Method for generating attack scenario in mobile cloud computing scene
A scenario generation and mobile cloud technology, applied in the field of dynamically generating attribute attack scenarios, can solve the problems of attack graph state explosion, error-prone, cumbersome, etc., and achieve the effect of improving accuracy and high applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
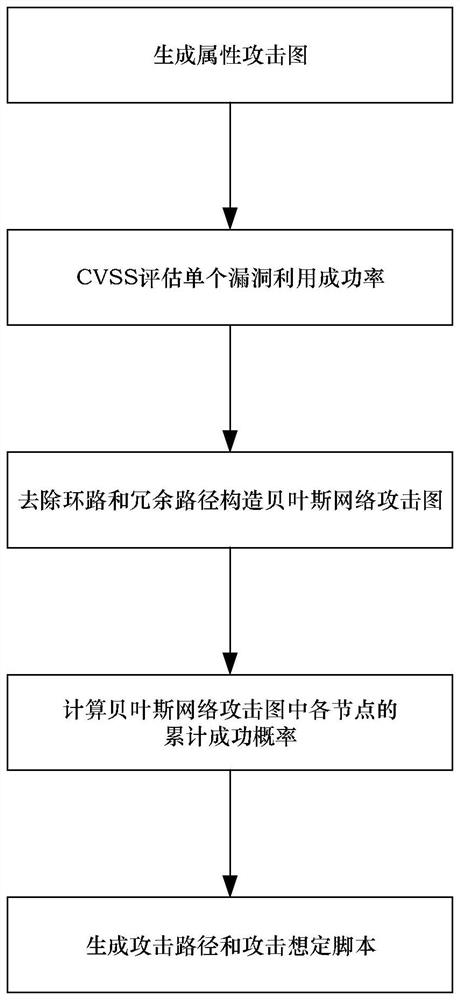
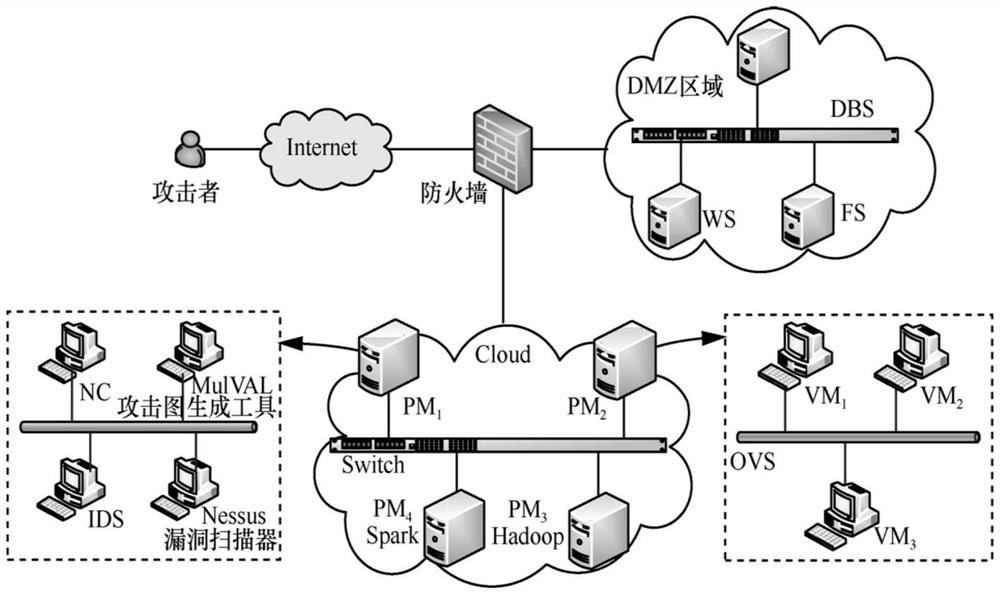
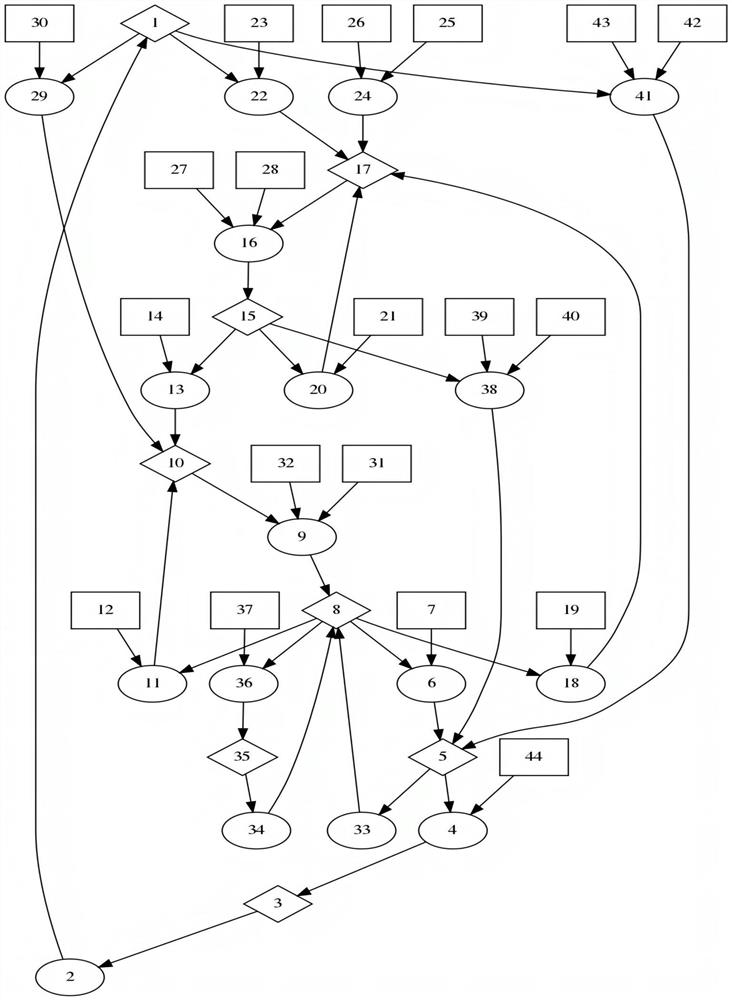
[0116] Mobile cloud platform computer scenarios such as figure 2 As shown, there are database servers (DBS, Datebase Server), website servers (WS, Web Server), and file servers (FS, FileServer) in the isolated area (DMZ, Demilitarized Zone). The first host PM 1 (PM, Parasitifer Machine) is divided into 4 virtual machines (VM, VirtualMachine), respectively running network controller (NC, Network Control), Nessus vulnerability scanner, MulVAL attack graph generation tool and intrusion detection system (IDS, Intrusion Detection System). The Nessus is a vulnerability scanning and analysis software. The translation of the MulVAL (Multistage Vulnerability Analysis) is multi-host multi-stage vulnerability analysis. The second host PM 2 It is divided into several virtual machines (VM, Virtual Machine), used as VMs used by cloud tenants, and the VMs are connected by a programmable open virtualization software switch (OVS, open vSwitch). OVS only completes the data forwarding func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com