Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
157 results about "Encryption software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Encryption software is software that uses cryptography to prevent unauthorized access to digital information. Cryptography is used to protect digital information on computers as well as the digital information that is sent to other computers over the Internet.
Protection of software against use without permit
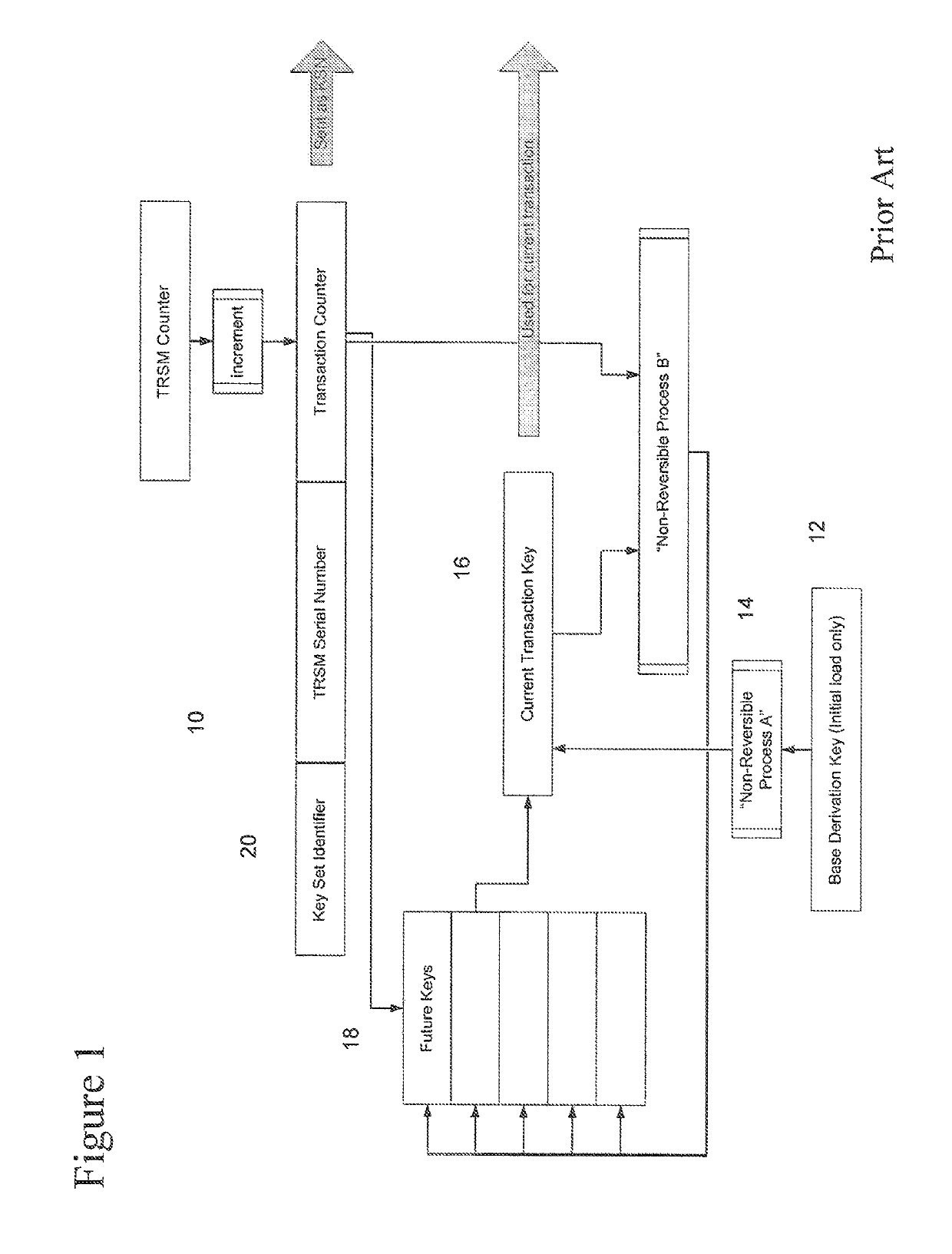
InactiveUS6266416B1Prevent illegal useKey distribution for secure communicationDigital data processing detailsComputer hardwareApplication program software
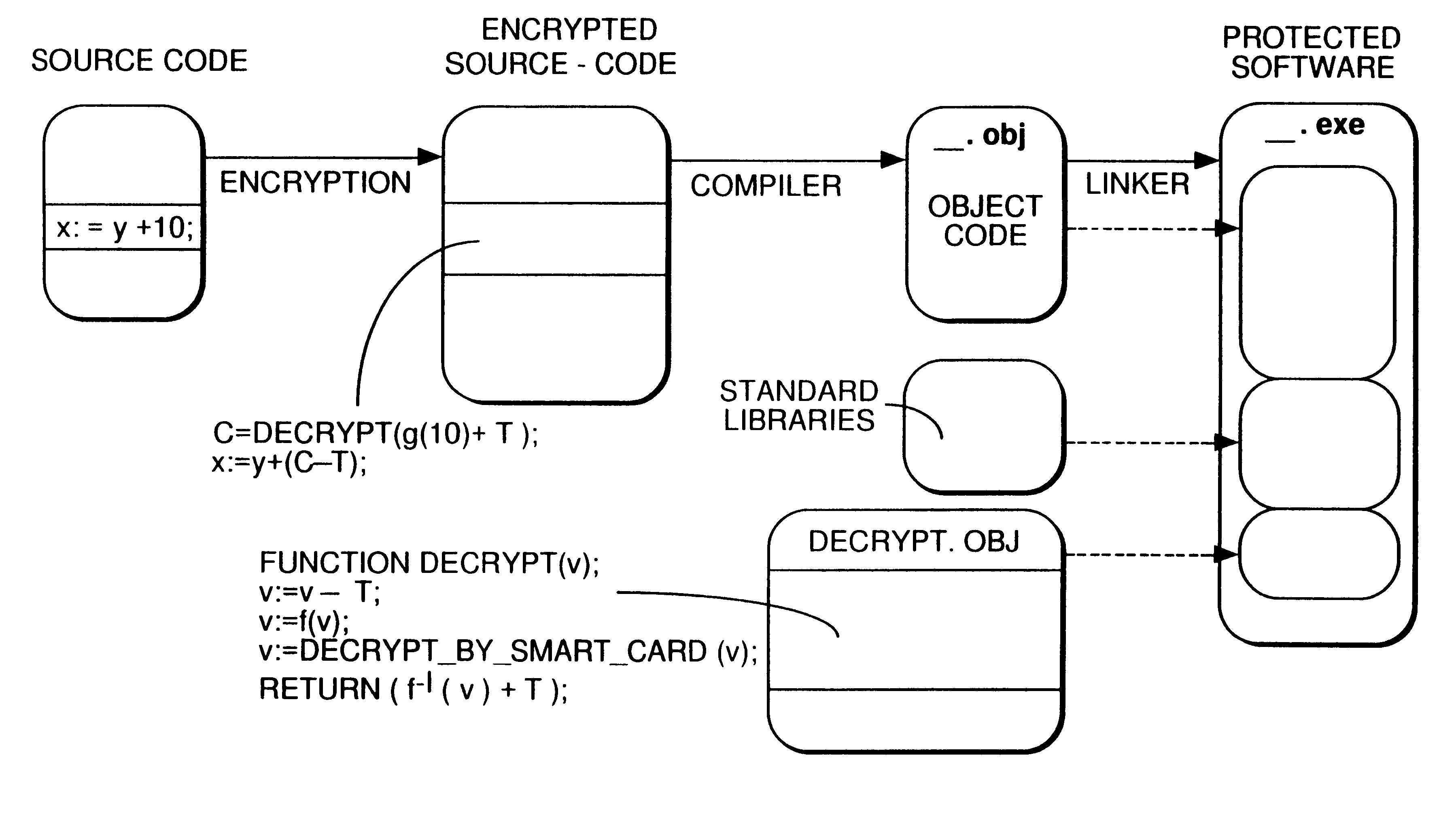
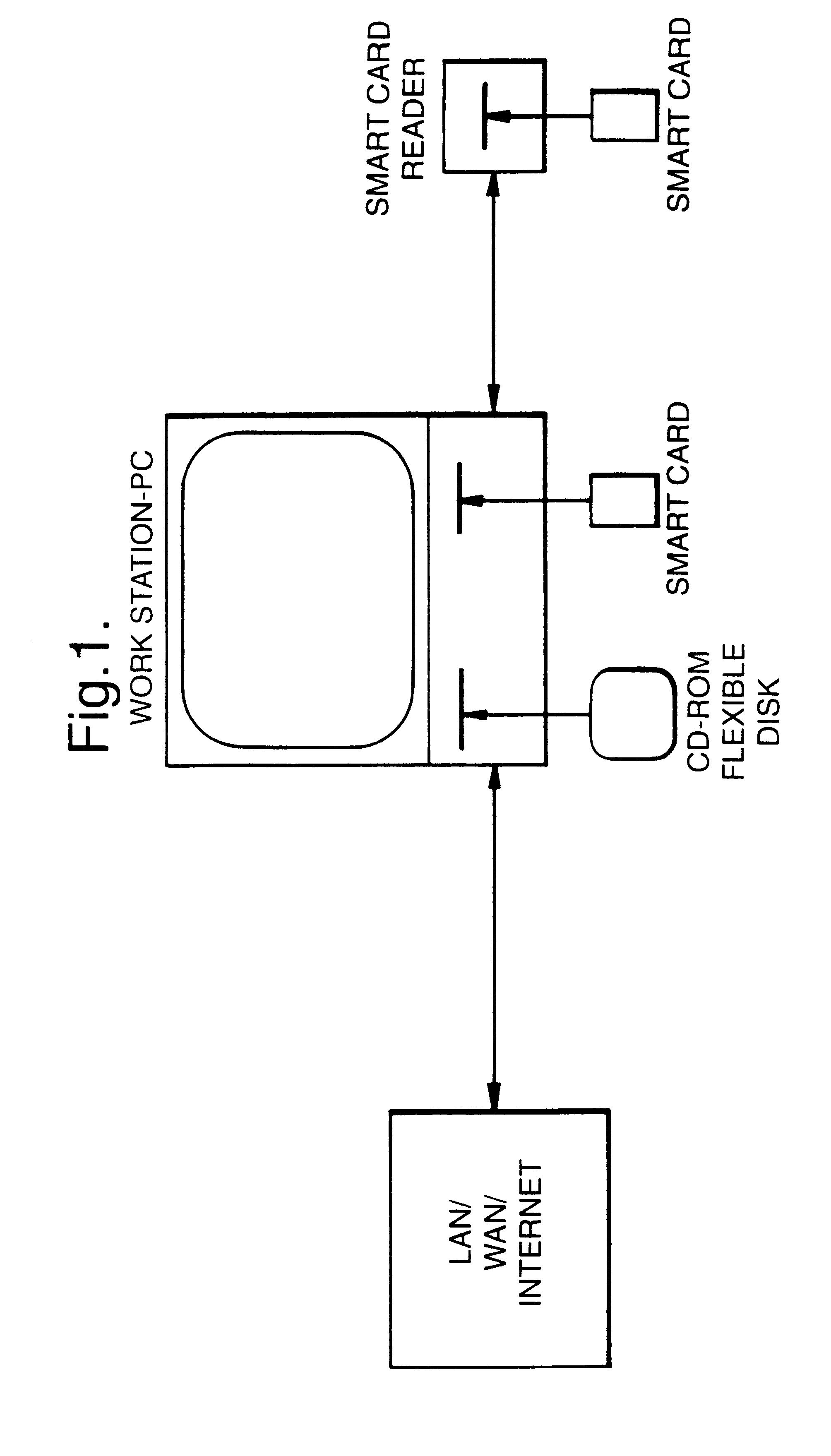
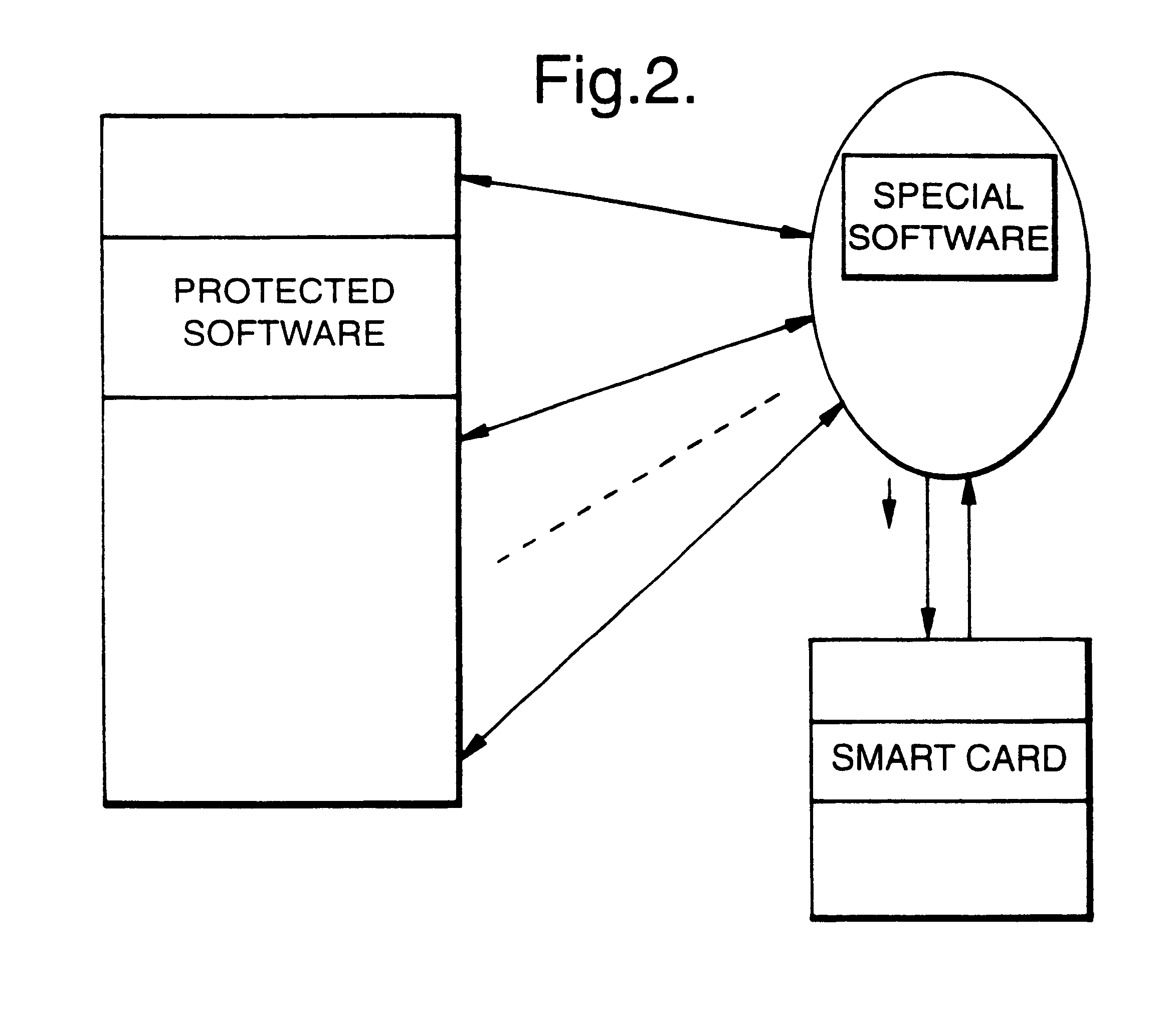
An arrangement to protect software, particularly freely distributed application software, against utilization without permission of the copyright holder. By encrypting the software employing a key (k1) which is different from that key (k2) which is employed in the decryption, better protection is obtained against unauthorized utilization when the decryption key is kept secret to the user. Further improved security is achieved by additionally executing scrambling-descrambling of the communication between the computer in which the software is utilized and the external unit in which the decryption key is stored. Also, the external unit is arranged such that it returns to the host computer, the result from its processing of data received from the host, the result then being utilized in the further execution of the respective program.
Owner:SOSPITA
Secure internet applications with mobile code
InactiveUS6907530B2Easy accessUser identity/authority verificationUnauthorized memory use protectionThe InternetMobile code
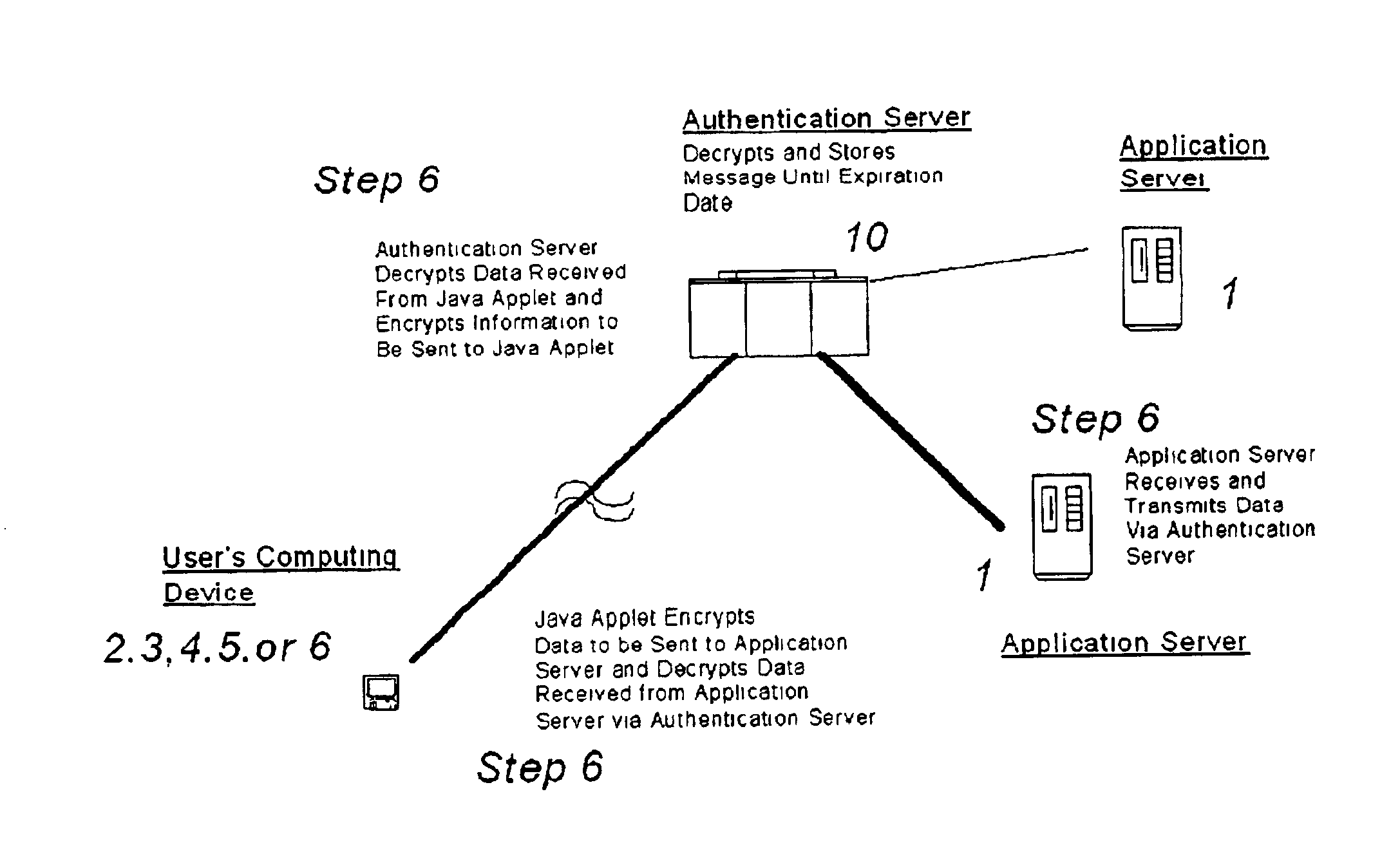
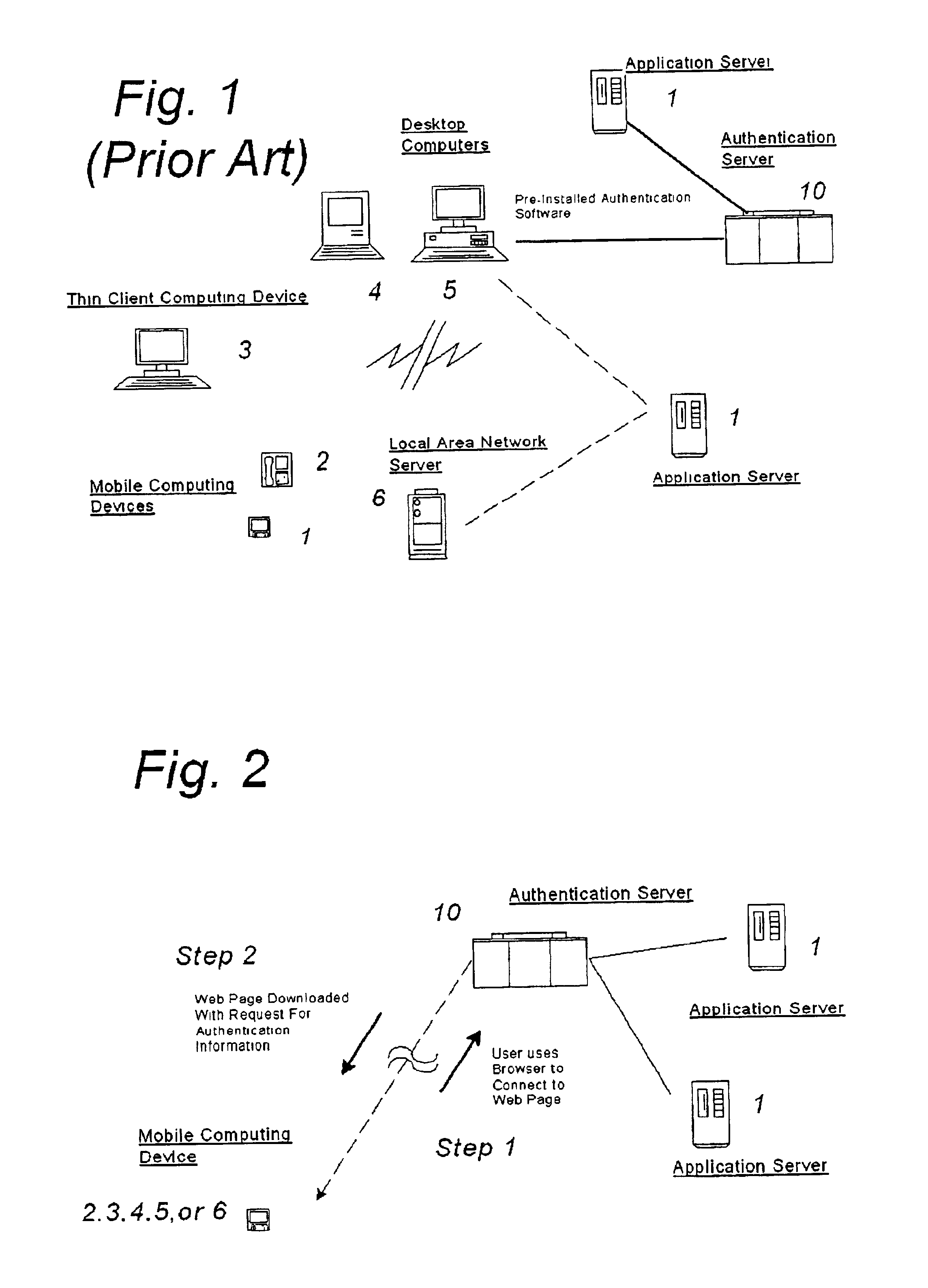
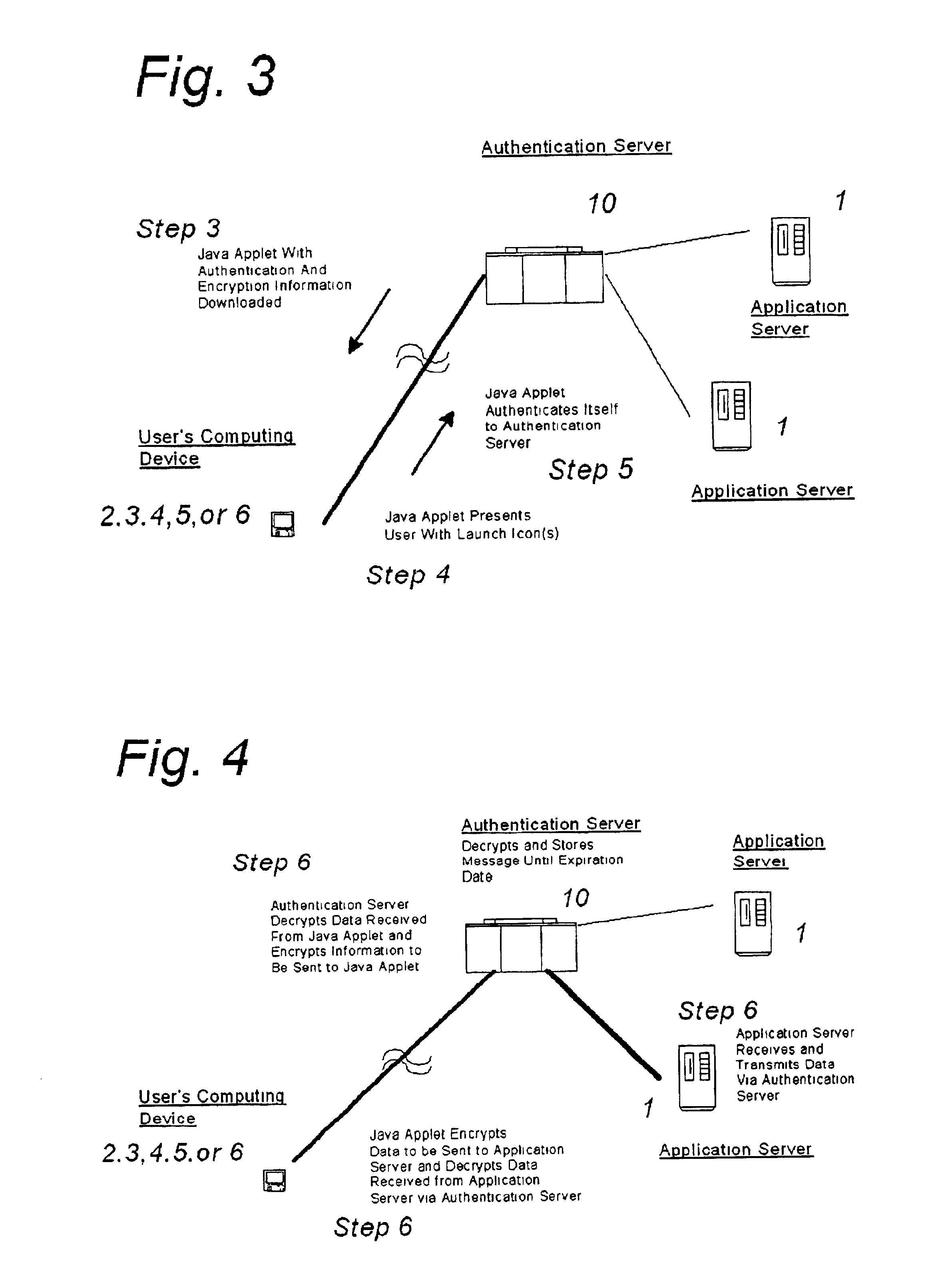
A system and method for securing pathways to a remote application server involves a gateway or authentication server, and a mobile code authentication and encryption client available for download from the gateway or authentication server. Upon connection of a user's computing device to the authentication server over the open network, the authentication server requests authentication information, such as a password, from the user, and upon authentication of the user by the authentication server, the authentication server downloads the mobile code authentication and encryption client to the user's computing device. The authentication and encryption client then authenticates itself to authentication server, after which a secure communications channel between the user's computing device and the authentication server is opened, the secure communications channel permitting transfer of data between the user's computing device and an application server. The system and method do not require pre-installation or any certificates or other authentication and encryption software on the user's computing device, enabling the system and method to be used with thin-client and mobile computing devices, as well as with conventional computers.
Owner:SSL SERVICES
System and method for providing customized secure access to shared documents
InactiveUS7299502B2Key distribution for secure communicationDigital data processing detailsDigital signatureClient-side
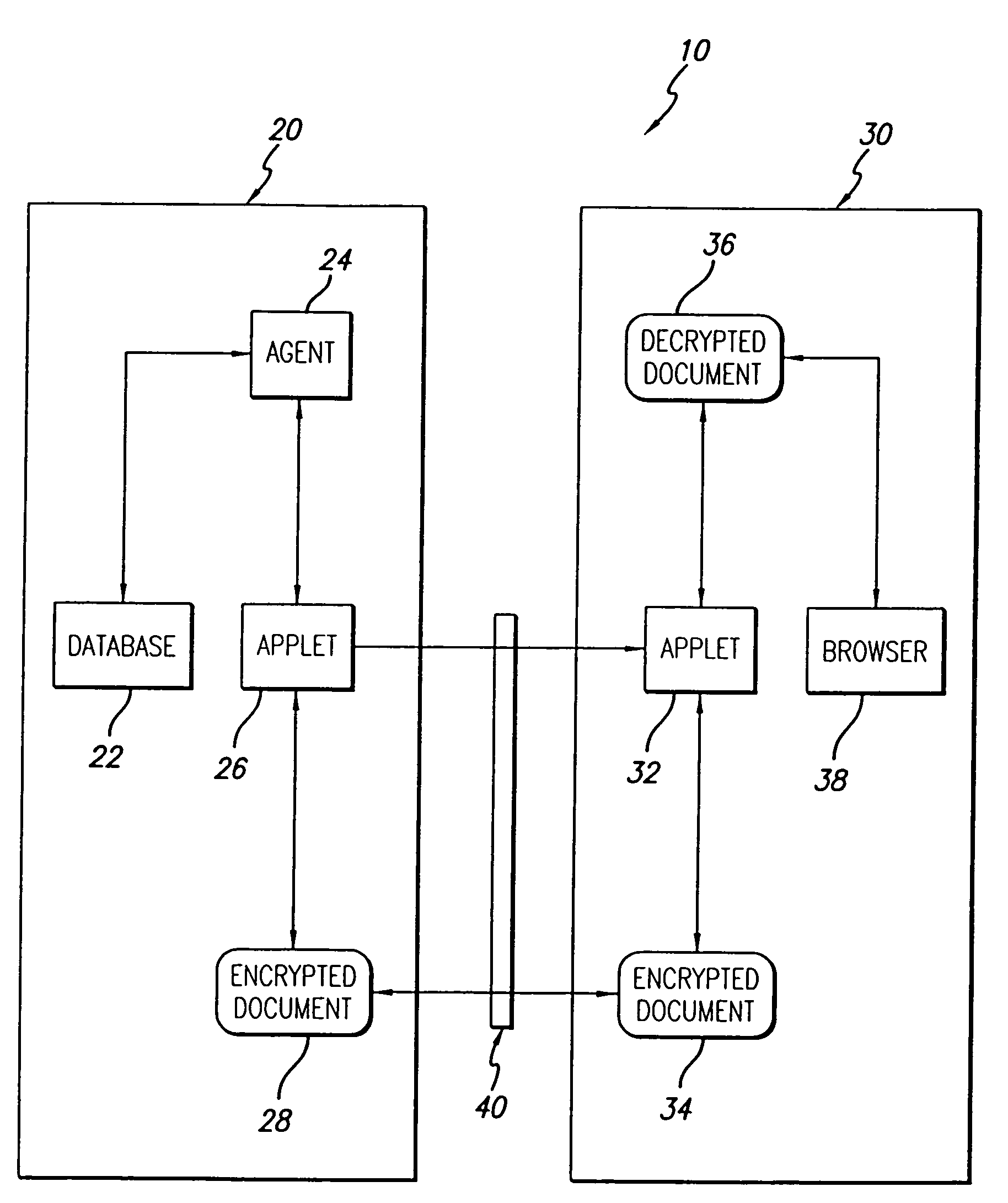
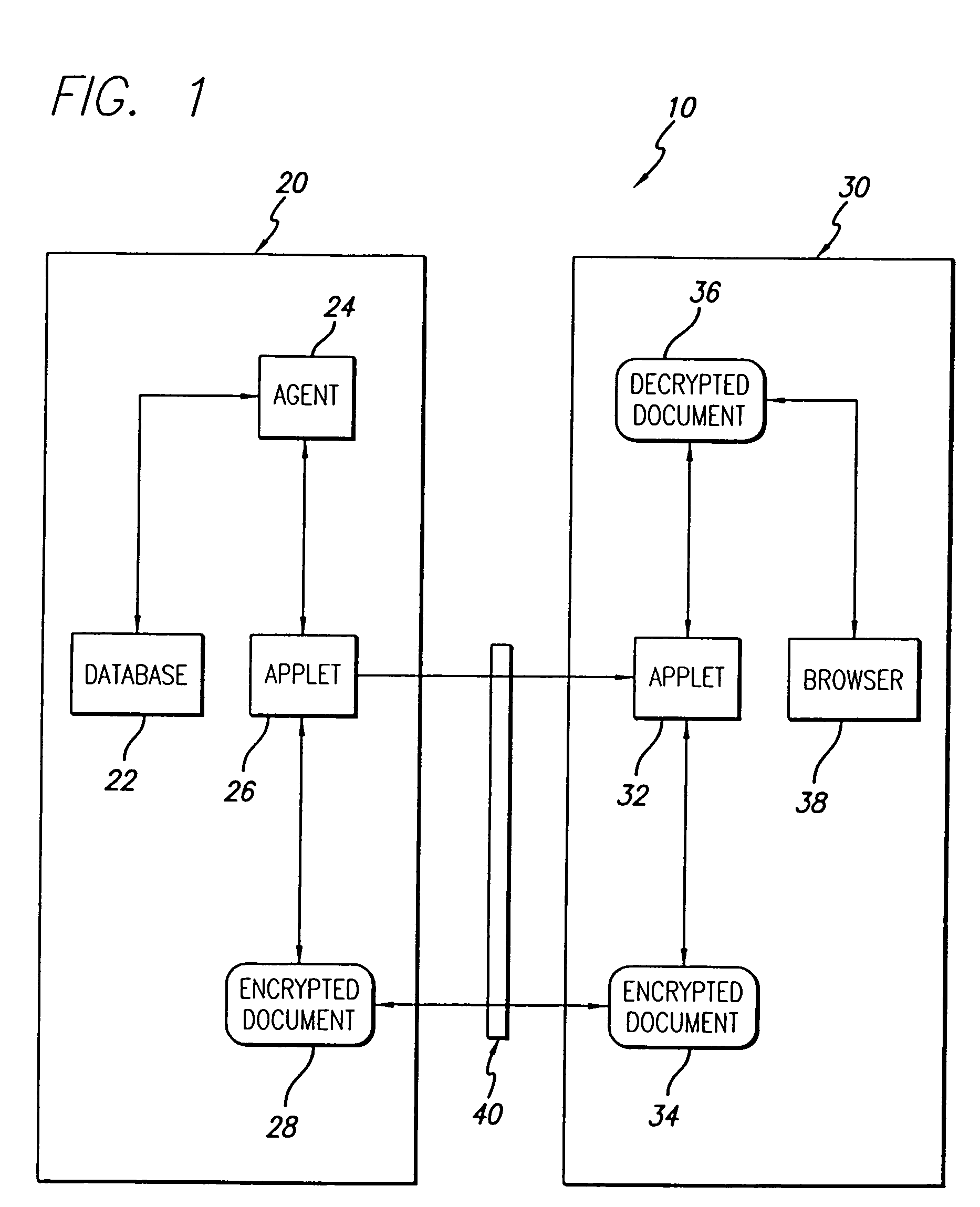
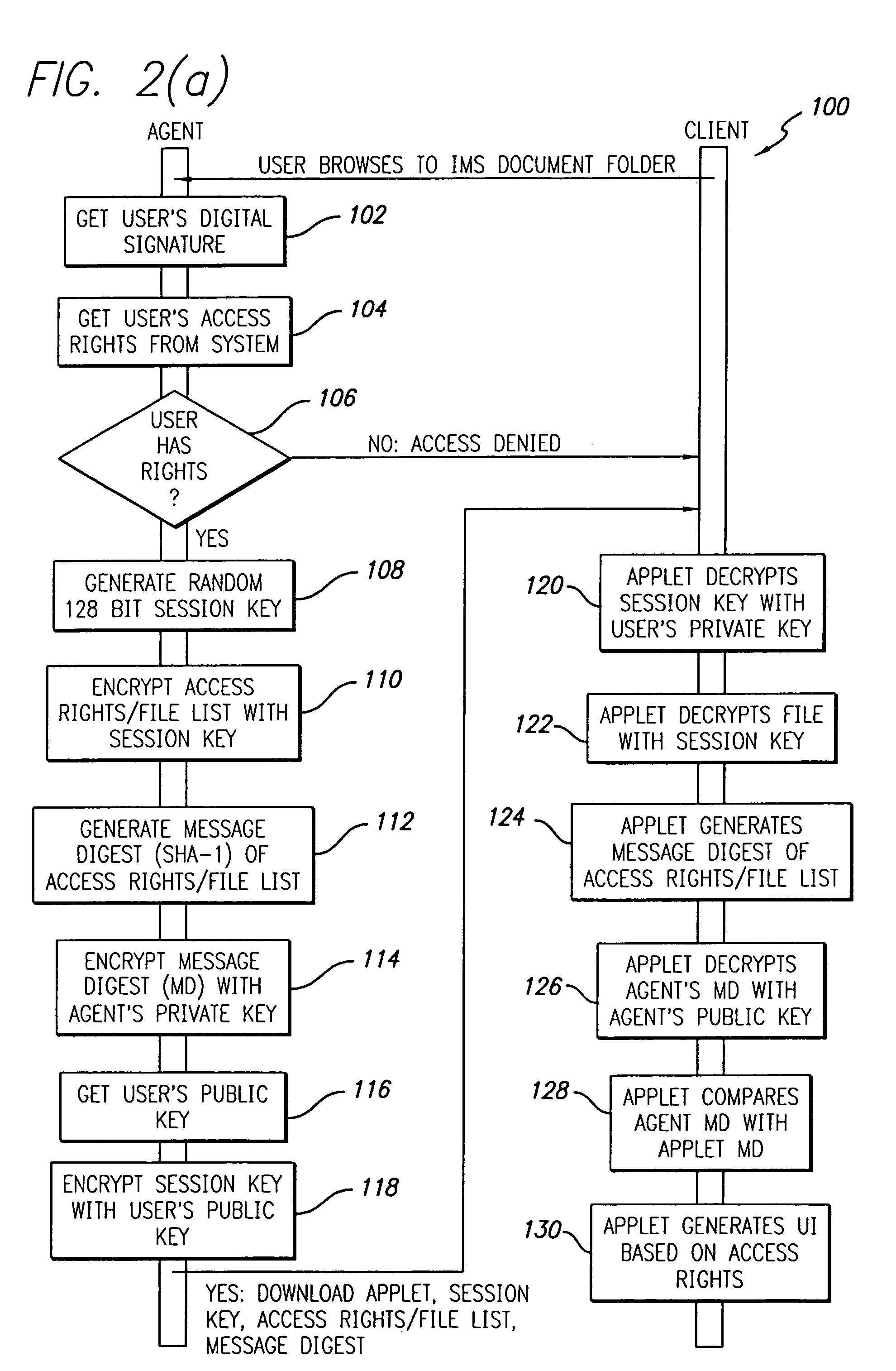
A document management system and method. The inventive system includes a server for providing data from a stored document. Software is provided on the server for encrypting the data. A communications subsystem is included for transporting the encrypted data from the server to the client. Software is provided at the client for decrypting the encrypted data. The inventive method includes the steps of: using a client machine to access a server via a network and to request data therefrom; encrypting at least a portion of said data on said server; communicating said encrypted data from said server to said client; and decrypting said data on said client. In the illustrative embodiment, the inventive method operates under the control of an agent residing on the server. The encrypting software is a first applet residing on the server and the decrypting software is a second applet residing on the client. In the illustrative implementation, the second applet is communicated from the server to the client. Several mechanisms are included for verifying the user's identity including a digital signature, a private key and a public key. In accordance with the invention, software is included for customizing the data based on the user's access rights; providing for secure modification of the shared document; and tracking submission, access, and changes in the document.
Owner:HEWLETT PACKARD DEV CO LP
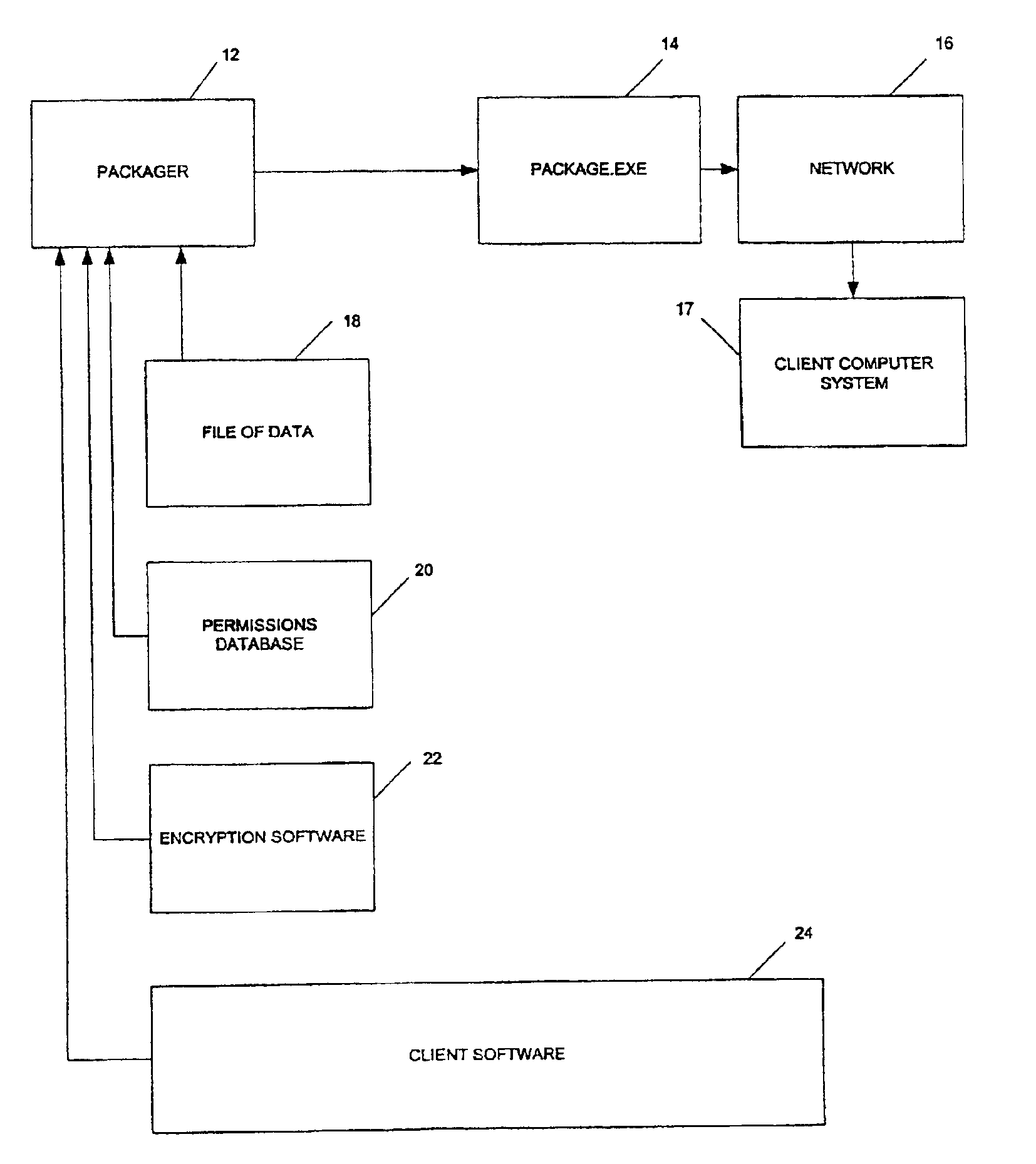
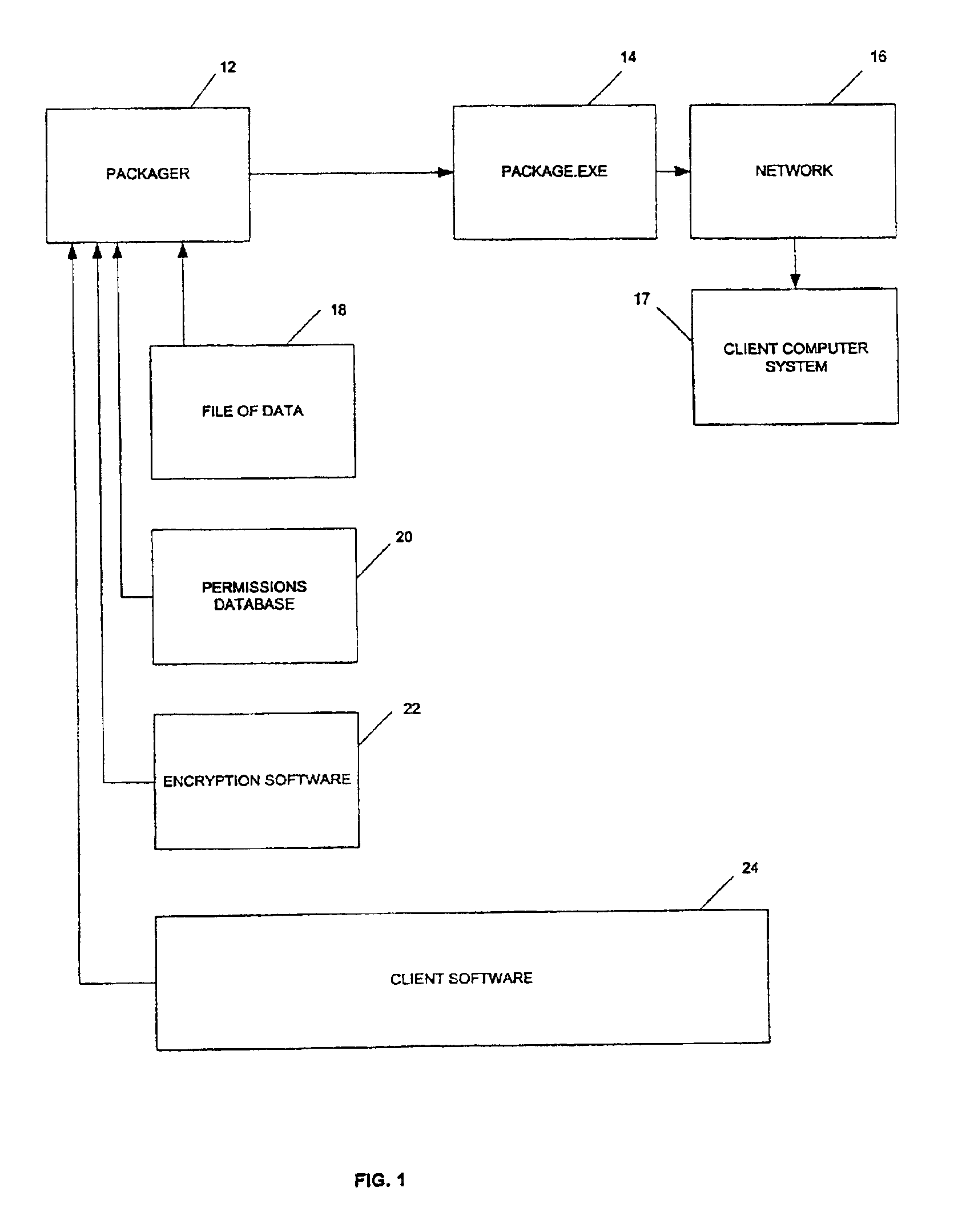
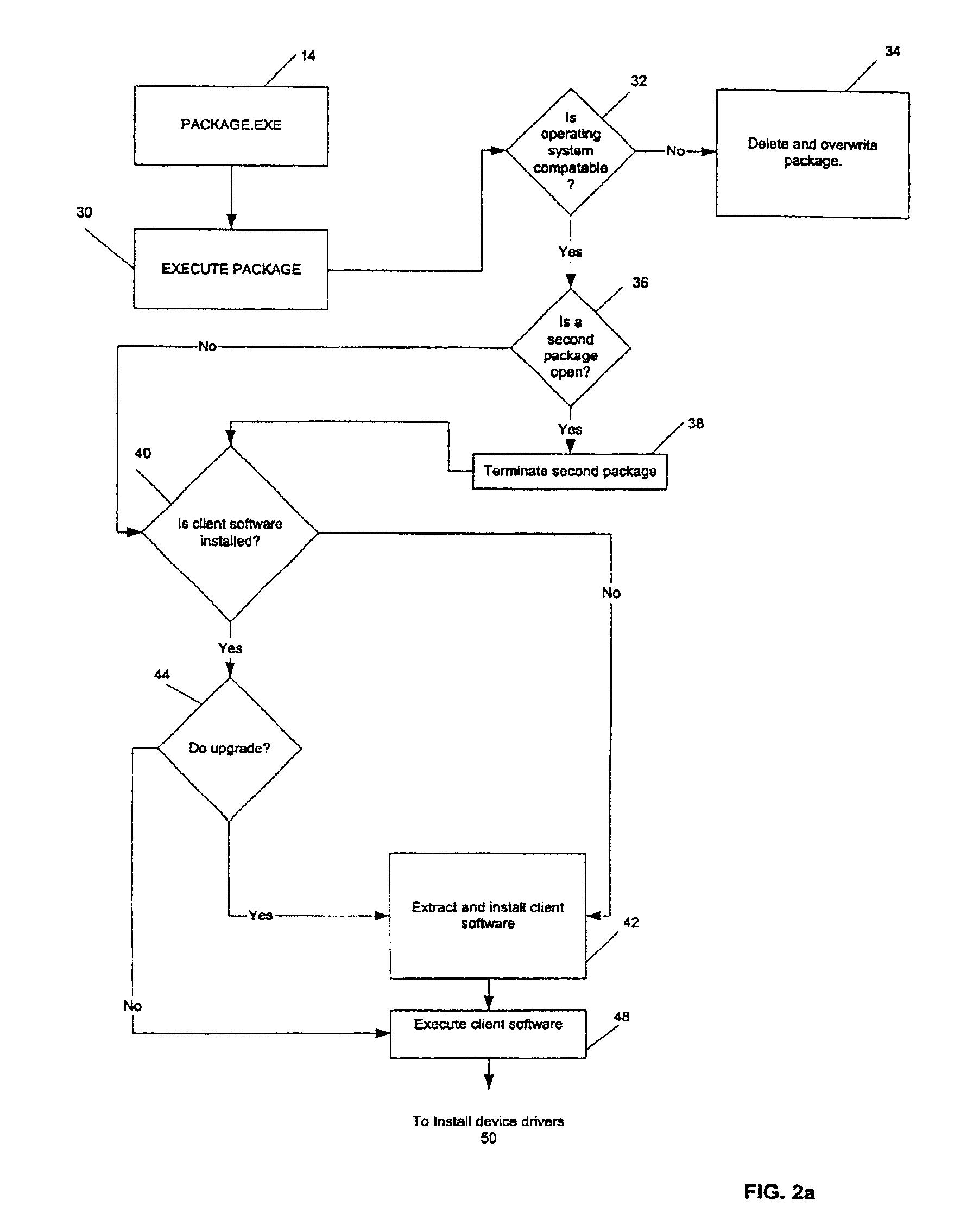
Method and apparatus for packaging and transmitting data
ActiveUS7039806B1Volume/mass flow measurementUser identity/authority verificationComputerized systemData file
A system and method for communicating a package of information. The system comprises a machine readable medium having information packaging software that generates a computer executable file (FIG. 1, 14) comprising a package of information. The packet information comprises the file of data and encryption software. The system communicates the package of information over a network (FIG. 1, 16) that is in communication with a machine readable medium. A client computer system (FIG. 1, 17) in communication with the network is adapted to receive the package of information and execute the computer executable. The computer system has a client permissions database (FIG. 1, 20) and a vault adapted to receive the package of information.
Owner:GIGAMEDIA ACCESS CORP
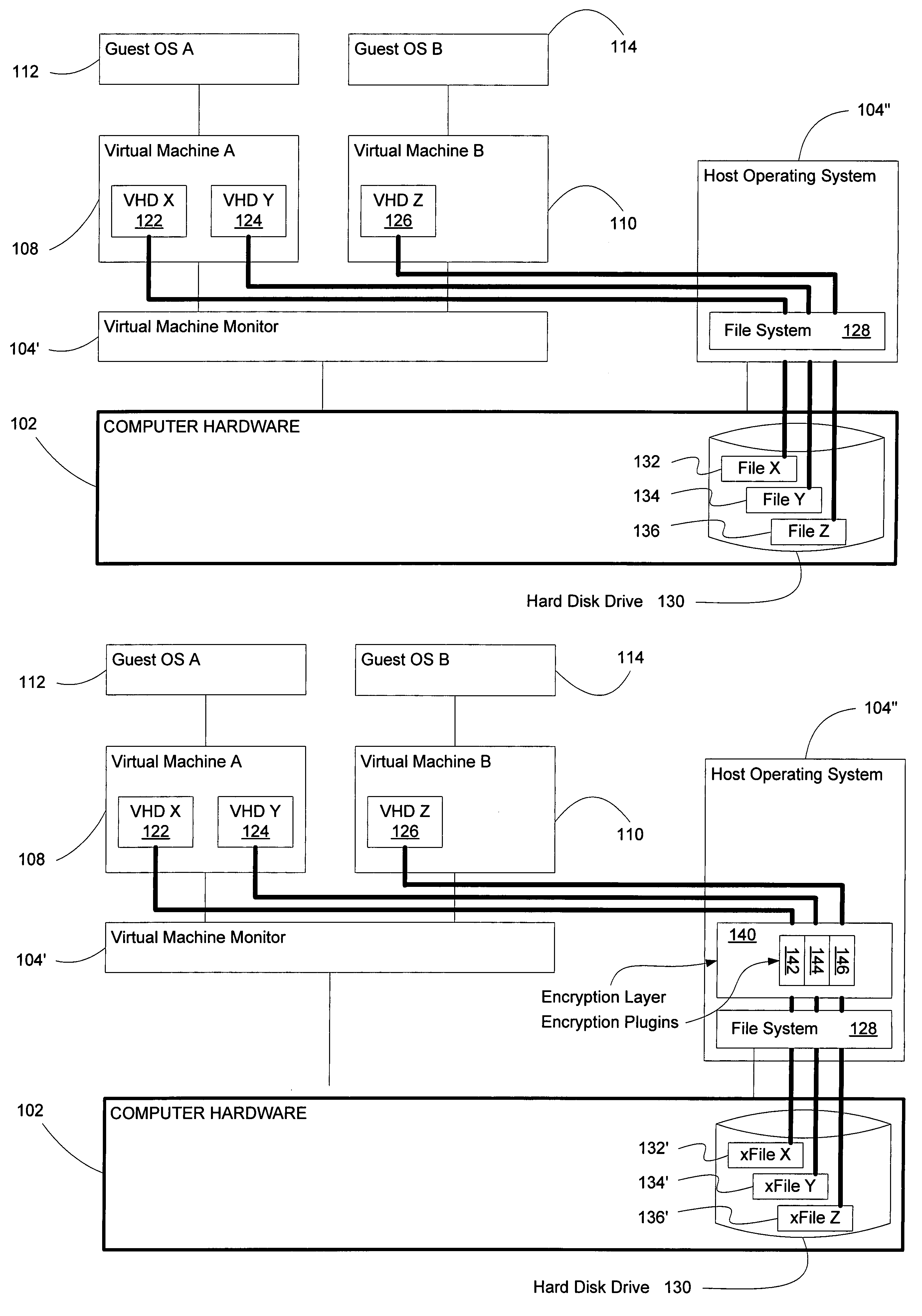
Systems and methods for data encryption using plugins within virtual systems and subsystems
ActiveUS7987497B1Improving data access securityImproved data access securityDigital data processing detailsUnauthorized memory use protectionHard disc driveData access
Several embodiments of the present invention provide a means for improving data access security in computer systems to support high-security applications, and certain of these embodiments are specifically directed to providing sector-level encryption of a virtual hard disk in a virtual machine environment. More specifically, certain embodiments are directed to providing sector-level encryption by using plug-ins in a virtual machine environment, thereby providing improved data access security in a computer system that supports high-security applications. Certain embodiments also use encryption plug-ins associated with standard encryption software for exchanging data between a virtual machine (VM) and its associated virtual hard drive(s) (VHDs). Moreover, several embodiments of the present invention are directed to the use of plug-in encryption services that interface with, and provide services for, a VM via a VM Encryption API (or its equivalent).
Owner:MICROSOFT TECH LICENSING LLC
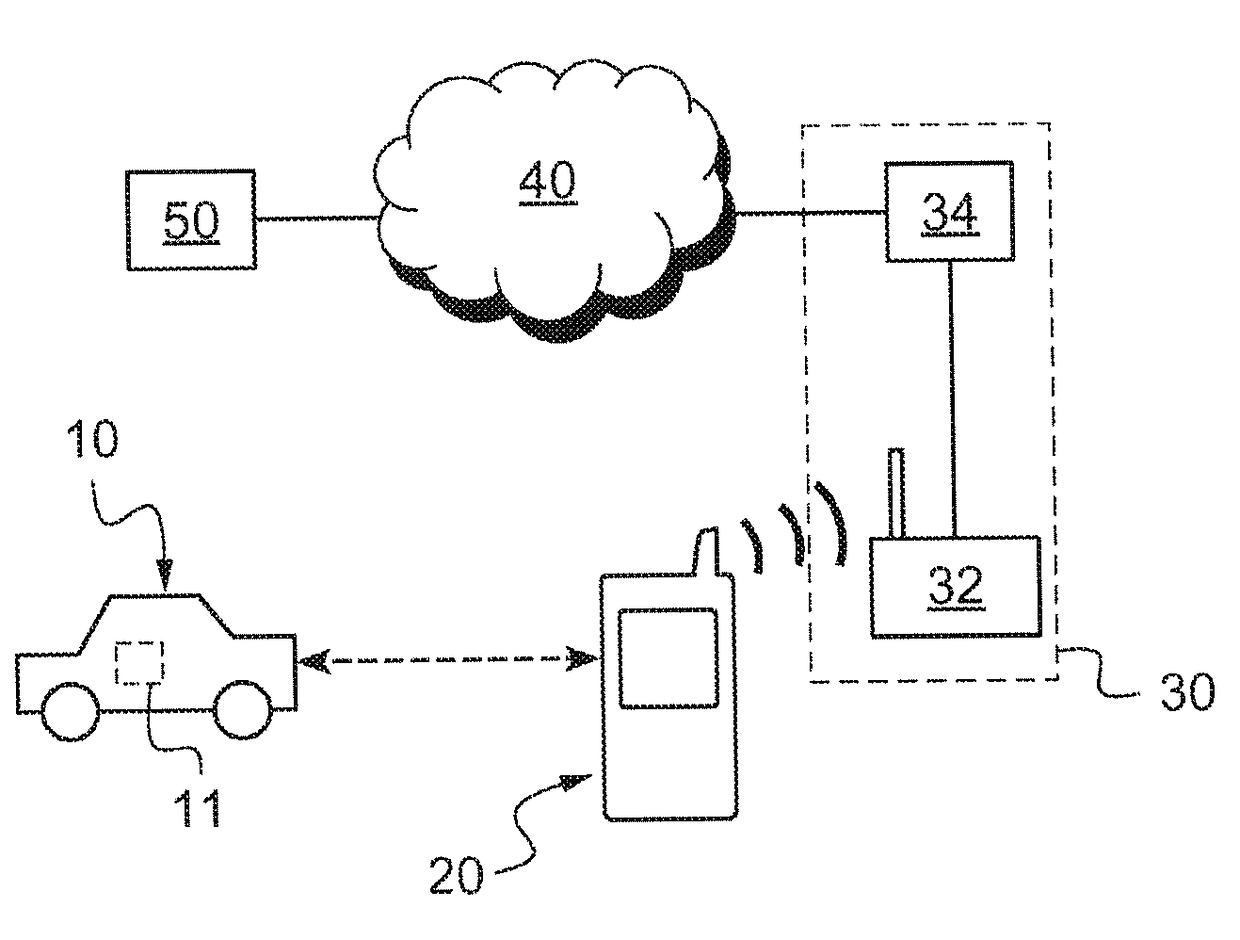
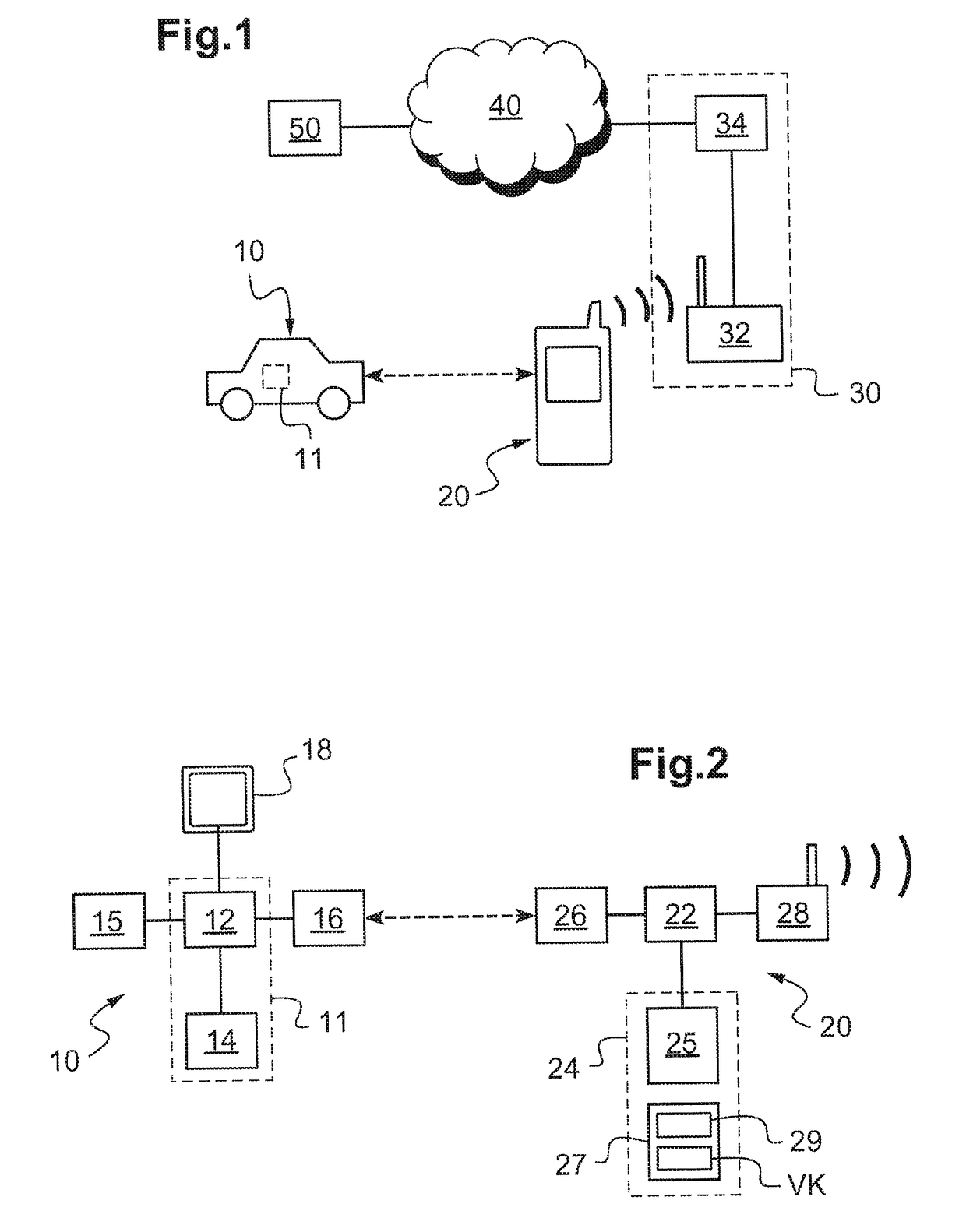
Method for secure transmission of a virtual key and method for authentication of a mobile terminal
ActiveUS20170330402A1Easy to processKey distribution for secure communicationAnti-theft devicesSecure transmissionComputer terminal
The invention relates to a method for transmission of a secure virtual key (VK) from a server (50, S) to a mobile terminal (20, T) capable of communicating with the server (50, S), comprising the steps of: a) reception by the server (50, S) of a certification request from the mobile terminal (20, T), b) provision and downloading on the mobile terminal (20, T), by the server (50, S), of a user application (25), and c) provision of the mobile terminal (20, T), by the server (50, S), with a virtual key (VK), and d) downloading and securing of the virtual key (VK) in a security element (27) of the mobile terminal (20, T), characterised in that said security element is formed by an encrypting software environment (27).
Owner:VALEO COMFORT & DRIVING ASSISTANCE
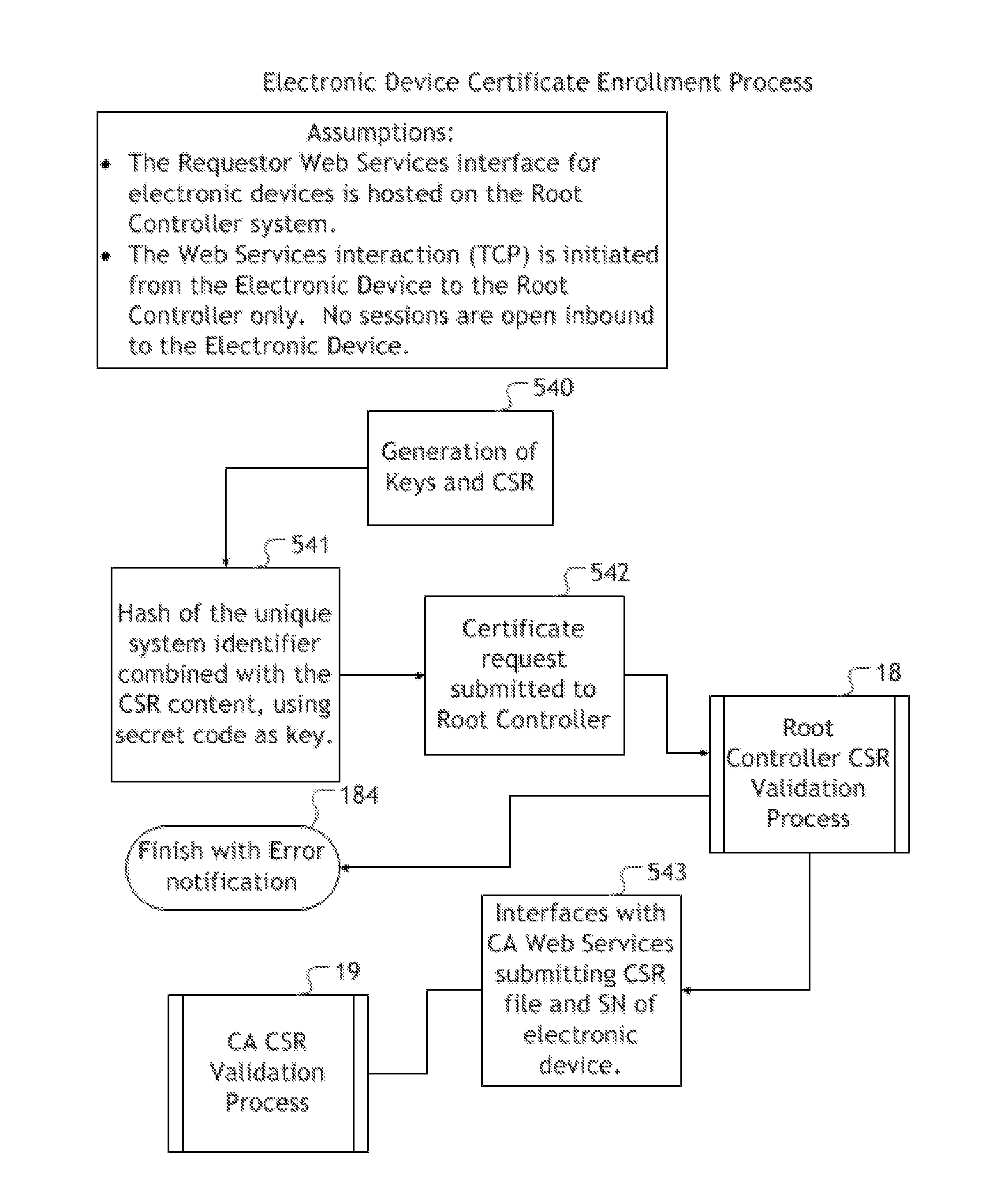
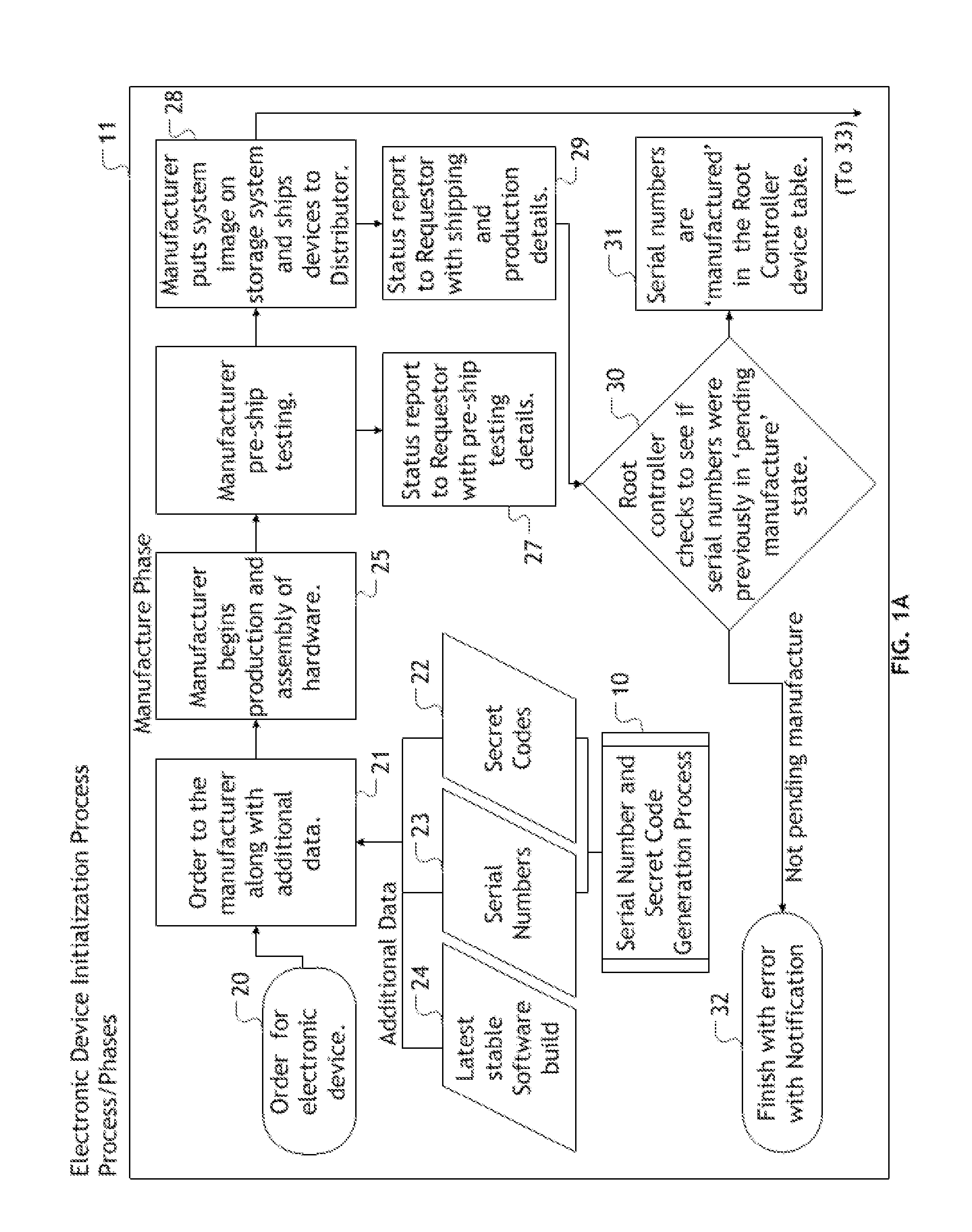
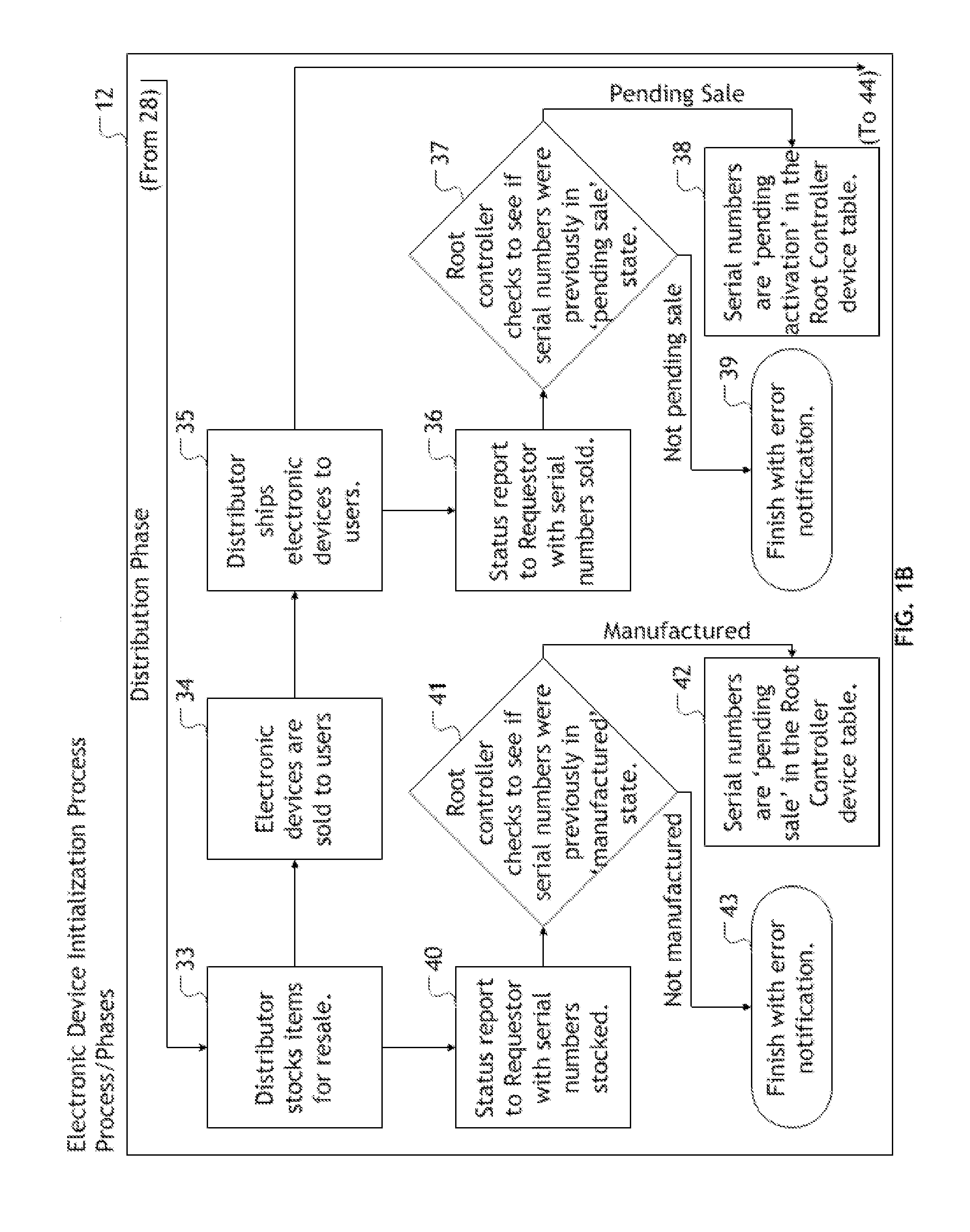
Secure installation of encryption enabling software onto electronic devices
A process / method is provided, which authenticates electronic devices allowing the installation and utilization of encryption enabling software capable of facilitating a public key infrastructure in combination with electronic devices without need for such encryption enabling software capable of facilitating a public key infrastructure to be installed at the same time as manufacture of the electronic device. The disclosed process / method may then provide a system for monitoring various metrics and statuses of the electronic devices through the manufacturing chain, distribution chain and product lifecycle. The process / method can be utilized to create electronic devices secured with encryption enabling software capable of facilitating a public key infrastructure, free from the security risks inherent with the current method of installing encryption enabling software onto electronic devices, which will render such secured electronic devices suitable for tasks requiring such enhanced security or encryption. Moreover, electronic devices utilizing the disclosed process / method to install encryption enabling software capable of facilitating a public key infrastructure will be enabled to benefit from and facilitate public key infrastructure functionality, including, but not limited to, the renew encryption enabling software on a defined renewal interval.
Owner:SMARTGUARD LLC
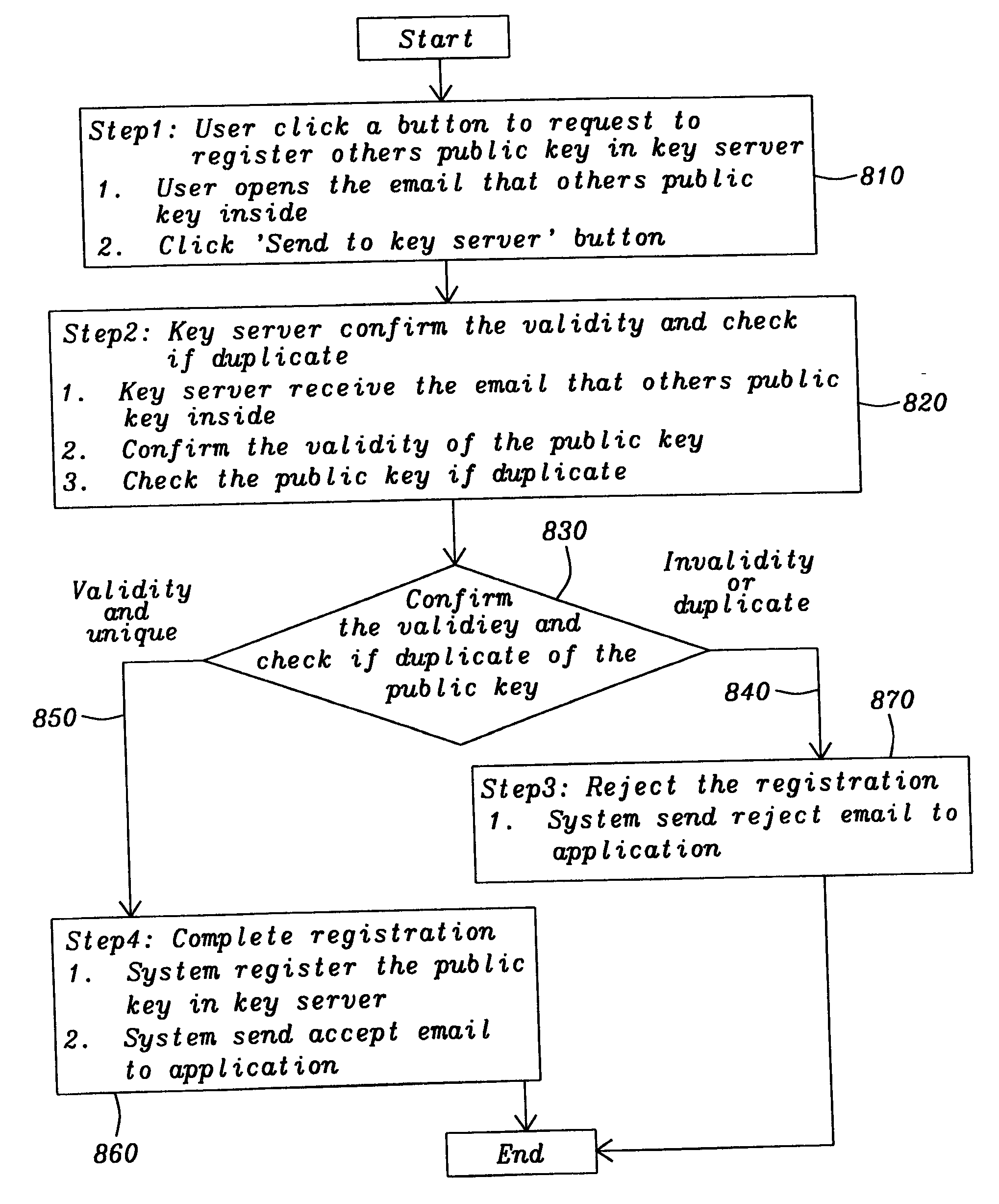
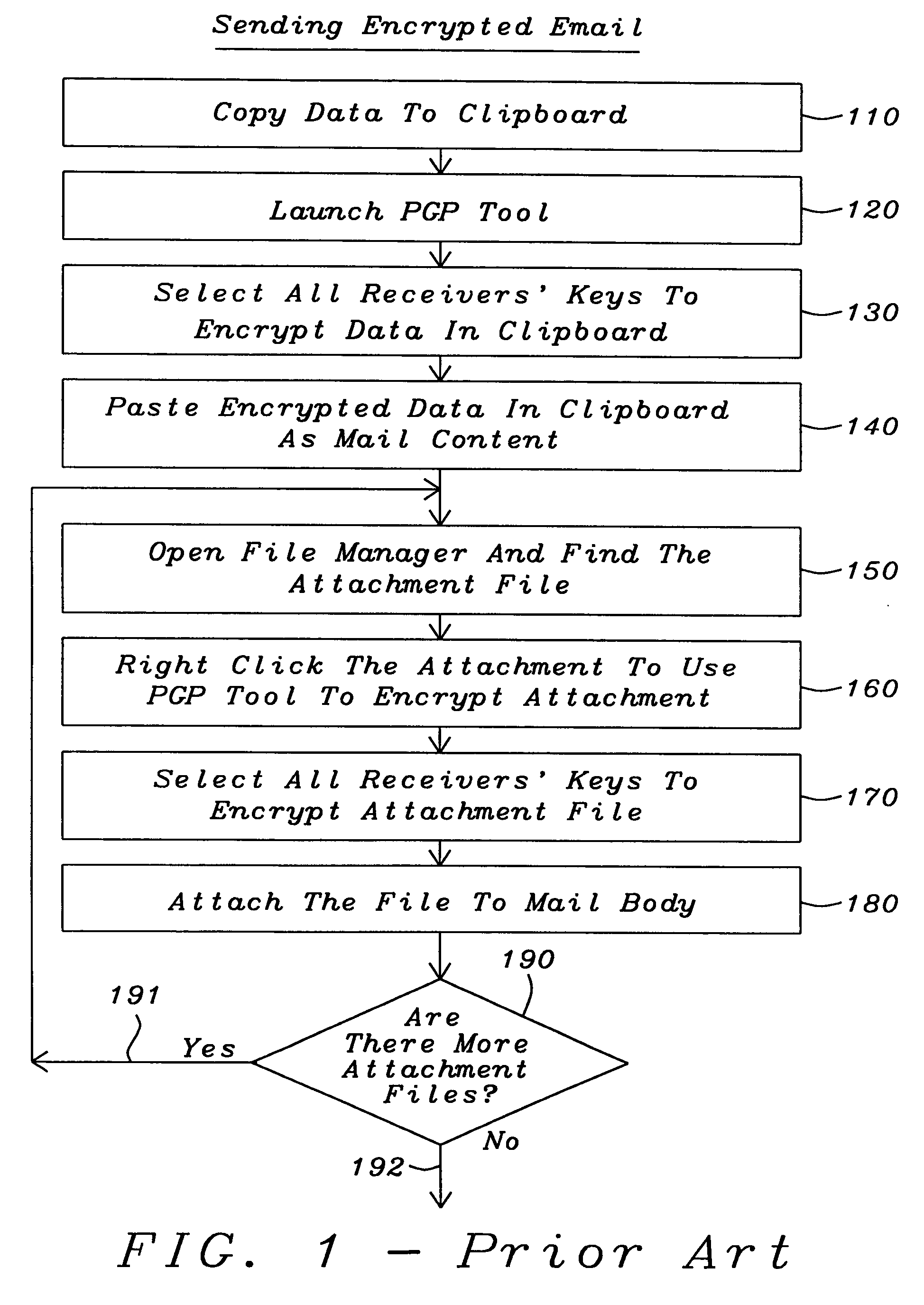
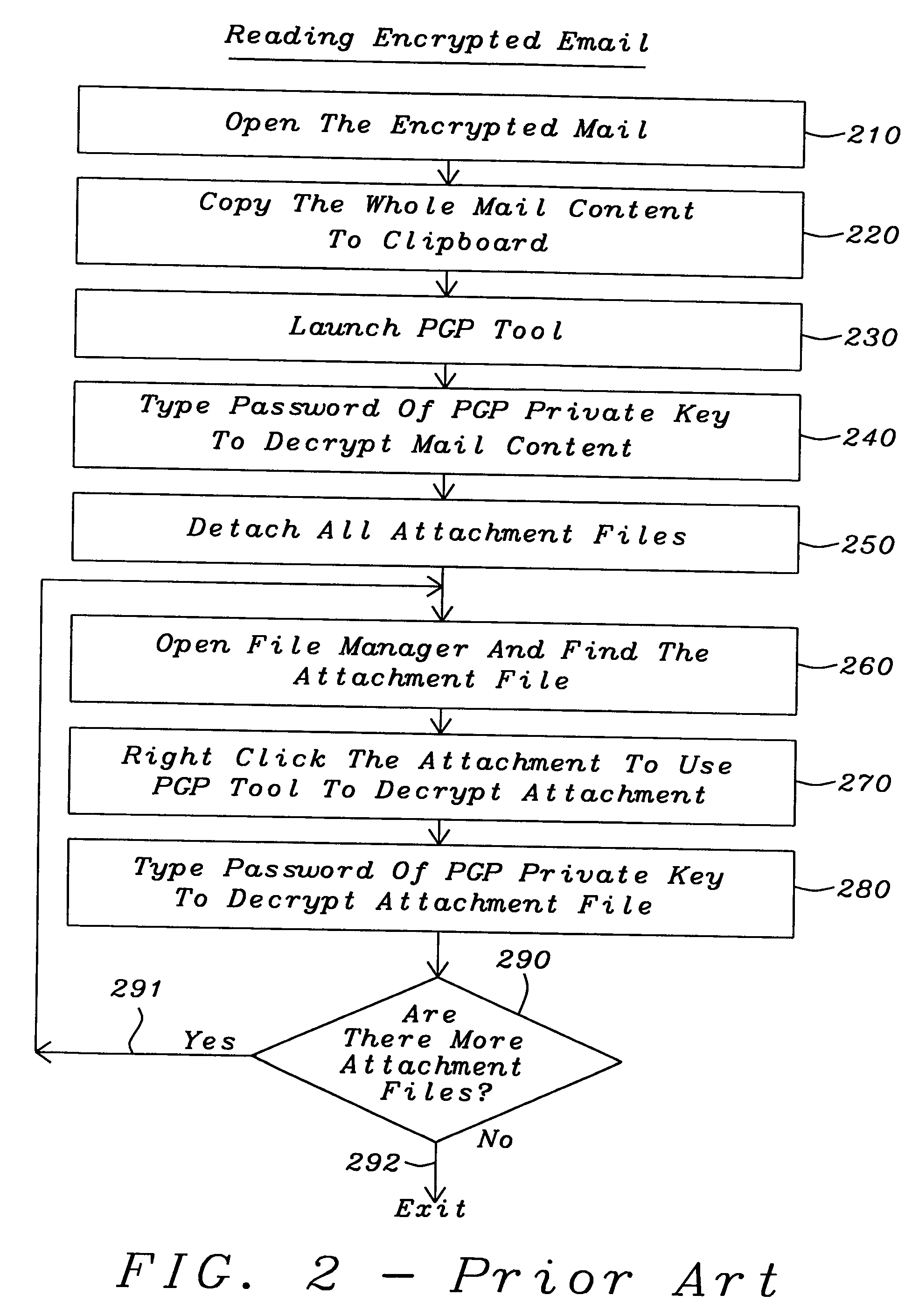
Integrate PGP and Lotus Notes to encrypt / decrypt email
InactiveUS20050086477A1Public key for secure communicationUser identity/authority verificationPasswordSoftware engineering
This invention provides a method, a system and a computer program for integrating encryption / decryption software and email software. In addition, it provides a method and a computer program for integrating encryption software (Pretty Good Privacy) encryption / decryption software and Lotus Notes email software with minimal process steps. Encryption / decryption software is public-key encryption / decryption software. The user can send encrypted email with just one step of clicking the send button. Also, the user can read encrypted email and attachments with just one step of keying in the password.
Owner:TAIWAN SEMICON MFG CO LTD
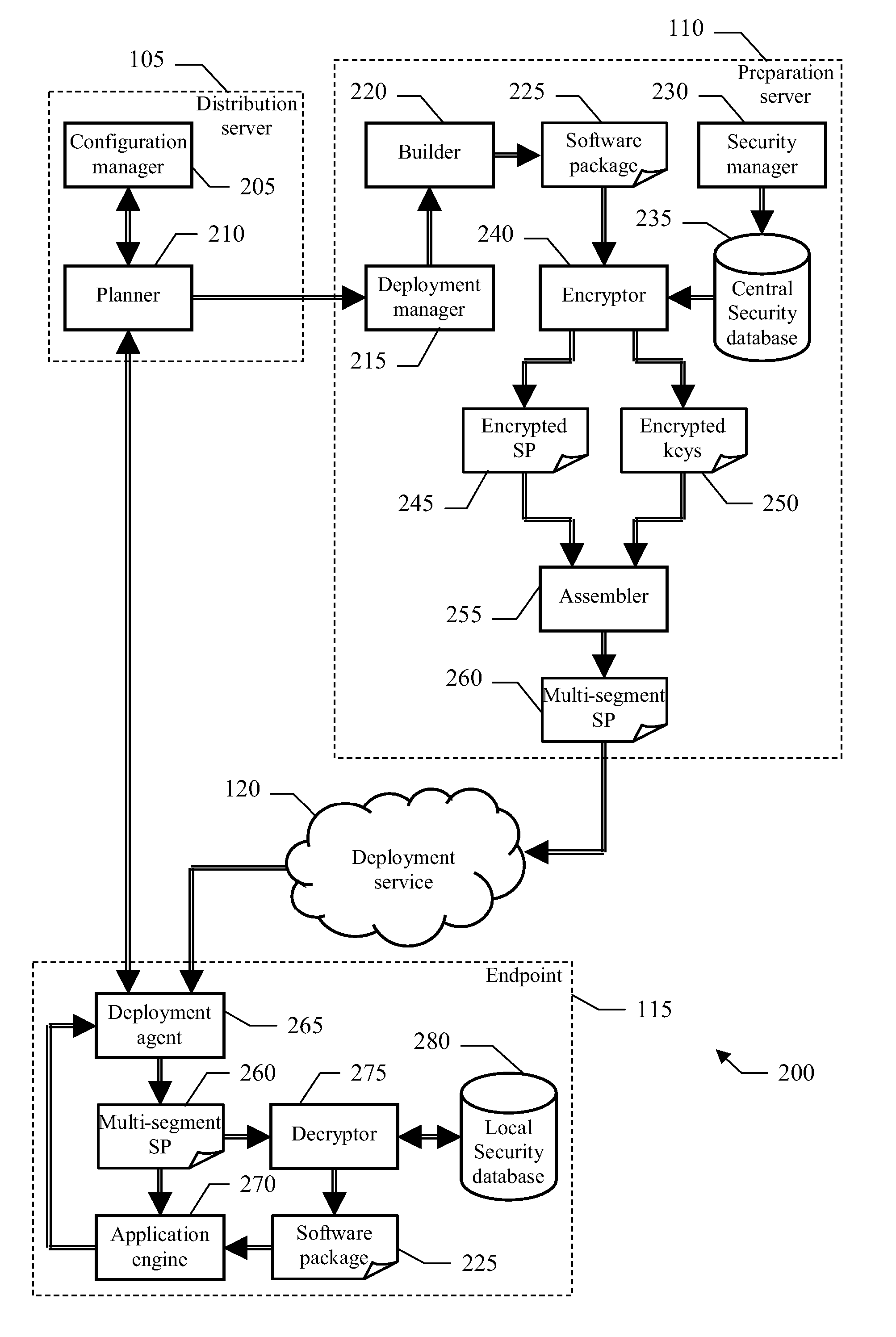
Method, system and computer program for deploying software packages with increased security
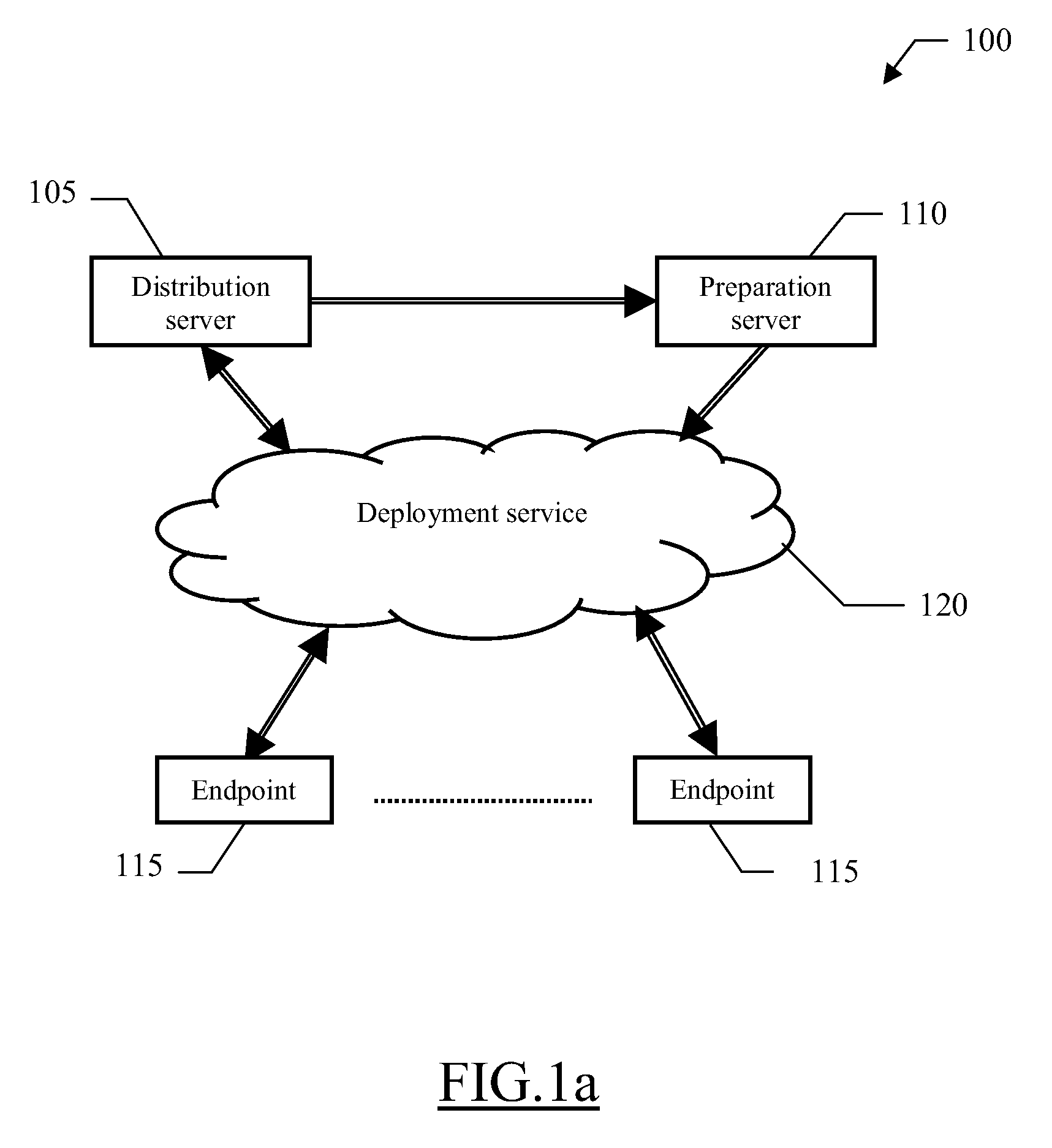
InactiveUS20070047735A1Key distribution for secure communicationPublic key for secure communicationComputer hardwareSoftware distribution
A software distribution method (300) with security add-on is proposed. Particularly, any software package to be deployed to selected target endpoints is encrypted (312-315) with a symmetric key (generated dynamically). The symmetric key is in turn encrypted (318-321) with a public key of each target endpoint. A multi-segment software package (embedding the encrypted software package and the encrypted symmetric keys) is then deployed (324-336, 360) to all the target endpoints. In this way, each target endpoint can decrypt (343-348) the encrypted symmetric key with a corresponding private key; it is then possible to decrypt (363-366) the encrypted software package with the symmetric key so obtained. As a result, the endpoint is able to apply (369) the decrypted software package. Therefore, the application of the software package can be restricted to the desired target endpoints only.
Owner:IBM CORP
Embedded system insuring security and integrity, and method of increasing security thereof
InactiveUS20070162964A1Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwareDigital rights management
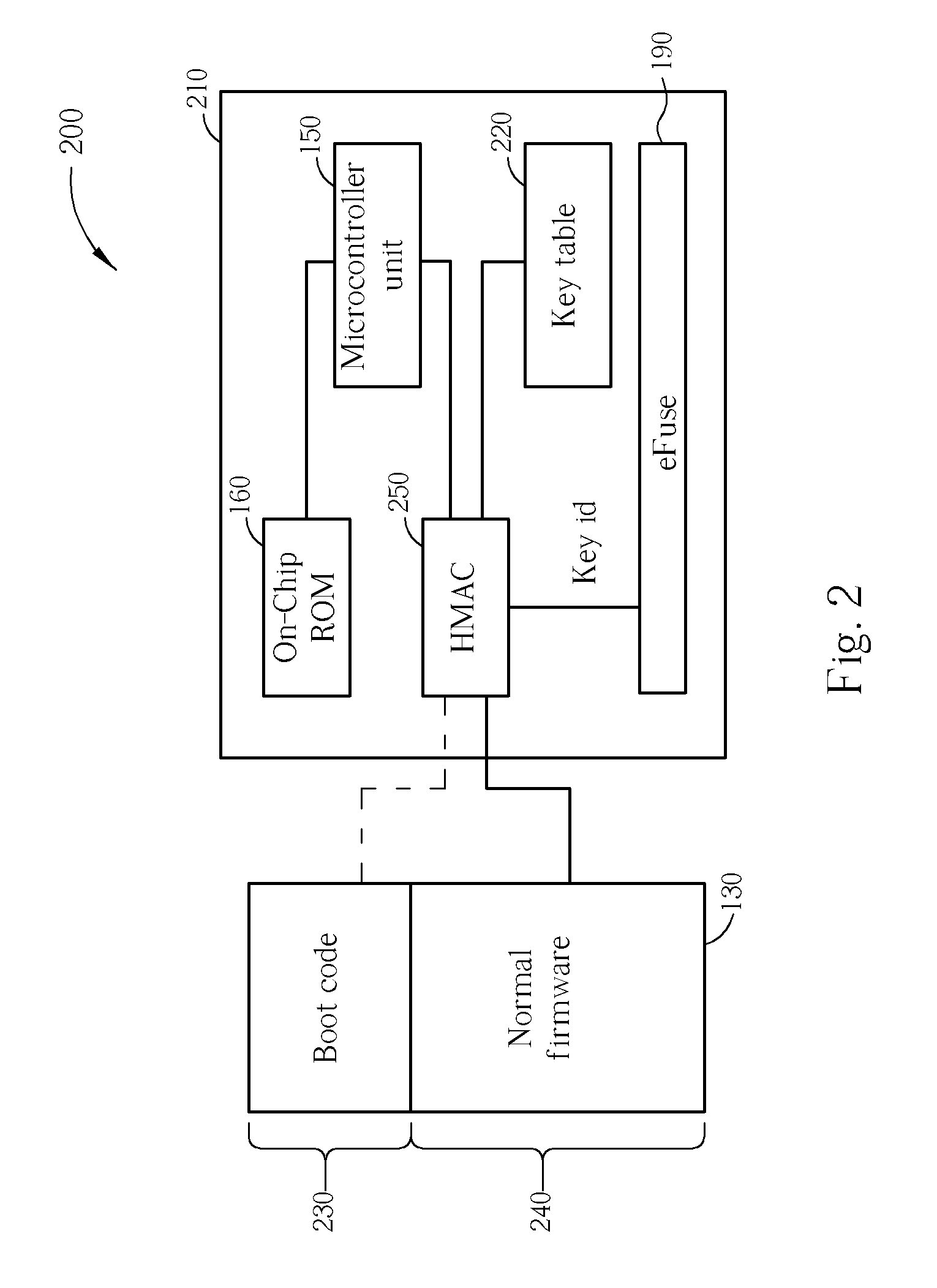
A system containing both software and hardware to perform secure operations especially suited for Digital Right Management. The system has hardware to accelerate Elliptic Curve calculations, hash algorithms, and various encryption algorithms. The system runs on encrypted software, and the software is checked for integrity before it boots.
Owner:MEDIATEK INC
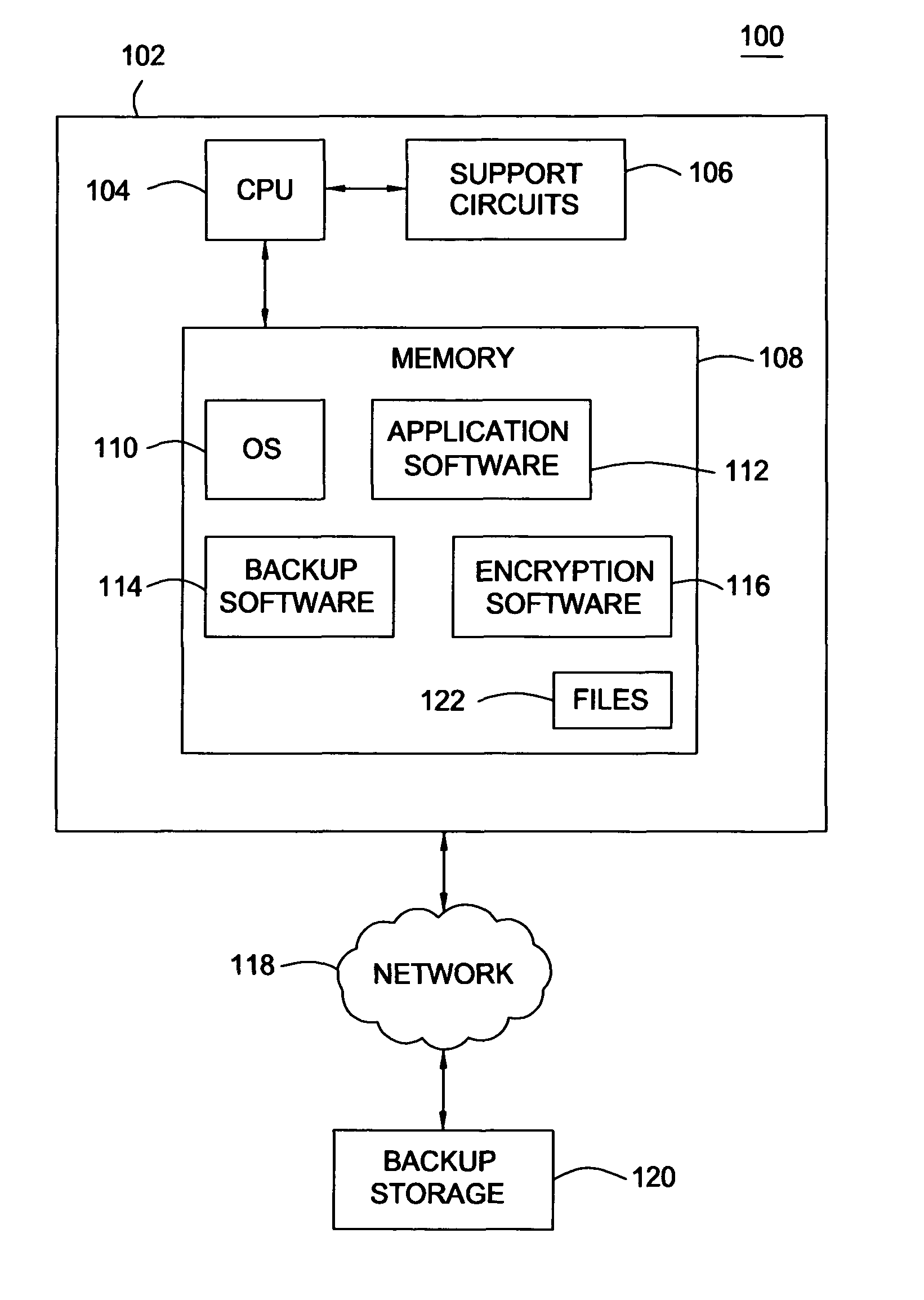
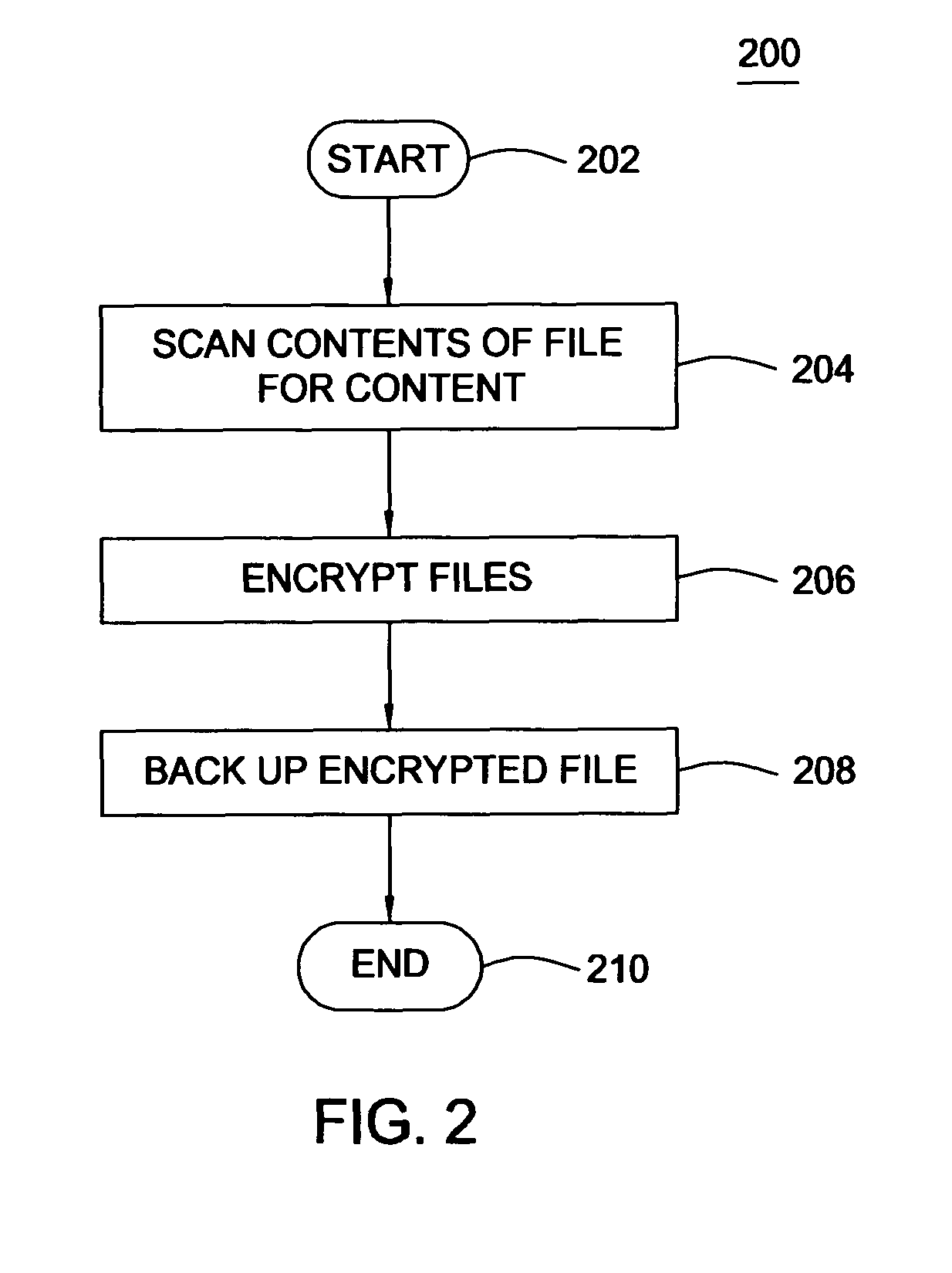
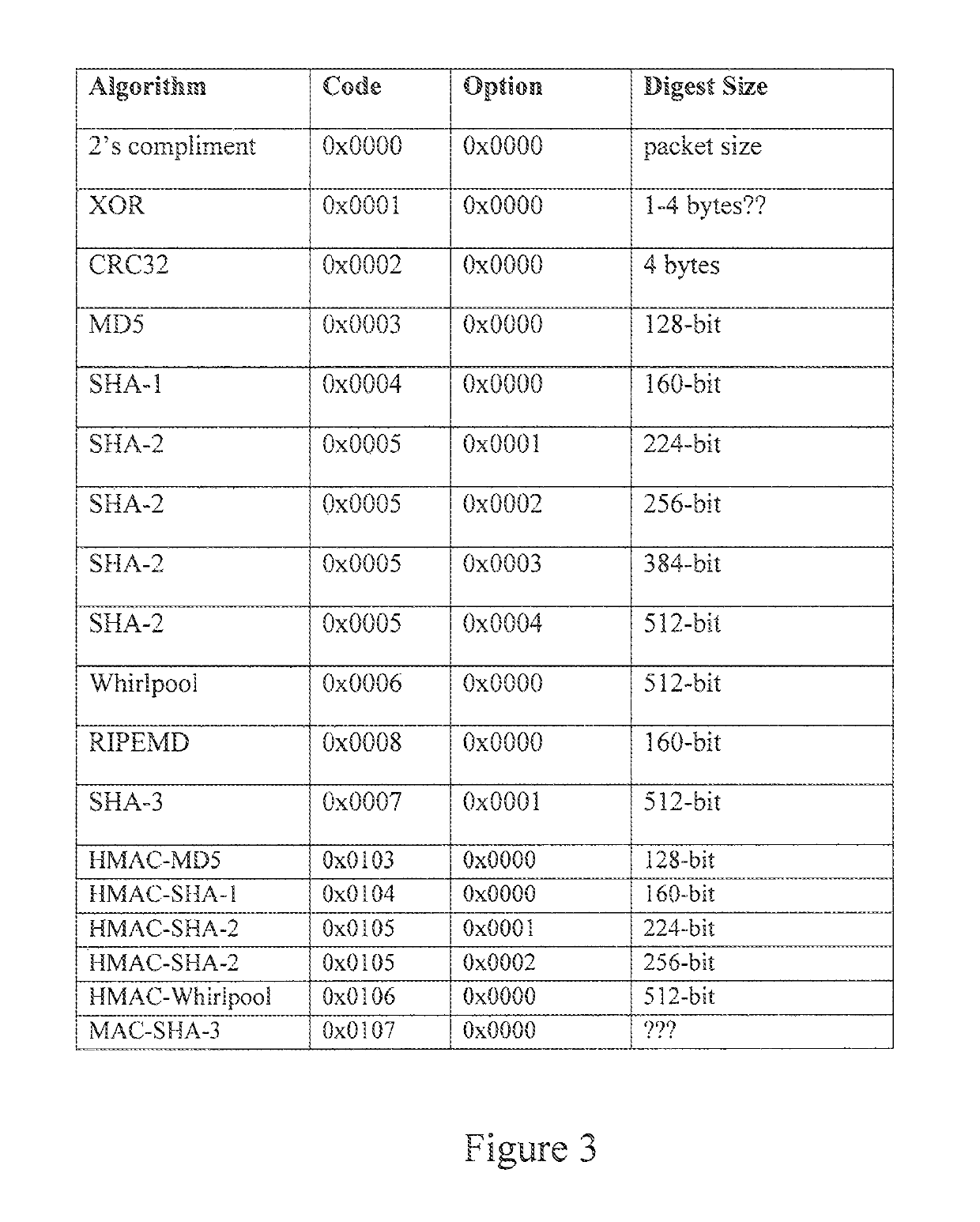
Method and apparatus for content based encryption
ActiveUS8127149B1Unauthorized memory use protectionHardware monitoringInternet privacyComputerized system
A method, system and computer-readable medium for encrypting a file on a computer system based on the content of the file. The method is setting an encryption policy, wherein the encryption policy is at least one attribute related to content of at least one file, scanning at least one file on a computer system for content, matching the content of the scanned at least one file to the at least one attribute set in the encryption policy and encrypting the scanned at least one file with a key in response to a match between the content of the scanned at least one file and the at least one attribute set in the encryption policy. The system is a computer system that includes policy-based encryption software that performs the steps embodied by the method.
Owner:CA TECH INC
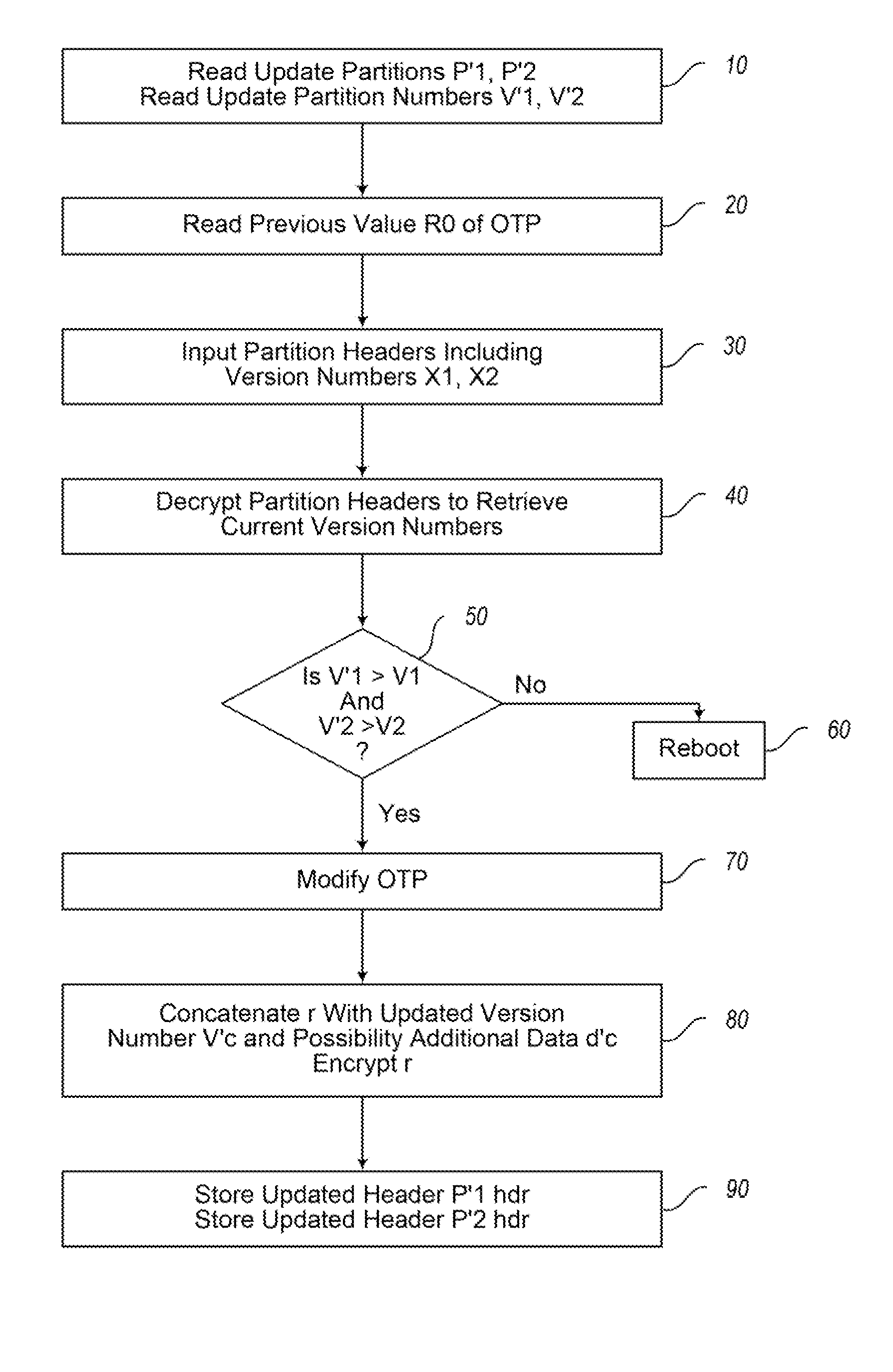
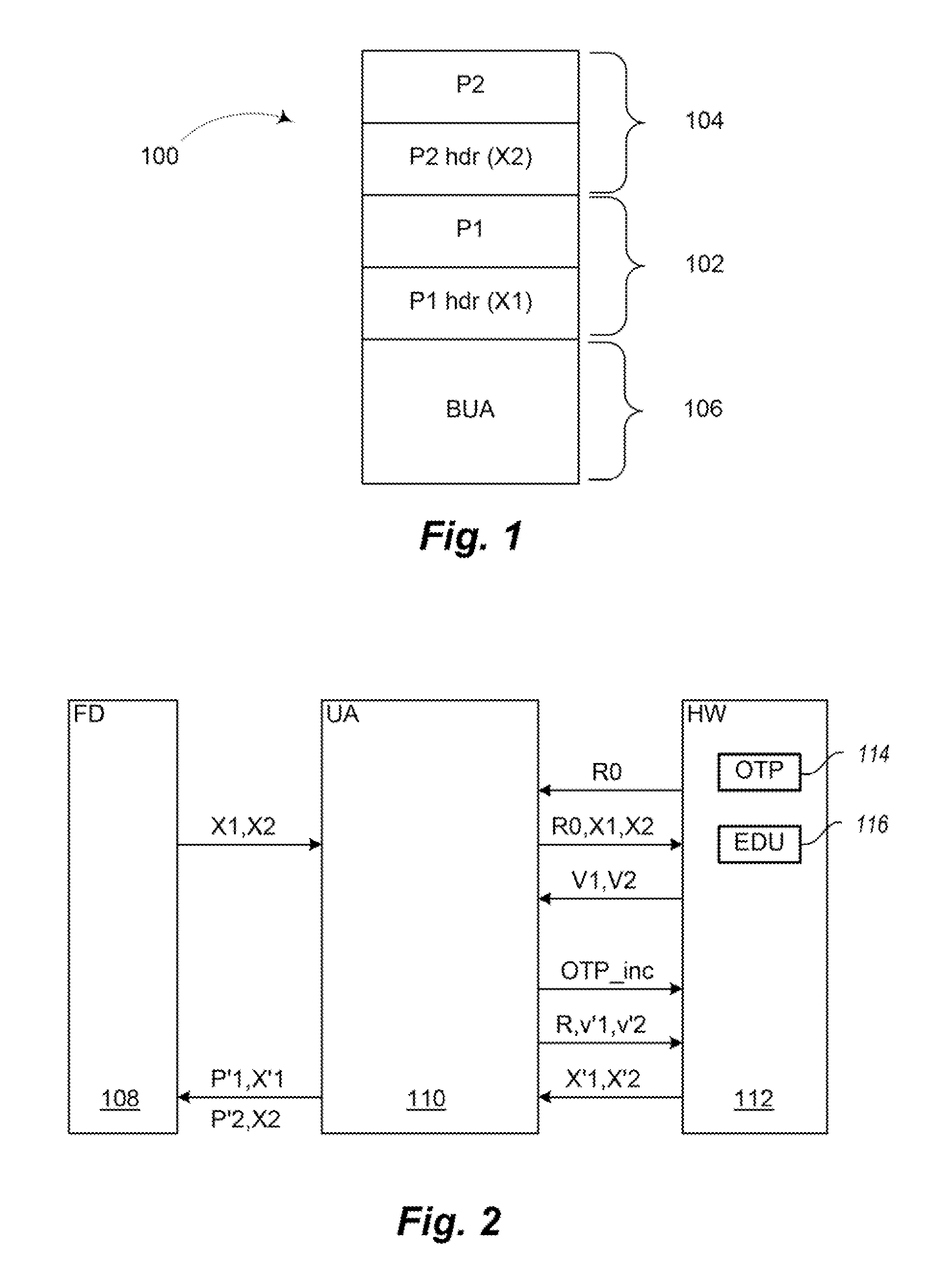
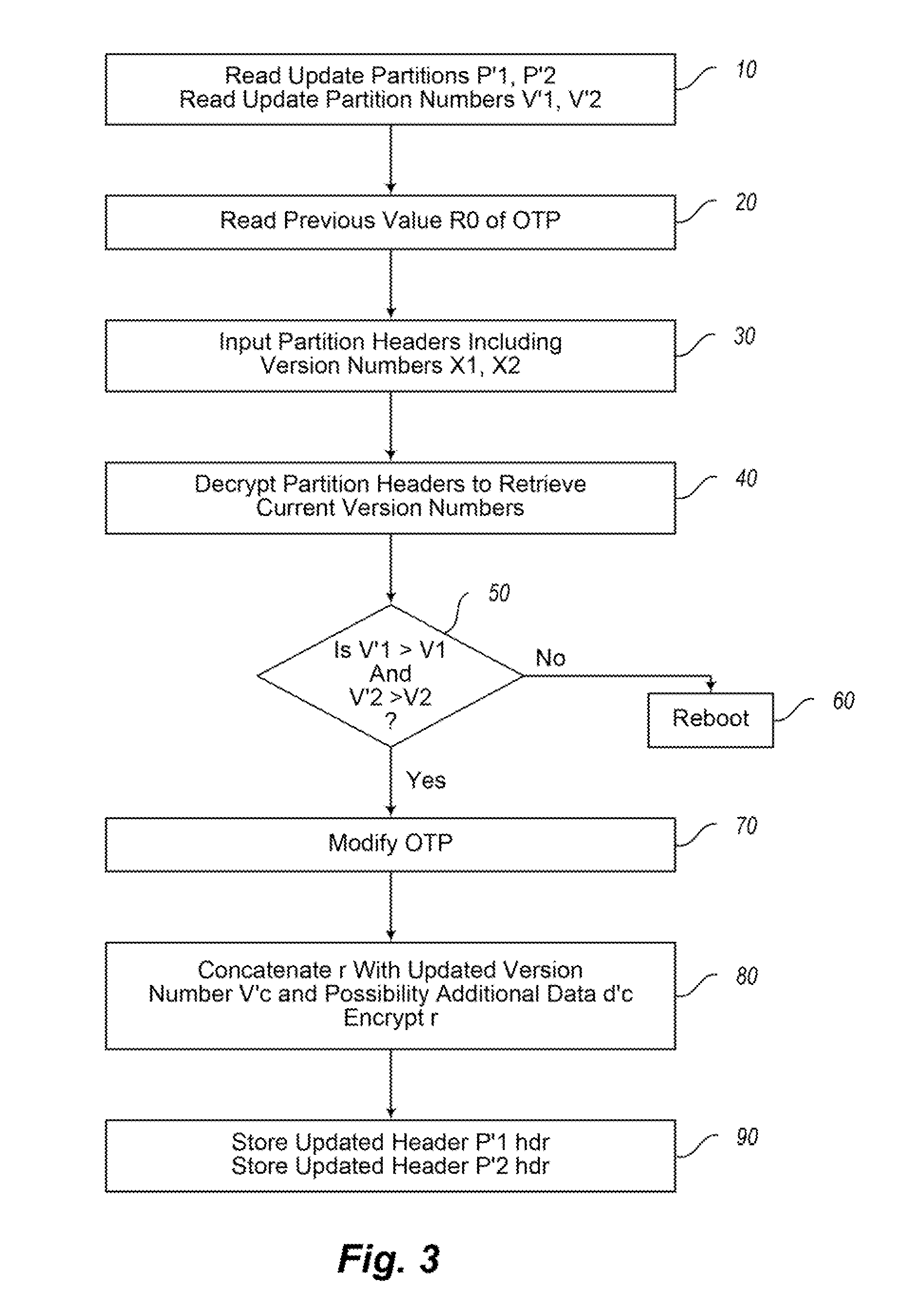
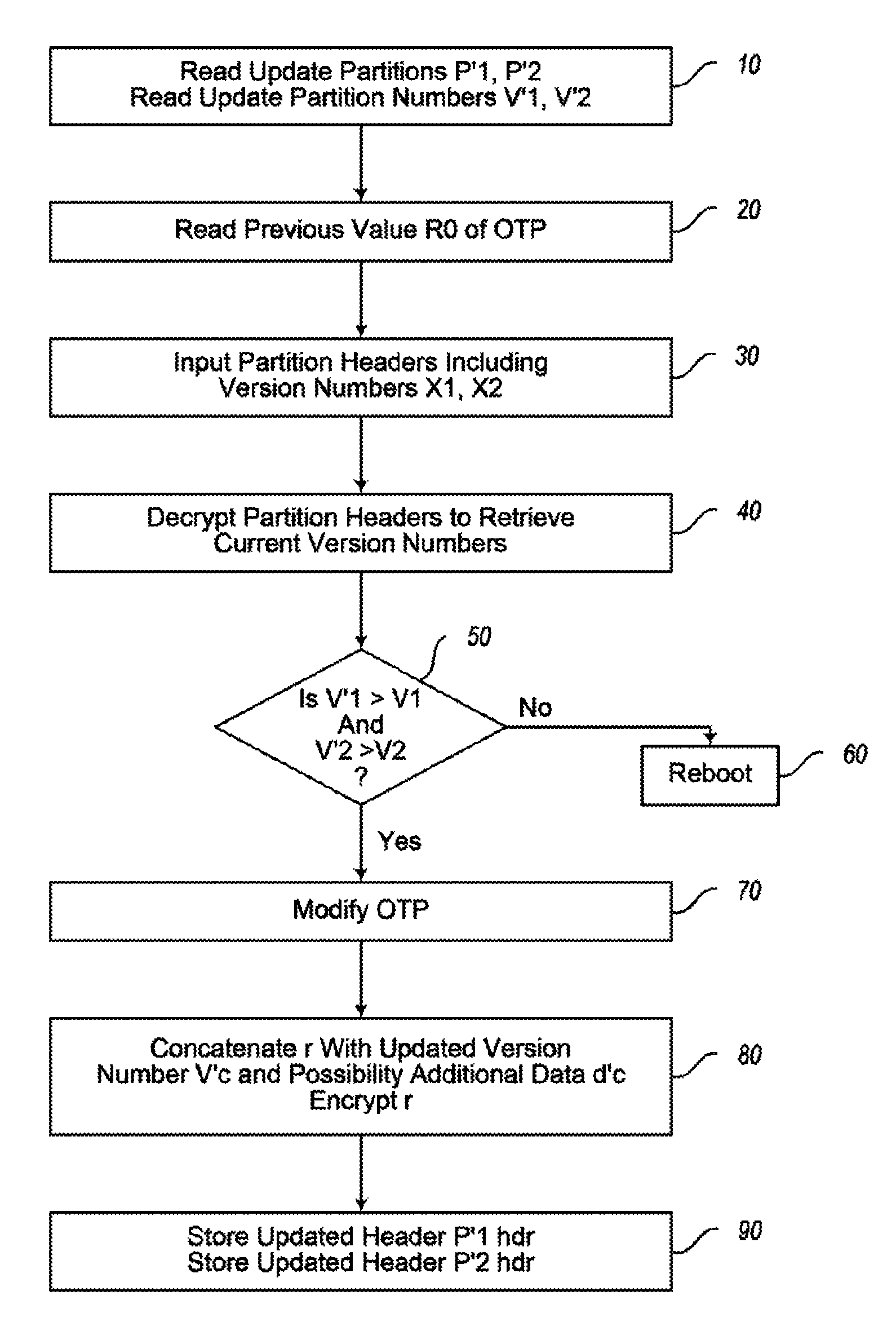
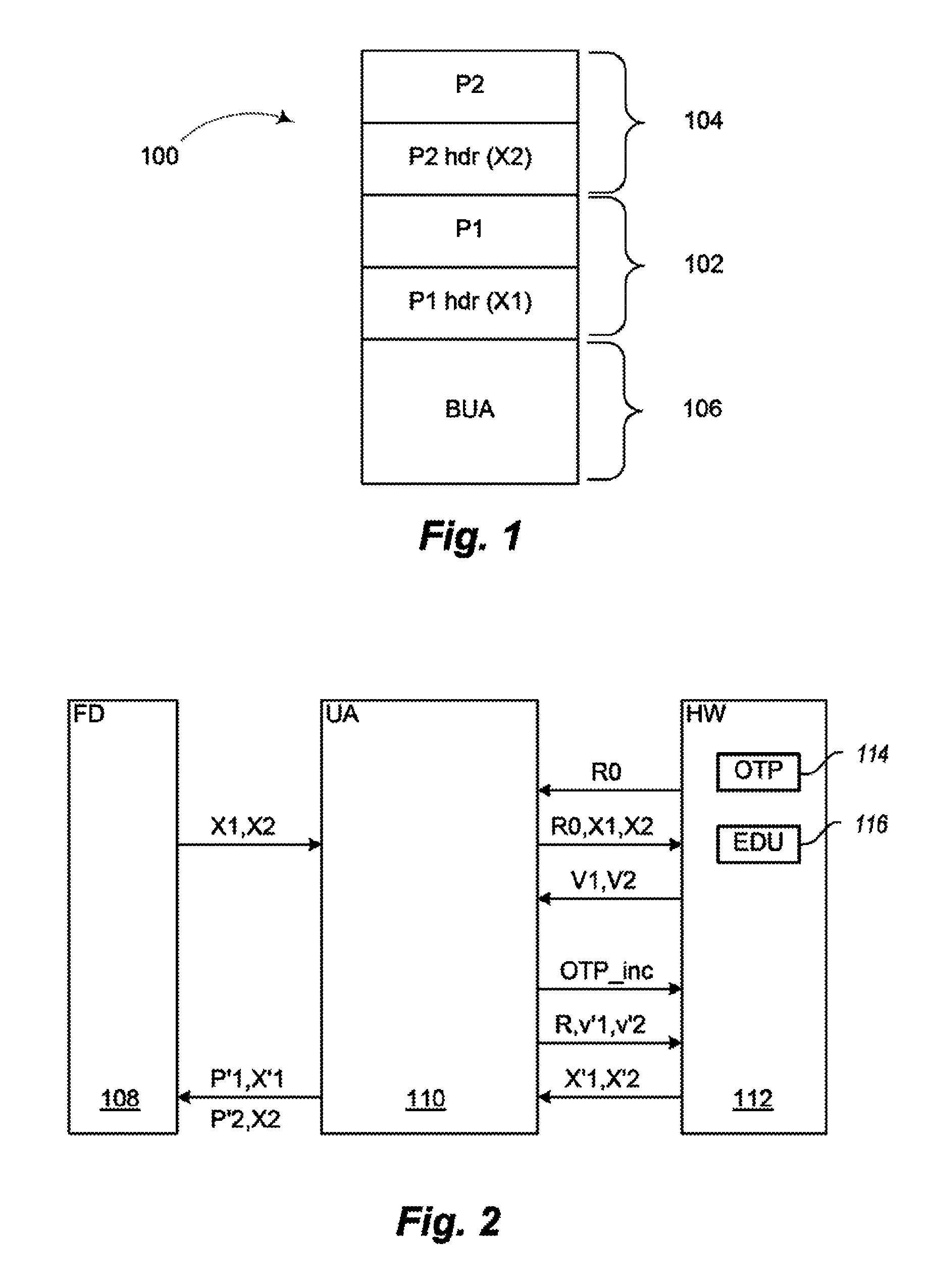
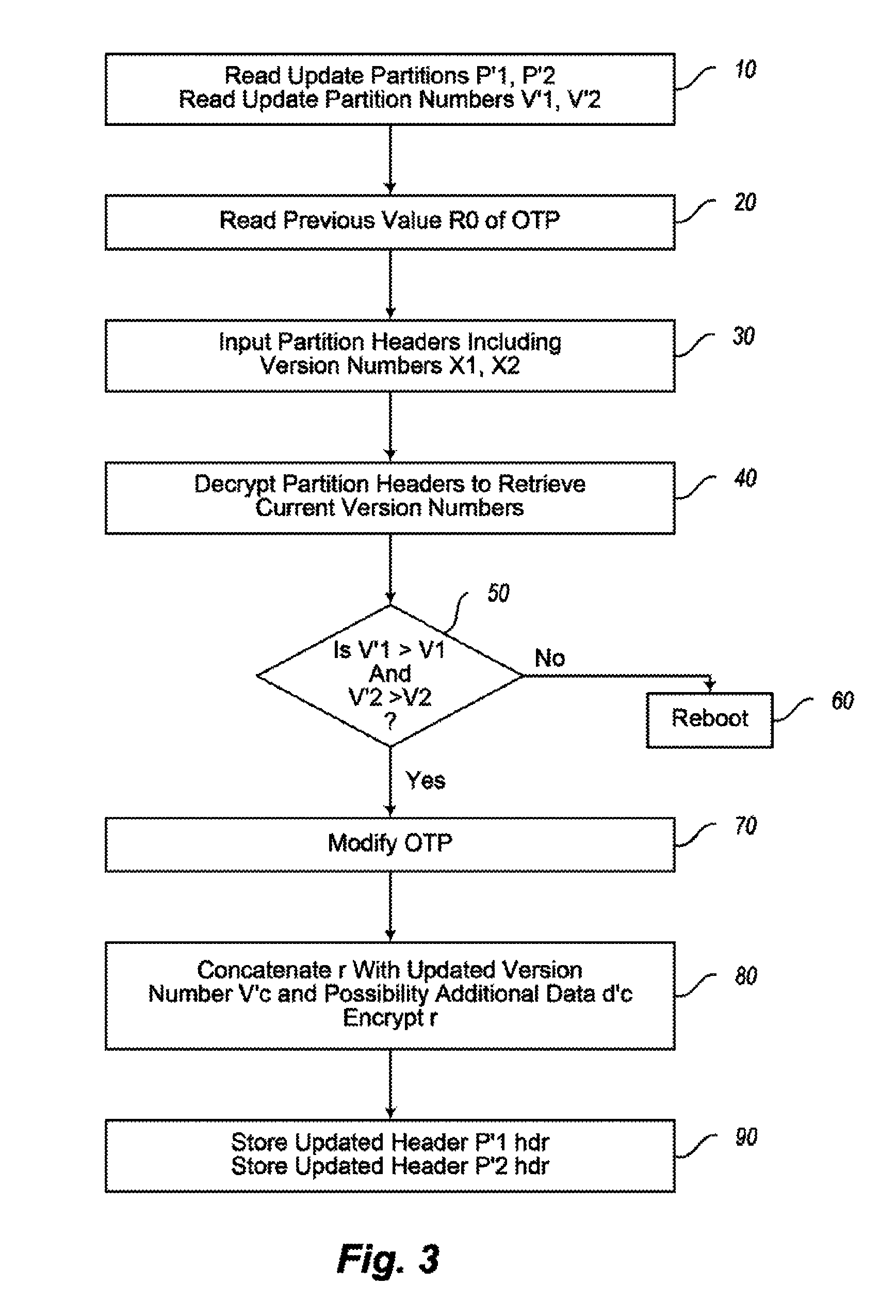
Electronic device and method of software or firmware updating of an electronic device
InactiveUS20110208975A1Low implementation costLow costUnauthorized memory use protectionHardware monitoringOne time programmableEncryption software
An electronic device is provided having a memory driver unit for reading partition headers including encrypted version numbers from a memory and for writing updated encrypted version numbers to the memory. The electronic device has an update agent unit for controlling a software or firmware update, a one-time programmable memory for storing a first value, and an encrypt-decrypt unit for decrypting the partition headers stored in the memory. The update agent is configured to compare the retrieved version numbers with a version number from a software or firmware update. The first value is incremented and stored in the one-time programmable memory if an update is performed. The encrypt-decrypt unit is configured to encrypt the version numbers of the software or firmware update based on the new first value. The memory driver unit is configured to write a new partition header with the updated encrypted version numbers into the memory.
Owner:ST ERICSSON SA
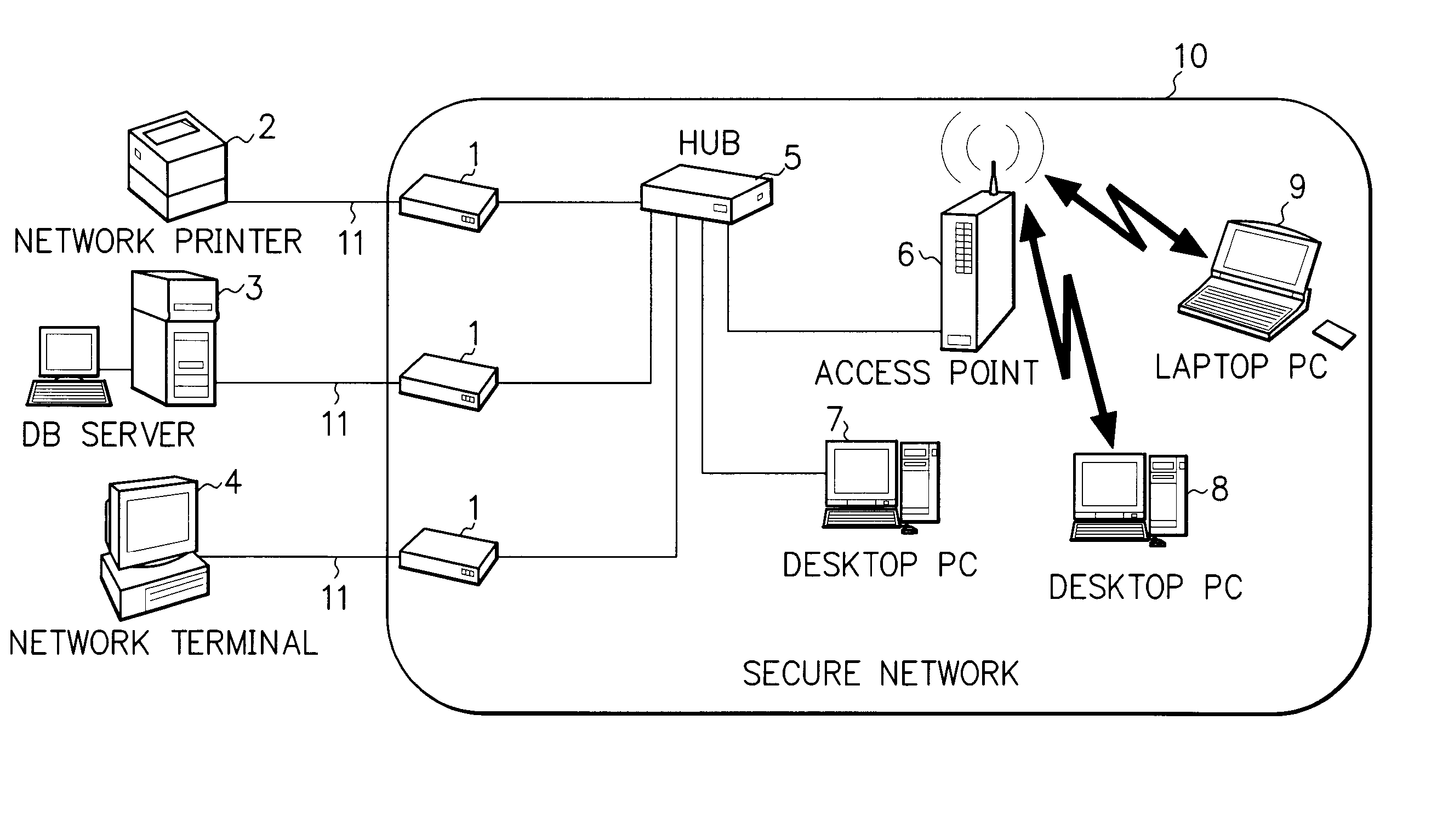
Encryption apparatus, encryption method, and encryption system
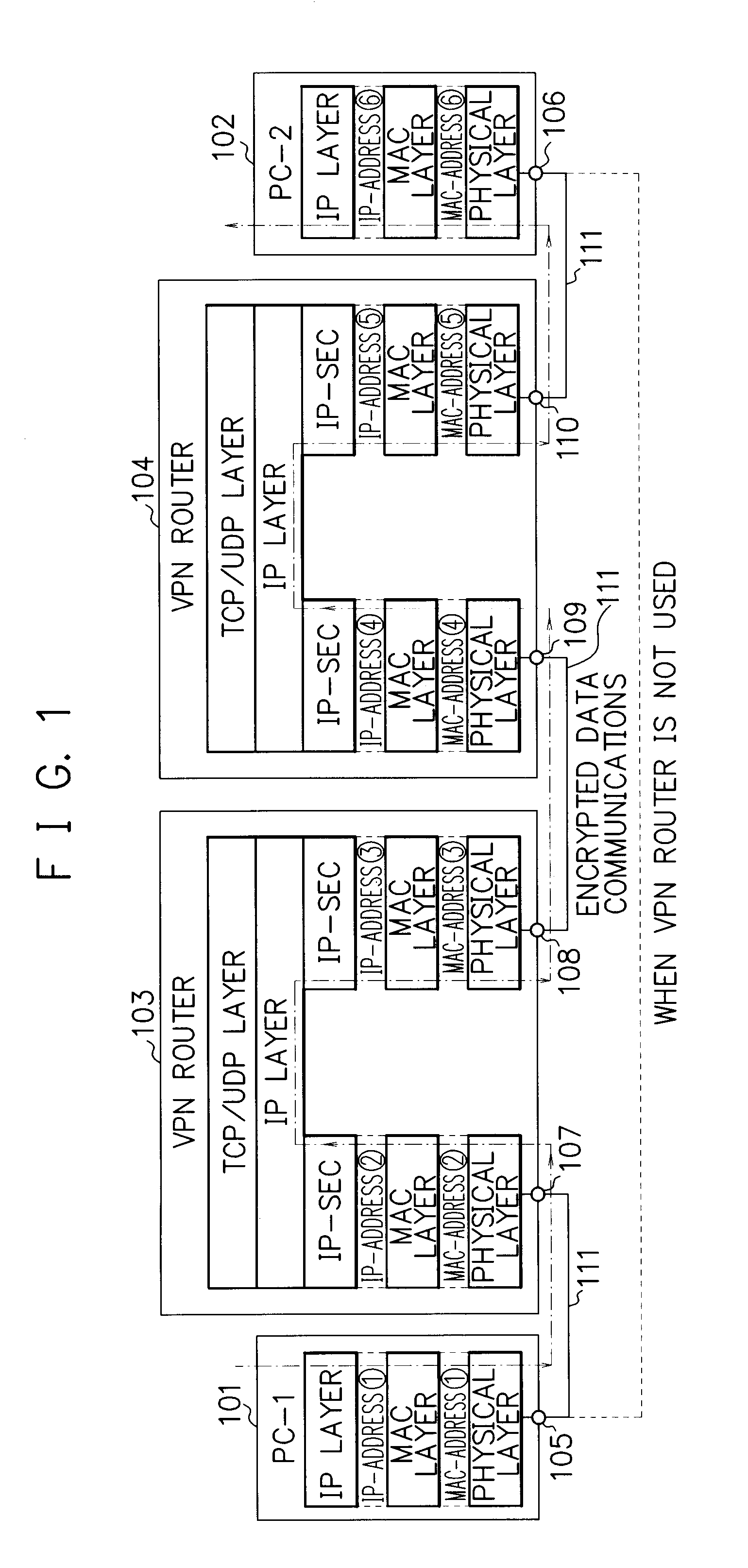
InactiveUS20050021949A1Risks of interceptionMultiple keys/algorithms usageData taking preventionPersonal computerEncryption software
An encryption apparatus 1 for performing an encrypting process and an encrypted data decrypting process is mounted to terminate the security by encryption between personal computers 7 to 9 on which encryption software is installed. For example, by connecting the apparatus between terminals 2 to 4 and the personal computers 7 to 9, the encryption can be used in an in-house LAN having the terminals 2 to 4 on which encryption software cannot be installed. Thus, a secure network 10 almost free of the risk of tapping of the confidential information in the LAN by an external unauthorized entry or attach can be successfully designed.
Owner:ONICIX GRP L A
Owner Controlled Transmitted File Protection and Access Control System and Method
InactiveUS20110162040A1Easy to controlLimited lifespanComputer security arrangementsTransmissionControl systemTime sensitive
An owner controlled file protection and control system that uses a protected file that is encrypted and has embedded with access and use control features. The file is selected and encrypted and combined with a set of encrypted policy rules by an encryption software program. The policy rules are one or more ‘access rules’ and ‘use rules’ that determine who, what, when, and where the protected file may be accessed and how the protected file will be used. They may be selectively changed at any time and may be location, time and date sensitive. The protected file may be sent to the recipient or stored in a file that the recipient may accessed. During use, each recipient must register with the system and is assigned a registered ID. Using the ‘access rule’, the owner may assign a particular recipient ID to the protected file. A recipient then uses a reader program to generate a request to access and use the protected file to a management server. Management server then reviews the policy rules associated with the protected file to determine if they are satisfied. If the rules are satisfied, then time sensitive digital certificate is sent to the recipient that allows the protected file to be accessed and used according to the policy rules.
Owner:FILELIFE
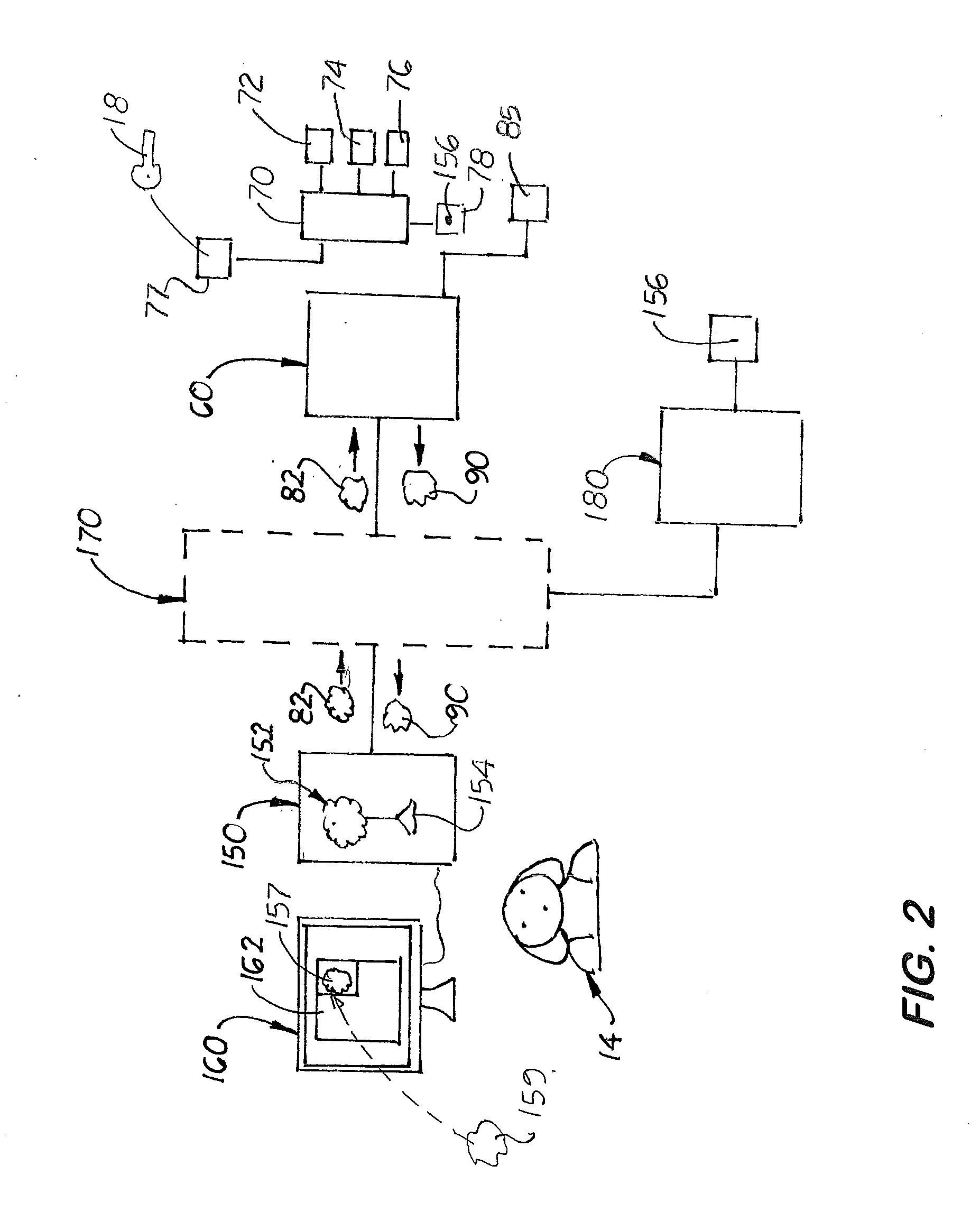
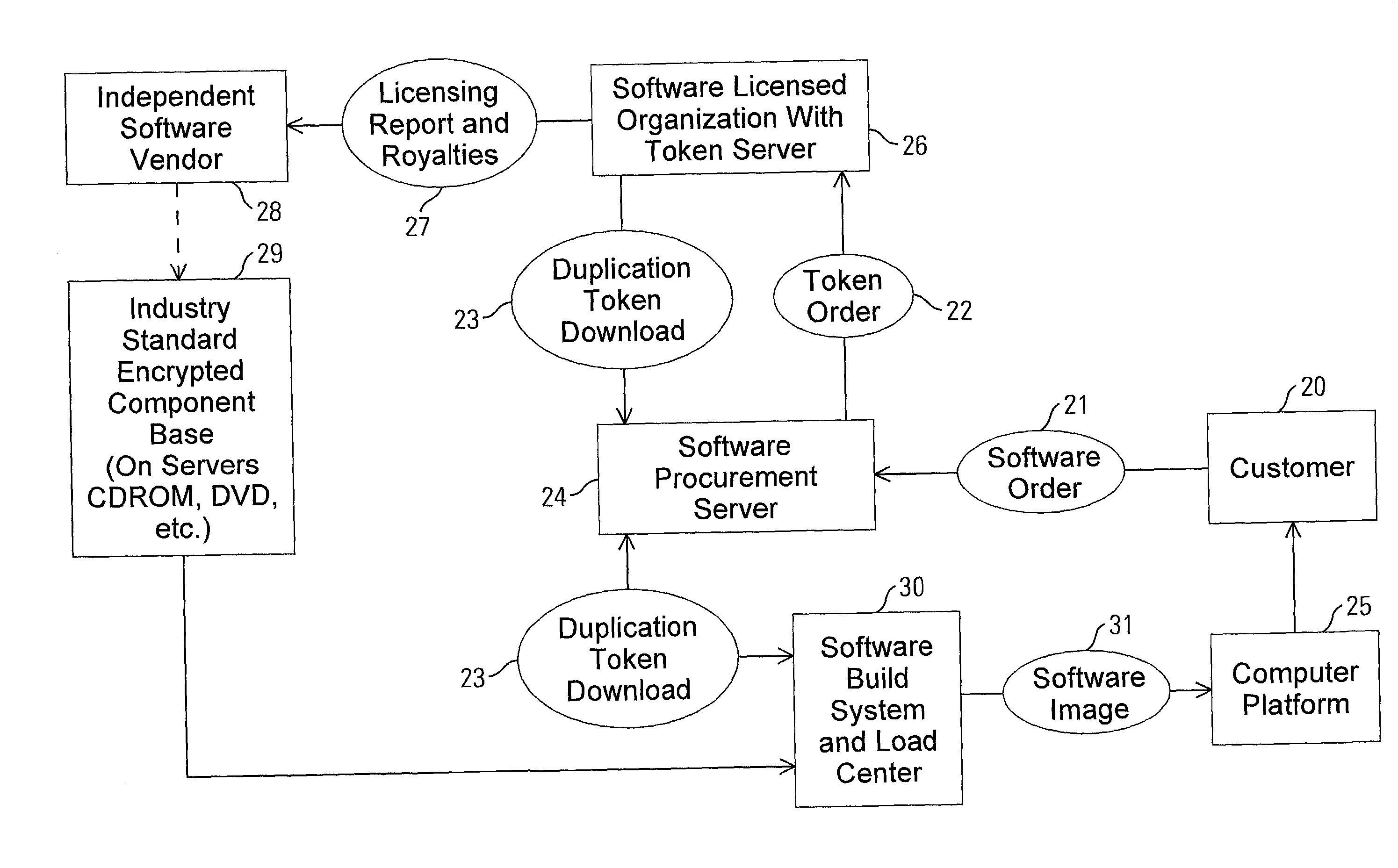
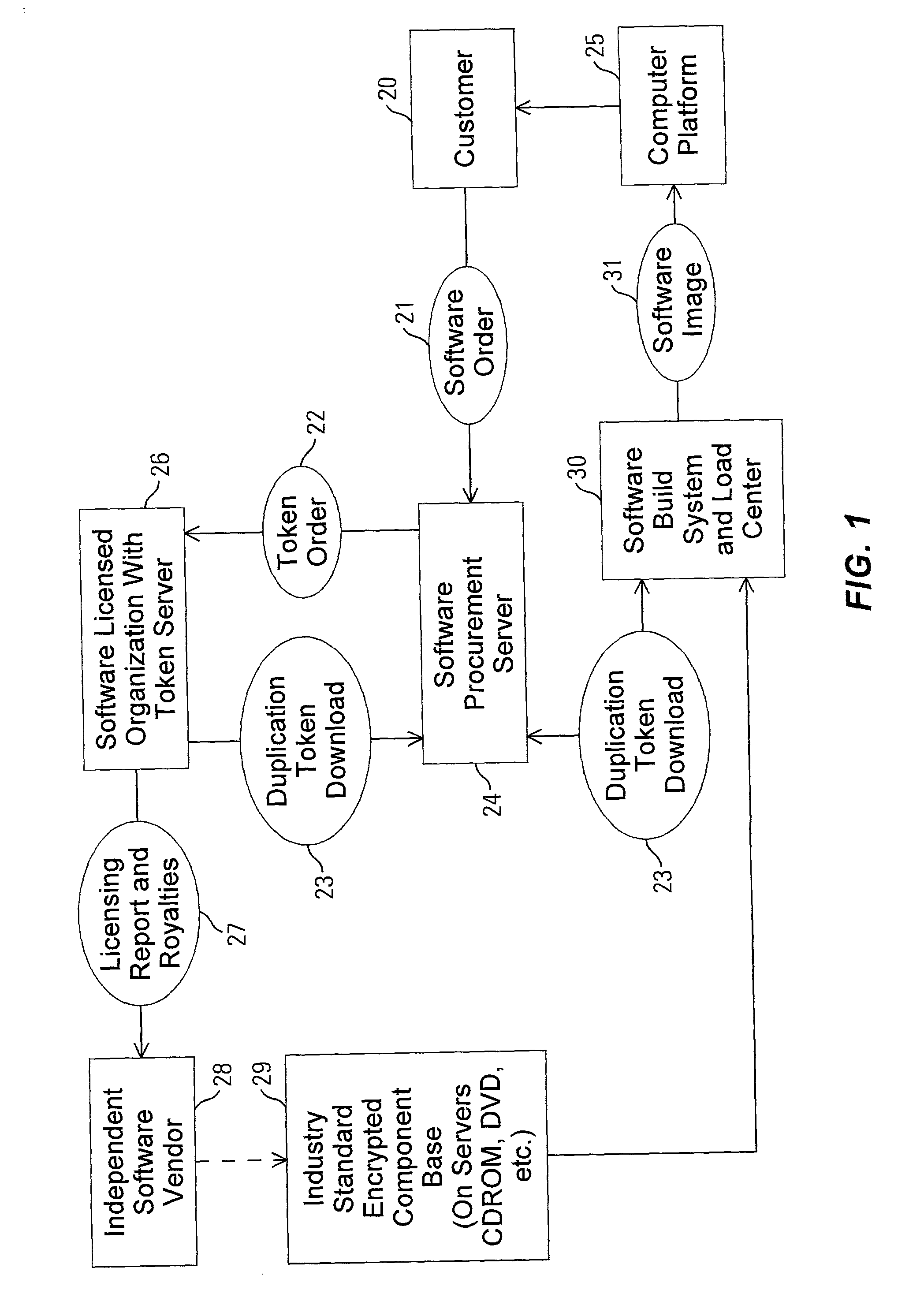
Method and apparatus for uniquely and securely loading software to an individual computer
InactiveUS20020128975A1Increase incomeTurn around timeKey distribution for secure communicationPublic key for secure communicationPersonal computerApplication software
A method and apparatus for uniquely and securely loading software to an individual computer includes requesting download of software components to a hardware platform and delivering a token from a token server responsive to the request. The token server is operated by an entity having rights to grant access to the software components. The token is passed to a system that builds software images. The system is operated by an organization that performs delivery of the software. The software components are assembled and decrypted with the system within an enabled secure process. A software image to be loaded onto the platform is created and bound to the hardware platform by encrypting the software image using an application specific encryption technique.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Protected IP telephony calls using encryption
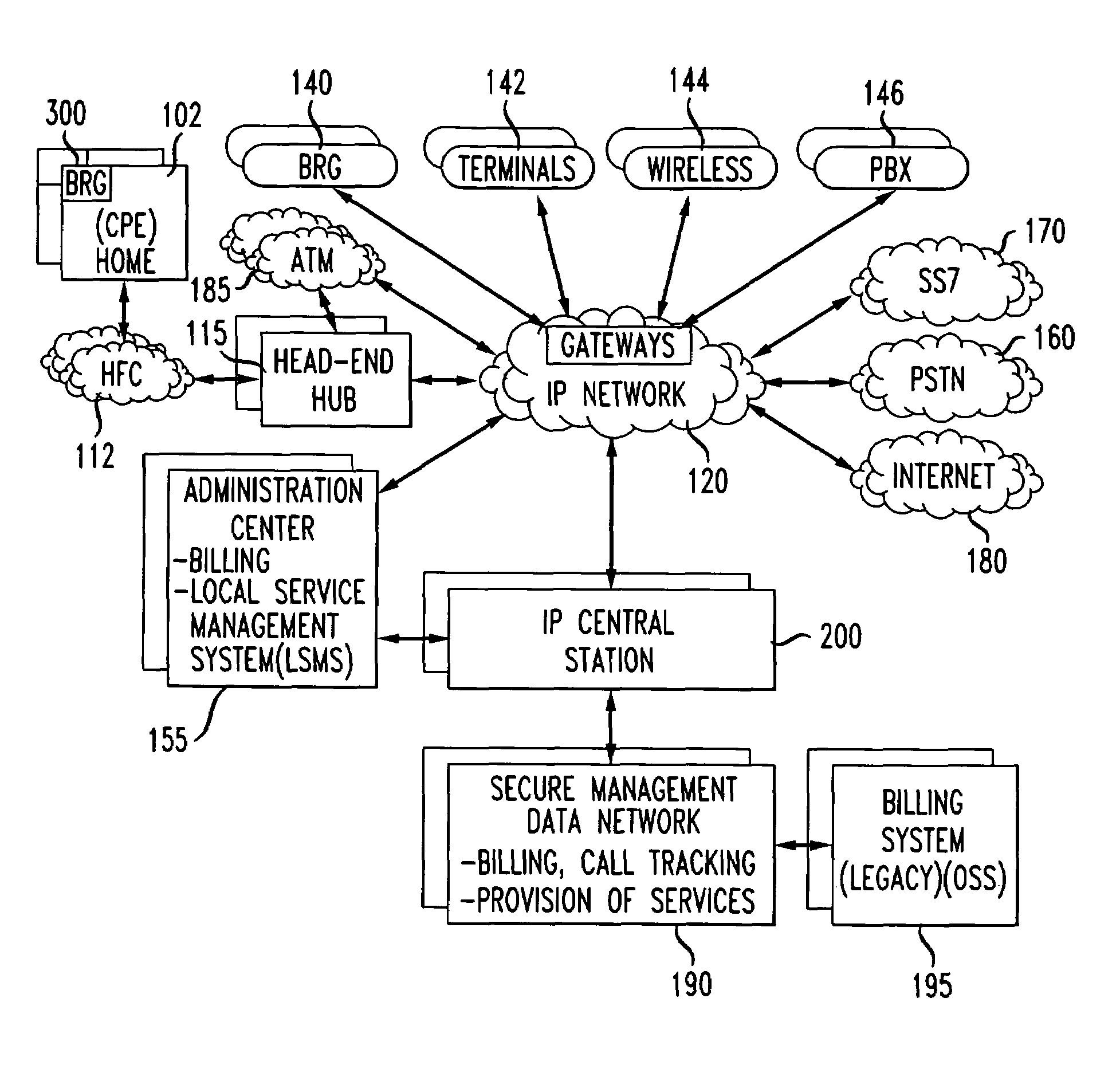
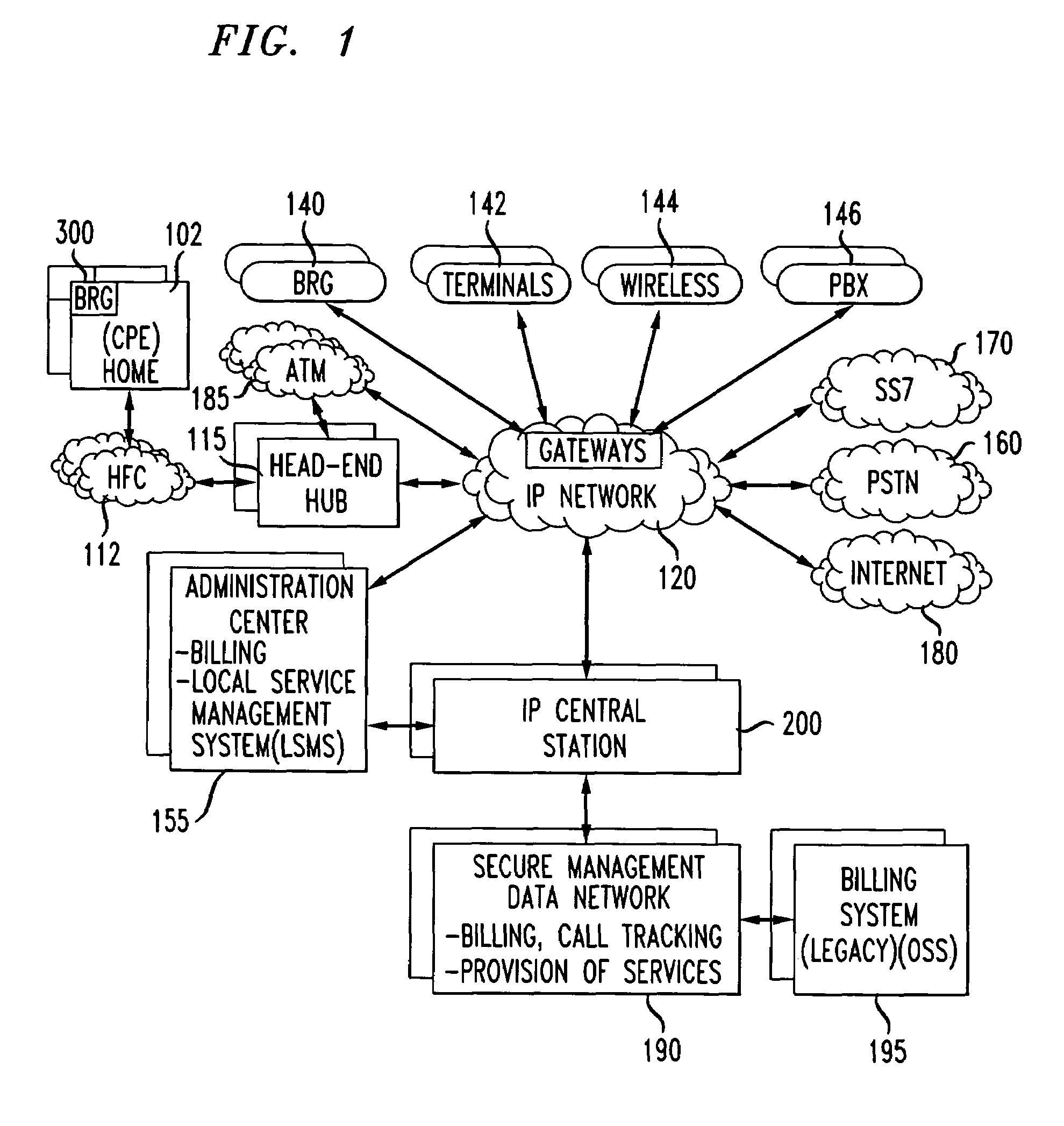
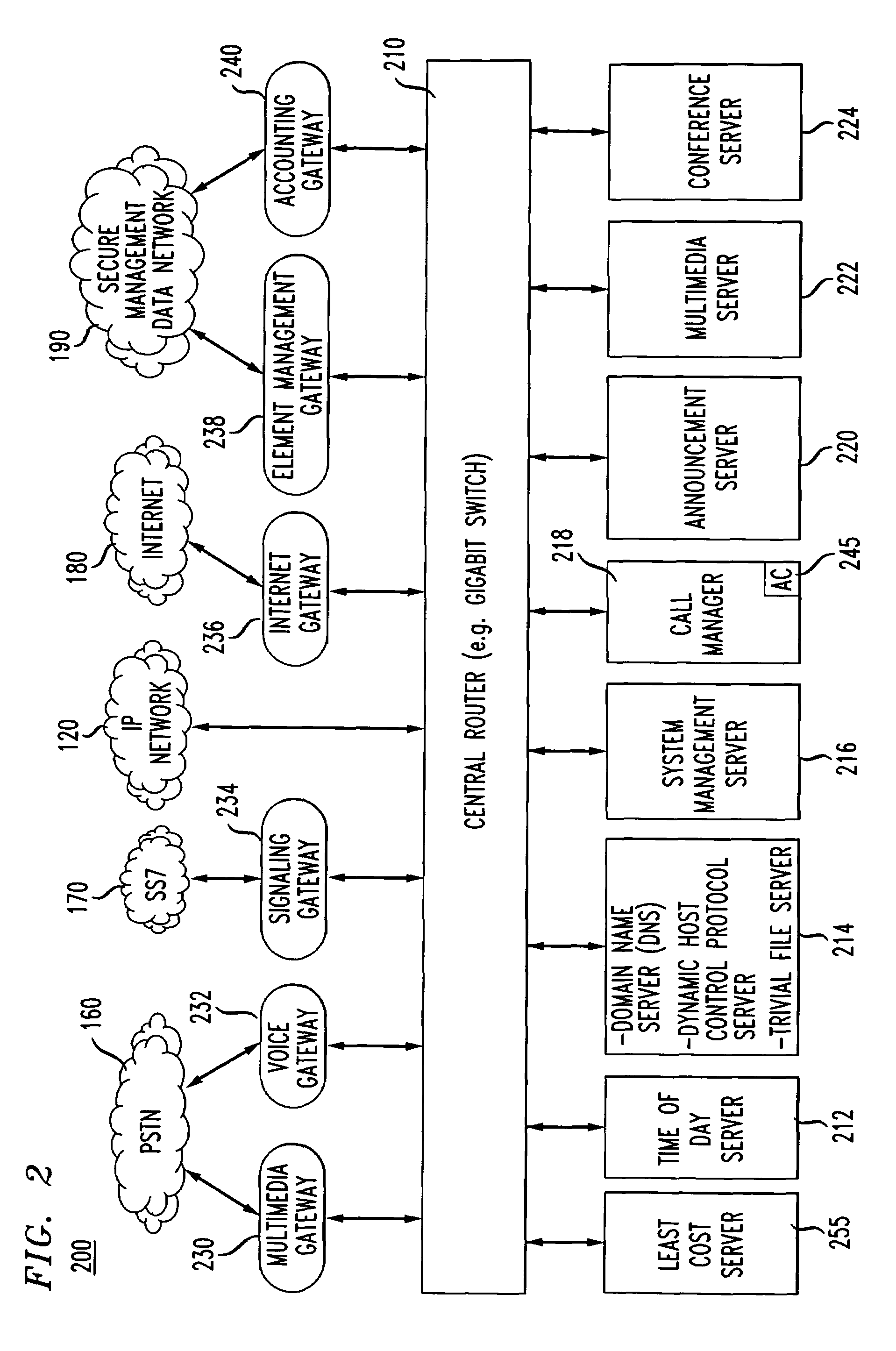
InactiveUS7734908B1Multiplex system selection arrangementsInterconnection arrangementsComputer scienceBroadband communication
Communication information transmitted in the broadband communication system may be in a packet format and secured using encryption techniques, for example encryption software, including a means for providing an initial security key and updated security keys to the various pieces of communication equipment located throughout the broadband communication system. When communication equipment, for example a gateway, is first registered with, for example, an IP central station, the IP central station assigns an initial encryption key to the gateway that is assigned and retained by a server, for example a call manager server, and the gateway (e.g., broadband residential gateway). This initial encryption key may be used to establish a secure two way communication between two pieces of communication equipment as an originating point communication equipment and a terminating point communication equipment.
Owner:RPX CORP
Software protection method, apparatus and equipment
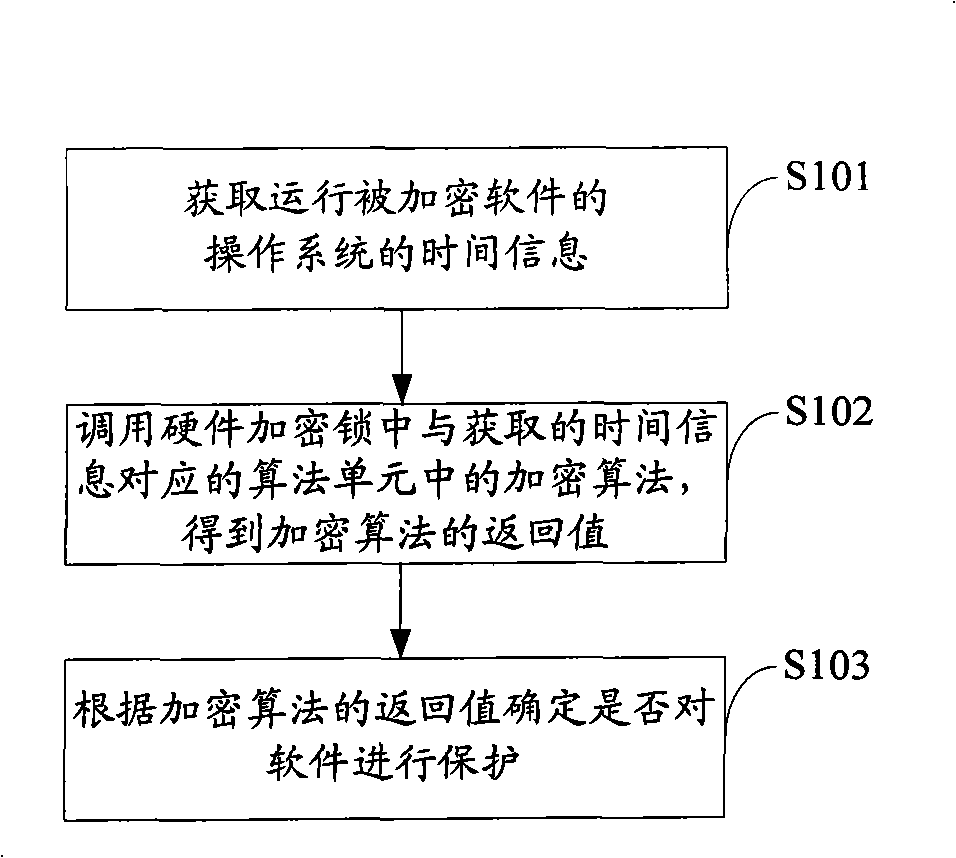
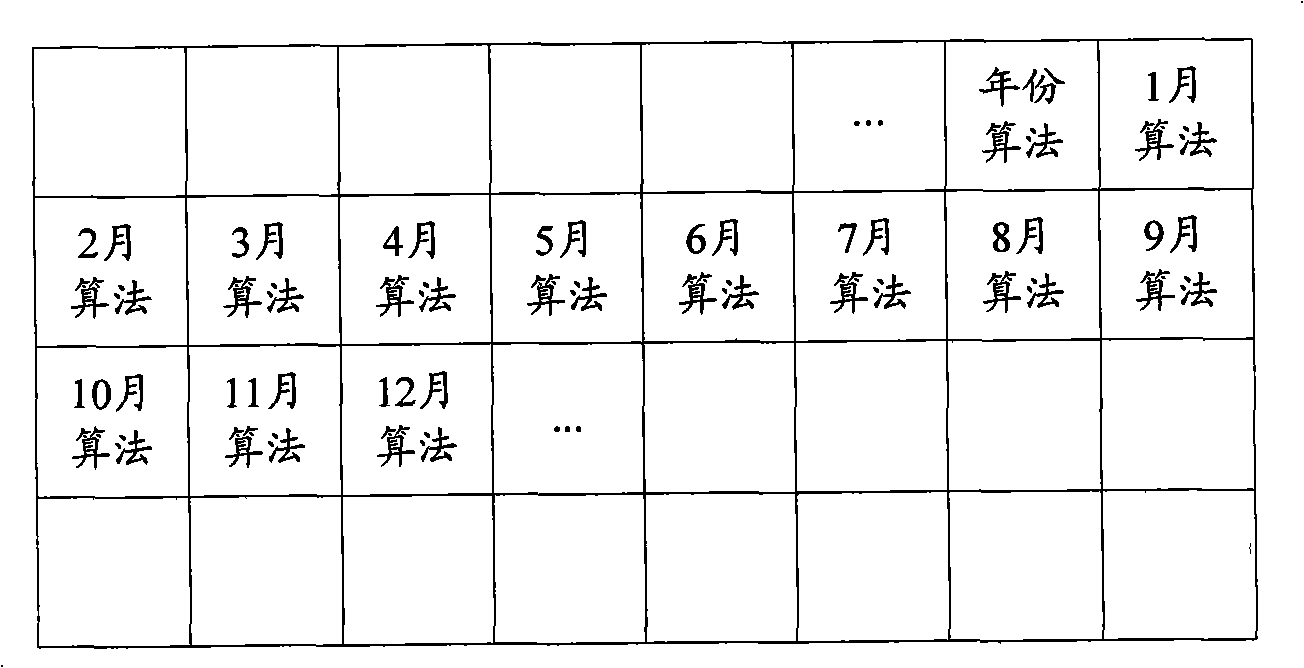
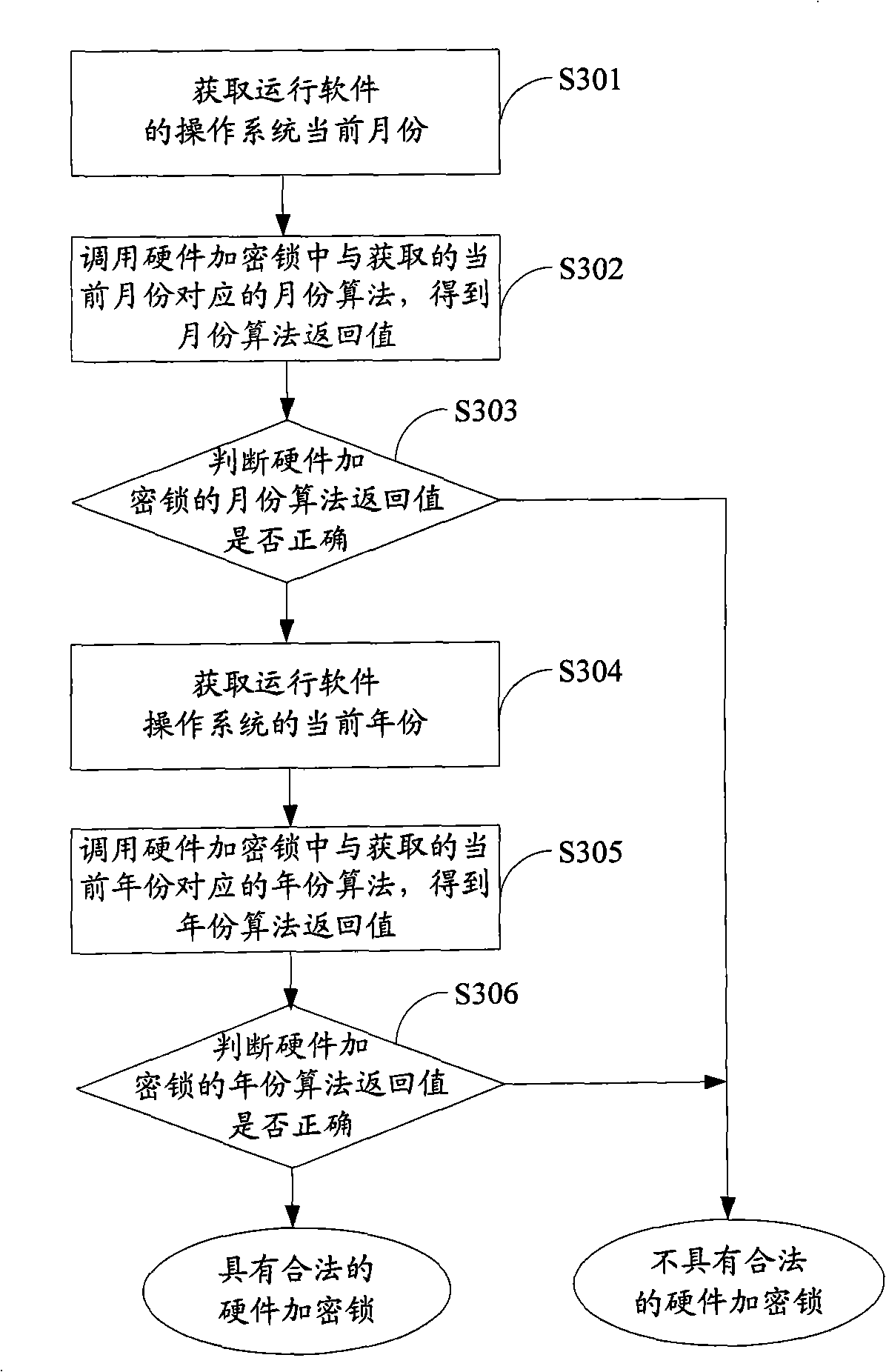
ActiveCN101404056AAchieve protectionReduce the risk of eavesdroppingPlatform integrity maintainanceProgram/content distribution protectionTemporal informationComputer hardware
The invention is applicable to the communication safety field and provides a software protection method, a device and equipment. The method comprises the following steps: current time information of an operation system which operates an encrypted software is obtained; an encryption algorithm in an algorithm unit which is corresponding to the obtained current time information is called from a hardware encryption lock, thereby obtaining a return value of the encryption algorithm; whether a software is protected or not is judged according to the return value of the encryption algorithm. The embodiment of the invention realizes the protection of the software and reduces the risk that communication information between the encrypted software and the hardware encryption lock is eavesdropped effectively by obtaining the time information of the operation system and calling the encryption algorithm which is corresponding to the time information from the hardware encryption lock.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
Gaming facility and method of operation thereof
InactiveUS20070178972A1Increase flexibilityEnabling executionApparatus for meter-controlled dispensingVideo gamesComputer hardwareWorkstation
A gaming system comprises one or more player stations, a repository containing a number of different software programs, and a download server communicable with the repository and each one of the player stations by means of a communication network. Each player station is identified by a unique code and is operable by a respective player to play a corresponding game. Each software program in the repository is executable on any player station to generate a simulation of a different game. One or more of selected software programs contained in the repository are encrypted, remotely from any of the player Stations, as a function of the unique identification code of a particular of the player stations. The download server is responsive to the encryption and downloads the encrypted software program or programs to the particular player station whose unique identification code was used for encryption. A security module associated with the particular player station decrypts the downloaded encrypted software program or programs to obtain therefrom a decrypted identification code. The security module enables execution of the downloaded encrypted software programs by the particular player station when the decrypted identification code is the same as the unique identification code of the particular player station, and disables execution of the downloaded encrypted software programs by the particular player station when the decrypted identification code is different from the unique identification code of the particular player station. The security module also disables execution of the software programs when the software program have not been encrypted.
Owner:WATERLEAF LTD
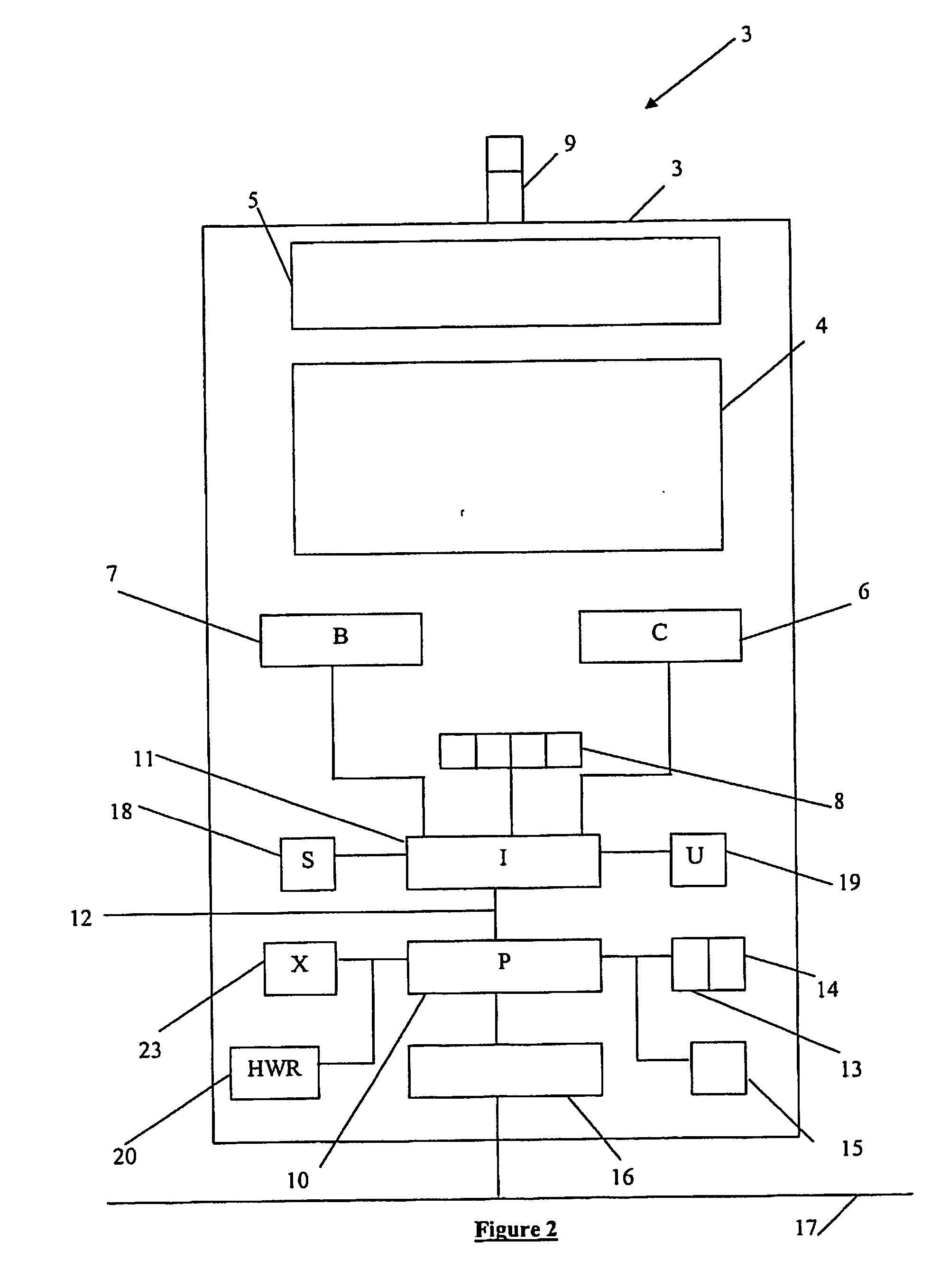
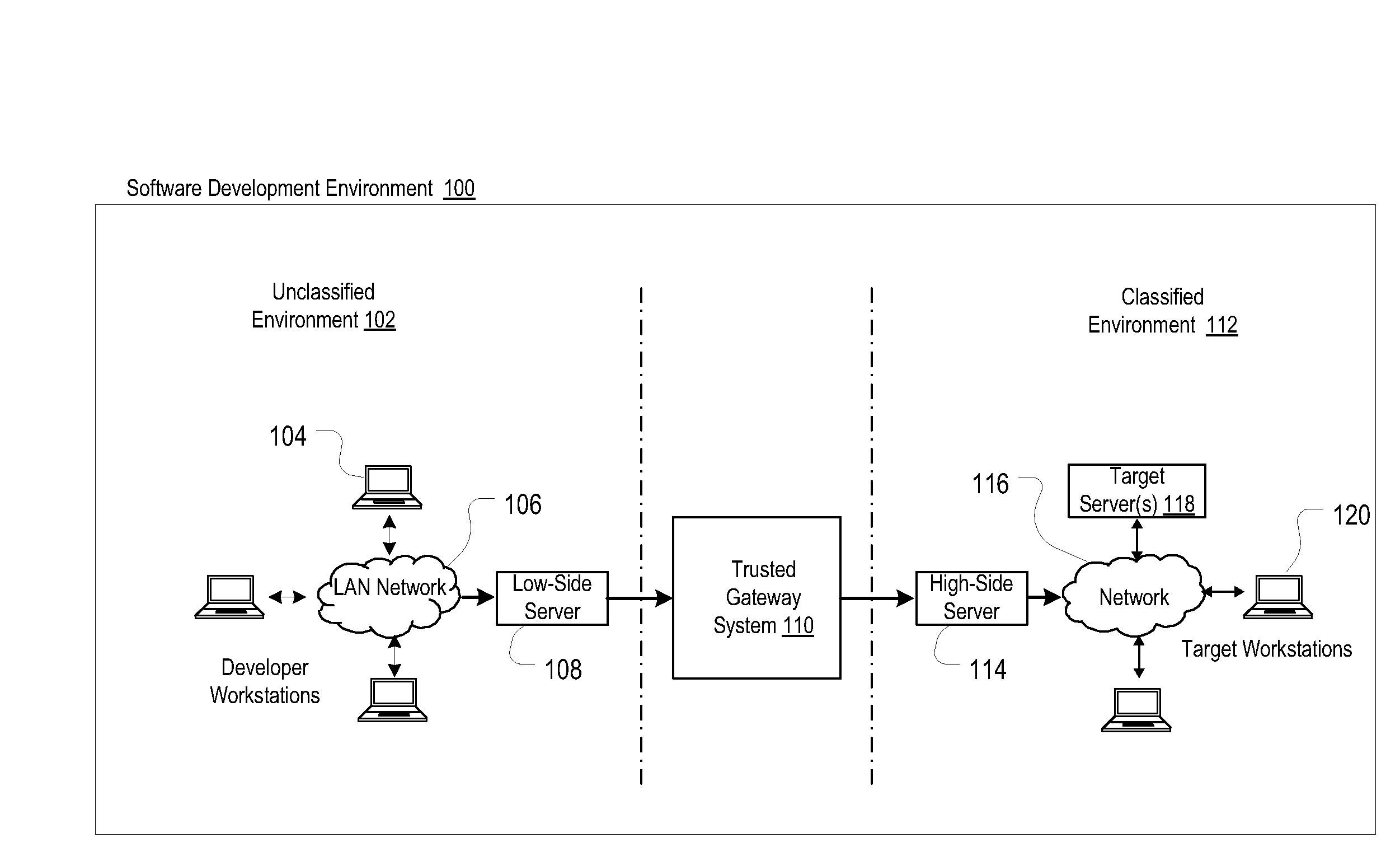
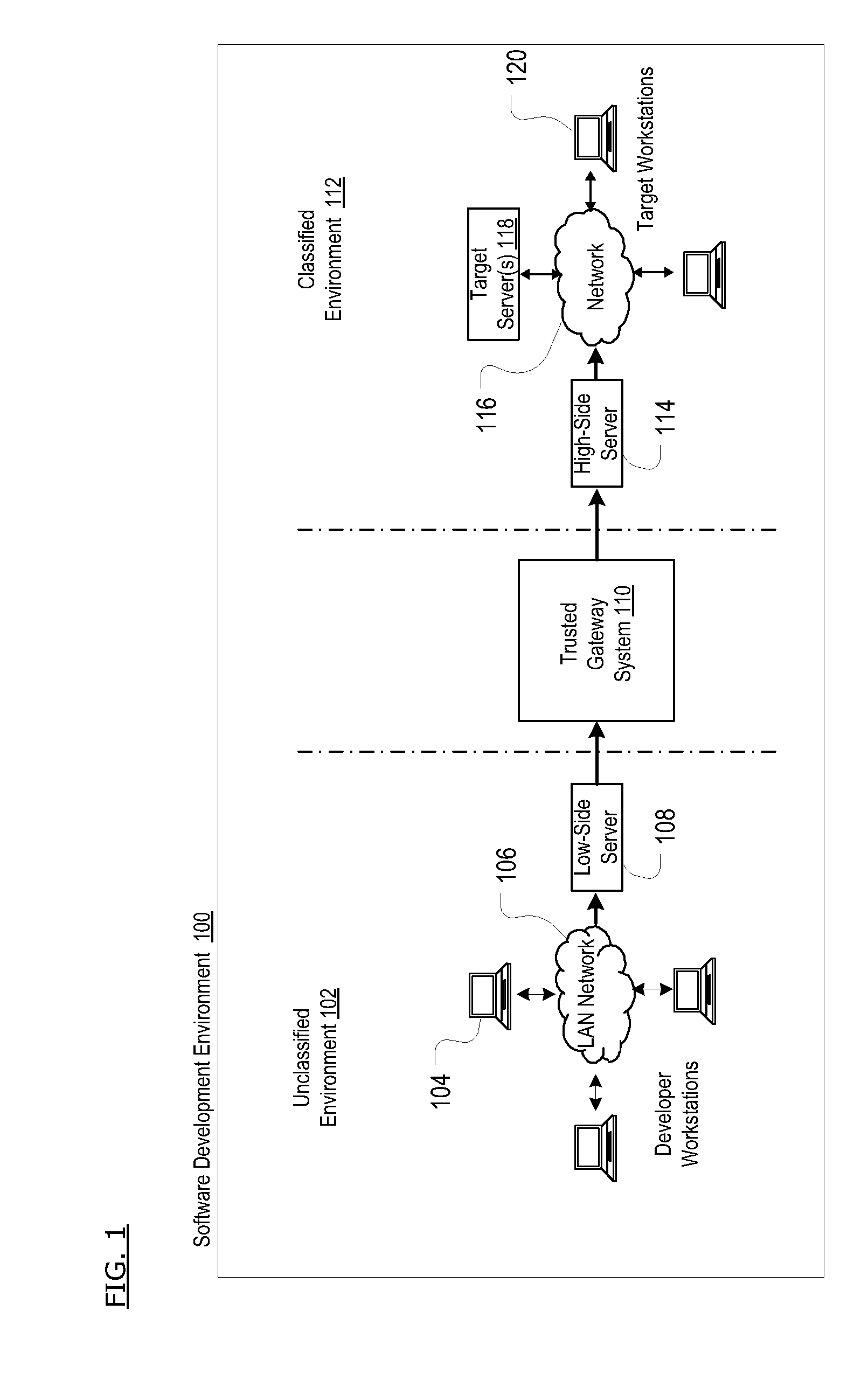
Method For Connecting Unclassified And Classified Information Systems
InactiveUS20090271858A1Small sizeAvoid easy removalMultiple digital computer combinationsProgram controlClassified informationM-government
A method and system that enables the connection of an unclassified information system to a classified information system while meeting all government requirements. The system utilizes a combination of COTS technologies (e.g., a Trusted Gateway System, type-2 encryption software, etc.), local administrative policies, and scriptable software applications.
Owner:LOCKHEED MARTIN CORP
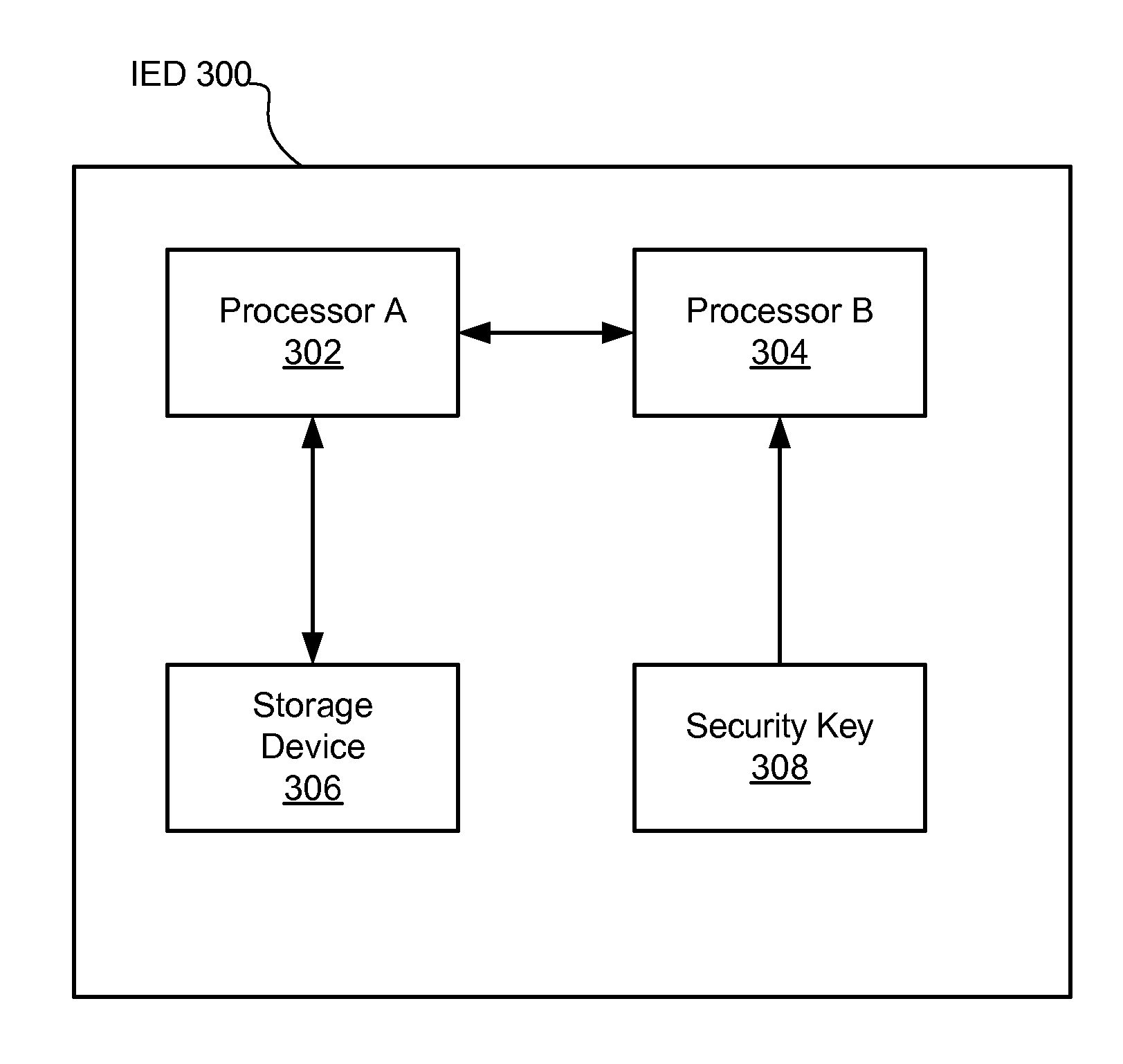
Security through layers in an intelligent electronic device
ActiveUS20150310191A1Improve securityPrevent password reuseTariff metering apparatusCurrent/voltage measurementPasswordIntelligent electronic device
The present disclosure provides for improving security in a meter or an intelligent electronic device (IED) through the use of a security key which is unique to each meter or IED. Such a key may be used to prevent password reuse among multiple meters. Such a key may also be used to encrypt critical components of the software, such that only when running on the correct meter can the components of the software be decrypted. Such a key may also be used to uniquely identify the device in a larger data collection and management system. The security key can also be used to prevent the direct copying of meters. The present disclosure also provides for a meter or IED that stores functional software separately from core software.
Owner:ELECTRO INDUSTRIES GAUGE TECH
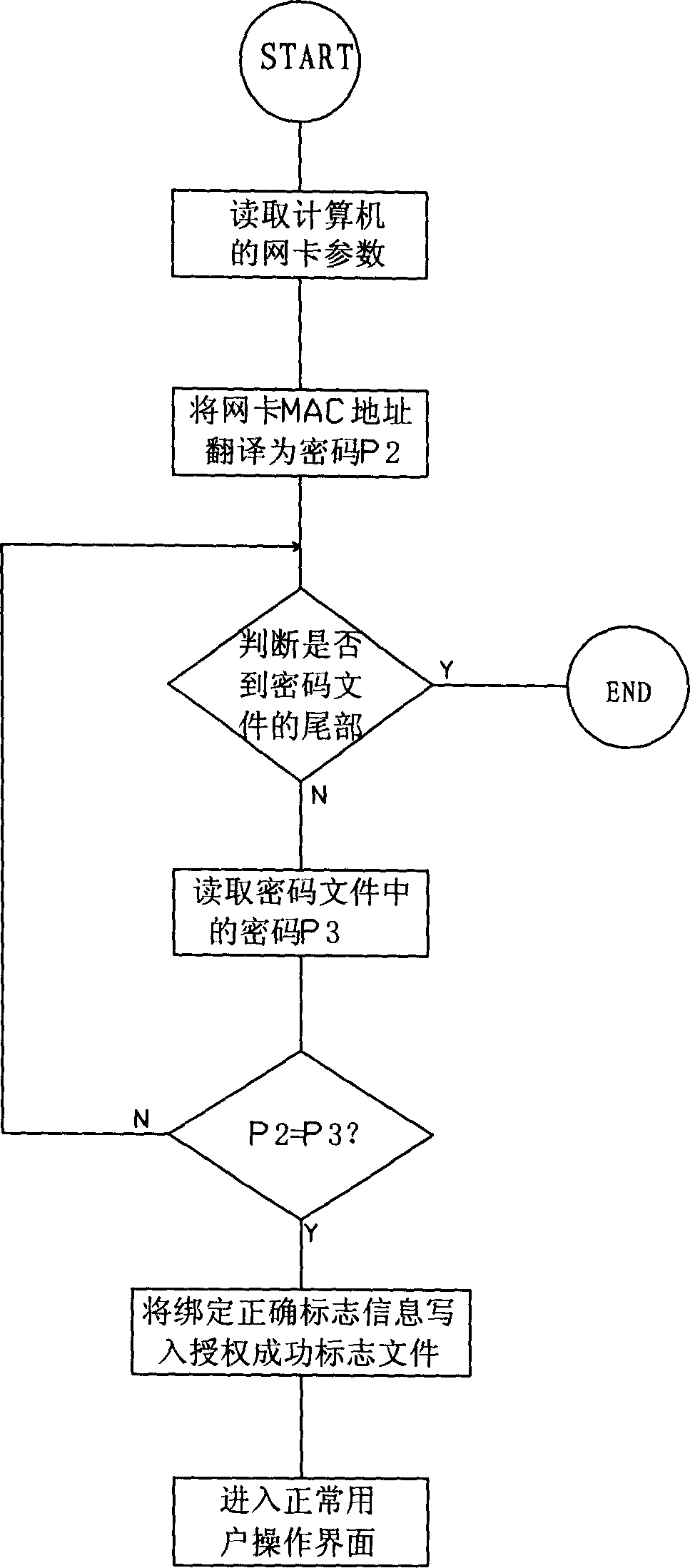
Method of preoenting software non-authorized use by using network card physical address
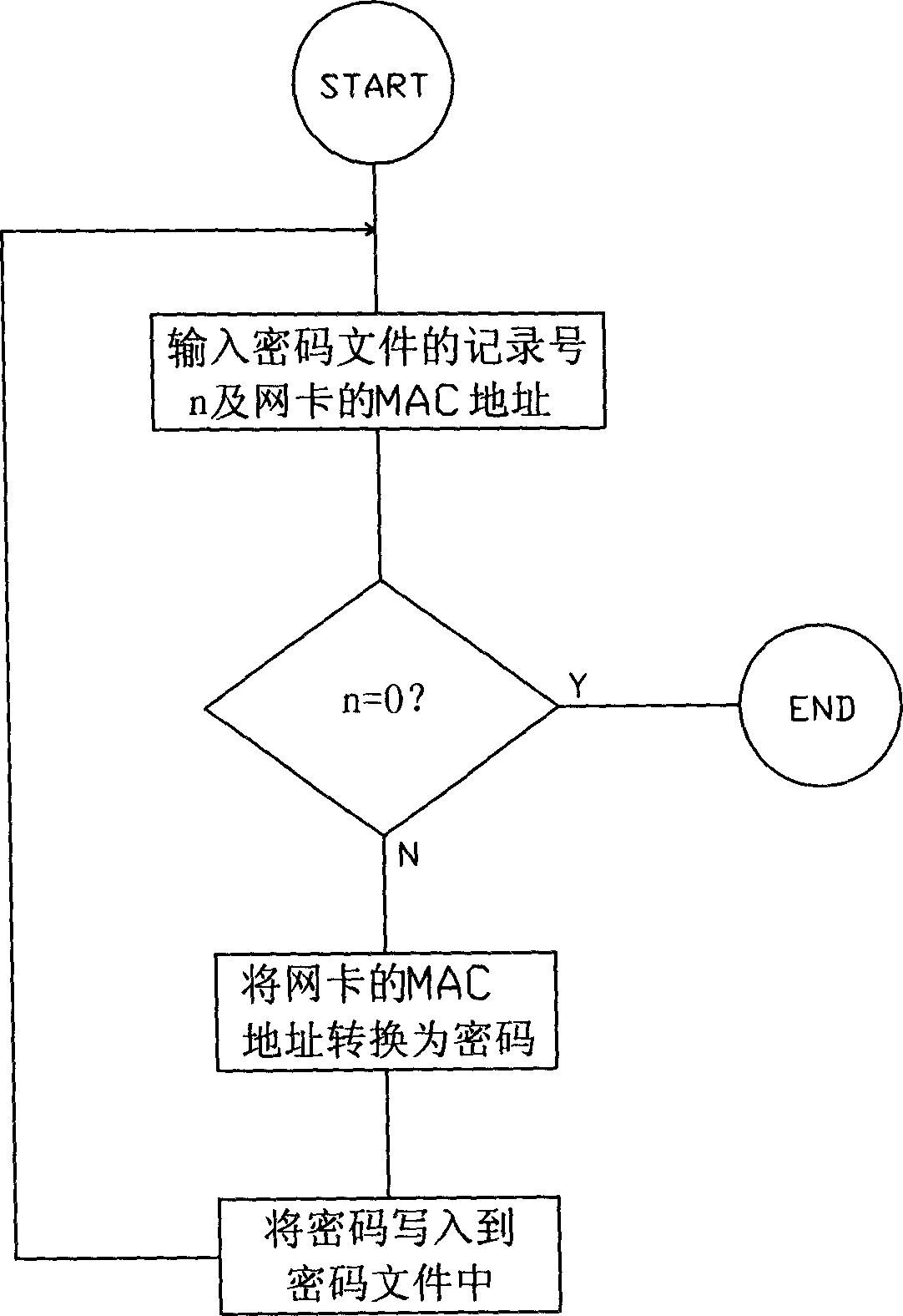
InactiveCN1794258ANot easy to damageNo damageDigital data processing detailsProgram/content distribution protectionPhysical addressSoftware development
This invention relates to a method for preventing non-authorized usage of software with MAC address, in which, a software development runner utilizes a ciphered software management program to convert the MAC of the customer end computer to a ciphered code and writes it to a ciphered code file to be provided to the customer, the customer end computer utilizes a ciphered software applied program to convert the local MAC address according to the same ciphered algorithm and compares it with the ciphered code fetched from the ciphered file, if they are the same, then the authorization is successful, which utilizes computer net cards to bind the ciphering applied software and a customer end computer, since each net card has an exclusive physical address in the world and if the address is bound, that means the software is bound onto the exclusive computer.
Owner:左长进
Electronic device and method of software or firmware updating of an electronic device
InactiveUS8543839B2Low implementation costLow costDigital data processing detailsUnauthorized memory use protectionControl softwareOne time programmable
An electronic device is provided having a memory driver unit for reading partition headers including encrypted version numbers from a memory and for writing updated encrypted version numbers to the memory. The electronic device has an update agent unit for controlling a software or firmware update, a one-time programmable memory for storing a first value, and an encrypt-decrypt unit for decrypting the partition headers stored in the memory. The update agent is configured to compare the retrieved version numbers with a version number from a software or firmware update. The first value is incremented and stored in the one-time programmable memory if an update is performed. The encrypt-decrypt unit is configured to encrypt the version numbers of the software or firmware update based on the new first value. The memory driver unit is configured to write a new partition header with the updated encrypted version numbers into the memory.
Owner:ST ERICSSON SA
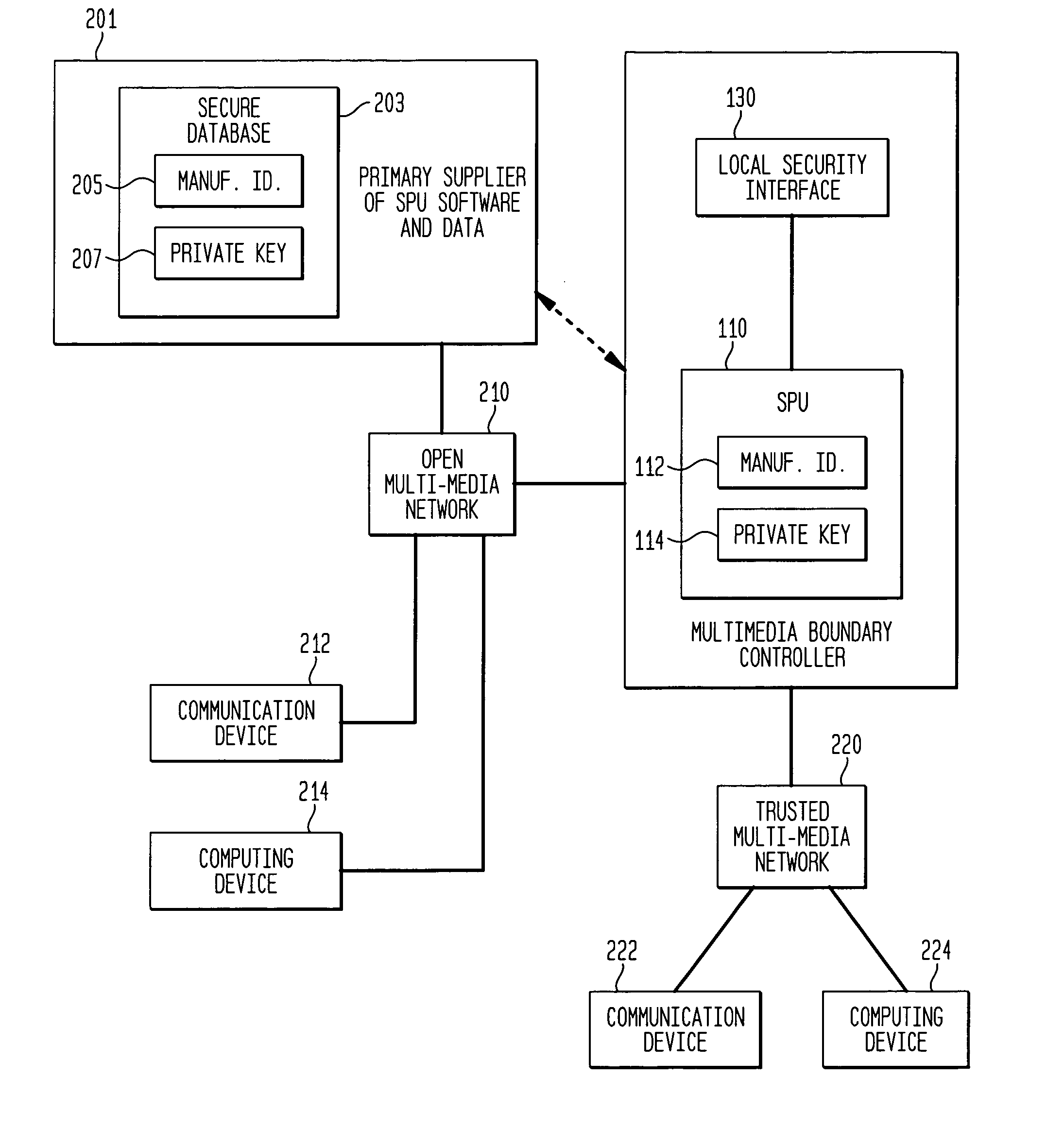
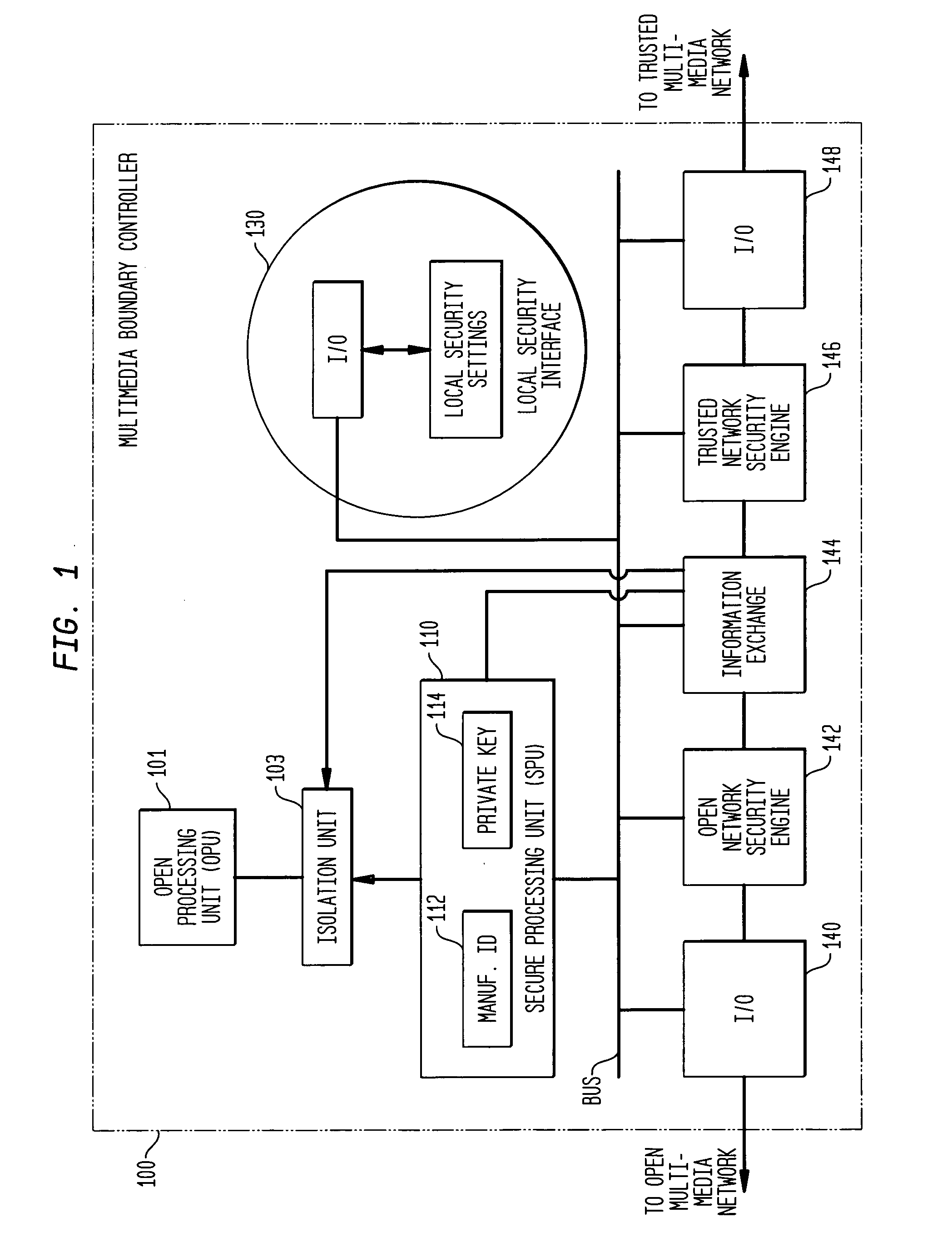
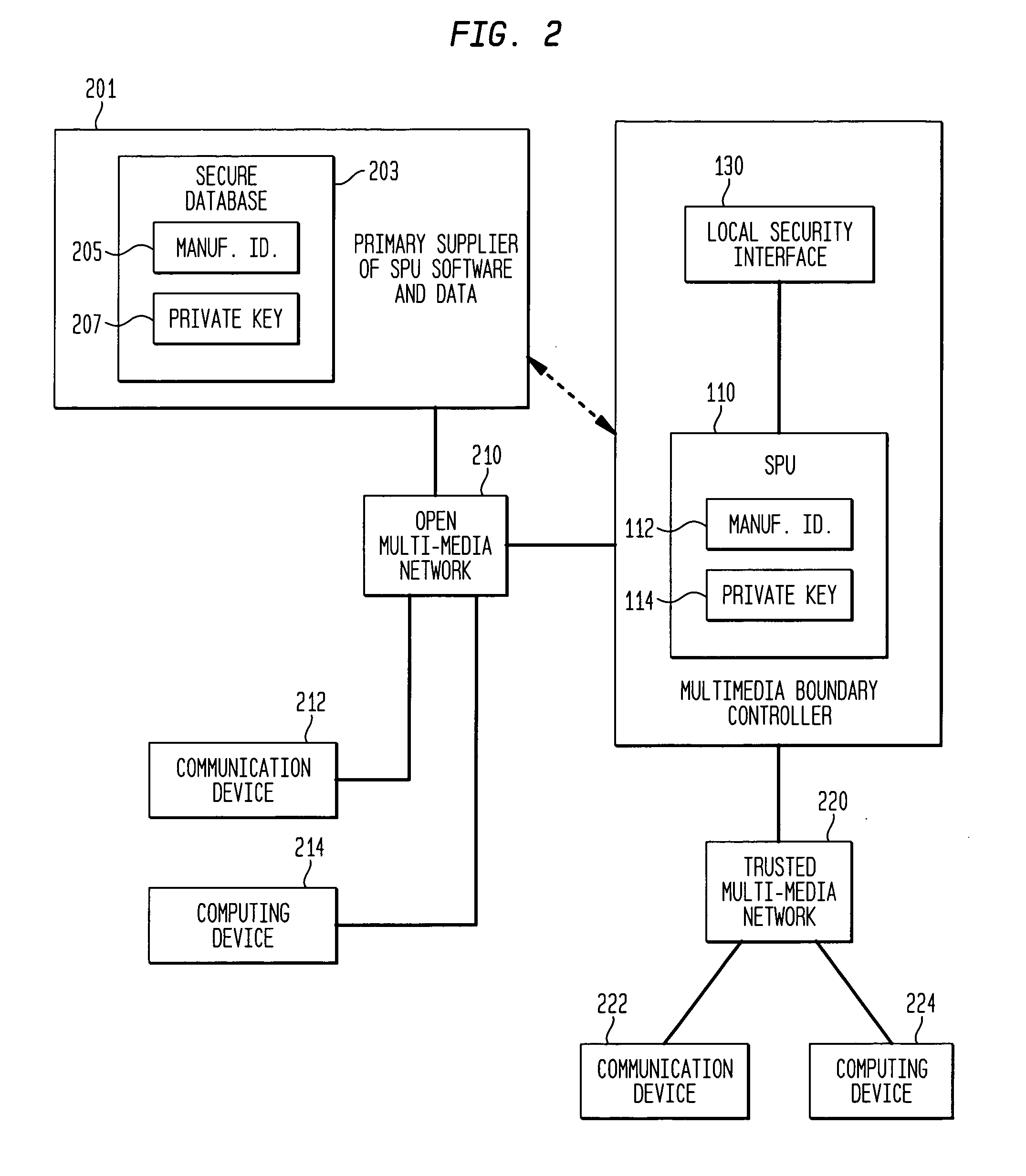
Secure data communication system
InactiveUS20050240991A1Contamination can be spreadInhibition of informationMultiple digital computer combinationsProgram controlSecure communicationCommunications system
This invention relates to methods and apparatus for securing communications between an open multimedia network and a trusted multimedia network. A multimedia boundary controller controls the communications between the two networks in order to intercept corrupting data such as viruses. The boundary controller contains an open network security engine for providing normal security and a trusted network security engine for implementing special software to provide additional protection. The unit is controlled by a secure processing unit which can prevent unwanted information from getting into the trusted network security engine and the trusted multimedia network. The secure processing unit communicates with a manufacturer of security software over the open network using encrypted messages. The encryption key is shared between the multimedia boundary controller and the manufacturer of software and is stored in a durable memory which can only be used directly by the secure processor's encryption software and hardware. Advantageously, this arrangement provides a high level of security for communications to and from a trusted multimedia network.
Owner:LUCENT TECH INC
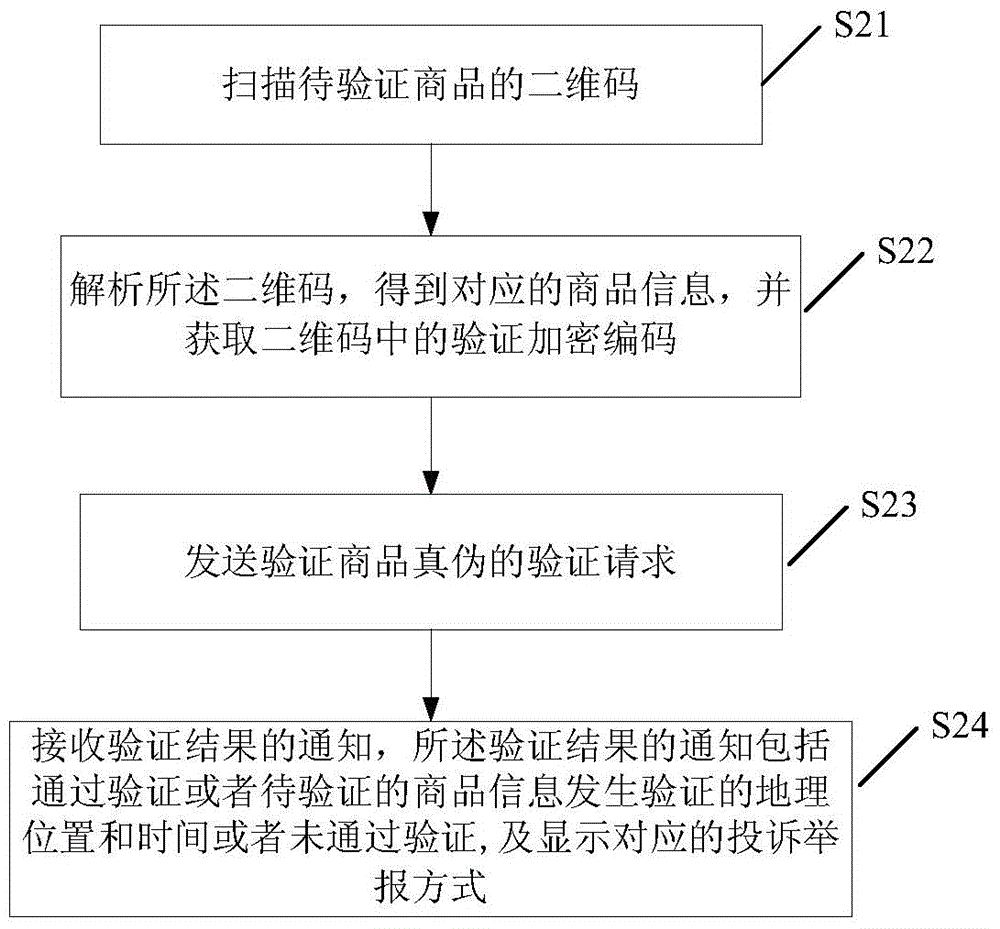
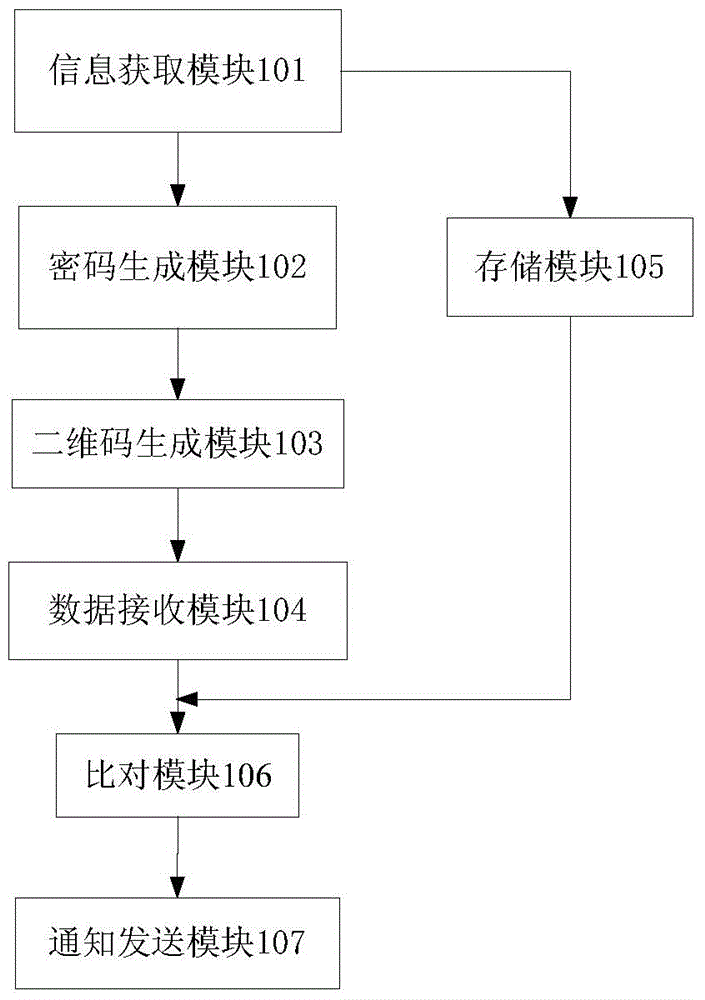
Method, system and device for two-dimension code authenticity
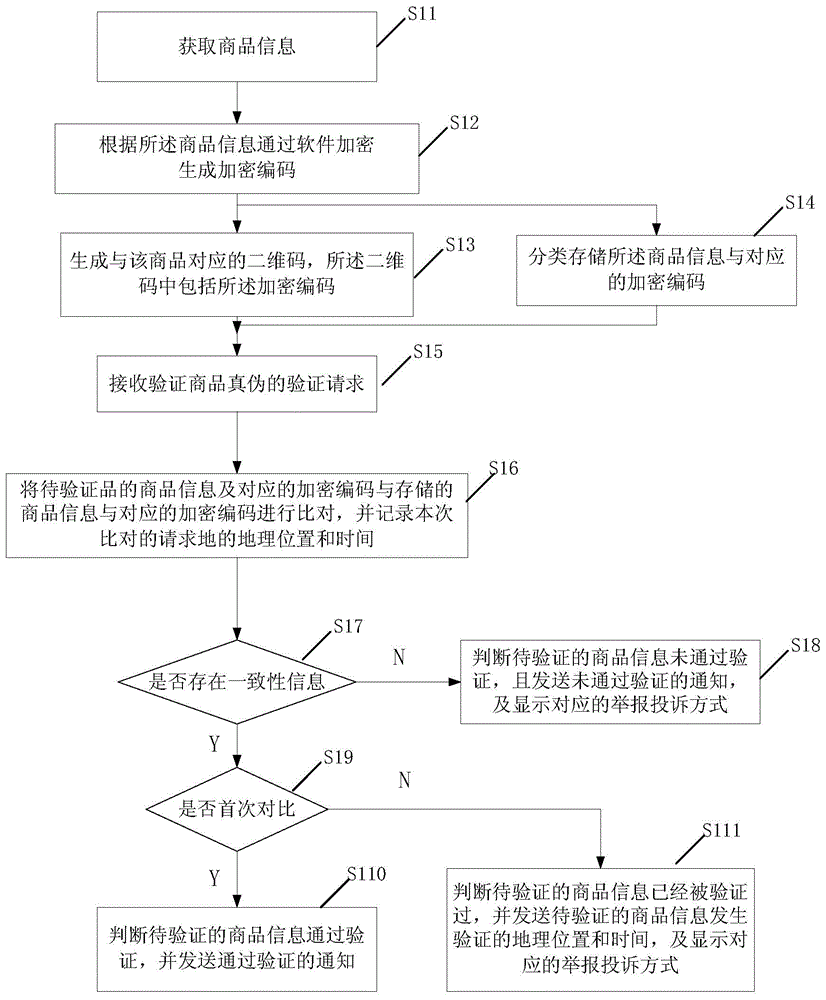
InactiveCN104881787AImprove experienceAvoid typosCommerceRecord carriers used with machinesValidation methodsUser input
The invention provides a method, system and device for two-dimension code authenticity. An encrypted code is generated by encryption software after information of an article is obtained and is contained in a generated two-dimension code. After a client application scans and analyzes the two-dimension code, the information details, contained in the two-dimension code, of the article are obtained, and the encrypted code, relative to the article and contained in the two-dimension code, is automatically obtained. A user only needs to provide a request of authenticity according to a prompt, and the encrypted code can be automatically updated to a server for authenticity. Operation of scraping coating and inputting a validation code is avoided. Experiences of the users are enriched, and a situation that the user inputs a wrong validation code is avoided.
Owner:JINGSHIJIA MEDIA TECH BEIJING
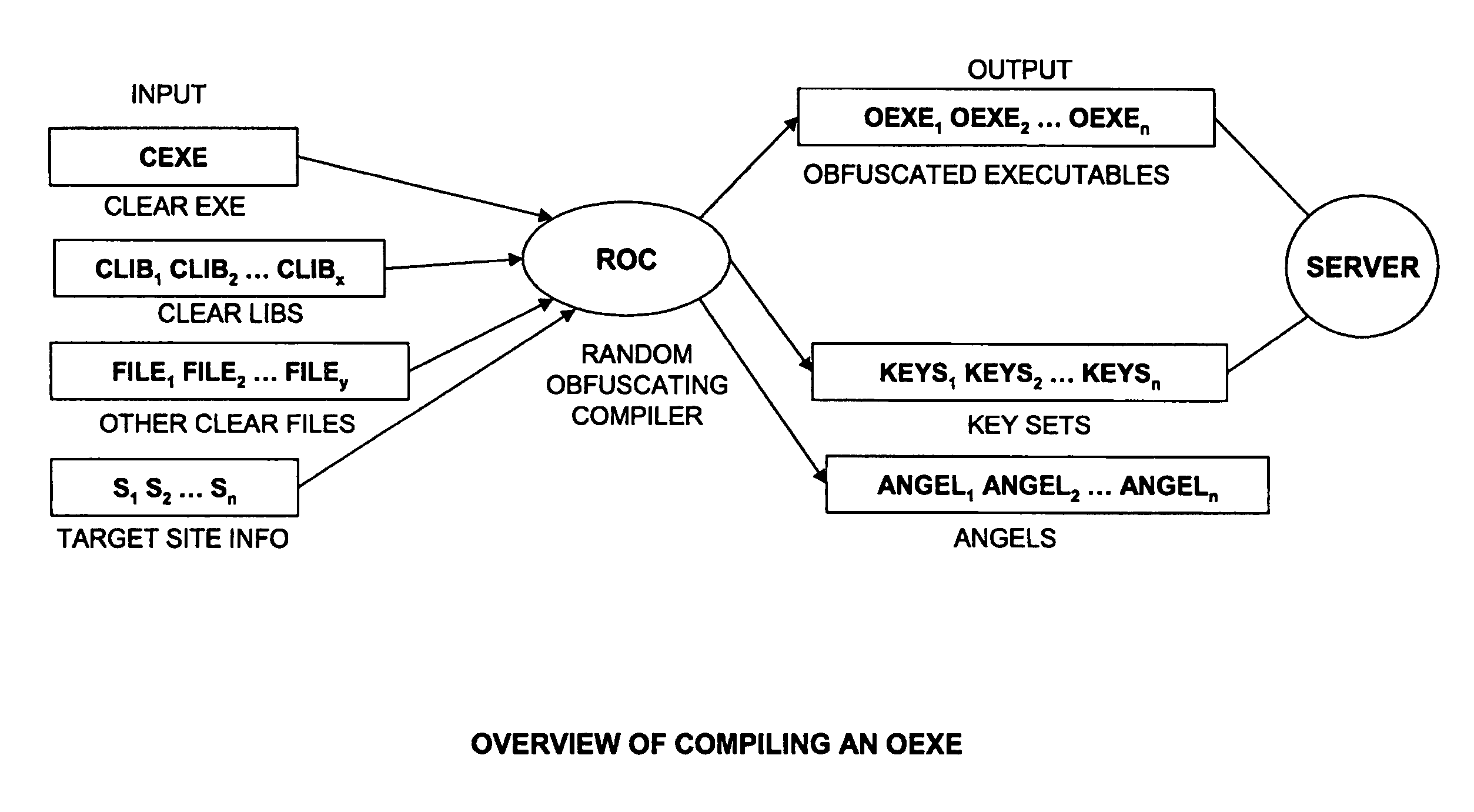
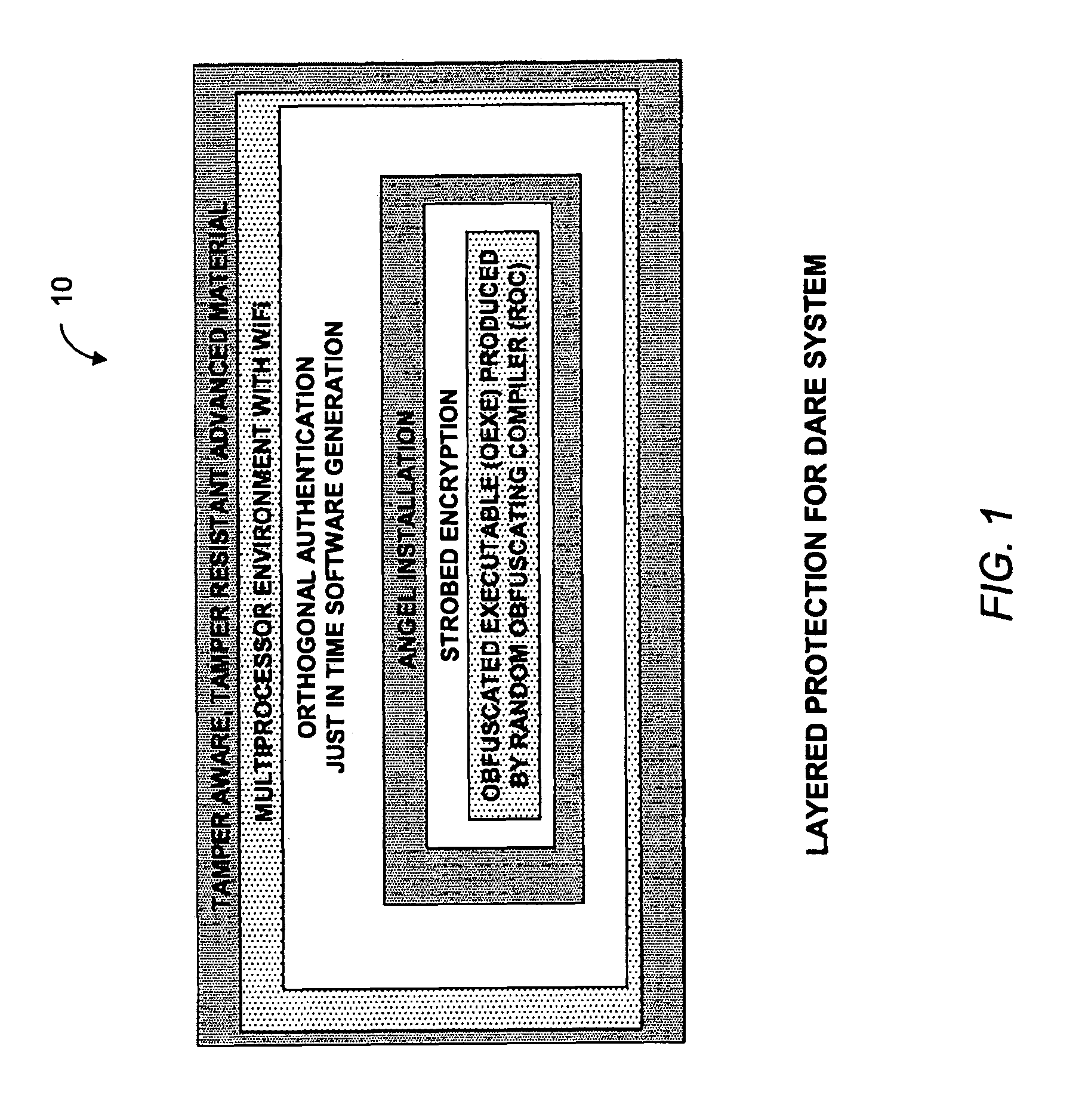
System and method for defending against reverse engineering of software, firmware and hardware
ActiveUS7841009B1Safe installationMemory loss protectionError detection/correctionEncryption softwareReverse engineering
A method for defending a software against reverse engineering in a target environment includes acquiring information from the target environment, encrypting the software to be protected with the acquired information, sending the encrypted software with the acquired information to an execution environment, acquiring information from the execution environment, comparing the information from the execution environment with the acquired information from the target environment to authenticate the execution environment as the target environment, and if the two set of information match, decrypting the software to be protected, and if two set of information do not match, destroying said software.
Owner:ANGEL SECURE NETWORKS
Software upgrading method based on OTA upgrading system and OTA upgrading system
ActiveCN110597538AGuaranteed safe isolationPrevent replay attacksDigital data protectionProgram/content distribution protectionSoftware engineeringSoftware upgrade
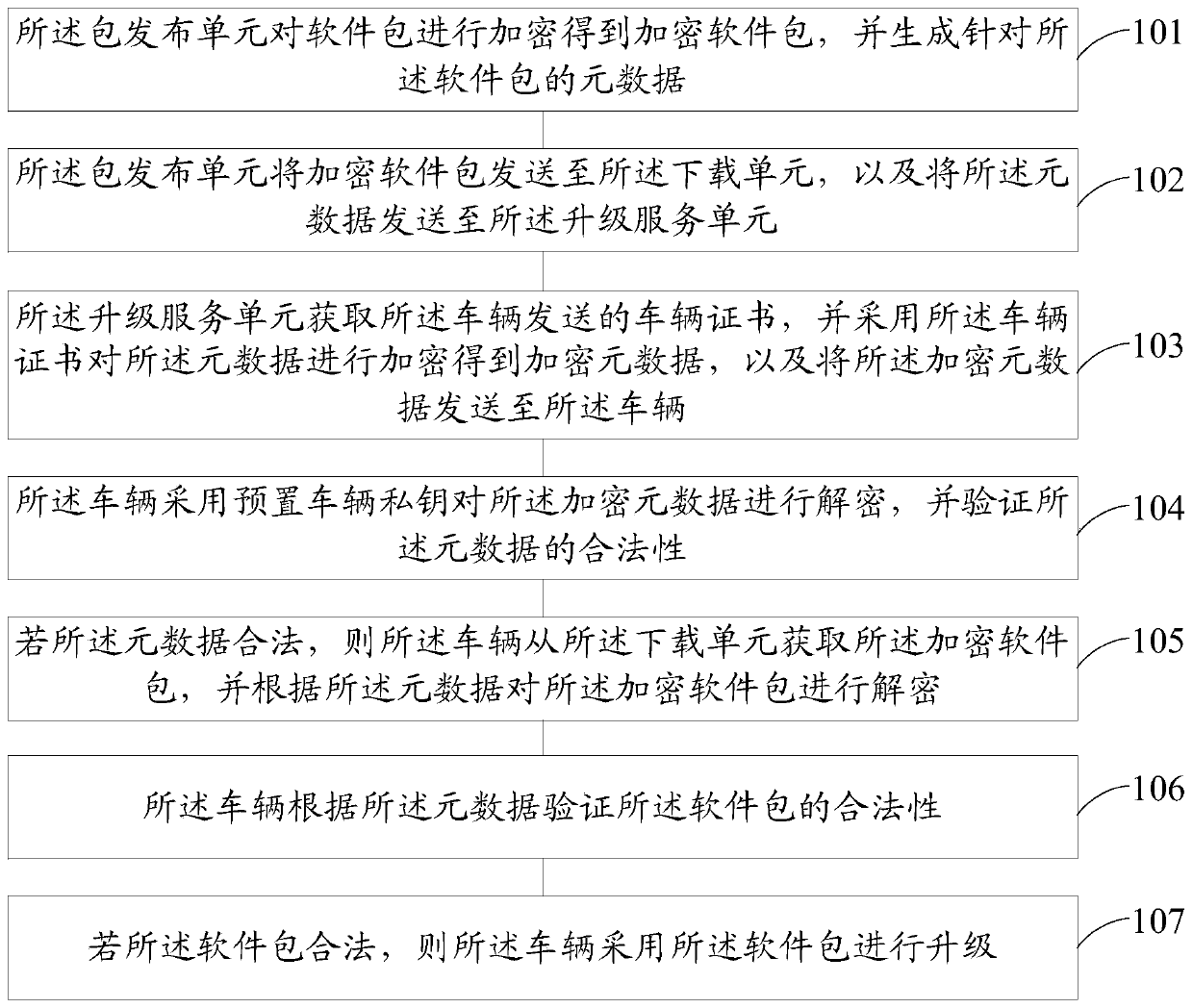
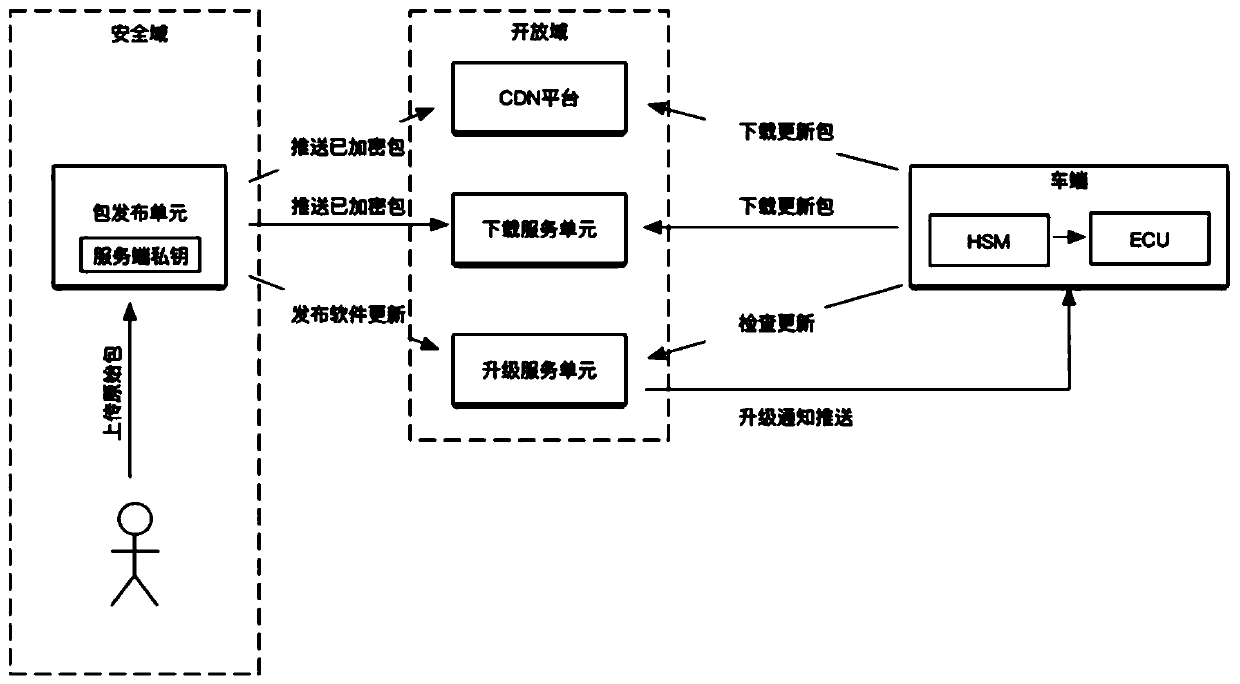
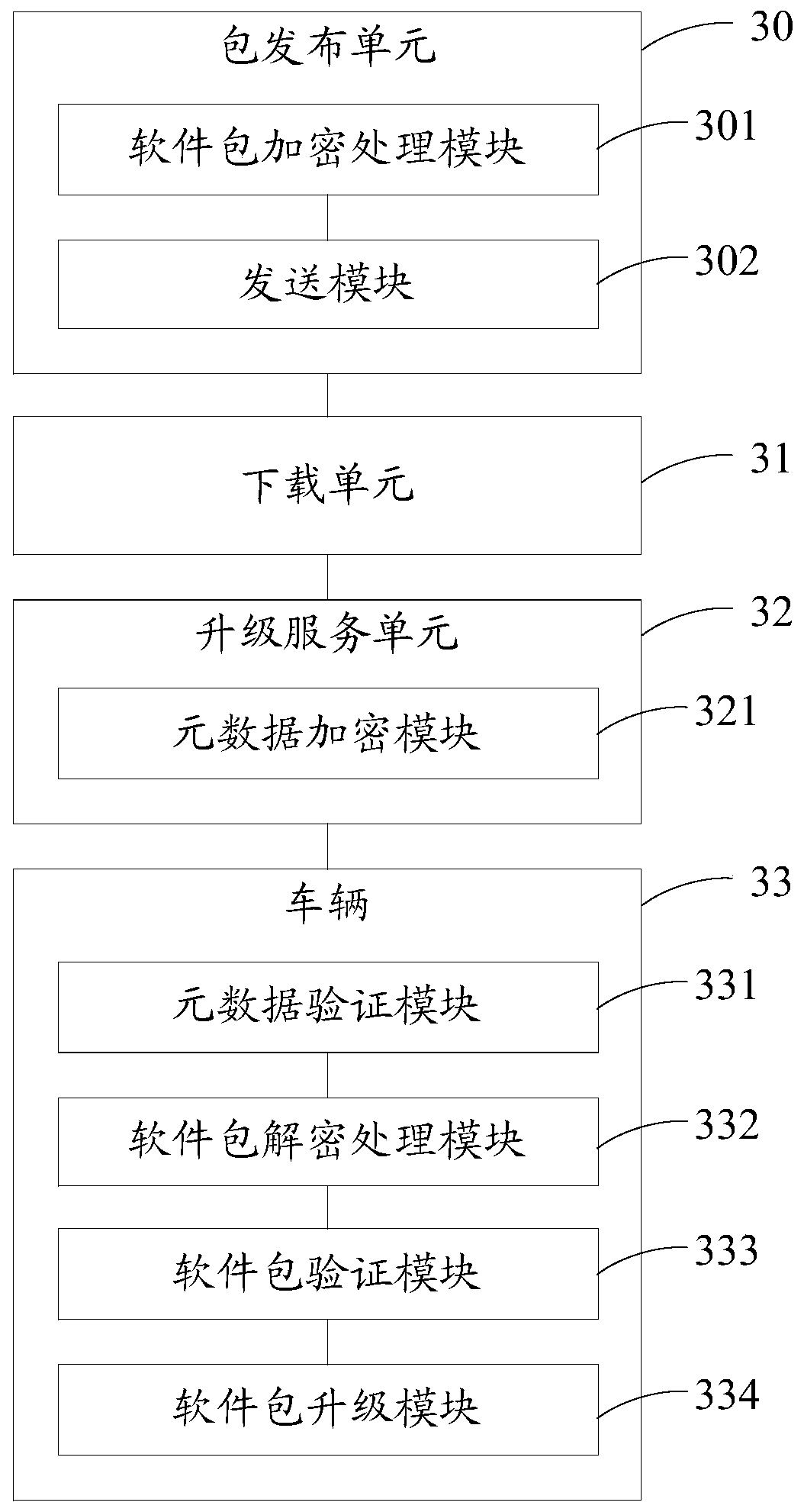
The embodiment of the invention provides a software upgrading method based on an OTA upgrading system and the OTA upgrading system, and the method comprises the steps that a package issuing unit encrypts a software package to obtain an encrypted software package, and generates metadata for the software package; a package issuing unit sends the encrypted software package to the downloading unit andsends the metadata to the upgrading service unit; an upgrading service unit acquires a vehicle certificate sent by a vehicle, encrypts the metadata by adopting the vehicle certificate to obtain encrypted metadata, and sends the encrypted metadata to the vehicle; enthe vehicle decrypts the encrypted metadata by adopting a preset vehicle private key, and verifies the legality of the metadata; if the metadata is legal, the vehicle acquires the encrypted software package from the downloading unit and decrypts the encrypted software package according to the metadata; the vehicle verifies the legality of the software package according to the metadata; and if the software package is legal, the vehicle is upgraded by adopting the software package. According to the embodiment of the invention, theproblems of tampering and replay attacks of the software package can be prevented.
Owner:GUANGZHOU XIAOPENG MOTORS TECH CO LTD
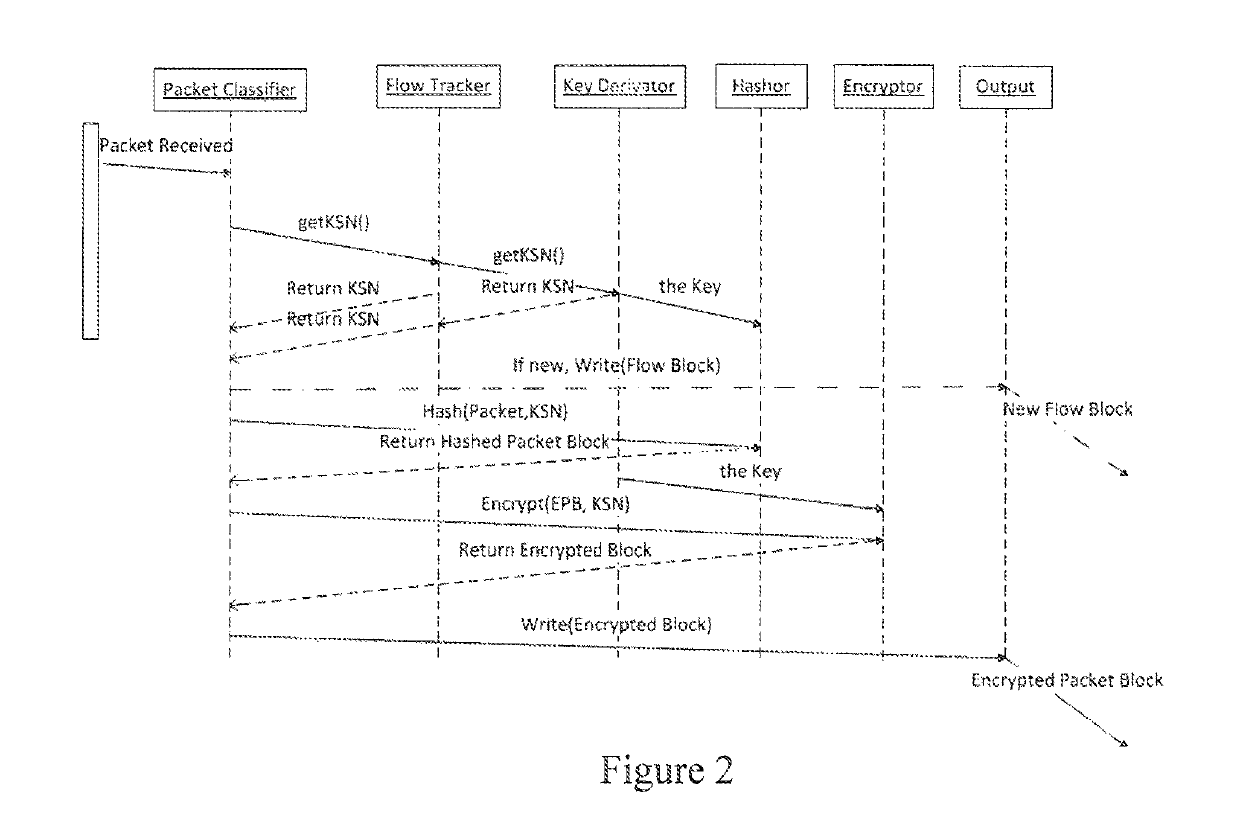
System, method and apparatus for network security monitoring, information sharing, and collective intelligence
ActiveUS10326803B1Easy to carryIncrease useTransmissionNetwork interface deviceCollective intelligence
A system, method and apparatus for network security monitoring, information sharing and collective intelligence between and among at least a first central processing unit and at least a second central processing unit connected together by a network. The system includes a network interface device with hardware-based logic for recognizing and cataloging individual sessions, wherein the network interface card is in communication with the network. The network interface device includes onboard cryptographic key management components with symmetric key algorithms, an onboard packet encryption software module using derived keys to encrypt network packets, and software for storing encrypted copies of network packets as blocks. Third party analyst hardware and software derive keys necessary to retrieve encrypted network packets.
Owner:UNIVERSITY OF TULSA
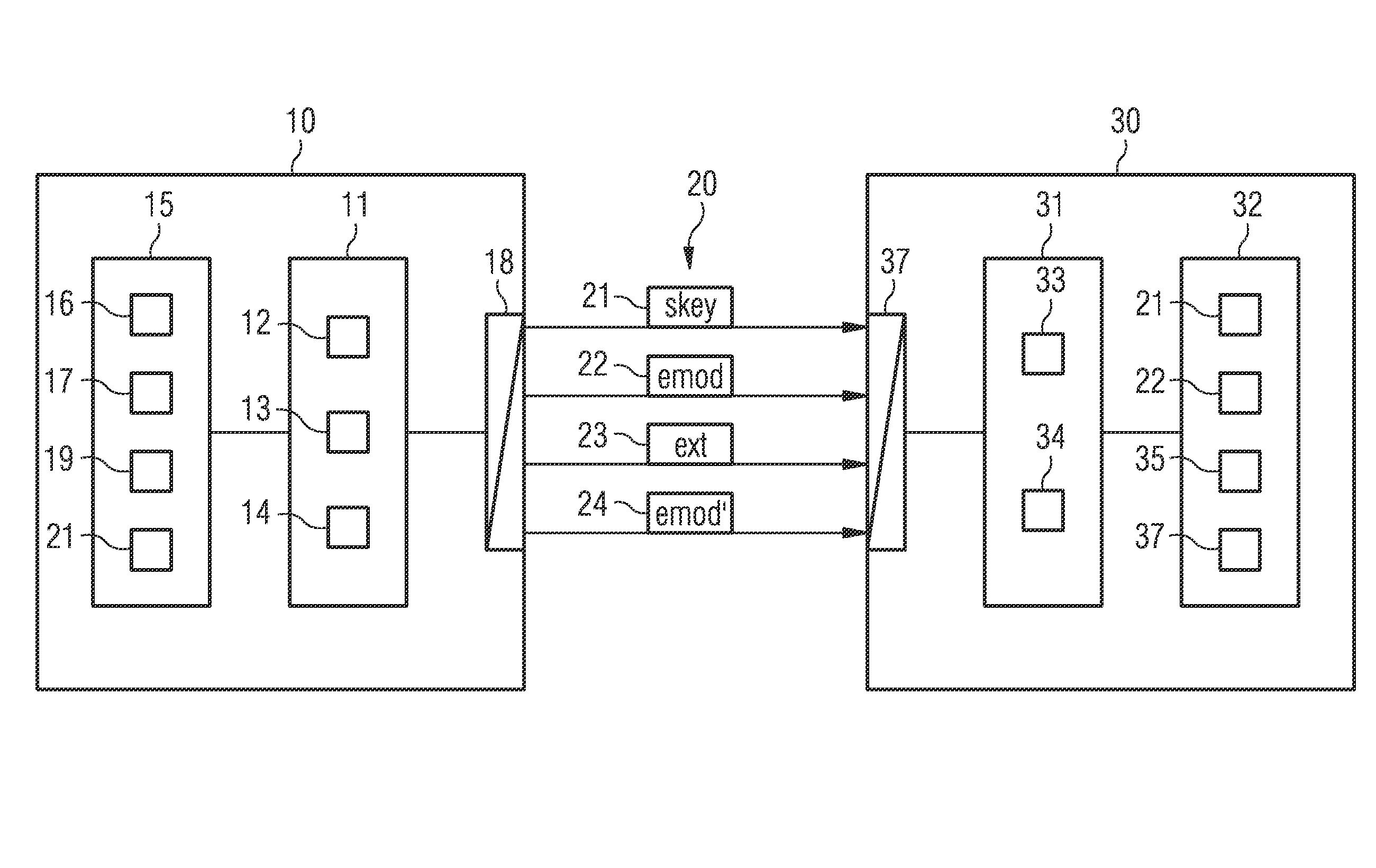
Protection of software models
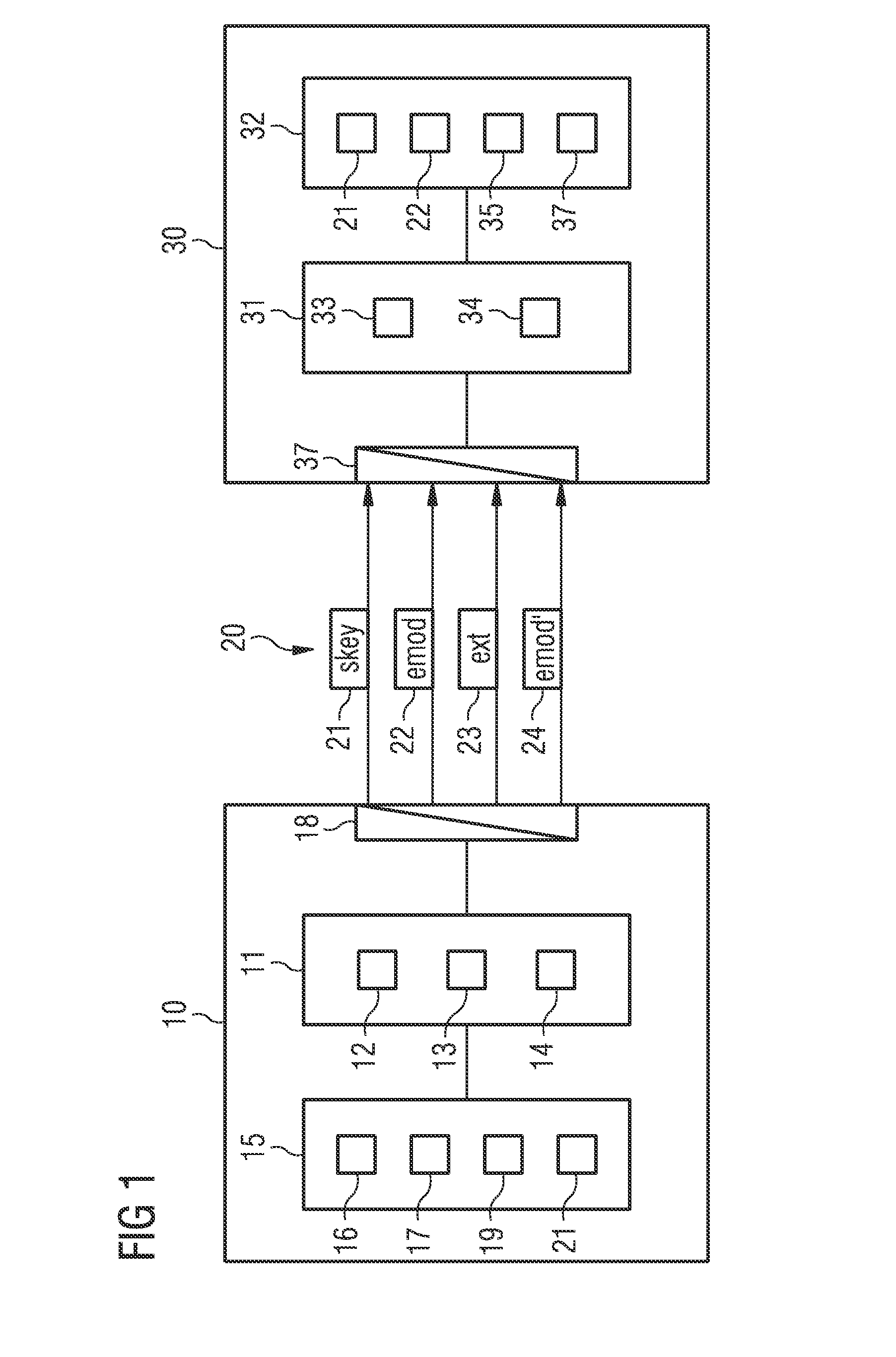
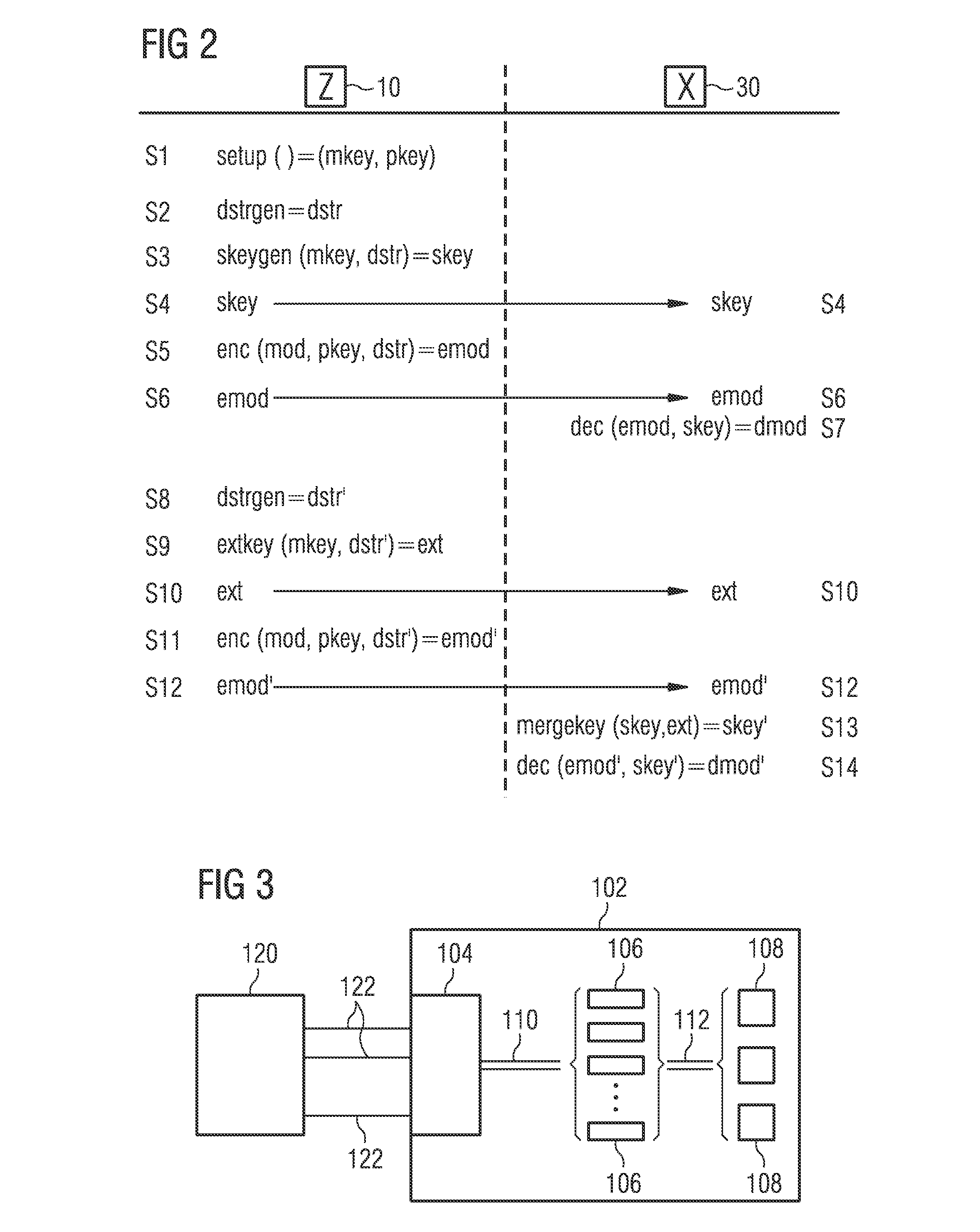
ActiveUS20160112195A1Avoids unnecessary management effortGuaranteed availabilityKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareEncryption
An encryption method is provided that has a software model of a technical system, the model including software components is encrypted by a public key and a decryption structure, wherein the latter includes definitions of component groups of the software model. The decryption structure is integrated at least partially into the encrypted software model. Correspondingly, in a decryption method according to the invention, via a secret key that likewise comprises definitions of component groups, only the particular component groups are decrypted whose definitions the secret key includes in agreement with the definitions of the encrypted software model. The definitions of the secret key can be extended after the fact by a key extension, so that additional component groups can be decrypted with an extended secret key.
Owner:DSPACE DIGITAL SIGNAL PROCESSING & CONTROL ENG
[mobile phone with file encryption function and method of encrypting/decrypting file thereof]
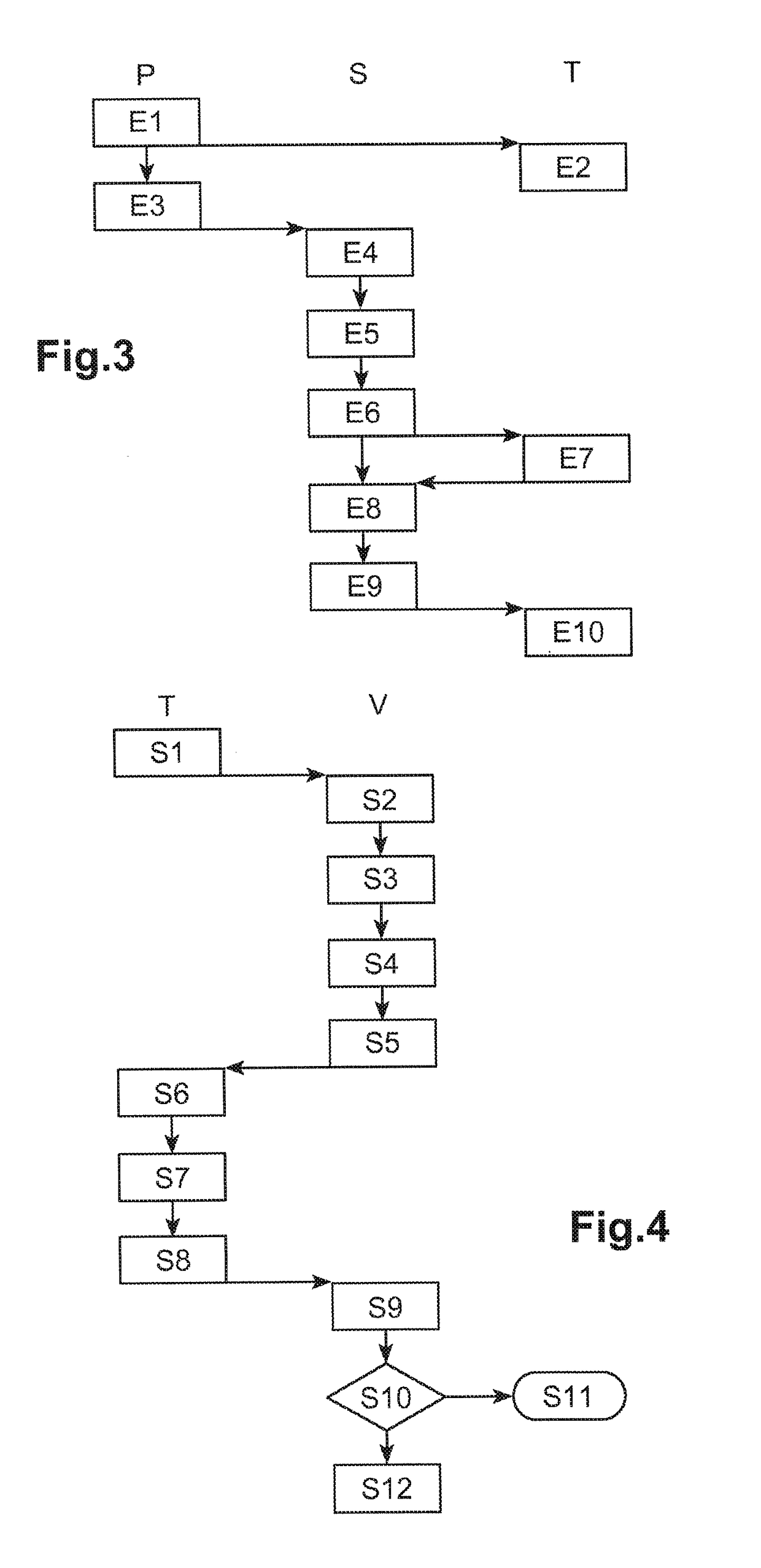
InactiveUS20050273604A1Avoid the needMemorizing a password can be effectively avoidedComputer security arrangementsSubstation equipmentData packEncrypted function
A mobile phone with file encryption function and method for encrypting file thereof are provided. The main unit of the mobile phone includes an encryption software. The second encryption software encrypts / decrypts the file stored in the computer based on a key. The method for encrypting file comprises: (a) establishing a transmission channel between the mobile phone and the computer; (b) sending the first file from said computer to the mobile phone; (c) encrypting / decrypting the first file based on a key to obtain a second file in the mobile phone; and (d) sending the second file from the mobile phone to the computer. Of course, the first file can be divided into a plurality of first packets in the computer. Then, the first packets can be sent to the mobile phone, encrypted / decrypted in the mobile phone, and sent back to the computer until all of the first packets have been encrypted / decrypted to obtain the second packets. Finally, the second packets can be combined to obtain the second file in the computer.
Owner:INVENTEC APPLIANCES CORP
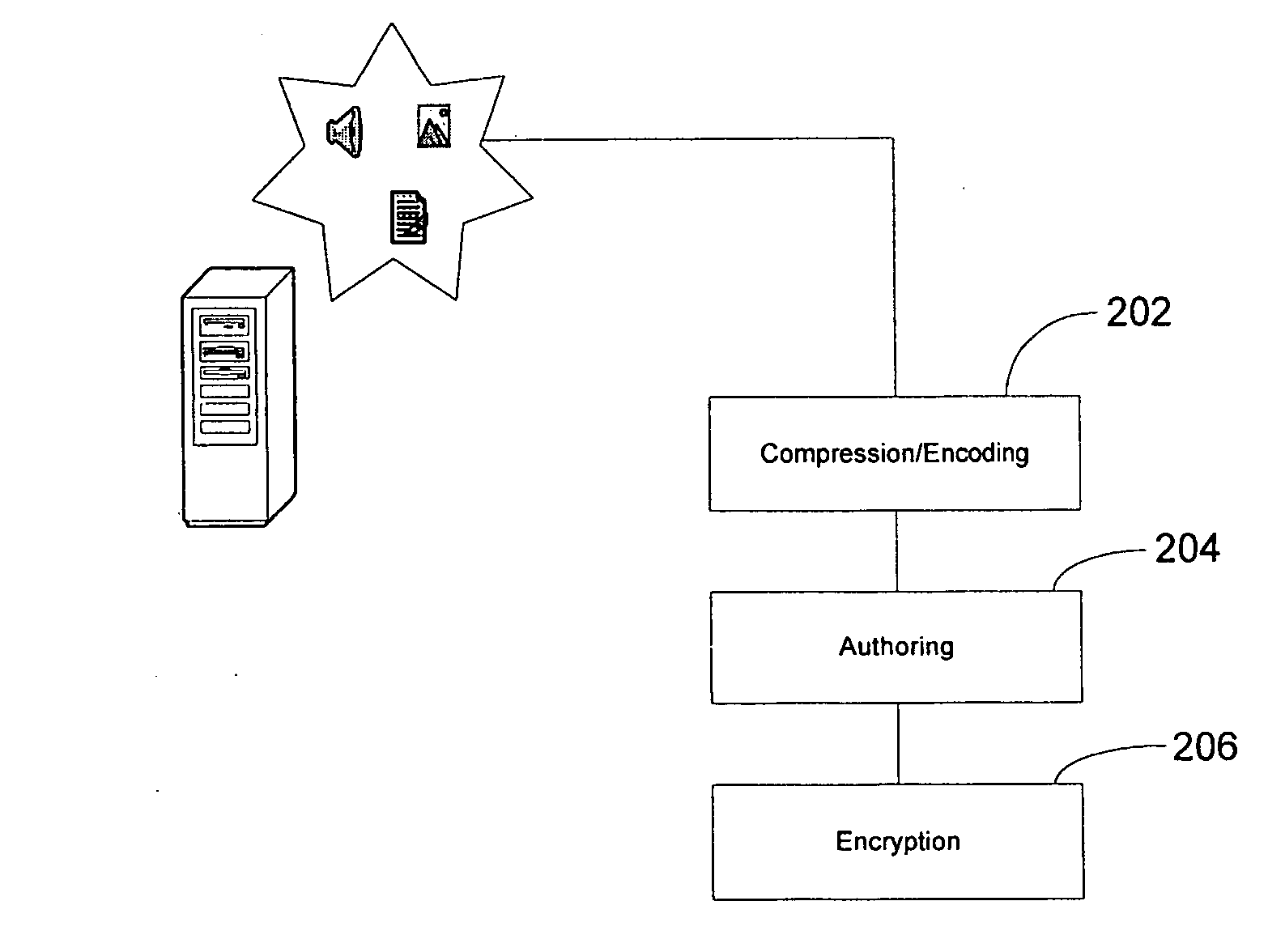
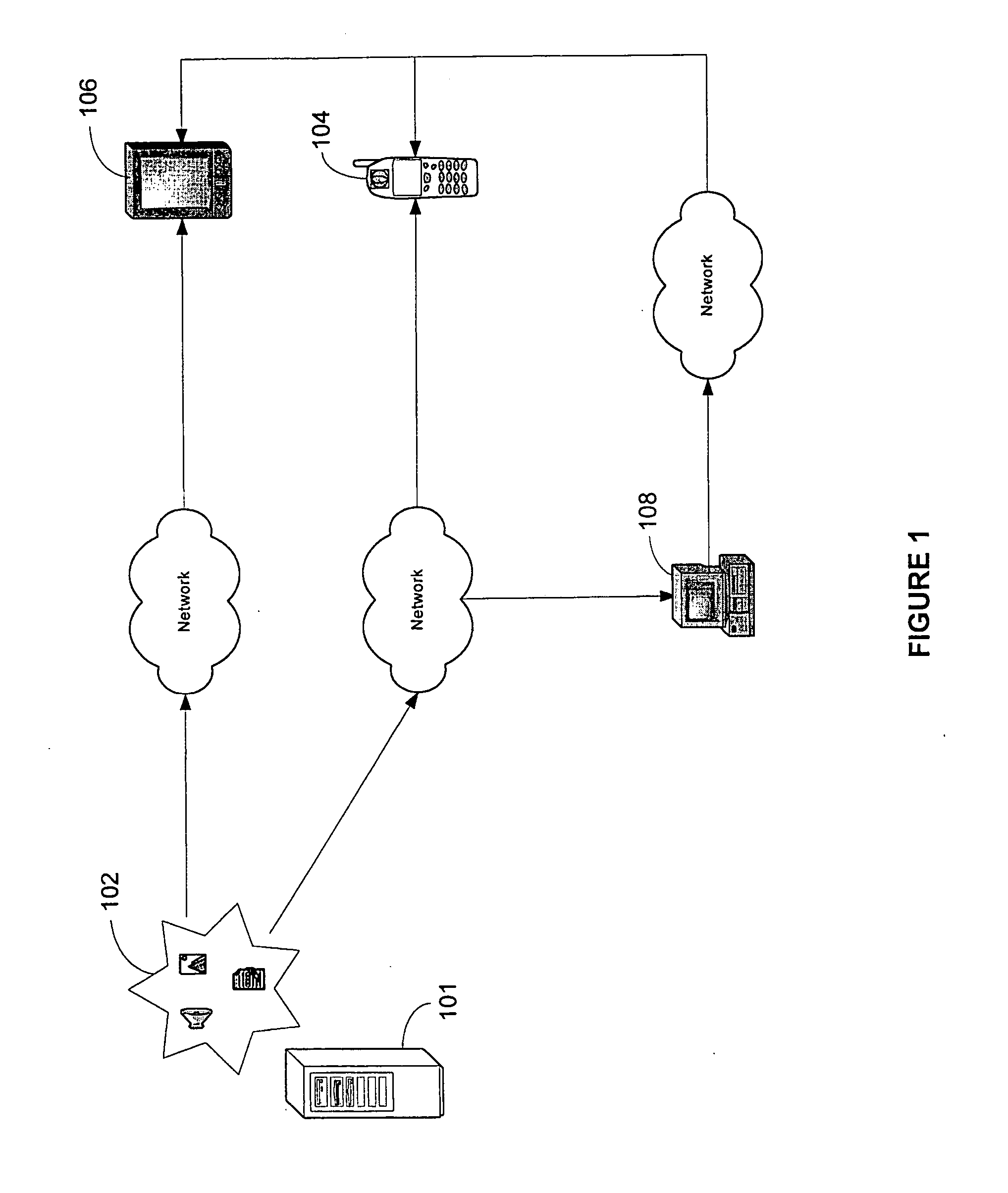
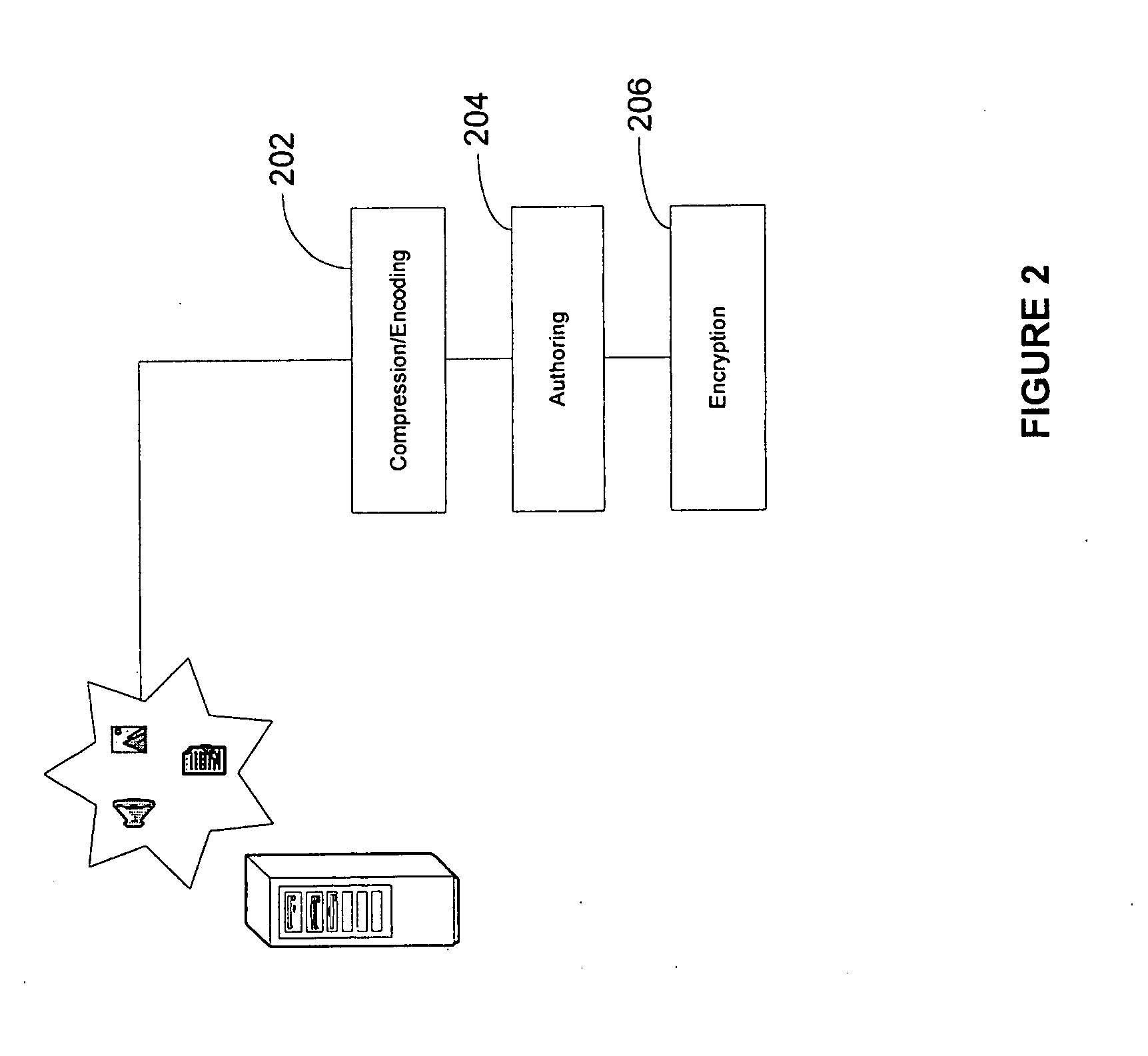
System for the compression, encoding, authoring, and encryption of data and media the storage of such content in external mobile telephone or personal digital assistant compatible memory devices
InactiveUS20070076876A1Television system detailsUnauthorised/fraudulent call preventionExternal storageMobile device
A unique combination of compression, encoding, authoring, and encryption software practices to store large data and media files onto external mobile handset and PDA compatible memory devices. The unique combination allows for a copy protected handset and PDA compatible external memory device with pre-installed data and media. A multimedia player is also written in the external memory device along with the processed data and / or media files, wherein the multimedia player is used to render the stored data and / or media files in a mobile device such as an external mobile handset or PDA. The memory device is inserted into a mobile handset or PDA for access by a user.
Owner:SHOPTEXT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com
![[mobile phone with file encryption function and method of encrypting/decrypting file thereof] [mobile phone with file encryption function and method of encrypting/decrypting file thereof]](https://images-eureka-patsnap-com.libproxy1.nus.edu.sg/patent_img/9378c43d-a26e-41ae-89f3-d29b37fbc31c/US20050273604A1-20051208-D00000.png)
![[mobile phone with file encryption function and method of encrypting/decrypting file thereof] [mobile phone with file encryption function and method of encrypting/decrypting file thereof]](https://images-eureka-patsnap-com.libproxy1.nus.edu.sg/patent_img/9378c43d-a26e-41ae-89f3-d29b37fbc31c/US20050273604A1-20051208-D00001.png)
![[mobile phone with file encryption function and method of encrypting/decrypting file thereof] [mobile phone with file encryption function and method of encrypting/decrypting file thereof]](https://images-eureka-patsnap-com.libproxy1.nus.edu.sg/patent_img/9378c43d-a26e-41ae-89f3-d29b37fbc31c/US20050273604A1-20051208-D00002.png)