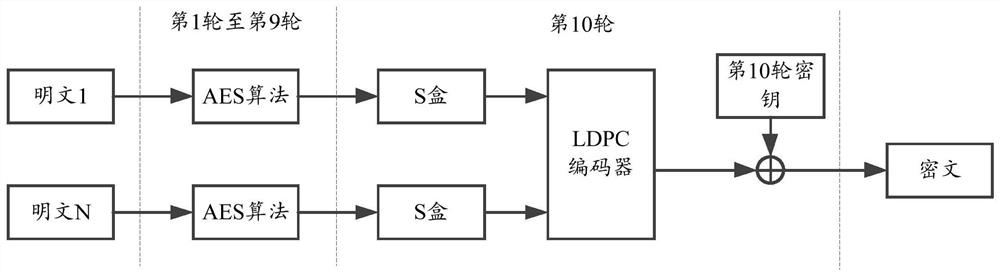
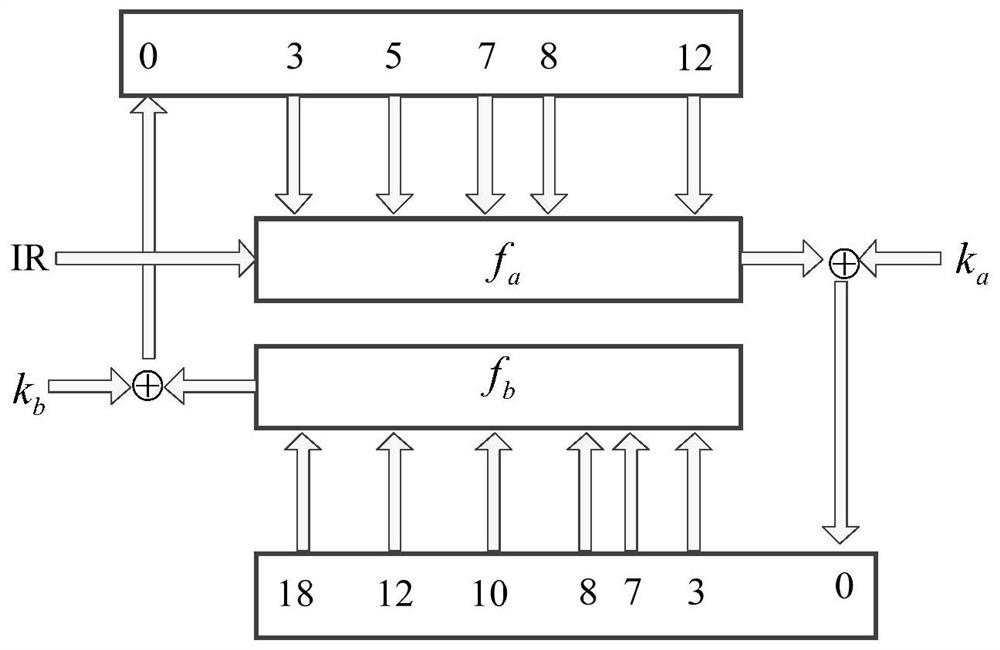
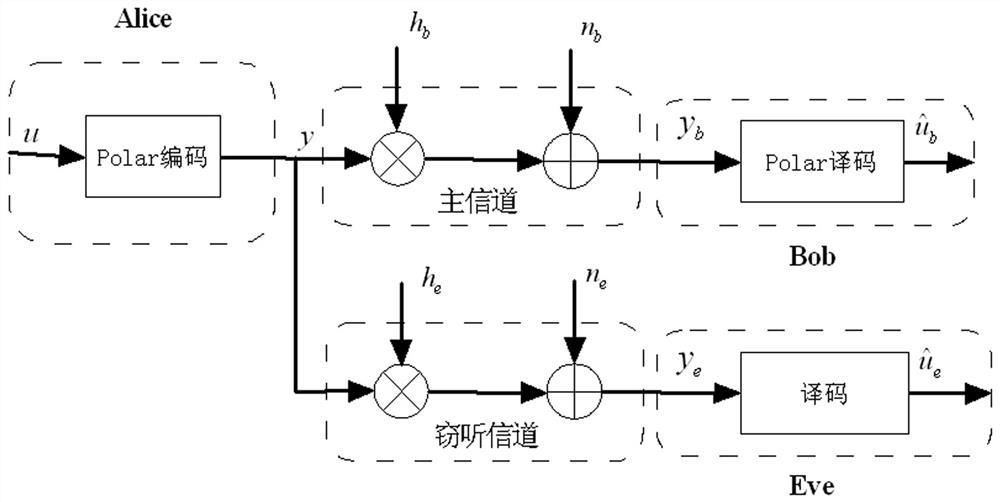
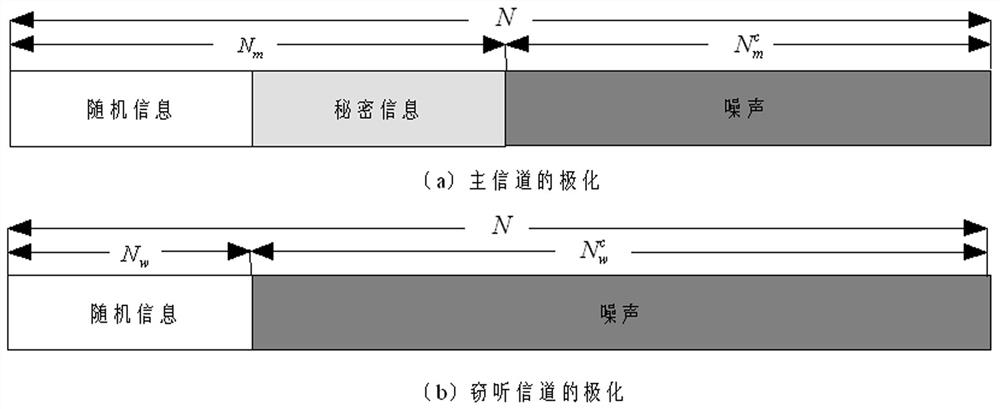
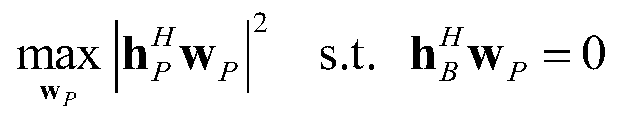Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
53 results about "Secure coding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Secure coding is the practice of developing computer software in a way that guards against the accidental introduction of security vulnerabilities. Defects, bugs and logic flaws are consistently the primary cause of commonly exploited software vulnerabilities. Through the analysis of thousands of reported vulnerabilities, security professionals have discovered that most vulnerabilities stem from a relatively small number of common software programming errors. By identifying the insecure coding practices that lead to these errors and educating developers on secure alternatives, organizations can take proactive steps to help significantly reduce or eliminate vulnerabilities in software before deployment.
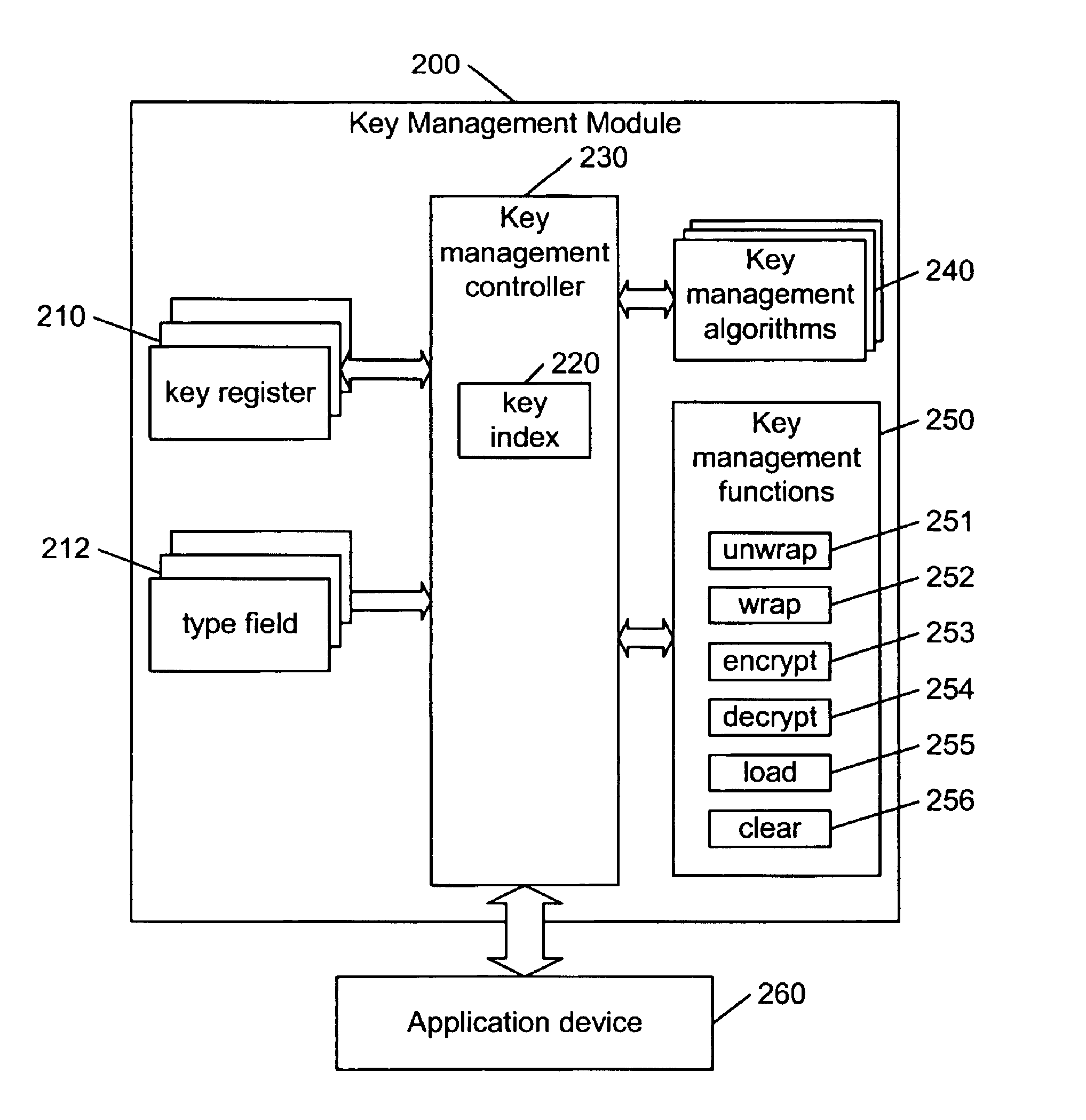
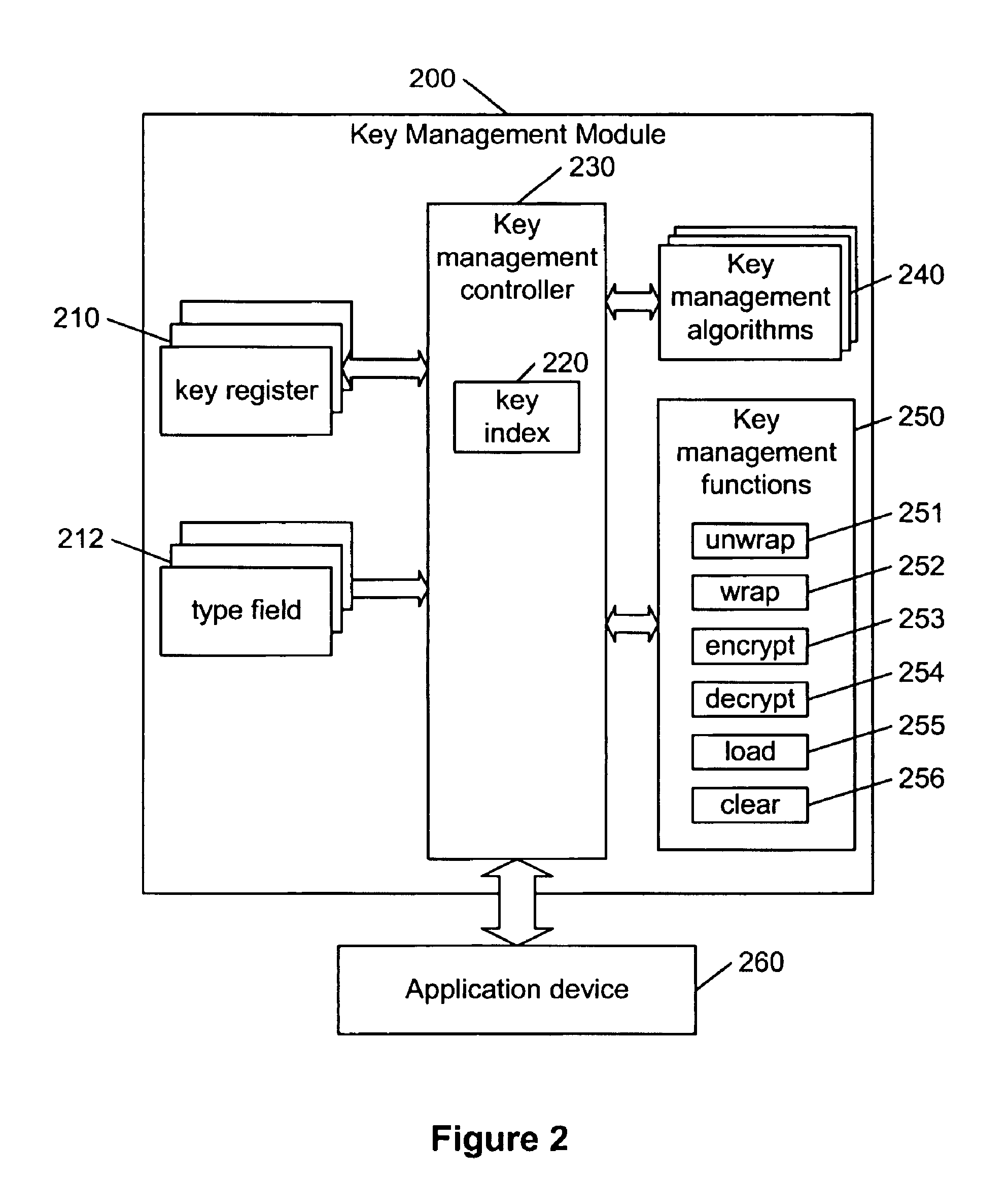
Hierarchical key management encoding and decoding
InactiveUS6907127B1Simple designSeparate applicationKey distribution for secure communicationDigital data processing detailsExclusive orInitialization vector
The present invention discloses a construction for key management module functionality which provides for secure encoding and decoding of messages which are up to two blocks long. A method for generating an encoded value having a first encoded value part and a second encoded value part from an unencoded value having a first unencoded value part and a second unencoded value part, comprising the steps of: obtaining an initialization vector; and generating the first and second encoded value parts. The first encoded value part is generated by: generating a first result by encrypting the first unencoded value part; generating a second result by performing an exclusive or operation on the first result and the second unencoded value part; generating a third result by performing an exclusive or operation on the second result and the initialization vector; generating a fourth result by encrypting the third result; generating a fifth result by performing an exclusive or operation on the fourth result and the first unencoded value part; and encrypting the fifth result. The second encoded value part is generated by encrypting the second result.
Owner:GOOGLE LLC
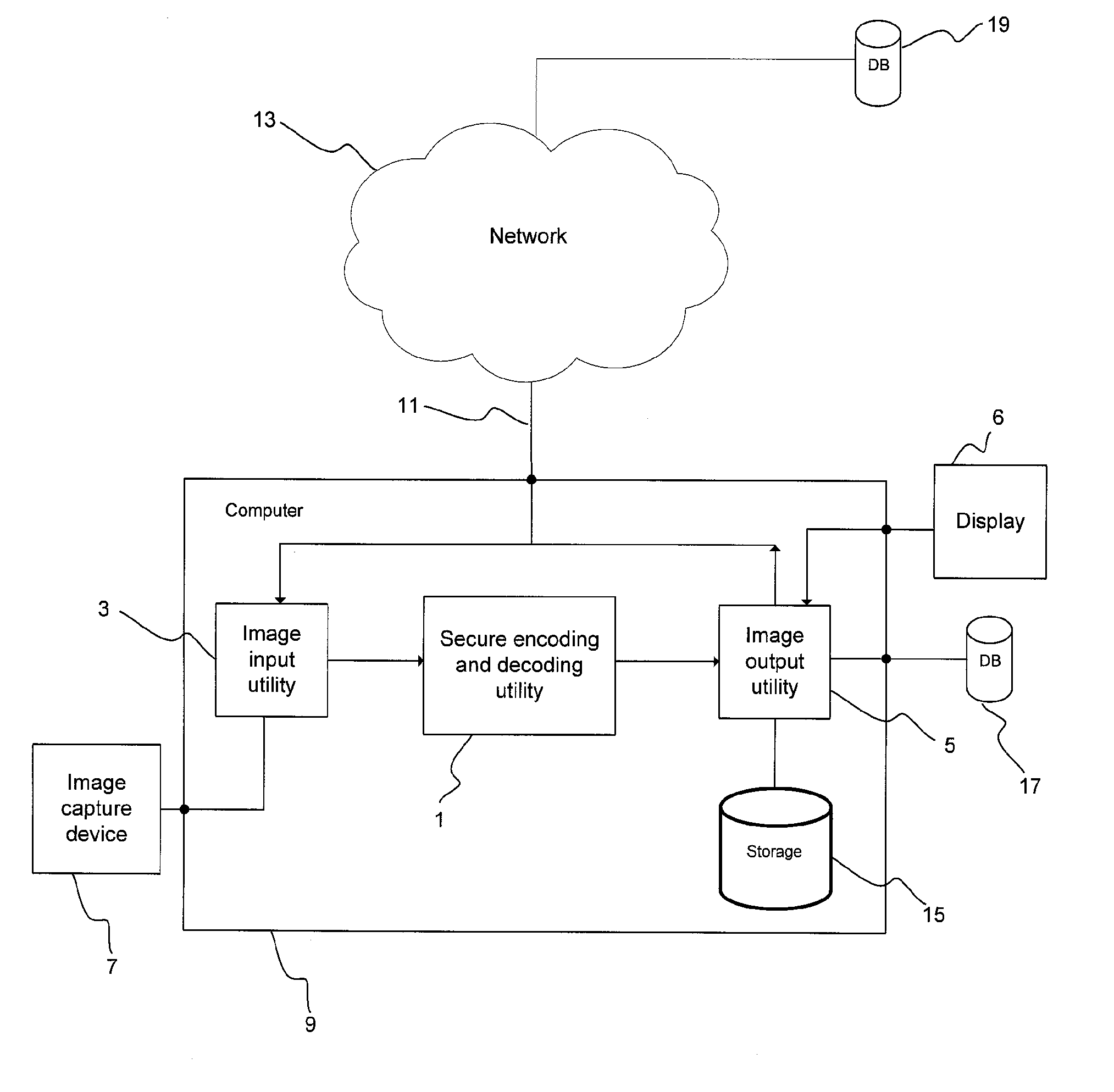
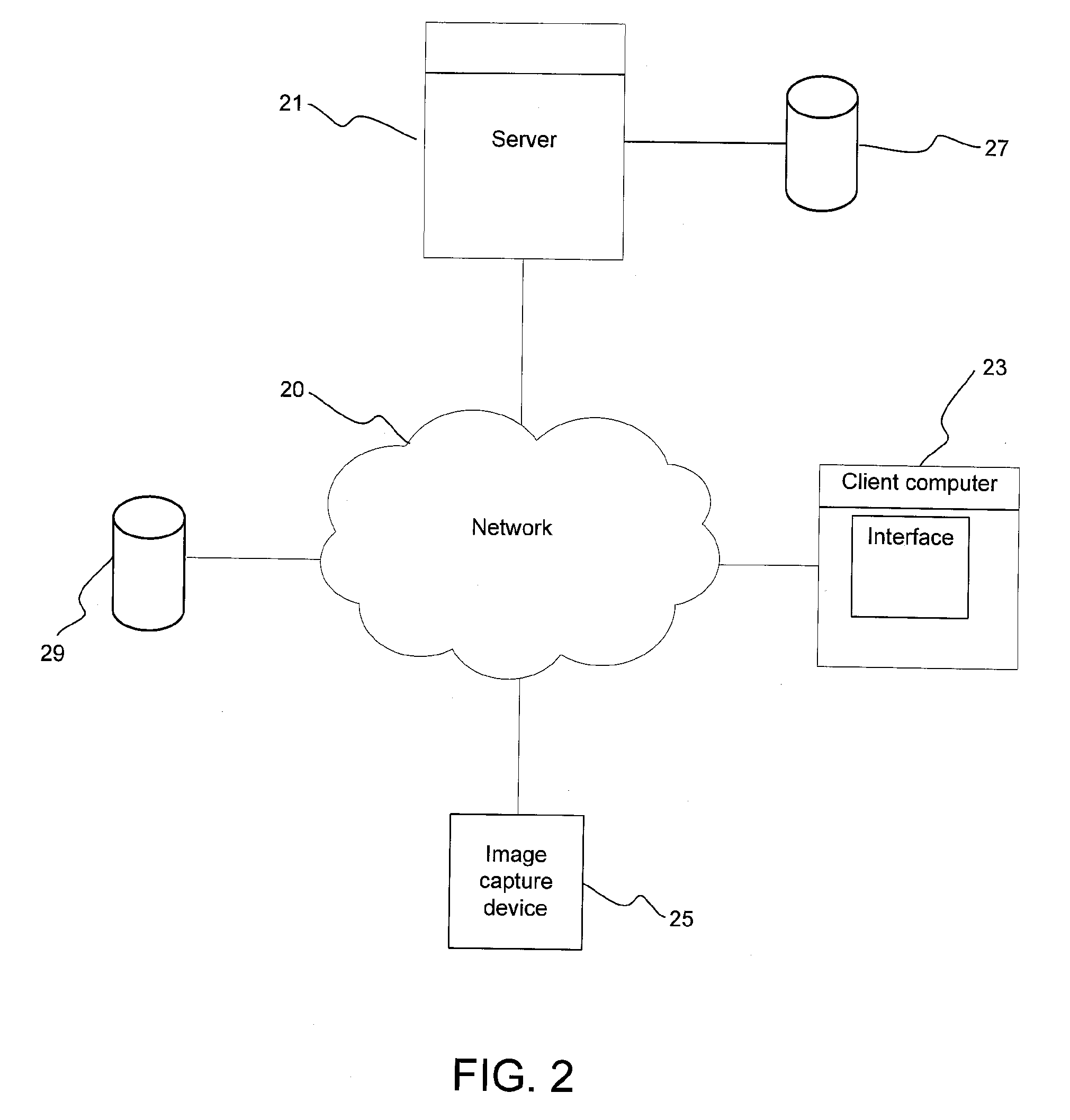
Method and system for secure coding of arbitrarily shaped visual objects
InactiveUS20110158470A1Easy to compressGood encryptionCharacter and pattern recognitionImage codingComputer graphics (images)Visual Objects
The present invention relates to a method and system for secure coding of arbitrarily shaped visual objects. More specifically, a system and method are provided for encoding an image, characterized by the steps of selecting one or more objects in the image from the background of the image, separating the one or more objects from the background, and compressing and encrypting, or facilitating the compression and encryption, by one or more computer processors, each of the one or more objects using a single coding scheme. The coding scheme also is operable to decrypt and decode each of the objects.
Owner:THE GOVERNINIG COUNCIL OF THE UNIV OF TORANTO
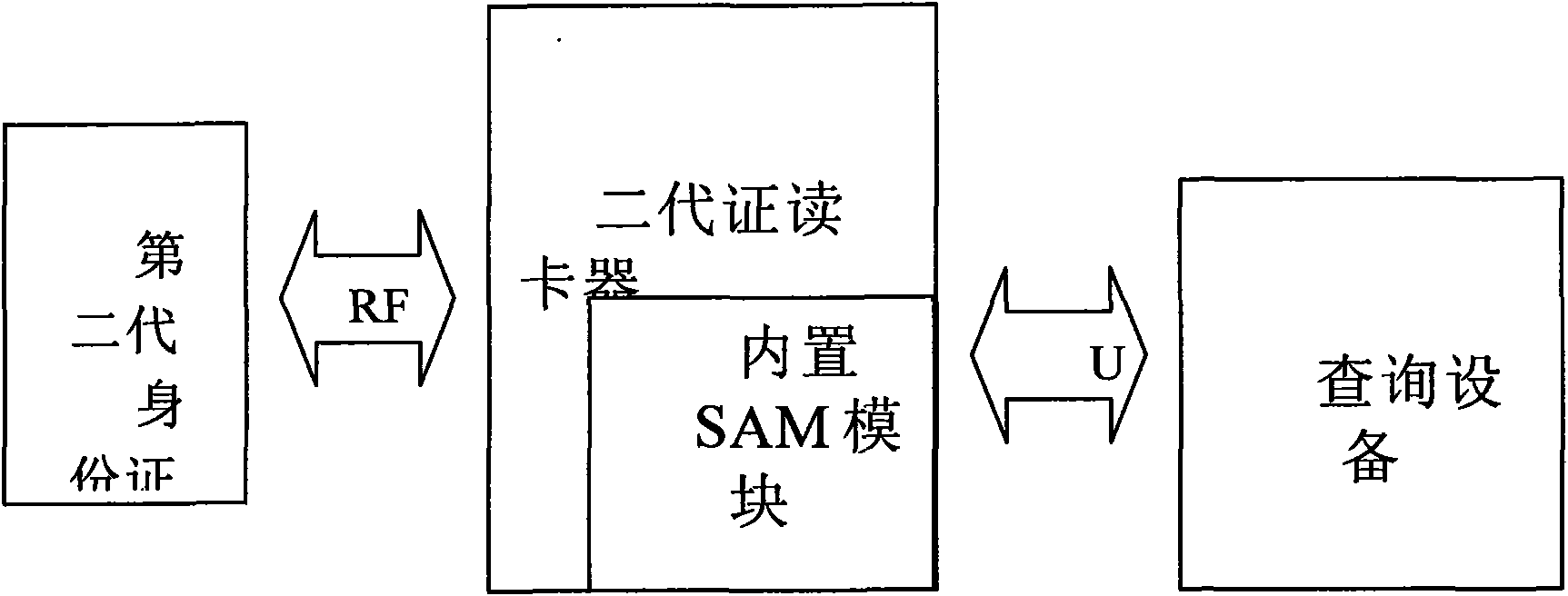
Second-generation ID card online inquiry system and method based on secure network
InactiveCN101656748ASolving the full range of mobile online applicationsRealize remote secure deliveryUser identity/authority verificationSpecial data processing applicationsRelevant informationNetwork link
The invention discloses a second-generation ID card online inquiry system based on a secure network, comprising an on-line service terminal, a secure network link module, an identification authentication and right management server and an identification relevant information database, wherein the on-line service terminal comprises a mobile multi-interface read module, a secure coding and decoding module and a terminal set, wherein the mobile multi-interface read module and the secure coding and decoding module are both connected to the same terminal set; the terminal set is connected with the identification authentication and right management server through the secure network link module; and a high-speed data link exists between the identification authentication and right management serverand the identification relevant information database. After the mobile multi-interface read module finishes reading a second-generation ID card, an identification information authentication inquiry request initiated from the terminal set by an operator is coded by the secure coding and decoding module and sent to the identification authentication and right management server by the secure networklink module, then information is obtained from the identification relevant information database after identification authentication and right judgment, and the information is fed back from the securenetwork link module to the terminal, thereby movably finishing the on-line authentication and inquiry of personal information with high security.
Owner:上海申远投资管理有限公司
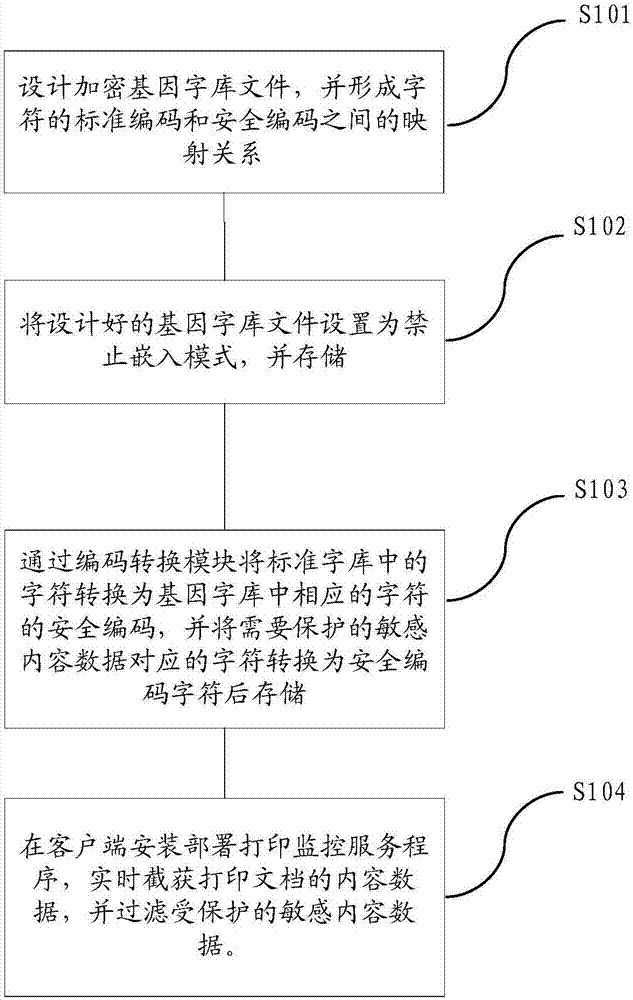
Information protection method and system of sensitive content data
ActiveCN107239713AImprove securityReduce risk of leakageDigital data protectionClient-sideSecure coding
The invention relates to an information protection method and system of sensitive content data. The method comprises the first step of designing a genetic word stock file, wherein the file comprises characters and security codes of the characters, and a several-for-one mapping relation is formed between the security code of each character and a standard code of the character in a standard word stock; the second step of setting the genetic word stock file into an embedding-forbidding mode, and conducting whole encryption and afterwards storing the encrypted file into a server instead of conducting installing directly in an operating system of a client side; the third step of converting the standard codes in the standard word stock into the security codes of corresponding characters in the genetic word stock, and converting the characters of the standard codes corresponding to the sensitive content data which needs to be protected into the characters of the security codes and afterwards storing the characters; the fourth step of deploying a printing and monitoring service program in the client side, intercepting content data of a printed file in real time, and filtering out the protected sensitive content data. According to the information protection method and system of the sensitive content data, the problem in the prior art that the safety is relatively low existing in the aspect that data leakage is prevented through a safe word stock encryption technology is solved.
Owner:李晓妮
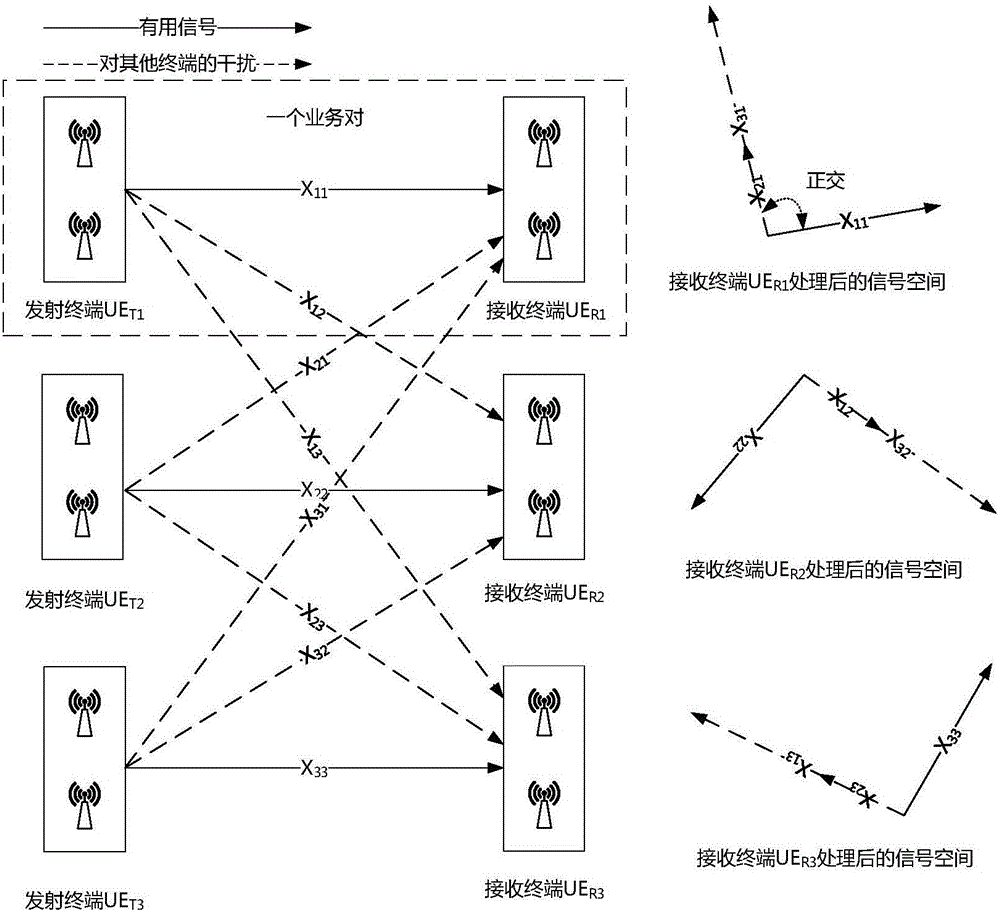
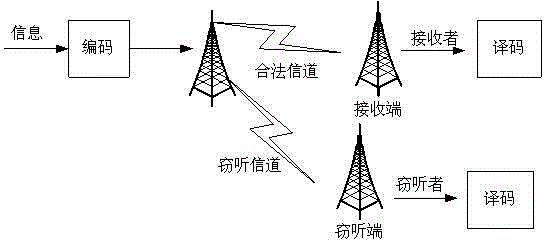
Unconditional physical layer secure cooperative transmission method based on interference alignment technology
ActiveCN106100710ARealize transmissionAvoid the risks of exchanging keysSpatial transmit diversityChannel estimationBinary-safePhysical layer
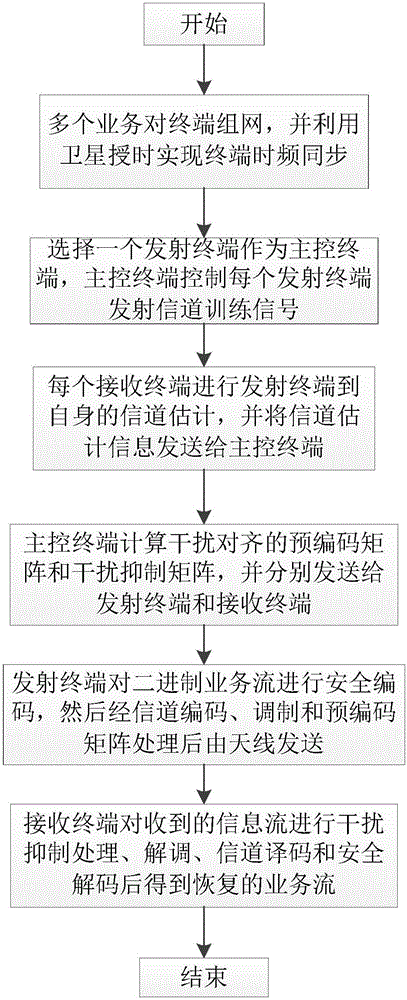
The invention provides an unconditional physical layer secure cooperative transmission method based on interference alignment technology. The method comprises the steps that networking and carrying out time-frequency synchronization are carried out at first, and a master control terminal is selected; all transmitting terminals sequentially transmit channel training signals; a receiving terminal carries out estimates a channel state and transmits the channel state to the master control terminal; the master control terminal calculates a precoding matrix and an interference suppression matrix, and then transmits the same to the other transmitting terminals and the receiving terminal; each transmitting terminal carries out binary secure coding on the original business flow, and the encoded bit stream is used as business input to carry out interference alignment transmission; and the receiving terminal carries out secure decoding on the received binary stream to acquire information stream of a user. Compared with the traditional scheme of encrypted and decrypted transmission based on keys, the risks brought by exchanging the keys are avoided firstly, secondly the error rate of an illegal user can approach 0.5 on the theory, so no valid information can be acquired from the information theory significance, and the complexity is relatively low.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Image compression secure coding method based on multidirectional sparse representation
InactiveCN101848390AIncrease the number of directionsIncrease flexibilityTelevision systemsDigital video signal modificationObjective qualityNoise shaping
The invention discloses an image compression secure coding method based on multidirectional sparse representation, comprising the following steps of: performing discrete dual-tree wavelet transform on an image and then performing directional filtering on each obtained high-frequency sub-band to obtain fine image directional sparse representation; performing rarefaction process on an obtained directional sub-band coefficient by using a noise shaping technology; interleaving the coefficients of each layer to ensure that the sub-band coefficients of neighbor layers have a parent child relation, and then performing quantitative coding on the coefficients by using SPIHT (Set Partitioning in Hierarchical Trees); and finally encrypting the coefficient symbols in a code stream in an XOR (Exclusive OR) manner and encrypting other partial code streams by using random arithmetic coding. As the code stream obtained by coding is encrypted by using the random arithmetic coding, the encryption efficiency is high, the effect is good, the security is high and no influence is brought to the image compression performance. The high-frequency components of the image are decomposed by using a directional filter, and therefore the directional representation is more flexible, sparser image representation is obtained, the image coding compression process is favored and the decoded image has better objective quality and subjective effect.
Owner:SOUTHWEST JIAOTONG UNIV
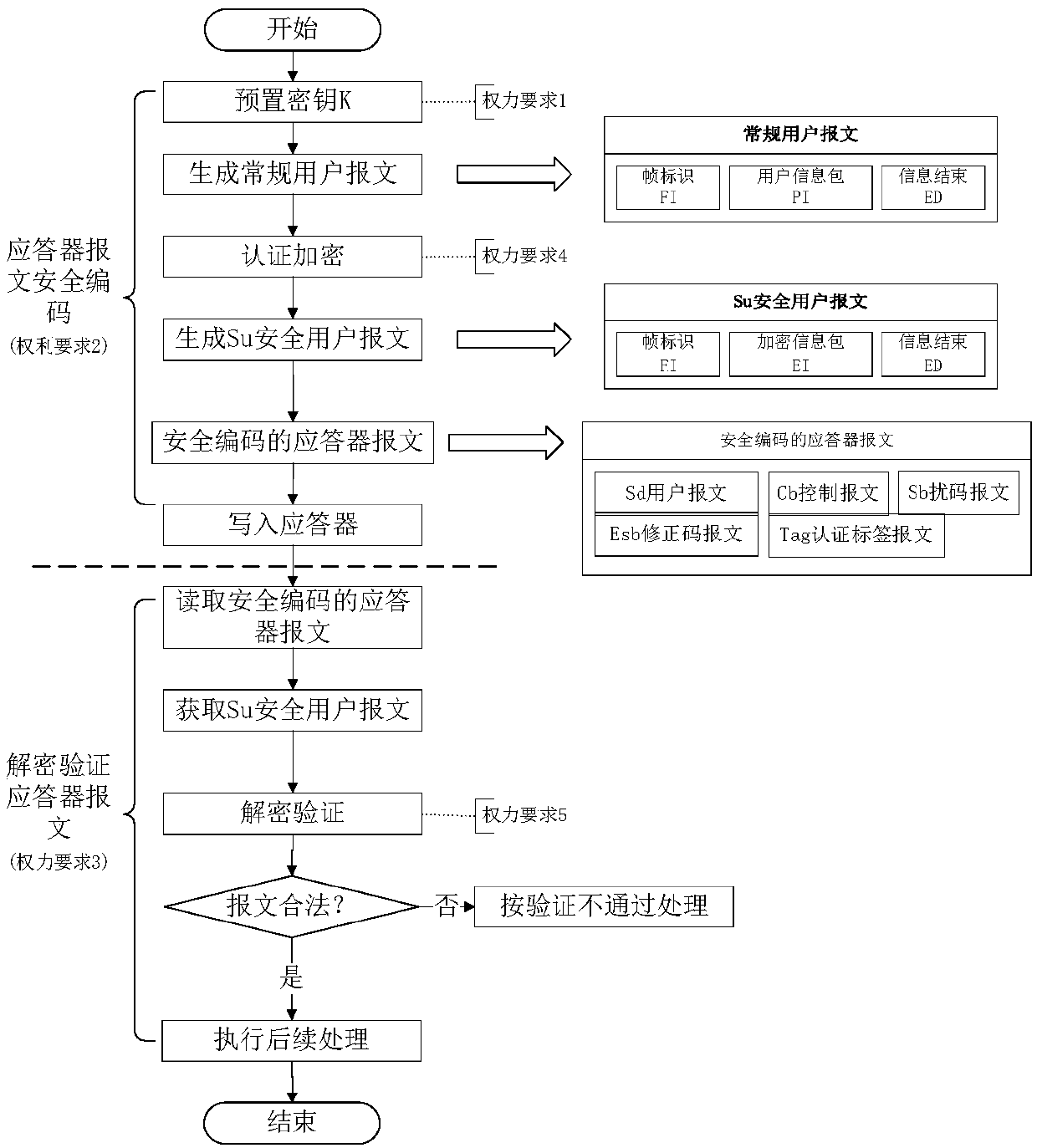
Secure coding and railway signal security protocol (RSSP-II)-based interface realization method
The invention relates to a secure coding and railway signal security protocol (RSSP-II)-based interface realization method. The method comprises the steps of receiving information from an RSSP-II communication layer, then converting the received information into information comprising coding information, dual-channel verification information and random error detection information by a receiving conversion module, wherein the information is involved in program operation of secure coding; and generating sent information in a program of secure coding, adding dual-channel verification informationand dual-channel random error detection information to MAC information of the sent information through a sending conversion module, then framing the MAC information with high bit coding information ofthe sent information to be sent out. Compared with the prior art, the method provides a detection mechanism for random errors generated in a process from receiving the information by the RSSP2-II communication layer to using the information by the coding program, and provides a detection mechanism for random errors generated in a process from generating information by the coding program to calculating an information verification code by an RSSP-II protocol layer, thereby making the interface safer.
Owner:CASCO SIGNAL
Information transmission method with combination of artificial scrambling and LDPC secure coding in satellite-ground link
ActiveCN106230552AEnsure safetyGuaranteed reliabilityKey distribution for secure communicationError preventionChannel state informationInformation transmission
The invention relates to an information transmission method with combination of artificial scrambling and LDPC secure coding in a satellite-ground link, and belongs to the technical field of satellite communication. The method includes: step 1, calculating a state vector of a main channel; step 2, calculating a state information matrix of the main channel; step 3, performing LDPC coding on to-be-sent information; step 4, constructing artificial noise z orthogonal to the main channel; step 5, calculating a sending weight of the to-be-sent information, wherein the sending weight enables a private interruption probability to be minimum; step 6, continuously sending the coded to-be-sent information, and sending the artificial noise by employing a multi-antenna emission mode; and step 7, performing decoding by employing a BP decoding algorithm by a receiving end. According to the method, in an information transmission process, channel state information is introduced to LDPC coding so that the security and the reliability of communication are guaranteed; the coding method based on the channel state information is employed so that problems during the application of the conventional encryption algorithm in the satellite communication process is avoided; and the complexity of satellite secret communication is reduced.
Owner:NORTHEASTERN UNIV
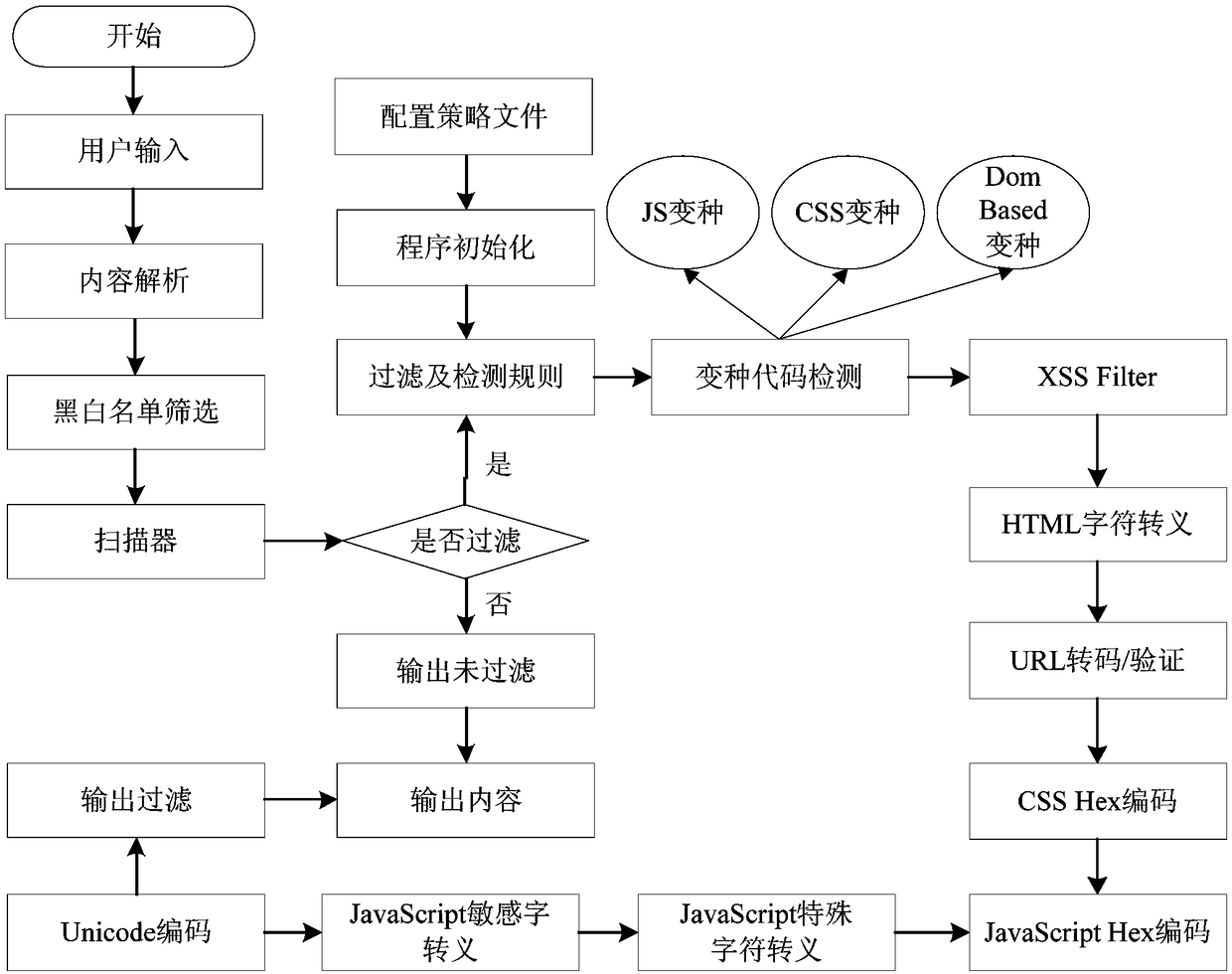
Cross-site scripting attack defense method, device, apparatus and storage medium
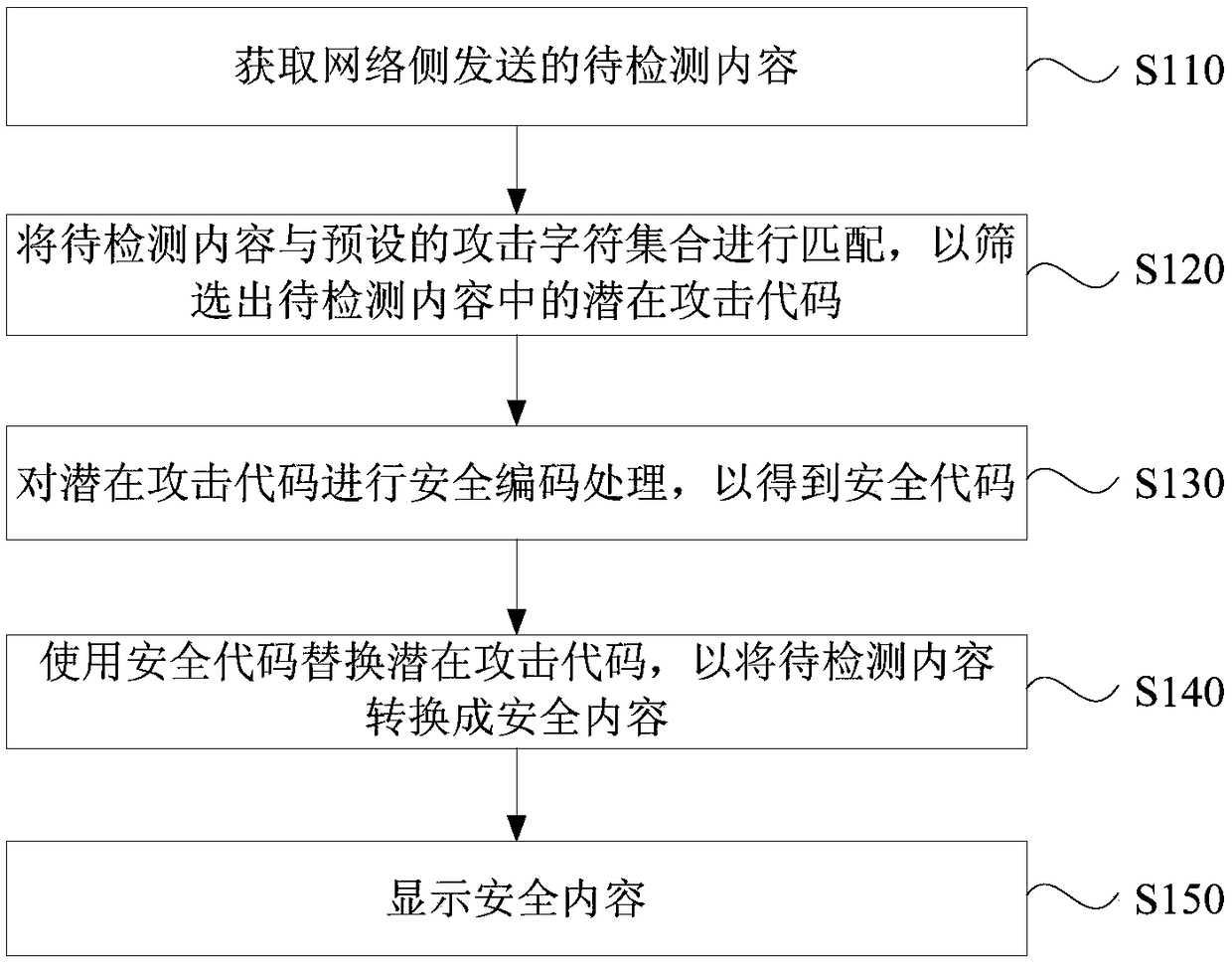
The invention discloses a cross-site script attack defence method, a device, an apparatus and a storage medium. The method comprises the following steps: obtaining the content to be detected sent by the network side; matching the content to be detected with a preset set of attack characters to screen potential attack codes in the content to be detected; performing security encoding processing on the potential attack code to obtain a security code; replacing the potential attack code with the security code to convert the content to be detected into secure content; displaying the secure content.The invention solves the technical problem that the XSS attack can not be dynamically defended in the prior art, the preset attack character set can be configured according to user requirements to ensure that the content to be detected input by the user conforms to the application specification of the application programming interface so as to effectively prevent the technical effect of XSS attacks.
Owner:彩讯科技股份有限公司
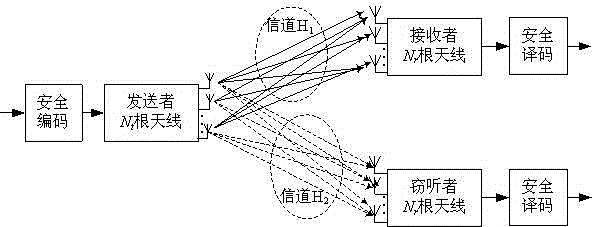
Method for establishing unconditionally secure communication model based on combination of beam forming and security coding
ActiveCN104917558AGuaranteed to receiveSpatial transmit diversityChannel estimationPrecodingSecure communication
The invention discloses a method for establishing an unconditionally secure communication model based on combination of beam forming and security coding. The method comprises the steps that a legal sending user sends pre-coded and modulated signals, and an eavesdropping user receives the signals and calculates an eavesdropping bit error rate; security coding parameters are calculated, a legal receiving user sends a pilot frequency sequence, the legal sending user estimates a legal channel, information of the legal channel is extracted, SVD pre-coding is carried out on the signals subjected to security coding and modulation, and the signals are sent; the legal receiving user or the eavesdropping user receives the signals and carries out decoding processing and carries out judgment and demodulation on the decoded signals, security decoding is carried out on a demodulated binary bit stream, and transmitted signals or eavesdropped signals are acquired. The eavesdropping user lacks information of the legal channel, so that pre-coding processing of the received signals cannot be relieved, and the bit error rate is high. The method disclosed by the invention can well achieve establishment of an advantageous channel in an eavesdropping signal model, and ensure the legal user to receive signals under a low bit error rate.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
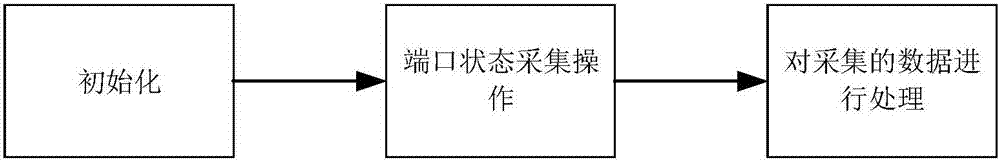
Safe processing method for data delay transmission in safe coding system
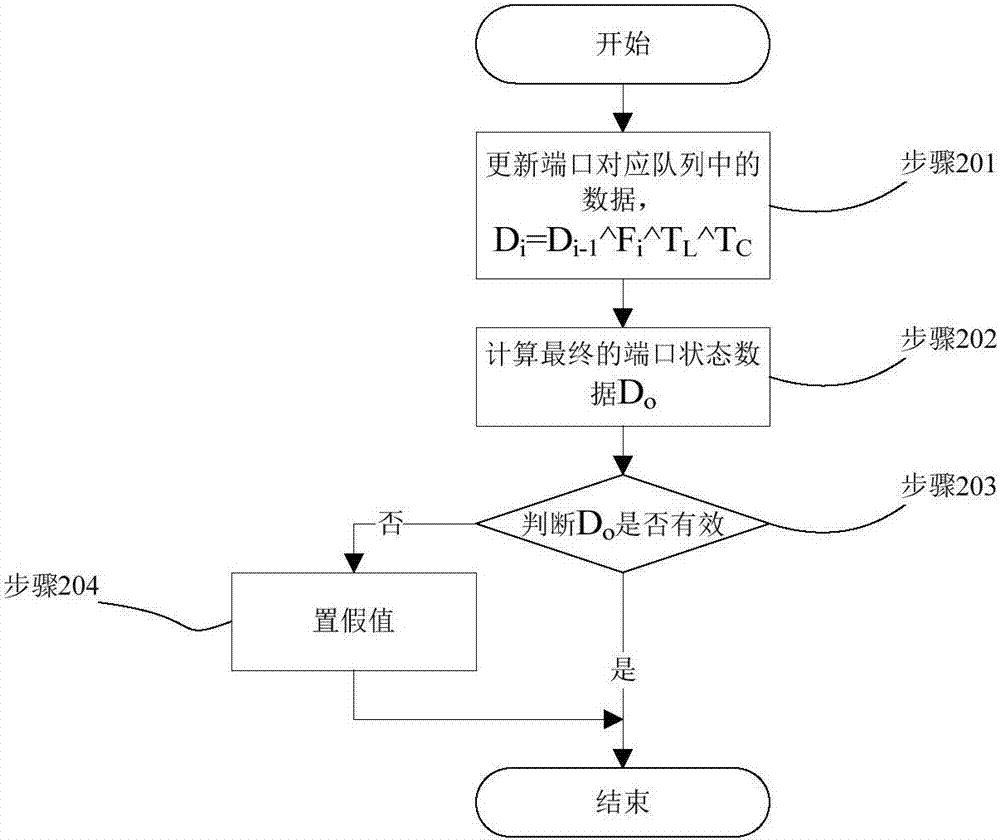
The invention relates to a safe processing method for data delay transmission in a safe coding system. A queue used for storing data of a port collected in a delay time window is firstly defined, every time the system collects the data stored in the window, the data is recomputed once, the finally sent state data of the port is a result of all data in the time window which has computed once, and safety of the result is judged. Compared with the prior art, the method provided by the invention has the advantage of high safety in output data.
Owner:CASCO SIGNAL
Random modulation-based combined channel and secure coding and decoding design method
InactiveCN103475462AImplement the encryption functionReduce coding complexityError preventionEncryption apparatus with shift registers/memoriesSecure codingPseudorandom permutation
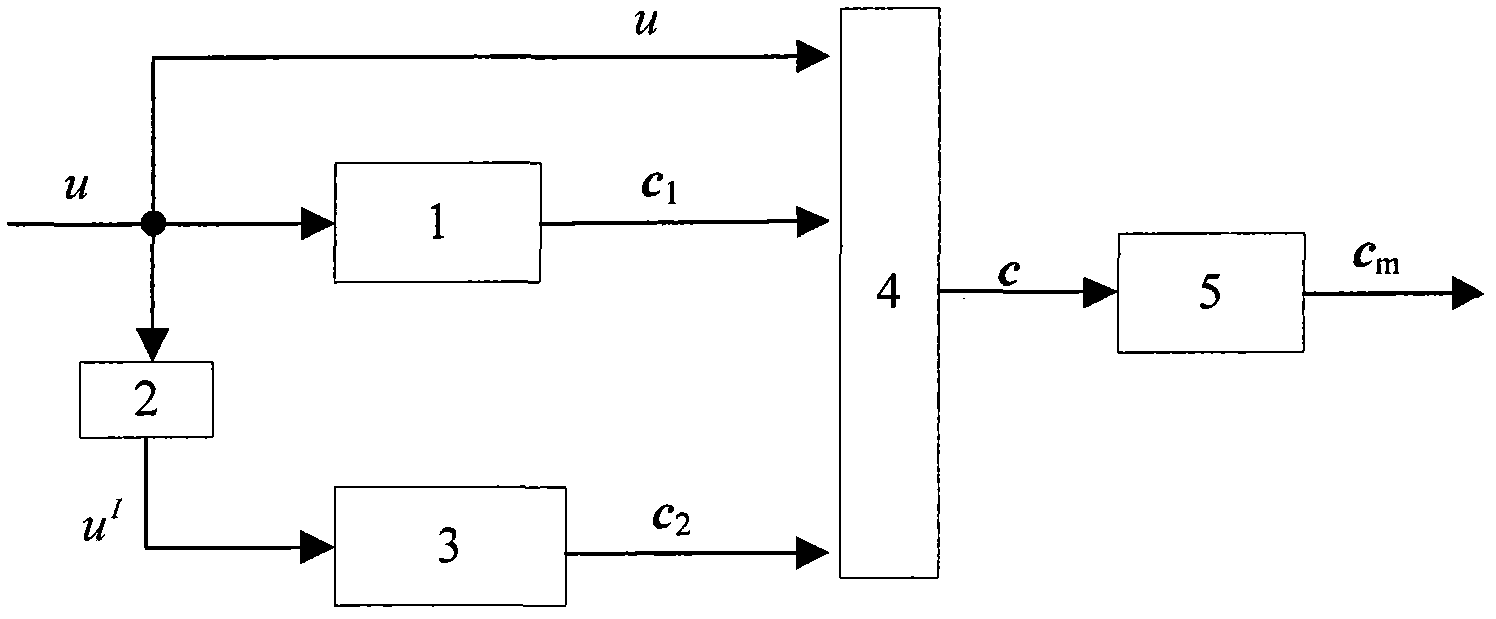
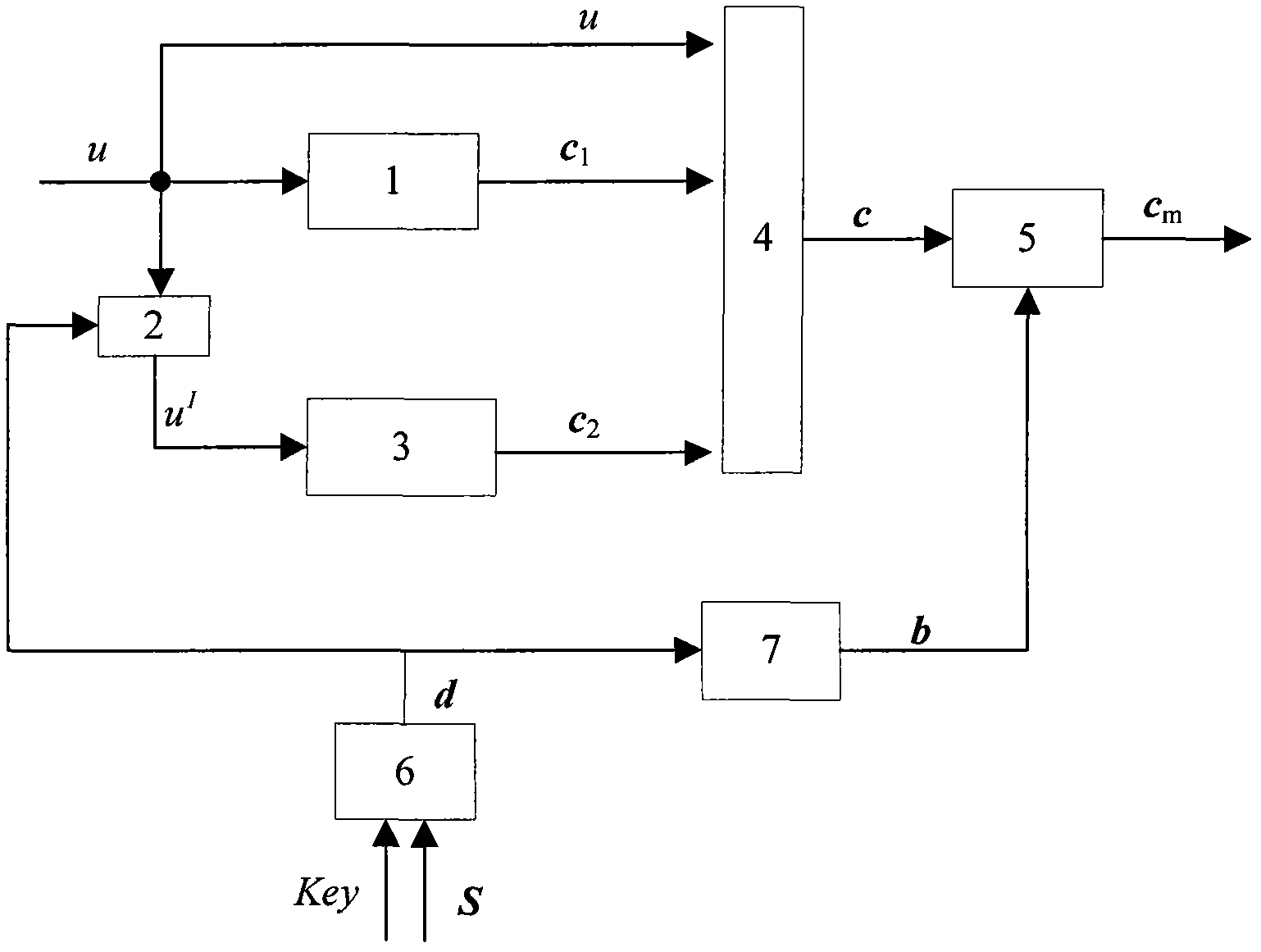
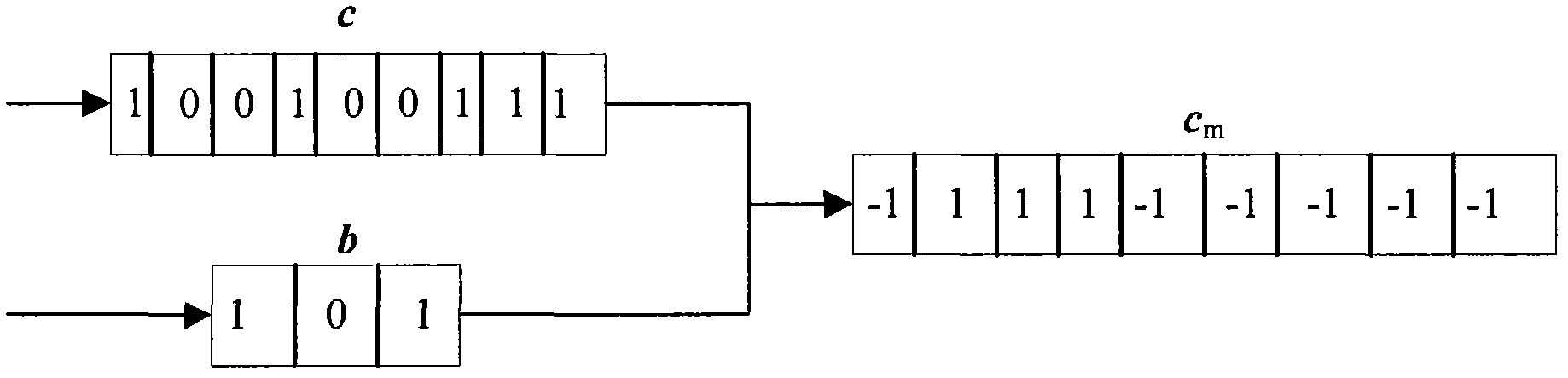
In allusion to the problem that a modulator of a routine Turbo code stream has no encryption function, a modulation and encryption method based on key control is designed according to a random modulation-based combined channel and secure coding and decoding design method. By the method, an interleaver is associated with a modulator. Firstly, length of the interleaver is set as N; S is natural sequence of the length N; a Key is adopted to generate a random permutation d of natural numbers having the length N, wherein d=f(S,Key), and f is a random permutation function; mod-2 operation is carried out on d to generate a binary sequence b having the length N; and finally, random modulation is carried out on a reused coded bit sequence c, and a modulation sequence cm is outputted. During demodulation, a receiving end adopts the same Key and random function f with a coding end to generate the binary sequence b having the length N, and demodulation is carried out to output the correct bit sequence c.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Channel polarization secure coding method based on robust soliton distribution
ActiveCN108631944AGuaranteed normal transmissionImprove securityChannel coding adaptationForward error control useRound complexityInformation transmission
The invention aims at providing a channel polarization secure coding method based on robust soliton distribution, and the method comprises the following steps: firstly, a sending end codes to-be-sentinformation based on robust soliton distribution; then, Polar coding is executed for the to-be-sent information which is coded based on robust soliton distribution; and a normal receiving end and an eavesdropping end respectively perform Polar decoding for the received information, finally, the normal receiving end and the eavesdropping end respectively perform belief propagation decoding for thereceived information subjected to Polar decoding, and restore the sent information. Compared with the existing technology, the method provided by the invention can improve transmission rate of information transmission while guaranteeing security and reliability of information transmission under the premise of slightly increasing secure coding and decoding complexity, and consequently improves validity of information transmission.
Owner:ZHONGBEI UNIV
Physical layer secure coding system based on Ethernet communication
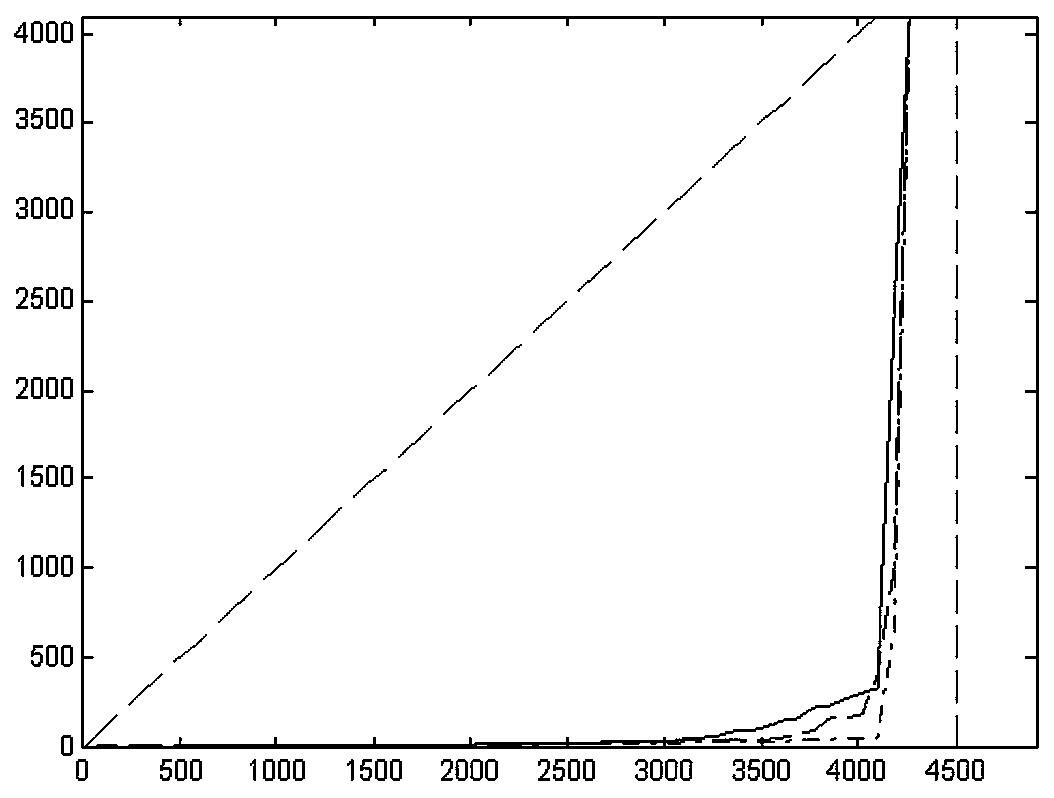
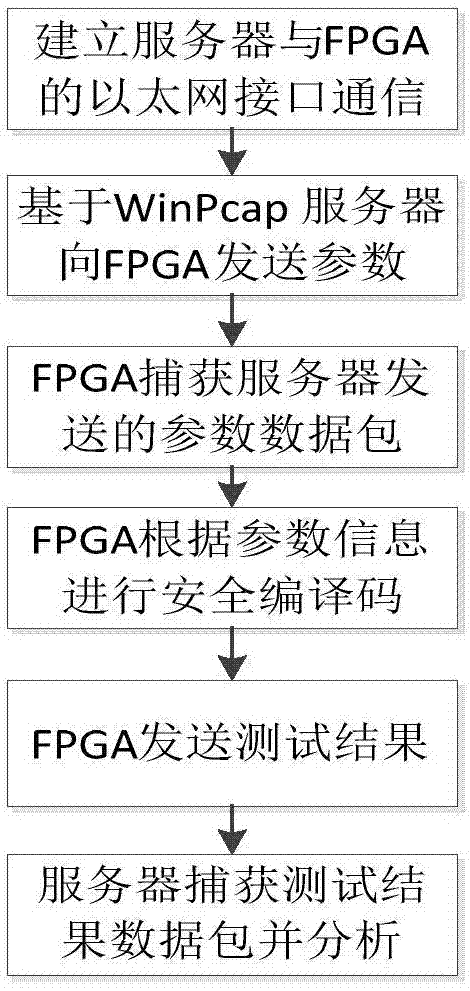
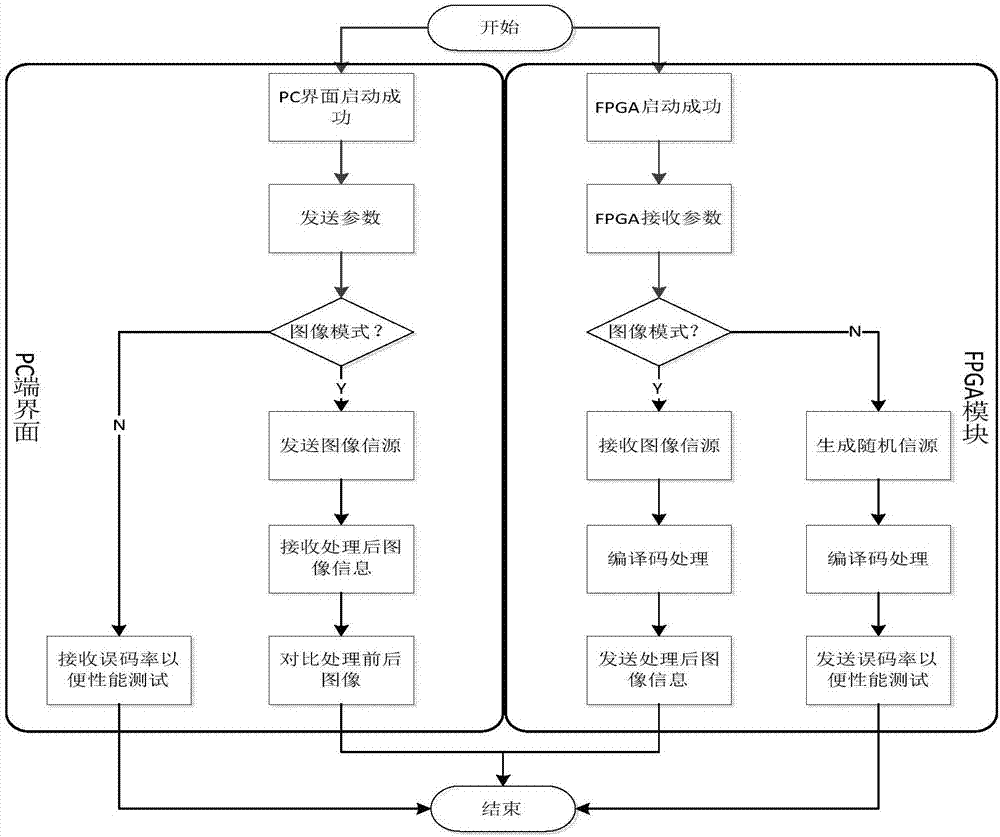
ActiveCN107342847AEasy to testGood secure coding performanceChannel coding adaptationPHYSecure coding
The invention relates to a physical layer secure coding system based on Ethernet communication. The system includes a server, an FPGA module and an Ethernet communication auxiliary platform. The FPGA module includes a physical layer PHY chip, an MAC controller and an FIFO memory. The FPGA module achieves the function of secure coding and decoding. According to the physical layer secure coding system based on Ethernet communication, communication is realized through the Ethernet communication auxiliary platform. High efficiency, high speed and high performance are obvious advantages of the Ethernet. With the Ethernet as a communication platform, the data transmission rate of the whole system will not affect the work efficiency of the system. Better coordination between hardware and software is realized. The function of physical layer secure coding is completed.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
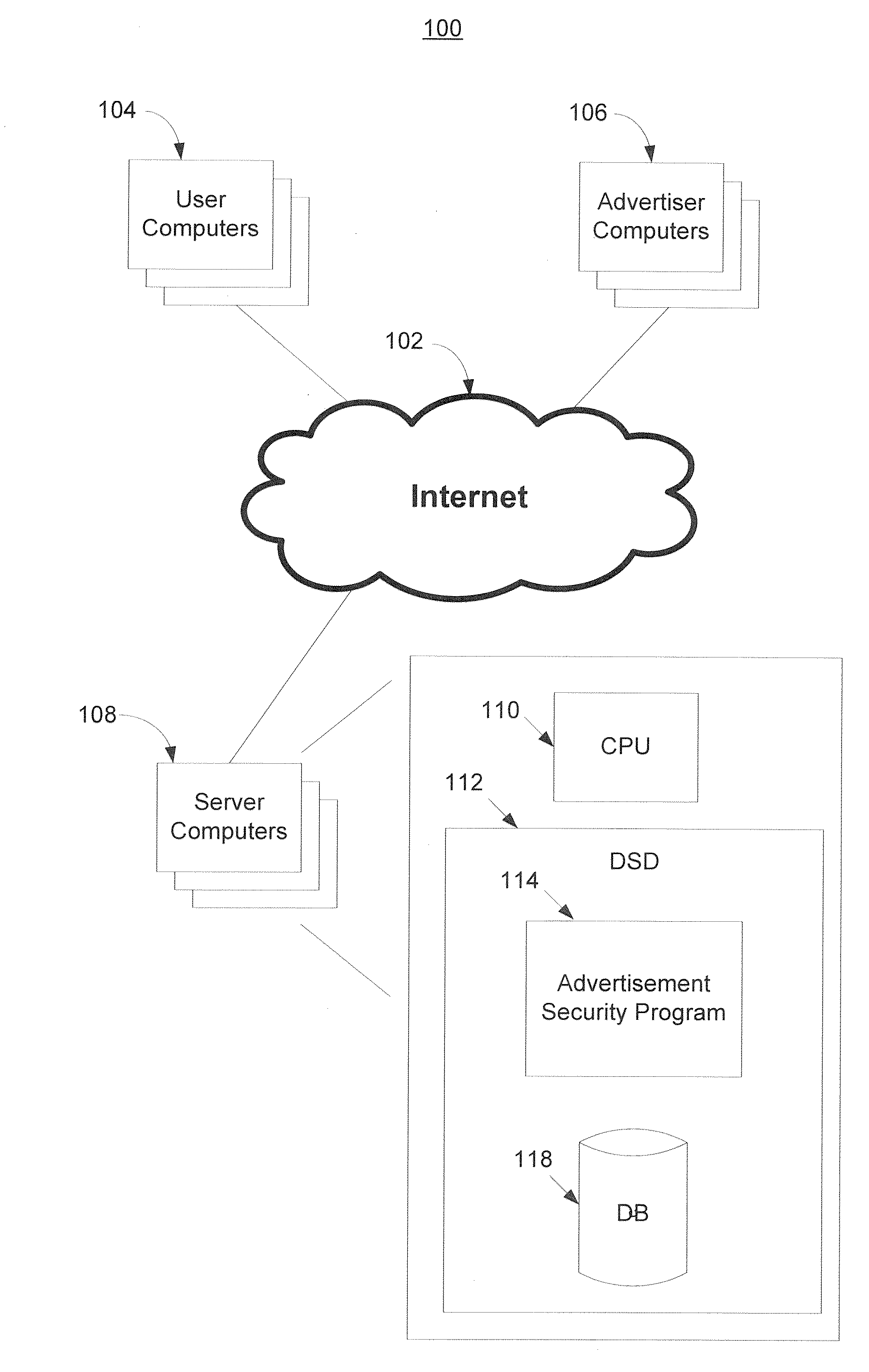
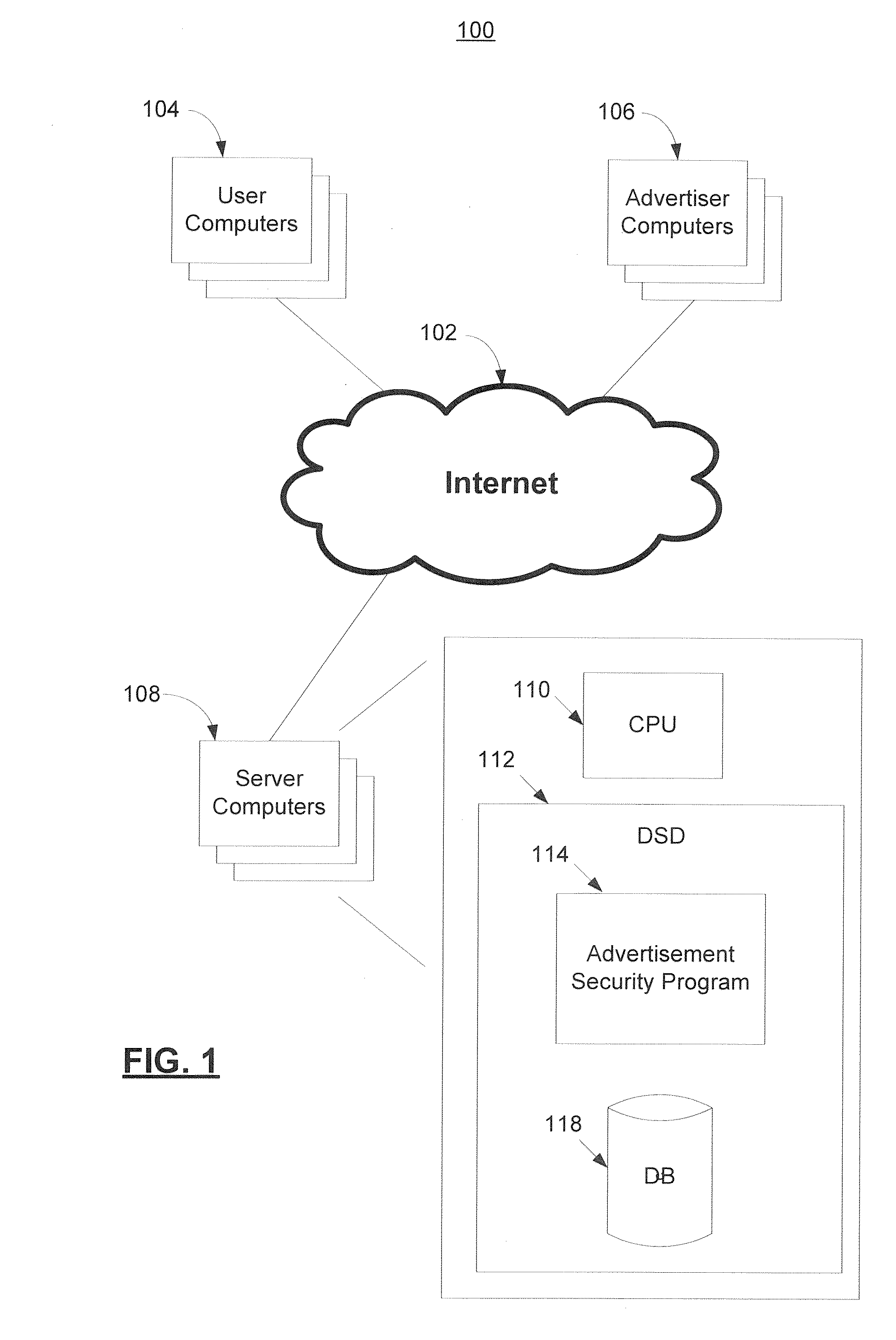
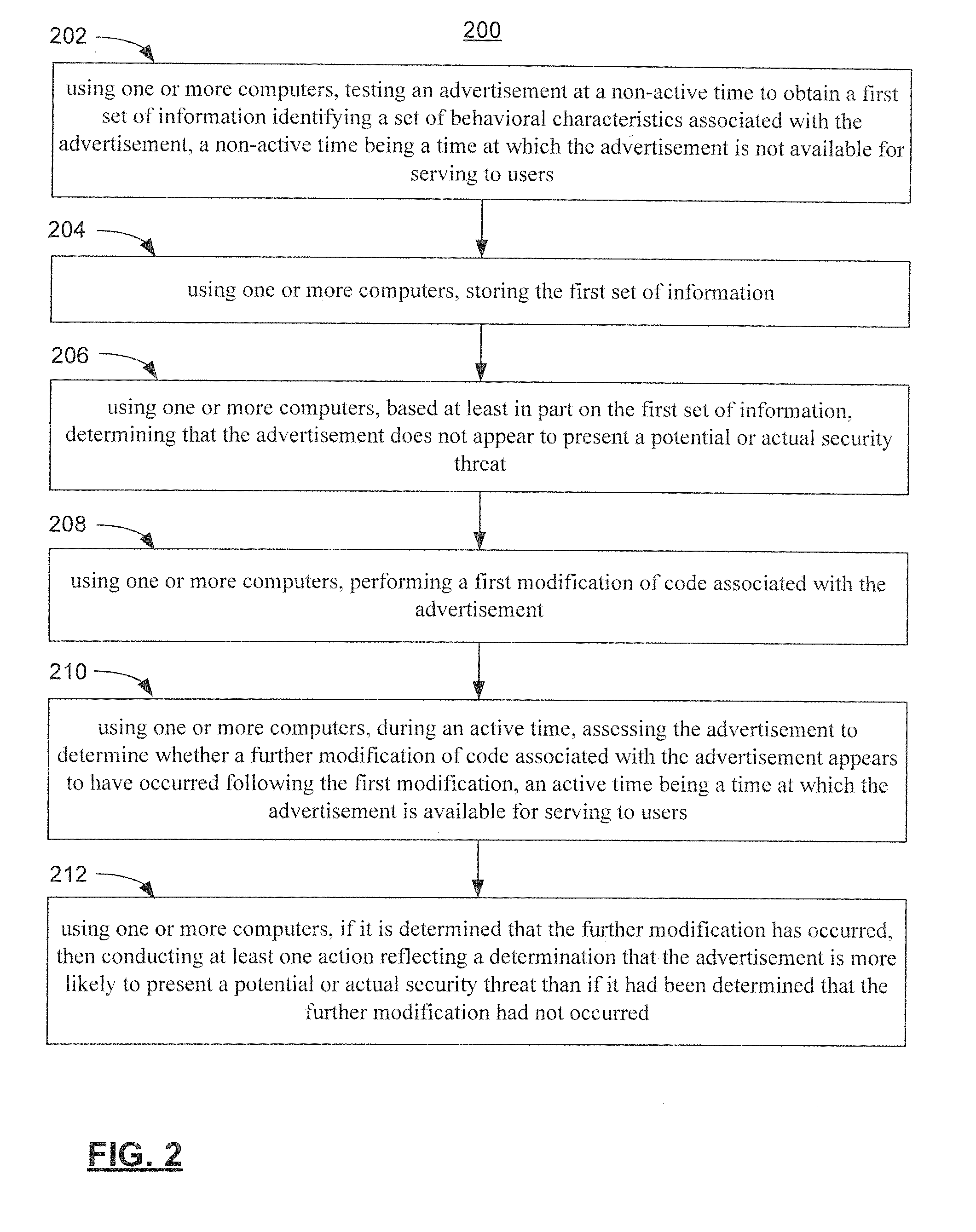
Security techniques for use in malicious advertisement management
The present invention provides methods and systems for use in malicious advertisement management. Methods and systems are provided in which, after an advertisement is determined not to present a security threat, whether initially or after removal any such threat, then a first modification is performed to code associated with the advertisement which may introduce a security coding. Further modification, which may breach the security coding, may indicate that the advertisement is more likely to present a security threat than if the further modification had not occurred.
Owner:OATH INC
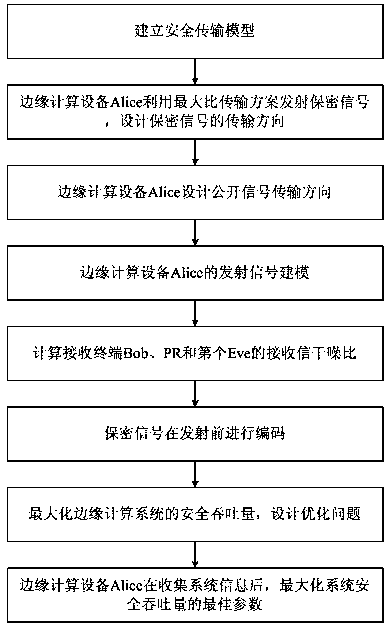
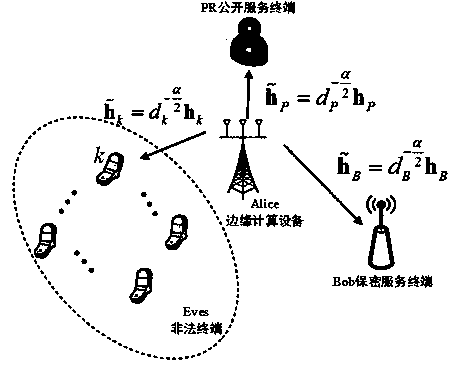
Low-complexity and low-time-delay secure transmission method
ActiveCN111246460AImprove confidentialityImprove securitySecurity arrangementHigh level techniquesQuality of serviceTelecommunications link
The invention discloses a low-complexity and low-time-delay secure transmission method. In an edge computing system, edge computing equipment needs to carry out signal security coding before signal transmission to improve confidentiality of data transmission, a Wyner security coding scheme is adopted, the edge computing equipment carries out offline design optimization on a codeword parameter, andthe designed coding parameters depend on statistical channel information of legal communication links and illegal communication links. In the whole edge computing secure transmission process, the codeword rate parameter is kept unchanged. In an energy-limited edge computing network, edge computing equipment Alice provides services for a secret service terminal Bob and a public service terminal PRat the same time, power cooperation is carried out between a public signal and a secret signal, and the security throughput of the edge computing system is maximized on the basis that the public service quality is met. The method is simple in design, low in calculation complexity and suitable for communication scenes such as multimedia video data transmission.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Channel security coding method for resisting joint eavesdropping in relay transmission
InactiveCN111884759AImprove securityReduce eavesdropping performanceError preventionInformation transmissionTrunking
The invention discloses a channel security coding method for resisting joint eavesdropping in relay transmission, which comprises the following steps that: 1) a source node S codes an original information sequence through an LDPC (Low Density Parity Check) code of which the dimension is M (1) * N check matrix to obtain a system code transmission codeword c (1) of which the length is N, and then modulates and transmits the obtained system code transmission codeword c (1) to a relay node R; 2) the relay node R decodes the received data to obtain an information sequence, encodes the information sequence through an LDPC code with a dimension of M (2) * N check matrix to obtain a system code transmission codeword c (2) with a length of N, and modulates and transmits the system code transmissioncodeword c (2) to a destination node D; and 3) the destination node D performs decoding solution according to the received information and a codebook used for transmission so as to recover an original information sequence, and the method can effectively improve the security of information transmission.
Owner:XI AN JIAOTONG UNIV
Secret communication transmission method and device and electronic equipment
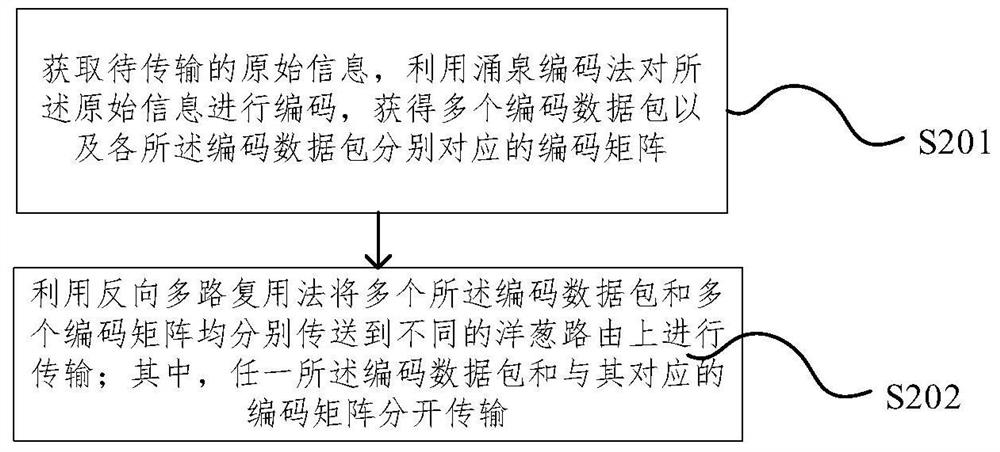
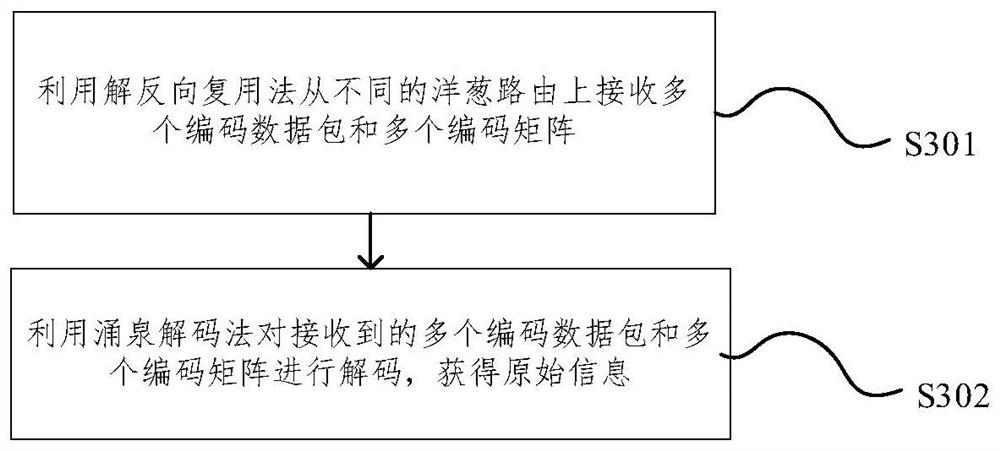
An embodiment of the invention provides a secret communication transmission method and device and electronic equipment. The method comprises the steps: obtaining to-be-transmitted original information, carrying out the coding of the original information through employing a Yongquan coding method, and obtaining a plurality of coding data packages and coding matrixes corresponding to the coding datapackages; respectively transmitting the plurality of coded data packets and the plurality of coding matrixes to different onion routes for transmission by using a reverse multiplexing method, whereinany coded data packet and the coding matrix corresponding to the coded data packet are transmitted separately. According to the method provided by the embodiment of the invention, the Yongquan codingmethod is used for safely coding the original information of the sending end, the coded data and the matrix data are separately transmitted, the reverse multiplexing technology is used for sending the coded data packet, and therefore the safety of the data is enhanced at the coding and decoding level; onion routing is also adopted to transmit each coded data packet and each coding matrix, encryption processing is also carried out in the transmission process, and the data security is also ensured in the transmission channel level.
Owner:TSINGHUA UNIV
Object trusted identity secure coding method
PendingCN107994990APrevent tamperingPrevent imitationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesOriginal dataSecure coding
The invention discloses an object trusted identity secure coding method. Original information of an object is segmented into one or more pieces of original data. The original data is encrypted to formone or more cipher identity quantity values. The cipher identity quantity values are publicized as public keys. Original attributes of the object are hidden, and verification and calculation also canbe carried out. The cipher identity quantity values are used as the public keys, so the possibility that original information is tampered and copied is prevented, the network application security ofan identity of the object is improved, and the identity is taken as the trusted identity on the network.
Owner:江苏信源久安信息科技有限公司
Secure coding and decoding method of railway transponder messages based on lightweight chaotic authentication encryption
InactiveCN108471348AImprove securityReduce bit error rateVehicle route interaction devicesSecuring communication by chaotic signalsCommunications securityDecoding methods
The invention discloses a secure coding and decoding method of railway transponder messages based on lightweight chaotic authentication encryption. The secure coding and decoding method comprises a dedicated lightweight chaotic authentication encryption method for transponder messages, a transponder message coding method based on authentication encryption, a corresponding decryption verification algorithm, and a transponder message decryption verification method based on the decryption verification algorithm. On the premise of maintaining the ETCS and CTCS standards, confidentiality, integrityand authentication protection is provided for the transponder messages, and security risks such as forgery, tampering and counterfeiting faced by the existing transponder messages are avoided. Meanwhile, in view of the limited computing resources of a transponder read-write device, a lightweight chaotic authentication encryption algorithm is used for providing lightweight information security protection for the transponder messages, so that the train-ground communication security of a transponder of a train control system is effectively enhanced.
Owner:SOUTHWEST JIAOTONG UNIV
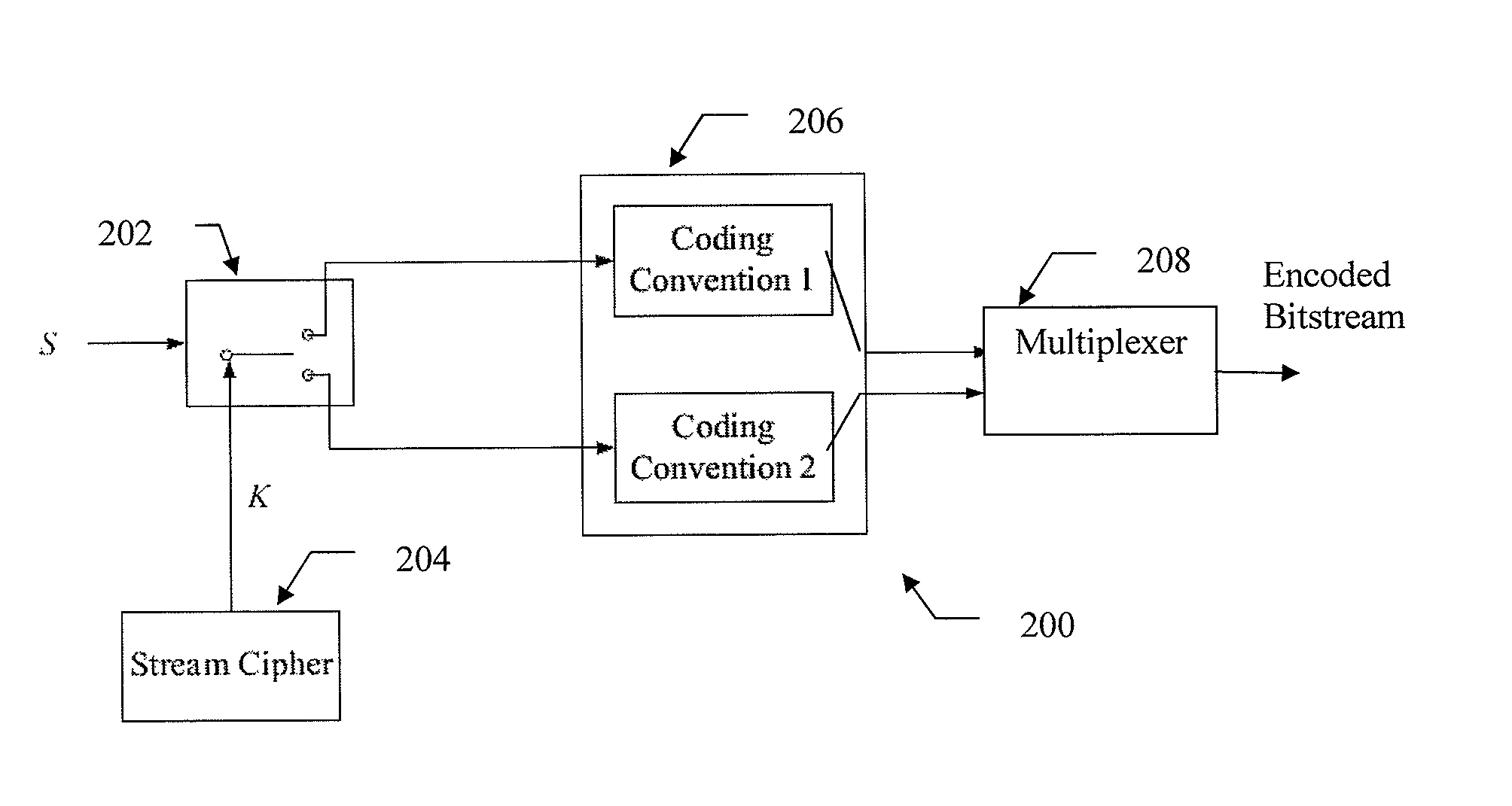
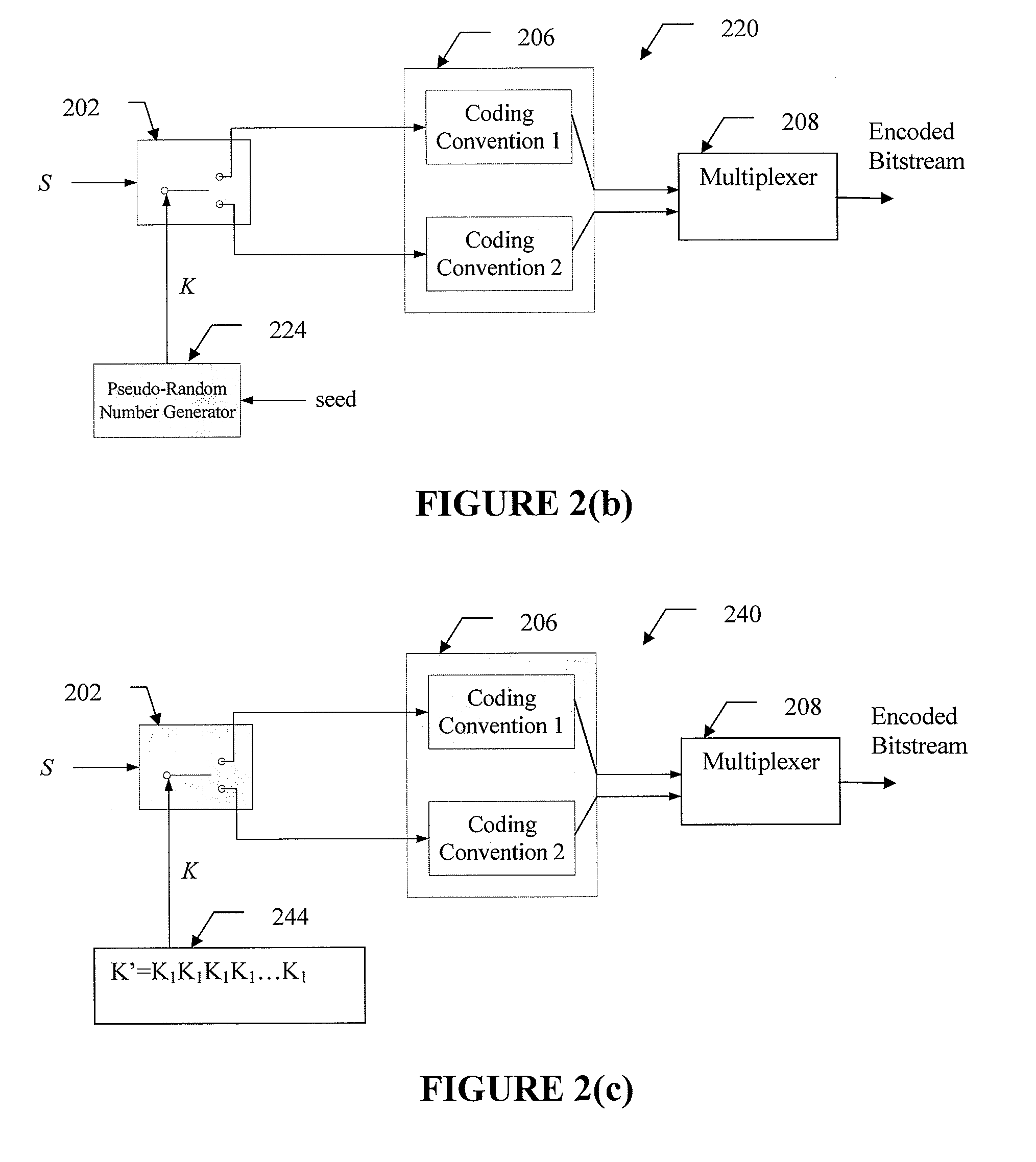
Method and system for encoding multimedia content based on secure coding schemes using stream cipher
ActiveUS8189776B2Improve the level ofReduce complexitySecret communicationTelevision systemsComputer hardwareCoding conventions
Owner:THE HONG KONG UNIV OF SCI & TECH
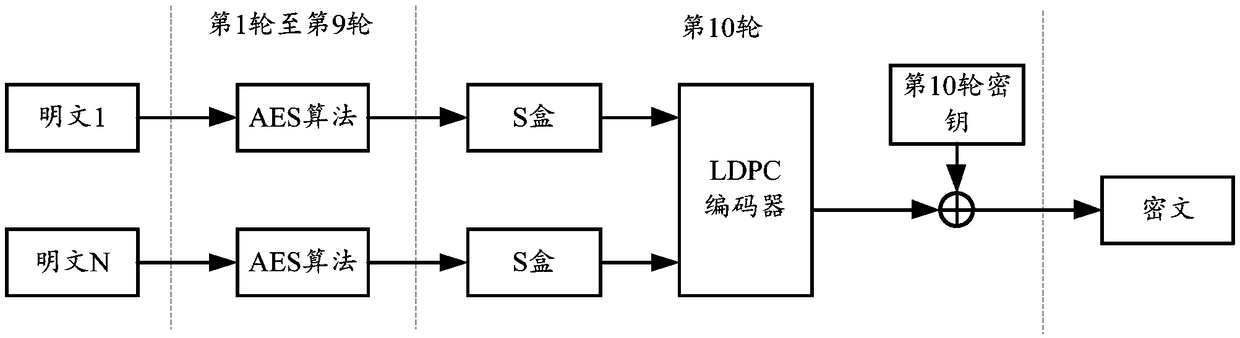
Secure coding method, decoding method and equipment
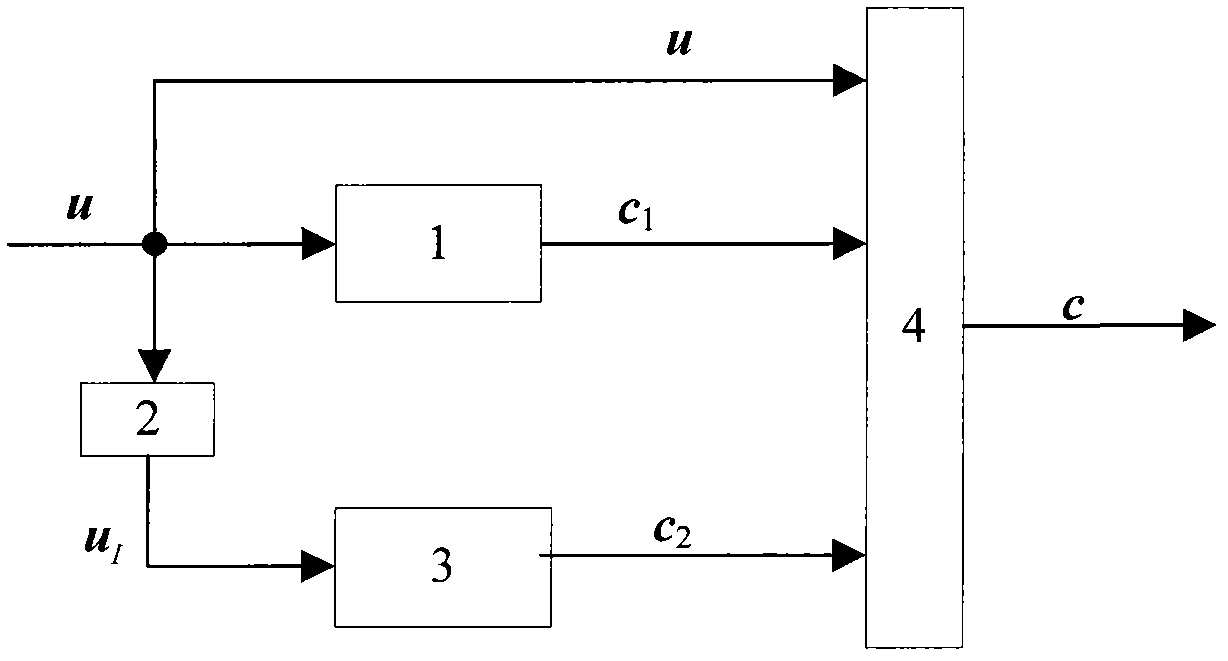
ActiveCN109327276AIncreased error diffusion performanceImprove securityEncryption apparatus with shift registers/memoriesForward error control usePlaintextComputer hardware
The invention discloses a secure coding method, a decoding method and equipment. The method comprises the following steps: performing, by a first encoder, coding processing in at least one round of encryption operation after at least one round of encryption operation in n rounds of encryption operations and / or in at least one round of encryption operation in the n rounds of encryption operations in the process of performing the n rounds encryption operations on a plaintext by applying an encryption algorithm, wherein the code rate of the first encoder is 1, and n is an integer more than 1; andperforming, by a second encoder, coding processing on the plaintext acquired after the n rounds of encryption operations, thus acquiring a coded result, wherein the code rate of the second encoder ismore than 1. The embodiment of the invention provides a lightweight secure coding scheme, which can combine a lower complexity encryption algorithm and a lower complexity coding algorithm to achievea low complexity secure coding algorithm on the premise of considering the security of the secure coding algorithm, and the low complexity secure coding algorithm is suitable for being applied to a lightweight Internet of things.
Owner:HUAWEI TECH CO LTD
Privacy protection method in edge computing environment
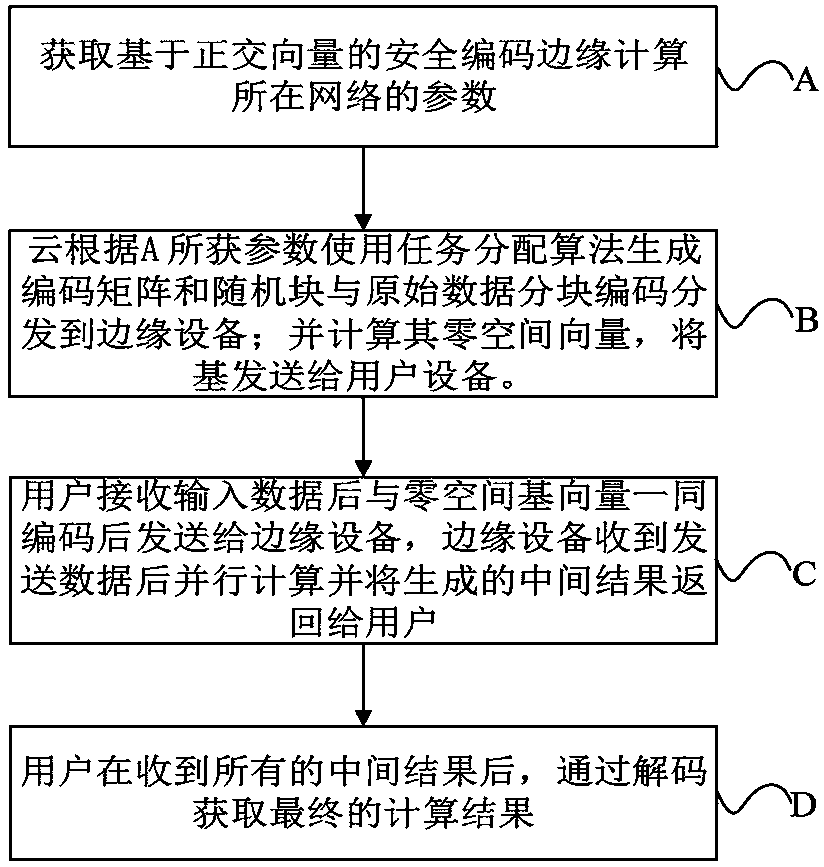
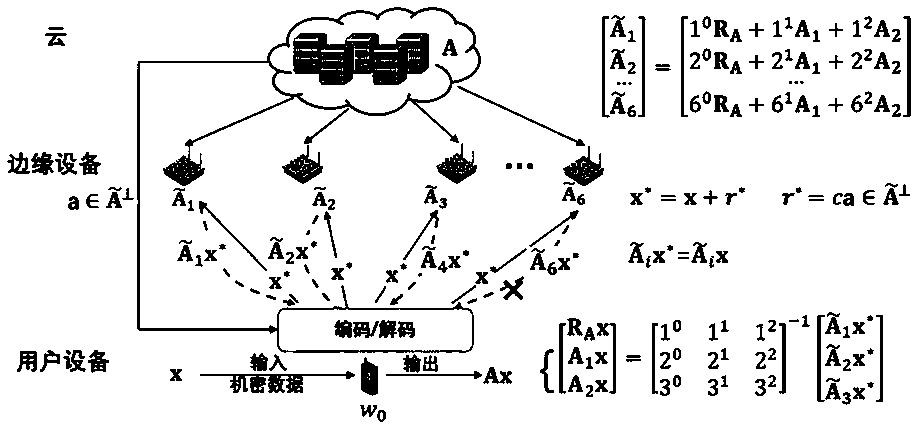
PendingCN111125752AGuaranteed privacy and securityReduce computing latencyDigital data protectionUser deviceAlgorithm
The invention discloses a privacy protection method in an edge computing environment, which is realized based on security coding of an orthogonal vector and comprises the following steps: acquiring parameters of a network where security coding edge computing based on the orthogonal vector is located; partitioning input data of one side of a calculation task by using a task allocation algorithm, adding a random block code, and allocating to a corresponding edge node; calculating a base vector of a null space vector of the coding matrix, and sending a base vector of a part of null space to userequipment according to the parameter of the A; after a user inputs data, generating an online calculation demand and after receiving all intermediate results returned by edge nodes, enabling a user todecode the intermediate results by using the coefficient coding matrix to obtain a required result. In edge calculation based on security coding, privacy of both sides of calculation is protected byadopting linear coding and adding random blocks, and meanwhile, the random blocks added by a user side are designed by utilizing orthogonality of a null space vector, so that communication load and decoding complexity are reduced, and low-delay, efficient and safe edge calculation privacy protection is obtained.
Owner:SUZHOU UNIV
CDMA secure coding and decoding method and system
ActiveCN113131967ARealize interconnectionImprove anti-interference abilitySecret communicationTransmissionCode division multiple accessEngineering
The invention provides a code division multiple access (CDMA) secure coding and decoding method and system, and the CDMA secure coding method comprises the steps: receiving a first clock signal, and converting the first clock signal into an analog signal; receiving a data signal and a second clock signal, and performing differential double-phase coding on the data signal to obtain a coded digital signal; conditioning and amplifying the analog signal, and coupling the analog signal with the coded digital signal to obtain a required baseband signal; coding the baseband signal to obtain a baseband coded signal; and performing CDMA coding on the baseband coding signal to obtain a CDMA coding signal. According to the CDMA safe coding and decoding method and system, interconnection and intercommunication of European railway operation control systems can be met, and the problems that an existing European train operation control system is poor in anti-interference performance, only suitable for short-distance transmission, high in bit error rate, high in receiving sensitivity threshold, free of multipath receiving and the like due to the fact that FSK, PSK and other signal systems are adopted are solved.
Owner:CRSC RESEARCH & DESIGN INSTITUTE GROUP CO LTD
Turbo code complexor design method in joint channel secure coding
InactiveCN103107816AWith encryptionReduce coding complexityError correction/detection using convolutional codesError correction/detection by combining multiple code structuresSequence controlEncrypted function
The invention discloses a complexor design method based on secret key control. The method aims at solving the problem that a conventional Turbo code encoder does not have an encryption function, and the method enables an interleaver to be associated with a complexor. The method includes the steps of firstly setting the length of the interleaver as N and setting S as sequence of natural numbers with the length equal to the N, using a secret key to generate N-length random arrangement S1 of natural numbers, that is, S1= f (S, Key), and f is a random function, secondly, carrying out module six calculation to the S1 to obtain a random N-length senary sequence controlled by the secret key, and finally, rearranging the output sequence of a coding bit stream, outputting the coding bit stream, obtaining an encryption bit stream, using the same secret key to obtain the random N-length senary sequence as the same as a coding end in a demultiplexing process, then using the sequence to confirm a correct output sequence of the bit stream, and finally obtaining a correct decoding result.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Data transmission method and related device
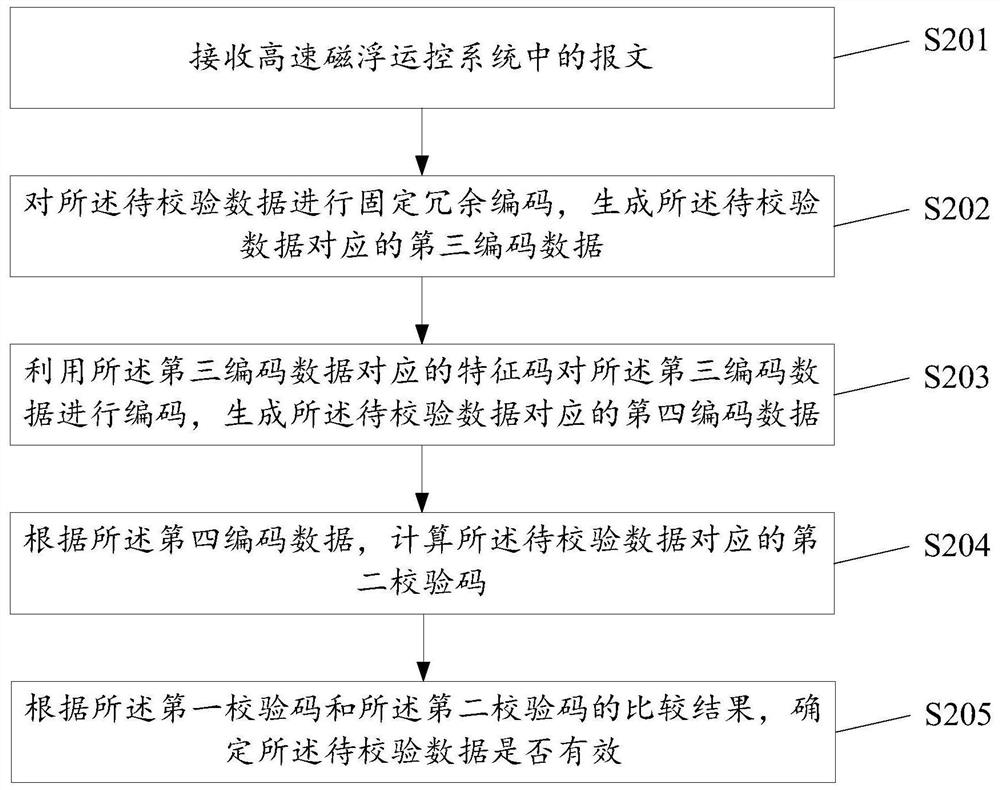
ActiveCN112187412AImplement redundant codingTo achieve unique encodingError preventionRailway traffic control systemsComputer hardwareControl system
Embodiments of the invention disclose a data transmission method and a related device. The method comprises the following steps: acquiring to-be-transmitted data for a high-speed magnetic levitation operation control system, carrying out fixed redundant coding on the to-be-transmitted data and generating first coded data corresponding to the to-be-transmitted data so as to achieve redundant codingof the data; then, coding the first coded data by using a feature code corresponding to the first coded data so as to generate second coded data corresponding to the to-be-transmitted data, thereby realizing unique coding of the data and further improving the security coding of the data; and then, calculating the check code of the to-be-transmitted data by utilizing the second coded data, whereinthe check code can be used for checking data in a message by the receiver, thereby ensuring the accuracy of the data in the transmission process. Moreover, the message adopted in the data transmission process carries the uncoded data to be transmitted, so the compressed transmission of the data is realized, and a bandwidth requirement on high-speed magnetic levitation 38G wireless communication is reduced.
Owner:CRRC QINGDAO SIFANG CO LTD
Secure encoding method, decoding method and device
ActiveCN109327276BIncreased error diffusion performanceImprove securityEncryption apparatus with shift registers/memoriesForward error control usePlaintextCiphertext
A secure encoding method, decoding method and device. The method includes: during the process of applying an encryption algorithm to perform n rounds of encryption operations on plaintext, after at least one round of encryption operations in the n rounds of encryption operations and / or during at least one round of encryption operations in the n rounds of encryption operations, passing The first encoder performs encoding processing, wherein the code rate of the first encoder is 1, and n is an integer greater than 1; the second encoder performs encoding processing on the ciphertext obtained after the above n rounds of encryption operations to obtain an encoding result , the code rate of the second encoder is greater than 1. The embodiment of the present application provides a lightweight secure coding scheme, which can combine the encryption algorithm with low complexity and the coding algorithm with low complexity under the premise of taking into account the security of the secure coding algorithm to realize a Low-complexity secure coding algorithm, this low-complexity secure coding algorithm is suitable for lightweight IoT applications.
Owner:HUAWEI TECH CO LTD
A Channel Polarization-Safe Coding Method Based on Robust Soliton Distribution
ActiveCN108631944BGuaranteed normal transmissionImprove securityChannel coding adaptationForward error control useInformation transmissionSoliton distribution
The invention aims at providing a channel polarization secure coding method based on robust soliton distribution, and the method comprises the following steps: firstly, a sending end codes to-be-sentinformation based on robust soliton distribution; then, Polar coding is executed for the to-be-sent information which is coded based on robust soliton distribution; and a normal receiving end and an eavesdropping end respectively perform Polar decoding for the received information, finally, the normal receiving end and the eavesdropping end respectively perform belief propagation decoding for thereceived information subjected to Polar decoding, and restore the sent information. Compared with the existing technology, the method provided by the invention can improve transmission rate of information transmission while guaranteeing security and reliability of information transmission under the premise of slightly increasing secure coding and decoding complexity, and consequently improves validity of information transmission.
Owner:ZHONGBEI UNIV
Secret communication method based on key fusion transformation
ActiveCN111934864BCompatibleGreat application potentialKey distribution for secure communicationCryptographic attack countermeasuresPlaintextCiphertext
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Safe Processing Method for Delayed Data Transmission in Secure Coding System
The invention relates to a safe processing method for data delay transmission in a safe coding system. A queue used for storing data of a port collected in a delay time window is firstly defined, every time the system collects the data stored in the window, the data is recomputed once, the finally sent state data of the port is a result of all data in the time window which has computed once, and safety of the result is judged. Compared with the prior art, the method provided by the invention has the advantage of high safety in output data.
Owner:CASCO SIGNAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com