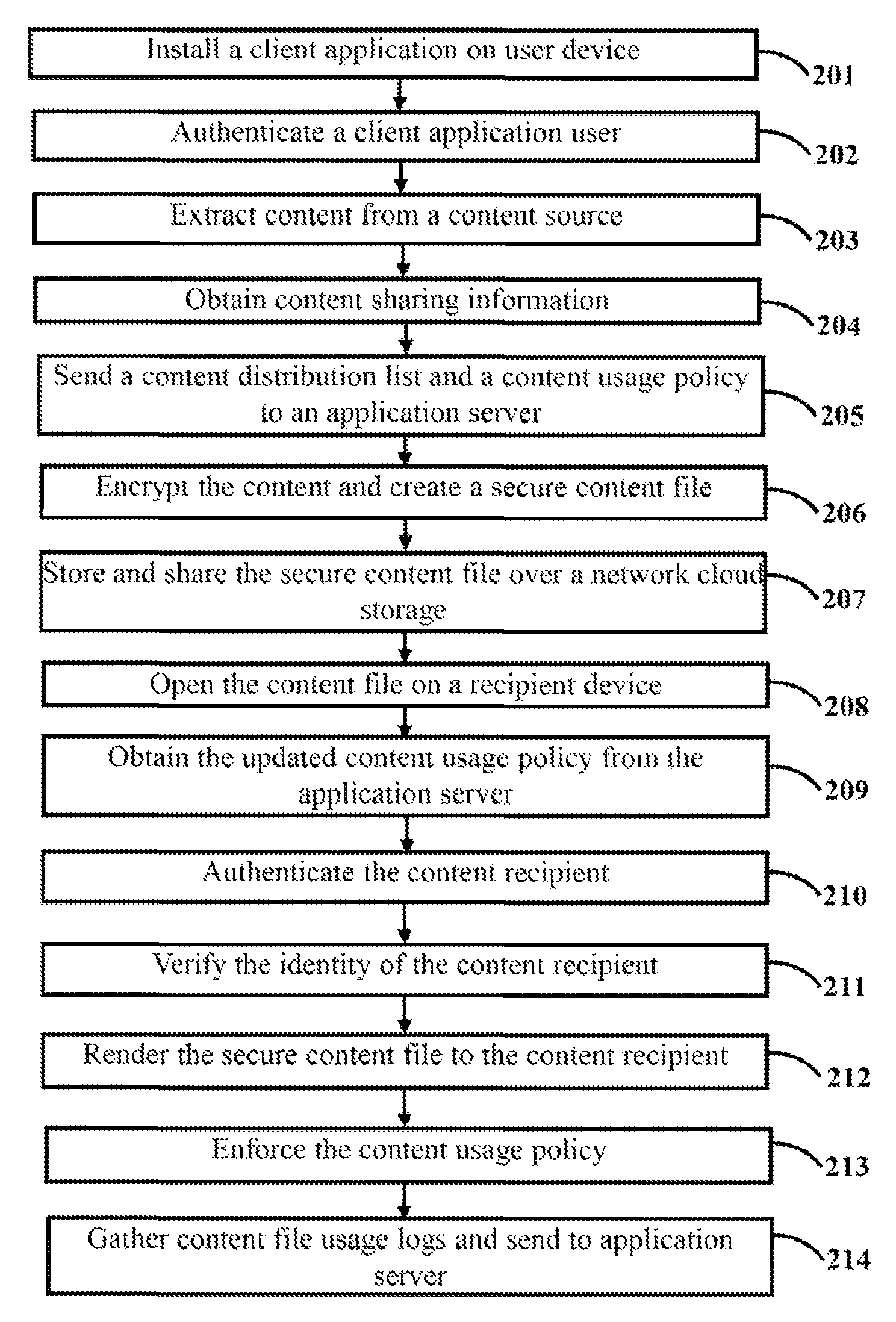
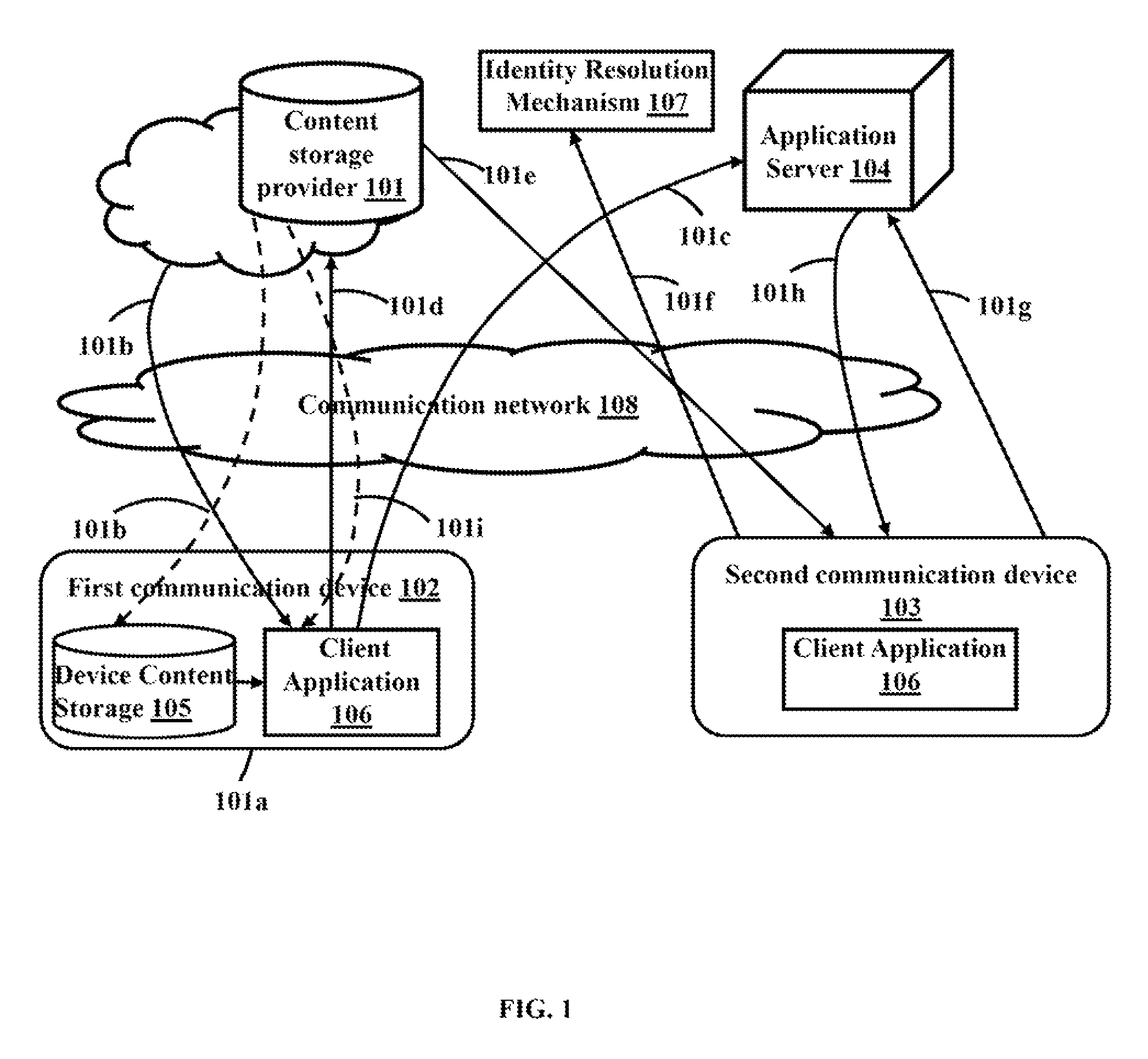
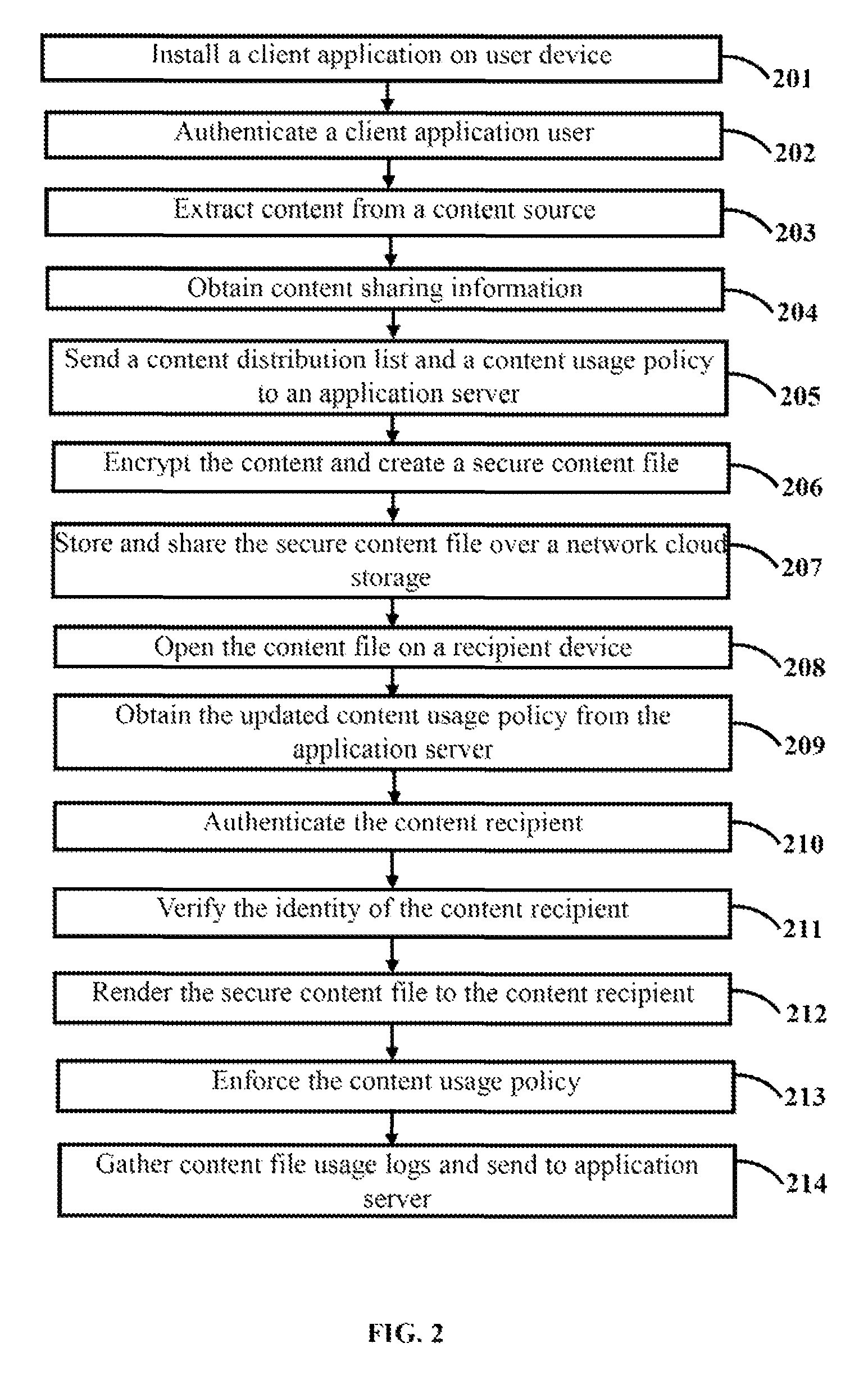
The various embodiments herein provide a method and system for secure data storage and sharing over a cloud based network. The method comprises installing a client application on a user device, authenticating a client application user, extracting content from a data source, obtaining content sharing information from a content storage provider, sending a content distribution list and a content usage policy to an application server, encrypting the content by the client application, creating and sharing a secure content file, decrypting the content file, finding the content usage policy and sharing information from the content file, obtaining an updated content usage policy from the application server, authenticating the content recipient using an authentication mechanism, verifying the identity of the content recipient using an identity resolution mechanism, rendering the secure content file to the recipient, enforcing the content usage policy and sending content usage logs to the application server.
Owner:SECURELYSHARE SOFTWARE PVT LTD
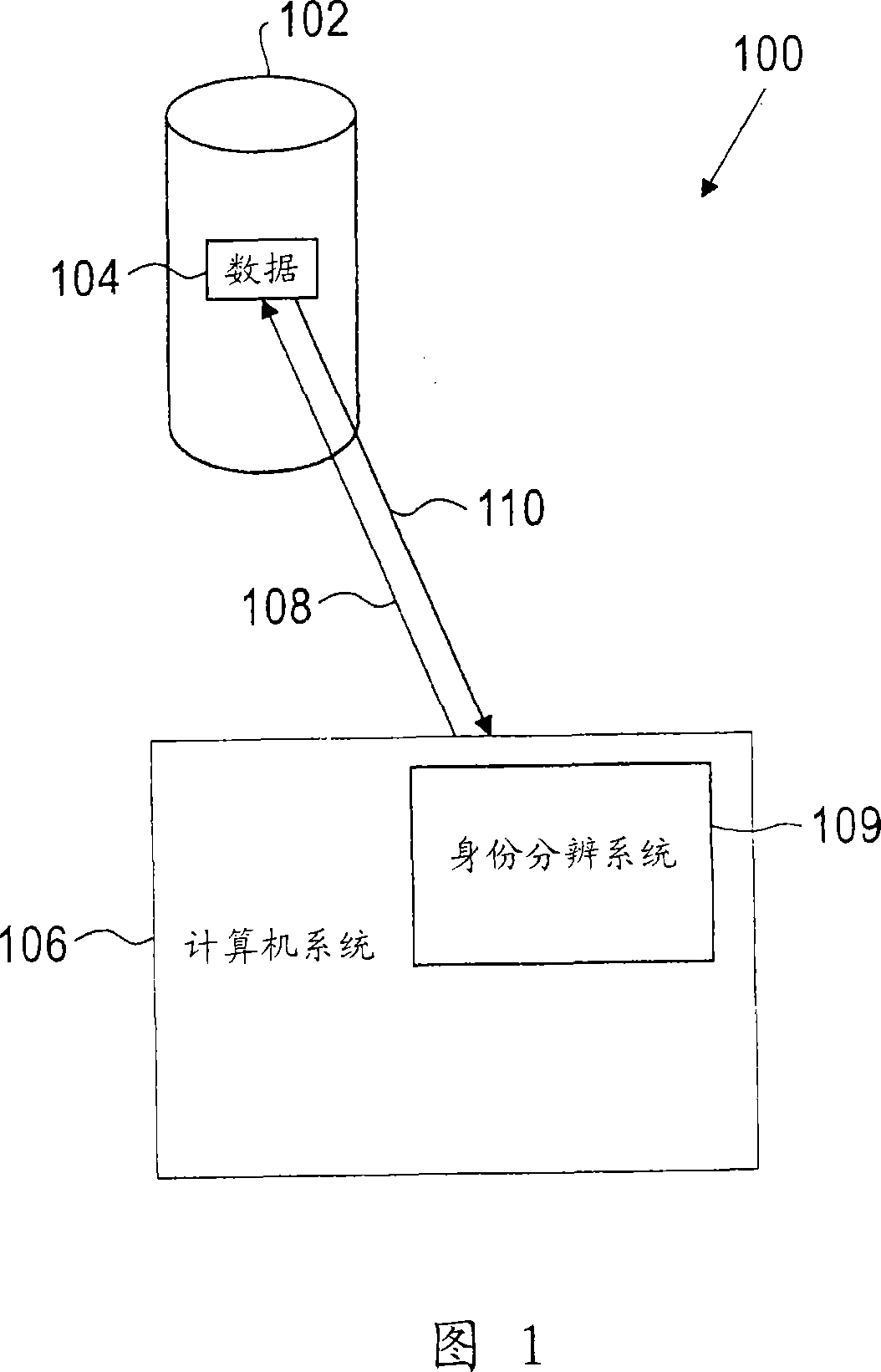
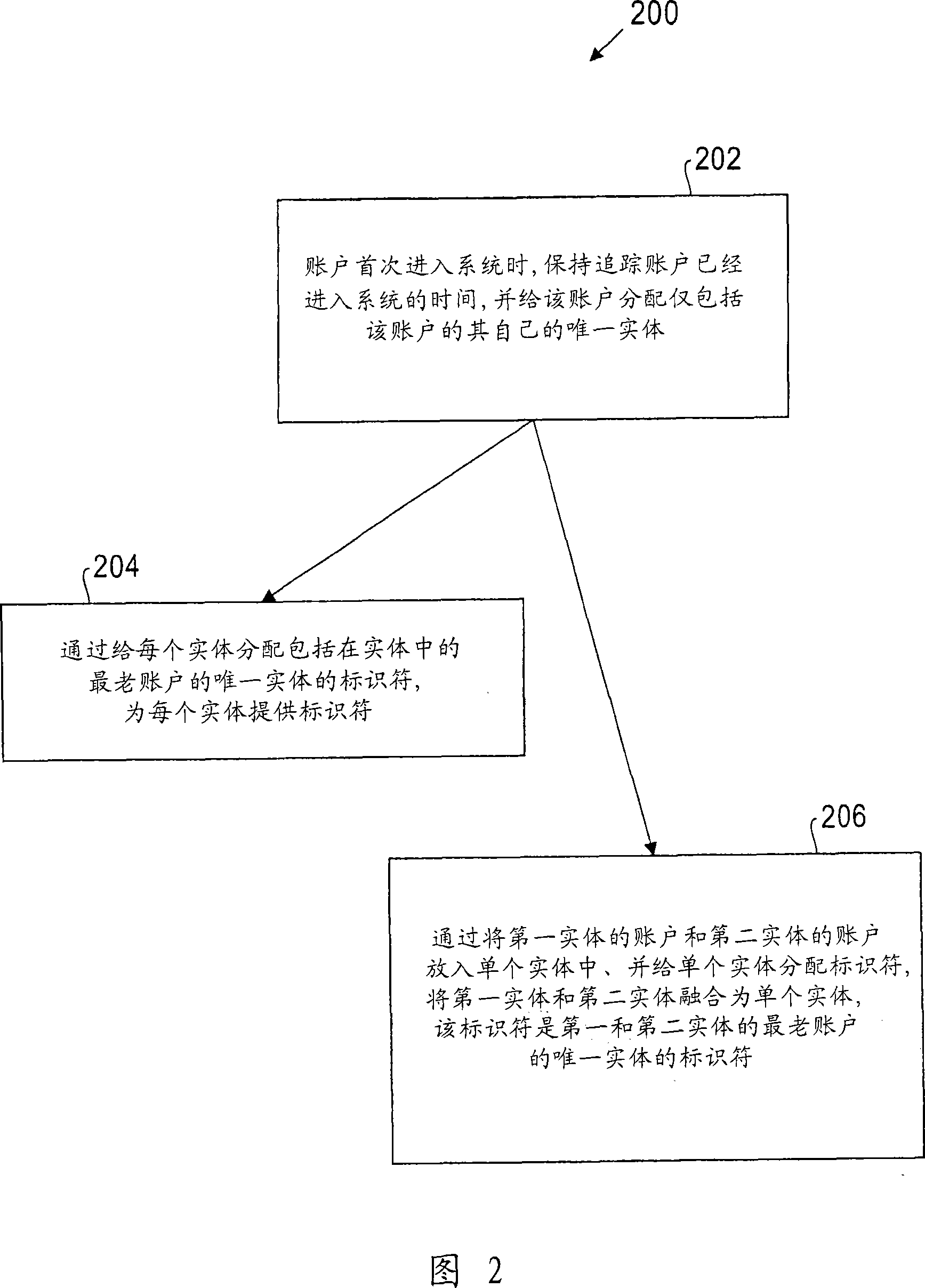
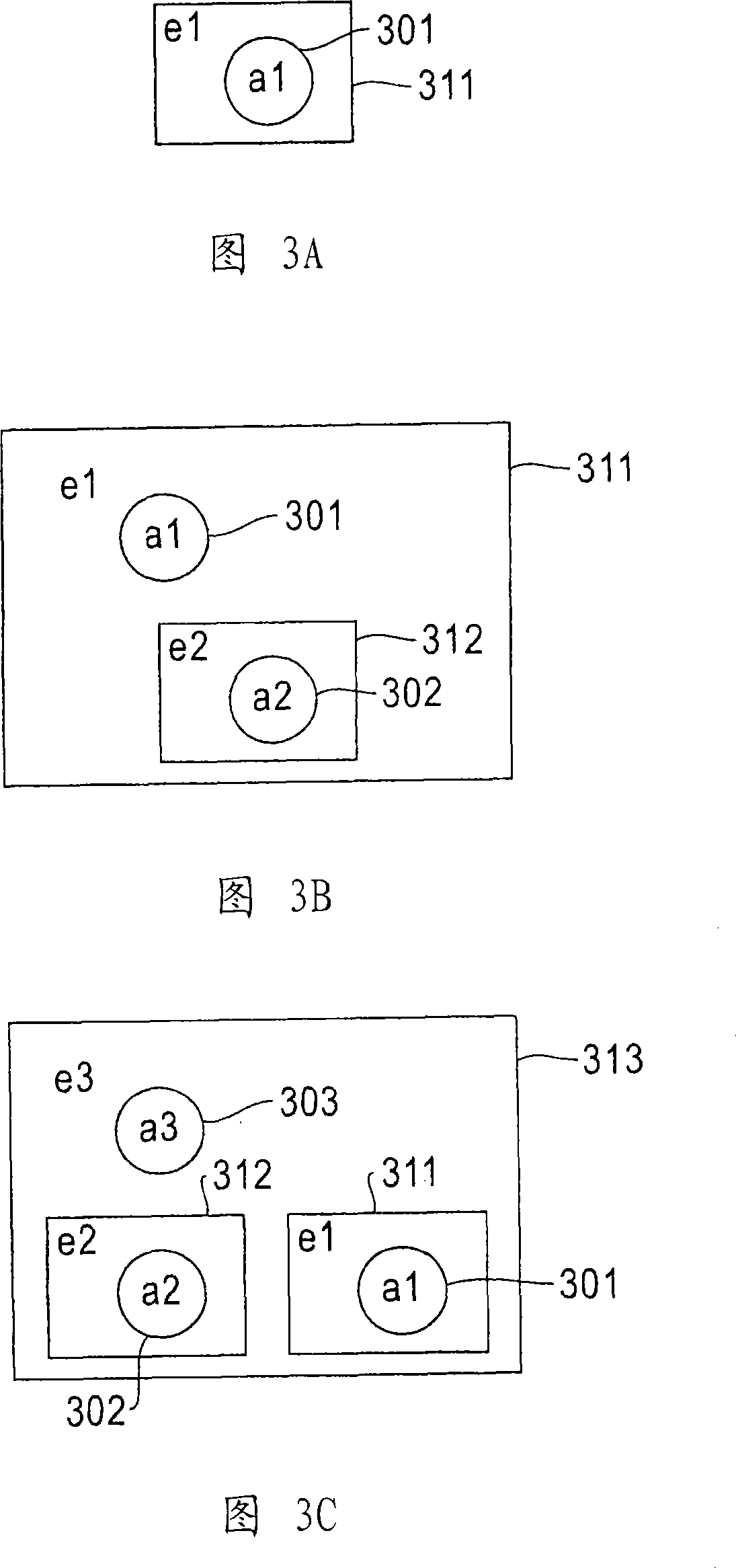
Tracking entities during identity resolution
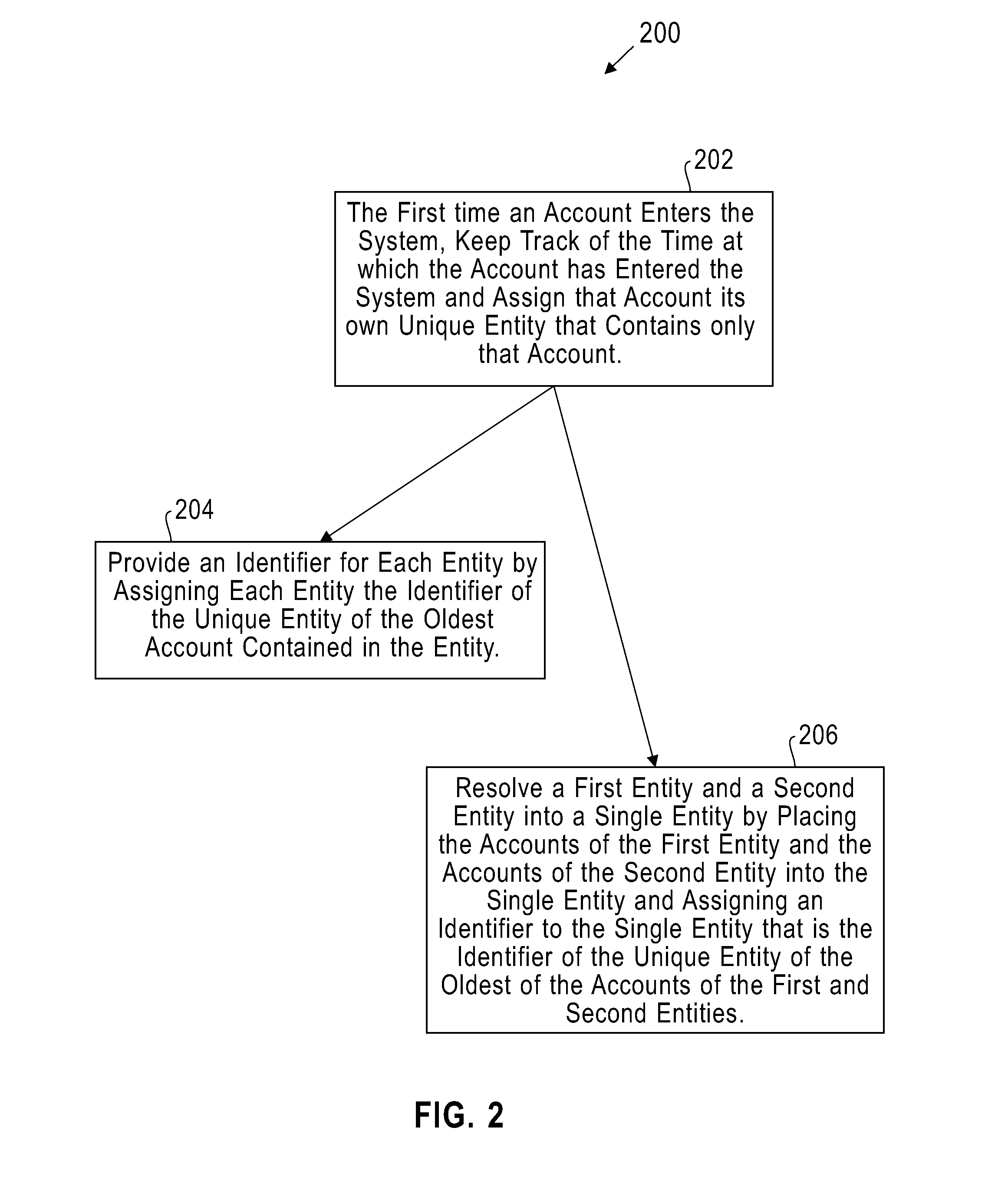
A method of tracking entities for identity resolution in database systems comprises assigning each account of a plurality of accounts a unique entity belonging only to the account and in which the account is contained; keeping track of the age of each account of the plurality of accounts; and assigning an identifier to any entity as the identifier of the unique entity of the oldest account contained in the entity. This simple method of assigning identifiers to accounts and entities solves a number of identity resolution problems known in the art including: lost entity identifier problem, lost entity version problem, entity switched warm bodies / accounts problem, and account drift problem.
Owner:IBM CORP
Method and system for secured data storage and sharing over cloud based network
ActiveUS9015483B2Digital data information retrievalDigital data processing detailsContent distributionUser device
The various embodiments herein provide a method and system for secure data storage and sharing over a cloud based network. The method comprises installing a client application on a user device, authenticating a client application user, extracting content from a data source, obtaining content sharing information from a content storage provider, sending a content distribution list and a content usage policy to an application server, encrypting the content by the client application, creating and sharing a secure content file, decrypting the content file, finding the content usage policy and sharing information from the content file, obtaining an updated content usage policy from the application server, authenticating the content recipient using an authentication mechanism, verifying the identity of the content recipient using an identity resolution mechanism, rendering the secure content file to the recipient, enforcing the content usage policy and sending content usage logs to the application server.
Owner:SECURELYSHARE SOFTWARE PVT LTD
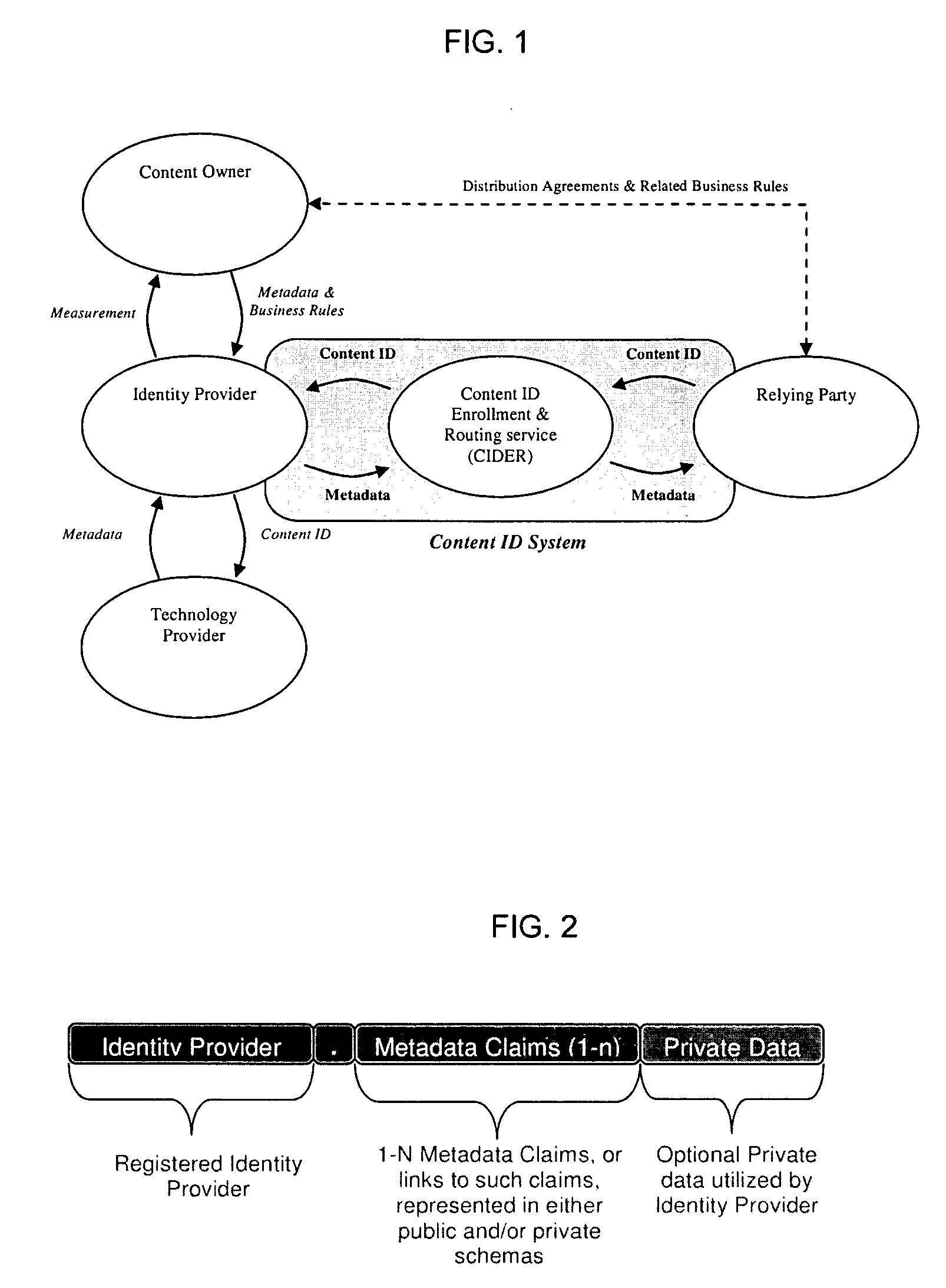
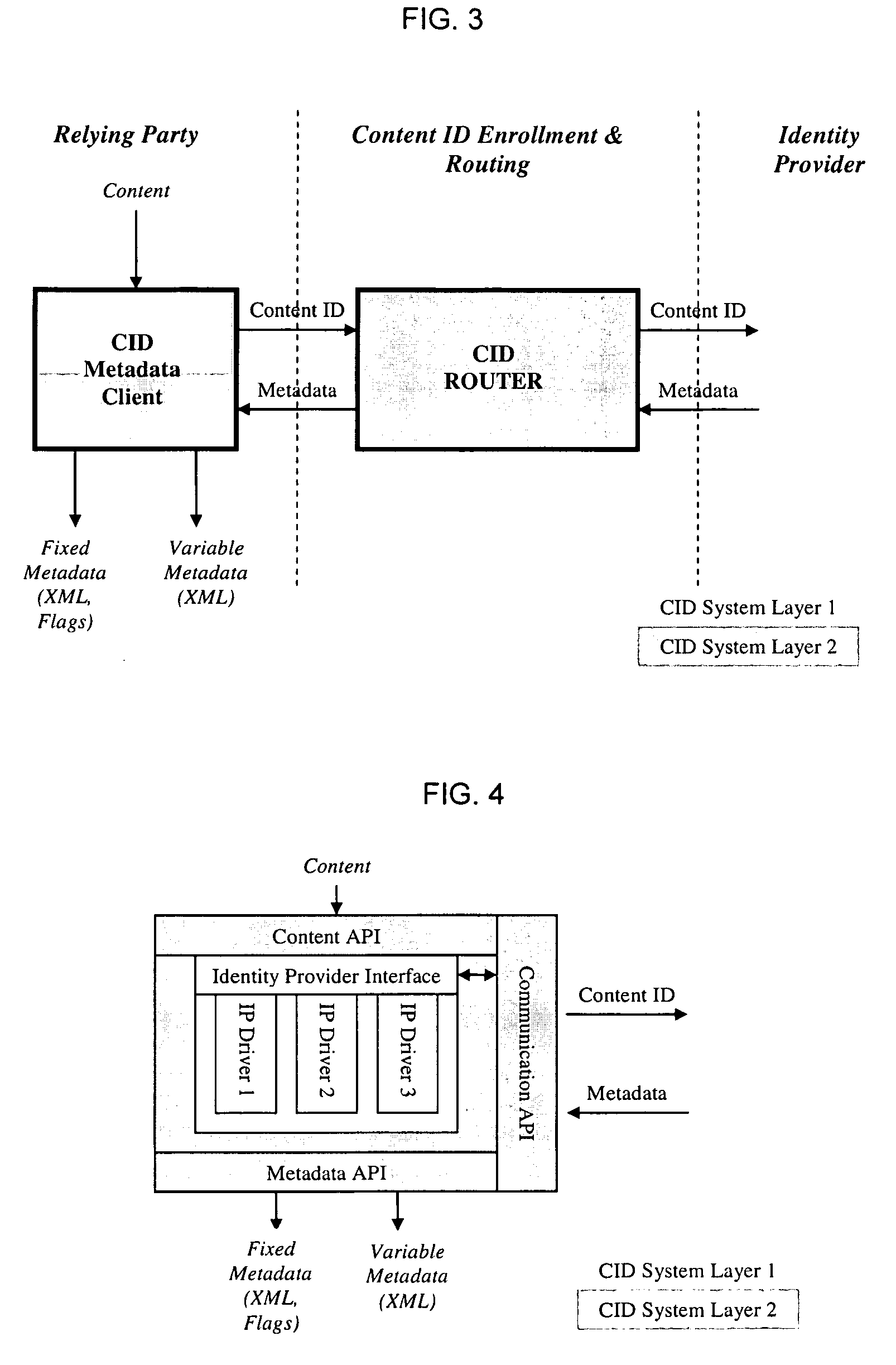
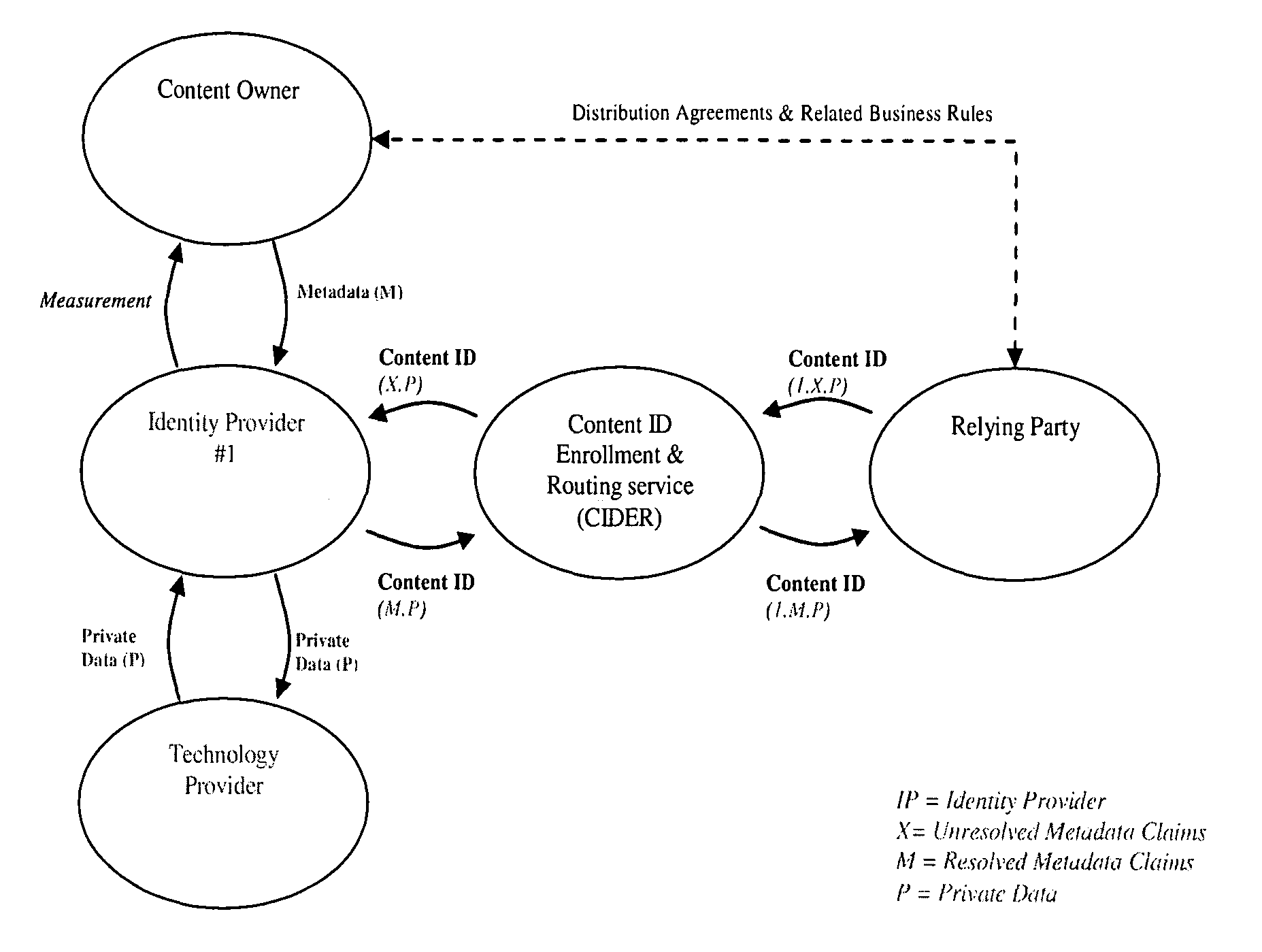
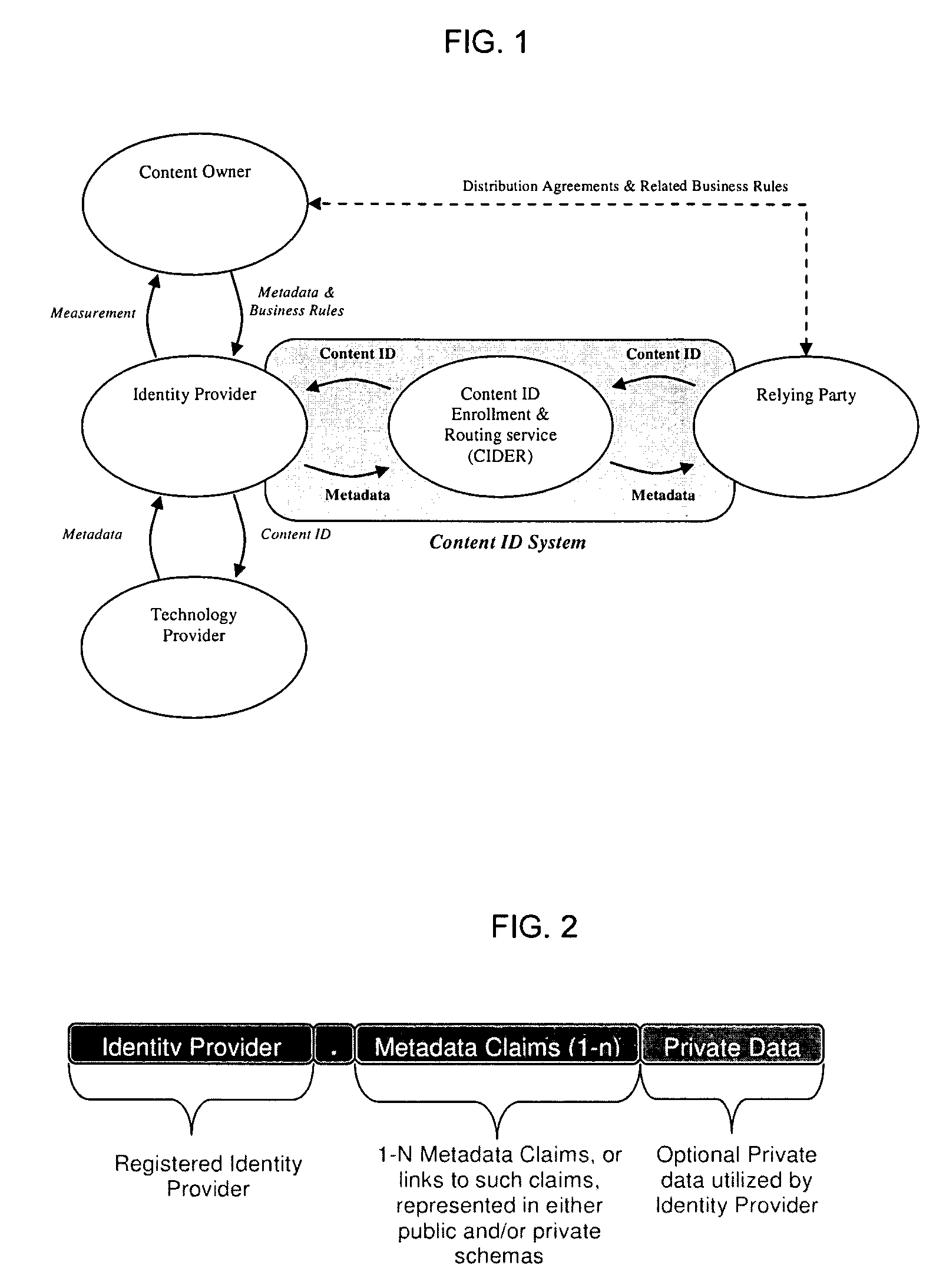
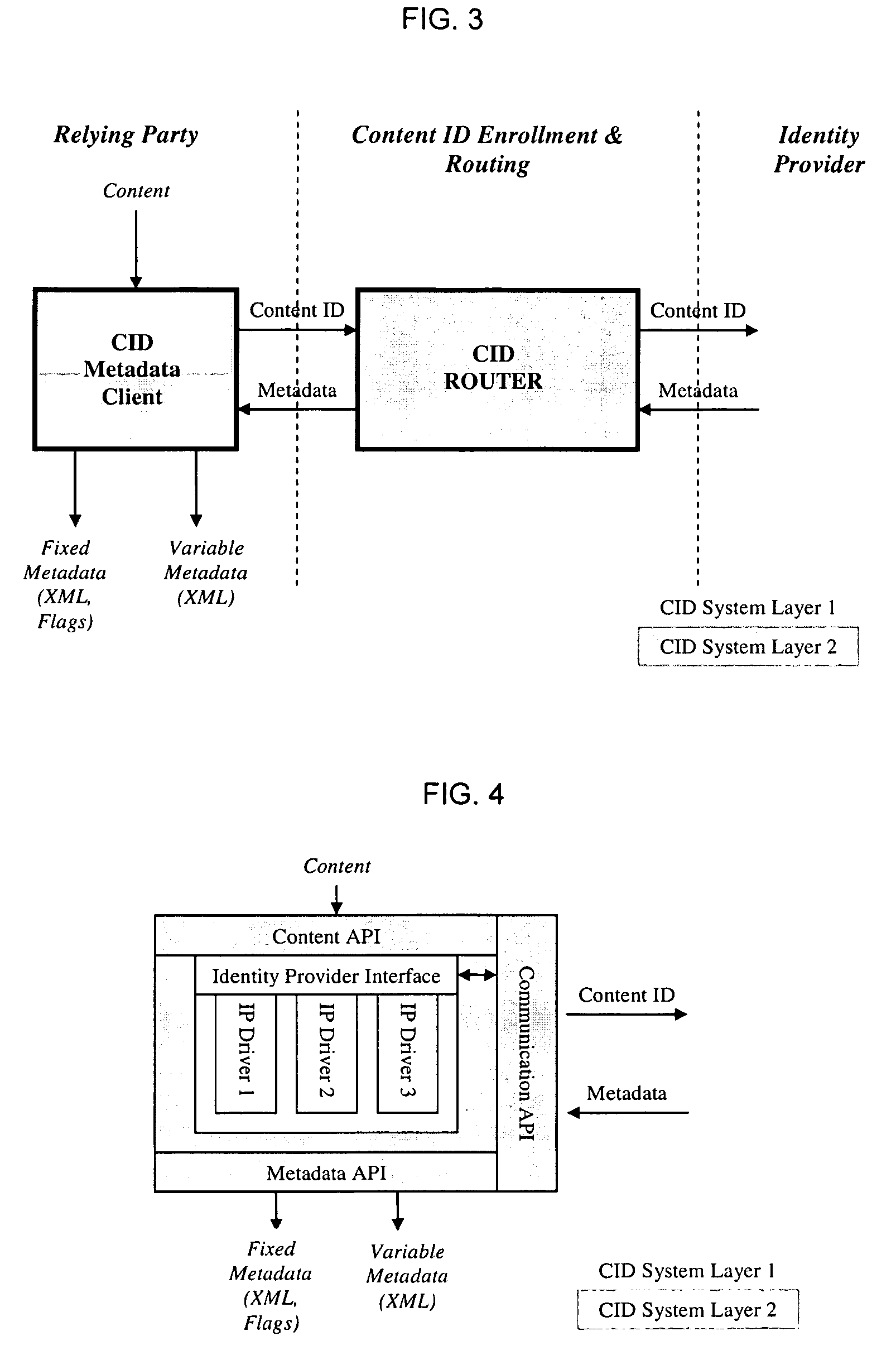
Layered Abstraction Systems and Methods for Persistent Content Identity
ActiveUS20080270575A1Ensure placementUser identity/authority verificationMetadata multimedia retrievalContent IdentifierComputer network
Owner:DIGIMARC CORP
Identity resolution for consumers with shared credentials
According to an embodiment, a data processing system for facilitating consumer identity resolution comprises: a memory storing a plurality of consumer records, each record comprising historical transaction records obtained from at least two different sources; a first logic module adapted to receive a request, the request including consumer credential information that potentially relates to each of the consumer records and a set of contextual transaction data; and a second logic module adapted to select one of the consumer records based on the consumer credential information, contextual transaction data, and historical transaction records. In an embodiment, at least one recommended electronic offer is selected by mapping the credential information to one of the consumer records. In an embodiment, the electronic offer is selected in response to a request for a receipt. In an embodiment, the electronic offer is included in a transaction receipt transmitted to a customer data processing system.
Owner:QUOTIENT TECH INC
Identity resolution for fraud ring detection
This disclosure provides systems, methods and apparatuses for identifying fraudulent accounts associated with an electronic payment service. In some implementations, a computing device may retrieve a data set including a number of attributes for each of a multitude of accounts, and may construct a plurality of different graphs each based on a unique set of the attributes. Each graph may include a plurality of nodes linked together by a multitude of edges, where each node identifies a corresponding account and each edge indicates one or more of the corresponding attributes that are common to a pair of accounts. The computing device may determine a likelihood of each graph correctly identifying fraudulent accounts by analyzing groups of nodes connected to each other by corresponding groups of edges using historical account data, and may select the graph having the greatest determined likelihood to predict whether any of the accounts is fraudulent.
Owner:INTUIT INC
Bluetooth device mutual recognition or mutual trust method
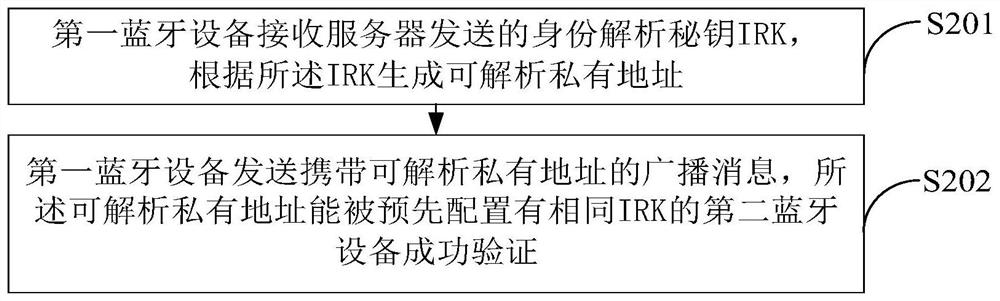
PendingCN112351390ASolve tedious technical problemsPrivacy protectionBroadcast service distributionTransmissionPrivate addressTerminal equipment
The invention is applicable to the technical field of communication, and provides a Bluetooth device mutual identification or mutual trust method, which comprises the following steps that: a first Bluetooth device receives an identity analysis key IRK sent by a server, and generates an analyzable private address according to the IRK; and the first Bluetooth device sends a broadcast message, the broadcast message carries the parsable private address, and the parsable private address can be successfully verified by a second Bluetooth device pre-configured with the same IRK. According to the invention, the technical problems of tedious user operation and low efficiency in related technologies are solved, and the technical effect of completing mutual recognition of the Bluetooth terminal devices without active operation of the user is achieved.
Owner:HUAWEI TECH CO LTD
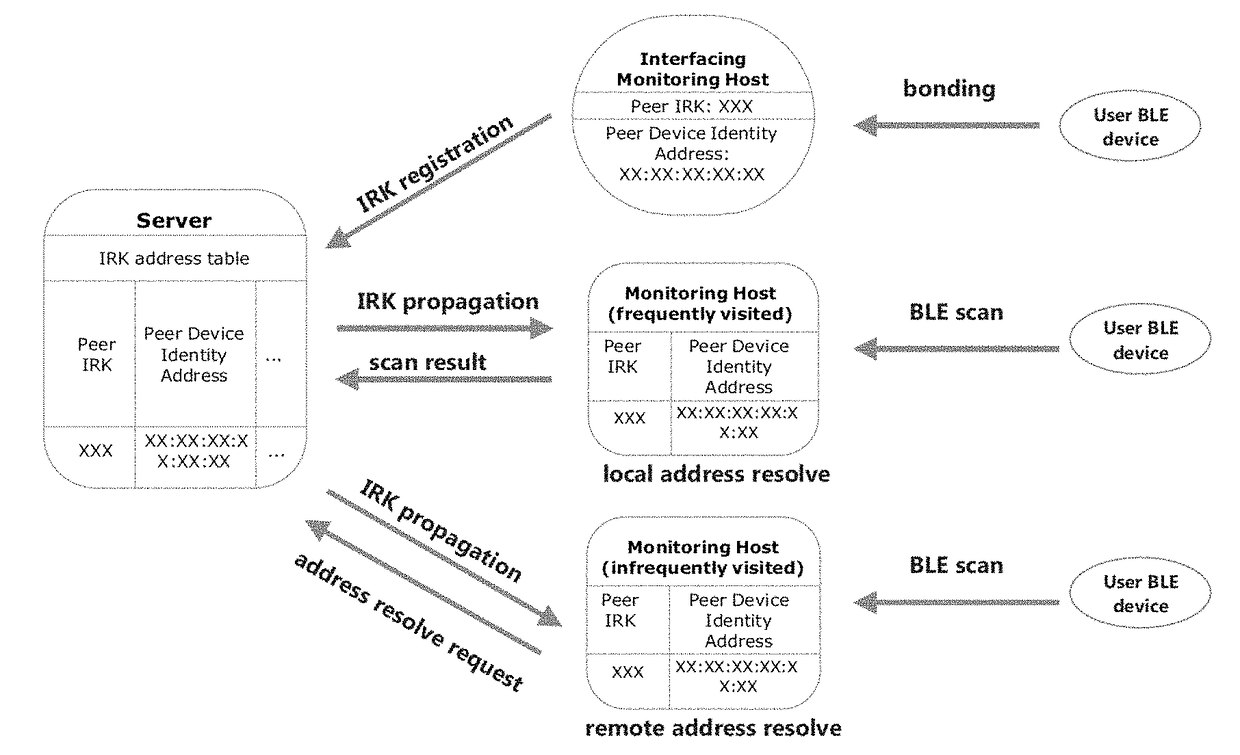
Privacy-preserving large-scale location monitoring
A privacy-preserving location monitoring system is provided, comprising monitoring hosts and a server. Immense resource requirement in large-scale location monitoring is lessened by allowing peripheral devices of users to bond to only one host. A peripheral device's one or more identity resolving keys (IRKs) retrieved by the host are sent to the server so as to register the IRKs to the server. The server propagates the IRKs to all other hosts. Furthermore, each host only stores the IRKs of peripheral devices frequently visiting the host. An incoming IRK not known by the host is sent to the server for resolving an identity of a peripheral device sending this IRK. The system is implementable in Bluetooth Low Energy (BLE) technology. Based on privacy features of BLU, different privacy protection mechanisms, including opt-in / out, k-anonymity and granularity-based anonymity, are provided.
Owner:TWINLY MARKETING TECH LTD
Layered abstraction systems and methods for persistent content identity
ActiveUS9092433B2Ensure placementUser identity/authority verificationMetadata multimedia retrievalContent IdentifierComputer network
Owner:DIGIMARC CORP
Identity analysis method and device
InactiveCN103297444APromotion of gradual substitutionReduce the burden onTransmissionDomain nameIp address
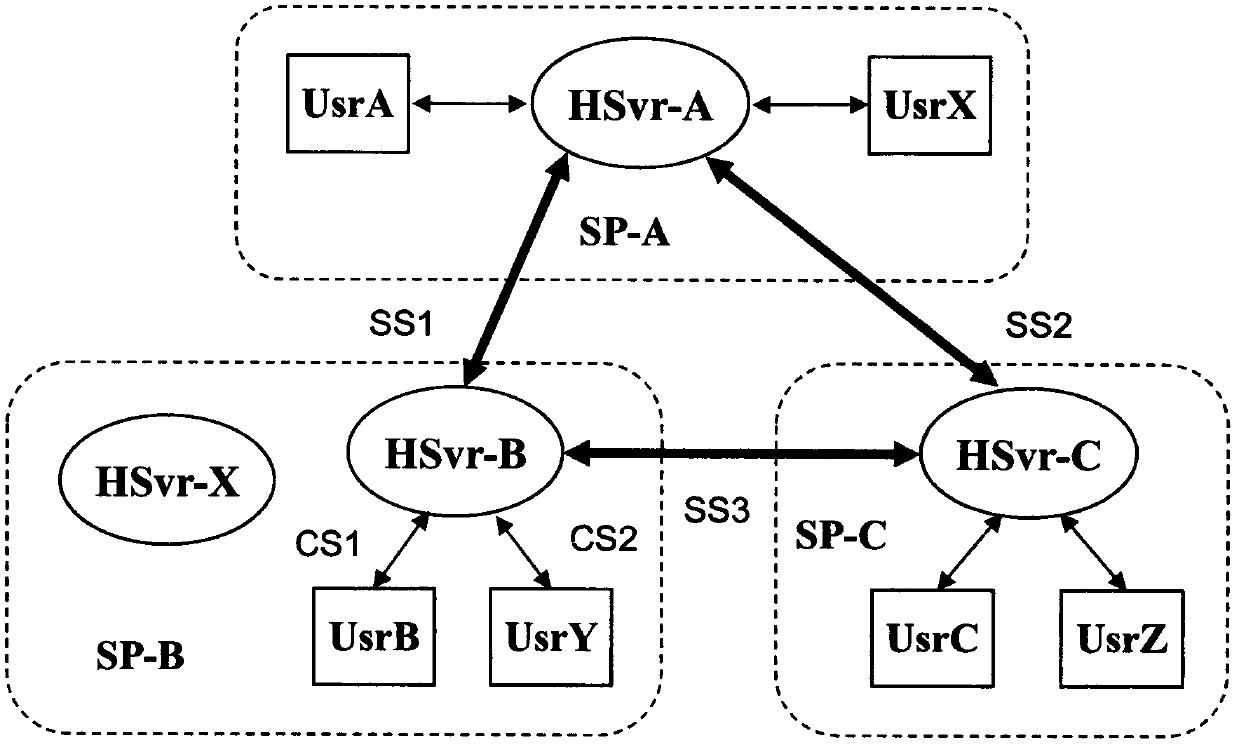
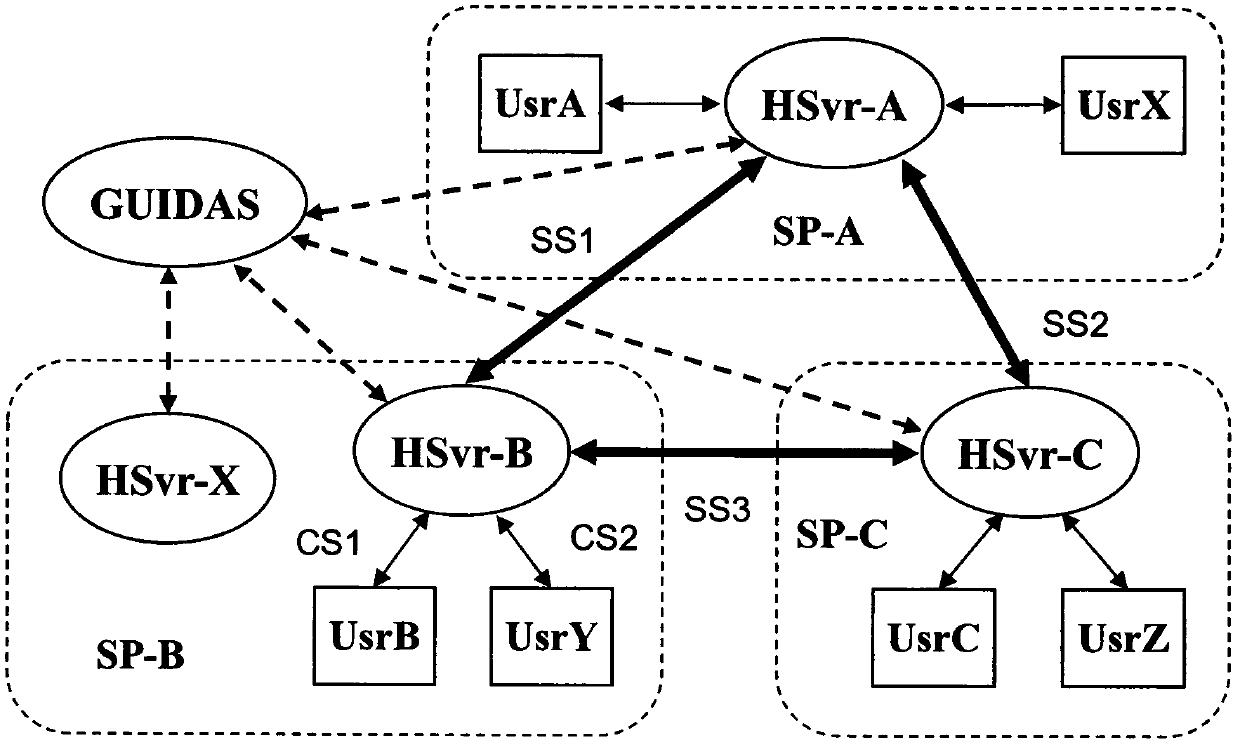
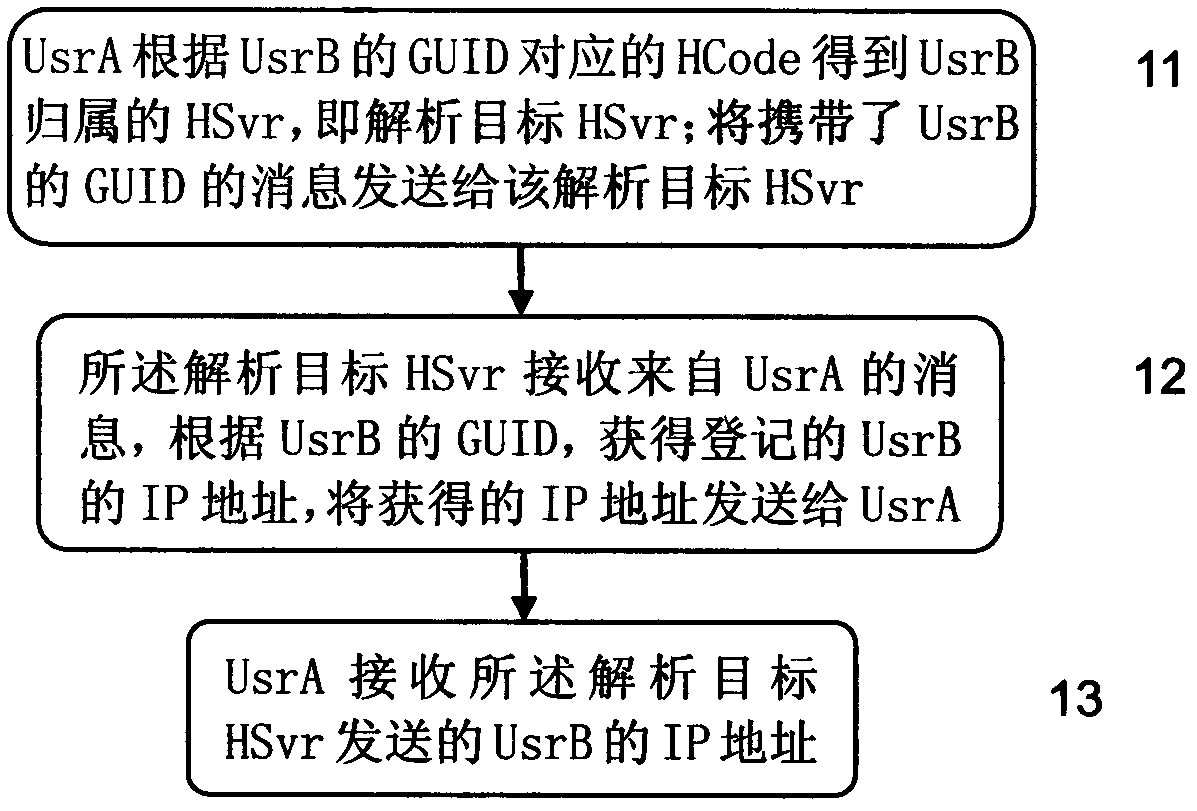
The invention discloses an identity analysis method. According to the method, corresponding relation of an HCode and an HSvr is established so that an Internet user can obtain an IP address registered corresponding to an analysis target by analyzing the target attributive HSvr. Accordingly, communication with a user can be achieved by analyzing the GUID of the user, so that communication between people is convenient. The invention further provides a host identification method, the user can identify a false GUID through the method, and the user cannot be cheated. The invention further provides a browsing method, information provided by a host indicated by the GUID can be browsed through a browser improved with the method, the user can be helped to issue a website based on the GUID, and the method helps to control domain name number expanding speed. The invention further provides the HSvr, and identity analysis service is provided for global users through the HSvr.
Owner:王正伟
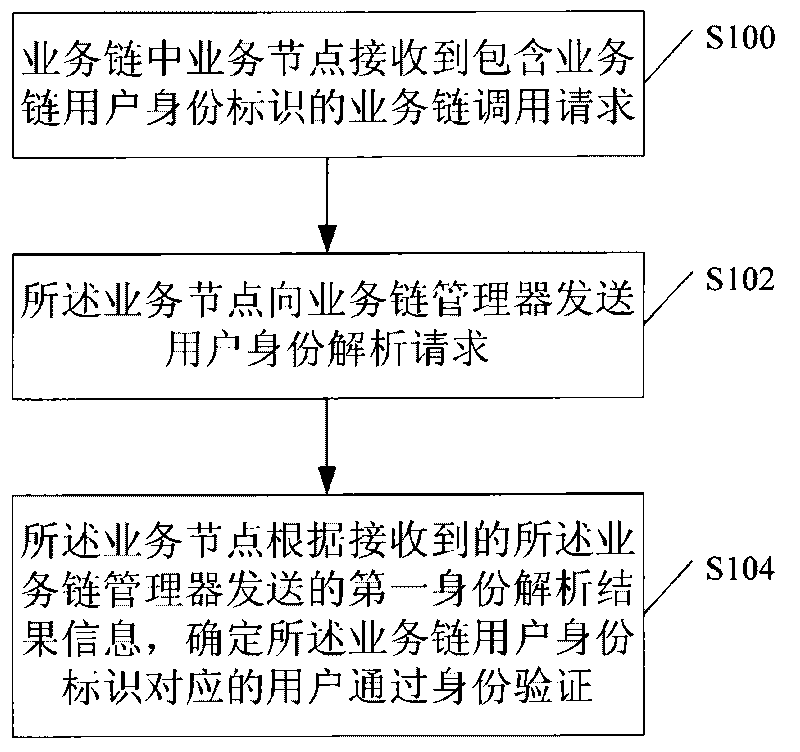
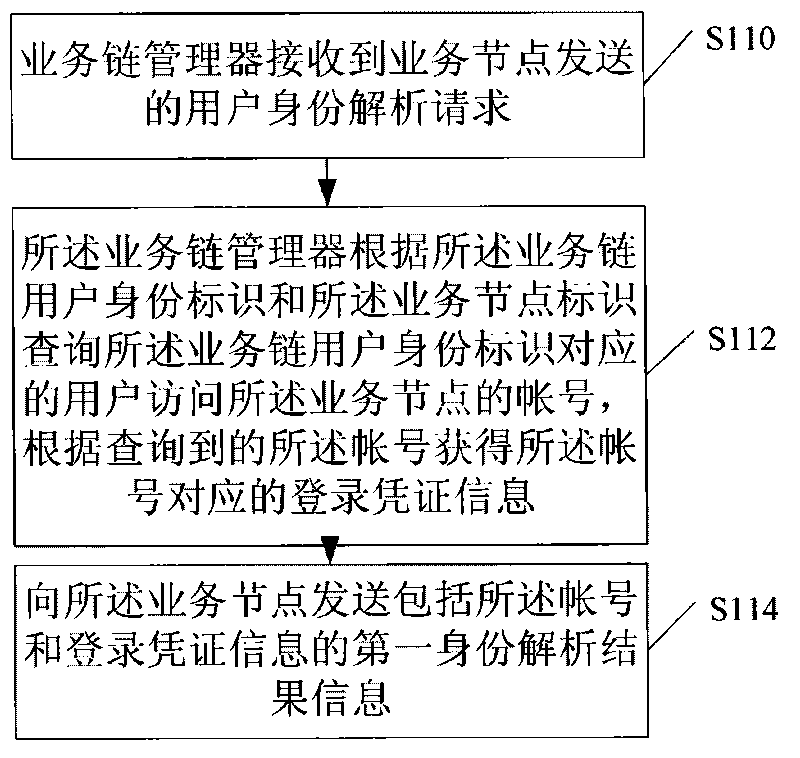
User identity verification method, equipment and system in business chain
ActiveCN101764791ASimple processUser identity/authority verificationInternet privacyUser authentication
The embodiment of the invention discloses a user identity verification method, equipment and a system in a business chain, wherein the method comprises the following steps: receiving business chain calling requests containing business chain user identity marks by business nodes in the business chain; sending user identity analysis requests which comprise the business chain user identity marks andthe business node marks of the business nodes to a business chain management device by the business nodes; and making sure that users corresponding to the business chain user identity marks pass the identity verification when the business nodes receive first identity analysis result information which is sent by the business chain management device and comprises the account and logging authentication information of the users corresponding to the business chain user identity marks to visit the business nodes. When being adopted, the invention has the advantage that the user identity verification can be realized by adopting a simple process flow.
Owner:HUAWEI TECH CO LTD
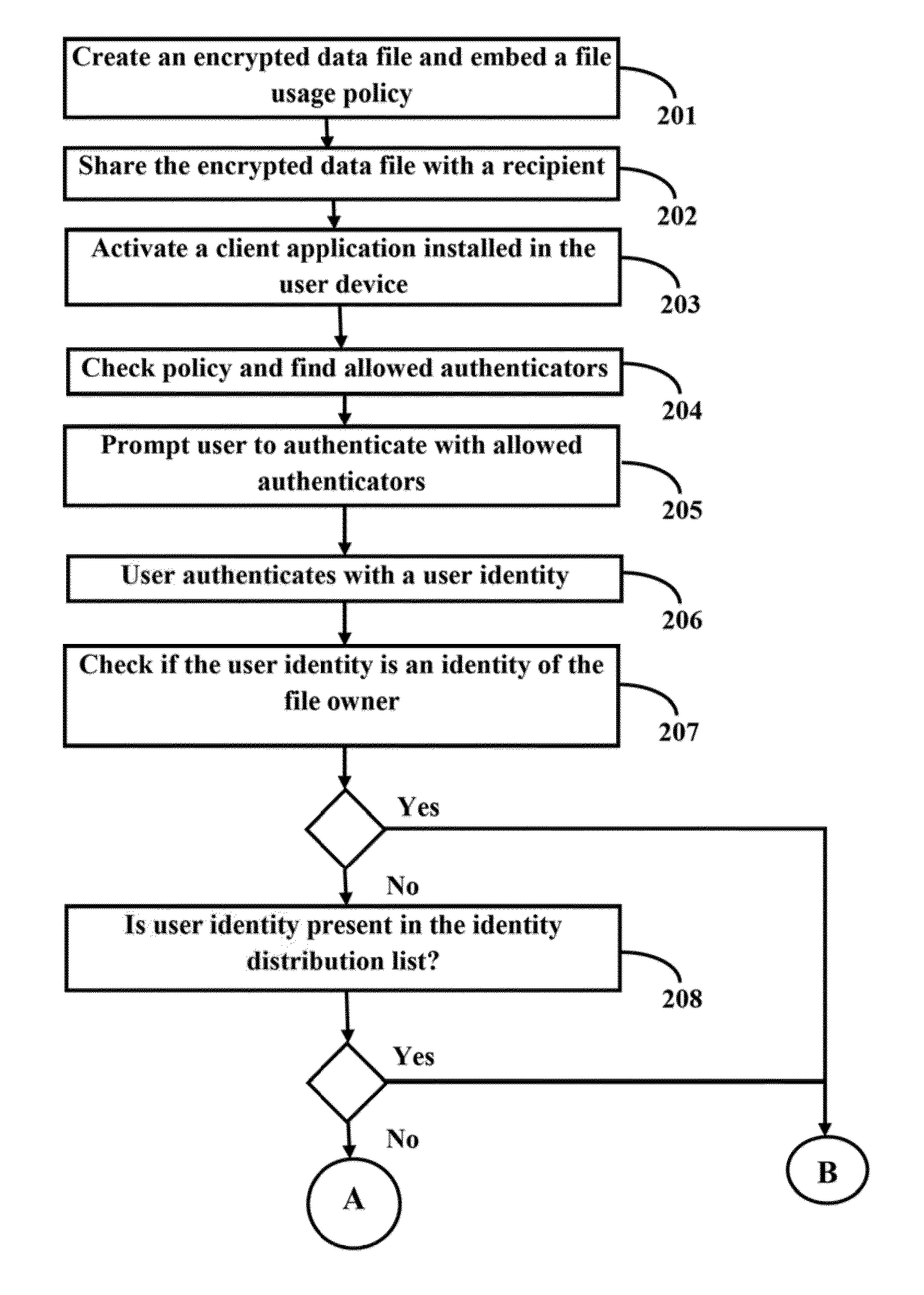
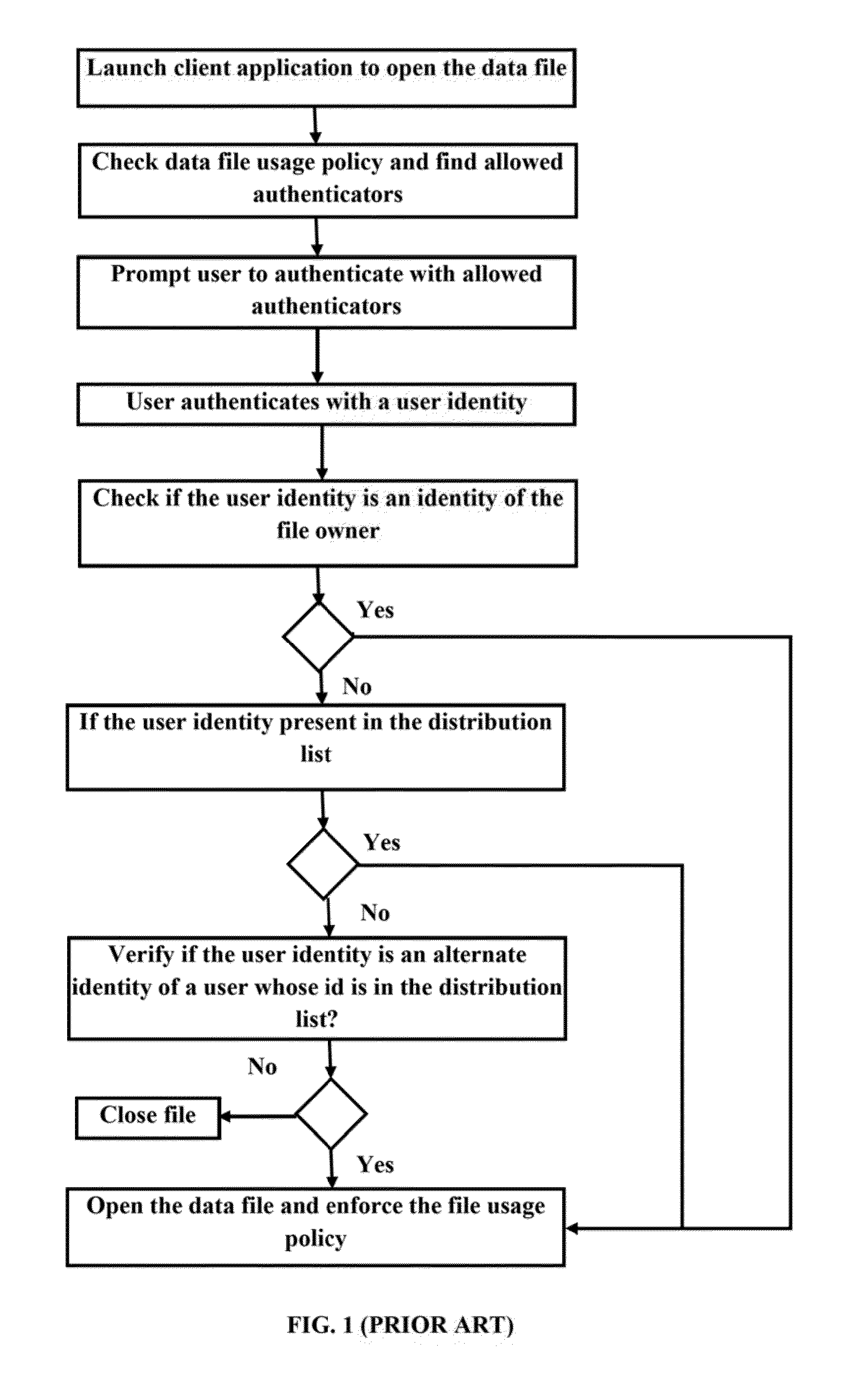
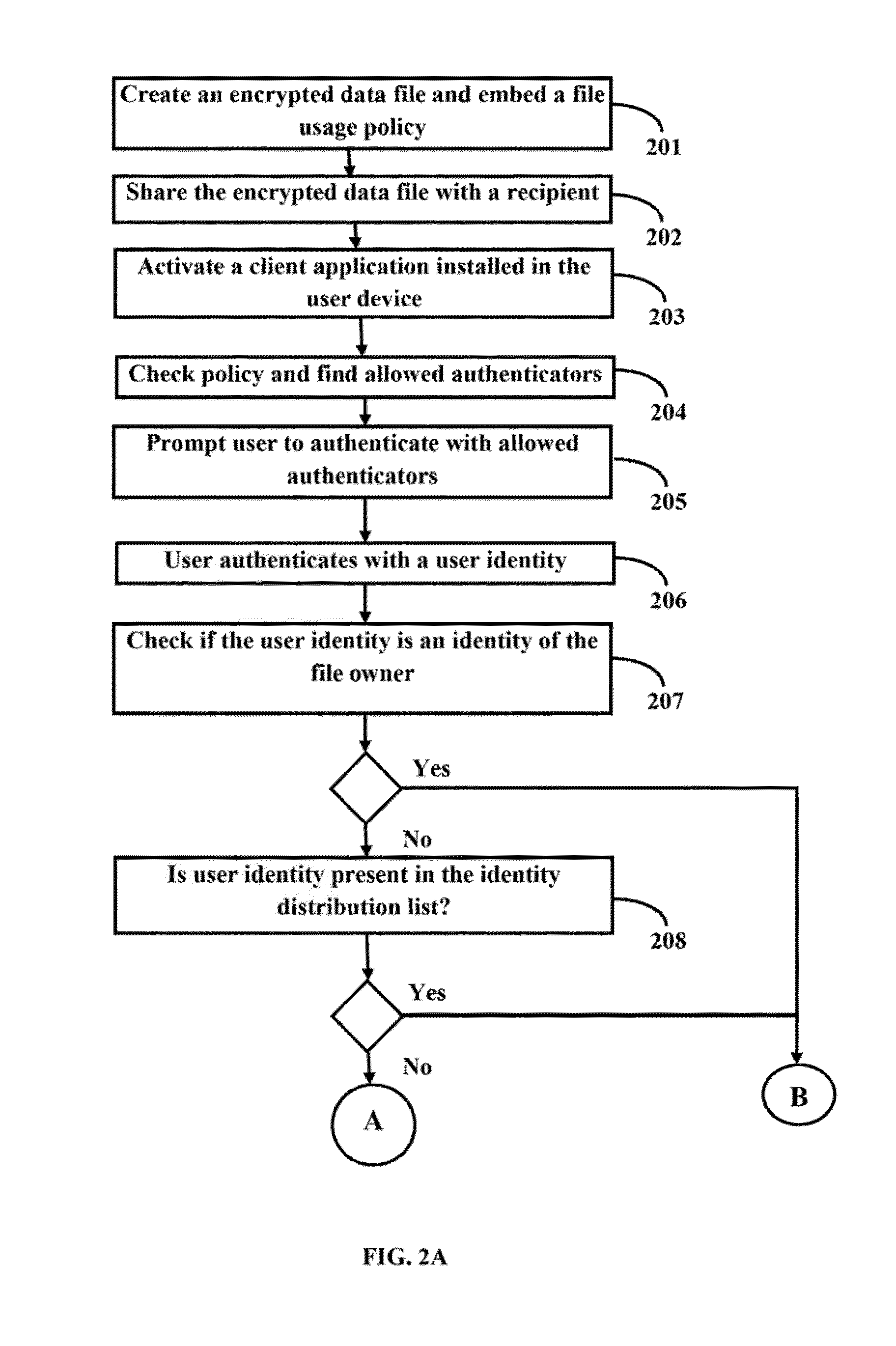
Method and system for providing access to encrypted data files for multiple federated authentication providers and verified identities
ActiveUS20150067802A1Eliminate needDigital data processing detailsMultiple digital computer combinationsApplication serverUser device
The embodiments herein disclose a method and system for providing access to an encrypted data tile by separating the concerns of Authentication, Identity Resolution and Authorization from Encryption thereby allowing for multiple federated authentication providers and verified identities. The method comprises of creating an encrypted data file, embedding a file usage policy to the data file, sharing the encrypted data file with an identity of an intended content recipient and an allowed authentication provider specified in the file usage policy, activating a client application installed in a user device to open the encrypted data file, fetching and updating the data file usage policy from an application server, prompting the user to authenticate with the allowed authentication provider, authenticating the user with a specified authentication provider, verifying if the authenticated user is allowed to open the data file, opening the data file on successful verification and enforcing the file usage policy.
Owner:SECURELYSHARE SOFTWARE PVT LTD
Tracking entities during identity resolution
Owner:INT BUSINESS MASCH CORP
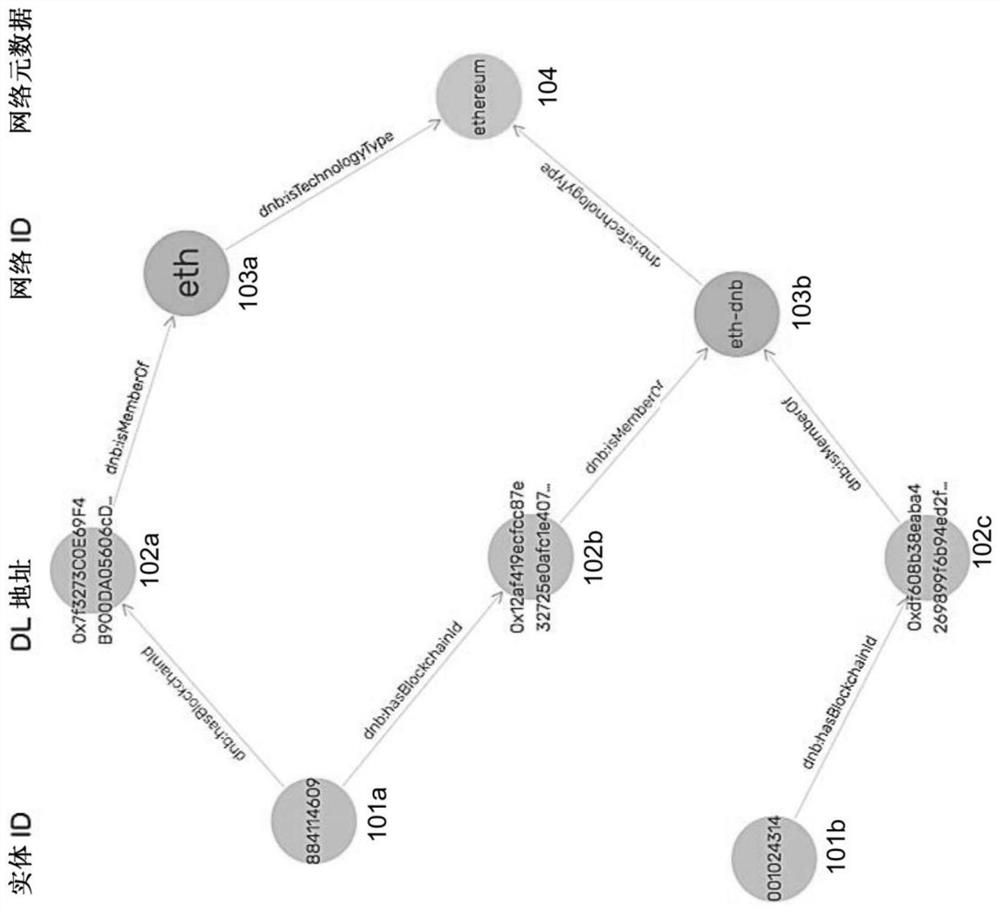
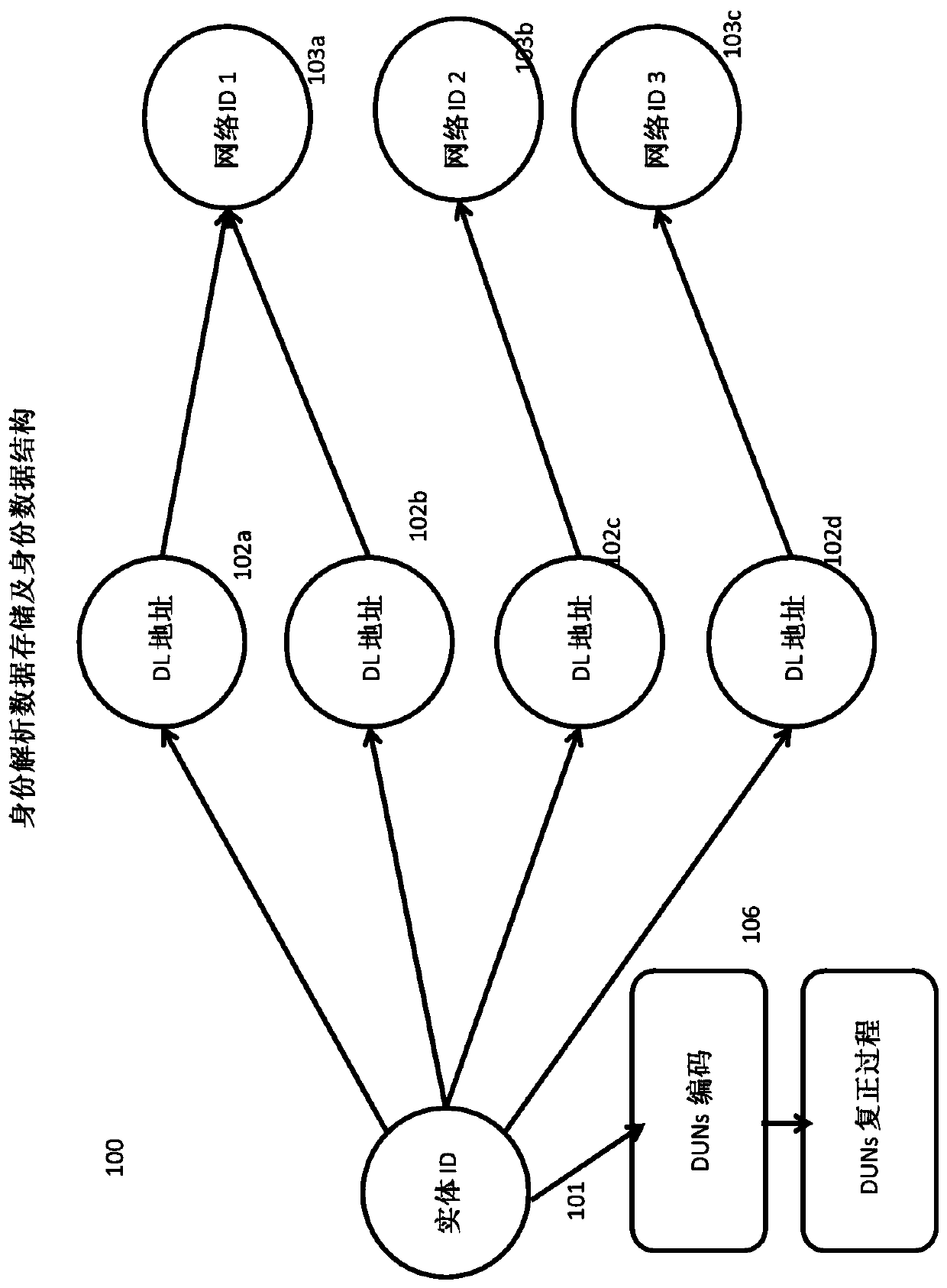
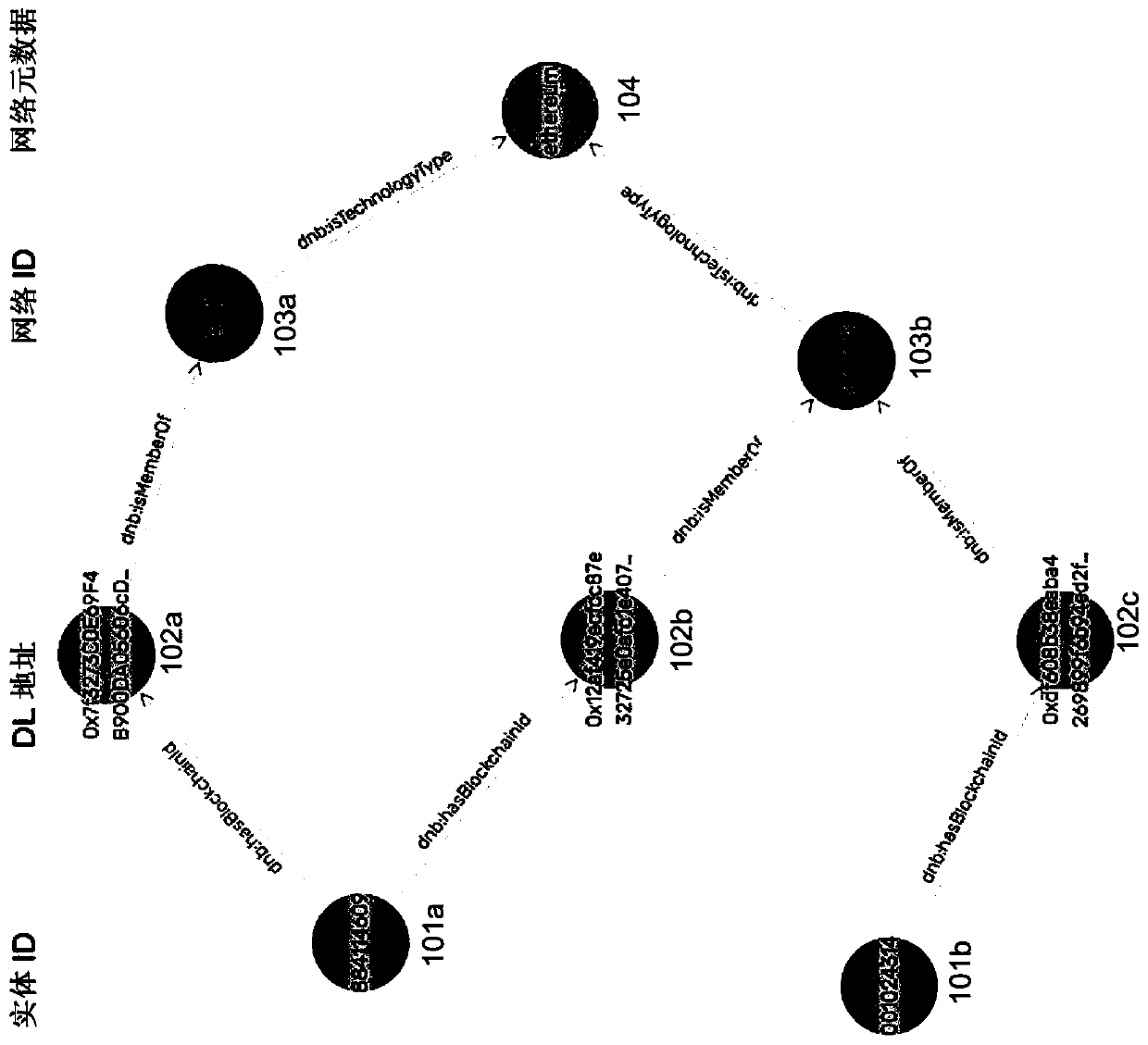
System and method for identity resolution across disparate distributed immutable ledger networks
PendingCN113204532AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMessage deliveryEngineering
A system and method for identifying previously unknown counterparties by registering distributed ledger public keys and / or addresses associated with specific business entities and / or individuals. The system and method are configured to provide tools for administering public facing distributed ledger identifiers using cryptographic proof messaging and transactions made on the Distributed Ledger. It also provides queries and lookups to discover public keys associated with entities and allows users to link identifiers on competing Distributed Ledgers to a disambiguated entity, thereby enabling cross Ledger transactions to occur.
Owner:THE DUN & BRADSTREET CORPORATION
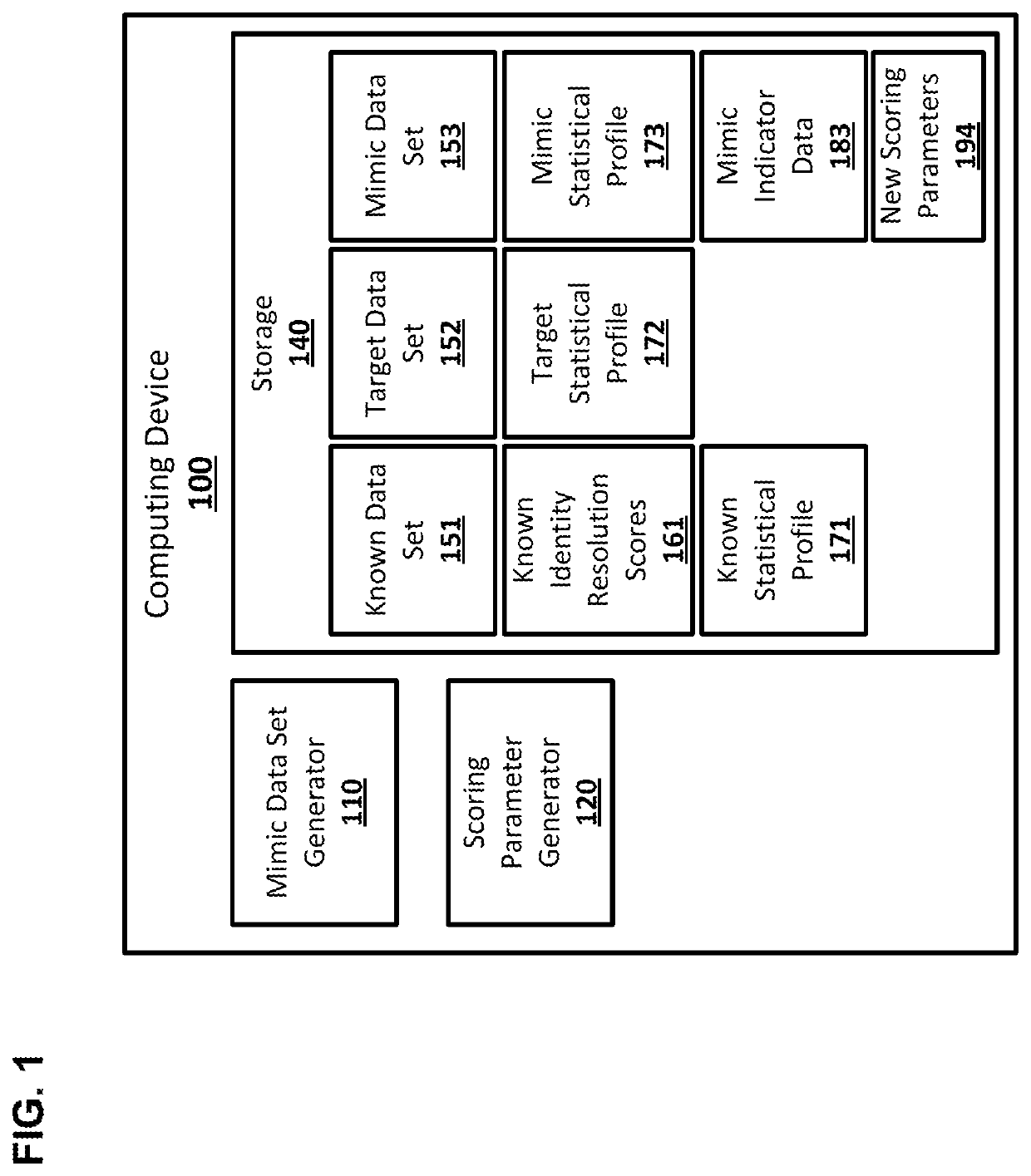
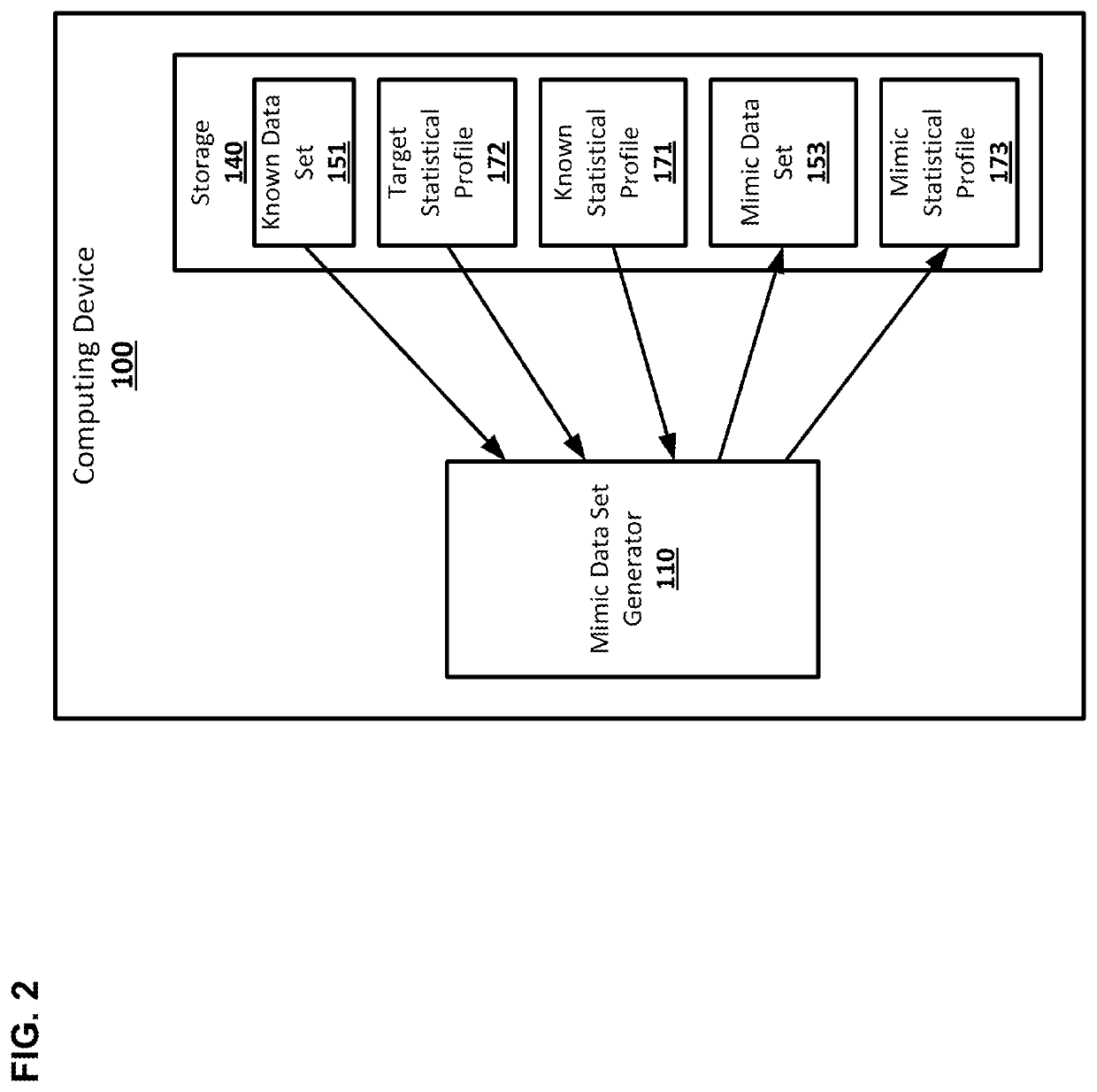
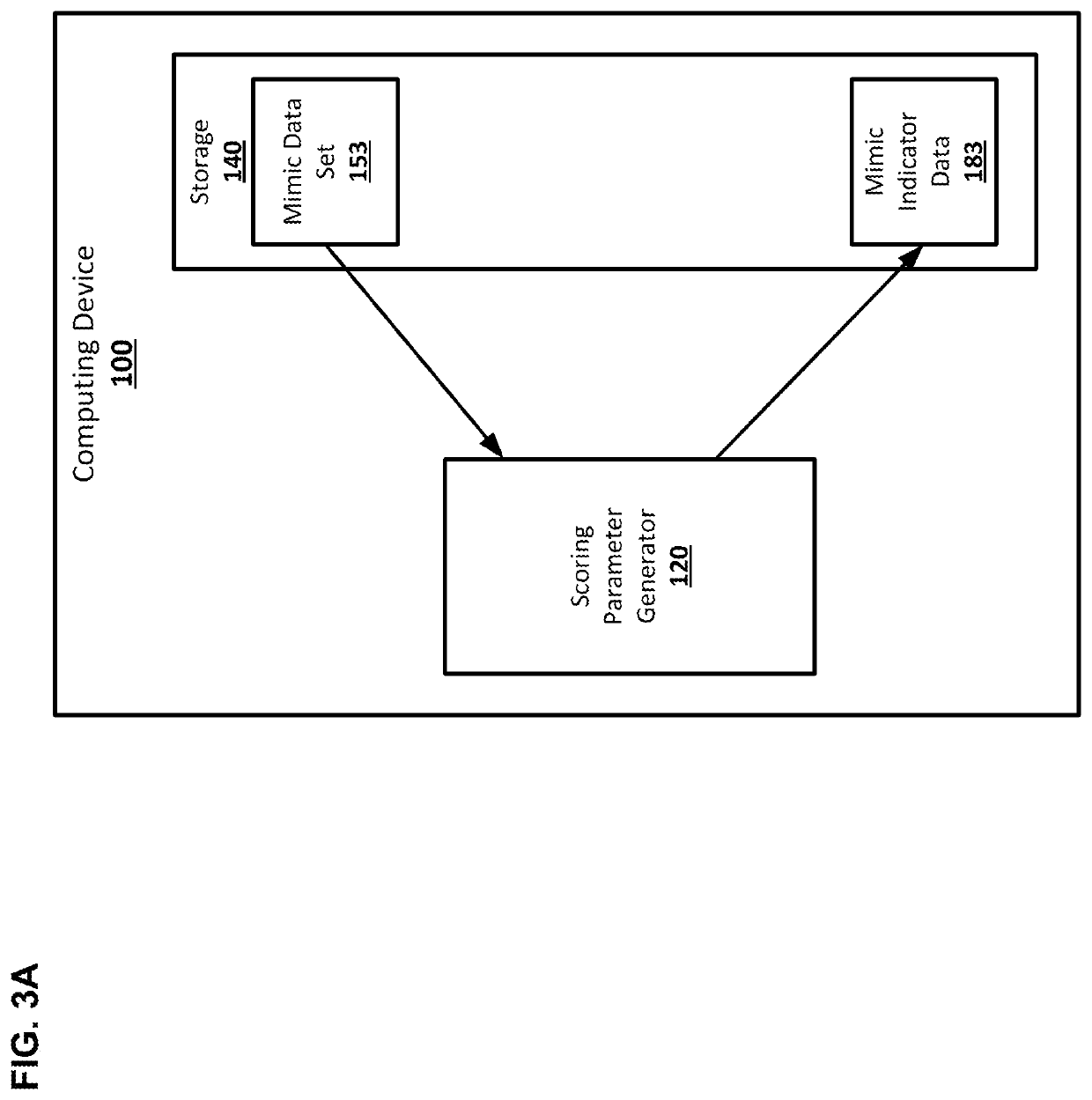
Scoring parameter generation for identity resolution
Systems and techniques are provided for scoring parameter generation for identity resolution. A second data set that has a statistical profile that matches a statistical profile of a third data set may be generated from a first data set. The first data set, the second data set, and the third data set may include records that comprise data about individuals. Identity resolution scores generated for the first data set may be matched to pairs of records from the second data set. New scoring parameters may be generated from the second data set and the identity resolution scores matched to the pairs of records from the second data set using regression. Identity resolution scores for pairs of records from the third data set may be generated using the new scoring parameters.
Owner:ACTIONIQ INC
Device connection method, electronic device, terminal and storage medium
ActiveCN111405082AImprove securityConnection managementTransmissionInformation repositoryComputer network
Owner:OPPO CHONGQING INTELLIGENT TECH CO LTD
Internet access method based on identity and location separation
An identity and position separation based on internet mainframe accessing method separates the double function of traditional IP address, the IP address is only used as position identify of mainframe, leading-in new name-space one end mainframe identity which is used as identifiers of mainframe and terminal identifier of transmission protocol. Leading-in identity resolver for resolving map relation between mainframe and IP address and dynamically updating binding between end mainframe identifiers and IP address. DNS resolving map relation between domain name and end identifiers and recording identified resolver IP address. In communication process communication node IP address can be changed but communication node EID keeps unchanged. Said invention can make fixation termination, mobile terminal, mobile network, self-organization network etc accessing internet in unitive mode.
Owner:BEIJING JIAOTONG UNIV
System and method for identity resolution across disparate distributed immutable ledger networks
ActiveCN111356995AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMessage deliveryEngineering
A system and method for identifying previously unknown counterparties by registering distributed ledger public keys and / or addresses associated with specific business entities and / or individuals. Thesystem and method are configured to provide tools for administering public facing distributed ledger identifiers using cryptographic proof messaging and transactions made on the Distributed Ledger. Italso provides queries and lookups to discover public keys associated with entities and allows users to link identifiers on competing Distributed Ledgers to a disambiguated entity, thereby enabling cross Ledger transactions to occur.
Owner:THE DUN & BRADSTREET CORPORATION
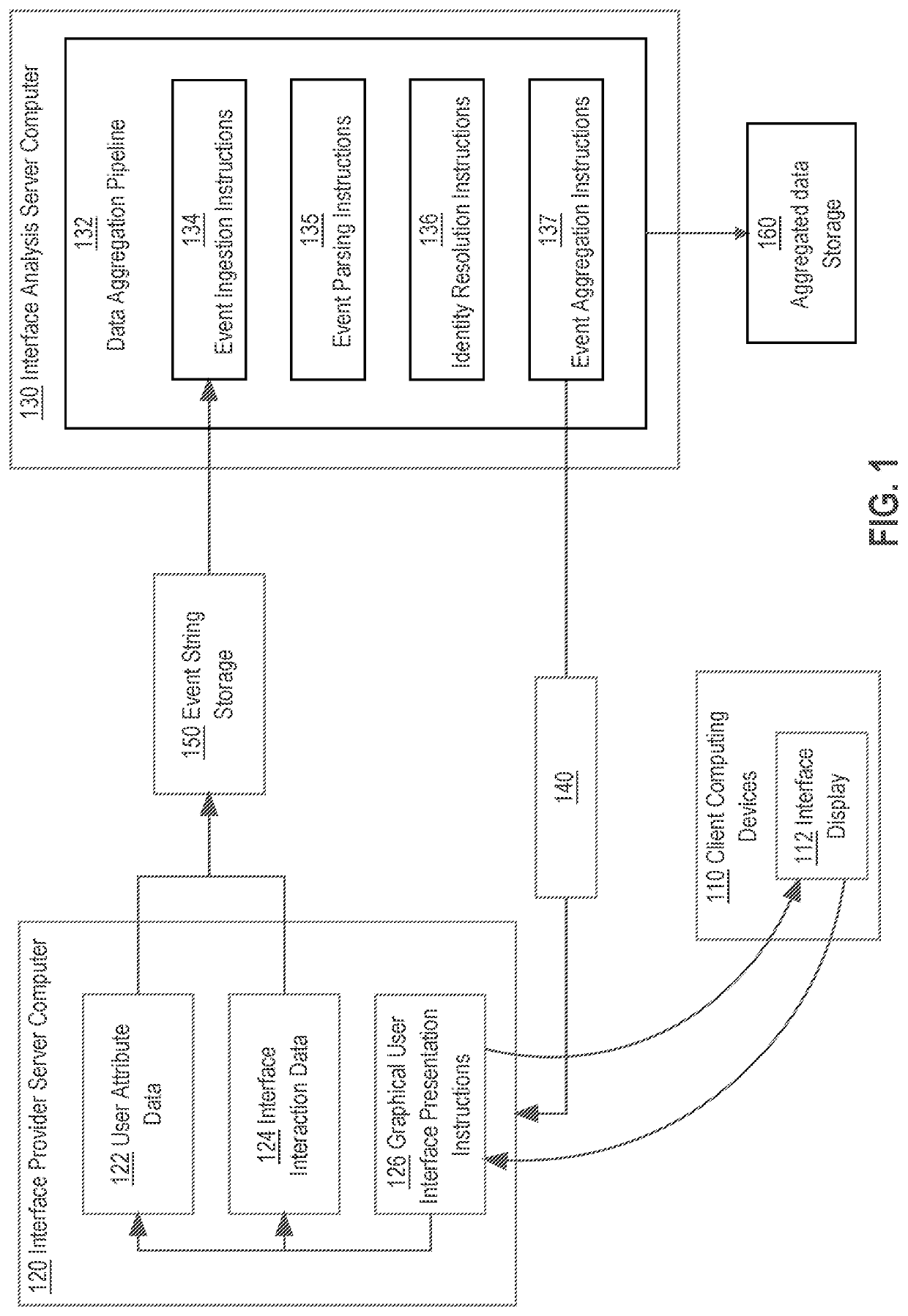
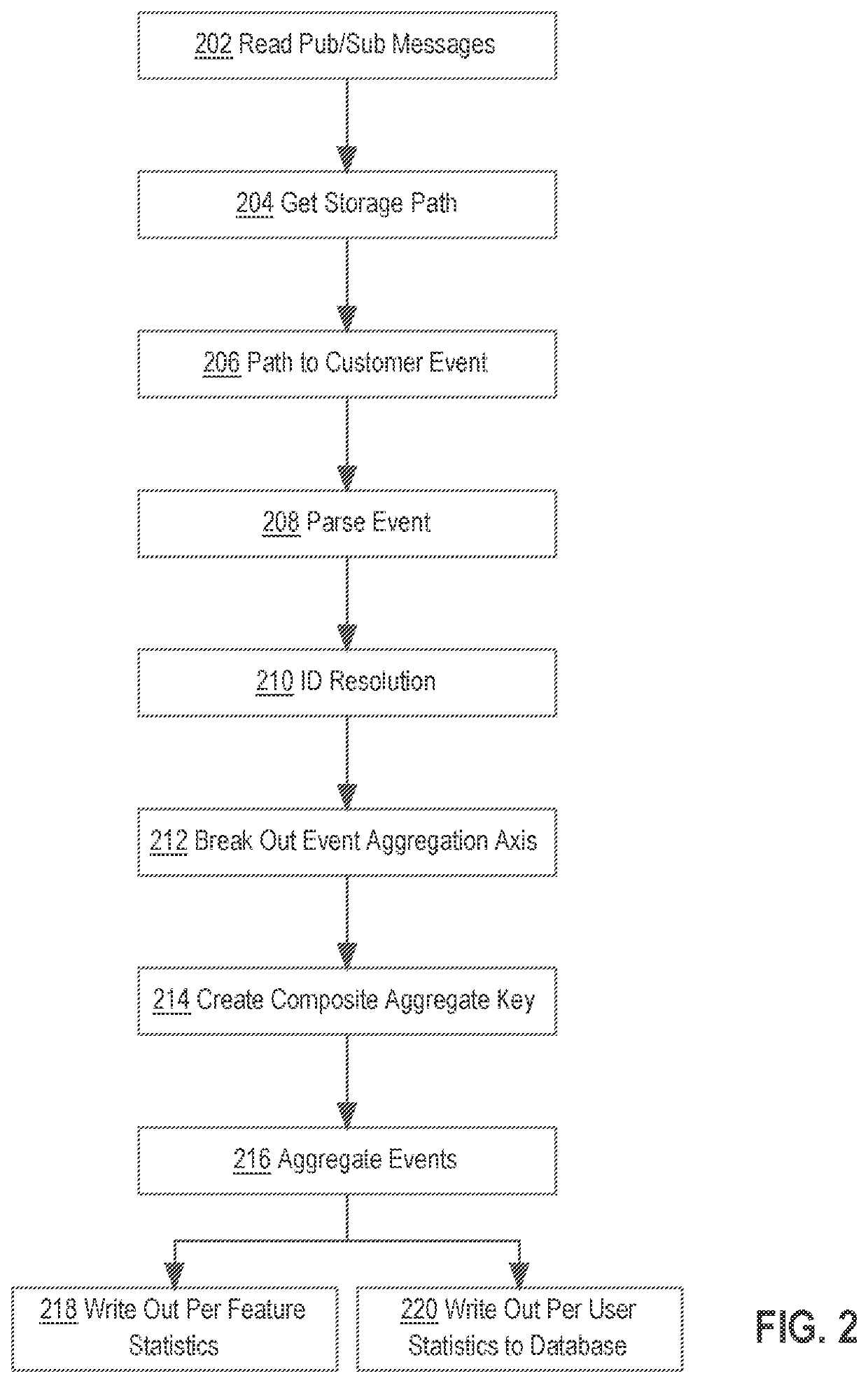
Real Time System for Ingestion, Aggregation, & Identity Association of Data from User Actions Performed on Websites or Applications
ActiveUS20210216536A1Natural language data processingWebsite content managementData ingestionWeb site
Systems and methods for data ingestion in real time are described herein. In an embodiment, a server computer receives a message comprising one or more client events from a storage device which publishes the message in response to storing the one or more client events. The server computer stores the one or more client events as raw event strings which are then parsed into parsed event strings. Identity resolution methods are performed on the parsed event strings. Feature groups are then identified in the parsed event strings and used to generate aggregation keys which are used to aggregate the feature groups prior to storing aggregated data in one or more aggregation tables.
Owner:AMPLITUDE INC
Shared chain of cone blockchain
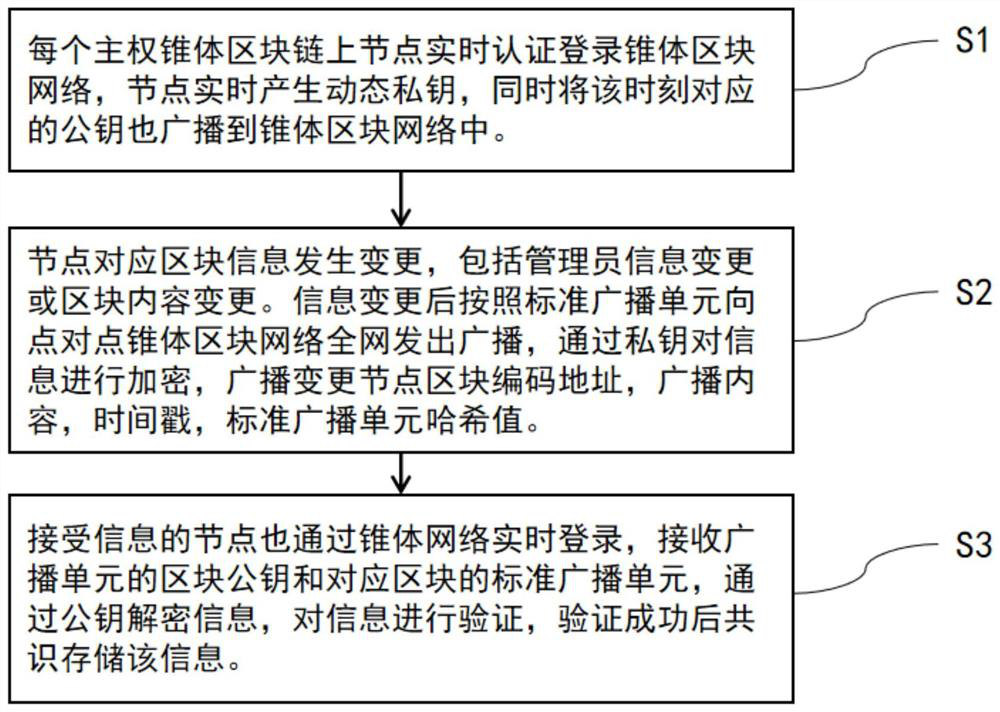
ActiveCN112751662AFix security issuesPrivacy protectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital identityInformation sharing
The invention belongs to the technical field of blockchains, and particularly relates to a shared chain of cone blockchains. The shared block comprises at least two sovereign cone blockchains, and the sovereign cone blockchains are connected through an alliance chain to form a sovereign alliance chain; nodes of all blocks in each sovereign cone blockchain can realize information sharing and consensus synchronization of public information through a public chain, and transmission and information authentication of the public information among the blocks are realized through the sovereign cone public chain. The security of blockchain shared information is solved, identity analysis and related authentication are carried out through identity management, identity information is stored in data blocks in a cone network, it is ensured that each information block stores complete digital identity information, copy accuracy is ensured, and meanwhile data privacy is also protected.
Owner:GLOBAL PRESTIGE INFORMATION TECH CO LTD
Method and device for Anti-tracking of bluetooth
ActiveUS20200145814A1Avoid tracesAvoid dataNear-field transmissionKey distribution for secure communicationComputer networkEngineering
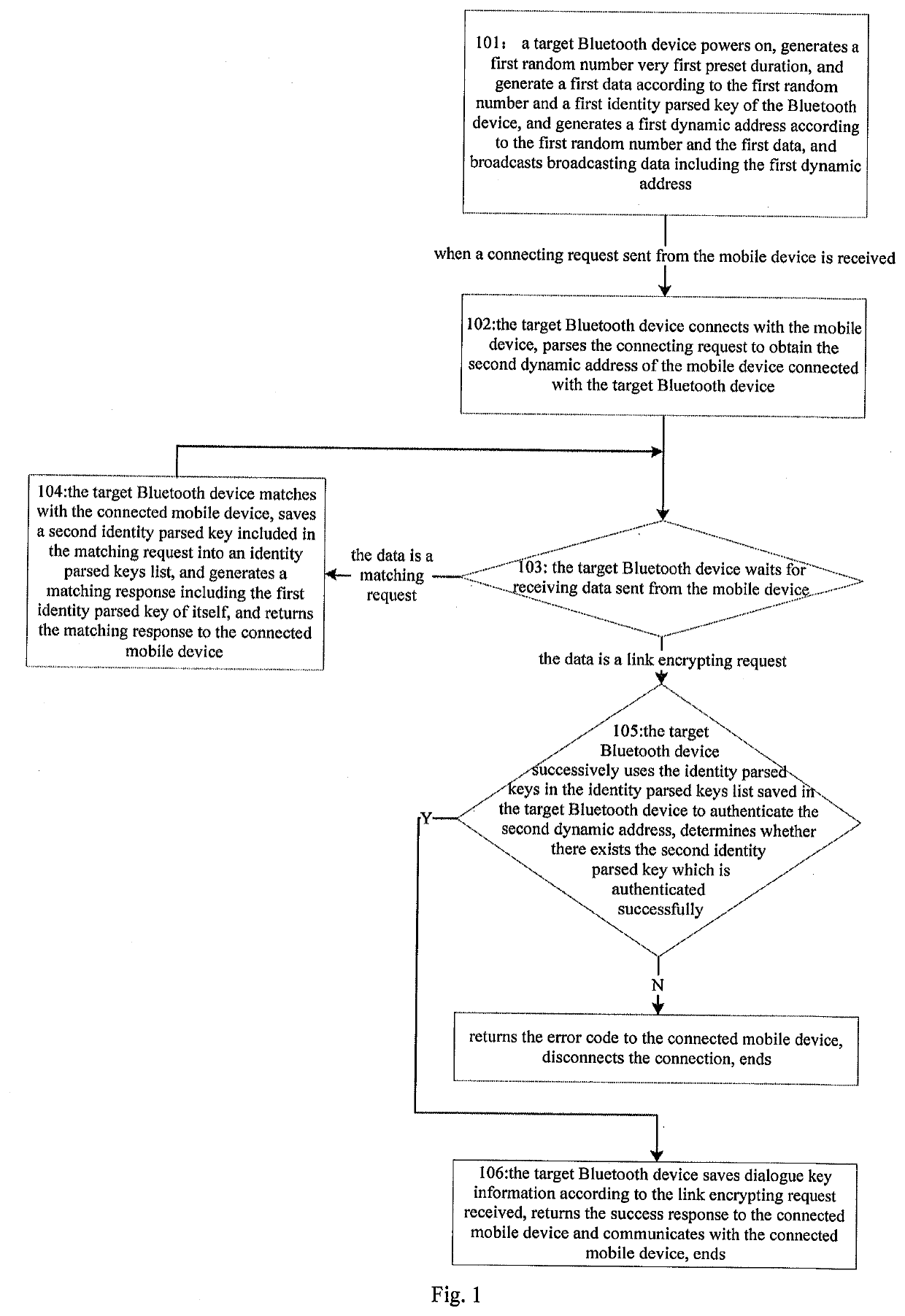
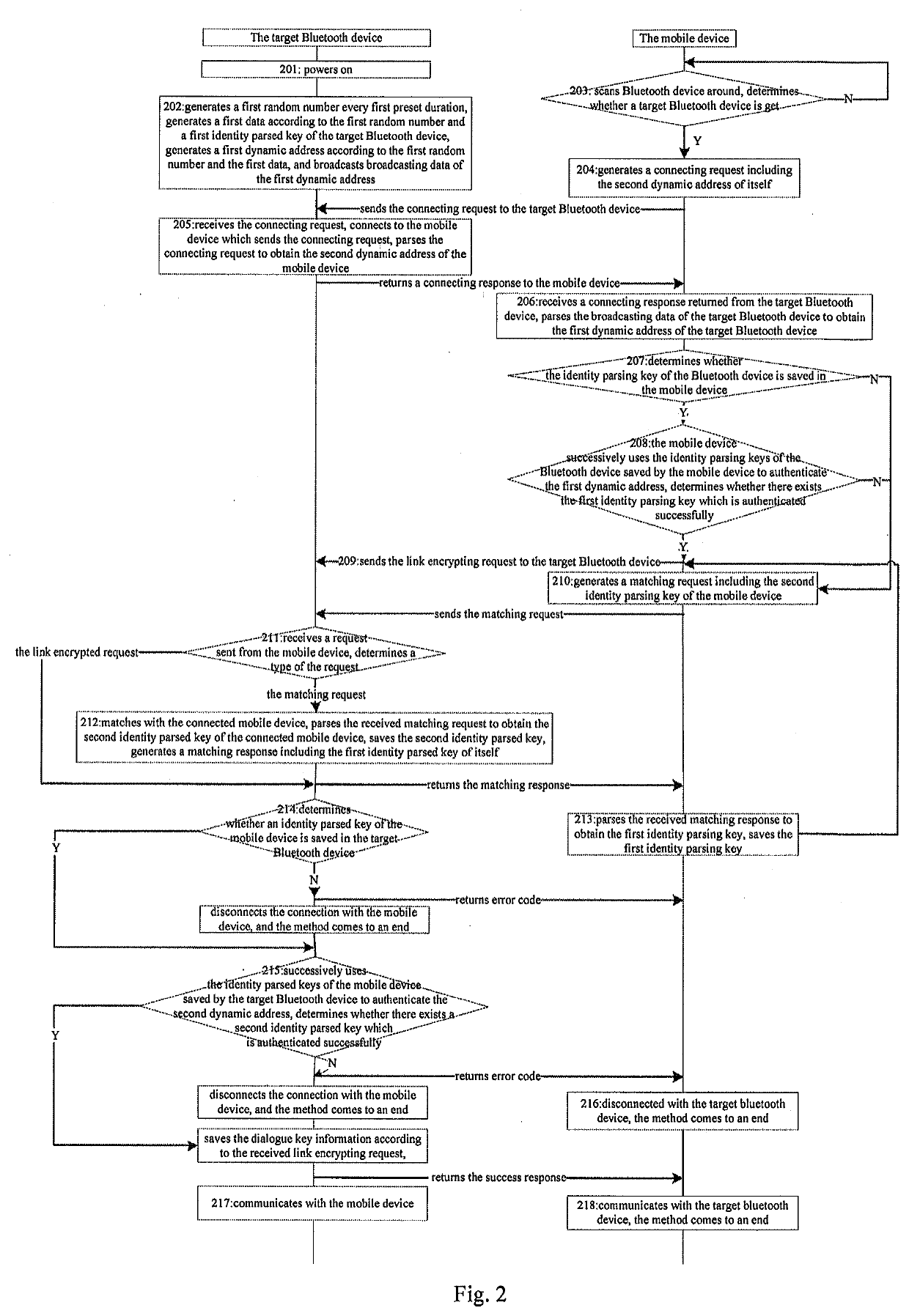
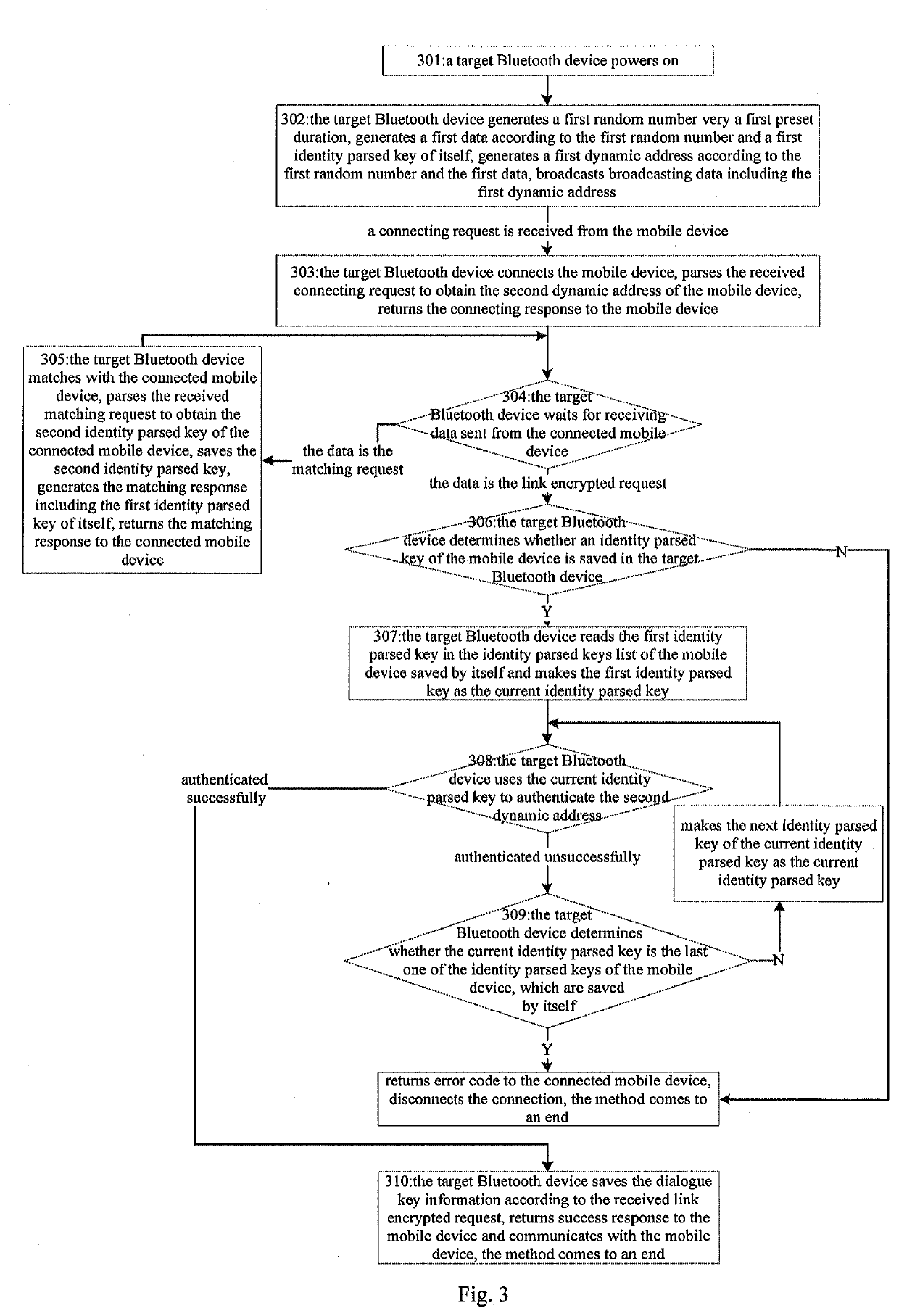
A method for anti-tracking of Bluetooth, comprising: a target Bluetooth device generating a first dynamic address every first pre-set time and broadcasting same; after connecting to a mobile device and obtaining a second dynamic address thereof, waiting to receive data sent by the mobile device; if the data is a pairing request, pairing with the mobile device, saving a second identity parsing key contained in the pairing request, returning a pairing response containing a first identity parsing key thereof to the mobile device, and continuing to wait to receive data; and if the data is a link encryption request, successively using identity parsing keys stored thereby of the mobile device to verify the second dynamic address, determining whether a second identity parsing key having been successfully verified exists, and if so, returning a success response to the connected mobile device and communicating with same, and ending the process, otherwise, returning an error code and disconnecting from same, and ending the process. In the present invention, a Bluetooth device periodically changes a dynamic address thereof, thereby effectively preventing data being stolen by a hacker.
Owner:FEITIAN TECHNOLOGIES
Network filtering using private resolvable addresses
PendingCN114365453AUser identity/authority verificationSecurity arrangementComputer networkTelecommunications
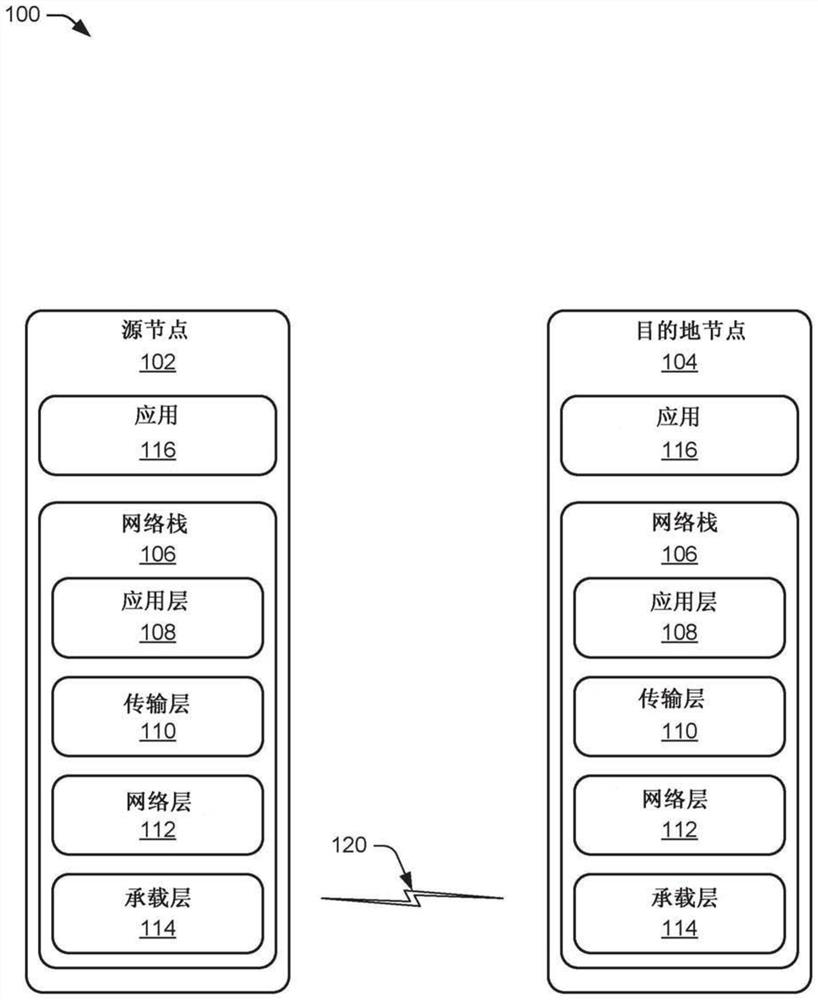
This document describes network filtering with private resolvable addresses in a wireless network (100). A source node (102) in the wireless network (100) hashing the identity resolution key and the value of the random digital segment to generate an address hash (502). The source node (102) forms an advertisement address (504) comprising a portion of the address hash and inserts the advertisement address in an advertisement extension packet (506). A source node (102) transmits an advertisement extension packet over a wireless network (100), an address hash being available by a destination node (104) to filter the advertisement extension packet (508).
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com