Electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and evaluation system based on the model
A technology for power information and risk assessment, applied in transmission systems, electrical components, electrical digital data processing, etc., can solve the inherent logic, network structure and security requirements that do not give the algorithm to determine the weight, taking into account the inapplicable vulnerability Threat assessment and other issues to achieve the effect of improving risk prevention capabilities, ensuring effectiveness and safety, and improving accuracy and timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042]The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments; however, a power information network vulnerability threat assessment model and system oriented to power CPS risk assessment of the present invention are not limited to the embodiments.
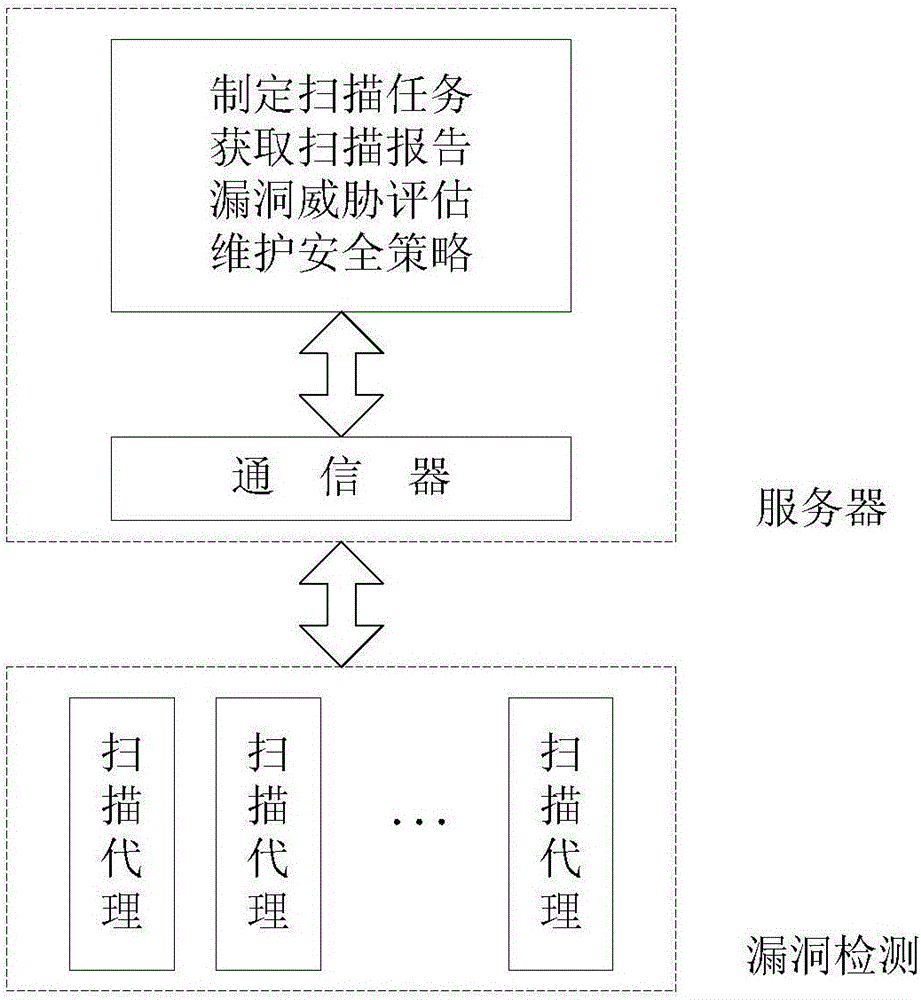
[0043] Embodiment, please refer to the accompanying drawings, a power information network vulnerability threat assessment model and system oriented to power CPS risk assessment of the present invention, its vulnerability scanning system includes distributed scanning agents scattered in various security areas and arranged in Servers in Zone III;
[0044] figure 1 It is a system logic model diagram of the present invention. As shown in the figure, the functions completed by the server arranged in Zone III include: formulating scanning tasks, obtaining scanning reports, assessing vulnerability threats and maintaining security policies; the communicator in the server...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com