Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36results about How to "Reduce the risk of eavesdropping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
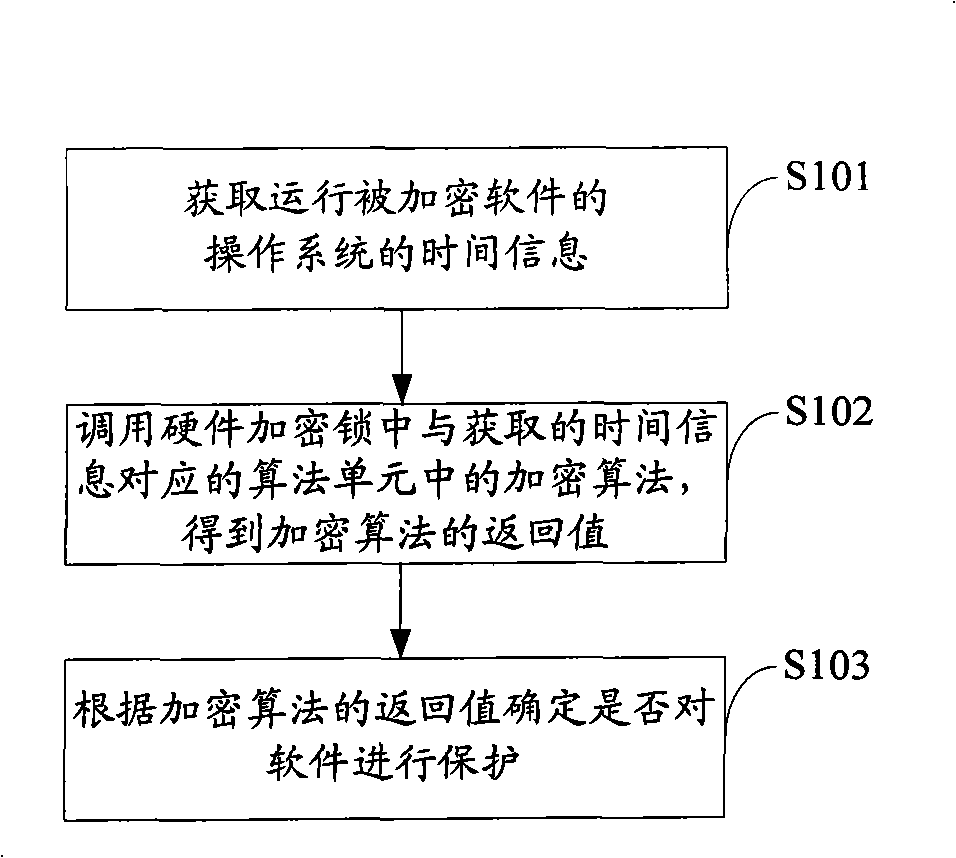
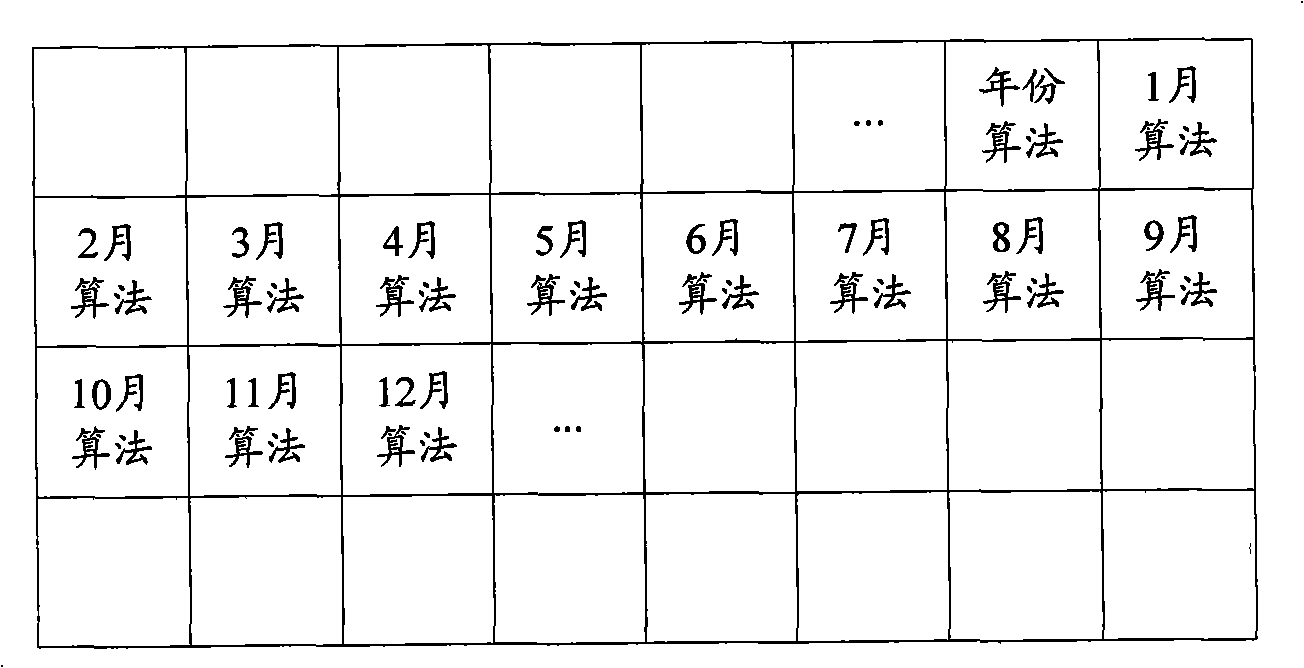
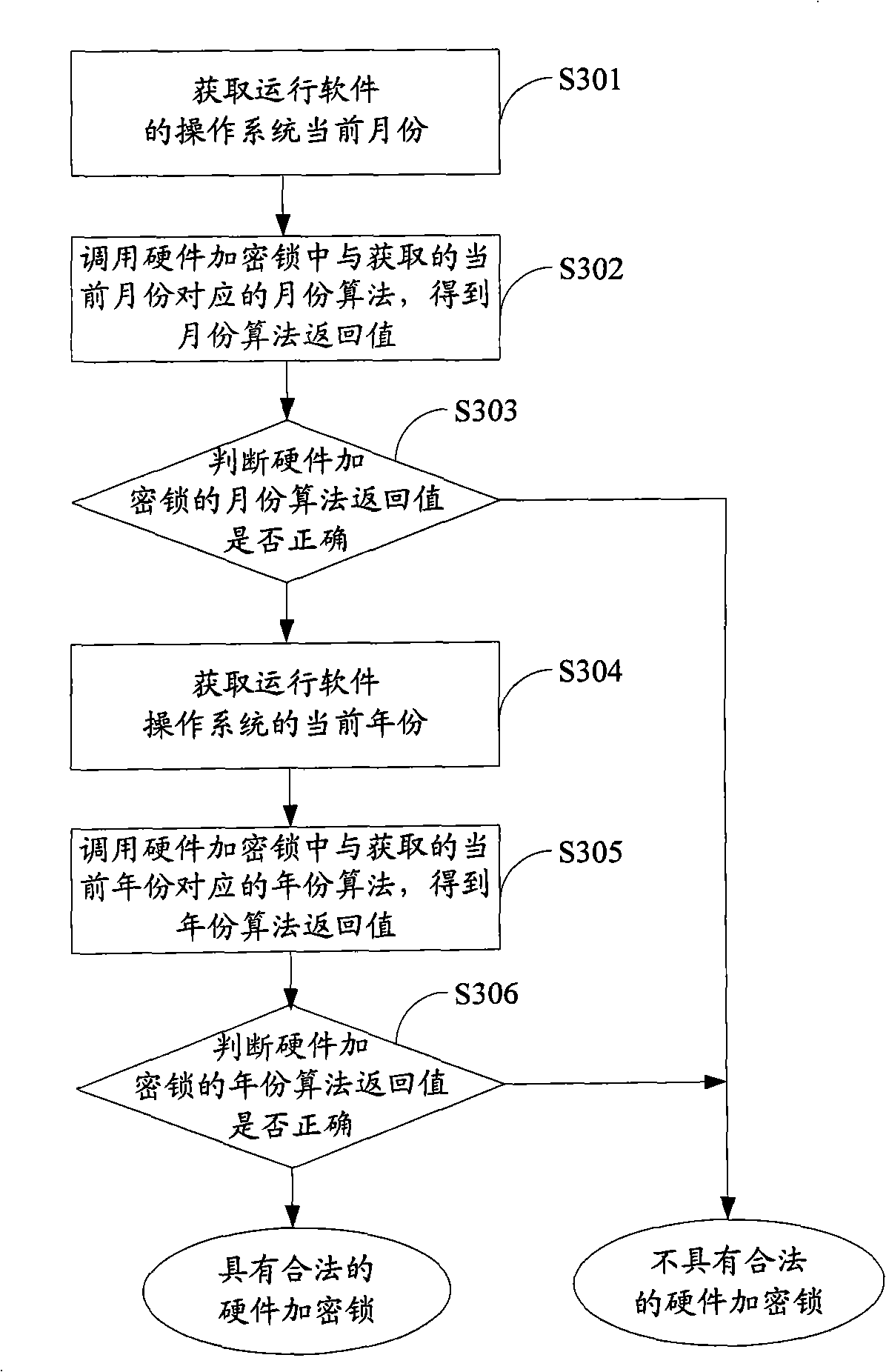
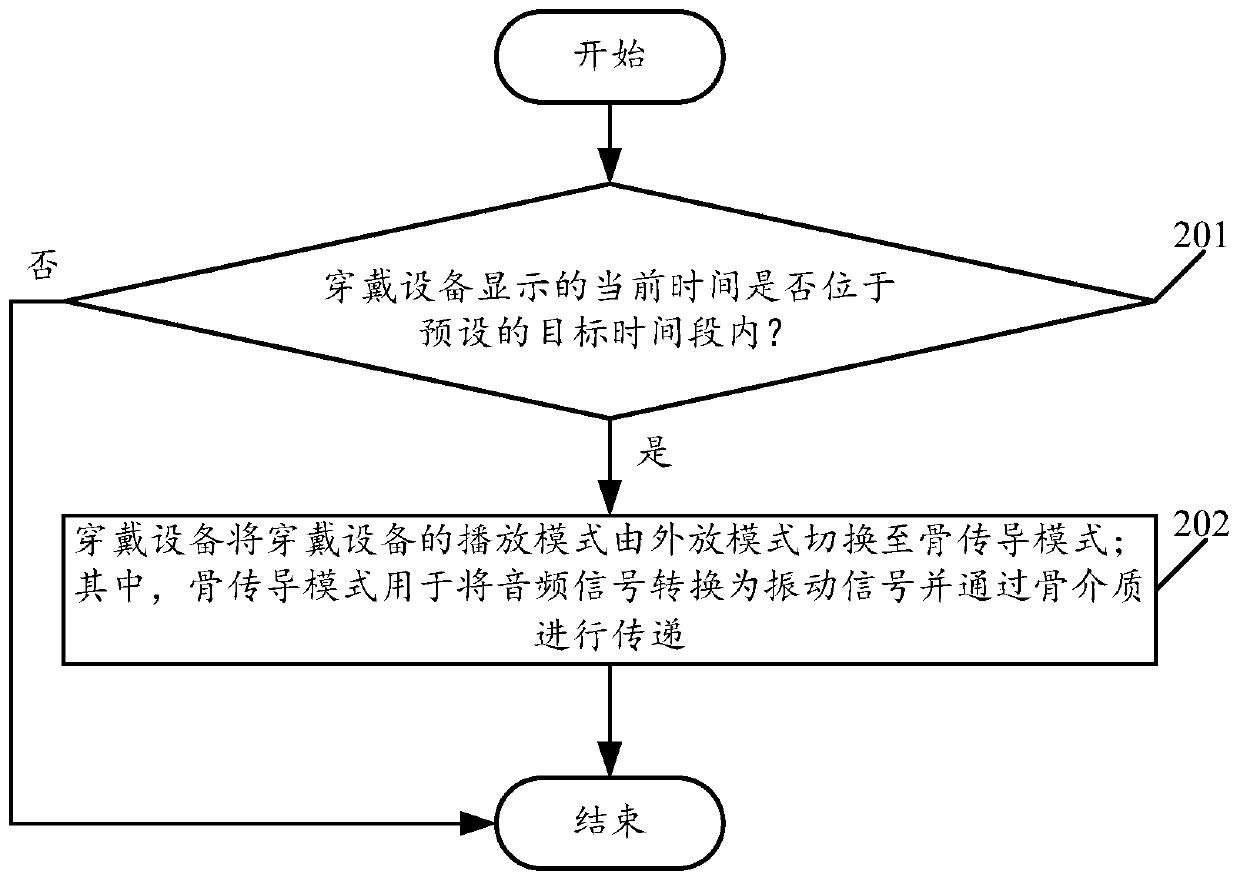
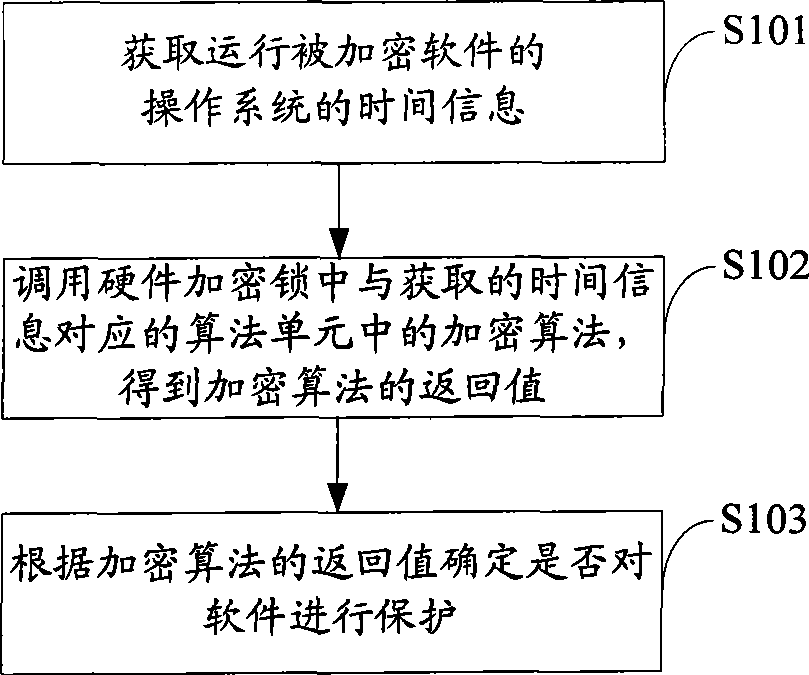
Software protection method, apparatus and equipment
ActiveCN101404056AAchieve protectionReduce the risk of eavesdroppingPlatform integrity maintainanceProgram/content distribution protectionTemporal informationComputer hardware
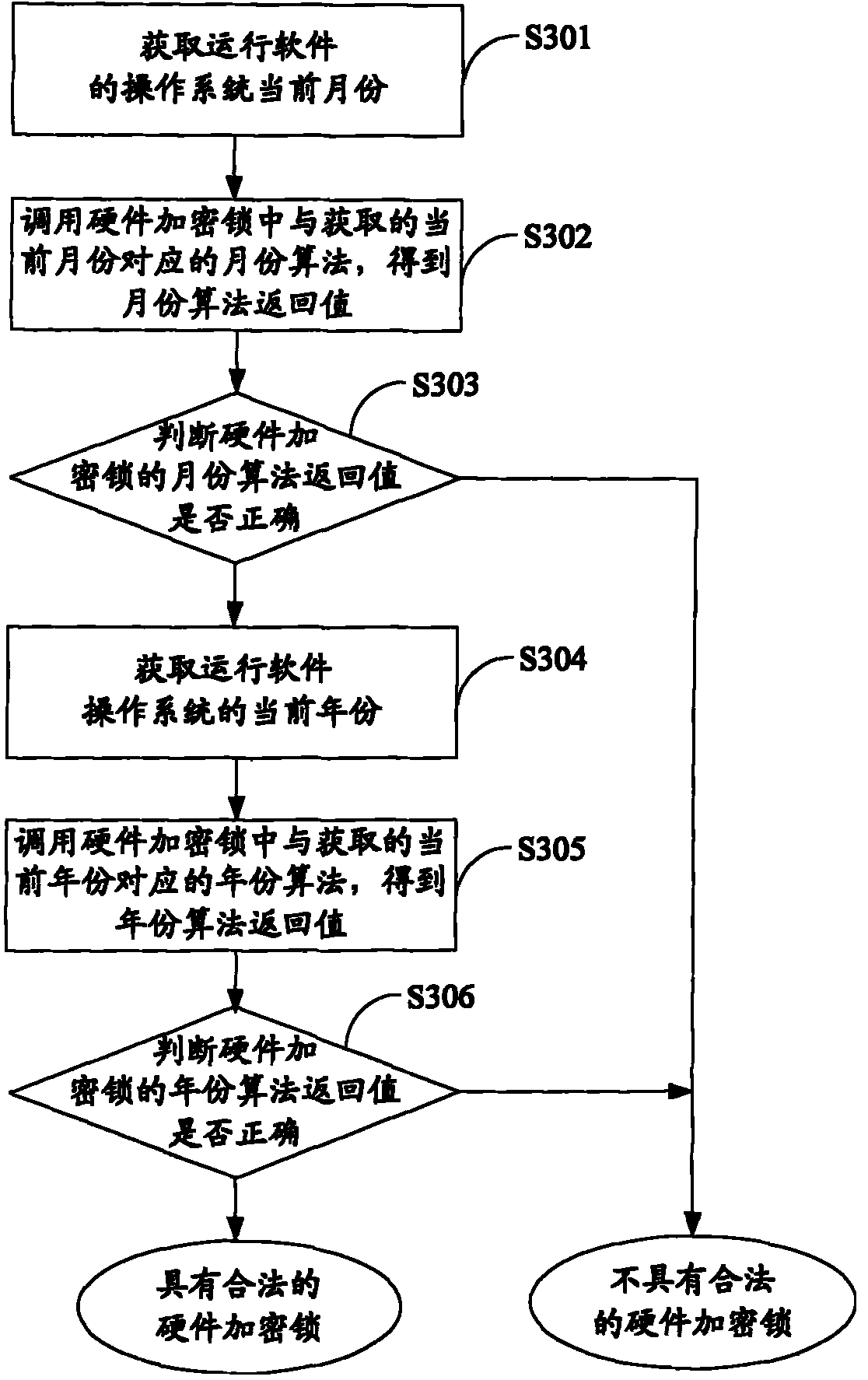
The invention is applicable to the communication safety field and provides a software protection method, a device and equipment. The method comprises the following steps: current time information of an operation system which operates an encrypted software is obtained; an encryption algorithm in an algorithm unit which is corresponding to the obtained current time information is called from a hardware encryption lock, thereby obtaining a return value of the encryption algorithm; whether a software is protected or not is judged according to the return value of the encryption algorithm. The embodiment of the invention realizes the protection of the software and reduces the risk that communication information between the encrypted software and the hardware encryption lock is eavesdropped effectively by obtaining the time information of the operation system and calling the encryption algorithm which is corresponding to the time information from the hardware encryption lock.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
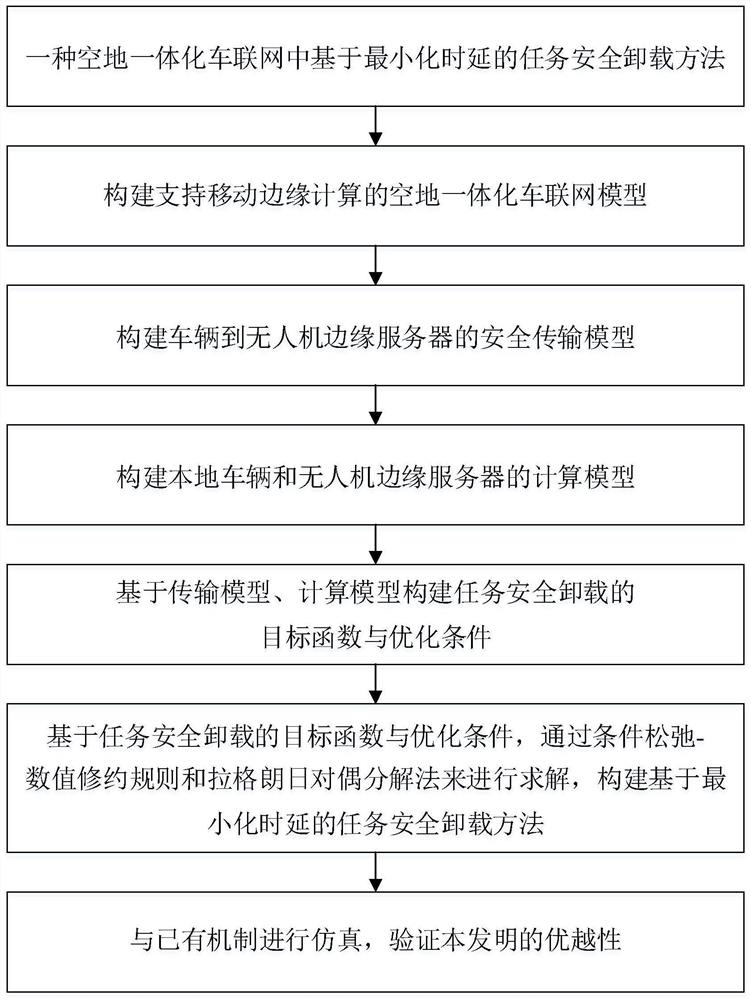
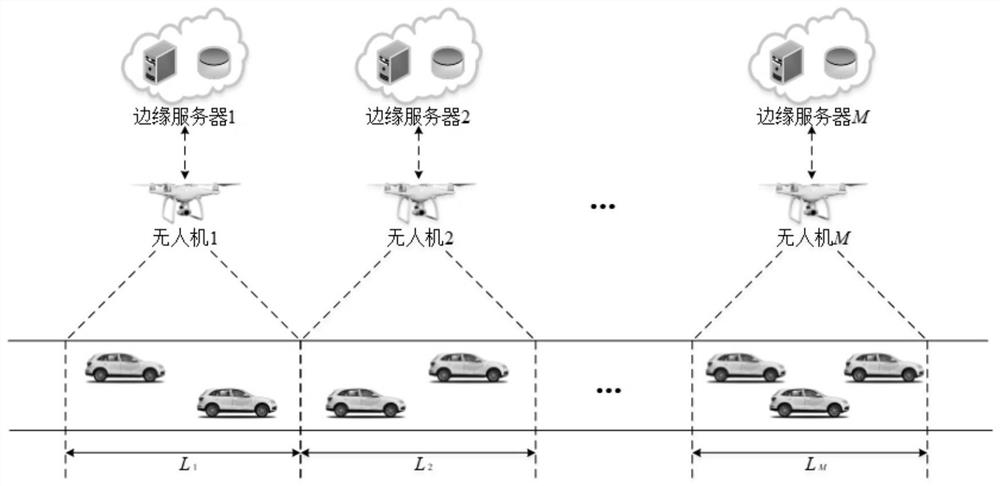
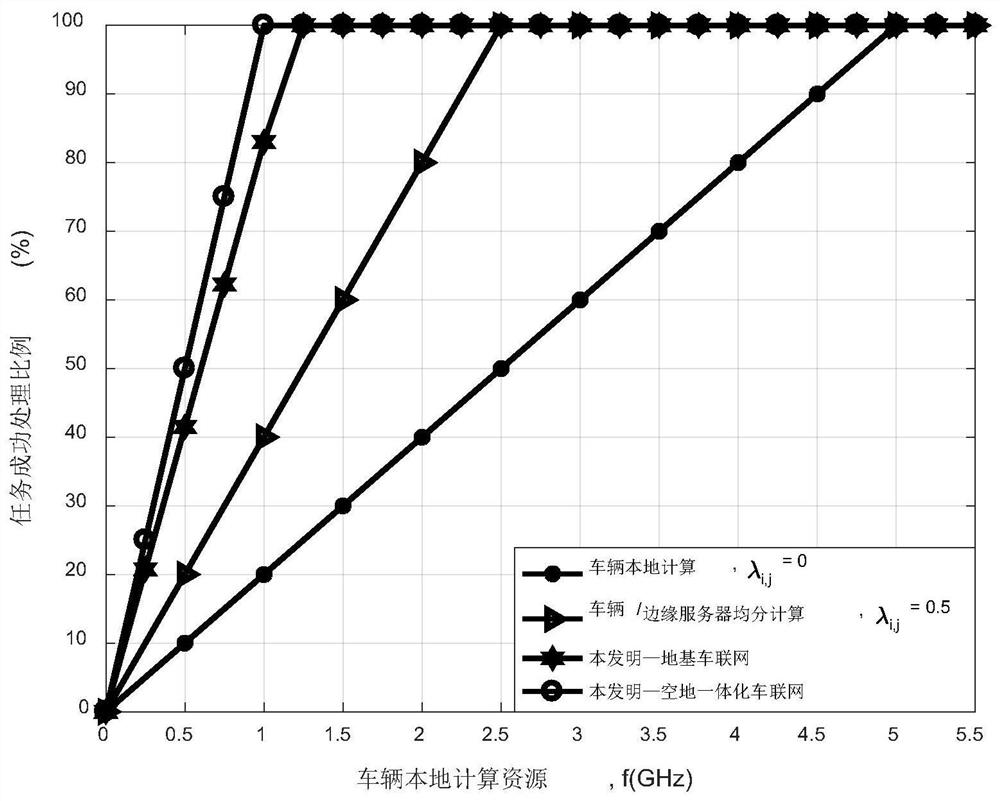
Task safety unloading method based on minimized time delay in air-ground integrated Internet of Vehicles
ActiveCN112737842AReduce the risk of eavesdroppingGuaranteed privacyRadio transmissionData switching networksEdge serverTime delays
The invention discloses a task safety unloading method based on minimized time delay in an air-ground integrated Internet of Vehicles, which comprises the following steps: firstly, constructing an air-ground integrated Internet of Vehicles model supporting mobile edge computing; secondly, analyzing and modeling a safe transmission mode from a vehicle to an unmanned aerial vehicle edge server and a calculation mode of a local vehicle and the unmanned aerial vehicle edge server, and formalizing an air-ground integrated Internet of Vehicles task unloading problem to be related to edge server selection, a transmission rate, resource allocation and task unloading; solving a multi-objective optimization problem taking minimization of time delay as an objective in combination with a conditional relaxation numerical value reduction rule and a Lagrange dual decomposition method, so that the task processing time delay can be effectively reduced, and the successful task processing proportion is improved.
Owner:RES & DEV INST OF NORTHWESTERN POLYTECHNICAL UNIV IN SHENZHEN +1
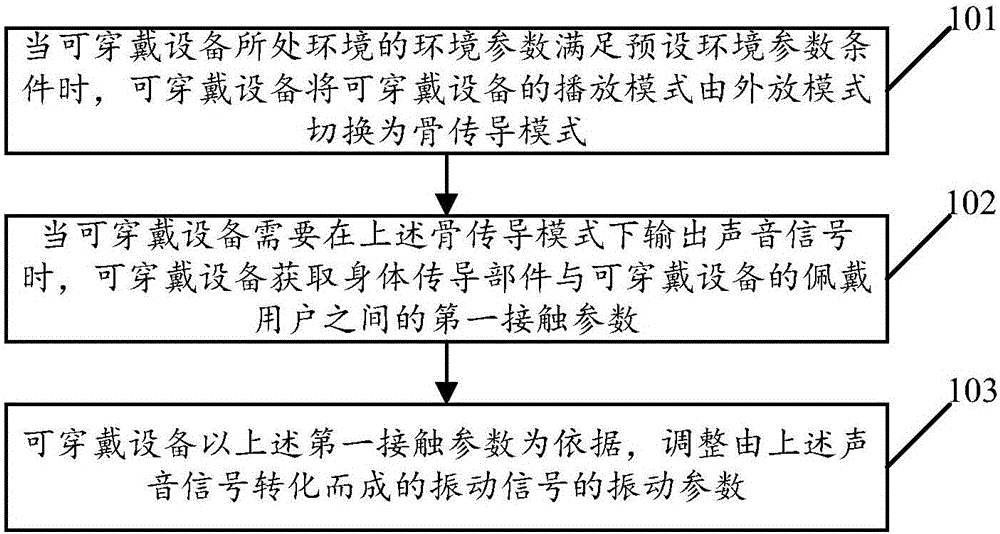
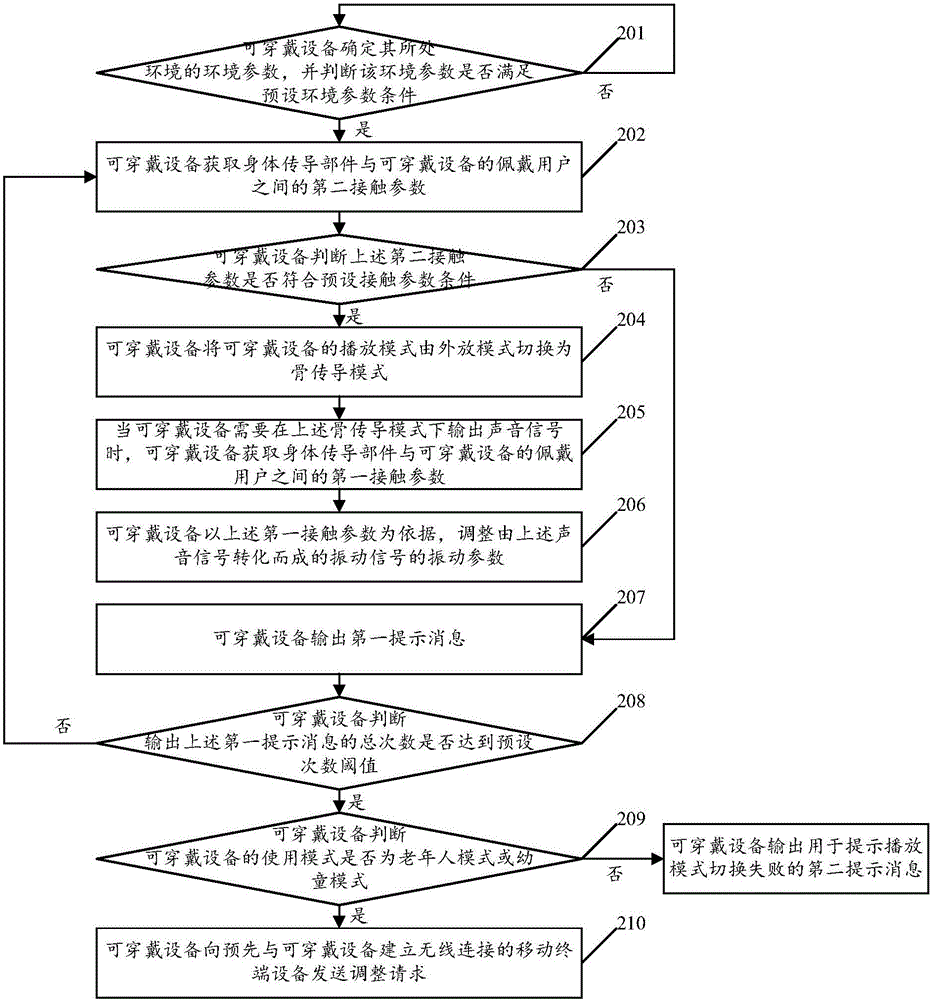
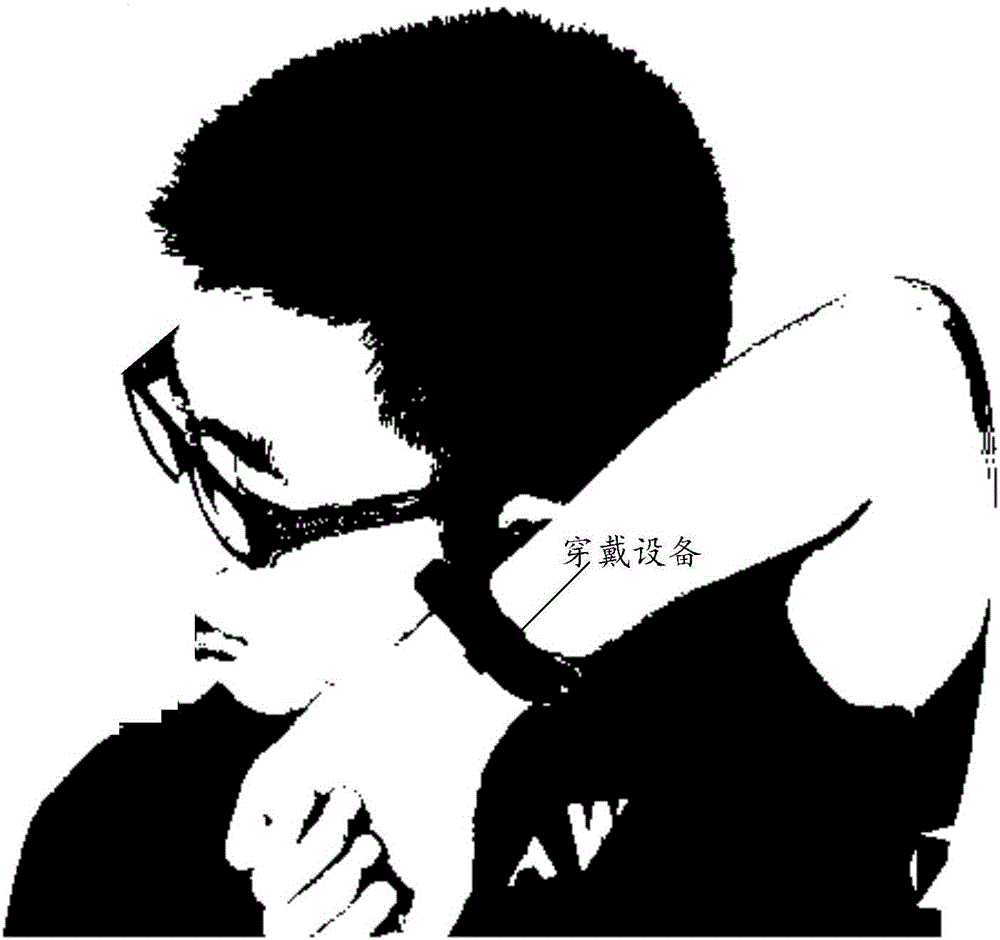
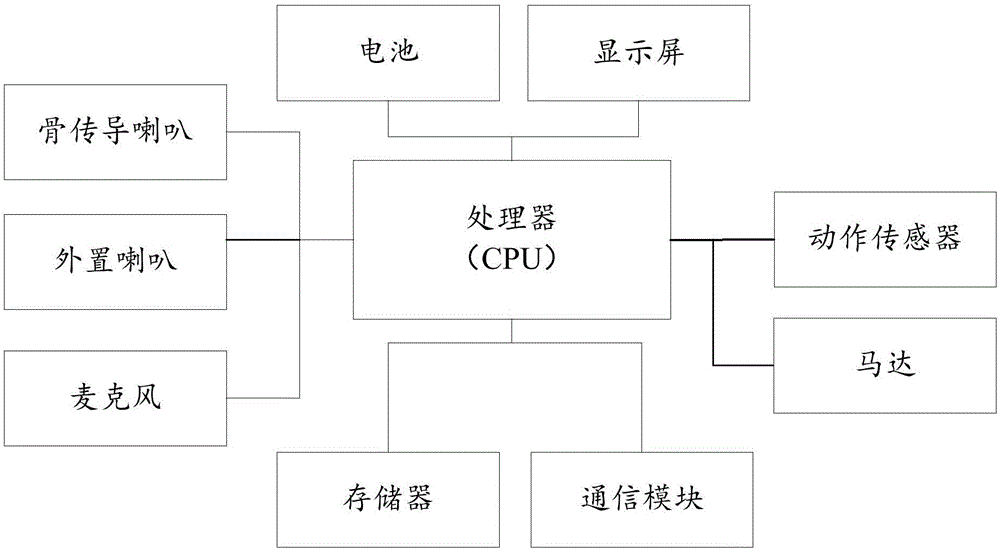
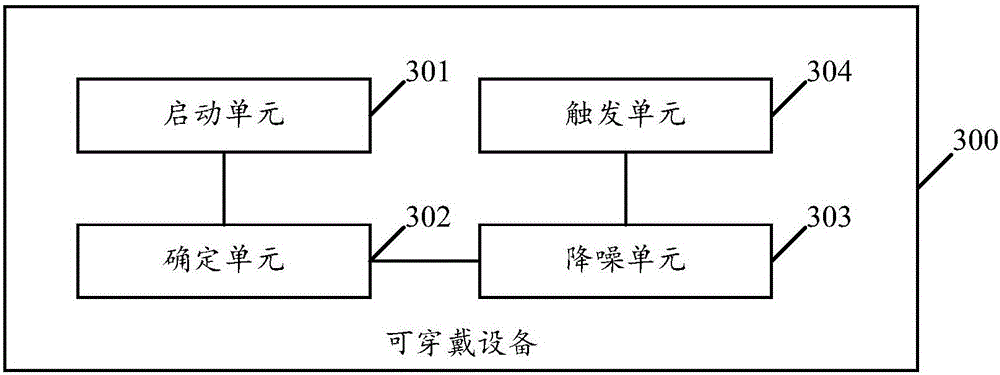
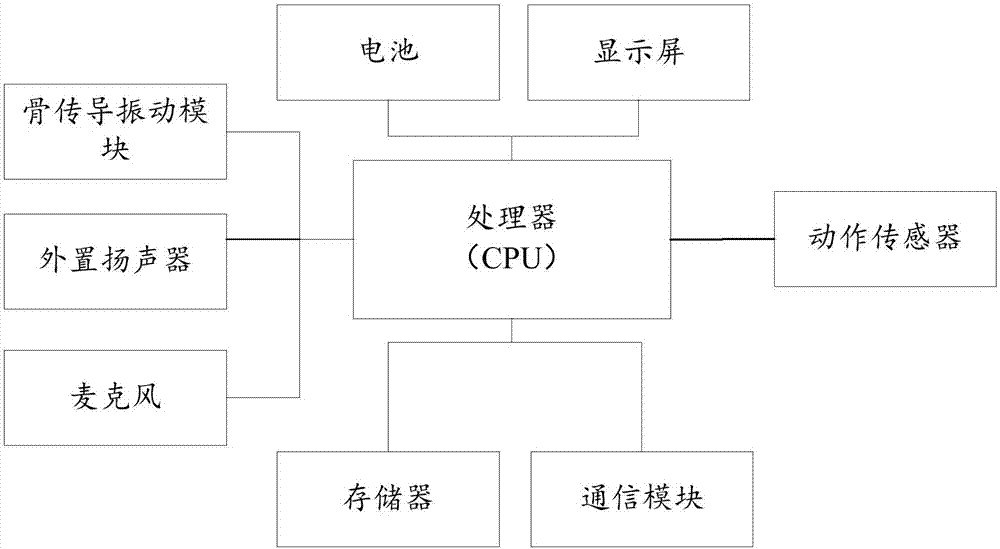
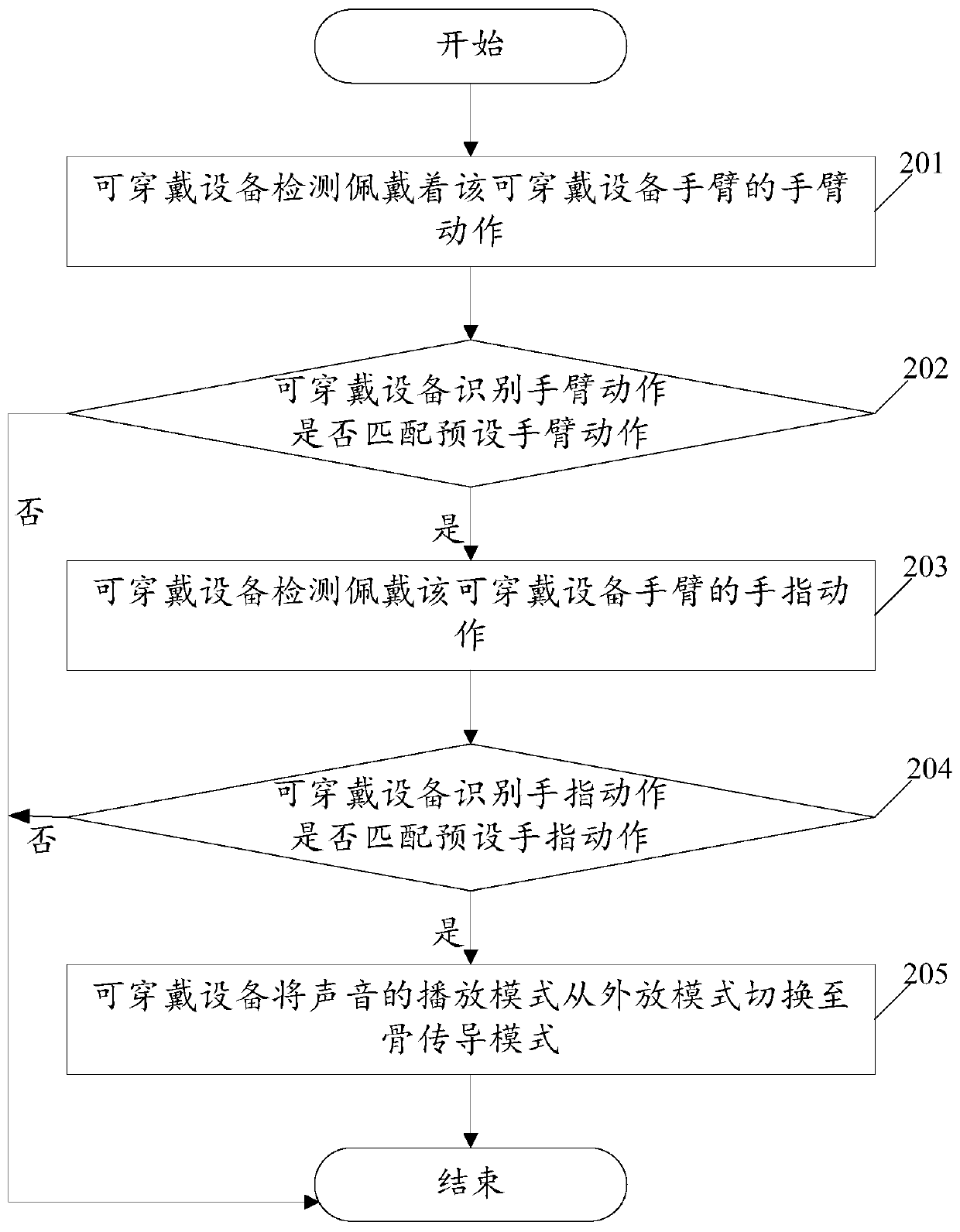
Playing mode control method of wearable device and wearable device
ActiveCN106656354AImprove privacyReduce manual operationsTransmissionTransducer circuitsAutomatic controlMode control
The embodiment of the invention relates to the technical field of wearable devices, and discloses a playing mode control method of a wearable device and the wearable device. The method comprises the following steps: when an environmental parameter of the environment where the wearable device is located satisfies a preset environmental parameter condition, switching the playing mode of the wearable device from an external playing mode into a bone conduction mode, when the wearable device needs to output a sound signal in the bone conduction mode, obtaining a first contact parameter between a body conduction component in the wearable device and a user of the wearable device, adjusting the vibration parameter of a vibration signal converted from the sound signal with reference to the first contact parameter, and transmitting the adjusted vibration signal through a bone medium. By implementation of the playing mode control method disclosed by the embodiment of the invention, the sound needing to be played can be automatically controlled through the contact parameter between the wearable device and the user, and the risk that the played sound is eavesdropped by people in the surrounding is effectively reduced.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
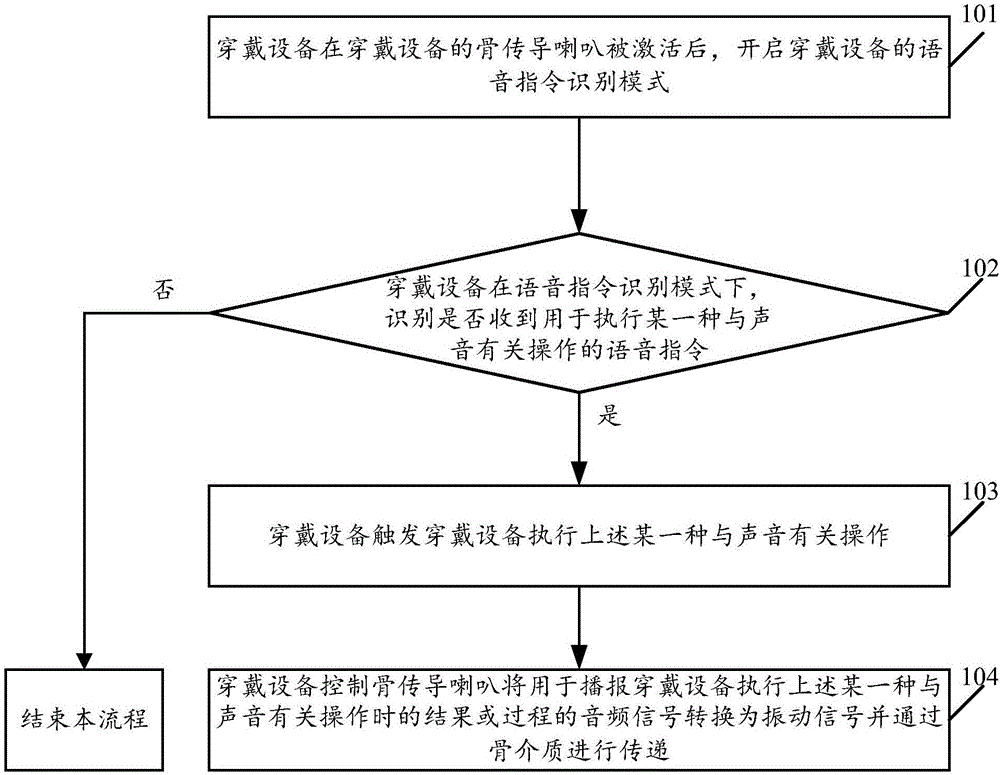
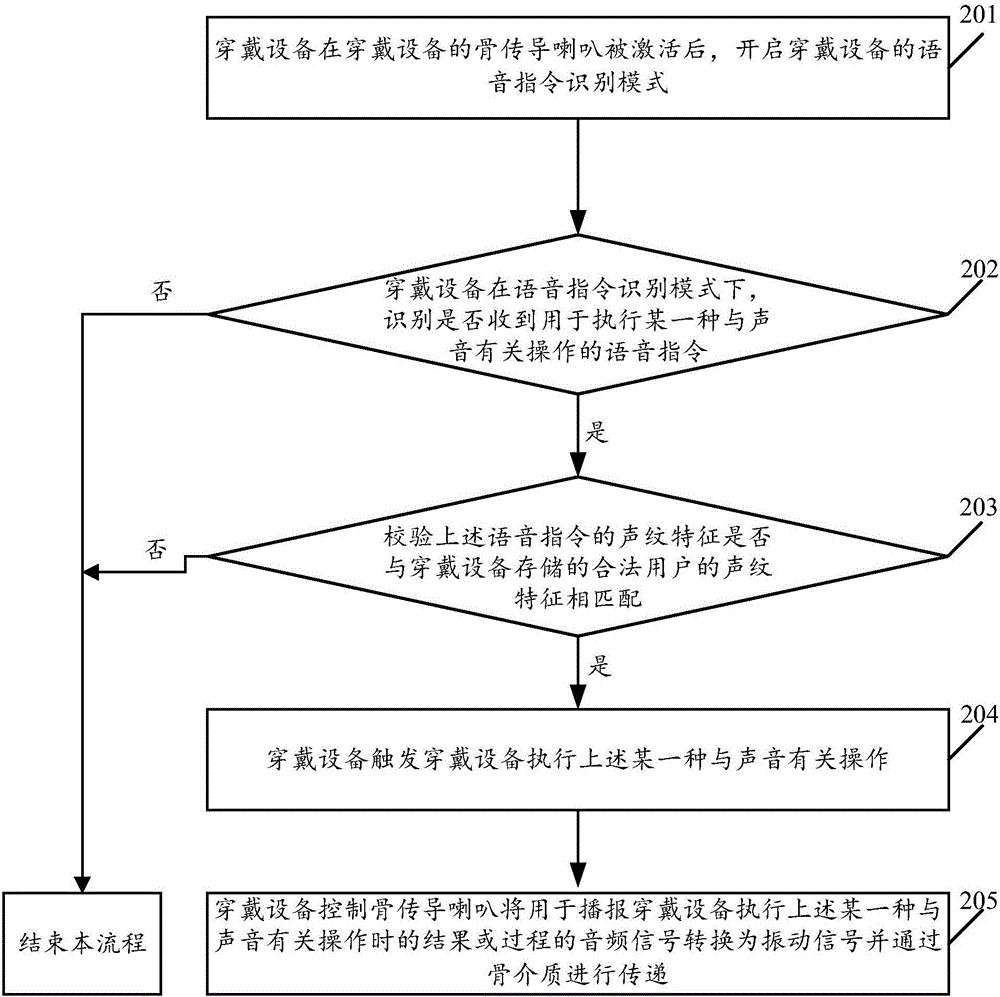
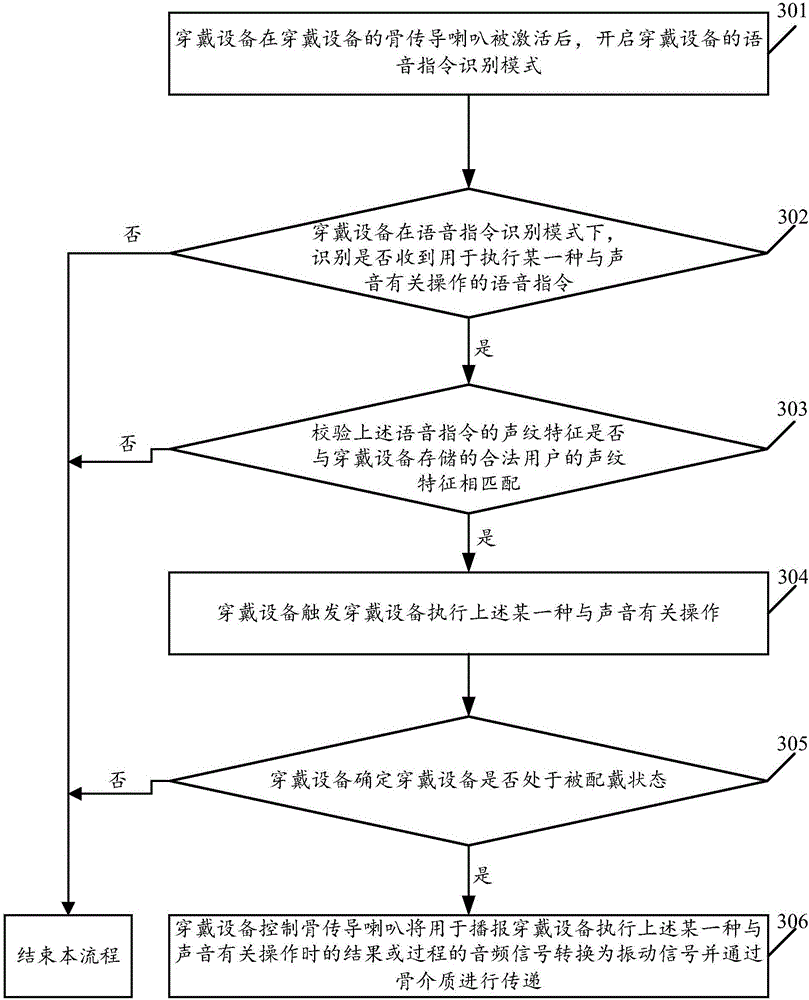
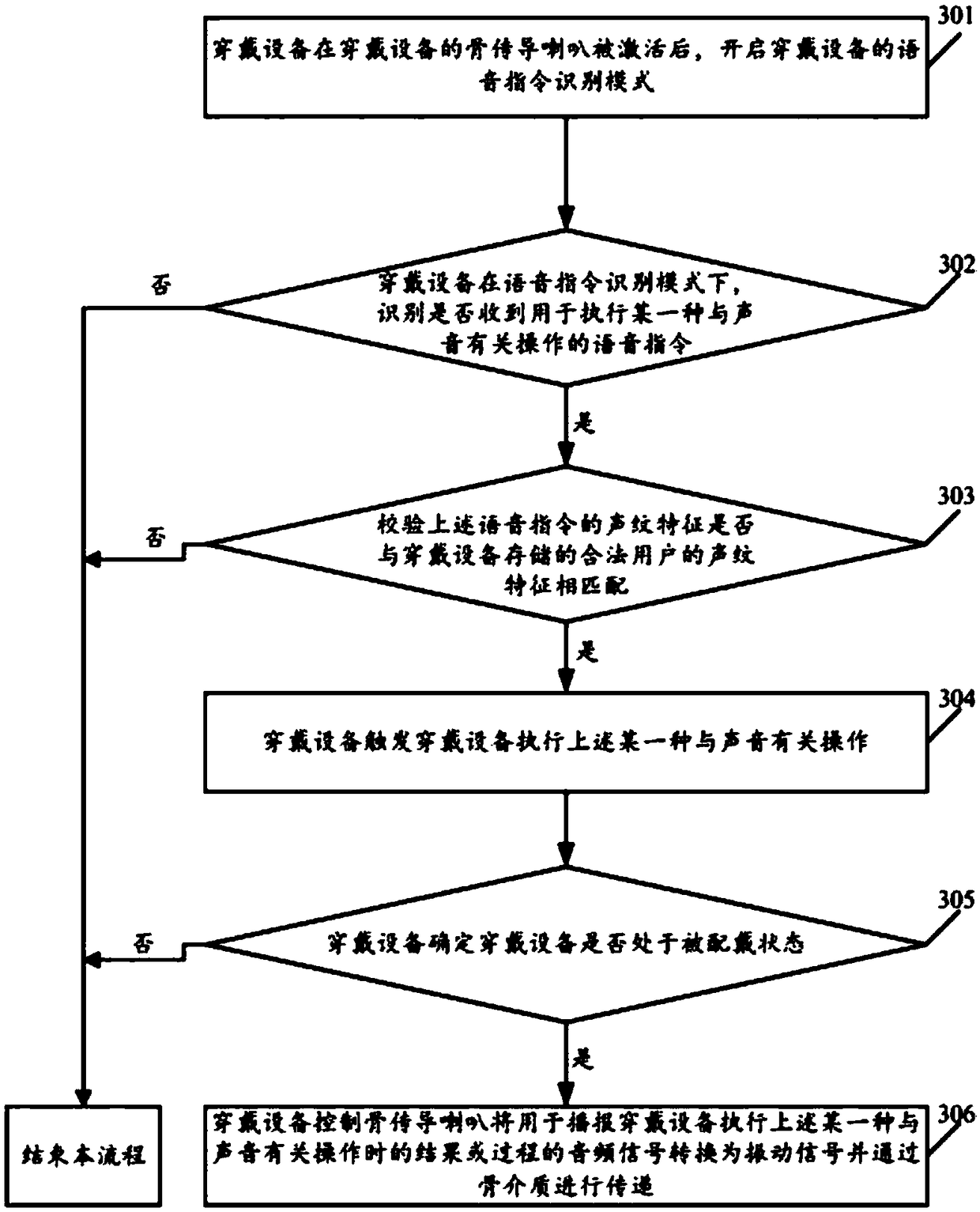
Method for controlling wearing equipment and wearing equipment
InactiveCN106847275AImprove convenienceReduce risk of leakageInput/output for user-computer interactionSound input/outputBone conduction hearingSpeech sound
The embodiment of the invention relates to the technical field of wearing equipment, and discloses a method for controlling the wearing equipment and the wearing equipment. The method comprises the steps of starting a voice instruction recognition mode of the wearing equipment after a bone conduction trumpet of the wearing equipment is activated; under the voice instruction recognition mode of the wearing equipment, recognizing whether a voice instruction used for executing certain operation related to voice is received or not; if the voice instruction is received, triggering the wearing equipment to execute the certain operation related to voice; besides, controlling the bone conduction trumpet to transform a sound signal used for broadcasting a result or process when the wearing equipment executes the certain operation related to voice into a vibration signal and transmitting the vibration signal through bone media. According to the method for controlling the wearing equipment, the wearing equipment can be controlled conveniently, and the risk that voice broadcast by the wearing equipment is intercepted by surrounding people is reduced.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
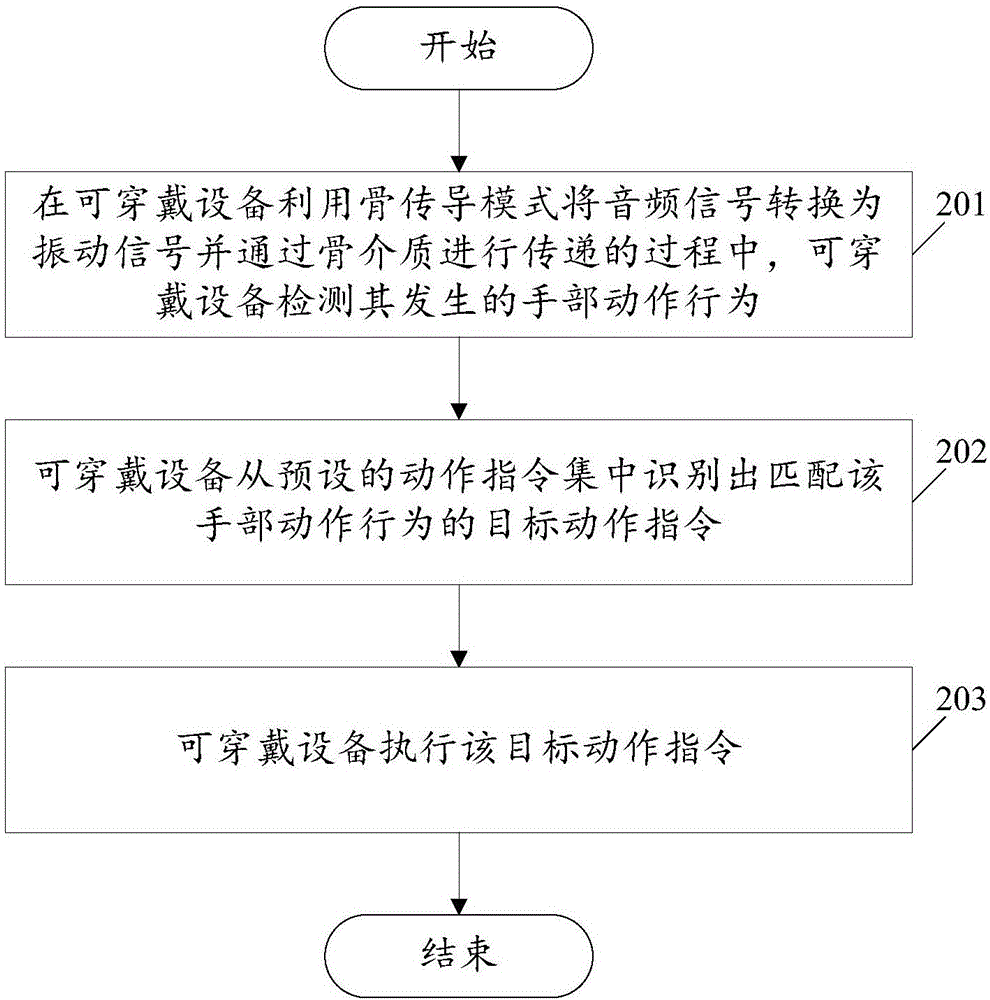
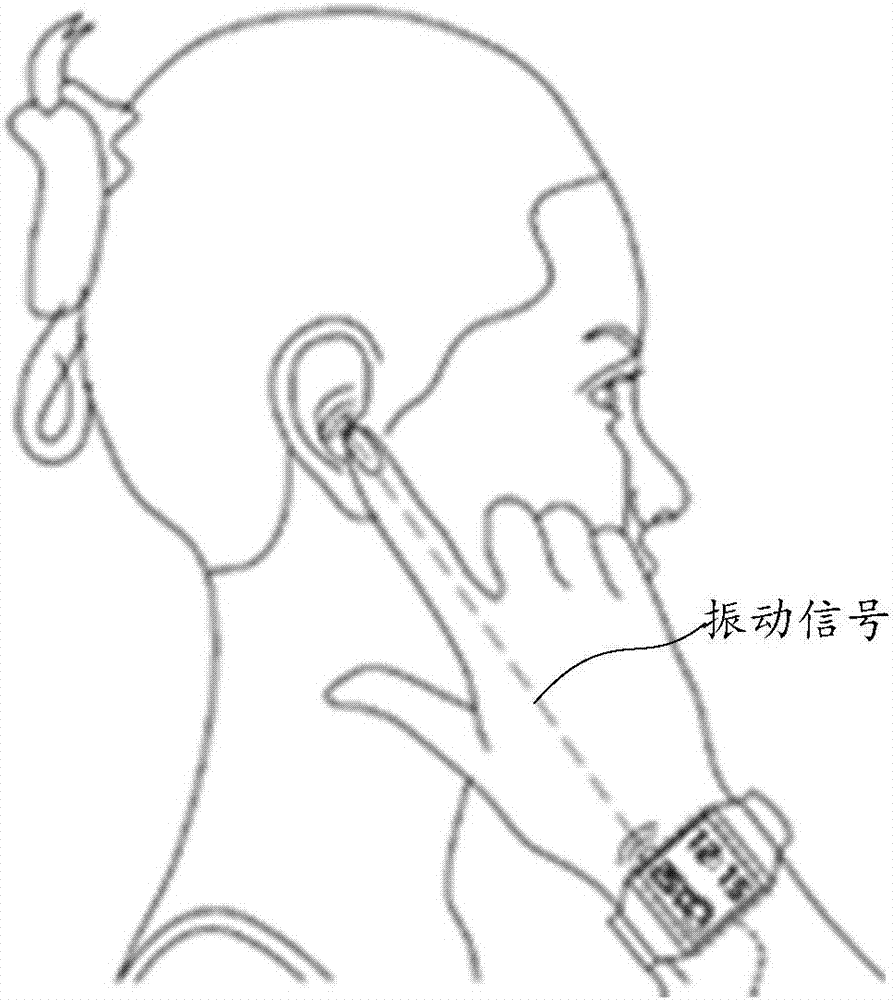
Control method for wearable device operation and the wearable device
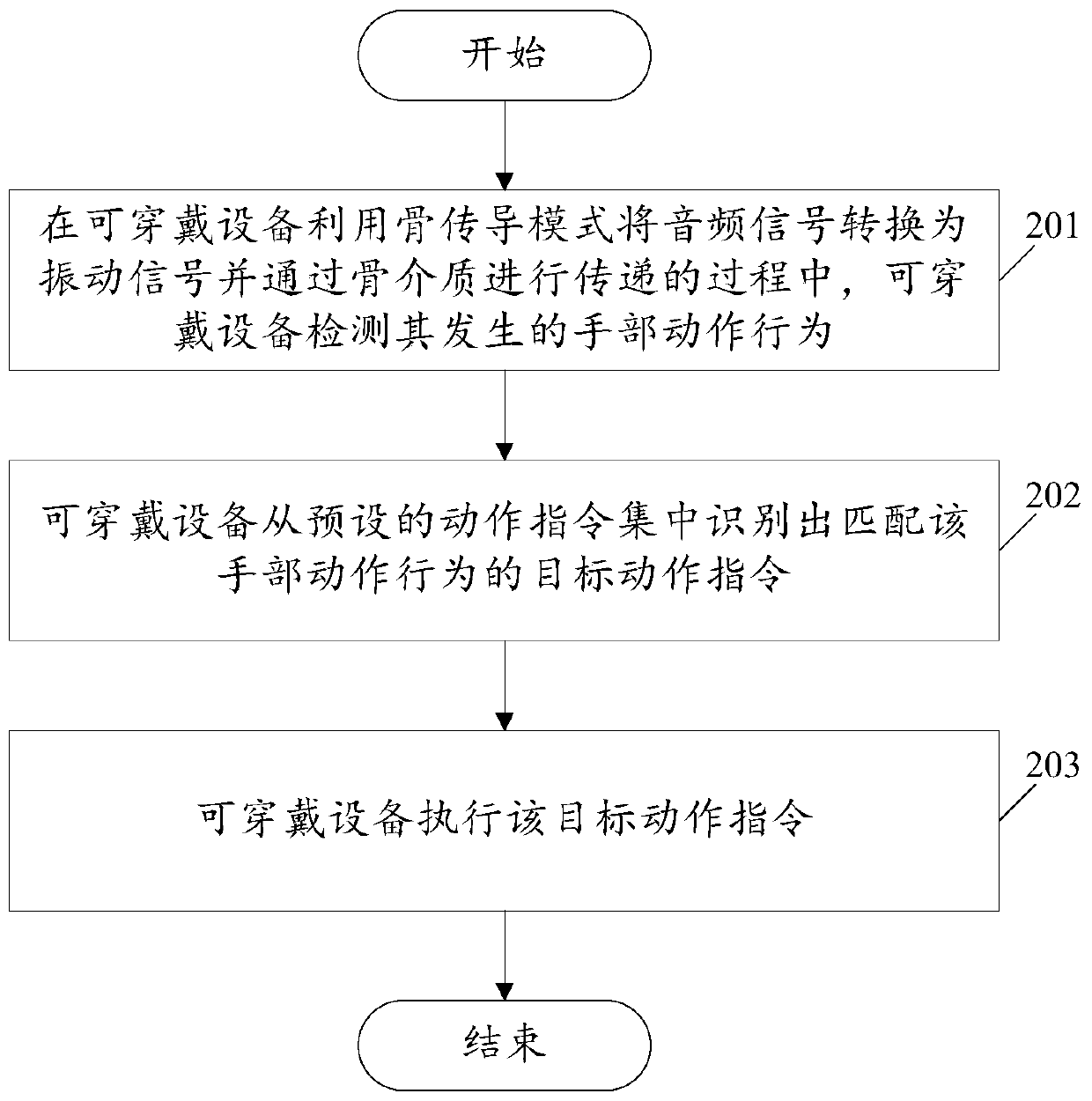
ActiveCN106685459AReduce the risk of eavesdroppingPrivacy protectionInput/output for user-computer interactionTransmissionUser privacyEngineering
An embodiment of the invention relates to the technical field of wearable devices and discloses a control method for wearable device operation and a wearable device. The method includes detecting hand actions of the wearable device when the wearable device utilizes a bone conduction mode to convert audio signals to vibration signals and transmits the vibration signals via bone medium; recognizing a target action command matching with the hand actions from a preset action command set; and performing the target action command on the wearable device. By applying the method provided by the invention, interception risks during audio playing of the wearable device are reduced, so that user privacy is protected. At the same time, simple and convenient operation control of the wearable device is realized, so that user experience is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
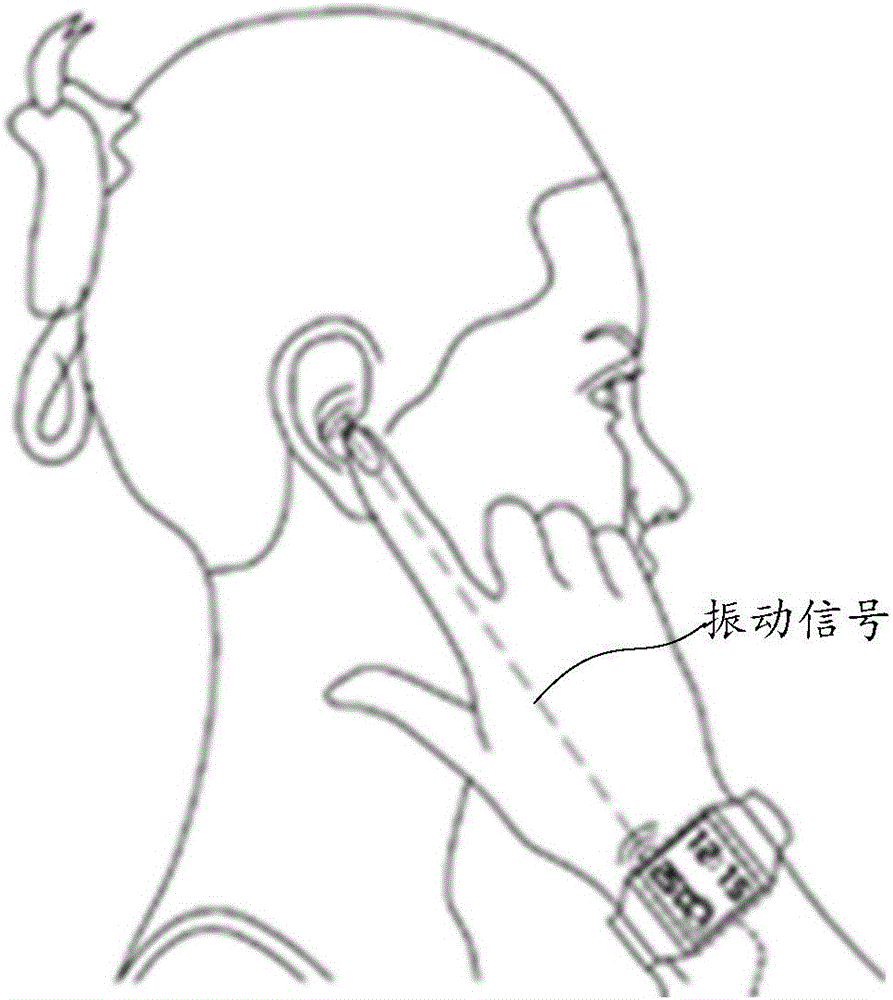
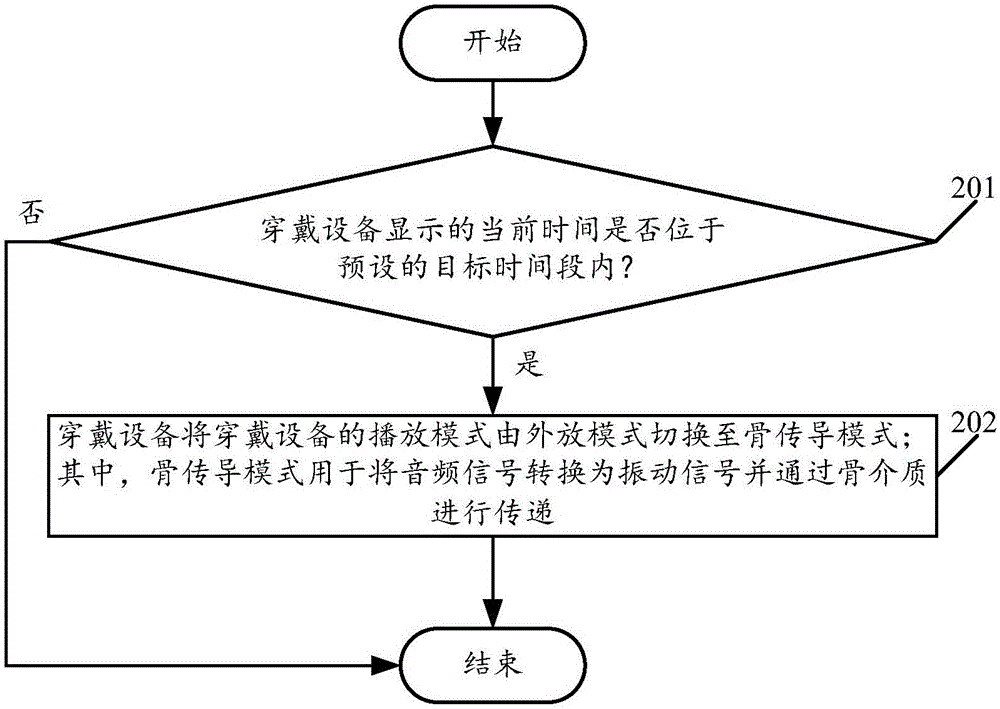
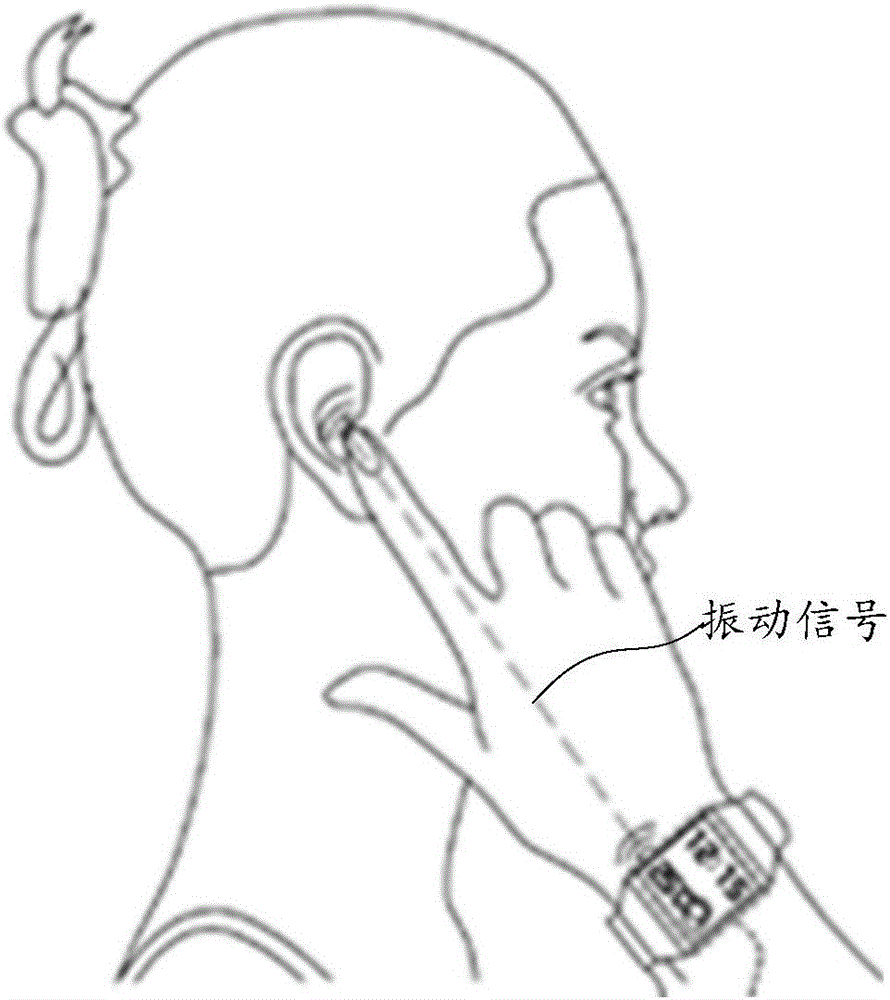
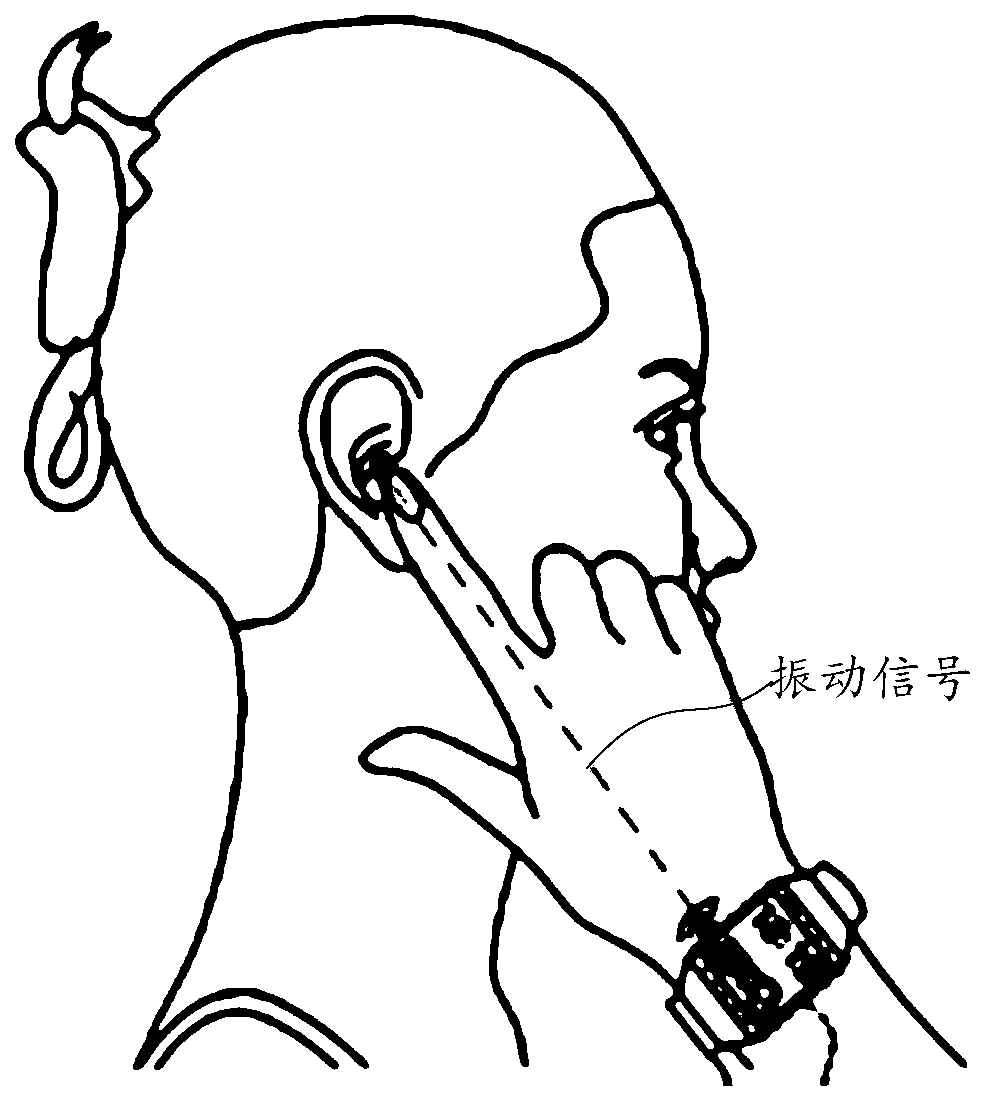
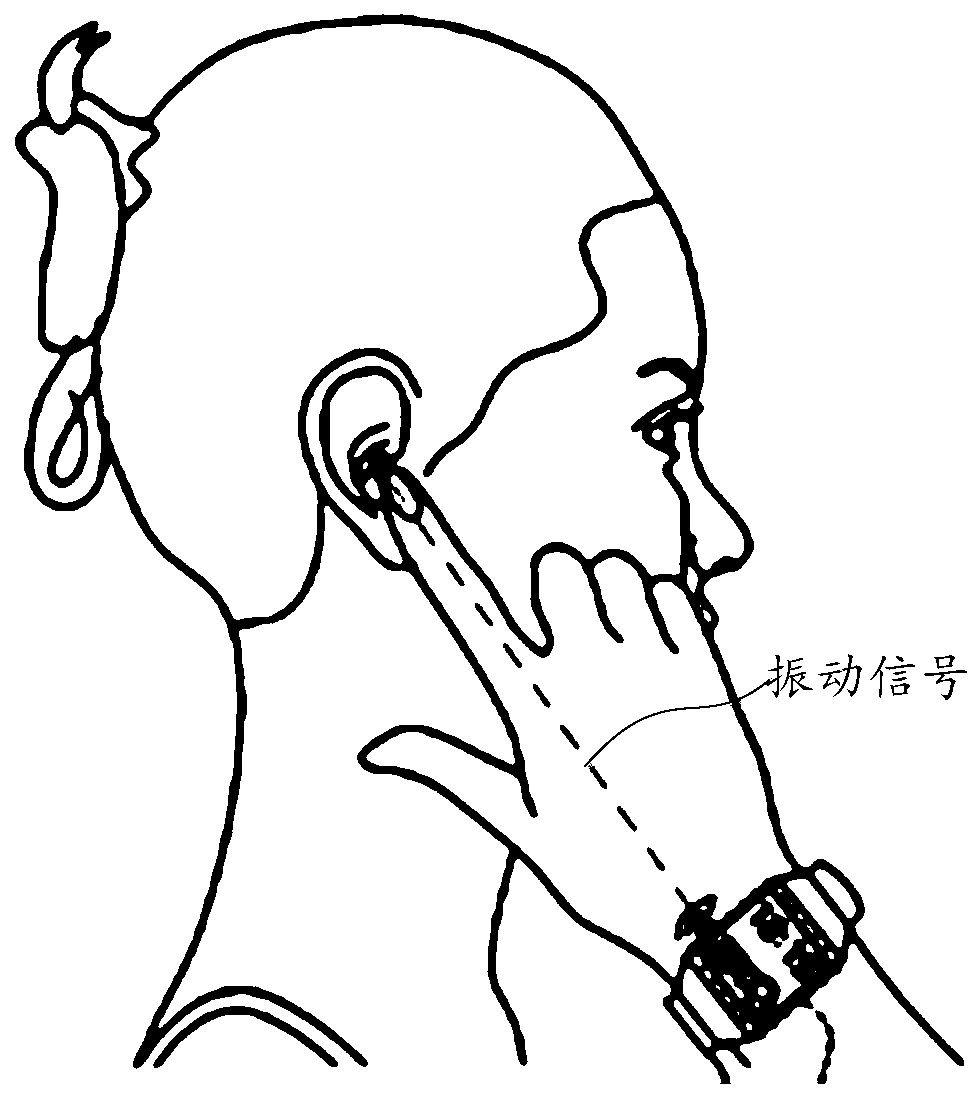
Playing mode switching method of wearable device and wearable device
ActiveCN106686187AAchieve private call effectClear and private call effectSubstation speech amplifiersBone conduction hearingAudio signal flow
The embodiment of the invention relates to the field of wearable devices and discloses a playing mode switching method of a wearable device and the wearable device. The method includes the steps that whether current time displayed by the wearable device is within a preset target time period or not is judged; if the current time is located in the target time period, the playing mode of the wearable device is switched from an outward playing mode to a bone conduction mode, wherein the bone conduction mode is used for converting audio signals into vibration signals and transmitting the vibration signals through bone media. By means of the method, the risk that calls are tapped by people around can be reduced, and calling convenience is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Wearable equipment and message play method thereof
InactiveCN106686231AImprove convenienceReduce the risk of eavesdroppingSubstation equipmentTransmissionComputer hardwareUser privacy
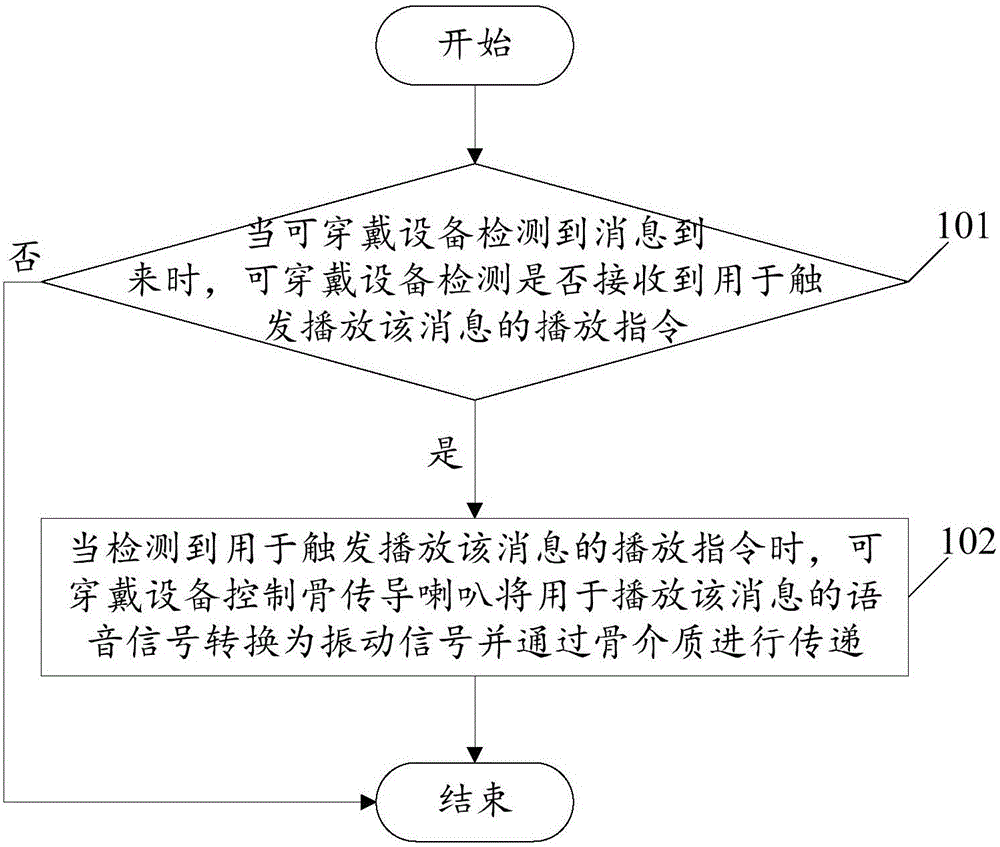
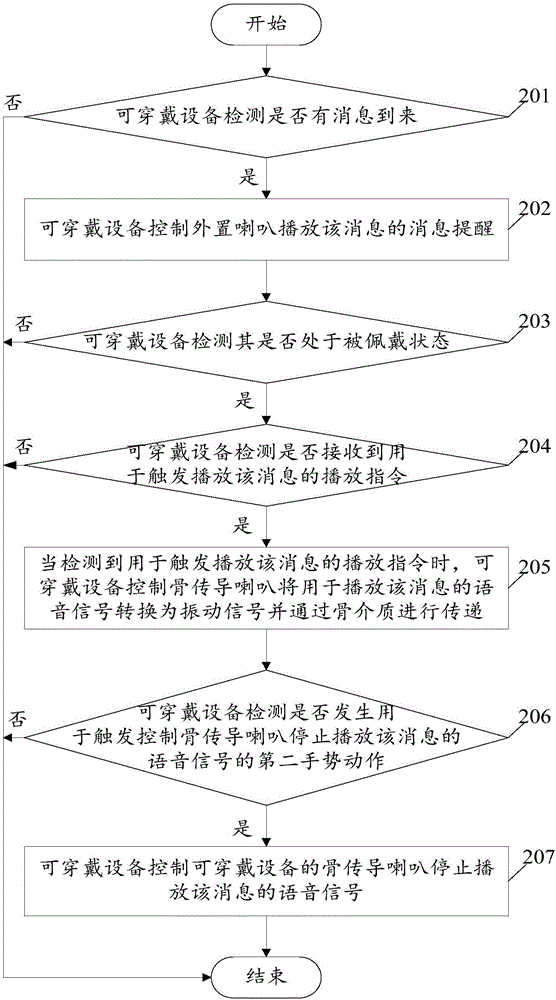
The invention relates to the technical field of wearable equipment, and discloses wearable equipment and a message play method thereof. The method comprises that when the wearable equipment detects arrival of a message, whether the wearable equipment receives a play instruction to trigger play of the message is detected; and if YES, a bone conduction loudspeaker of the wearable equipment is controlled to convert a voice signal to play the message into a vibration signal and transmit the bone signal via a bone medium. According to embodiments of the invention, the message receiving convenience is improved, sound leakage is not caused due to the fact that the bone conduction loudspeaker converts the voice signal into the vibration signal and transmit the vibration signal via the bone medium, the risk that the message is eavesdropped can be reduced, and the user privacy is protected.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
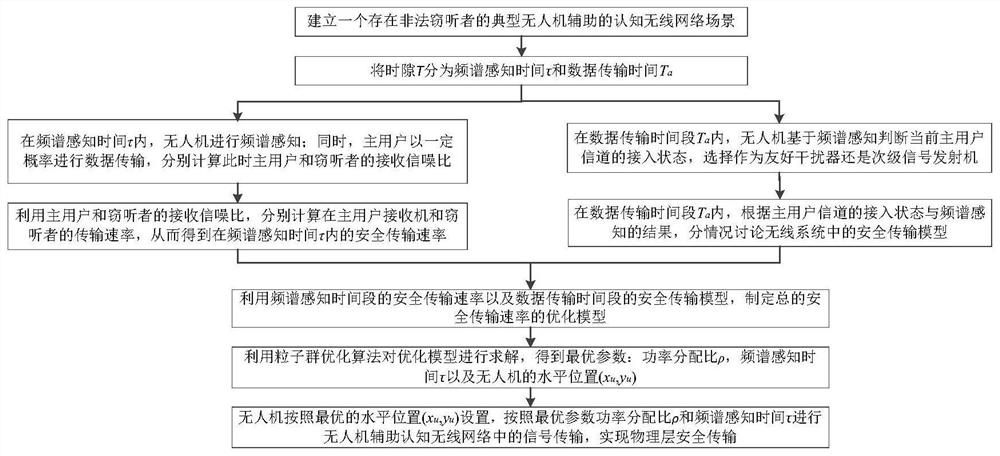
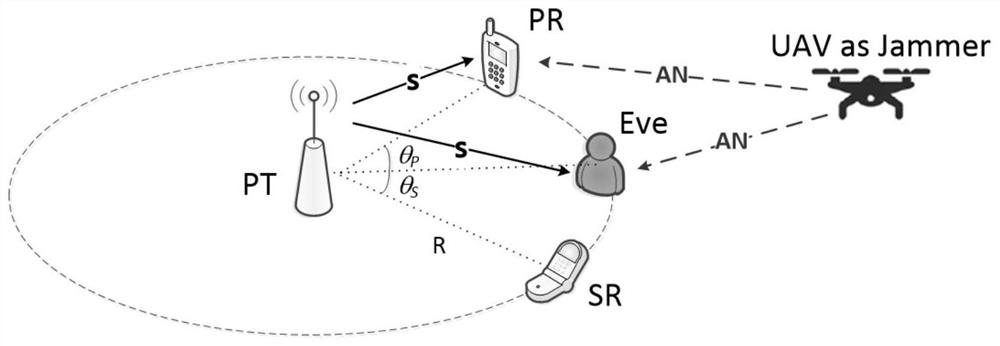
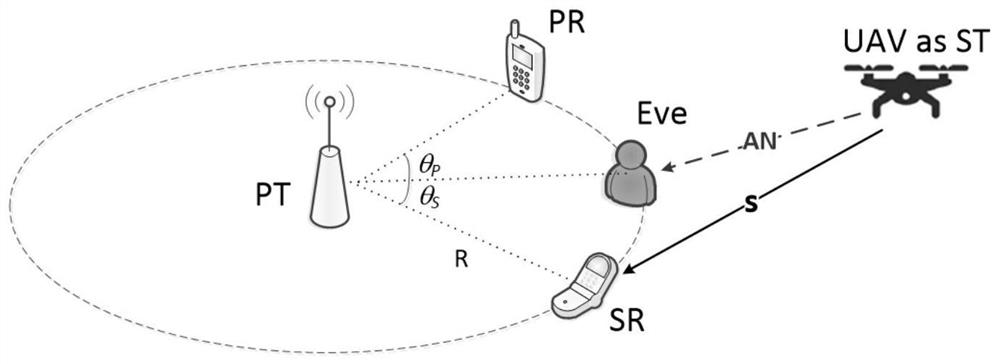
Physical layer secure transmission method in unmanned aerial vehicle assisted cognitive wireless network
ActiveCN112566127AImprove secure transmission performanceGuaranteed safe transmissionInternal combustion piston enginesTransmission monitoringInterference (communication)Frequency spectrum
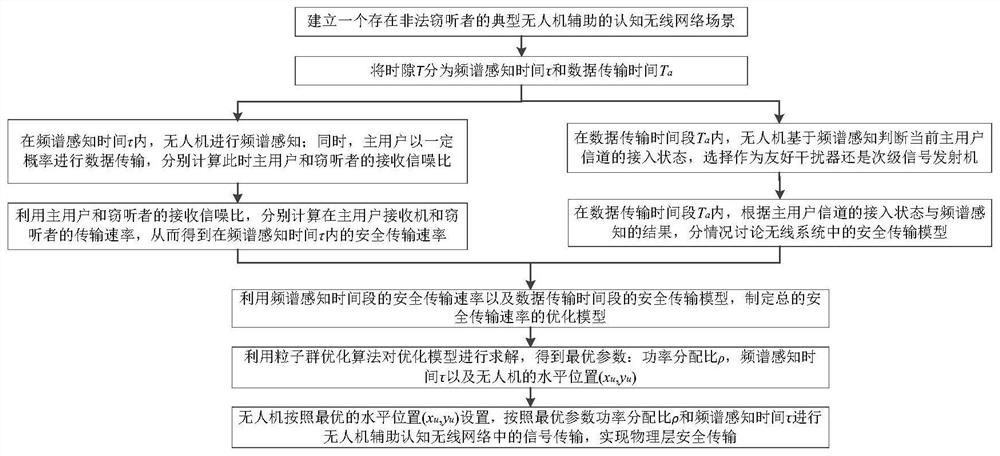
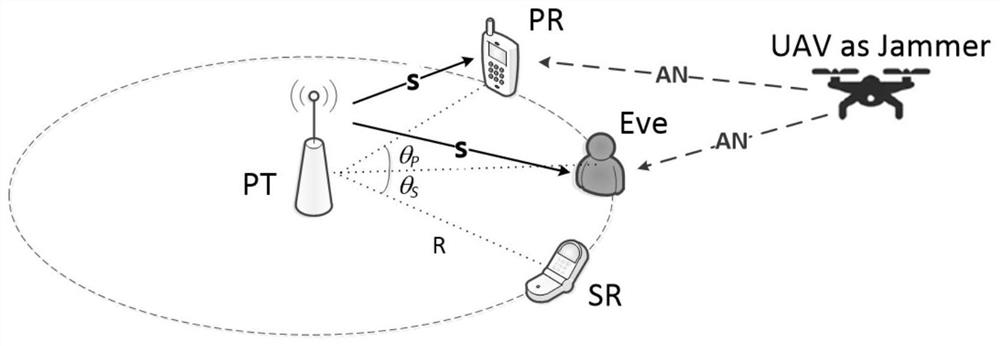
The invention provides a physical layer secure transmission method based on an unmanned aerial vehicle assisted cognitive wireless network, and belongs to the field of wireless communication. The method specifically comprises the following steps: establishing a wireless communication scene comprising an unmanned aerial vehicle, a primary user transmitter, a primary user receiver, a secondary userreceiver and an eavesdropper, and then, in a frequency spectrum sensing time tau of a time slot T, enabling the unmanned aerial vehicle to perform spectrum sensing, wherein the main user may perform data transmission, and calculates the safe transmission rate at the moment; meanwhile, in the data transmission time period Ta of the time slot T, enabling the unmanned aerial vehicle to judge the access state of the current main user channel based on spectrum sensing, selecting the current main user channel as a friendly interference unit or a secondary signal transmitter, and discussing a securetransmission model in four situations; based on this, formulating an optimization model of the total secure transmission rate; performing solving by using a particle swarm optimization algorithm; andenabling the unmanned aerial vehicle to perform signal physical layer safety transmission according to the obtained optimal parameters. According to the invention, the secure transmission of the primary and secondary users is considered, so that the secure transmission performance of the system is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
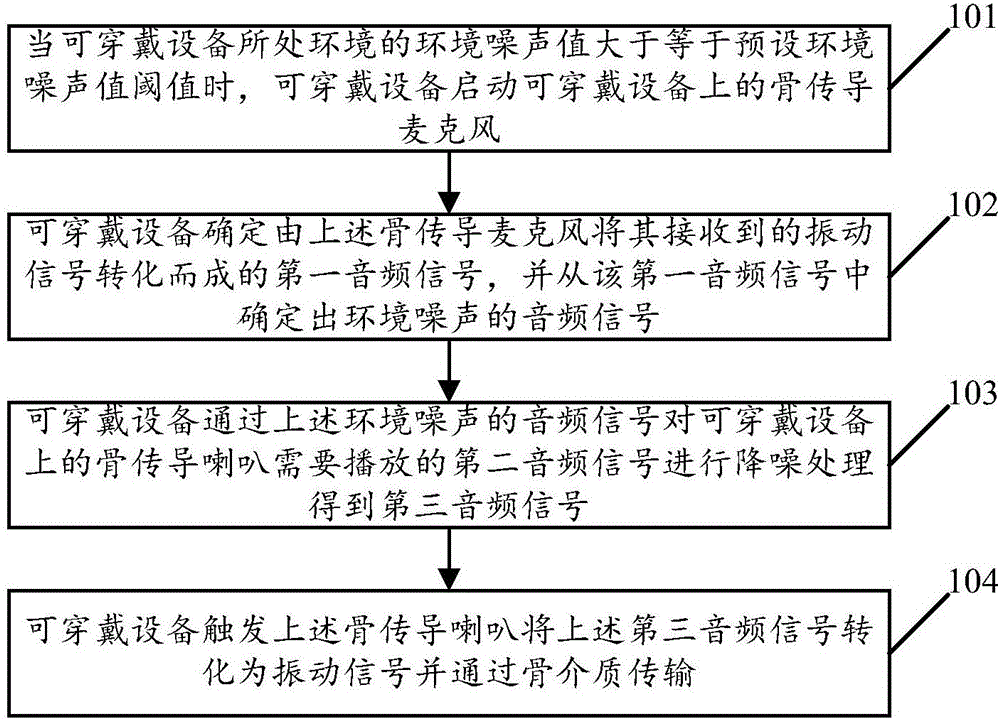
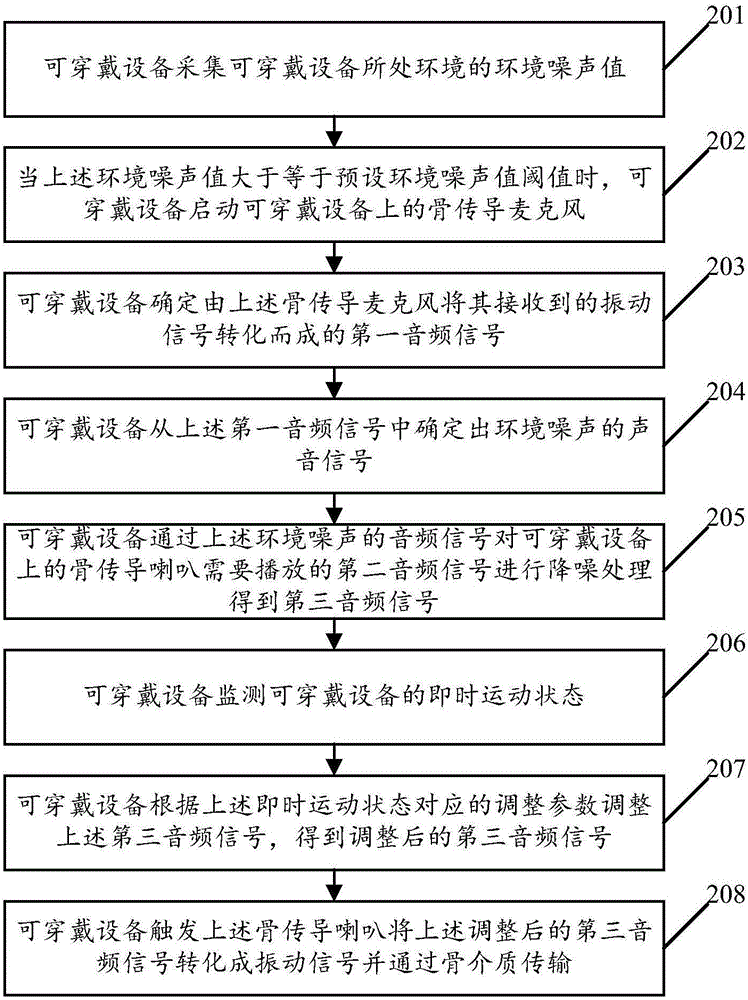
Play mode control method of wearable equipment and wearable equipment
InactiveCN106792354AReduce distractionsReduce the risk of eavesdroppingSignal processingTransducer circuitsEnvironmental noiseMode control
An embodiment of the invention relates to the technical field of wearable equipment and discloses a play mode control method of wearable equipment and the wearable equipment. The method comprises steps as follows: when an environmental noise value of an environment where the wearable equipment is located is larger than or equal to a preset environmental noise threshold value, a bone conduction microphone on the wearable equipment is started, first audio signals converted from received vibration signals by the bone conduction microphone are determined, audio signals of environmental noise are determined from the first audio signals, second audio signals required to be played by a bone conduction speaker on the wearable equipment are subjected to noise reduction treatment by means of the audio signals of environmental noise, and third audio signals are obtained and converted by the bone conduction horn into vibration signals to be transmitted through bone media. With the adoption of the embodiment of the invention, the risk of eavesdropping for played voice by people around can be effectively reduced, and interference of the environmental noise to the played voice can be effectively reduced.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
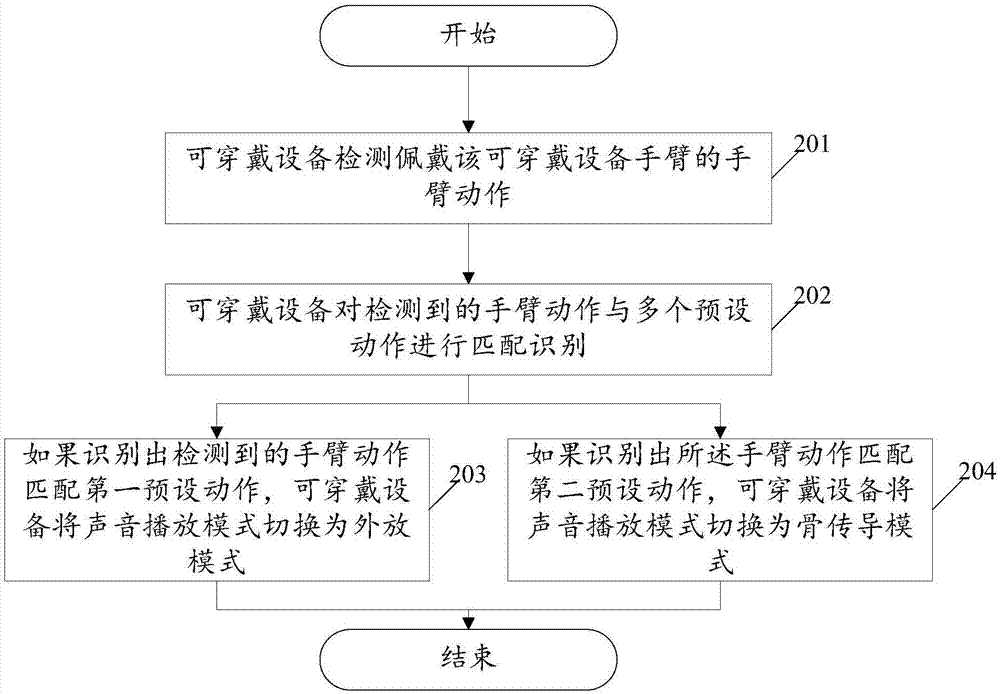
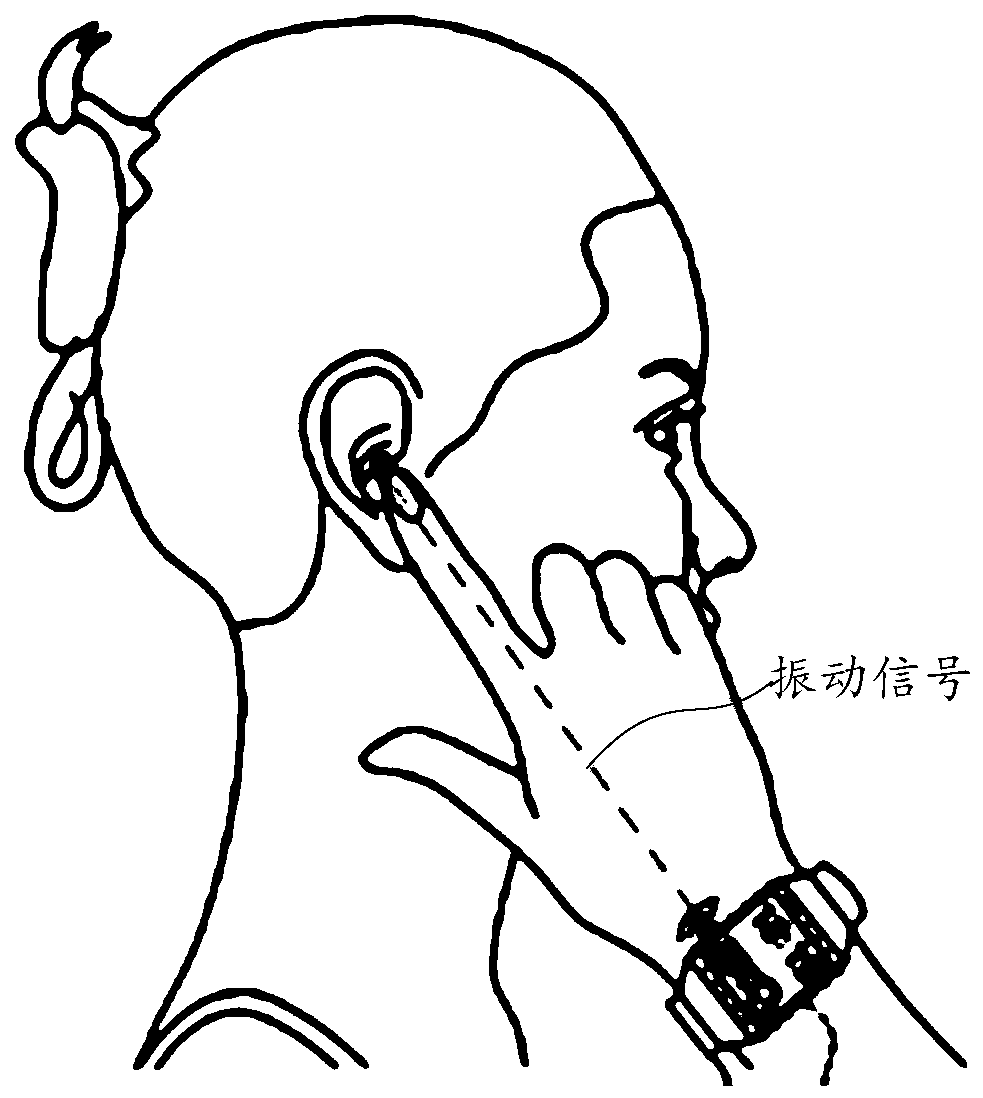
Control method for switching playing mode of wearable equipment and wearable equipment
InactiveCN107070474AReduce the risk of eavesdroppingProtect user privacySubstation speech amplifiersSound input/outputUser privacyLoudspeaker
The embodiment of the invention relates to the technical field of wearable equipment, and discloses a control method for switching a playing mode of wearable equipment and the wearable equipment. The method comprises the steps of detecting the arm action of an arm wearing the wearable equipment; performing matching recognition on the arm action with a plurality of preset actions; if the condition that arm action is matched with the first preset action is recognized, switching the sound playing mode of the warble equipment to a loudspeaker mode; if the condition that the arm action is matched with the second preset action is recognized, switching the sound playing mode of the wearable equipment to a bone conduction mode, wherein the bone conduction mode is used for converting an audio signal into a vibration signal and transmitting the signal via a bone medium. With the application of the method and the equipment provided by the embodiment of the invention, an eavesdropping risk when sound plays is reduced, and thus user privacy is improved; and usage experience of the wearable equipment is also improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
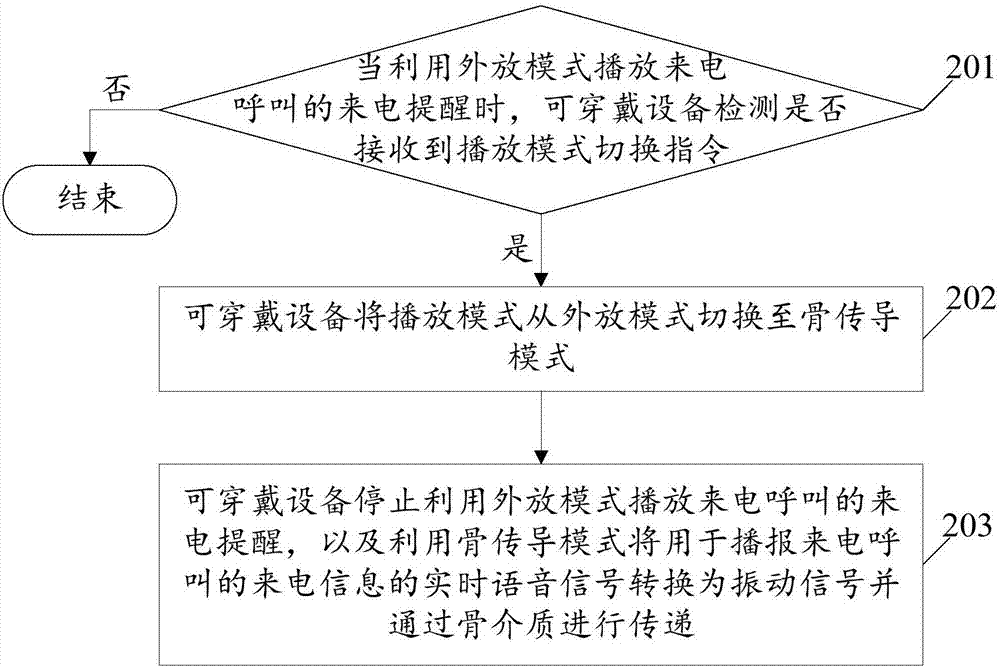
Wearable equipment call reminding method and wearable equipment
ActiveCN106856416AAvoid missing callsReduce the risk of eavesdroppingTransmissionTransducer circuitsEmbedded systemLoudspeaker
The embodiment of the invention relates to the technical field of wearable equipment, and discloses a wearable equipment call reminding method and wearable equipment. The method comprises the steps that when the wearable equipment plays the call reminder of a call by using a loudspeaker mode, whether the wearable equipment receives a play mode switching instruction is detected; if the wearable equipment receives the play mode switching instruction, the playing mode of the wearable equipment is switched to a bone conduction mode from the loudspeaker mode; and using the loudspeaker mode to play the call reminder of the call is stopped, and real-time voice signals used for playing call information of the call are converted into vibration signals by using the bone conduction mode and the vibration signals are transmitted through the bone medium. With application of the wearable equipment call reminding method and the wearable equipment, the user is enabled to timely know the call information of the call to avoid missing the call, and the risk of interception of the call information can also be reduced so as to achieve the effect of protecting the privacy of the user.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
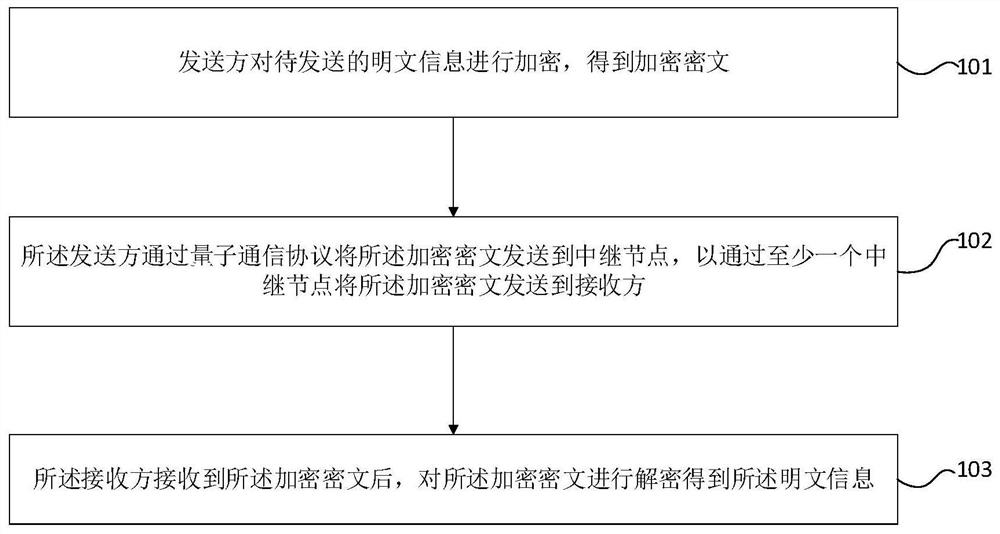
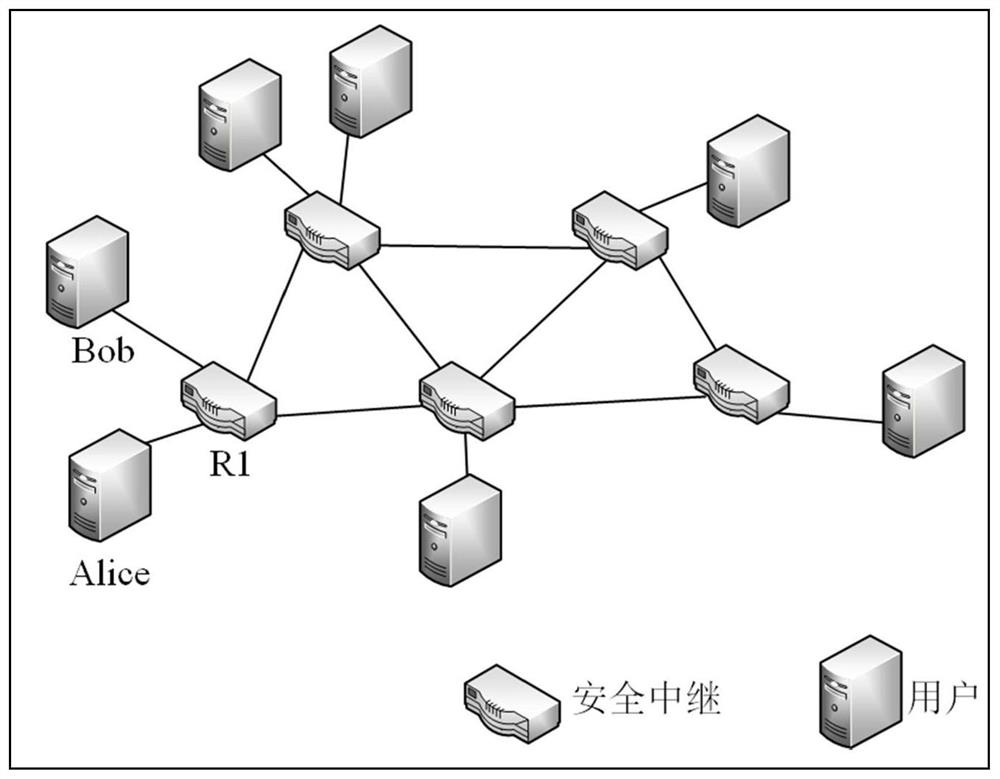
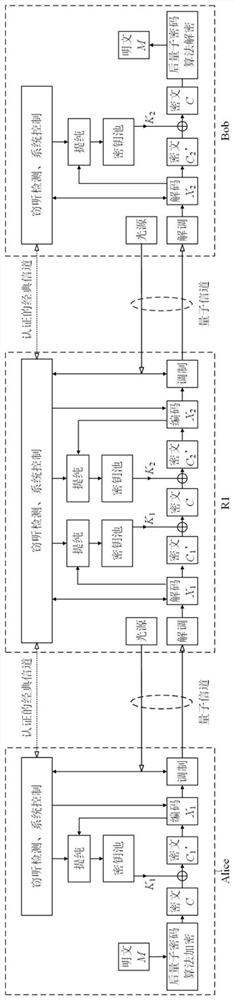
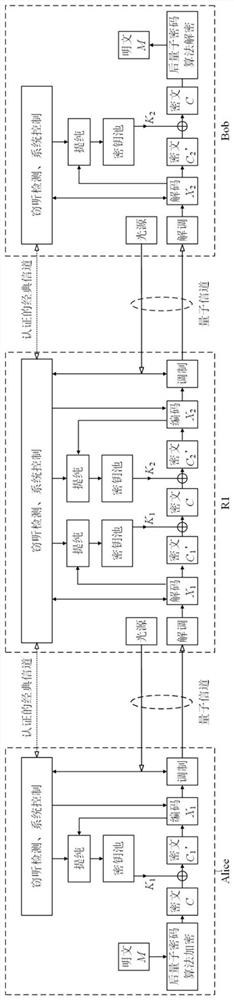
Quantum communication method and communication network based on secure relay
ActiveCN112787807AReduce the risk of eavesdroppingImprove securityKey distribution for secure communicationPhotonic quantum communicationCiphertextTrunking
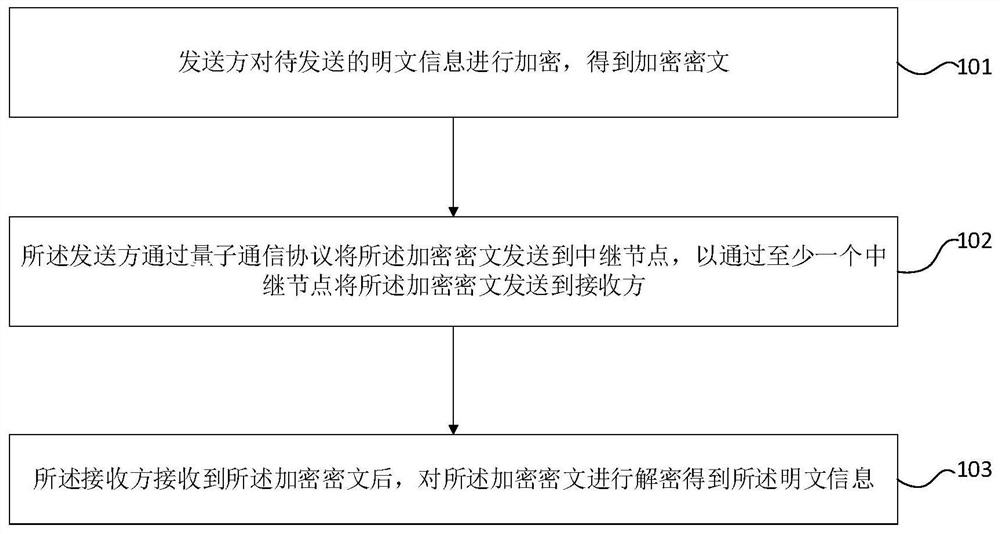
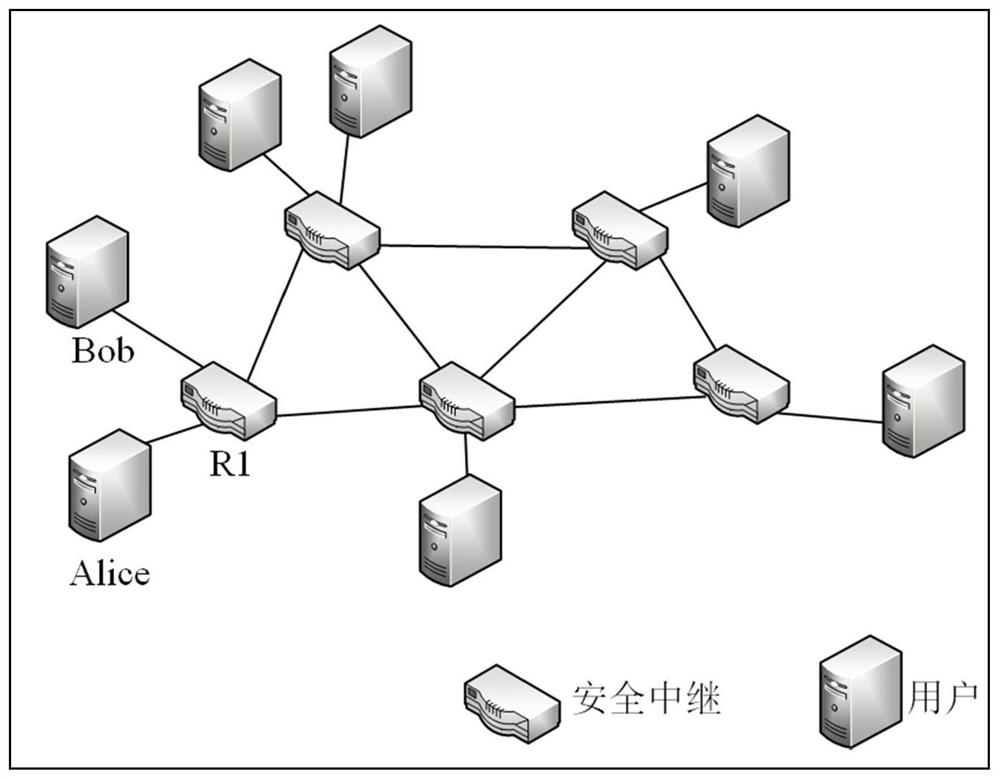
The invention provides a quantum communication method and communication network based on a secure relay; the method comprises the steps: the to-be-sent plaintext information is encrypted by a sender to generate an encrypted ciphertext; the sender sends the encrypted ciphertext to a relay node through a quantum communication protocol, so that the encrypted ciphertext is sent to a receiver through at least one relay node; and after receiving the encrypted ciphertext, the receiver decrypts the encrypted ciphertext to obtain the plaintext information. The encrypted ciphertext is transmitted step by step through at least one relay node and is not limited by the distance between a sender and a receiver, so that the encrypted ciphertext can be transmitted remotely. Meanwhile, before the information arrives at the receiver, the plaintext information is transmitted in the form of encrypted ciphertext and is not decrypted, so that the risk that the information is eavesdropped is reduced, and the security is improved.
Owner:TSINGHUA UNIV
Device and method for selecting cooperative relay node
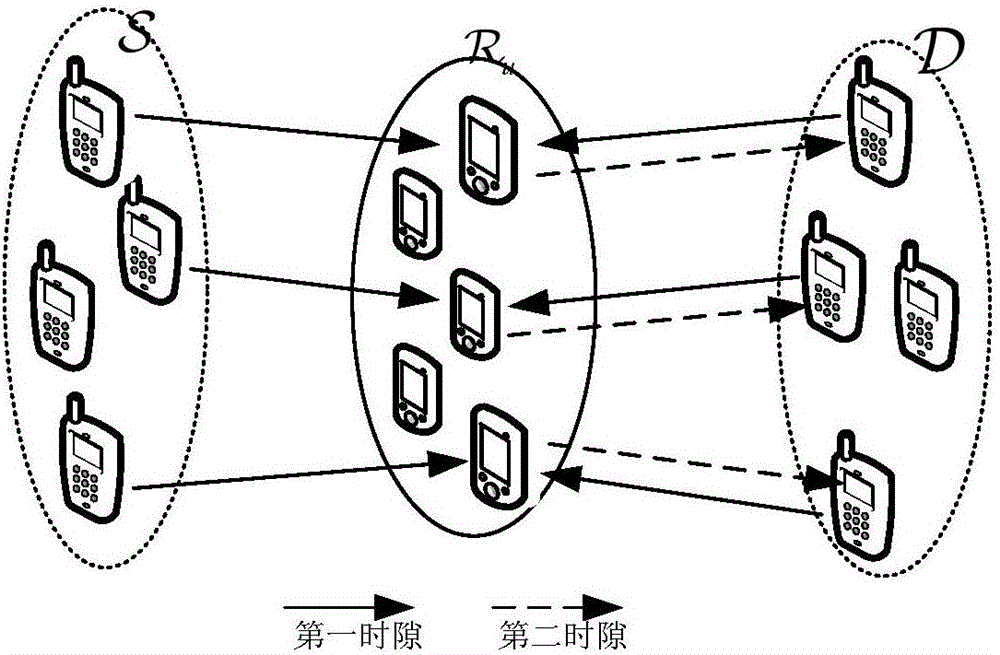
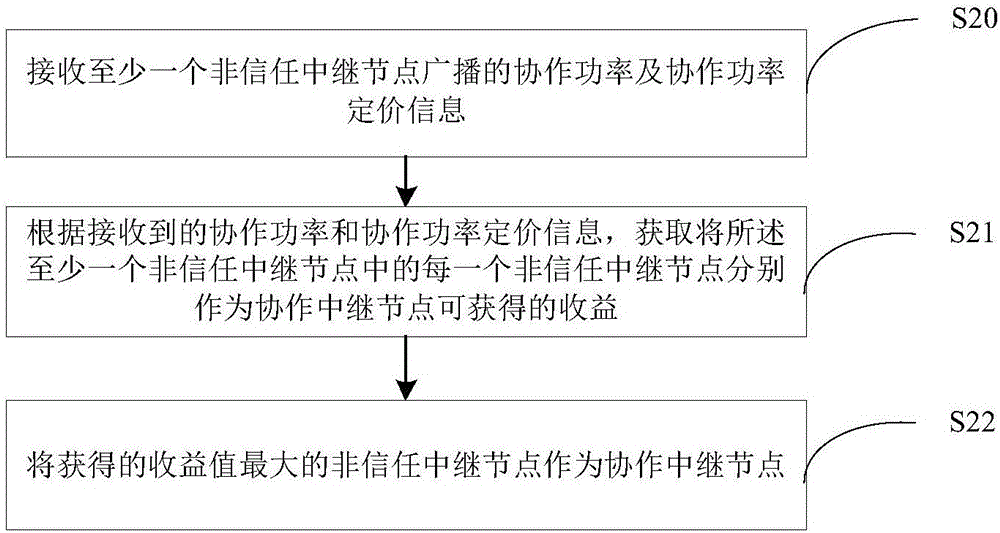
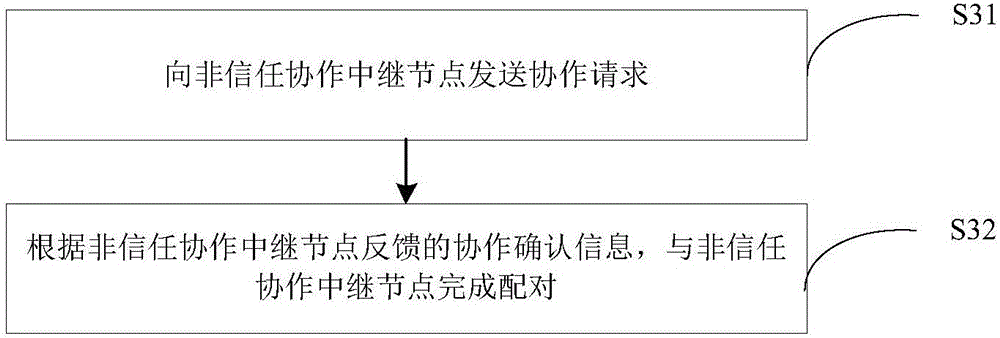
InactiveCN106358258AFast convergenceReduce communication costsHigh level techniquesWireless communicationSecure communicationComputer science
The invention discloses a device and a method for selecting a cooperative relay node. The method comprises the steps of receiving cooperative power and cooperative power pricing information broadcast by at least one relay node; acquiring revenue capable of being obtained when each relay node serves as a cooperative relay node according to the received cooperative power and cooperative power pricing information; taking the relay node with the maximum revenue value as the cooperative relay node. With implementation of the method, the cooperative relay node of each source-target node pair can be obtained rapidly; the cooperative relay node is determined according to the cooperative power and the cooperative power pricing information of the relay nodes, and the relay node capable of obtaining the maximum revenue is taken as the cooperative relay node, communication cost can be reduced, and secure communication efficiency can be increased.
Owner:CHONGQING UNIV +1
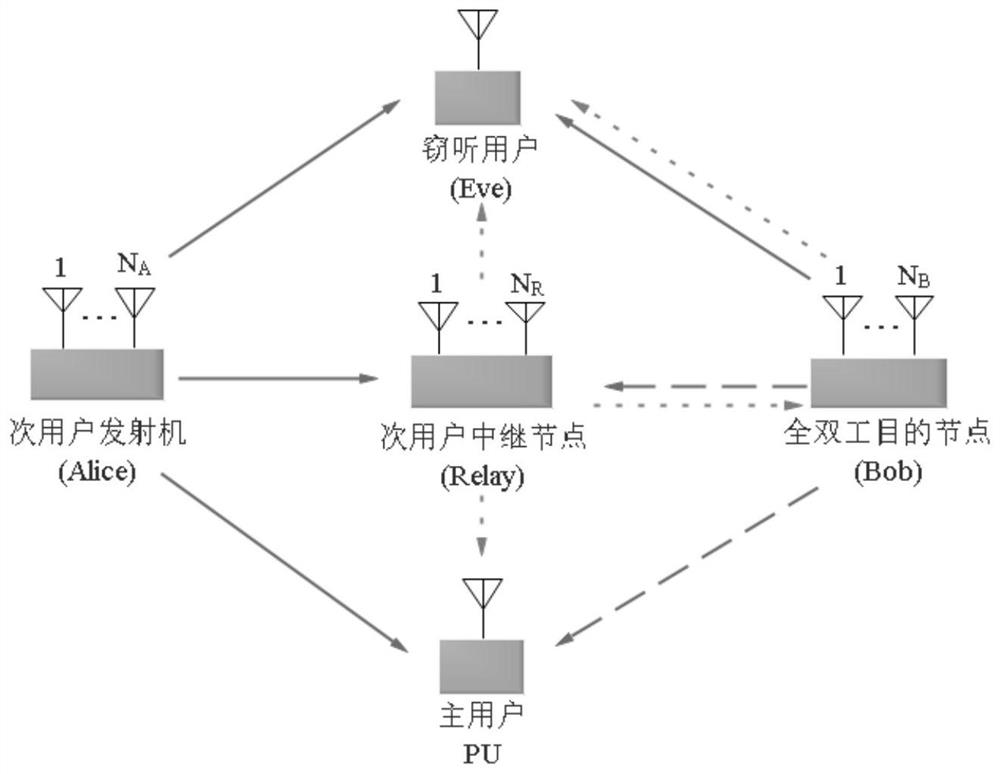
Full duplex cognitive multiple-input-multiple-output relay cooperation method in non-ideal channel state
PendingCN111800217AReduce the risk of eavesdroppingImprove secure transmission performanceSite diversitySpatial transmit diversityMulti inputWireless transmission
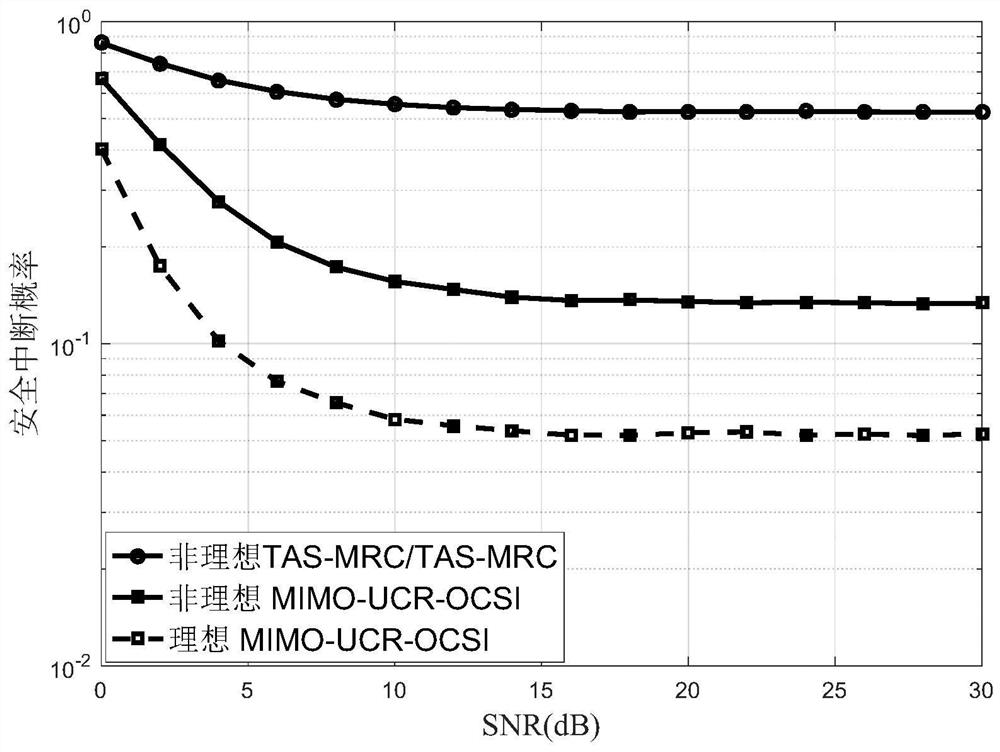
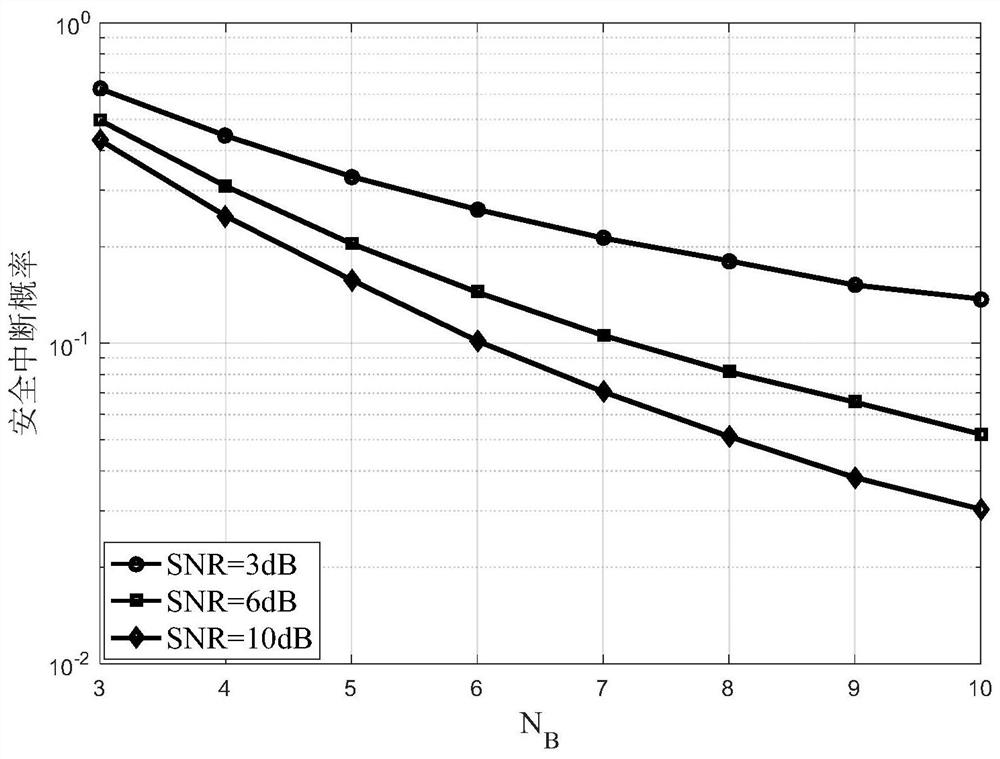
The invention discloses a full duplex cognitive multiple-input-multiple-output relay cooperation method in a non-ideal channel state, and belongs to the technical field of multi-antenna full duplex wireless transmission. Firstly, according to a channel estimation model in a first time slot non-ideal channel state, a secondary user transmitter selects and configures an optimal antenna to send a signal to a secondary user relay node under a primary user interference temperature constraint condition, and a full duplex destination node transmits a directional interference signal to an eavesdropping user in a zero-forcing beamforming mode; then, according to a channel estimation model in a second time slot non-ideal channel state; and the secondary user relay node forwards data to the full-duplex destination node under the constraint condition of the interference temperature of the primary user, any LB antenna in the full-duplex destination node receives signals, and the remaining NB-LB antenna of the full-duplex destination node transmits artificial interference to an eavesdropping user. According to the method, the physical layer security transmission performance of the full duplex cognitive wiretapping network under the non-ideal channel is effectively improved, and the risk that the whole network system is wiretapped is reduced.
Owner:ZUNYI MEDICAL UNIVERSITY
Method for controlling wearable device and wearable device thereof
InactiveCN109448715AImprove convenienceReduce risk of leakageSpeech recognitionComputer hardwareBone conduction hearing
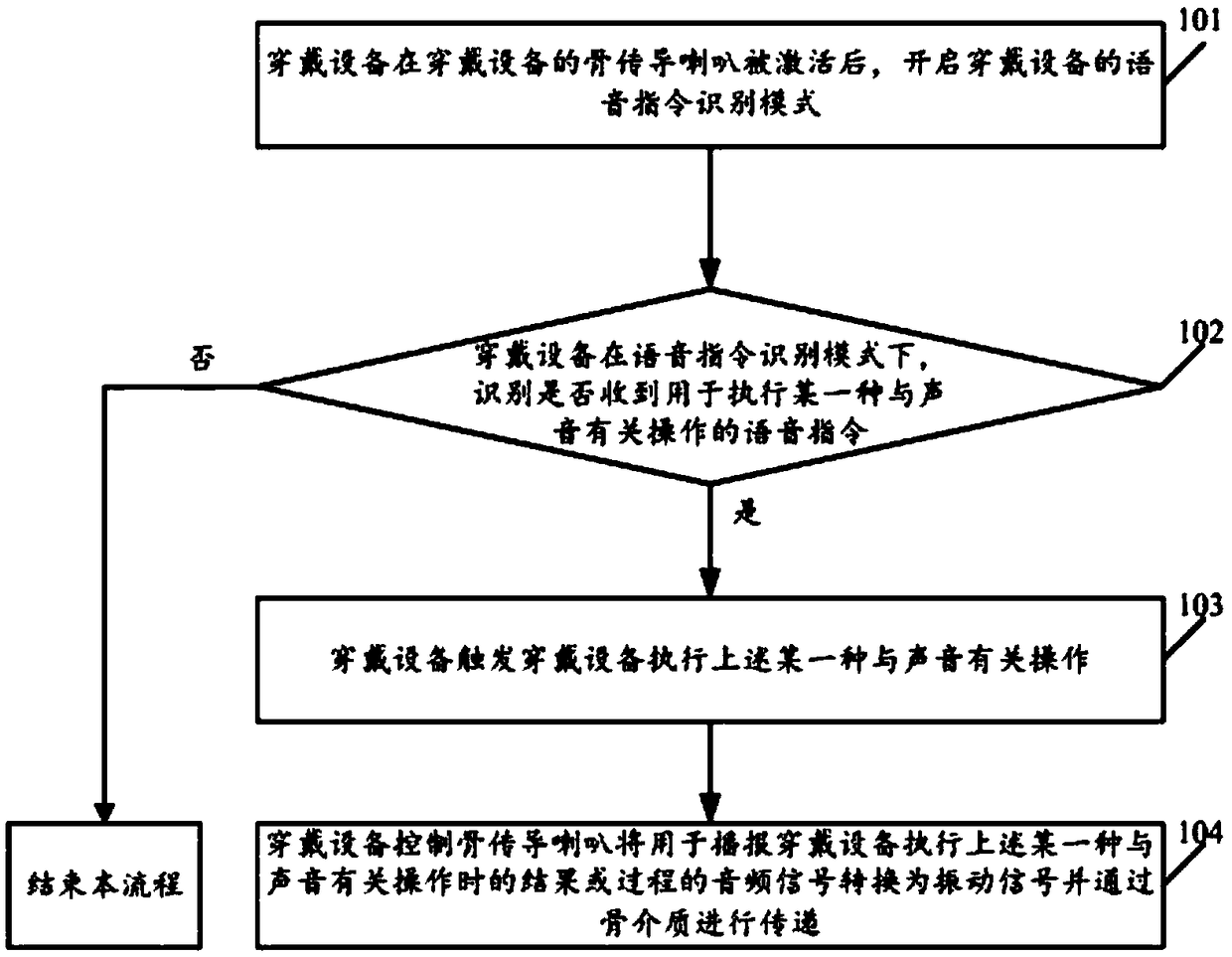
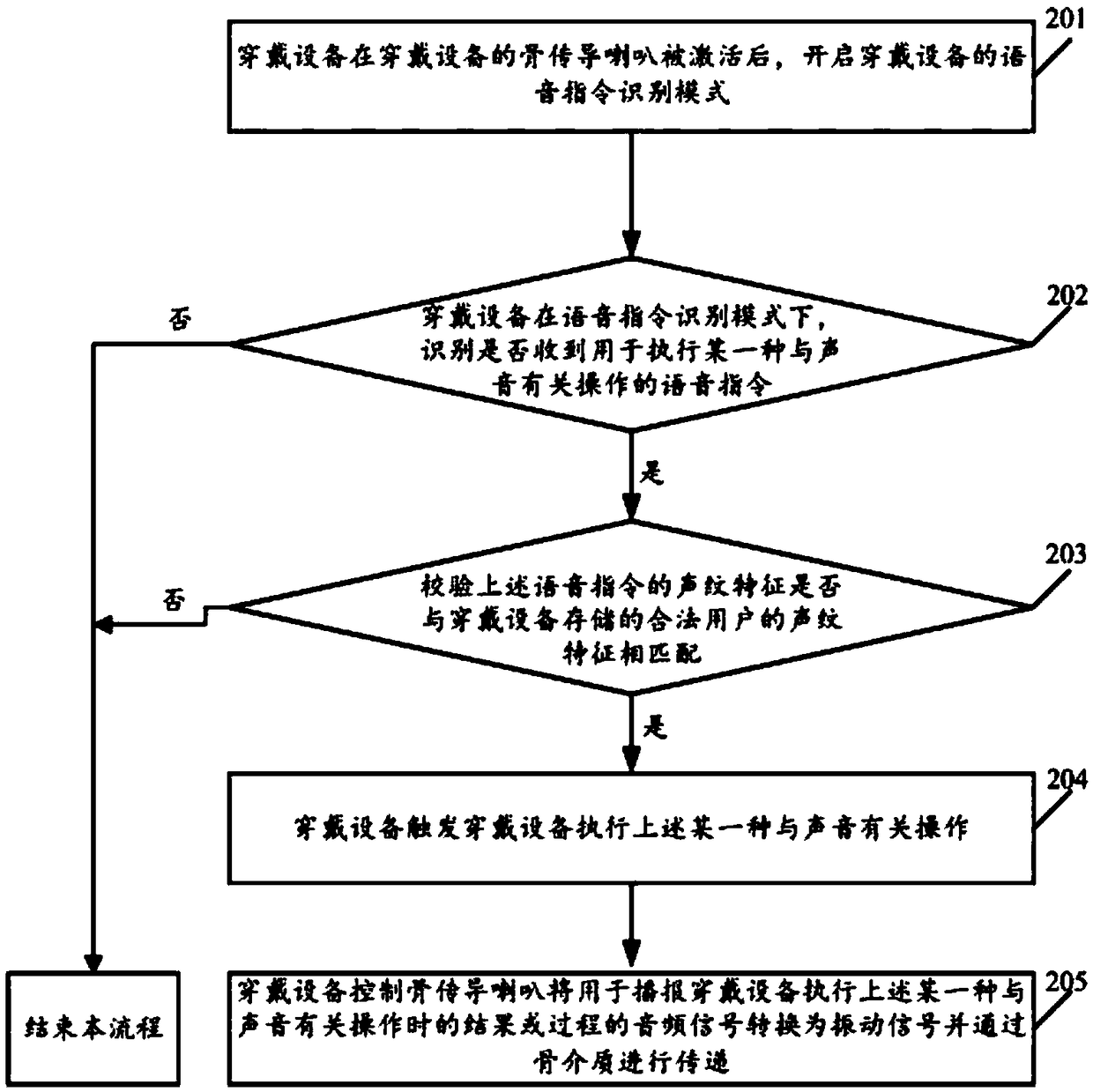
The invention relates to the field of wearable devices, and disclose a method for controlling a wearable device and the wearable device thereof. The method includes the following steps: after a bone conduction horn of the wearable device is activated, turning on a voice instruction recognition mode of the wearable device; in the voice command recognition mode of the wearable device, identifying whether a voice command for performing a certain sound-related operation is received or not; if the voice command is received, triggering the wearable device to perform the above-mentioned certain sound-related operation; and controlling the bone conduction horn to convert an audio signal used to broadcast a result or a process of the certain sound-related operation executed by the wearable device to a vibration signal and transmits the vibration signal through a bone medium. By implementing the embodiments of the present invention, the wearable device can be conveniently controlled, and the risk that the sound played by the wearable device is eavesdropped by the surrounding person is reduced.
Owner:GUANGZHOU HEDY COMPUTER CO LTD
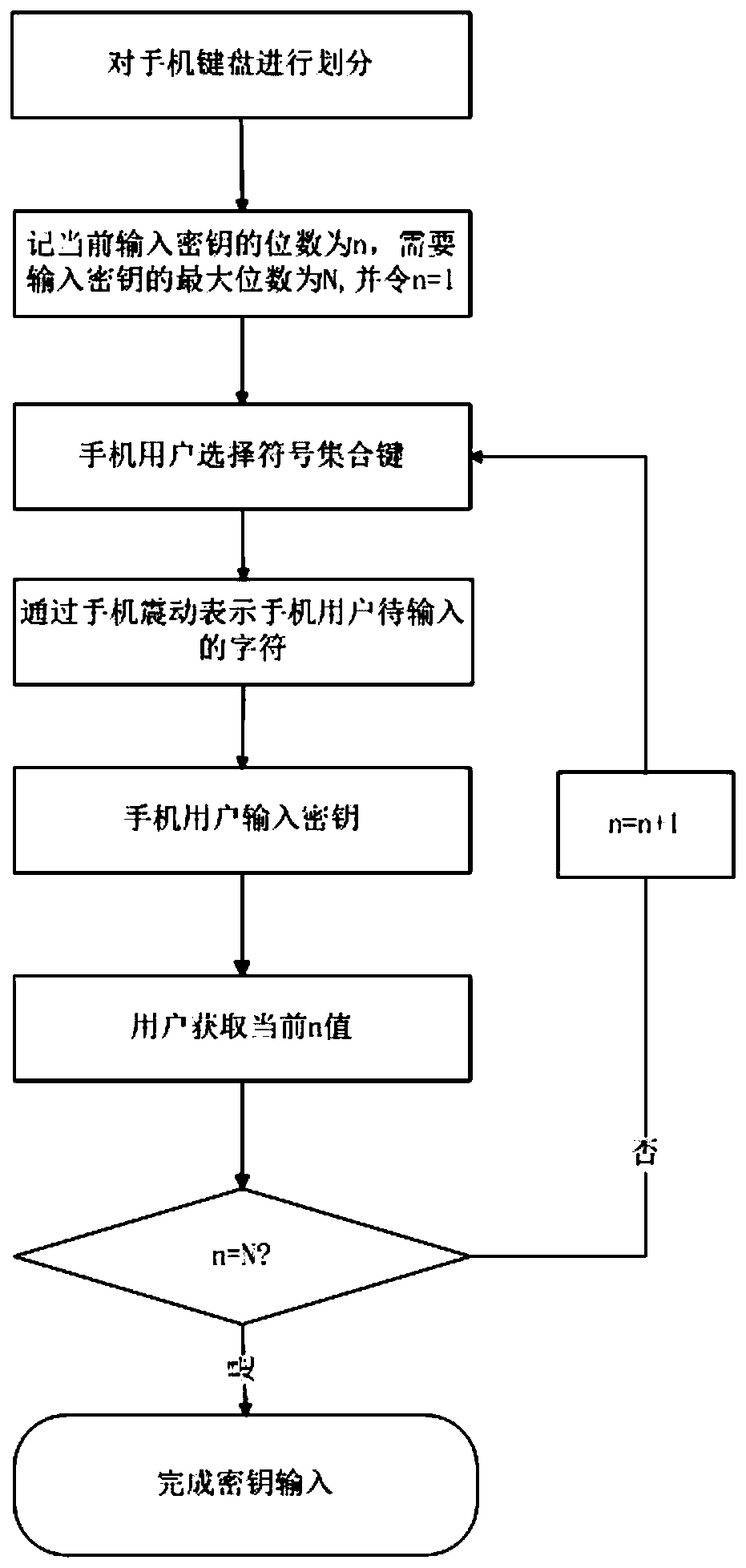
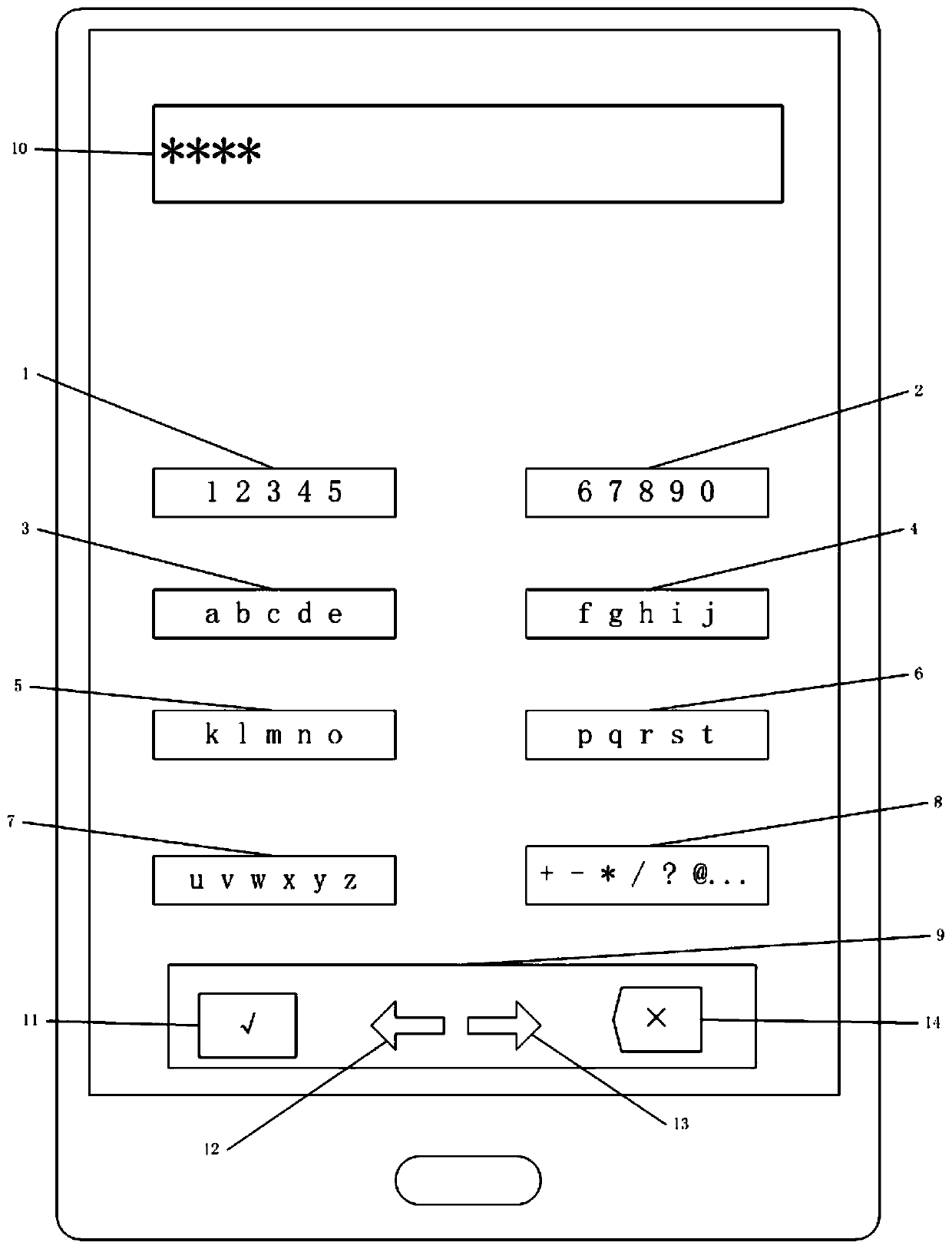
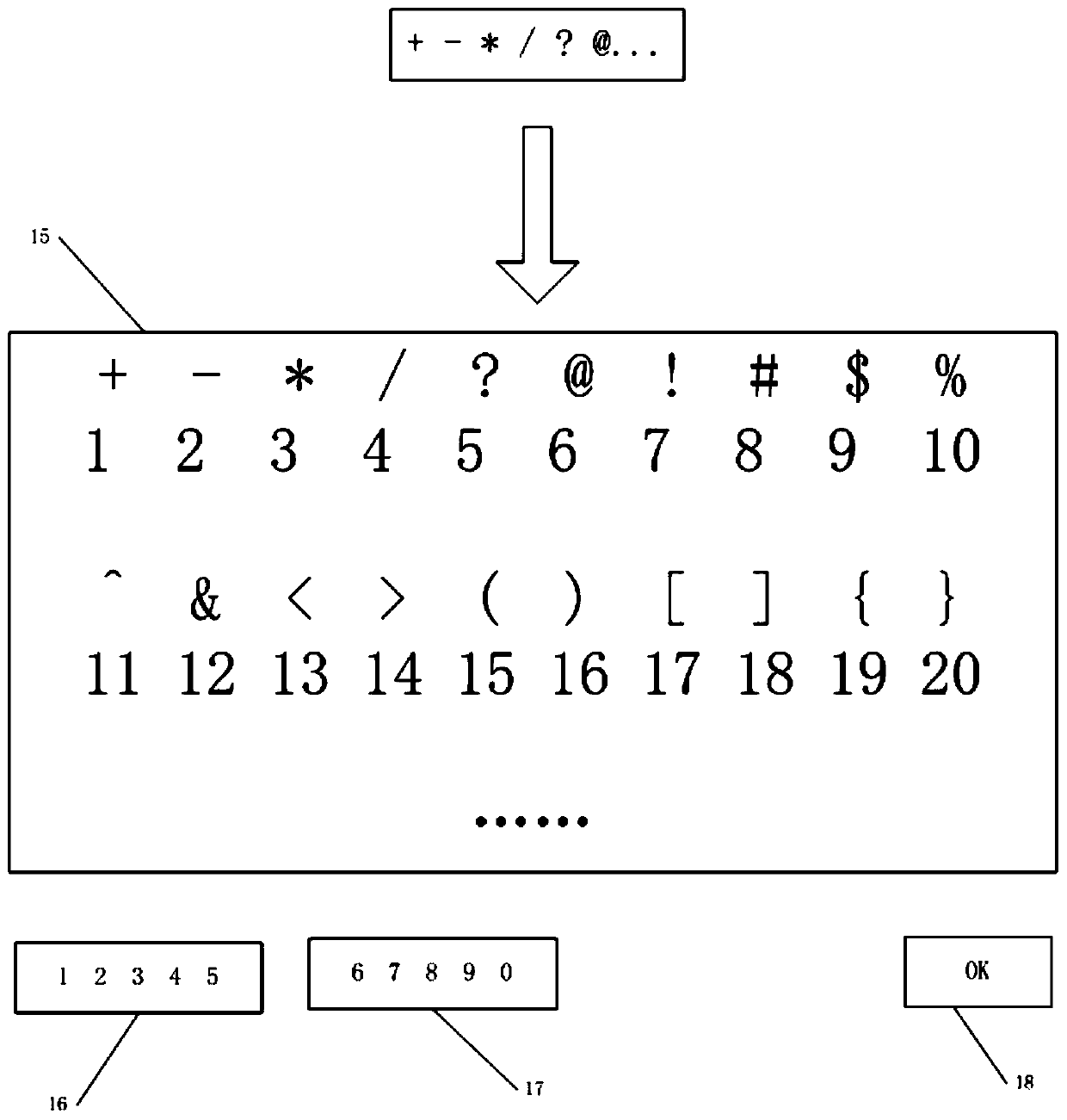
Anti-peeping secret key input method for mobile phone
PendingCN110532759AImprove convenienceReduce the risk of key eavesdroppingInternal/peripheral component protectionDigital data authenticationKey leakageComputer hardware
The invention provides an anti-peeping secret key input method for a mobile phone, which aims to avoid secret key leakage caused by peeping when a mobile phone user uses the mobile phone to input a secret key in a public occasion. The method comprises the following implementation steps: dividing keys on a mobile phone keyboard into a plurality of set keys; the mobile phone user selecting a set keyaccording to a secret key which needs to be input by himself / herself; representing a Morse code of a random character of the set key selected by the user through mobile phone vibration; the user determining the number of character position cyclic backward movement times according to the number of mobile phone vibration times and inputs a secret key; and judging whether the secret key reaches themaximum digit or not, if so, completing secret key input, and otherwise, inputting the next secret key. The mobile phone keys are rearranged and the mobile phone vibration prompt is used for assistingthe user to input the secret key, so that the secret key is prevented from being leaked due to peeping of the keyboard when the secret key is input, any additional auxiliary equipment is not needed,and the safety and convenience are ensured.
Owner:XIDIAN UNIV
A playback control method of a wearable device and the wearable device
ActiveCN106686188BReduce the risk of eavesdroppingImprove transmission efficiencySubstation speech amplifiersTransmissionEngineeringBone conduction hearing
The embodiment of the invention relates to the wearable device technology field, and discloses a play control method of a wearable device and a wearable device. The method comprises: when a voice play demand is detected, starting bone conduction horn on the wearable device, determining a first audio signal of the bone conduction horn requiring playing voice, loading the first audio signal to a predetermined ultrasonic wave audio signals, and controlling the bone conduction horn to convert the ultrasonic wave audio signals loading the first audio signal to a first vibration signal and transmitting the first vibration signal through a bone medium. According to the embodiment of the invention, the play control method of the wearable device and the wearable device can reduce the risk that the voice is eavesdropped by people around and improve the users' convenience to listen to sound.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
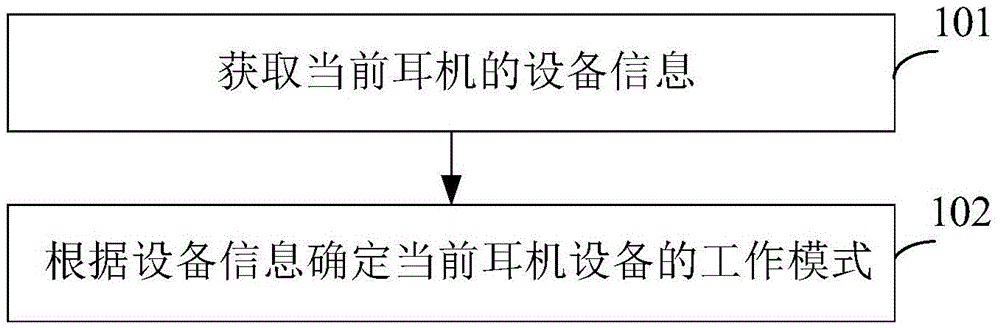
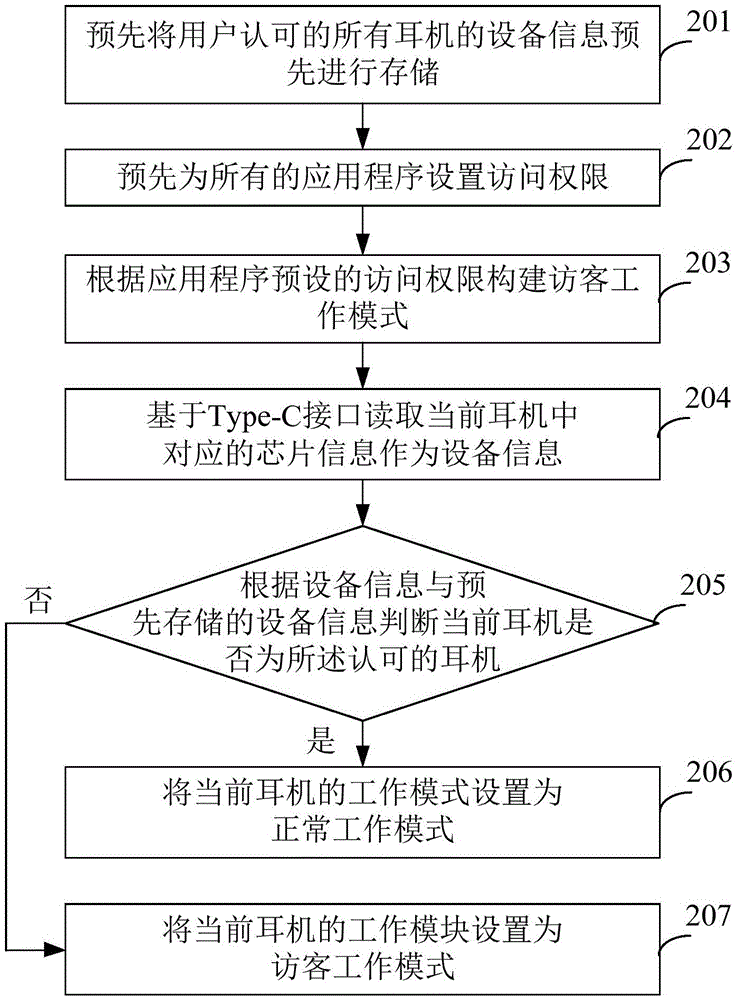
Earphone work mode selection method and apparatus
InactiveCN105828232AReduce the risk of eavesdroppingImprove information securityHearing devicesEarpiece/earphone mechanical/electrical switchesInformation securityComputer science
The embodiments of the invention provide an earphone work mode selection method and apparatus. Equipment information of current earphones is obtained based on a Type-C interface through an obtaining module, and a determining module, according to the equipment information, determines a work mode matching the current earphones. According to the embodiments of the invention, through arranging different access authorities for different work modes, correspondingly, the current earphones under the different work modes have the different access authorities for accessed equipment, such that the information security of the accessed equipment is improved, and the risk that private information of the accessed equipment is eavesdropped is reduced.
Owner:LETV HLDG BEIJING CO LTD +1
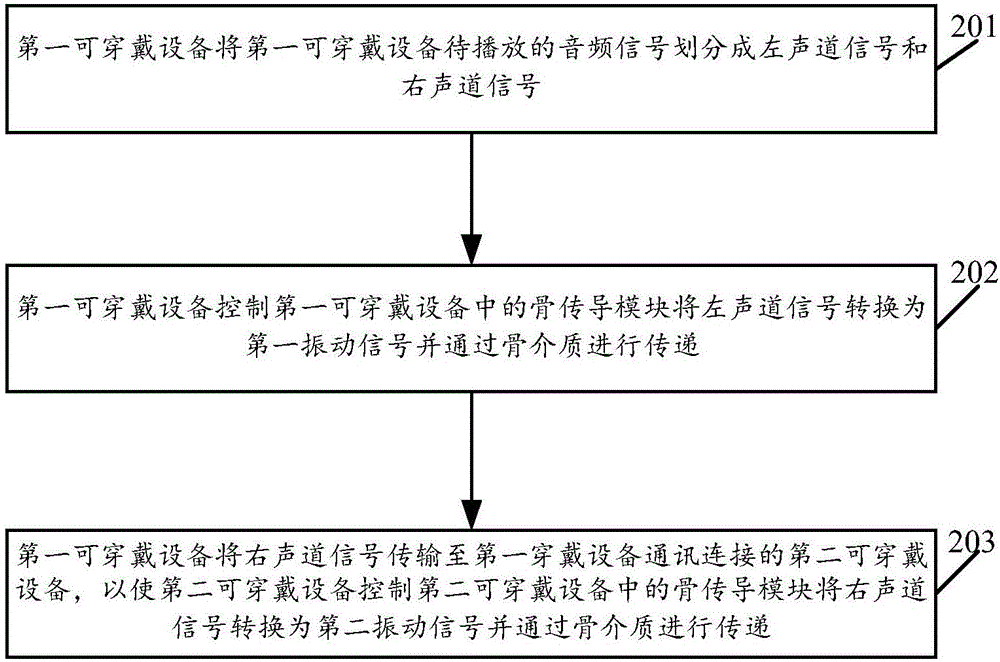
Audio signal processing method, device and system
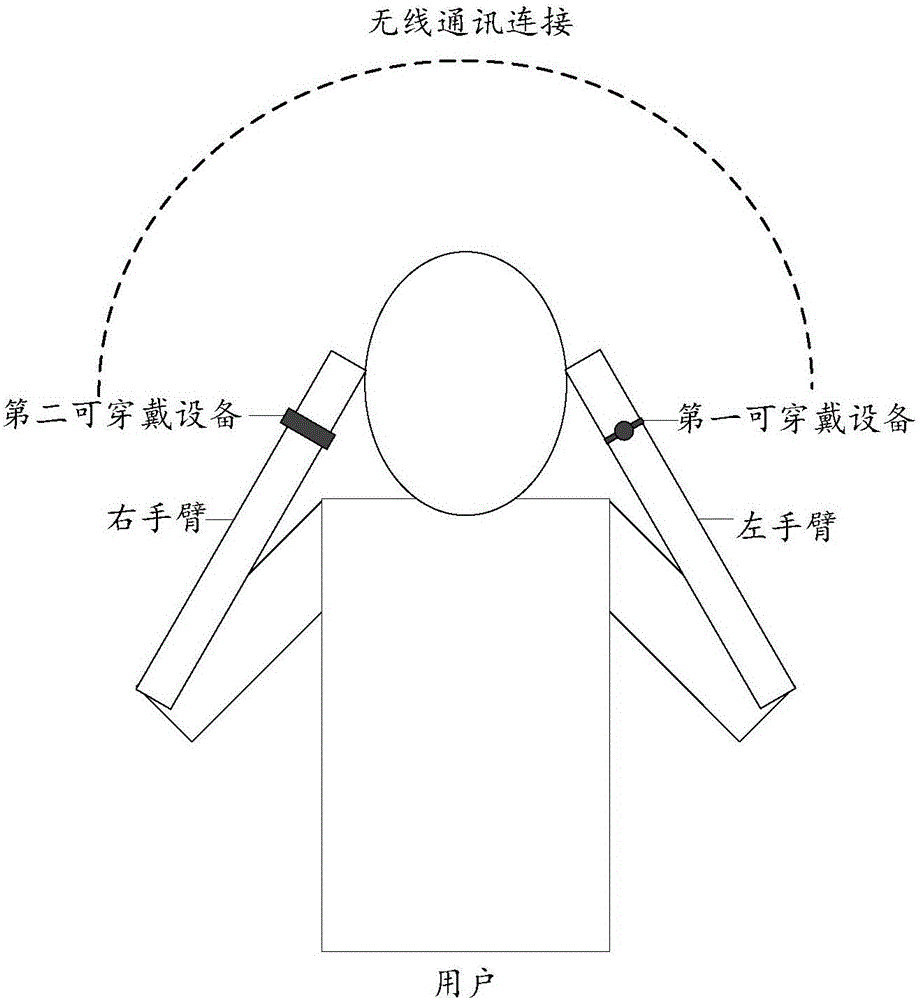
ActiveCN106658339AClear Stereo EffectEasy to listen toTwo-channel systemsStereophonic soundVIT signals
The embodiment of the invention relates to the field of audio signal processing, and discloses an audio signal processing method, device and system. The method comprises the following steps of: dividing an audio signal to be played by first wearable equipment into a left channel signal and a right channel signal; controlling a bone conduction module in the first wearable equipment to convert the left channel signal into a first vibration signal and transmit the first vibration signal through a bone medium; and, transmitting the right channel signal into second wearable equipment in communication connection with the first wearable equipment, so that the second wearable equipment controls the bone conduction module in the second wearable equipment to convert the right channel signal into a second vibration signal and transmit the second vibration signal through the bone medium. By means of the embodiment of the invention, sound can be listened conveniently; the risk that sound is eavesdropped by people around can be reduced; and the stereophonic effect is obtained.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
A control method for wearable device operation and wearable device
ActiveCN106685459BReduce the risk of eavesdroppingPrivacy protectionInput/output for user-computer interactionTransmissionTarget–actionUser privacy
An embodiment of the invention relates to the technical field of wearable devices and discloses a control method for wearable device operation and a wearable device. The method includes detecting hand actions of the wearable device when the wearable device utilizes a bone conduction mode to convert audio signals to vibration signals and transmits the vibration signals via bone medium; recognizing a target action command matching with the hand actions from a preset action command set; and performing the target action command on the wearable device. By applying the method provided by the invention, interception risks during audio playing of the wearable device are reduced, so that user privacy is protected. At the same time, simple and convenient operation control of the wearable device is realized, so that user experience is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Operation control method of wearable device and wearable device
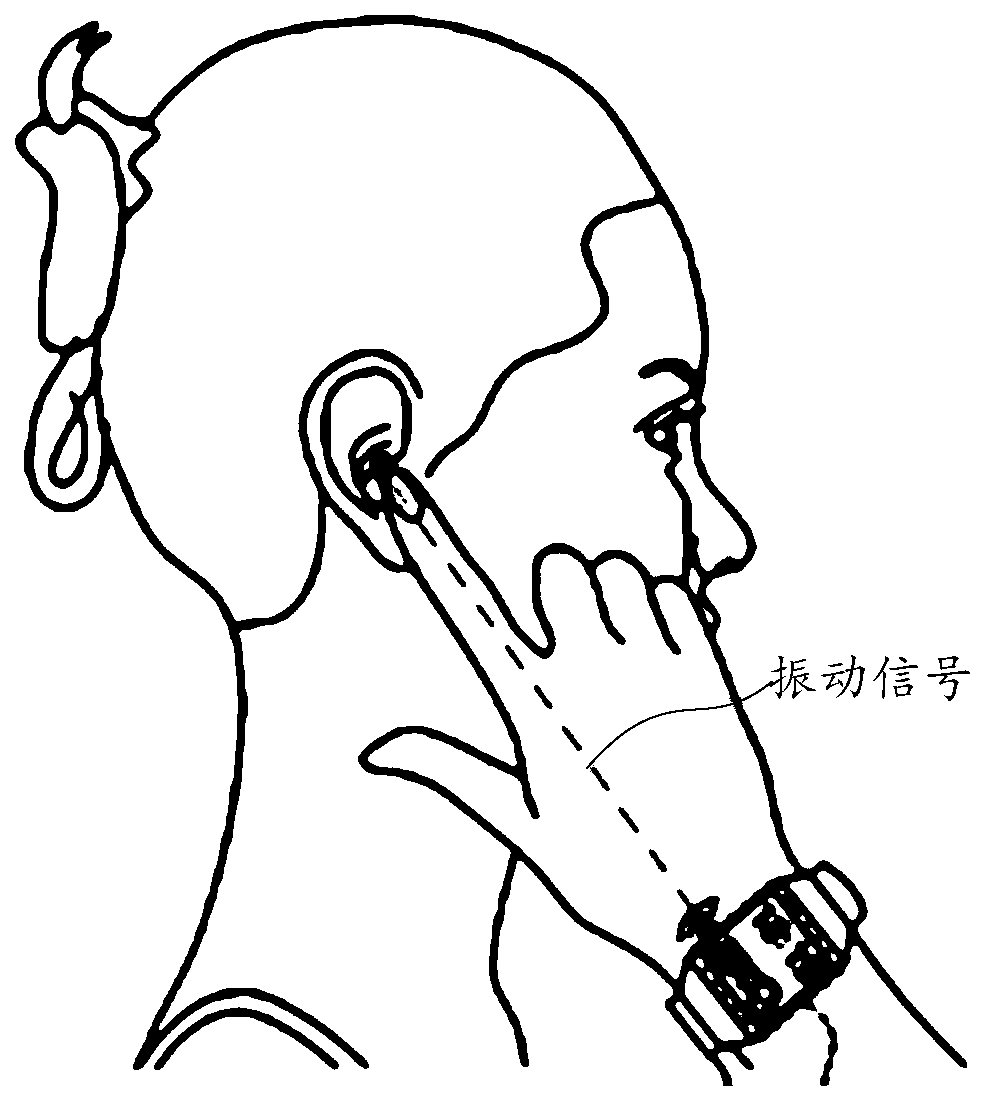
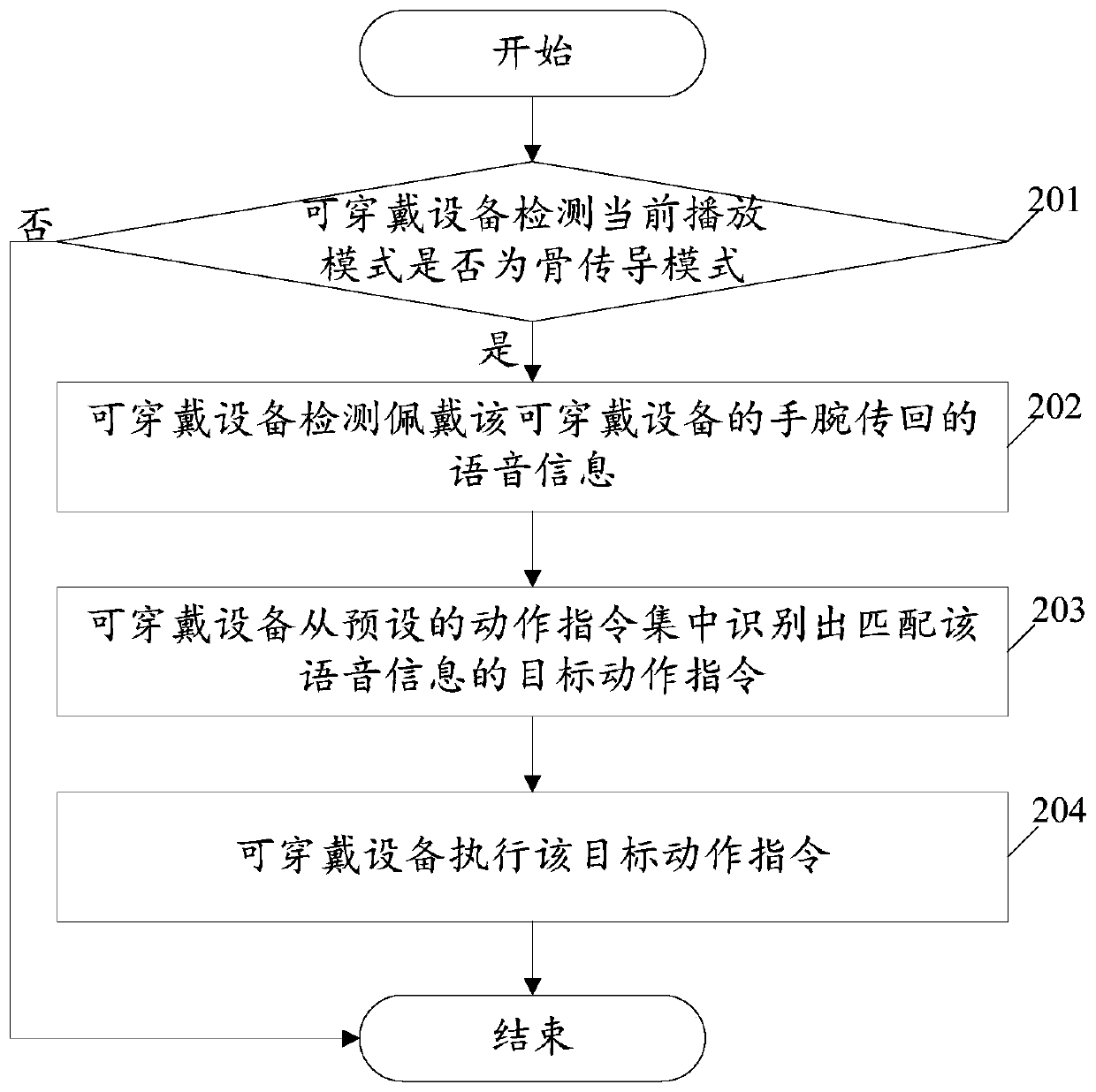
ActiveCN106713569BReduce the risk of eavesdroppingPrivacy protectionSpeech recognitionTelephone set constructionsTarget–actionUser privacy
The embodiment of the invention relates to the technical field of wearable equipment, and discloses a wearable equipment operating control method and wearable equipment. The method comprises the steps of detecting whether the current playing mode of the wearable equipment is a bone conductive mode, wherein the bone conductive mode is used for converting an audio signal into a vibration signal and then transmitting the vibration signal via a bone medium; if the current playing mode is the bone conductive mode, detecting a voice message sent back by a wrist wearing the wearable equipment; recognizing a target action command matched with the voice message from a preset action command set; and executing the target action command on the wearable equipment. With the application of the method and the equipment provided by the embodiment of the invention, an eavesdropping risk when sound plays is reduced, and thus user privacy is improved; meanwhile, the wearable equipment can be operated by a hand, and thus user experience is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
A playback mode switching method of a wearable device and the wearable device
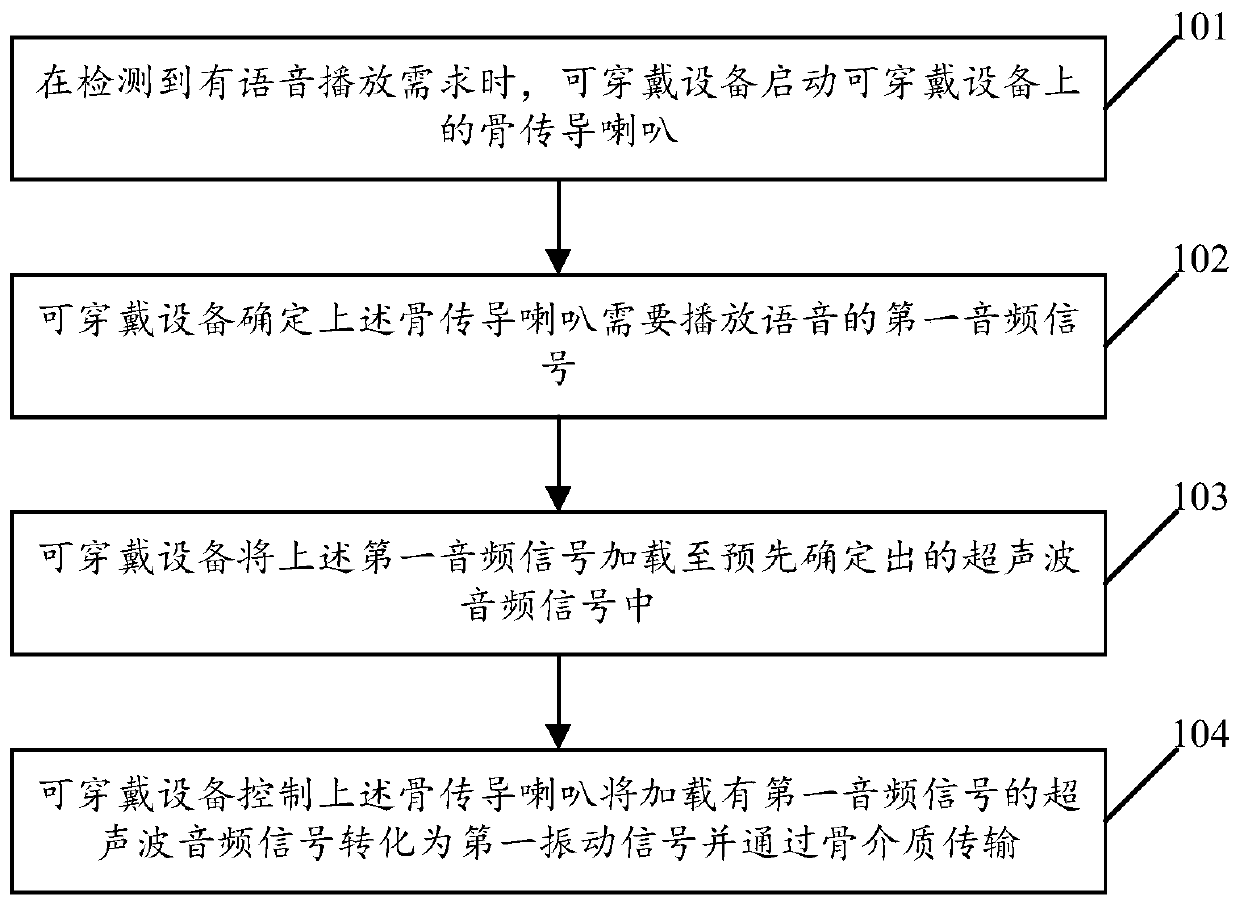
ActiveCN106686187BAchieve private call effectClear and private call effectSubstation speech amplifiersCurrent meterEngineering
The embodiment of the invention relates to the field of wearable devices and discloses a playing mode switching method of a wearable device and the wearable device. The method includes the steps that whether current time displayed by the wearable device is within a preset target time period or not is judged; if the current time is located in the target time period, the playing mode of the wearable device is switched from an outward playing mode to a bone conduction mode, wherein the bone conduction mode is used for converting audio signals into vibration signals and transmitting the vibration signals through bone media. By means of the method, the risk that calls are tapped by people around can be reduced, and calling convenience is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Software protection method, apparatus and equipment
ActiveCN101404056BAchieve protectionReduce the risk of eavesdroppingPlatform integrity maintainanceProgram/content distribution protectionTemporal informationComputer hardware
The invention is applicable to the communication safety field and provides a software protection method, a device and equipment. The method comprises the following steps: current time information of an operation system which operates an encrypted software is obtained; an encryption algorithm in an algorithm unit which is corresponding to the obtained current time information is called from a hardware encryption lock, thereby obtaining a return value of the encryption algorithm; whether a software is protected or not is judged according to the return value of the encryption algorithm. The embodiment of the invention realizes the protection of the software and reduces the risk that communication information between the encrypted software and the hardware encryption lock is eavesdropped effectively by obtaining the time information of the operation system and calling the encryption algorithm which is corresponding to the time information from the hardware encryption lock.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
A physical layer secure transmission method in UAV-assisted cognitive wireless network
ActiveCN112566127BImprove secure transmission performanceGuaranteed safe transmissionInternal combustion piston enginesTransmission monitoringSecure transmissionSimulation
The invention proposes a physical layer security transmission method in a UAV-assisted cognitive wireless network, which belongs to the field of wireless communication. , and the wireless communication scenario of the eavesdropper, then, within the spectrum sensing time τ of the time slot T, the UAV performs spectrum sensing; the primary user may perform data transmission, and calculate the safe transmission rate at this time; at the same time, in the time slot T data transmission time period T a Inside, the UAV judges the access status of the current primary user channel based on spectrum sensing, chooses to be a friendly jammer or a secondary signal transmitter, and discusses the safe transmission model in four cases; based on this, the optimization model of the total safe transmission rate is formulated ; Use the particle swarm optimization algorithm to solve the problem; the UAV performs the safe transmission of the signal physical layer according to the optimal parameters obtained. The invention considers the safe transmission of primary and secondary users, thereby improving the safe transmission performance of the system.
Owner:BEIJING UNIV OF POSTS & TELECOMM
A base station forwarding multi-antenna processing method considering wireless physical layer security
ActiveCN105978610BReduce the risk of eavesdroppingReduce the probability of interruption of secure transmissionRadio transmissionPhysical layerEavesdropping
The invention relates to a base-station forwarding multi-antenna processing method concerning wireless physical layer safety. A multi-antenna uplink receiving matrix and a downlink transmitting pre-coding matrix of a base station are used for reducing the risk of the eavesdropping of private information between a transmitter and a receiver. The method effectively inhibits malicious eavesdropping behaviors of a malicious eavesdropper through increasing number of base station side antennas. In an actual scene, the private information is transmitted through a base station relay, and the base station can obtain the statistical information of an eavesdropping channel in the actual scene, thereby reducing the outage probability of safety transmission between the transmitter and the receiver. The method is simple and practical, is easy to implement, and is good in application prospect.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +2
A kind of play mode switching control method of wearable device and wearable device
ActiveCN106788540BPrivacy protectionReduce the risk of eavesdroppingSubstation equipmentTransmissionEngineeringBone conduction hearing
An embodiment of the invention relates to the technical field of wearable equipment and discloses a play mode switching control method of wearable equipment and the wearable equipment. The method comprises steps as follows: an arm action of an arm where the wearable equipment is worn is detected; whether the arm action is matched with a preset arm action is recognized; if the arm action is matched with the preset arm action, a finger action of the arm where the wearable equipment is worn is detected; whether the finger action is matched with a preset finger action is recognized; if the finger action is matched with the preset finger action, a sound play mode of the wearable equipment is switched from a loud speaker mode to a bone conduction mode; the bone conduction mode is used for converting audio signals into vibration signals to be transmitted through bone media. With implementation of the embodiment of the invention, the eavesdropping risk of the wearable equipment during sound playing is reduced, so that privacy of a user is improved, and use experience of the wearable equipment is also improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
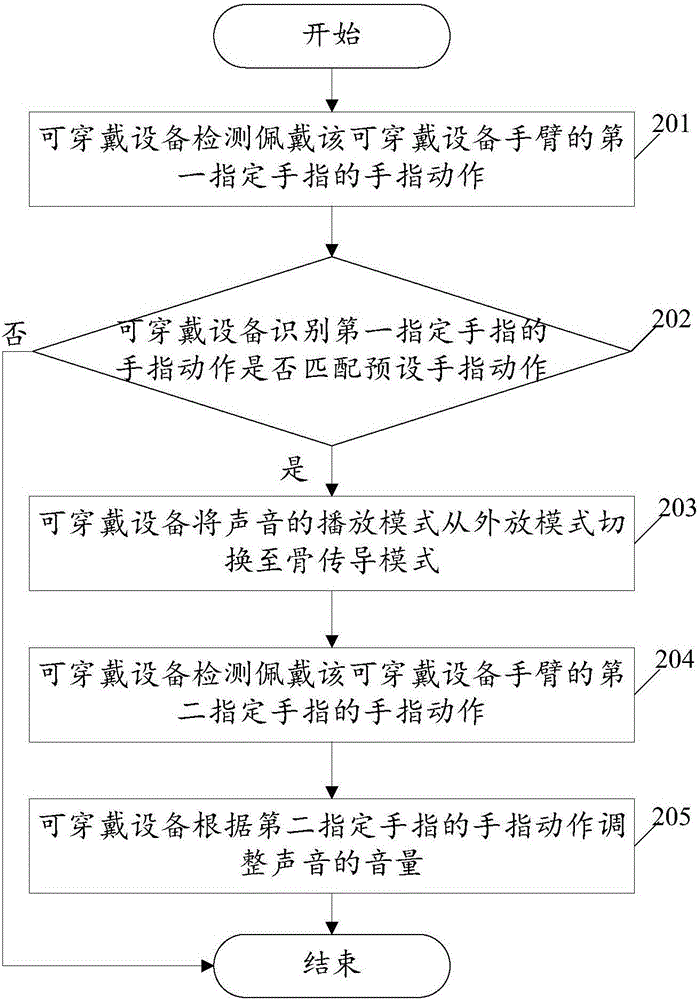
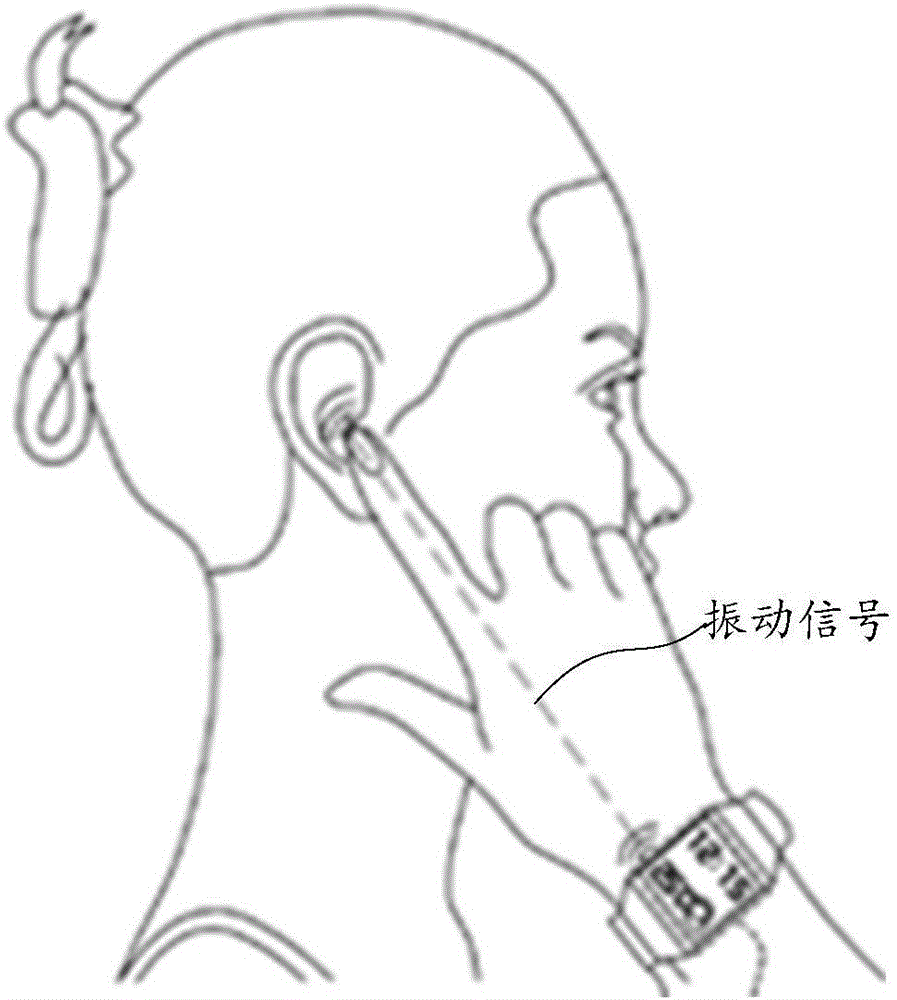
Volume adjusting method of wearable device and wearable device
ActiveCN106686497APrivacy protectionPrivacy is simple and convenientSignal processingTransmissionBone conduction hearingLoudspeaker
An embodiment of the invention relates to the technical field of wearable devices and discloses a volume adjusting method of a wearable device and the wearable device. The method includes detecting finger actions of a first specific finger of an arm with the wearable device; identifying whether the finger actions of the first specific finger match with predetermined finger actions or not; if the finger actions of the first specific finger match with the predetermined finger actions, switching the sound transmitting mode of the wearable device from a loudspeaker mode to a bone conduction mode, wherein the bone conduction mode is used for converting audio signals to vibration signals and transmitting the vibration signals via bone medium; detecting finger actions of a second specific finger of the arm with the wearable device; adjusting the volume of the wearable device according to the finger actions of the second specific finger. By applying the method and device provided by the embodiment of the invention, interception risks during audio playing of the wearable device are reduced and volume can be adjusted conveniently and quickly, so that user experience is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
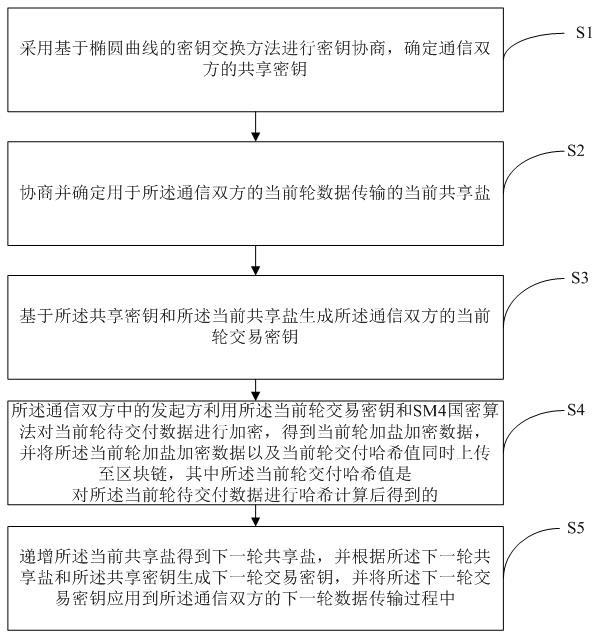
Block chain industrial data encryption method and device based on national secret and storage medium
InactiveCN114338047AGood encryptionImprove securityKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeEngineering
The invention relates to a block chain industrial data encryption method and device based on national secret and a storage medium, and the method comprises the steps: carrying out the key negotiation through employing a key exchange method based on an elliptic curve, and determining a shared key; negotiating and determining the current shared salt of the current round of data transmission; generating a current round transaction key based on the shared key and the current shared salt; the initiator encrypts the current round of to-be-delivered data by using the current round of transaction key and the SM4 national secret algorithm, and simultaneously uploads the current round of salted encrypted data and the current round of delivery hash value of the current round of to-be-delivered data to the block chain; and progressively increasing the current shared salt to obtain a next round of shared salt, generating a next round of transaction key according to the next round of shared salt and the shared key, and applying the next round of transaction key to a next round of data transmission process of the two communication parties. According to the method, the repudiation resistance, anonymity and integrity of the transaction can be enhanced, the continuous encryption delivery of the data on the block chain is realized, and the key leakage hazard can be reduced.
Owner:HKUST TIANGONG INTELLIGENT EQUIP TECH (TIANJIN) CO LTD
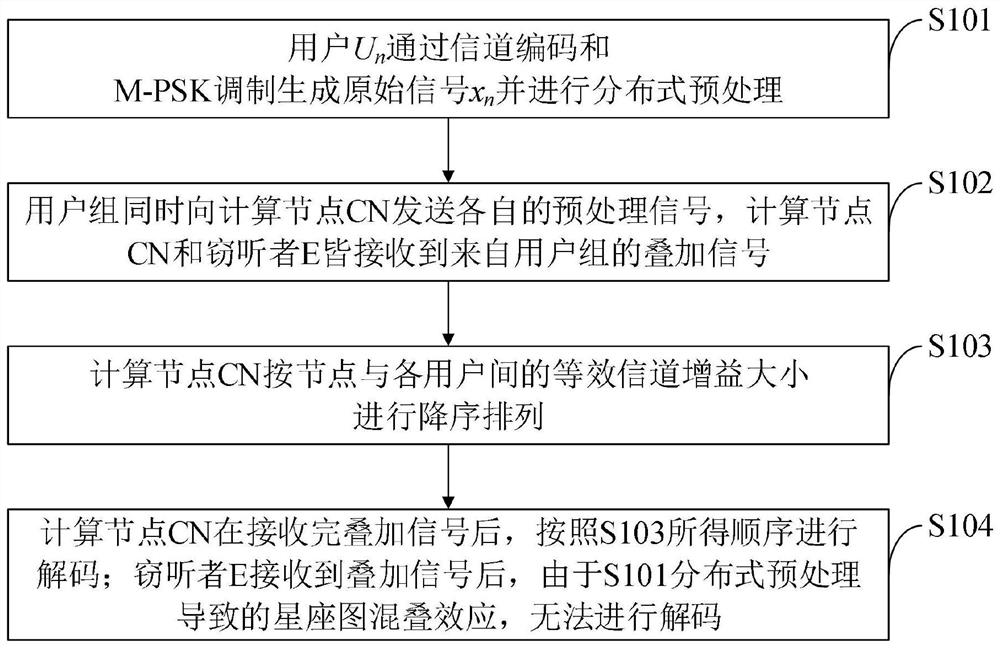
NOMA multi-user security computing unloading method and system
ActiveCN114244587AImprove securityImprove performanceNetwork traffic/resource managementSecurity arrangementSecure transmissionPhysical layer
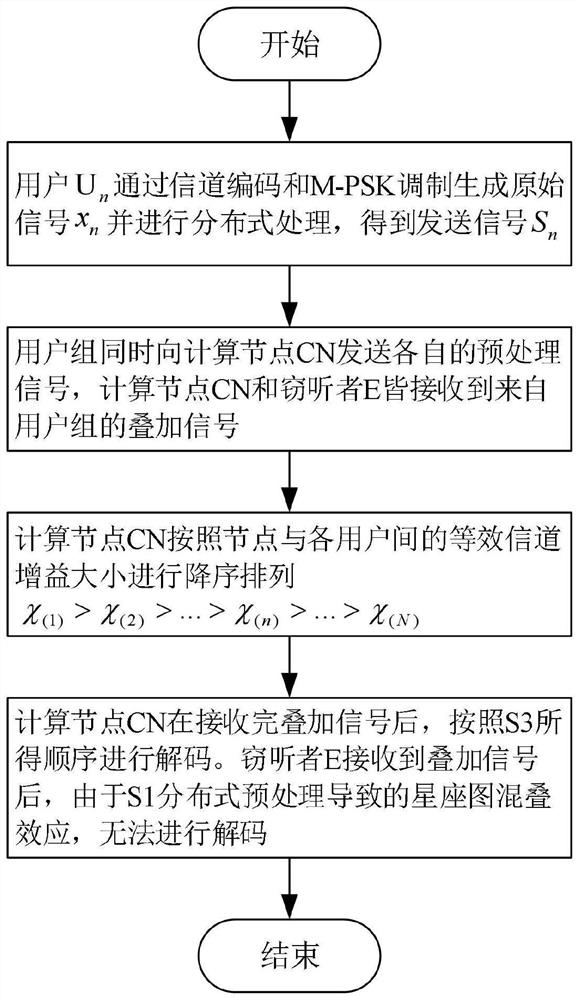
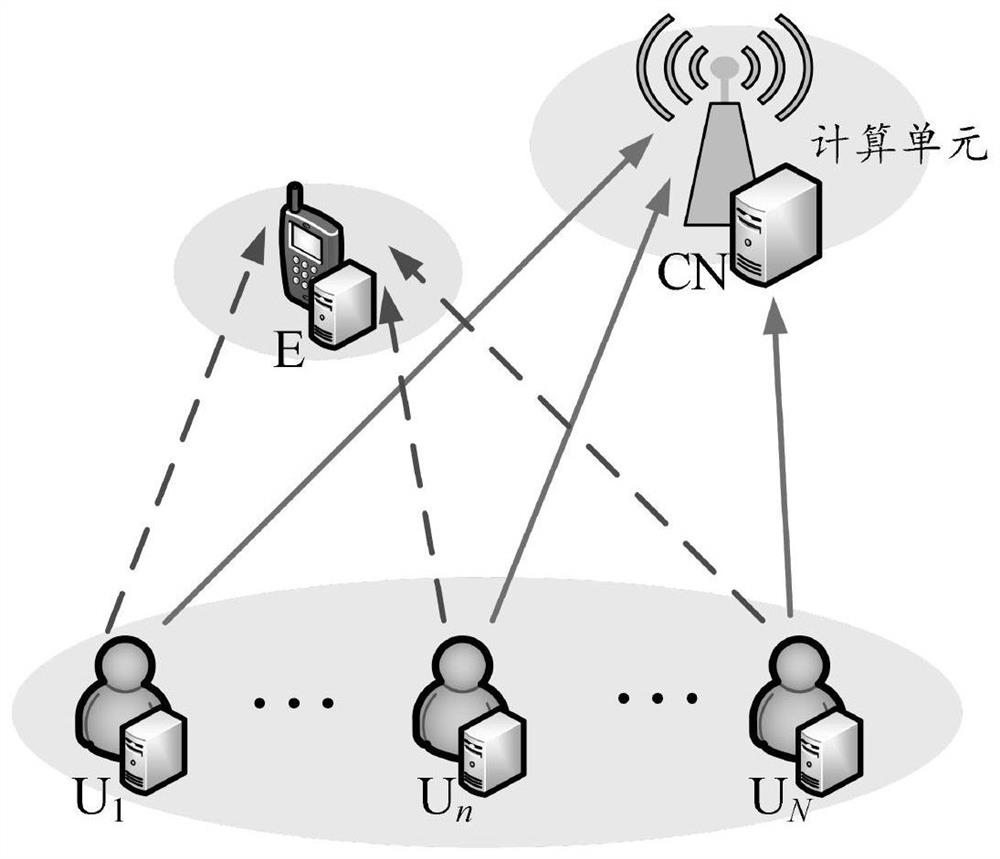
The invention belongs to the technical field of wireless communication, and discloses an NOMA multi-user secure computing unloading method and system, and the method comprises the steps: a user Un generates an original signal xn through channel coding and M-PSK modulation, and carries out the distributed preprocessing; the user group sends respective preprocessing signals to the computing node CN at the same time, and the computing node CN and the eavesdropper E both receive superposed signals from the user group; the computational nodes CN are arranged in a descending order according to the equivalent channel gains between the nodes and the users; the CN decodes the superposed signals in sequence after receiving the superposed signals; after an eavesdropper E receives the superposed signal, the superposed signal cannot be decoded due to a constellation diagram aliasing effect caused by distributed preprocessing. According to the method, the physical layer security performance of multi-user communication transmission can be improved, guarantee is provided for NOMA security transmission of a multi-user computing task, the eavesdropping risk is effectively reduced, and the network performance is improved.
Owner:XIDIAN UNIV
A quantum communication method and communication network based on secure relay
ActiveCN112787807BReduce the risk of eavesdroppingImprove securityKey distribution for secure communicationPhotonic quantum communicationCiphertextTrunking
The present invention provides a quantum communication method and communication network based on a secure relay. The sender encrypts plaintext information to be sent to obtain encrypted ciphertext; the sender sends the encrypted ciphertext to the relay through a quantum communication protocol The node is configured to send the encrypted ciphertext to a receiver through at least one relay node; after receiving the encrypted ciphertext, the receiver decrypts the encrypted ciphertext to obtain the plaintext information. The encrypted ciphertext is transmitted step by step through at least one relay node, and the distance between the sender and the receiver is not limited, so that the encrypted ciphertext can be transmitted over a long distance. At the same time, before reaching the recipient, the plaintext information is transmitted in the form of encrypted ciphertext, without decryption, which reduces the risk of information being eavesdropped and improves security.
Owner:TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com