Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
119results about How to "Protect user privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
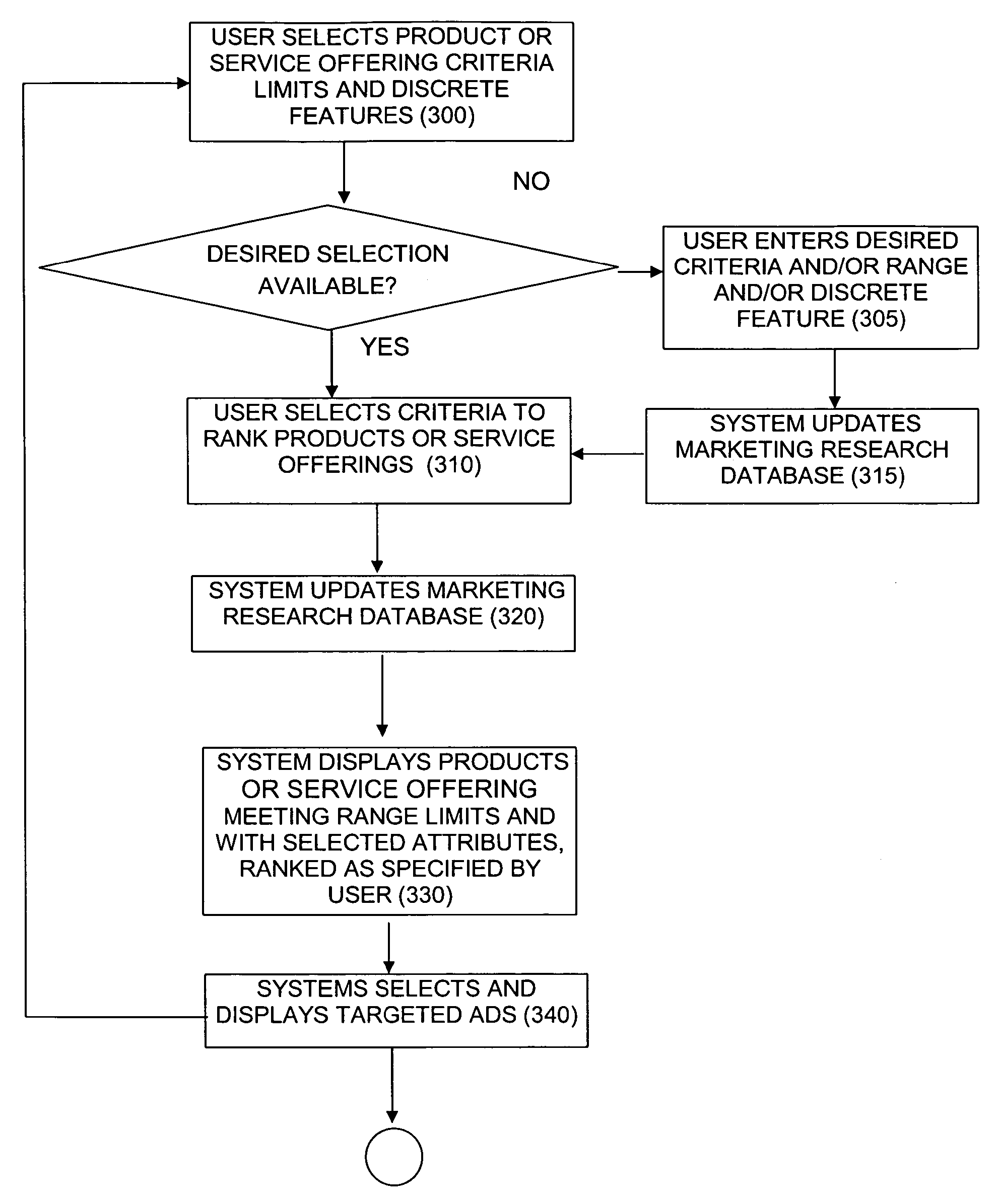
Method and apparatus for obtaining consumer product preferences through product selection and evaluation
InactiveUS20020026390A1Facilitates taskProtect user privacyDigital data information retrievalAdvertisementsProduct selectionWorld Wide Web
A method and system for obtaining consumer preferences over a communication network from consumers. The system searches the product database for products or services based on consumer's search criteria. The system displays the products or services and / or advertisements related to the consumer's search criteria in accordance with the ranking parameter(s) specified by the user. The consumer's preferences, i.e., the search criteria and the ranking parameter(s), are stored in the database for future references, e.g., determine consumer trends, etc.
Owner:III HLDG 1
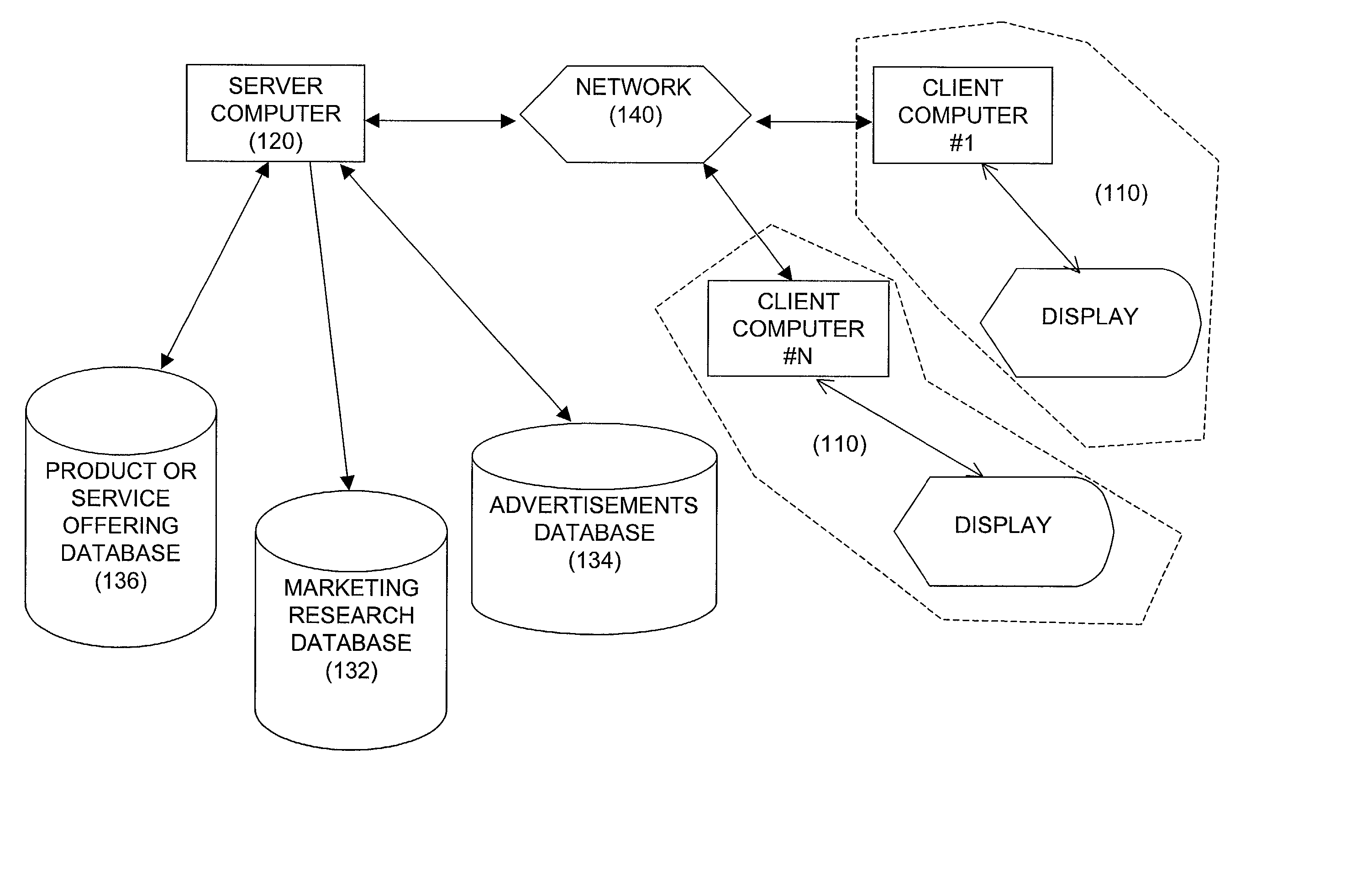
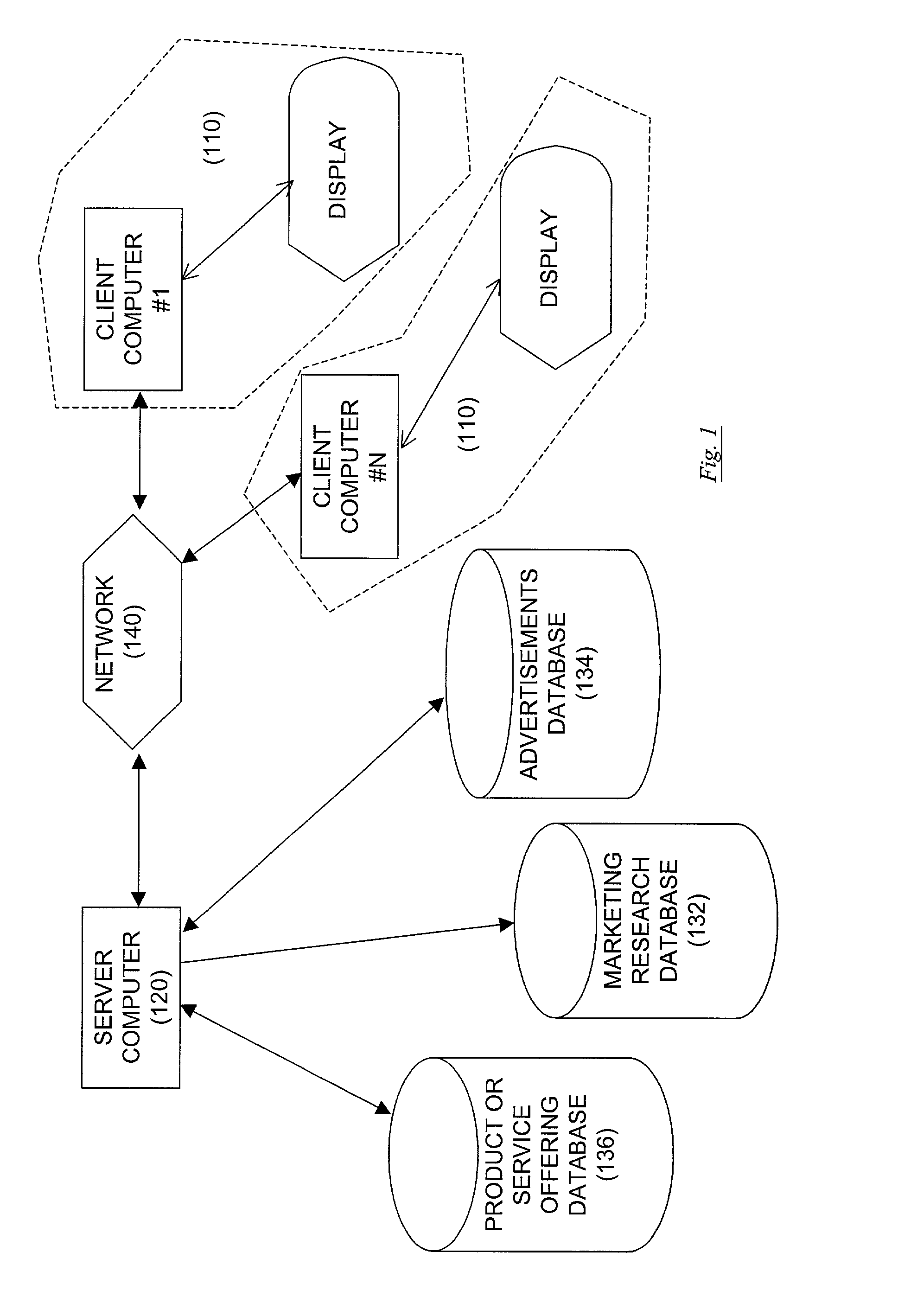
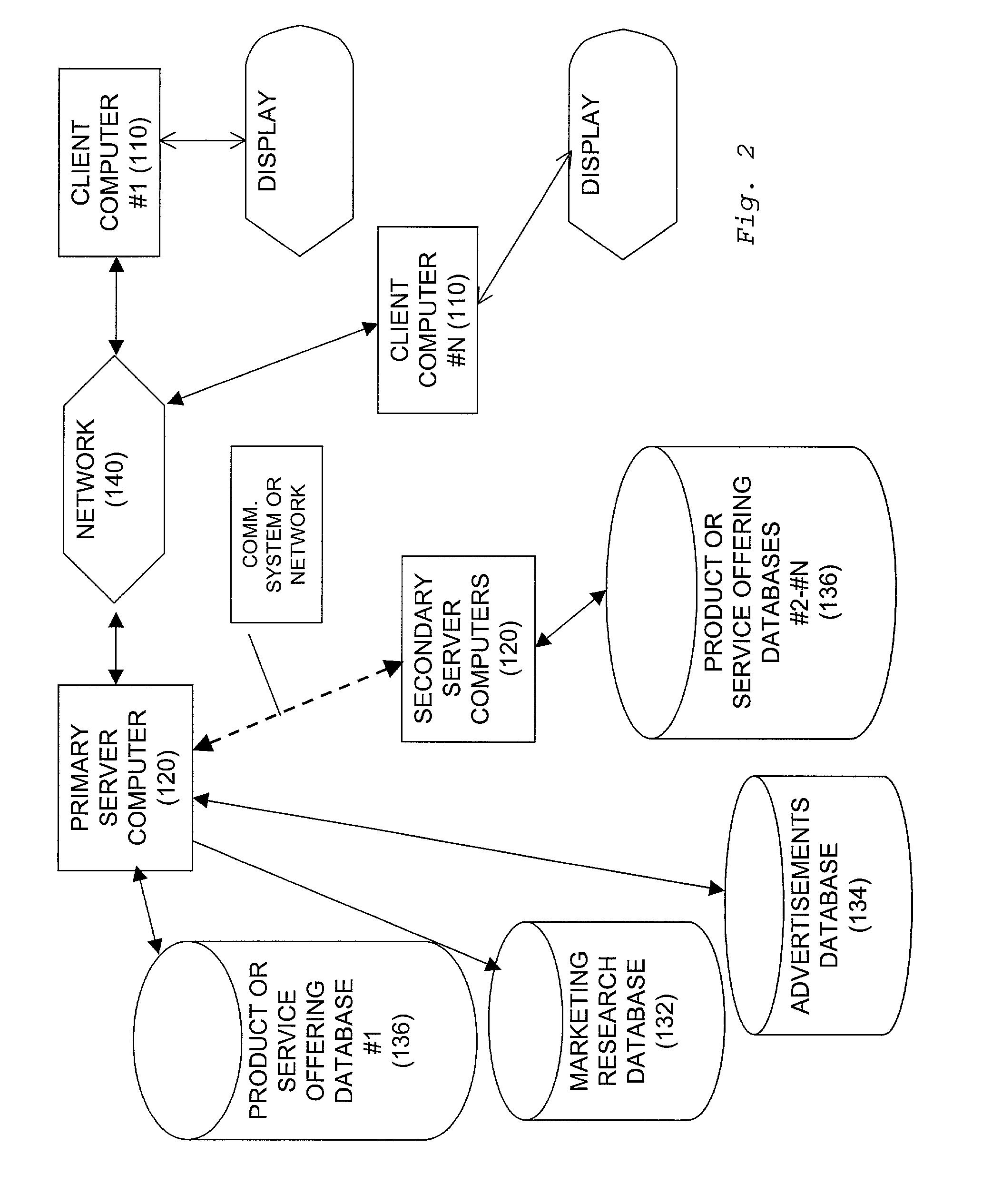
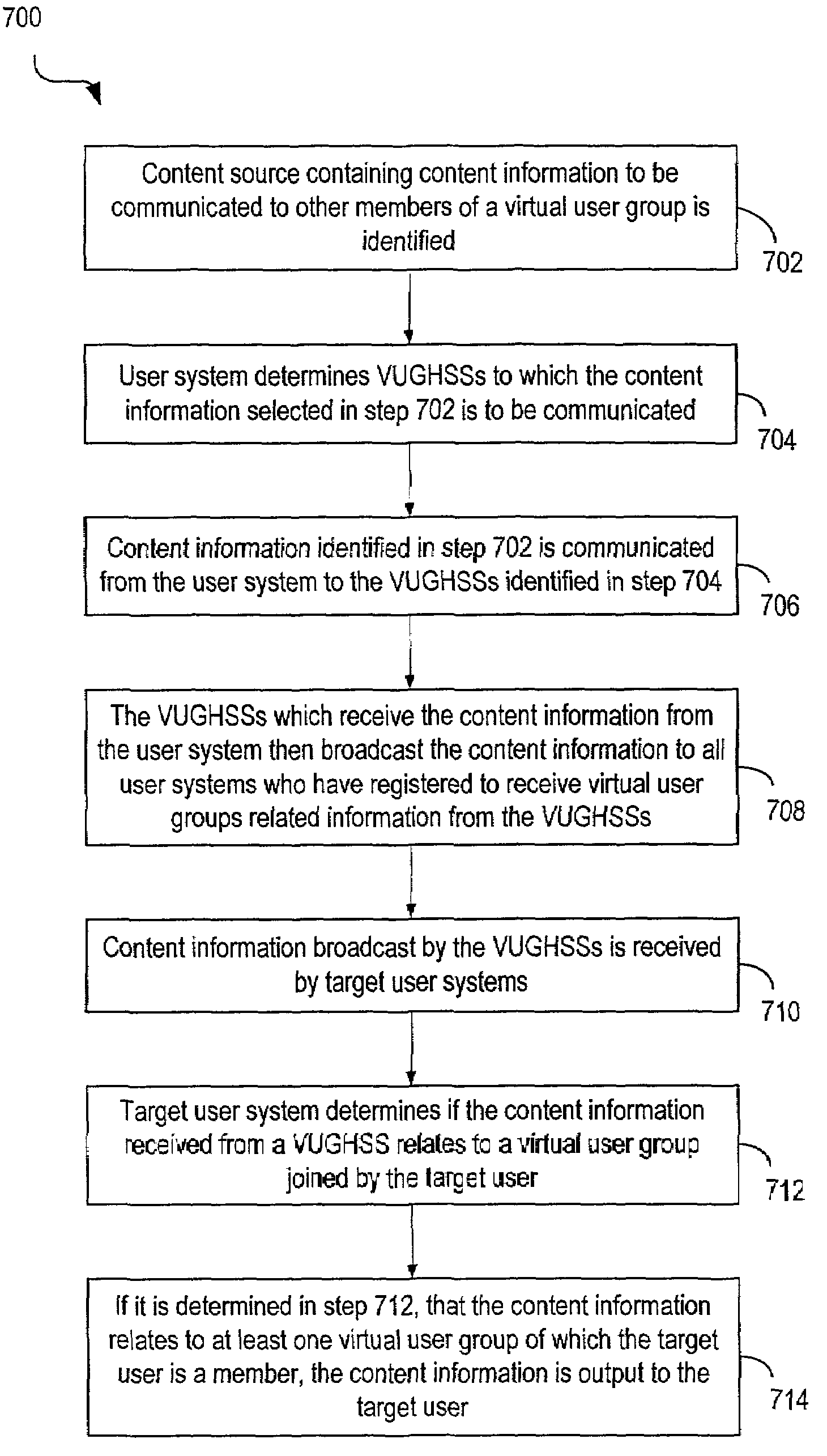
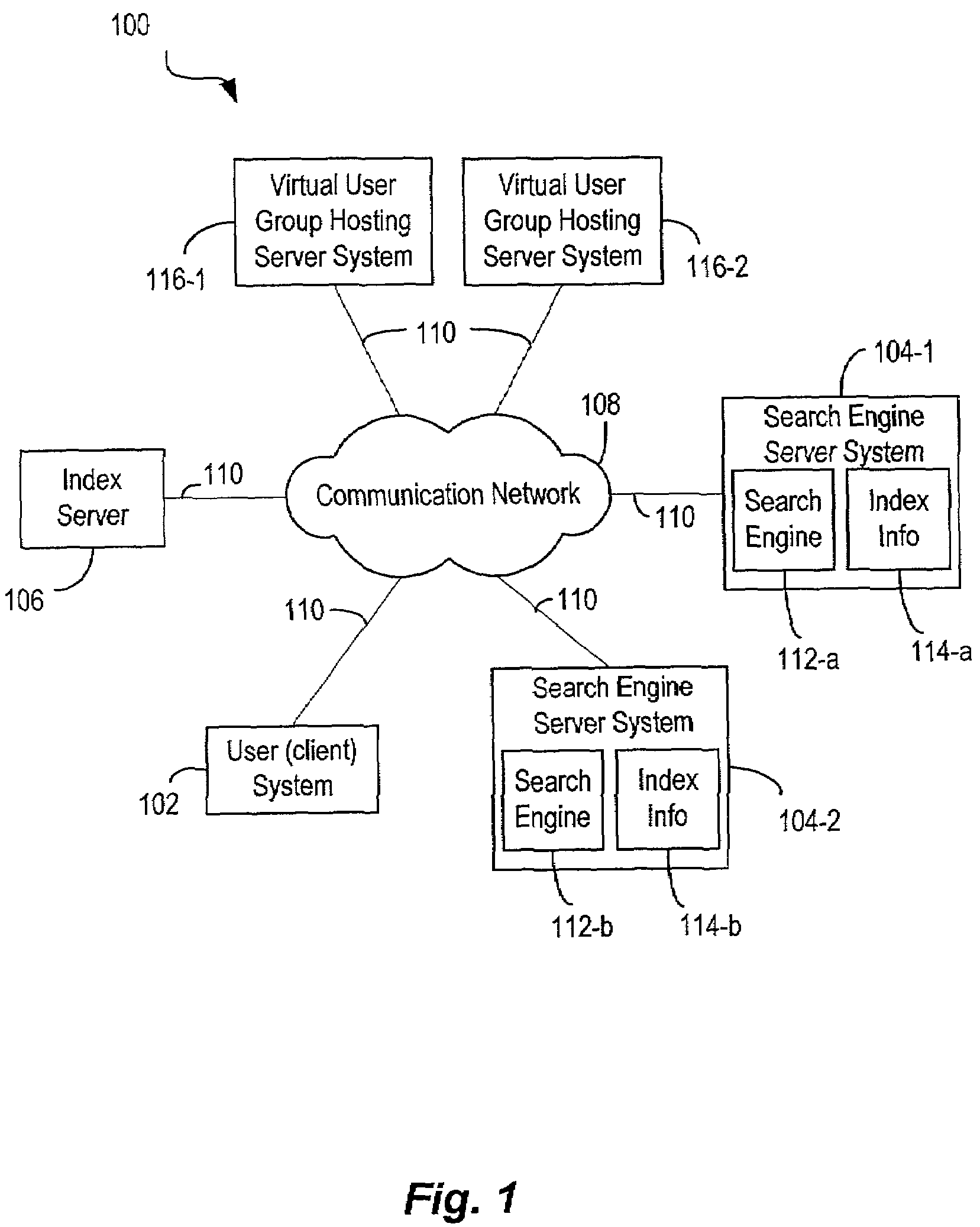
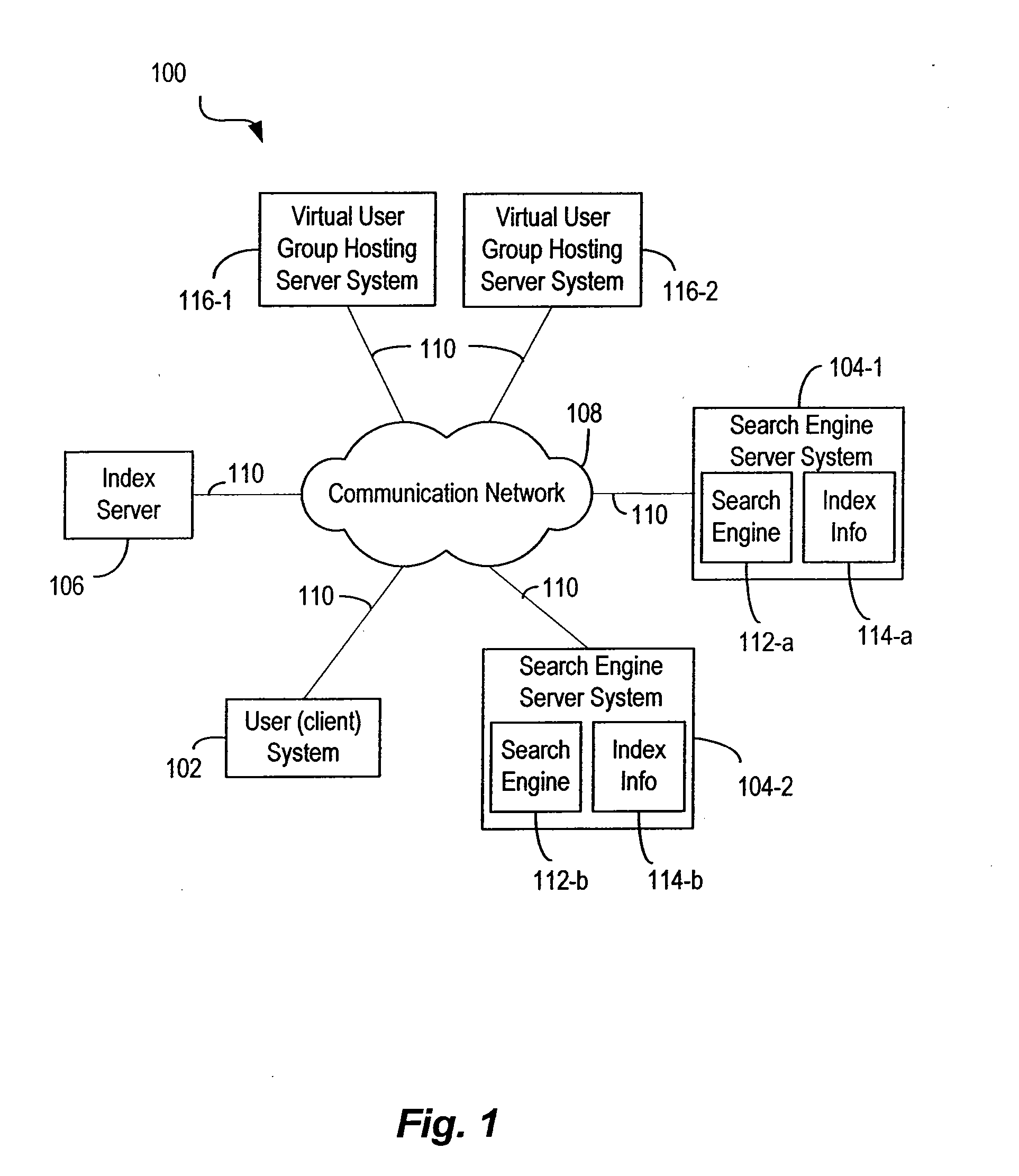
Techniques for sharing content information with members of a virtual user group in a network environment without compromising user privacy
InactiveUS7177904B1Protect user privacyWithout compromising the user's privacyComputer security arrangementsMultiple digital computer combinationsRelevant informationVirtual user
Techniques for sharing content information between members of a virtual user group without compromising the privacy of the members. A user can identify content information to be shared with other members of a virtual user group using a user computer system. The content information is then communicated to the other members of the virtual user group and can be accessed by members of the virtual user group in such a manner that the privacy of the user and of the other members of the virtual user group is not compromised. The present invention preserves user privacy by controlling and minimizing the amount of user-related information available / accessible to server systems hosting the virtual user groups.
Owner:MICRO FOCUS LLC
System, method and apparatus for electronically searching for an item
ActiveUS20060195428A1Protect user privacyMore revenueWeb data indexingSpecial data processing applicationsMultiple categoryInformation retrieval
The present invention provides provides a system, method and apparatus for electronically searching for an item by receiving a search request comprising a requested category and one or more requested attributes of the item and storing the search request in a search index based on the requested category and the requested attribute(s). The search index includes one or more categories and each category is defined by a taxonomy of attributes. The search index is then searched for any previously stored search requests that match the requested category and the requested attribute(s), a result of the search is determined and a search response that includes the result of the search is sent.
Owner:YOUR COMMAND
Method and apparatus for obtaining consumer product preferences through product selection and evaluation
InactiveUS7072847B2Facilitates taskProtect user privacyDigital data information retrievalAdvertisementsProduct selectionWorld Wide Web
Owner:III HLDG 1
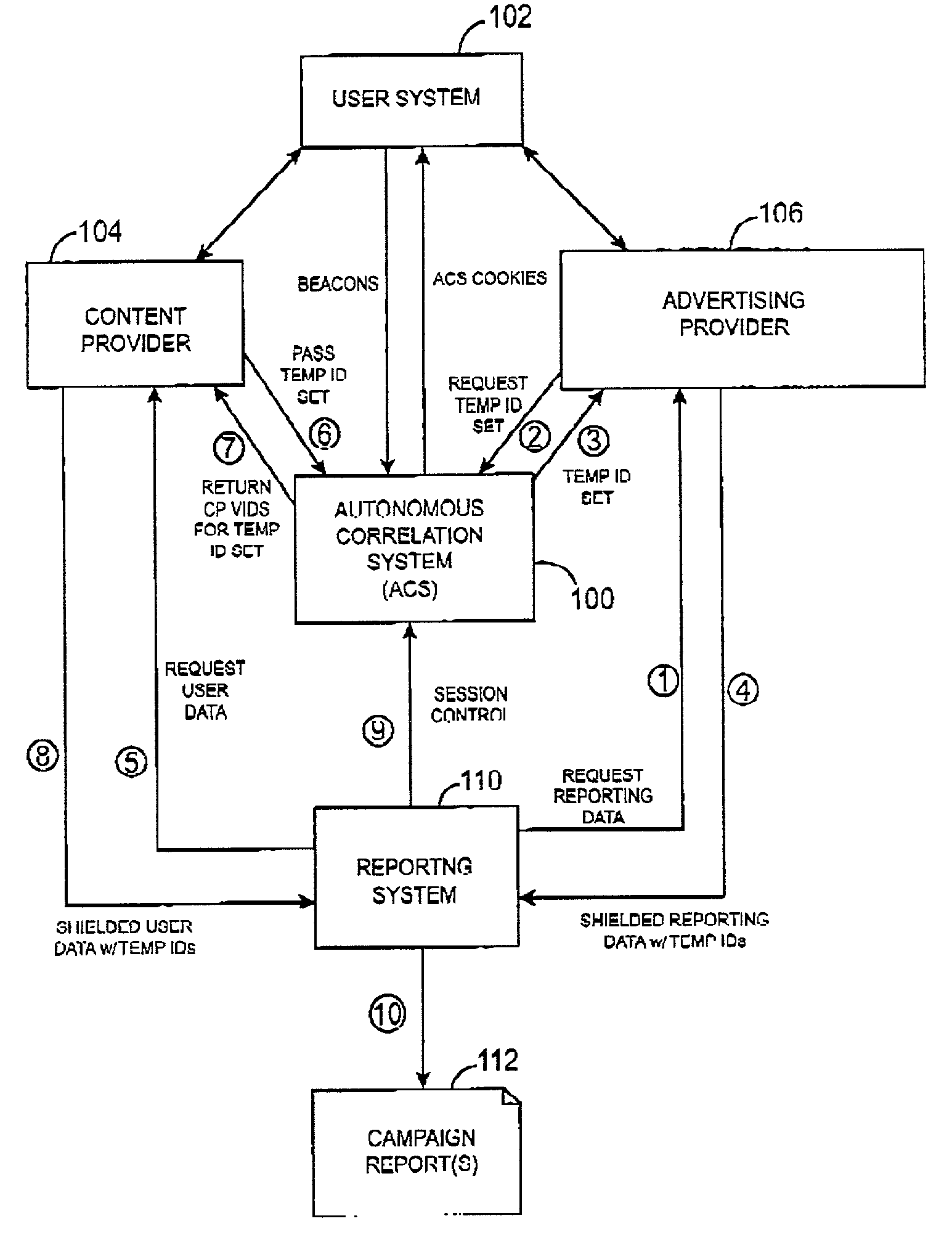
System and method for correlating user data from a content provider and user data from an advertising provider that is stored on autonomous systems
ActiveUS7257546B2Increase valueProtect user privacyAdvertisementsAnalogue secracy/subscription systemsReference databaseUser identifier
An autonomous correlation system correlates user data from a content provider and advertising view data from an advertising provider, wherein the user data is present on one autonomous system and the advertising view data is present on another autonomous system distinct from the one autonomous system, the systems being autonomous in that each is normally secured against unconstrained access by another. The autonomous correlation system comprises logic to accept a first message from a user, wherein the first message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a first user identifier associated with the user by a presenter of the object; a reference database for storing an association between the first user identifier and the user; logic to accept a second message from the user, wherein the second message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a second user identifier associated with the user by a presenter of the object; wherein the reference database stores an association between the second user identifier and the user.
Owner:PINTEREST
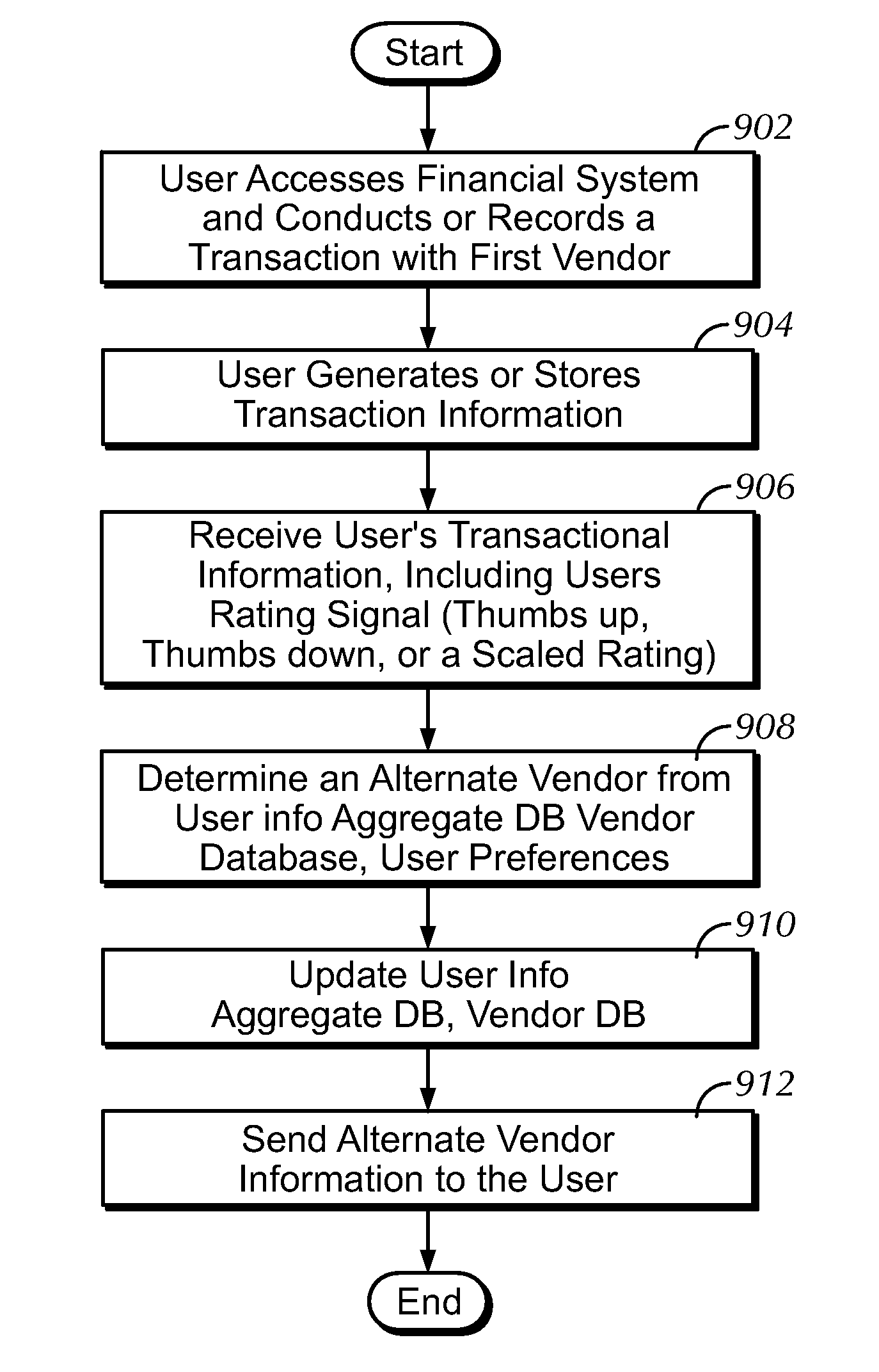
Vendor comparison, advertising and switching
ActiveUS7870025B2Easy to switchProtect user privacyBuying/selling/leasing transactionsMarketingMultimediaUser information
A method for switching vendors, including sending an invitation to a user to rate a first vendor in response to the user designating the first vendor as a payee, receiving a rating assigned to the first vendor, determining a second vendor as an alternative to the first vendor based on the rating being below a predefined threshold, sending information associated with the second vendor to the user, receiving a request from the user to switch from the first vendor to the second vendor, sending a cancellation notice to the first vendor in response to receiving the request, transmitting user information to a computer of the second vendor for setting up a new account, and charging the second vendor a fee for sending the information associated with the second vendor to the user.
Owner:INTUIT INC
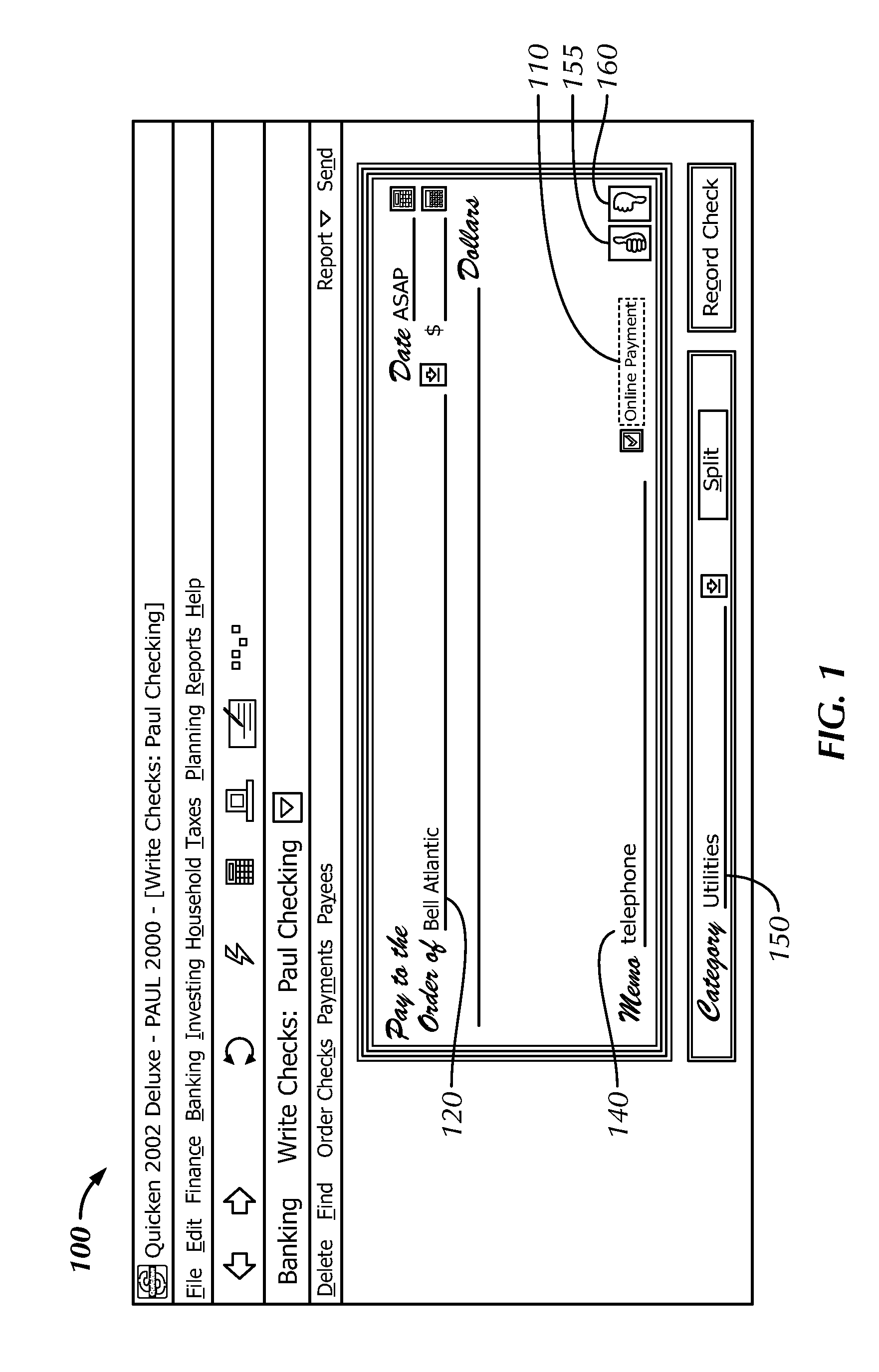
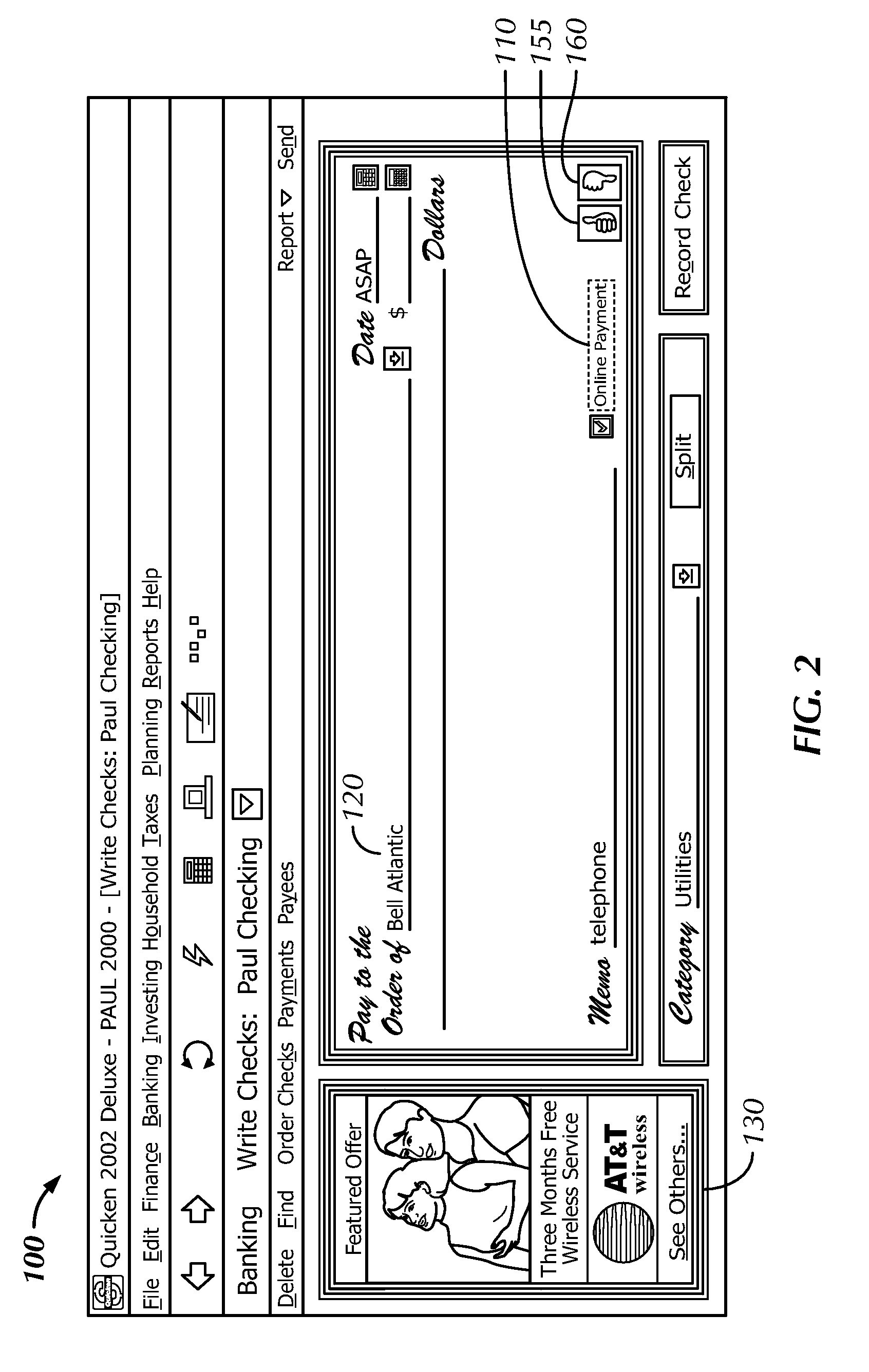
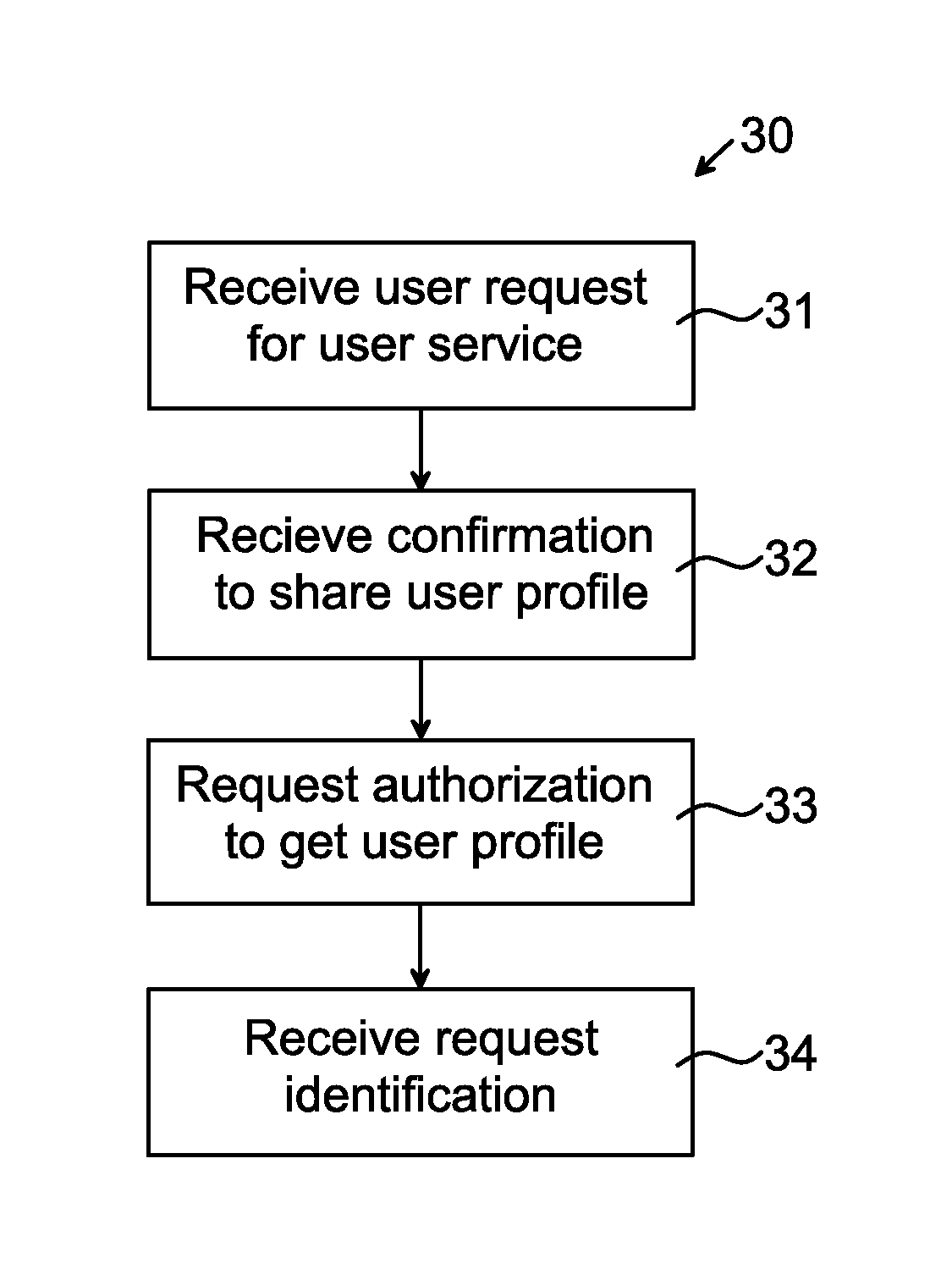
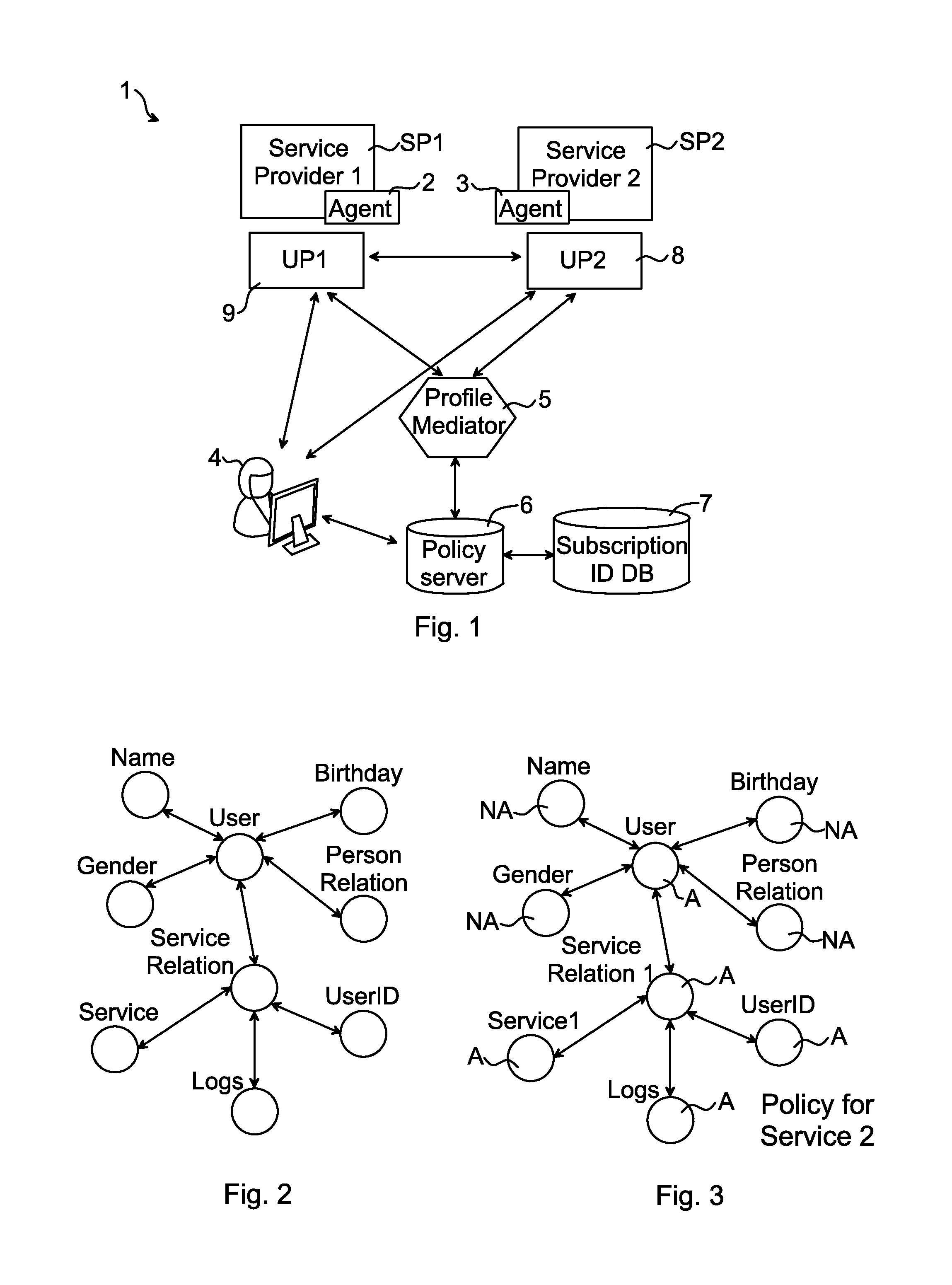
Methods for Exchanging User Profile, Profile Mediator Device, Agents, Computer Programs and Computer Program Products
InactiveUS20140006512A1Easy to handleMaintaining the integrity of the userTransmissionMarketingService provisionUser profile
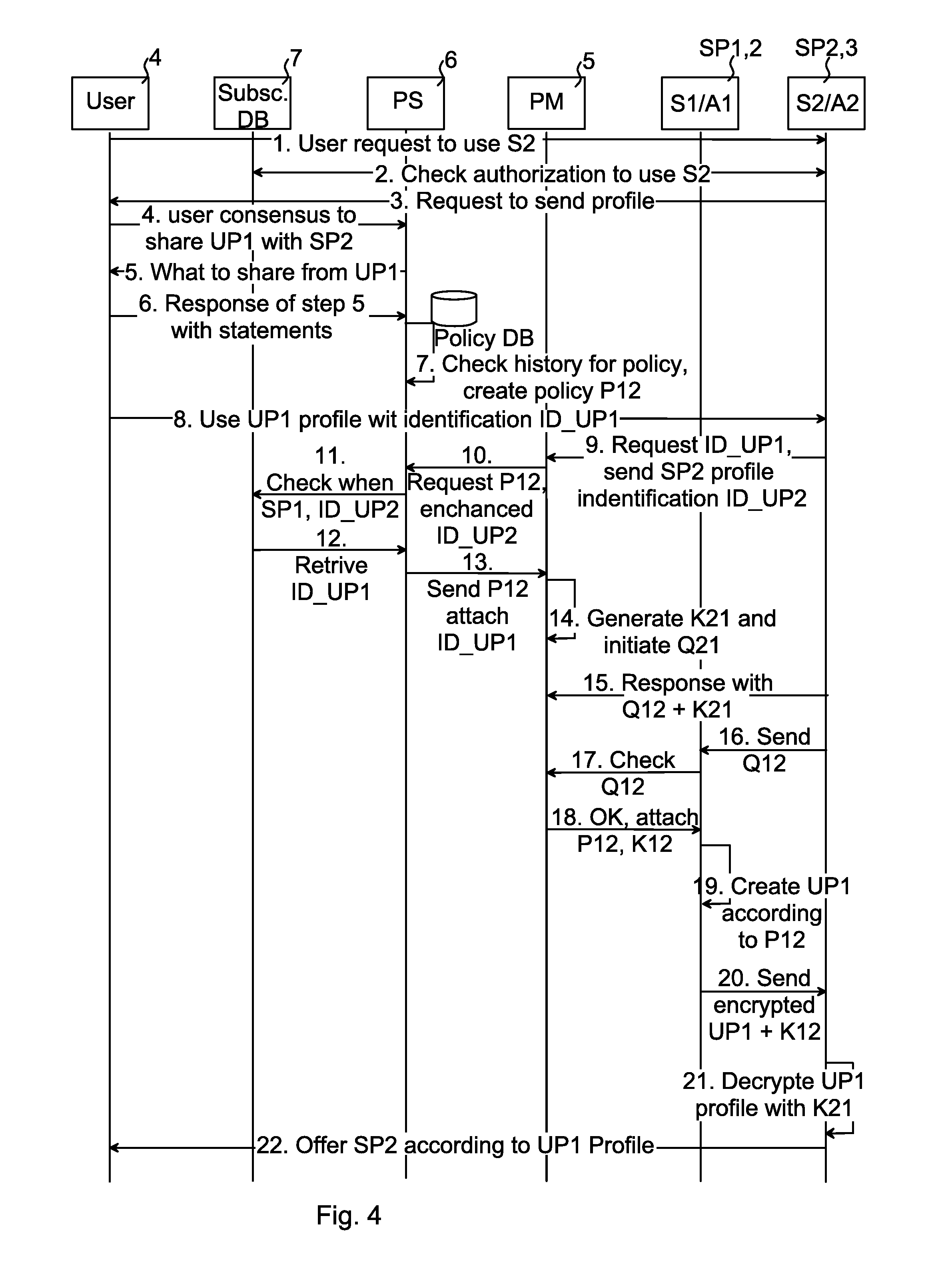
The invention relates to a method 20 performed in a profile mediator device 5 for exchanging user profile UP1 of a user between a first service provider SP1 having a first user profile UP1 for the user, and a second service provider SP2. The method 20 comprises: receiving 21 from the second service provider SP2 a request for the user profile UP1; retrieving 22 a policy corresponding to the user profile UP1; generating 23 a request identification Q12 for the request; and sending 24 the request identification Q12 to the second service provider SP2, the request identification Q12 enabling the first service provider SP1 to exchange the user profile UP1 with the second service provider SP2 in accordance with the policy. The invention also relates to a profile mediator device, agents, computer programs and computer program products.
Owner:TELEFON AB LM ERICSSON (PUBL)
Mobile device tracking prevention method and system
ActiveUS20150024787A1Protect user privacyCompromising privacySpecial service provision for substationDevices with wireless LAN interfaceProduction rateNetwork access point
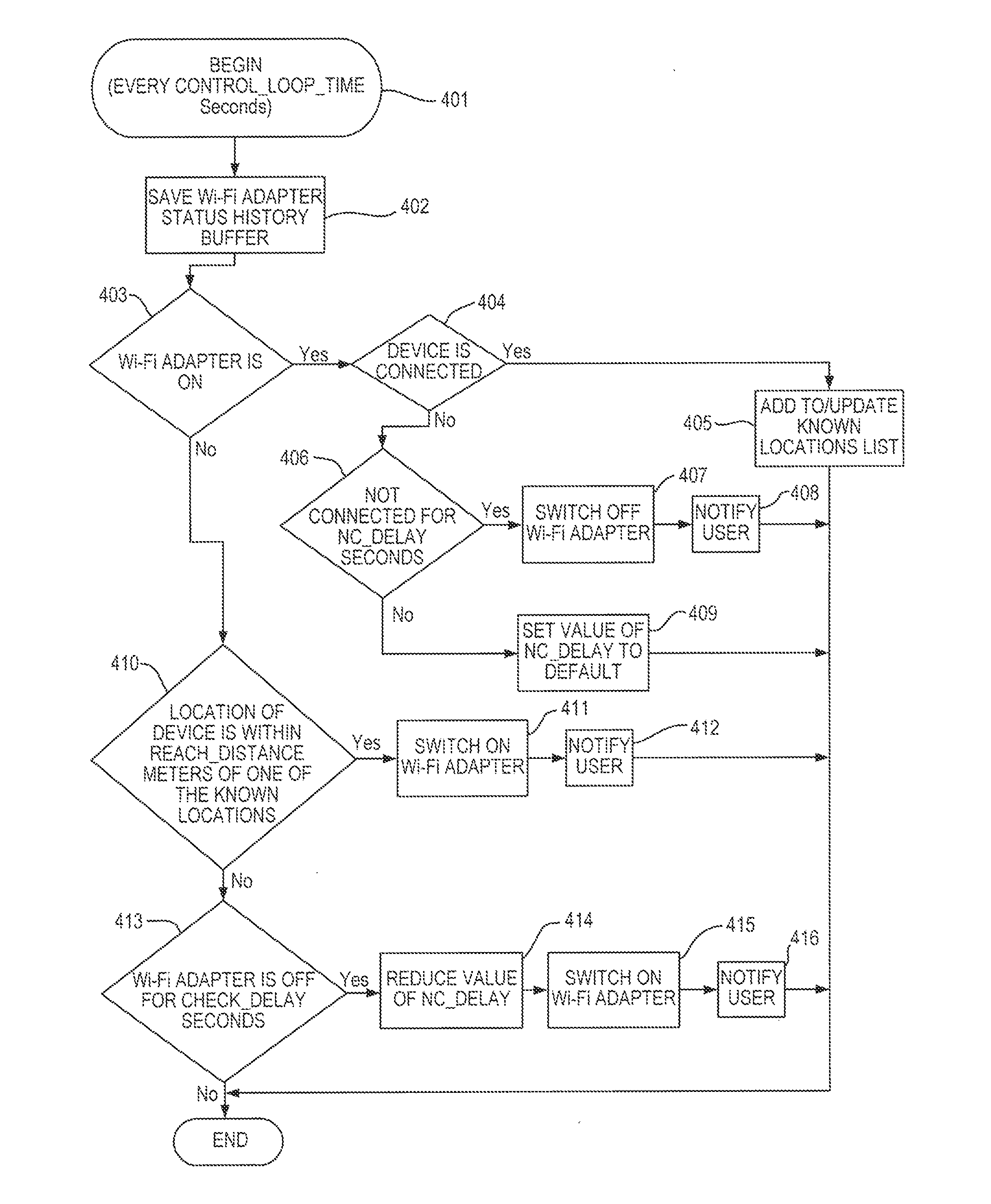
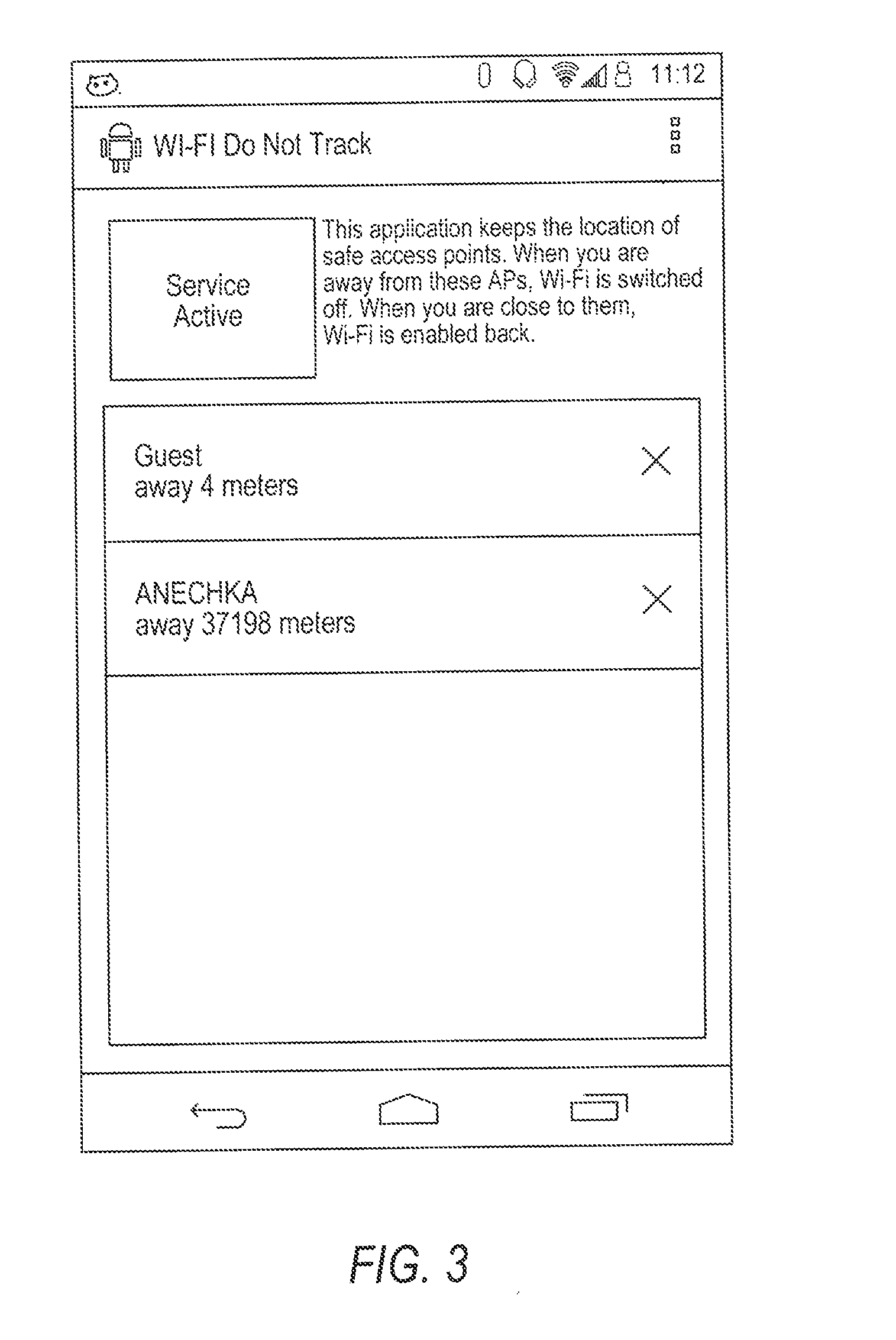
A mobile device tracking prevention method and system includes monitoring a mobile device for movement, determining whether an operating state of a wireless module of the mobile device should be adjusted when movement of the mobile device is detected, and controlling the operating state of the wireless module based on the determination. One or more of the actual geographic location of the mobile device, network IDs broadcasted by nearby network access points, and signal strengths of the access points as detected by the mobile device can be monitored to detect movement of the mobile device. Changes to any of these may be indicative of movement of the mobile device, which may serve as the basis for enabling or disabling the wireless module to prevent tracking of the mobile device without sacrificing user productivity.
Owner:AVAST SOFTWARE
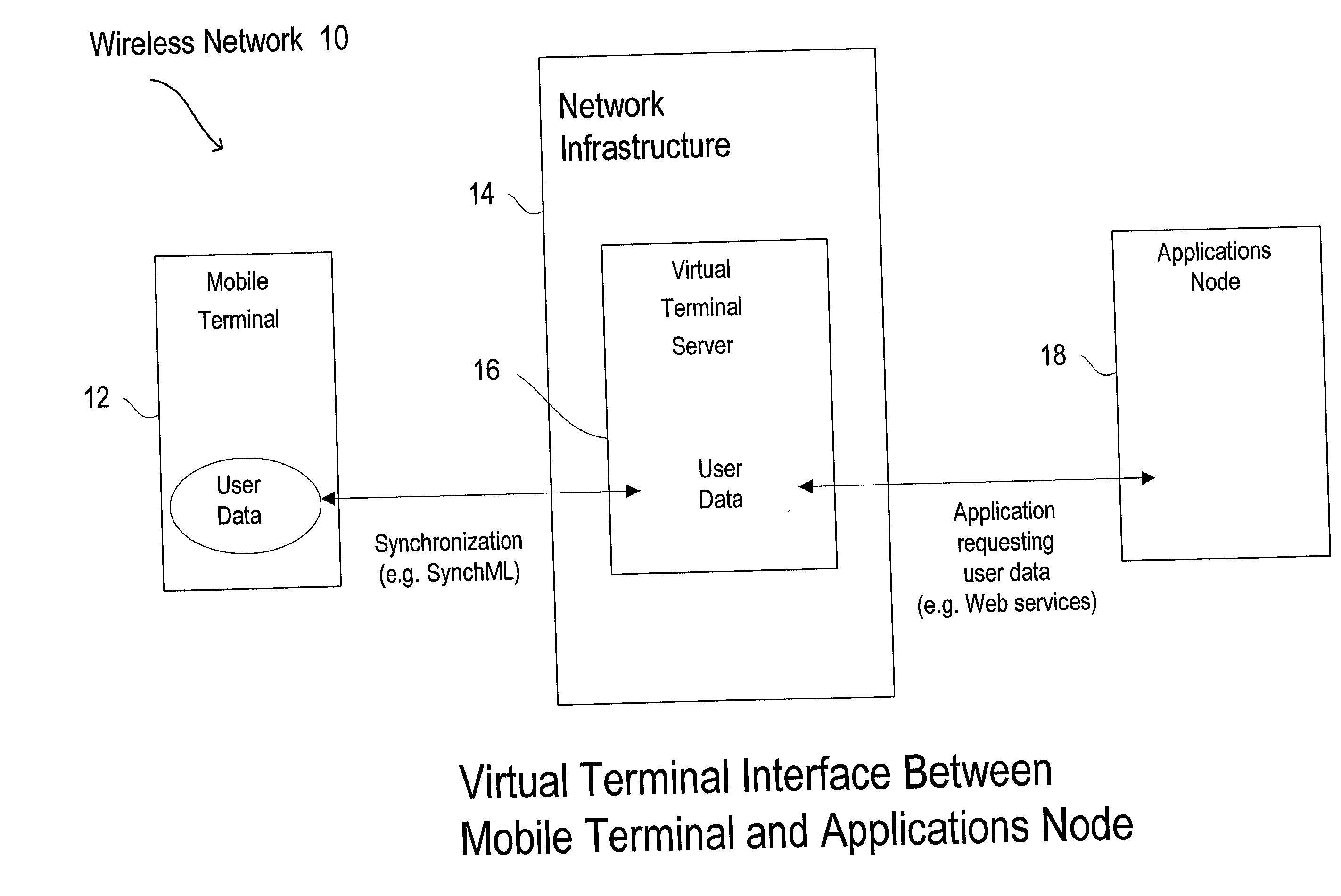
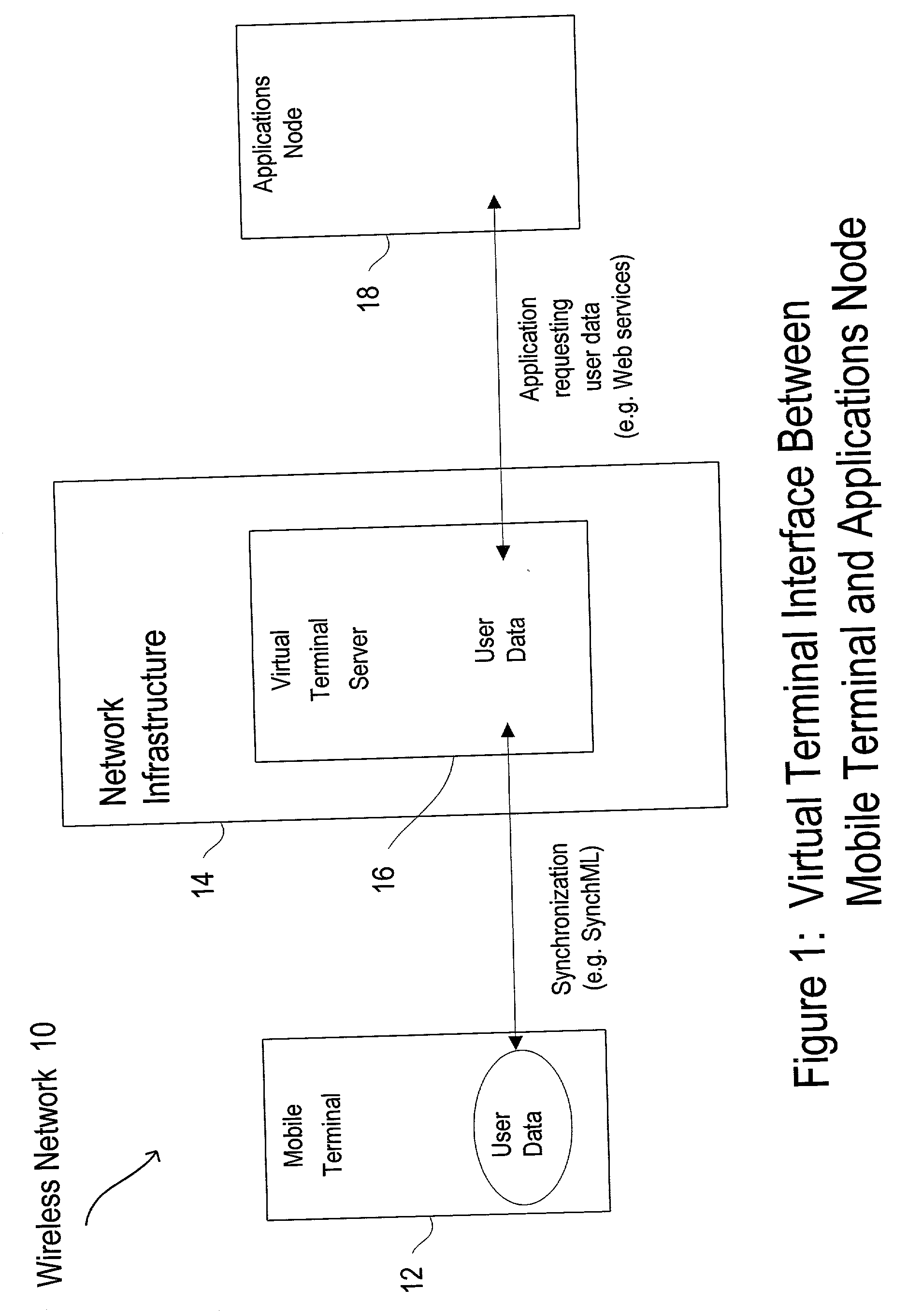
Virtual terminal for mobile network interface between mobile terminal and software applications node
InactiveUS20030145044A1Blocking in networkProvide controlMultiple digital computer combinationsElectric digital data processingVirtual terminalMobile Web
A method and apparatus are provided for sharing information about an end user of a mobile terminal with an applications node in a wireless network, in which a virtual terminal arranged between the mobile terminal to the applications node provides end user information about the end user of the mobile terminal to the applications node from a centralized point. The mobile terminal stores end user information and has a mobile terminal user interface for managing the provision of the end user information. The mobile terminal also stores end user rules or preferences controlling how different types of the end user information can be used and to whom the end user information can be given in the wireless network. The end user of the mobile terminal also requires manual confirmation so that the end user will be prompted each time certain end user information is requested by the applications node. The mobile terminal user interface manages these end user rules and preferences.
Owner:NOKIA CORP
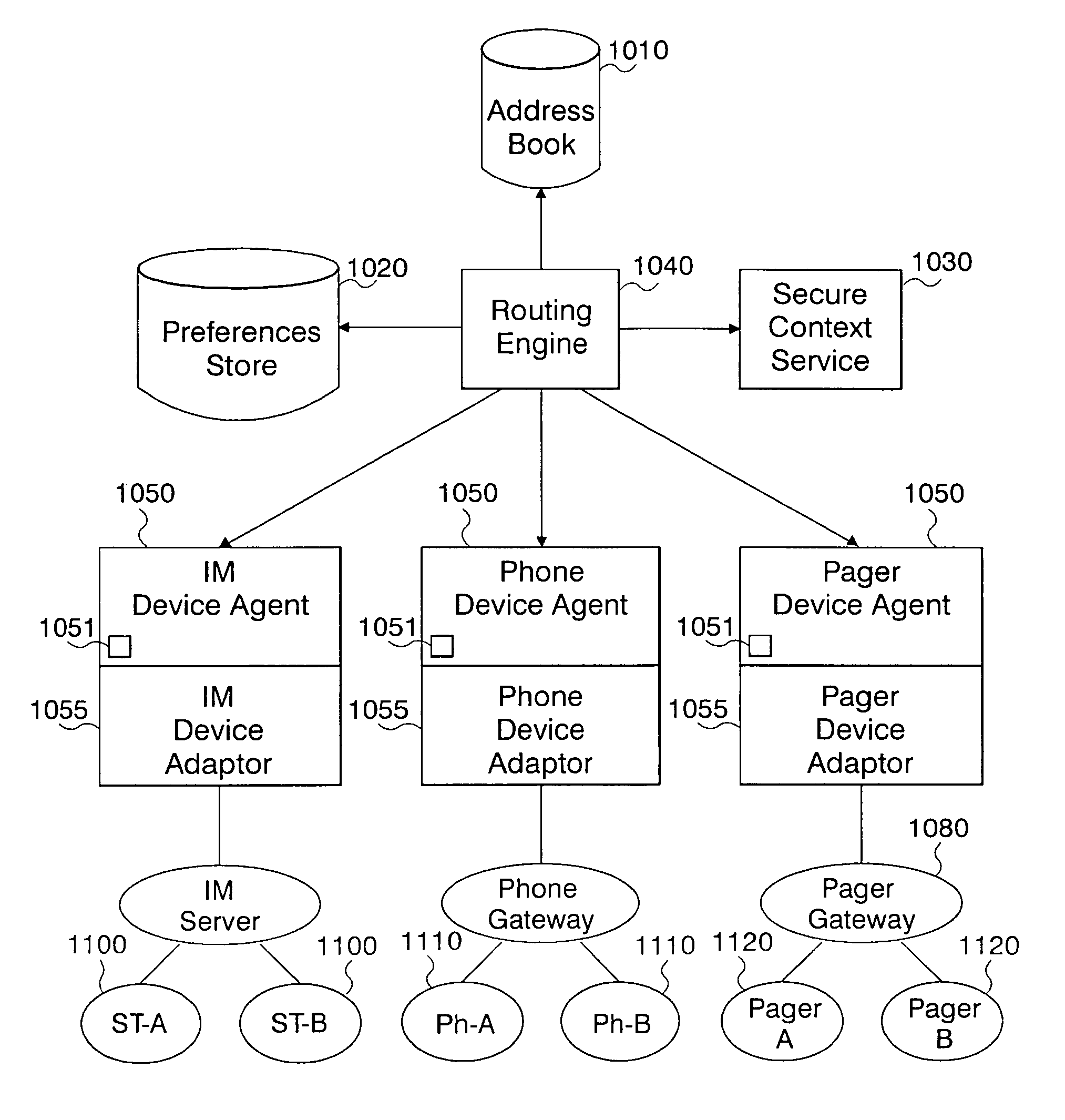
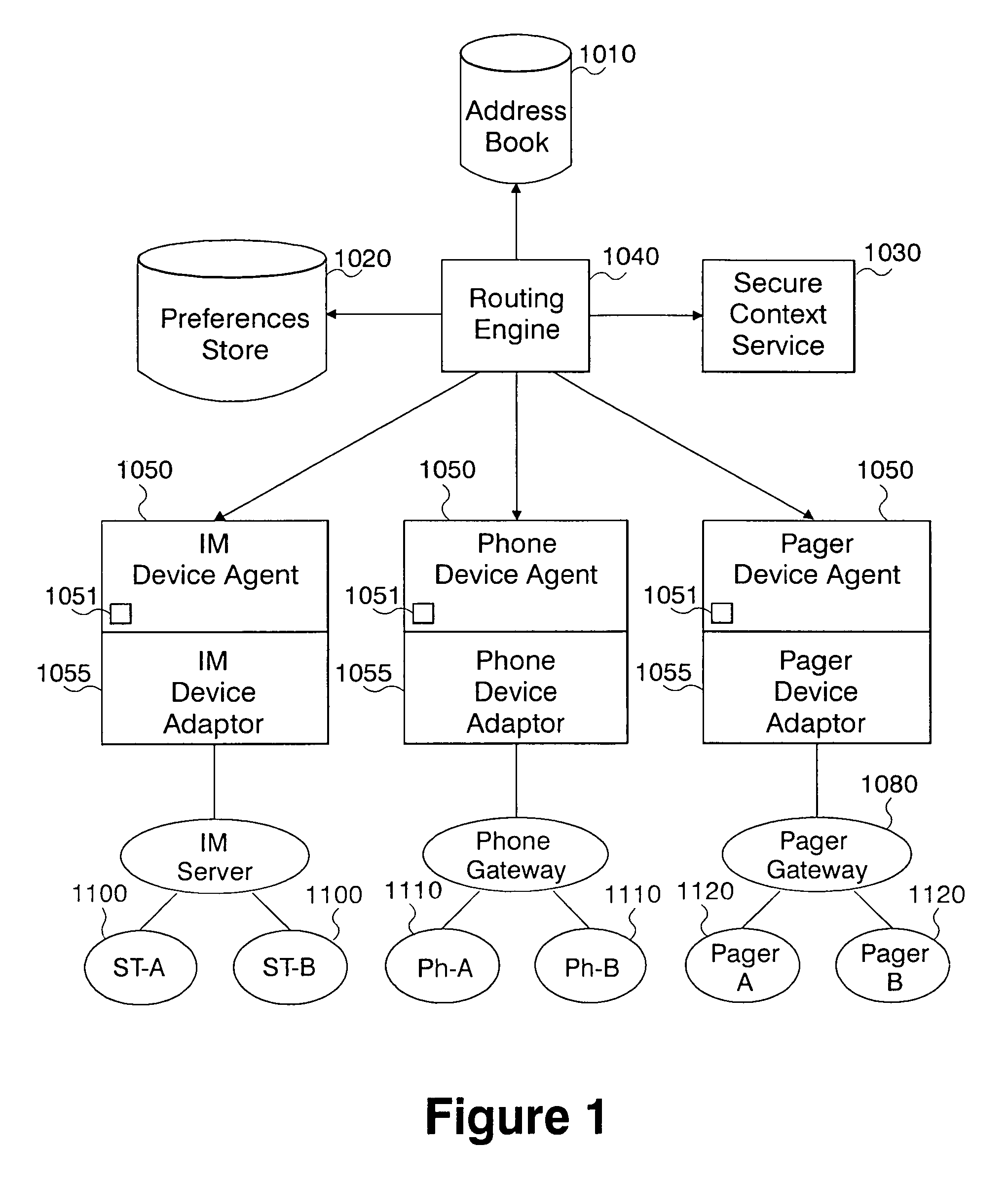
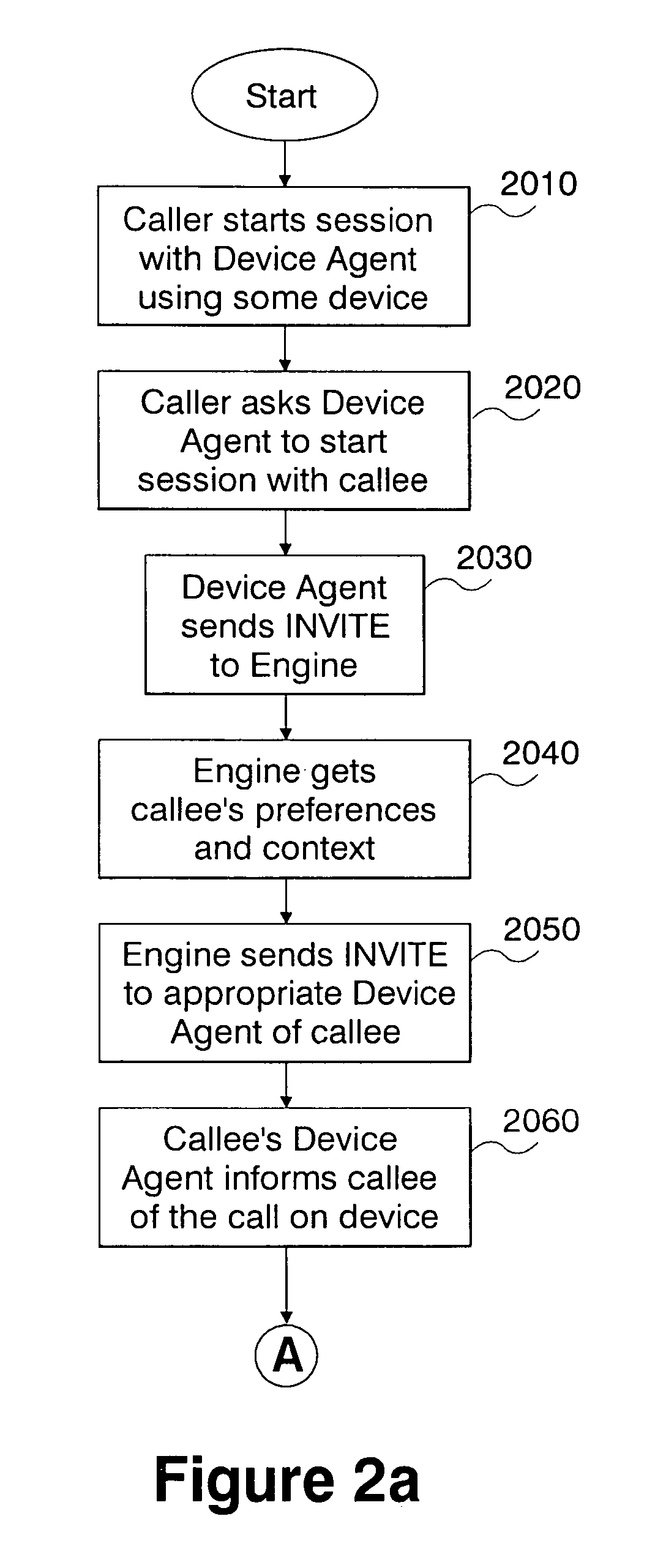
System and method for context-aware unified communications
ActiveUS7706785B2Protect user privacyPrivacy protectionSpecial service for subscribersMultiple digital computer combinationsUnified communicationsCall control
A system and method for context-aware unified communication for enabling communications between users over a common communications platform or heterogeneous communications platforms. The system comprises: agents associated with a respective caller and callee communications device for generating commands providing call control between the caller and callee devices; a routing engine for routing call commands between caller and callee via respective device agents to establish a communication session, and enabling exchange of conversation messages between the caller and callee communications devices over said single or heterogeneous communications platforms; a device for monitoring dynamic context of a callee and obtaining callee's preferences for receiving communications so that the routing engine enables a call setup between a caller and callee communications devices based on the callee's preferences or dynamic context information; and, further enabling either caller or callee to migrate a call to another communications device without disrupting a flow of a conversation.
Owner:TWITTER INC
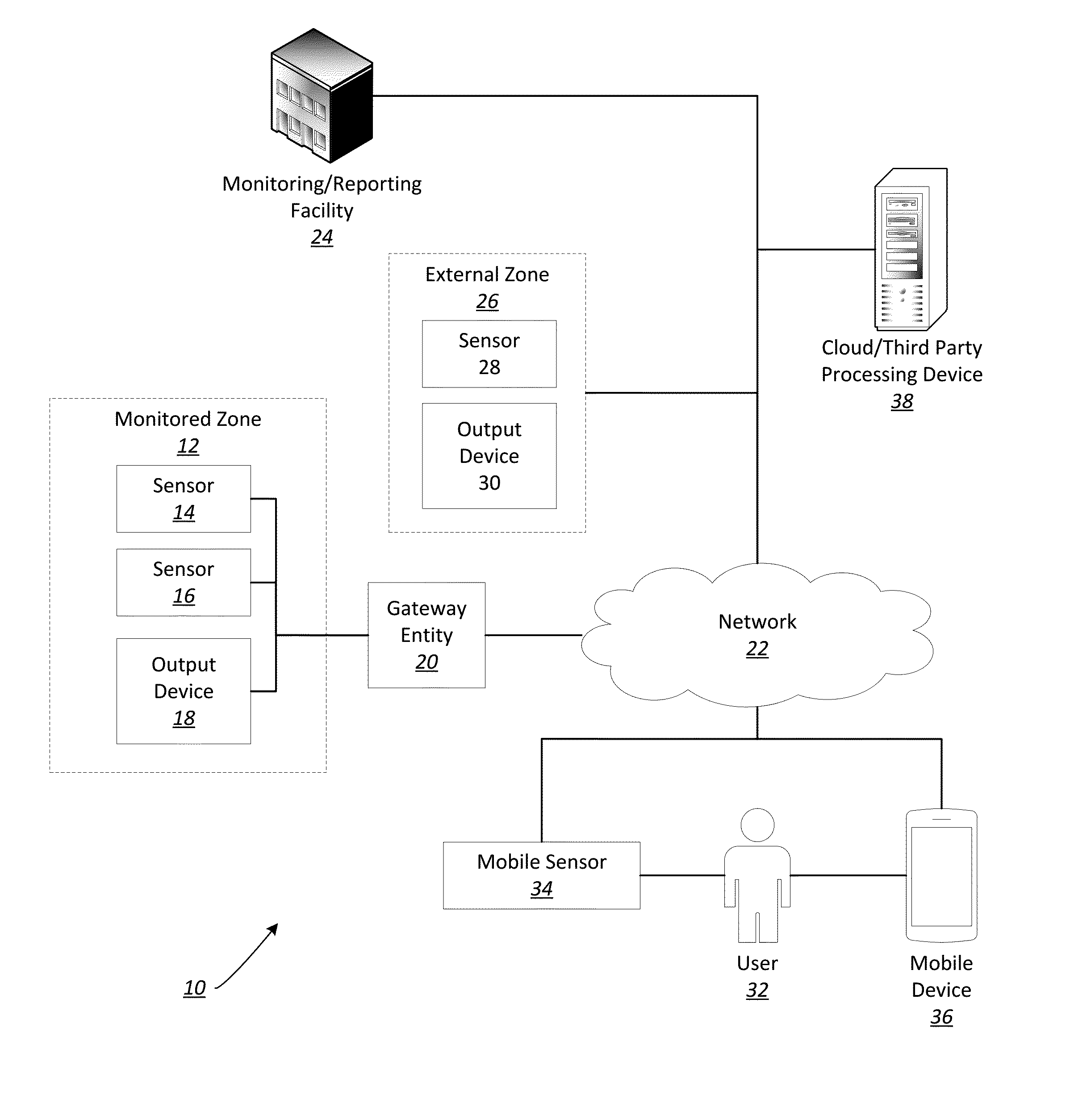
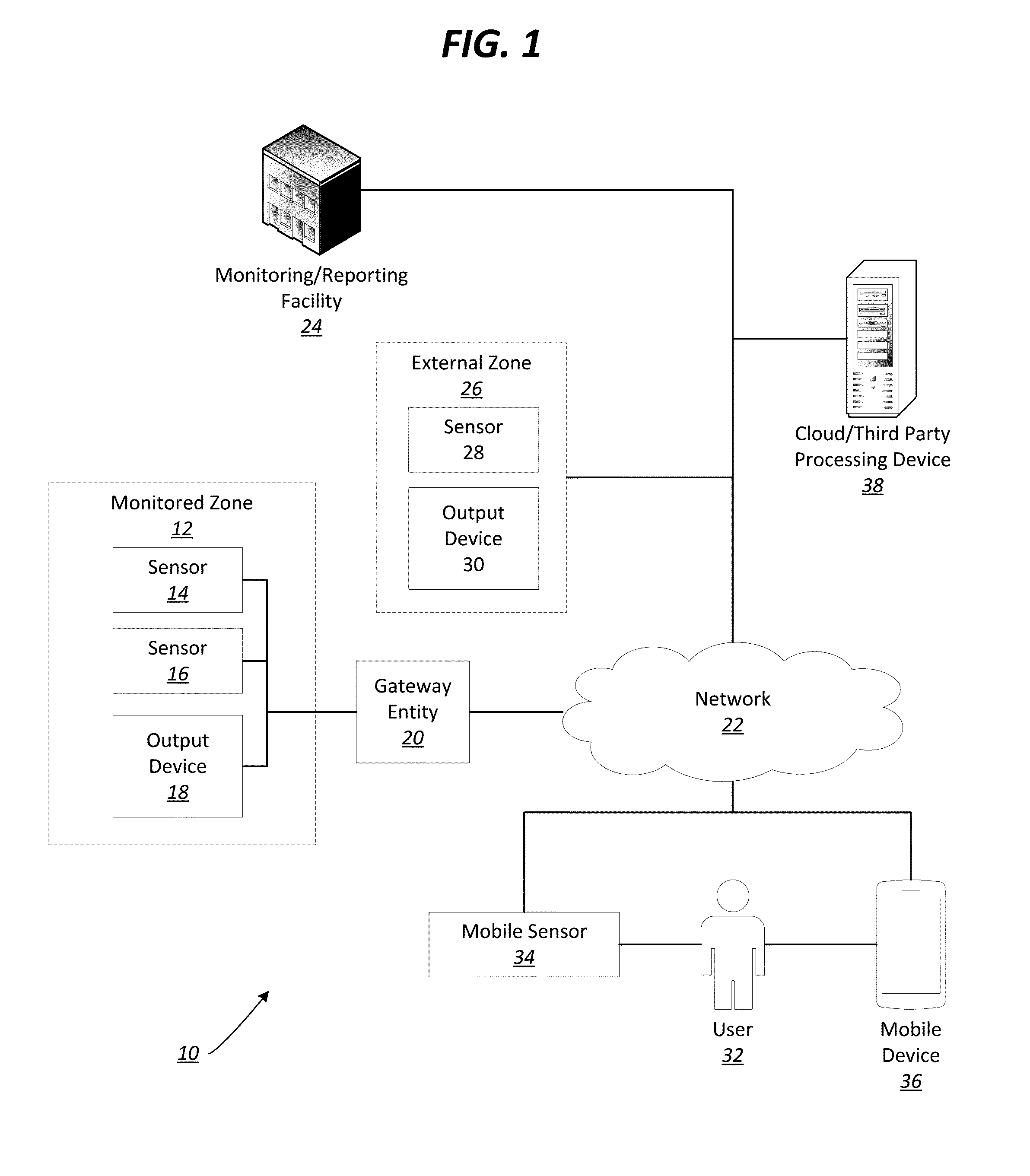
Intelligent smoke sensor with audio-video verification
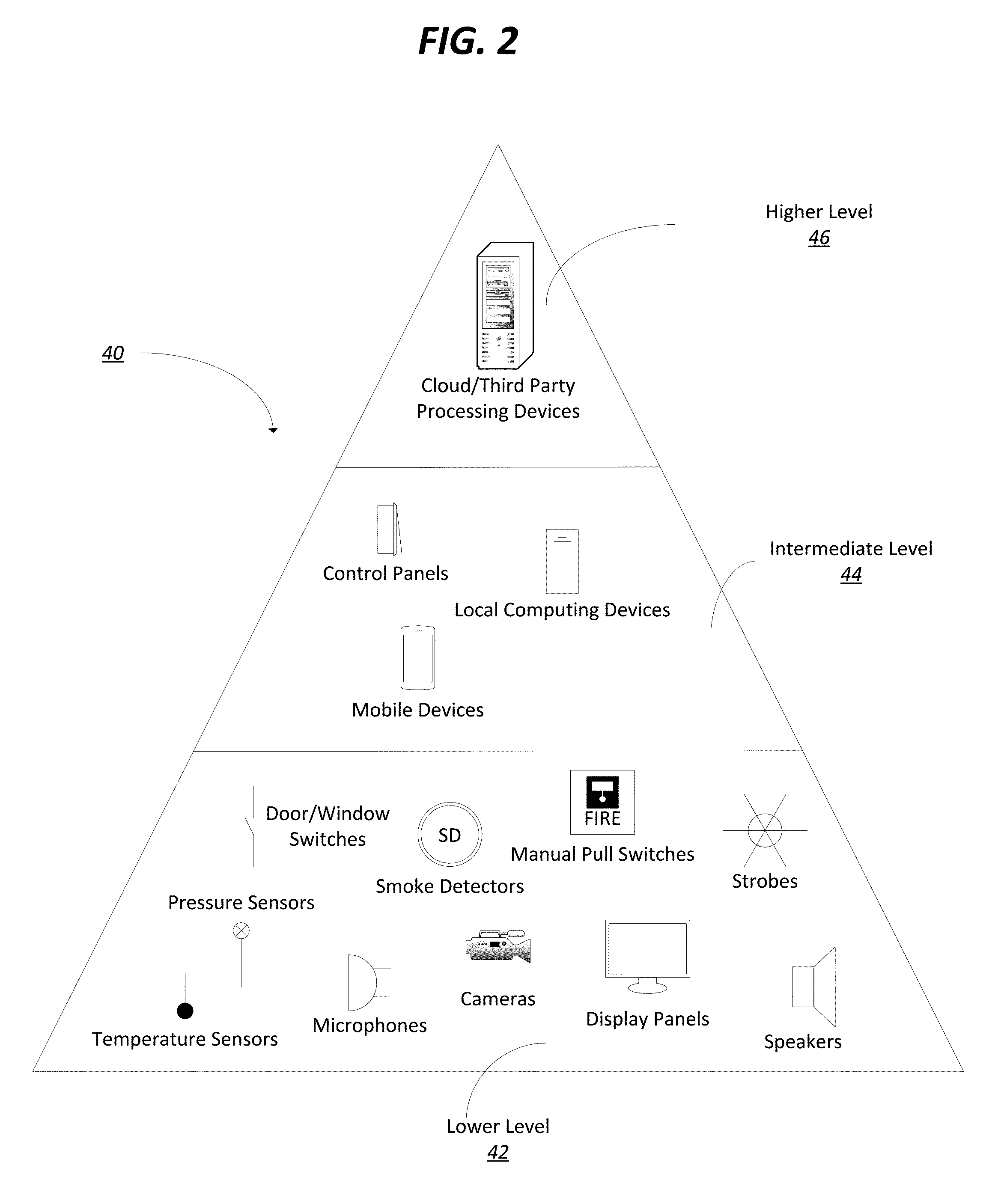
ActiveUS20160133108A1Protect privacyReduce occurrenceNetwork connectionsFire alarm smoke/gas actuationProcess systemsAudio frequency
A method and system architecture for automation and alarm systems is provided. An intelligent fire detection sensor is provided that provides input data to a gateway device for processing and facilitates two-way communication with users and a third-party monitoring service. The system architecture is hierarchically organized, allowing devices to process system data differently at different levels of the hierarchy. Processing of at least some of the sensor data is overseen by the gateway device, which may determine, based on the processing, to activate one or more secondary sensors at the fire detector (such as an optical camera). The gateway device and fire detection sensor may interact cooperatively to process voice commands and / or gesture data, and to recognize false alarms.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
Home gateway apparatus
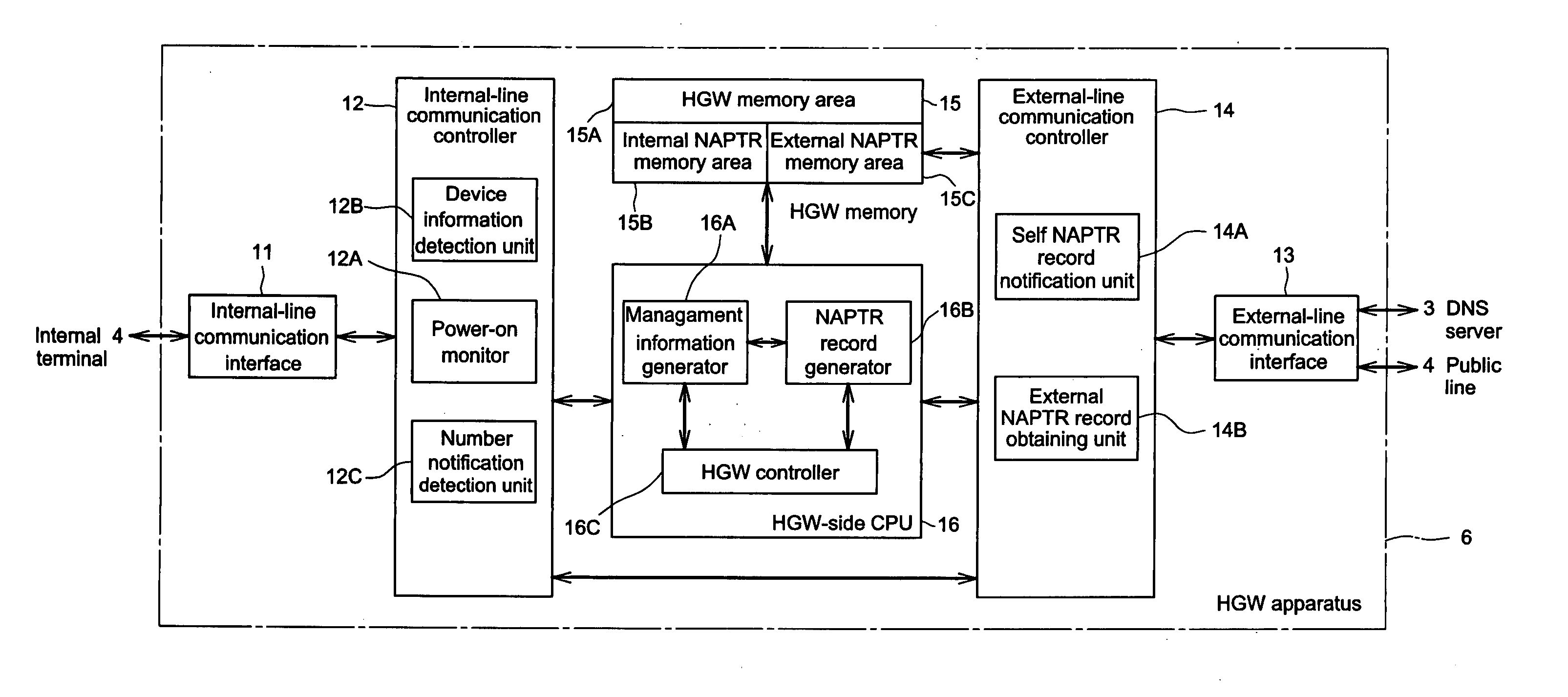
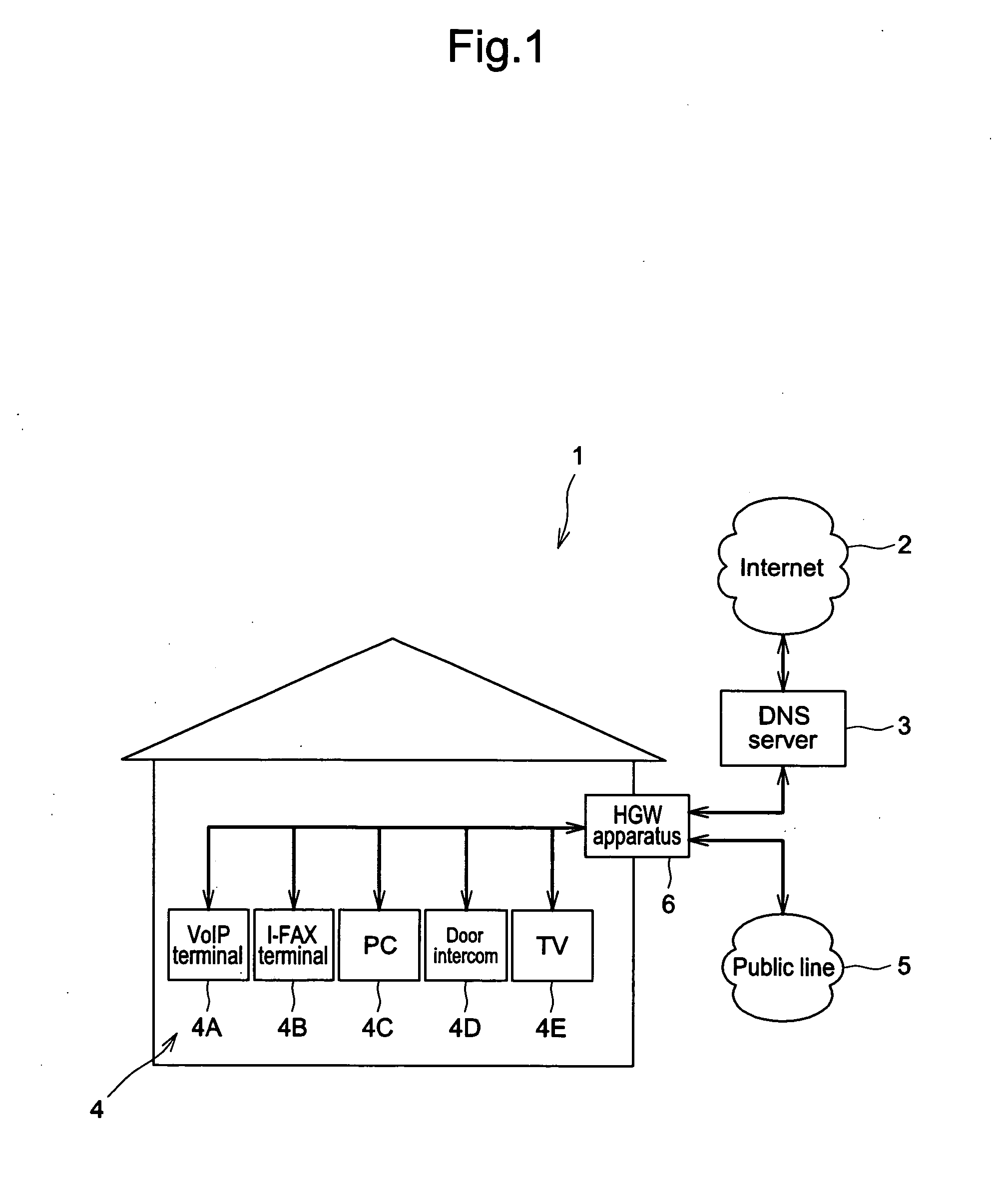
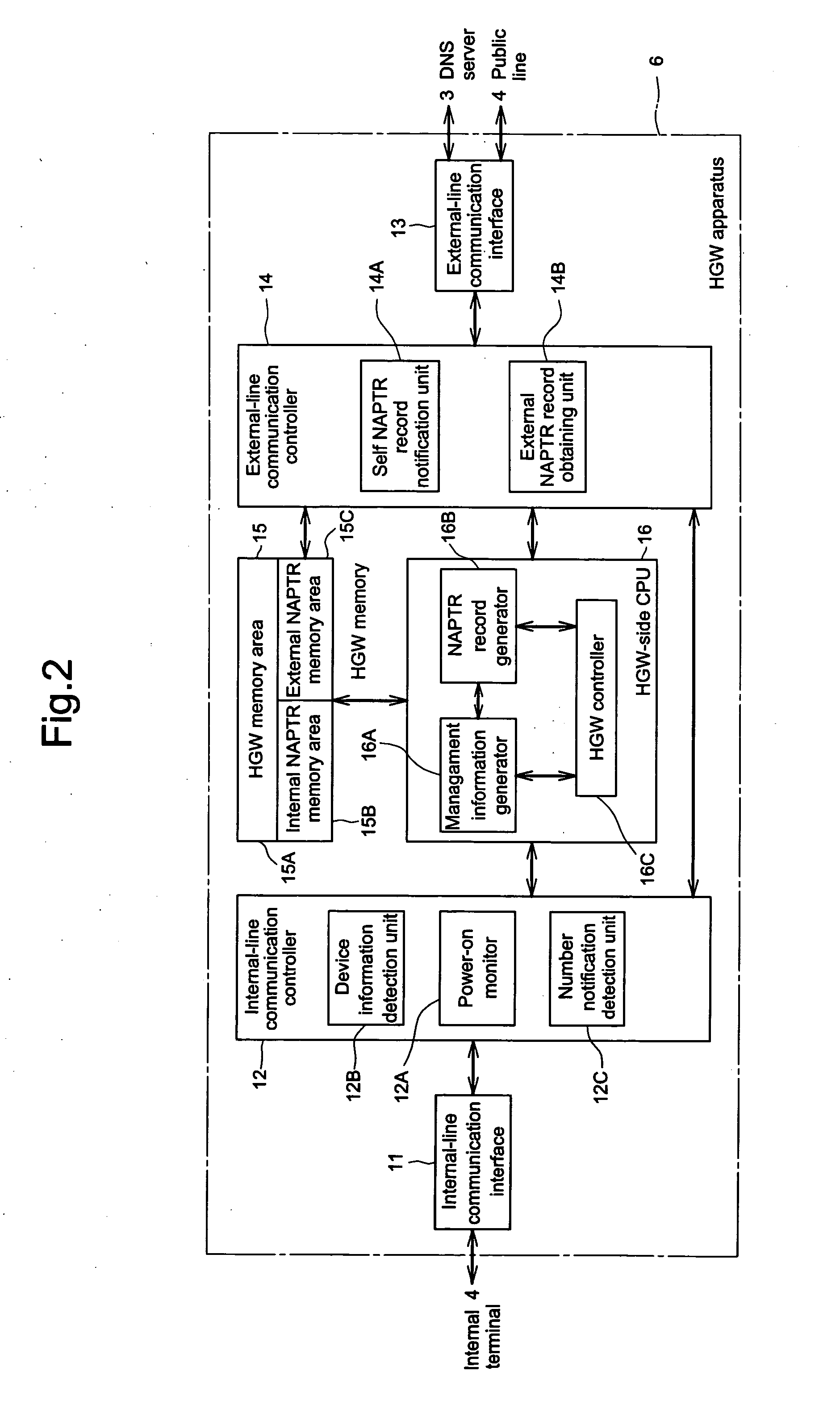
InactiveUS20050144322A1Reduce processing workloadProtect user privacySpecial service for subscribersMultiple digital computer combinationsComputer terminalComputer science
A home gateway apparatus is connected to a DNS server that stores and manages telephone numbers and an external NAPTR record corresponding to each telephone number. The home gateway apparatus also includes and mutually connects a plurality of internal terminals. The home gateway apparatus includes an NAPTR record generator that generates an internal NAPTR record of all internal terminals; an internal NAPTR memory area that stores the generated internal NAPTR record; an external NAPTR memory area that stores an external NAPTR record, which is selected from the internal NAPTR record to be allowed to be disclosed to the DNS server; and a self NAPTR record notification unit that notifies the DNS server of the external NAPTR record so that the DNS server can register the external NAPTR record in association with a telephone number.
Owner:PANASONIC CORP
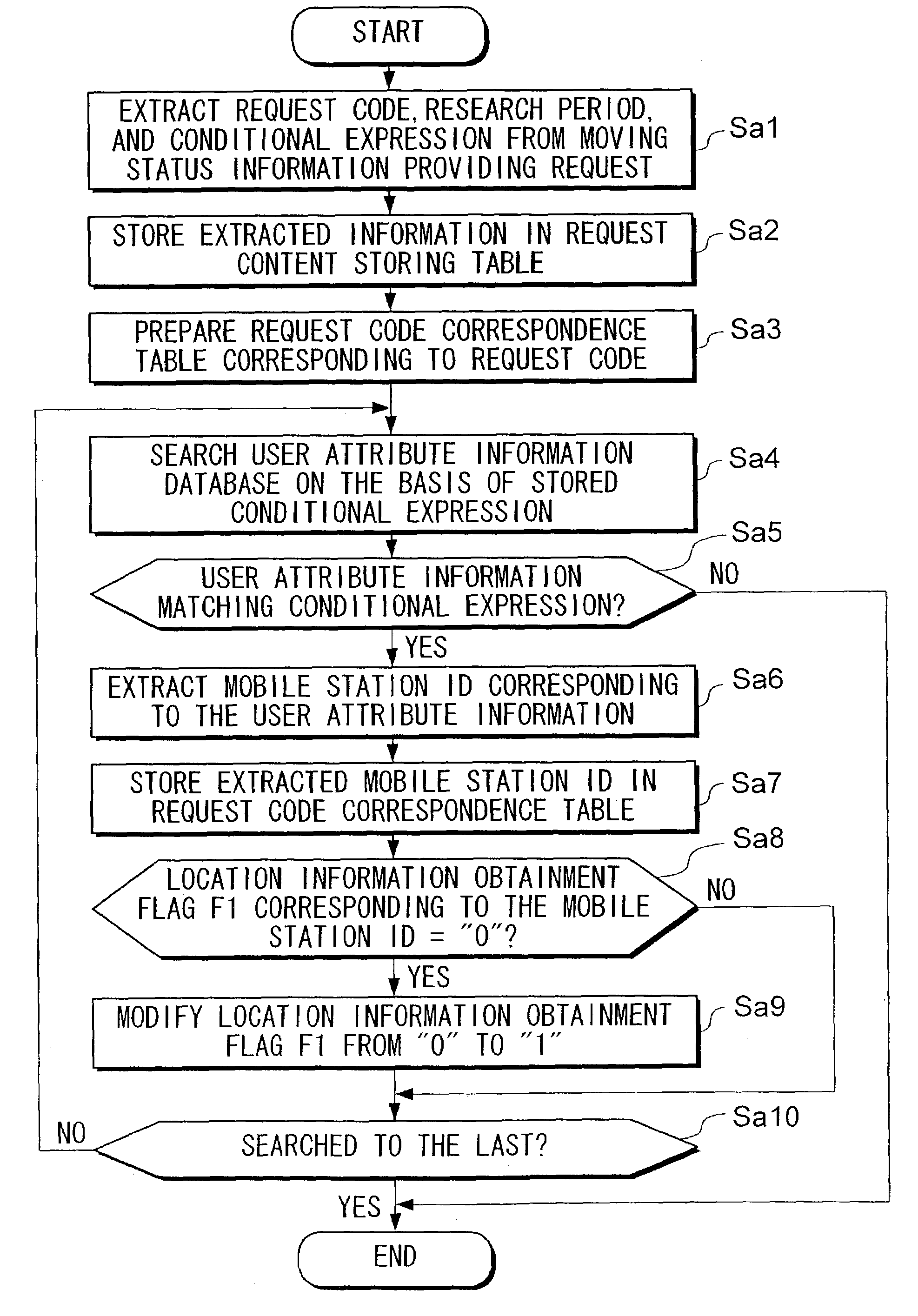
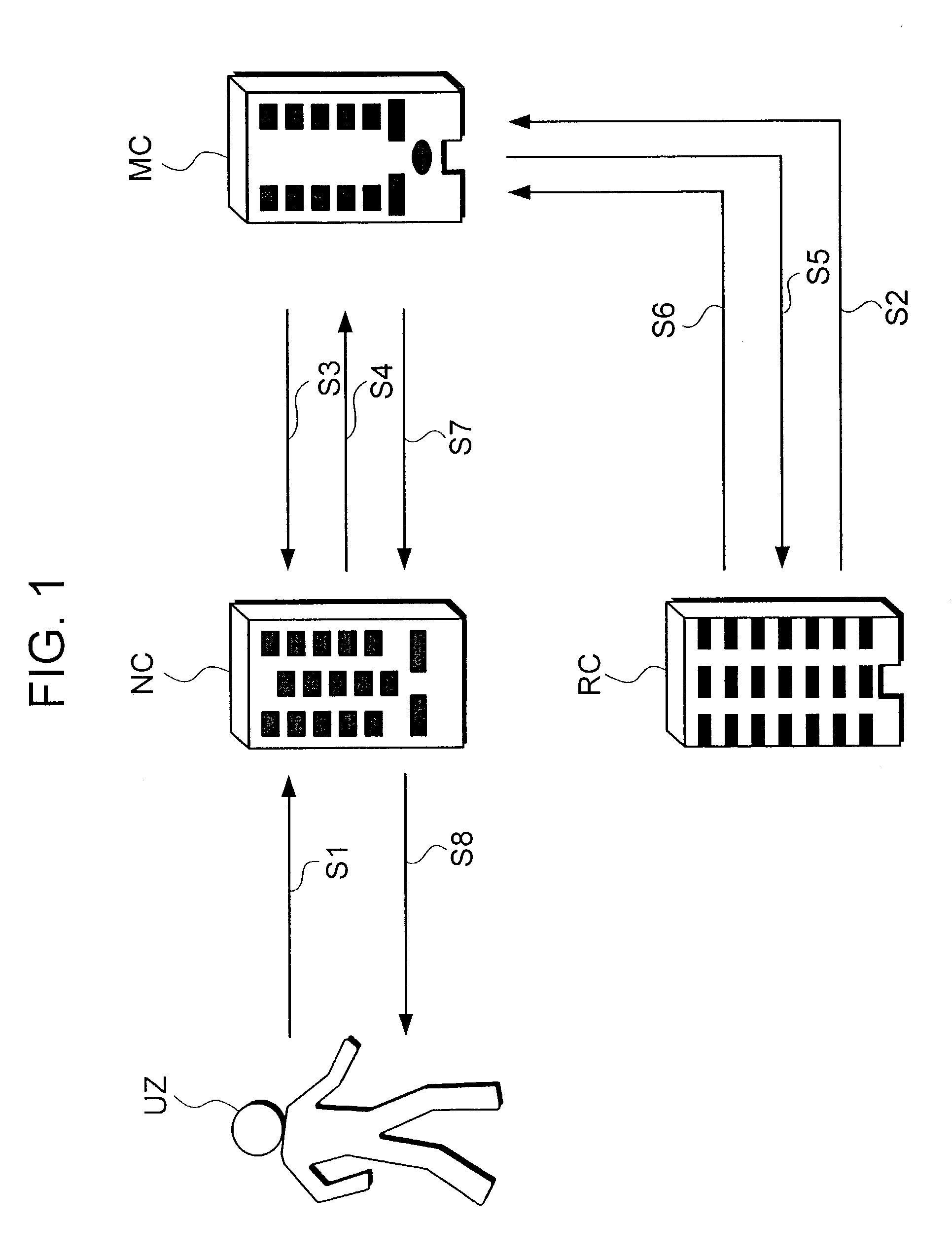
Moving status information providing method and server
InactiveUS7130611B2Protect user privacyRoad vehicles traffic controlSpecial service for subscribersConditional expressionMobile station
Research server 4 transmits to moving status search server 3 a request for providing moving status information containing a conditional expression, designating attributes of users to be researched. Moving status search server 3 extracts users having user attribute information (information such as address, occupation or the like, of each user) matching the conditional expression and obtains location information from mobile stations 1 which the users possess. In this way, moving status search server 3 generates moving status information on the basis of location information of users having user attribute information matching the conditional expression, and transmits the generated moving status information to research server 4.
Owner:NTT DOCOMO INC
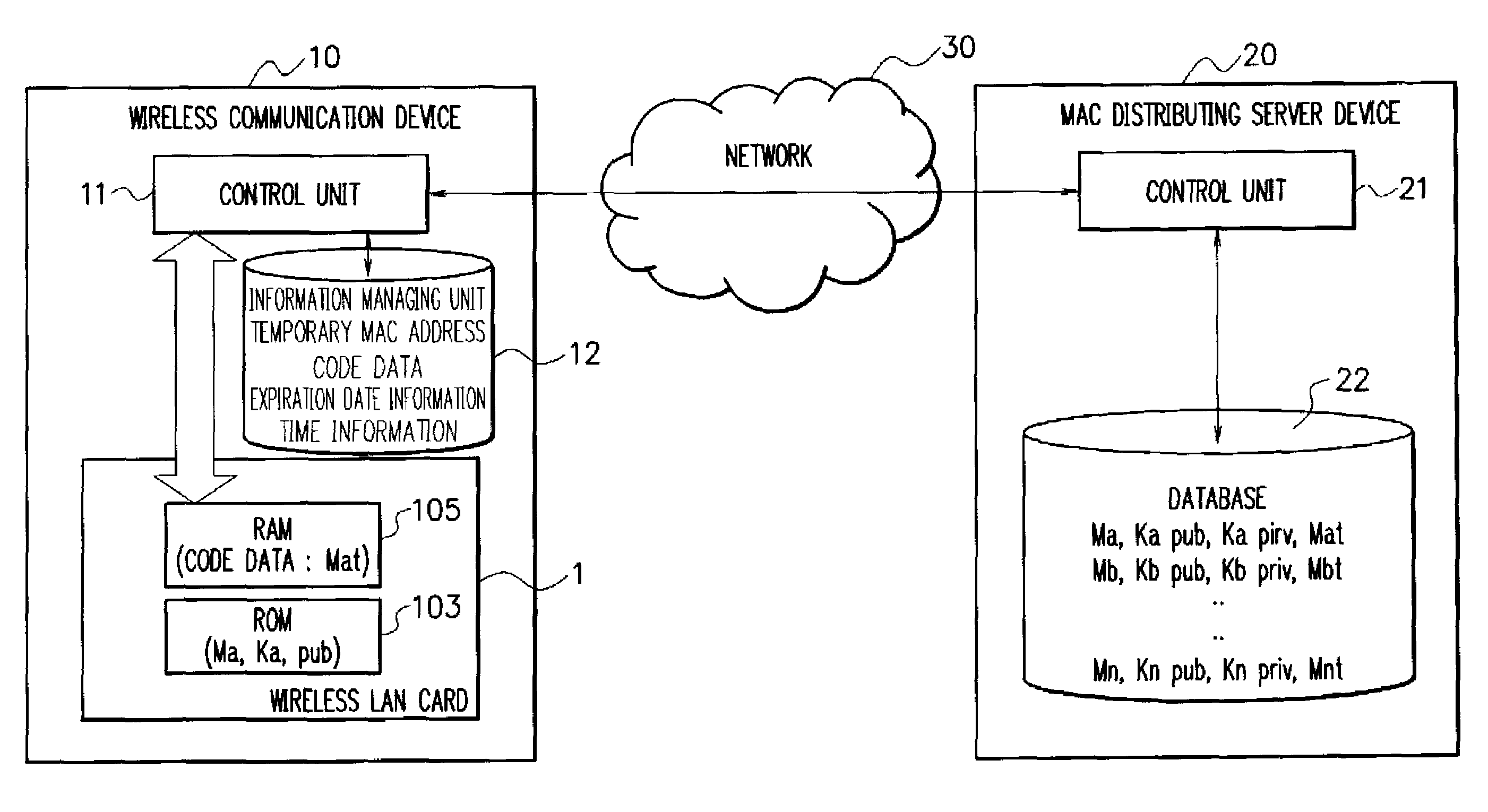
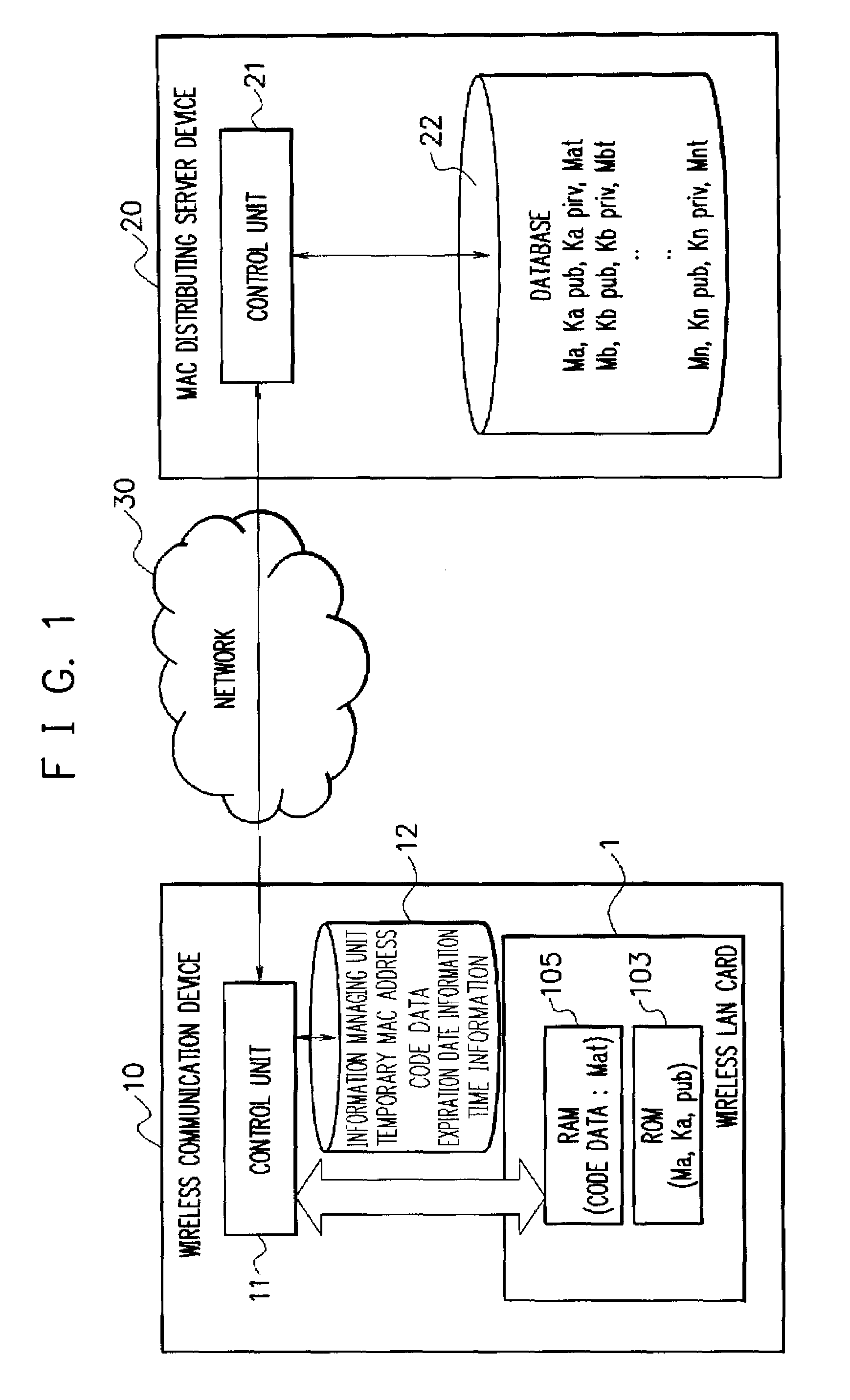
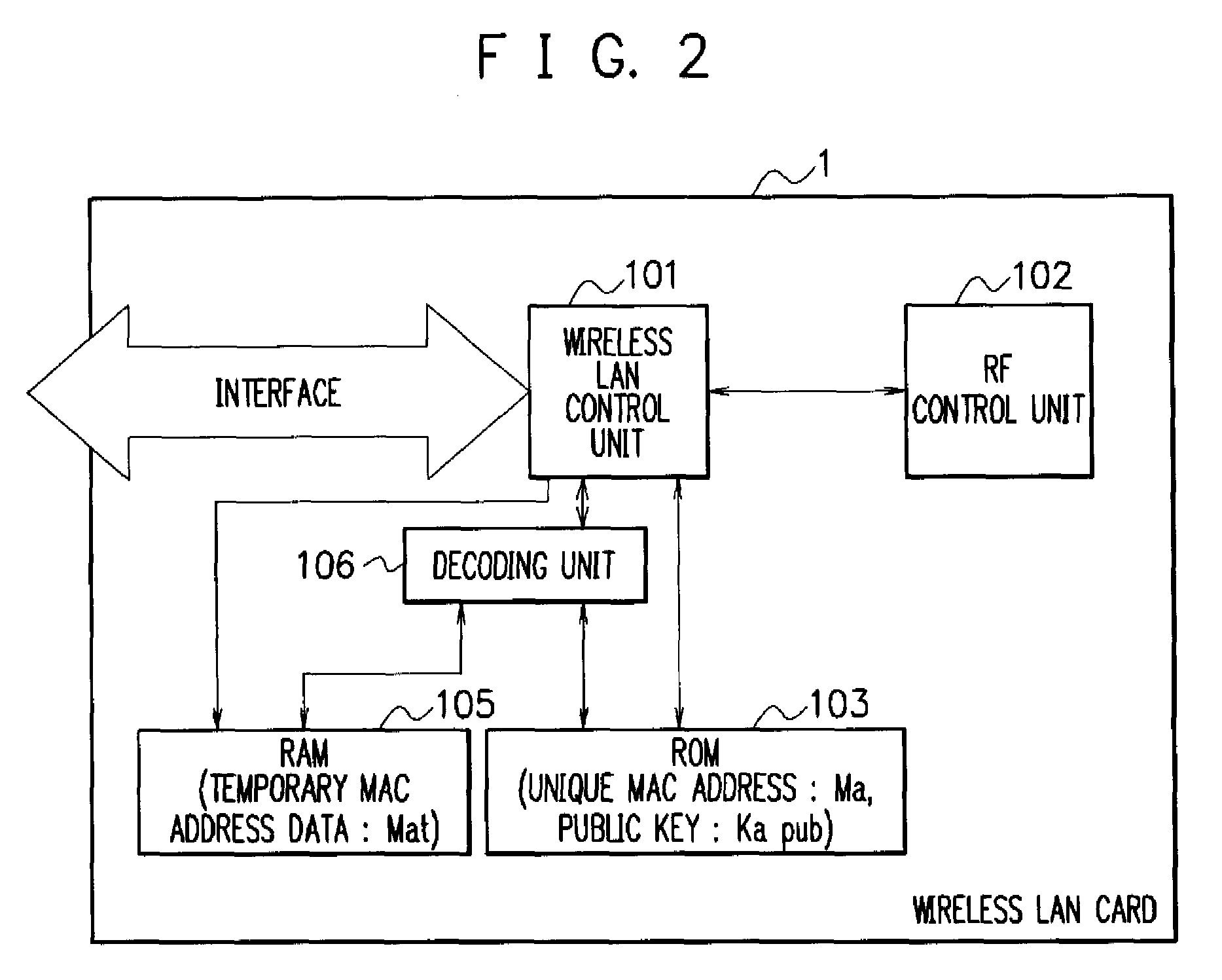
Wireless communication device, mac address management system, wireless communication method, and program
ActiveUS20070211653A1Maintaining secrecyProtect user privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareDistributed servers
A MAC address management system acquires code data obtained by encoding a temporary MAC address that can be temporarily used and decodes the acquired code data to perform wireless communication. The MAC address management system includes a MAC distributing server device in which a temporary MAC address which can be temporarily used is stored and a wireless communication device that acquires the temporary MAC address from the MAC distributing server device and performs wireless communication by using the acquired temporary MAC address, the wireless communication device acquires code data obtained by encoding the temporary MAC address from the MAC distributing server device, decodes the acquired code data, and performs wireless communication by using the decoded temporary MAC address.
Owner:NEC CORP
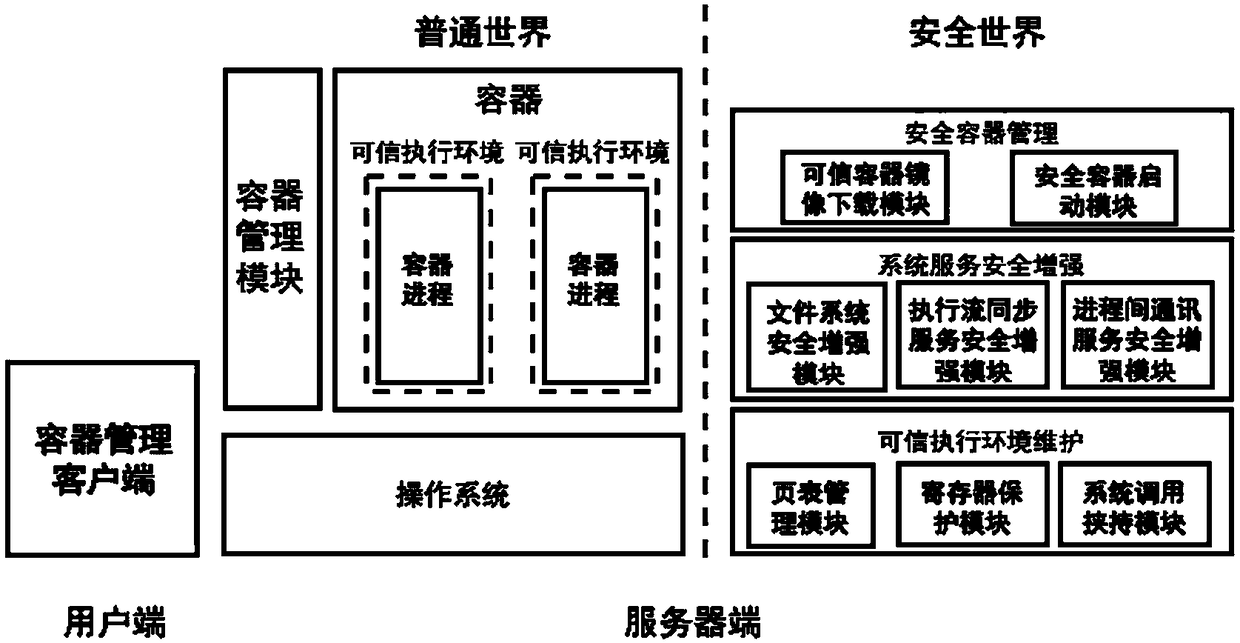
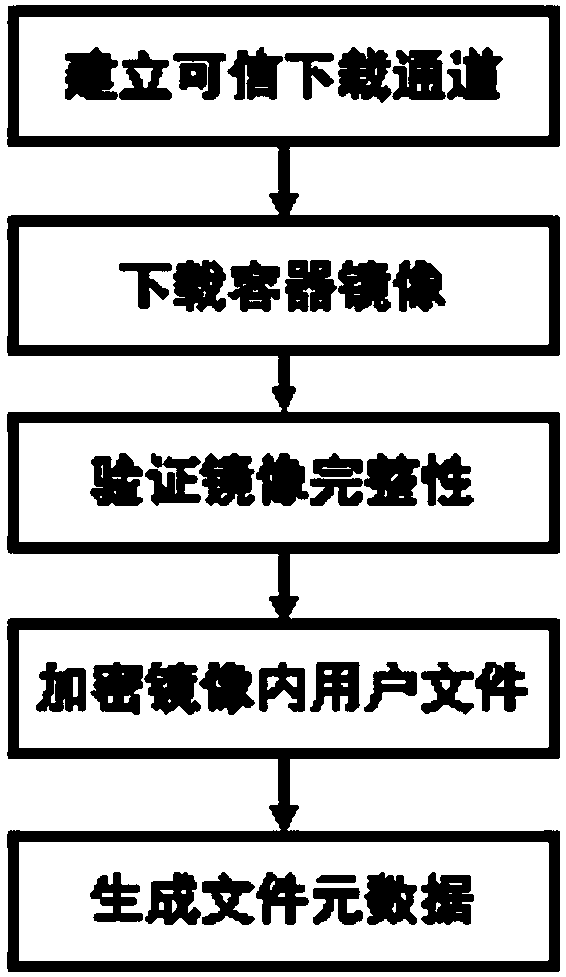
Container isolation enhancement system based on ARM TrustZone
ActiveCN108733455AProtect user privacyAvoid attackSoftware simulation/interpretation/emulationPage tableClient-side
The invention provides a container isolation enhancement system based on an ARM TrustZone. The system comprise a container management client side which runs at a client side; an untrusted operation system, an untrusted container management module and a trusted execution environment which run in the ordinary world of a server side; and a page table management module, a register protection module, asystem call hijacking module, a file system safety enhancement module, an execution flow synchronous service safety enhancement module, an interprocess communication service safety enhancement module, a trusted container mirror image downloading module and a safety container starting module which run in the safety world of the server side. According to the container isolation enhancement system based on the ARM TrustZone, an existing application program safely runs on a malicious operation system which is completely controlled by an attacker so that different applications of different users in the container can perform safe communication and synchronous control flow; and the users do not need to make any modification on an existing mirror image.
Owner:SHANGHAI JIAO TONG UNIV
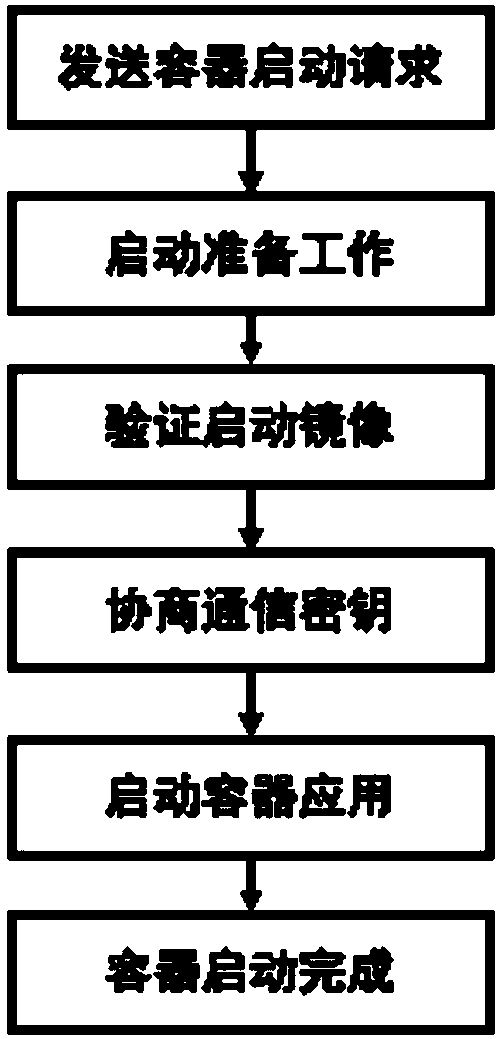
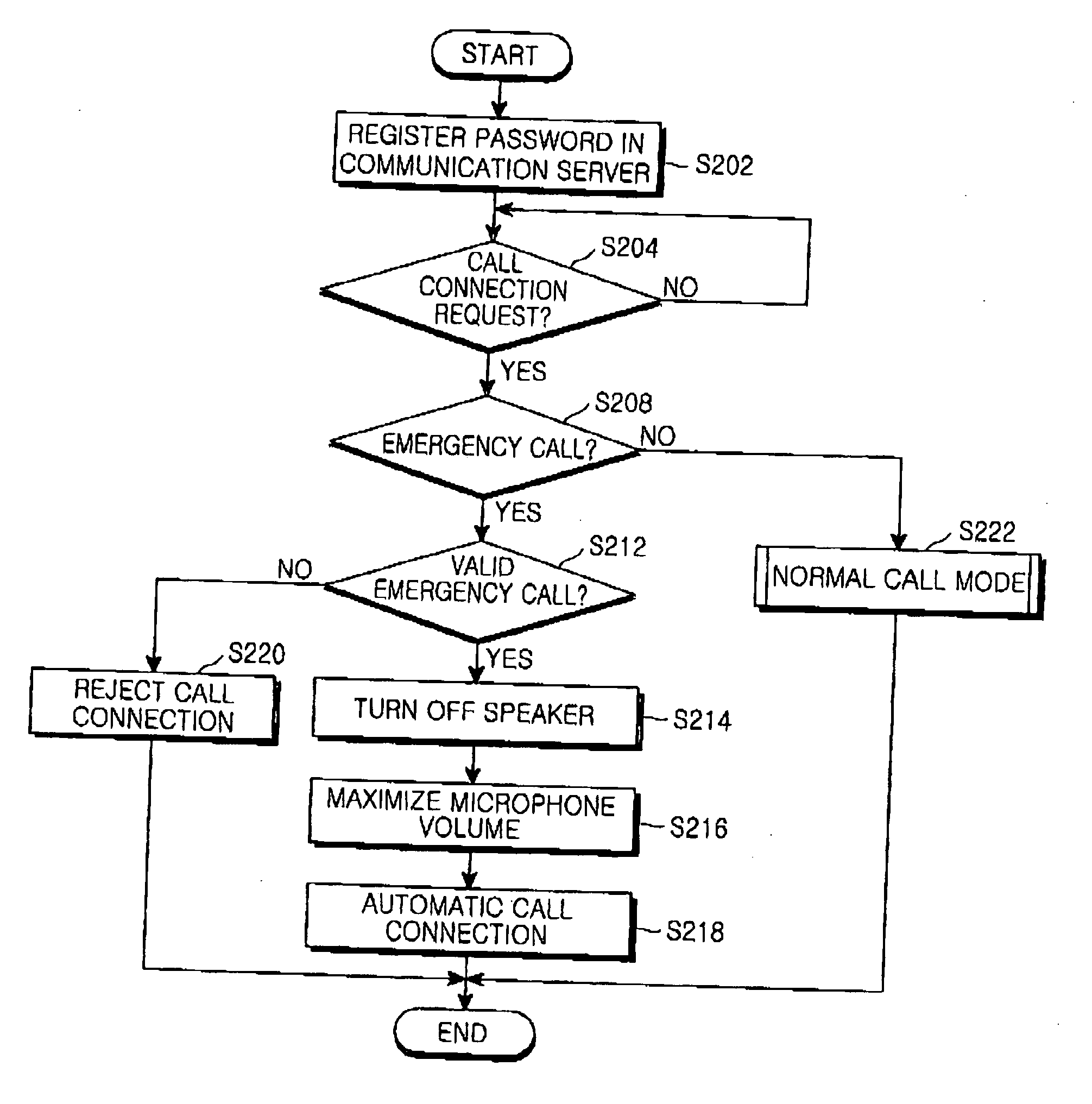
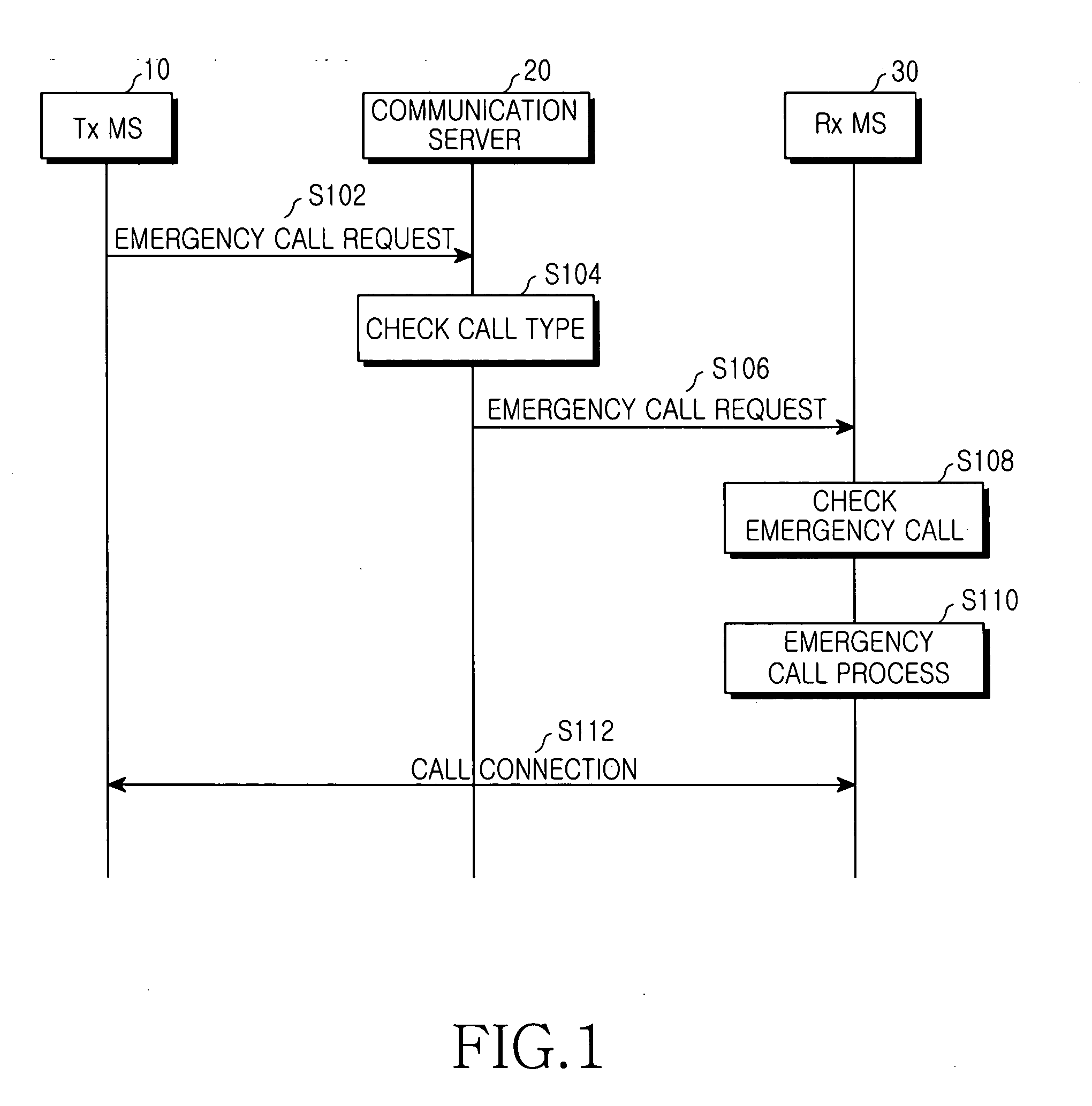
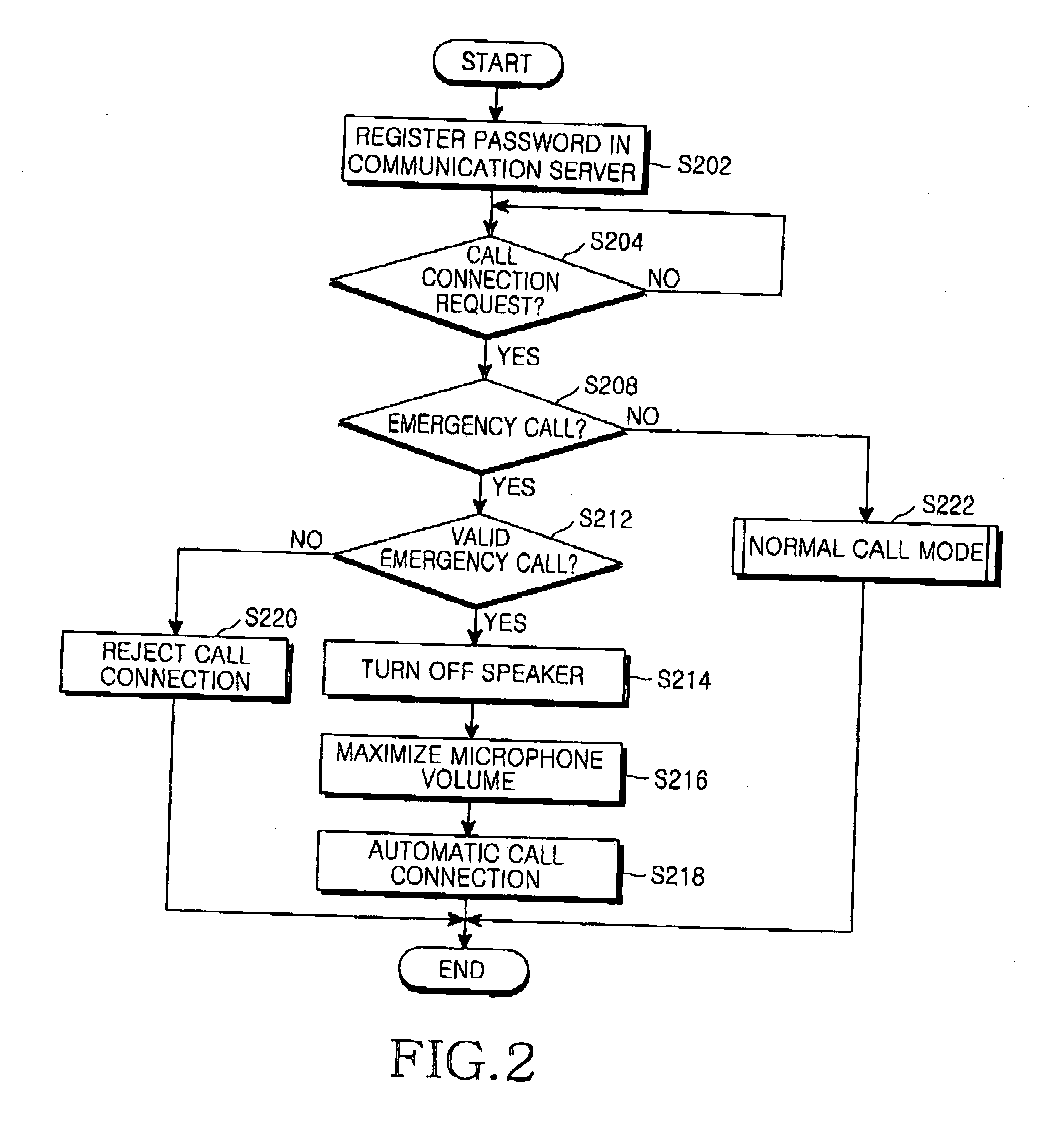
Method for connecting a call in a mobile station during an emergency situation
InactiveUS20050096008A1Privacy protectionProtect user privacyAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersTelecommunicationsPassword
A method for automatically connecting a call in a mobile station during an emergency situation. In the method a call connection request message including a service identifier previously set for automatic call connection and a password is received. Next, whether the call connection request message is valid is determined using the password included in the received call connection request message. If the call connection request message is valid, devices for outputting an alert signal of the mobile station are turned off, and a response signal for call connection in response to the call connection request message is automatically generated.
Owner:SAMSUNG ELECTRONICS CO LTD
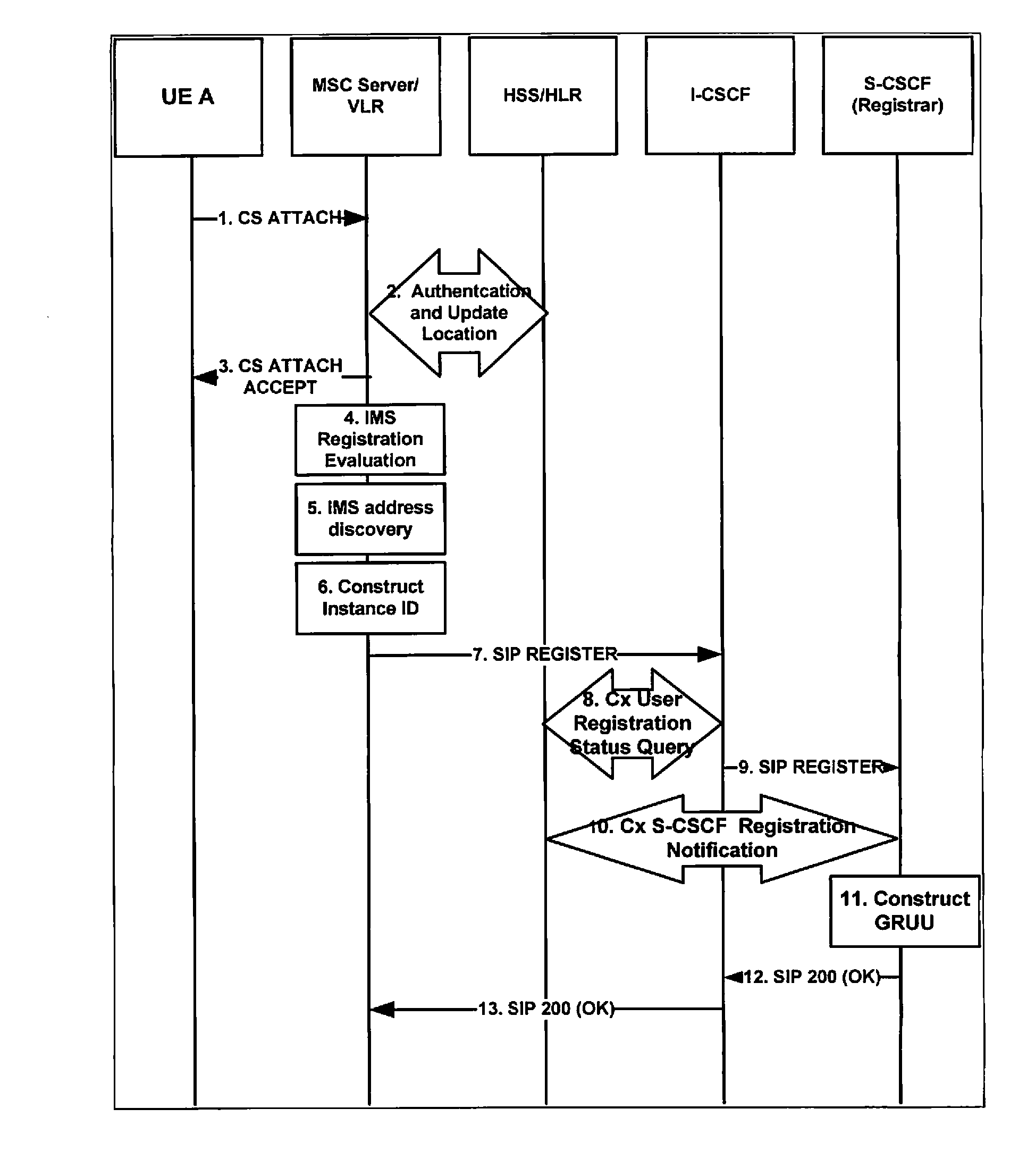
Method and apparatus for instance identifier based on a unique device identifier
ActiveUS20100009681A1Protect user privacyEnsure consistencyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer networkUnique device identifier
A method and apparatus for use in a communications network whereby an Instance Identifier (ID) is created to uniquely identify a device such as a mobile device or User Equipment (UE) in the communications network.
Owner:TELEFON AB LM ERICSSON (PUBL)
Techniques for sharing content information with members of a virtual user group in a network environment without compromising user privacy
InactiveUS20070162570A1Without compromising the user's privacyProtect user privacyComputer security arrangementsMultiple digital computer combinationsVirtual userInternet privacy
Techniques for sharing content information between members of a virtual user group without compromising the privacy of the members. A user can identify content information to be shared with other members of a virtual user group using a user computer system. The content information is then communicated to the other members of the virtual user group and can be accessed by members of the virtual user group in such a manner that the privacy of the user and of the other members of the virtual user group is not compromised. The present invention preserves user privacy by controlling and minimizing the amount of user-related information available / accessible to server systems hosting the virtual user groups.
Owner:MICRO FOCUS LLC
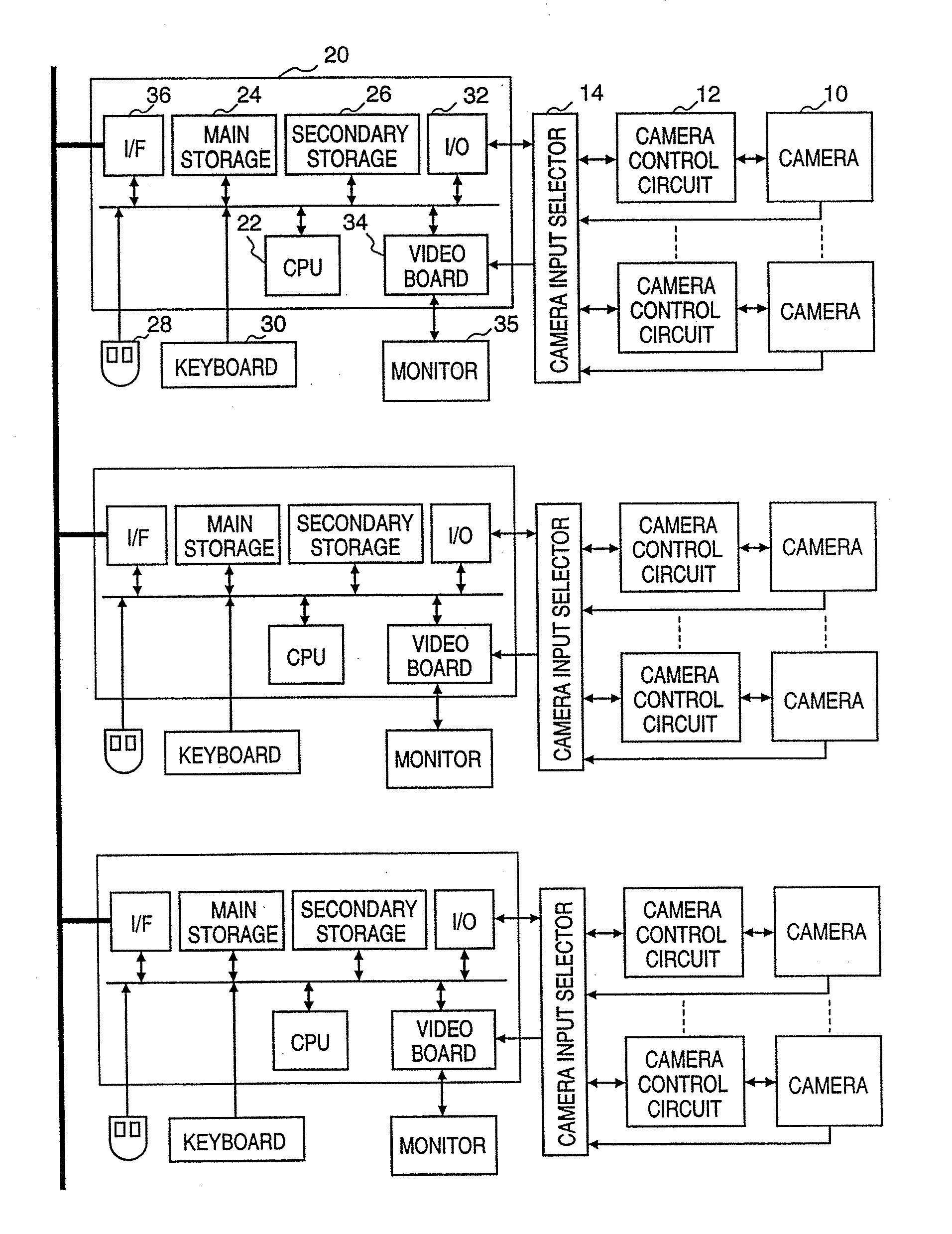
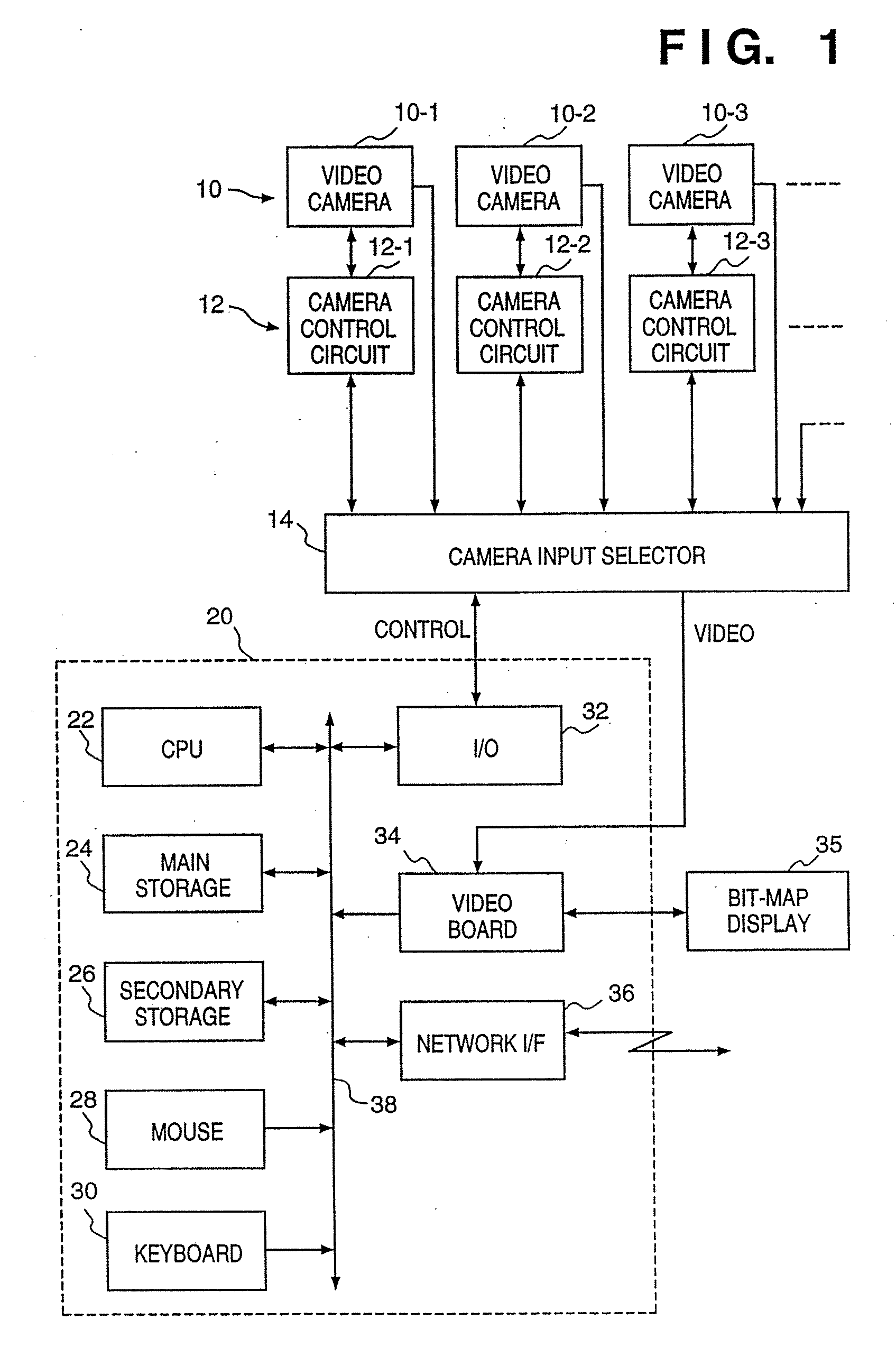
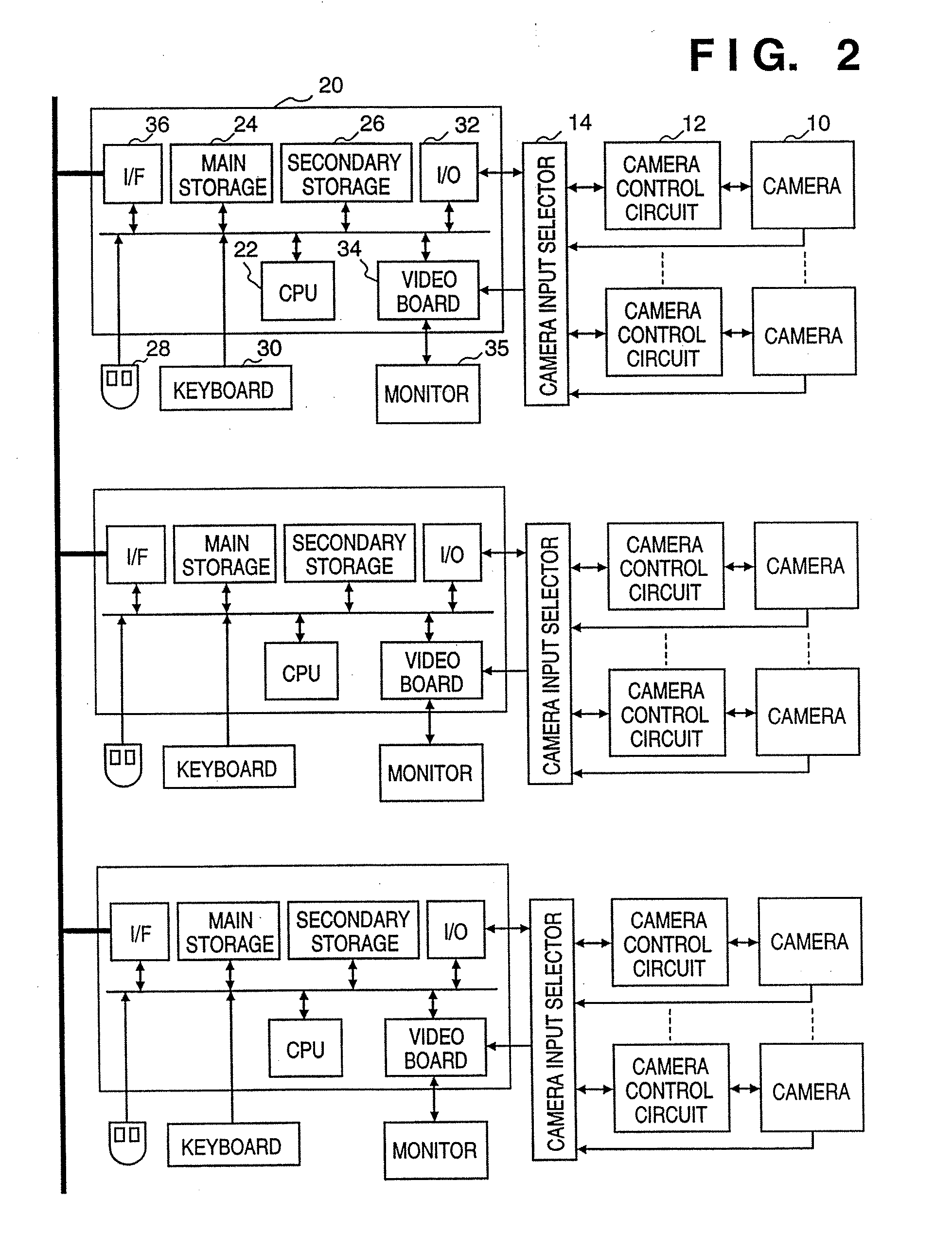
Image input system
InactiveUS20070097460A1Protect user privacyEasy to operateTelevision system detailsColor television detailsVideo cameraView angle
This invention provides an image input system capable of setting an arbitrary imaging inhibited area. This system displays a map showing the positions of cameras arranged in an office and the directions in which these cameras can be aimed, or displays the view angles of the cameras. An operator designates an imaging inhibited area on the map. In accordance with the designated imaging inhibited area, a limiting direction is calculated for each camera, and each camera is so controlled as not to point in that direction. Even when cameras are fixed, the system controls display so that an imaging inhibited area is not displayed.
Owner:CANON KK
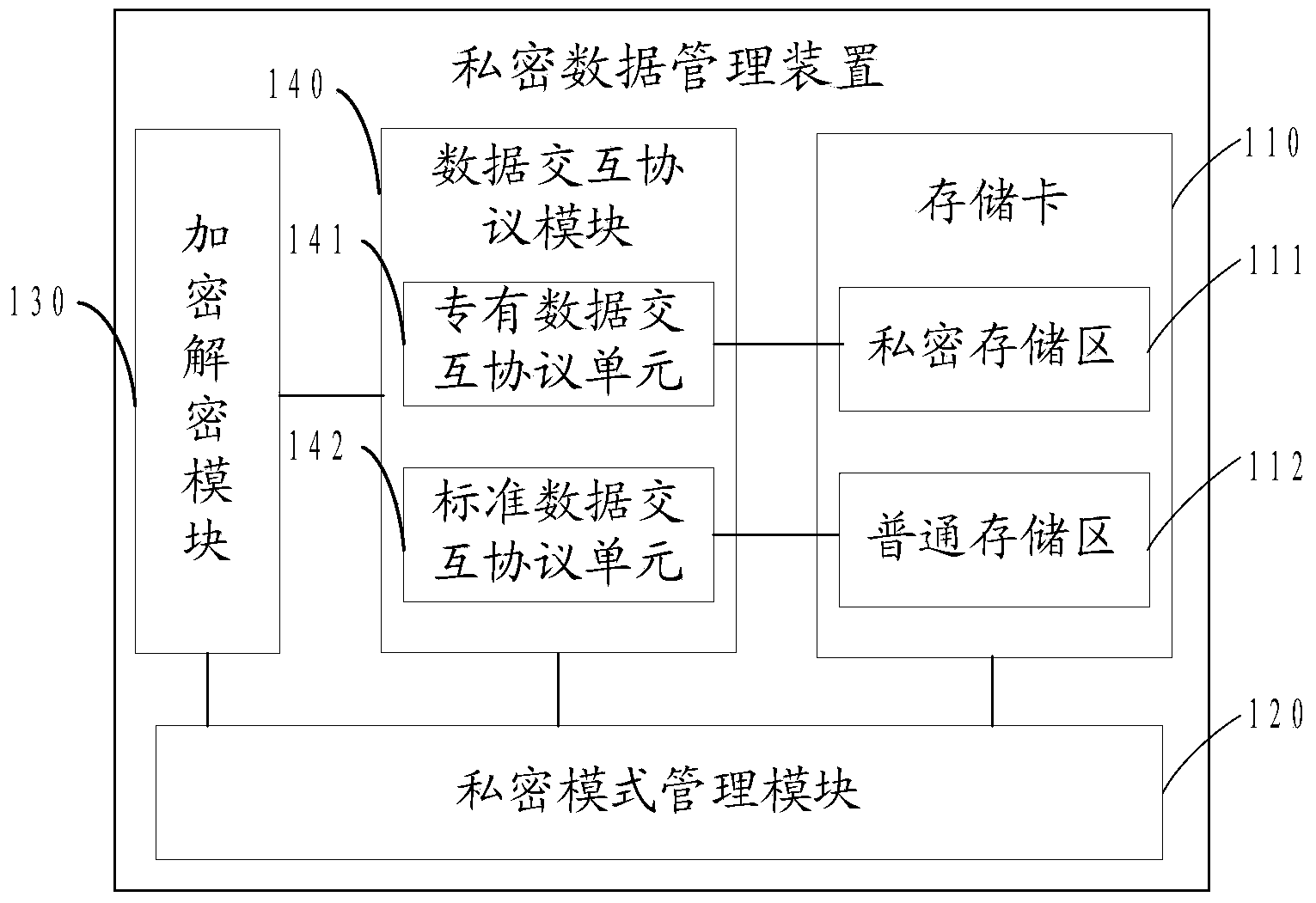
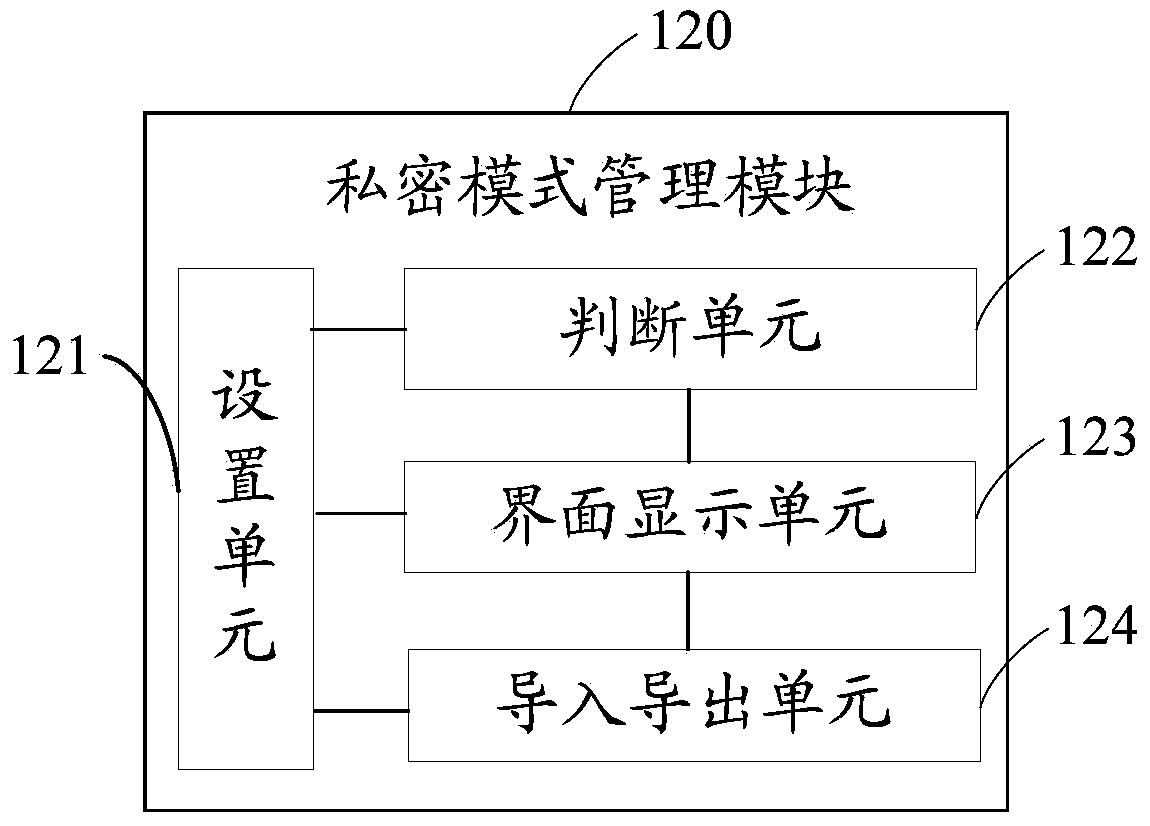
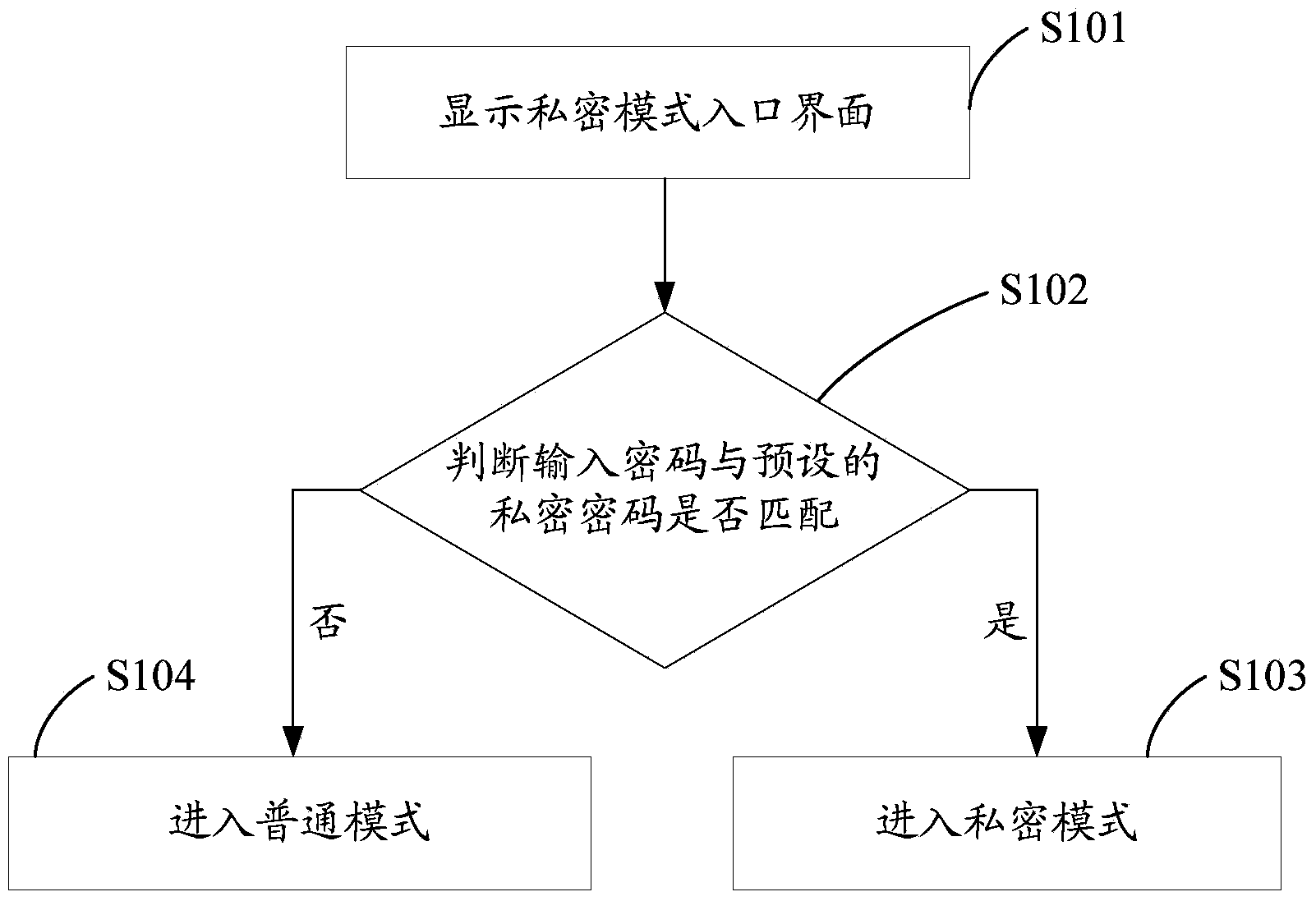
Secret data management device and secret data management method as well as mobile terminal
InactiveCN103413102AProtect user privacyImprove securityDigital data protectionSubstation equipmentPoint of entryInteraction protocol
The invention discloses a secret data management device and a secret data management method as well as a mobile terminal. The secret data management device comprises a storage card, a data interaction protocol module and a secret mode management module, wherein the storage card comprises a secret storage region for storing secret data and an ordinary storage region for storing ordinary data; the secret mode management module is used for displaying a secret mode inlet interface and judging whether codes input into the secret mode inlet interface are matched with the preset secret codes or not, if the input codes are matched with the preset secret codes, the secret mode management module enters a secret mode, and the secret data of the secret storage region is displayed; and the data interaction protocol module comprises a specific data interaction protocol unit and a standard data interaction protocol unit, the specific data interaction protocol unit is used for processing the secret data of the secret storage region in the secret mode, and the standard data interaction protocol unit is used for processing the ordinary data of the ordinary storage region in an ordinary mode.
Owner:NUBIA TECHNOLOGY CO LTD
Method and apparatus for obtaining consumer product preferences through interactive product selection and evaluation
InactiveUS7979314B2Facilitates taskProtect user privacyDigital data information retrievalSpecial data processing applicationsProduct selectionWorld Wide Web
A method and system for obtaining consumer preferences over a communication network from consumers. The system searches the product database for products or services based on consumer's search criteria. The system displays the products or services and / or advertisements related to the consumer's search criteria in accordance with the ranking parameter(s) specified by the user. The consumer's preferences, i.e., the search criteria and the ranking parameter(s), are stored in the database for future references, e.g., determine consumer trends, etc.
Owner:III HLDG 1
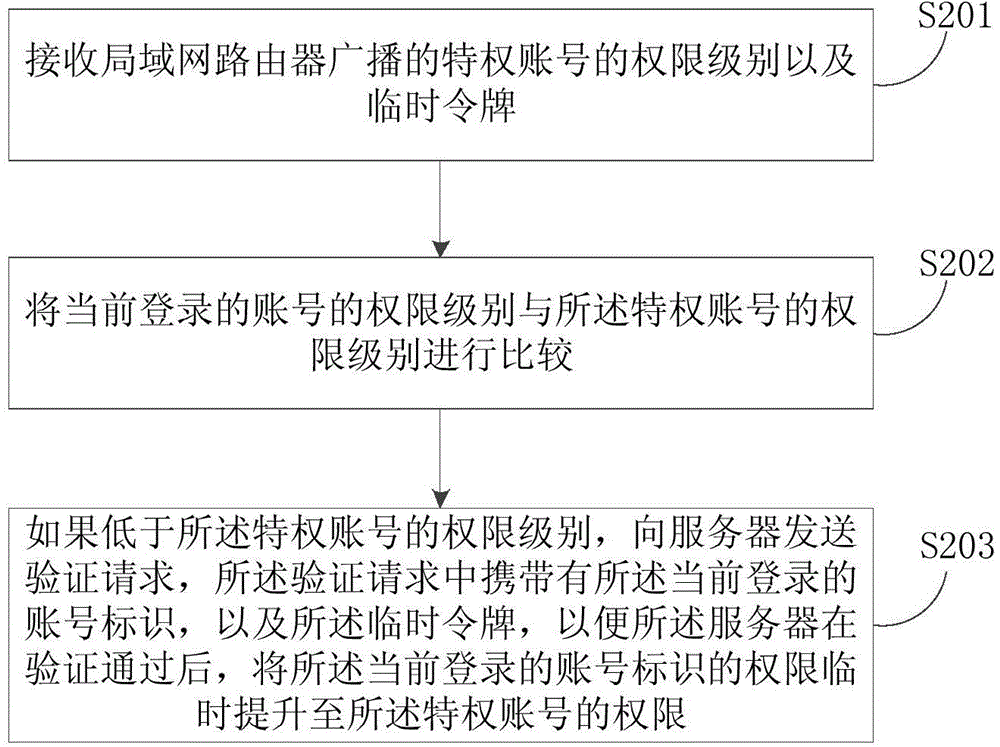
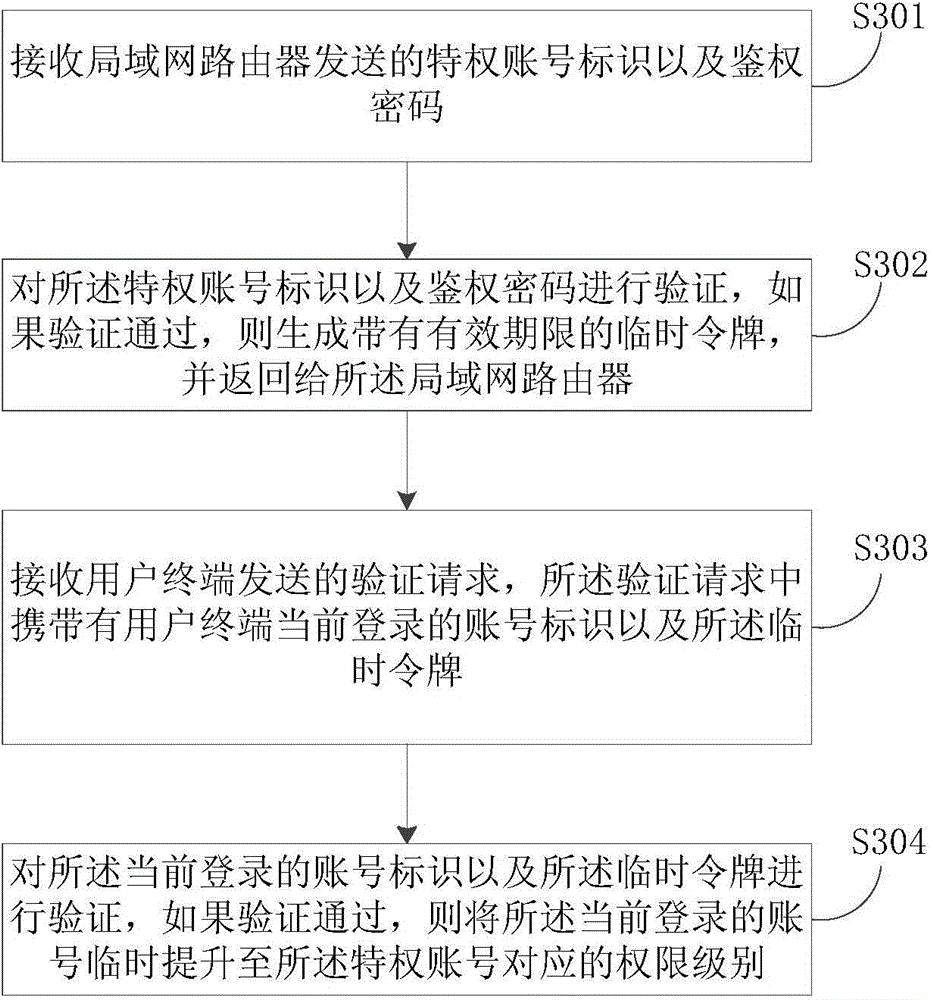
Account number permission control method and device
ActiveCN104702415AProtect user privacyImprove safety and convenienceUser identity/authority verificationUser privacyLocal memories
The embodiment of the invention discloses an account number permission control method and device. The account number permission control method comprises the steps of determining a privilege account number accessed to a current local area network and obtaining the permission level of the privilege account number and an authentication password; sending a privilege account number identification and the corresponding authentication password to a server to perform verification, and returning a temporary token marked with expiry date through the server if the verification is passed; receiving the temporary token returned by the server and then saving the temporary token in a local memory, and broadcasting the permission level of the privilege account number and the temporary token at regular intervals, so that the temporary token is utilized to request the server to temporarily improve the permission level of the temporary token to the permission level of the privilege account number if the permission level of the currently logined account number is lower than that of the privilege account number after a user terminal receives a broadcasting message. By means of the account number permission control method and device, the privacy of a user is protected, and safety and convenience are improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
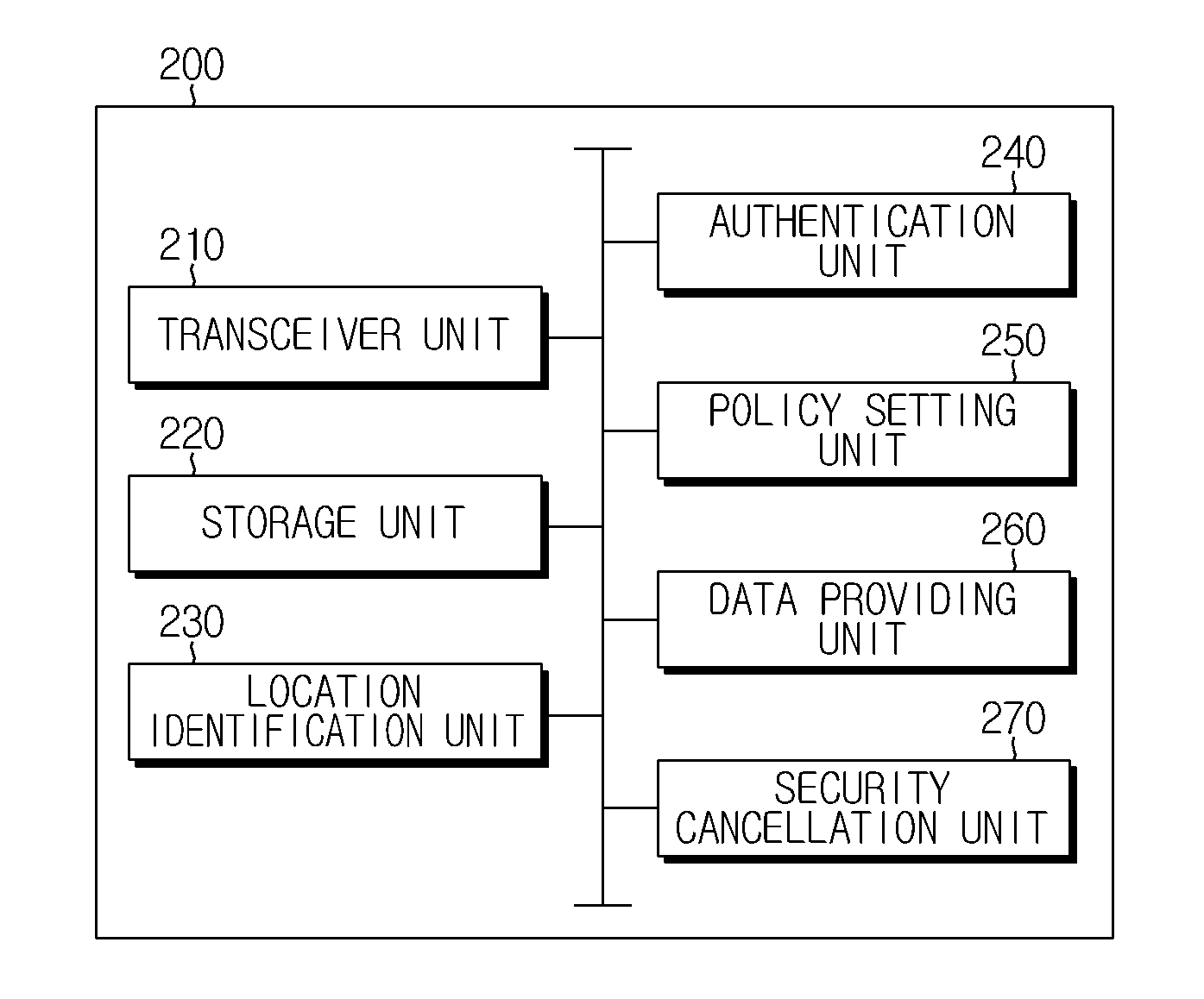
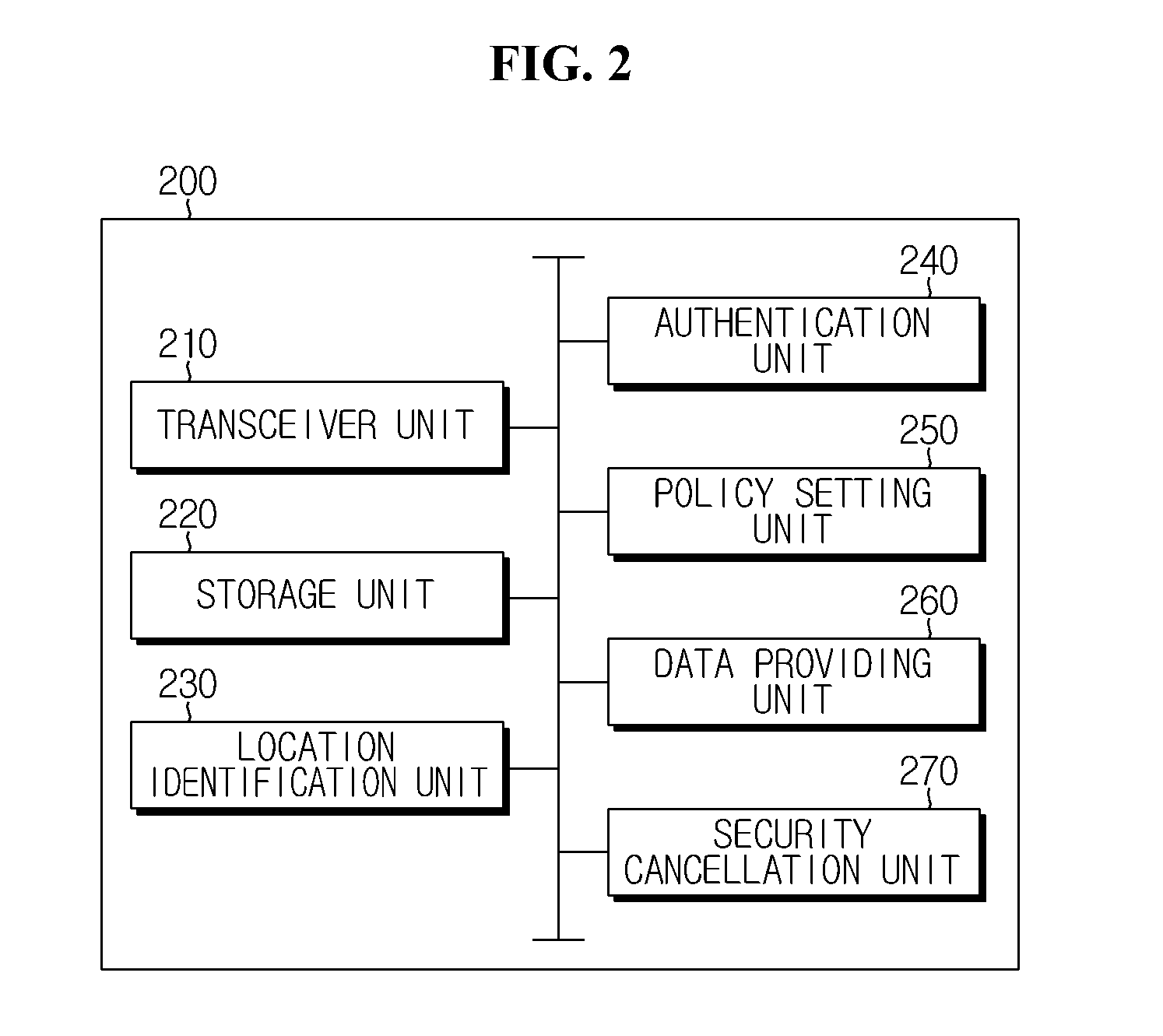
Method of Controlling Access to Network Drive, And Network Drive System
ActiveUS20150341359A1Improve securityProtect user privacyDigital data processing detailsDigital data protectionData storingCommunication device
A network drive system for controlling access to a network drive based on location information on a communication device according to the present technology includes: a storage unit storing a network drive that stores security data and general data; a receiving unit receiving a request for access to the network drive from a first communication device; a location checking unit checking whether the distance between the first communication device and a second communication device designated as a device for controlling access to the network drive is within a critical value; and a policy setting unit that applies a policy allowing the first communication device to access general data stored in the network drive or applies a policy disallowing the first communication device to access general data stored in the network drive, according to results of the determining by the location checking unit.
Owner:FACECON
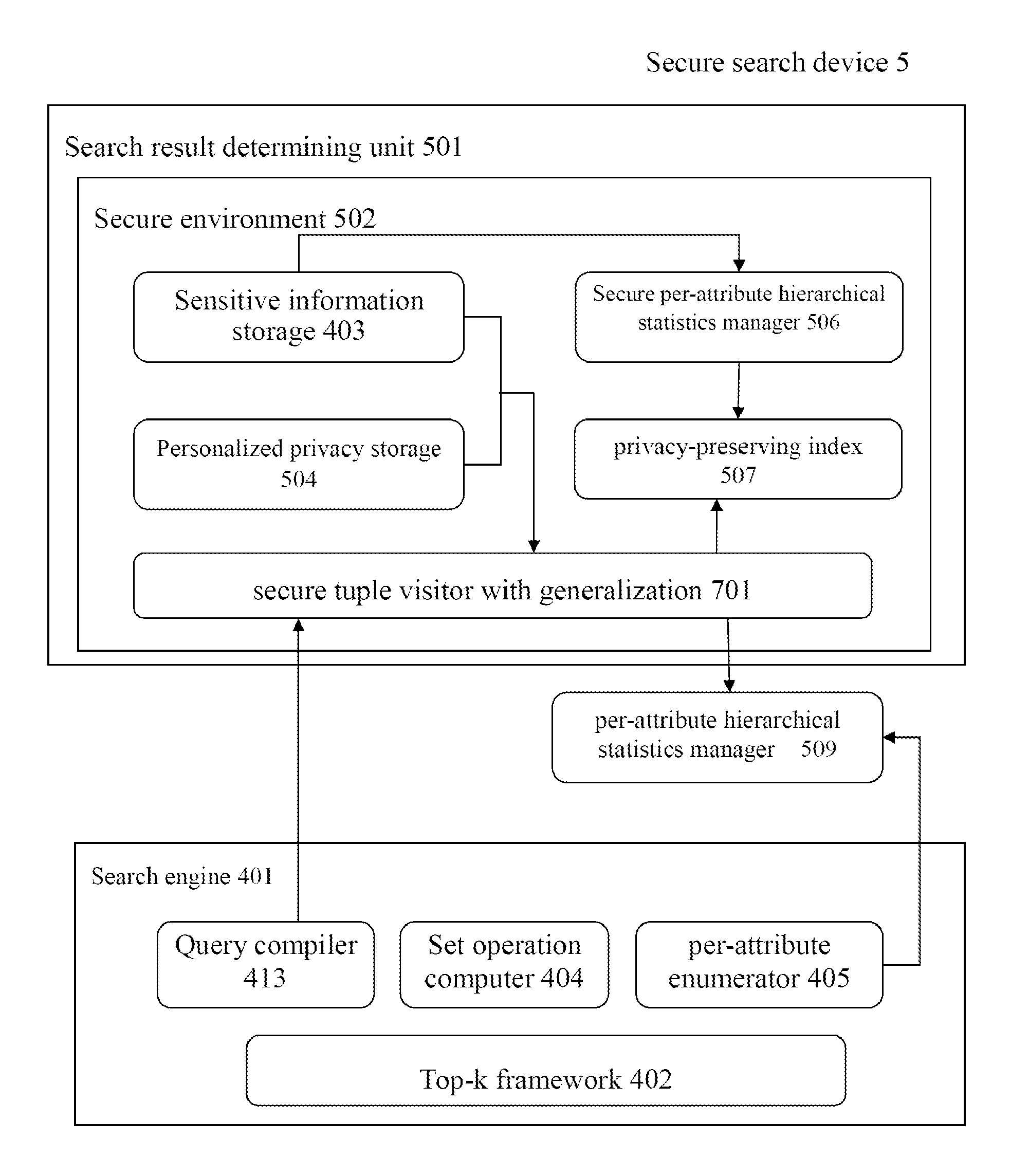
Secured searching
InactiveUS20130054554A1Protect user privacyDigital data information retrievalDigital data processing detailsInformation retrievalComputer device
A method and system for a secured search. The method includes the steps of: receiving a search request from a searching user; determining search results to be returned to the searching user based on a security schema; and returning the search results to the searching user, where at least one of the steps is carried out by using a computer device.
Owner:IBM CORP
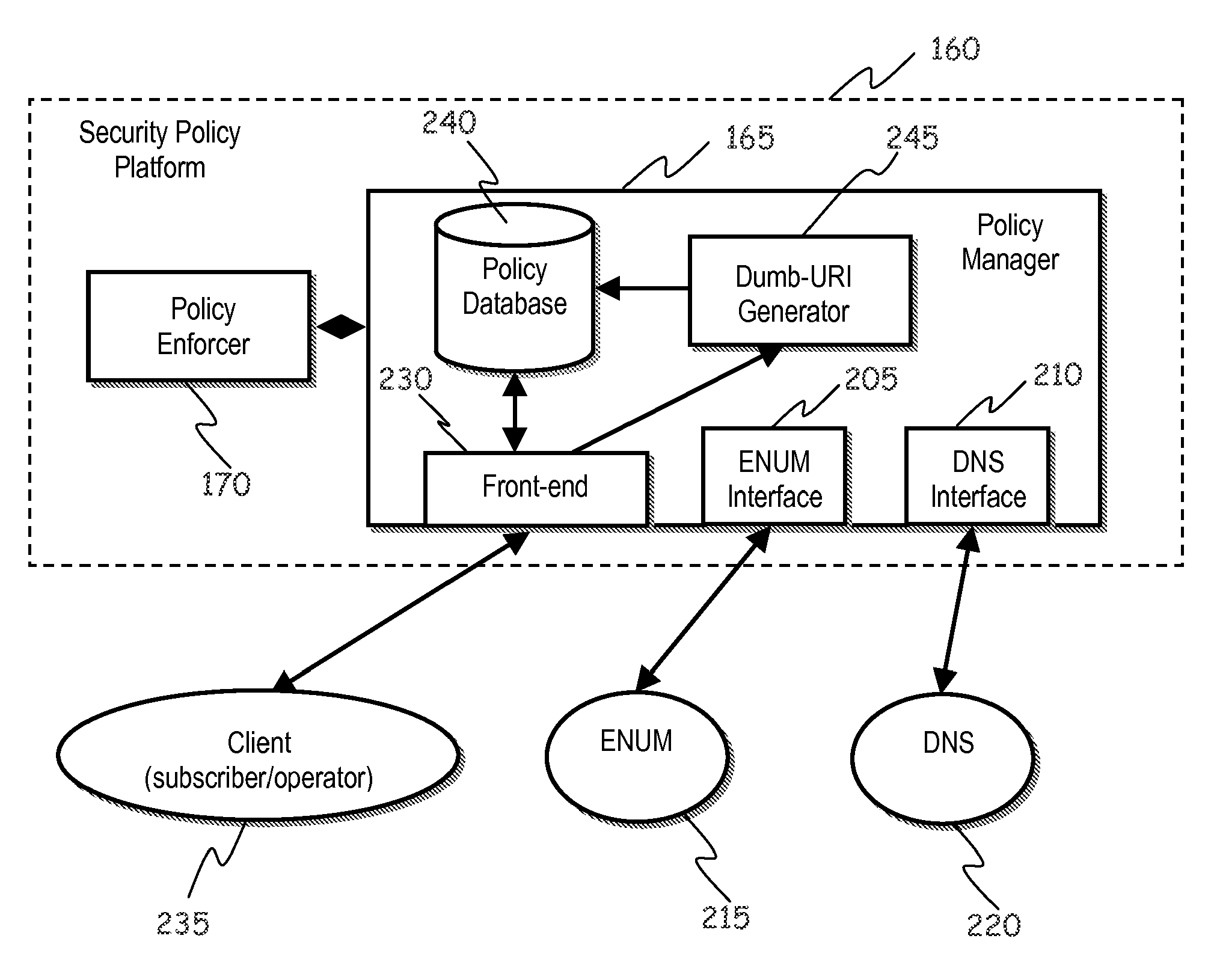
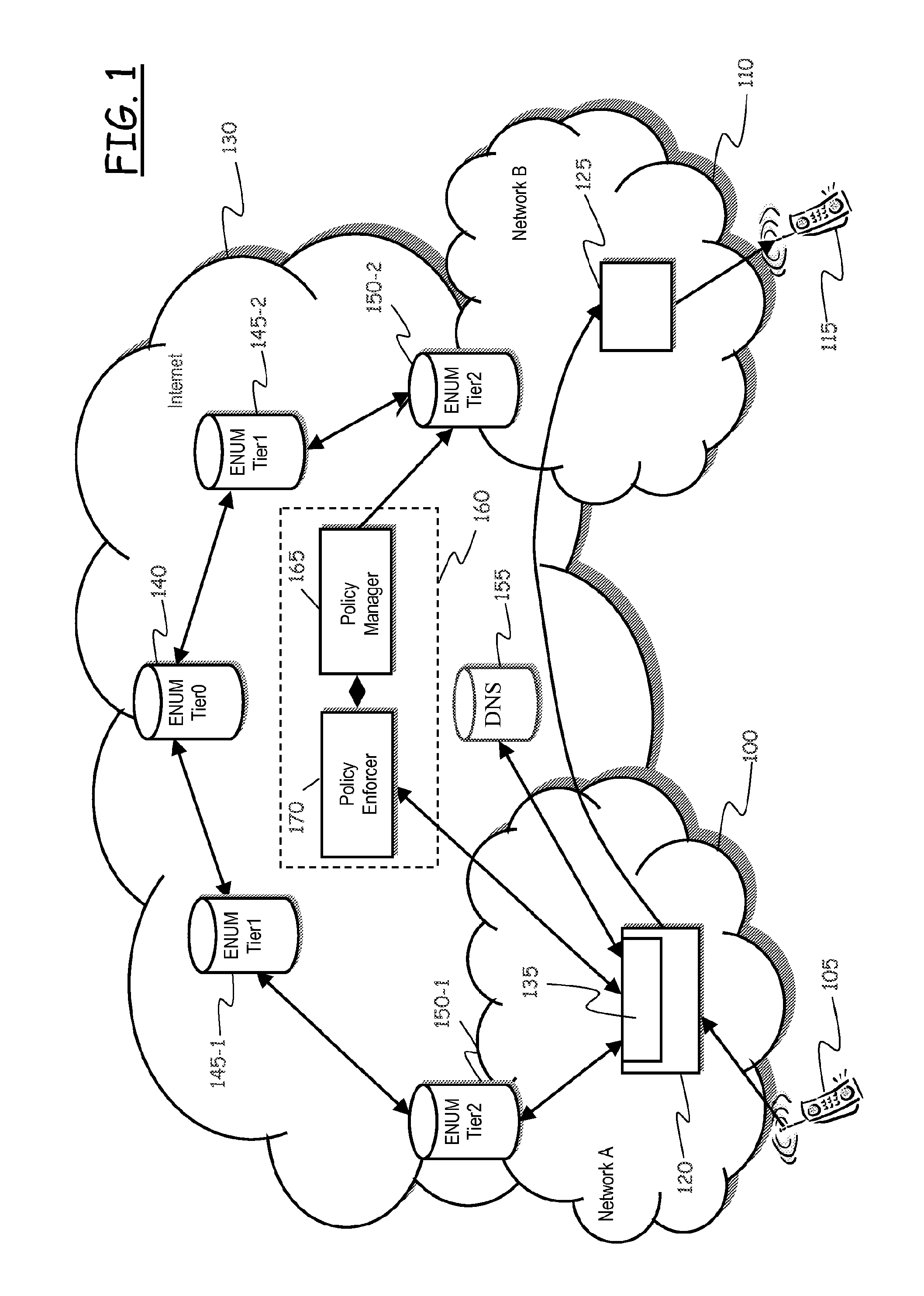
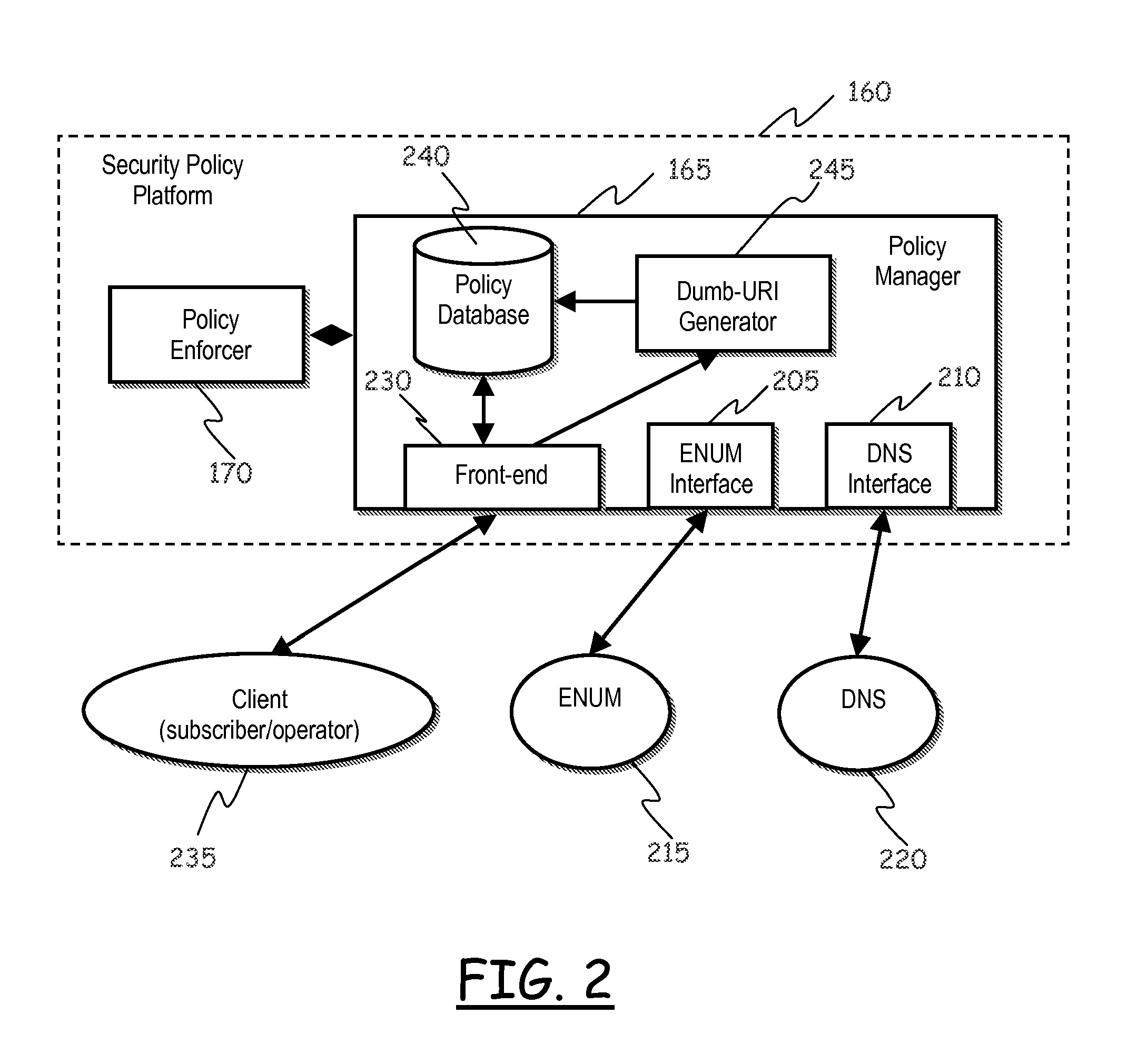
Enhancing ENUM Security
ActiveUS20110016145A1Guaranteed privacyProtect user privacyInterconnection arrangementsDigital data processing detailsThe InternetTelenet
A method of providing telecommunication services includes generating a fictitious contact information univocally associated with a telephone number assigned to a subscriber; and storing the fictitious contact information in a database, like an ENUM database. Responsive to a request, received from a requester, of a contact information corresponding to the telephone number and adapted to allow contacting over the Internet the subscriber assignee of the telephone number, the method includes having the database providing the fictitious contact information; and conditioning a resolution of the fictitious contact information for the provisioning of the contact information to the satisfaction of at least one security rule adapted to assess properties of at least one among the requester and the request. In a case that the request from the requester satisfies the at least one security rule, the method resolves the fictitious contact information and provides the requester with the contact information.
Owner:TELECOM ITALIA SPA
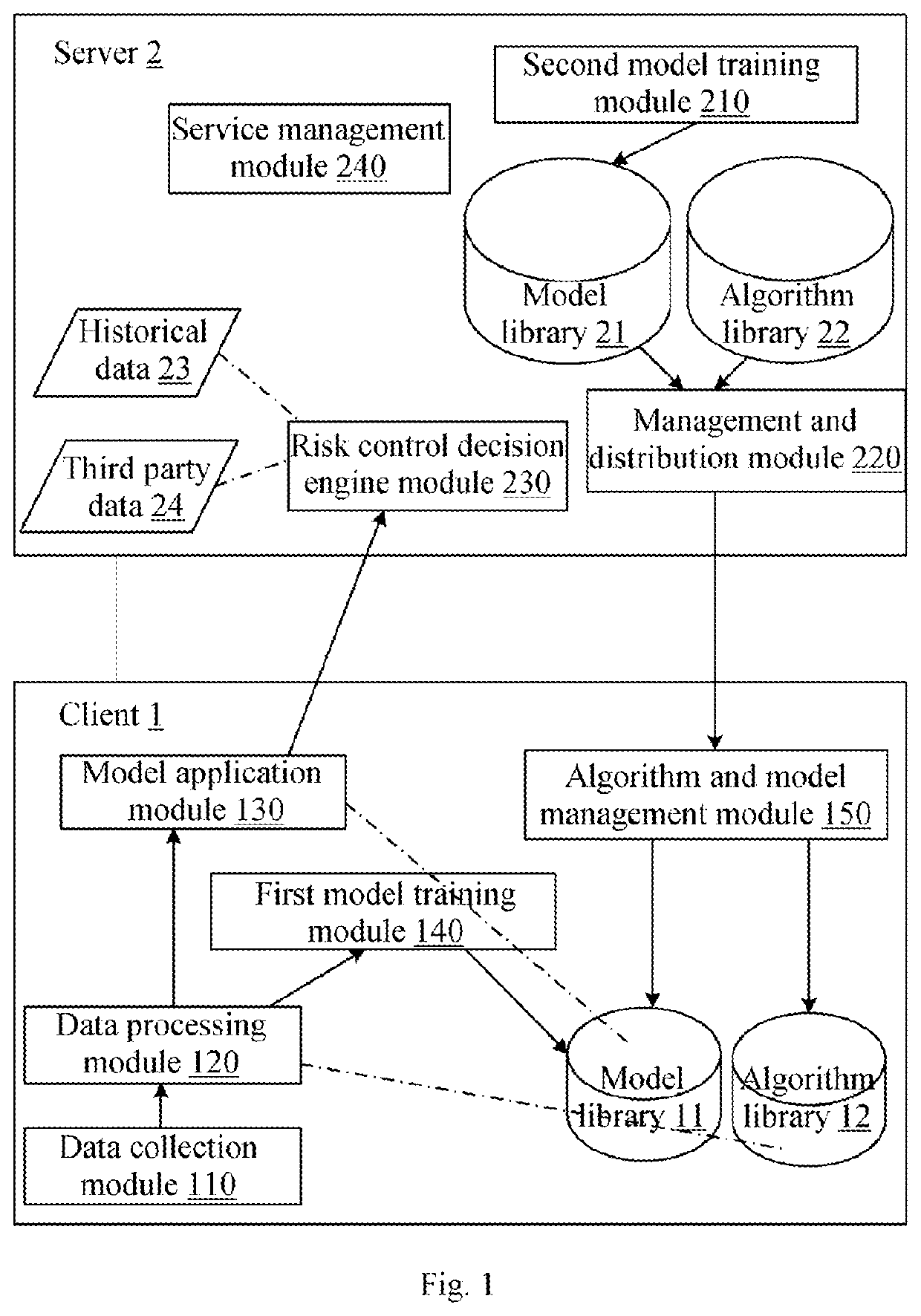
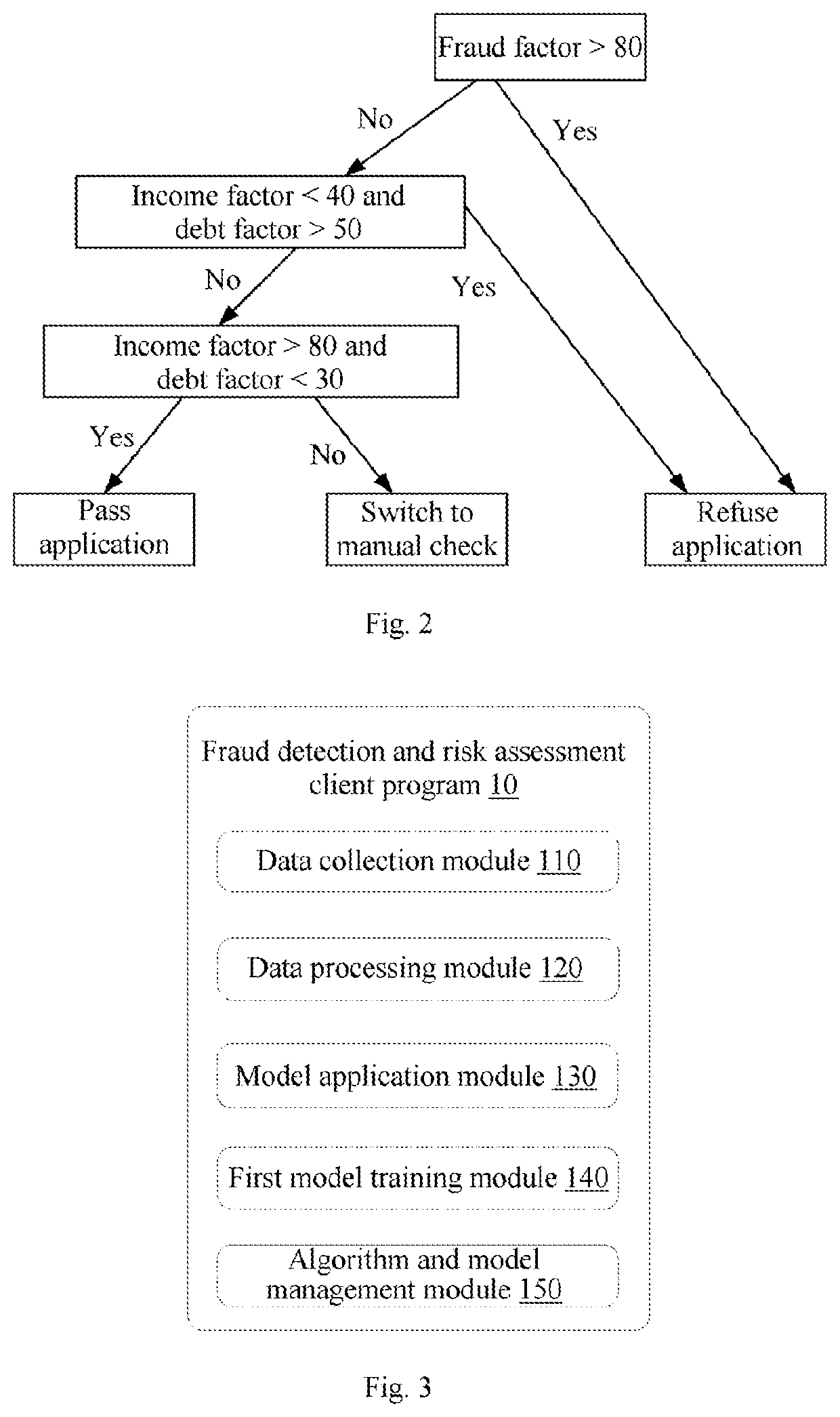
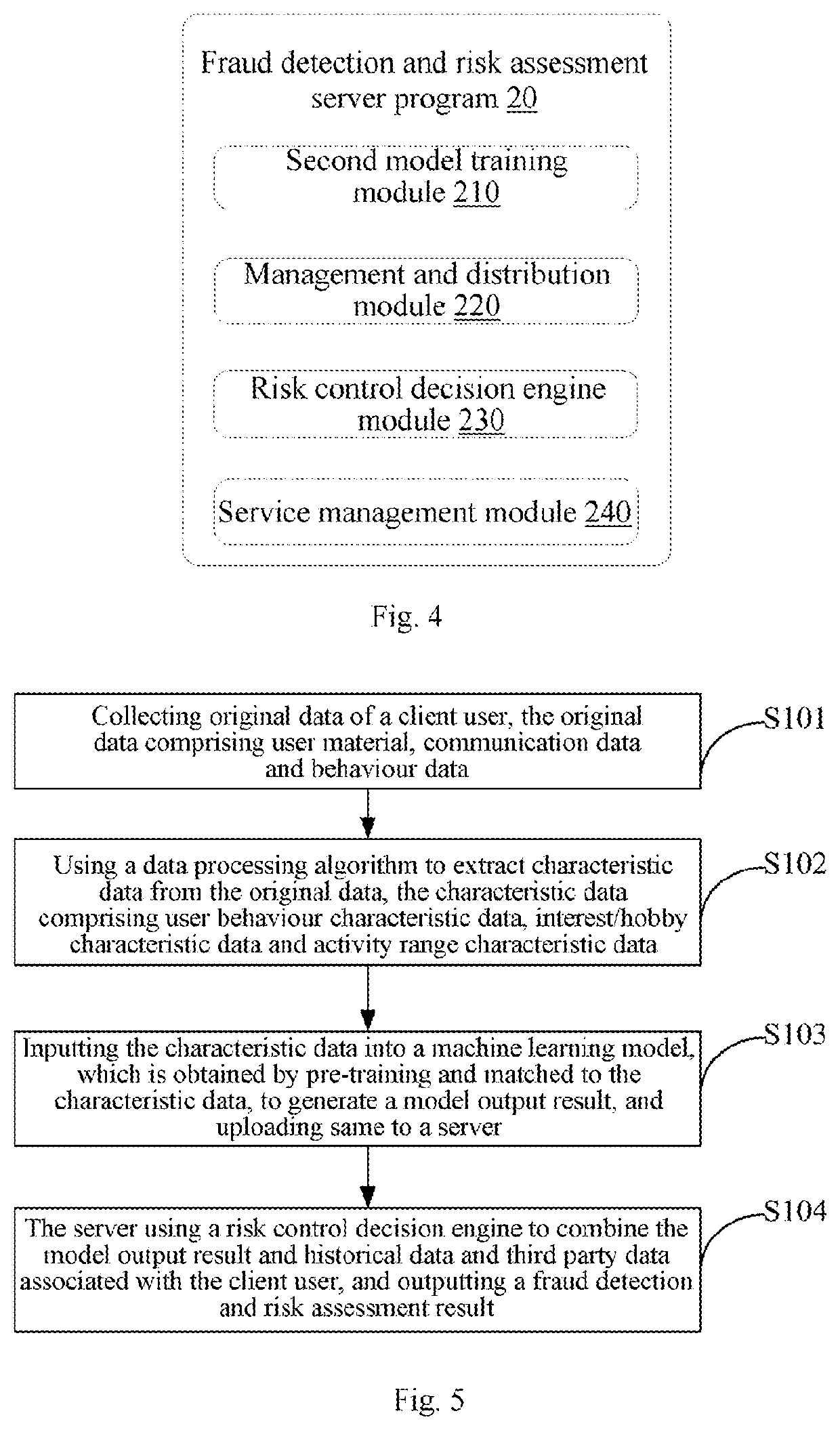
Fraud detection and risk assessment method, system, device, and storage medium
PendingUS20210019657A1Protect user privacyAlleviate the pressure of data transmissionEnsemble learningVersion controlOriginal dataReliability engineering
The present application provides a fraud detection and risk assessment method, a system, a device, and a computer readable storage medium. Said method comprises the following steps: acquiring original data of a client user; using a data processing algorithm to extract characteristic data from the original data; inputting the characteristic data into a pre-trained machine learning model matching the characteristic data, generating a model output result, and uploading same onto a server; and outputting a fraud detection and risk assessment result using a risk control decision engine in conjunction with the model output result, historical data associated with the client user, and third party data. By using the present application, the computing capability of a client device can be fully utilized, reducing the computing pressure on the server. As the client does not need to upload the original data to the server, the present application can also reduce the data transmission pressure on the client and the server and reduce the risk of leakage of the user's private data and security information.
Owner:WELAB INFORMATION TECH SHENZHEN LTD
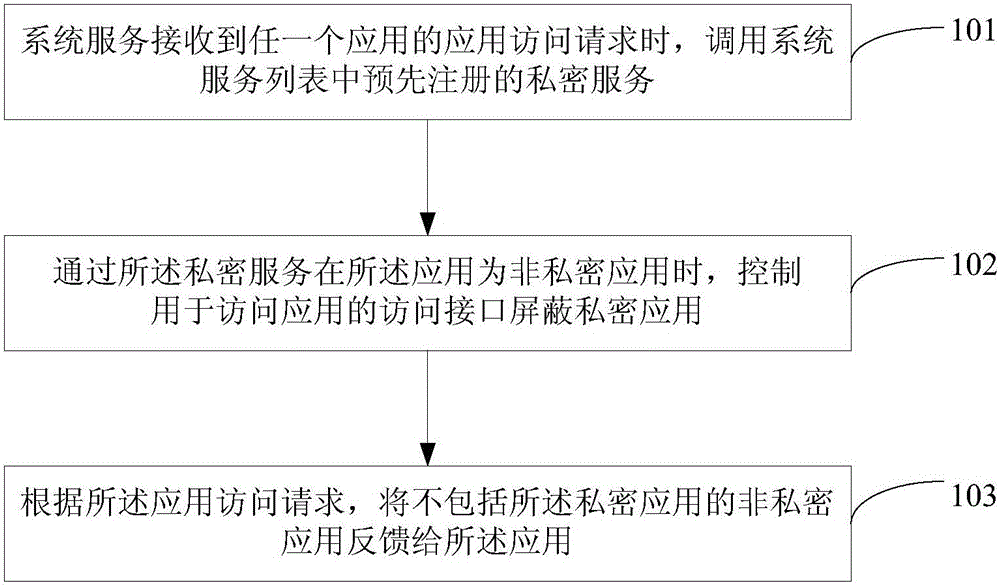
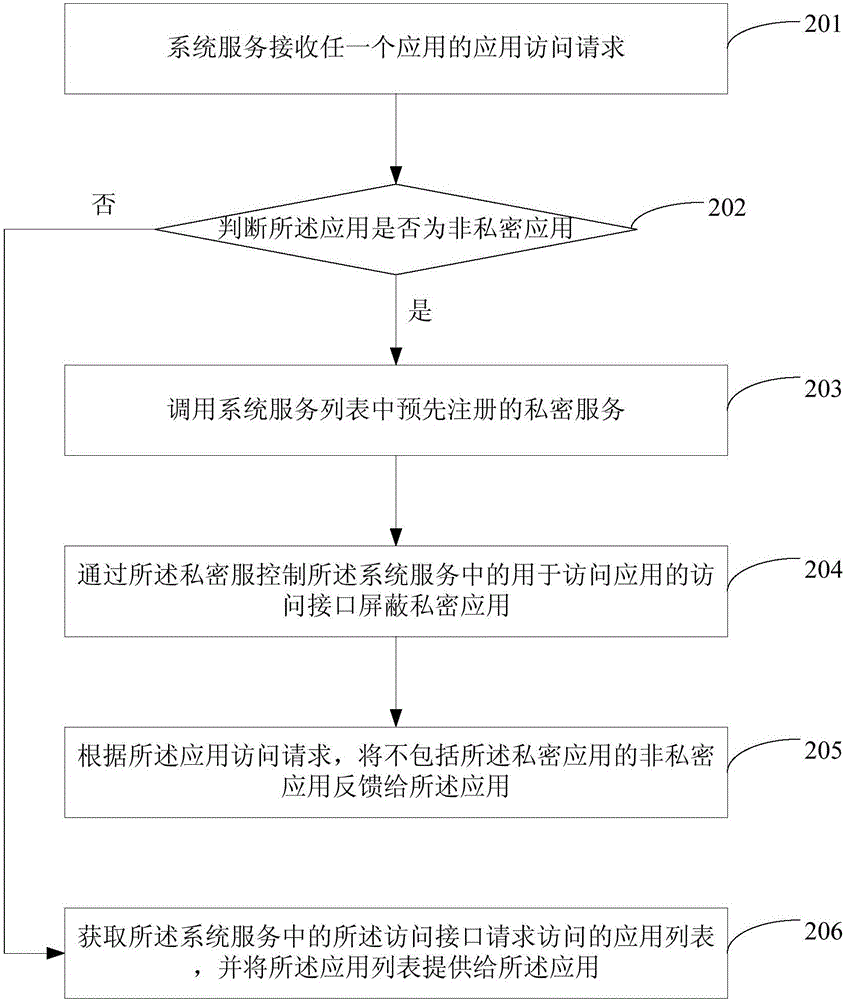
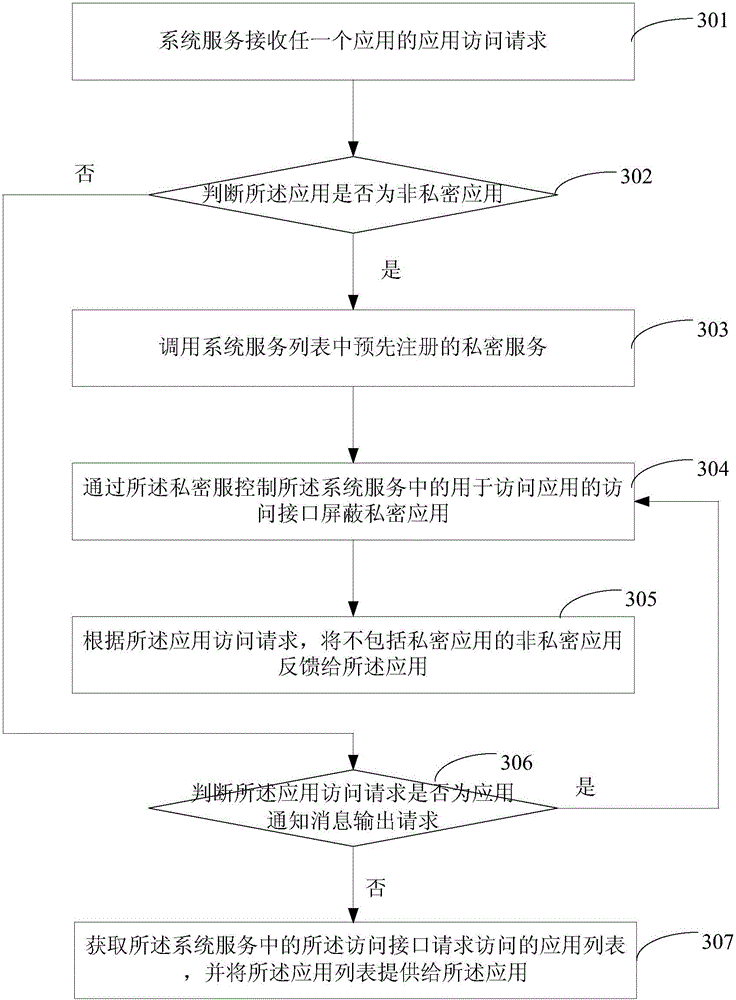
Application access control method and device
The embodiment of the invention provides an application access control method and an application access control device. The method comprises the steps of when a system service receives an application access request of any application, calling a pre-registered private service in a system service list; when the application where the private service is located is the non-private application, controlling an access interface, used for accessing the application, in the system service to shield the private application, wherein the private application is the application, requested by a user to be hidden according to a hiding request of the user, determined by the private service; and feeding the non-private application not including the private application back to the application according to the application access request. According to the method provided by the embodiment of the invention, the non-private application cannot access the private application in any case, thus the user privacy is effectively protected, and the security is improved.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
Method and system for located tracking and warning of mobile terminal group
InactiveCN1571553AProtect user privacyReduce intermediate linksPosition fixationTelephonic communicationApplication serverBackground information
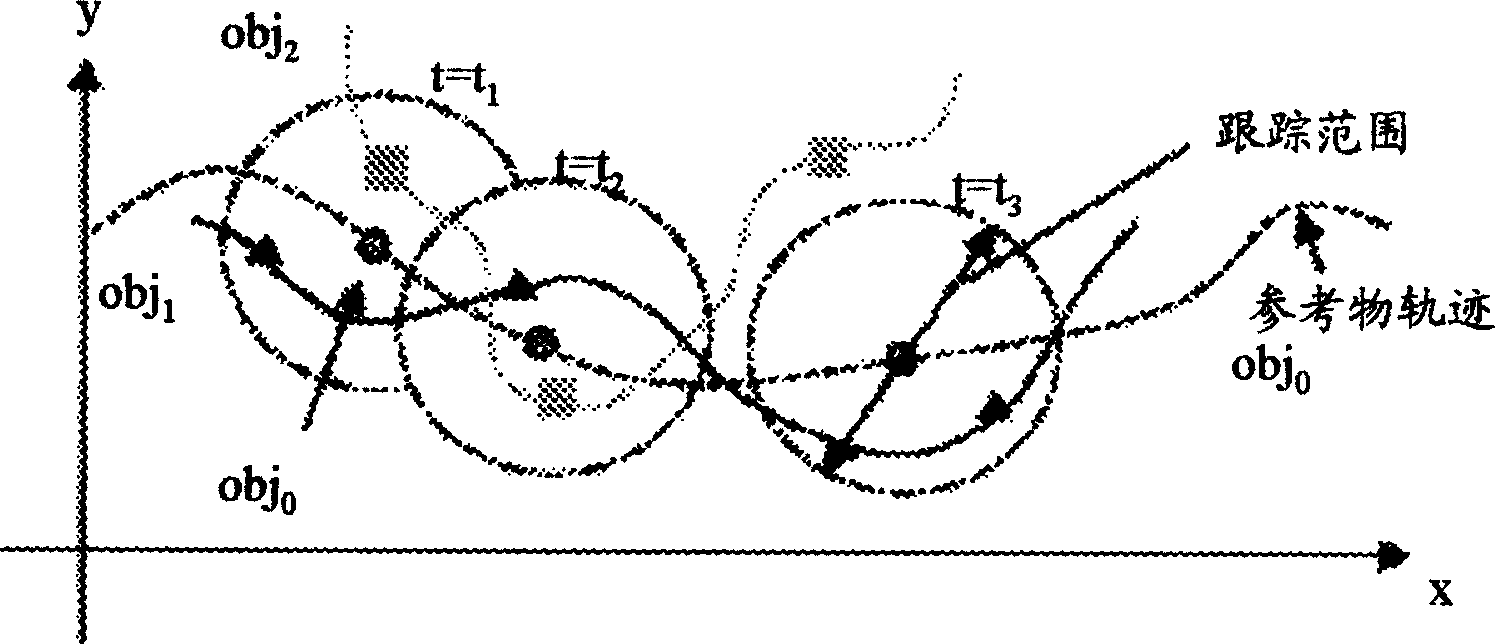
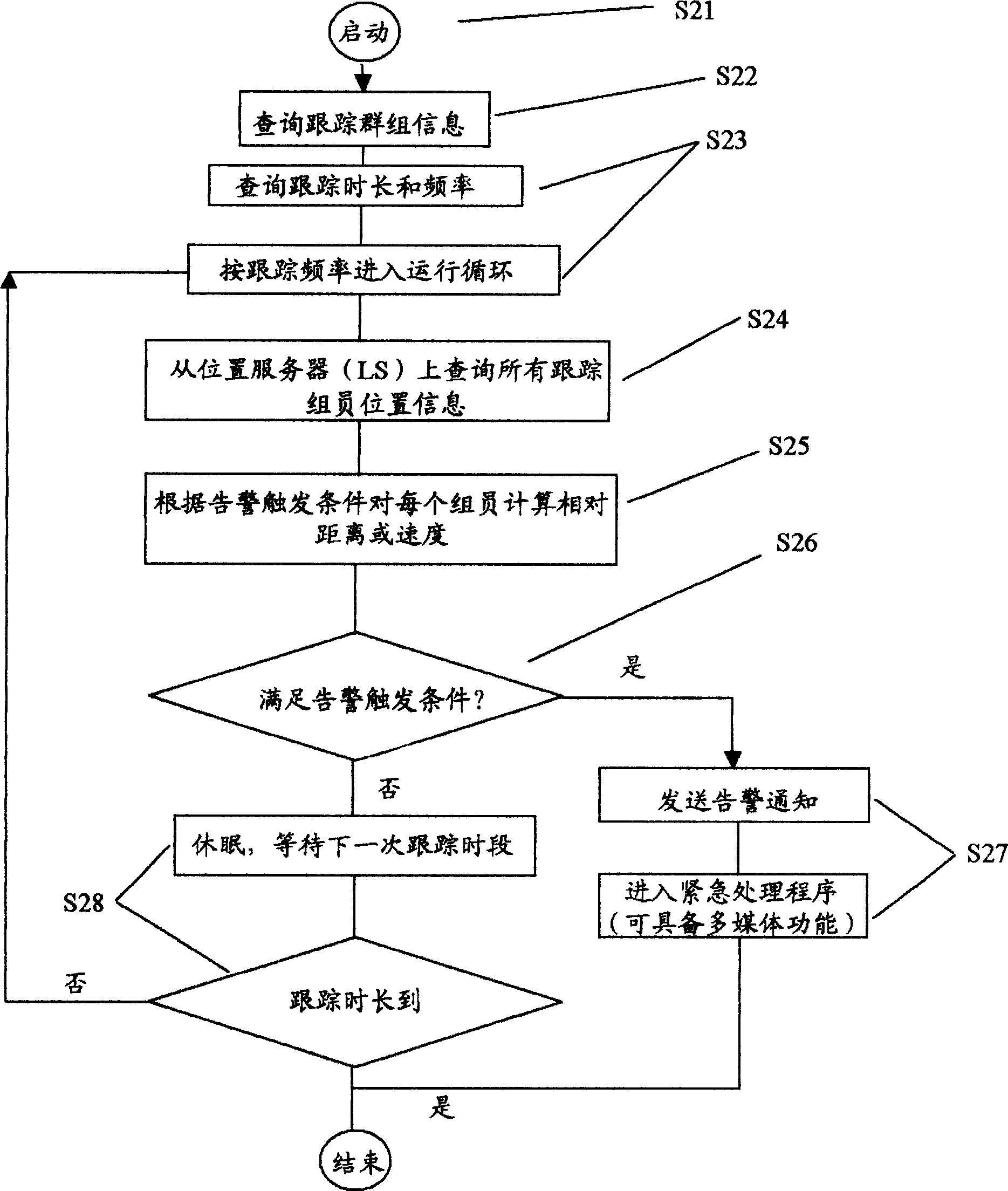
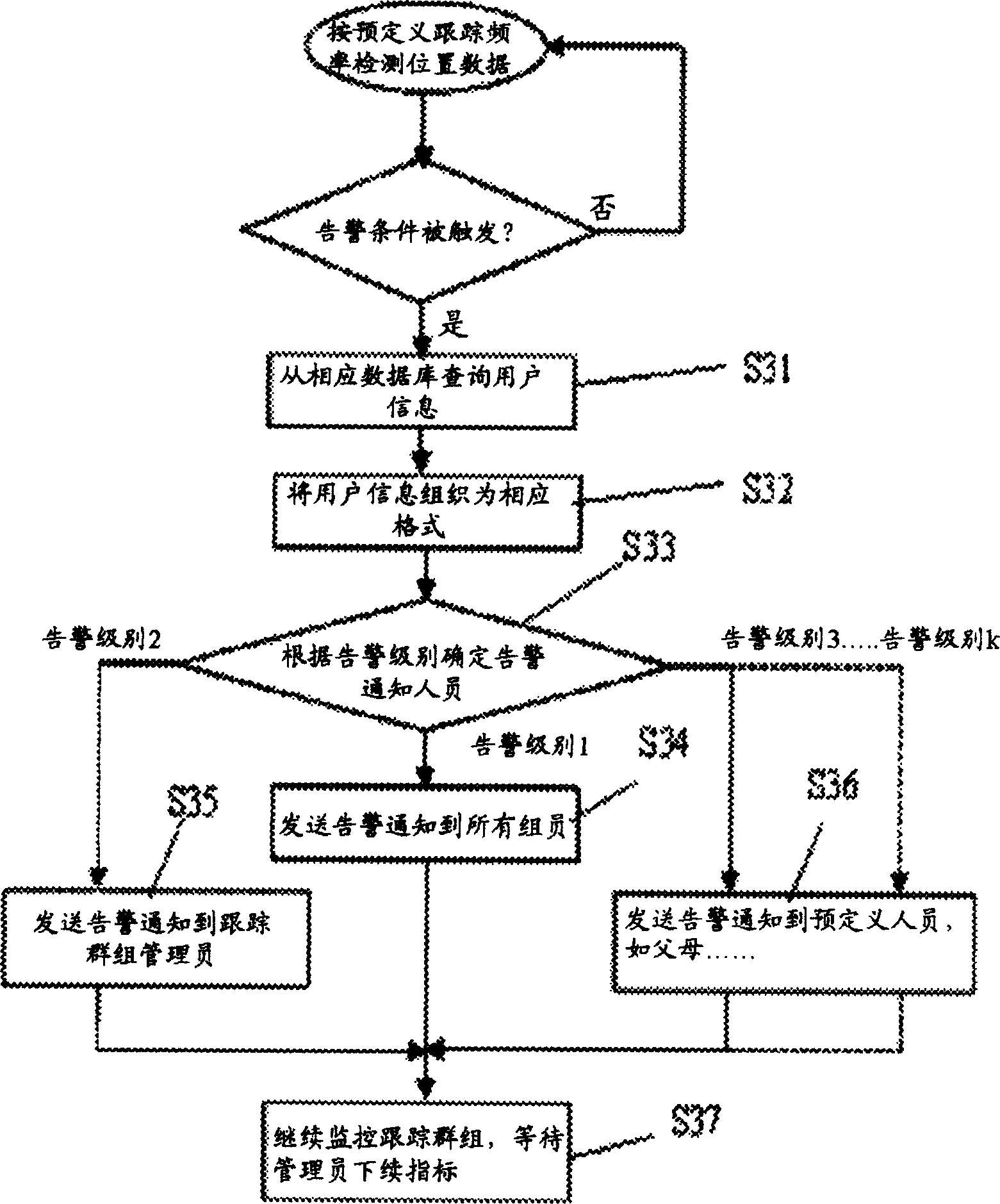
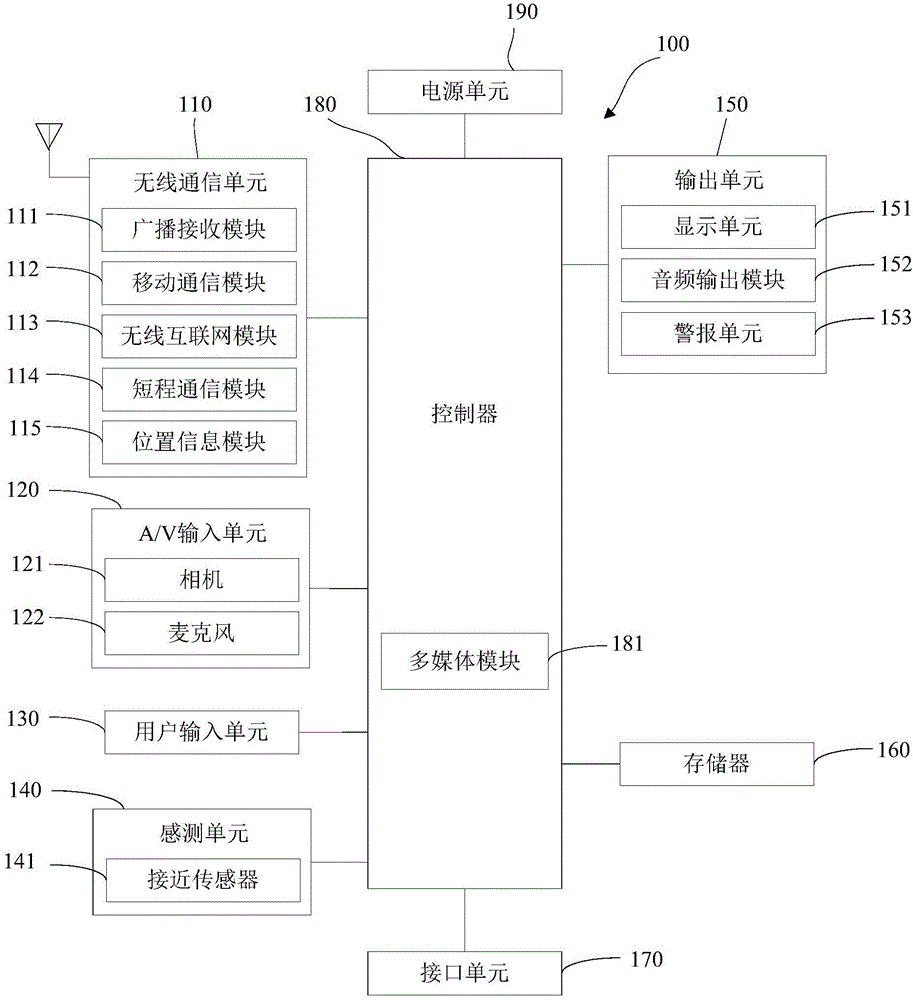
This invention is a position tracking alarm method of mobile terminal groups. A concept group is built and the parameters are given. Several mobile targets are invited to join in the group. Tracking monitoring service is started to inquire the background information and current position of the tracked target. Then result is got after computing according to the local position information and alarm toggle condition to judge whether to alarm. Emergency processing mechanism is started when alarm toggle condition is sufficient. If it doesní»t meet the alarm condition, then next tracking or finishing service is processed after a certain time. Multimedia and text mode are used to transmit information and emergency mechanism between members in the group. Software of position tracking alarm system of mobile terminal groups includes core business software package of position tracking alarm system, multimedia data base and mobile terminal adaptive software package. Hardware includes application server, wireless network, position server, database server and mobile terminal. Business software package is set in application server to get position information to compute from position server through application server, and send multimedia transfer instruction and text information through application server. Position server gets position information of the mobile terminal through wireless core network, and then sends the information to tracking alarm system.
Owner:吴坚
Projection processing method and apparatus, and terminal
ActiveCN106657651AProtect user privacyImprove user experienceSubstation equipmentSelective content distributionUser privacyDisplay device
The invention discloses a projection processing method. The method comprises the following steps: detecting a projection instruction of projecting a screen of a terminal to a display device for display; judging whether a running application of the terminal comprises a preset refusal projection content according to the projection instruction; and when the judgment result is yes, projecting the screen of the terminal to the display device for display after filtering the running application belonging to the preset refusal projection content in the terminal. The invention further discloses a projection processing apparatus and a terminal. The problem of user privacy leakage after the screen of the terminal is projected to the display device for display in the prior art is solved, and the user privacy contents are projected to the display device after being filtered so as to effectively improve the user privacy and enhance the user experience.
Owner:NUBIA TECHNOLOGY CO LTD
Authentication method, authentication system and authentication program
InactiveUS20140342701A1Protect user privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareUse of services
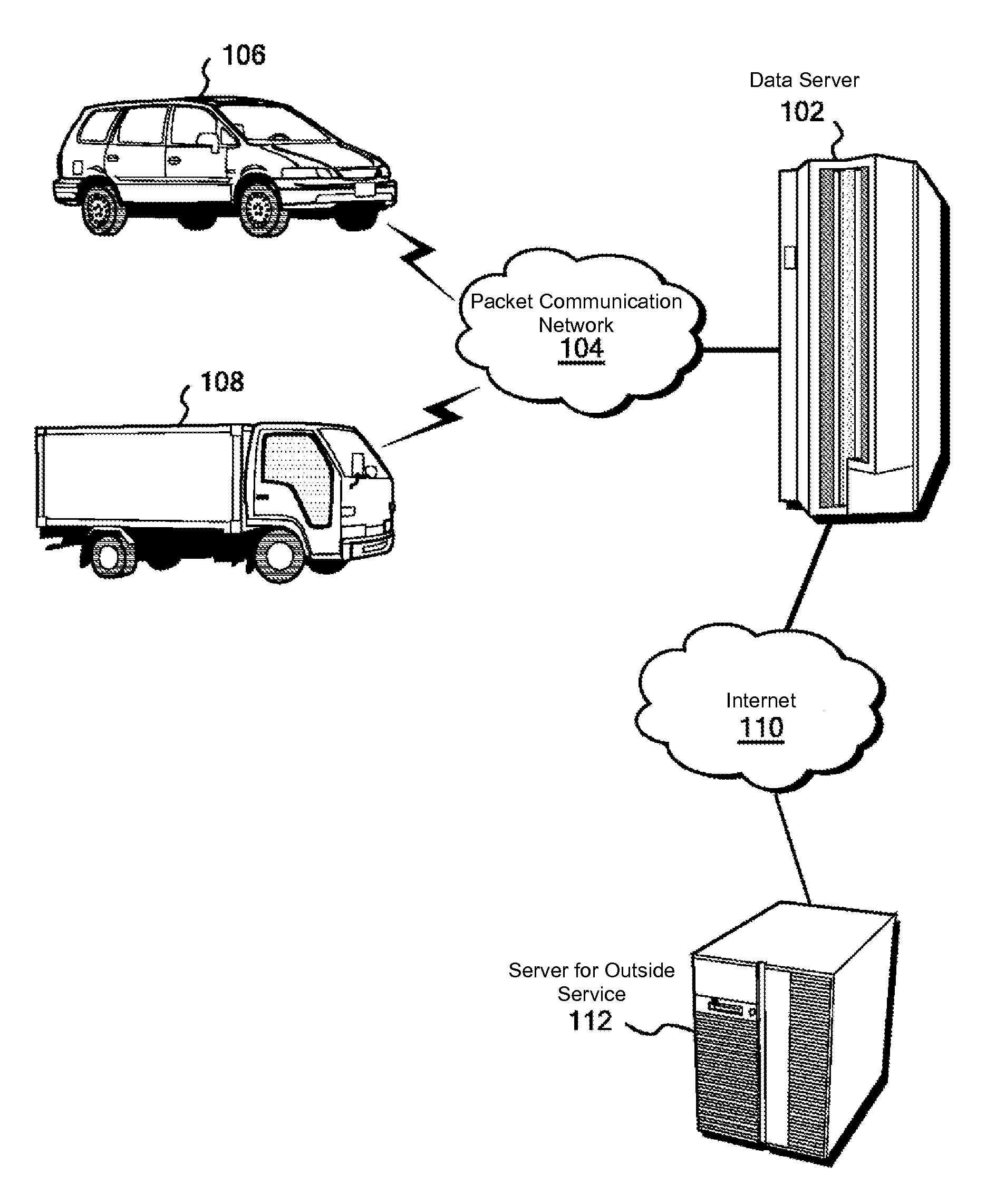
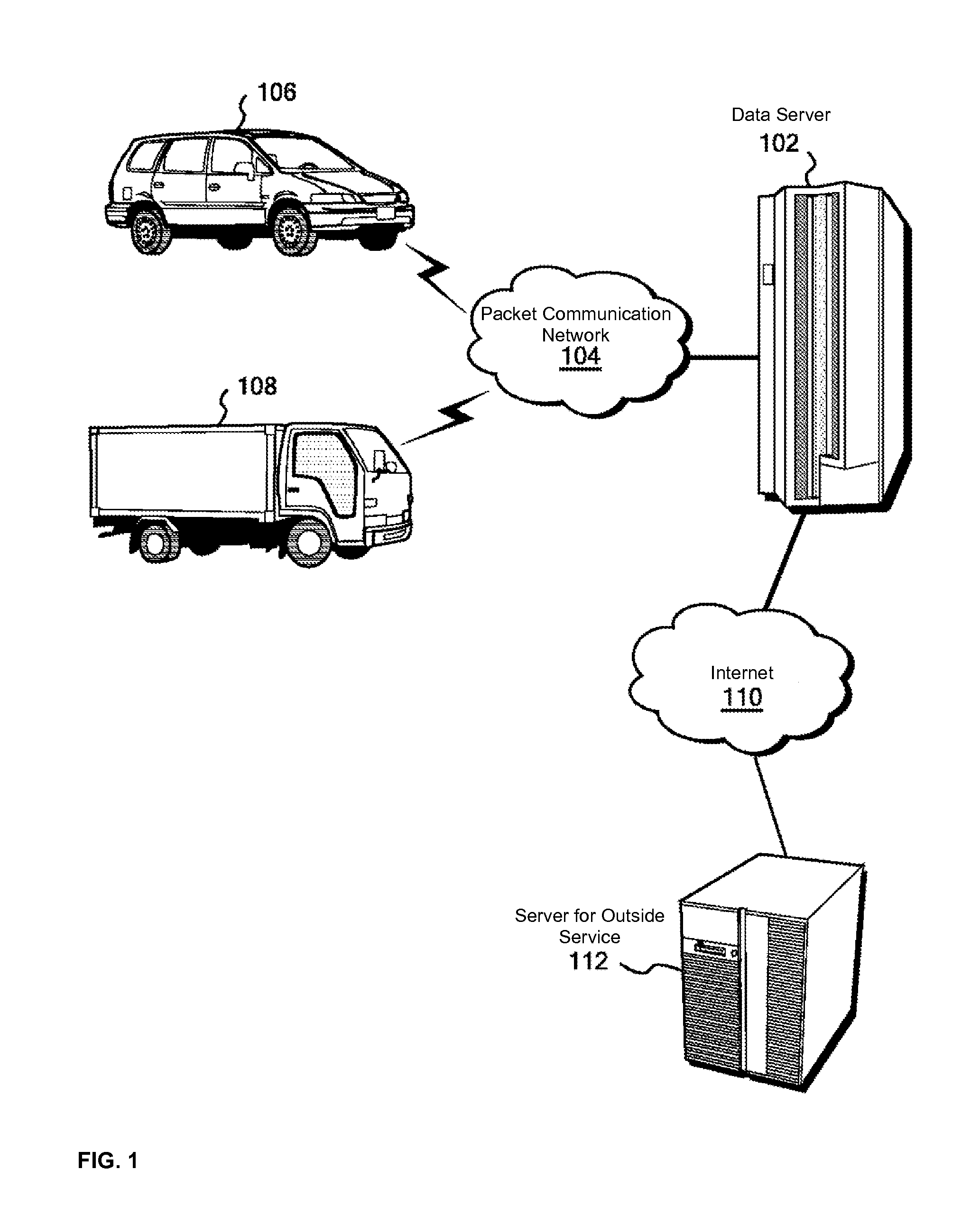
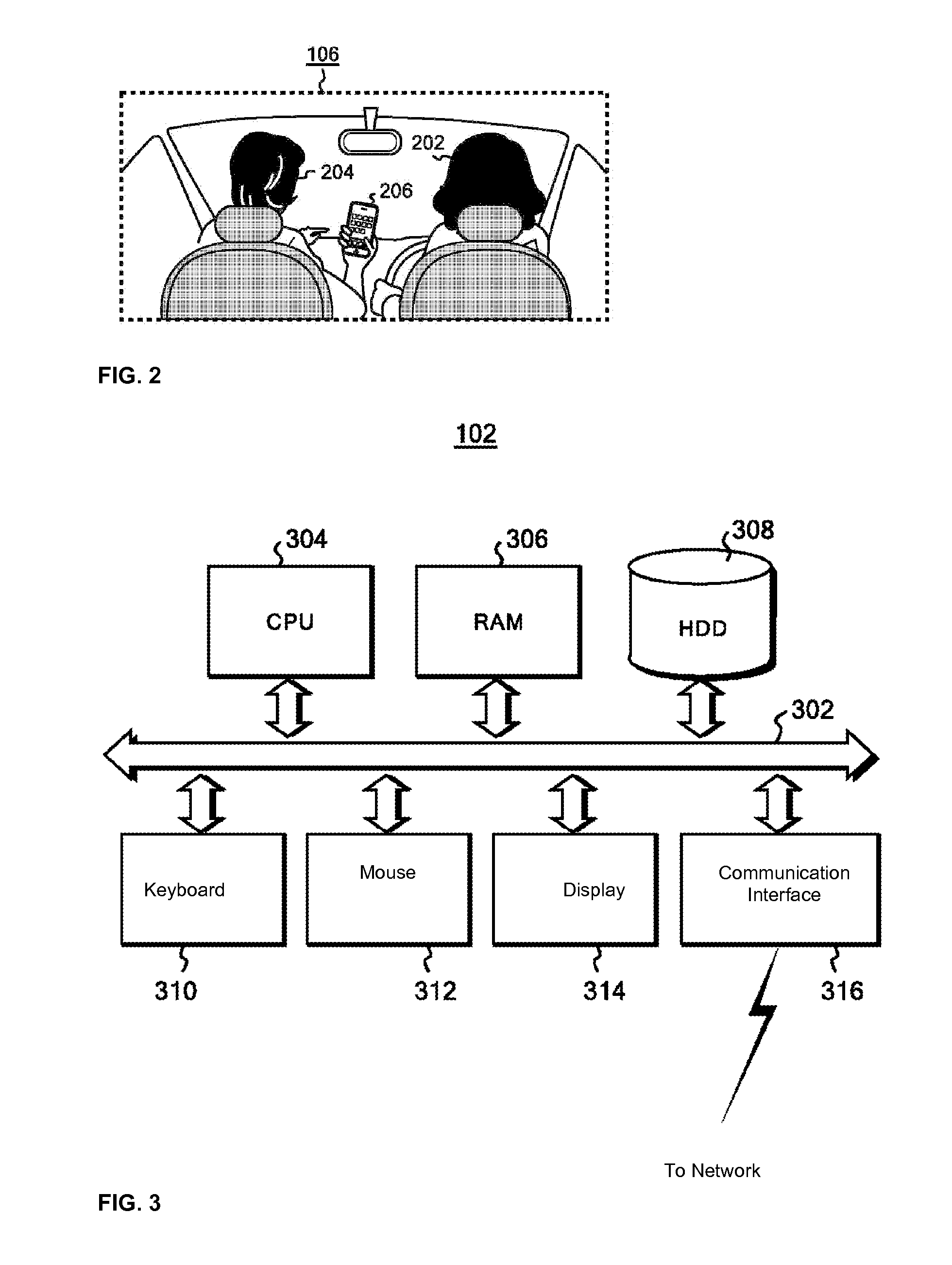
A data server to authenticate a passenger anonymously and allow an outside service to provide a service on the basis of this authentication. A passenger in an automobile uses a portable terminal with an acceleration sensor to send the acceleration sensor log in the portable terminal to a data server. The data server calculates the degree of similarity between the acceleration sensor log and time-series data related to acceleration obtained from probe data acquired from the automobile, and verifies that the portable terminal is indeed inside the automobile by confirming that there is a sufficiently high correlation between the log and the time-series data. The data server provides an access permission code to the portable terminal in response to successful acceleration authentication. The portable terminal provides the access permission code to an outside service, and the outside service accesses probe data in the data server using the access permission code.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com