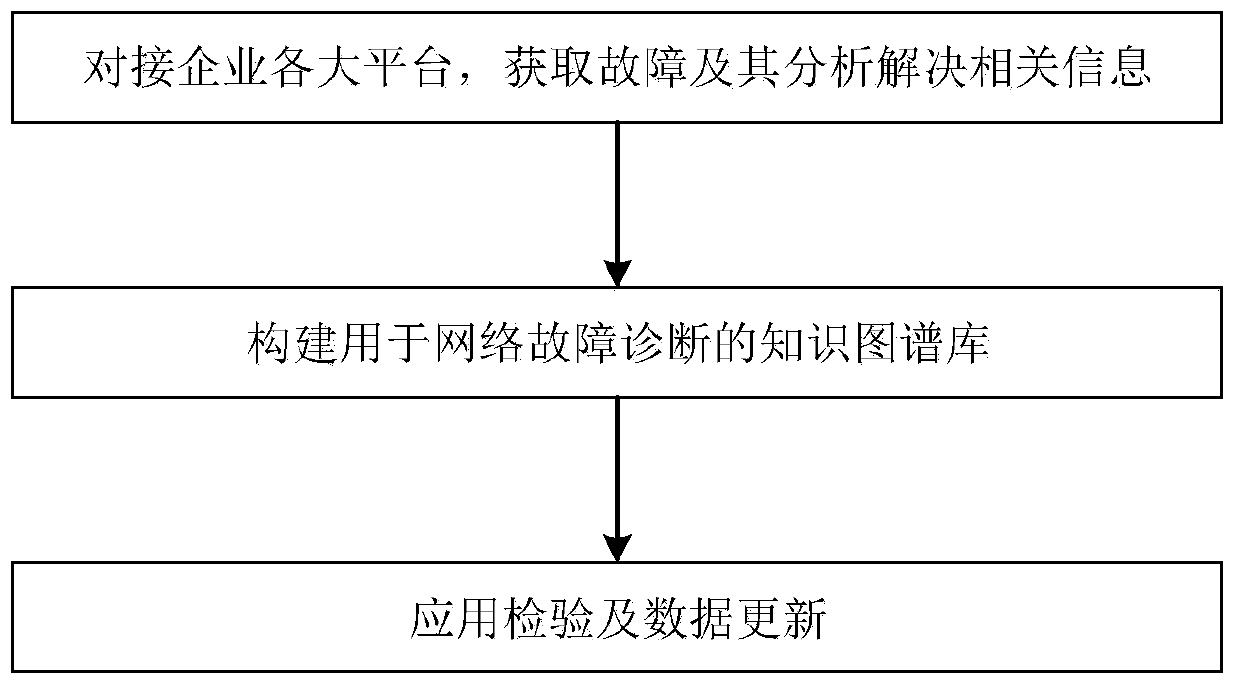
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
203 results about "Datasource" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
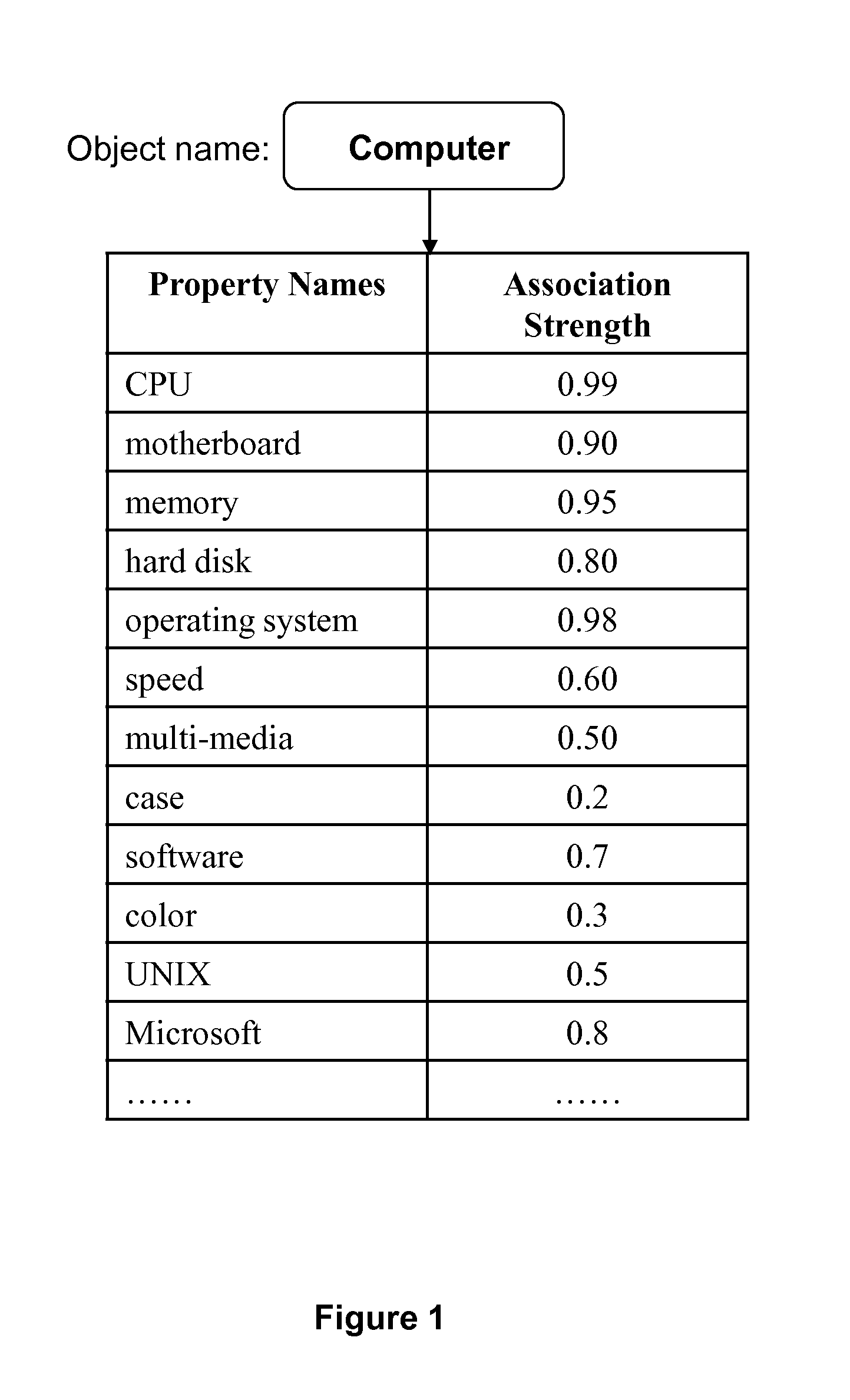
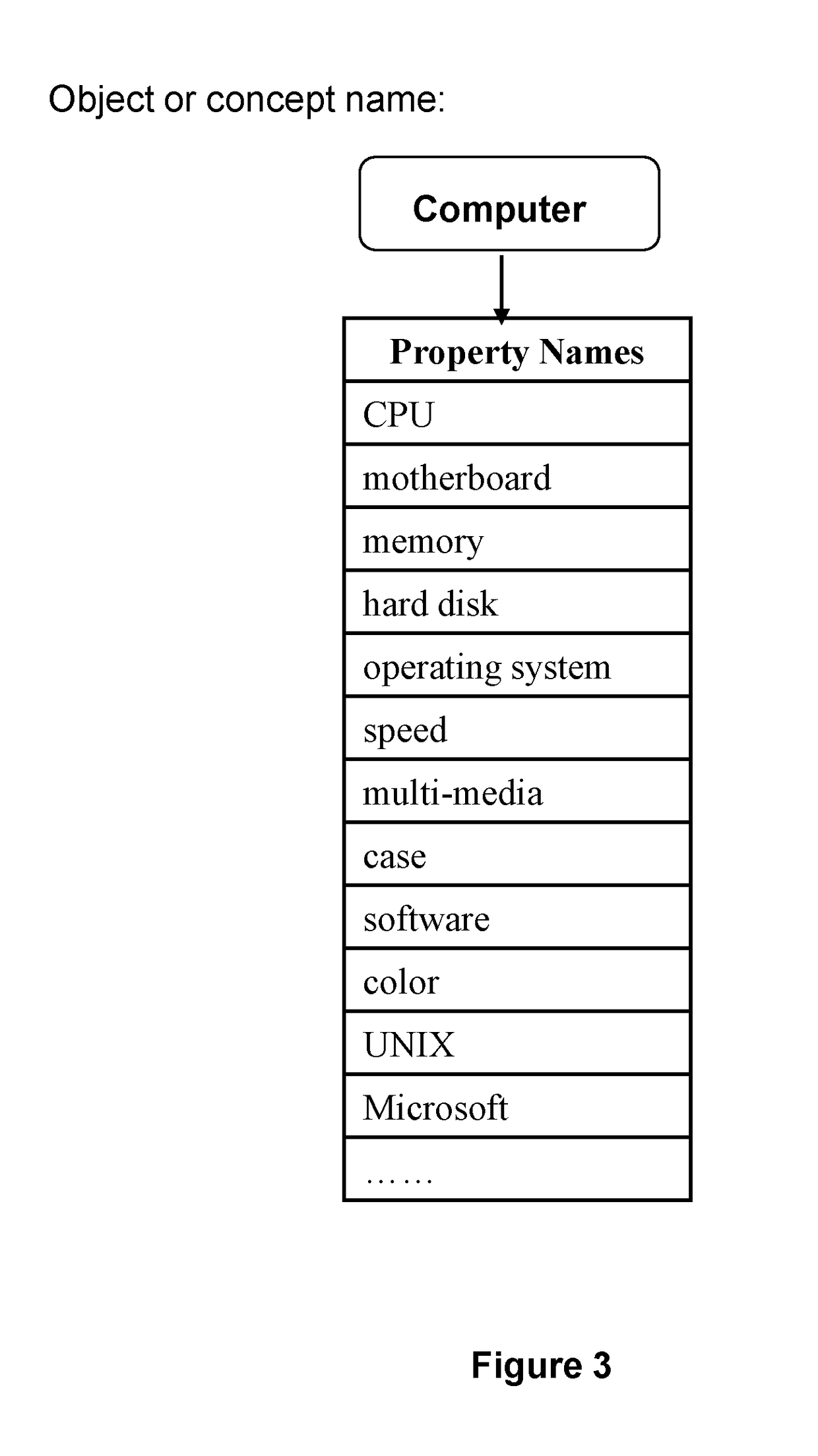
DataSource is a name given to the connection set up to a database from a server. The name is commonly used when creating a query to the database. The data source name (DSN) need not be the same as the filename for the database. For example, a database file named friends.mdb could be set up with a DSN of school. Then DSN school would be used to refer to the database when performing a query.
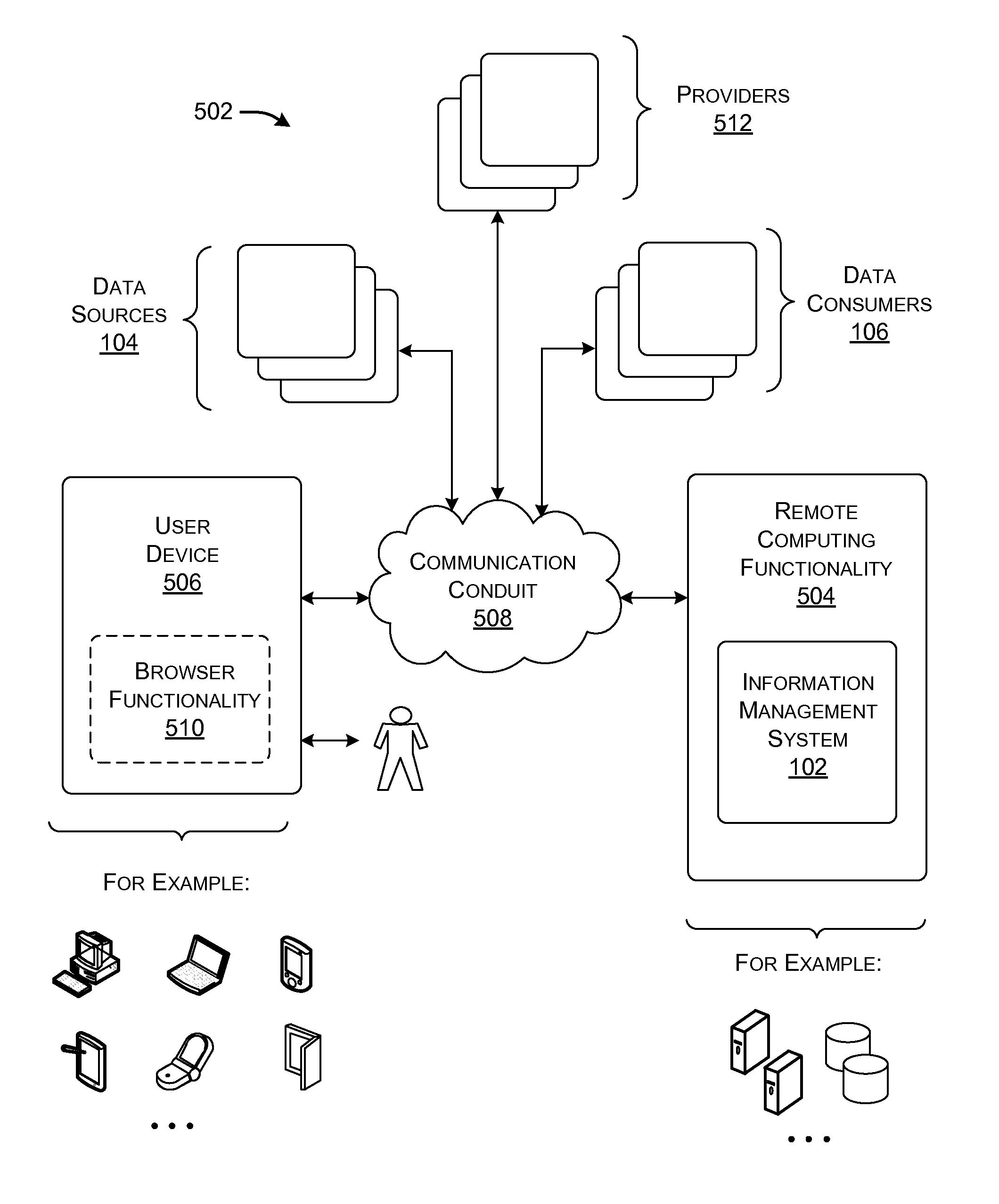
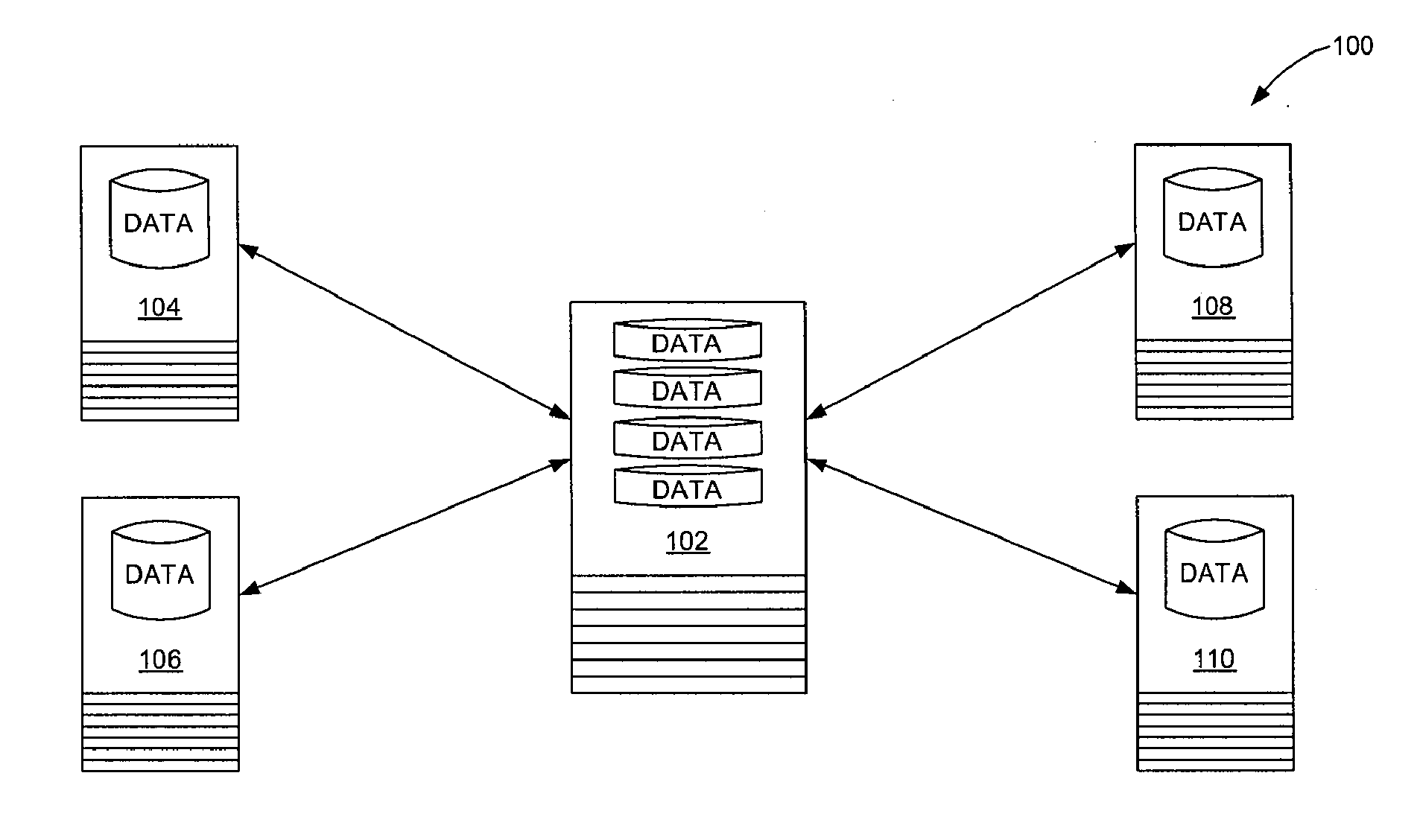
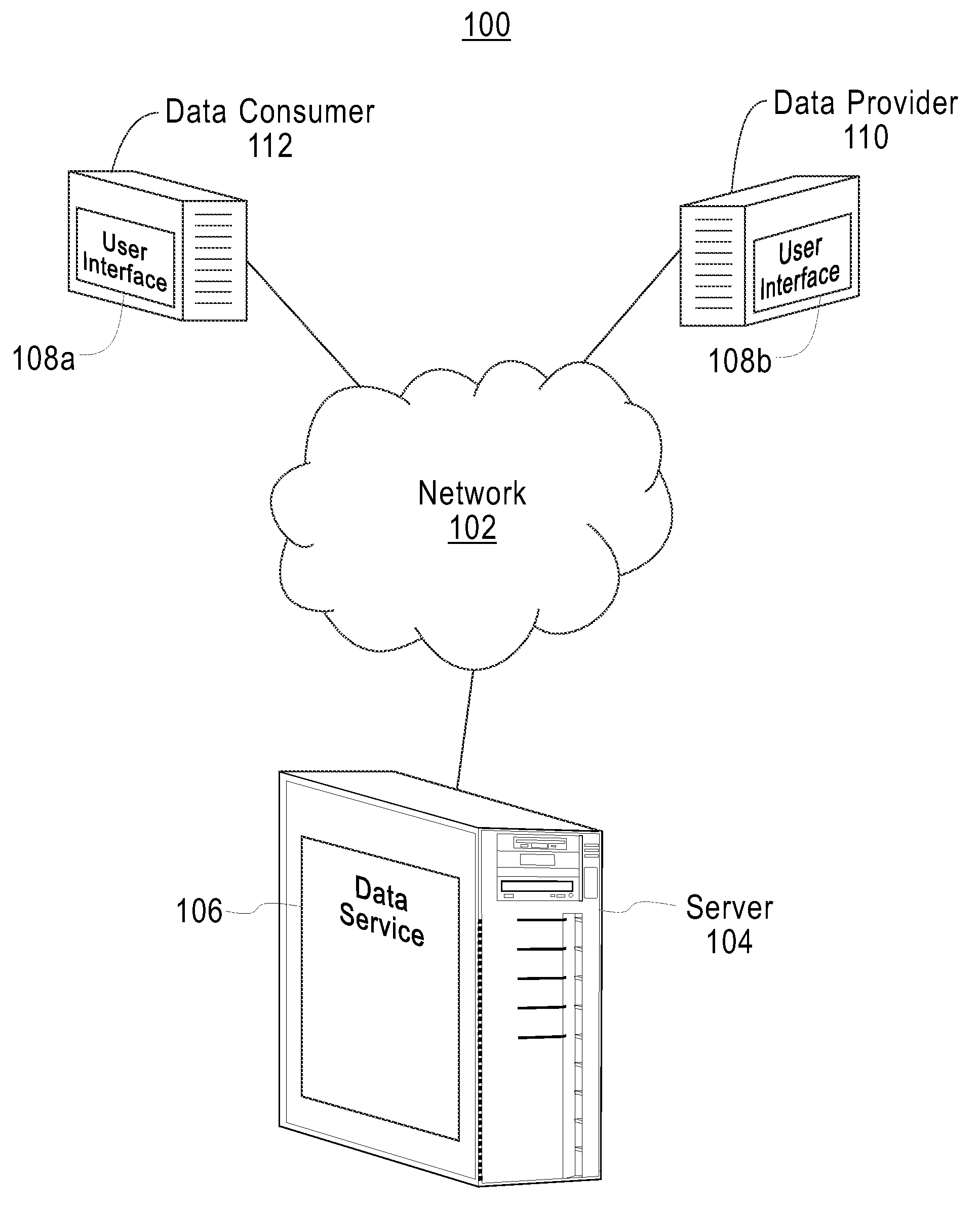
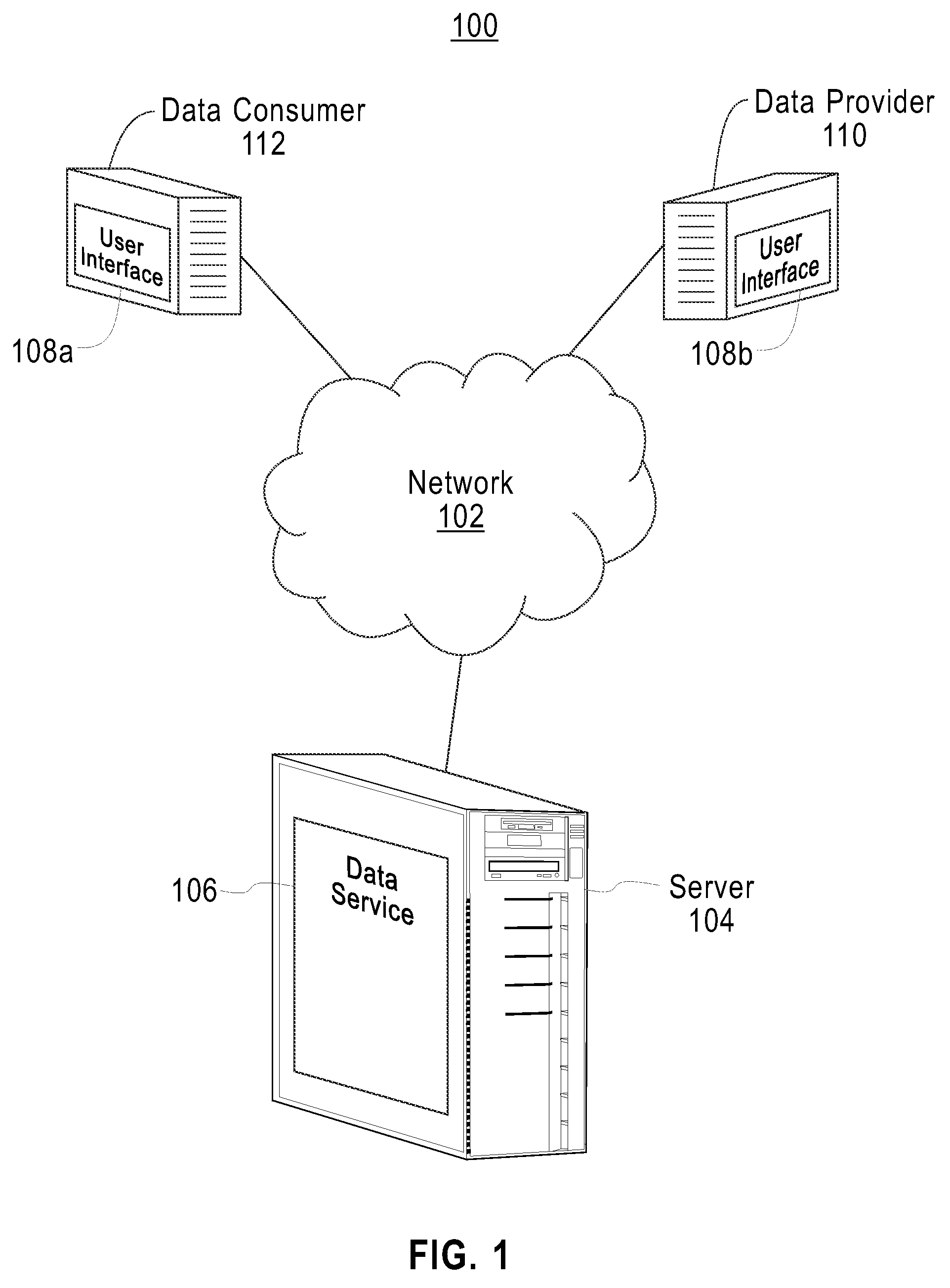
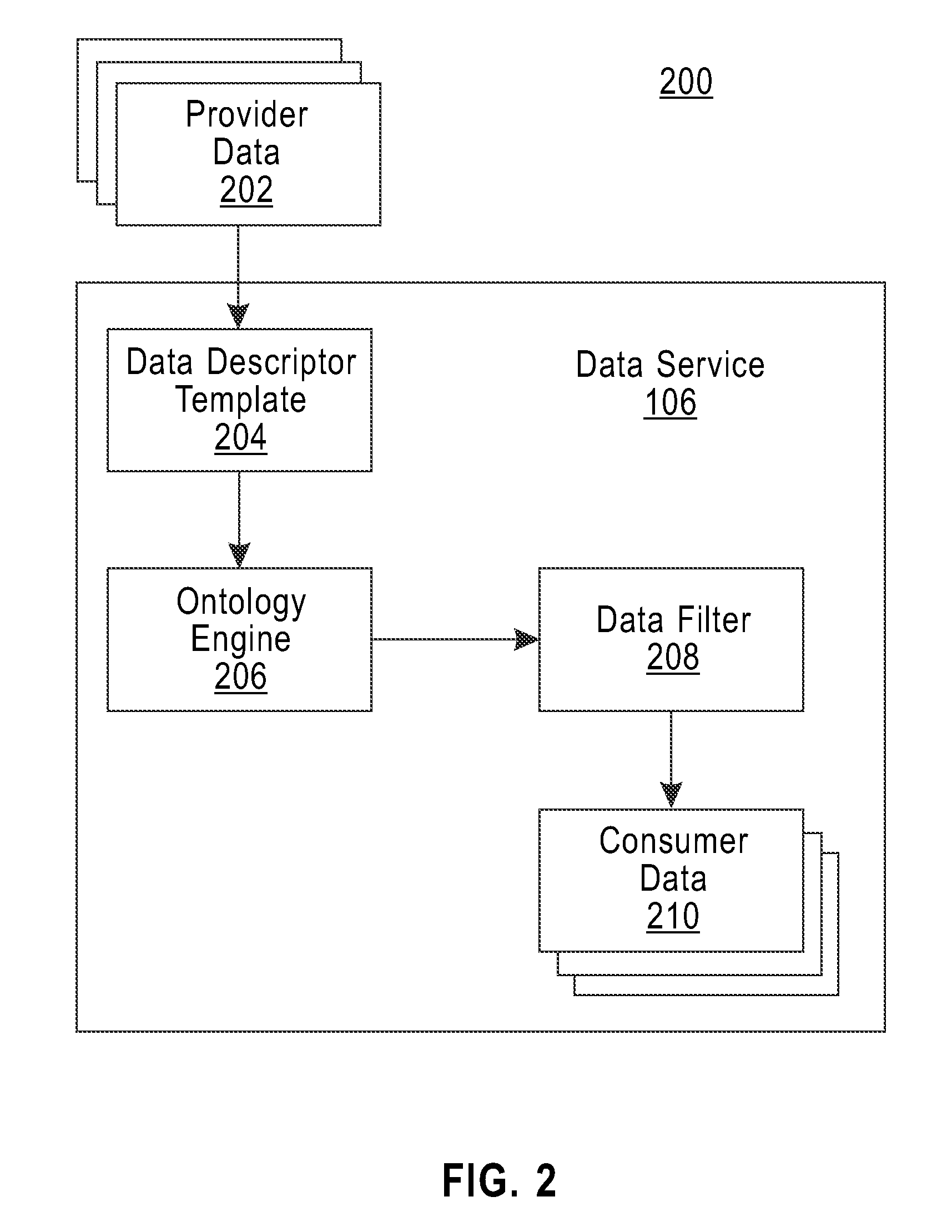
Distributing collected information to data consumers based on global user consent information
InactiveUS20120254320A1Well formedTelemedicineMultiple digital computer combinationsInformation functionDatasource
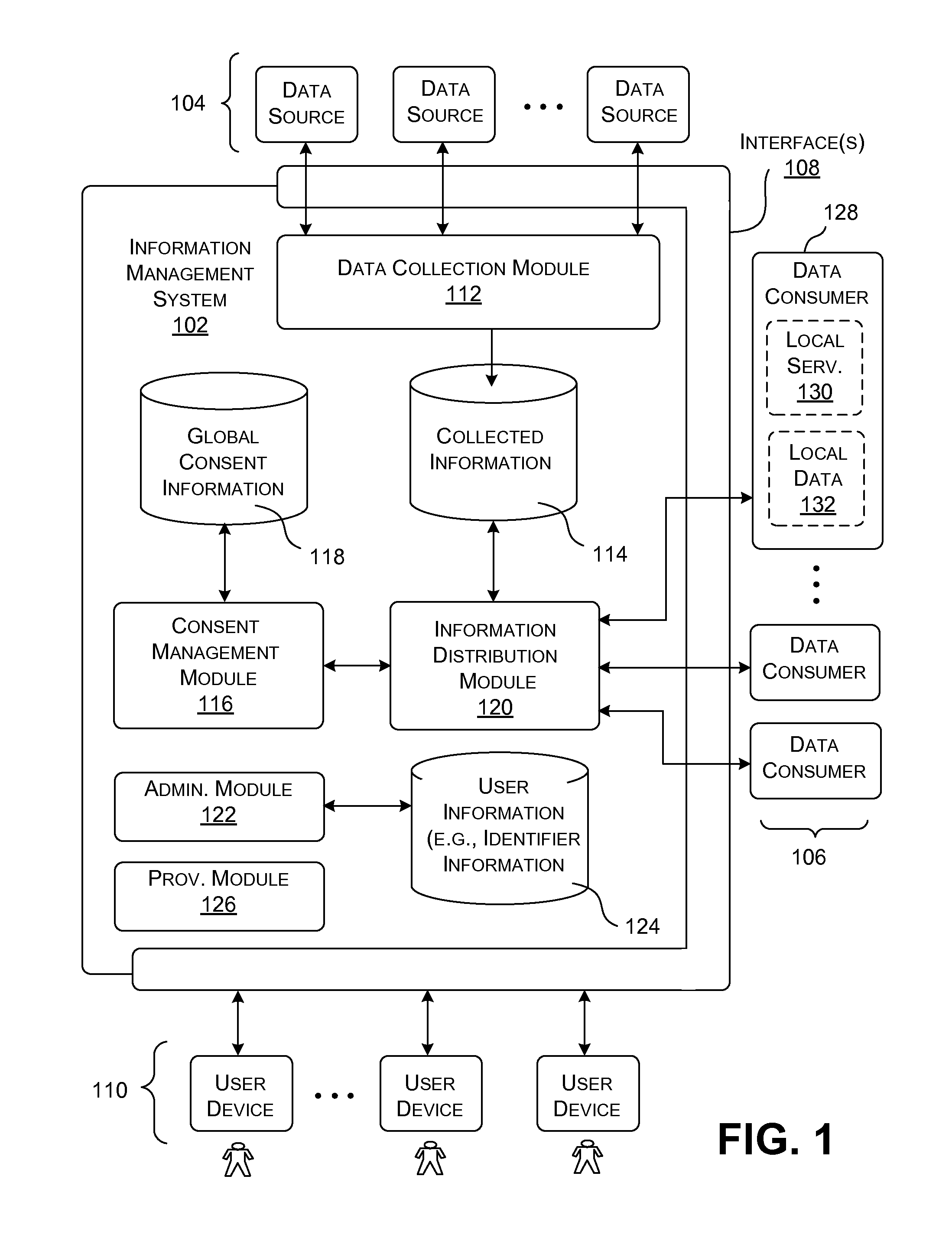
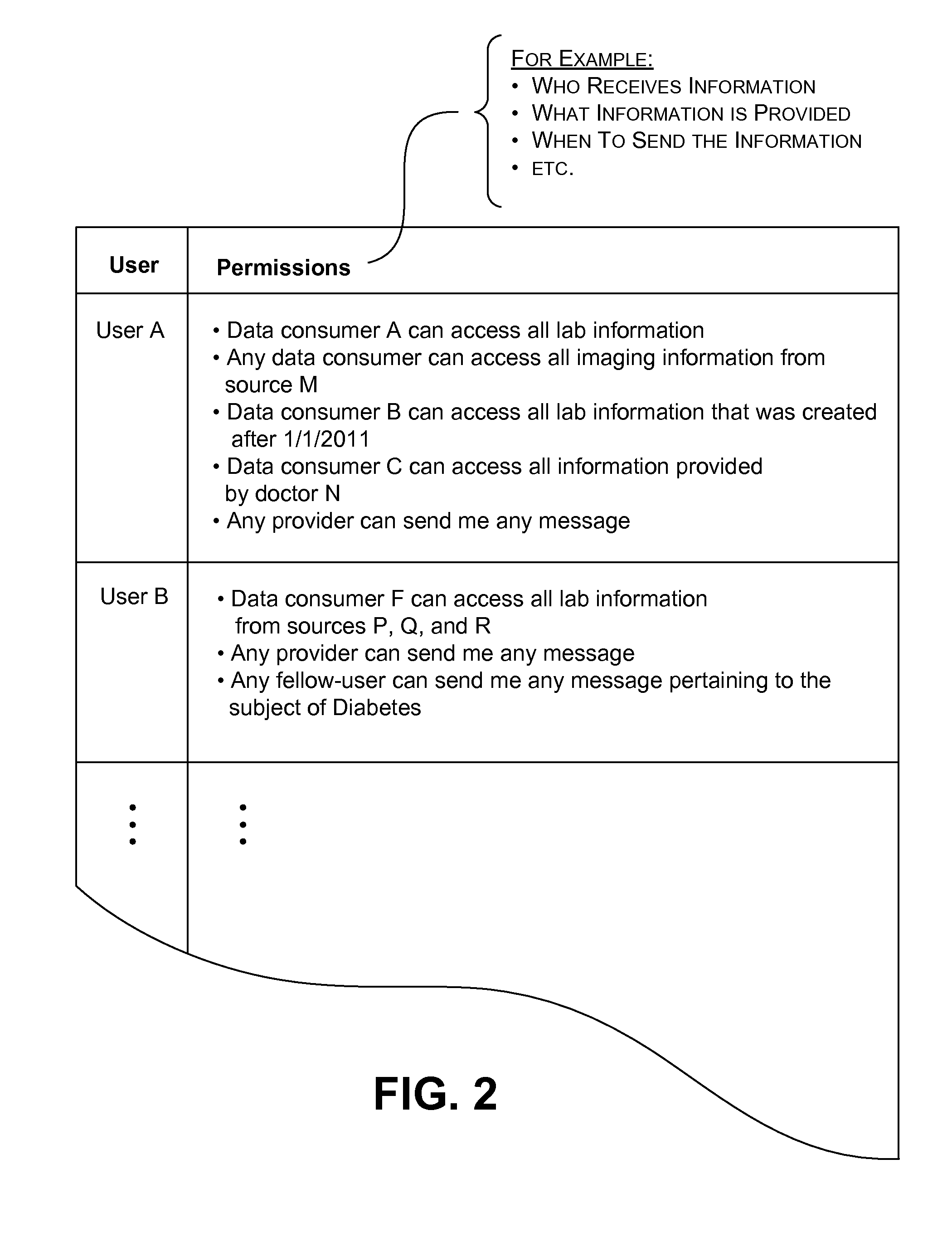
An information management system is described herein which maintains collected information that pertains to users, received from one or more data sources. The information management system also maintains a store of consent information. The consent information describes, for each user, at least one permission rule (established by the user) which enables at least one data consumer to receive at least part of the collected information for that user. Upon the occurrence of a triggering event, an information distribution module operates by distributing identified part(s) of the collected information to appropriate data consumer(s), as governed by the consent information. In this manner of operation, the consent information functions as global metadata which, from a centralized platform, governs the dissemination of the collected information to any data consumer in an application-agnostic manner.
Owner:MICROSOFT TECH LICENSING LLC
Declarative external data source importation, exportation, and metadata reflection utilizing HTTP and hdfs protocols
ActiveUS20160092476A1Accurate resolutionDigital data information retrievalDigital data processing detailsExternal dataDatasource
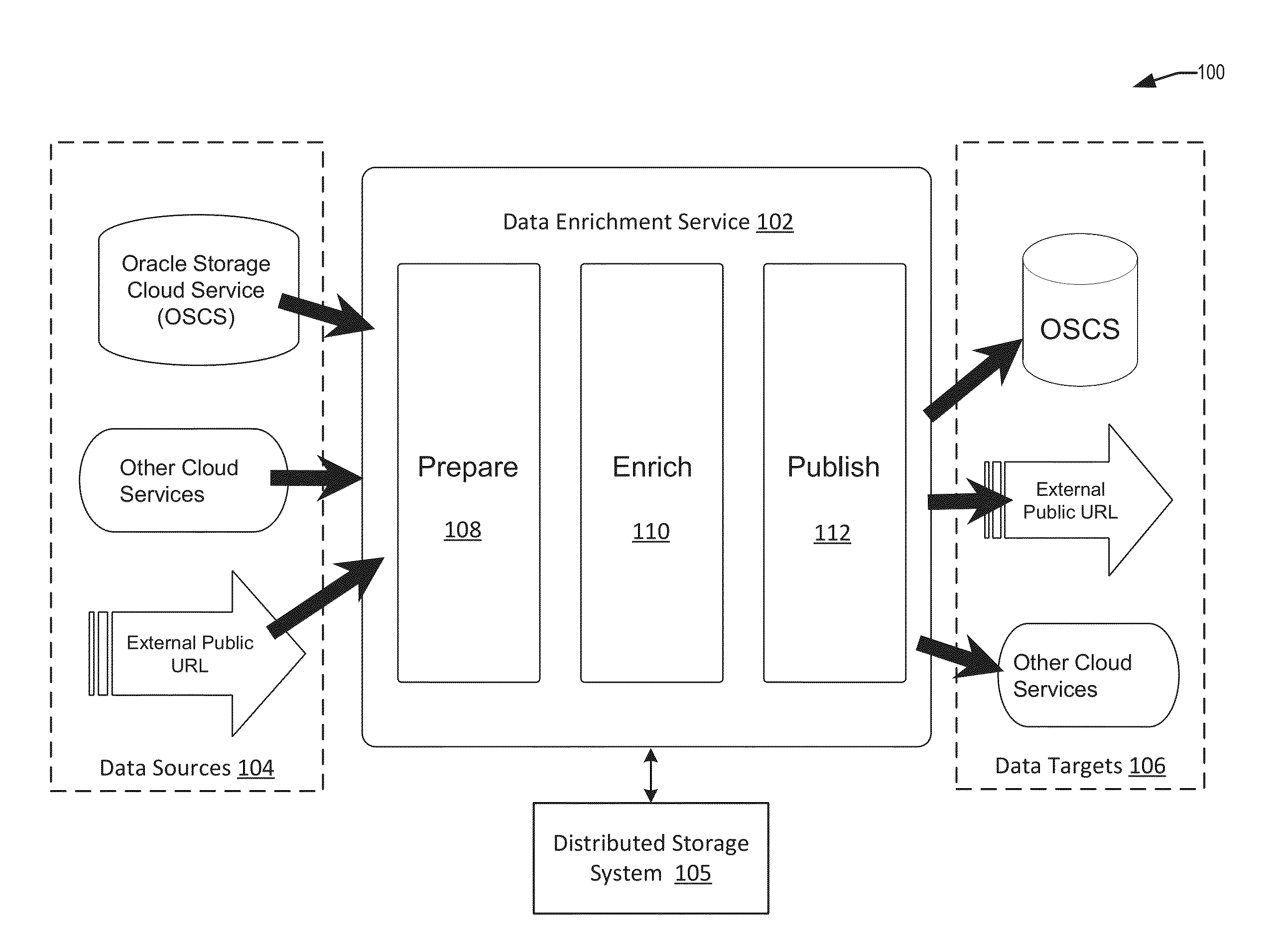
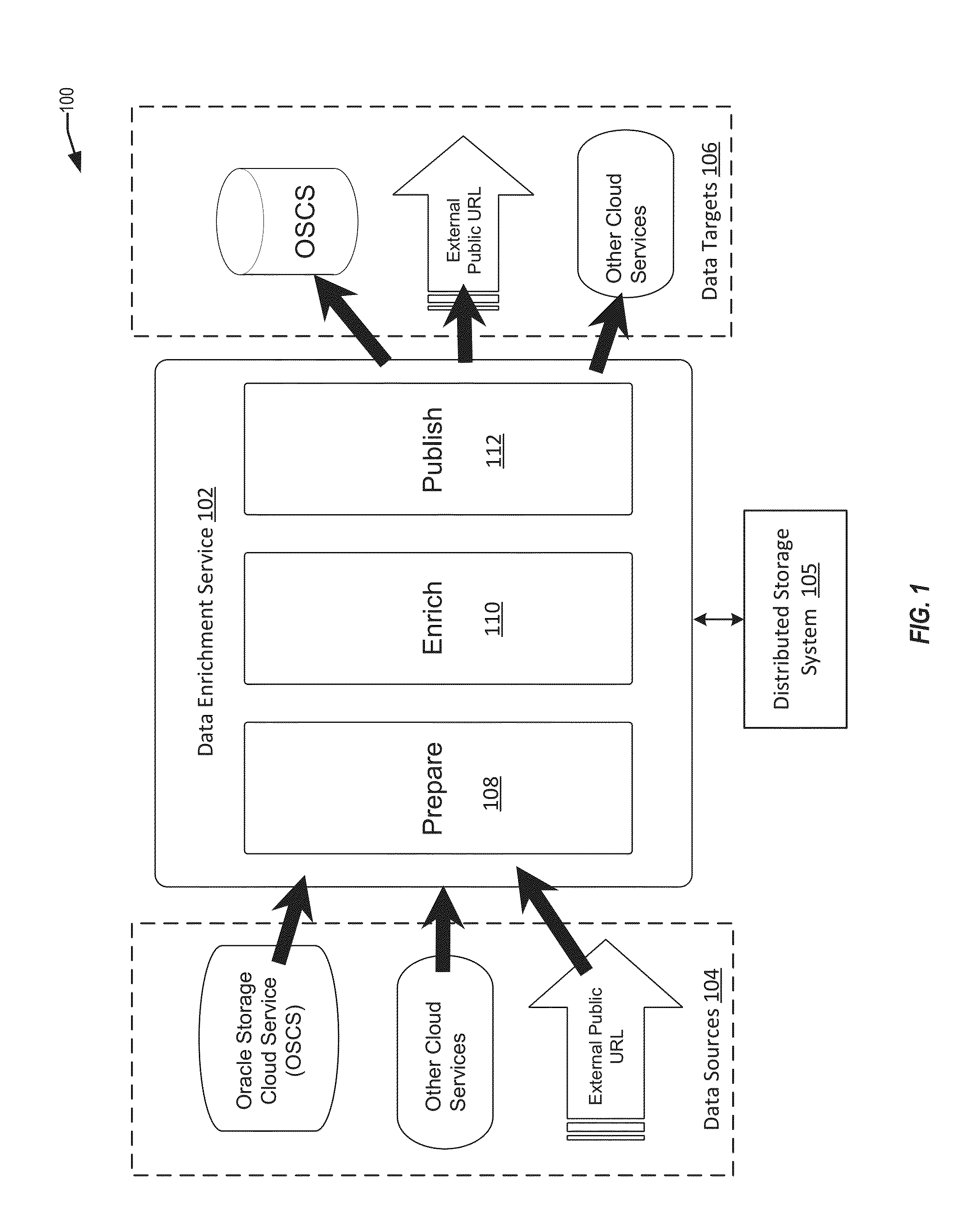
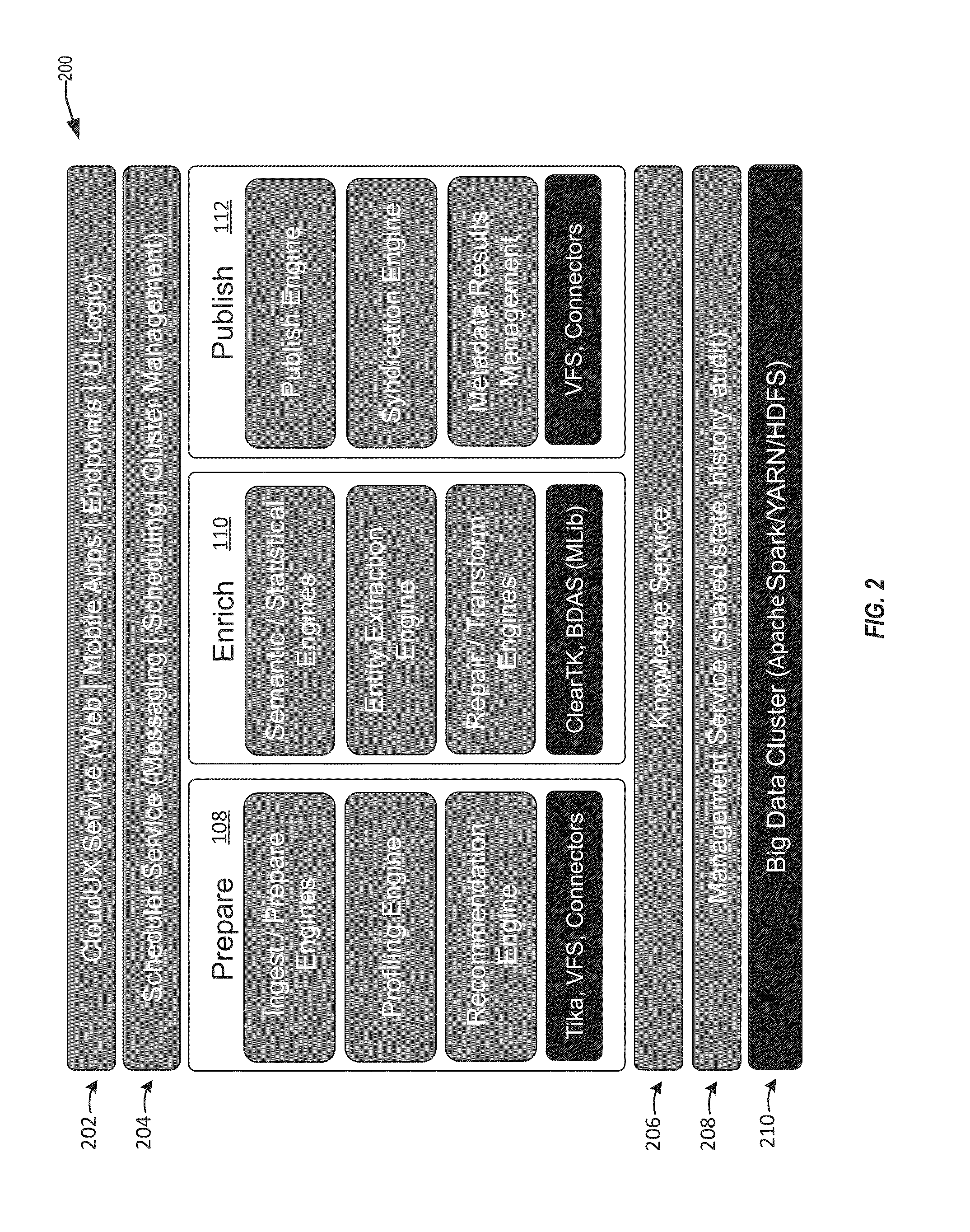
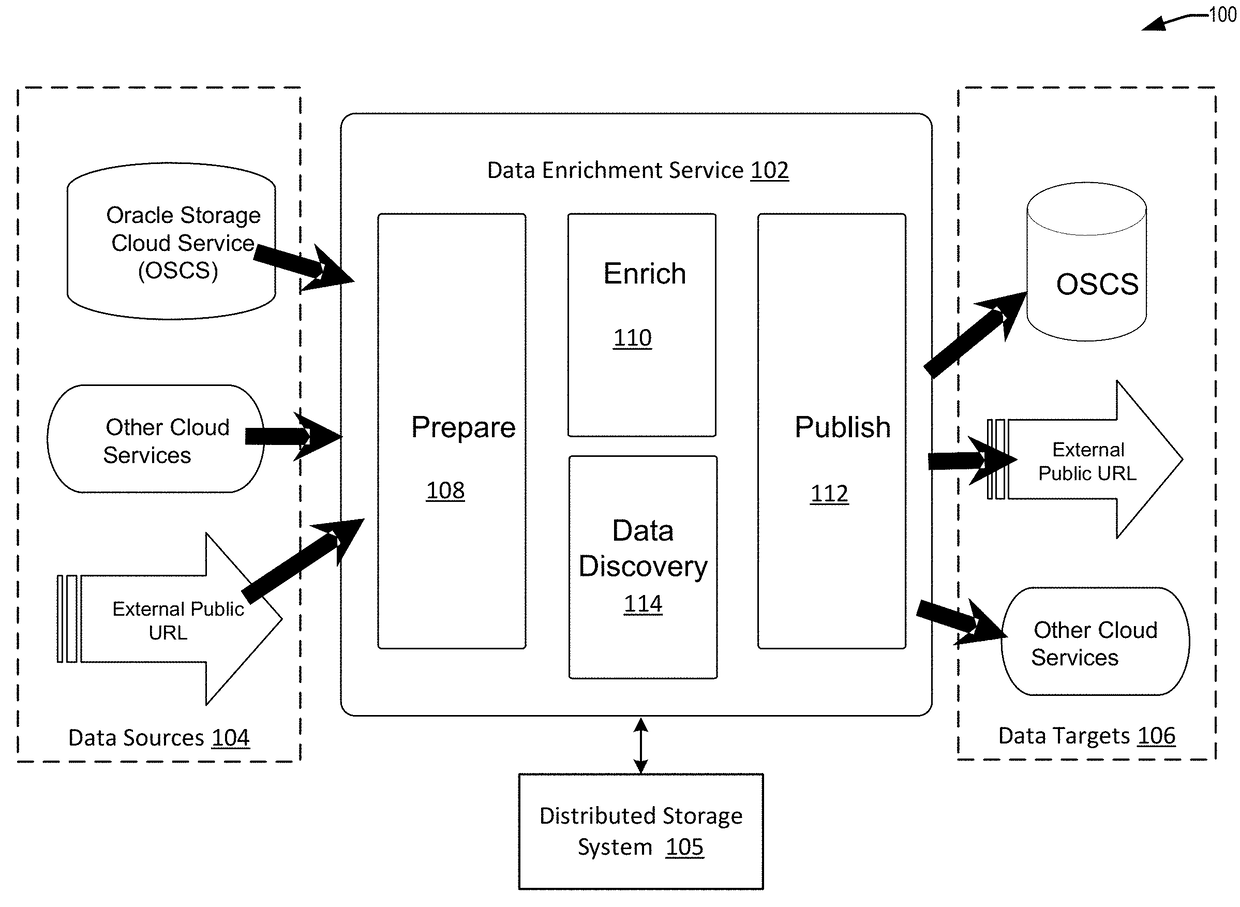
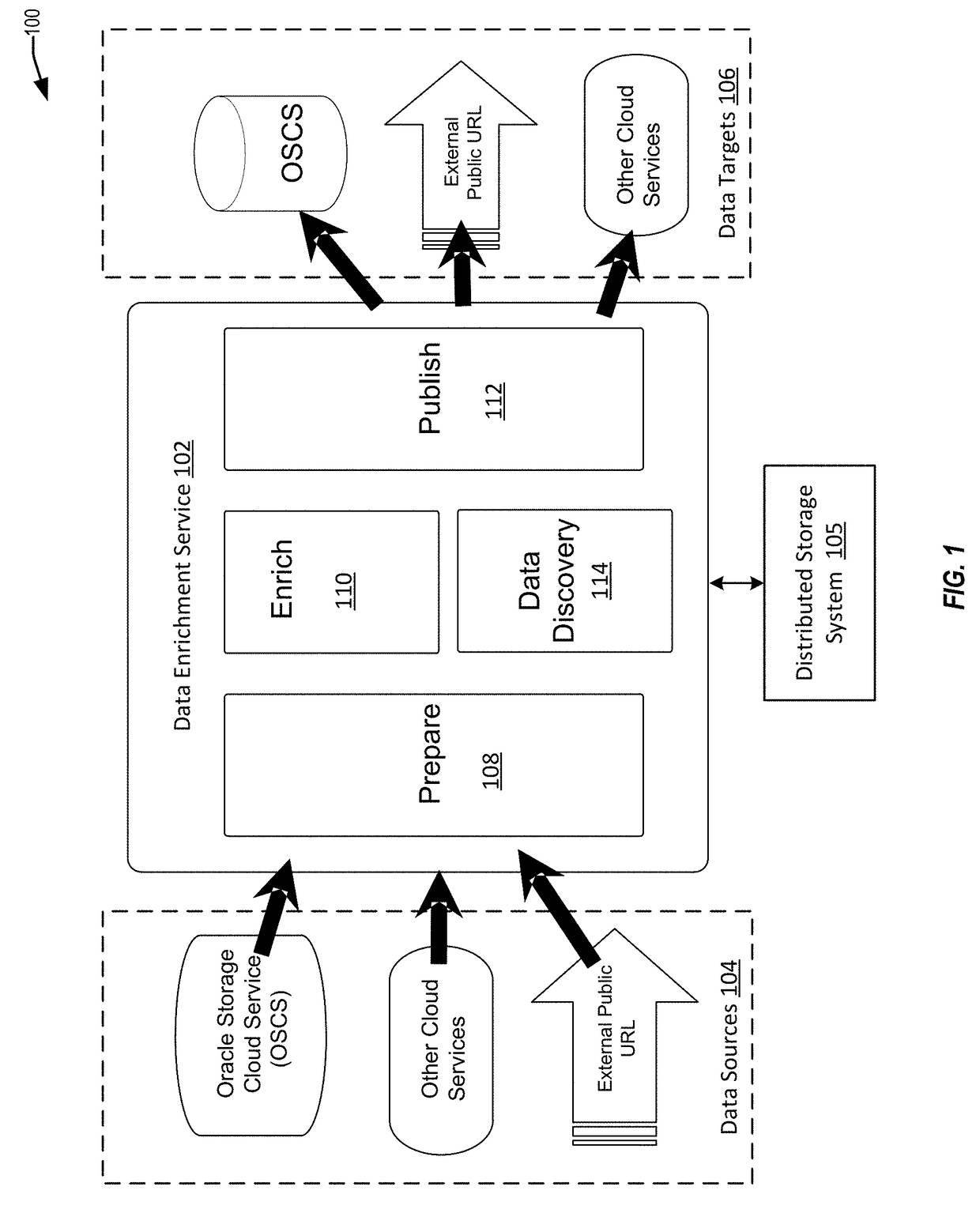
Techniques are disclosure for a data enrichment system that enables declarative external data source importation and exportation. A user can specify via a user interface input for identifying different data sources from which to obtain input data. The data enrichment system is configured to import and export various types of sources storing resources such as URL-based resources and HDFS-based resources for high-speed bi-directional metadata and data interchange. Connection metadata (e.g., credentials, access paths, etc.) can be managed by the data enrichment system in a declarative format for managing and visualizing the connection metadata.
Owner:ORACLE INT CORP
Techniques for relationship discovery between datasets
ActiveUS20180075104A1Increase valueIncrease usageDigital data information retrievalSpecial data processing applicationsData setDatasource
Owner:ORACLE INT CORP
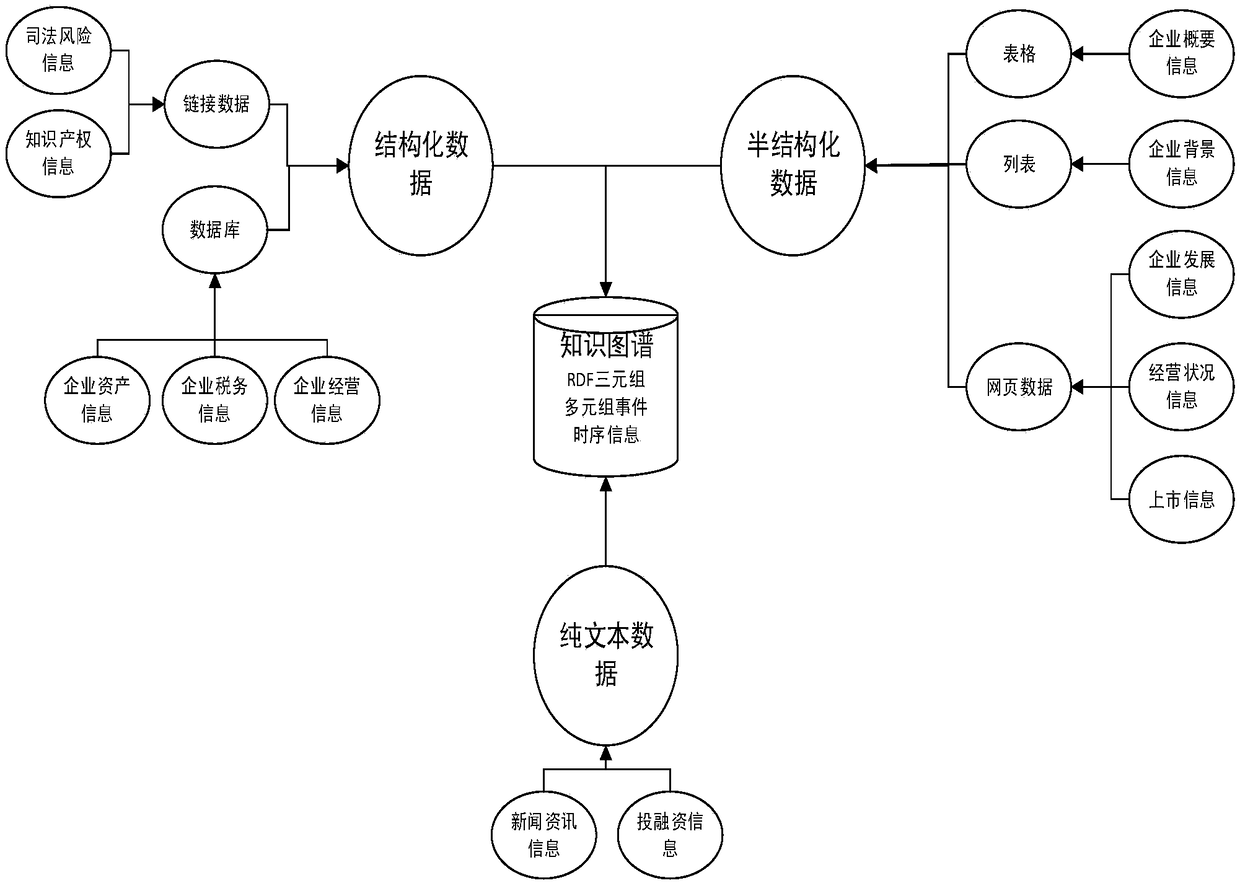
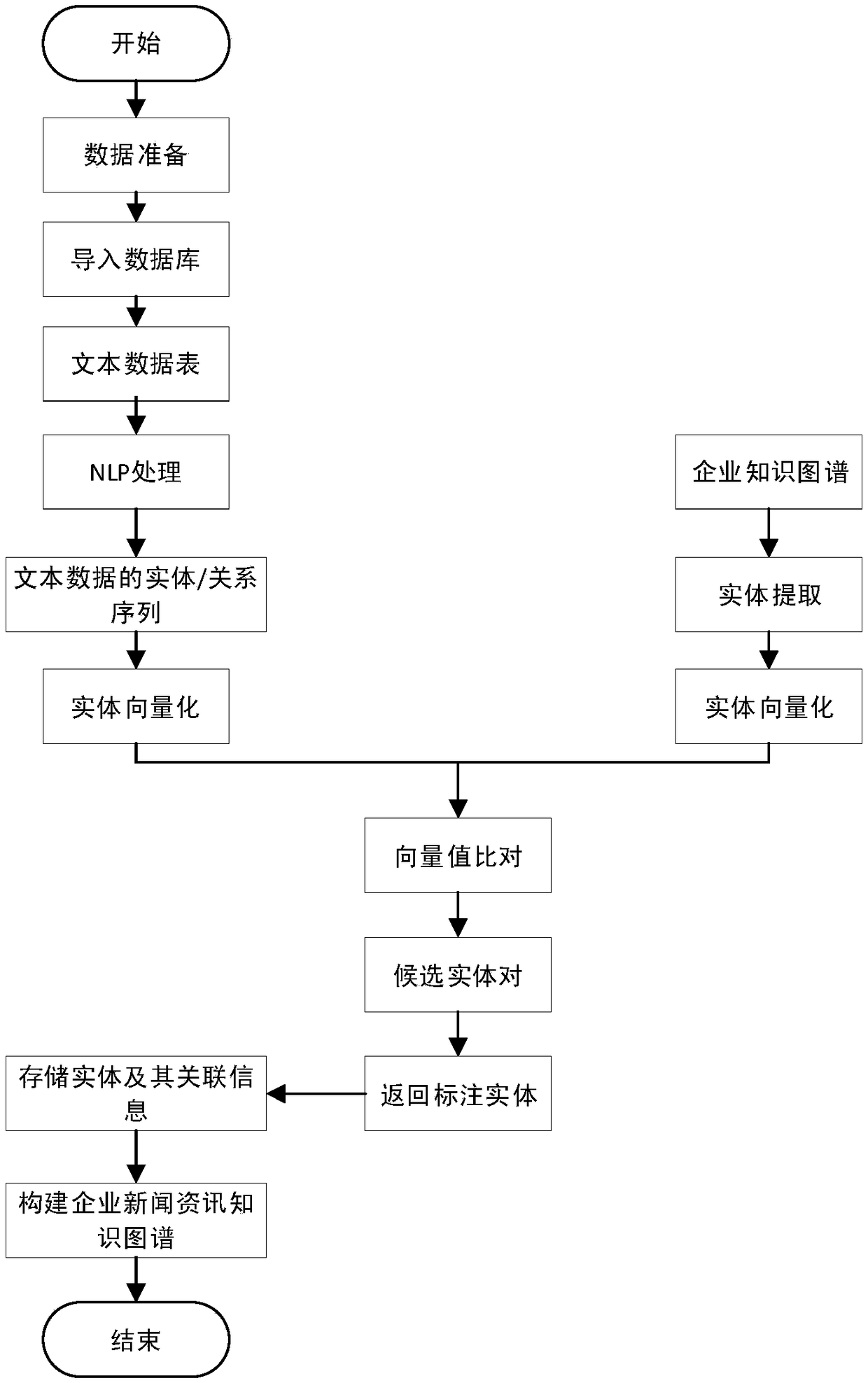
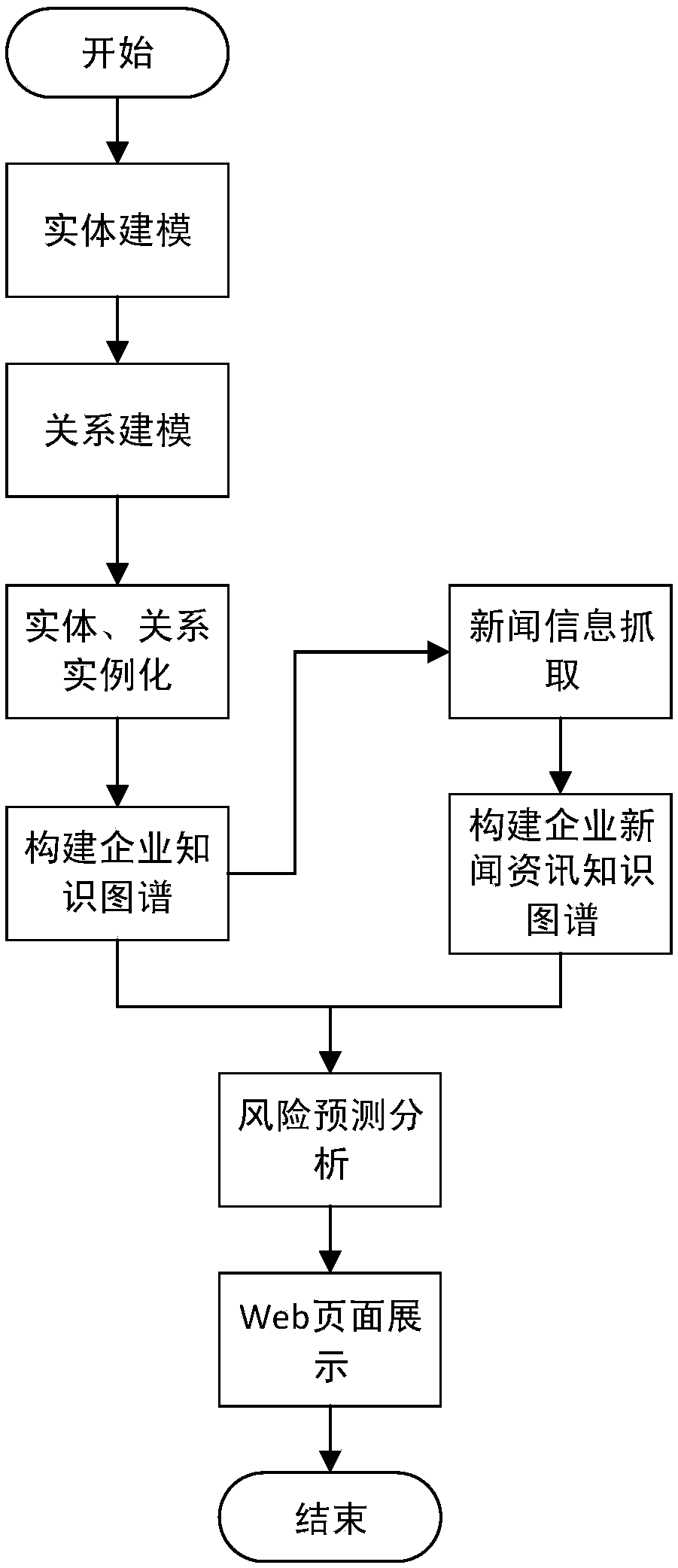
Knowledge graph-based enterprise risk prediction method and system
InactiveCN108596439ARealize knowledge extractionImplement storageResourcesSpecial data processing applicationsDatasourceKnowledge extraction
The invention discloses a knowledge graph-based enterprise risk prediction method and system. The method comprises the steps of 1) constructing entities of an enterprise knowledge graph, establishingrelationships between the entities, and extracting knowledge from set data sources to form the enterprise knowledge graph; 2) capturing news information of enterprises and related entities, processingthe captured news information based on the enterprise knowledge graph, marking relationships between the related entities and events, and storing marked information in a structured knowledge base toform an enterprise news information knowledge graph; and 3) performing enterprise risk prediction based on the enterprise knowledge graph and the enterprise news information knowledge graph. The blankof an existing knowledge graph in the field of enterprise risk analysis is filled; and the constructed enterprise knowledge graph and enterprise news information knowledge graph have relatively highpracticality.
Owner:BEIJING ZTE DIGITAL TECH
Real-time, stream data information integration and analytics system
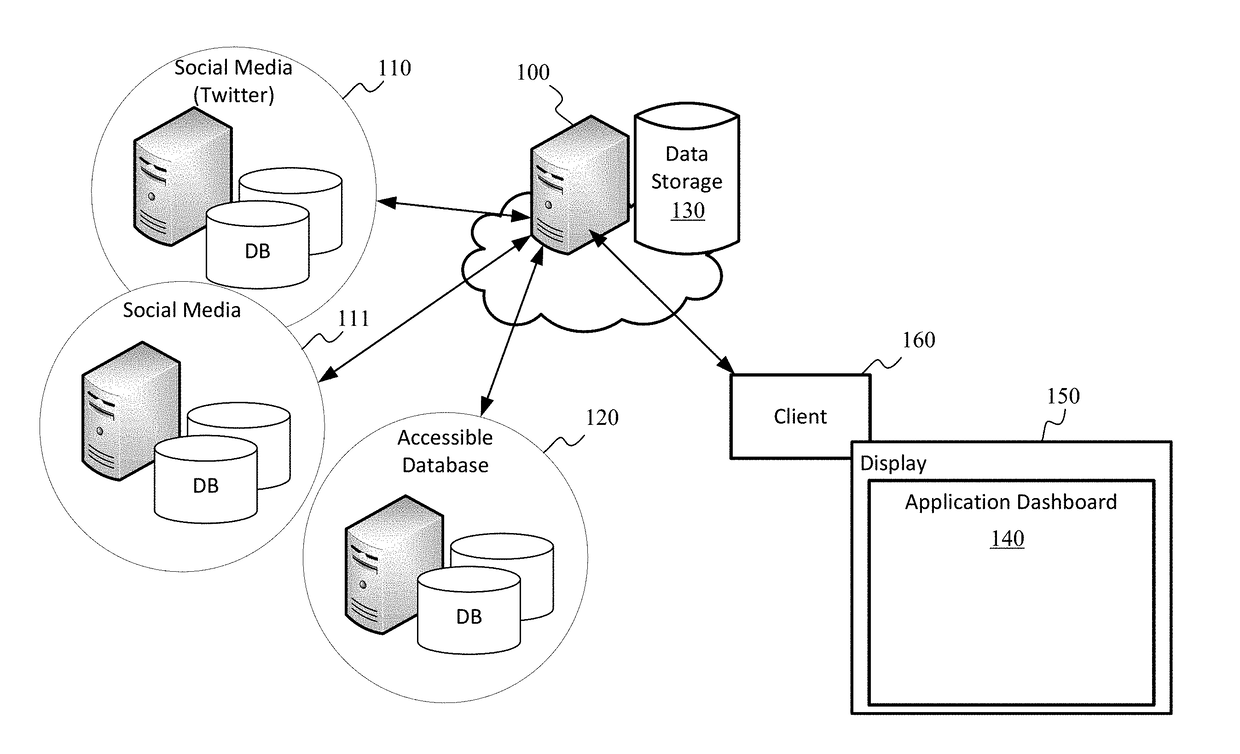
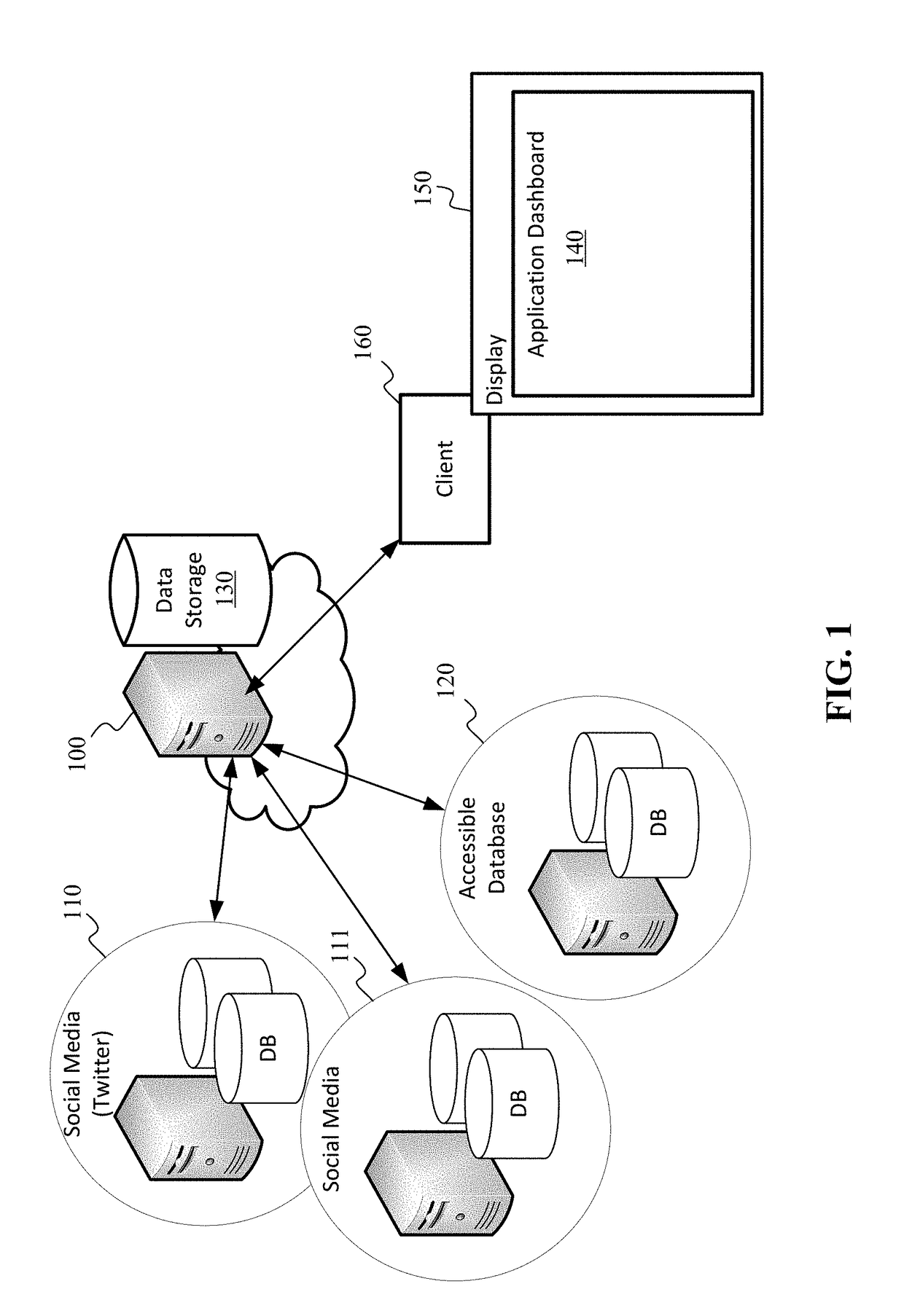
A real-time, stream data information integration and analytics system can include an information engine that performs real-time entity extraction to create key-value pairs of attributes for a personal profile and integrates similar personal profiles generated from same or different data sources into a single person-of-interest profile. The real-time, stream data information integration and analytics system can further include a real-time analytics module that performs a variety of analytics using the person-of-interest profiles and updates the person-of-interest profiles with scores and other results of the variety of analytics. The variety of real-time analytics can include sentiment analysis and at least some aspects of threat detection analysis. The sentiment analysis can be used to provide a recommender system and the threat detection analysis can be used to identify and predict threats and opportunities.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
System and methods for searching objects and providing answers to queries using association data
InactiveUS9367608B1Novel methodSemantic analysisDigital data processing detailsData setDocumentation procedure
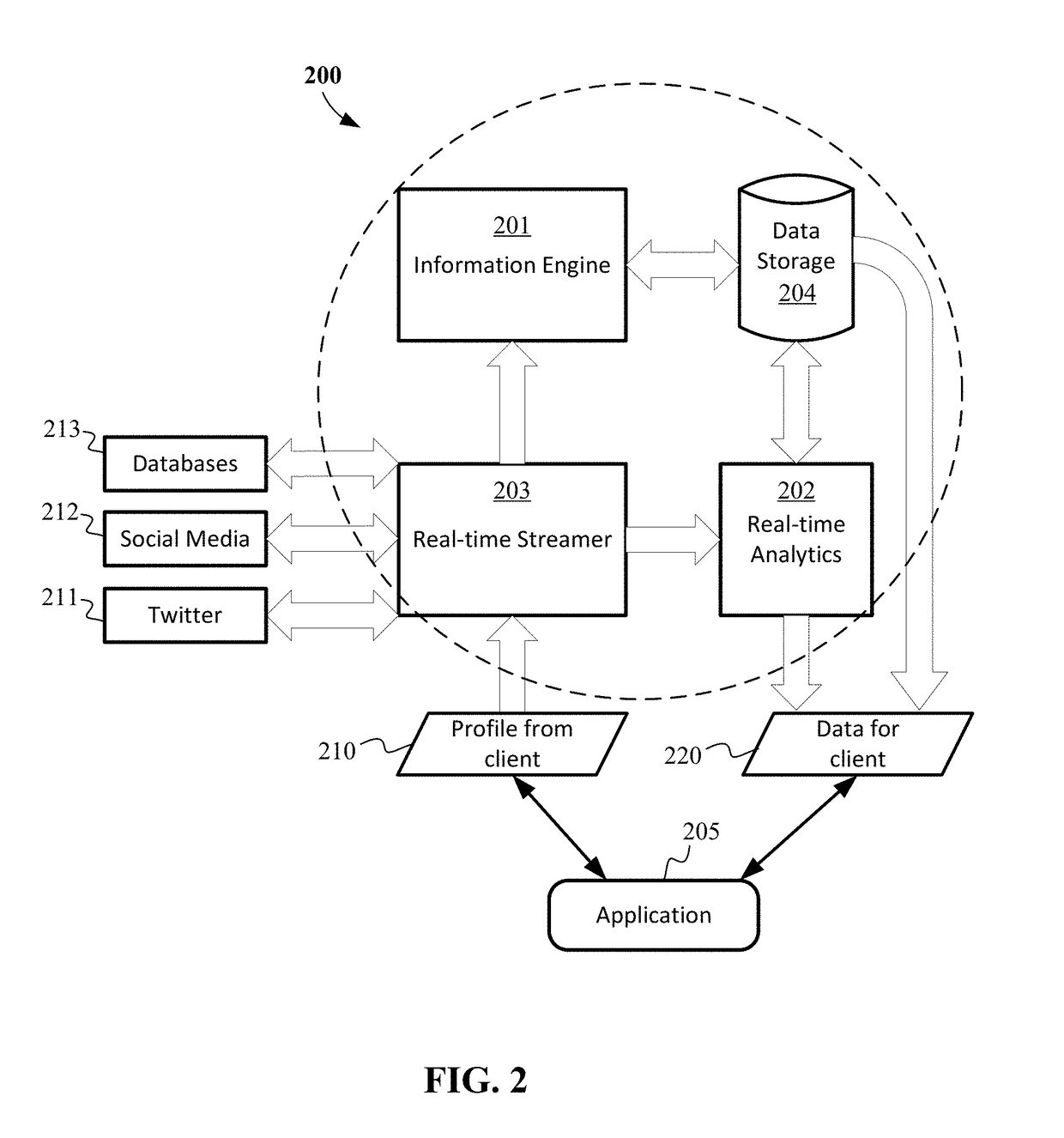
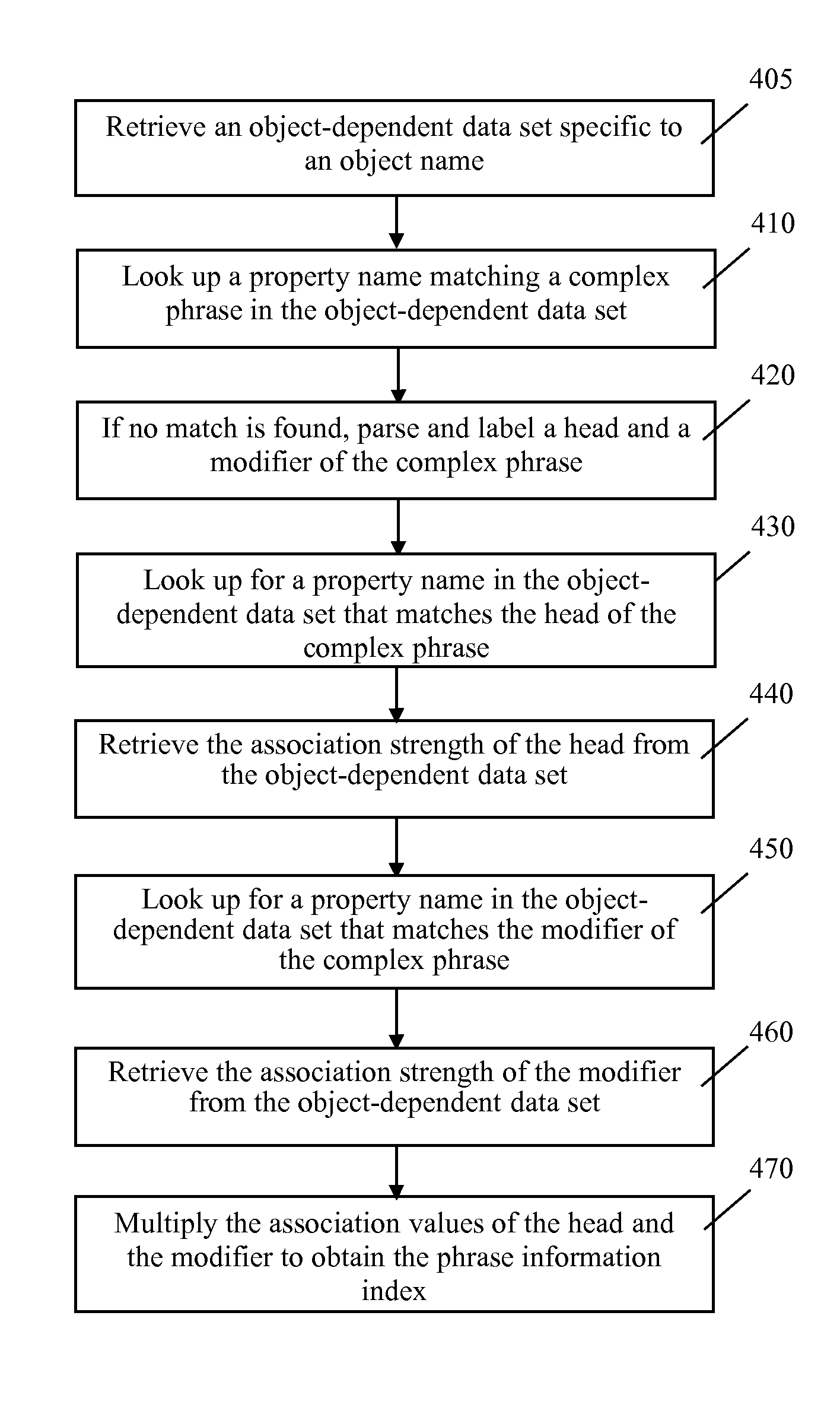
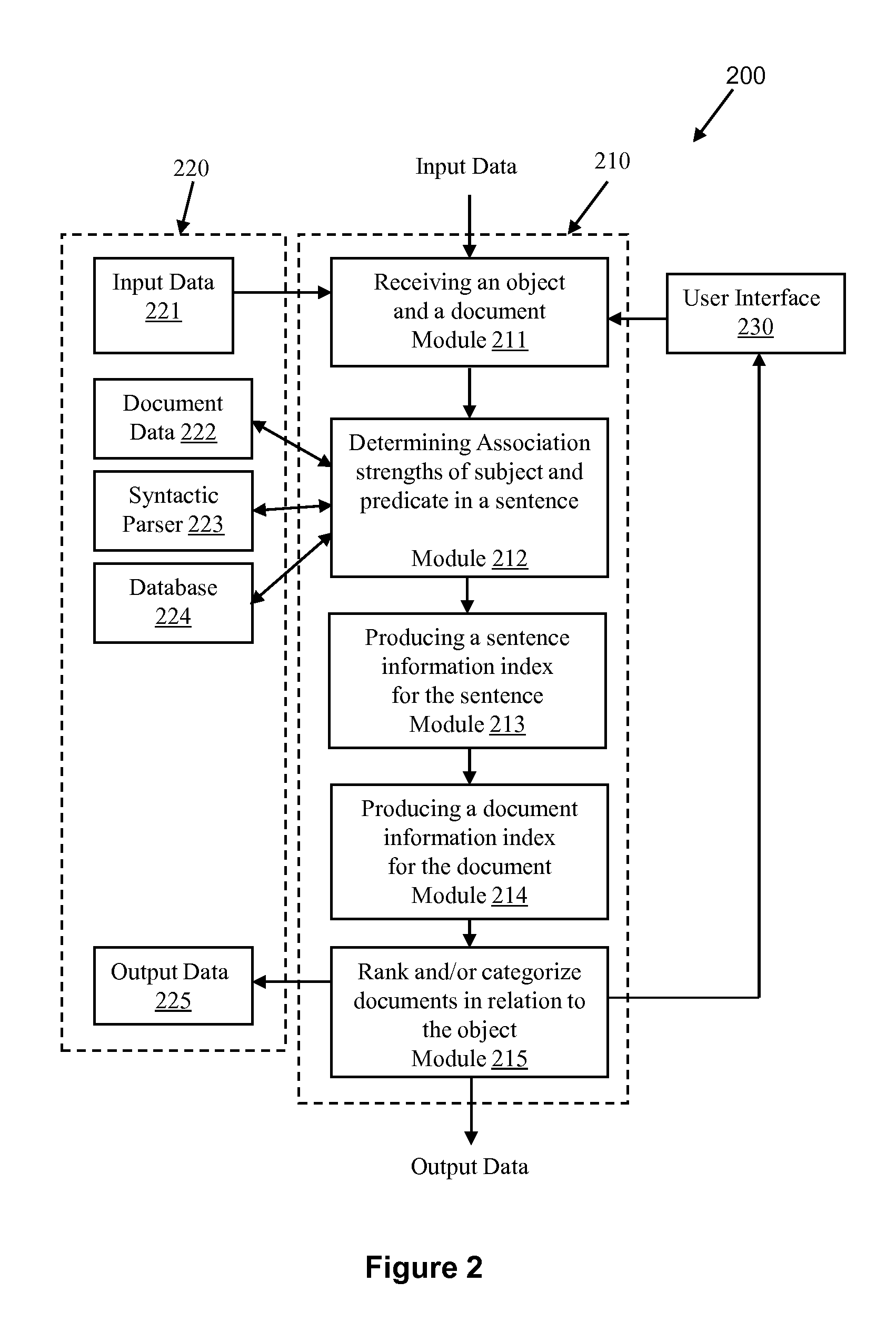
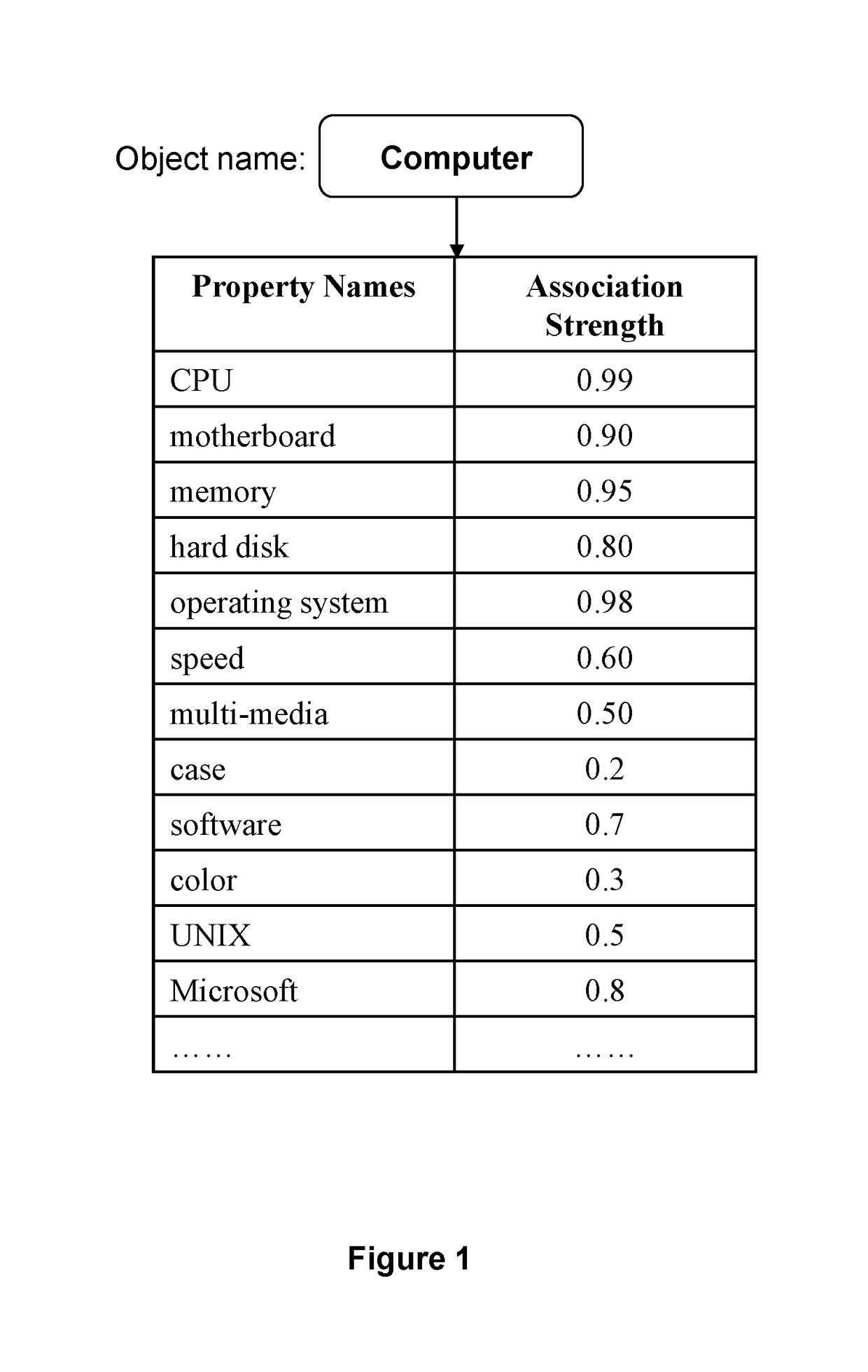
System and methods are disclosed for providing answers to search queries, and for searching using association data without requiring keyword matching. Datasets representing objects and their properties are created from unstructured data sources based on natural language analysis methods, and can be used to answer queries about objects or properties of objects. Implementations include general information search engines and embodiments for searching products, services, people, or other objects without knowing the names of such objects, or searching for information about known objects by using either keyword-based queries or natural language queries such as asking questions. System and methods are also provided for creating a structured or semi-structured representation of various unstructured data, in contrast to the conventional term-vector or term-document matrix representation.
Owner:LINFO IP LLC
System and method for managing facility content and equipment information
InactiveUS20110276886A1Low costEasy to integrateGeometric CADInput/output for user-computer interactionDatasourceData file
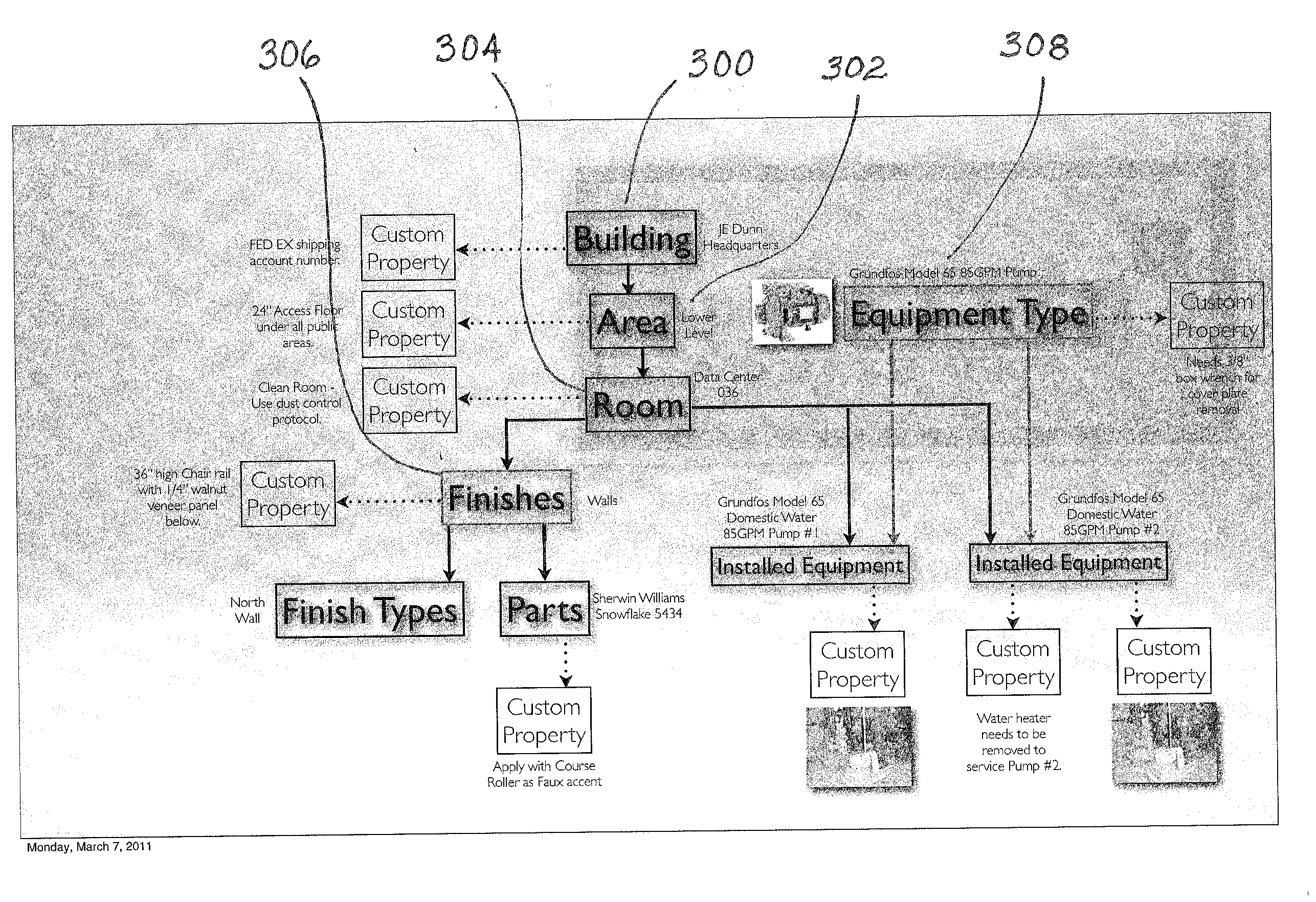
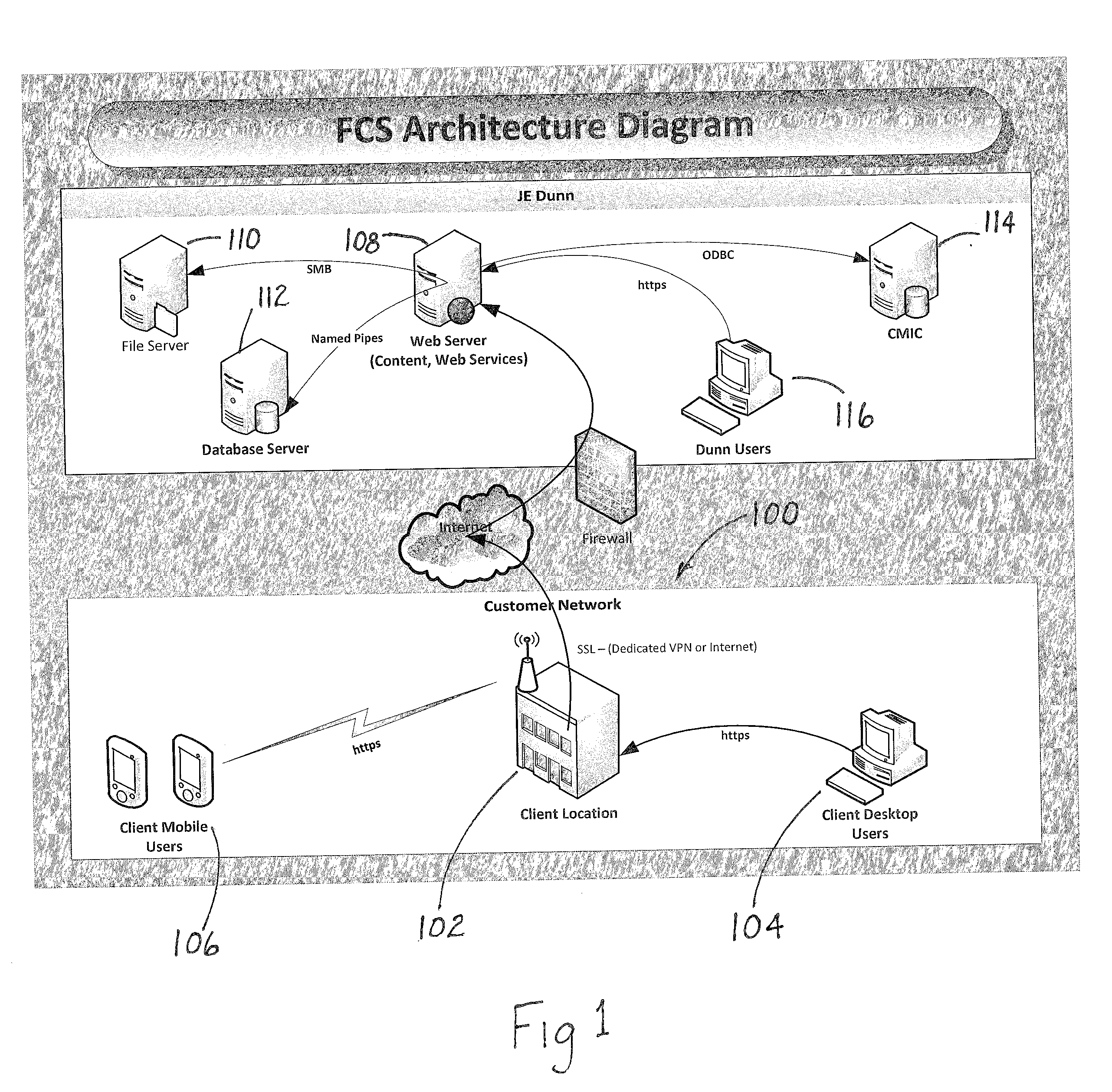
A system and method that provides a unique building maintenance tool which leverages the information collected during the design and construction phase of the building lifecycle. User access BIMs, Revit schedules and other data sources within the unique construction process to provide clients with a post occupancy view previously unobtainable. The solution provides for simple integration with external data sources through data file import or direct integration. The intent of the data integration model is to reduce costs of ongoing implementations providing a scalable model. Mobile access to information is a central component of customer appeal and will be a focal point of the design process. With the present invention mobile users can use mobile devices to scan 2 dimensional barcodes or QR Codes or other georeferencing technologies including RFIDs, thereby using the mobile device as the primary navigation portal to room and equipment information and images. The present invention provides building management functionality by leveraging extracted building data of a database constructed from construction process data as a basis for data organization, which includes detailed equipment specifications.
Owner:SITE 10 01 INC
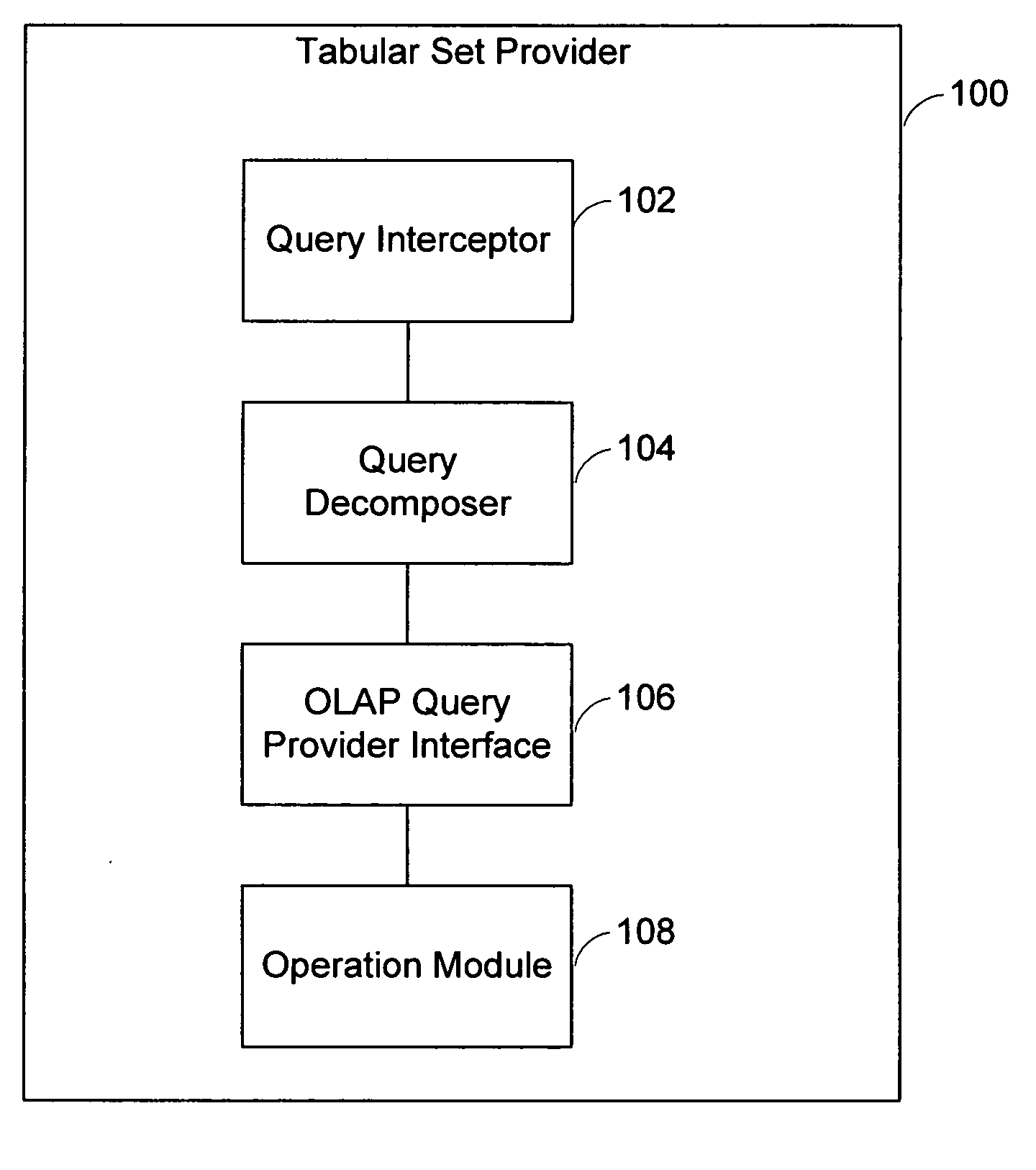
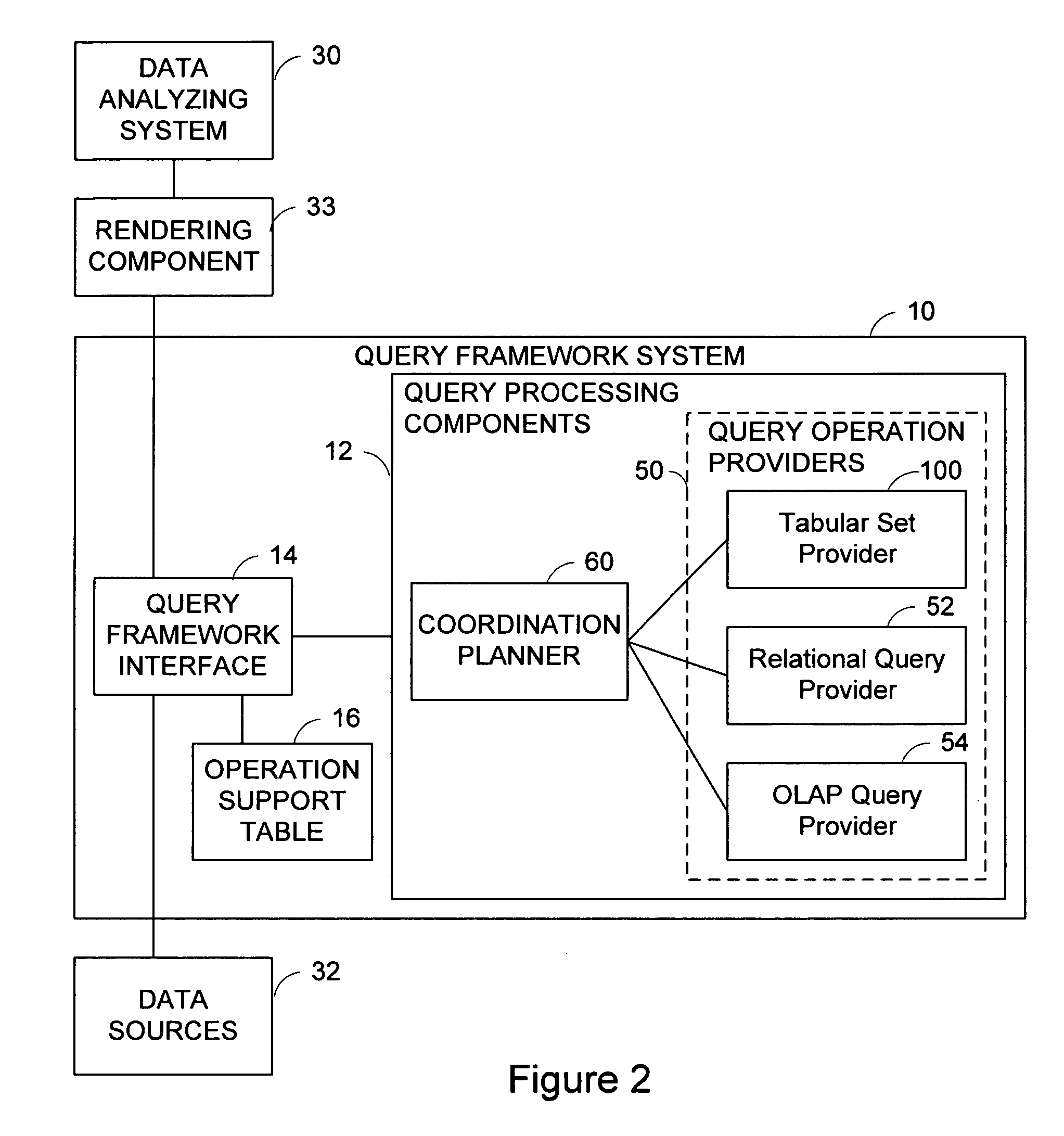
System and method for processing and decomposition of a multidimensional query against a relational data source
ActiveUS20060294087A1Multi-dimensional databasesSpecial data processing applicationsDatasourceData mining
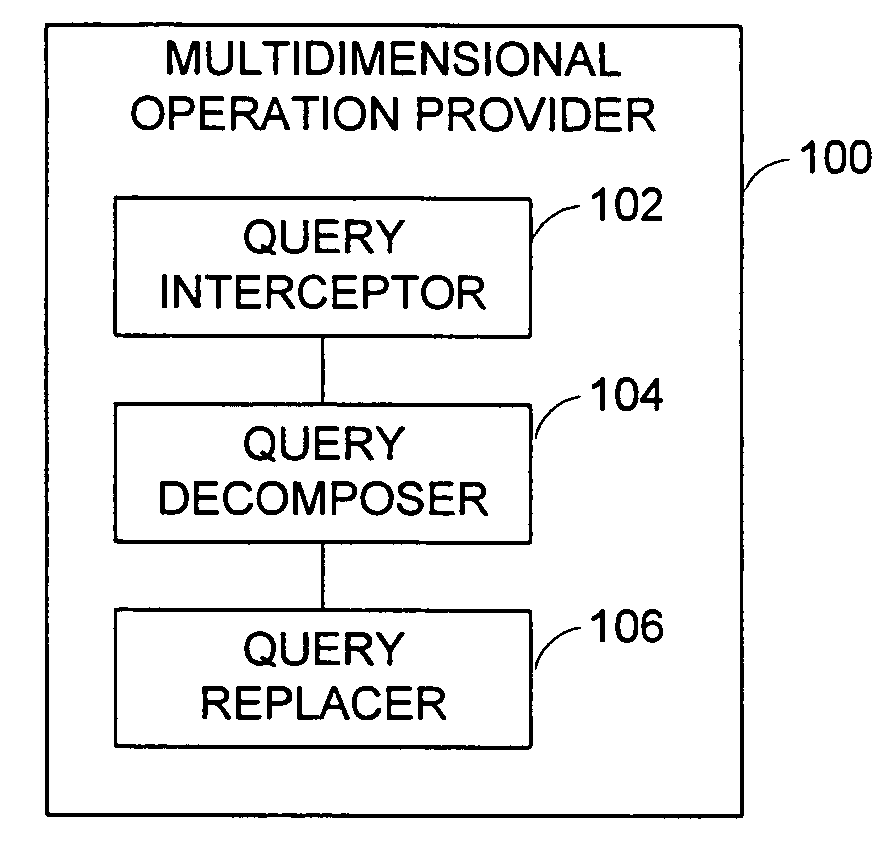
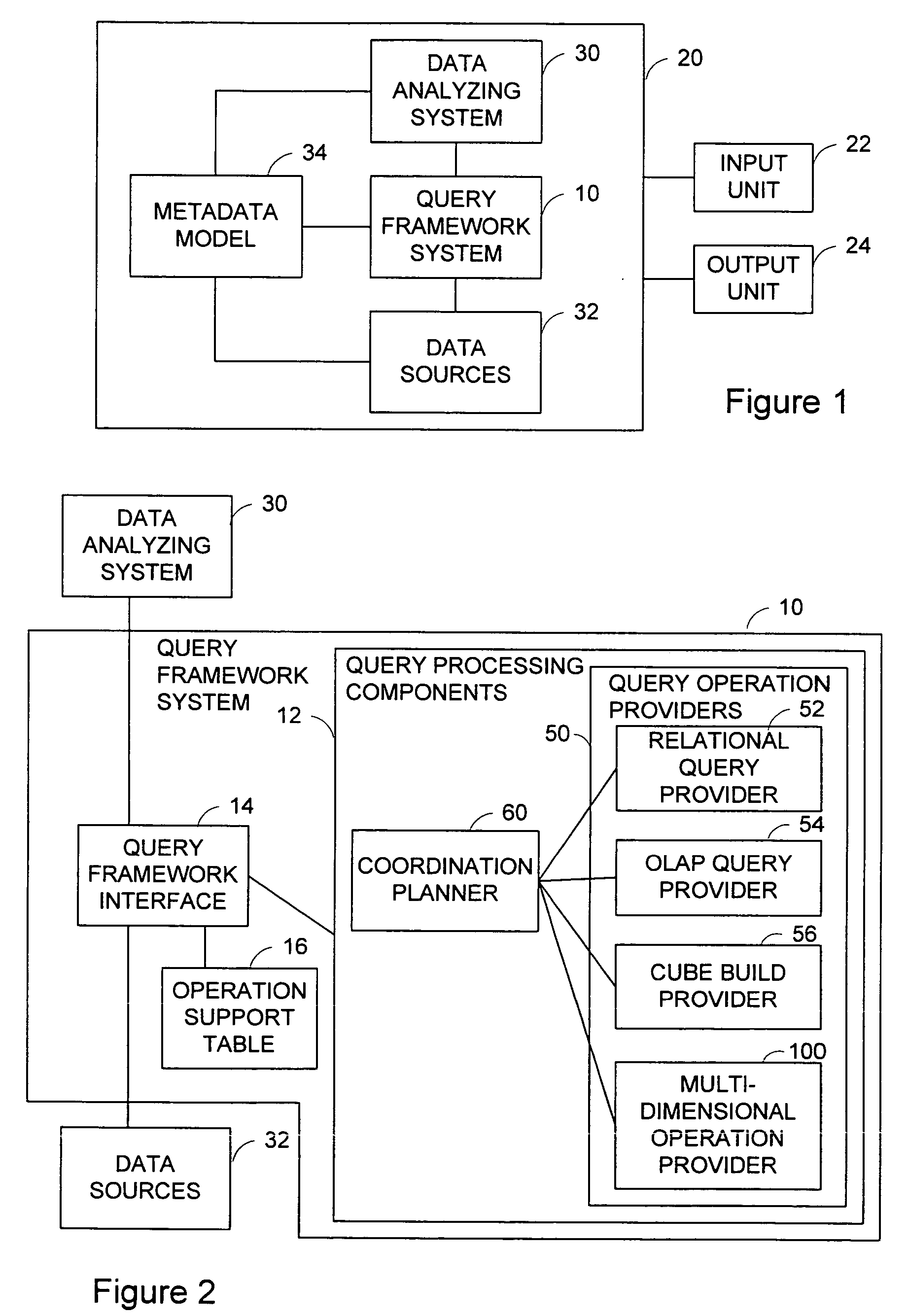
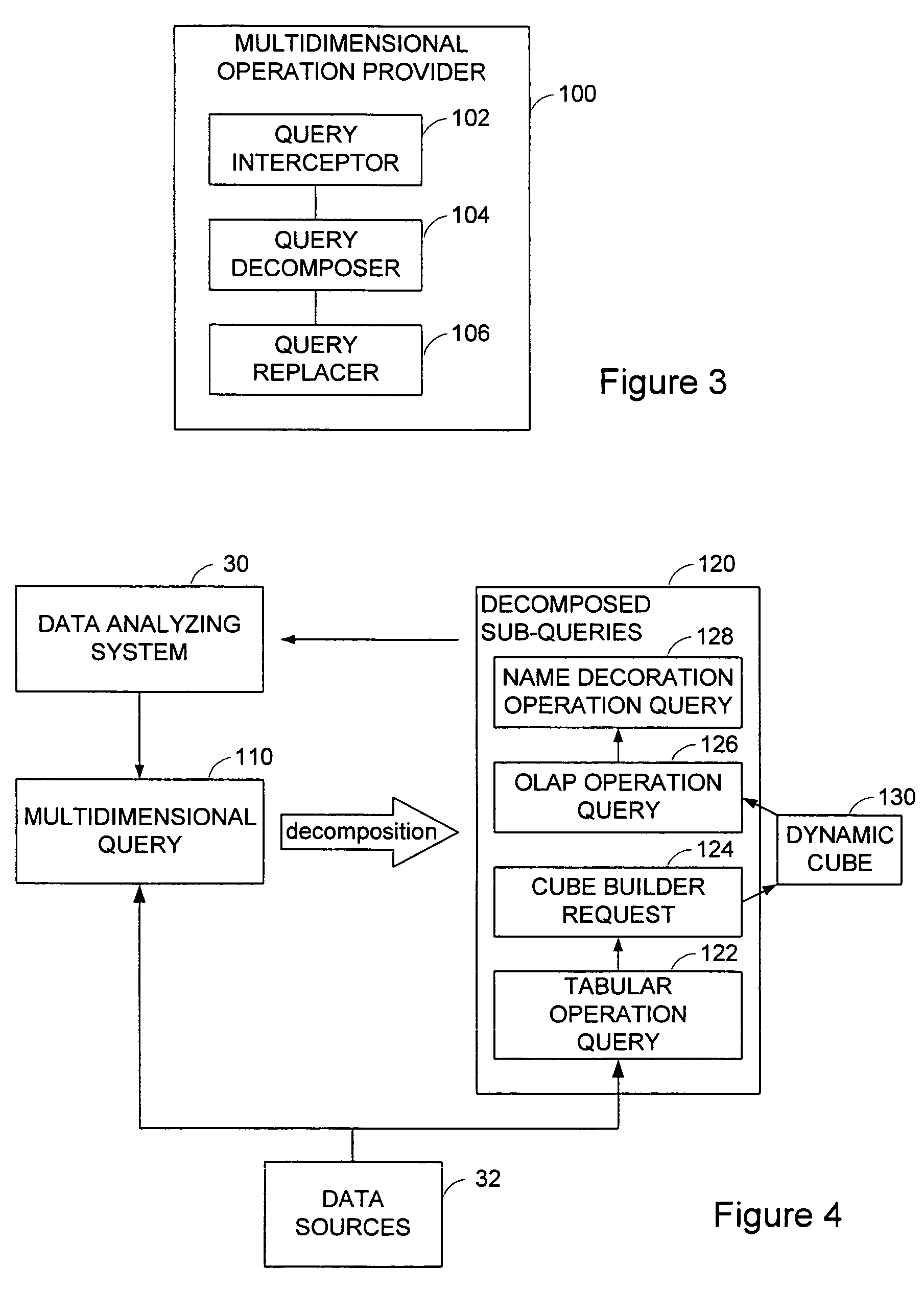
A multidimensional operation provider is provided for processing a multidimensional query against a relational datasource. The multidimensional operation provider comprises a query interceptor, a query decomposer and a query replacer. The query interceptor detects and intercepts a multidimensional query that is issued against one or more relational data sources. The query decomposer decomposes expressions of the multidimensional query into one multidimensional expression and / or one or more relational expressions. The query replacer replaces the multidimensional query with a stack of operations expressed by the decomposed multidimensional expressions and / or the relational expressions.
Owner:IBM CORP
Fast statistical query method for mass medical data
ActiveCN103049556AAvoid visitingRapid positioningSpecial data processing applicationsDistributed File SystemDatasource
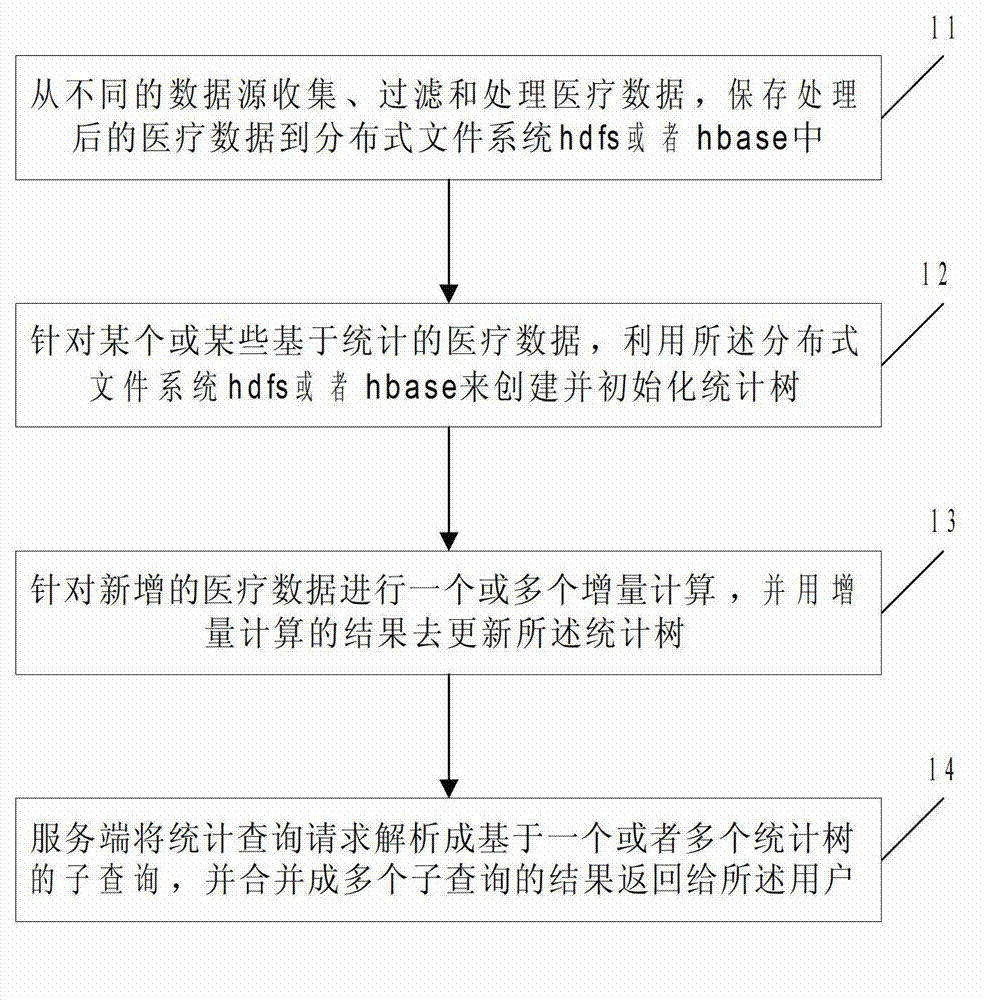
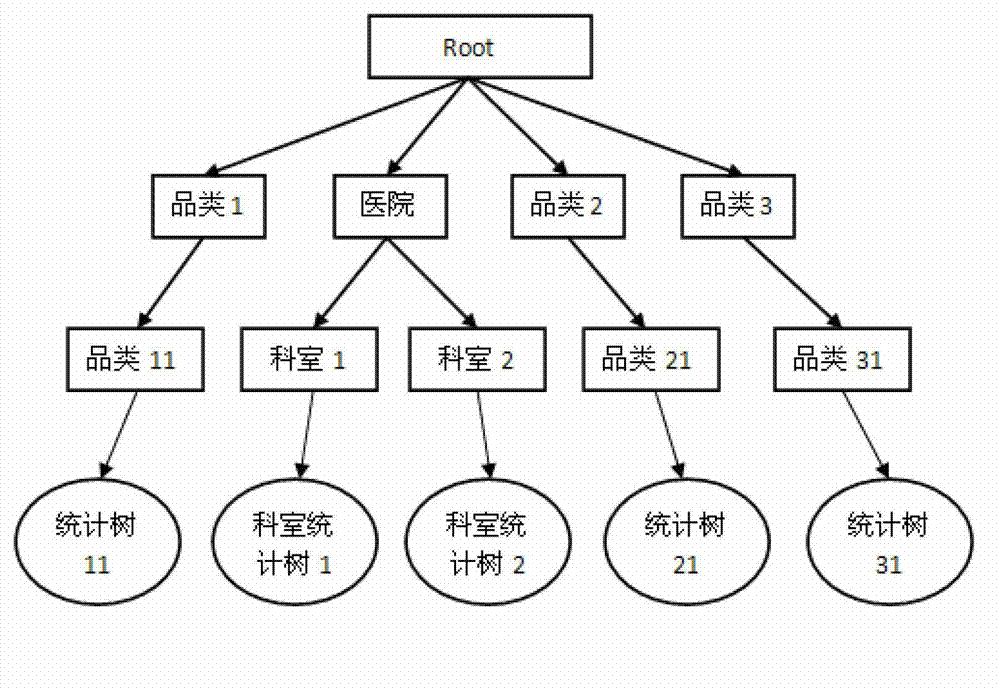
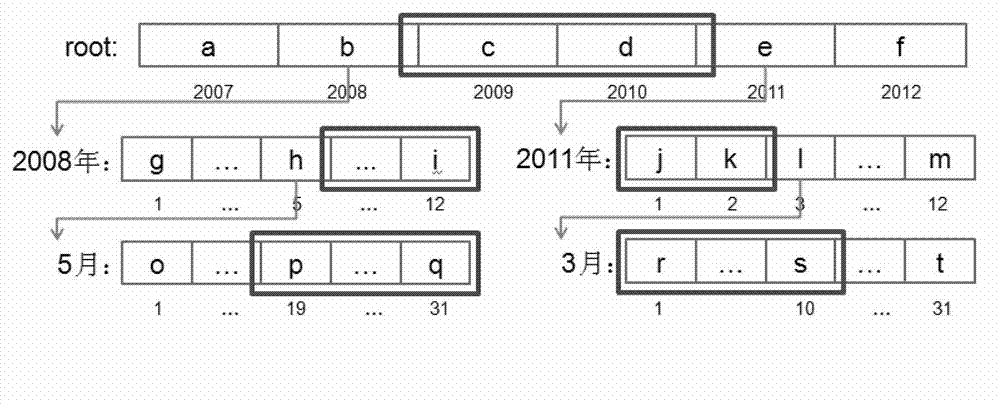
The invention discloses a fast statistical query method for mass medical data. The method includes: firstly, collecting, filtering and processing medical data from different data sources, and storing processed medical data into an HDFS (Hadoop distributed file system) or HBase; using the HDFS or HBase to create and initialize statistics trees for one or certain statistics-based medical data; subjecting the newly added medical data to single or multiple incremental computations, and updating the statistics tree by results of the incremental computations; allowing a server to respond to a statistical query request from a user according to the one or a plurality of created statistics trees, to analyze the statistical query request into sub-queries based on one or the plurality of statistics trees, and to combine into a plurality of sub-query results fed back to the user. The position of statistical data can be located quickly by the method, access to mass data is avoided, system load is lightened, and query efficiency and access concurrency are increased.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
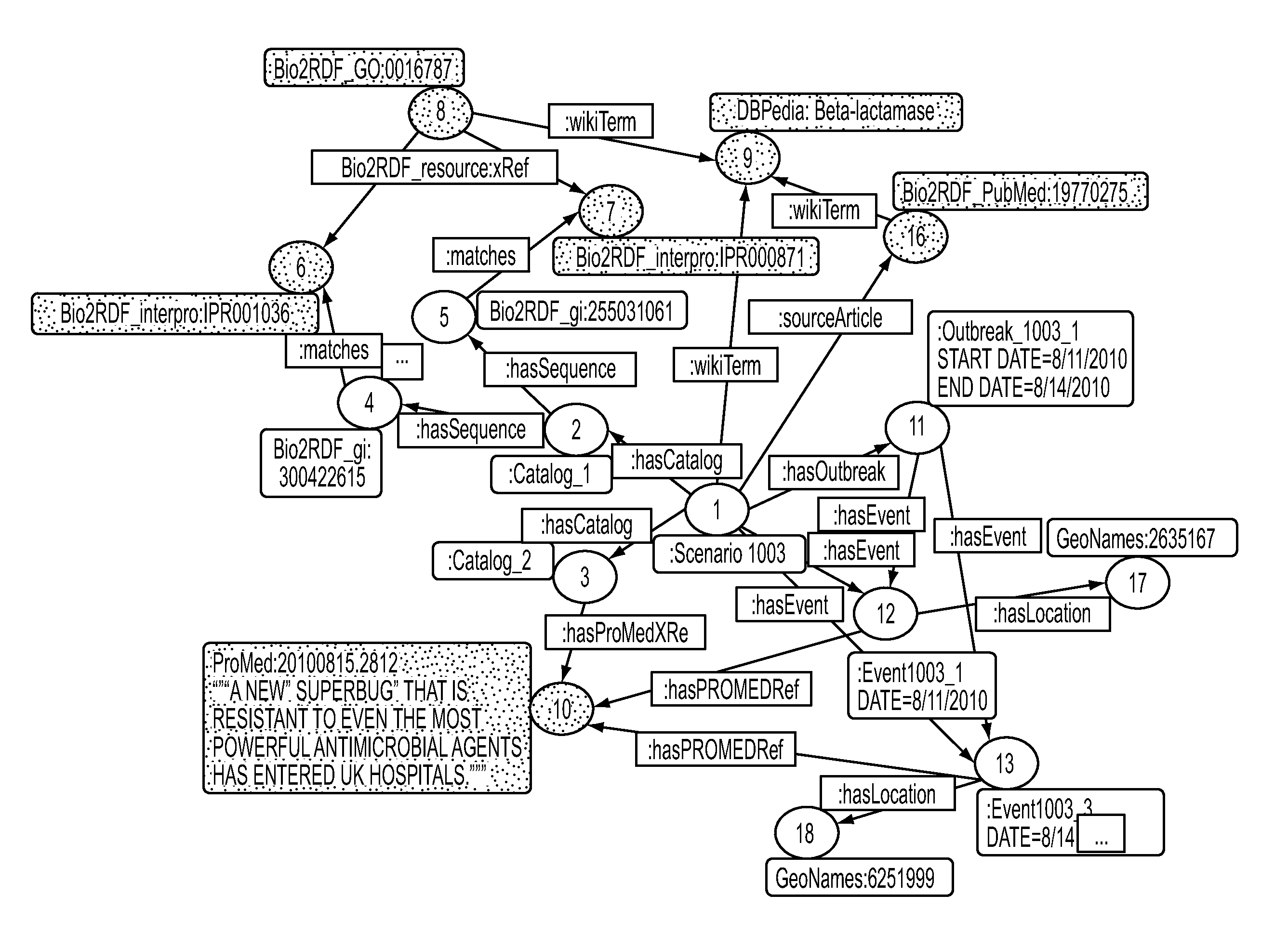
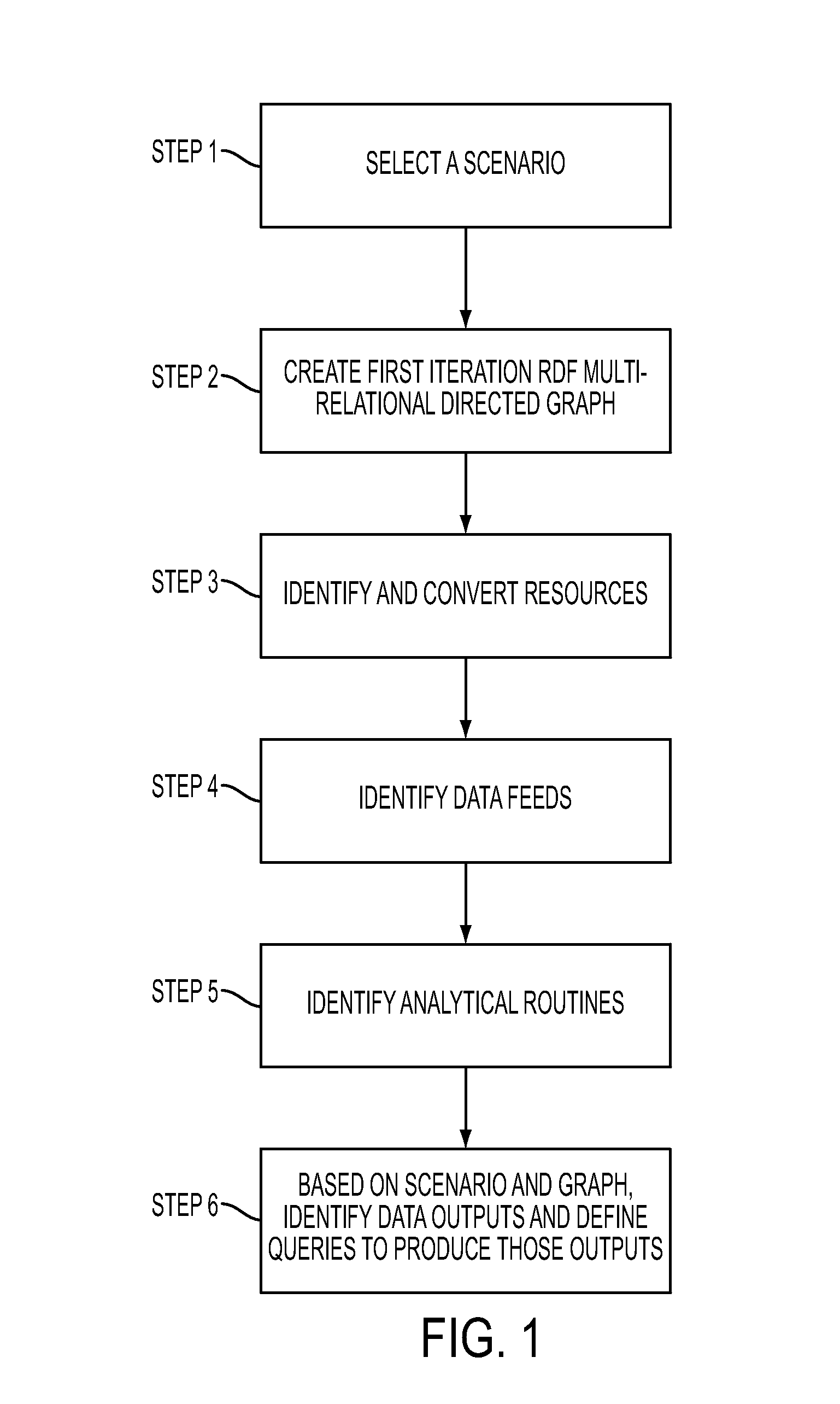
Scenario driven data modelling: a method for integrating diverse sources of data and data streams
ActiveUS20130124574A1Digital data information retrievalDigital data processing detailsData feedData stream
A system and method of integrating diverse sources of data and data streams is presented. The method can include selecting a scenario based on a topic, creating a multi-relational directed graph based on the scenario, identifying and converting resources in accordance with the scenario and updating the multi-directed graph based on the resources, identifying data feeds in accordance with the scenario and updating the multi-directed graph based on the data feeds, identifying analytical routines in accordance with the scenario and updating the multi-directed graph using the analytical routines and identifying data outputs in accordance with the scenario and defining queries to produce the data outputs from the multi-directed graph.
Owner:UT BATTELLE LLC
Methods for information extraction, search, and structured representation of text data
InactiveUS10146751B1Facilitate decision-makingDigital data information retrievalNatural language data processingJob descriptionUser-generated content
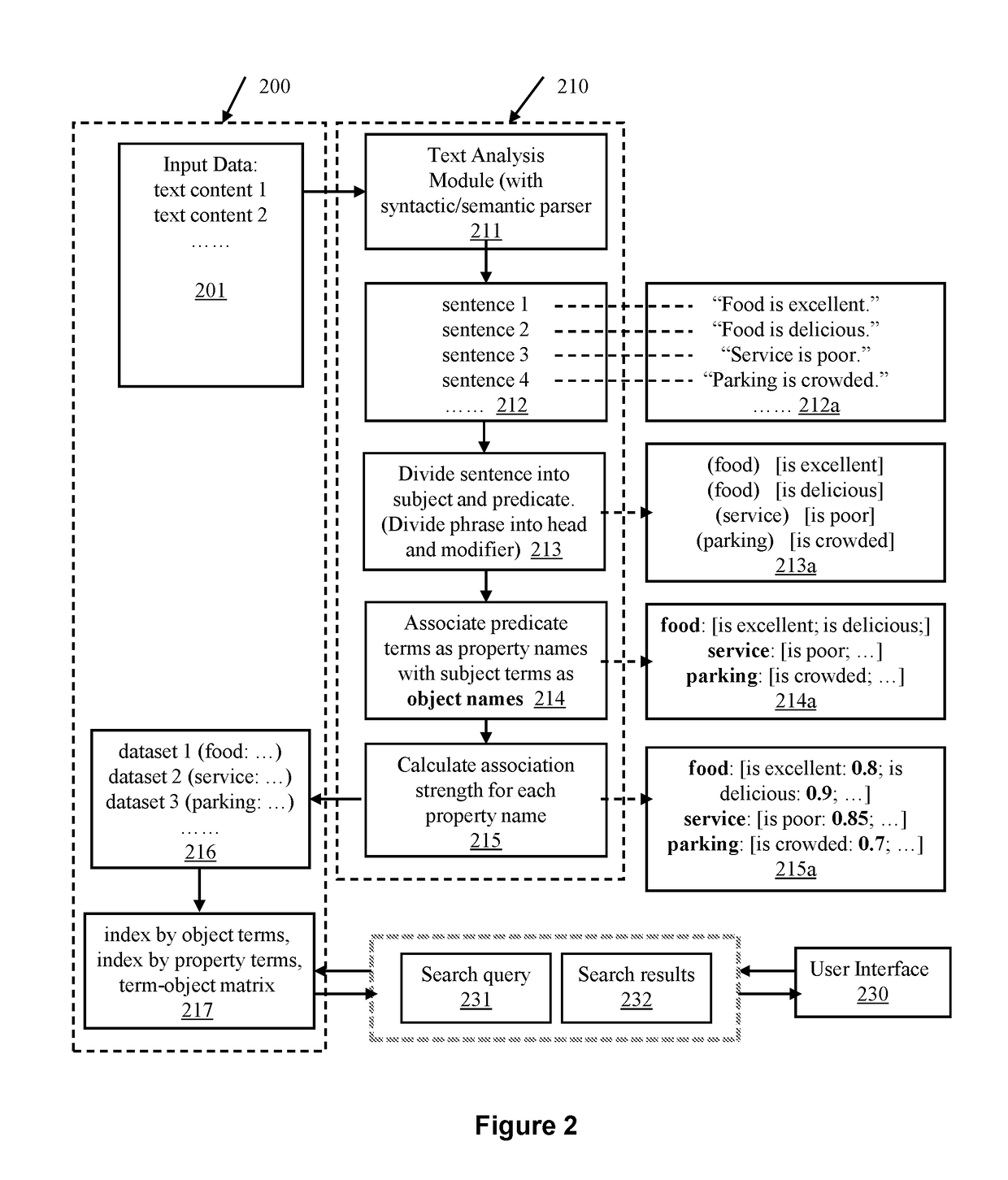
System and methods for creating structured or semi-structured representations of information extracted from unstructured text data sources are described. In some embodiments, without requiring a predefined target data structure, the methods identify the grammatical and semantic attributes and context information in a text content, and create object-properties association data as knowledge and information extracted from the unstructured data, and represent such information in a structured or semi-structured format to facilitate search and trend analysis. In some other embodiments, the methods identify the types of information contained in the unstructured data, and for a pre-defined target information type, the methods identify the context and content of the portion of the text that represents the target information type, and extract the text, attach a tag or label to the extracted text, and store or display the data in a database table format or xml format for further pattern and trend analysis. Applications of the present system and methods include effectively analyzing user-generated contents such as customer feedback, reviews, comments, technical support forum messages, resume or job description documents, and other types of text contents.
Owner:LINFO IP LLC
Method and system for accessing anonymized data
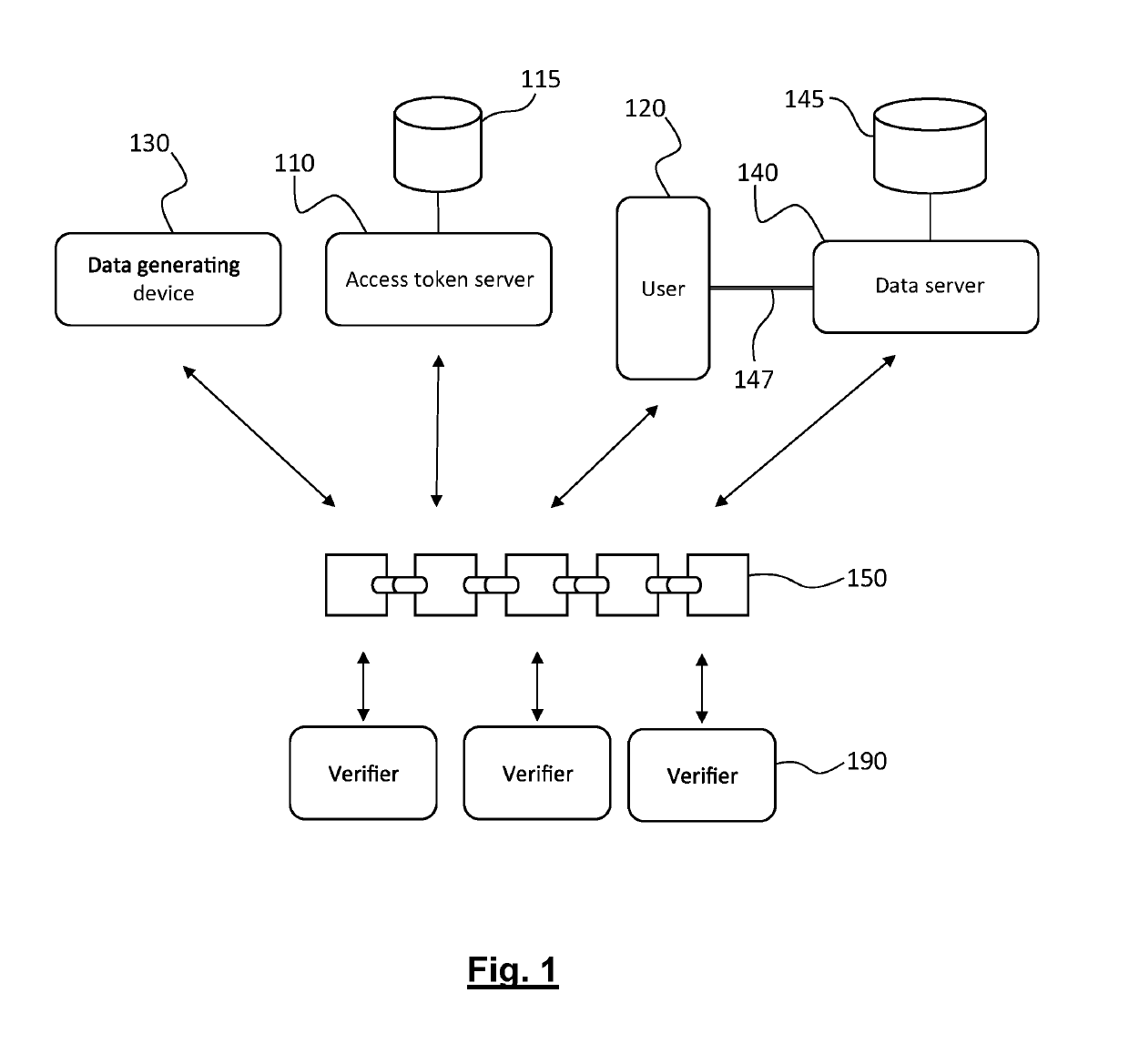
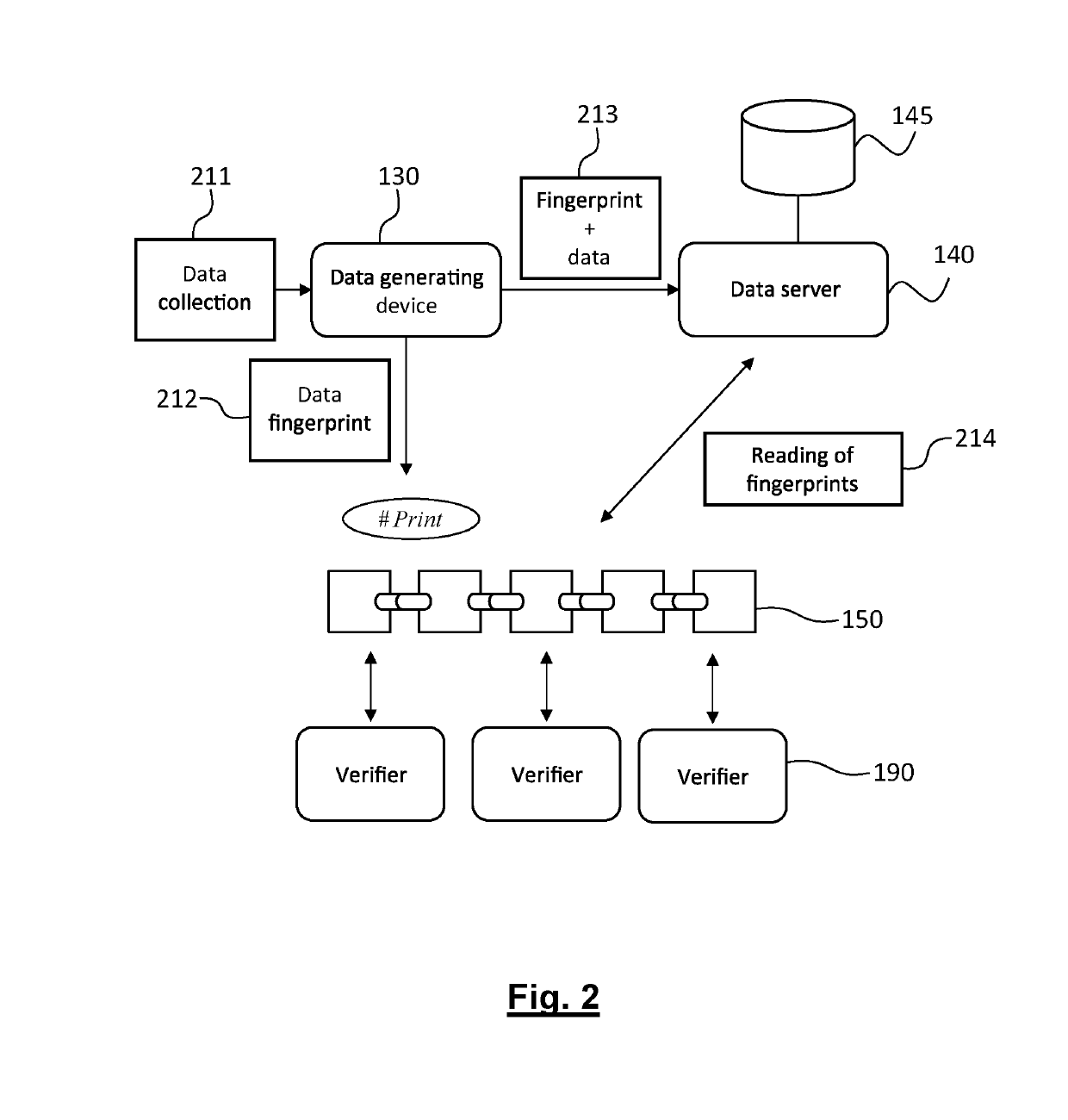
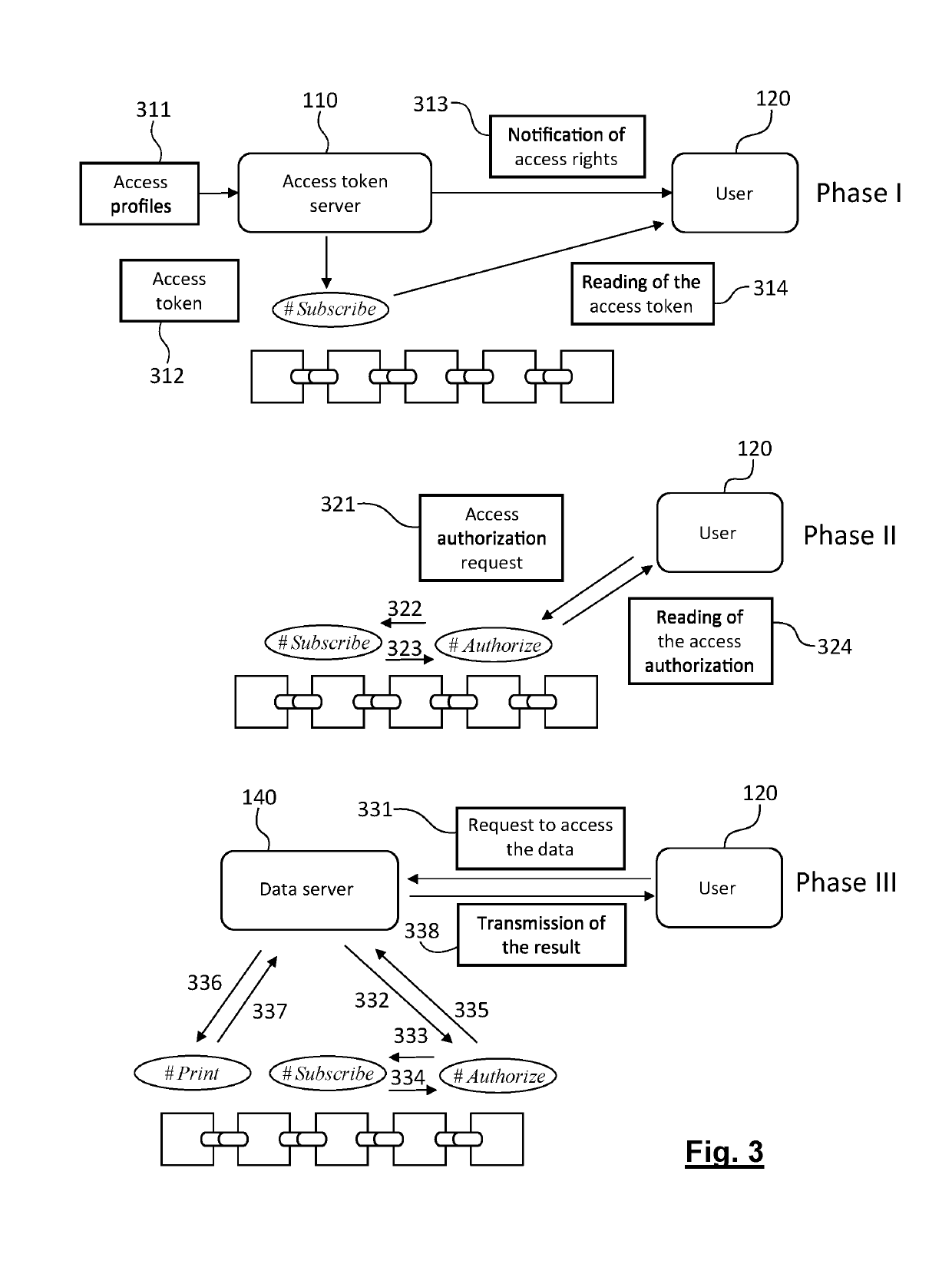
ActiveUS20190294822A1Database updatingEncryption apparatus with shift registers/memoriesDatasourceDatabase
A method for anonymized storage of personal data and a method for managing access to the data. The anonymization of data is achieved by making independent, thanks to the use of a blockchain, the identifiers of the data sources and the users on the one hand, and the personal data on the other hand. The personal data are stored at addresses indexed by their hashed values in a first database and the identifiers are stored with their corresponding access profiles in a second database. The link between these two independent databases is ensured by cryptographic elements recorded in the ledger of the blockchain
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
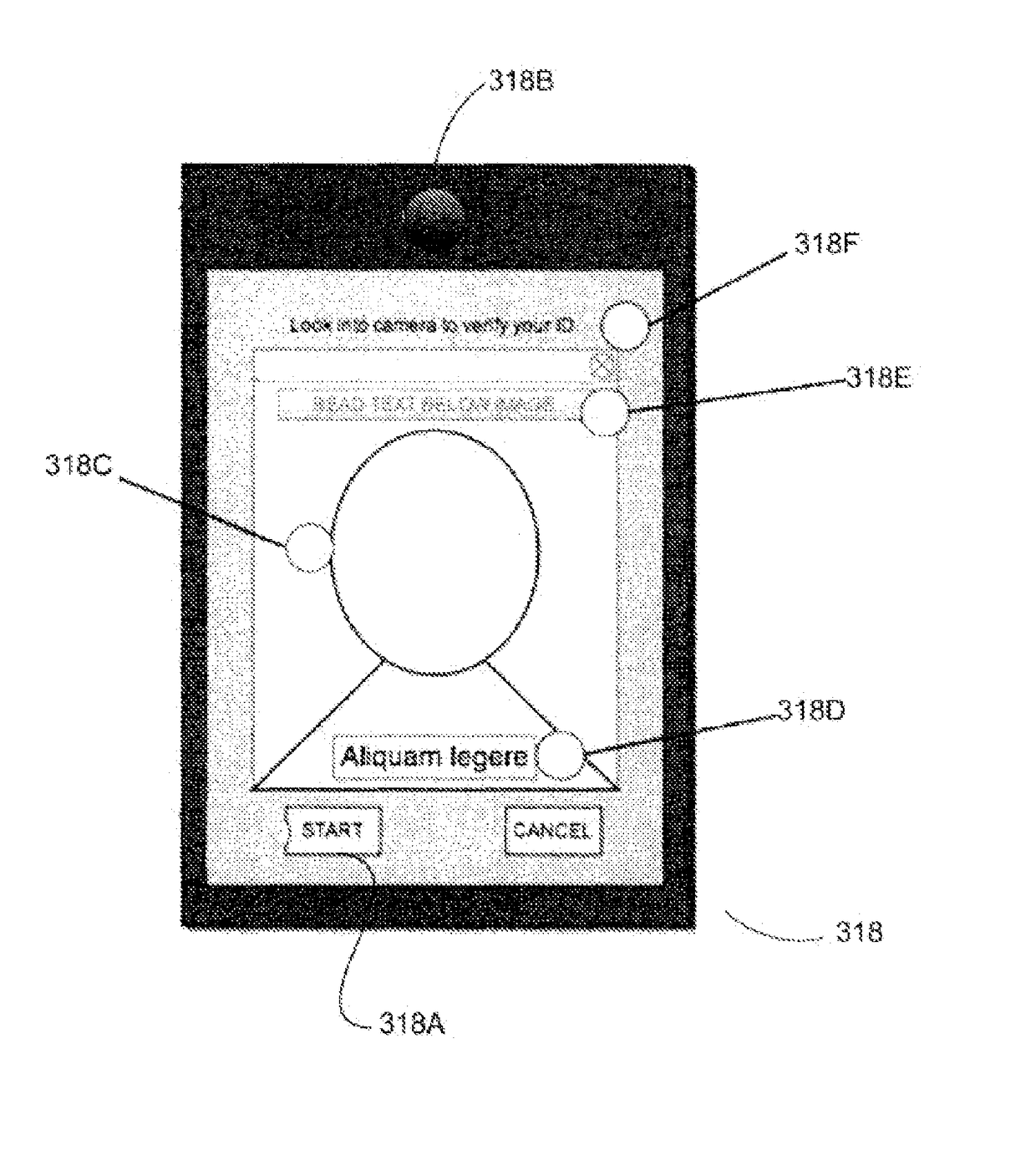
Analyzing facial recognition data and social network data for user authentication
Tools, strategies, and techniques are provided for evaluating the identities of different entities to protect business enterprises, consumers, and other entities from fraud by combining biometric activity data with facial recognition data for end users. Risks associated with various entities can be analyzed and assessed based on a combination of user liveliness check data, facial image data, social network data, and / or professional network data, among other data sources. In various embodiments, the risk assessment may include calculating an authorization score or authenticity score based on different portions or combinations of the collected and processed data.
Owner:SOCURE
Techniques for implementing information services with tentant specific service level agreements
InactiveUS20140101299A1Specific access rightsDigital computer detailsService-level agreementDatasource
A technique for selecting an information service implementation includes receiving a service request that includes a tenant identifier that uniquely identifies a calling tenant. Transformation logic to service the service request is selected based on the received tenant identifier. One or more data sources and one or more data targets are selected for the service request based on the received tenant identifier. Data from the selected data sources is processed using the selected transformation logic and the processed data is stored at the selected data targets.
Owner:IBM CORP
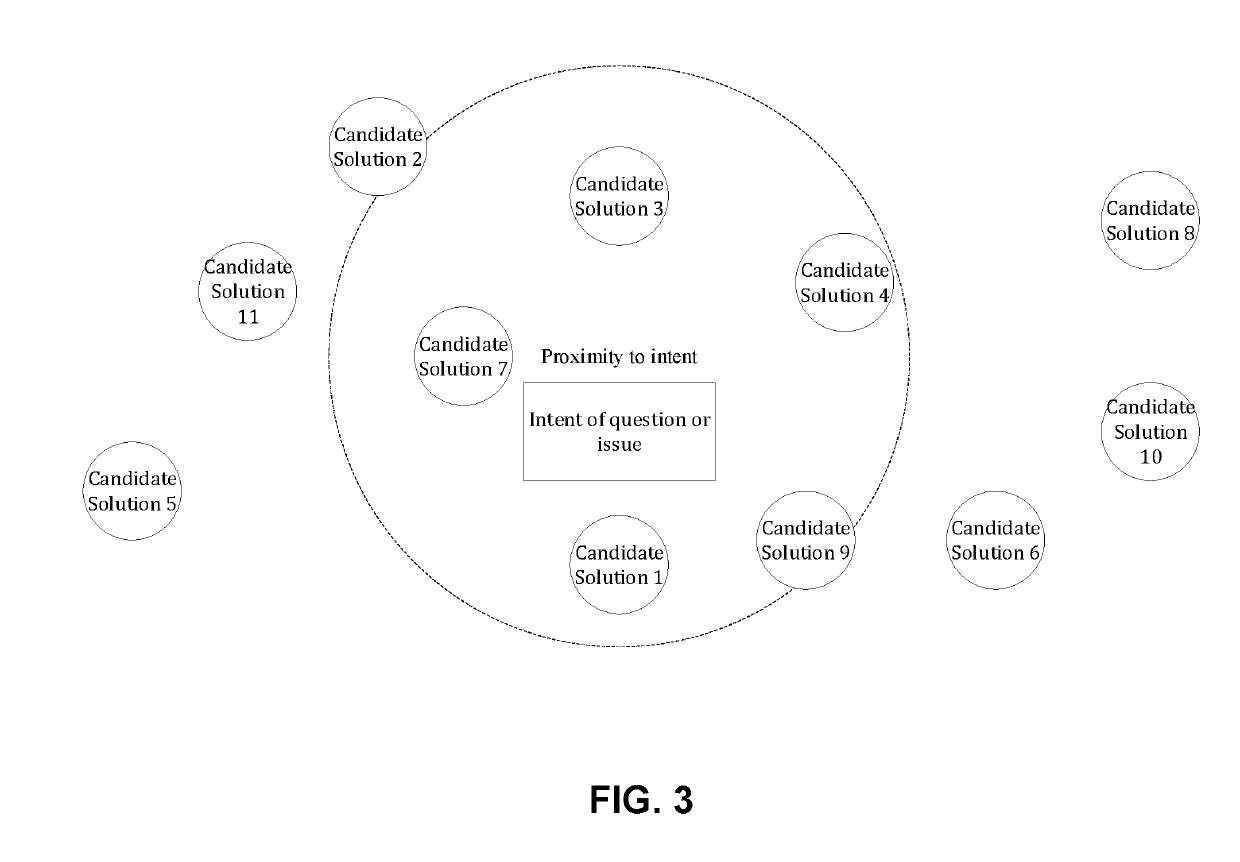
Intent Based Dynamic Generation of Personalized Content from Dynamic Sources
InactiveUS20190163691A1Promote resultsSave effortNatural language translationSpeech recognitionPersonalizationNatural language understanding
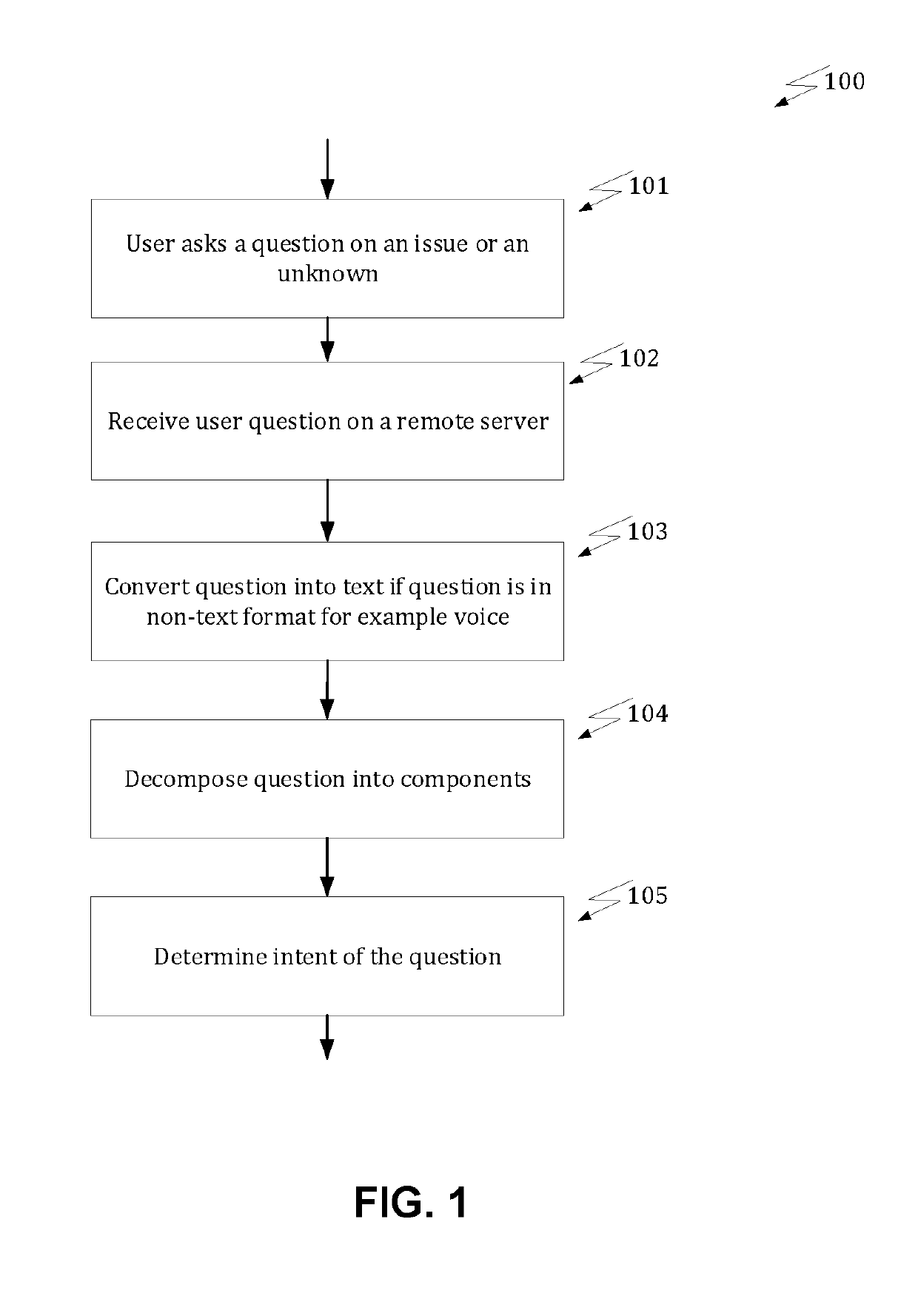
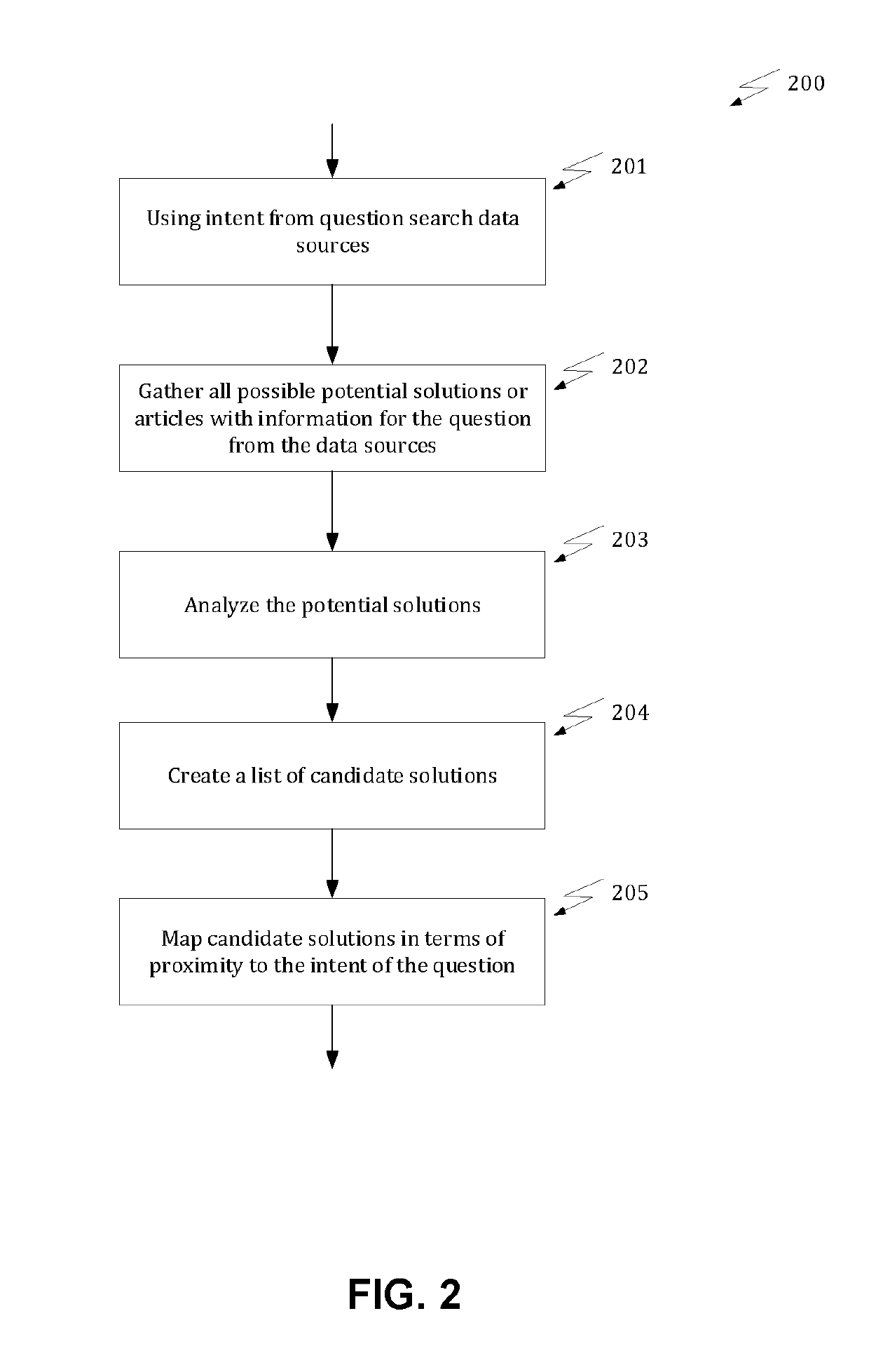
A method is provided for generating automated responses to customer questions. Terms of a customer question are received, which are then decomposed into components of the question. An intent is determined from at least one of the components. A query is formulated with the intent. The query is searched in a plurality of data sources to obtain raw search results. These raw search results are compared, and those results proximate to the intent are selected. After redundant and non-informative results are removed, these proximate search results are stored in a cache. The cache is further analyzed / processed to eliminate redundant parts. At least one of natural language understanding (NLU), natural language generation (NLG) or generative neural nets (GNN) is applied to the remaining text in the cache to generate a natural language answer to the customer question.
Owner:CROWDCARE
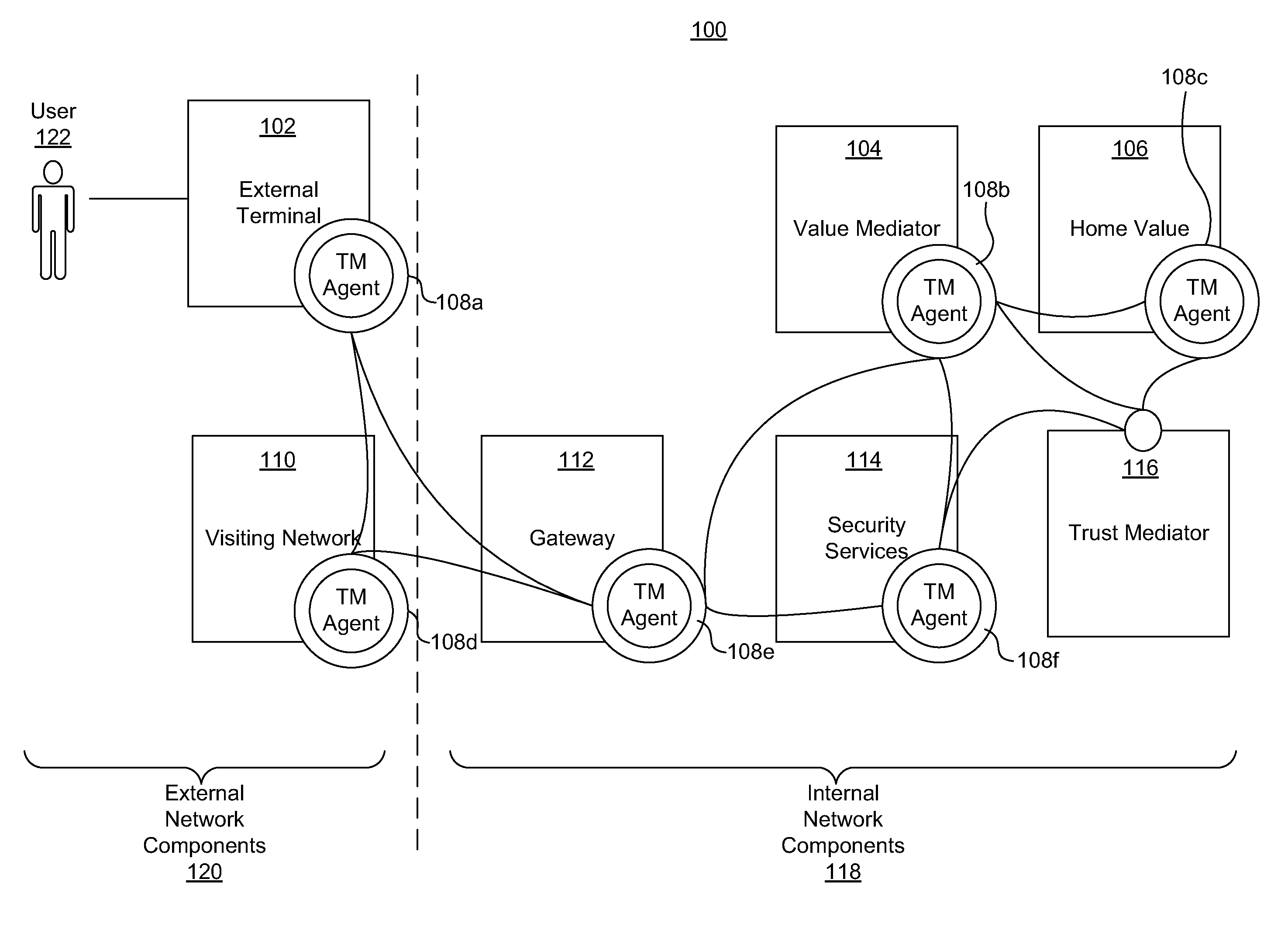
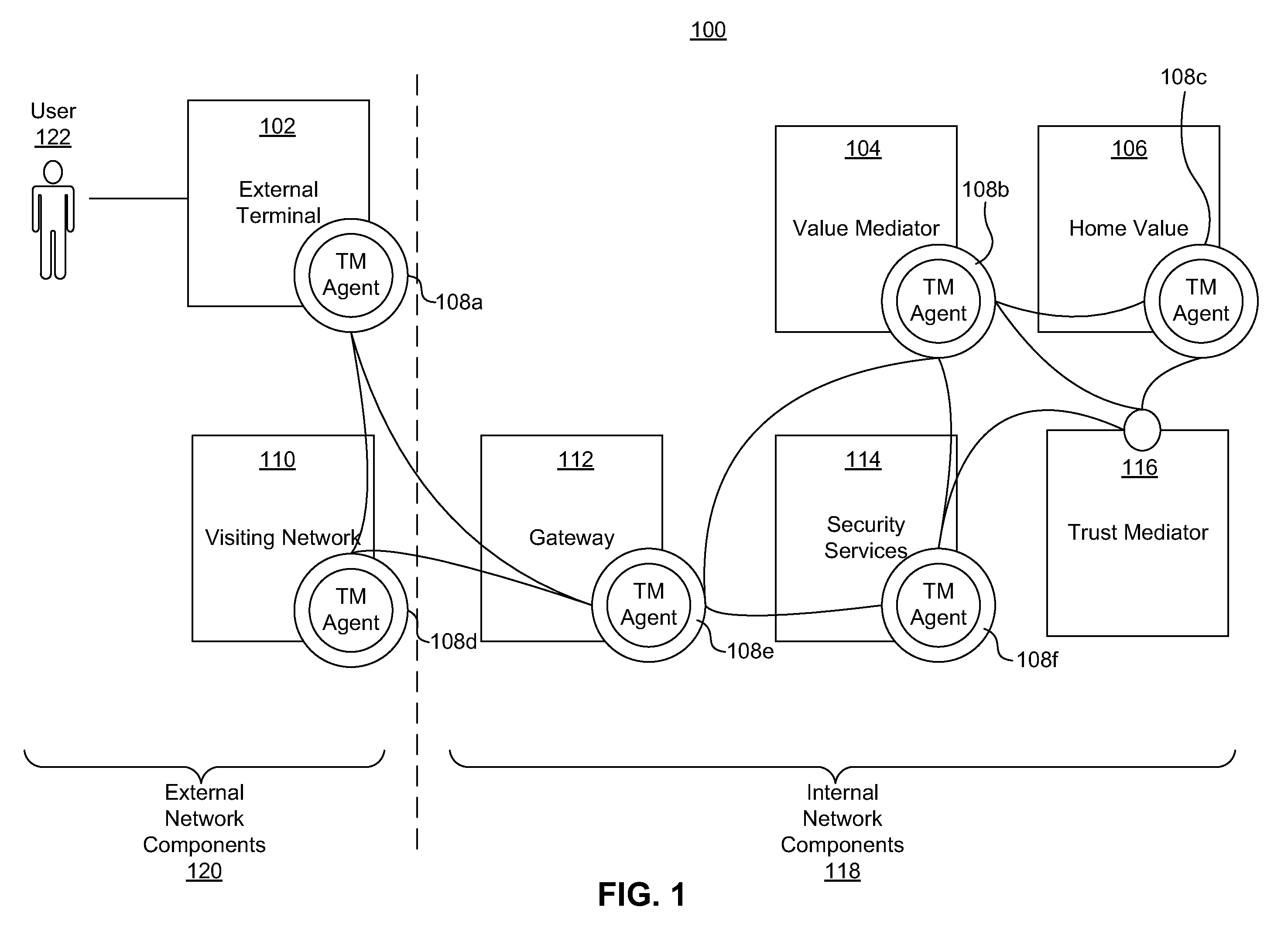
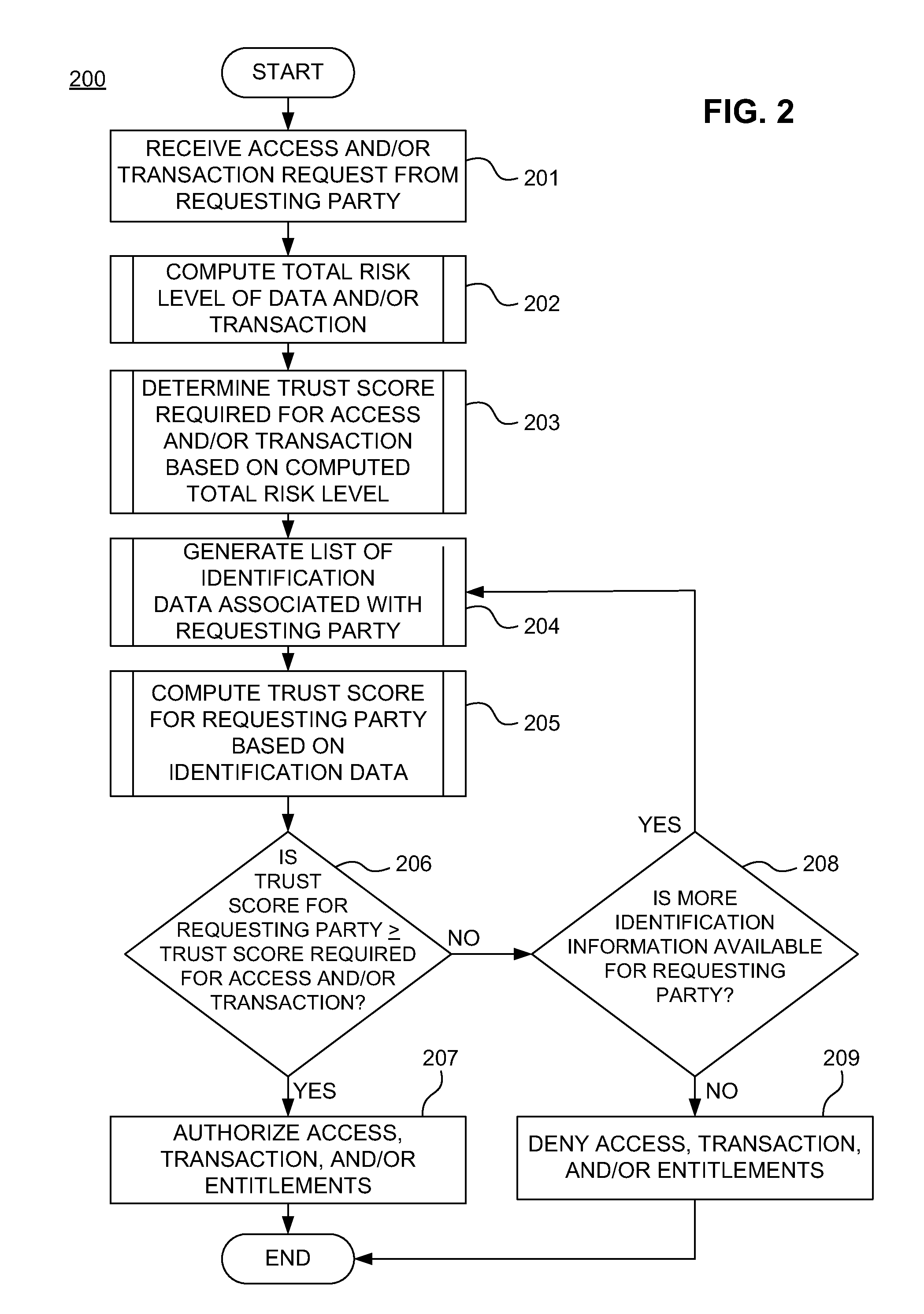
Dynamic pairing system for securing a trusted communication channel
ActiveUS20110313925A1Shorten the time to marketIncrease propensityFinancePayment architectureTotal riskInternet privacy
A system for securing a trusted communications channel for a mobile financial transaction is provided by receiving, from a user via an external terminal, a request for an access control entitlement to complete a financial transaction. A total risk level associated with the financial transaction is computed. A required trust score is determined based on the total risk level. User identification data associated with the user is received from one or more data sources. The user identification data is validated. A user trust score associated with the user is computed based on the validated identification data. The user trust score is compared to the required trust score. The access control entitlement is transmitted to the user via the external terminal if the user trust score is greater than or equal to the required trust score.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
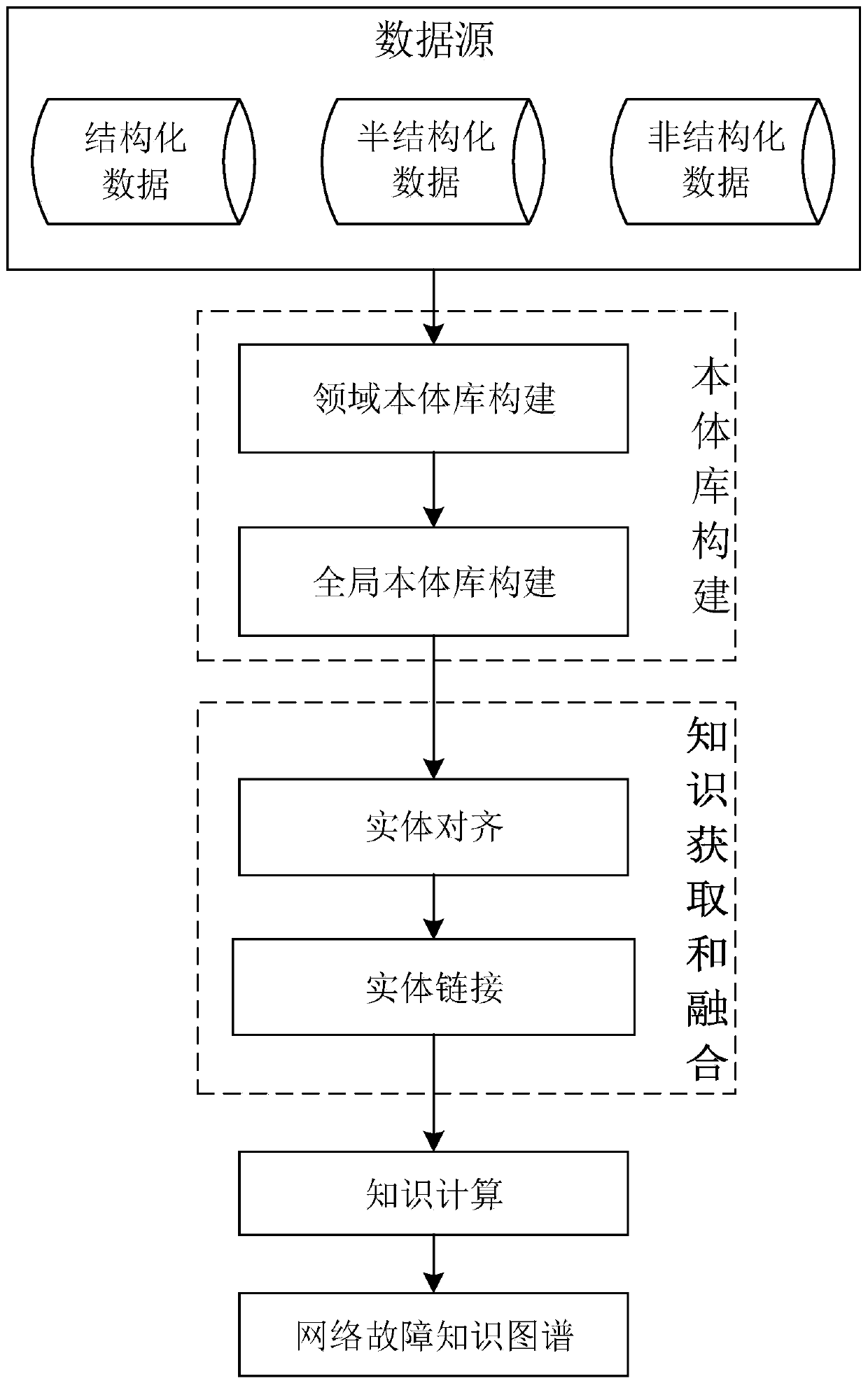
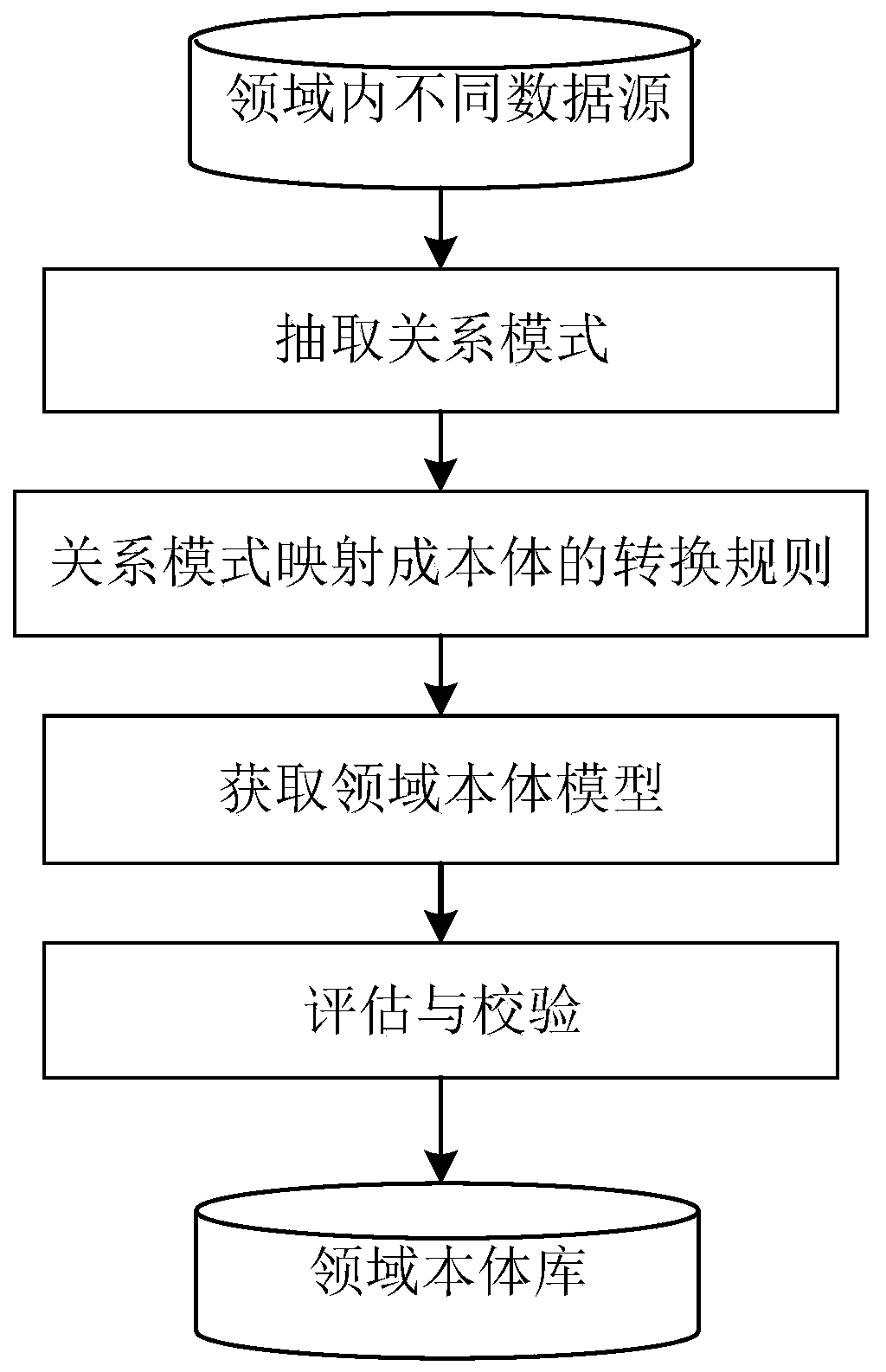
Construction method of knowledge graph library for network fault analysis and application thereof
The invention discloses a construction method of a knowledge graph library for network fault analysis and application thereof, and relates to the technical field of network communication. The method comprises: using an intelligent method to carry out data acquisition on communication network data; constructing ontology libraries in different fields, constructing a global ontology library by adopting a data fusion and mapping technology according to the ontology libraries in different fields, and finally constructing a knowledge map library with consistent semantic relationships of various datasources through entity alignment, entity linking and knowledge calculation in sequence. The constructed knowledge graph library is used for retrieving possible reasons for causing the network fault,suggestions of a fault solution are provided for a user, rapid positioning and solution of the network fault are facilitated, the fault processing efficiency is improved, and meanwhile the influence of human factors is reduced.
Owner:WUHAN FIBERHOME TECHNICAL SERVICES CO LTD
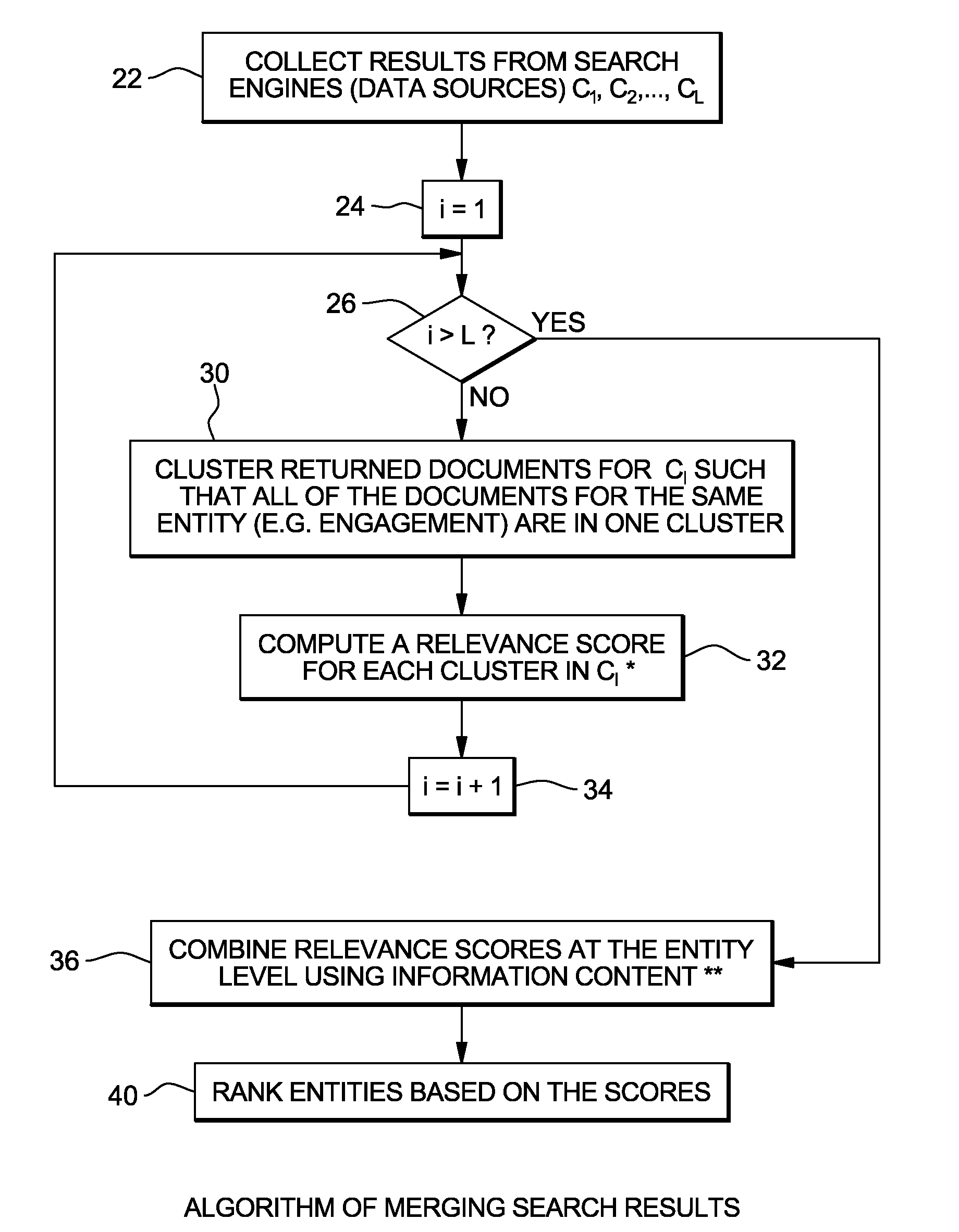
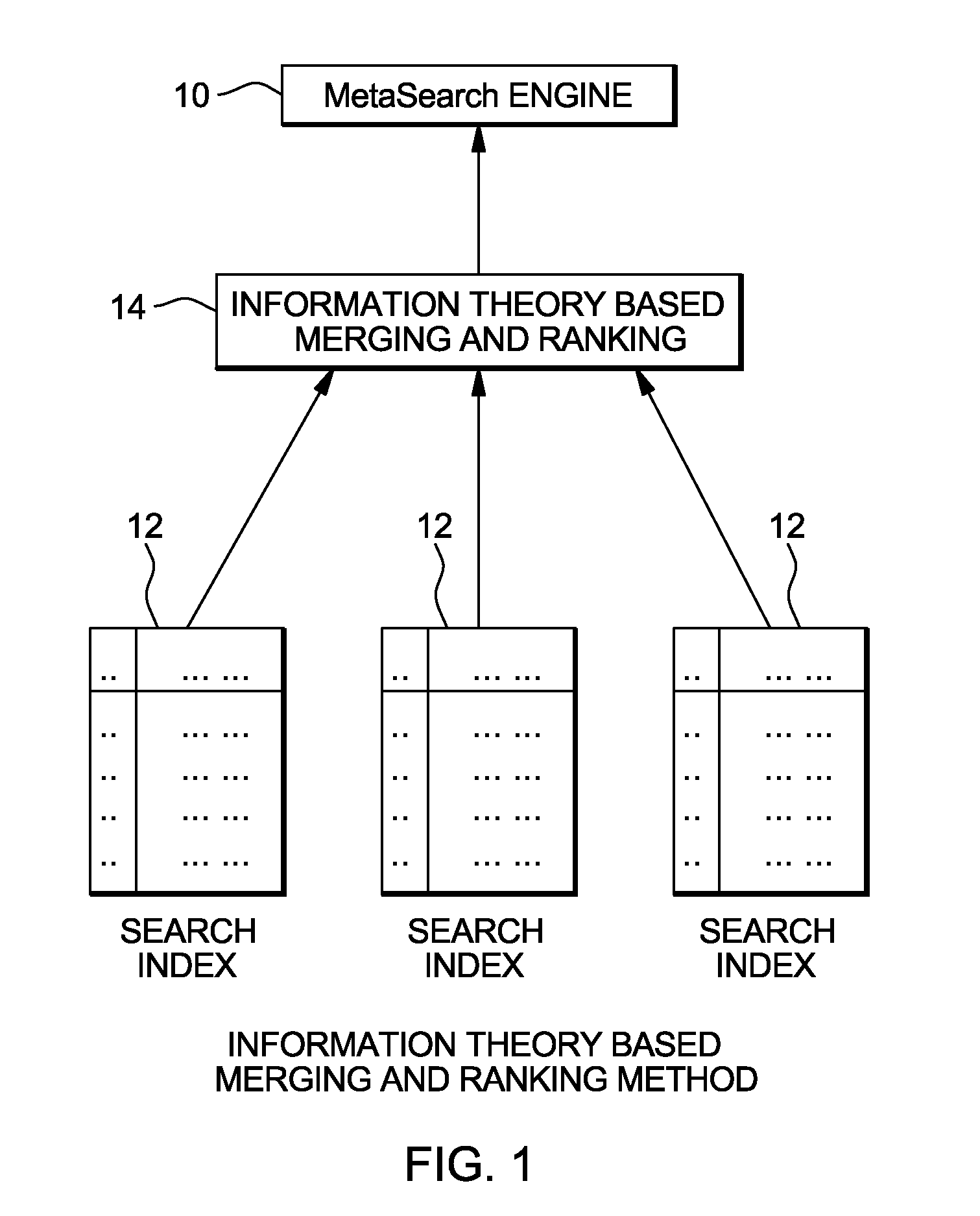
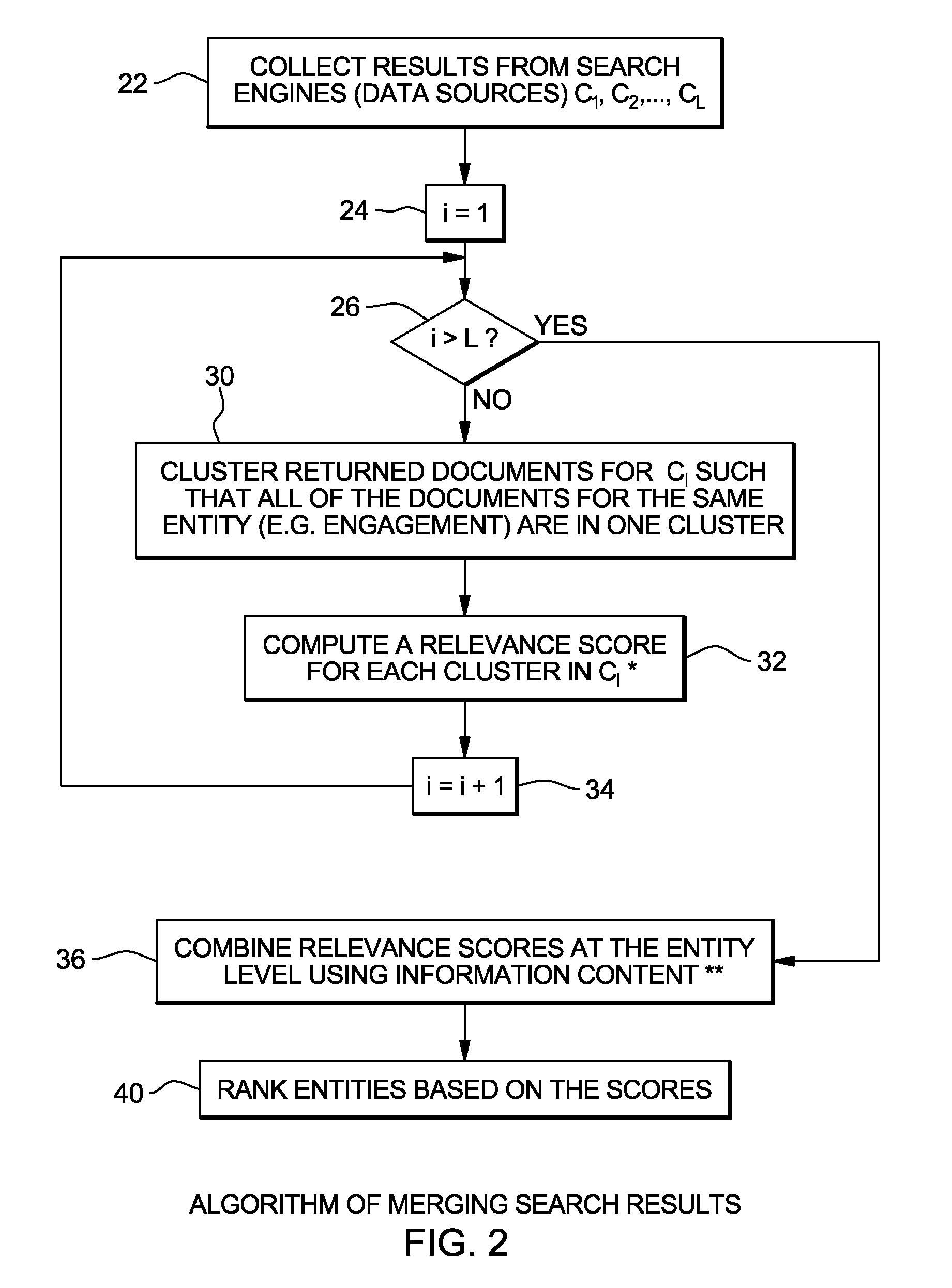
Information theory based result merging for searching hierarchical entities across heterogeneous data sources
A method, system, and computer program product are disclosed for merging search results. In one embodiment, the method comprises identifying a query, splitting the query into sub-queries, and calculating information content for each of the sub-queries. This method also comprises executing each of the sub-queries to obtain a plurality of search results, and combining the search results based on the information content calculated for the sub-queries. In an embodiment, the execution of each of the sub-queries includes identifying a multitude of search results for at least one of the sub-queries; and the combining includes grouping said multitude of search results into a plurality of clusters, and computing a relevance score for each of said clusters. In the embodiment the combining further includes merging the clusters based on the relevance scores computed for the clusters as well as the information content calculated for the sub-queries.
Owner:IBM CORP
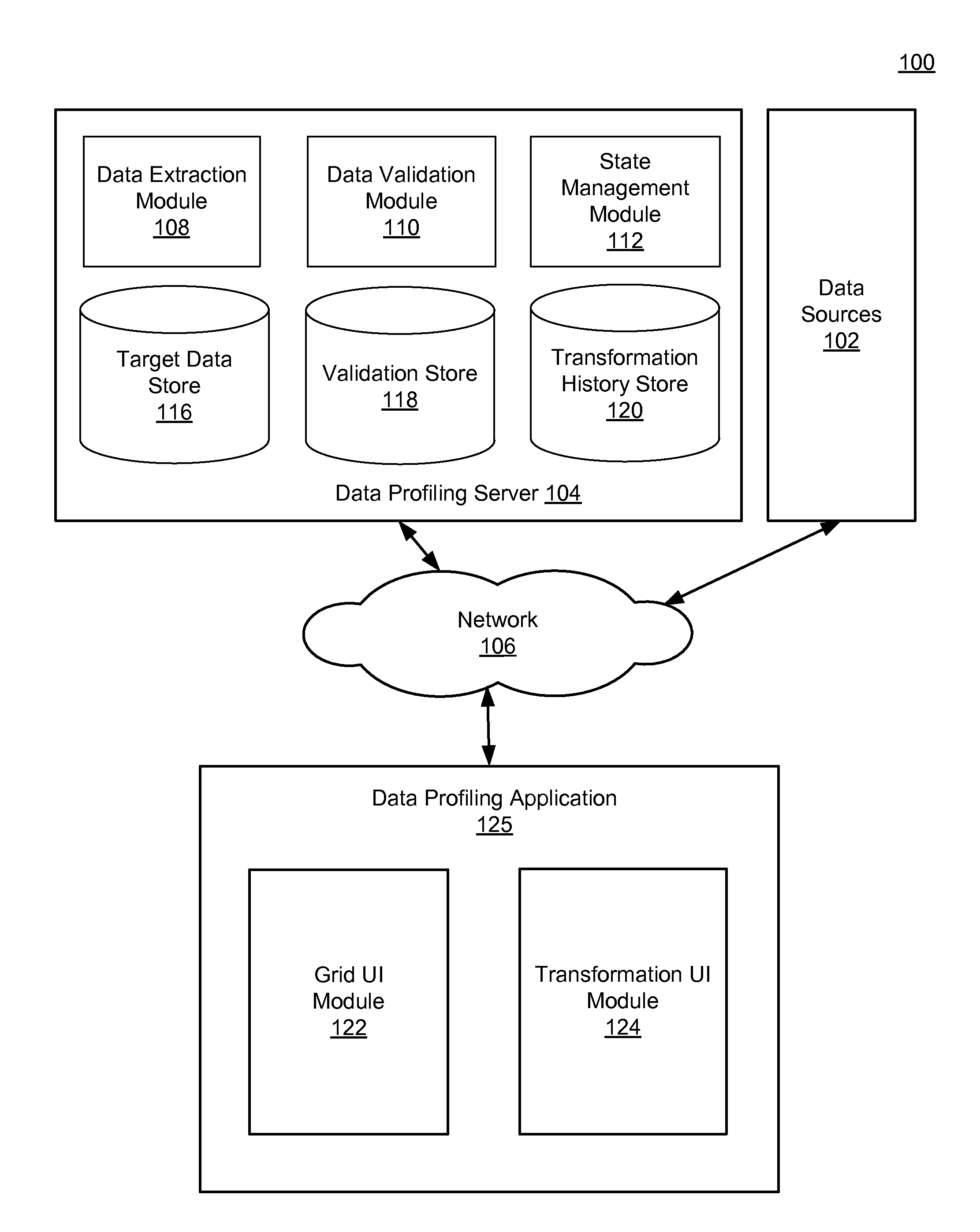
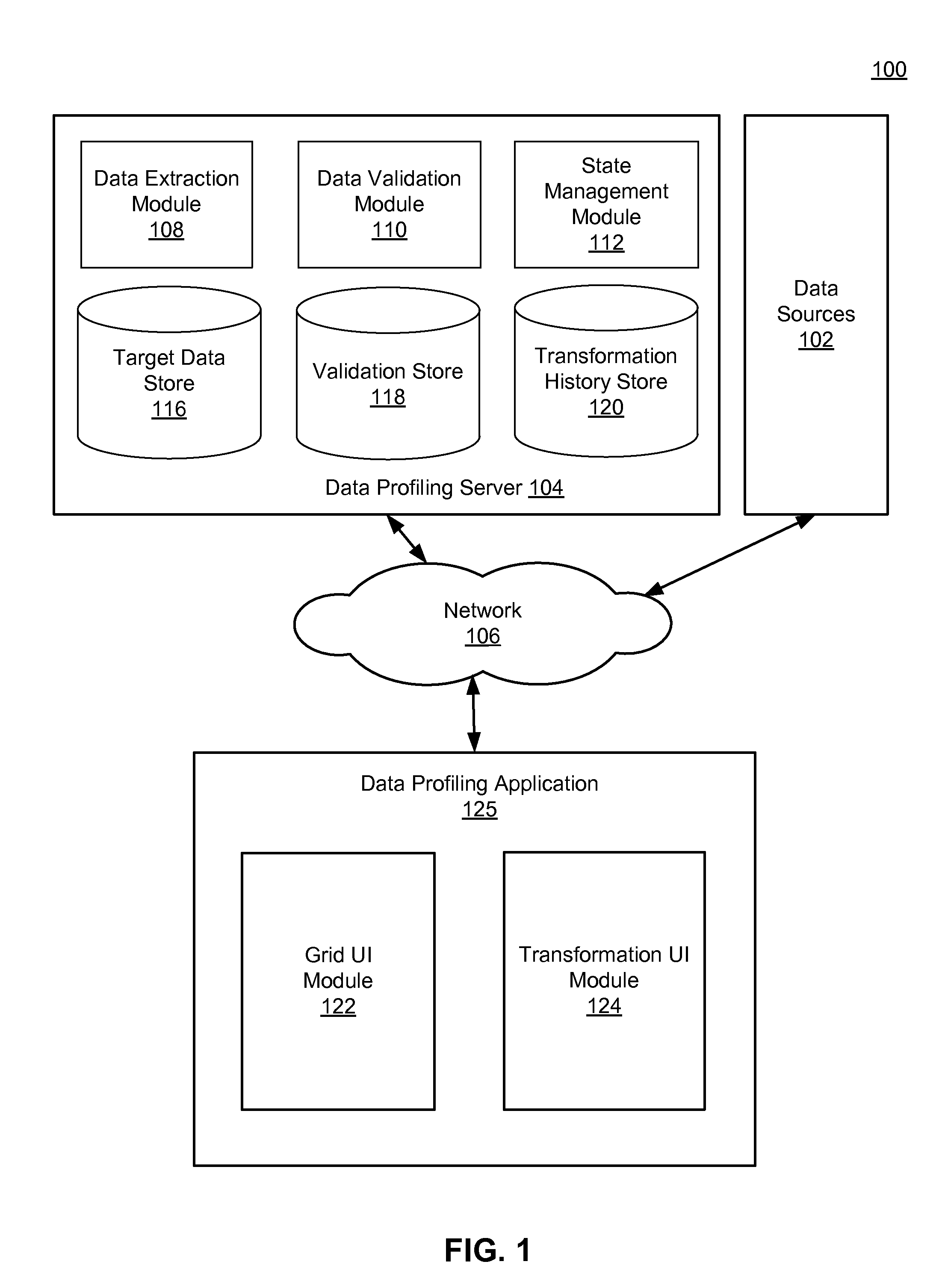
Grid format data viewing and editing environment
ActiveUS20150324437A1Quick identificationReduce consumptionDigital data information retrievalDigital data processing detailsData viewDatasource
A data profiling server extracts data from multiple data sources and stores the extracted data in a target data store. Validation functions are performed on the extracted to determine whether the data conforms to validation rules associated with the target data store and / or business logic definitions. For data that does not conform to the validation rules, the data profiling server identifies recommended transformations to be applied to the data to correct any errors that cause the data to not conform with the validation rules. A data profiling application presents to a user the data extracted from the multiple data sources in a grid structure. The grid structure also includes error indicators identifying the data that does not conform to the validation rules and specifies the recommended transformations identified by the data profiling server.
Owner:INFORMATICA CORP
Using commercial share of wallet to compile marketing company lists
InactiveUS20140012633A1Accurate balanceEfficient managementMarket predictionsFinanceDatasourceCommercial Sources
Commercial size of spending wallet (“CSoSW”) is the total business spend of a business including cash but excluding bartered items. Commercial share of wallet (“CSoW”) is the portion of the spending wallet that is captured by a particular financial company. A modeling approach utilizes various data sources to provide outputs that describe a company's spend capacity. Marketing companies that sell lists compile those lists by searching one or more databases for names and / or businesses that match certain criteria. Those marketing companies can use the CSoW / CSoSW modeling approach to show predicted spend and / or revenues for each company on a list. This makes the list more valuable to list buyers.
Owner:EXPERIAN MARKETING SOLUTIONS
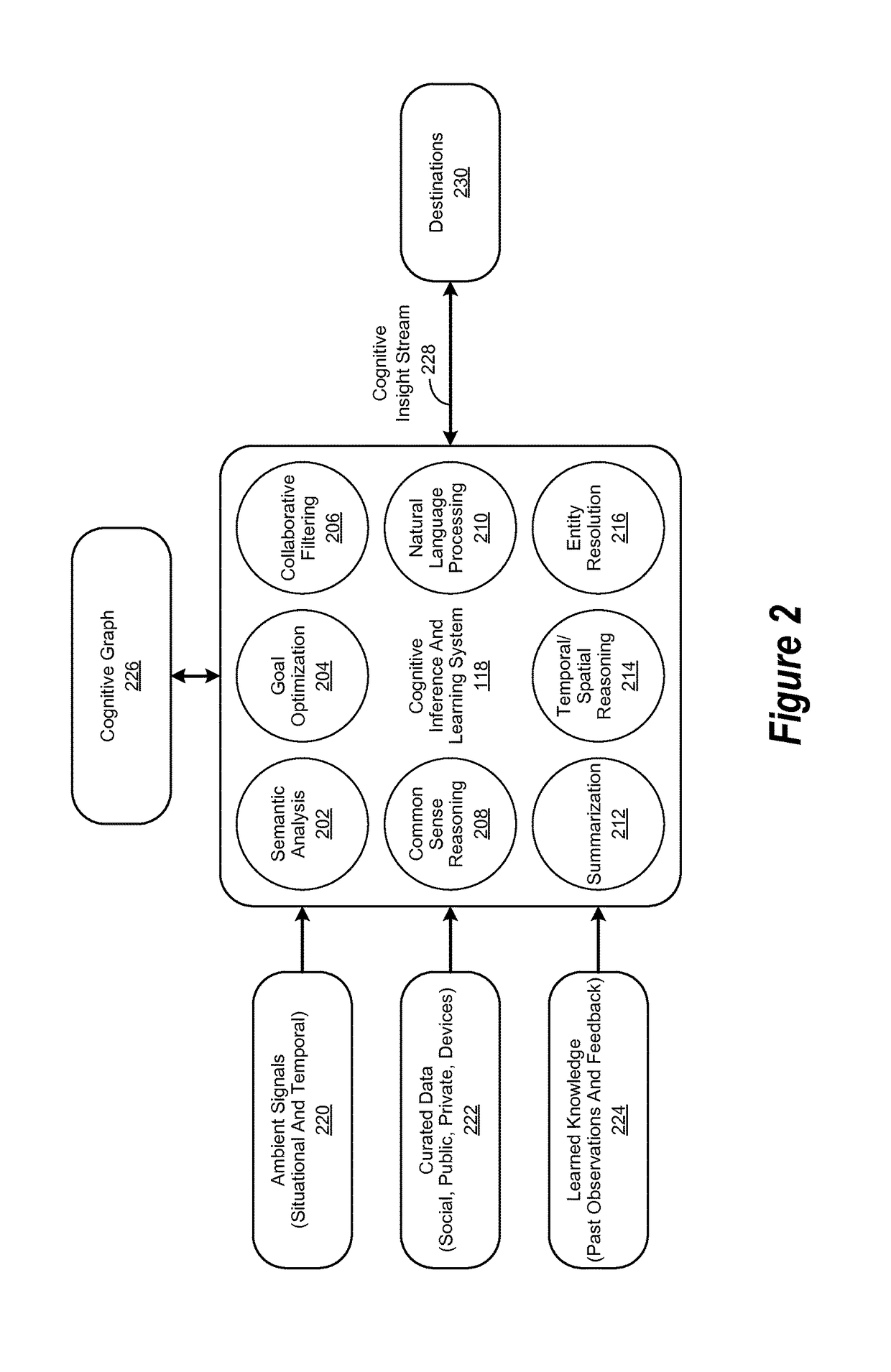
Weighted cognitive personas and profiles
A method, system and computer-usable medium for performing cognitive computing operations comprising receiving streams of data from a plurality of data sources; processing the streams of data from the plurality of data sources, the processing the streams of data from the plurality of data sources performing data enriching for incorporation into a cognitive graph; defining a cognitive persona within the cognitive graph, the cognitive persona corresponding to an archetype user model, the cognitive persona comprising a set of nodes in the cognitive graph, links among the set of nodes being weighted to provide a weighted cognitive graph; associating a user with the cognitive persona; and, performing a cognitive computing operation based upon the cognitive persona associated with the user.
Owner:TECNOTREE TECH INC
A method and system for constructing a health knowledge graph
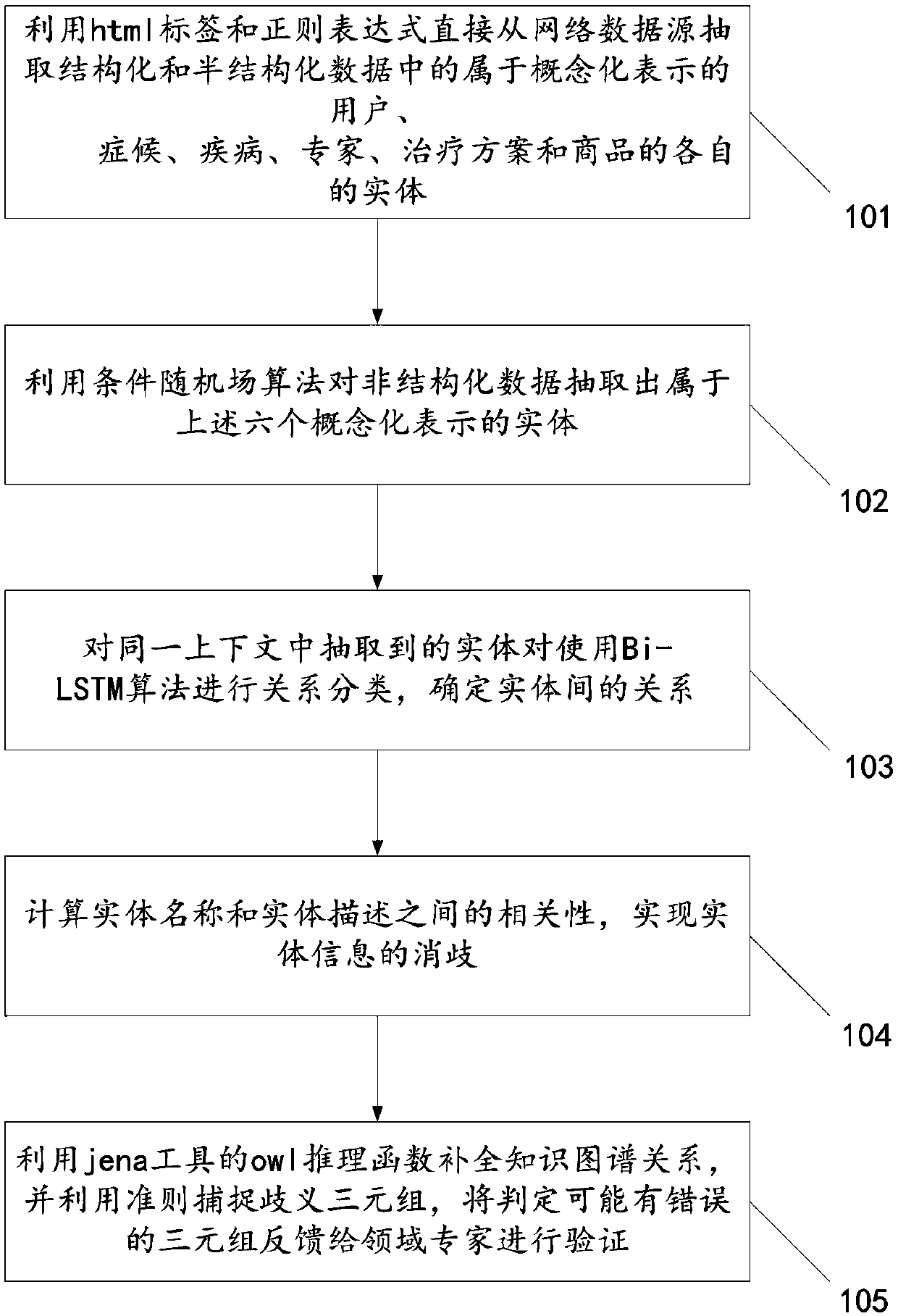
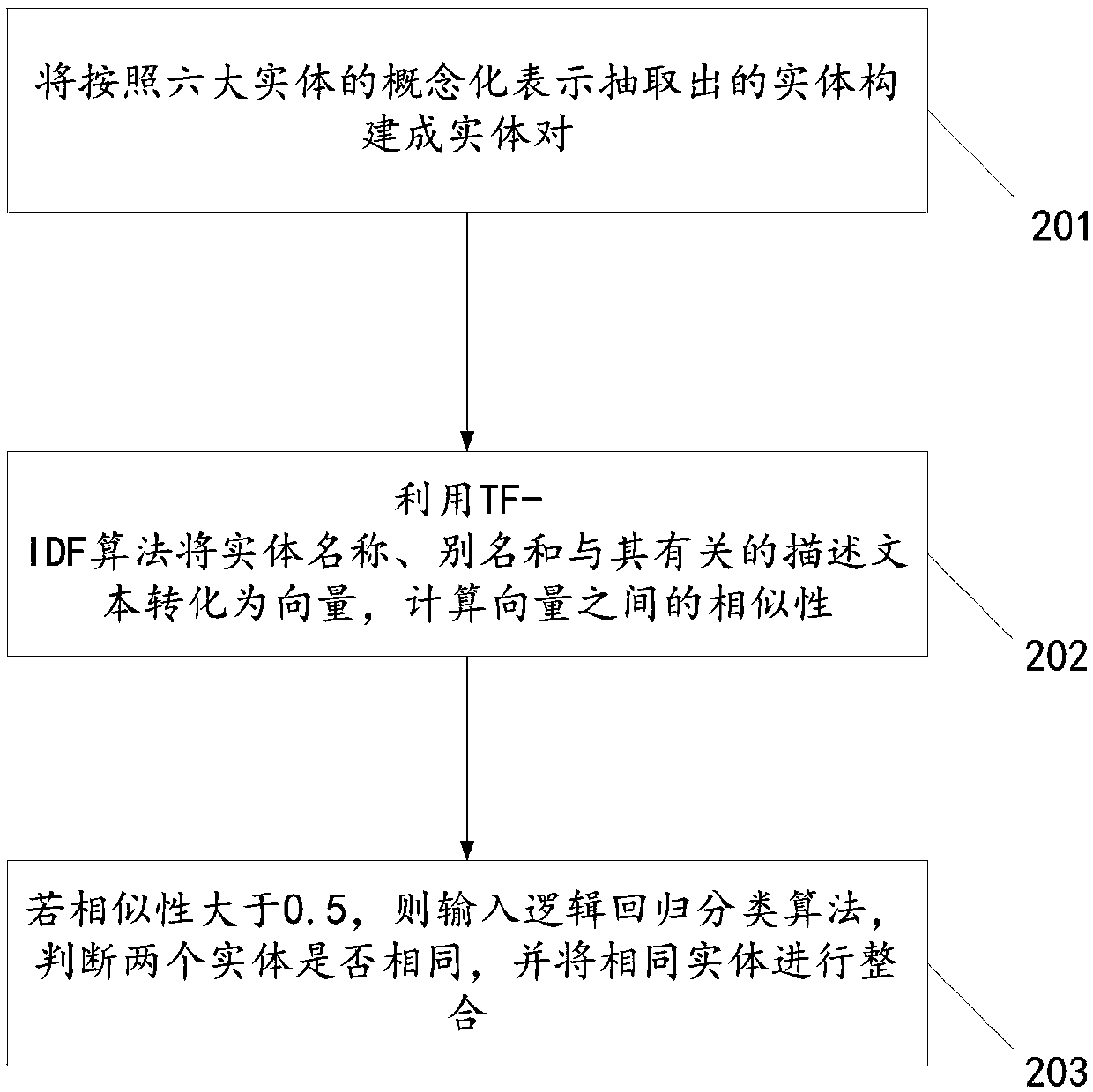
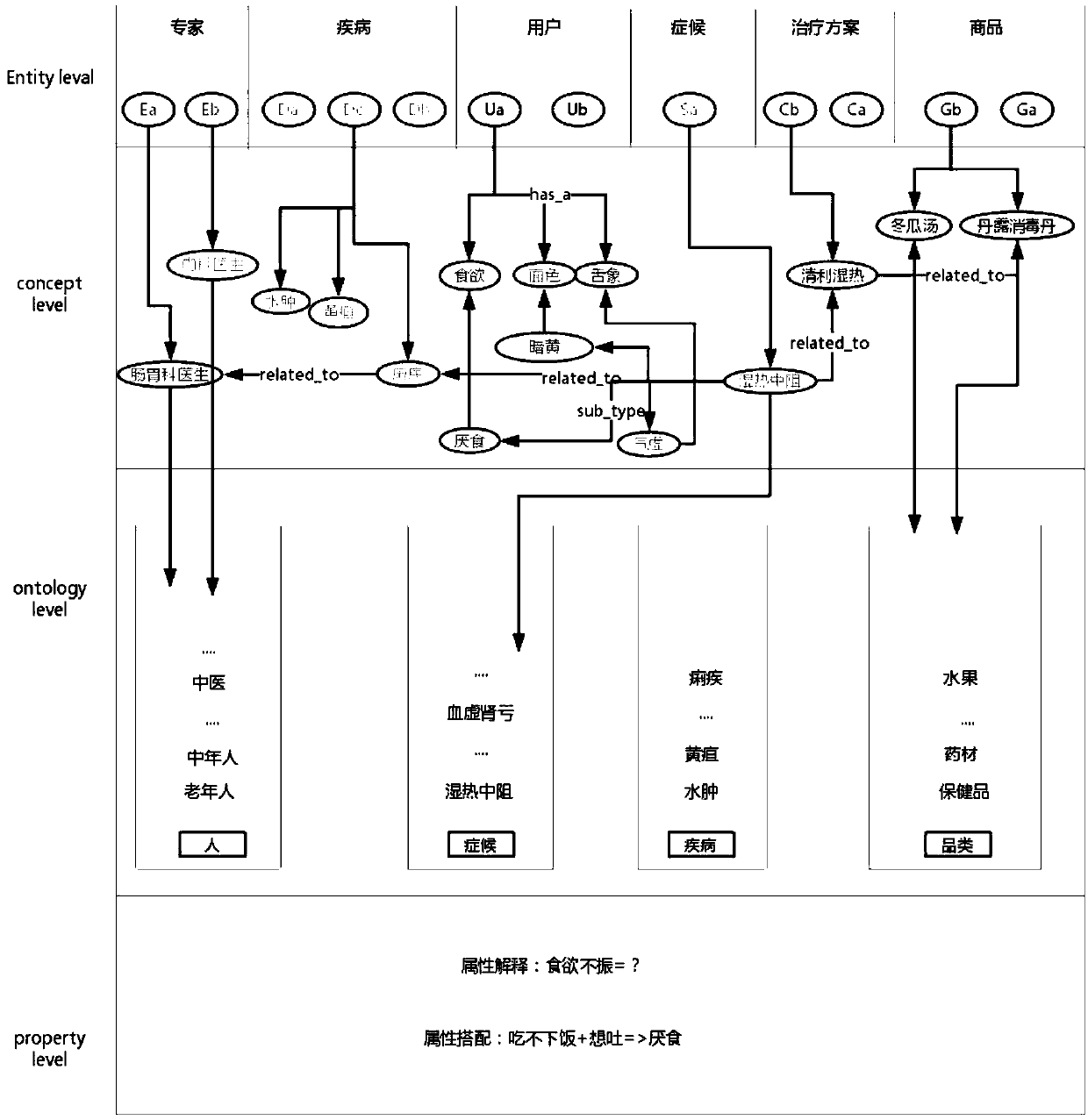
ActiveCN109669994AEasy to buildStrong knowledgeDatabase modelsSemantic tool creationDiseaseConditional random field
The invention relates to a method for constructing a health knowledge graph. The method comprises the following steps of directly extracting entities of users, symptoms, diseases, experts, treatment schemes and commodities belonging to generalized representations in structured and semi-structured data from a network data source by utilizing an html label and a regular expression; extracting entities belonging to the six summarized representations from the unstructured data by using a conditional random field algorithm; using Bi-pairs of entities extracted in the same context The LSTM algorithmcarries out relation classification and determines a relation between entities; calculating the correlation between the entity names and the entity descriptions and achieving the disambiguation of the entity information; and complementing the knowledge graph relation by using an owl reasoning function of a jena tool, capturing ambiguous triplet by using a criterion, and feeding back the triplet which is judged to be possibly wrong to a domain expert for verification. The method has the beneficial effects that the health knowledge graph of the traditional Chinese medicine theory is constructed, the incomplete relation is automatically complemented by applying the knowledge reasoning technology, and the more perfect health graph is constructed.
Owner:JILIN UNIV
Knowledge Graph Based Query Generation
InactiveUS20160328443A1Digital data information retrievalSpecial data processing applicationsQuery planData set
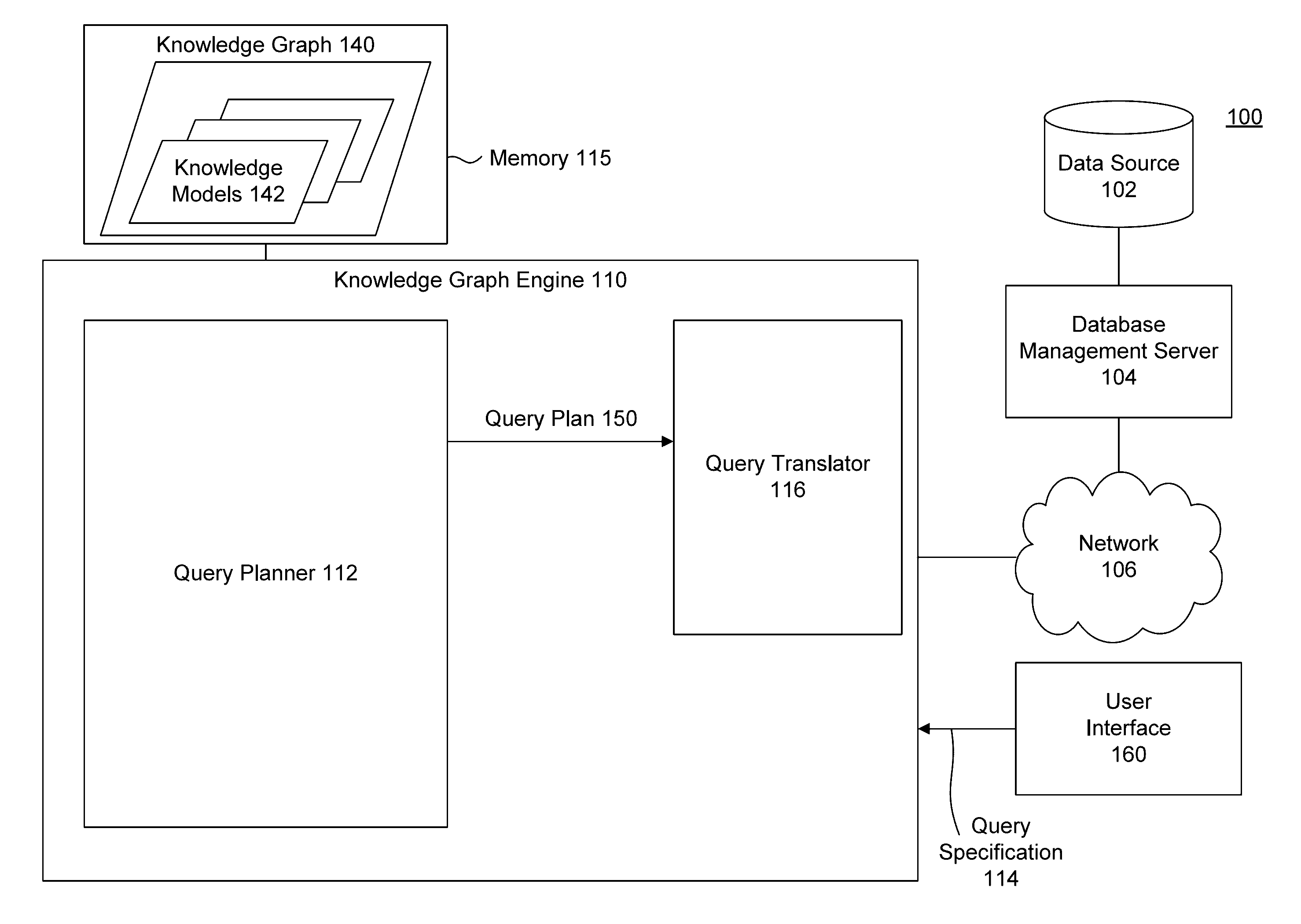
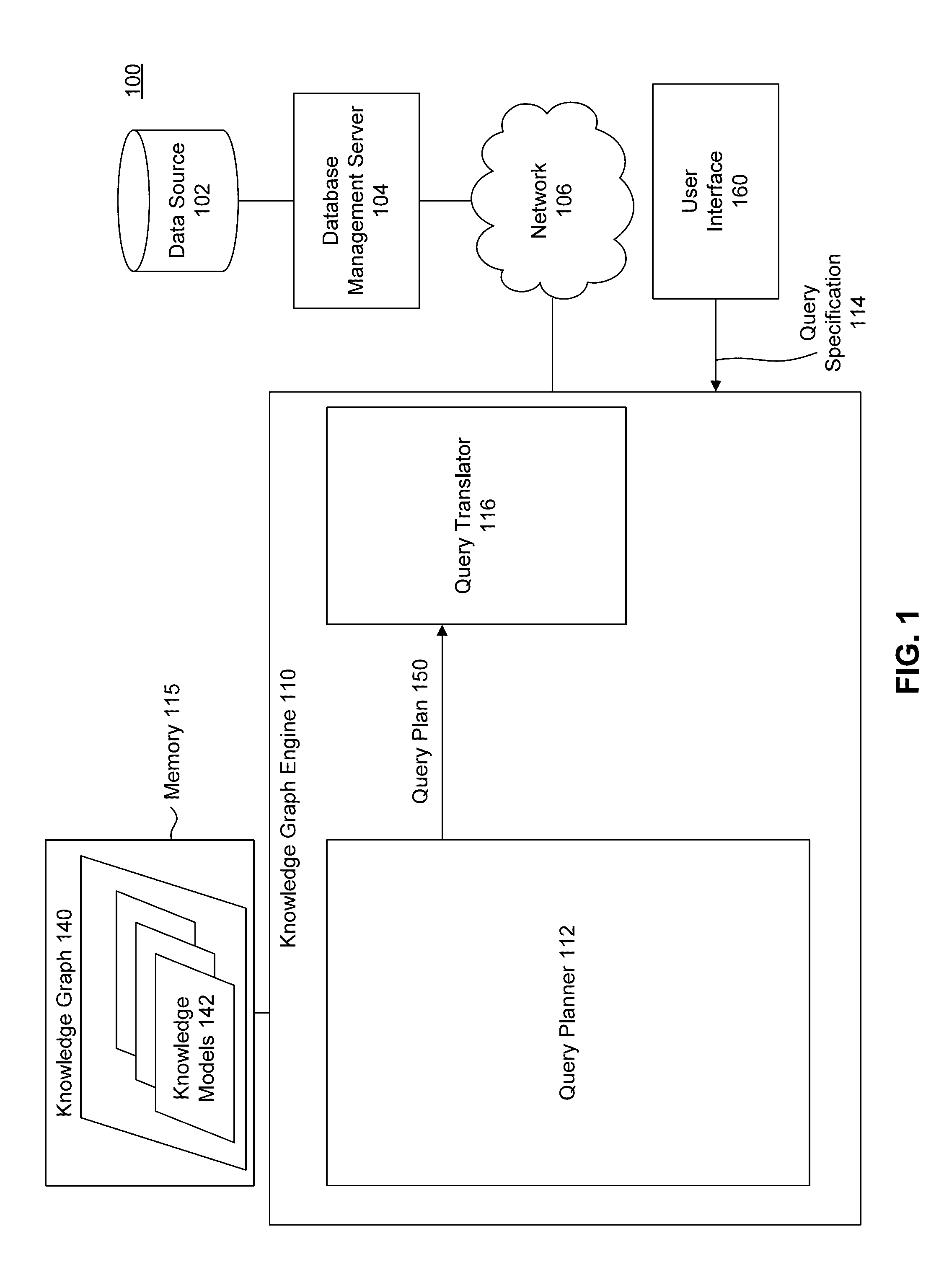
Computer-implemented methods, systems and program storage devices for knowledge graph based query generation are disclosed herein. A computer-implemented method includes storing electronically a knowledge graph that represents relationships between a plurality of knowledge models. Further steps include: receiving a query specification that identifies a knowledge model for a query dataset; determining with a computing device a path based on path cost criteria, where the path covers a portion of the knowledge graph across one or more knowledge models to one or more data sources; and generating an initial query plan according to one or more knowledge models along the determined path to fulfill the query specification with data from one or more data sources.
Owner:VERO ANALYTICS
Incremental compiling of a declarative program
InactiveUS20140306964A1Drawing from basic elementsVisual/graphical programmingDatasourceDependency graph
The incremental compiling of a recalculation user interface. As an example, the recalculation user interface may be a spreadsheet program although the principles may apply to an visualization of data sinks that are interconnected to data sources via a transformation chain. The transformation chain includes multiple declarative transformations. A dependency graph is generated through analysis of the declarative transformations of the transformation chain. As the user interacts with the recalculation user interface, the user may cause one or more changes to the transformation chain. The dependencies associated with the transformations may be identified and may be largely isolated. The compiler may then compile that one or more affected dependencies, without compiling the entire recalculation user interface.
Owner:MICROSOFT TECH LICENSING LLC
System and method for multidimensional extension of database information using inferred groupings
ActiveUS20070005154A1Optimization rangePowerful and flexibleMedical data miningData processing applicationsDatasourceData mining
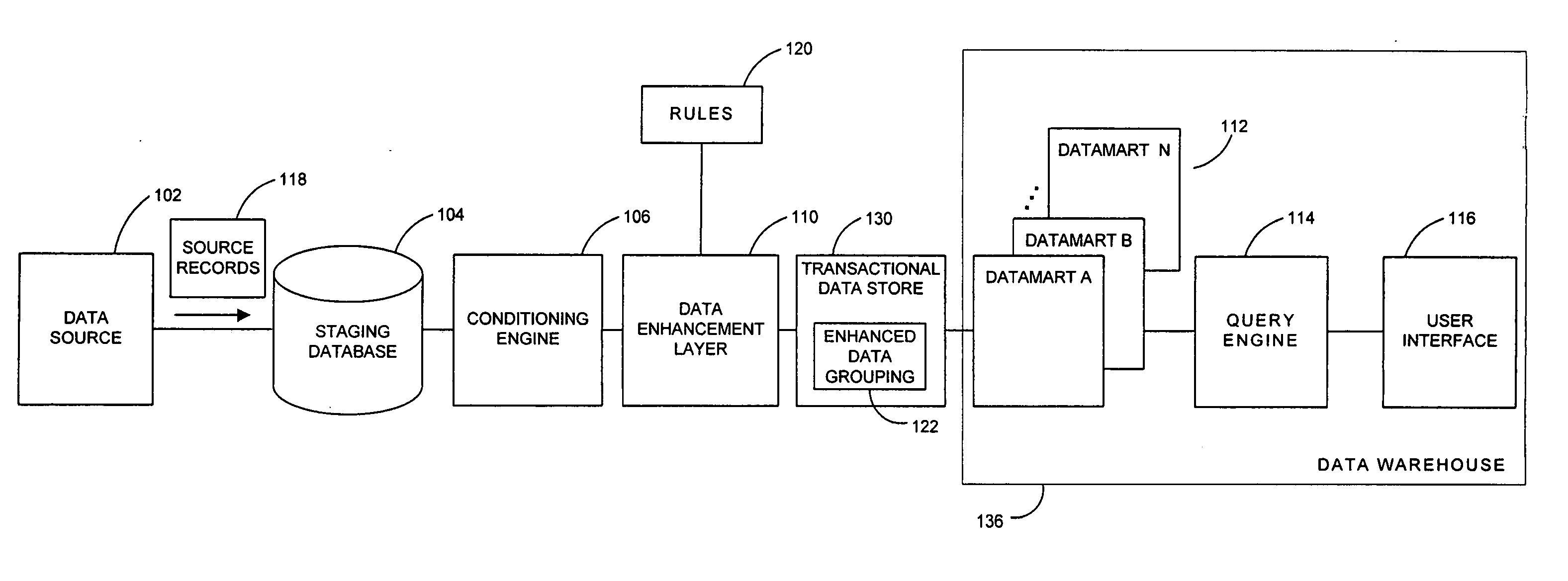
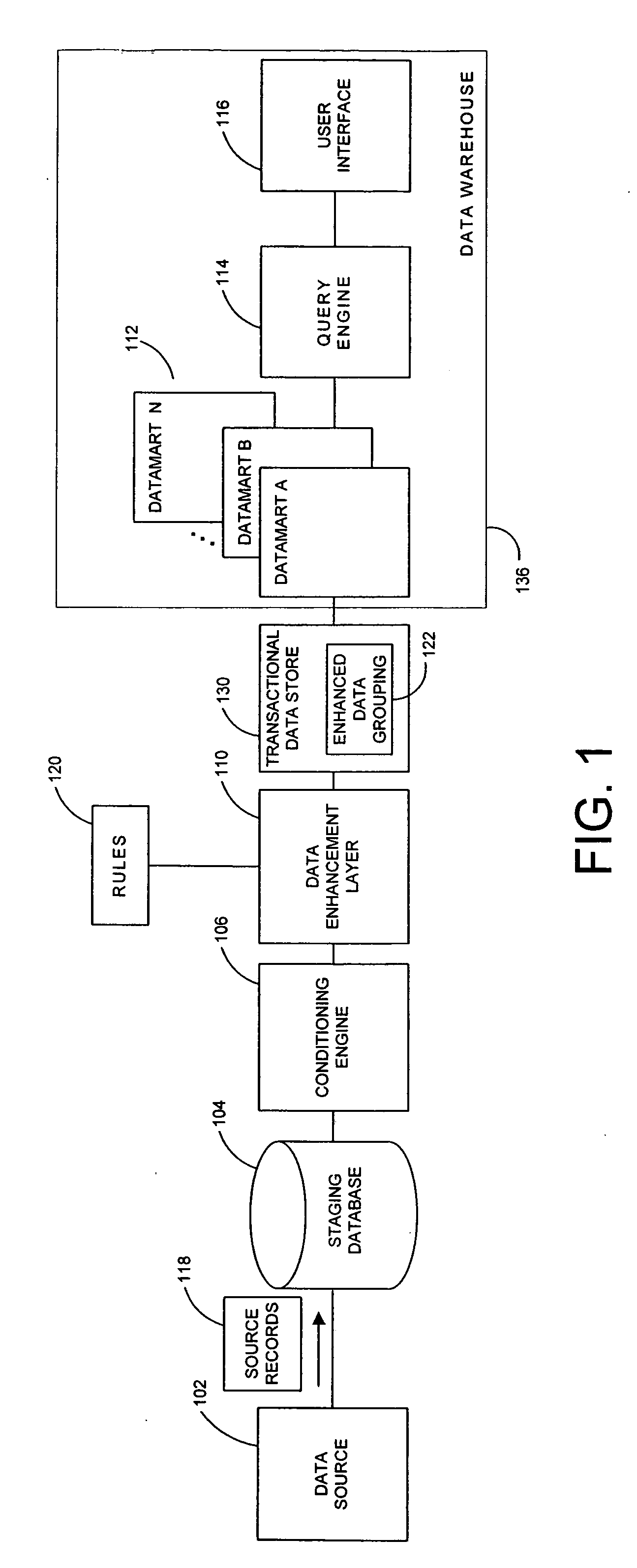
A system and method for receiving medical or other database information and pregrouping and extending that data include a data enhancement layer configured to generate additional stored dimensions capturing the data and relevant attributes. Data sources such as hospitals, laboratories and others may therefore communicate their clinical data to a central warehousing facility which may assemble and extend the resulting aggregated data for data mining purposes. Varying source format and content may be conditioned and conformed to a consistent physical or logical structure. The source data may be extended and recombined into additional related dimensions, pre-associating meaningful attributes for faster querying and storage. The attributes, data and other pieces of information may likewise in embodiments be subjected to an inference analysis to determine whether previously unidentified or unexploited relationships may exist within the universe of source data, for instance using correlation, inference or other analytic techniques. Newly detected, identified or inferred data groupings, which may for instance reveal hidden trends or patterns residing in the data, may then be added back to the enhanced data groupings. Users running analytics against the resulting medical or other datamarts may therefore access a richer set of related information, more powerful sets of predictive models as well as have their queries and other operations run more efficiently.
Owner:CERNER INNOVATION
Policy based data collection, processing, and negotiation for analytics
An approach for ontological policy based data collection, processing, and negotiation for data in view of analytics is provided. The approach searches one or more data sources for data related to a data request. The approach collects data related to the data request from the one or more data sources. The approach determines whether one or more attributes generated from the data request match one or more descriptors associated with the data related to the data request. The approach creates one or more annotated ontologies for the data related to the data request. The approach displays a hierarchical visualization of the one or more annotated ontologies for the data related to the data request. The approach updates the one or more annotated ontologies for the data related to the data request based, at least in part, on an evaluation of the quality of the one or more data selections.
Owner:IBM CORP
System and Method for Account Access
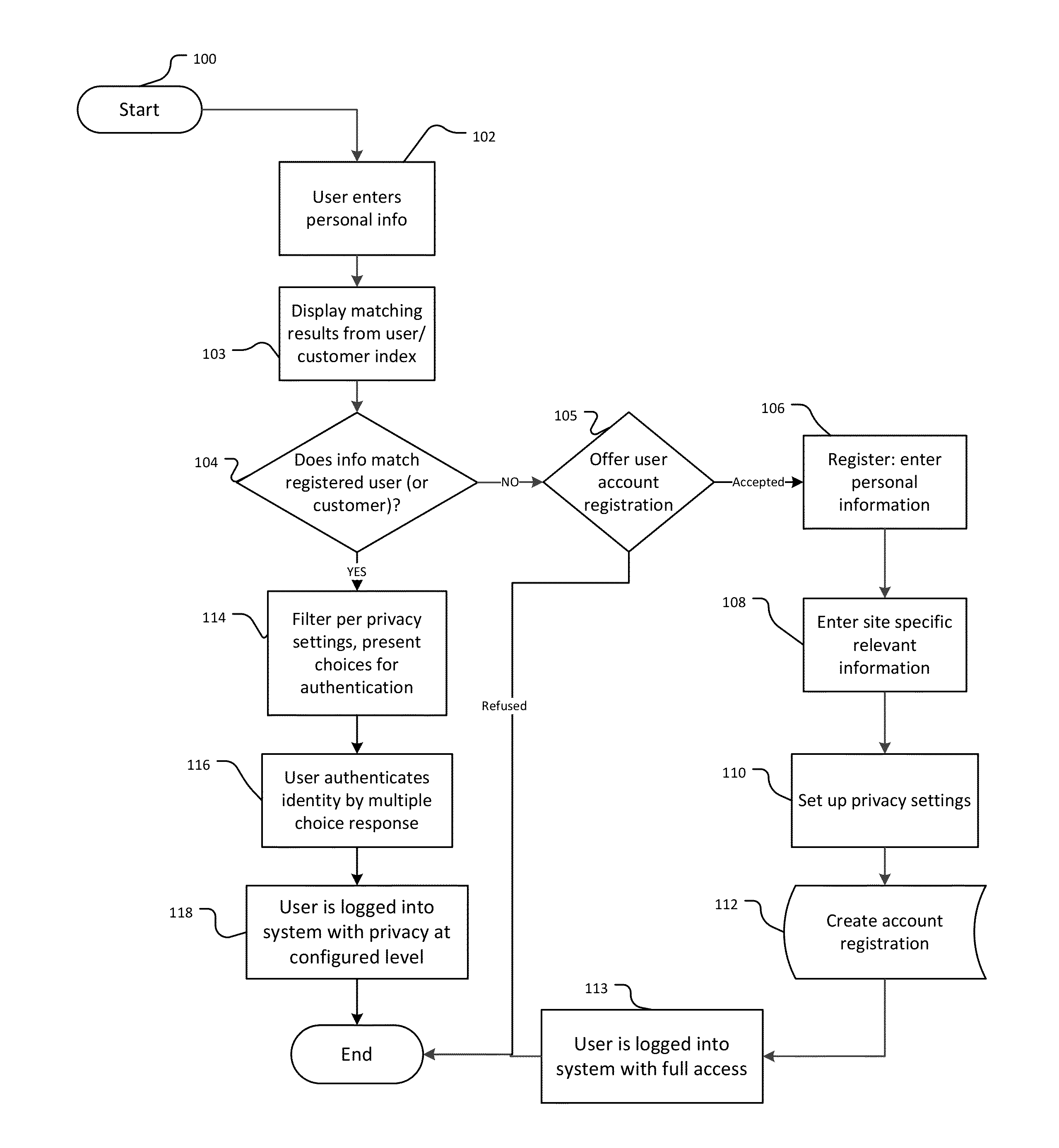
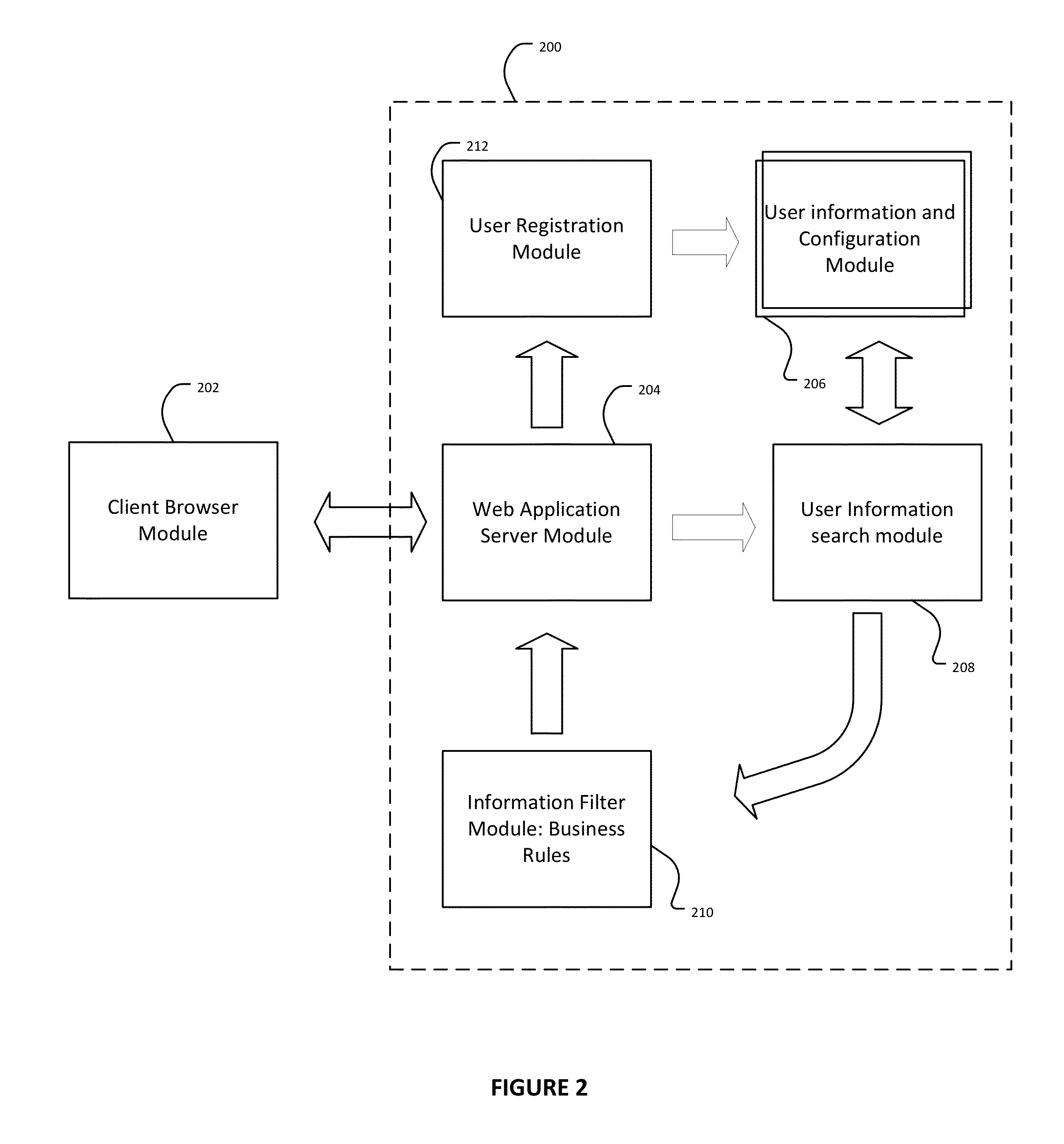
InactiveUS20140282949A1Without compromising user privacySimple and safe processDigital data processing detailsMultiple digital computer combinationsLimited accessUser input
The longstanding problems of user password management and security, and user authentication are addressed. Disclosed is a system and method for providing a means for a user to identify themselves with configurable levels of authentication in order to receive limited access or services while protecting user privacy. As a user inputs information related to their identity into an interface, the system searches an indexed database which may include both registered users and / or unregistered customers indexed from disparate data sources. The system presents the user matching results from the search in an obscured form from which the user selects and authenticates his or her identity. Unregistered users identified during the process may be automatically registered in certain embodiments, or no account may be needed in other embodiments
Owner:KAARYA
System and method of providing relational set operations for OLAP data sources
A tabular set provider is provided for processing a data agnostic business intelligence query with relational set operations, herein called a relational query against a multidimensional datasource. The tabular set provider comprises a query interceptor, a query decomposer, an OLAP query provider interface, and an operation module. The query interceptor is provided for detecting and intercepting a data agnostic Business intelligence query that has relational set operations that is issued against one or more multidimensional data sources. The query decomposer is provided for decomposing the operands of the set operation in the input query into one or more sub-queries. The OLAP query provider interface is provided for sending the OLAP supported sub-queries to an OLAP query provider and receiving results. The operation module is provided for using set operation functionality provided by a relational query provider that performs the set operations locally on the results of the OLAP data extraction.
Owner:SAP AG
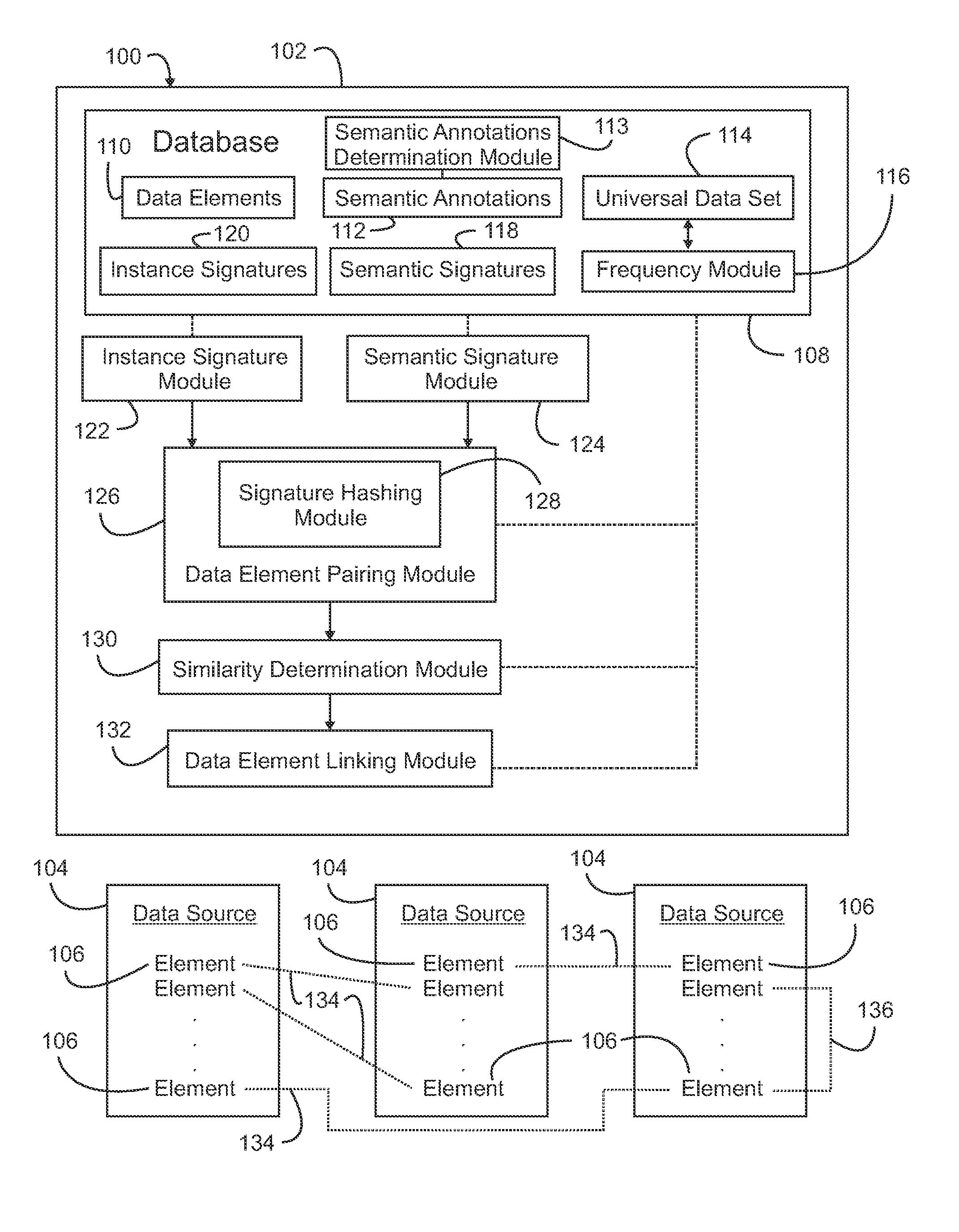
Linking Data Elements Based on Similarity Data Values and Semantic Annotations
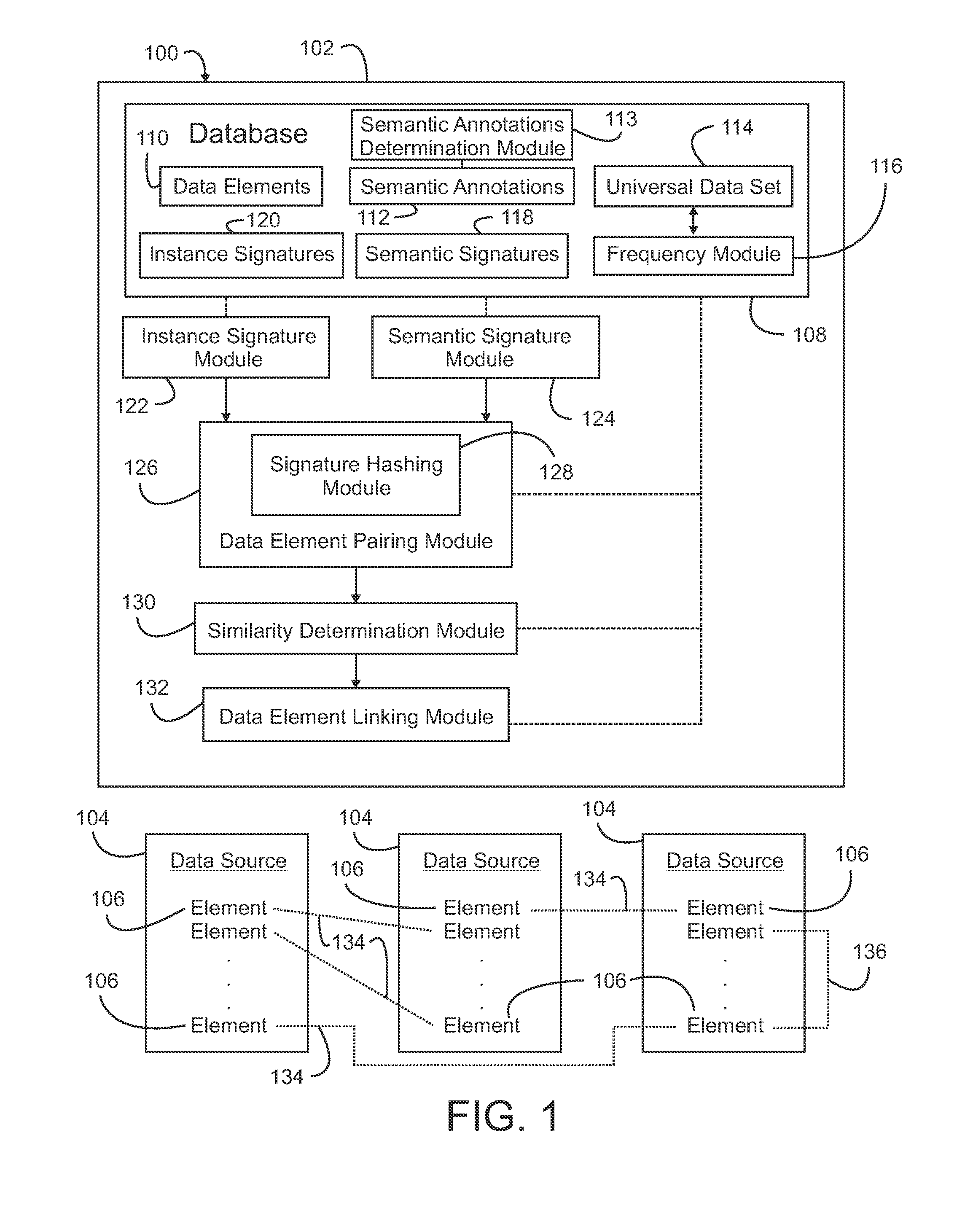
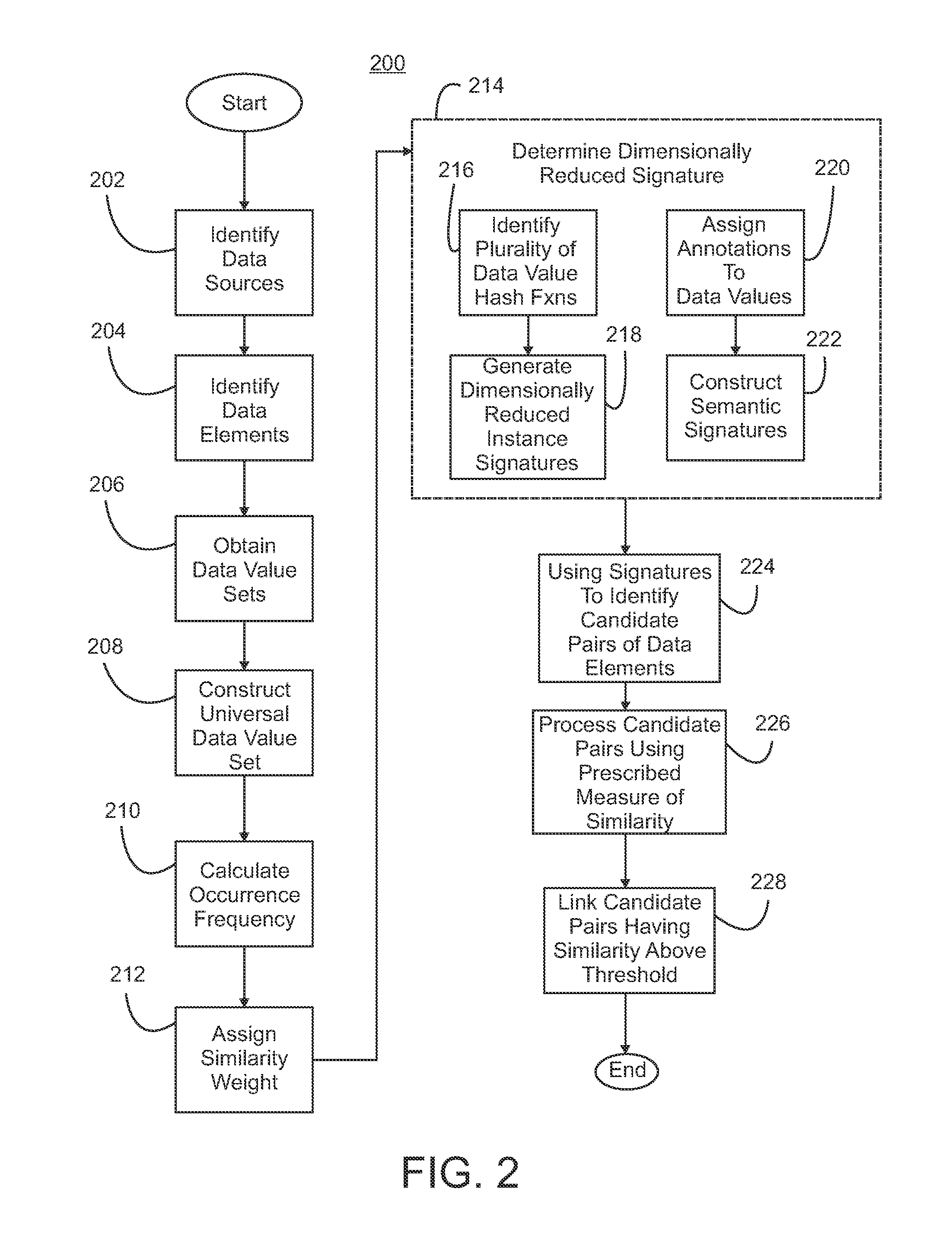
InactiveUS20130332467A1Reduce in quantityLow costWeb data indexingDigital data processing detailsHash functionDatasource
Data elements from data sources and having a data value set are linked by using hash functions to determine a dimensionally reduced instance signature for each data element based on all data values associated with that data element to yield a plurality of dimensionally reduced instance signatures of equivalent fixed size such that similarities among the data values in the data value sets across all data elements is maintained among the plurality of instance signatures. Candidate pairs of data elements to link are identified using the plurality of instance signatures in locality sensitive hash functions, and a similarity index is generated for each candidate pair using a pre-determined measure of similarity. Candidate pairs of data elements having a similarity index above a given threshold are linked.
Owner:IBM CORP
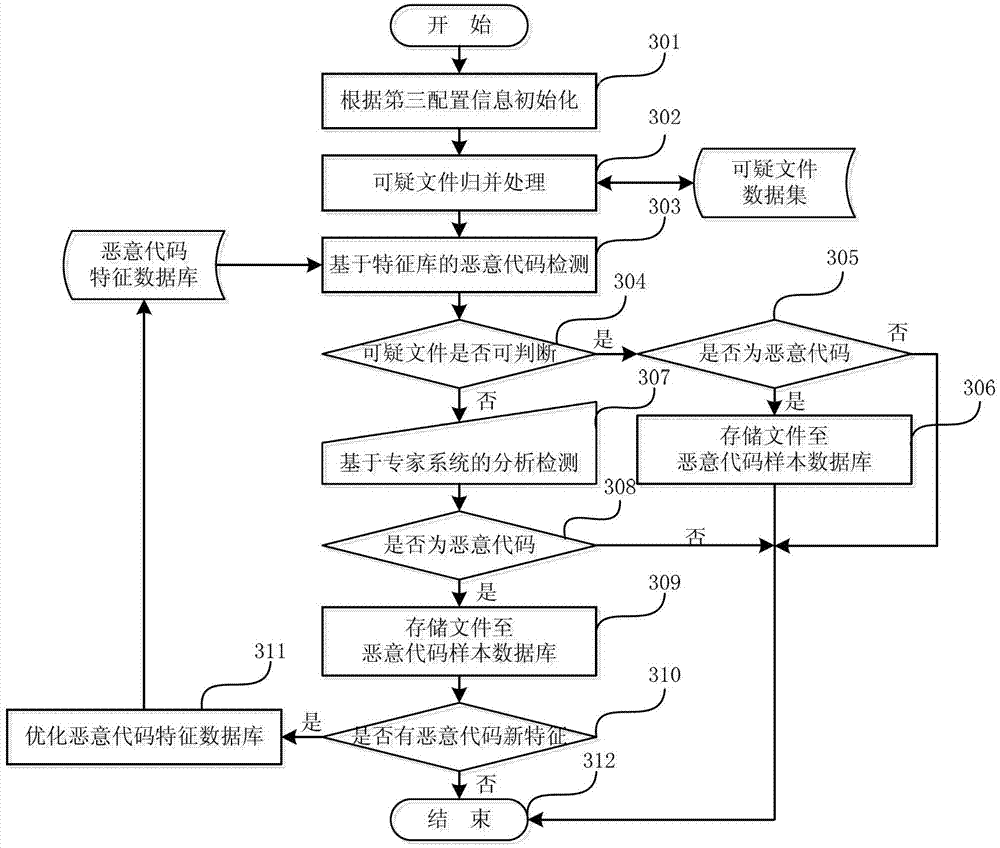
Malicious code capturing method and system
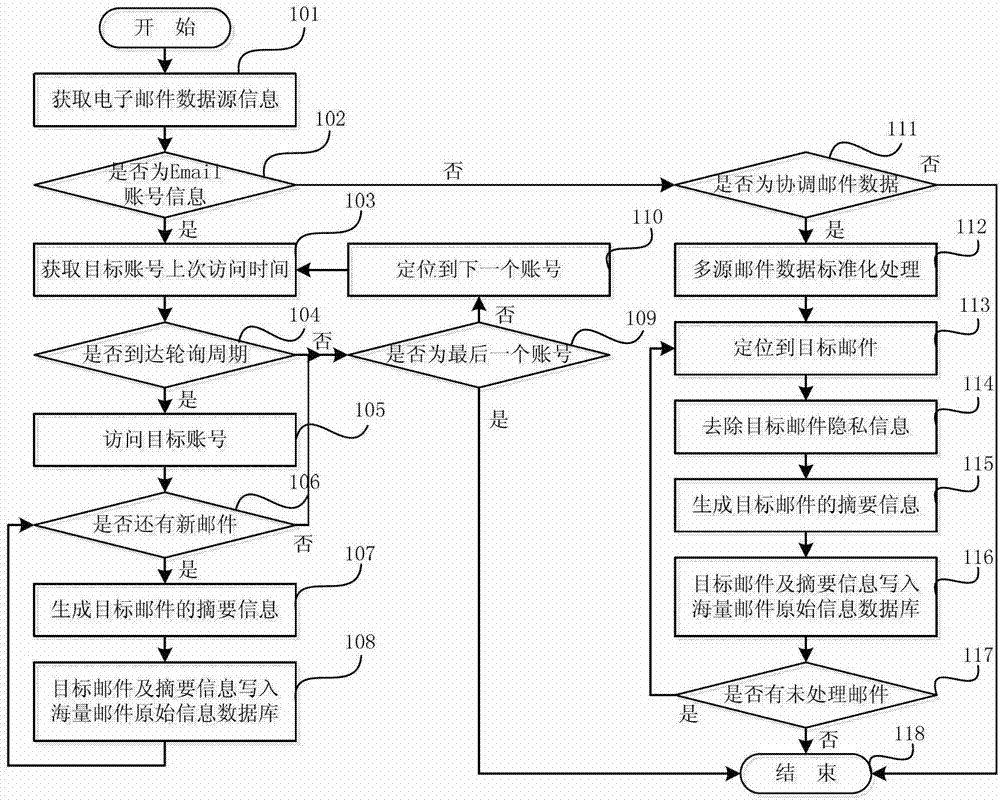
ActiveCN102833240AImprove capture abilityExpand coverageComputer security arrangementsTransmissionDatasourceElectronic mail
The invention relates to malicious code capturing method and system. The malicious code capturing method includes acquiring email data from various email data sources; analyzing the email data, recording files, which cannot be eliminated according to set false negative rate, as suspicious files, and storing the suspicious files to suspicious file database; and detecting the suspicious files by malicious code feature database and manual detection; and storing the suspicious files with unusual detection results to malicious code sample database. The malicious code capturing method and system are applicable to a related honeypot and honeynet system, coverage range of captured objects can be increased, and capability of capturing malicious codes is improved.
Owner:INST OF INFORMATION ENG CAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com