Method, system and device for two-dimension code authenticity
A verification method and verification system technology, which is applied in the field of commodity anti-counterfeiting, can solve problems such as poor user experience and poor anti-counterfeiting effect, and achieve the effect of avoiding input errors and enriching experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
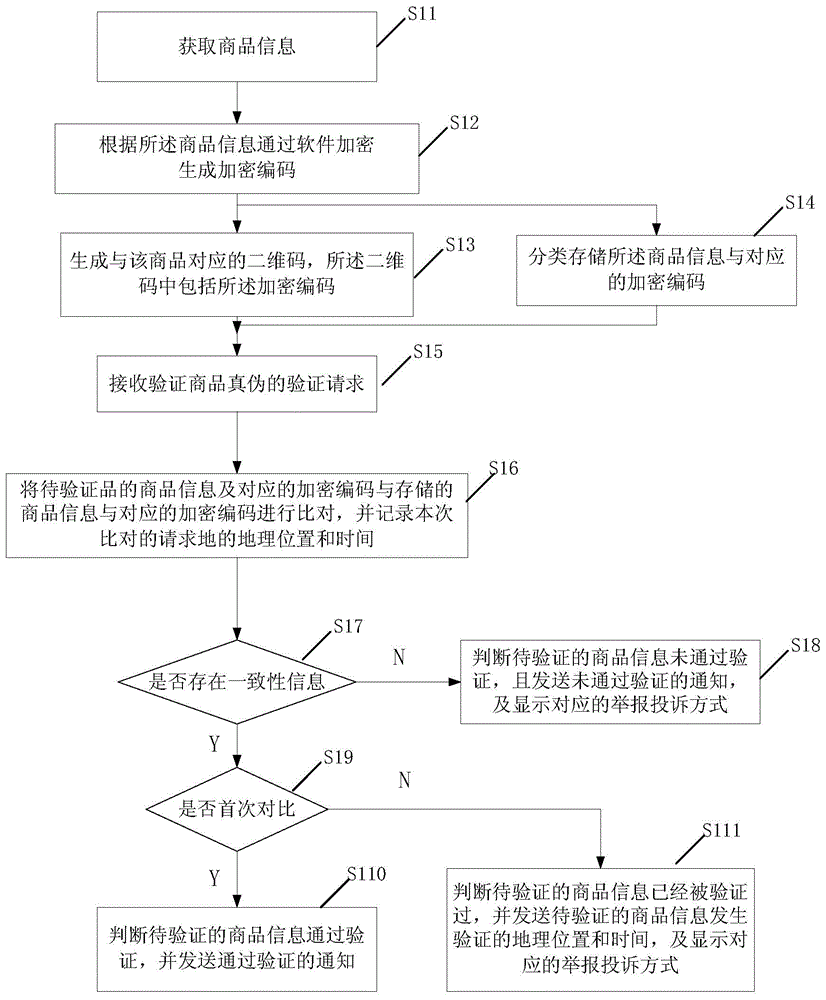
[0059] This embodiment provides a two-dimensional code anti-counterfeiting verification method, which is applied to the server side, such as figure 1 shown, including the following steps:
[0060] S11: Acquiring product information, wherein the product information includes but not limited to product name, product number (quantity, code range), product pattern, promotional website link and so on.
[0061] S12: Generate an encrypted code according to the commodity information, this step is realized by a computer software encryption program.
[0062] S13: Generate a two-dimensional code corresponding to the commodity, and form a two-dimensional code file, which can be printed or printed. The two-dimensional code includes the encrypted code.
[0063] S14: Classify and store the commodity information and corresponding encryption codes. It can be classified according to product category or other rules, and can be stored in the directory of the corresponding product model to form ...
Embodiment 2
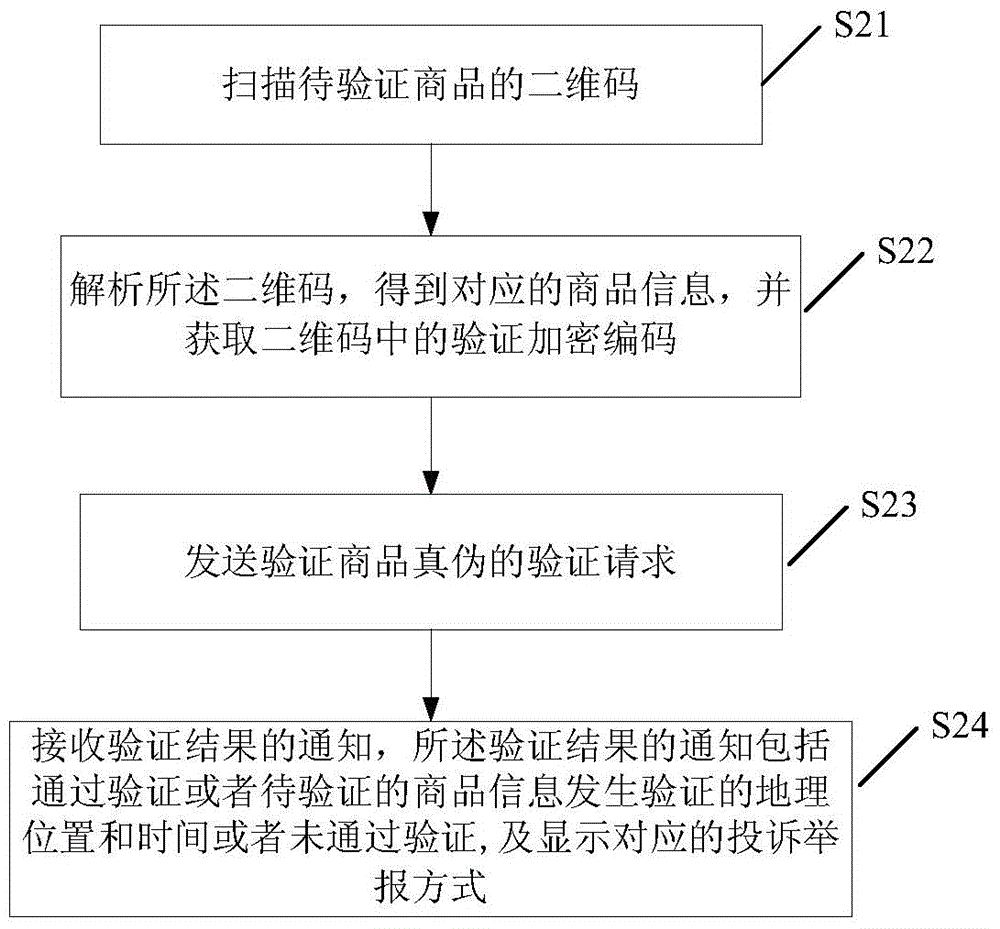
[0079] This embodiment provides a two-dimensional code anti-counterfeiting verification method, which is applied to the client, such as figure 2 shown, including the following steps:
[0080] S21: Scan the QR code of the product to be verified. This step is realized by client software, wherein the client software can be the dedicated software in the present invention, or existing software in the prior art can be used.
[0081] S22: Analyze the two-dimensional code to obtain corresponding commodity information, and obtain the encrypted code in the two-dimensional code.
[0082] S23: Send a verification request to verify the authenticity of the commodity, the verification request includes the geographical location of the request, the request time, the MAC address of the client sending the request, the commodity information of the commodity to be verified and the corresponding encryption code.
[0083] S24: Receive a notification of a verification result, where the notificatio...
Embodiment 3
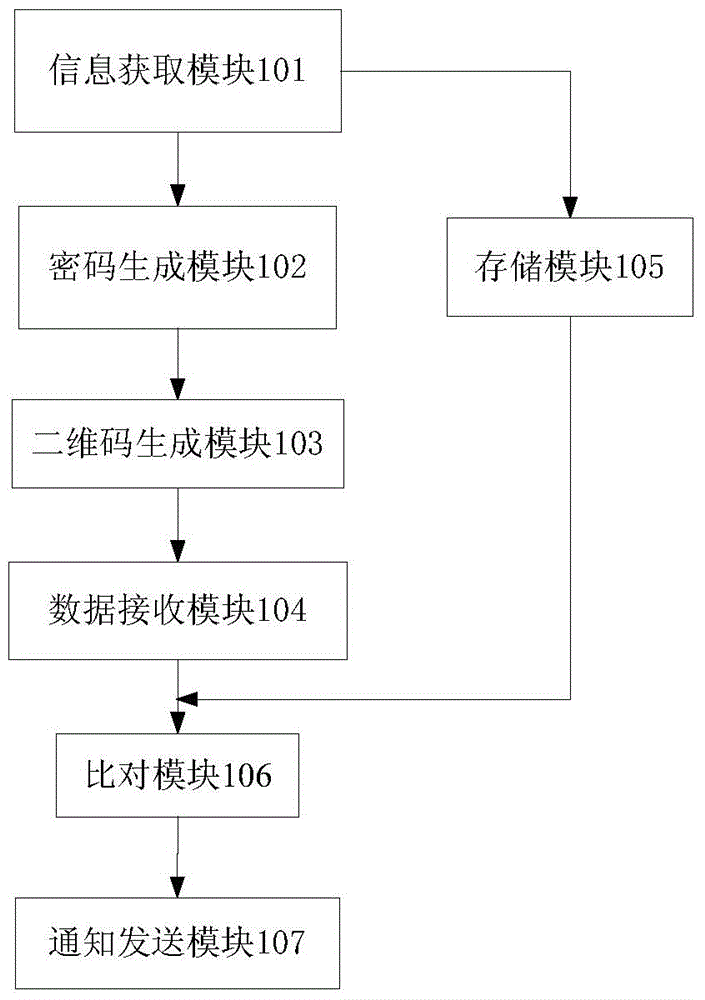
[0086] This embodiment provides a two-dimensional code anti-counterfeiting verification system, which is applied to the server side, such as image 3 shown, including:
[0087] The information acquisition module 101 is configured to acquire commodity information.
[0088] A password generating module 102, configured to automatically generate encrypted codes according to the commodity information.
[0089] The two-dimensional code generating module 103 is configured to generate a two-dimensional code corresponding to the commodity, the two-dimensional code including the encrypted code.
[0090] The storage module 105 is configured to classify and store the commodity information and corresponding encryption codes.
[0091] The data receiving module 104 is configured to receive a verification request for verifying the authenticity of the commodity, and the verification request includes the geographical location of the request, the MAC address of the client sending the request, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com