Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2663 results about "Temporal information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
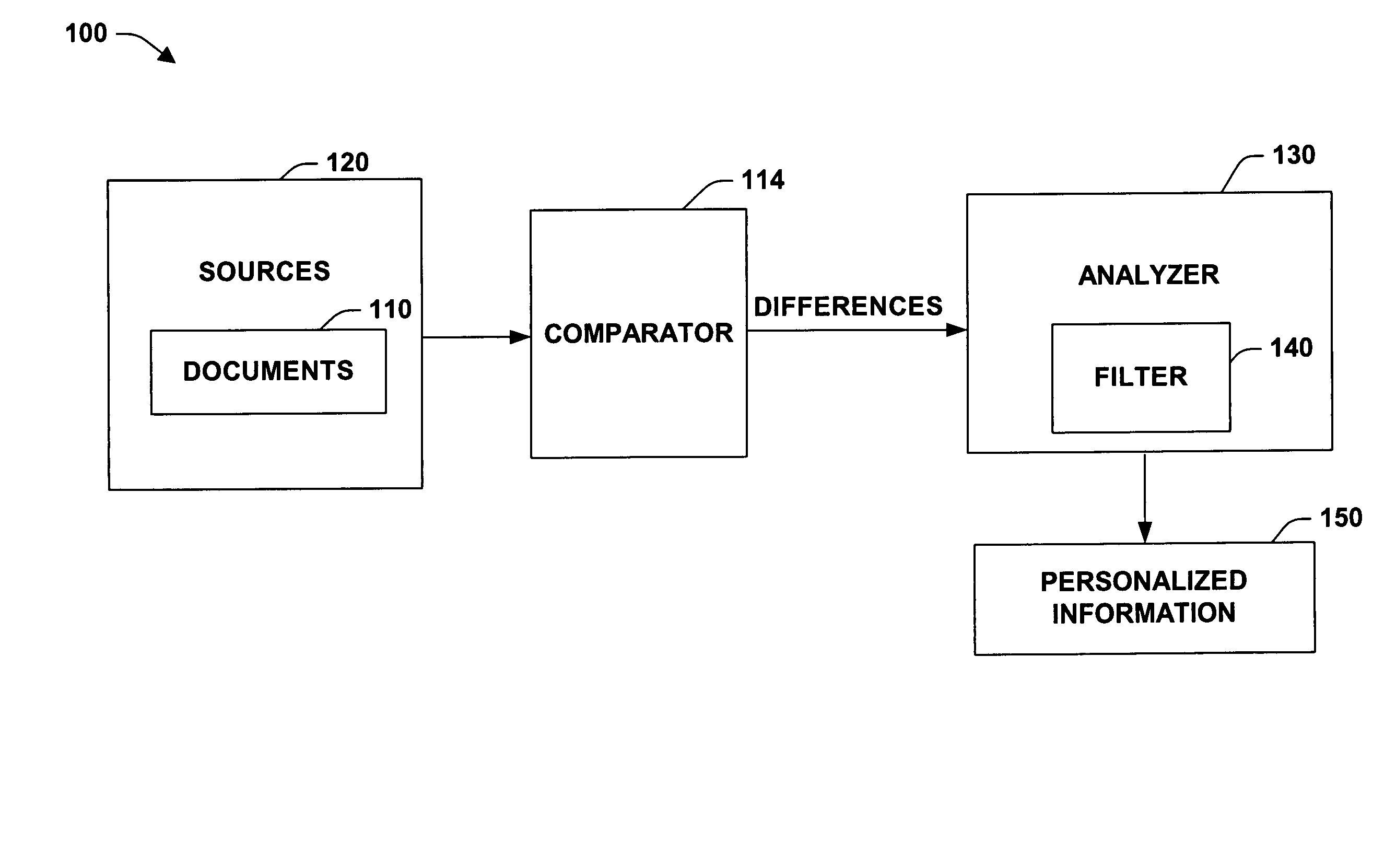
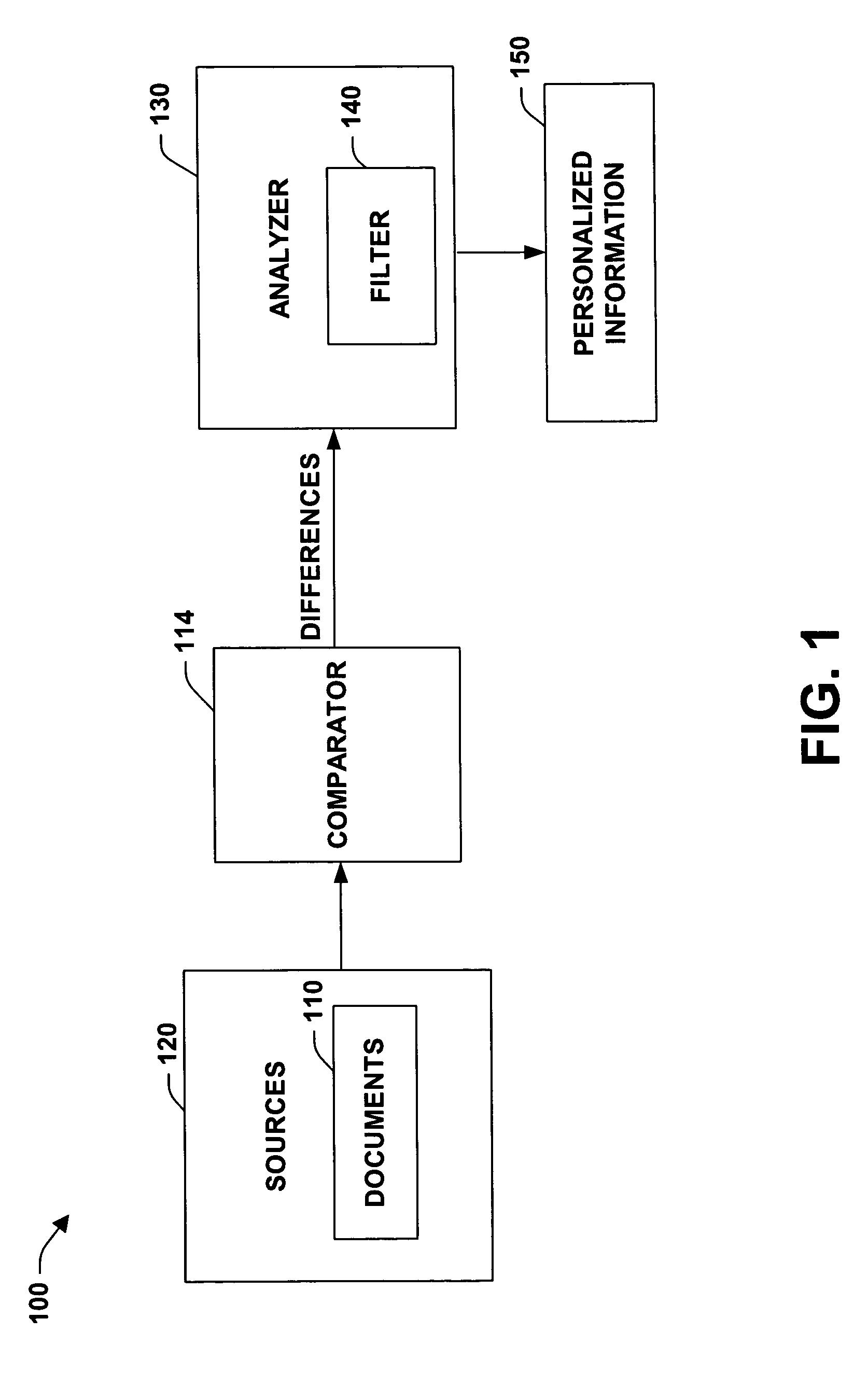
Temporal information is information whose validity is defined by a start and end date.
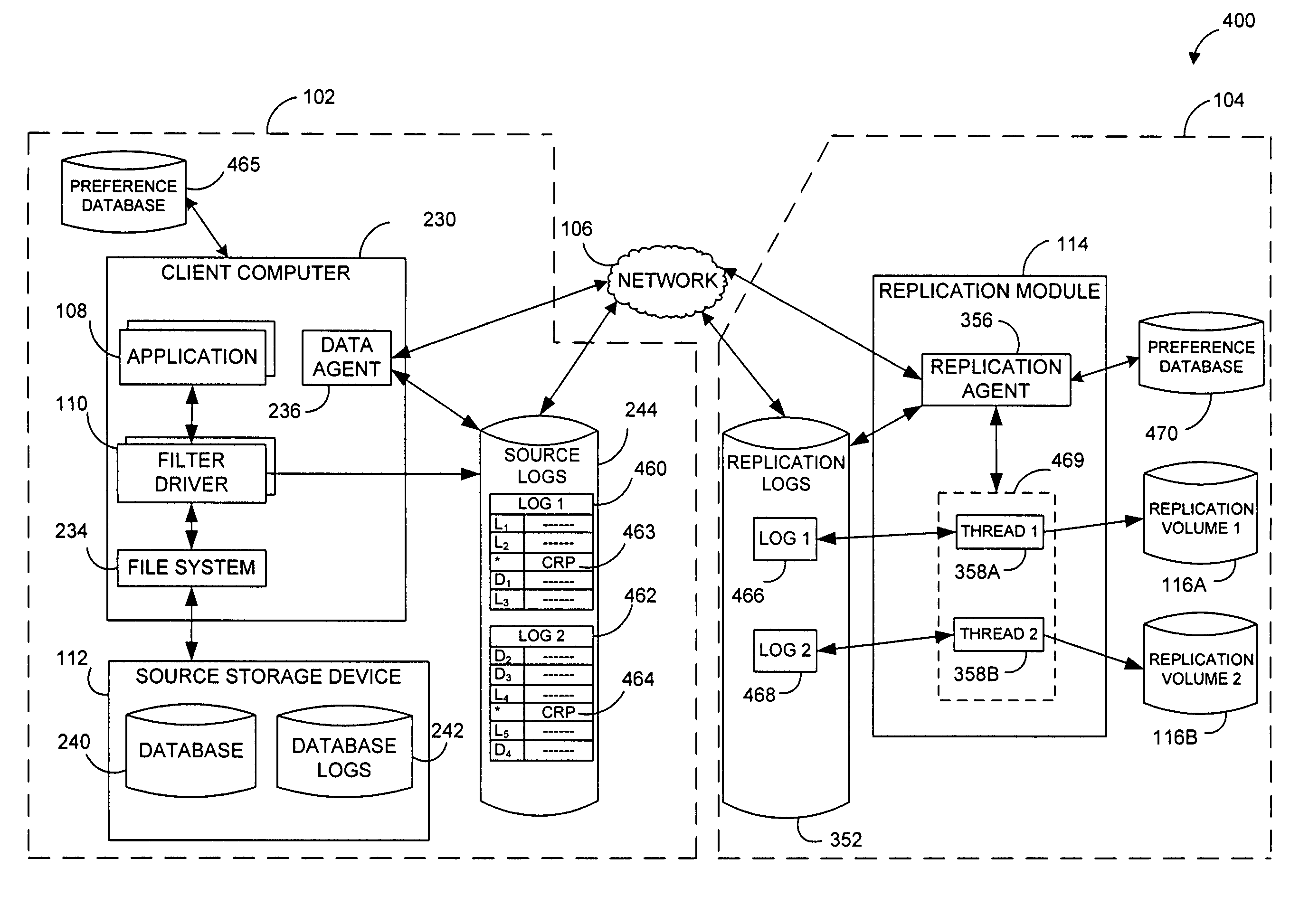
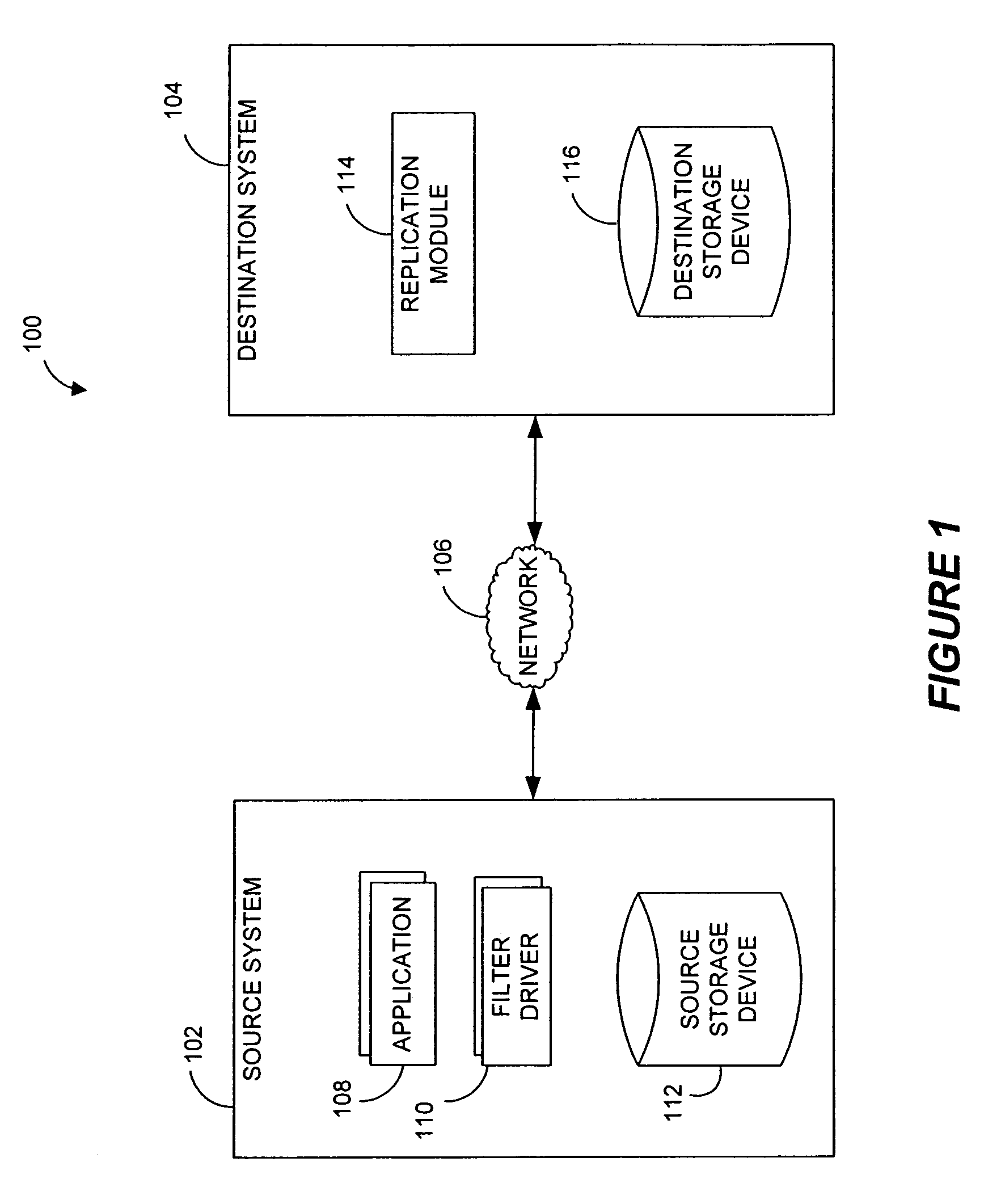
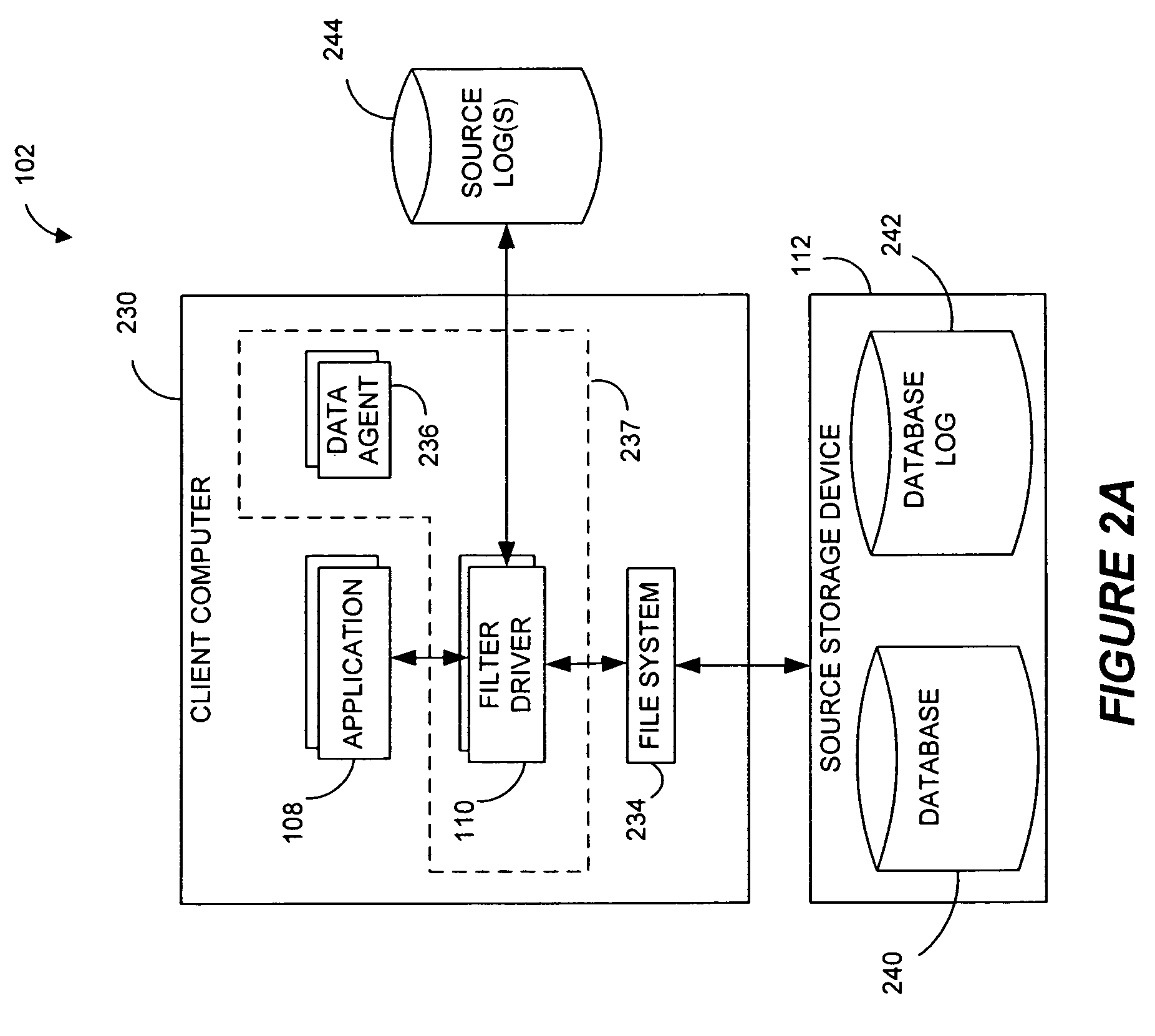
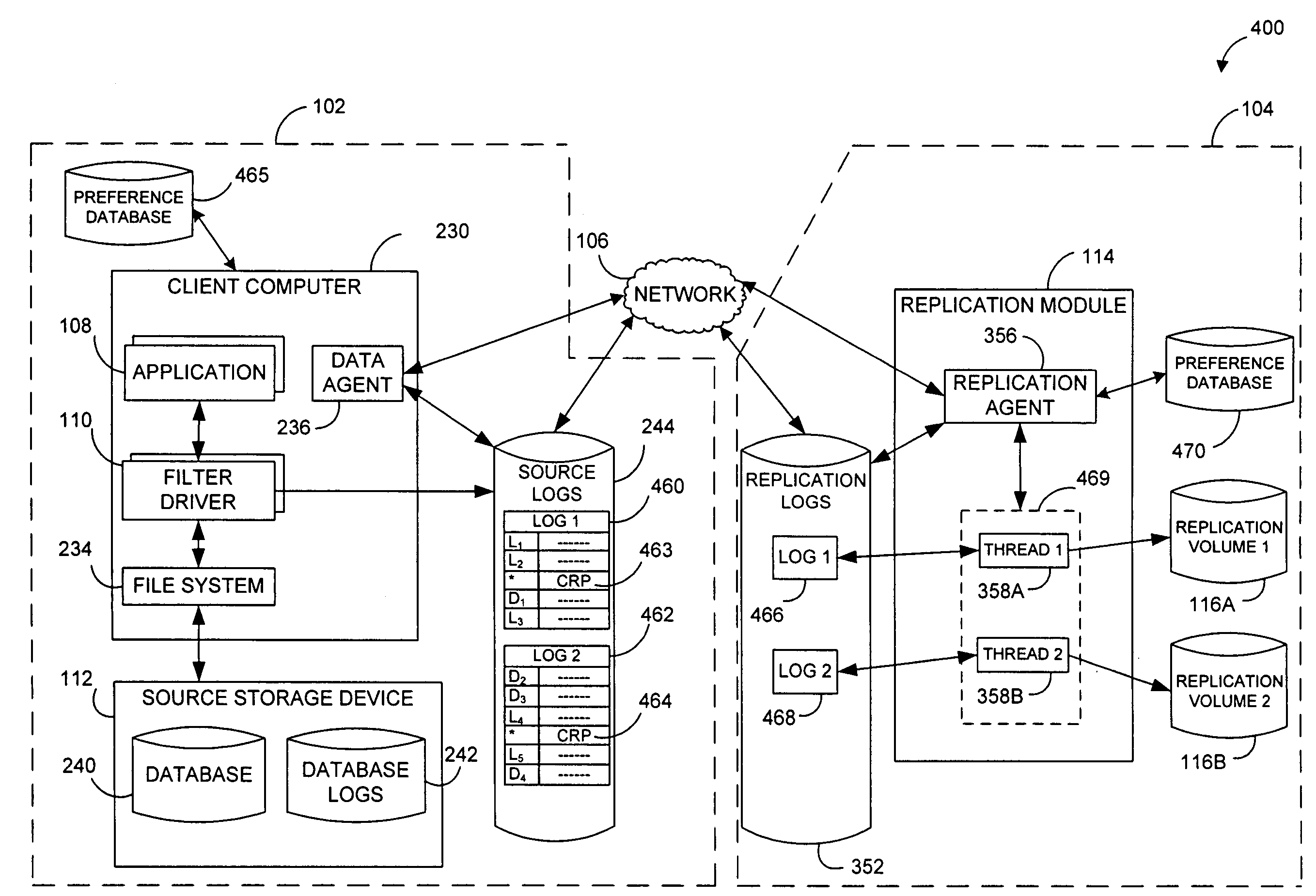
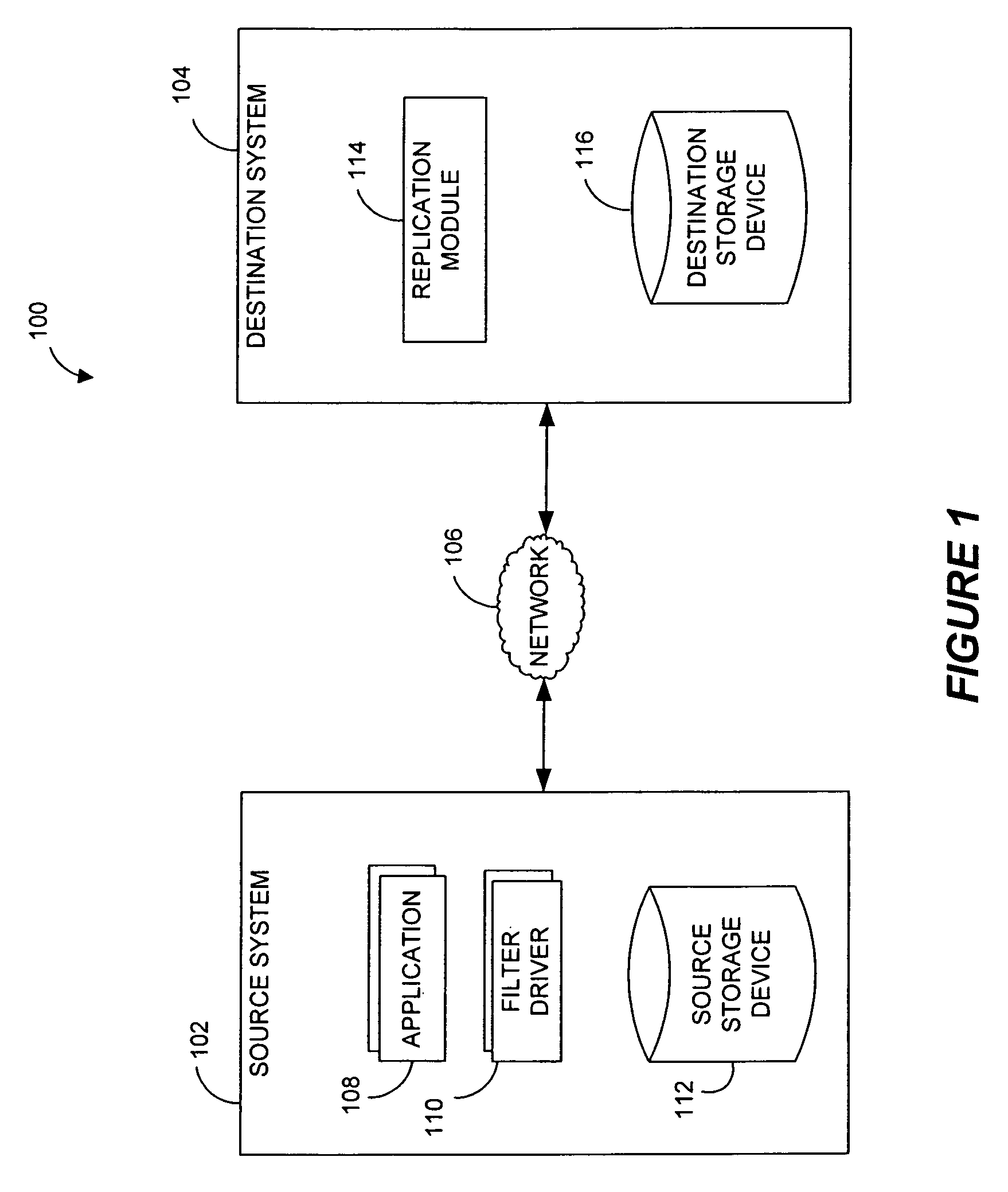
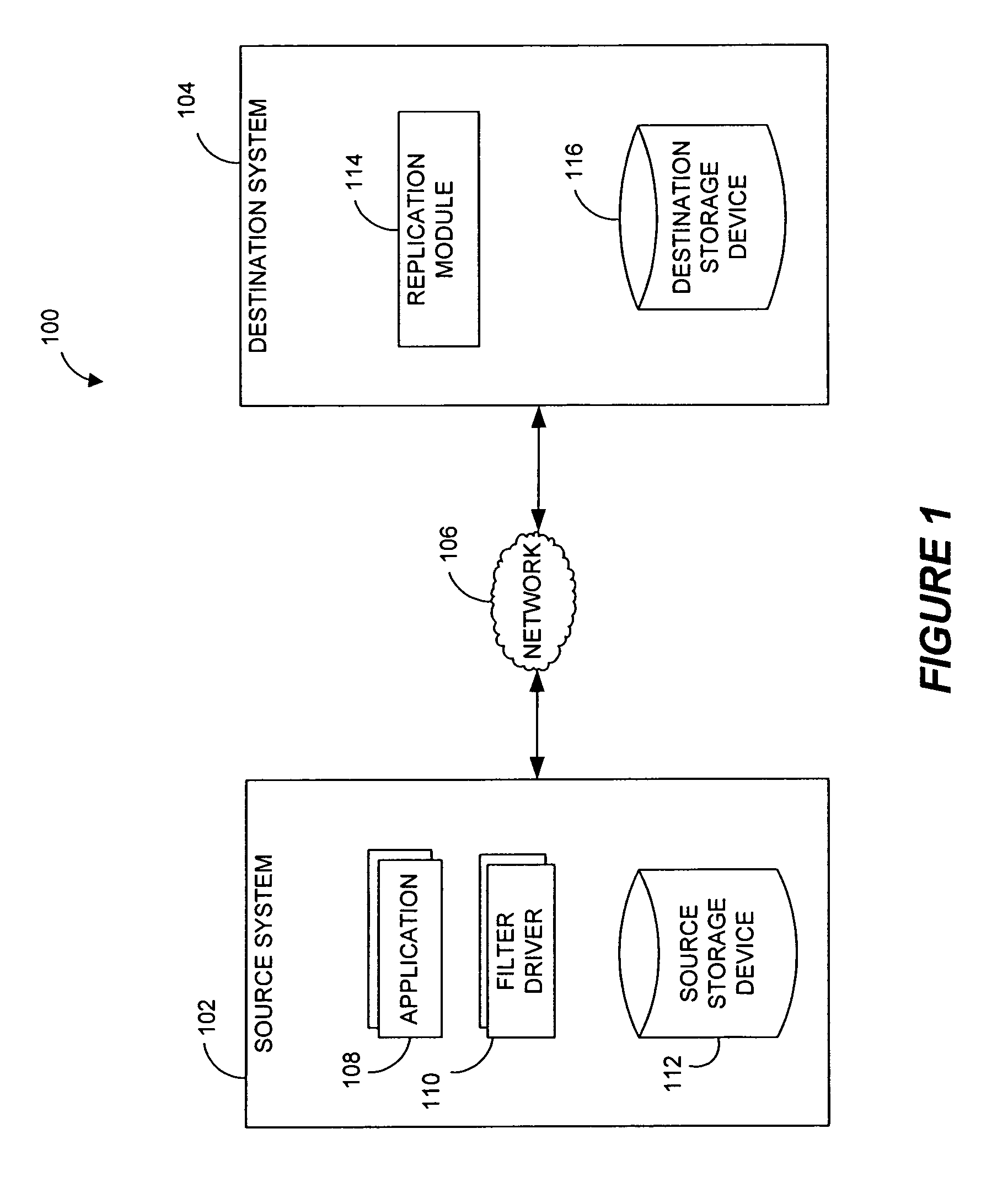
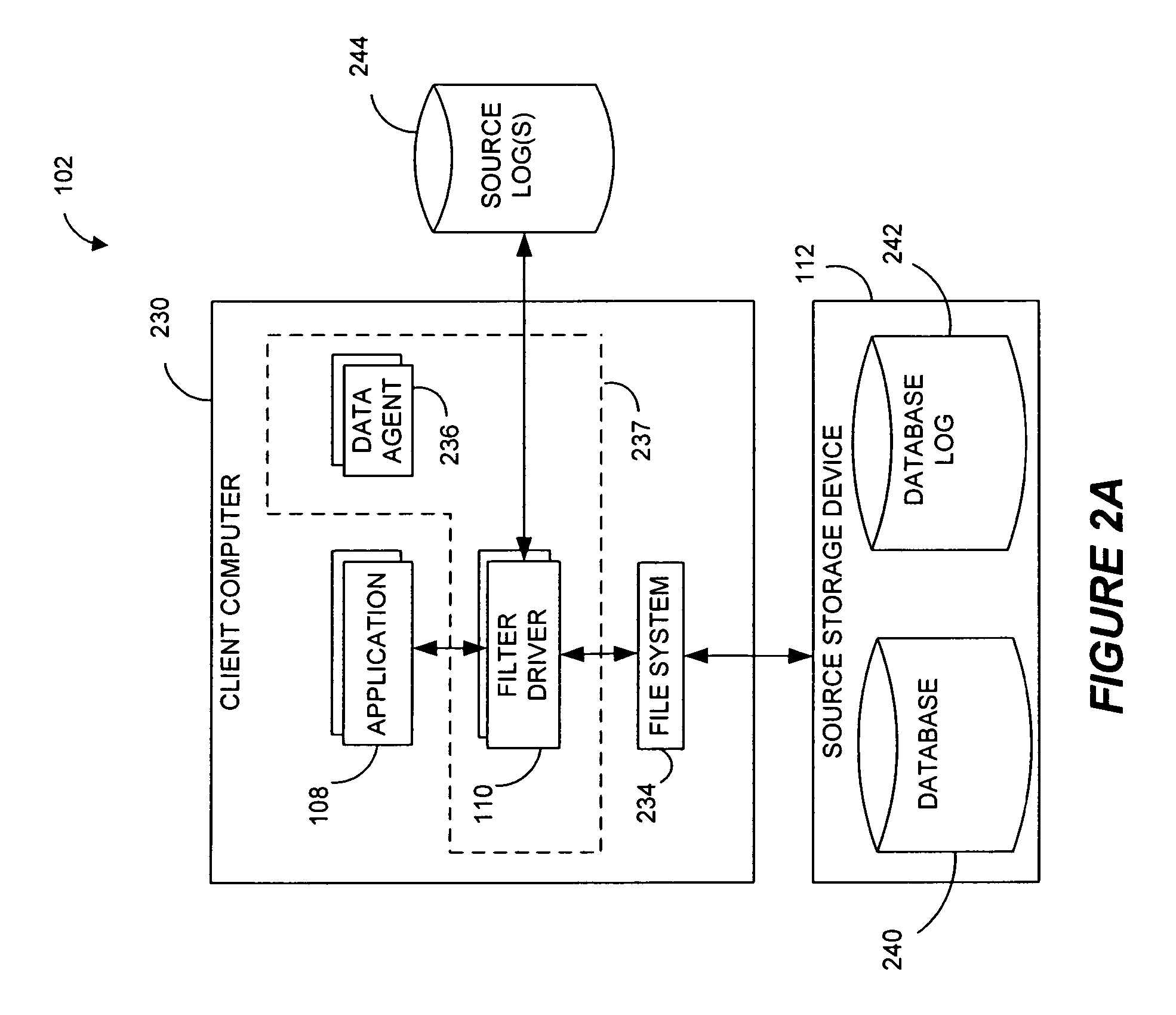
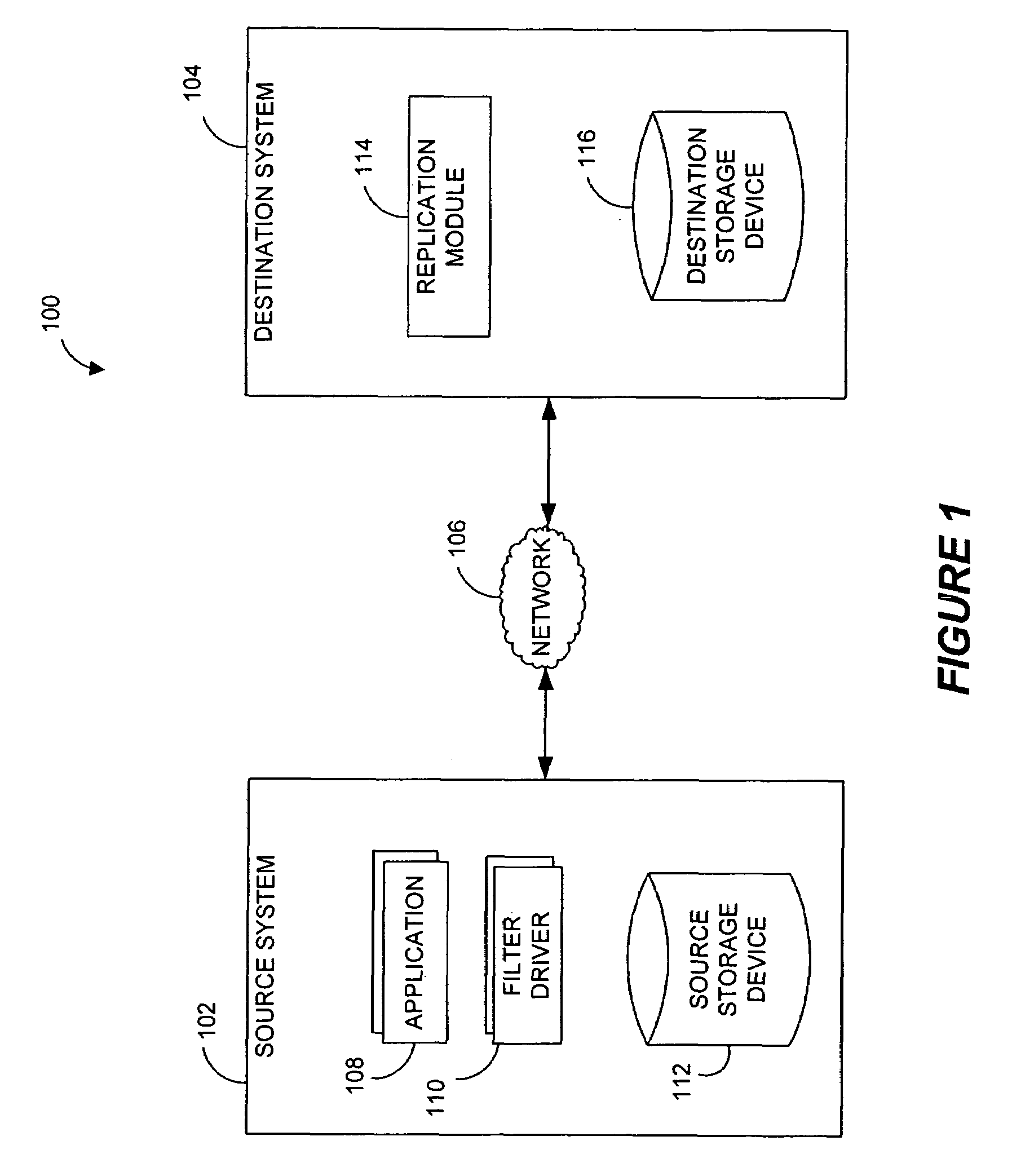
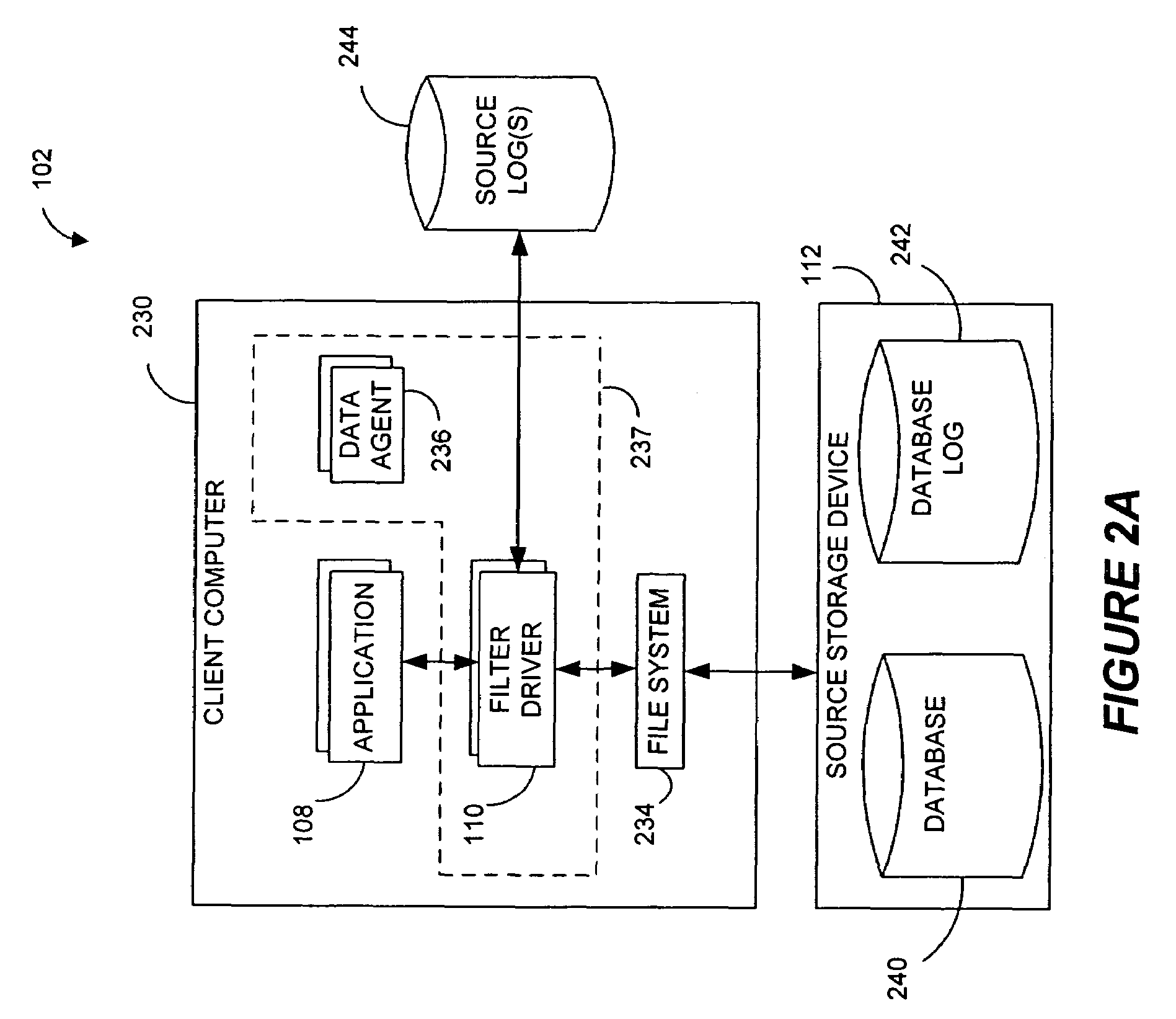
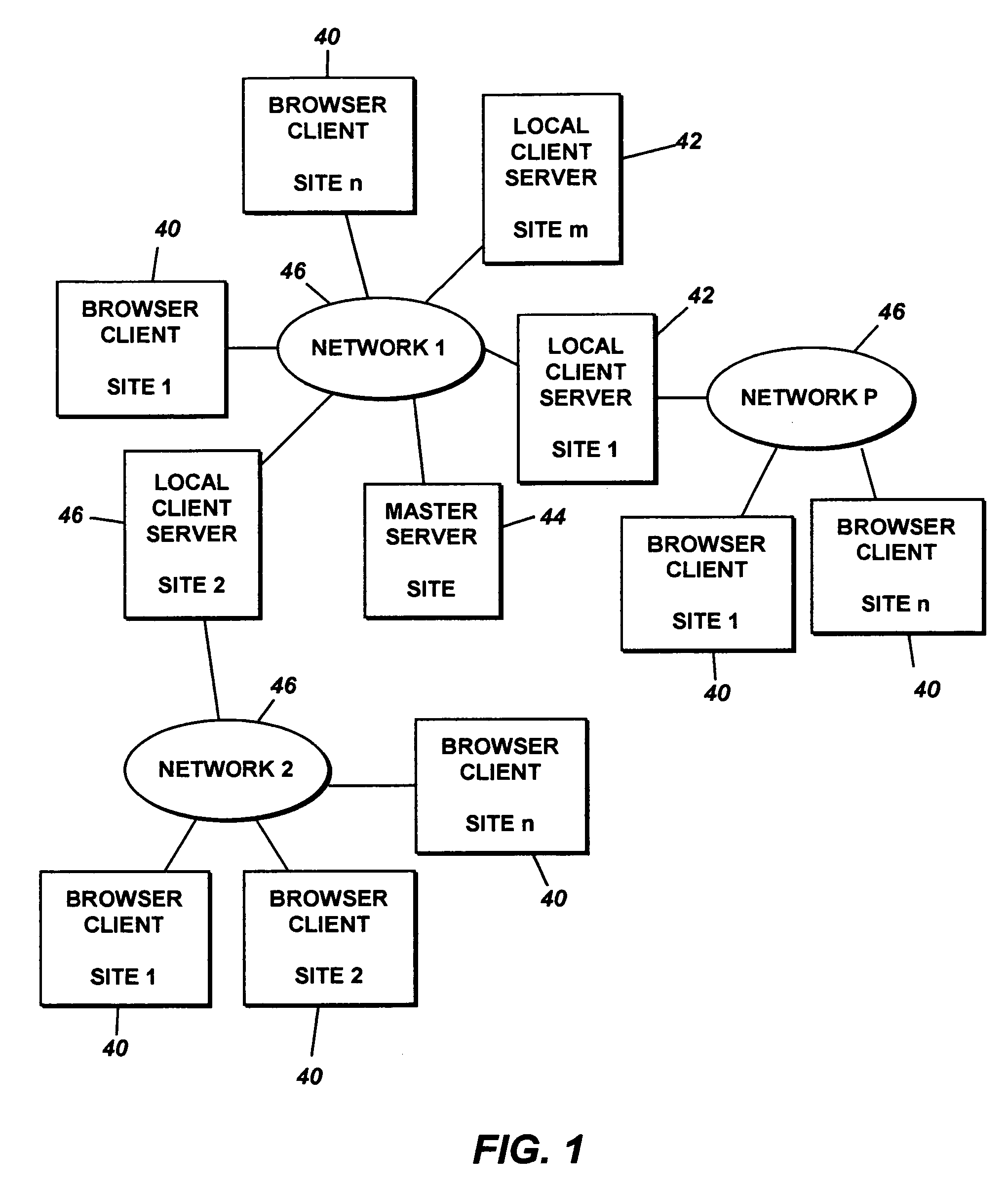
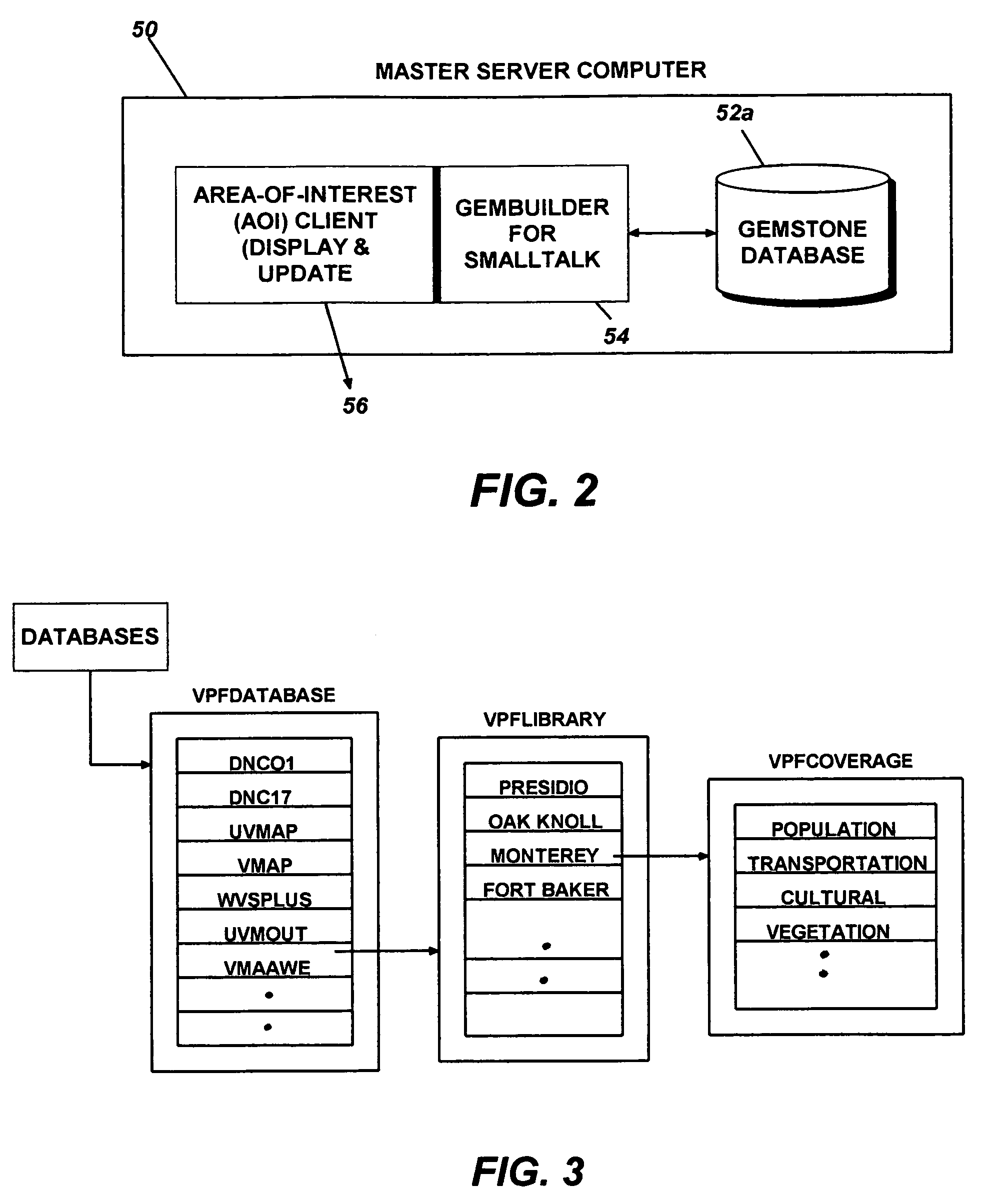
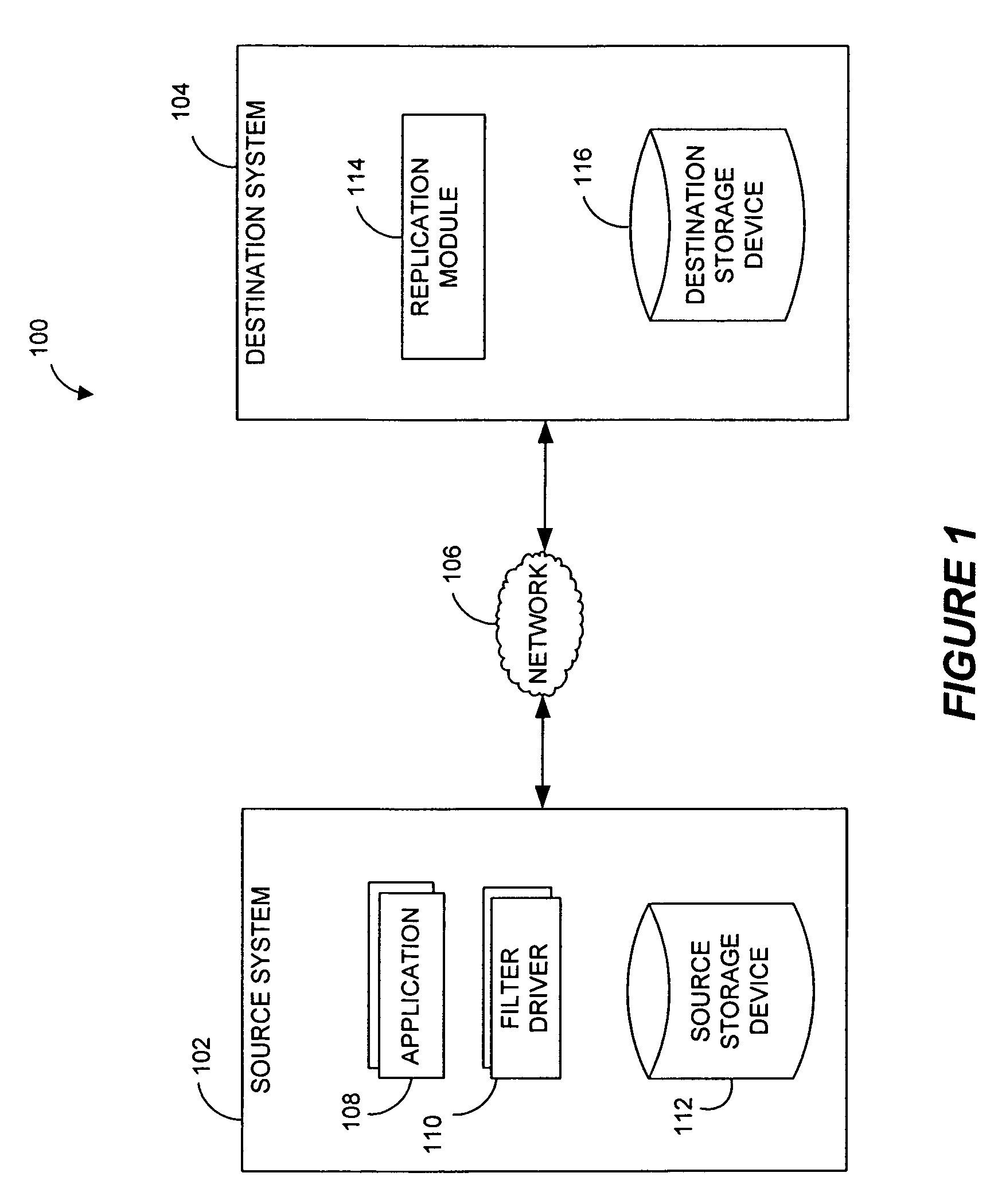
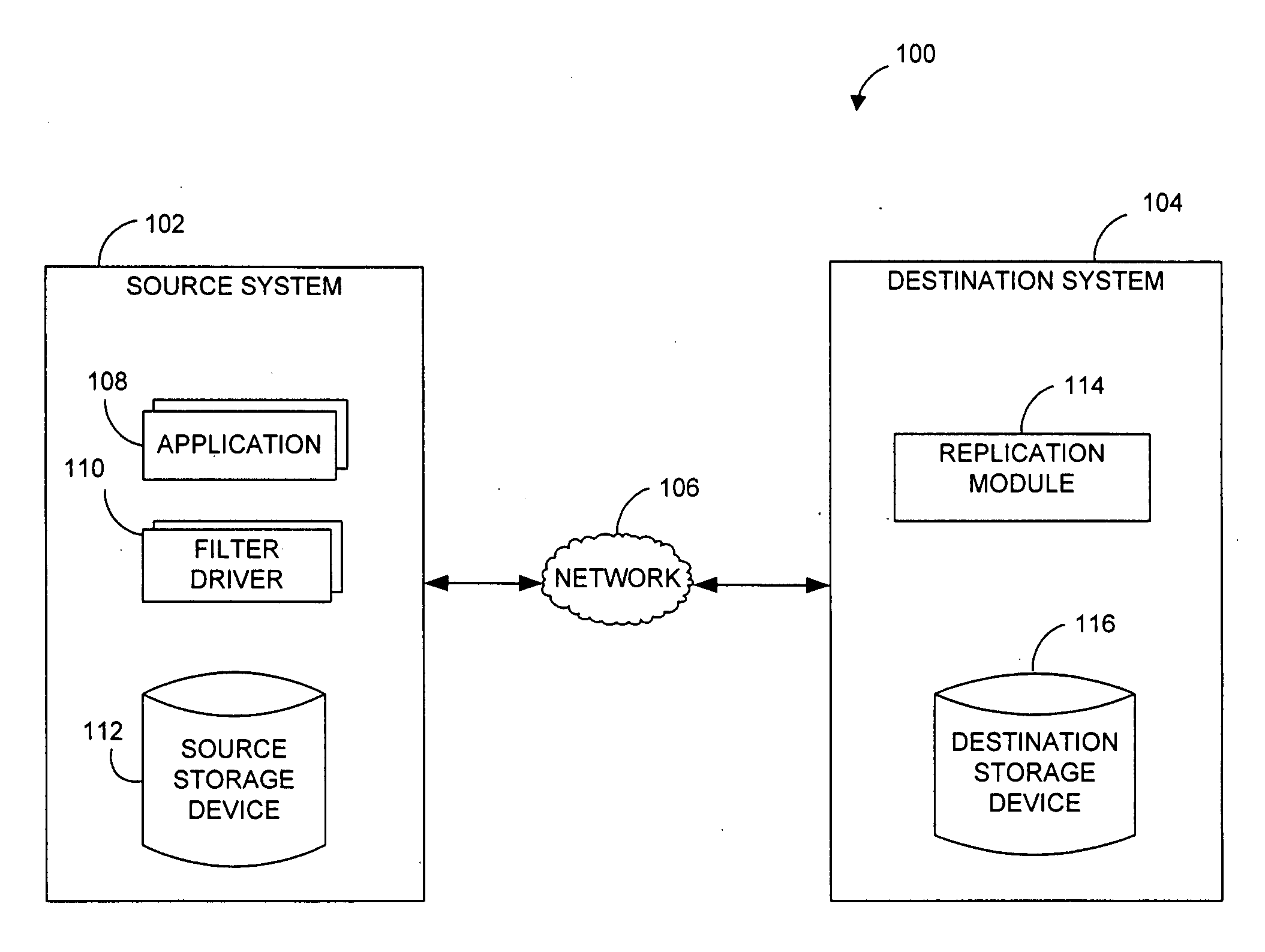
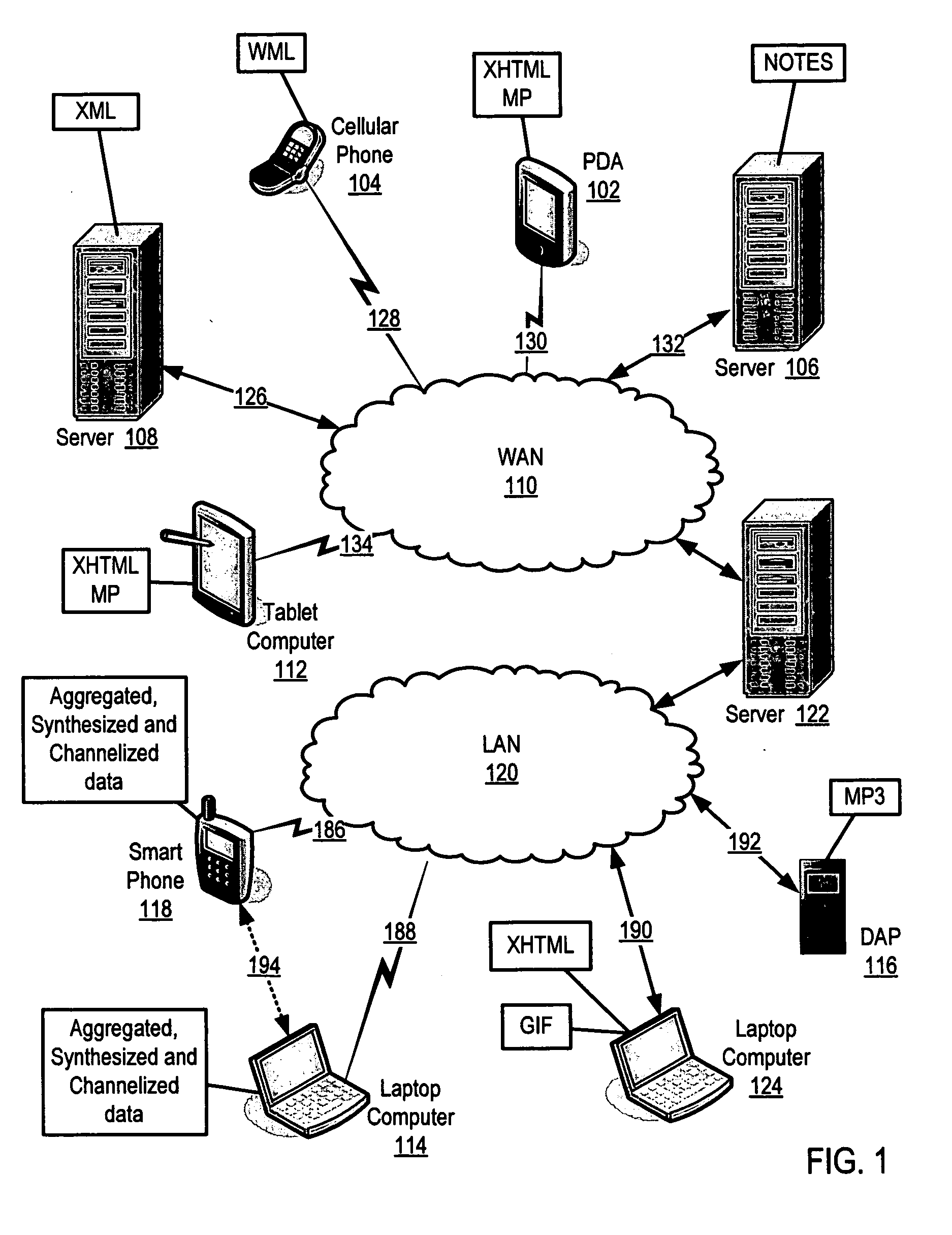
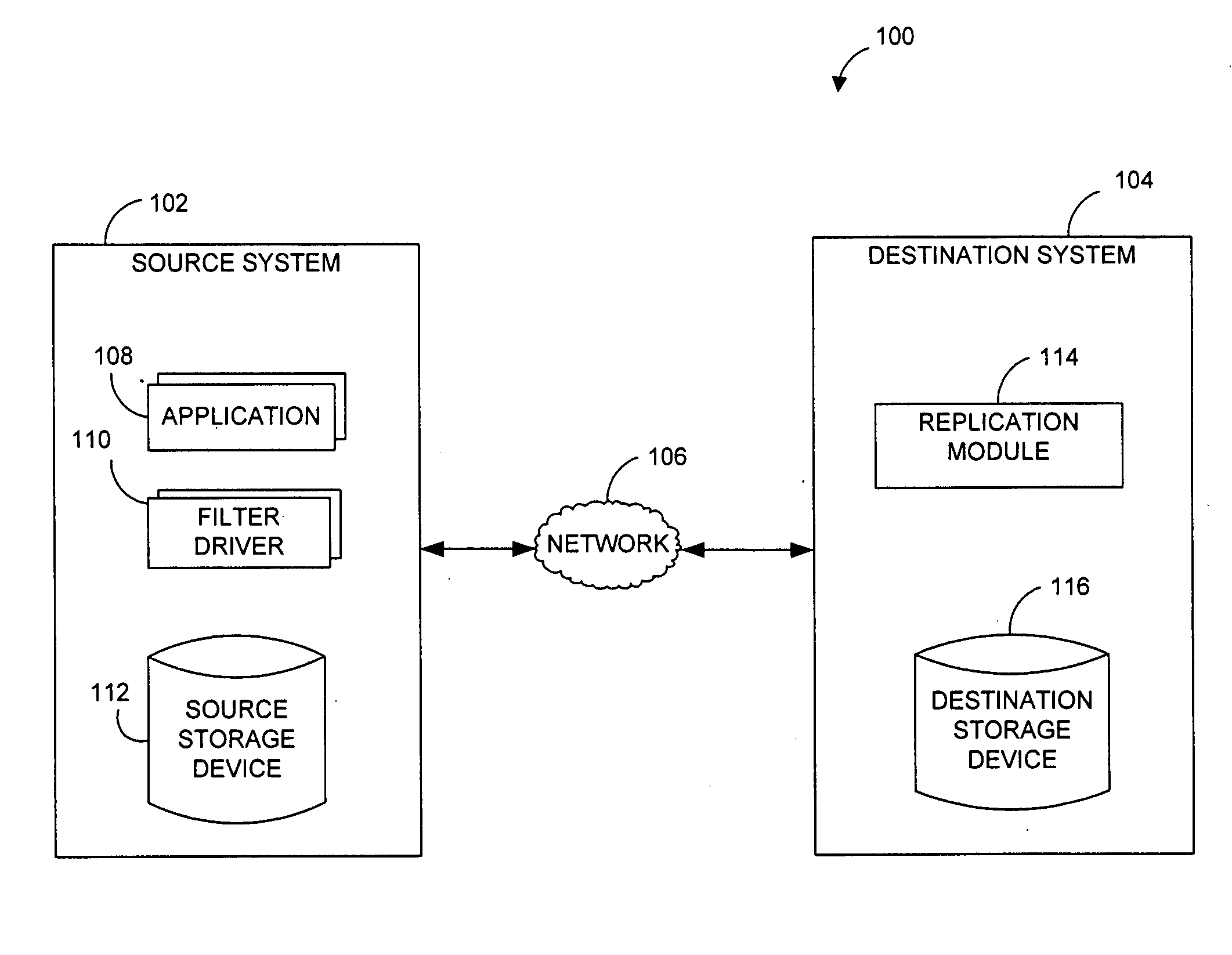
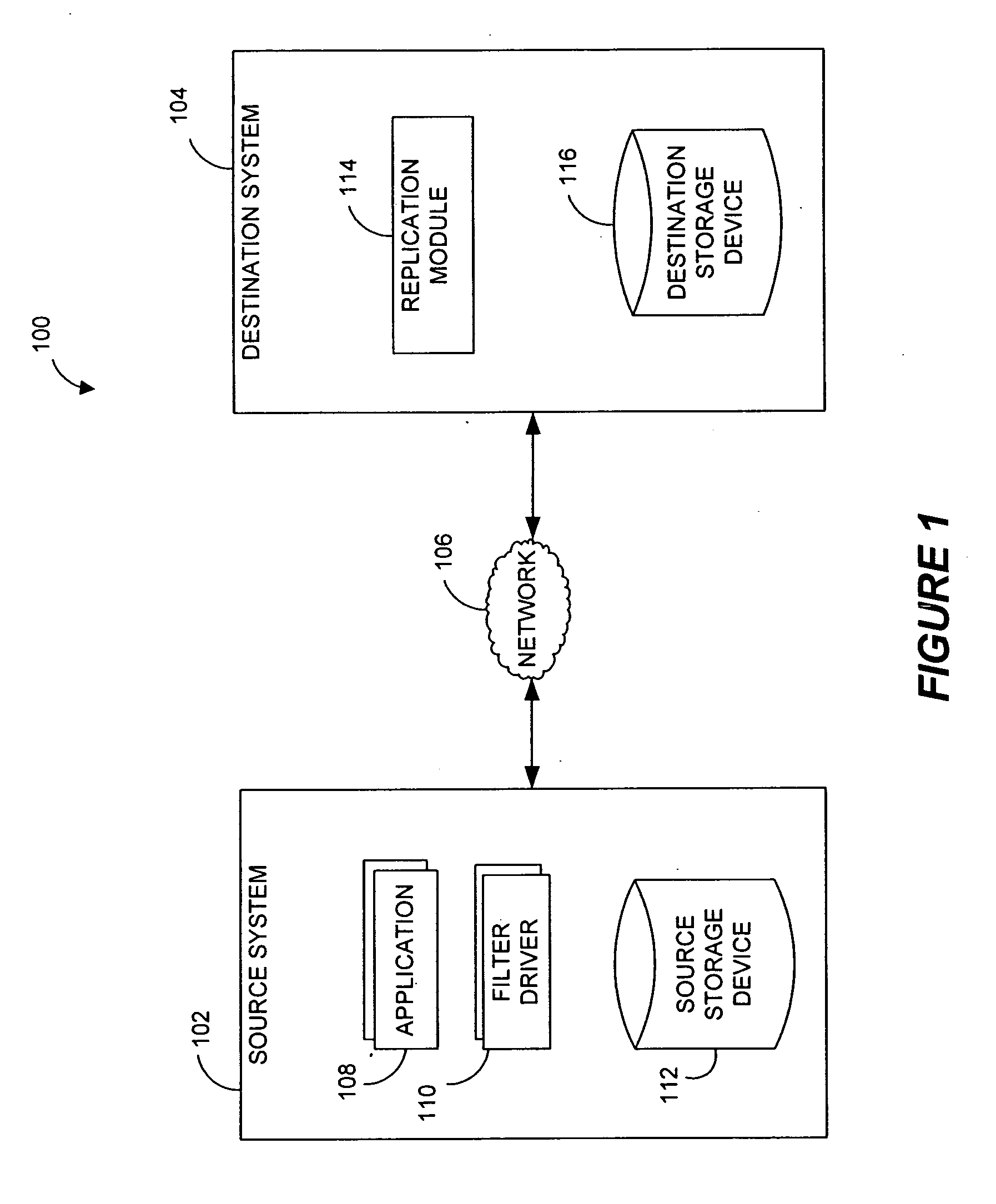
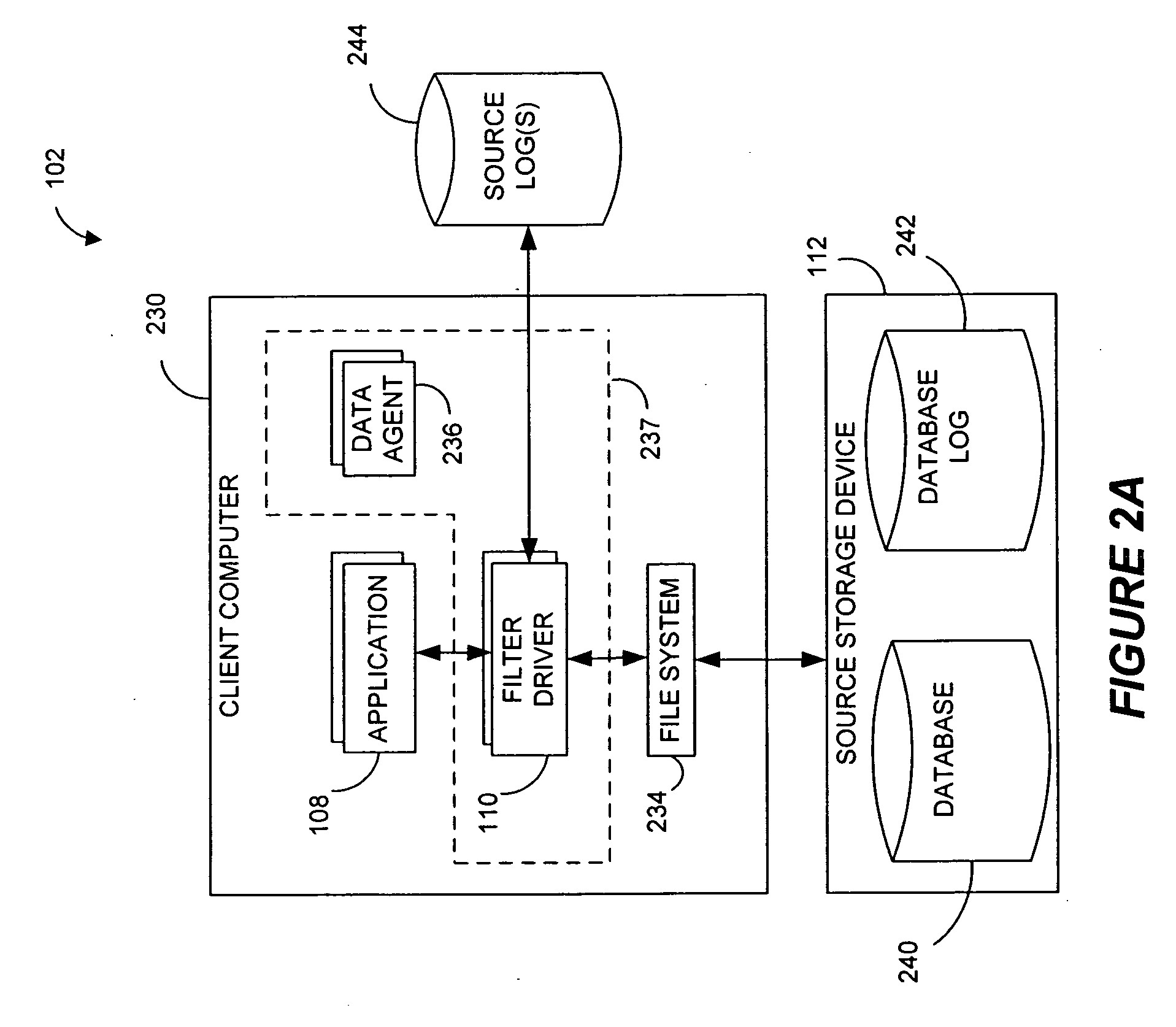
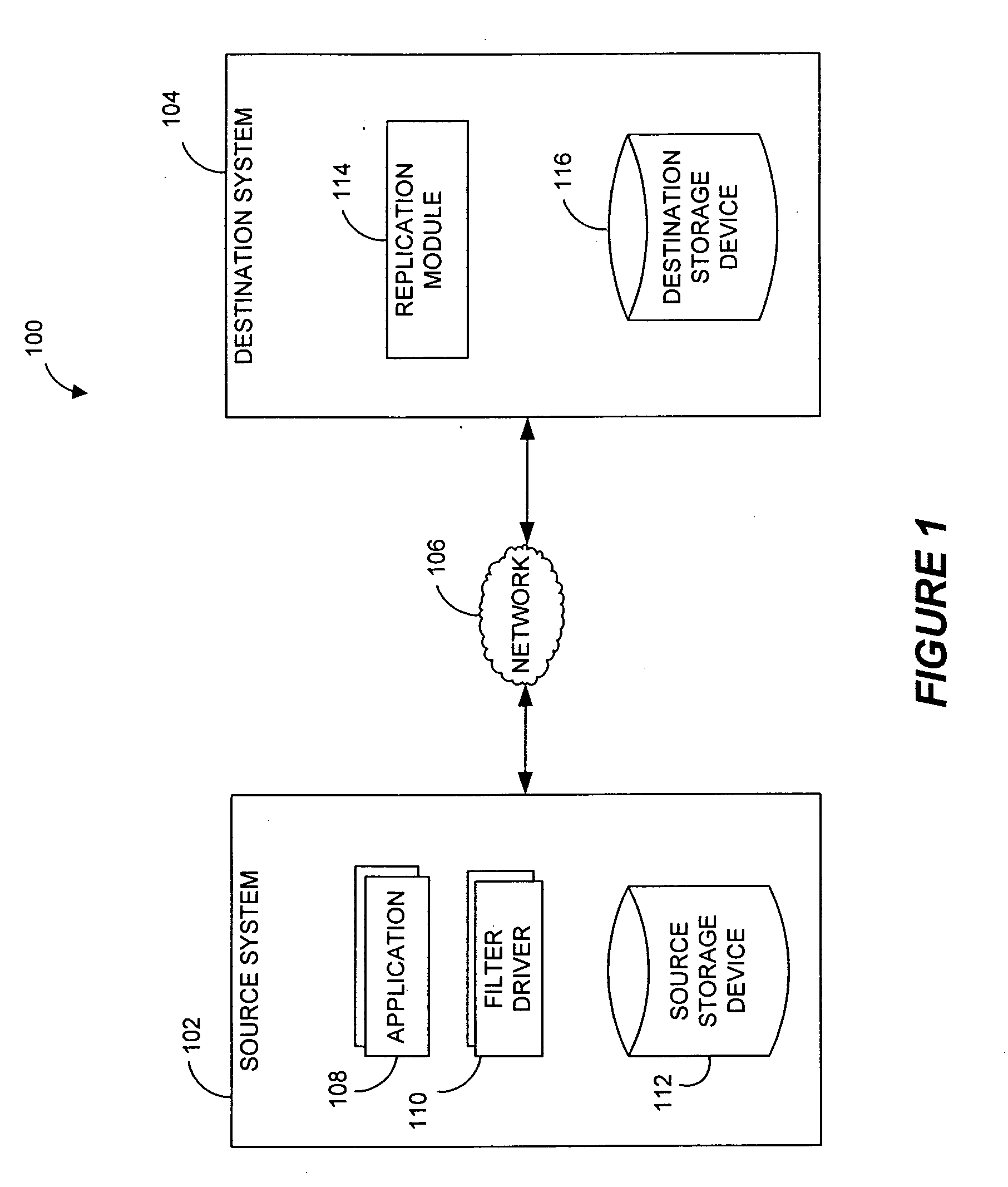
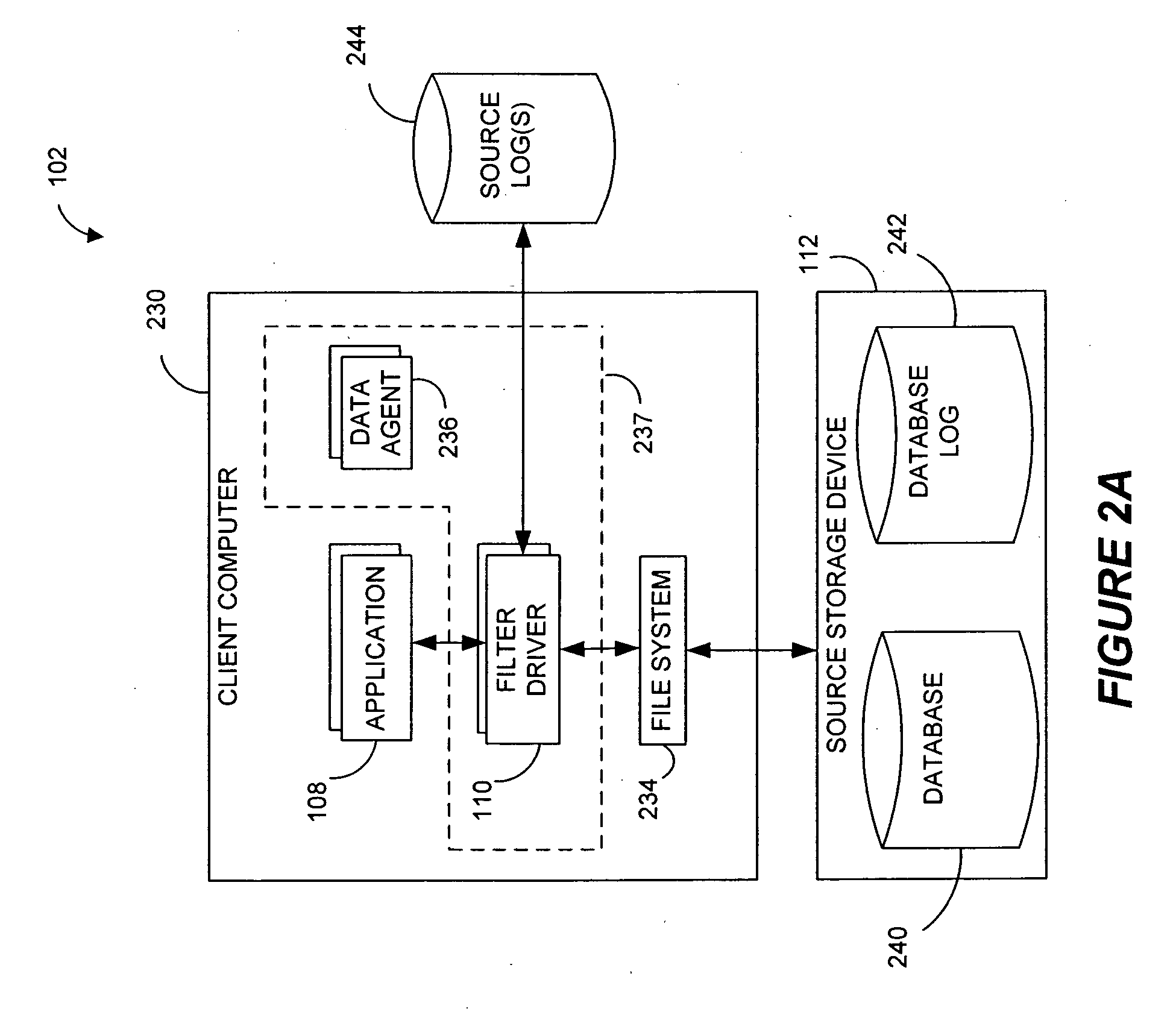
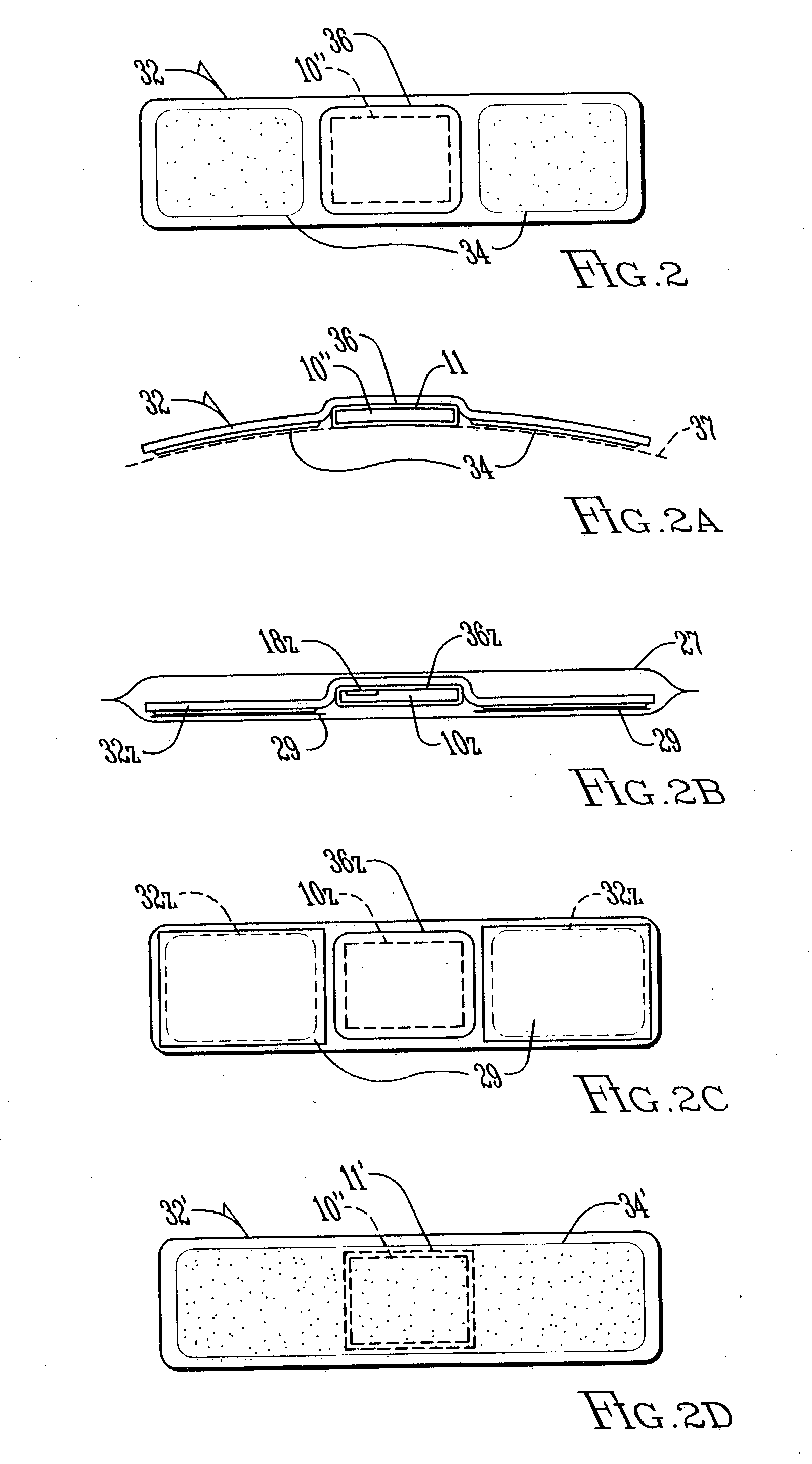
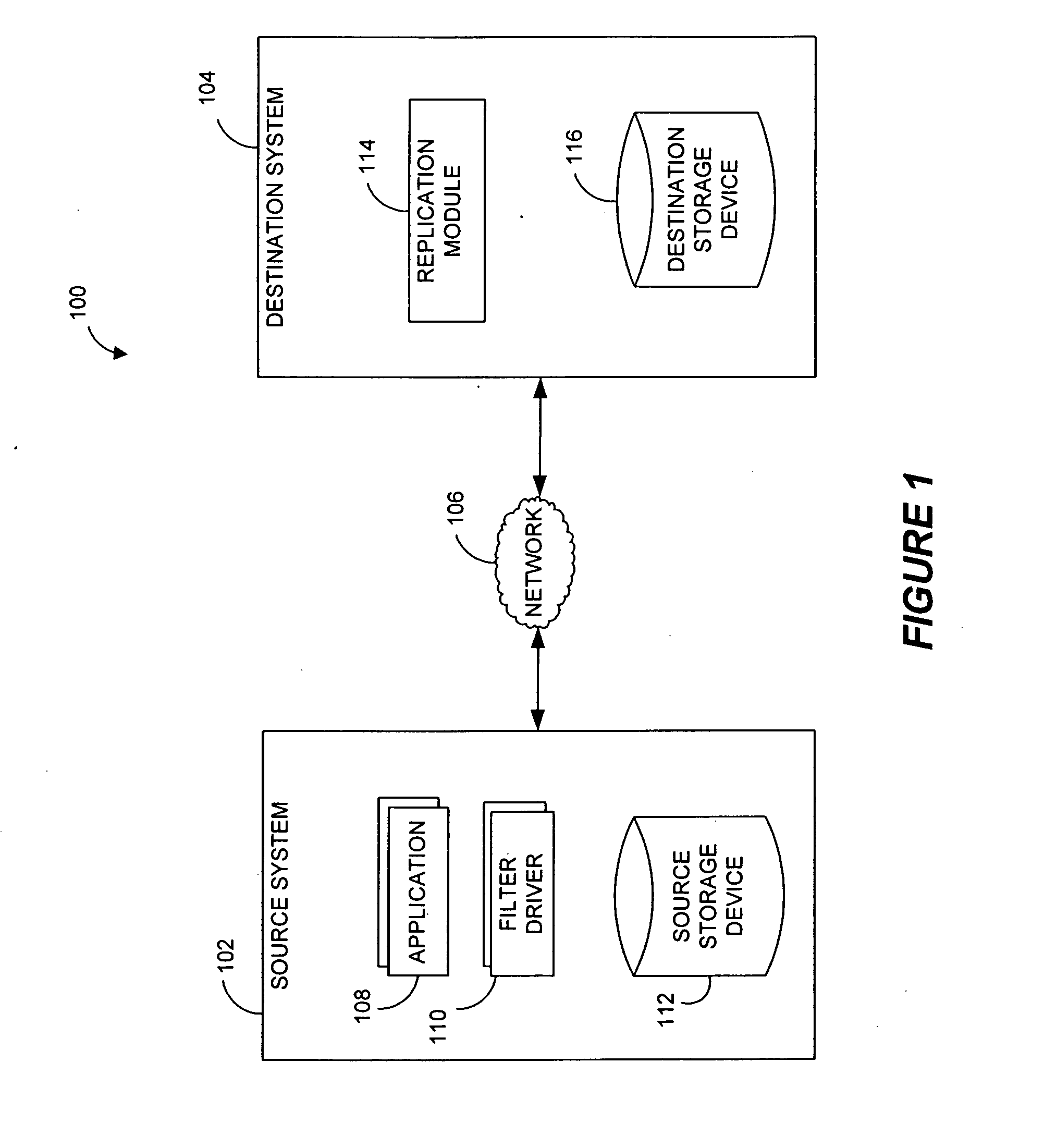
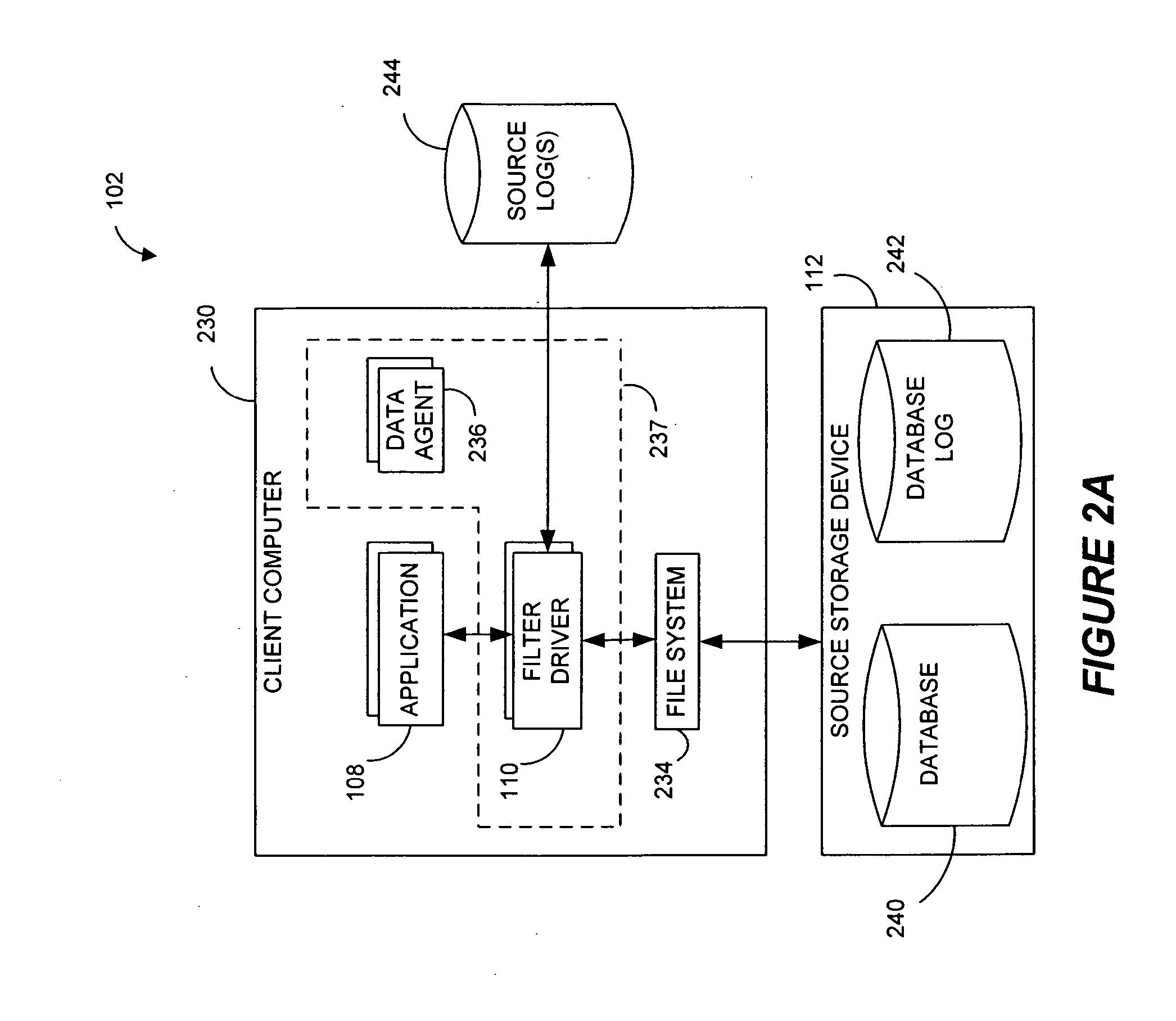
Systems and methods for monitoring application data in a data replication system
InactiveUS7617262B2Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationData management
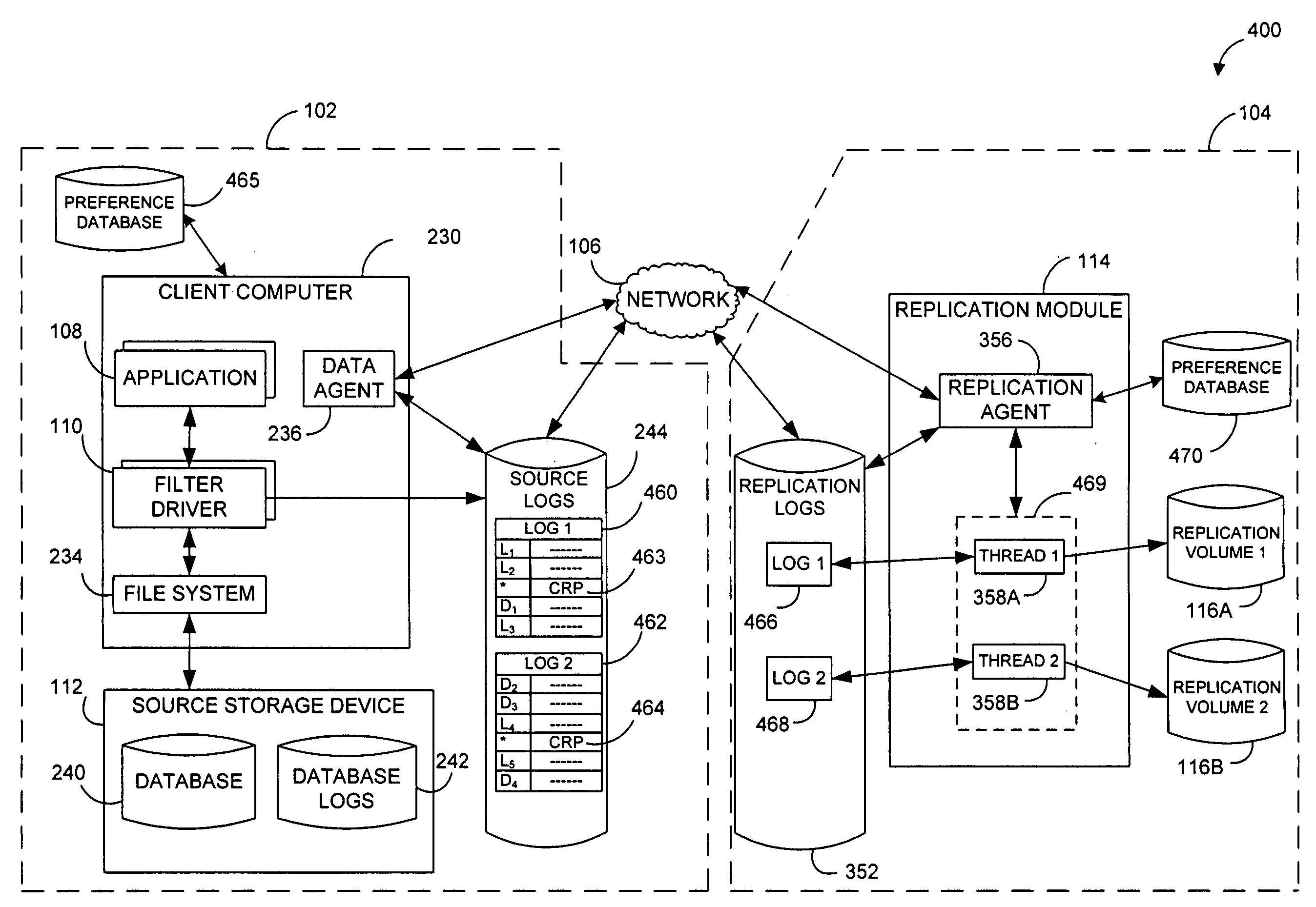
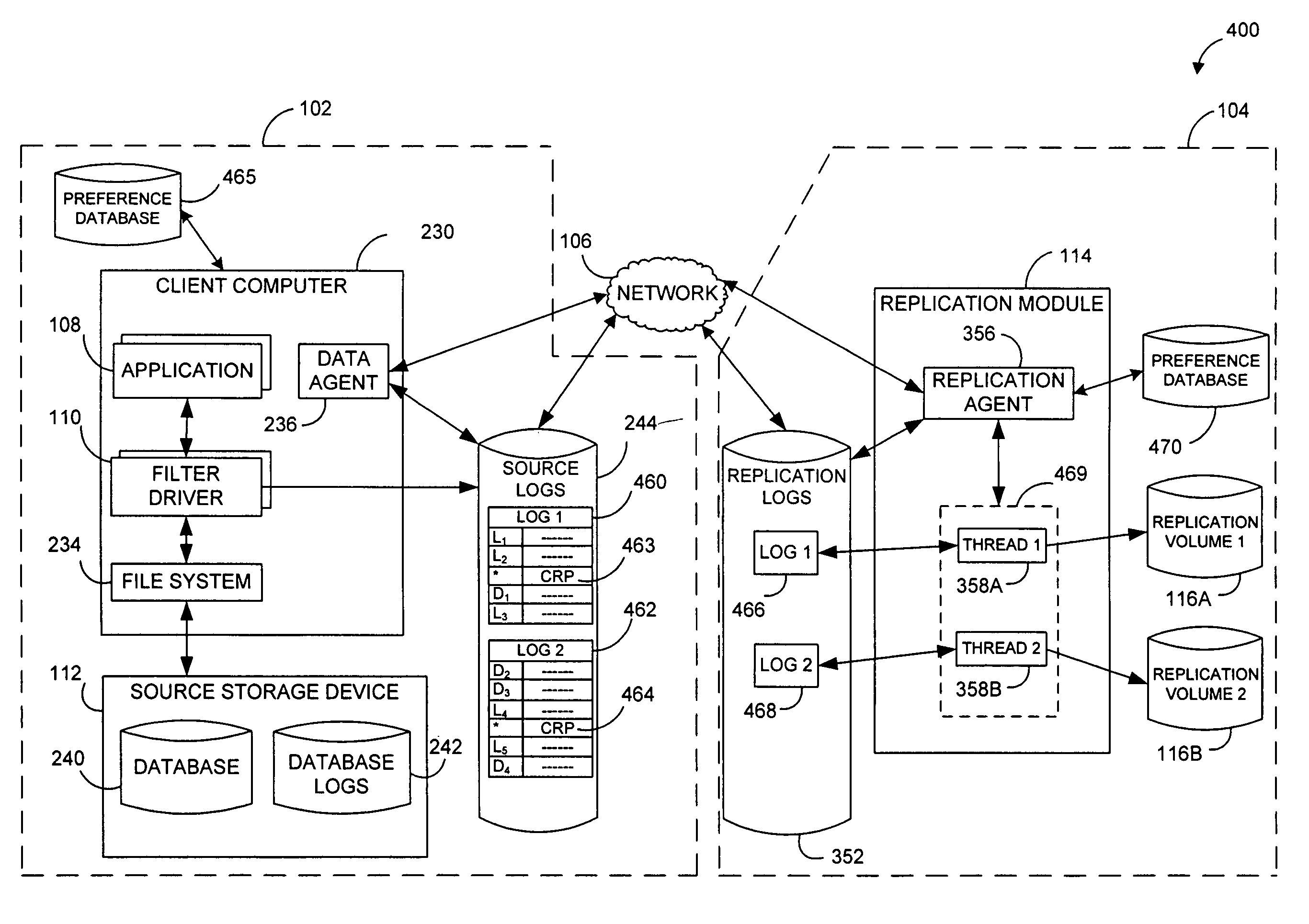
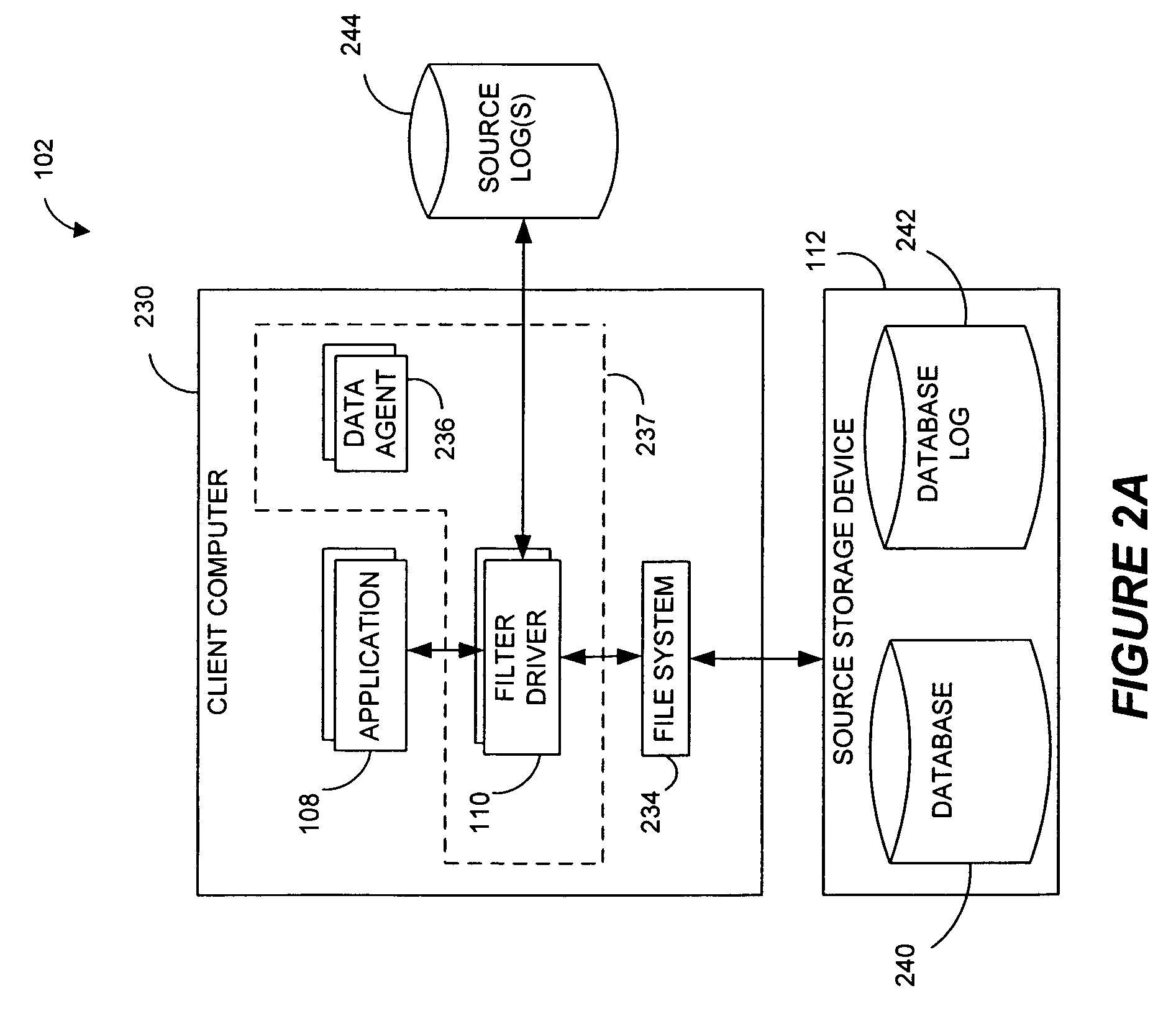
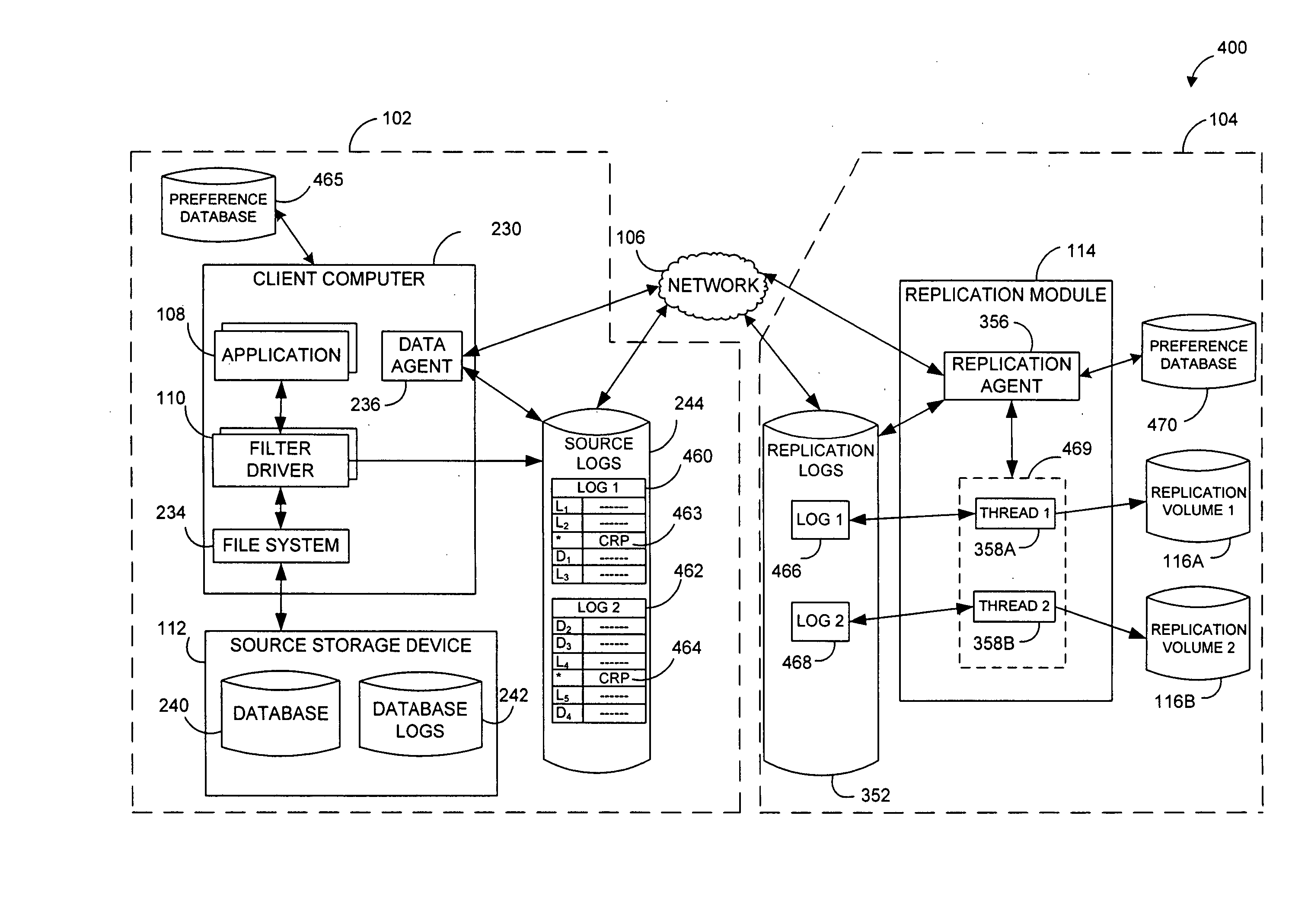
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Systems and methods for performing data replication
ActiveUS7651593B2Reduce impactReduce memory requirementsError detection/correctionDistillation separationTemporal informationData management
Owner:COMMVAULT SYST INC
Miniaturized cell array methods and apparatus for cell-based screening
InactiveUS6103479AImprove throughputIncrease contentBioreactor/fermenter combinationsMaterial nanotechnologyTemporal informationHigh-Throughput Screening Methods
The present invention discloses devices and methods of performing high throughput screening of the physiological response of cells to biologically active compounds and methods of combining high-throughput with high-content spatial information at the cellular and subcellular level as well as temporal information about changes in physiological, biochemical and molecular activities. The present invention allows multiple types of cell interactions to be studied simultaneously by combining multicolor luminescence reading, microfluidic delivery, and environmental control of living cells in non-uniform micro-patterned arrays.
Owner:CELLOMICS
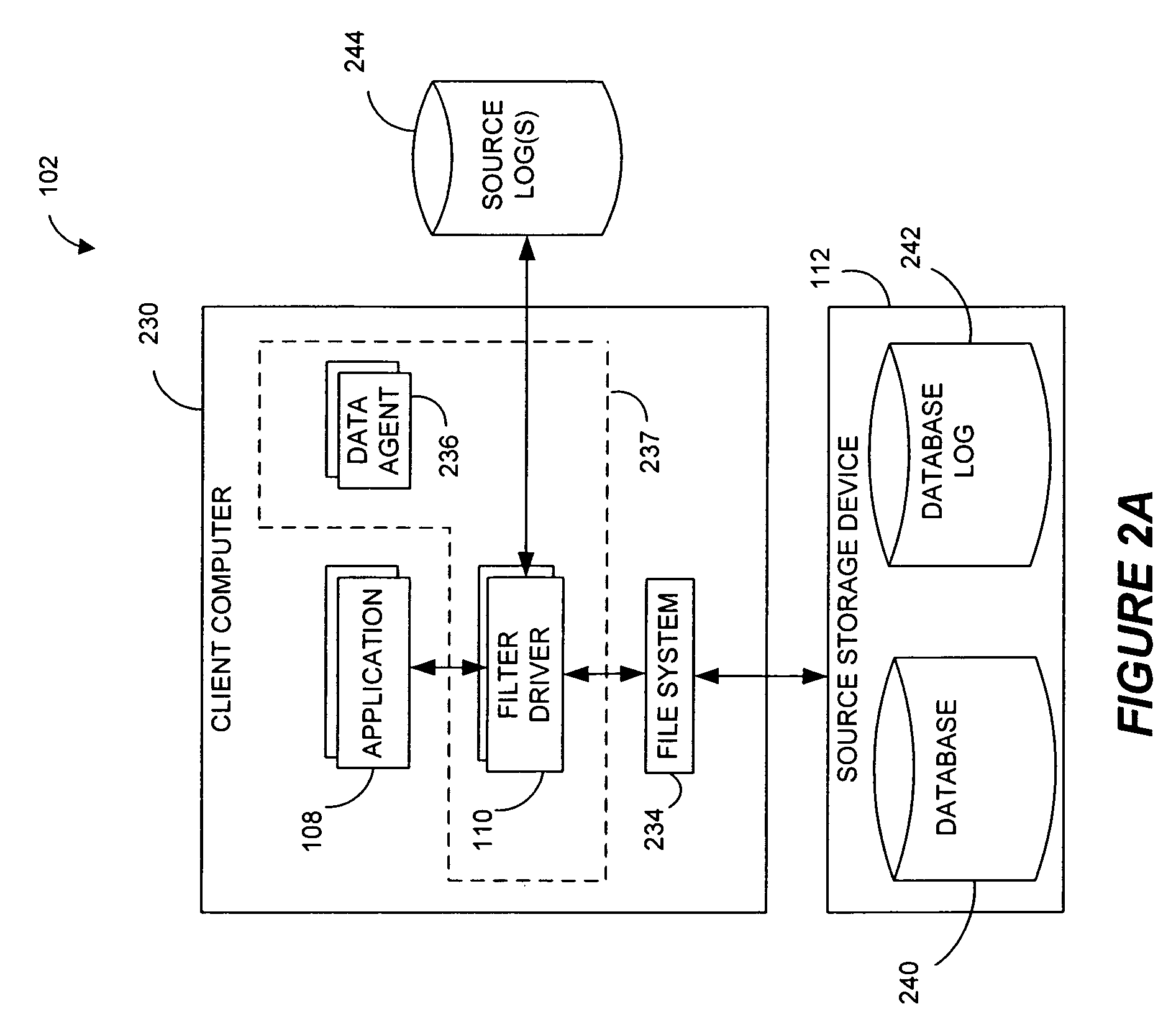
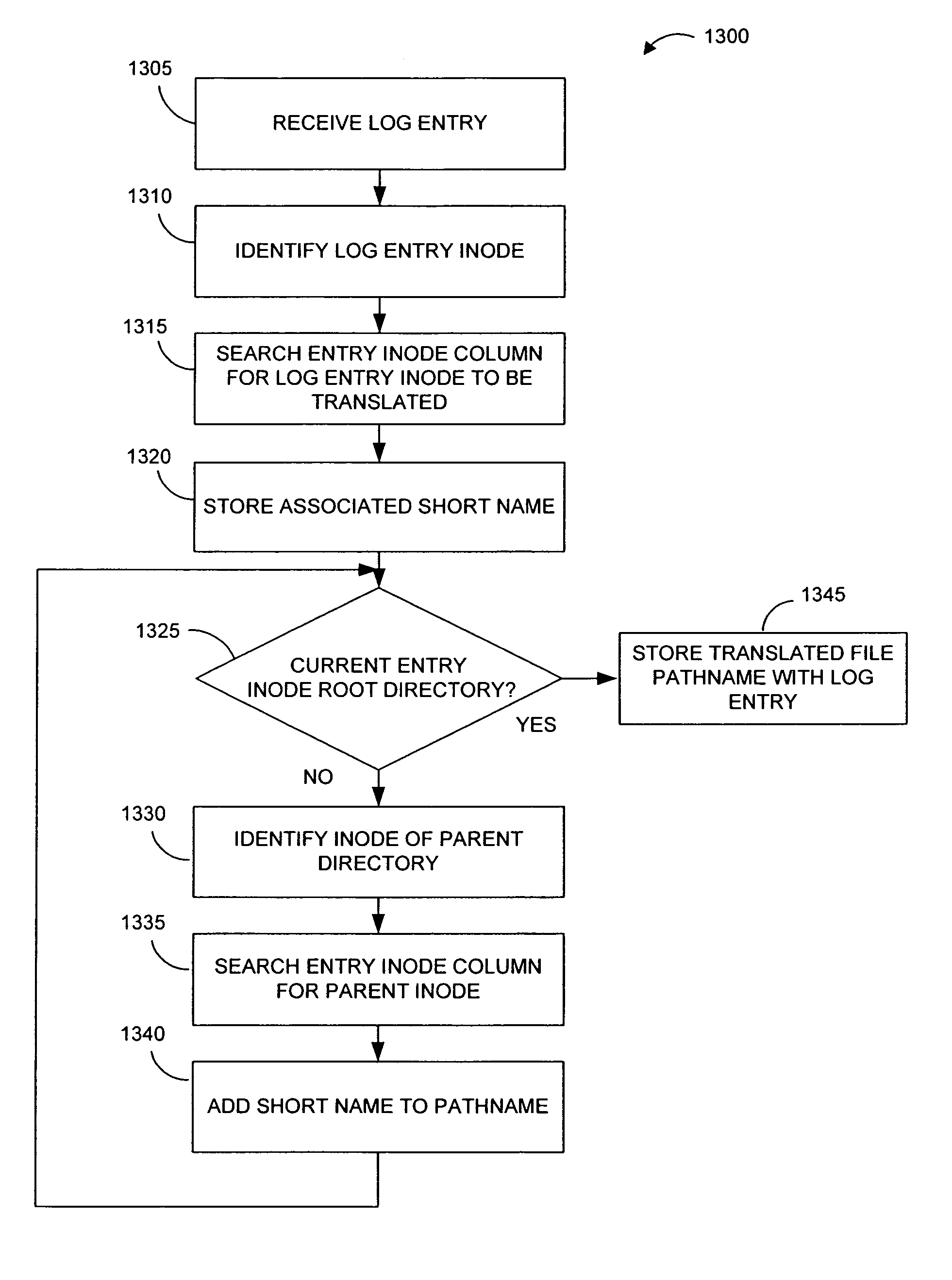
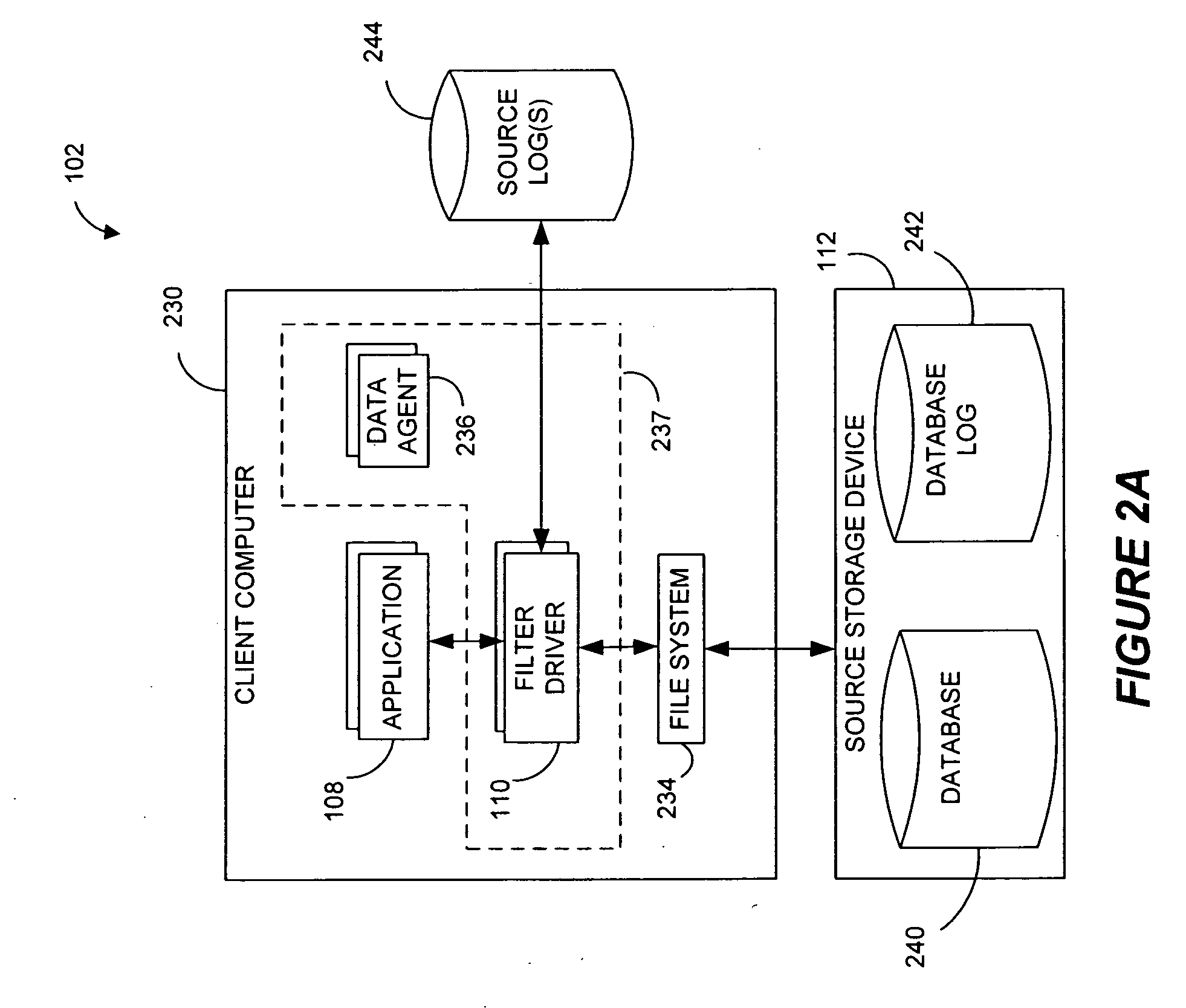
Pathname translation in a data replication system
InactiveUS7636743B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Owner:COMMVAULT SYST INC
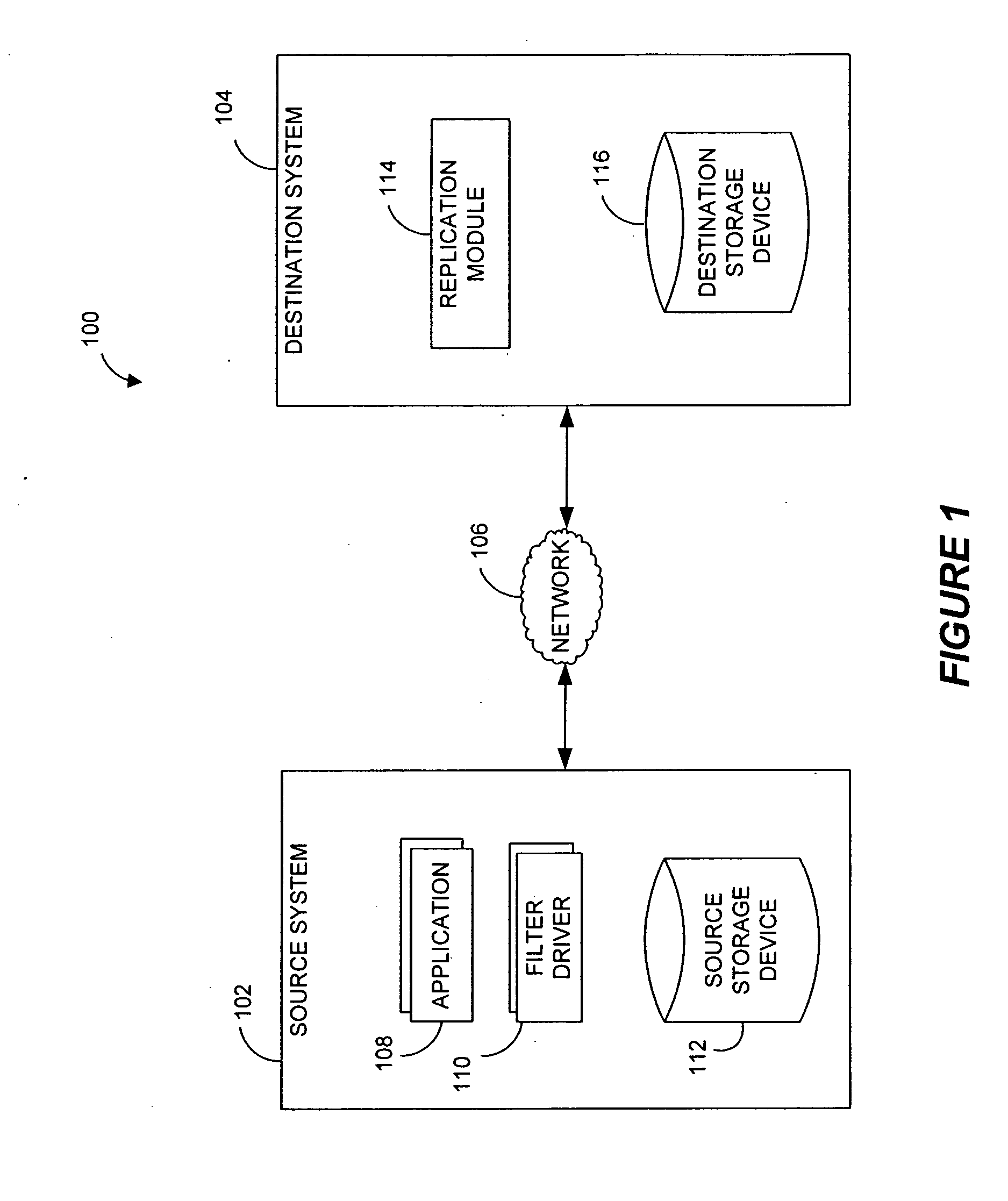
Destination systems and methods for performing data replication
InactiveUS7617253B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
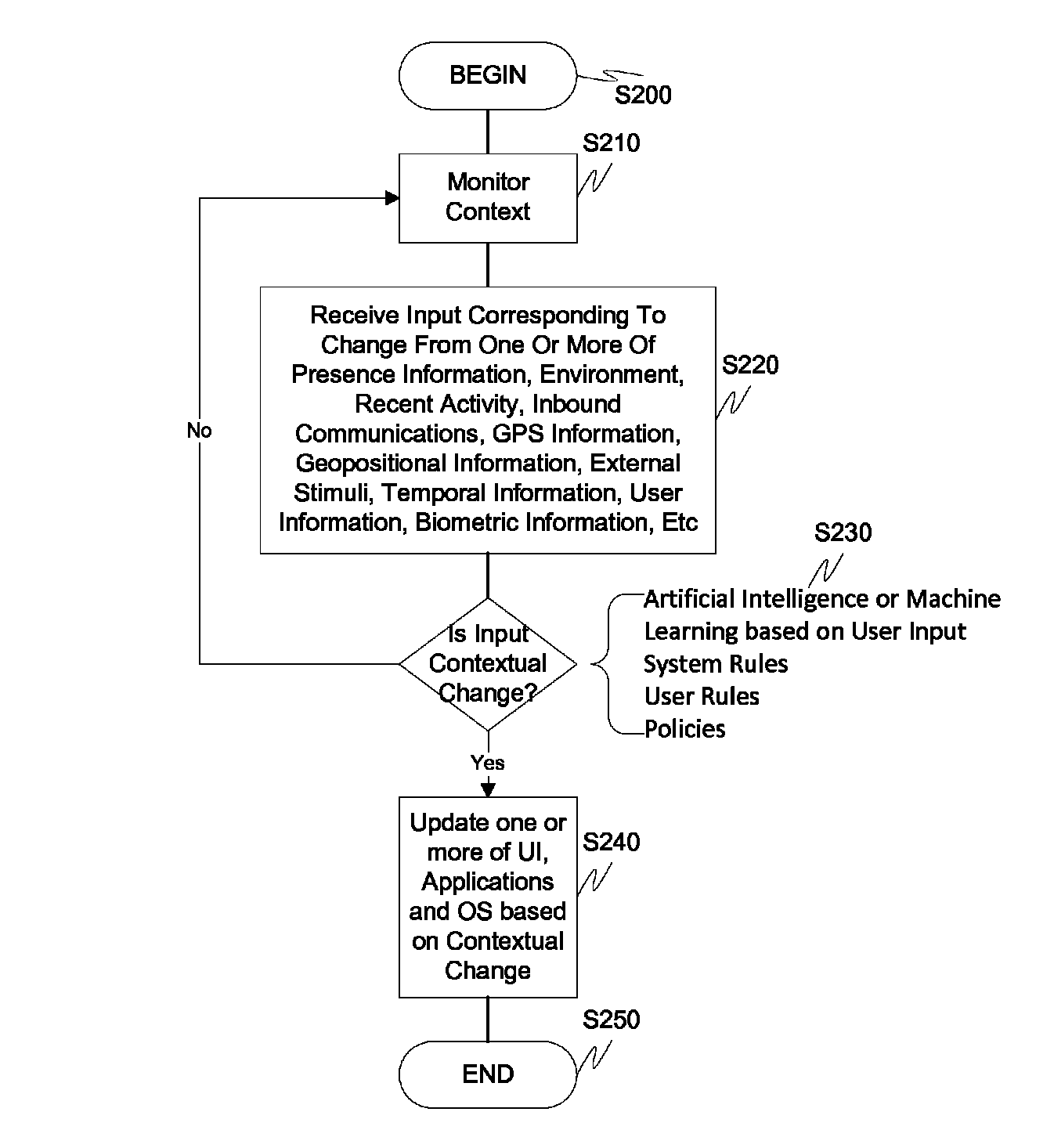
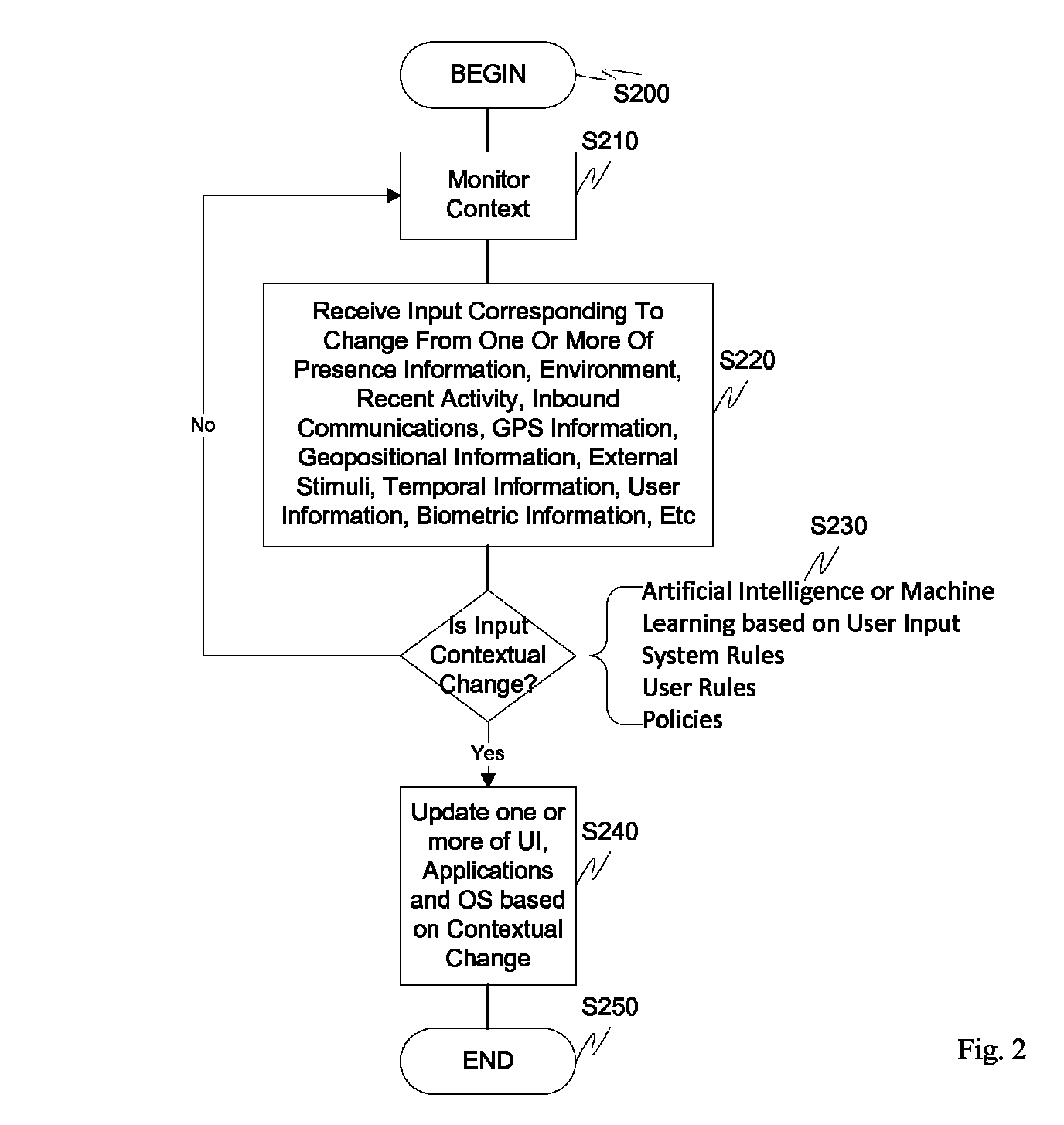
Screen icon manipulation by context and frequency of use
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
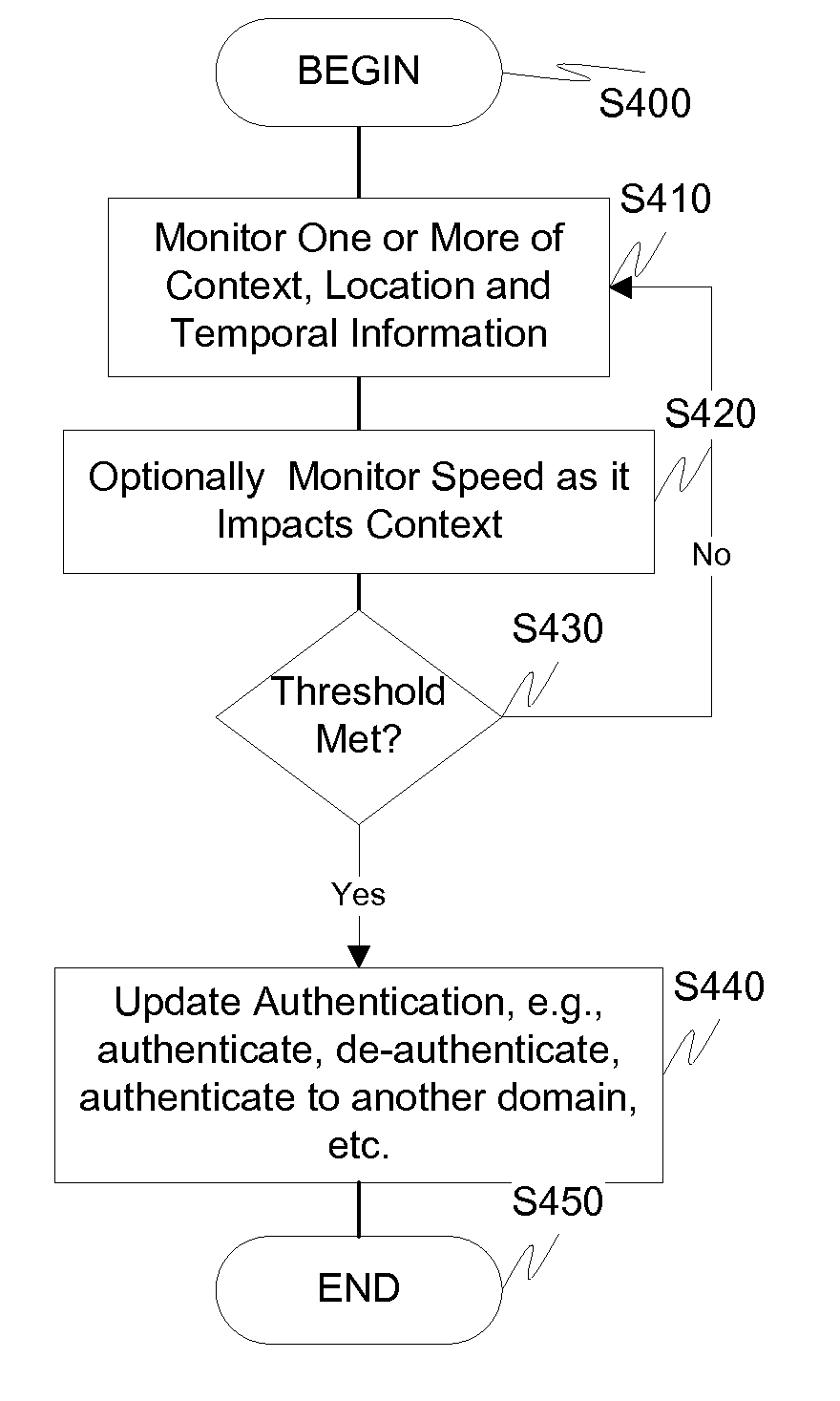
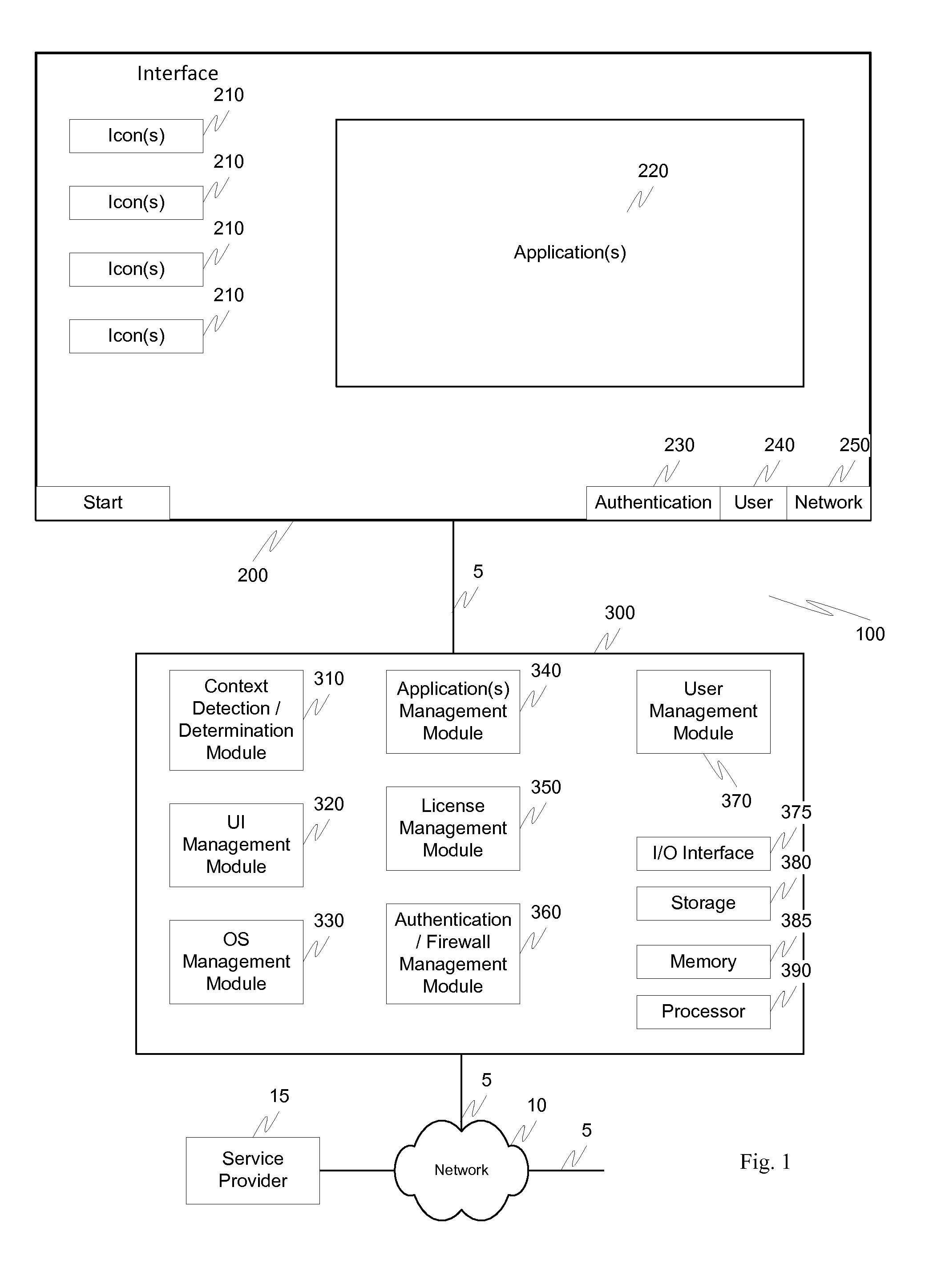
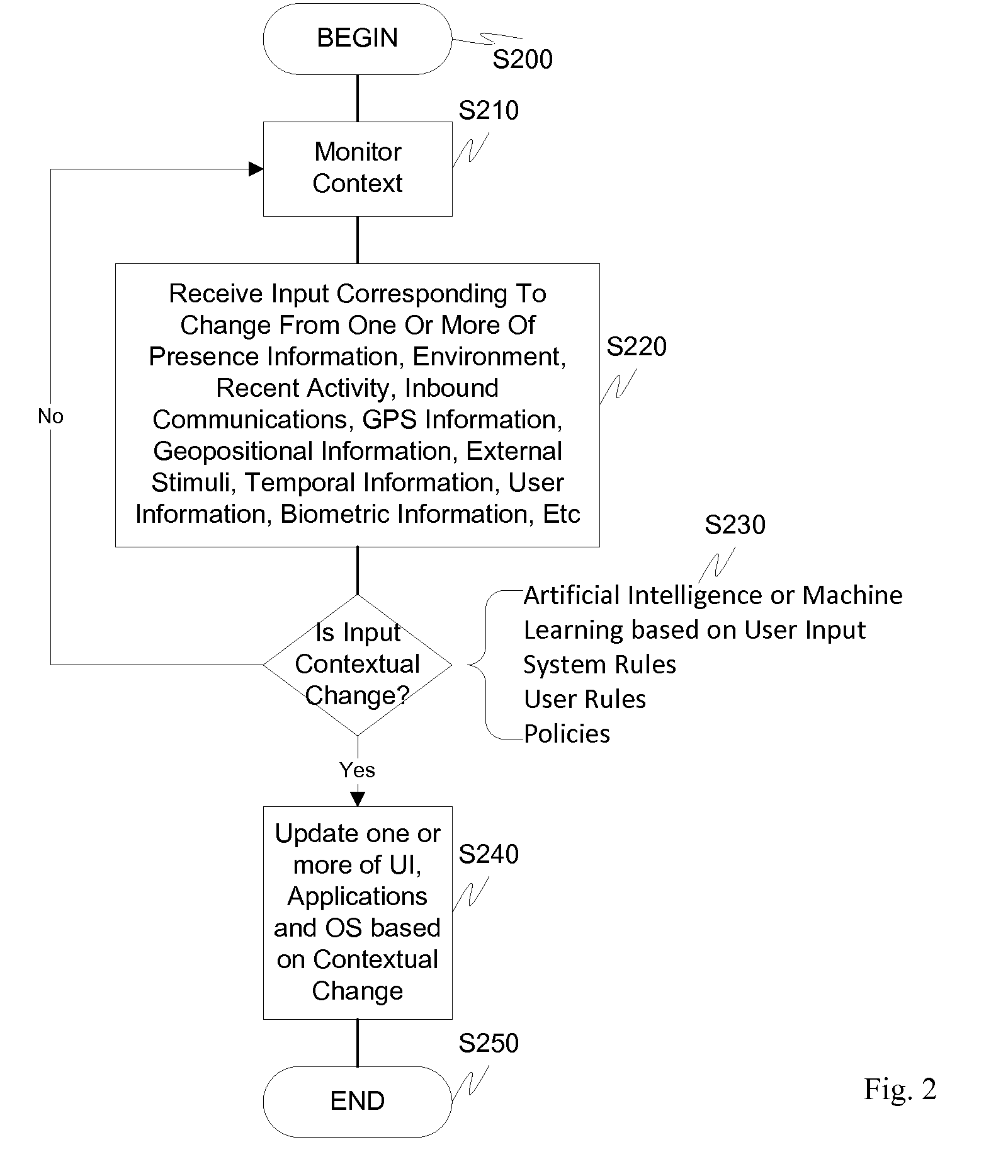
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
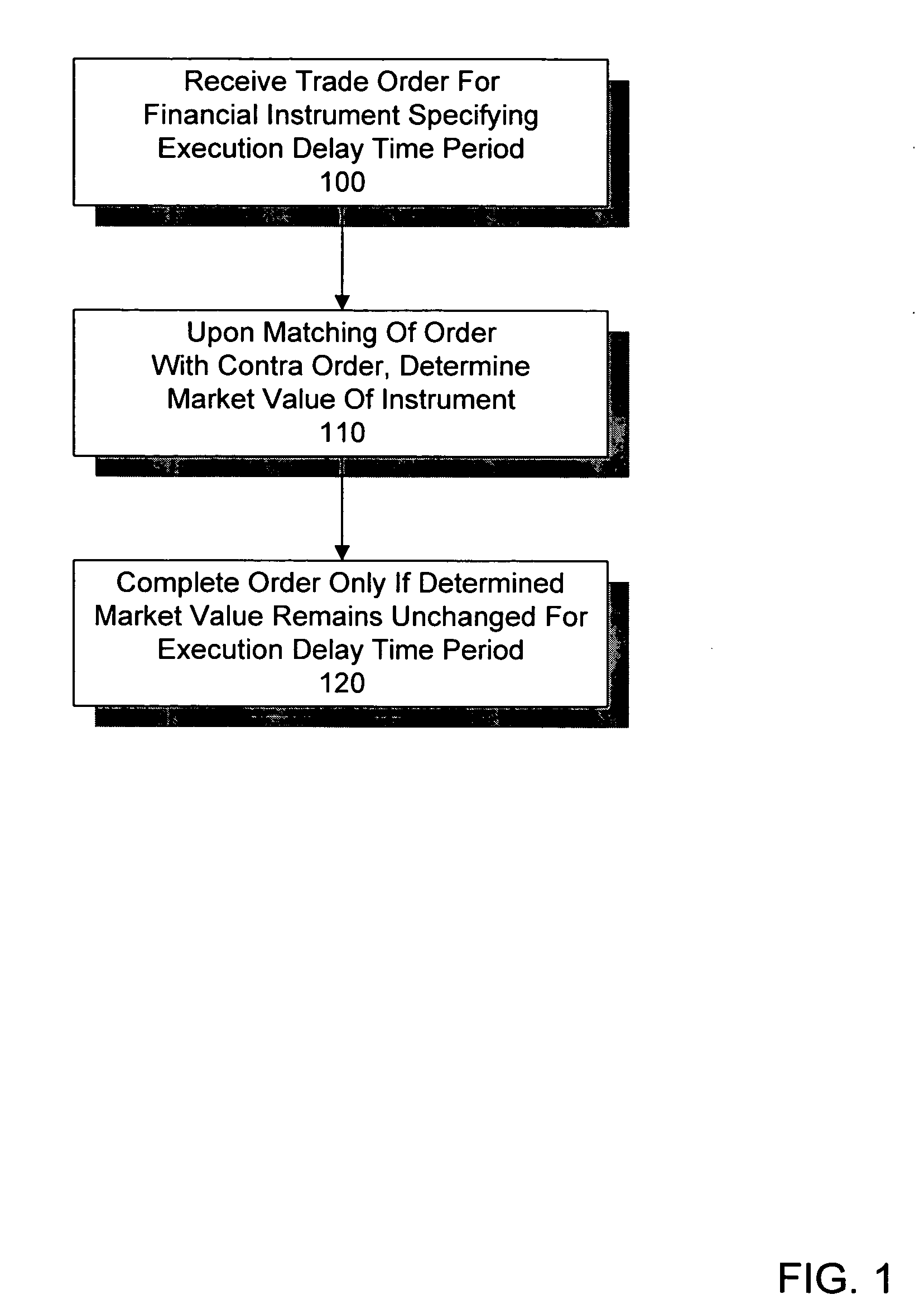
System and method for execution delayed trading
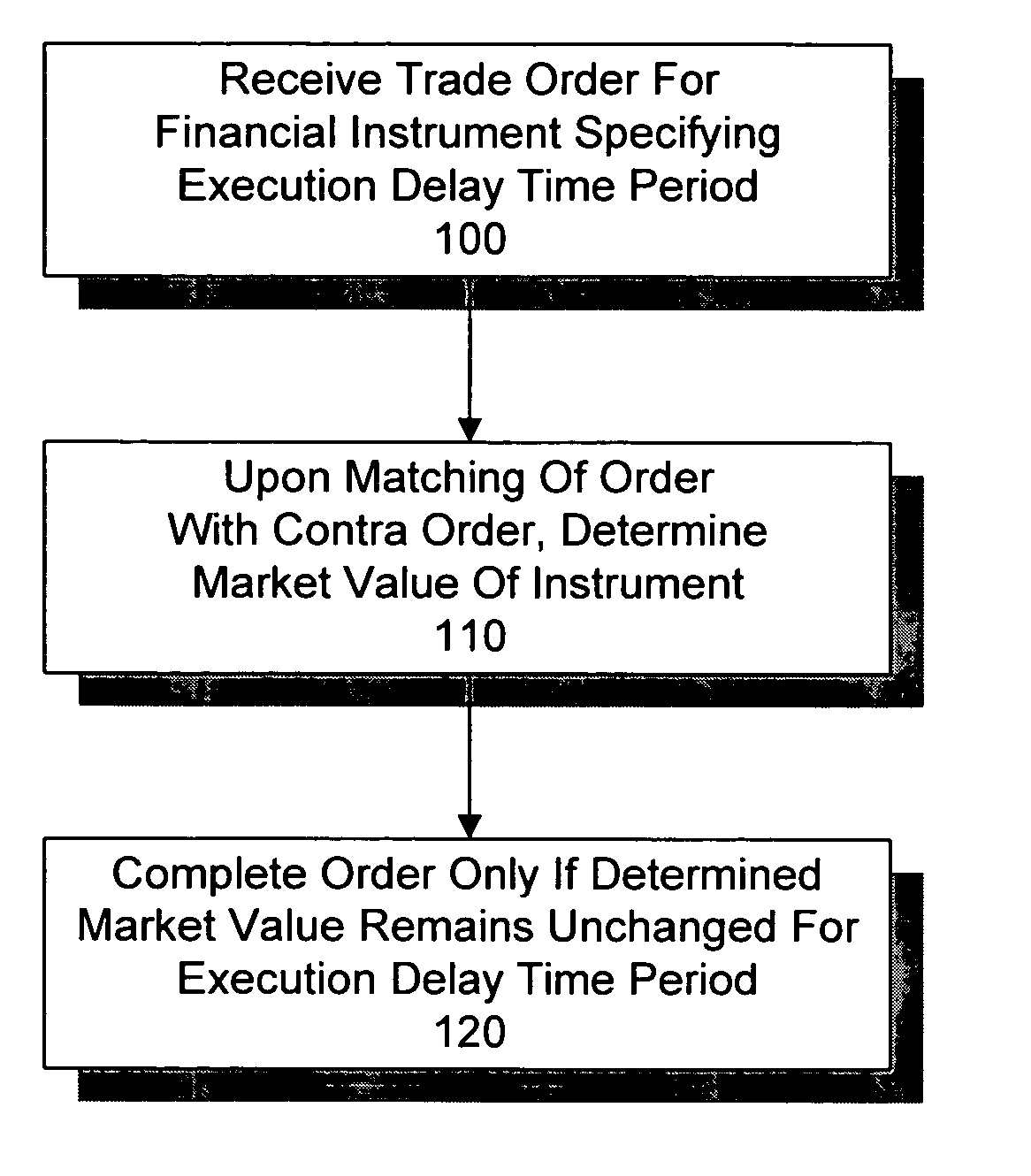
InactiveUS20050075963A1Low costImprove liquidityFinanceSpecial data processing applicationsTemporal informationOrder form
Owner:DEEP LIQUIDITY
Screen icon manipulation by context and frequency of Use
ActiveUS8972878B2More user confidenceDigital data authenticationSubstation equipmentTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
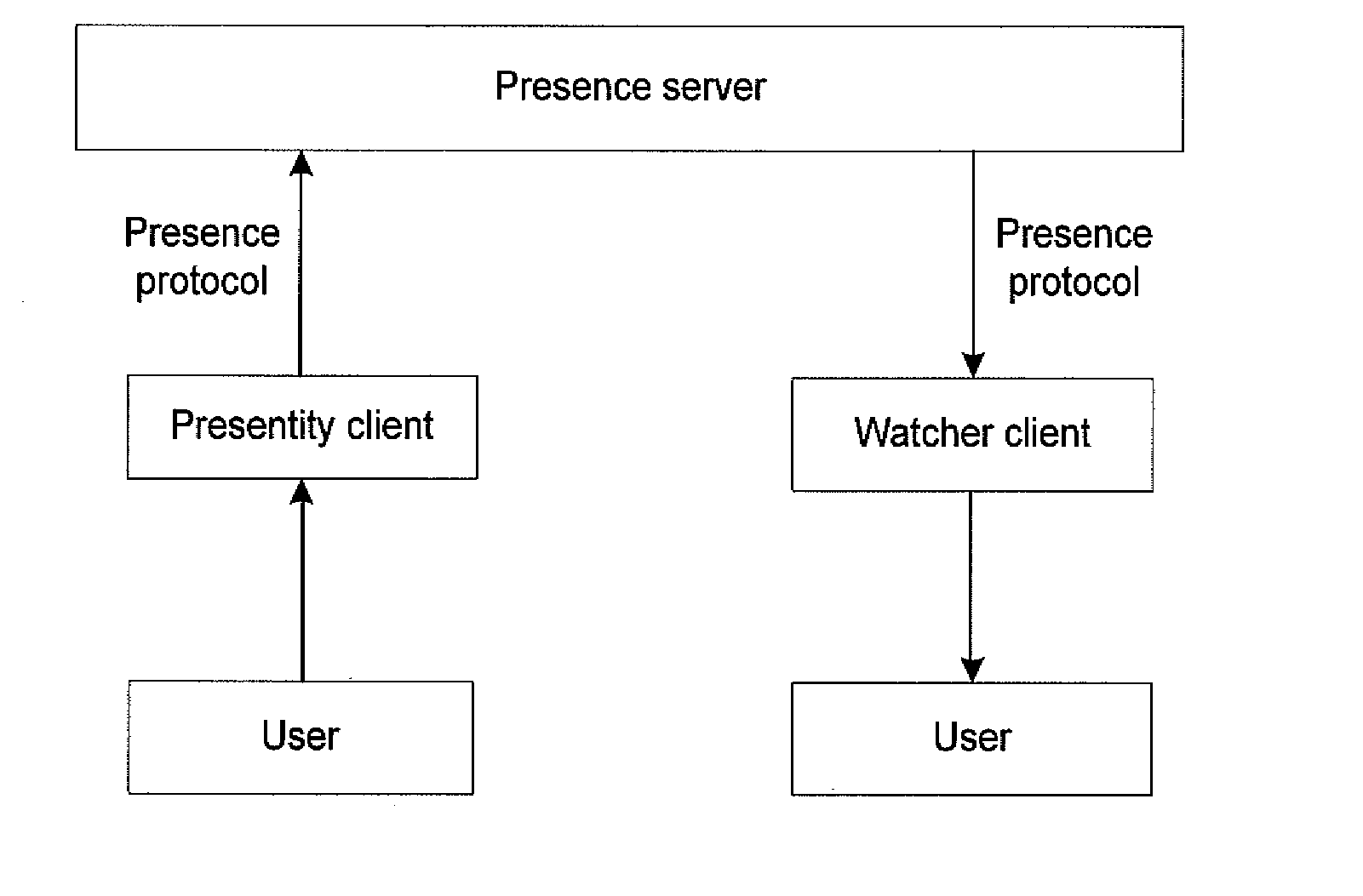
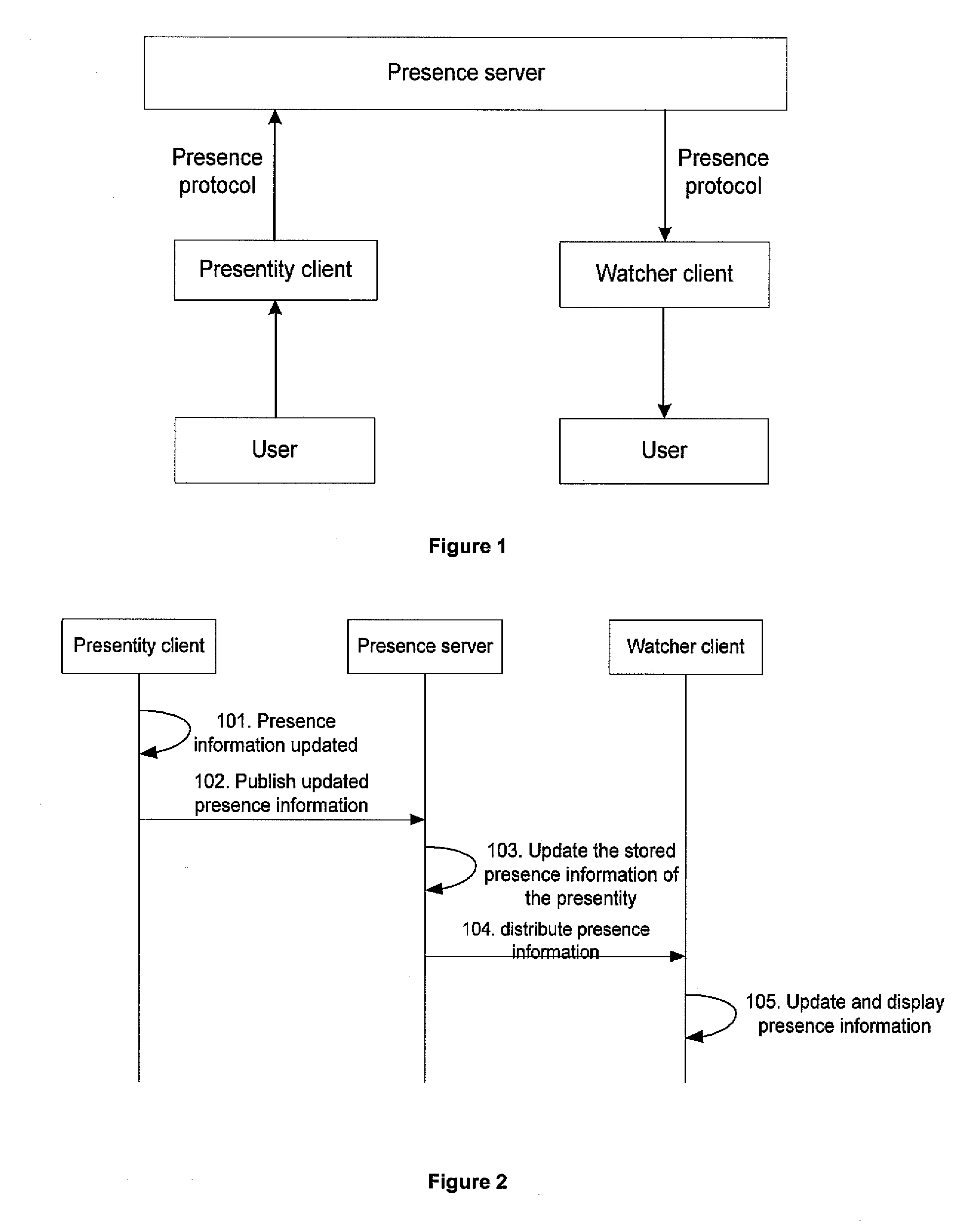
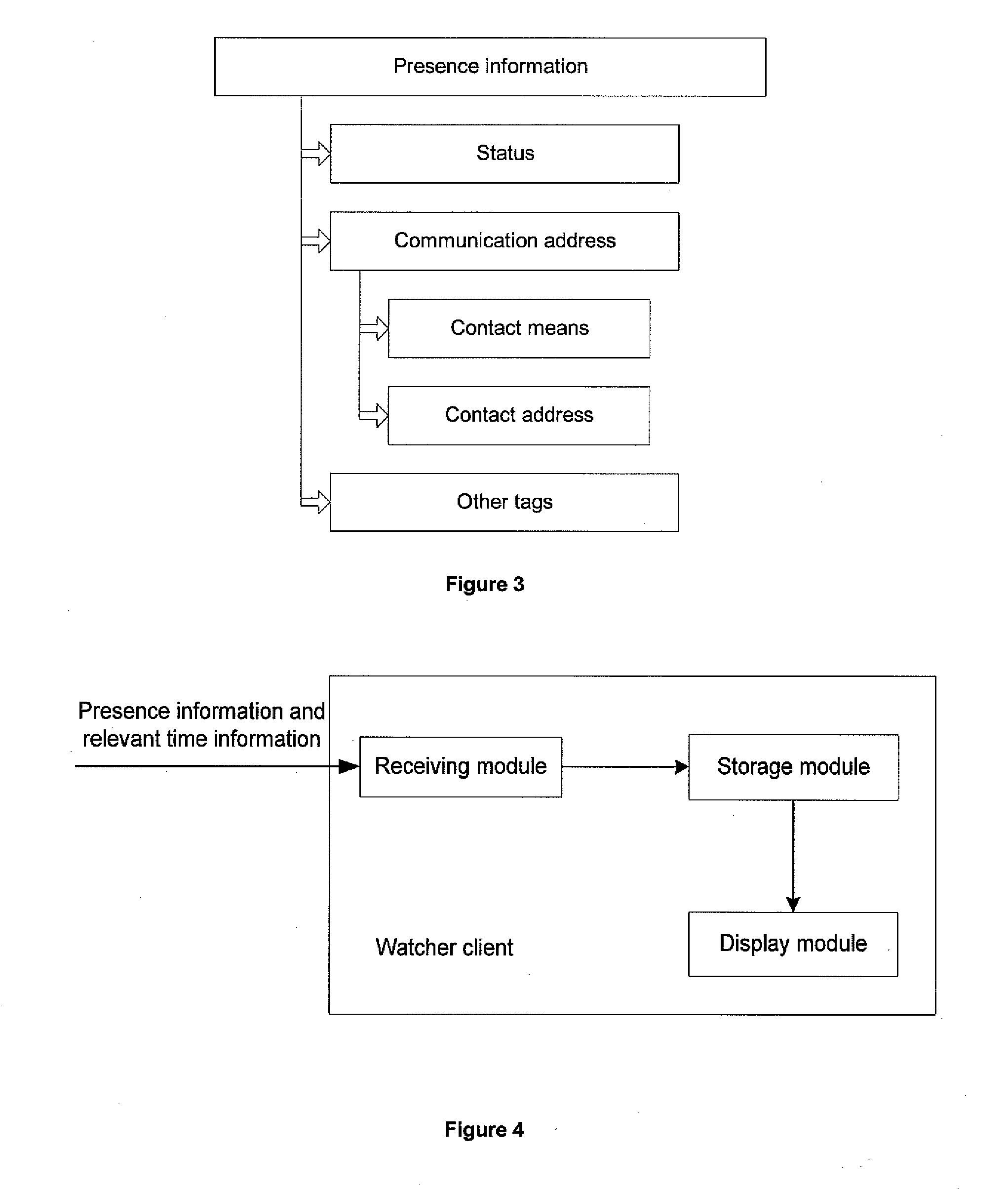
Method and apparatus for providing presence information
InactiveUS20070233859A1Digital computer detailsData switching networksTemporal informationState of art
The present invention discloses a method for providing presence information, a watcher, a presence server, a presence system and a presentity. It enables the provisioning of history and future presence information, while the prior arts can provide only presence information corresponding to the current time. The method provided by the present invention includes: setting time elements of presence information; recording relevant time information of presence information in the time elements; providing the watcher with presence information together with relevant time information.
Owner:HUAWEI TECH CO LTD
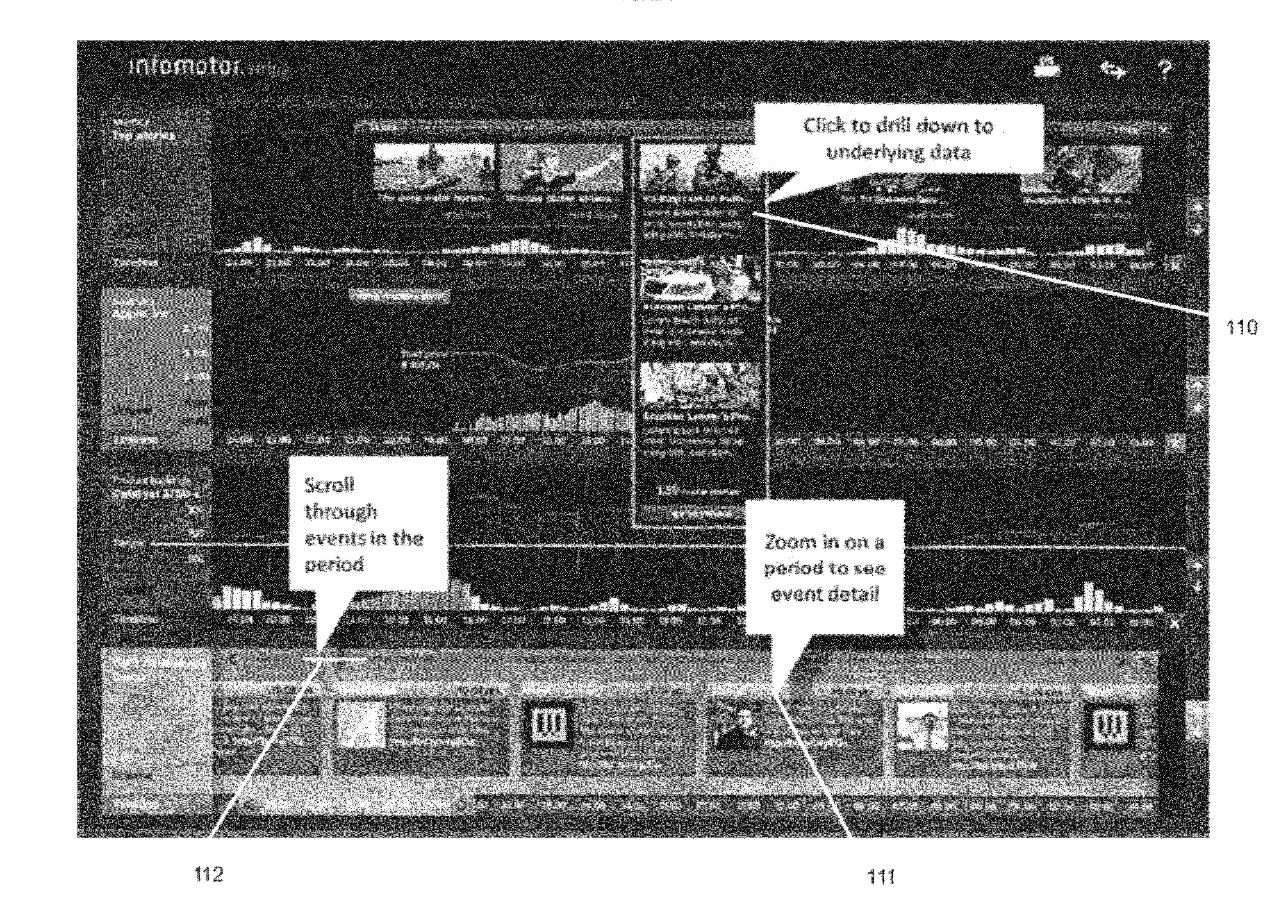
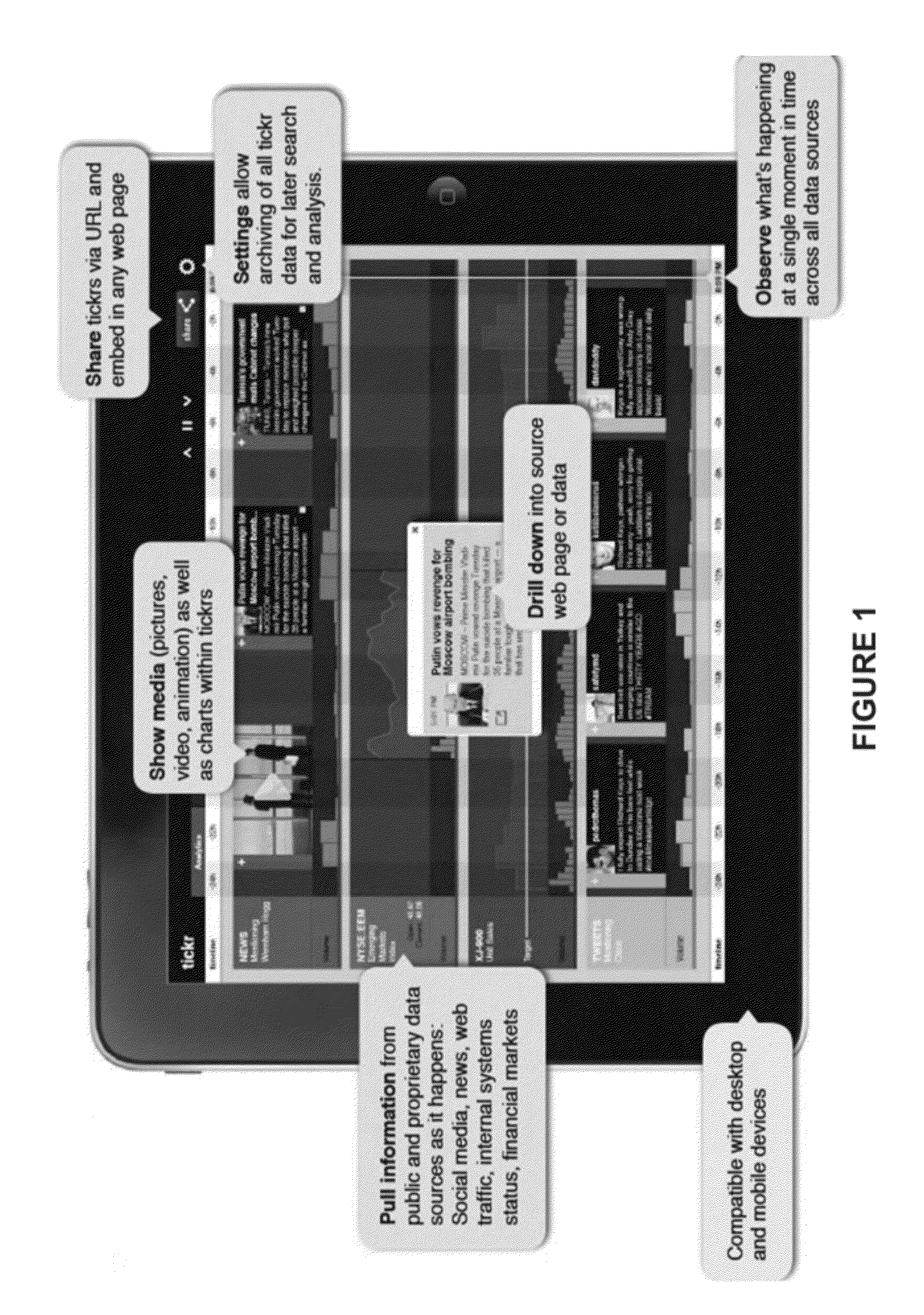
Multi-dimensional visualization of temporal information
ActiveUS20120173985A1Not simpleDigital data information retrievalSpecial data processing applicationsTemporal informationRelevant information
Various kinds of business and other information are tracked in real time. A coherent information visualization, for example as a time line, automatically, simultaneously presents relevant information to a user across multiple dimensions. Tools are provided that allow the user to establish and manipulate multi-dimensional linkages to develop insights into information gathered from multiple domains.
Owner:TICKR
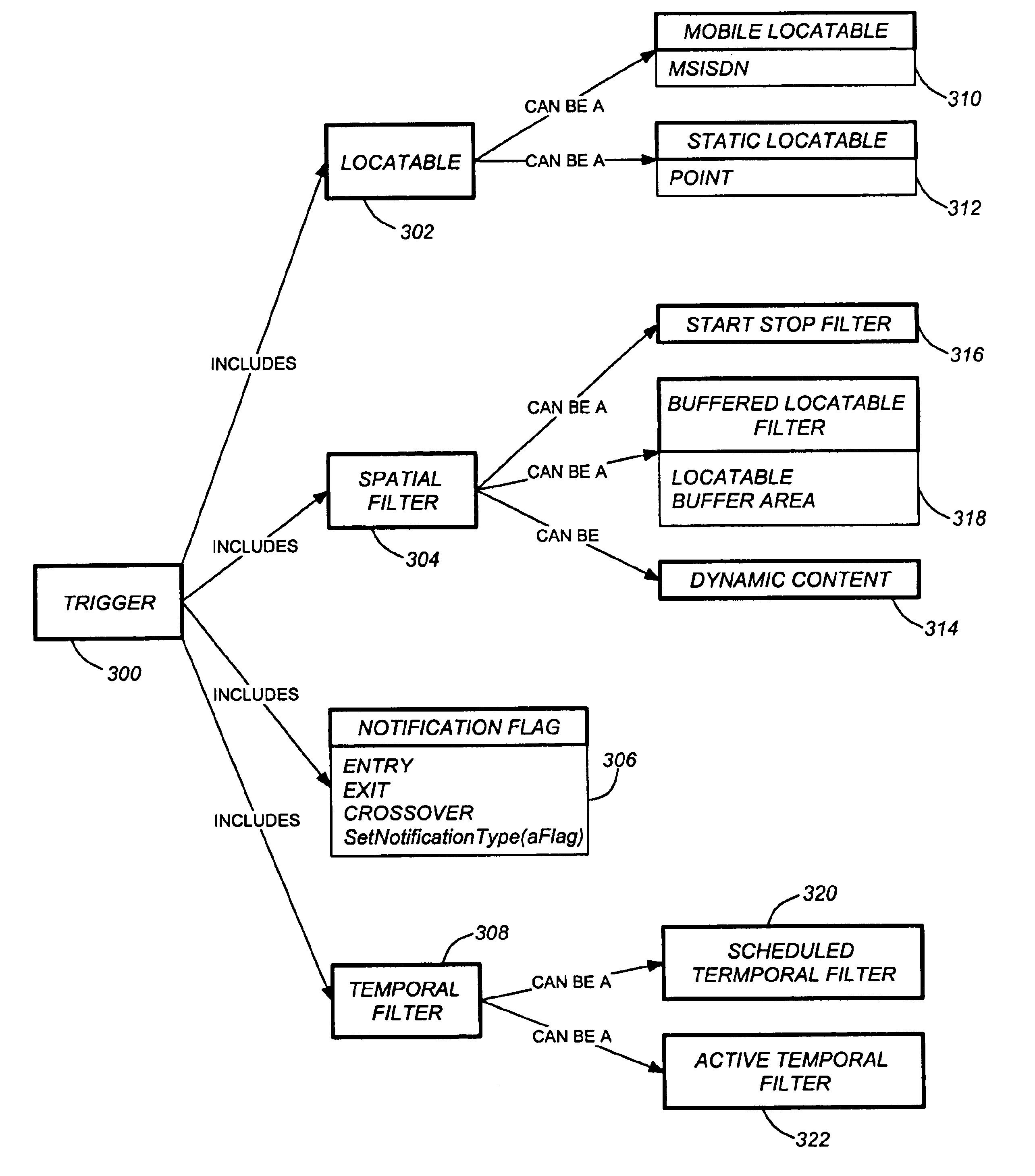
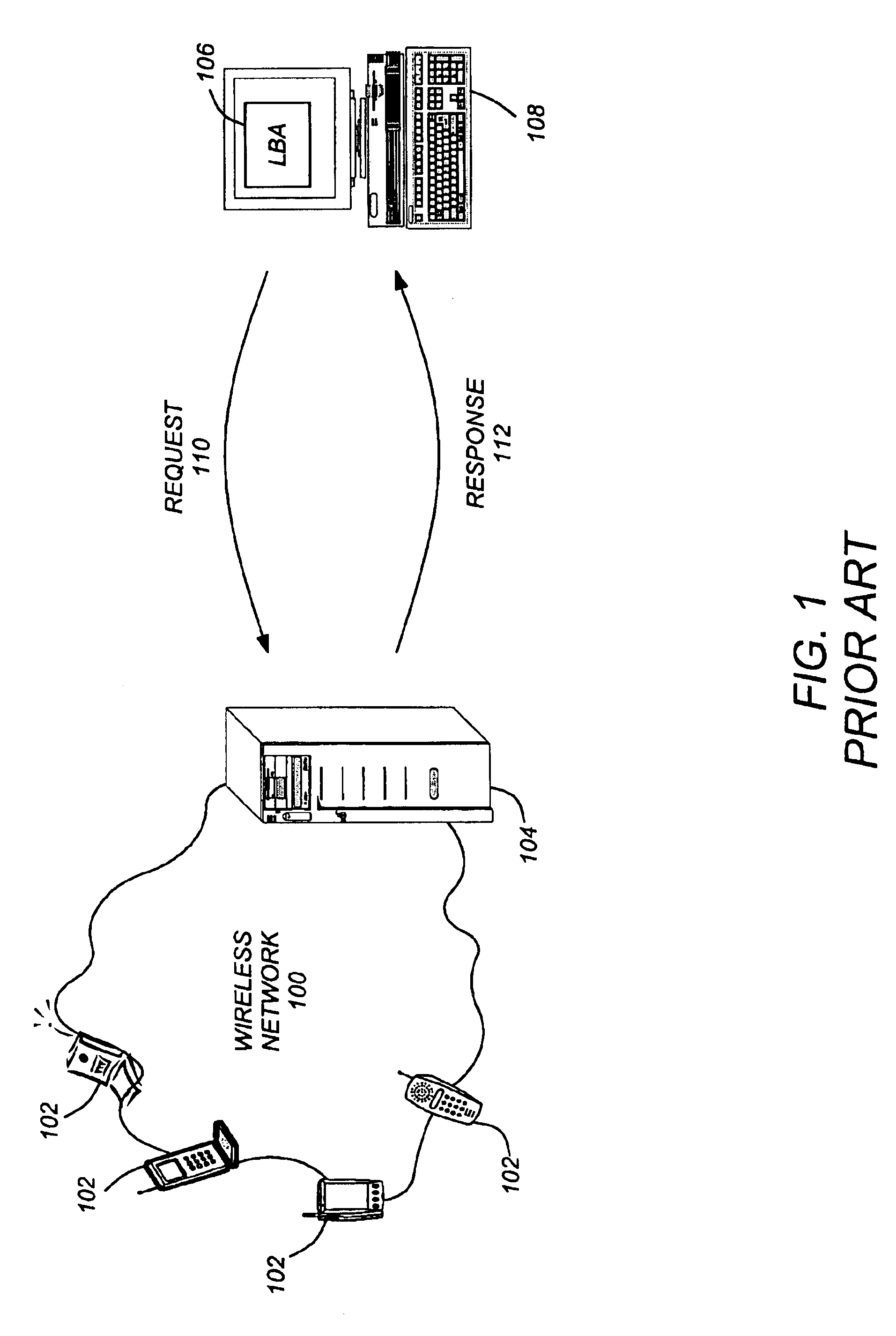
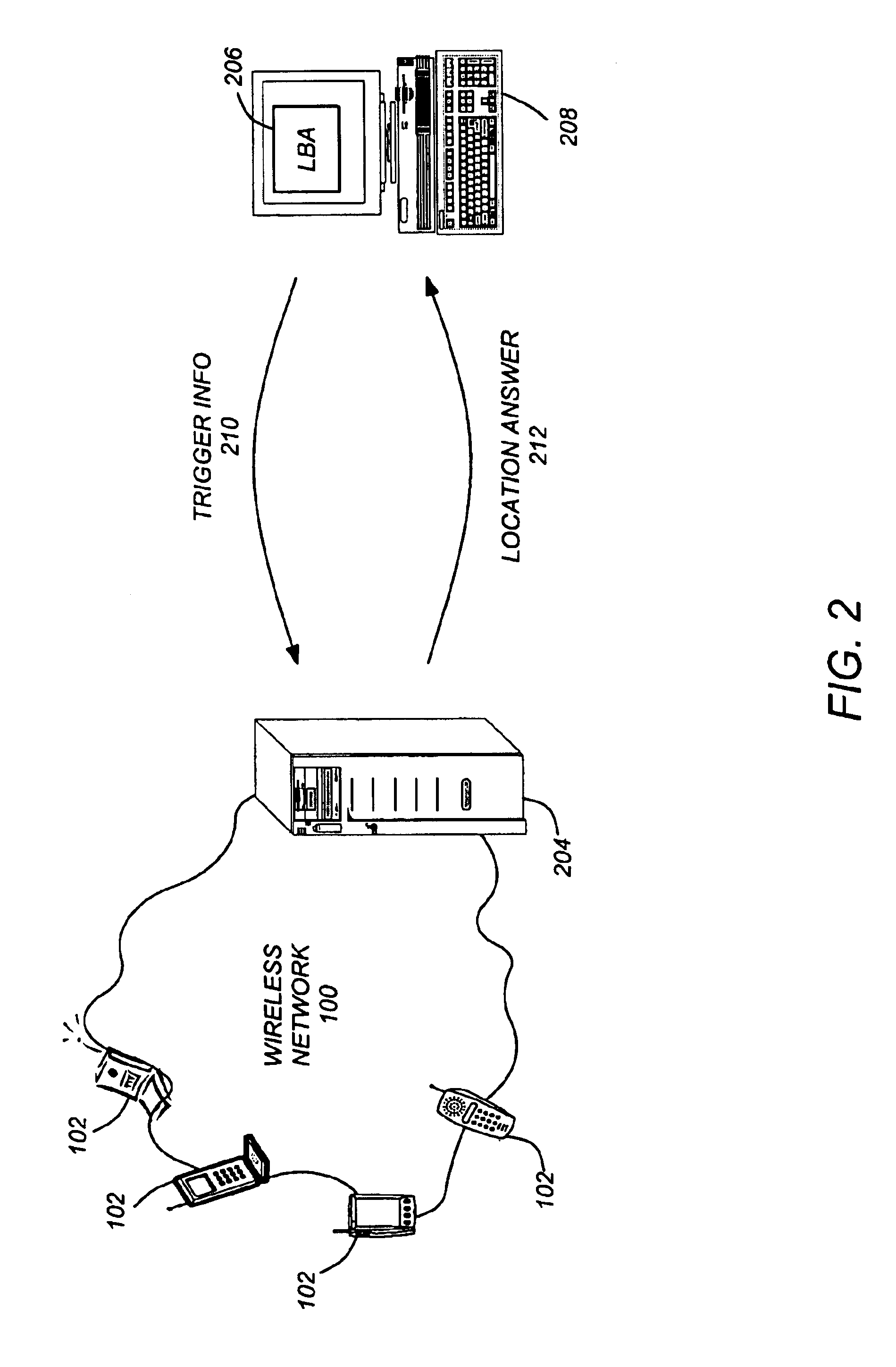
Use of triggers and a location hypercube to enable push-based location applications
ActiveUS6985747B2Minimizing pollingImprove performanceTelephonic communicationRadio/inductive link selection arrangementsTemporal informationComputer science
A method, system, and article of manufacture enable the use of location based applications (LBA). A location server (LS) on a wireless network receives trigger information from a LBA that is located outside of the wireless network. The trigger information defines a source locatable, spatial information (defining spatial criteria for a target locatable), a notification flag (describing) an interaction between the source locatable and the spatial criteria), and temporal information (defining a time period the trigger will be active). The LS determines if the triggers are active based on the temporal information and obtains updated locations if the trigger is active. Active triggers are evaluated to determine if a trigger alert has been caused by the locatables interacting with each other pursuant to the spatial information and notification flag. A location answer is pushed to the LBA if a trigger alert has been caused.
Owner:TELECOMM SYST INC
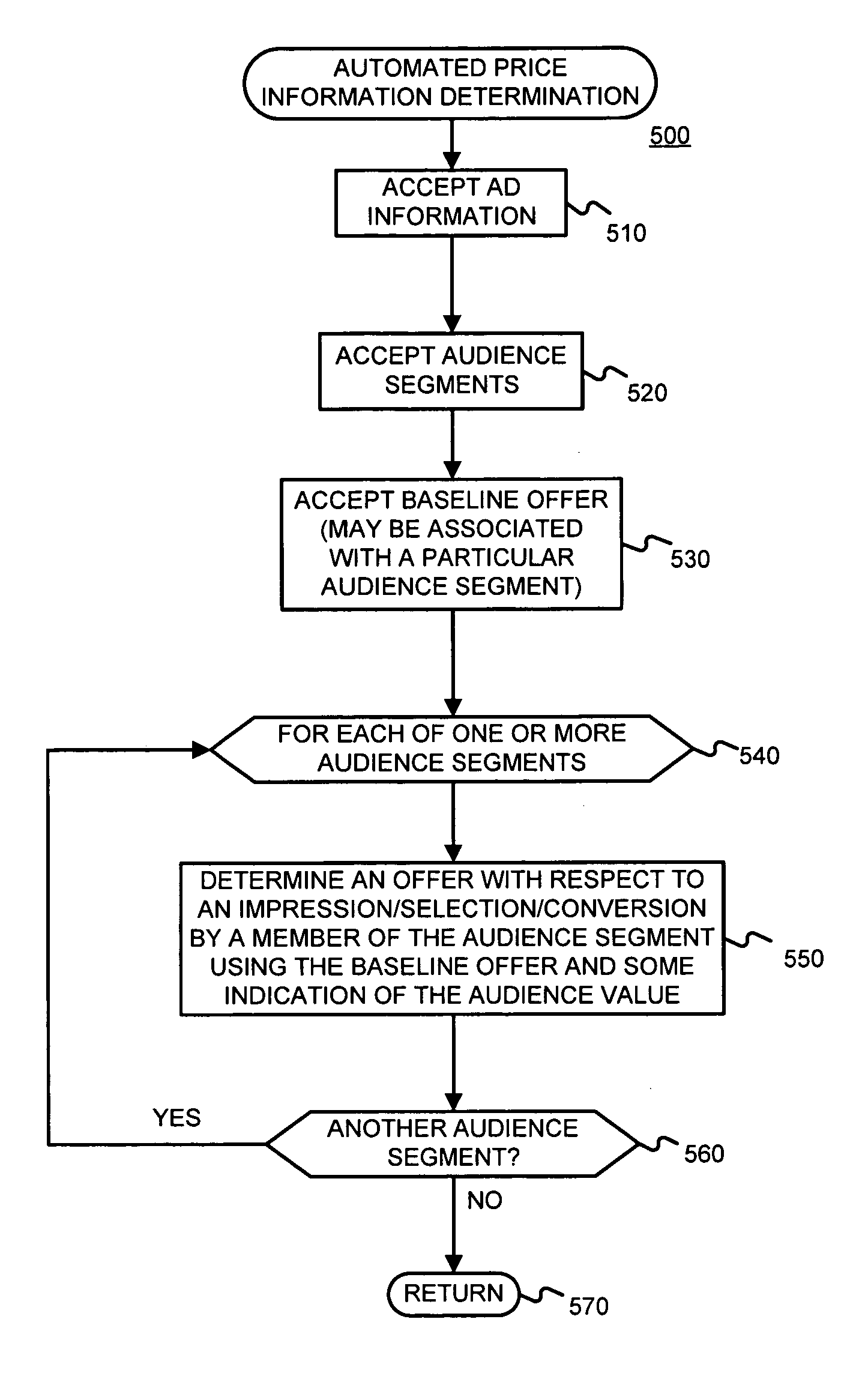
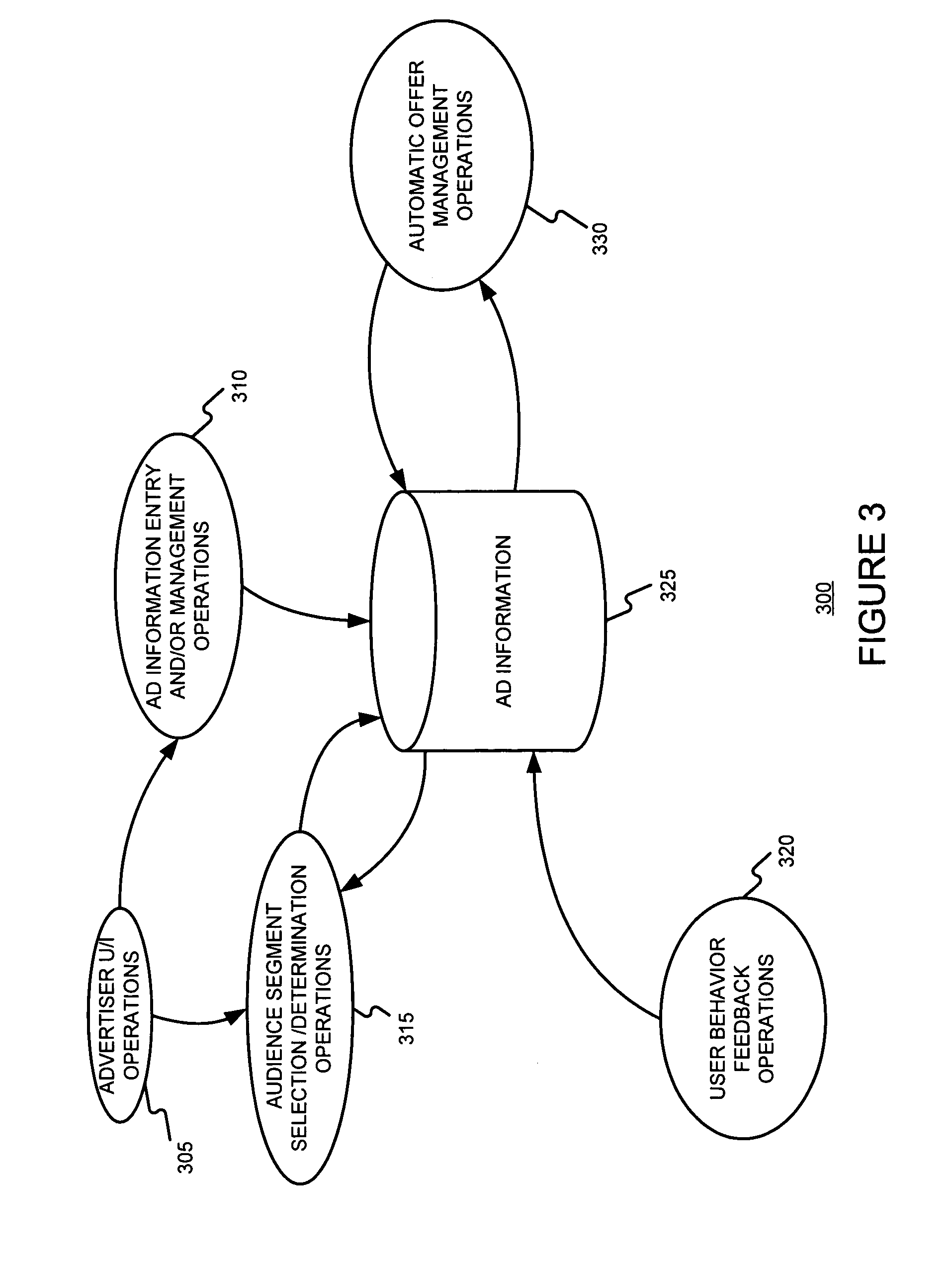
Automated offer management using audience segment information
An advertiser's management of an advertising campaign may be assisted by (a) accepting information defining a plurality of audience segments to which an advertisement may be served, (b) accepting a first offer, and (c) determining, using the first offer, a second offer associated with at least one of the plurality of audience segments. The act of determining a second offer associated with one of the plurality of audience segments may use an indication of value assigned to the one audience segment. The indication of value may be automatically determined, and / or provided by an advertiser. The indication of value may be expressed as functions, rules, and / or parameter values. The information defining a plurality of audience segments may be one or more of (a) location information, (b) user information, (c) temporal information, and (d) client device information.
Owner:GOOGLE LLC
Method for transmitting time information via a data packet network
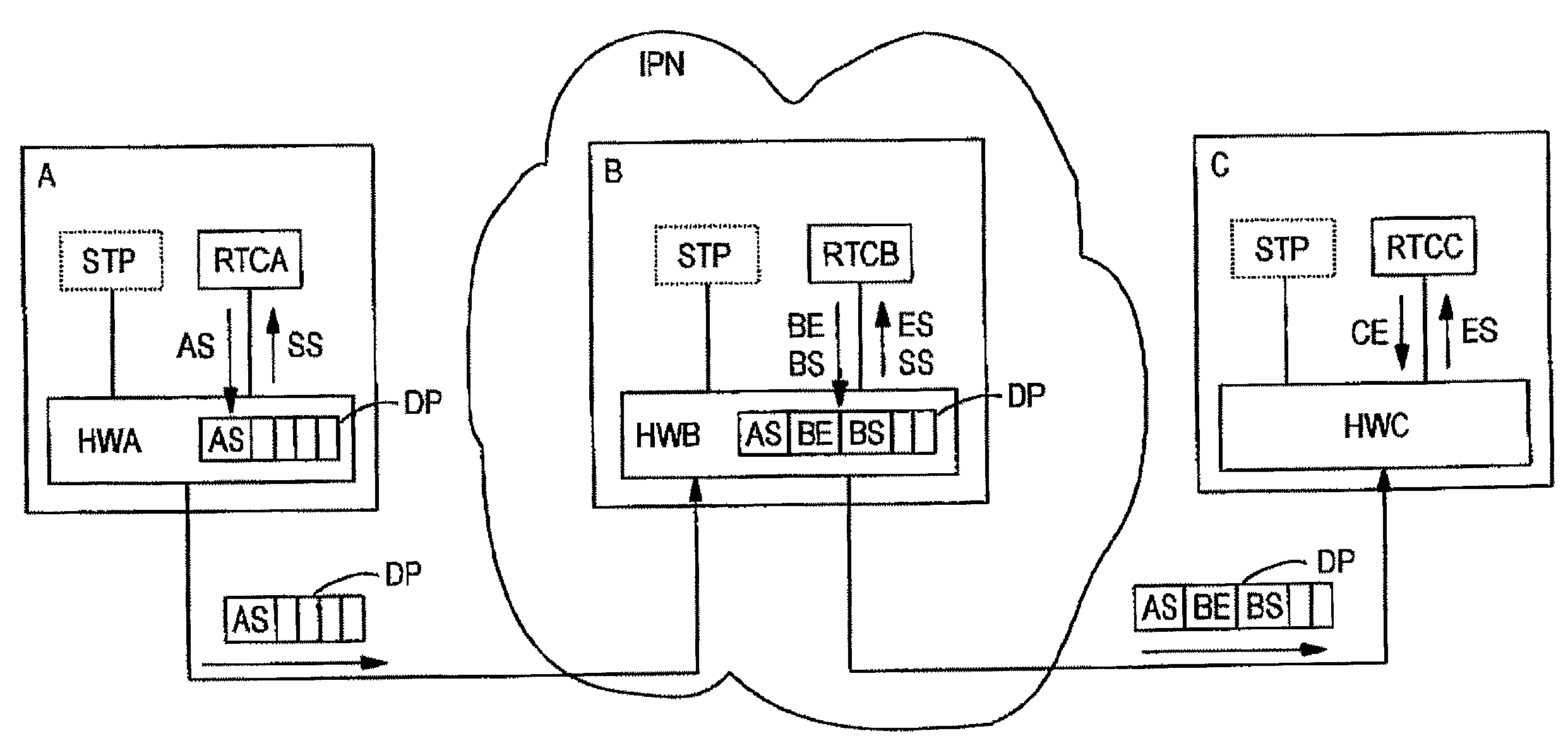
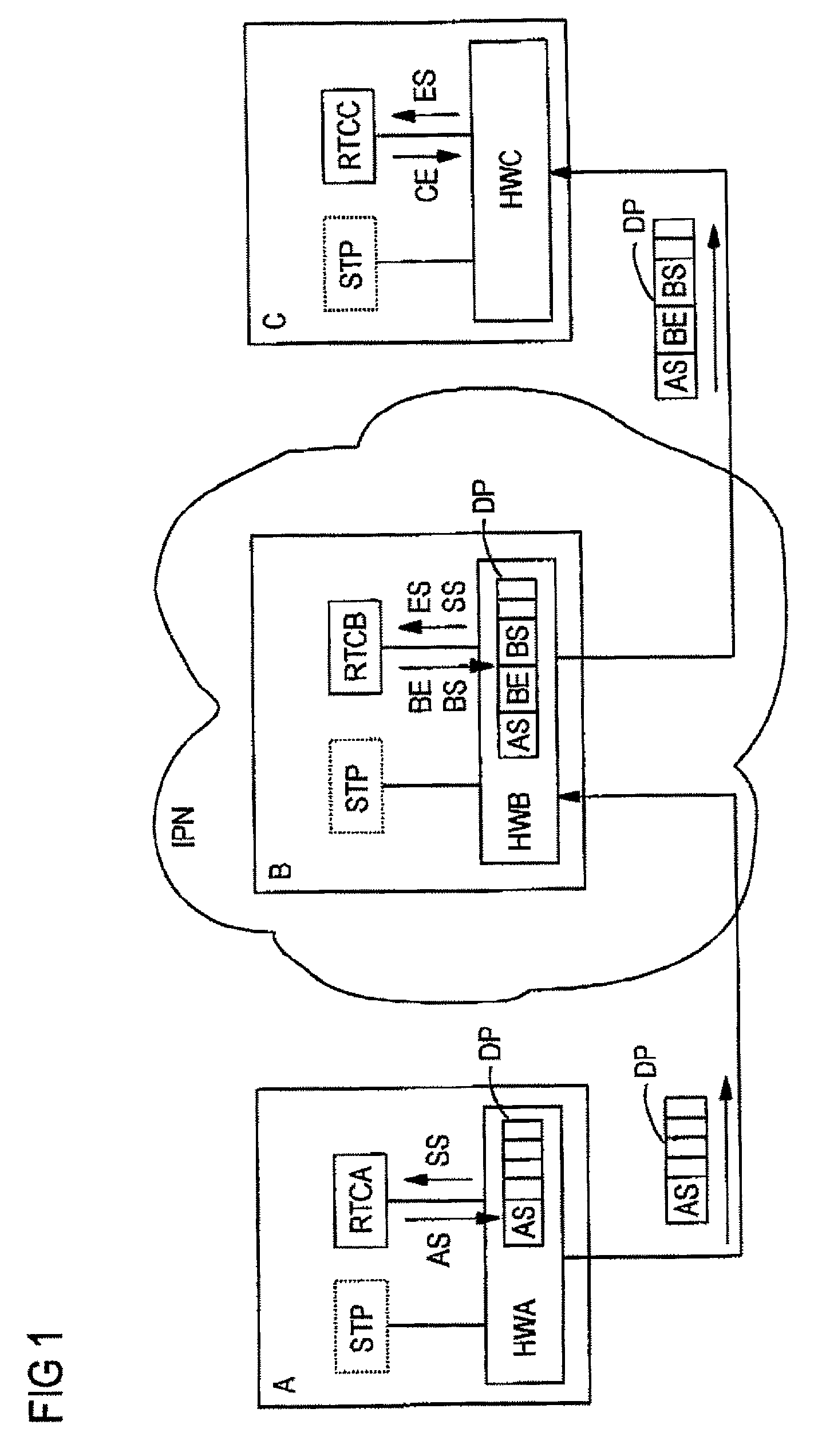
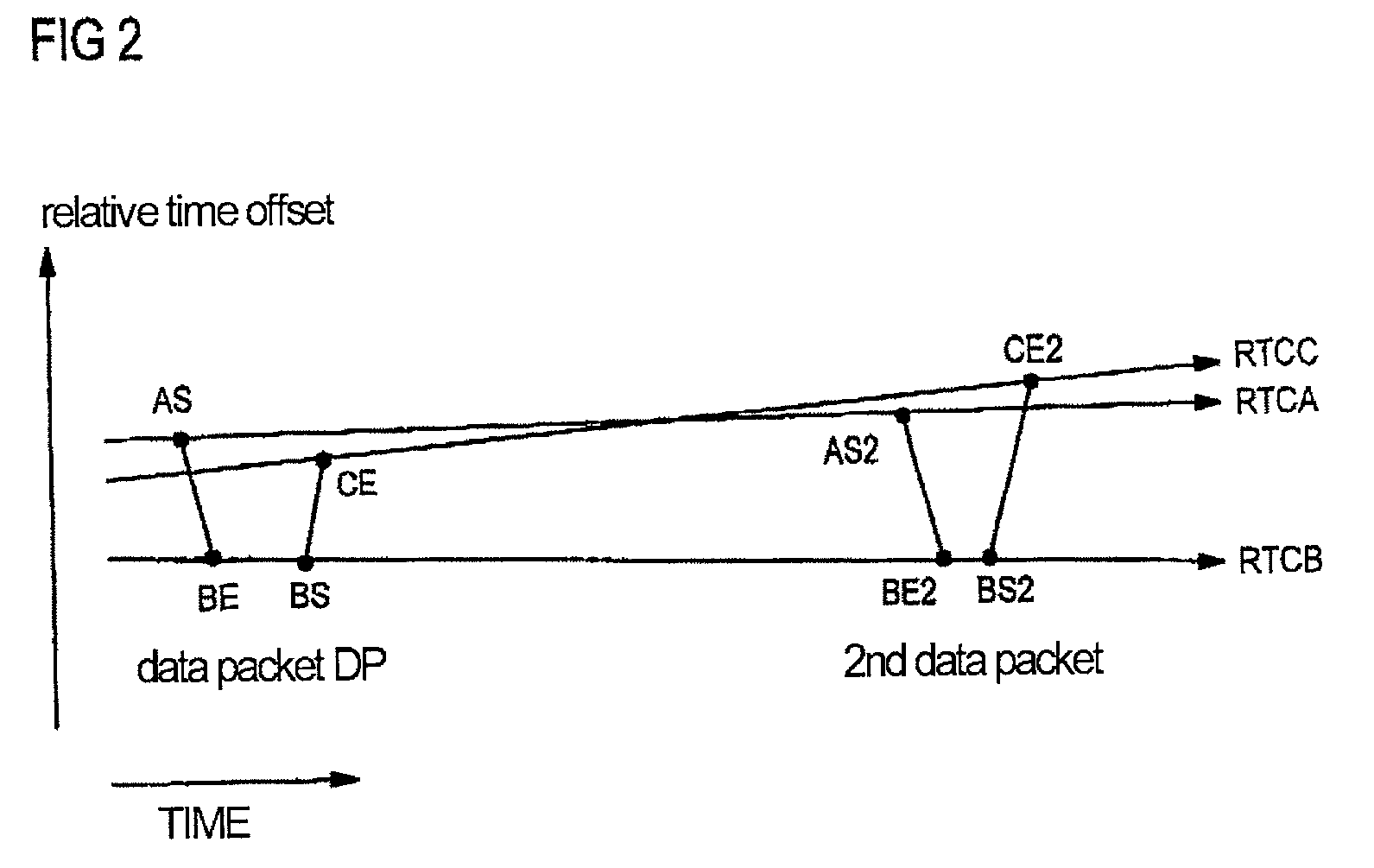
InactiveUS7372846B2Accurate timingHigh synchronization accuracyTime-division multiplexData switching by path configurationTemporal informationNetworked Transport of RTCM via Internet Protocol
Time information which is to be transmitted via a data packet network is called up from a time information source and is transmitted to a data packet transmission module. The data packet transmission module controls the transmission time of a data packet in which the time information is transmitted via the data packet network. The transmission time and the calling of the time information are aligned with respect to one another in time by a transmission signal which is generated by the time information source or by the data packet transmission module and indicates the transmission time.
Owner:RINGCENTRAL INC
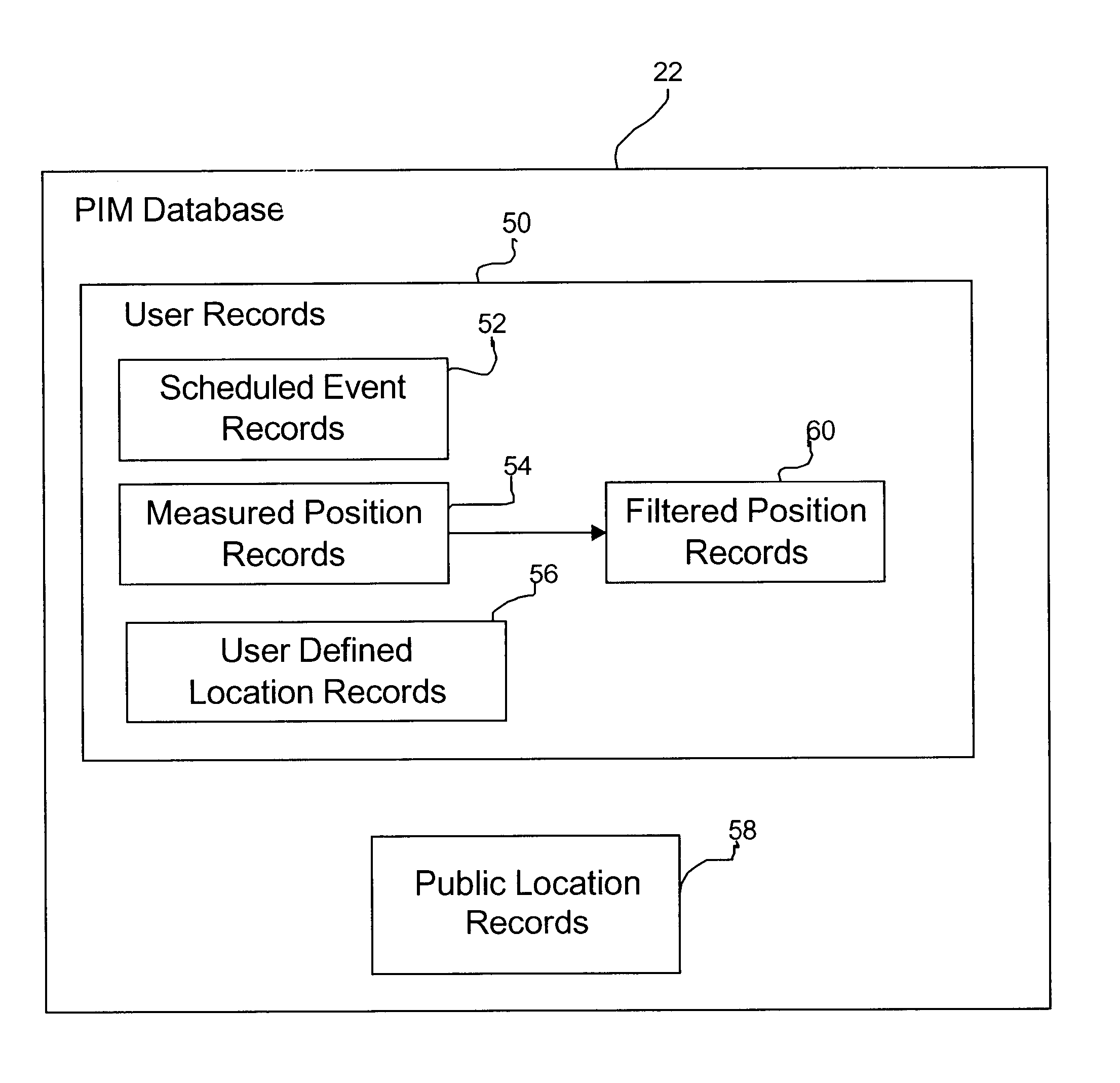
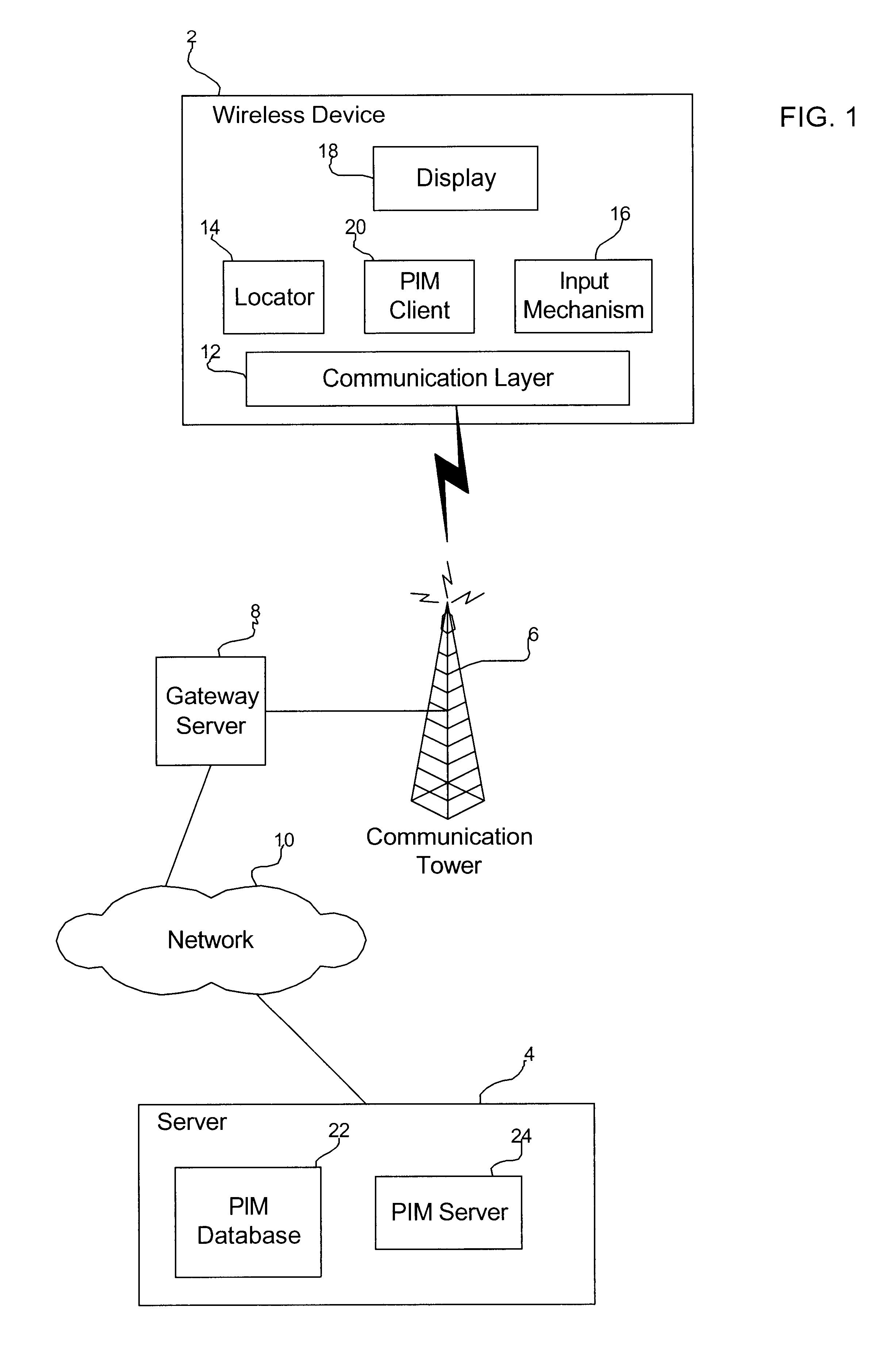
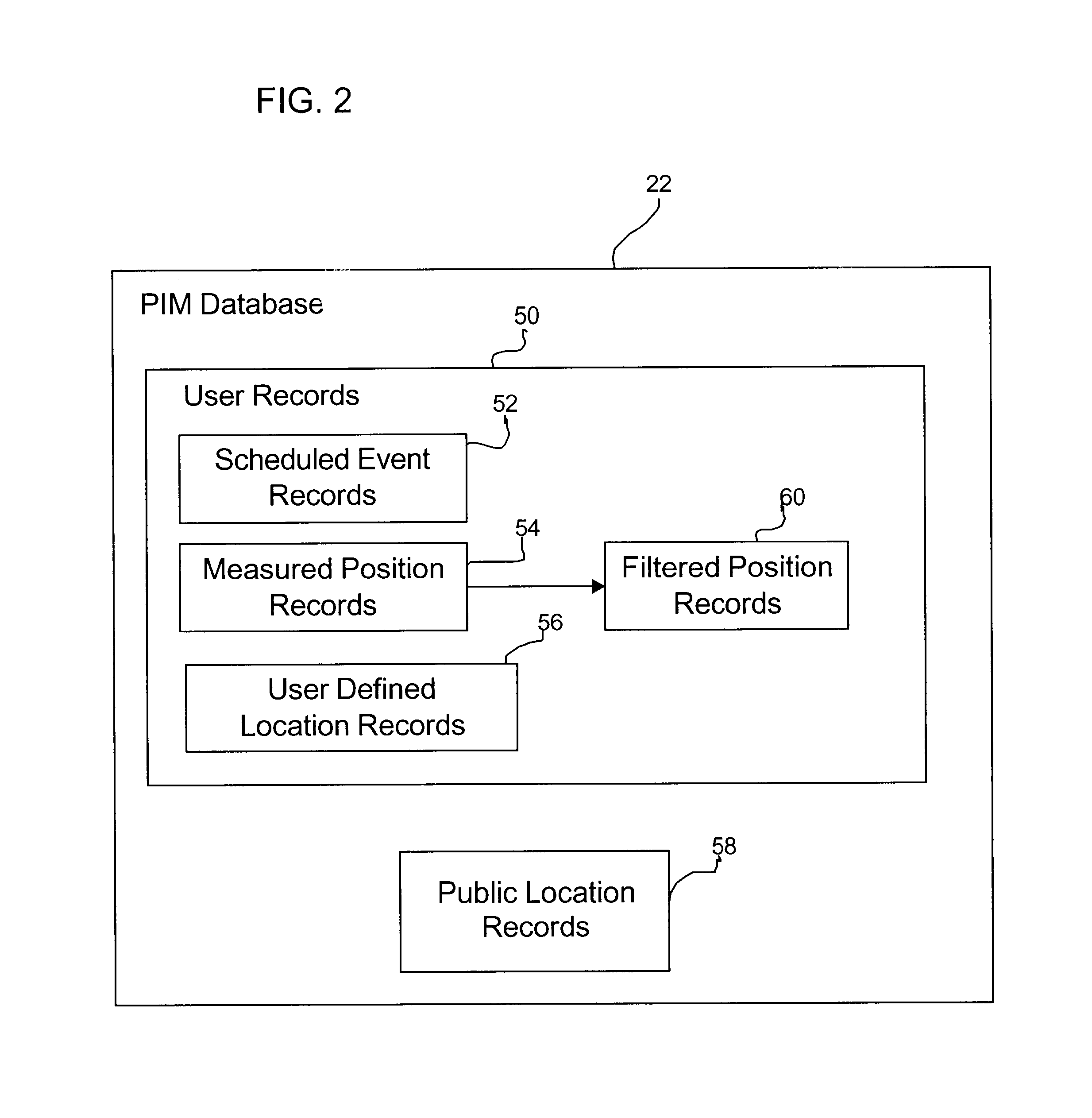
Method, system, and program for mining data in a personal information manager database
InactiveUS6751626B2Information can be usedRegistering/indicating time of eventsDigital data processing detailsTemporal informationTime segment
Provided is a method, system, and program for analyzing data within a personal information management program. Position records are provided in a database for at least one user. Each position record includes a time period value and event information indicating an event that occurred with respect to the user during the time period. The time period value and event information in each position record is based on time information and position coordinates generated by a wireless device associated with the user that indicate a location of the wireless device for time periods. The database is queried to determine position records for one user that satisfy at least one search criteria. Information is generated characterizing data in the determined position records.
Owner:MEDIATEK INC
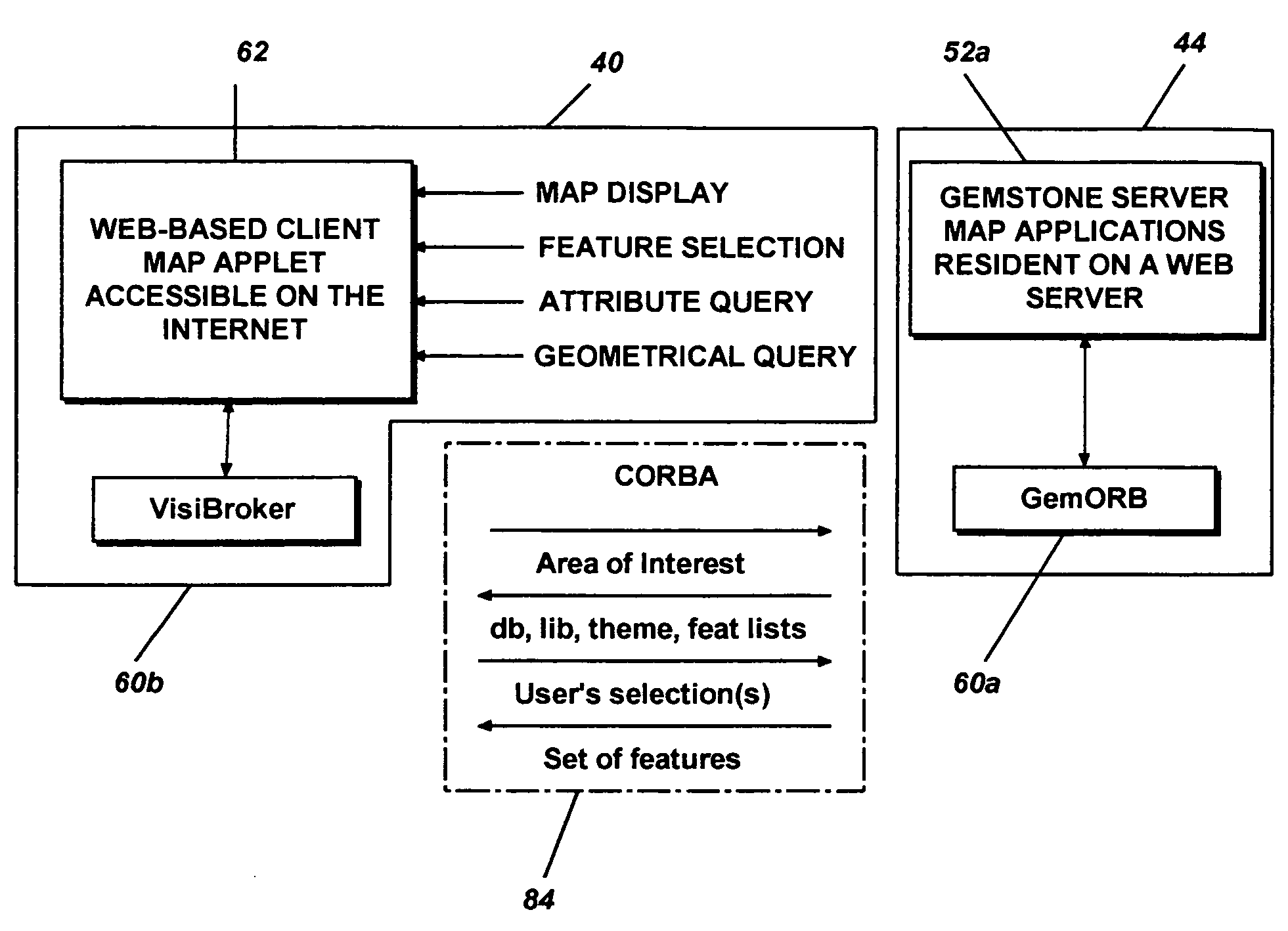
Distributed object-oriented geospatial information distribution system and method thereof
InactiveUS6985929B1Road vehicles traffic controlMultiple digital computer combinationsTemporal informationDistributed object
A distributed object-oriented geospatial database system and method thereof over the Internet using Web-based technology to perform data-driven queries, such as retrieving, viewing and updating, geospatial data of the object oriented geospatial database, such as vector, raster, hypertext and multimedia data, including data types or formats of ESRI shape files, GSF, oceanographic ASCII text data by NAVOCEANO and geospatial data with temporal information and supporting 3D display of the geospatial data. The object-oriented geospatial database system is implemented in a heterogeneous object-oriented development and integration environment through the Common Object Request Broker Architecture (CORBA).
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
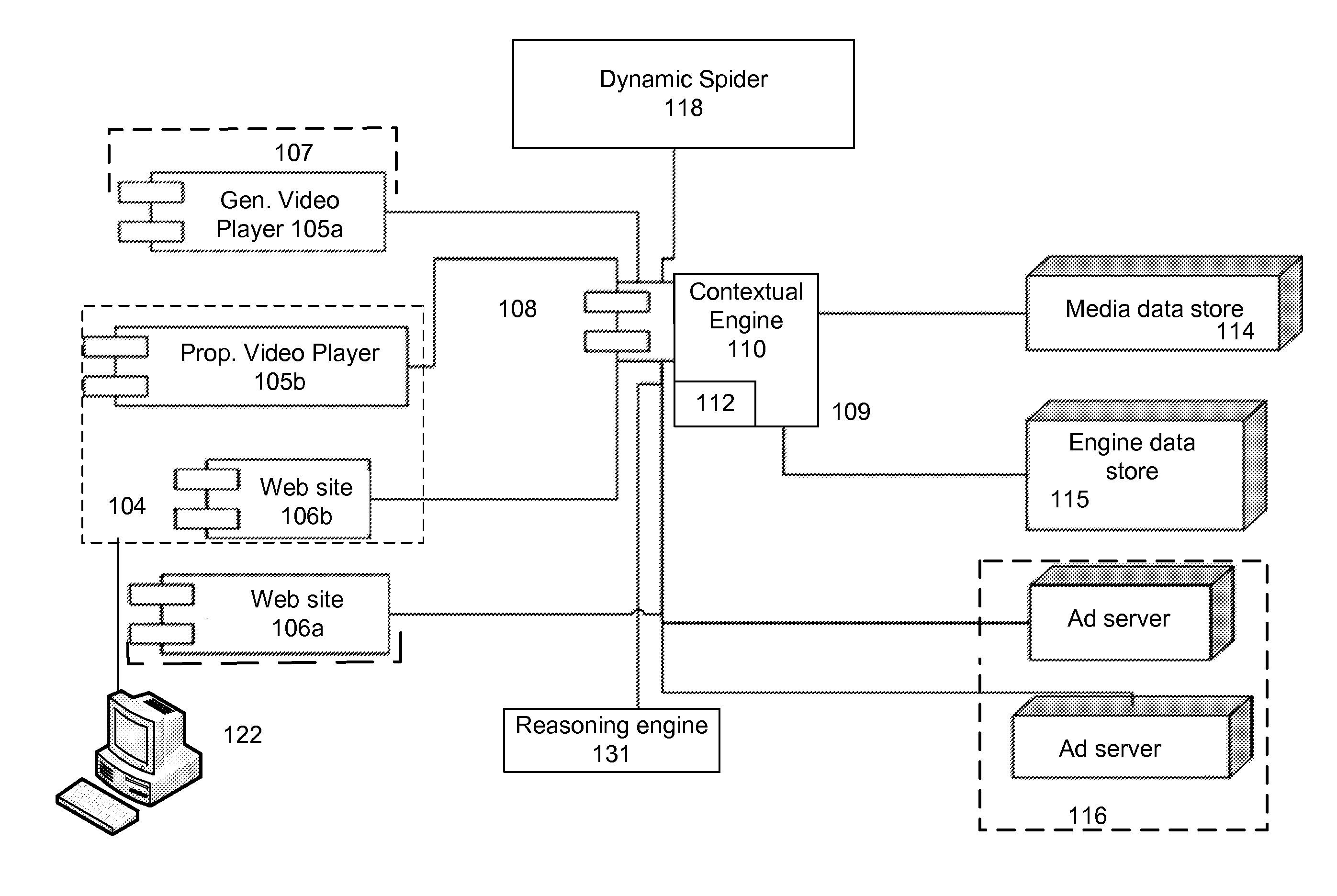
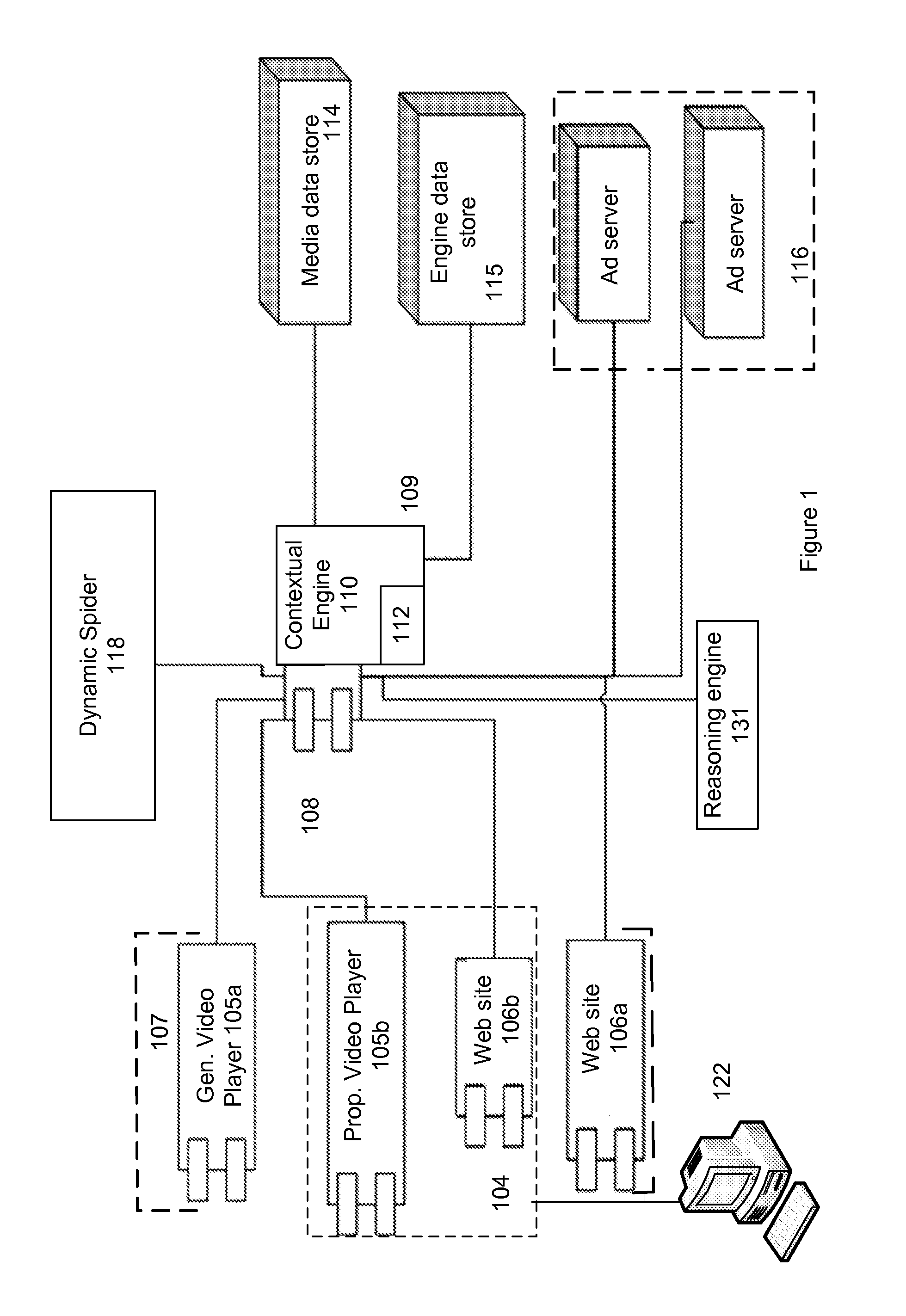
Various methods and apparatuses for an engine that pairs advertisements with video files
InactiveUS20090119169A1Metadata video data retrievalMultiple digital computer combinationsTemporal informationTemporal context
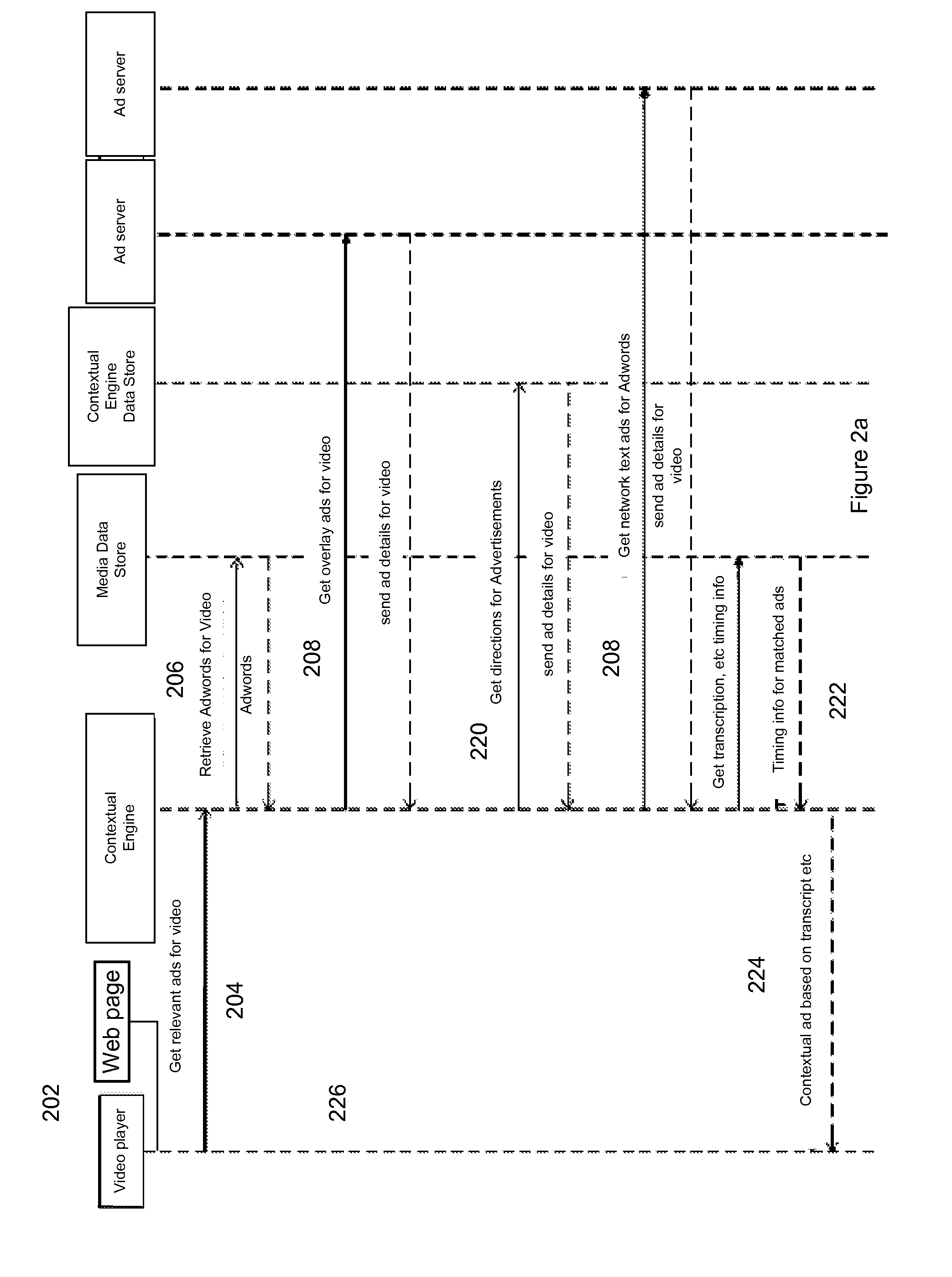
A system to pair advertisements with media files is described. A request is processed to find one or more relevant advertisements and determine when to display each relevant advertisement at a temporally contextual point within a video file when the video file is played on a web page. The video file's key concepts and timing information are retrieved from a database. A request is generated for advertisements that contextually match the content in the key conceptual points found in the content of the video file. The timing information is retrieved regarding when the key conceptual points, relevant to returned advertisements that contextually match, chronologically appear in the video file. Contextual relevant advertisements are supplied with temporal information on when the placement of advertisements is most contextually relevant to the content being played in the video file.
Owner:RHYTHMONE
Network redirector systems and methods for performing data replication
InactiveUS7962709B2Reduce impactReduce memory requirementsDigital data information retrievalDigital data processing detailsTemporal informationNetwork redirector
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Systems and methods for monitoring application data in a data replication system
InactiveUS20070185939A1Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationGoal system
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
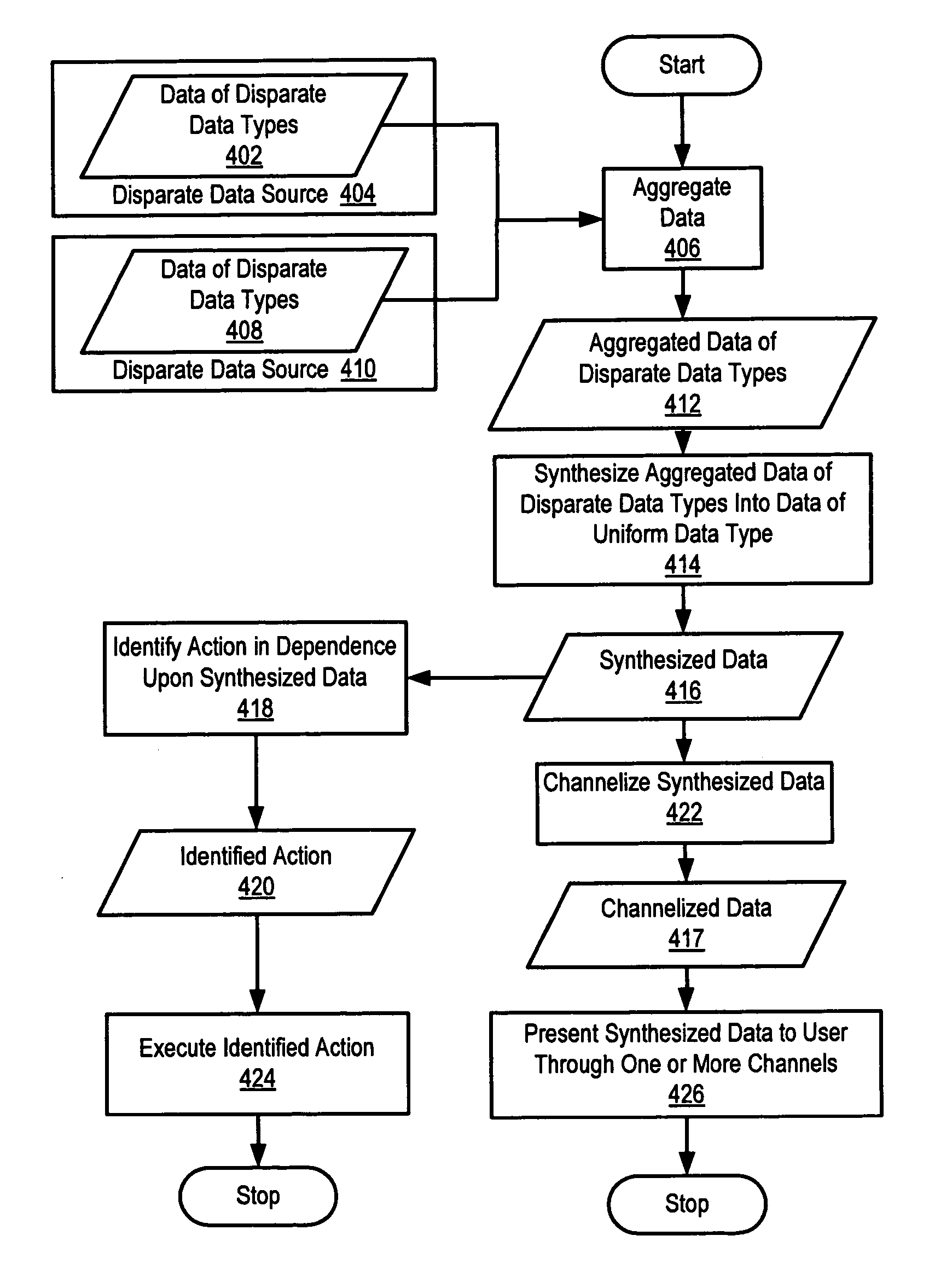
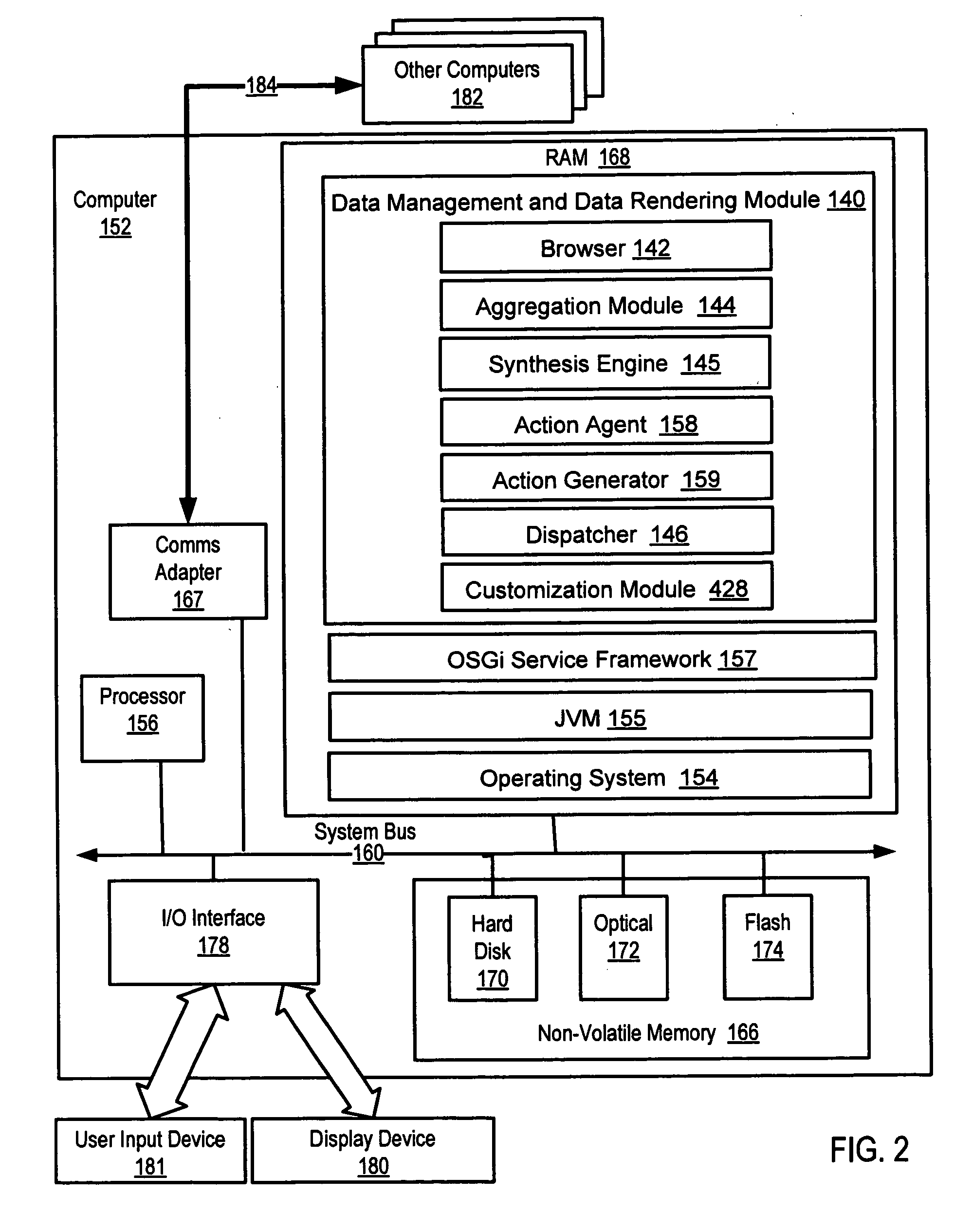
Management and rendering of calendar data
InactiveUS20070061712A1Digital data information retrievalDigital computer detailsTemporal informationPaper document
Methods, systems, and products are disclosed for management and rendering of calendar data, including receiving aggregated calendar data in native form, synthesizing the aggregated native form calendar data into a synthesized calendar document including one or more synthesized calendar events, and presenting at least one synthesized calendar event. Synthesizing the aggregated native form calendar data into a synthesized calendar document including one or more synthesized calendar events includes translating aspects of the aggregated native form calendar data into text and markup. Aspects of the aggregated native form calendar data include a calendar event. A calendar event includes date and time information and an event description.
Owner:IBM CORP
Destination systems and methods for performing data replication
InactiveUS20070185937A1Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
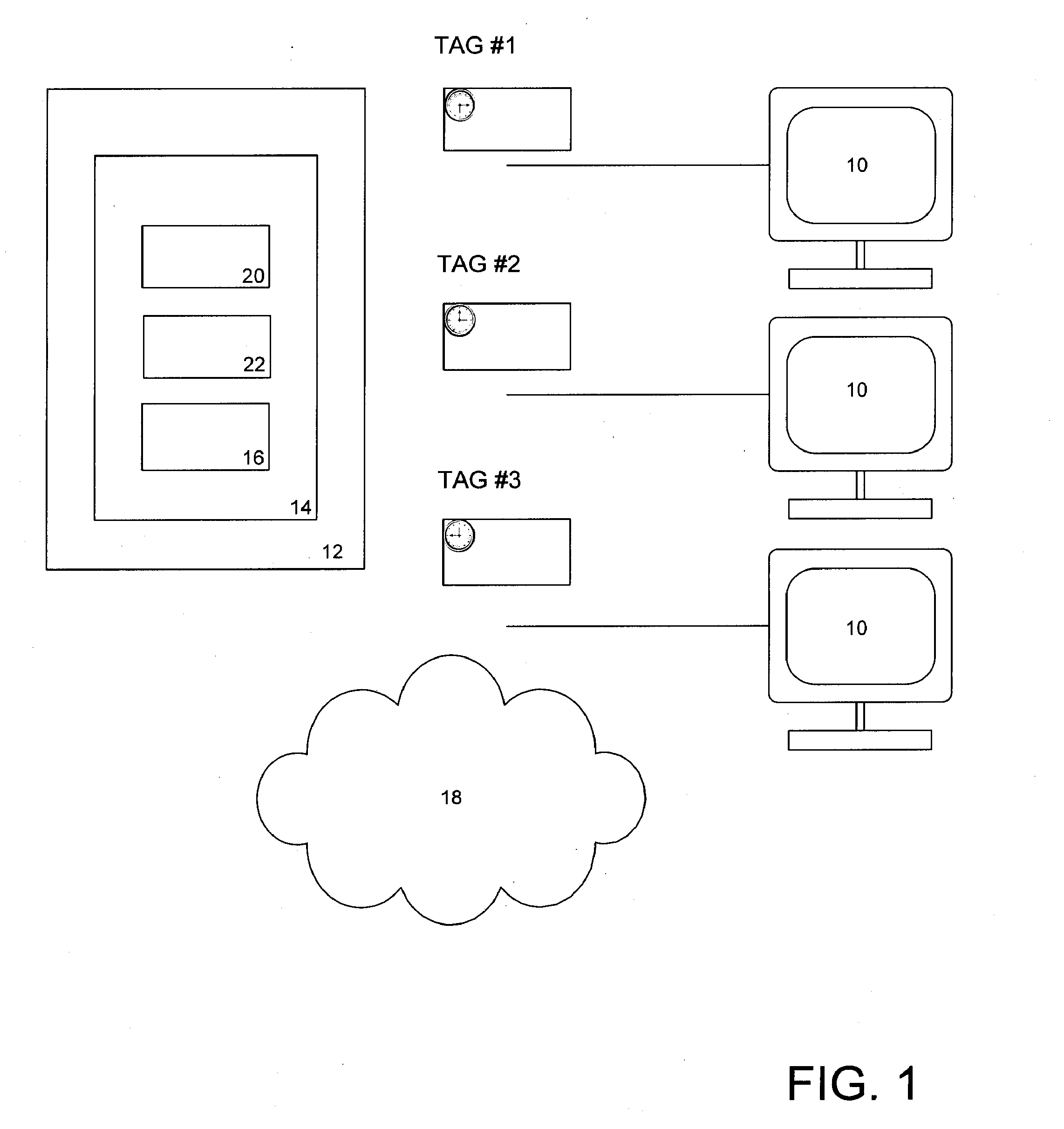
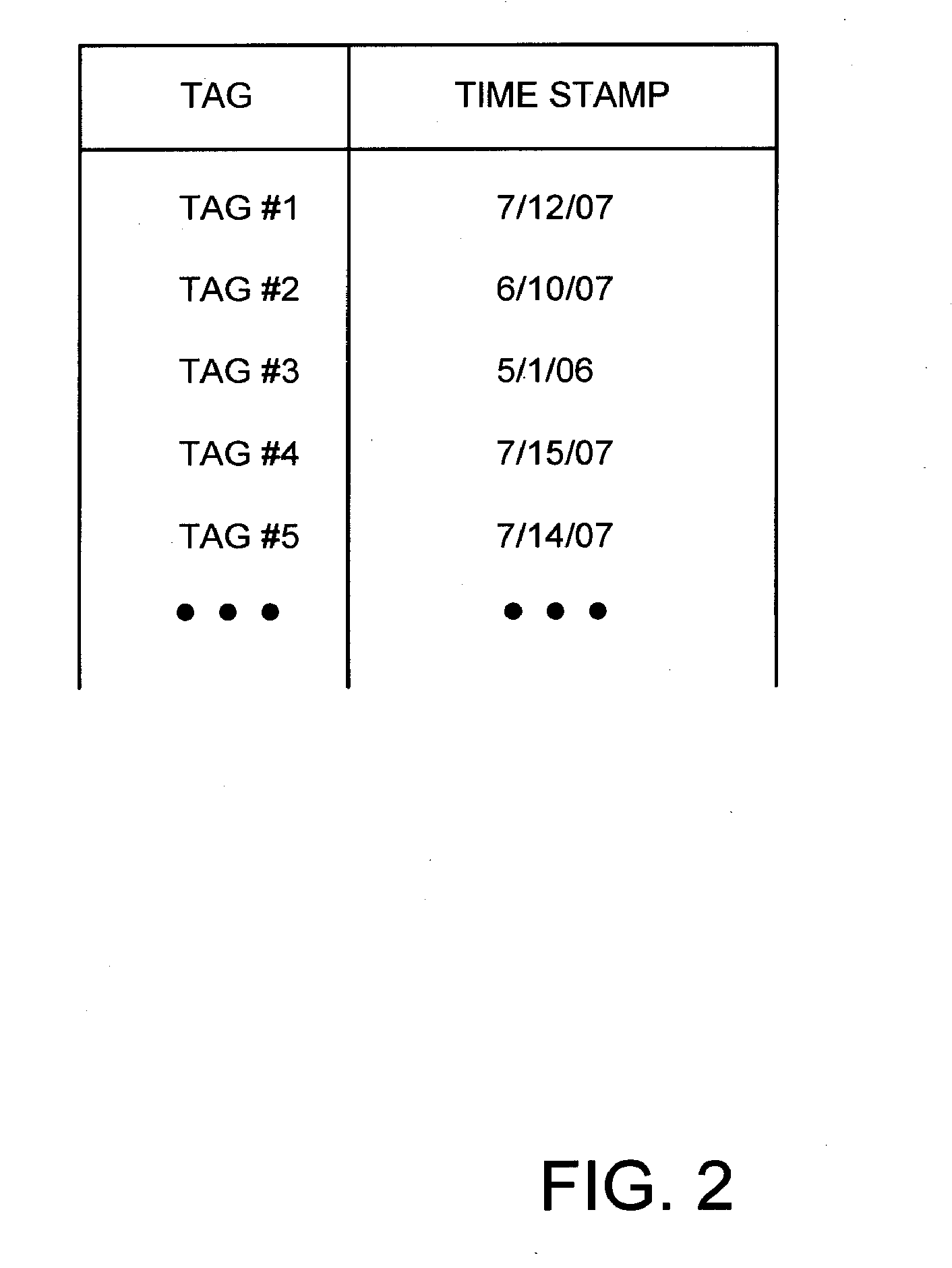
Methods and Apparatus for Detecting Fraud with Time Based Computer Tags
ActiveUS20090083184A1Detection of potentialPrevention of potentialComputer security arrangementsPayment architectureTemporal informationBank account
Systems and methods for creating and analyzing computer tag information for the prevention or detection of potential fraud. Computers and other devices accessing the Web carry device tags with date and time information describing when they were issued by a security tag server. A server time stamp may be inserted into time based computer tags such as a cookies indicating when they were created. Such time stamp information can be encrypted and analyzed during future attempts to access a secure network such as a customer attempting to log into an online banking account. When the time stamp information from the tag is compared to other selected information about the user, device and / or account, including but not limited to last account log-in date / time or account creation date, the invention may be used to detect suspicious activity.
Owner:THE 41ST PARAMETER
Principles and methods for personalizing newsfeeds via an analysis of information novelty and dynamics
InactiveUS7293019B2Minimize time and disruptionData processing applicationsDigital data information retrievalPersonalizationTemporal information
A system and methodology is provided for filtering temporal streams of information such as news stories by statistical measures of information novelty. Various techniques can be applied to custom tailor news feeds or other types of information based on information that a user has already reviewed. Methods for analyzing information novelty are provided along with a system that personalizes and filters information for users by identifying the novelty of stories in the context of stories they have already reviewed. The system employs novelty-analysis algorithms that represent articles as a bag of words and named entities. The algorithms analyze inter- and intra-document dynamics by considering how information evolves over time from article to article, as well as within individual articles.
Owner:MICROSOFT TECH LICENSING LLC
Buffer configuration for a data replication system
InactiveUS20070183224A1Reduce impactReduce memory requirementsError detection/correctionDatabase distribution/replicationTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Product integrity systems and associated methods
InactiveUS20050080566A1Soften contactAvoid breakingForce measurement using piezo-electric devicesLinear/angular speed measurementAccelerometerTransceiver
The invention provides a smart sensor in the form of an adhesive bandage. The sensor may be used in many applications such as within sports, the shipping industry and medical and health industries. The sensor sticks to people and objects and wirelessly communicates with remote receivers. Internal detectors sense conditions associated with movement and / or the environment of the sensor. In one example, an accelerometer detects impact and drop distance of a package in transit; the sensor is either within a label or attached to a product within the package. The sensor may also prevent theft and assist in tracking package disposition so as to reduce lost packages. The sensors of the invention may also be used in fitness and health, such as to monitor body functions of heart rate and respiration; these sensors also may initiate immediate wireless warnings for improper functions so that persons may obtain immediate assistance. Sensors of the invention are also useful for sports media broadcasts; multiple sensors may attach to athletes so that wireless performance data is made available, in near real time, to audiences and media observers. Data from sensors of the invention may also change the computer gaming community; that is, certain sensors tracking real performance data may relay information used within gaming so as to govern computer gaming motions. Typically, sensors of the invention communicate by an RF transmitter or transceiver. Groups of sensors may be combined within a common canister that imparts date and time information and “power on” when dispensed.
Owner:TVIPR
Rolling cache configuration for a data replication system
InactiveUS20070226438A1Reduce impactReduce memory requirementsMemory loss protectionDigital data processing detailsTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
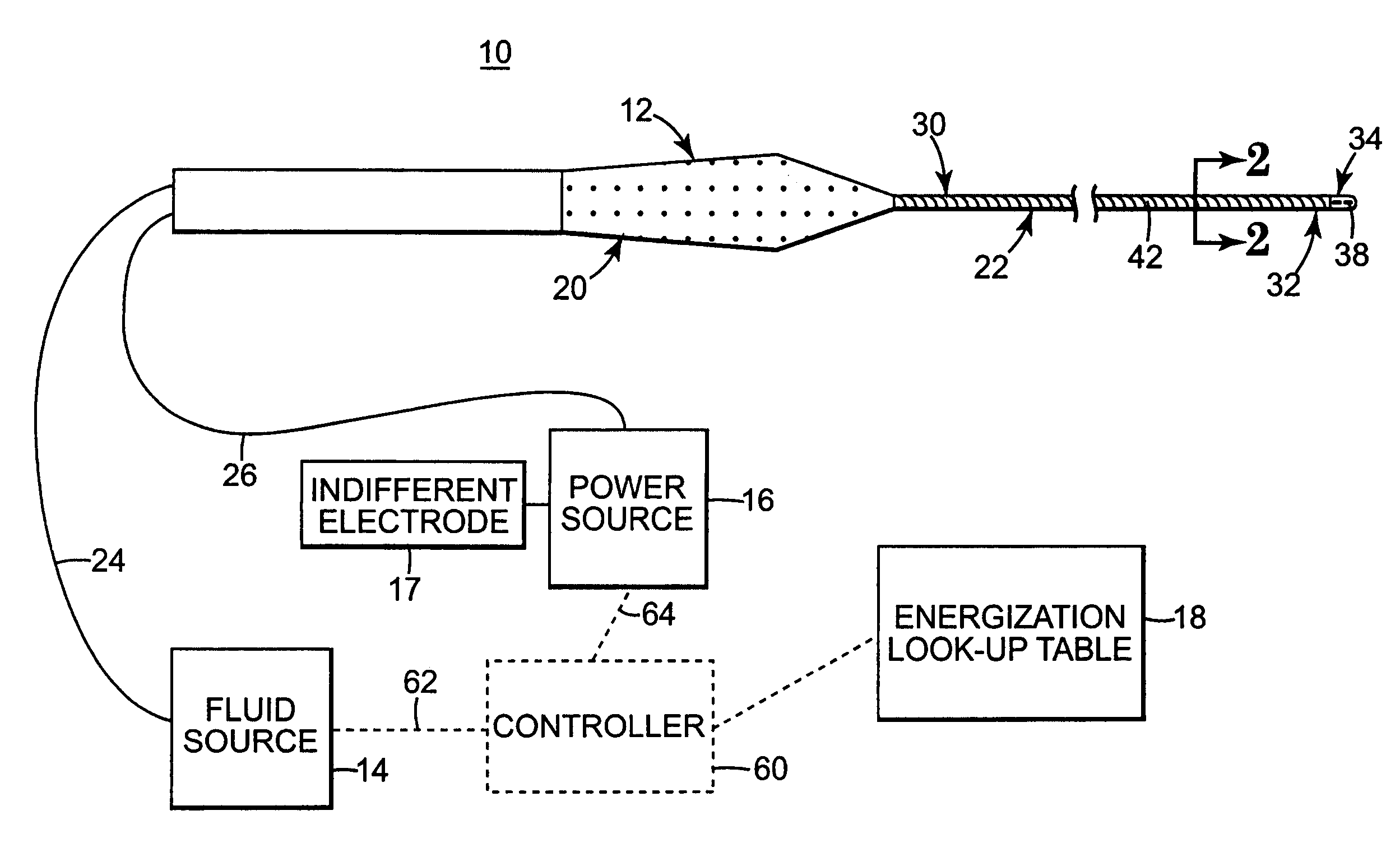
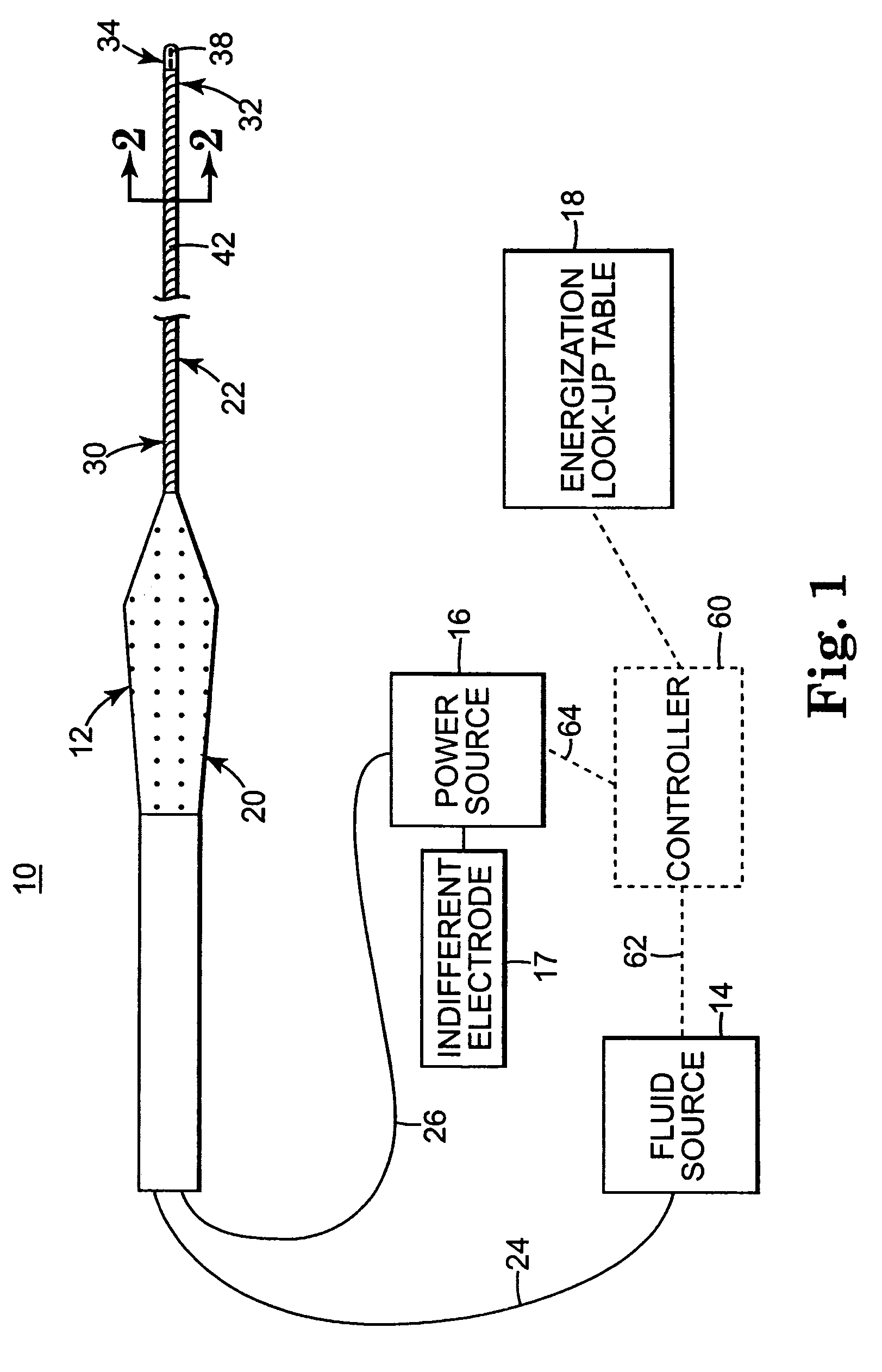
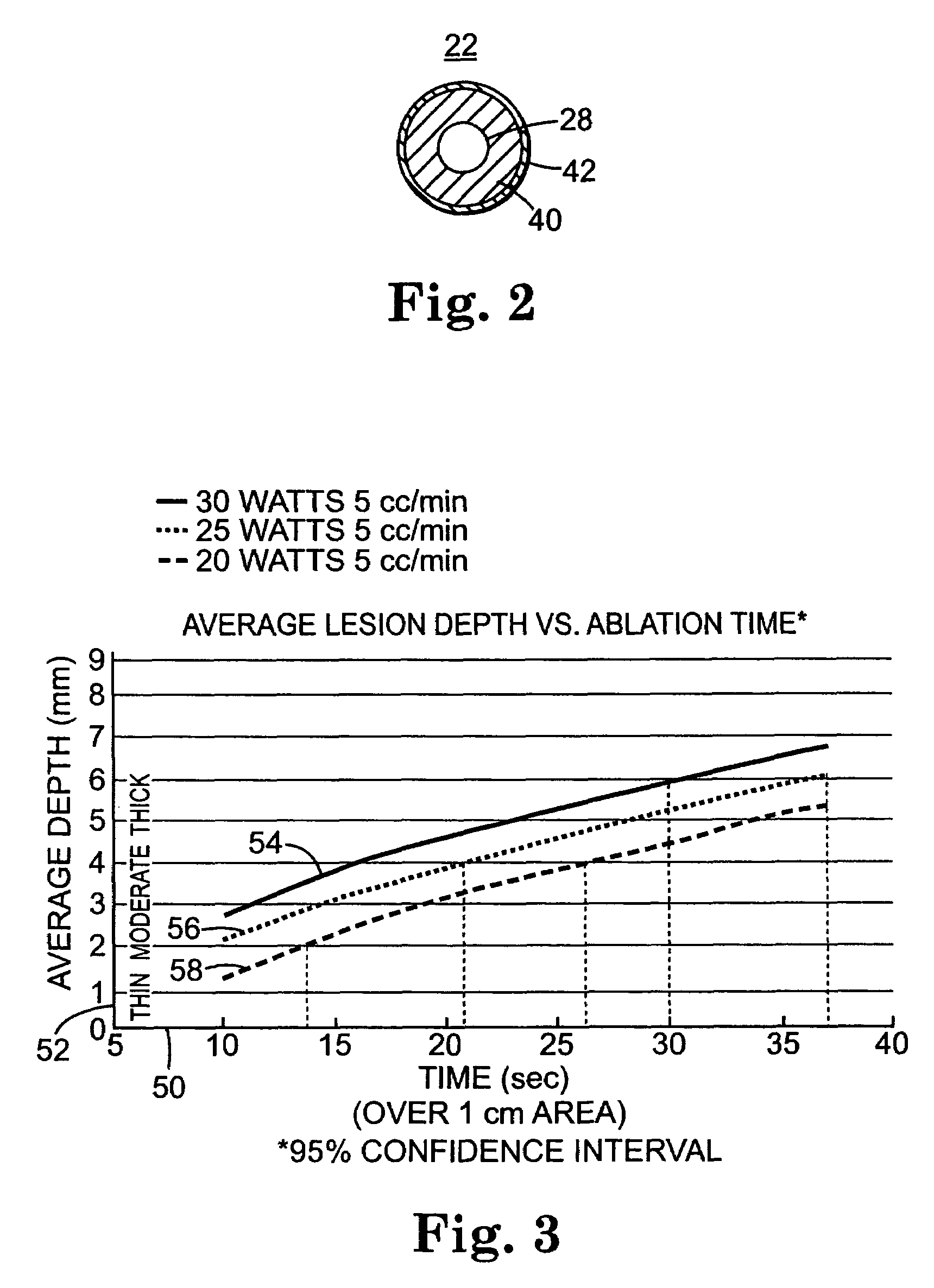
System and method of performing an electrosurgical procedure
Owner:MEDTRONIC INC
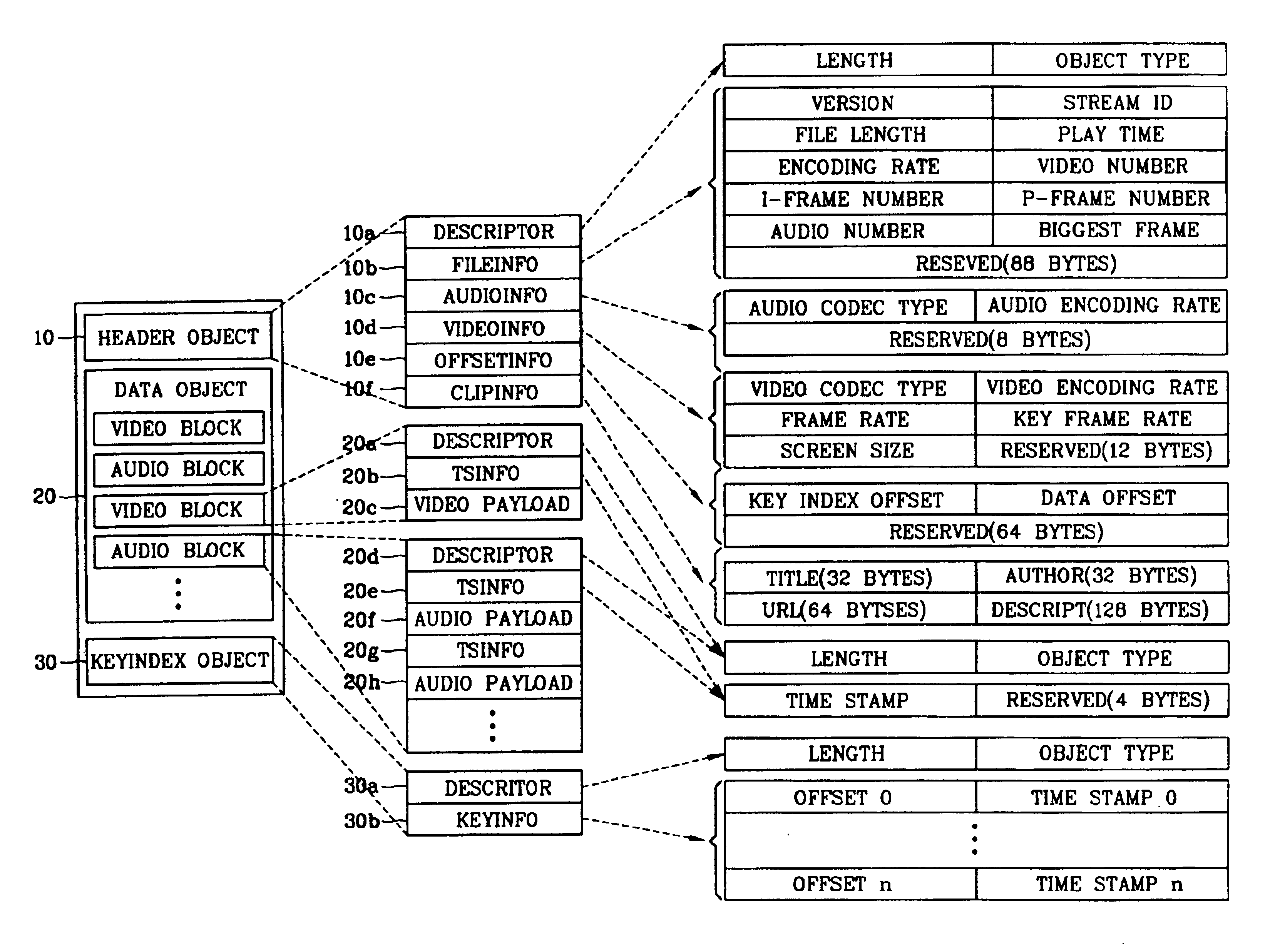
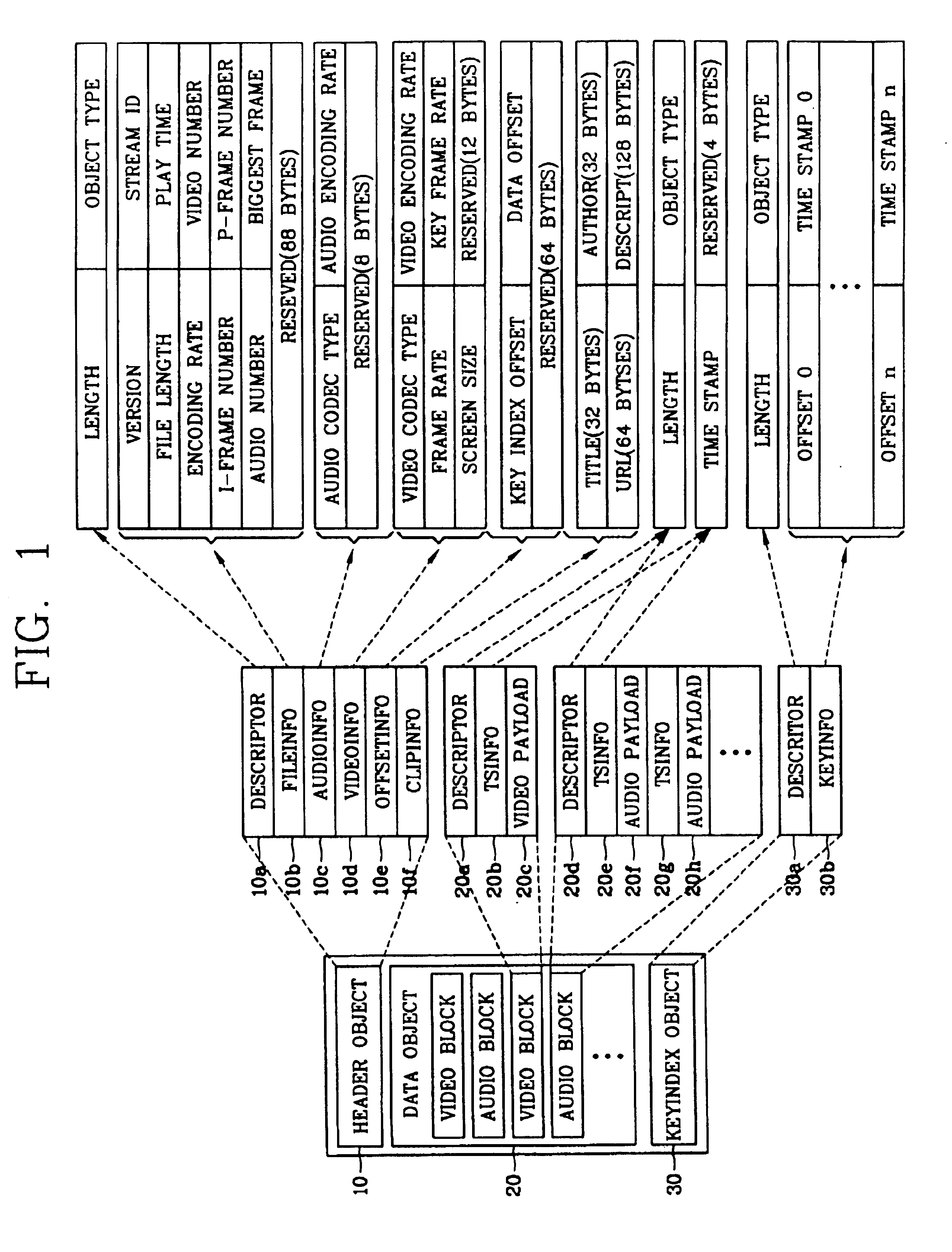
Apparatus and method for providing file structure for multimedia streaming service
InactiveUS6856997B2Reduce bandwidth wasteFast data transferData processing applicationsPulse modulation television signal transmissionData synchronizationTemporal information
In a file structure for a streaming service and a method for providing a streaming service, a file structure includes a header object having basic information about a file and information for an application service, a data object synchronizing multimedia data with temporal information and storing it, and a key index object storing an offset and temporal information of a video block having a key frame in video blocks as a basis on a time axis for random access and reproduction. Accordingly, data can be transmitted quickly by not including unnecessary additional data, an application region can be expanded by including other media file besides a video and an audio files, because a random access and random reproduction by key index information are possible, it is possible to support various reproduction functions such as a fast play, a reverse play and random reproduction, etc.
Owner:LG ELECTRONICS INC
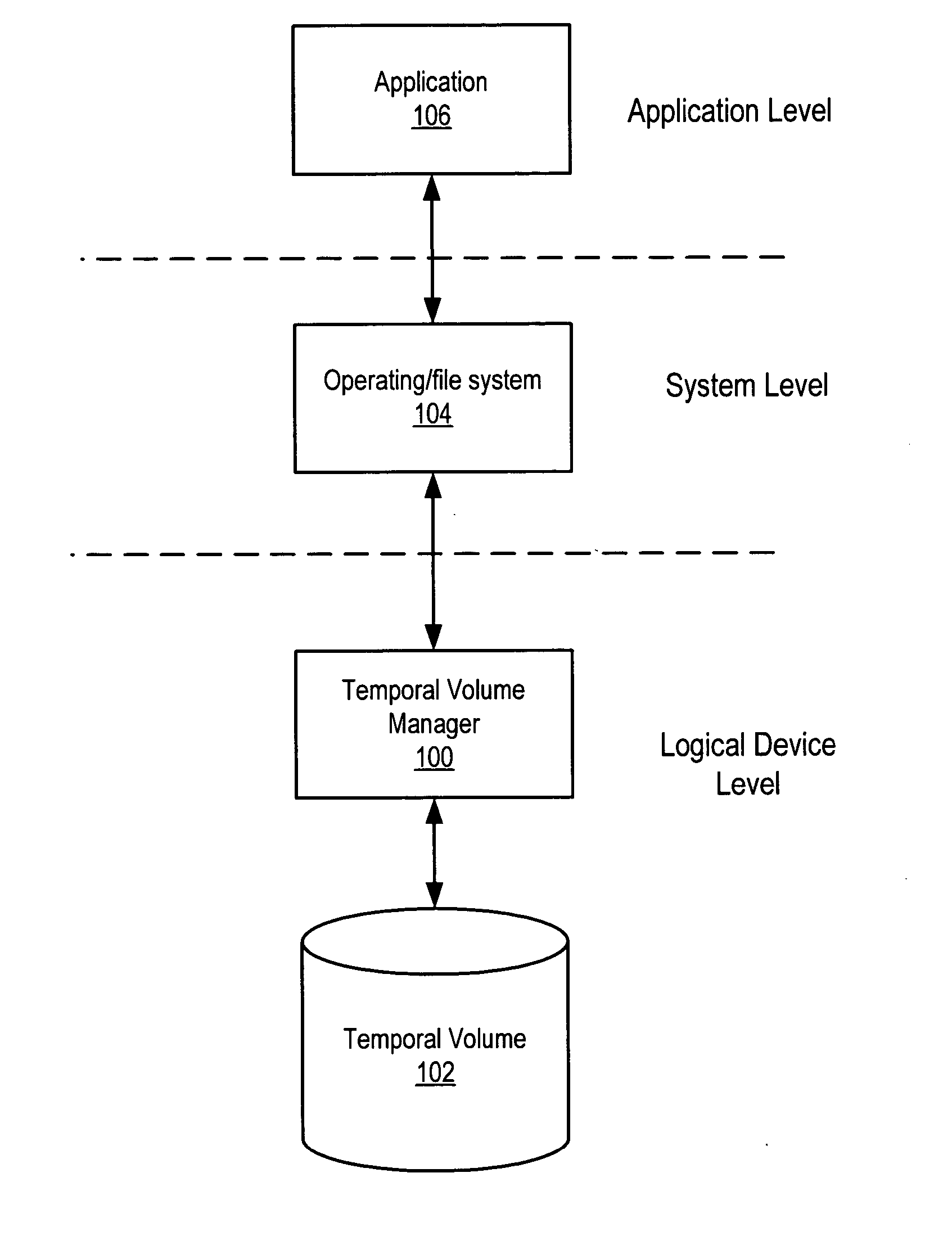
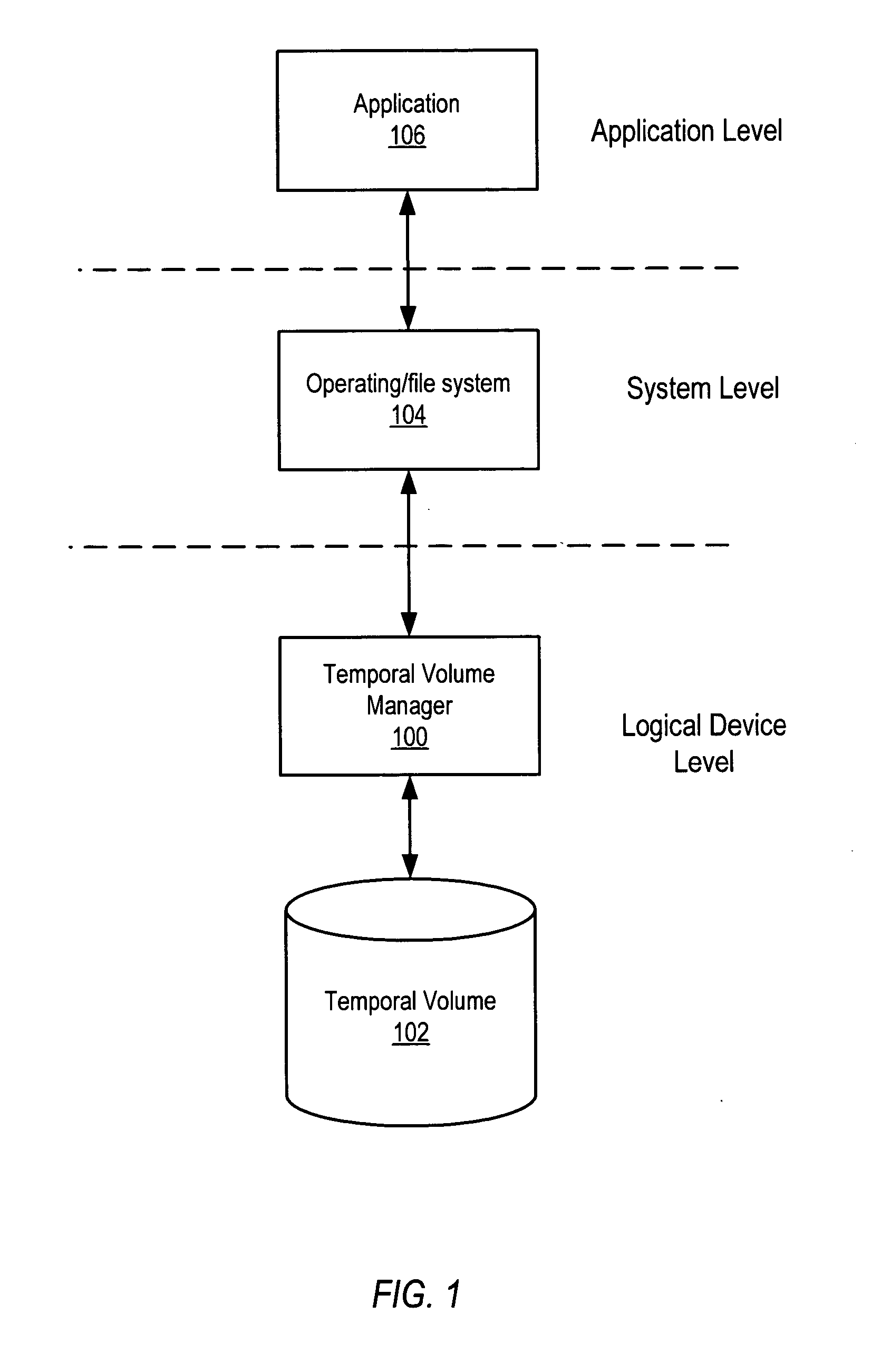
System and method for maintaining temporal data in data storage
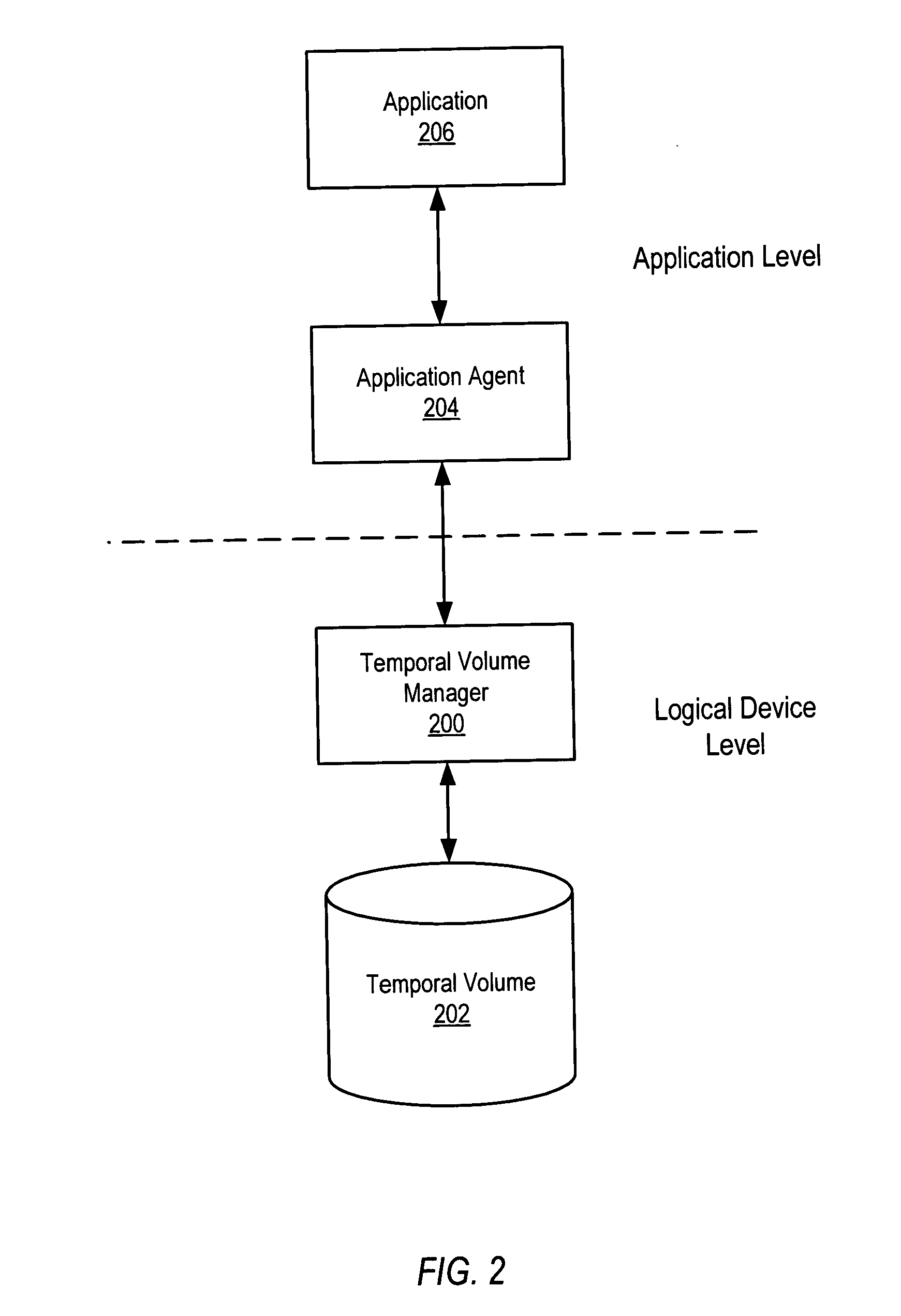
ActiveUS20050071379A1Data processing applicationsDigital data information retrievalTemporal informationTemporal database
System and method for maintaining temporal data in data storage at the logical device level. Embodiments of the temporal volume manager may provide an interface that allows applications and / or application agents to communicate with the temporal volume manager to manage and keep track of the temporal information on one or more temporal volumes. Embodiments may provide an infrastructure for applications that work on the history of data such as temporal databases, versioning file-systems / repositories, data archives, and streaming media to manage temporal data. In one embodiment, if an application does not want to use the temporal volume directly, application agents may be used to access the temporal volume. Embodiments may provide I / O controlled, application-controlled, and / or periodic checkpointing of temporal data on the temporal volume. One embodiment may provide a mechanism for generating temporal images (e.g. point-in-time and slice-in-time images) of a temporal volume that may have their own independent history.
Owner:SYMANTEC OPERATING CORP
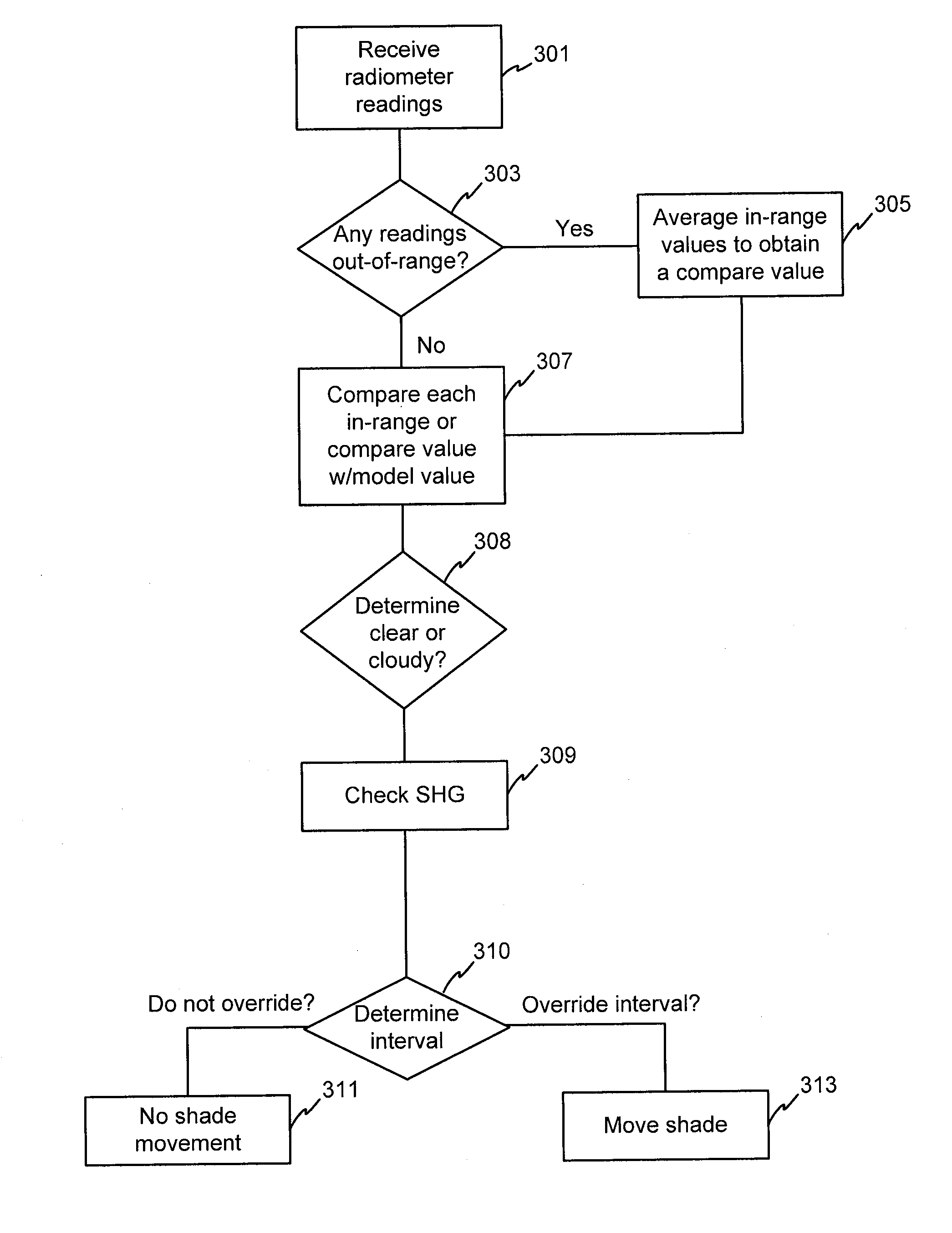
Automated shade control relectance module
Automated shade systems comprise motorized window coverings, sensors, and controllers that use algorithms to control operation of the automated shade control system. These algorithms may include information such as: 3-D models of a building and surrounding structures, shadow information, reflectance information, lighting and radiation information, ASHRAE clear sky algorithms, log information related to manual overrides, occupant preference information, motion information, real-time sky conditions, solar radiation on a building, a total foot-candle load on a structure, brightness overrides, actual and / or calculated BTU load, time-of-year information, and microclimate analysis.
Owner:MECHOSHADE SYST LLC
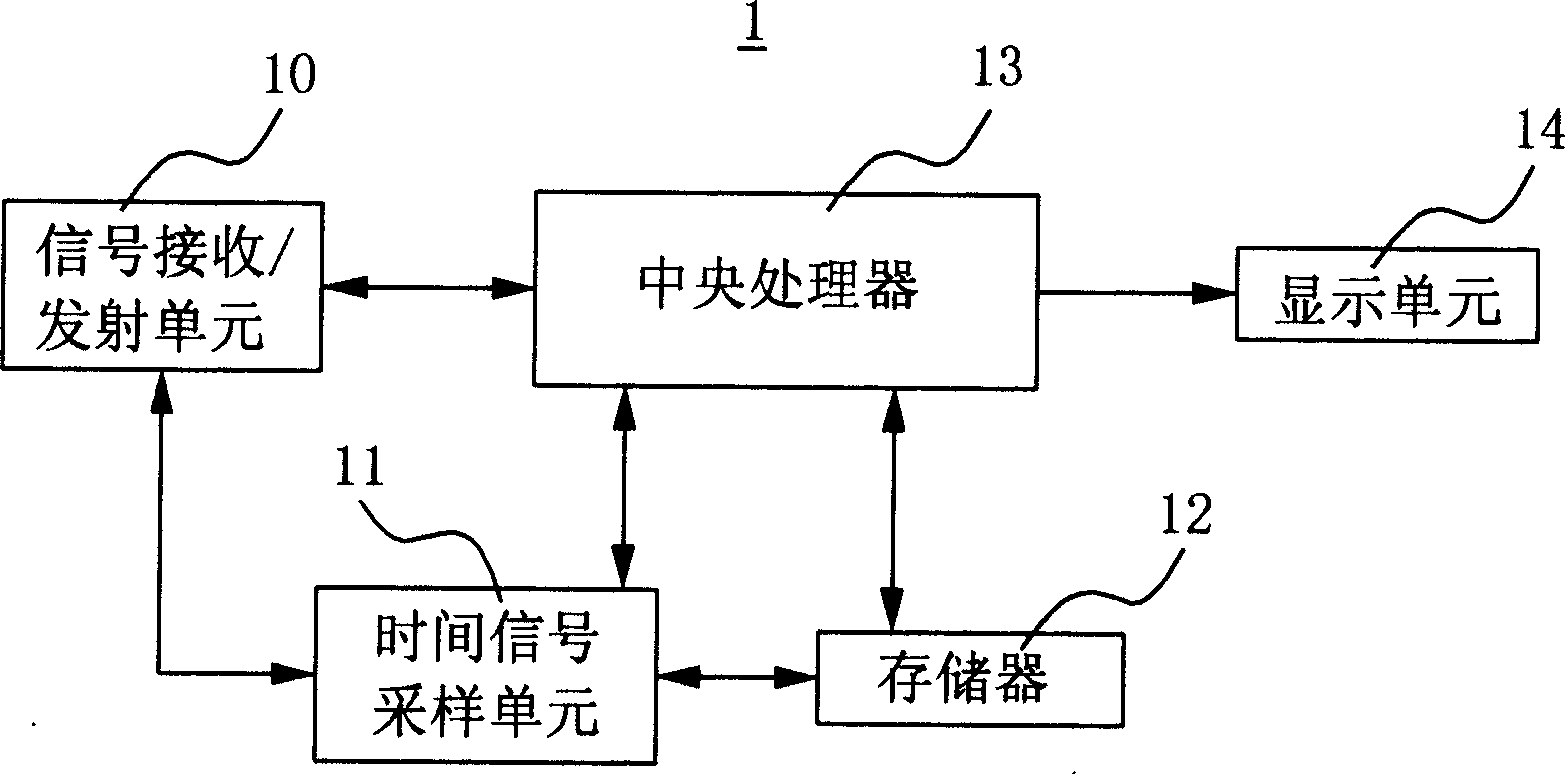
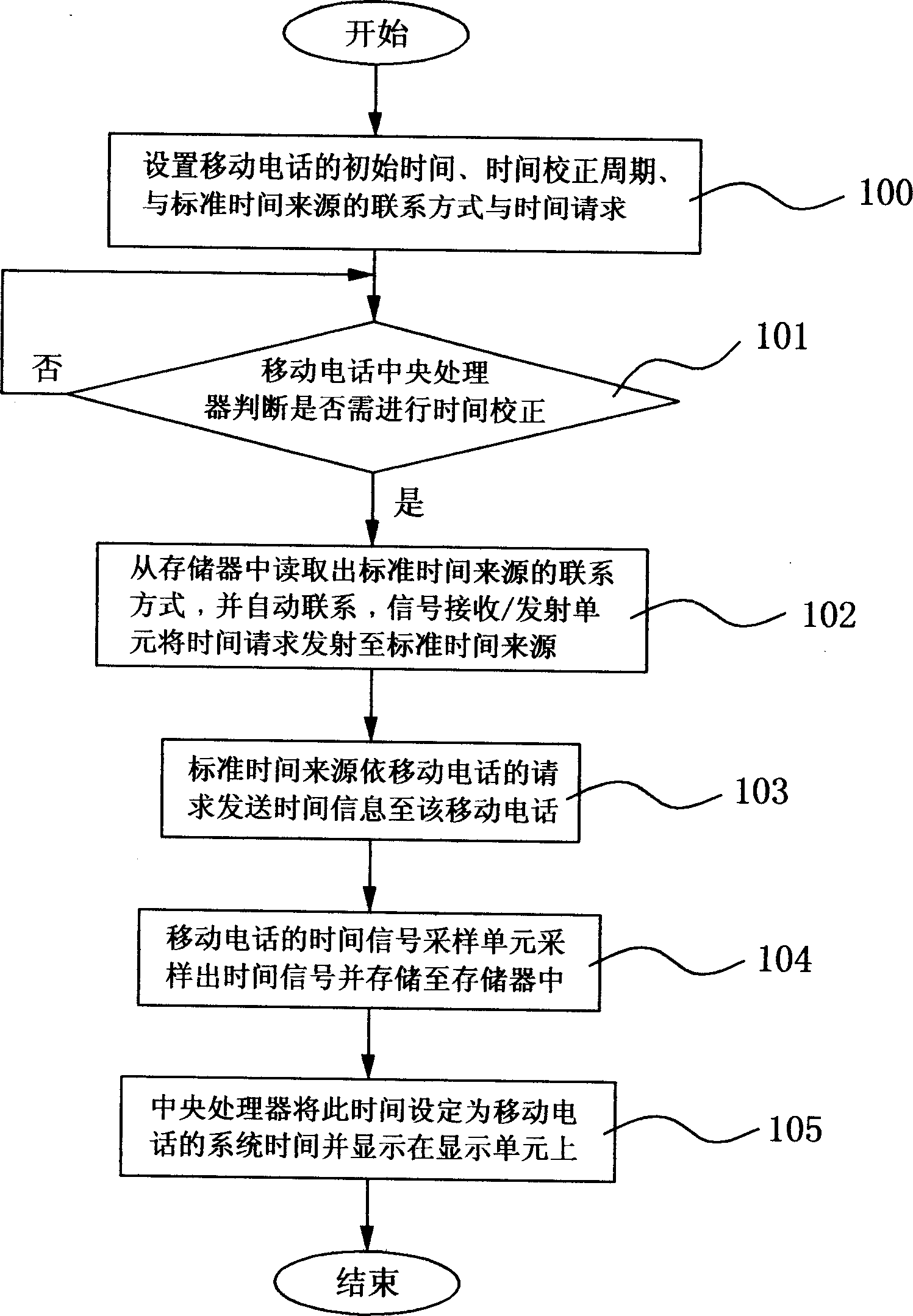
Mobile phone time automatic correction method
InactiveCN1801829ALow costMiniaturization hindranceSetting time indicationRadio-controlled time-piecesTemporal informationAutocorrection
Said invention provides a mobile telephone time autocorrection method. It contains signal reception / transmitting unit, time signal sampling unit memory unit, central processing unit and display unit, said method mainly setting mobile telephone initial time, time adjustment cycle, and standard time source connection mode and time request , when need proceeding time correction, said mobile telephone automatically transmitting time request to standard time source and taking standard time then configuring said standard time as system time of mobile telephone to reach higher time precision by using normal quartz oscillator.
Owner:KUNDA COMP TECHKUSN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com