Unknown vulnerability risk assessment method based on text analysis
A technology of unknown vulnerability and text analysis, applied in the field of network unknown vulnerability risk assessment, which can solve problems such as assessing vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention is described in further detail now in conjunction with accompanying drawing.
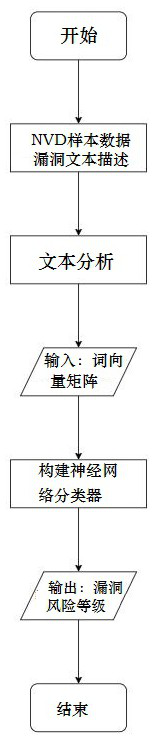
[0041] Such as figure 1 Shown, the present invention a kind of unknown vulnerability risk assessment method based on text analysis, comprises the following steps:
[0042] Step 1: Take the National Vulnerability Database, NVD as the sample data source to obtain the existing vulnerability text description;
[0043] Step 2: Perform text analysis on the sample vulnerability text description, and extract the vector matrix, specifically:
[0044] 2.1: Use the natural language processing tool jieba to segment the text;
[0045] 2.2: Remove punctuation marks and stop words;
[0046] 2.3: Use natural language processing tools to extract stem parts and remove invalid parts;
[0047] 2.4: Use the term frequency-inverse document frequency TF-IDF (term frequency-inverse document frequency) method to establish a keyword vector matrix, specifically:
[0048] 2.4.1: Calculate word...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com