Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
285 results about "Secure communication channel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
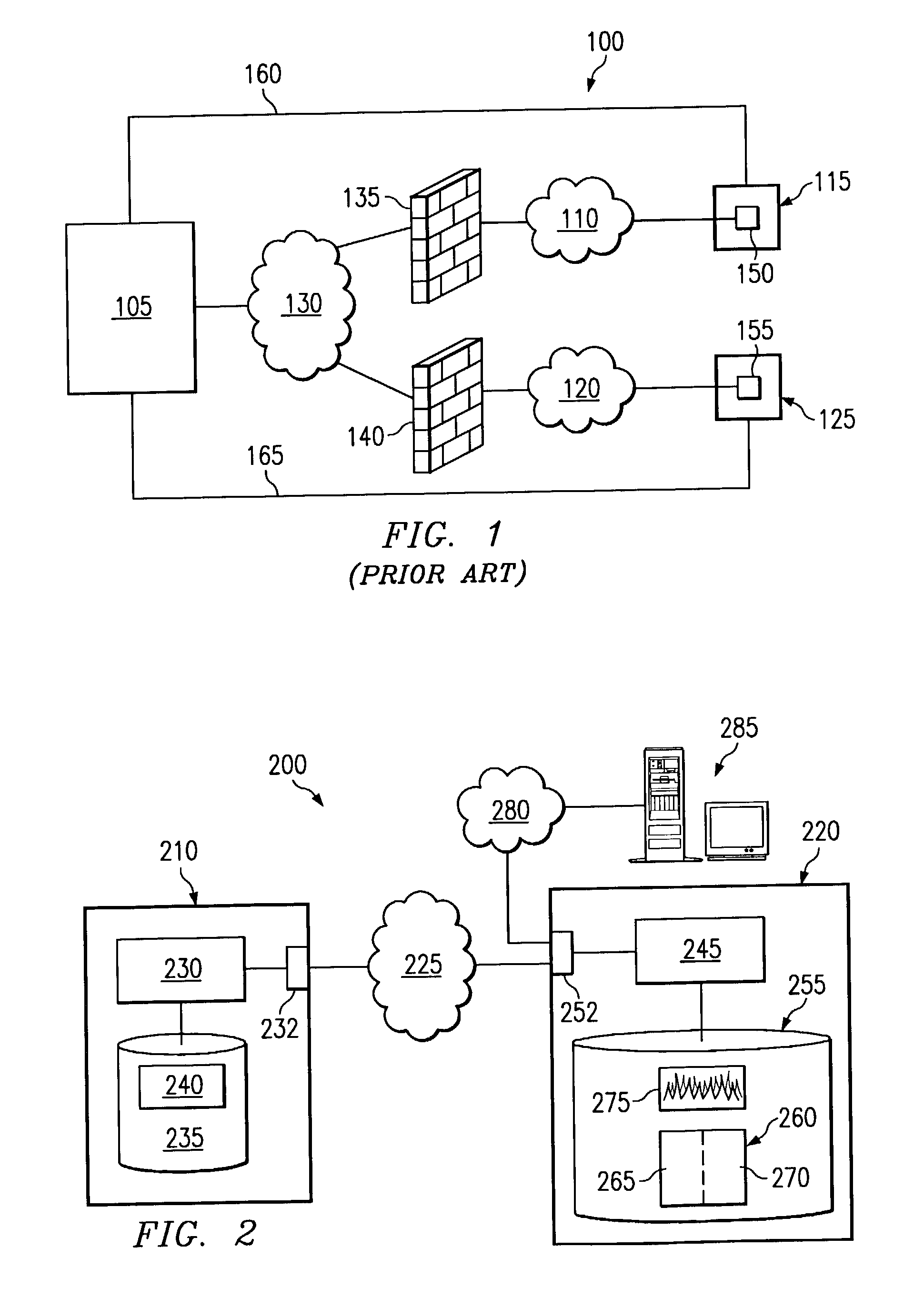
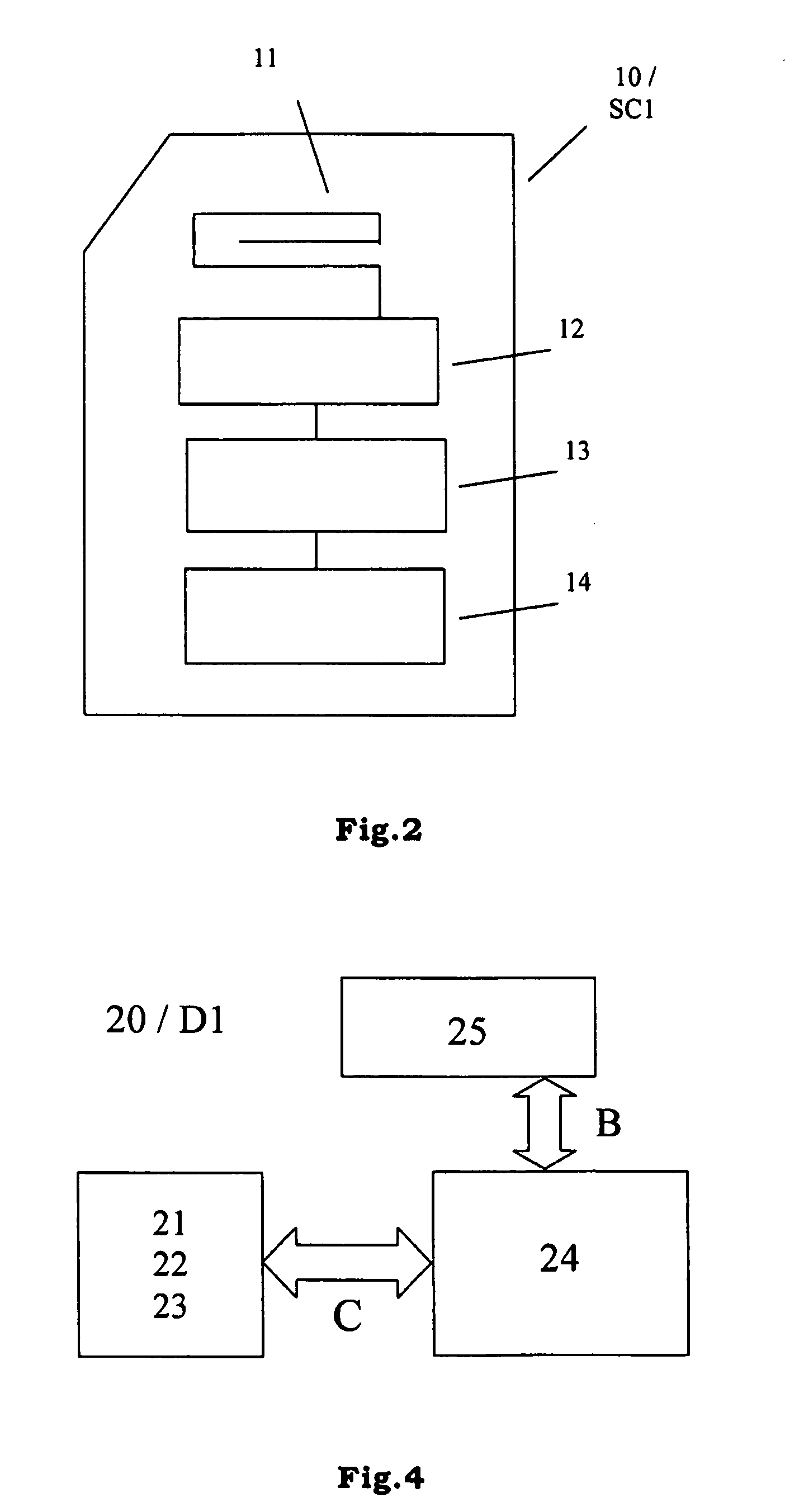
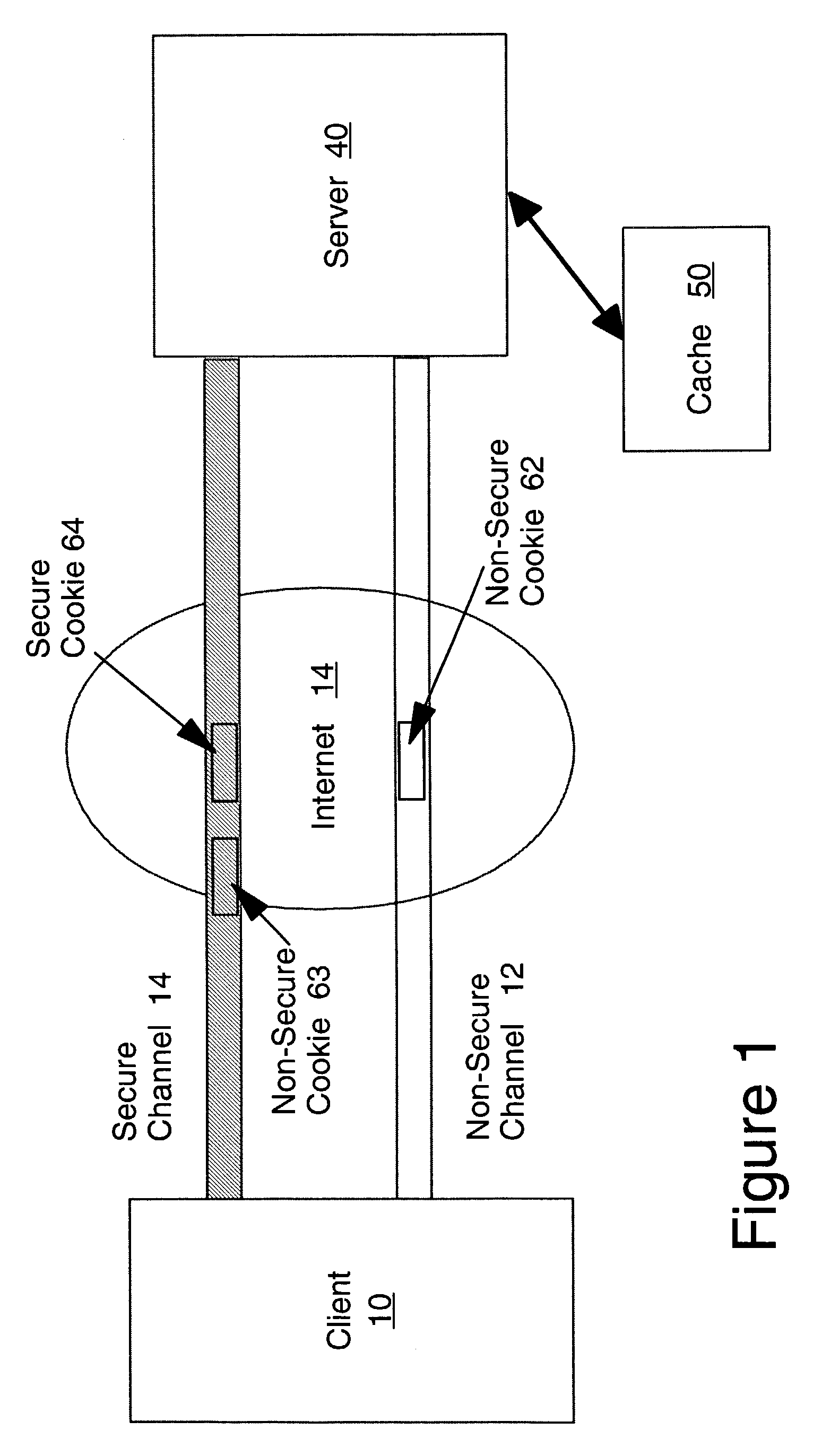
Communication Channels. By default, the communication channels are not secure. To secure them, you can configure the channels to use the Secure Sockets Layer (SSL) protocol. SSL is a cryptographic protocol that provides security and data integrity for communications over TCP/IP networks.
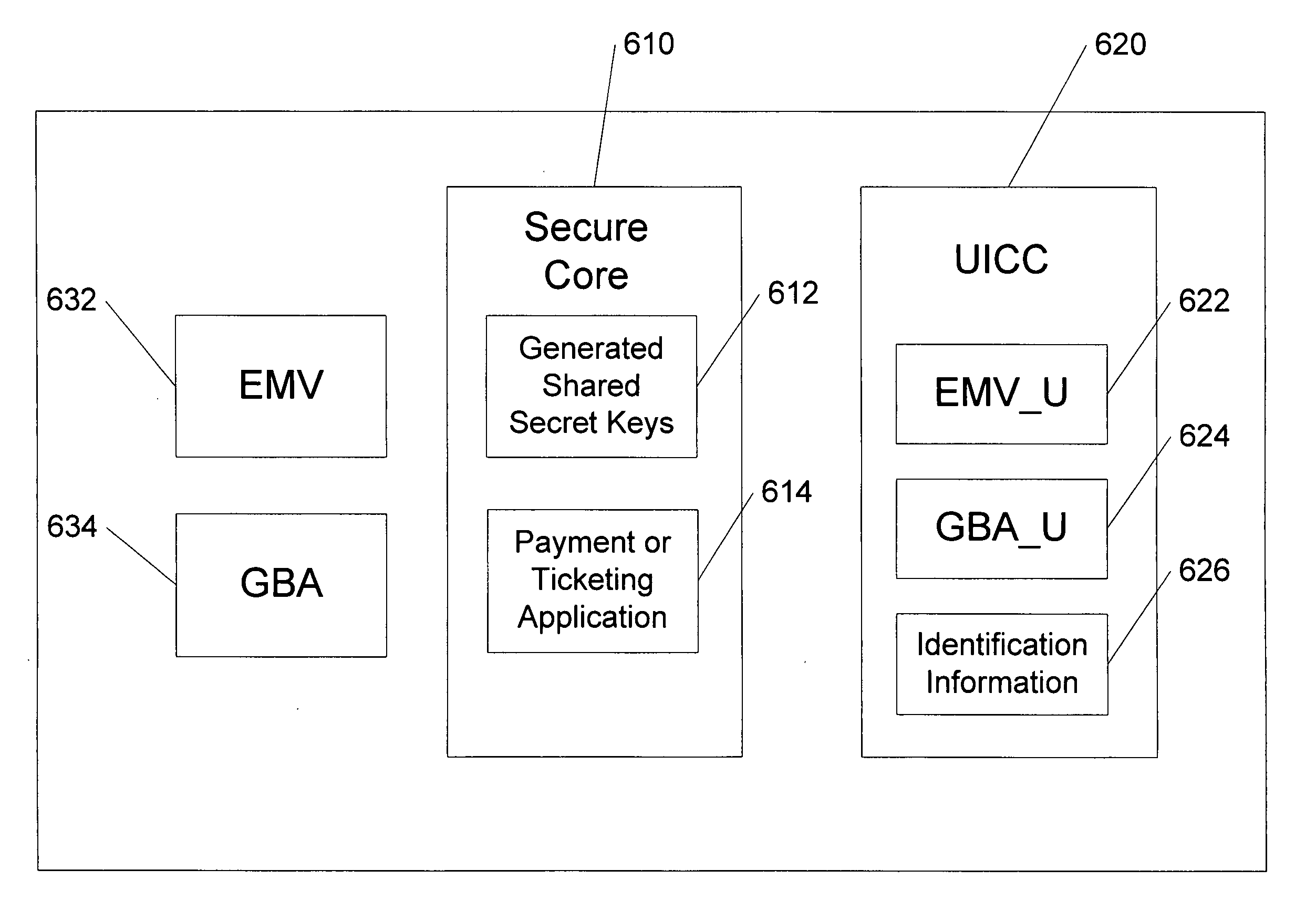
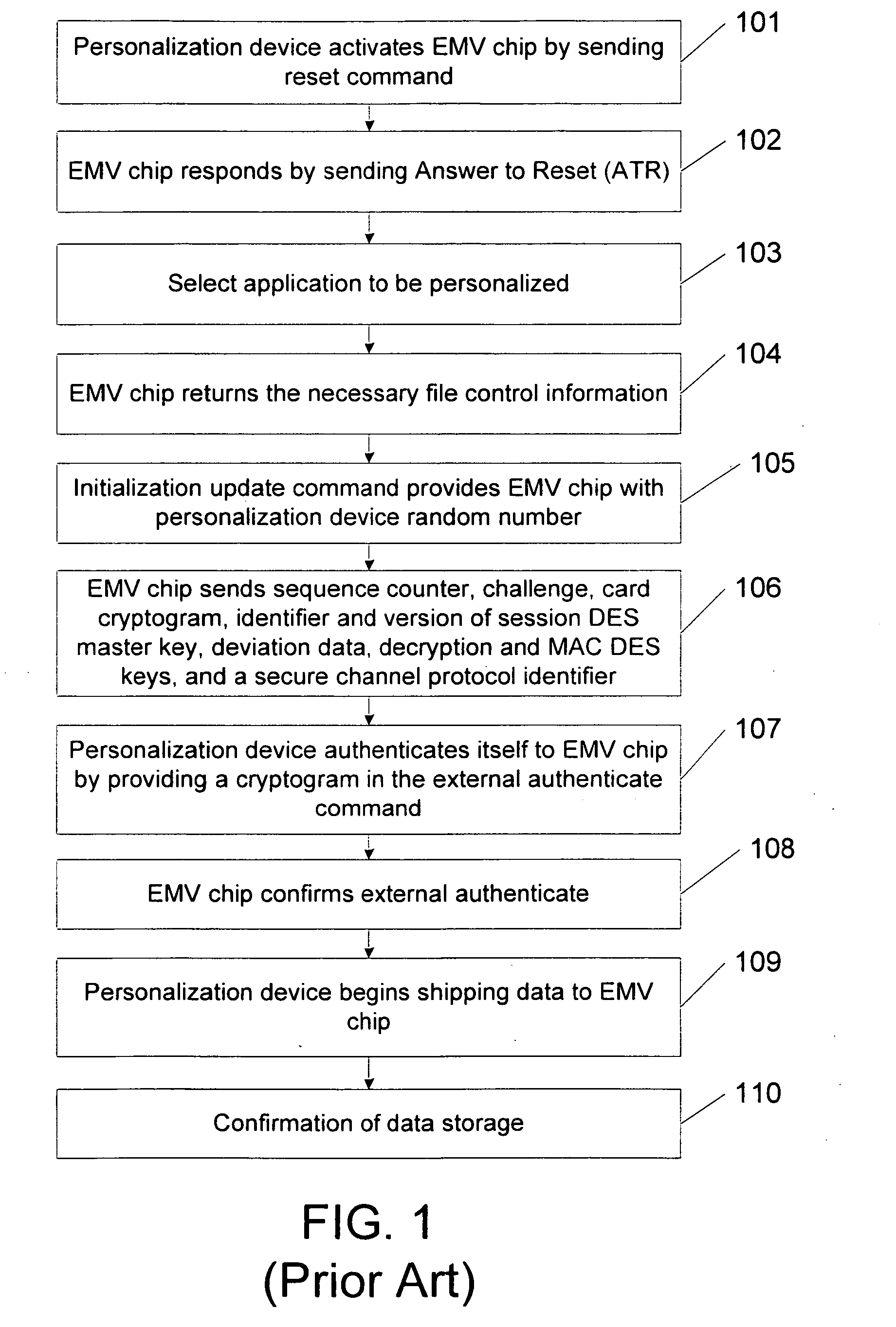
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
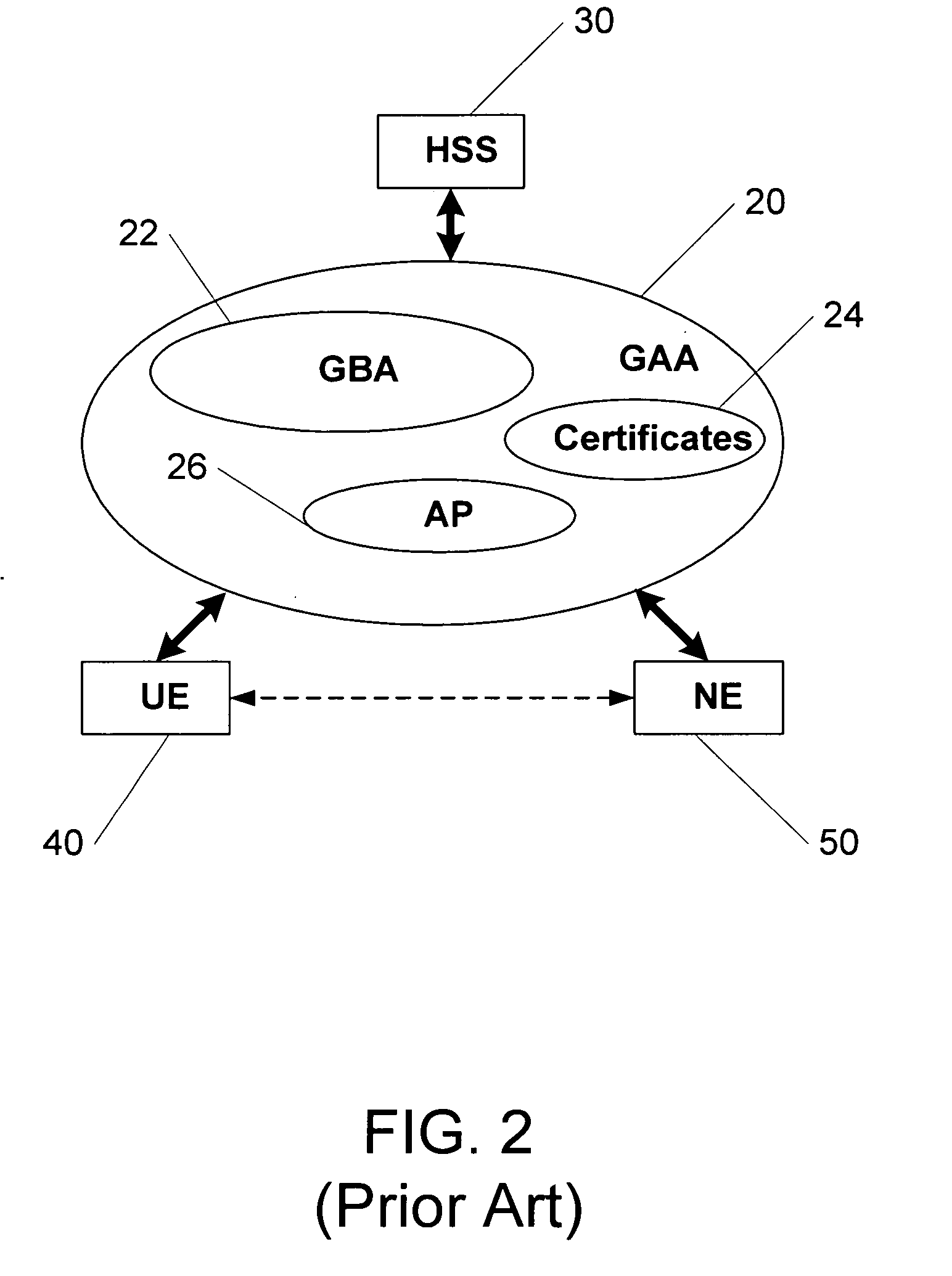
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
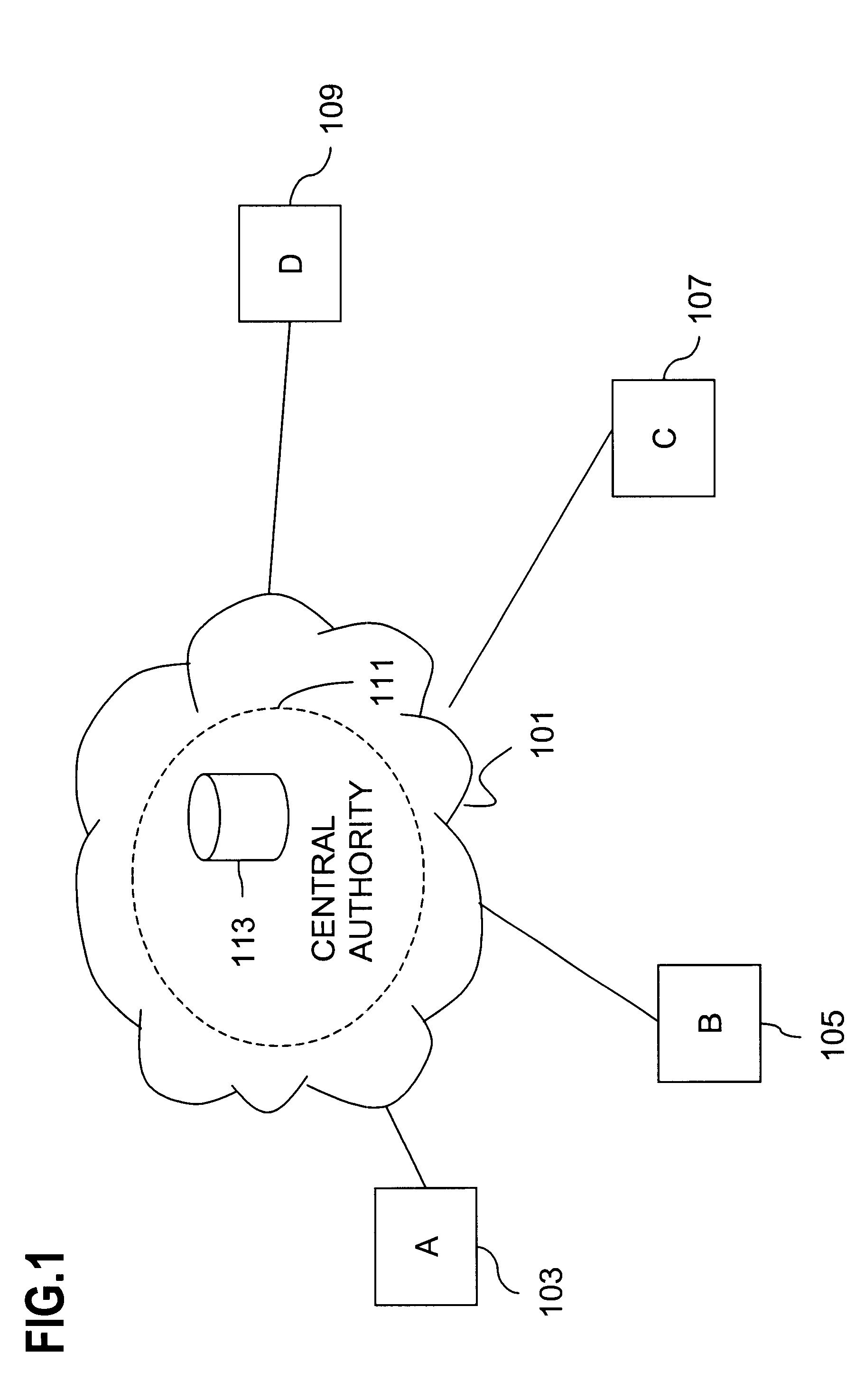
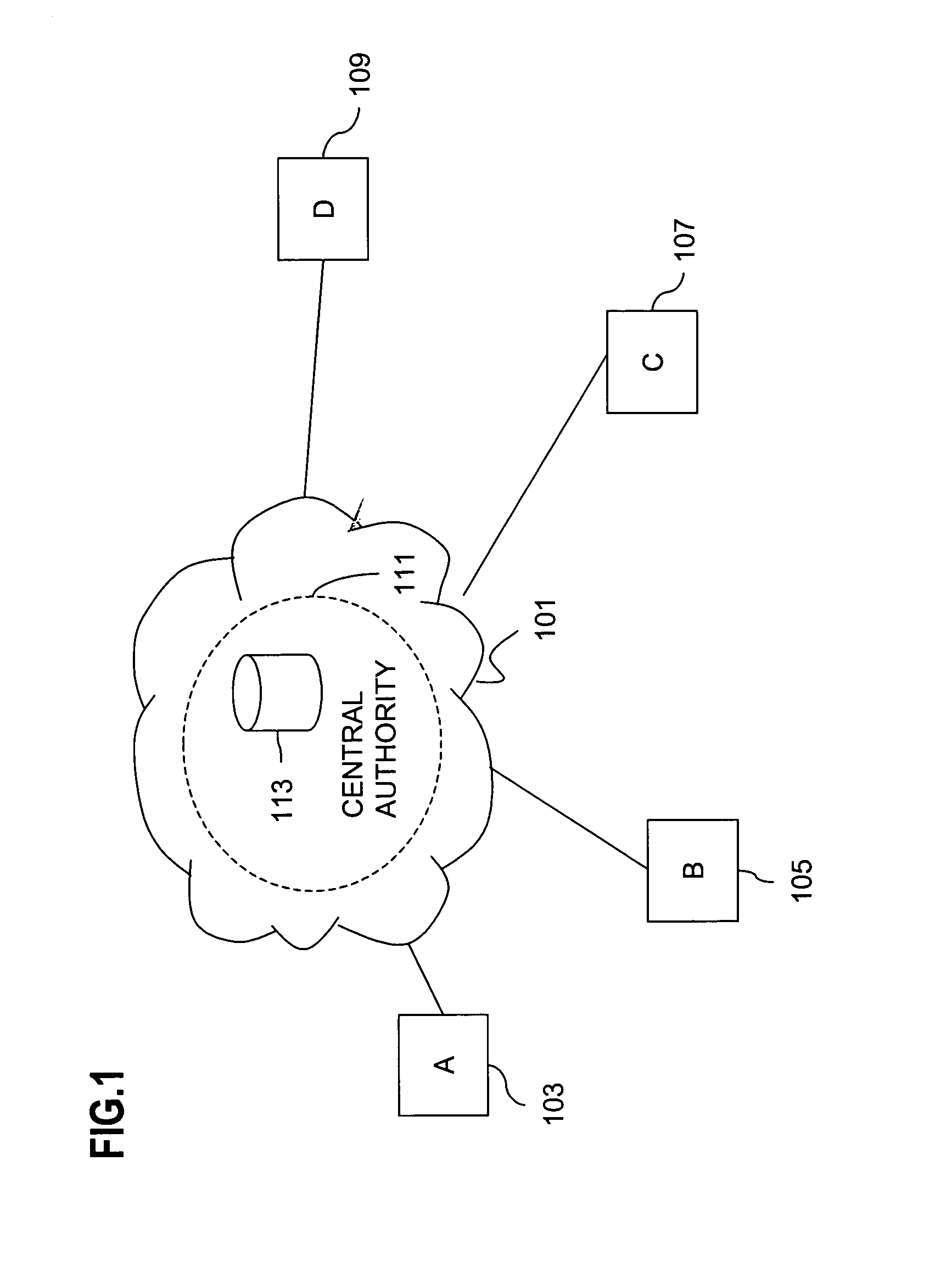
Method and apparatus for creating a secure communication channel among multiple event service nodes
InactiveUS7013389B1Easy to scaleUser identity/authority verificationSecure communicationGroup session
An approach for establishing secure multicast communication among multiple event service nodes is disclosed. The event service nodes, which can be distributed throughout an enterprise domain, are organized in a logical tree that mimics the logical tree arrangement of domains in a directory server system. The attributes of the event service nodes include the group session key and the private keys of the event service nodes that are members of the multicast or broadcast groups. The private keys provide unique identification values for the event service nodes, thereby facilitating distribution of such keys. Because keys as well as key version information are housed in the directory, multicast security can readily be achieved over any number of network domains across the entire enterprise. Key information is stored in, and the logical tree is supported by, a directory service. Replication of the directory accomplishes distribution of keys. Event service nodes may obtain current key information from a local copy of the replicated directory.
Owner:CISCO TECH INC
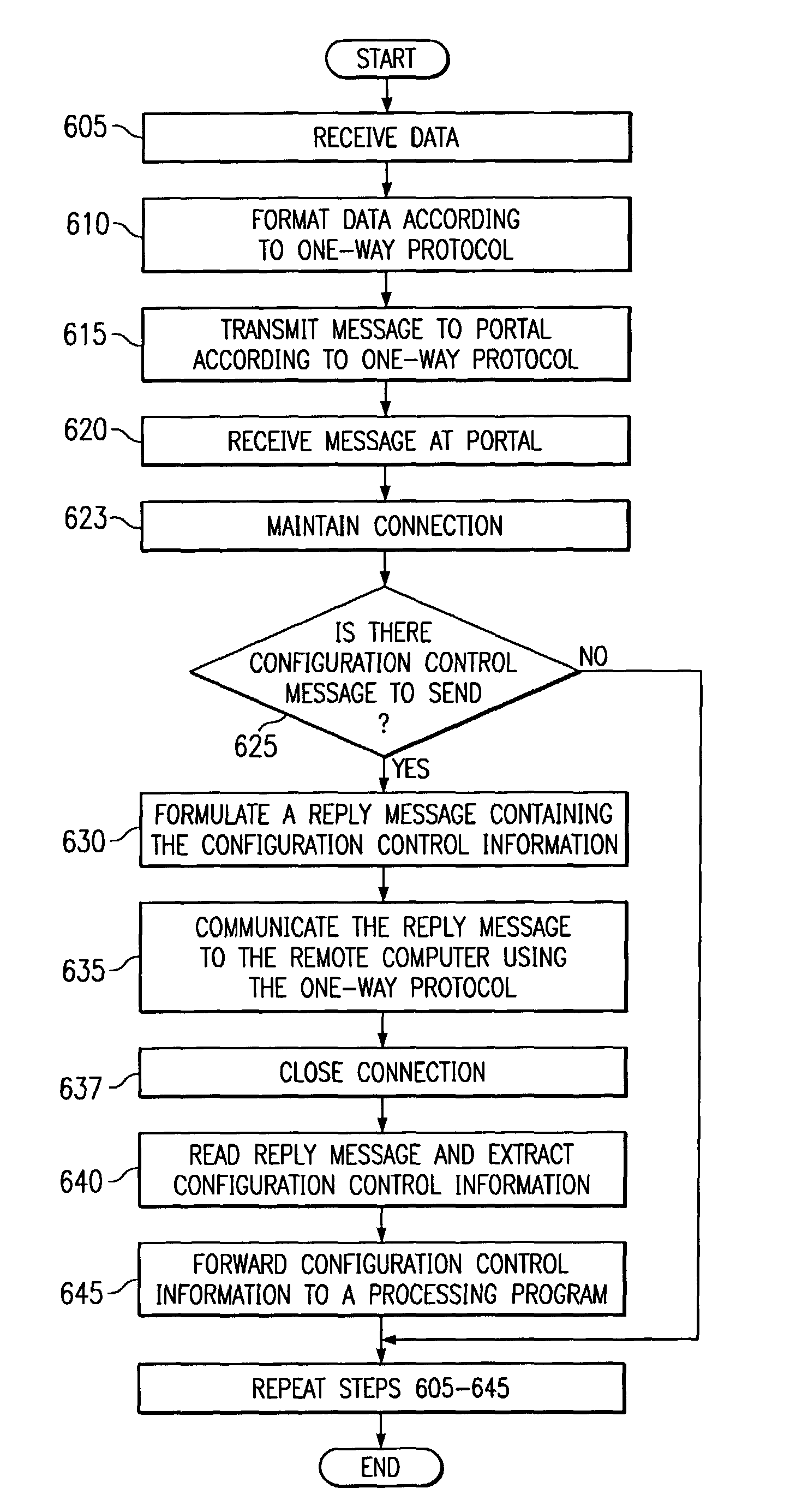
System and method for secure communications with a remote software program
ActiveUS7877783B1Communication securityAmount of timeDigital data processing detailsData switching networksSecure communicationLeased line
In one embodiment of the present invention, a messaging program at a remote computer can send a first message to a portal computer according to a one-way protocol such as HTTP. A portal program at the portal computer can receive the first message and determine if information should be sent to the portal computer. If so, the portal computer can generate a reply message that includes the information and send the reply message to remote computer on the same connection over which the first message was received. In this manner, the portal computer can send configuration control information and other information to the messaging program without requiring leased lines, dial-up connections or a VPN. Moreover, since the communication according to the one-way protocol was initiated at the remote computer, a firewall will allow the remote computer to receive the reply message.
Owner:BMC SOFTWARE
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECH OY
System and method of exploiting the security of a secure communication channel to secure a non-secure communication channel
InactiveUS6986040B1Key distribution for secure communicationUser identity/authority verificationSecure communicationApplication server
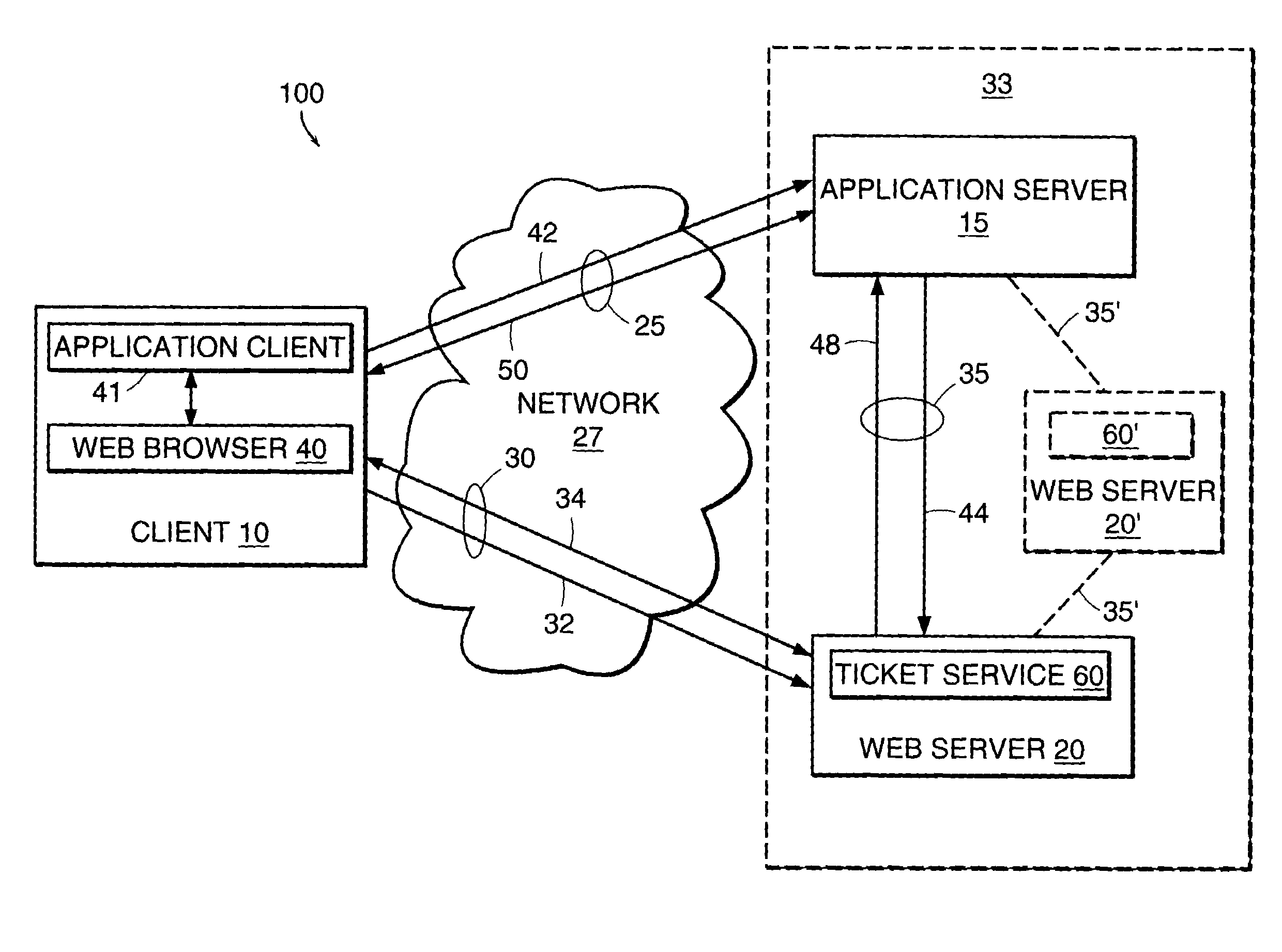
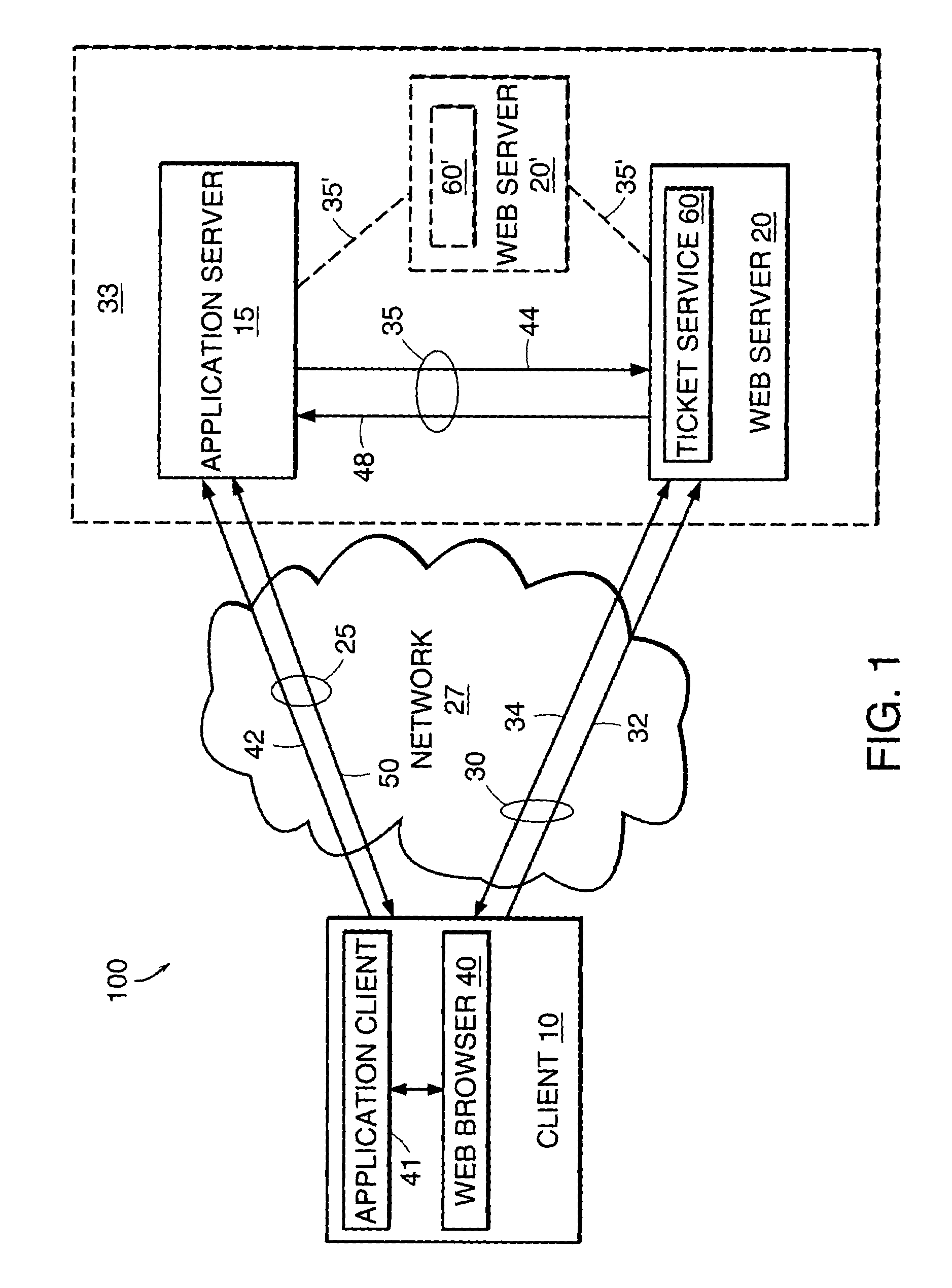
The present invention features a system and method for establishing a secure communication channel between a client and an application server. In one embodiment, a ticket service generates a ticket having an identifier and a session key. A communications device obtains the ticket from the ticket service and transmits the ticket to a client over a secure communication channel. The client transmits the identifier of the ticket to an application server over an application communication channel. The application server then obtains a copy of the session key of the ticket from the ticket service. Communications exchanged between the client and the application server over the application communication channel are then encrypted using the session key to establish the application communication channel as a secure communication channel.
Owner:CITRIX SYST INC
WIFI authentication method
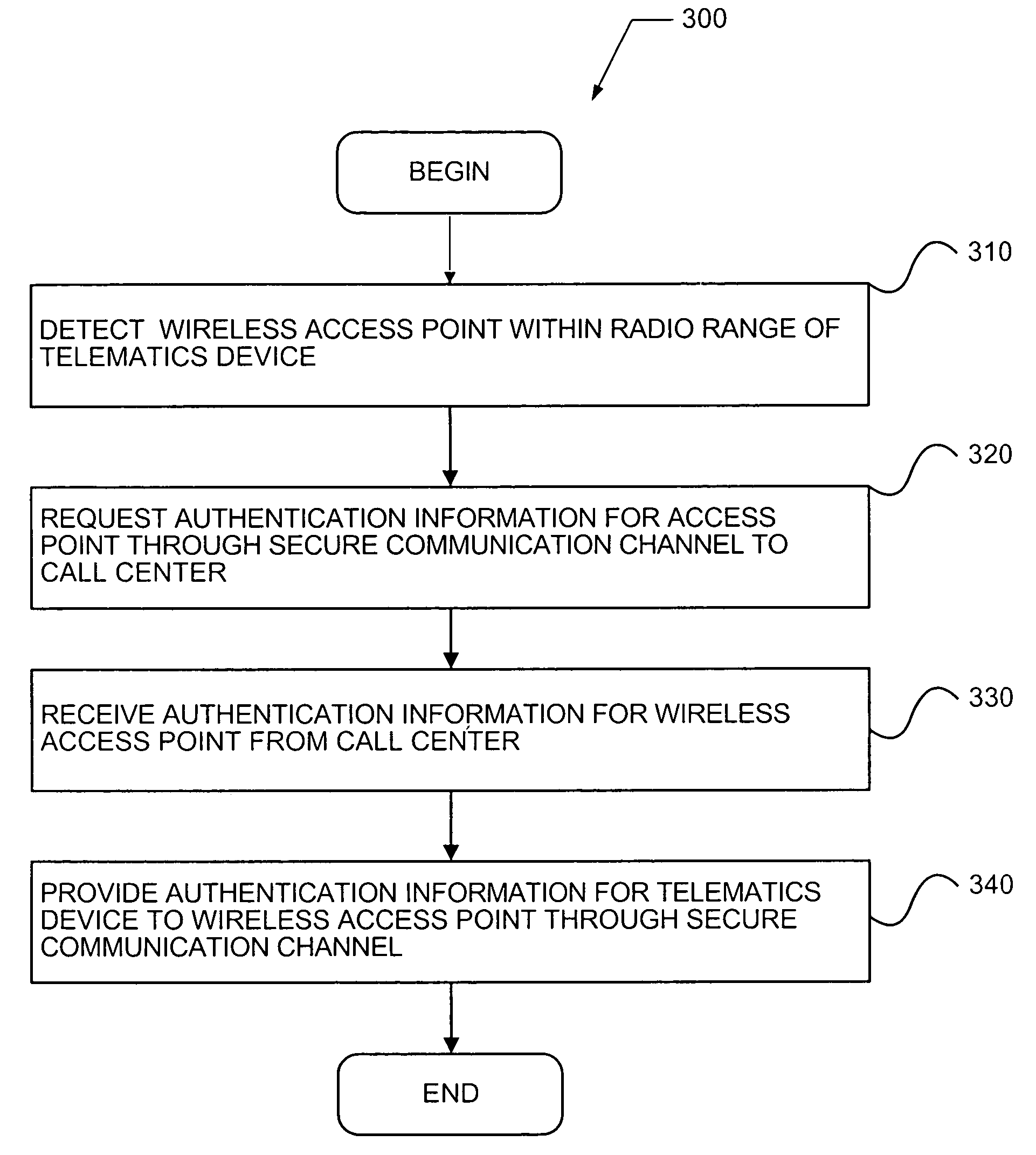
ActiveUS7548744B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure authenticationTelematics
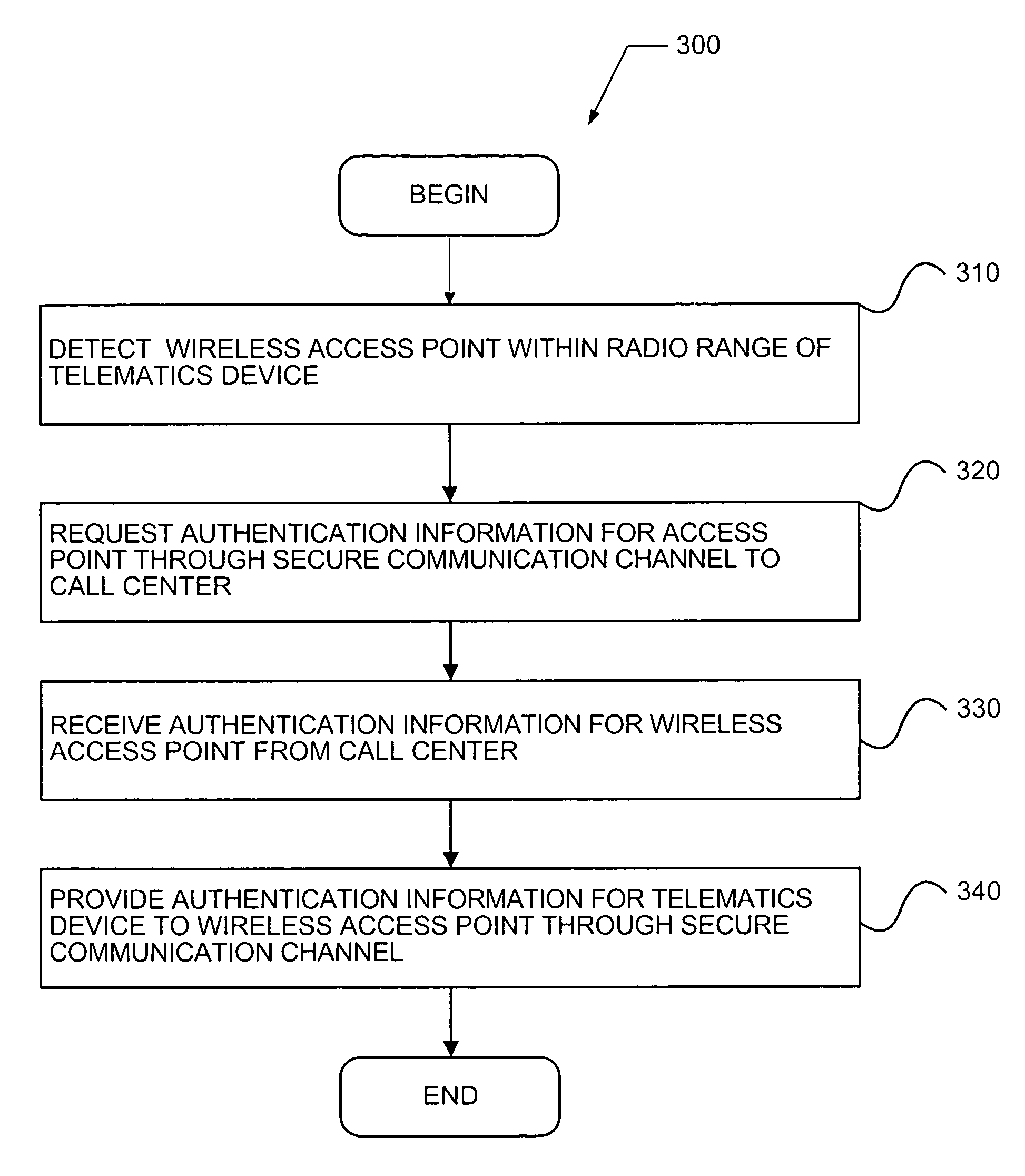
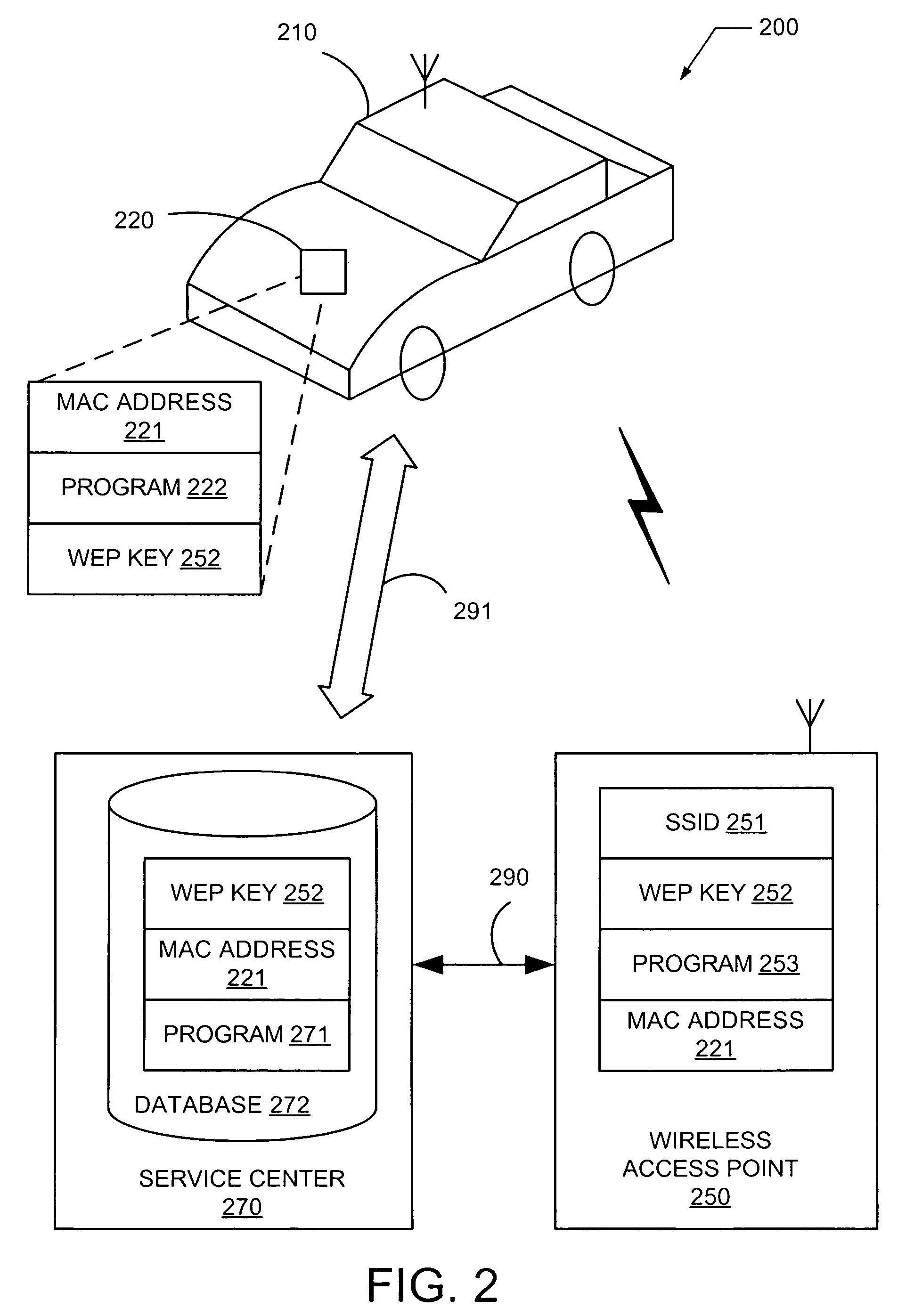
A system and method provides secure authentication of a wireless communication channel for a vehicle telematics device that includes detecting a wireless access point within radio range of a telematics device, requesting authentication information for the access point through a first secure communication channel to a call center, receiving authentication information for the wireless access point from the call center through the first secure communication channel, and providing authentication information for the telematics device to the wireless access point through a second secure communication channel. A computer readable medium storing a computer program is described for implementing one or more steps of the method.
Owner:GENERA MOTORS LLC
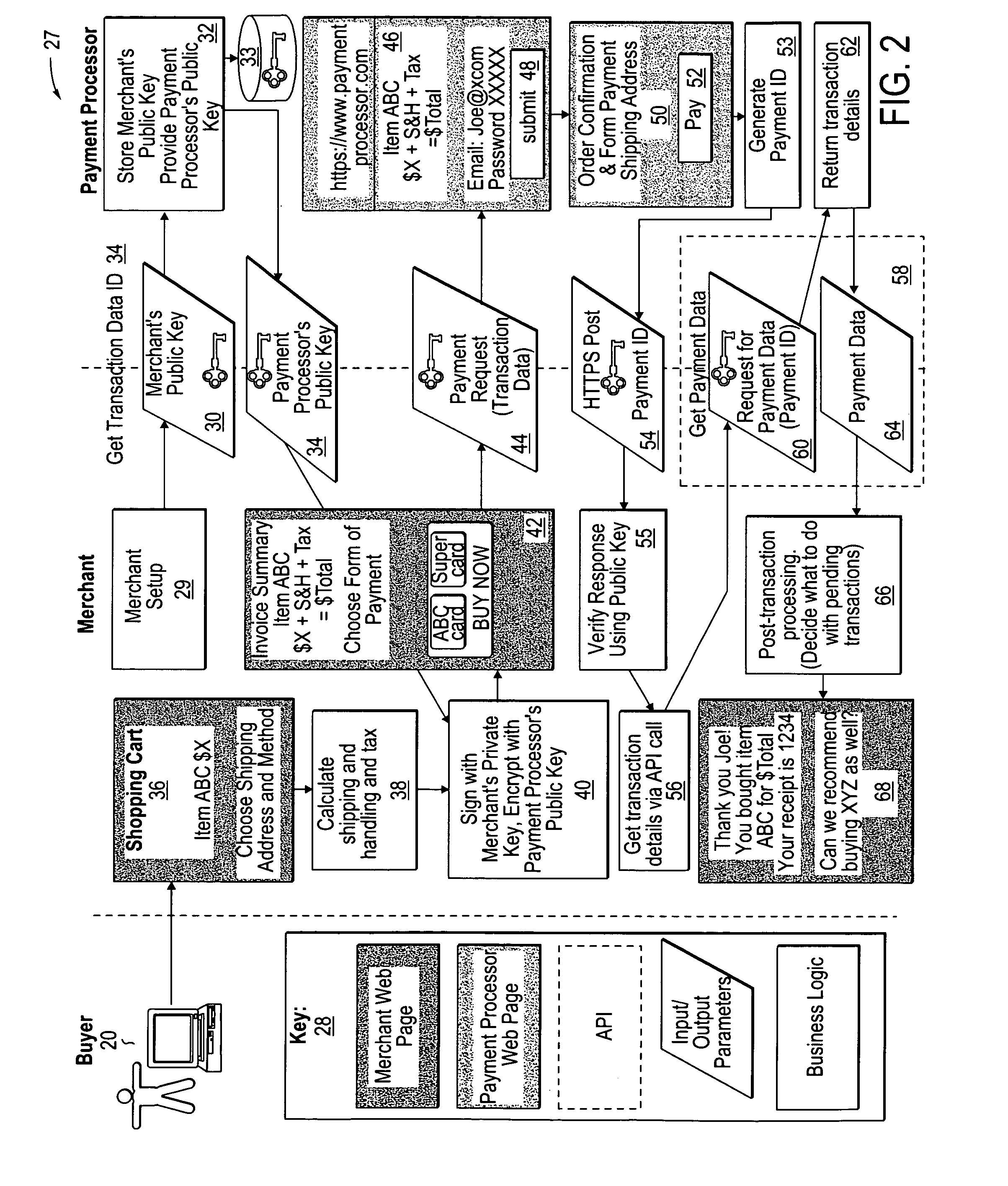
Method and system to facilitate securely processing a payment for an online transaction
ActiveUS20050256806A1Buying/selling/leasing transactionsPayment circuitsMerchant servicesInternet privacy
A computer-implemented method, to facilitate processing a payment for an online transaction, includes, responsive to receiving secure transaction data from a merchant server, using a payment processor to generate a transaction data identifier to identify the transaction data. The payment processor communicates the transaction data identifier to the merchant server. In response to receiving a request to process a payment, including the transaction data identifier, the payment processor requests user credentials from a user. Upon receiving user credentials from the user, the payment processor verifies the user credentials. The payment processor processes the payment and generates a payment identifier to identify payment data associated with the payment. The payment processor communicates the payment identifier to the merchant server. Upon receiving a request for payment data, including the payment identifier, over a secure communication channel from the merchant server, the payment processor communicates the payment data to the merchant server.
Owner:PAYPAL INC
Secure internet applications with mobile code
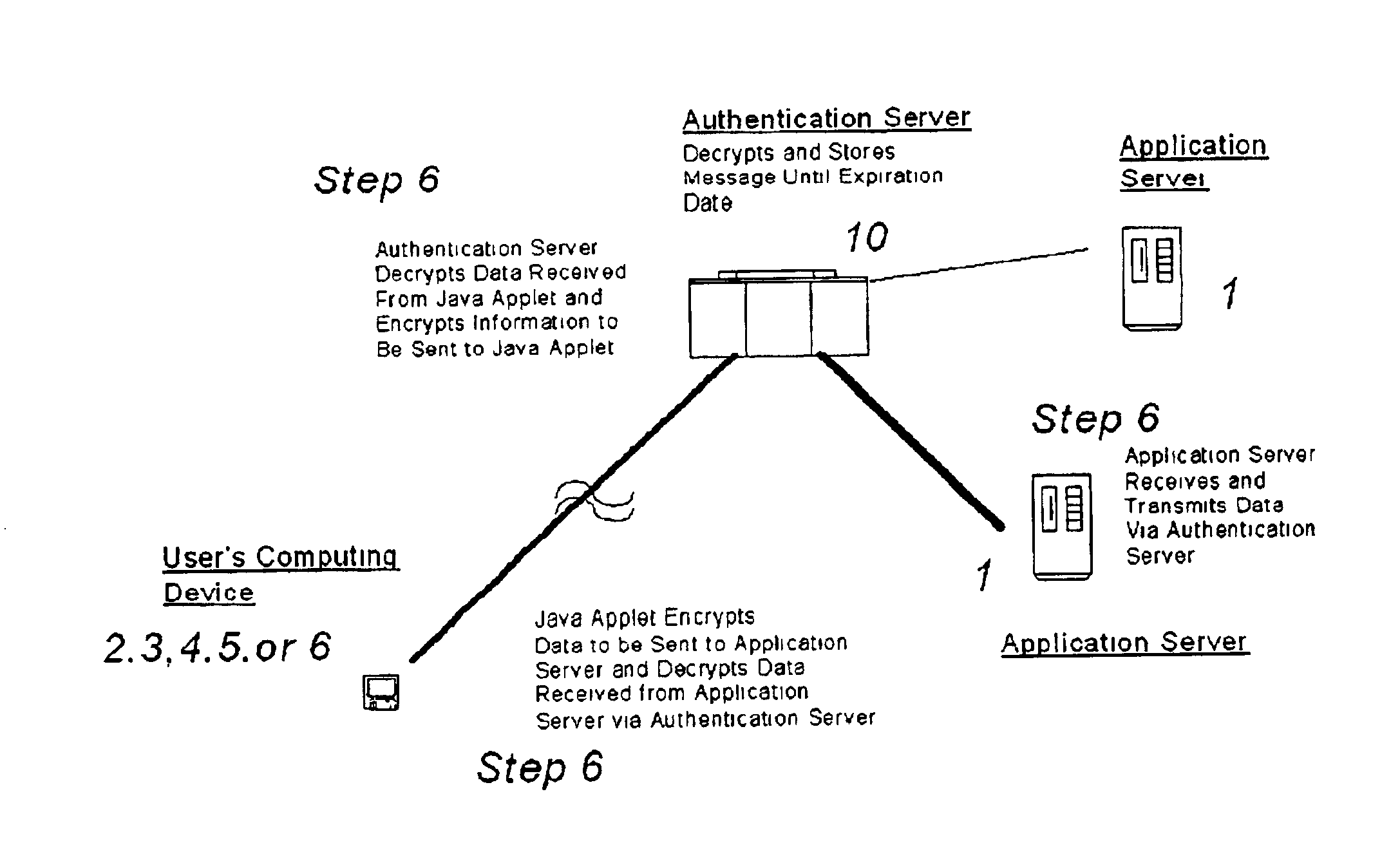
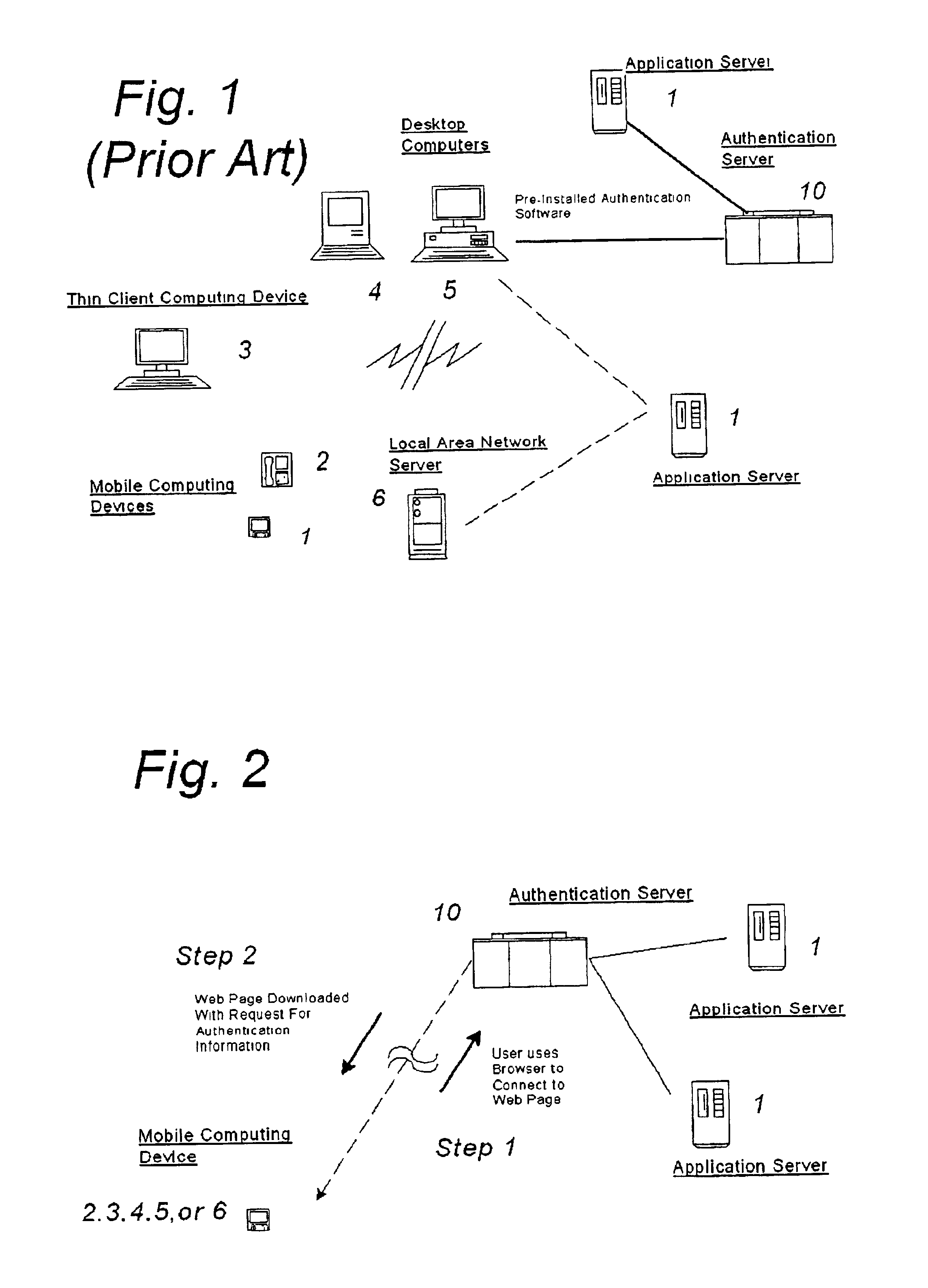
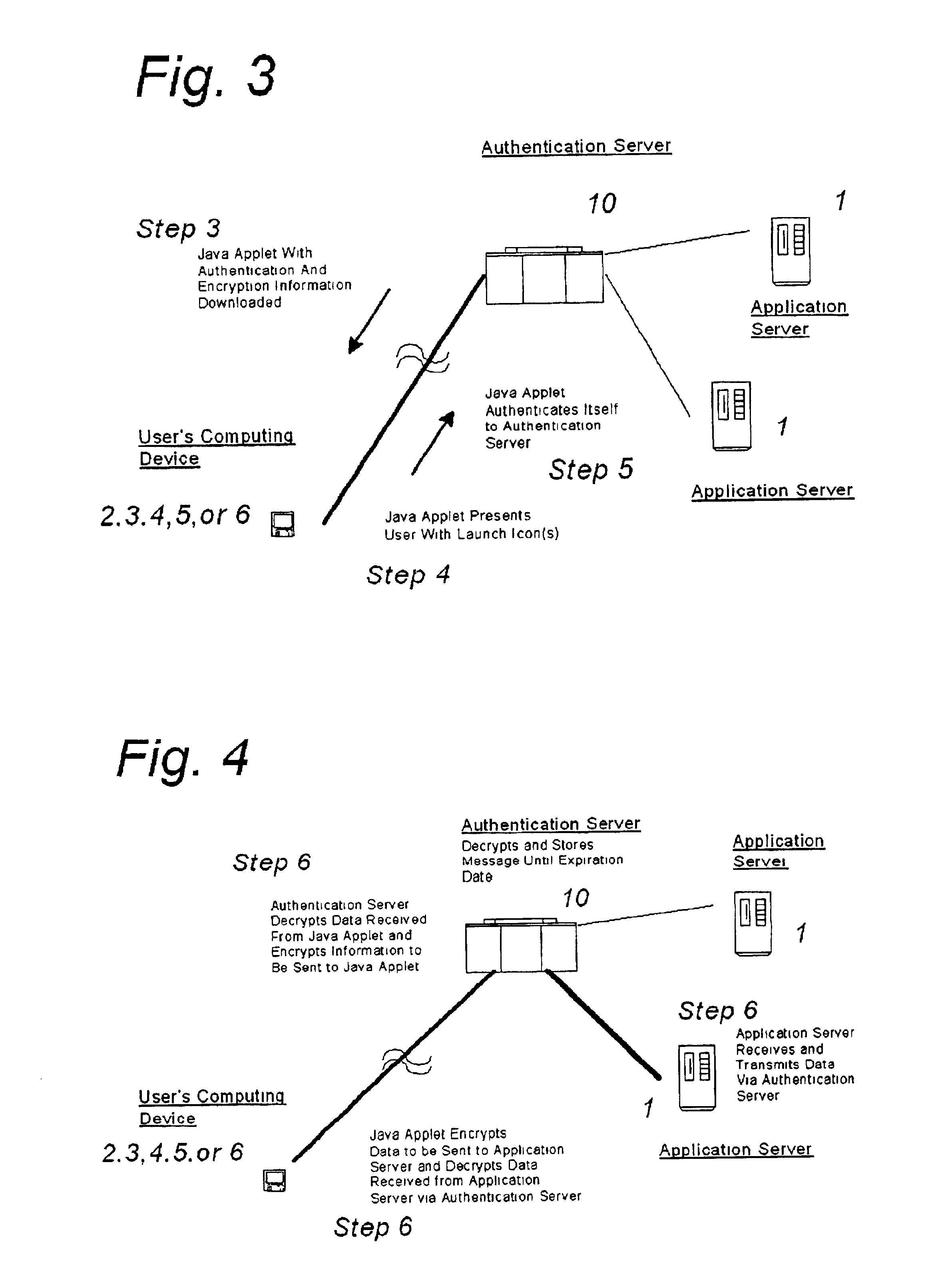
InactiveUS6907530B2Easy accessUser identity/authority verificationUnauthorized memory use protectionThe InternetMobile code
A system and method for securing pathways to a remote application server involves a gateway or authentication server, and a mobile code authentication and encryption client available for download from the gateway or authentication server. Upon connection of a user's computing device to the authentication server over the open network, the authentication server requests authentication information, such as a password, from the user, and upon authentication of the user by the authentication server, the authentication server downloads the mobile code authentication and encryption client to the user's computing device. The authentication and encryption client then authenticates itself to authentication server, after which a secure communications channel between the user's computing device and the authentication server is opened, the secure communications channel permitting transfer of data between the user's computing device and an application server. The system and method do not require pre-installation or any certificates or other authentication and encryption software on the user's computing device, enabling the system and method to be used with thin-client and mobile computing devices, as well as with conventional computers.
Owner:SSL SERVICES
Method and system for content downloads via an insecure communications channel to devices
ActiveUS20050076210A1Easy to downloadKey distribution for secure communicationDigital data processing detailsPlaintextSecure communication
The present teachings provide for a method and system for facilitating content download to one or more remote devices via an insecure communication channel. The method comprises the steps of receiving at least one shared secret from a device via an insecure communications channel, each shared secret encoded and functioning as an identifier for the device, transmitting an encrypted file, from a file server, to the device associated with the encoded shared secret, receiving the shared secret in a plaintext form a via a secure communications channel, receiving a confirmation authorizing the release of a decryption key, and sending a decryption key corresponding to the transmitted file, for which the authorization for the release of the decryption key has been received. The decryption key is encrypted using the shared secret if transmission is via the insecure channel.
Owner:MARQETA
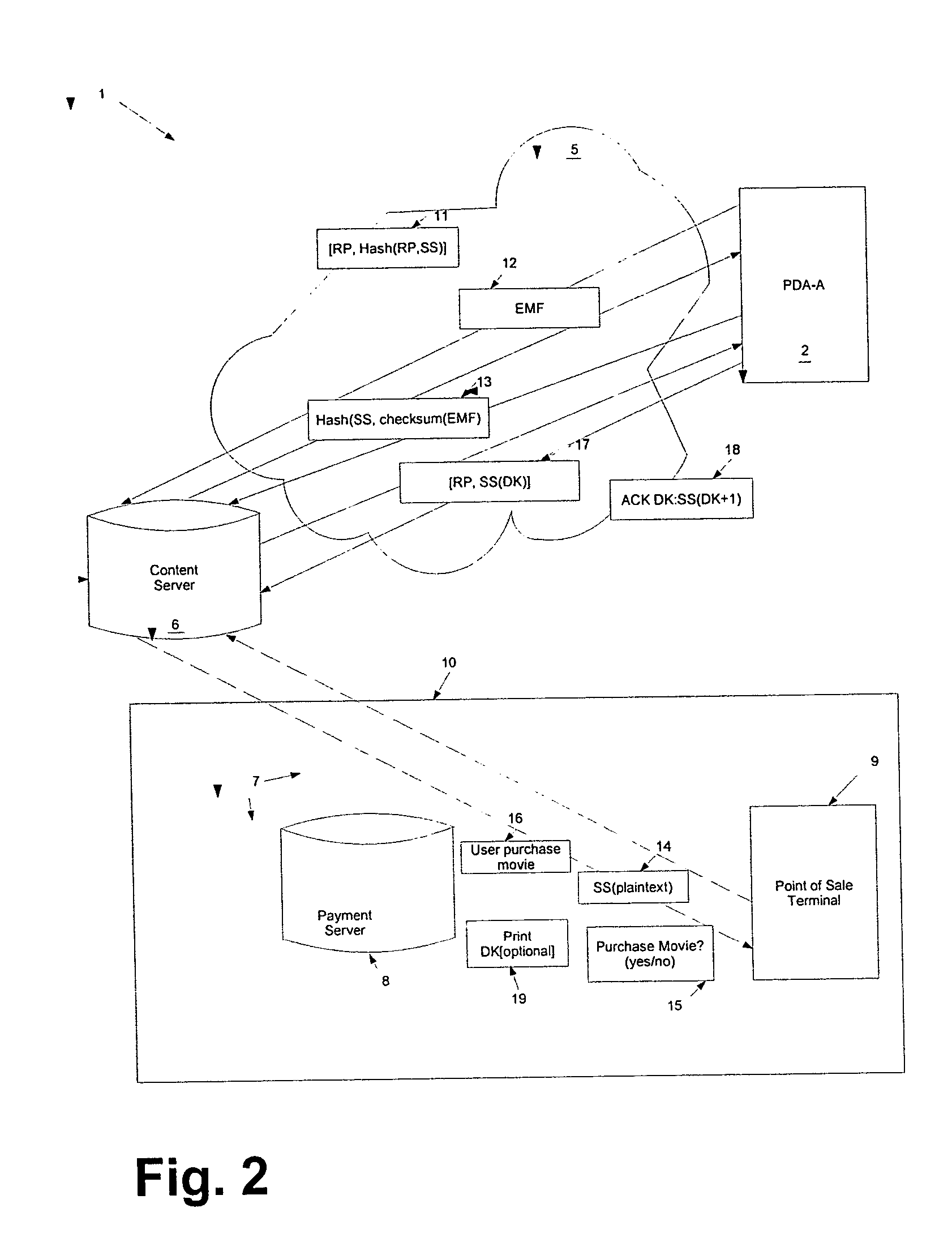
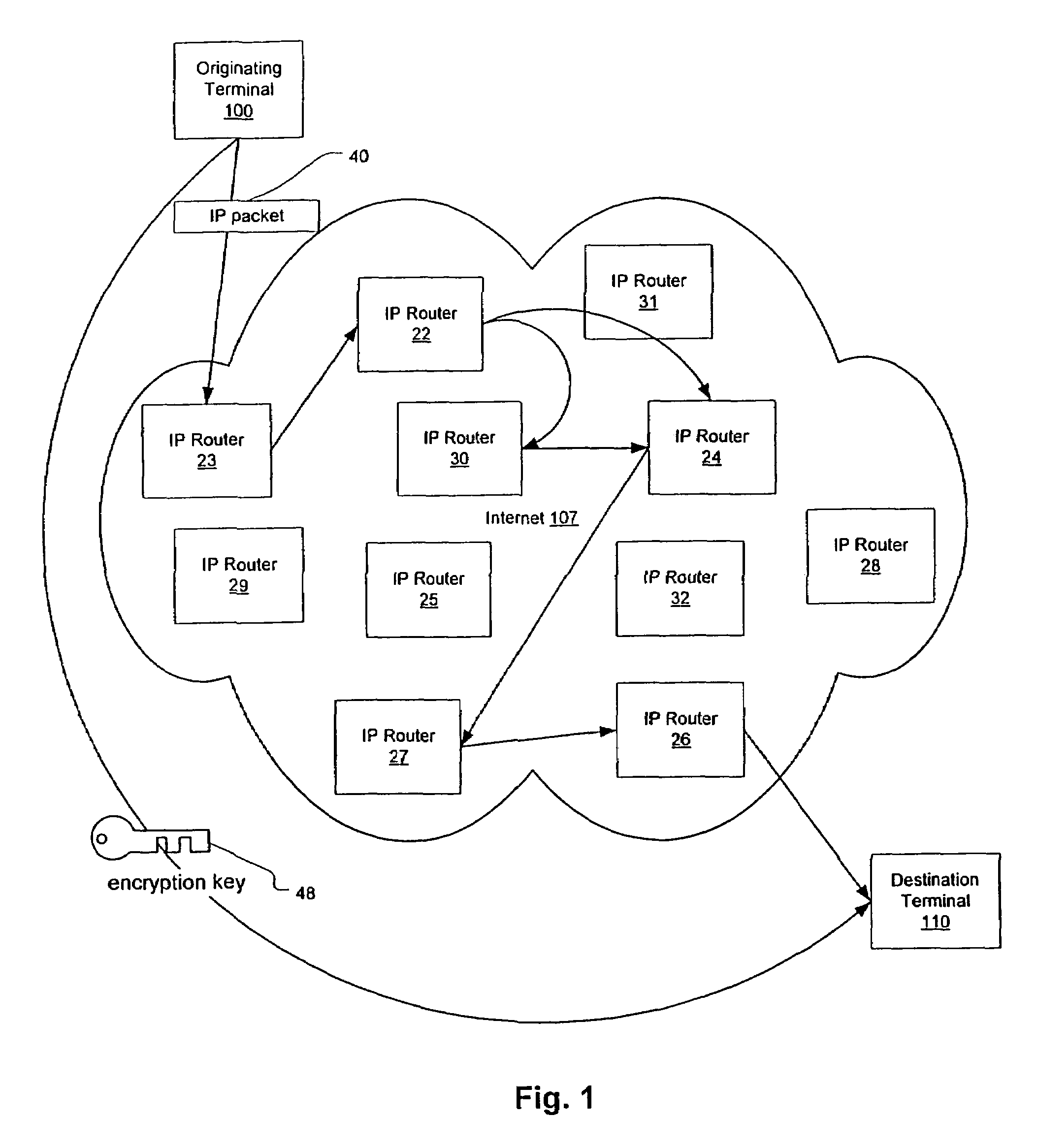
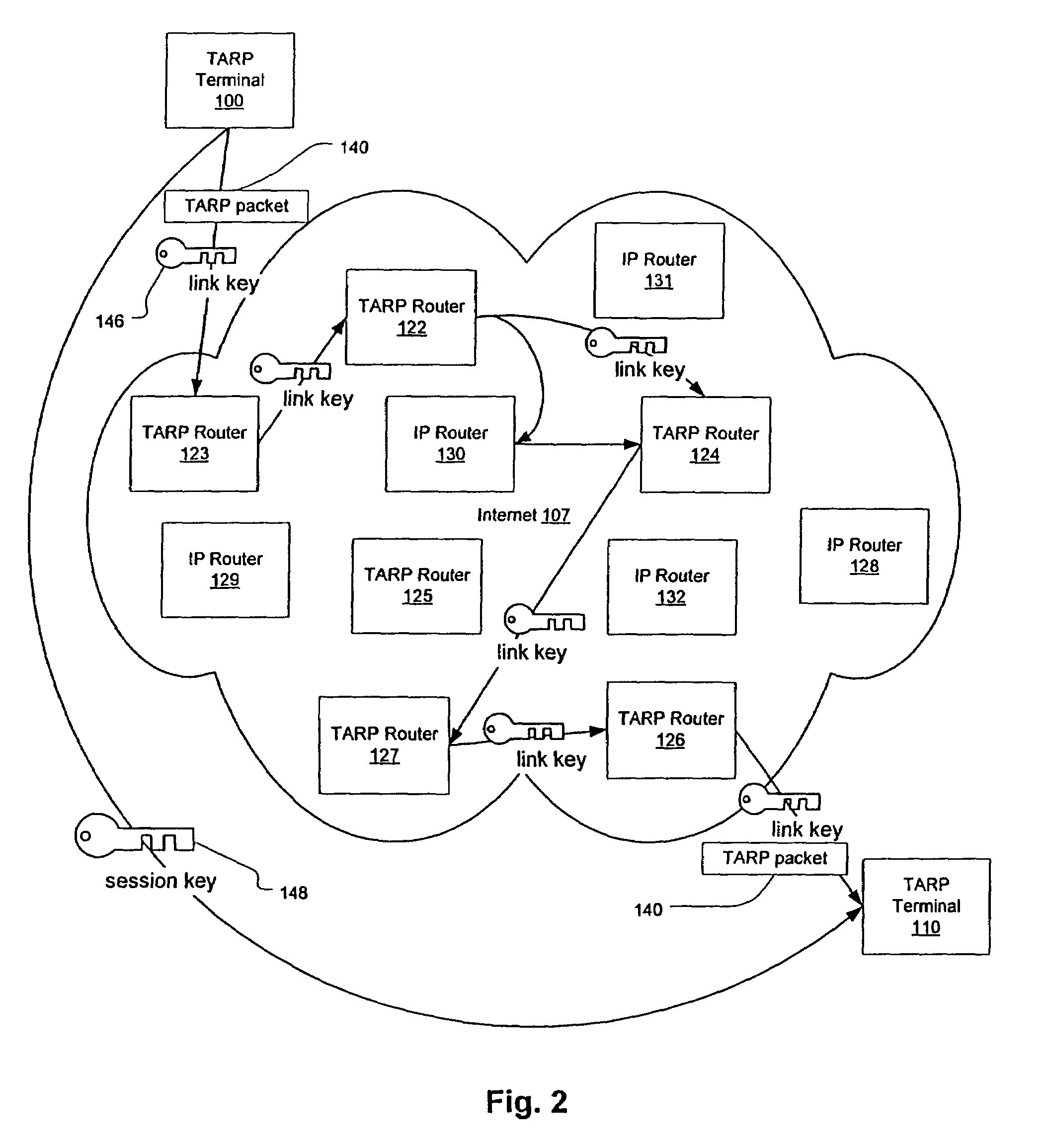
Agile network protocol for secure communications with assured system availability
InactiveUS7010604B1Reduce network loadSmall sizeKey distribution for secure communicationData stream serial/continuous modificationDiscriminatorComputer hardware
A plurality of computer nodes communicates using seemingly random IP source and destination addresses and (optionally) a seemingly random discriminator field. Data packets matching criteria defined by a moving window of valid addresses are accepted for further processing, while those that do not meet the criteria are rejected. In addition to “hopping” of IP addresses and discriminator fields, hardware addresses such as Media Access Control addresses can be hopped. The hopped addresses are generated by random number generators having non-repeating sequence lengths that are easily determined a-priori, which can quickly jump ahead in sequence by an arbitrary number of random steps and which have the property that future random numbers are difficult to guess without knowing the random number generator's parameters. Synchronization techniques can be used to re-establish synchronization between sending and receiving-nodes. These techniques include a self-synchronization technique in which a sync field is transmitted as part of each packet, and a “checkpoint” scheme by which transmitting and receiving nodes can advance to a known point in their hopping schemes. A fast-packet reject technique based on the use of presence vectors is also described. A distributed transmission path embodiment incorporates randomly selected physical transmission paths.
Owner:VIRNETX
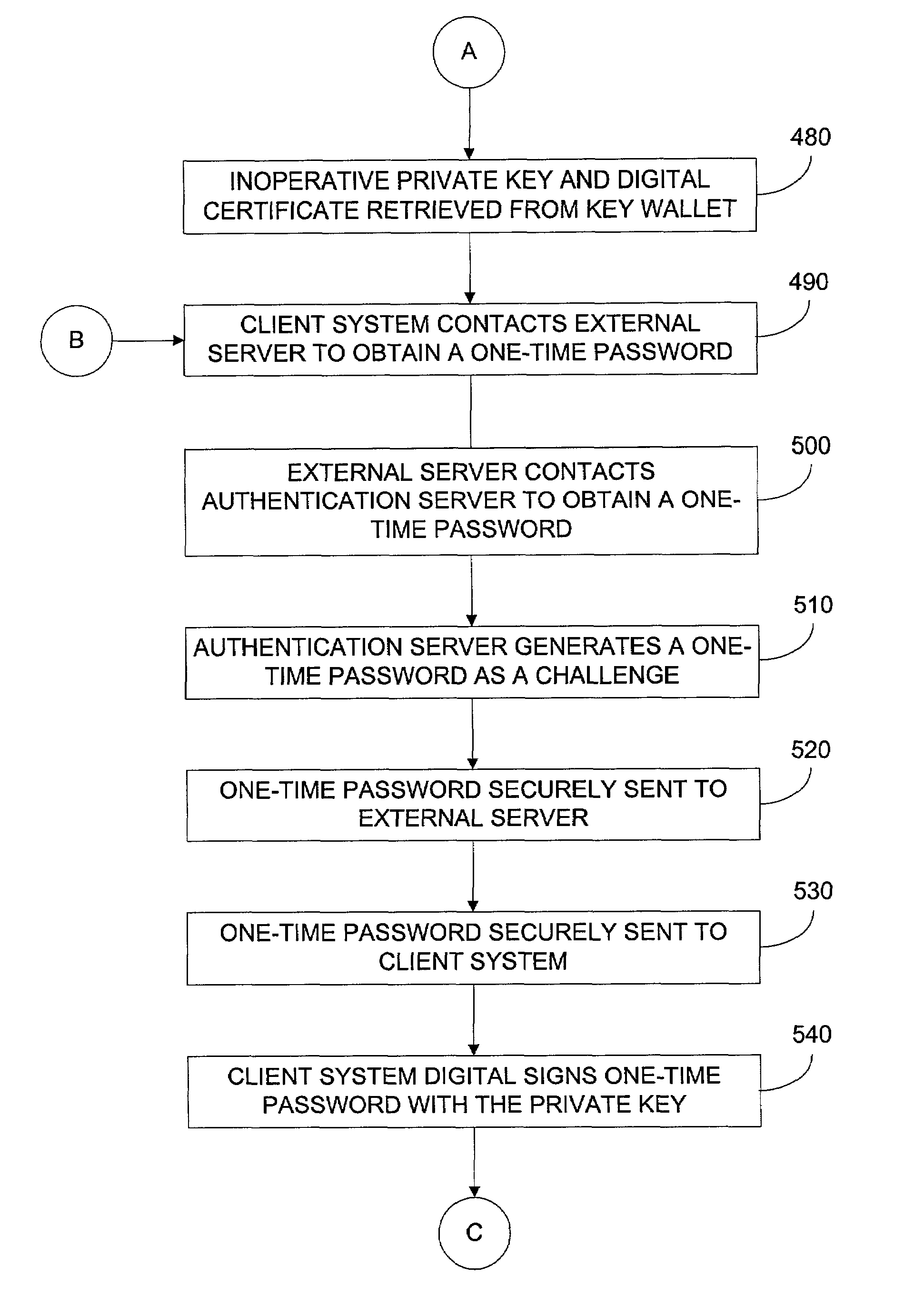
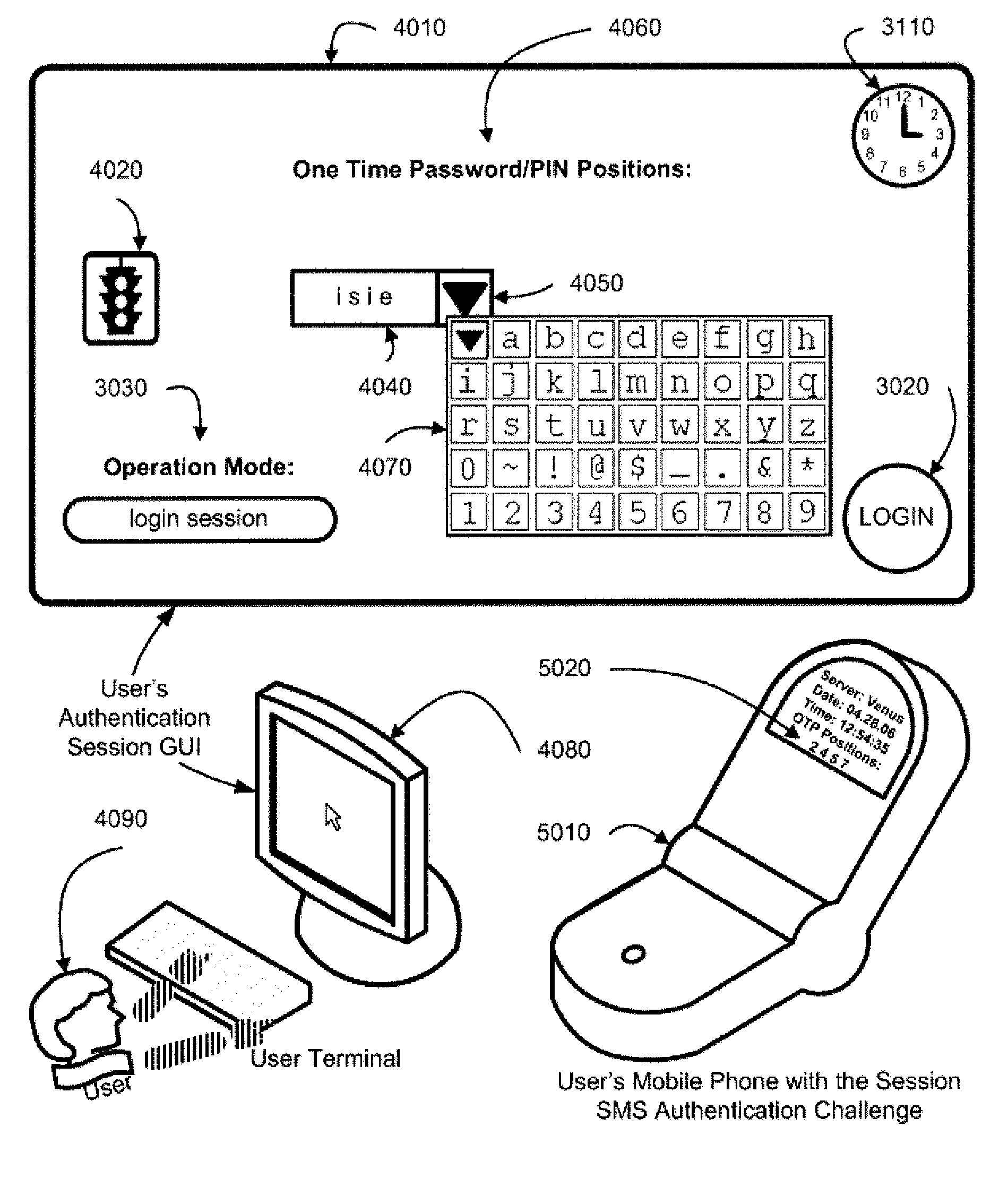
Methods for pre-authentication of users using one-time passwords
InactiveUS6983381B2User identity/authority verificationData resettingDigital signatureAuthentication server
A method for communicating passwords includes receiving at a server a challenge from a authentication server via a first secure communications channel, the challenge comprising a random password that is inactive, communicating the challenge from the server to a client computer via a second secure communications channel, receiving at the server a challenge response from the client computer via the second secure communications channel, the challenge response comprising a digital certificate and a digital signature, the digital certificate including a public key in an encrypted form, the digital signature being determined in response to the random password and the private key, and communicating the challenge response from the server to the authentication server via the first secure communications channel, wherein the random password is activated when the authentication server verifies the challenge response.
Owner:CA TECH INC
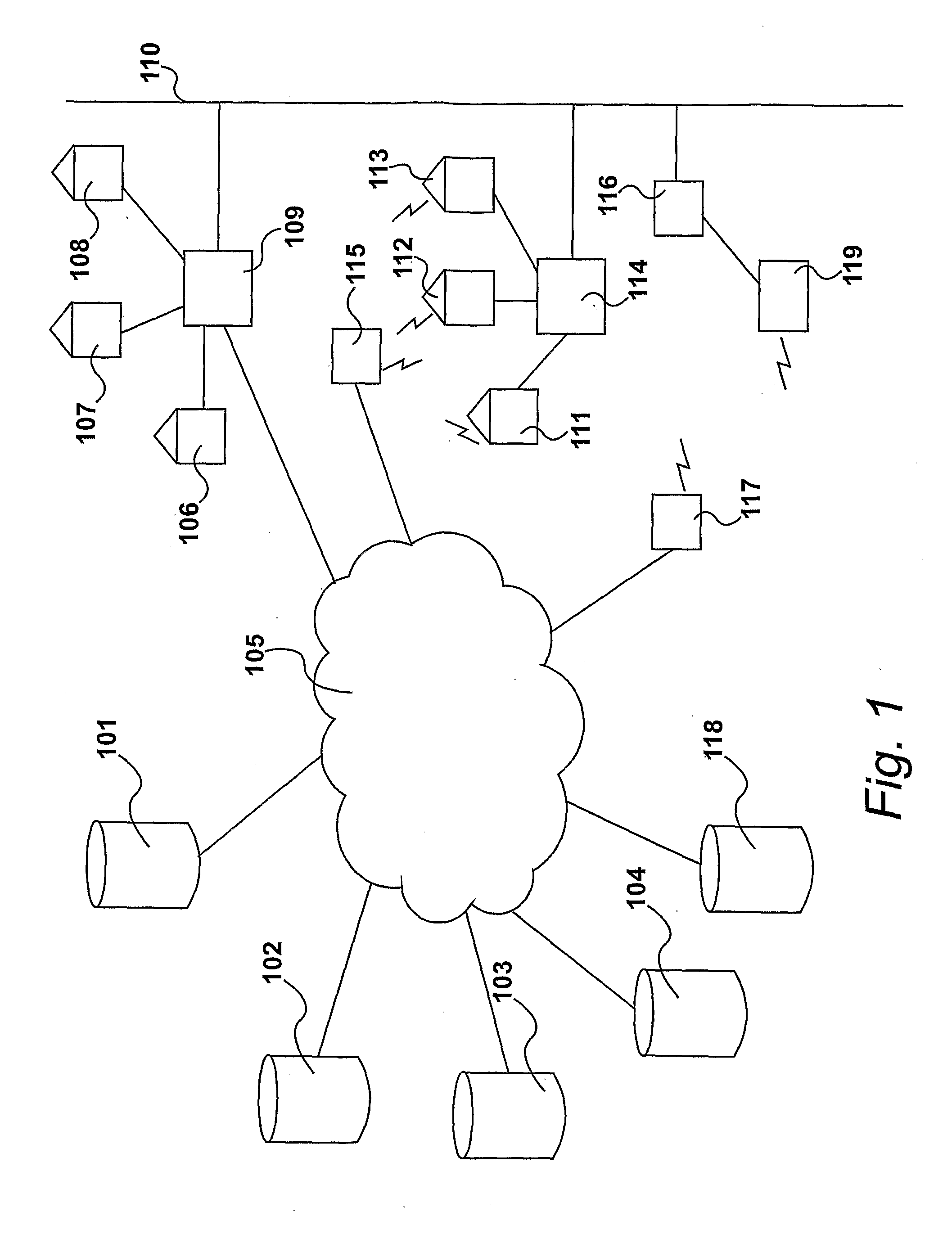
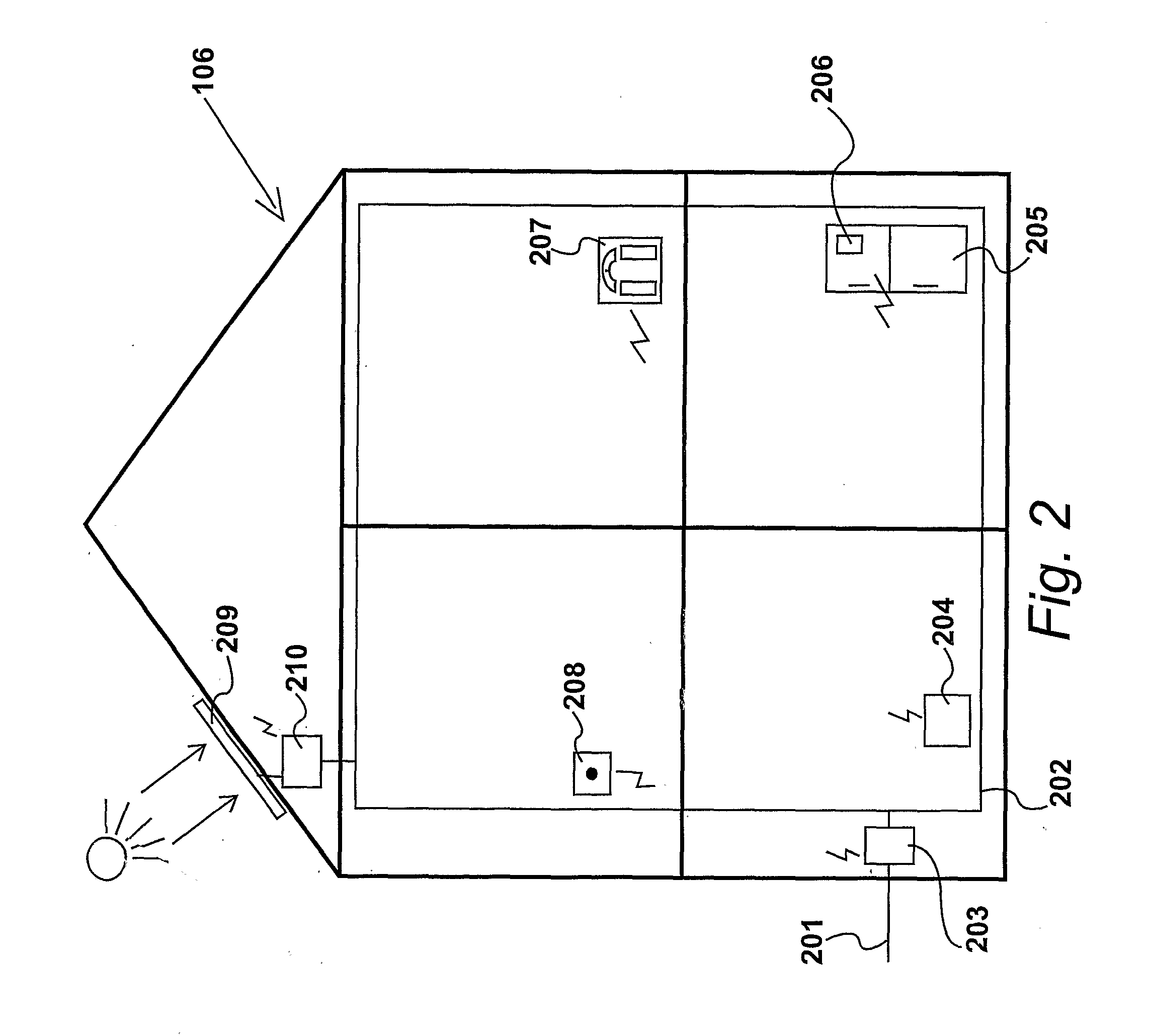
Facilitating secure communication between utility devices
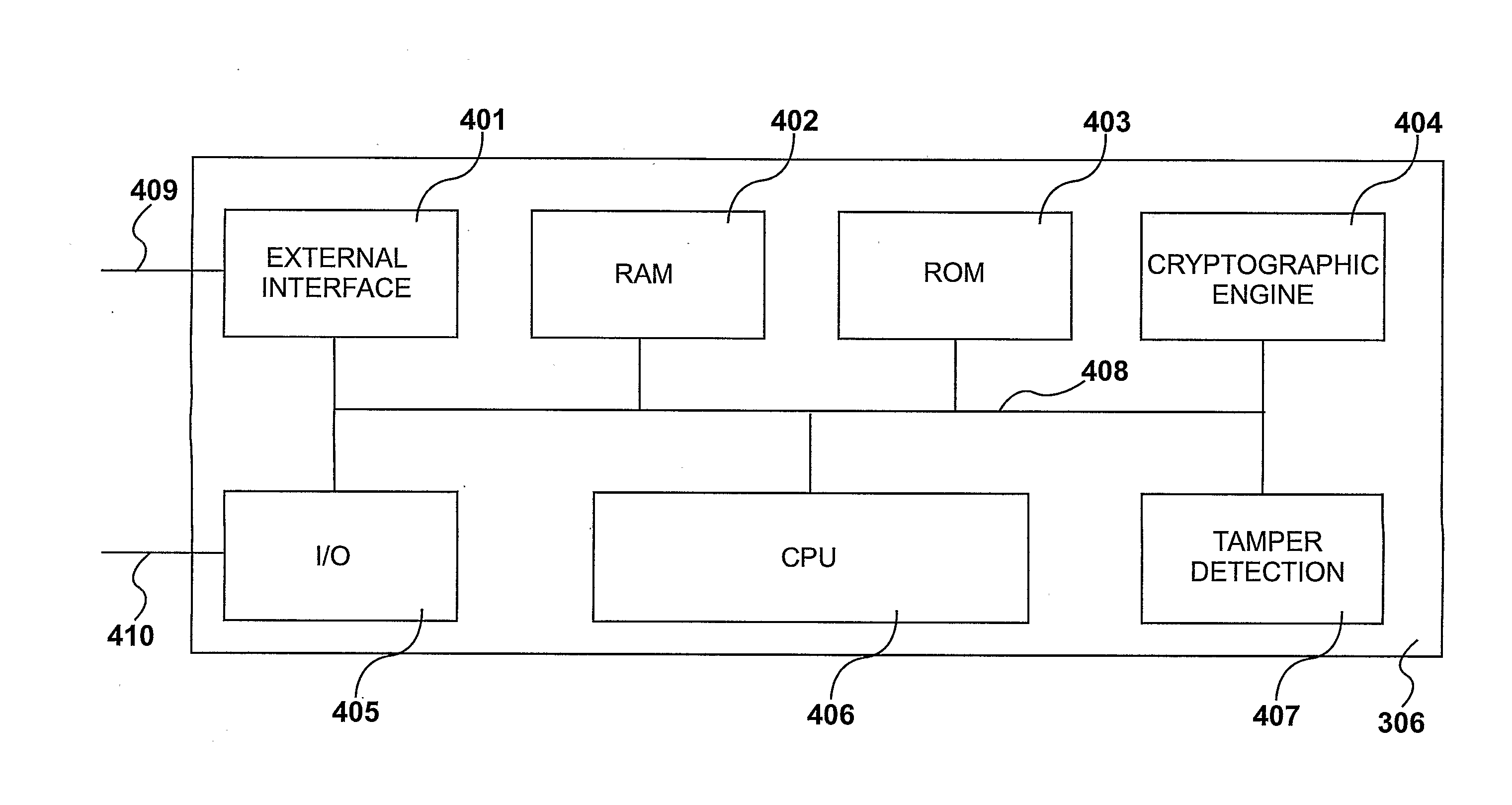
InactiveUS20110296169A1Facilitate communicationSecuring communicationHome automation networksMicrocontrollerTamper resistance
Communication is facilitated between a plurality of servers (101,102,103) and a plurality of local devices (204,206,207,208,210). An apparatus comprises a first network interface for communicating with the servers, a second network interface for communicating with the local devices, and a microcontroller having a processor, memory, a cryptographic engine for carrying out cryptographic calculations, and a tamper-resistance element configured to resist tampering with the apparatus. A plurality of programs, each comprising instructions and data, are stored in the memory. The processor is configured to, for a first local device, identify a first program which is associated with the first local device, and using the first program, provide a secure communications channel between the first local device and a first server. The processor is unable to accept commands from any other of the programs to access or change the first program, and the processor is unable to route messages over the secure communications channel that are not from or to the first local device and the first server.
Owner:PALMER CHARLES GRAHAM
Method and apparatus for securely invoking a rest API
An embodiment of the present invention provides a system that enables a user to securely invoke a REST (Representational State Transfer) API (Application Programming Interface) at an application server. A client can establish a secure communication channel with an application server, and can send a request to the application server to invoke the REST API. The client can then receive a security token from an authentication system in response to authenticating the user with the authentication system. Next, the client can receive a nonce and a timestamp from the application server. The client can then determine a security token digest using the security token, the nonce, and the timestamp. Next, the client can resend the request to the application server to invoke the REST API with the security token digest. The application server can invoke the REST API if the security token digest is valid.
Owner:INTUIT INC
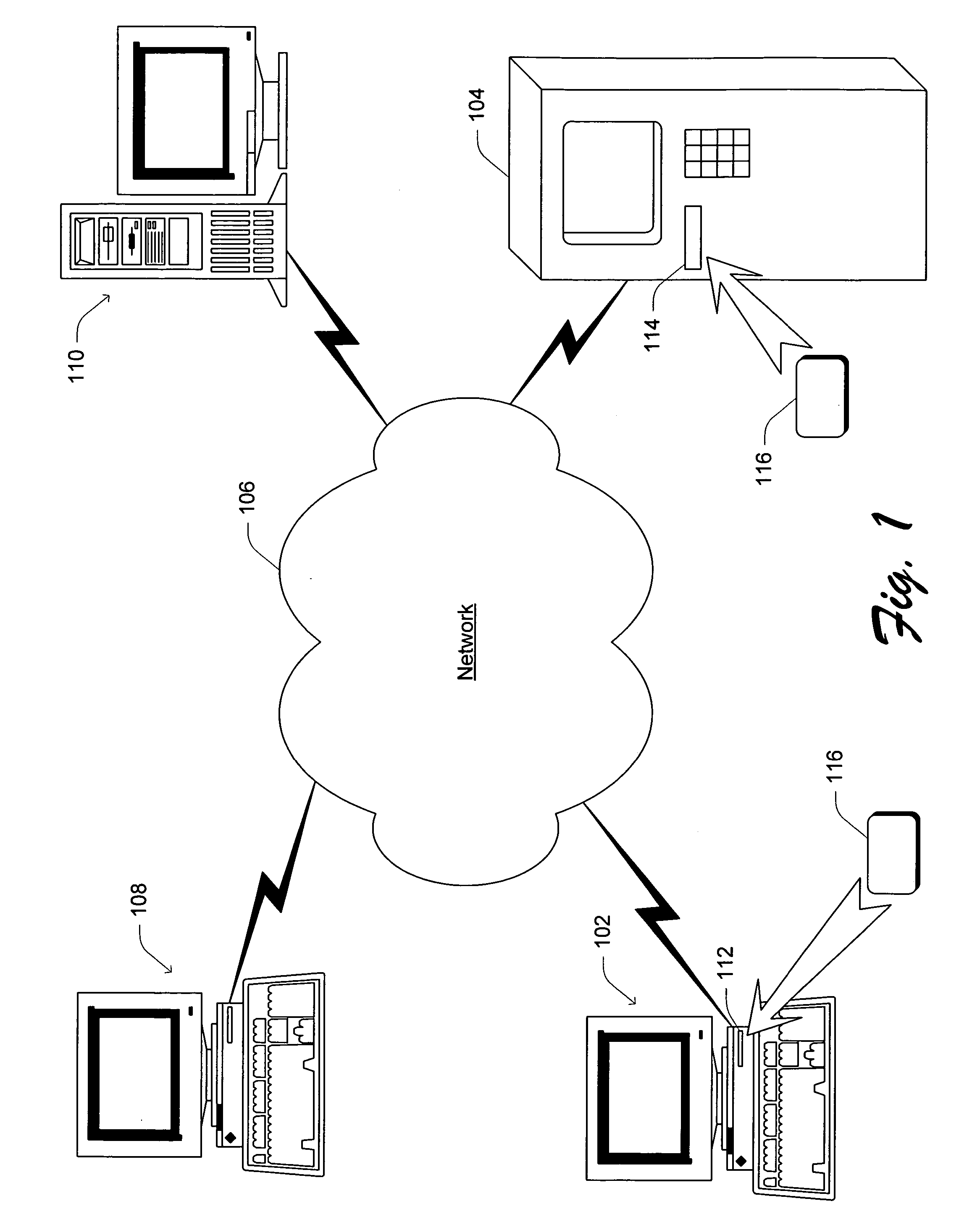
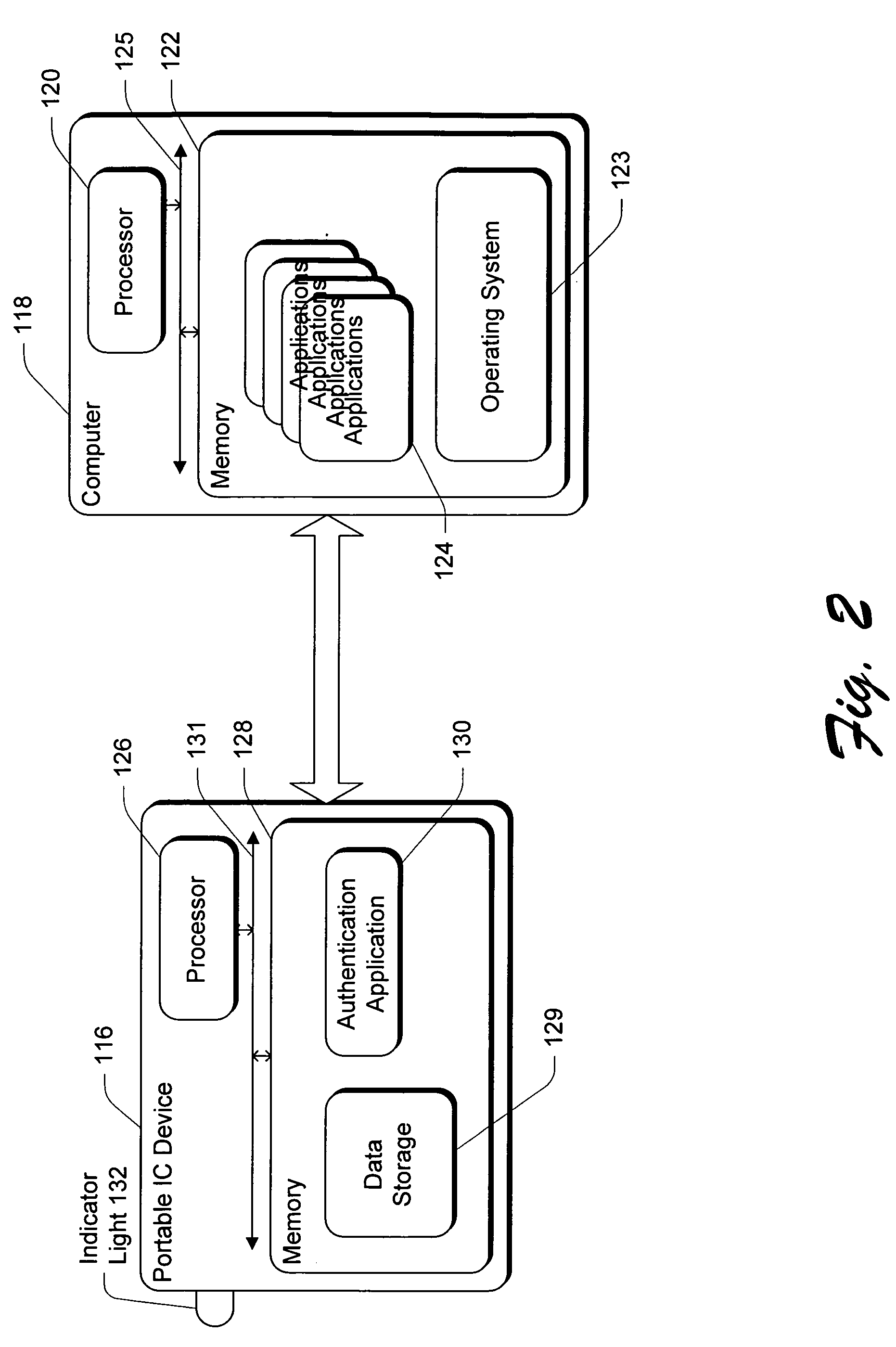
Method and apparatus for authenticating an open system application to a portable IC device
InactiveUS20060036851A1Specific access rightsUser identity/authority verificationSecure communicationApplication software
A secure communication channel between an open system and a portable IC device is established. An application running on the open system desiring access to the information on the portable IC device authenticates itself to the portable IC device, proving that it is trustworthy. Once such trustworthiness is proven, the portable IC device authenticates itself to the application. Once such two-way authentication has been completed, trusted communication between the open system and the portable IC device can proceed, and private information that is maintained on the portable IC device can be unlocked and made available to the application.
Owner:MICROSOFT TECH LICENSING LLC
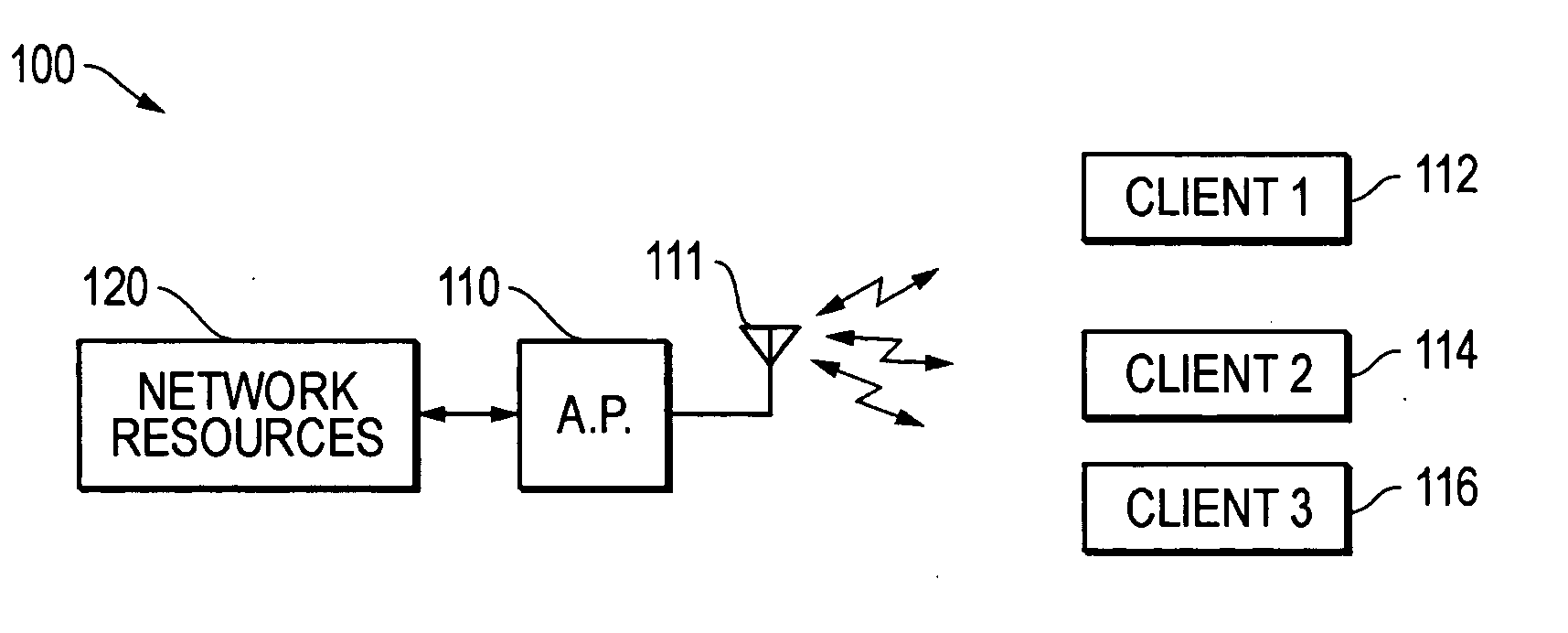
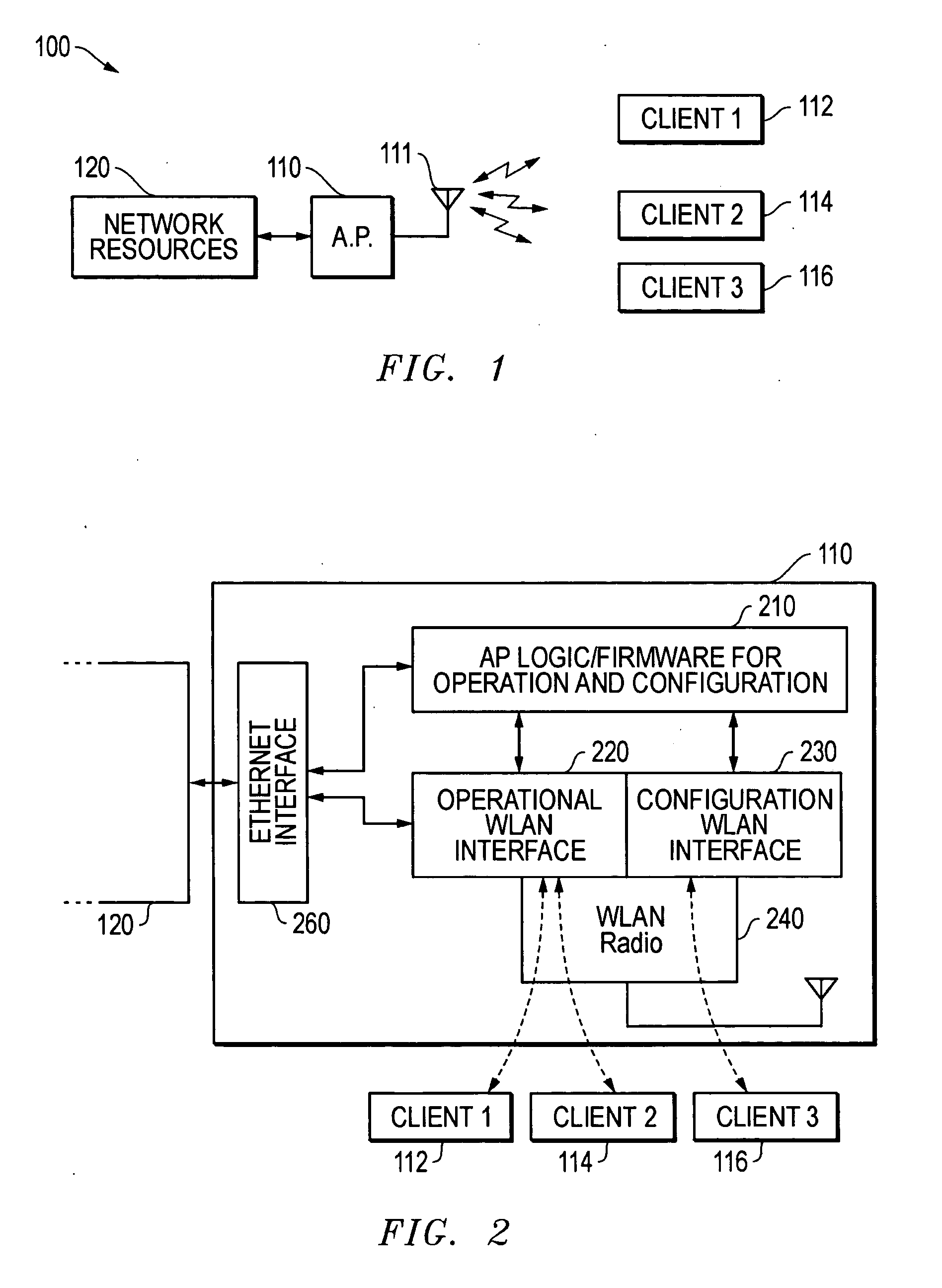
Virtual access point for configuration of a LAN
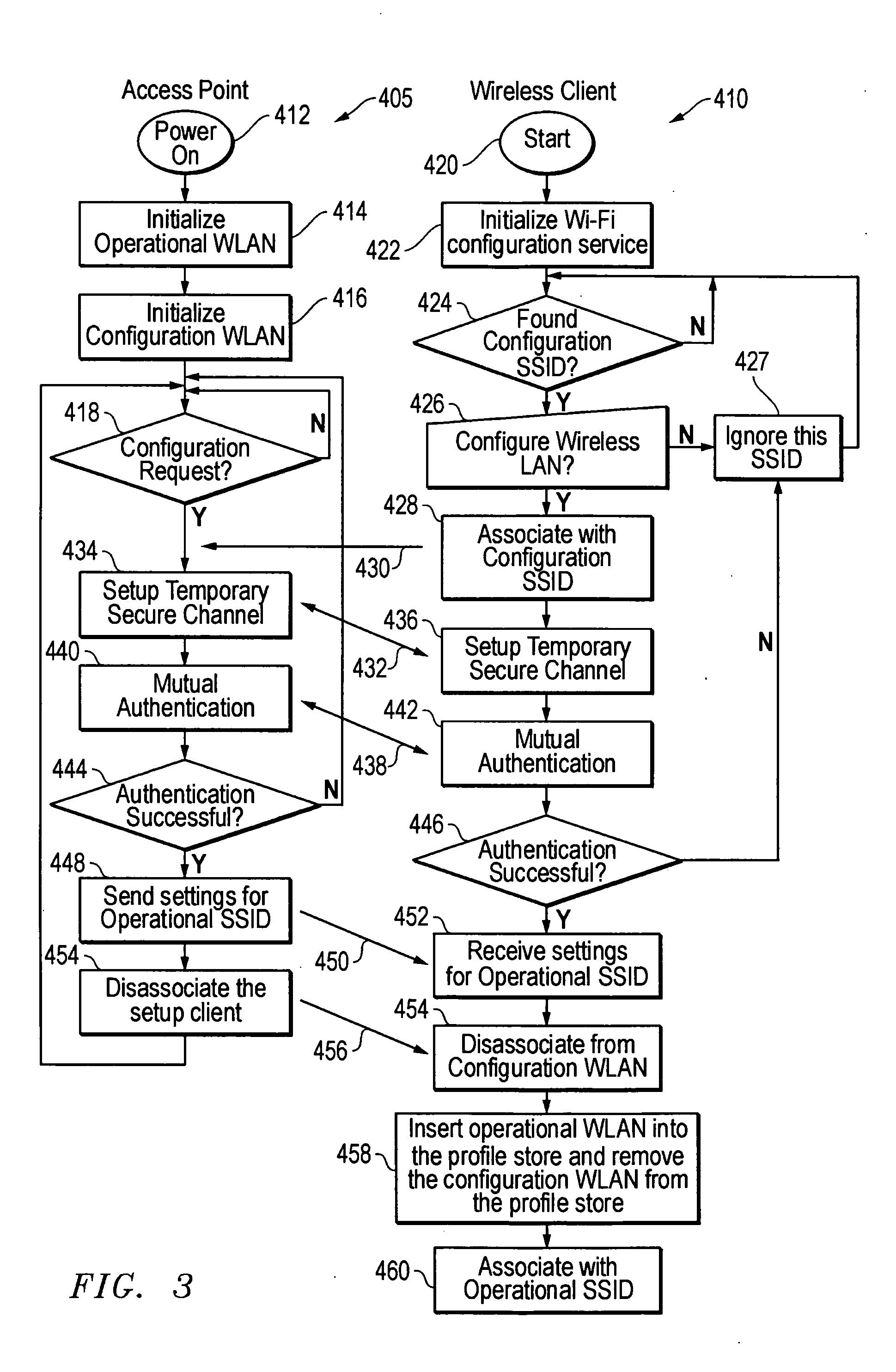
ActiveUS20070206527A1Eases setup of that communication channelEasy to identifyNetwork topologiesConnection managementSecure communicationClient-side
A technique is disclosed for setting up and configuring a LAN. More particularly, secure communications may be configured between an access point (AP) and a client device. Virtual AP technology is utilized to assist the configuration of the network. In particular, at least two wireless networks are provided in a single A, a configuration LAN and an operational LAN, by utilizing virtual AP technology. The configuration LAN is utilized to provide communication between the AP and the client devices that is related to network setup, configuration, modification, etc. and the operational LAN provides normal LAN data communication. The configuration LAN may be provided in a relatively insecure manner that eases setup of that communication channel and the operational LAN may be provided in a more fully secure communication channel. Different types of service set identifiers (SSIDs) may be provided for configuration LANs and operational LANs so as to more easily identify the type of LAN through its SSID.
Owner:DELL PROD LP
Partitioned scheme for trusted platform module support
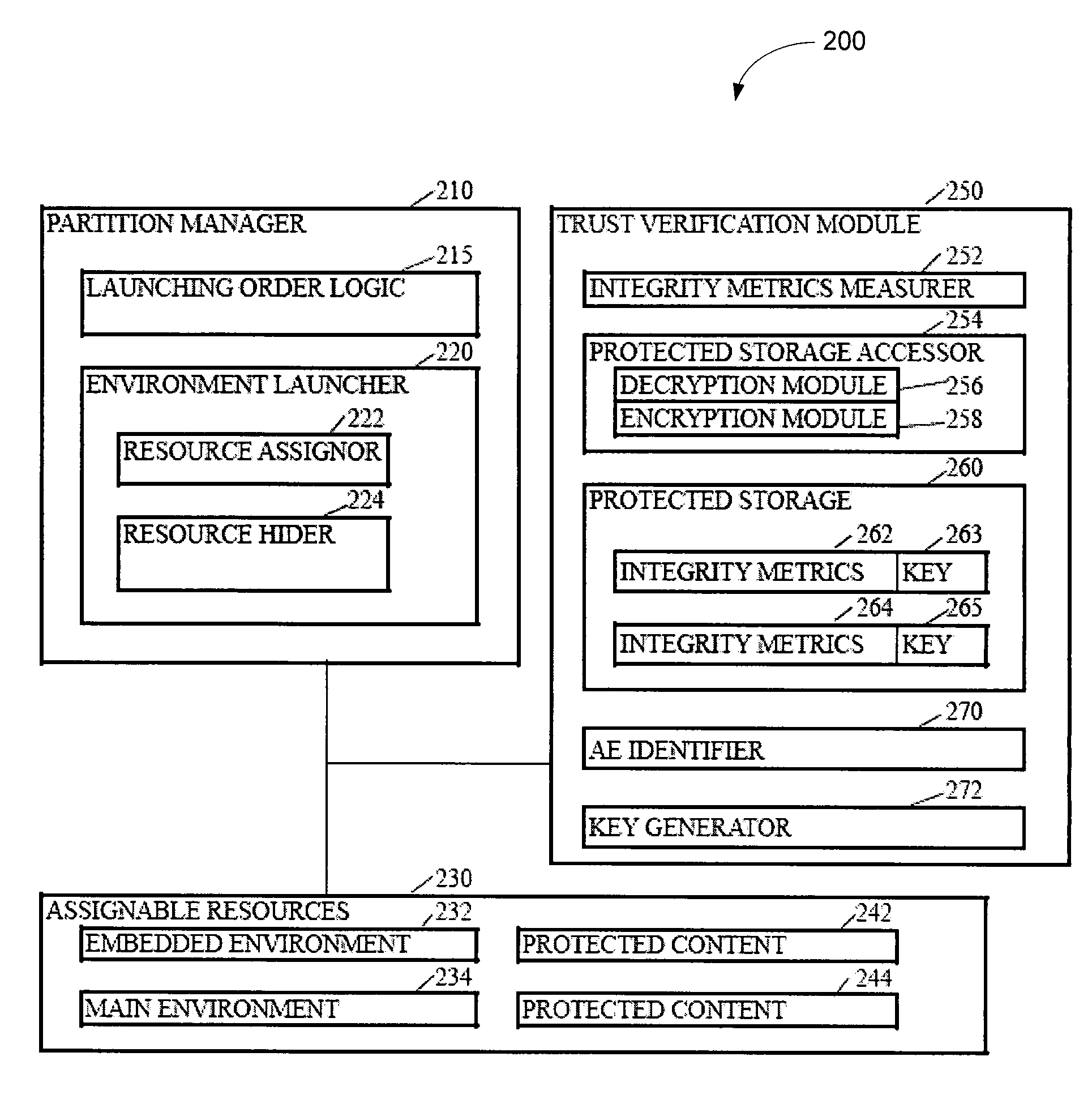
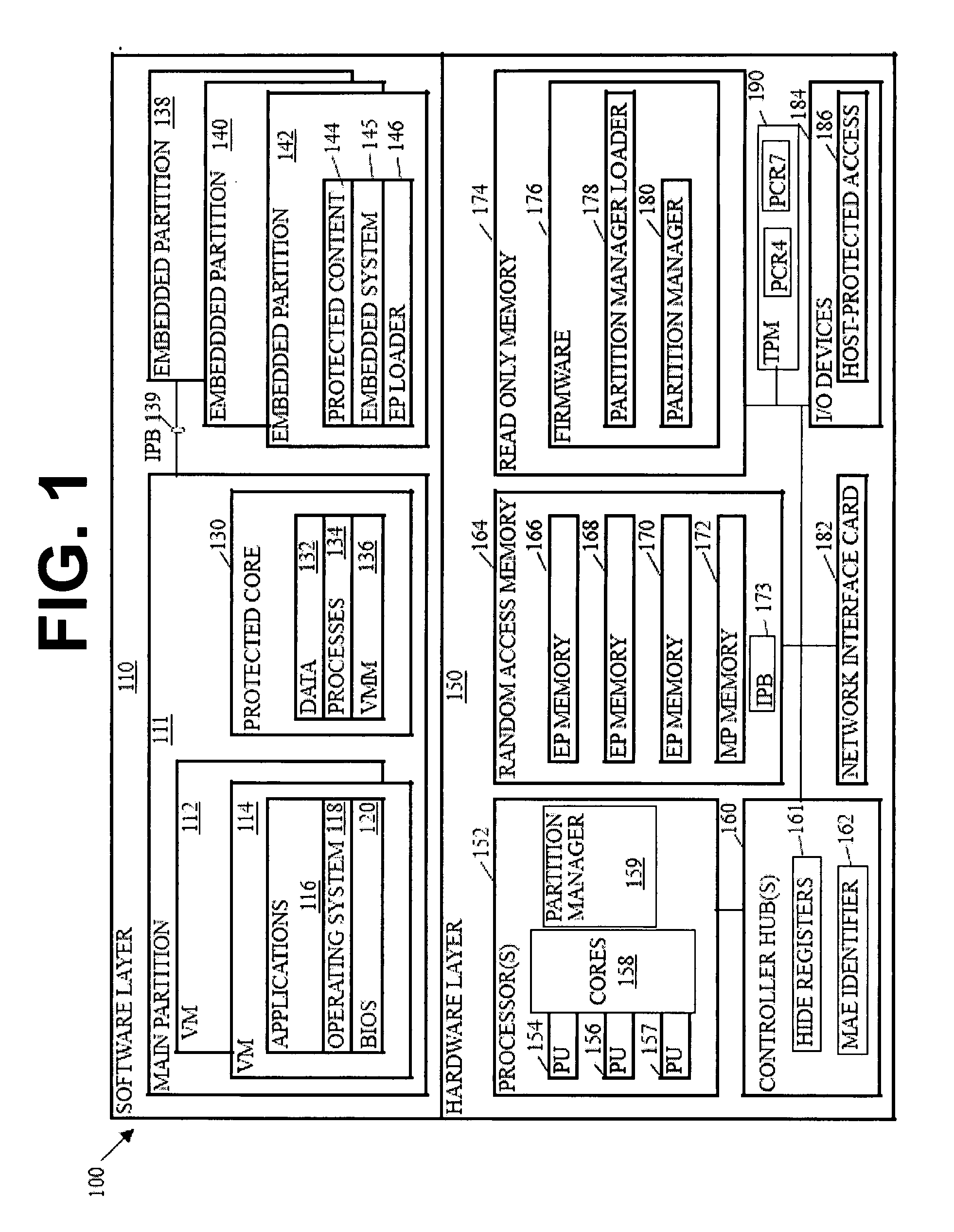
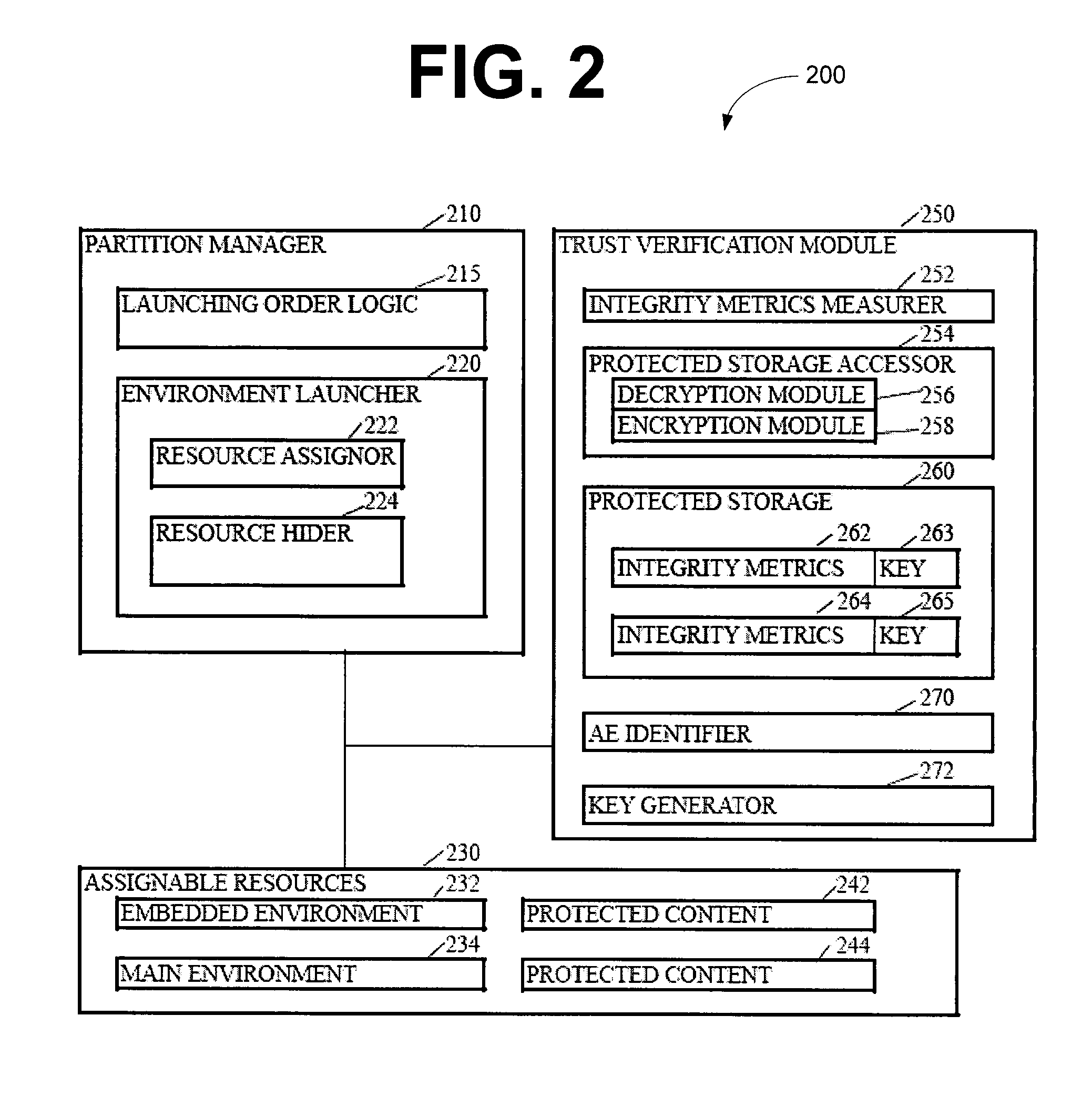
InactiveUS20090007104A1Computer security arrangementsSoftware simulation/interpretation/emulationComputer hardwareOperational system
The subject mater herein relates to processing of sensitive data and, more particularly, to a partitioned scheme for trusted platform module support. Various embodiments provide systems, methods, and software that instantiate one or more emulated trusted platform modules in respective sequestered processor cores. In some embodiments, a trusted platform module in instantiated in a processor core, sequestered for the trusted platform module, for each operating system or virtual machine operating on a computing device. The operating system may then communicate with the appropriate trusted platform module over a secure communication channel, such as an interpartition bridge.
Owner:INTEL CORP
Method and system for facilitating online gaming
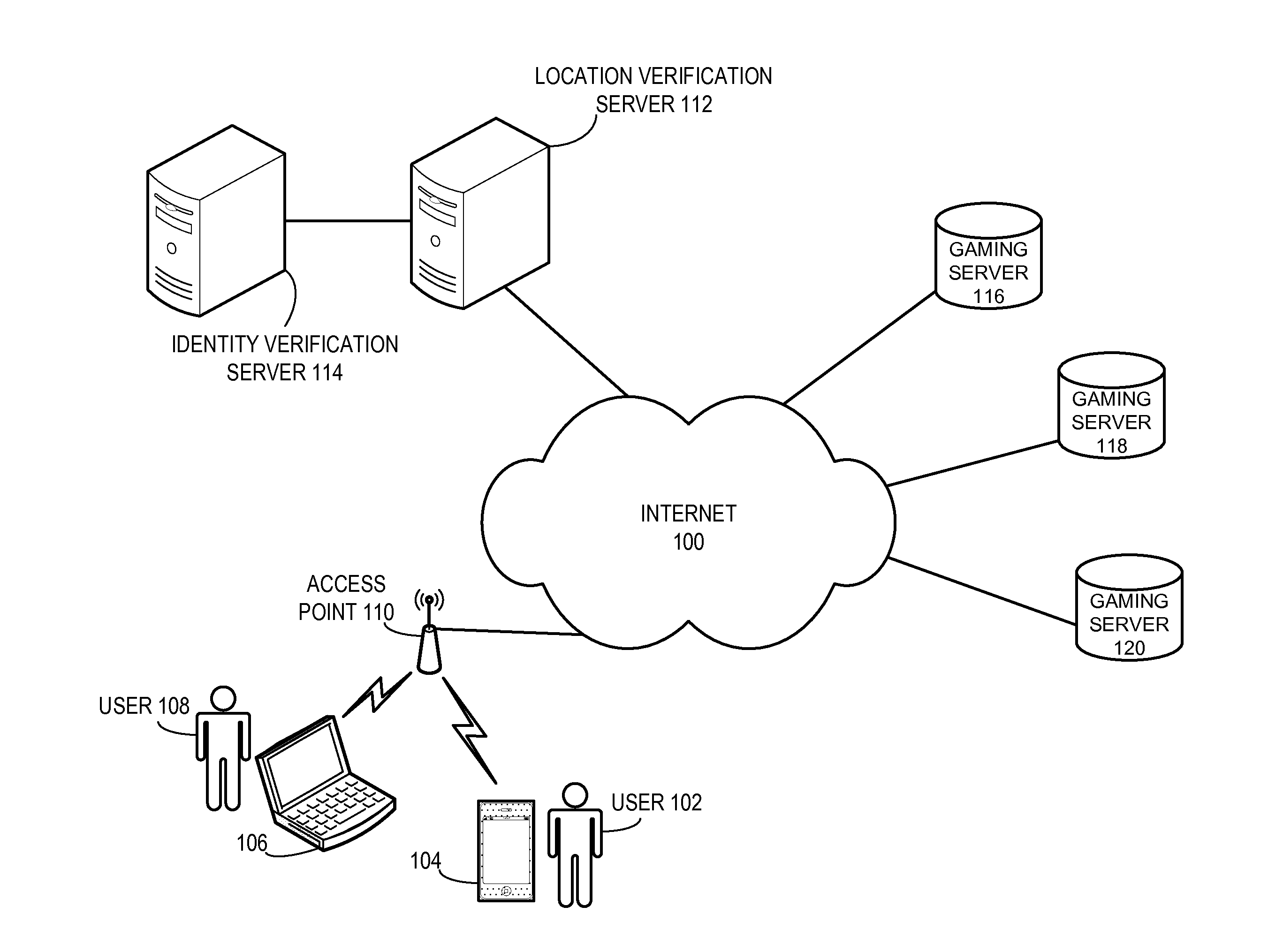
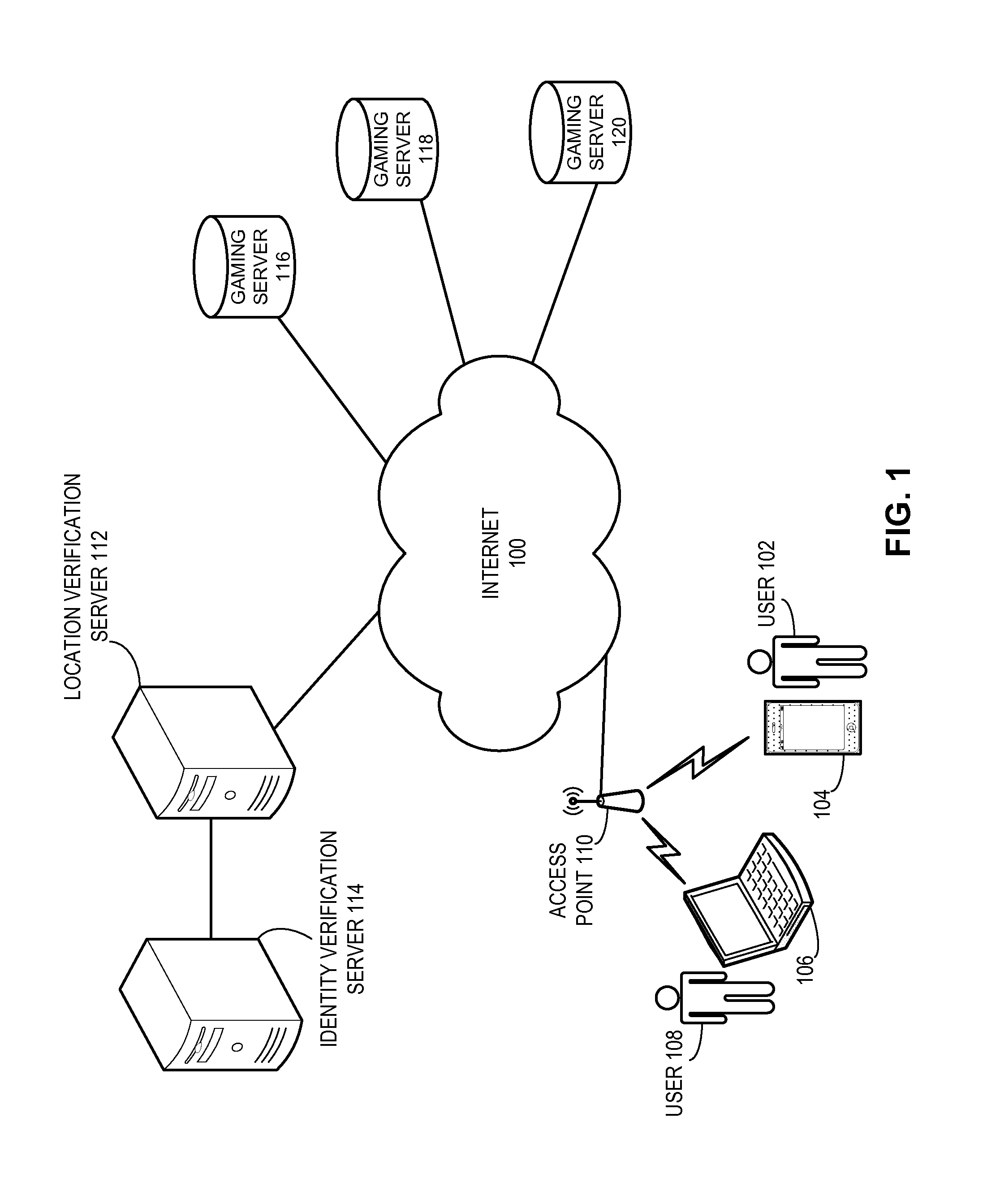
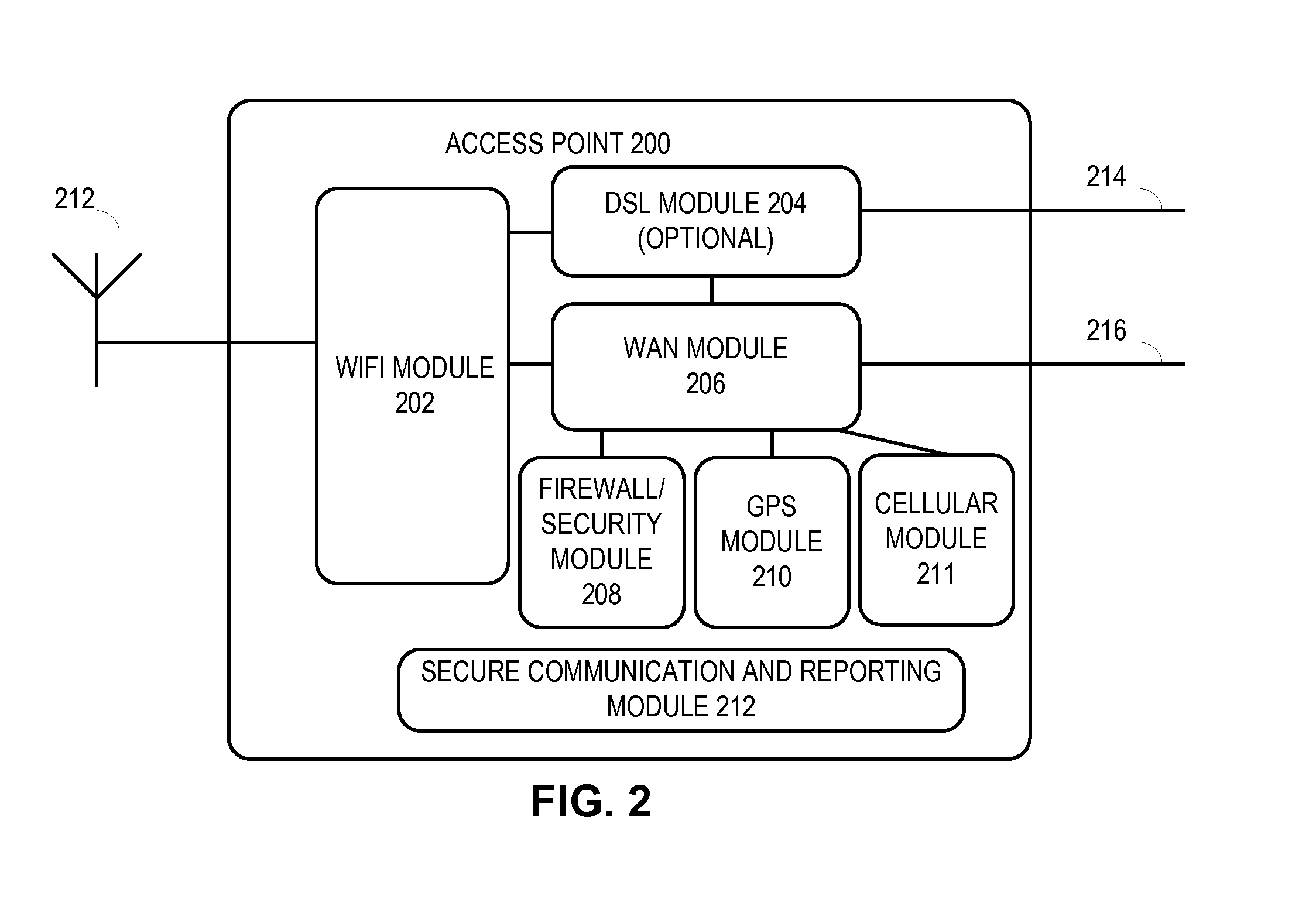
InactiveUS20150089595A1Convenient verificationPrecise positioningDigital data processing detailsMultiple digital computer combinationsSecure communicationIp address
One embodiment provides a system that facilitating location verification of a wireless access point and associated user devices. During operation, the access point establishes a secure communication channel with a location verification server. The access point then transmits to the location verification server an identifier of the access point, an external IP address of the access point, and location information for the access point via the secure communication channel. Next, the access point receives a packet from a user device, replaces the packet's source IP address with the access point's external IP address, and transmits the packet, thereby allowing the user device's physical location to be verified.
Owner:YAO SHUN +1
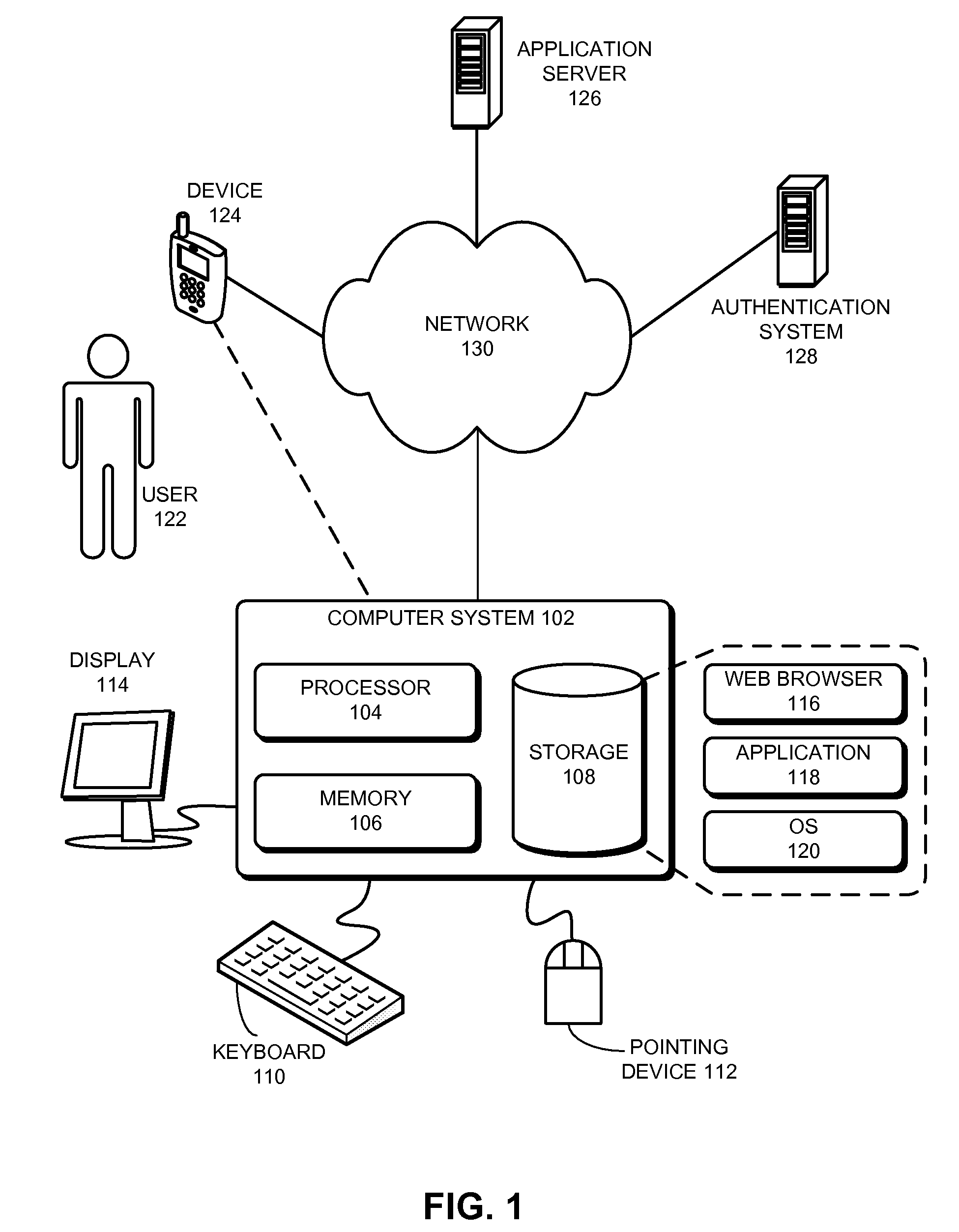
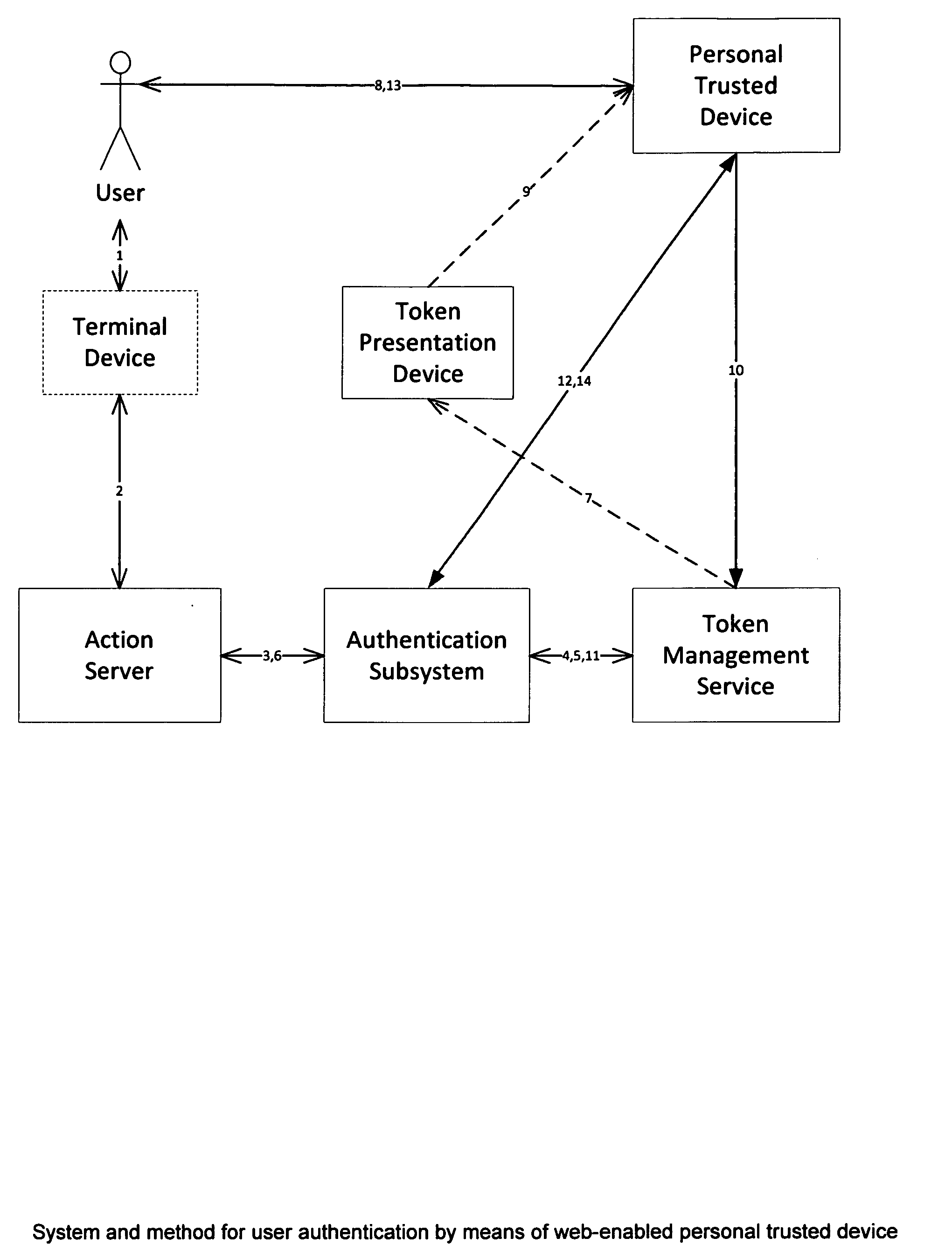
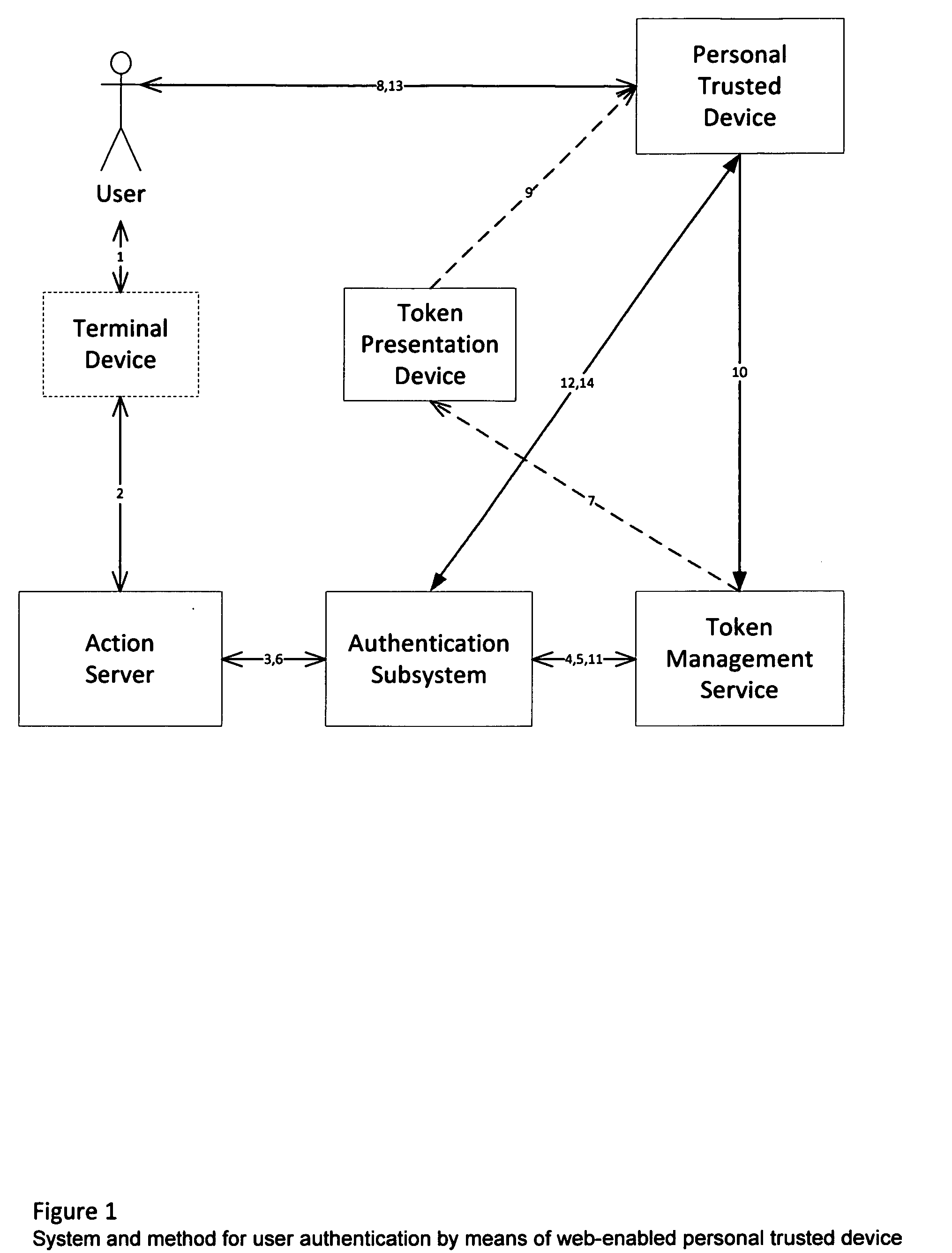
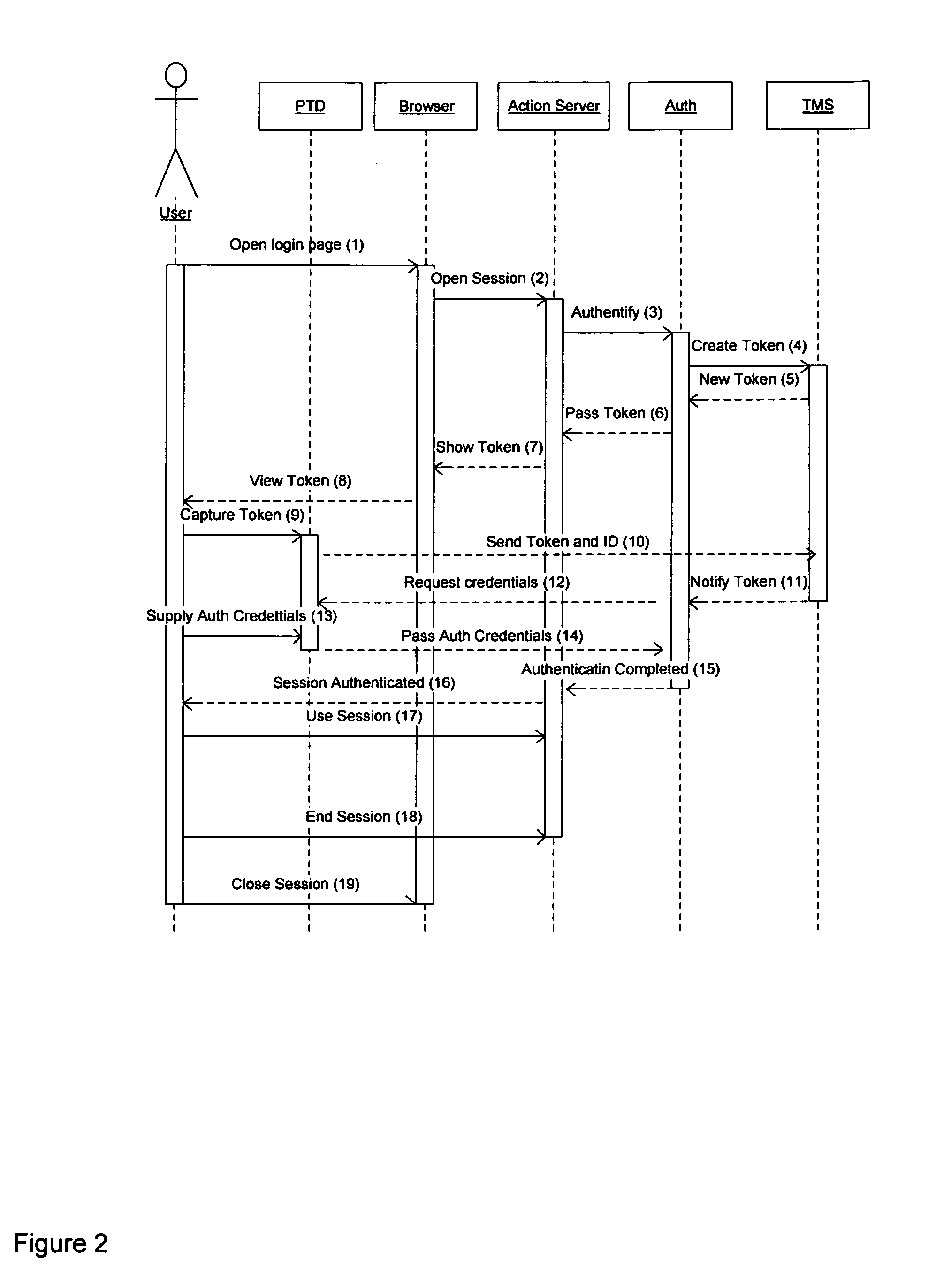
System and method for user authentication by means of web-enabled personal trusted device
InactiveUS20120192260A1Digital data processing detailsUser identity/authority verificationWeb applicationInternet privacy
A system of token-based user authentication for the purpose of authorizing user access to protected resources, such as web applications, computer systems or computer controlled devices. The system utilizes a personal trusted device (PTD), which is owned and operated by one specific user, to establish secure communication channels that are subsequently used to pass user credentials to authentication service. Association of a PTD with servers controlling access to resources is performed by publishing and capturing unique tokens via sensors embedded in PTD, such as an optical camera.
Owner:ADJOY INC
Method and arrangement for secure user authentication based on a biometric data detection device
InactiveUS20100049987A1Easy to carrySafe storageDigital data processing detailsUser identity/authority verificationBiometric dataComputer module
Owner:TELECOM ITALIA SPA
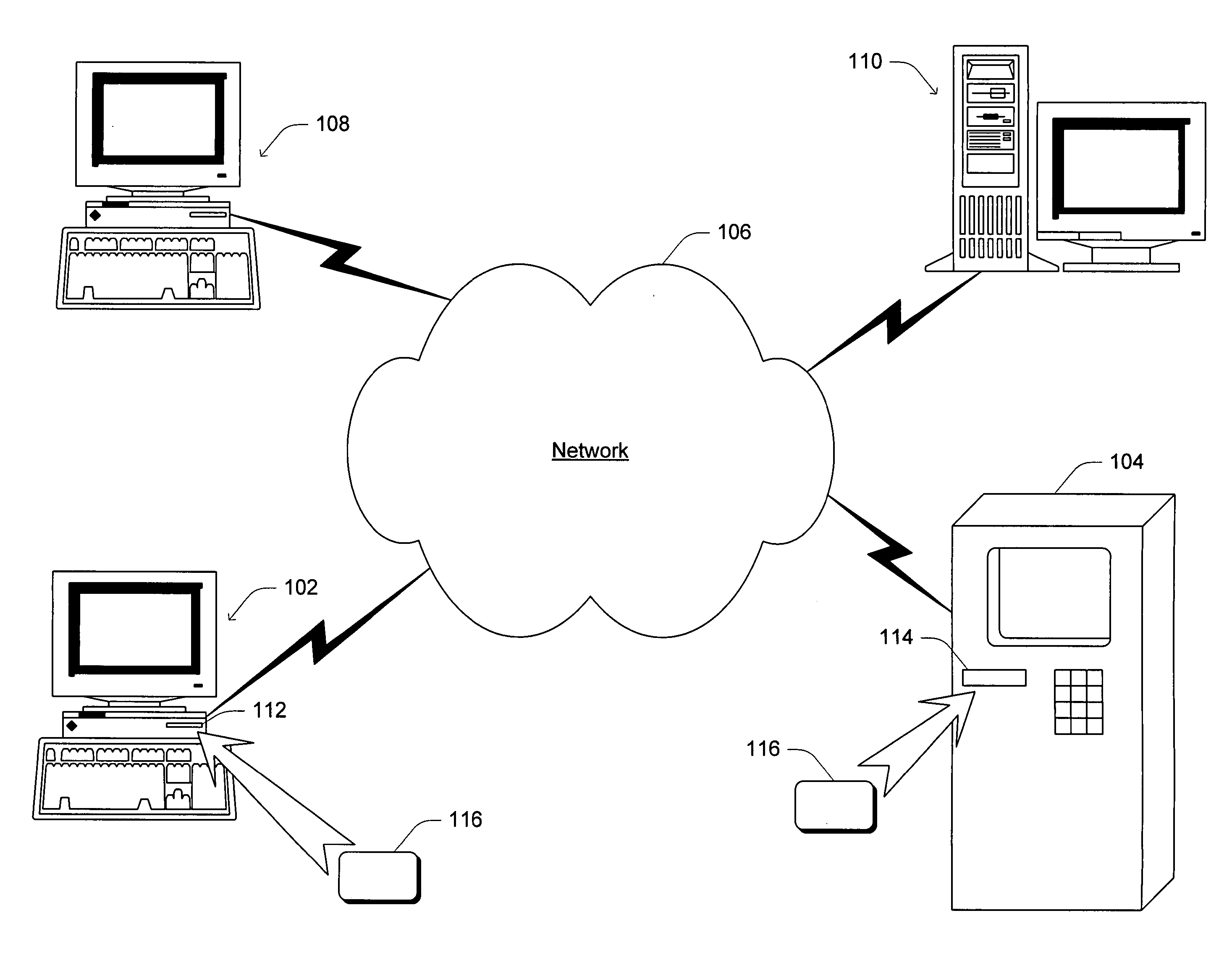
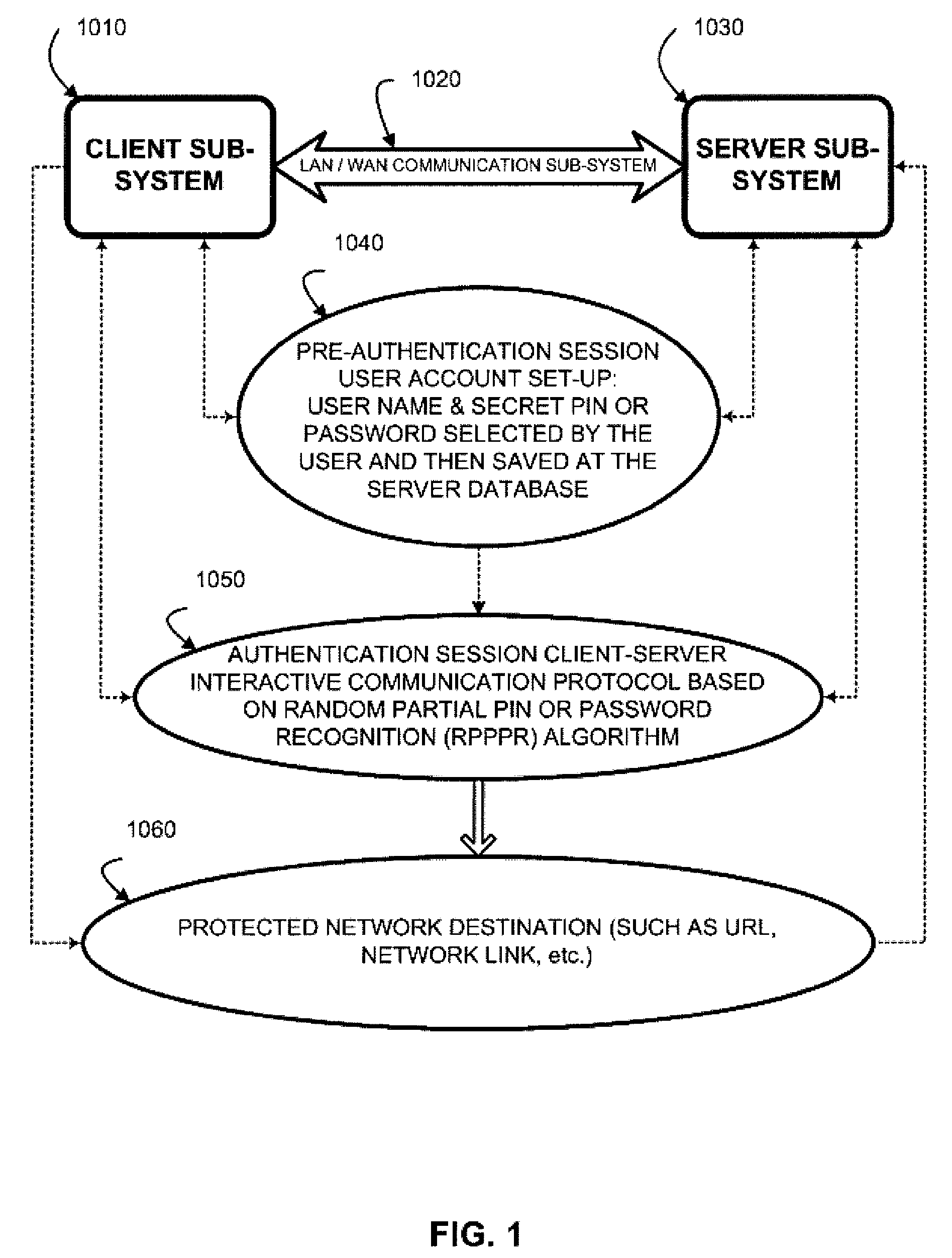
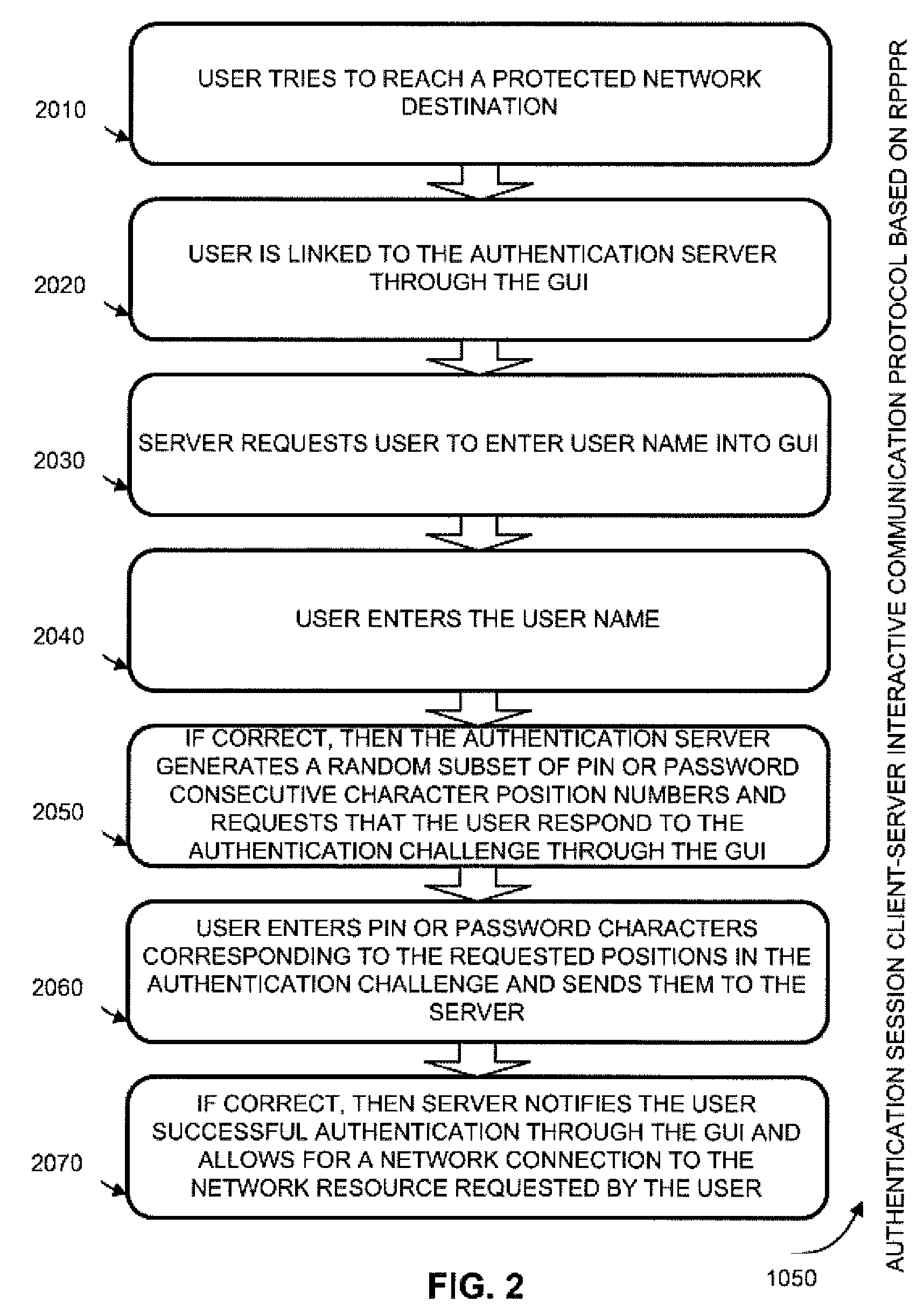
Two-channel challenge-response authentication method in random partial shared secret recognition system
ActiveUS8006300B2Digital data processing detailsUnauthorized memory use protectionClient-sideServer-side
Random partial shared secret recognition is combined with using more than one communication channel between server-side resources and two logical or physical client-side data processing machines. After a first security tier, a first communication channel is opened to a first data processing machine on the client side. The session proceeds by delivering an authentication challenge, identifying a random subset of an authentication credential, to a second data processing machine on the client side using a second communication channel. Next, the user enters an authentication response in the first data processing machine, based on a random subset of the authentication credential. The authentication response is returned to the server side on the first communication channel for matching. The authentication credential can be a one-session-only credential delivered to the user for one session, or a static credential used many times.
Owner:AUTHERNATIVE INC
WIFI authentication method
ActiveUS20050136892A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure authenticationTelematics
A system and method provides secure authentication of a wireless communication channel for a vehicle telematics device that includes detecting a wireless access point within radio range of a telematics device, requesting authentication information for the access point through a first secure communication channel to a call center, receiving authentication information for the wireless access point from the call center through the first secure communication channel, and providing authentication information for the telematics device to the wireless access point through a second secure communication channel. A computer readable medium storing a computer program is described for implementing one or more steps of the method.
Owner:GENERA MOTORS LLC
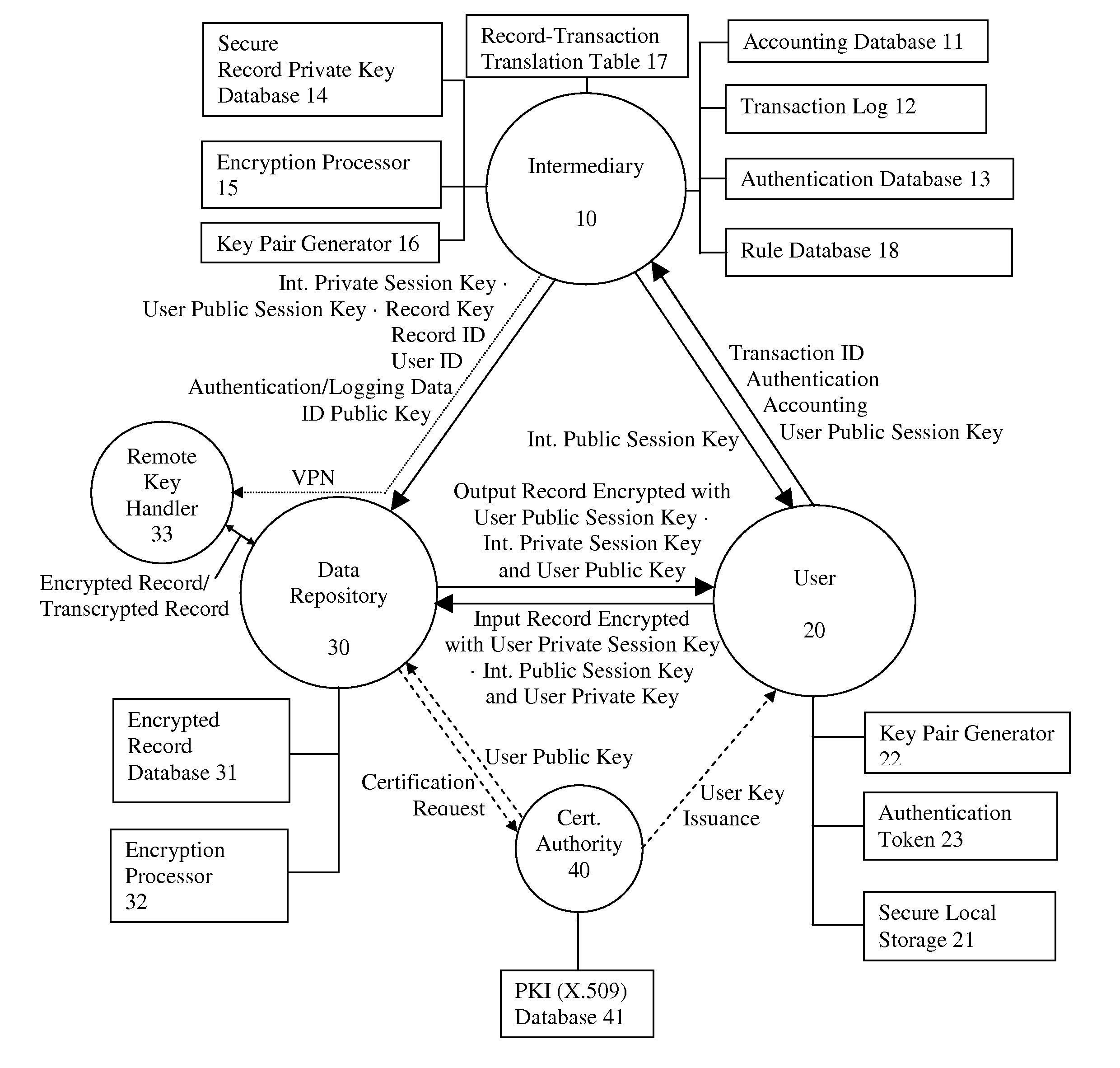
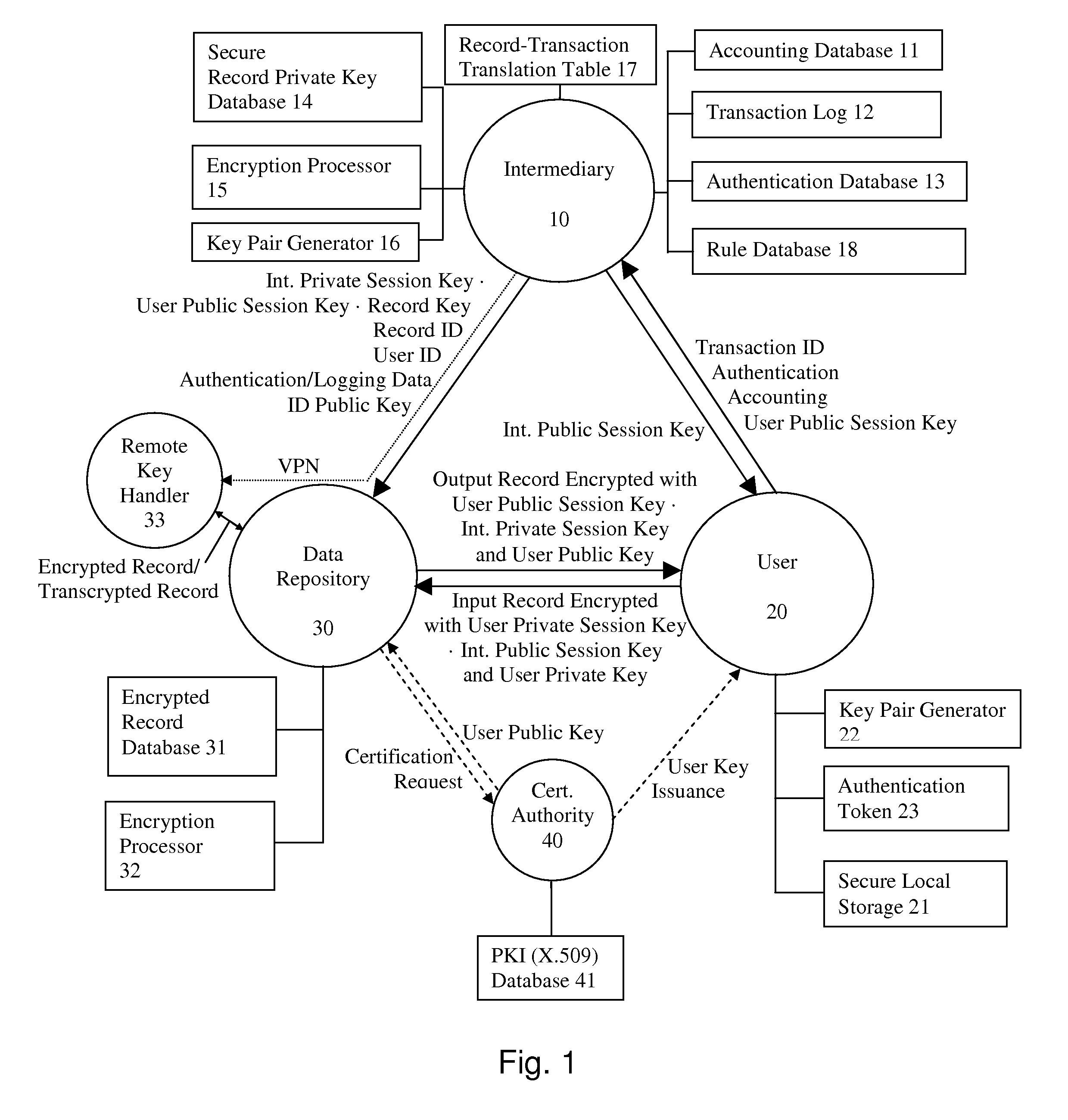
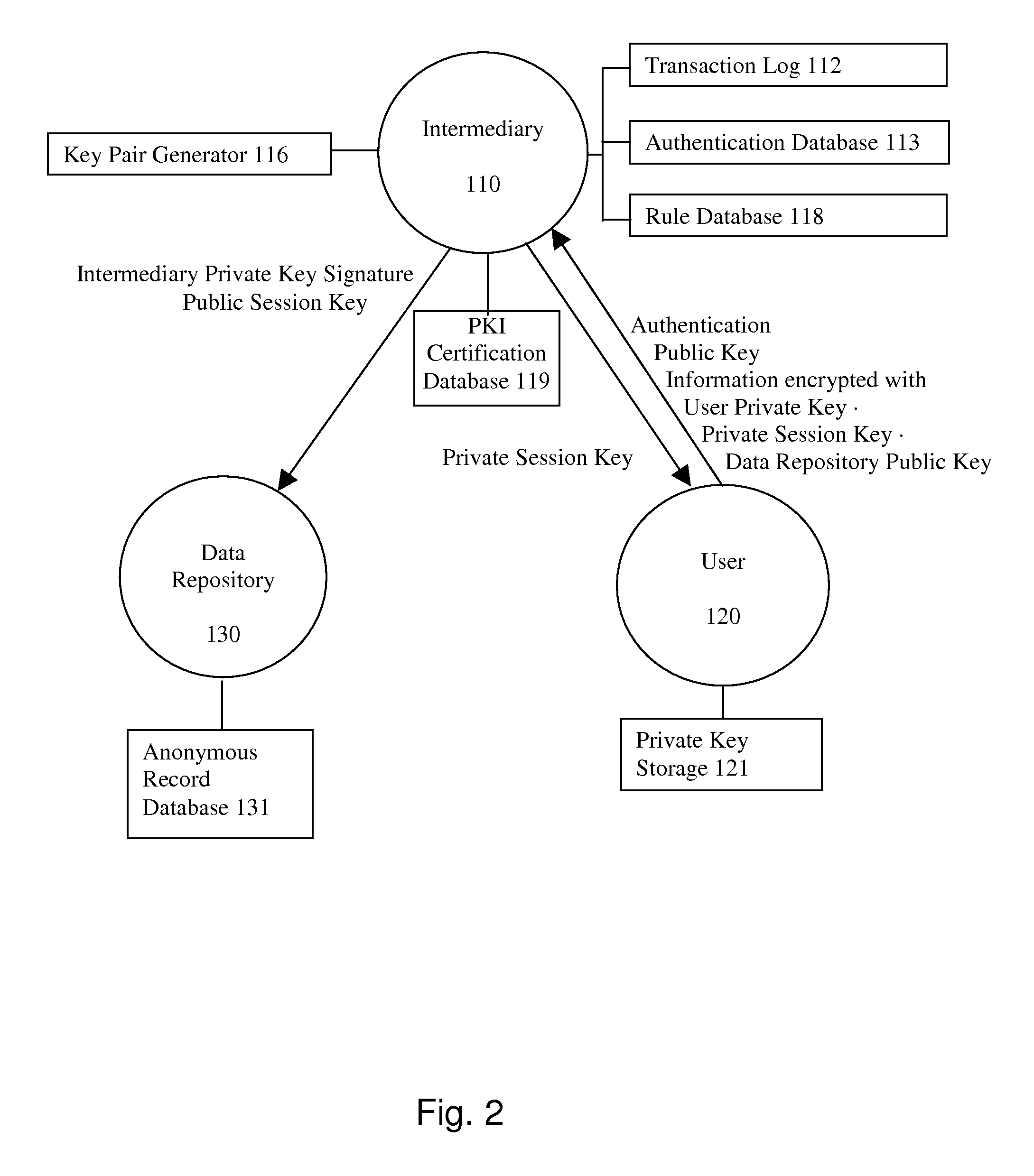
System and method for secure communications involving an intermediary
ActiveUS8566247B1Reduce liabilityReduce riskPublic key for secure communicationInformation retrieval from punched cardsSecure communicationKey exchange
A system and method for communicating information or a cryptographic key therefore between a first party and a second party, comprising the steps of receiving, by an intermediary, an identifier of desired information and accounting information for a transaction involving the information from the first party, transmitting an identifier of the first party to the second party, and negotiating, by the intermediary, a comprehension function for obscuring at least a portion of the information communicated between the first party and the second party. The data transmission may be made secure with respect to the intermediary by providing an asymmetric key or direct key exchange for encryption of the communication between the first and second party. The data transmission may be made secure with respect to the second party by maintaining the information in encrypted format at the second party, with the decryption key held only by the intermediary, and transmitting a secure composite of the decryption key and a new encryption key to the second party for transcoding of the data record, and providing the new decryption key to the first party, so that the information transmitted to the first party can be comprehended by it. According to the present invention, asymmetric key encryption may be employed to provide the establishment of secure communications channels involving an intermediary, without making the intermediary privy to the decryption key or the message.
Owner:RPX CORP
Method and system for secure data transmission
ActiveUS20170338951A1Reduce the amount requiredImprove securityKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationClient-side
One embodiment described herein provides a system and method for establishing a secure communication channel between a client and a server. During operation, the client generates a service request comprising a first dynamic message, transmits the first service request to the server, which authenticates the client based on the first dynamic message, and receives a second dynamic message from the server in response to the first dynamic message. The client authenticates the server based on the second dynamic message, and negotiates, via a quantum-key-distribution process, a secret key shared between the client and the server. The client and server then establish a secure communication channel based on at least a first portion of the secret key.
Owner:ALIBABA GRP HLDG LTD
TLS tunneling
InactiveUS7529933B2Reduce interceptionProtect normal transmissionUser identity/authority verificationSecret communicationSecure communicationWireless mesh network
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
Secure cache of web session information using web browser cookies
InactiveUS7197568B2Not be easily alteredDigital data information retrievalDigital data processing detailsWeb browserHash-based message authentication code
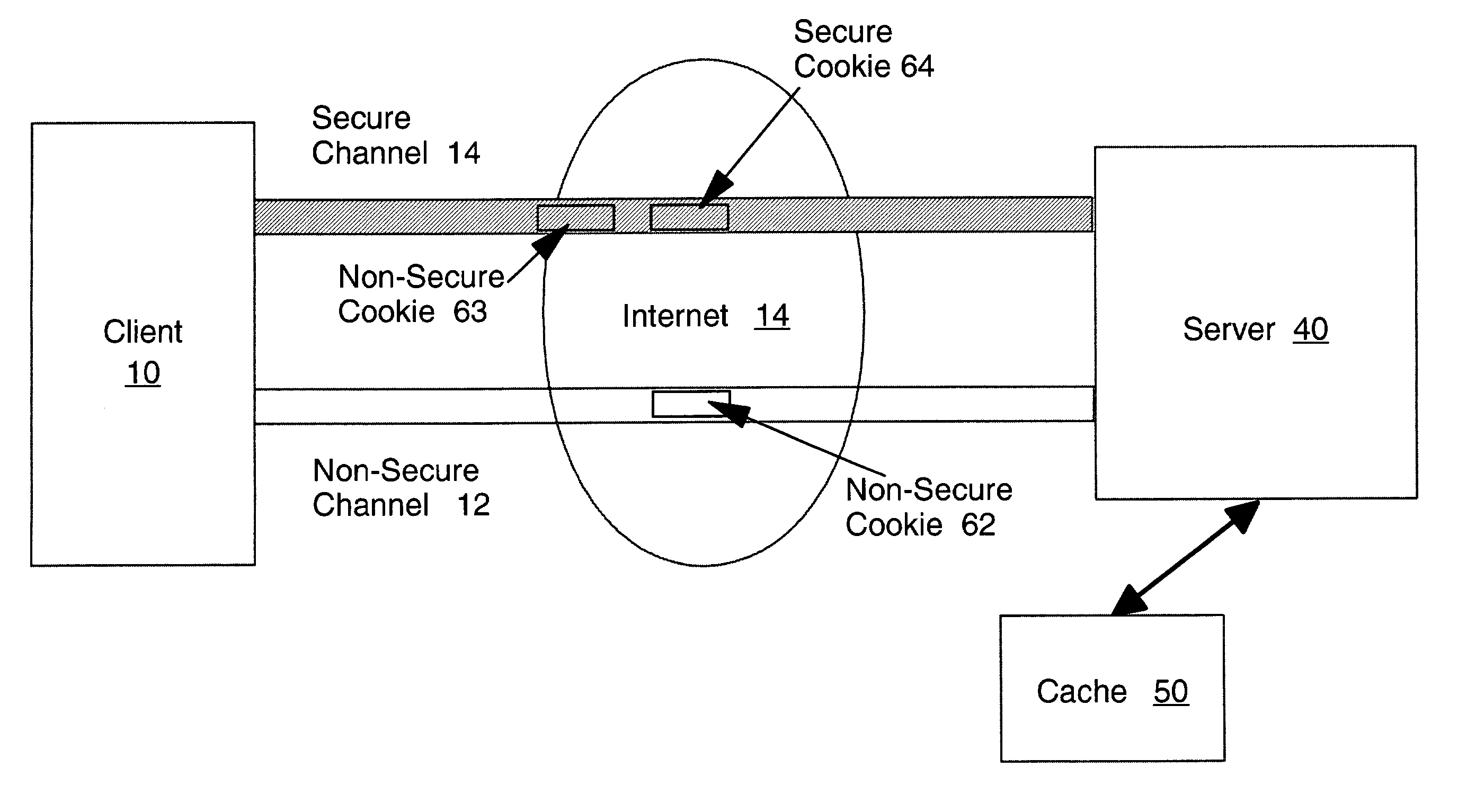
A secure method and system for accessing a cache for web session is provided using web browser cookies. The cache for the web session data uses an encoded identifier, determined using for example the Keyed-Hash Message Authentication Code, based on information identifying a client. The client communication is accompanied by a cookie (persistent state object) that also includes the identifier encoded in the same manner. This encoded identifier in the received cookie is used for accessing the cached data. Where a secure communication channel is available, such as a secure socket layer (SSL connection), a second cookie which is only transmitted over SSL is used as a signature for the first cookie.
Owner:IBM CORP
Apparatus and method for establishing secure communication channels in an internet of things (IOT) system
An apparatus and method are described for secure wireless communication. For example, one embodiment of an apparatus comprises: a first local wireless communication module to establish local wireless communication channels with a second local wireless communication module; a data structure managed by the first local wireless communication module, the data structure comprising a set of characteristics, each characteristic identified with an characteristic ID and having a value buffer associated therewith containing data associated with the characteristic; the first wireless communication module to form a first network socket using the data structure by defining a first characteristic for receiving data packets transmitted by the second local wireless communication module and a second characteristic for transmitting outgoing data packets to the second local wireless communication modules; wherein the incoming data packets are to be temporarily buffered in a first value buffer associated with the first characteristic and wherein the outgoing packets are to be temporarily buffered in a second value buffer associated with the second characteristic.
Owner:AFERO
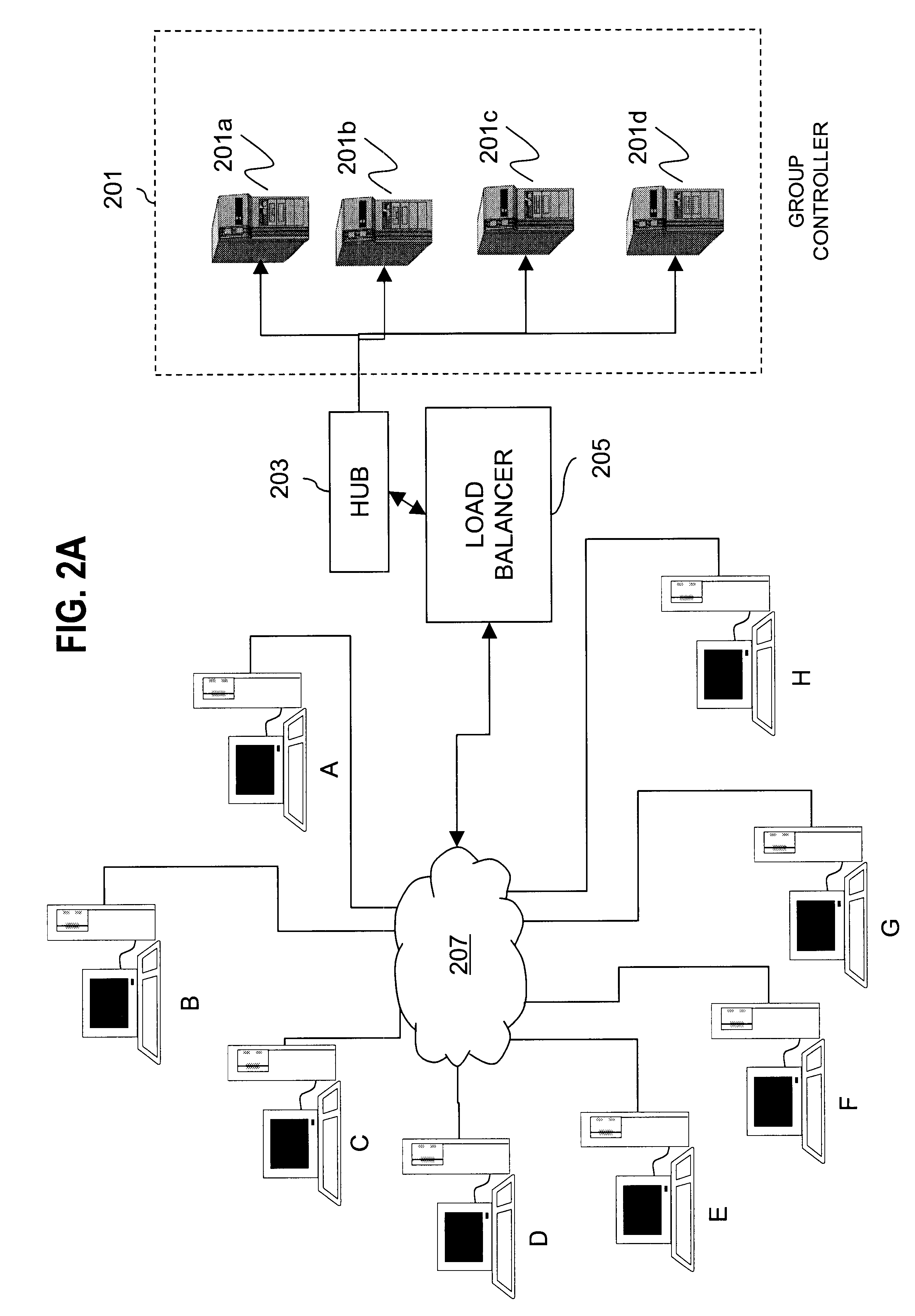
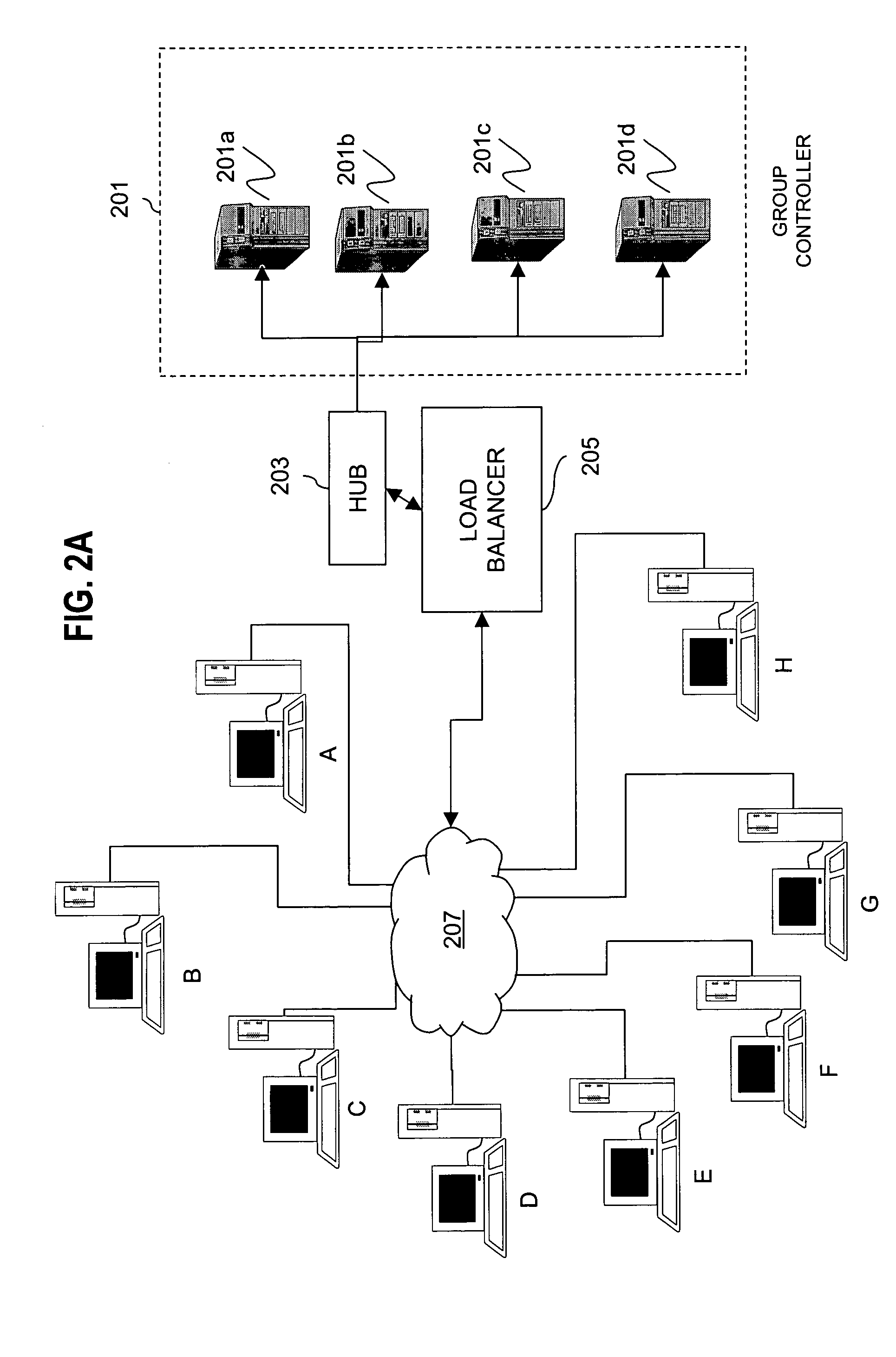
Method for overcoming the single point of failure of the central group controller in a binary tree group key exchange approach
InactiveUS7260716B1Improve scalabilityLess attentionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkStructure of Management Information
An approach for managing addition or deletion of nodes in a multicast or broadcast group, which avoids introducing a single point of failure at a group controller, certificate authority, or key distribution center, is disclosed. A central group controller utilizes a binary tree structure to generate and distribute session keys for the establishment of a secure multicast group among multiple user nodes. The central group controller is replicated in a plurality of other group controllers, interconnected in a network having a secure communication channel and connected to a load balancer. The secure communication channel is established using a public key exchange protocol. The load balancer distributes incoming join / leave requests to a master group controller. The master group controller processes the join or leave, generates a new group session key, and distributes the new group session key to all other group controller replicas. Each group controller is successively designated as master group controller in real time when a former master group controller crashes or relinquishes its master authority.
Owner:CISCO TECH INC
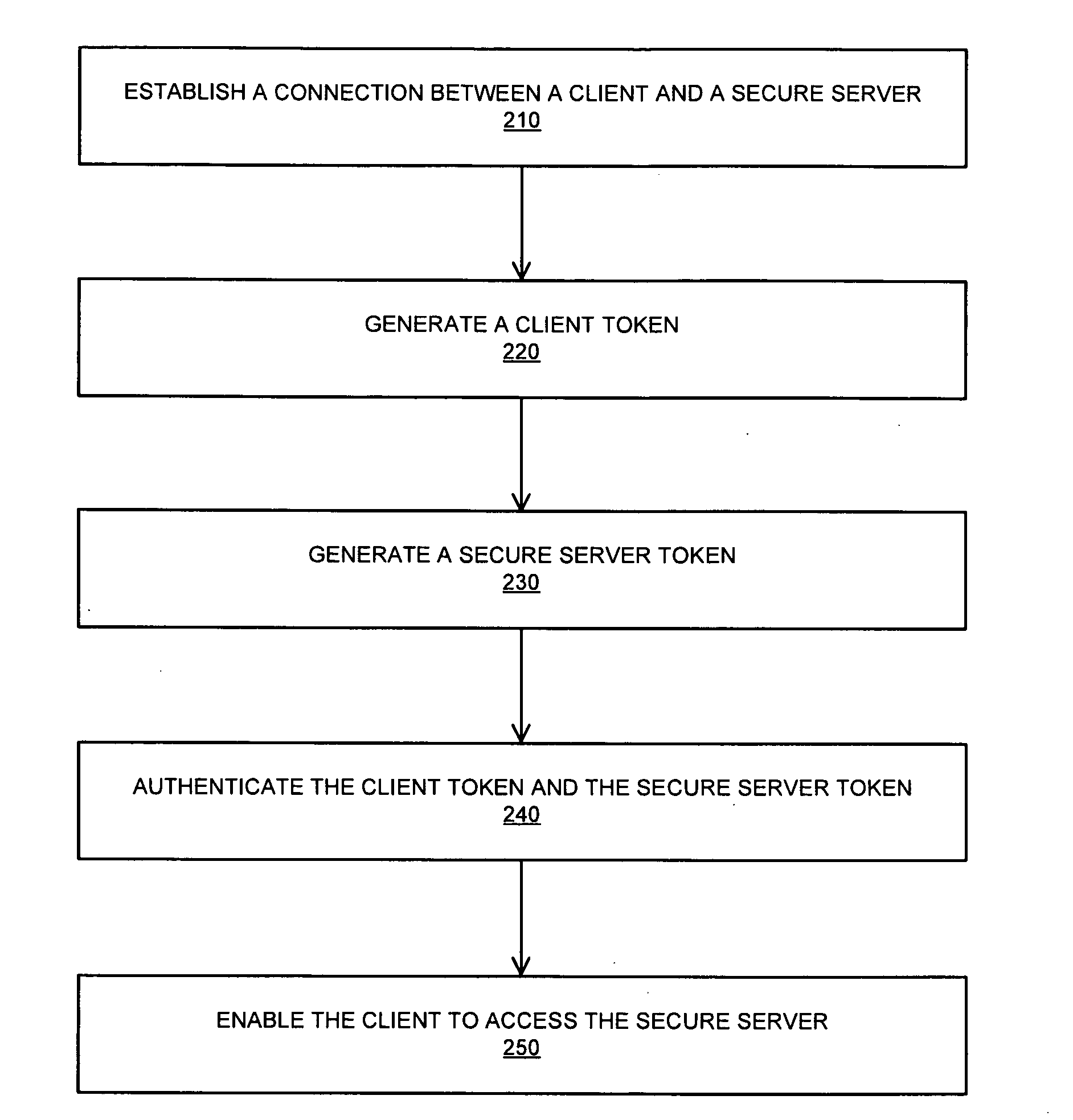
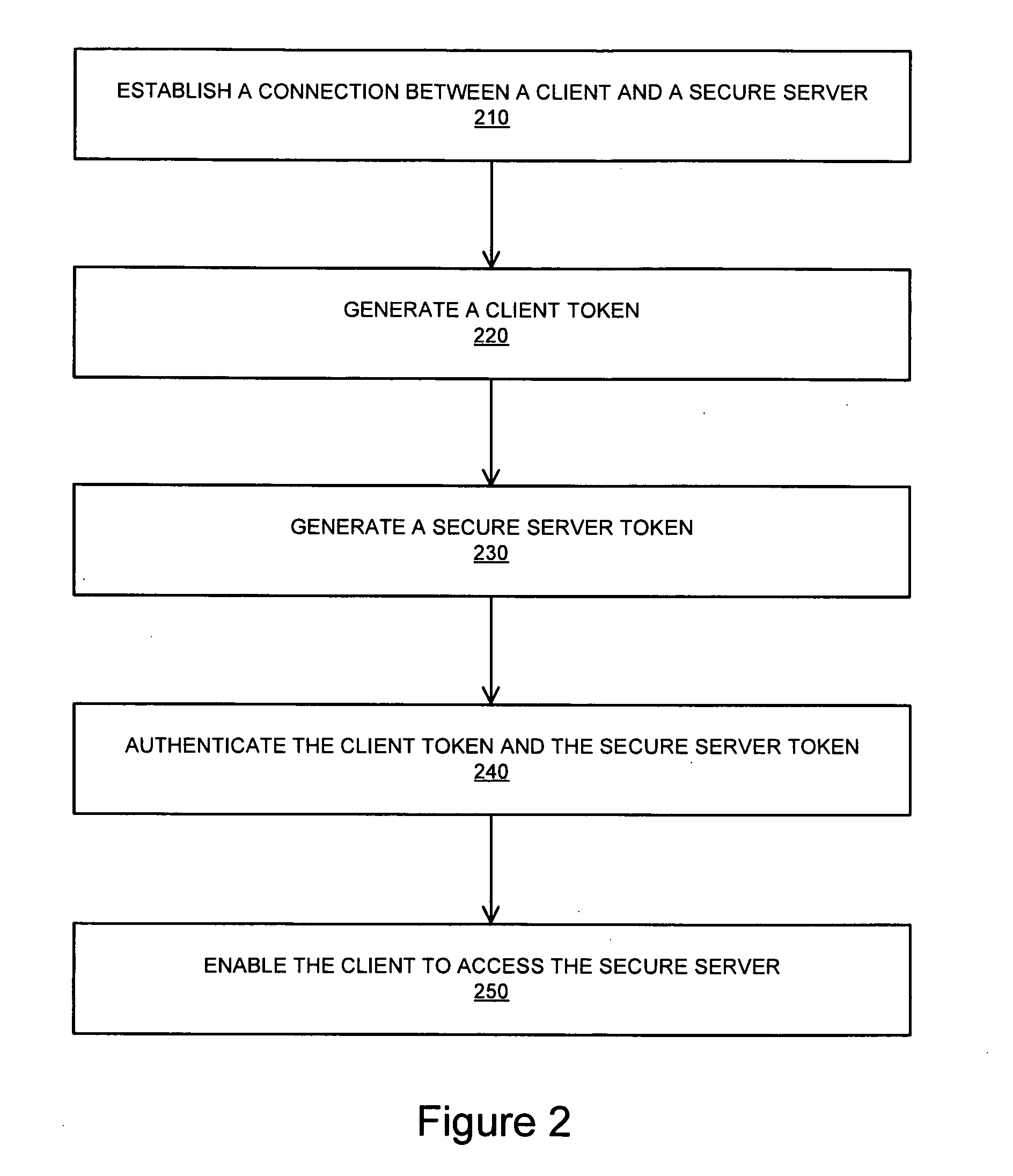
Systems and methods for establishing a secure communication channel using a browser component
InactiveUS20100318802A1Digital data processing detailsUser identity/authority verificationClient-sideSecure communication channel
A system for providing a secure channel for communication comprises a client comprising a browser, a secure server and a browser component installed on the client that enables a user to establish a connection with the secure server, the browser component configured to generate a first token. The secure server is configured to generate a second token, and wherein the client is provided with access to the secure server upon verification of the first token and the second token.
Owner:BALAKRISHNAN AJIT
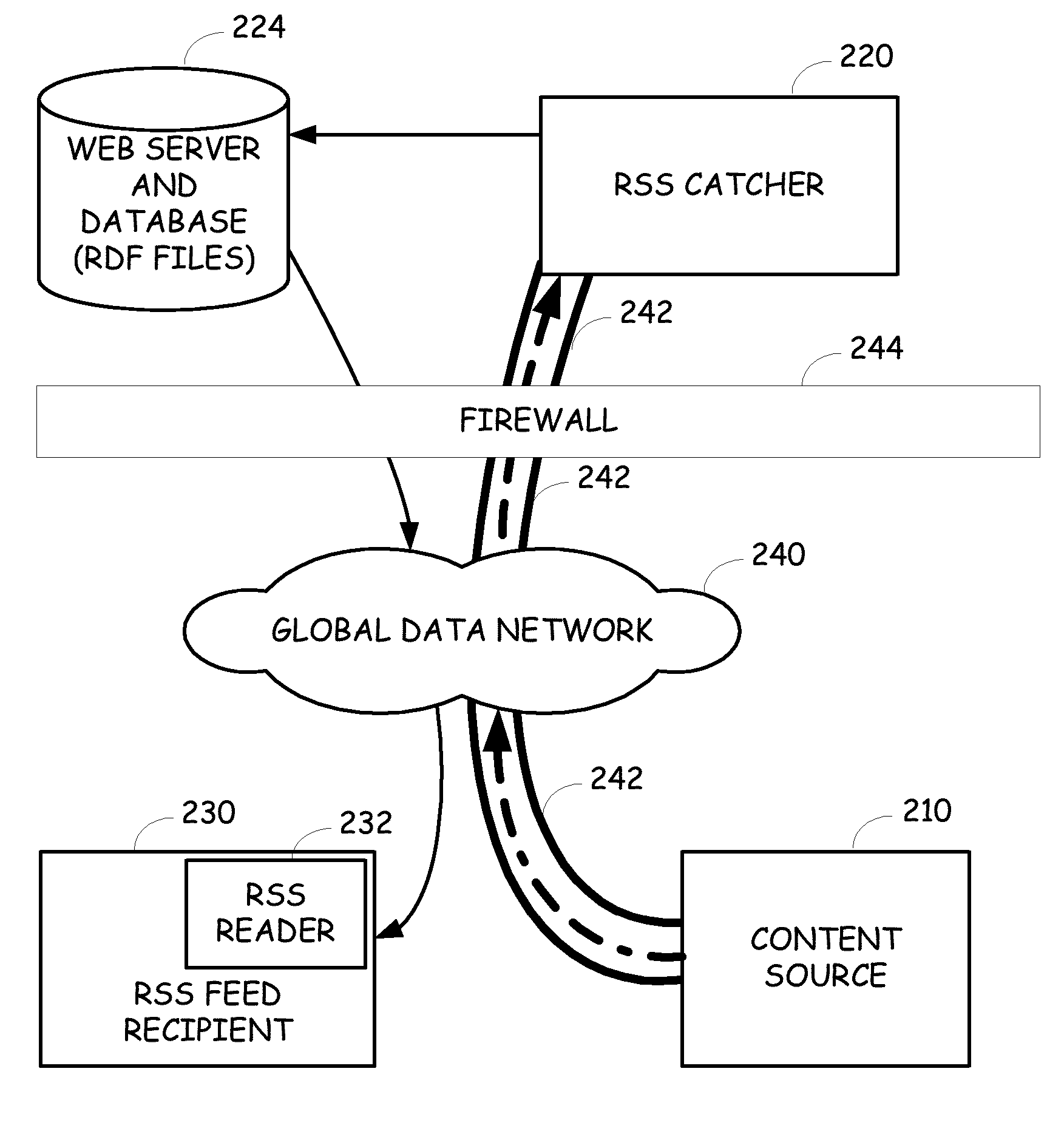
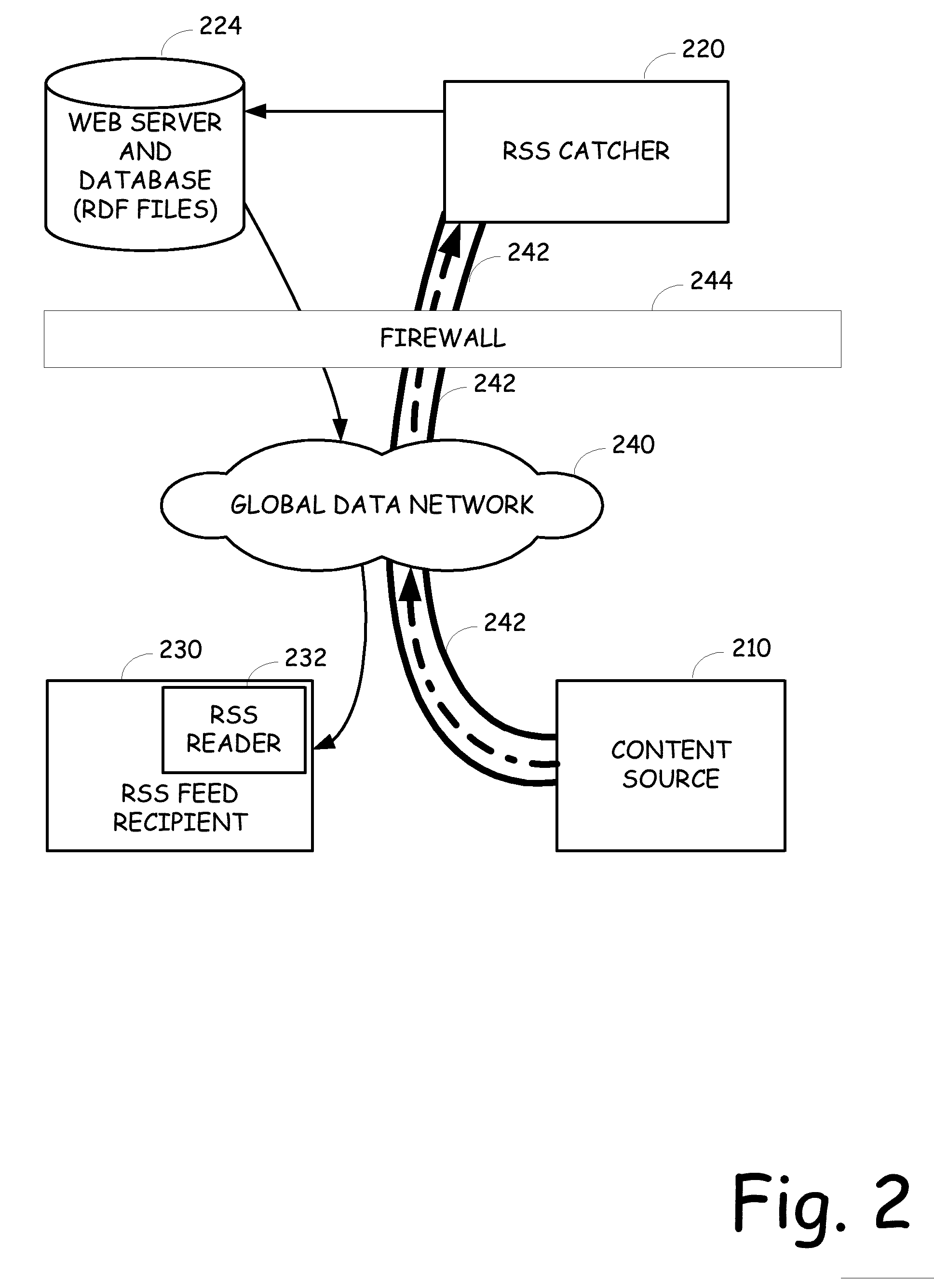
Provision of secure rss feeds using a secure rss catcher
InactiveUS20070094365A1Computer security arrangementsMultiple digital computer combinationsPersonalizationInternet privacy
A device that resides behind a firewall and receives content to be further directed towards one or more users, such as high-volume emails. The device captures the incoming content that is delivered over a secure communication channel from an external content source and creates personalized RDF or XML files for the intended recipients. The URLs associated with the files include a unique code that is generated using at least a portion of the addressing information or other parameters of the message. An RSS reader can then be employed to read the content from the RDF or XML file.
Owner:ACOUSTIC LP
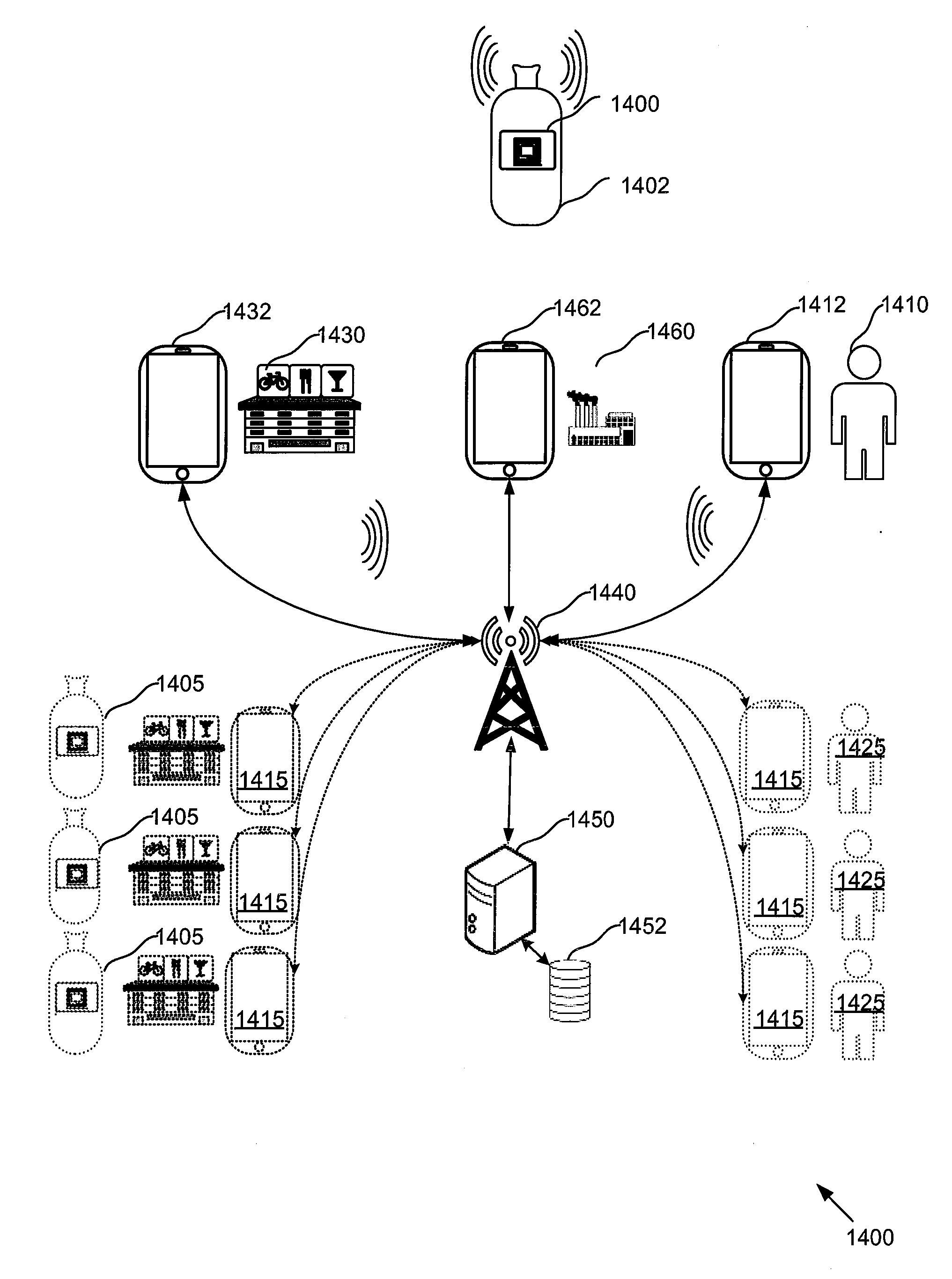
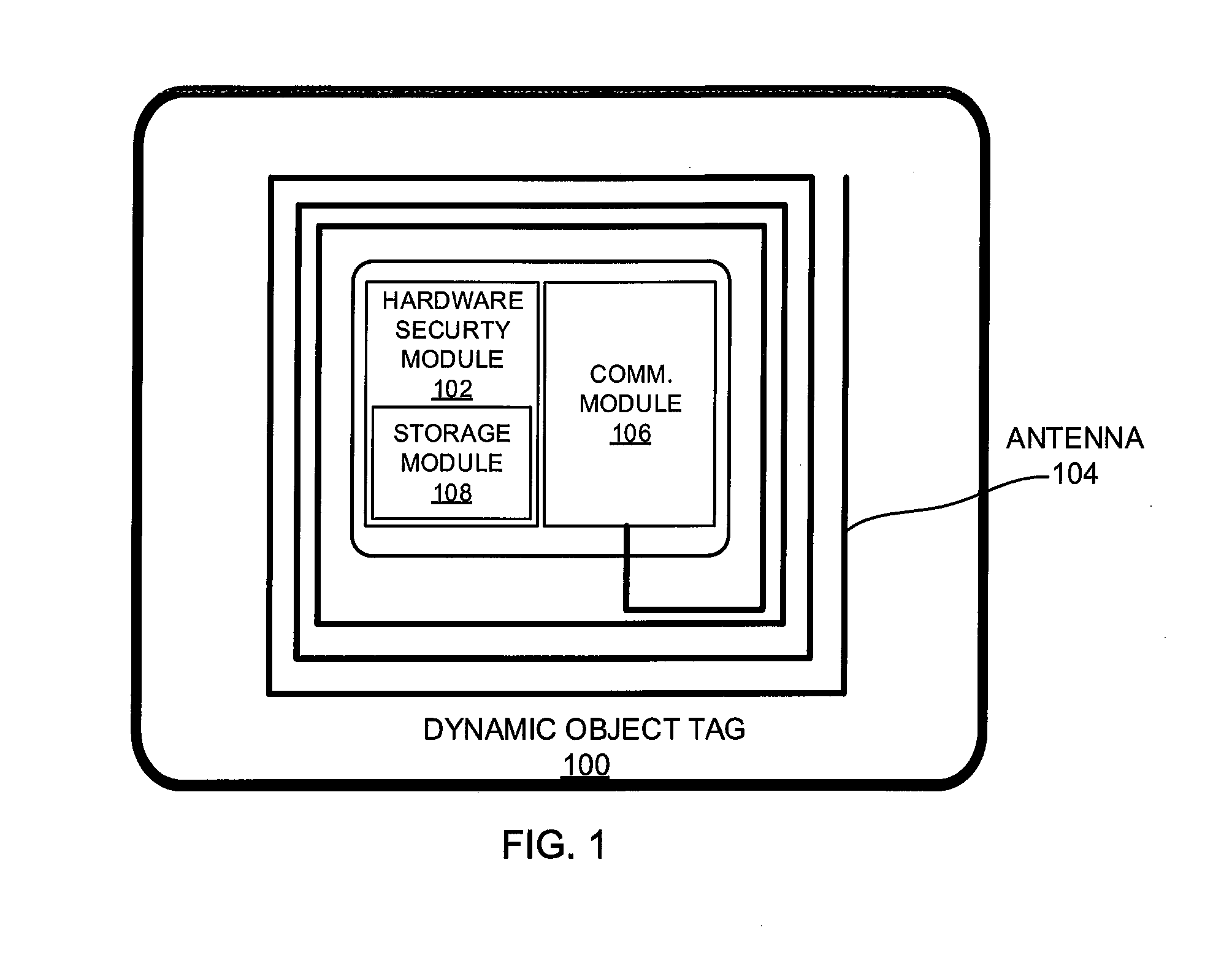
Dynamic object tag and systems and methods relating thereto
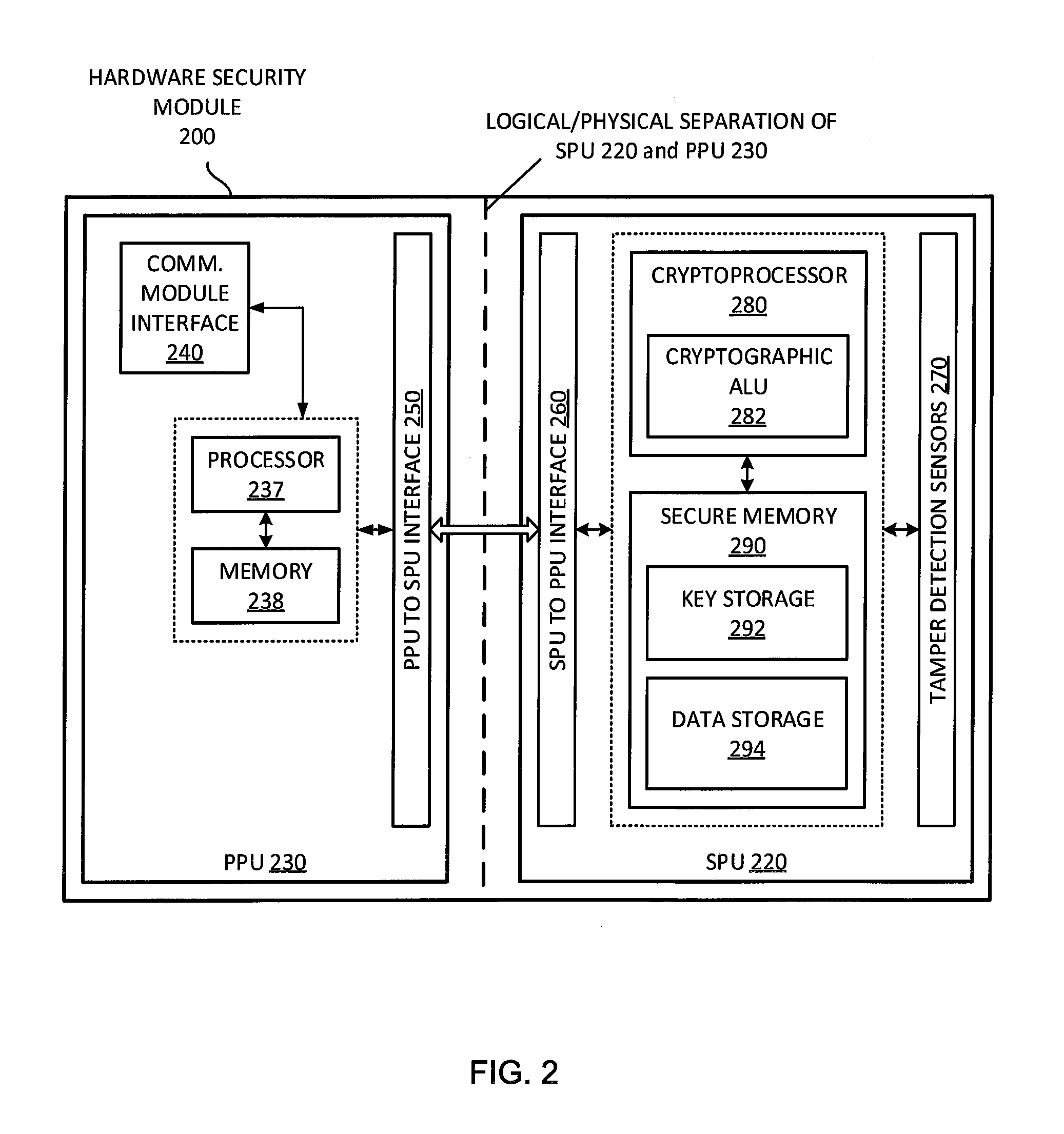
ActiveUS20150254677A1Cryptography processingDigital data processing detailsHardware security moduleSecure communication channel
A dynamic object tag for a product and systems and methods relating thereto is disclosed. The dynamic object tag comprises a hardware security module, including an electronic storage module, and a communication module for communicating with an interrogation device. The hardware security module is adapted to establish a secure communication channel with the interrogation device, to exchange dynamic authentication parameters with the interrogation device, and to communicate product information stored on the electronic storage module to the interrogation device over the secure communication channel.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com