Bug repair method based on hierarchical bug threat assessment
A vulnerability repair, hierarchical technology, applied in the field of vulnerability threat assessment, can solve the problem of inability to classify vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
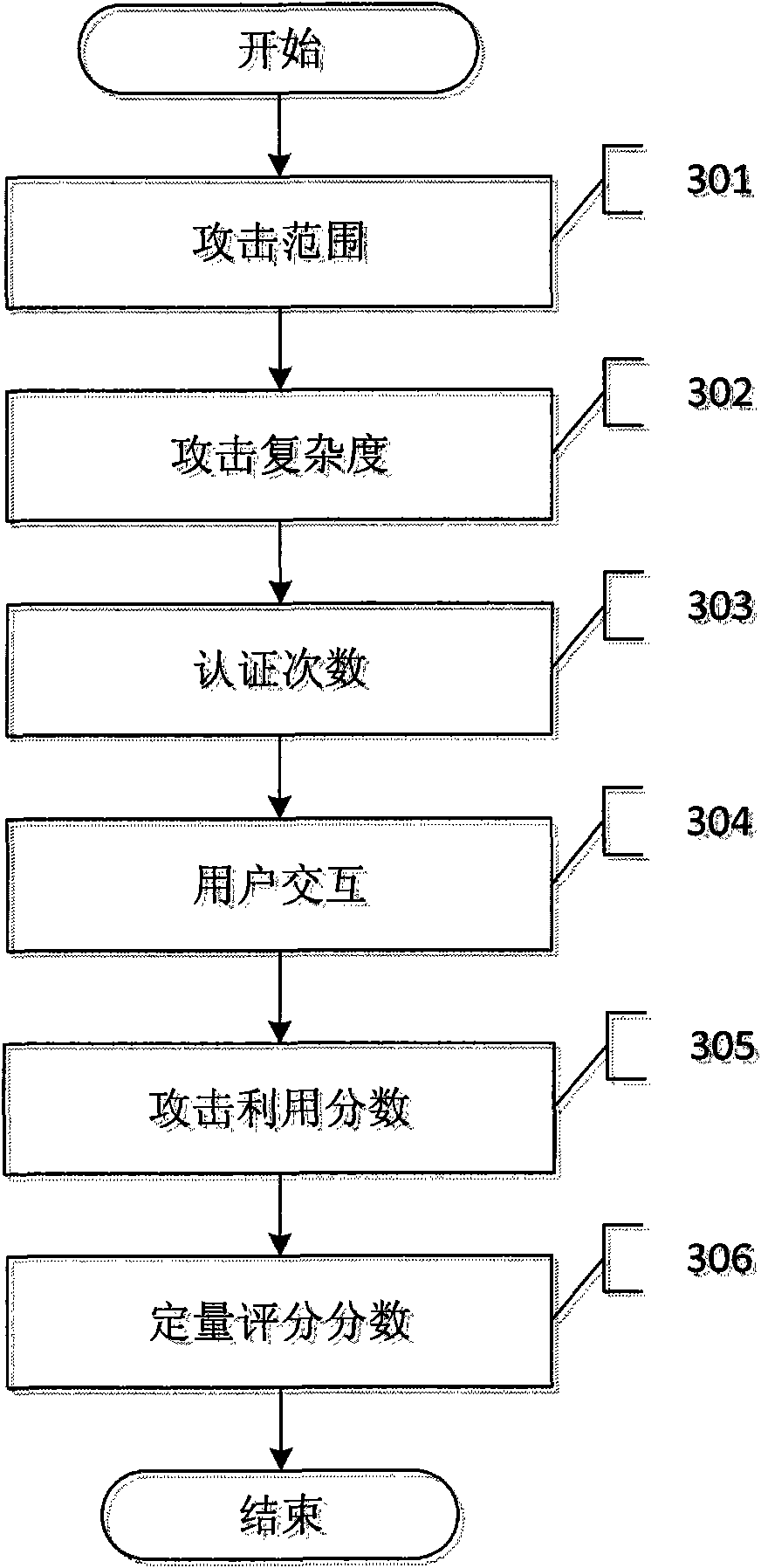
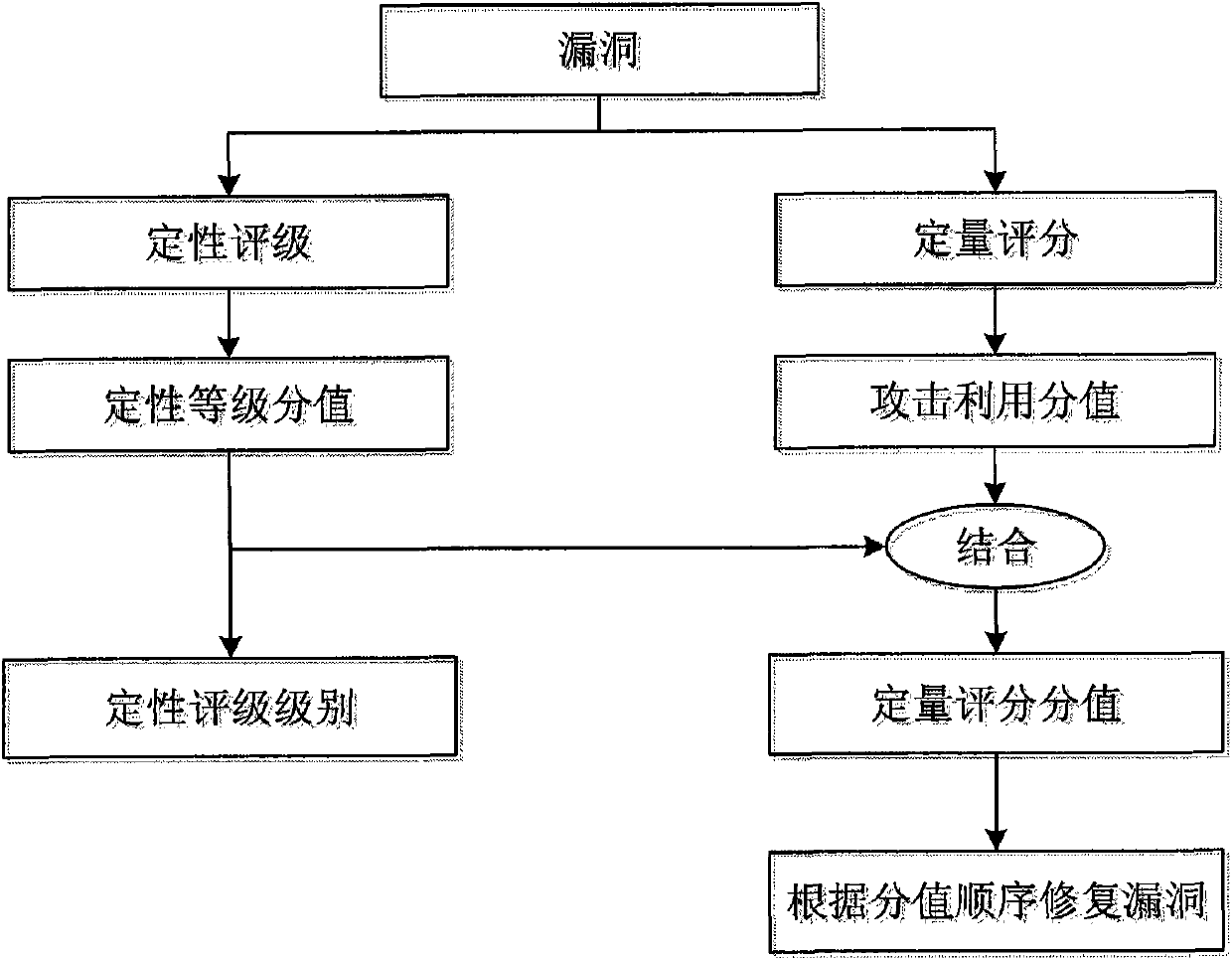
[0059] The present invention includes two parts, qualitative rating and quantitative scoring. The two parts of the present invention will be further described in detail below referring to the accompanying drawings in combination with Table 1-Table 9 and the vulnerability with CVE number CVE-2008-4250. The vulnerability numbered CVE-2008-4250 describes a buffer overflow vulnerability in the Windows system when the server service receives a specially crafted RPC request. Remote attackers may use this vulnerability to execute arbitrary programs on the target.
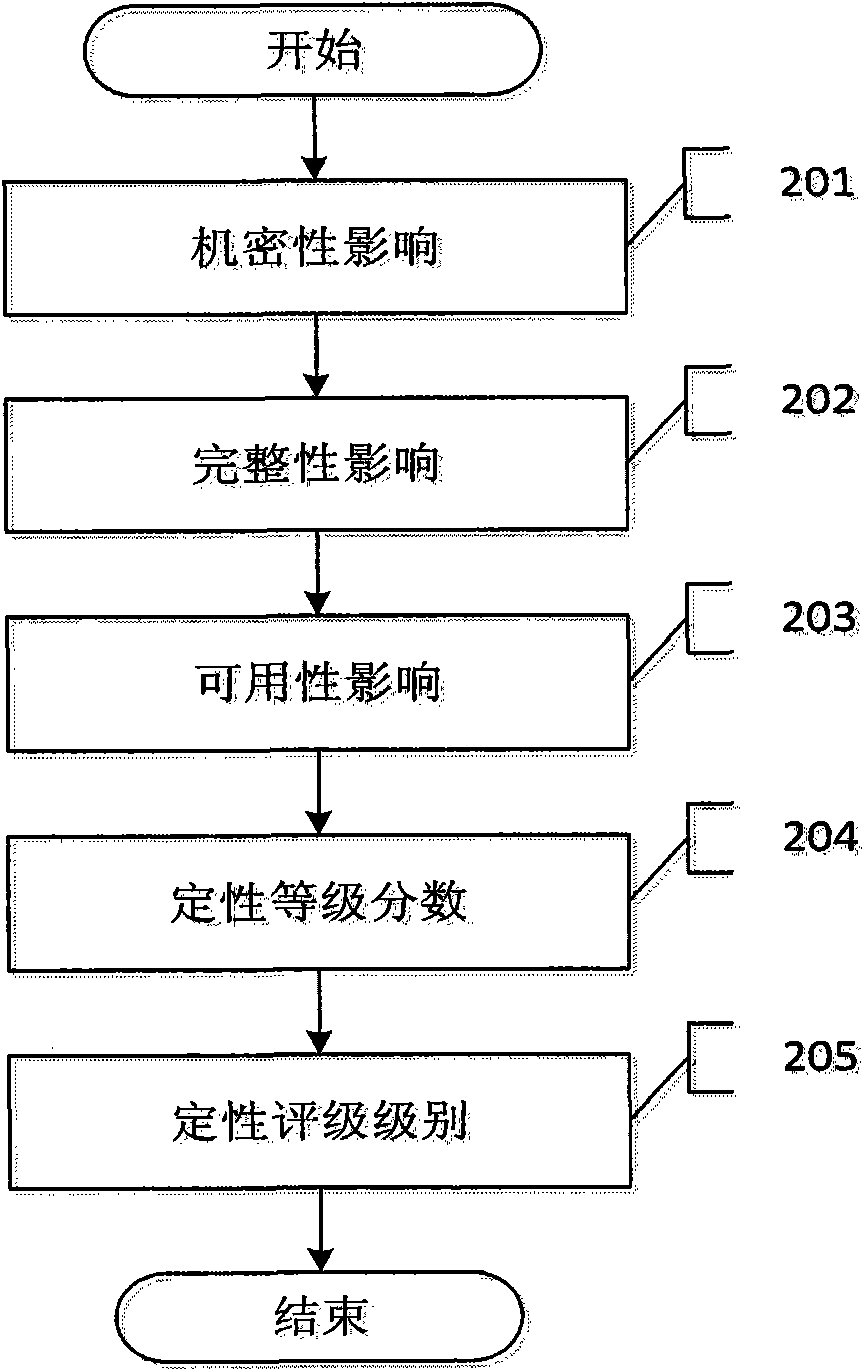
[0060] Such as figure 2 As shown, the specific implementation process of the vulnerability qualitative rating method of the present invention for the CVE-2008-4250 vulnerability includes the following steps:
[0061] Step 201: Analyze the impact of vulnerabilities on confidentiality. Since this vulnerability can cause an attacker to execute arbitrary programs on the target, an attacker can read the entire data of the sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com