Multilayer impact factor-based security vulnerability threat quantification method
An impact factor, multi-level technology, applied in the field of network security, can solve the problems of regardless of the degree of attention of the vulnerability, the evaluation is highly subjective, and the objective threat of the vulnerability cannot be well reflected, so as to achieve efficient acquisition and avoid bias. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
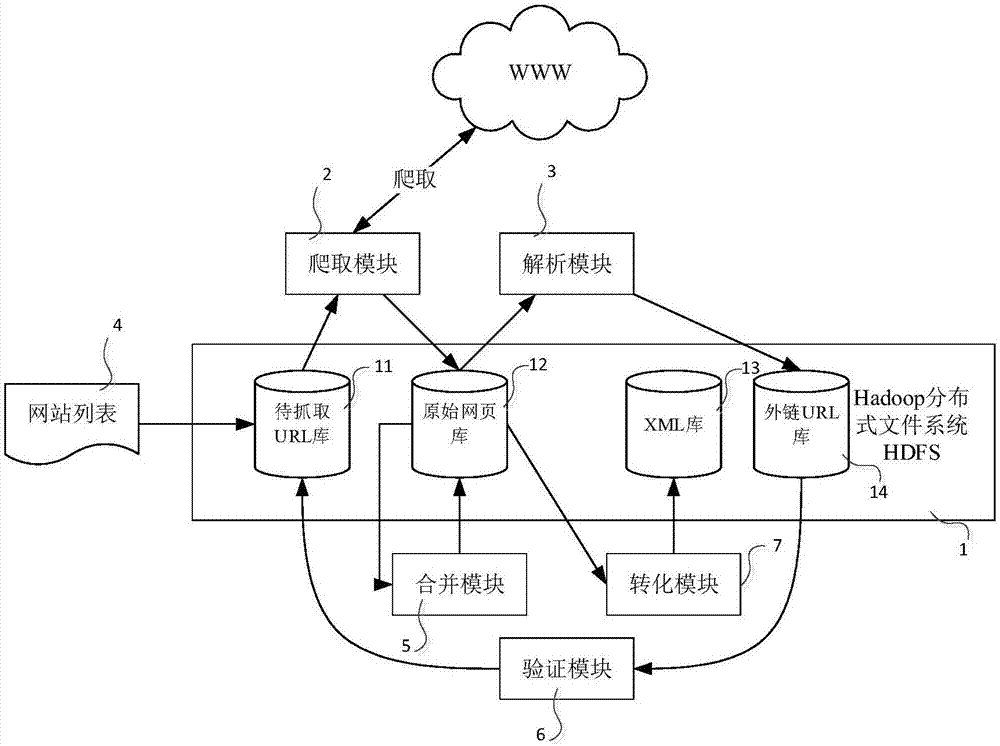
[0039] figure 1 Shown is a schematic diagram of the basic framework of a distributed crawler, such as figure 1 As shown, the distributed crawler includes five functional modules: crawling module 2, parsing module 3, verification module 6, merging module 5 and transformation module 7. Crawling module 2 generates a list to be crawled according to the website list 4 in the URL library 11, and then sends the list segmentation to the crawler node to crawl the webpage; Parse, save the external chain address parsed in the external chain URL library 14; verification module 6 is to verify that the link in the external chain URL library 14 ensures that the address that has been visited is removed; the merging module is to link ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com