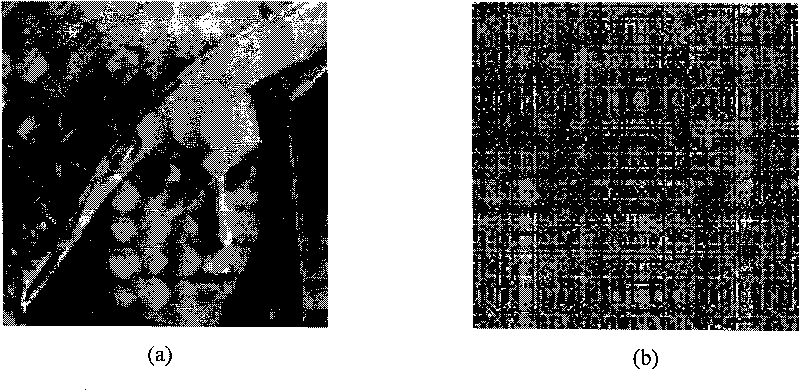Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
476results about How to "Good encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
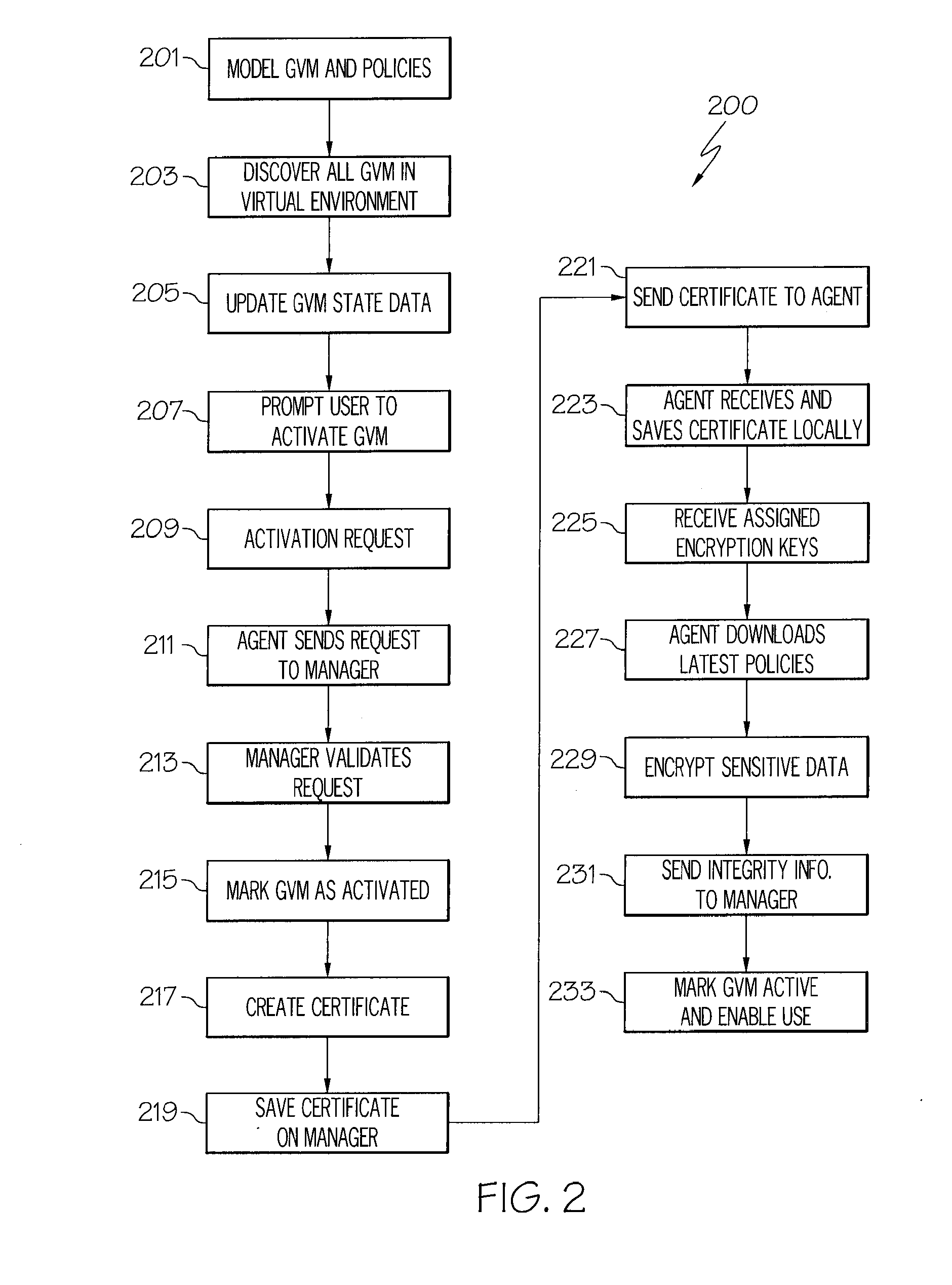
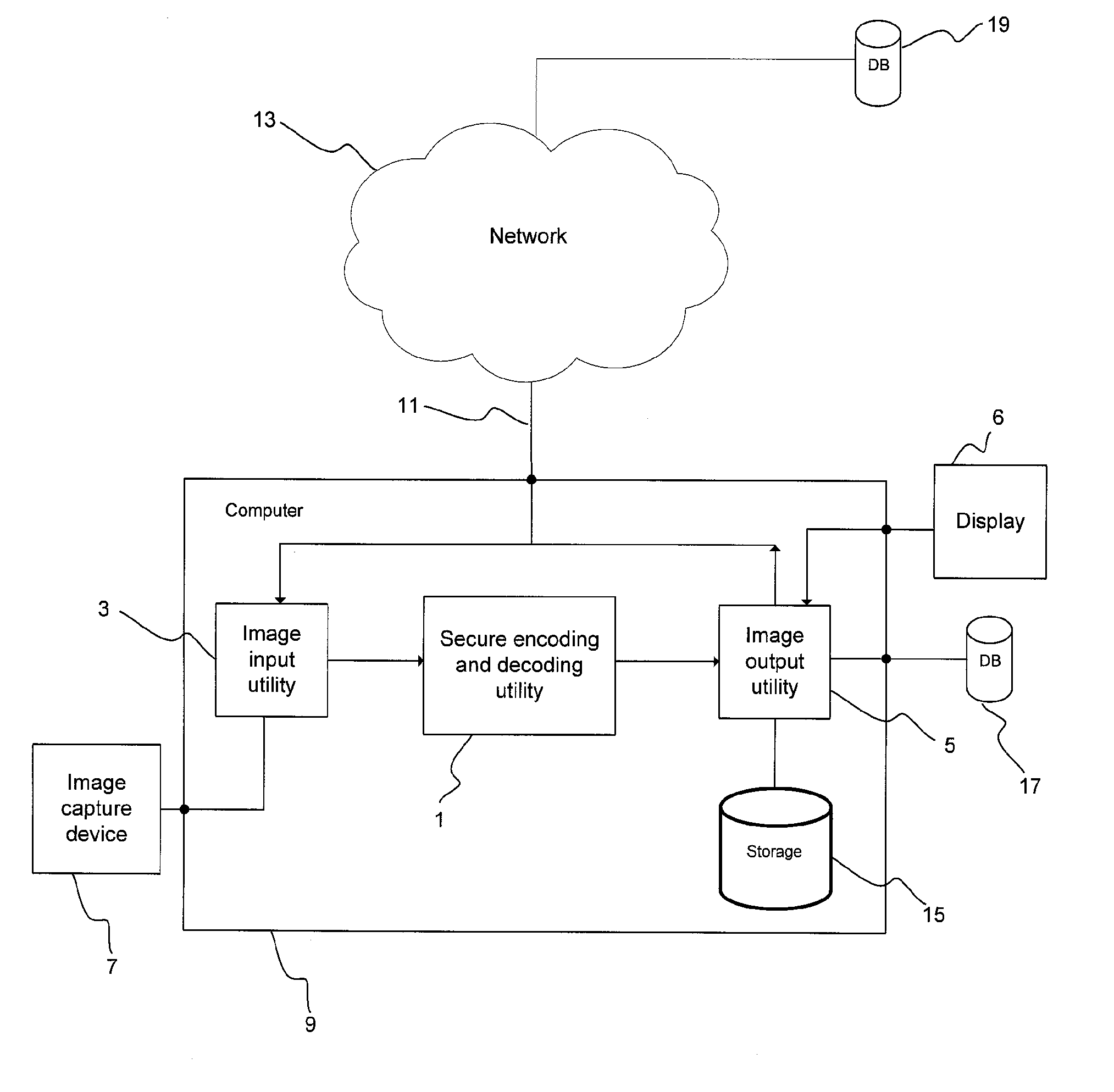
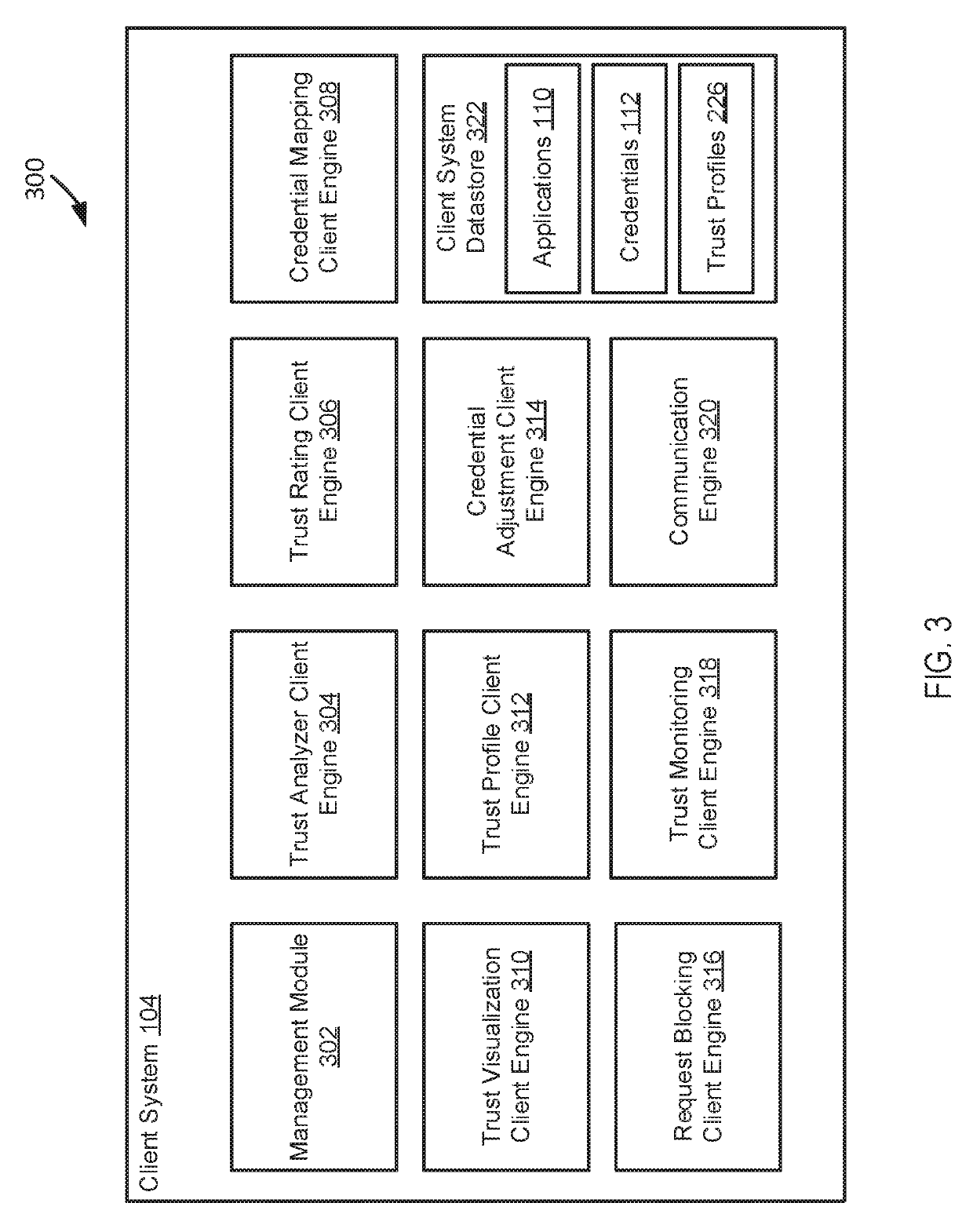
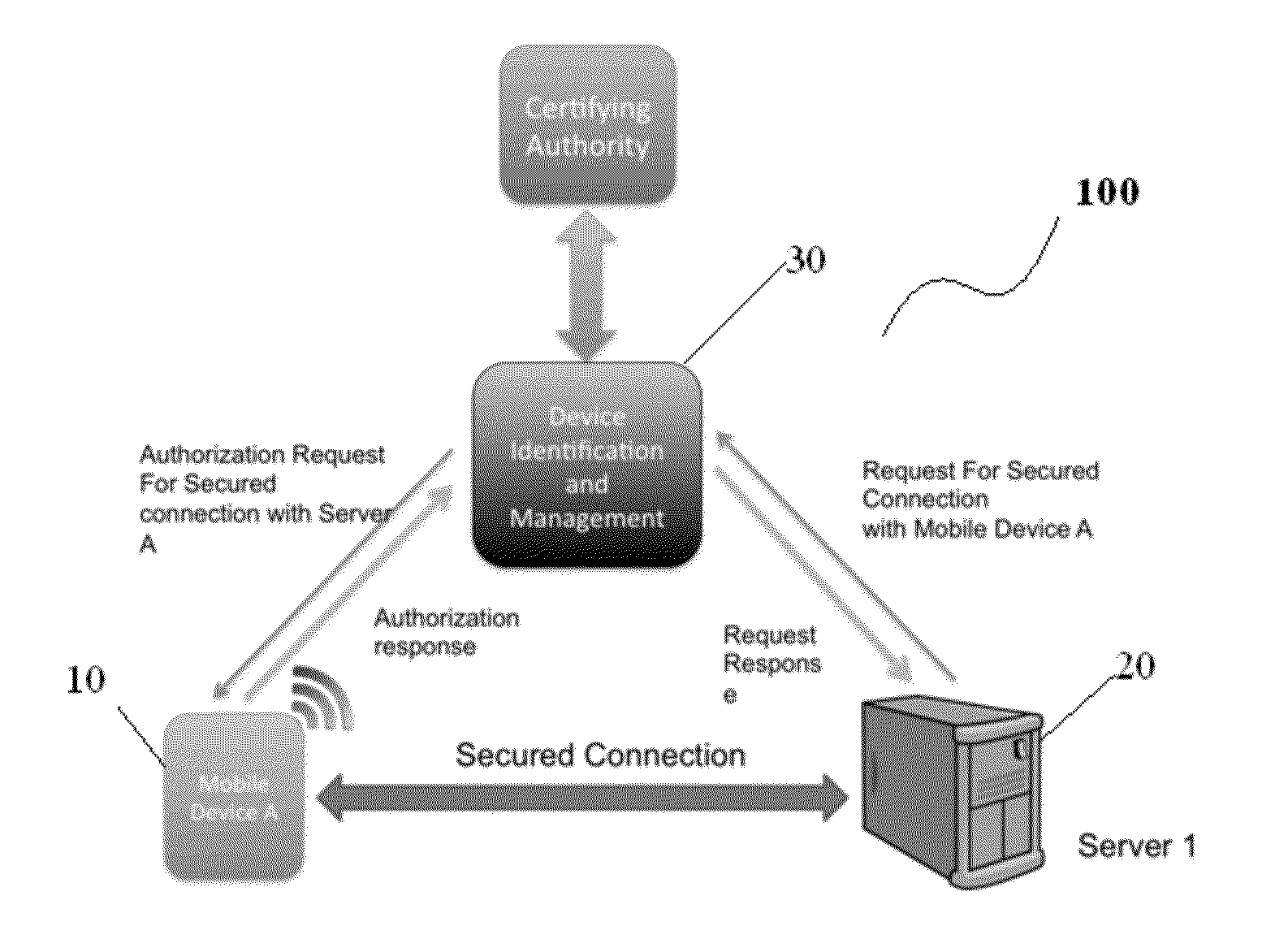
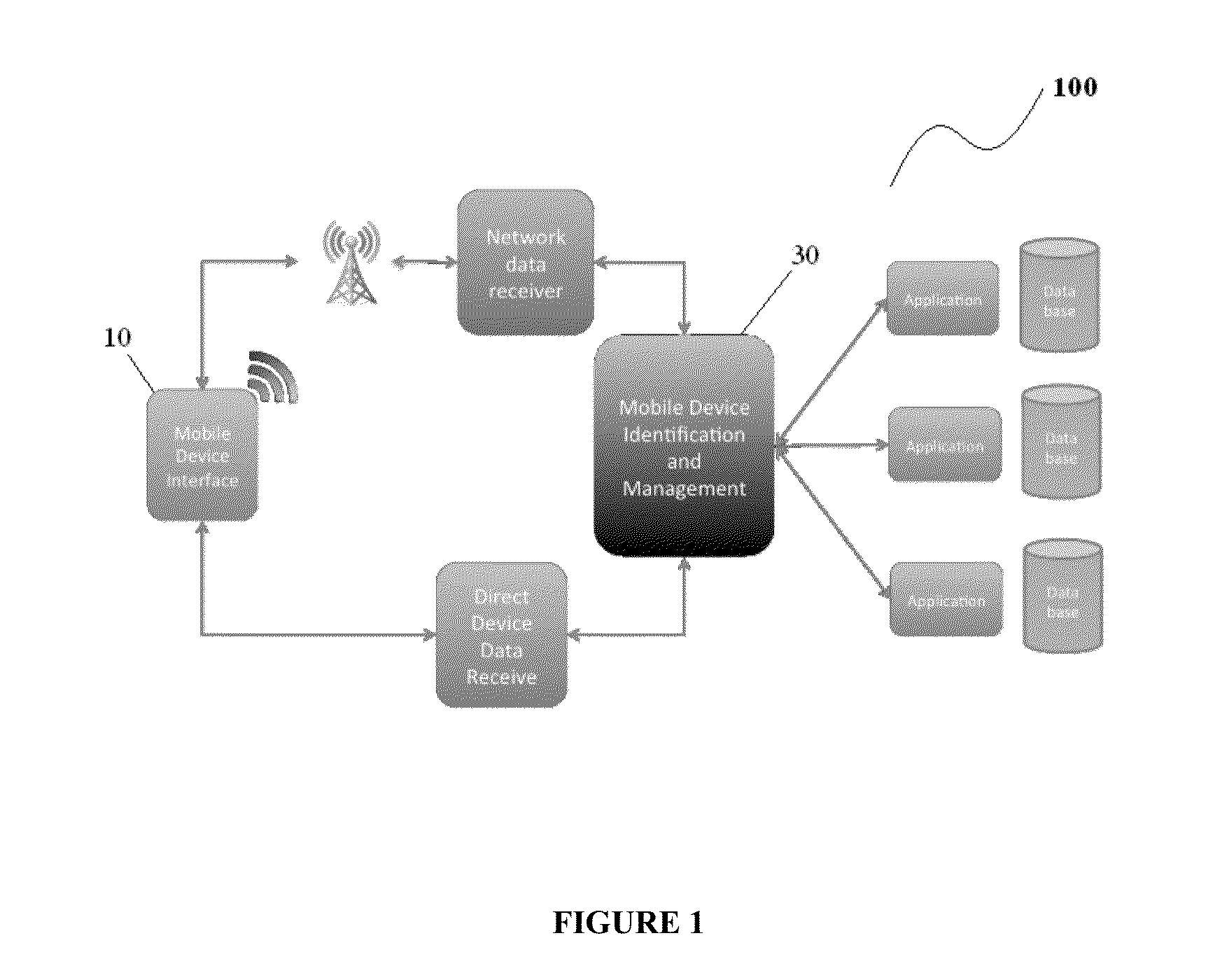
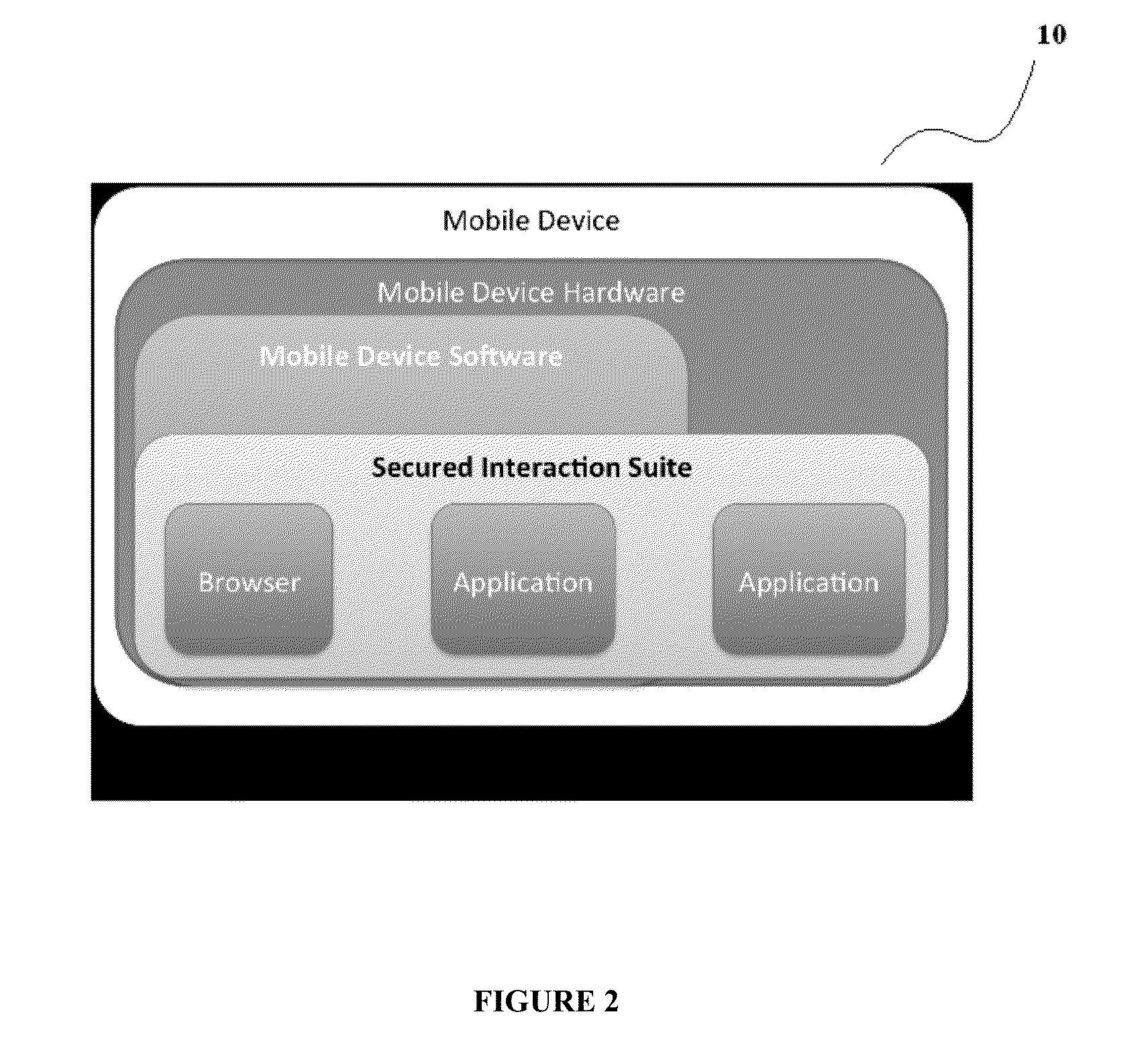
System and method for enforcement of security controls on virtual machines throughout life cycle state changes
ActiveUS20140096134A1Improve securityStrong security policyPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtual computingData storing
Systems and methods associated with virtual machine security are described herein. One example method includes instantiating a guest virtual machine in a virtual computing environment. The method also includes installing a life cycle agent on the guest virtual machine, assigning an identifying certificate, a set of policies, and an encryption key to the guest virtual machine, and providing the certificate, policies, and encryption key to the guest virtual machine. The certificate, policies, and encryption key may then be used by the guest virtual machine to authenticate itself within the virtual computing environment and to protect data stored on the guest virtual machine.
Owner:CA TECH INC
Inventory manager-chip kiosk
InactiveUS20070060307A1Easily trackReduce and eliminate number of timeApparatus for meter-controlled dispensingVideo gamesReceiptEngineering
A chip dispensing kiosk including a vault for holding casino chips, a dispensing assembly for dispensing selected numbers of casino chips and security and input systems to allow a pit boss to access the kiosk and have the kiosk dispense selected numbers of chips. The kiosk is interactive with the casino's accounting system so as to report the dispensing of casino chips or receipt of casino chips.
Owner:JCM AMERICAN CORP
BIOS integrated encryption
InactiveUS7376968B2Easy to decryptFacilitate secure rebooting of a computer systemDigital data processing detailsDigital computer detailsOperational systemComputerized system
A system and method for facilitating BIOS integrated encryption is provided. An interface is defined between the operating system and the BIOS. The operating system employs this interface to provide BIOS code information to facilitate decryption of data that is encrypted on the system. In the pre-operating system boot phase, the BIOS employs the decryption information provided from this interface in order to decrypt the data. The decrypted information can be employed to facilitate secure rebooting of a computer system from hibernate mode and / or secure access to device(s).
Owner:MICROSOFT TECH LICENSING LLC
Color image encryption and decryption method based on multiple-fractional-order chaotic systems
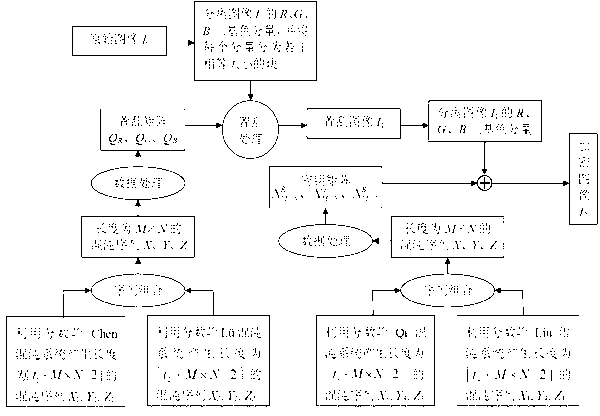
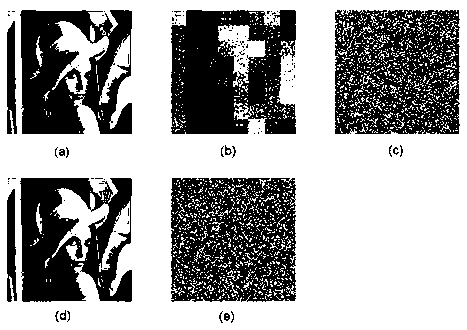
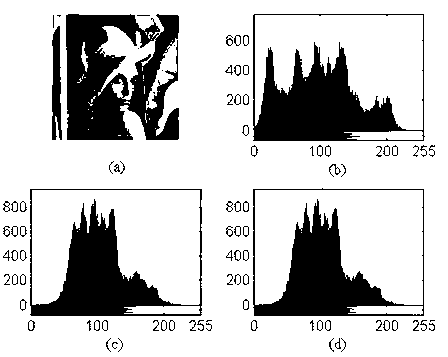
ActiveCN102982499ARich Dynamic BehaviorBig Key SensitivityImage data processing detailsKey spaceAlgorithm
The invention discloses a color image encryption and decryption method based on multiple-fractional-order chaotic systems. An encryption algorithm comprises an original image scrambling stage and a scrambling image encryption stage. Firstly, two different fractional-order chaotic systems are utilize to generate three scrambling arrays and respectively process R, G and B three primary color component arrays of an original color image I0 in a scrambling mode to obtain scrambled image I1. Furthermore, another two different fractional-order chaotic systems are utilize to generate three secret key arrays and carries out exclusive OR operation on elements on the secret key arrays and pixel of the scrambled image I1 one by one to change values of all pixel points of the scrambled image I1 to obtain encrypted image I2, and the image decryption is a reversed process of the encryption. The method uses the multiple-fractional-order chaotic systems so as to greatly enhance safety. Furthermore, the algorithm secret keys are large in space, high in secret key sensitiveness and strong in impact resistance.
Owner:HENAN UNIVERSITY
Fully Homomorphic Encryption from Monoid Algebras
ActiveUS20170134158A1Improve securityReduce chancePublic key for secure communicationCommunication with homomorphic encryptionCiphertextSecurity parameter
A blueprint that produces a family of FHE schemes given any homomorphic monoidal encryption scheme. The ciphertext space is a subspace of the monoid algebra over F2 generated by the initial encryption monoid. The method can be generally applied to any monoid encryption schemes. Advantageously, monoid encryption schemes produce efficient FHE schemes with the inventive blueprint. Furthermore, the corresponding FHE scheme can correctly decrypt and efficiently compute circuits with low (polynomial in the security parameter) additive depth, a feature not realized by prior encryption methods.
Owner:CERTSIGN SA
Method and system for secure coding of arbitrarily shaped visual objects
InactiveUS20110158470A1Easy to compressGood encryptionCharacter and pattern recognitionImage codingComputer graphics (images)Visual Objects
The present invention relates to a method and system for secure coding of arbitrarily shaped visual objects. More specifically, a system and method are provided for encoding an image, characterized by the steps of selecting one or more objects in the image from the background of the image, separating the one or more objects from the background, and compressing and encrypting, or facilitating the compression and encryption, by one or more computer processors, each of the one or more objects using a single coding scheme. The coding scheme also is operable to decrypt and decode each of the objects.
Owner:THE GOVERNINIG COUNCIL OF THE UNIV OF TORANTO
Systems and methods for analyzing, assessing and controlling trust and authentication in applications and devices
ActiveUS10366241B2Good encryptionIncrease ratingsDigital data protectionDigital data authenticationInternet privacyPersonal details
Owner:THE PRIVACY FACTOR
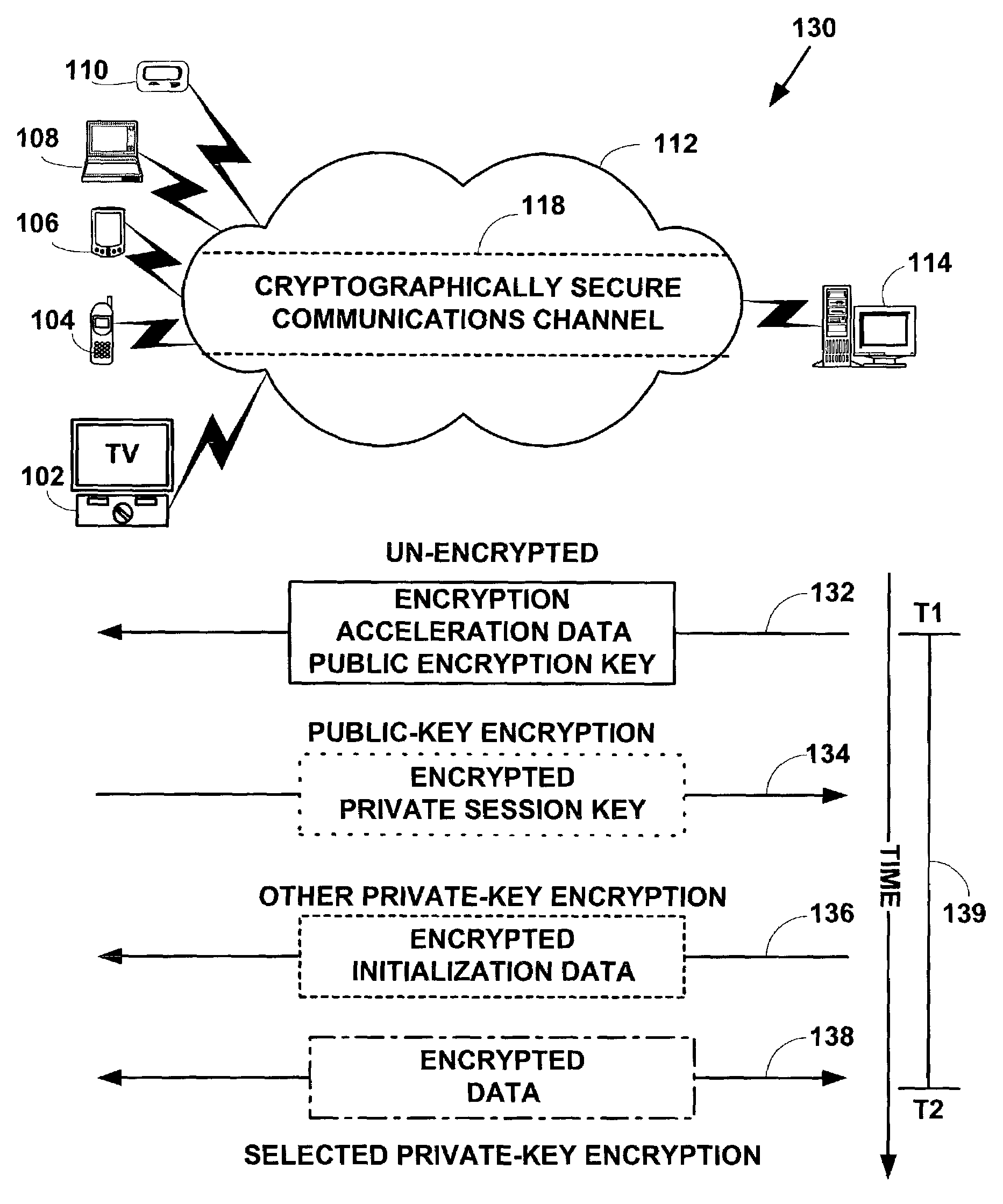
Method and system for accelerated data encryption
ActiveUS7221757B2Reduce in quantityQuick exchangeKey distribution for secure communicationPublic key for secure communicationComputer hardwareSecure communication channel
An encrypted private session key for a private-key encryption method is quickly exchanged between a first device and a second device by computing encryption acceleration data using a public key for a public-key encryption method. The encryption acceleration data and the public key are sent to and used on the second device to encrypt a private session key exchanged between the first device and second device. The private-key encryption method is quickly initialized on the second device using encryption initialization data for the private-key encryption method computed on the first device using the exchanged private session key sent to the second device. The encryption acceleration data and encryption initialization data reduce a number of calculations needed on the second device to initialize and use the private-key encryption method, thereby reducing the overall time needed to create a cryptographically secure communications channel between the first device and the second device.
Owner:OPEN TV INC
Optical touch screen, optical touch screen light source and touch pen
ActiveCN101630213AAchieve conversionPromote conversionInput/output processes for data processingTouchpadTouchscreen
Owner:李甲明
Color image encryption method based on cellular neural network hyperchaos and DNA sequence
The invention belongs to the technical field of information security, and particularly relates to a color image encryption method based on cellular neural network hyperchaos and a DNA sequence. The method provided by the invention comprises the steps of separating red, green and blue three primary color components of a color plaintext image; updating and generating parameters and initial values of a six-order cellular neural network hyperchaotic system and a Logistic-Sine mapping system through the plaintext image, respectively carrying out iterative operation on the two chaotic systems, and obtaining red, green and blue components of an encrypted image according to a DNA encoding rule and a DNA decoding rule; and finally, changing the pixel values of the encrypted image through key stream and a bitwise XOR operation to obtain a final ciphertext image. The decryption is a reverse operation of the encryption process. Compared with the existing image encryption method, the color image encryption method provided by the invention has the advantages of high security, good encryption effect, strong robustness, no information loss and the like, and thus being capable of being widely used in military, remote sensing, remote medical treatment, commerce and other fields.
Owner:FUDAN UNIV
Digital image encryption method based on DNA sequence and multi-chaotic mapping
ActiveCN101706946AEasy to implementEasy to controlGenetic modelsImage data processing detailsChaotic systemsDigital image
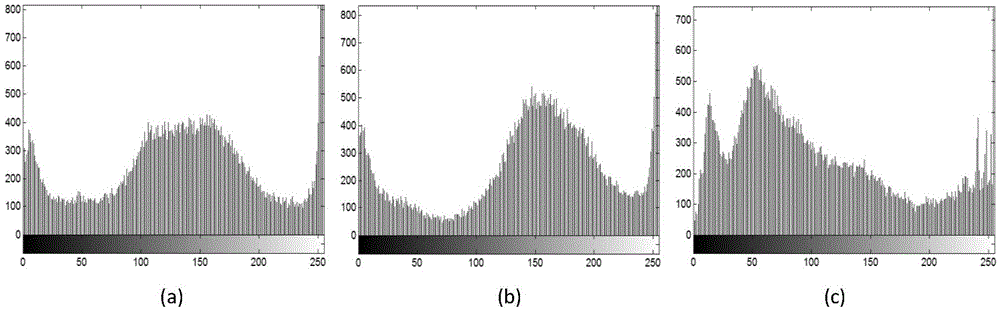
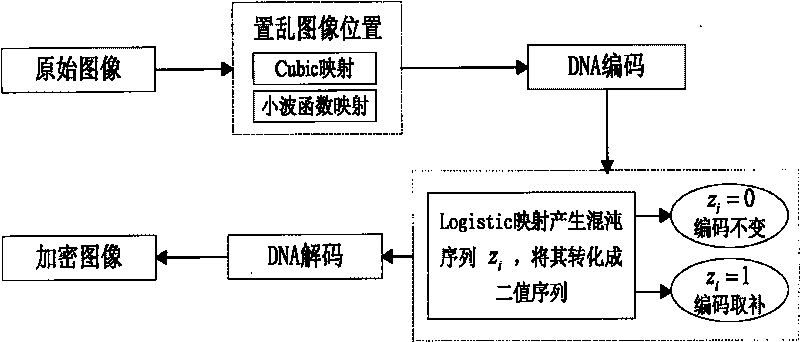
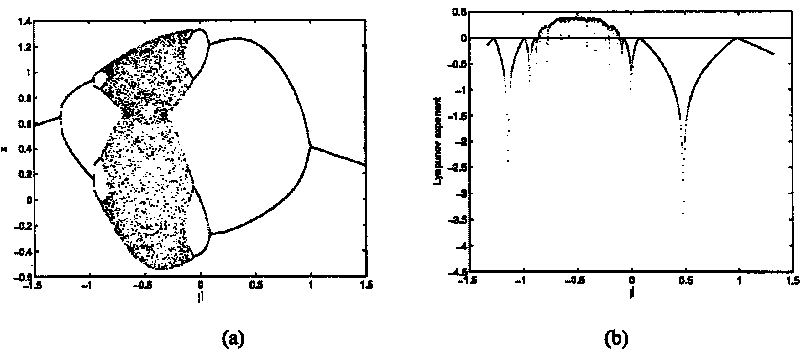
The invention discloses a novel digital image encryption method belonging to the field of DNA calculation and image encryption, and provides a digital image encryption method based on a DNA sequence and multi-chaotic mapping. The traditional encryption algorithm based on chaos has the defects that a key space is small, a chaos system is easy to analyze and forecast, and the like; and almost of the current encryption systems based on DNA need complex biological operation and are hard to realize. In order to overcome the defects, the invention provides the digital image encryption method based on a DNA sequence and multi-chaotic mapping, comprising the following steps of: firstly, scrambling the positions of pixels of images by utilizing a two-dimension chaotic sequence generated by Cubic mapping and Haar wavelet functions, and then disrobing the pixel values of the images under the action of a chaotic sequence generated by the DNA sequence and the Logistic mapping. The experimental result shows that the algorithm is easy to realize, has better encryption effect on images, large key space and high sensitivity to keys and can effectively resist exhaustive attack and statistical attack.
Owner:DALIAN UNIV
Authentication and secured information exchange system, and method therefor
InactiveUS20150082025A1Facilitates authorizationGood encryptionKey distribution for secure communicationUser identity/authority verificationAuthentication serverServer appliance
Identity based encryption (IBE). An IBE server assigns a private and public key pair to a client device based on a unique identification of the client device. To establish an encrypted session with the client device a server device requests the client device's public key from the IBE server. Authentication of the client and the server by the IBE server is based on credentials or a token. Assigned keys are securely stored in an embedded trusted platform provided in the client device.
Owner:DESHPANDE NACHIKET GIRISH
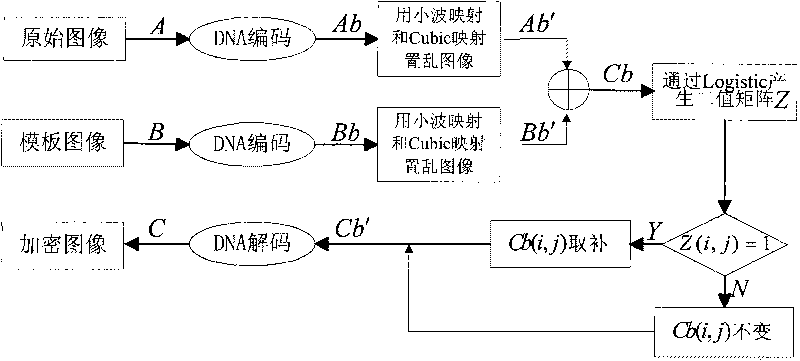
Image fusion encryption method based on DNA sequences and multiple chaotic mappings
ActiveCN101706947AGood encryptionLarge key spaceGenetic modelsChaos modelsChaotic systemsImage fusion
The invention discloses an image fusion encryption algorithm based on DNA sequences and multiple chaotic mappings, belonging to the field of DNA computation and image encryption. The traditional chaos-based encryption algorithm has the defects that the key space is small, the chaotic system is easy to be analyzed and predicted, and the like, and the existing image fusion based encryption method features difficult control of fusion parameters and low safety. To overcome the above defects, the invention first utilizes the two-dimensional chaotic sequence based scrambled coded original image and the template image which are generated by the Cubic mapping and the wavelet function to obtain two DNA sequence matrices, then carries out addition operation on the two scrambled DNA sequence matrices and finally utilizes the chaotic sequence generated by Logistic mapping and the DNA sequence matrices obtained by addition operation to interact to obtain the encrypted image. The experimental results show that the algorithm can effectively encrypt the digital images and has higher safety.
Owner:DALIAN UNIV
Image encryption method based on DNA sub-sequence operation
ActiveCN101702240AGood encryptionLarge key spaceGenetic modelsImage codingComputer visionDigital image
The invention discloses a novel digital image encryption method, which belongs to the field of DNA calculation and image encryption, in particular an image encryption method based on DNA sub-sequence operation. Current encryption systems based on DNA mostly need complex biological operations that are difficult to realize. Compared with traditional encryption methods based on DNA, the method of the invention abandons the complex biological operations, combines the DNA sub-sequence operations including extending, cutting, deleting and transposition and Logistic chaotic mapping to scramble pixel positions and pixel values of images. The experimental results indicate that the method has the advantages of easy realization, good encryption effect for images, large key space and strong sensibility to key and effective resistance to savage attacks and statistical attacks.
Owner:DALIAN UNIV
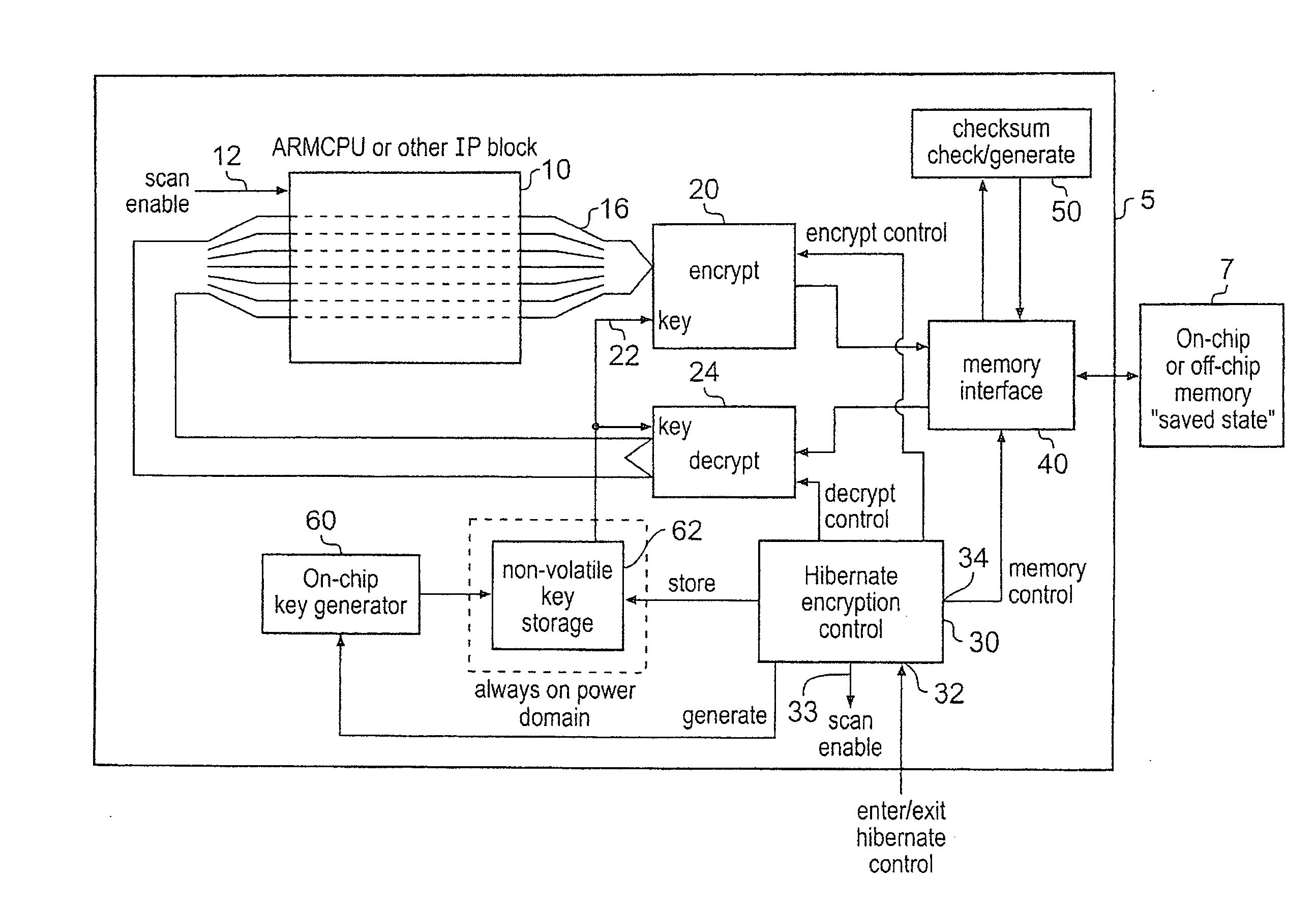
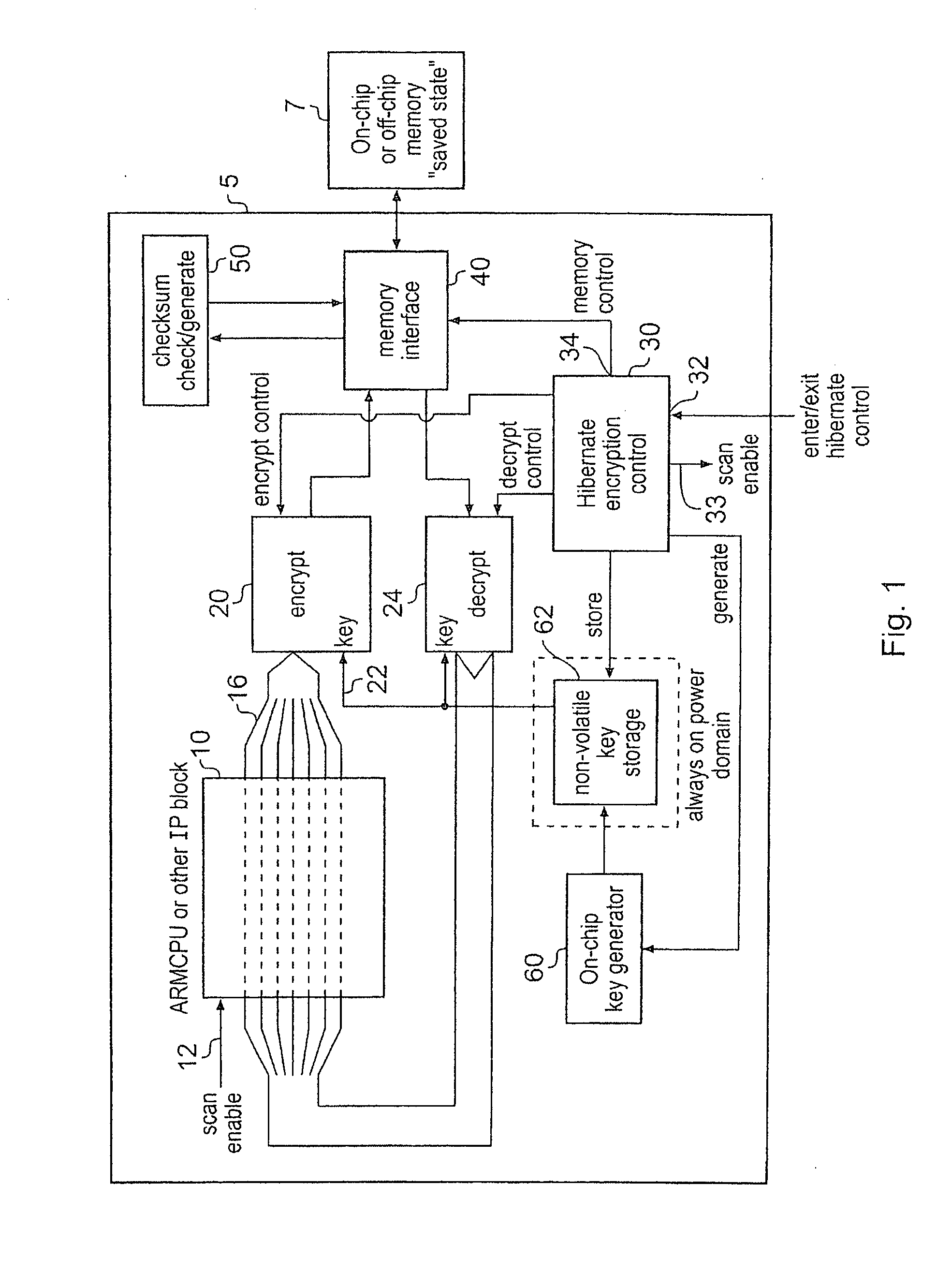
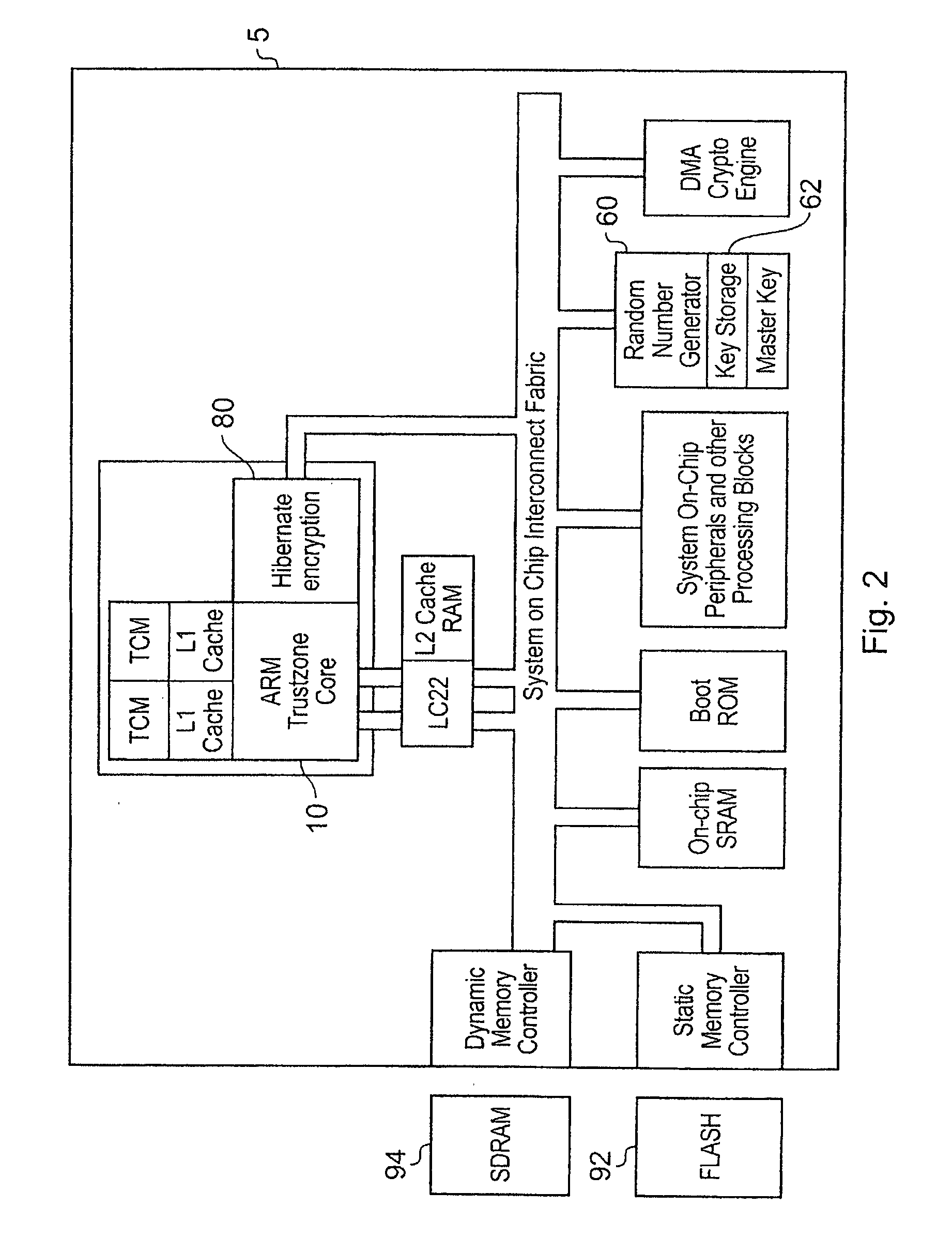
Hibernating a processing apparatus for processing secure data
InactiveUS20080201592A1Performed quickly and efficientlyEffective encryptionElectrical testingInternal/peripheral component protectionElectricityComputer hardware
A data processing apparatus for processing secure data is disclosed. The data processing apparatus comprising: processing circuitry comprising a plurality of state retention cells in the form of scan chains for holding a current state of said processing circuitry, at least some of the state retention cells being arranged in series; encryption circuitry; and a hibernate signal input; said data processing apparatus being responsive to receipt of a hibernate signal at said hibernate signal input to switch from an operational mode in which said data processing apparatus is powered up, to a low power mode in which at least said processing circuitry is powered down, said data processing apparatus being operable prior to powering down said processing circuitry, to output a state of said processing circuitry from said plurality of state retention cells and to encrypt said output state using said encryption circuitry and to save said encrypted state to said storage device.
Owner:ARM LTD
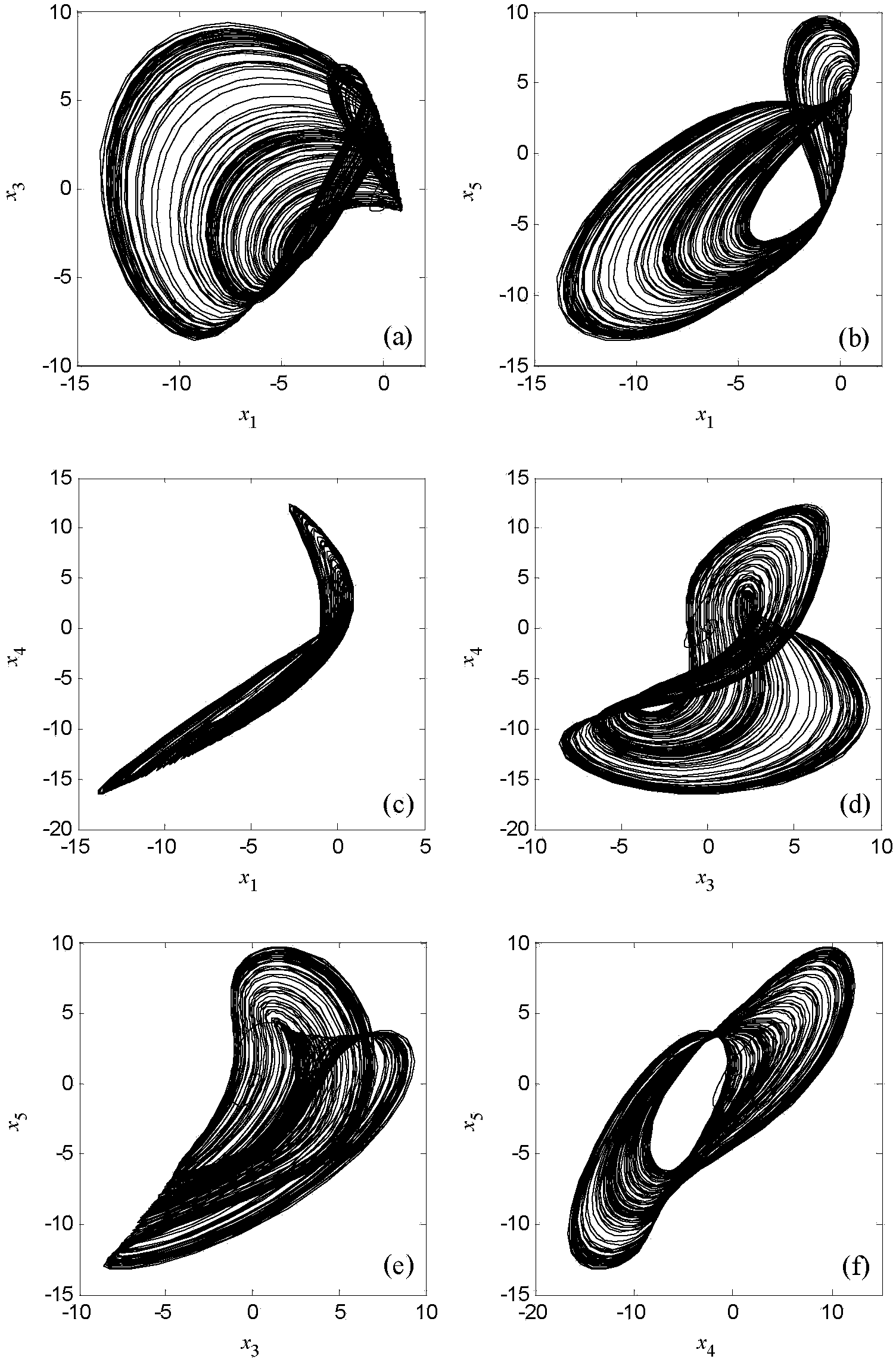
Five-dimensional chaotic system and chaotic signal generator based on five-dimensional chaotic system
InactiveCN103634099AStrong anti-deciphering abilityGood encryptionSecuring communicationDigital analog converterChaotic systems
The invention discloses a five-dimensional chaotic system and a chaotic signal generator based on the five-dimensional chaotic system, and relates to the information encryption field. The five-dimensional chaotic system provided by the invention is small in quantity of occupied digit circuit multiplying units, easy to implemented and large in chaotic system parameter range, so that complex chaotic signals are obtained, and the information encryption safety is improved. The five-dimensional chaotic system is used for inputting five chaotic signals and has typical chaotic attractors. An FPGA (Field Programmable Gate Array) in the chaotic signal generator is used for generating a five-dimensional chaotic system circuit, and the five chaotic signal output ends are respectively connected with the digital signal input ends of first, second, third, fourth and fifth digital analog converters. One end of a dial switch is connected with a power supply while the other end of the dial switch is respectively connected with the power supply ends of the five digital analog converters. The signals output by the five digital analog converters are voltage signals. The chaotic signal generator can provide a five-dimensional chaotic signal source which has various association of variation, is used for information encryption and has good chaotic characteristics.
Owner:HARBIN UNIV OF SCI & TECH
A multi-channel color image chaotic encryption method based on DNA coding
ActiveCN109918923AGood encryptionImprove execution efficiencyImage codingDigital data protectionColor imageHash function
The invention discloses a multi-channel color image chaotic encryption method based on DNA coding, relates to the field of digital image encryption, and aims to solve the problems that an existing image chaotic encryption scheme is insufficient, and a high-dimensional continuous time chaotic system is complex in discrete process algorithm, so that the safety of an encrypted image is low, and the acquisition of a discrete chaotic sequence is time-consuming. A six-dimensional discrete hyper-chaotic system is used for generating six groups of chaotic sequences, and a Hash function SHA-256 is usedfor generating a system iteration initial value; RGB (red, green and blue) components of the color image are extracted, DNA (deoxyribonucleic acid) coding is performed on each component to obtain a DNA matrix, the DNA matrixes is merged, a recombinant DNA matrix is constructed, and row and column scrambling operation is executed; Then, the scrambled DNA matrix is splitted into three matrixes withthe same size, respectively DNA calculation is carried out on the three matrixes and the three chaotic key matrixes subjected to DNA coding, and DNA decoding operation is carried out on the obtainedmatrixes; diffusion encryption operation is performed on the decoding matrix, wherein the encryption round number is determined by SHA-256. The encryption effect is good and the security is high.
Owner:HARBIN UNIV OF SCI & TECH
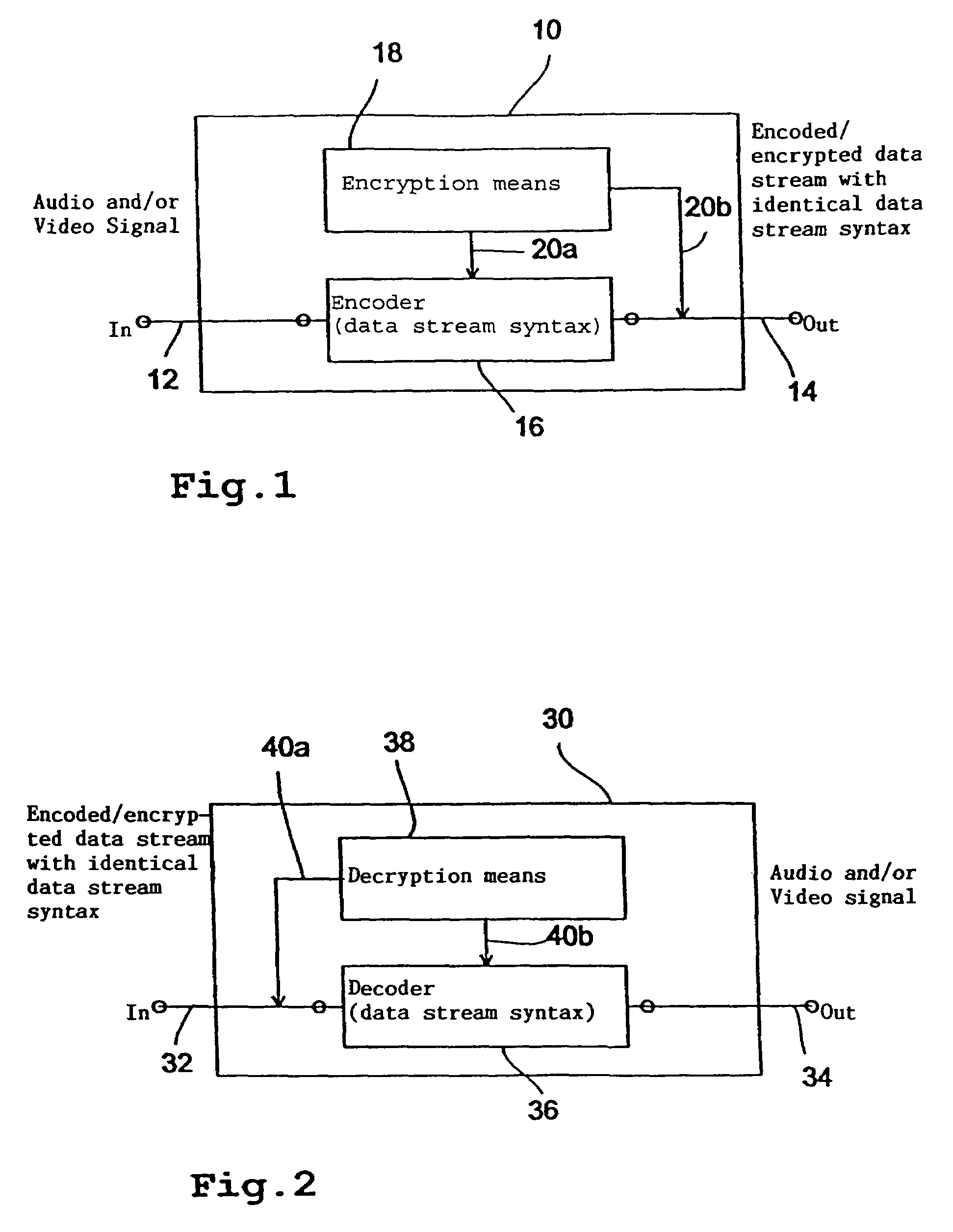
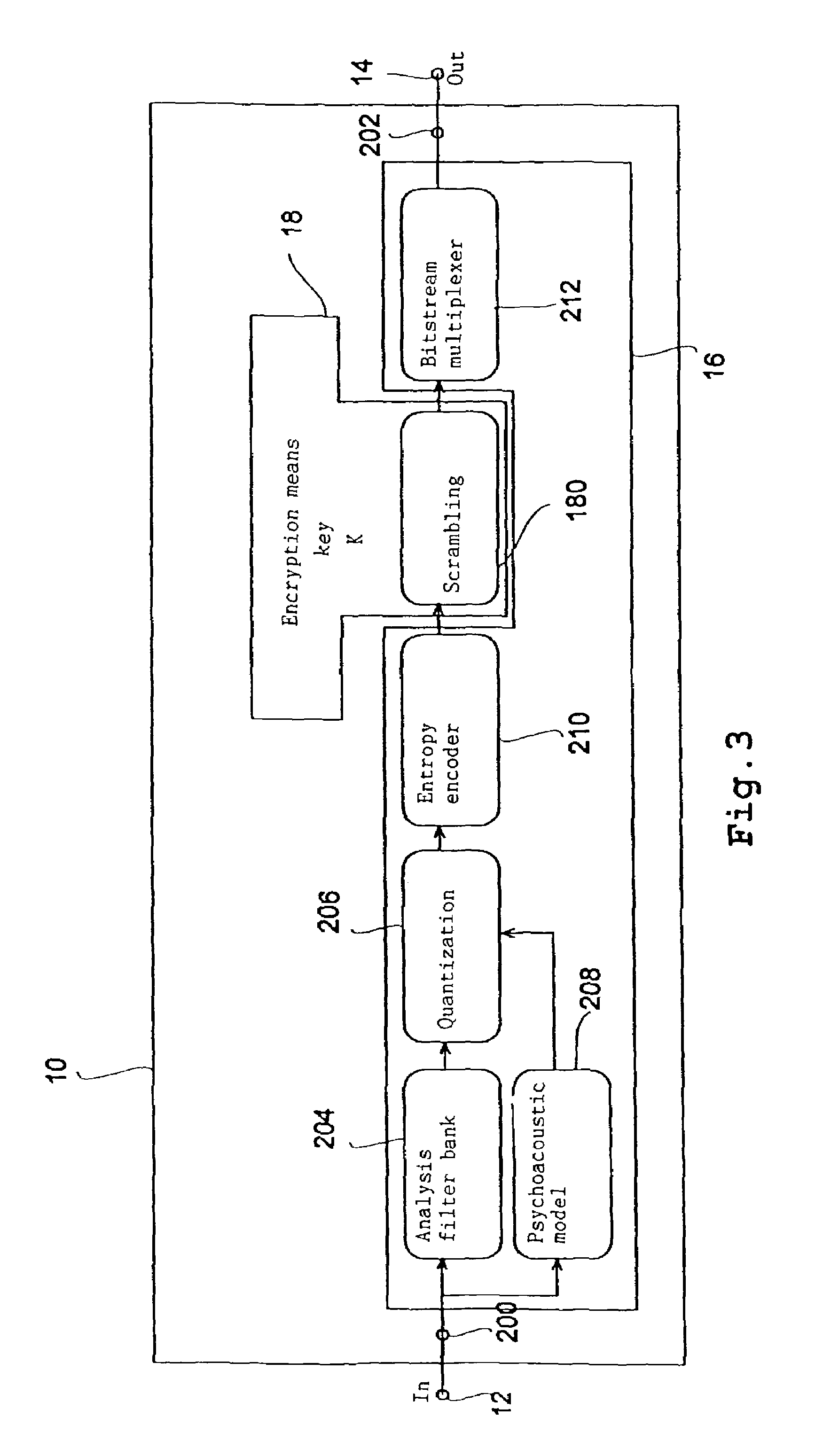
Device and method for producing an encoded audio and/or video data stream
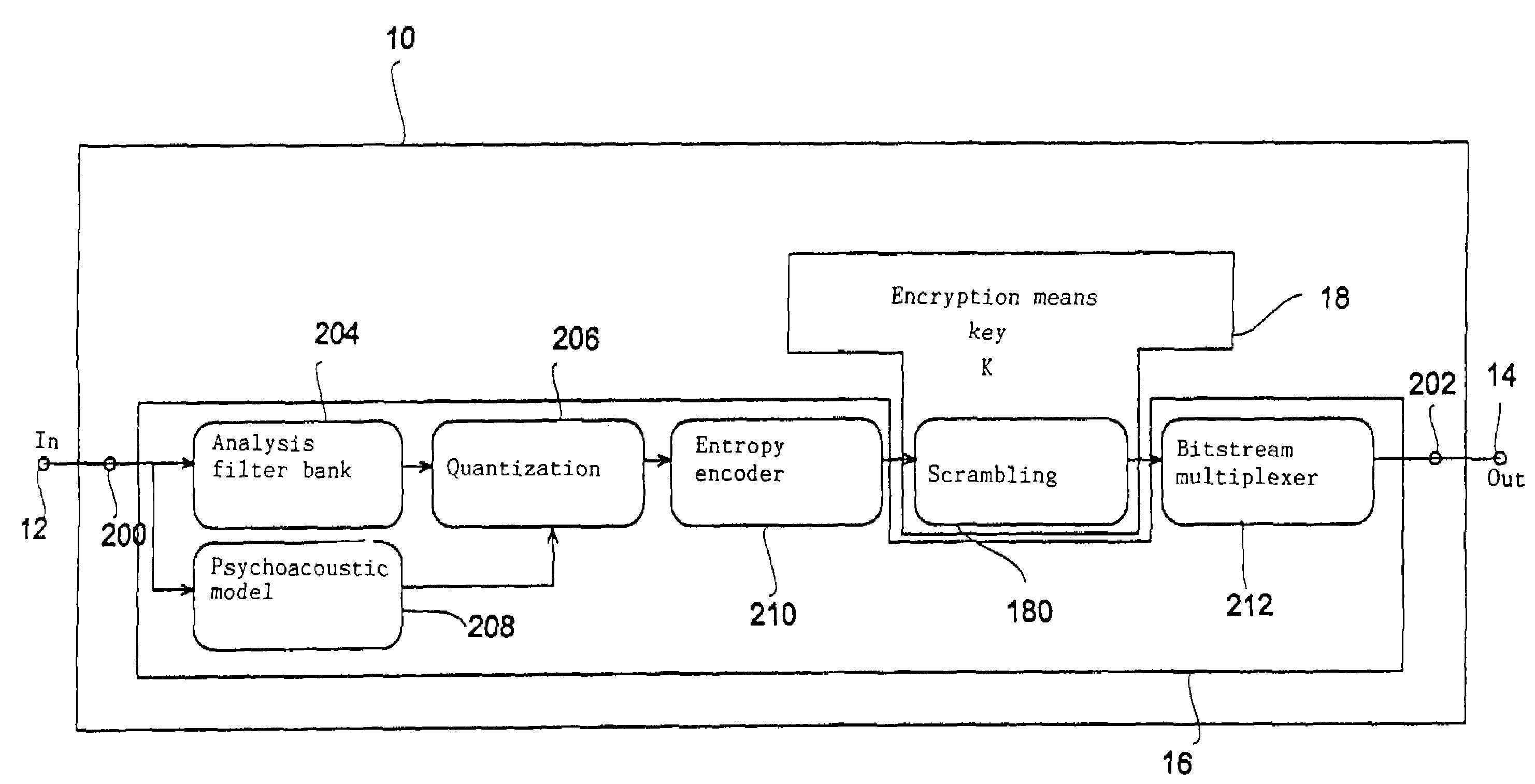
InactiveUS7308099B1Maximum flexibilityLow costSpeech analysisCharacter and pattern recognitionComputer hardwareData stream
An apparatus for generating an encrypted data stream representing an audio and / or video signal comprises an encoder for encoding an input signal to generate a data stream with a predefined data stream syntax as output signal. The apparatus further comprises an encryption means coupled with the decoder in order to influence encoder internal data and / or the output signal of the encoder in a uniquely reversible manner based on a key such that the generated encrypted data stream comprises payload information differing from payload information of a data stream that would be generated by the apparatus without the presence of an encryption means and that the generated encrypted data stream comprises the predefined data stream syntax. Thereby, a flexible data stream encryption is achieved, wherein the degree of encryption can be freely selected such that the owner of a decoder who does not possess the key, still obtains a rough idea of the audio and / or video signal which might cause him to buy the key in order to hear or view the audio and / or video signal in its full quality. The encoder-specific encryption and decryption concept can be implemented into already existing encoders / decoders with little effort.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
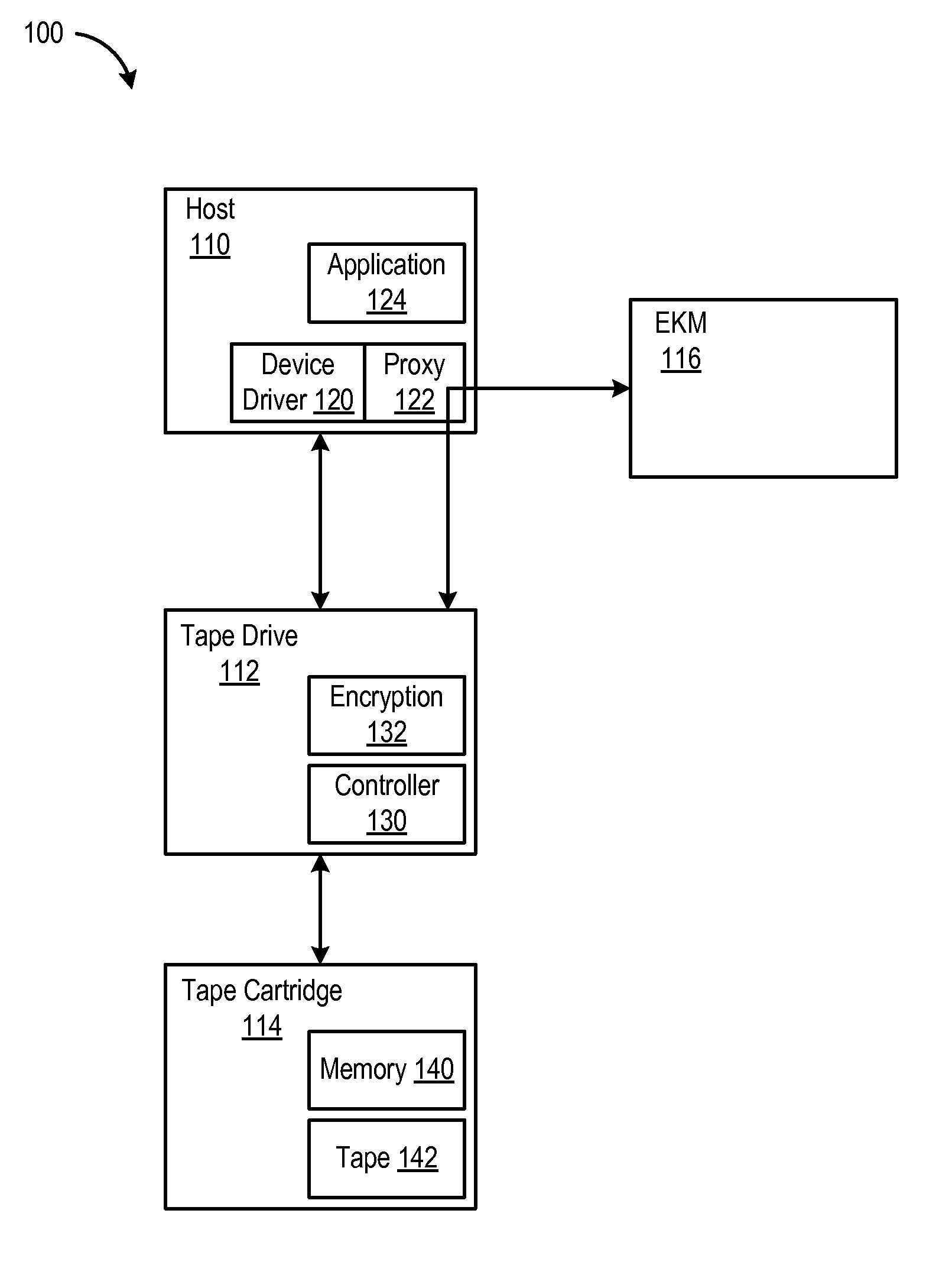
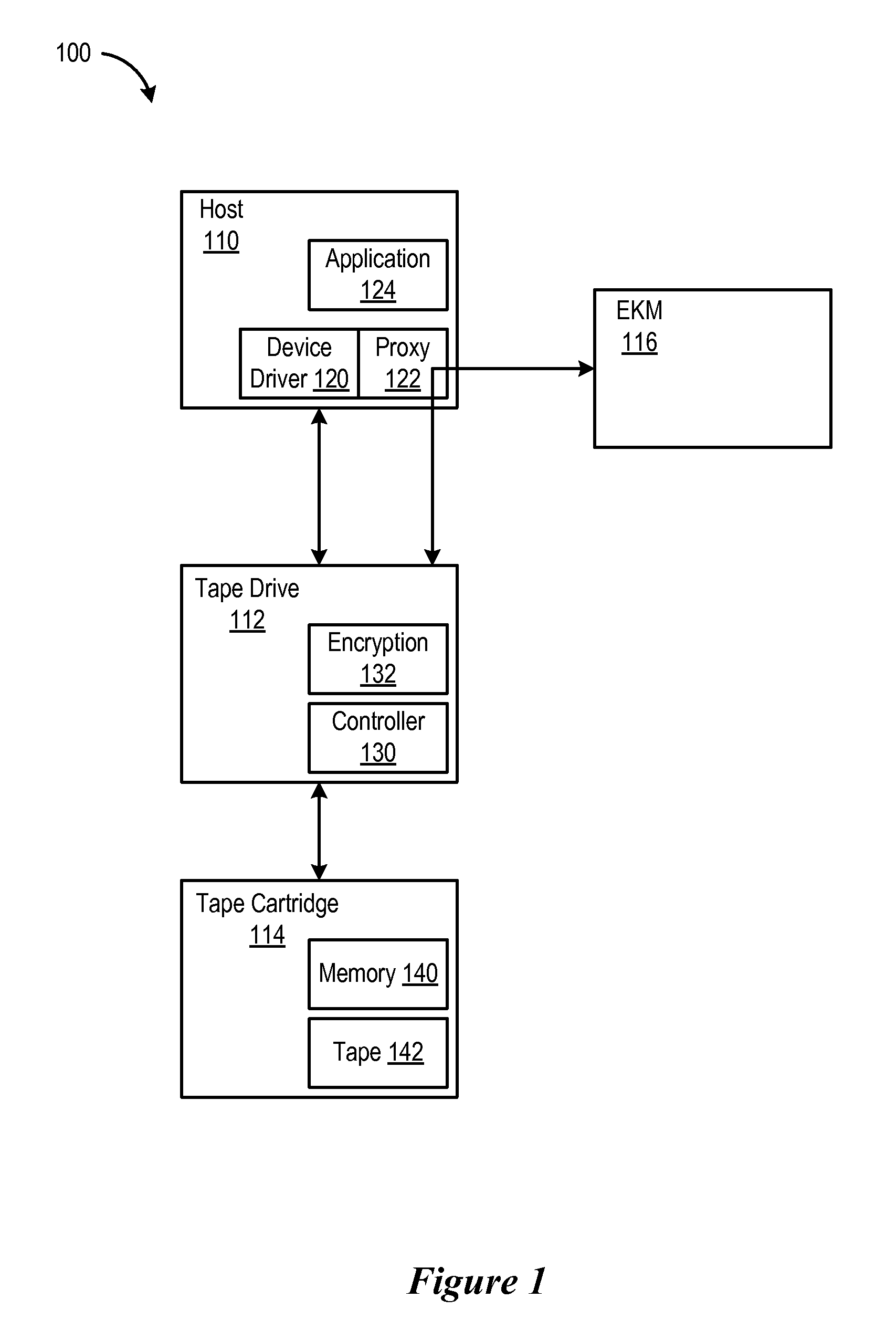
Use of Device Driver to Function as a Proxy Between an Encryption Capable Tape Drive and a Key Manager
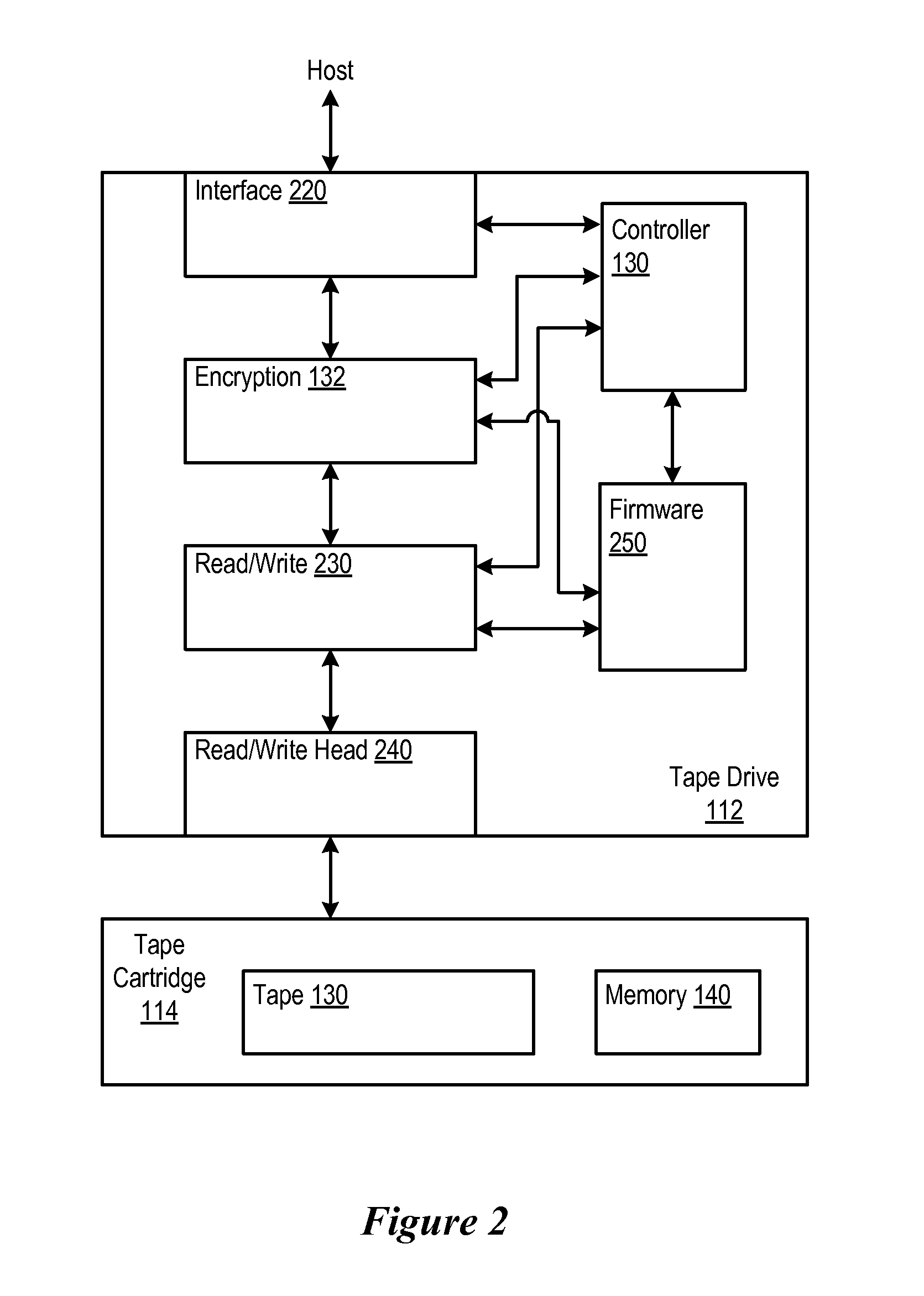
InactiveUS20080065898A1Facilitates encryptionFacilitate operationKey distribution for secure communicationInput/output to record carriersEncrypted functionTape drive
A tape system is provided with an encryption capable tape drive and an encryption enabled tape drive device driver for the encryption capable tape drive. The encryption enabled tape drive device driver functions as a proxy which connects the encryption capable tape drive to a key manager which serves keys to the tape drive. When the encryption capable device driver causes a command to be sent to the drive, the tape drive is configured to respond with a message that is intended for a key manager such as an External Key Manager (EKM). The encryption capable device driver recognizes that this is a message intended for the EKM and forwards that message to the EKM (e.g., via an Internet Protocol (IP) connection). The EKM then responds to the key request by issuing a new key (for a new cartridge which is to be written from beginning of tape (BOT)) or an existing key (for a cartridge which needs to be read). The device driver connects all EKM responses to the encryption capable tape drive and the EKM from which the encryption capable tape drive obtains its keys.
Owner:IBM CORP
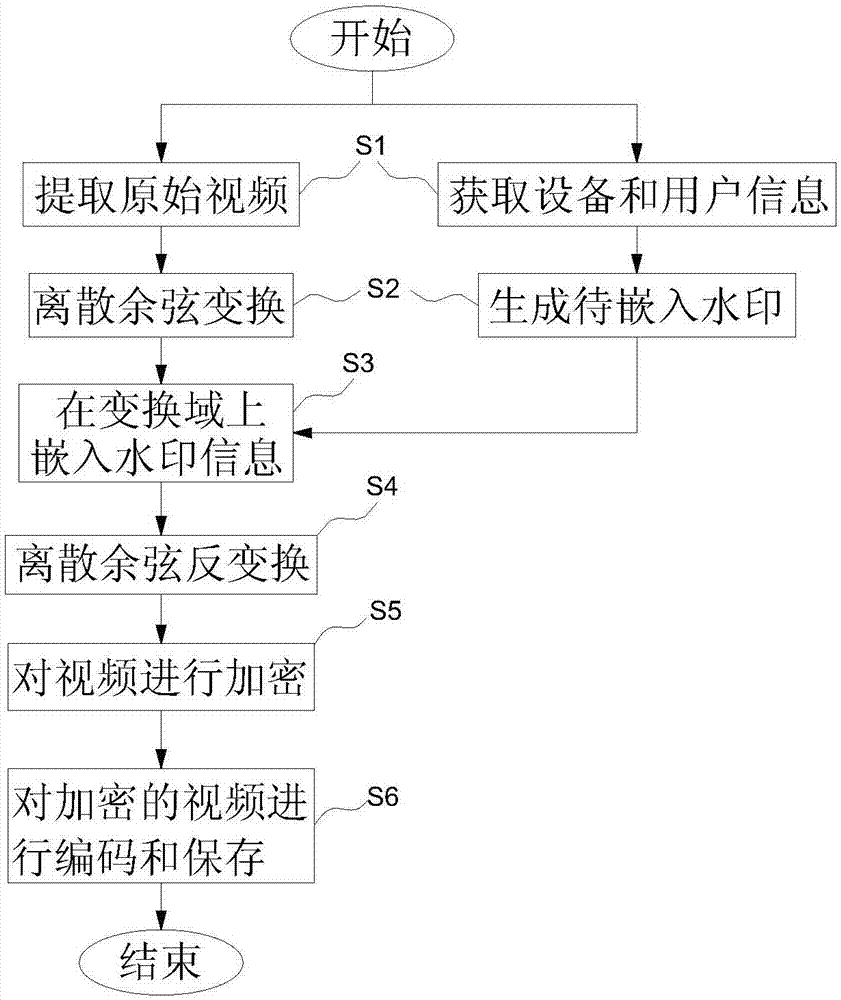
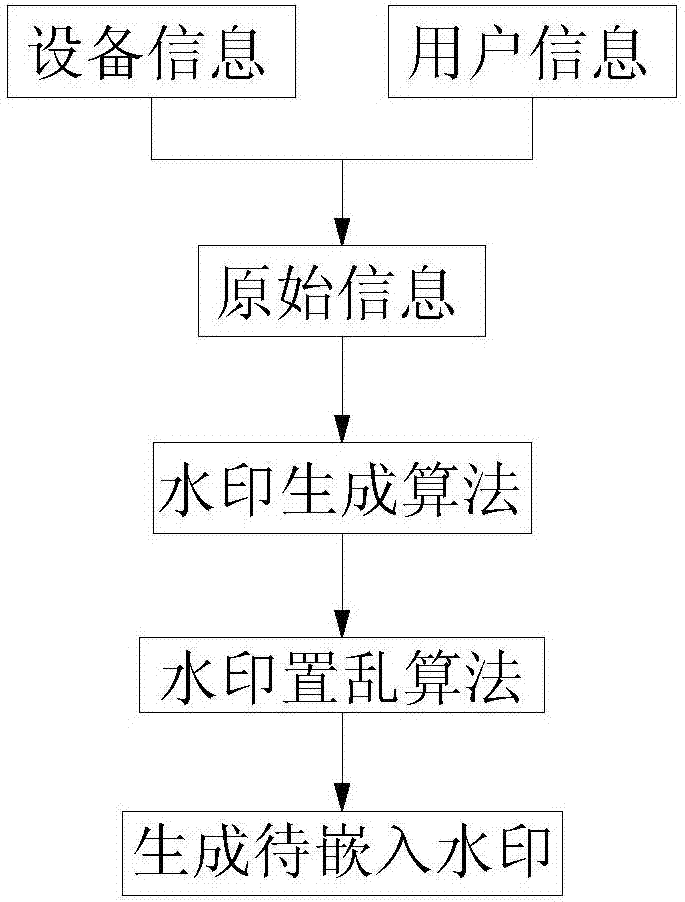
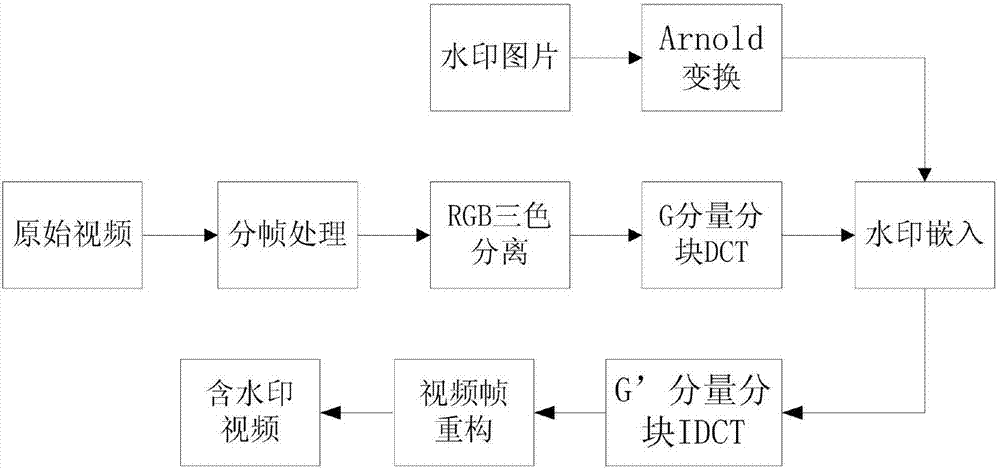
Video source tracing and encryption method based on watermark technology
InactiveCN107027055AAvoid damageGuaranteed video qualityDigital video signal modificationSelective content distributionSource tracingExtraction algorithm
The invention relates to a video source tracing and encryption method based on a watermark technology. The method comprises the steps of extracting an original video and obtaining device information and user information; transforming the original video from a time domain to a frequency domain through adoption of a discrete cosine transform algorithm, and generating a to-be-embedded watermark through adoption of a watermark generation algorithm; embedding the to-be-embedded watermark through adoption of a watermark embedding algorithm, thereby generating the video containing the watermark; generating a time domain video containing the watermark through adoption of an inverse transform algorithm; carrying out encryption through adoption of a key frame extraction algorithm and a video head information encryption algorithm, thereby forming an encrypted video file; and coding and storing the encrypted video file. According to the method, the generated video containing the watermark is good in quality, high in concealment and security and good in video sensuality; the method is good in encryption effect and high in security; relatively good source tracing and encryption effects are achieved; the video sharing security and circulation traceability are realized.
Owner:ANHUI SUN CREATE ELECTRONICS
System and method for encryption and decryption based on quantum key distribution
ActiveUS20170324550A1Facilitate secure encryption and decryptionFacilitating secure encryption and decryptionKey distribution for secure communicationProtocol for Carrying Authentication for Network AccessKey distribution
One embodiment of the present invention provides a system for facilitating storage encryption and decryption. During operation, the system receives a first request to encrypt data which is to be stored on a remote device, wherein the first request indicates the data. The system updates a key based on a dynamic key refreshment protocol. The system determines a key label for the updated key. The system encrypts the data based on the updated key, and transmits the encrypted data and the key label to the remote device, thereby facilitating secure encryption and decryption of data on the remote device.
Owner:ALIBABA GRP HLDG LTD
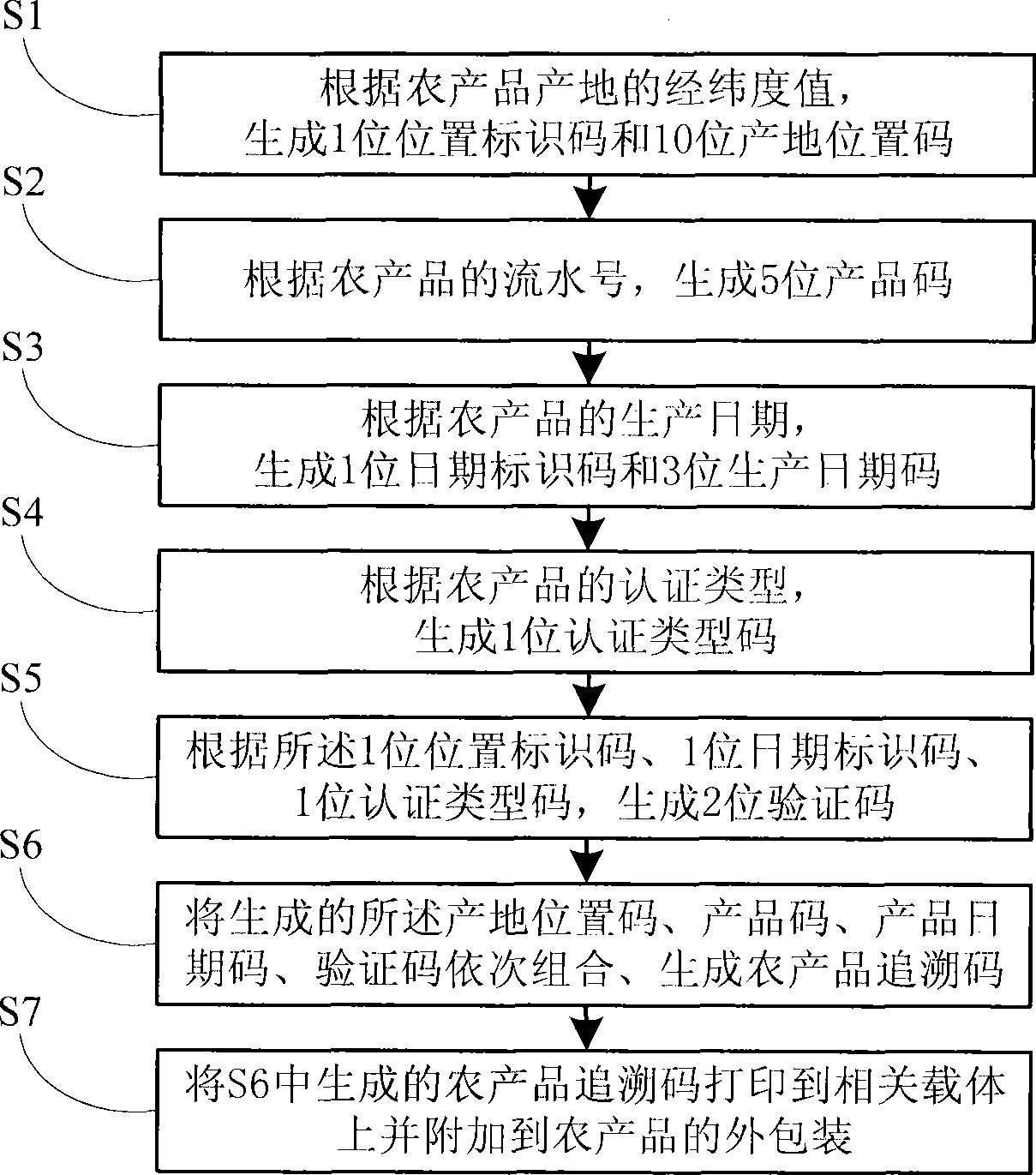
Method for encoding agricultural product backdate code
The invention relates to a method for coding tracing codes of agricultural products. The method comprises the following steps: generating one position identifying code of agricultural products and ten position codes of a manufacturing location; generating five product codes of agricultural products; generating one date identifying code of agricultural products and three production date codes; generating one authentication type code of agricultural products; generating two identifying codes of agricultural products; generating tracing codes of agricultural products; and printing the tracing codes of agricultural products generated on the relevant carrier and attaching an outer packing of agricultural products. The encoding scheme designed in the invention is difficult to indicate indicial meanings upon the figure composition, the length is shorter, and the encryption is better; during the product tracing, under the condition of separating from a database, the coding method can trace geographical positions of information close relevant to quality security of agricultural products enterprises, production dates and product authentication types and the like, so as to lay the foundation of accurate positioning to the enterprise and rapid taking emergency measures during generating the problem of quality security of agricultural products.
Owner:BEIJING RES CENT FOR INFORMATION TECH & AGRI
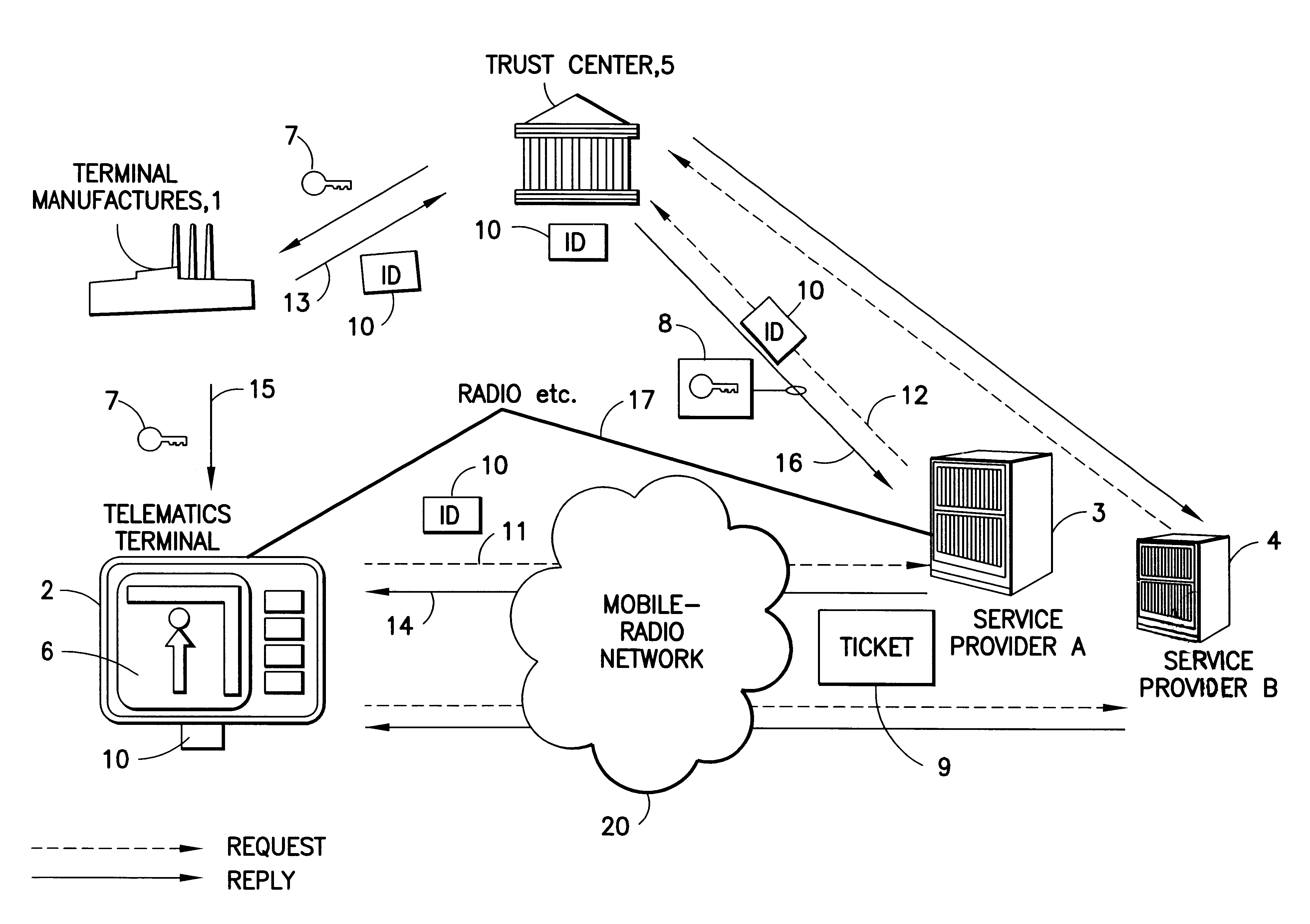
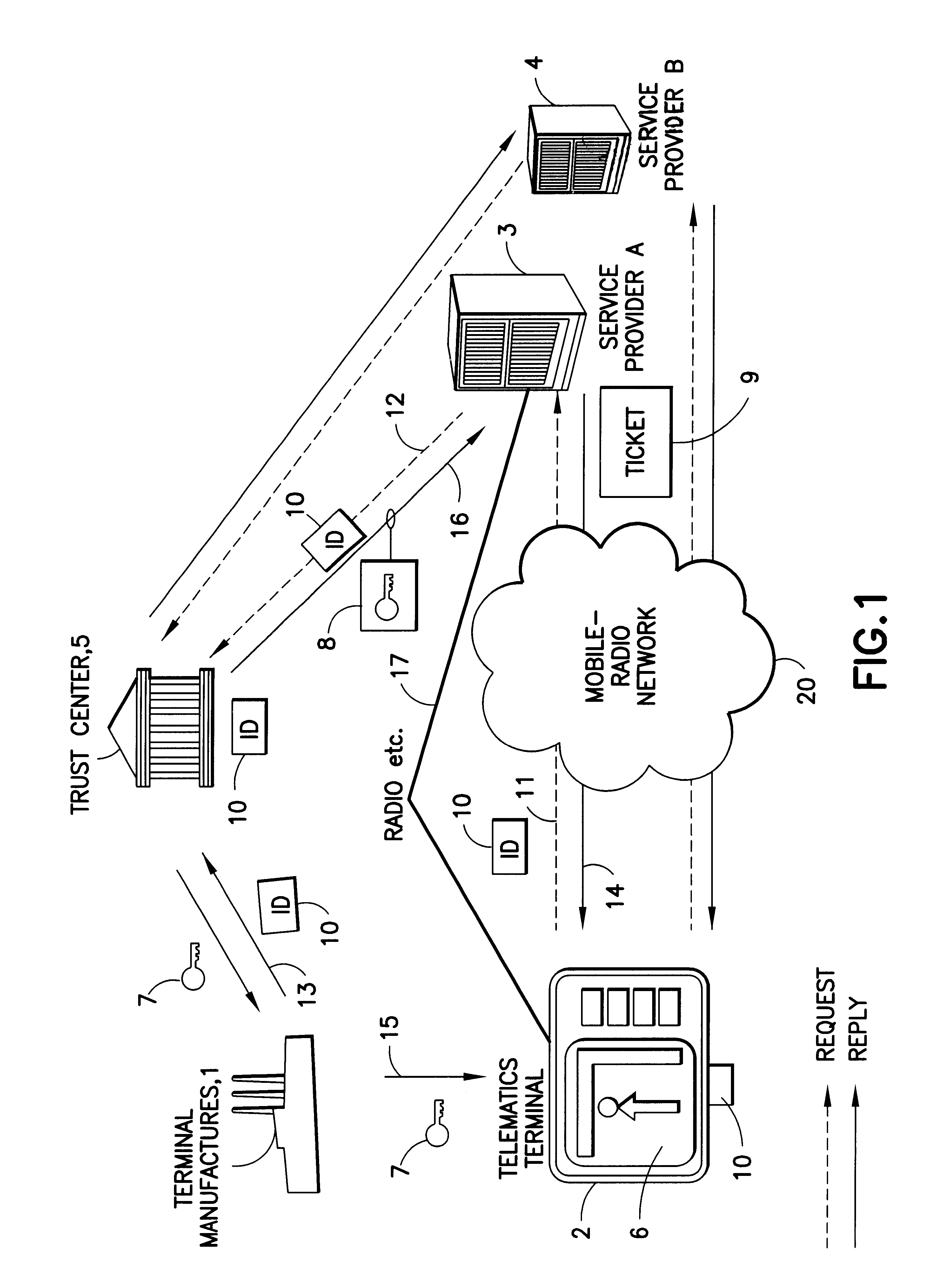
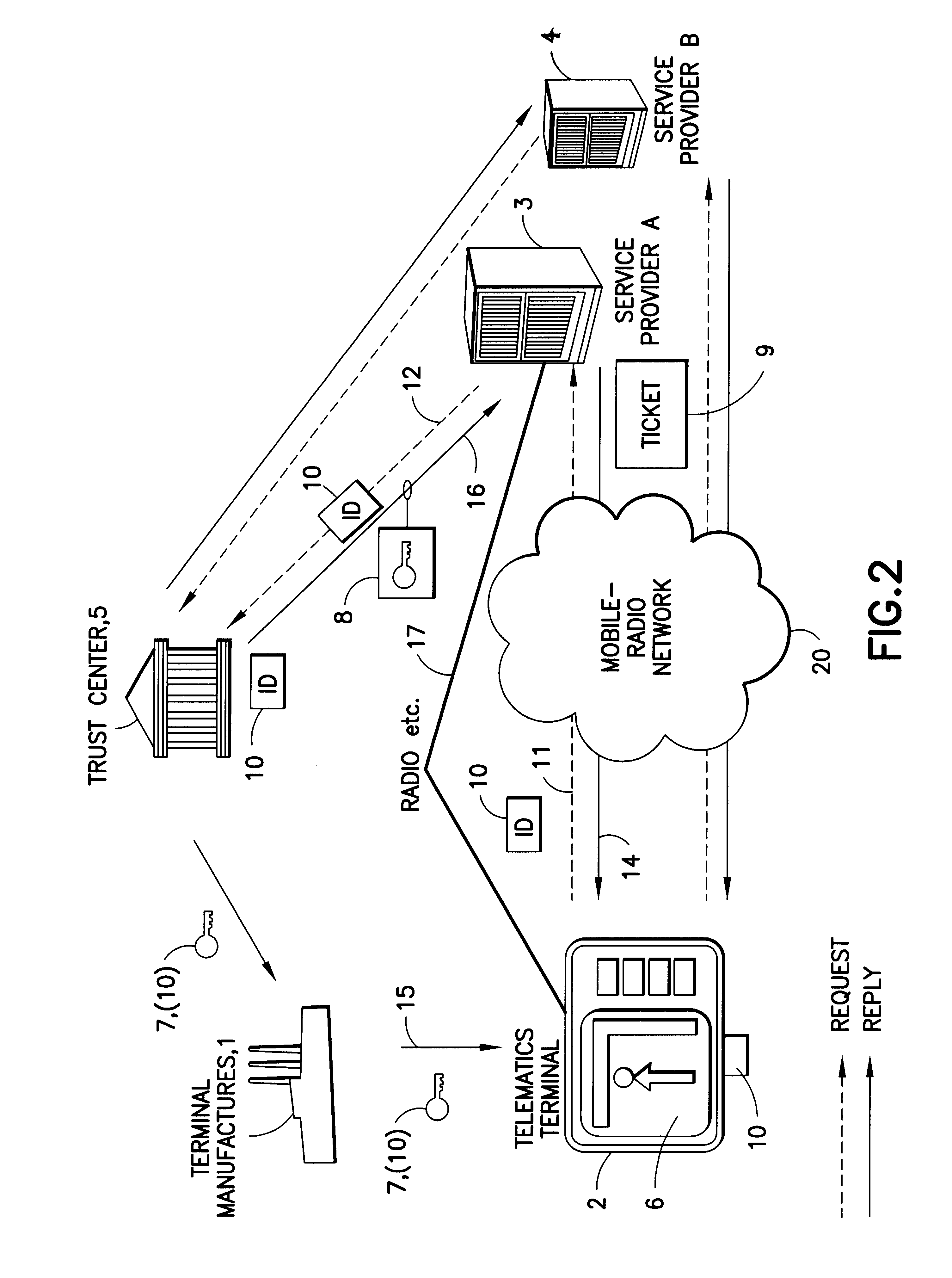
Method for inserting a service key in a terminal and devices for implementing said method
InactiveUS6611194B1Excessive complexityEfficientlyKey distribution for secure communicationElectric signal transmission systemsComputer networkEnd user
A secure and efficient key management system for utilizing a service key for retrieving service data transmitted to a terminal from a service center via a communication channel. A service key is inserted into a terminal and is used to enable the decryption of the received encrypted service data from the service center. The service center requests and obtains a coding key from a trust center when the service center receives a service key transmission request from the from the terminal. The service key transmission request includes a terminal identity number. The service center forwards the request to the trust center which returns the coding key associated with a decoding key corresponding to the specific terminal. The service center encrypts the service key with the coding key and transmits the service key to the terminal. The service key is decrypted in the terminal using the decoding key input to the terminal by the terminal manufacturer. Once the service key has been decrypted, the service data can correspondingly be decrypted to use by the terminal user.
Owner:SIRIUS XM CONNECTED VEHICLE SERVICES
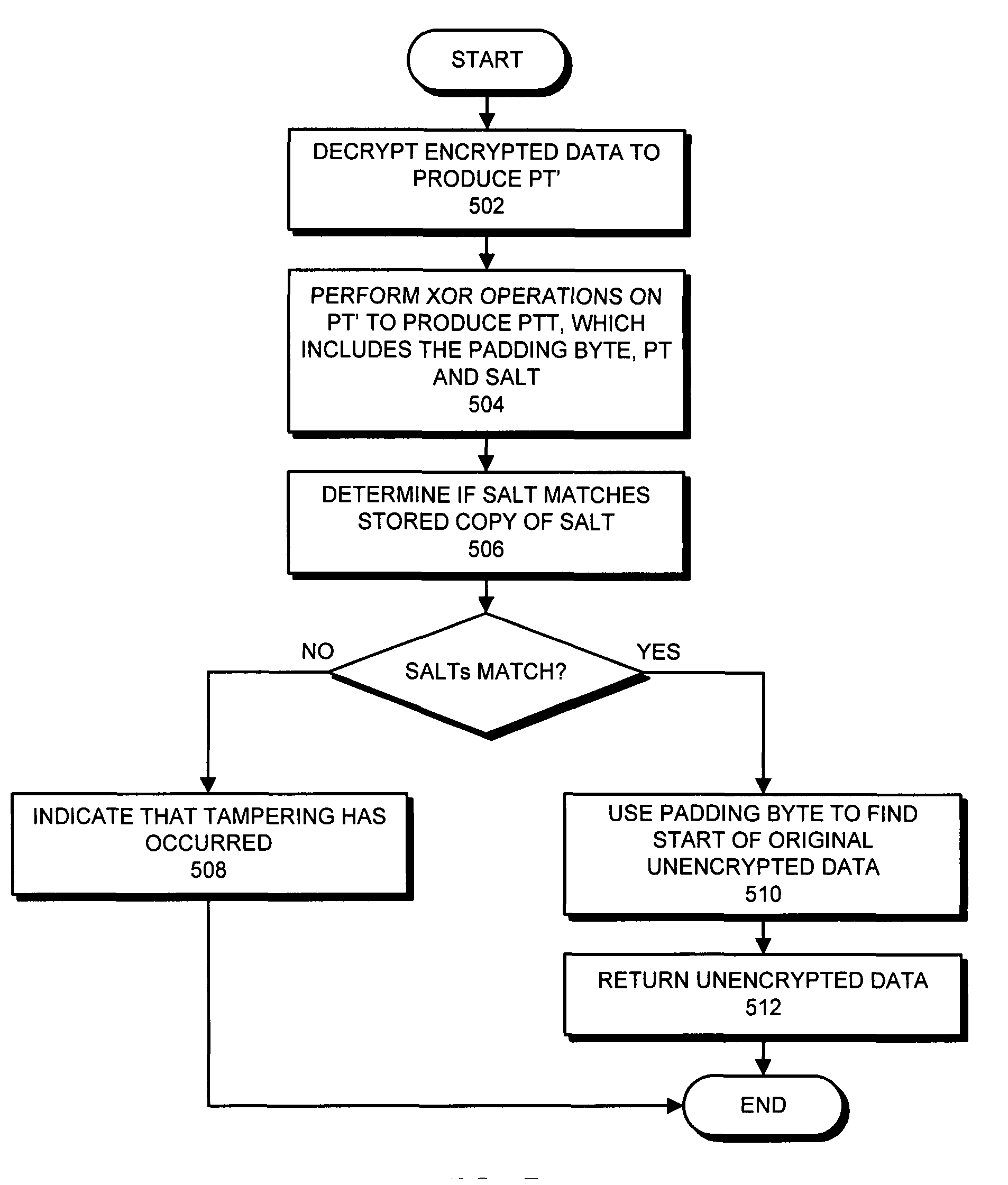
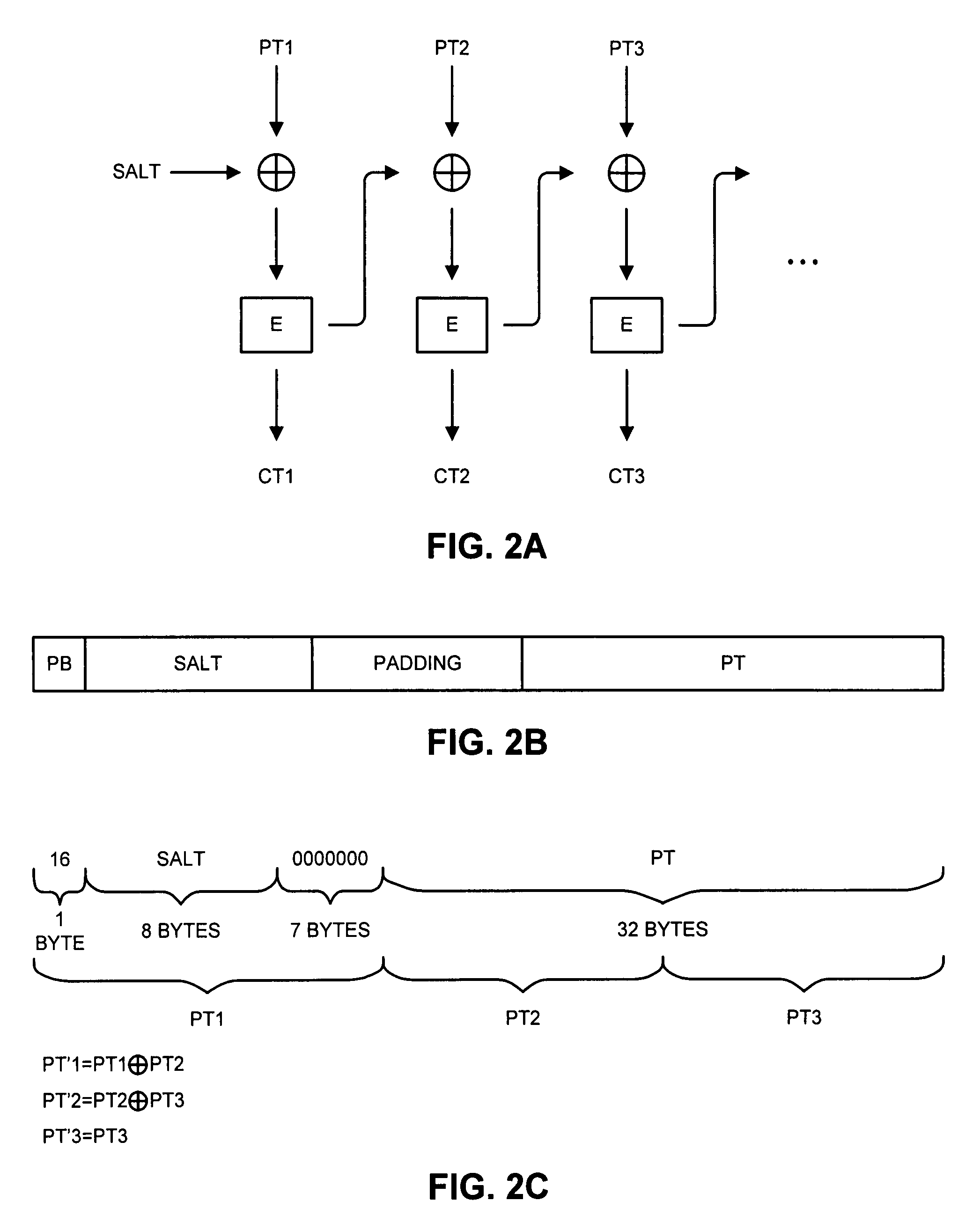
Method and apparatus for encrypting data to facilitate resource savings and tamper detection
ActiveUS8744076B2Good encryptionEasy to determinePublic key for secure communicationUser identity/authority verificationPlaintextComputer hardware
One embodiment of the present invention provides a system that facilitates encrypting data. During operation, the system receives unencrypted data to be encrypted. Next, the system preprocesses the unencrypted data to create preprocessed unencrypted data, wherein preprocessing the unencrypted data involves generating a salt (wherein the salt facilitates in determining if the subsequently encrypted data has been altered) and concatenating the salt and the unencrypted data to create the preprocessed unencrypted data. Next, the system encrypts the preprocessed unencrypted data to create the encrypted data. Because the salt has already been applied to the plaintext data, it does not need to be reapplied during the encryption phase as is typically done in encryption. Finally, the system stores a copy of the salt with the encrypted data.
Owner:ORACLE INT CORP
Data encryption method and system
InactiveCN102567687AEncryption guaranteedGood encryptionDigital data protectionSecuring communicationComputer hardwareData transmission
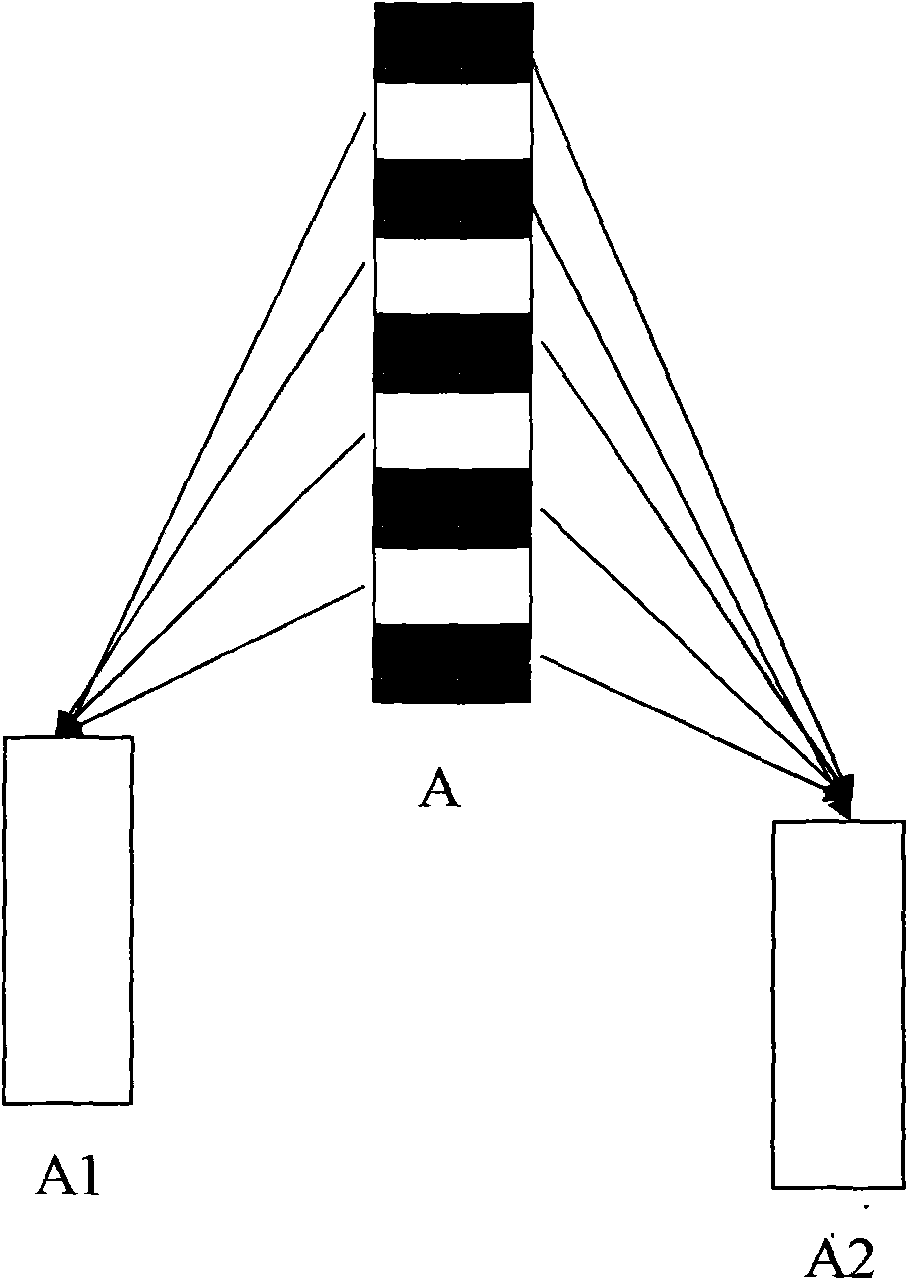
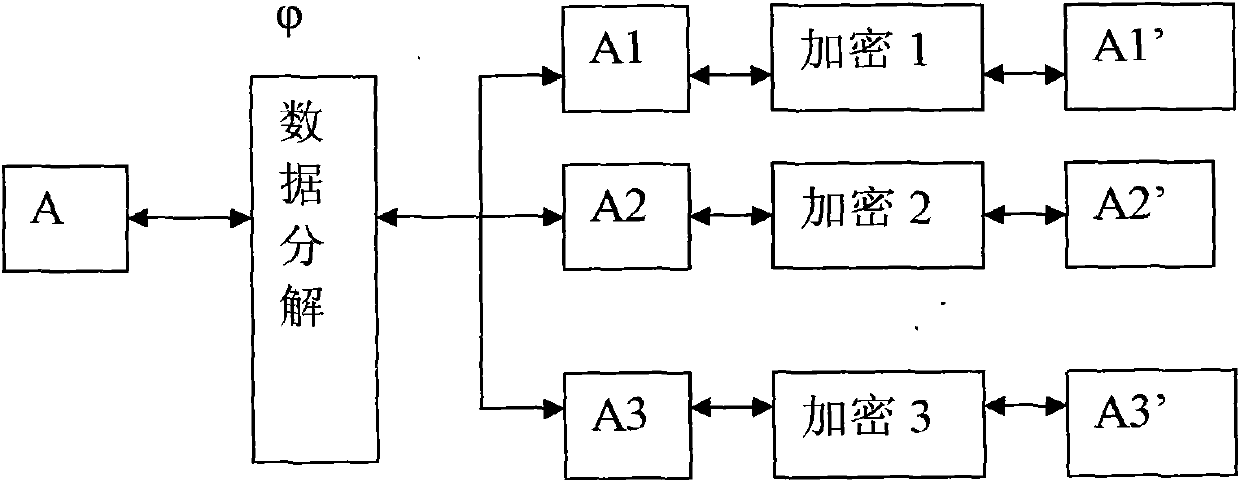
The invention relates to a data encryption method and a system. The data encryption method is characterized in that raw data is decomposed into at least two parts of data according to a preset function relationship. A data encryption storage method is characterized in that the preset function relationship is decomposed into at least parts of data, and the disassembled data is respectively stored in different memories. A data encryption transmission method is characterized in that a sending end decomposes raw data A into at least two parts according to the preset function relationship; the two parts are sent to a data receiving end via different data transmitting channels; and the data receiving end respectively receives the data, and combines and reduces the data into the raw data A according to the corresponding function relationship. As various combination modes are provided, the decryption difficulty is high after encryption, and the original encryption index is enhanced by times to guarantee the encryption effect of numbers. Only disassembly is required, and therefore, good encryption effect is achieved. In addition, the data encryption method has the advantages of low calculation amount and high encryption and decryption efficiency.
Owner:成都科创知识产权研究所
Anti-pirate method and device for software capable of unloading and reinstalling
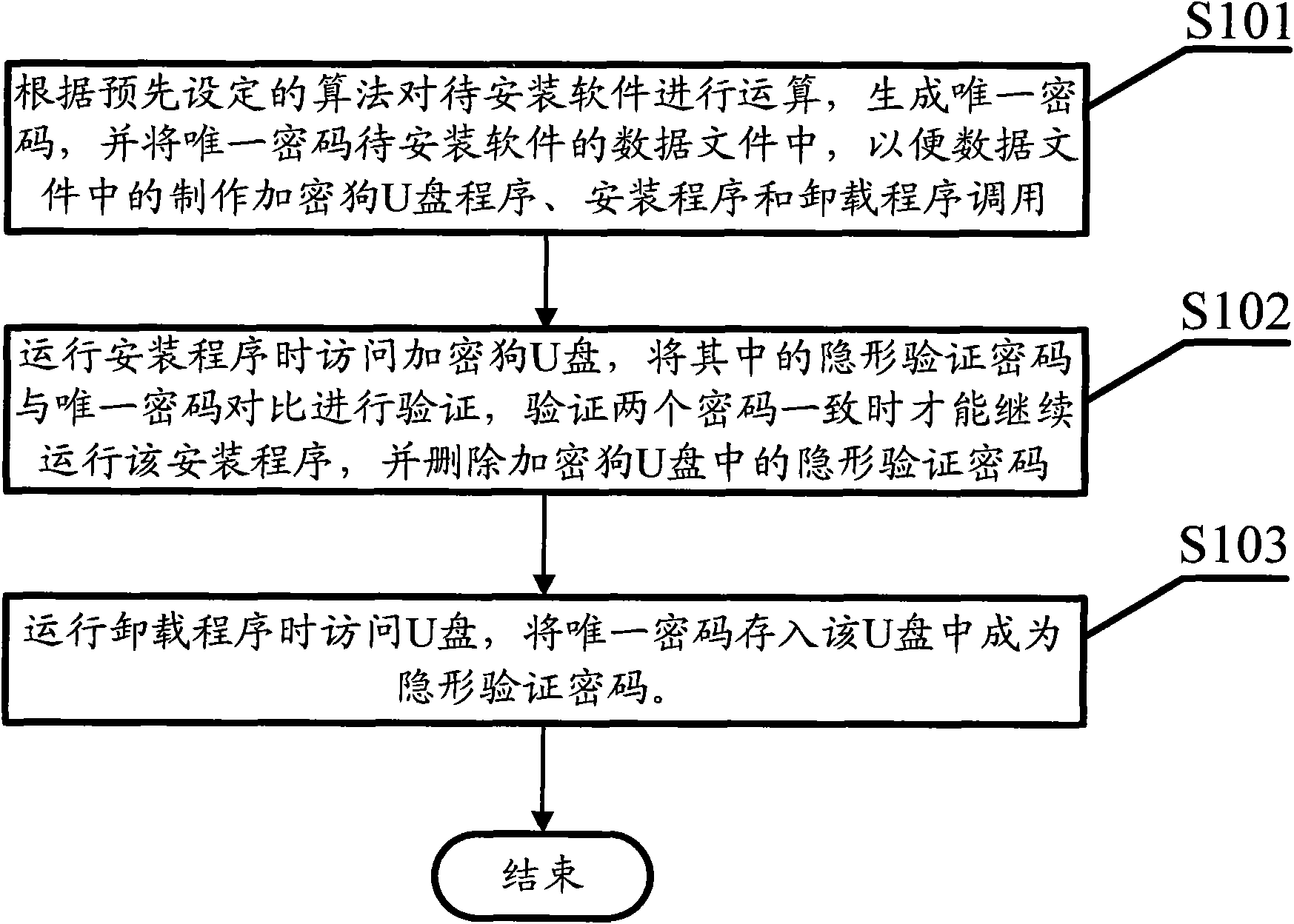
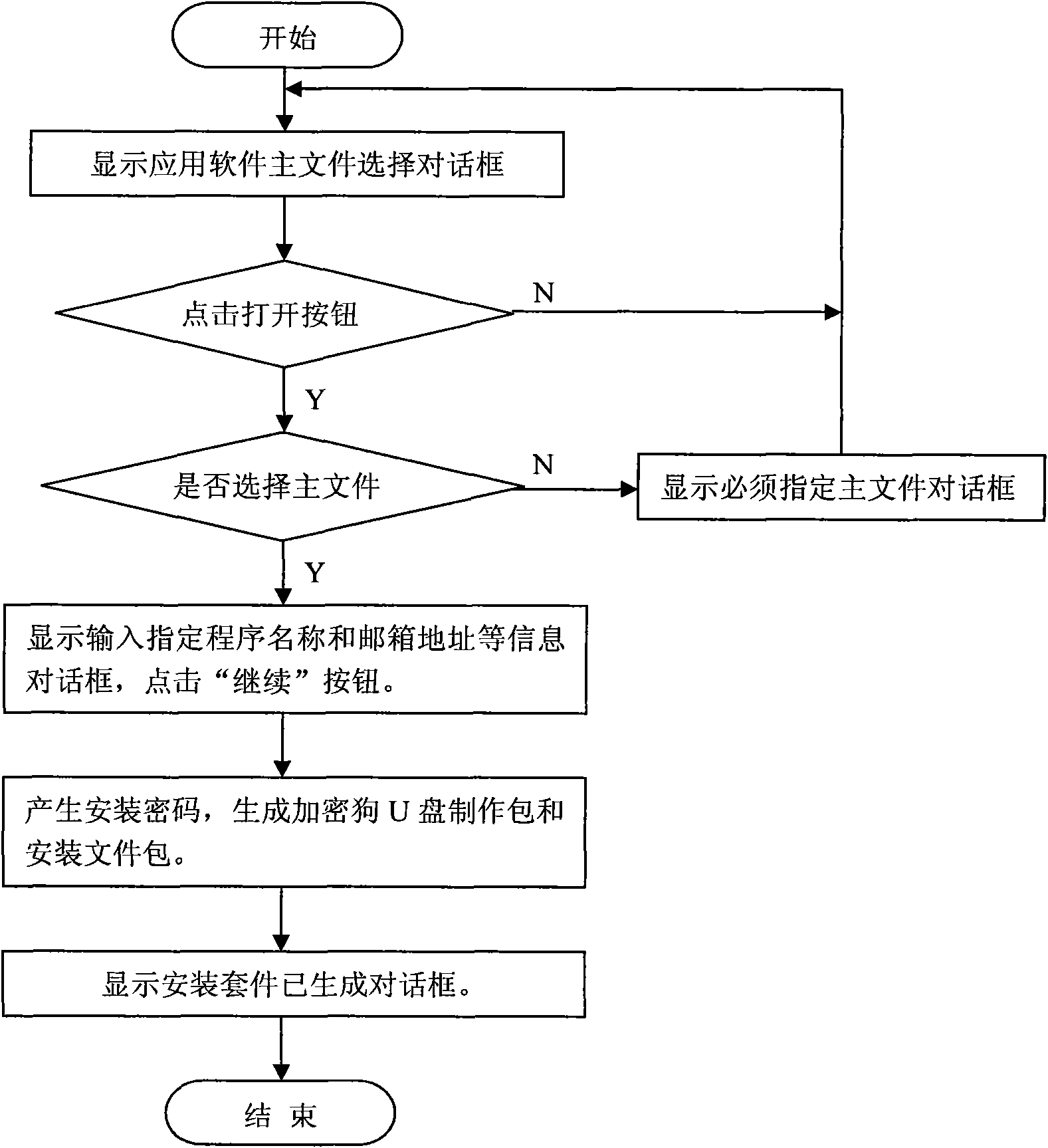
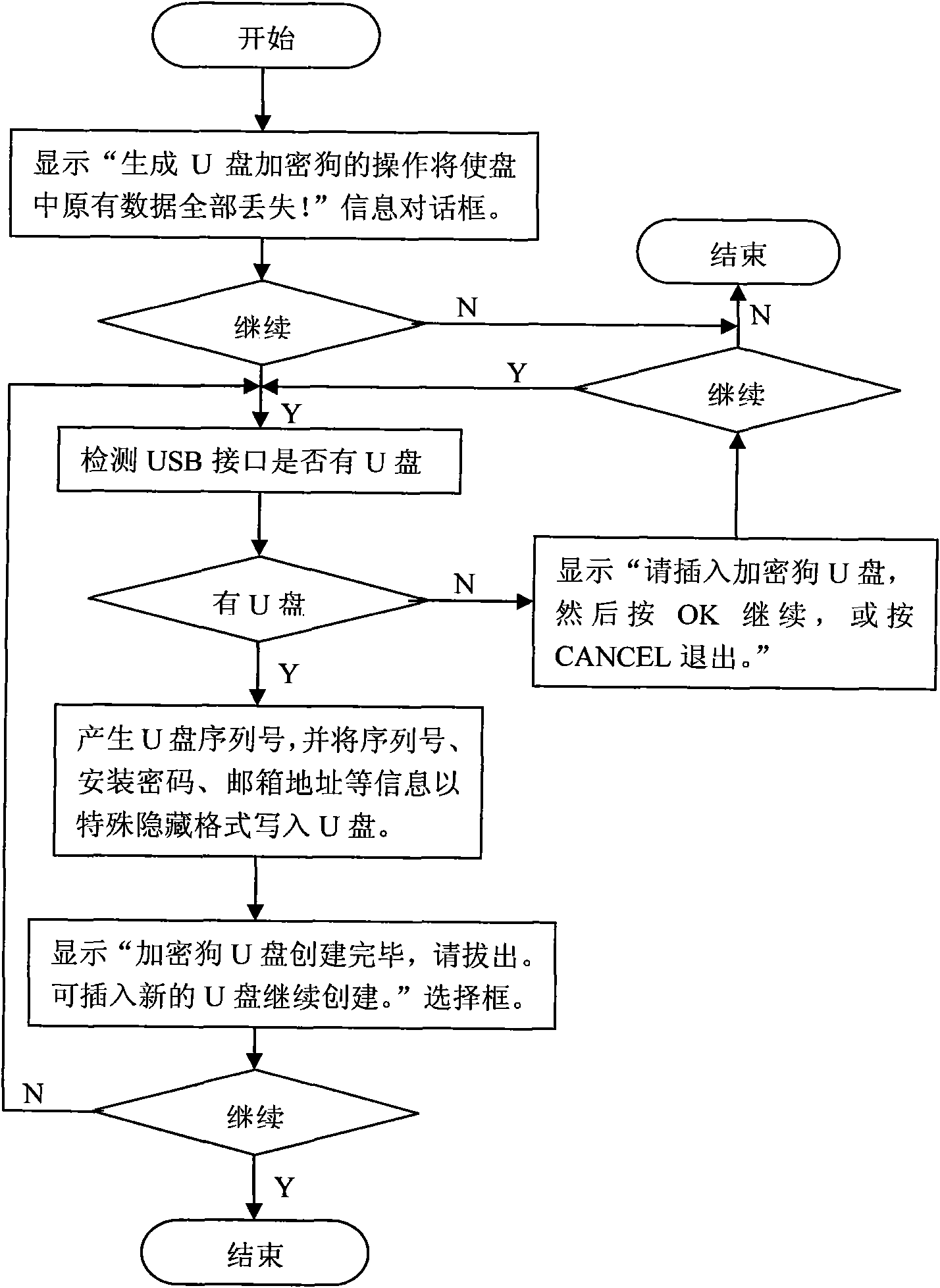
InactiveCN101661545AGood encryptionSimple and efficient operationProgram loading/initiatingProgram/content distribution protectionData fileSoftware
The invention discloses an anti-pirate method and a device for software capable of unloading and reinstalling. The method comprises the following steps: carrying out encryption algorithm on software to be installed according to preset algorithm to generate a unique cipher, and storing the unique cipher into a data file of the software to be installed so as to be called by the data file for manufacturing a dongle U disk program, an installation program and an unloading program; accessing the dongle U disk when the installation program is run, and verifying stealth verification cipher read fromthe dongle U disk with the unique cipher in the data file of the software to be installed, continuing to run the installation program when the two ciphers are in accordance, and deleting the stealth verification cipher in the dongle U disk; and accessing the U disk when the unloading program is run, storing the unique cipher into the U disk to become the stealth verification cipher. The method adopts a mode of stealth verification cipher which is disabled after installation, avoids repeated installation of the software, has good encryption performance and simple and convenient operation, and does not use a slot of an external port of a computer.
Owner:JIANGHAN UNIVERSITY
Nitrogen carbide quantum dot fluorescence ink
The invention discloses nitrogen carbide quantum dot fluorescence ink. By virtue of a hydrothermal synthesis method, a colorless and transparent nitrogen solution with strong fluorescence characteristics is prepared, and nitrogen carbide quantum dots of the water solution are uniform in shape and controllable in size; a maximal fluorescence-emission peak can be detected at 368 nanometers by virtue of excitation of a 250-nanometer wavelength, and most emission peaks are projected to invisible regions; when the nitrogen carbide quantum dot fluorescence ink is applied to encrypted storage protection of fluorescence information, the encrypted information cannot be read by virtue of ultraviolet color development, and fluorescence signals can be converted into readable information by virtue of a specific instrument. Compared with a traditional method, the method has the advantages that read equipment is relatively specific, and the information encryption is relatively strong.
Owner:FUZHOU UNIV
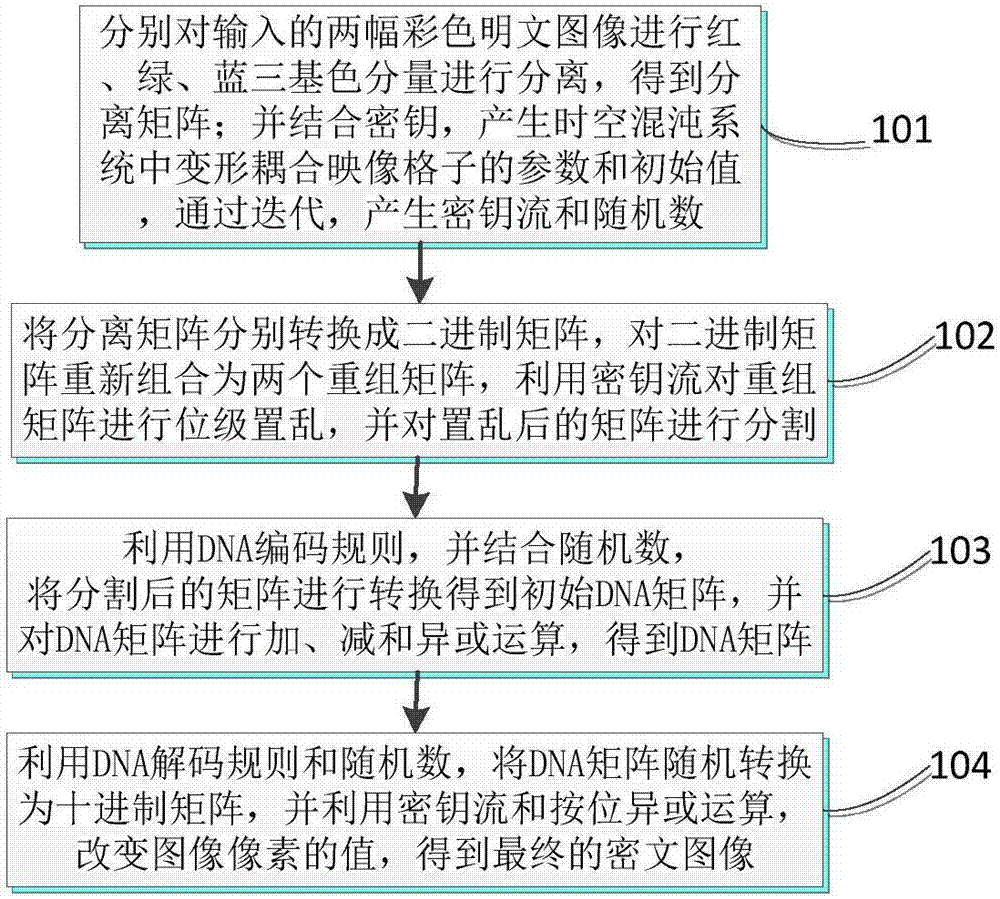
Double color image encryption method based on DNA sequence operation and deformed coupled map lattices
The invention discloses a double color image encryption method based on DNA sequence operation and deformed coupled map lattices. The method comprises: utilizing a secret key and two color plaintext images to generate parameters and initial values of iterating the deformed coupled map lattices, and generating secret key streams of L1, L2, K1 and K2 and random numbers of d1, d2 and d3 through iteration; separating red, green and blue trichromatic components of the plaintext images, transforming the components into binary matrices, and recombining the six binary matrices to obtain recombination matrices of A and B, utilizing the secret key streams of L1 and L2 to carry out bit-level scrambling on the matrices of A and B, and dividing the same into six binary matrices; utilizing a DNA encoding rule and combining the random numbers of d1, d2 and d3 to transform the binary matrices into DNA matrices, and executing DNA addition, subtraction and exclusive OR operations; and utilizing a DNA decoding rule to transform the DNA matrix into decimal matrices, utilizing the secret key streams of K1 and K2 and the bitwise exclusive OR operation to change values of image pixels, and obtaining ciphertext images of C1 and C2. The method can encrypt the two plaintext images at the same time, and has the advantages of high security, good encryption effect, no information loss, fast encryption speed and the like.
Owner:HENAN UNIVERSITY
Chip tray loading device and process
InactiveUS20070060313A1Reduce and eliminate number of timeEasy to monitorApparatus for meter-controlled dispensingVideo gamesEngineeringReceipt
A chip dispensing kiosk including a vault for holding casino chips, a dispensing assembly for dispensing selected numbers of casino chips and security and input systems to allow a pit manager to access the kiosk and have the kiosk dispense selected numbers of chips. These chips may be dispensed individually, in stacks or automatically loaded into a table chip tray back module. The kiosk is interactive with the casino's accounting system so as to report the dispensing of casino chips or receipt of casino chips. One preferred embodiment consists of a casino back room, cage, or Pit area chip tray management device that can be utilized by casino personnel to physically accept and count dumped gaming chips, communicate information with an ICT Intelligent Chip Tray Module, and automatically reload the chip tray per computer controlled specifications for any given table ID or chip loading requirement.
Owner:JCM AMERICAN CORP
Design of six-dimensional fractional-order hyperchaotic system and chaotic signal generator
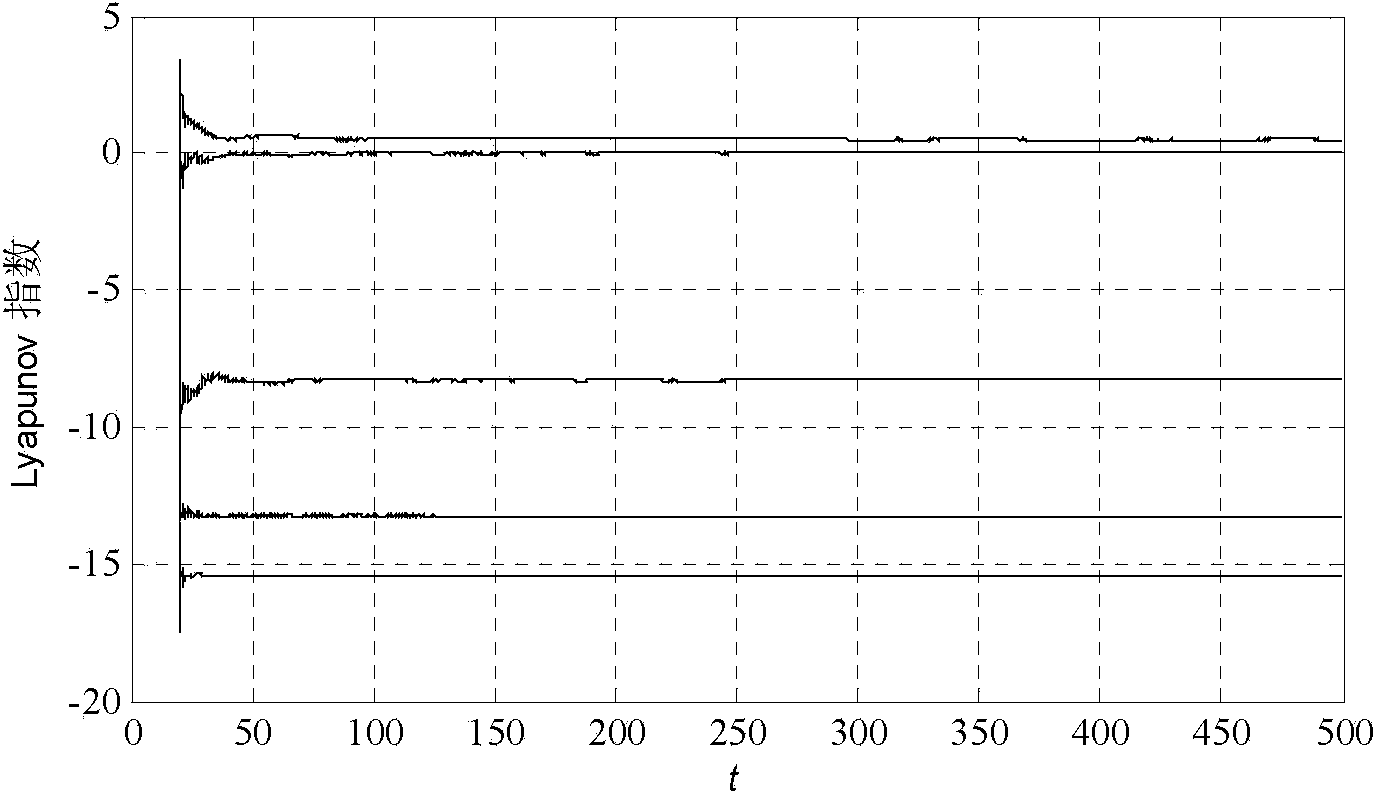
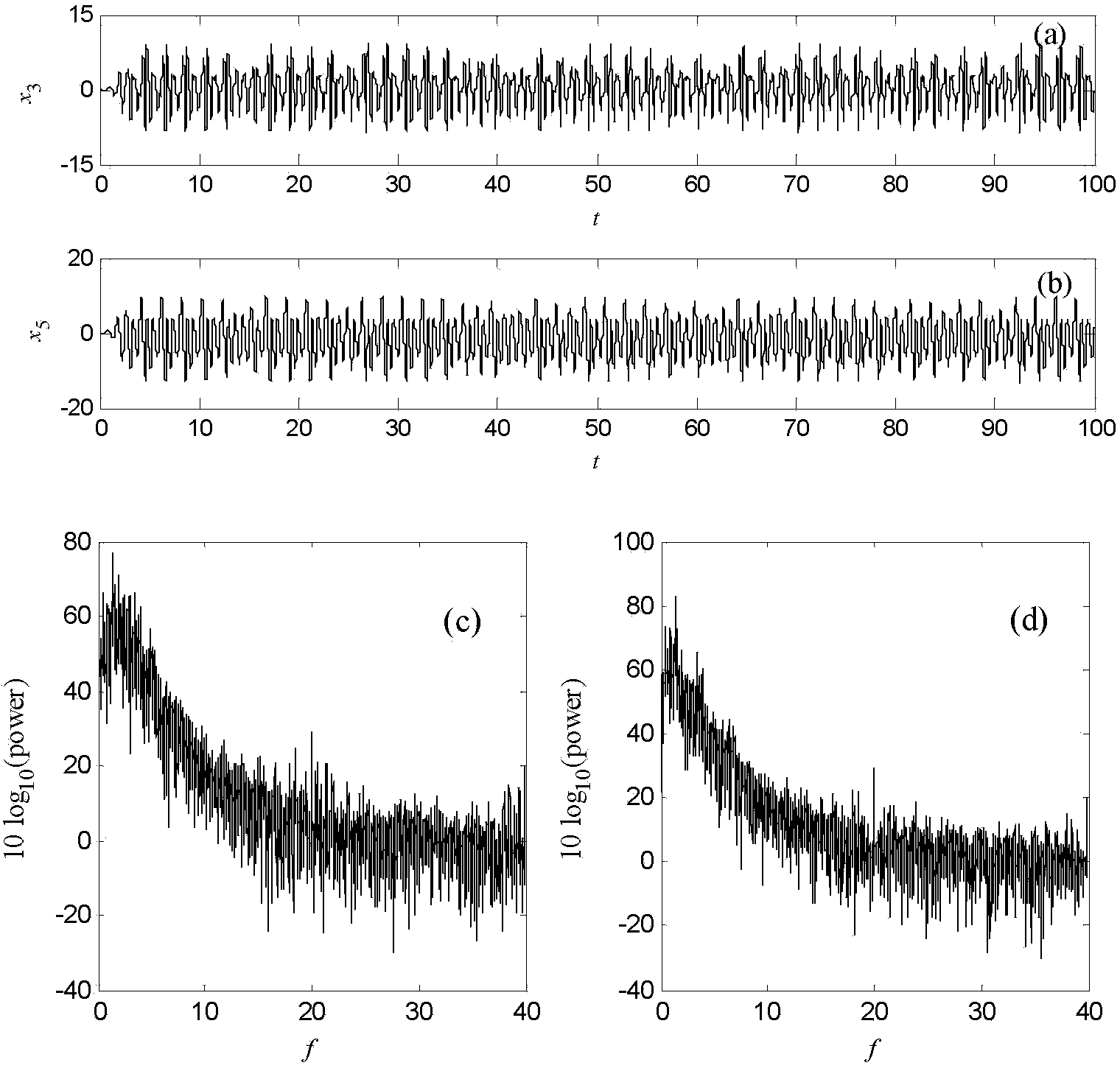
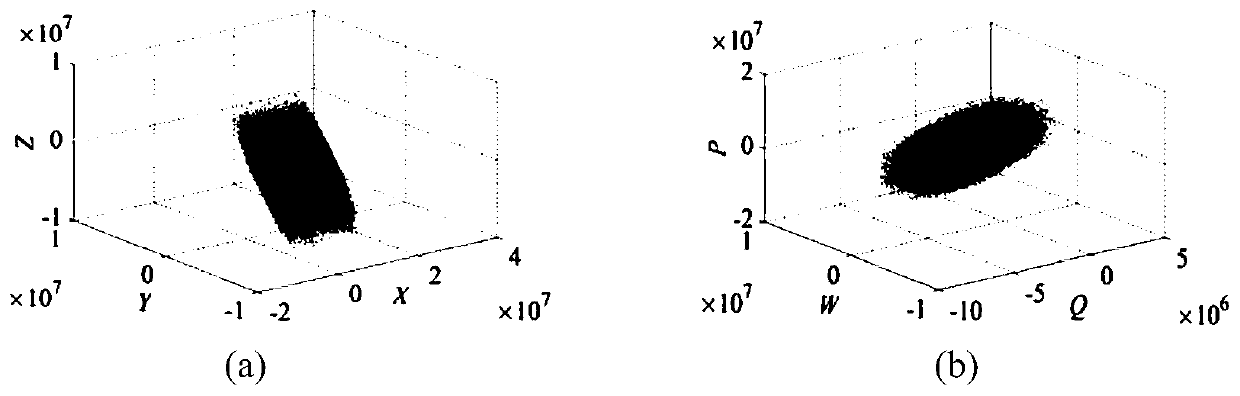
ActiveCN107359980AGood encryptionStrong anti-deciphering abilitySecuring communication by chaotic signalsChaotic systemsSignal generator
The invention discloses a six-dimensional fractional-order hyperchaotic system and a chaotic signal generator, and relates to the field of information encryption. The six-dimensional fractional-order hyperchaotic system disclosed by the invention is high in dimensionality; the system has more than two positive Lyapunov indexes, shows the hyperchaotic characteristic and obtains a more complex chaotic signal so as to improve safety of chaotic information encryption. Fractional-order differentiation has memory capacity, and is more suitable for characteristic description of a circuit system than the integer order. The six-dimensional fractional-order hyper system is used for outputting six paths of chaotic signals. A FPGA in the chaotic signal generator is used for generating a six-dimensional hyperchaotic system circuit; an six-path chaotic signal output end of the FPGA is respectively connected with digital signal input ends of a first path, second path, third path, fourth path, fifth path and sixth path of digital-to-analog converters; one end of a dial switch is connected with a power supply; the other end of the dial switch is respectively connected with power supply ends of the six paths of digital-to-analog converters; and signals output by the six paths of digital-to-analog converters are all voltage signals. The chaotic signal generator can provide a six-dimensional chaotic signal source which has various variable combination forms, is used for information encryption and has the excellent chaotic characteristic.
Owner:HARBIN UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com