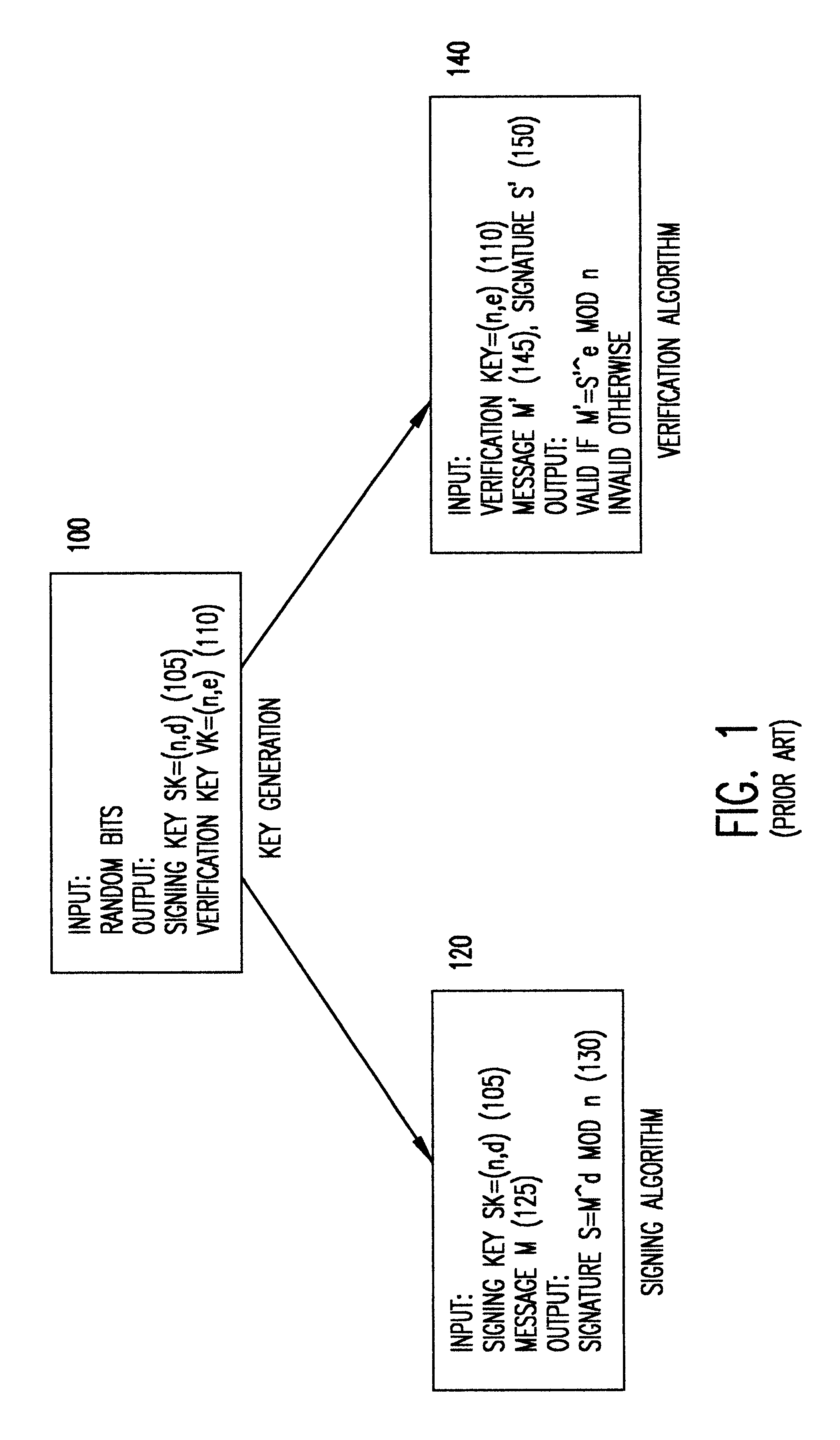
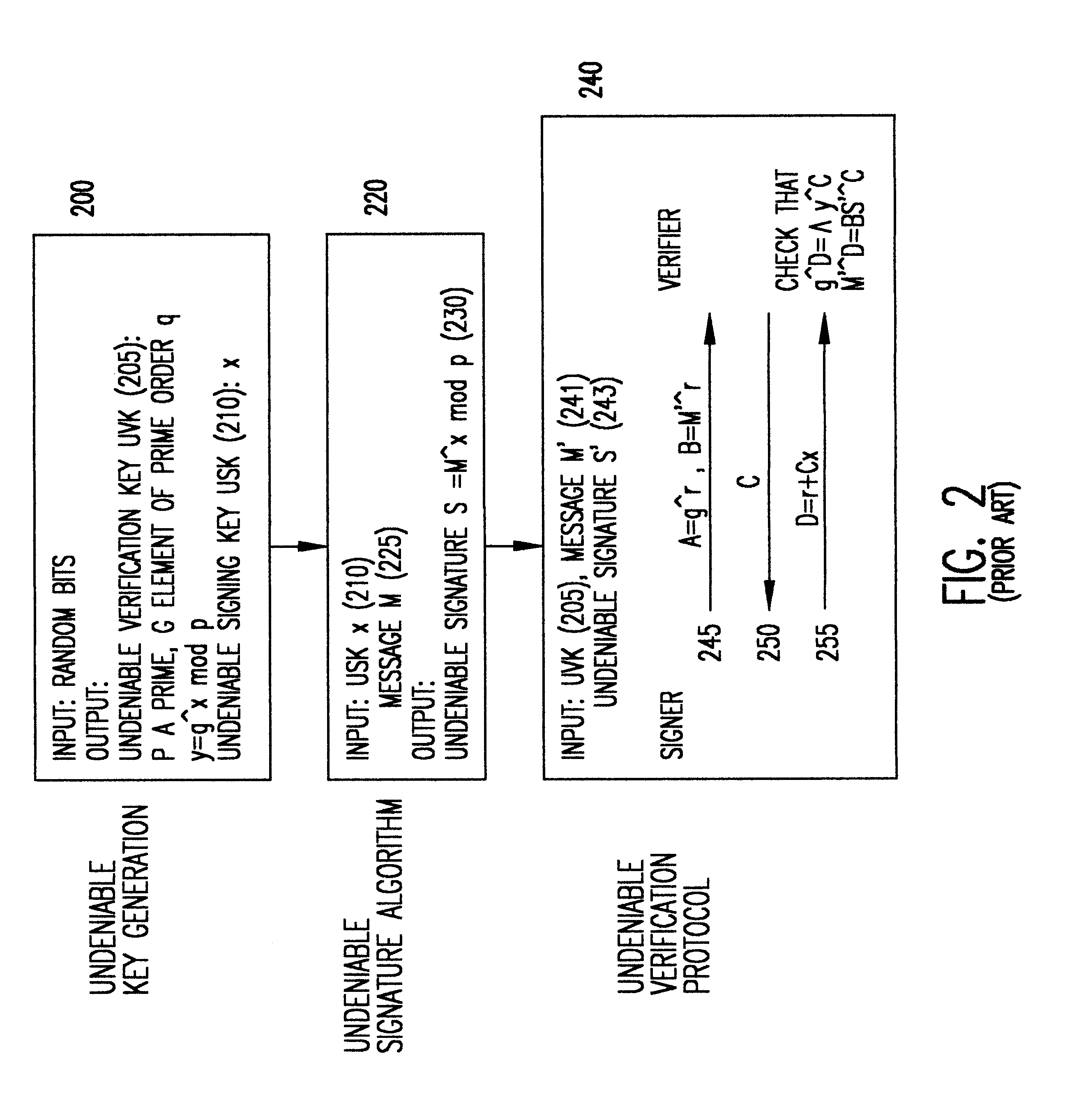
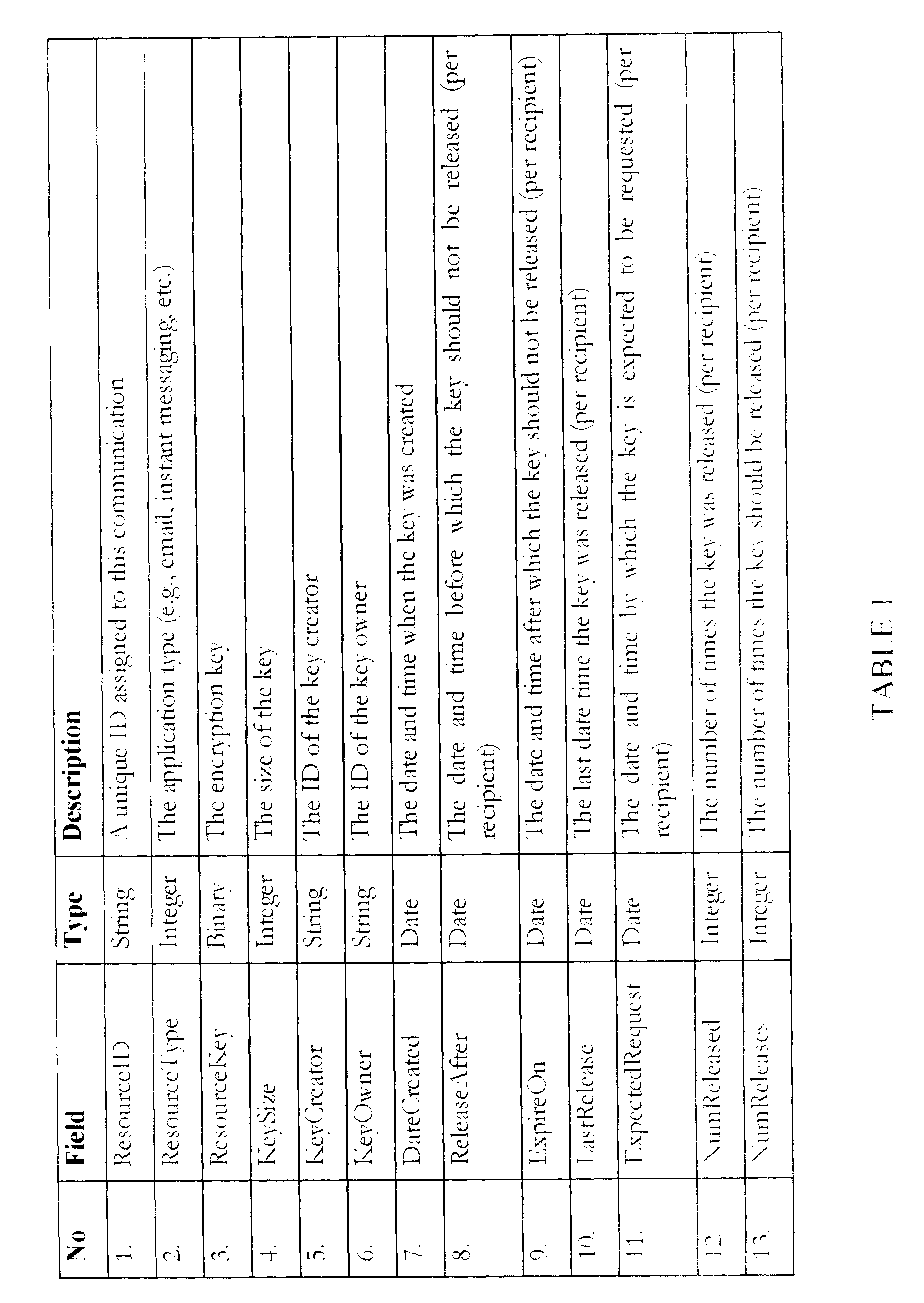
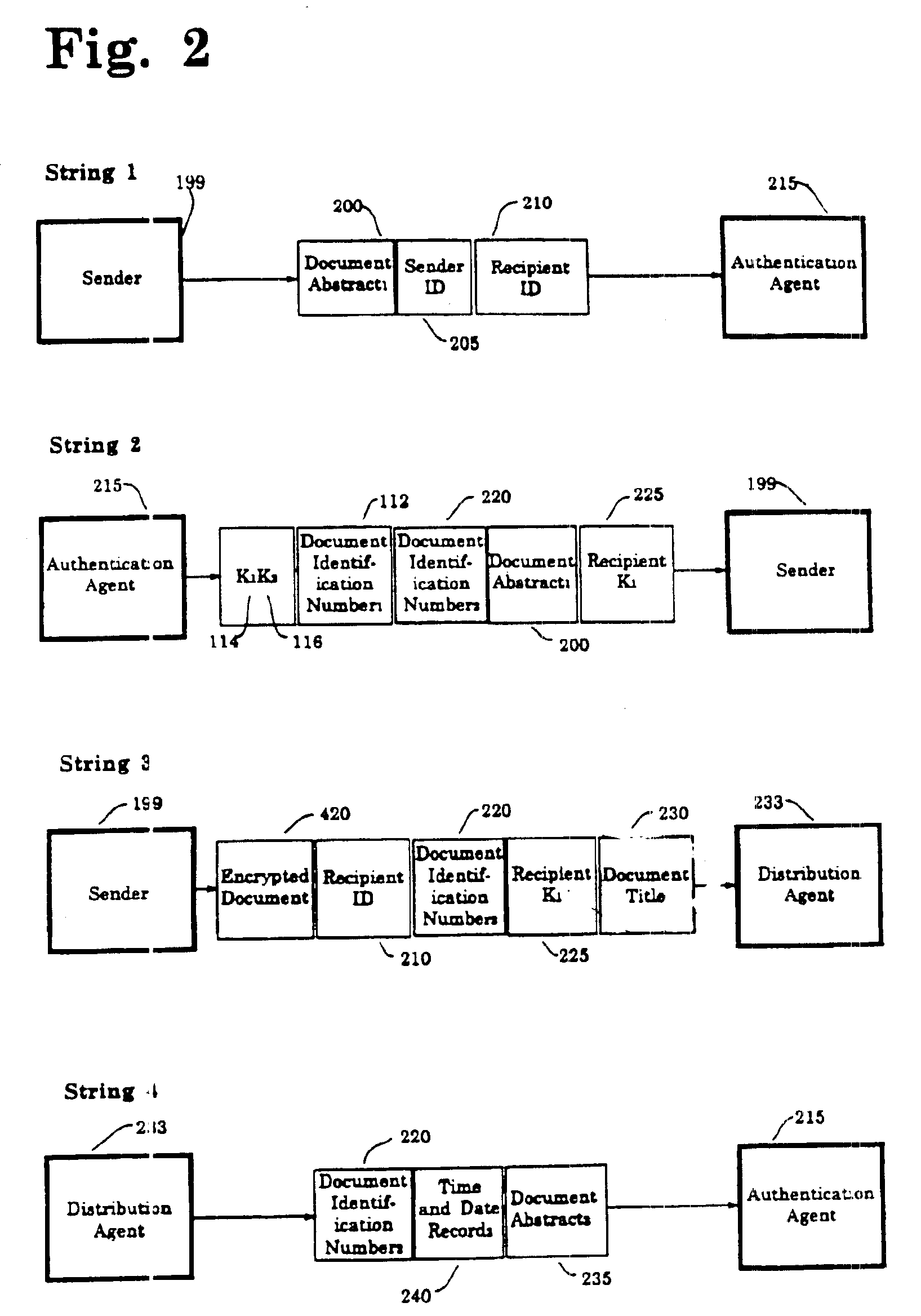
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
445 results about "Non-repudiation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
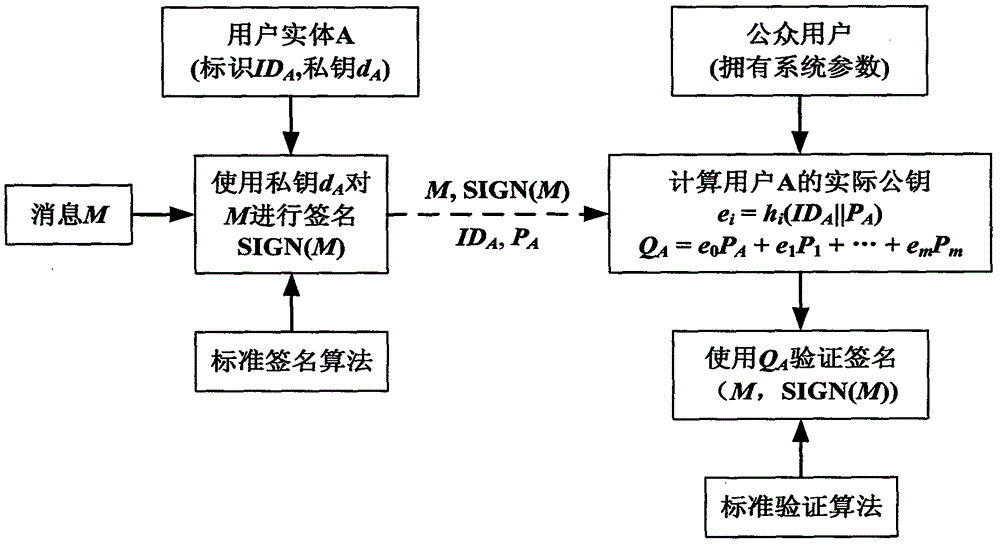
Non-repudiation refers to a situation where a statement's author cannot successfully dispute its authorship or the validity of an associated contract. The term is often seen in a legal setting when the authenticity of a signature is being challenged. In such an instance, the authenticity is being "repudiated".
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
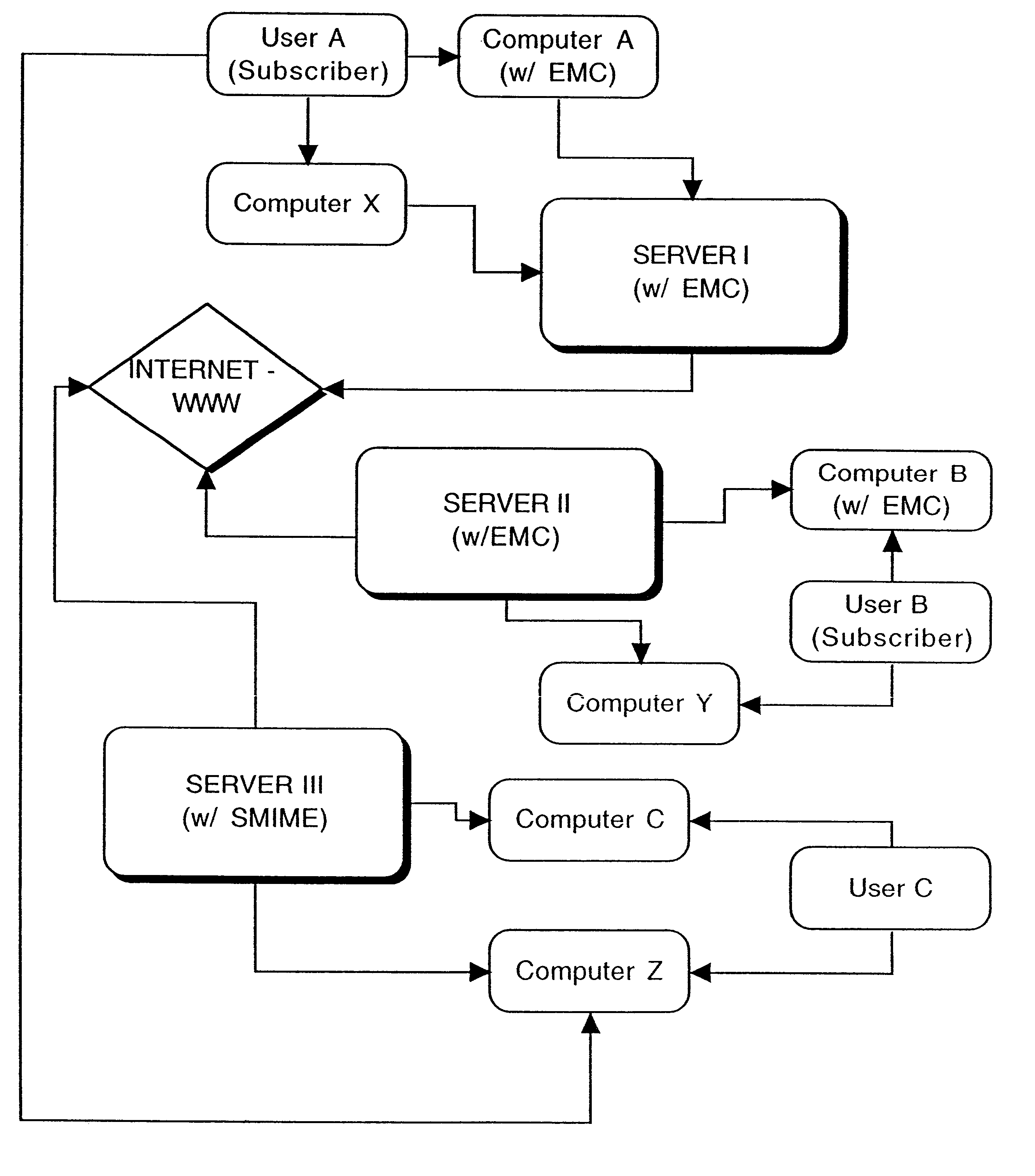
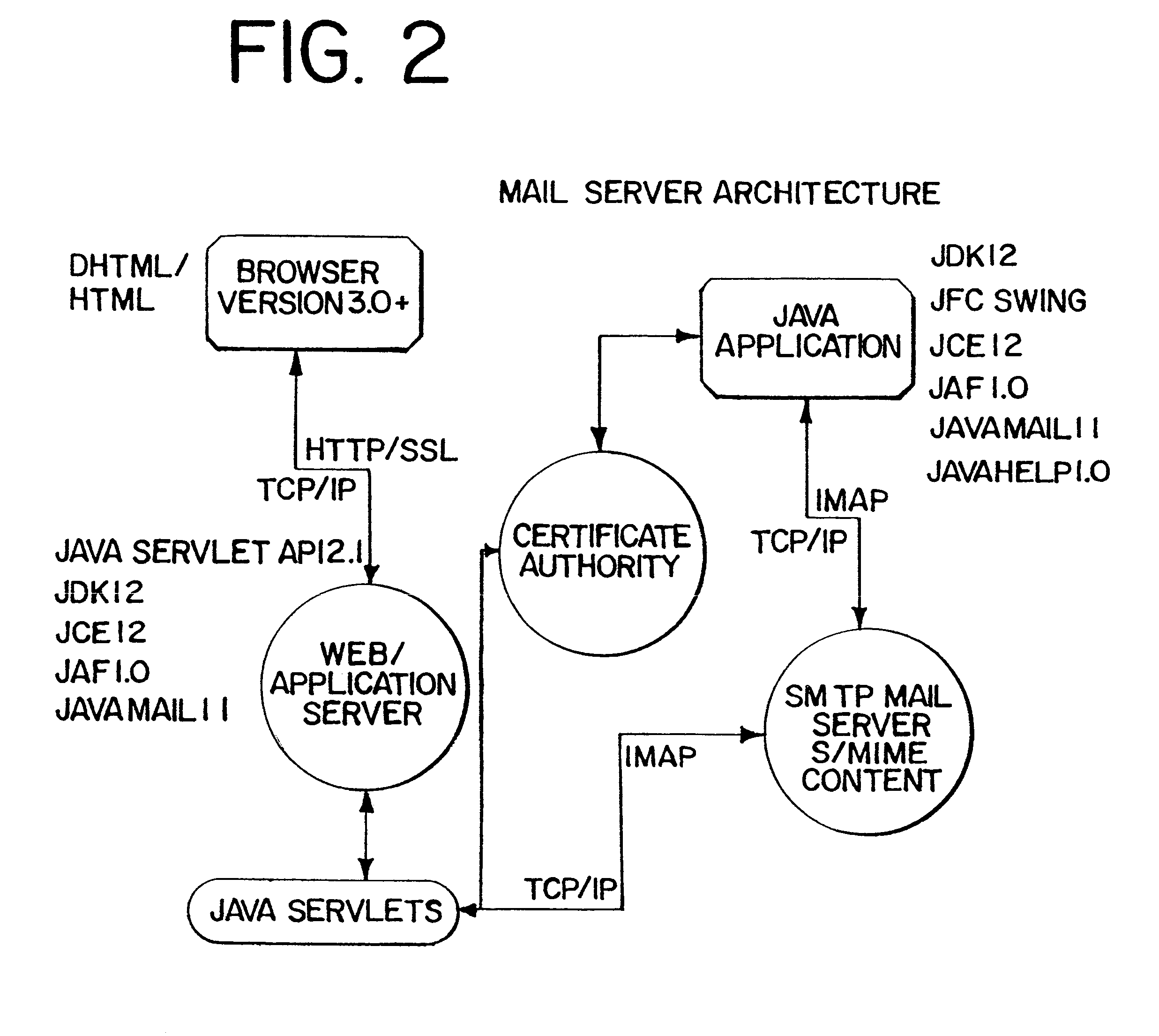
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
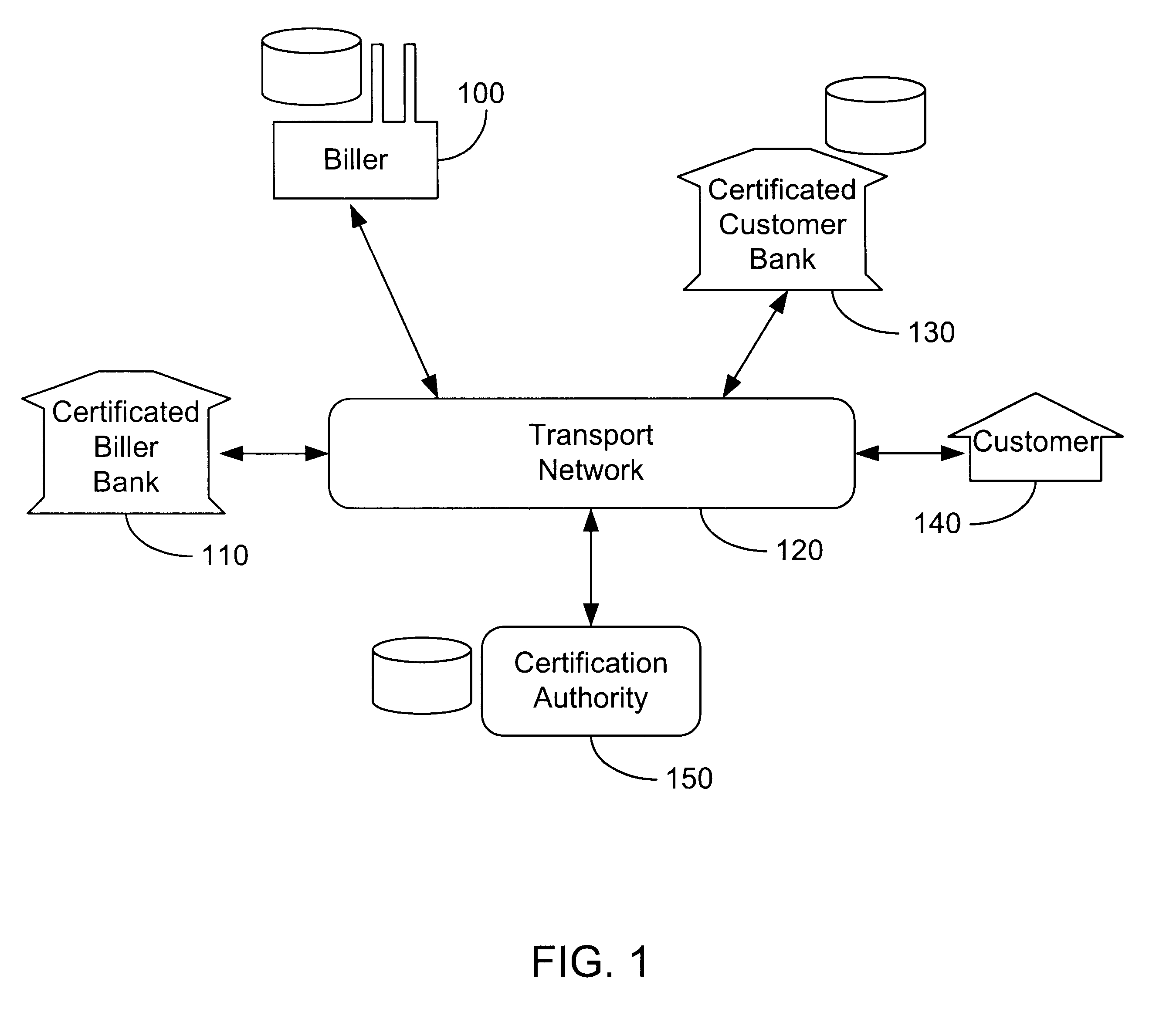
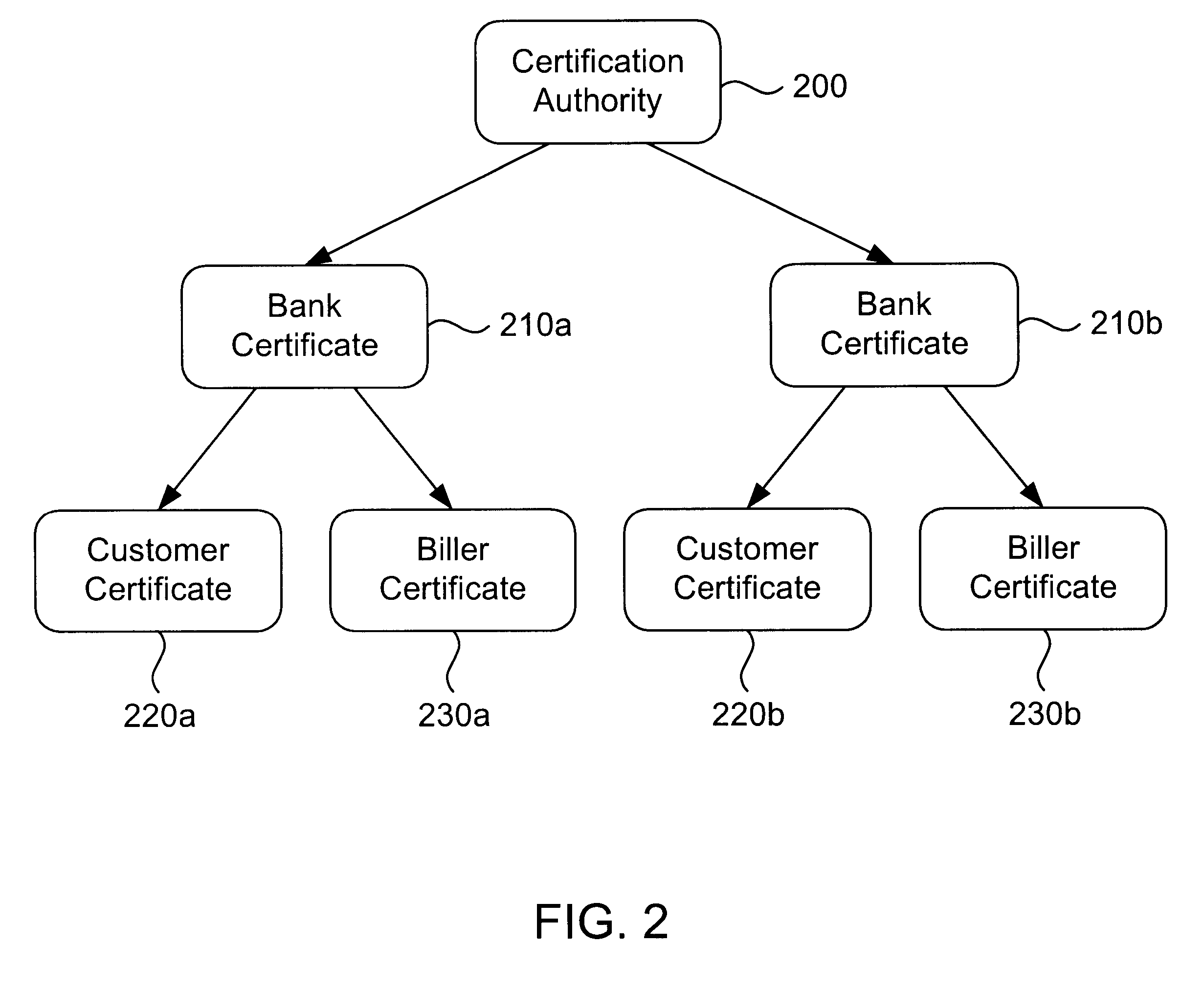
Secure interactive electronic account statement delivery system
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
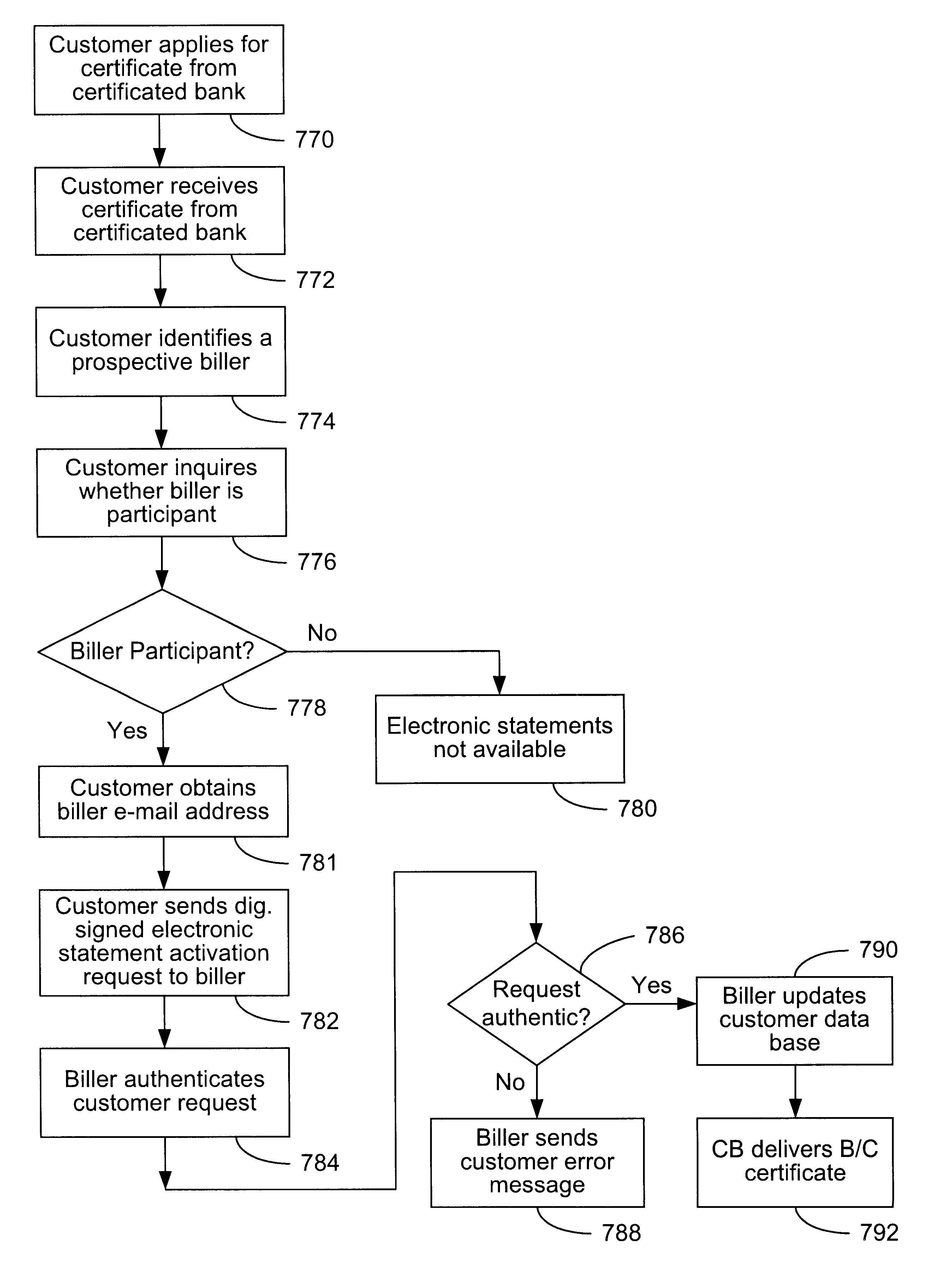
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
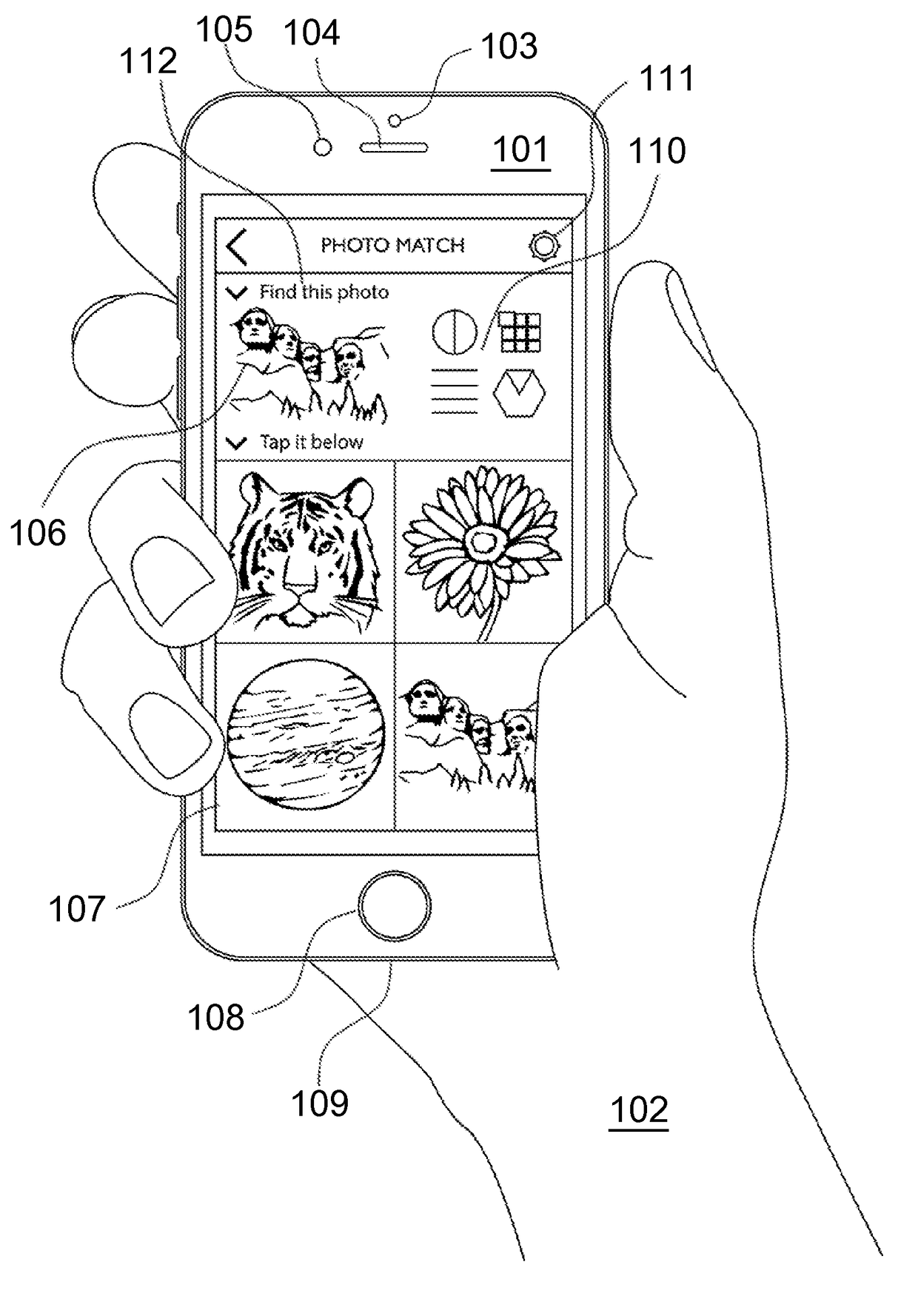
Mutual authentication security system with detection and mitigation of active man-in-the-middle browser attacks, phishing, and malware and other security improvements.
ActiveUS20170346851A1Multiple keys/algorithms usagePublic key for secure communicationWeb sitePhishing
A strong, unified and comprehensive new computer security and authentication solution is disclosed. It is ideal for everyday users, and invents faster and easier enrollments, faster usage, easier usage, numerous aspects of stronger security including token based rapid mutual-authentication with protection against phishing, MitM, malware and user carelessness, secure resilience against token loss or theft, continuing protection in harsh situations, non-repudiation benefits, biometric encryption, code self-defenses, improved deployment, lower costs, new revenue opportunities, and more. One aspect's flow, visually-enforced mutual-authentication is: customer visits protected web site's login page, gets identified via Cookies, site displays one random photograph on said page, triggers customer's smartphone to automatically show a grid of random photos, one of which matches the login page photo, and customer taps it to login. Disclosed techniques teach how to block fraudulent sites and activity by preventing these producing any matching photo the customer can tap.
Owner:DRAKE CHRISTOPHER NATHAN TYRWHITT
Non-repudiation of e-mail messages
InactiveUS6904521B1User identity/authority verificationData switching networksElectronic mailNon-repudiation
A technique, and system(s) implementing the technique, allow an encrypted message to be sent directly to a recipient, and when the recipient opens the message, the recipient's system sends a request to an arbiter server to retrieve decryption information to decrypt the message. When the arbiter server receives the request for the decryption information, the arbiter server generates evidence of the request and sends the decryption information to the recipient. In this way, an evidentiary trail, that cannot be repudiated, can be used to establish that the recipient received and attempted to open the message.
Owner:MCAFEE LLC
Method for implementing an intelligent content rating middleware platform and gateway system
InactiveUS20050135264A1Highly scalable, manageable and reliableMetering/charging/biilling arrangementsError preventionCyber operationsMiddleware
The method for implementing an Intelligent Content Rating middleware platform and gateway system disclosed herewith provides telecommunications carriers and network operators with the ability to define routing and actions based on HTTP / SIP based content and subscriber context through a powerful, extensible Layer 4-7 switching fabric technology. The invention mediates communications between applications and networks for IP packet flows, personal messaging, location-based services and billing. Furthermore, it enables advanced context-sensitive dialogue scenarios with the wireless subscriber such as, but not limited to, Advice-of-Charge dialogues. The art permits telecommunications network operators and like entities to introduce real-time rating of data services for both prepaid and post-paid subscribers. Further advances in the art include the validation of digital signatures, combined with authentication and non-repudiation techniques to ensure subscriber privacy remains protected.
Owner:REDKNEE INC
Undeniable certificates for digital signature verification
InactiveUS6292897B1Less-expensive computationUser identity/authority verificationThird partyUndeniable signature
A signer uses an undeniable signature scheme to sign his public key to thereby create an "undeniable certificate" which can be used to verify the signer's digital signature on any message signed using the signer's corresponding private key. Hence, once the undeniable certificate is received by the recipient, the recipient and the signer engage one time in a confirmation protocol or denial protocol to the satisfaction of the recipient that the undeniable certificate has in fact been signed by the signer thus certifying signer's public key. Thereafter, the recipient can use the certified public key to verify any documents signed by the signer with no further interaction with the signer. However, third parties are precluded from verifying the signer's signature since they do not possess the confirmed undeniable certificate and corresponding public key. Digital signatures can now be verified between two parties using a public key as in traditional digital signatures but which avoids verifiability by third parties.
Owner:IBM CORP
Telecommunications adapter providing non-repudiable communications log and supplemental power for a portable programmable device
InactiveUS6119179ABatteries circuit arrangementsDigital data processing detailsHand heldConference call
A portable adapter that provides non-repudiable telecommunications services to bar-code reading hand-held computers and palm-top or tablet-type mobile computers is disclosed. The adapter provides supplemental power supply and processing capacity that supports API communications functions, such as interactive voice recognition, conference calling, data encryption, VoIP packetization and other signal-format conversions that are not implemented on mobile computers. In particular, the device automatically logs IP packet identifiers and DOV dialing and status signals, without the user having access to edit this information, thereby providing a "non-repudiation" record of all communications. The adapter also supports intensive use of the host computer's serial port by supplementing the power available from the host computer's battery, or replacing that battery with a connector. For plant inspection and inventory auditing, ground-based cellular communications are implemented for supporting on-site work, including conference calling to discuss apparent pilferage or imminent safety hazards, and removable WORM recording media for documenting these discussions. For repair shop use, a standard phone jack or 10-base-T connector allows the device to upload engine test-data, with reports or estimates dictated by the mechanic to the repair shop's LAN server. For hospital use, the device includes removable WORM media for logging patient test results and examination reports. The hospital device also uses a dedicated local-area RF or IR transmitter, with location-specific encryption, to protect the privacy of lab reports received by the device, and to limit use of these devices to hospital's own premises.
Owner:HIPPO
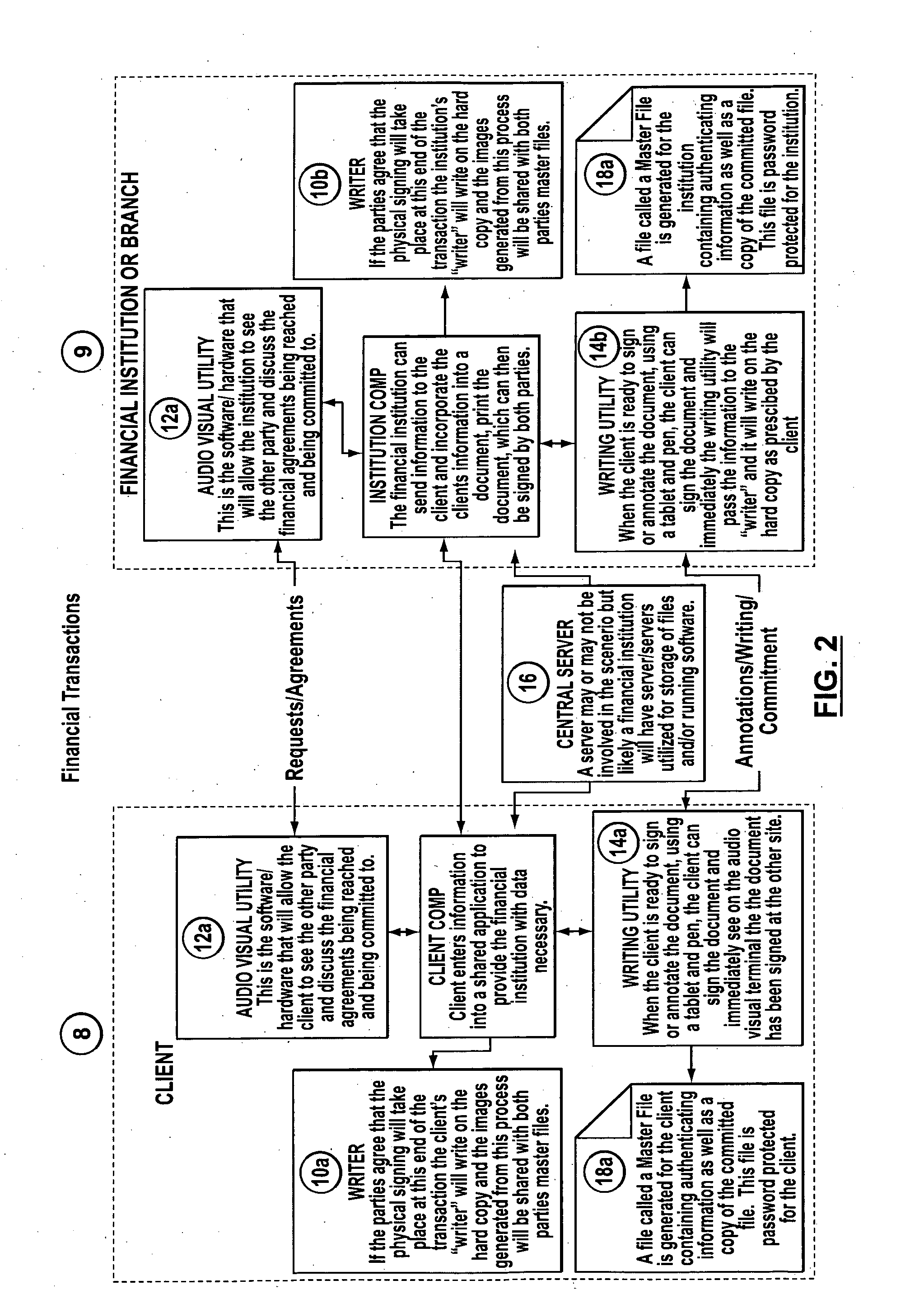
System, method and computer program, for enabling entry into transactions on a remote basis
A system, method and computer program for enabling transactions on a remote basis is provided. The method of the present invention comprises the steps of: (1) providing a first computer at a location of a customer, and providing a second computer at a location of a financial institution, the first computer and the second computer being linked so as to provide a two-way audiovisual communication system; (2) providing an authentication request at the second computer and communicating the request to the first computer; (3) the customer reviewing the request and providing a signature or other writing as an input to an input device connected to the first computer; (5) transmitting the signature from the first computer to the second computer; (6) receiving the signature and providing the signature to a plotting device connected to the second computer; and (7) applying the signature to a transactional document, wherein the audiovisual information received by the second computer and the signature received by the second computer in combination provide a means of transaction authentication and non-repudiation.
Owner:SYNGRAFFI CORP
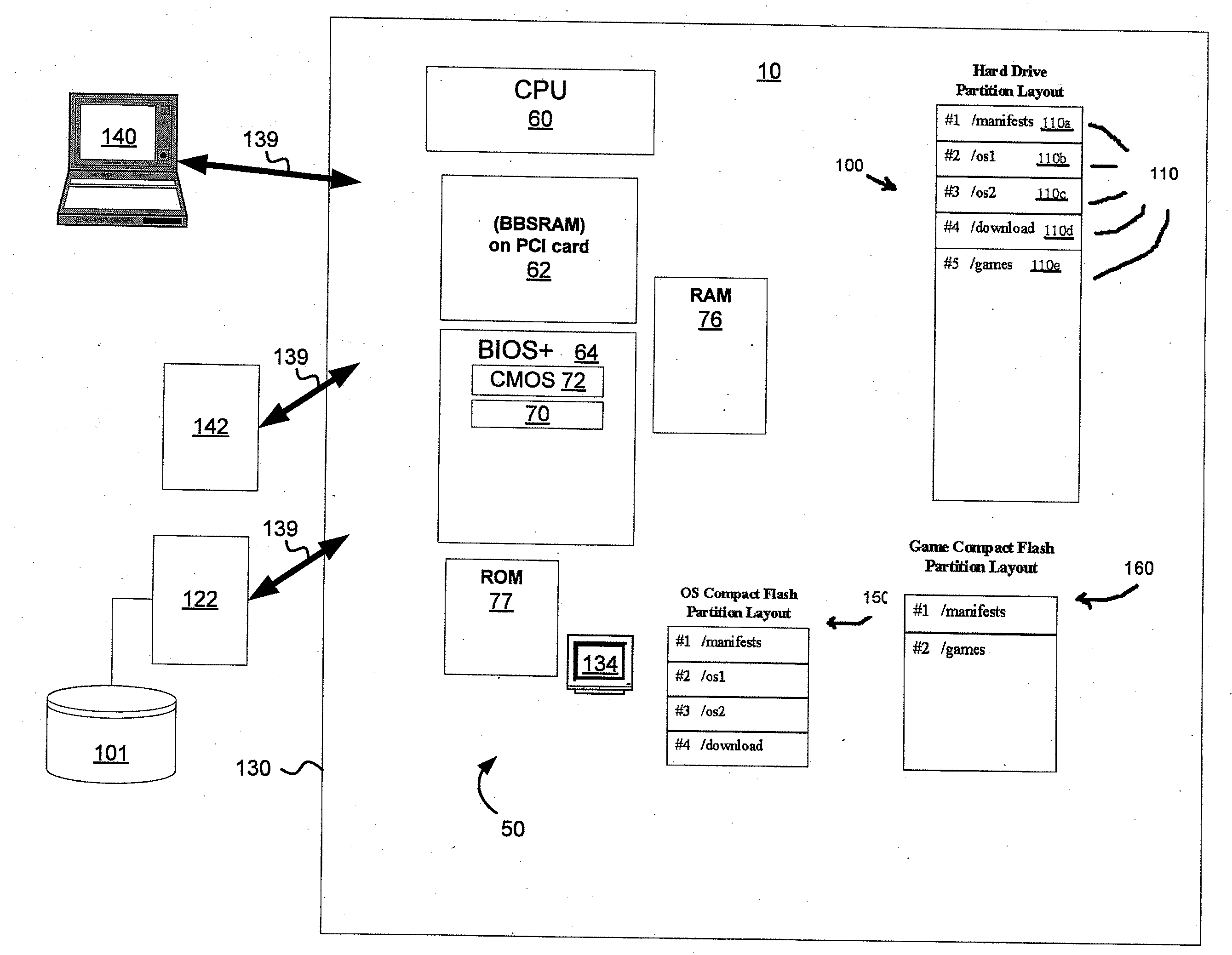
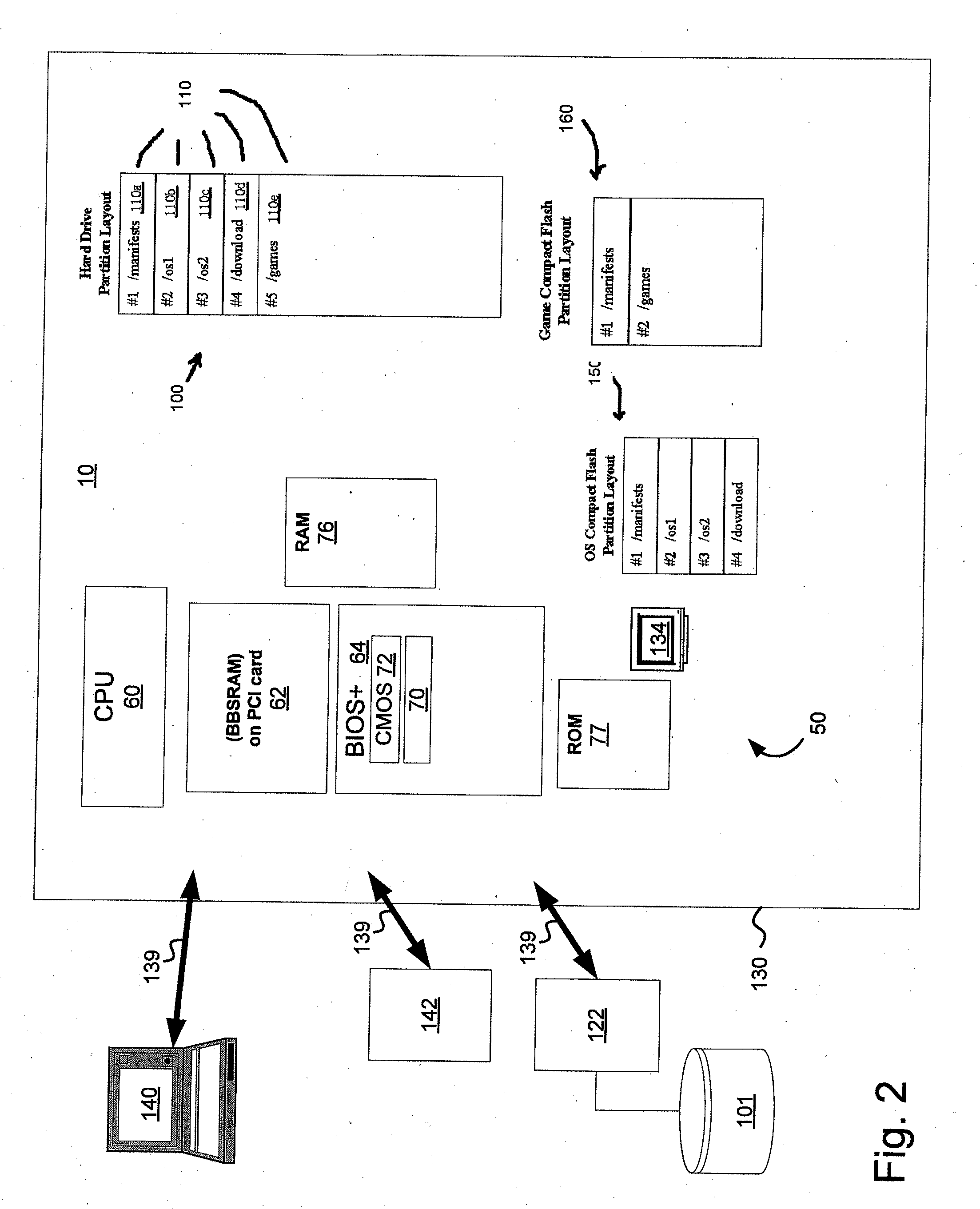
Data Integrity and Non-Repudiation
ActiveUS20080045342A1Reduce boot timeImprove loading timeUnauthorized memory use protectionHardware monitoringComputer hardwareData integrity
Disclosed is a system and method that uses digital signature technology to authenticate the contents of one or more manifests located on a storage device. Each manifest contains a list of file records, where each record contains the name of a file stored on the storage device, and a signature value derived from the contents of the file. At boot time, the gaming machine first authenticates the contents of the manifest and then authenticates the contents of the files using the signature value stored in the manifest. Files are verified using the signature, as they are needed, during the boot up of the operating system and throughout normal operation. This method reduces the boot time of the gaming machine and eliminates the need to check digital signatures for each individual file or over the entire contents of a non-secure media. Similarly, a method of adding authentication ability to legacy software components without necessarily altering the legacy software components is disclosed. Introduction of a stronger authentication algorithm, or when a private key has been compromised would normally require the software component to be re-built to support the new algorithm or private / public key pair; however, a method is disclosed where algorithms and key pairs may be changed and applied to legacy software without having to re-built, re-test, re-sign, or re-submit the component to regulatory agencies for approval. Also disclosed is a system and method of establishing a trusted environment containing a gaming operating system and associated authentication module, file system drivers, and / or network drivers that may be used to in the process of authenticating contents of one or more manifests located on a storage device.
Owner:LNW GAMING INC
Pseudonymous public keys based authentication
InactiveUS20110302412A1High security requirementsImprove securityUser identity/authority verificationAuthentication systemNon-repudiation
Systems and methods for pseudonymous public keys based authentication are described that enable an authentication to achieve pseudonymity and non-repudiation, for example, at the same time. Pseudonymity may provide, for example, that a user can show to different parties different digital identifiers for authentication instead of, for example, always using a single digital identifier everywhere, which may lead to a breach of privacy. Non-repudiation may provide, for example, that the authentication data at the server side can be used, for example, to verify a user's authentication request, but not to generate an authentication request, which might lead to user impersonation. A user may use a physical token to generate the authentication request corresponding to the user's identity to pass the authentication.
Owner:NORTHWESTERN UNIV
Method for electronic commerce using security token and apparatus thereof
InactiveUS20050097060A1Securing communicationPayments involving neutral partyConfidentialityExtensible markup
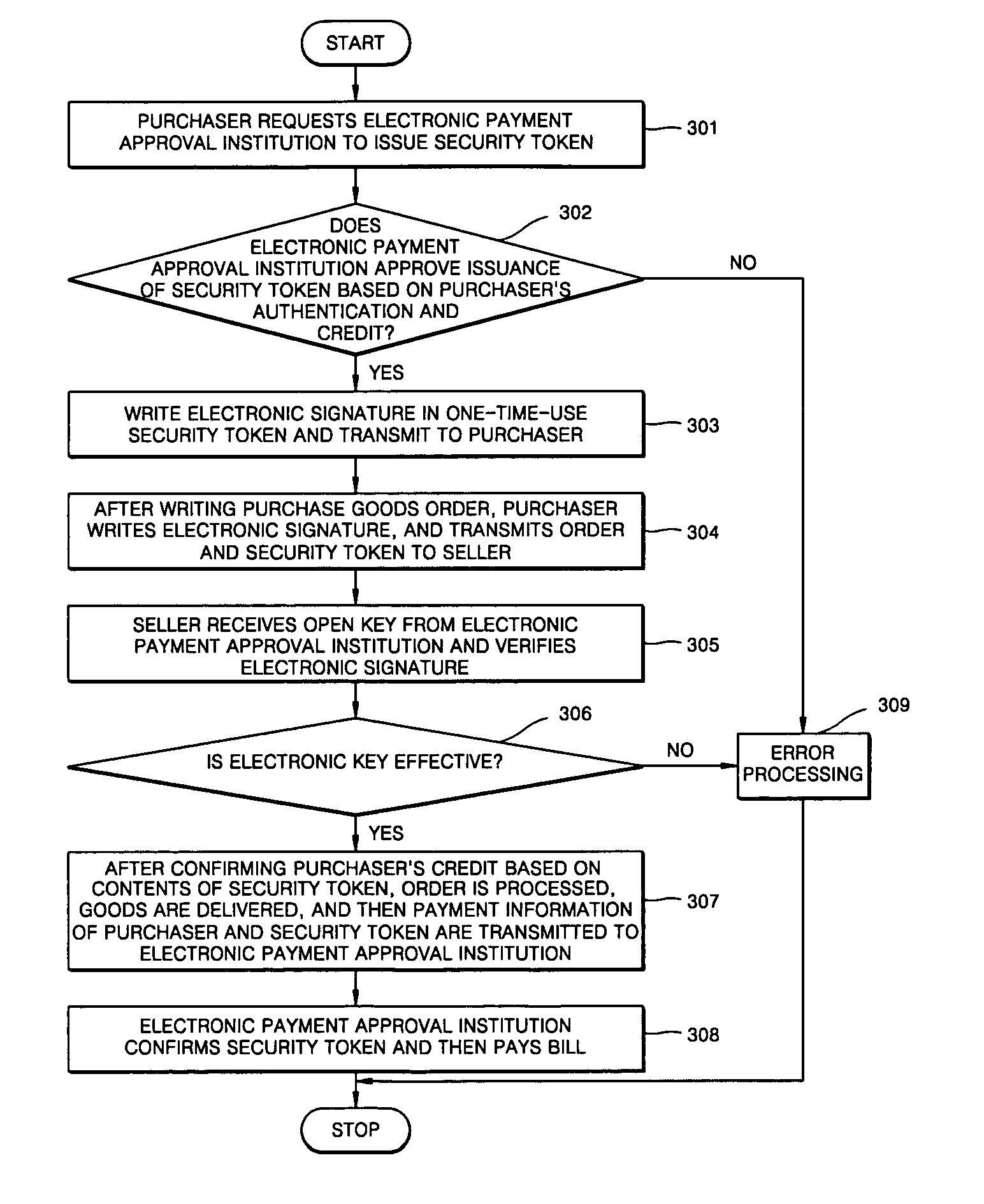
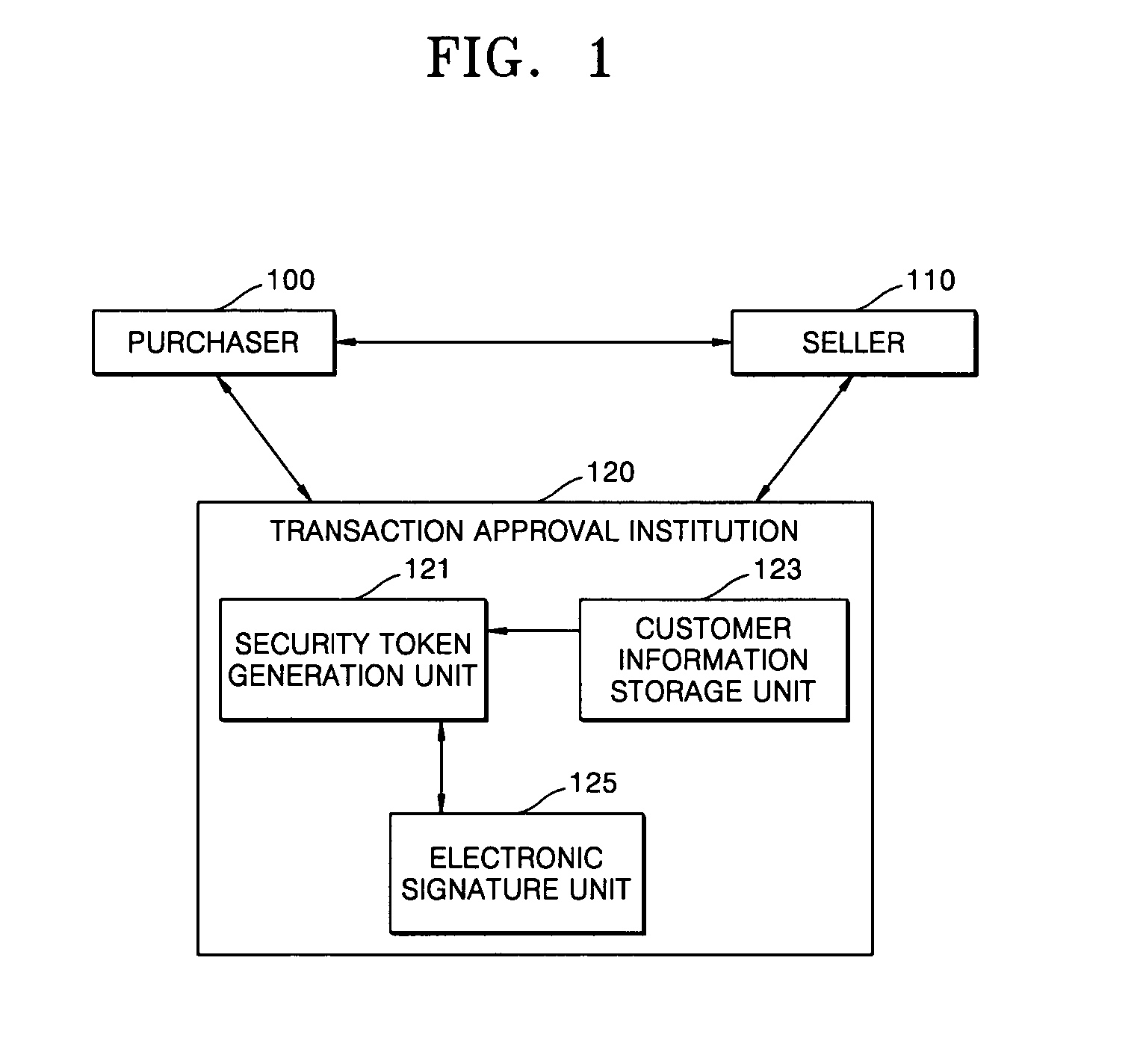
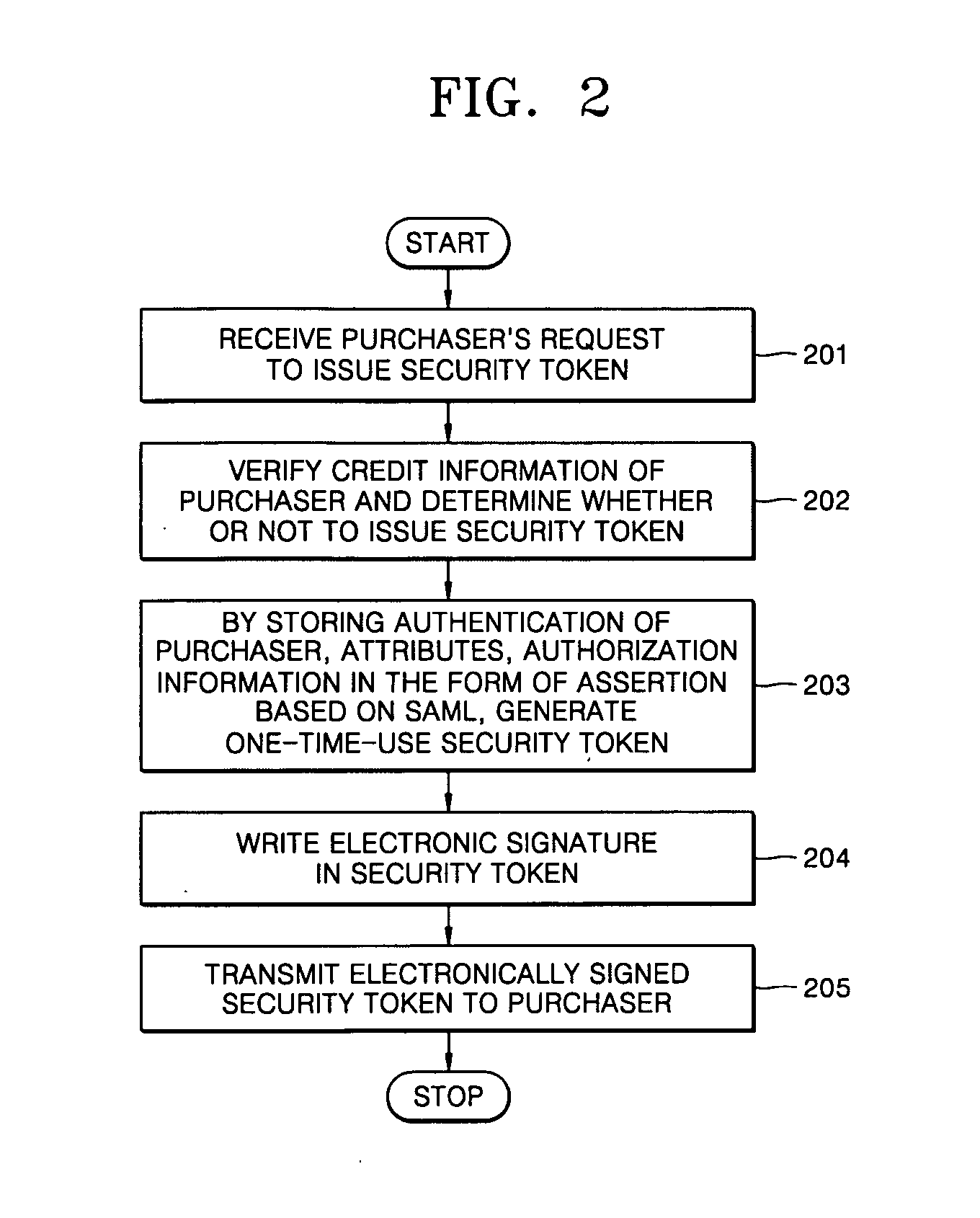
A method for electronic commerce using a security token and an apparatus thereof are provided. The electronic commerce method using a security token comprises a transaction approval institution generating a security token based on a security assertion markup language (SAML), using credit information of a purchaser who requests to issue a security token, and transmitting the security token to the purchaser; the purchaser writing an electronic signature on an order and transmitting the order together with the security token to a seller; the seller verifying the received order and security token, and then delivering goods according to the order to the purchaser; and the transaction approval institution performing payment for the seller and the purchaser. The method can solve the problems of personal information leakage and privacy infringement that may happen when a purchaser sends his personal information to a seller for electronic commerce. Since the token is one-time-use data, even if a security token sent is counterfeited or stolen, the loss can be minimized. In addition, by writing an extensible markup language (XML) electronic signature in the security token, authentication, integrity, and non-repudiation for a transmitted message can be guaranteed and through simple object access protocol (SOAP) security technology, confidentiality is maintained.
Owner:ELECTRONICS & TELECOMM RES INST
Implementing nonrepudiation and audit using authentication assertions and key servers
InactiveUS7376835B2Providing serviceMultiple level of strengthKey distribution for secure communicationUser identity/authority verificationKey serverCommunications system
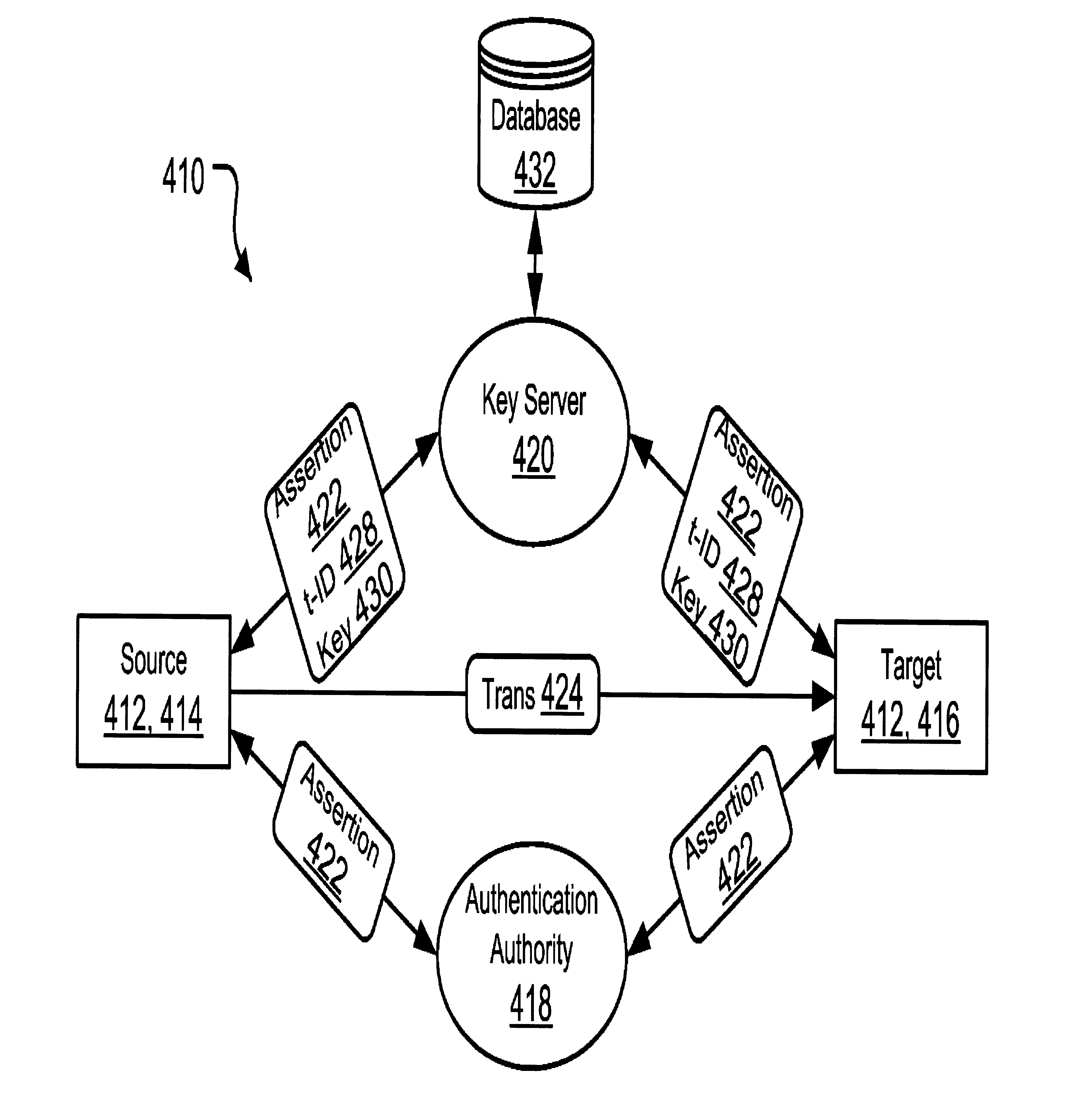
A communication system (410) wherewith sources (414) and targets (416) employ a key server (420) to exchange transactions (424). A first request to the key server includes a source assertion (422) from an authentication authority (418), and optionally a key (430). The key server provides a transaction ID (428), and the key if not already provided, in reply to this request. The key server stores the transaction ID and source assertion. The source encrypts the transaction and sends it with the transaction ID to the targets. A second request to the key server includes a target assertion and the transaction ID. The key server provides the key in reply to this request. The key server also stores the target assertion in association with the transaction ID. The respective assertions then establish the source and targets of the transaction in a manner that cannot plausibly be repudiated.
Owner:PROOFPOINT INC
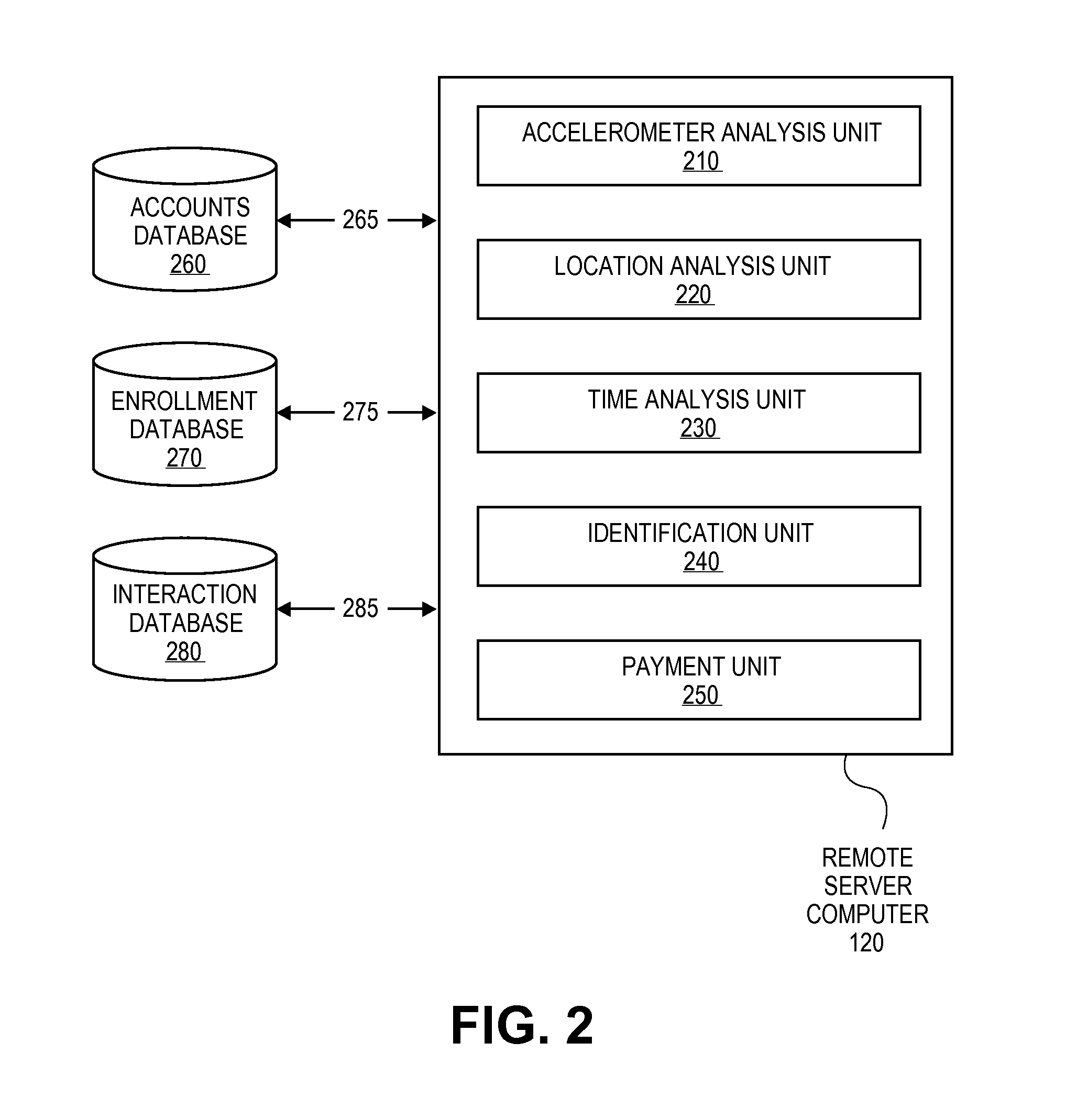
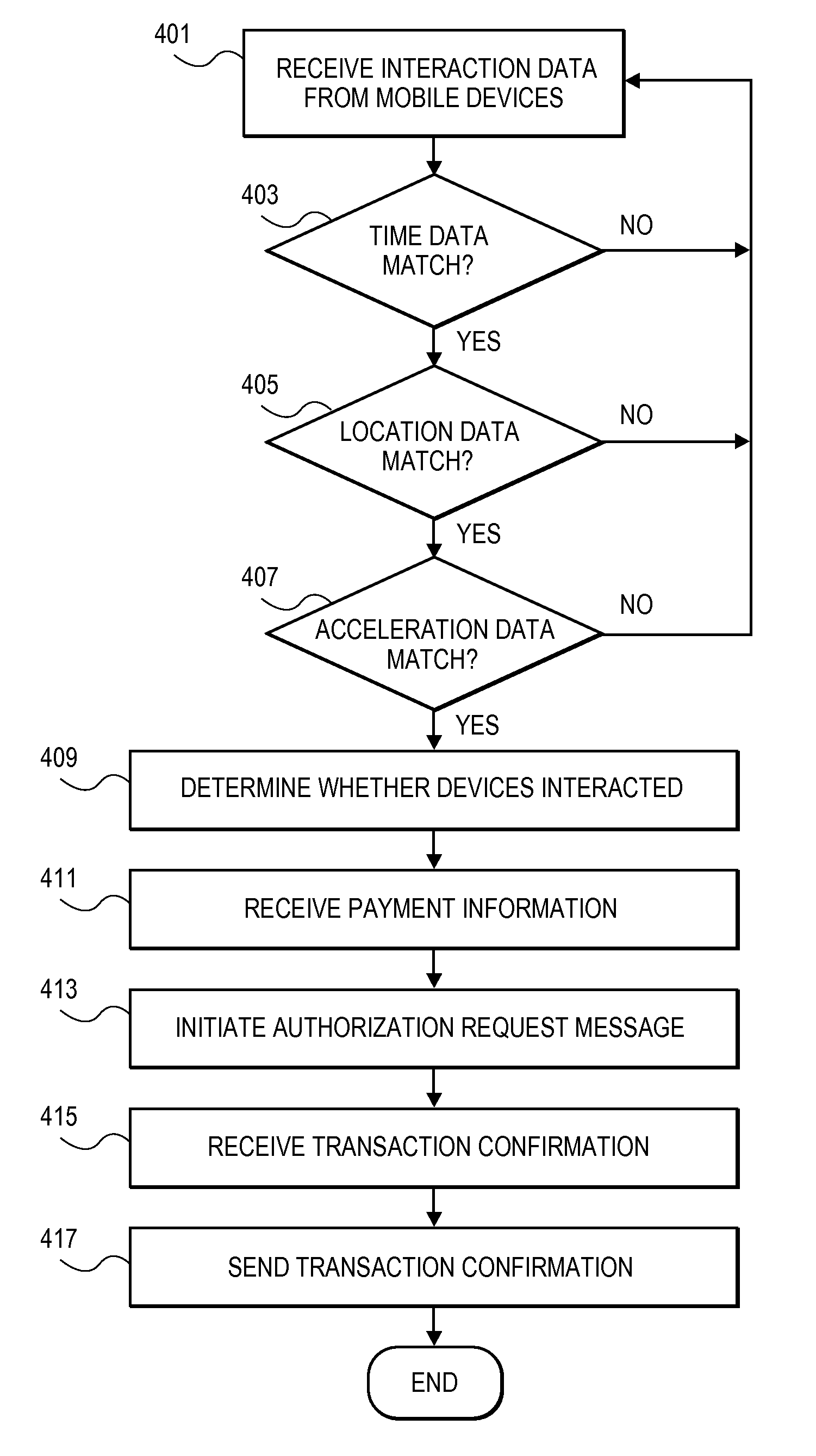
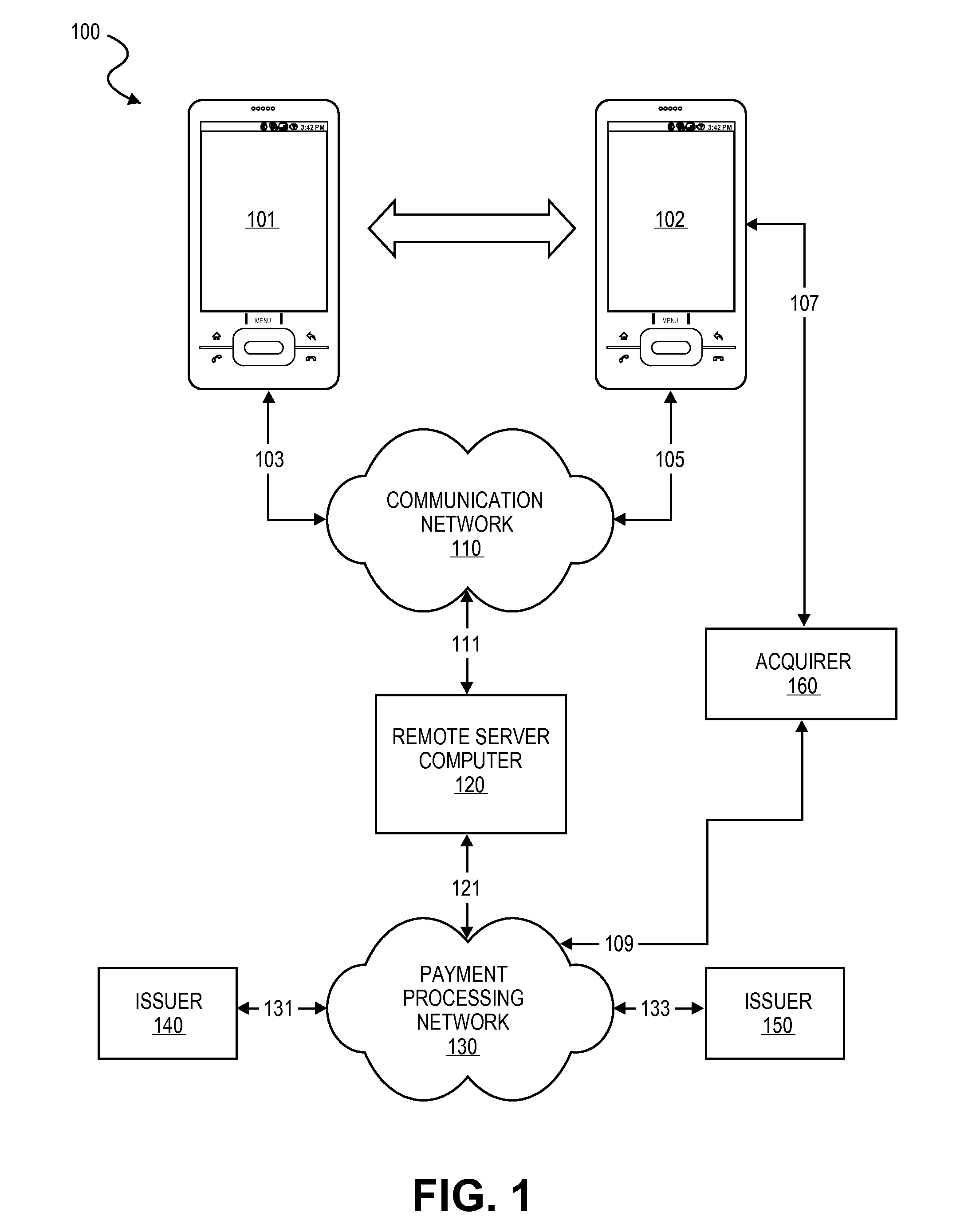
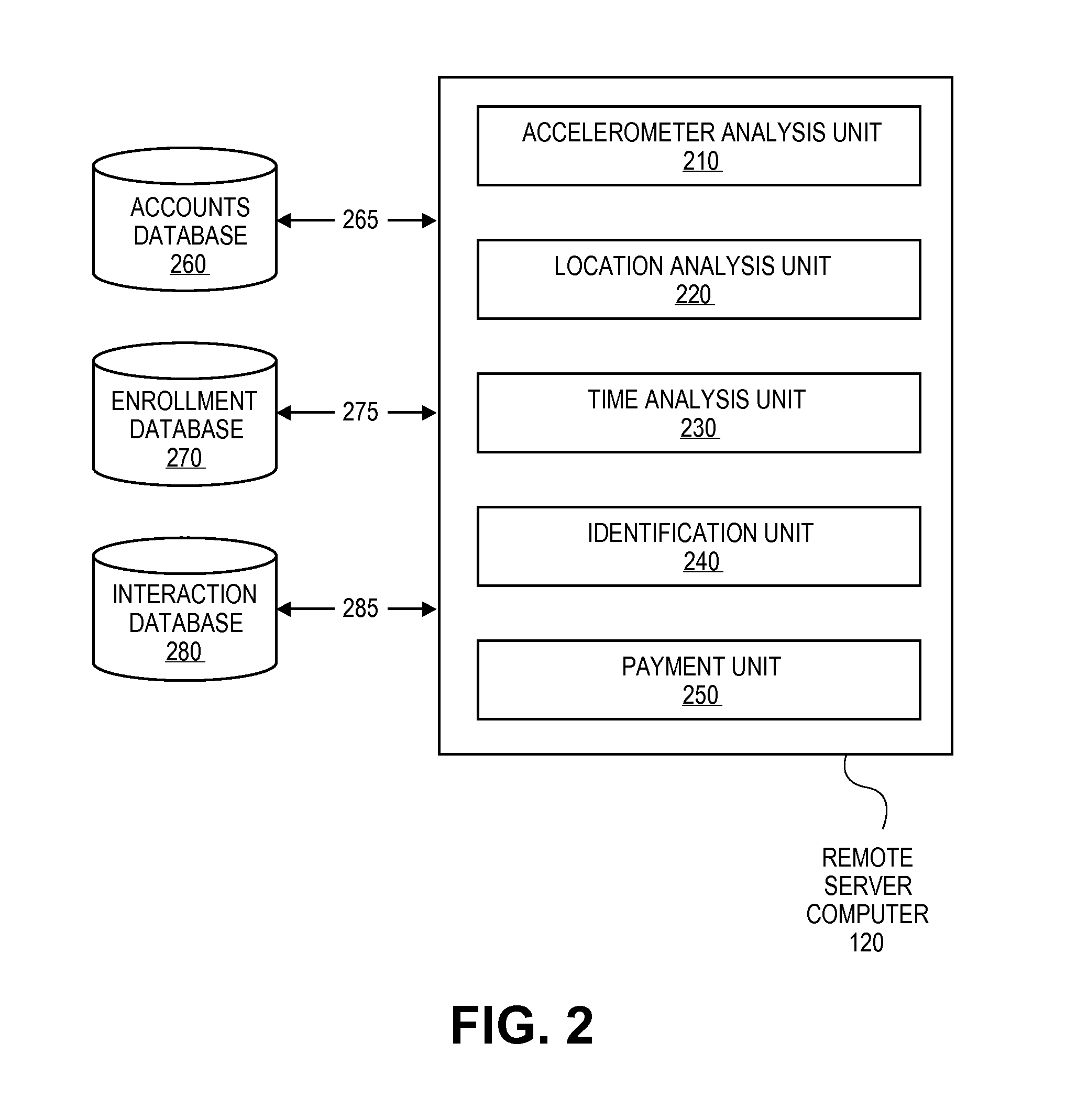
Transaction Using A Mobile Device With An Accelerometer
Embodiments of the invention may use a first accelerometer to measure first acceleration data of a first device. Other interaction data, including time data and geographic location data, generated by the first device may also be recorded. First acceleration data is compared by a remote server computer to second acceleration data generated by a second accelerometer in a second device. If the first and second accelerometer data are substantially equal, it can be determined that the devices have interacted and communications can be initiated. After communications are initiated, a financial transaction is conducted. Accelerometer data may be stored and / or used as part of the authentication process in a payment processing network. Other embodiments of the invention use the accelerometer to generate movement security data to make financial transaction more secure. Accelerometer data is used for authentication, security, encryption, session keys, non-repudiation, or fraud protection.
Owner:VISA INT SERVICE ASSOC
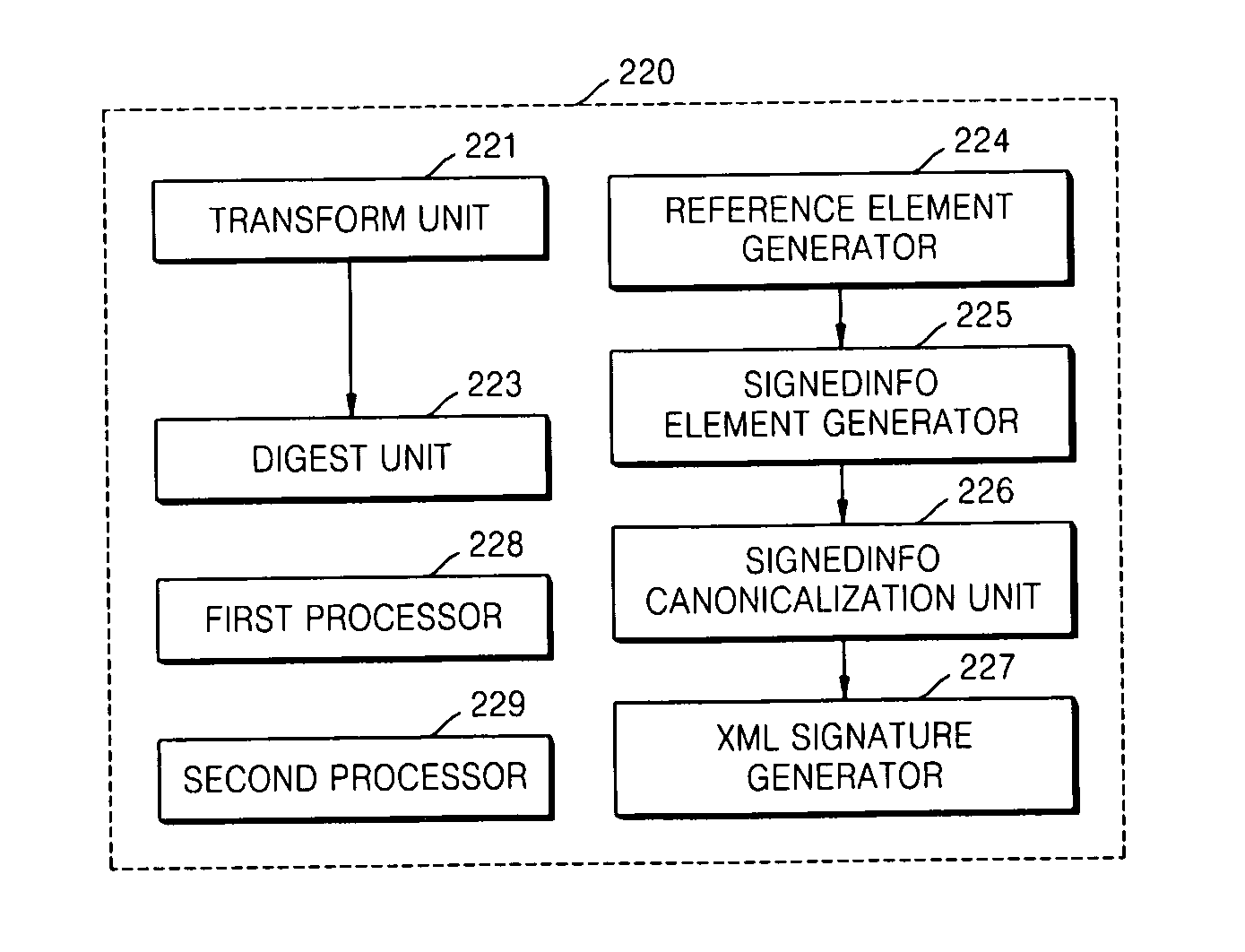
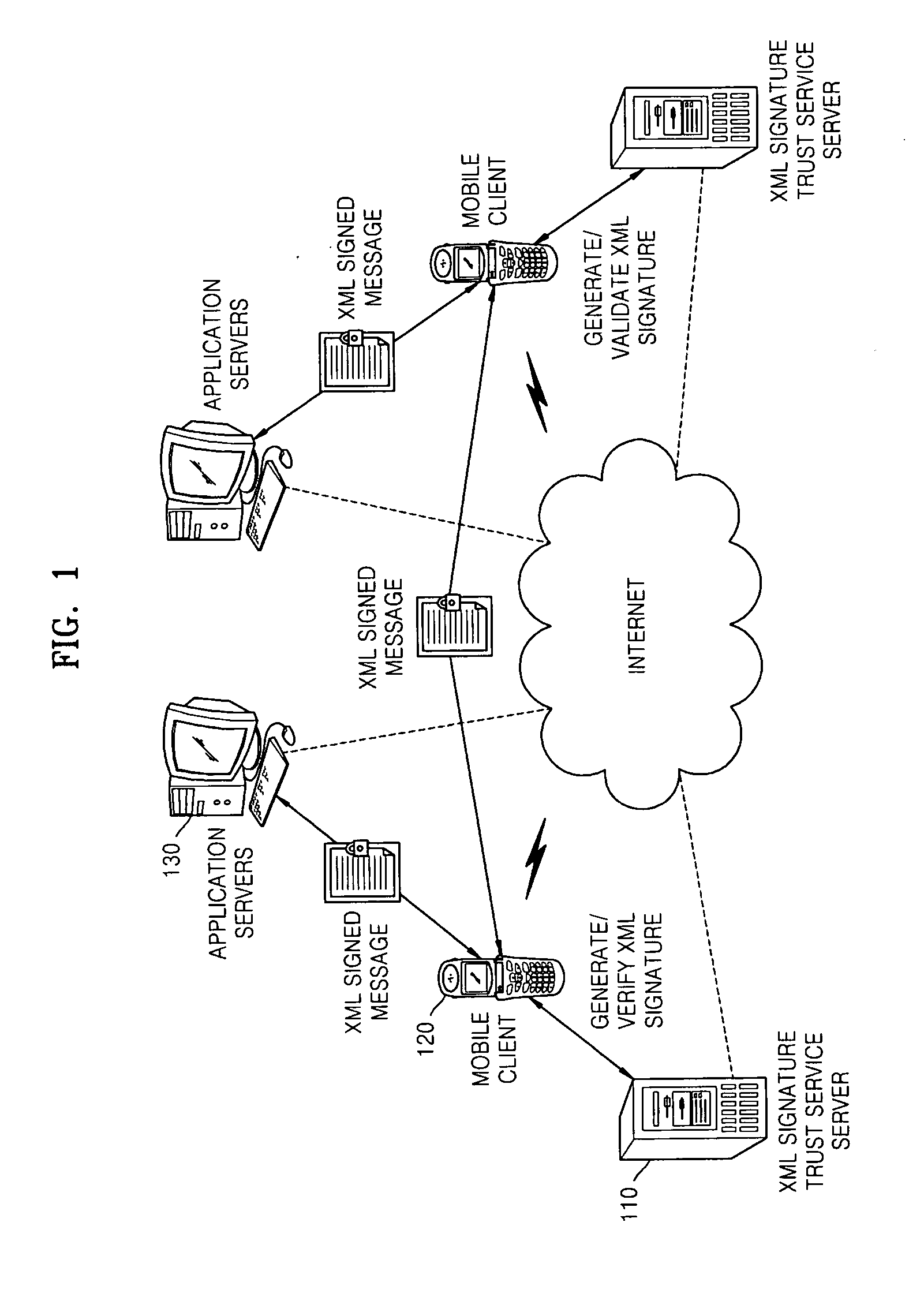
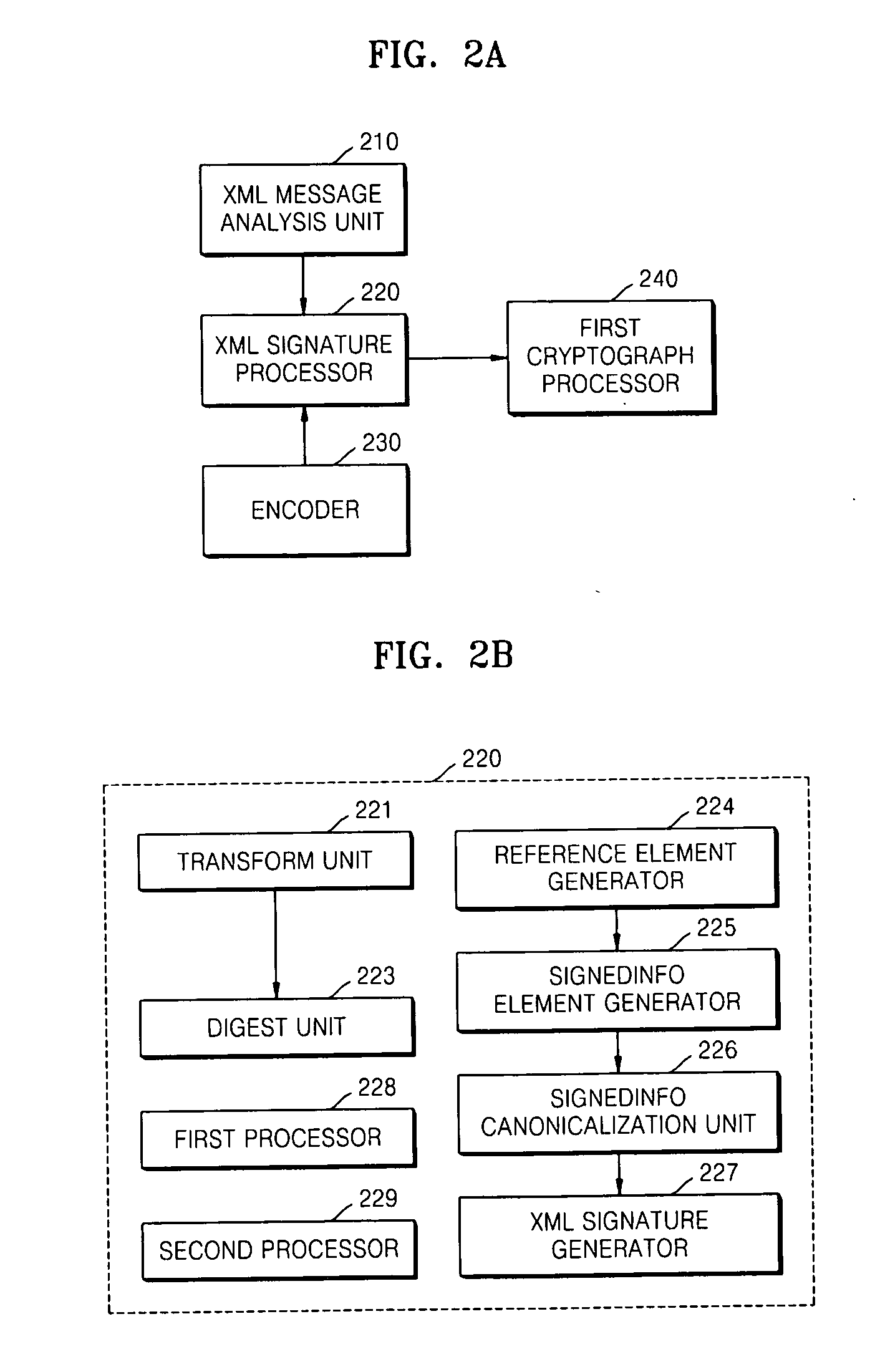
Method and apparatus for providing XML signature service in wireless environment
InactiveUS20070136361A1Digital data processing detailsDigital data protectionLimited resourcesE-commerce
Provided are a mobile extensible Markup Language (XML) signature service providing apparatus and method. The mobile XML signature service providing apparatus includes: an XML message analyzing unit authenticating a mobile client, according to an XML signature template generation request or an XML signature verification request received from the mobile client; an XML signature processor generating an XML signature template and a SignedInfo element in a canonicalized format if the authentication is successful, and verifying an XML signature; and an encoder providing key information and at least one setting value for the generation of the XML signature template and verification of the XML signature, to the XML signature processor. Therefore, the mobile XML signature service providing apparatus and method provide authentication, integrity, non-repudiation, etc. with respect to messages received / transmitted in a wireless environment, are applied to a wireless environment having limited resources, are compatible with an XML signature for an existing wired environment that is to be applied to wired-and-wireless integration electronic commerce, and minimizes a change in an existing wired environment when a mobile XML signature is applied.
Owner:ELECTRONICS & TELECOMM RES INST
Method for authenticating electronic documents
InactiveUS6963971B1Improve privacyImprove user securityKey distribution for secure communicationUser identity/authority verificationThird partyElectronic document
A secure method for sending registered, authenticated electronic documents. The invention validates sender and recipient identities, provides for non-repudiation of authenticated documents by sender and recipient, provides an evidence trail, and protects the integrity of the document. The invention is constructed so that a sender can be supplied with proof that the intended recipient received and opened an authenticated document. A neutral third party acts as a document registration agent, and witness to the transmission and receipt of the authenticated document. In the event of a dispute between sender and recipient, the third party can provide an irrefutable record of the contents of the document and of the history of the transmission and receipt of the document Because the third party never has possession of the electronic document, the method provides maximum privacy for sender and recipient. The method is readily adaptable to both key recovery and key escrow.
Owner:BUSH GEORGE +4
Method and system with authentication, revocable anonymity and non-repudiation
The present invention relates to a method of access to a service consisting in i) identifying and registering a client (C), ii) authenticating the client to an anonymous certification authority, iii) authenticating the client by producing an anonymous signature and opening and maintaining an anonymous authentication session with a server (Se), and iv) selectively allowing contact between the server (Se) and the anonymous certification authority (ACA) to revoke the anonymity of the client (C) using the signature provided in step iii). The invention also relates to a system for opening and maintaining an authentication session guaranteeing non-repudiation.
Owner:FRANCE TELECOM SA
Apparatus, system, and method for an electronic payment system
InactiveUS20070022375A1Reduce transaction cost burdenFinanceDigital computer detailsClosed loopGoal system
The present contrivance is an apparatus, system, and method for an electronic payment system. The present contrivance provides an electronic payment system that provides advertising for compensation. Further the present contrivance provides an anonyfier that can separate accesser identity information from transaction information. Further, the present contrivance provides an advertising targeting system that determines advertising that does not conflict with providers provisions. Further, the present contrivance provides a payment release system based on delivery verification. Further, the present contrivance provides a credit auction providing accessers and creditors with a dynamic credit market. The present contrivance also provides a system that converts identification cards and other forms of ID into non repudiation devices. The present contrivance also enables the extension of closed loop payment systems.
Owner:WALKER DAVID H
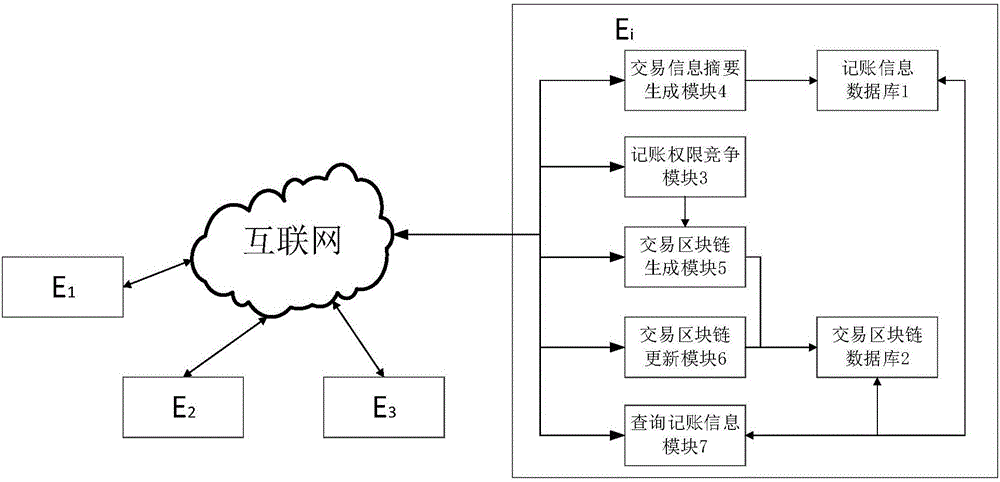
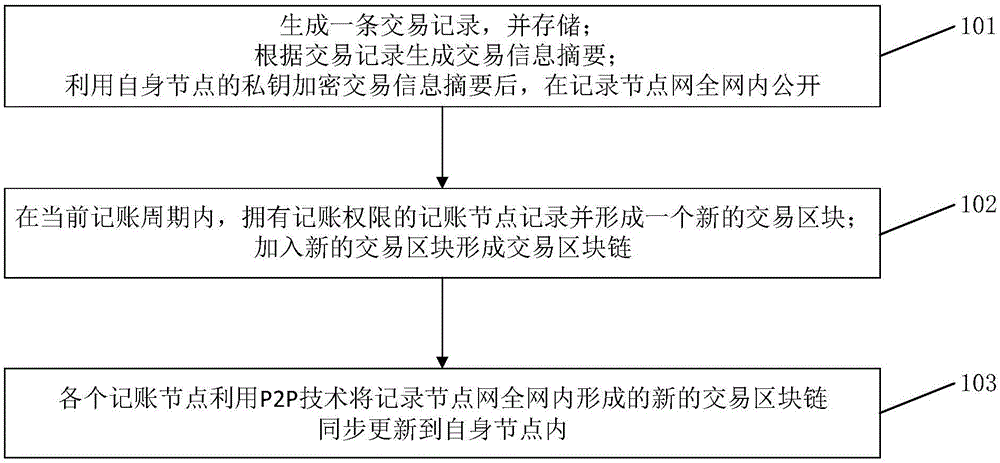
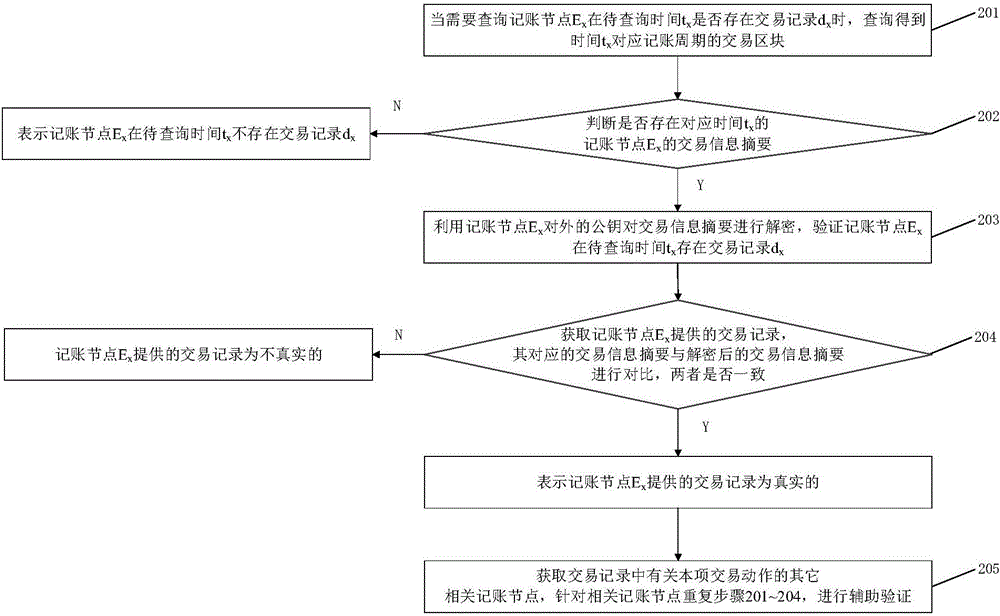
Cloud manufacturing service transaction information recording system and method based on block chain
ActiveCN106790431AOvercome opacityOvercoming data discrepanciesResourcesTransmissionComputer moduleData recording
The invention relates to a cloud manufacturing service transaction information recording system and method based on a block chain. The system comprises a plurality of book keeping nodes; a plurality of book keeping nodes are communicated with each other to form a recording node network; each book keeping node comprises a book keeping information database, a transaction block chain database, a book keeping permission competition module, a transaction information abstract generation module, a transaction block chain generation module and a transaction block chain updating module; the method is applied to the recording node network; recording node network comprises a plurality of book keeping nodes communicated with each other; each book keeping node contests for book keeping permissions in different book keeping periods in a competing mode; and the method comprises a transaction information recording process and a transaction information inquiry verification process. Compared with the prior art, according to the cloud manufacturing service transaction information recording system and method disclosed by the invention, a data recording method and a data structure in the cloud manufacturing service transaction process are improved, and non-repudiation and inquiry verification of transaction can be conveniently implemented.
Owner:TONGJI UNIV
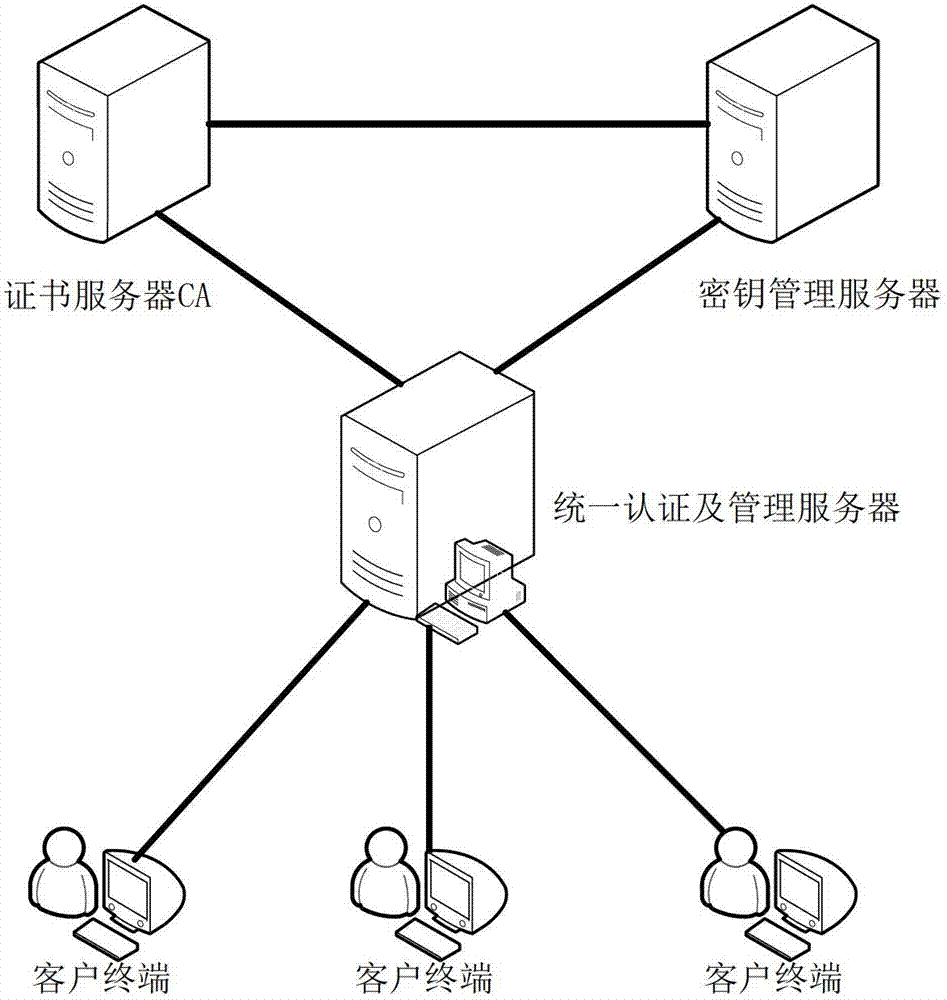
File safe protection system and method thereof
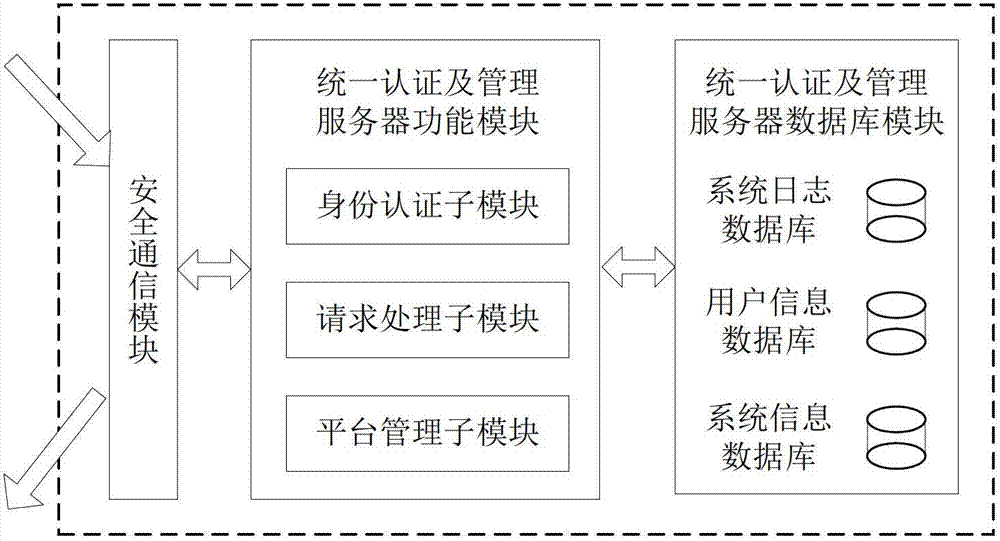
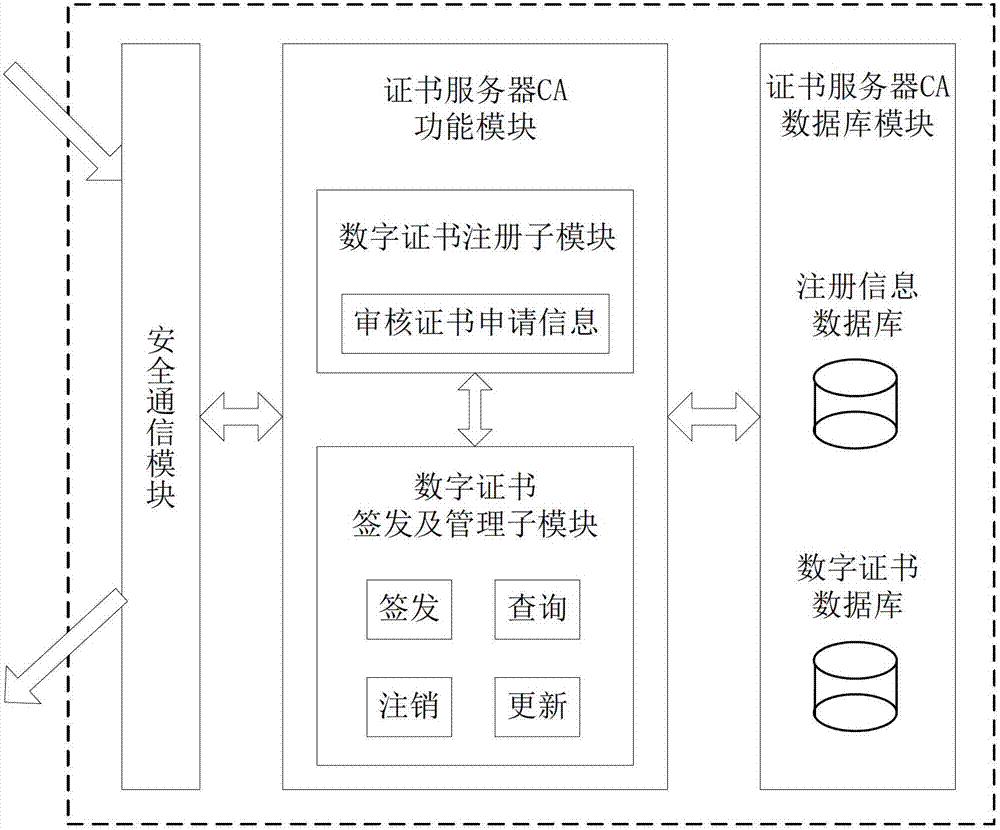
ActiveCN102970299ASimple structureEasy to buildKey distribution for secure communicationUser identity/authority verificationConfidentialityComputer terminal
The invention discloses a file safe protection system and a method, which mainly solves the problems of network illegal invasion, information stealing and tamping, impersonation and weak deny resistance in the conventional information system. The file safe protection system consists of a unified authentication and management server, a certificate server CA, a secret key management server and a client terminal; the unified authentication and management server is used as a middle node and is used for processing or transmitting a service request sent by the client terminal; the certificate server CA processes a certificate service request of the client terminal and provides basic support for identification; and the secret key management server processes the secrete key service requests of the client terminal and the certificate server CA, and is used for encrypting and decrypting a file for the client terminal and providing parameter support for a digital certificate signed by the certificate server CA. With the adoption of the file safe protection system and method provided by the invention, identification, confidentiality, integration and non-repudiation services can be provided; and the file can be safely protected in transmission, storage, sharing and access processes.
Owner:XIDIAN UNIV
System and method for nameless biometric authentication and non-repudiation validation
InactiveUS20070175986A1High degreeProvide protectionDigital data authenticationIndividual entry/exit registersNon-repudiationBiometric trait
Owner:LIBERTY PEAK VENTURES LLC
Multi-tier transaction processing method and payment system in m- and e- commerce
A server executes a protocol that automates transactions involving a customer and a merchant agreeing to trade money in the customer's account for goods or services available from the merchant. The protocol protects personal identifying information of the customer from disclosure to the merchant, and protects all parties from repudiation of the specific transaction. The protocol defines a pre-authenticated form of the specific transaction; obtains authorization from the customer and the merchant to commit on their behalf to the pre-authenticated transaction; and obtains authorization from the bank to commit resources for settlement with the merchant. After obtaining authorizations, a transaction clearance code is generated completing a record of the pre-authenticated transaction for non-repudiation, for proof of a right to receive settlement from the third party and for proof of a right to receive the goods or services from the merchant.
Owner:AUTHERNATIVE INC
EFFICIENT TECHNIQUE TO ACHIEVE NON-REPUDIATION AND RESILIENCE TO DoS ATTACKS IN WIRELESS NETWORKS
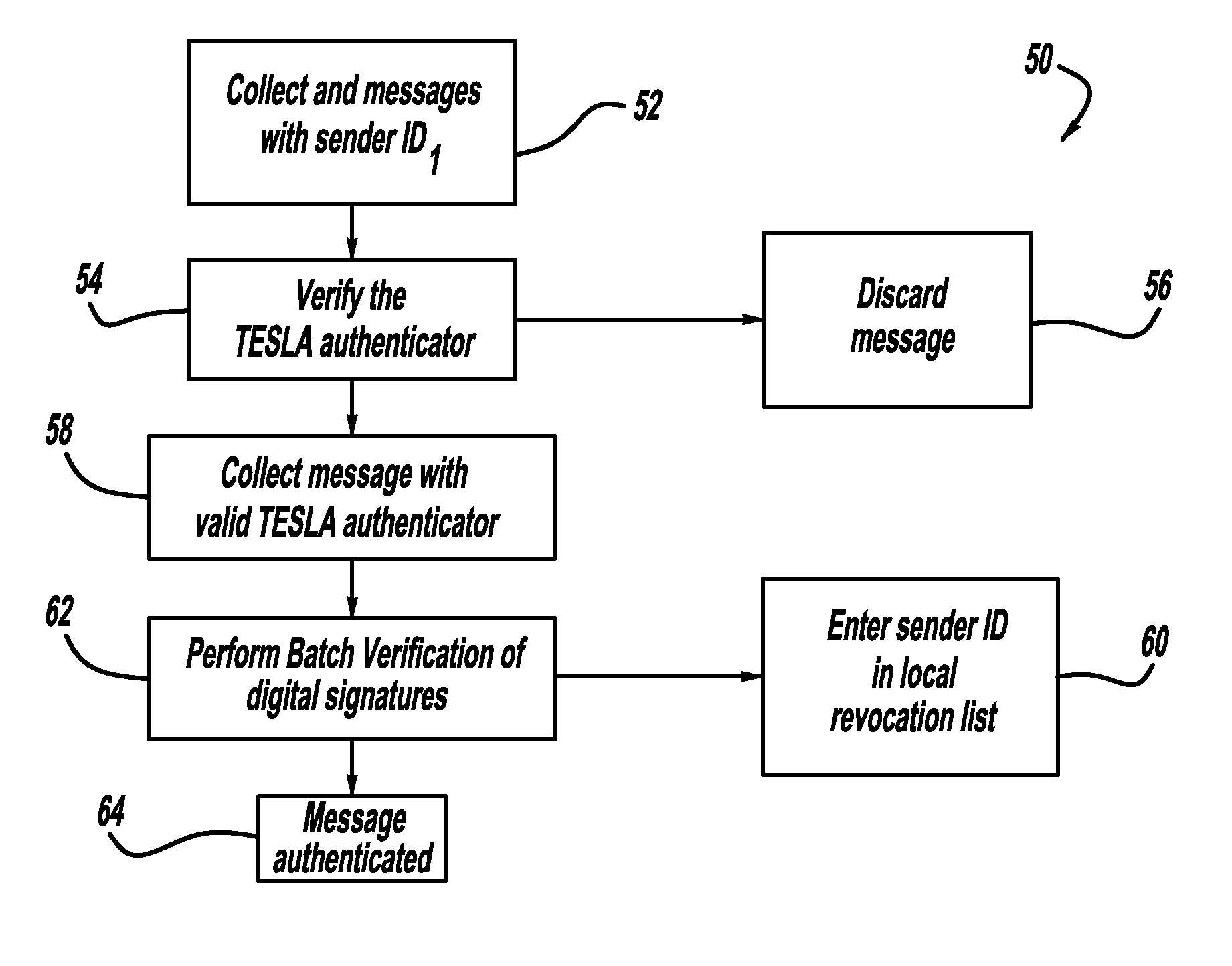
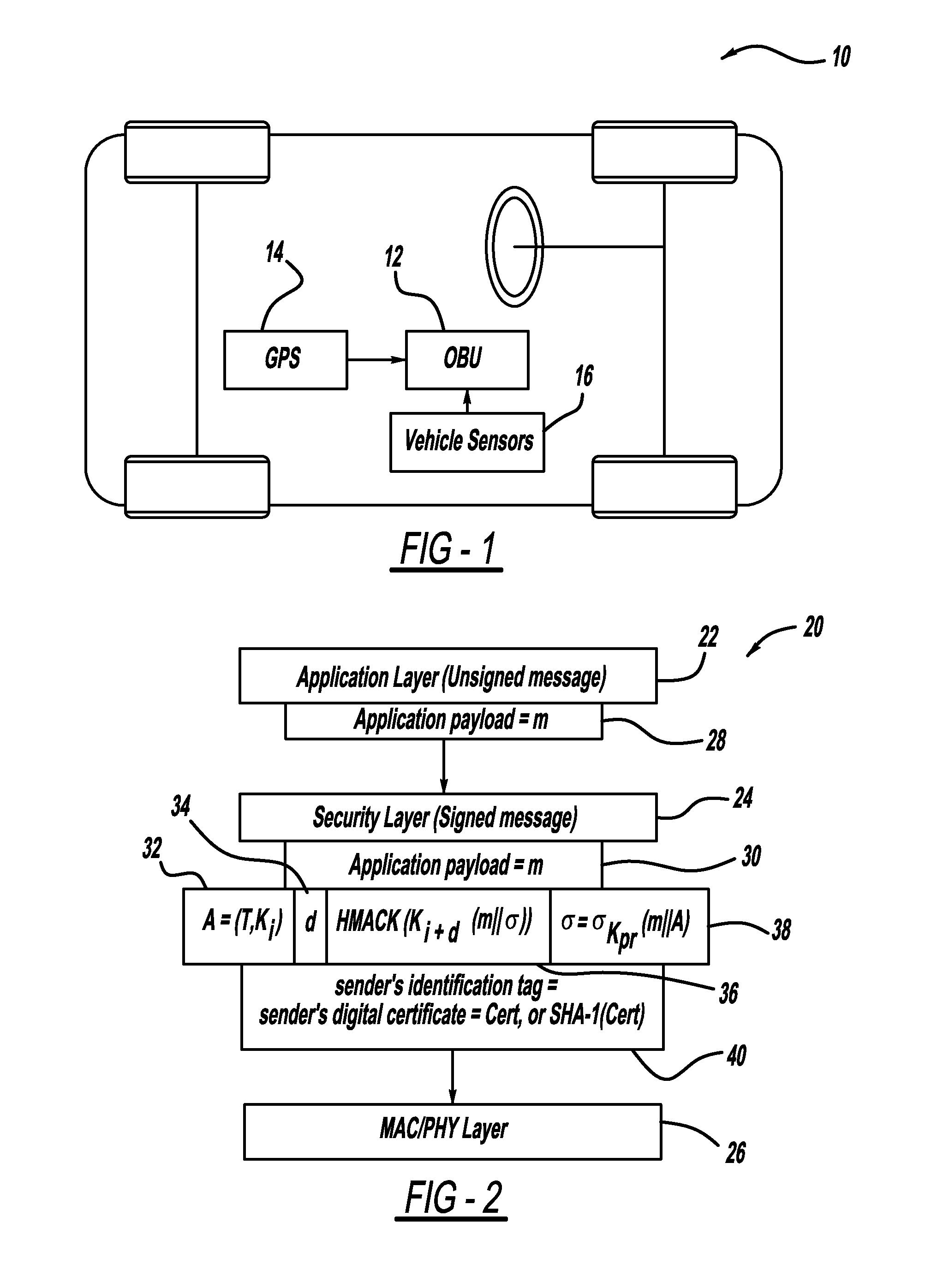
ActiveUS20110238997A1Multiple keys/algorithms usageRoad vehicles traffic controlDigital signatureNon-repudiation
A computationally efficient message verification strategy that achieves non-repudiation and resilience to computational denial of service attacks in conjunction with a broadcast authentication protocol that authenticates messages using a combination of a digital signature and a TESLA MAC. When messages are received at a receiver, the verification strategy separates the messages into messages with the same sender identification. The strategy then determines whether the TESLA MAC authenticator is valid for each message and discards those messages that do not have a valid TESLA MAC. The strategy collects the messages that have a valid TESLA MAC for each sender identification and performs a batch verification process on the group of messages to determine if the messages in the group have a valid digital signature. This strategy verifies each message in the group of messages if the batch verification process shows that the group of messages has a valid digital signature.
Owner:GM GLOBAL TECH OPERATIONS LLC
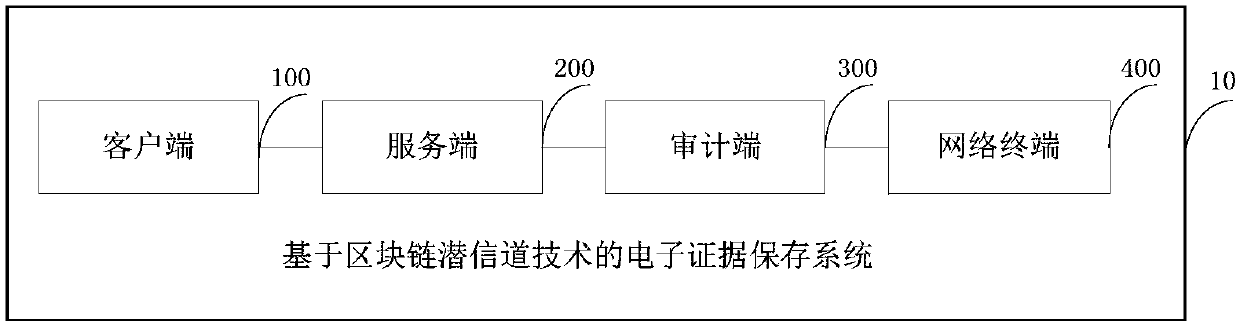
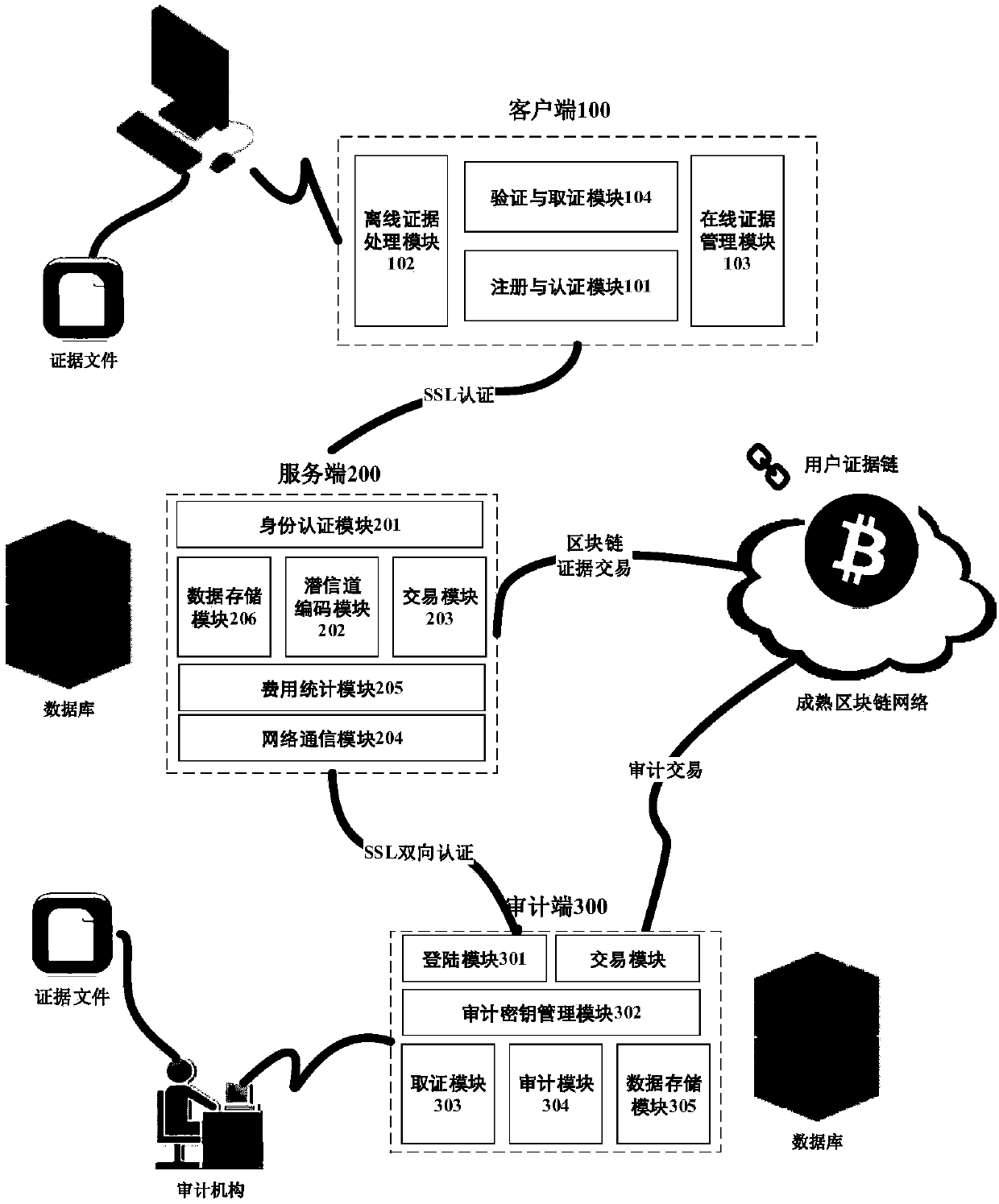
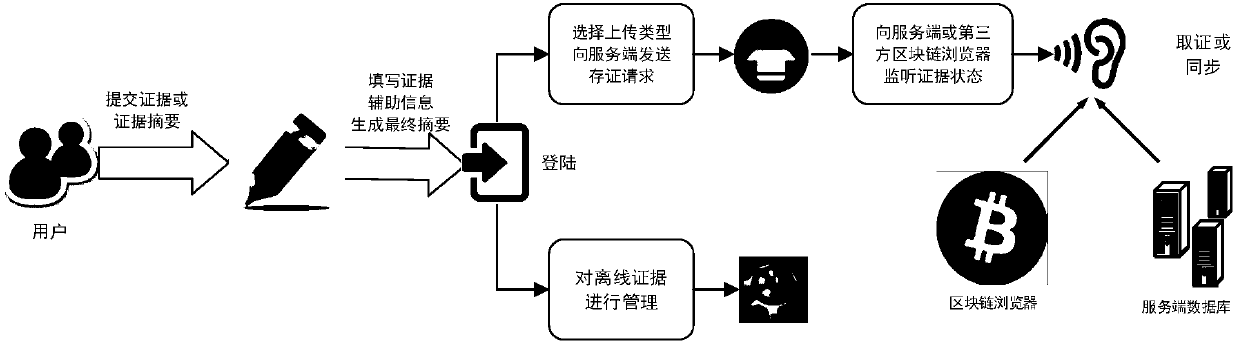
Electronic evidence preservation system based on block chain subliminal channel technology
ActiveCN107682308AAchieving processing powerAchieving covert storageDigital data protectionTransmissionNetwork terminationSubliminal channel
The invention discloses an electronic evidence preservation system based on a block chain subliminal channel technology, which comprises a client, a server, an auditing terminal and a network terminal, and is characterized in that the client is used for performing off-line acquisition and processing, online management and evidence collection on a user electronic evidence; the server generates an existence proof for the evidence and performs hosting and recovery on the chain evidence according to a user address; the auditing terminal is used for auditing the chain evidence, generating a corresponding transaction on a block chain and constructing an auditing proof so as to main the integrity, the timeliness and the non-repudiation of an auditing result; and the network terminal is used for performing state synchronization and real-time evidence collection on the user evidence on the chain. The system can dig a cryptographic basis of the subliminal channel preserved electronic evidence and the auditing result thereof in a mature block chain system, thereby realizing safe processing and hidden preservation for the electronic evidence, thus improving the safety and timeliness of electronic evidence preservation, and effectively reducing the preservation cost.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
Blockchain-based electronic evidence storing method and system and blockchain-based electronic evidence verifying method and system
InactiveCN108717431AEnhancing AdoptabilityGuaranteed legalityDigital data protectionSpecial data processing applicationsTamper resistanceData set
The invention relates to a blockchain-based electronic evidence storing method and system and a blockchain-based electronic evidence verifying method and system. The electronic evidence storing methodcomprises the steps of after an evidence storing person passes the identity authentication, forming an evidence storing data set according to an electronic evidence set formed by evidence collection,the identity information of the evidence storing person and an evidence storing time stamp; signing the evidence storing data set and submitting to a blockchain system by the evidence storing person;and generating a two-dimensional code through a smart contract, wherein the two-dimensional code comprises the certificate data set, the signature of the evidence storing person, the relevant information of an evidence storing transaction in a blockchain and a URL (Uniform Resource Locator) address pointing to the evidence storing transaction. The electronic evidence verifying method comprises the steps of after an evidence verifying person passes the identity authentication, scanning the two-dimensional code to view the relevant information; clicking on the URL to view the evidence storing transaction; and carrying out the consistency comparison of the electronic evidence set. The methods disclosed by the invention have the beneficial effects that the supporting information is added intothe electronic evidence set and the applicability of the electronic evidence is guaranteed; the storing of the electronic evidence set is carried out through the blockchain system and the tamper resistance of the electronic evidence is guaranteed; and the legality and the non-repudiation of the operators are guaranteed through the signature verification of the evidence storing person and the evidence verifying person.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Dynamic virtual network and method
InactiveUS20070033252A1Improve efficiencyMaximize compatibilityMultiple digital computer combinationsOffice automationBusiness-to-businessExchange network
A system and method of operating hardware and services to allow participating members to find and establish partnerships, communicate, transact business and share information. The dynamic virtual network comprises the business exchange network, the network authority and the access device. The present invention employs the network authority, a neutral body regulating the trading partners and playing a passive role qualifying participating businesses, ensuring security and integrity, and guaranteeing non-repudiation of business transactions. The access device provides a number of services facilitating direct business-to-business relationships, communications, and transactions. The dynamic virtual network can also provide a set of services giving structure and organization beyond that of the public internet. These services enable participating businesses to find prospective partners, arrange partnerships, communicate with their partners, transact business and share information via the internet, exclusively among partners. The invention provides software and hardware to satisfy the specialized demands of business-to-business commercial transactions.
Owner:AMTECH SYST
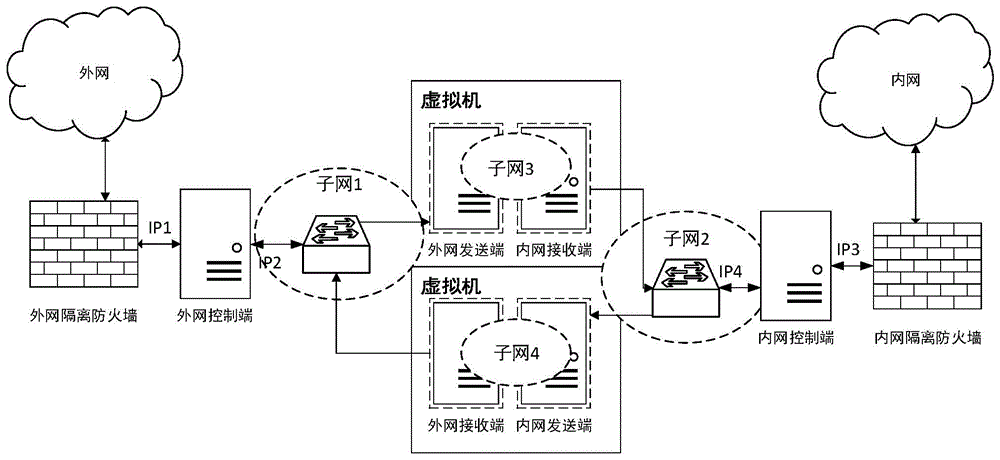
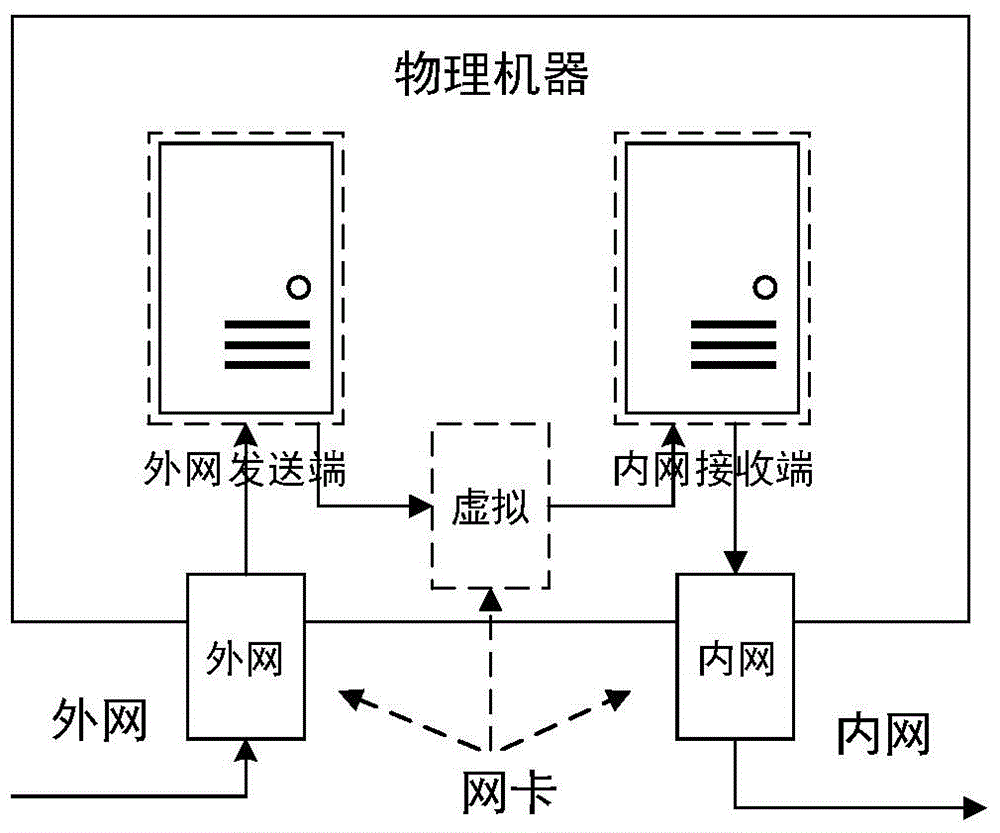
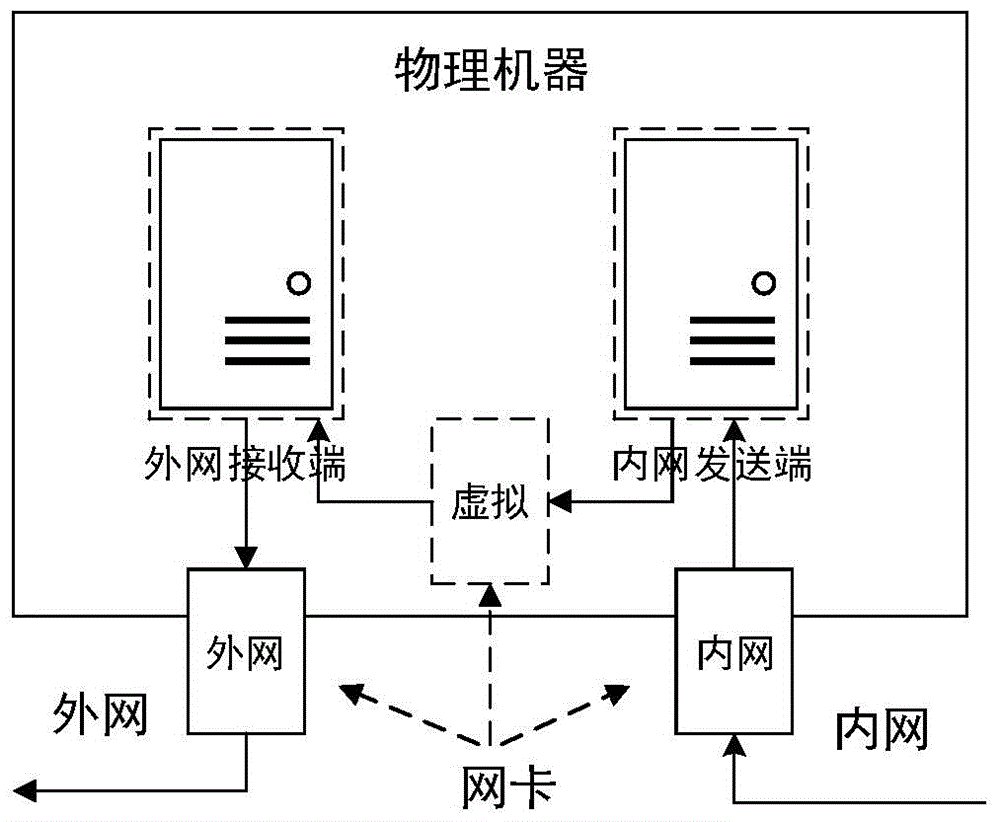
Network safety isolation file transmission control method
InactiveCN104363221AEnsure safetyKeep Content SafeSecuring communicationComputer hardwareConfidentiality
The invention relates to a safety isolation file transmission control method, in particular to a file transmission control method between taxation network safety isolation systems. A transmission control system comprises an external network isolation firewall, an external network control end, an external network transmitting end, an external network receiving end, an internal network transmitting end, an internal network receiving end, an internal network control end and an internal network isolation firewall. A computer system, a virtual machine system and the isolation firewalls are combined to achieved a relatively universal safety data transmission manner, safe and reliable bidirectional data transmission is achieved by the control method with a special safety protocol, confidentiality, completeness and non-repudiation during information transmission are achieved by safety techniques such as data encryption, digital signatures and information authentication codes, data exchanging performance is increased while safety of internal and external network systems is guaranteed, and the whole system can work reliably and stably.
Owner:QINGDAO WEIZHIHUI INFORMATION
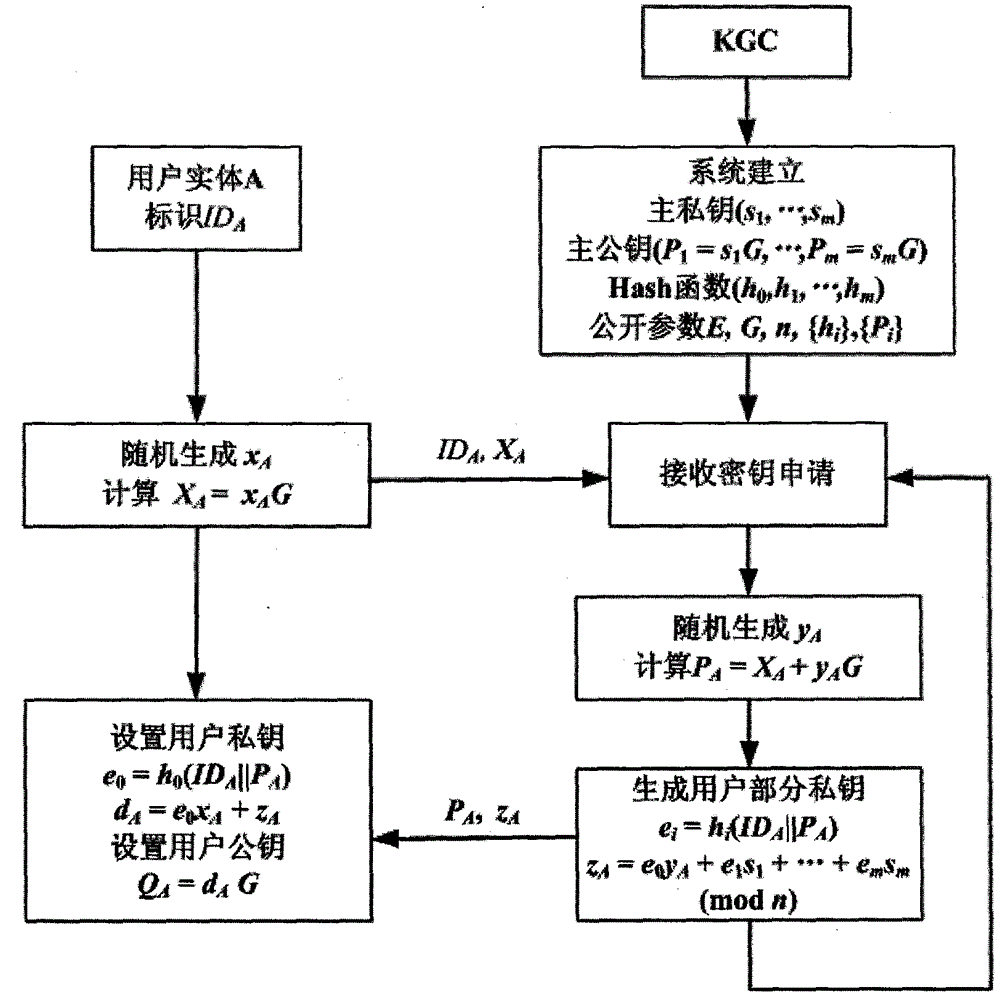
Achievement method of certificate-less public key cryptosystem without bilinear pairing operation
ActiveCN104539423AEfficient managementImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCommunications securityInformation security
The invention provides an achievement method of a certificate-less public key cryptosystem without bilinear pairing operation and belongs to the field of information safety. The achievement method is used for solving the problems of generation of a secret key of a user, usage and authentication of a public key of the user. According to the achievement method, firstly, a user sets a secret value and calculates a temporary public key, then a secret key generating center generates the other part of the secret key for the user and enables the two parts to be bound, and finally the user synthesizes a his / her actual public and secret key pair. The defect that public key replacement and signature counterfeit possibly exist in a common certificate-less cryptosystem is overcome, the user has complete control right on the secret key, the secret key can be revoked and re-generated, and the signature of the user has non-repudiation. The achievement method adopts a public key cryptographic algorithm of a standard elliptic curve, does not adopt the bilinear pairing operation, is few in occupied resources and high in safety and can operate without the secret key generating center when being applied to signature, authentication and secret key negotiation. By means of the achievement method, identity authentication, communication security and non-repudiation application demands of large-scale systems and low-power-consumption devices can be met.
Owner:北京百旺信安科技有限公司 +1
Secure prescription computer
InactiveUS20080112615A1Reduce usagePaper-money testing devicesDrug and medicationsDocument preparationMedical prescription
A method to secure unique information about a handwritten document and to provide verification of document's authenticity, integrity and non-repudiation. The method includes the following steps: creating a document having an area of interest containing information, segmenting the area of interest on the document into a plurality of elements, obtaining the average gray scale of each element, inserting the average gray scale of each element into an identifier, and attaching the identifier to the document.
Owner:PITNEY BOWES INC
Transaction using a mobile device with an accelerometer
Embodiments of the invention may use a first accelerometer to measure first acceleration data of a first device. Other interaction data, including time data and geographic location data, generated by the first device may also be recorded. First acceleration data is compared by a remote server computer to second acceleration data generated by a second accelerometer in a second device. If the first and second accelerometer data are substantially equal, it can be determined that the devices have interacted and communications can be initiated. After communications are initiated, a financial transaction is conducted. Accelerometer data may be stored and / or used as part of the authentication process in a payment processing network. Other embodiments of the invention use the accelerometer to generate movement security data to make financial transaction more secure. Accelerometer data is used for authentication, security, encryption, session keys, non-repudiation, or fraud protection.
Owner:VISA INT SERVICE ASSOC
Internet of Vehicles distributed authentication method based on controllable privacy
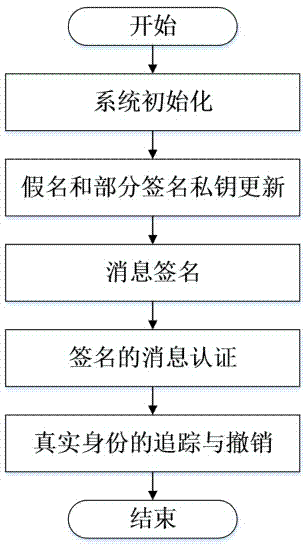
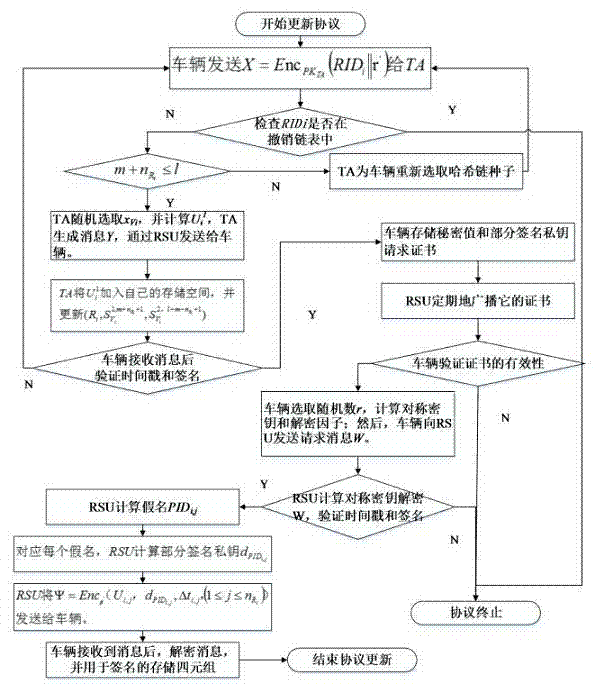
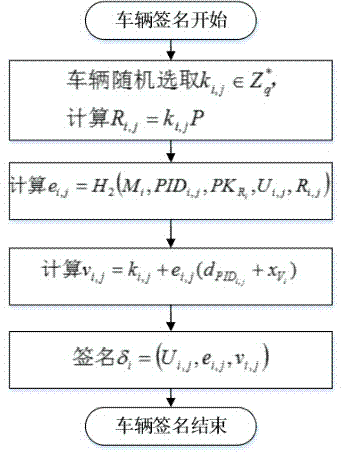
InactiveCN104853351AReduce the burden onSolve the problem of non-repudiationSecurity arrangementTrusted authorityStructure of Management Information
The invention discloses an Internet of Vehicles distributed authentication method based on controllable privacy, relates to the field of vehicle network communication safety, and specifically relates to an Internet of Vehicles distributed authentication method based on controllable privacy. The method specifically includes five following steps: system initialization; private key update of fake names and a part of signatures; message signature; message authentication of signatures; and real identity tracking and revocation. According to the method, the double hash chain is employed to establish the fake names, the communication cost for invalidating a vehicle identity is irrelevant to the numbers of the fake names and a part of the signature private keys of the vehicle, a vehicle user can update multiple parts of signature private keys by the adoption of one authorization, and the burden of trusted authority (TA) and road-side units (RSU) is reduced; when a message with a controversial signature occurs, the TA can distinguish whether the signature is forged by the RSU according to re-signature of the message uploaded by the vehicle, and the problem of non-repudiation in the distributed environment is solved. According to the method, the security is high, the cost is low, and the method is applicable to node high-speed movement, topology structure volatility, and large-scale VANET network.
Owner:JIANGSU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com