Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
61results about How to "Improve user security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
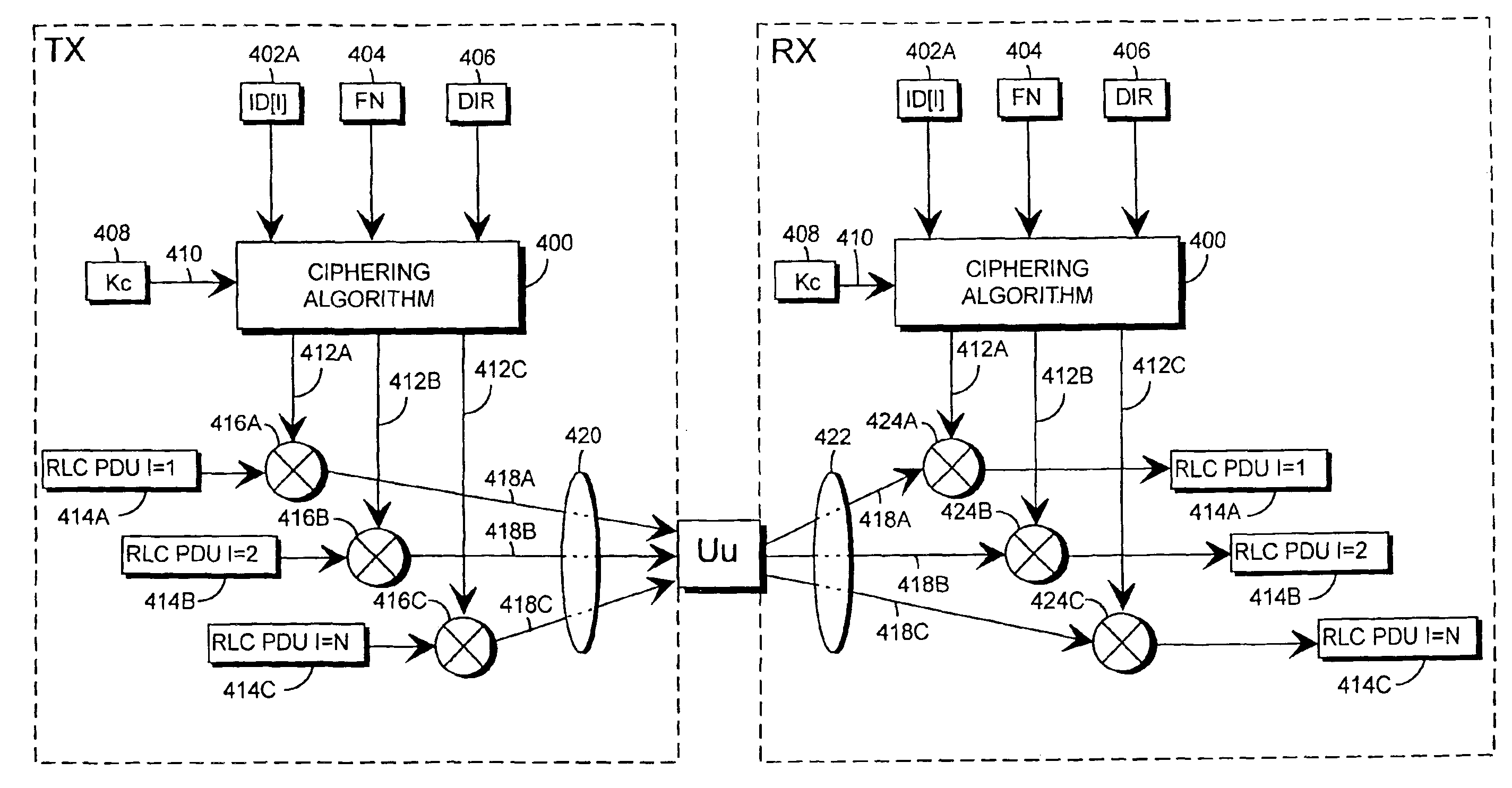
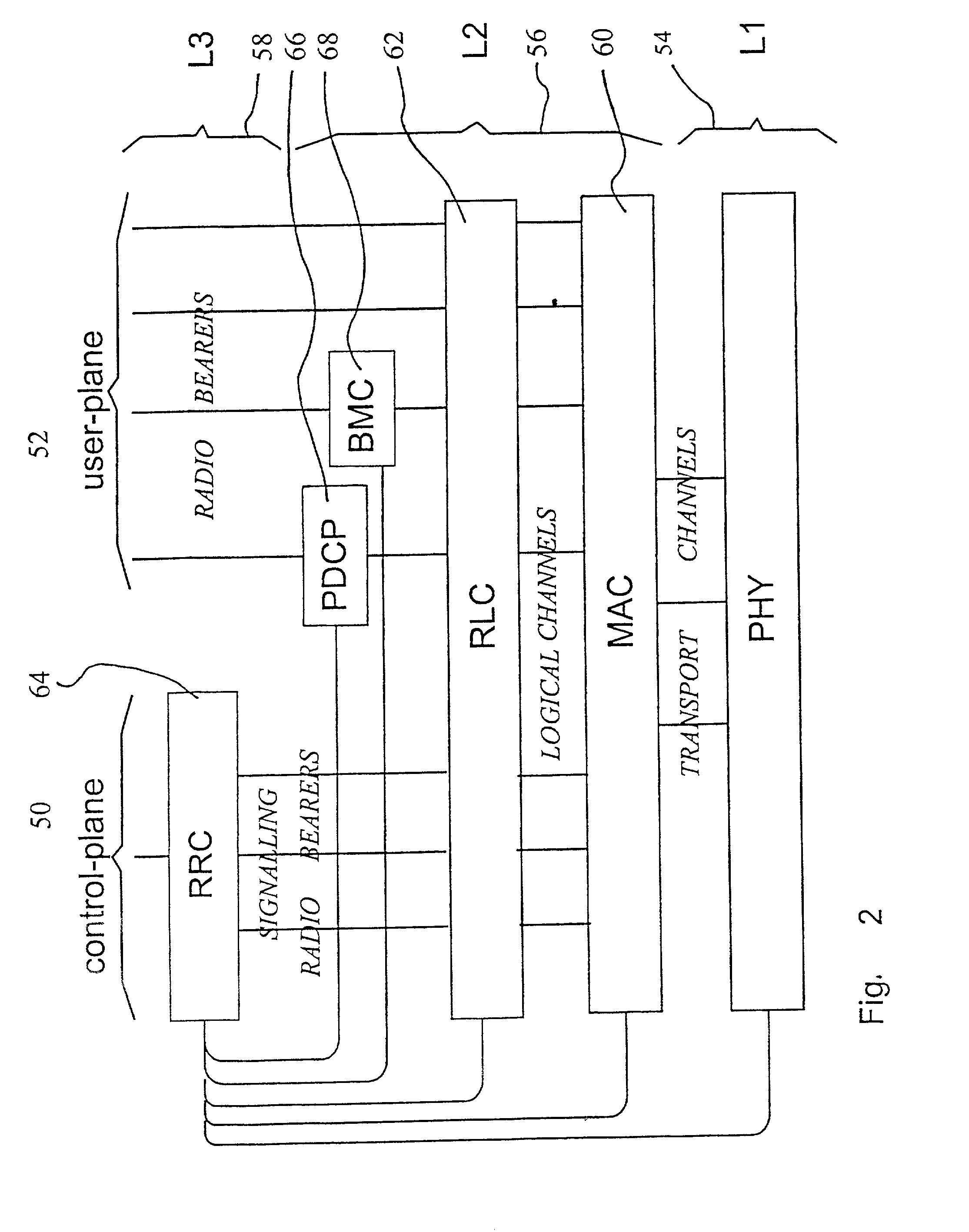
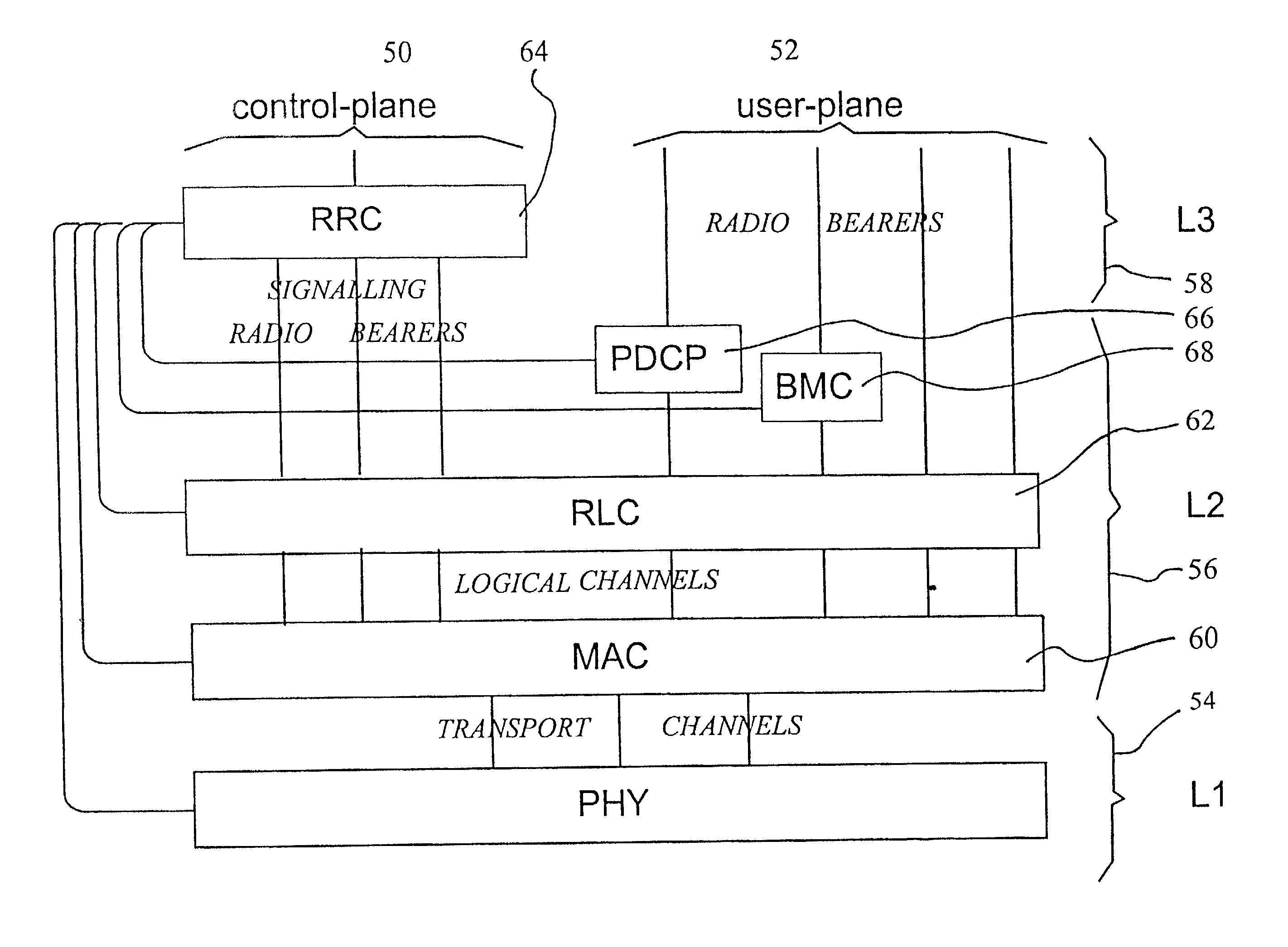
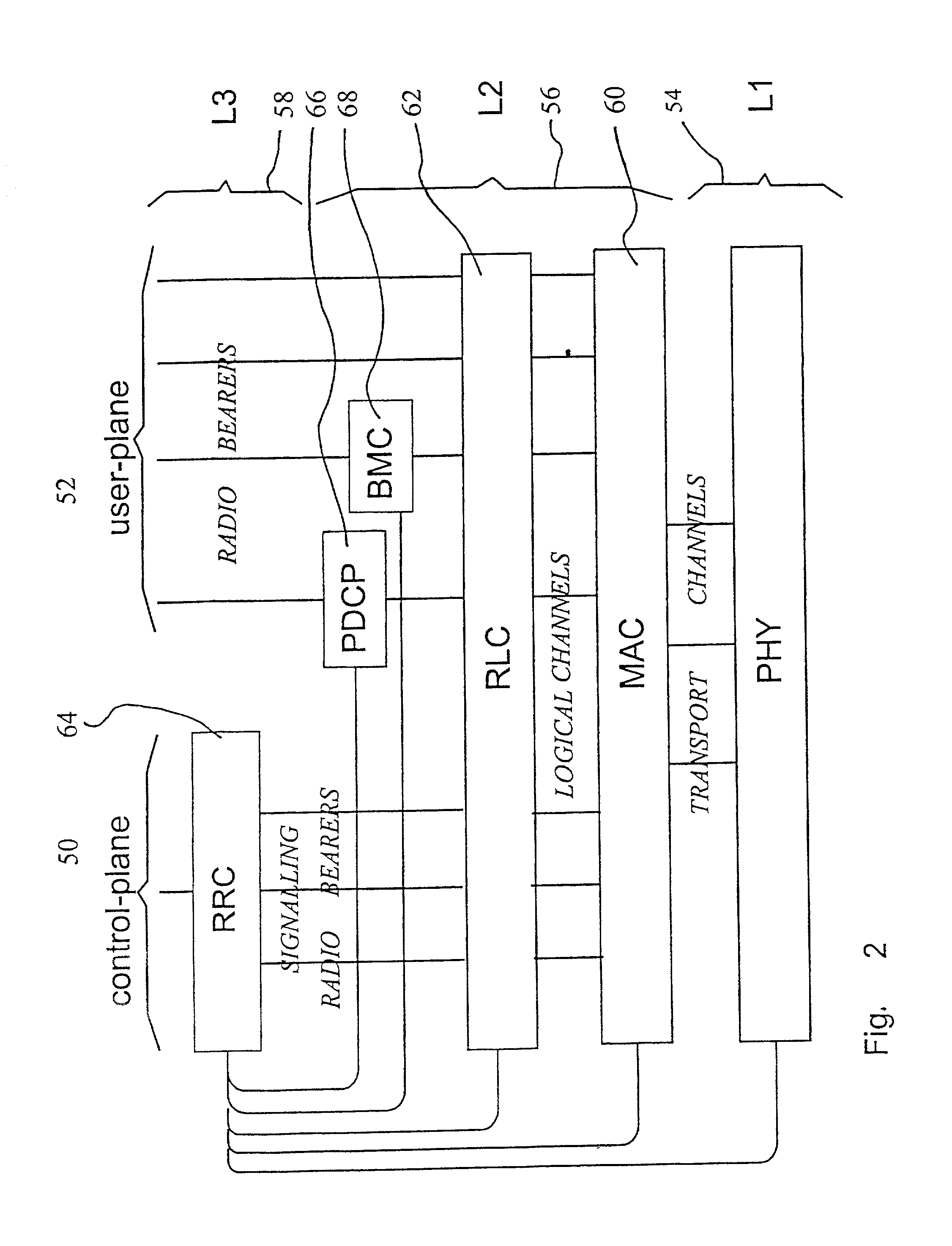
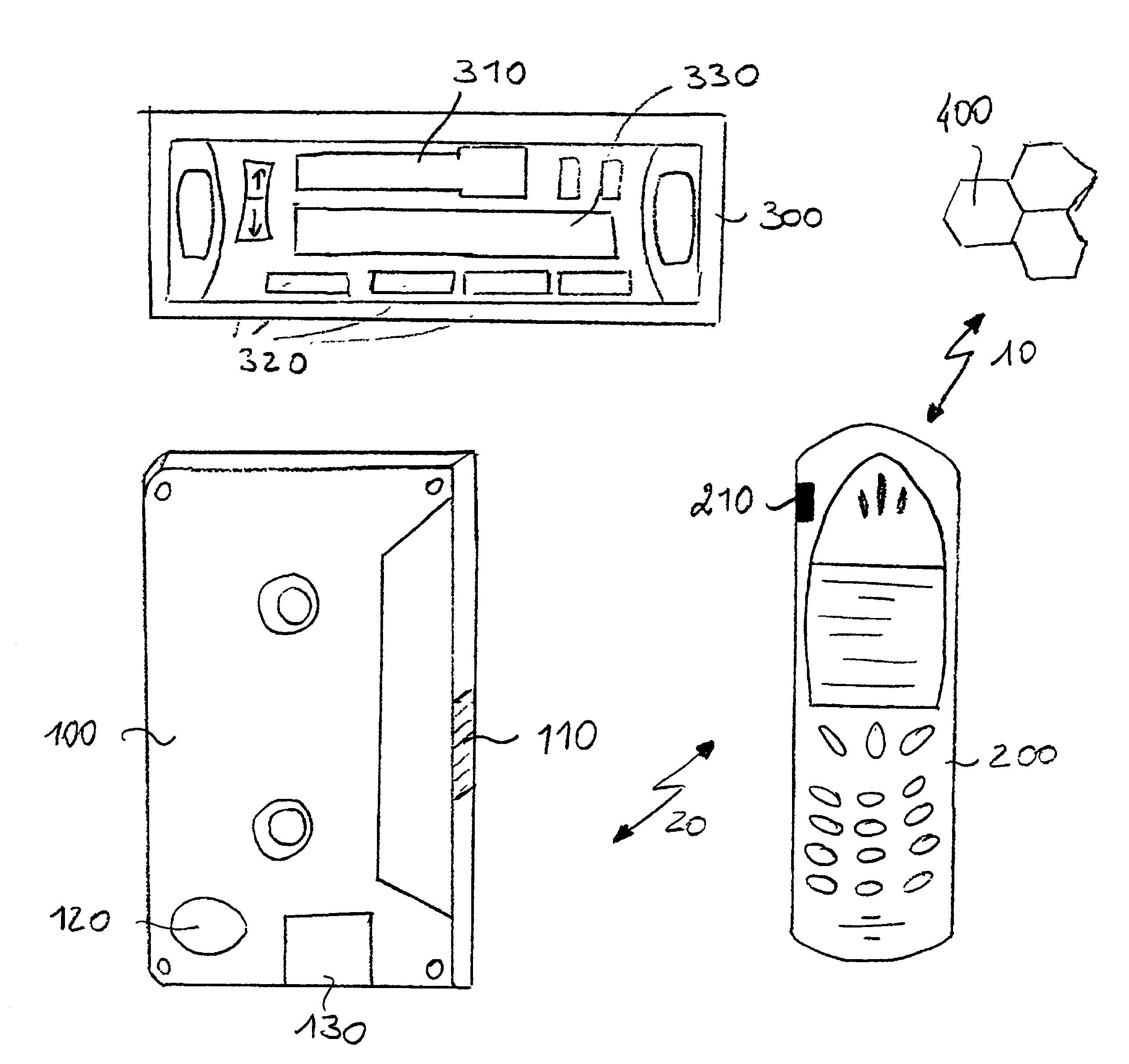
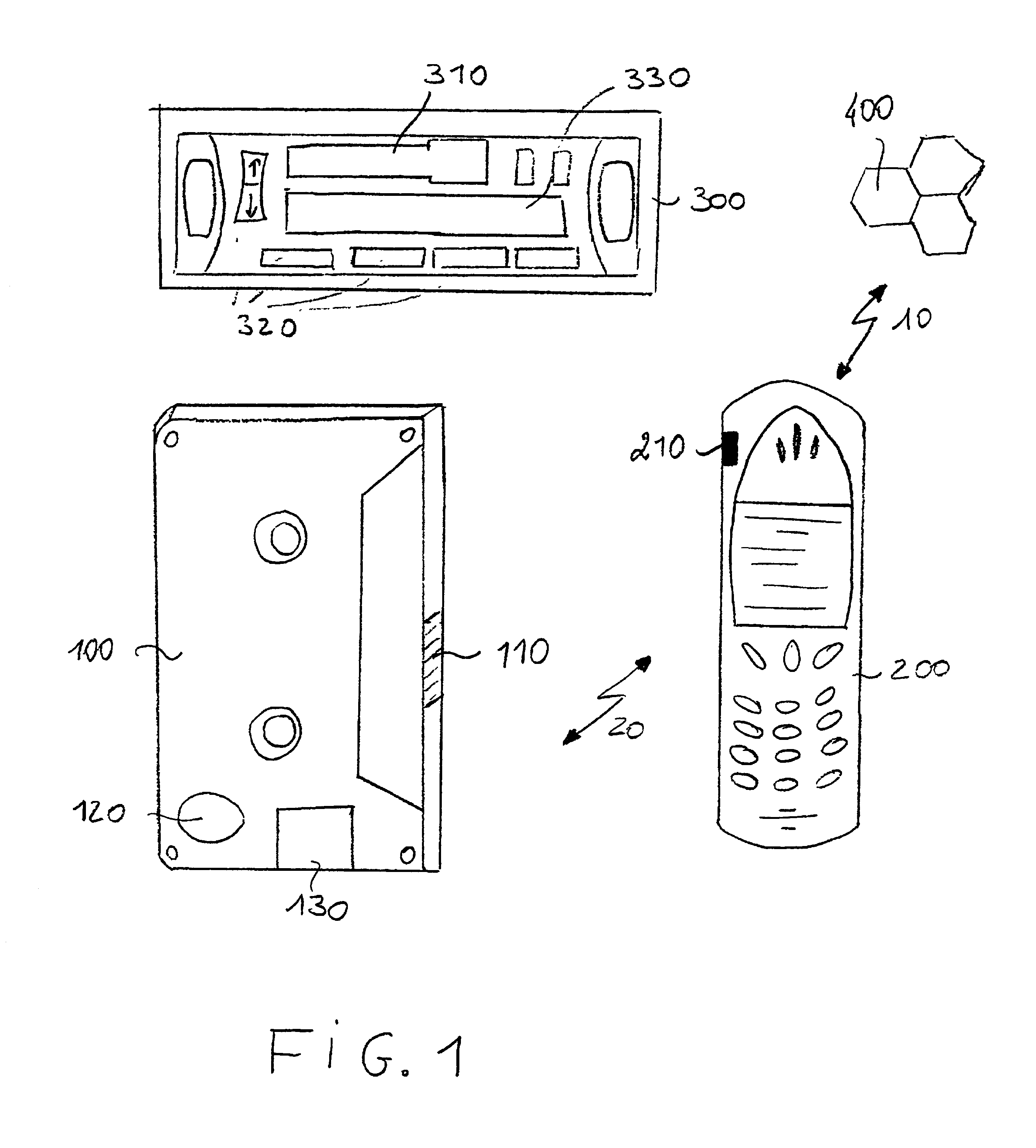
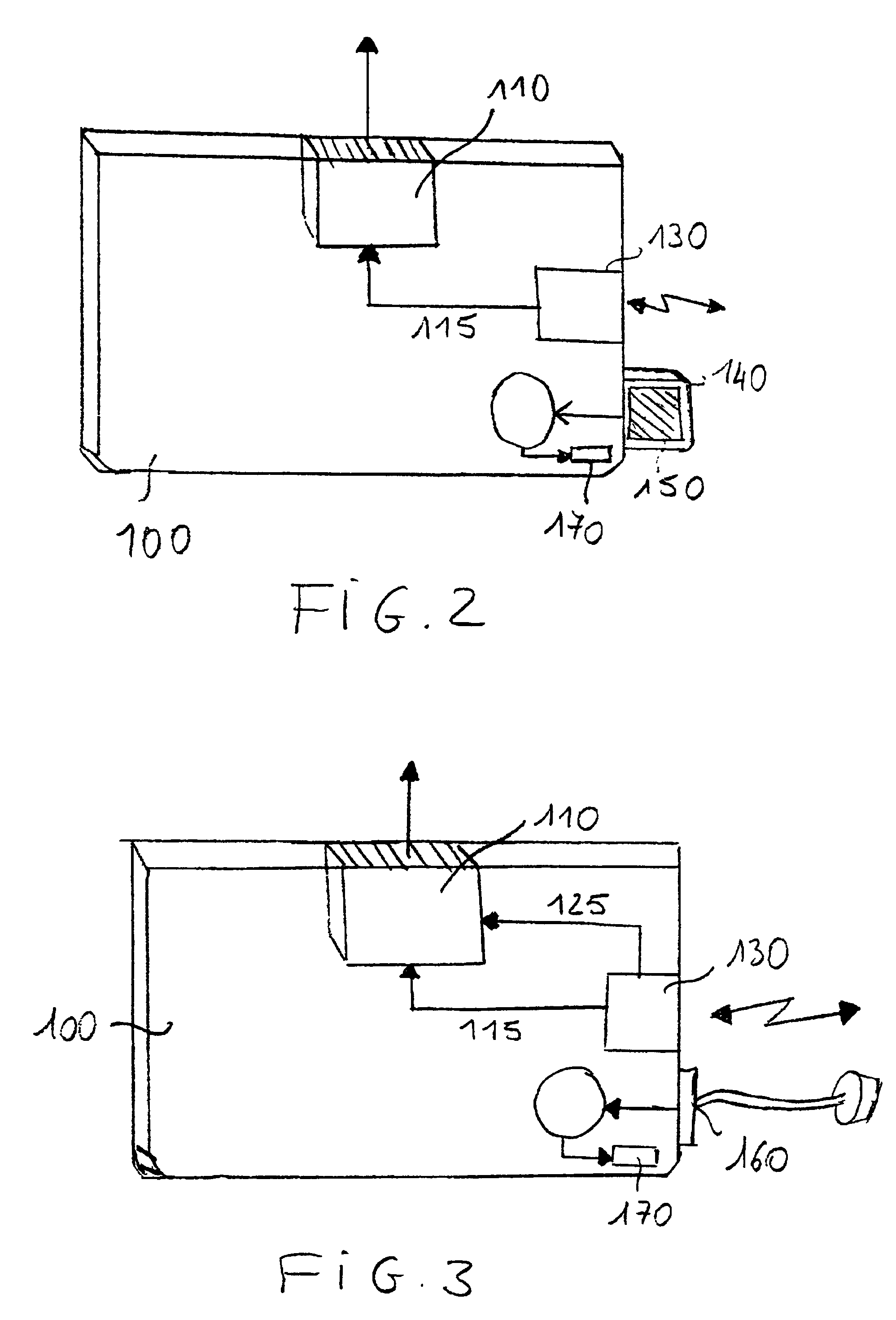
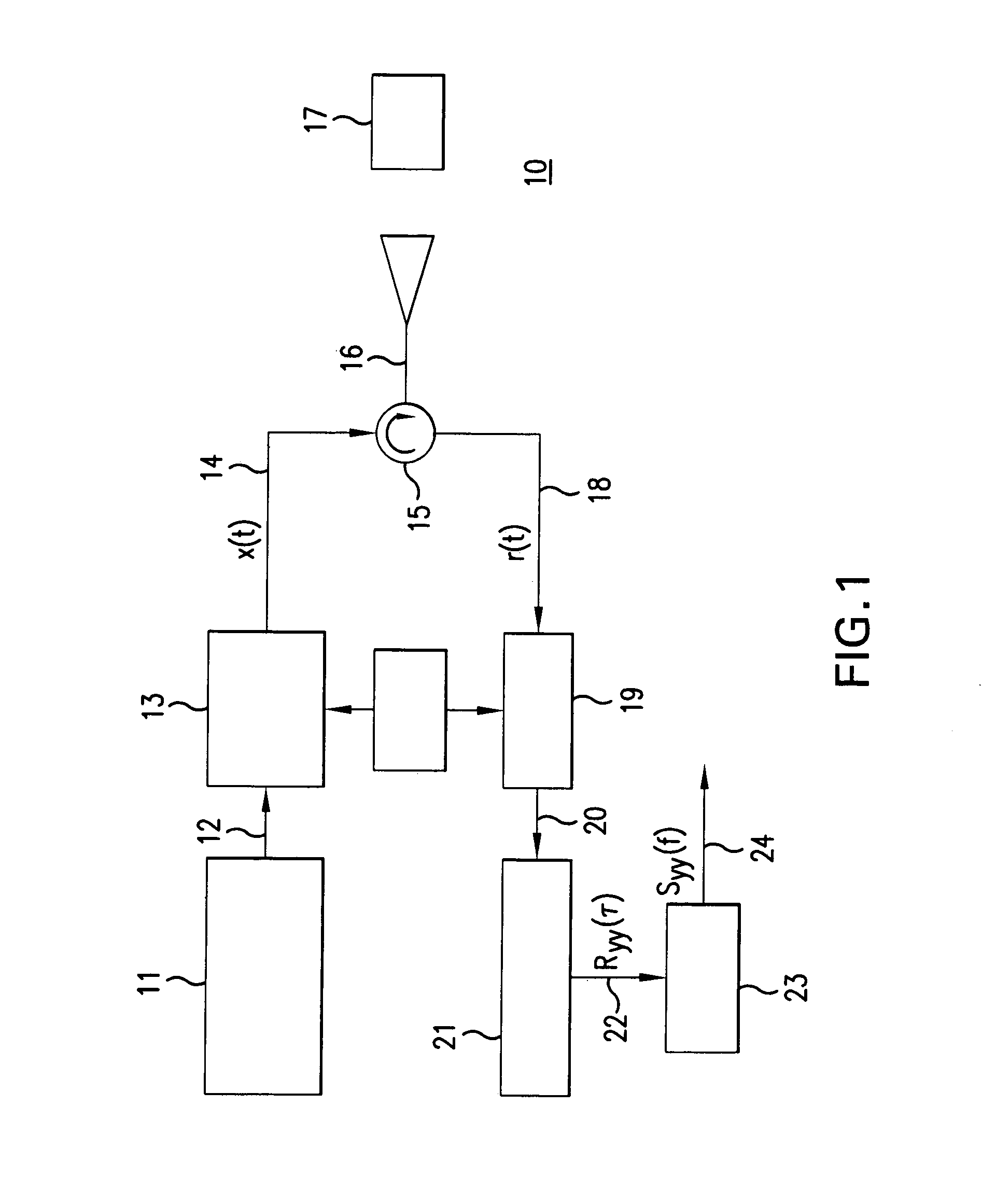
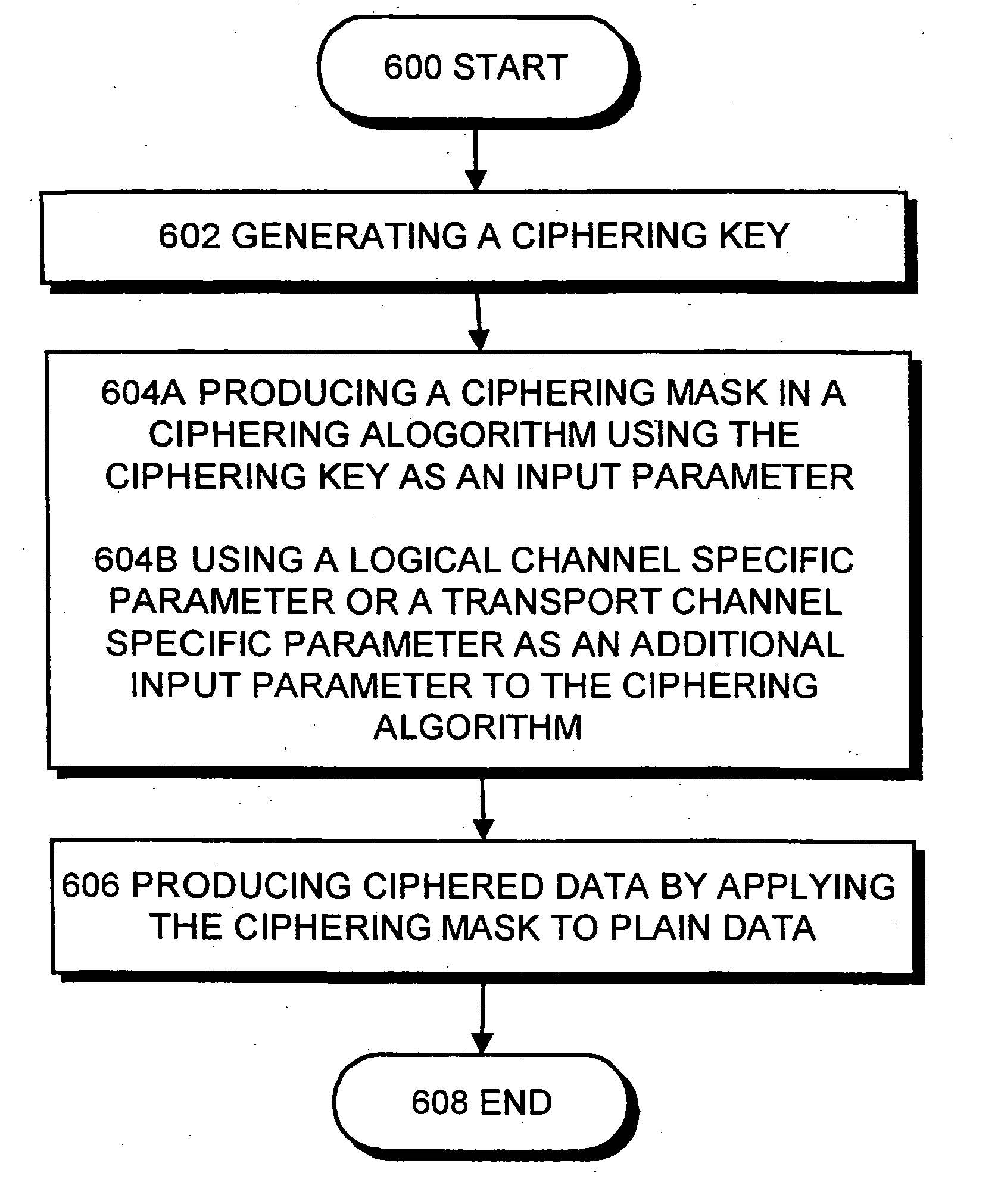
Method of ciphering data transmission in a radio system
InactiveUS6882727B1Enhance user securityFlexibly controlData stream serial/continuous modificationRadio/inductive link selection arrangementsData transmissionRadio networks
The invention relates to a method of ciphering data transmission in a radio system, and to a user equipment using the method, and to a radio network subsystem using the method. The method includes the steps of: (602) generating a ciphering key; (604A) producing a ciphering mask in a ciphering algorithm using the ciphering key as an input parameter; (604B) using a logical channel specific parameter or a transport channel specific parameter as an additional input parameter to the ciphering algorithm; and (606) producing ciphered data by applying the ciphering mask to plain data.
Owner:NOKIA TECHNOLOGLES OY
Integrity check in a communication system
InactiveUS20020044552A1Improve user securityPrevent replay attacksError preventionTransmission systemsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
Owner:NOKIA TECHNOLOGLES OY
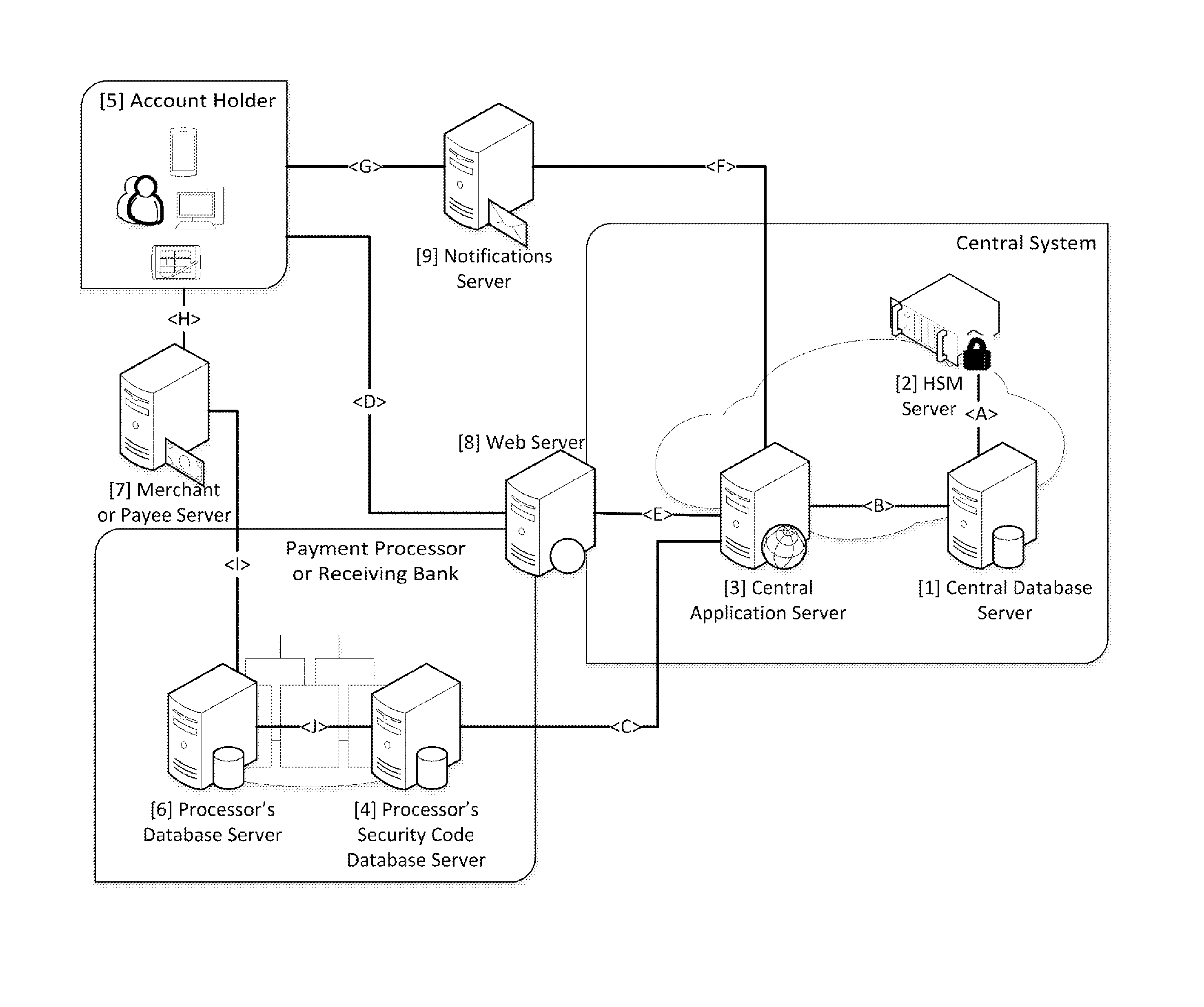
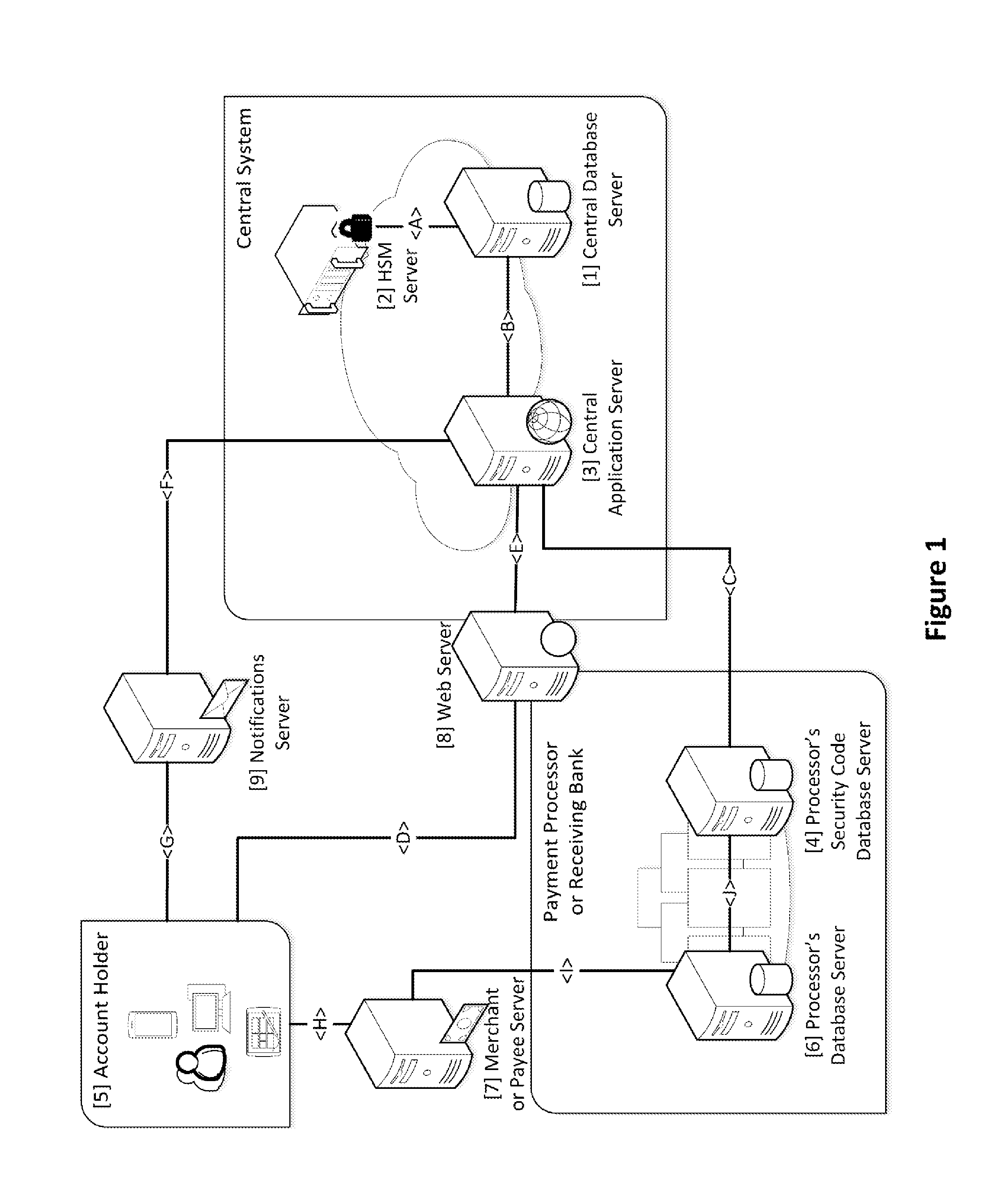
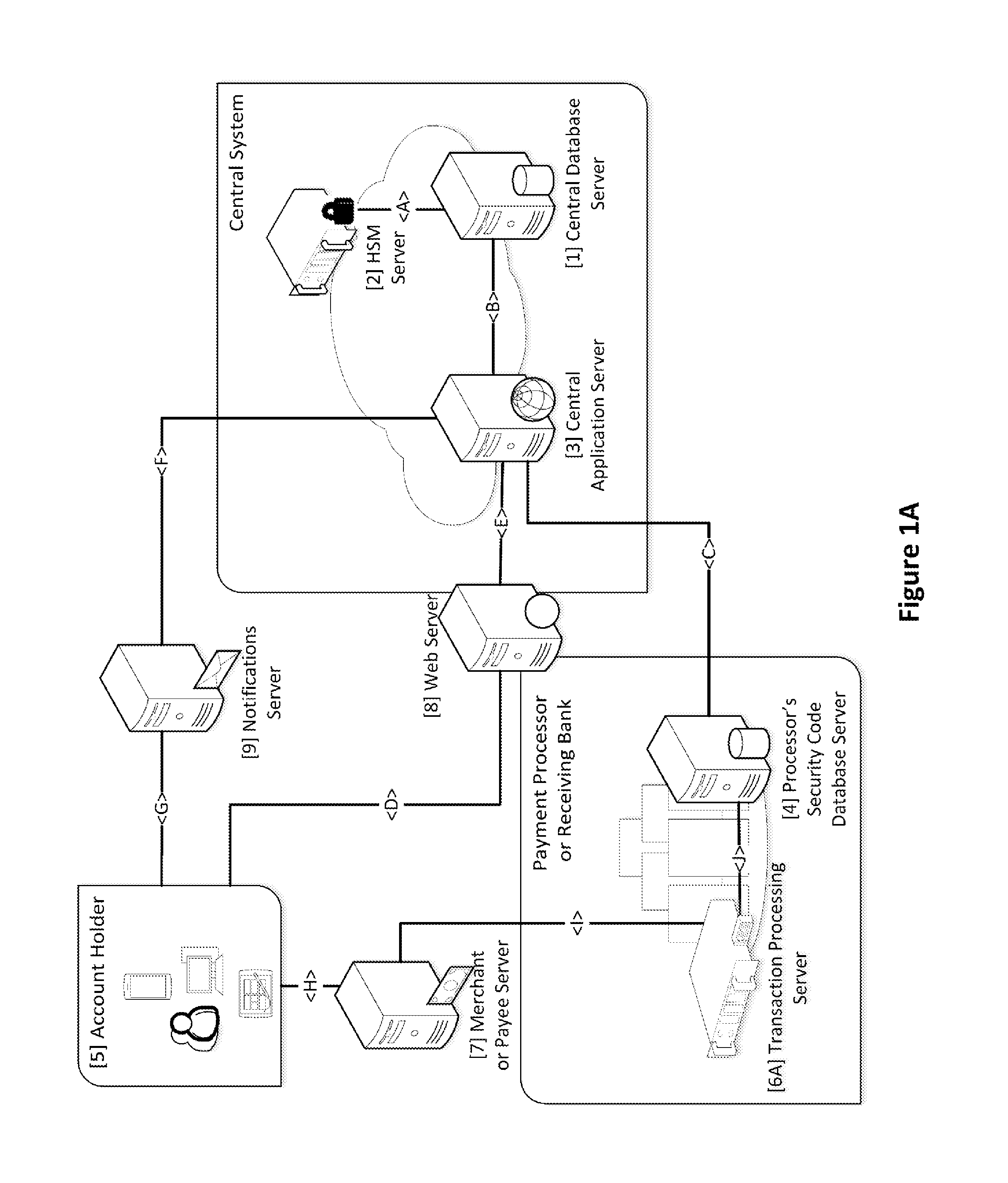
Security for electronic transactions and user authentication
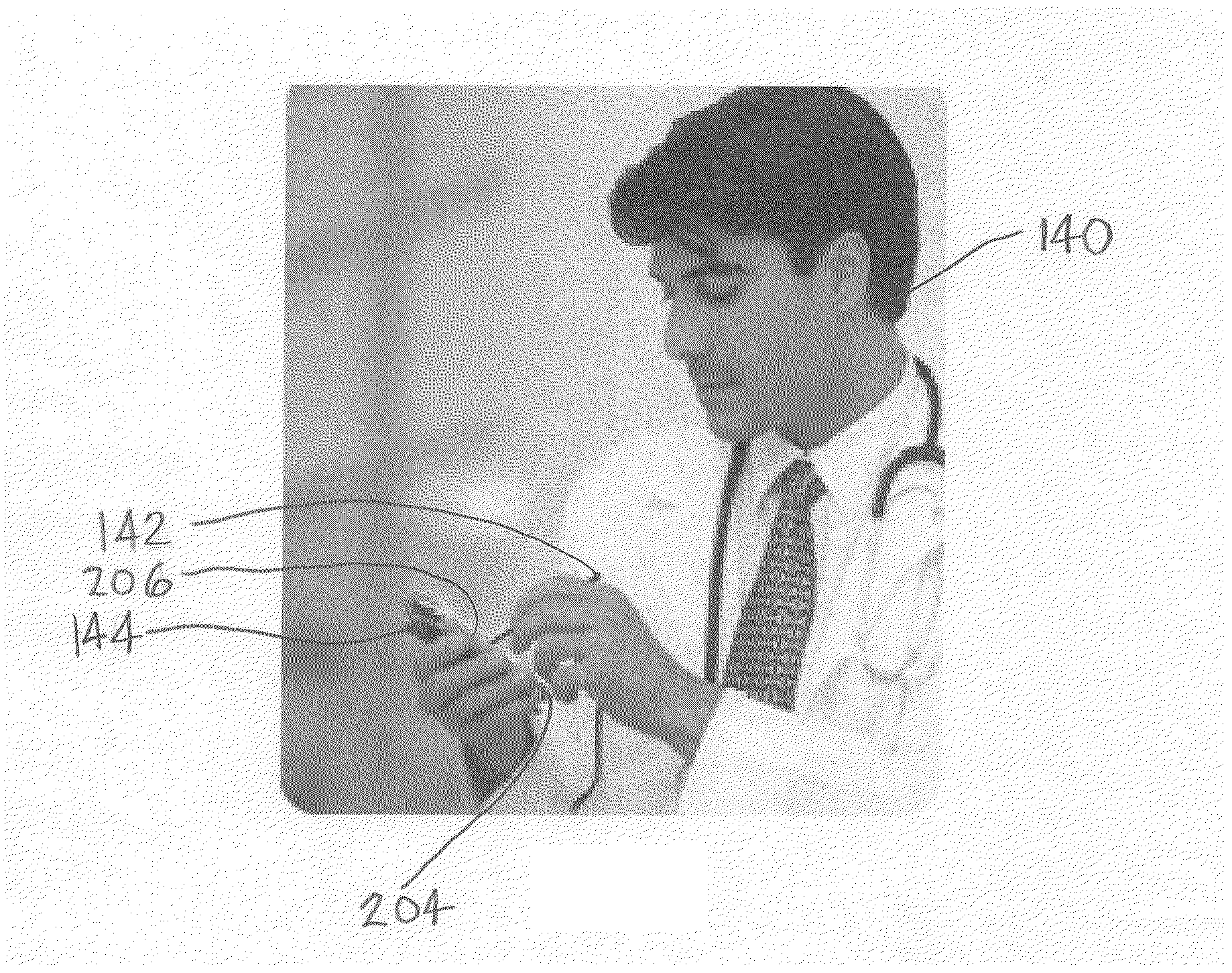
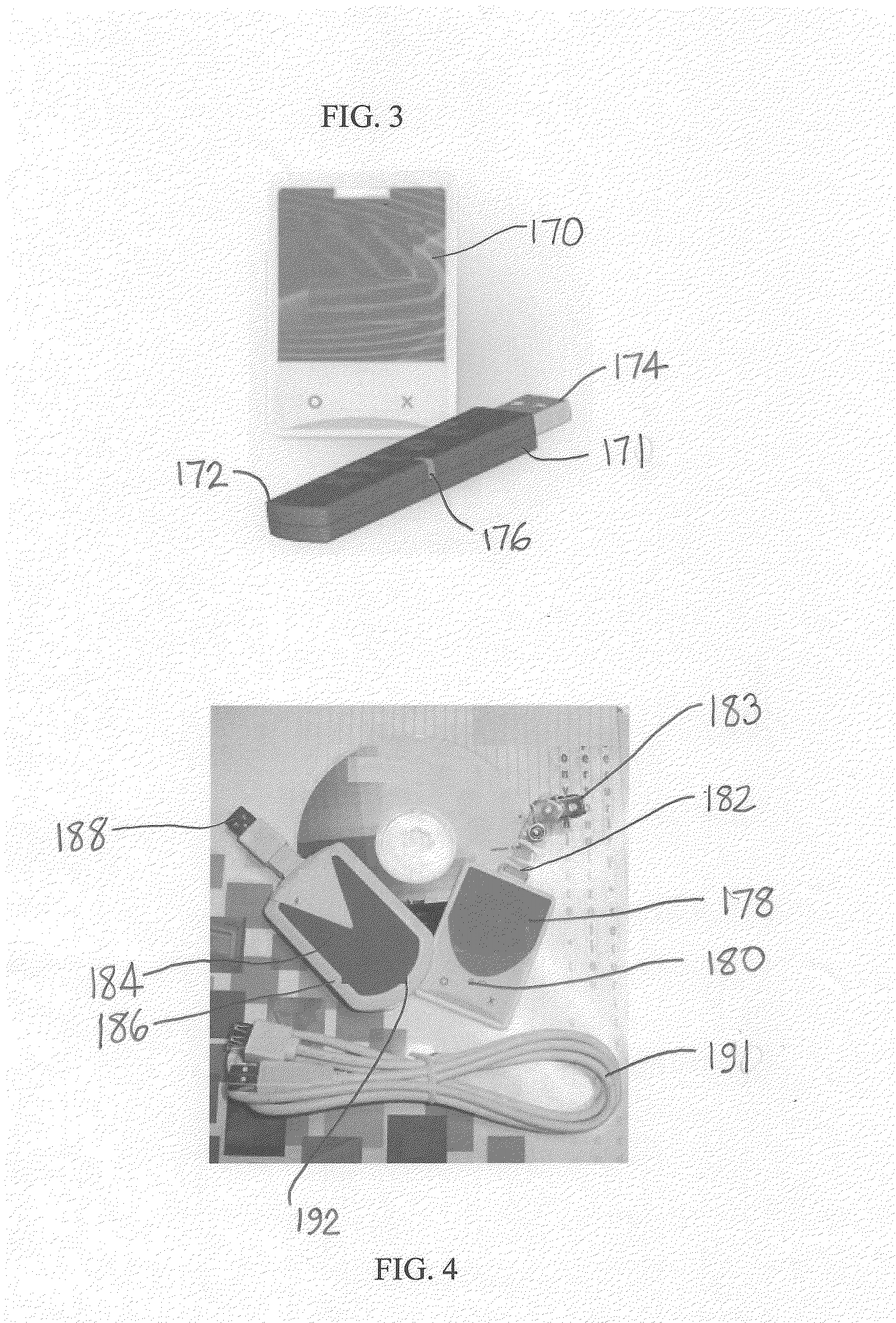
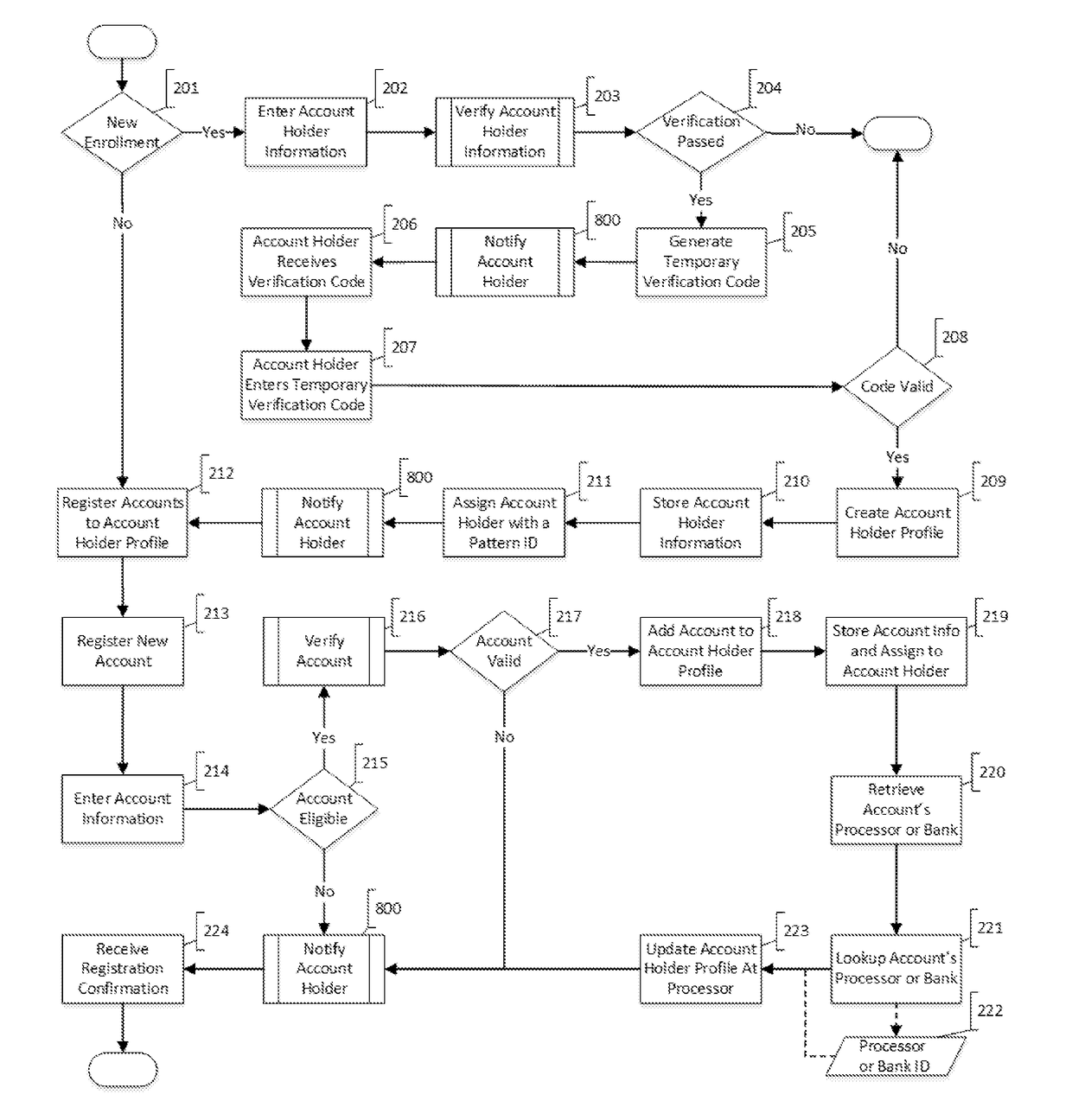
InactiveUS20170004506A1Increase randomnessImprove user securityCryptography processingProtocol authorisationUser authenticationPayment transaction
System and method for generating, disseminating, controlling, and processing limited-life security codes used to authenticate users, particularly for electronic financial transactions, such as payment transactions or interacting with automated teller machines and the like. Providing a user with a single security code usable across multiple accounts or other secured systems is contemplated, each security code having a limited lifetime (e.g., one day). In a particular example of the present invention, a plurality of similarly situated users (each needing authenticated access to a plurality of accounts or other secured systems using the security code) are each assigned a set or group of respective security codes. In a preferred example, each security code is a random number from a random number generator. The respective security codes for each user correspond to a respective security code validity period of limited duration. Thus, a table or matrix that associates the plurality of users with the respective sets of randomly selected security codes (each having their respective validity periods) is generated, and that matrix is provided to the respective entities (such as banks, payment processors, computer networks generally, etc.) to which each user requires secured access. In parallel, at least a current security code (for example, for the current validity period) is provided to each user, and this is how the respective entities being accessed can track which code from which user is currently valid.
Owner:TENDER ARMOR LLC
Integrity check in a communication system
InactiveUS7009940B2Improve user securityPrevent replay attacksError preventionFrequency-division multiplex detailsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
Owner:NOKIA TECHNOLOGLES OY
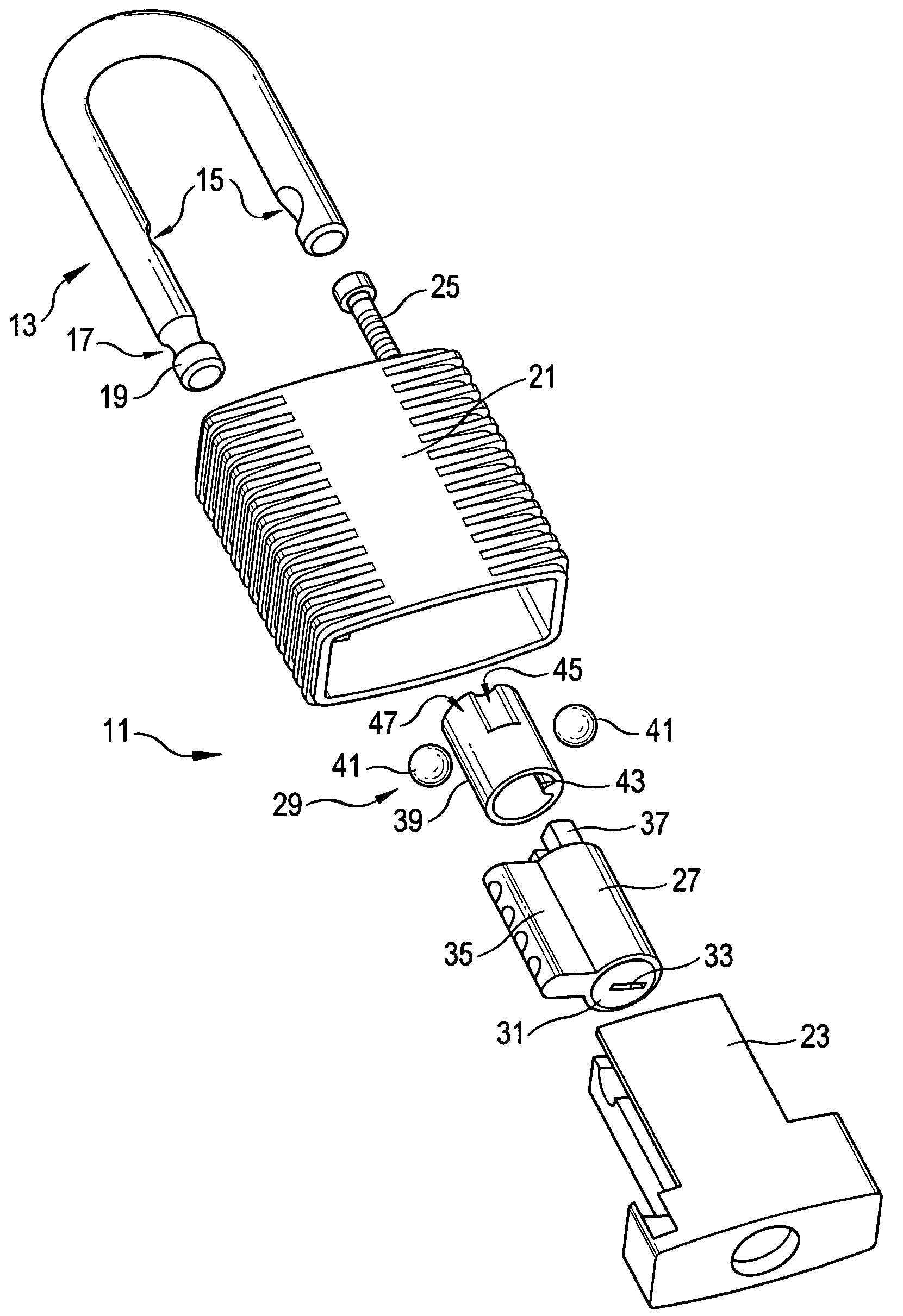
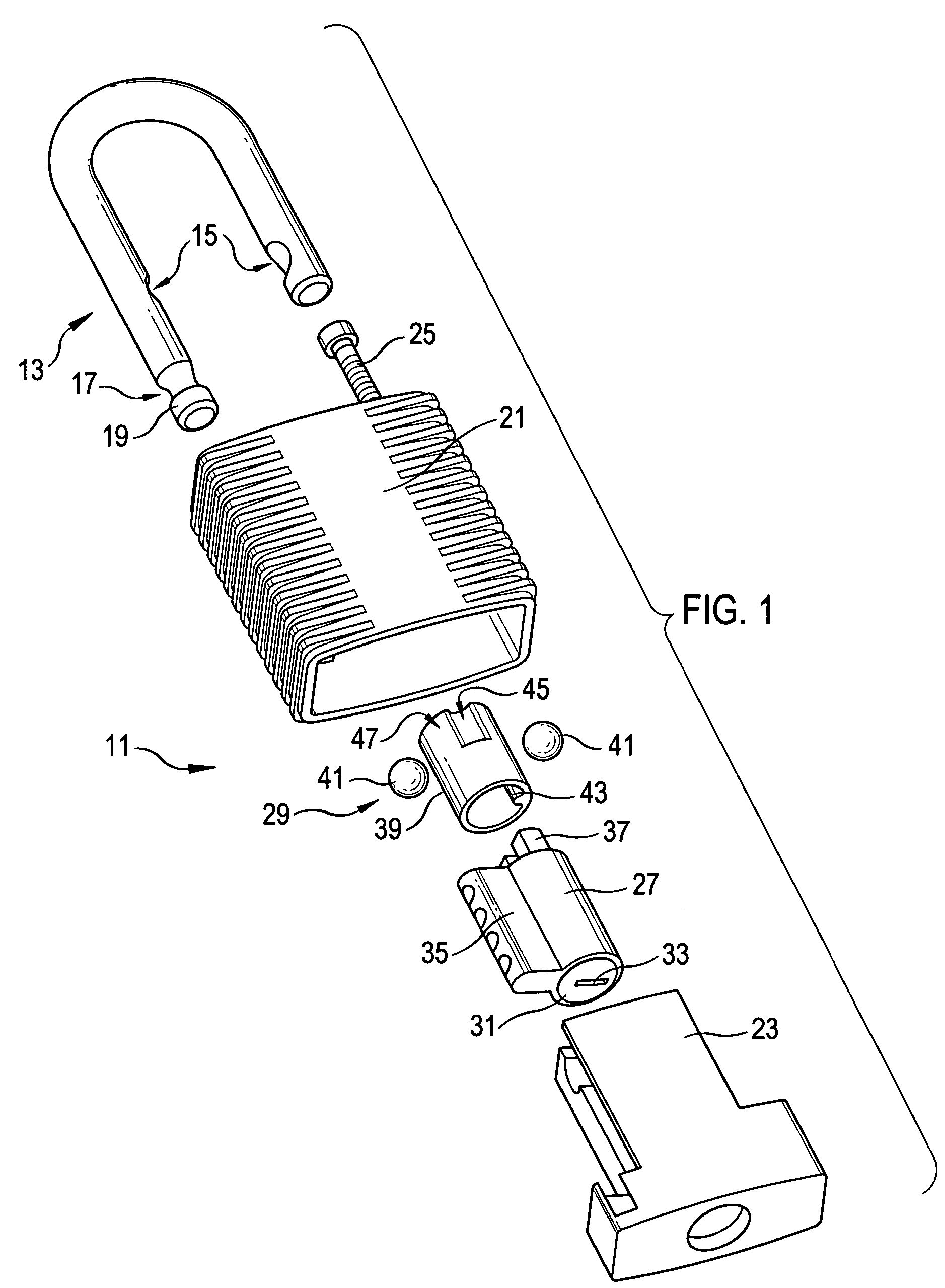
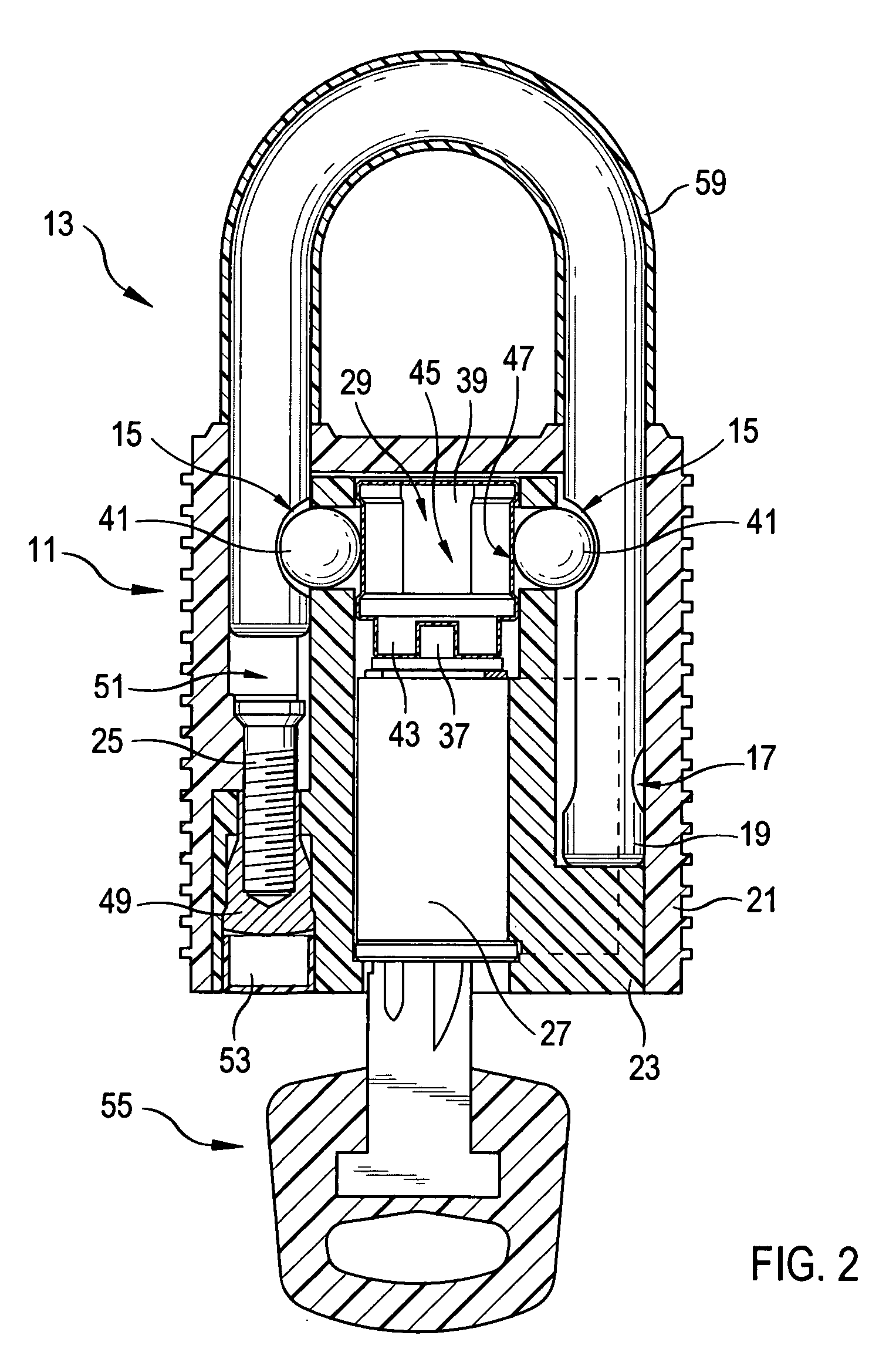
Padlock
ActiveUS7278283B2Improve mechanical stabilityImprove guidancePadlocksCarpet fastenersEngineeringElectrical and Electronics engineering
Owner:ABUS AUGUST BREMICKER SOEHNE AG
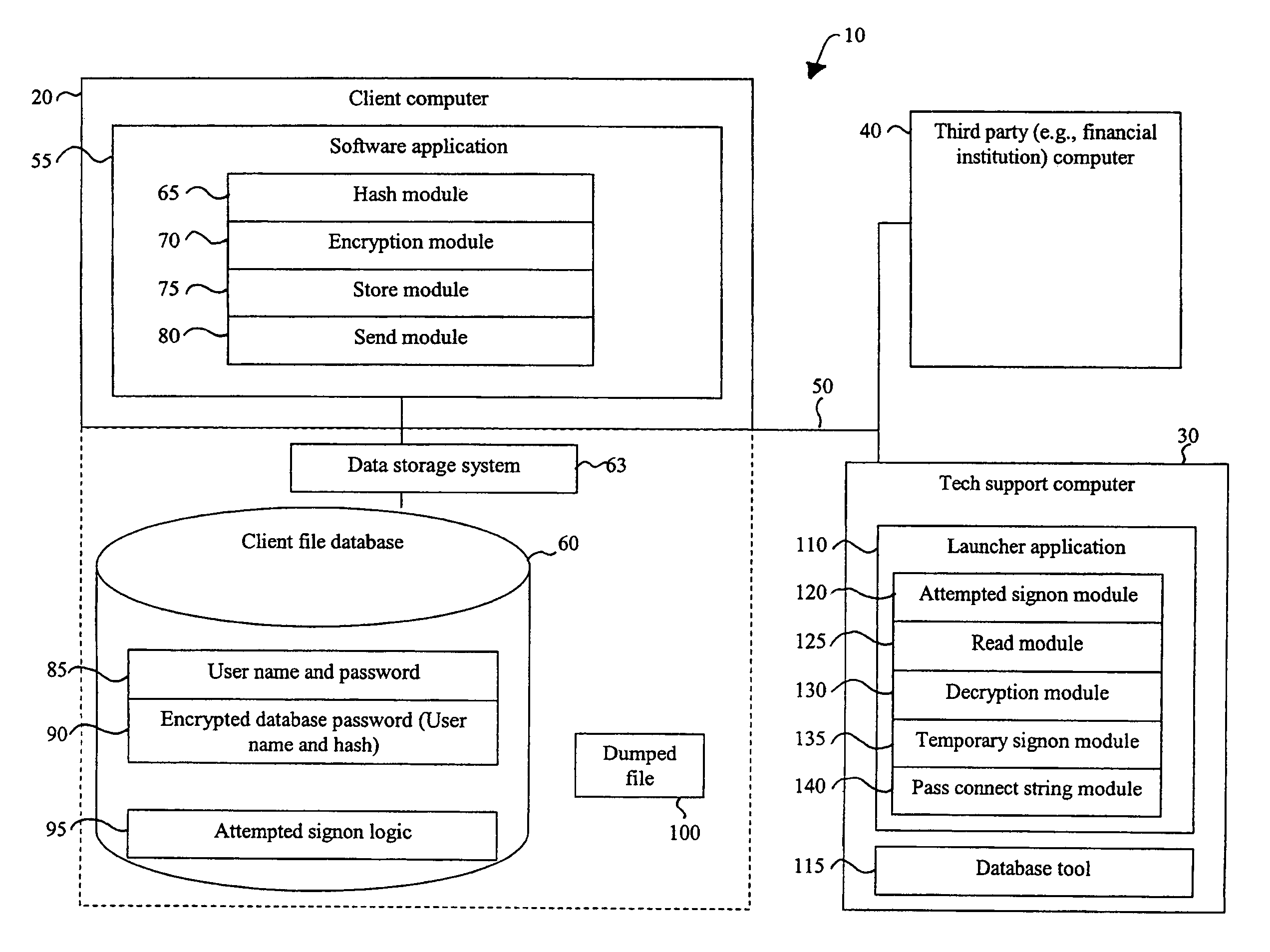
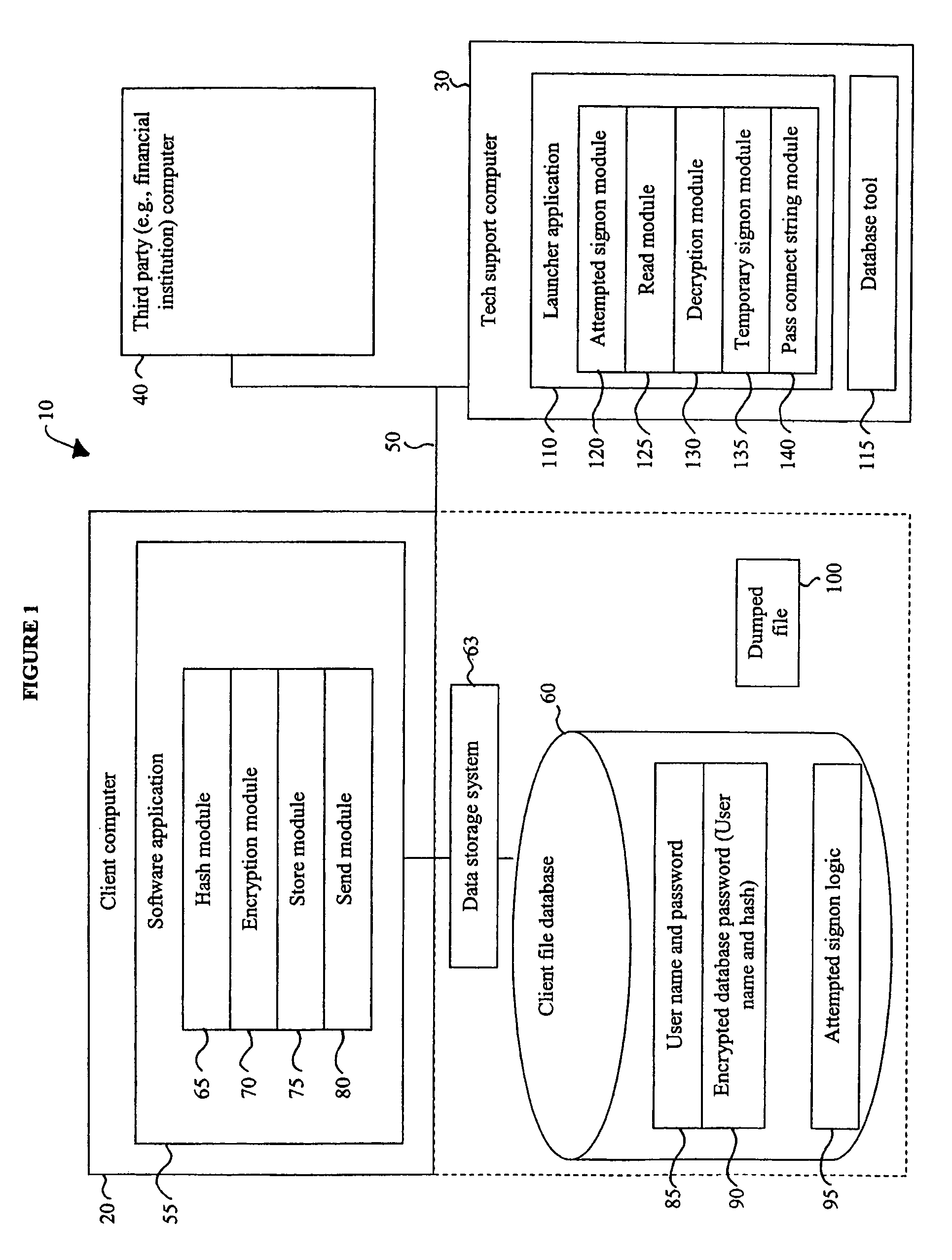
Recovery access to secure data
ActiveUS7644285B1Improve securityImprove user securityKey distribution for secure communicationDigital data processing detailsInternet privacyPassword
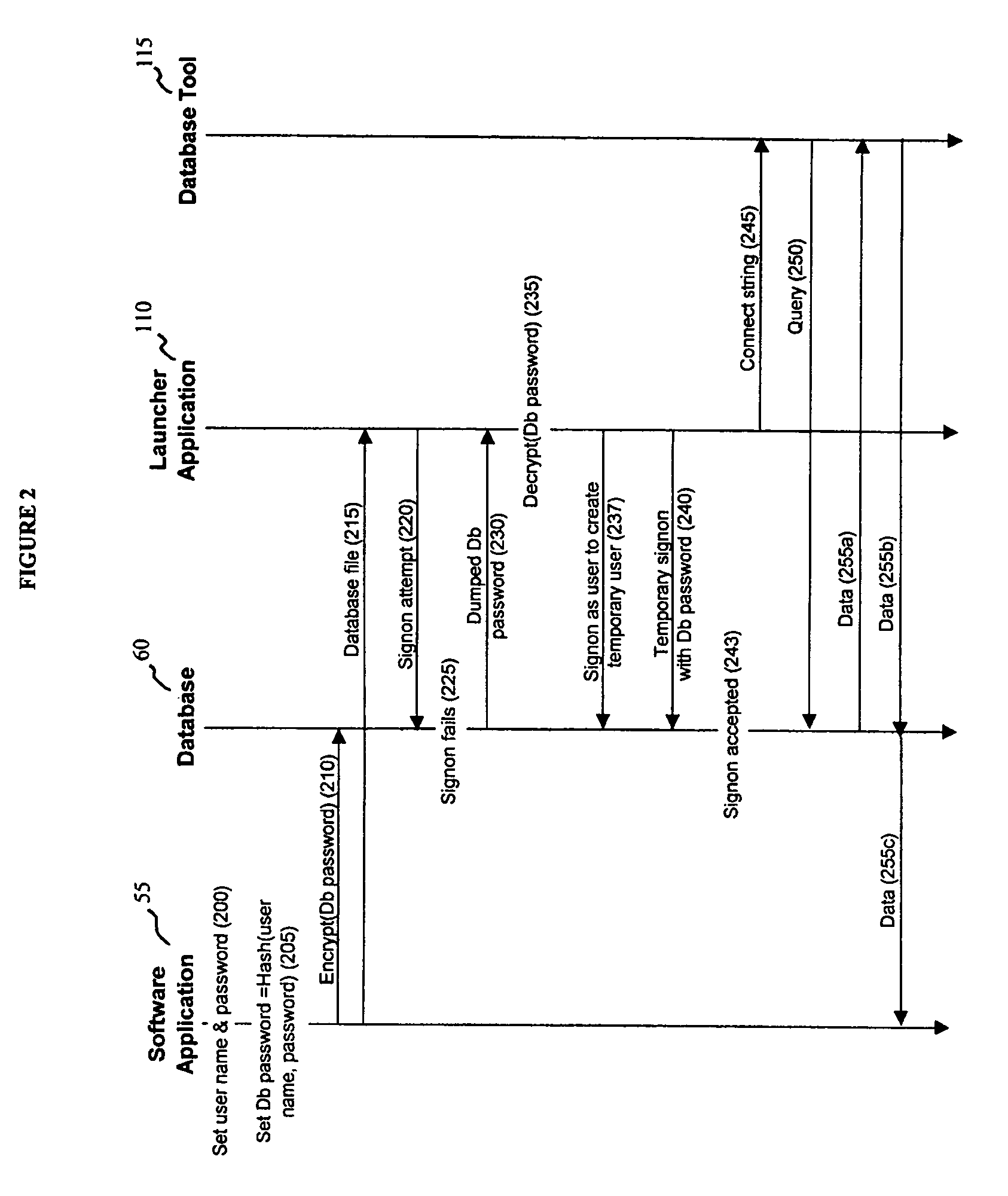
A security mechanism affords data recovery engineers the ability to access and recover secure data from user files without knowledge of the user's password. The mechanism uses a launcher application to access the database by establishing a temporary, restricted user session. The launcher application also passes a handle to an industry standard database tool, allowing the data recovery engineer to recover the user file data. The recovered data then can be accessed by the software application.
Owner:INTUIT INC
System and method for locking electronic devices
InactiveUS20070164847A1Improve user securityUnauthorised/fraudulent call preventionDigital data processing detailsPosition sensorExit point
A system and method are provided for locking electronic devices when the devices are not in the same location as a user associated with the device. The system includes a plurality of users each having an identification tag and a plurality of electronic devices each having an identification tag. Location sensors are provided in a room and at entry and exit points for detecting the location of the tags. A database stores the location information of tags and associations of a user with one or more devices. A remote locking means invokes a lock command or an unlock command on an electronic device depending on whether or not the electronic device is in the same location as a user associated with the device. In one embodiment, the identification tags are radio frequency identification transponders and the location sensors are radio frequency identification readers.
Owner:IBM CORP
Bluetooth cassette-like device for a hands-free cell-phone kit
InactiveUS7117021B2Manipulation can be minimizedImprove abilitiesNear-field transmissionSubstation speech amplifiersDriver/operatorComputer module
A hands-free kit for cell-phones combines the wireless capabilities of Bluetooth and the sound and visual functionalities of a tape player. A device that has a shape of a conventional magnetic cassette comprises a Bluetooth module. The module automatically detects a data communication initiated with the portable apparatus over a wireless network when the device is inserted in the tape player. Then the module automatically configures the apparatus to transmit to the device a low frequency signal representative of the communicated data. The device converts the received low frequency signal into a magnetic signal further communicated to the tape player for play out and / or display. Thus, when a cell-phone rings, a driver inserts the device in his tape player and the cell is picked up and the conversation played out loud on the loud speakers in the car.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
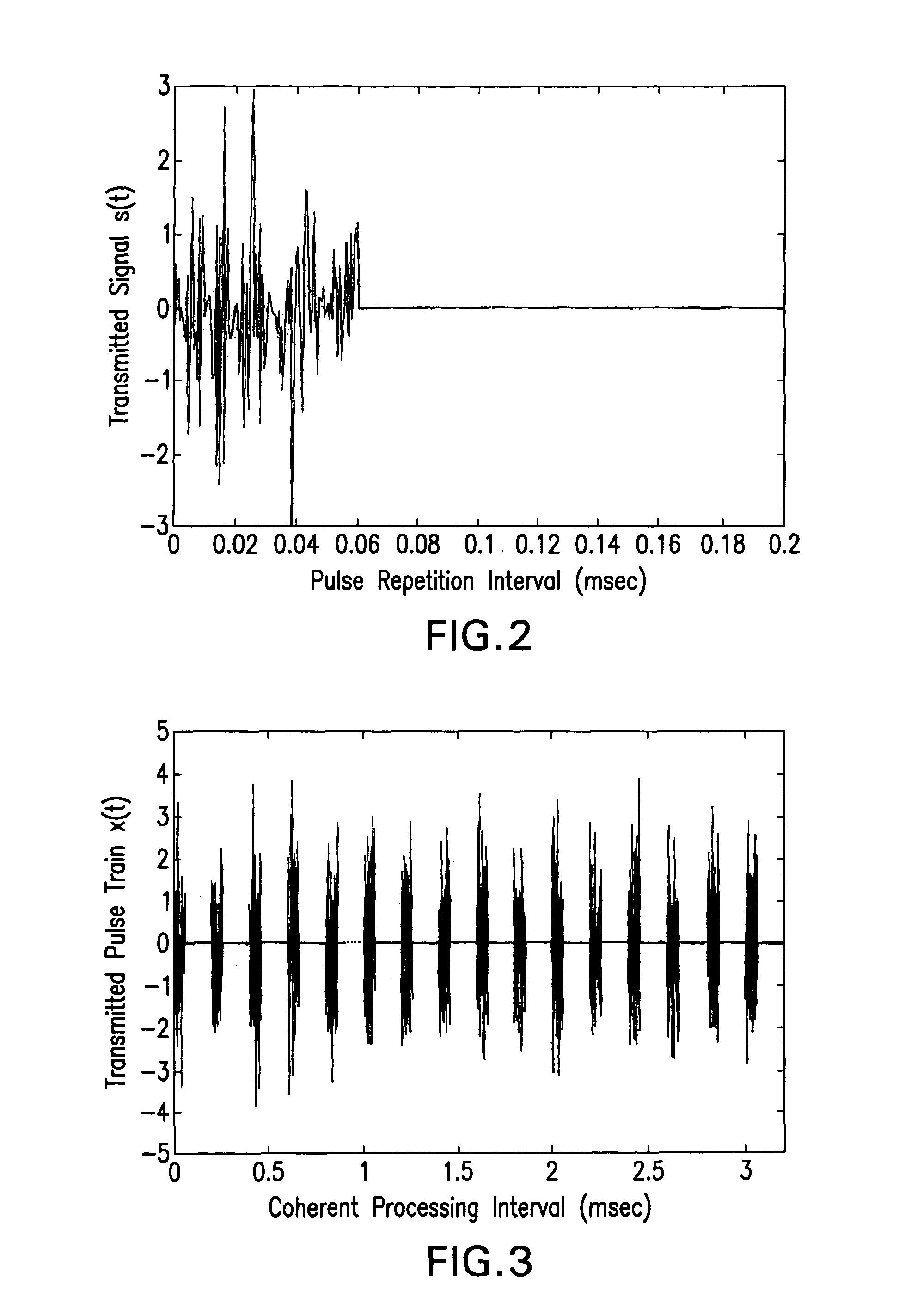
Noise correlation radar devices and methods for detecting targets with noise correlation radar
InactiveUS8035551B1Instantaneous band widthIncrease the carrier frequencyRadio wave reradiation/reflectionRadar systemsFrequency modulation
A pulsed compression noise correlation radar uses noise modulation and pulse compression technology to scramble recognizable transmit signal characteristics and reduce transmit energy. The pulsed noise correlation radar advantageously uses pulse compression technology, a pulsed linear frequency modulated noise correlation mixer, and a new and innovative noise fused waveform to automatically correlate the pulsed linear frequency modulated (LFM) noise waveform with the received signal. The pulsed noise correlation radar apparatus and system now make it possible to effectively reduce transmitting power, preserve high band widths through oversampling in the receiver, and achieve multi-channel array frequency diversity. A secure pulsed compression noise correlation radar system and methods for undetected target detection with pulsed noise correlation radar and a pulsed LFM fused noise waveform are also provided.
Owner:ARMY US SEC THE
Integrity check in a communication system
InactiveUS20060159031A1Improve user securityPrevent replay attacksError prevention/detection by using return channelTransmission systemsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
Owner:NOKIA TECH OY
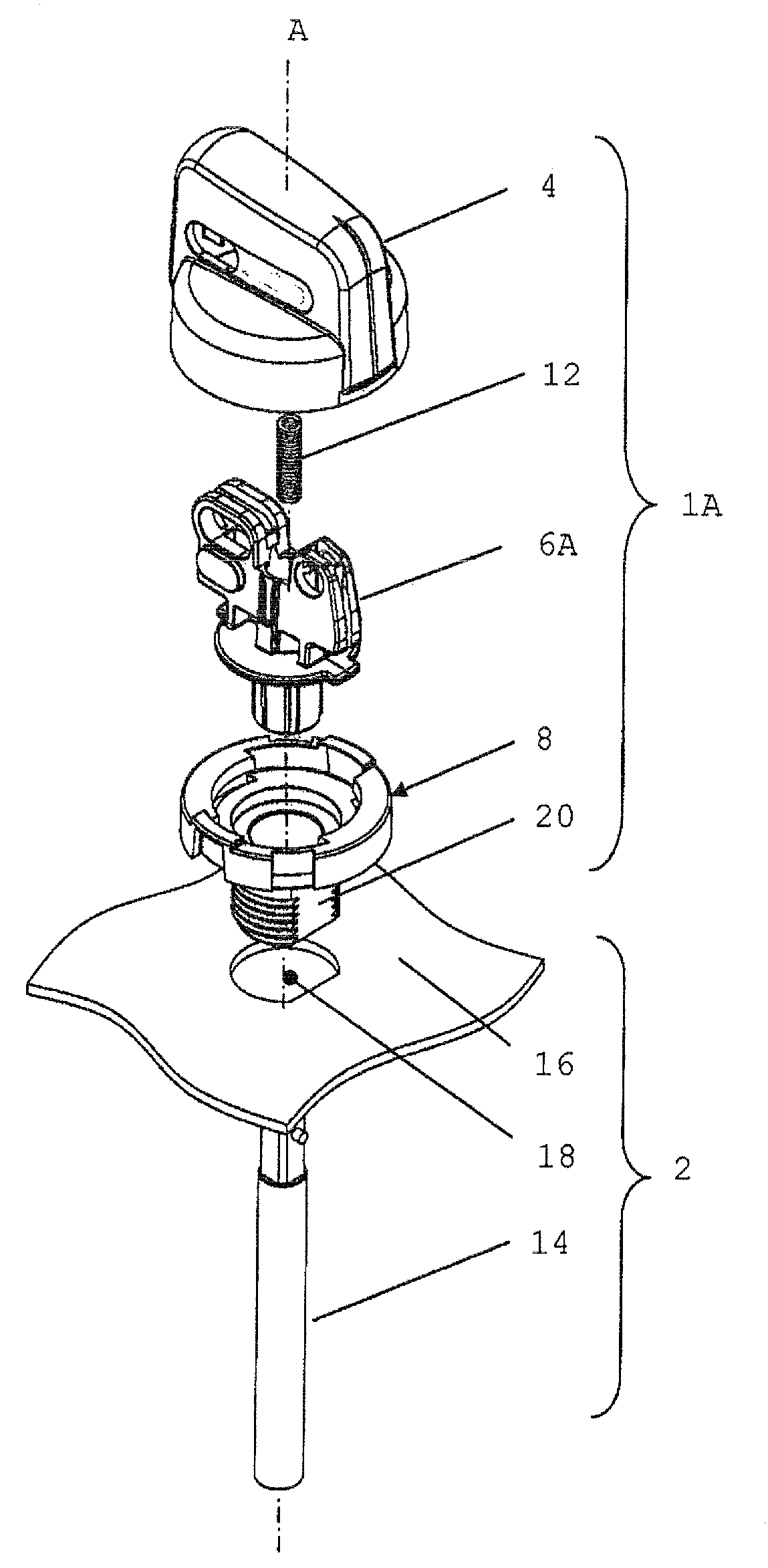
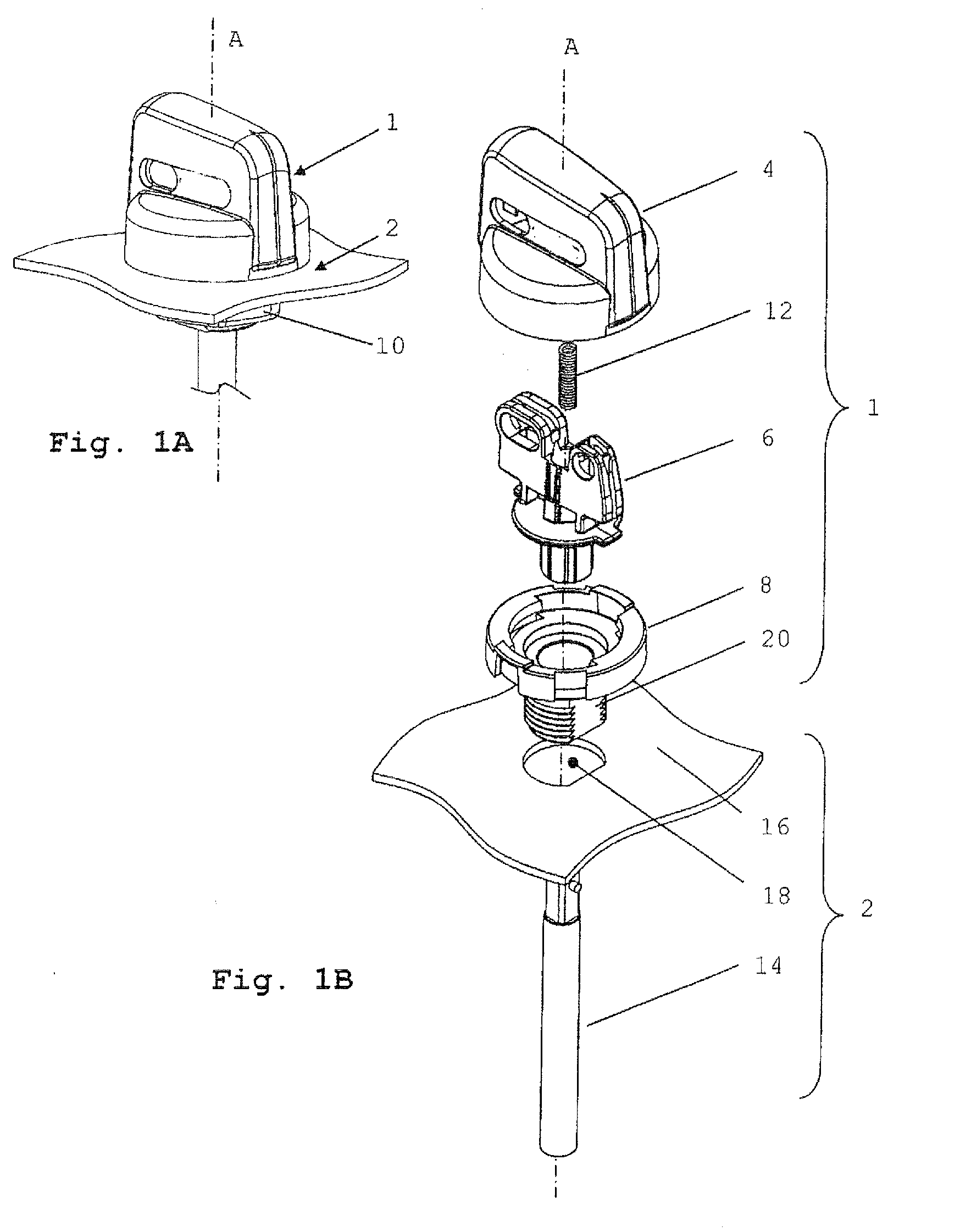
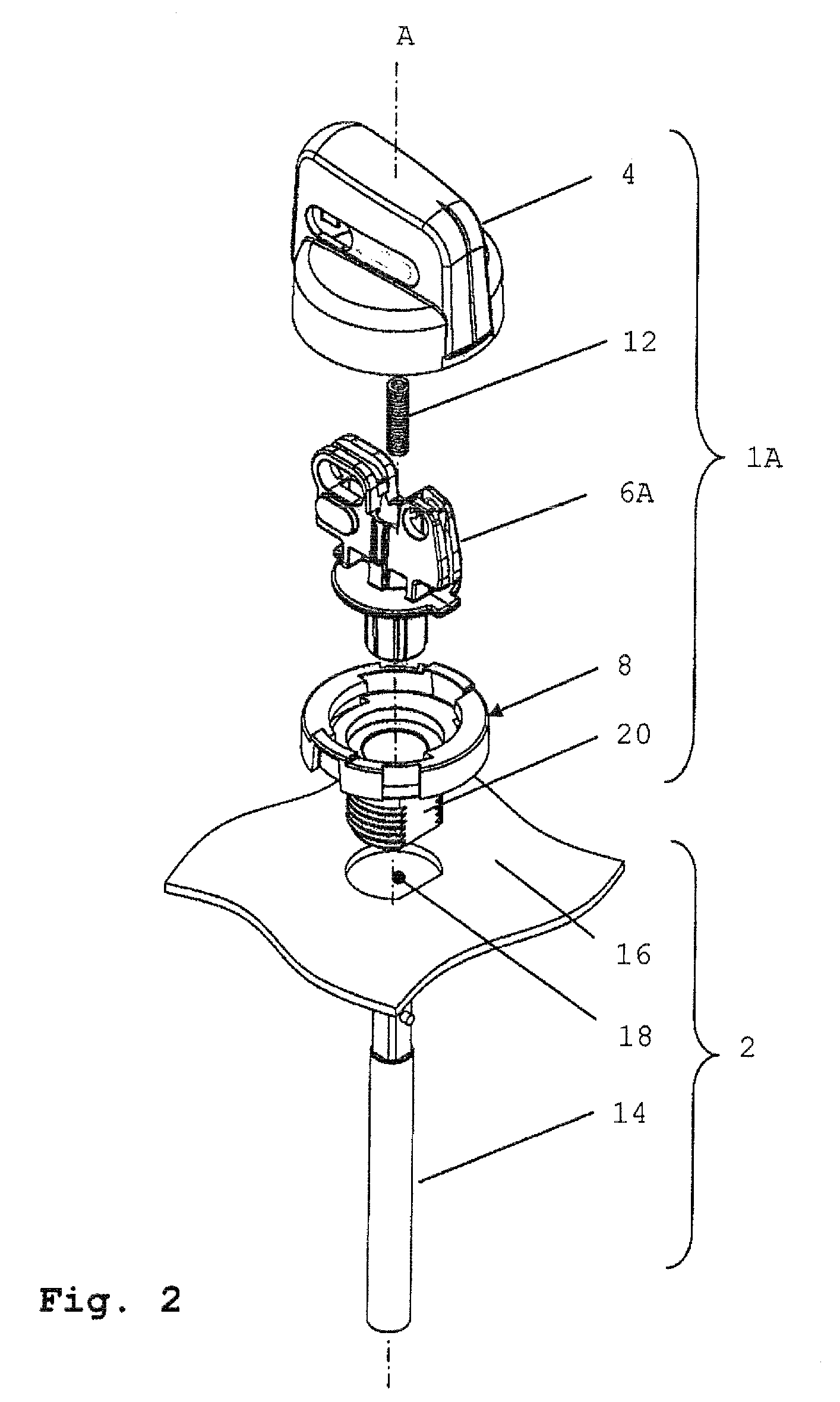
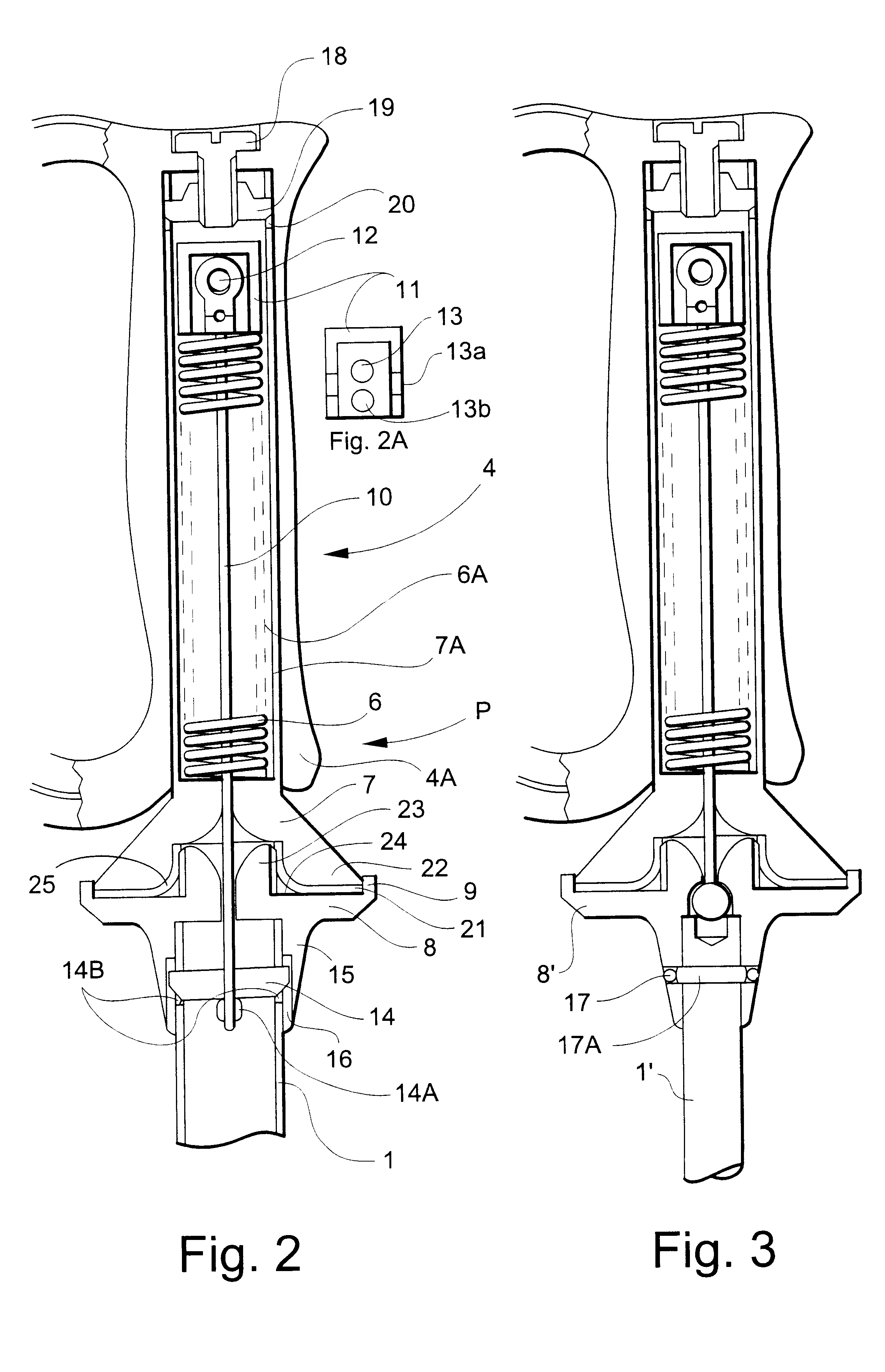
Safety Rotary Operator Assembly
ActiveUS20100294632A1Operational safety be improveIncrease safetyControlling membersMechanical apparatusEngineeringMechanical engineering
A rotary operator assembly (1A) includes a grip member (4), a spindle member (6A), and an operator body member (8). The spindle member (6A) is attached to the operator body member (8), being rotatable with respect to the operator body member (8) about an operative axis of rotation (A). The grip member (4) is movably coupled to the spindle member (6A) and the operator body member (8) and is translatable between a first translational position and a second translational position with respect to the operator body member (8). The grip member (4) and the operator body member (8) include cooperating means for blocking rotation of the grip member (4) with respect to the operator body member (8) about the operative axis of rotation in the first position and for allowing rotation of the grip member (4) with respect to the operator body member (8) about the operative axis of rotation in the second position from a first angular position to a second angular position. The grip member (4) is configured to operably couple with the spindle member (6A) in at least the second translational position, and the grip member (4) comprises at least one portion cooperating with at least one portion of the spindle member (6A) for preventing translation of the grip member (4) between the first translational position and the second translational position in the first angular position.
Owner:EWAC HLDG
Electronic Medical Record Process
InactiveUS20130317848A1Convenient and economical and effectiveUser friendlyDrug and medicationsOffice automationMedical recordUser identifier
A user friendly improved process can include: transmitting and detecting a user identification (ID) signal providing an electronic code of a physician or other medical personnel; electronically comparing the user ID signal with an electronic database of authorized users to determine if the physician or other medical personnel is an authorized user; and authorizing access to each electronic medical record (EMR) of patients of the authorized user. After access is allowed, the authorized user can input patient information, prescriptions and physician's notes into the EMR, generate the user's signature on the EMR as well as view, transmit and print the signed prescription or EMR.
Owner:SAVIN ANDREW
Security for electronic transactions and user authentication
InactiveUS20180197171A1Improve user securityMinimizing adoption burdenCredit schemesDebit schemesPayment transactionFinancial transaction
System and method for generating, disseminating, controlling, and processing limited-life security codes used to authenticate users, particularly for electronic financial transactions, such as payment transactions. Providing a user with a single security code usable across multiple accounts or other secured systems is contemplated, each security code having a limited lifetime. Each security code is a random number from a random number generator. The respective security codes for each user correspond to a respective security code validity period of limited duration. Thus, a table or matrix that associates the plurality of users with the respective sets of randomly selected security codes (each having their respective validity periods) is generated, and that matrix is provided to the respective entities to which each user requires secured access. In parallel, at least a current security code is provided to each user, and this is how the respective entities being accessed can track which code from which user is currently valid.
Owner:TENDER ARMOR LLC
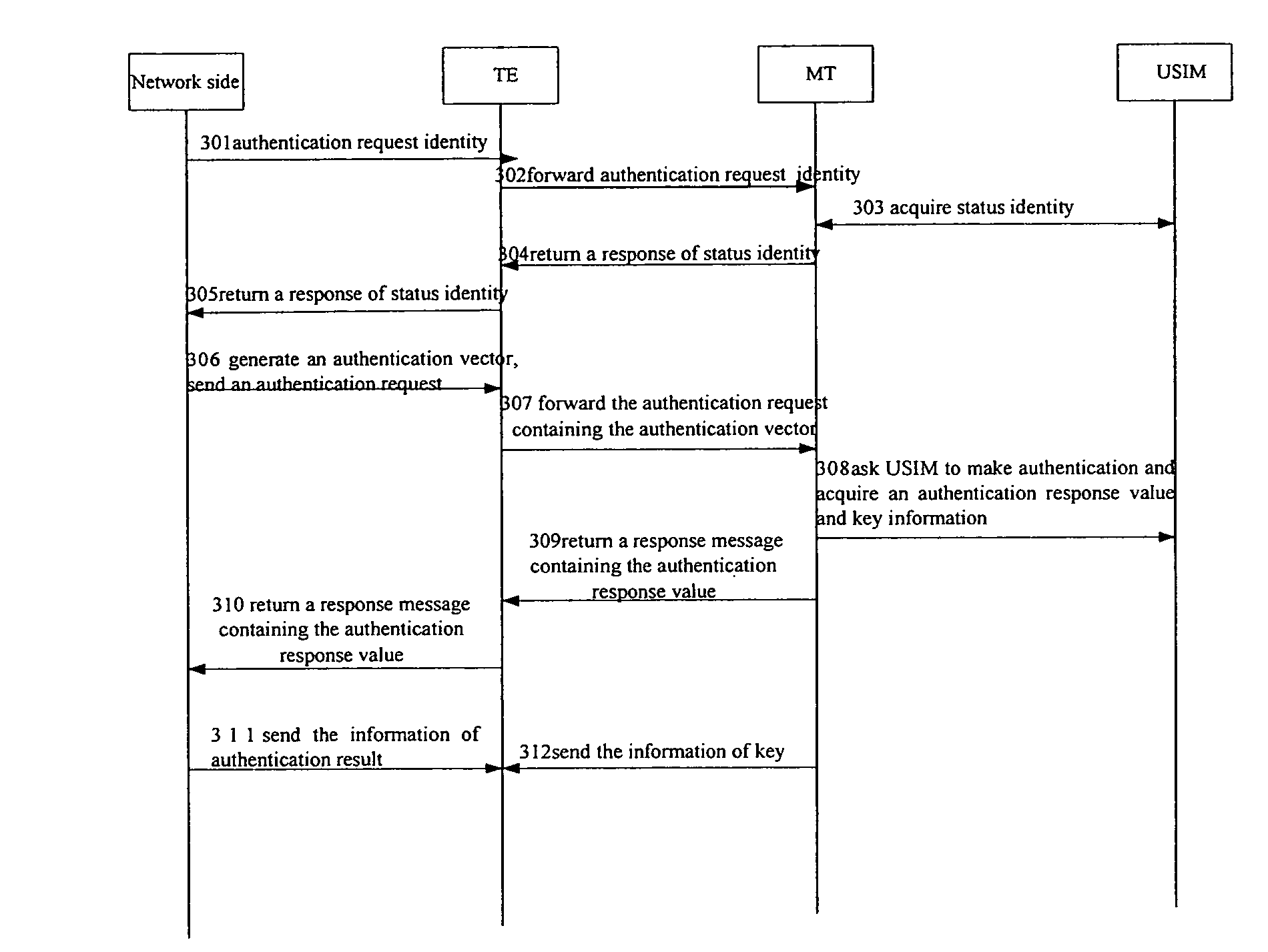
Method For Managing Local Terminal Equipment Accessing A Network
ActiveUS20080101276A1Save network resourcesFunction increaseUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTerminal equipmentUser Facility
Methods for managing a local Terminal Equipment (TE) accessing a network are provided. One is to set in a Mobile Terminal (MT) a management list containing the identities of local TEs, and to decide according to the information of the management list whether to accept a request message from the TE, thereby implementing the management of local TE that accesses the network using resources of the MT, improving the function of the MT, and at the same time, enhancing the security of users' accounts. In accordance with this invention, a user is able to define an authority for the TE to access and learn the current state of the TE, which gives the user facilities for daily use. The other method is to modify the existing procedure such that the MT will not send the key(s) information to the TE until having received a notice of successful authentication from the TE or having decided that the message forwarded by the TE is a response message of successful authentication, which makes the procedure more reasonable and saves the network resources the method further includes a management list containing the identities of local TEs on the basis of the modified procedure.
Owner:HUAWEI TECH CO LTD
Method and device for robust detection, analytics, and filtering of data/information exchange with connected user devices in a gateway-connected user-space
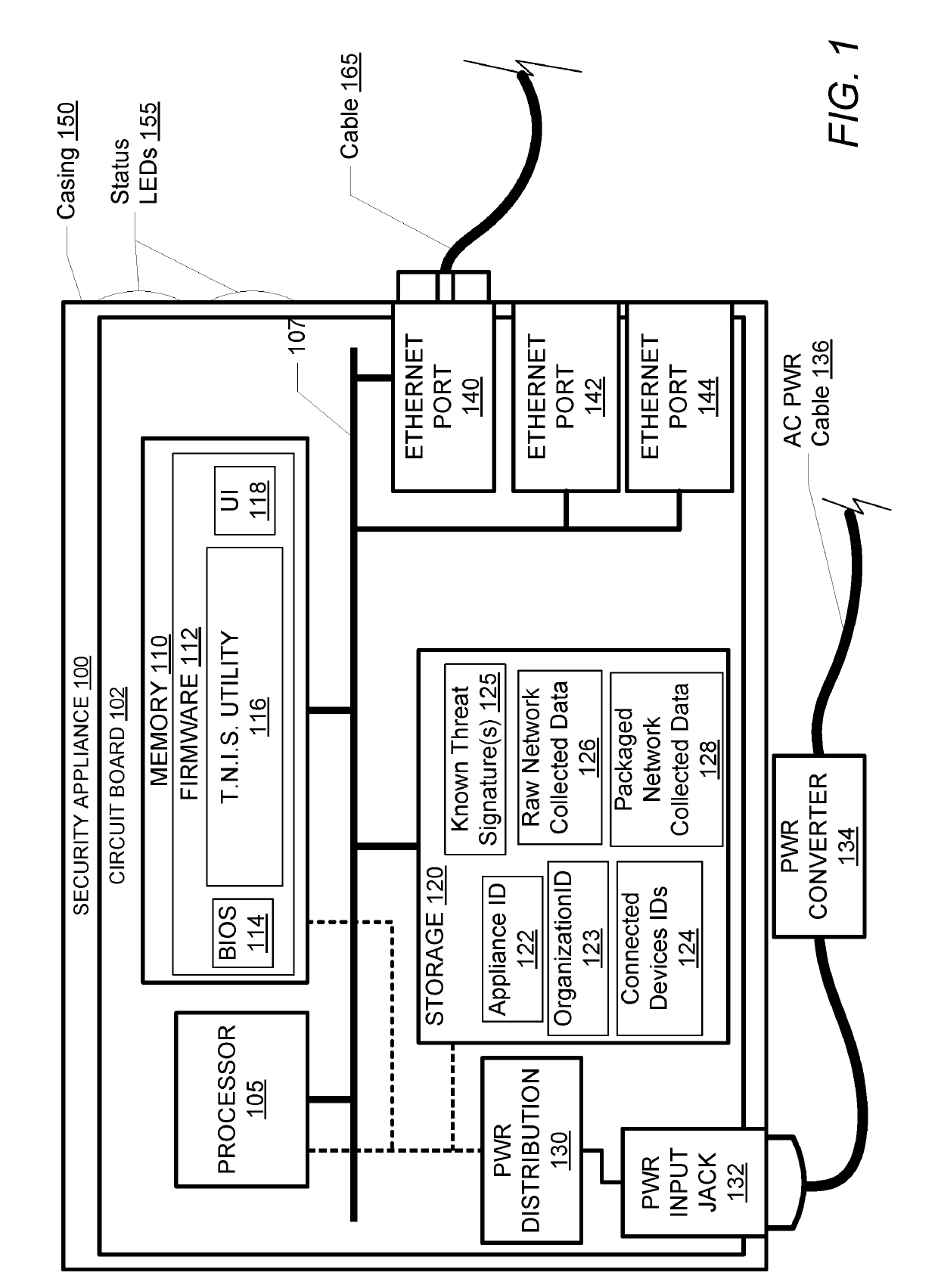
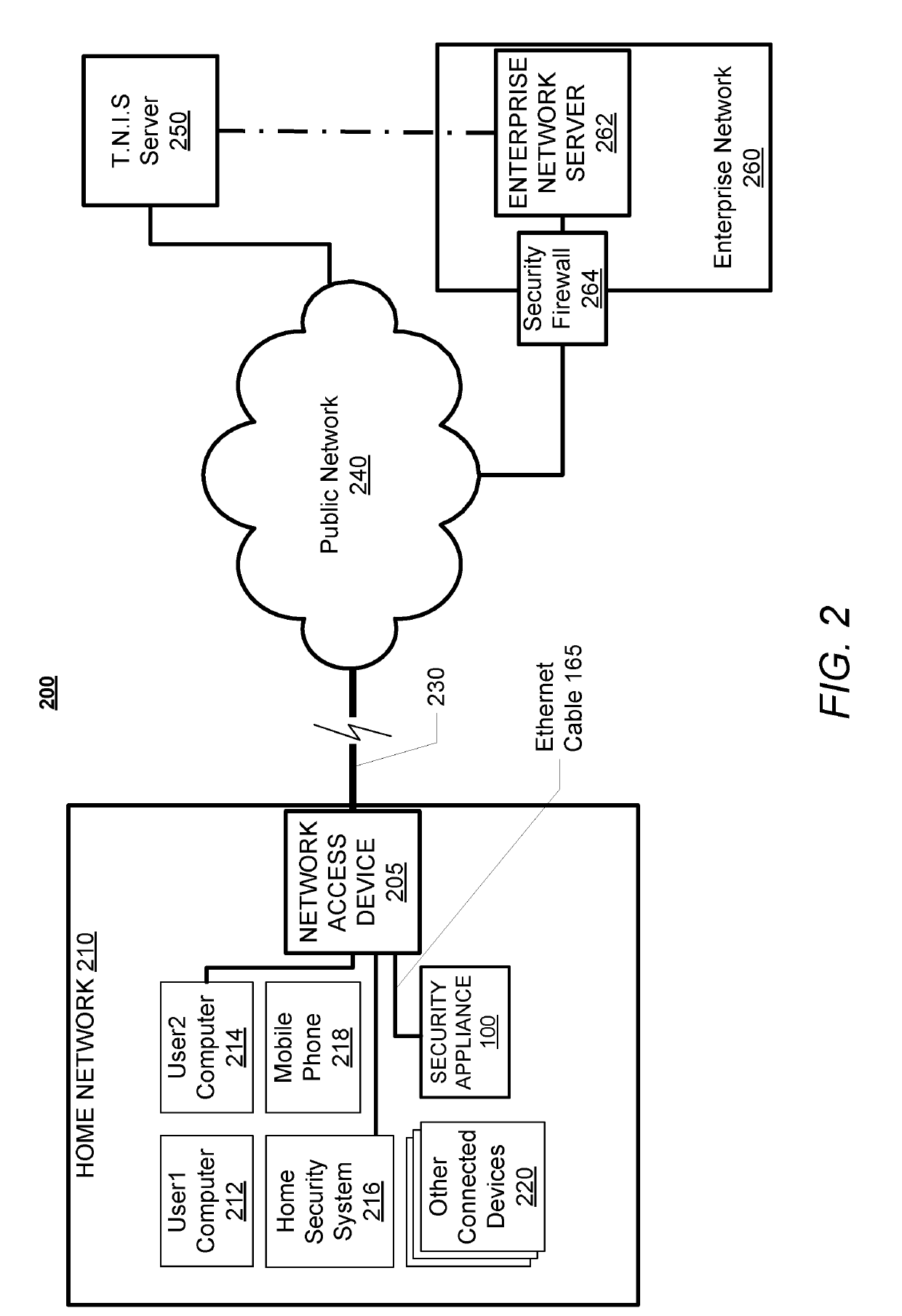
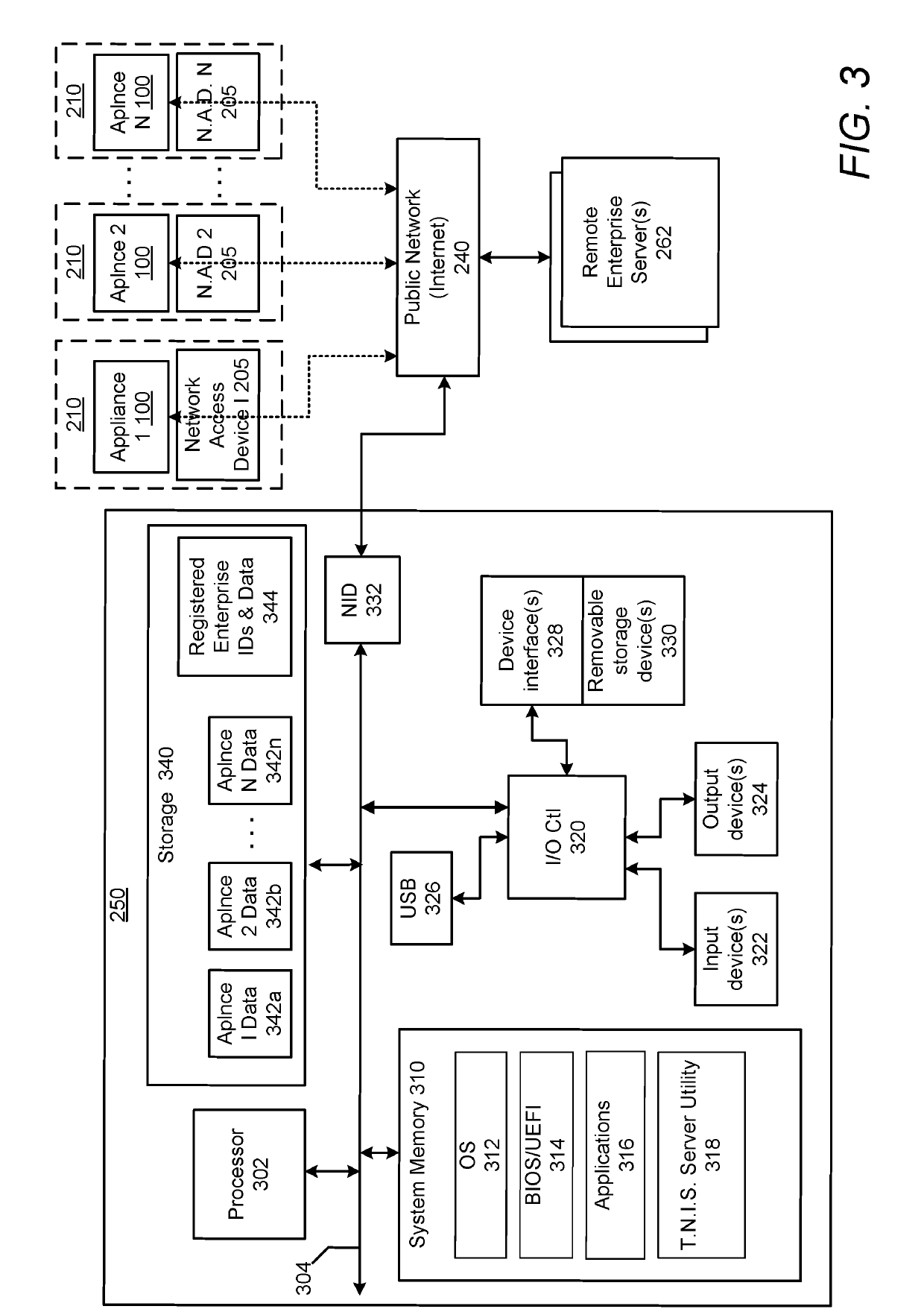
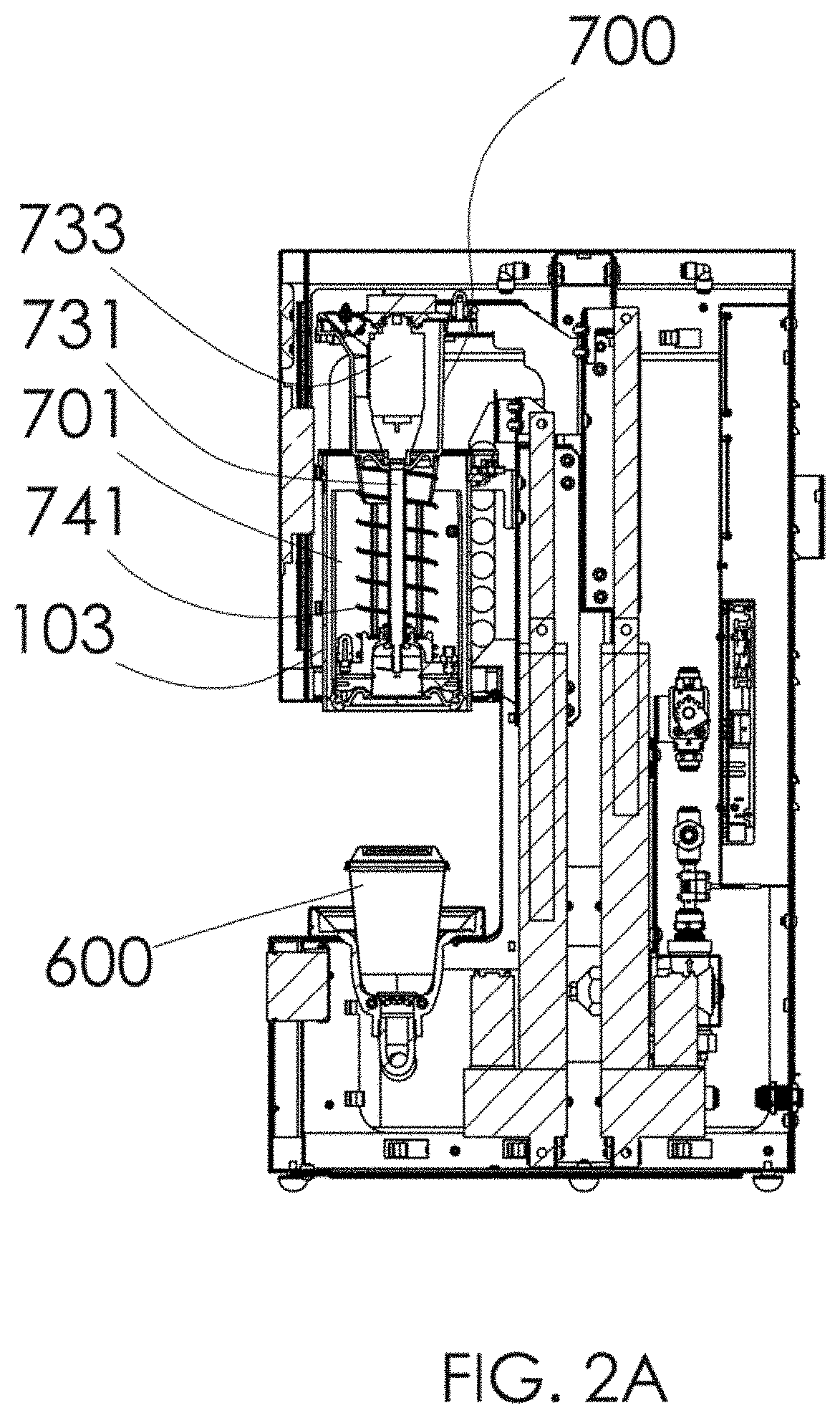
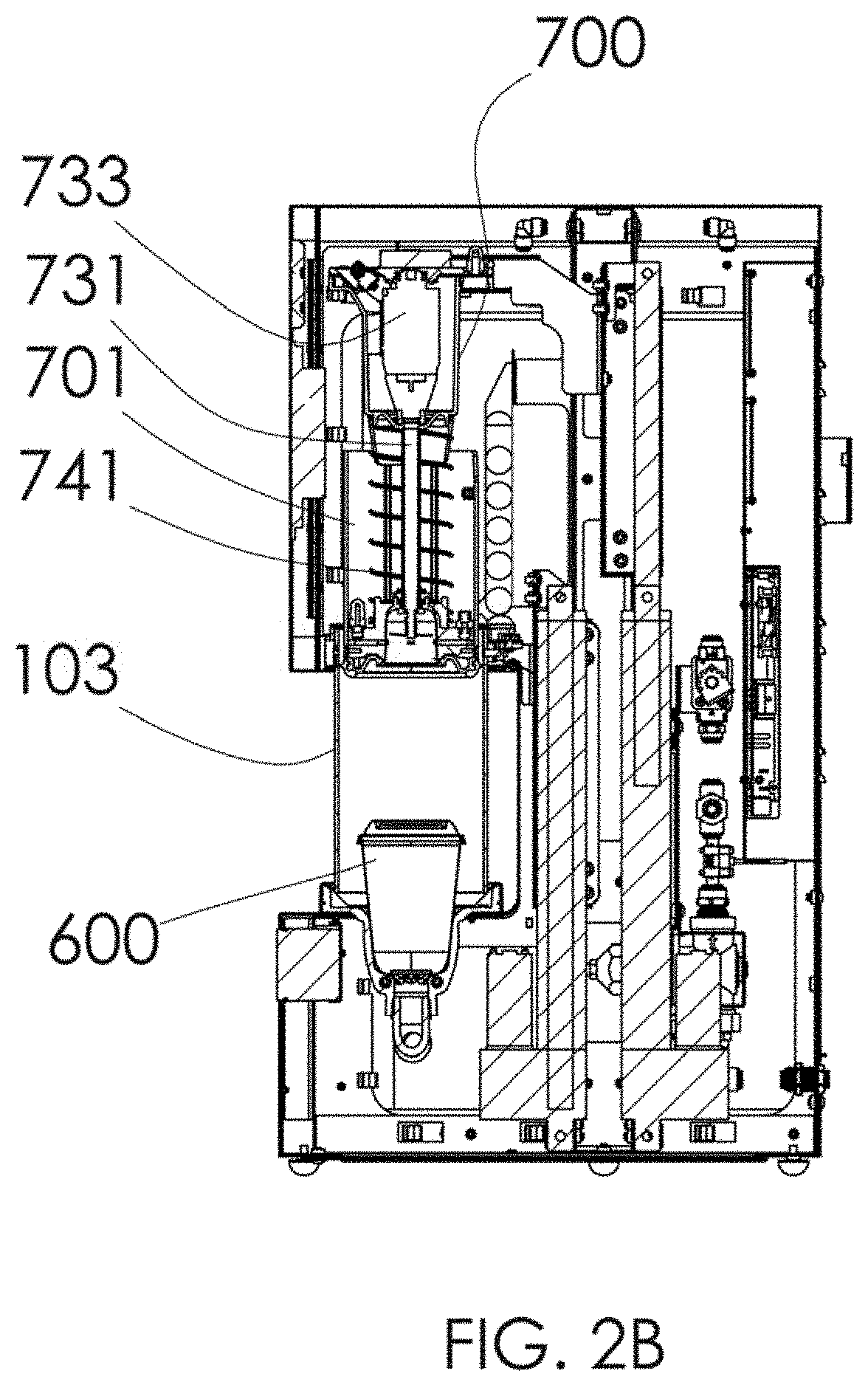
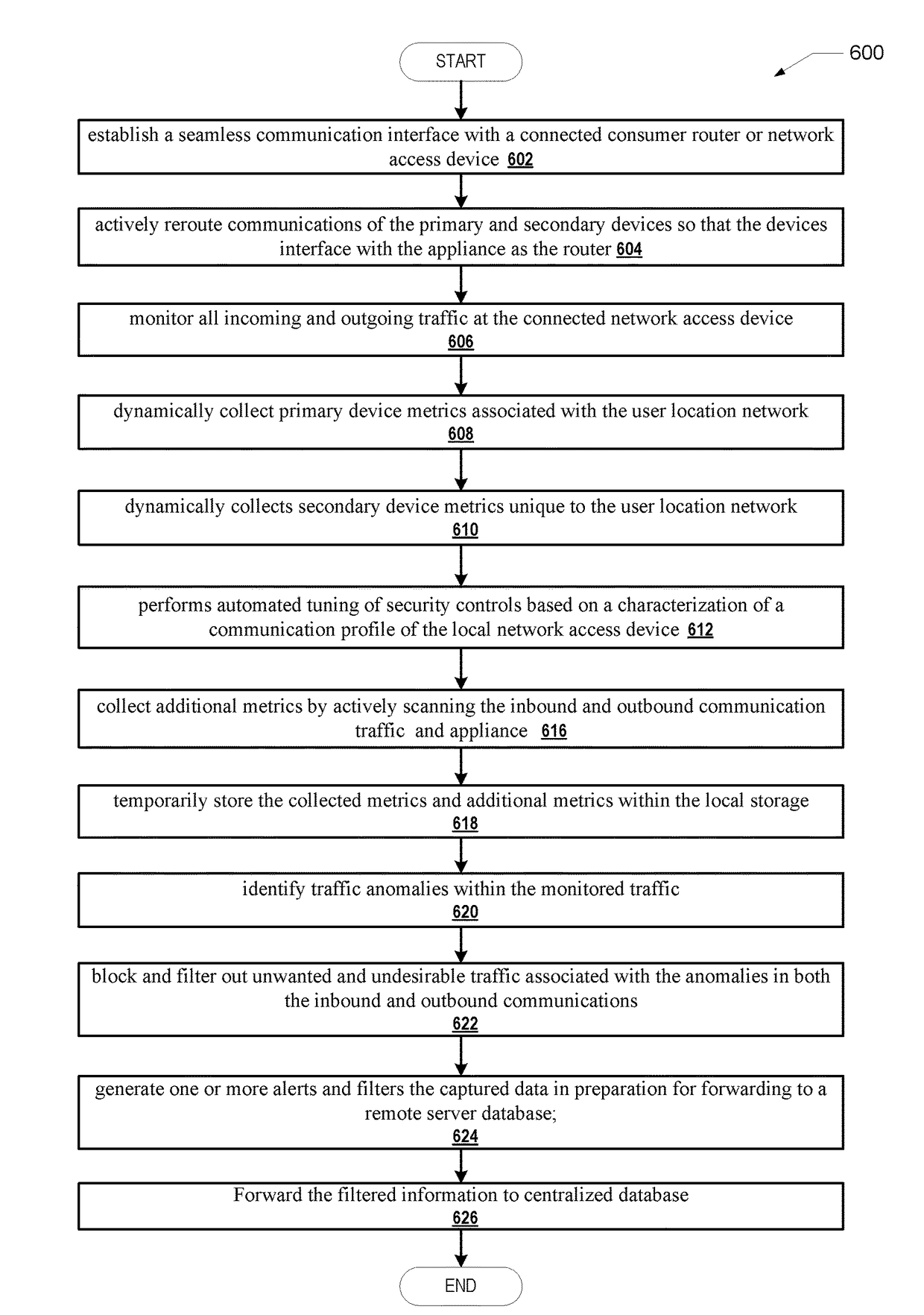
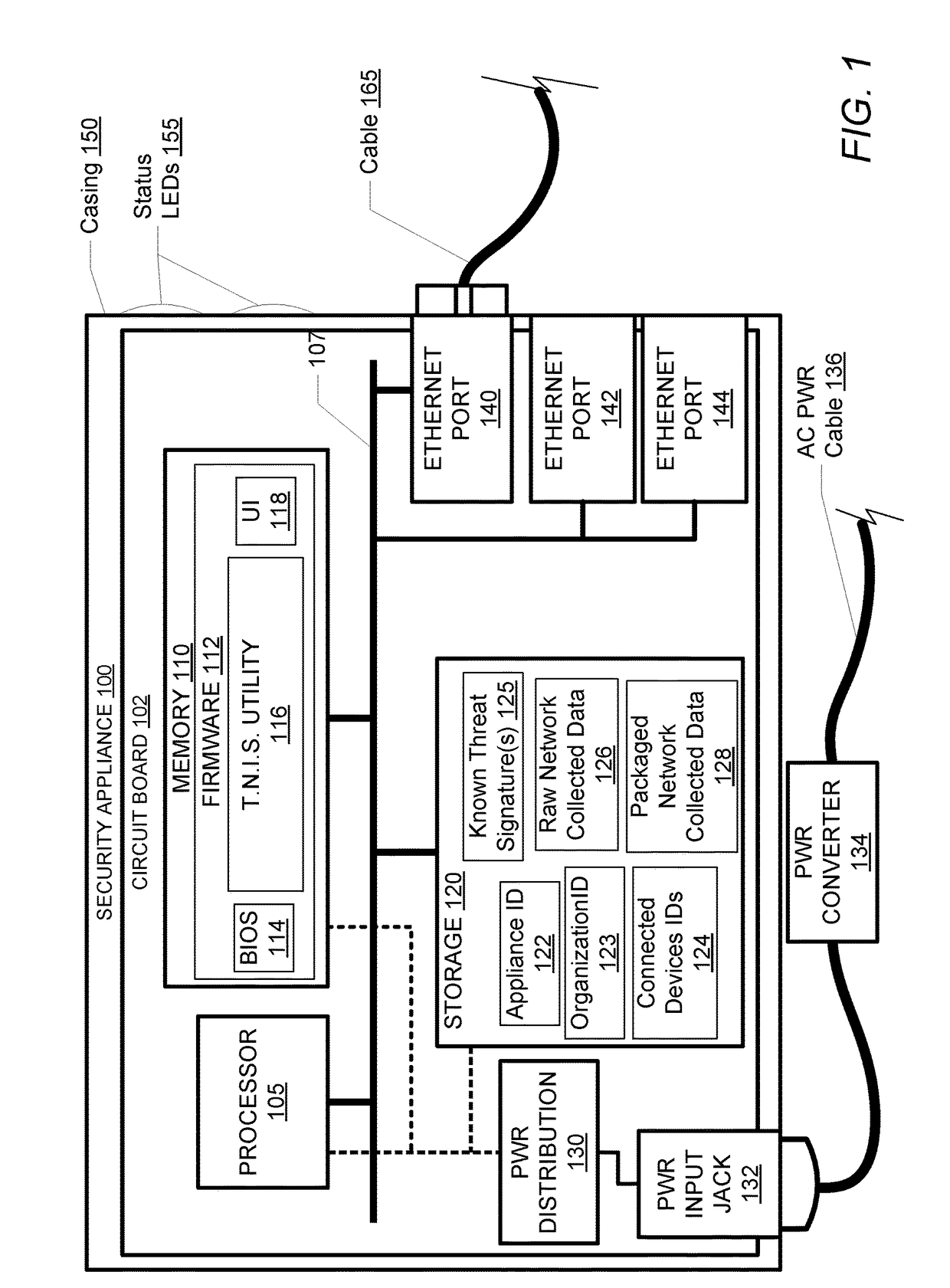
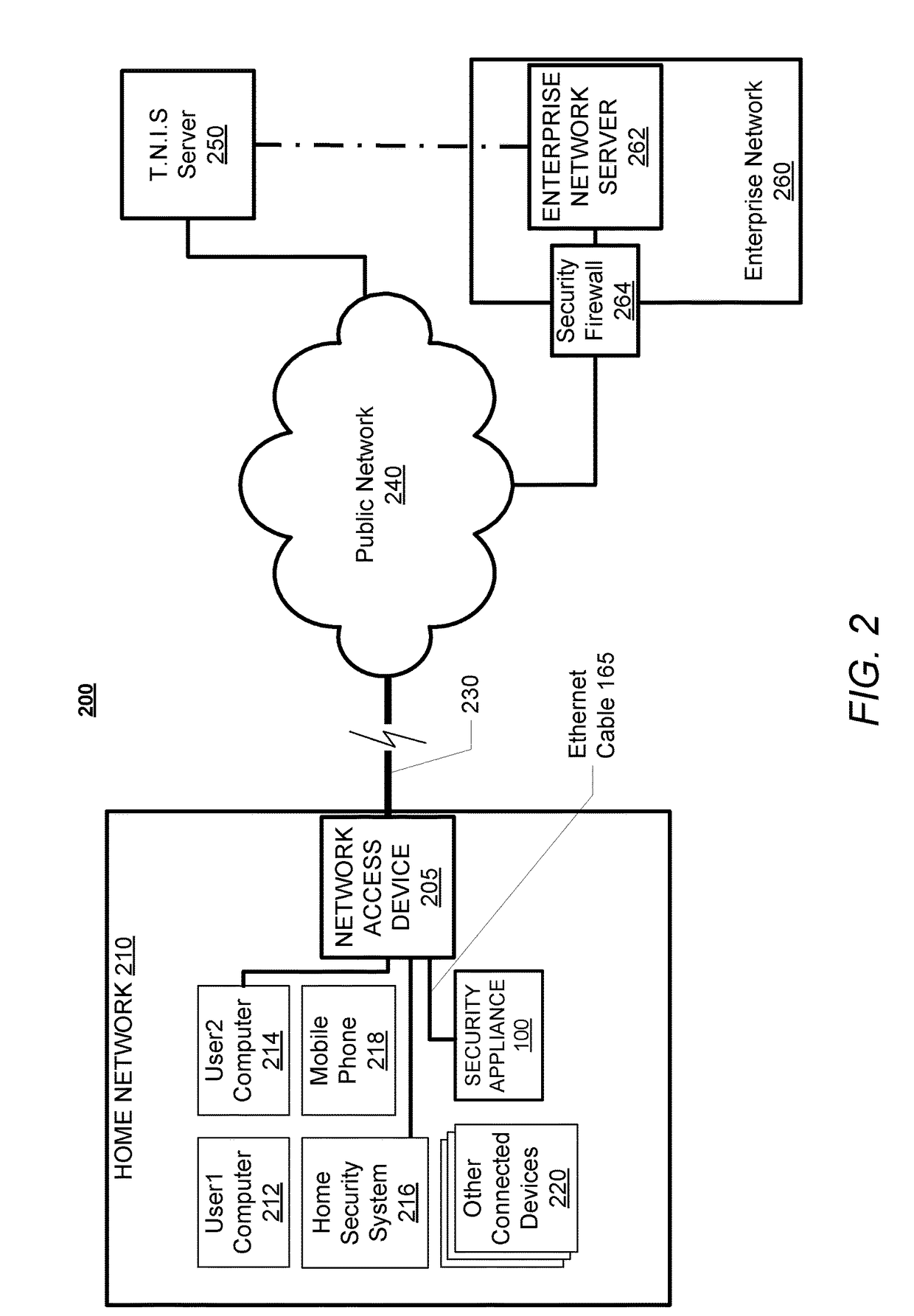
InactiveUS10250624B2Improve user securityImprove network securityComputing modelsTransmissionTraffic capacityCommunication interface
A security appliance includes: a network port enabling direct connection to a gateway; a storage module having stored thereon firmware for operating the security appliance; and a processor that executes the program code of the firmware. The firmware configures the appliance to: establish a seamless communication interface with a connected gateway; monitor traffic coming into and going out from the connected gateway; and identify traffic anomalies within the monitored traffic. The firmware further configures the appliance to: in response to identifying one or more of the traffic anomalies: forward information about the identified traffic anomalies to a centralized database for evaluation and reporting; and initiate steps to prevent further occurrence of the traffic anomalies, without user approval.
Owner:OAK TREE LOGIC LLC
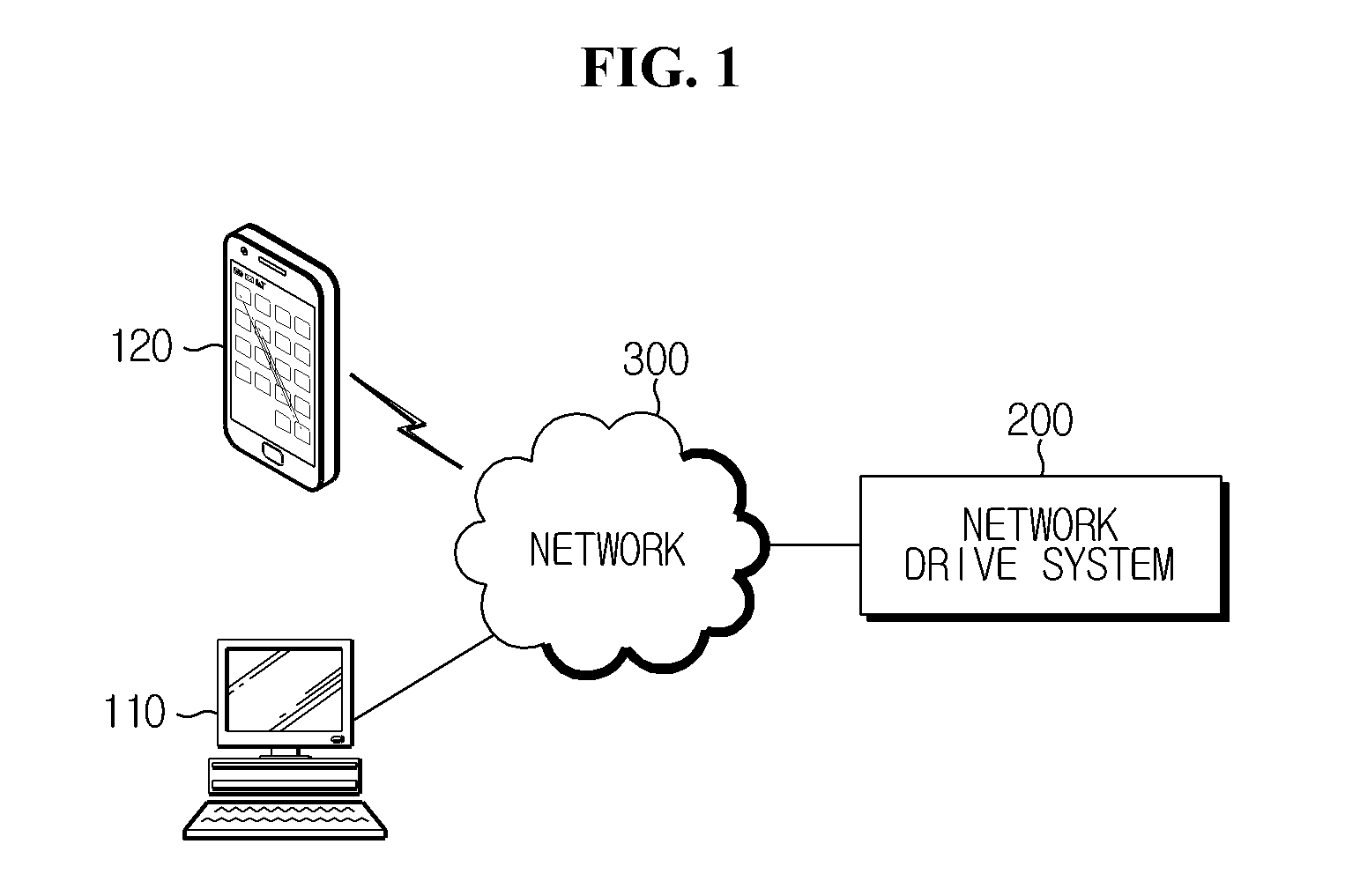
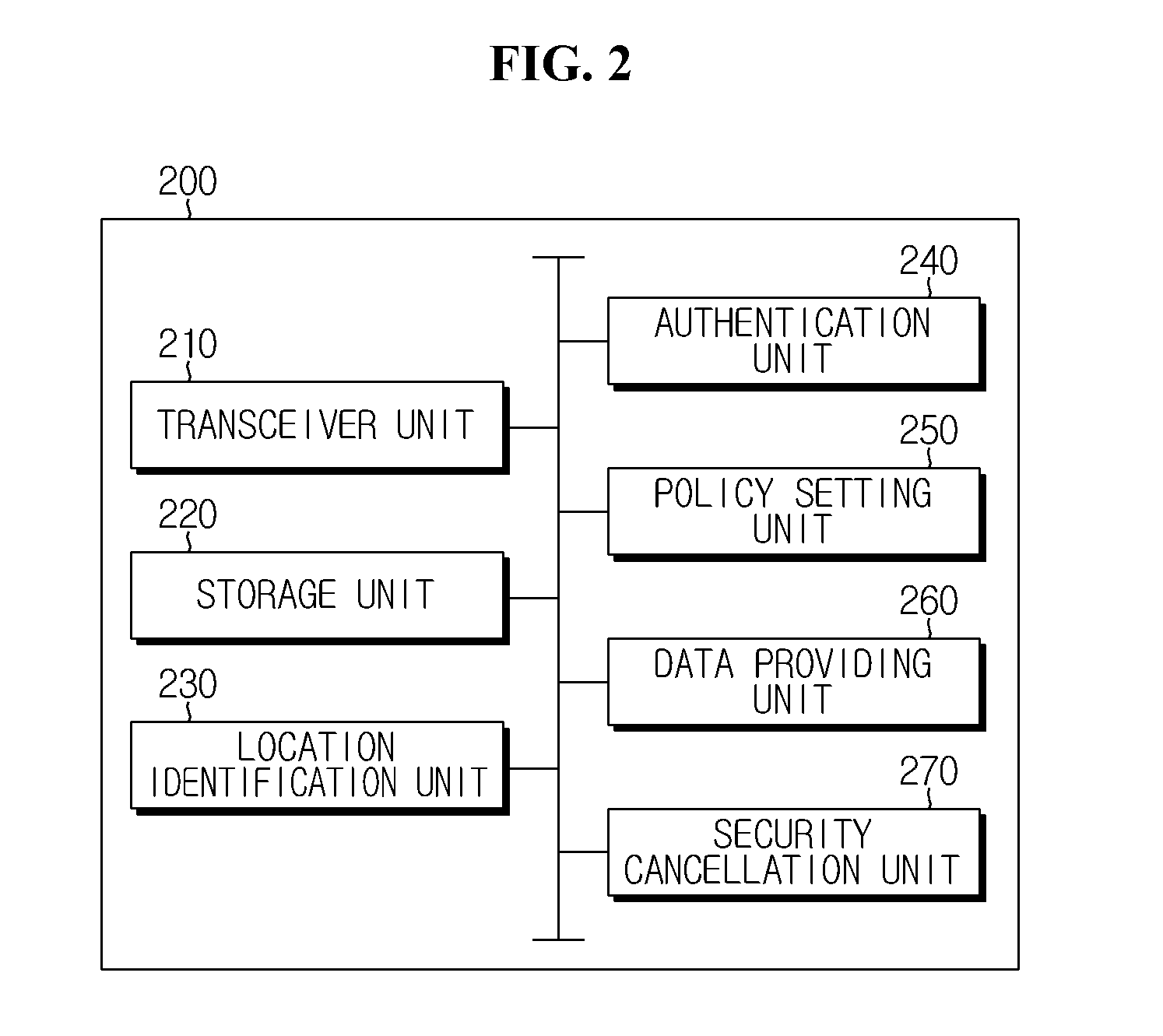
Method of Controlling Access to Network Drive, And Network Drive System
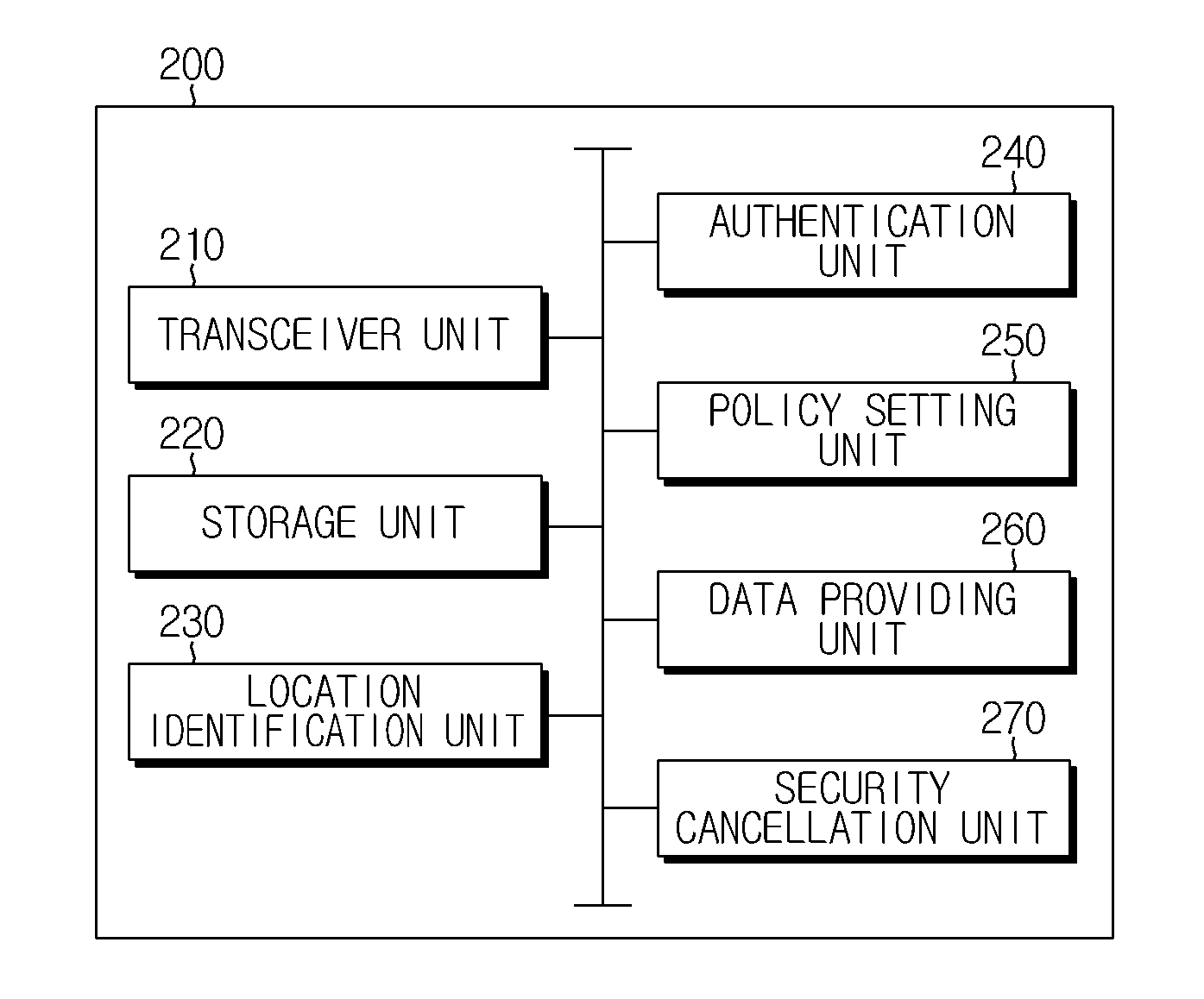
ActiveUS20150341359A1Improve securityProtect user privacyDigital data processing detailsDigital data protectionData storingCommunication device
A network drive system for controlling access to a network drive based on location information on a communication device according to the present technology includes: a storage unit storing a network drive that stores security data and general data; a receiving unit receiving a request for access to the network drive from a first communication device; a location checking unit checking whether the distance between the first communication device and a second communication device designated as a device for controlling access to the network drive is within a critical value; and a policy setting unit that applies a policy allowing the first communication device to access general data stored in the network drive or applies a policy disallowing the first communication device to access general data stored in the network drive, according to results of the determining by the location checking unit.
Owner:FACECON
Cable hook attachment for ladders
ActiveUS20140367194A1Improve user securityImprove securityScaffold accessoriesLaddersEngineeringMechanical engineering
A fixed strand grabber and a removable strand grabber are presented for use on a conventional ladder. The strand grabber includes a hook member connected to a top support and a bottom lever. The bottom lever has a portion that extends past and encloses the open interior of the hook that protrudes from the forward side of the ladder. As the ladder is lowered over a cable, the hooks move upward which in turn causes the bottom lever to rotate upward. A portion of the bottom lever encloses the open interior of the hook thereby locking the cable therein. In this way improved safety is provided as the cable is prevented from accidently slipping out of the open interior of the hook which improves user safety. The system also provides an attachment point for a safety lock. In addition, the removable strand grabber provides a V-brace for using against utility poles.
Owner:BOLINSKI ERIC C
User data protection method in server apparatus, server apparatus and computer program
InactiveUS20090248950A1Improve user securityImprove securityDigital data processing detailsUnauthorized memory use protectionVirtualizationServer appliance
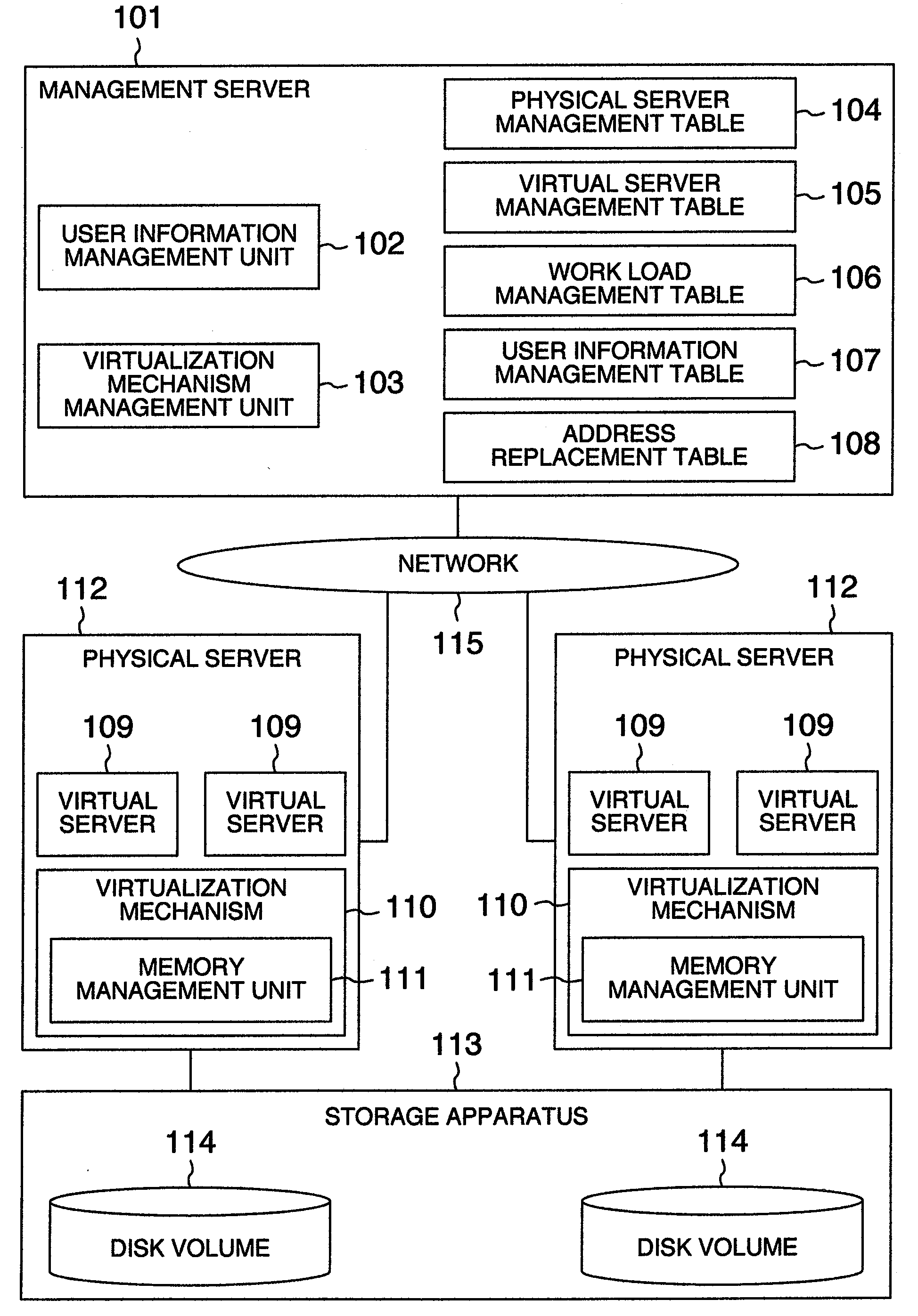
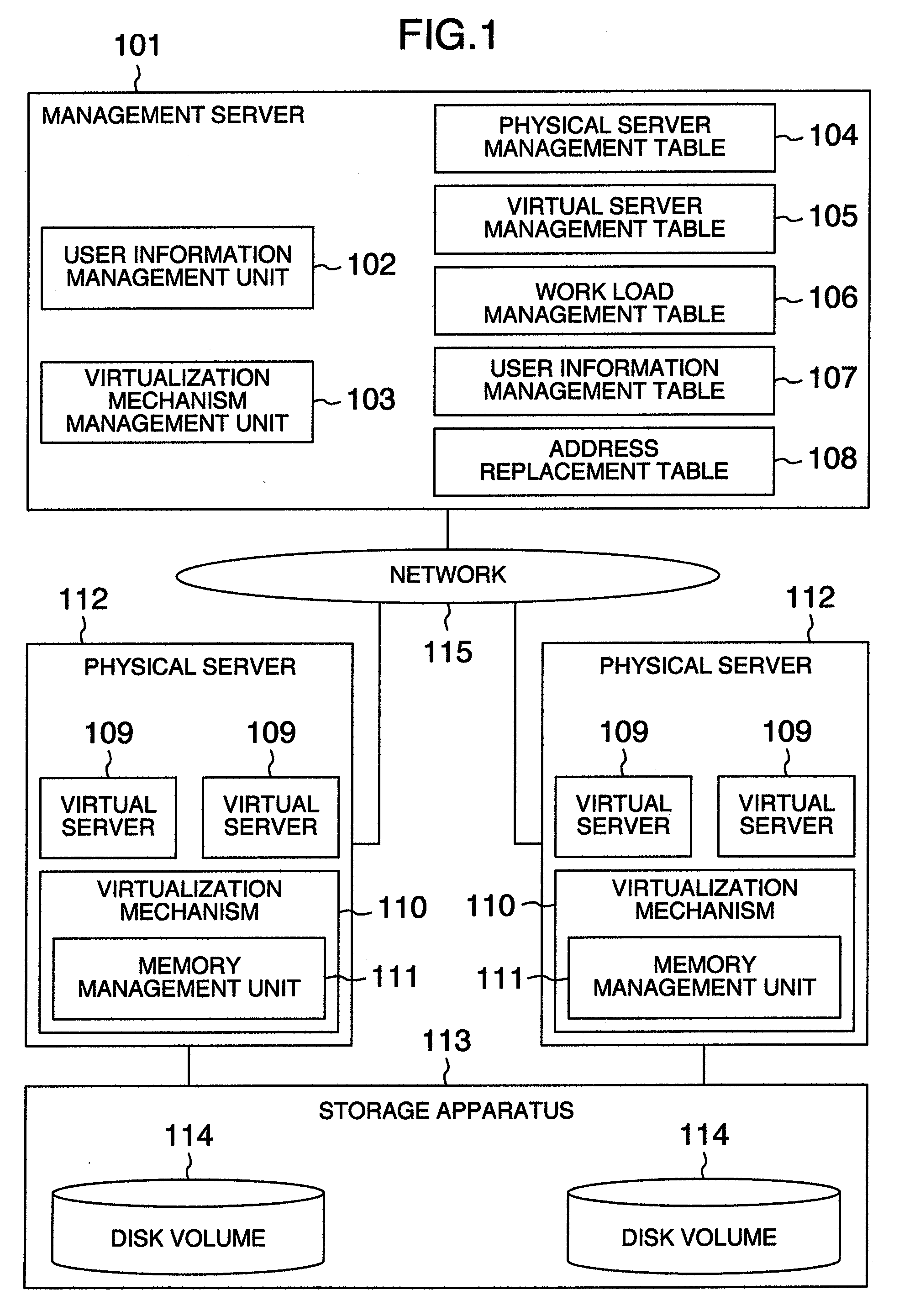
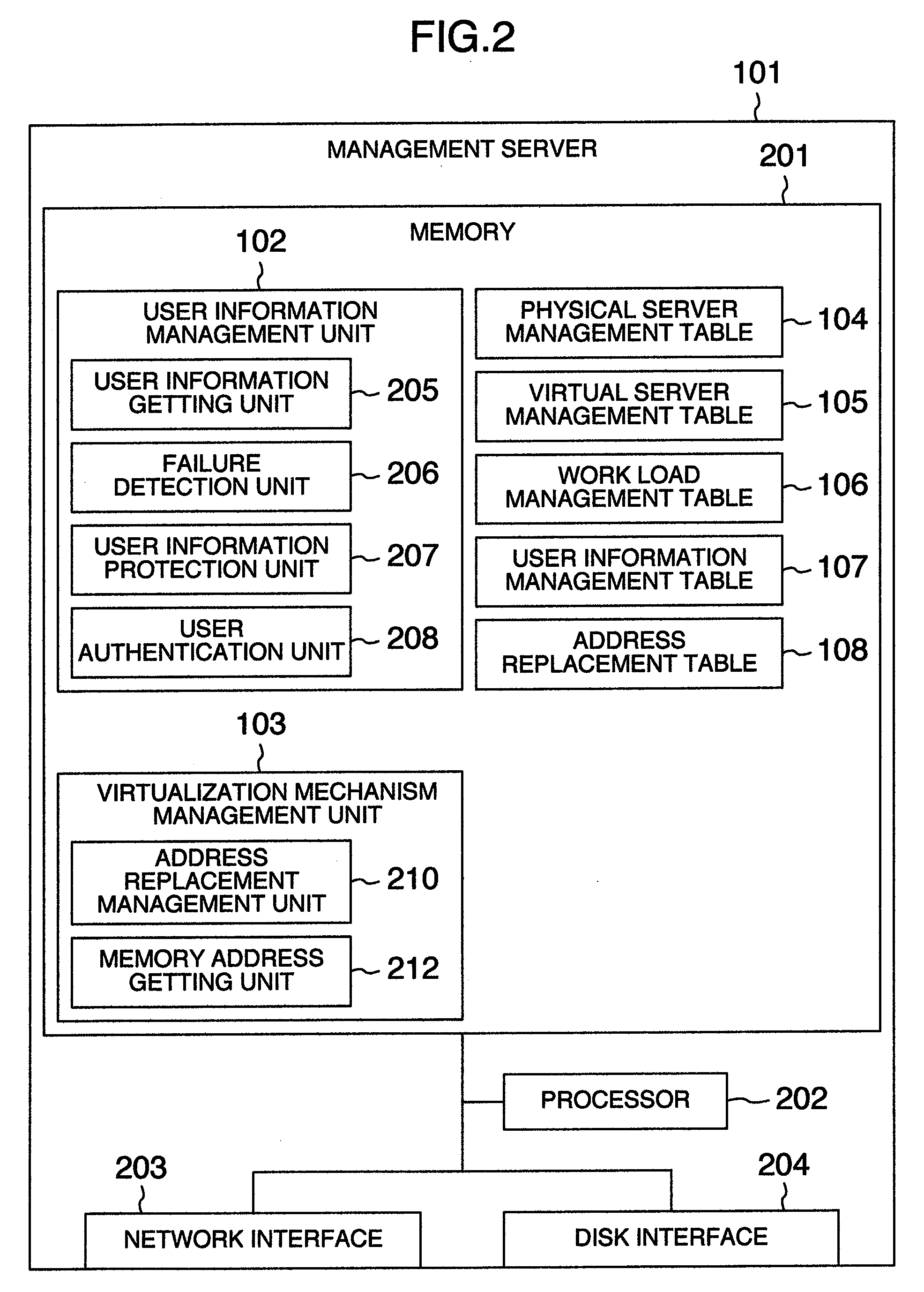
A user data protection method in which a management server includes an address replacement table having correspondence relation of memory addresses of a memory assigned to a virtual server and memory addresses of a memory assigned to a virtualization mechanism which is different from that at usual time, comprising the steps of: making, when an event occurs, the virtual server send virtual server identifier information for identifying the virtual server to the management server; making the management server detect the event; making the management server specify the virtual server in which the event occurs in accordance with the virtual server identifier information; sending the address replacement table to the virtualization mechanism of the physical server including the specified virtual server; and changing the correspondence relation of the memory addresses of the virtual server and the memory addresses of the virtualization mechanism on the basis of the address replacement table.
Owner:TAMAKI MASARU +3
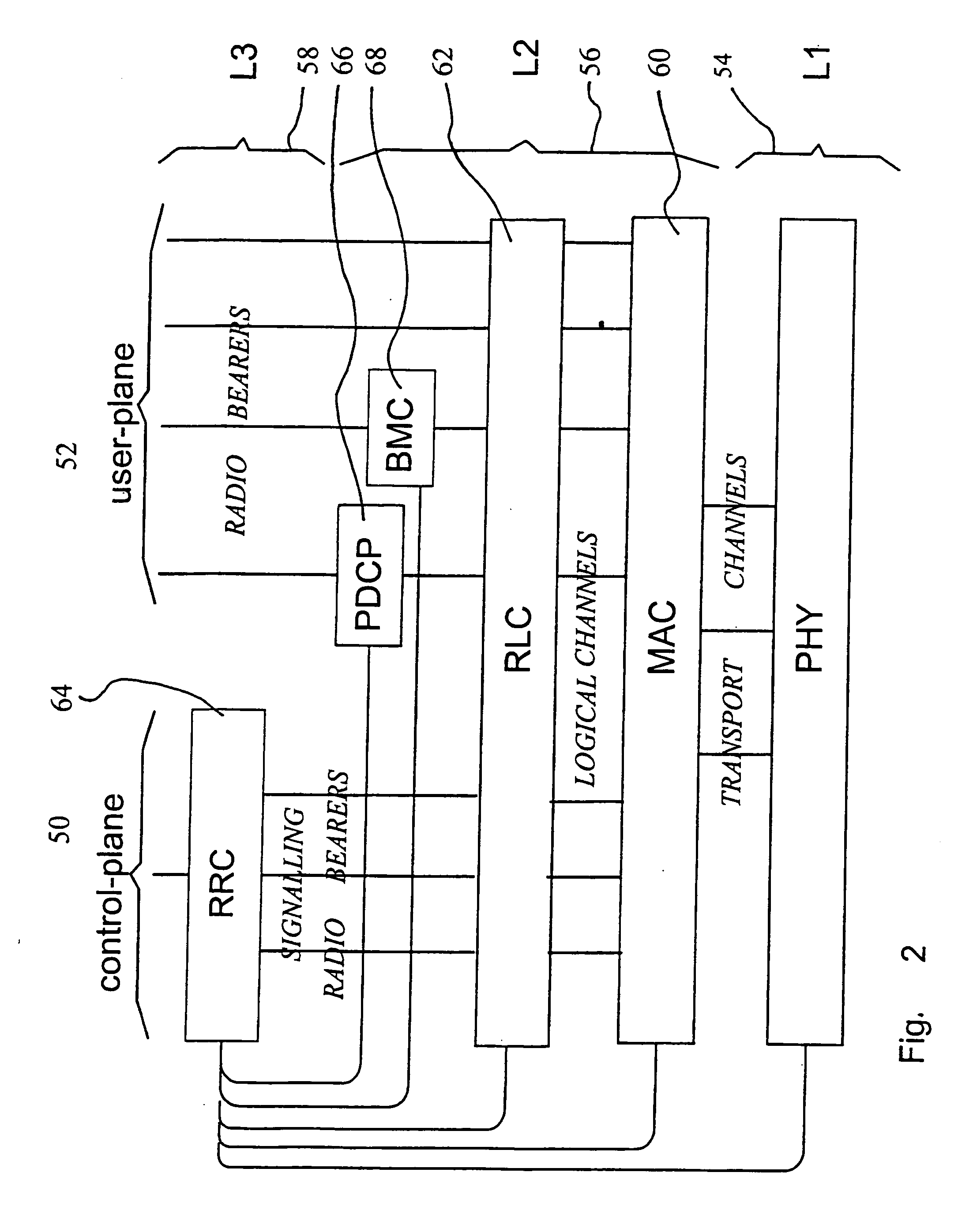
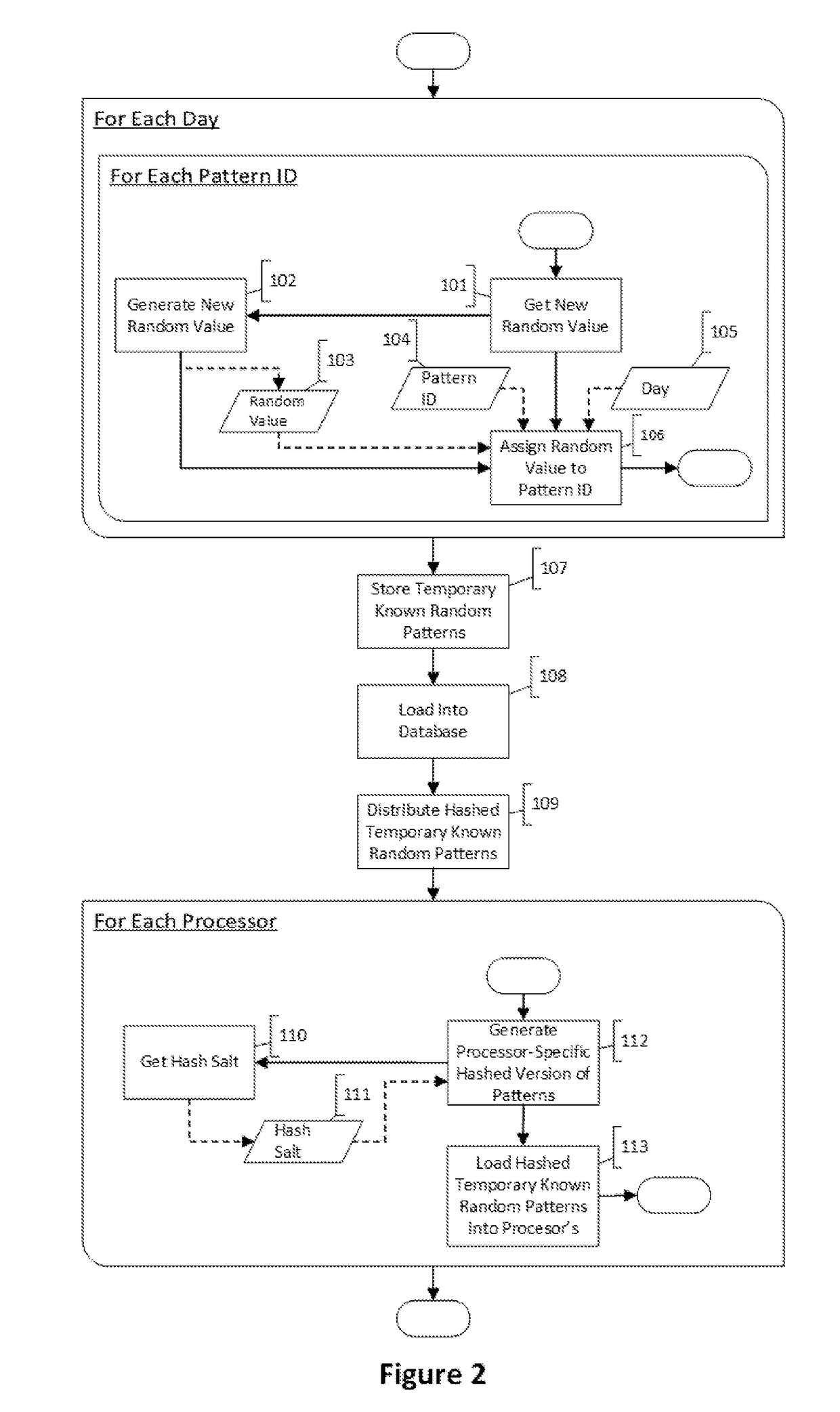
Method of ciphering data transmission in a radio system
InactiveUS20060120530A1Flexible controlImprove user securityData stream serial/continuous modificationSecret communicationComputer hardwareRadio networks
The invention relates to a method of ciphering data transmission in a radio system, and to a user equipment using the method, and to a radio network subsystem using the method. The method includes the steps of: (602) generating a ciphering key; (604A) producing a ciphering mask in a ciphering algorithm using the ciphering key as an input parameter; (604B) using a logical channel specific parameter or a transport channel specific parameter as an additional input parameter to the ciphering algorithm; and (606) producing ciphered data by applying the ciphering mask to plain data.
Owner:NOKIA TECHNOLOGLES OY
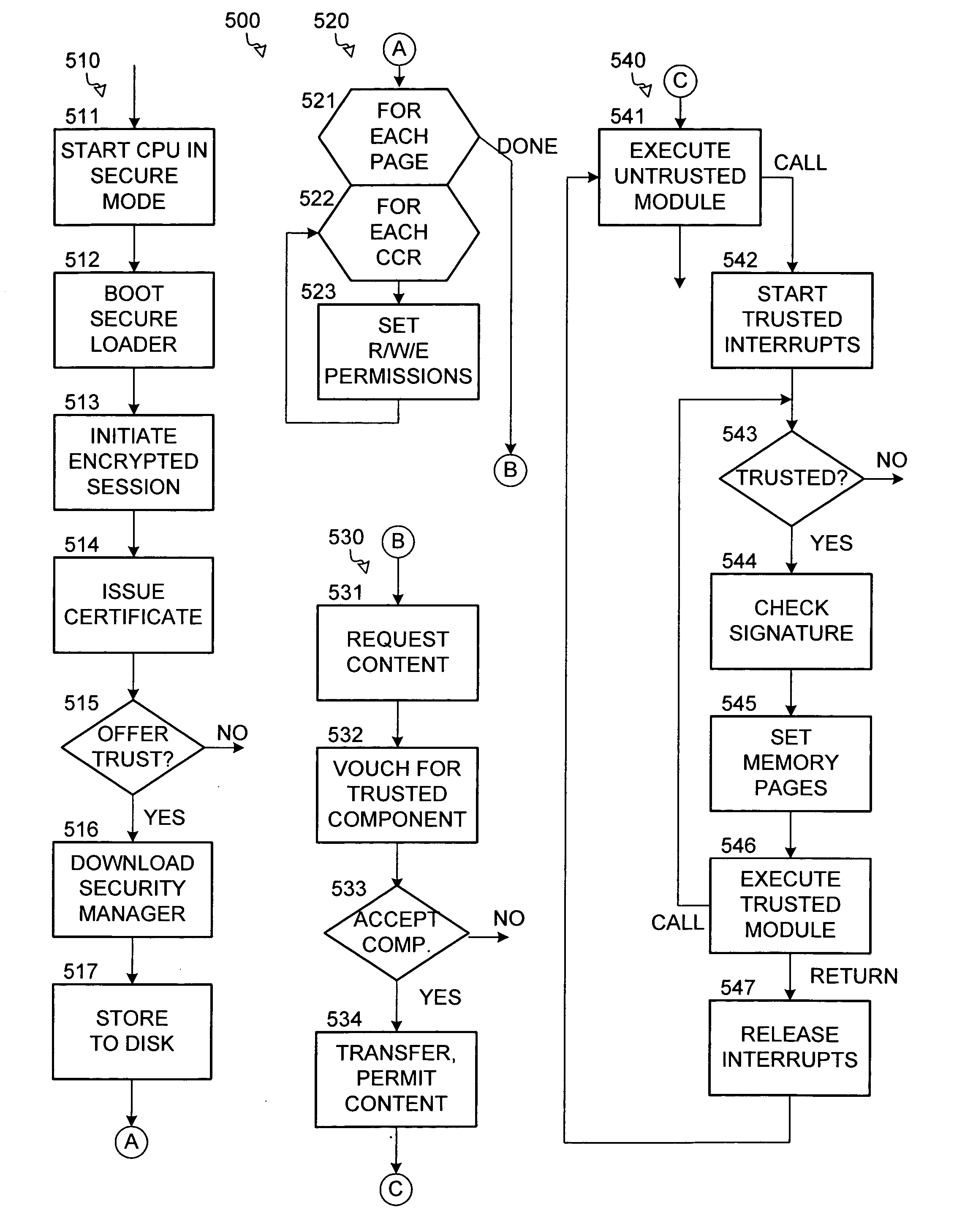
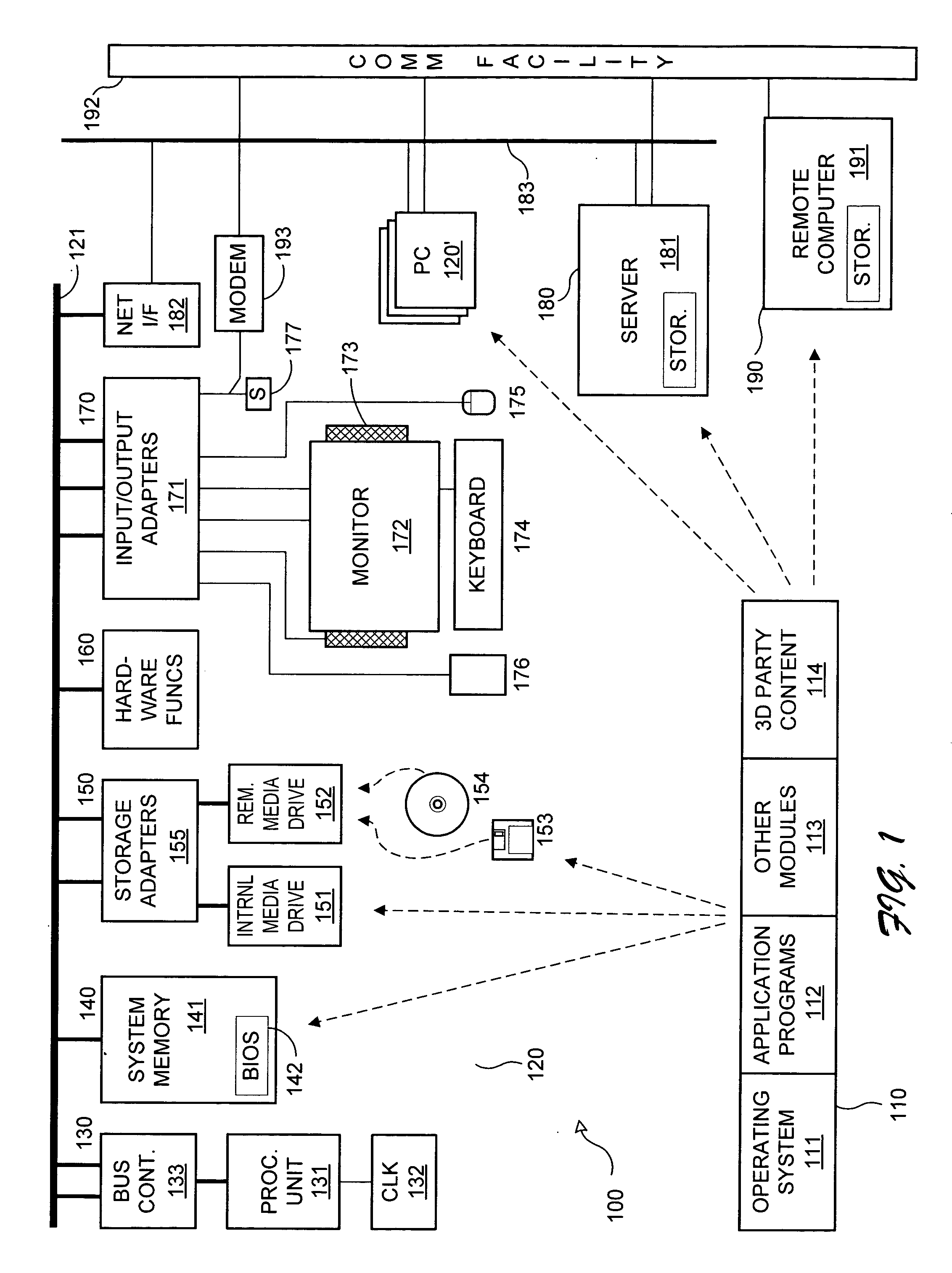
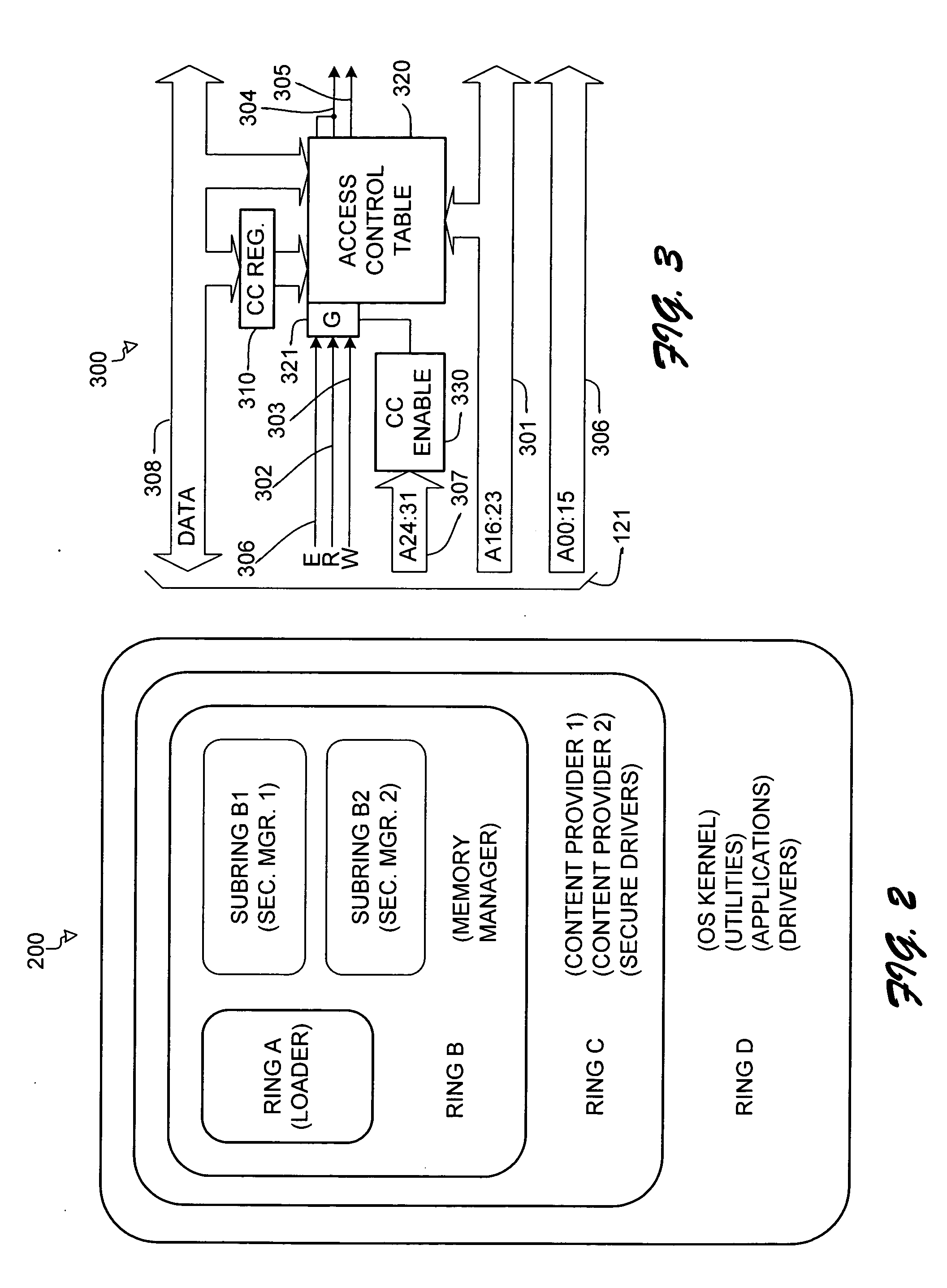
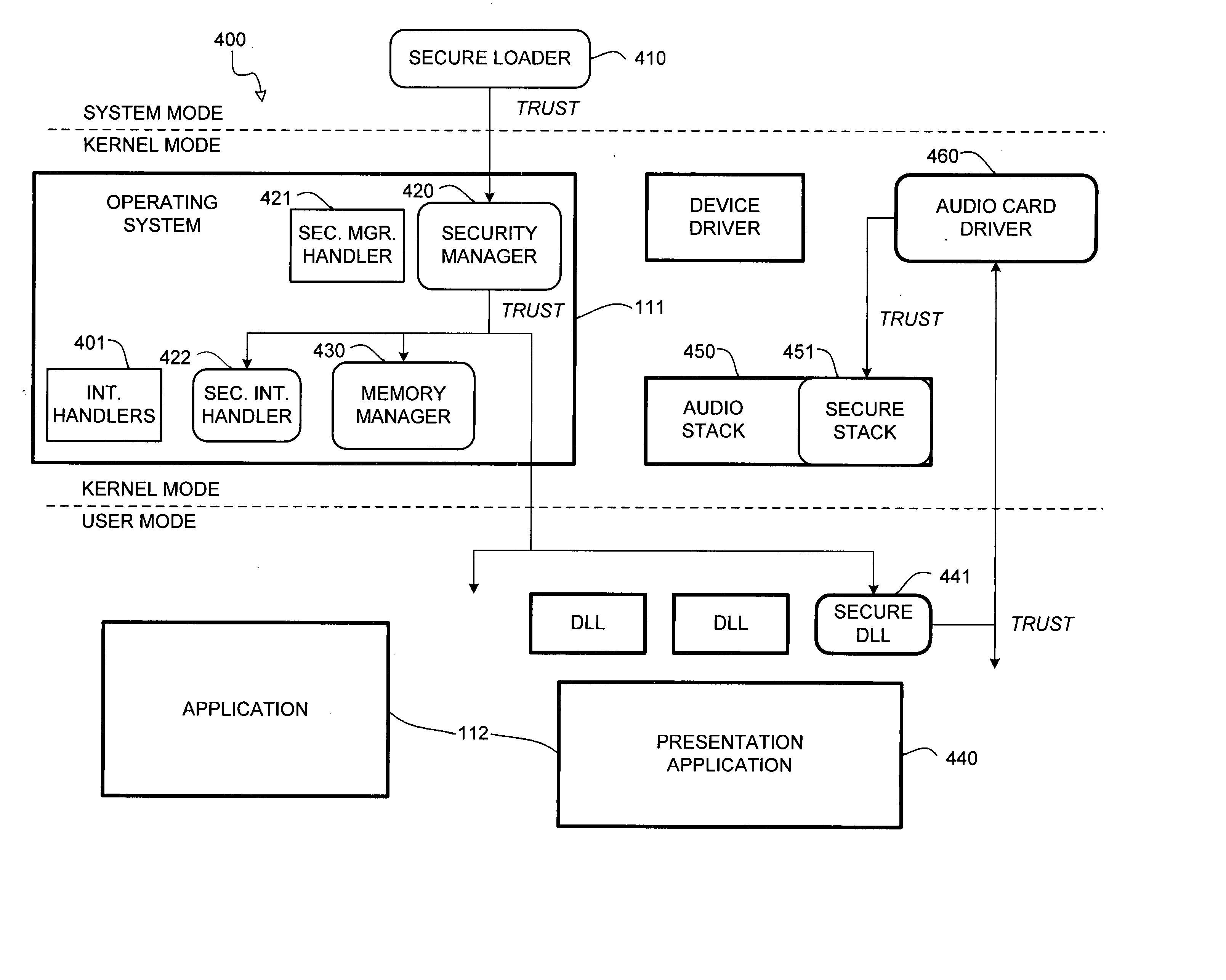
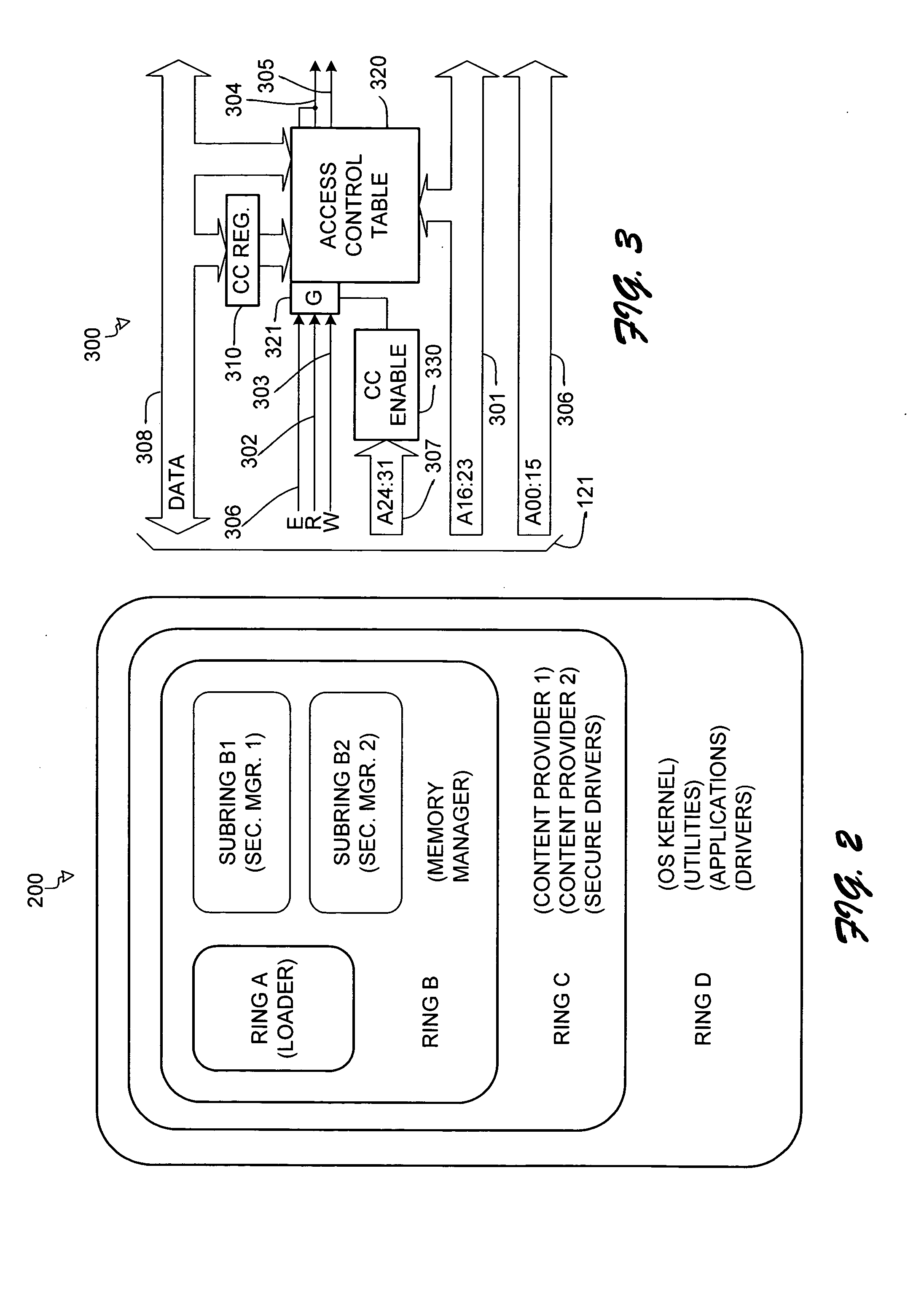
Hierarchical trusted code for content protection in computers
InactiveUS20050235362A1Improve user securityDigital data processing detailsUser identity/authority verificationCode moduleSecurity management
An architecture for protecting premium content in a nonsecure computer environment executes only a small number of code modules in a secure memory. The modules are arranged in a hierarchy of trust, where a module names other modules that it is willing to trust, and those modules in turn name other modules that they are willing to trust. A secure loader loads a security manager that oversees a number of content-providing modules for manipulating the content. A memory manager assigns permissions to various pages of the secure memory. The memory has rings of different security. The security model can be extended to program modules and other devices on the computer's bus, such as DMA controllers and peripherals.
Owner:MICROSOFT TECH LICENSING LLC
Hierarchical trusted code for content protection in computers
InactiveUS20050097355A1Improve user securityDigital data processing detailsUser identity/authority verificationPeripheralSecurity management
An architecture for protecting premium content in a nonsecure computer environment executes only a small number of code modules in a secure memory. The modules are arranged in a hierarchy of trust, where a module names other modules that it is willing to trust, and those modules in turn name other modules that they are willing to trust. A secure loader loads a security manager that oversees a number of content-providing modules for manipulating the content. A memory manager assigns permissions to various pages of the secure memory. The memory has rings of different security. The security model can be extended to program modules and other devices on the computer's bus, such as DMA controllers and peripherals.
Owner:MICROSOFT TECH LICENSING LLC
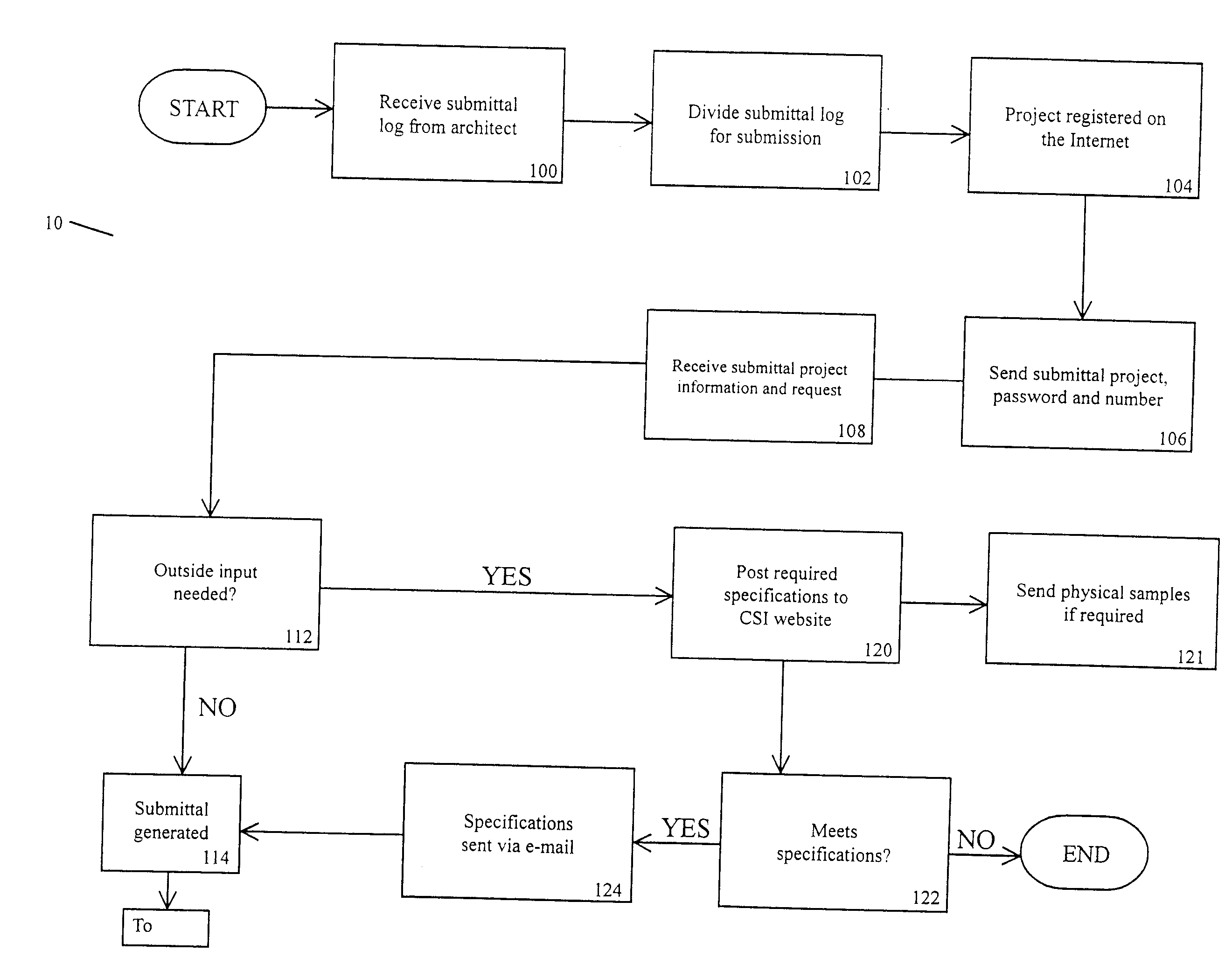
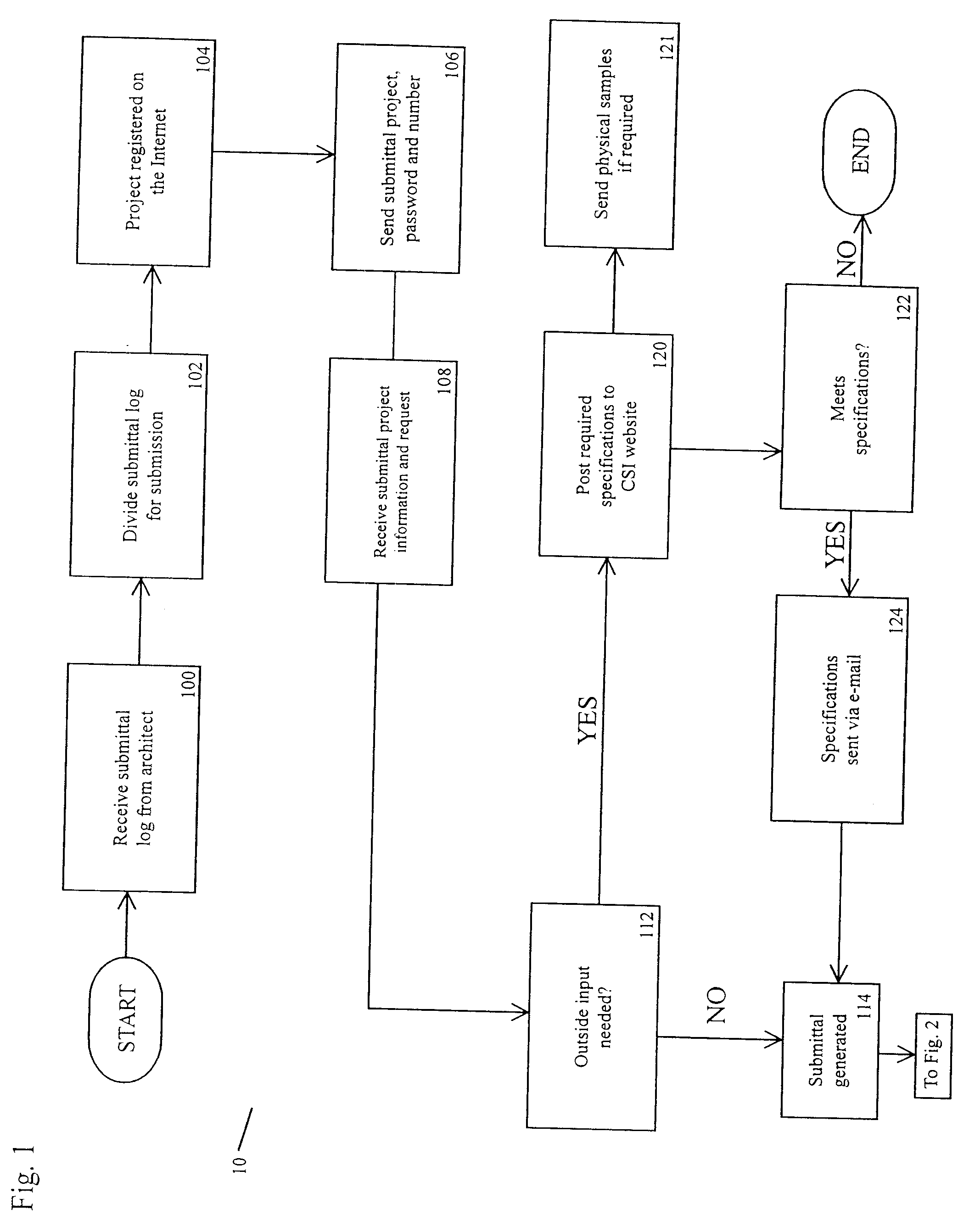
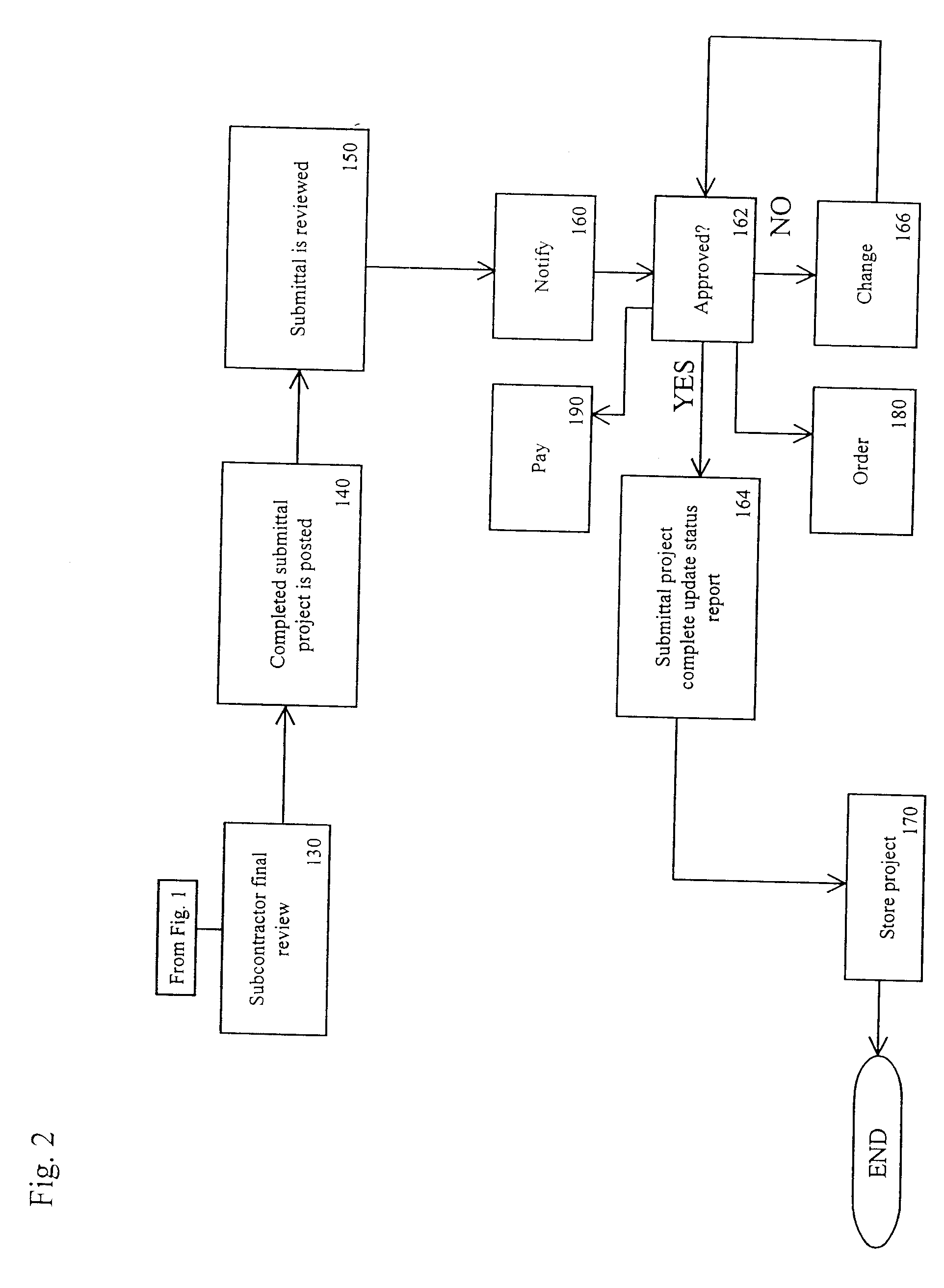
Construction project submittal management
InactiveUS20080288364A1Improve reliabilityImprove user securityMarket predictionsAnimal feeding devicesEngineeringConstruction management
A network based construction project management system. The system includes network accessible databases of project information including drawings and specifications. The system allows for varying amount of access for various user including general contractors, subcontractors, architects and project owners. The system allows for the effective creation, management and long term accessible storage of project submittals.
Owner:HARRIS ELBERT
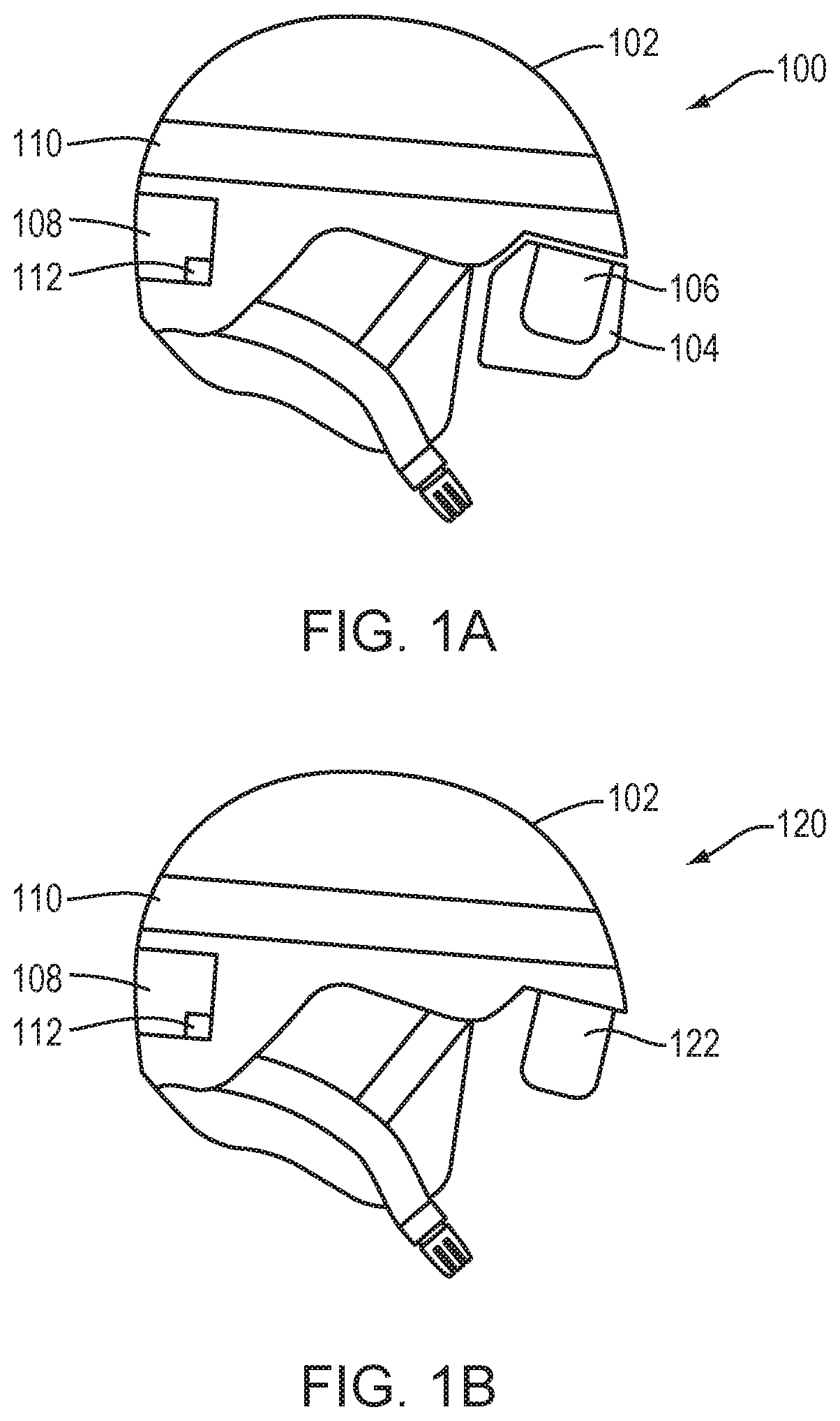
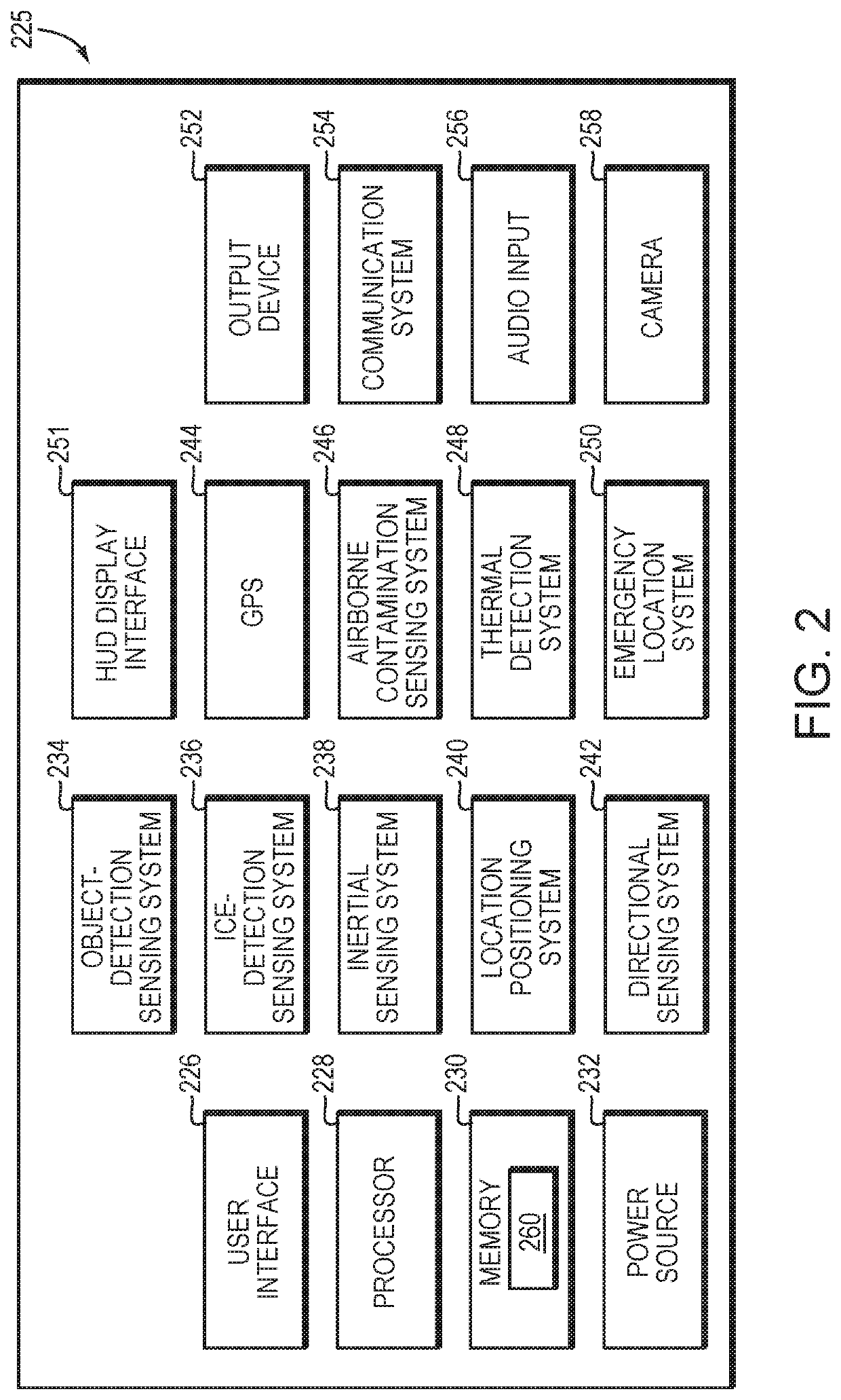
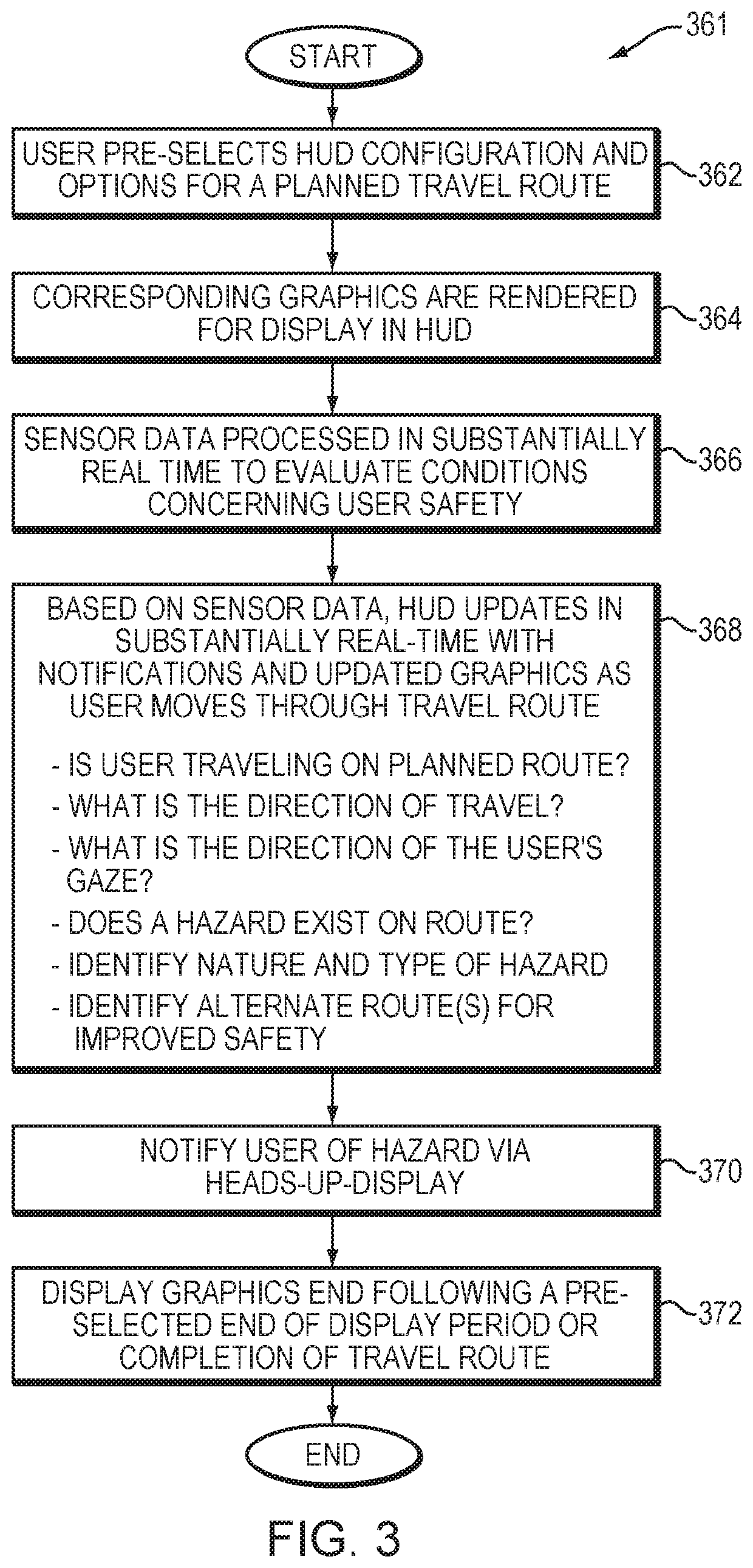
Smart safety helmet with heads-up display
ActiveUS20200015536A1Improve user securityImprove securityInstruments for road network navigationGogglesComputer hardwareGraphics
A safety system is configured to be worn by a user. The safety system includes a helmet, a transparent display screen coupled to the helmet and configured to provide eye safety for the user, the transparent display screen configured to display graphical information to the user in substantially real time. According to one embodiment, if a hazard is identified in a first route, the apparatus communicates an identification of the hazard for display to the user via the transparent display screen. Further, if the hazard is identified in the first route, the apparatus communicates an identification of a second route for display to the user via the transparent display screen, the second route avoiding the hazard with each of the first route and the second route rendered in the transparent display screen. According to various embodiments, the apparatus operates in substantially real time to evaluate conditions in the first route based on information provided by the at least one sensing system to determine whether the hazard exists.
Owner:CICCAGLIONE SARAH NICOLE
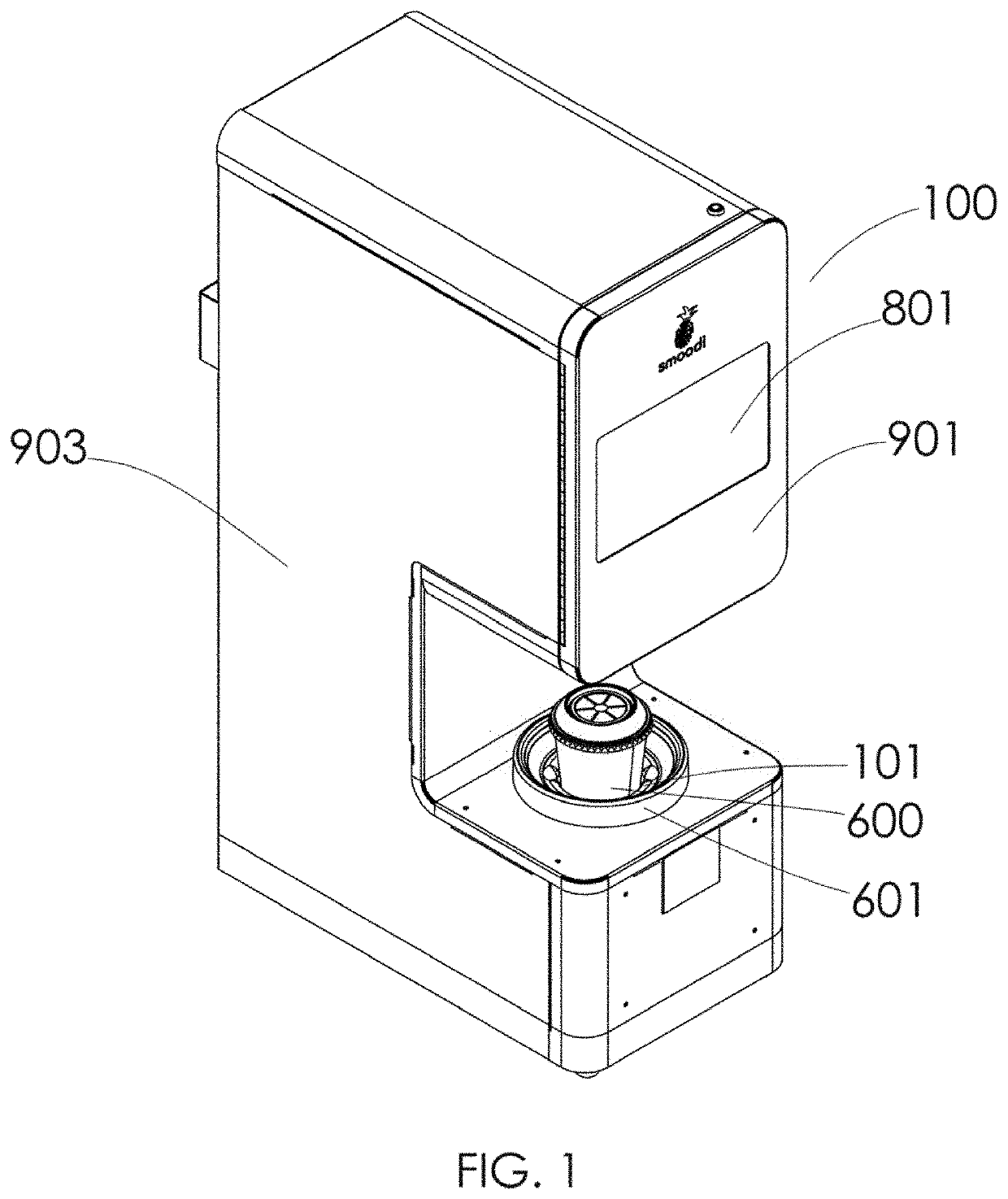
Self-cleaning automated blended drink machine
PendingUS20210274974A1Improve user securityImprove securityKitchen equipmentFood scienceIceboxProcess engineering
A stand-alone automated machine for the automatic blending of drinks. The machine will generally puree materials including fresh or frozen fruits and vegetables provided in large particulate sections or chunks within a cup which is available from a neighboring refrigerator or freezer unit. The blending machine can handle all aspects of drink blending as well as automatic cleaning, sanitization, and / or sterilization cycles.
Owner:SMOODI INC
Method and device for robust detection, analytics, and filtering of data/information exchange with connected user devices in a gateway-connected user-space
InactiveUS20180041529A1Improve user securityImprove network securityComputing modelsTransmissionUser deviceOperation safety
A security appliance includes: a network port enabling direct connection to a gateway; a storage module having stored thereon firmware for operating the security appliance; and a processor that executes the program code of the firmware. The firmware configures the appliance to: establish a seamless communication interface with a connected gateway; monitor traffic coming into and going out from the connected gateway; and identify traffic anomalies within the monitored traffic. The firmware further configures the appliance to: in response to identifying one or more of the traffic anomalies: forward information about the identified traffic anomalies to a centralized database for evaluation and reporting; and initiate steps to prevent further occurrence of the traffic anomalies, without user approval.
Owner:OAK TREE LOGIC LLC
Securing passwords by using dummy characters
ActiveUS20210157900A1Improve user securityDigital data authenticationTransmissionInternet privacyPassword
Various systems and methods are provided for using dummy characters to provide enhanced security of a user's login credentials. The functionality disclosed herein provides specific steps for the creation, evaluation, storage, and use of such dummy characters in conjunction with a user's login credentials. Dummy characters can be thought of as characters that are not part of a user's actual password, but which are mixed in and around the actual characters when the password is being entered, in order to protect a user's true password from prying eyes and nefarious actors. Dummy characters can be associated with a specific user and / or a specific device or devices associated with a specific user. The functionality provided herein prevents a nefarious actor from simply repeating an entire password string (including the dummy characters) on a device that is not associated with the user whose credentials the nefarious actor is attempting to misappropriate.
Owner:DELL PROD LP
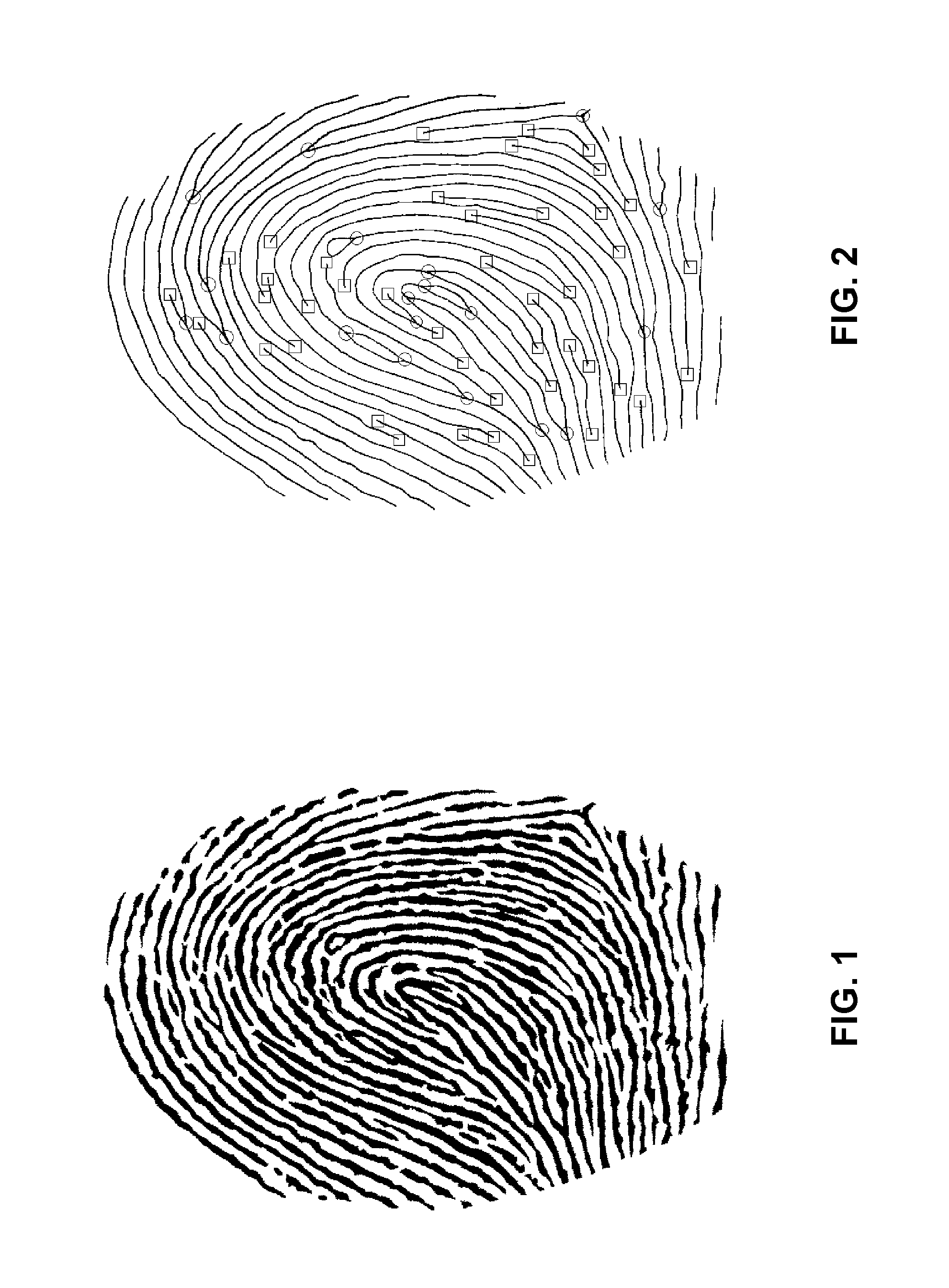
Fingerprint enrolment algorithm
InactiveUS9483679B2Limited desirabilityExtension of timeImage enhancementImage analysisPattern recognitionMinutiae
A method of enrolling a fingerprint using a narrow-width fingerprint scanner is described. The method may include the steps of receiving first, second, and third fingerprint image strips, respectively representing overlapping portion of the fingerprint, extracting minutiae from each of the fingerprint image strips, matching the extracted minutiae to determine relative positions of the fingerprint image strips, combining the extracted minutiae based on their relative positions to produce a combined set of minutiae representing a larger portion of the fingerprint, and determining that the fingerprint has been successfully enrolled if a width of the larger portion is greater than a predetermined minimum width, or, if not, requesting further fingerprint image strips until the width of the larger portion of the fingerprint is greater than the predetermined minimum width.
Owner:ZWIPE
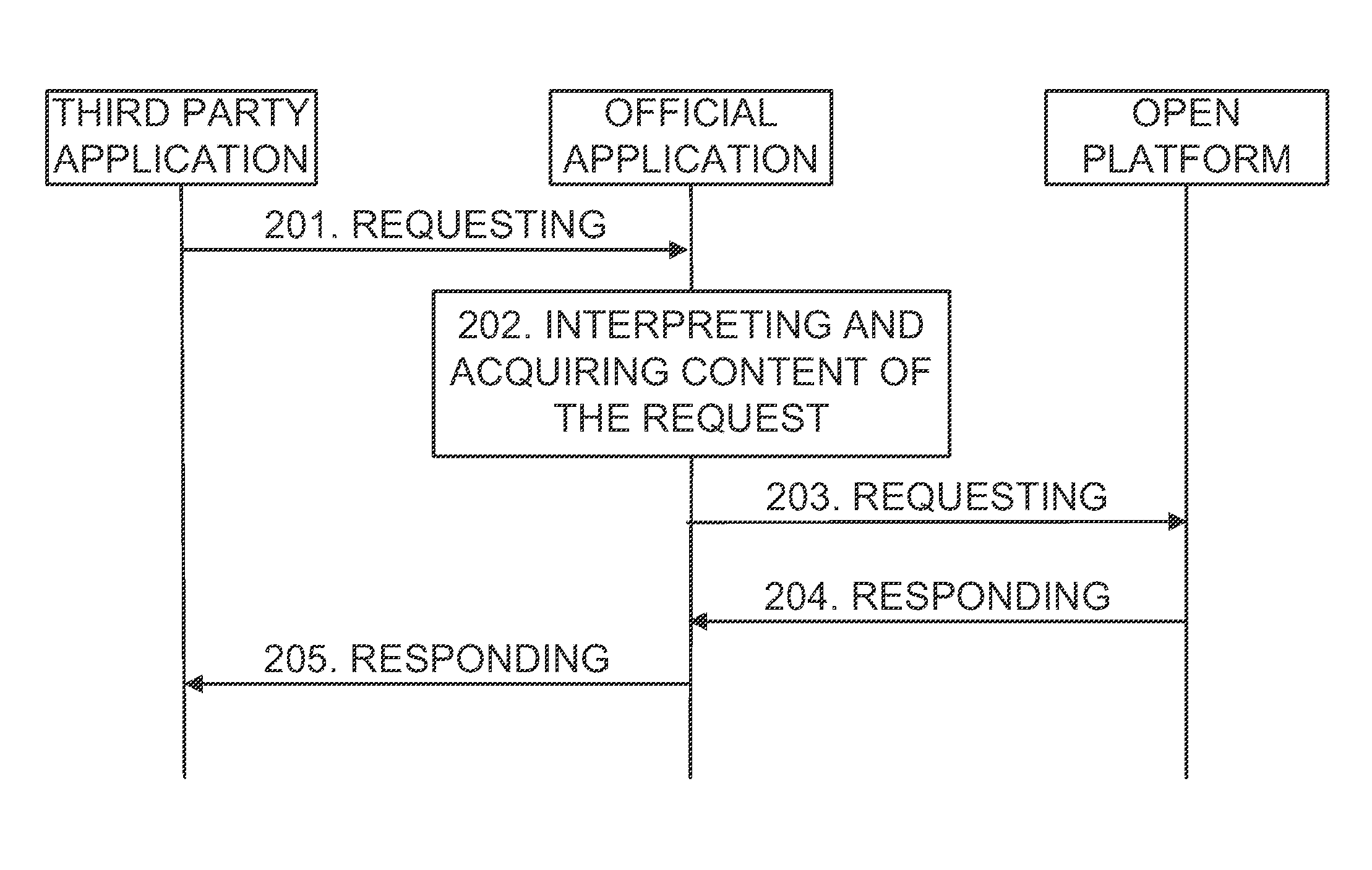
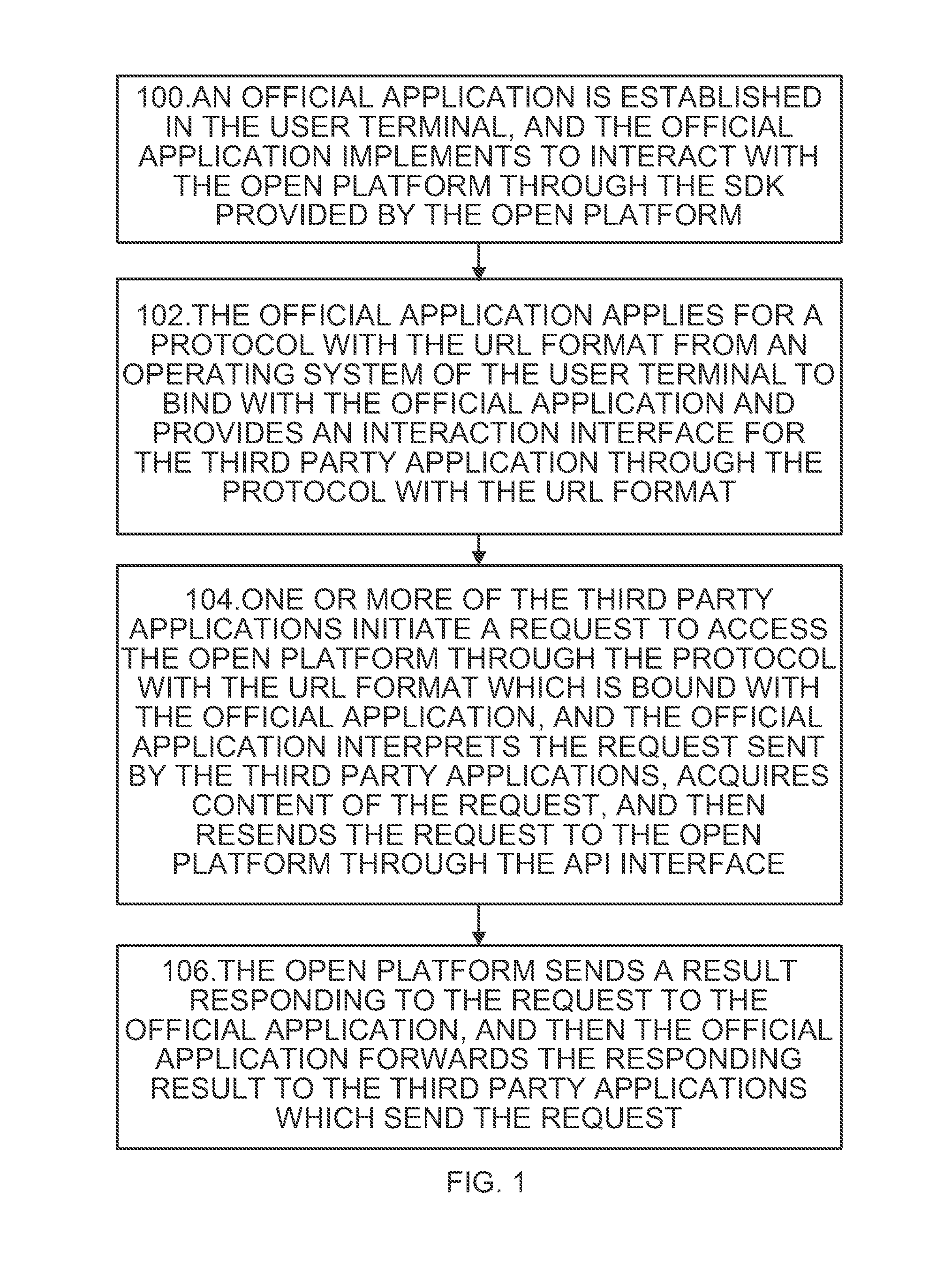
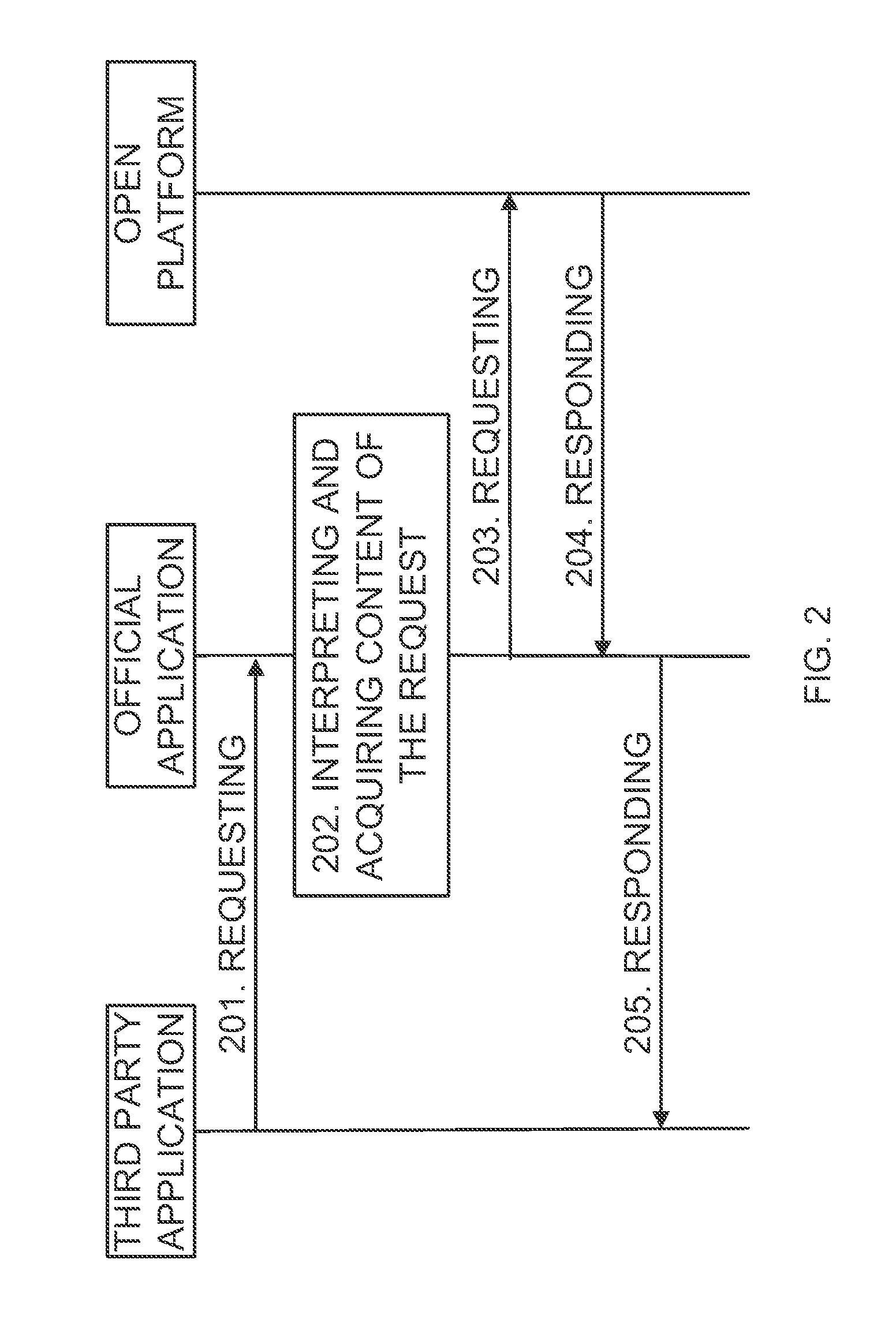
Method and device for proxy access of open platform
ActiveUS9032489B2Reduce development costsImprove user securityDigital data processing detailsMultiple digital computer combinationsThird partyOperational system
Disclosed are a method and device for a proxy access of an open platform for solving technical problems that resource occupancy is excessive, a password security is low, and a local file cannot be uploaded. In the present invention, an official application is established in a user terminal, and the official application interacts with the open platform by an SDK provided by the open platform; the official platform is bound by applying for a protocol with the URL format from an operating system of the user terminal, and provides an interaction interface for the third party application through the protocol with the URL format. Therefore, the present invention reduces the system resource which the third party application occupies in the user terminal and the development cost of the third party application, and protects the security of the user's account.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Transaction device with noise signal encryption
ActiveUS7392396B2Good encryptionImprove user securityUnauthorized memory use protectionHardware monitoringNoise componentEncryption
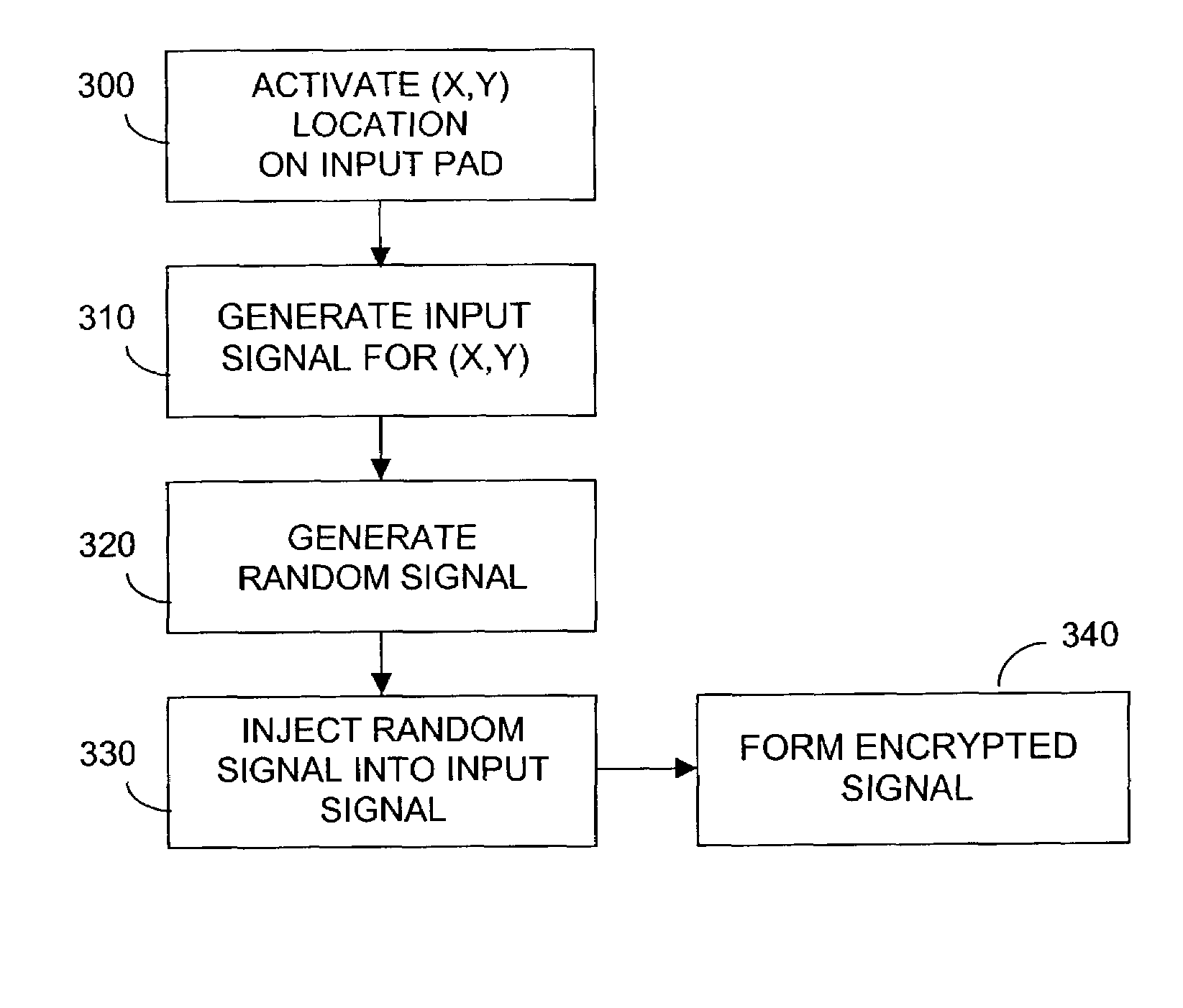
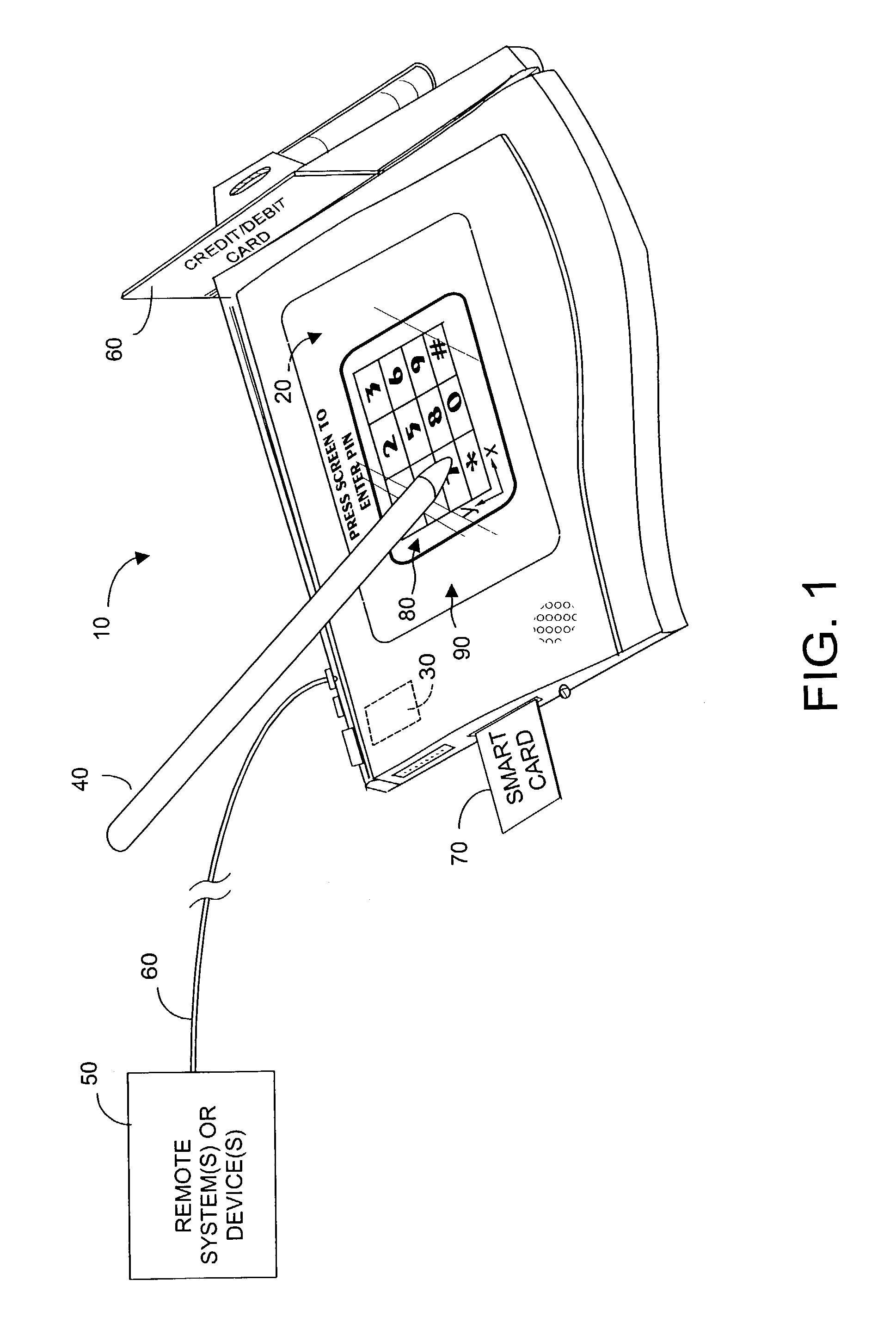
A transaction device adds or injects a random noise component into signals representing (x,y) coordinate signals associated with user interface with an input screen associated with the device. The noise component can be generated by converting to analog the output of a random number generator, and then adding the noise component to the x-axis and / or y-axis component of the (x,y) coordinate signal. Alternatively the noise component can be injected into the x-axis and / or y-axis operating potential for the input screen. The result is a masking of the original (x,y) positional information. The randomly generated number is only available internal to the device. The device can use this number to de-crypt the true (x,y) signals, which signals can then be re-encrypted before transmitting from the device.
Owner:SYMBOL TECH LLC
Safety athletic pole
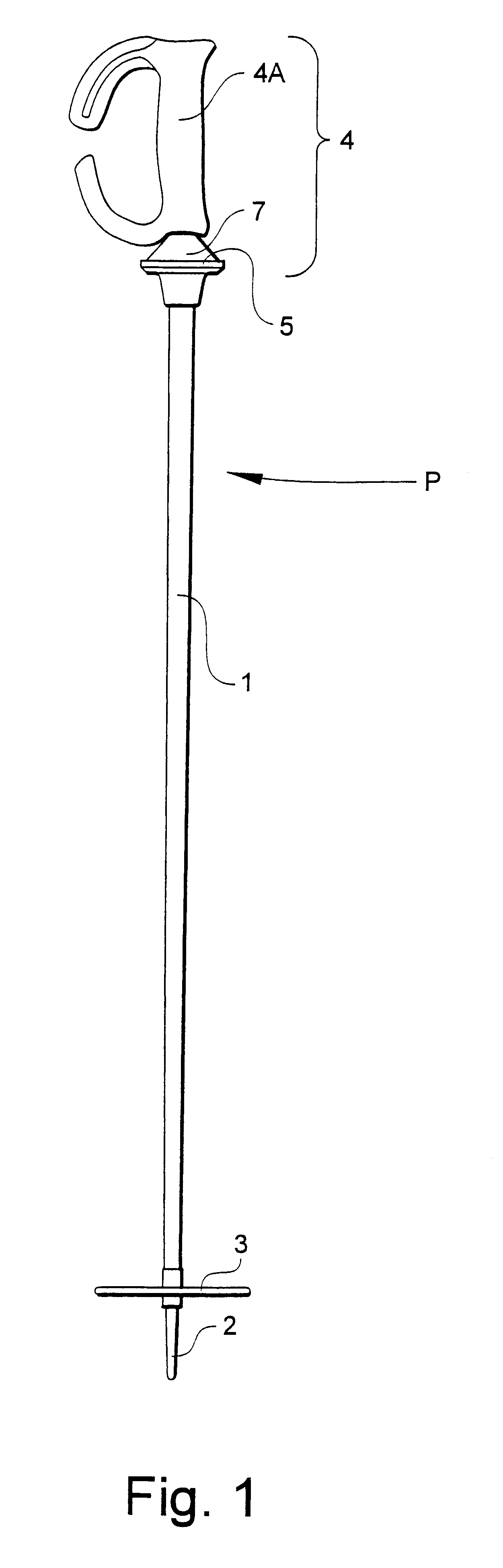
InactiveUS6203063B1Improve user securityProlong lifeWalking sticksYielding couplingEngineeringBending force
An athletic pole including a handle, a shaft, and a handle-to-shaft transition assembly, the transition assembly adapted for allowing the handle to articulate. The transition assembly includes an enlarged shaft base on the shaft, the shaft base including a handle-base-engaging surface. The transition assembly also includes an enlarged handle base on the handle. The handle base and the shaft base are biased together by a tension force into a mating, coaxially aligned position when any bending forces applied to the pole are insufficient to overcome the tension force, the handle being pivotable to an articulated position relative to the shaft upon the application of a predetermined bending force on the pole sufficient to overcome the tension force. During handle articulation, the enlarged dimensions of the handle base and the shaft base allow the periphery of the handle base to travel across and engage the handle-base-engaging surface of the shaft base such that, after an initial range of handle articulation, the bending force necessary to continue articulation or to maintain the handle in a desired articulated position is reduced relative to the bending force that would prevail if the periphery of the handle base were not allowed to travel across the handle-base-engaging surface toward the center of the shaft base.
Owner:BUJOLD ED
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com