Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
255 results about "Interaction protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Interaction protocols are possible communication scenarios between individual agents in multi-agent systems. FIPA defines markup for interaction protocol diagrams and several standard interaction protocols, including Dutch auction, English auction and reply-response.
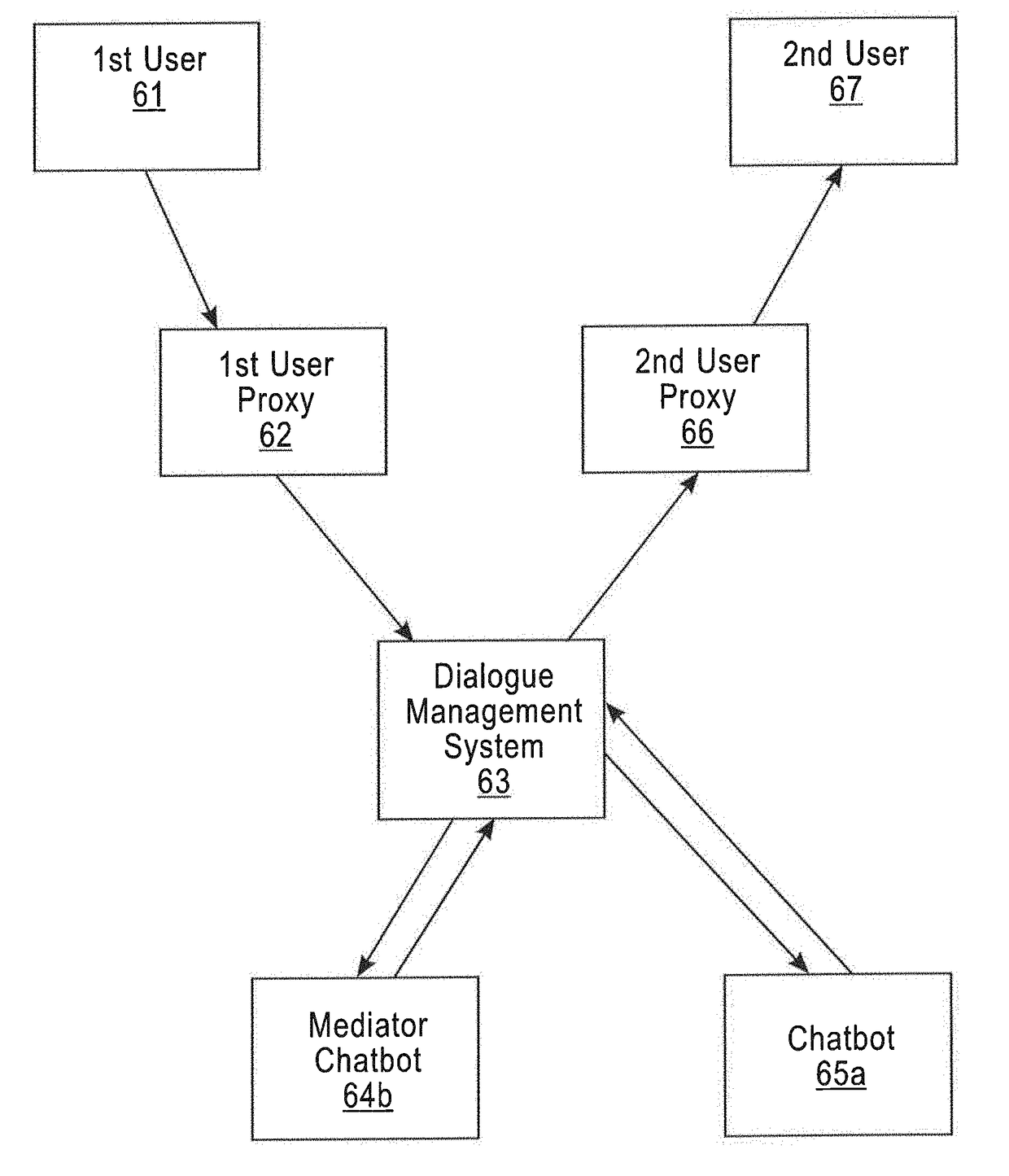
Creating coordinated multi-chatbots using natural dialogues by means of knowledge base
InactiveUS20180025726A1Natural language data processingSpeech recognitionDialog systemNetwork connection
A system for coordinating multiple chatbots in a group conversation using natural dialog systems, including a creation unit that enables a user to create a group chat with chatbots; a response unit that allows the user to reply to any utterance extracted from a message received from a member of the group chat; a transmission unit that sends messages to every member of the group chat; a development unit that develops chatbots that understand natural language and interact in a group chat using natural dialogue; a network connection; a first database that stores a knowledge base extracted from all the utterances exchanged by members of the group chat; a second database that stores all interactions between the user and the group chat, and a third database that stores all interaction protocols used by the members of the group chat.
Owner:IBM CORP
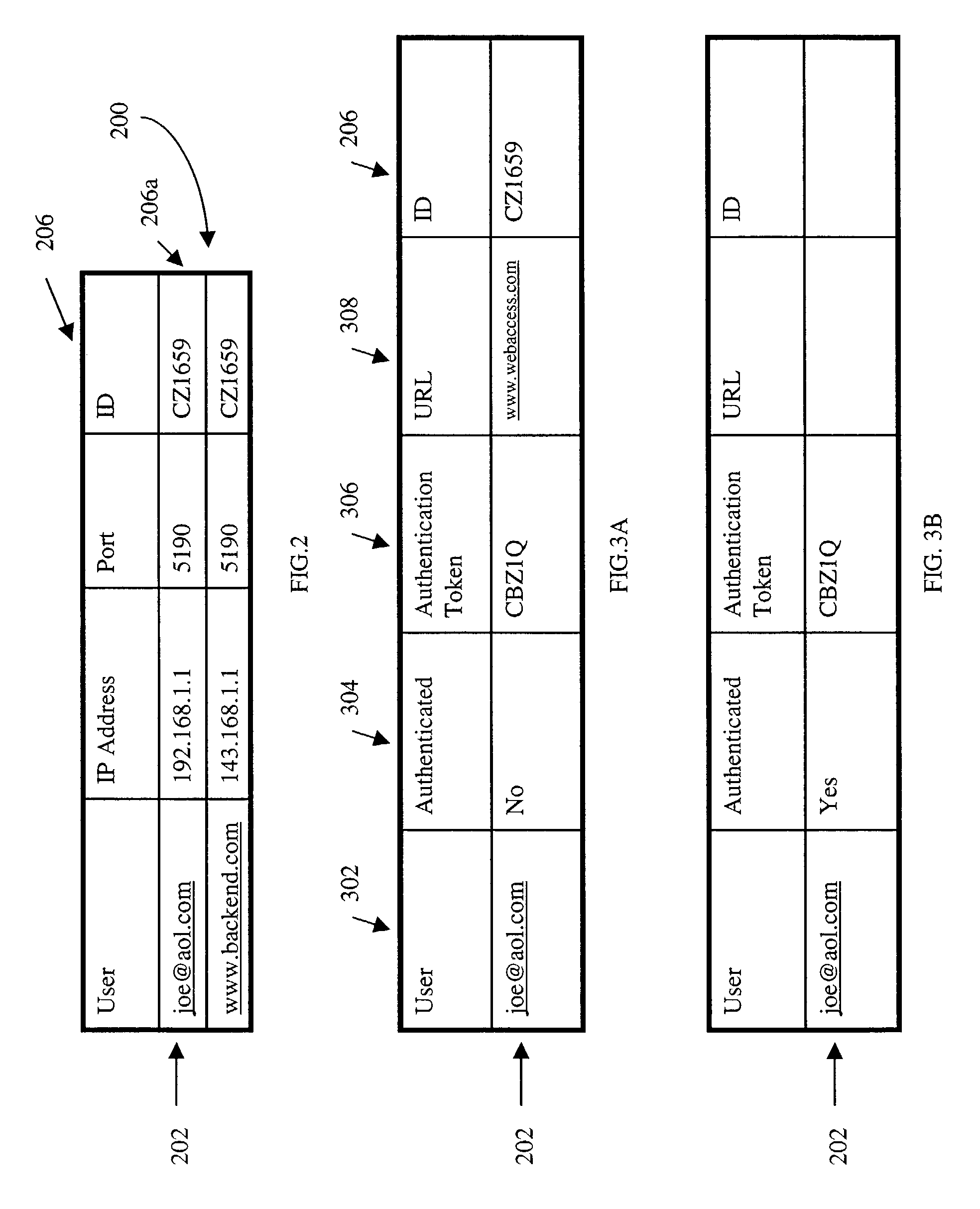
Method and system for integrating interaction protocols between two entities
InactiveUS20040139095A1Shorten the timeEnhance RosettaNetMultiple digital computer combinationsTransmissionGuidelineMessage passing
A method of and system for defining a common interactions protocol between two entities is described. The method comprises inputting a description of each entity's messaging guidelines, the description including the entity's constraints on interacting with the other entity; calculating the union of the two descriptions; determining whether the union is satisfiable using a constraint resolver; providing the intersection of the two descriptions as the common interactions protocol if the union is satisfiable; and indicating where any incompatibility lies if the union is not satisfiable.
Owner:QUALCOMM INC
Eye tracking human-machine interaction method and apparatus
InactiveCN101311882AAccurate outputSimple protocol for interactionInput/output for user-computer interactionCharacter and pattern recognitionComputer graphics (images)Man machine
The invention relates to a view line tracking man-machine interactive method, including: view line tracking information is collected and a view line focus position is obtained according to the view line tracking information; facial image information is collected and facial action is recognized according to the facial image information; a control command corresponding to the facial action is output according to the view line focus position. the invention also relates to a view line tracking man-machine interactive device which comprises a view line tracing processing unit which is used for the view line tracking operation, a facial action recognition unit for collecting the facial image information and recognizing the facial action according to the facial image information and a control command output unit which is respectively connected with the view line tracking processing unit and the facial action recognition unit and is used for outputting the control command corresponding to the facial action according to the view line focus position. the embodiment of the invention provides a non-contact view line tracking man-machine interactive method and a device with interaction protocols.
Owner:HUAWEI TECH CO LTD
Method and device for realizing three-screen interaction
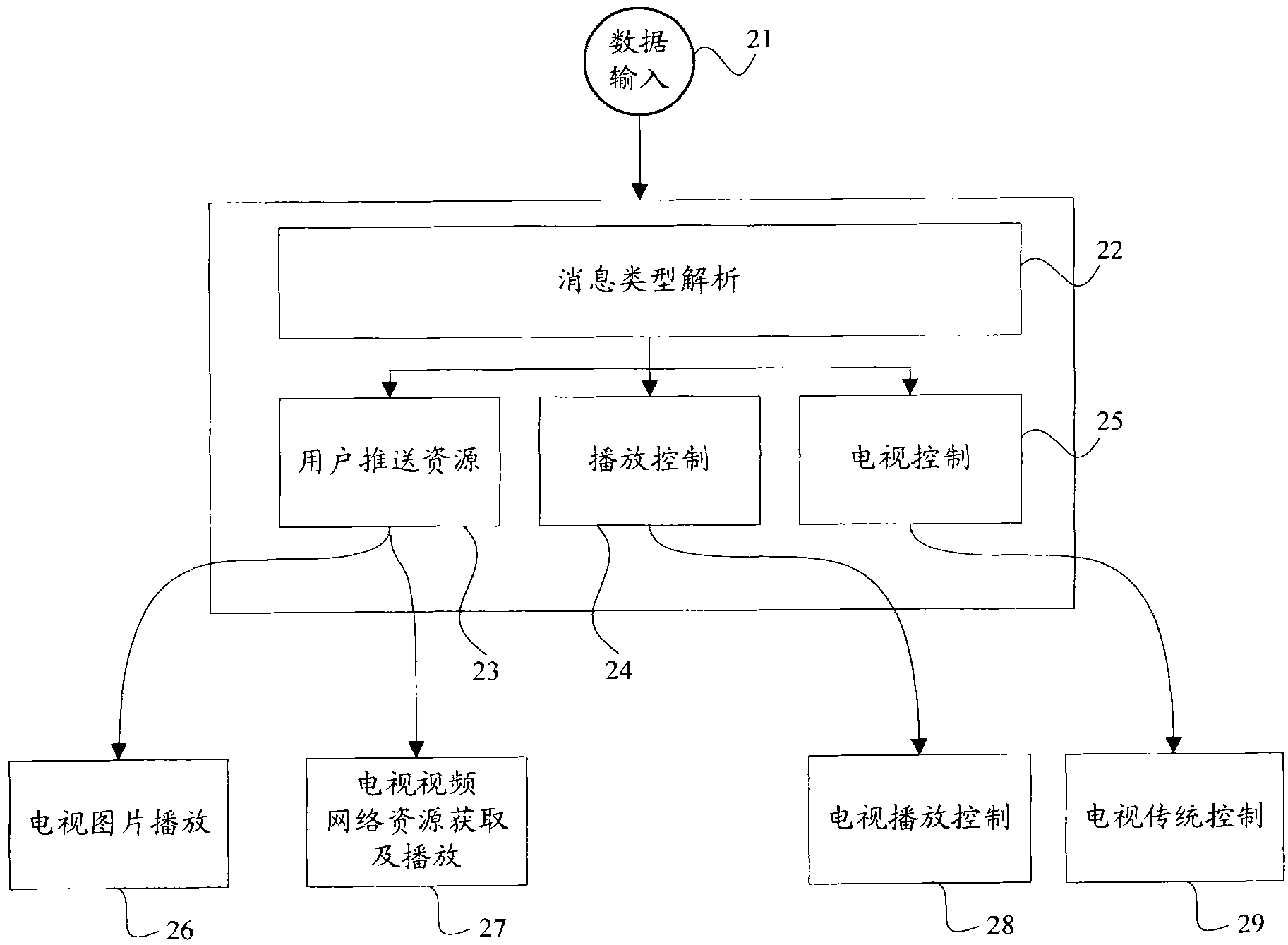
InactiveCN102130900AEasy to controlAchieve interactionTelephonic communicationTransmissionMessage typePersonal computer
The invention discloses a method and device for realizing three-screen interaction. The method comprises the following steps: on the basis of taking a mobile phone or a personal computer (PC) as an operating terminal (OT) and a television as a display terminal, binding the OT with the display terminal, and establishing a communication connection by virtue of a three-screen interaction protocol; and sending messages to the display terminal by the OT through the three-screen interaction protocol, receiving and analyzing the messages by the display terminal, and carrying out corresponding processes in accordance with message types. In the method, the mobile phone or the PC is taken as the OT, and the television is taken as the independent display terminal, thus the problems that network resources are short, the control is not convenient and the like in the existing television can be solved at the same time of realizing the three-screen interaction.
Owner:HISENSE BROADBAND MULTIMEDIA TECH
Multi-screen interaction video and audio content switching method and media player
InactiveCN102510541ARealize multi-screen interactionLow costSelective content distributionData streamMultimedia
The invention discloses a multi-screen interaction video and audio content switching method and a media player. The method comprises the following steps: when a screen needs to be switched, connecting source equipment with target equipment; generating video and audio content switching data by use of the current playing position of the recorded current played video and audio, original compressed data stream from the previous key frame of the current playing frame to the tail part of the current playing frame as well as parameters and control information required by coding the current played video and audio; transmitting to the media player of the target equipment according to a multi-screen interaction protocol; switching the data by the media player of the target equipment according to the received video and audio content; and according to the current playing position, continuously playing the video and audio from the previous key frame of the current playing frame. According to the invention, multi-screen interaction can be flexibly realized among all equipment, video and audio pictures can be seamlessly switched, the target equipment is continuously remotely controlled on the source equipment to play, the source equipment is switched back to continuously play, low network bandwidth is occupied, and convenience is provided for users.
Owner:TCL NEW TECH HUIZHOU
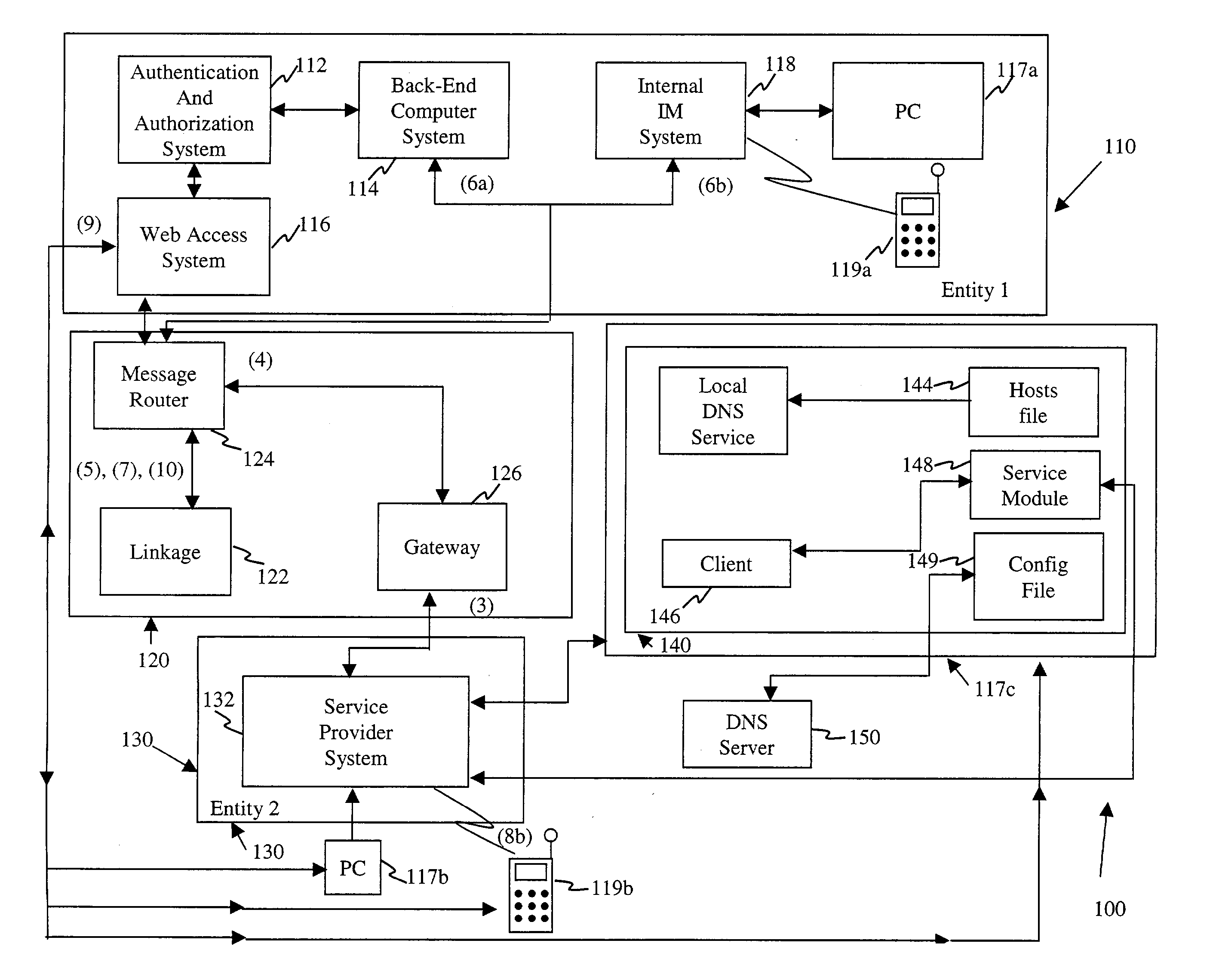
System and method for add-on services, secondary authentication, authorization and/or secure communication for dialog based protocols and systems
InactiveUS20040088546A1Improve overall utilizationSpecial service provision for substationFinanceSecure communicationComputerized system
The present invention relates generally to a system and method that provides add-on services and / or facilitates authentication, authorization and / or secure communications of a user using a dialog based interactive protocol and accessing a first computer system, separately from the authentication and security mechanism(s) provided by a second computer system using a dialog based interactive protocol system.
Owner:CA TECH INC
IPTV Presence And Interaction Protocol
InactiveUS20110173300A1Reduced availabilityImprove viewing experienceMultiple digital computer combinationsTelevision systemsNon real timeMultimedia
Disclosed are techniques for a protocol that provides for a TV viewing experience with interaction by allowing for social collaboration of non co-located TV viewers and integrating the TV viewing experience with social networking concepts and interactive multimedia communication. The protocol enables a digital video distribution system (e.g., IPTV) to provide a user with presence, channel, and grouping information regarding other users in the IPTV system and available video content. The protocol also enables users of the IPTV system to interact using real-time and / or non-real time communication.
Owner:VIDYO
Method and system for integrating interaction protocols between two entities
InactiveUS7516229B2Way of increaseMultiple digital computer combinationsTransmissionGuidelineMessage passing
Owner:QUALCOMM INC
Method and system for establishing ESP security alliance in communication system
InactiveCN101110672AGuaranteed privacyImprove efficiencyKey distribution for secure communicationUser identity/authority verificationCommunications systemSecurity association
To create an ESP security association in a communication system, three methods are provided. I. A AAA server directly creates a security key and a mobile node MN for the ESP security association to obtain a security key from the AAA server or independently work out a safety security key, a preset a cryptographic algorithm and a SPI configured in advance. II. ESP security association parameters and MN are coordinated between a home agent HA and the mobile node MN to obtain a security key from the AAA server or independently calculate a same security key. III. The MN accesses to a shared key for bound updating of the current MN and the HA created during authentication as a preset key in the process of key interaction protocol, thus completing mutual authentication in the key protocol authentication and creating an ESP security association based on negotiation of the key interaction protocol. A security association is created between a HA and a MN with three methods above to ensure safety of service between consequent HA and MN.
Owner:HUAWEI TECH CO LTD
Voice-control electric appliance and voice control method thereof
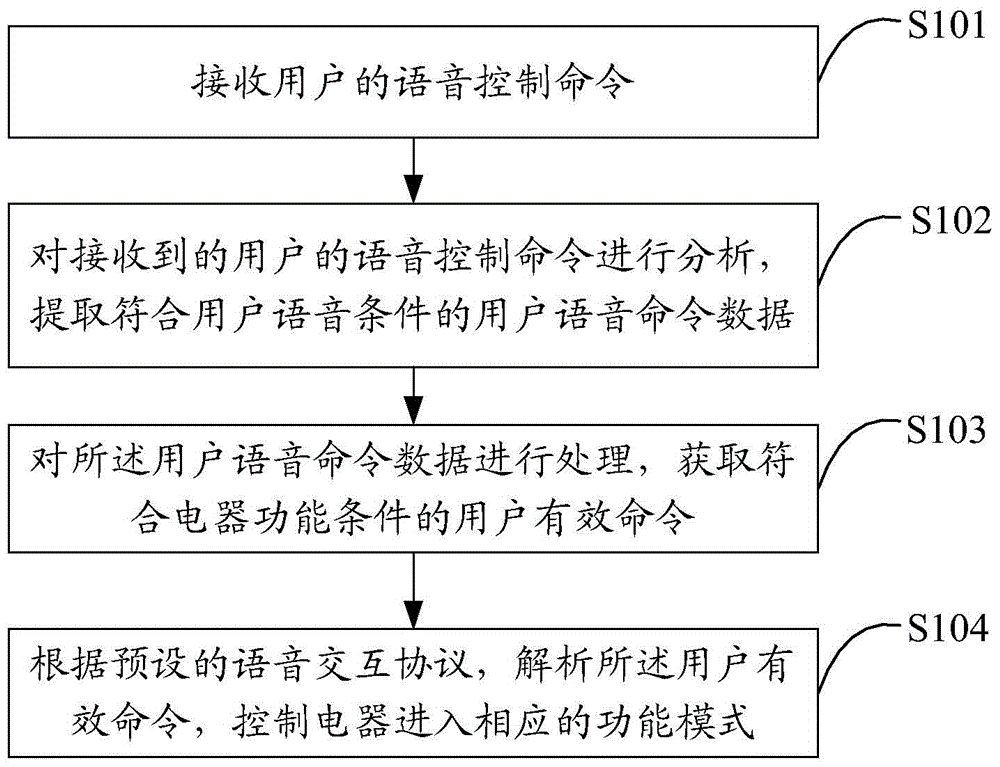
InactiveCN104464729AAchieve the purpose of cookingSolve operational problemsSpeech recognitionProgramme control in sequence/logic controllersSpeech soundSpeech control
The invention relates to a voice-control electric appliance and a voice control method of the voice-control electric appliance. The voice control method of the voice-control electric appliance comprises the steps that a voice control command of a user is received; the received voice control command of the user is analyzed, so that user voice command data meeting the user voice condition are extracted; the user voice command data are processed, so that a user effective command meeting the electric appliance function condition is obtained; the user effective command is analyzed according to a preset voice interaction protocol, and the electric appliance is controlled to be in the corresponding function mode. According to the voice-control electric appliance and the voice control method of the voice-control electric appliance, the user can directly control domestic appliances such as an electric cooker by giving out a voice command, the purpose of cooking is realized, and the problem of complicated and inconvenient operation is solved for the user.
Owner:FOSHAN SHUNDE MIDEA ELECTRICAL HEATING APPLIANCES MFG CO LTD +1
Implementation method of streaming media quality monitoring report based on user experience interaction
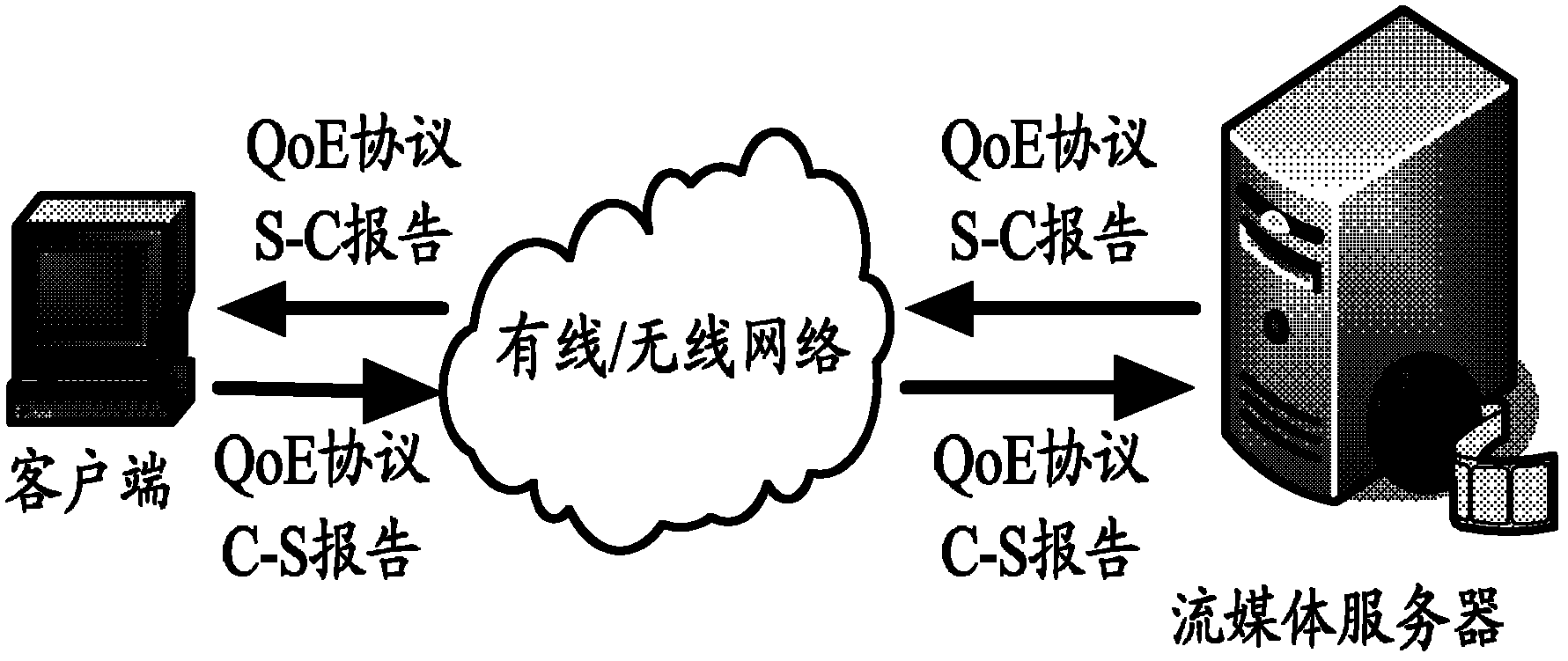
InactiveCN102868666AImprove service qualityDoes not affect transport playbackData switching networksLate resultsClient-side
The invention relates to an implementation method of a streaming media quality monitoring report based on user experience interaction. The implementation method comprises the steps that: a user-defined two-way-transmission experience quality QoE interaction protocol and relative network environment parameters and business performance parameters are firstly set; a server monitors the streaming media transmission state; a client monitors the streaming media receiving state and estimates the user experience quality; an S-C (server-client) report and a (client-server) report are respectively generated and are transmitted through a network; and the real-time interaction of streaming media quality monitoring reports is realized between the client and the server. In the invention, according to the base of the existing network technology, the multi latest results of the streaming media quality monitoring and monitoring technology are widely absorbed, and the method is comprehensively provided. The method disclosed by the invention has the advantages that the operation steps are simple, the occupied bandwidth resources are few, the computing difficulty is low, the existing network does not need be updated and reformed, and the implementation is easy, the method has an important significance to the operation and management of the streaming media in the existing network, and has a good population and application prospect.
Owner:北京东方文骏软件科技有限责任公司 +1
Residential power monitoring method and system based on power line communication
The invention discloses a residential power monitoring method and system based on power line communication. The method comprises that all household electrical appliances and an intelligent electric meter in a house are connected with a central controller to complete networking; the central controller collects power utilization data of each household electric appliance, stores the data in a database, and displays the data via reports; and the central controller detects whether abnormity occurs the household electrical appliances, and if yes, warming is sent to a user terminal. According to the invention, all the household electrical appliances are connected to the residential intelligent network, simple interaction protocols are combined with instant messaging technology to monitor and analyze the appliances in the network as well as the power utilization condition of the appliances, early warning is given to the appliance that is connected to the network newly, and alarming is raised against abnormal power utilization condition.
Owner:SHENZHEN COOCAA NETWORK TECH CO LTD
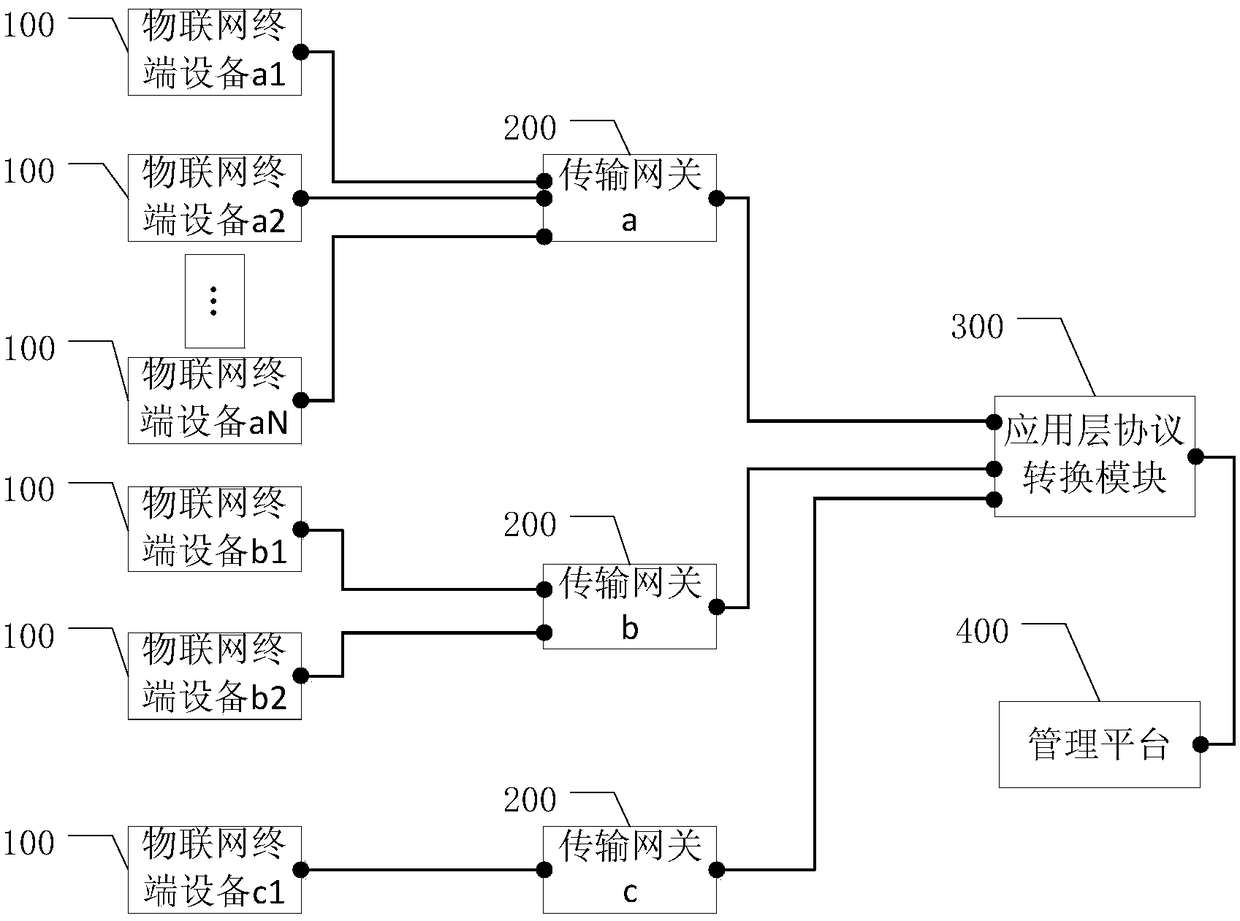
Data processing method in Internet of Things, and Internet of Things access system
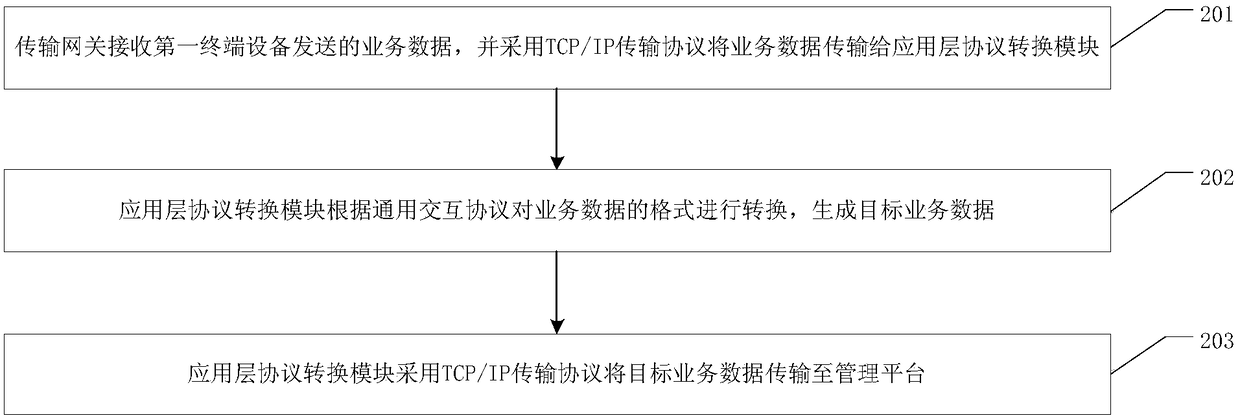
The embodiment of the invention provides an Internet of Things system and terminals of IOT management method in the Internet of Things, and is used for reducing the workload of erection of the Internet of Things, and increasing the richness of terminals of IOT on an Internet of Things platform. A data processing method in the Internet of Things provided by the embodiment of the invention is applied to the Internet of Things system, and the Internet of Things system comprises a transmission gateway, an application layer protocol conversion module and a management platform, and the data processing method specifically comprises the following steps: receiving service data sent by first terminal equipment by the transmission gateway, and transmitting the service data to the application layer protocol conversion module by adopting a TCP / IP transmission protocol; converting the format of the service data by the application layer protocol conversion module according to a general interaction protocol to generate target service data, wherein the management platform and the application layer protocol conversion module uniformly adopt the general interaction protocol for application layer datainteraction; and transmitting the target service data to the management platform by the application layer protocol conversion module by adopting the TCP / IP transmission protocol.
Owner:SHENZHEN SUNDRAY NETWORK SCI TECH
Method and device for detecting encryption algorithm and secret key
ActiveCN103516511AAvoid lossPrevent the situationMultiple keys/algorithms usageComputer hardwarePlaintext
The invention provides a method and a device for detecting an encryption algorithm and a secret key. The method comprises the steps of identifying a detected terminal and obtaining the type of the detected terminal and password equipment used by the detected terminal; determining the detected algorithm type according to the password equipment used by the detected terminal; for the detected algorithm type, selecting a set correlation calculation example to carry out calculation, comparing the detected algorithm type with a cipher-text generated after the detected terminal carries out password calculation according to an input plaintext, and generating the detection result of the detected algorithm type; obtaining the length, the strength, the life cycle and the interaction protocol of the secret key used by the detected terminal, carrying out password calculation according to the set technical specification, and generating the detection result of the secret key. The method can automatically identify the algorithm used by terminal equipment, and checks whether the algorithm conforms to the specification of the national password authority, the device is compatible with all types of interfaces, compliance inspection of use of the encryption algorithm and management of the secret key is carried out on the terminal, and terminals breaking the rule and illegal terminals are prevented from being accessed.
Owner:STATE GRID CORP OF CHINA +4
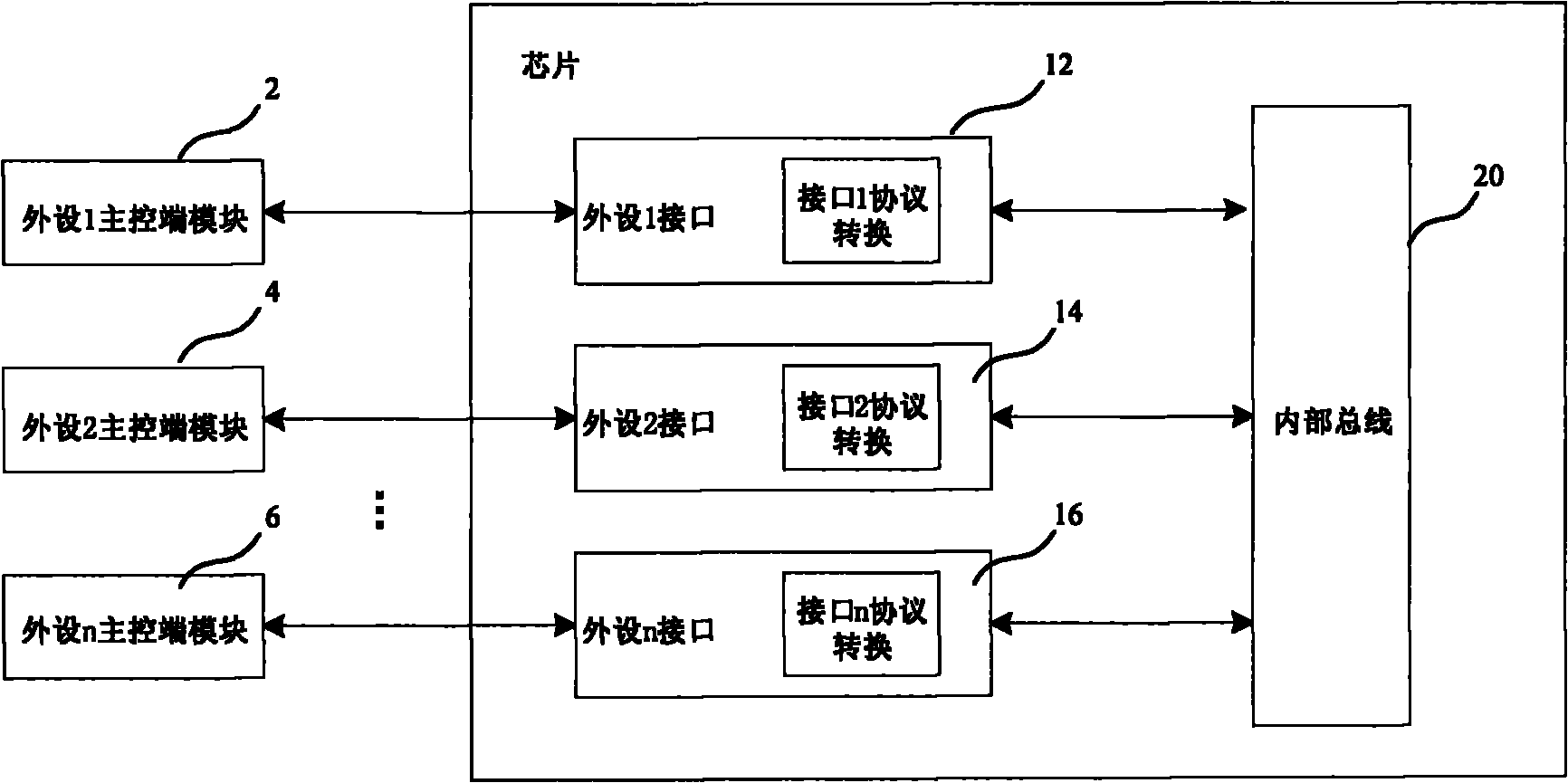
Data interaction system with a plurality of external interfaces and method
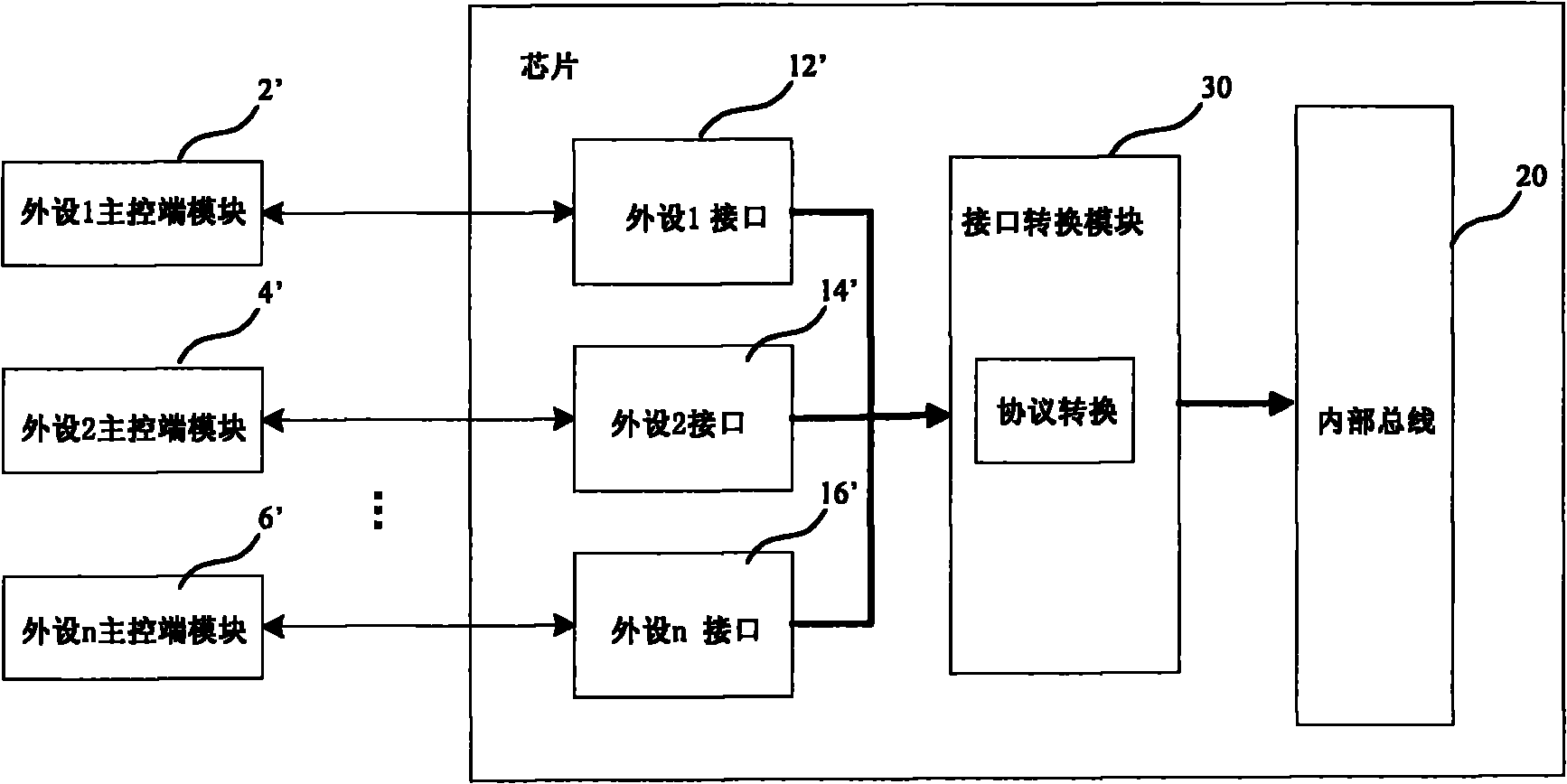
InactiveCN101770442ASimplify validationImprove reusabilityElectric digital data processingInteraction systemsInteractive design
The invention provides a data interaction system with a plurality of external interfaces, which comprises a plurality of external main control end modules, a plurality of external interface modules and interface conversion modules, wherein the external main control end modules correspond to the external interface module, command words and data are predefined according to an interaction protocol with an internal bus and are transmitted through the external interface modules, the external interface modules are respectively used for transmitting the corresponding command words and the data to the interface conversion modules, and the interface conversion modules analyze and convert the command words and the data according to the data interaction protocol for executing the data interaction with the internal bus. The invention can improve the consistency and the importance of the interactive design of the external interfaces and the internal data.
Owner:ISVUE TECH
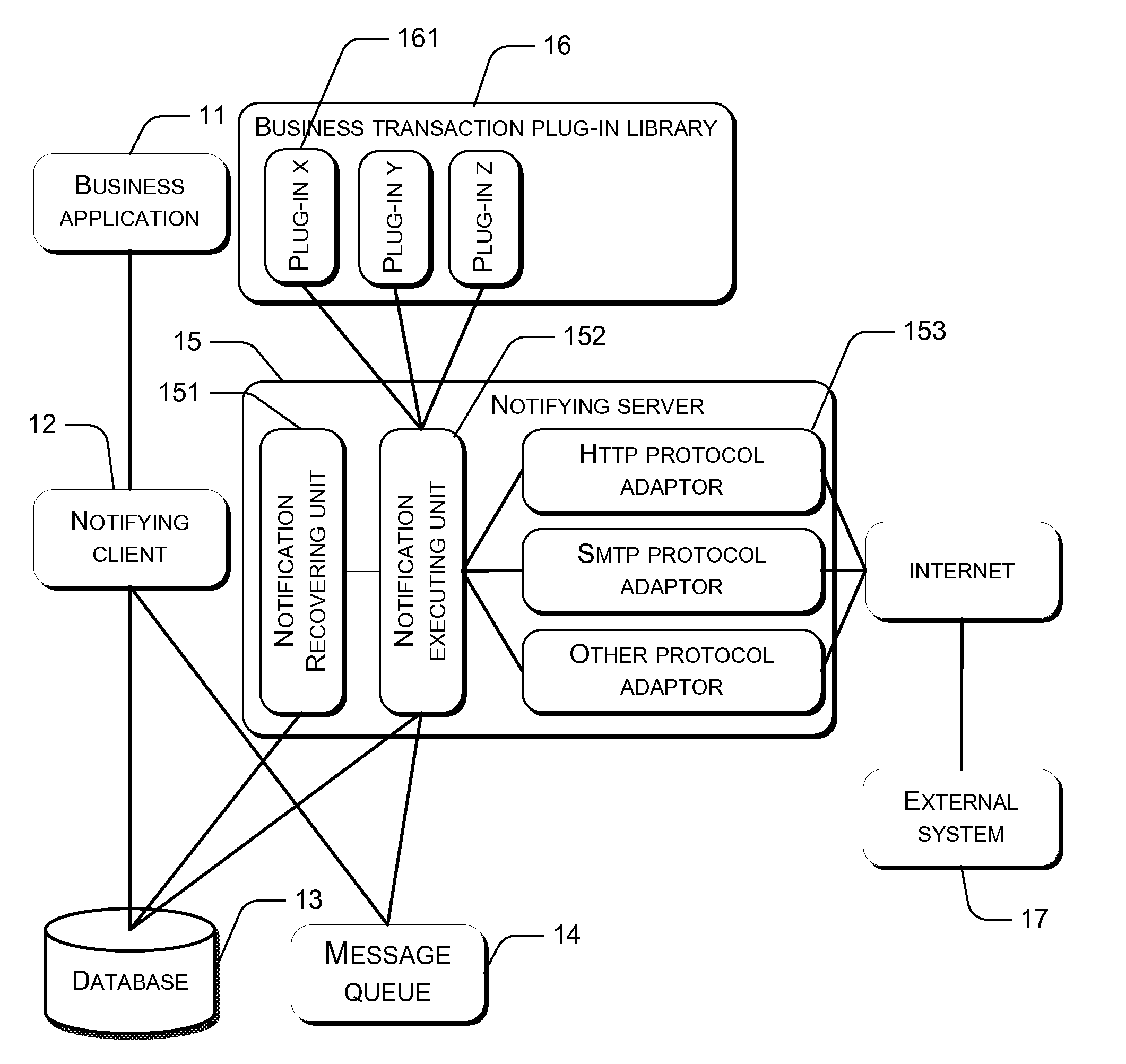
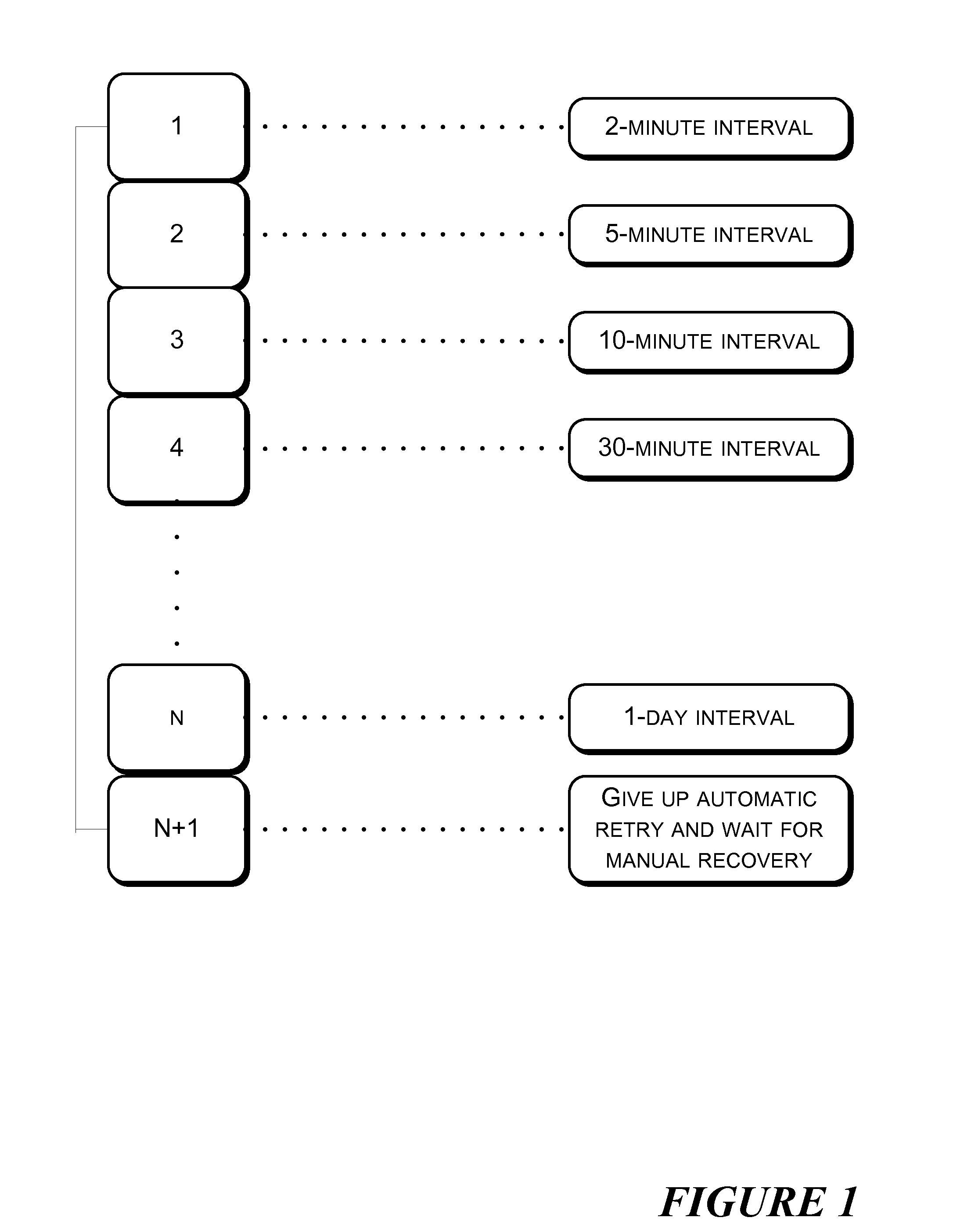
Method and System for Message Retransmission and Intersystem Message Delivery
ActiveUS20090300449A1Minimize the numberMaximizing timelinessError prevention/detection by using return channelTransmission systemsTransmission protocolThe Internet
The present invention discloses a method and a system for resending messages with a minimized number of retries and maximized timeliness of delivering the message to the receiving party. The method sets a retry period for a message that needs to be resent, determines a retry time according to the retry period, and sends the message after the retry time is reached. The retry period increases as the number of retries increases. The method and the system can ensure reliable delivery of notification messages and support many transmission protocols between different systems, does not require the receiving party to implement complicated interaction protocols to reliably receive a notification message, and is suitable for widespread use in the Internet. Moreover, the disclosure supports multiple transaction processing, can be used as a common business transaction application platform, and allows flexible expansion of multiple transactions and multiple protocols.
Owner:ADVANCED NEW TECH CO LTD
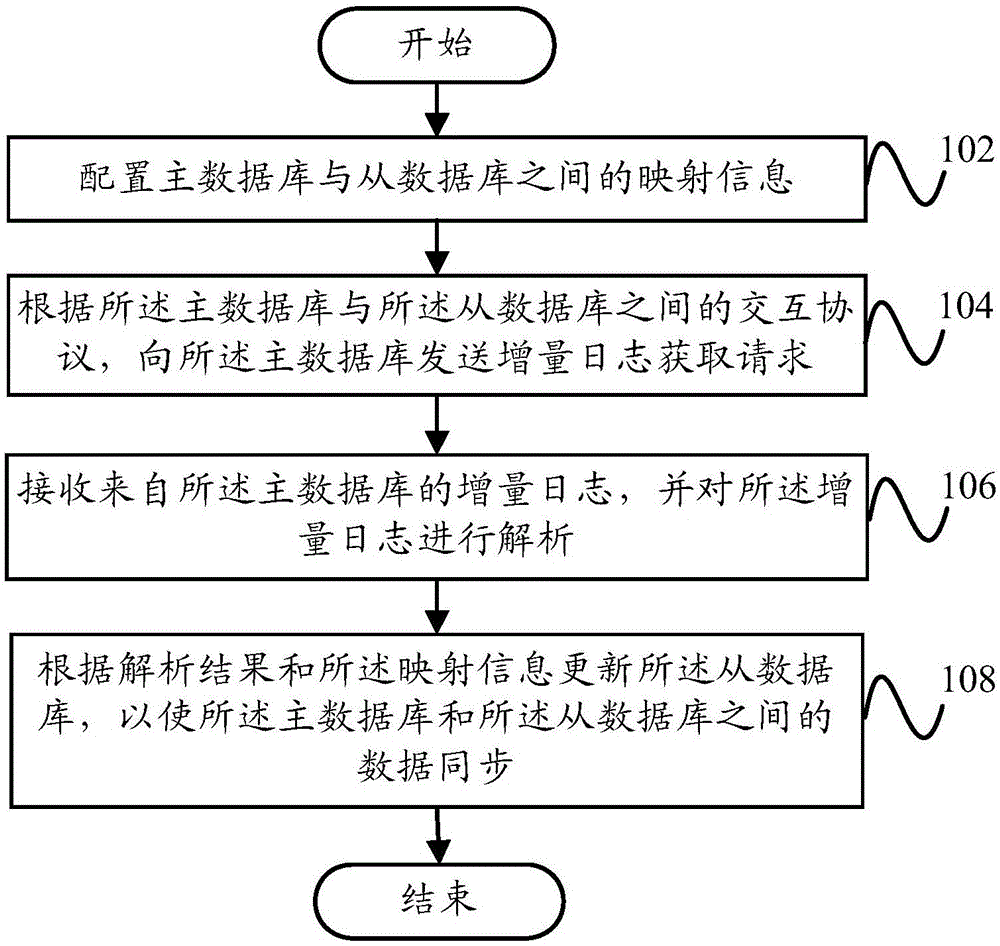
Data synchronization method and data synchronization device based on incremental log analysis
InactiveCN106294713AData synchronizationDatabase distribution/replicationSpecial data processing applicationsData synchronizationData mining
The invention discloses a data synchronization method and a data synchronization device based on incremental log analysis. The data synchronization method based on the incremental log analysis comprises the steps of configuring mapping information between a master database and a slave database; according to an interaction protocol between the master database and the slave database, sending an incremental log obtaining request to the master database; receiving an incremental log from the master database and carrying out analysis on the incremental log; and according to an analysis result and the mapping information, updating the slave database so as to achieve data synchronization between the master database and the slave database. Through the technical scheme of the invention, the data synchronization can be realized more accurately and safely.
Owner:ZICT TECH CO LTD
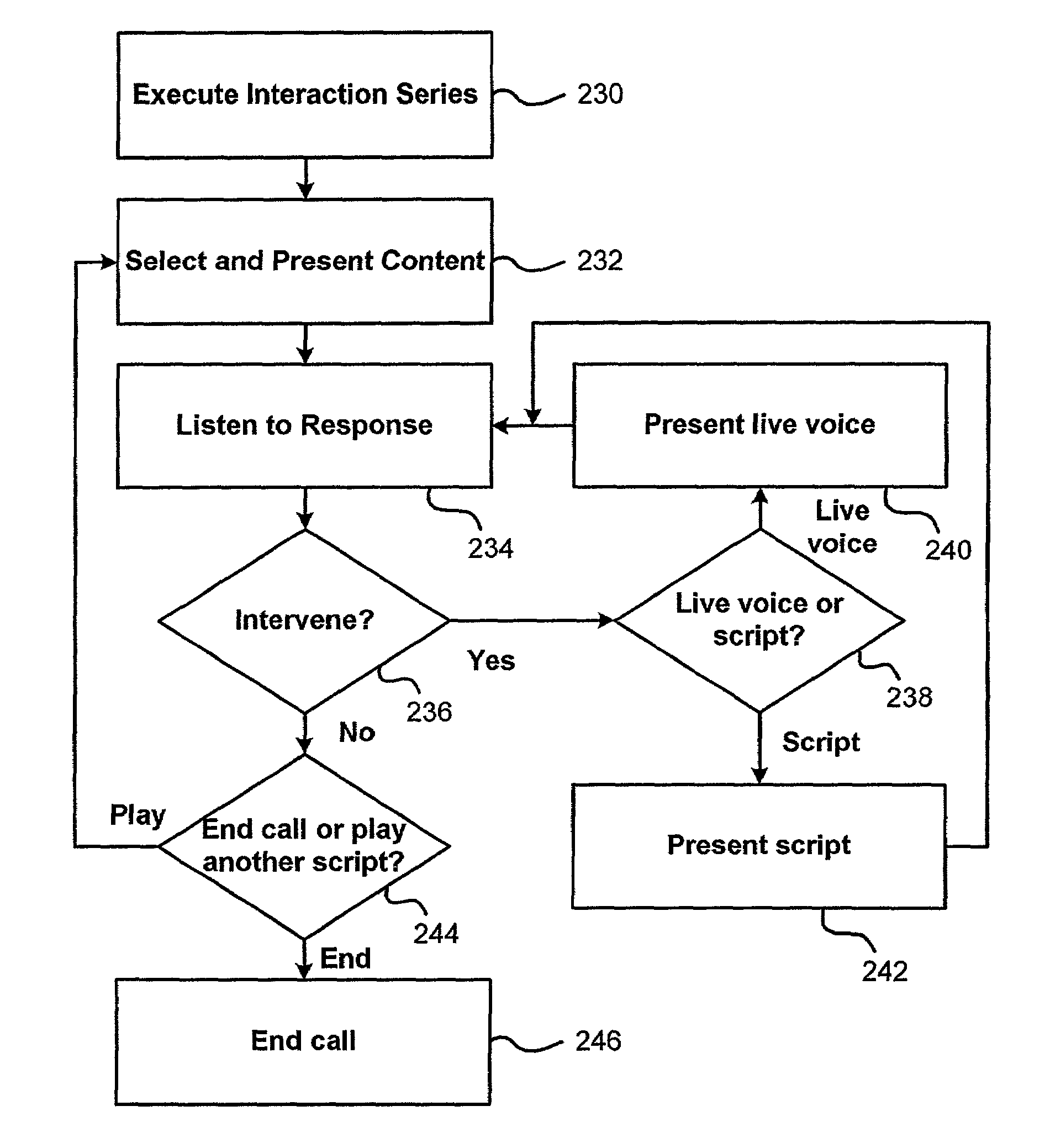
Voice transition script caller
InactiveUS7933387B1Solve problemsReduce in quantityAutomatic call-answering/message-recording/conversation-recordingManual exchangesLive voiceHuman agent
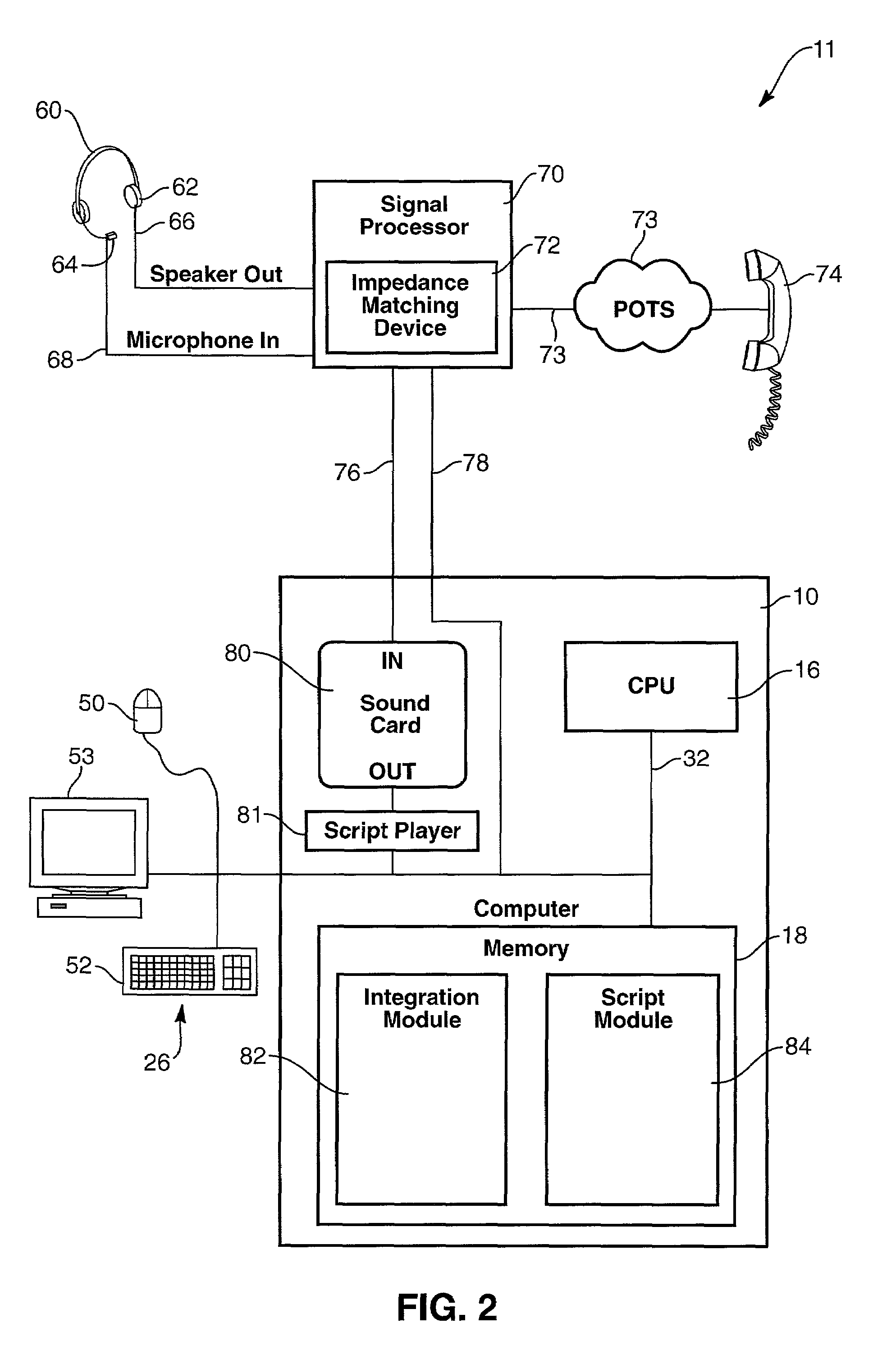
A system allows an agent to execute an interaction protocol, to create an interaction between the agent and a contact. The agent or a computer dialing system initiates a call to a contact and the agent selectively interleaves responses to the contact with a live voice or with a recorded script. The interleaving of responses to the contact from the human agent and the recorded script approximates seamless transitions. The system includes a script player for outputting scripted voice waveforms over a phone line to a contact and a signal processor configured to provide a normalized signal selected from the output device and the script player.
Owner:NOGUAR LC
Multi-drone cluster navigation method
InactiveCN109445456AAppropriate distanceTo achieve the purpose of the clusterPosition/course control in three dimensionsControl vectorNetwork model
The invention discloses a multi-drone cluster navigation method. The method comprises steps that an interaction protocol among drones is determined; according to the interaction protocol, a flight status of each drone of the drone cluster is determined by utilizing sensing devices and / or positioning devices of the drones; control vectors of the drones are determined; a revenue function is determined according to the flight status of the drones; based on the flight status, the control vectors and the revenue function, the learning algorithm is utilized to train a neural network model centrallyto obtain a control function used for describing the mapping relationship from the flight status to the control strategy of the drones, and the control function is shared among the drones of the multi-drone cluster; based on the control function, a corresponding control command is generated by each drone according to its own flight status to implement autonomous cluster navigation.
Owner:TSINGHUA UNIV
System and method for authentication with out-of-band user interaction
ActiveUS20190080331A1Digital data authenticationSpeech recognitionInteraction systemsInternet privacy
Systems and methods for authenticating a party to a secure transaction may include receiving, from a first computing device on behalf of a first party at a second computing device of a second party, information associated with a secure transaction between the parties, receiving, from the first device at the second device, video or audio evidence of actions taken by the first party, capturing, by the second computing device during presentation of the video or audio evidence, acknowledgement of actions taken by the first party as observed or heard by the second party in the evidence, determining, dependent on the acknowledgement, whether the actions observed or heard by the second party match expected actions of the first party in accordance with an out-of-band user interaction protocol, and determining whether to accept the information associated with the secure transaction dependent on whether the observed or heard actions match the expected actions.
Owner:WALRUS SECURITY INC
Multi-screen interaction method and terminal equipment
InactiveCN105430482AImprove compatibilityAvoid the defect that multi-screen interaction cannot be performedSelective content distributionTerminal equipmentComputer terminal
The invention discloses a multi-screen interaction method and terminal equipment. The method includes: after a source terminal is connected to a local area network, if a system external interface of the source terminal detects a multi-screen interaction instruction triggered by a user, protocol search information is sent to the local area network, and at least a multi-screen interaction protocol is packaged in a bottom system of the source terminal; a search response message returned by at least a target terminal connected to the local area network is obtained, the search response message is sent by the target terminal after obtaining the protocol search information, and the search response message carries protocol types supported by the target terminal; after the condition that the user selects an interaction terminal from the target terminals is determined, a target protocol is taken from the at least one multi-screen interaction protocol, and the target protocol is the multi-screen interaction protocol corresponding to the protocol type supported by the interaction terminal; and multi-screen interaction between the source terminal and display equipment corresponding to the interaction terminal is performed according to the target protocol.
Owner:1VERGE INTERNET TECH BEIJING
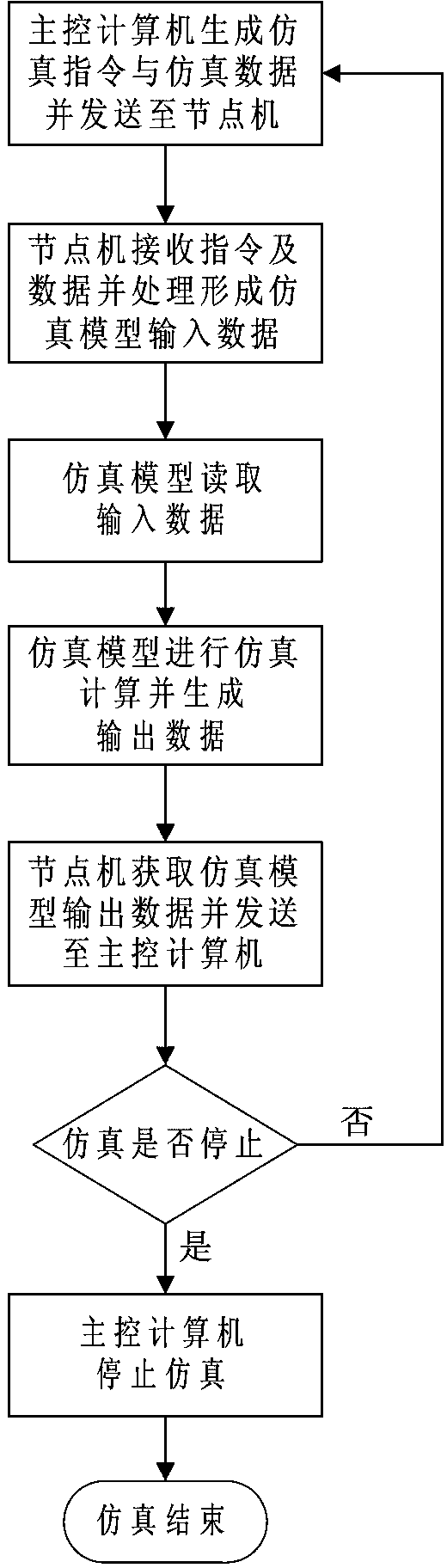
Method for dispatching distributed simulation models in aircraft simulation system
InactiveCN103279622AImprove design efficiencyPrecise deliverySpecial data processing applicationsSystems designData stream
The invention relates to a method for dispatching distributed simulation models in an aircraft simulation system and belongs to the technical field of aircraft system design. The dispatching method is based on a data flow dispatching idea, simulation progress is driven through a data flow, the simulation begins when the data flow is generated, and the simulation is finished when the data flow is terminated. The method for dispatching the distributed simulation models of the aircraft simulation system is achieved by formulating a data interaction protocol between the simulation models and a distributed simulation platform and designing a simulation model execution sequence algorithm. By means of the method, the concurrent design simulation of an aircraft can be achieved, the design efficiency of the aircraft is effectively improved, accurate transferring of simulation data is ensured, and correct execution of a simulation task is further guaranteed.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Log cluster scanning and analysis method used for large-scale server cluster
ActiveCN104917627AComprehensiveEfficientData switching networksSpecial data processing applicationsInteraction protocolData mining
The invention relates to the system monitoring and system management field and aims at providing a log cluster scanning and analysis method used for a large-scale server cluster. The log cluster scanning and analysis method used for the large-scale server cluster comprises one machine log analysis, cluster log analysis, log cluster analysis and log data exchange. By using the method in the invention, a simplicity of one machine log processing, high efficiency of one machine and cluster log exchange after unification processing, ''pushing'' and ''pulling'' log interaction protocol promptness, cluster log association analysis comprehensiveness, event database structure integrity and high efficiency and event prediction accuracy are possessed.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Method for implementing information issue and sharing of mobile browser
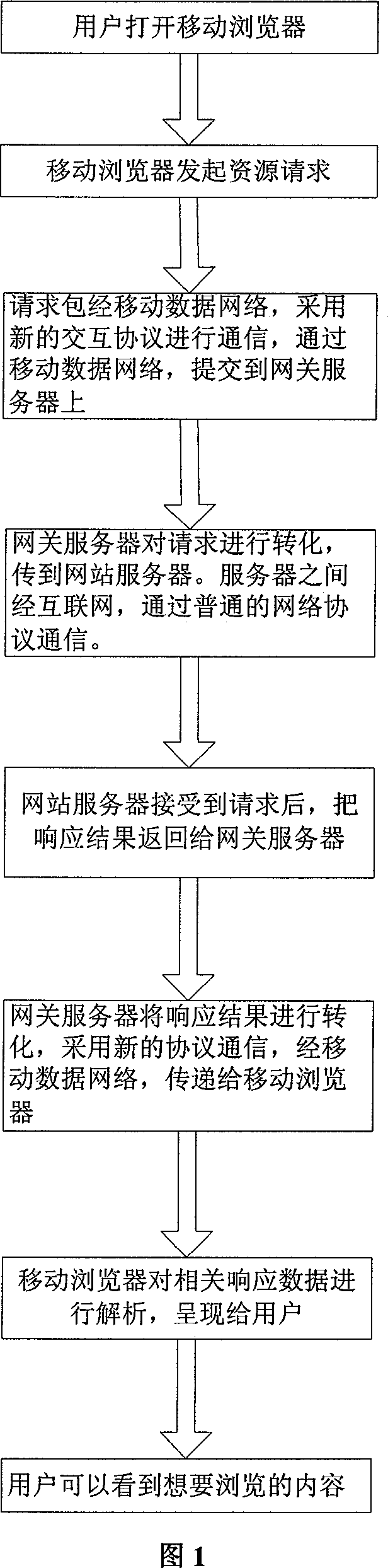
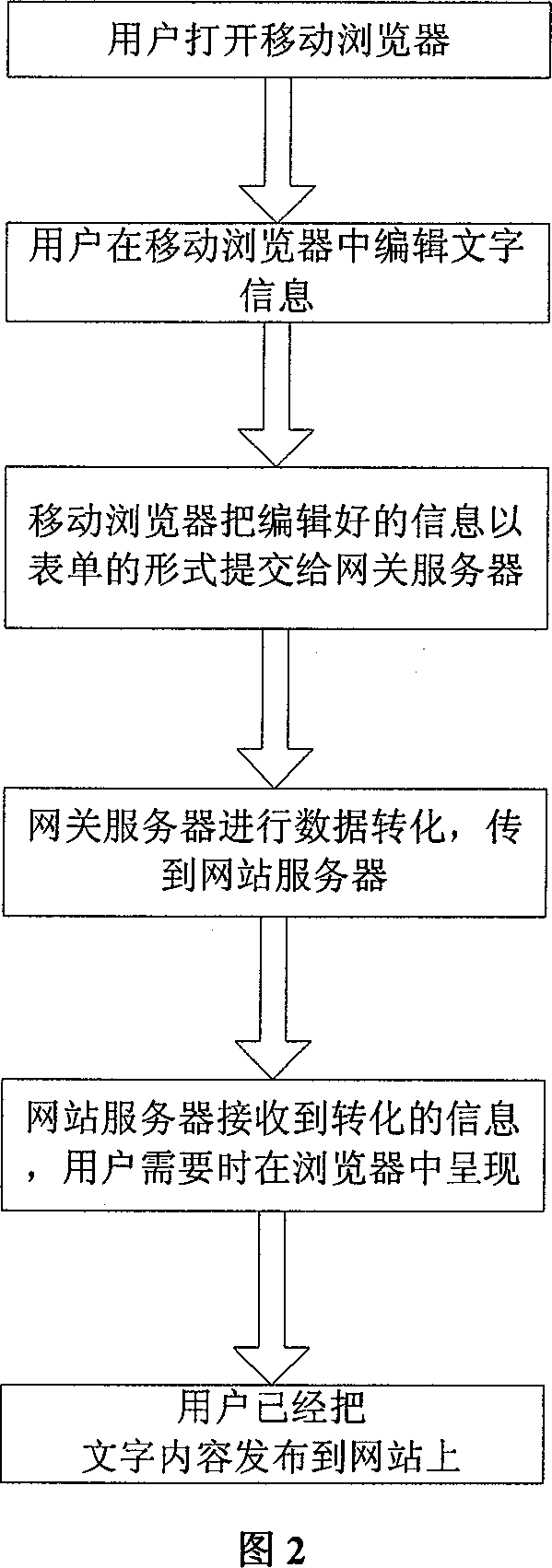
InactiveCN101115076AImprove request response speedHigh speedNetwork connectionsMedia serverWeb content
The invention provides a method of realizing information publishing and sharing by a mobile browser. The invention is characterized in that: the mobile browser is respectively connected with a gateway server which can convert a protocol and a media server that stores multimedia information by making use of a special communication and interaction protocols through mobile data network and which jointly achieves to brow web content completely and quickly and to publish and share multiple information of users by making use of a website server which provides the websites which can be published and shared. The invention enables users to publish and share multiple information which comprise multimedia information by using the mobile browser, thereby enhancing the experience in using and improving the development of the technology of mobile browser.
Owner:蒋晓海
Live broadcast control method and device, computer readable storage medium and terminal
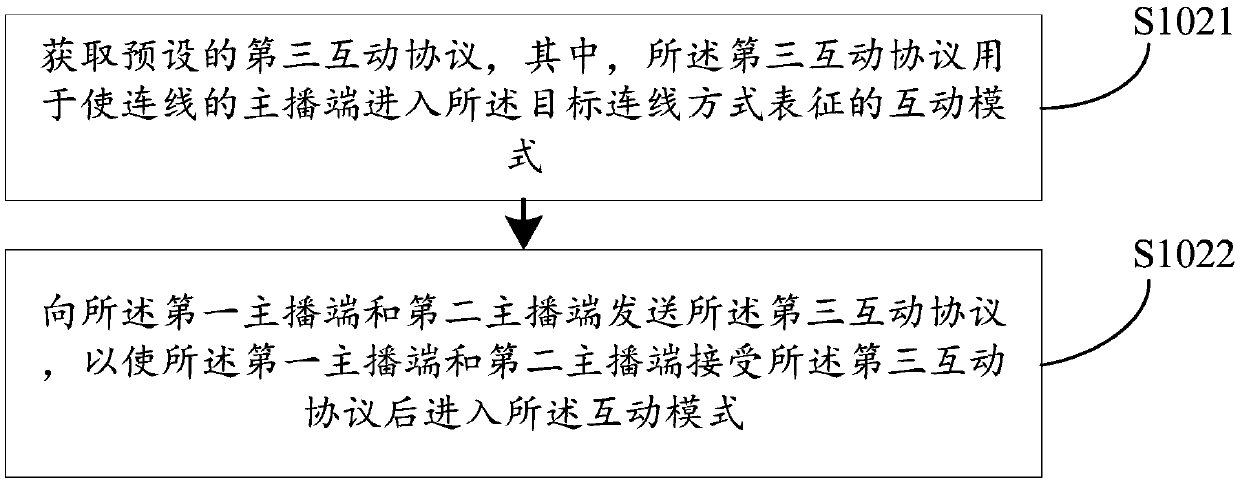
InactiveCN109587509AImprove interactivityHigh activitySelective content distributionAtmosphereMultimedia
The embodiment of the invention discloses a live broadcast control method and device, a computer readable storage medium and a terminal. The method comprises the following steps of acquiring a first interaction protocol sent by a client terminal; calling the progress information of the target connection mode of a target anchor end pointed by the first interaction protocol according to the first interaction protocol; and sending the progress information to the client terminal so that the progress of the target connection mode is displayed when the target anchor end is in a connected state afterthe client terminal obtains the progress information. Through anchor connection and interaction, a live broadcast material can be greatly increased and a live broadcast content is enriched through interaction based on the existing live broadcast content. The progress of the connection can be set and the progress is sent to the client terminal synchronously so that an audience can clearly know a connection process, the interactive ability of the audience is improved, an atmosphere in a connected live broadcast room is further enlivened, and audience activity is increased.
Owner:GUANGZHOU BAIGUOYUAN INFORMATION TECH CO LTD
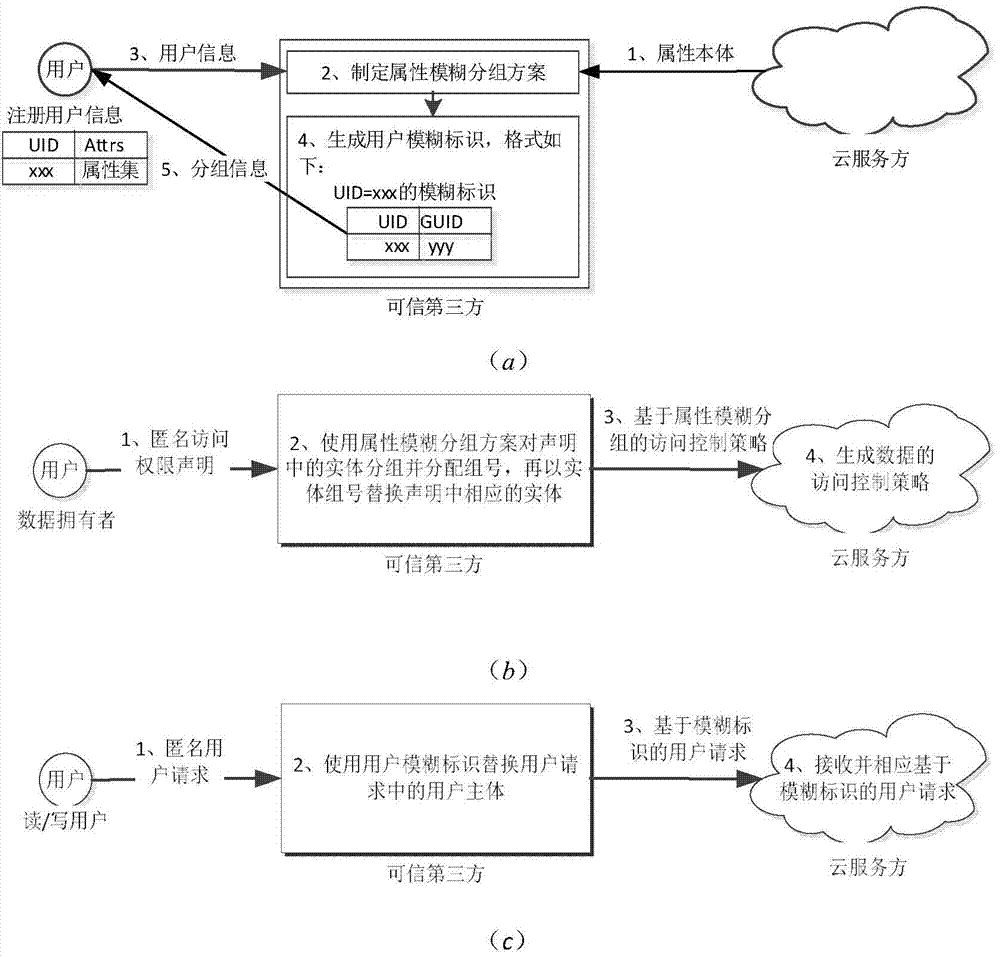
Privacy protection method based on trusted third party attribute fuzzy grouping under cloud environment
The invention relates to a privacy protection method based on trusted third party attribute fuzzy grouping under the cloud environment. The method comprises an attribute fuzzy grouping access control method and an interaction protocol based on trusted third party protection, and is mainly used for three stages of cloud user registration, cloud end data creation and cloud end data access, and the stages support direct interaction and indirect interaction. Through the access control method based on attribute fuzzy grouping, conversion of an access entity, an access control policy and user requests is achieved on the three stages by the trusted third party, leakage of privacy information of users can be effectively avoided, and authenticity of anonymous access users is ensured. Through the interaction protocol based on trusted third party protection, interaction behaviors of the user, the trusted third party and the cloud service party are stipulated, data encryption, timestamp and other technological means are added to the protocol, and safety of user data, user identities and attribute privacy is guaranteed in the interaction process of the user, the trusted third party and the cloud service party.
Owner:BEIJING UNIV OF TECH
Online game message interaction protocol on mobile platform based on CS architecture
InactiveCN101094227AIncrease independenceIncrease flexibilityError preventionData switching networksHand held devicesByte
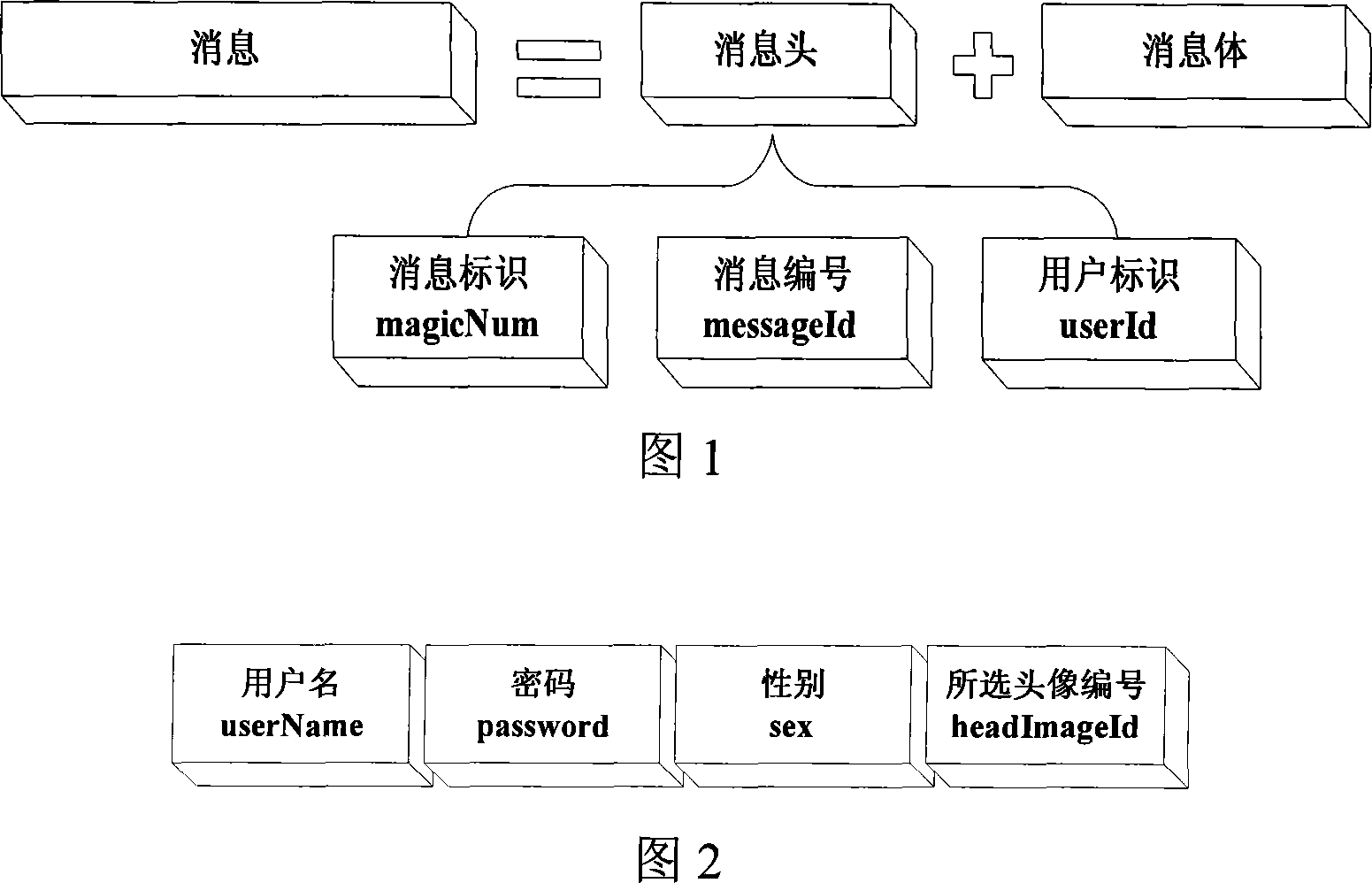
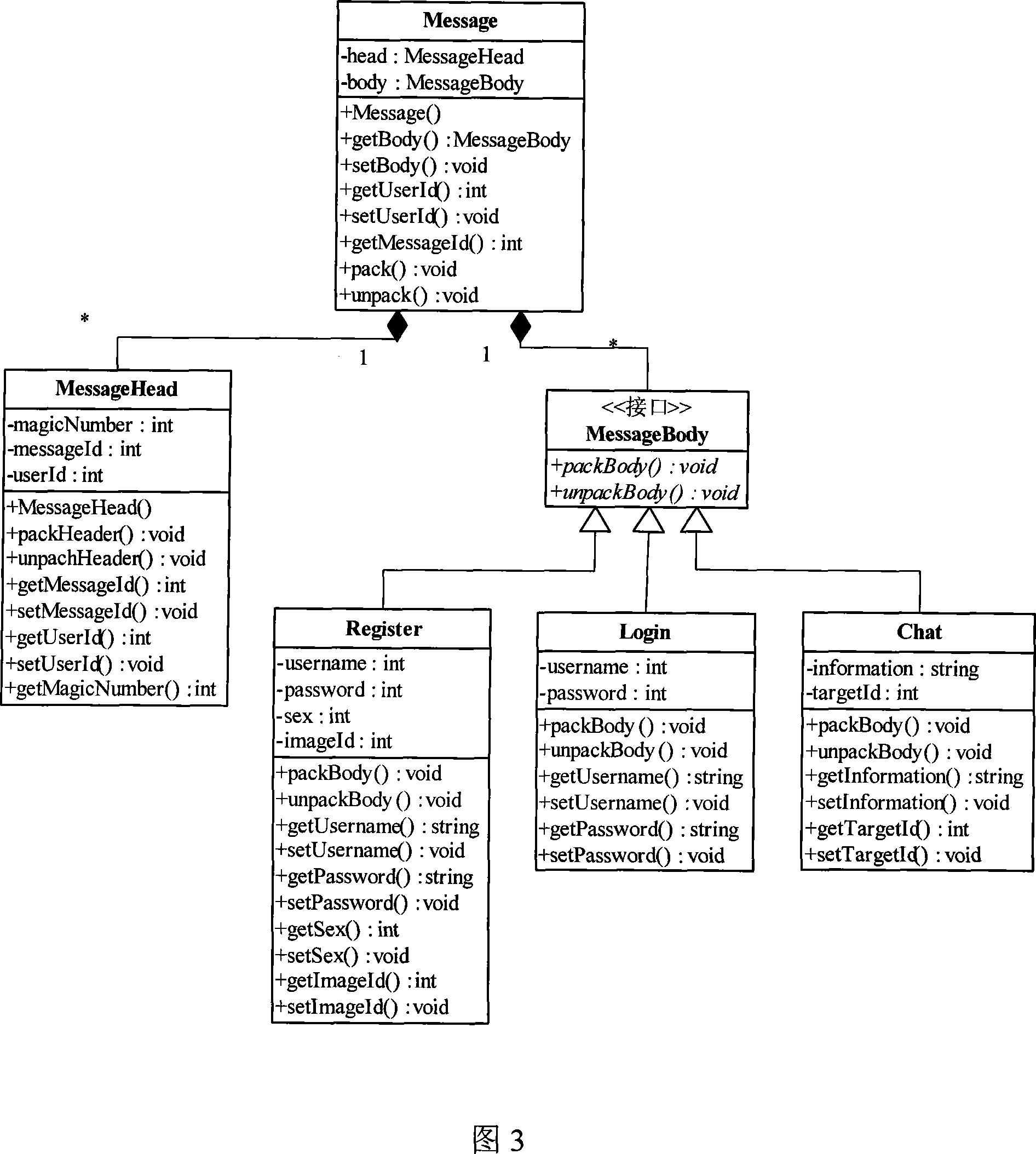
The method comprises: using bitstream-based message designing approach to divide a message into both message head and message body parts; using the object oriented design ideal to pack said message; said designed message comprising a MessageHead and a Messagebody; said message is packet into one message packet.
Owner:SUN YAT SEN UNIV
System and method for add-on services, secondary authentication, authorization and/or secure communication for dialog based protocols and systems
InactiveUS7475240B2Improve overall utilizationSpecial service provision for substationFinanceSecure communicationInternet privacy
In an authentication system, a first computer system provides a desired service and a second computer system provides a dialog-based interactive protocol service (e.g., an instant messaging service). Users of a second computer system can be authenticated by the first system using a mechanism separate from the dialog based interactive protocol system, so the users can then access the first system using the dialog based interactive protocol systems (even though the systems are not owned or necessarily trusted by the first system). The authentication system enables communication between the first and second computer systems by establishing the dialog session between the computer systems and transmitting to the second computer system a link to a site used to authenticate this computer system. The authentication system associates authentication information (e.g., a unique identifier and / or an authorization token, etc.) with the dialog and uses this information to enable the second computer system to have authorized communications with the first.
Owner:CA TECH INC
Interactive data processing method and device
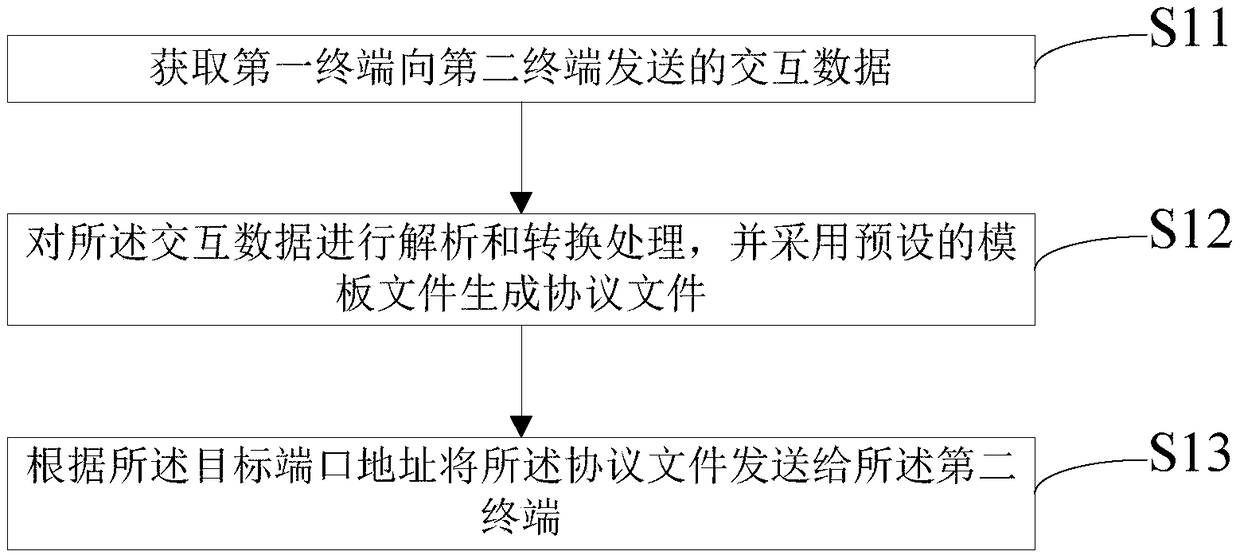
InactiveCN109408247AMechanism to automatically generate checksumsInterprogram communicationComputer hardwareCross-platform
An interactive data processing method and device is provided by an embodiment of the present invention. The method comprises the following steps: acquiring the interaction data sent by the first terminal to the second terminal, analyzing and converting the interaction data, adopting a preset template file to generate a protocol file, and sending the protocol file to the second terminal according to the target port address. According to the invention, by acquiring interaction data sent from the first terminal to the second terminal, analyzing and converting the interactive data, generating a protocol file by adopting a preset template file, and sending the protocol file to the second terminal according to the target port address, the mechanism of automatically generating cross-platform andcross-language protocol interface codes and protocol parameter verification by maintaining the data interaction protocol through the configuration file is realized.
Owner:天津龙拳风暴科技有限公司
Bluetooth test method, terminal device and computer readable memory medium
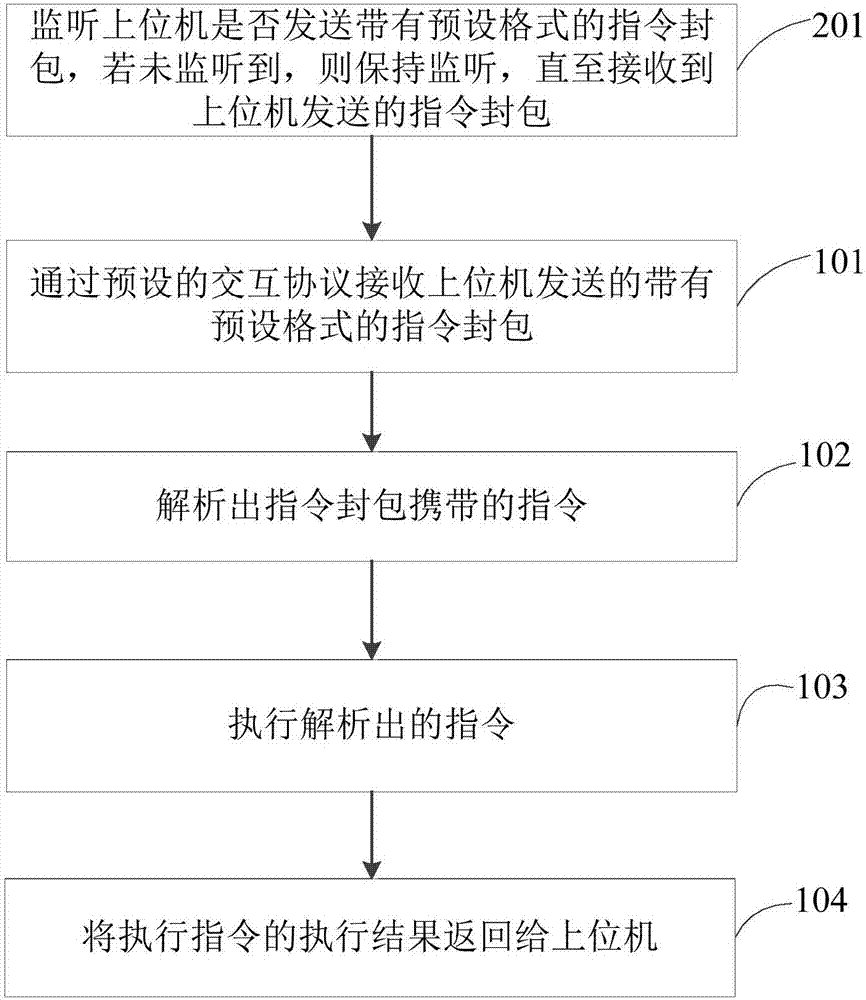
InactiveCN107317638AImprove test efficiencyIncrease the number of testsTransmission monitoringWireless commuication servicesTest efficiencyAutomatic test equipment
The invention provides a Bluetooth test method, a terminal device and a computer readable memory medium and relates to the technical field of a Bluetooth test. The method comprises the steps of receiving an instruction packet which is sent an upper computer and is equipped with a preset format through a preset interaction protocol; analyzing an instruction carried by the instruction packet; performing the analyzed instruction; and returning an instruction performance result to the upper computer. According to the embodiment of the invention, the upper computer sends the instruction packet of the preset format to a lower computer for a communication test through the preset interaction protocol, and the lower computer analyzes and performs the instruction and returns the instruction performance result to the upper computer. Through application of the automatic test method, the existing test method of requiring artificial participation at the sides of the upper computer and the lower computer is replaced, the test times can be increased, an application range of a test place can be expanded, and the test efficiency of a Bluetooth product can be improved.
Owner:PAX COMP TECH SHENZHEN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com