Internet access method based on identity and location separation
An access method and Internet technology, applied in the field of Internet access, can solve problems such as large routing overhead, large address translation overhead, and limited number of access nodes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0027] An Internet access method based on the separation of identity and location;
[0028] 160-bit source EID
160-bit destination EID
16-bit source port number
16-bit destination port number
32-bit serial number
32-digit confirmation number
4 digits
Ministry length
6 reserved bits
6 flag bits
16 bit windows
16 bit checksum
16-bit urgent pointer
options (if any)
data
[0029] Table 1 TCP packet format using EID as terminal identifier
[0030] 160-bit source EID
160-bit destination EID
16-bit source port number
16-bit destination port number
16-bit UDP length
16-bit UDP checksum
data
[0031] Table 2 UDP packet format using EID as terminal identifier
[0032] In order to resolve the mapping between EID and IP address, a new device——Identity Resolution Server (IRS) is introduced. The IRS is responsibl...
Embodiment 2
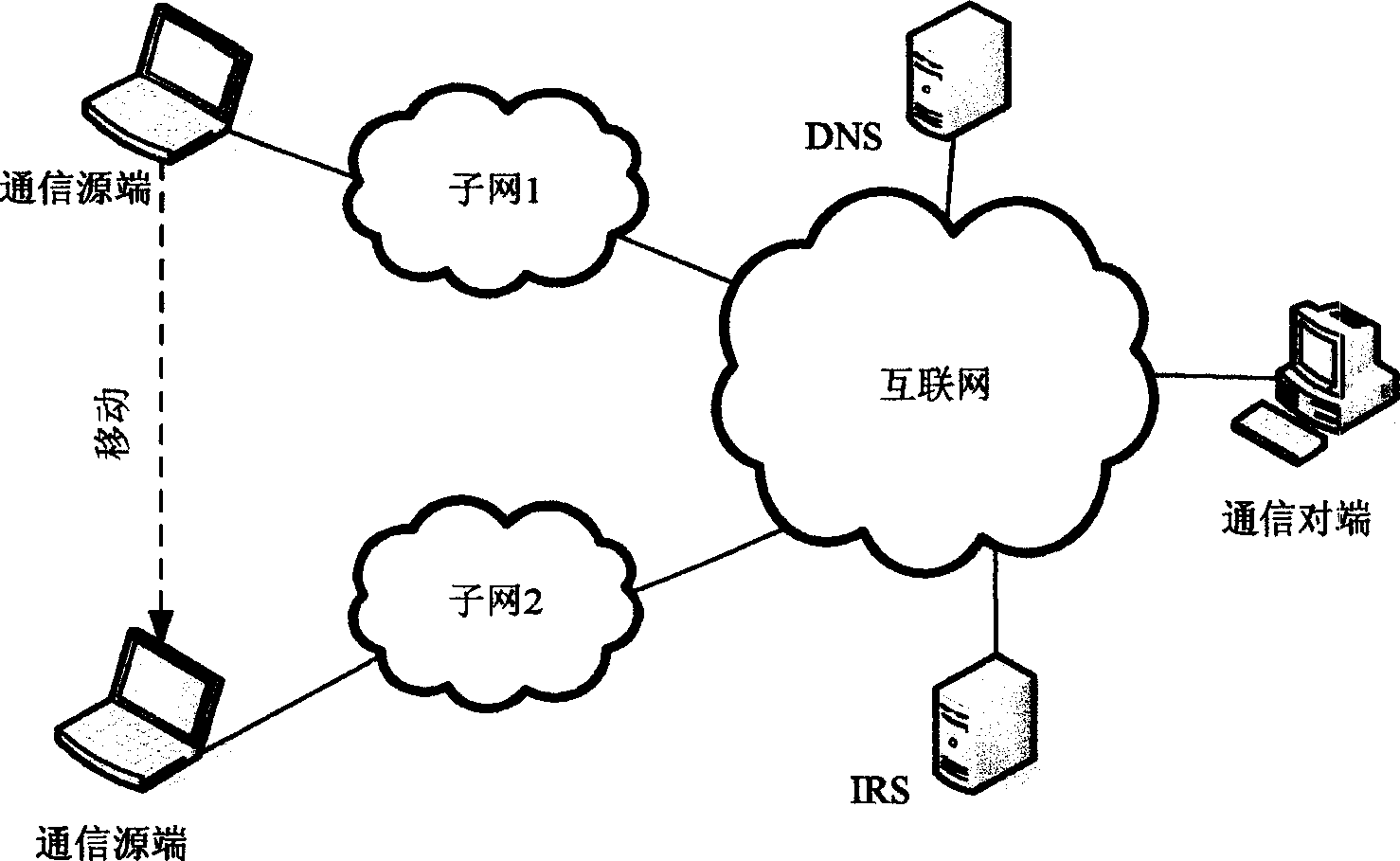
[0057] Such as figure 1 shown. figure 1 Shown in is a fixed host and a single host that communicates with nodes in the Internet when it moves. figure 1 The communication source in the network moves during the communication process. It originally connected to the Internet through subnet 1, and then connected to the Internet through subnet 2 after moving.
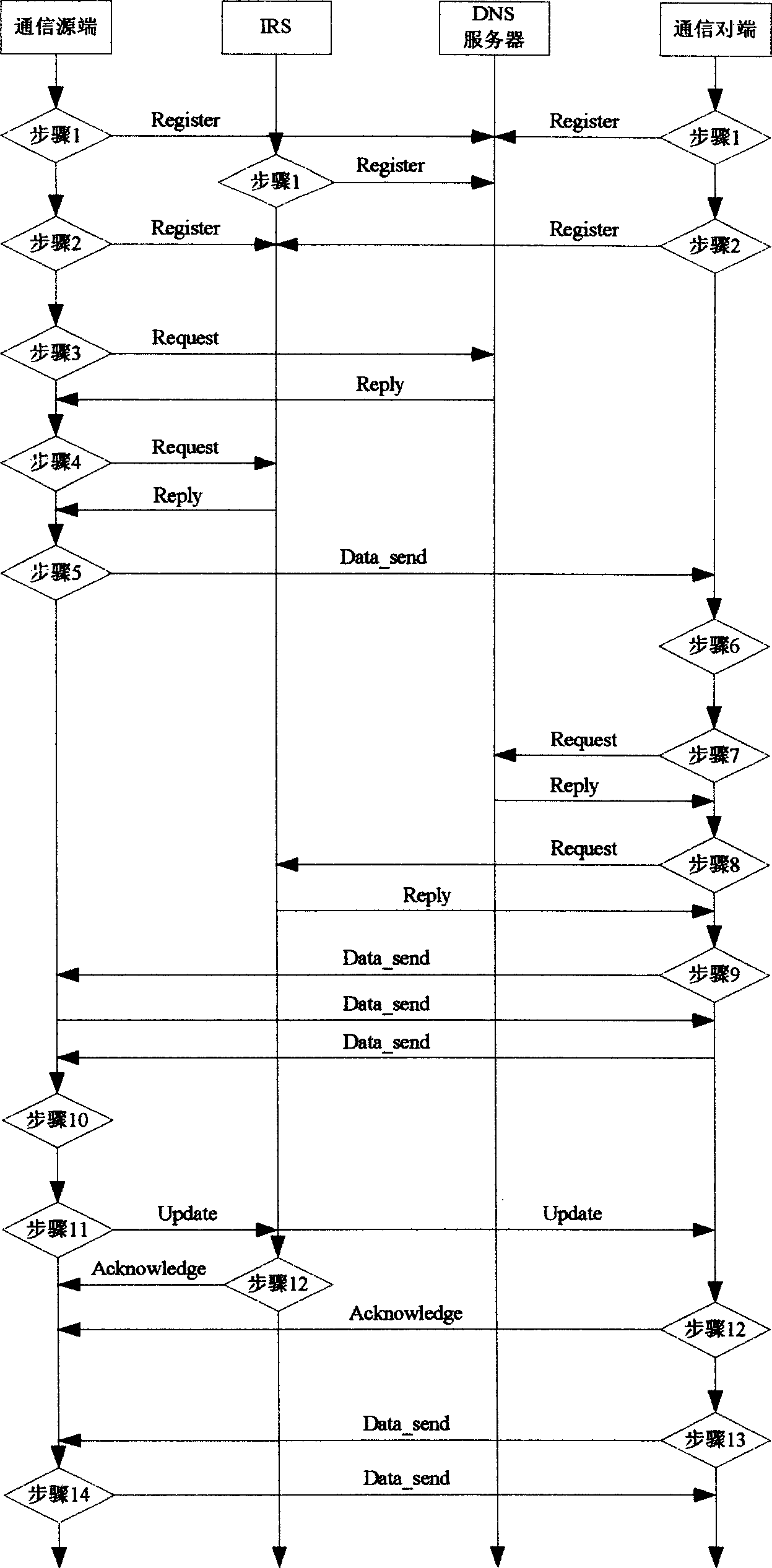
[0058] Step 1: All nodes register their end host identifiers in the DNS server, such as the communication source registering EID 1 , the communication peer registers EID 2 , the IRS registers its own end host identifier EID in the DNS server IRS and address IP IRS .
[0059] Step 2: All nodes register their end host identifiers and current IP addresses in the IRS, such as the communication source registering EID 1 and IP 1 , the communication peer registers EID 2 and IP 2 .
[0060] Step 3: The communication source searches for the DNS server and obtains the EID of the communication peer 2 and IRS EID IRS and IP ...
Embodiment 3
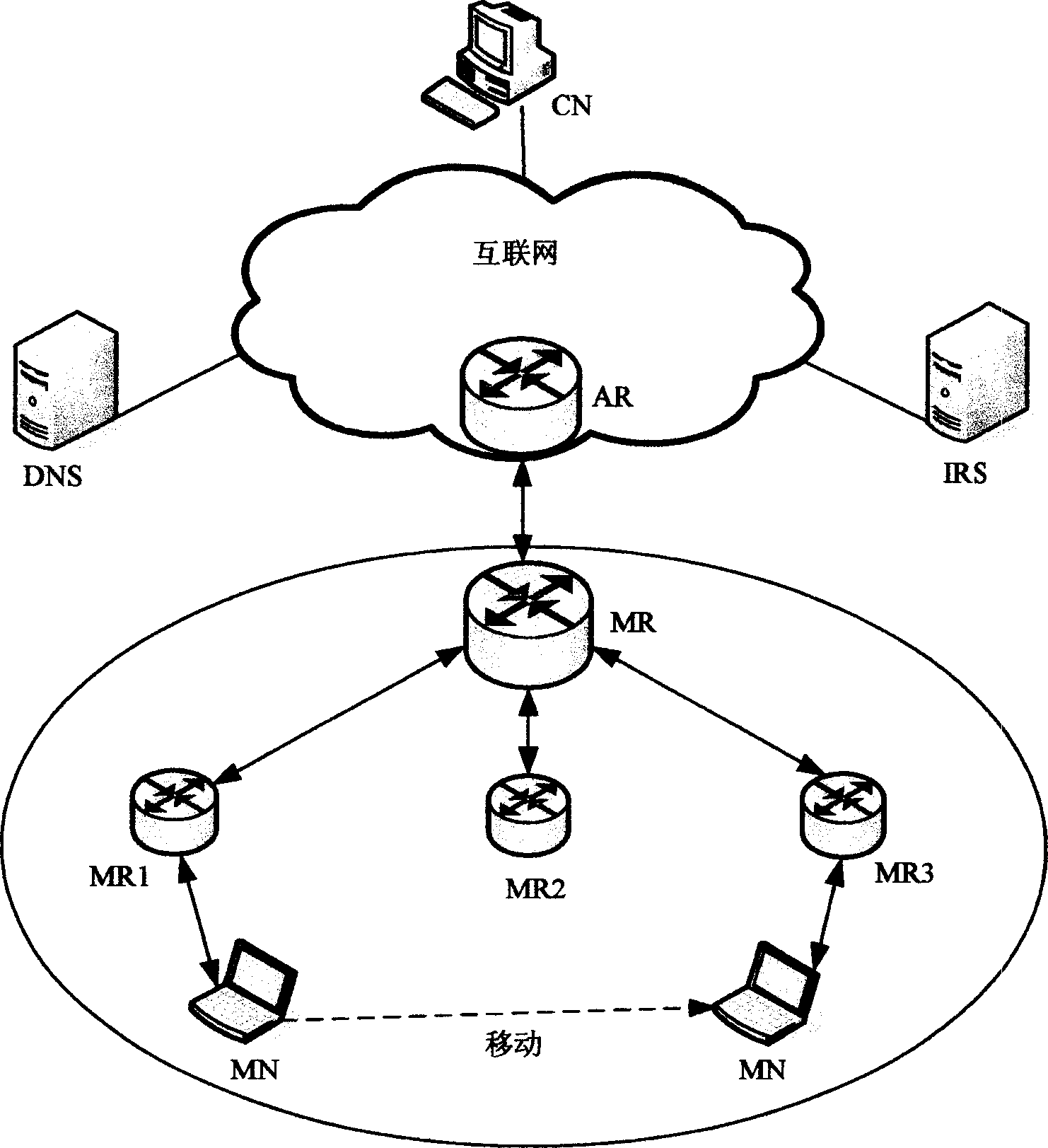
[0074] Such as image 3 shown. image 3 What is shown in is that the nodes in the mobile network communicate with the nodes in the Internet, AR is an access router (Access Router), and MR has enough address space to assign a unique address to each host belonging to its own network . For simplicity, only four mobile routers are shown in the figure.
[0075] The communication steps between MN and CN are as follows:
[0076] Step 1: All nodes register their end host identifiers in the DNS server, such as MN registering EID MN 、CN registration EID CN、MR registration EID MR , the IRS registers the EID in the DNS server IRS and address IP IRS .
[0077] Step 2: All nodes register their end host identifiers and current IP addresses in the IRS, such as MN registration EID MN and IP MN 、CN registration EID CN and IP CN 、MR registration EID MR and IP MR .
[0078] Step 3: MN queries the DNS server to obtain the EID of CN CN , IRS EID IRS and address IP IRS , MR's EID ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com