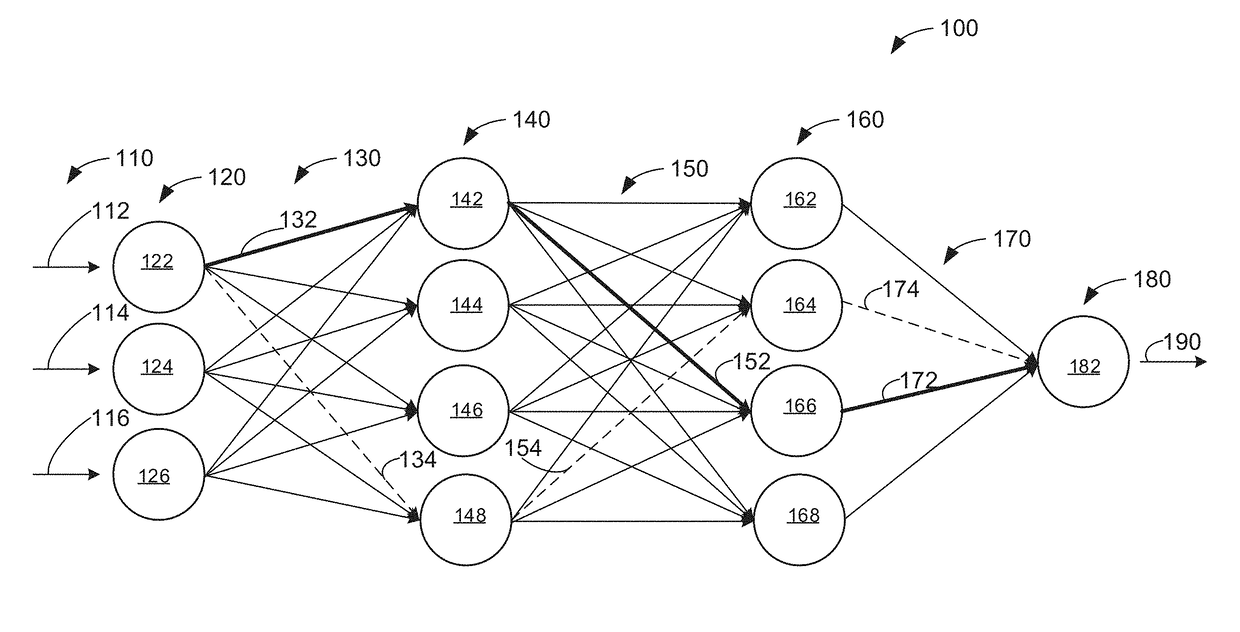
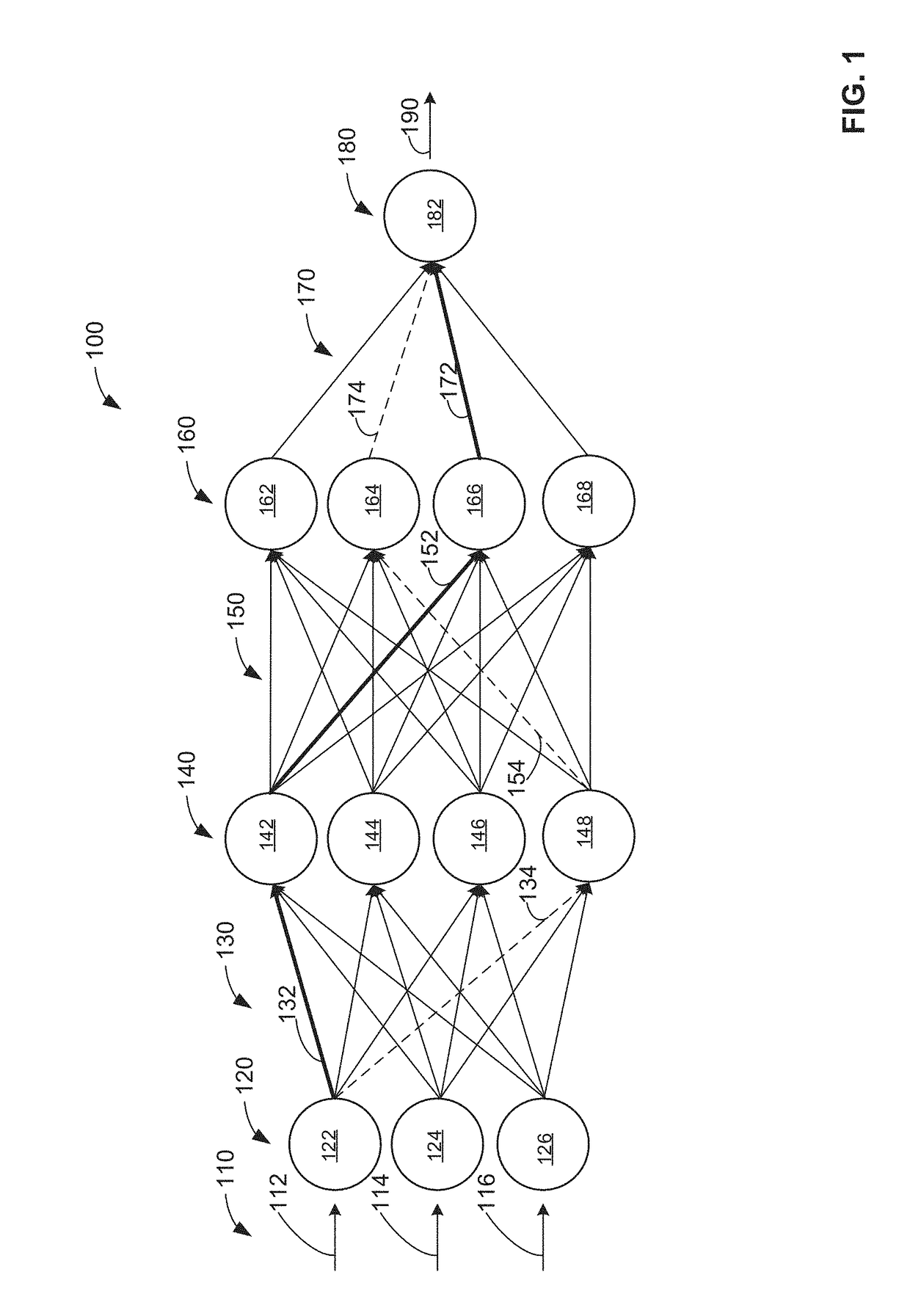
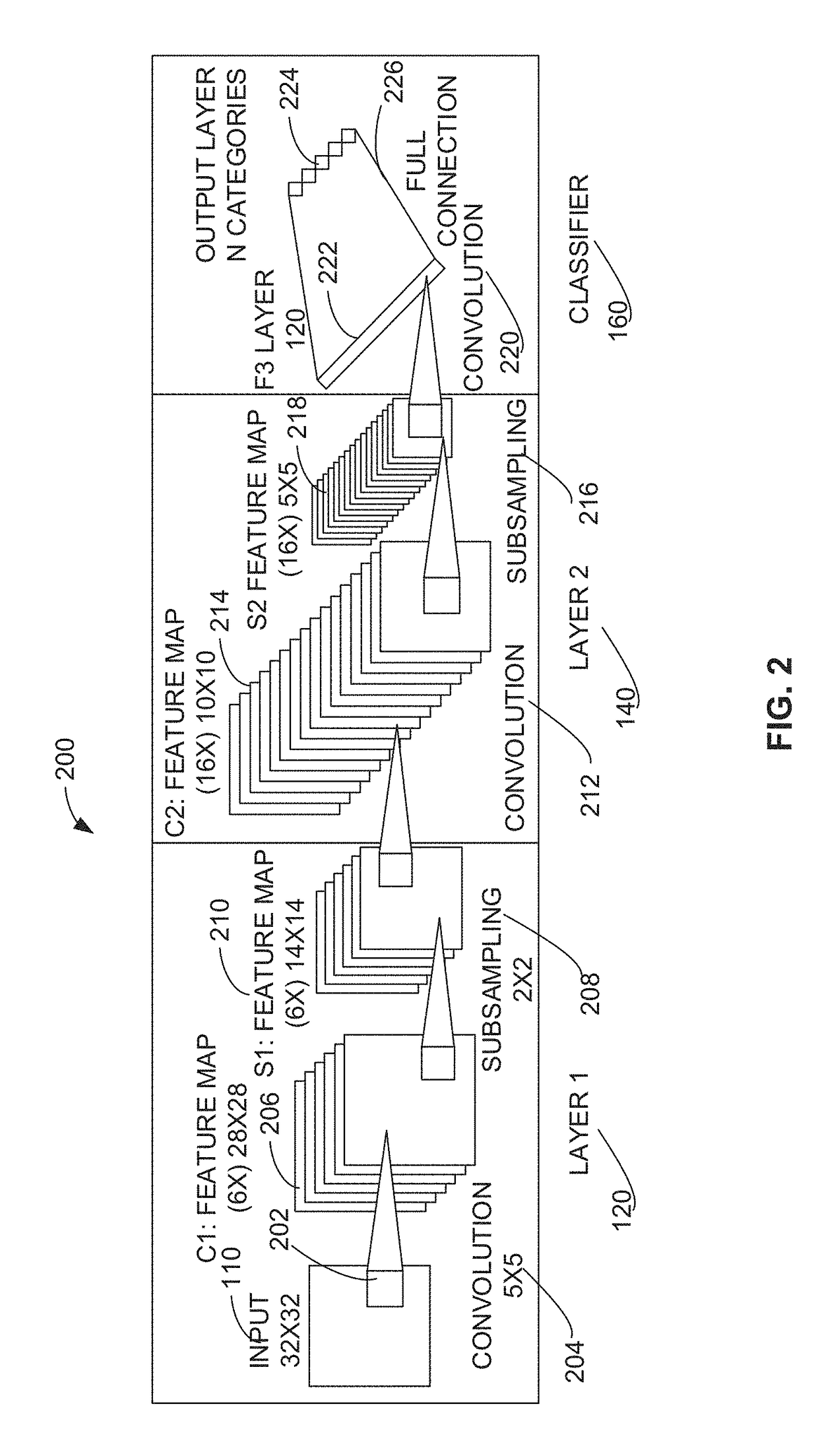
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1505 results about "Goal system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Each system more or less adopts the same principles of goal setting, but each one has a different emphasis – so goal setting systems that work well for one person may not work for someone else. That’s why it’s important to look into goal setting systems properly before choosing one.
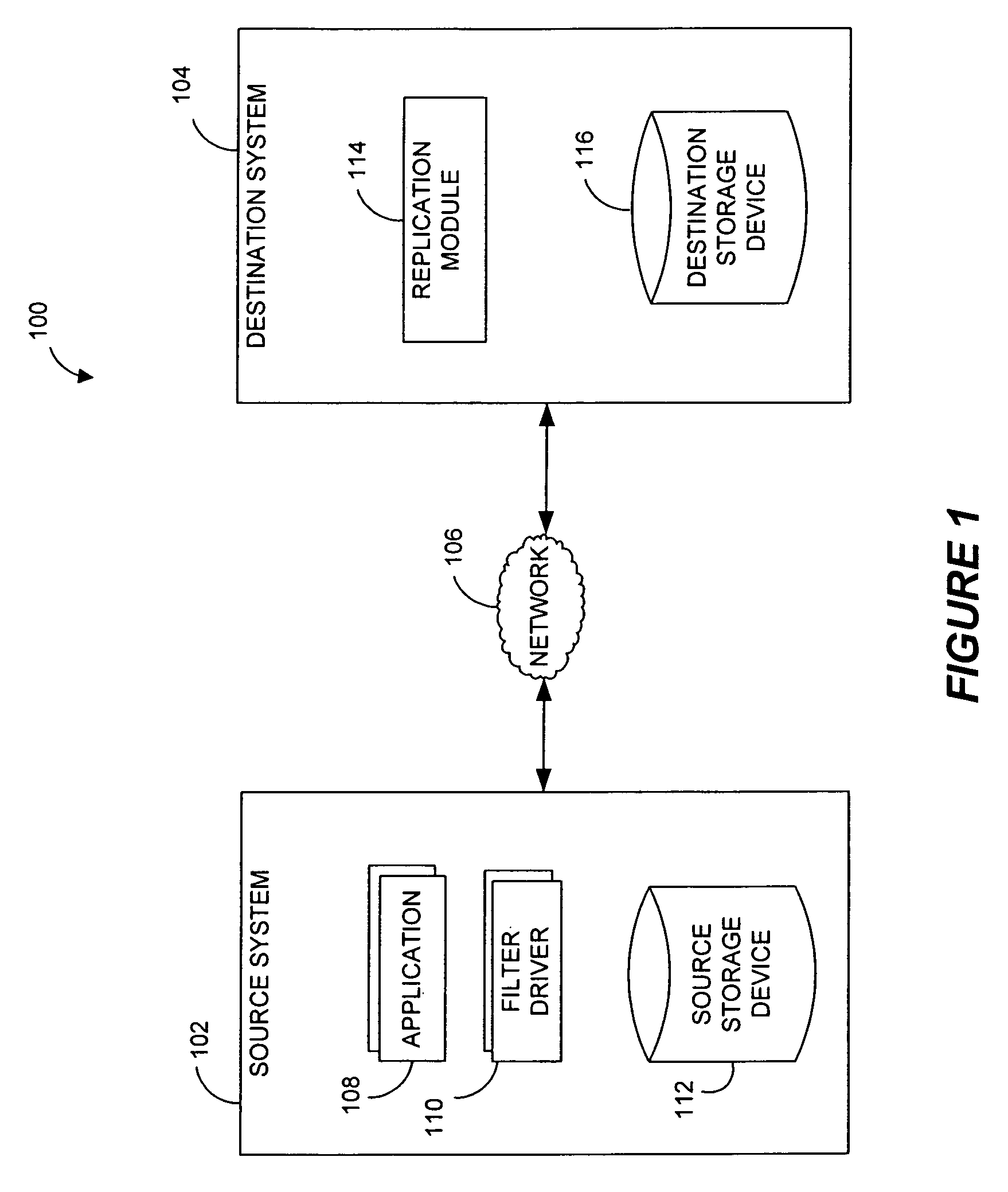
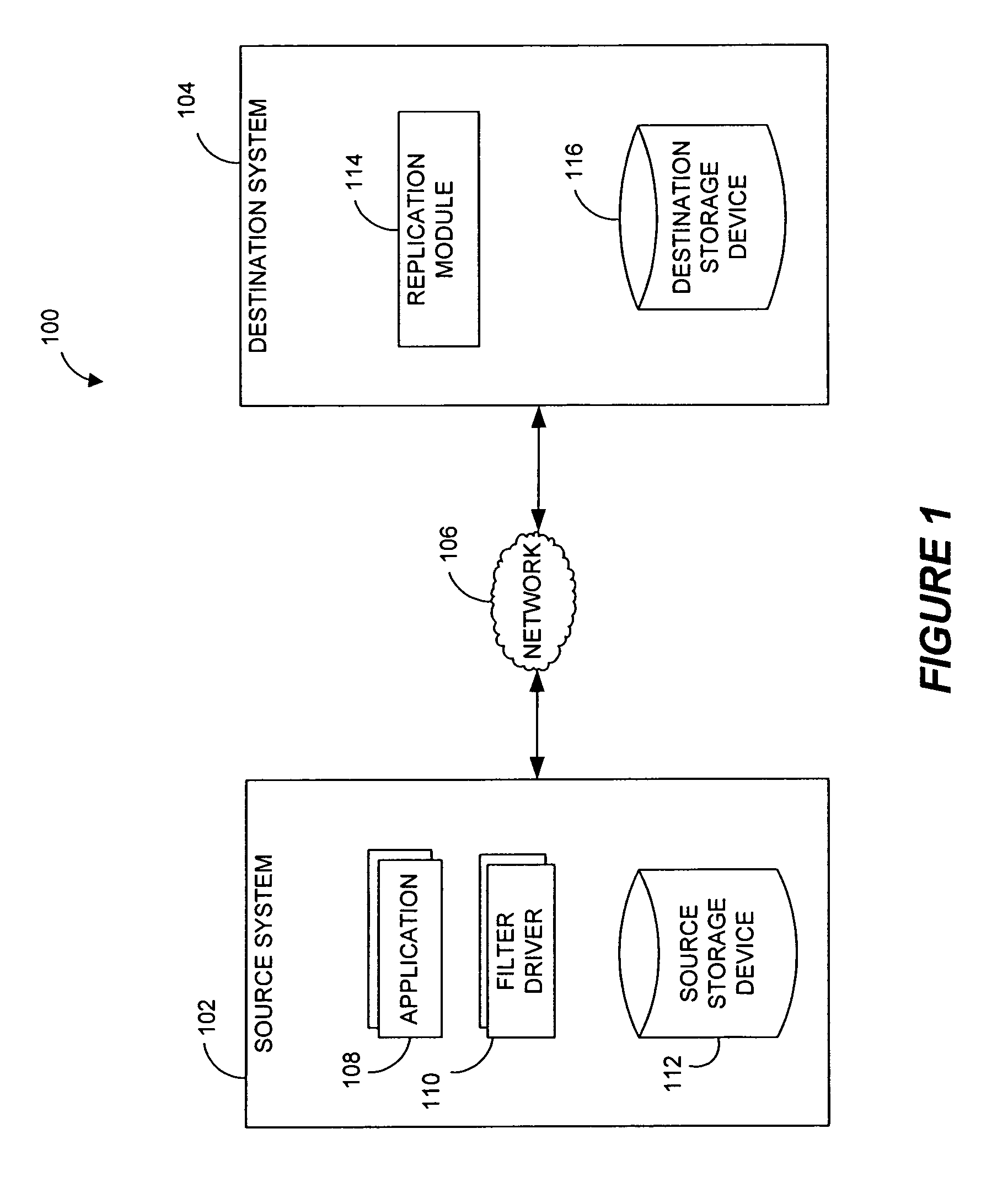
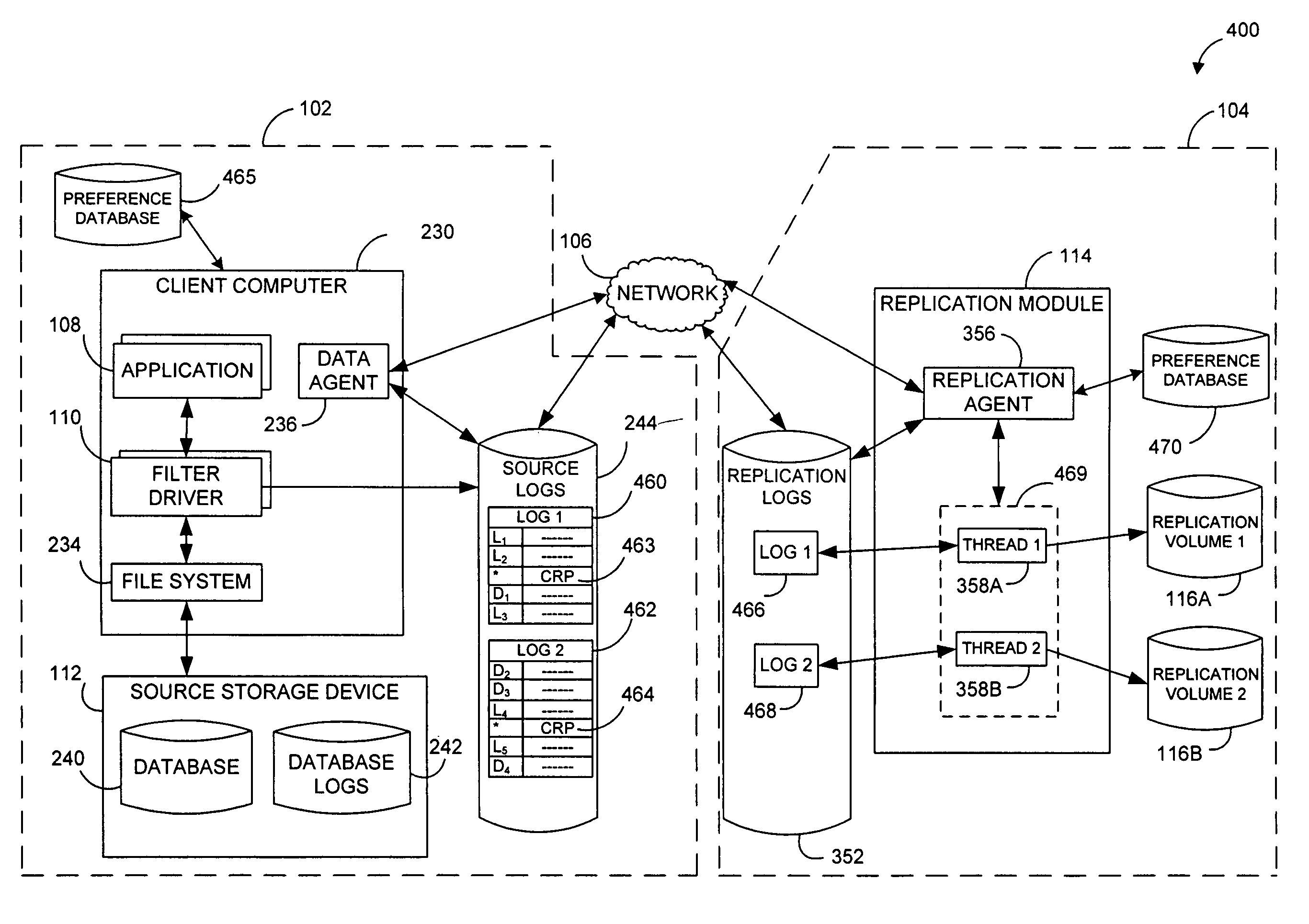
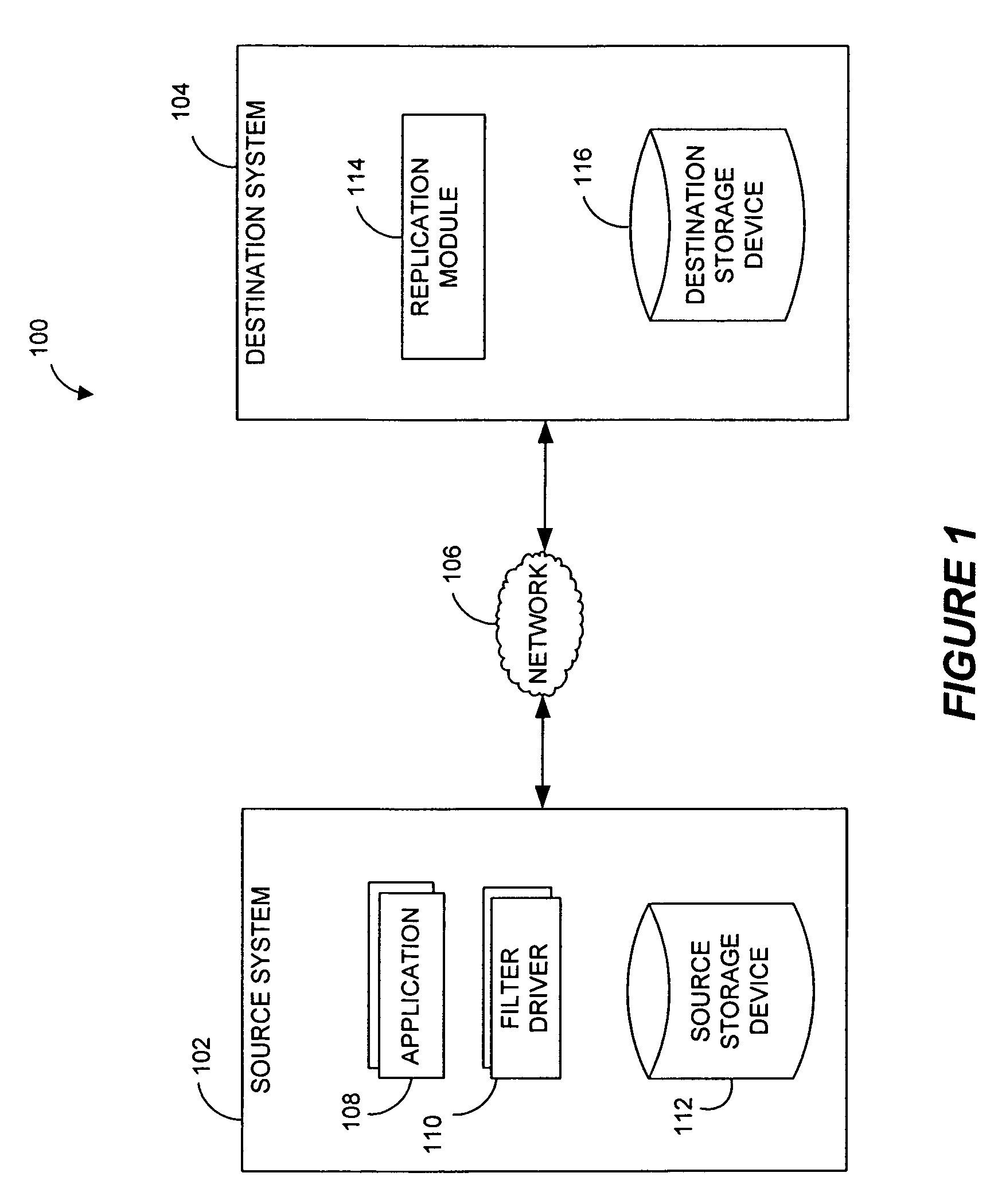
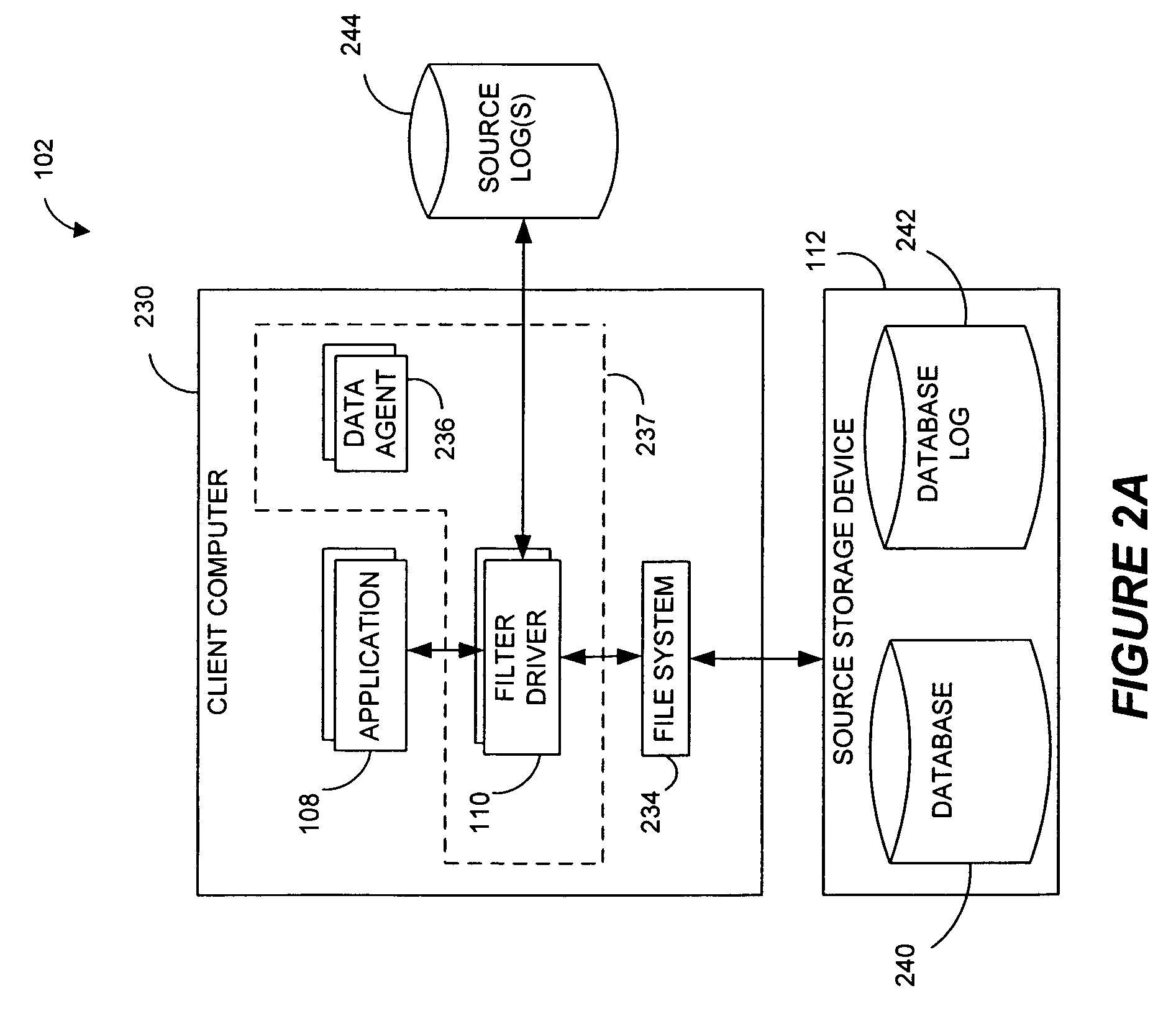
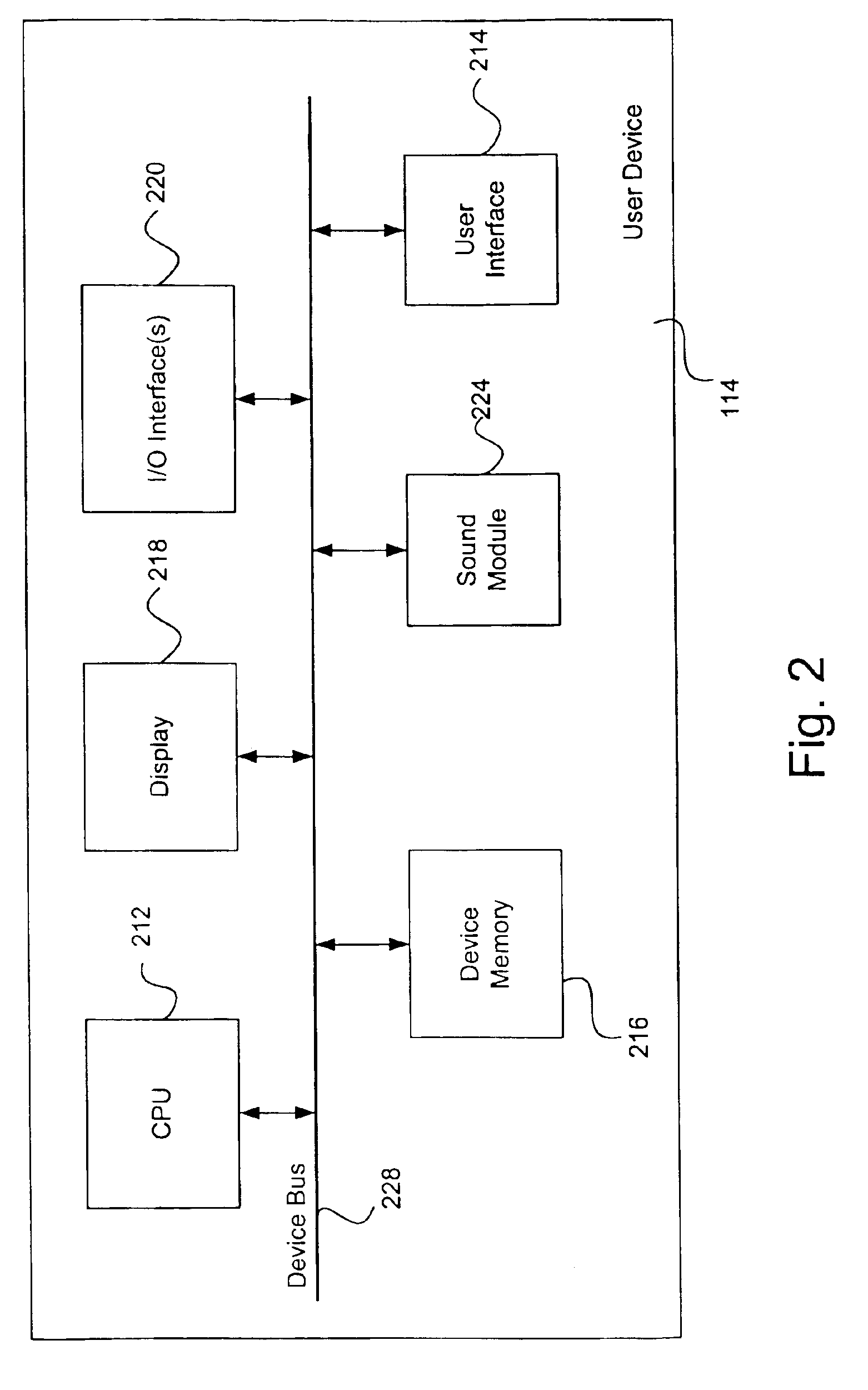
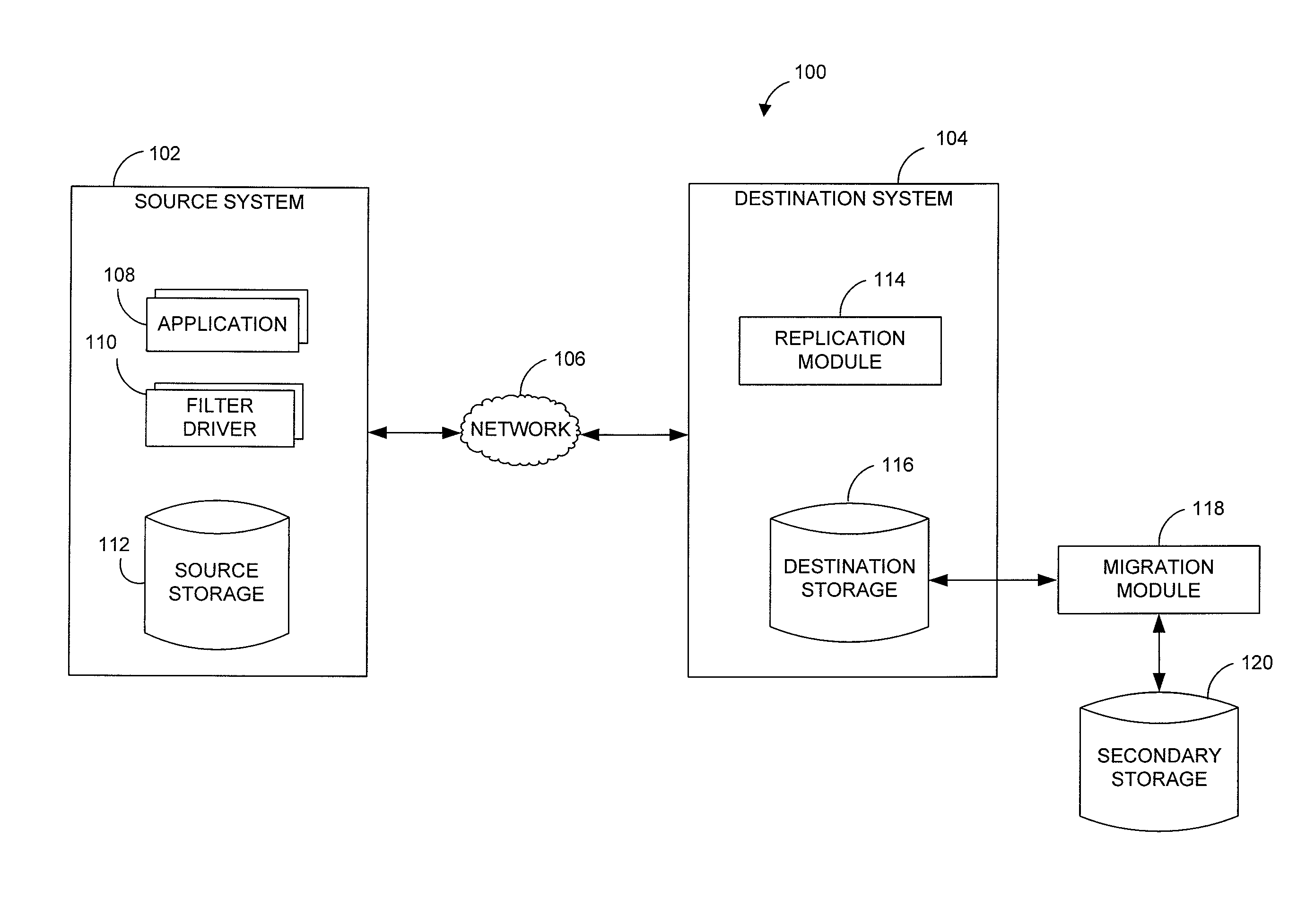
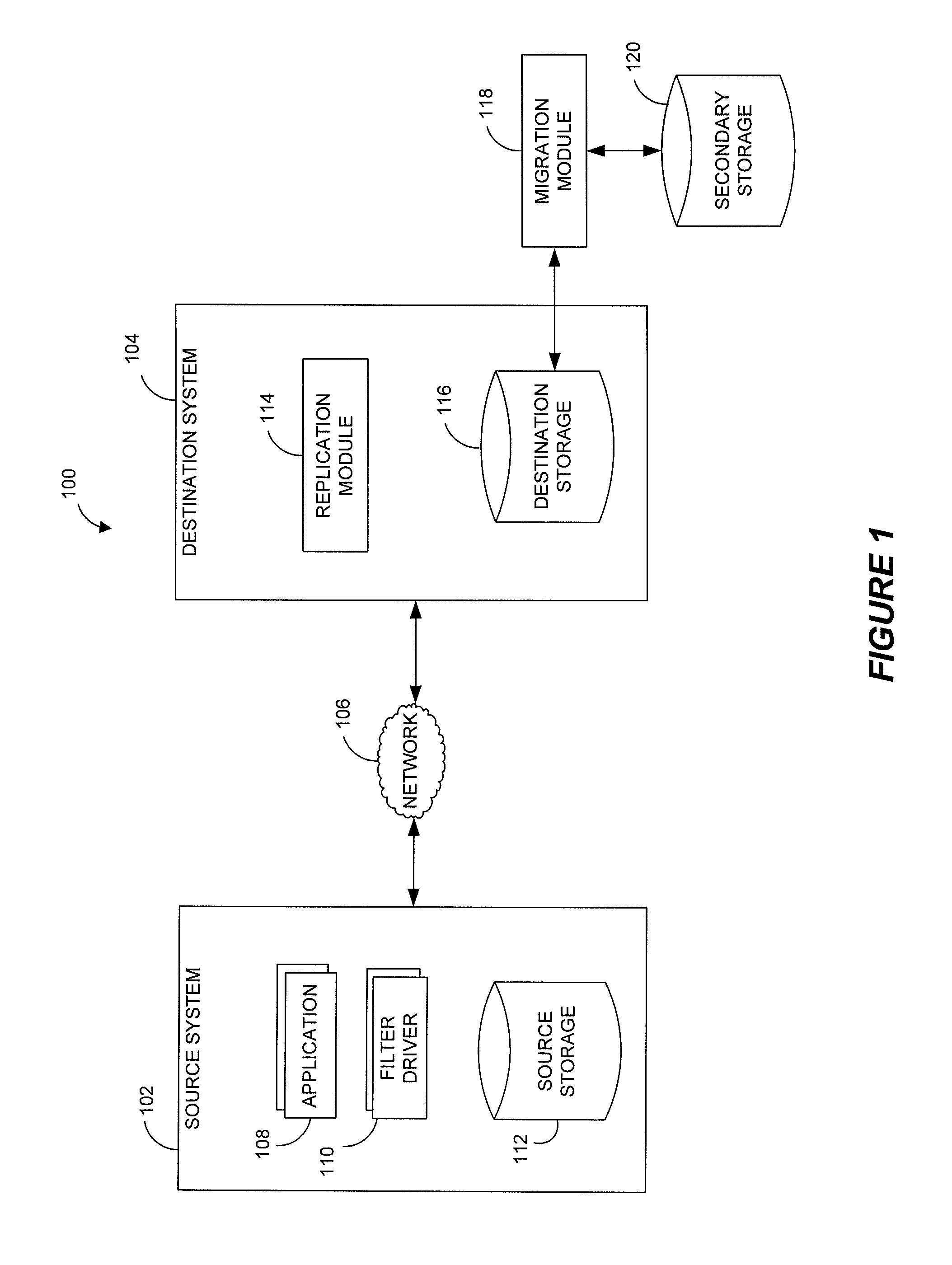
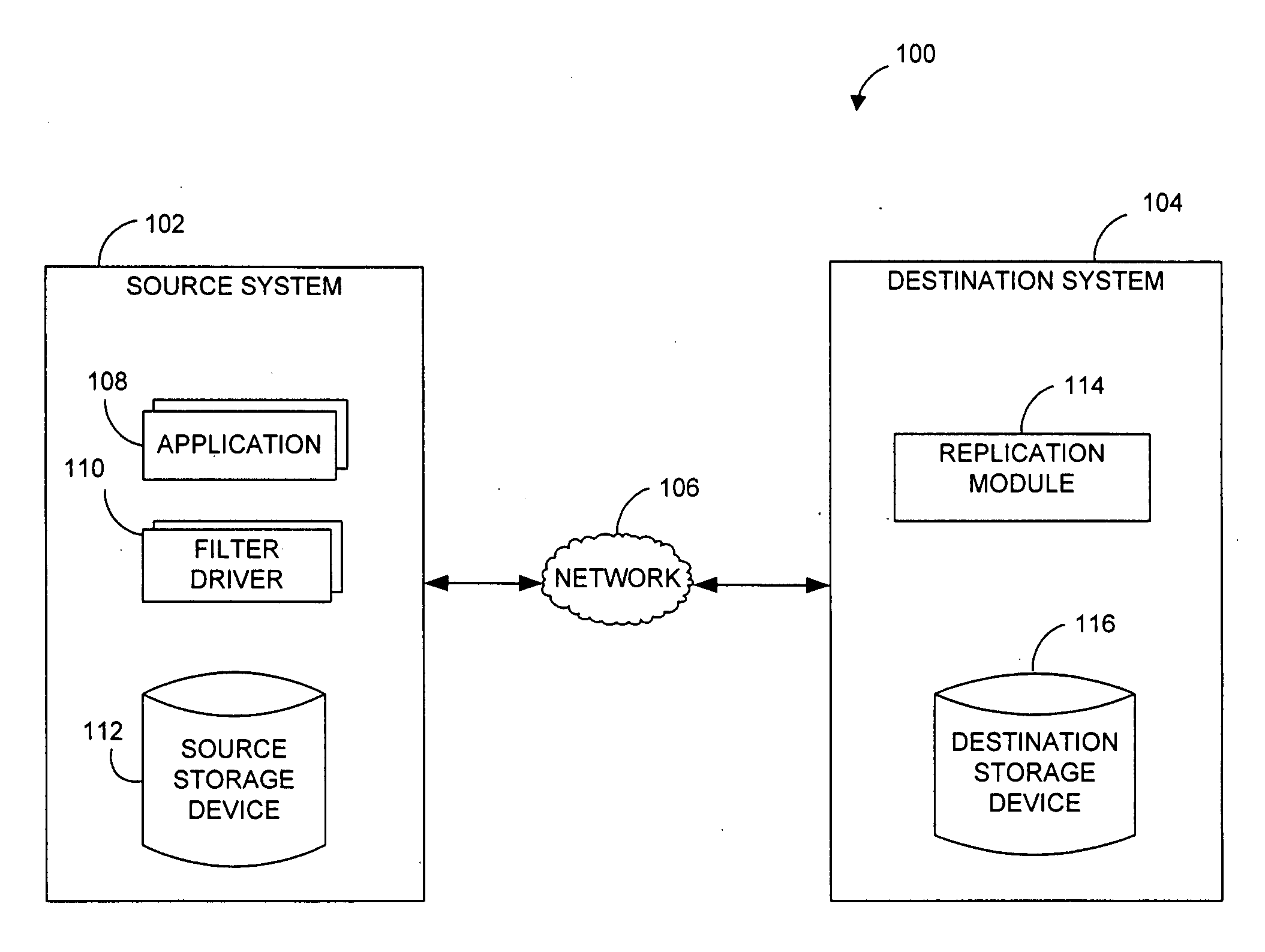
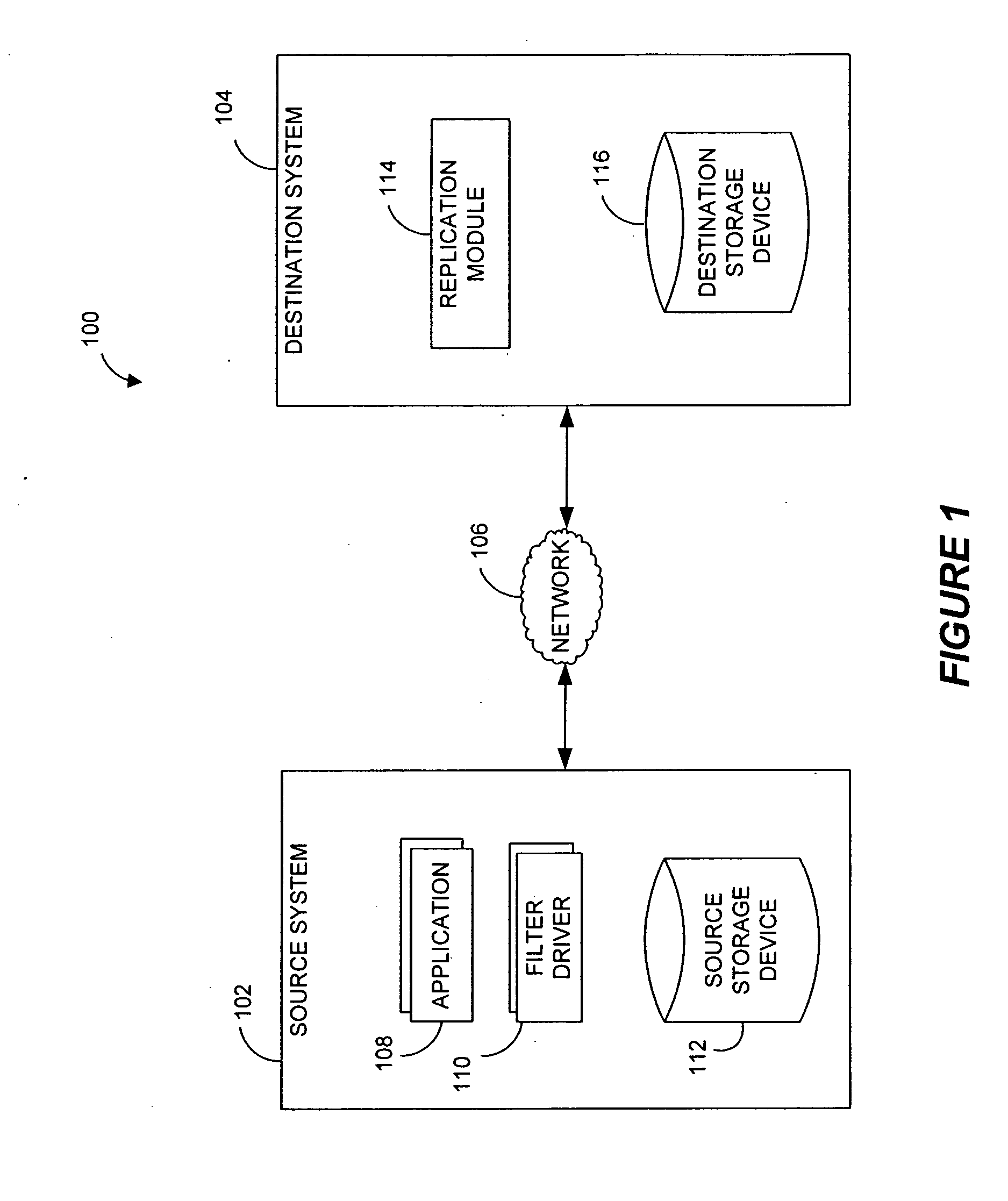
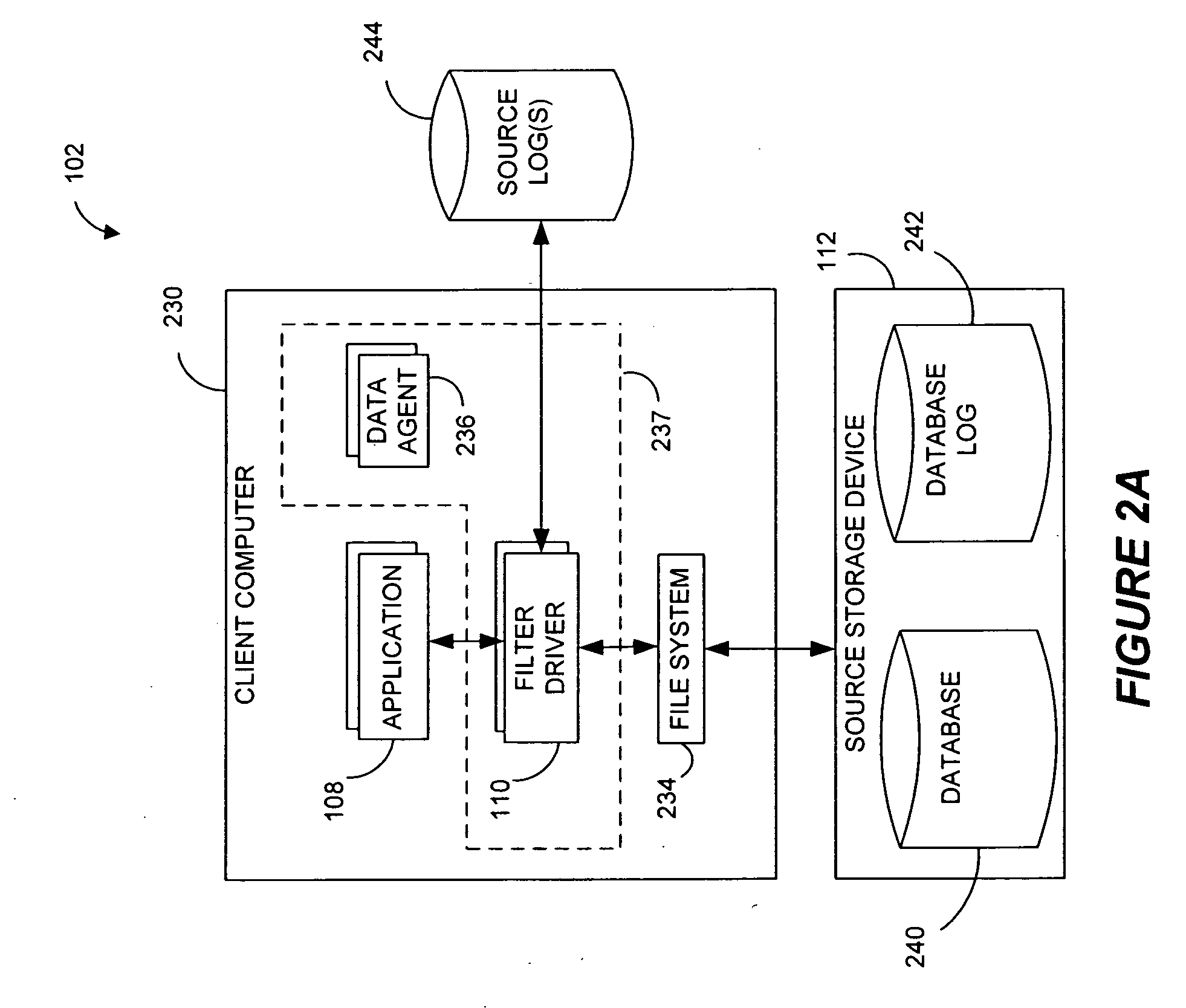
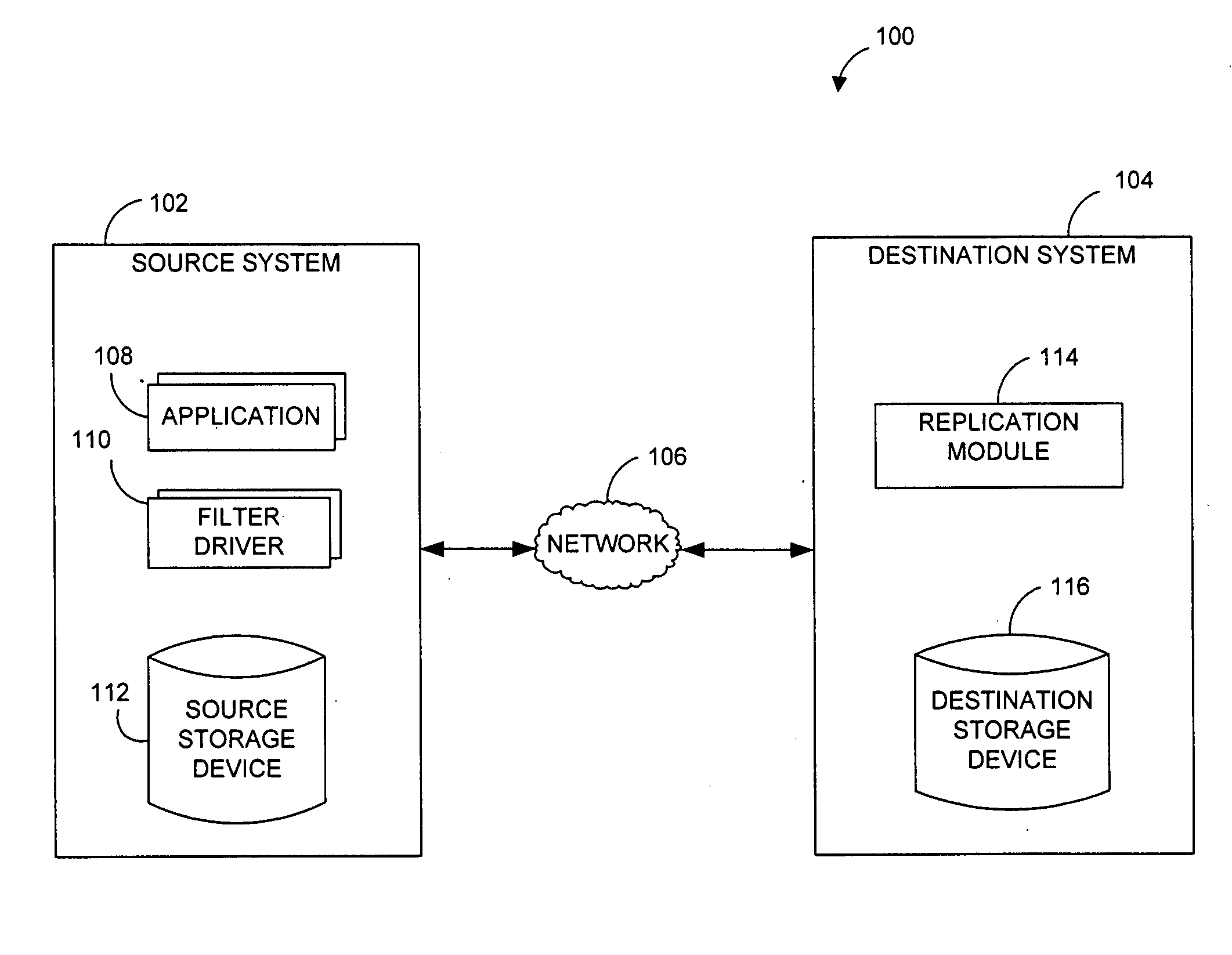
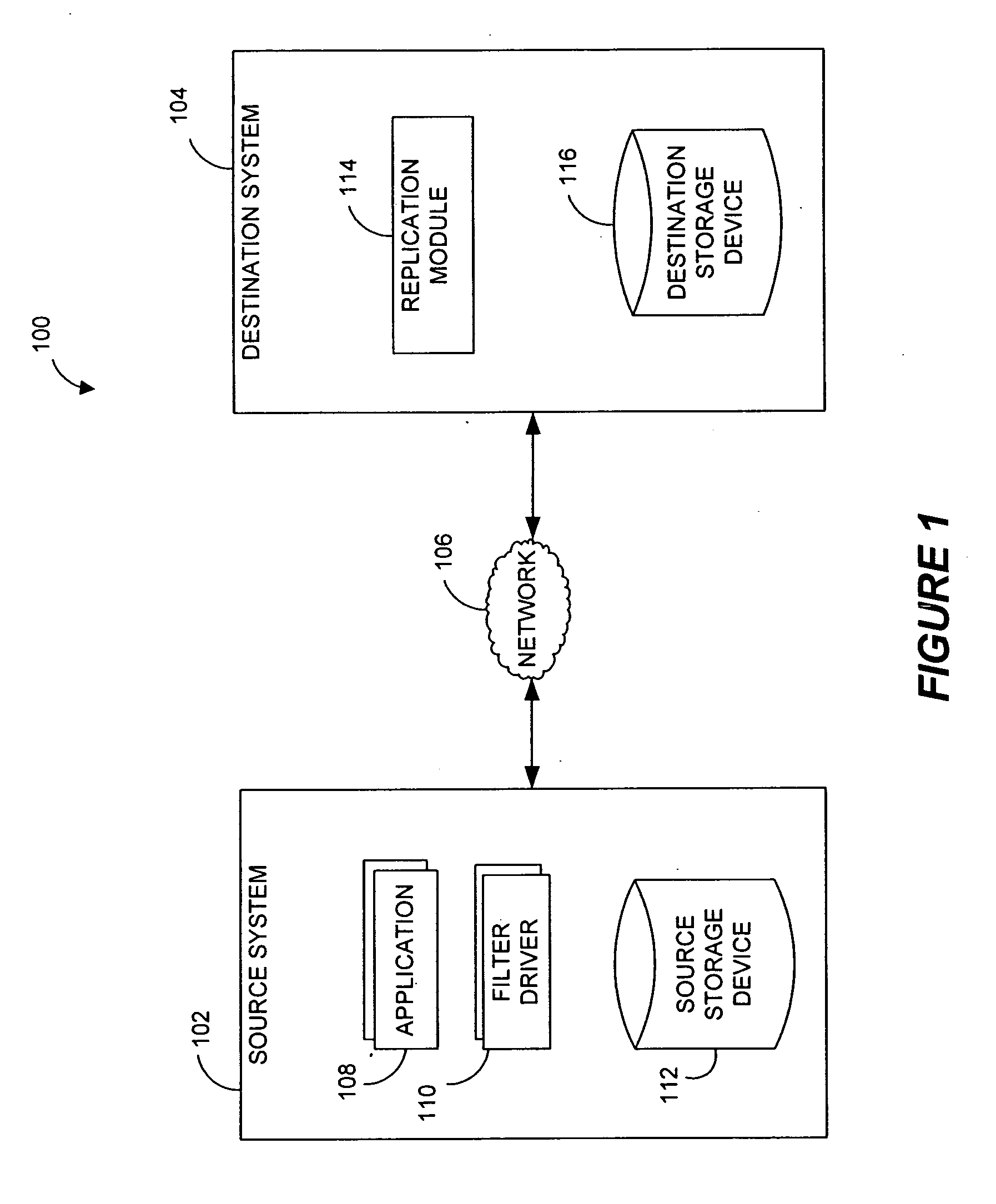
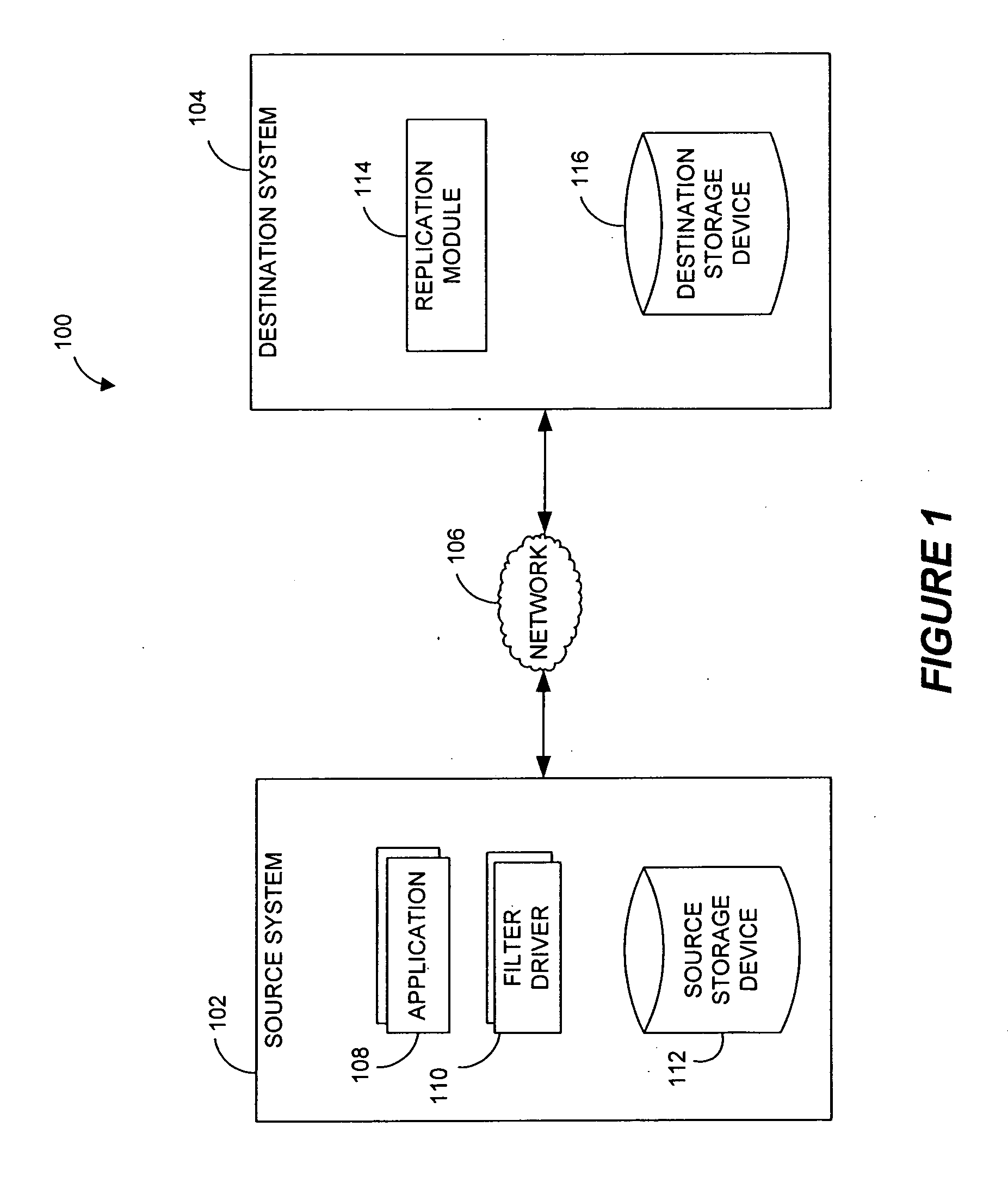
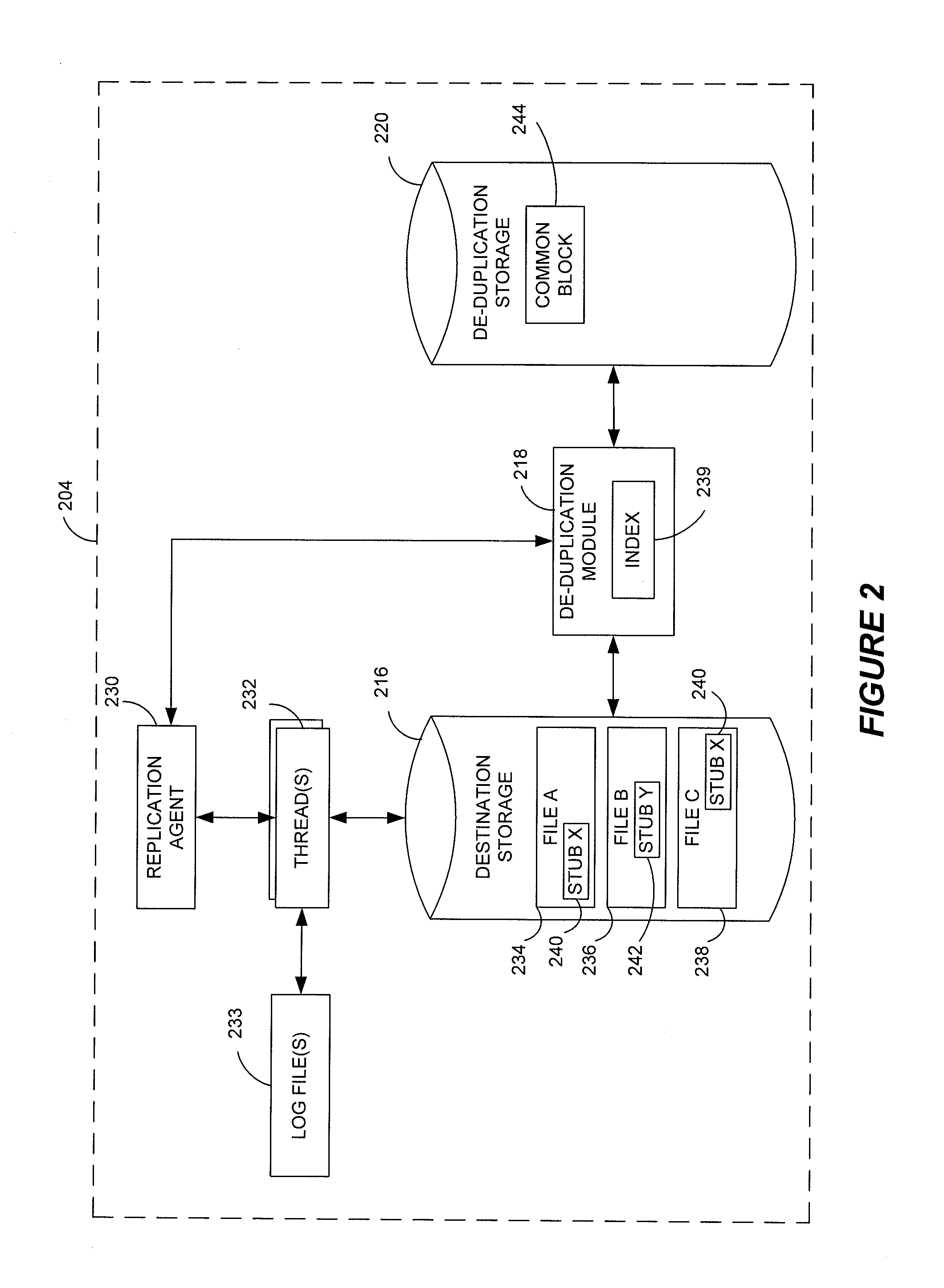
Systems and methods for monitoring application data in a data replication system
InactiveUS7617262B2Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationData management
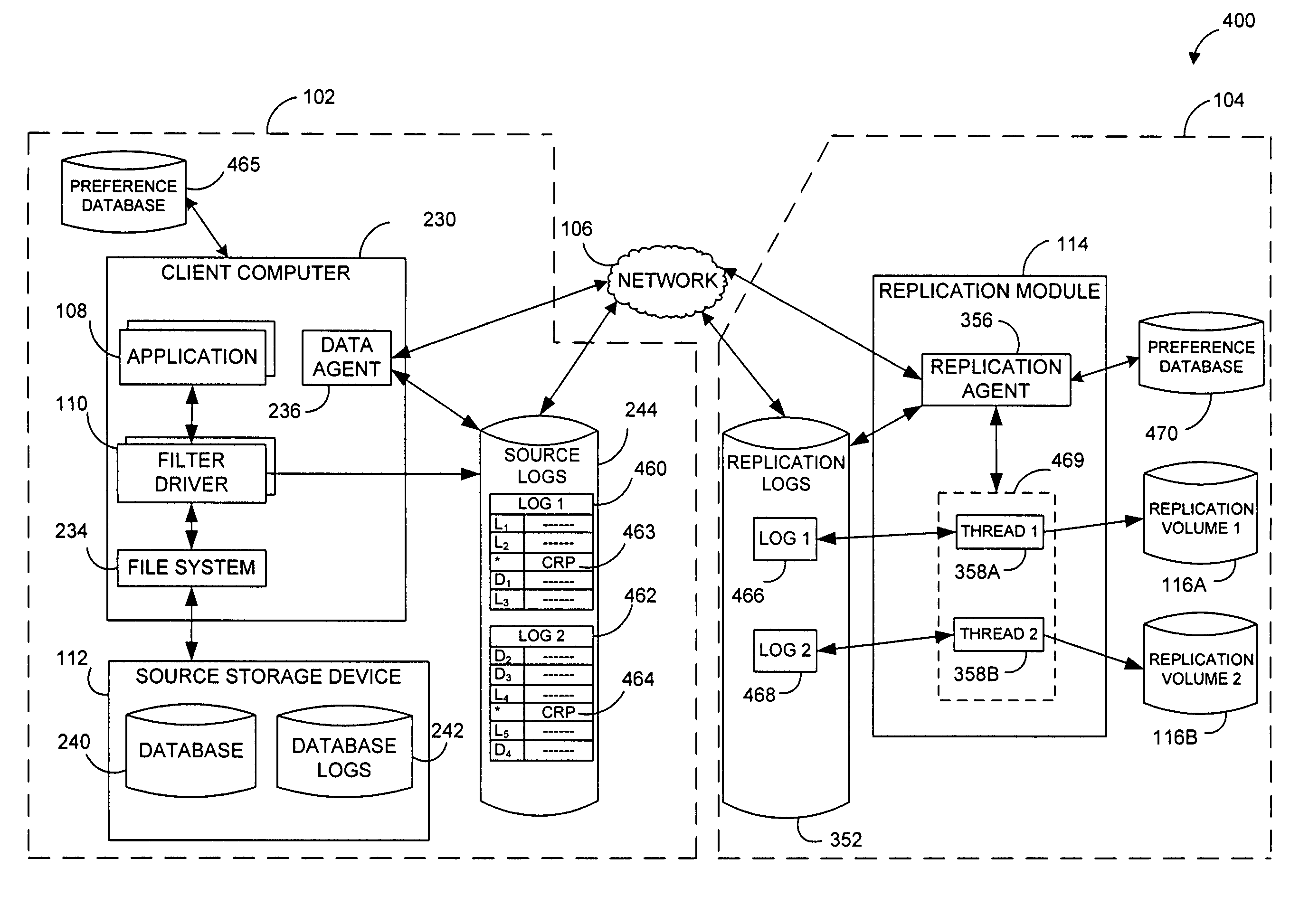
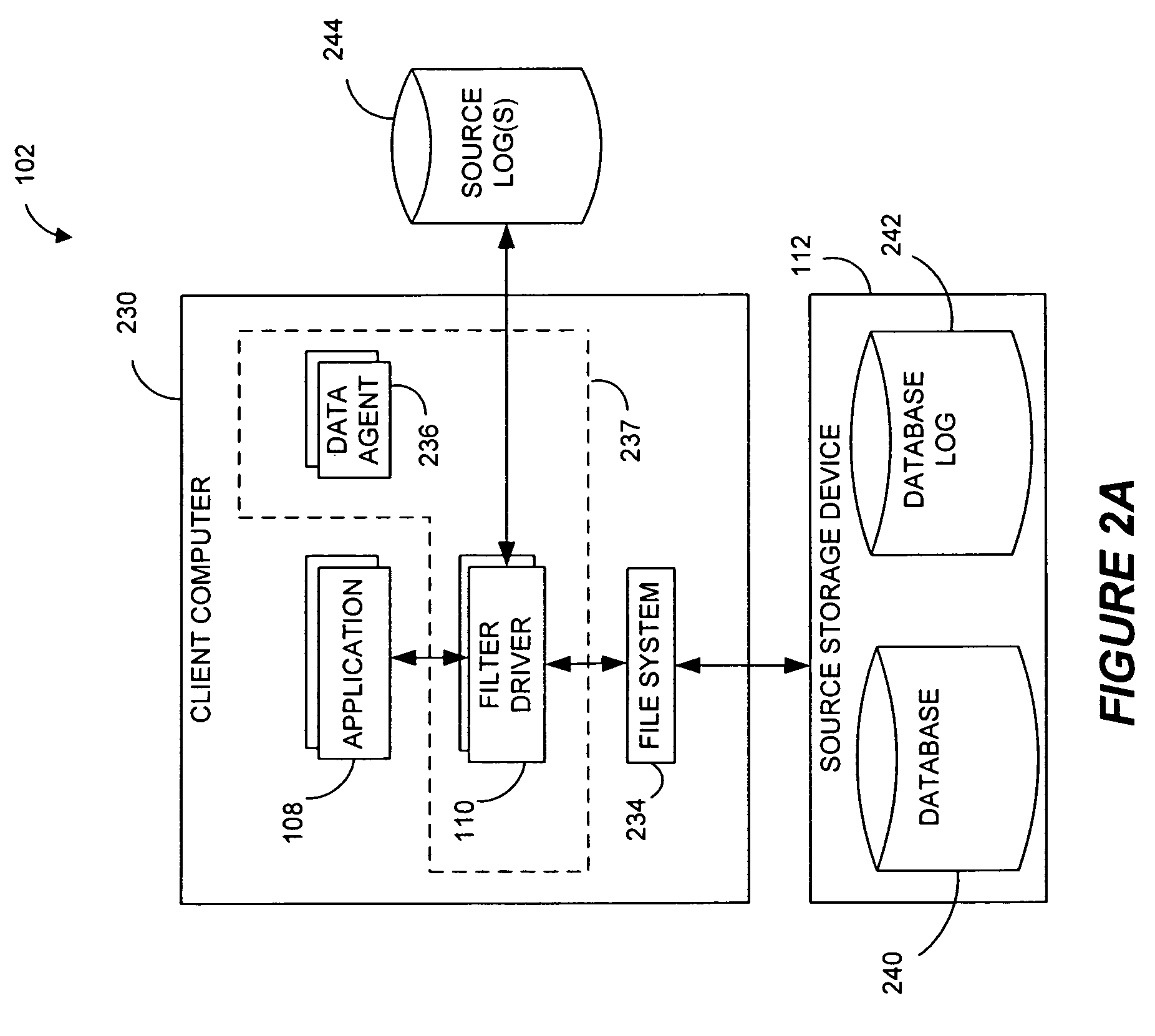
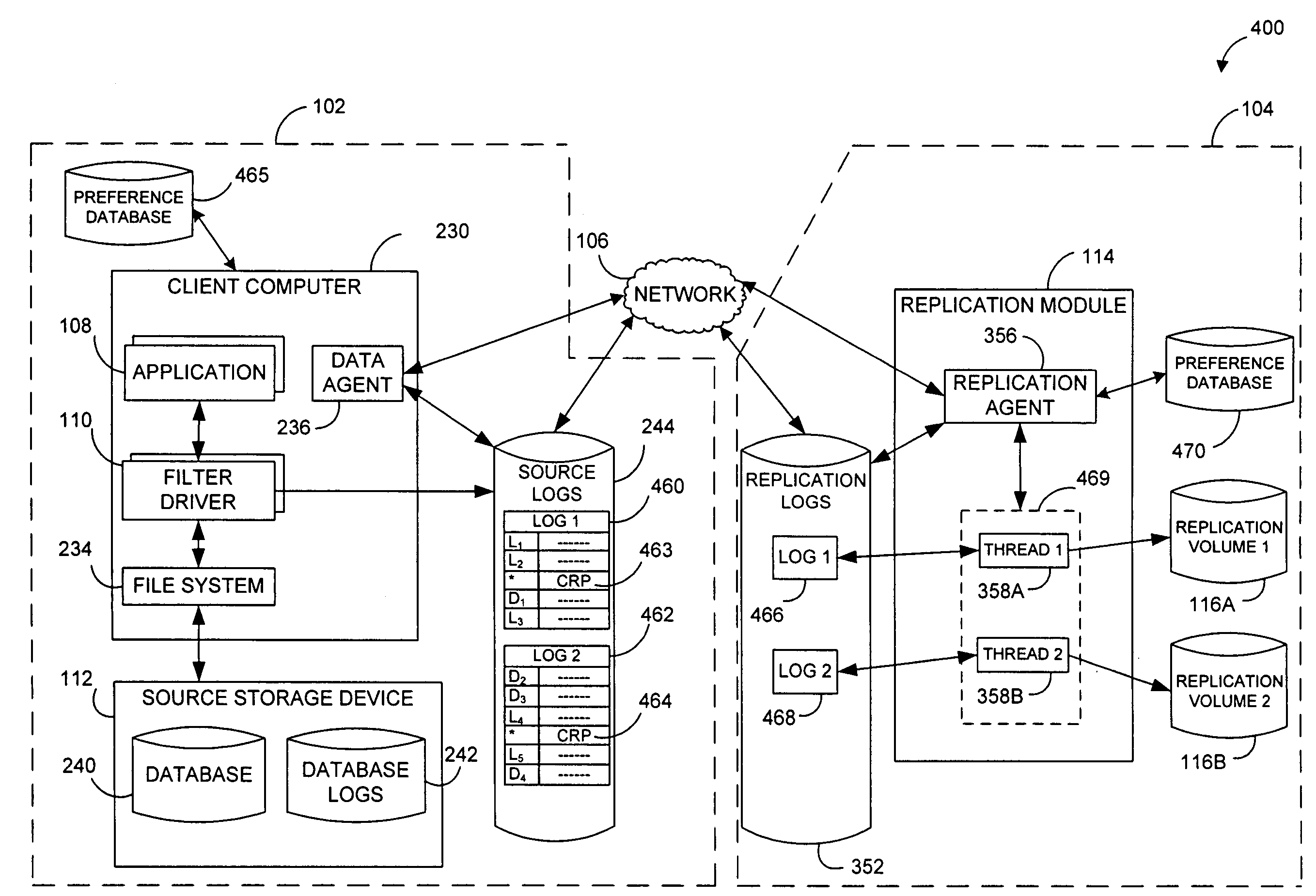
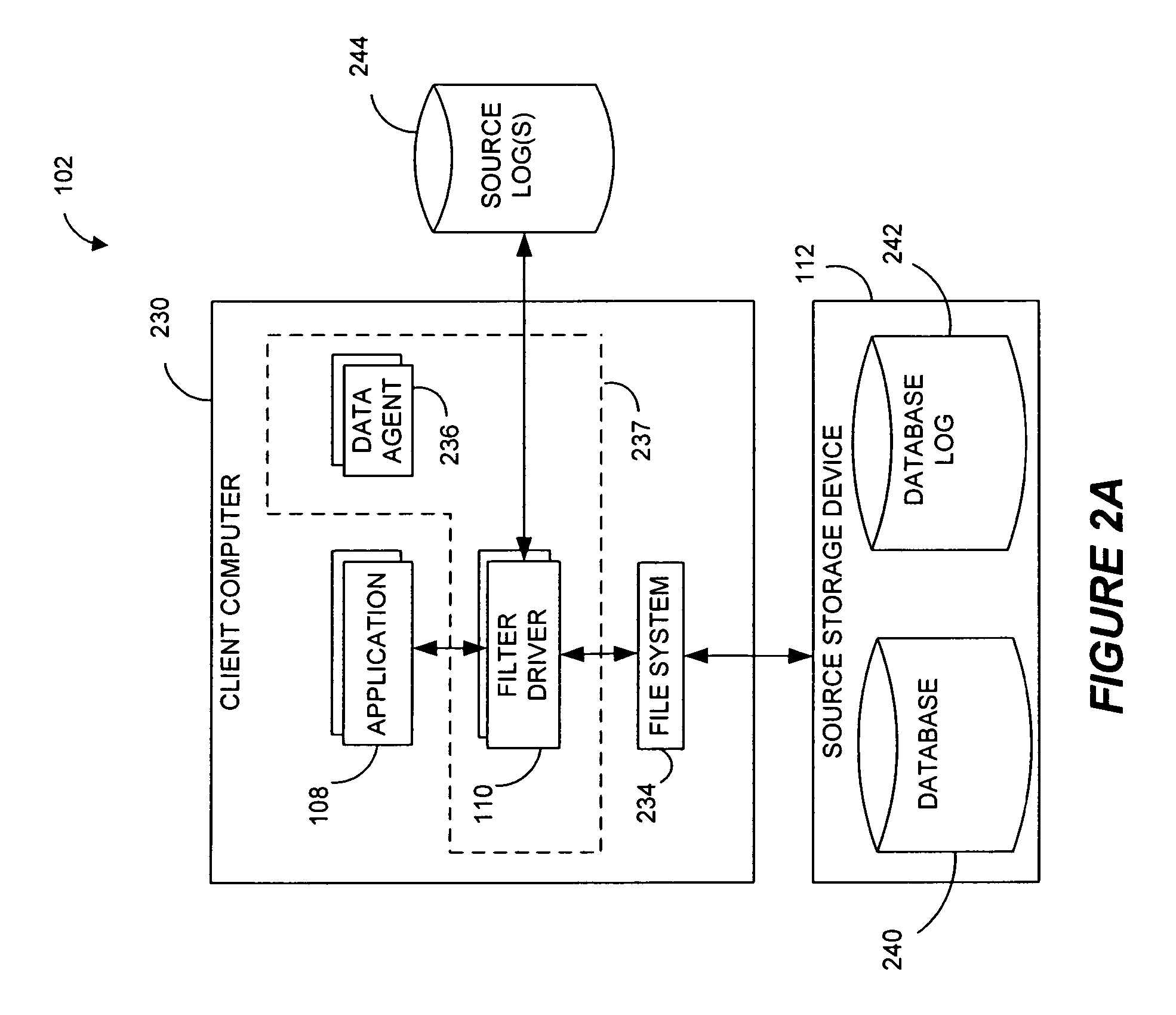
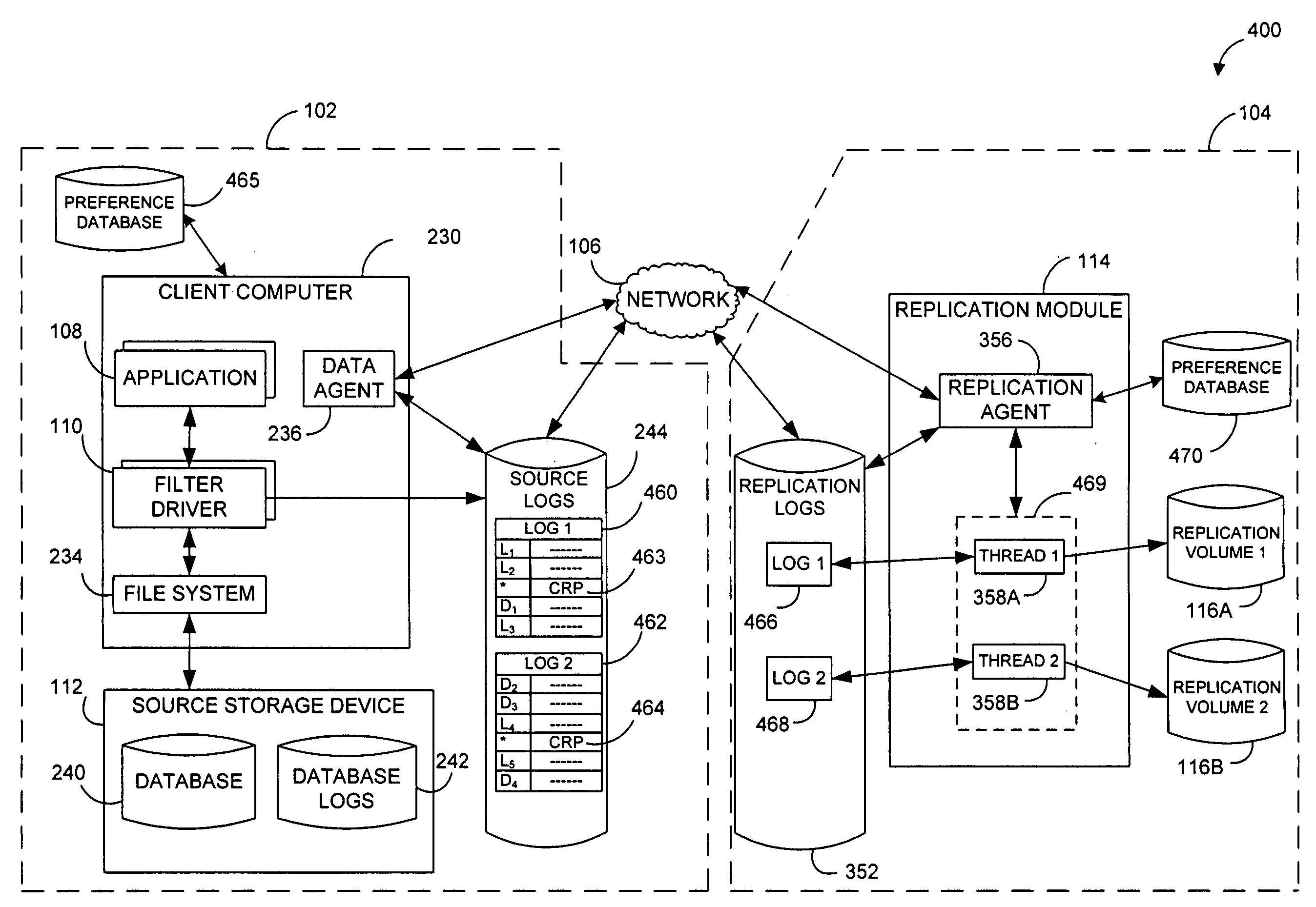
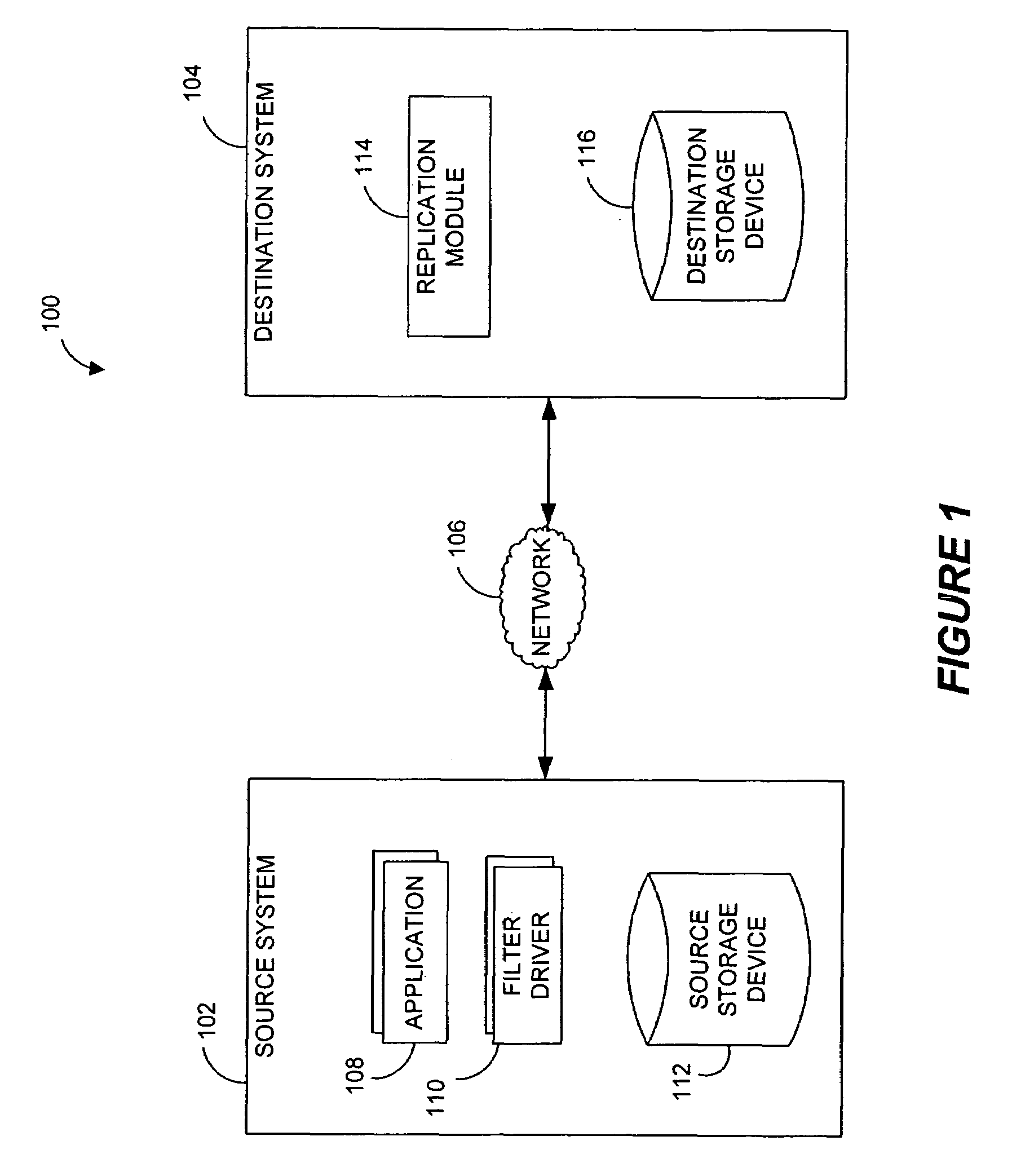
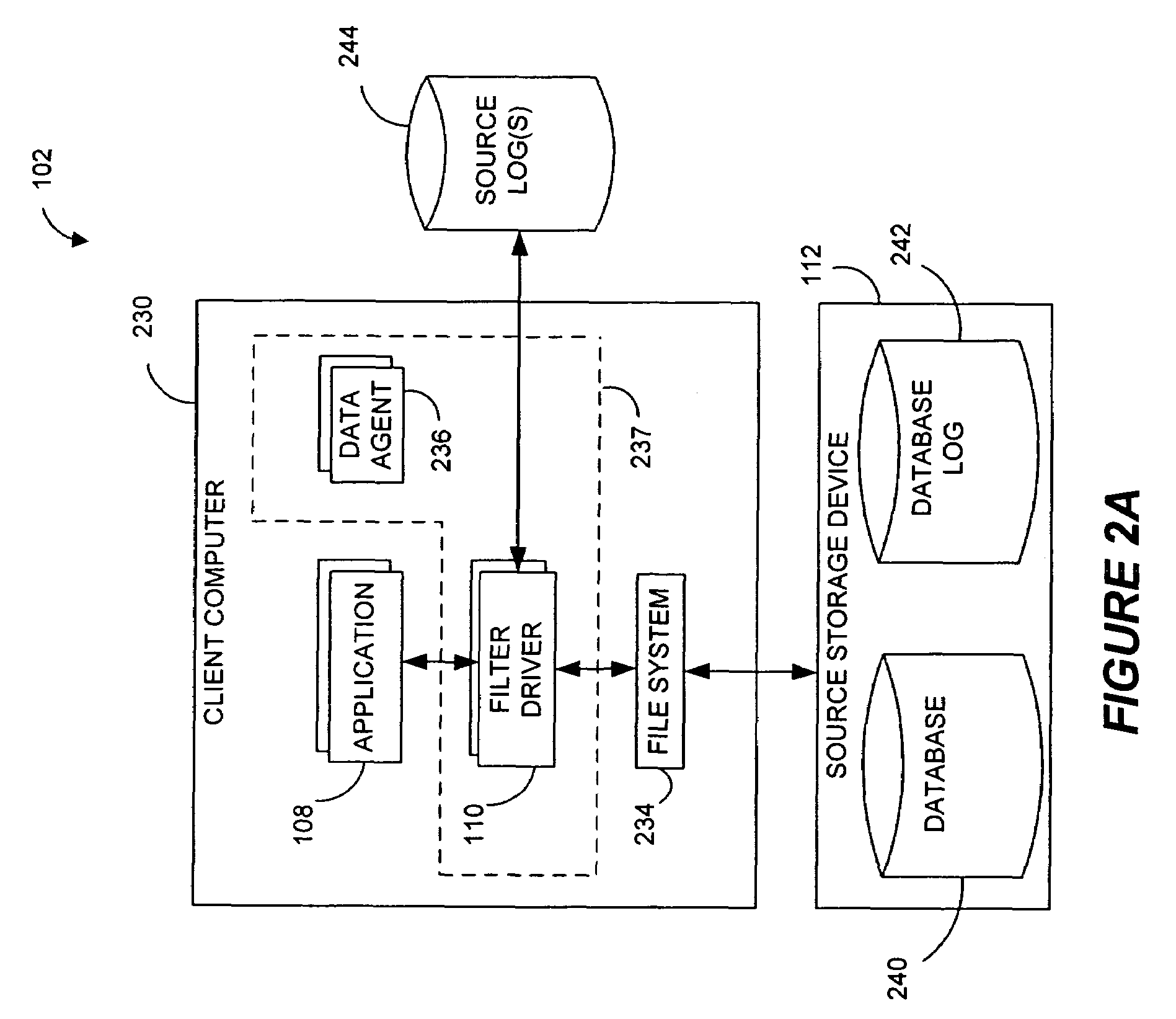
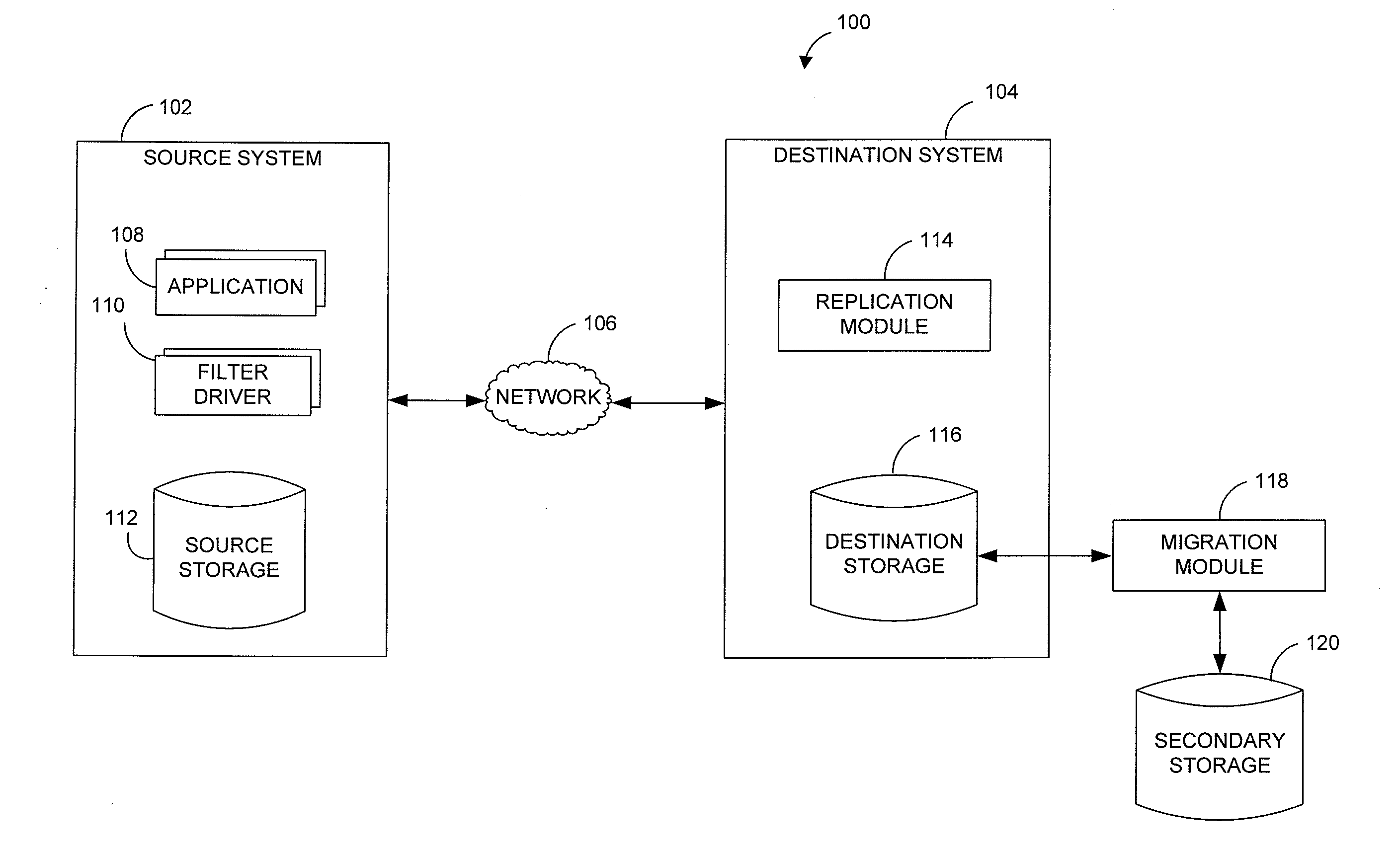
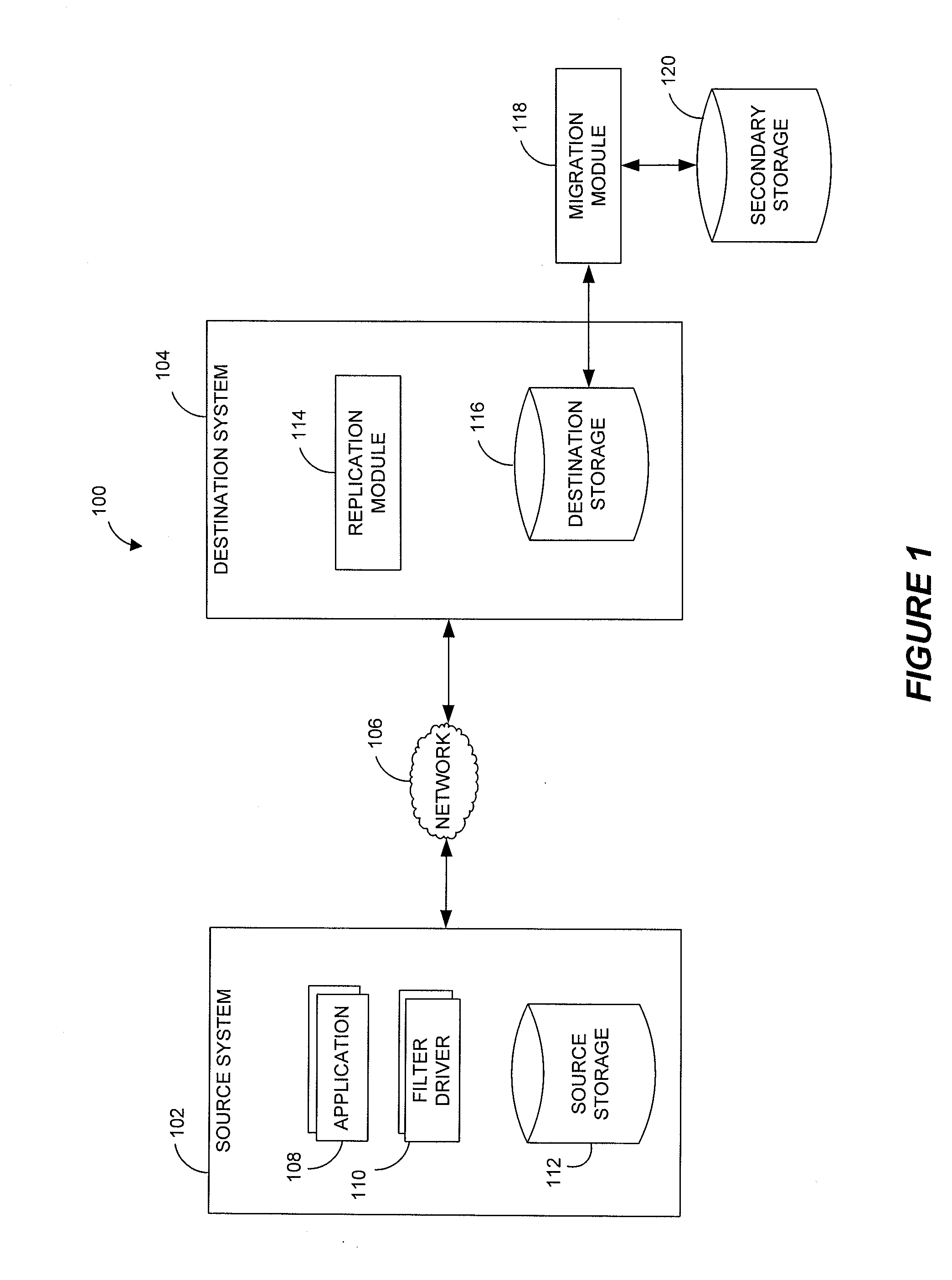
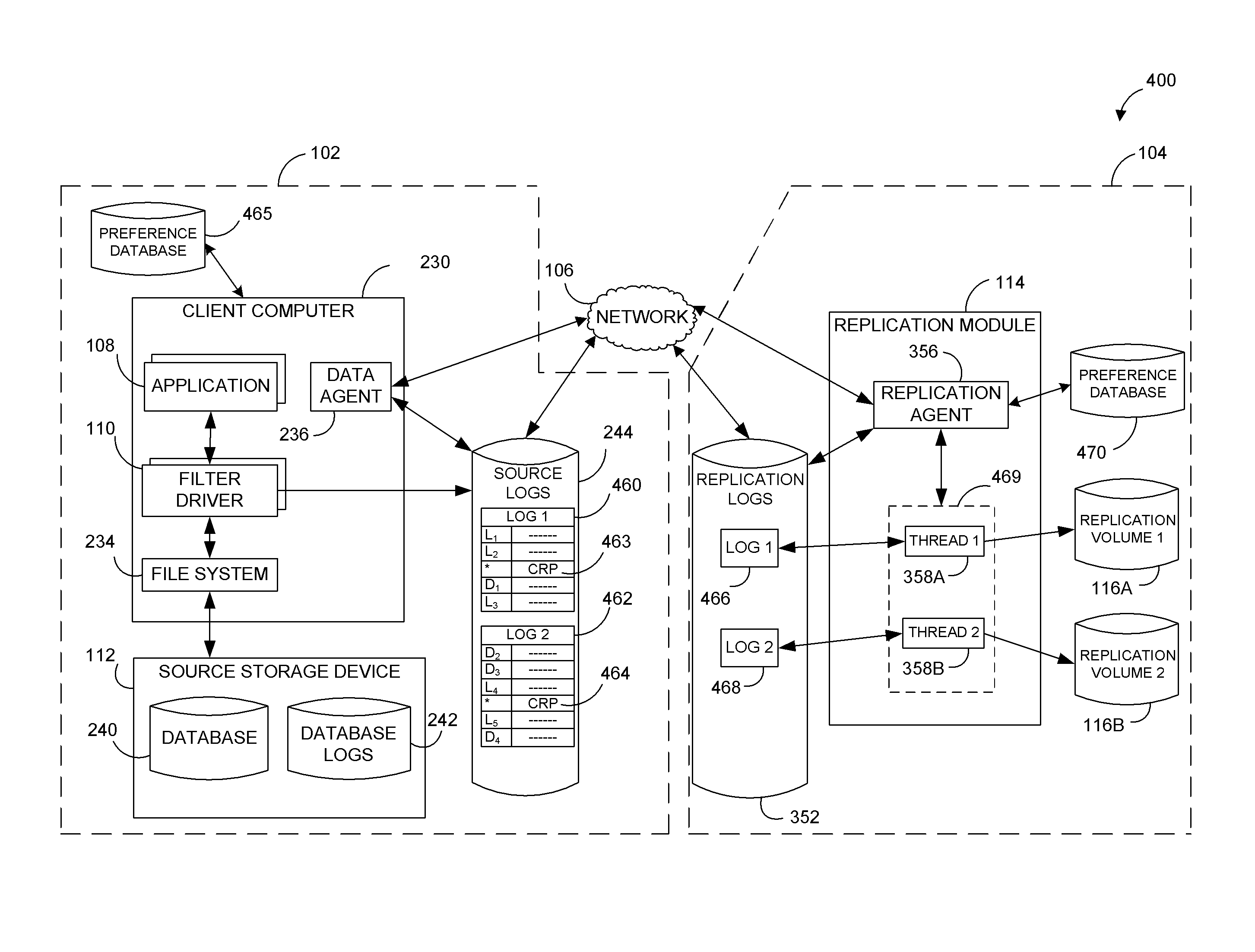
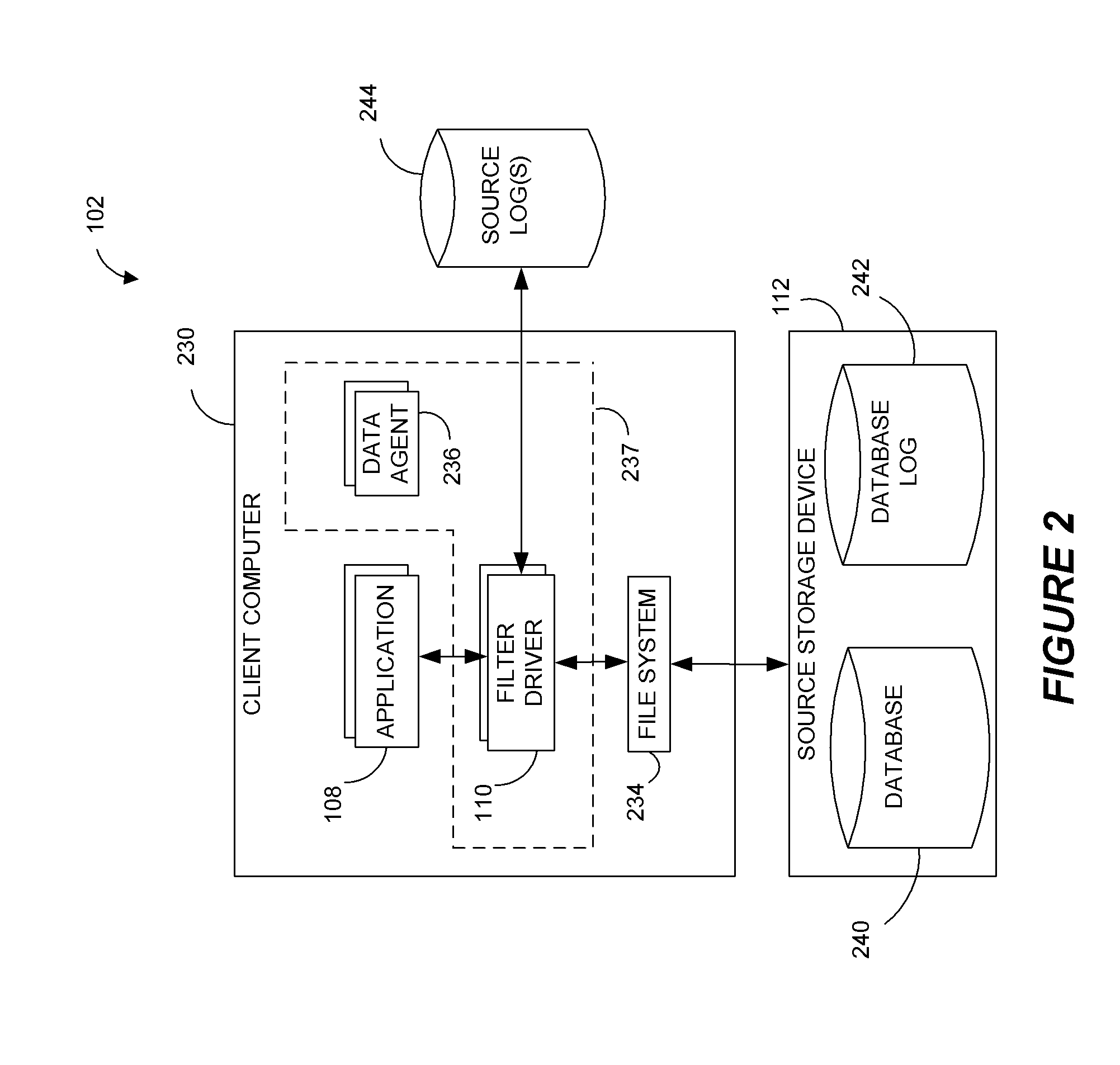
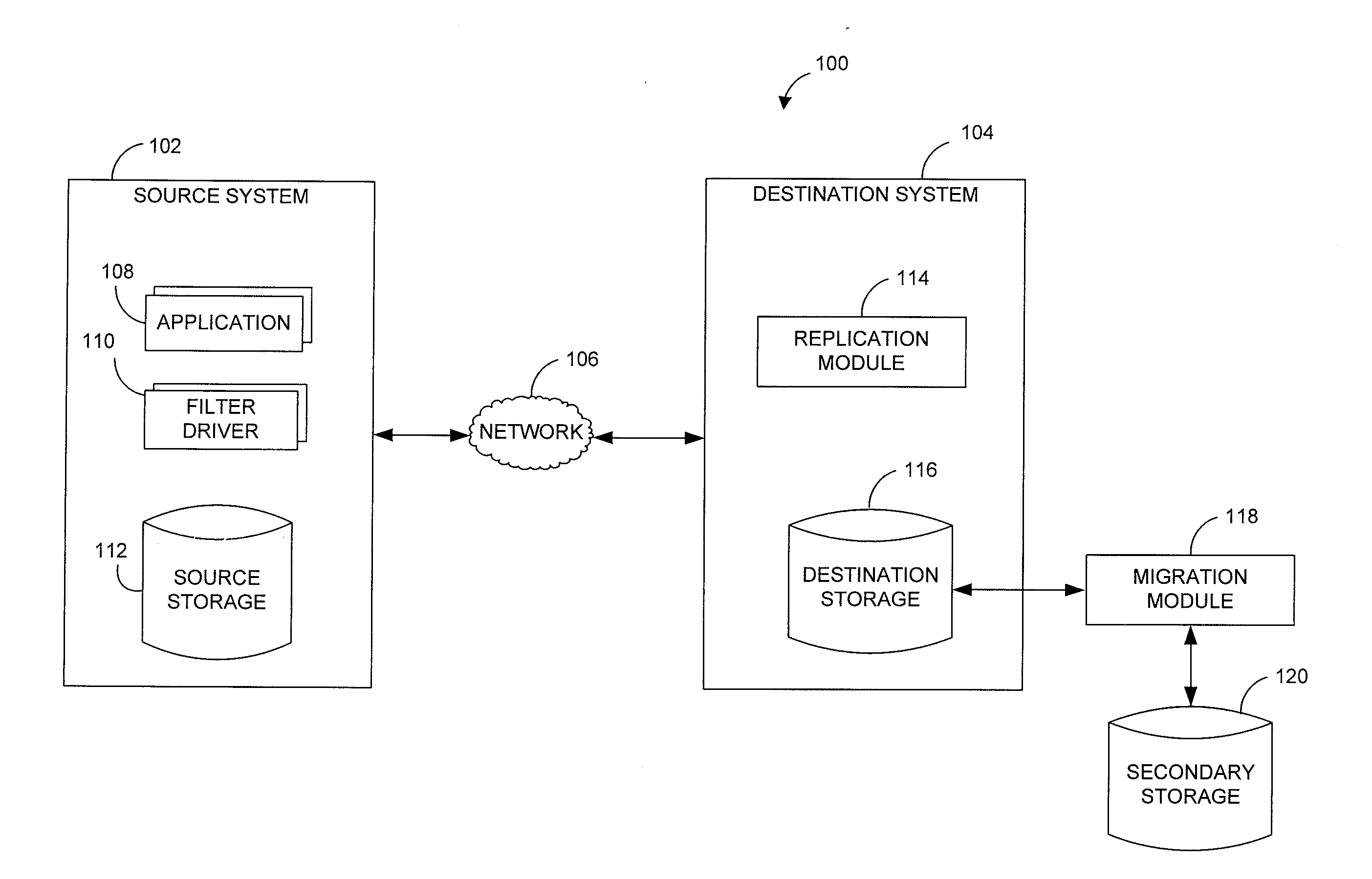
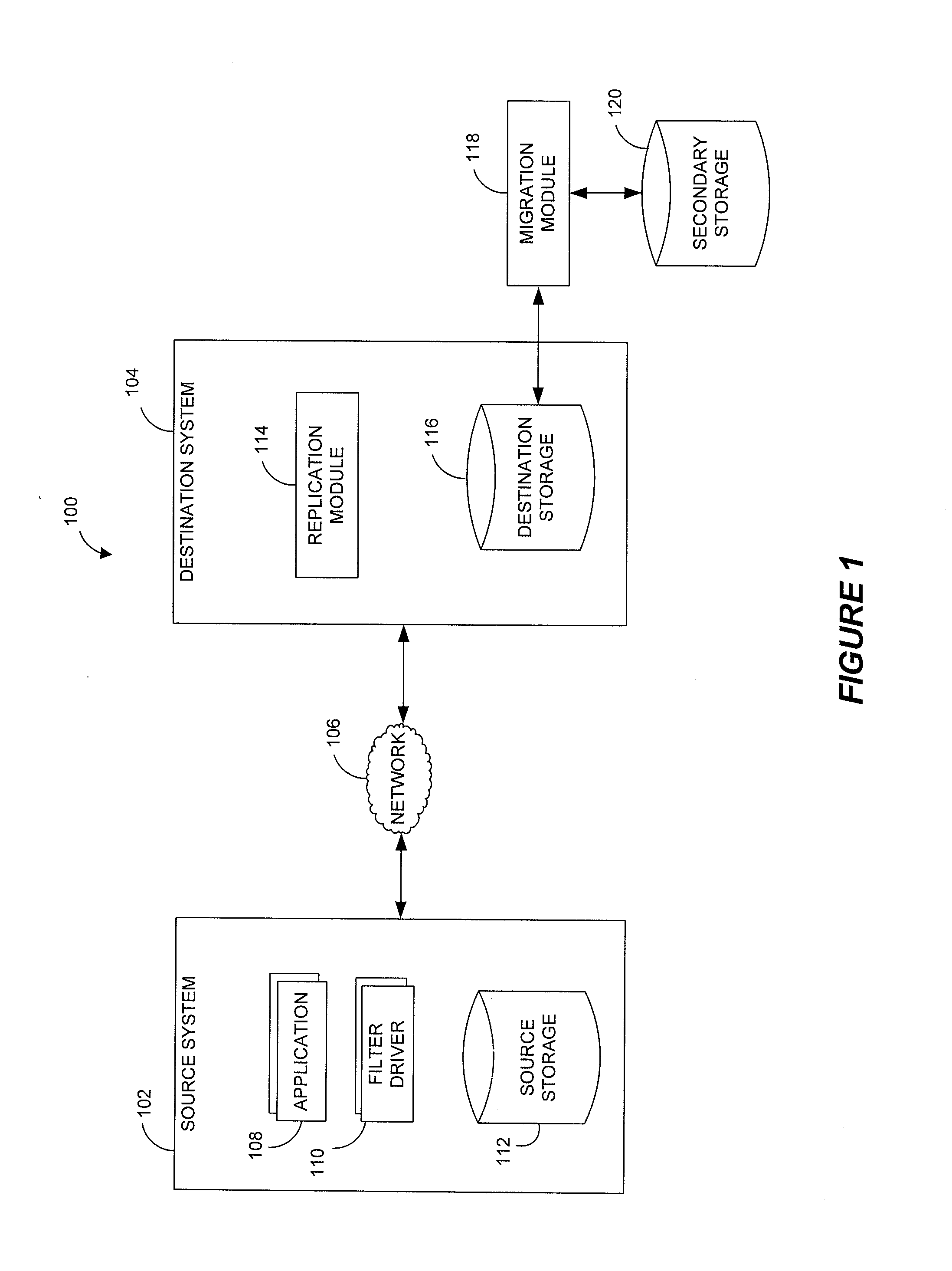
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Systems and methods for performing data replication
ActiveUS7651593B2Reduce impactReduce memory requirementsError detection/correctionDistillation separationTemporal informationData management
Owner:COMMVAULT SYST INC
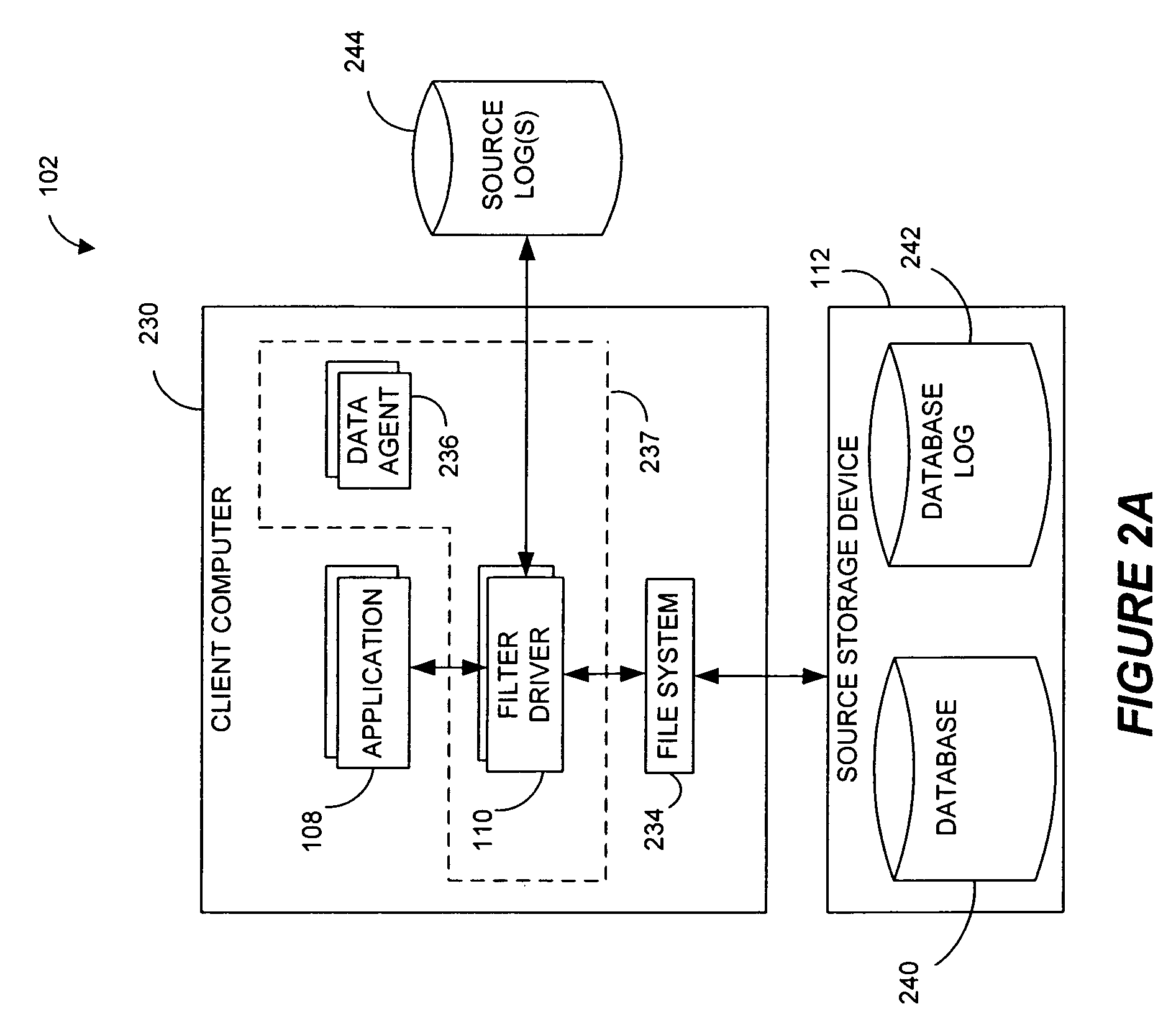
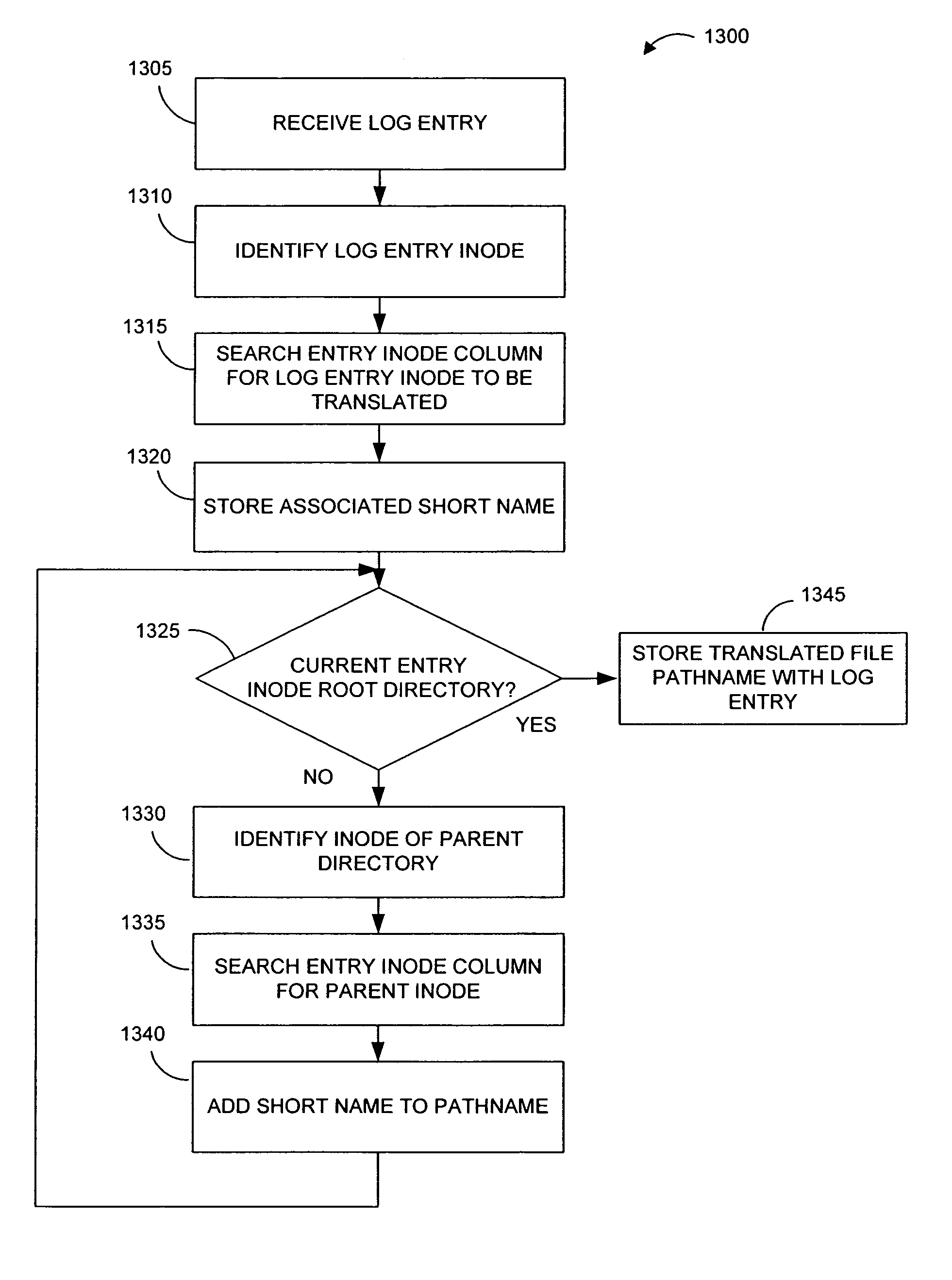
Pathname translation in a data replication system
InactiveUS7636743B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Owner:COMMVAULT SYST INC
Destination systems and methods for performing data replication
InactiveUS7617253B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
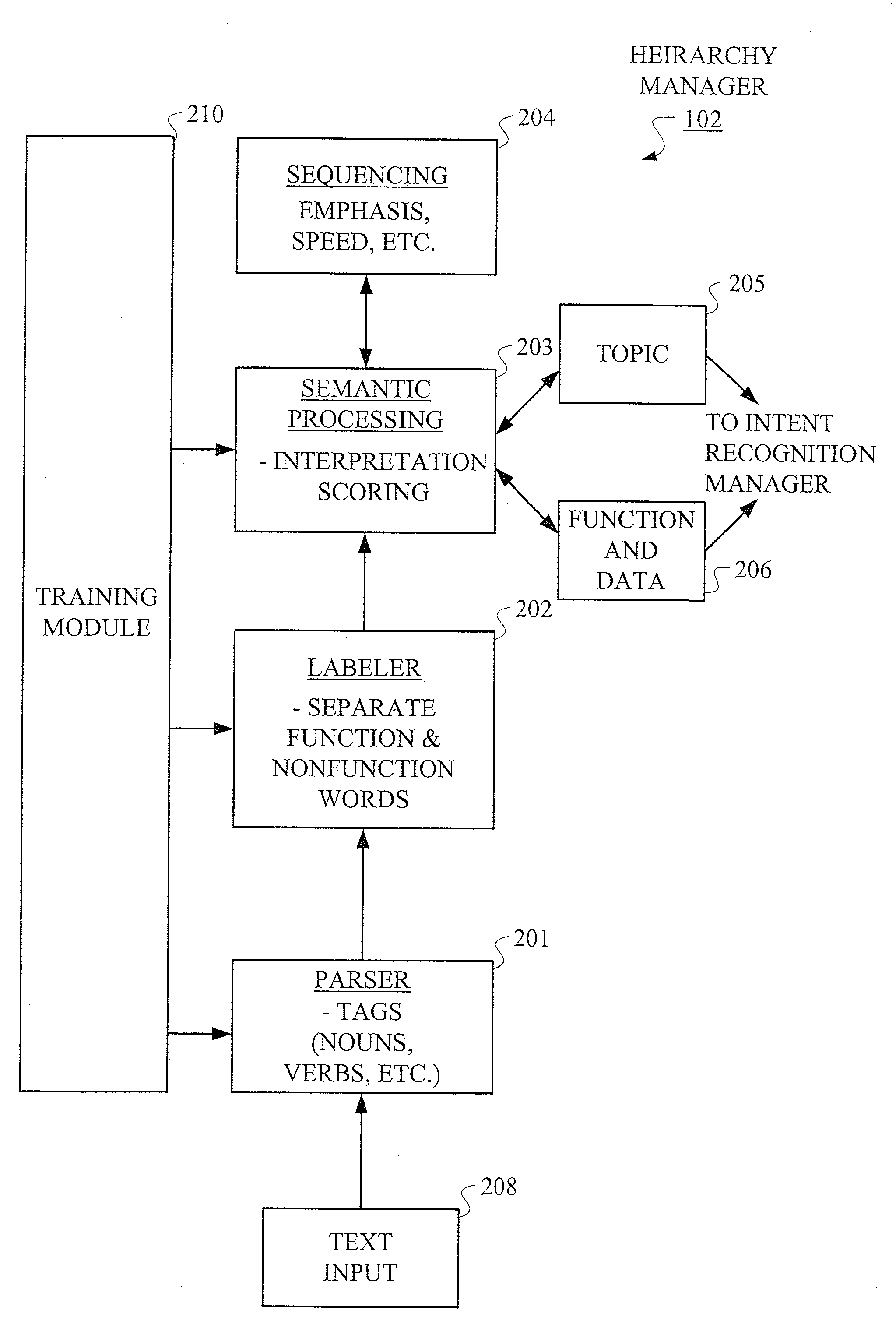
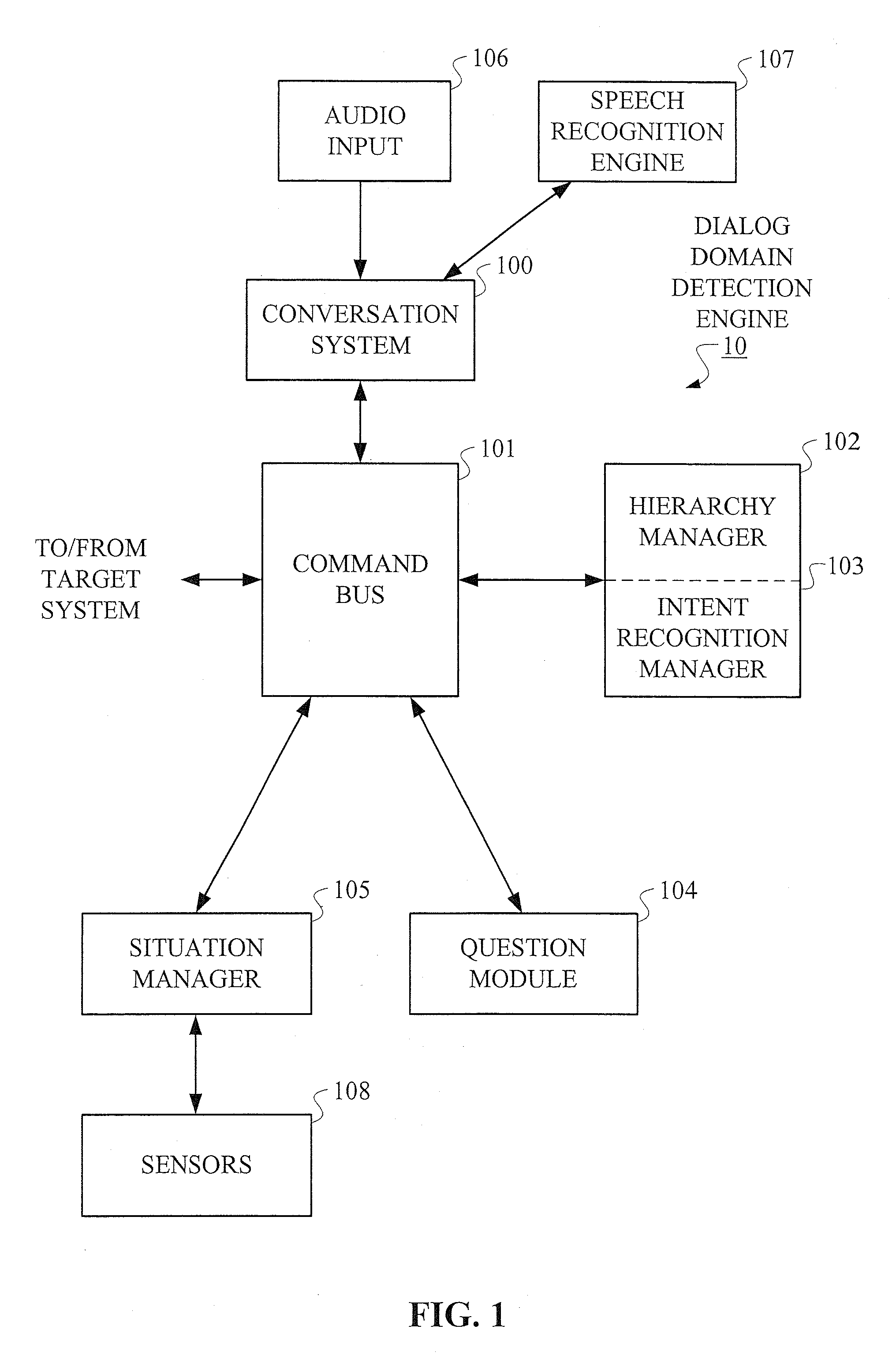
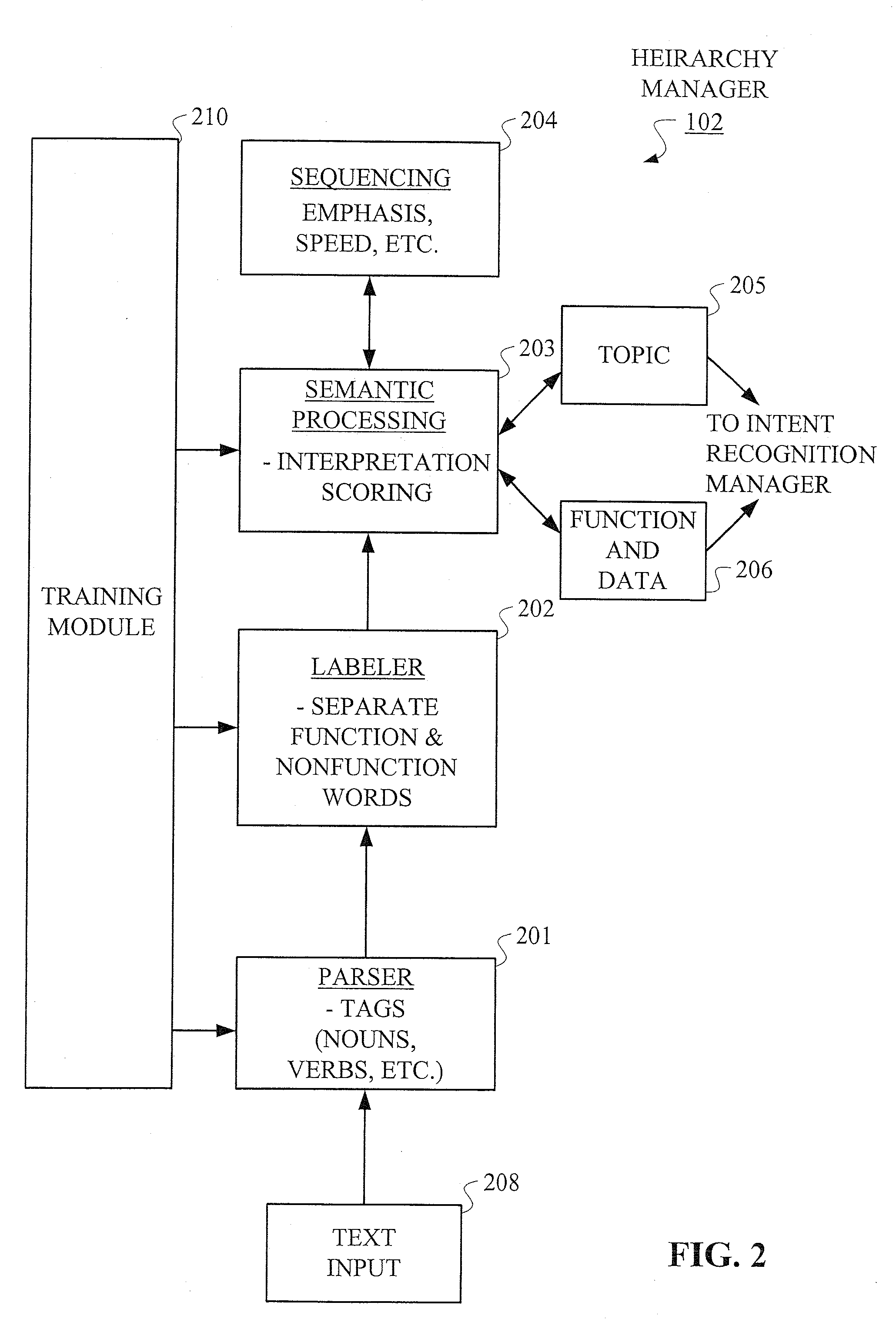
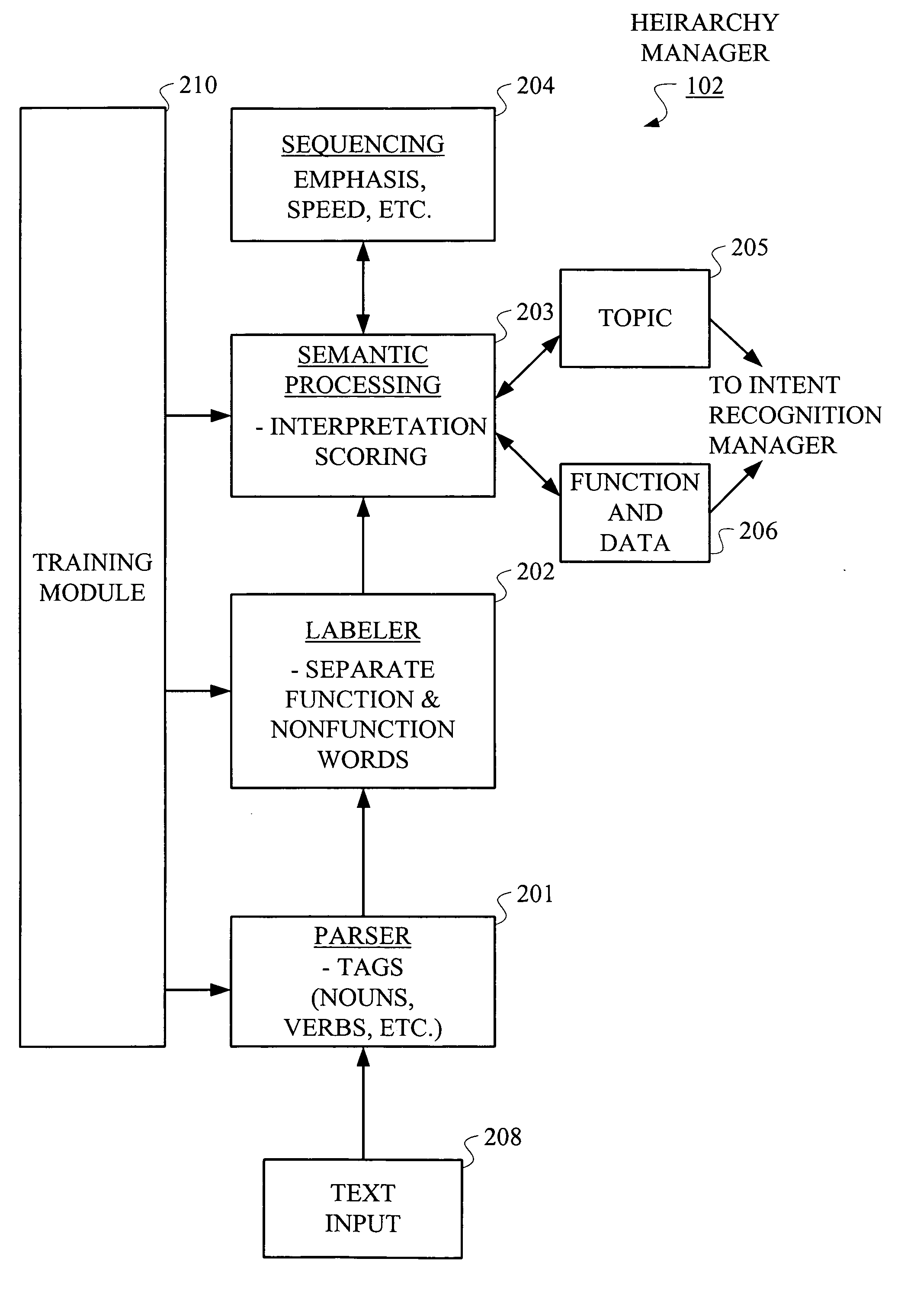
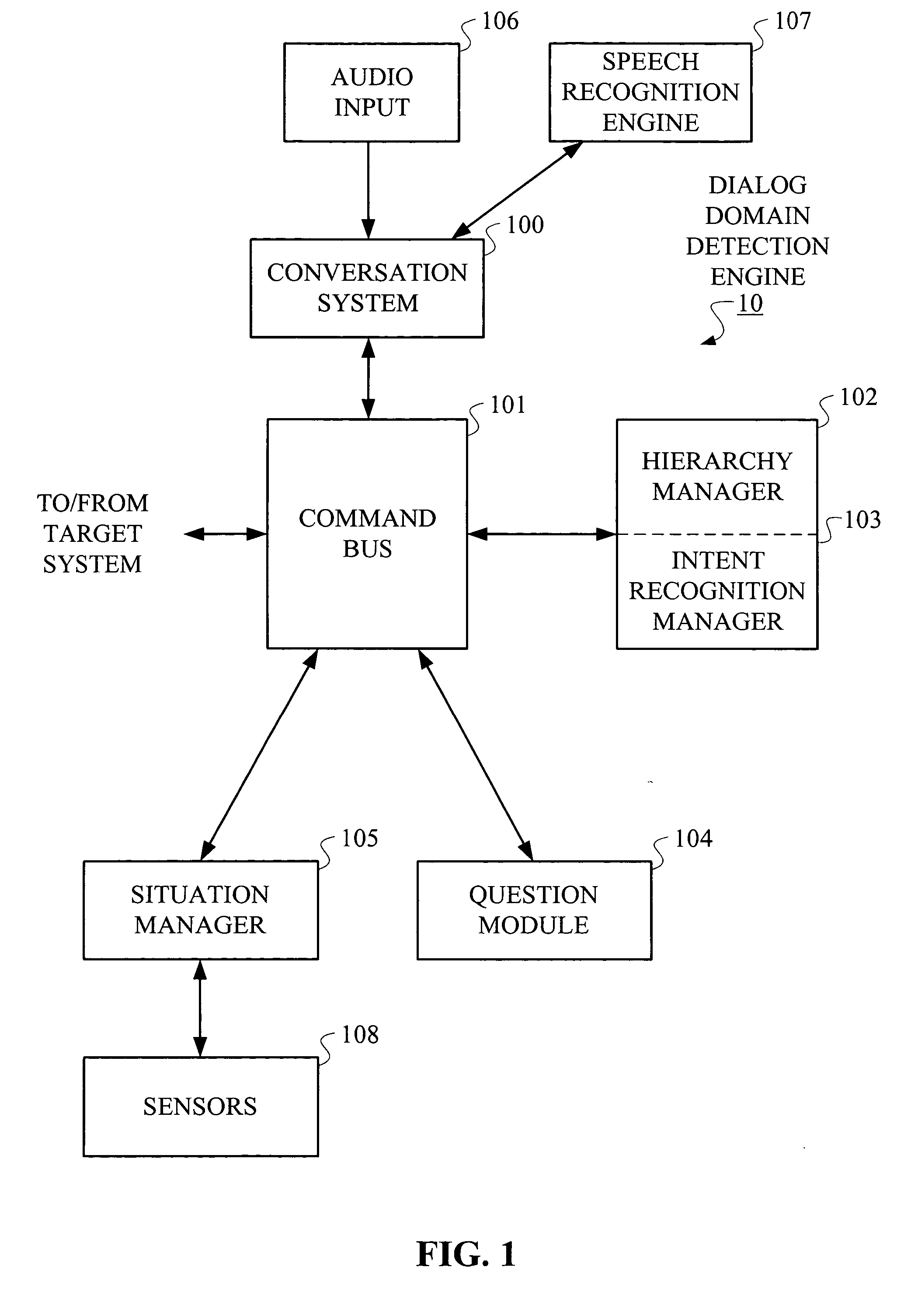
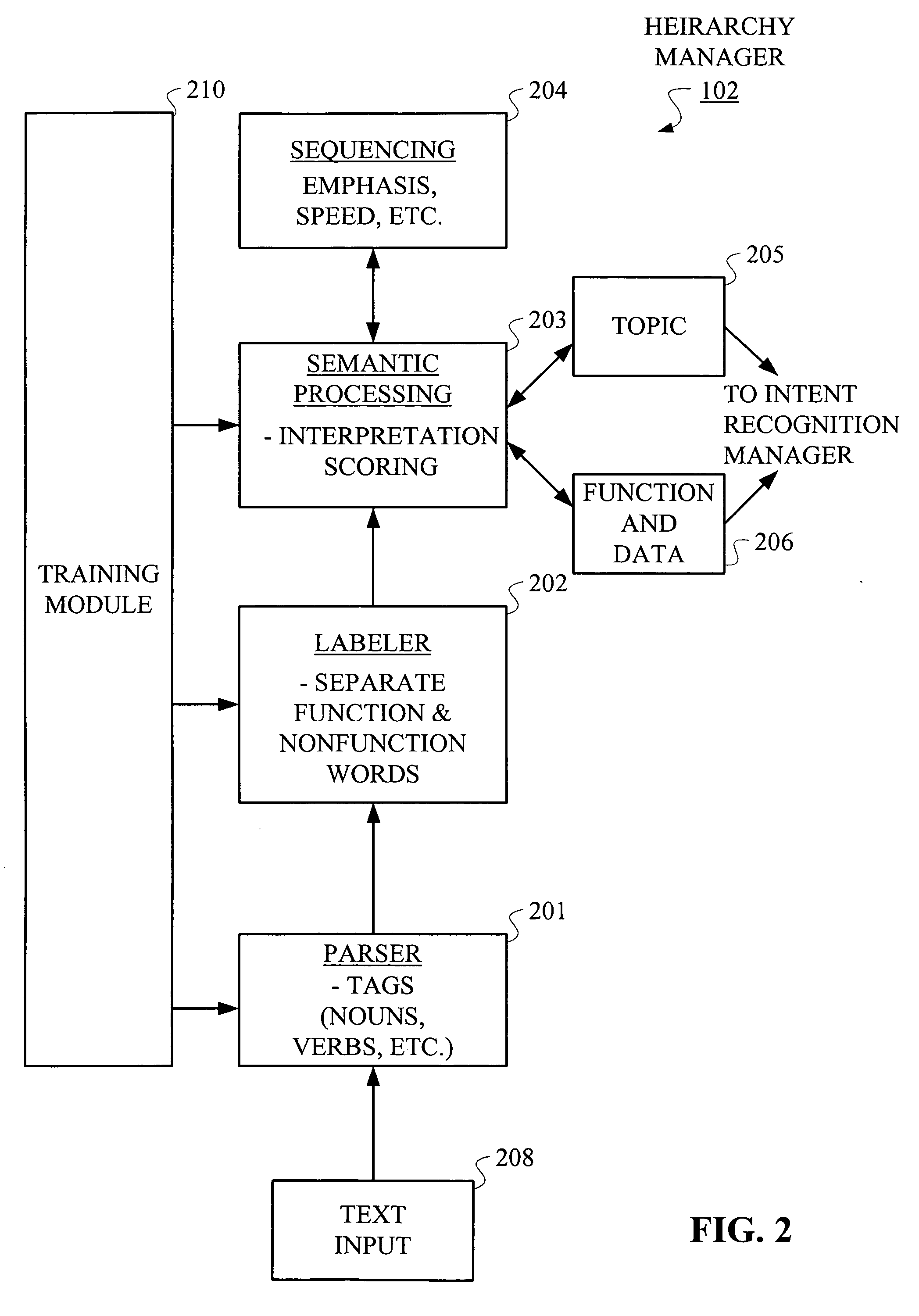
Hierarchical Methods and Apparatus for Extracting User Intent from Spoken Utterances
Improved techniques are disclosed for permitting a user to employ more human-based grammar (i.e., free form or conversational input) while addressing a target system via a voice system. For example, a technique for determining intent associated with a spoken utterance of a user comprises the following steps / operations. Decoded speech uttered by the user is obtained. An intent is then extracted from the decoded speech uttered by the user. The intent is extracted in an iterative manner such that a first class is determined after a first iteration and a sub-class of the first class is determined after a second iteration. The first class and the sub-class of the first class are hierarchically indicative of the intent of the user, e.g., a target and data that may be associated with the target. The multi-stage intent extraction approach may have more than two iterations. By way of example only, the user intent extracting step may further determine a sub-class of the sub-class of the first class after a third iteration, such that the first class, the sub-class of the first class, and the sub-class of the sub-class of the first class are hierarchically indicative of the intent of the user.
Owner:NUANCE COMM INC
Hierarchical methods and apparatus for extracting user intent from spoken utterances
Improved techniques are disclosed for permitting a user to employ more human-based grammar (i.e., free form or conversational input) while addressing a target system via a voice system. For example, a technique for determining intent associated with a spoken utterance of a user comprises the following steps / operations. Decoded speech uttered by the user is obtained. An intent is then extracted from the decoded speech uttered by the user. The intent is extracted in an iterative manner such that a first class is determined after a first iteration and a sub-class of the first class is determined after a second iteration. The first class and the sub-class of the first class are hierarchically indicative of the intent of the user, e.g., a target and data that may be associated with the target. The multi-stage intent extraction approach may have more than two iterations. By way of example only, the user intent extracting step may further determine a sub-class of the sub-class of the first class after a third iteration, such that the first class, the sub-class of the first class, and the sub-class of the sub-class of the first class are hierarchically indicative of the intent of the user.
Owner:NUANCE COMM INC
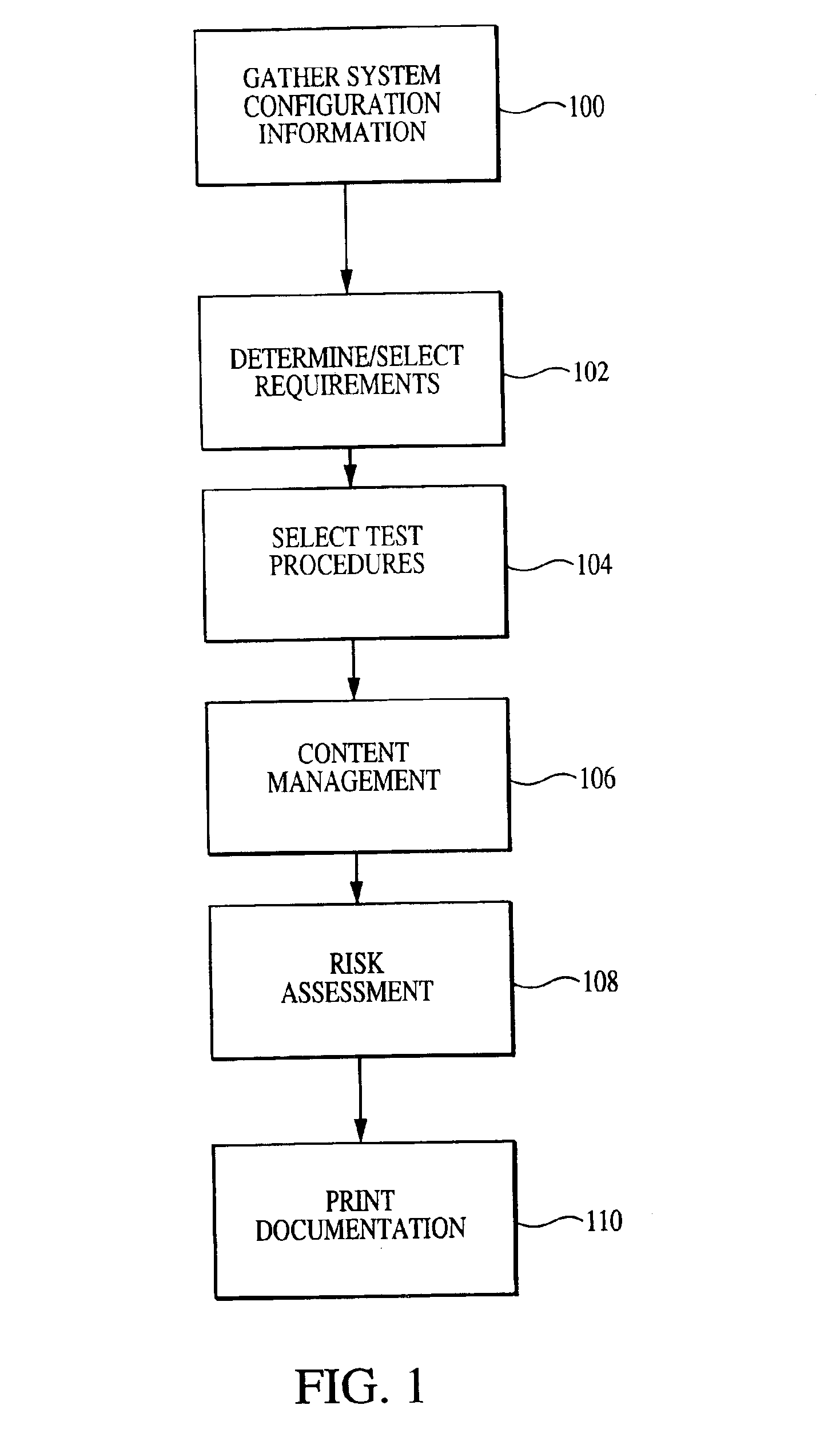
Enhanced system, method and medium for certifying and accrediting requirements compliance utilizing robust risk assessment model
InactiveUS6983221B2Enhances and facilitates security risk assessmentsFinanceError detection/correctionComputer-aidedGoal system
Owner:TELOS CORP
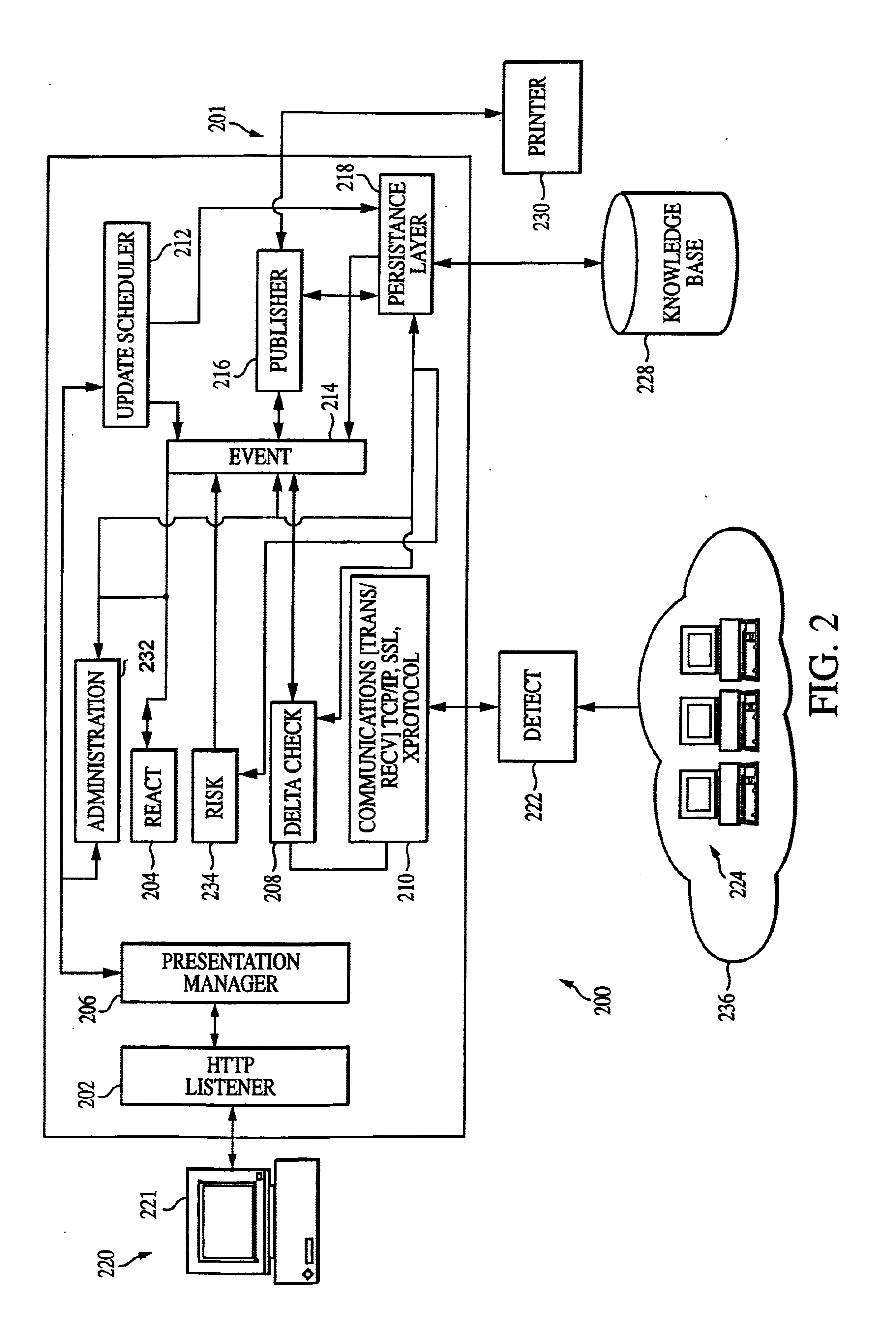
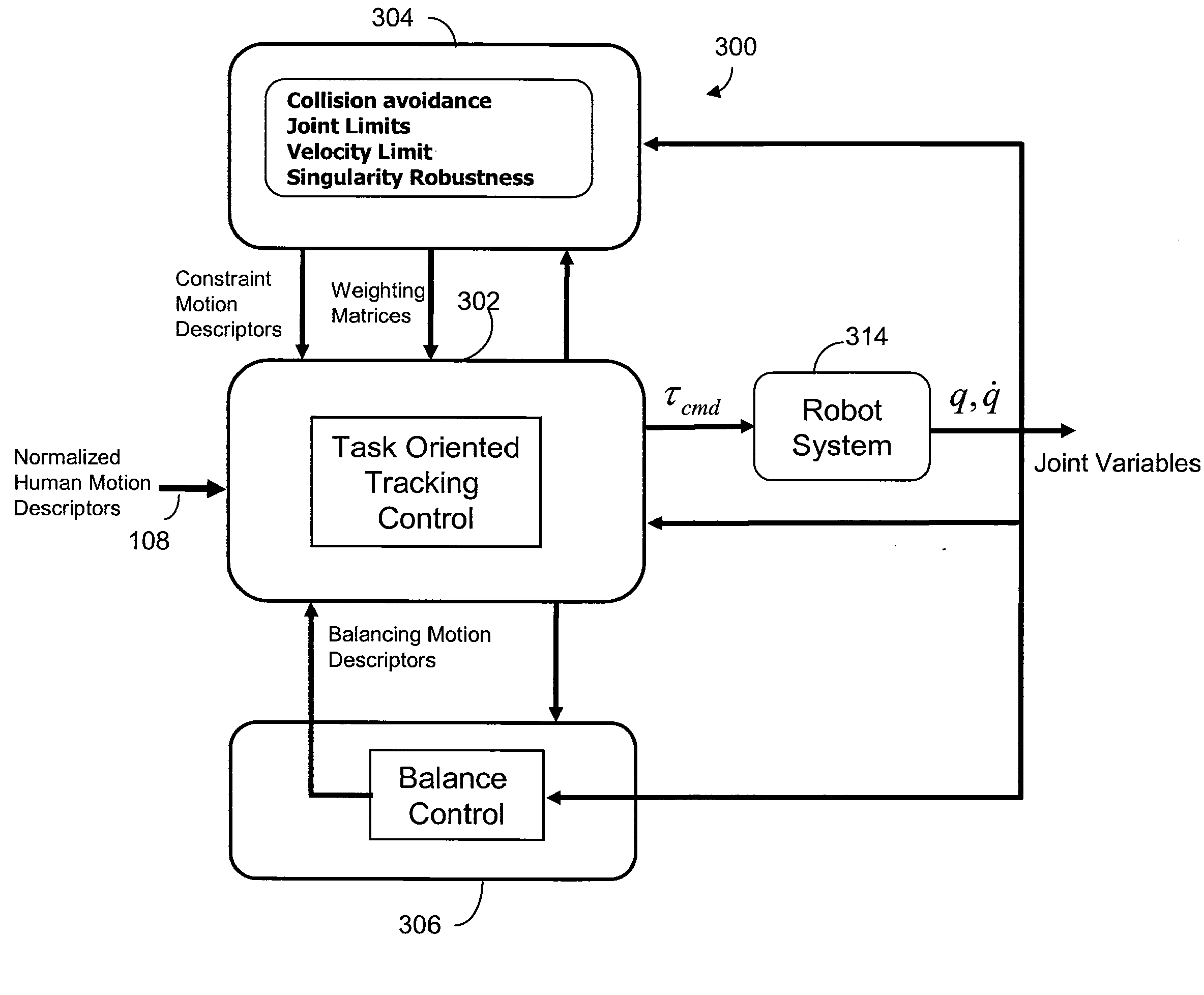
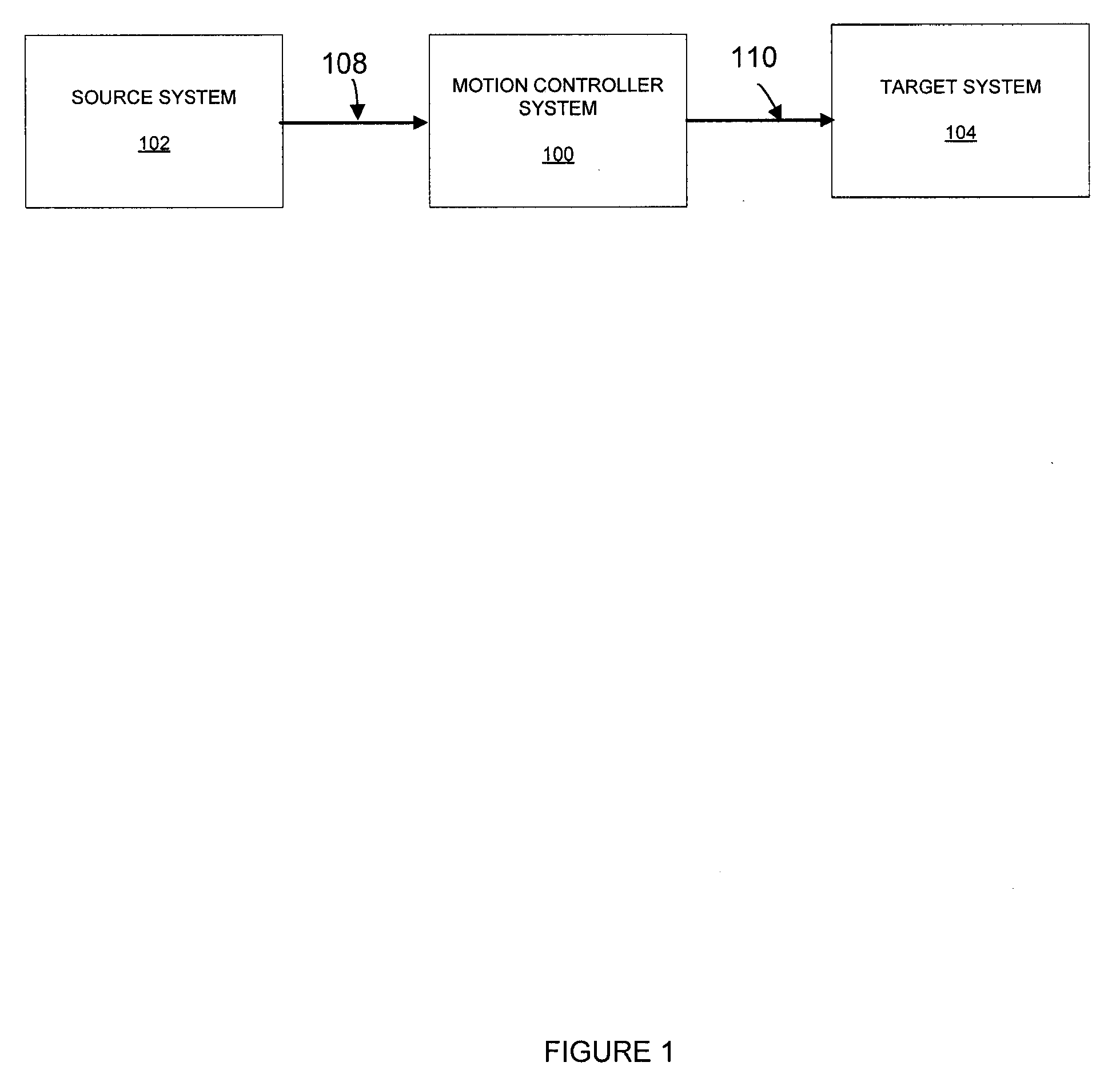
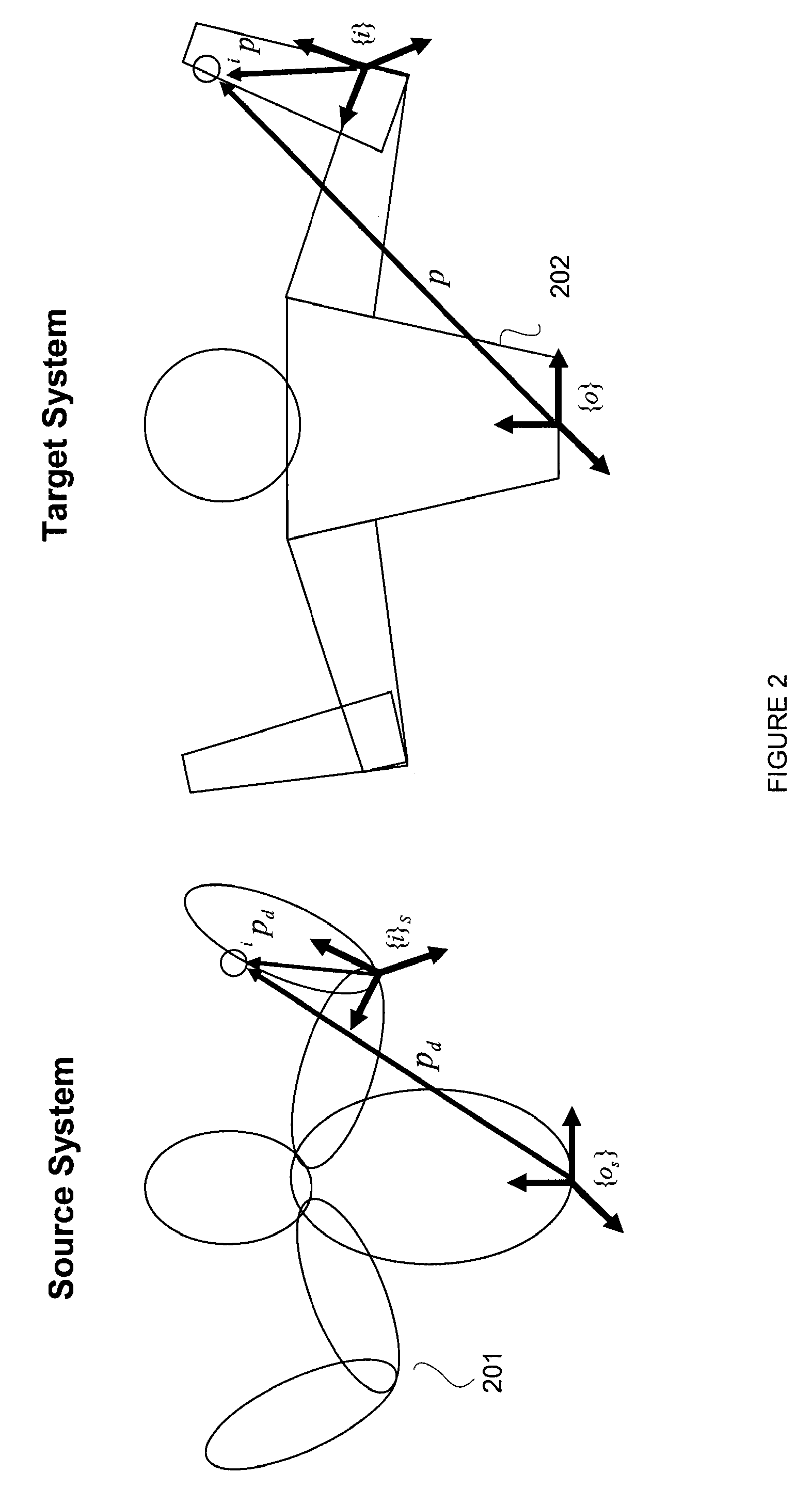
Control Of Robots From Human Motion Descriptors
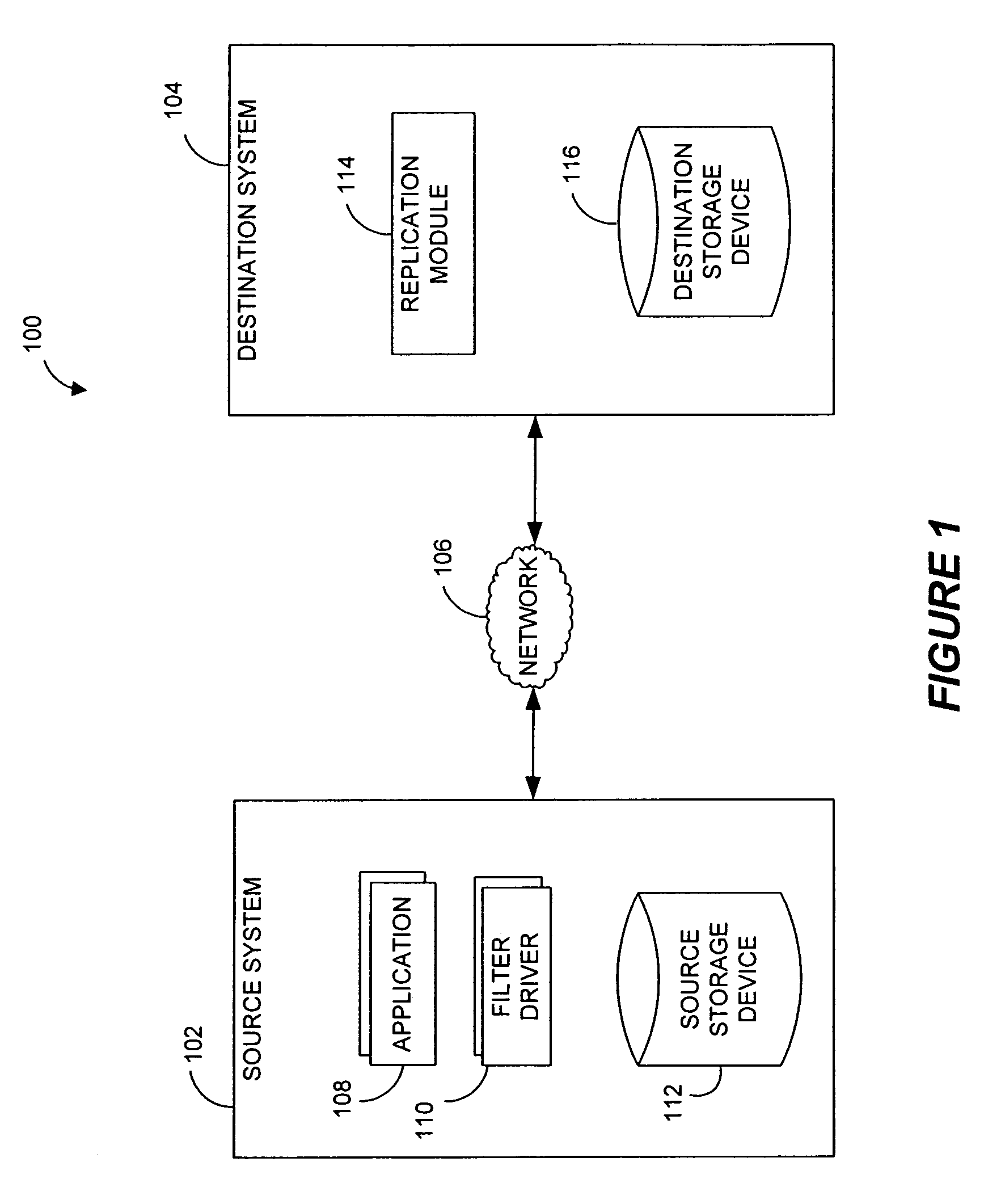
A control system and method generate torque comments for motion of a target system in response to observations of a source system. Constraints and balance control may be provided for more accurate representation of the motion as replicated by the target system.
Owner:HONDA MOTOR CO LTD
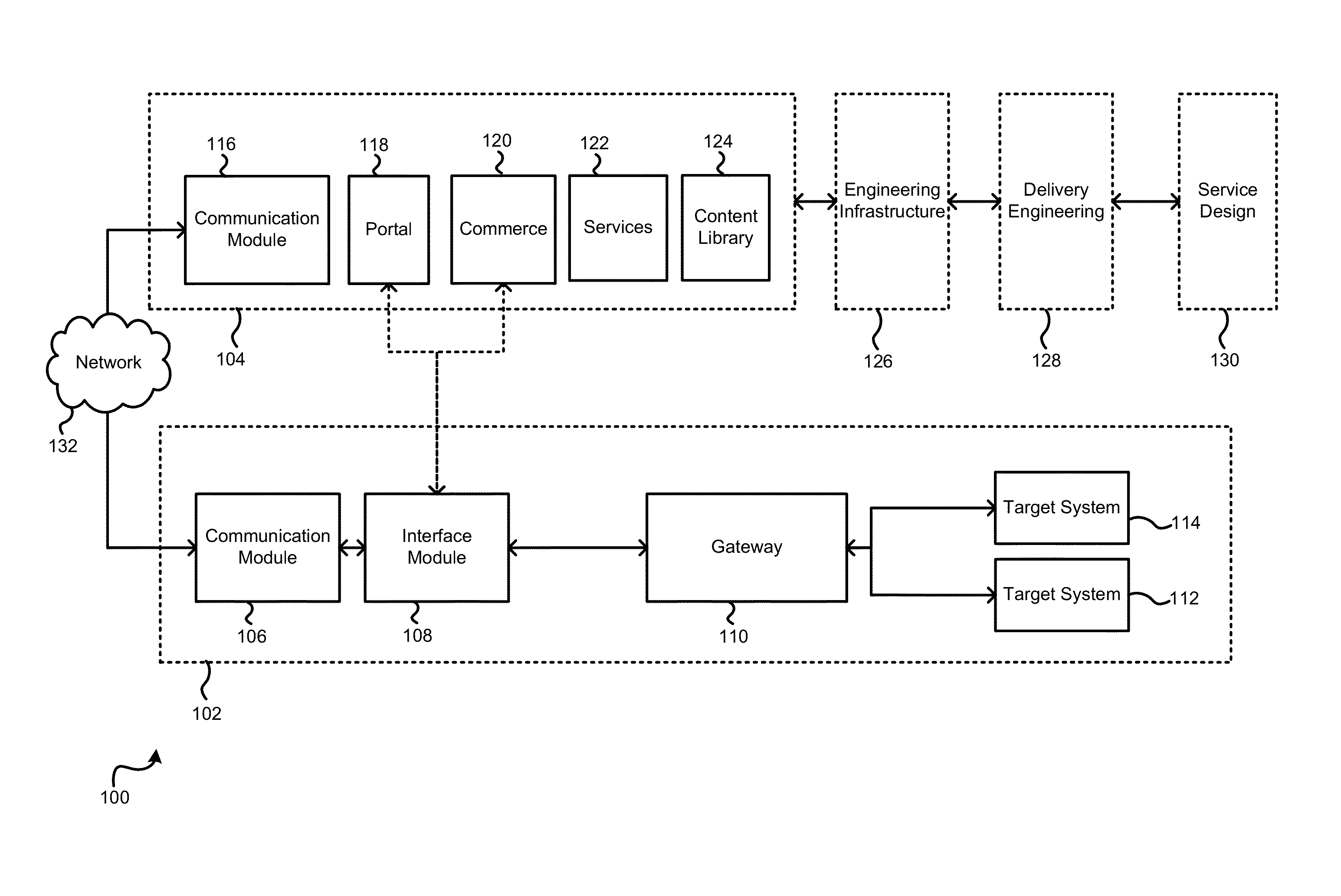
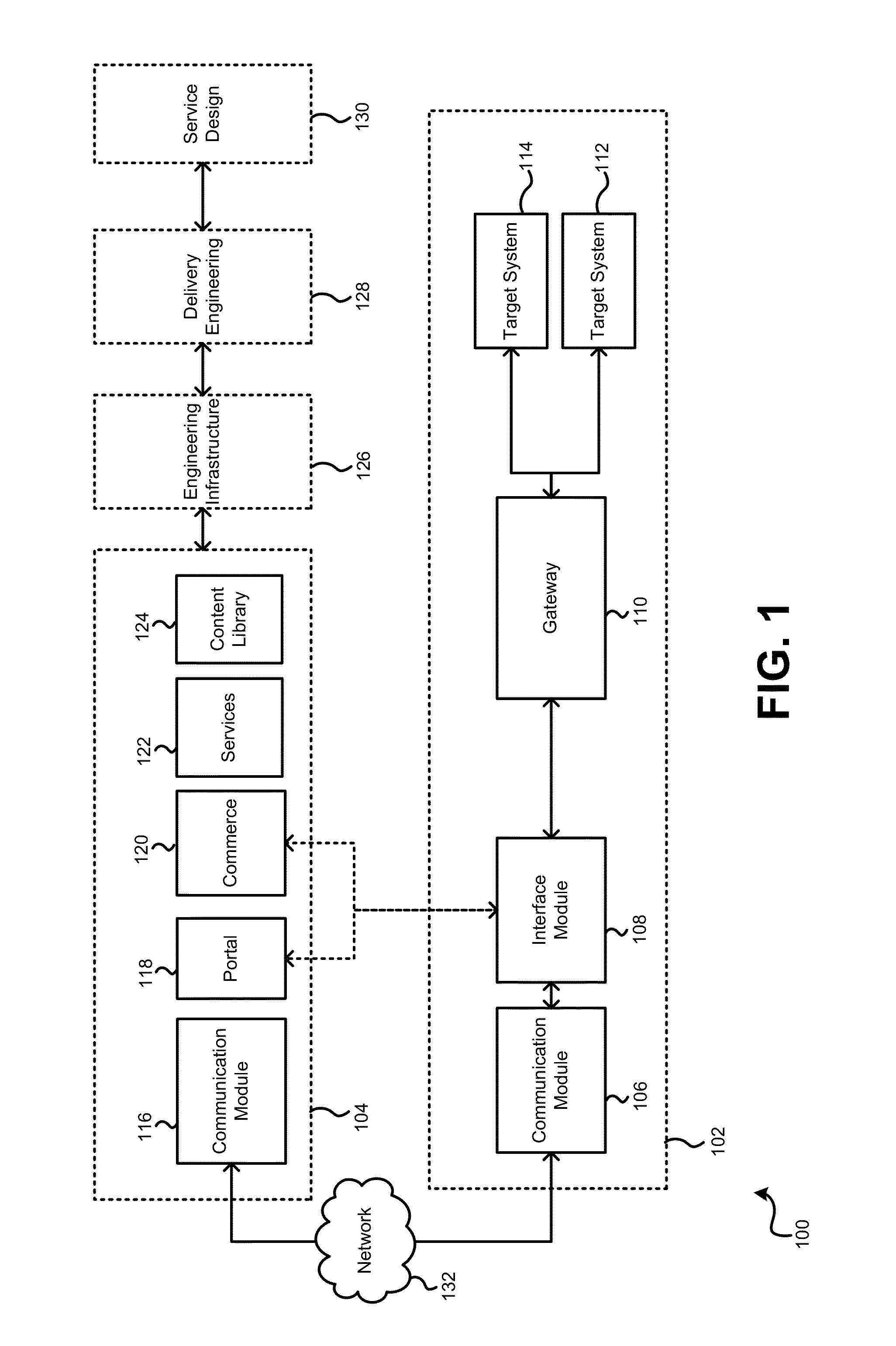
Hardware system design improvement using deep learning algorithms
Methods and apparatus for deep learning-based system design improvement are provided. An example system design engine apparatus includes a deep learning network (DLN) model associated with each component of a target system to be emulated, each DLN model to be trained using known input and known output, wherein the known input and known output simulate input and output of the associated component of the target system, and wherein each DLN model is connected as each associated component to be emulated is connected in the target system to form a digital model of the target system. The example apparatus also includes a model processor to simulate behavior of the target system and / or each component of the target system to be emulated using the digital model to generate a recommendation regarding a configuration of a component of the target system and / or a structure of the component of the target system.
Owner:GENERAL ELECTRIC CO
Network redirector systems and methods for performing data replication
InactiveUS7962709B2Reduce impactReduce memory requirementsDigital data information retrievalDigital data processing detailsTemporal informationNetwork redirector
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
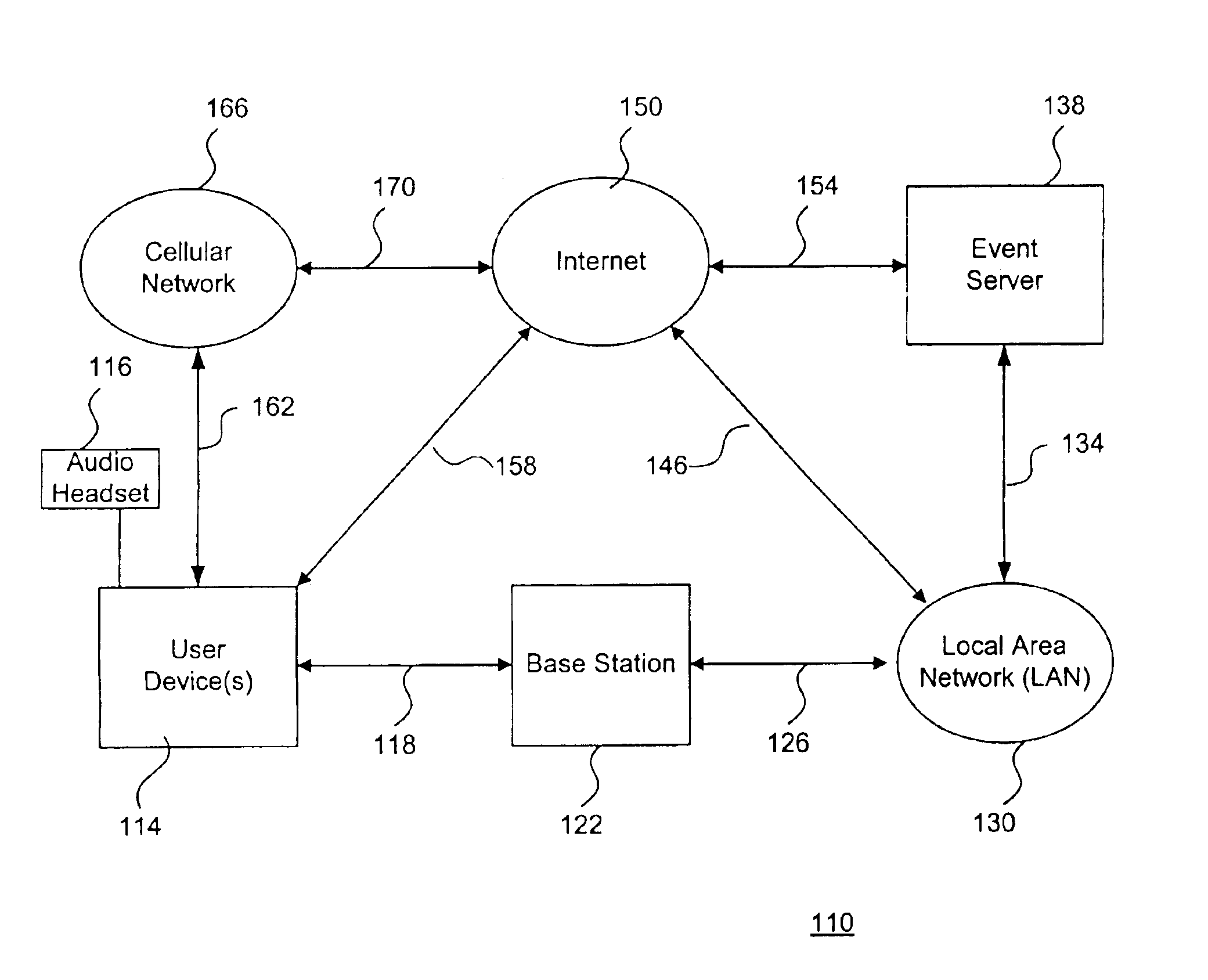
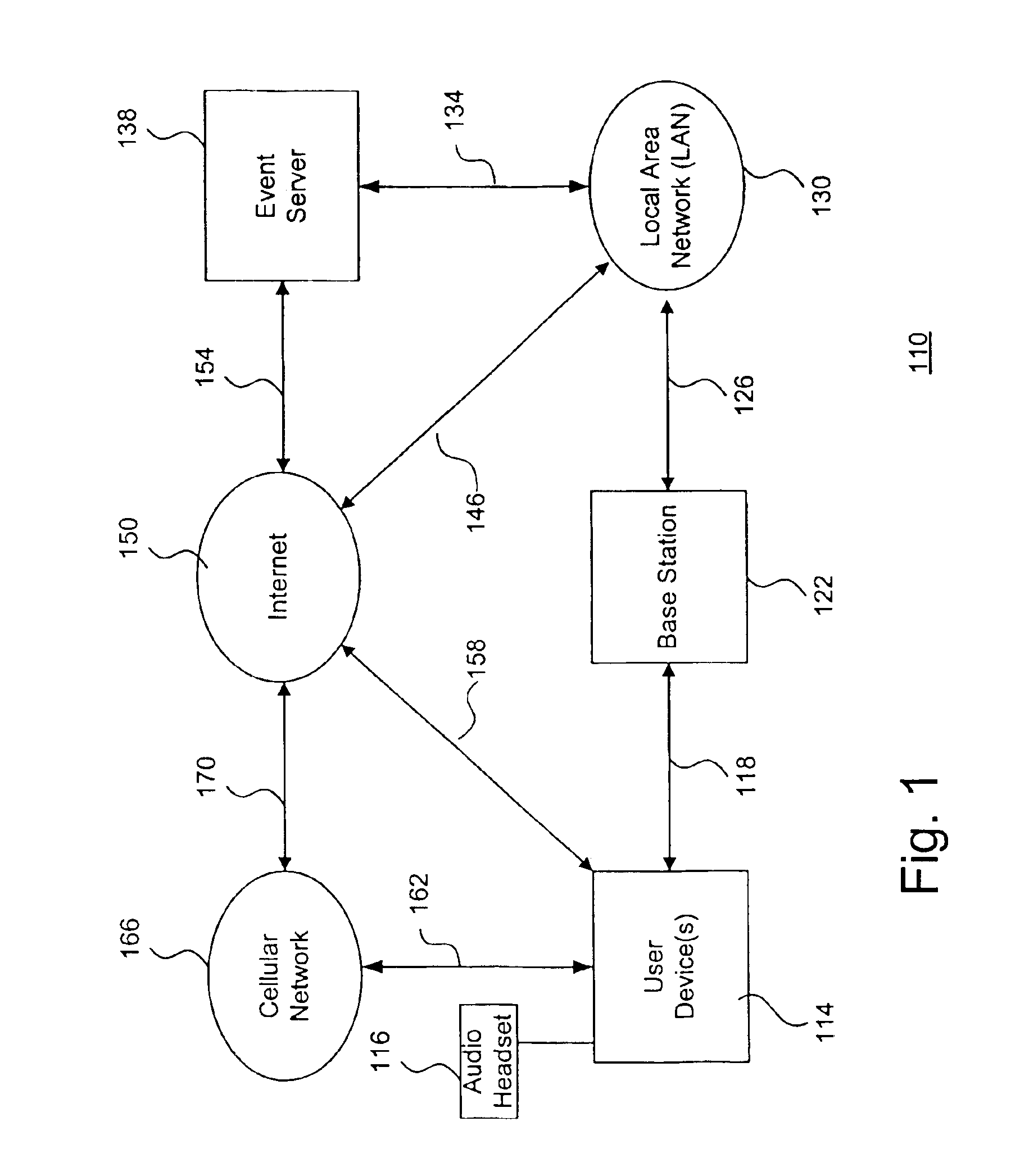
System and method to support gaming in an electronic network
InactiveUS6884162B2Apparatus for meter-controlled dispensingVideo gamesUser deviceRelevant information
A system and method to support electronic gaming in an electronic network includes an event server that provides restricted access to various types of game services. One or more system users may utilize corresponding wireless portable user devices for connecting to the event server to thereby gain access to the foregoing game services as game participants. The system users may thereby utilize the user devices to access the event server for accessing appropriate gaming services and related information. In addition, a source system user may utilize a source user device to perform a transfer procedure for transferring ownership rights of an electronic certificate related to the electronic gaming to a target system user through a target user device. The foregoing transfer procedure may be conducted through the event server, or may occur directly from the source user device to the target user device.
Owner:SONY CORP +1
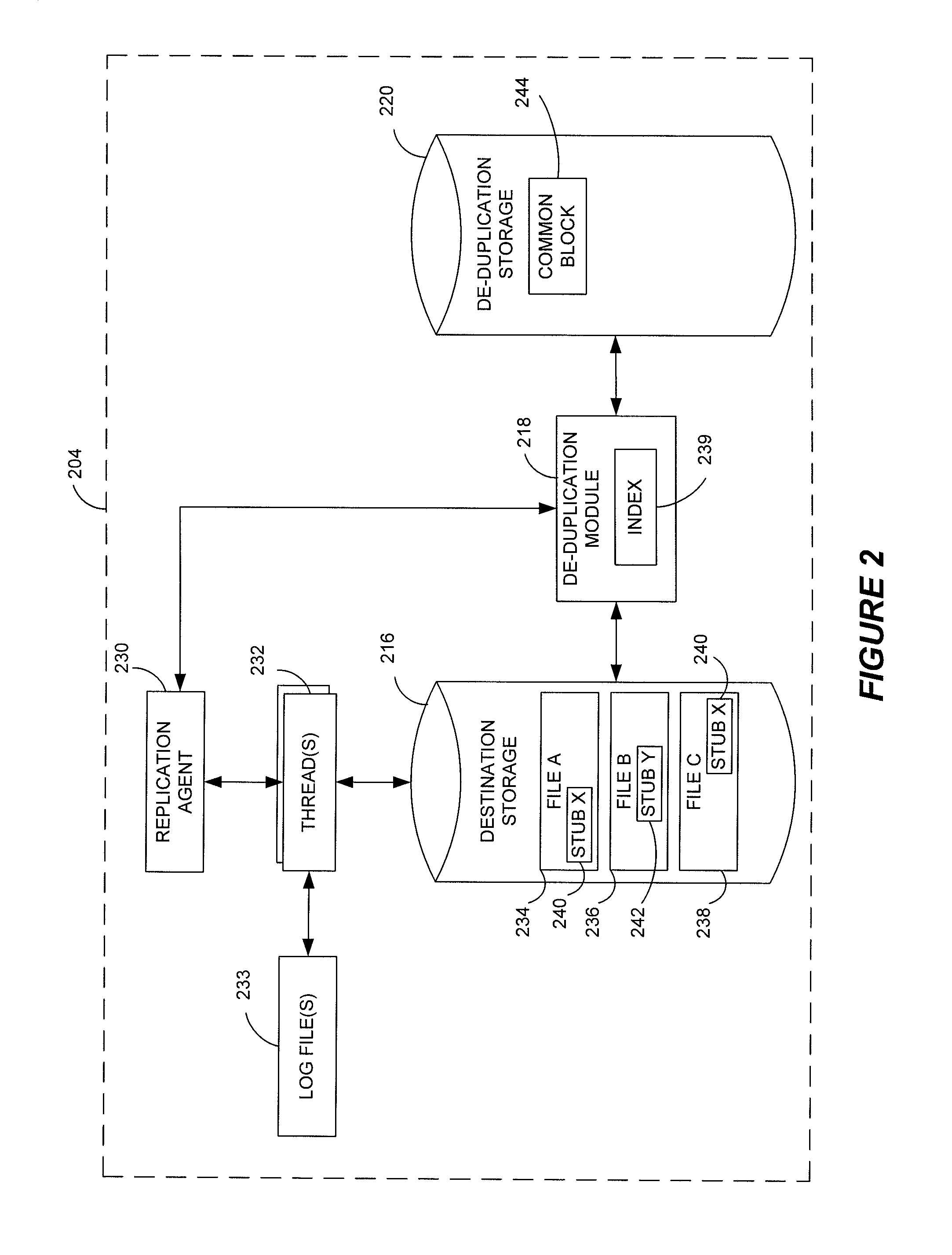
Data restore systems and methods in a replication environment
ActiveUS8352422B2Digital data information retrievalDigital data processing detailsData managementGoal system
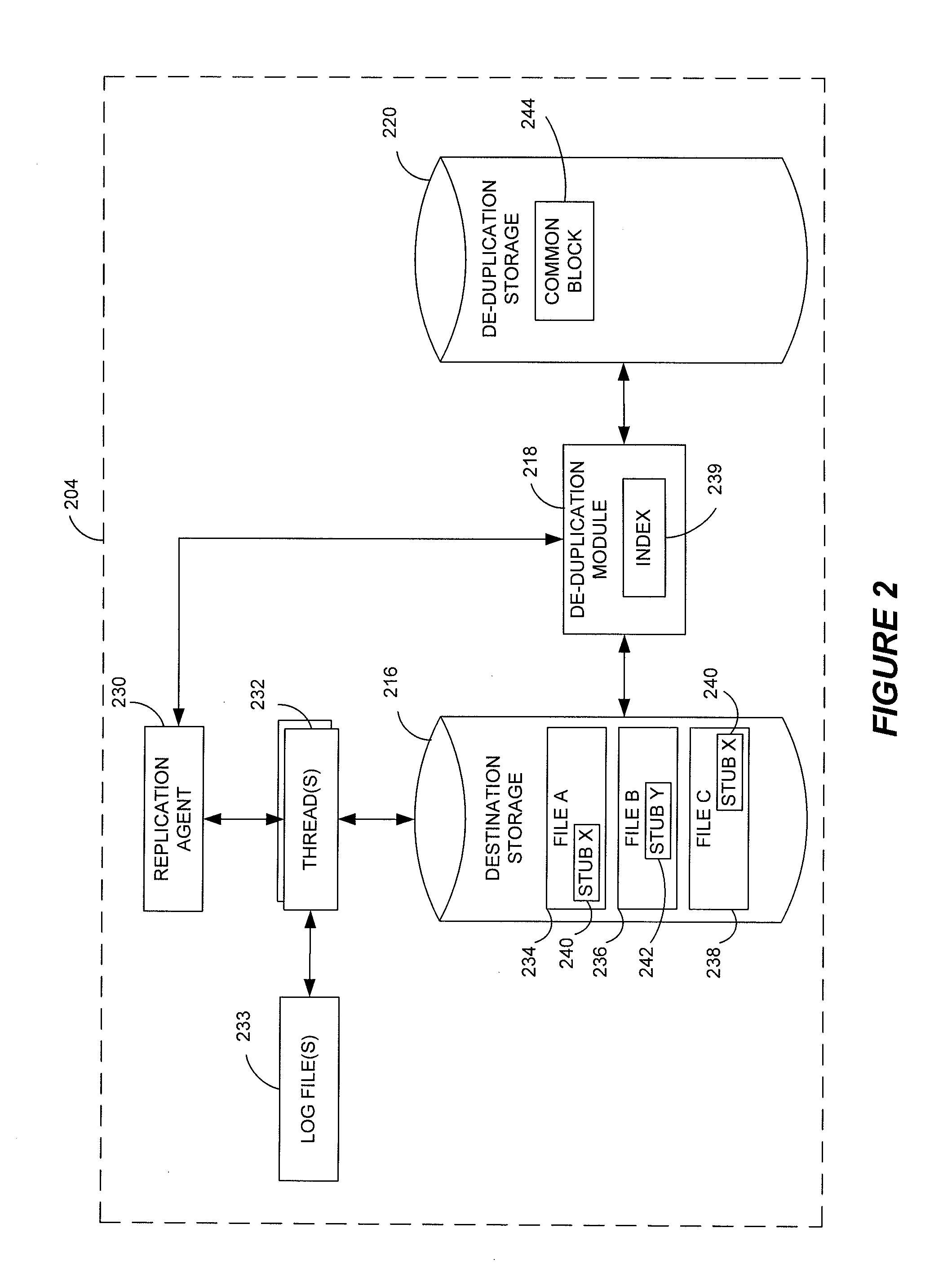
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication data or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
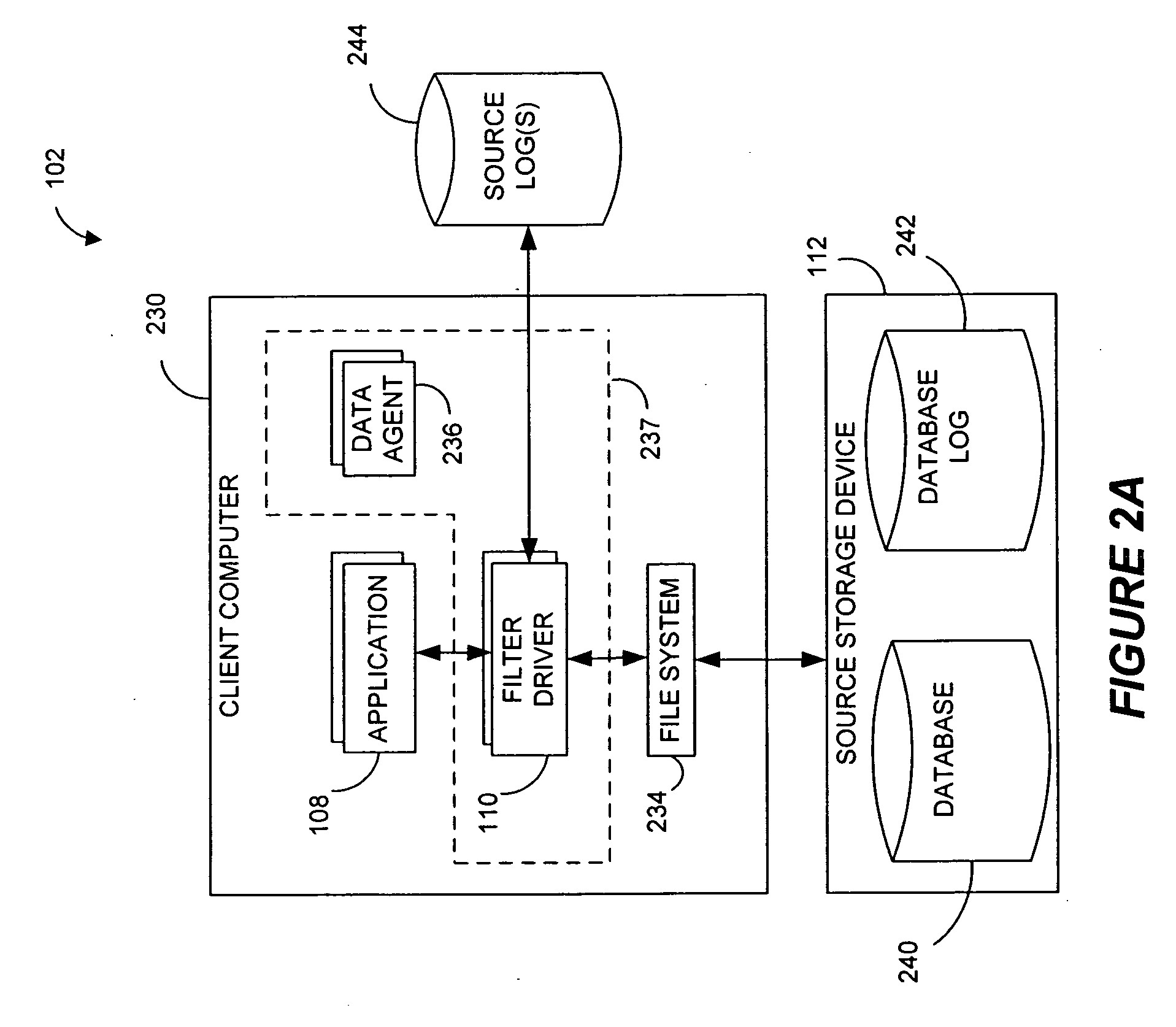
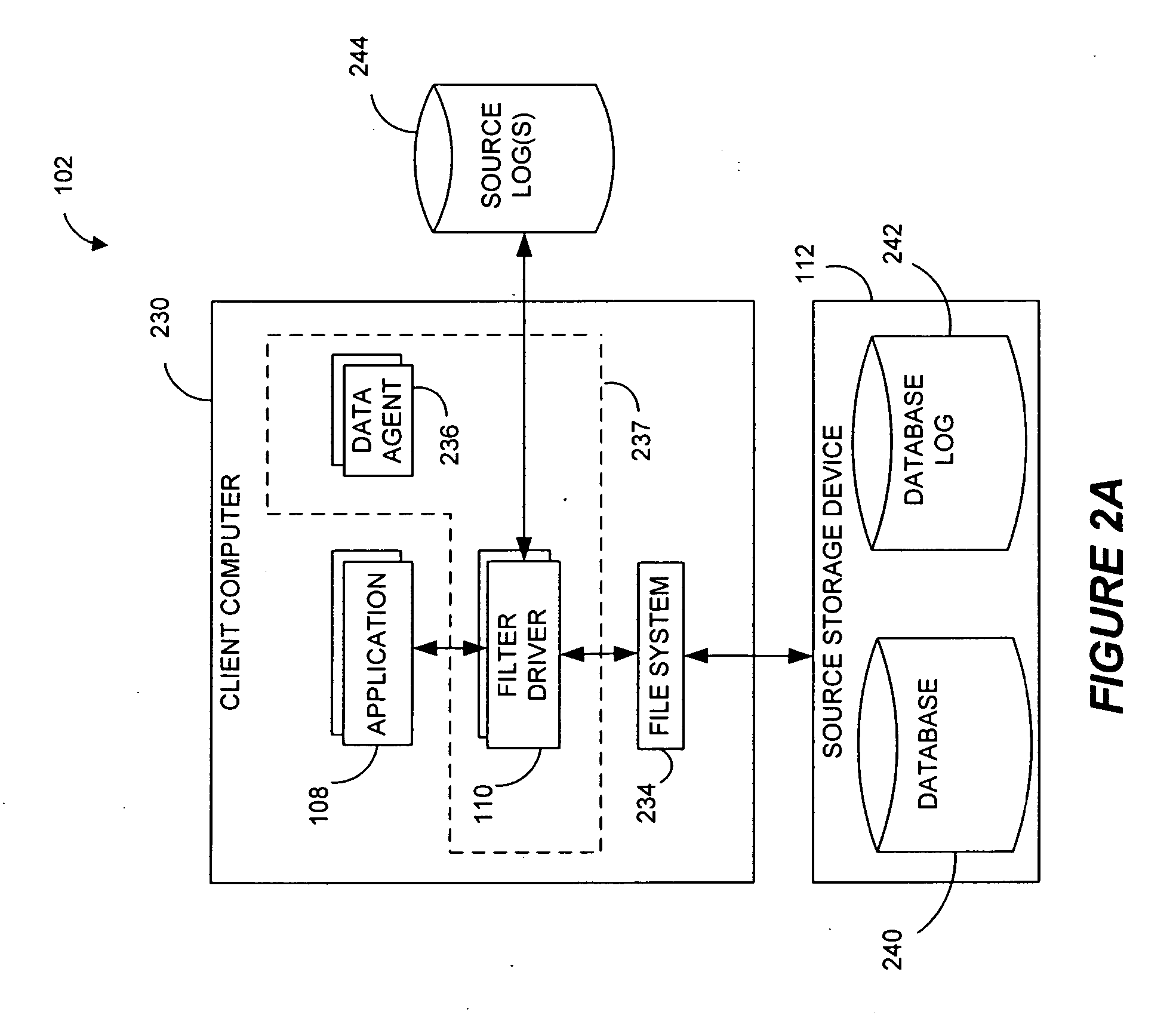
Systems and methods for monitoring application data in a data replication system
InactiveUS20070185939A1Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationGoal system
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Destination systems and methods for performing data replication
InactiveUS20070185937A1Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
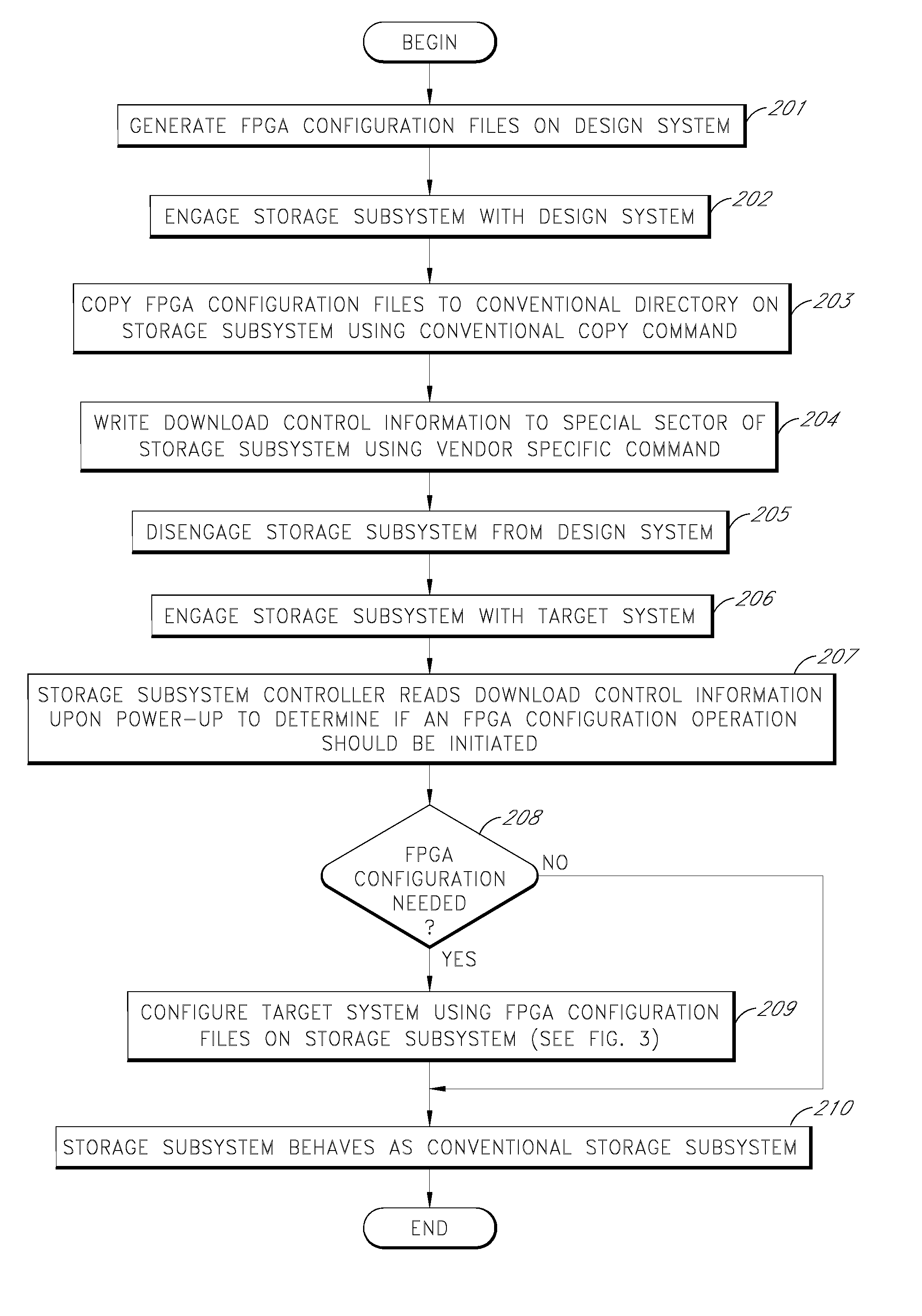
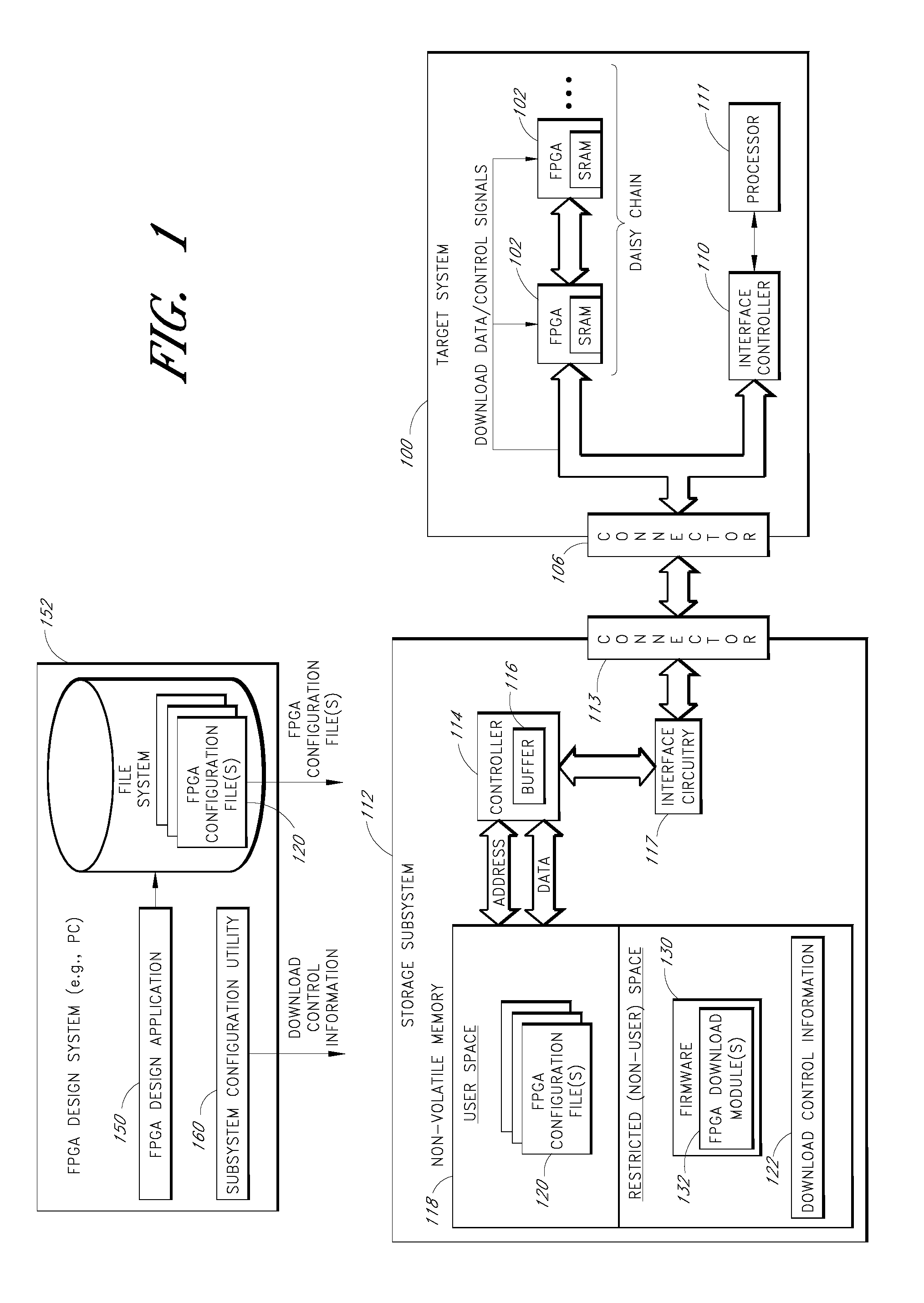
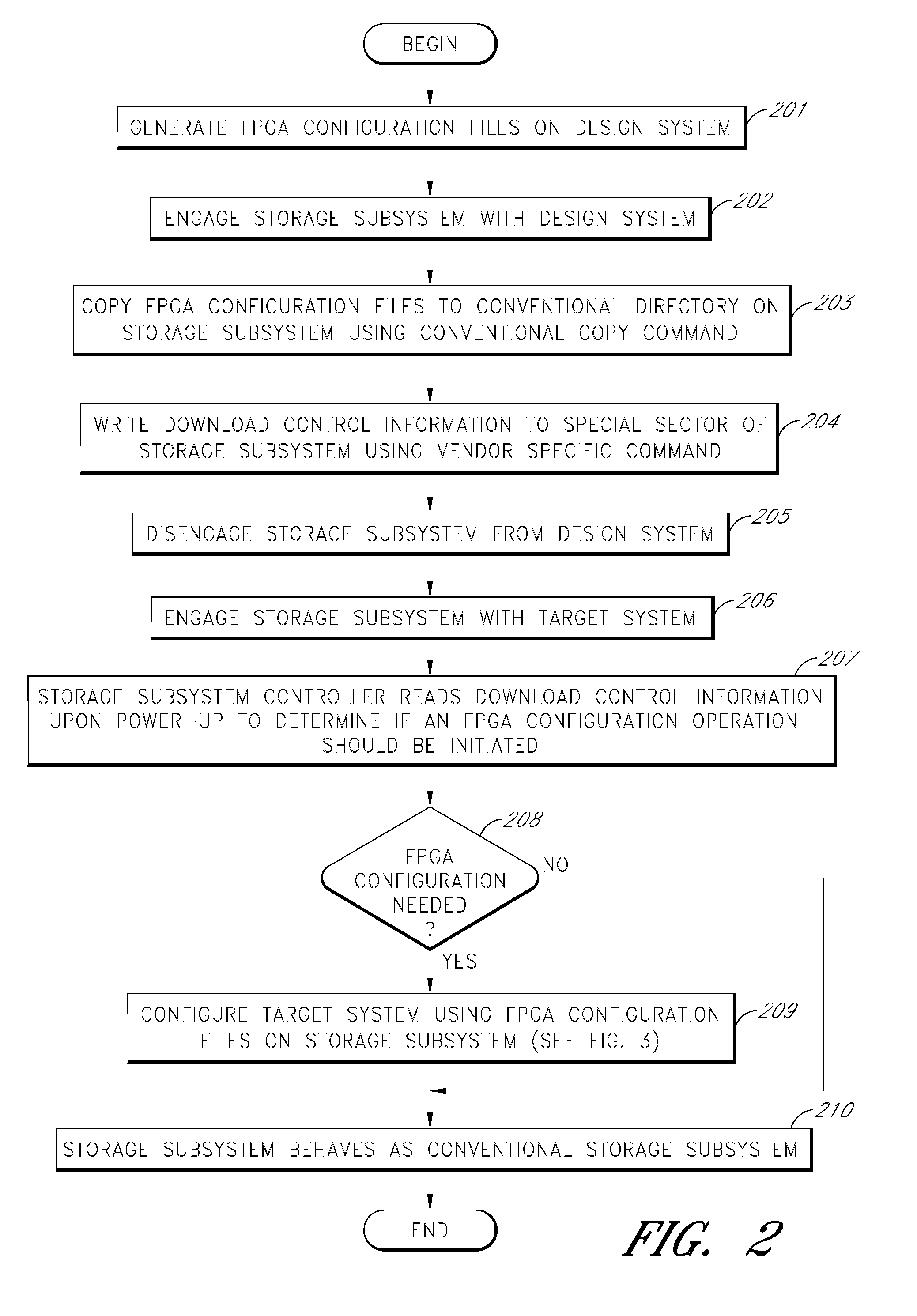
Storage subsystem capable of programming field-programmable devices of a target computer system
InactiveUS8161227B1Avoid the needInput/output to record carriersError preventionProgrammable logic deviceGoal system
A non-volatile storage subsystem is capable of serving as a configuration controller for configuring / programming one or more field-programmable devices, such as FPGAs, of a target computer system. The storage subsystem may be in the form of a memory card or drive that plugs into a standard slot or external port of the target system. When connected to the target system, the storage subsystem uses the appropriate download interface / protocol to stream or otherwise send configuration data stored in its non-volatile storage to the target system's field-programmable device(s). Thus, the need for a configuration controller in the target system is avoided. Once the configuration process is complete, the storage subsystem preferably acts as a standard storage subsystem, such as an ATA storage drive, that may be used by the target system to store data.
Owner:WESTERN DIGITAL TECH INC
System and methods for advertisement and event promotion
InactiveUS20080215426A1Guaranteed uptimeEfficient managementAdvertisementsGoal systemTargeted advertising
The present invention is directed to a system and methods for targeted advertisement and event promotion. The system comprises a web-based application which enables event promoters to create, execute and manage event promotional campaigns using advertisements, targeted promotional messages, target user search tools, session tracking tools, campaign analytical tools, event pricing tools, reporting tools, embedded calendar applications and other tools and services provided by the system. The system combines these tools to enable promoters to communicate with and market events to highly targeted audiences utilizing a wide array of communication tools. Furthermore, each promotional or advertisement campaign enriches and grows promoter's target user list thus continually enlarging the overall group of trusted and targeted system users.
Owner:GULDIMANN MARC +4
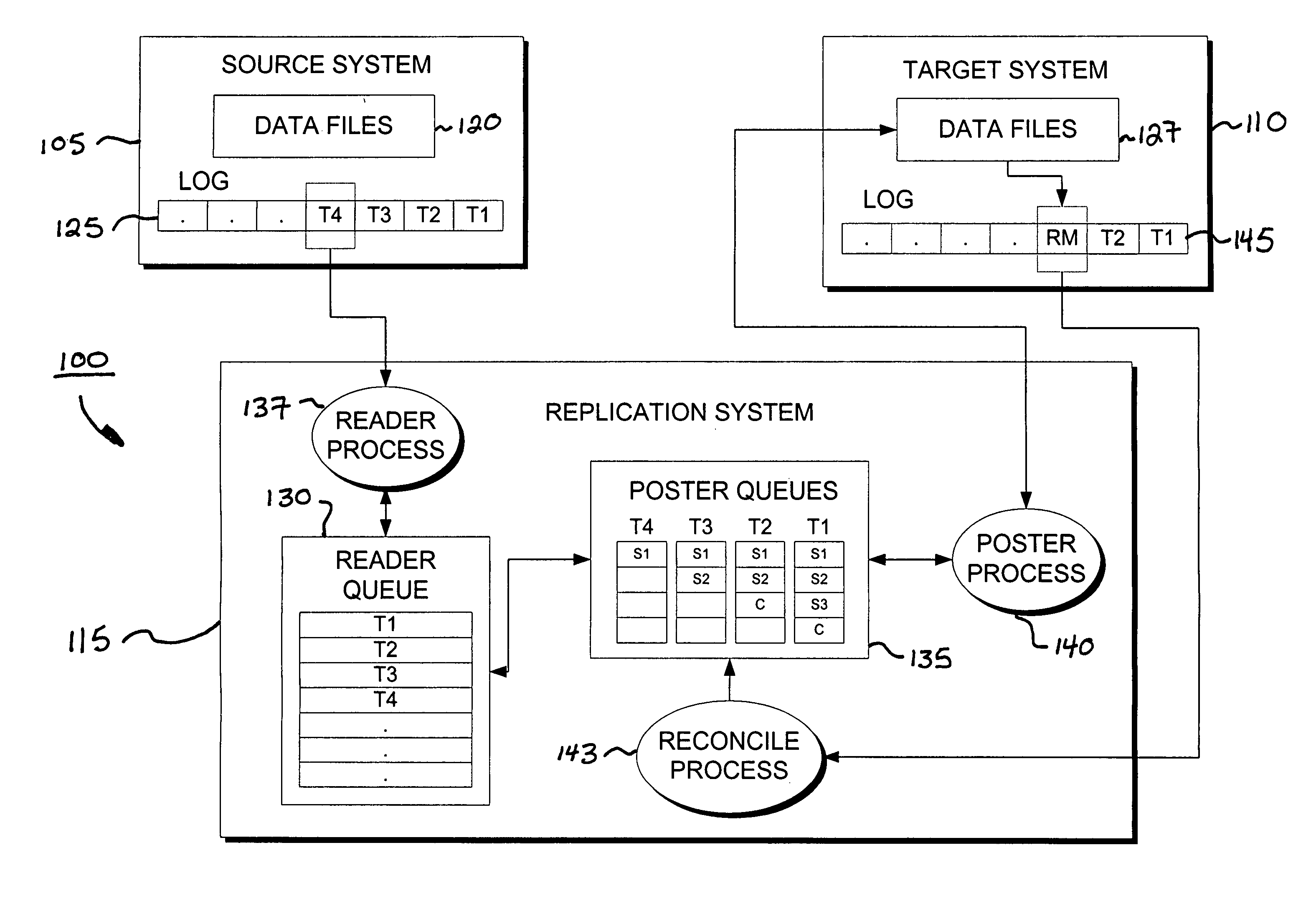
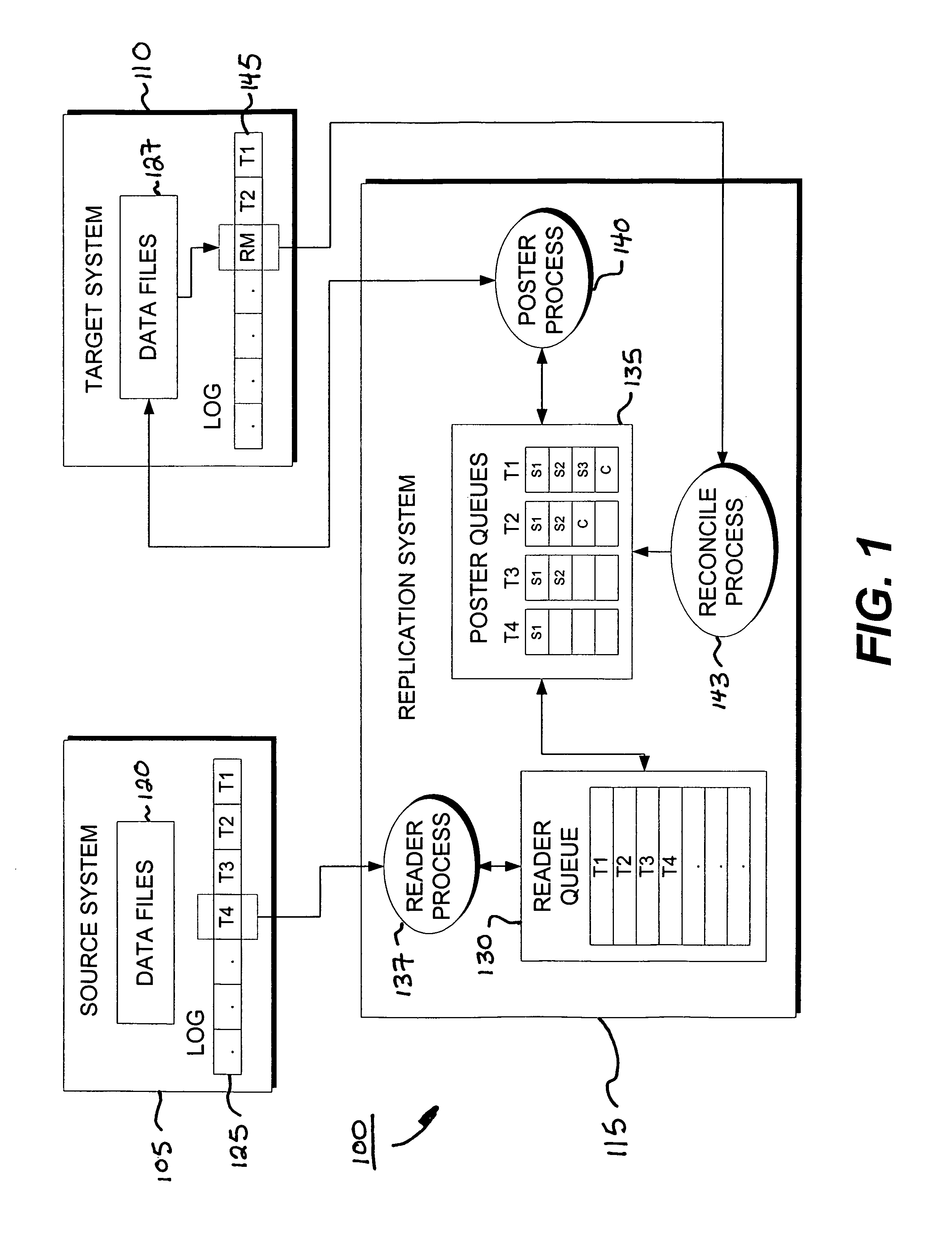
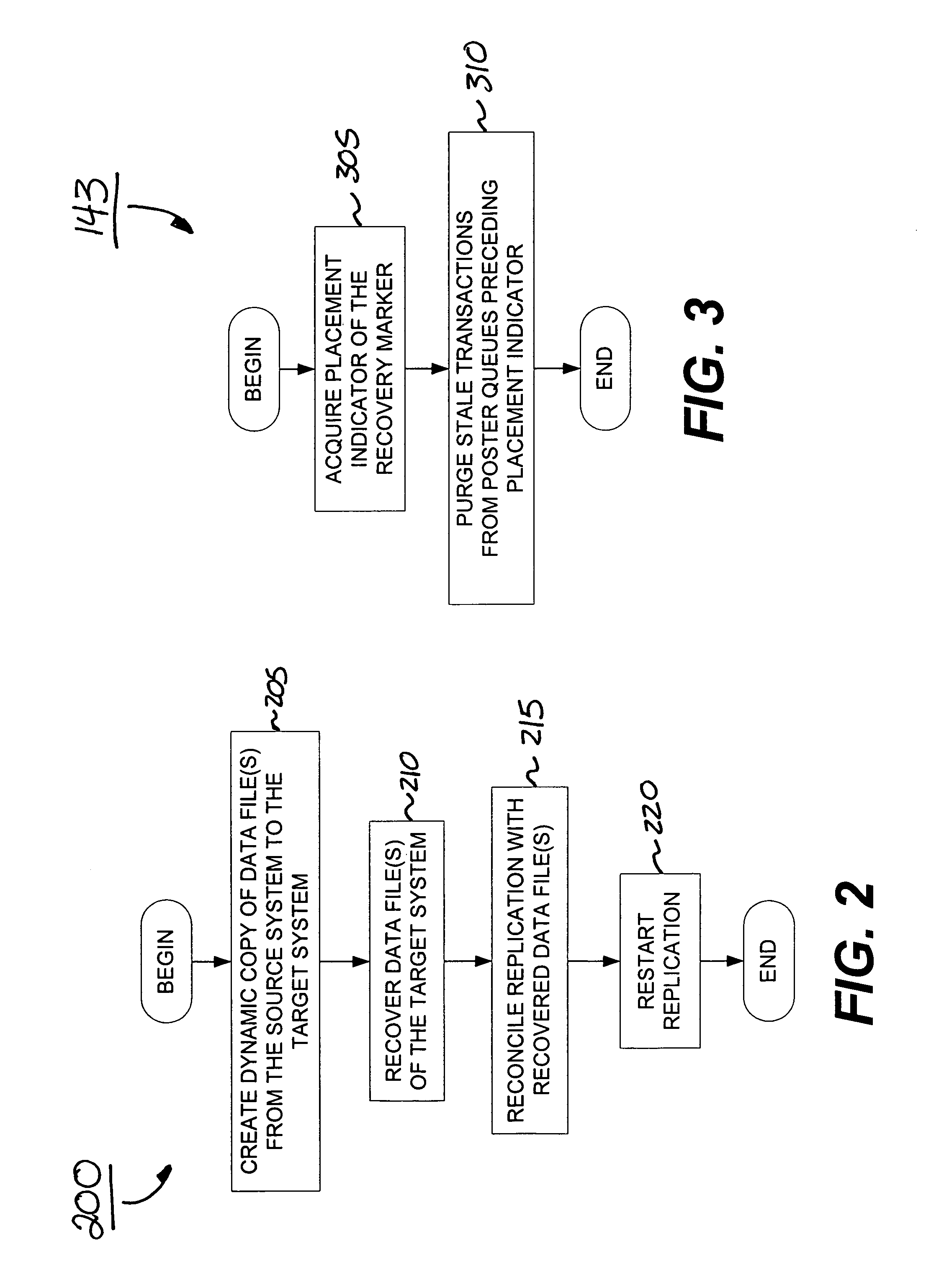
System and method for reconciling transactions between a replication system and a recovered database
InactiveUS7065538B2Purging stale transactions from the replication systemData processing applicationsDatabase distribution/replicationRecovery positionGoal system
The invention is a reconcile system for providing data replication between a source system and a target system. The reconcile system includes a reconcile process that determines a recovery position for a failed or otherwise desynchronized target system, and purges queues of the reconcile system of stale transactions occurring before the recovery position, thereby ensuring synchronization between the source and target systems.
Owner:QUEST SOFTWARE INC
Pathname translation in a data replication system
InactiveUS20070185852A1Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationGoal system
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
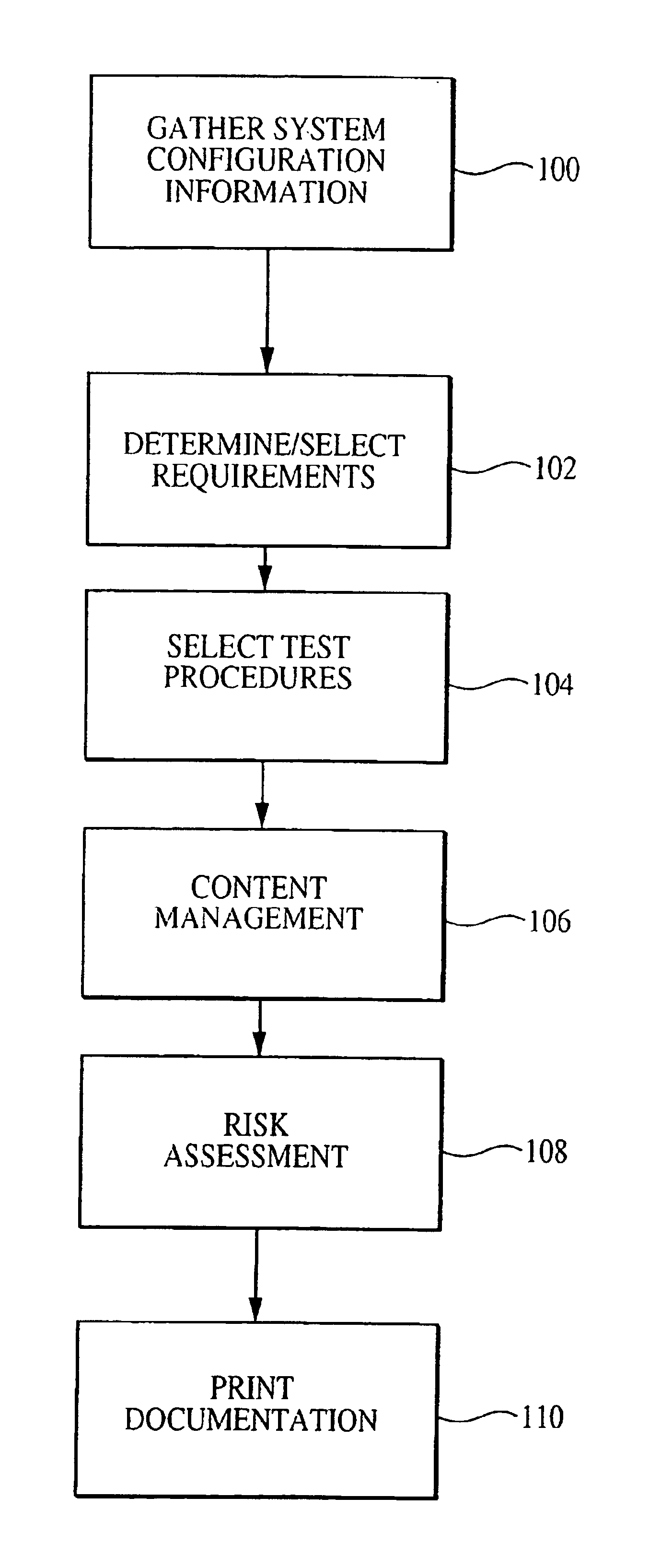
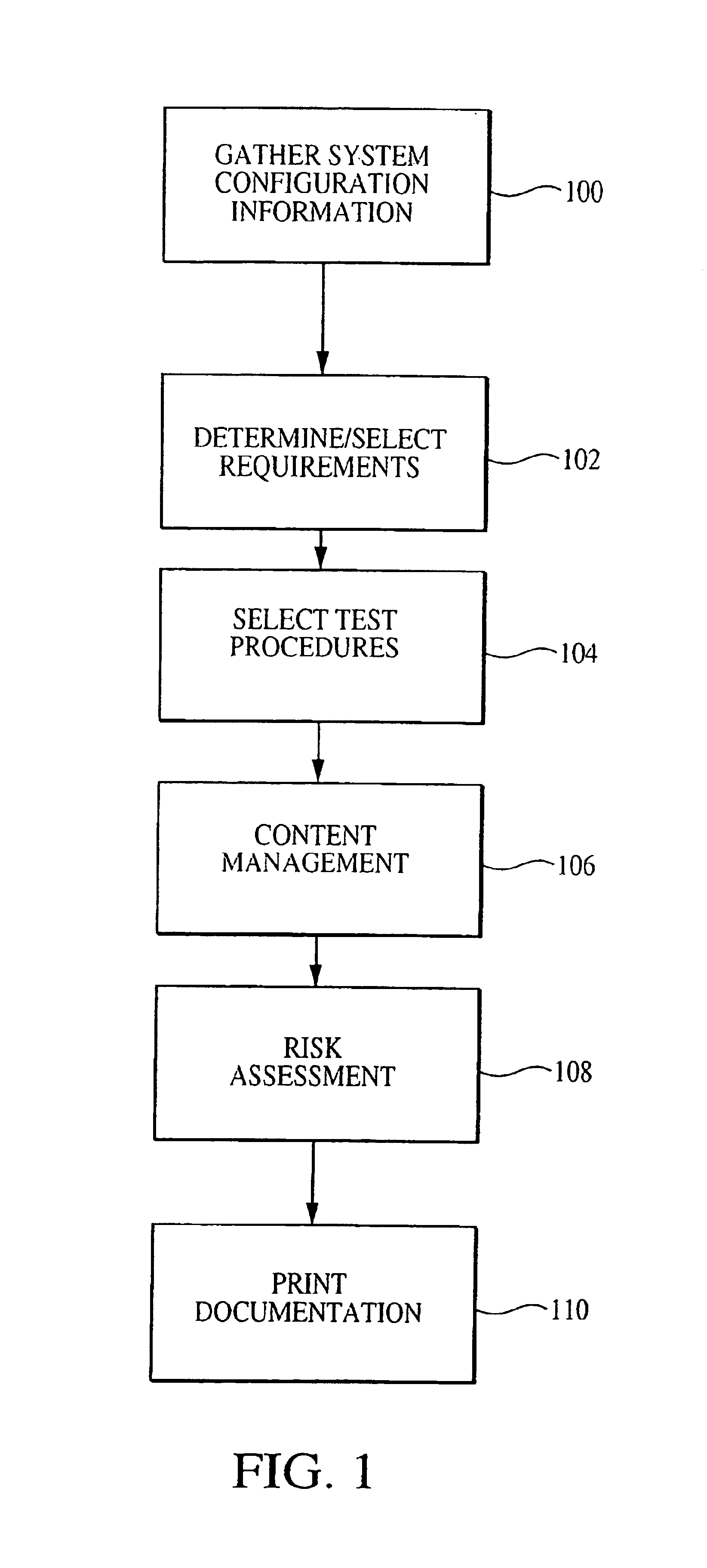
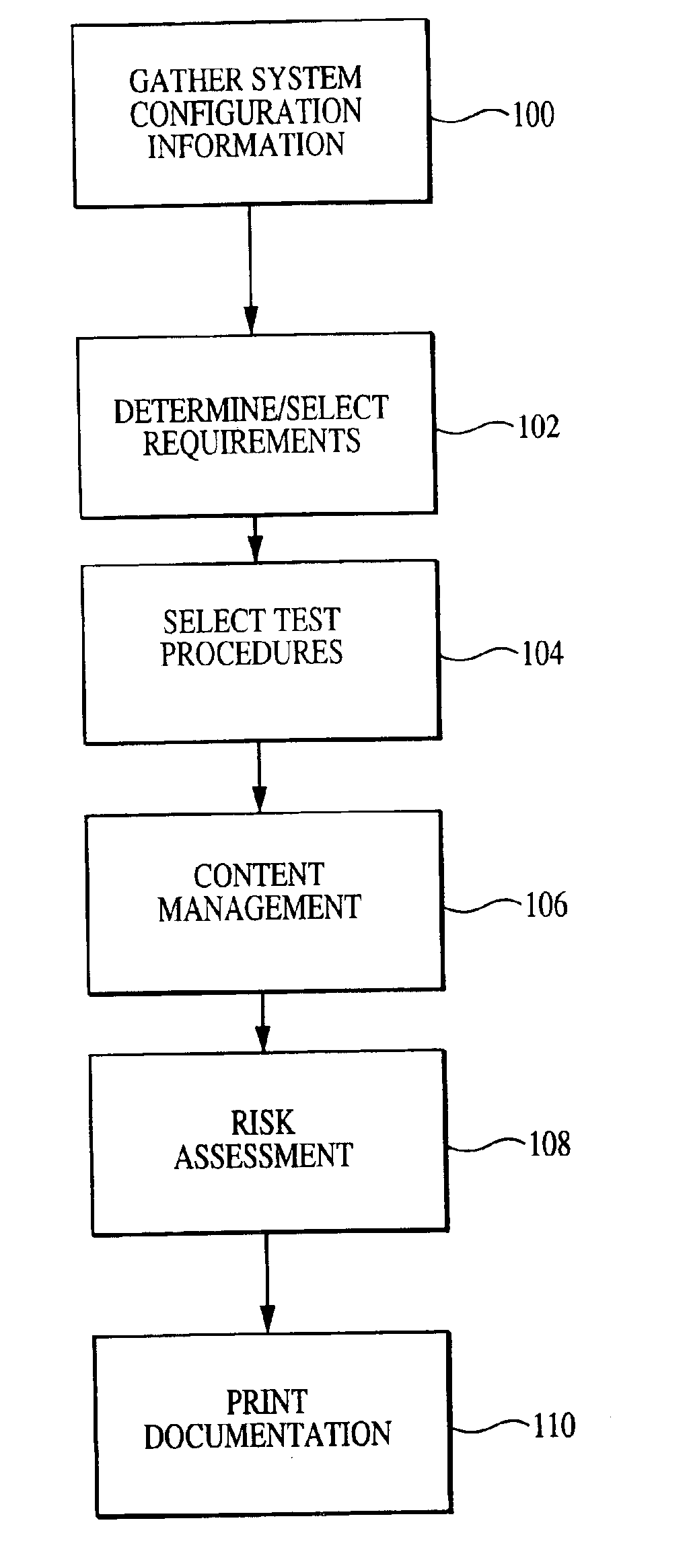
Enhanced system, method and medium for certifying and accrediting requirements compliance utilizing continuous risk assessment
InactiveUS6980927B2Enhances and facilitates security risk assessmentsMemory loss protectionError detection/correctionTechnical standardComputer-aided
A computer-assisted system, medium and method of providing a risk assessment of a target system. The method includes electronically scanning, on a predetermined basis, hardware and / or software characteristics of components within a target system to obtain and store target system configuration information, receiving and storing target system operational environment information, using information collected in the scanning and receiving steps to select one or more security requirements in accordance with the at least one predefined standard, regulation and / or requirement, selecting one or more test procedures used to determine target system compliance with the security requirements, and producing a risk assessment of the target system.
Owner:TELOS CORP
System and method for quantifying the dynamic response of a target system
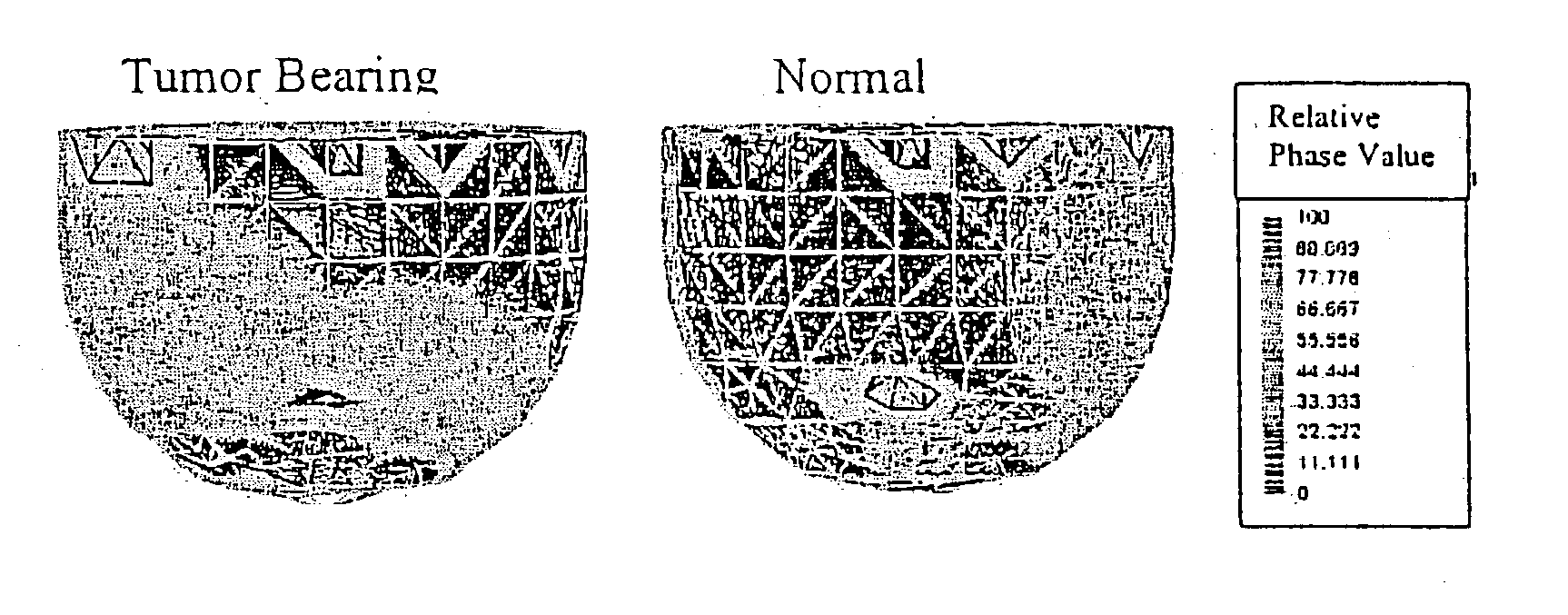
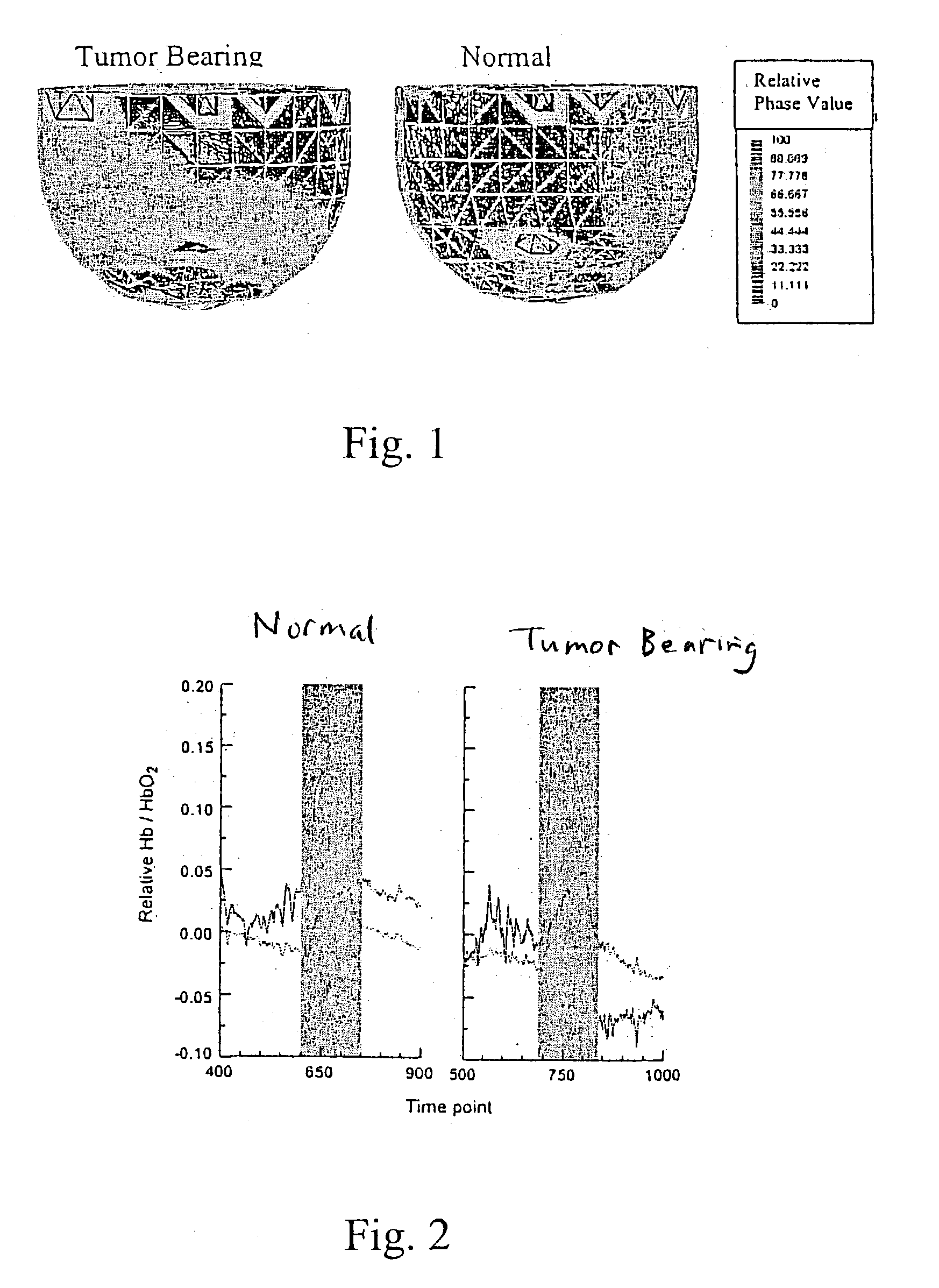
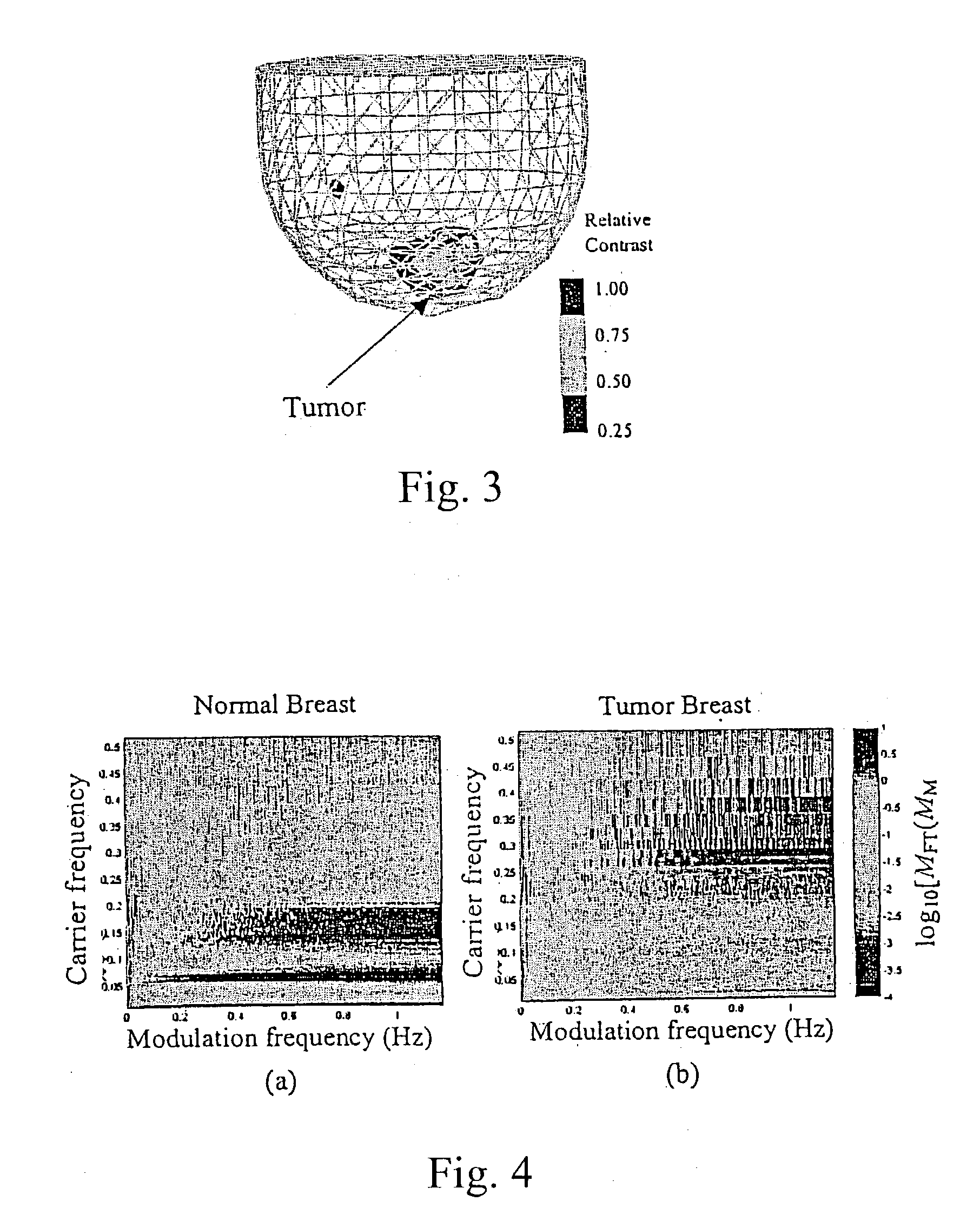
A time series of optical tomography data is obtained for a target tissue site in a human (or animal), using an optical wavelength, such as near infrared, at which hemoglobin is absorptive, to observe properties of the vasculature of the human. The data may be compared to baseline data of a corresponding tissue site, e.g., from a healthy human, or from another, corresponding tissue site of the human. For example, a suspected cancerous breast of a human may be compared to a known healthy breast to detect differences in the vasculature. Measures may be made of flow, oxygen supply / demand imbalance, and evidence of altered regulation of the peripheral effector mechanism. The function of the target tissue site may be analyzed, along with the coordinated interaction between multiple sites of the target system. A provocation may be administered to identify surrogate markers of an underlying state or process.
Owner:US DEPT OF HEALTH & HUMAN SERVICES
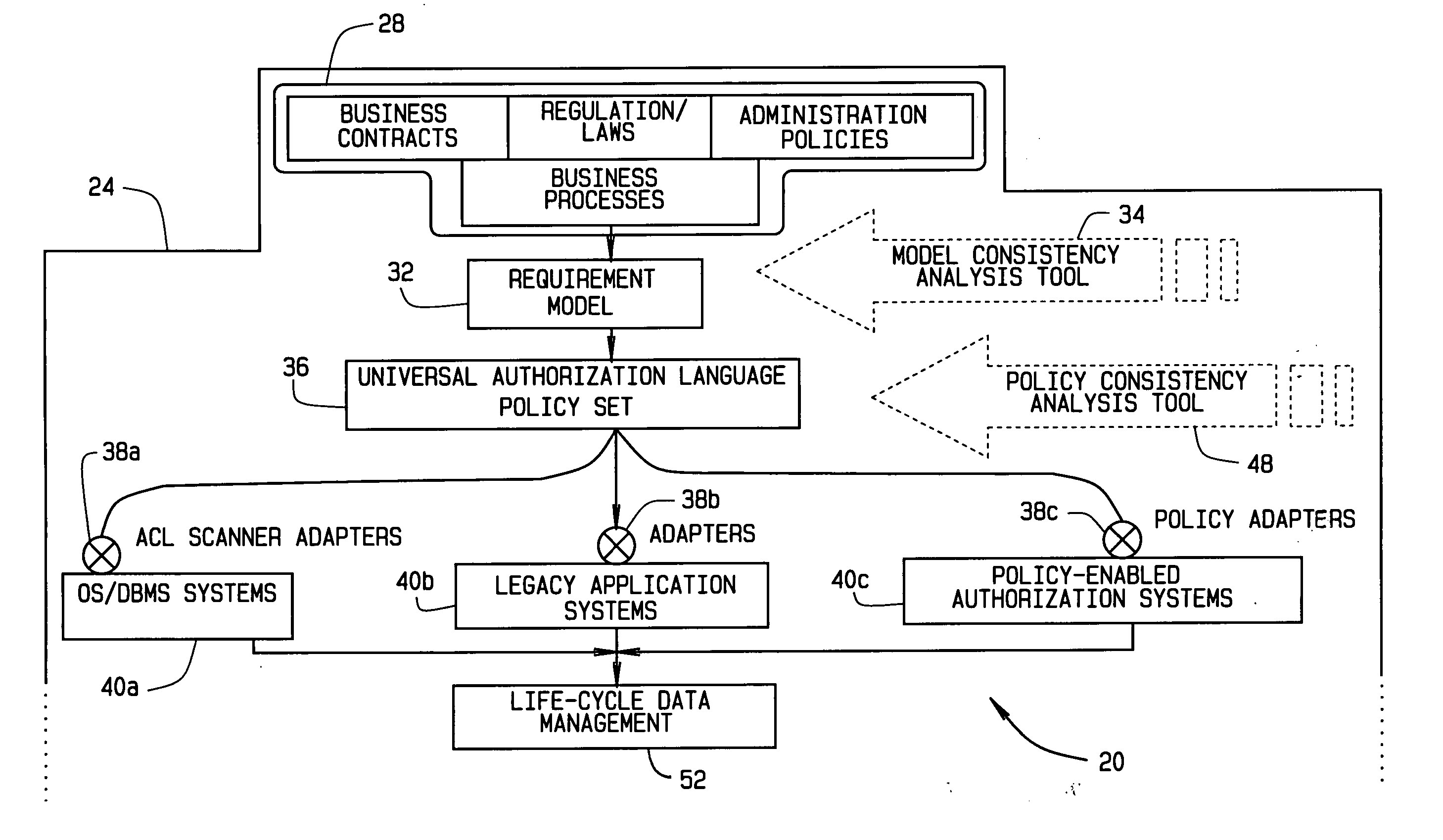
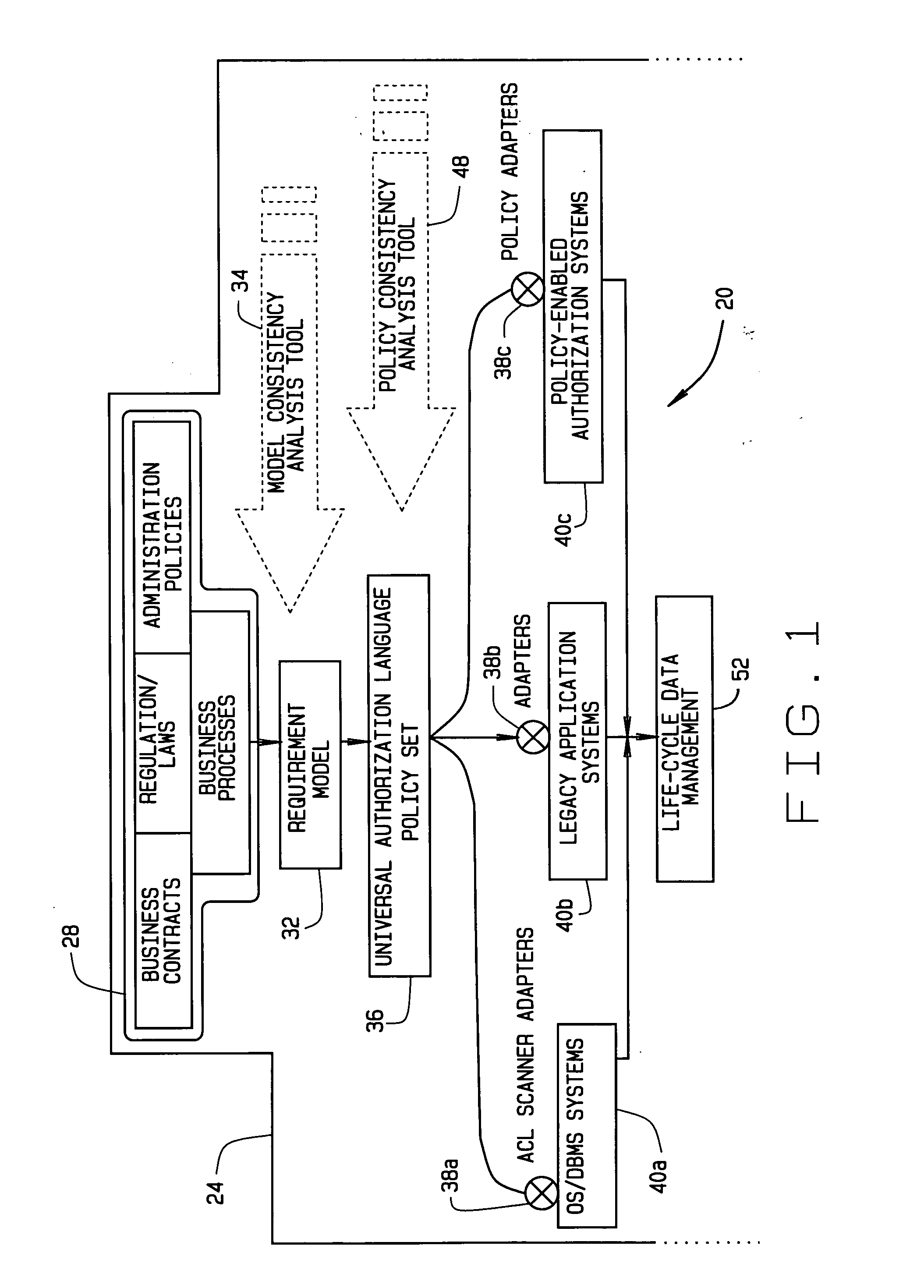
Implementing access control policies across dissimilar access control platforms
ActiveUS20070056019A1Digital data processing detailsAnalogue secracy/subscription systemsSet representationGoal system
A method of implementing access control requirements to control access to a plurality of system resources. The requirements are modeled as contents of security policies. The security policy contents are integrated into a policy set. Representations of the integrated policy set are generated, each representation corresponding to a target system that controls access to the resources. The policy set representation(s) are integrated with the corresponding target system(s) to implement the policy set. This method makes it possible to implement high-level security requirements correctly and consistently across systems of a system-of-systems (SoS) and / or distributed system.
Owner:THE BOEING CO
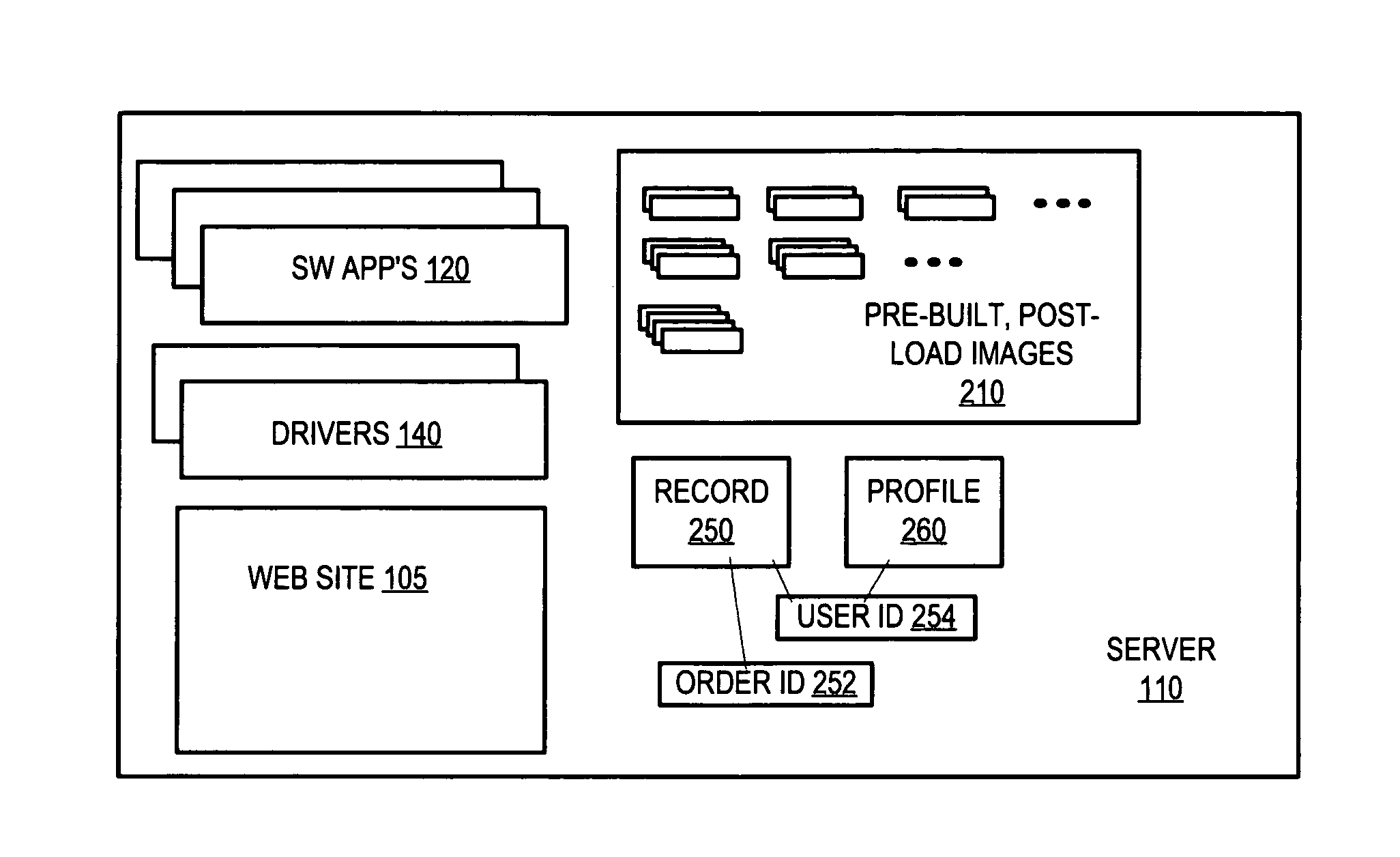
Method, apparatus and computer program product for deploying software via post-load images
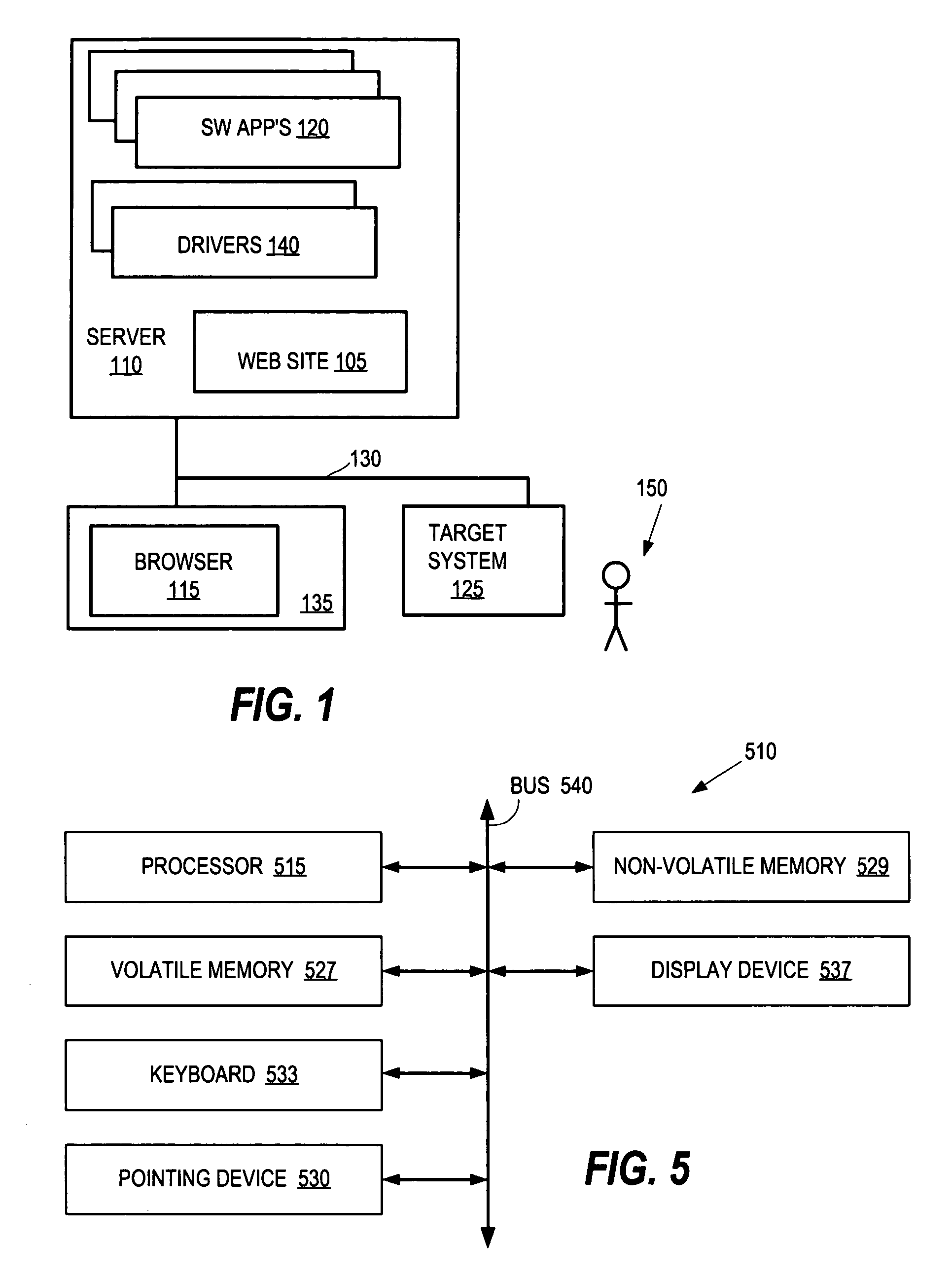
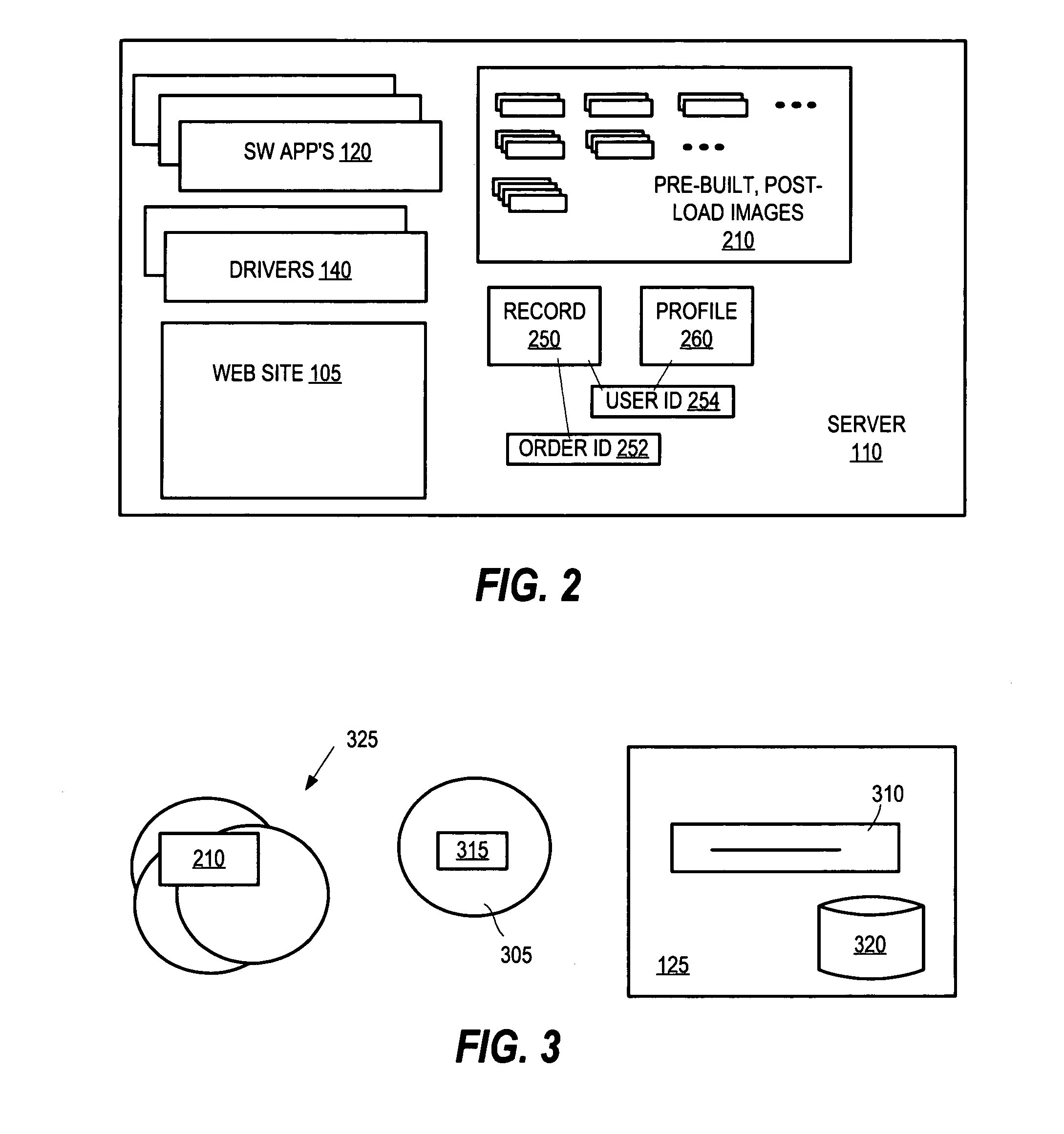
A method for deploying software includes providing a Web site on a server coupled to a network for presenting a user with an interface. The server has an array of post-load images stored thereon for combinations of the software and hardware that the user may select. The server receives a user selection of software applications for deploying to a target computer system and of hardware for the target system and responsively determines what drivers correspond to the indicated hardware. The server then selects a certain one of the post-load images having the software applications that have been selected by the user and has the drivers for the hardware that have been selected by the user.
Owner:ACTIVISION PUBLISHING
Stubbing systems and methods in a data replication environment
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication dath or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
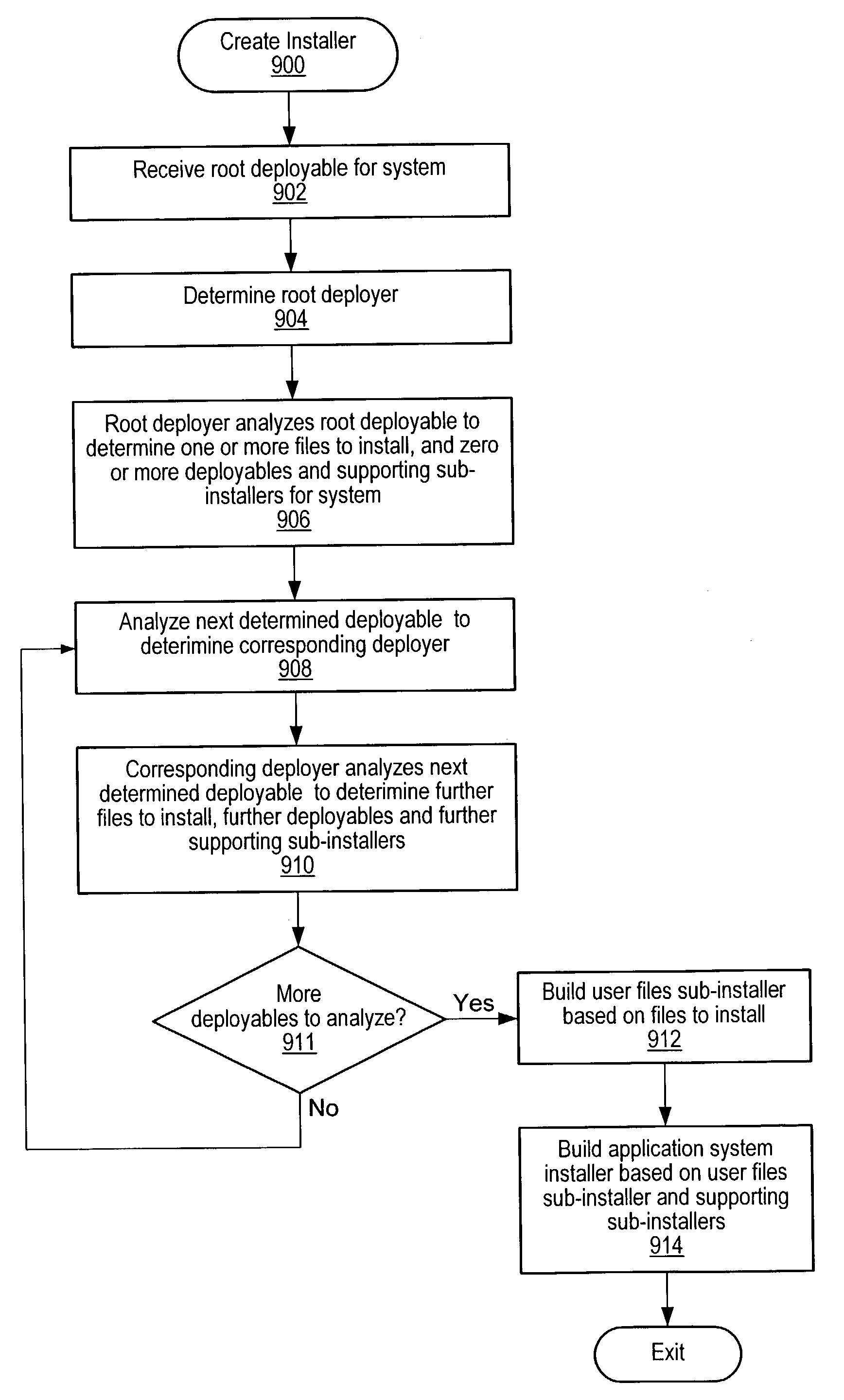
Creation of application system installer
System and method for creating an application system installer. A root deployable for an application system is received, and programmatically analyzed to determine a root deployer. The root deployer is programmatically analyzed to determine zero or more deployables, and one or more files-to-install. For each respective deployable, a respective deployer is programmatically determined that analyzes the respective deployable to determine any further deployables and files-to-install. This process is repeated for each of the further deployables until all deployables for the respective deployable have been determined and analyzed, and all files-to-install have been determined. The application system installer is then generated using the determined files-to-install, where the installer is operable to programmatically deploy the application system onto a target system to perform the function. Determining zero or more deployables may also include determining one or more supporting sub-installers, where the installer is then generated using the determined files-to-install and supporting sub-installers.
Owner:NATIONAL INSTRUMENTS
Systems and methods for performing data replication
ActiveUS8489656B2Easy to operateDigital data information retrievalDigital data processing detailsFile systemData operations
Preparing source data to be replicated in a continuous data replication environment. Certain systems and methods populate a file name database with entries having a unique file identifier descriptor (FID), short name and a FID of the parent directory of each directory or file on a source storage device. Such information is advantageously gathered during scanning of a live file system without requiring a snapshot of the source storage device. The database can be further used to generate absolute file names associated with data operations to be replayed on a destination storage device. Based on the obtained FIDs, certain embodiments can further combine write operations to be replayed on the destination storage device and / or avoid replicating temporary files to the destination system.
Owner:COMMVAULT SYST INC
Stub file prioritization in a data replication system
ActiveUS20110246429A1Digital data information retrievalDigital data processing detailsGoal systemData management
Stubbing systems and methods are provided for intelligent data management in a replication environment, such as by reducing the space occupied by replication data on a destination system. In certain examples, stub files or like objects replace migrated, de-duplicated or otherwise copied data that has been moved from the destination system to secondary storage. Access is further provided to the replication data in a manner that is transparent to the user and / or without substantially impacting the base replication process. In order to distinguish stub files representing migrated replication data from replicated stub files, priority tags or like identifiers can be used. Thus, when accessing a stub file on the destination system, such as to modify replication data or perform a restore process, the tagged stub files can be used to recall archived data prior to performing the requested operation so that an accurate copy of the source data is generated.
Owner:COMMVAULT SYST INC
Systems and methods for providing companion services to customer equipment using an ip-based infrastructure
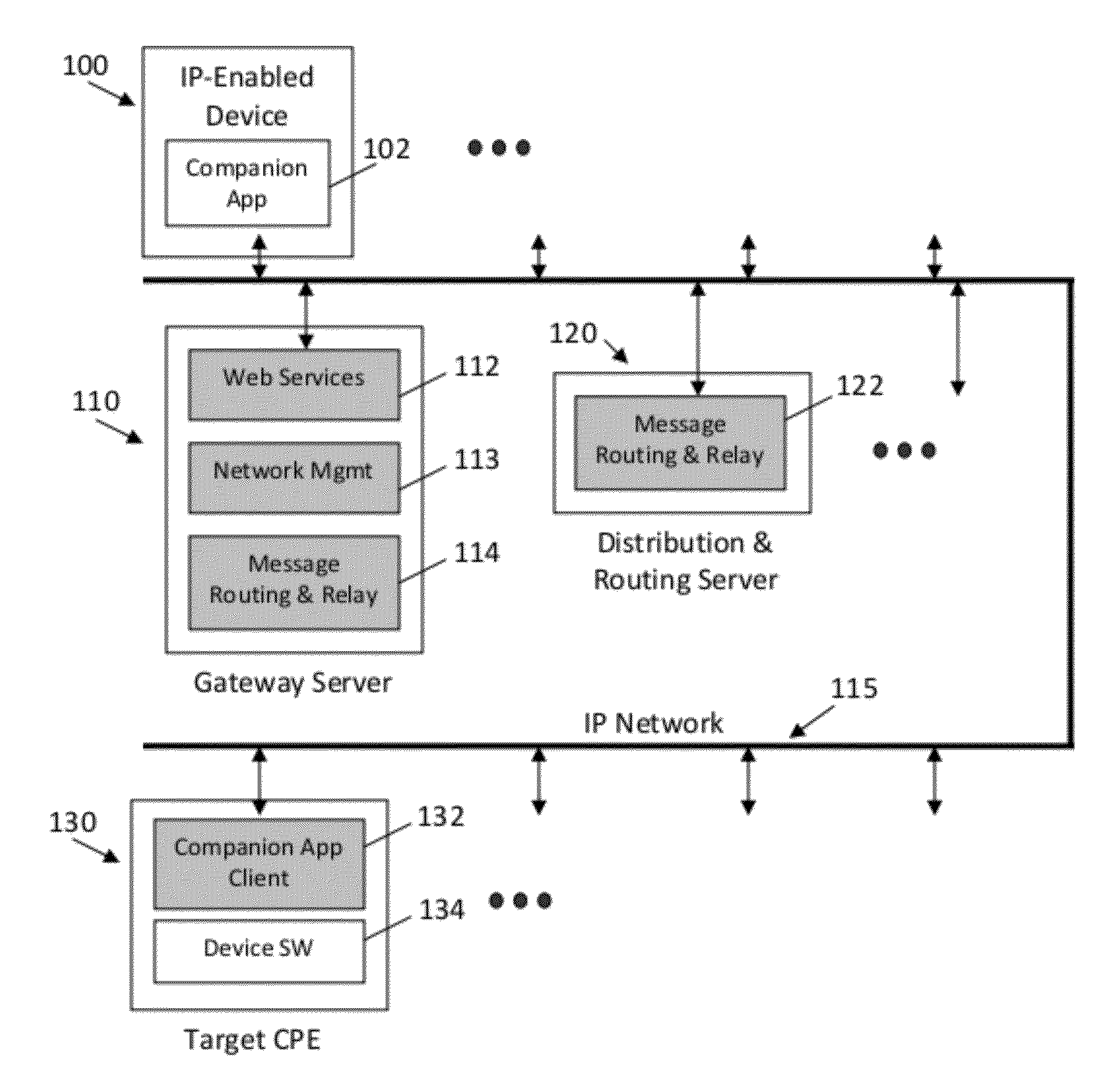
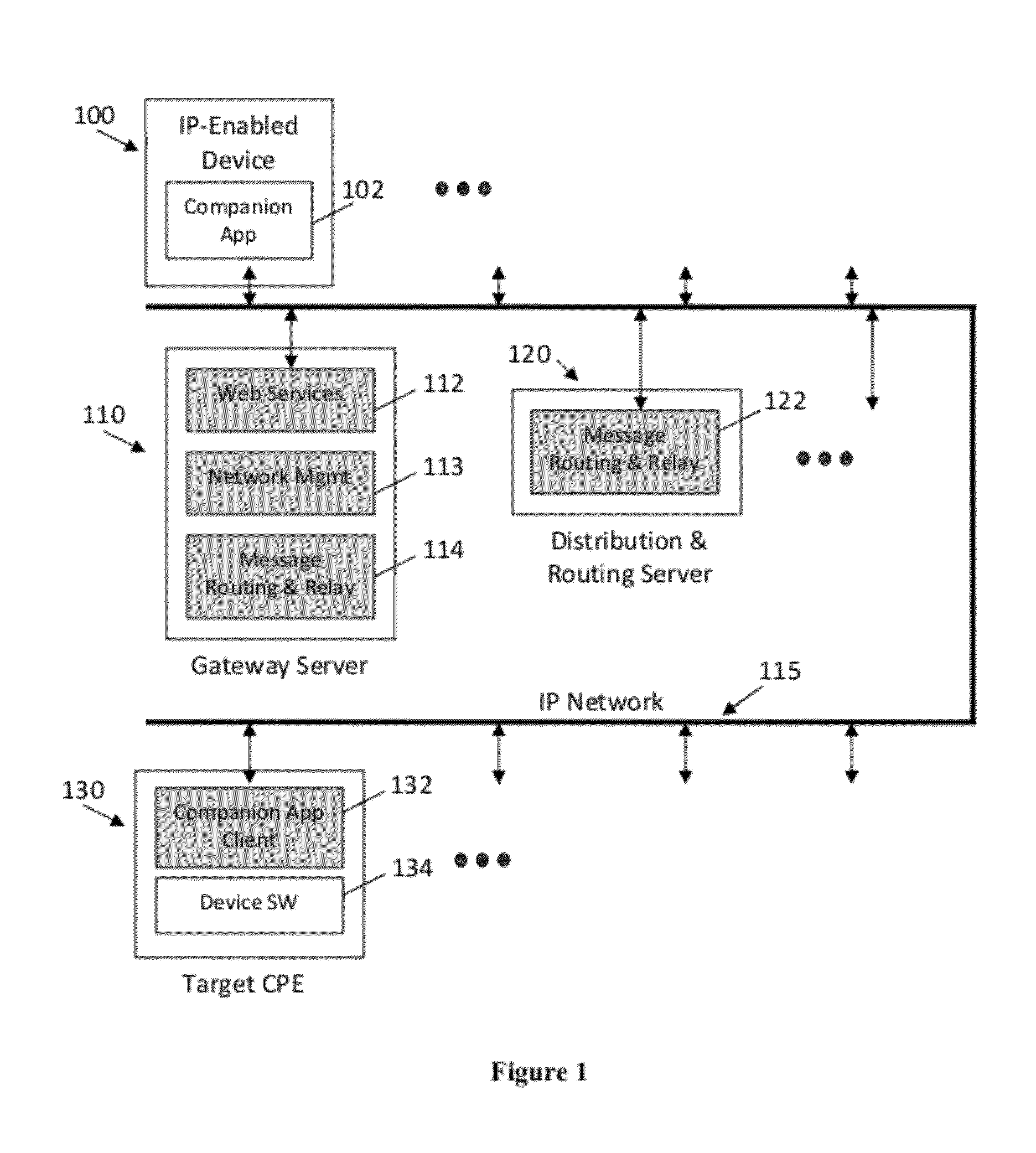
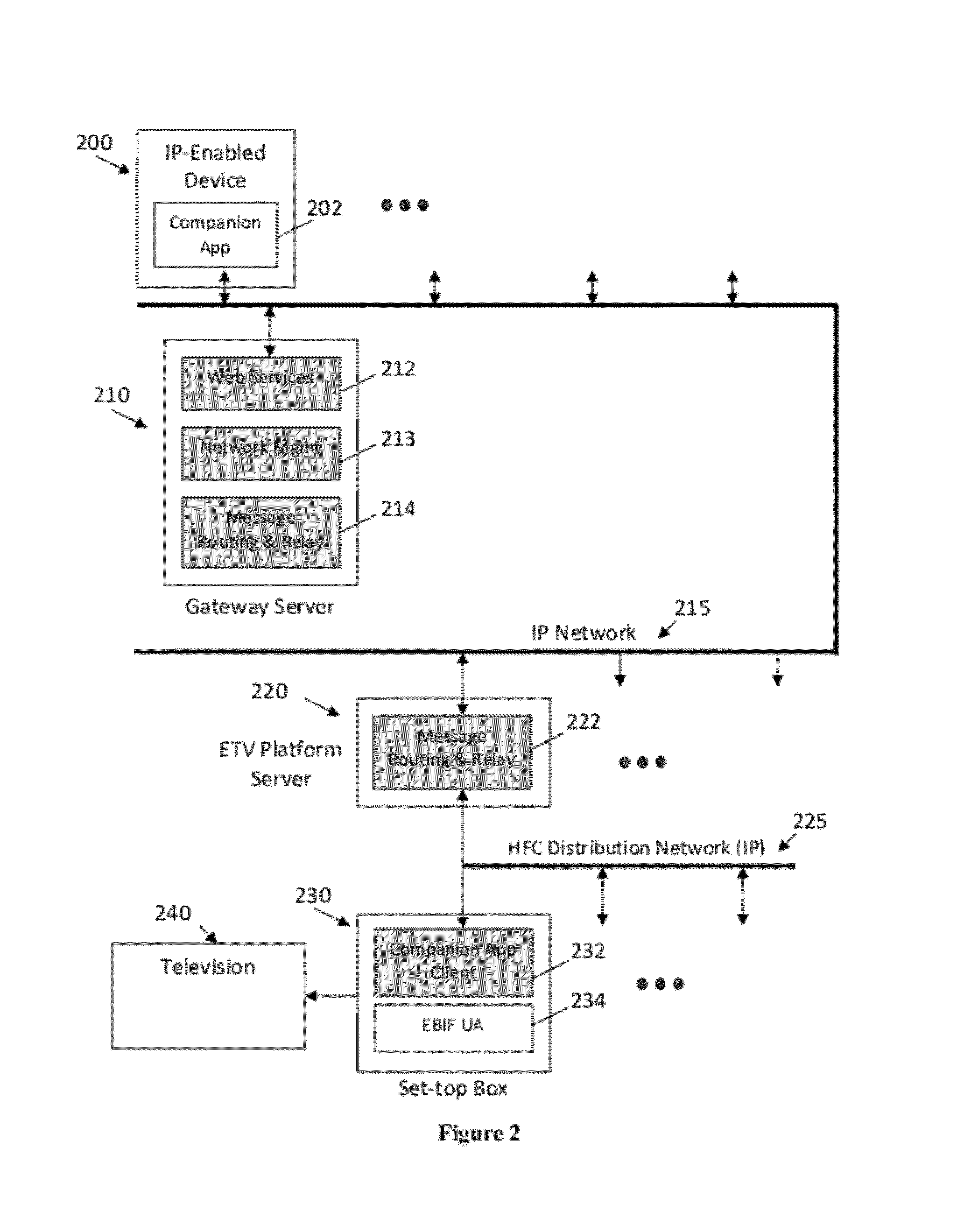
ActiveUS20120096503A1Eliminate needLess riskMultiple digital computer combinationsTwo-way working systemsDigital videoThe Internet
Disclosed herein are systems and methods for providing companion services to customer premises equipment (CPE) using an IP-based service infrastructure. The infrastructure allows IP-enabled devices such as tablet PCs, smart phones, PDAs, and laptop computers to provide supplementary services to target systems and devices located at customer premises. Target systems and devices (CPE) may be TVs, PCs, set-top boxes, digital video recorders, or other electronics. An embodiment is disclosed which allows a mobile device to provide companion services to a television through a link with a set-top box in a cable TV network using the Internet.
Owner:FOURTHWALL MEDIA
Systems and methods for operating system migration
InactiveUS20060026587A1Specific program execution arrangementsMemory systemsOperational systemGoal system
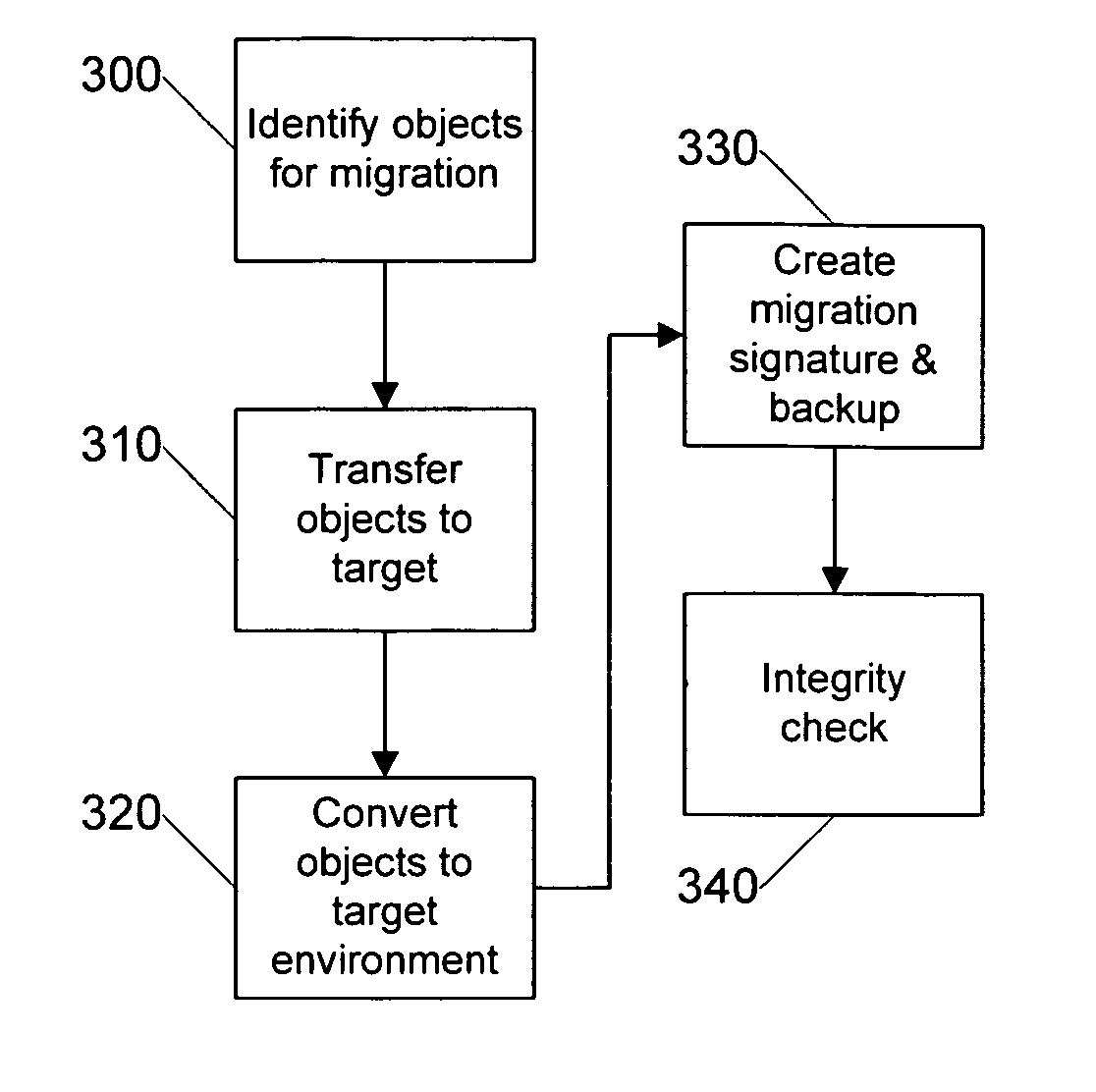
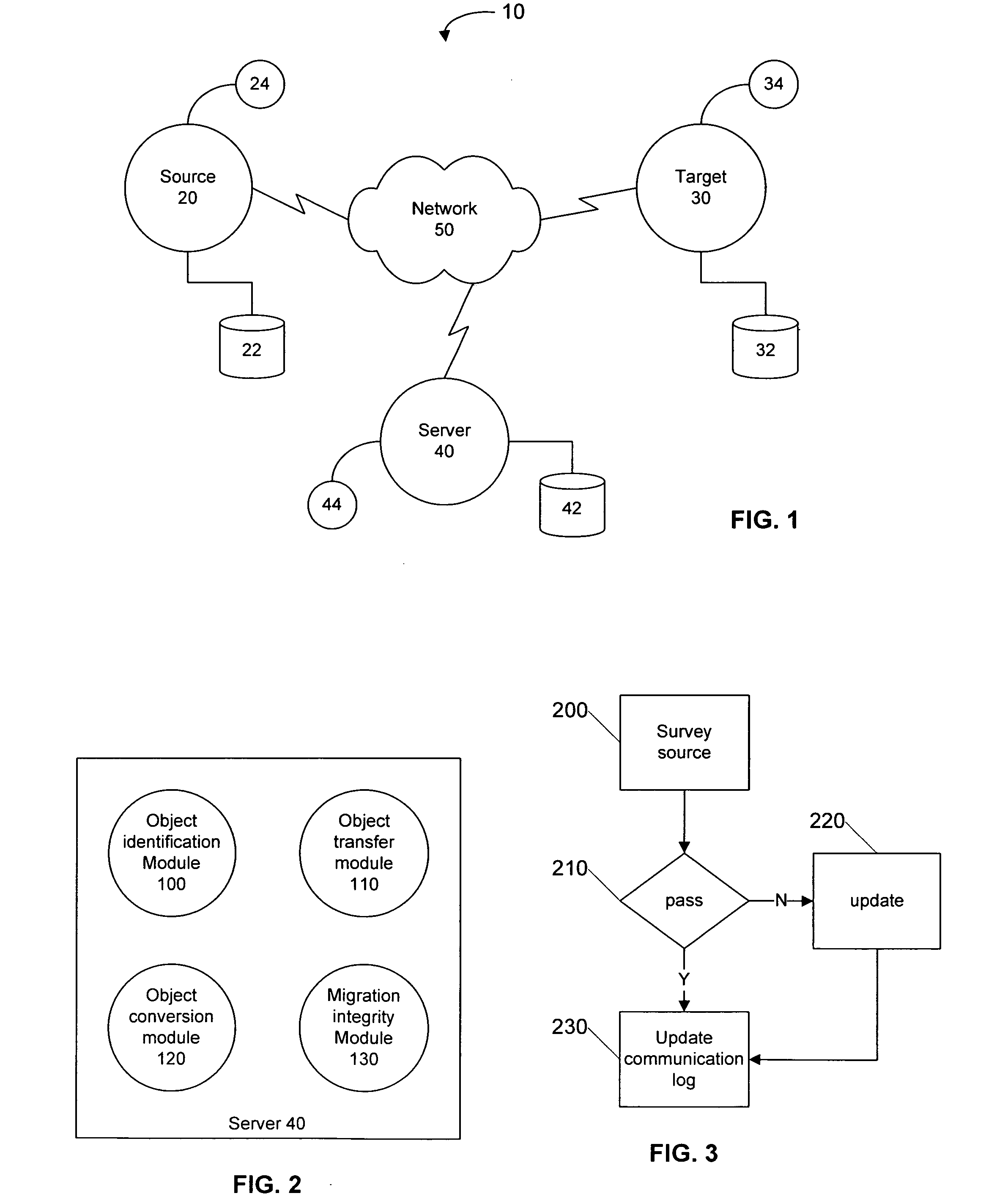
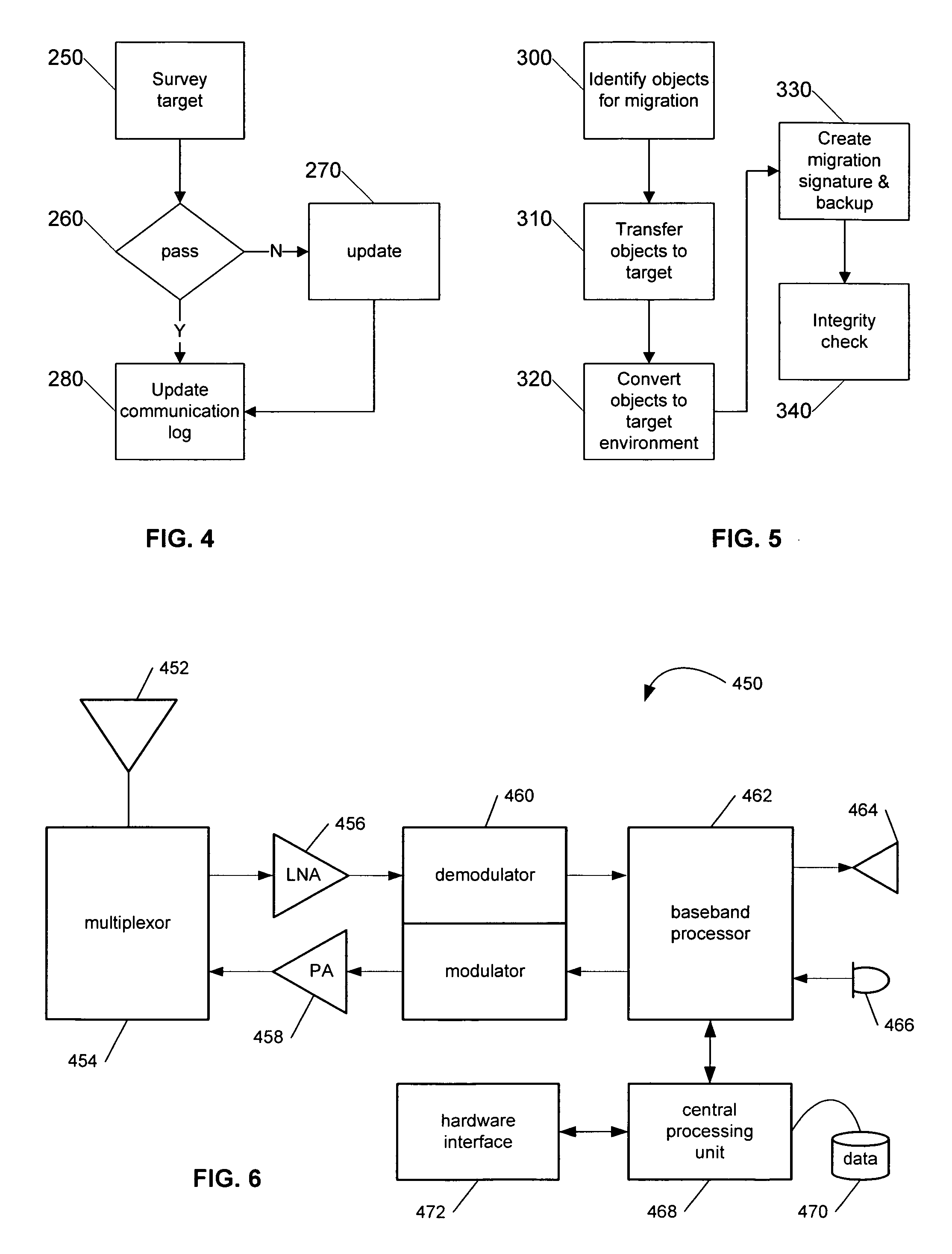
The present invention provides for systems and methods that recognize source and target devices and automatically identify, transfer, and convert user profiles, user settings, data, applications, and other information from the source device with its source operating system to the target device with its target operating system. The system surveys both the source device and the target device to ensure that each device has the appropriate resources and configuration to support the migration. Objects to be migrated are then identified, transferred to the target system and converted as necessary to create a similar environment on the target device as the previous environment on the source device. The post transfer integrity of the target device is then analyzed to ensure that the target system continues to work for its intended purpose and to further ensure that the migrated environment is also operational on the target device.
Owner:MONARCH LX LLC
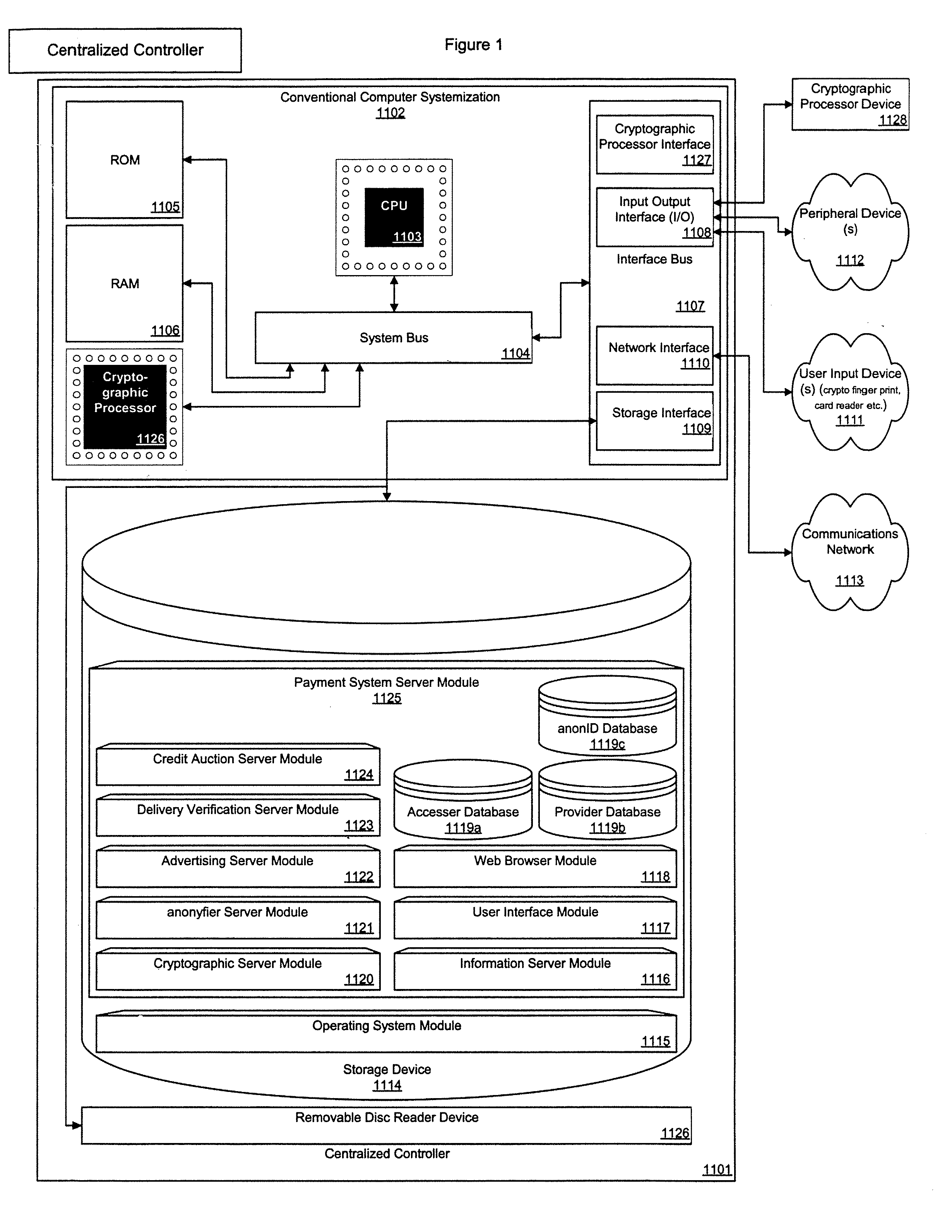
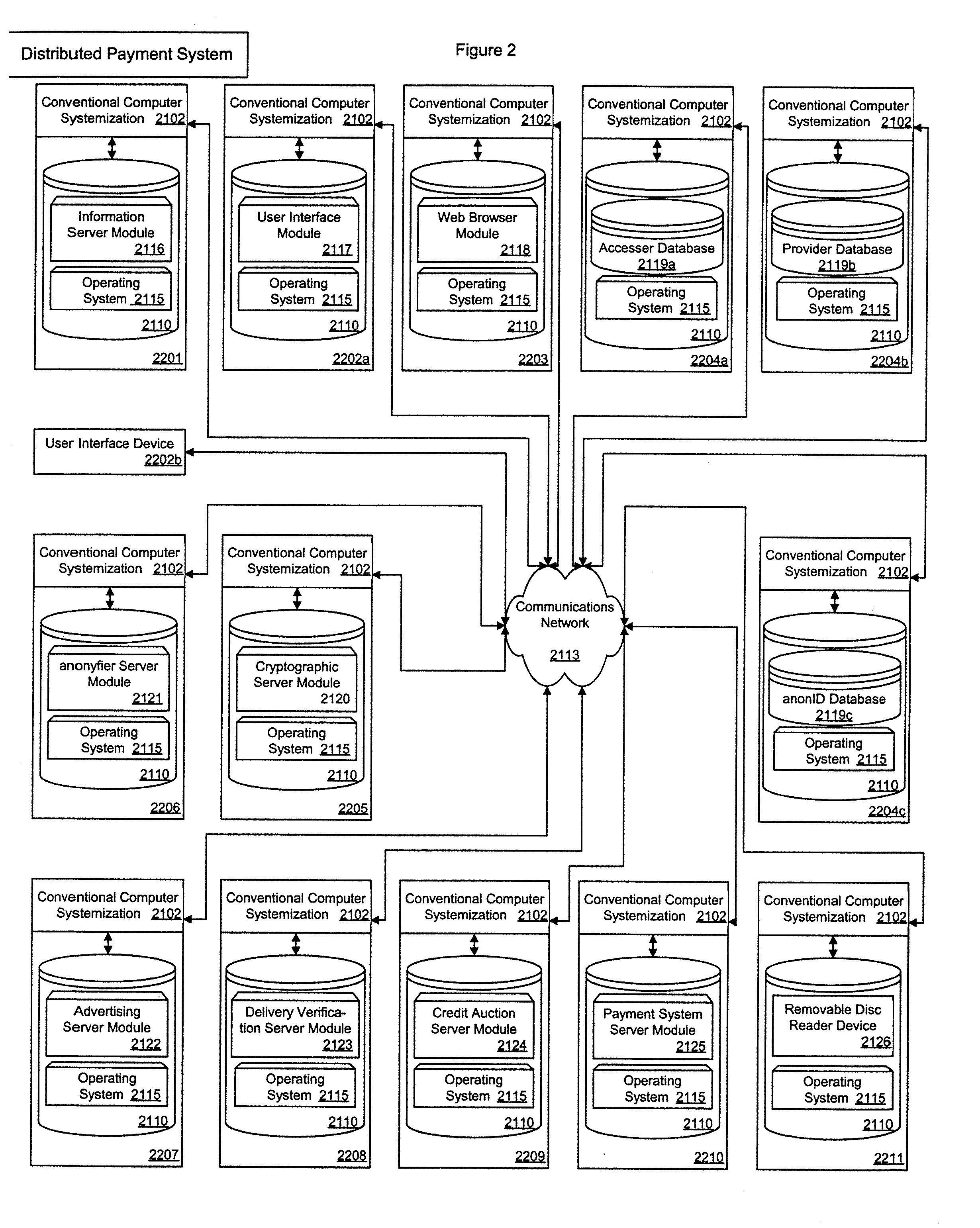
Apparatus, system, and method for an electronic payment system
InactiveUS20070022375A1Reduce transaction cost burdenFinanceDigital computer detailsClosed loopGoal system
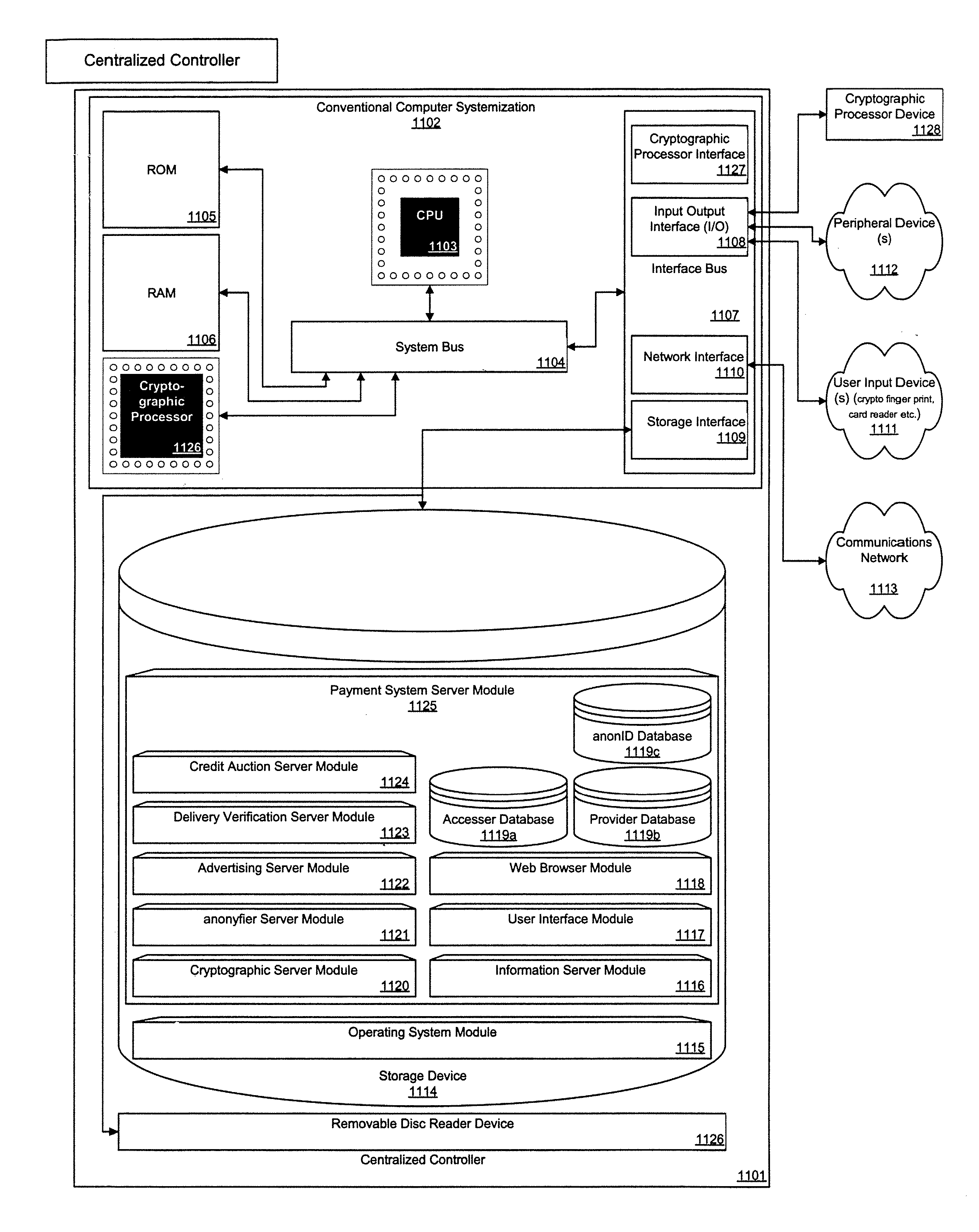
The present contrivance is an apparatus, system, and method for an electronic payment system. The present contrivance provides an electronic payment system that provides advertising for compensation. Further the present contrivance provides an anonyfier that can separate accesser identity information from transaction information. Further, the present contrivance provides an advertising targeting system that determines advertising that does not conflict with providers provisions. Further, the present contrivance provides a payment release system based on delivery verification. Further, the present contrivance provides a credit auction providing accessers and creditors with a dynamic credit market. The present contrivance also provides a system that converts identification cards and other forms of ID into non repudiation devices. The present contrivance also enables the extension of closed loop payment systems.
Owner:WALKER DAVID H
Migration services for systems
Systems and methods for systems migration are provided. A migration engine to perform system migration operations is provided. One or more processors may be configured to execute instructions to perform one or more of the following. Information indicative of one or more migration candidates corresponding to one or more system components in a source system may be collected. A migration strategy may be determined at least partially based on the information indicative of one or more migration candidates. The one or more migration candidates may be mapped to one or more system components of a target system. One or more scripts configured to copy system data and / or application data corresponding to the one or more system components in the source system for migration to the target system may be generated. One or more storage media coupled to the one or more processors may retain the instructions.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com