NOMA multi-user security computing unloading method and system
A computing offloading and multi-user technology, which is applied in the field of NOMA multi-user secure computing offloading, can solve the security threats of computing task offloading, difficulties in key distribution and management, computing task eavesdropping, etc. System security, the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
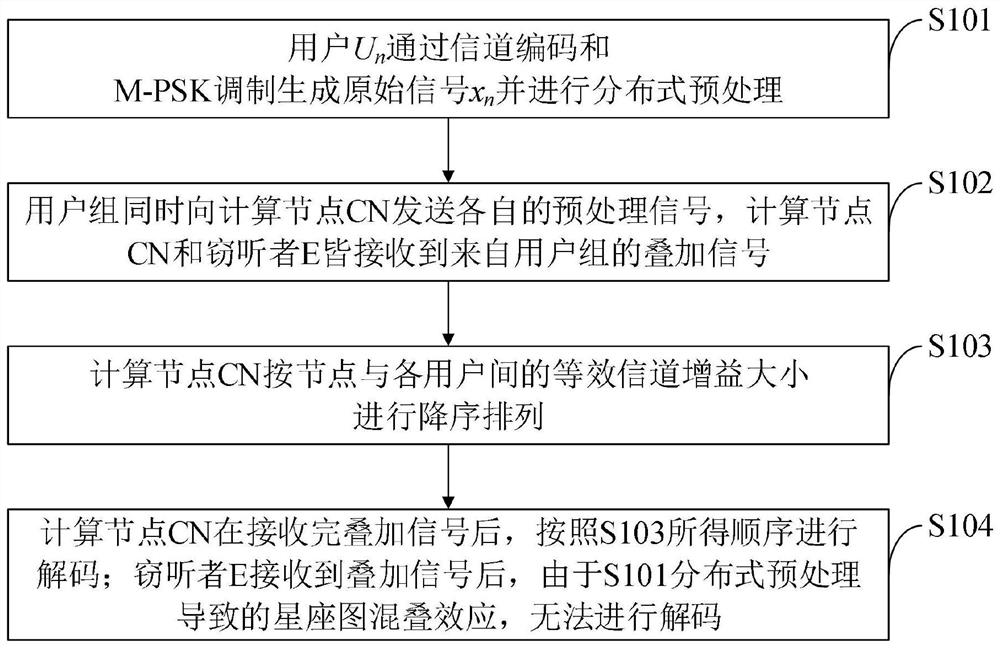
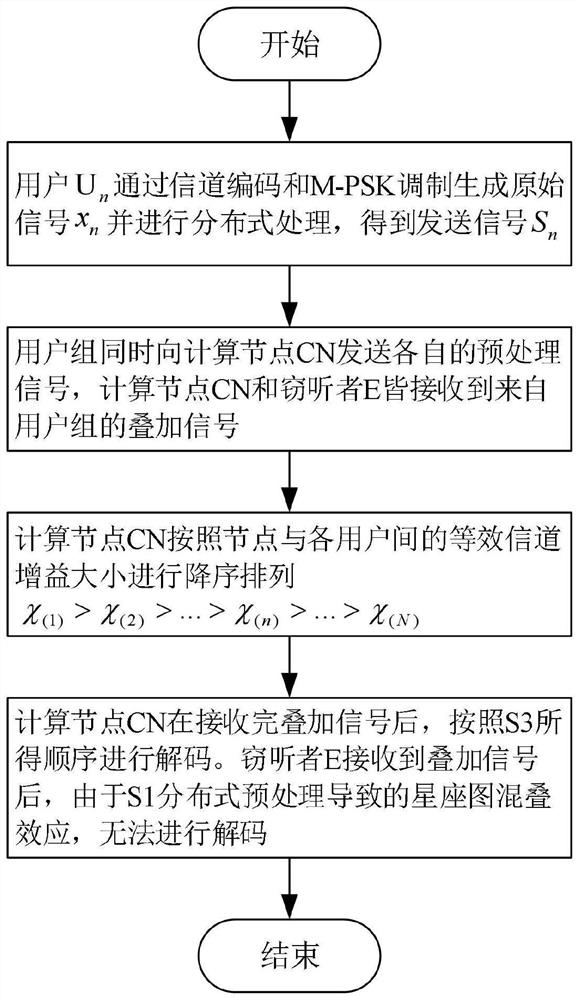
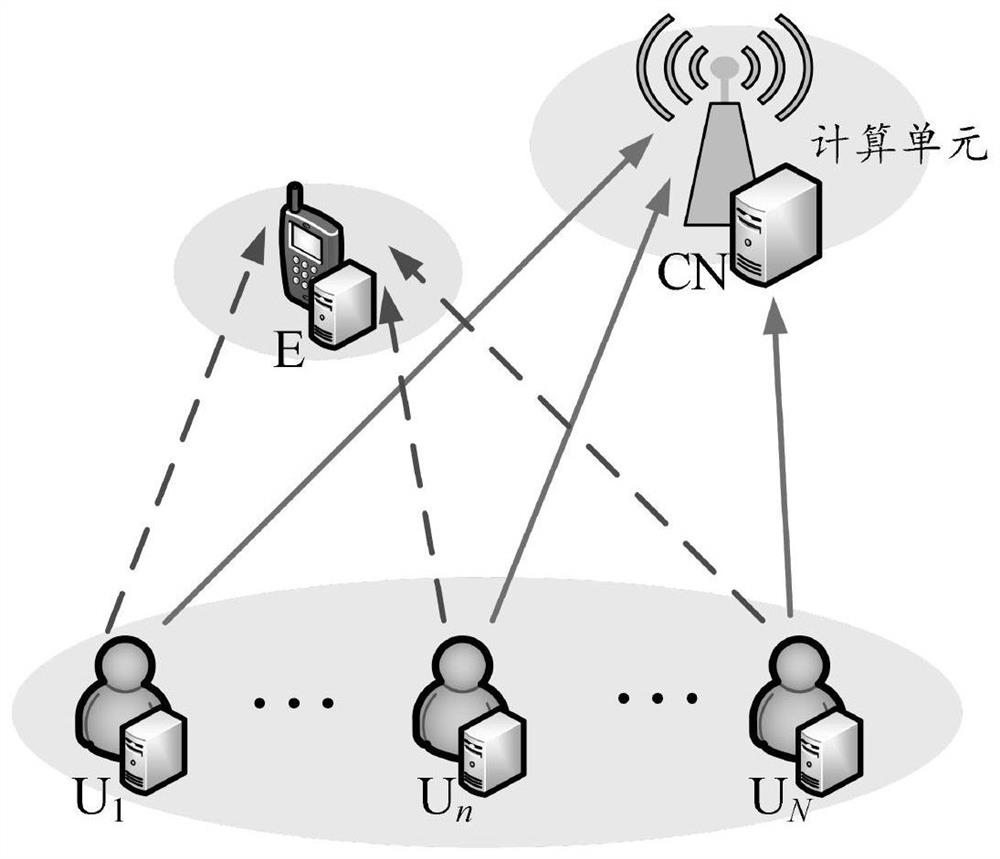
[0061] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. The present invention is applicable to communication scenarios with high communication security requirements such as banks, hospitals, and transportation. For example, in intelligent medical systems, private information such as patient medical records, prescriptions, and treatment plans may be leaked or tampered with during collection, storage, and transmission. In intelligent transportation, private information such as the vehicle's location and driving trajectory also has the risk of being exposed and illegally tracked and used. The present invention can effectively reduce the probability of data leakage and the risk of being eavesdropped. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com