Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
582 results about "ASCII" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
ASCII (/ˈæskiː/ ASS-kee), abbreviated from American Standard Code for Information Interchange, is a character encoding standard for electronic communication. ASCII codes represent text in computers, telecommunications equipment, and other devices. Most modern character-encoding schemes are based on ASCII, although they support many additional characters.
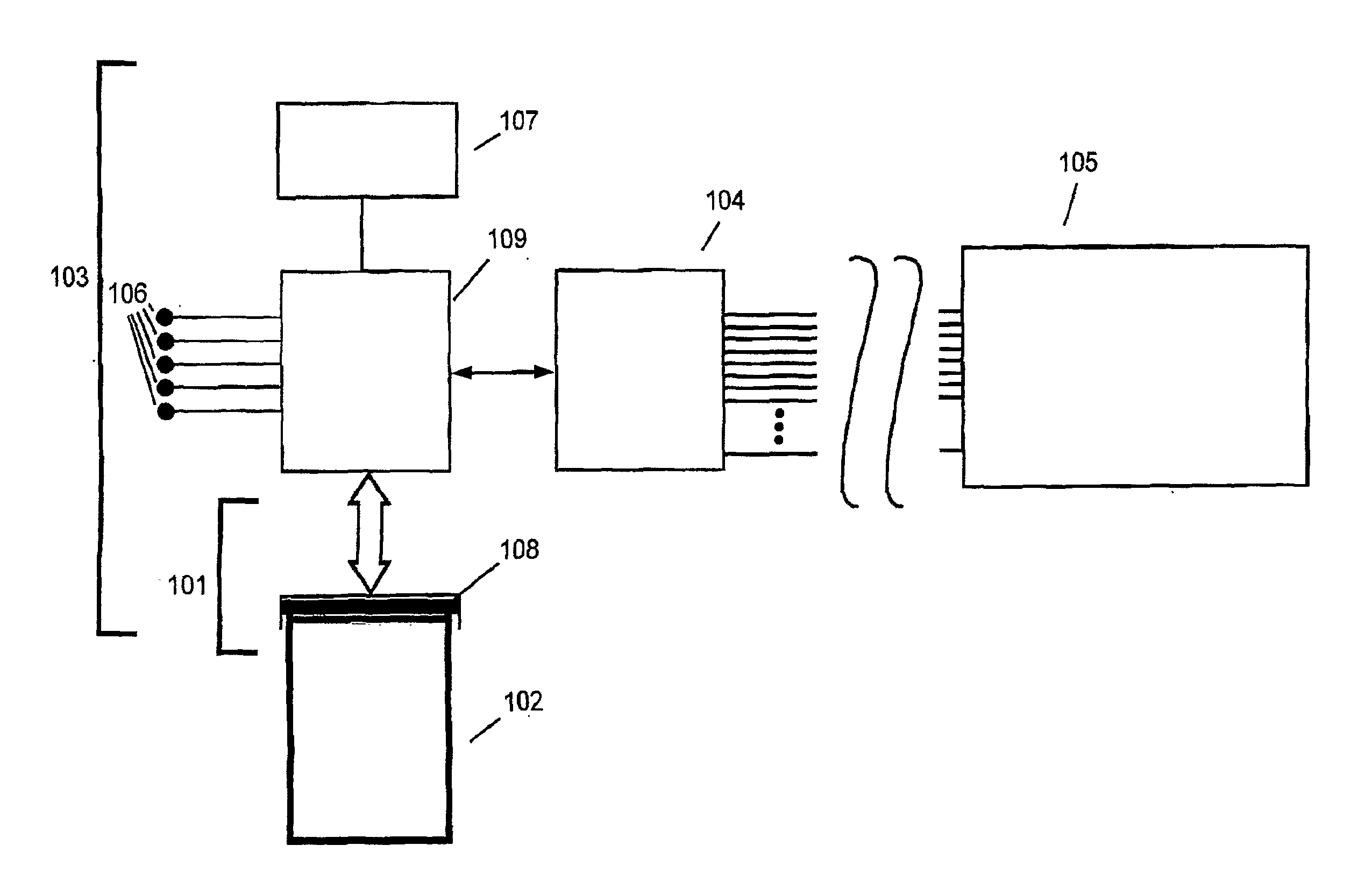
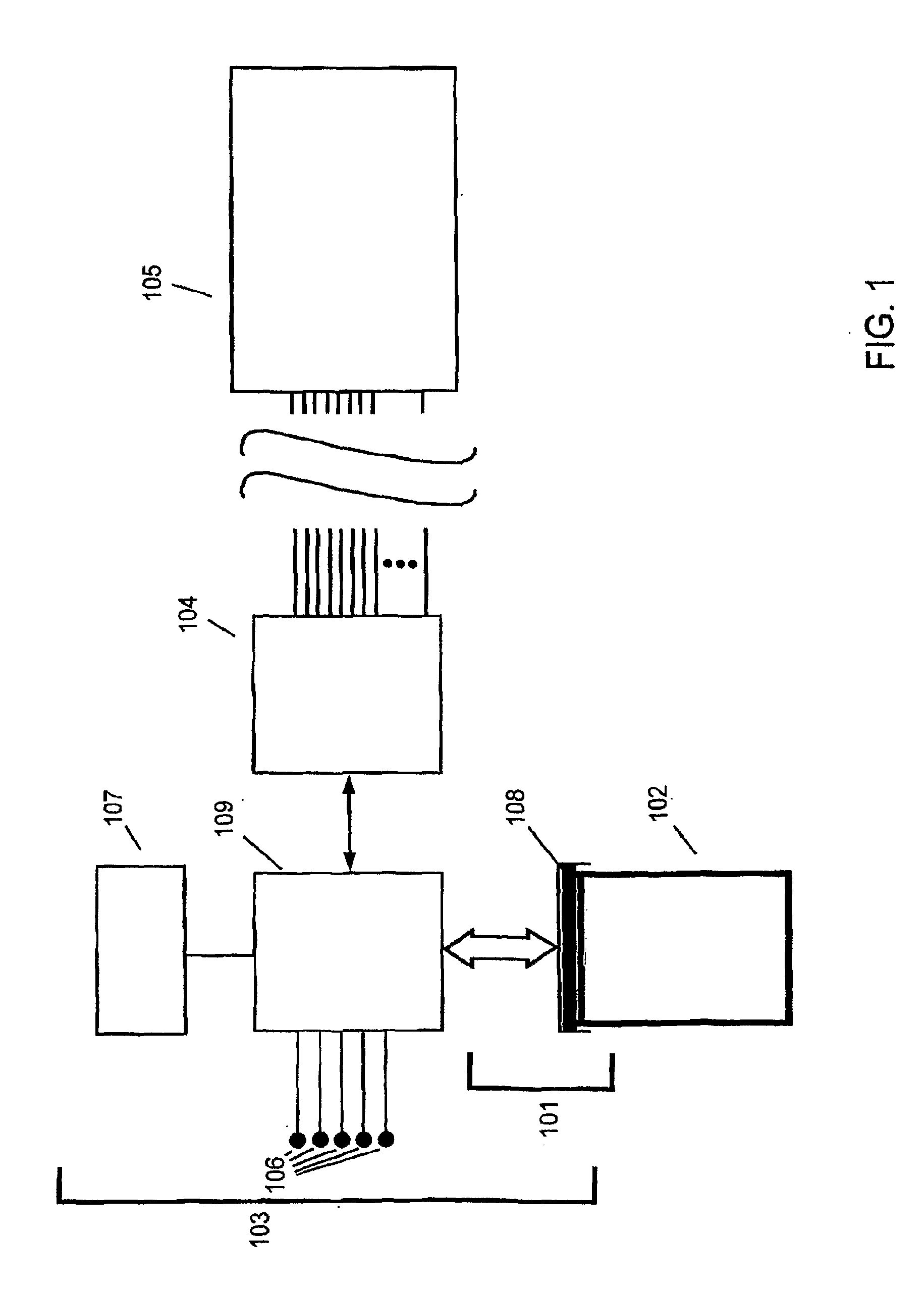
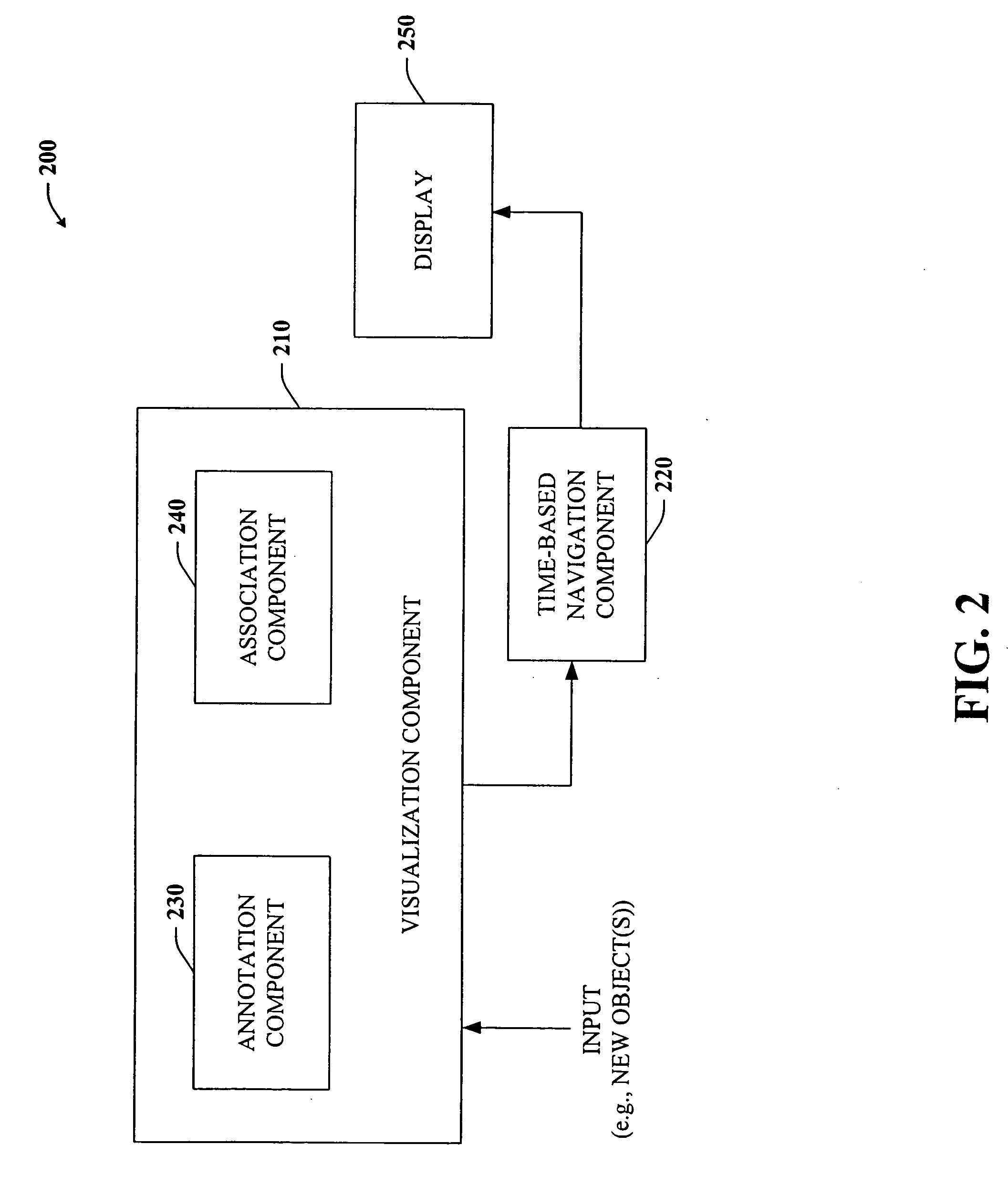
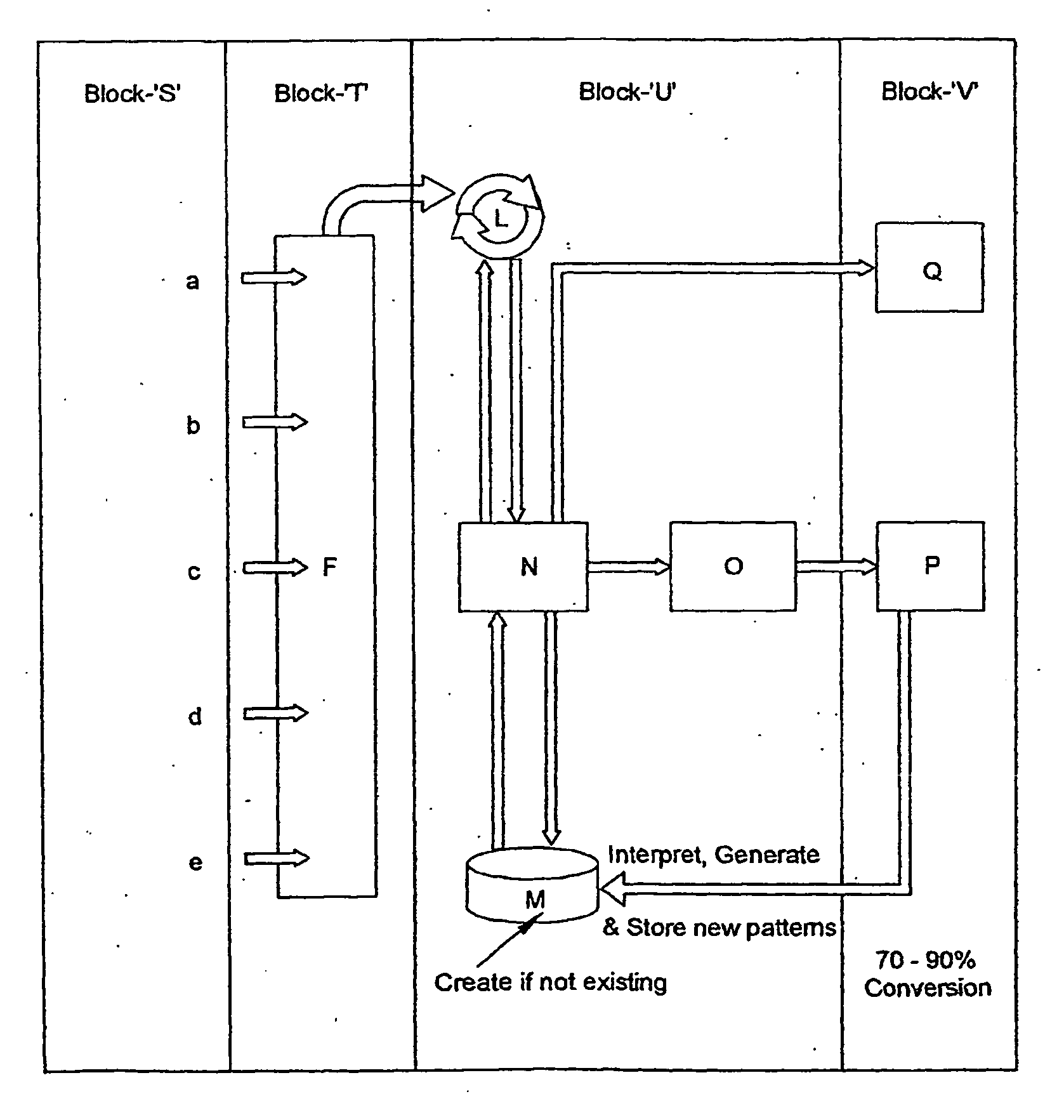
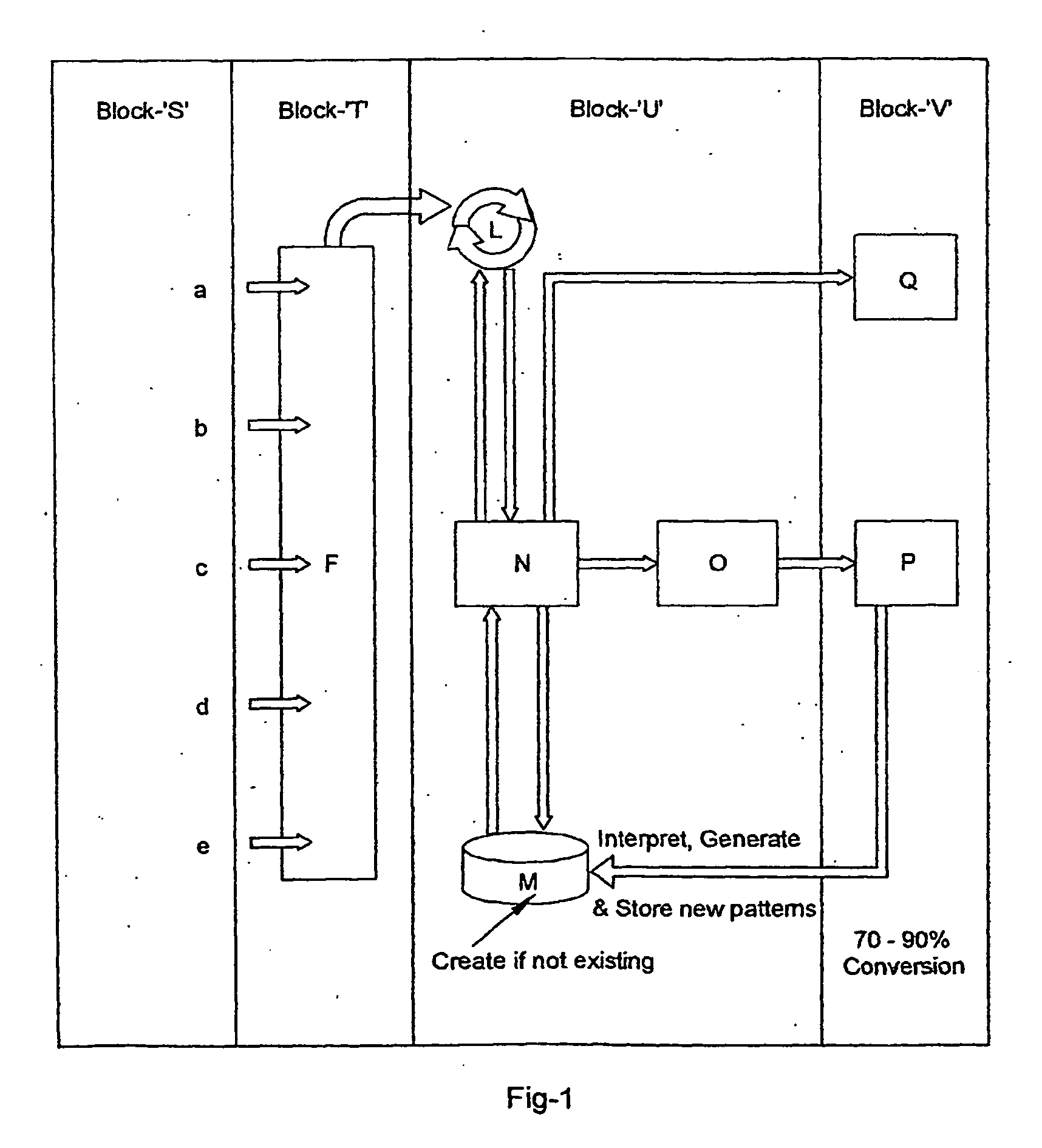
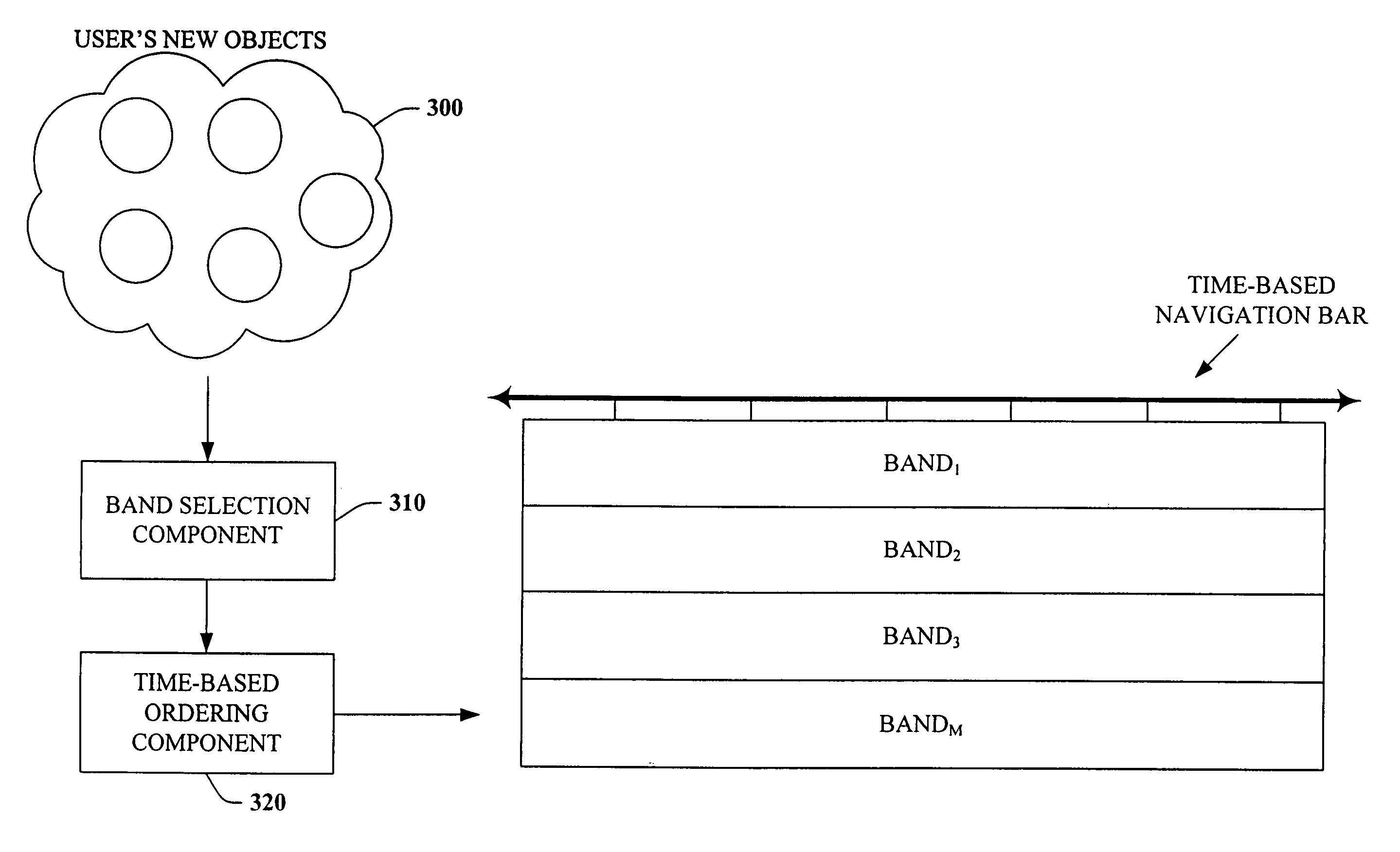
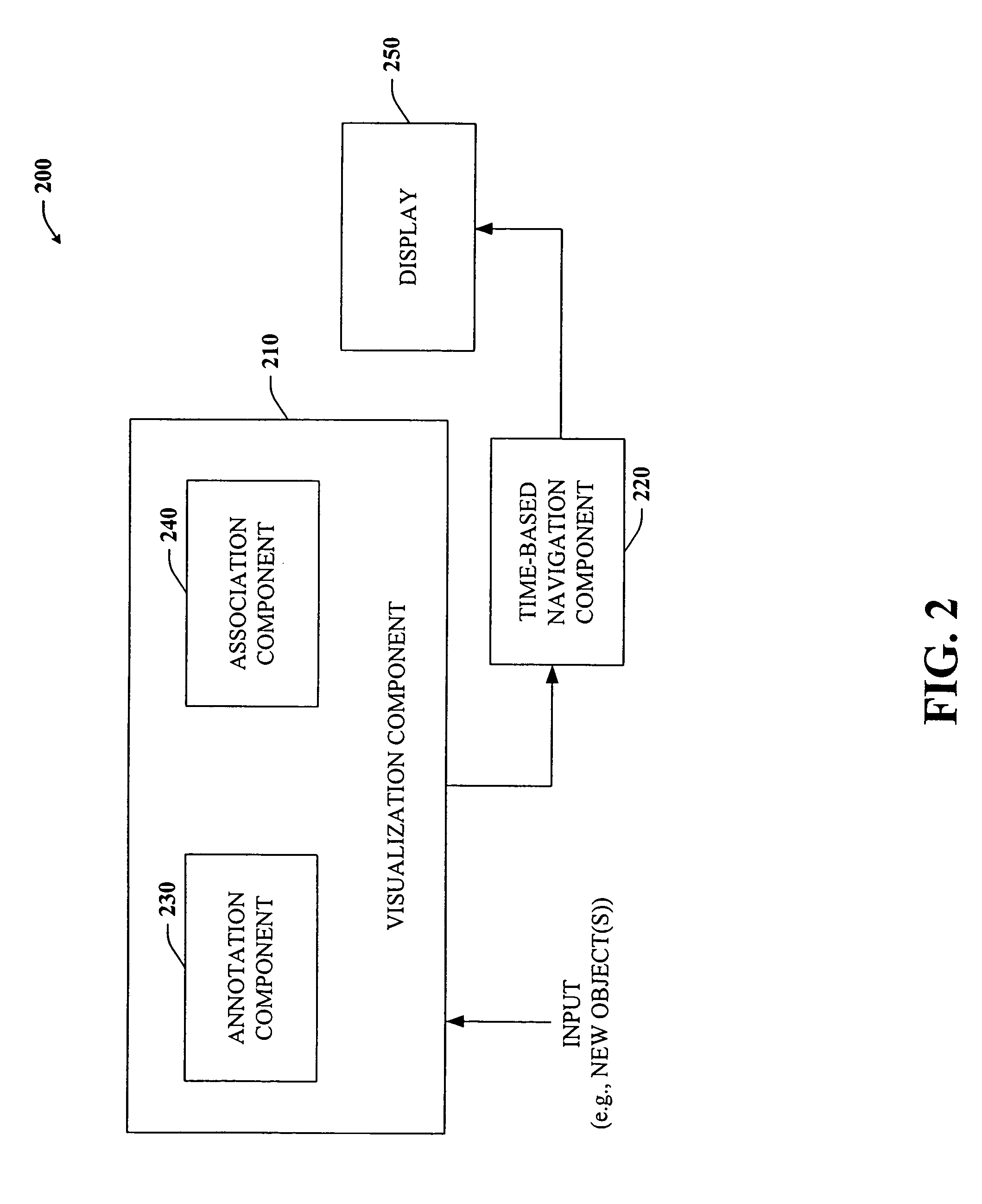
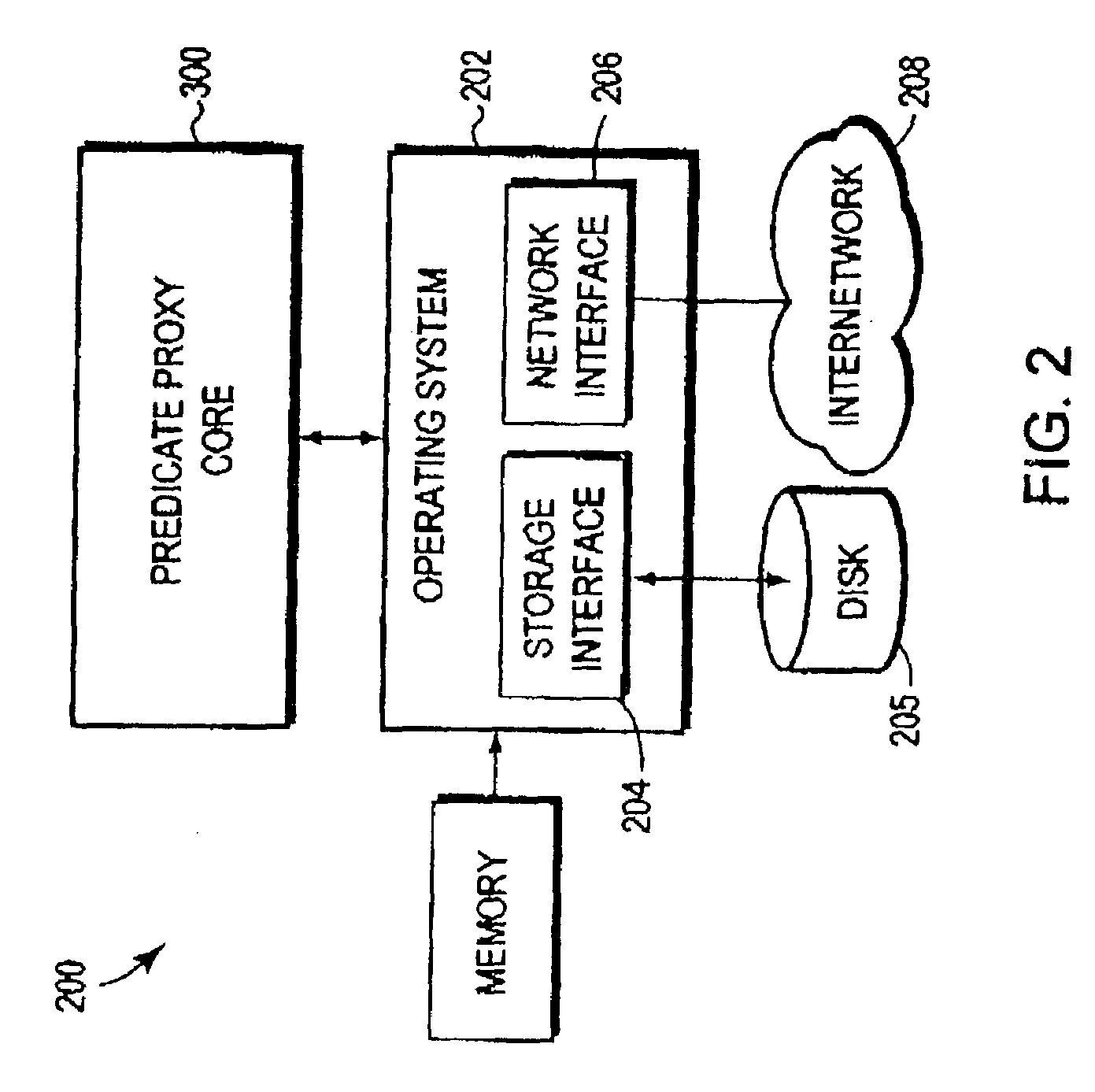
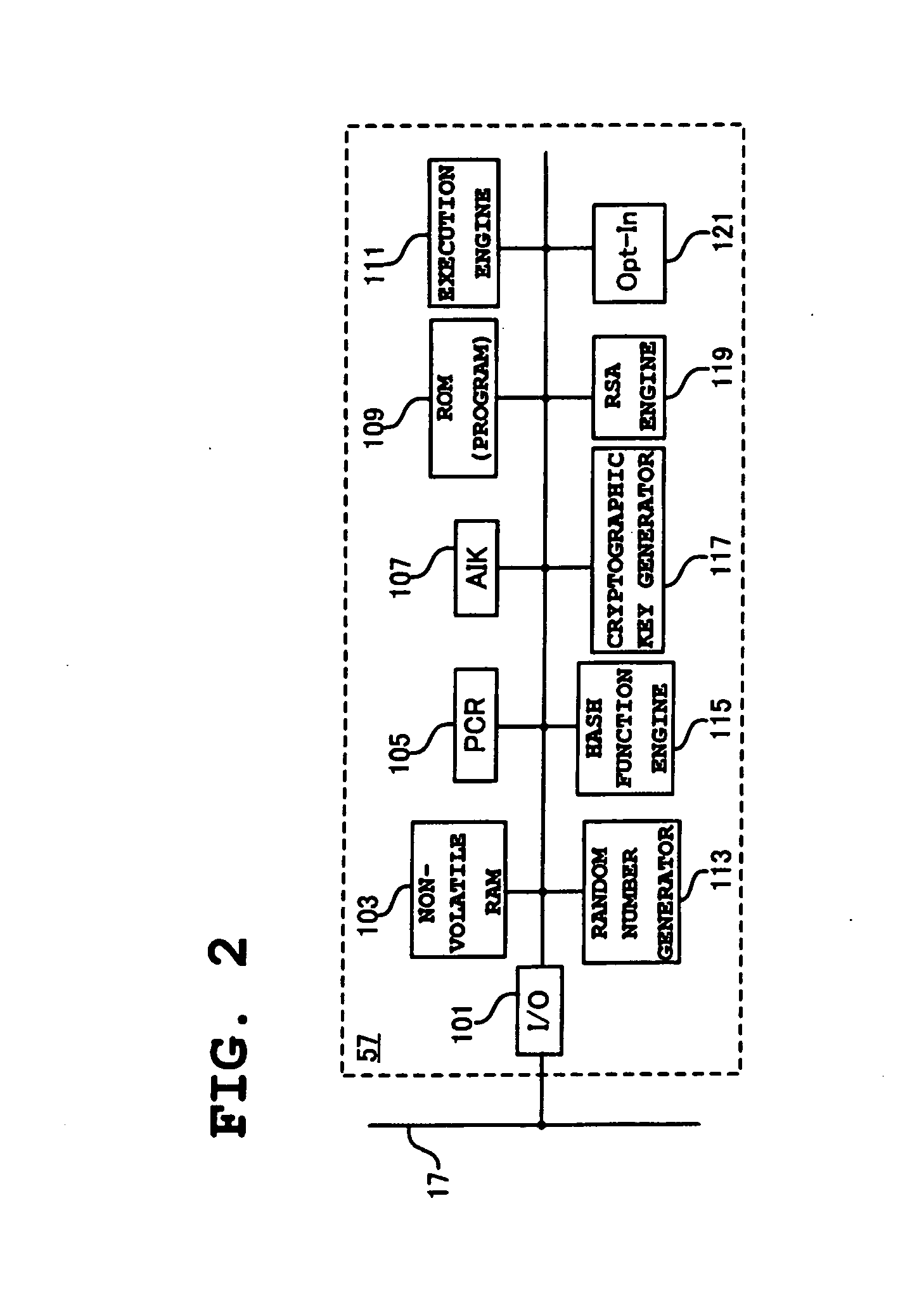
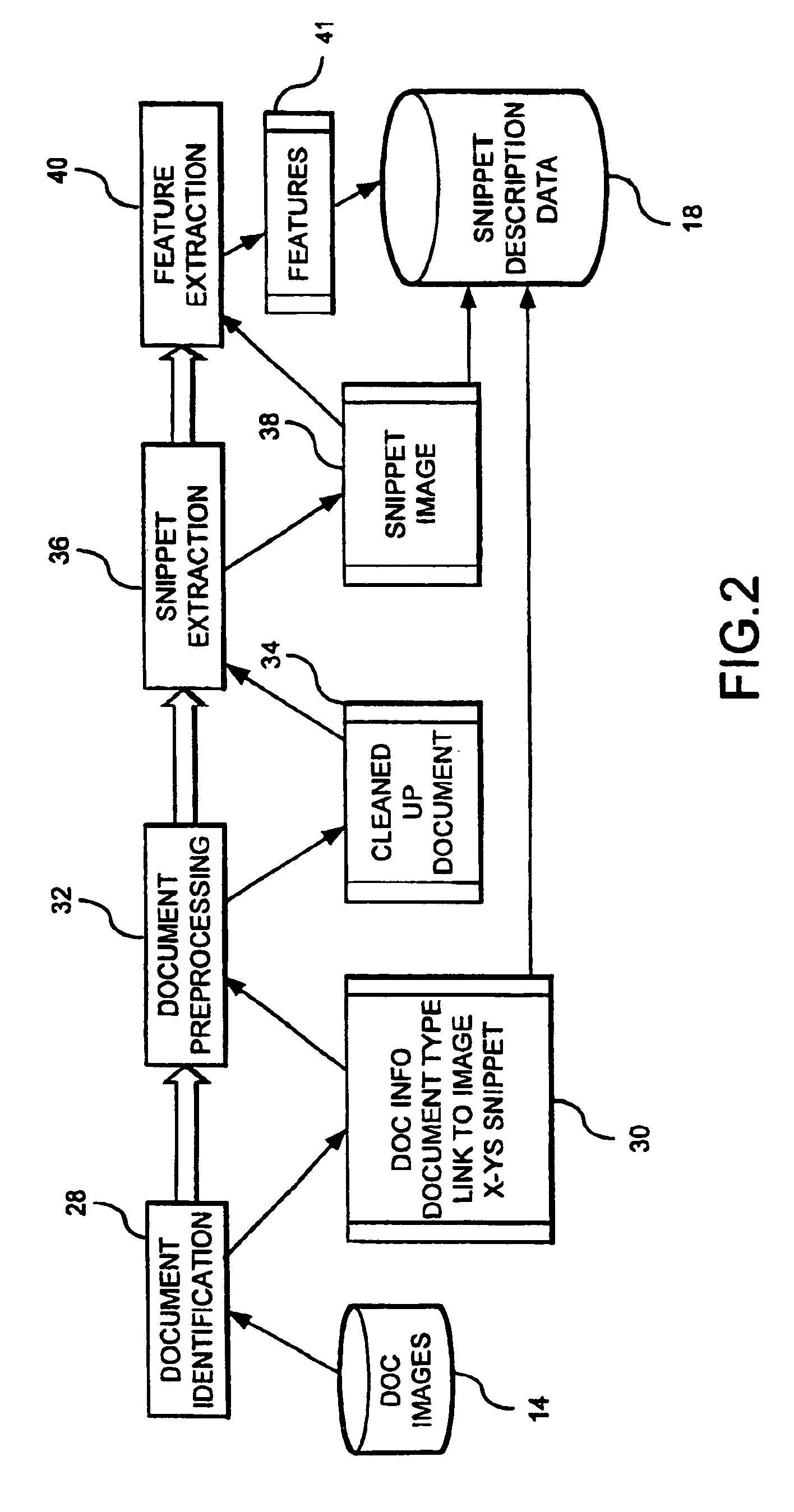
Architecture and engine for time line based visualization of data
InactiveUS20060156246A1Easy to watchFacilitate navigating and managingData processing applicationsVisual data miningLevel of detailThumbnail
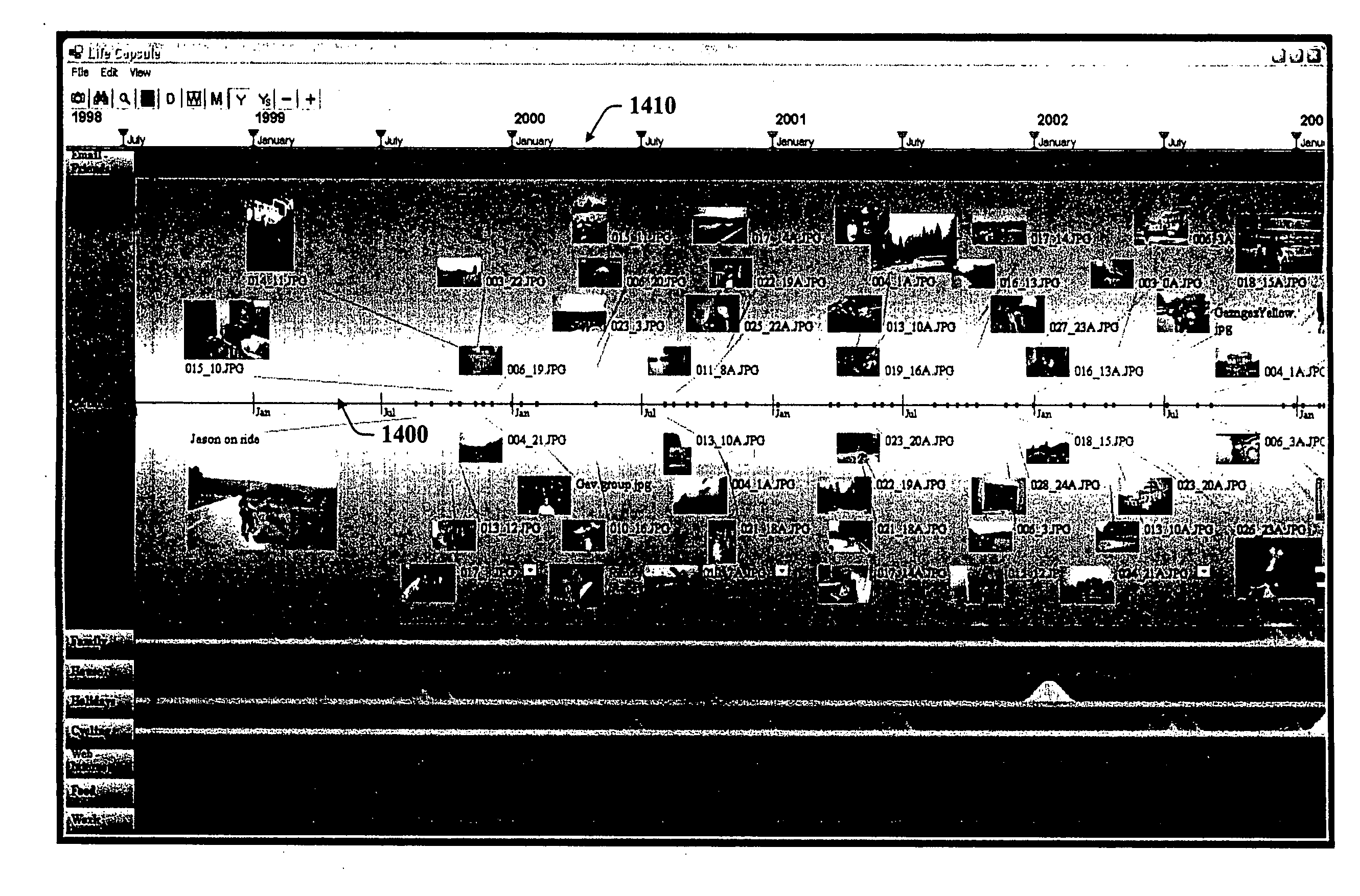
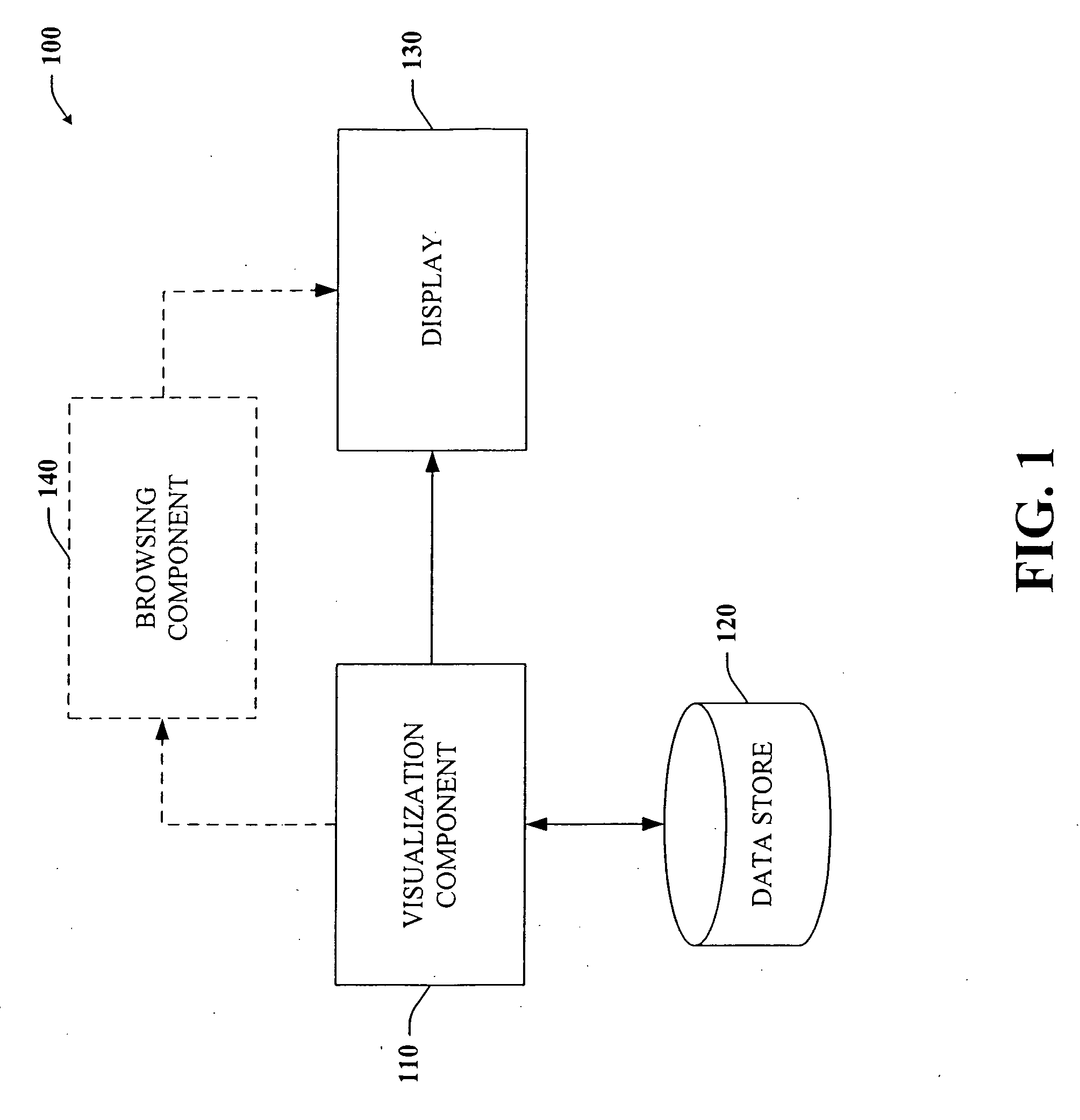
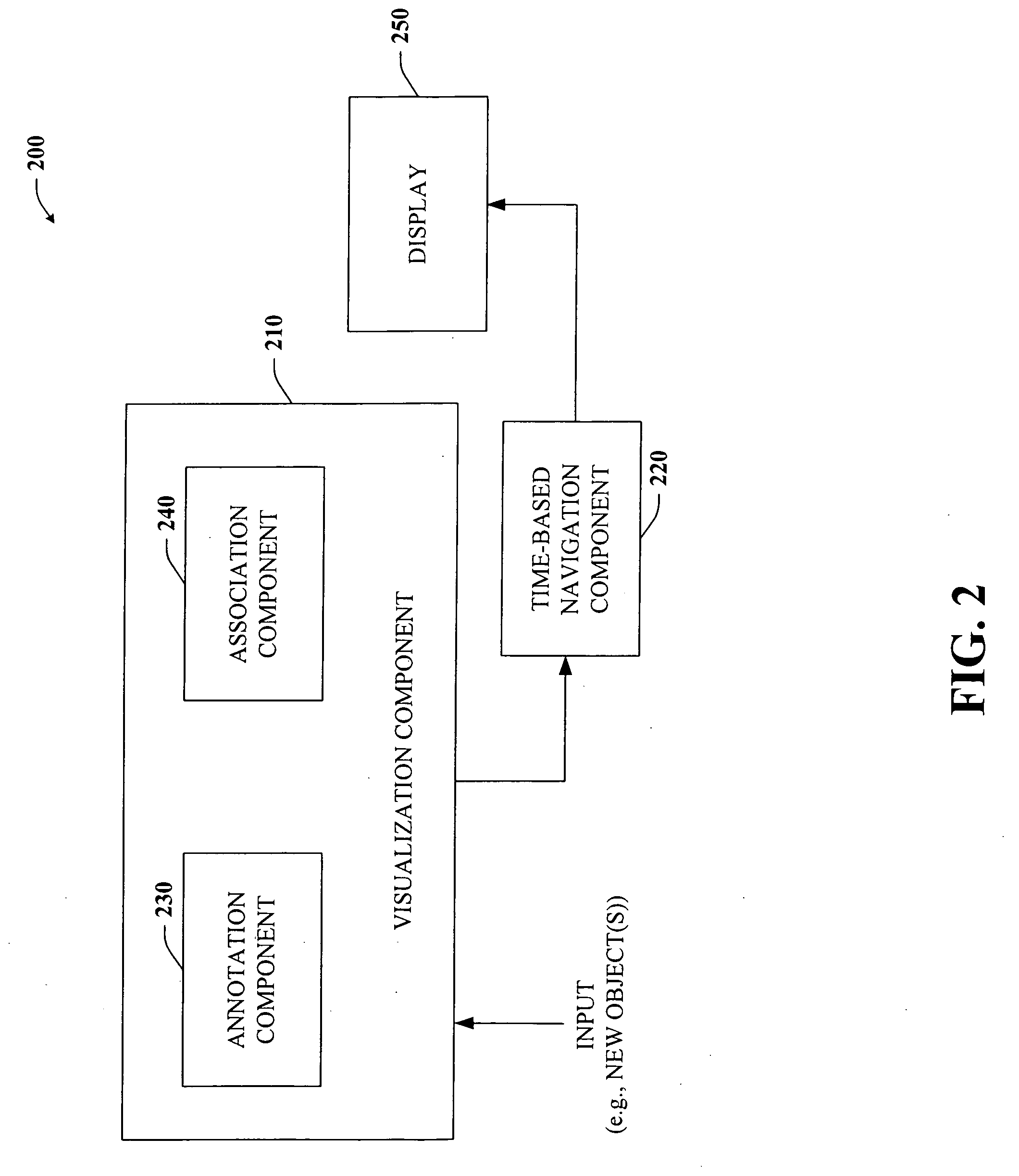
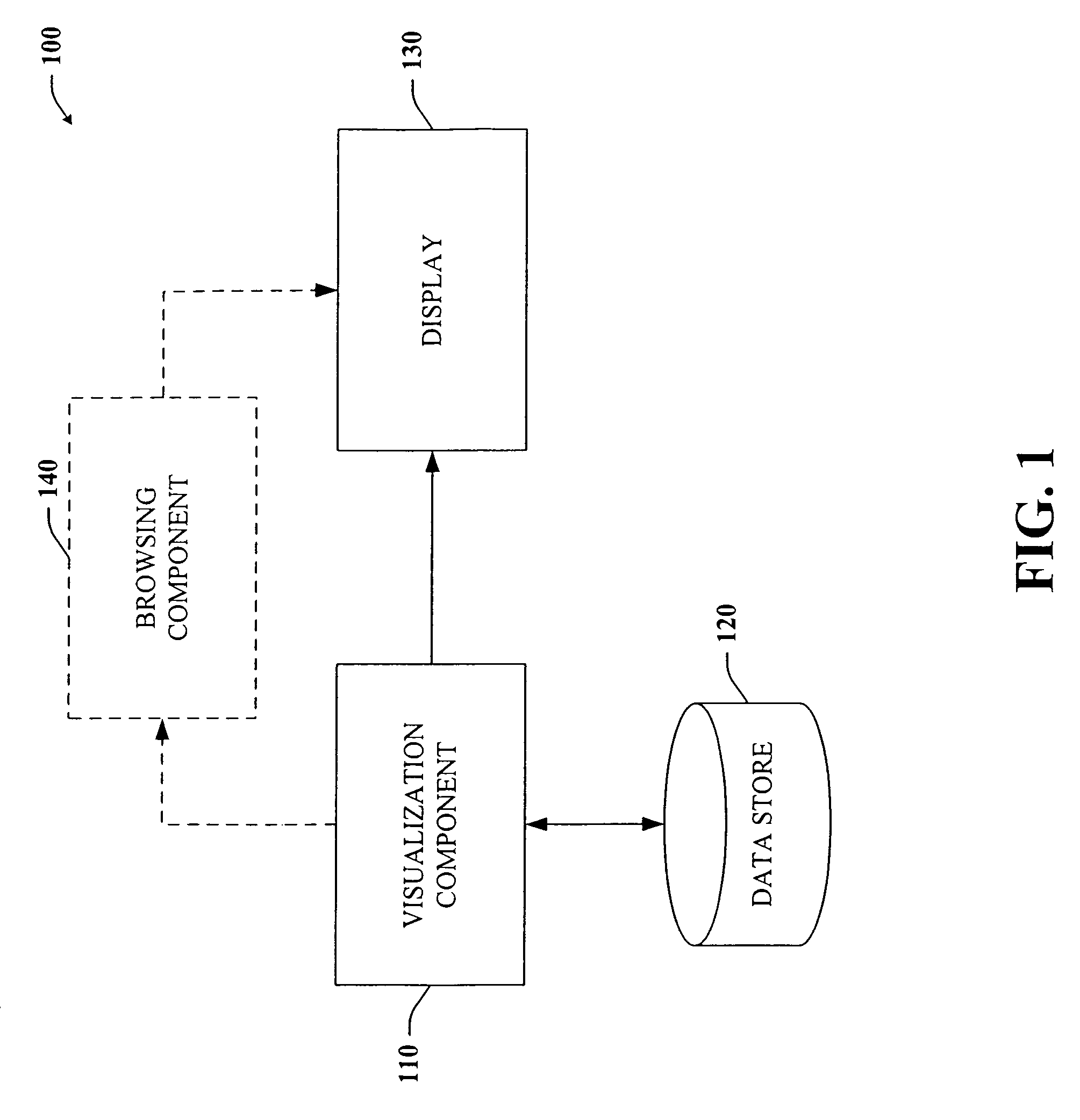
The subject invention provides a unique system and method that facilitates management and navigation of various data objects by making use of a unique time-line based navigation tool. In particular, objects can organized into a plurality of bands based on their respective subject matter. Each band can be created to designate a particular topic. Objects are organized within the appropriate bands based in part on a time parameter such as a time or date that the object was created, for example. The navigation tool allows a user to navigate or browse through the bands and objects according to a desired time parameter or range of time. Zooming and other browsing options are available to the user to view objects of interest at varying levels of detail. The objects are represented as ASCII thumbnails that are operational. Thus, the content of any object can be modified directly via the thumbnail.
Owner:MICROSOFT TECH LICENSING LLC
Pure adversarial approach for identifying text content in images
ActiveUS20080131006A1Effective approachData switching networksCharacter recognitionSearch termsASCII
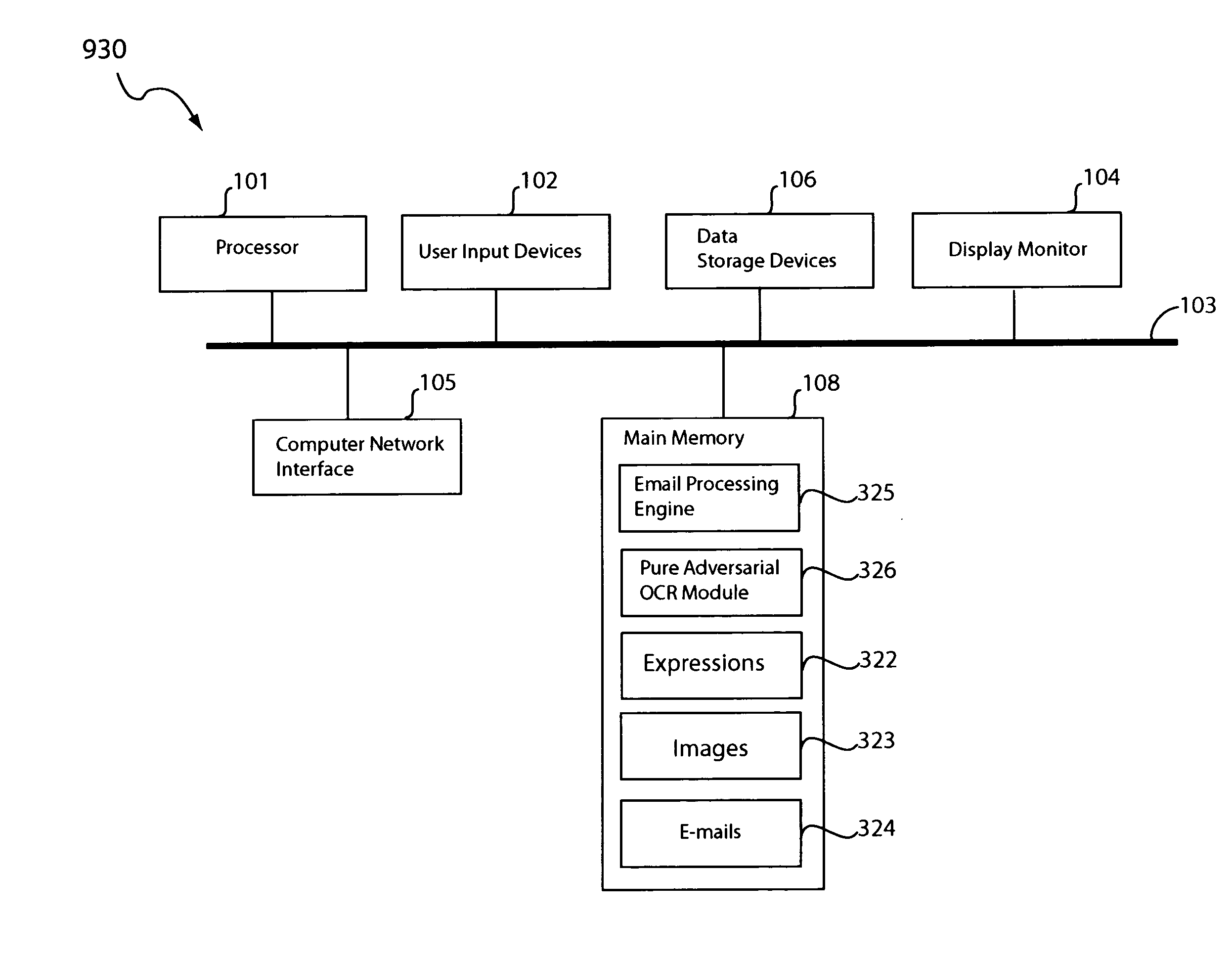
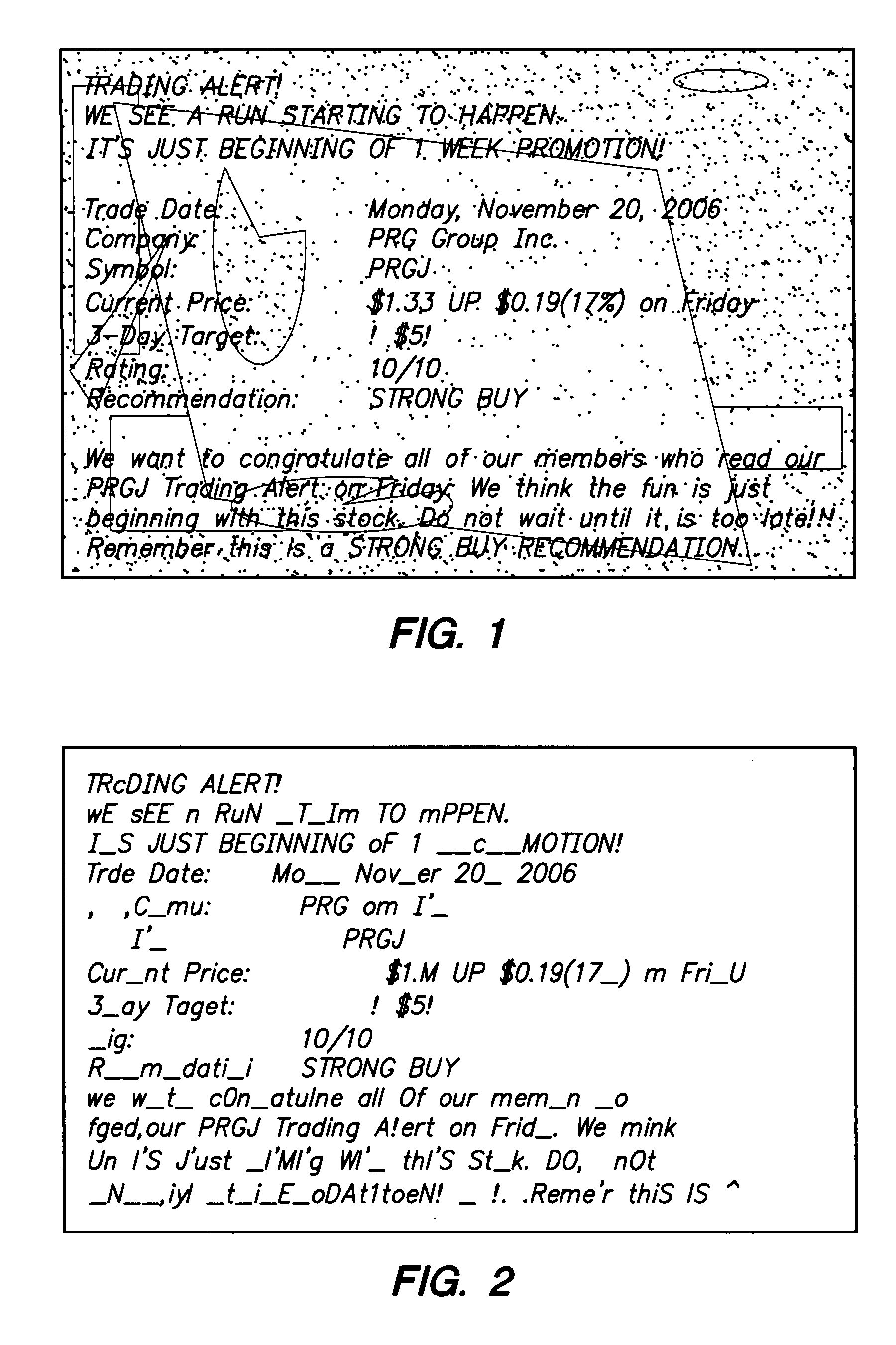
A pure adversarial optical character recognition (OCR) approach in identifying text content in images. An image and a search term are input to a pure adversarial OCR module, which searches the image for presence of the search term. The image may be extracted from an email by an email processing engine. The OCR module may split the image into several character-blocks that each has a reasonable probability of containing a character (e.g., an ASCII character). The OCR module may form a sequence of blocks that represent a candidate match to the search term and calculate the similarity of the candidate sequence to the search term. The OCR module may be configured to output whether or not the search term is found in the image and, if applicable, the location of the search term in the image.
Owner:TREND MICRO INC
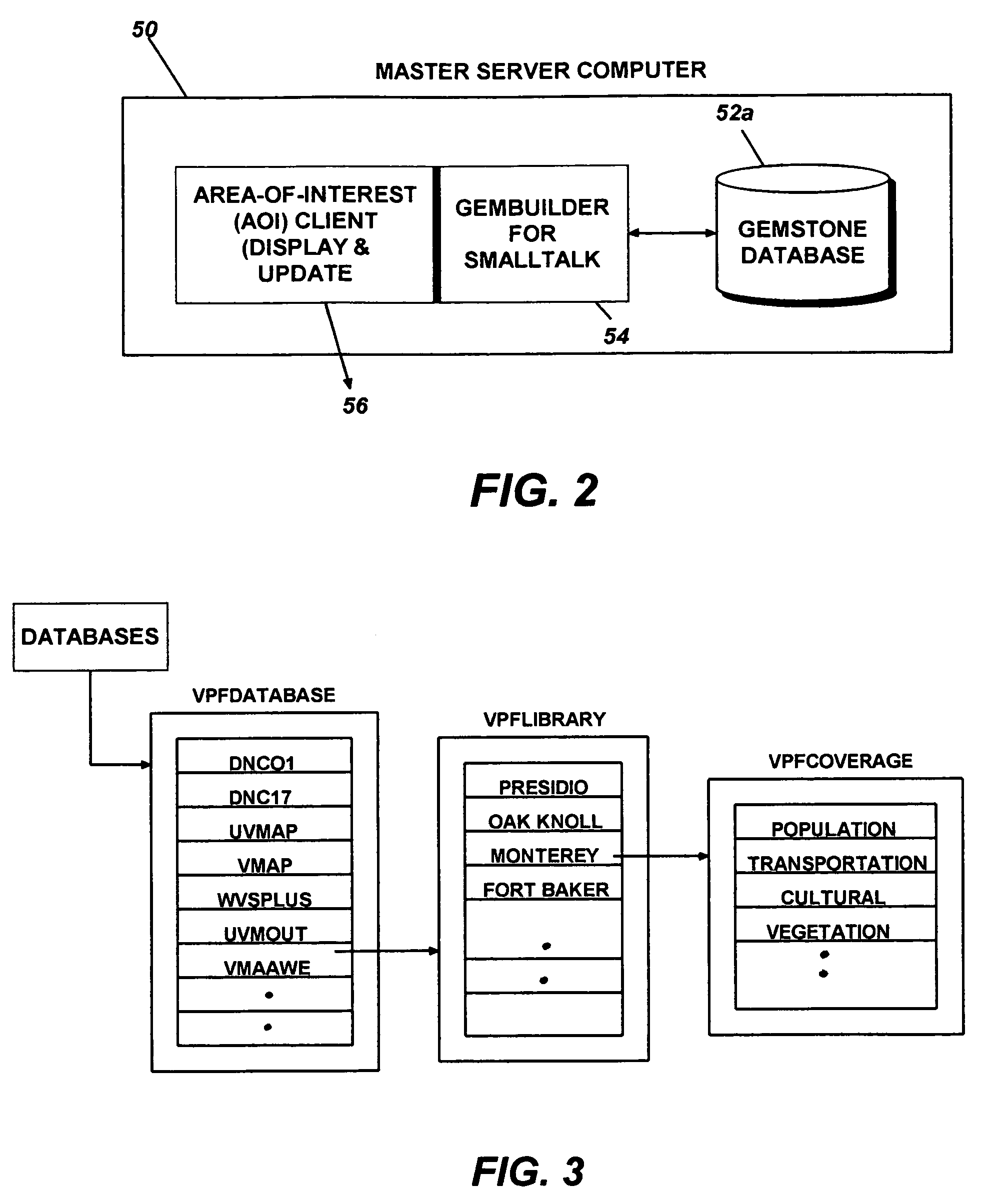
Distributed object-oriented geospatial information distribution system and method thereof
InactiveUS6985929B1Road vehicles traffic controlMultiple digital computer combinationsTemporal informationDistributed object
A distributed object-oriented geospatial database system and method thereof over the Internet using Web-based technology to perform data-driven queries, such as retrieving, viewing and updating, geospatial data of the object oriented geospatial database, such as vector, raster, hypertext and multimedia data, including data types or formats of ESRI shape files, GSF, oceanographic ASCII text data by NAVOCEANO and geospatial data with temporal information and supporting 3D display of the geospatial data. The object-oriented geospatial database system is implemented in a heterogeneous object-oriented development and integration environment through the Common Object Request Broker Architecture (CORBA).
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
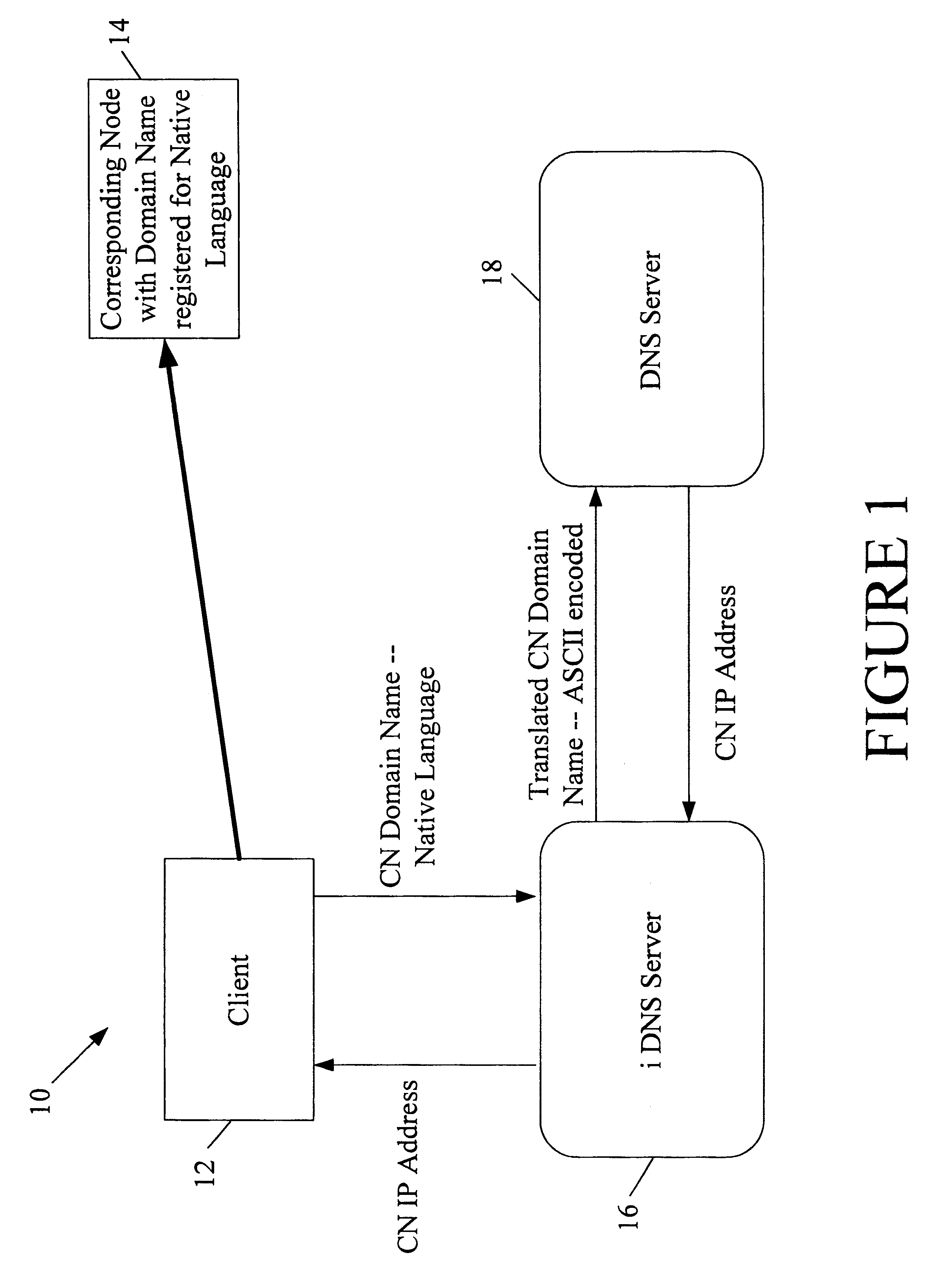
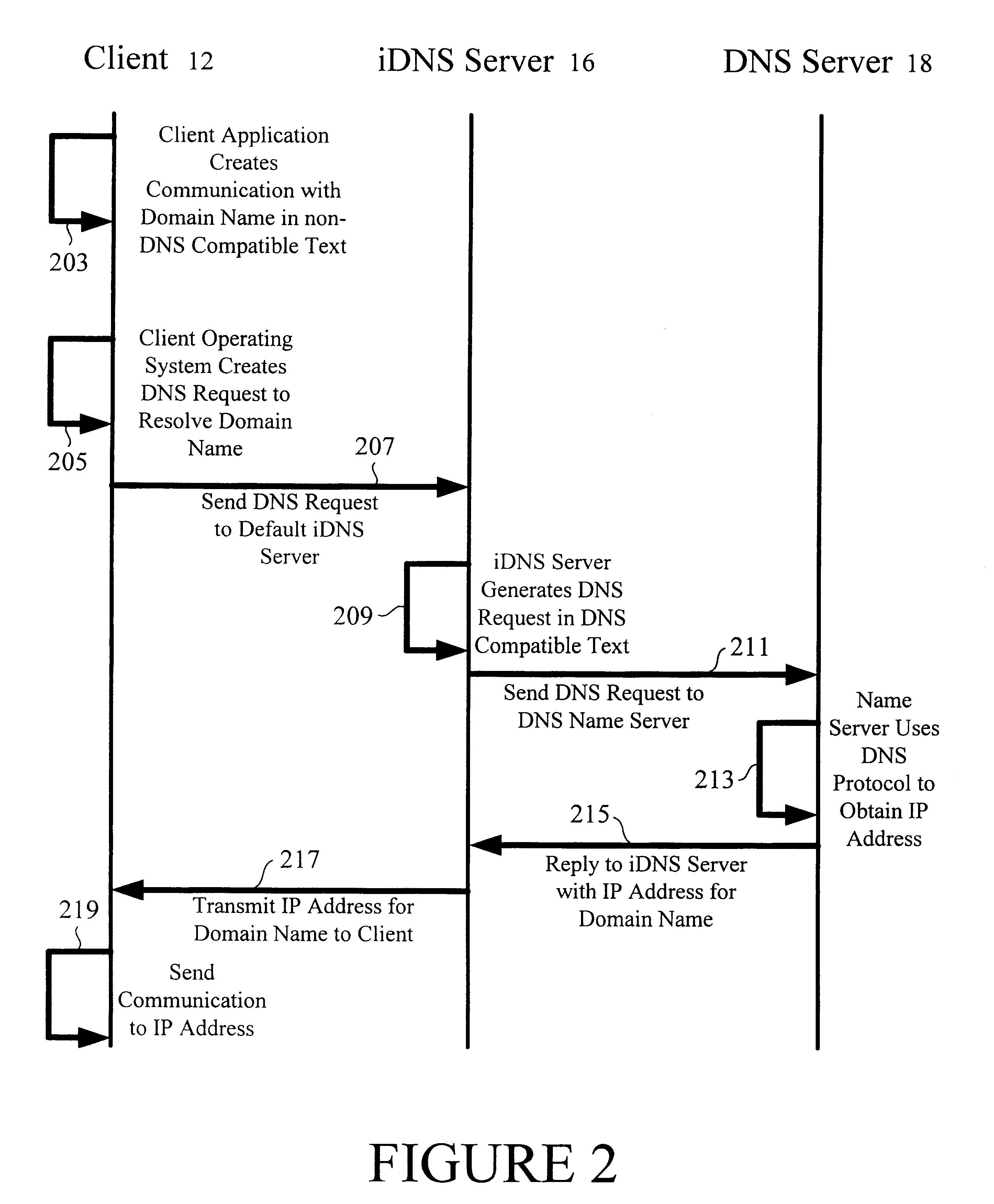
Multi-language domain name service
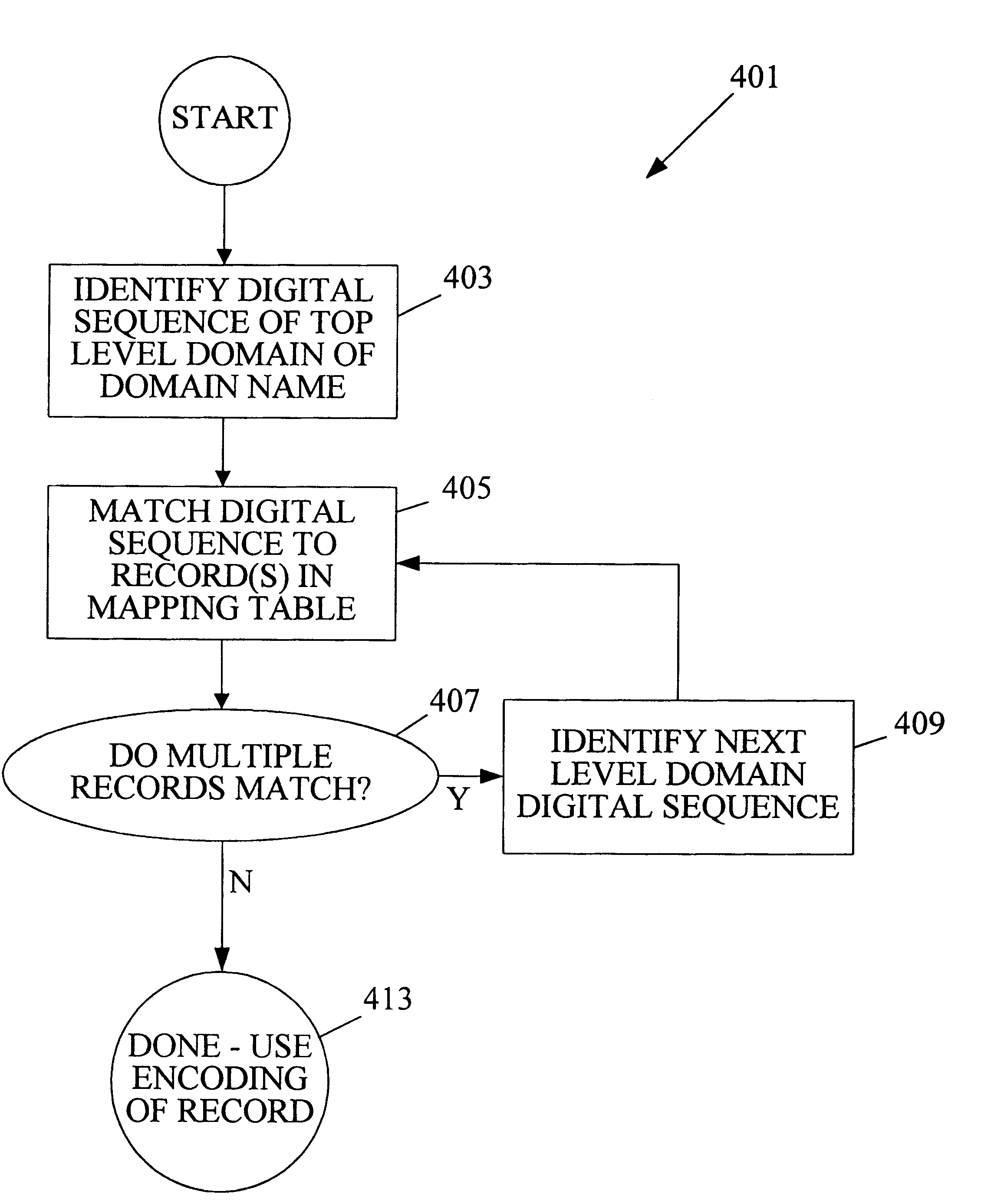
InactiveUS6314469B1Avoid ambiguityAvoid placingDigital data processing detailsNatural language data processingIp addressMulti language
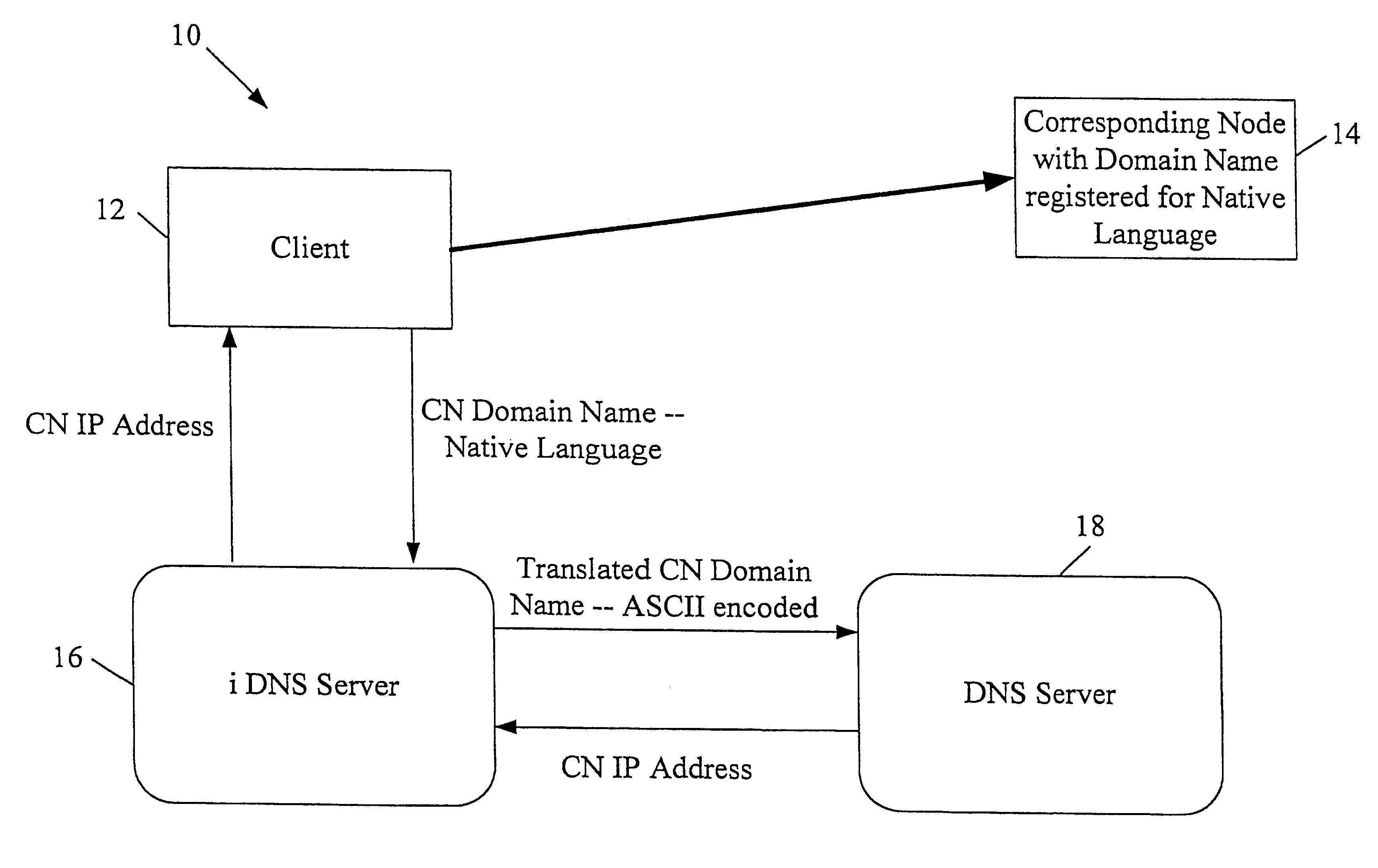
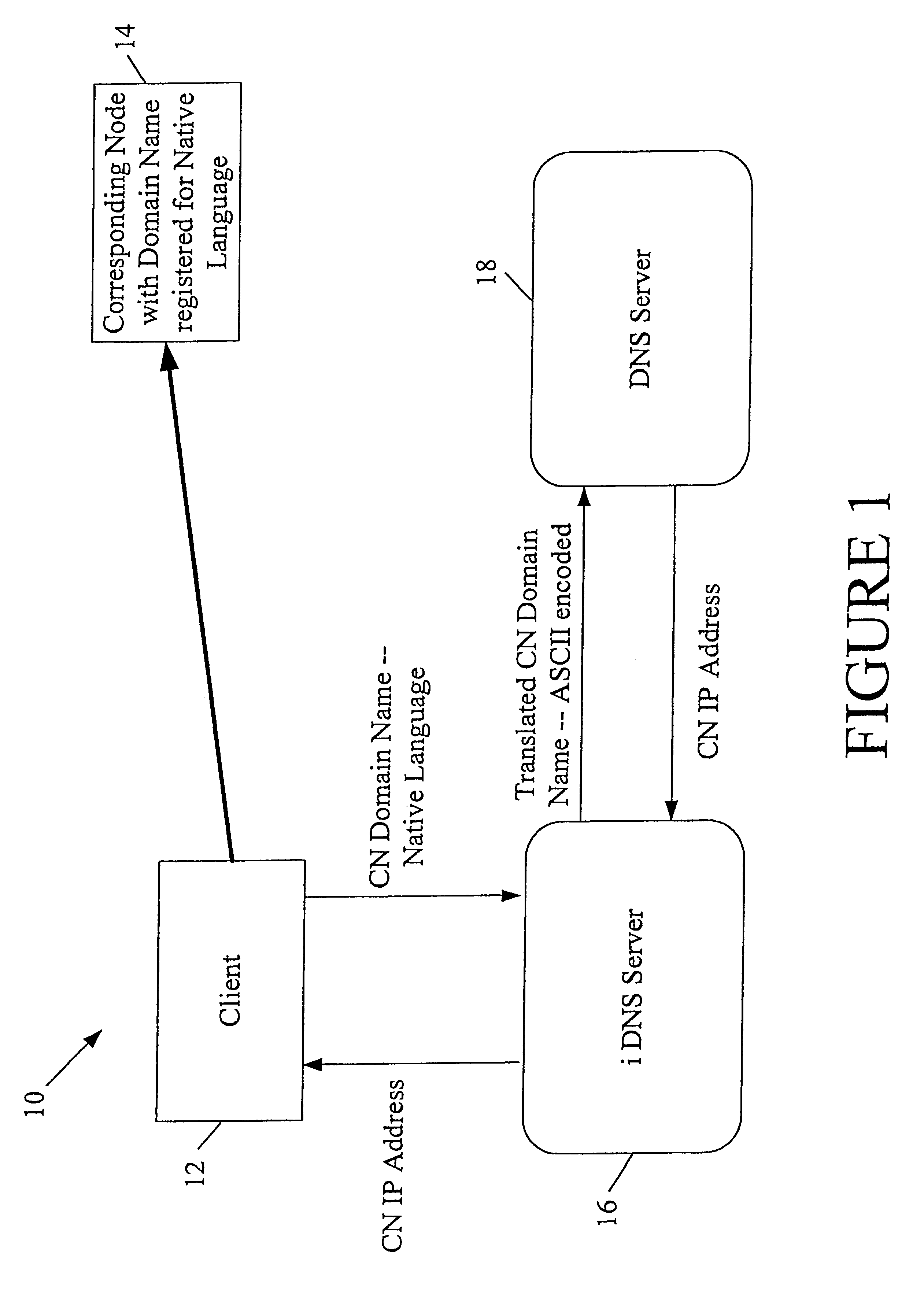
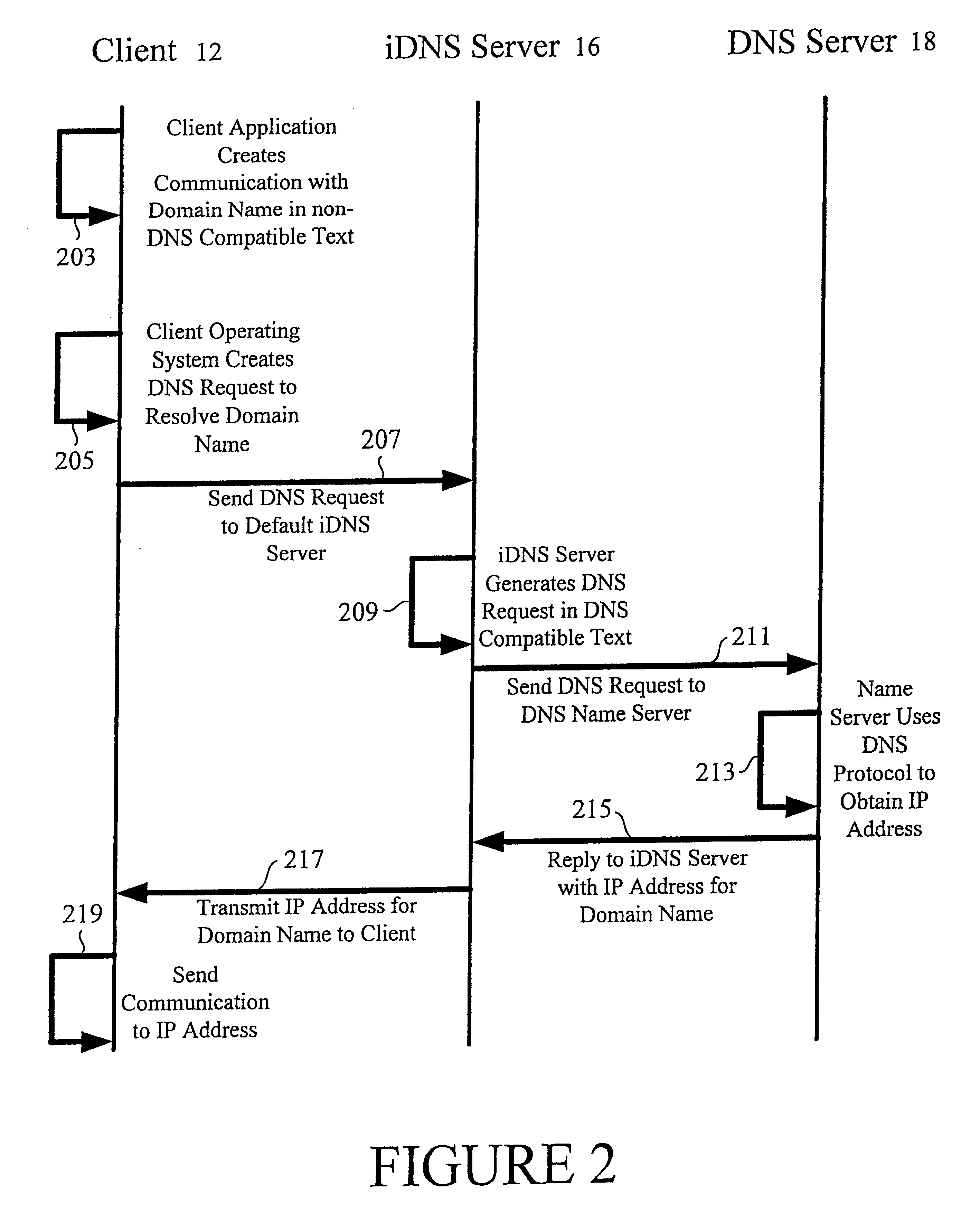
A multilingual Domain Name System allows users to use Domain Names in non-Unicode or ASCII encodings. An international DNS server (or iDNS server) receives multilingual DNS requests and converts them to a format that can be used in the conventional Domain Name System. When the iDNS server first receives a DNS request, it determines the encoding type of that request. It may do this by considering the bit string in the top-level domain (or other portion) of the Domain Name and matching that string against a list of known bit strings for known top-level domains of various encoding types. One entry in the list may be the bit string for ".com" in Chinese BIG5, for example. After the iDNS server identifies the encoding type of the Domain Name, it converts the encoding of the Domain Name to Unicode. It then translates the Unicode representation to an ASCII representation conforming to the universal DNS standard. This is then passed into a conventional Domain Name System, which recognizes the ASCII format Domain Name and returns the associated IP address.
Owner:I DNS NET INT
Architecture and engine for time line based visualization of data
InactiveUS7788592B2Facilitate navigating and managingUser may experienceData processing applicationsDigital data processing detailsLevel of detailThumbnail
The subject invention provides a unique system and method that facilitates management and navigation of various data objects by making use of a unique time-line based navigation tool. In particular, objects can organized into a plurality of bands based on their respective subject matter. Each band can be created to designate a particular topic. Objects are organized within the appropriate bands based in part on a time parameter such as a time or date that the object was created, for example. The navigation tool allows a user to navigate or browse through the bands and objects according to a desired time parameter or range of time. Zooming and other browsing options are available to the user to view objects of interest at varying levels of detail. The objects are represented as ASCII thumbnails that are operational. Thus, the content of any object can be modified directly via the thumbnail.
Owner:MICROSOFT TECH LICENSING LLC
Email analysis using fuzzy matching of text
InactiveUS20050262210A1Easy to analyzeEfficient and accurate analysisMultiple digital computer combinationsData switching networksData miningASCII
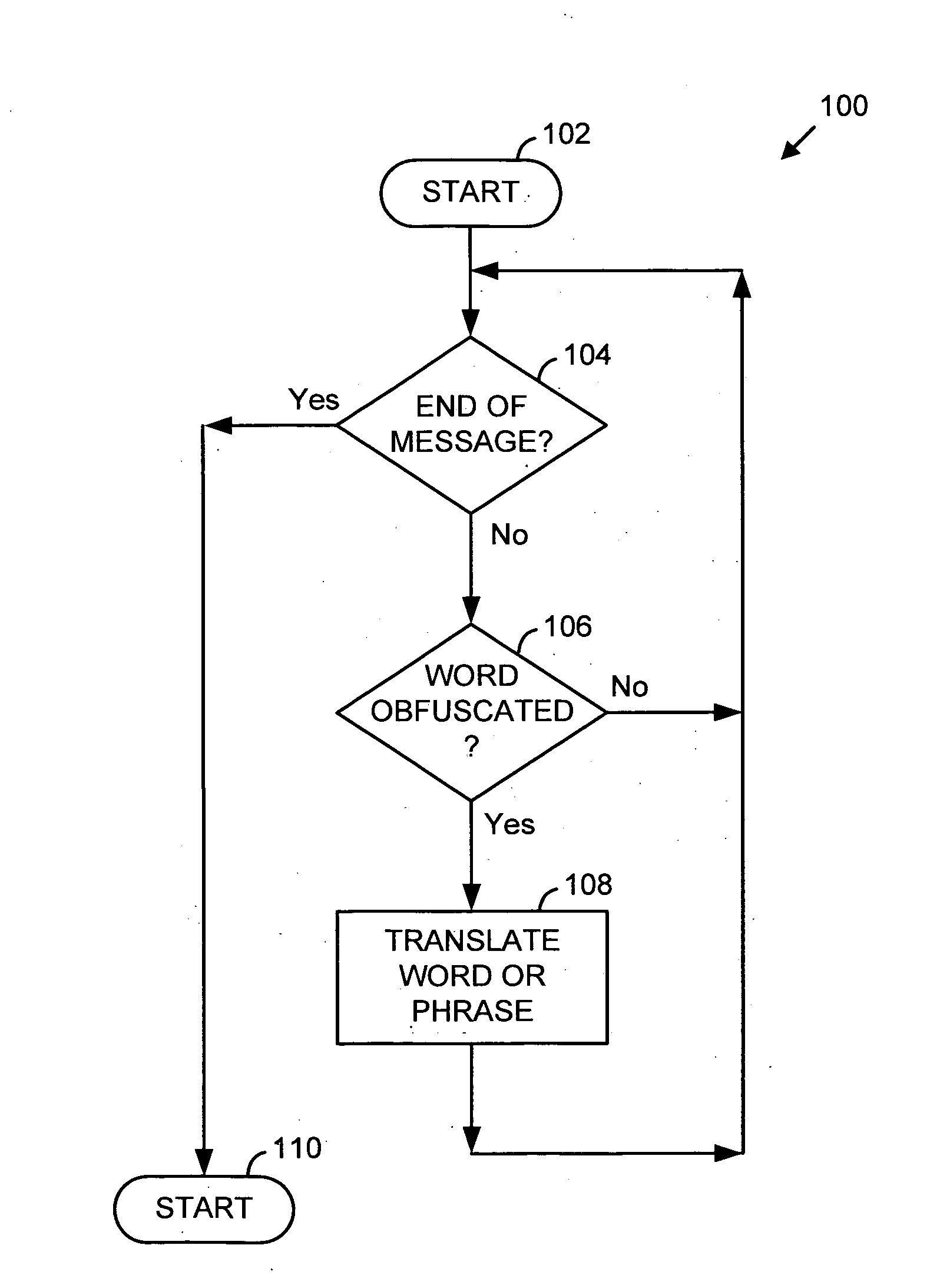
Translation of text or messages provides a message that is more reliably or efficiently analyzed for purposes as, for example, to detect spam in email messages. One translation process takes into account statistics of erroneous and intentional misspellings. Another process identifies and removes characters or character codes that do not generate visible symbols in a message displayed to a user. Another process detects symbols such as periods, commas, dashes, etc., interspersed in text such that the symbols do not unduly interfere with, or prevent, a user from perceiving a spam message. Another process can detect use of foreign language symbols and terms. Still other processes and techniques are presented to counter obfuscating spammer tactics and to provide for efficient and accurate analysis of message content. Groups of similar content items (e.g., words, phrases, images, ASCII text, etc.) are correlated and analysis can proceed after substitution of items in the group with other items in the group so that a more accurate detection of “sameness” of content can be achieved. Dictionaries are used for spam or ham words or phrases. Other features are described.
Owner:GOZOOM COM
Multi-language domain name service
InactiveUS6446133B1Avoid placingDigital data processing detailsNatural language data processingDomain nameIp address
A multilingual Domain Name System allows users to use Domain Names in non-Unicode or ASCII encodings. An international DNS server (or iDNS server) receives multilingual DNS requests and converts them to a format that can be used in the conventional Domain Name System. When the iDNS server first receives a DNS request, it determines the encoding type of that request. It may do this by considering the bit string in the top-level domain (or other portion) of the Domain Name and matching that string against a list of known bit strings for known top-level domains of various encoding types. One entry in the list may be the bit string for ".com" in Chinese BIG5, for example. After the iDNS server identifies the encoding type of the Domain Name, it converts the encoding of the Domain Name to Unicode. It then translates the Unicode representation to an ASCII representation conforming to the universal DNS standard. This is then passed into a conventional Domain Name System, which recognizes the ASCII format Domain Name and returns the associated IP address.
Owner:I DNS NET INT
Universalthermostat expansion port
InactiveUS20100182743A1Rapid productionLine/current collector detailsTemperature control using digital meansElectricityTemperature control
In one aspect, the invention relates to a configurable thermostat including a thermostat core having a user interface. The user interface includes a plurality of user interface keys, a display, a temperature sensor, and a temperature control. The configurable thermostat also includes a universal thermostat expansion port. The universal thermostat expansion port is disposed on the thermostat core. The universal thermostat expansion port includes at least one electrical connector. The electrical connector electrically couples a daughter board to the thermostat core, wherein the daughter board is communicately coupled to the thermostat core by an ASCII communications protocol. According to another aspect of the invention, a method for configuring a thermostat uses a personal computer with a thermostat having a user removable memory. Yet another aspect of the invention is a method for rapidly producing a thermostat having new features without needing to redesign the entire thermostat.
Owner:CARRIER CORP
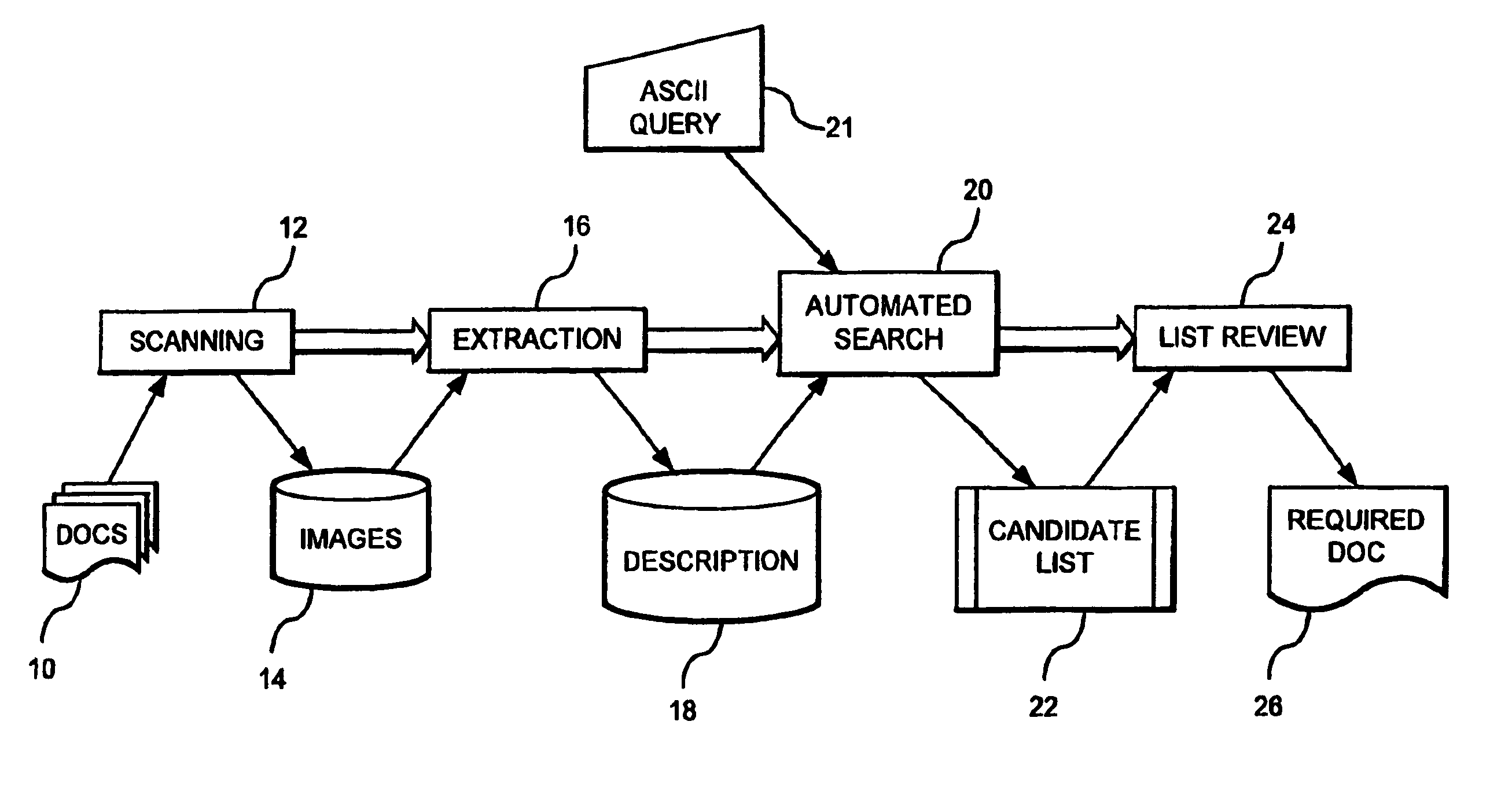
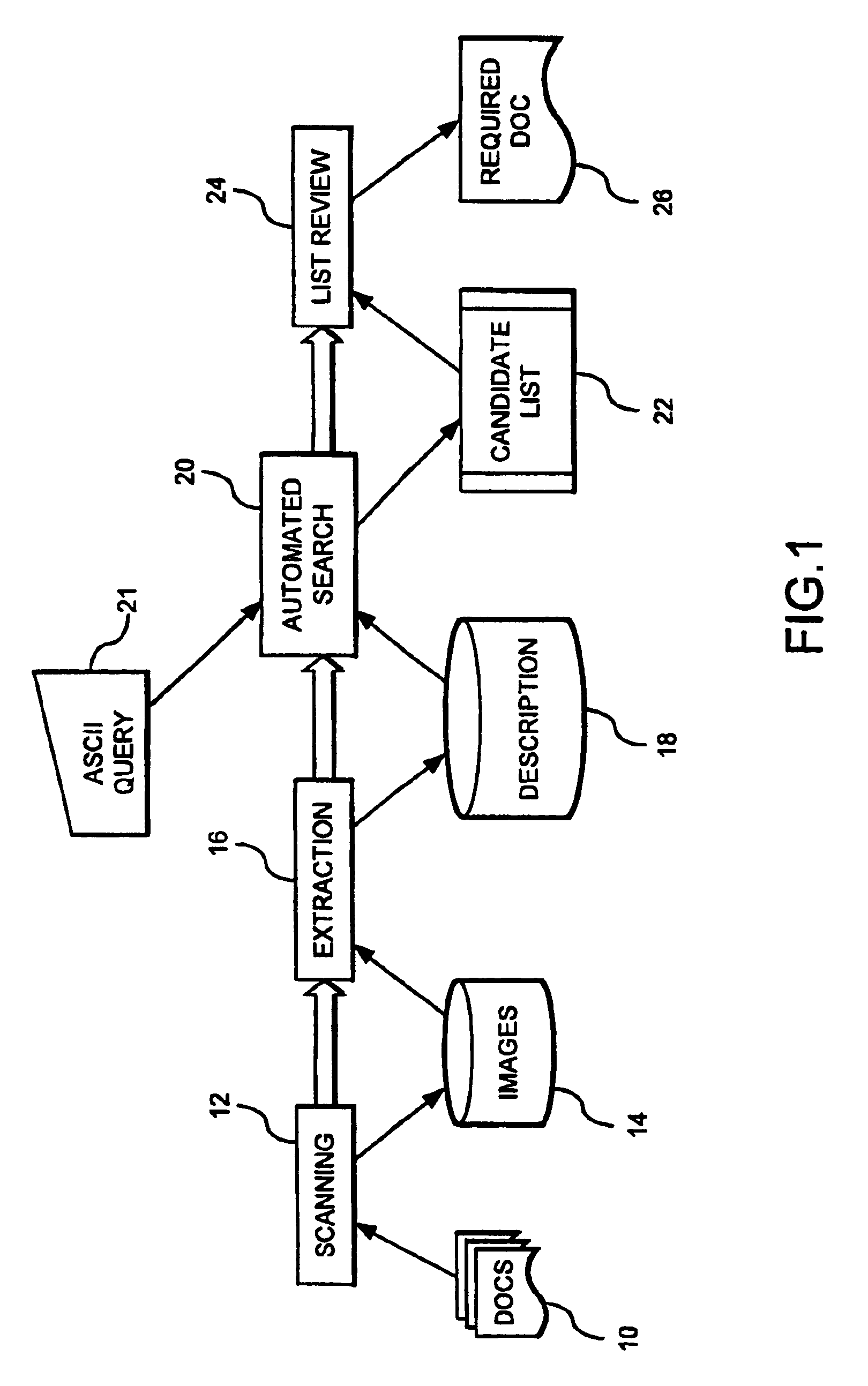
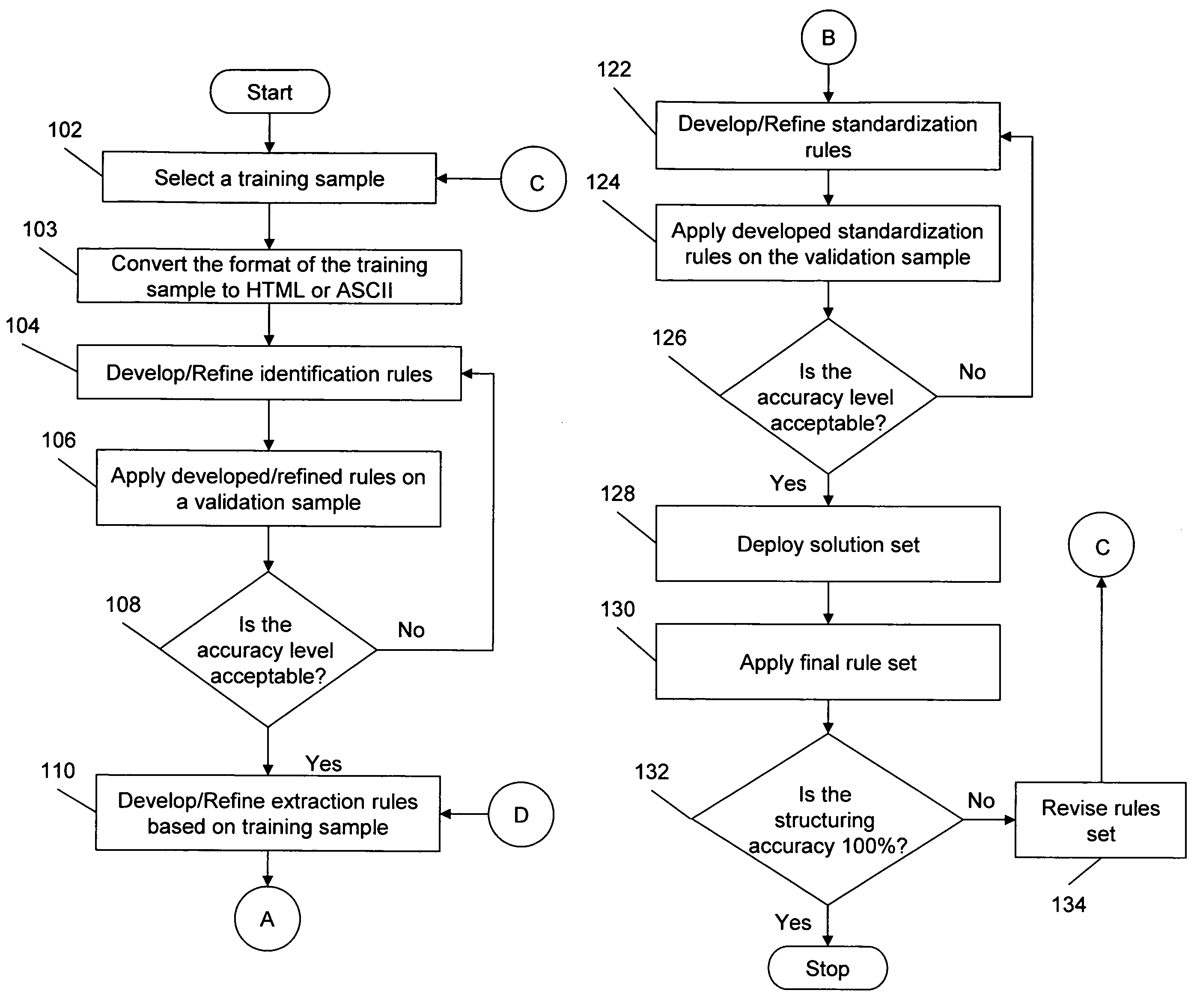
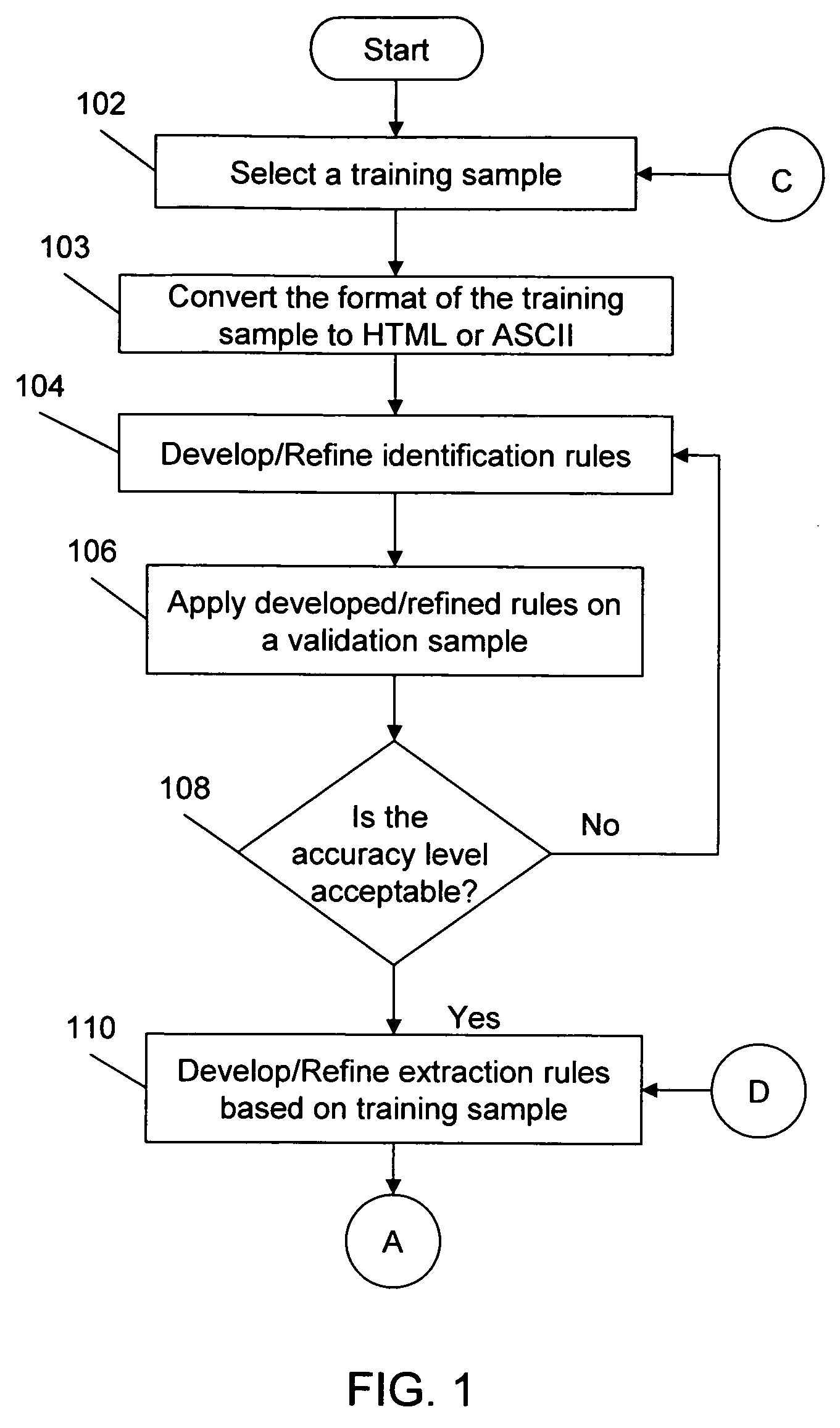
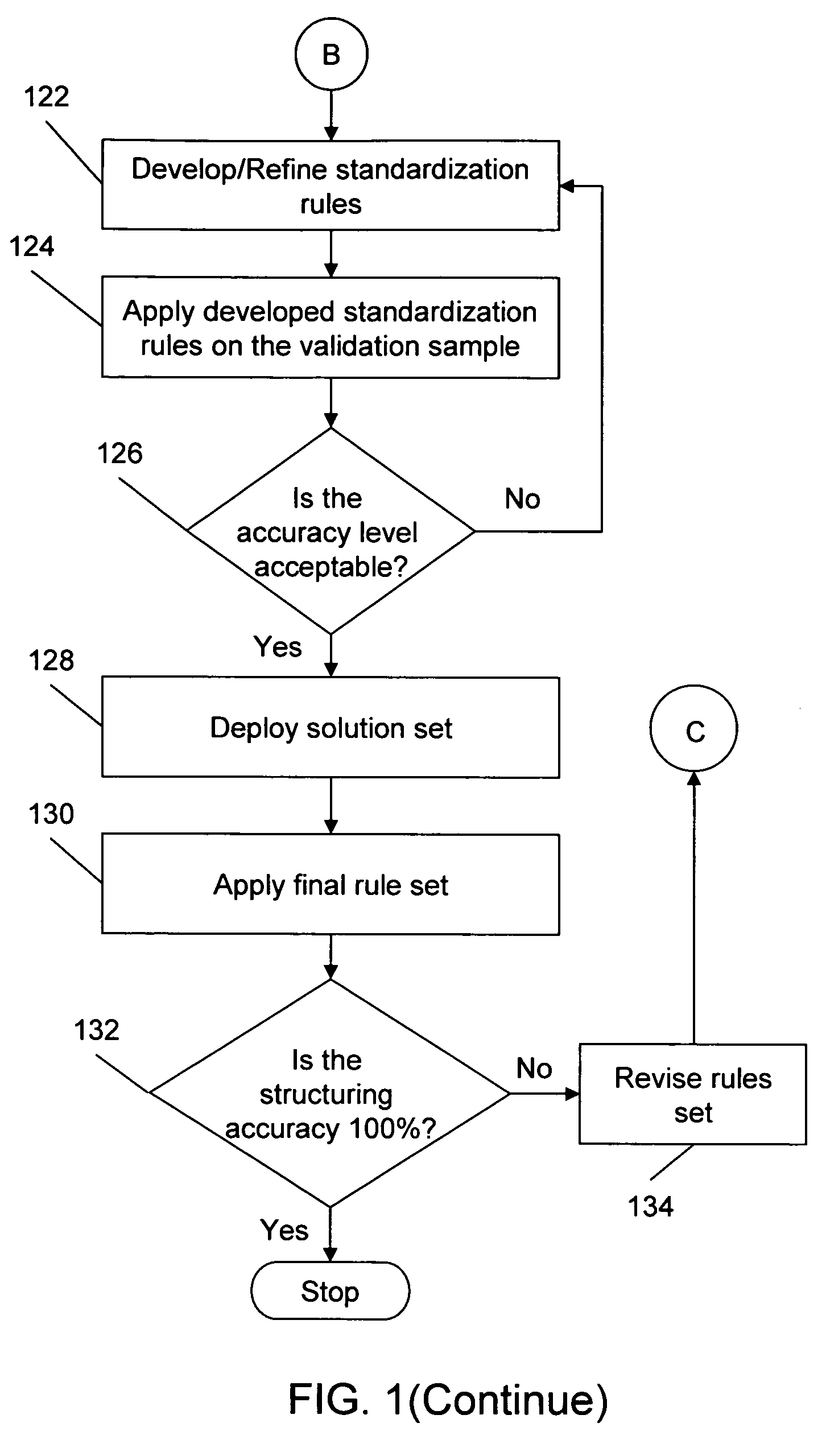
Method for extracting, interpreting and standardizing tabular data from unstructured documents
ActiveUS20060288268A1Eliminate manual effortMaximum flexibilityData processing applicationsDigital data information retrievalPortable document formatPaper document
A system, method, and computer program for automatically identifying, parsing, and interpreting tabular data from unstructured documents stored in various formats such as ASCII text, Unicode text, HTML, PDF text, and PDF image format is provided. A set of table identification, parsing / tokenizing, and interpreting / mapping rules are developed with grammar descriptors. These rules are then applied to a set of documents to identify a table, parse the content of the table, and interpret the parsed content, if required, thereby standardizing the tabular data.
Owner:RAGE FRAMEWORKS +1
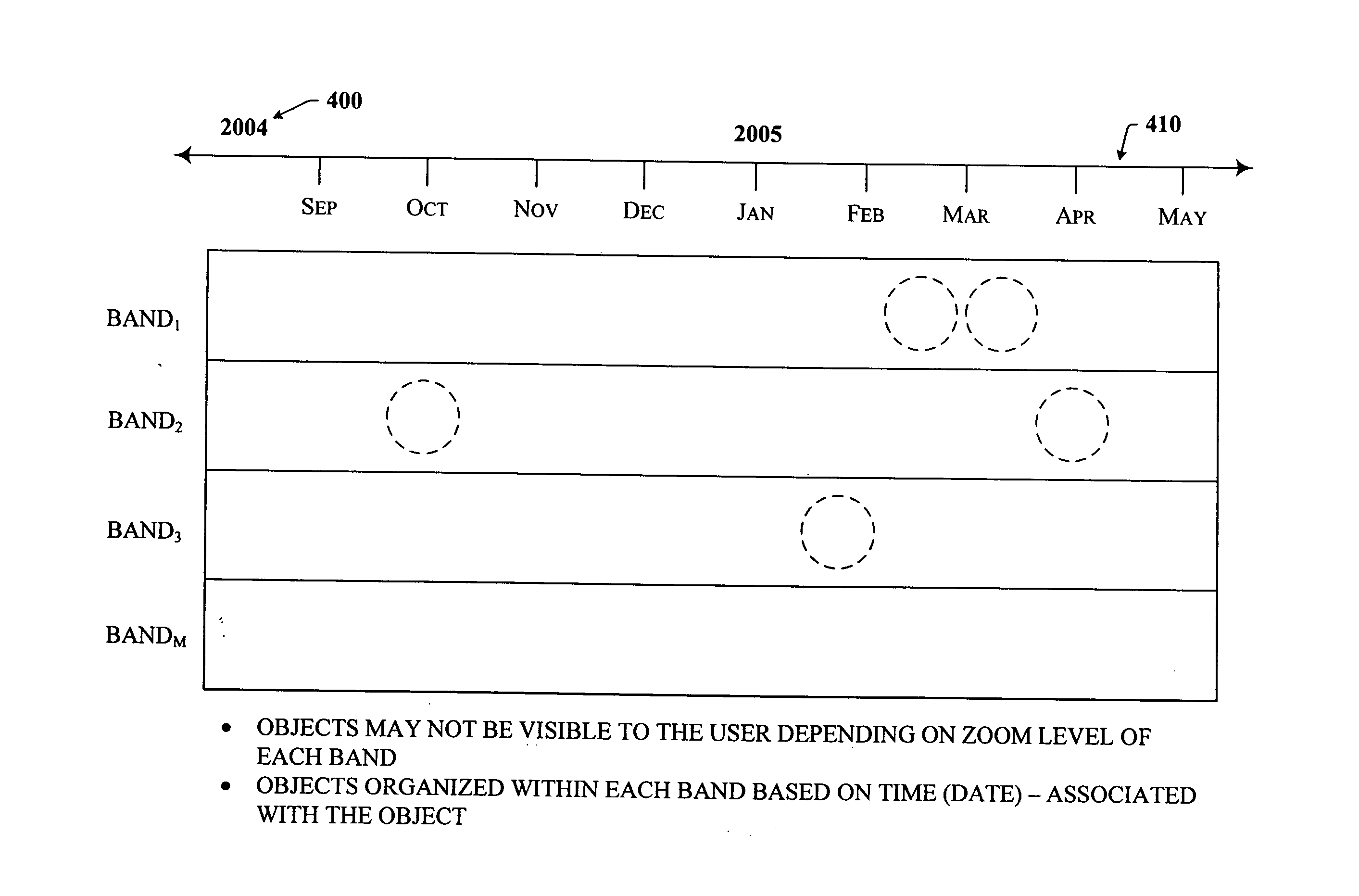
File management system employing time line based representation of data
ActiveUS20060155757A1Easy to watchFacilitate navigating and managingData processing applicationsDigital data information retrievalLevel of detailThumbnail
The subject invention provides a unique system and method that facilitates management and navigation of various data objects by making use of a unique time-line based navigation tool. In particular, objects can organized into a plurality of bands based on their respective subject matter. Each band can be created to designate a particular topic. Objects are organized within the appropriate bands based in part on a time parameter such as a time or date that the object was created, for example. The navigation tool allows a user to navigate or browse through the bands and objects according to a desired time parameter or range of time. Zooming and other browsing options are available to the user to view objects of interest at varying levels of detail. The objects are represented as ASCII thumbnails that are operational. Thus, the content of any object can be modified directly via the thumbnail.
Owner:MICROSOFT TECH LICENSING LLC
Email analysis using fuzzy matching of text
InactiveUS7644127B2Efficient and accurate analysisEasy to analyzeMultiple digital computer combinationsData switching networksData miningASCII
Translation of text or messages provides a message that is more reliably or efficiently analyzed for purposes as, for example, to detect spam in email messages. One translation process takes into account statistics of erroneous and intentional misspellings. Another process identifies and removes characters or character codes that do not generate visible symbols in a message displayed to a user. Another process detects symbols such as periods, commas, dashes, etc., interspersed in text such that the symbols do not unduly interfere with, or prevent, a user from perceiving a spam message. Another process can detect use of foreign language symbols and terms. Still other processes and techniques are presented to counter obfuscating spammer tactics and to provide for efficient and accurate analysis of message content. Groups of similar content items (e.g., words, phrases, images, ASCII text, etc.) are correlated and analysis can proceed after substitution of items in the group with other items in the group so that a more accurate detection of “sameness” of content can be achieved. Dictionaries are used for spam or ham words or phrases. Other features are described.
Owner:GOZOOM COM
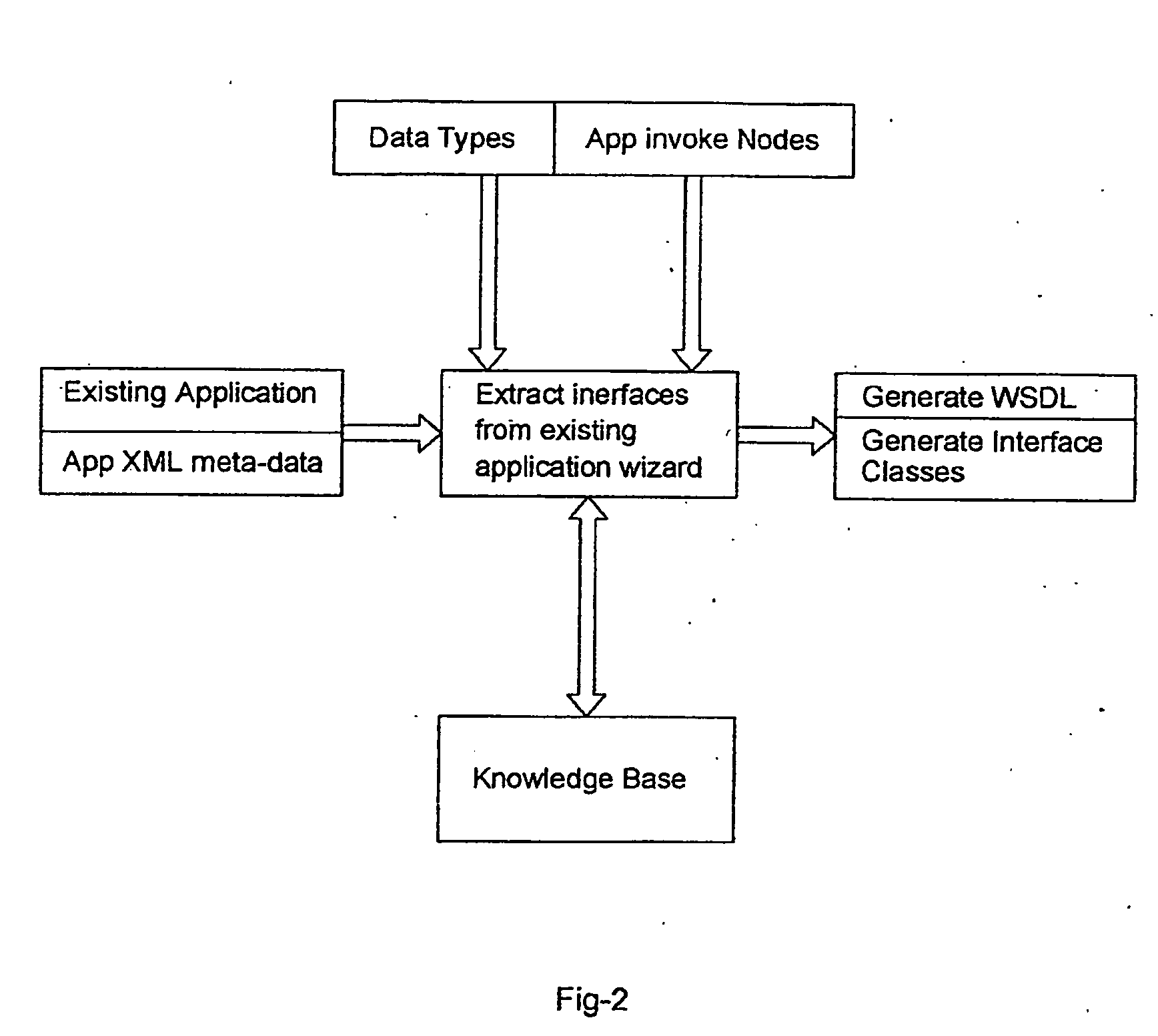
Apparatus for Migration and Conversion of Software Code from Any Source Platform to Any Target Platform
ActiveUS20070256058A1Improve quality controlProgram code adaptionSpecific program execution arrangementsSource codeASCII
An apparatus migrates and / or converts any source application working on any platform into a format of any target platform. It comprises an inputting means for accepting the entire source code of sample part in ASCII to analyze the business logic of the source application and corresponding data; an analyzing means for analyzing the source schemes; a setting up means for generating (updating or creating) custom knowledge base; a processing means for conversion of source code in format of target specification; and A documenting means for generation of reports during review of the process stage and a summary report after the end of the conversion process, which consists of the code that is not converted automatically.
Owner:EVOLVEWARE
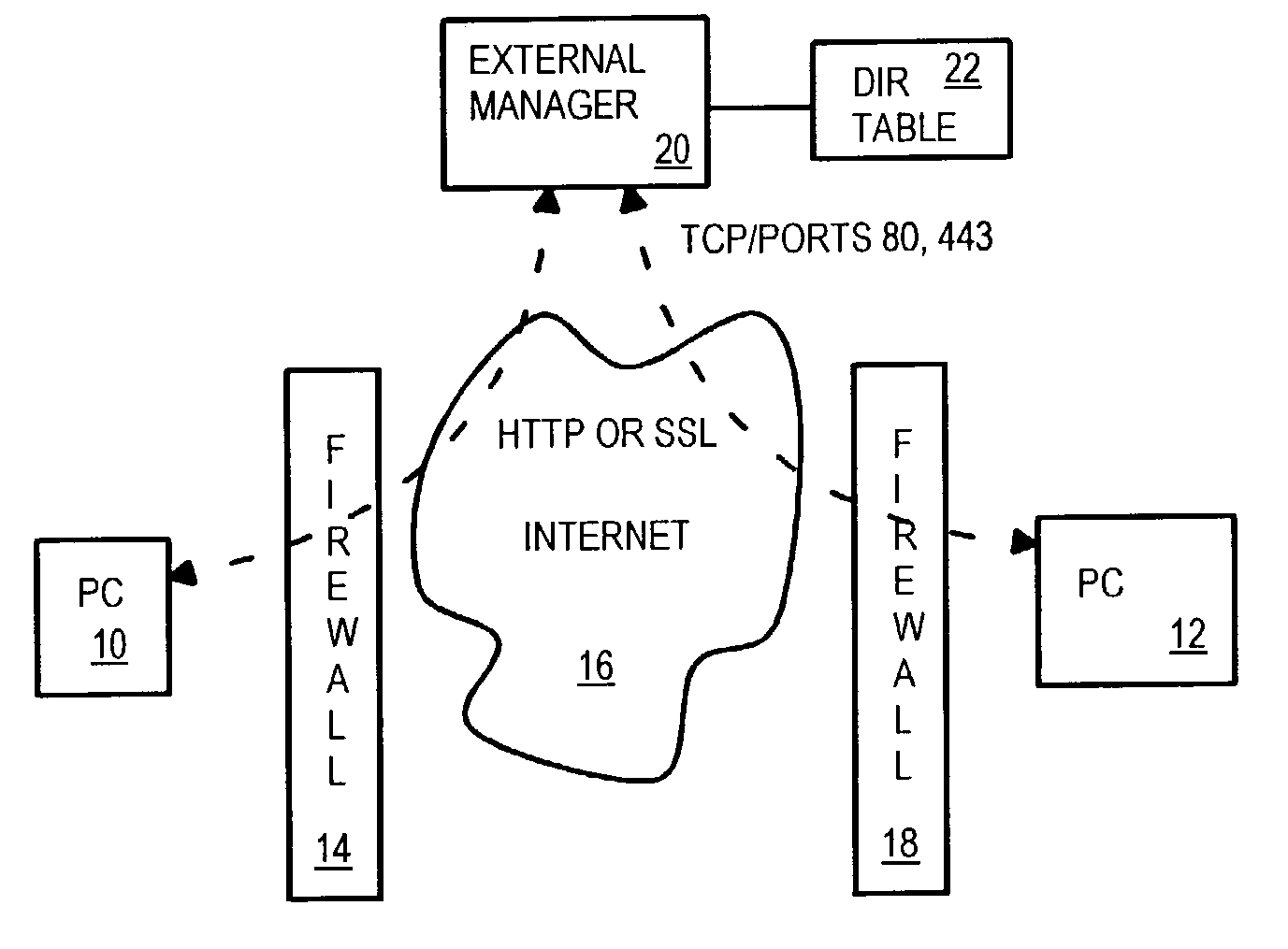
Firewall-tolerant voice-over-internet-protocol (VoIP) emulating SSL or HTTP sessions embedding voice data in cookies
A voice-over-Internet-Protocol (VoIP) client codes audio data as printable ASCII characters, then embeds the ASCII audio data inside a cookie that is sent over the Internet within an HTTP GET message. The GET message is sent to a server acting as a call proxy or external manager that forwards the audio data to a remote client. Return audio data is sent back to the client in the normal data field of an HTTP response message from the server. When the client receives the HTTP response, it sends another GET message without audio data, allowing the server to send another response. This empty GET allows VoIP to pass through strict firewalls that pair each HTTP response with a GET. For secure-sockets layer (SSL), client and server exchange pseudo-keys in hello and finished messages that establish the SSL session. Audio data is streamed in SSL messages instead of encrypted data.
Owner:GOOGLE LLC
File management system employing time line based representation of data
ActiveUS7716194B2Facilitate navigating and managingUser may experienceData processing applicationsDigital data information retrievalLevel of detailThumbnail
The subject invention provides a unique system and method that facilitates management and navigation of various data objects by making use of a unique time-line based navigation tool. In particular, objects can organized into a plurality of bands based on their respective subject matter. Each band can be created to designate a particular topic. Objects are organized within the appropriate bands based in part on a time parameter such as a time or date that the object was created, for example. The navigation tool allows a user to navigate or browse through the bands and objects according to a desired time parameter or range of time. Zooming and other browsing options are available to the user to view objects of interest at varying levels of detail. The objects are represented as ASCII thumbnails that are operational. Thus, the content of any object can be modified directly via the thumbnail.
Owner:MICROSOFT TECH LICENSING LLC
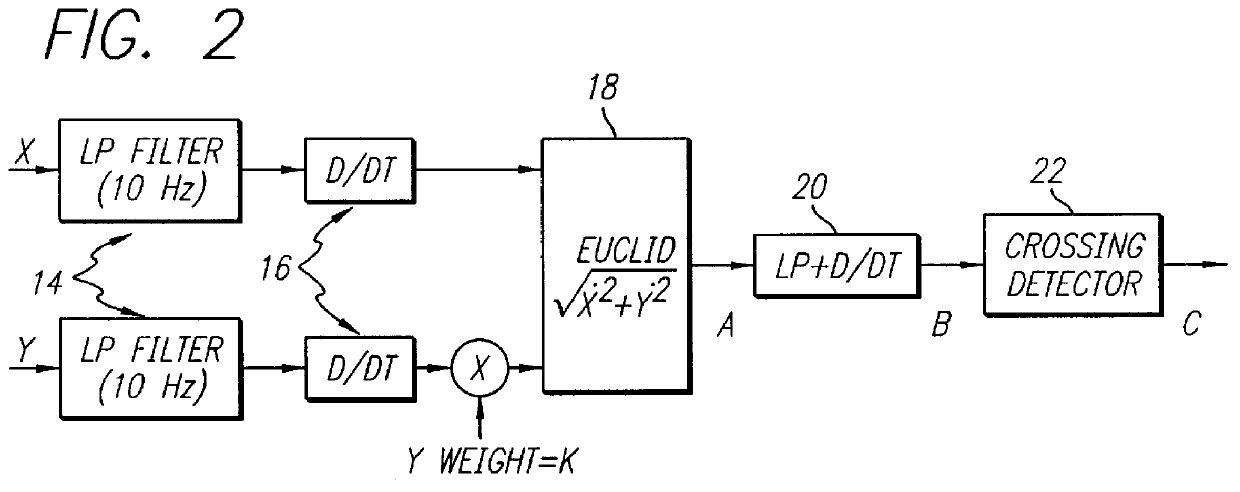
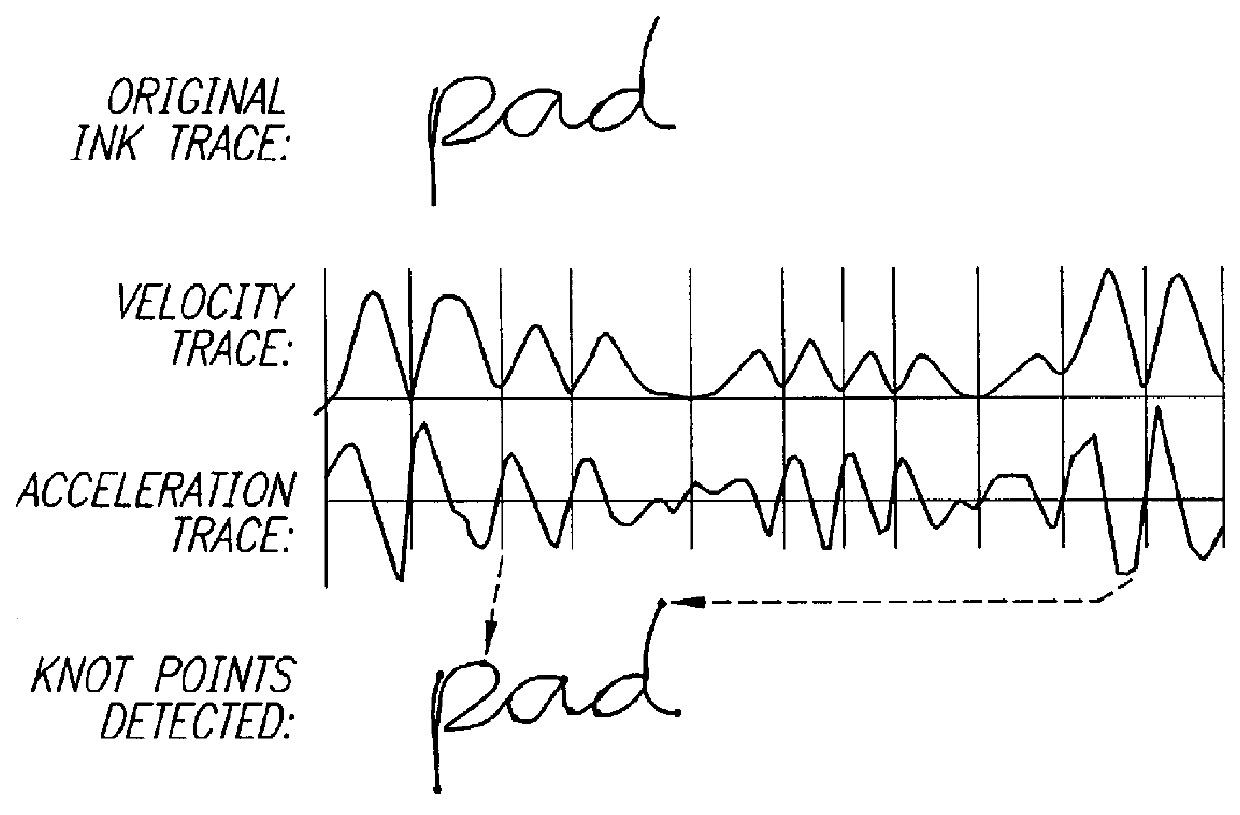
Scribble matching
InactiveUS6018591ASave powerImprove performanceCharacter and pattern recognitionAlgorithmElastic matching
The present invention relates to scribble matching methods, ie. methods for searching samples of electronic ink without having first to translate the ink into ASCII text. The methods of the present invention find application in pen-based computer devices. The invention entails the identification and encoding of velocity minima in the input scribble. Three scribble matching algorithms are described-a syntactic matcher, a word matcher and an elastic matcher. The syntactic matcher encodes the input scribble according to the shape of the scribble in the region of the velocity minima. The word matcher encodes the input scribble according to the heights of the velocity minima from a reference line, using a continuous height encoding scheme. The elastic matcher encodes the input scribble according to a classification of the velocity minima and intermediate points. The use of velocity minima in the encoding of scribble input provides a stable set of points and leads to improved performance in comparison with known scribble matching methods.
Owner:HEWLETT PACKARD DEV CO LP
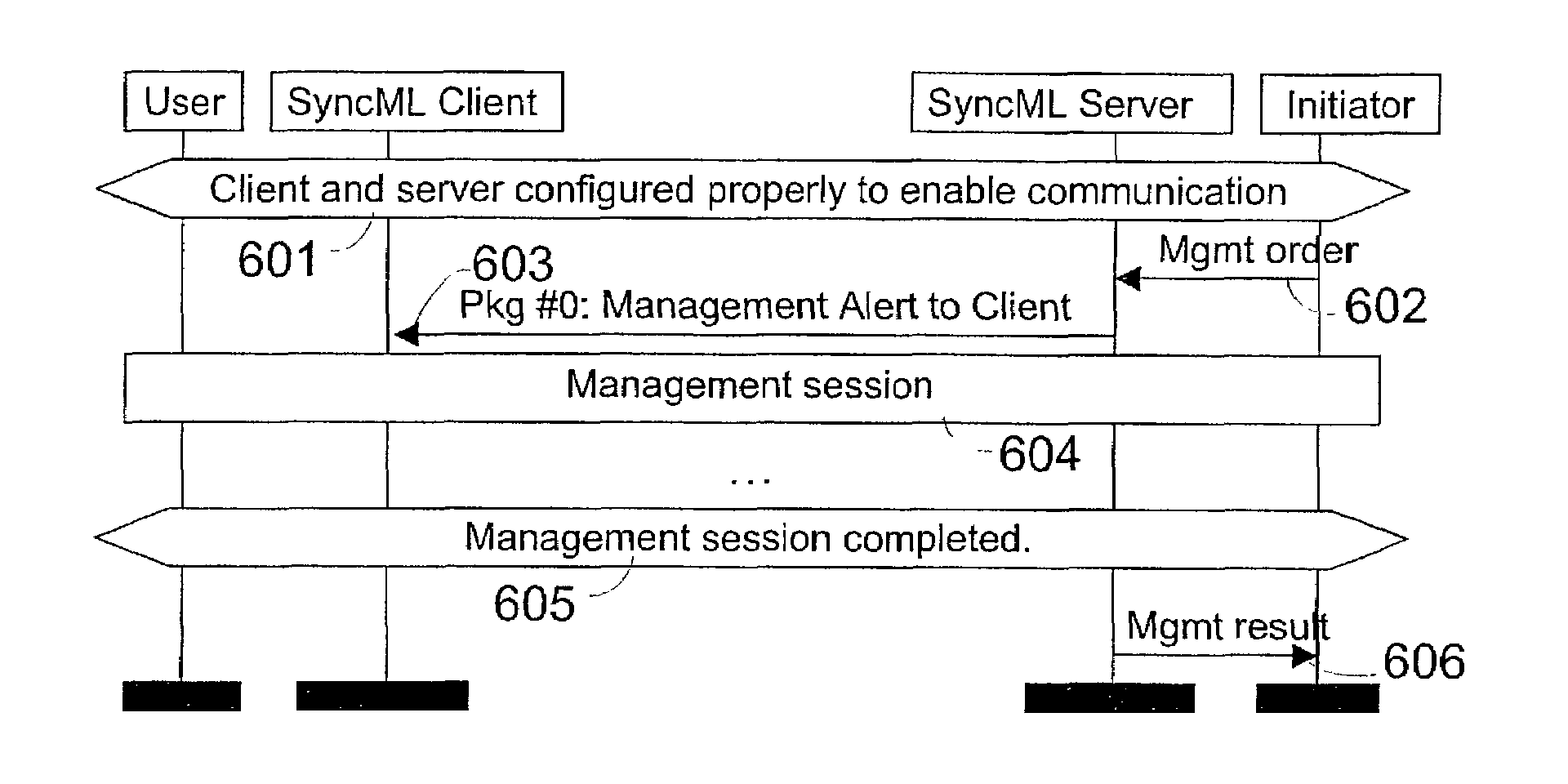
Starting a session in a synchronization system
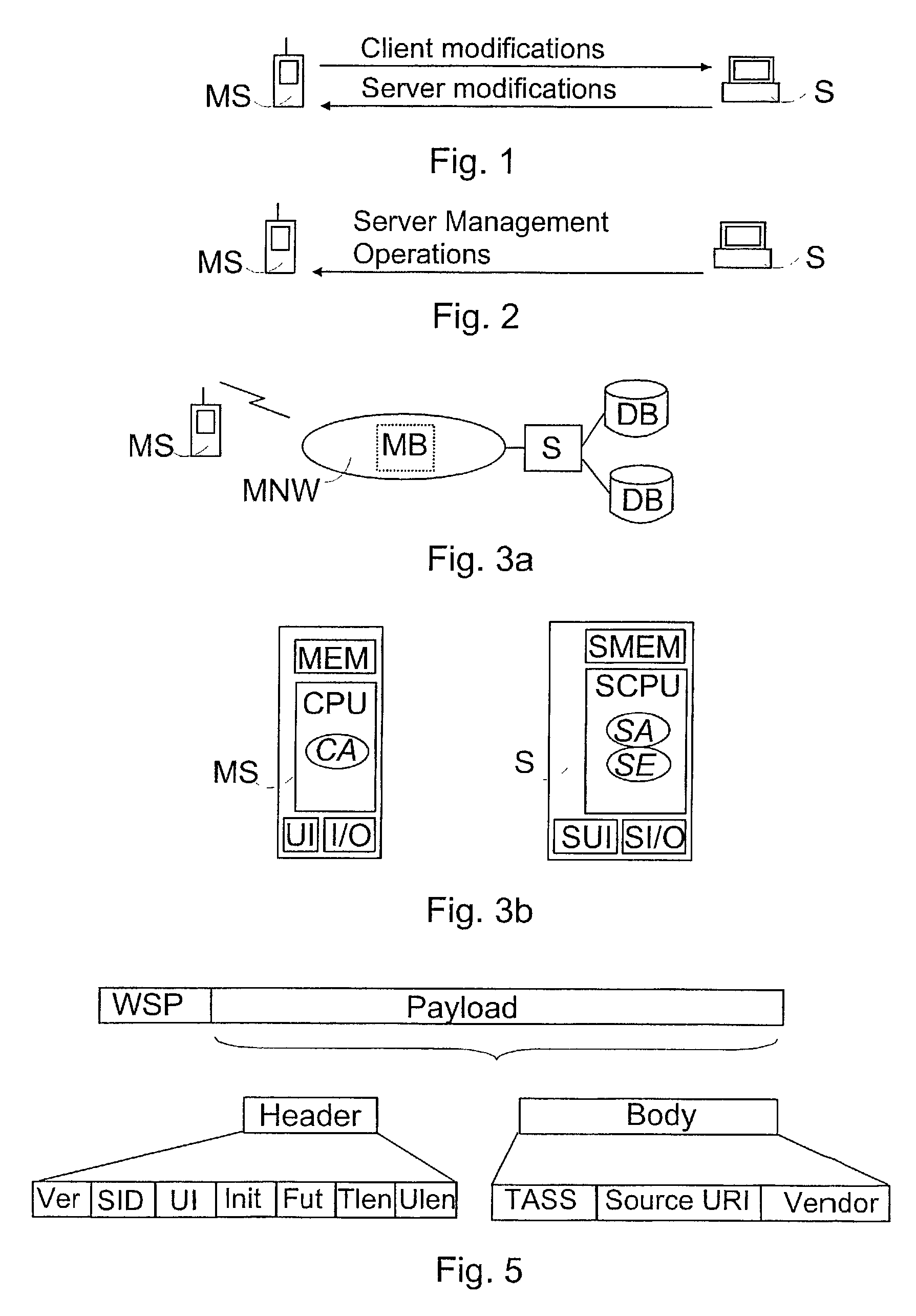
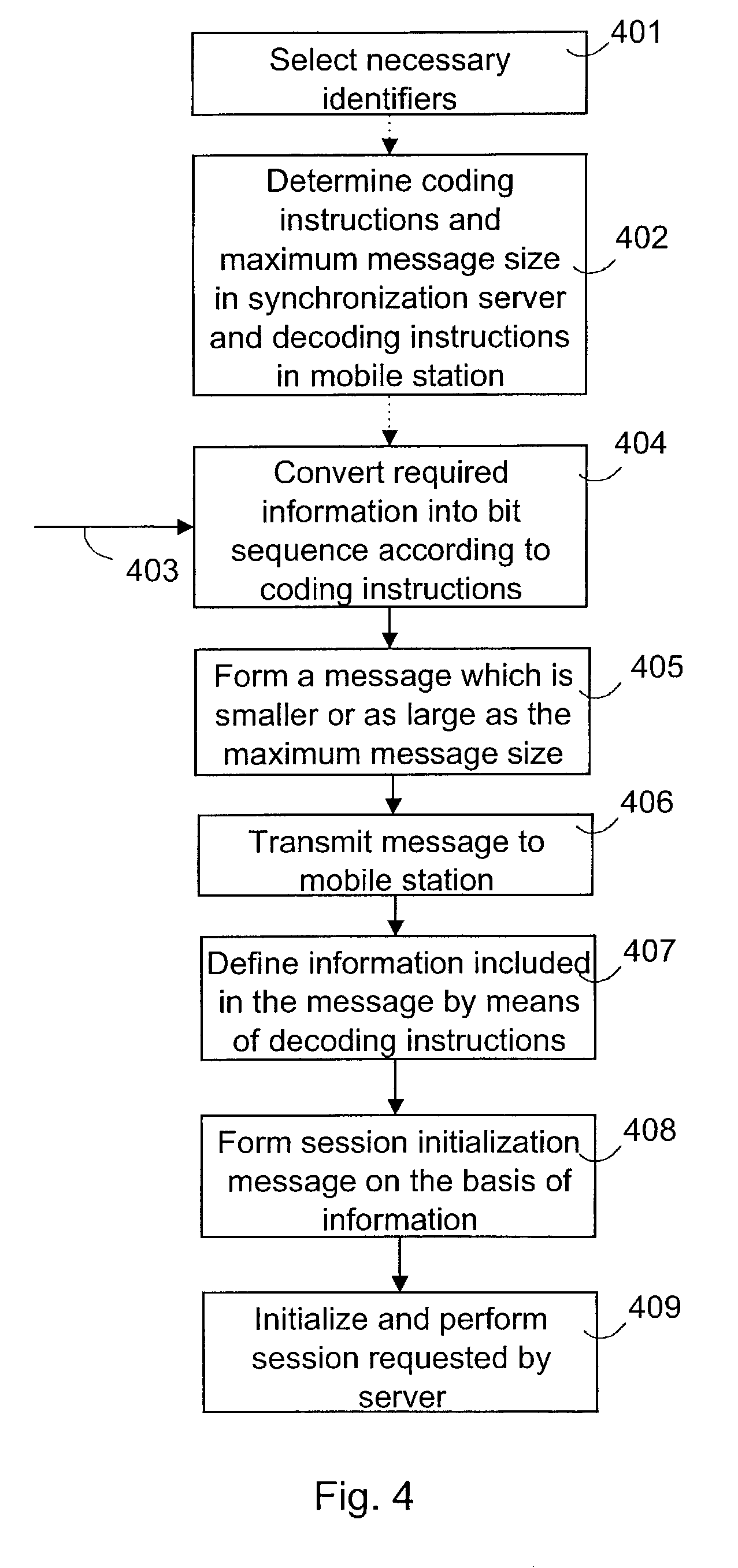
InactiveUS7155521B2Less spaceSave transmission resourcesMultiple digital computer combinationsSynchronisation signal speed/phase controlMobile stationMaximum size
A method of starting a session in a synchronization system. The maximum size of a message that is to be sent from a synchronization server to a mobile station for the request, and coding instructions, by which at least one of the identifiers can be coded into a bit sequence requiring substantially fewer bits than its ASCII presentation, are determined in the synchronization server. Decoding instructions, by means of which the original identifier is obtained from the bit sequence, are determined in the mobile station. When the purpose is to transmit a request indicating the need for starting a session to at least one mobile station, a message is formed, is shorter or as long as the maximum size and includes the pre-selected identifiers, at least one of which is presented as a bit sequence defined according to the coding instructions. The mobile station forms a session initialization message on the basis of the information included in the message received from the server, at least part of information being defined from the received bit sequence according to the decoding instructions.
Owner:NOKIA TECHNOLOGLES OY
Predicate indexing of data stored in a computer with application to indexing cached data
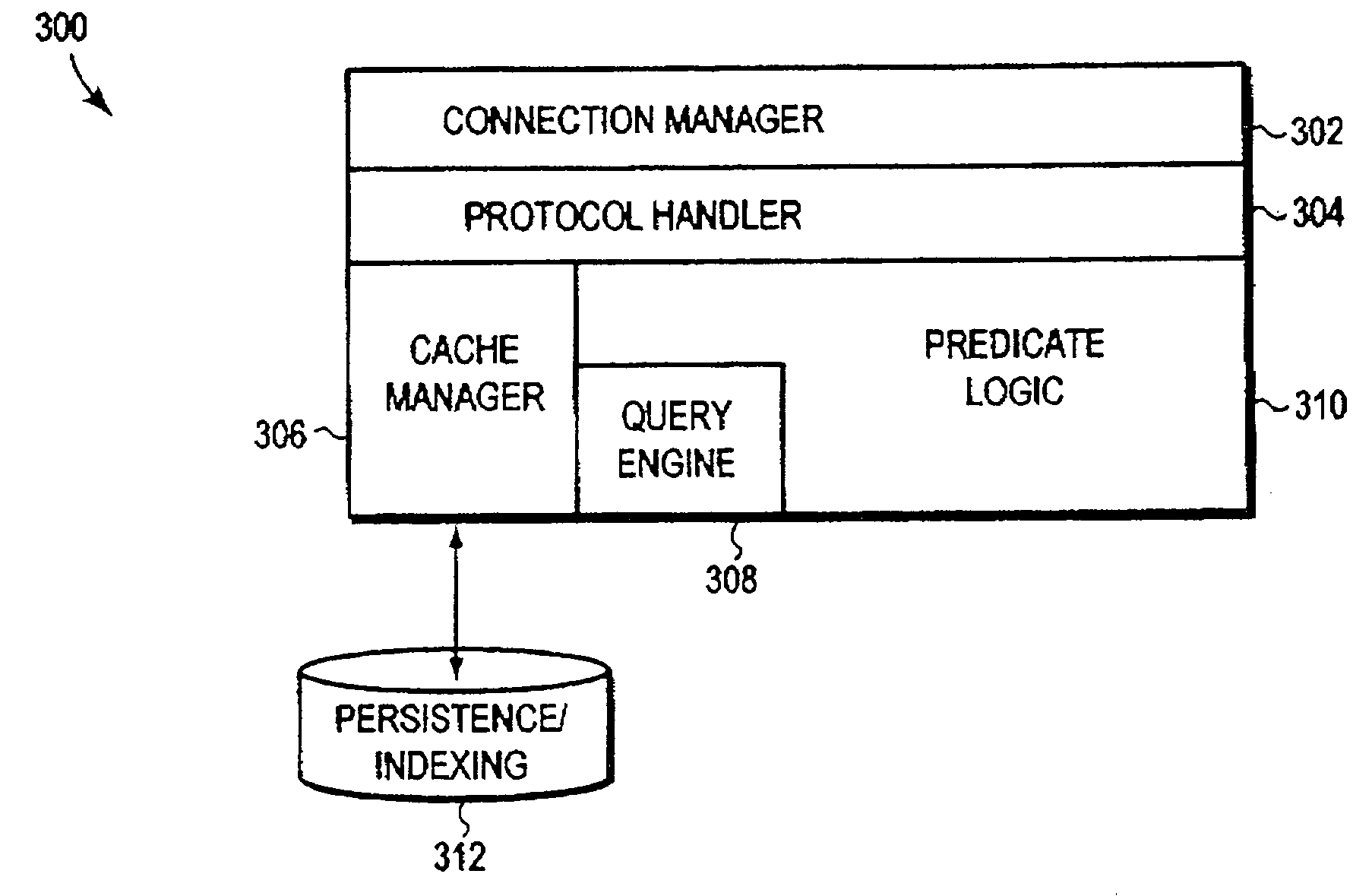
InactiveUS7191170B2Digital data information retrievalData processing applicationsTheoretical computer scienceA-normal form
The invention relates to a directory proxy caching system that is constructed based on a predicate, i.e., a query from a client. Broadly stated, the predicate is formed by the query (request) issued by the client. Once the data is found in the directory, then the data is stored in a cache of a proxy server. The data is indexed in the proxy server by the predicate. The predicate is used to form an index by sorting the predicate into a normal form. Steps in sorting the predicate into the normal form include the following. Each symbol of the predicate is represented by a numerical representation, for example the ASCII value used to represent the symbol in ordinary text files. The predicate is expressed as a plurality of primitive predicates, and individual predicates of the plurality of primitive predicates are joined by logical connectors. The logical connectors, and each term in the primitive predicates are represented by numbers. The logical connectors and the predicates are sorted in numerical order of the numbers to form the normal form of the predicate. The information retrieved by the predicate is stored into a cache using the normal form of the predicate as an index. The next request using a previously used predicate can then be found in the cache by the next request being sorted into normal form and used as an index into the cache.
Owner:ORACLE INT CORP
Systems and methods for managing a life journal
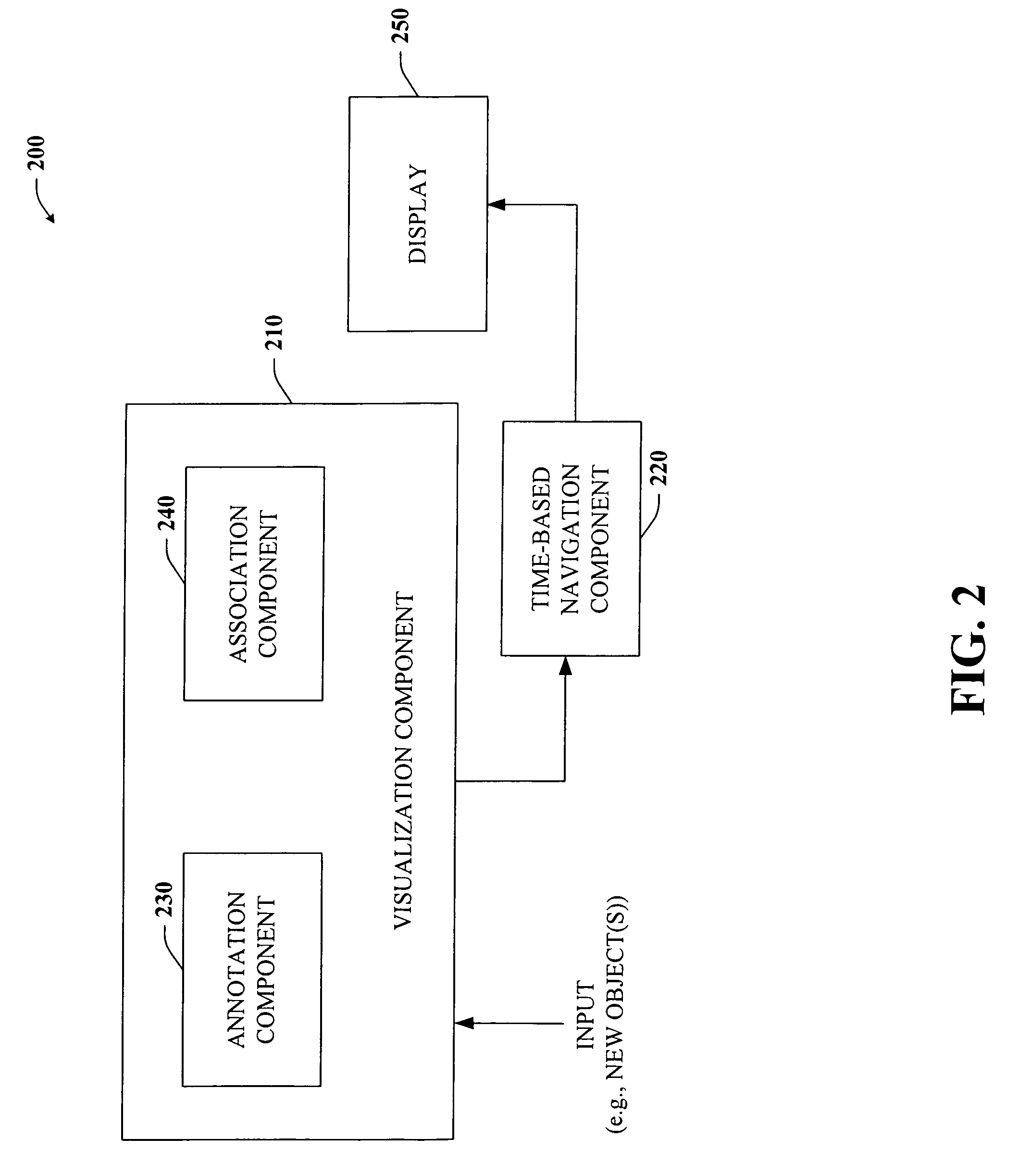
ActiveUS20060156245A1Easy to watchFacilitate navigating and managingData processing applicationsOther databases browsing/visualisationTime rangeLevel of detail
The subject invention provides a unique system and method that facilitates management and navigation of various data objects by making use of a unique time-line based navigation tool. In particular, objects can organized into a plurality of bands based on their respective subject matter. Each band can be created to designate a particular topic. Objects are organized within the appropriate bands based in part on a time parameter such as a time or date that the object was created, for example. The navigation tool allows a user to navigate or browse through the bands and objects according to a desired time parameter or range of time. Zooming and other browsing options are available to the user to view objects of interest at varying levels of detail. The objects are represented as ASCII thumbnails that are operational. Thus, the content of any object can be modified directly via the thumbnail.
Owner:MICROSOFT TECH LICENSING LLC
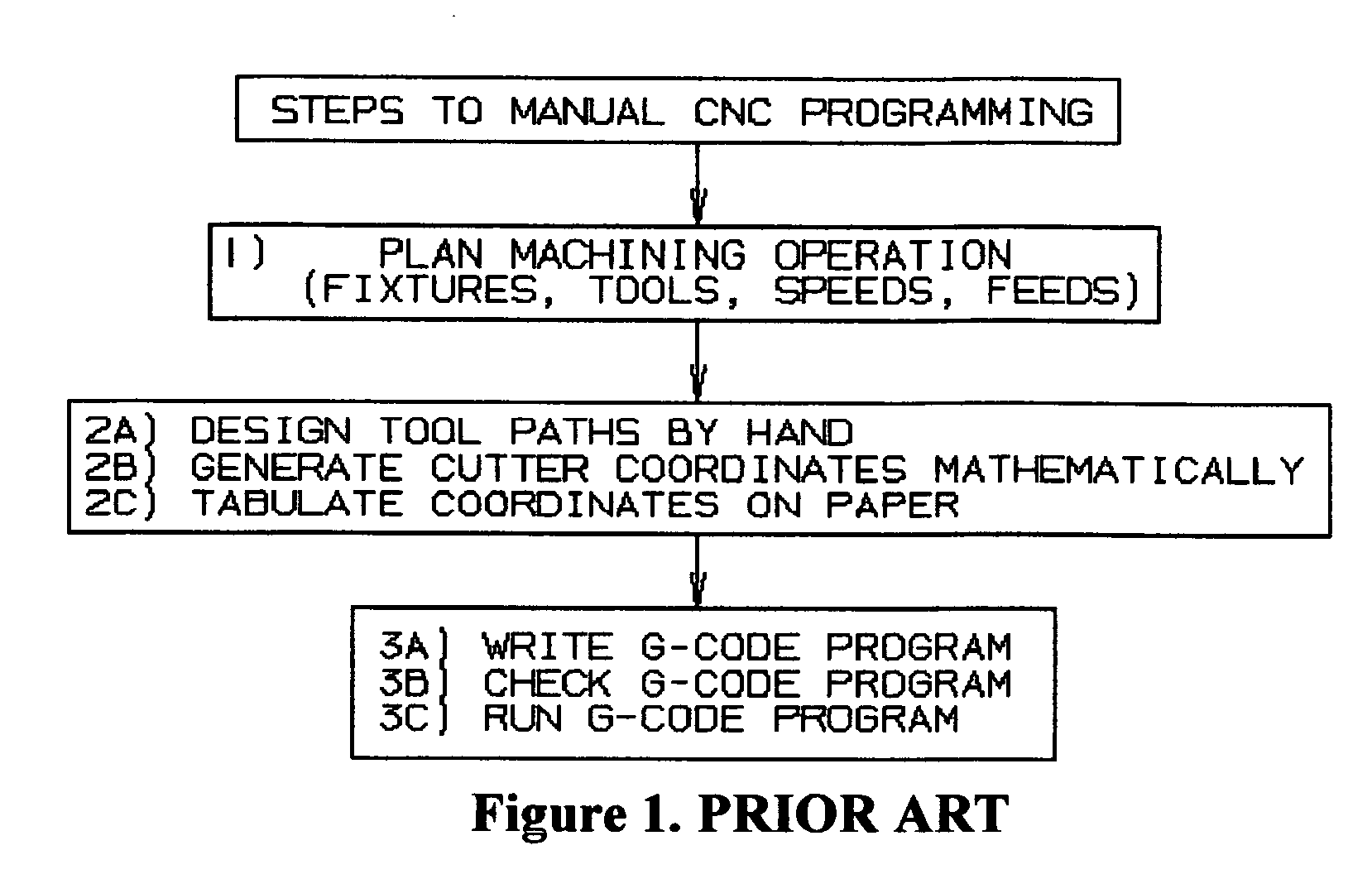
Manual CNC programming system and technique to use computer aided design systems to determine cutter location information
ActiveUS20070191982A1Simply carry-outComputer controlSimulator controlComputer Aided DesignCutter location
A manual computer numerical control (CNC) programming method and system (which may be embodied in whole or part in an article of manufacture or apparatus) in which coordinates may be manually entered into a text editor into a file format known as the coordinate work sheet (CWS) including verification, modification and conversion of the CWS to G-Code, the coordinate work sheet format being a comma delimited ASCII text file, and further including cutter on / off commands and using computer aided design (CAD) data to generate the coordinate work sheet (CWS).
Owner:SULLIVAN DOUGLAS G
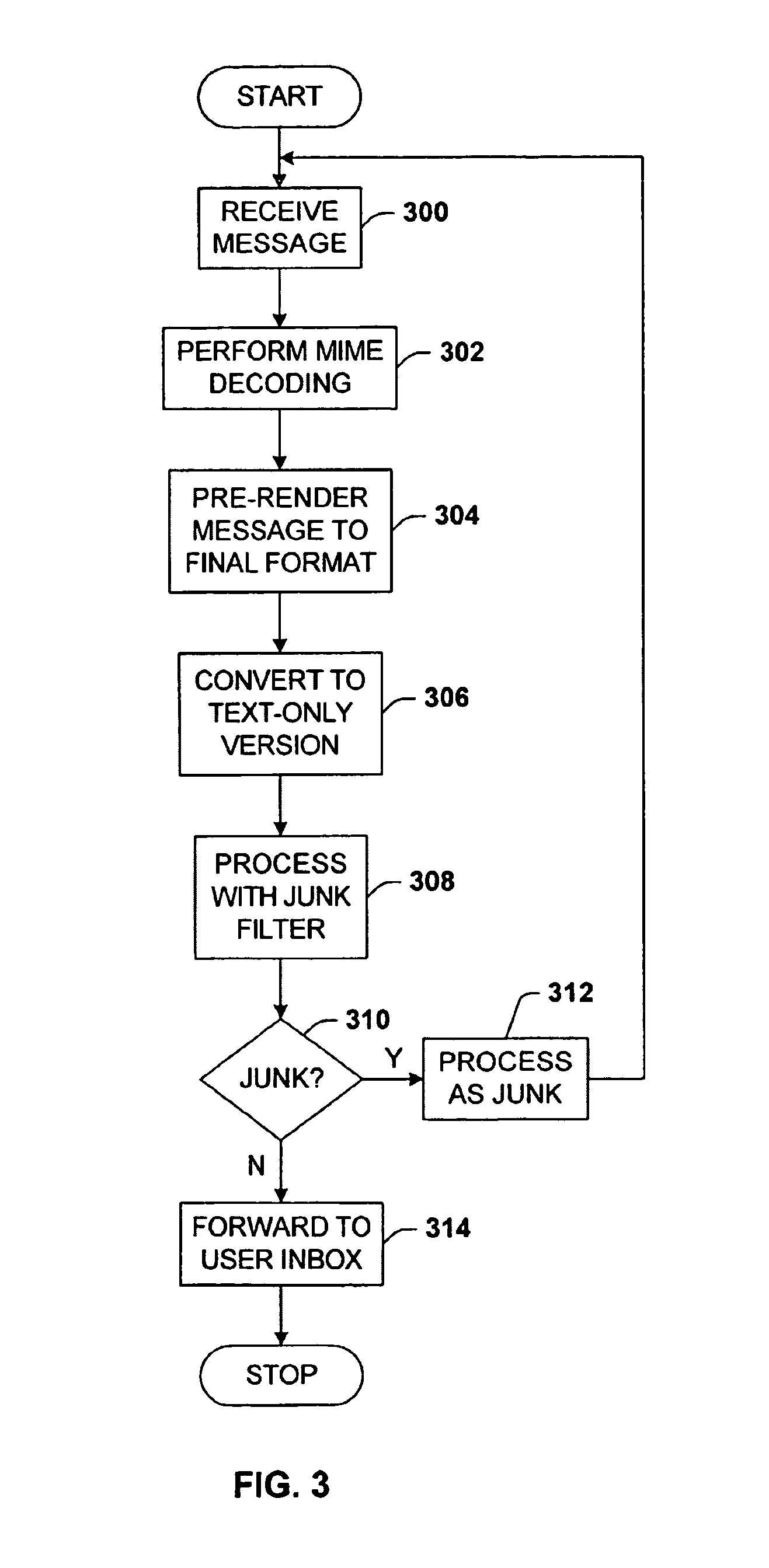
Message rendering for identification of content features
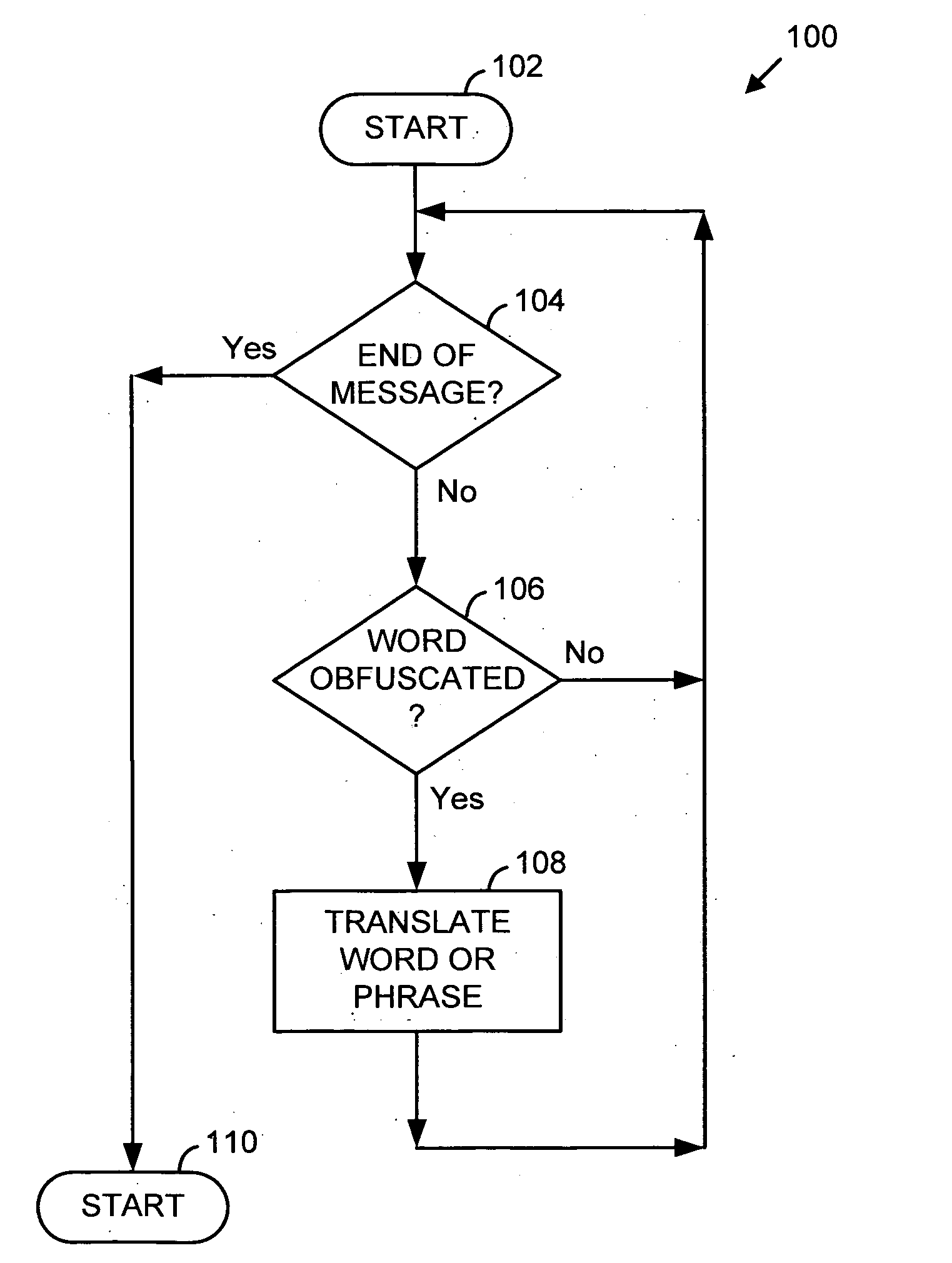
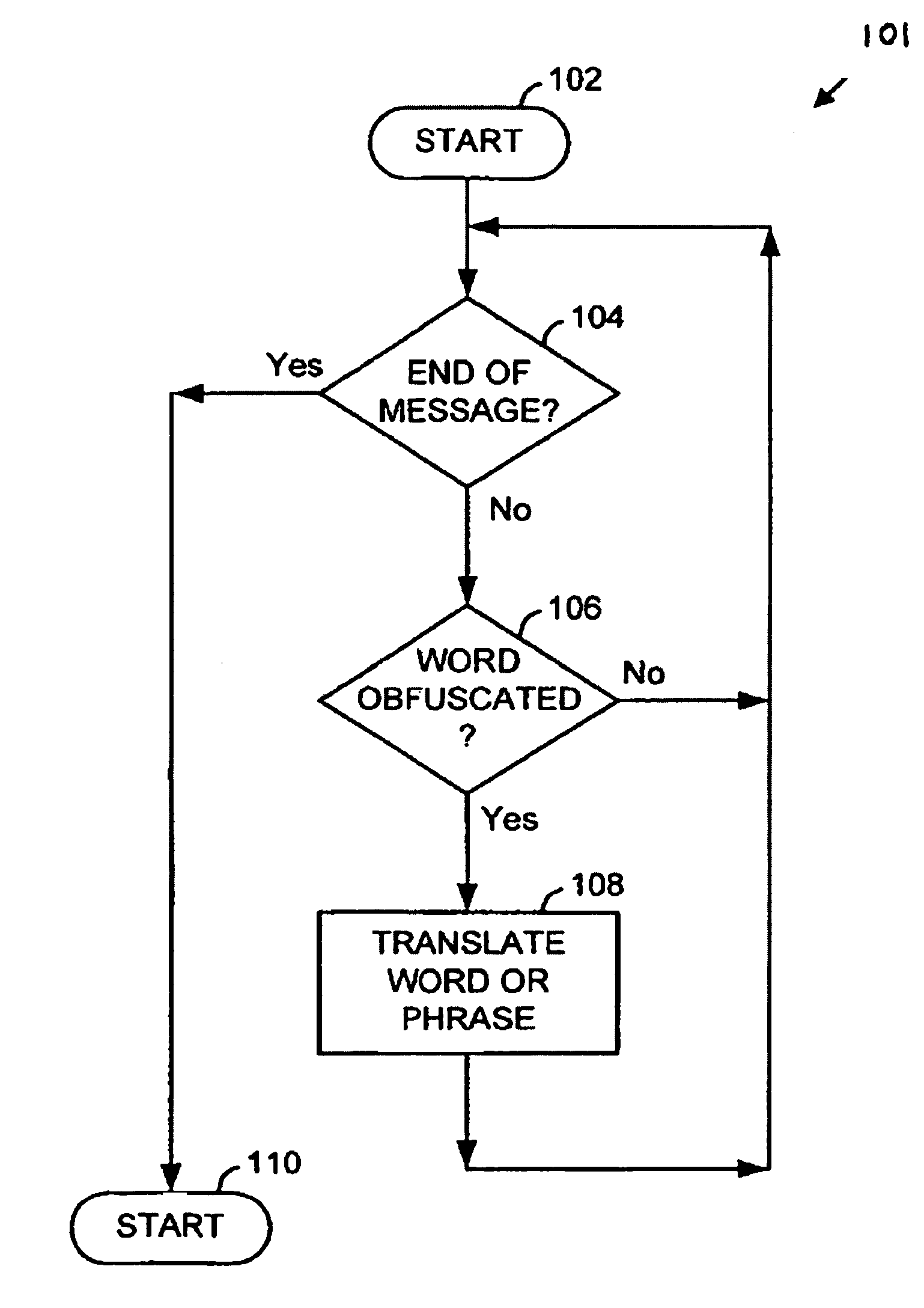
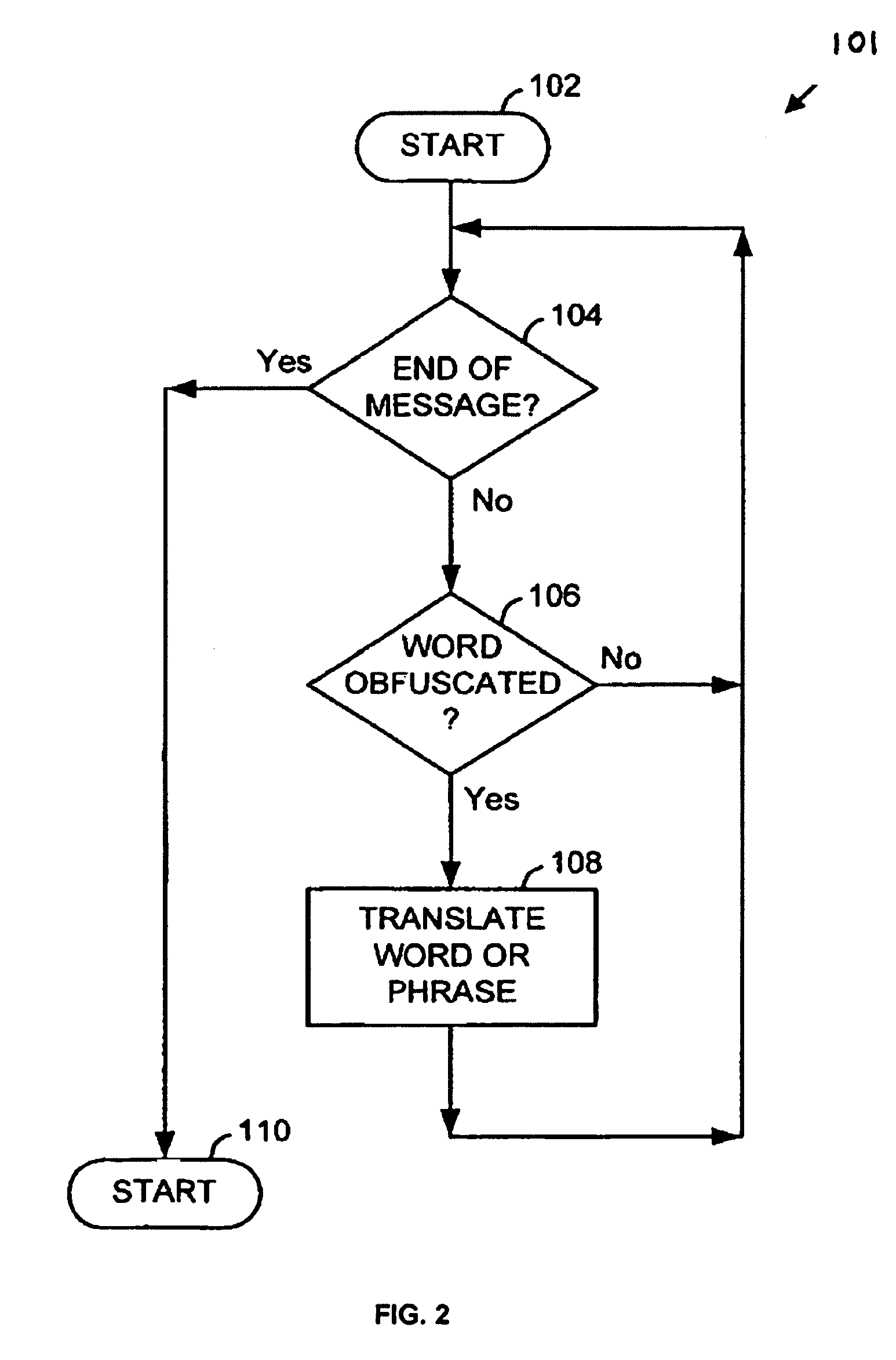
InactiveUS7483947B2Remove colorMemory loss protectionError detection/correctionGraphicsSchema for Object-Oriented XML
Architecture for detecting and removing obfuscating clutter from the subject and / or body of a message, e.g., e-mail, prior to filtering of the message, to identify junk messages commonly referred to as spam. The technique utilizes the powerful features built into an HTML rendering engine to strip the HTML instructions for all non-substantive aspects of the message. Pre-processing includes pre-rendering of the message into a final format, which final format is that which is displayed by the rendering engine to the user. The final format message is then converted to a text-only format to remove graphics, color, non-text decoration, and spacing that cannot be rendered as ASCII-style or Unicode-style characters. The result is essentially to reduce each message to its common denominator essentials so that the junk mail filter can view each message on an equal basis.
Owner:MICROSOFT TECH LICENSING LLC
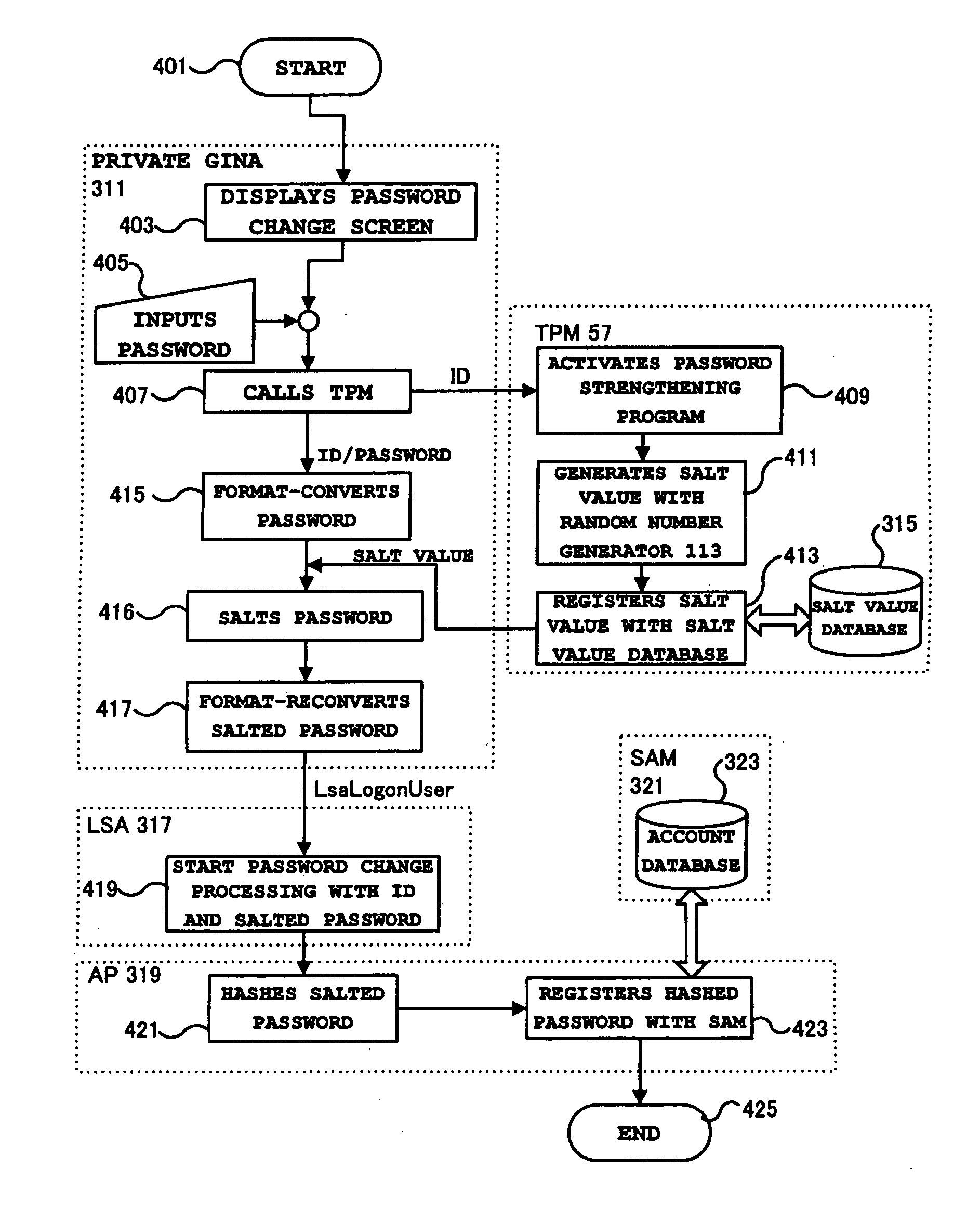
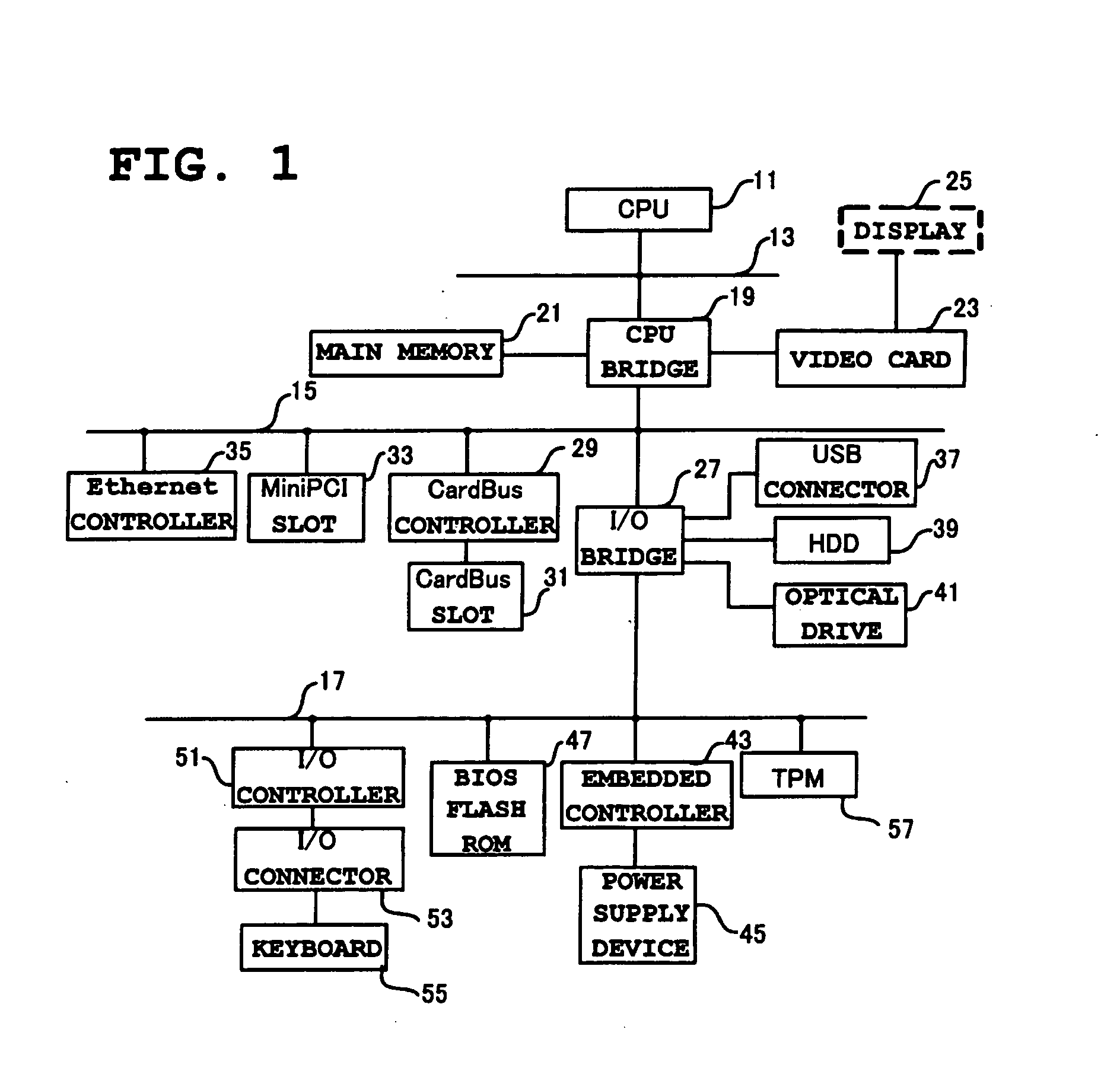
Authentication password storage method and generation method, user authentication method, and computer
ActiveUS20080092216A1Protection attackImprove protectionDigital data processing detailsUser identity/authority verificationOperational systemPassword
Protection of an authentication password stored in a database held by a SAM of Windows® is strengthened. A GINA, a part of the OS, receives an authentication password in ASCII codes. The authentication password is converted to first UNICODES, and the first UNICODES are salted with a random number and converted to second UNICODES. The random number used for salting is associated with a user account and a password and stored in a read / write protected non-volatile memory or a non-volatile memory which can be accessed only by a BIOS. An LSA of the OS can process UNICODES without being changed.
Owner:LENOVO PC INT
System for email processing and analysis
InactiveUS8918466B2Multiple digital computer combinationsData switching networksEmail addressComputerized system
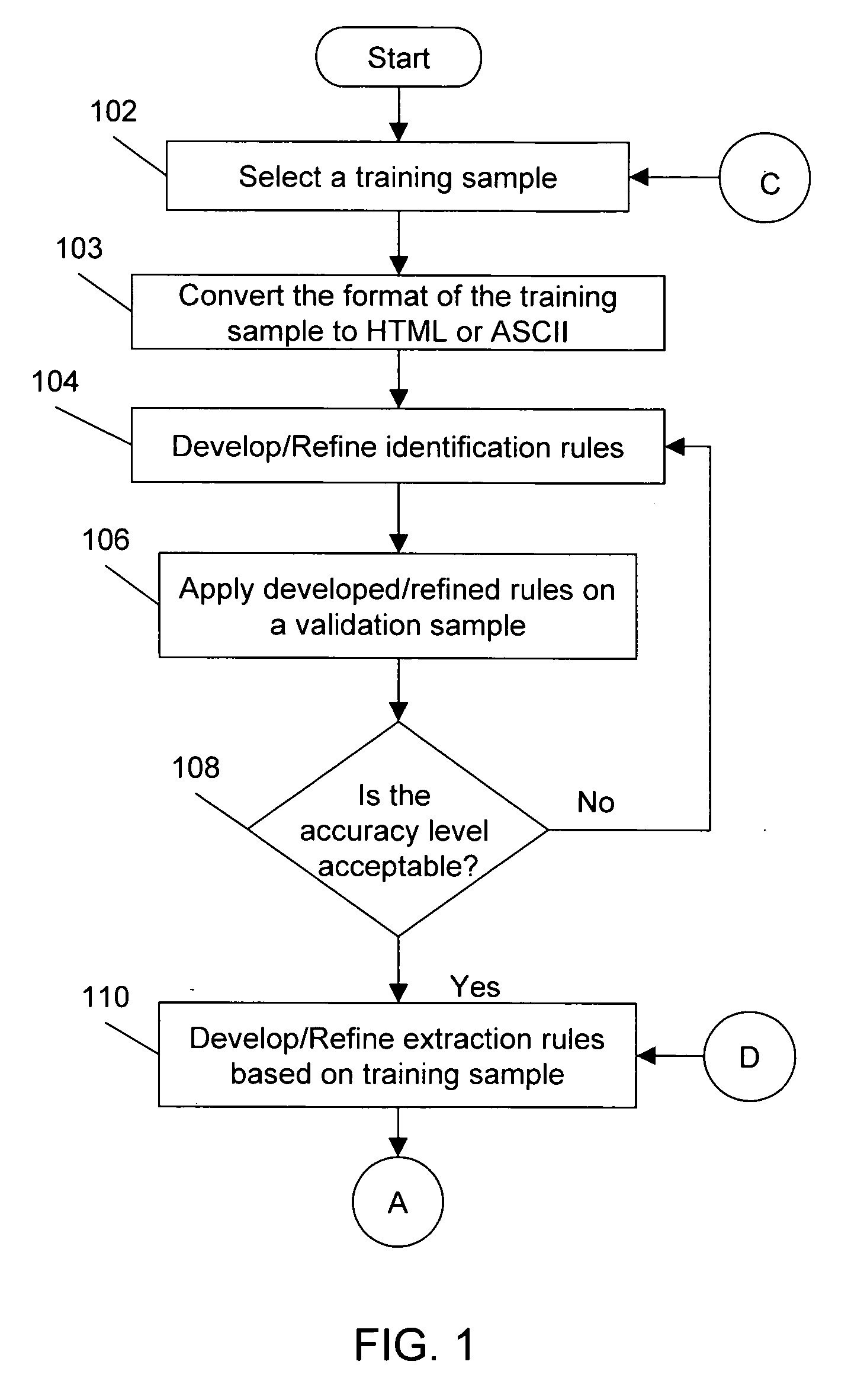
Various features are provided for analyzing and processing email messages including determining if an email message is unwanted, and blocking unwanted messages. Email traffic is monitored by analyzing email messages addressed to known invalid email addresses. Email messages addressed to invalid email addresses are sent to a central control site for analysis. One embodiment tries to ensure that the distance between the invalid addresses and closest valid addresses is significant enough so that the invalid addresses are not inadvertently used for non-spam purposes. Another embodiment of the invention provides for distributed “thin client” processes to run on computer systems or other processing platforms. The thin clients emulate an open relay computer. Attempts at exploiting the apparent open relay computer are reported to a control center and the relay of email messages can be inhibited. Another embodiment provides for analysis and tuning of rules to detect spam and legitimate email. The approach adjusts various factors according to changing, current email data that is gathered from present, or recent, email traffic. Another embodiment takes into account statistics of erroneous and intentional misspellings. Groups of similar content items (e.g., words, phrases, images, ASCII text, etc.) are correlated and analysis can proceed after substitution of items in the group with other items in the group so that a more accurate detection of “sameness” of content can be achieved. Another embodiment uses authentication and security methods for validating email senders, detecting the sameness of messages, tracking the reputation of the sender, and tracking the behavior of the sender. Another embodiment profiles users to intelligently organize user data, including adapting spam detection according to a user's perceived interests.
Owner:GOZOOM COM
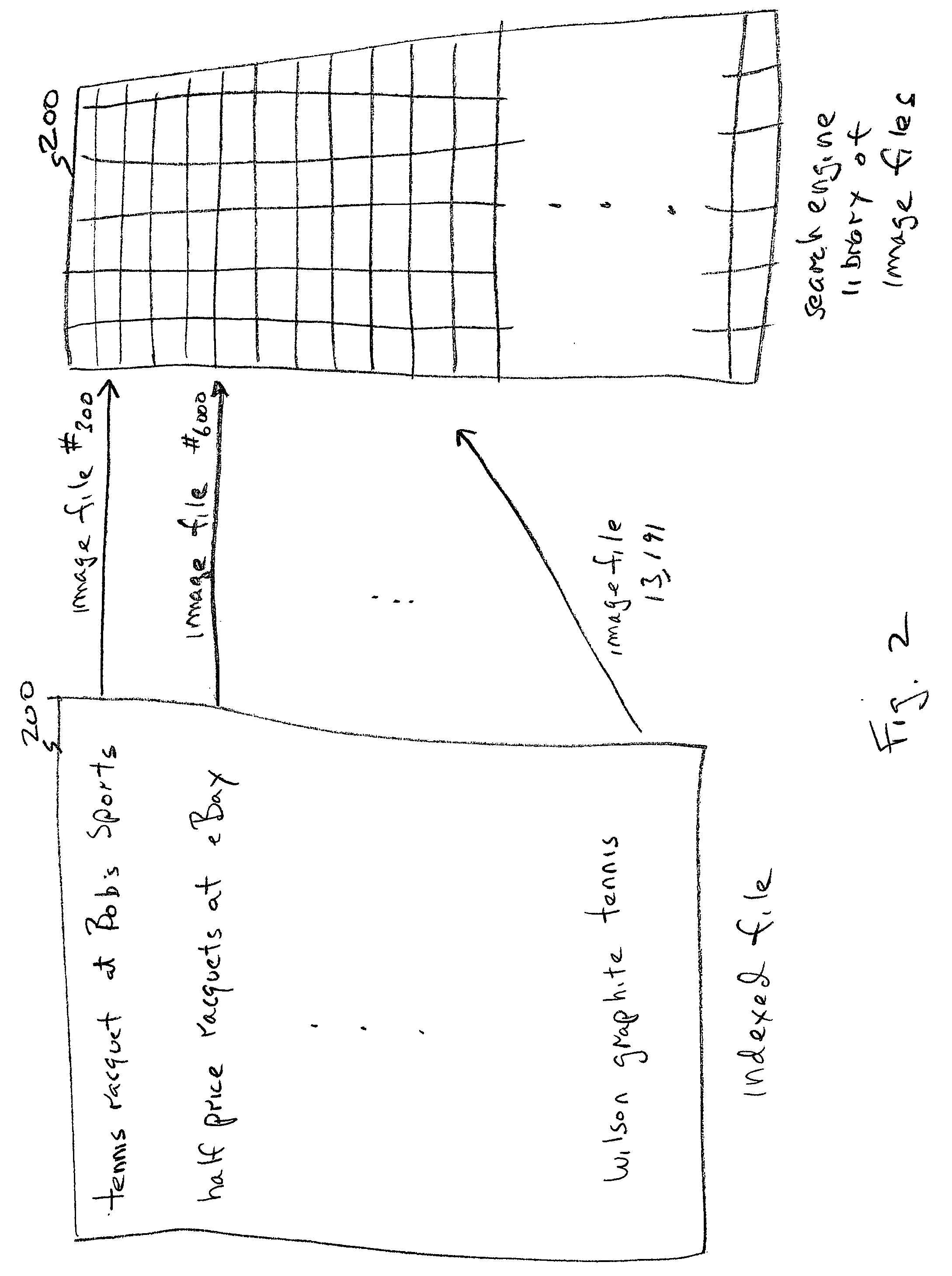
System and method for automatically locating searched text in an image file
InactiveUS20050097080A1Special data processing applicationsTagged Image File FormatDocument preparation
A system and method is provided for locating searched terms in an image file received from a search engine. The method comprises: submitting a search term to a search engine having an indexed file database of image files, for example, a text search term such as a keyword, ASCII symbols, word patterns, or data patterns; receiving an indexed file cross-referencing image indexed files to the search term, for example, the image files may be a tagged image file format (TIFF) or portable document (PDF) format document; performing optical character recognition (OCR) on the selected image file; locating coordinates in the image file corresponding to the search term; and, automatically displaying the image file at the coordinates. Typically, the location process causes the search term to be displayed, or even highlighted.
Owner:SHARP LAB OF AMERICA INC
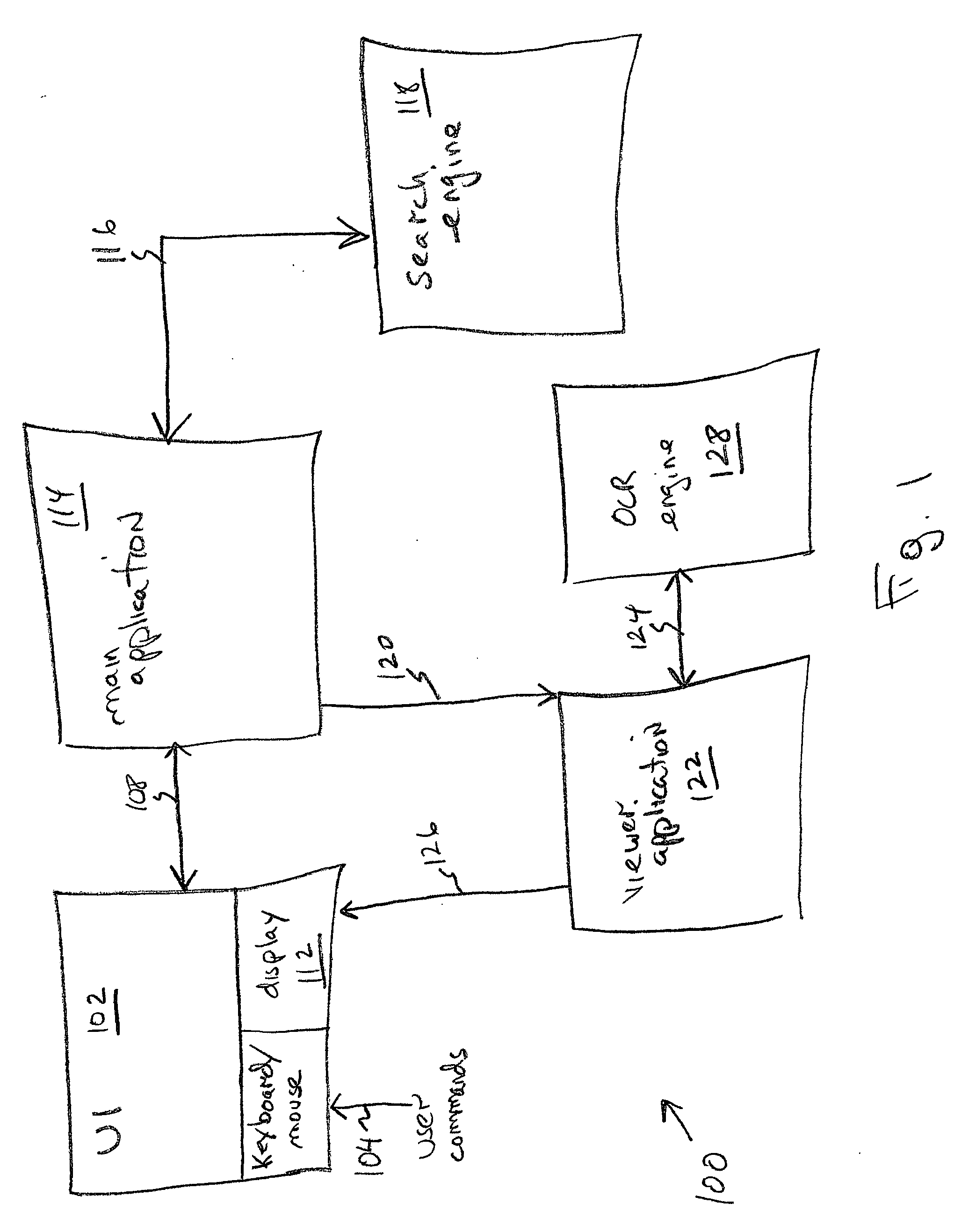
Automated search on cursive records not having an ASCII index
InactiveUS6917709B2Digital data information retrievalData processing applicationsData miningImage matching
Images of handwritten cursive records are extracted, and an automated search on the images of the cursive records is performed based on an ASCII query for a record. A cursive equivalent of the ASCII query is matched to the images of the cursive records, and a similarity value is generated to indicate the extent of match between features of the cursive equivalent of the ASCII query and features of each cursive record. The records are sorted based upon their similarity value determined in the matching process. This provides a candidate list of cursive record images to be manually examined by a user for the purpose of making a final determination as to whether any of the cursive records on the candidate list satisfy the query.
Owner:PARASCRIPT
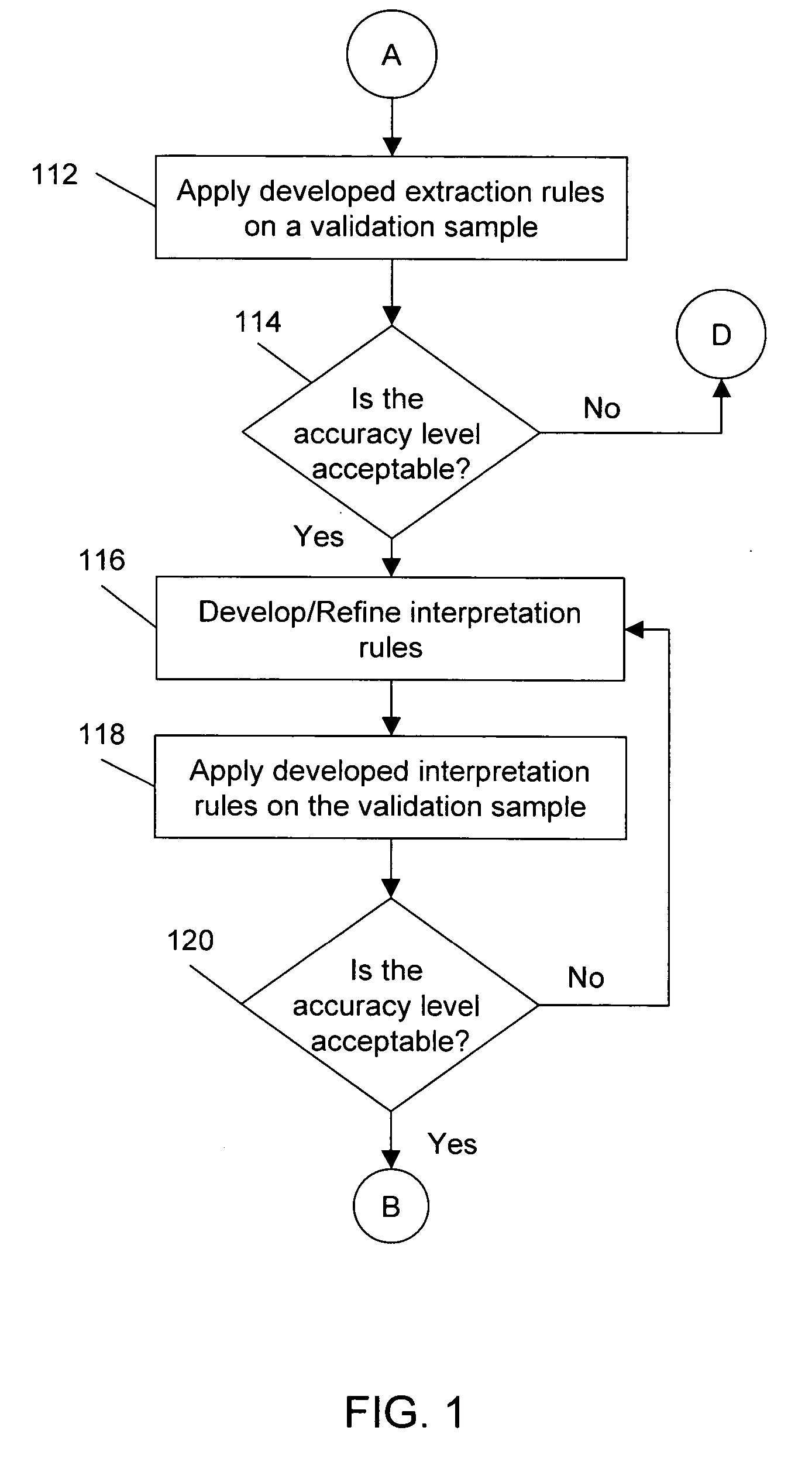
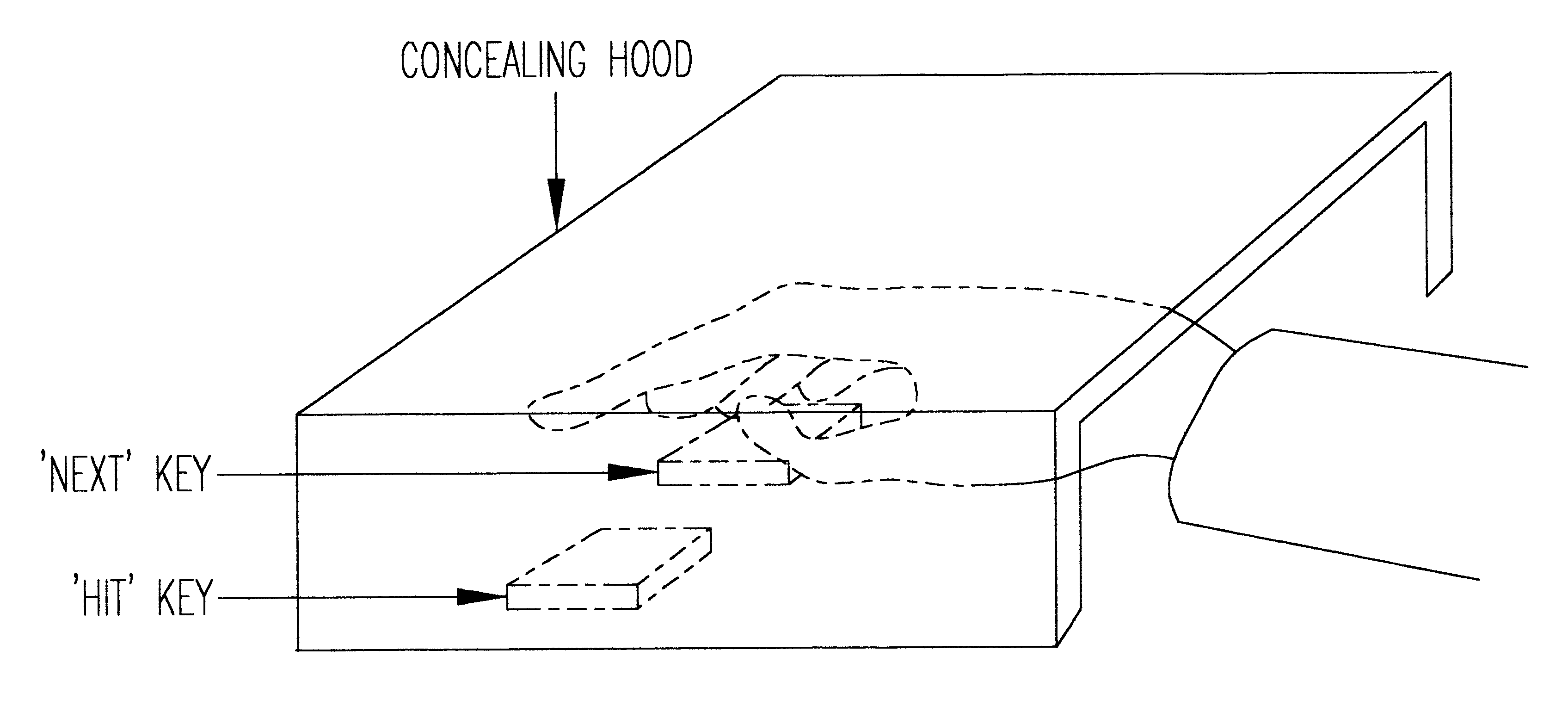
Method for non-disclosing password entry
InactiveUS6658574B1Easy to implementAvoid viewingDigital data processing detailsUser identity/authority verificationPasswordComputerized system
Password entry is done by displaying to a user distinct codes corresponding to characters in the user's password. The user then serially enters codes corresponding to characters while concealing the entry. Only a limited number of keys are used for password entry. In one example, two keys, a "HIT" key and a "NEXT" key, are provided within a concealing hood, and the password in entered serially as a number of "HIT" key hits. The user is prompted to enter digits corresponding to symbols of his or her password with a display of unique m-ary number codes assigned mutually exclusively to different characters. The scheme can be easily implemented in existing computer systems entirely through a conventional ASCII keyboard or mouse, by using adjacent keys on the keyboard or left and right mouse buttons. As the method requires only a few keys, concealing the keys to prevent viewing of key entry is possible.
Owner:GOOGLE LLC
Movement and attitude controlled mobile station control
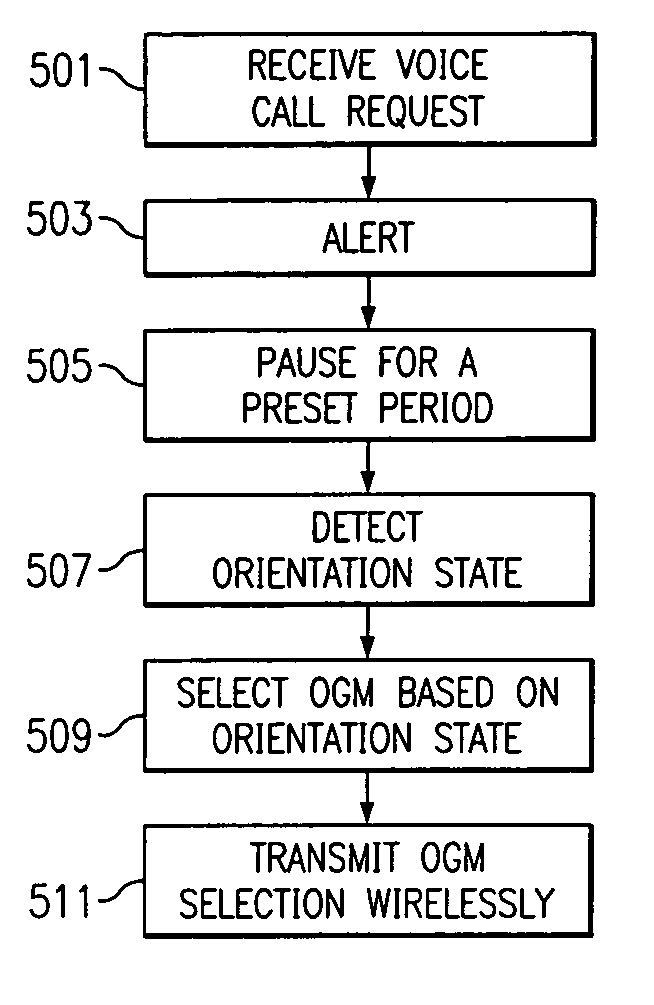
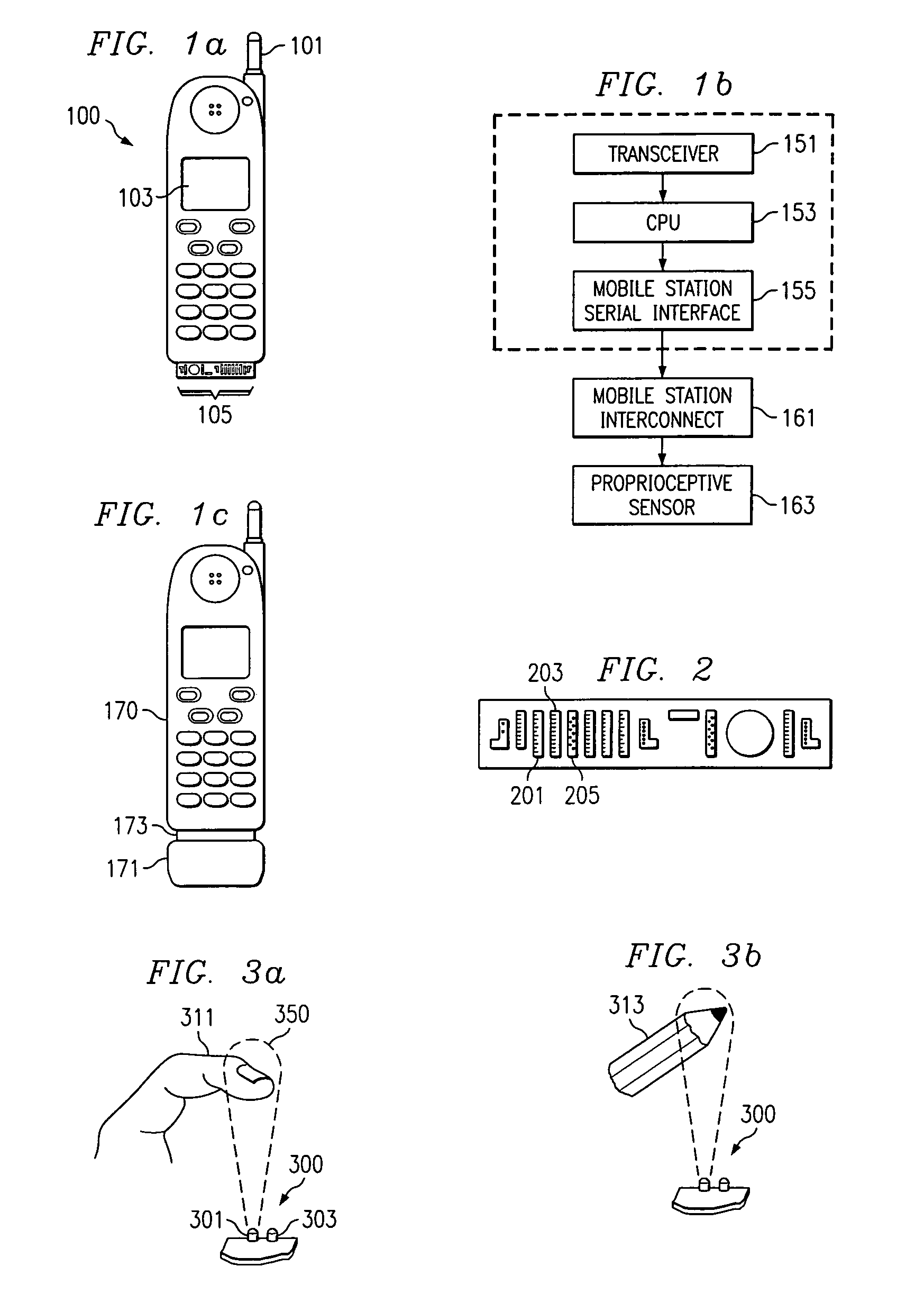
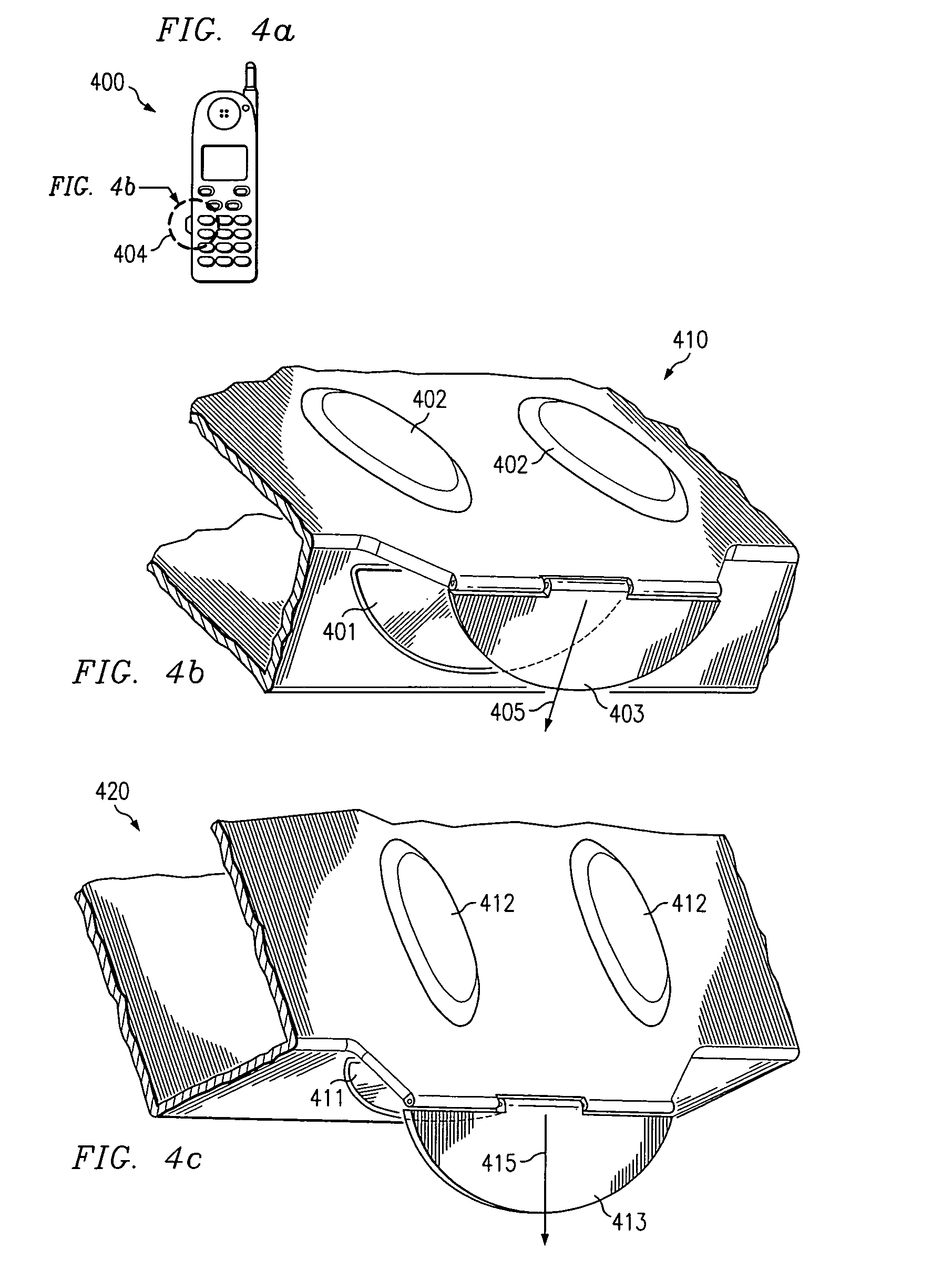
InactiveUS7024228B2Transparent to userEliminate needAutomatic call-answering/message-recording/conversation-recordingDevices with sensorAttitude controlOn board
A mobile station embodiment (400) is provided with a reflection detector (401) which may provide supplemental inputs along with keys (402) such that a character encoding, such as, e.g. ASCII, is selected on the basis of the reflection detector (401) alone, or in combination with keys (402) either pushed down or released. A movable target or pendulum (405) may provide an ability to sense the near space along a direction that the reflection detector is sensitive to. Signals may be transmitted from the reflection detector (401) and pass across a void or other great distance before being reflected, if at all. If such signals are reflected toward the reflection detector (401), and the signals have not been overly attenuated, the reflection detector (401) may provide a ‘reflect’ signal to any on-board processor of the mobile station (400). The pendulum (405) may be influenced by wind, gravity or acceleration (405) to operate as a reflector to cooperate with the reflection detector (401) and generate a ‘reflect’ signal.
Owner:NOKIA TECHNOLOGLES OY
Method for extracting, interpreting and standardizing tabular data from unstructured documents
ActiveUS7590647B2Automate quicklyMaximum flexibilityData processing applicationsDigital data information retrievalDocumentationData mining
A system, method, and computer program for automatically identifying, parsing, and interpreting tabular data from unstructured documents stored in various formats such as ASCII text, Unicode text, HTML, PDF text, and PDF image format is provided. A set of table identification, parsing / tokenizing, and interpreting / mapping rules are developed with grammar descriptors. These rules are then applied to a set of documents to identify a table, parse the content of the table, and interpret the parsed content, if required, thereby standardizing the tabular data.
Owner:RAGE FRAMEWORKS +1
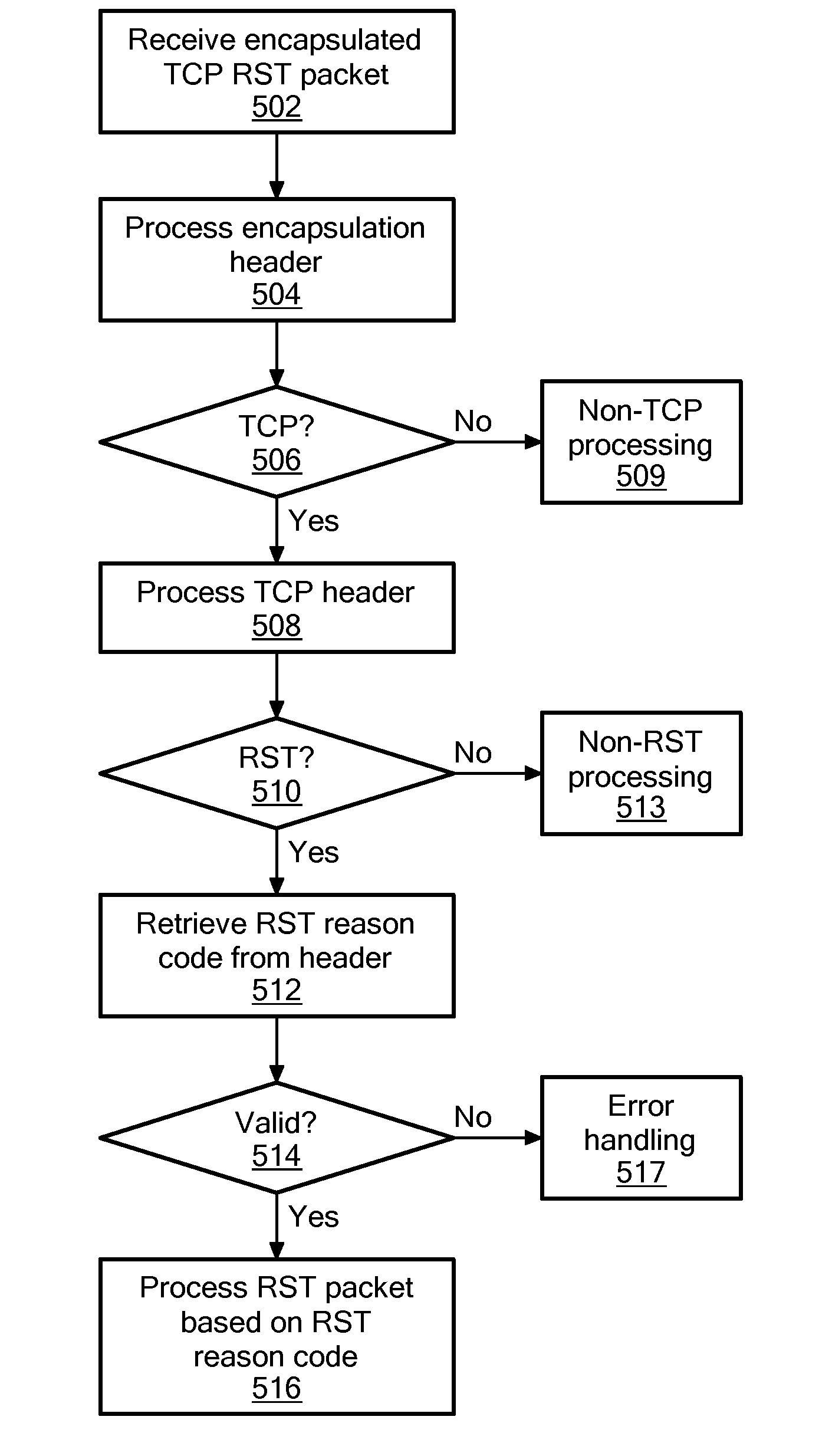
System and method for conveying the reason for TCP reset in machine-readable form
An RST reason code is conveyed in a predetermined field of the TCP or IP header for a TCP RST packet in order to indicate the reason for the RST. In this way, an enhanced TCP device that receives the RST packet can access the RST reason code in machine-readable form and, unlike prior art implementations in which ASCII text is carried in the TCP payload to provide a RST reason, without having to process the payload of the TCP packet.
Owner:HITACHI VANTARA LLC
Method and system for cutting index participle
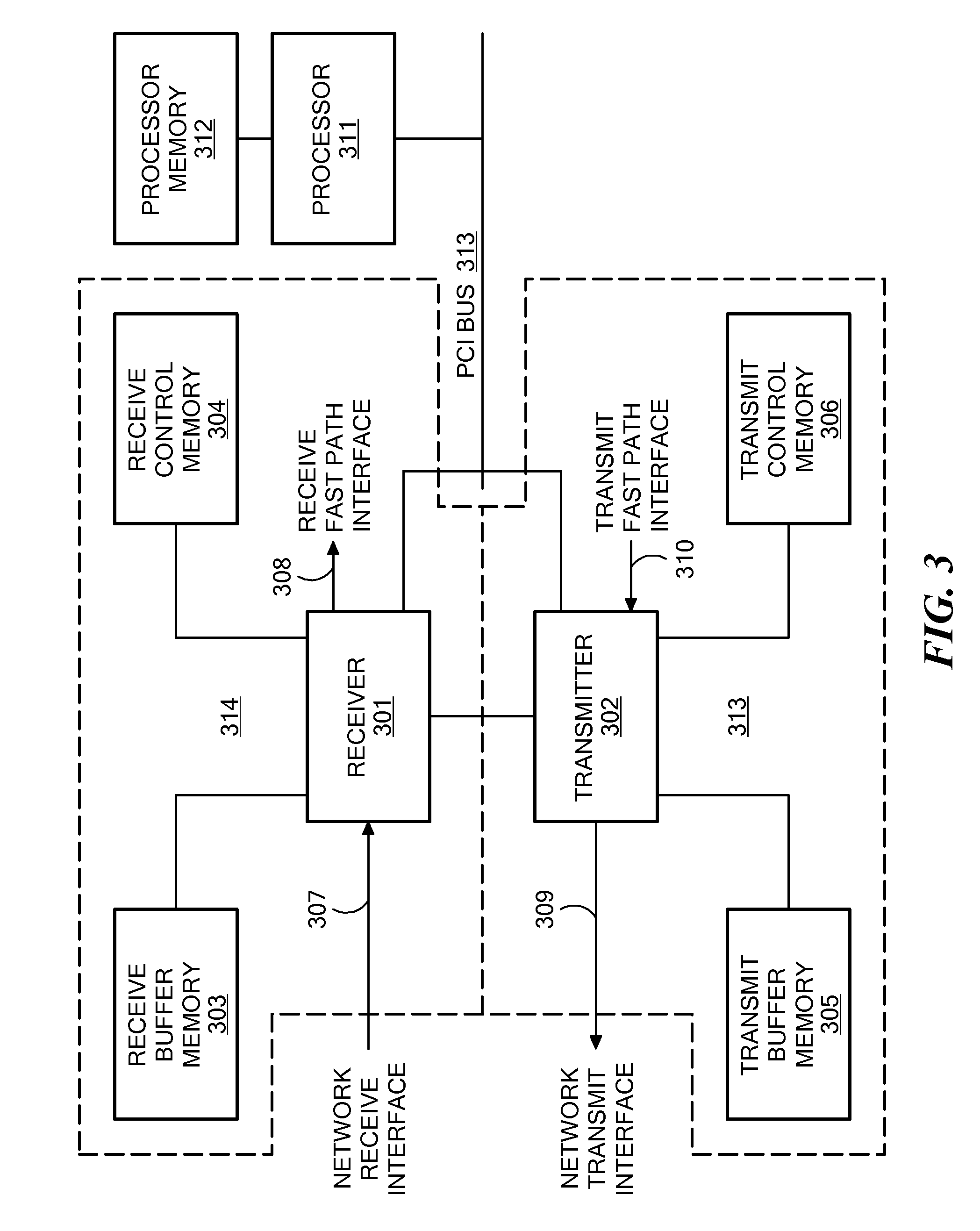
ActiveCN101071420AResolve accuracySolve a certain amount of redundant wordsSpecial data processing applicationsChinese charactersEnglish characters
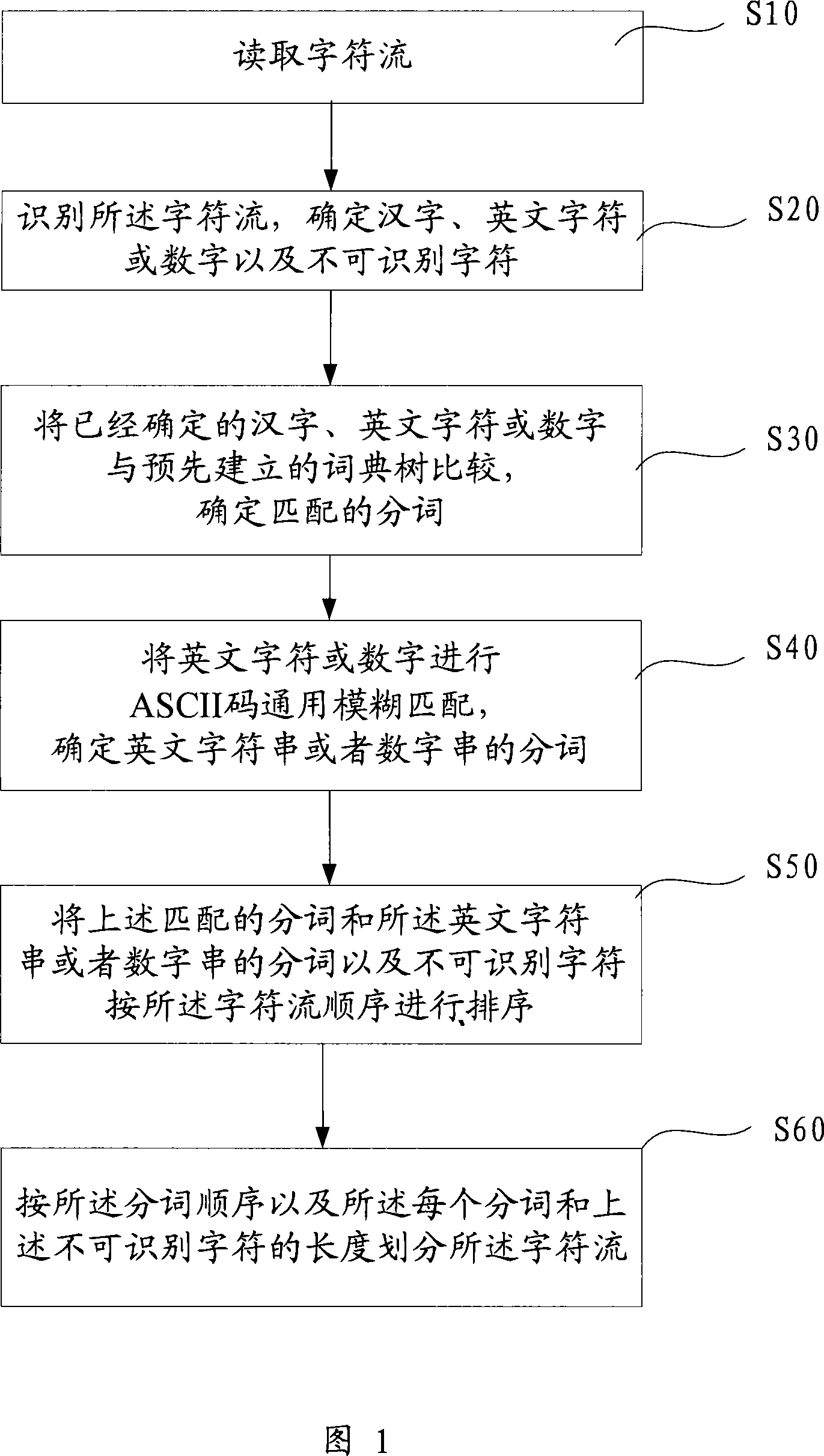
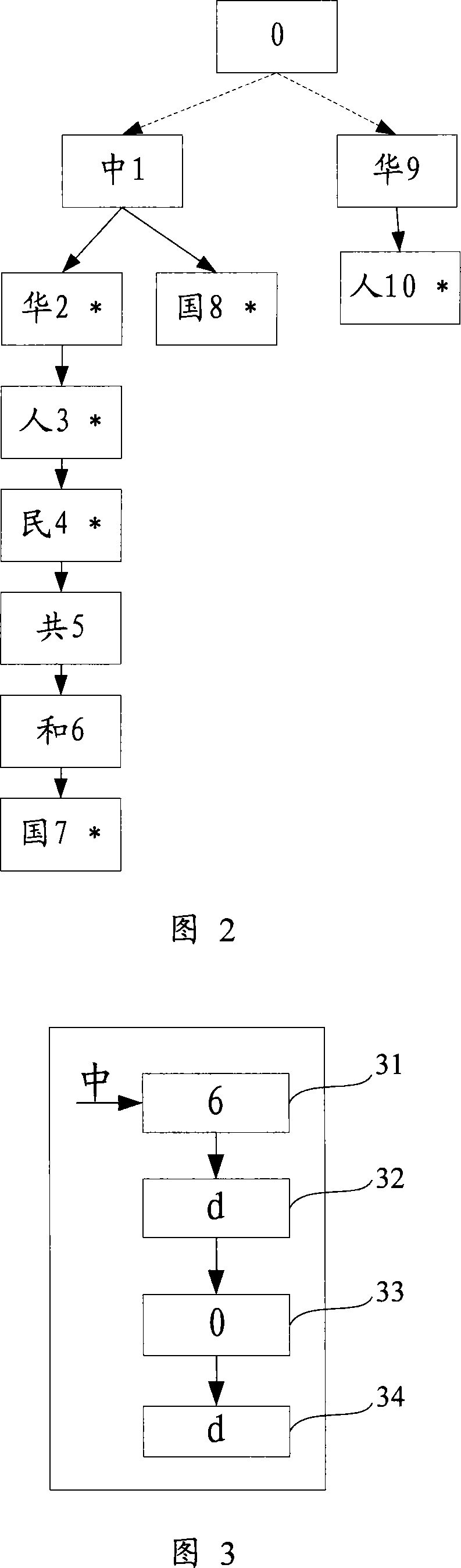
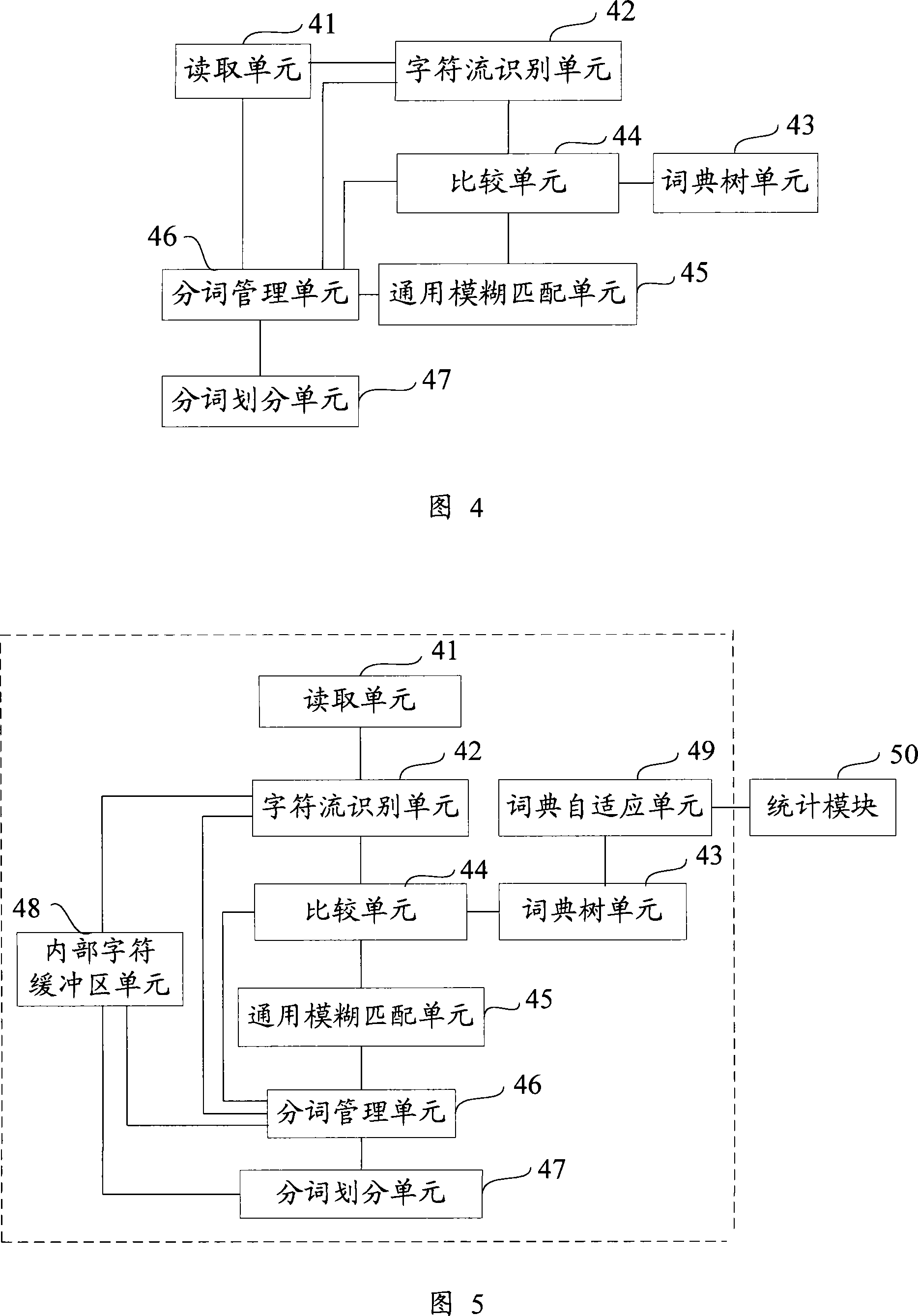
The invention discloses a segmentation index segmentation method. Including the following steps: read the character stream; identification described the character stream to identify Chinese characters and English characters, as well as an identification number or character; already identified Chinese and English characters or Digital and pre-built 1.1 tree comparison, the sub-set match words; English characters or figures generic fuzzy matching ASCII codes to determine English string or string of digital-term matching the above mentioned English words and string or digital string of words and non-recognition of characters referred to the character stream by order of ranking; The words and figures mentioned in the English string or strings of the sort described in the order of the character stream. The invention also openly segmentation Index segmentation system. The invention provides a cut-word indexing method and system can simultaneously address the precise words, a certain amount of redundant words and word-term problems, enhance the user experience.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
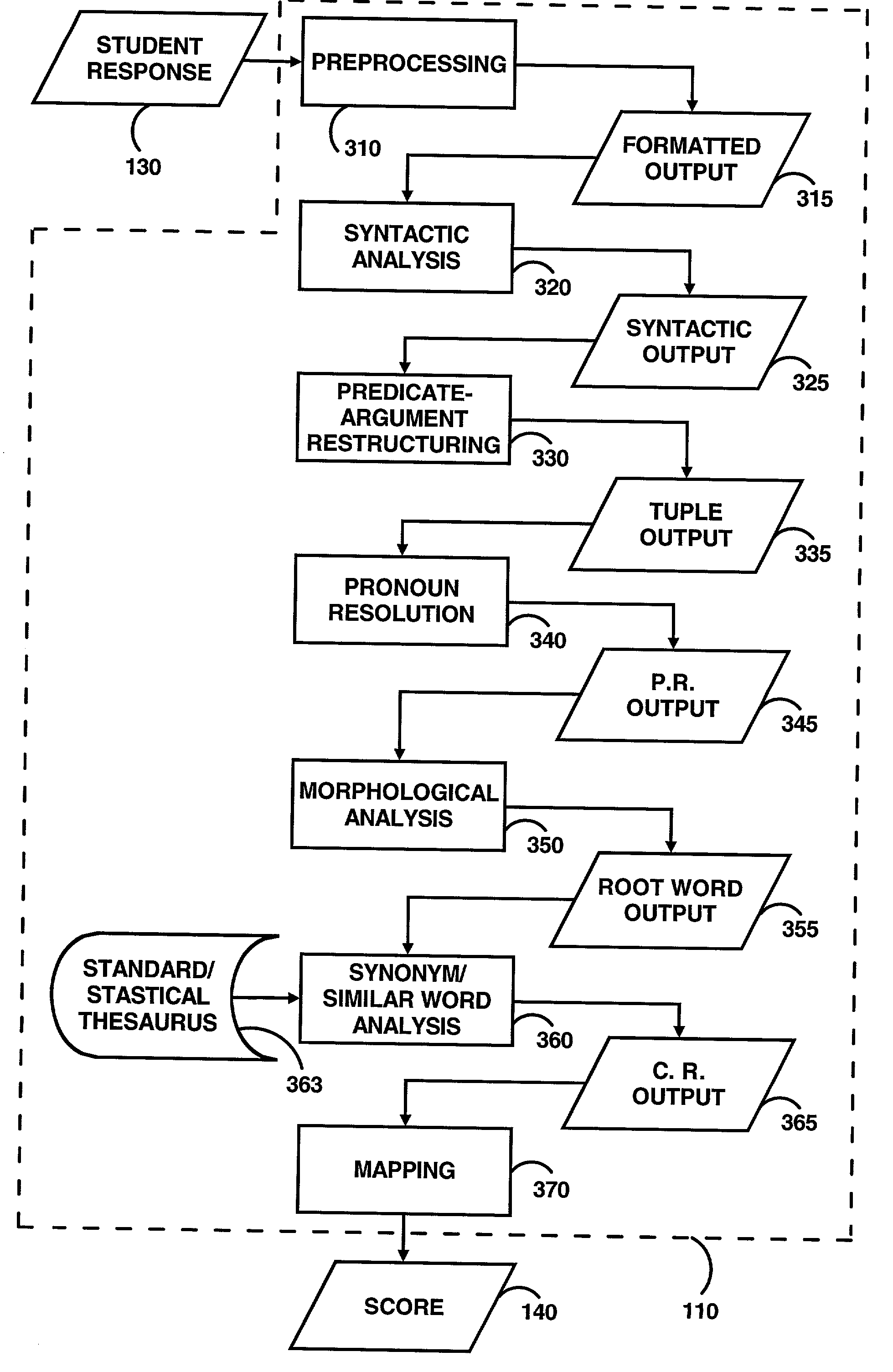
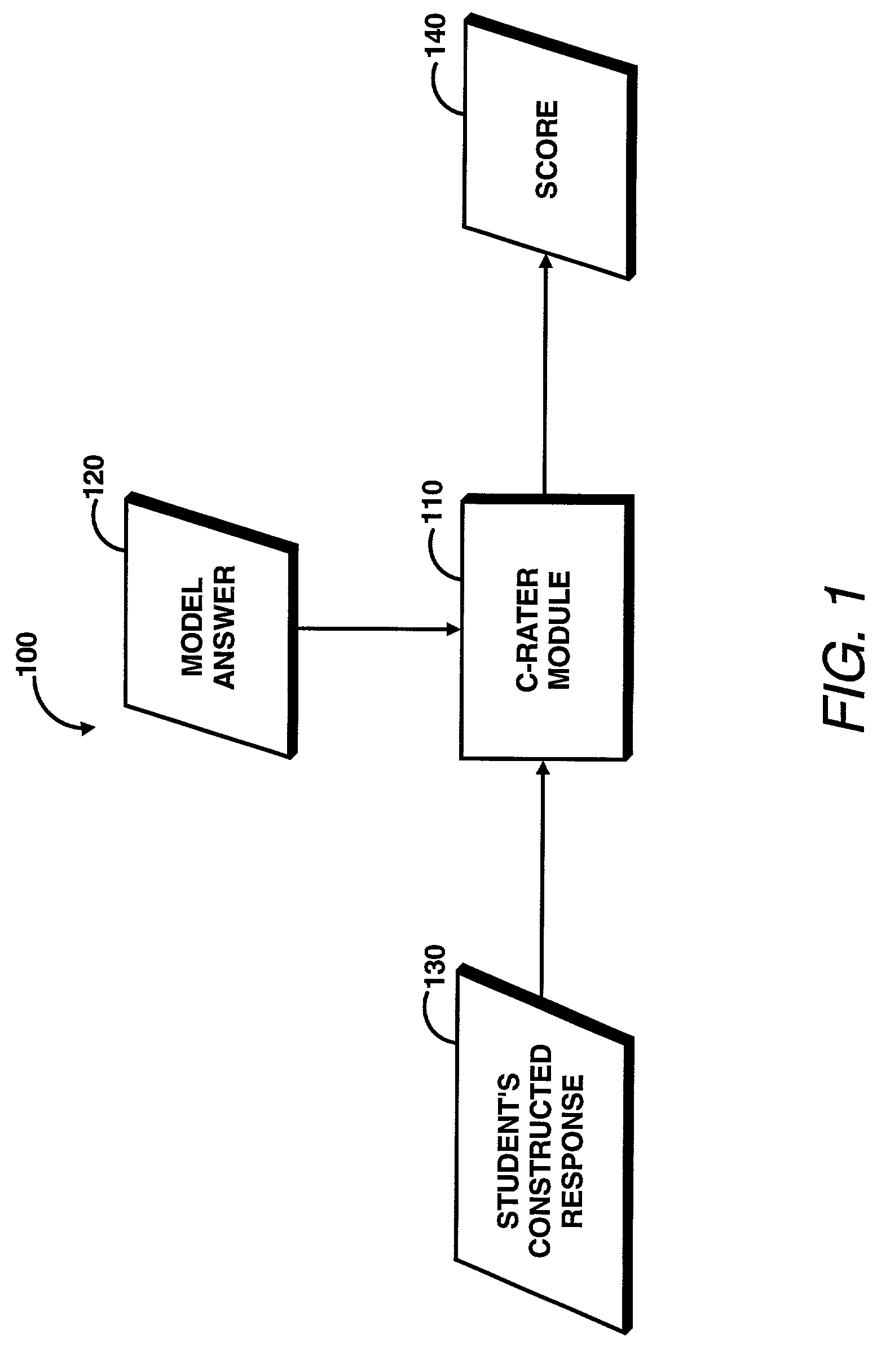
System for rating constructed responses based on concepts and a model answer
ActiveUS20030200077A1Digital data information retrievalNatural language data processingWord processingData mining
A concept rater module is utilized to automatically grade or score constructed responses based on a model answer. The concept rater module may be configured to accept a model answer as input. The model answer may be used as a grading key by the concept rater module. The concept rater module may be further configured to accept student responses in a file format. The file format may be ASCII text, a formatted word processing (e.g., WORDPERFECT, MICROSOFT WORD, etc.) and the like. The concept rater module maybe further configured to process a student response into a canonical representation of the student response. The canonical representation of the student response is compared against the model answer by the concept rater module. From the comparison, a score is generated which represents the students ability to cover all the key concepts.
Owner:EDUCATIONAL TESTING SERVICE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com