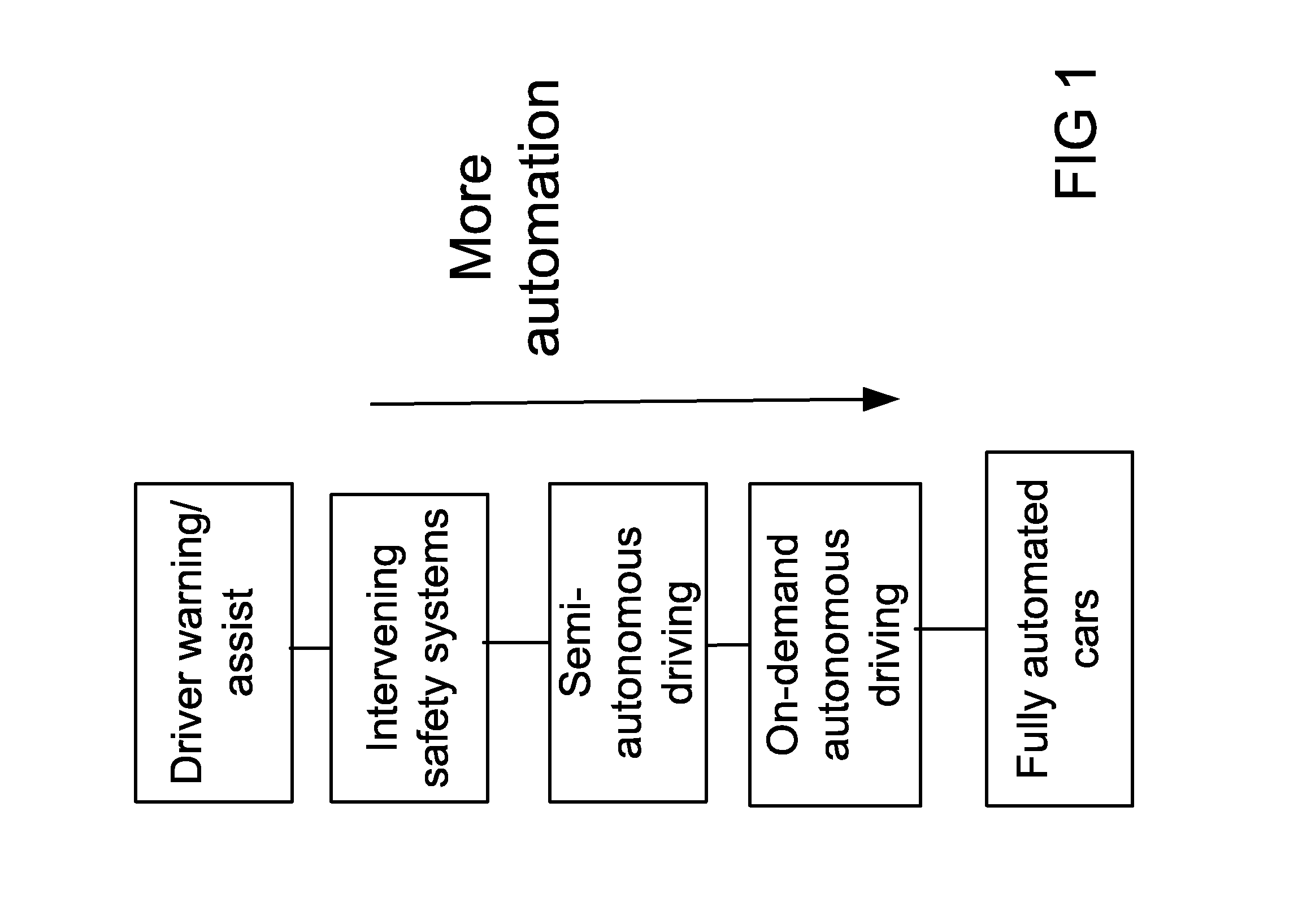
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
233 results about "Threat assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
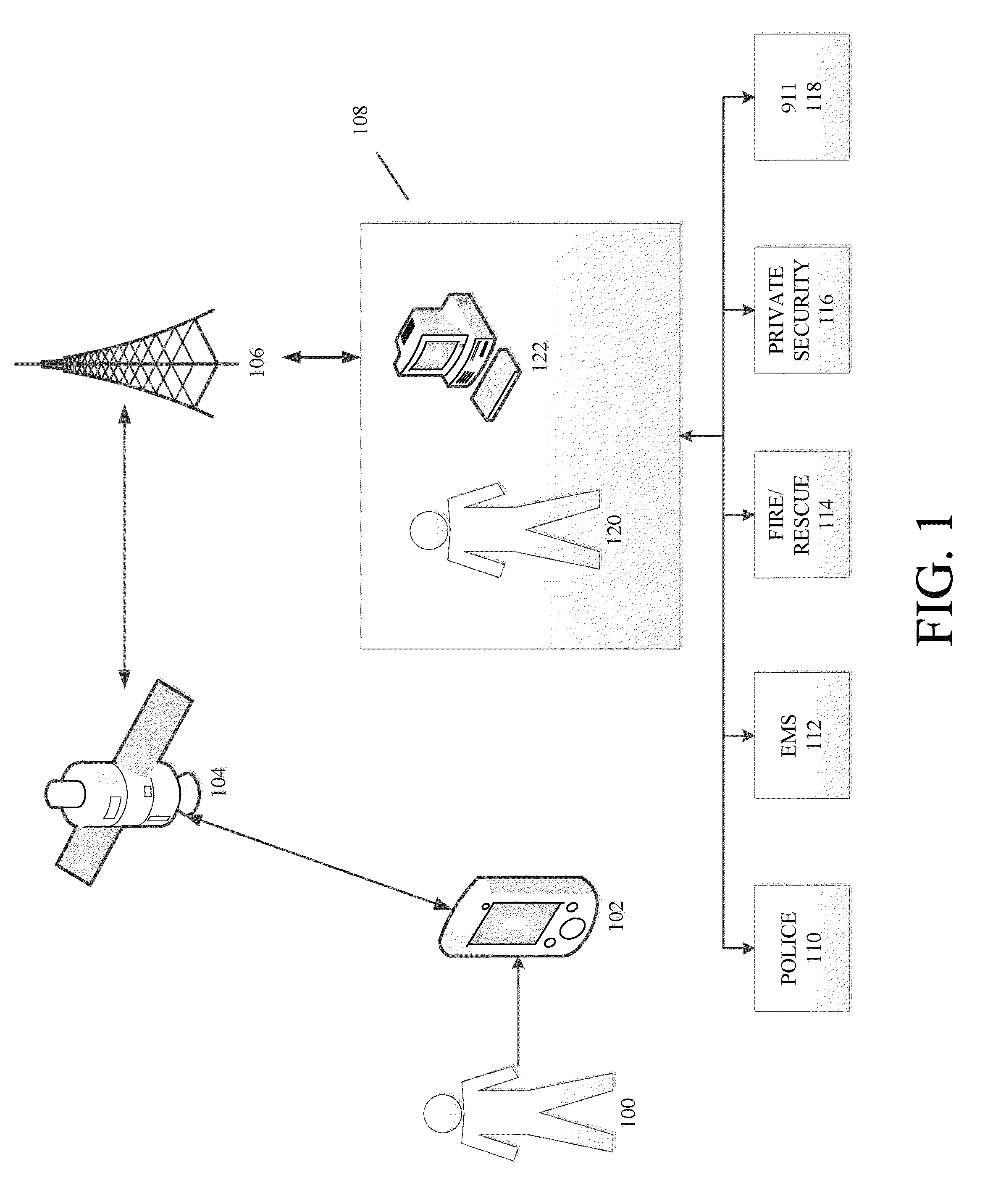
Threat Assessment is the practice of determining the credibility and seriousness of a potential threat, as well as the probability that the threat will become a reality. Threat assessment is separate to the more established practice of violence-risk assessment, which attempts to predict an individual's general capacity and tendency to react to situations violently. Instead, threat assessment aims to interrupt people on a pathway to commit "predatory or instrumental violence, the type of behavior associated with targeted attacks," according to J. Reid Meloy, PhD, co-editor of the International Handbook of Threat Assessment. "Predatory and affective violence are largely distinctive modes of violence."
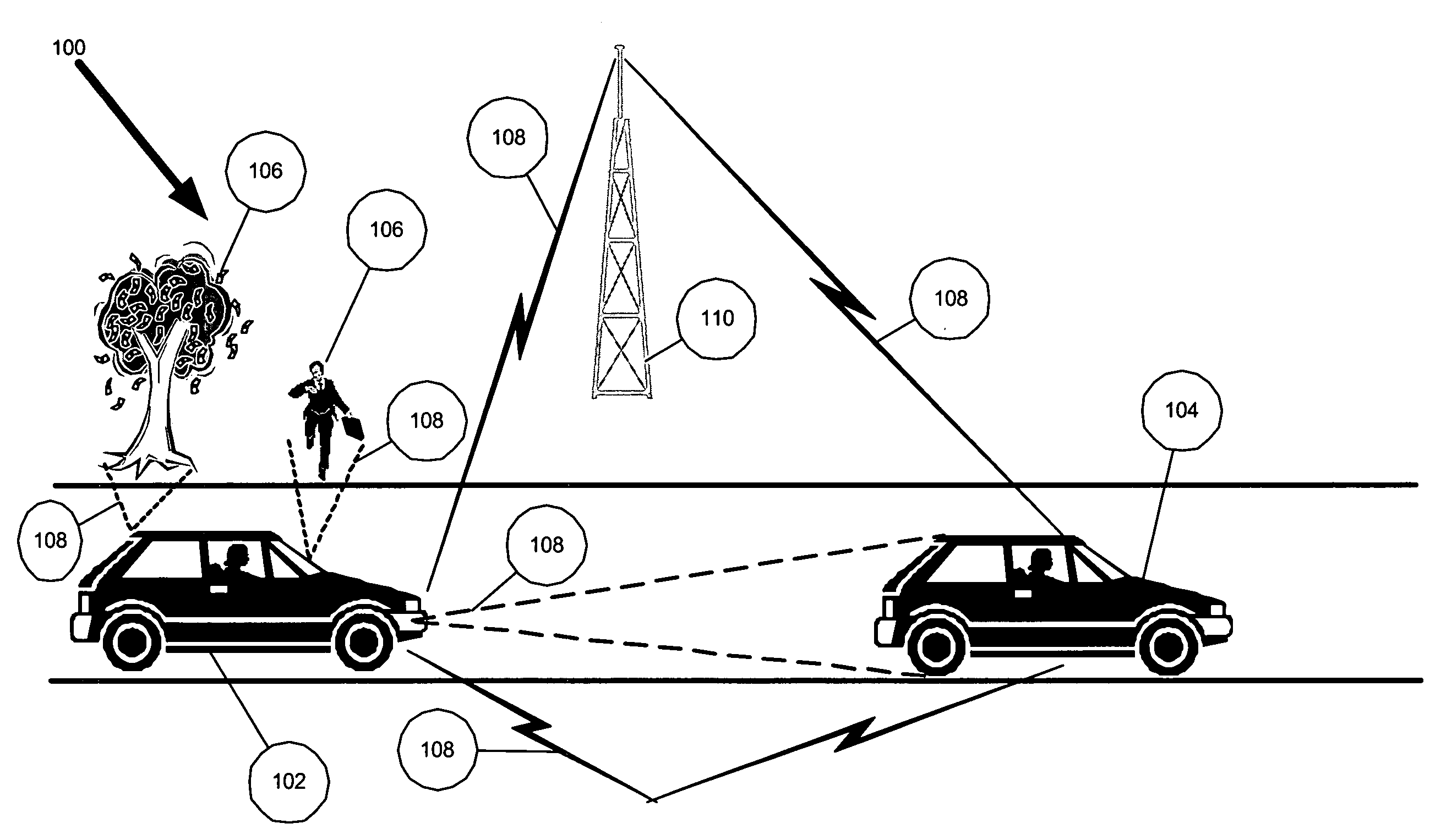
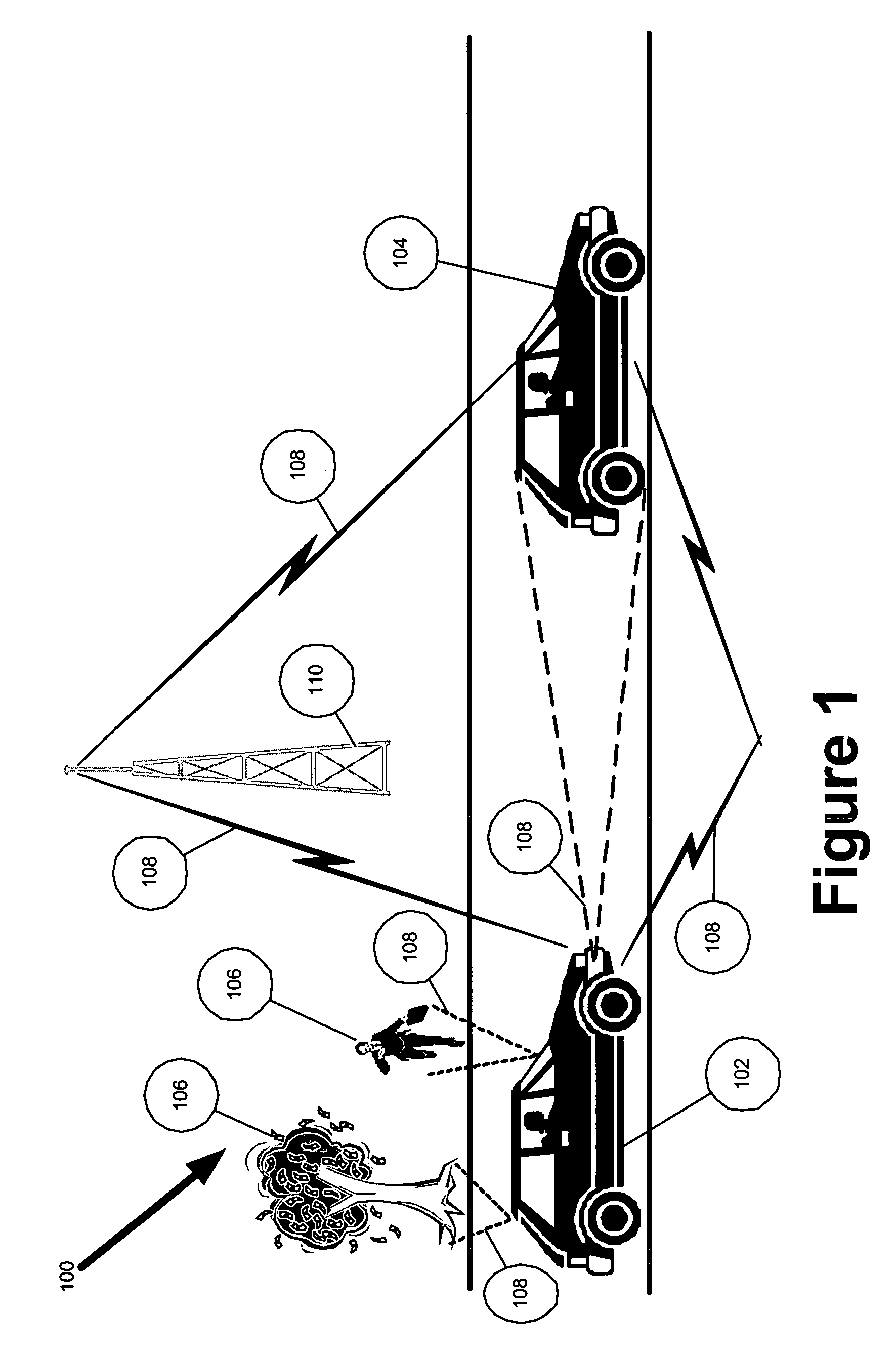
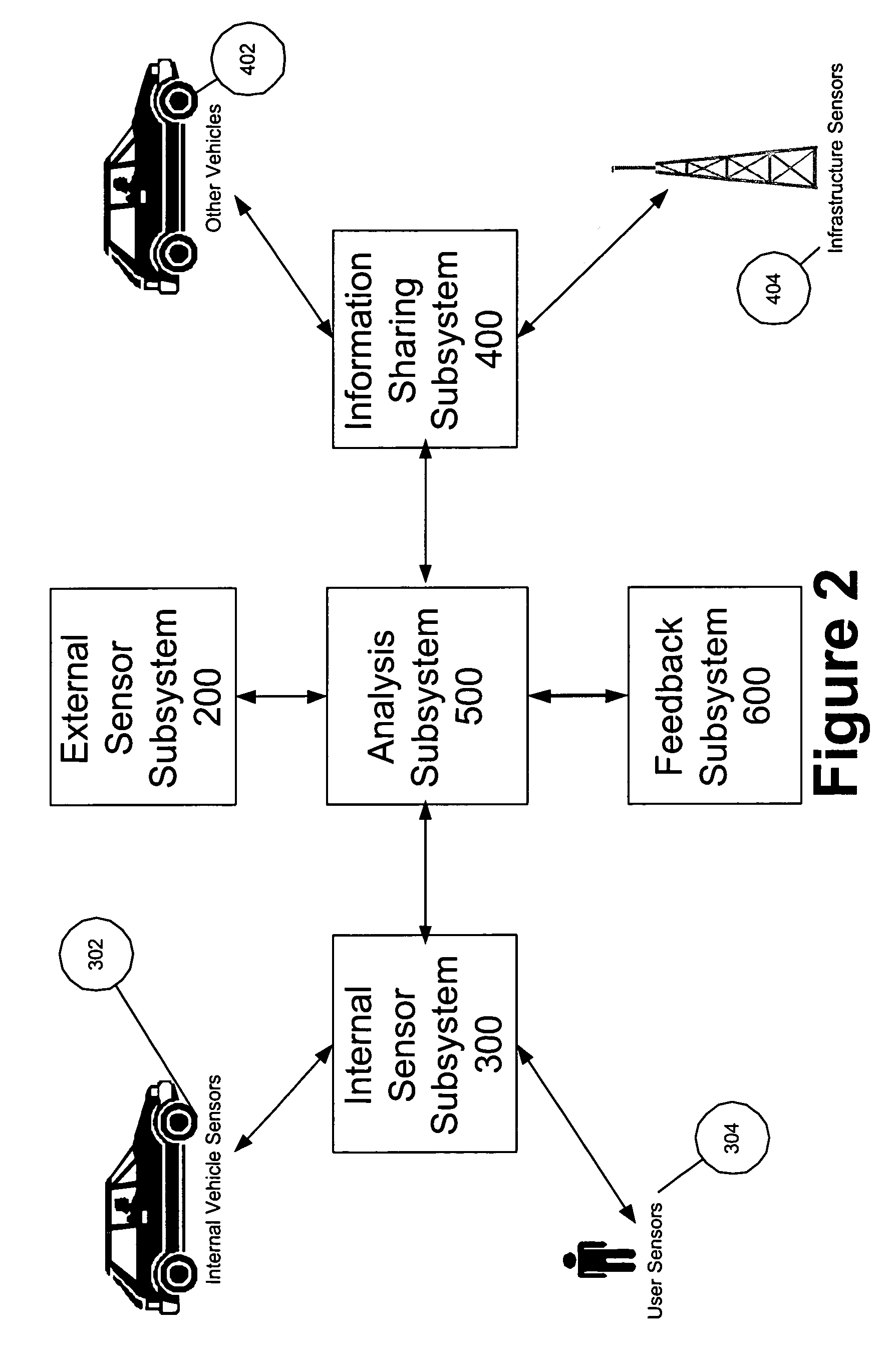
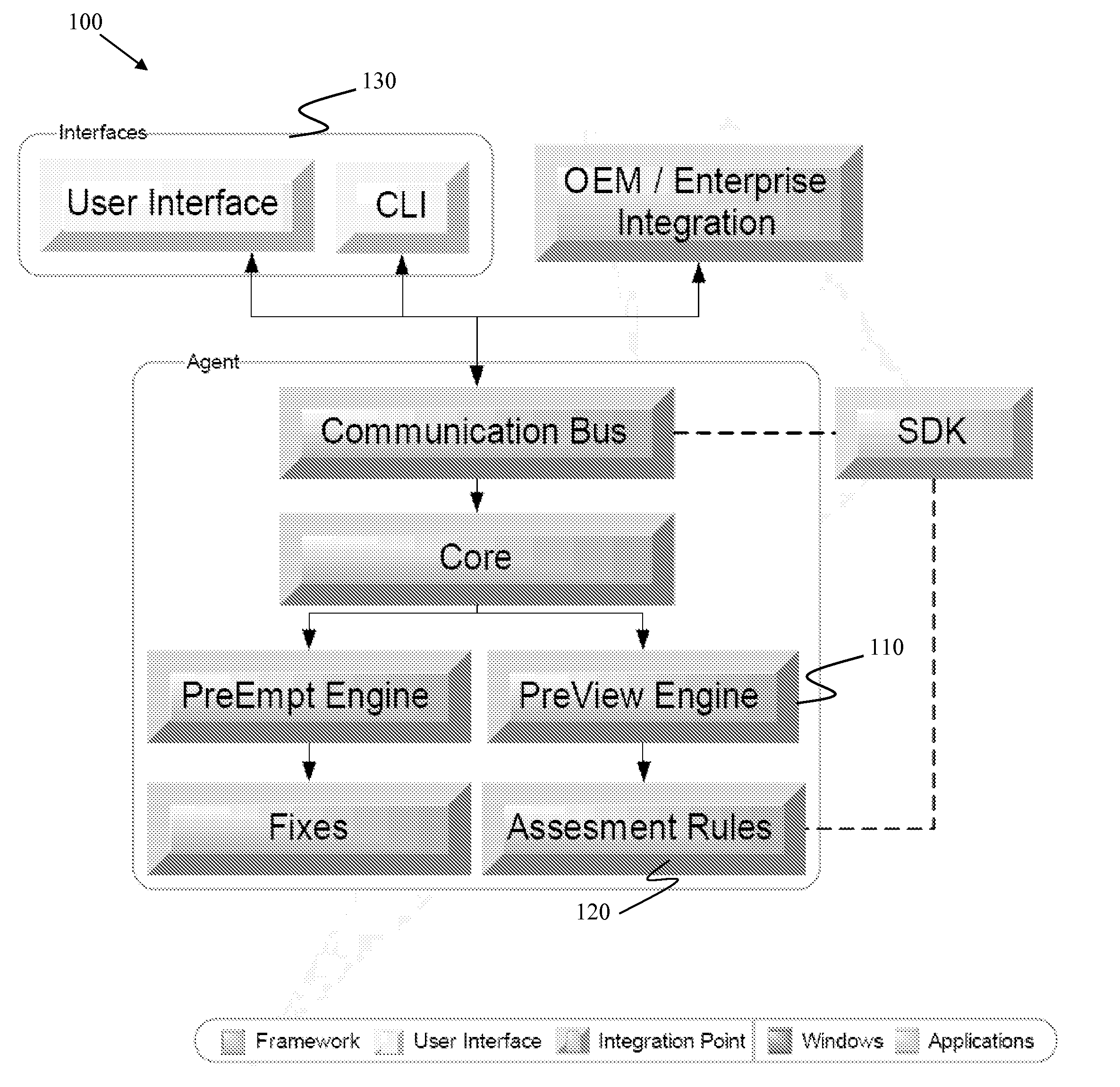
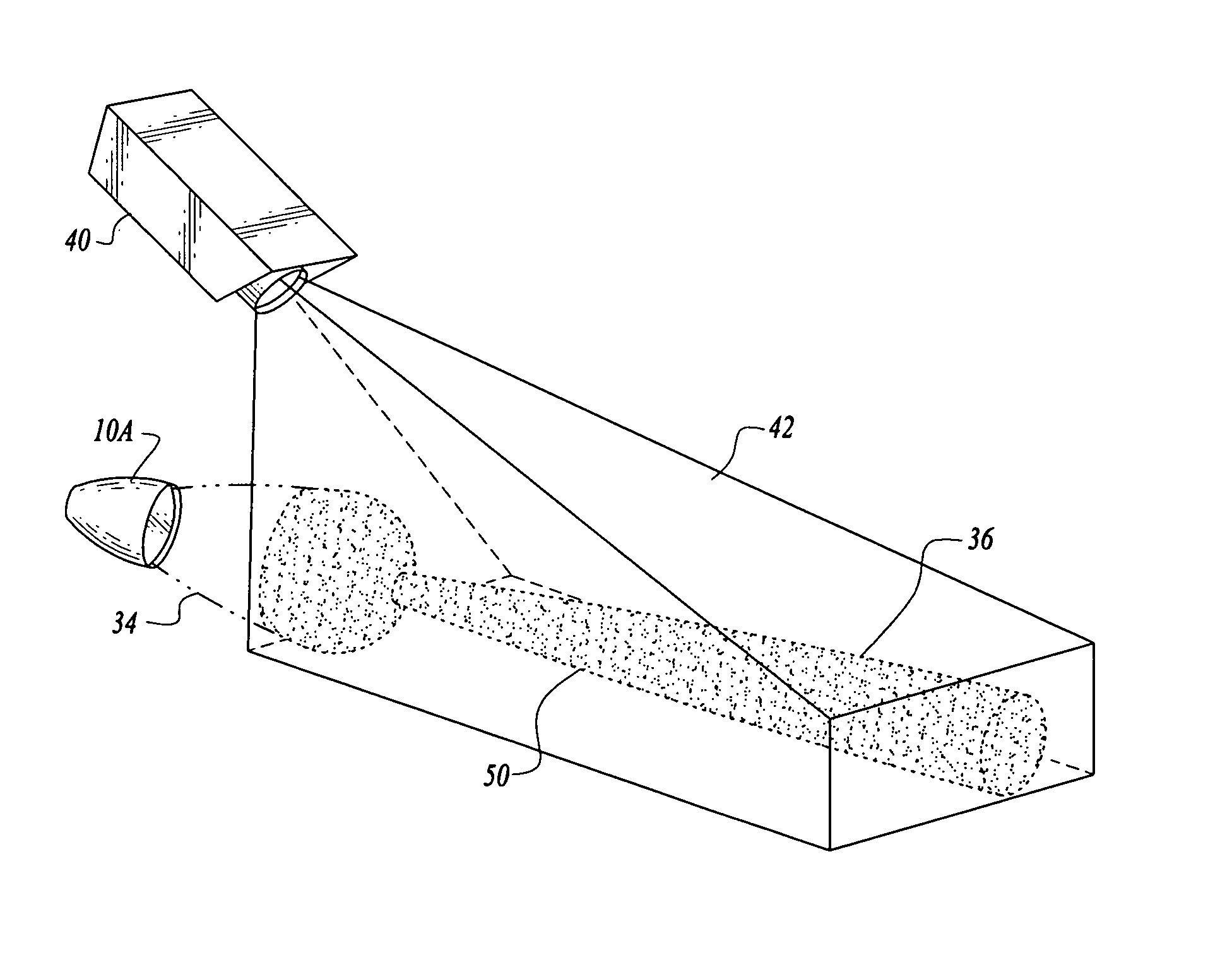
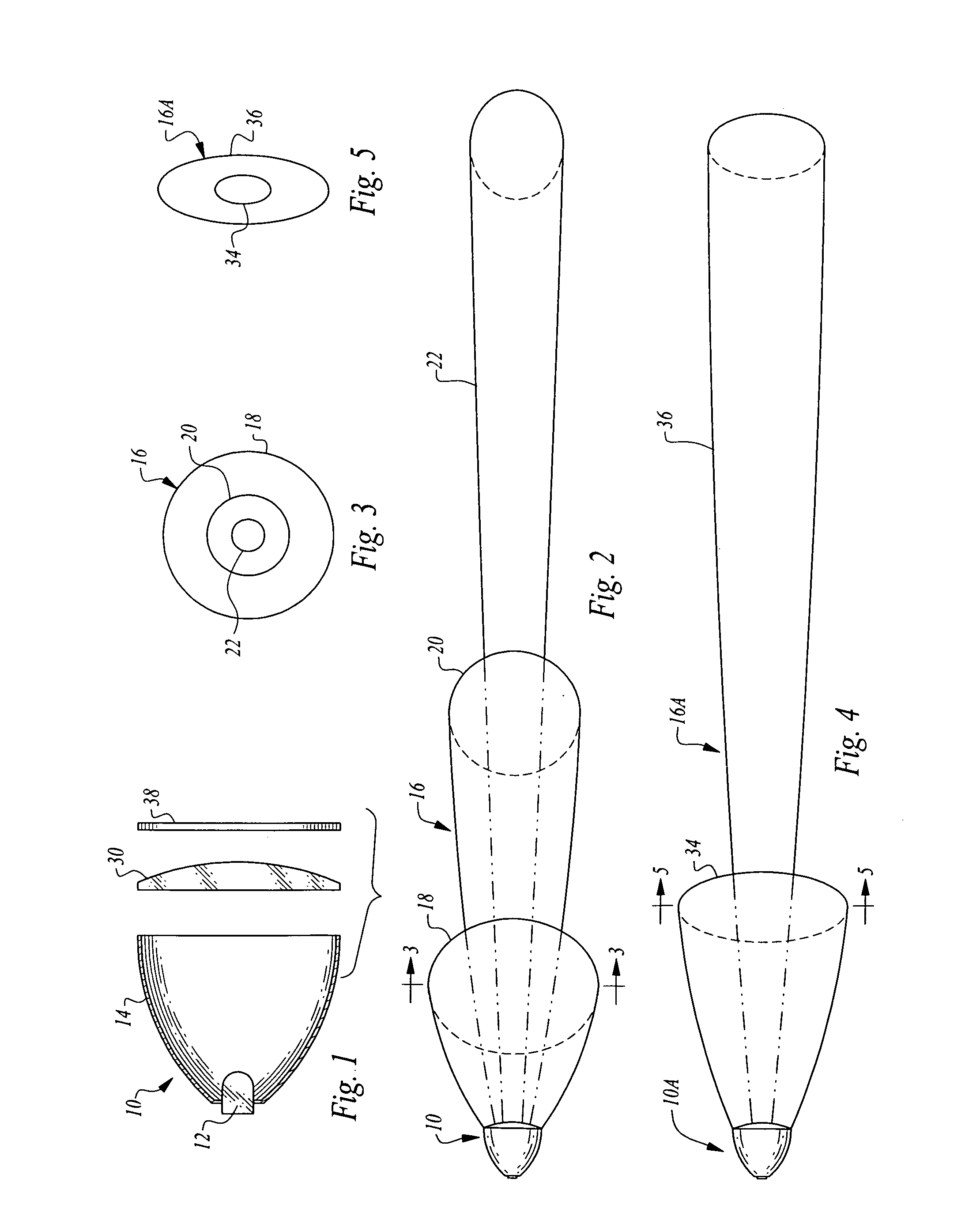
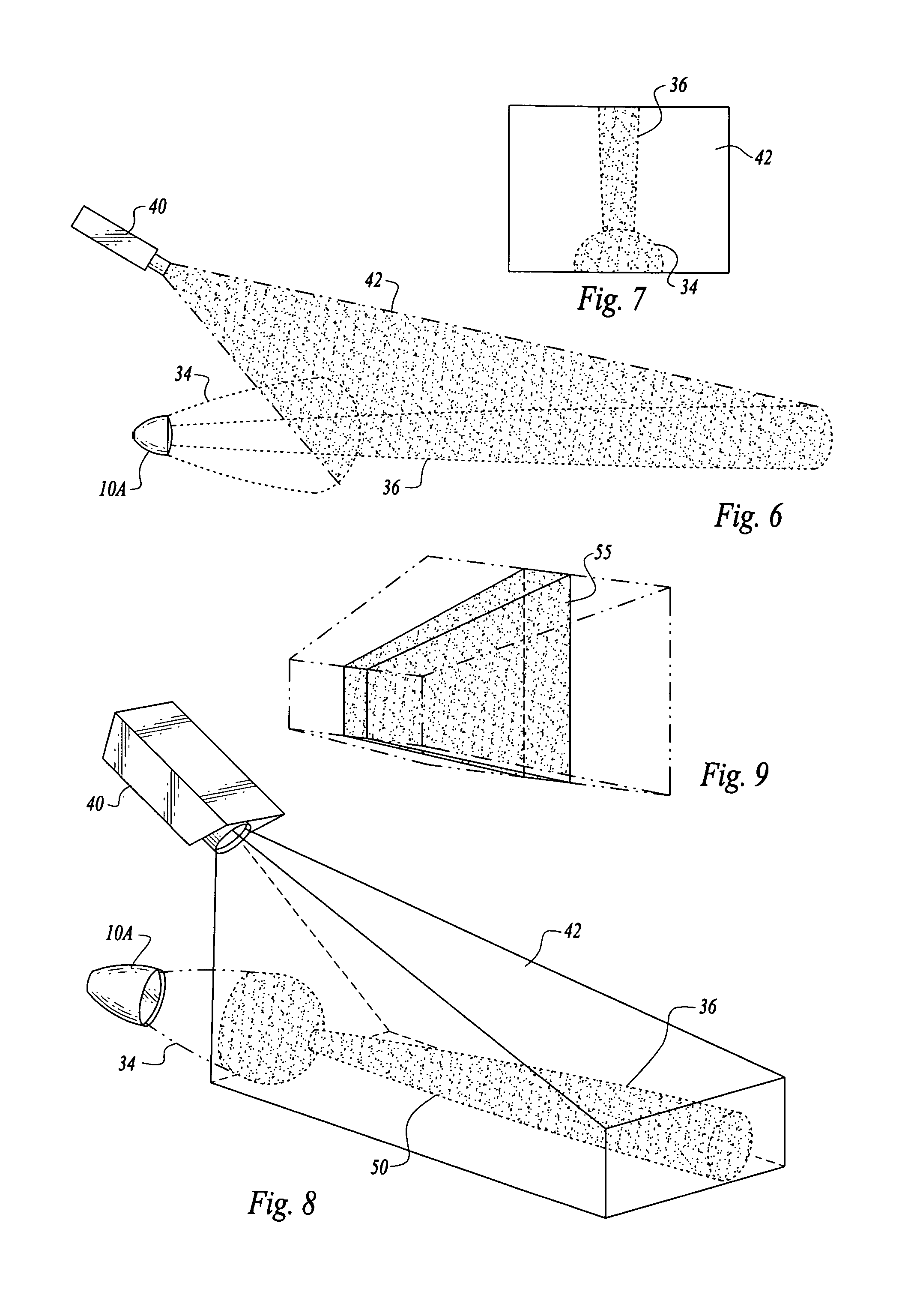
Multi-sensor integration for a vehicle
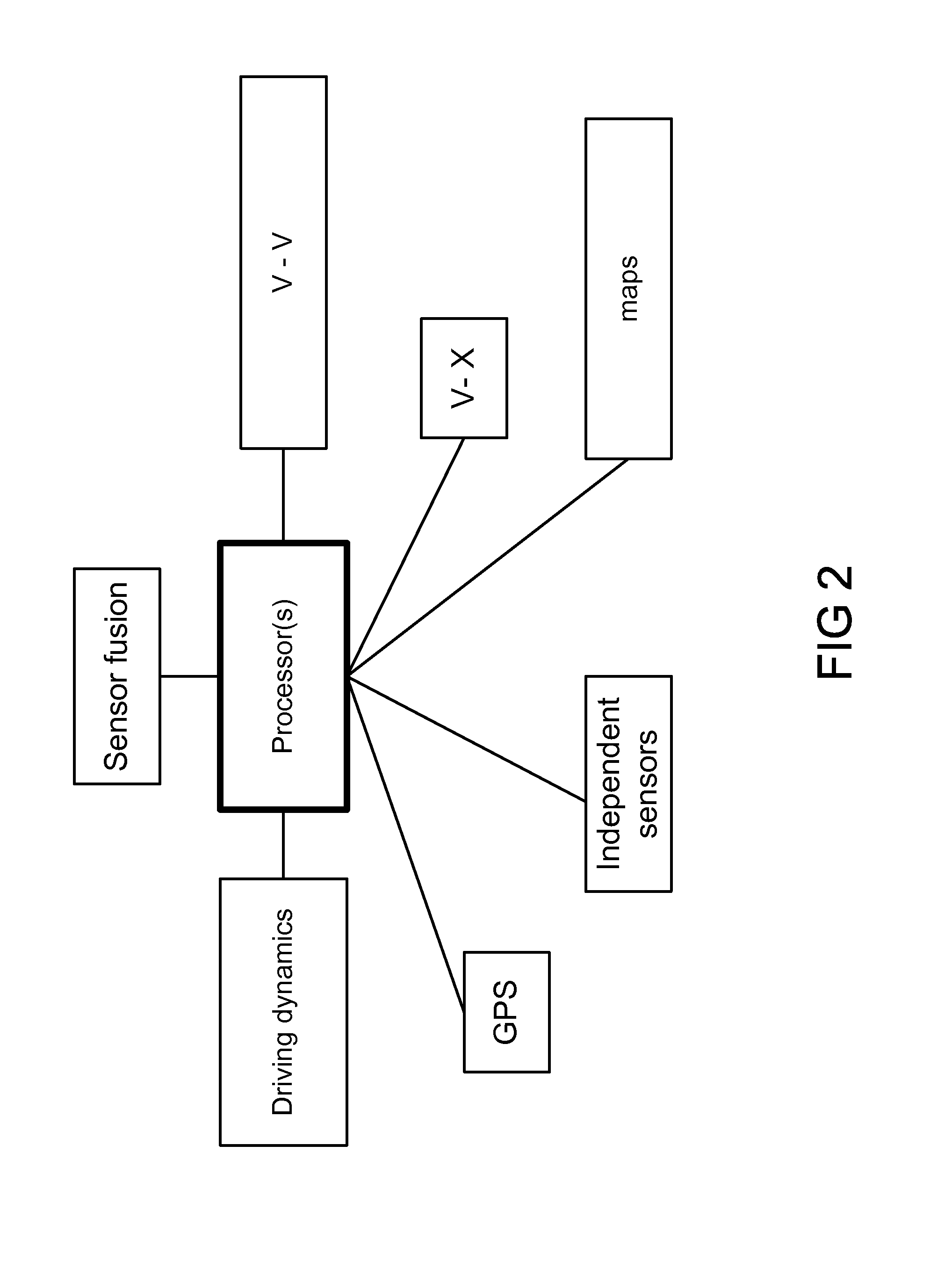
A sensor system for use in a vehicle that integrates sensor data from more than one sensor in an effort to facilitate collision avoidance and other types of sensor-related processing. The system include external sensors for capturing sensor data external to the vehicle. External sensors can include sensors of a wide variety of different sensor types, including radar, image processing, ultrasonic, infrared, and other sensor types. Each external sensor can be configured to focus on a particular sensor zone external to the vehicle. Each external sensor can also be configured to focus primarily on particular types of potential obstacles and obstructions based on the particular characteristics of the sensor zone and sensor type. All sensor data can be integrated in a comprehensive manner by a threat assessment subsystem within the sensor system. The system is not limited to sensor data from external sensors. Internal sensors can be used to capture internal sensor data, such a vehicle characteristics, user attributes, and other types of interior information. Moreover, the sensor system can also include an information sharing subsystem of exchanging information with other vehicle sensor systems or for exchanging information with non-vehicle systems such as a non-movable highway sensor system configured to transmit and receive information relating to traffic, weather, construction, and other conditions. The sensor system can potentially integrate data from all different sources in a comprehensive and integrated manner. The system can integrate information by assigning particular weights to particular determinations by particular sensors.
Owner:YAZAKI NORTH AMERICA
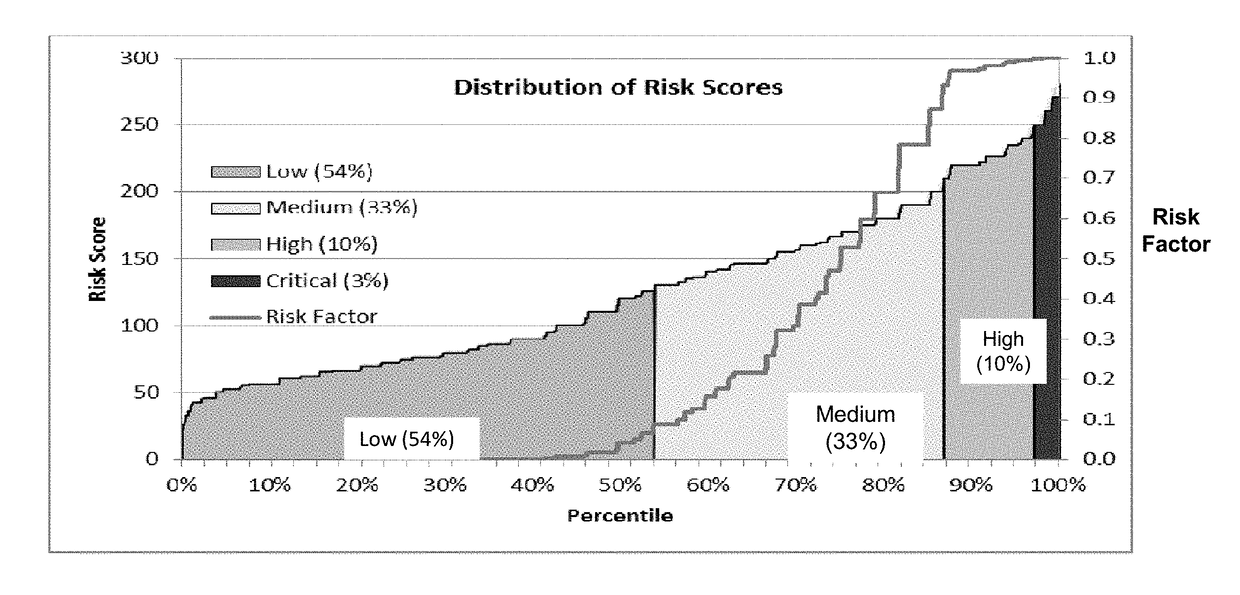
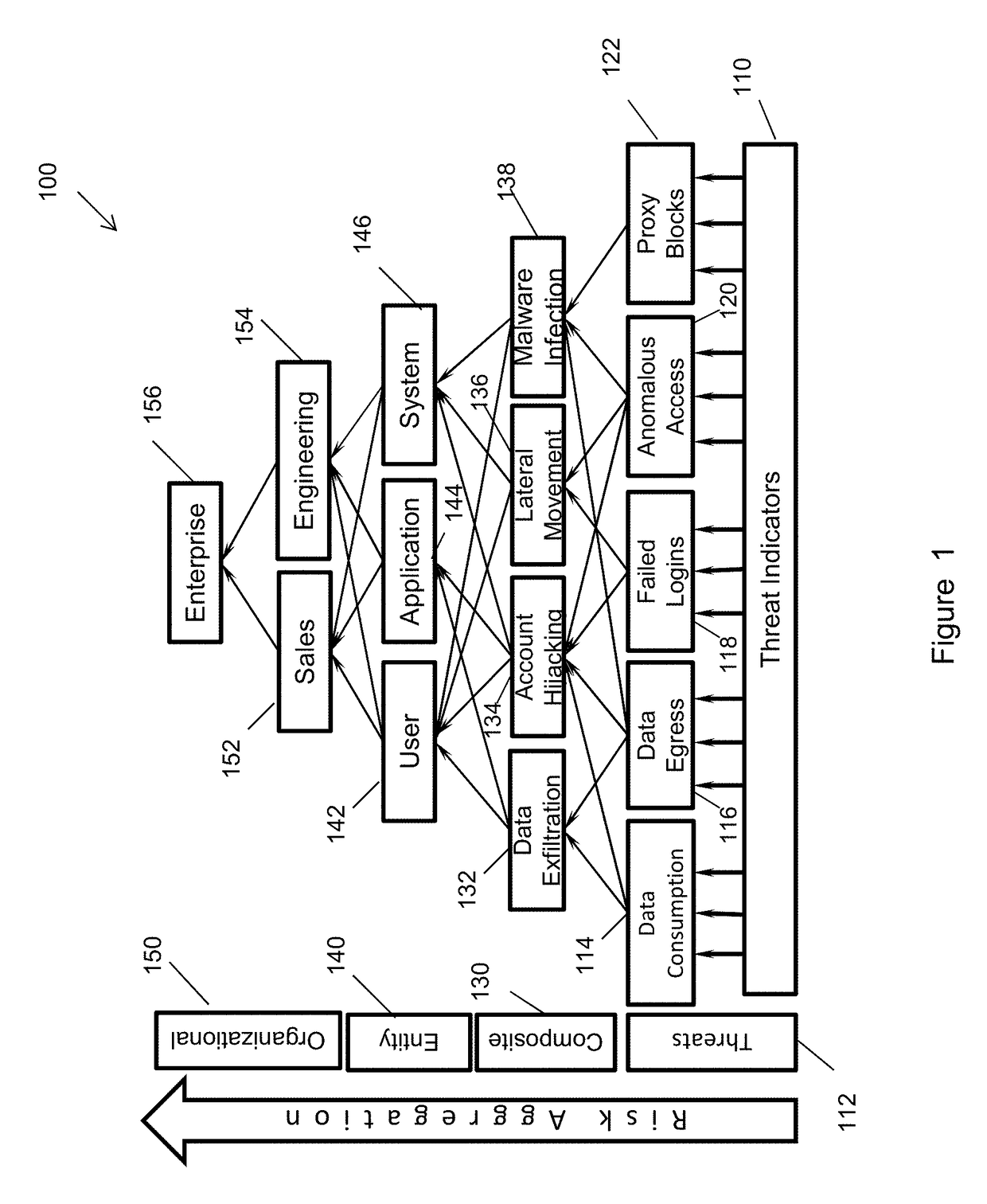
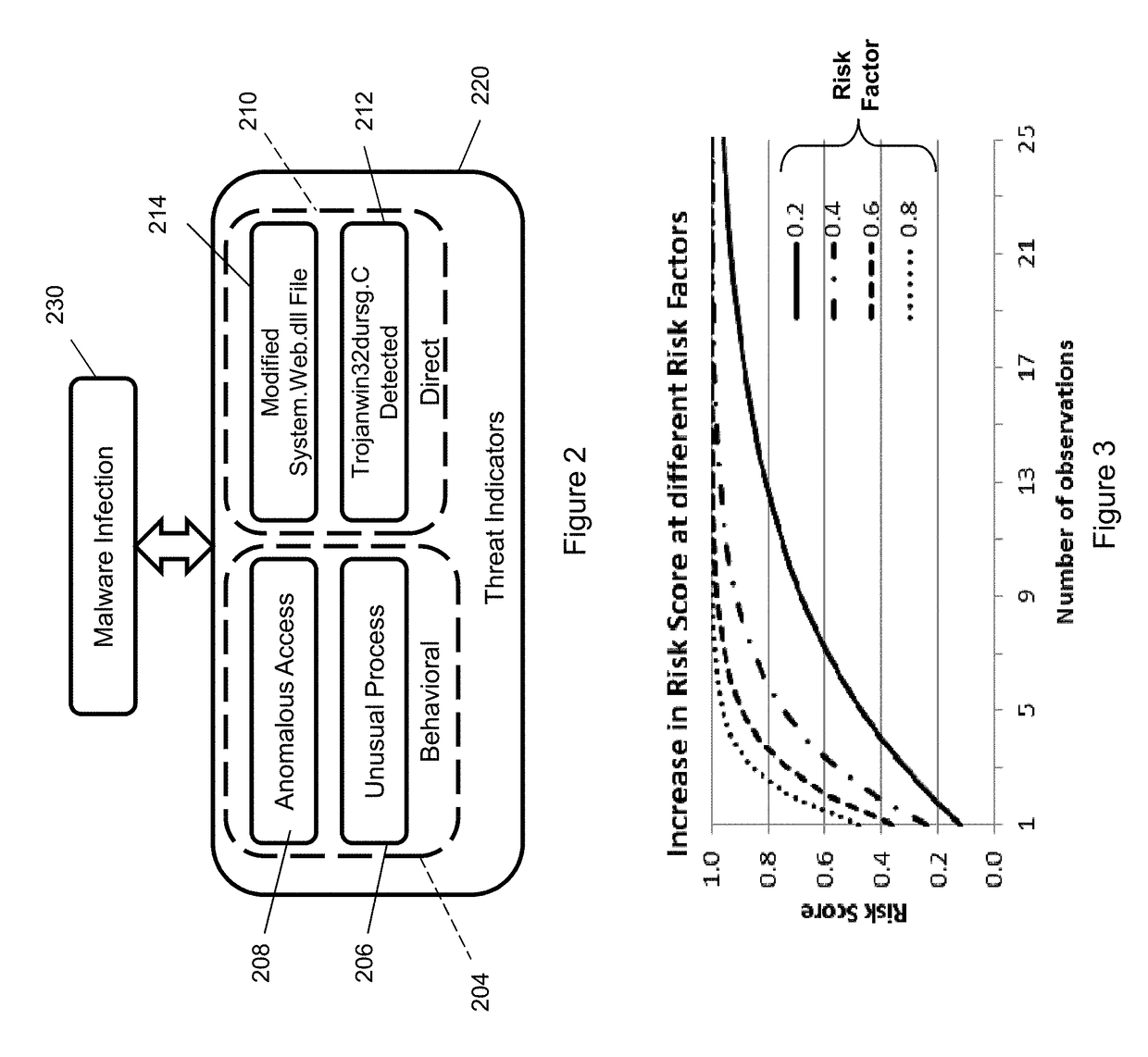
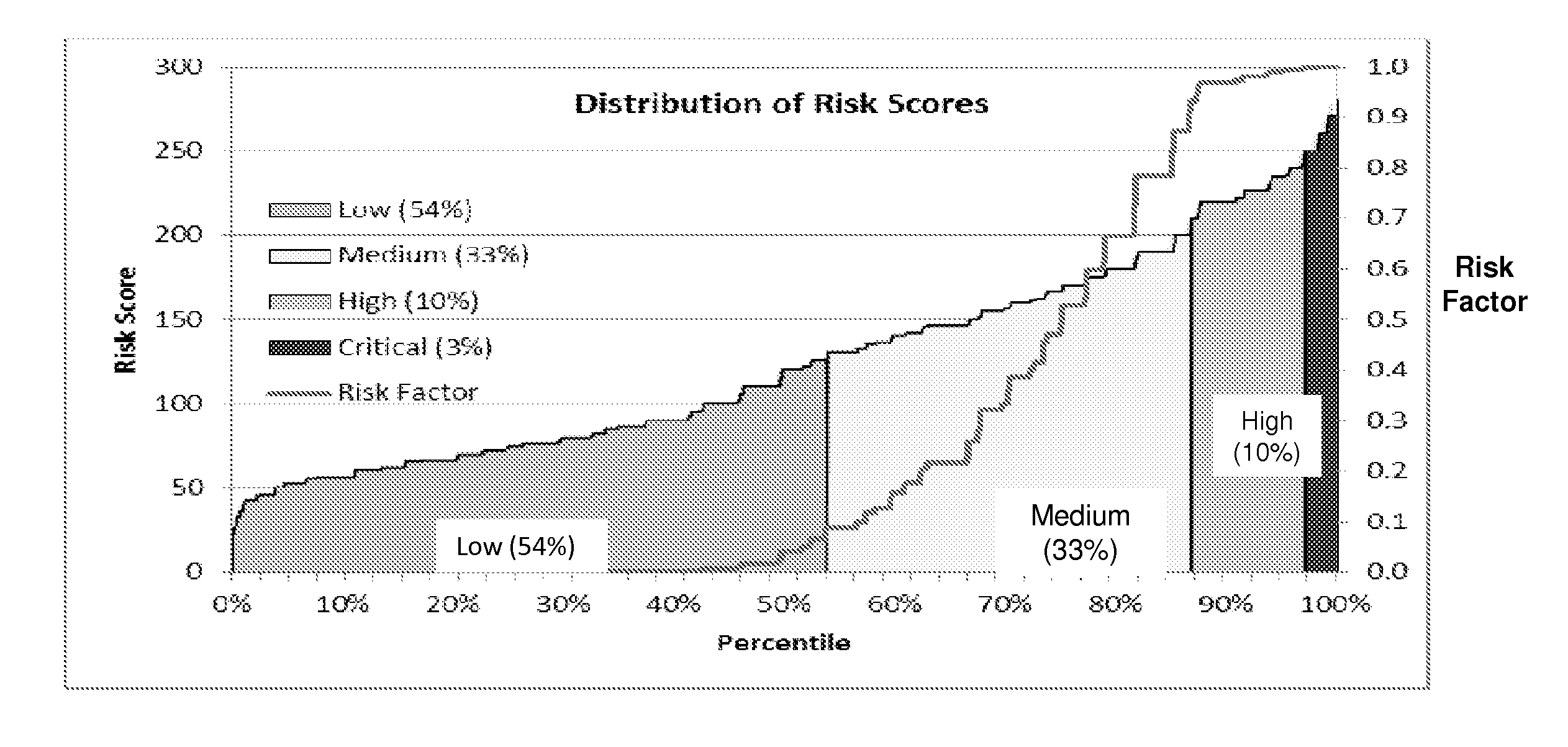
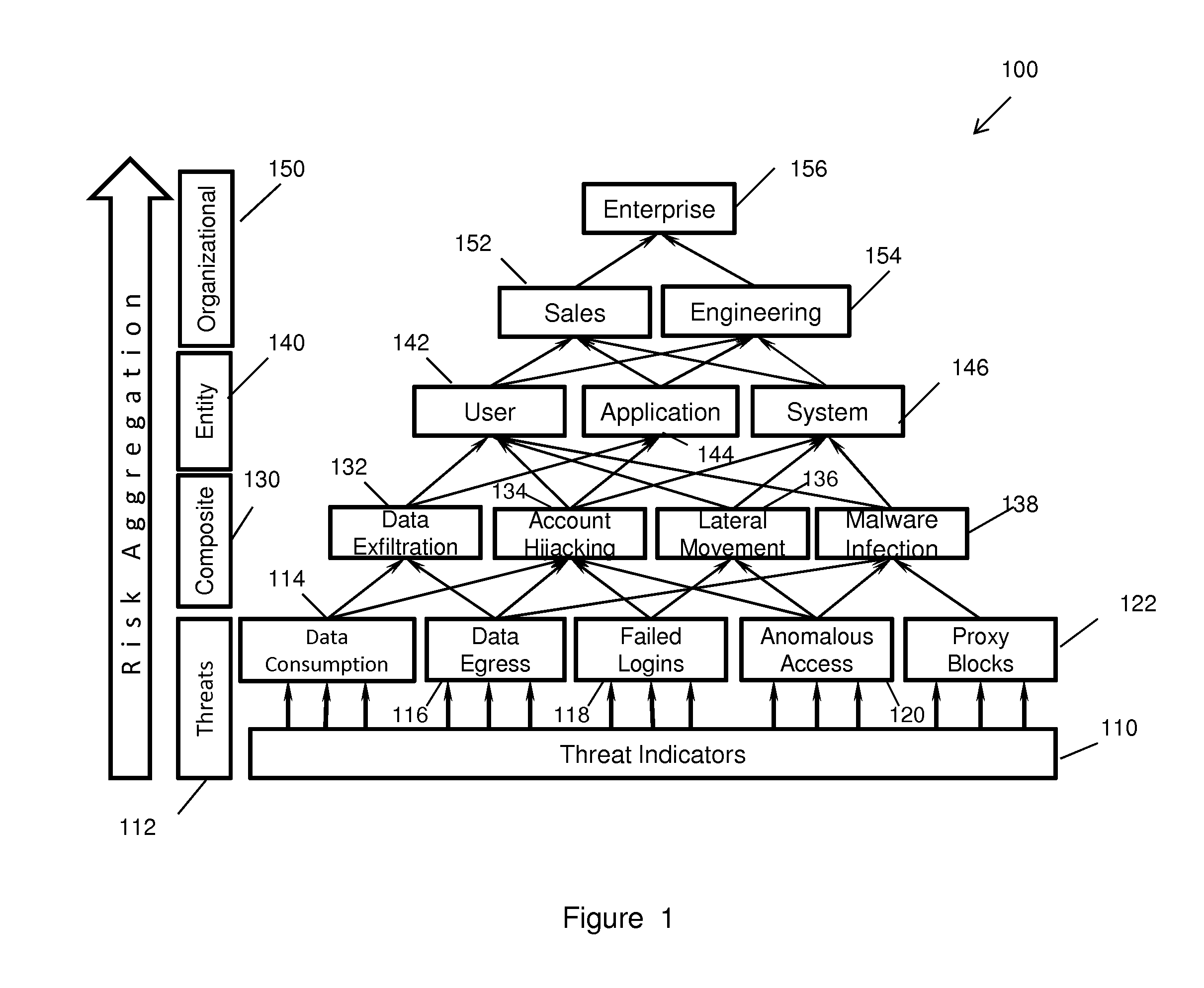
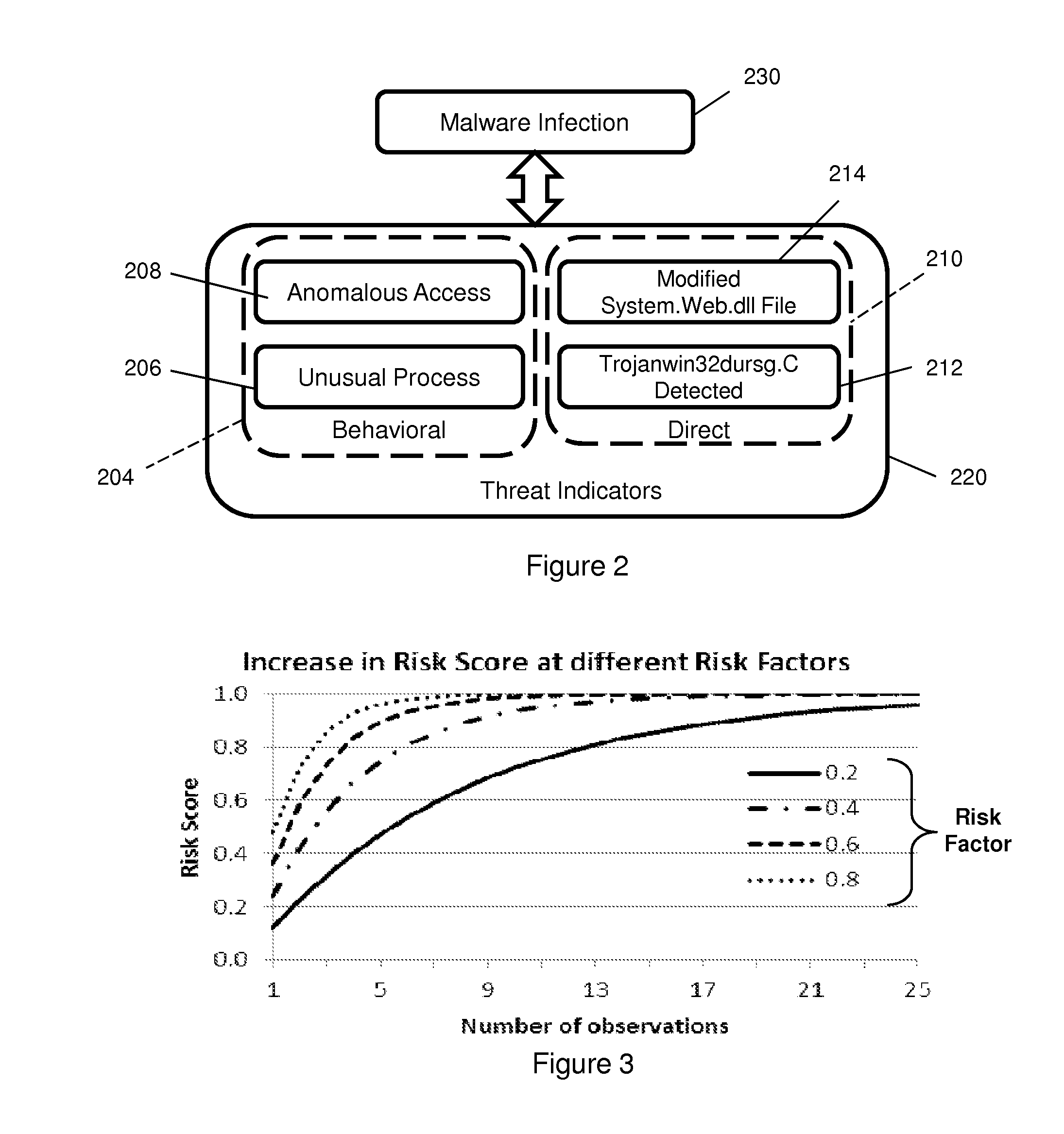
Risk scoring for threat assessment
Threat risks to an enterprise are detected and assessed by assembling singular threats identified using both direct and behavioral threat indicators into composite threats to create complex use cases across multiple domains, and to amplify risks along kill chains of known attacks for early detection. Composite threat risk scores are computed from risk scores of singular threats to exponentially increase with the number of events observed along the kill chain. Composite threats are combined with normalized values of static risk and inherent risk for an entity of the enterprise to produce an entity risk score representative of the overall risk to the entity.
Owner:SECURONIX INC
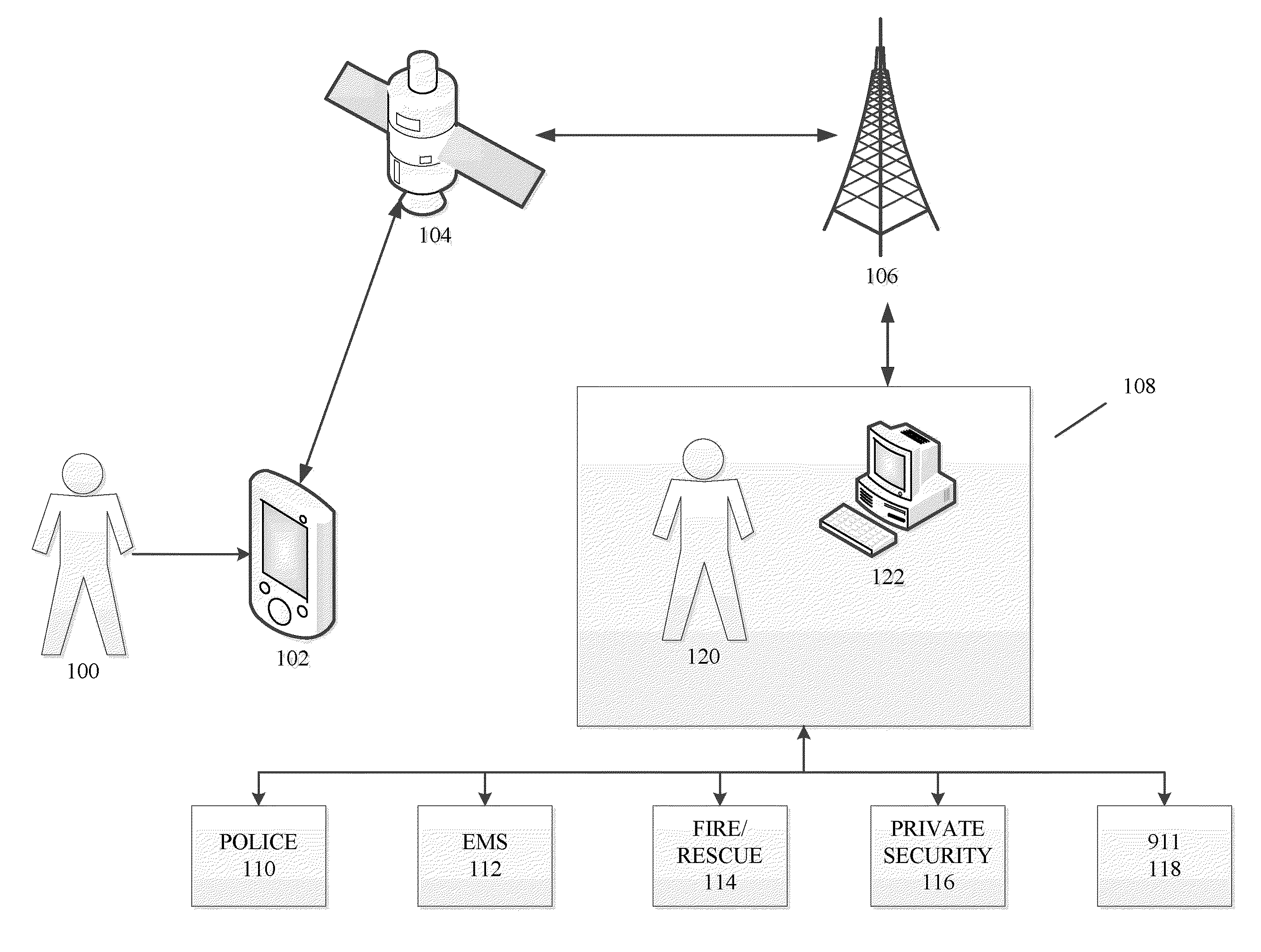
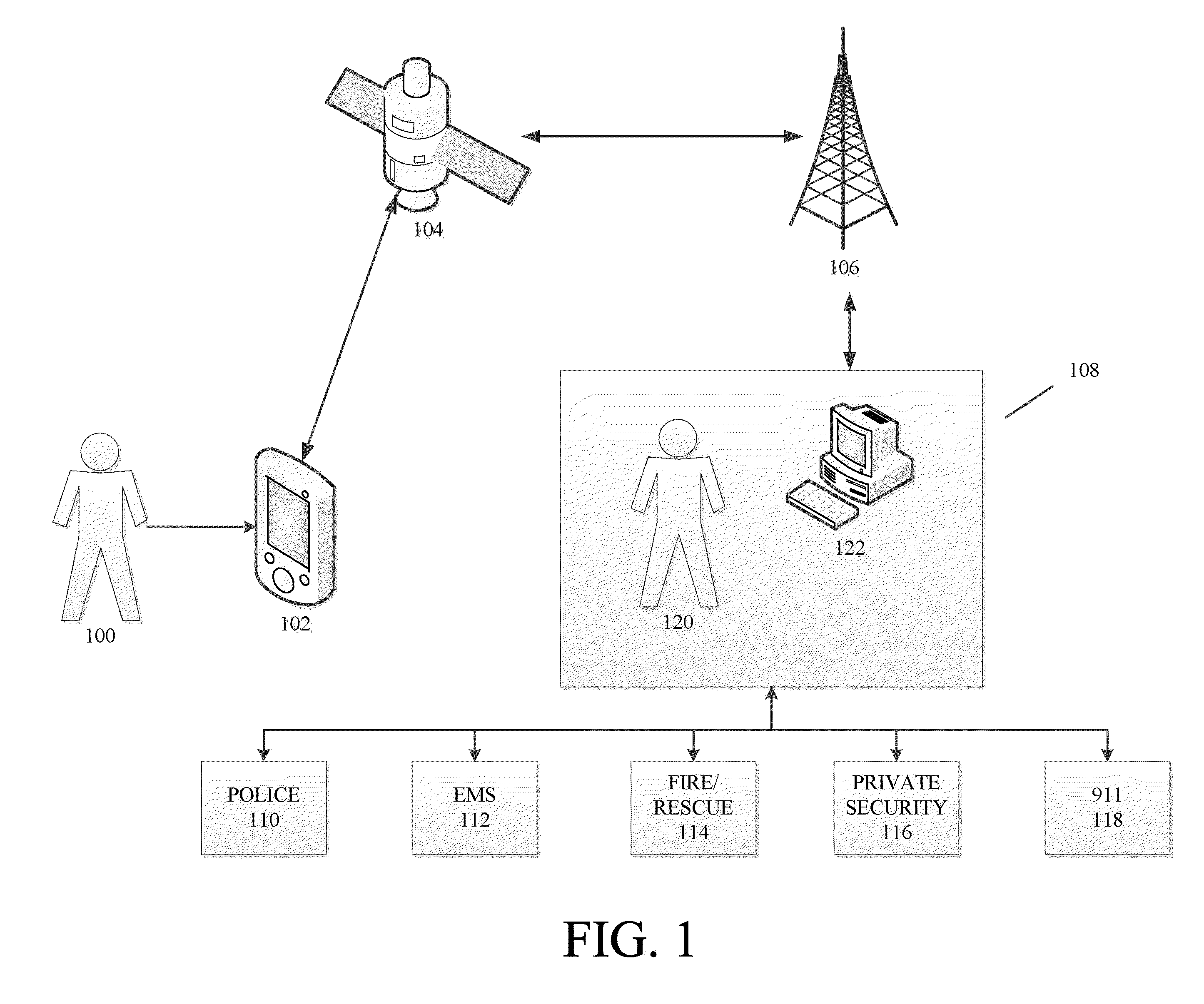
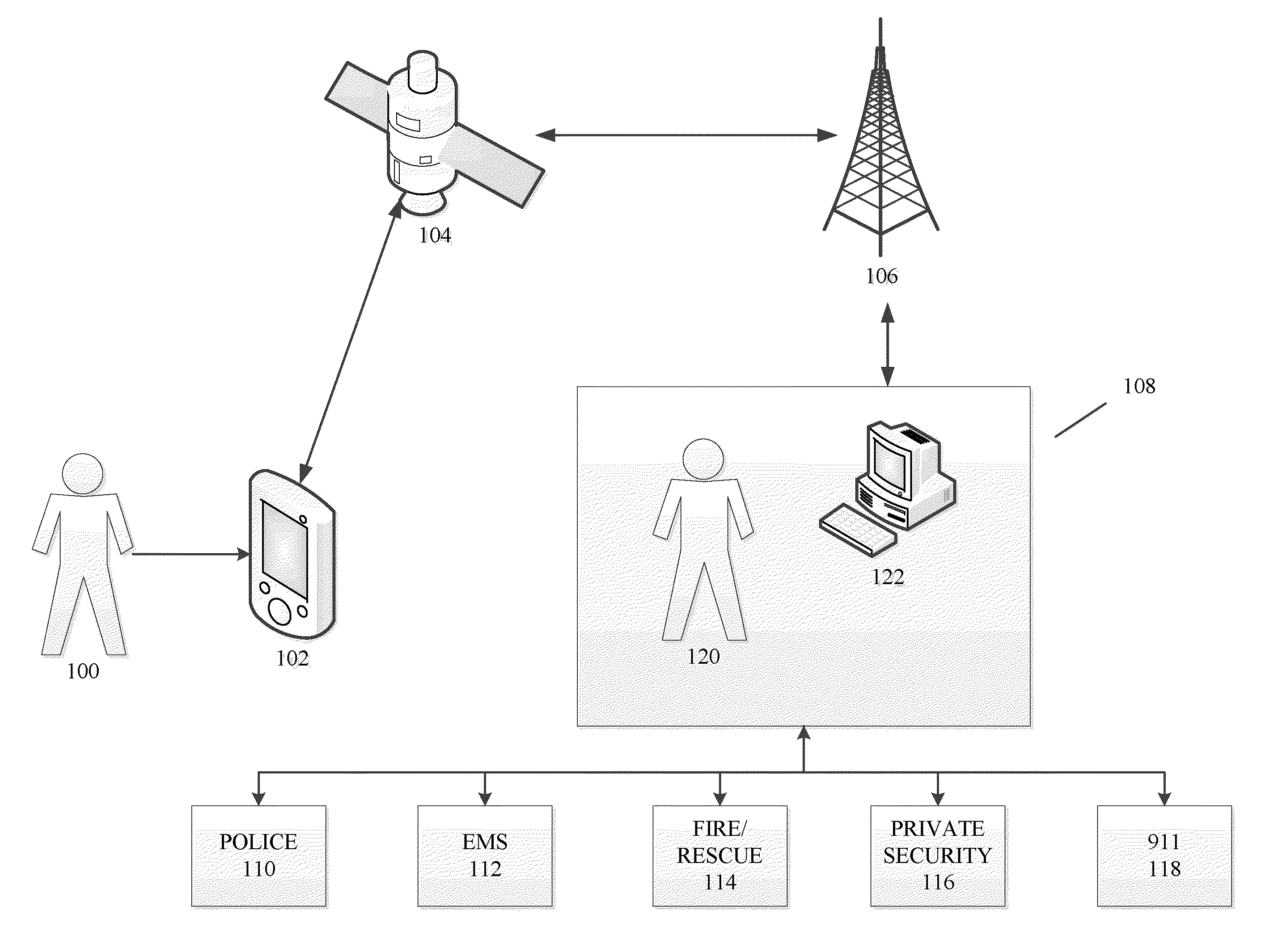
Methods and systems for threat assessment, safety management, and monitoring of individuals and groups
InactiveUS20110046920A1Improve security levelReduce morbidityError detection/correctionMultiple digital computer combinationsComputer scienceSecurity management
The disclosure generally relates to methods and systems anticipating a potentially threatening or dangerous incident, and providing varying levels of response to a user. In an exemplary embodiment, the present invention provides varying levels of assistance to a user prior to, during, and after a threatening incident occurs. By providing assistance prior to a threatening incident occurring, the system may be able to thwart potential attacks, bodily harm, robberies, break-ins, and other criminal or dangerous activity. The assistance can be, for example, in the form of deterrents, alerting first responders to go to the scene, sending security personnel to the scene, remotely monitoring the scene, remotely interacting with the scene, providing information and advice to the user.
Owner:STRIDER
Integrated framework for vehicle operator assistance based on a trajectory and threat assessment
ActiveUS20120083947A1Autonomous decision making processDigital data processing detailsState spaceHazard avoidance
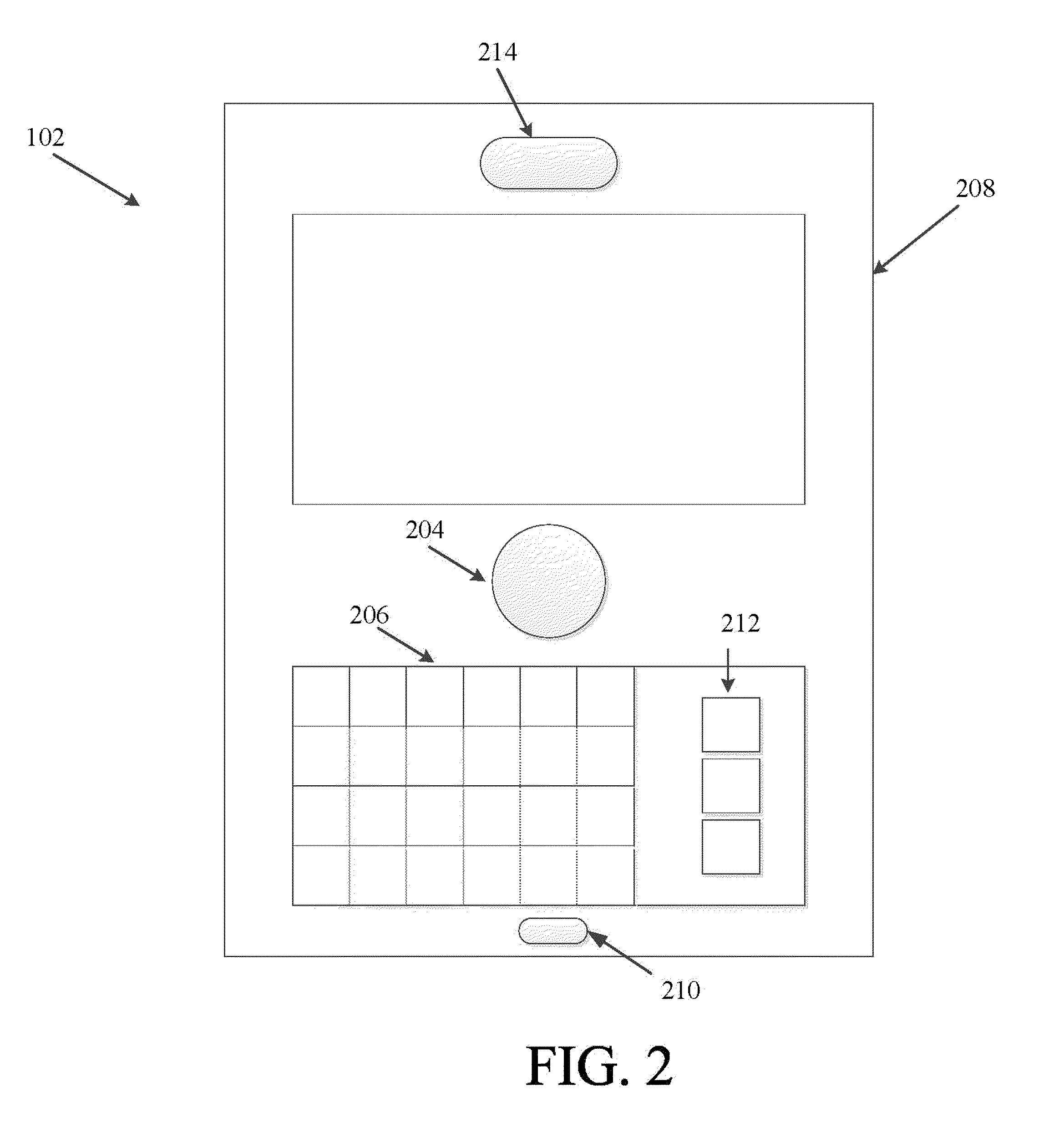
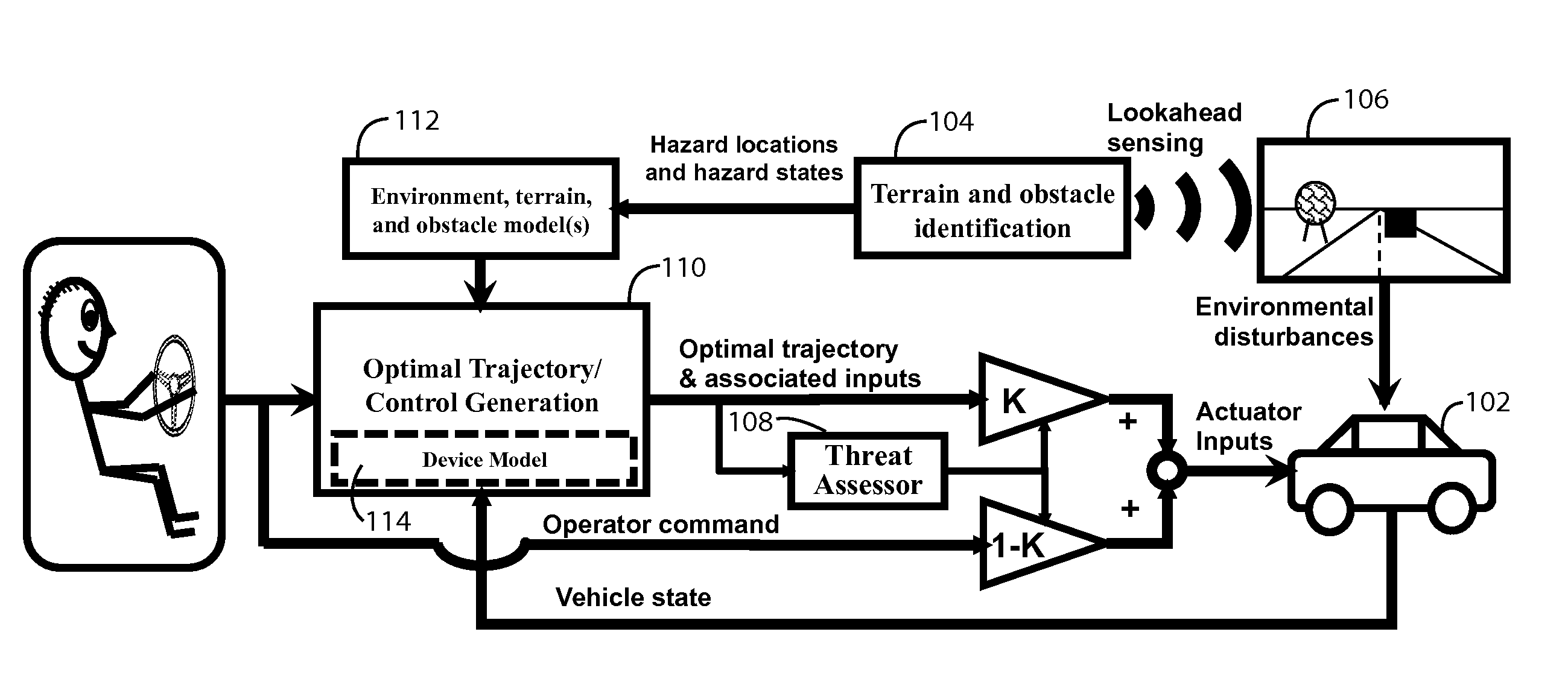
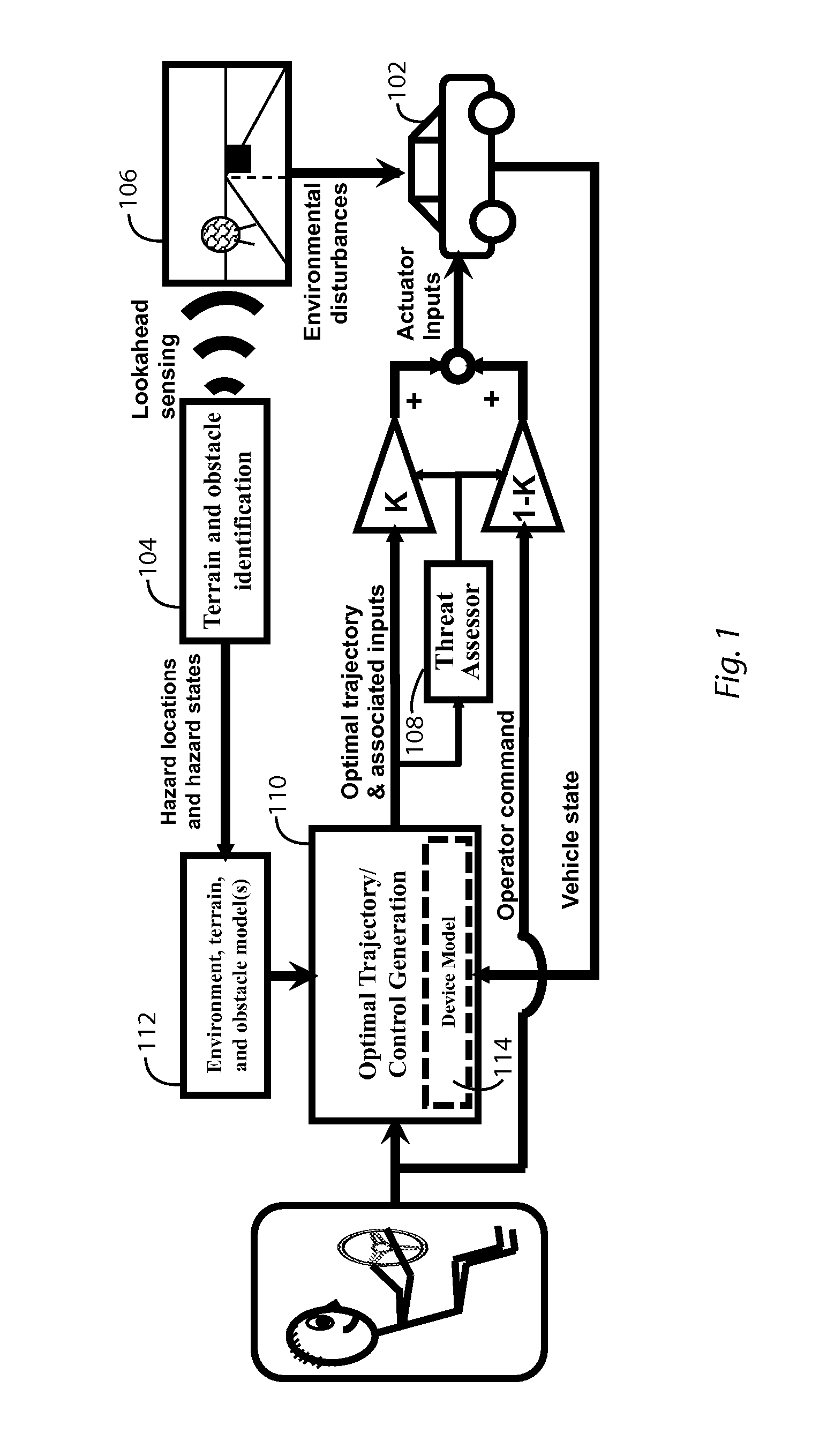
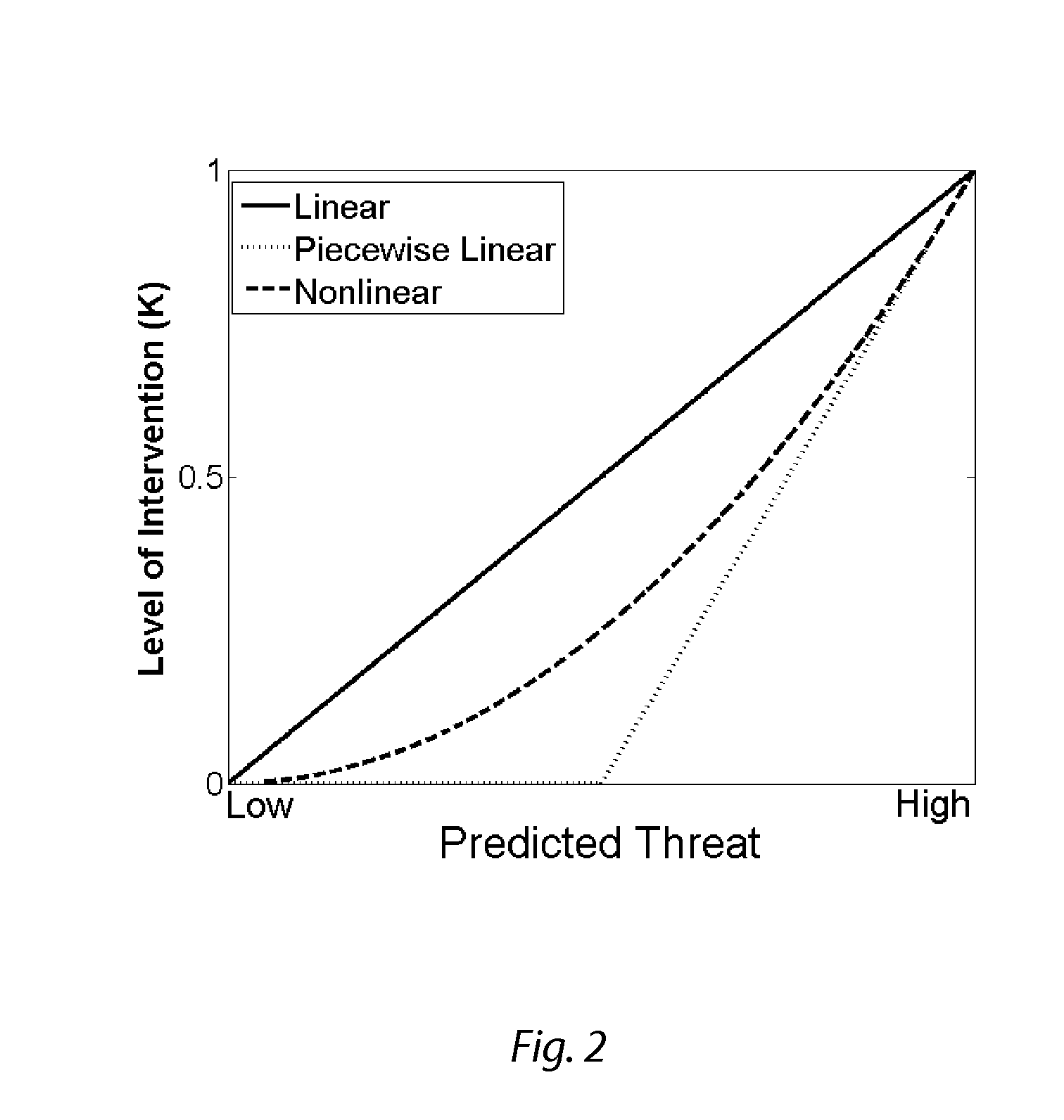
Various types and levels of operator assistance are performed within a unified, configurable framework. A model of the device with a model of the environment and the current state of the device and the environment are used to iteratively generate a sequence of optimal device control inputs that, when applied to a model of the device, generate an optimal device trajectory through a constraint-bounded corridor or region within the state space. This optimal trajectory and the sequence of device control inputs that generates it is used to generate a threat assessment metric. An appropriate type and level of operator assistance is generated based on this threat assessment. Operator assistance modes include warnings, decision support, operator feedback, vehicle stability control, and autonomous or semi-autonomous hazard avoidance. The responses generated by each assistance mode are mutually consistent because they are generated using the same optimal trajectory.
Owner:MASSACHUSETTS INST OF TECH
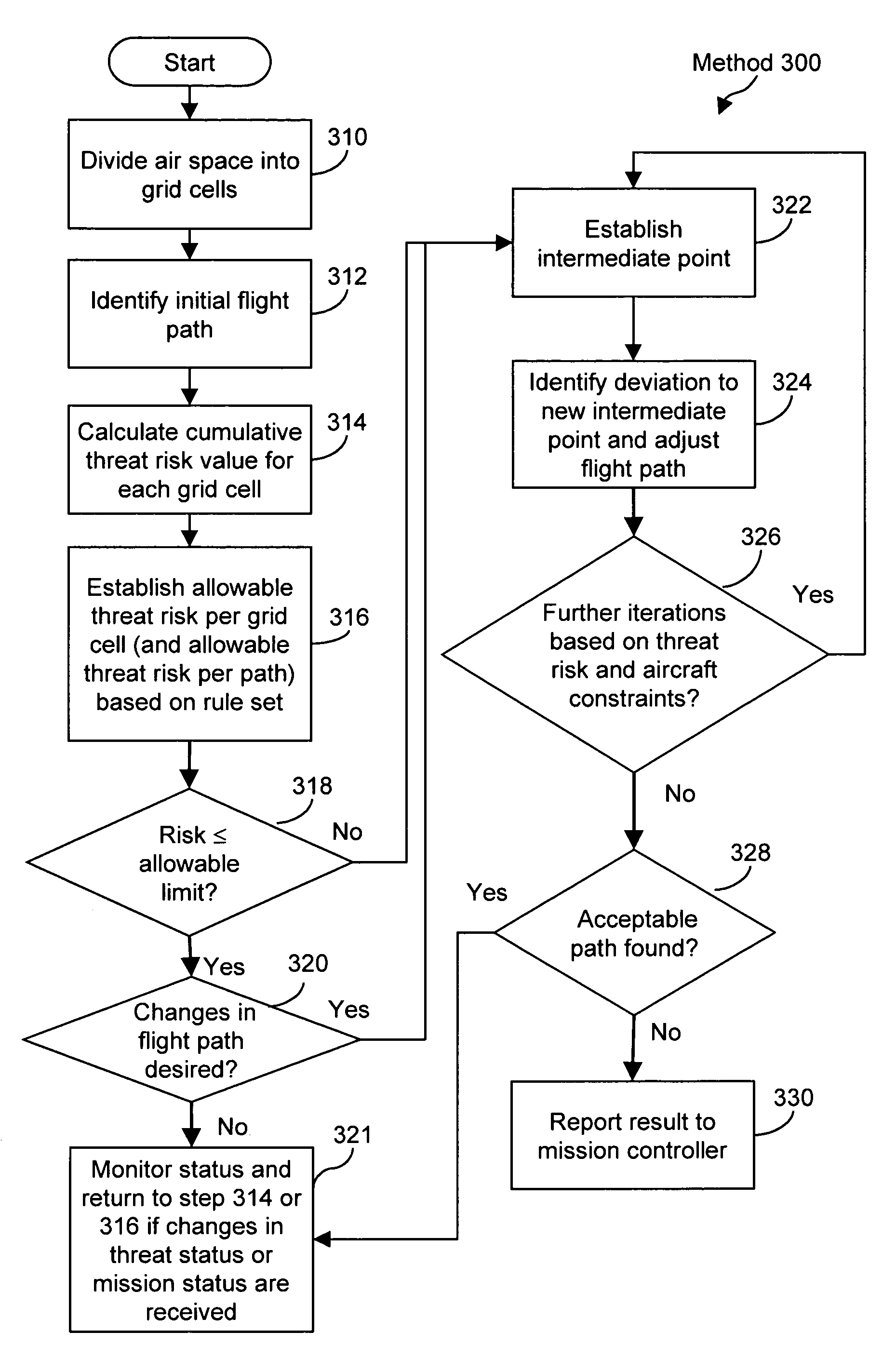
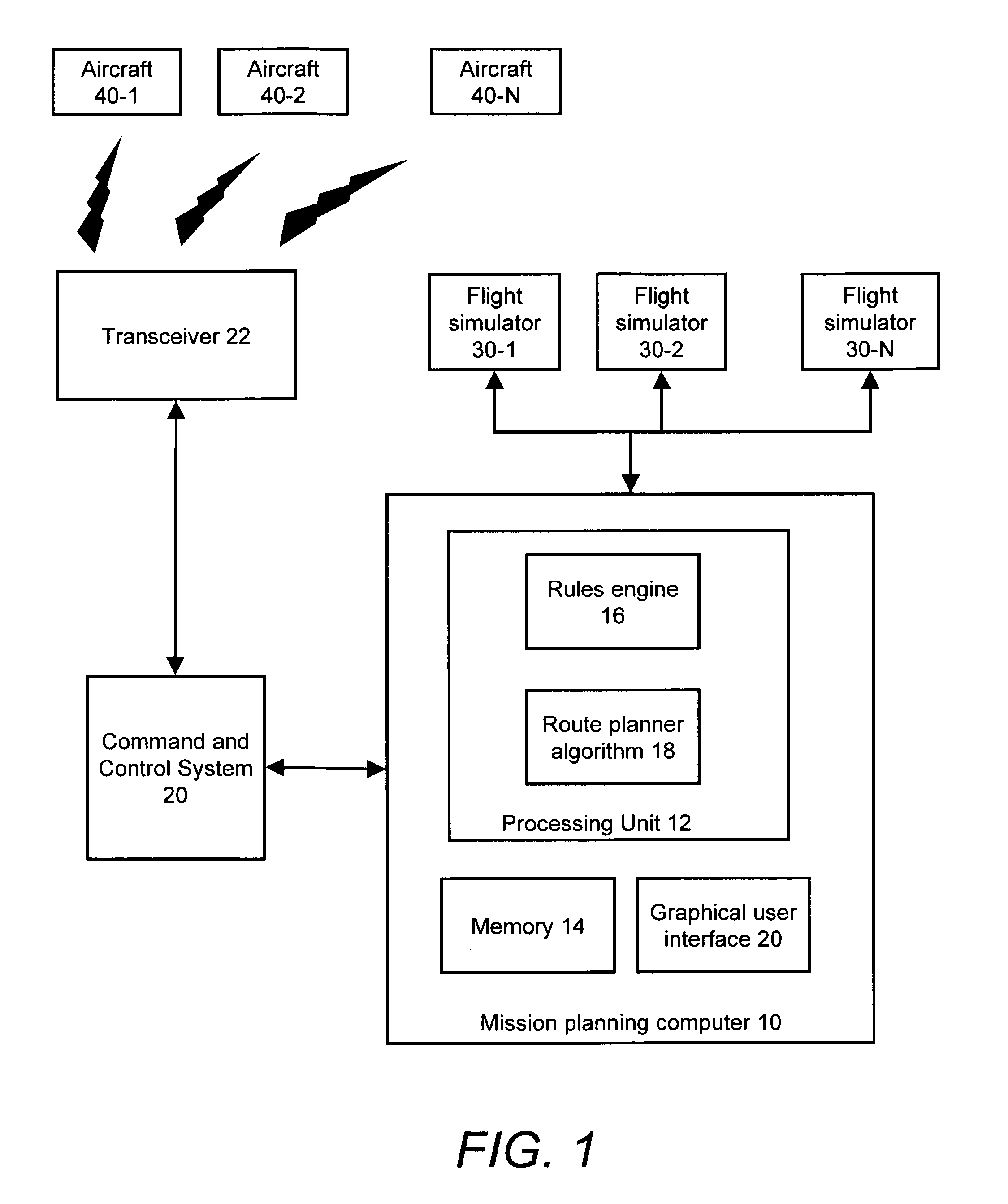
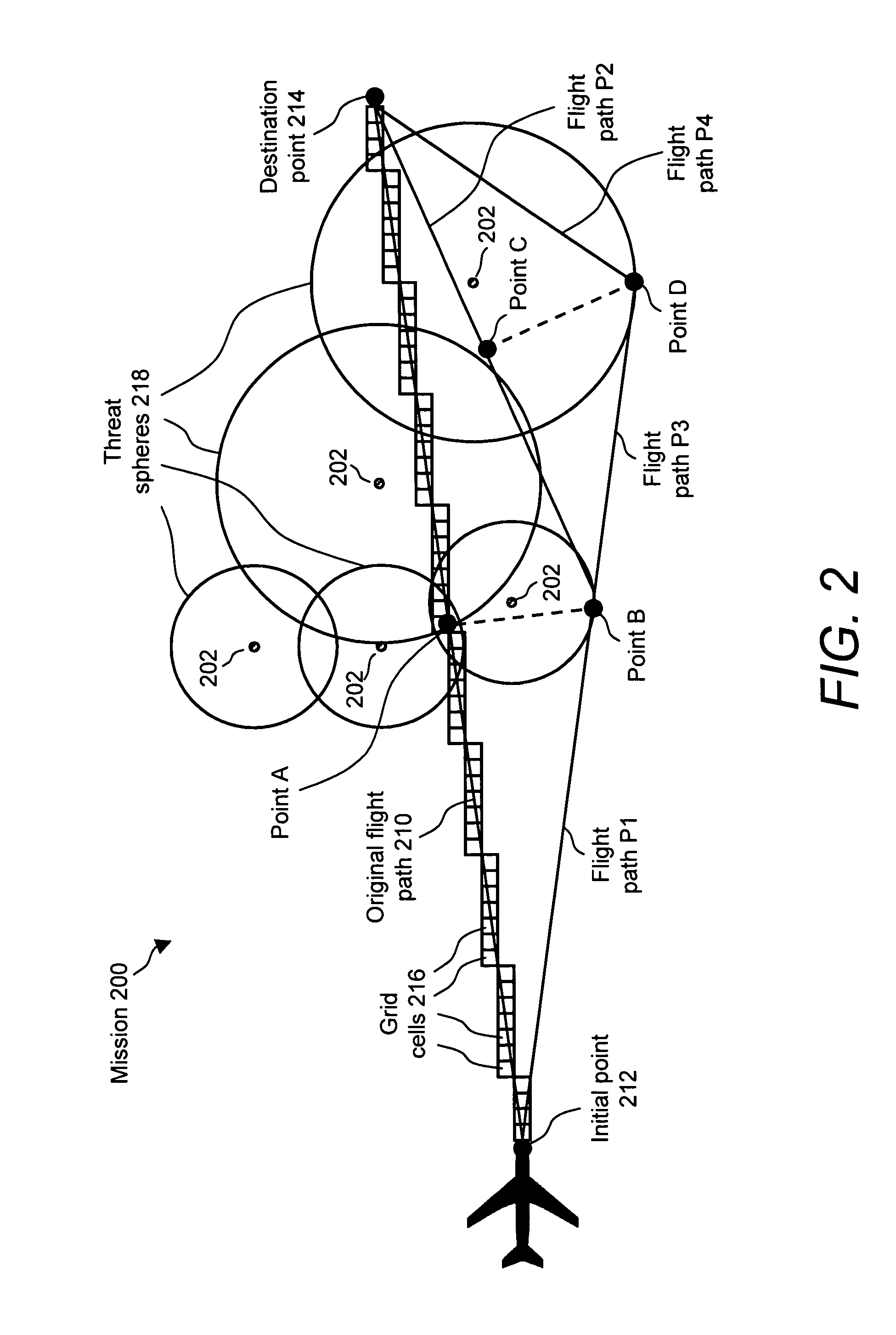
Method and system for route planning of aircraft using rule-based expert system and threat assessment
ActiveUS7194353B1Reduce errorsReduce manpowerInstruments for road network navigationAnti-collision systemsRule based expert systemGrid cell
A method and system or determining a flight path for an aircraft between an initial point and a destination point are described. An airspace is divide into a set of grid cells, and a flight path is established between the initial point and the destination point. A cumulative threat risk value for each of the grid cells is calculated, and an allowable threat risk per grid cell is established based on a rule set. An intermediate point from which to deviate the flight path is identified based upon an analysis of the cumulative threat risk values of the grid cells, if the threat risk value of any of the grid cells intersecting the flight path exceeds the allowable threat risk. A deviation from the intermediate point to a new intermediate point is determined such that the new intermediate point has a cumulative threat risk value lower than or equal to the allowable threat risk per grid cell. The flight path is adjusted between the initial point and the destination point to pass through the new intermediate point, thereby providing a modified flight path.
Owner:ACCENTURE GLOBAL SERVICES LTD
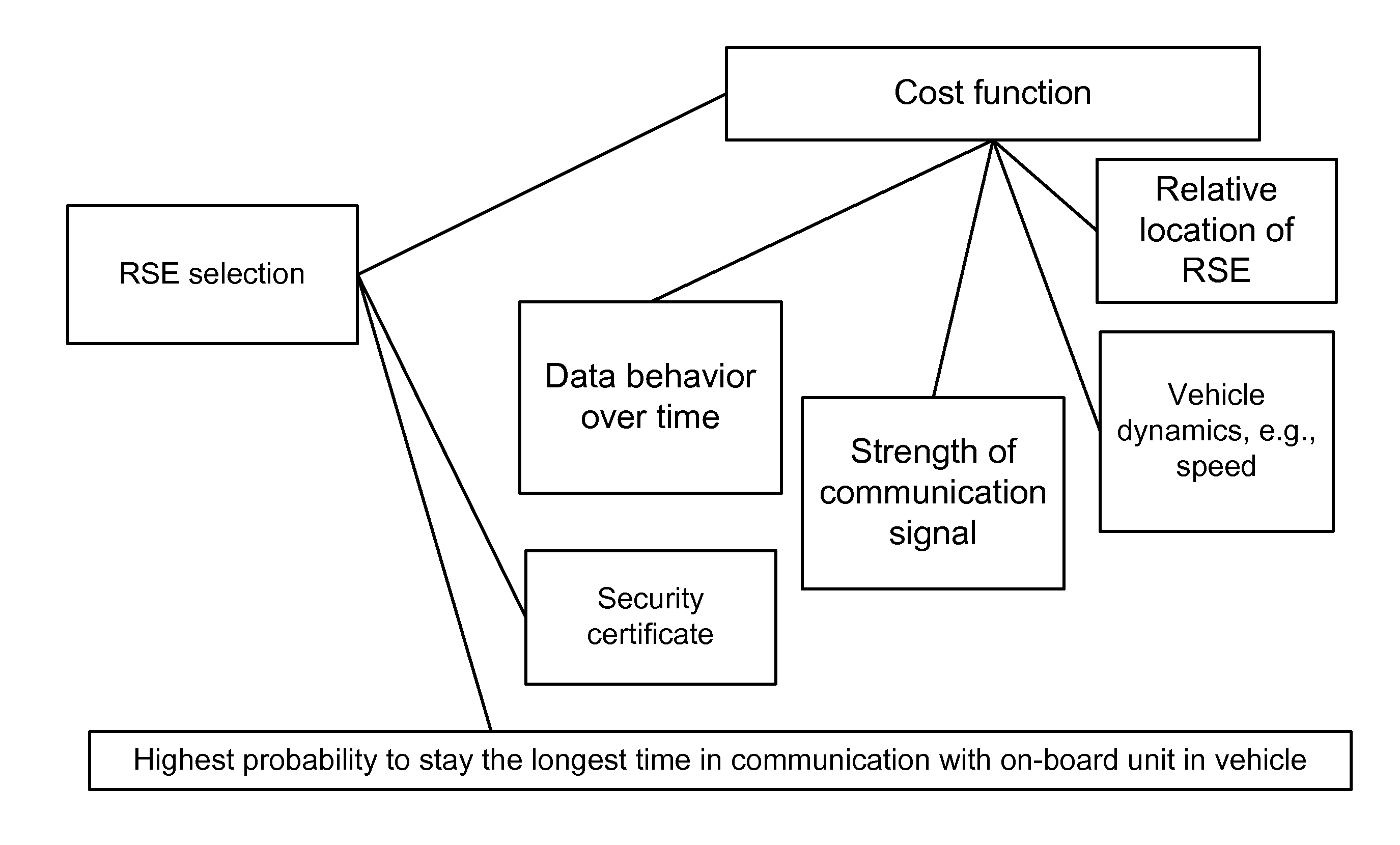
System and method for road side equipment of interest selection for active safety applications
ActiveUS20140358324A1Road vehicles traffic controlDigital data processing detailsActive safetyTraffic signal
In one example, we describe a method and infrastructure for DSRC V2X (vehicle to infrastructure plus vehicle) system. In one example, some of connected vehicle applications require data from infrastructure road side equipment (RSE). Examples of such applications are road intersection safety application which mostly requires map and traffic signal phase data to perform the appropriate threat assessment. The examples given cover different dimensions of the above issue: (1) It provides methods of RSE of interest selection based solely on the derived relative geometric data between the host vehicle and the RSE's, in addition to some of the host vehicle data, such as heading. (2) It provides methods of RSE of interest selection when detailed map data is communicated or when some generic map data is available. (3) It provides methods of RSE of interest selection when other vehicles data is available. Other variations and cases are also given.
Owner:HARMAN INT IND INC
Aircraft collision sense and avoidance system and method
ActiveUS20070210953A1Small sizeReduce weightRadio wave reradiation/reflectionAircraft traffic controlMulti target trackingFlight vehicle
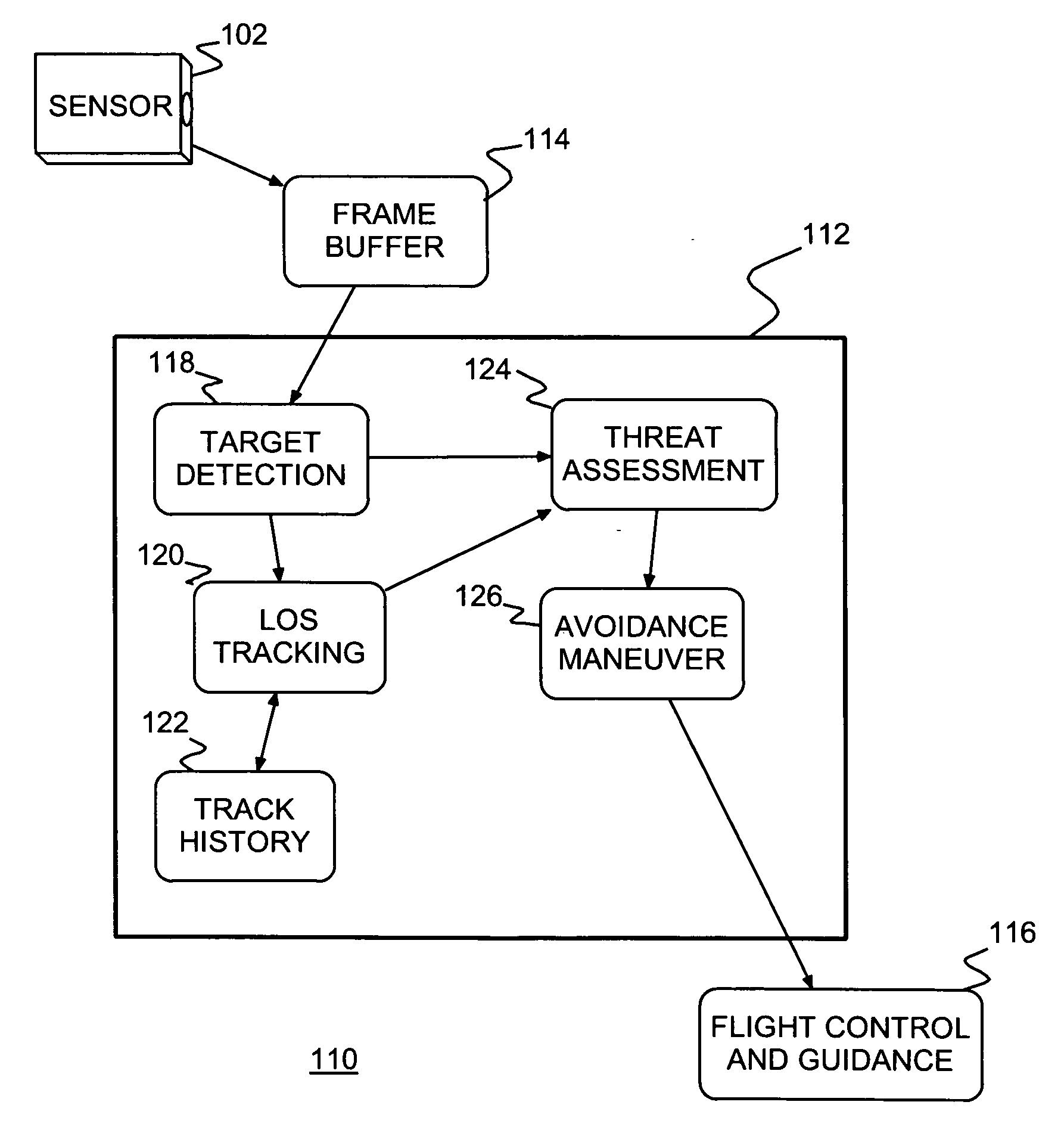
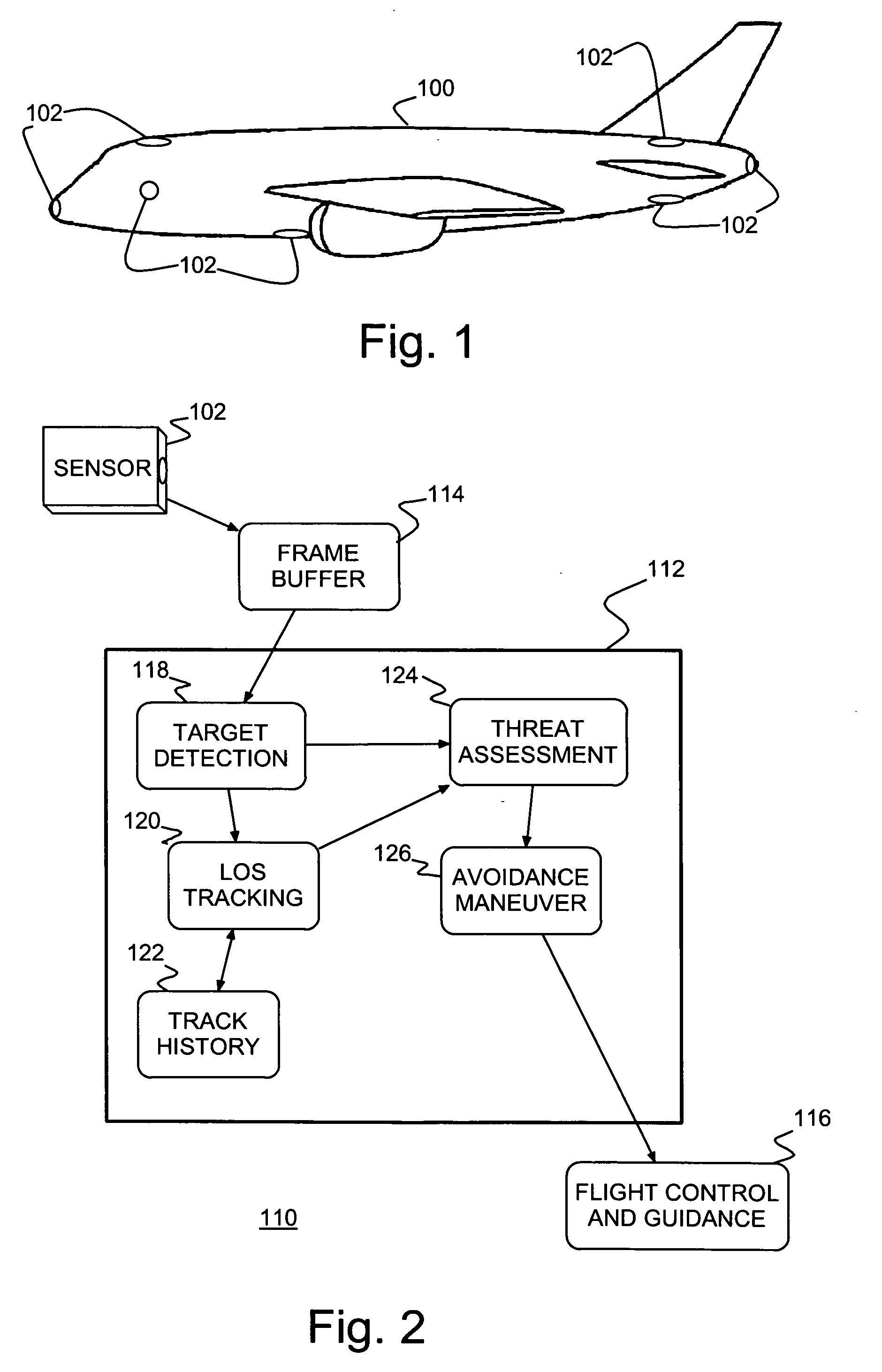
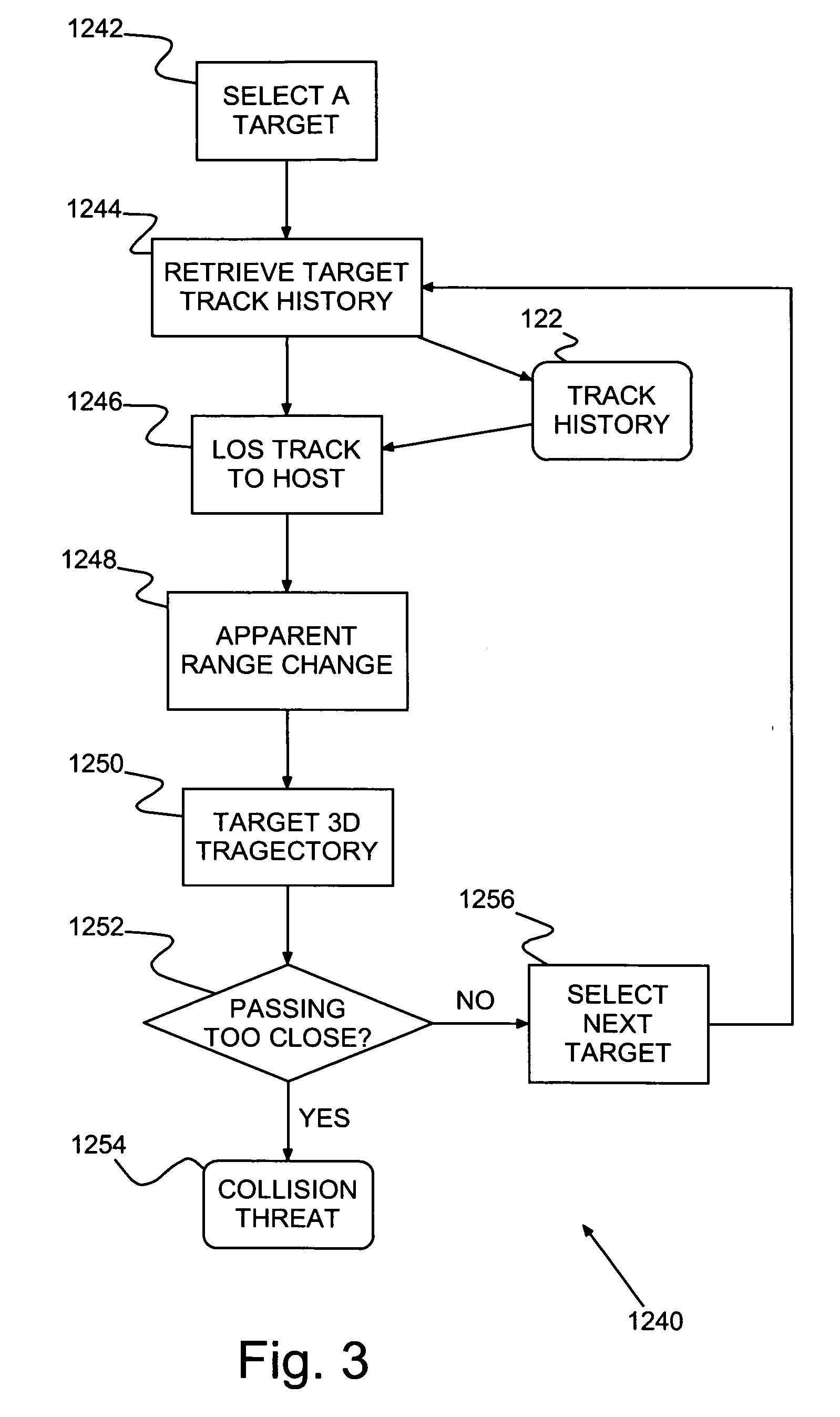
A collision sense and avoidance system and method and an aircraft, such as an Unmanned Air Vehicle (UAV) and / or Remotely Piloted Vehicle (RPV), including the collision sense and avoidance system. The collision sense and avoidance system includes an image interrogator identifies potential collision threats to the aircraft and provides maneuvers to avoid any identified threat. Motion sensors (e.g., imaging and / or infrared sensors) provide image frames of the surroundings to a clutter suppression and target detection unit that detects local targets moving in the frames. A Line Of Sight (LOS), multi-target tracking unit, tracks detected local targets and maintains a track history in LOS coordinates for each detected local target. A threat assessment unit determines whether any tracked local target poses a collision threat. An avoidance maneuver unit provides flight control and guidance with a maneuver to avoid any identified said collision threat.
Owner:THE BOEING CO
Systems and Methods for Vulnerability Detection and Scoring with Threat Assessment
InactiveUS20080028470A1Memory loss protectionUnauthorized memory use protectionSeverity levelComputer science
Certain embodiments of the present invention provide a system for vulnerability detection and scoring with threat assessment including an analysis engine adapted to perform at least one of automated and semi-automated analysis of a computing system of at least one of known threats, vulnerabilities, and risk factors. The analysis engine is further adapted to determine a security score for the computing system based on the analysis and a schedule indicating a severity level for each threat, vulnerability, and risk factor.
Owner:REMINGTON MARK +3
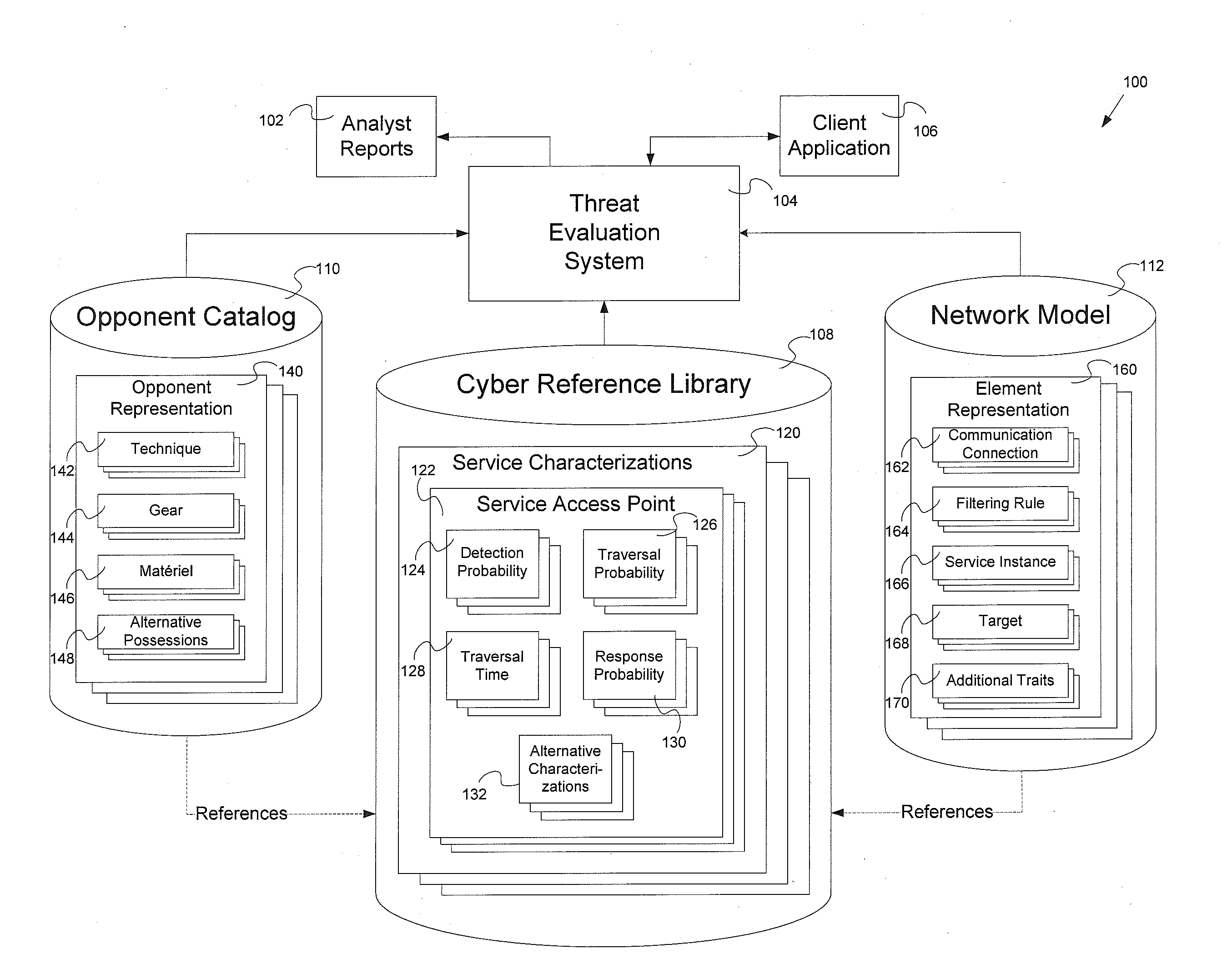
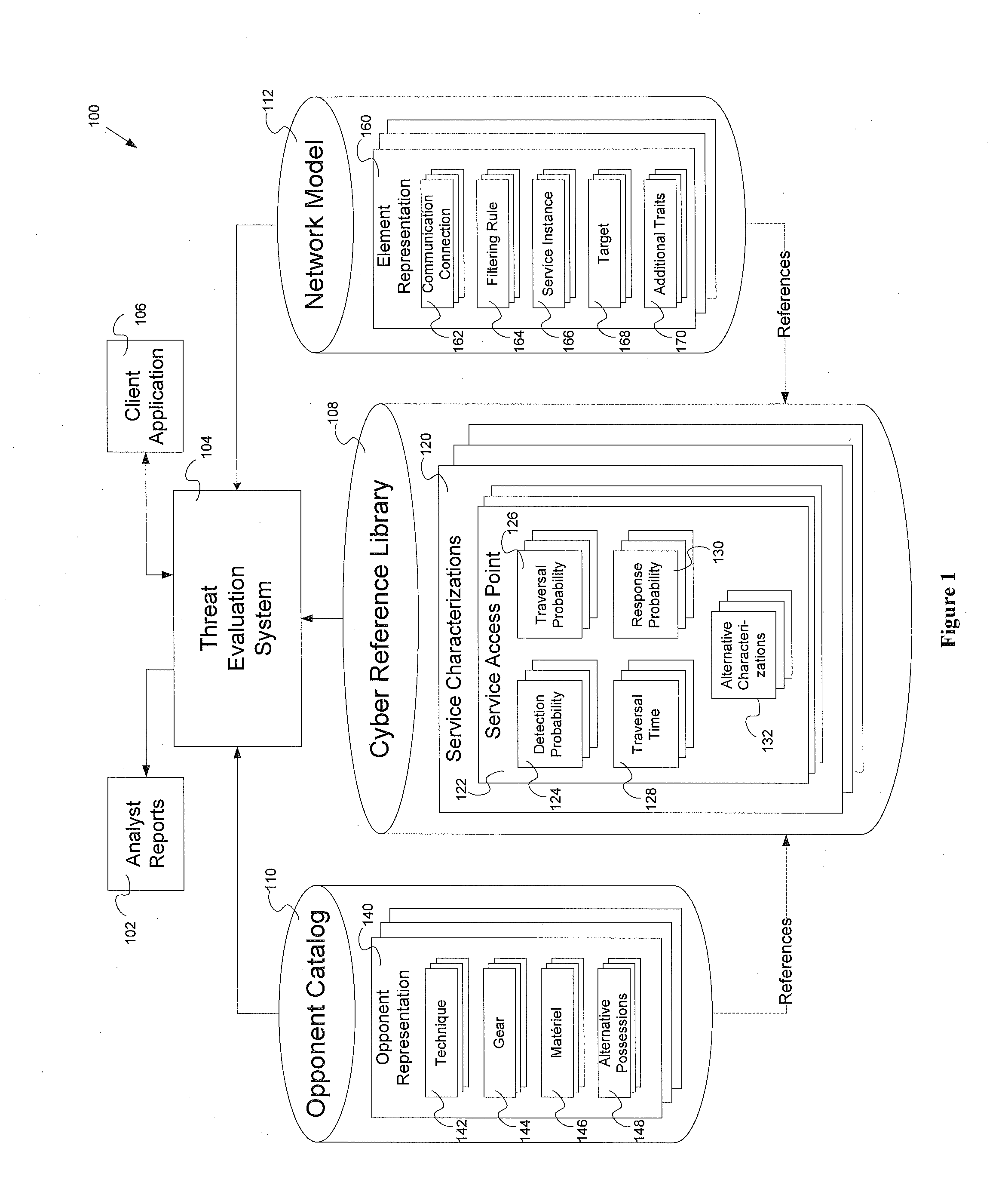
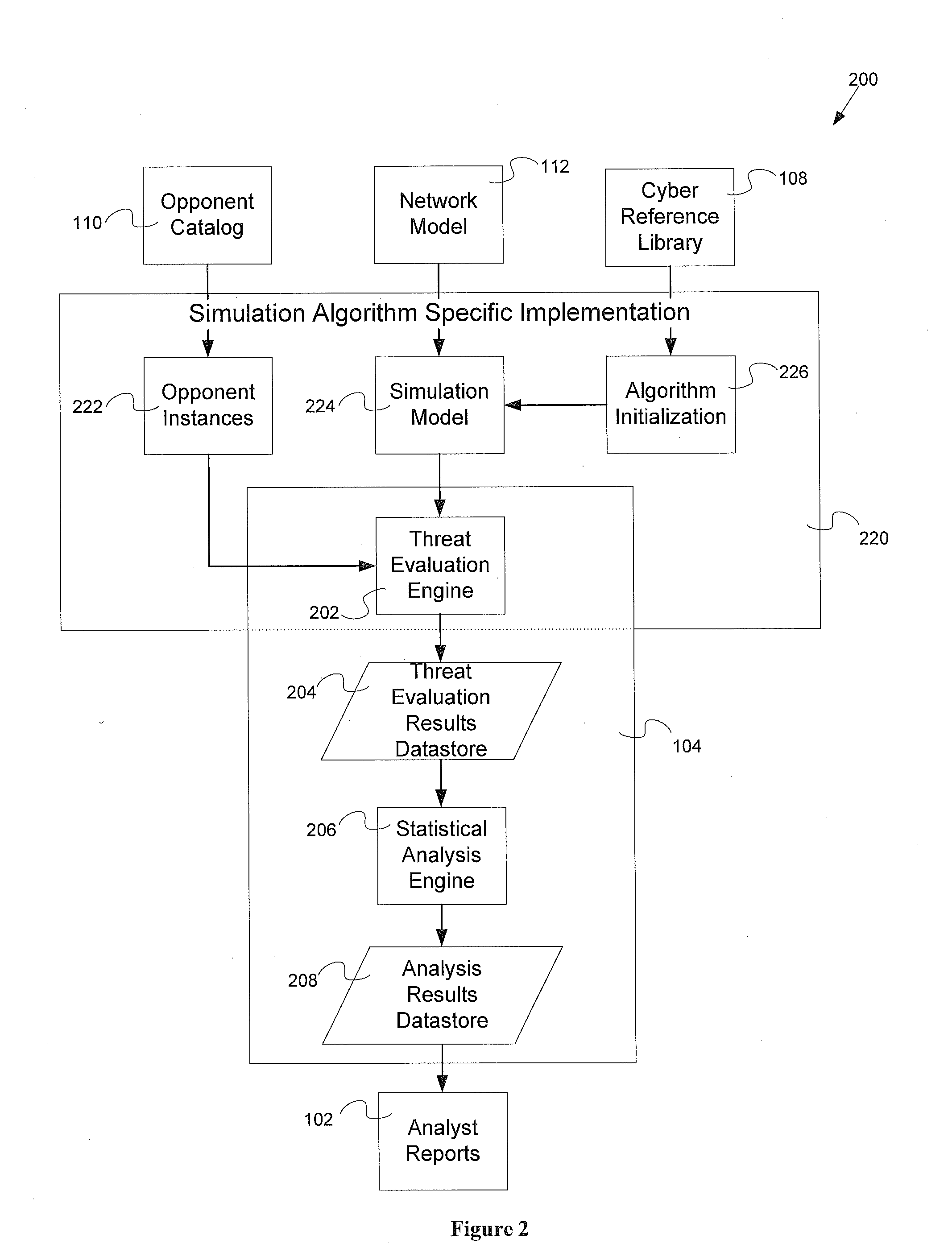
Threat evaluation system and method
InactiveUS20130347116A1Memory loss protectionError detection/correctionStatistical analysisNetwork model
Systems and methods of evaluation of threats to elements of a client computer application having a cyber reference library, an opponent catalog and a network model. The systems and methods produce a set of analyst reports evaluating the threats to the client computer application. One embodiment of the system for evaluating at least one threat to a client computer application has a threat evaluation engine which performs a plurality of algorithms, where each algorithm of has implementation specific needs for input into the individual algorithm, a threat evaluation results data store, a statistical analysis engine, and an analysis results data store.
Owner:OPPLEO SECURITY
System and method for road side equipment of interest selection for active safety applications
ActiveUS8954205B2Digital data processing detailsRoad vehicles traffic controlActive safetyTraffic signal
In one example, we describe a method and infrastructure for DSRC V2X (vehicle to infrastructure plus vehicle) system. In one example, some of connected vehicle applications require data from infrastructure road side equipment (RSE). Examples of such applications are road intersection safety application which mostly requires map and traffic signal phase data to perform the appropriate threat assessment. The examples given cover different dimensions of the above issue: (1) It provides methods of RSE of interest selection based solely on the derived relative geometric data between the host vehicle and the RSE's, in addition to some of the host vehicle data, such as heading. (2) It provides methods of RSE of interest selection when detailed map data is communicated or when some generic map data is available. (3) It provides methods of RSE of interest selection when other vehicles data is available. Other variations and cases are also given.
Owner:HARMAN INT IND INC
Deterent for unmanned aerial systems
ActiveUS20170192089A1Defence devicesDirection/deviation determining electromagnetic systemsNon destructiveAutomated algorithm
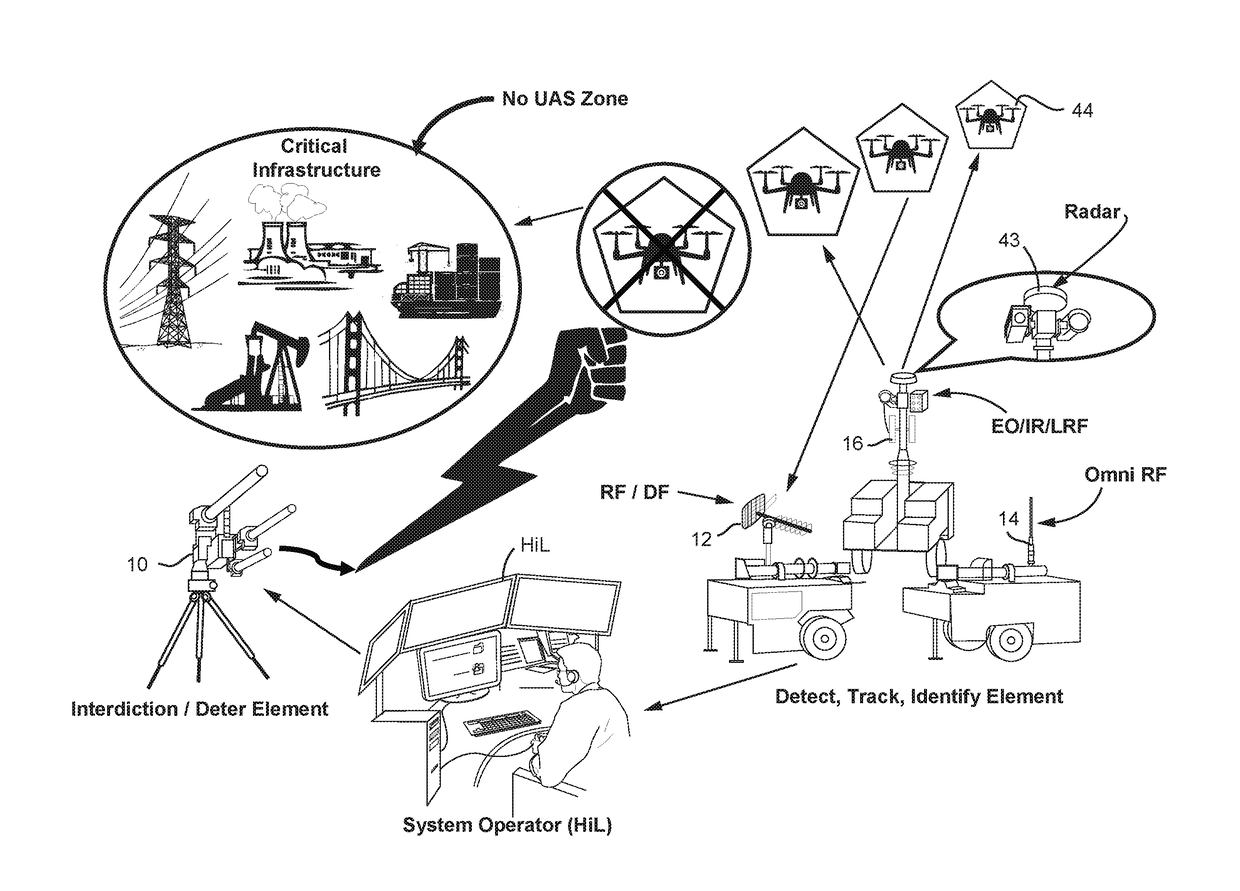
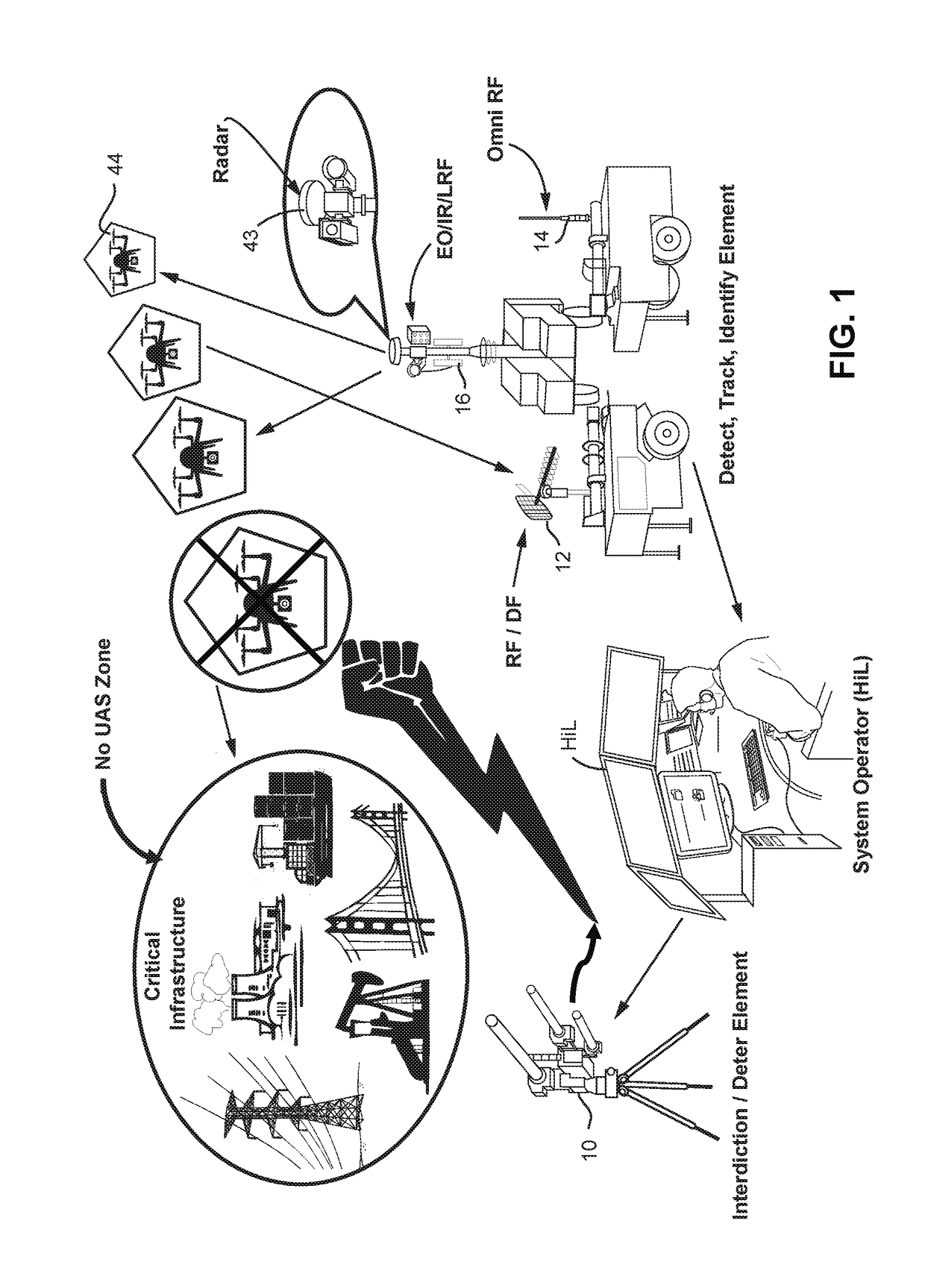
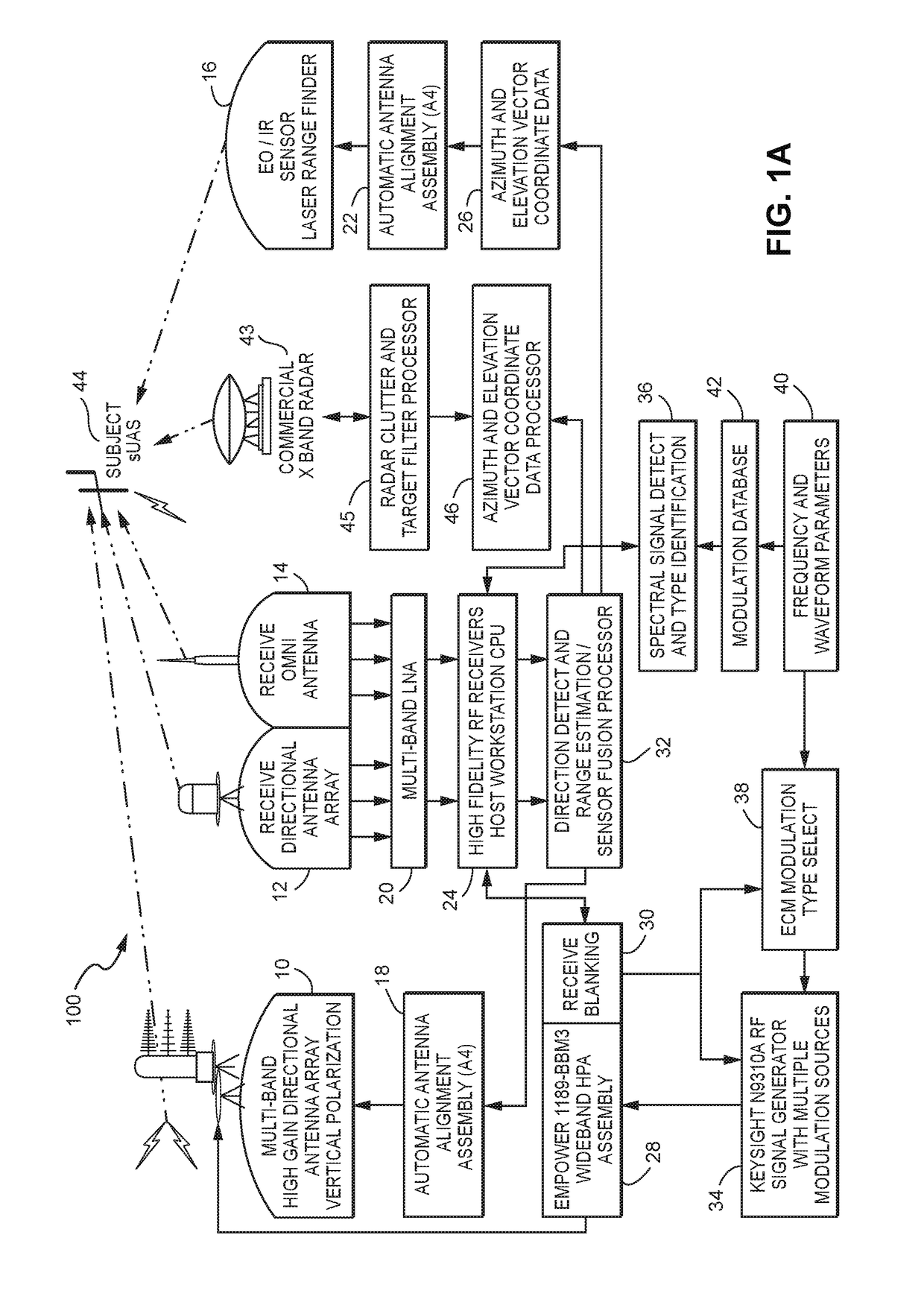
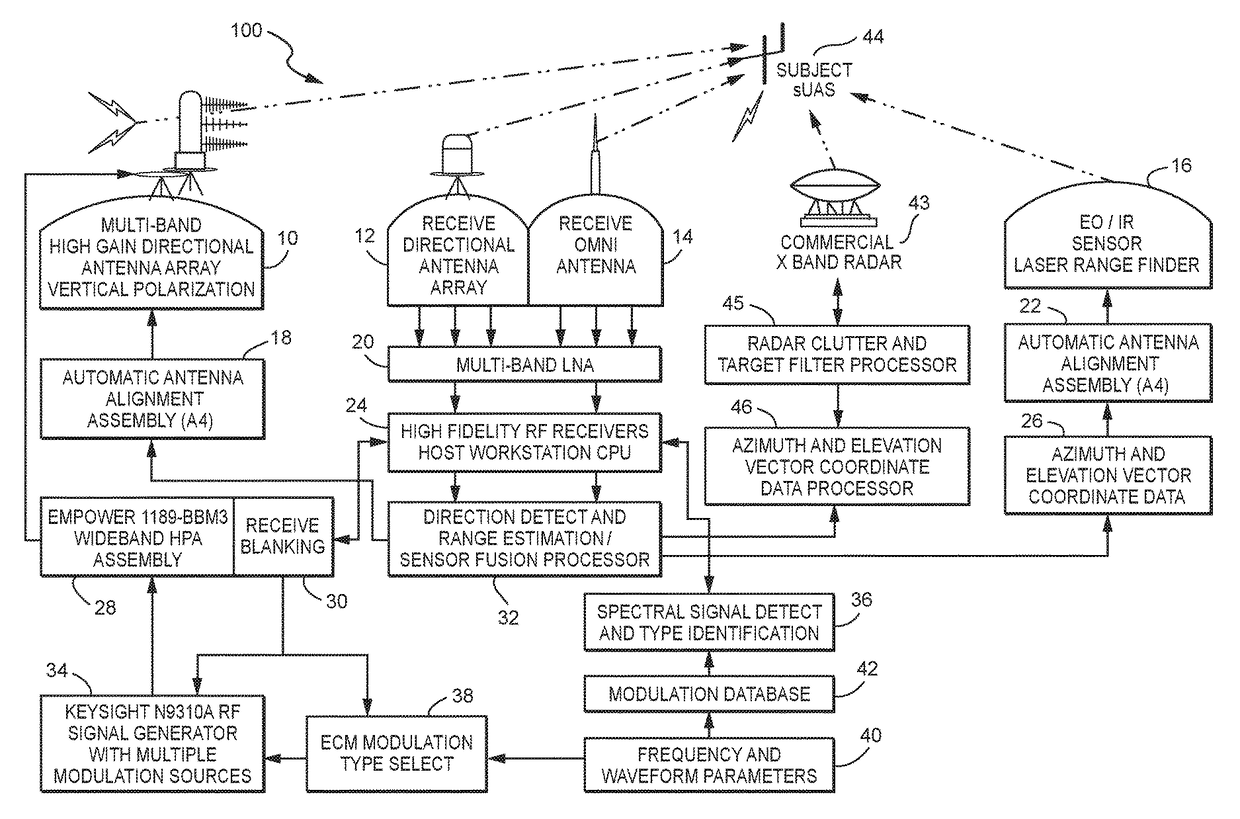
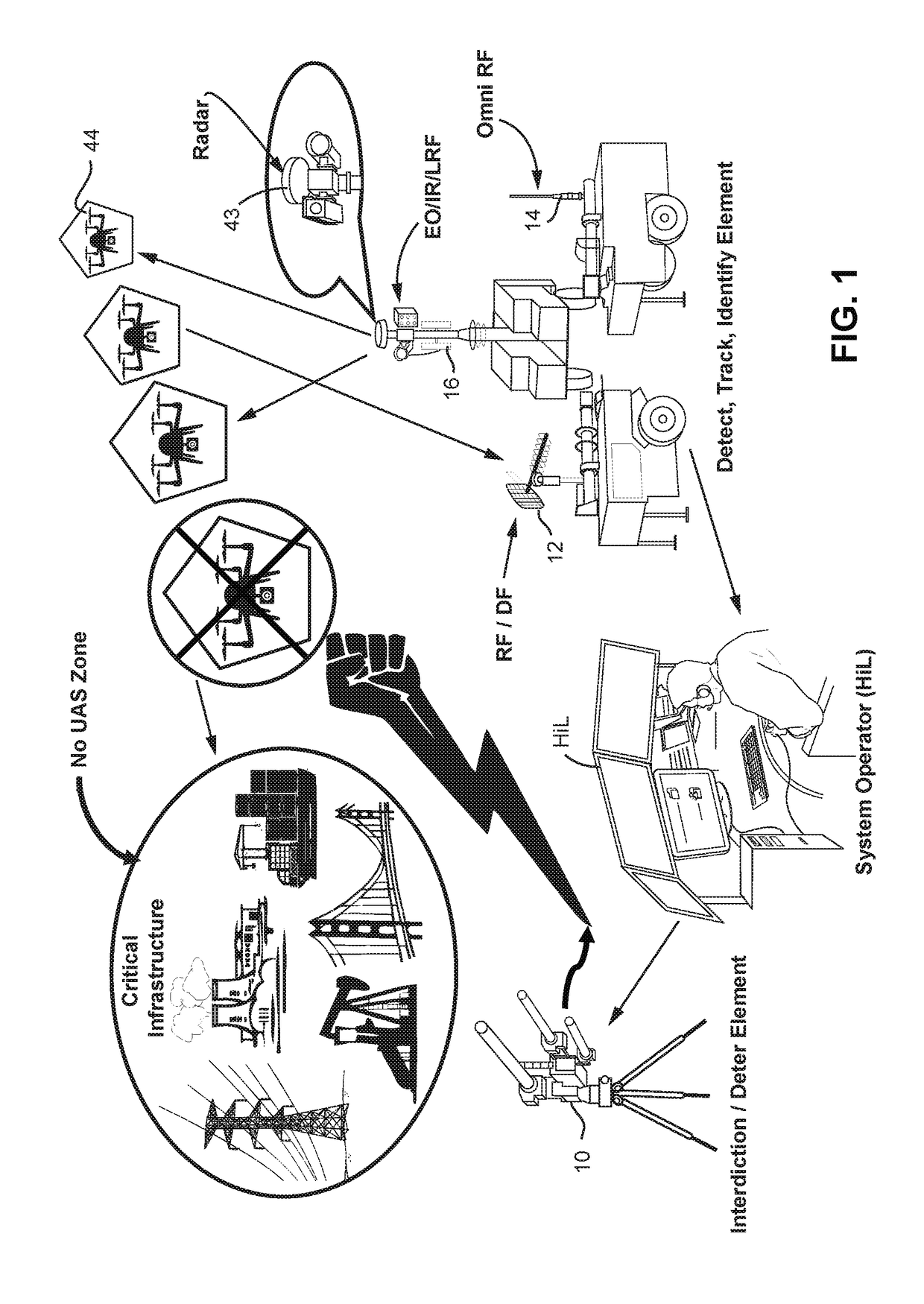
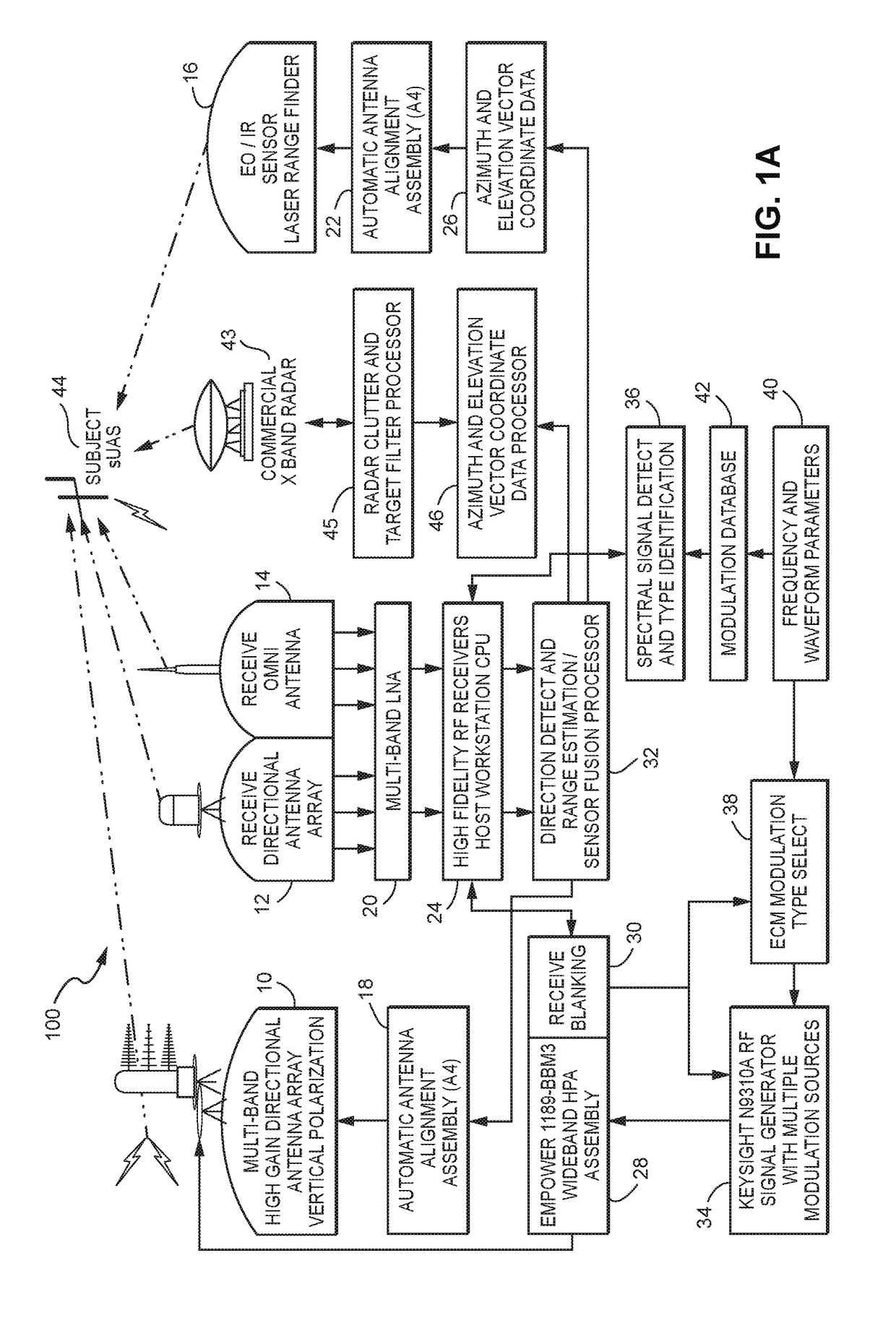
A system (100) for providing an integrated multi-sensor detection and countermeasure against commercial unmanned aerial systems / vehicles (44) and includes a detecting element (103, 104, 105), a tracking element (103,104, 105) an identification element (103, 104, 105) and an interdiction element (102). The detecting element detects an unmanned aerial vehicle in flight in the region of, or approaching, a property, place, event or very important person. The tracking element determines the exact location of the unmanned aerial vehicle. The identification / classification element utilizing data from the other elements generates the identification and threat assessment of the UAS. The interdiction element, based on automated algorithms can either direct the unmanned aerial vehicle away from the property, place, event or very important person in a non-destructive manner, or can disable the unmanned aerial vehicle in a destructive manner. The interdiction process may be over ridden by intervention by a System Operator / HiL.
Owner:XIDRONE SYST INC
Risk Scoring For Threat Assessment
Threat risks to an enterprise are detected and assessed by assembling singular threats identified using both direct and behavioral threat indicators into composite threats to create complex use cases across multiple domains, and to amplify risks along kill chains of known attacks for early detection. Composite threat risk scores are computed from risk scores of singular threats to exponentially increase with the number of events observed along the kill chain. Composite threats are combined with normalized values of static risk and inherent risk for an entity of the enterprise to produce an entity risk score representative of the overall risk to the entity.
Owner:SECURONIX INC
Methods and systems for threat assessment, safety management, and monitoring of individuals and groups
InactiveUS8630820B2Reduce morbidityMaintain awarenessTelephonic communicationNuclear monitoringComputer scienceIndividual person
Owner:STRIDER
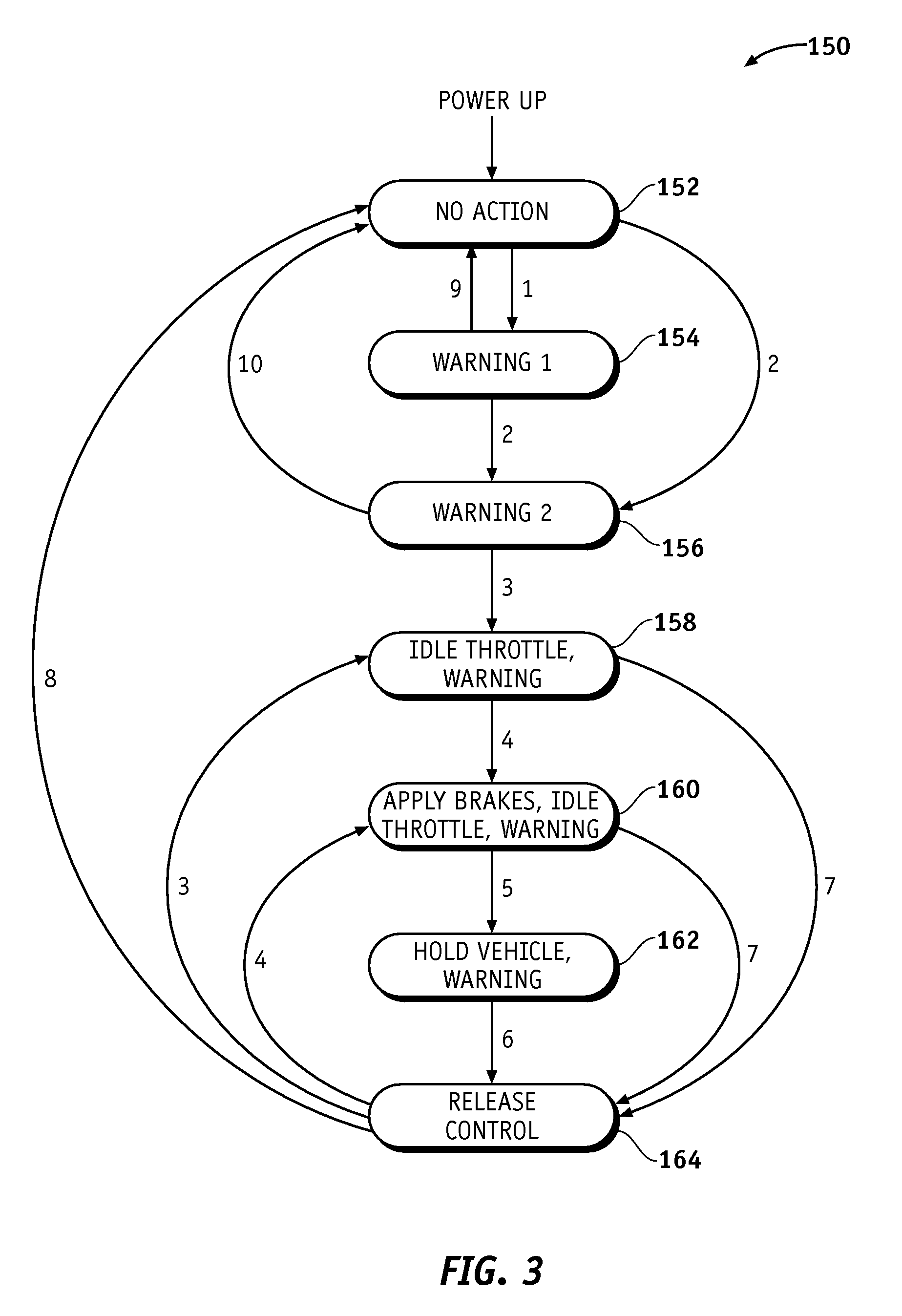
Threat Assessment State Processing for Collision Warning, Mitigation and/or Avoidance in Ground-Based Vehicles
ActiveUS20080167781A1Reduce the required powerRestore powerAnalogue computers for trafficAnti-collision systemsEngineeringDetect and avoid
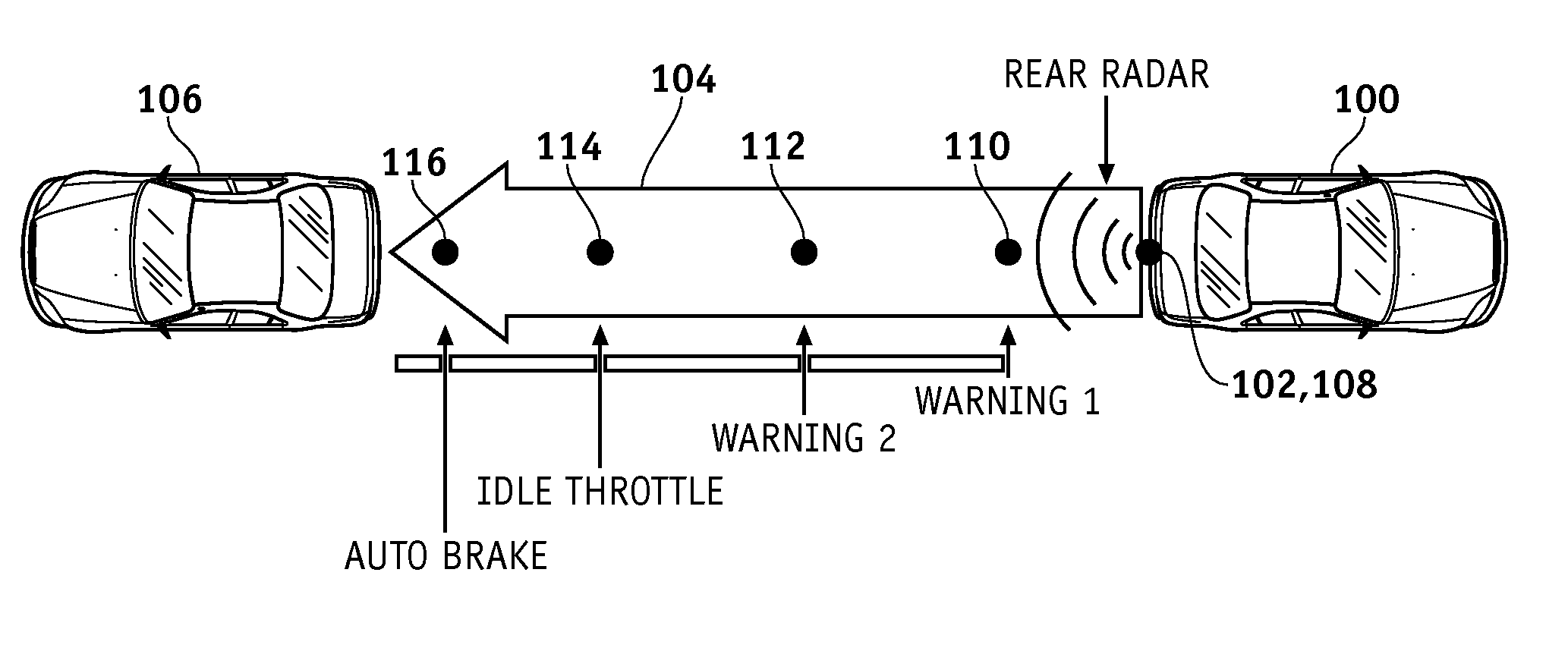
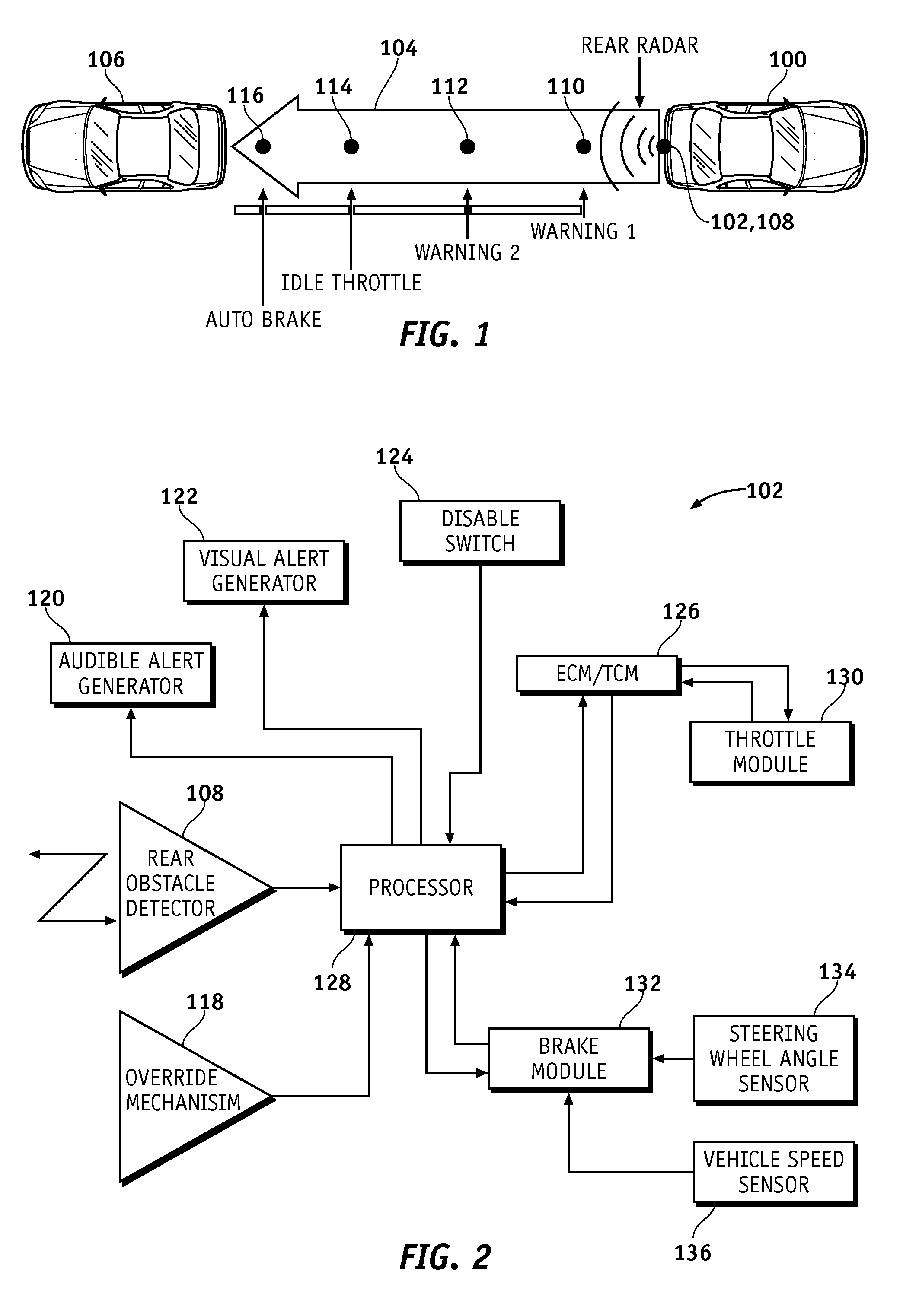
A method and apparatus is provided for detecting and avoiding an obstacle using a system of a vehicle. The method includes the steps of detecting a distance between the obstacle and the vehicle, generating an action when the distance between the obstacle and the vehicle is less than a threshold, determining whether an override of the system has been initiated, and disabling the action if it is determined that the override has been initiated. The system includes an obstacle detector, an action generator, an override mechanism, and a processor configured to implement the steps of the method set forth above.
Owner:GM GLOBAL TECH OPERATIONS LLC
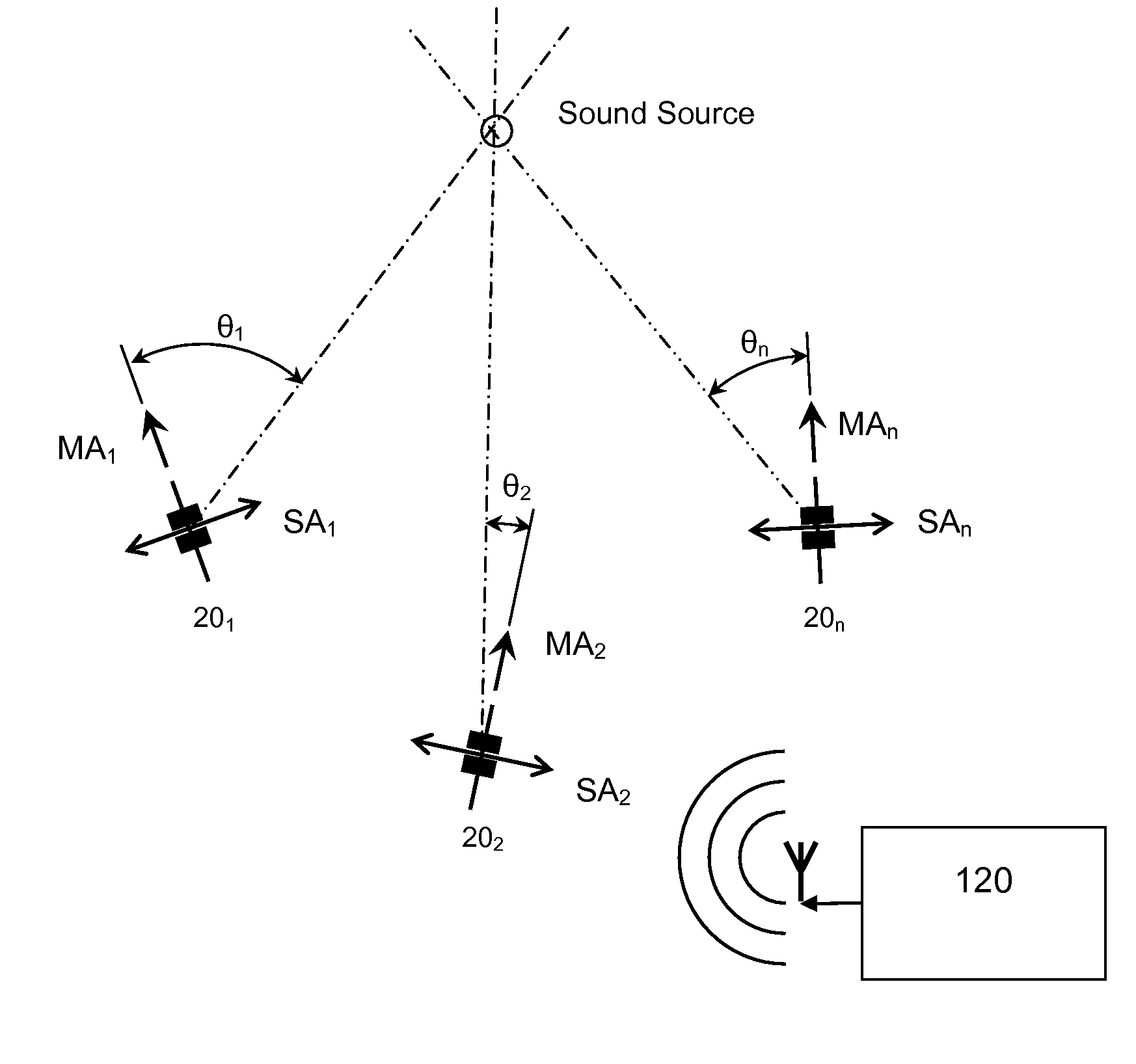
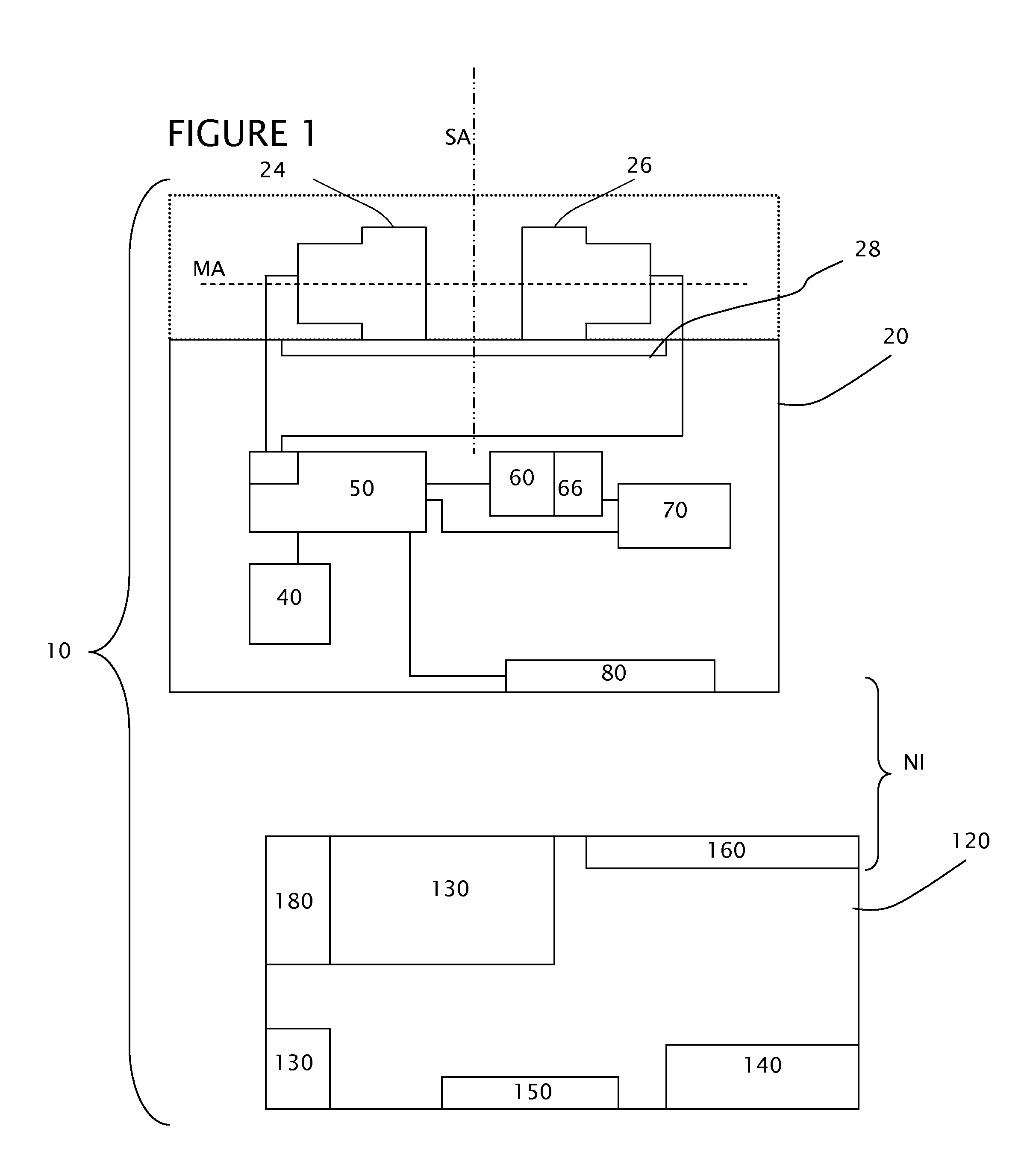
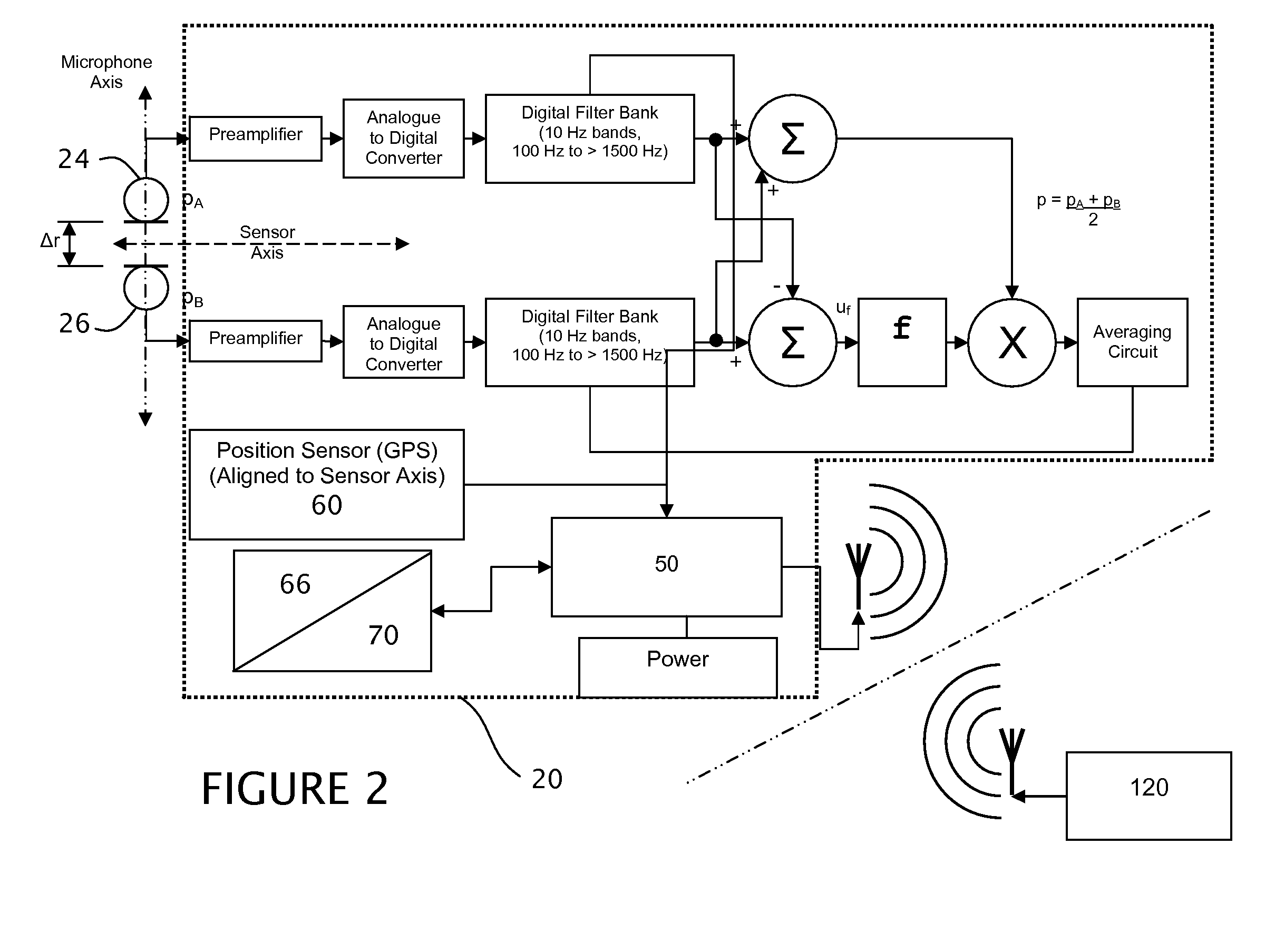
Multiple acoustic threat assessment system
InactiveUS20100008515A1Accurate trackingMicrophones signal combinationTransducer casings/cabinets/supportsAcoustic sensorLight spectrum
A system is provided for locating and identifying an acoustic event. An acoustic sensor having a pair of concentric opposing microphones at a fixed distance on a microphone axis is used to measure an acoustic intensity, from which a vector incorporating the acoustic event is identified. A second acoustic sensor or movement of the first acoustic sensor is used to provide a second vector incorporating the acoustic event. Combination of the first and the second vector locates the acoustic event in space. A command unit in communication with the acoustic sensors can be used for combining the vectors as well as comparing a signal spectra of the acoustic event to stored identified spectra to provide an identification of acoustic event.
Owner:CBRNE GROUP +1
Security threat detection system
ActiveUS8305447B1Low costDetect motion effectivelyCharacter and pattern recognitionColor television detailsVisibilityLight beam
Owner:WONG THOMAS K
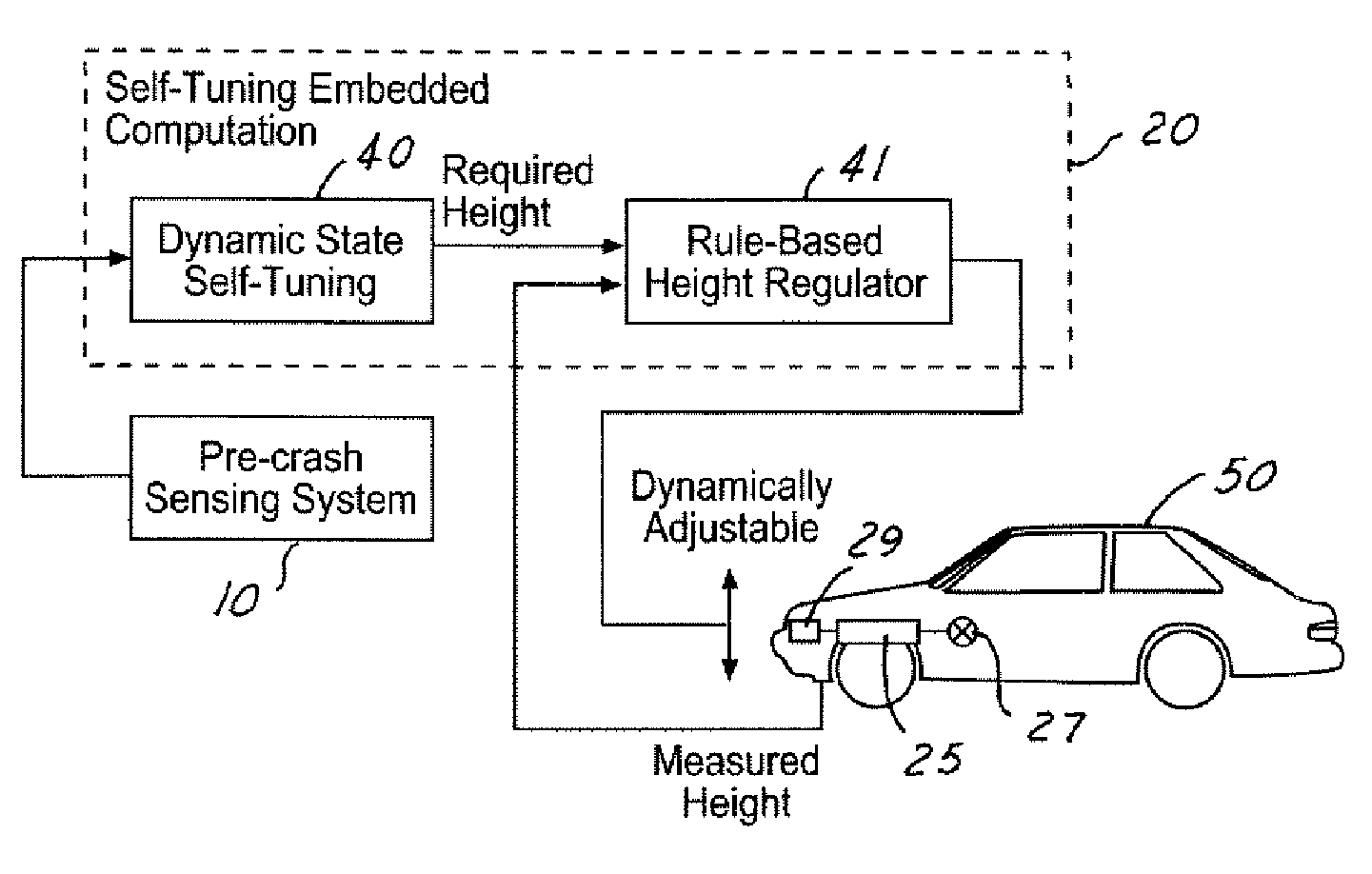
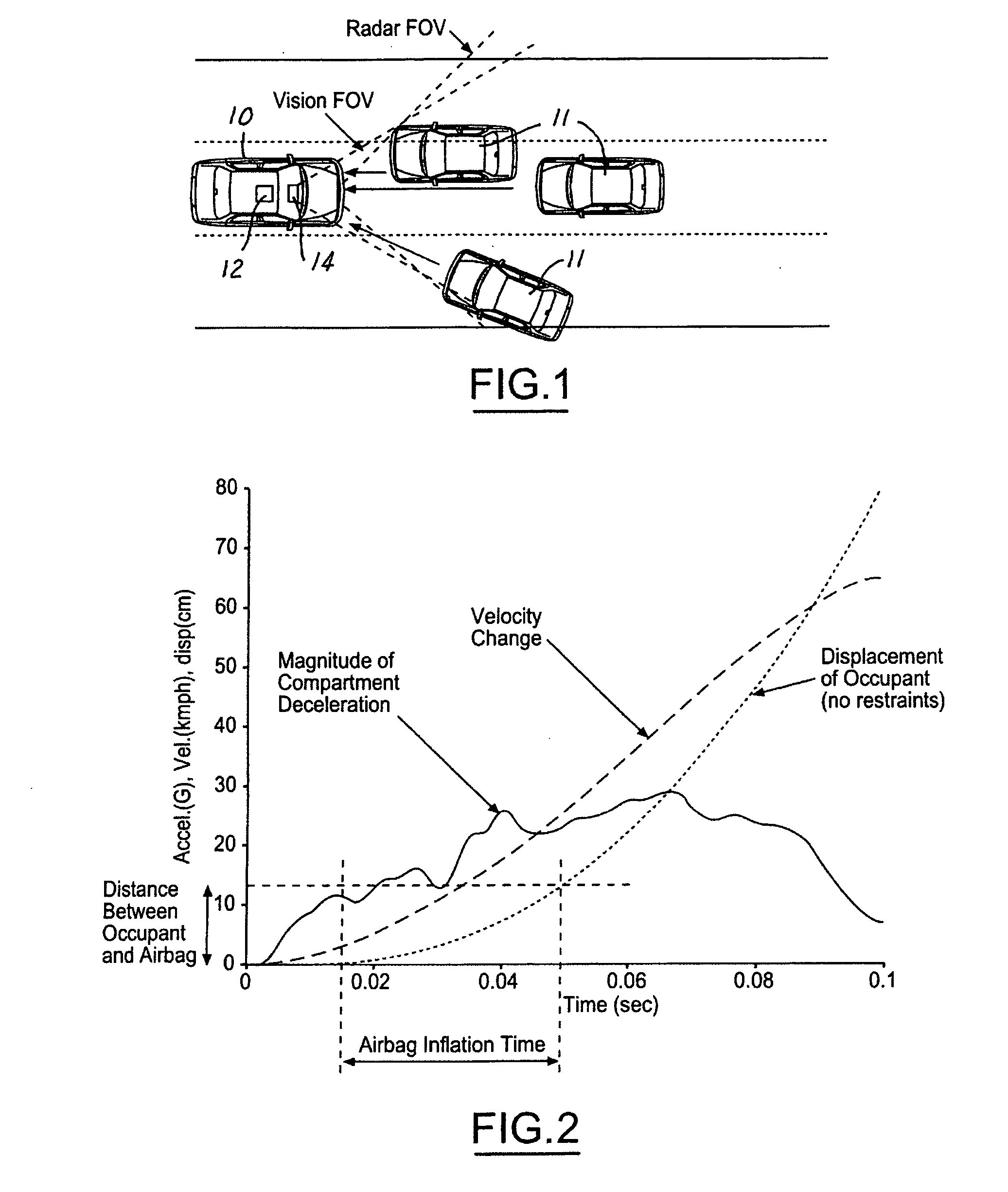
Adaptive vehicle safety system for collision compatibility
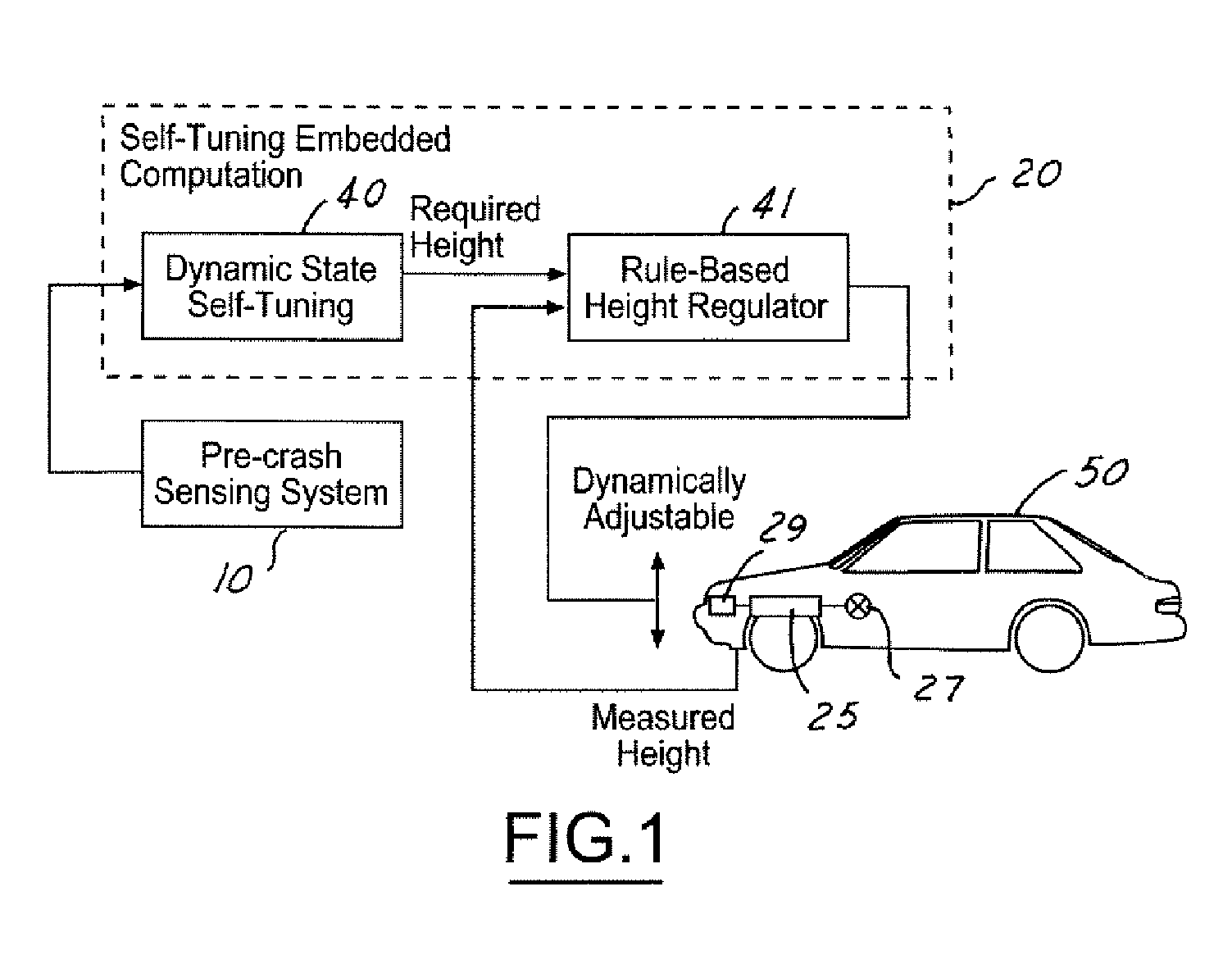
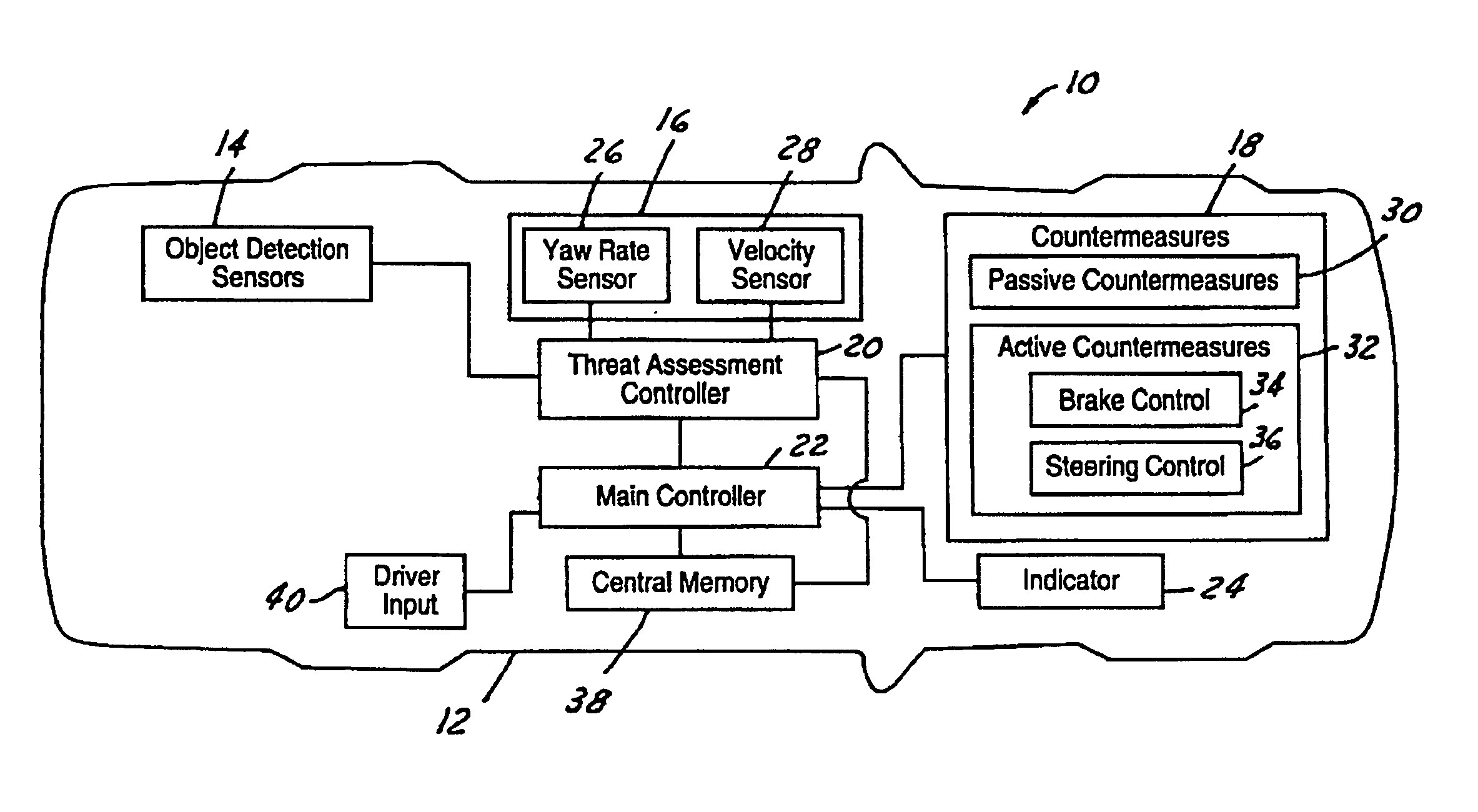
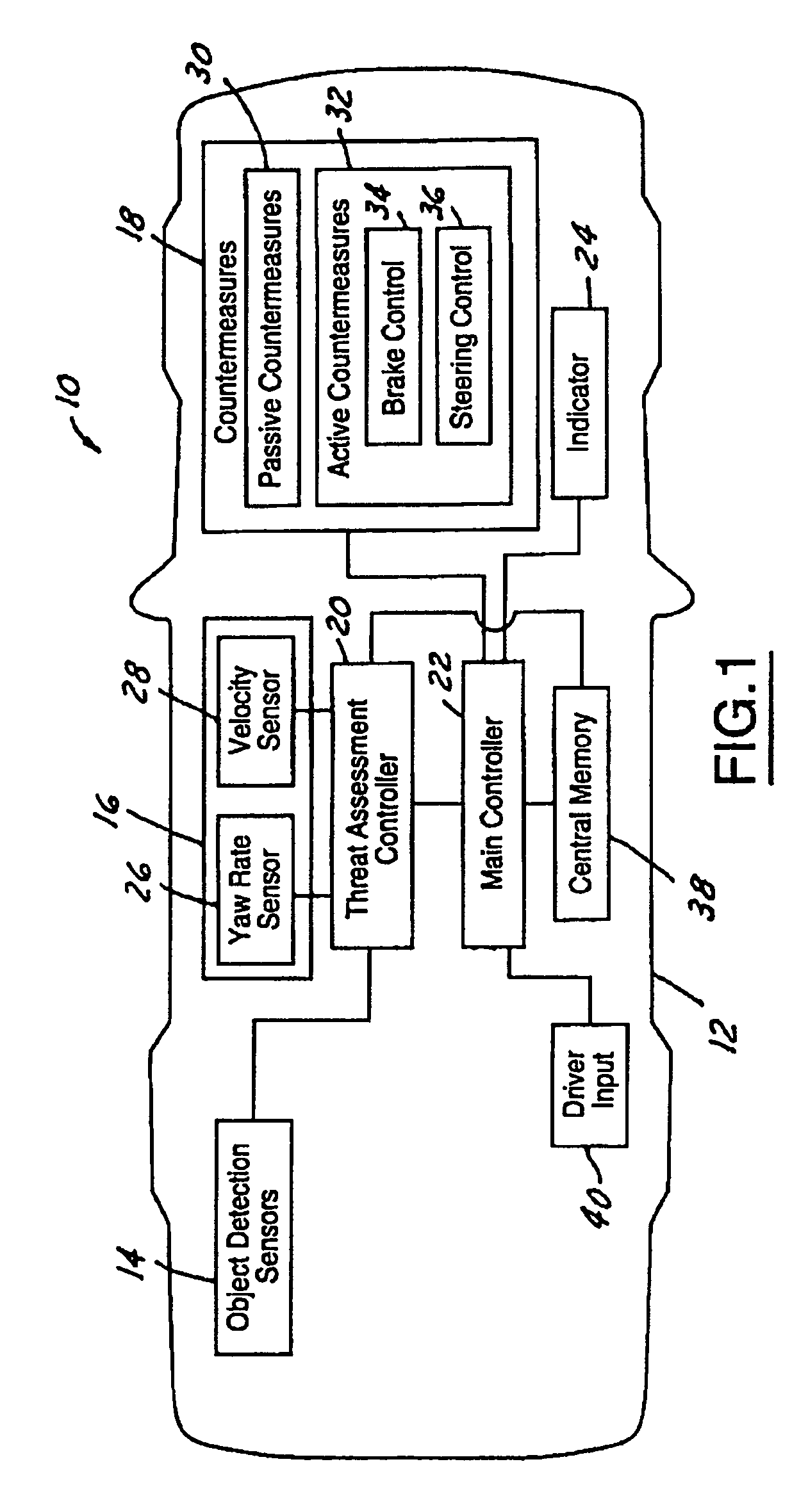
ActiveUS6944544B1Improved and robust occupant protectionIncrease awarenessDigital data processing detailsPedestrian/occupant safety arrangementRide heightVehicle dynamics
A safety system for a host vehicle includes a pre-crash sensing system generating host vehicle dynamics data, a target vehicle threat assessment, and target vehicle bumper or doorsill location data. A ride-height, Dynamic State Self-Turning (DSST) controller generates a reference ride-height signal as a function of the host vehicle dynamics data, target vehicle threat assessment, and target vehicle bumper or doorsill location data. A Rule-Based Height Regulator (RBHR) controller is feedback communication with an adjustable suspension system, is programmed to continuously adjust the host vehicle ride-height with reference to the ride-height signal, and the host vehicle bumper location to optimize the collision conditions between the two vehicles until just prior to impact.
Owner:FORD GLOBAL TECH LLC +1
Probabilistic target selection and threat assessment method and application to intersection collision alert system
A system and method for providing target selection and threat assessment for vehicle collision avoidance purposes that employ probability analysis of radar scan returns. The system determines a travel path of a host vehicle and provides a radar signal transmitted from a sensor on the host vehicle. The system receives multiple scan return points from detected objects, processes the scan return points to generate a distribution signal defining a contour of each detected object, and processes the scan return points to provide a position, a translation velocity and an angular velocity of each detected object. The system selects the objects that may enter the travel path of the host vehicle, and makes a threat assessment of those objects by comparing a number of scan return points that indicate that the object may enter the travel path to the number of the scan points that are received for that object.
Owner:GM GLOBAL TECH OPERATIONS LLC
Countering security threats with the domain name system
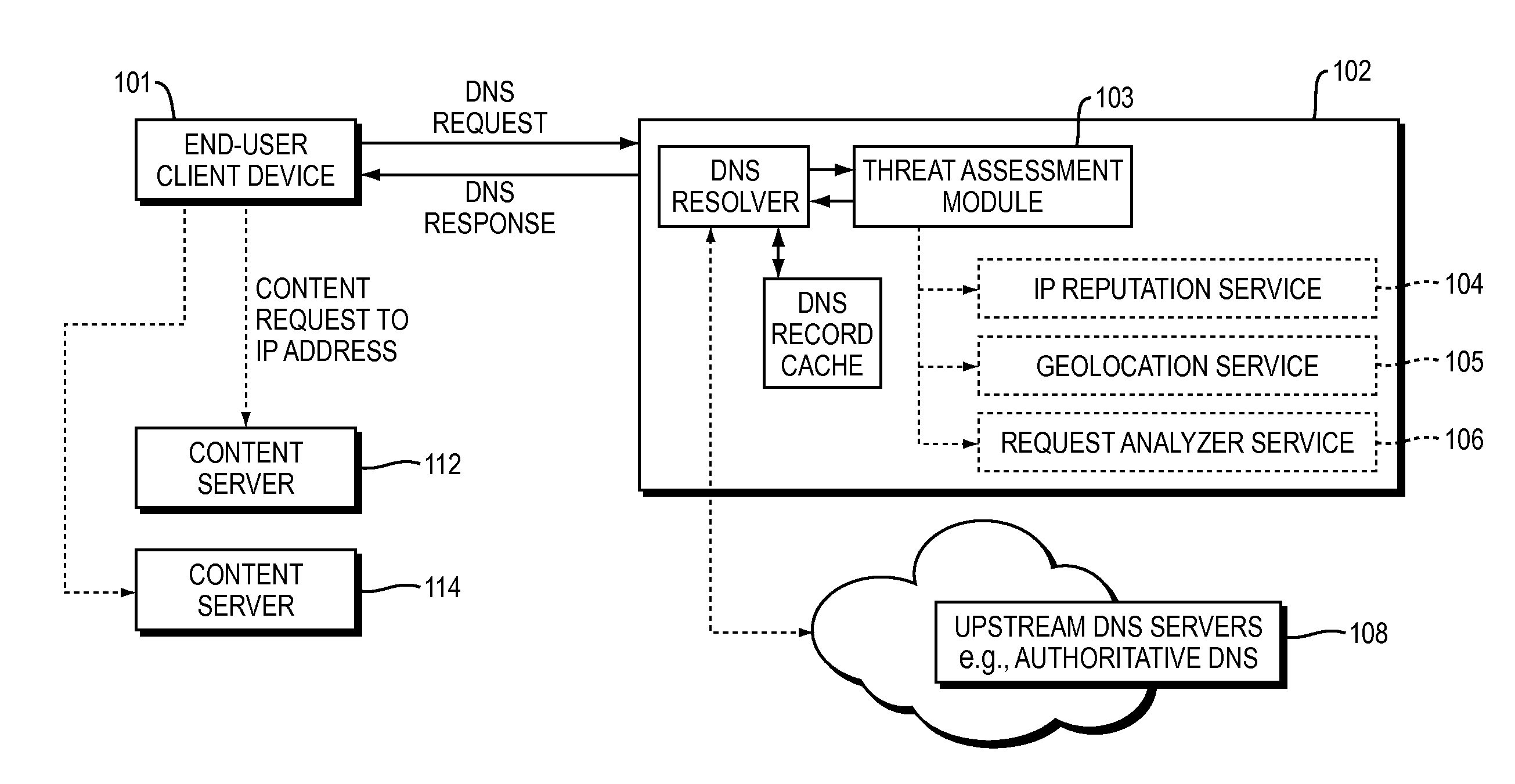
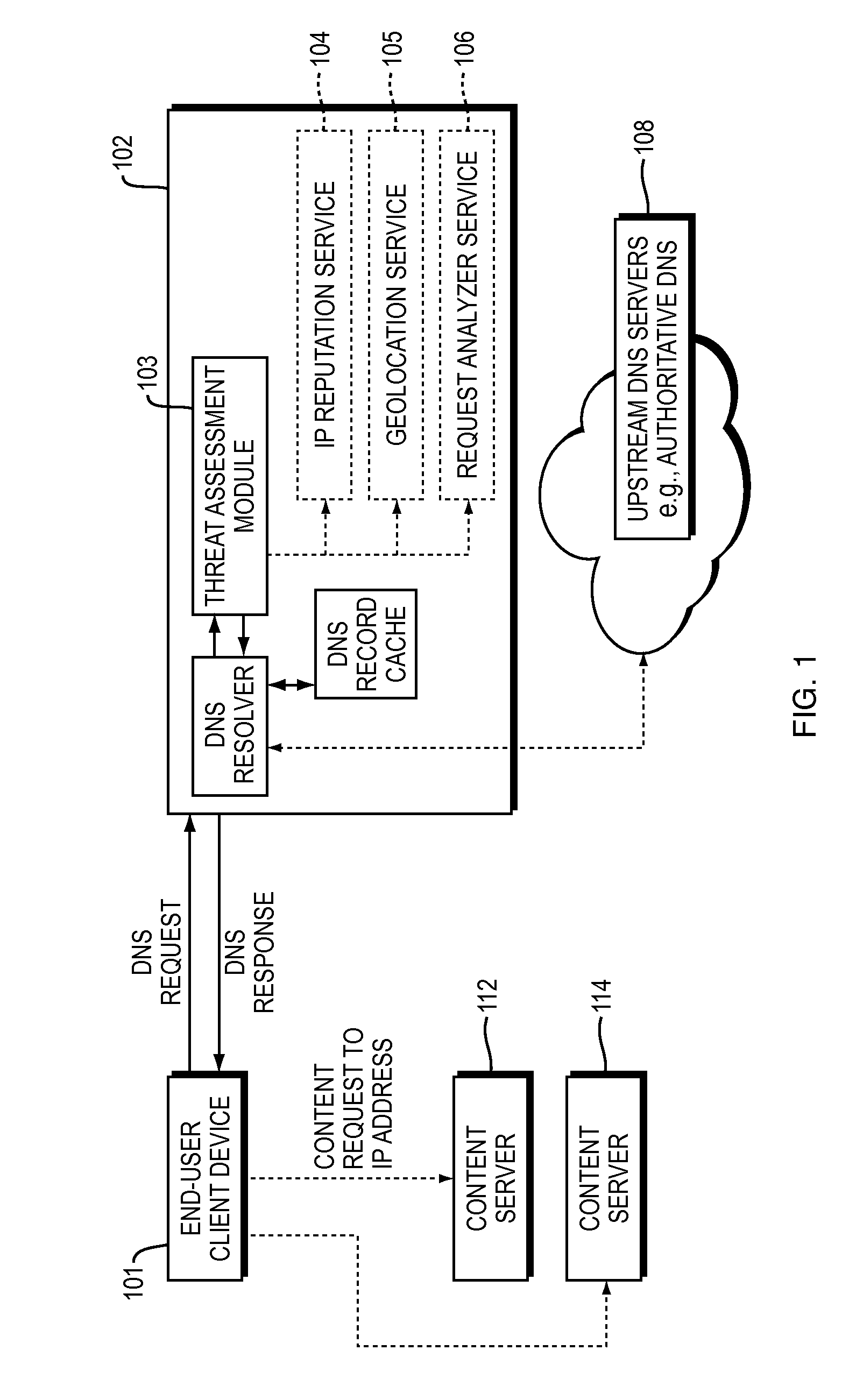
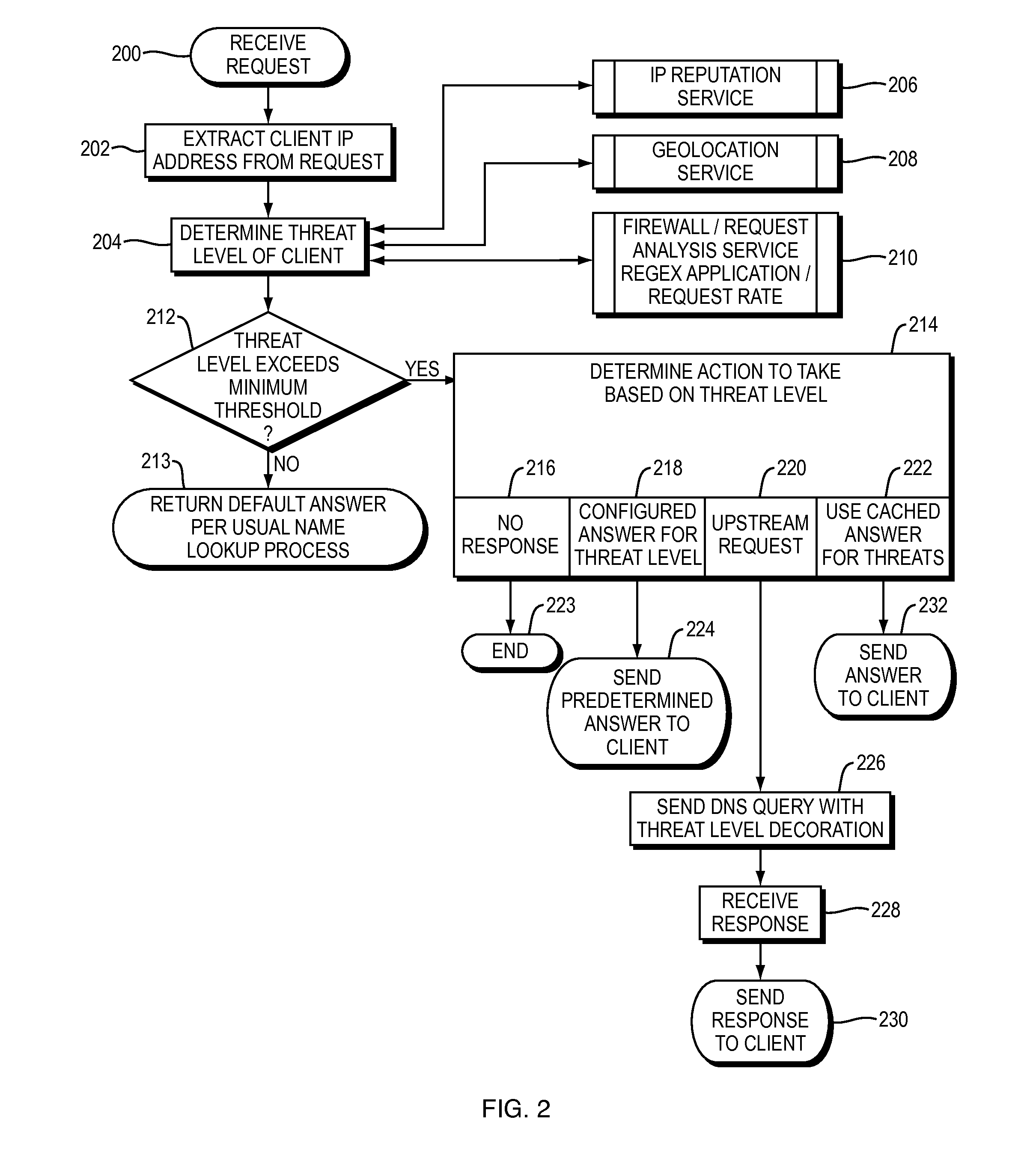
ActiveUS20150180892A1Easy to controlGood mitigateMemory loss protectionError detection/correctionDomain nameDomain Name System
Described herein are methods, systems, and apparatus in which the functionality of a DNS server is modified to take into account security intelligence when determining an answer to return in response to a requesting client. Such a DNS server may consider a variety of security characteristics about the client and / or the client's request, as described more fully herein. Such a DNS server can react to clients in a variety of ways based on the threat assessment, preferably in a way that proactively counters or mitigates the perceived threat.
Owner:AKAMAI TECH INC
Active attack detection system
Owner:MEADOW HILLS
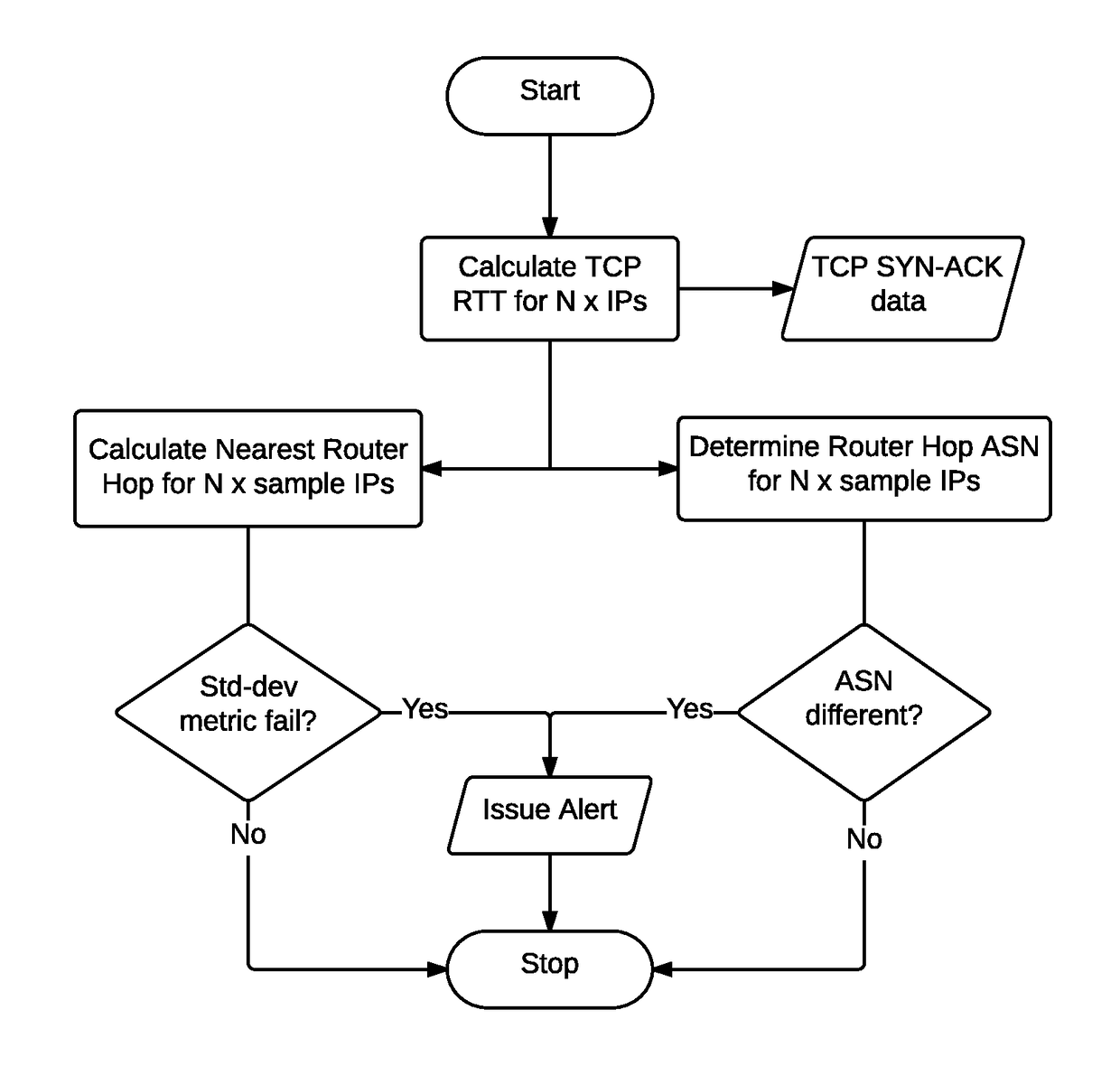
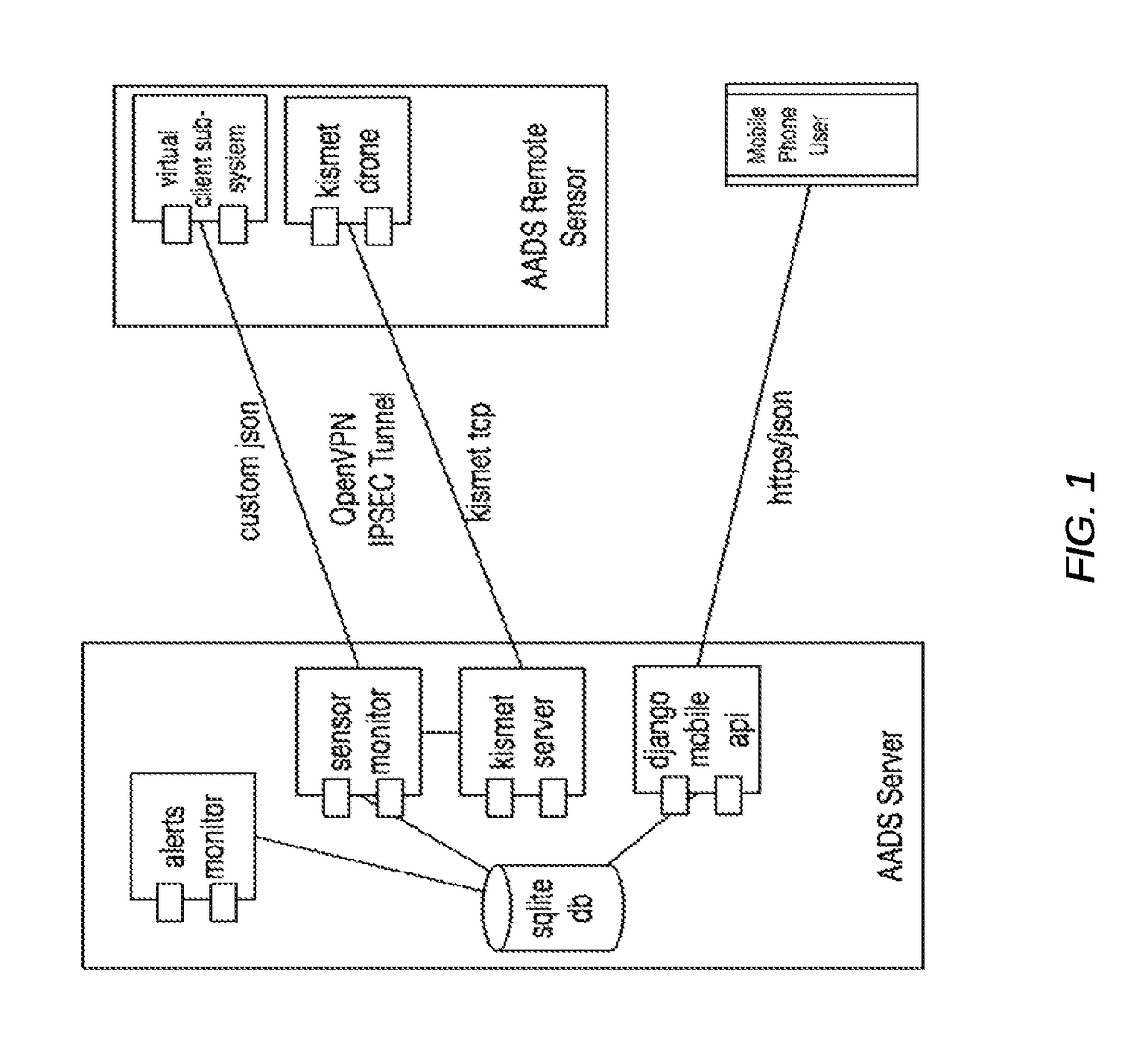
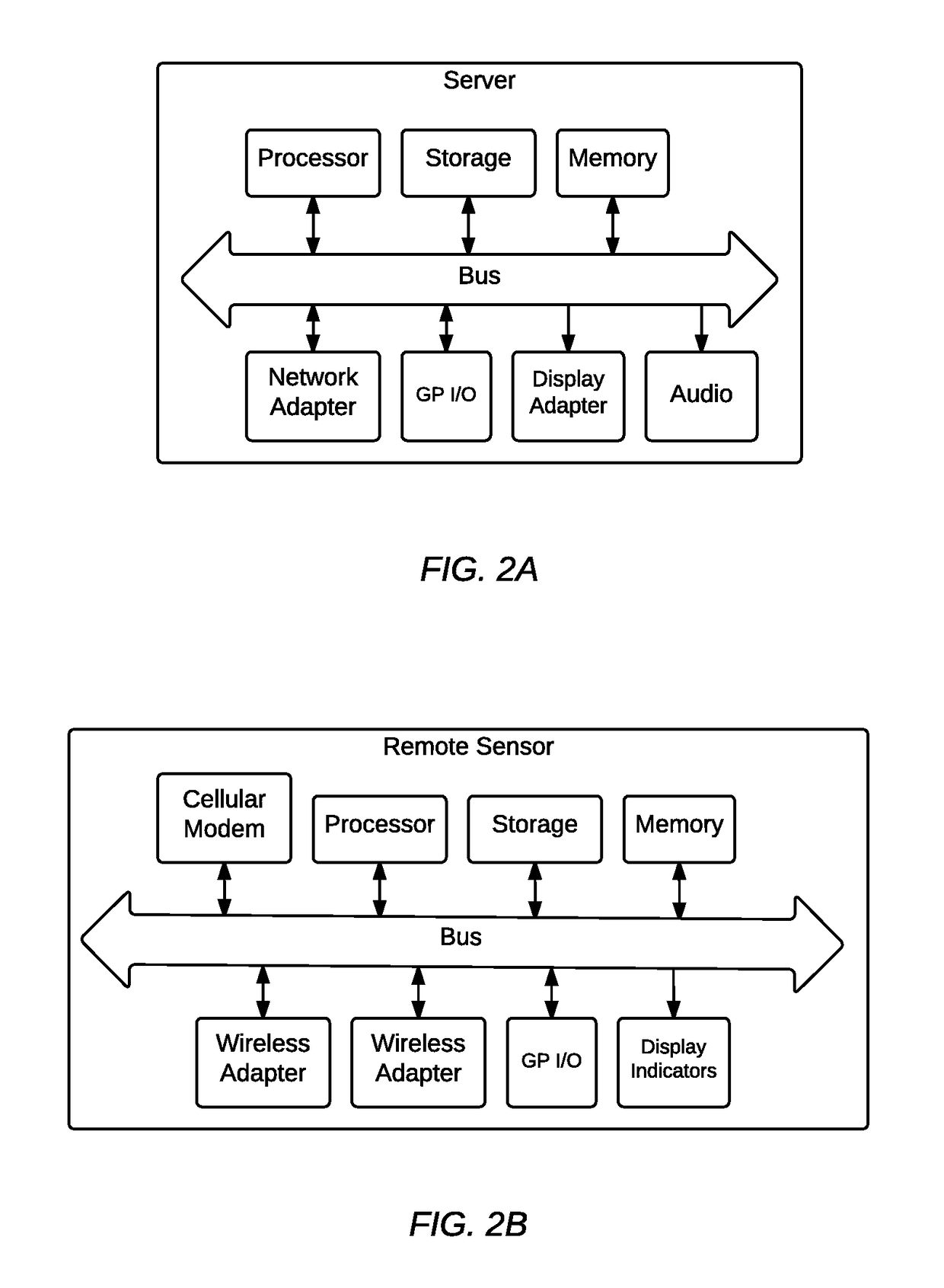
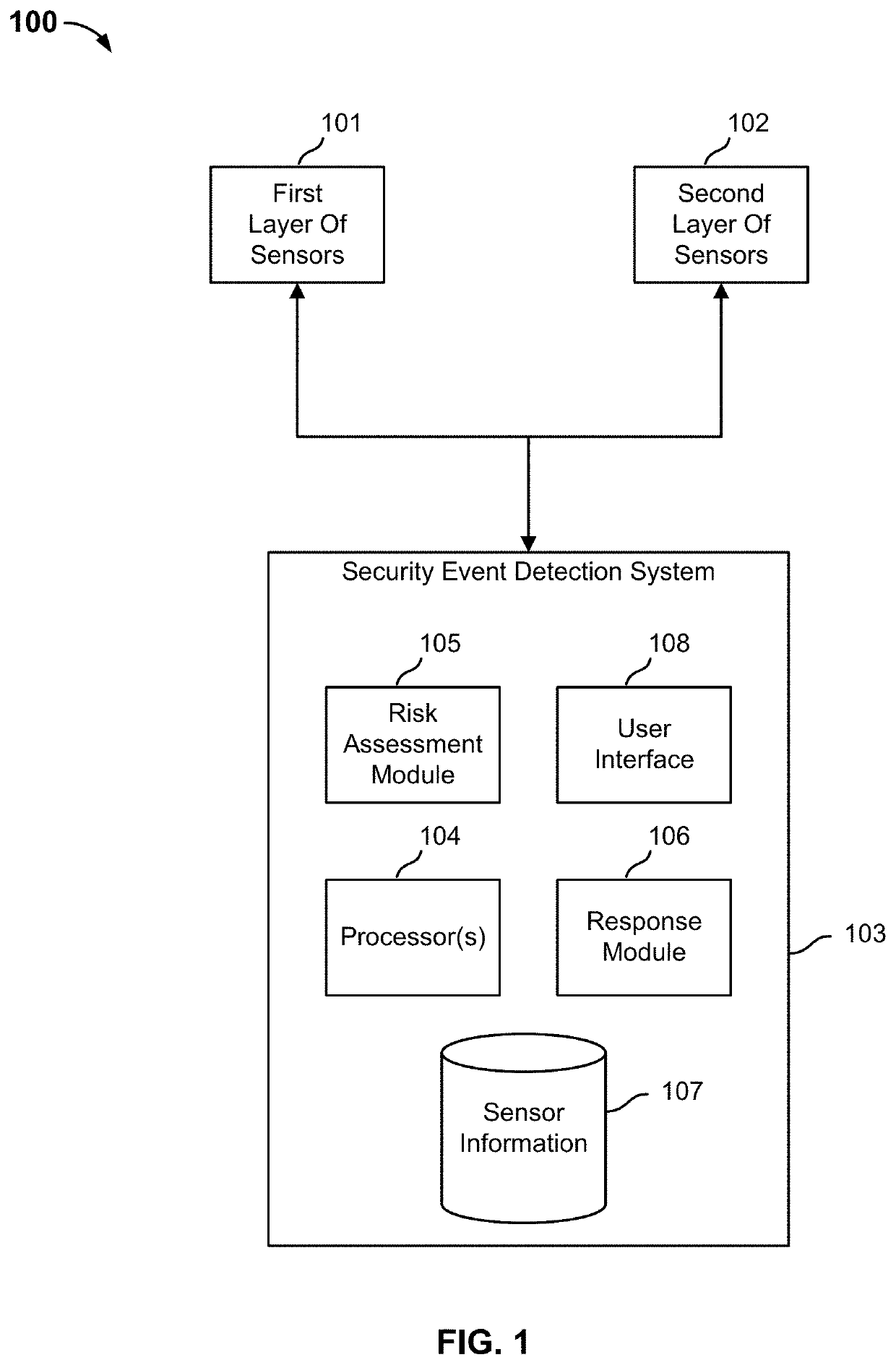
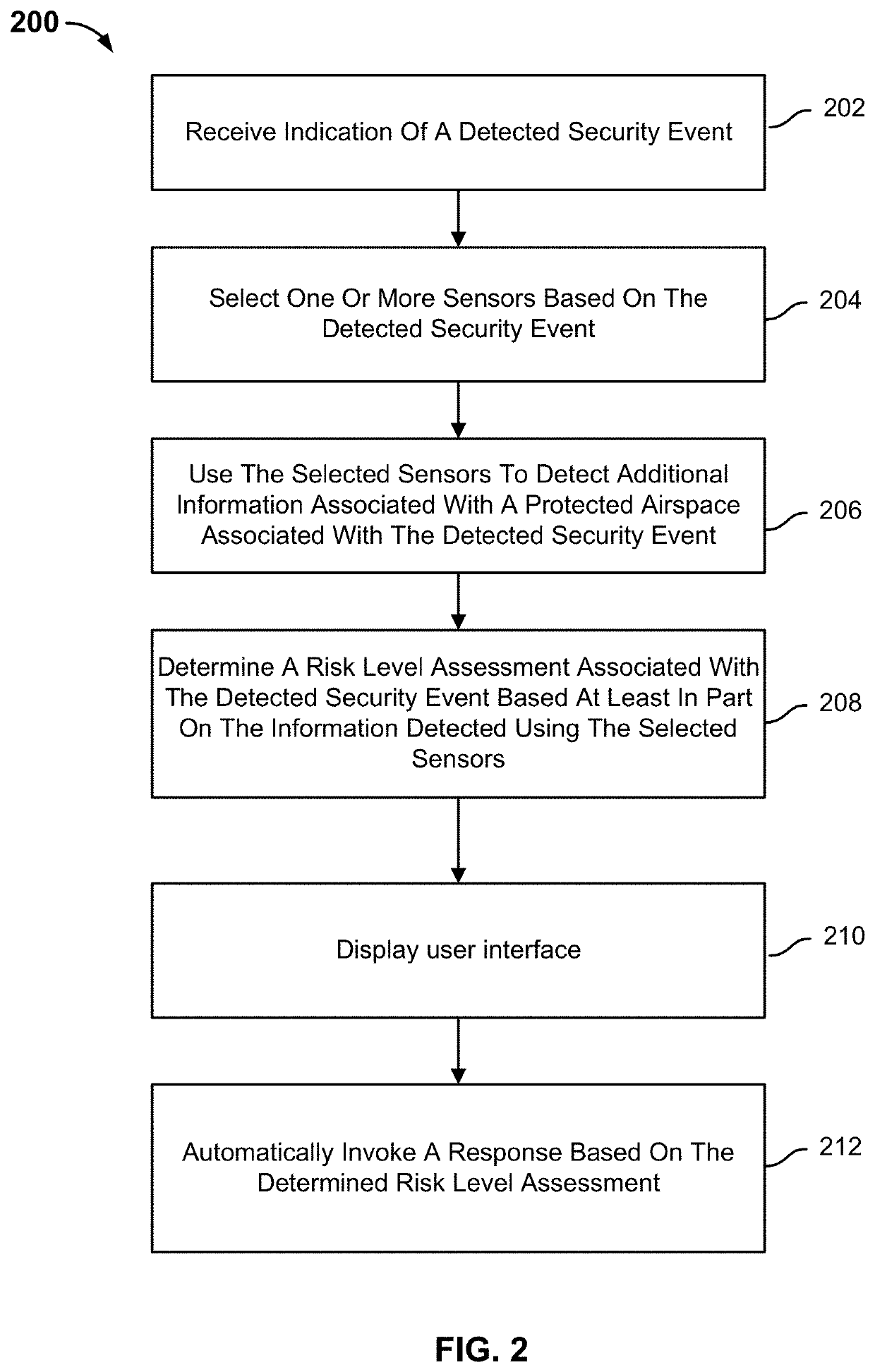
Security event detection and threat assessment
An indication of a detected security event is received. One or more sensors are selected based on the detected security event. The selected sensors are used to detect additional information associated with a protected airspace associated with the detected security event. A risk level assessment associated with the detected security event is determined based at least in part on the additional information detected using the selected sensors. A response is automatically invoked based on the determined risk level assessment.
Owner:AIRSPACE SYST INC
Hazard and Threat Assessment System
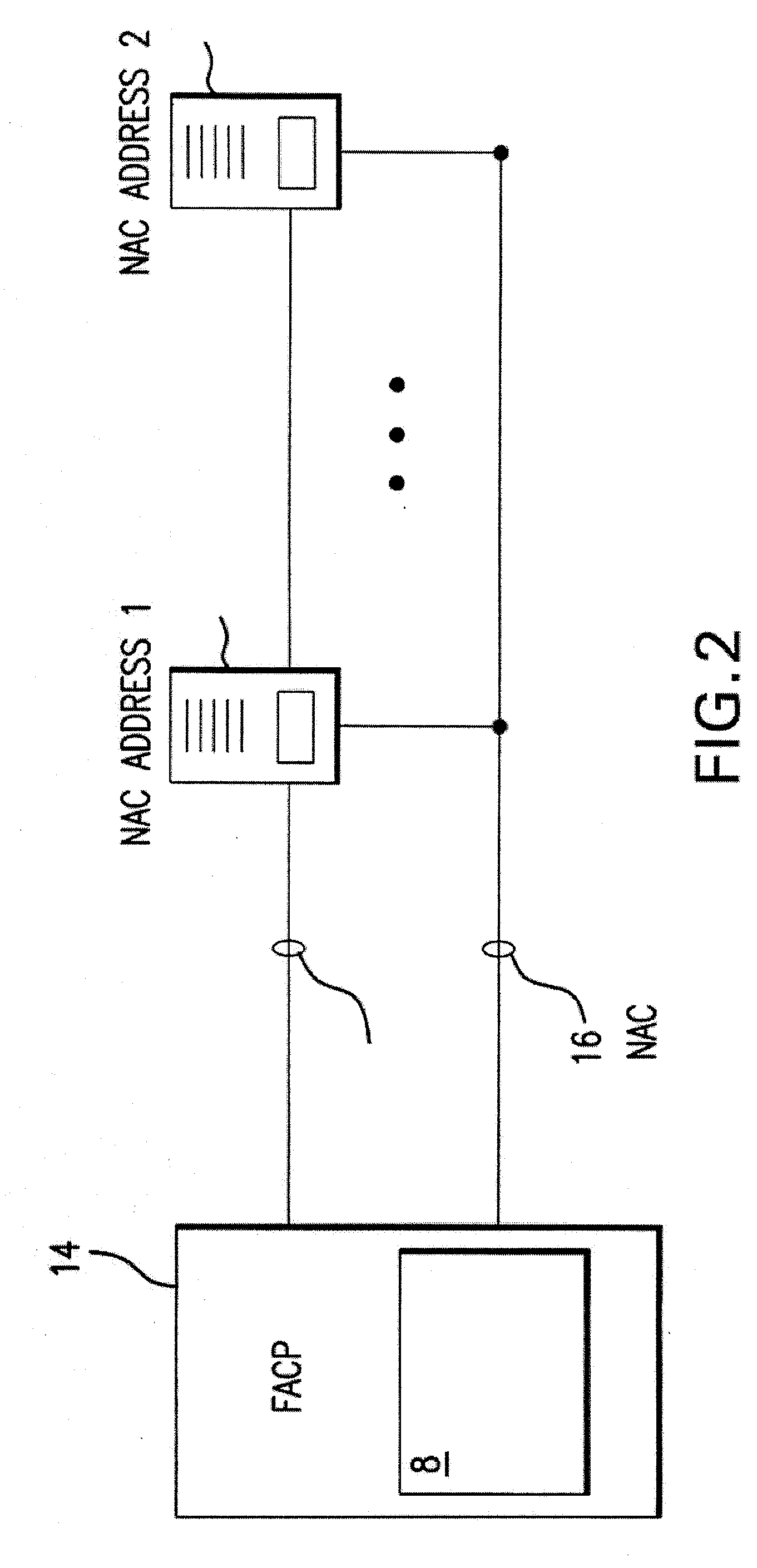
A fire alarm system for graphically illustrating a fire alarm event is provided. The fire alarm system may receive fire alarm information from one or more fire sensors in a building, and may determine a rate of change of at least one aspect of the fire sensor. The rate of increase of temperature, the length that the fire sensor has been activated, the progression of the fire, etc. The rate of change may be graphically illustrated to enable the operator to quickly assess the fire alarm event. A fire alarm system, whose actions are modified by the rate of change of the fire alarm event, is also provided. Depending on the rate of change, one or more input devices (e.g., cameras or other sensors) one or more output devices (e.g., sprinklers, notification appliances, etc.) in the fire alarm system may be controlled.
Owner:SIMPLEXGRINNELL
Threat level identification and quantifying system
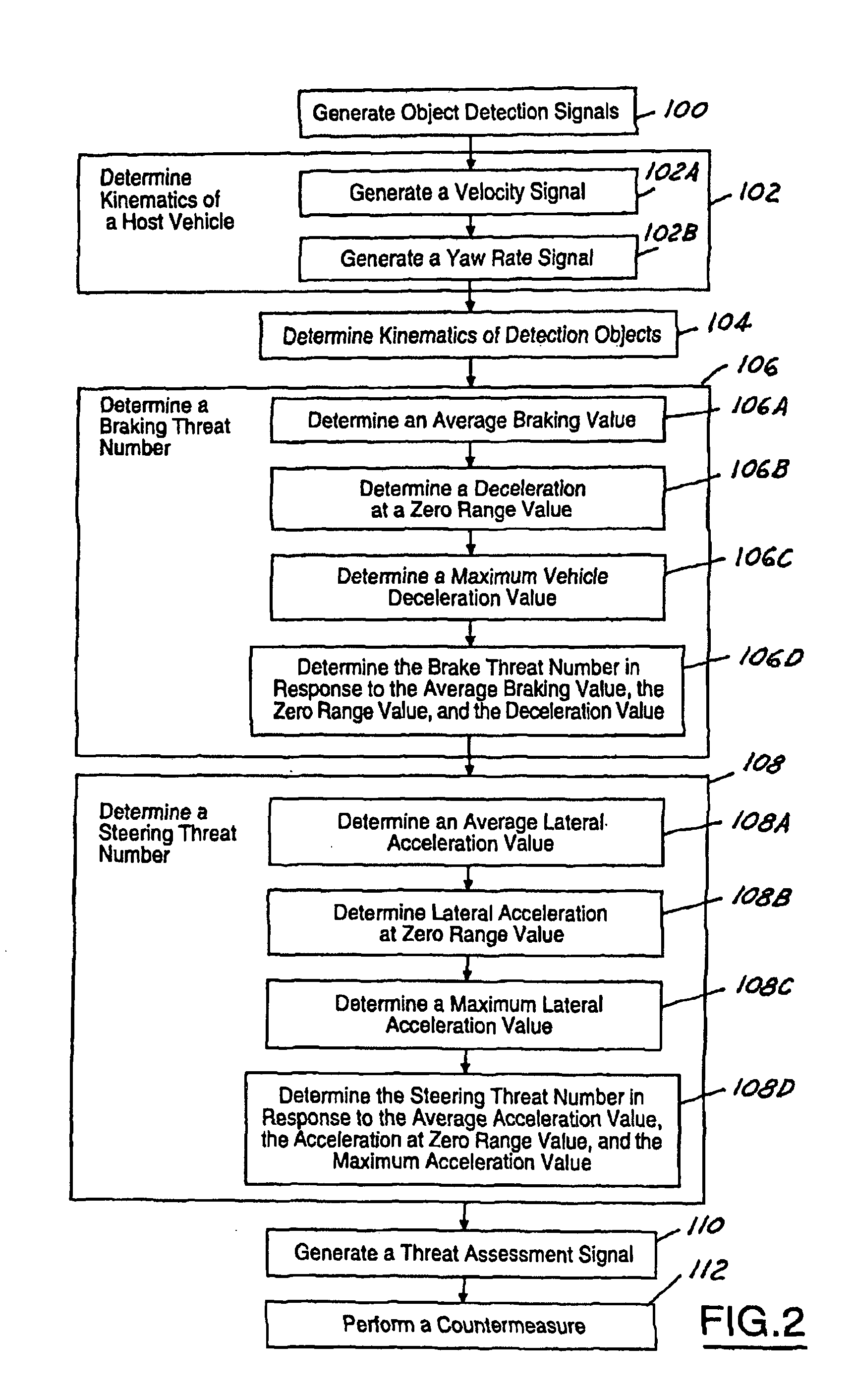
ActiveUS7034668B2Technique is effectiveSimplifies threat assessmentBrake system interactionsDigital data processing detailsKinematicsEngineering
Methods of performing threat assessment of objects for a vehicle include detecting an object. Kinematics of the vehicle and of the object are determined. A brake threat number and a steering threat number are determined in response to the kinematics of the vehicle and the object. The threat posed by the object is determined in response to the brake threat number and the steering threat number.
Owner:FORD GLOBAL TECH LLC
Deterent for unmanned aerial systems
ActiveUS9715009B1Defence devicesDirection/deviation determining electromagnetic systemsNon destructiveCountermeasure
Owner:XIDRONE SYST INC
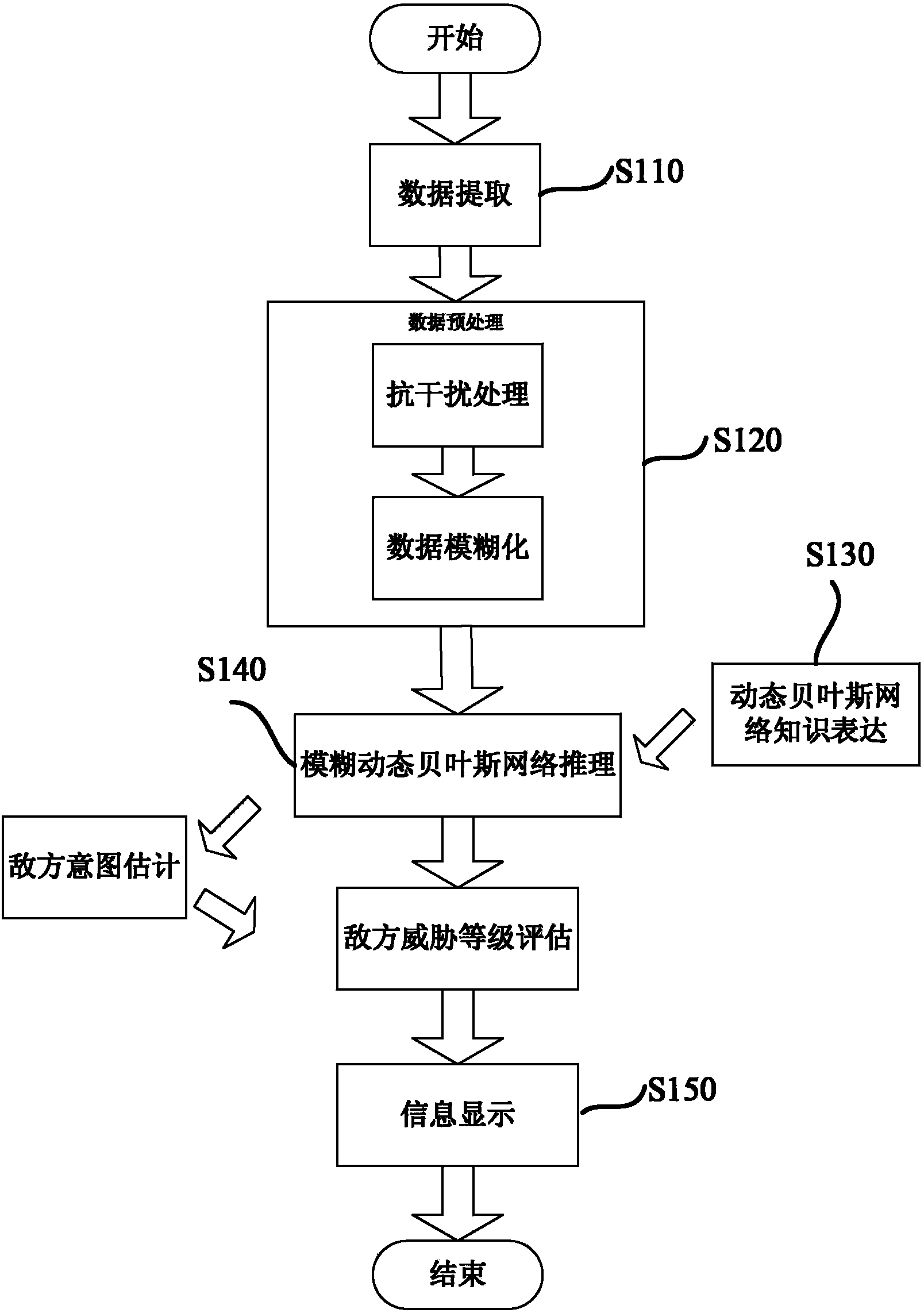
State threat assessment method based on fuzzy dynamic Bayesian network
ActiveCN103488886AImprove anti-interference abilityImprove real-time performanceSpecial data processing applicationsTemporal changeNetwork model
The invention discloses a state threat assessment method based on a fuzzy dynamic Bayesian network. The method includes extracting data to be processed from acquired data; processing the acquired data in a jamming proofing manner, and processing the data processed in the jamming proofing manner in a fuzzy manner; performing knowledge representation on the process of battlefield state threat assessment, determining concept and expression of events and attributes, and establishing a dynamic Bayesian network model about battlefield threat assessment; inputting fuzzy variables into the network model to obtain the fuzzy dynamic Bayesian network, performing inference on the fuzzy dynamic Bayesian network to acquire a state forecasting result, and acquiring the threat assessment grade based on the state forecasting result. According to the method, the dynamic Bayesian network is established, knowledge representation is performed on data changing with the time, timeliness and effectiveness of the data are enhanced, the data processed in a fuzzy manner are inputted as inputting evidences, accuracy and efficiency of inference are improved, and a semantic model of the state threat assessment can be expressed better.
Owner:TSINGHUA UNIV
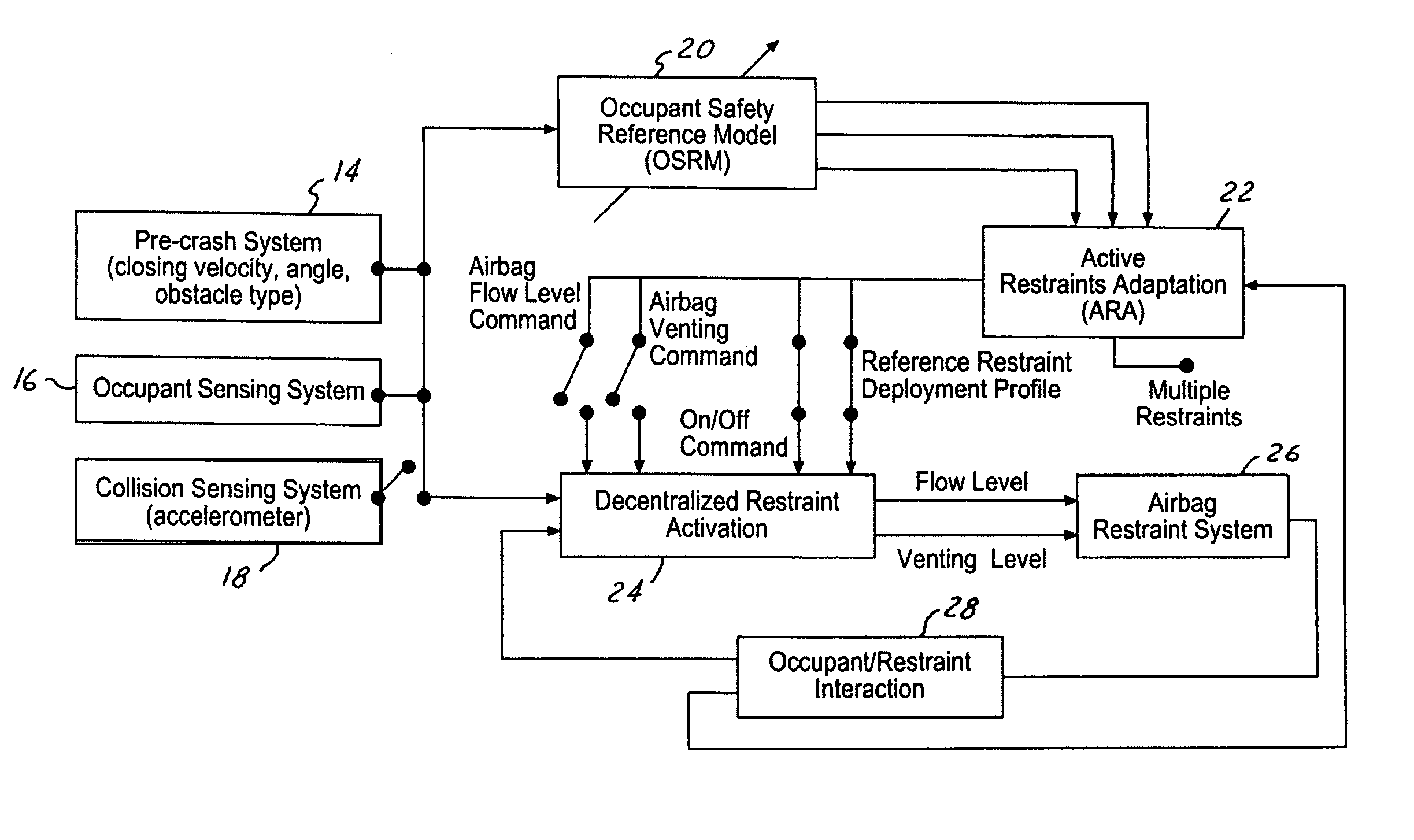
Active adaptation of vehicle restraints for enhanced performance robustness
InactiveUS20060052924A1Dissipate kinetic energyReduce harmDigital data processing detailsAnti-collision systemsVehicle dynamicsReference model
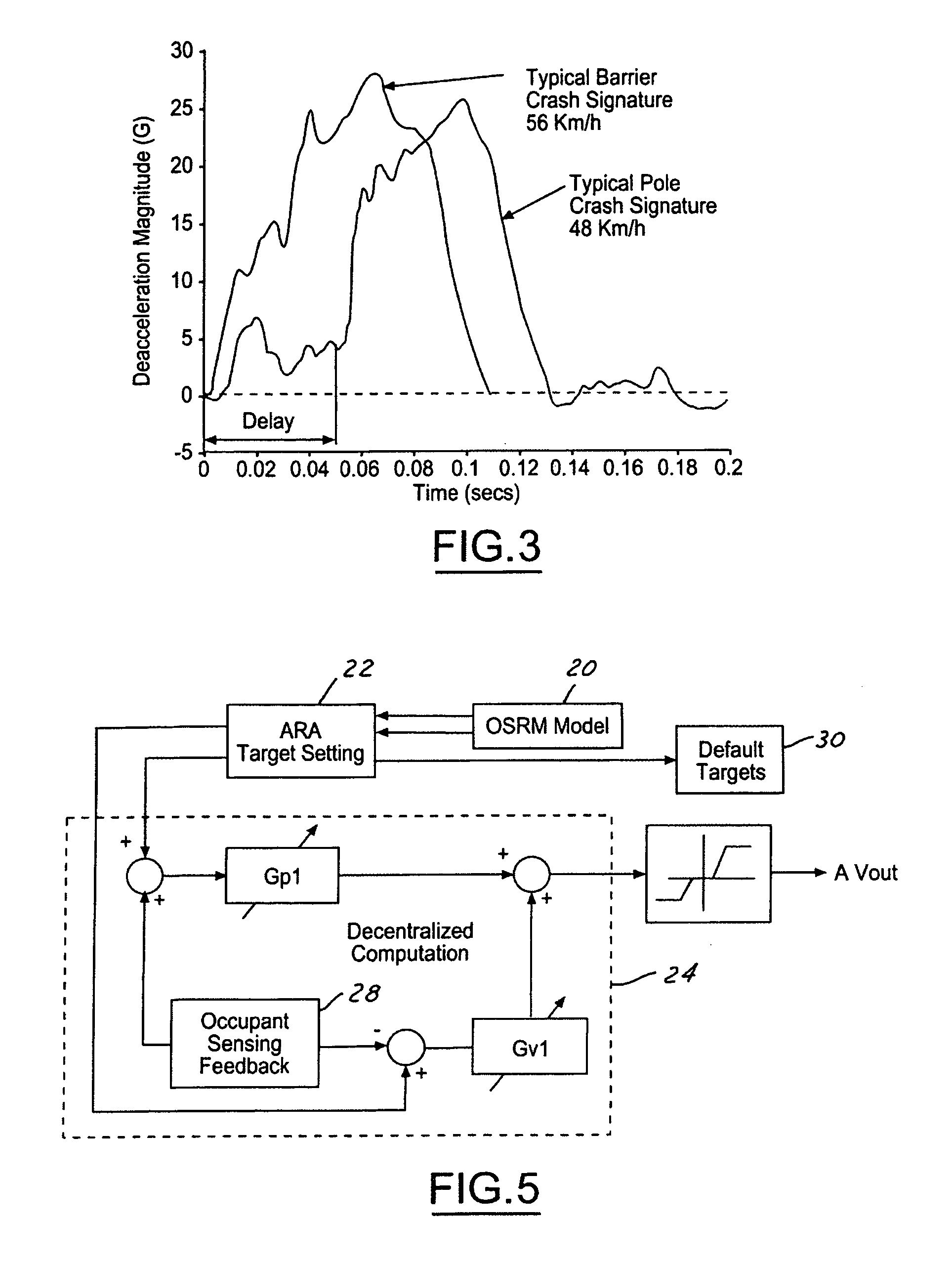
A vehicle crash safety system includes a pre-crash sensing system generating an object threat assessment and vehicle dynamics data, an occupant sensing system generating occupant characteristic data, and an Occupant Safety Reference Model (OSRM) controller for generating a reference safety restraint deployment profile as a function of the object threat assessment, vehicle dynamics data and occupant characteristic data. An active restraint adaptation (ARA) controller in operative communication with the OSRM controller and a decentralized restraint controller. The ARA controller sends restraint deployment targets, and the safety restraint deployment profile to the decentralized restraint controller. The ARA controller may modify input signals to the decentralized controller based on the real-time occupant position trajectory. The decentralized restraint controller is adapted to operate the restraint system as a function of signals from the ARA controller and real-time occupant-restraint system interactions.
Owner:FORD MOTOR CO
Electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and evaluation system based on the model
ActiveCN105763562AImprove accuracyImprove timelinessPlatform integrity maintainanceTransmissionDistributed structureStructure of Management Information
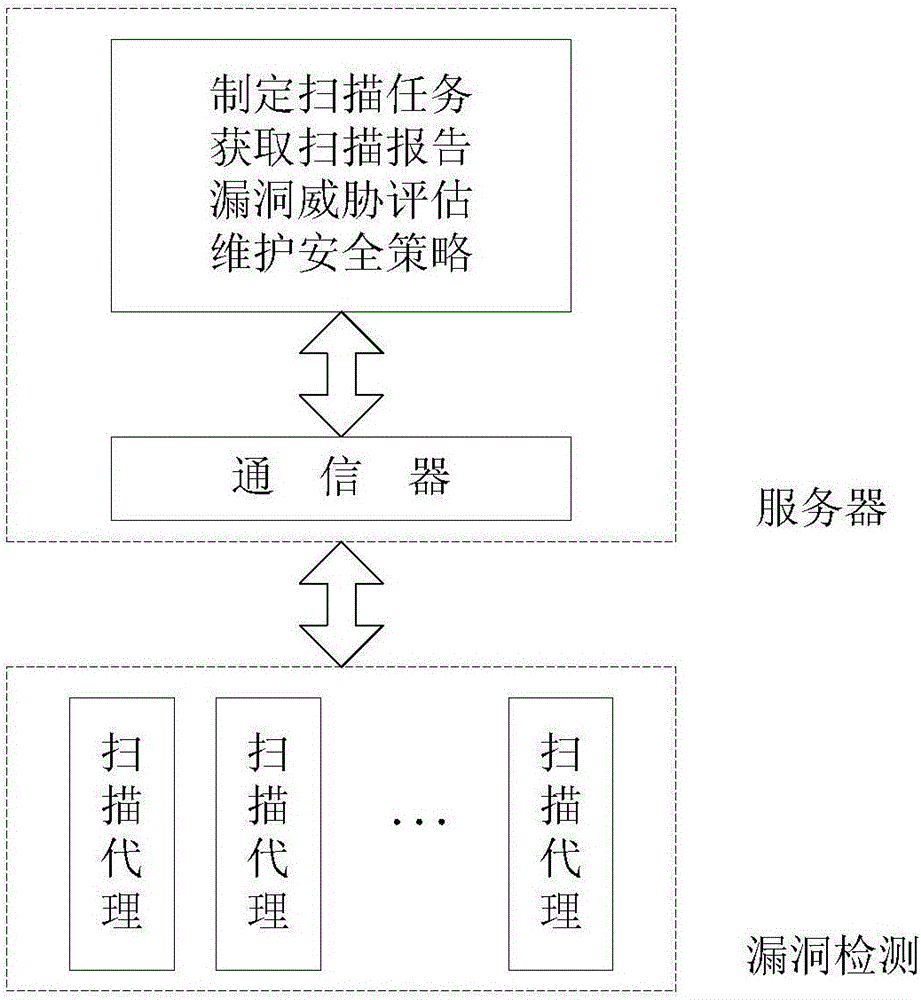
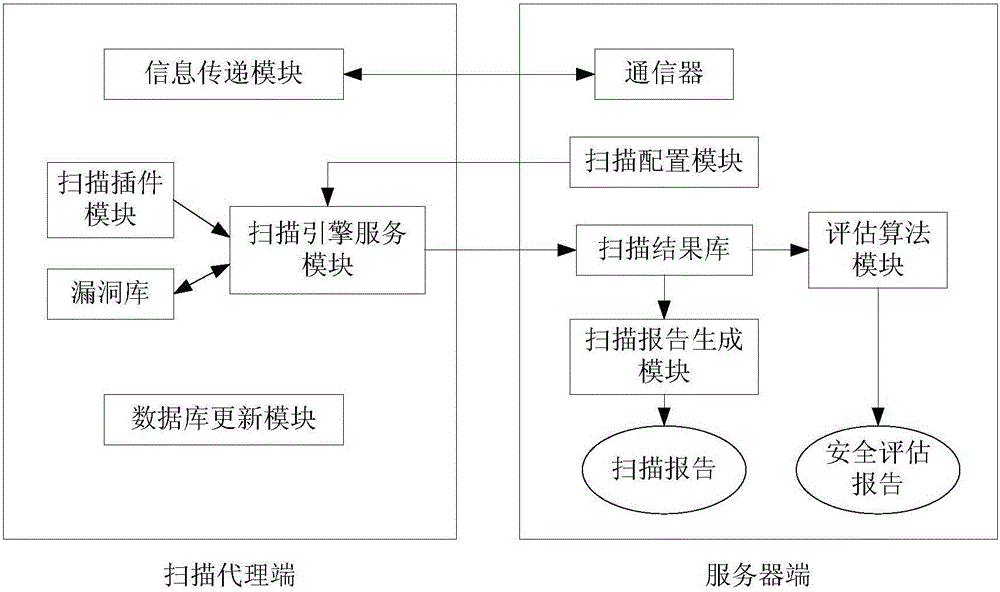
The invention discloses an electric power information network vulnerability threat evaluation model establishment method faced to electric power CPS risk evaluation and an evaluation system based on the model, the model selects three groups of security vulnerability evaluation factors including vulnerability distribution threat degree, access approach and utilization complexity; an analytic hierarchy process is adopted to establish a vulnerability threat degree evaluation model, and a parameter construction method is provided; on the basis of quantitative evaluation, the evaluation result defines a vulnerability threat level, and the objectivity of quantitative evaluation and visibility of qualitative evaluation are considered; and the system related to the invention comprises a vulnerability detection part and a server part which adopt distributed structure. According to the invention, a vulnerability scanning system and a security area of the electric power information network are combined, an electric power information network vulnerability threat evaluation algorithm based on CVSS and analytic hierarchy process is adopted to perform vulnerability threat evaluation, so that the system can be safer and more accurate for performing vulnerability scanning and safety evaluation on the electric power information network.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
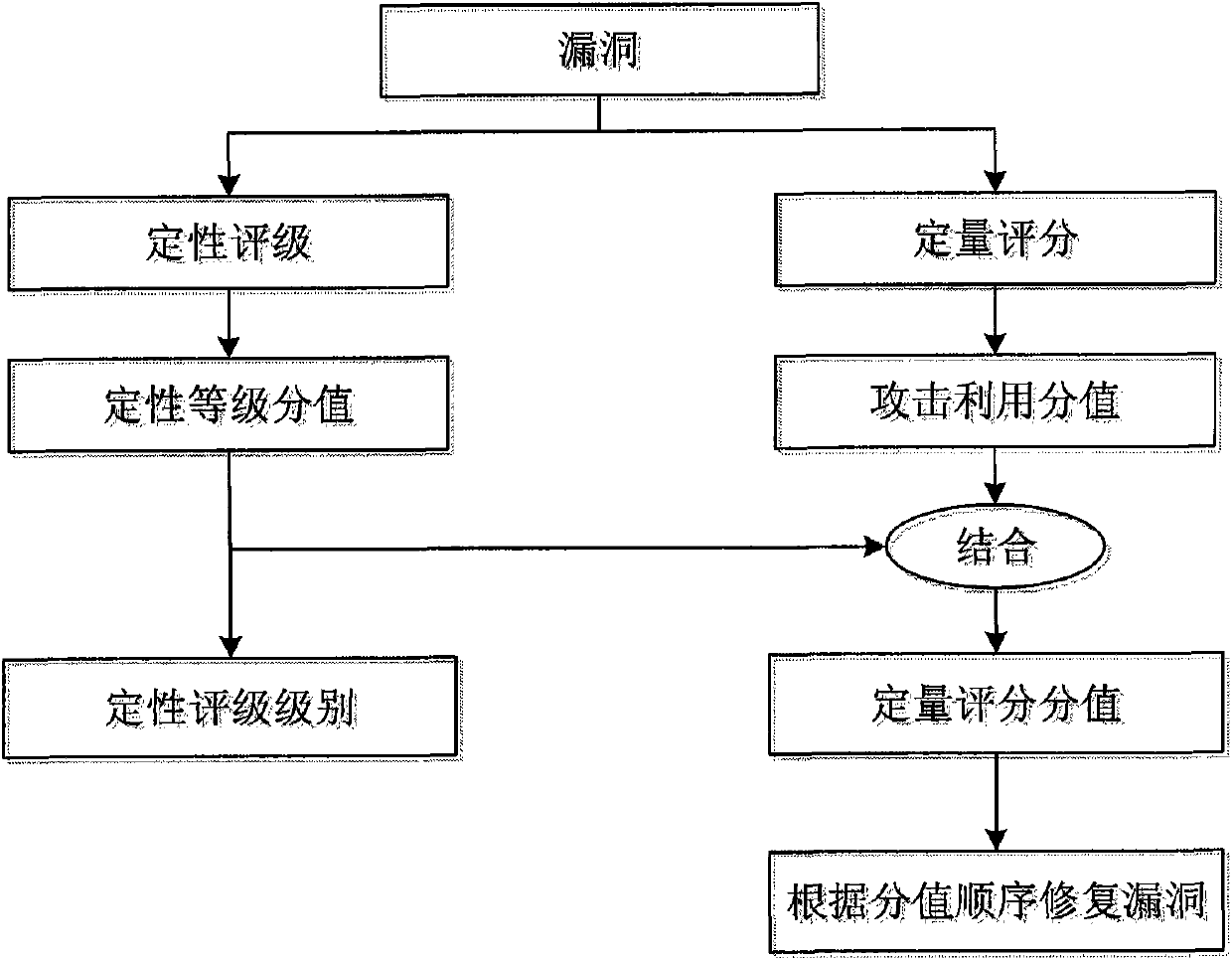
Bug repair method based on hierarchical bug threat assessment
The invention discloses a bug repair method based on hierarchical bug threat assessment. The method comprises the following steps: (1) extracting a plurality of information security attributes of the target system, a bug to be tested, and required attack conditions for the bug in the utilized process; (2) attacking the bug, and recording the value of the required attack conditions for the bug in the utilized process and the degree of damage after the bug is successfully utilized; (3) obtaining the qualitative grade score of the bug according to the degree of damage; (4) obtaining the attack utilization score of the bug according to the value of the required attack conditions; (5) obtaining the quantitative grade score according to the attack utilization value and the qualitative grade score; (6) and after determining the bug processing sequence according to the quantitative grade score of the bug to be tested, and repairing the bug. The method combines the advantages of qualitative and quantitative bug assessment methods, and divides the bugs as detailed as possible on the basis of visually giving out the bug threat degree, thereby helping the user to repair a great deal of bugs.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
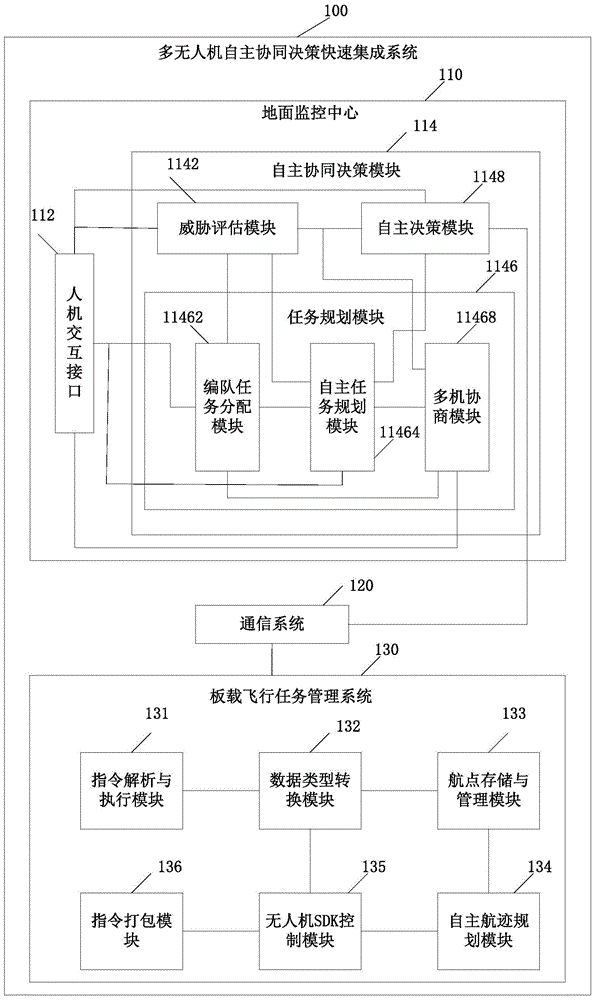
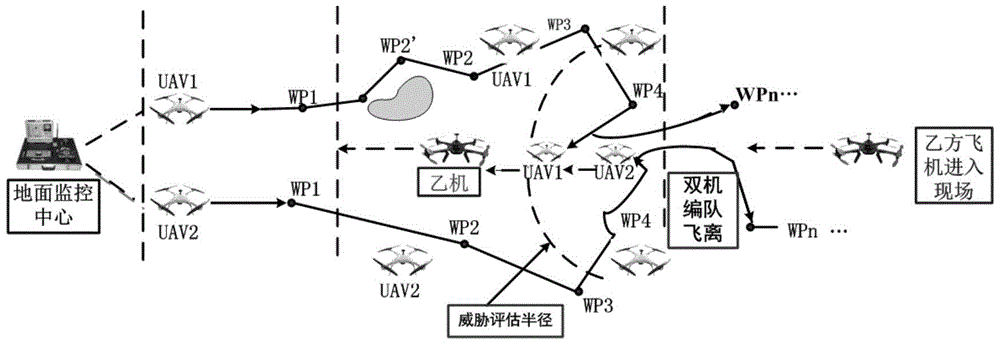
A multi-unmanned-aerial-vehicle autonomous collaborative-decision-making fast integration system
ActiveCN105700553AImprove AI performanceQuickly integrate applicationsPosition/course control in three dimensionsHuman–computer interactionParsing
The invention discloses a multi-unmanned-aerial-vehicle autonomous collaborative-decision-making fast integration system. The system comprises a ground monitor center, a communication system and an onboard flight mission management system. The ground monitor center comprises a man-machine interaction interface and an autonomous collaborative-decision-making module. The collaborative-decision-making module comprises a threat assessment module, a task planning module and an autonomous decision-making module. The task planning module comprises a formation task distribution module, an autonomous task planning module and a multi-machine negotiation module. The onboard flight mission management system comprises an instruction parsing and execution module, an instruction packing module, a data type conversion module, a waypoint storage and management module, an autonomous track planning module and an unmanned aerial vehicle SDK control module. The unmanned aerial vehicle SDK control module is configured to control an unmanned aerial vehicle. Through the embodiment of the invention, technical problems of how to realize multi-unmanned-aerial-vehicle autonomous collaborative fast integration application and system modularization and how to raise artificial intelligence performance of the system are solved.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
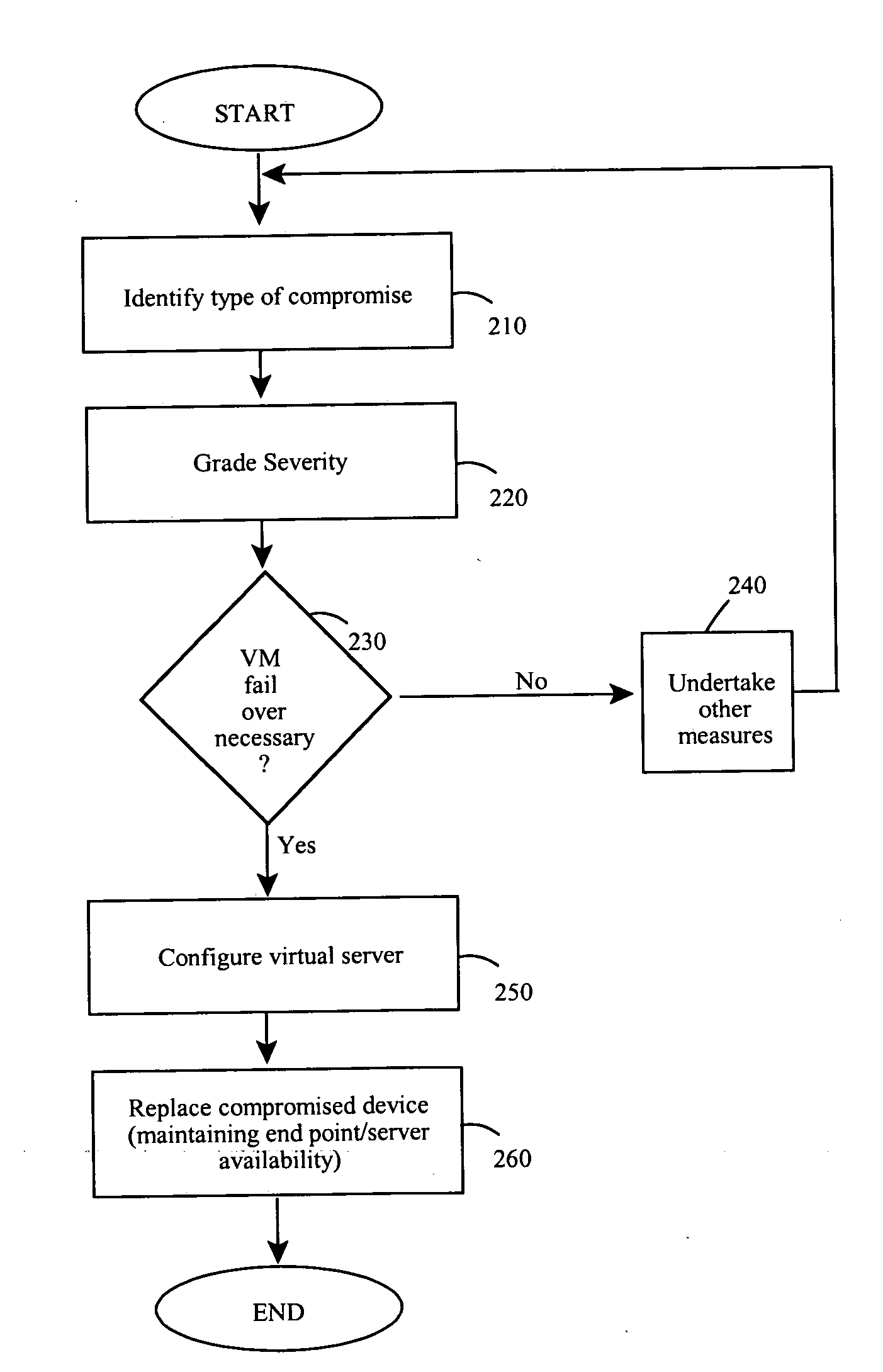
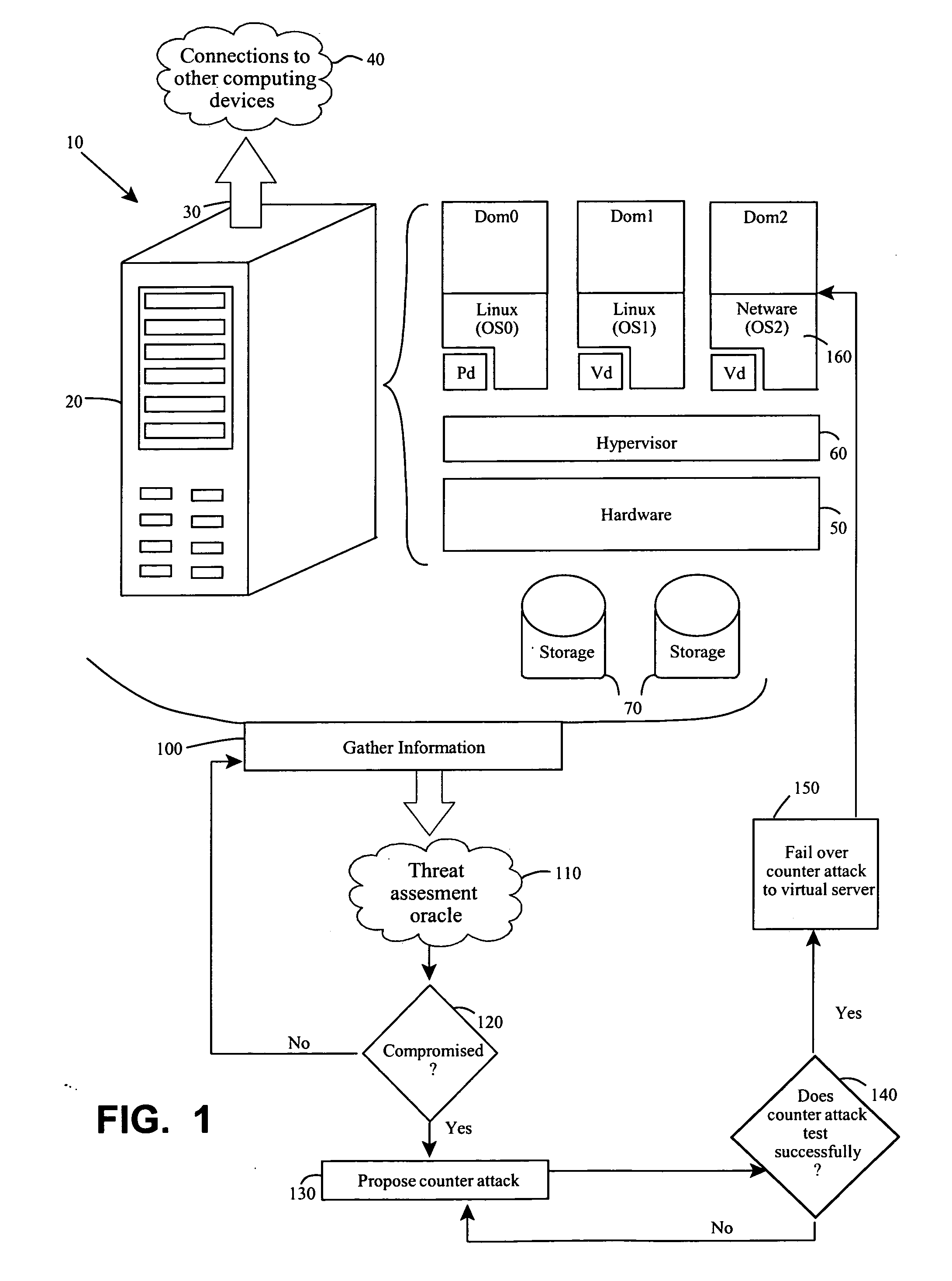
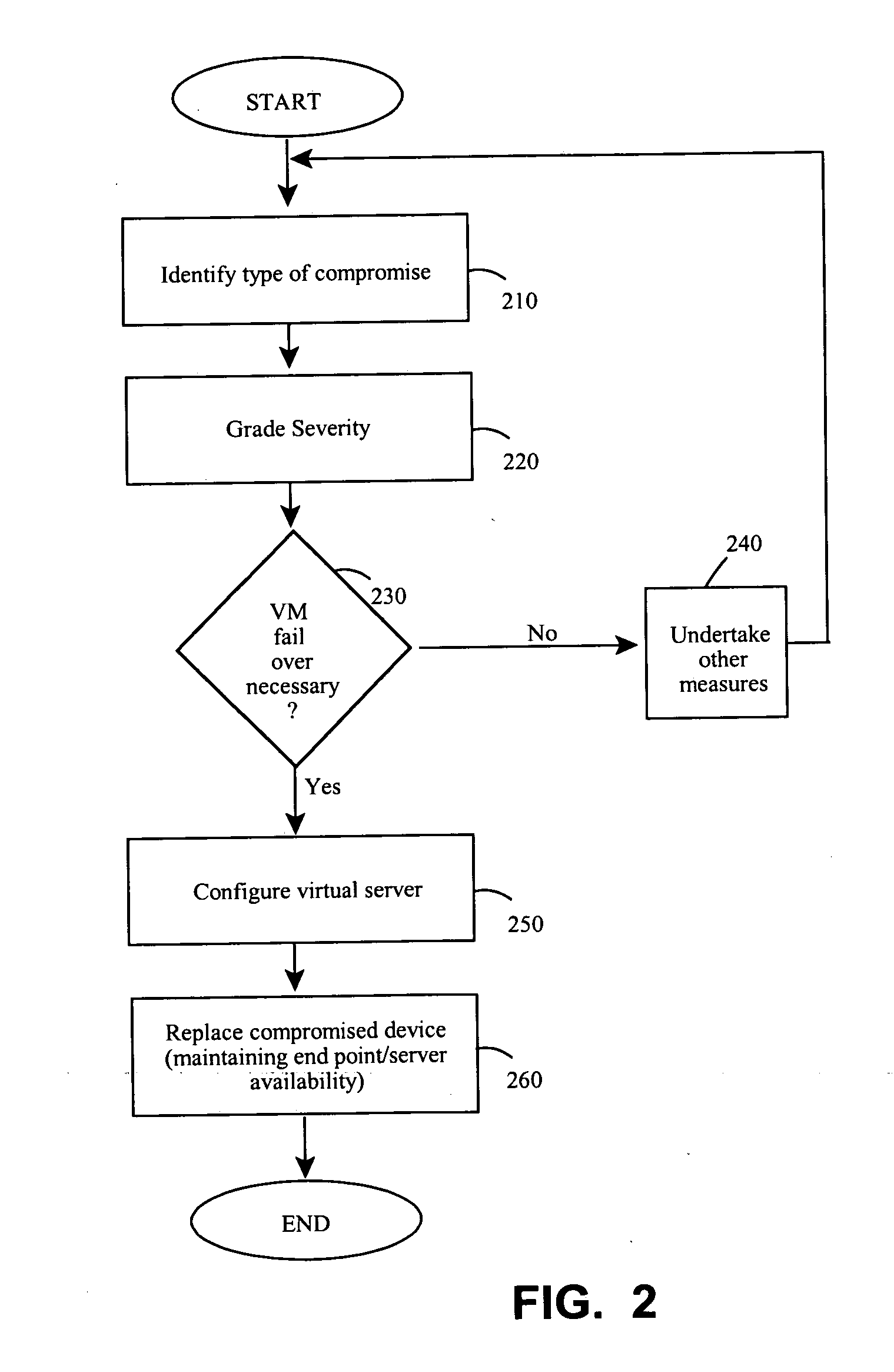
Endpoint security threat mitigation with virtual machine imaging
InactiveUS20110078797A1Quick changeMaintain availabilityMemory loss protectionError detection/correctionCountermeasureEndpoint security
Methods and apparatus involve the mitigation of security threats at a computing endpoint, such as a server, including dynamic virtual machine imaging. During use, a threat assessment is undertaken to determine whether a server is compromised by a security threat. If so, a countermeasure to counteract the security threat is developed and installed on a virtual representation of the server. In this manner, the compromised server can be replaced with its virtual representation, but while always maintaining the availability of the endpoint in the computing environment. Other features contemplate configuration of the virtual representation from a cloned image of the compromised server at least as of a time just before the compromise and configuration on separate or same hardware platforms. Testing of the countermeasure to determine success is another feature as is monitoring data flows to identifying compromises, including types or severity. Computer program products and systems are also taught.
Owner:NOVELL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com