Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
888 results about "Protocol for Web Description Resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Protocol for Web Description Resources (POWDER) is the W3C recommended method for describing Web resources. It specifies a protocol for publishing metadata about Web resources using RDF, OWL, and HTTP.
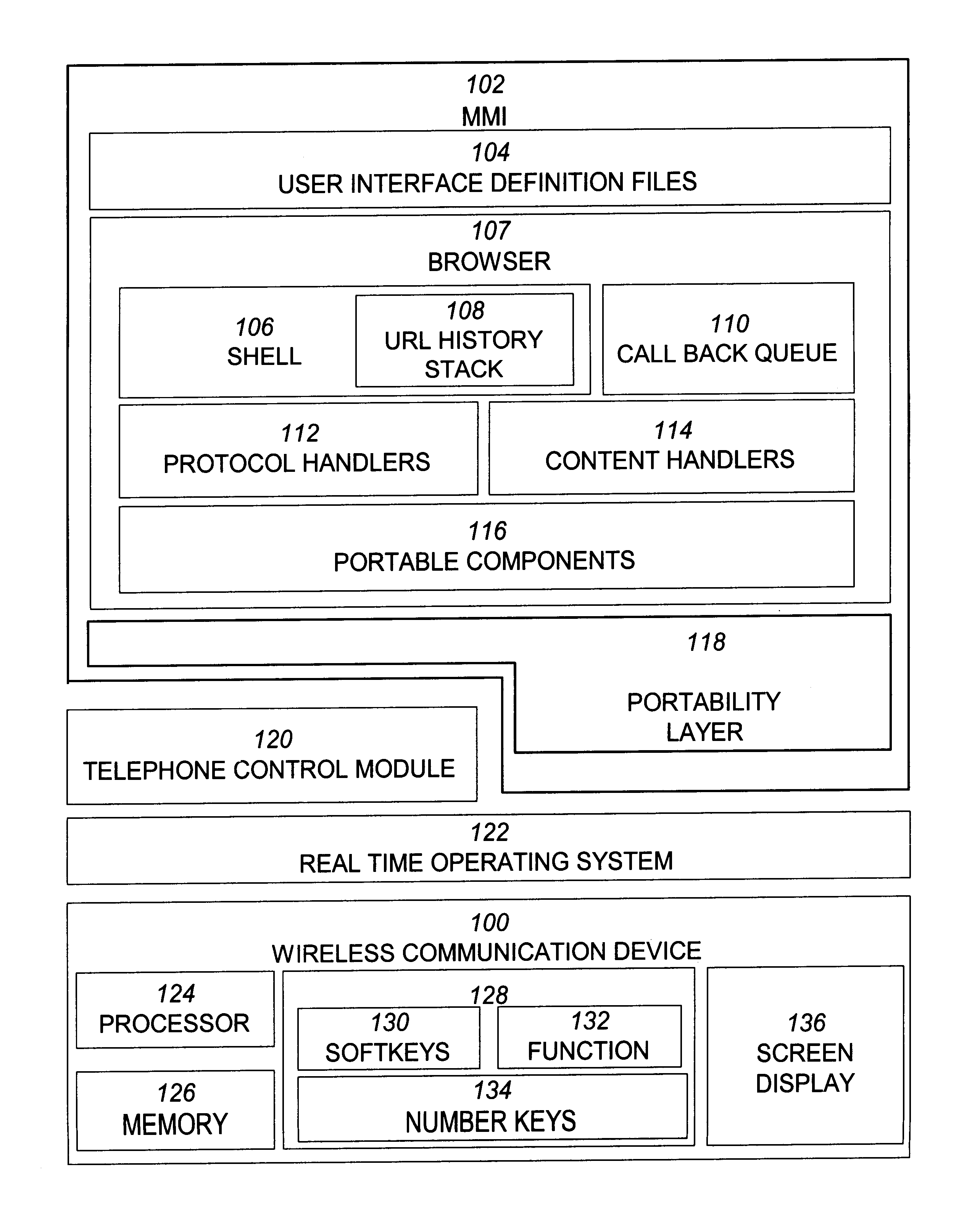
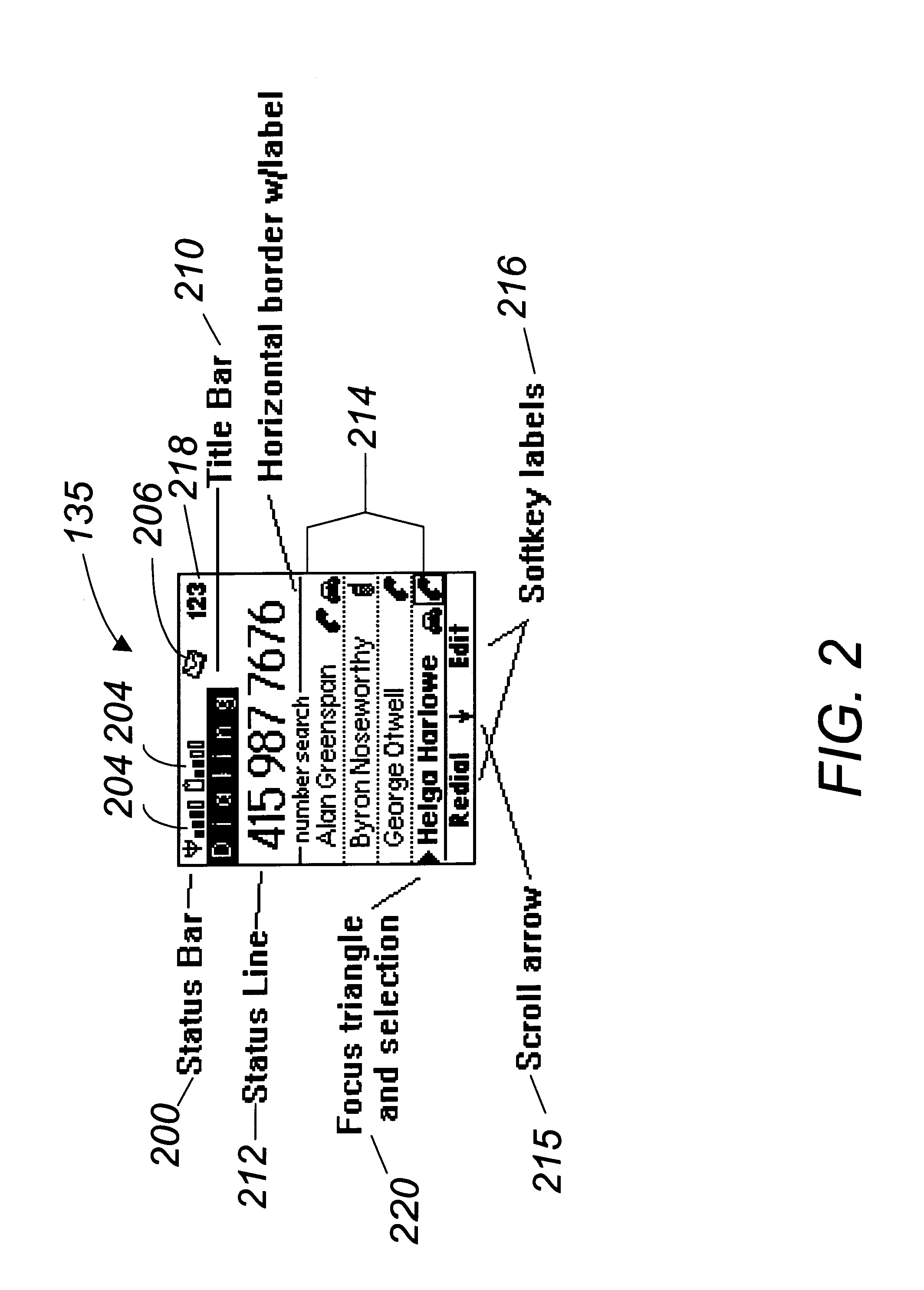
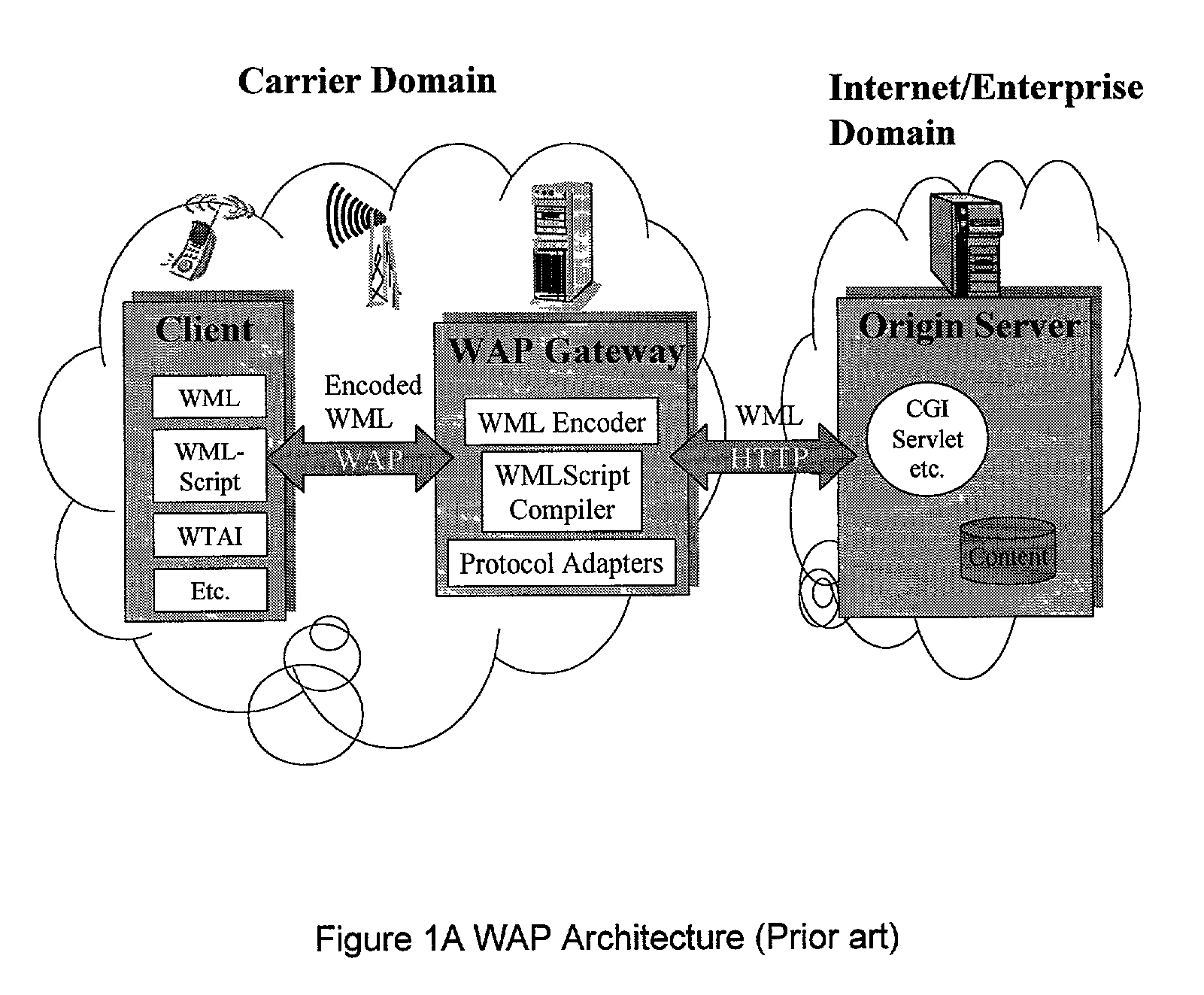
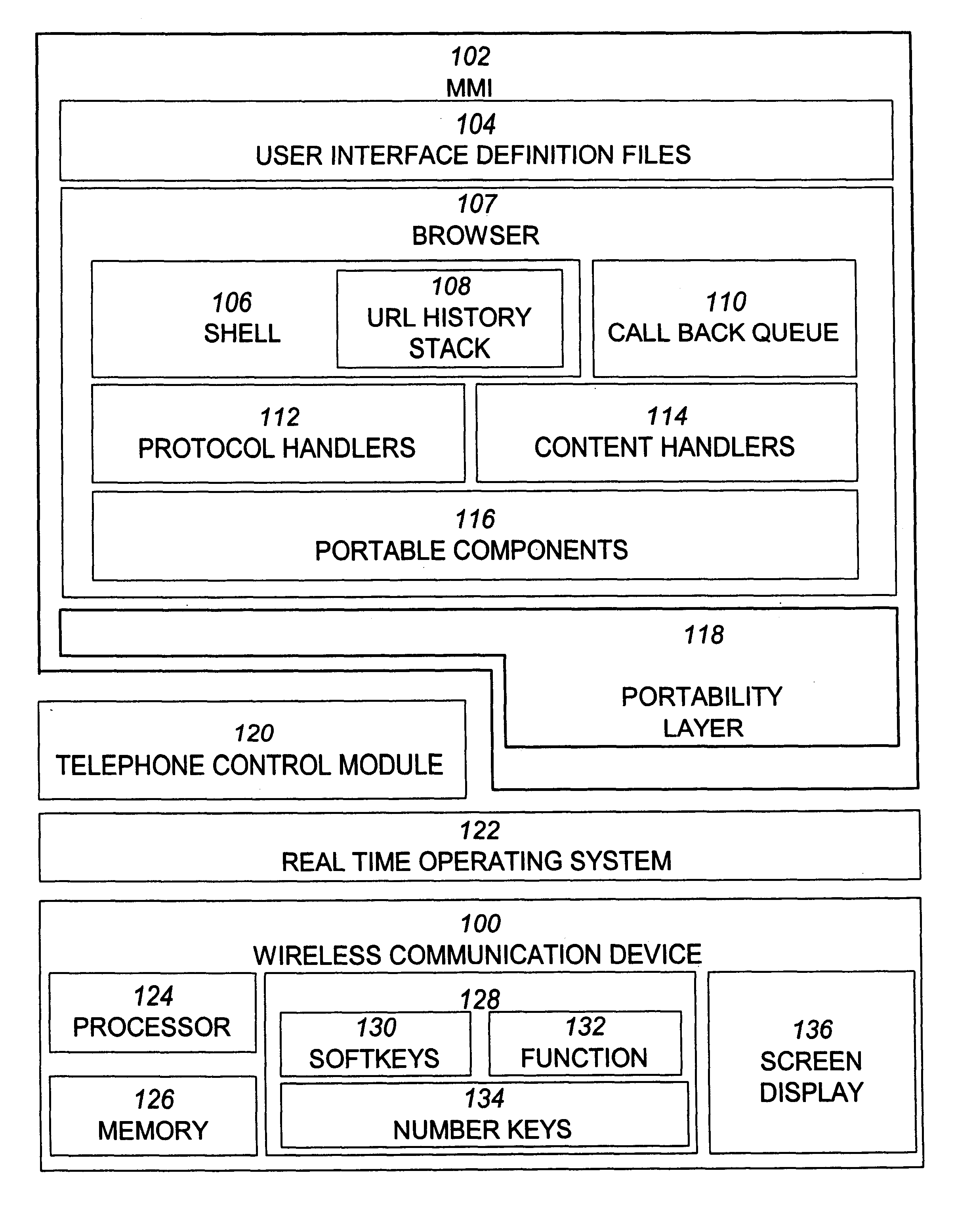
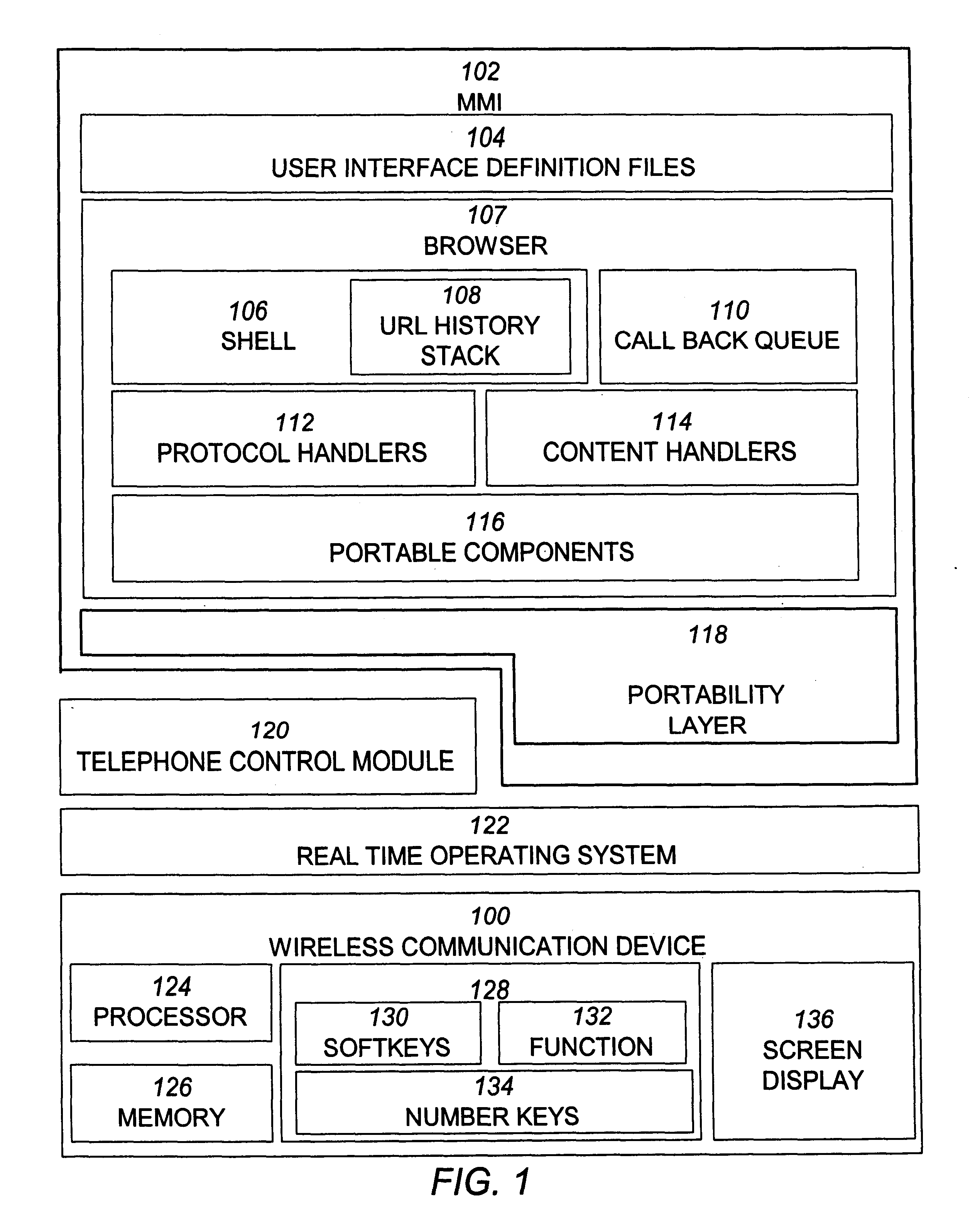
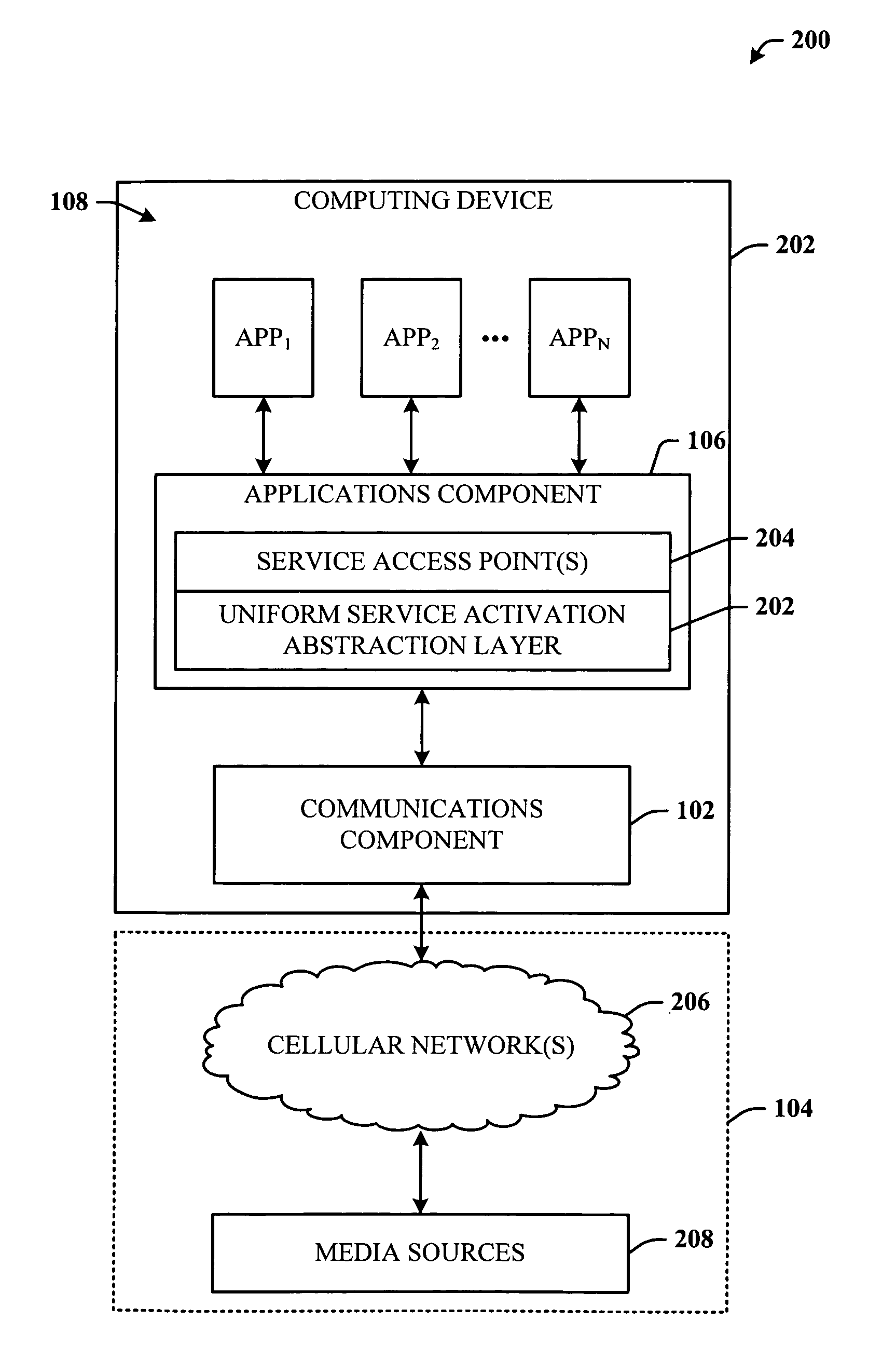
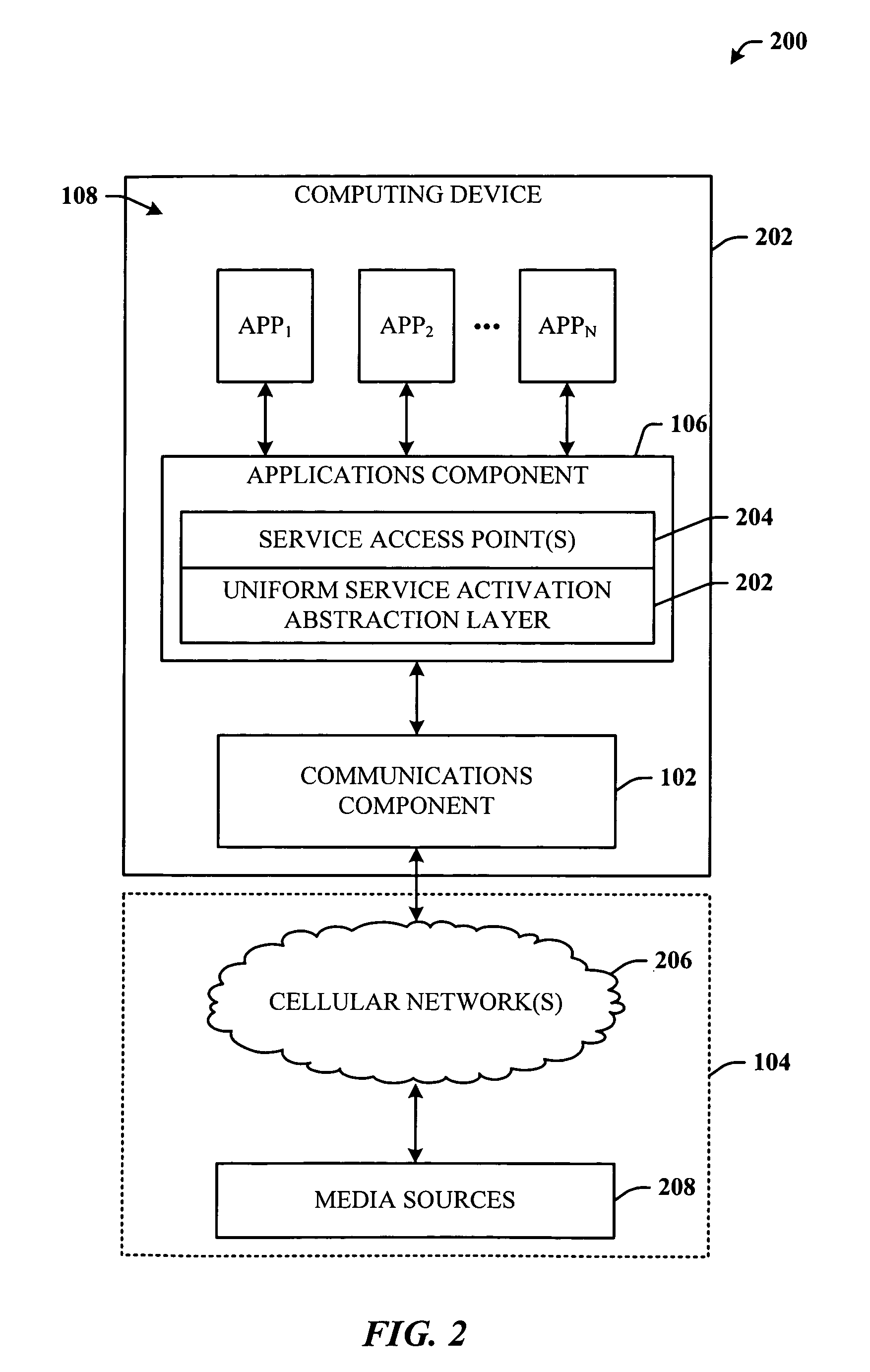
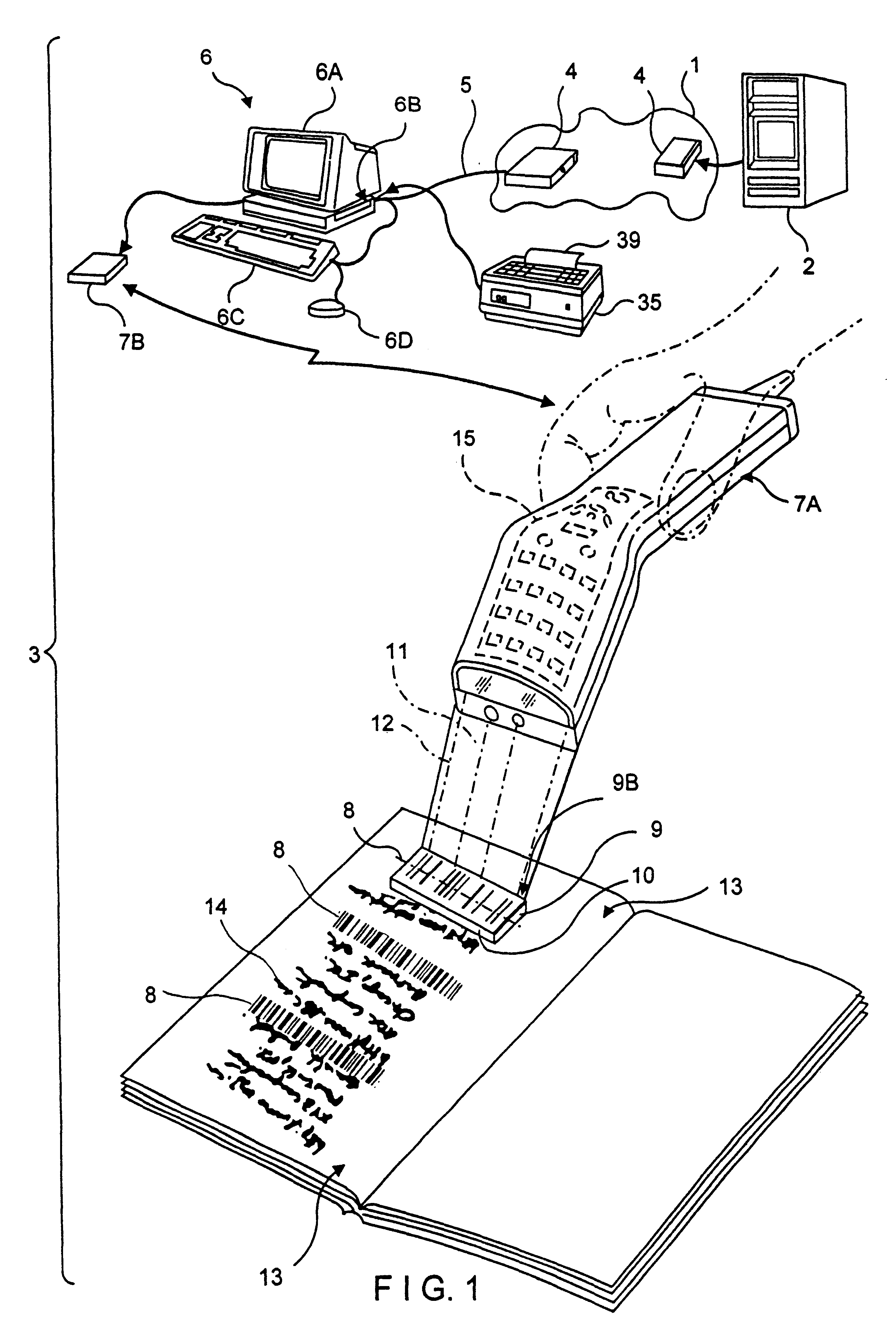
Wireless communication device with markup language based man-machine interface
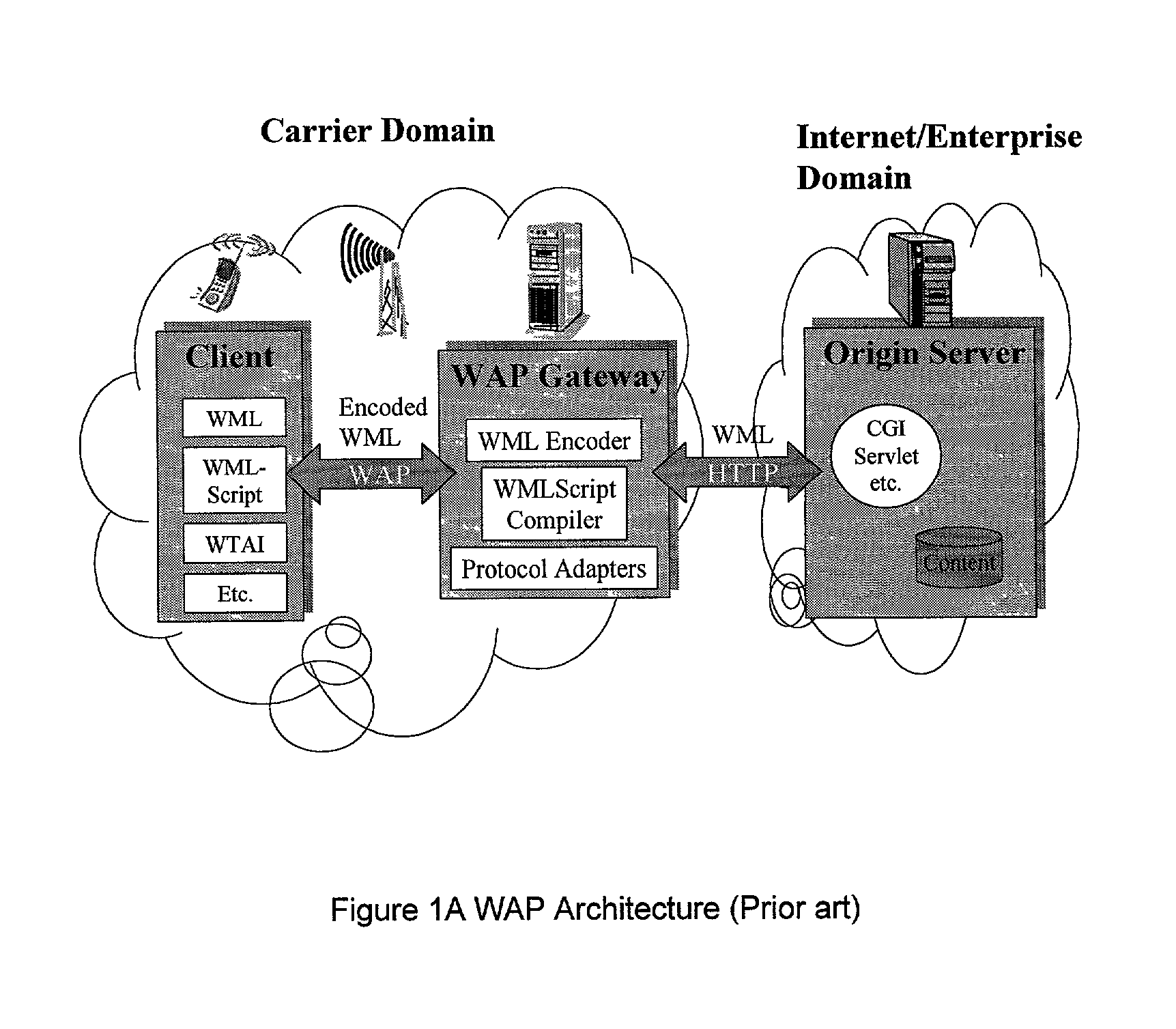
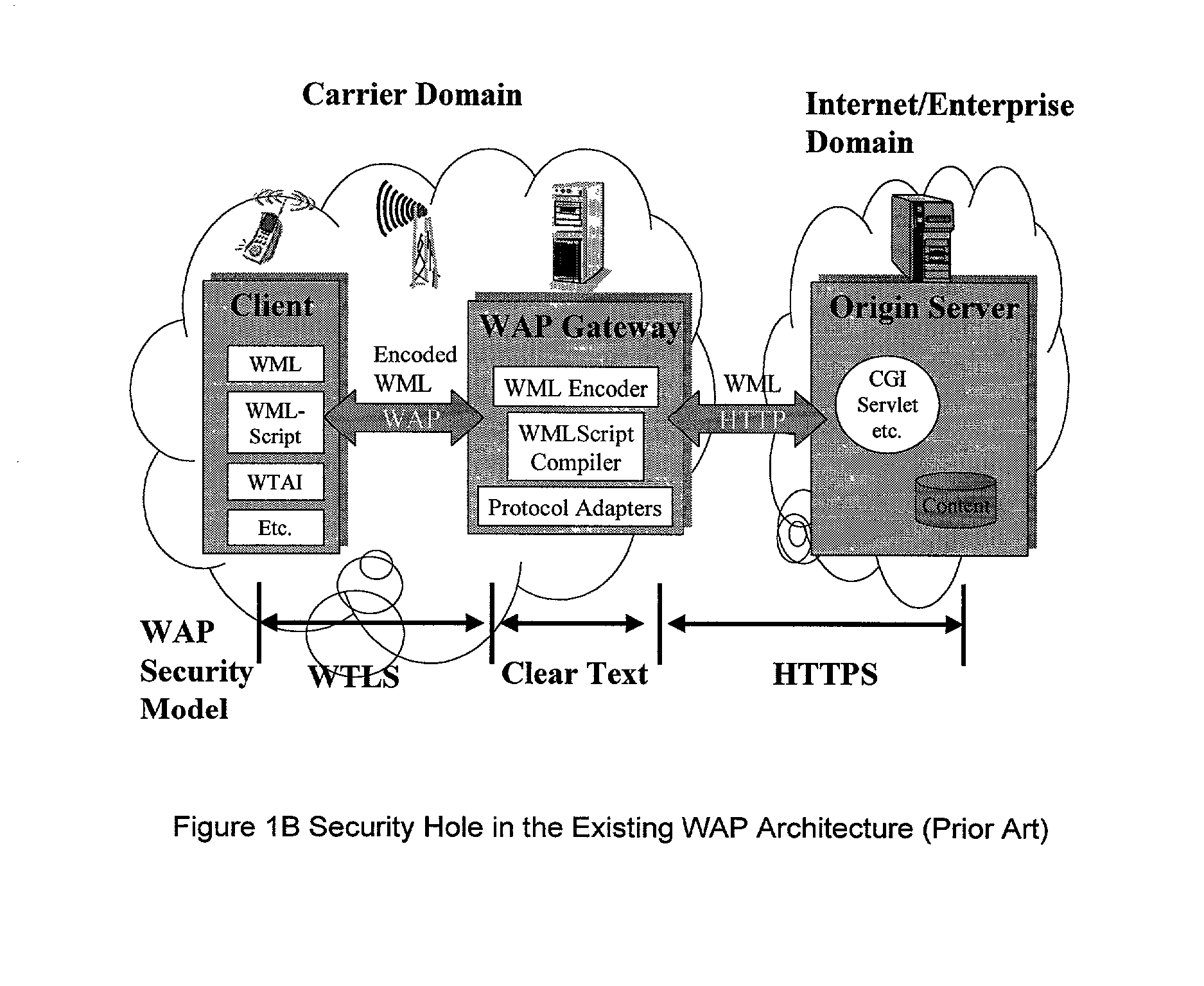
A system, method, and software product provide a wireless communications device with a markup language based man-machine interface. The man-machine interface provides a user interface for the various telecommunications functionality of the wireless communication device, including dialing telephone numbers, answering telephone calls, creating messages, sending messages, receiving messages, establishing configuration settings, which is defined in markup language, such as HTML, and accessed through a browser program executed by the wireless communication device. This feature enables direct access to Internet and World Wide Web content, such as Web pages, to be directly integrated with telecommunication functions of the device, and allows Web content to be seamlessly integrated with other types of data, since all data presented to the user via the user interface is presented via markup language-based pages. The browser processes an extended form of HTML that provides new tags and attributes that enhance the navigational, logical, and display capabilities of conventional HTML, and particularly adapt HTML to be displayed and used on wireless communication devices with small screen displays. The wireless communication device includes the browser, a set of portable components, and portability layer. The browser includes protocol handlers, which implement different protocols for accessing various functions of the wireless communication device, and content handlers, which implement various content display mechanisms for fetching and outputting content on a screen display.
Owner:ACCESS
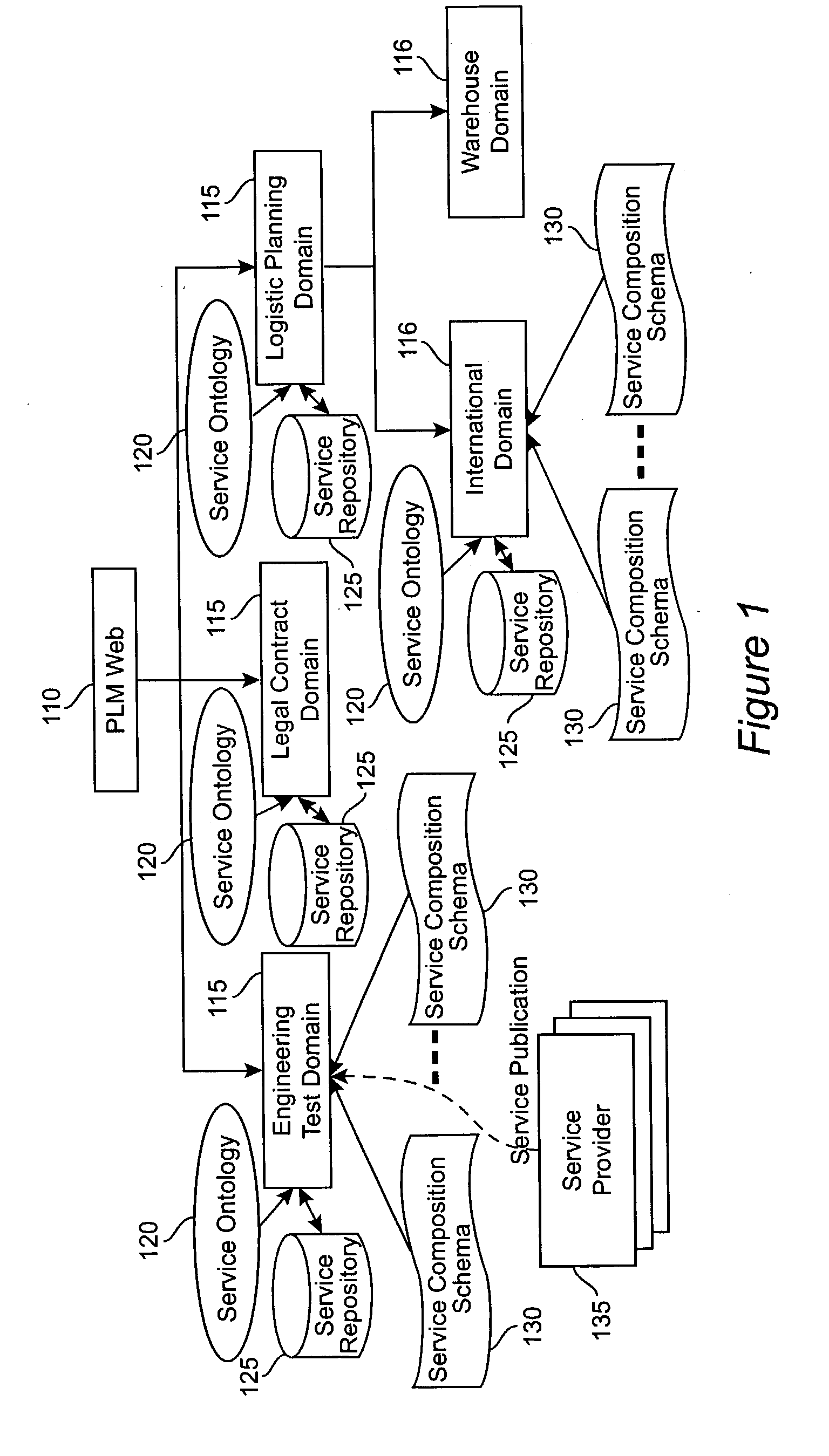
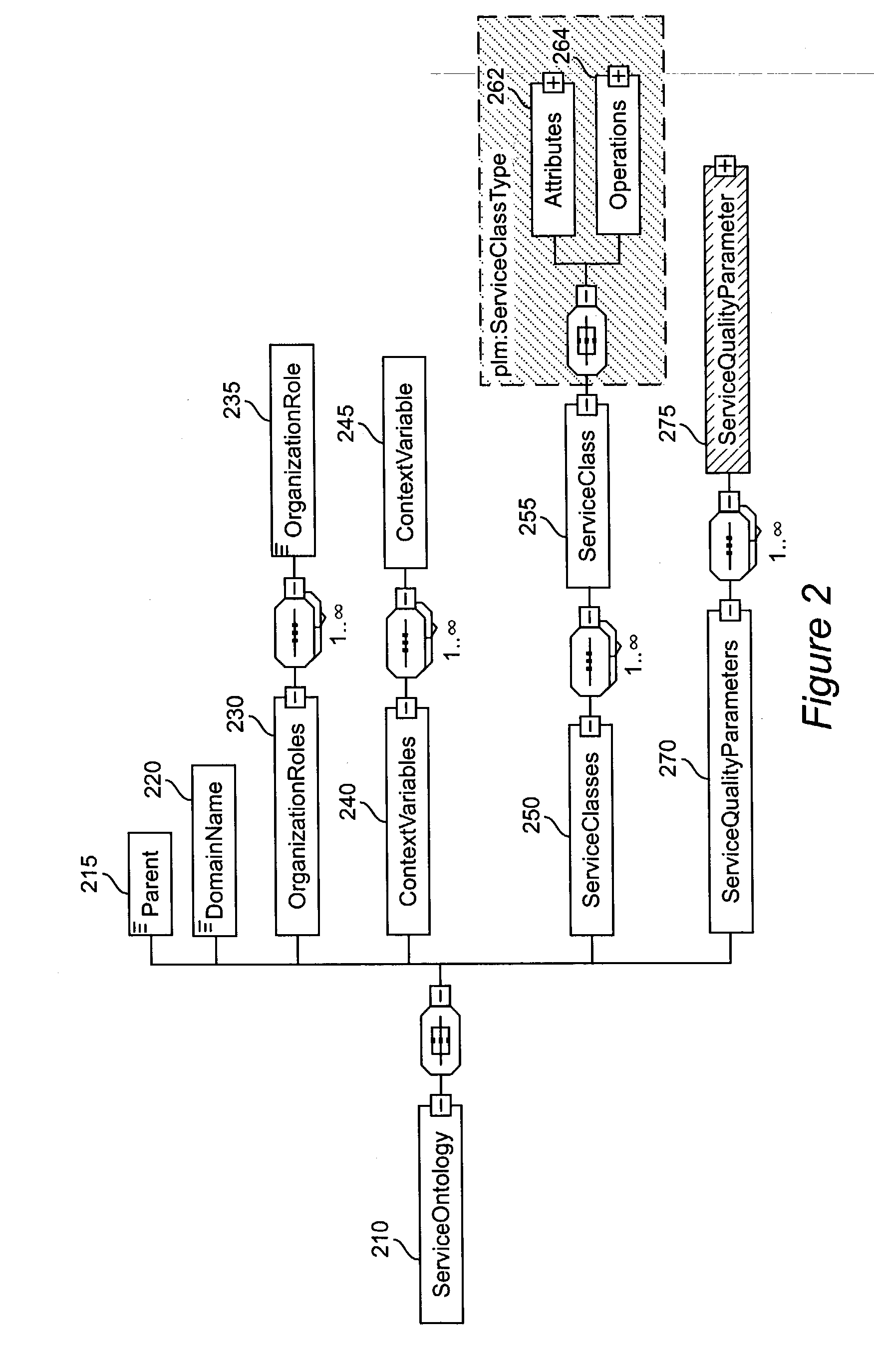
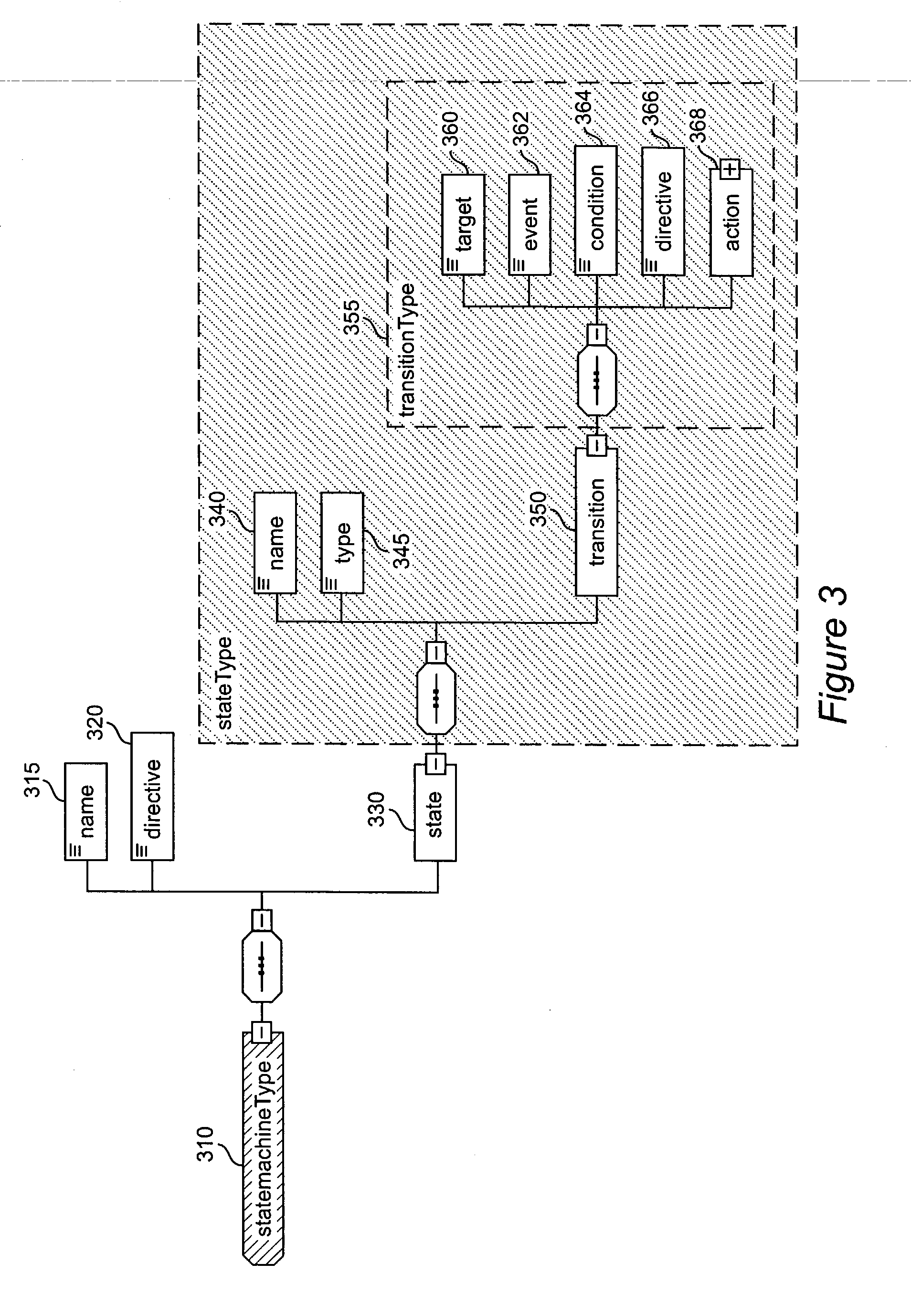
Method and apparatus for product lifecycle management in a distributed environment enabled by dynamic business process composition and execution by rule inference
InactiveUS20040162741A1Detect and resolve conflictOffice automationResourcesDistributed servicesNetwork topology
A system and method for supporting Product Lifecycle Management over a distributed service network topology that connects a hierarchy of functional domains, each domain having a service ontology and one or more service composition schemas defined by the service ontology. Each service composition schema models a business process in its domain. Descriptions of services provided to each domain are published to a service repository by providers of the services, in conformity with one of the service composition schemas. There is a business process proxy provided by the service provider for each service description, which encapsulates for public access the internal processes of the service provider. The invention makes use of an event messaging protocol that enables service collaboration and ad-hoc workflow composition. Each business process is implemented by an ad-hoc workflow comprised of one or more tasks connected by one or more business rules. For each business process there is a business flow manager that dynamically composes ad-hoc workflow prior to execution and dynamically modifies the ad-hoc workflow as the business process executes. The business flow manager uses backward-chain inferencing and then forward-chain inferencing to generate the ad-hoc workflows, based on user identification of a target task. The business flow manager is able to stop execution of the workflow and regenerate a workflow for remaining tasks in response to events received over the network from service providers, and is also able to detect conflicts in the workflows at composition time and at execution time.
Owner:IBM CORP
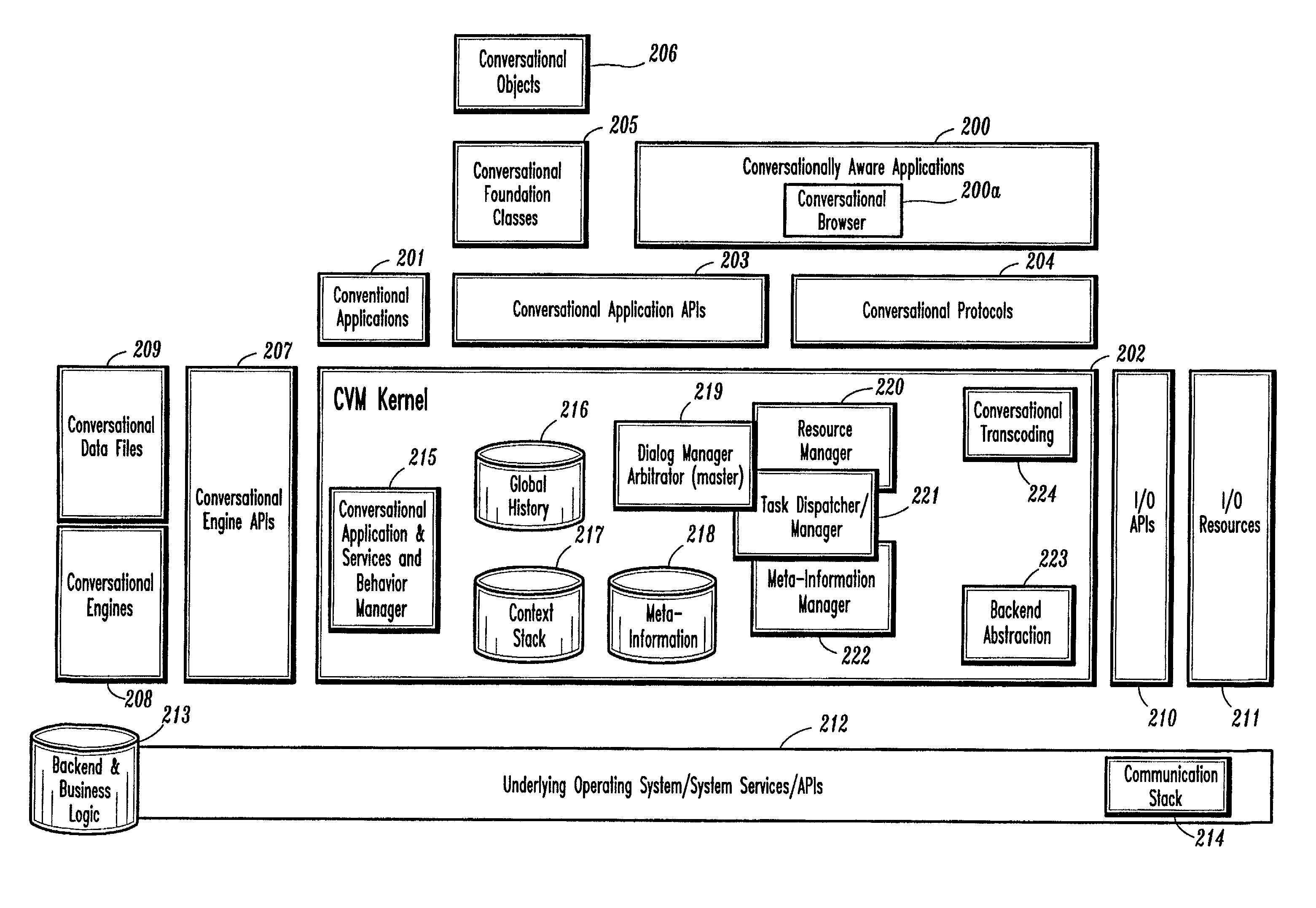
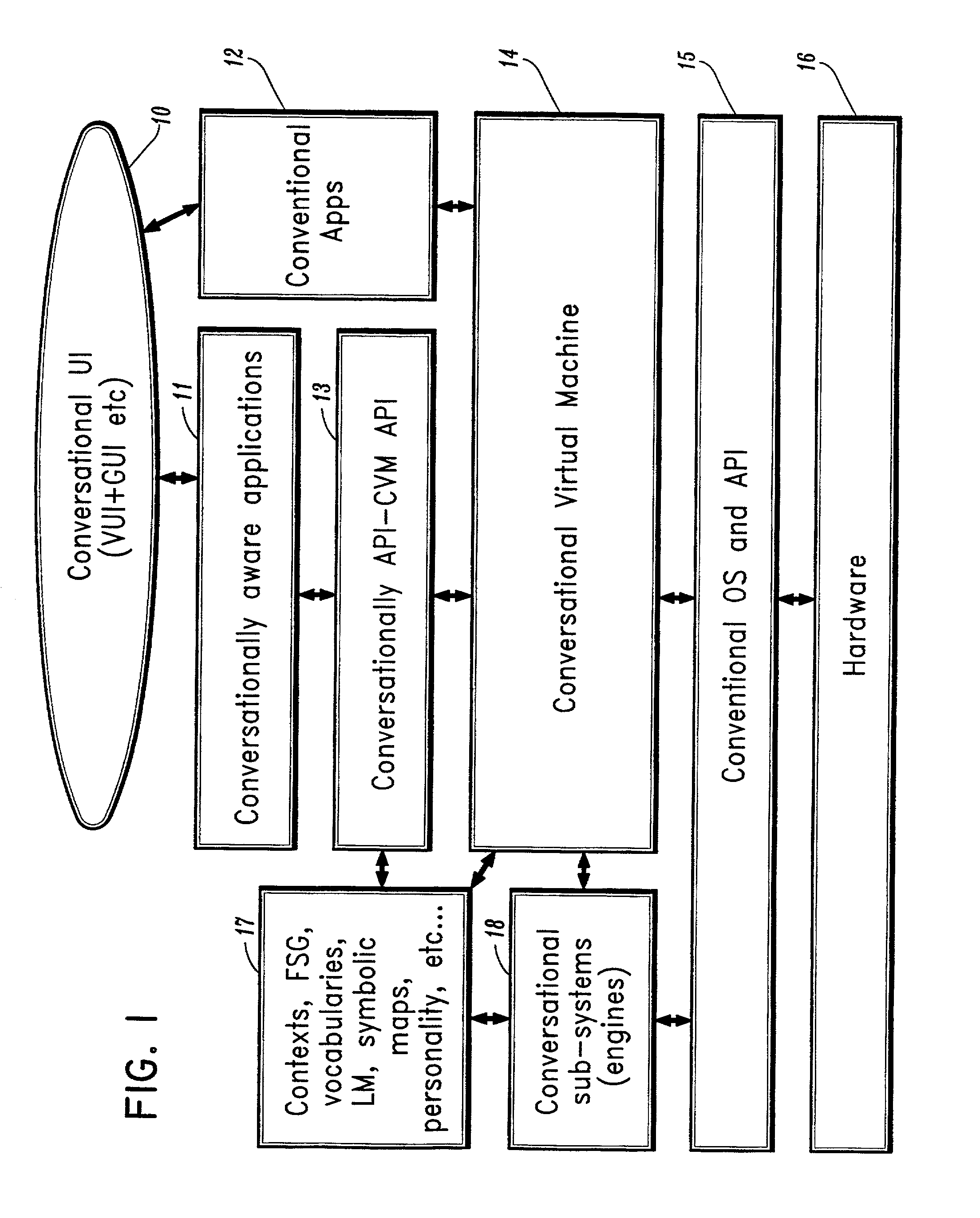
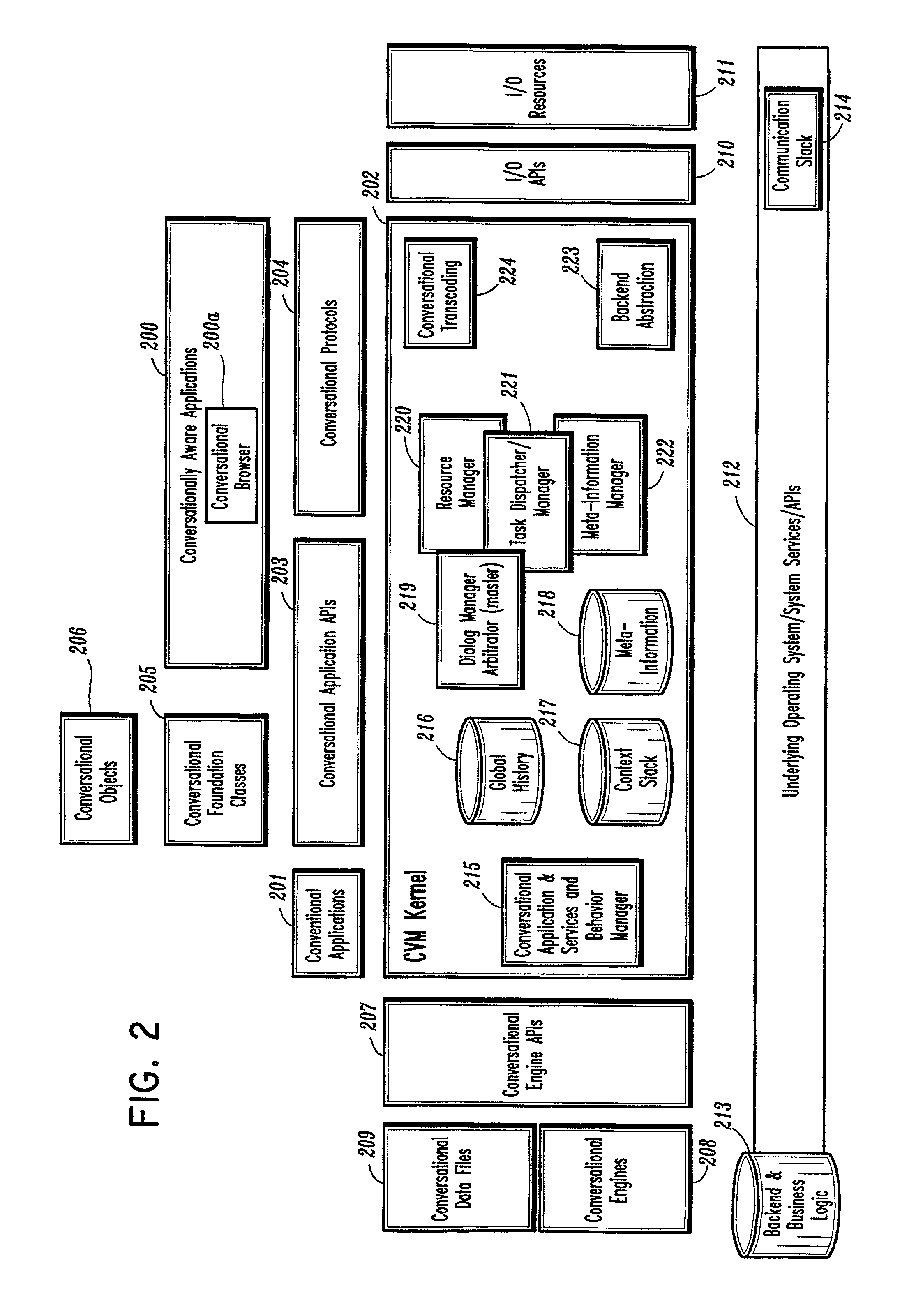
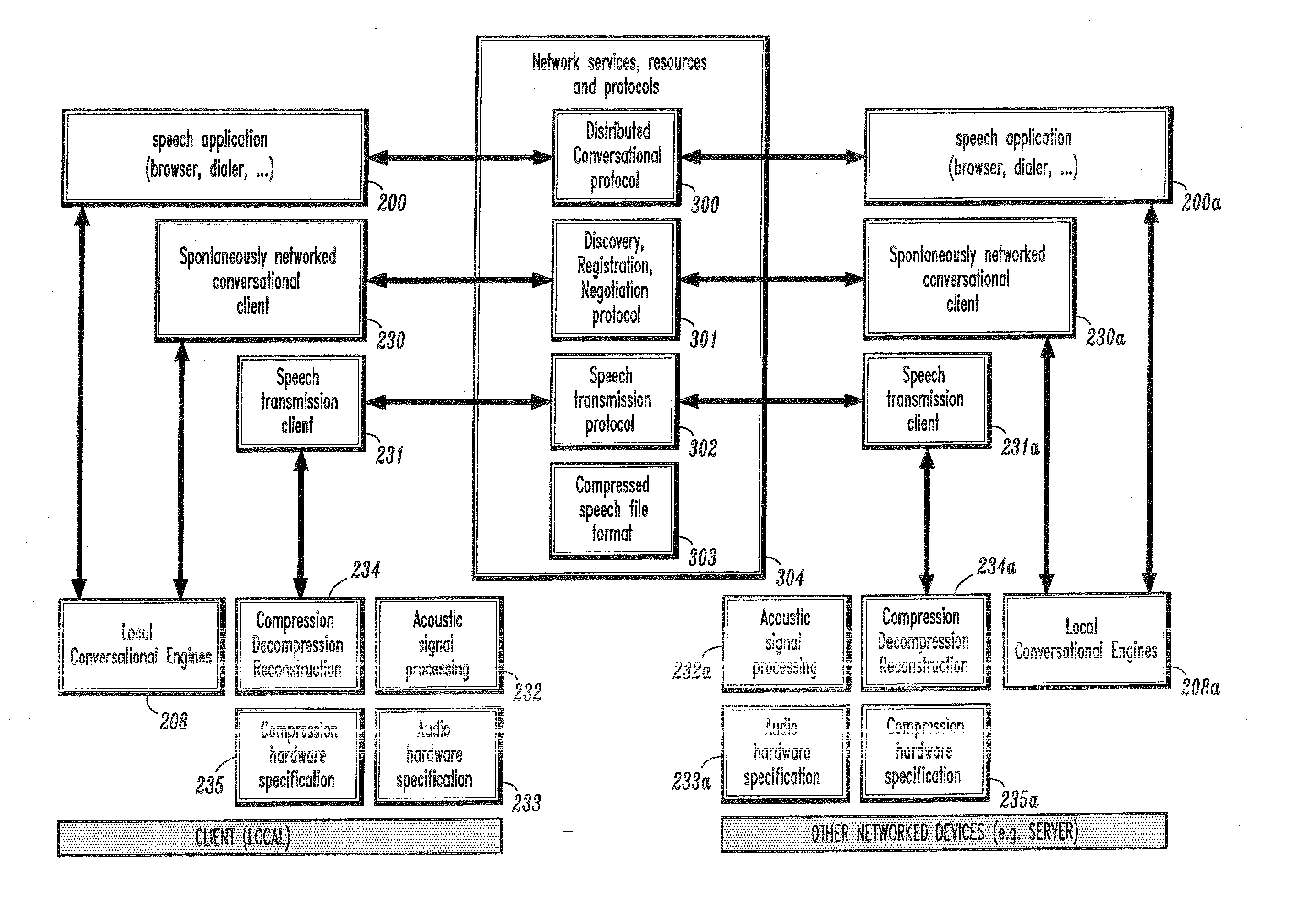
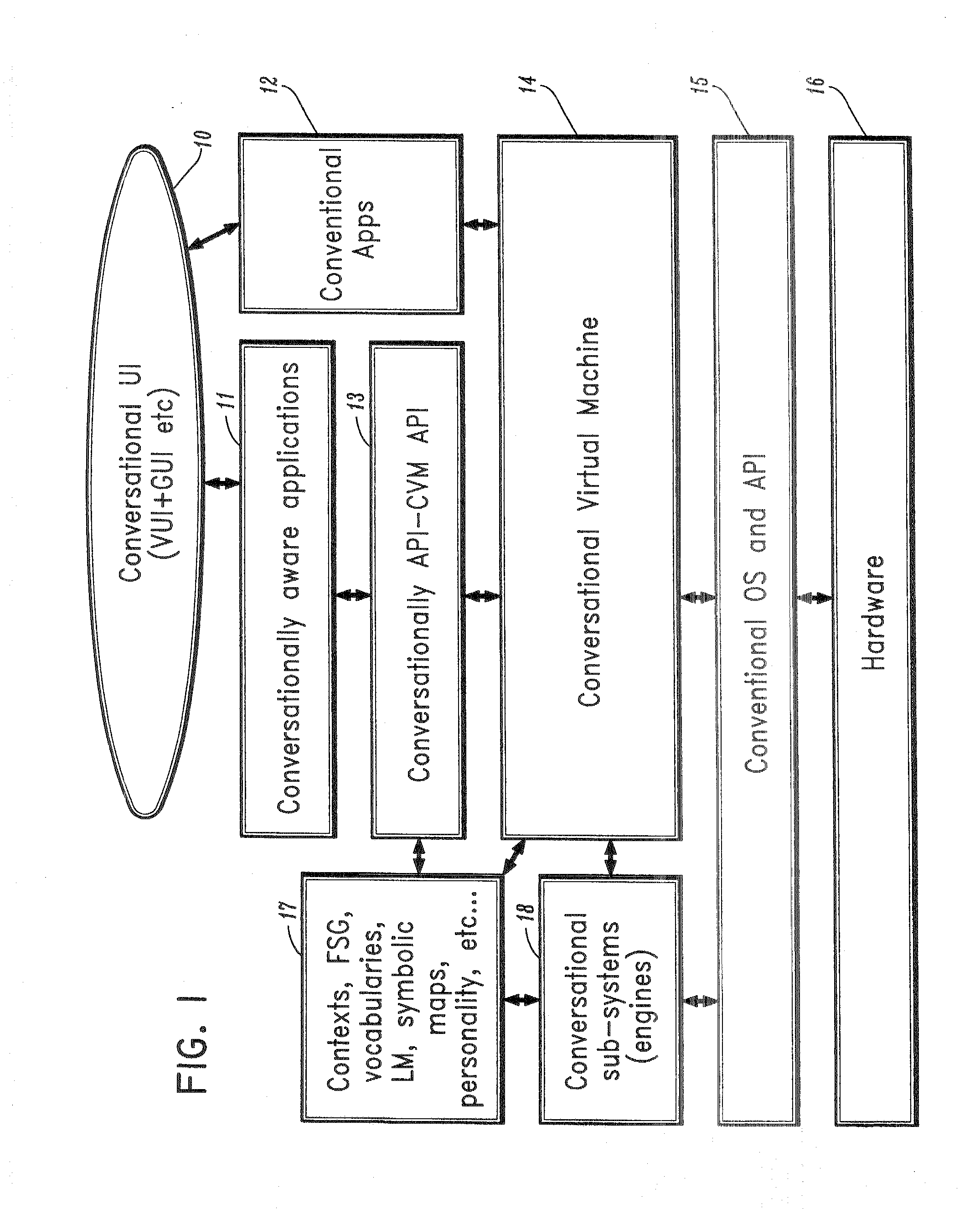
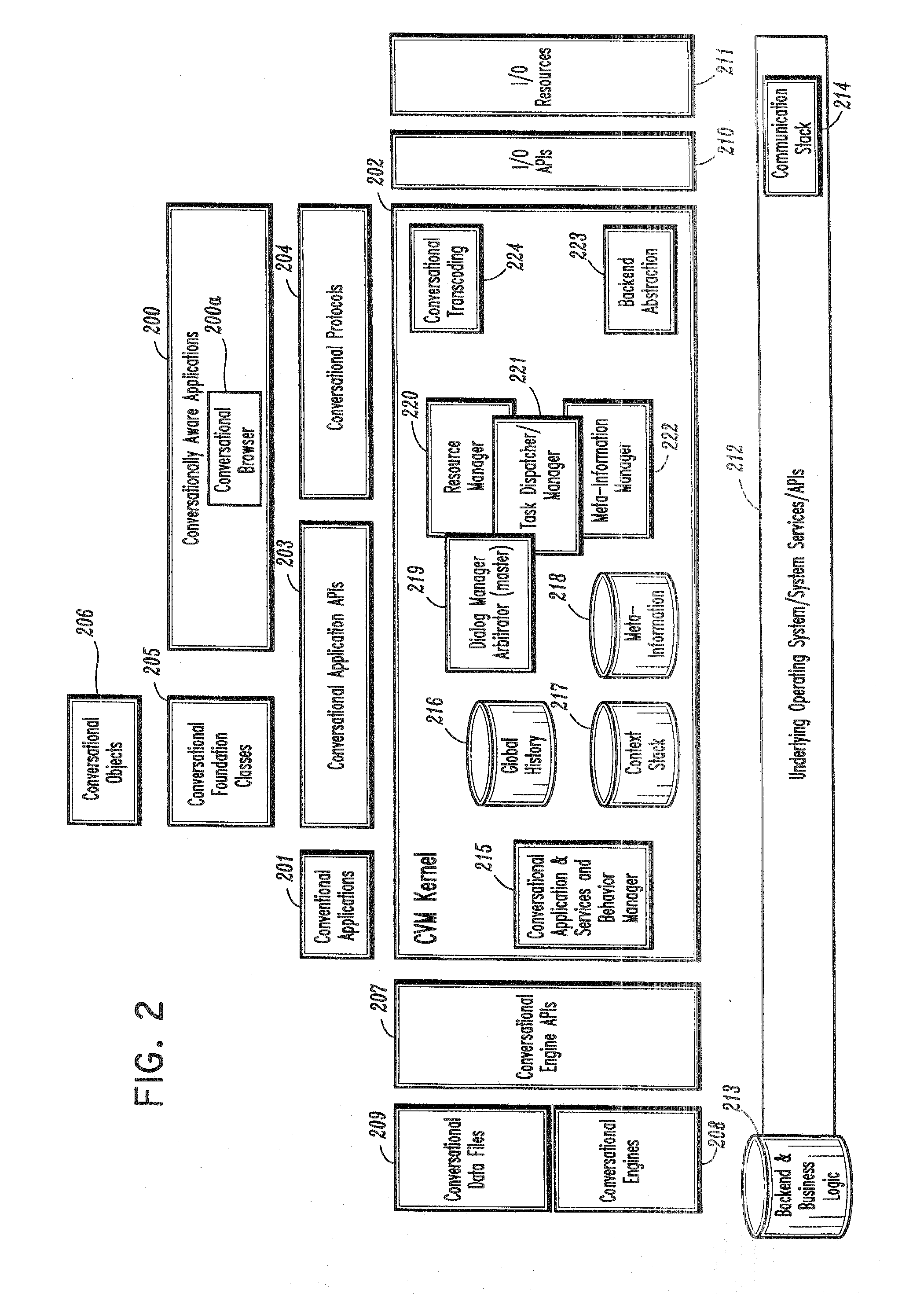
Conversational computing via conversational virtual machine
InactiveUS7137126B1Limitation for transferReduce degradationInterconnection arrangementsResource allocationConversational speechApplication software
A conversational computing system that provides a universal coordinated multi-modal conversational user interface (CUI) (10) across a plurality of conversationally aware applications (11) (i.e., applications that “speak” conversational protocols) and conventional applications (12). The conversationally aware maps, applications (11) communicate with a conversational kernel (14) via conversational application APIs (13). The conversational kernel (14) controls the dialog across applications and devices (local and networked) on the basis of their registered conversational capabilities and requirements and provides a unified conversational user interface and conversational services and behaviors. The conversational computing system may be built on top of a conventional operating system and APIs (15) and conventional device hardware (16). The conversational kernel (14) handles all I / O processing and controls conversational engines (18). The conversational kernel (14) converts voice requests into queries and converts outputs and results into spoken messages using conversational engines (18) and conversational arguments (17). The conversational application API (13) conveys all the information for the conversational kernel (14) to transform queries into application calls and conversely convert output into speech, appropriately sorted before being provided to the user.
Owner:UNILOC 2017 LLC
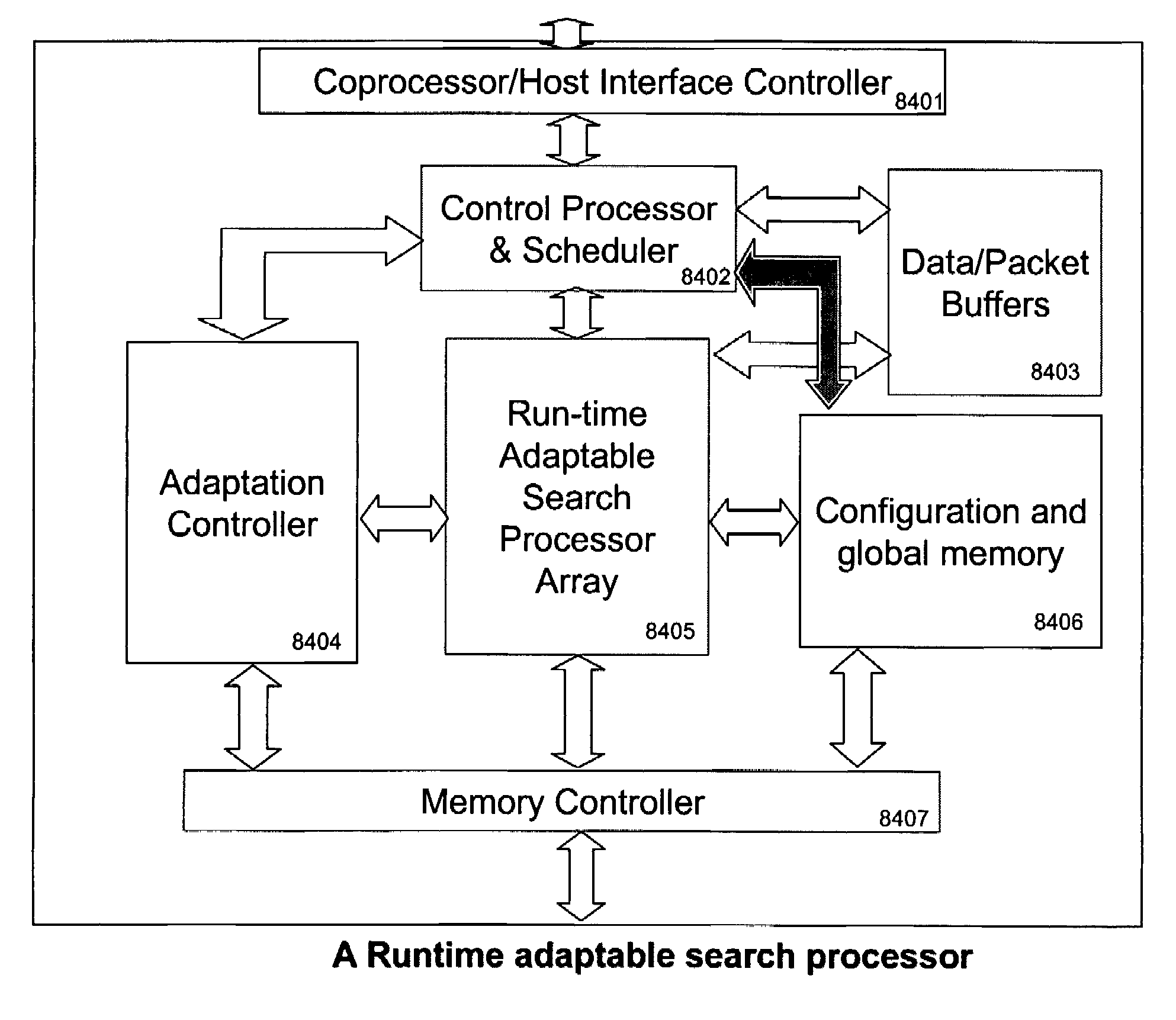
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
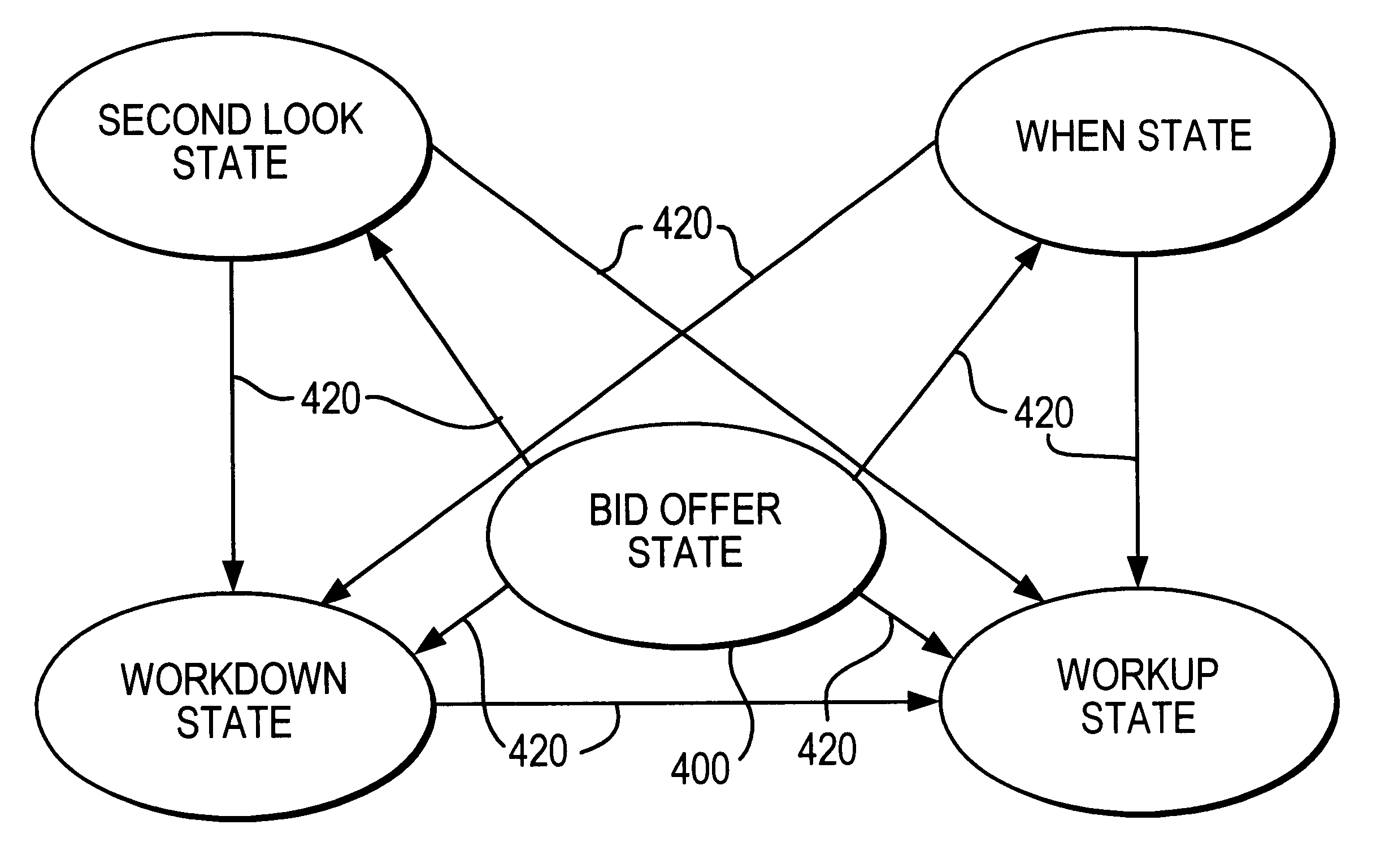
Automated price improvement protocol processor
InactiveUS6850907B2Distribute quicklyFast exchangeFinanceBuying/selling/leasing transactionsData processing systemProtocol processing
A data processing system for implementing transaction management of auction-based trading for specialized items such as fixed income instruments. The data processing system provides a highly structured trading protocol implemented through a sequence of trading paradigms. The system employs a distributed computer processing network linking together a plurality of commonly configured program controlled workstations. The protocol and its program controlling logic enhances trading efficiency, rewards market Makers, and fairly distributes market opportunity to system users.
Owner:CANTOR FITZGERALD LP +1
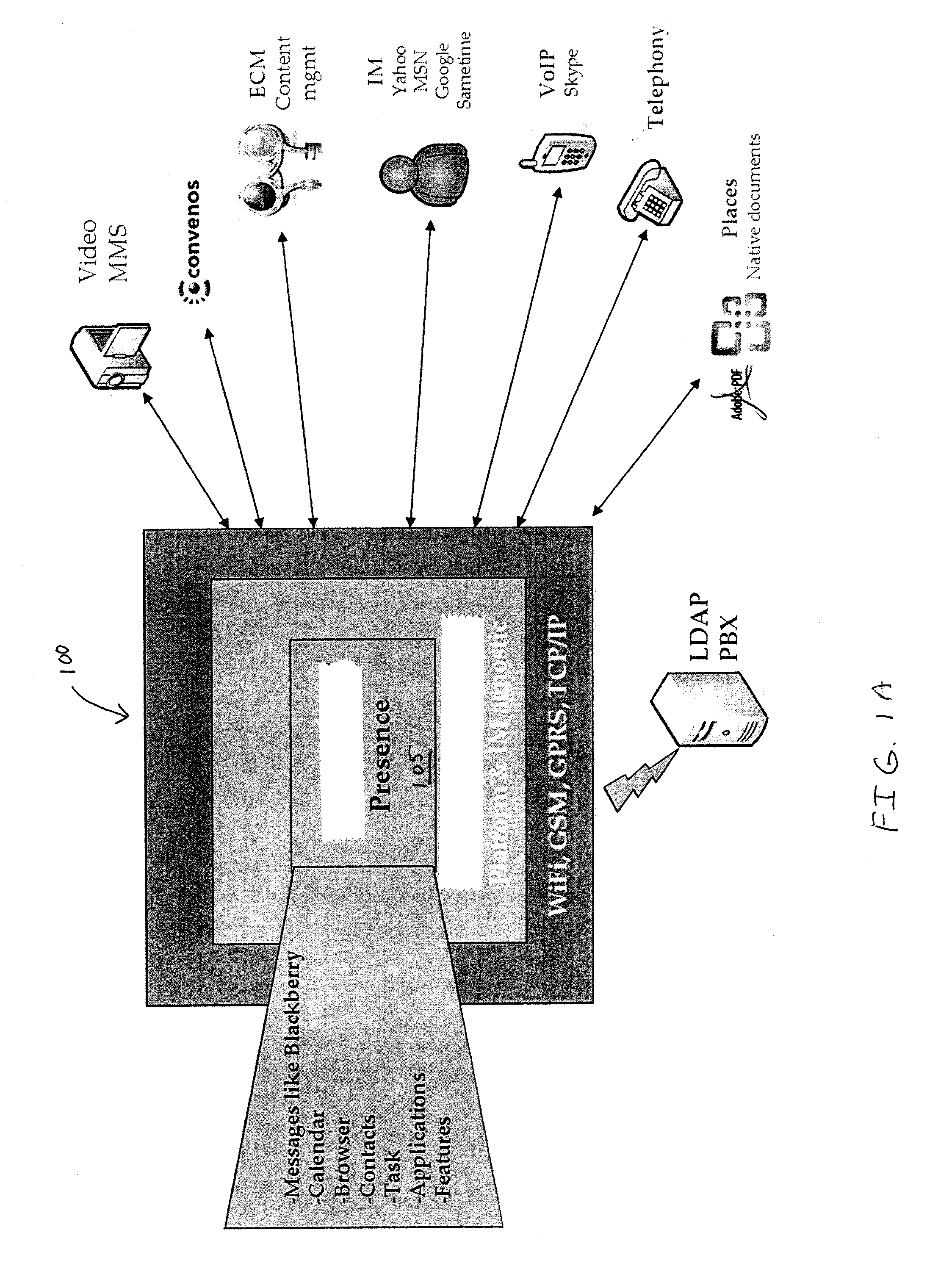
Apparatus, system, method, and computer program product for collaboration via one or more networks
InactiveUS20090019367A1Work well togetherFacilitate conferencing and collaborationDigital data protectionMultiple digital computer combinationsVirtual conferenceSpeech sound
A collaboration architecture supports virtual meetings, including web conferencing and collaboration. Presence information is aggregated from different types of communication services to provide a generic representation of presence. In one implementation, collaboration lifecycle management is provided to manage meetings over the lifecycle of a project. Audio options include voice over internet protocol (VoIP) and conventional PTSN phone networks, which are supported in one implementation by an audio conferencing server.
Owner:CONVENOUS
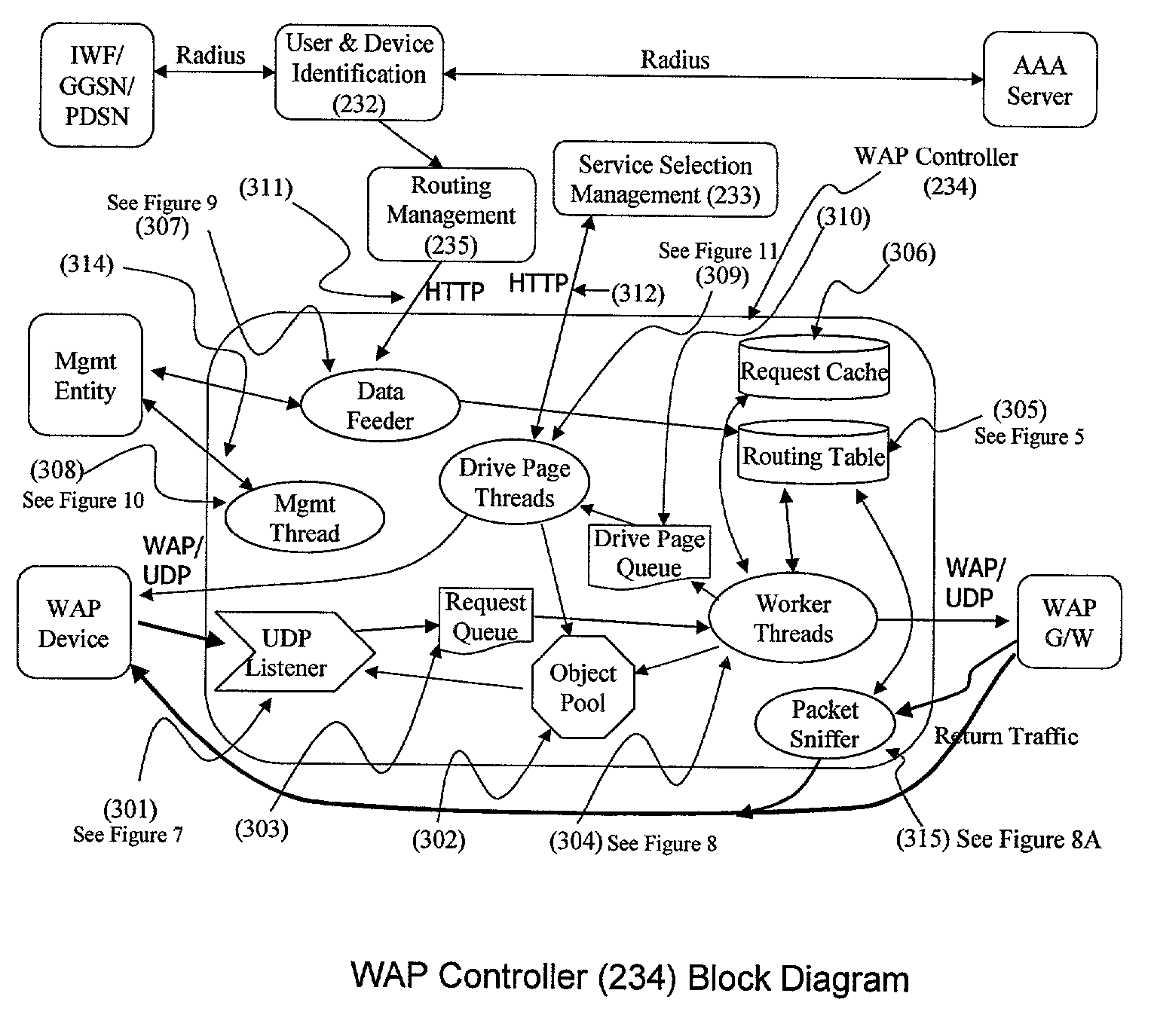
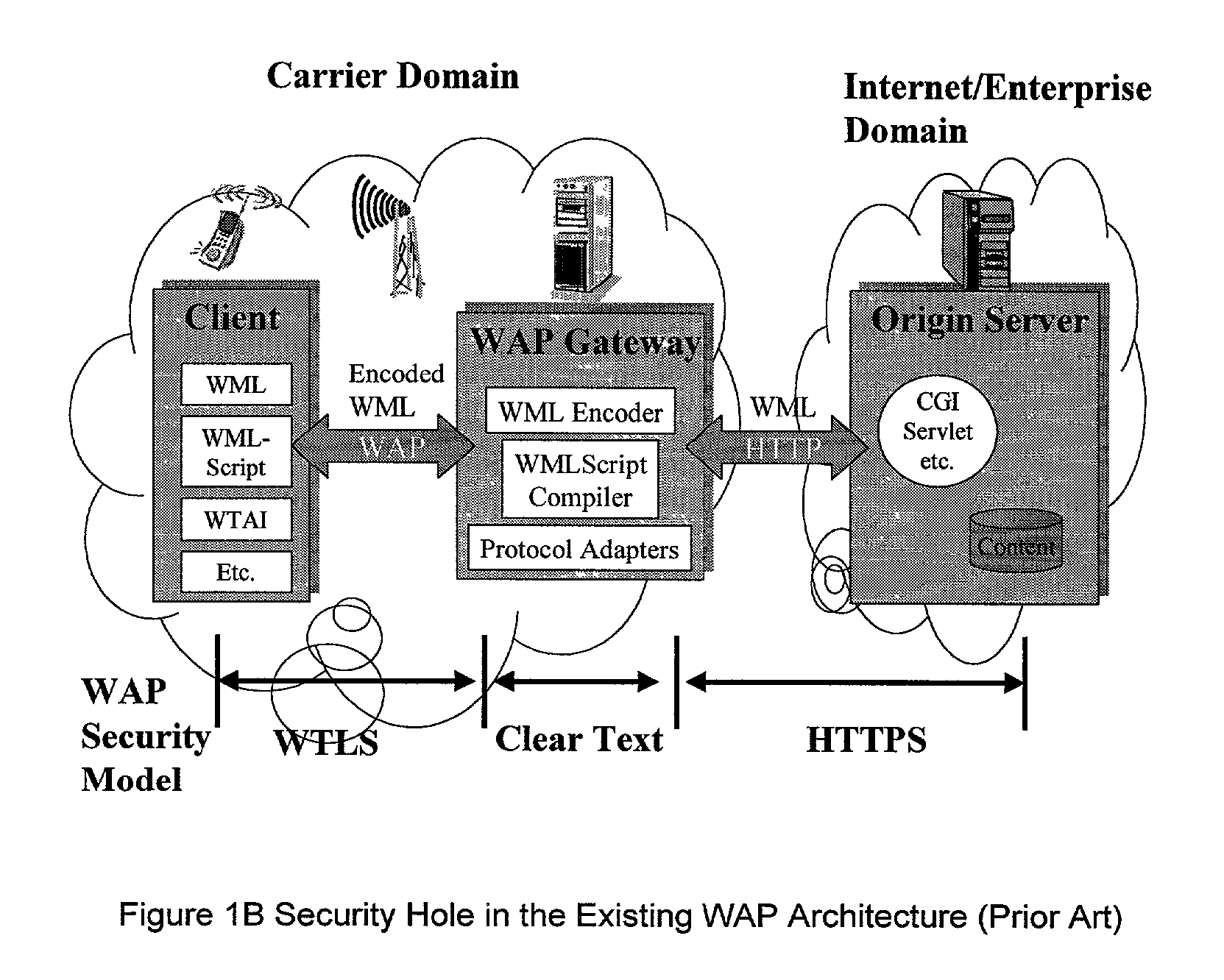
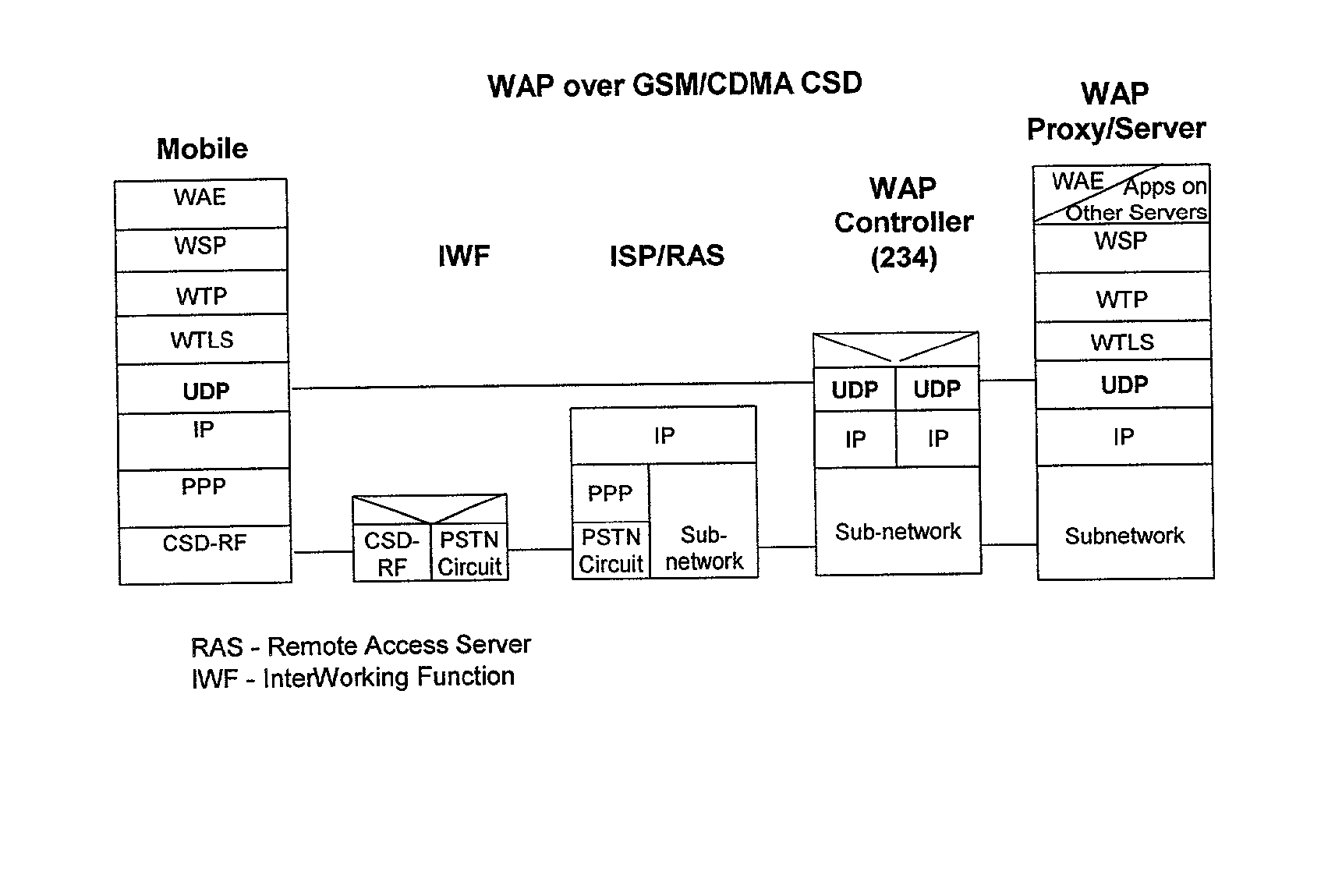
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protocol) gateways simultaneously
ActiveUS7039037B2Time-division multiplexData switching by path configurationCyber operationsComputer network
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYST INC
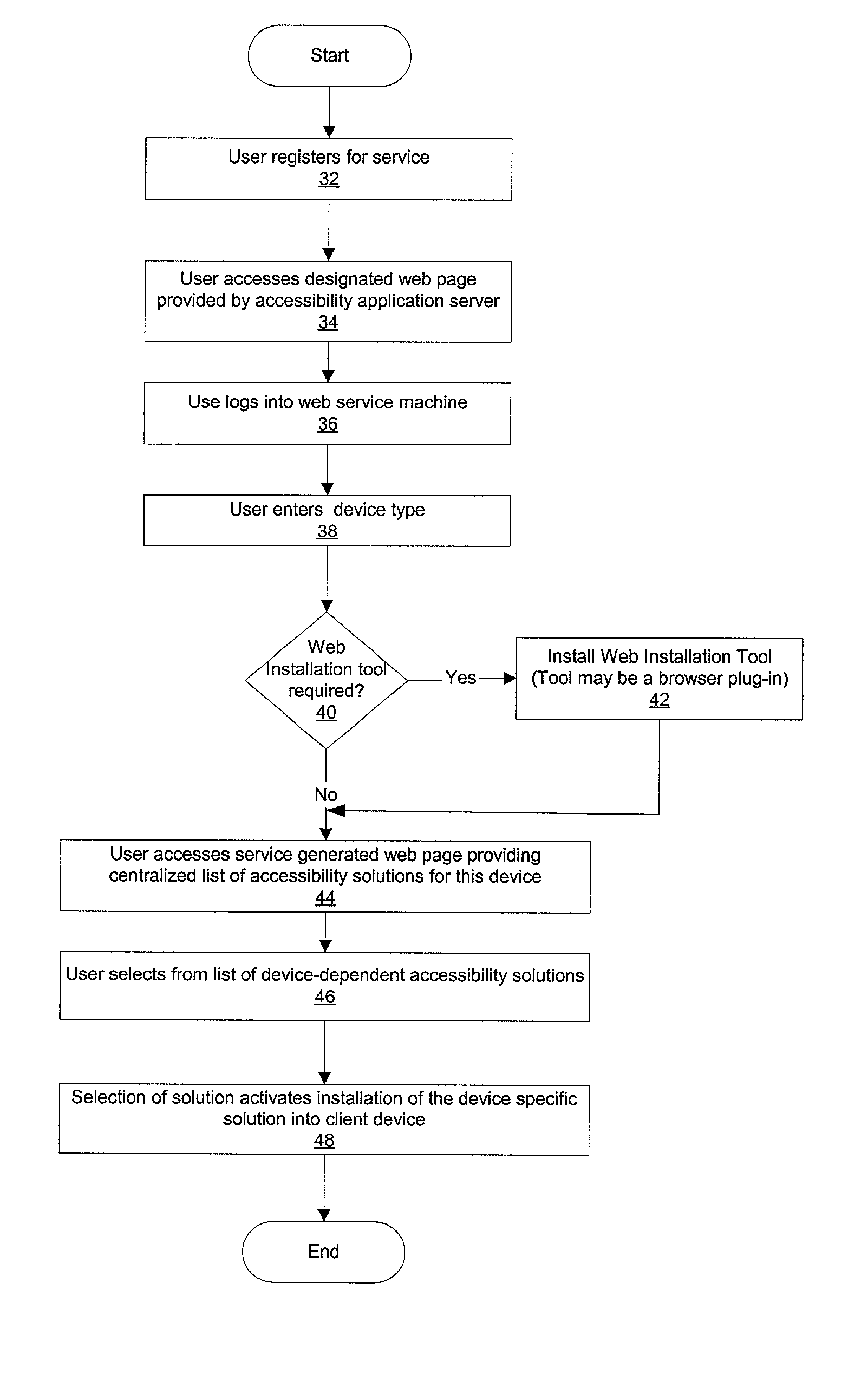
Method and system for providing a central repository for client-specific accessibility
InactiveUS20030061317A1Digital data information retrievalMultiple digital computer combinationsService provisionTranscoding
A method and system that provide a central repository for client specific accessibility applications to a user from an accessible server. The repository is updated on a periodic basis with new solutions provided by the service provider, who also manages licensing agreements between the user and the owner of the accessibility application. Accessibility programs, such as page magnification, screen readers, background changes, input modification, etc., are downloaded into the client device being used by the user customer by clicking link buttons from a web page generated by the service provider's server. The accessibility programs downloaded are then resident on the client device until changed by the user. In a preferred embodiment, the service provider also provides a universal transcoding service to apply the user selected accessibility transformations to any type of client device used by the user.
Owner:IBM CORP
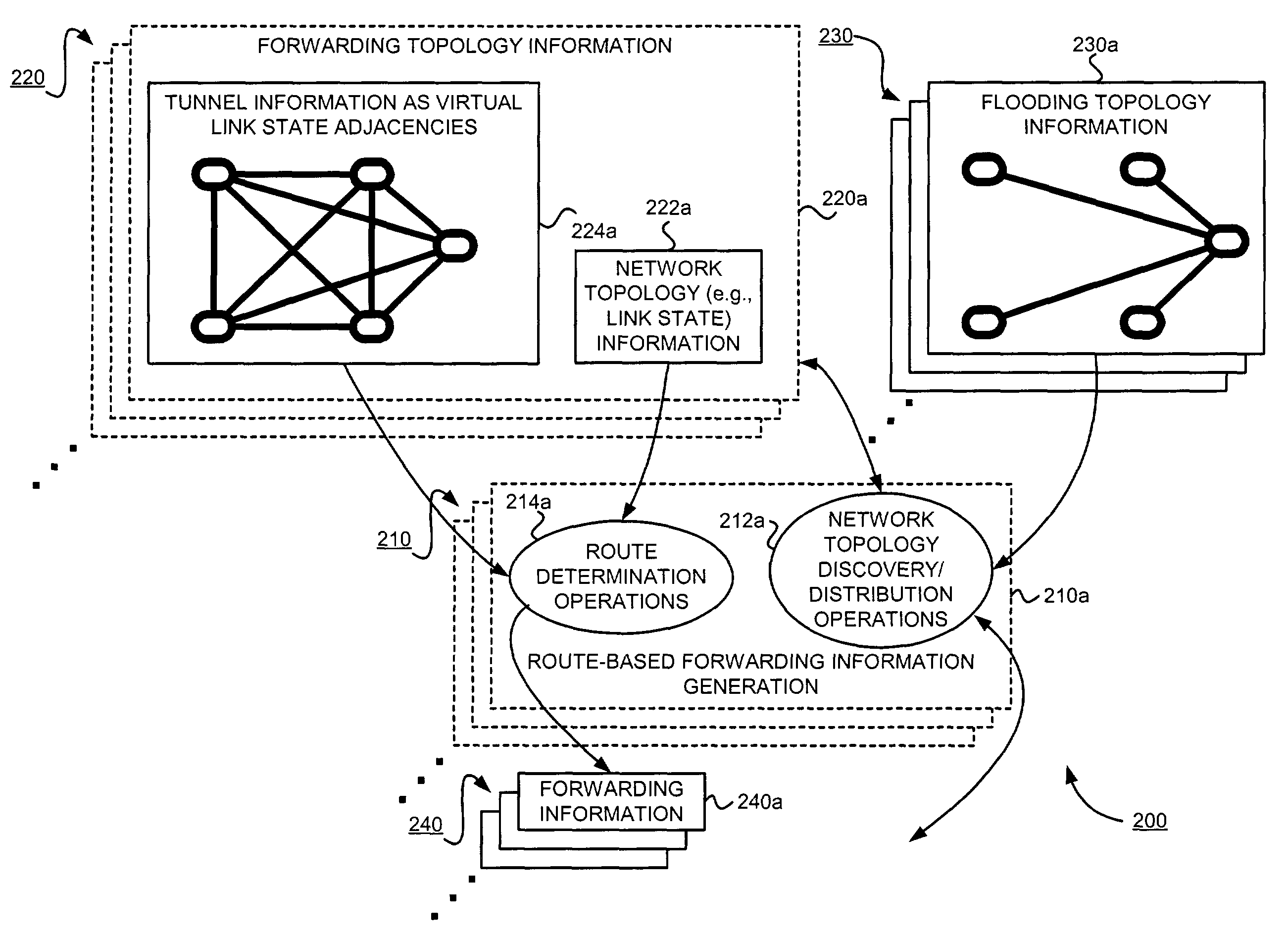
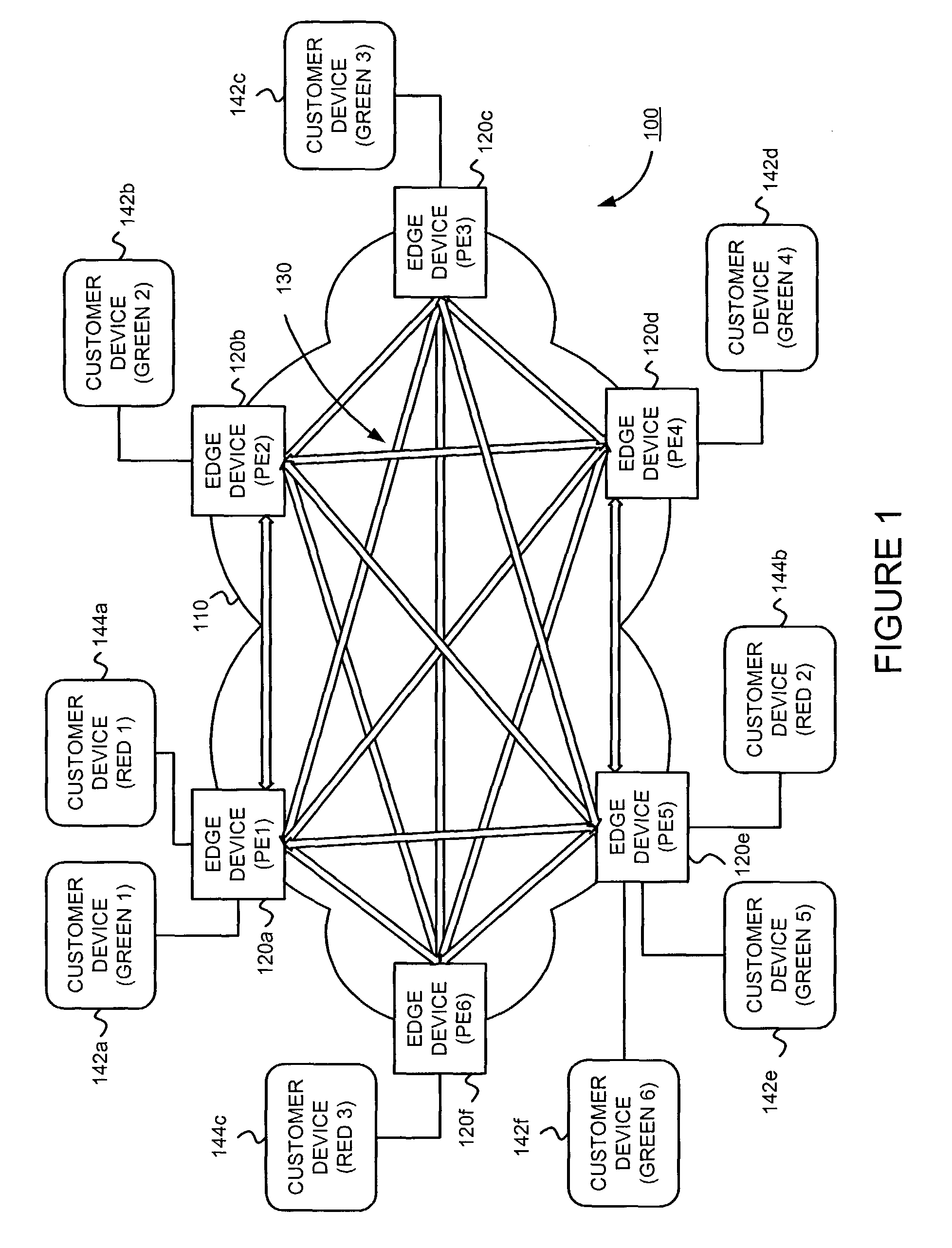
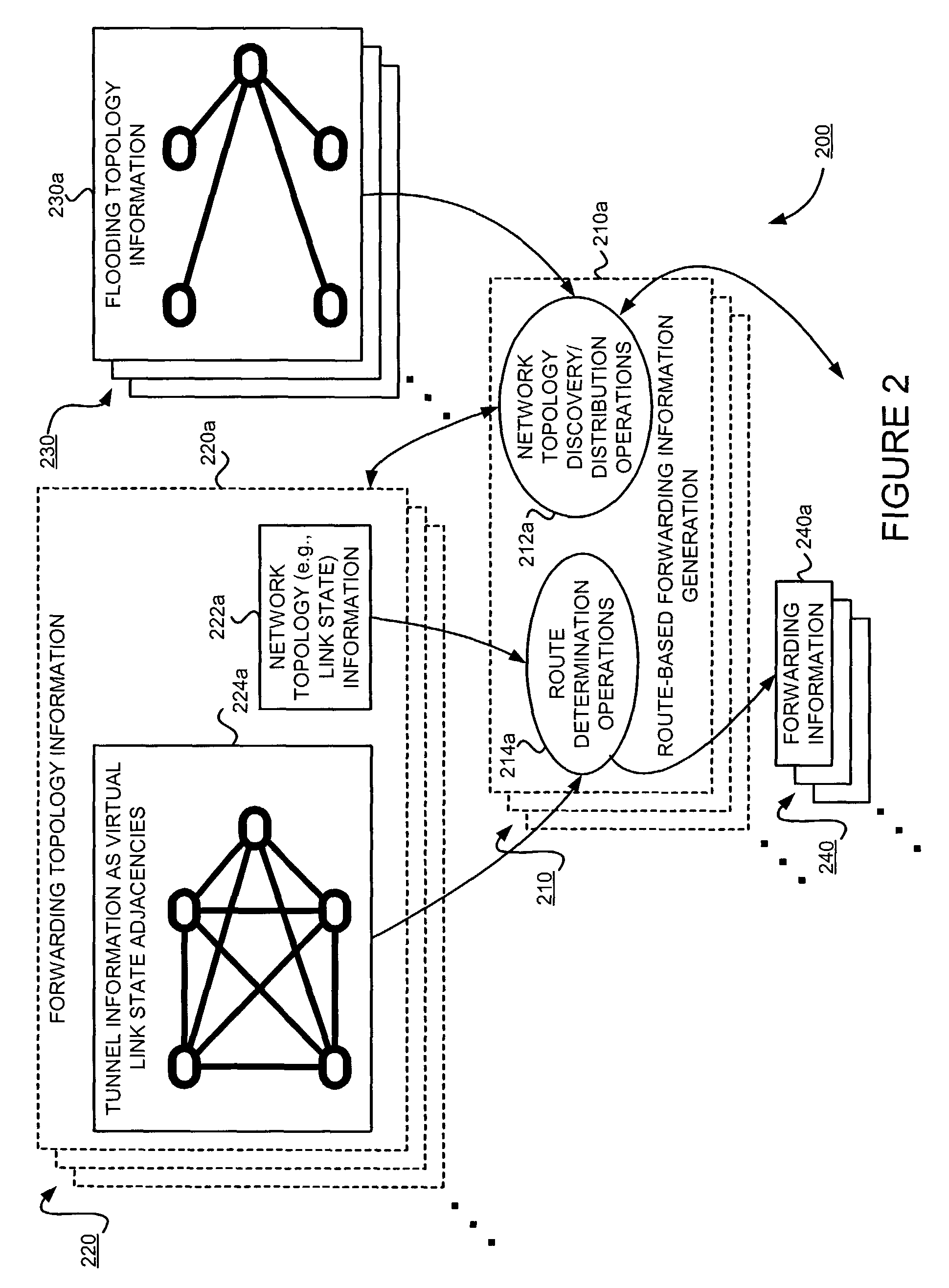
Supporting virtual private networks using a first network topology for forwarding and a subset of the first network topology or a smaller topology for signaling
InactiveUS7792987B1Avoid problemsError preventionTransmission systemsBorder Gateway ProtocolTTEthernet
Virtual Private Networks (VPNs) are supported in which customers may use popular internet gateway protocol (IGPs) without the need to convert such IGPs, running on customer devices to a single protocol, such as the border gateway protocol (BGP). Scaling problems, which might otherwise occur when multiple instances of an IGP flood link state information, are avoided by using a flooding topology which is smaller than a forwarding topology. The flooding topology may be a fully connected sub-set of the forwarding topology.
Owner:JUMIPER NETWORKS INC
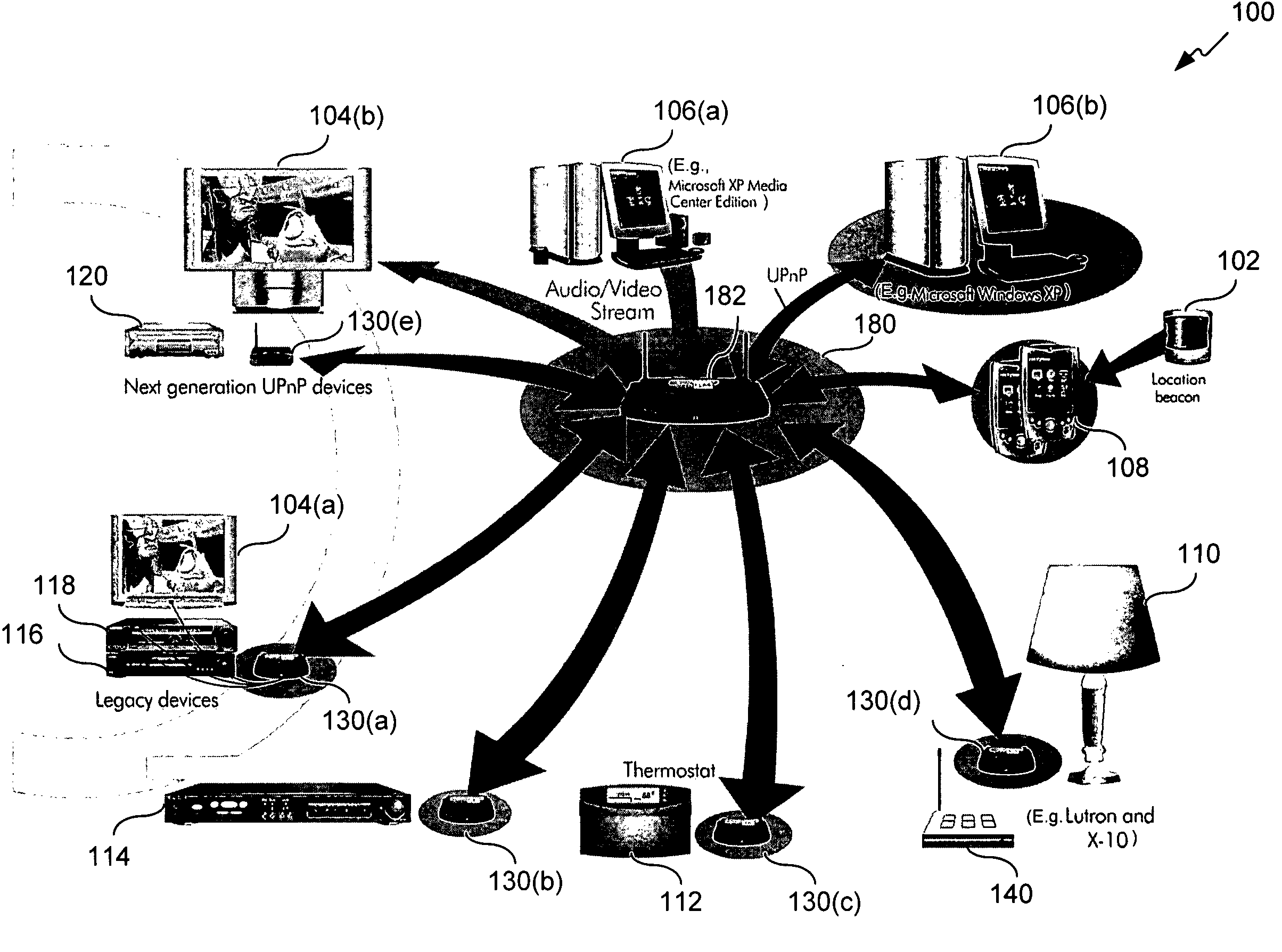
Method of controlling a device to perform an activity-based or an experience-based operation
ActiveUS7668990B2Television system detailsElectric signal transmission systemsClient-sideOperation Activity
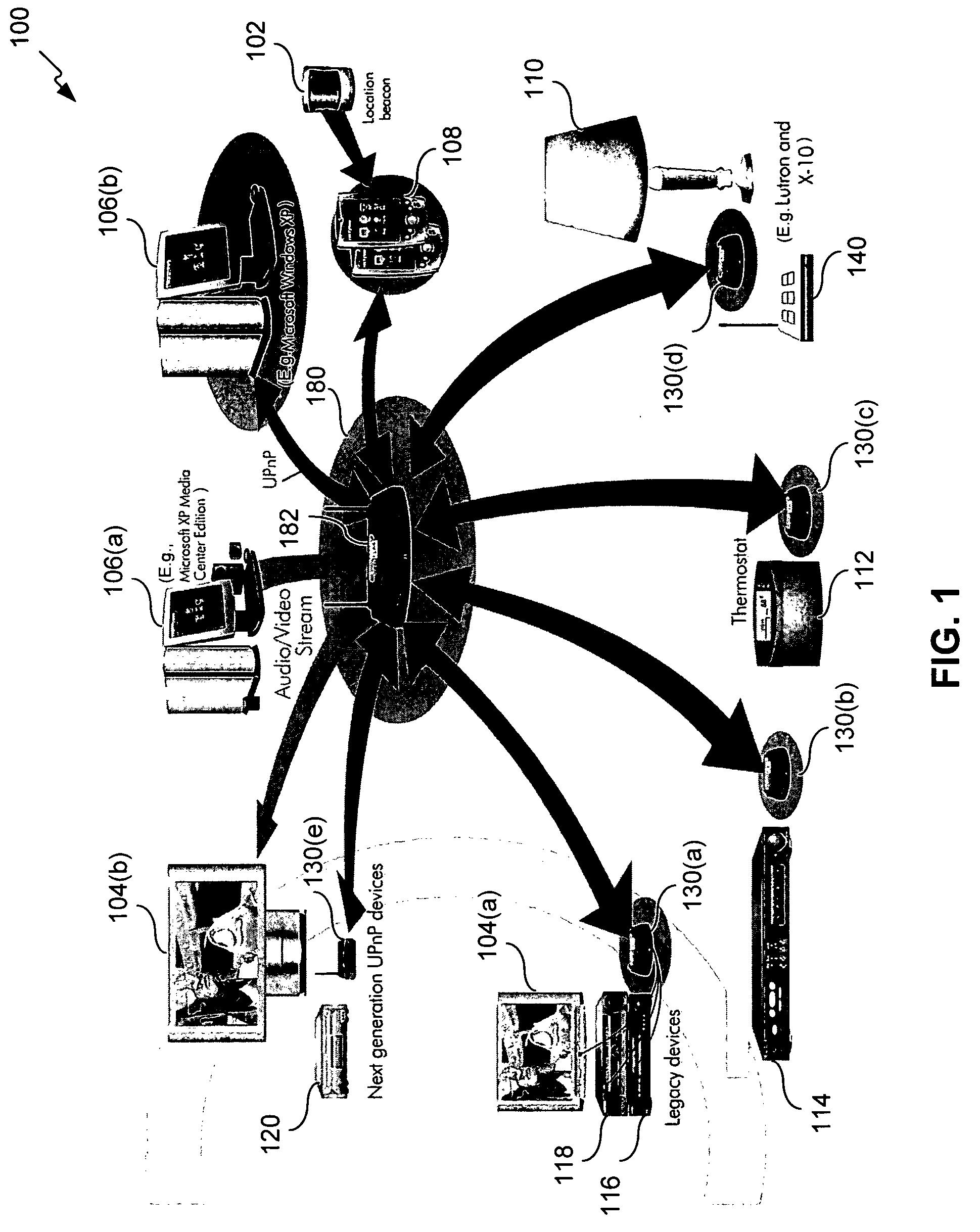
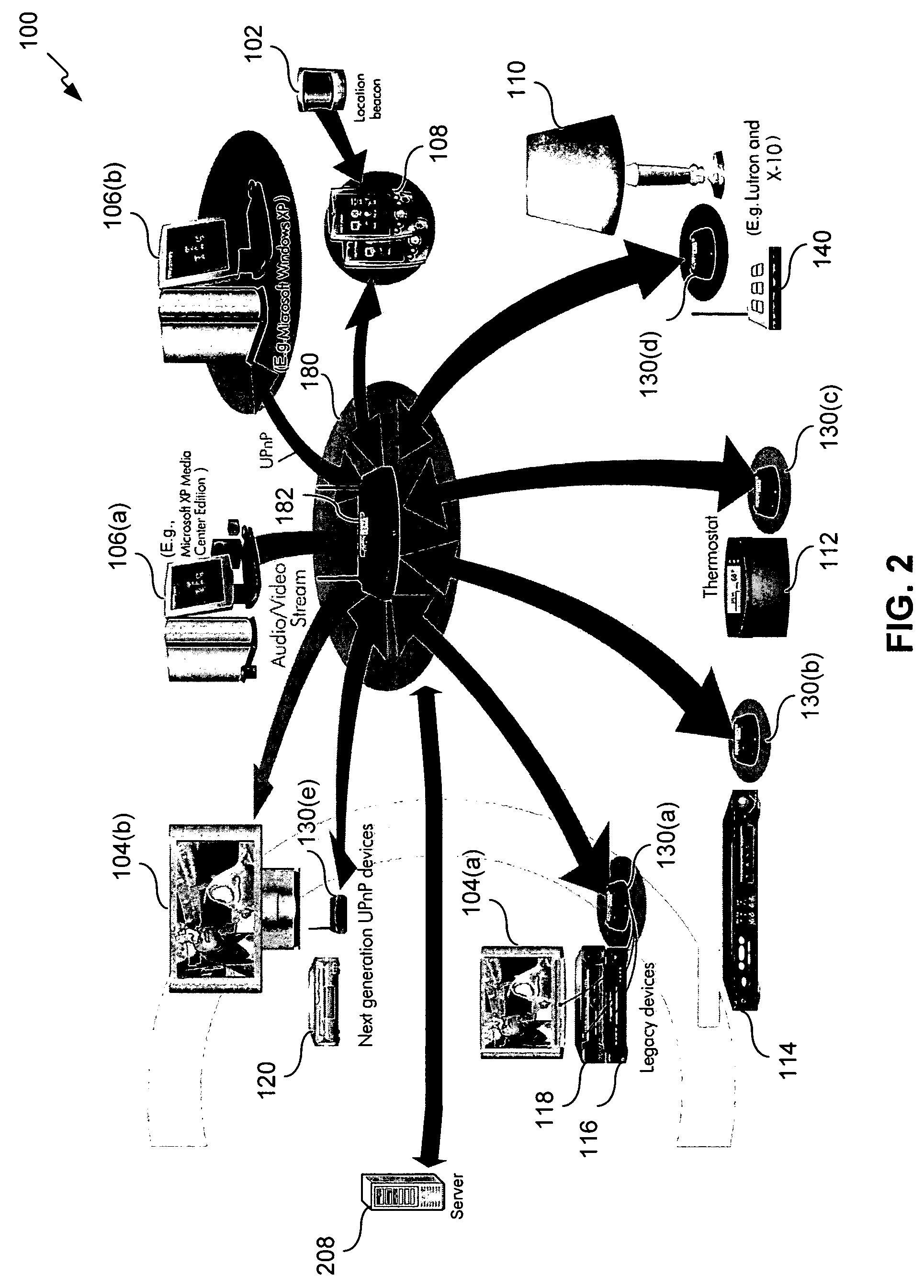
Activity-based or experienced-based operations are created and defined during an initialization or setup session for one or more system component, with minimum or no user interaction. The system components include legacy and / or non-legacy devices, which are configured and managed within a controlled environment, such as a home or business peer-to-peer or client-server network. During an initialization or setup session, relevant device information and device metadata are collected via a conventional or discovery protocol interface. For a legacy device that is not automatically discoverable, a user adds the legacy device to the controlled environment by inputting the device information. The device information can also be automatically collected from an accessible database. Once the device information has been collected, the system components are configured to support one or more activity-based or experienced-based operations.
Owner:MICROSOFT TECH LICENSING LLC
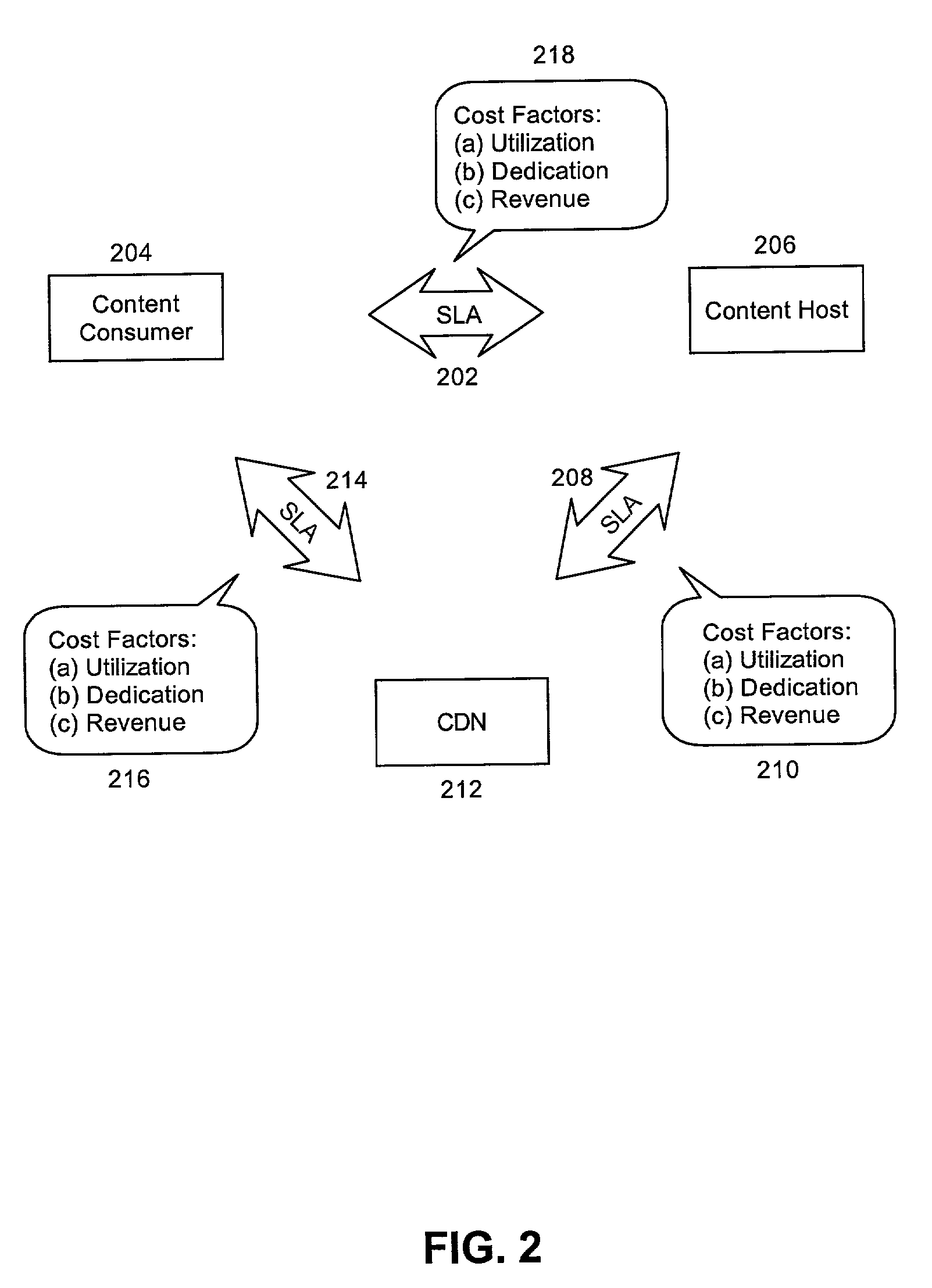
Multi-tier service level agreement method and system
ActiveUS7099936B2Overcome limitationsMultiple digital computer combinationsResourcesService-level agreementEdge server
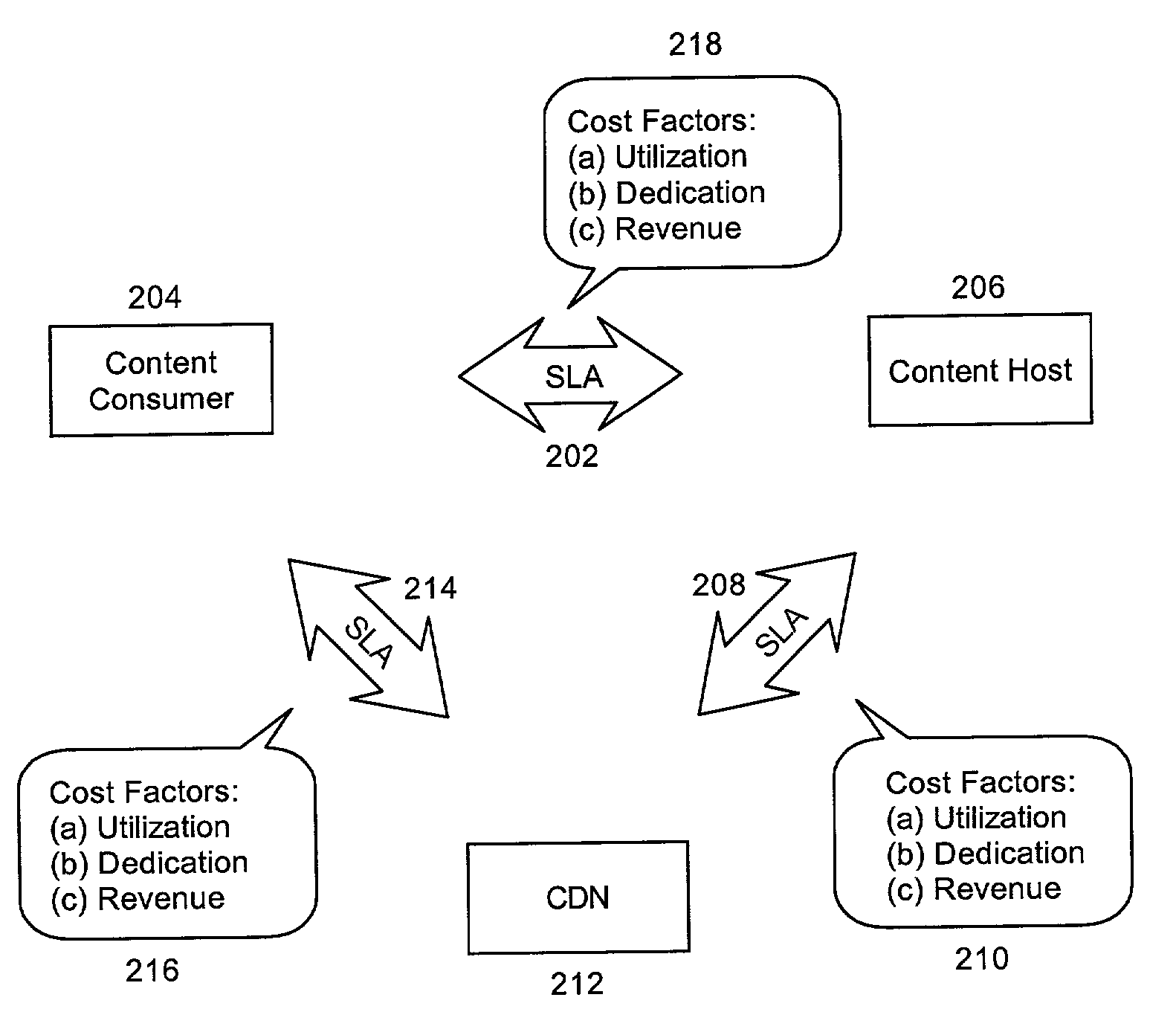
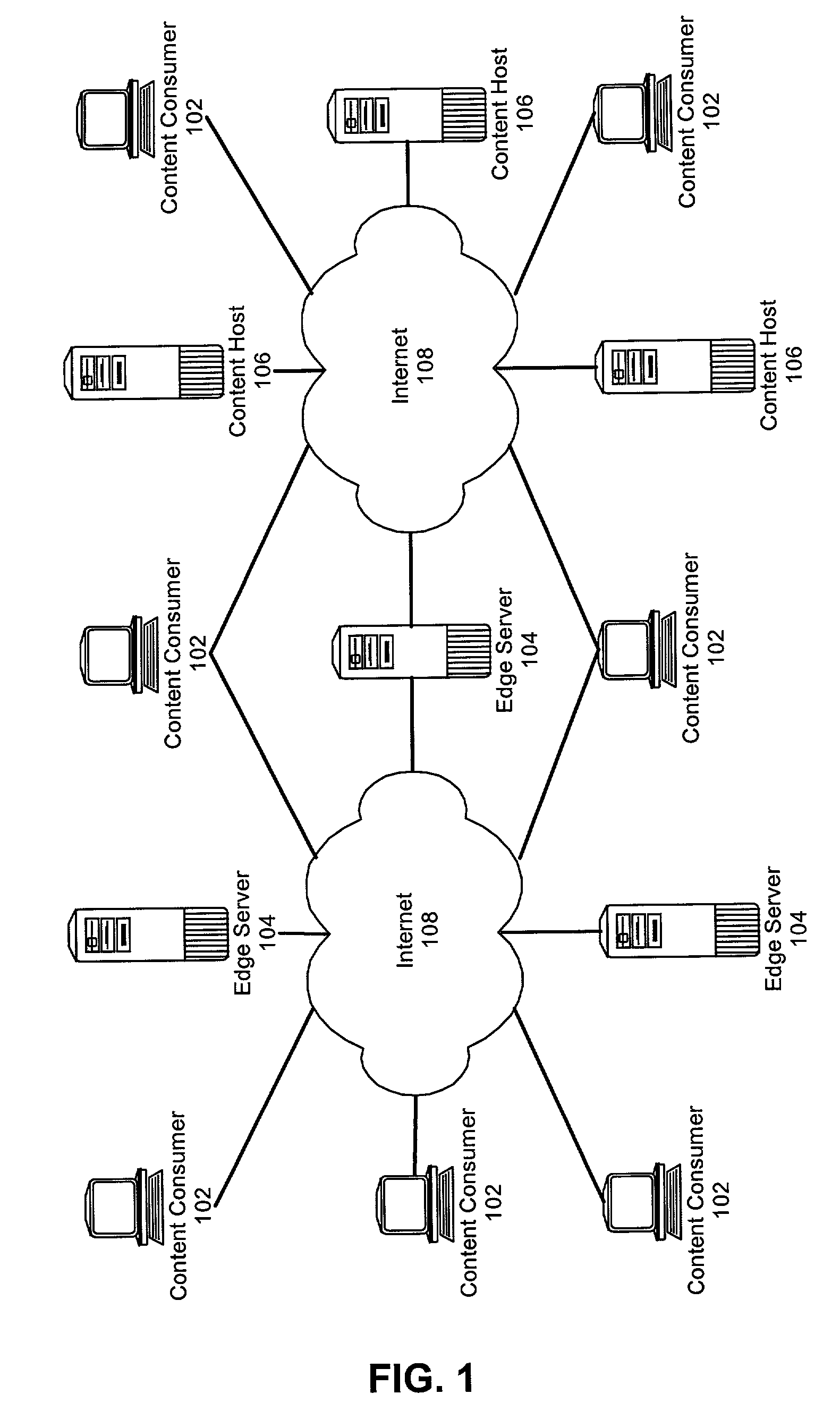
A method for managing multi-tier SLA relationships. The method can include first computing costs of utilizing edge server resources in a CDN, costs of dedicating content host resources in a content host in lieu of the utilization, and prospective revenues which can be generated by the content host providing services based on the resources to content consumers. Minimum QoS levels can be identified which must be maintained when providing the services to the content consumers according to QoS terms in established SLAs between the content host and individual ones of the content consumers. Finally, a new SLA can be established between the content host and the CDN. Importantly, the new SLA can include QoS terms for selectively allocating resources in the CDN. Moreover, the QoS terms can optimize revenues generated by the content host providing services based on the selective allocation of resources and the computed costs.
Owner:IBM CORP
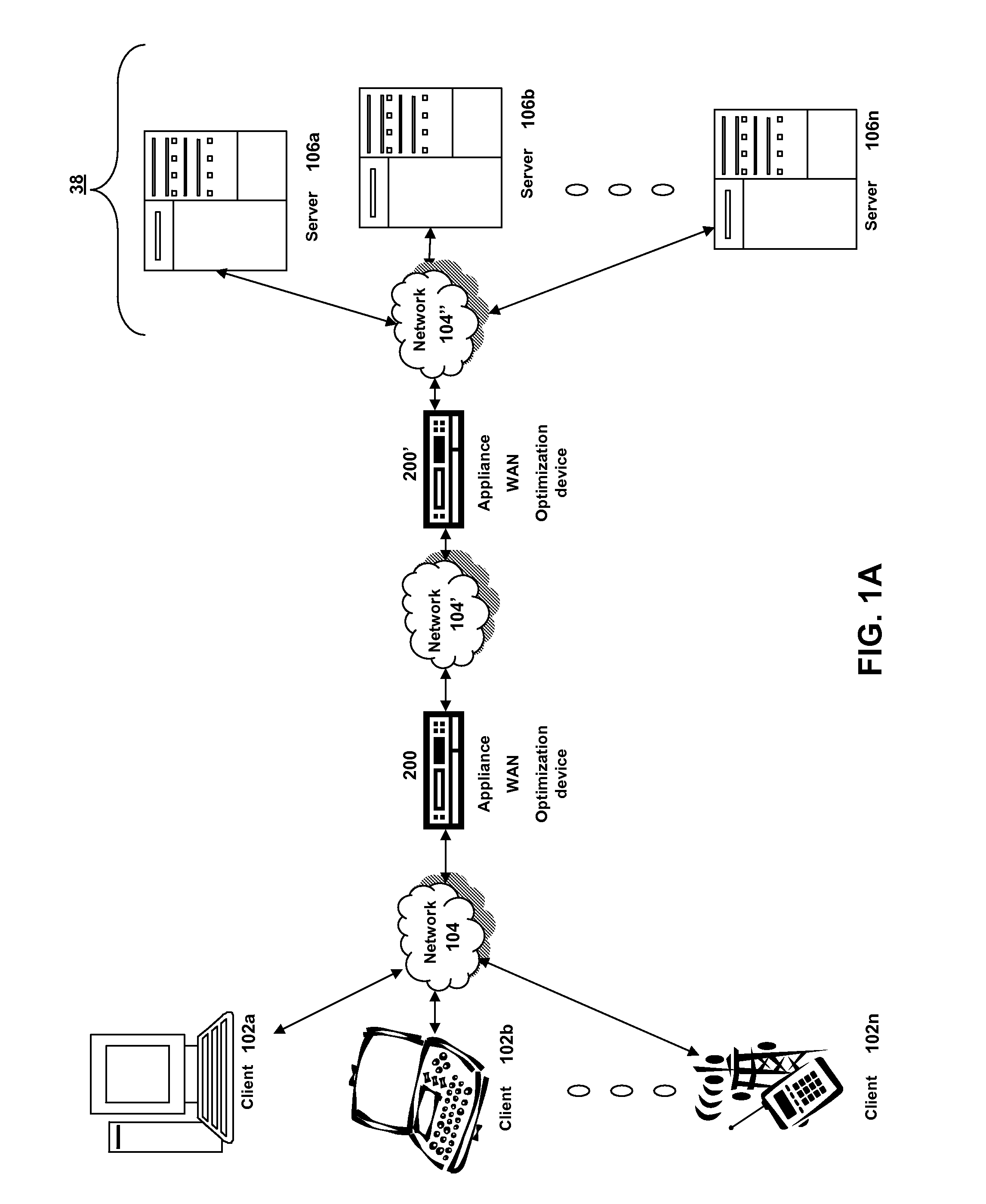
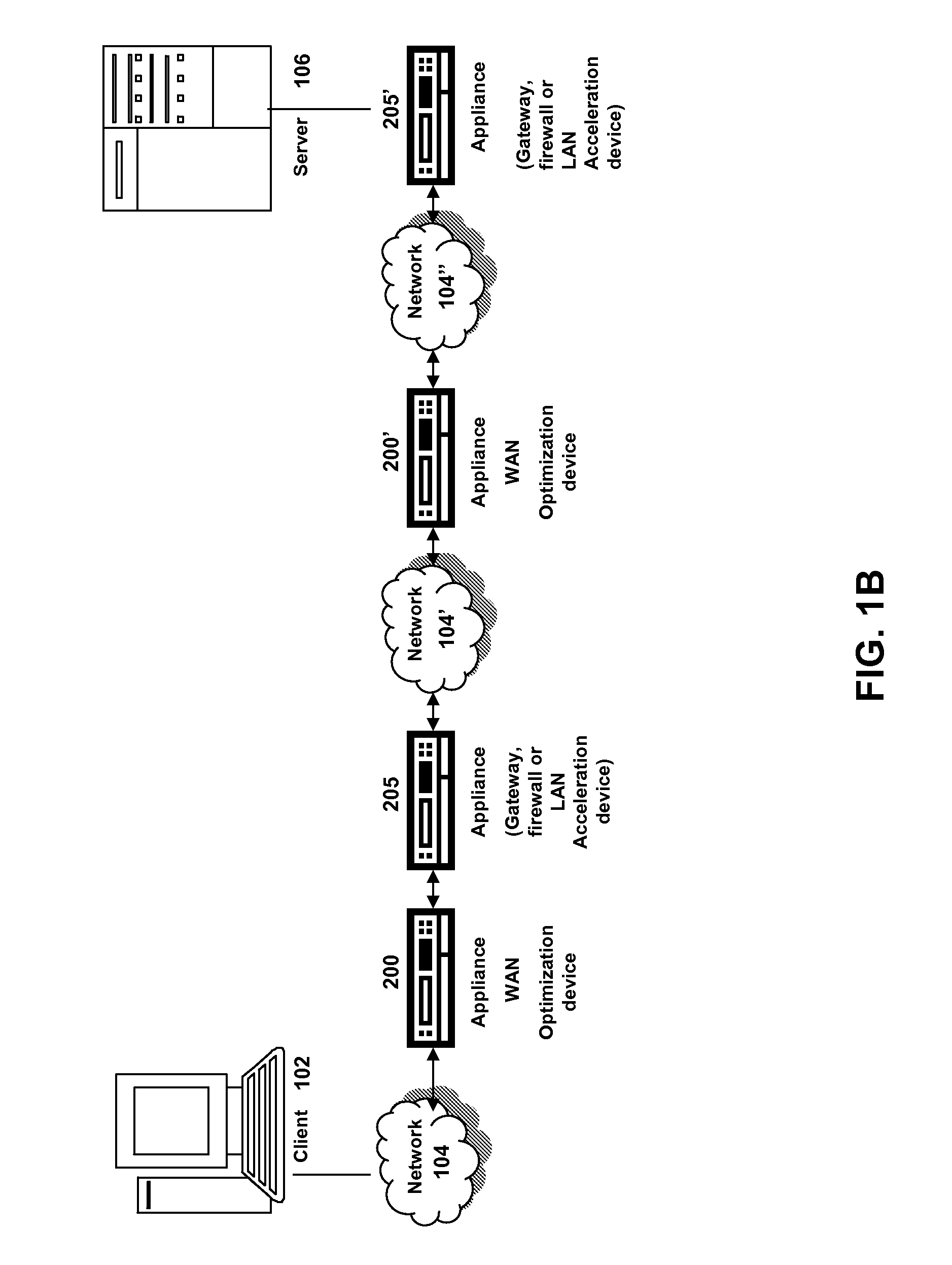
Wireless communication device with markup language based man-machine interface
A system, method, and software product provide a wireless communications device with a markup language based man-machine interface. The man-machine interface provides a user interface for the various telecommunications functionality of the wireless communication device, including dialing telephone numbers, answering telephone calls, creating messages, sending messages, receiving messages, establishing configuration settings, which are defined in markup language, such as HTML, and accessed through a browser program executed by the wireless communication device. This feature enables direct access to Internet and World Wide Web content, such as Web pages, to be directly integrated with telecommunication functions of the device, and allows Web content to be seamlessly integrated with other types of data, since all data presented to the user via the user interface is presented via markup language-based pages. The browser processes an extended form of HTML that provides new tags and attributes that enhance the navigational, logical, and display capabilities of conventional HTML, and particularly adapt HTML to be displayed and used on wireless communication devices with small screen displays. The wireless communication device includes the browser, a set of portable components, and portability layer. The browser includes protocol handlers, which implement different protocols for accessing various functions of the wireless communication device, and content handlers, which implement various content display mechanisms for fetching and outputting content on a screen display.
Owner:ACCESS
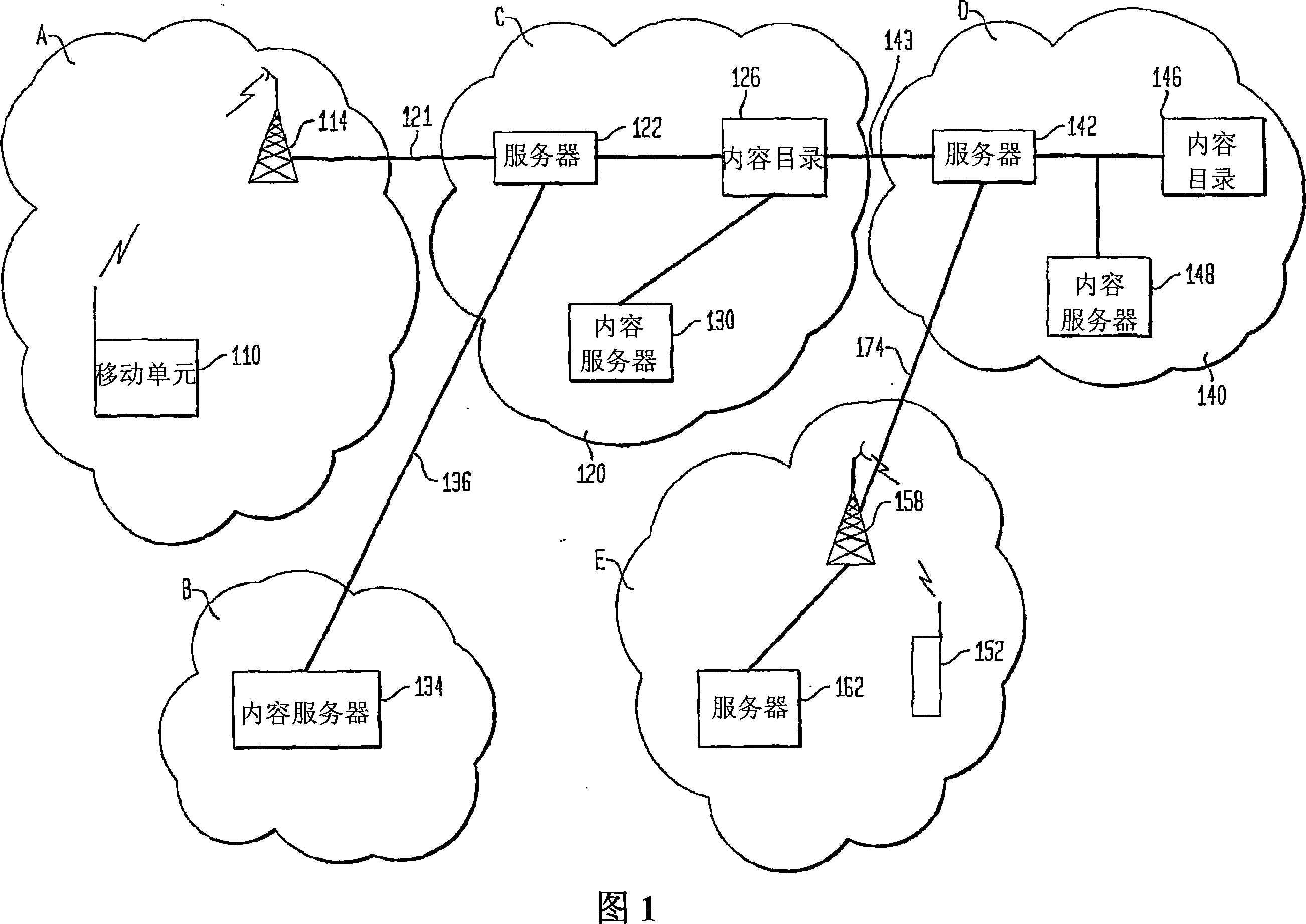
Method, apparatus and system for a location-based uniform resource locator
An aspect of the present invention is a method for routing content information to a mobile user or client application. The method preferably comprises re-directing a user request to one or more gateway servers provided via an overlay network. In another aspect, the present invention is an apparatus that includes a proxy service that intercepts content information requests to the Internet and re-directs the content requests to an overlay. Another aspect of the present invention comprises a location-based Uniform Resource Locator that includes a protocol semantic portion and a location-based resolver address portion that identifies one or more resources on a network based on the geographical location of the resources.
Owner:TELCORDIA TECHNOLOGIES INC +1
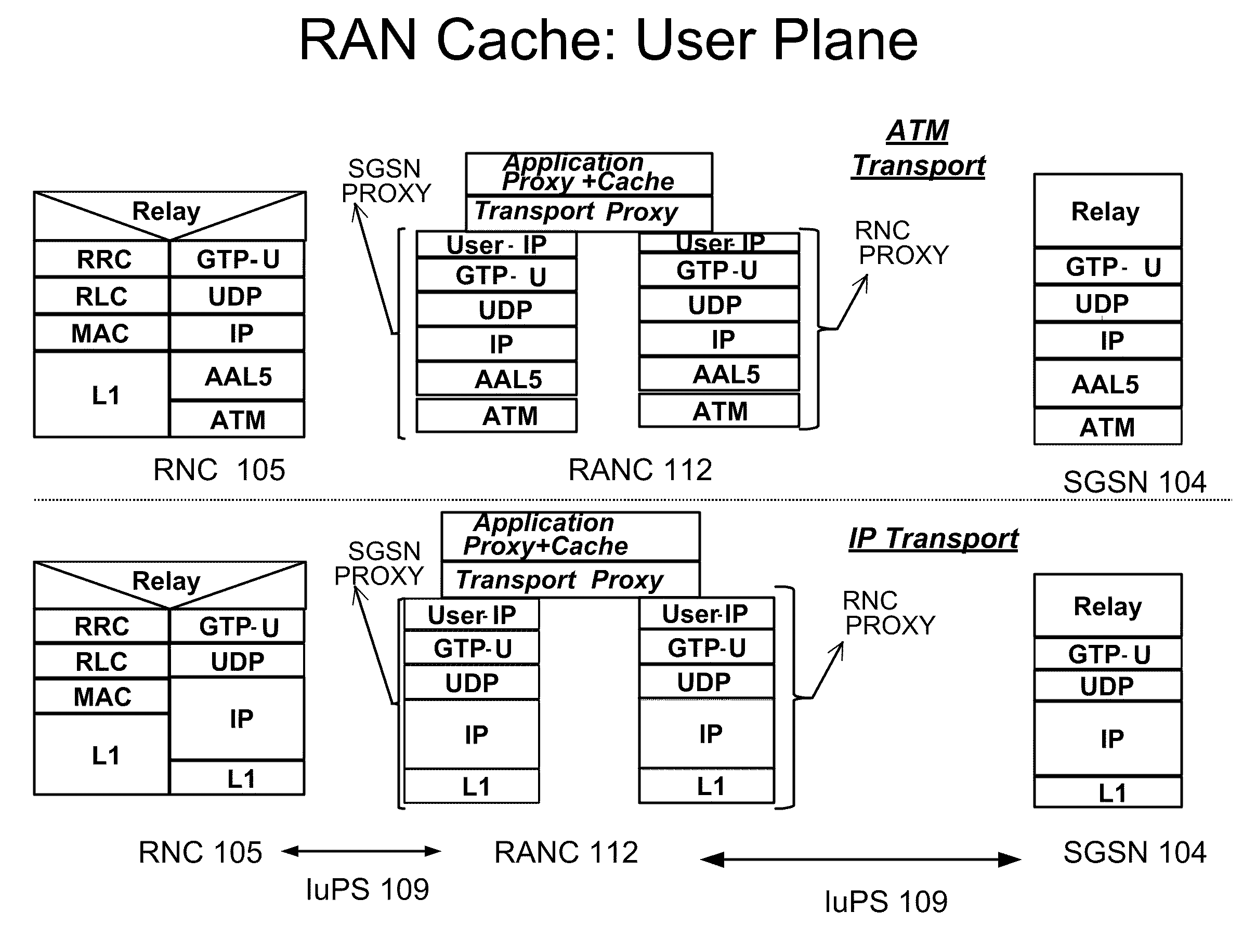
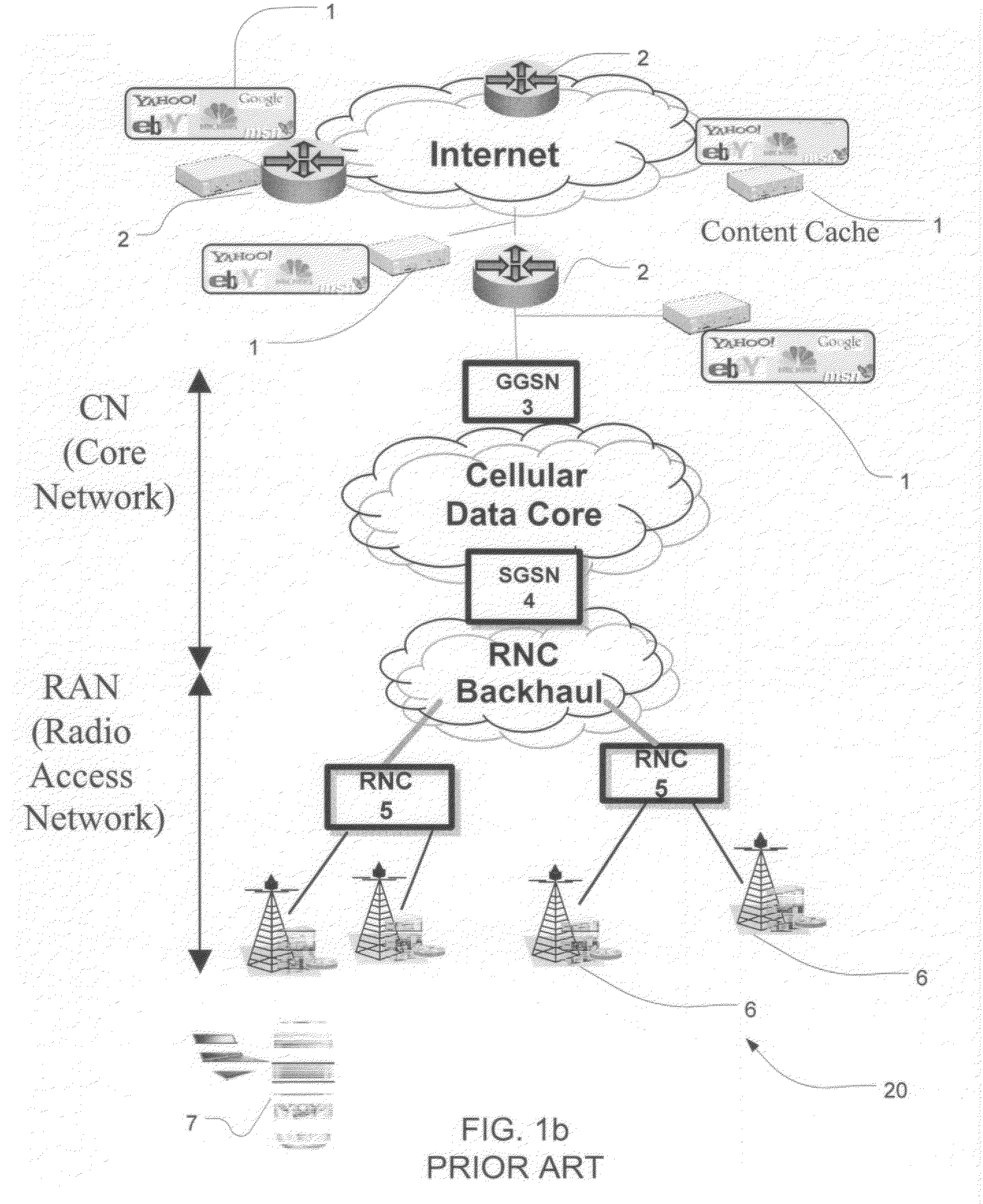
Content Caching in the Radio Access Network (RAN)
ActiveUS20100034089A1Reducing back-haul bandwidthImprove user experienceError preventionNetwork traffic/resource managementNetwork packetRadio access network
A system and method to intercept traffic at standard interface points as defined by Cellular / Wireless networks (GSM / GPRS, 3G / UMTS / HSDPA / HSUPA, CDMA, WIMAX, LTE), emulate the respective protocols on either side of the interception point, extract user / application payloads within the intercepted packets, perform optimizations, and re-encapsulate with the same protocol, and deliver the content transparently is disclosed. The optimizations include but are not limited to Content Caching, prediction & pre-fetching of frequently used content, performance of content-aware transport optimizations (TCP, UDP, RTP etc.) for reducing back-haul bandwidth, and improvement of user experience. An additional embodiment of the current invention includes injecting opportunistic content (location based, profile based or advertisement content) based on the information derived while monitoring control plane protocols.
Owner:RIBBON COMM SECURITIES CORP
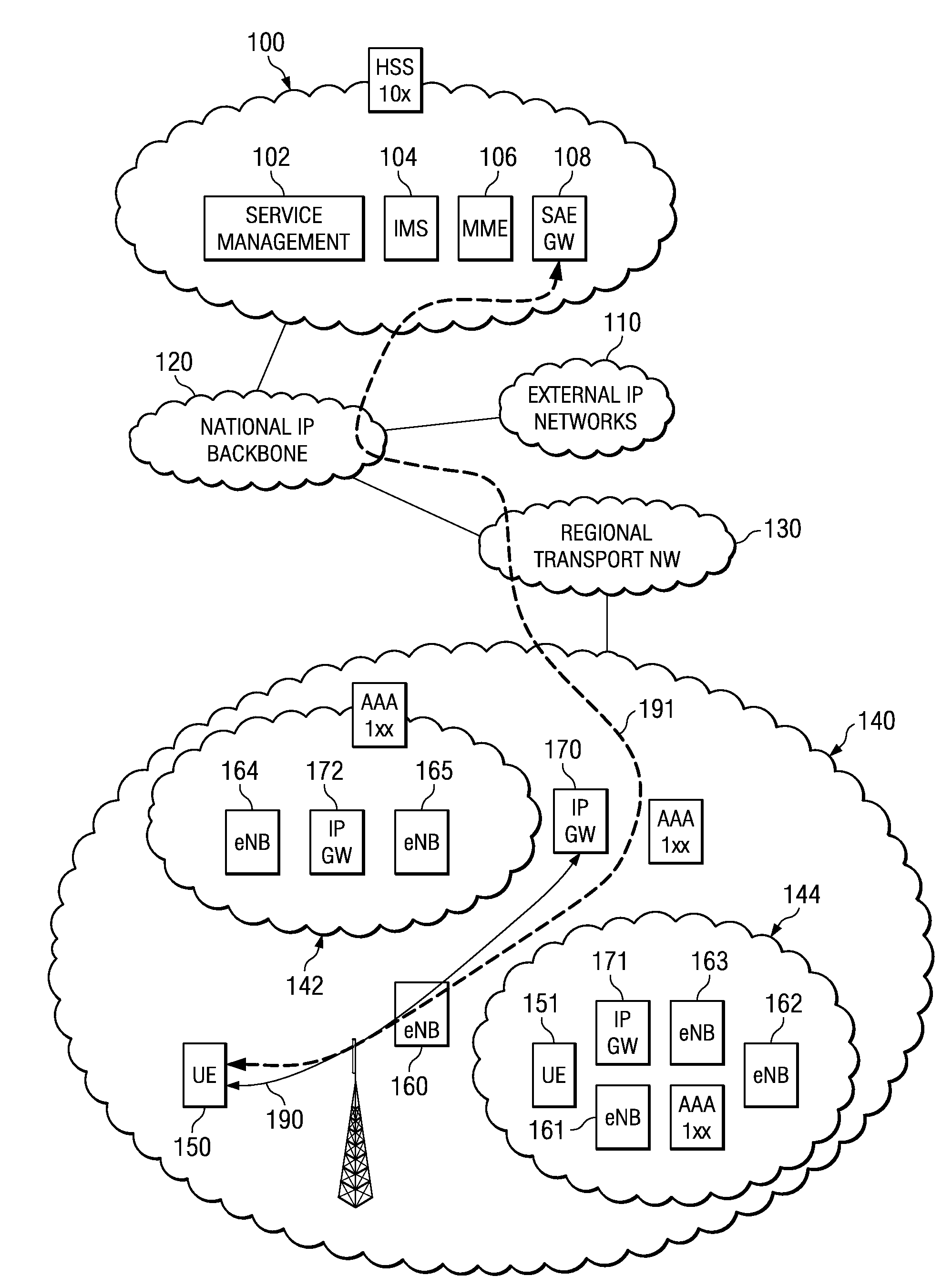
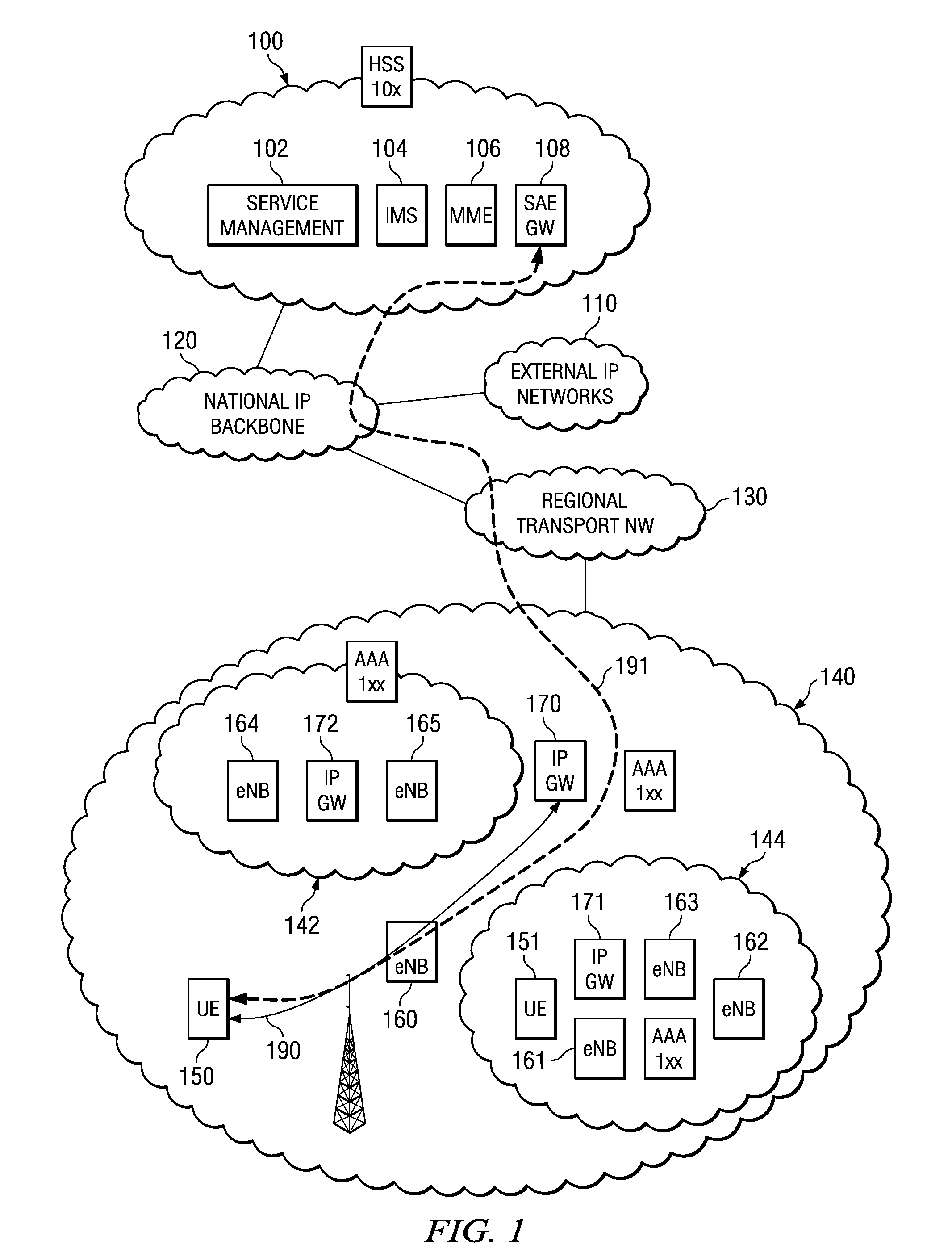
System and Method for Providing Local IP Breakout Services Employing Access Point Names
A method, apparatus and system are provided for acquiring an access point name for an application employing a local Internet protocol breakout service. In one embodiment, the apparatus includes a user management subsystem (820) configured to initiate an Internet protocol application. The apparatus also includes a local breakout service monitoring subsystem (810) configured to monitor availability of a local Internet protocol local breakout service and to obtain an access point name from the local Internet protocol local breakout service when the local Internet protocol local breakout service is available. The apparatus also includes an access point name selection control subsystem (830) configured to bind the access point name to the Internet protocol application.
Owner:NOKIA TECHNOLOGLES OY
QoS channels for multimedia services on a general purpose operating system platform using data cards
InactiveUS7609700B1Increase data rateMultiplex system selection arrangementsSpecial service provision for substationComputer hardwareSession Initiation Protocol
Upper layer applications discover, establish and manage the QoS connectivity through a SIP (session initiation protocol) that serves as a unified interface. In one implementation, this is IP Multimedia Subsystem-centric, further supporting applications that utilize SIP for session control. This capability extends to the data card universe allowing UMTS data card vendors to establish concurrent QoS-based sessions using multiple primary PDP (packet data protocol) contexts based on a set of SIP triggers, further allowing applications running on a computing system to transparently utilize the established pipes based on the individual QoS requirements.
Owner:CINGULAR WIRELESS LLC
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protecol) geteways simultaneously
ActiveUS20030035409A1Time-division multiplexData switching by path configurationCyber operationsTraffic capacity
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYSTEMS
Method and apparatus for provisioning network devices using instructions in extensible markup language
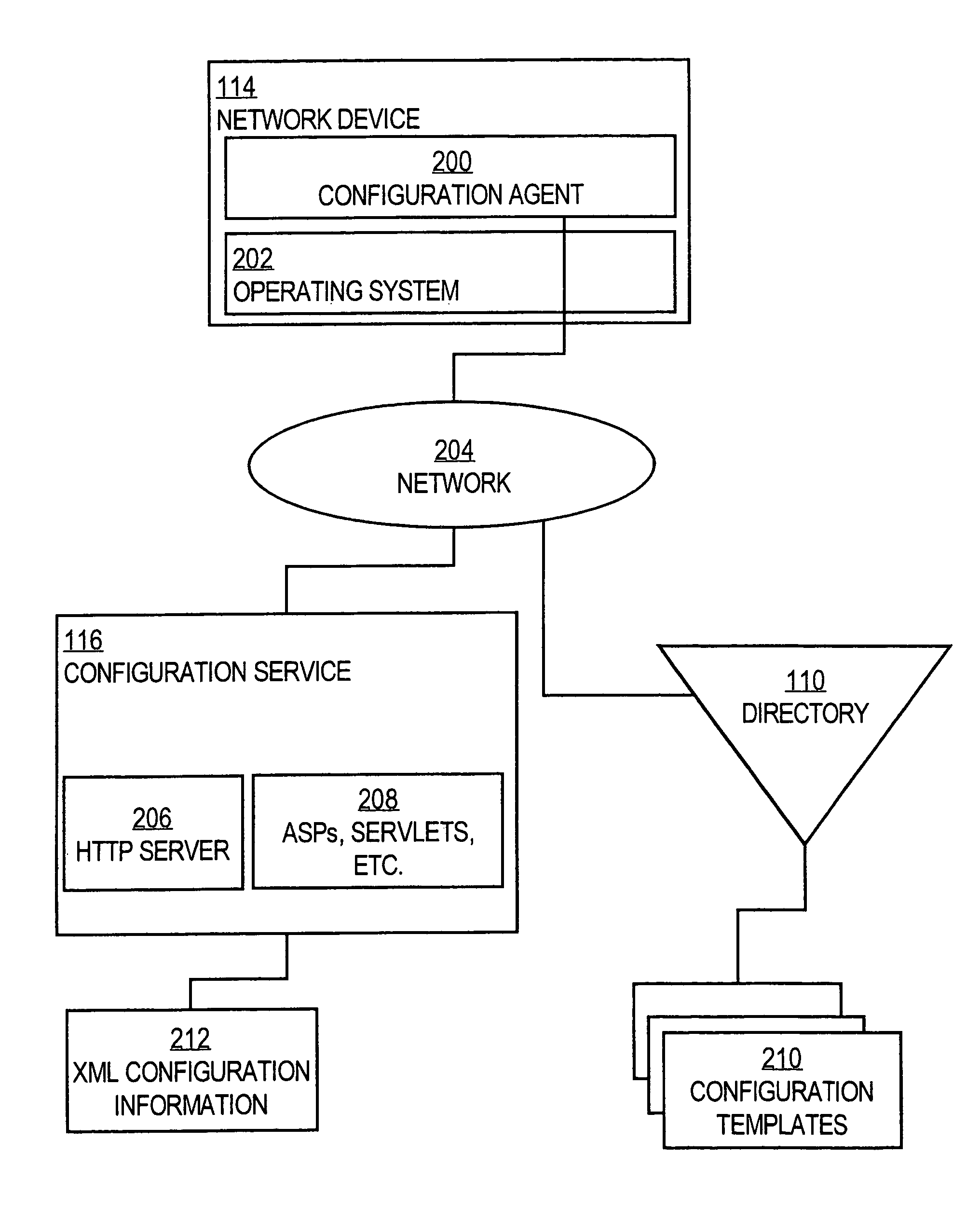
InactiveUS7054924B1Reliable transportationMultiple digital computer combinationsTransmissionReliable transmissionExtensible markup
A method is disclosed for carrying out network device provisioning and configuration, and communication of other information to a network device, automatically and in an assured manner. A configuration service receives a request from a network device to provide configuration information. The configuration service retrieves a template representing the configuration from a storage location, e.g., a directory service. The configuration service also retrieves one or more parameter values specific to the device. Device-specific values are instantiated for the generic parameters in the template, based on the retrieved values. The resulting configuration is stored in XML format using XML tags to delimit configuration commands, tested for well-formed-ness, and syntax checked. A reliable transport protocol carries the configuration information to the device. At the device, a configuration agent syntax checks the embedded configuration information, and then applies the configuration information to the device. As a result, automatic network provisioning may be accomplished remotely, without requiring a skilled technician to visit customer premises to carry out configuration. The process may be integrated with an event service to enable multiple devices to concurrently receive re-configuration without special synchronization logic.
Owner:CISCO TECH INC
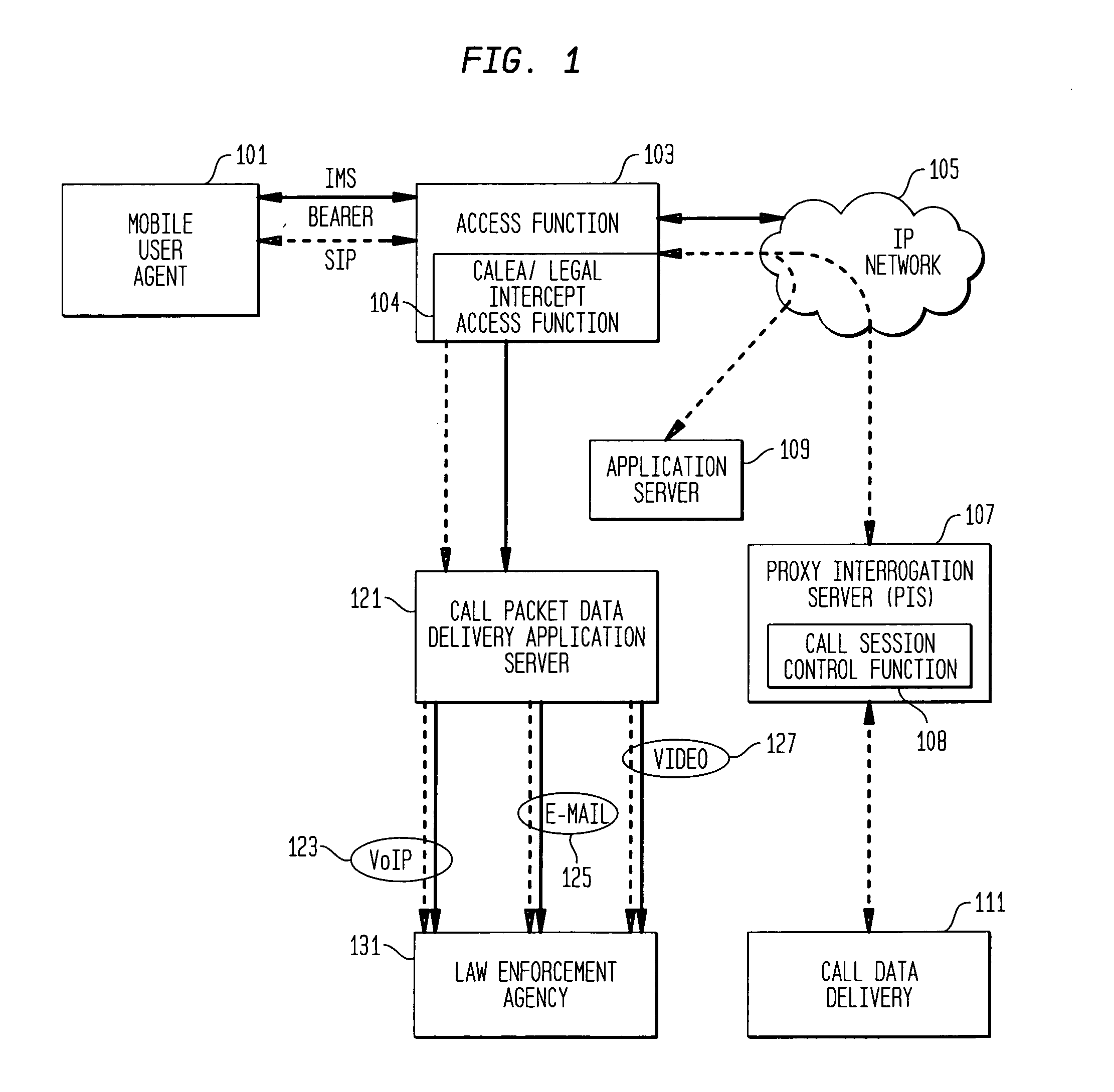
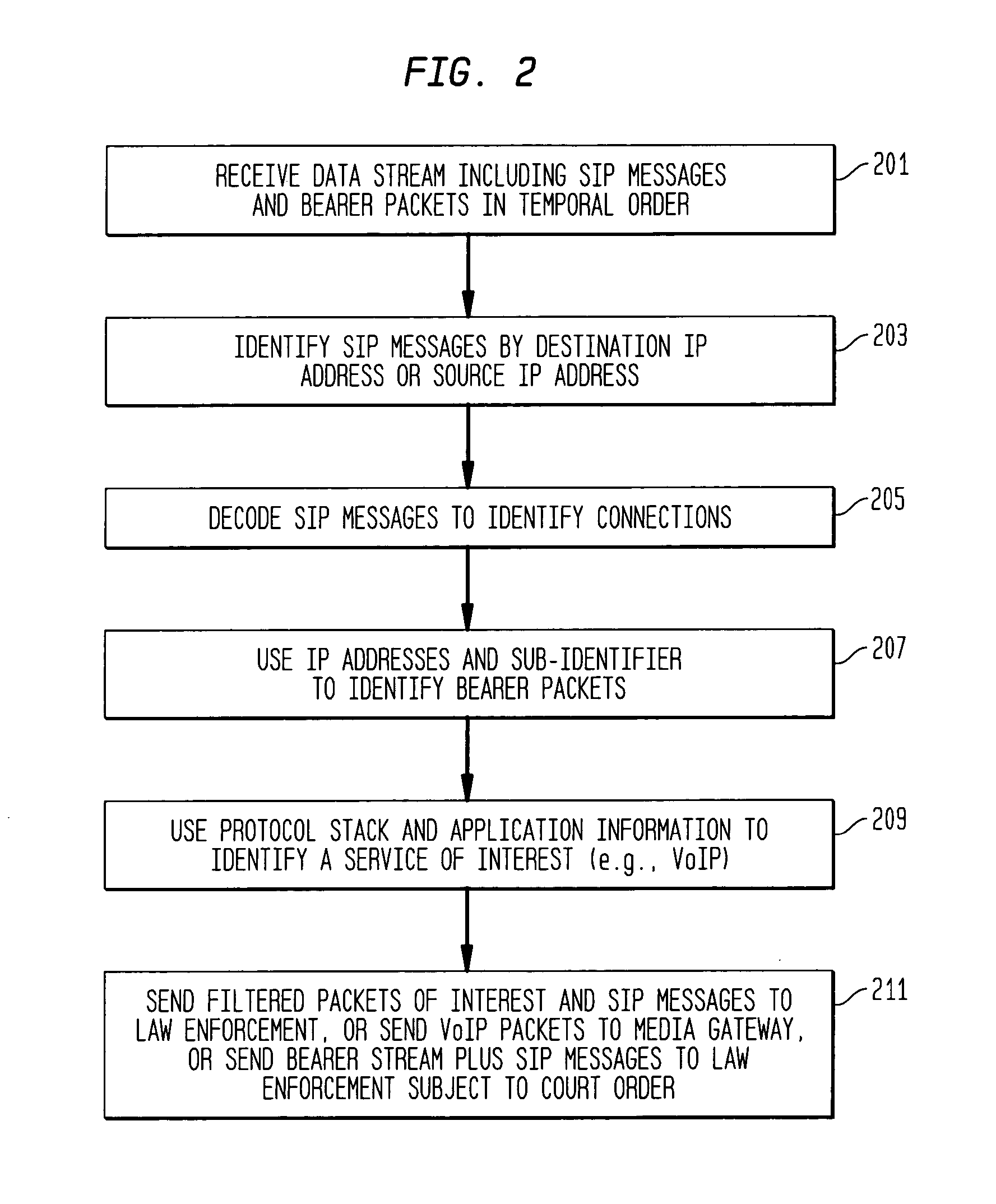
Providing CALEA/LegaI Intercept information to law enforcement agencies for internet protocol multimedia subsystems (IMS)
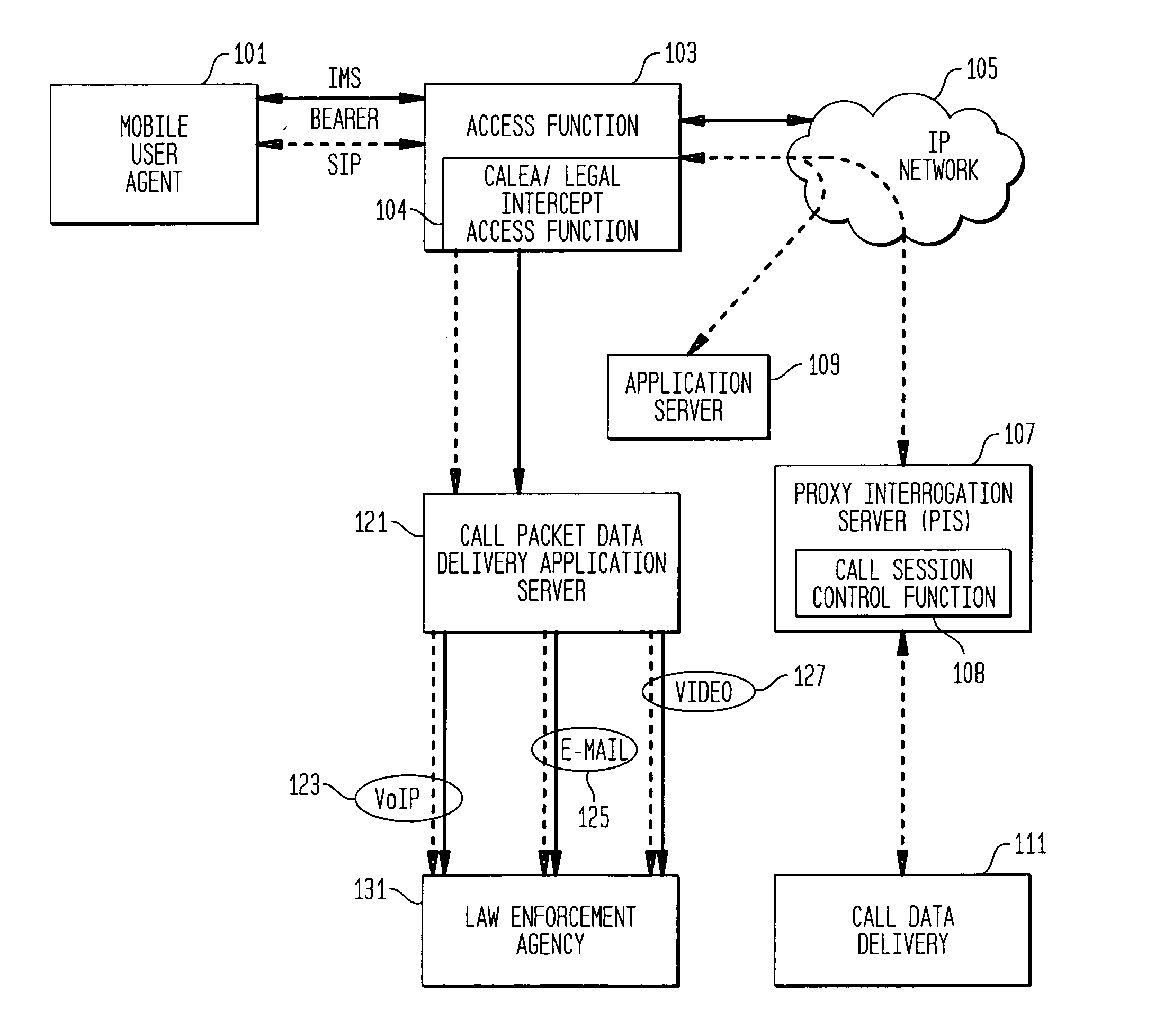
ActiveUS20060072550A1Supervisory/monitoring/testing arrangementsRadio/inductive link selection arrangementsData connectionApplication server
A method and apparatus for providing useful packet data to a CALEA / Legal Intercept collection function. At an access point to a network such as the Internet, sources and destinations of data connections are examined to determine whether any of the bearer messages should also be routed to a CALEA / Legal Intercept monitoring system. If this condition is recognized, the bearer messages and corresponding signaling control messages are correlated in a call packet delivery application server and then delivered to a CALEA / Legal Intercept monitoring system. Advantageously, the monitoring receives as a bundled message set the bearer message and the control messages used to route and otherwise process these bearer messages.
Owner:ALCATEL-LUCENT USA INC
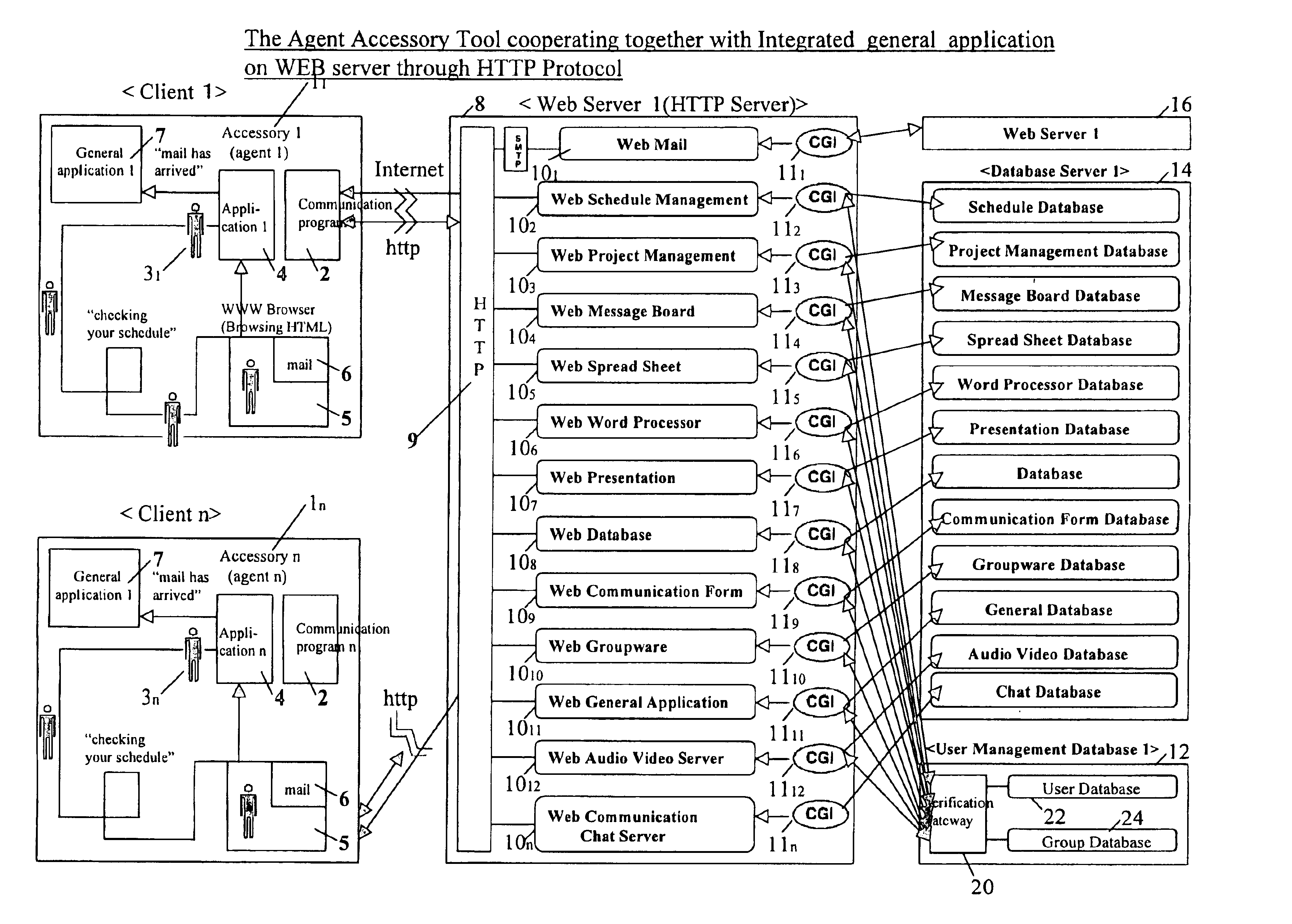
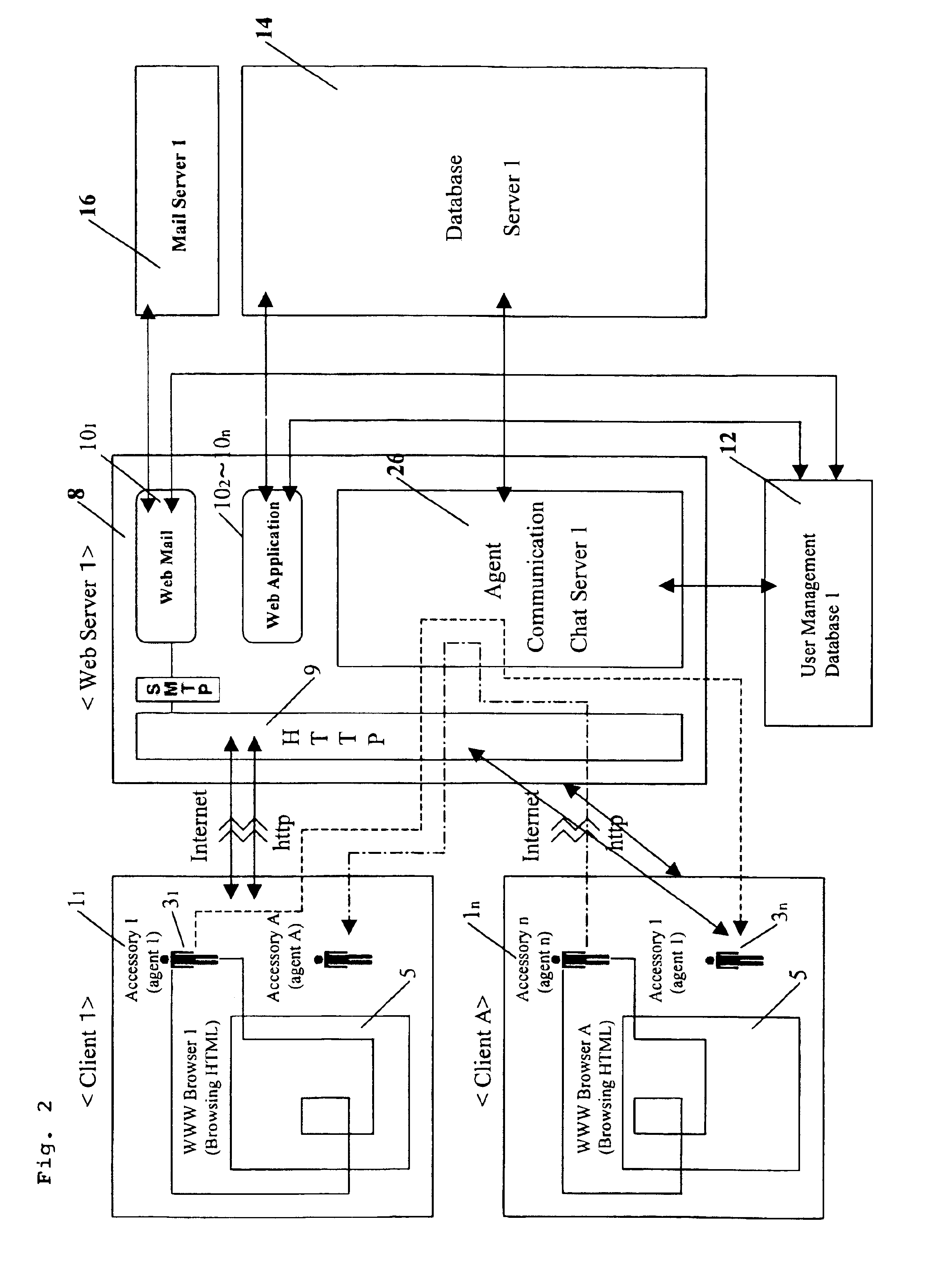
Agent accessory tool cooperating with integrated application on WEB server by HTTP protocol
InactiveUS6842779B1Multiple digital computer combinationsSpecial data processing applicationsWeb applicationExternal application
An agent accessory tool which enables integration of a Web-type application operating within a browser area and general application operating outside browser area is provided. The agent accessory tool includes an agent program interlocking by HTTP incorporated in a personal computer (hereinafter referred to as PC) of each of a plurality of clients, and a Web server having a CGI interface for executing communication software and an external application of the HTTP concerned to each client PC through a communication line. In this agent accessory tool interlocking with the integrated application on the Web server by the HTTP, the agent program accesses various data of a CGI program through the Web server under input conditions, and music and images to each client. When, as a result, the data are updated from previous access data or in conformity to predetermined conditions, an accessory tool including an avatar (digital actor) is caused to appear on the display of the PC of the client, and is also caused to conduct a predetermined action / reaction so as to transmit the existence of information, the non-conformity to the predetermined conditions, and music and images to each client. As a result, the agent accessory tool operates integrally with the Web application by accessing the Web server, without booting the browser software.
Owner:NISHIZAWA YASUO
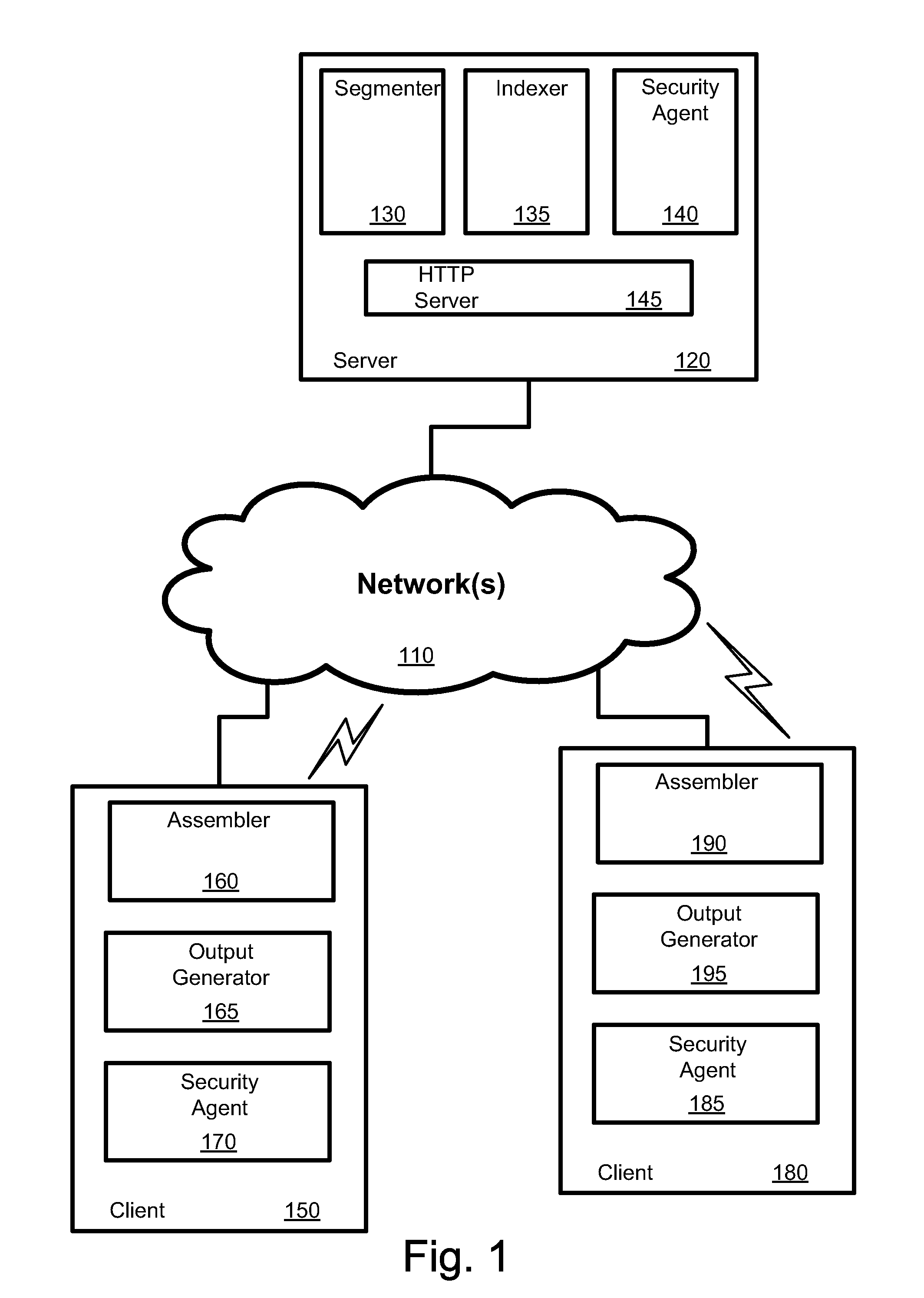
File Aggregation in a Switched File System
InactiveUS20090077097A1Digital data information retrievalMemory loss protectionFile systemGlobal file system
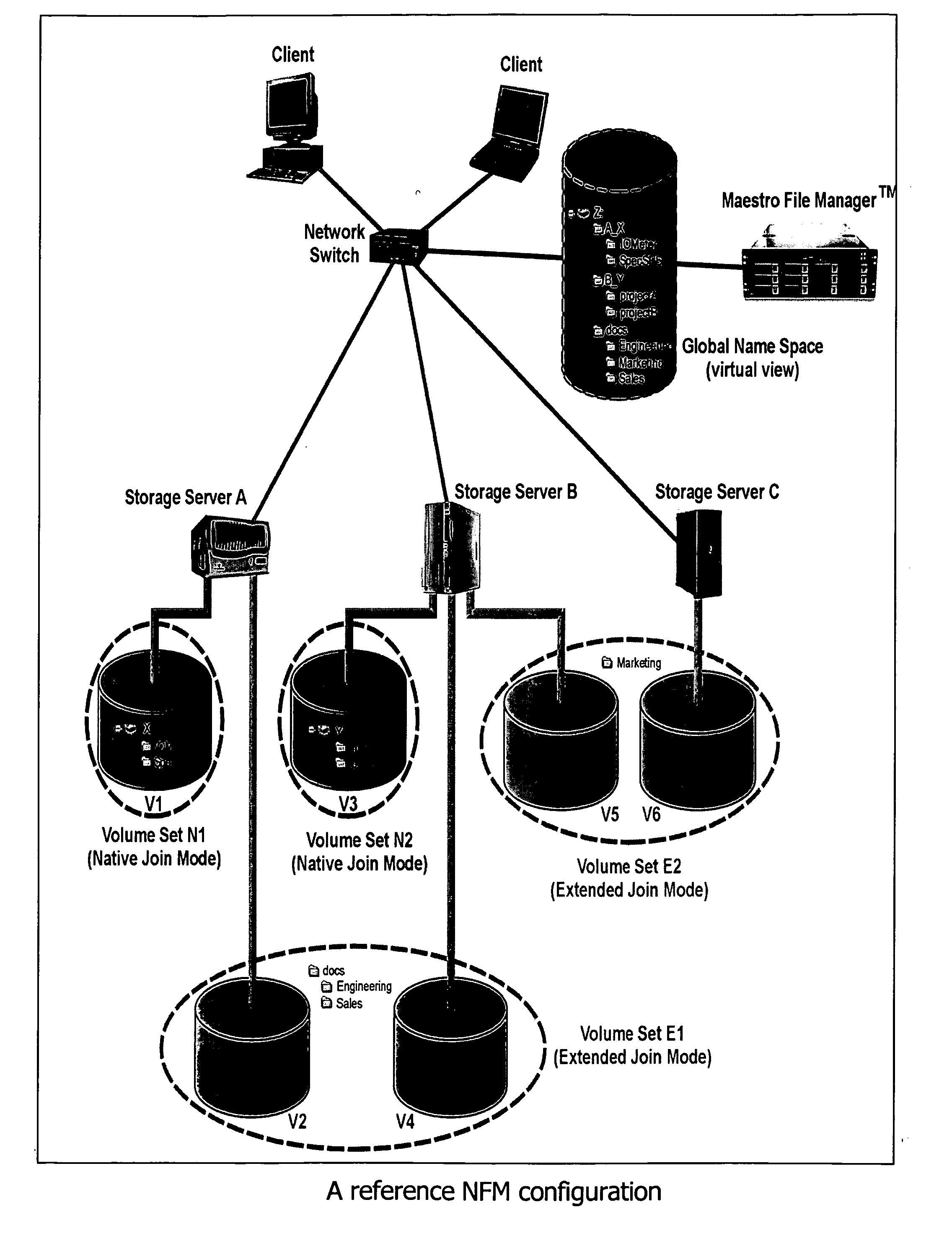
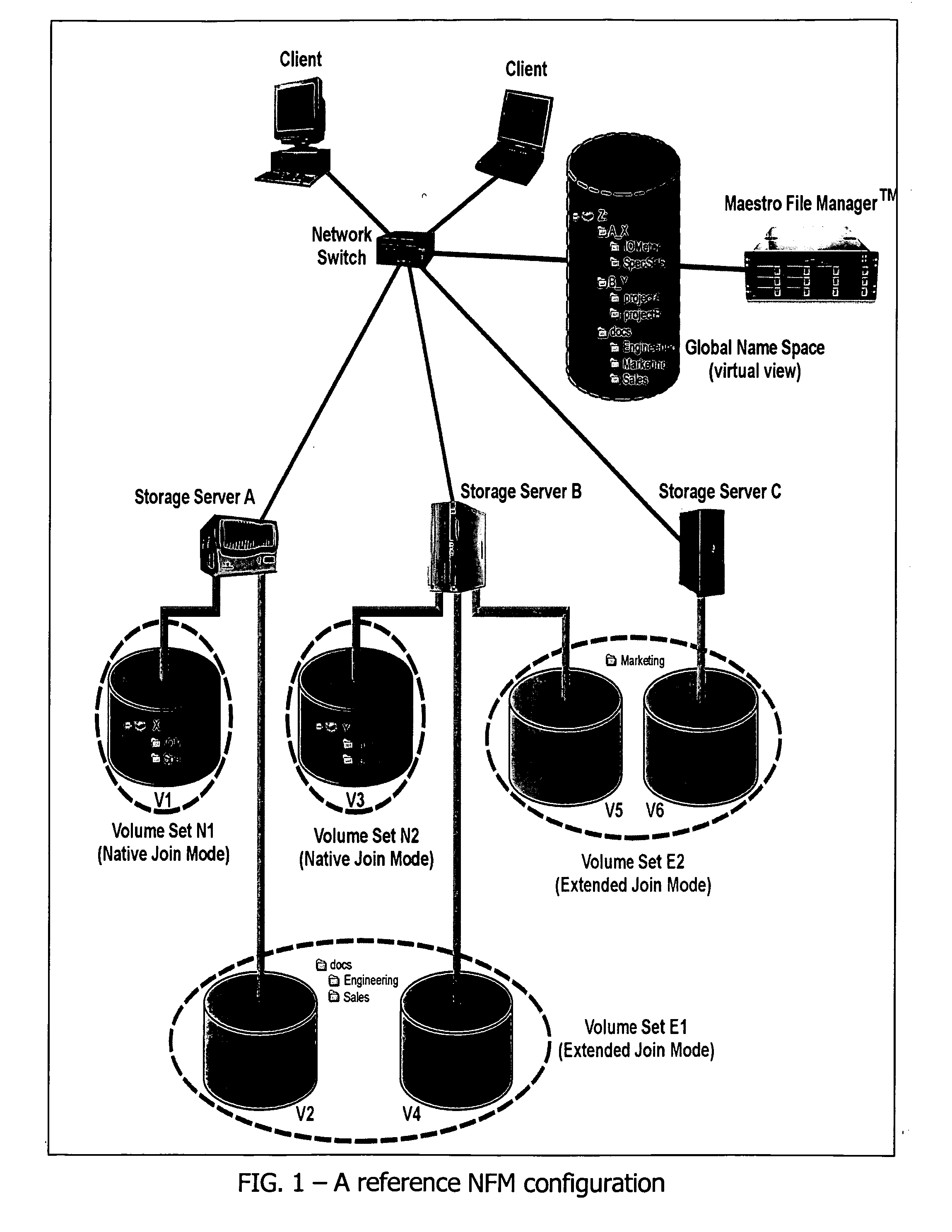
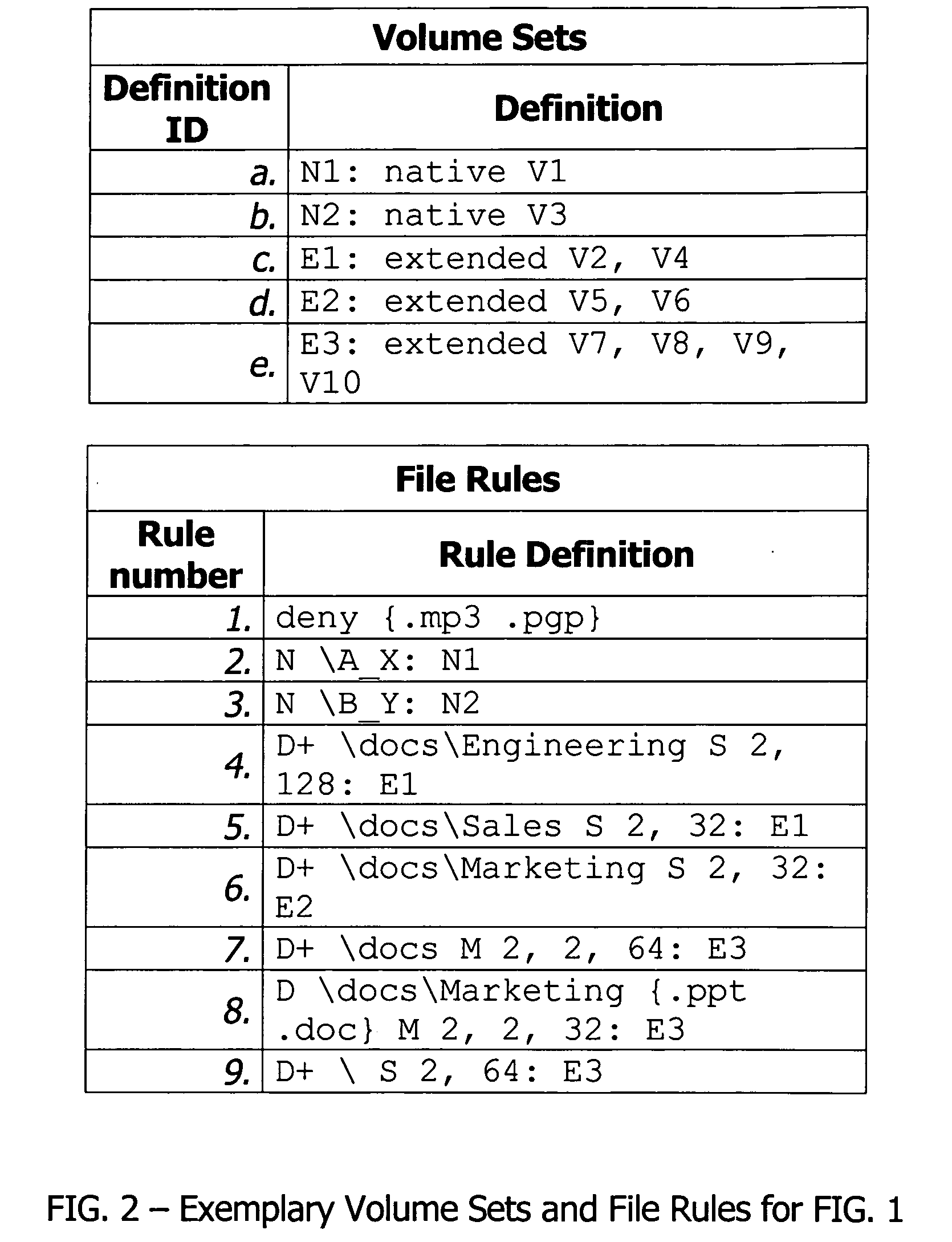
In a switched file system, a file switching device is logically positioned between clients and file servers and communicates with the clients and the file servers using standard network file protocols. The file switching device appears as a server to the client devices and as a client to the file servers. The file switching device aggregates storage from multiple file servers into a global filesystem and presents a global namespace to the client devices. The file switching device typically supports a “native” mode for integrating legacy files into the global namespace and an “extended” mode for actively managing files across one or more file servers. Typically, native-mode files may be accessed directly or indirectly via the file switching device, while extended-mode files may be accessed only through the file switching device. The file switching device may manage file storage using various types of rules, e.g., for managing multiple storage tiers or for applying different types of encoding schemes to files. Rules may be applied to pre-existing files.
Owner:RPX CORP
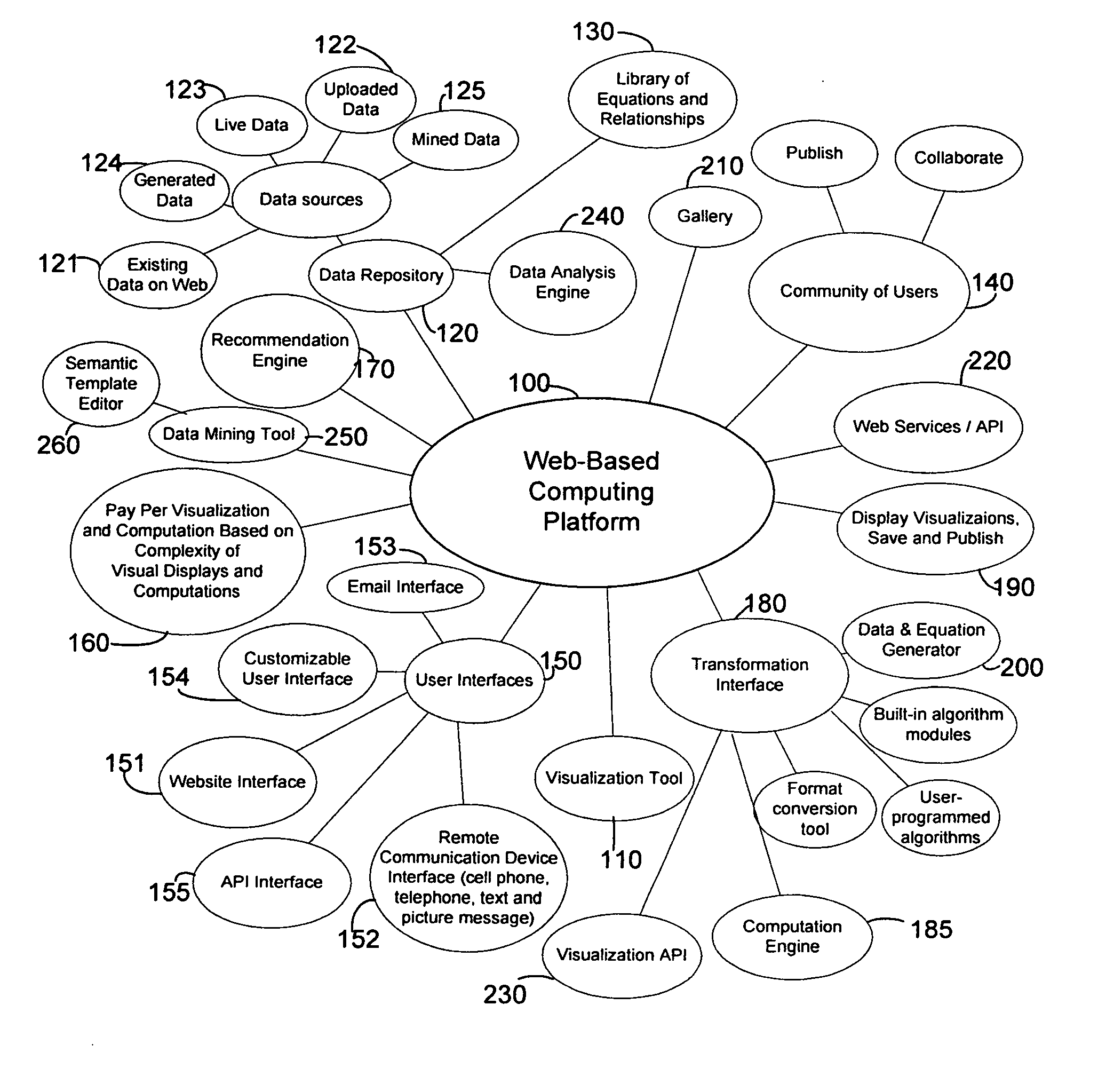
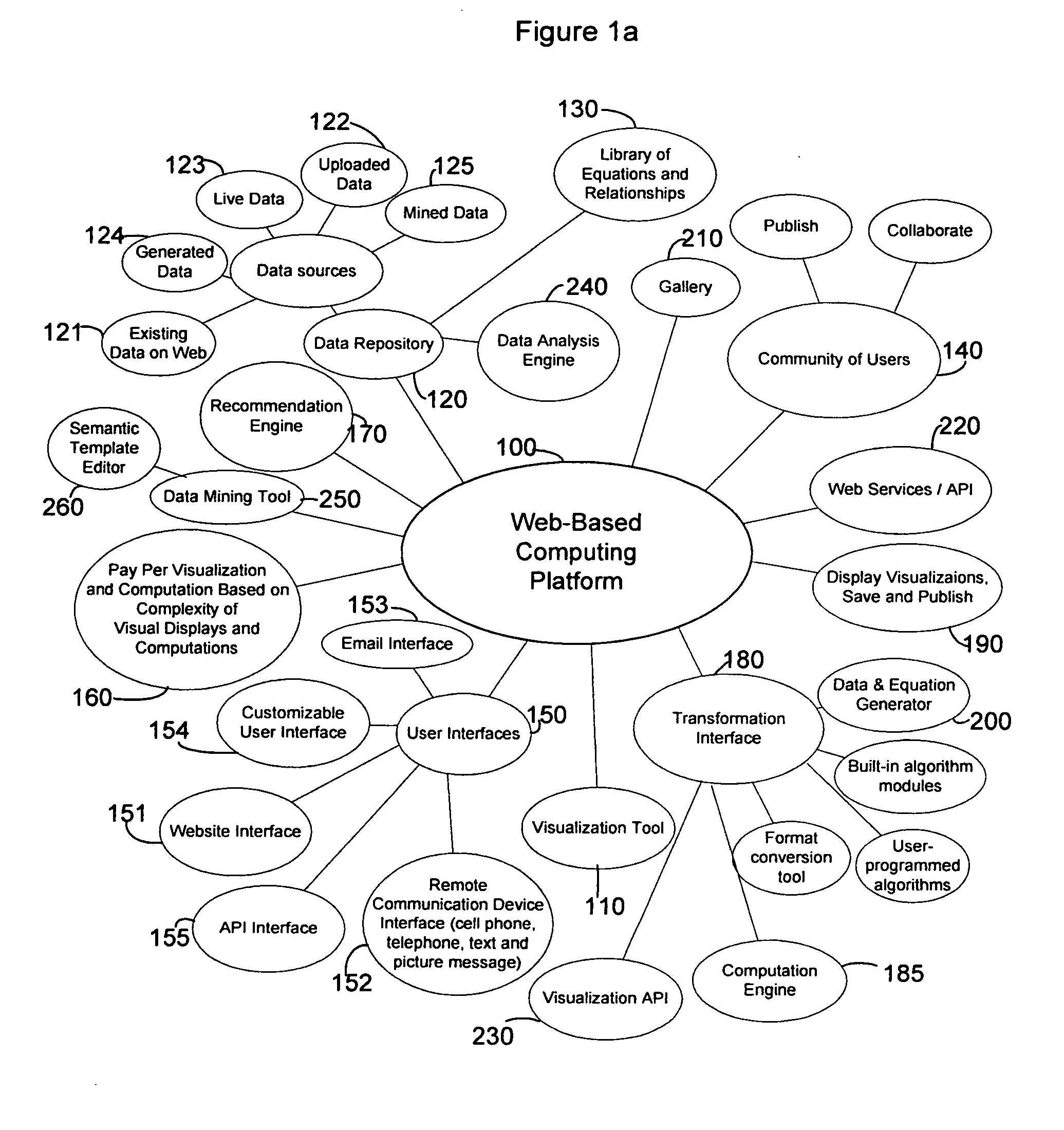
Method of extracting data and recommending and generating visual displays
A method of recommending and generating visual displays of data by executing a visualization tool that operates as part of a comprehensive Web-based computing platform can be accessed via a website, customizable interface, email, telephone, or other remote communication device. The visualization tool operates by accessing the data source and then executing an analysis engine to parse numerical and other forms of data. If necessary, a data mining tool can also be used to download data and a semantic template editor can be used to generate a template for parsing any type of data. The data and data format are identified, and the visualization tool executes a recommendation engine that considers the data and data format and recommends suitable visual display styles and visual display options and recommends additional compatible algorithms. Additionally, users can provide their own compatible algorithms for data processing. The user then selects one or more display styles or graphs and display options. If there are compatible algorithms, the user can select a pre-programmed algorithm or a user-generated algorithm as well. The computation engine executes the algorithms, performs calculations associated with the chosen visual display style, and outputs a file according to a given API protocol. A presentation program uses the output file to generate a visual display. Finally, the visualization tool delivers the display to the user, saves the display, and / or publishes the display.
Owner:YUAN MAX
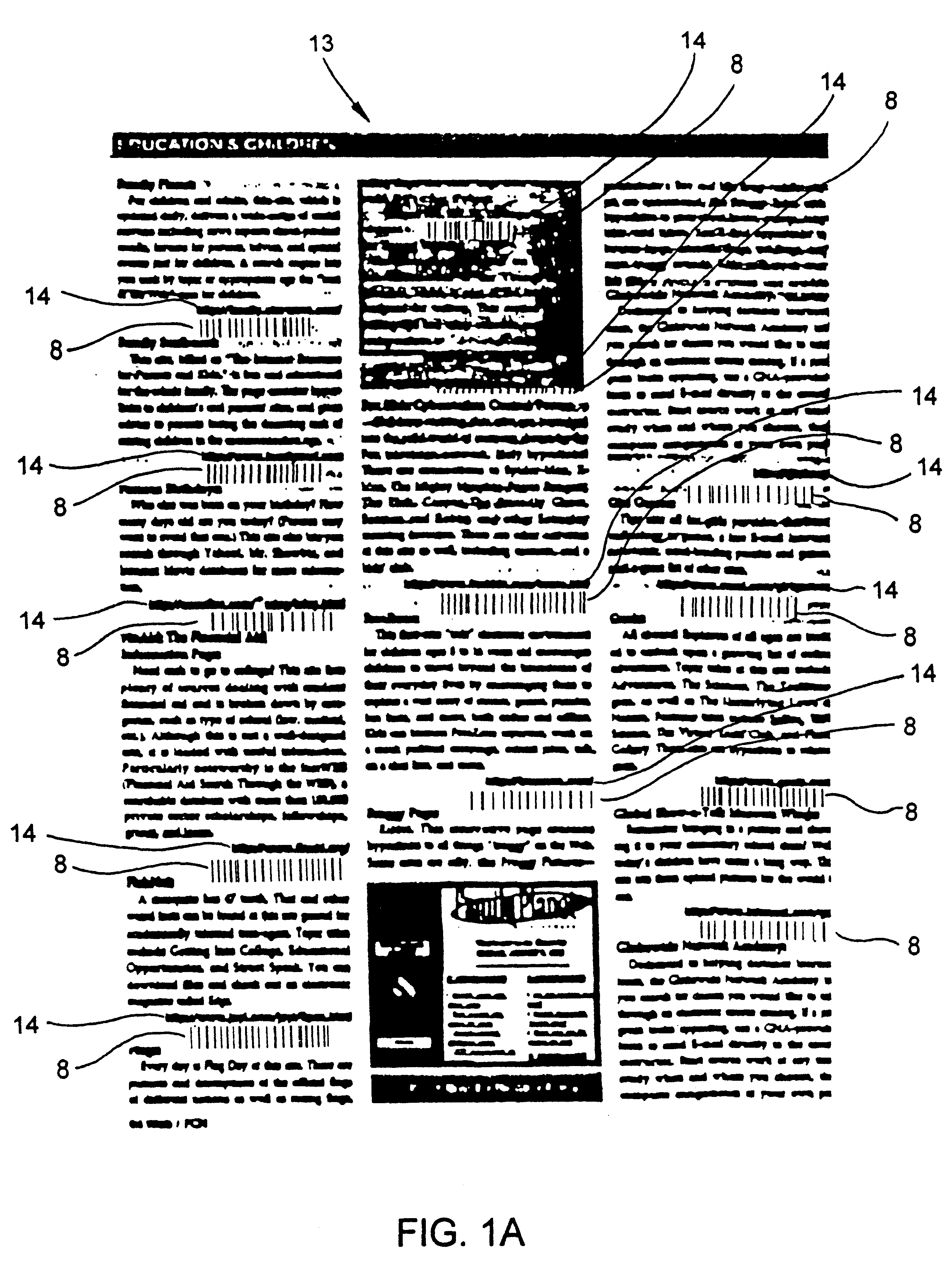
Web-based television system and method for enabling a viewer to access and display HTML-encoded documents located on the World Wide Web (WWW) by reading bar code symbols printed in a WWW-site guide using a wireless bar-code driven remote control device
InactiveUS6321991B1Digital data information retrievalTransmission systemsTelecommunications linkInternet information services
A Web-based television system for enabling an operator to access and display HTML-encoded documents located on the WWW. The system comprises one or more Internet information servers, an Internet terminal unit, and television set having a wireless remote control device and an audio-visual monitor. The Internet information servers store a plurality of HTML-encoded documents at a plurality of storage locations specified by a plurality of Uniform Resource Locators (URLs). The Internet terminal unit is operably connected to the infrastructure of the Internet and embodies a GUI-based Internet browser program, supporting the TCP / IP networking protocol. The television set is operably connected to the Internet terminal unit. The wireless remote control device includes a bar code symbol reader for reading bar code symbols, and an IR-based communication circuit for establishing a wireless communication link with the Internet terminal unit. A WWW-site guide is provided to television viewers. On the guide, a plurality of bar code symbols are preprinted along with a plurality of Web-site descriptions. Each preprinted bar code symbol is encoded with information related to one of the plurality of URLs. The bar code symbol reader is programmed for reading the bar code symbols in the WWW-site guide. In response to reading each bar code symbol, the bar code symbol reader produces information related to one of the URLs, and this information is transmitted, over the wireless information communication link, to the Internet terminal unit. Thereupon, the GUI-based Internet browser uses the TCP / IP networking standard and the produced information to automatically access the HTML-encoded document specified by the related URL, and automatically display the accessed HTML-encoded document on the audio-visual monitor of the television set, for viewing purposes.
Owner:METROLOGIC INSTR
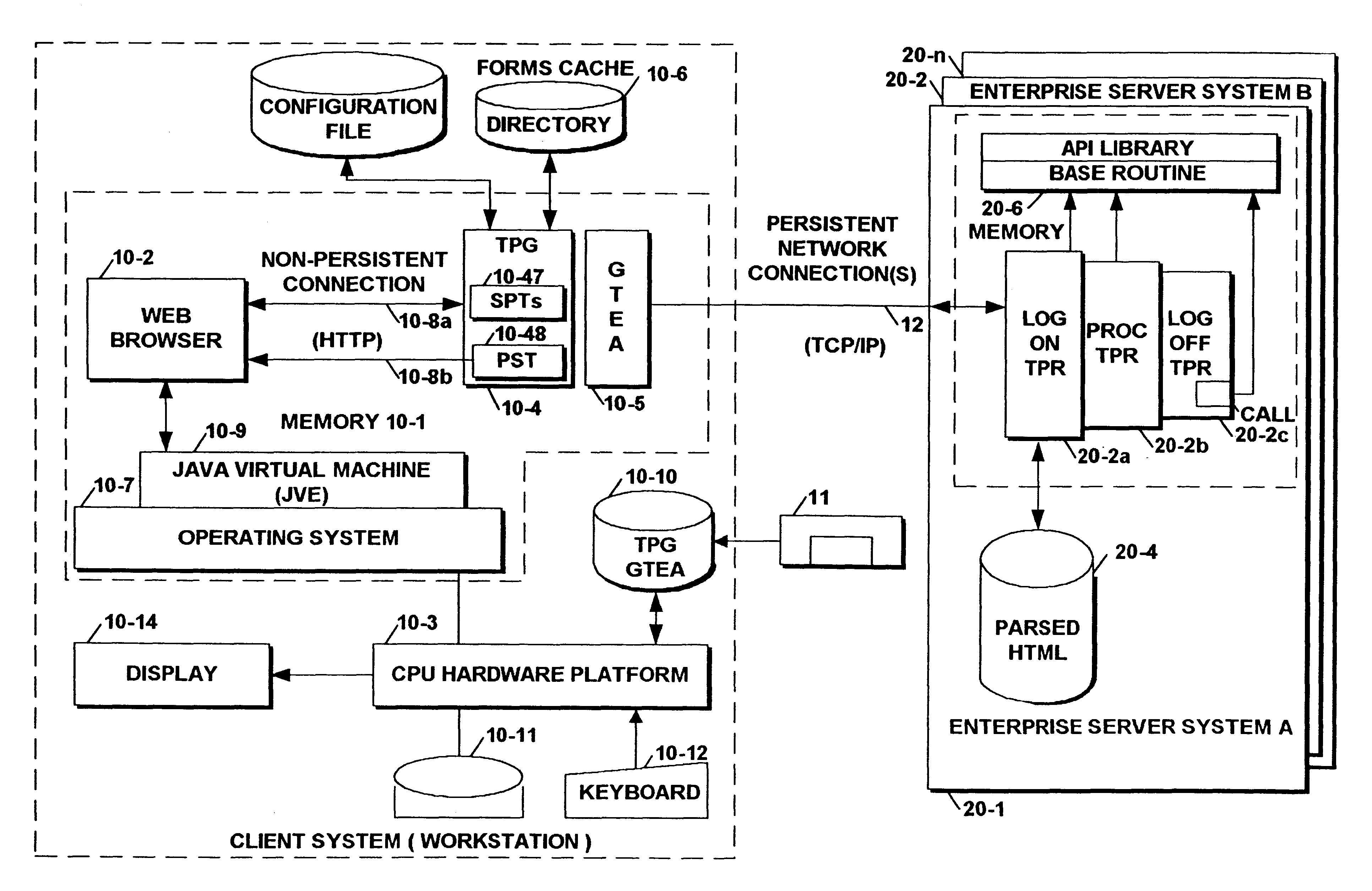
Method and system for providing session pools for high performance web browser and server communications
InactiveUS6338089B1Function increaseReduce the burden onMultiple digital computer combinationsSpecial data processing applicationsWeb browserClient-side
A client system utilizes a standard browser component and a transaction protocol gateway (TPG) component that operatively couples to the standard browser component. The browser component initiates the utilization of new session connections and reuse of existing session connections through the use of session pools as a function of the coding of the universal resource locators (URLs) contained in each issued request. The gateway component builds a plurality of session pool table structures at client system startup that define an initial number of pre-established persistent session connections for enabling communication with a number of server systems. Each browser URL is passed to the TPG component that examines a context field within the URL. If the context field has been set to a predetermined value, the TPG component in lieu of opening a new session connection to the designated server system, obtains a pre-established session connection from a session pool. Then the TPG component moves an entry corresponding to the session connection information to the PST component for enabling the browser component to communicate with a particular server system over the pre-established persistent session connection.
Owner:BULL HN INFORMATION SYST INC
Conversational computing via conversational virtual machine
InactiveUS20070043574A1Limitation for transferReduce degradationInterconnection arrangementsInterprogram communicationConversational speechApplication software
A conversational computing system that provides a universal coordinated multi-modal conversational user interface (CUI) 10 across a plurality of conversationally aware applications (11) (i.e., applications that “speak” conversational protocols) and conventional applications (12). The conversationally aware applications (11) communicate with a conversational kernel (14) via conversational application APIs (13). The conversational kernel 14 controls the dialog across applications and devices (local and networked) on the basis of their registered conversational capabilities and requirements and provides a unified conversational user interface and conversational services and behaviors. The conversational computing system may be built on top of a conventional operating system and APIs (15) and conventional device hardware (16). The conversational kernel (14) handles all I / O processing and controls conversational engines (18). The conversational kernel (14) converts voice requests into queries and converts outputs and results into spoken messages using conversational engines (18) and conversational arguments (17). The conversational application API (13) conveys all the information for the conversational kernel (14) to transform queries into application calls and conversely convert output into speech, appropriately sorted before being provided to the user.
Owner:NUANCE COMM INC
Generating and providing alert messages in a communications network
InactiveUS6871214B2Special service for subscribersMultiprogramming arrangementsSpeech soundComputer science
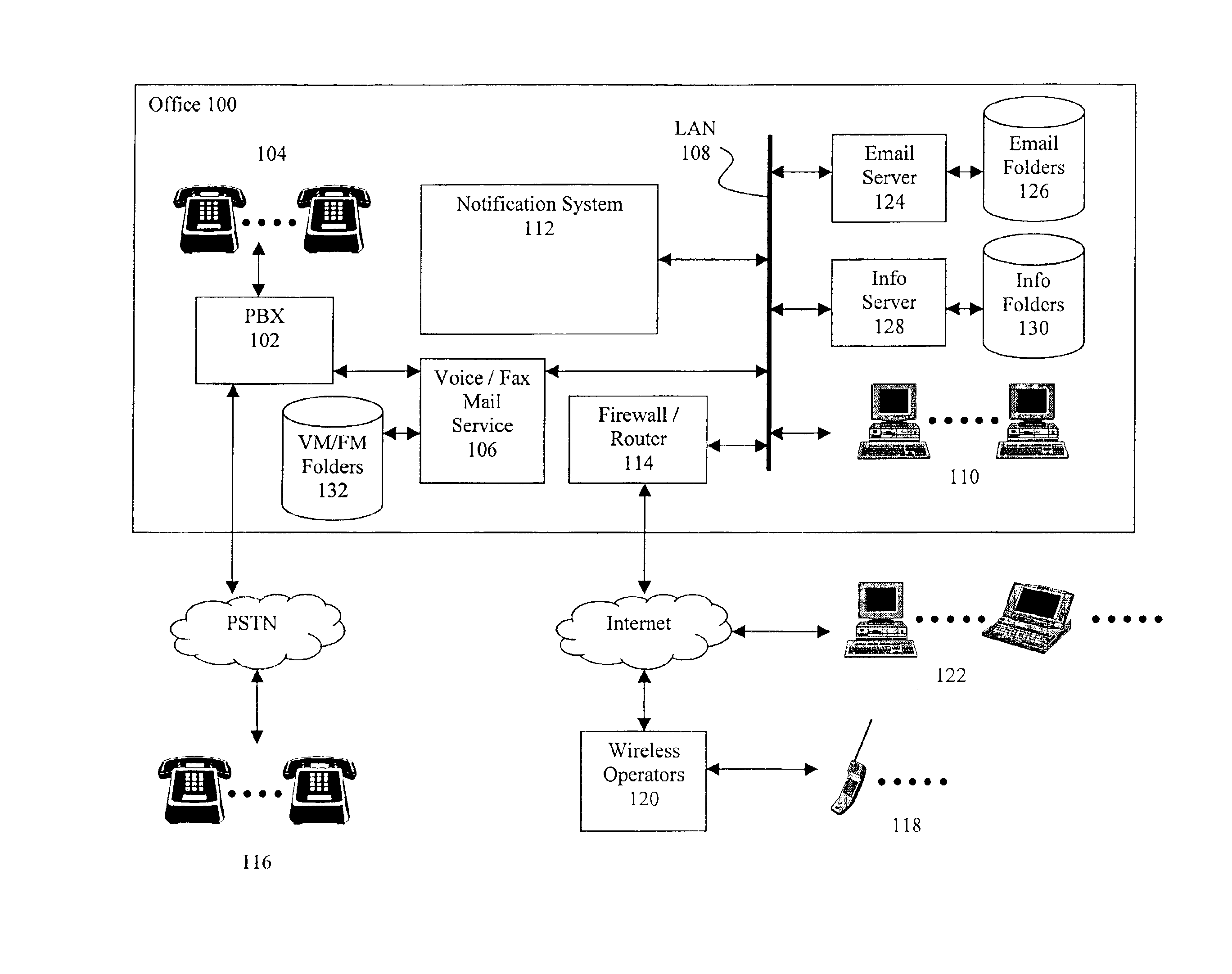
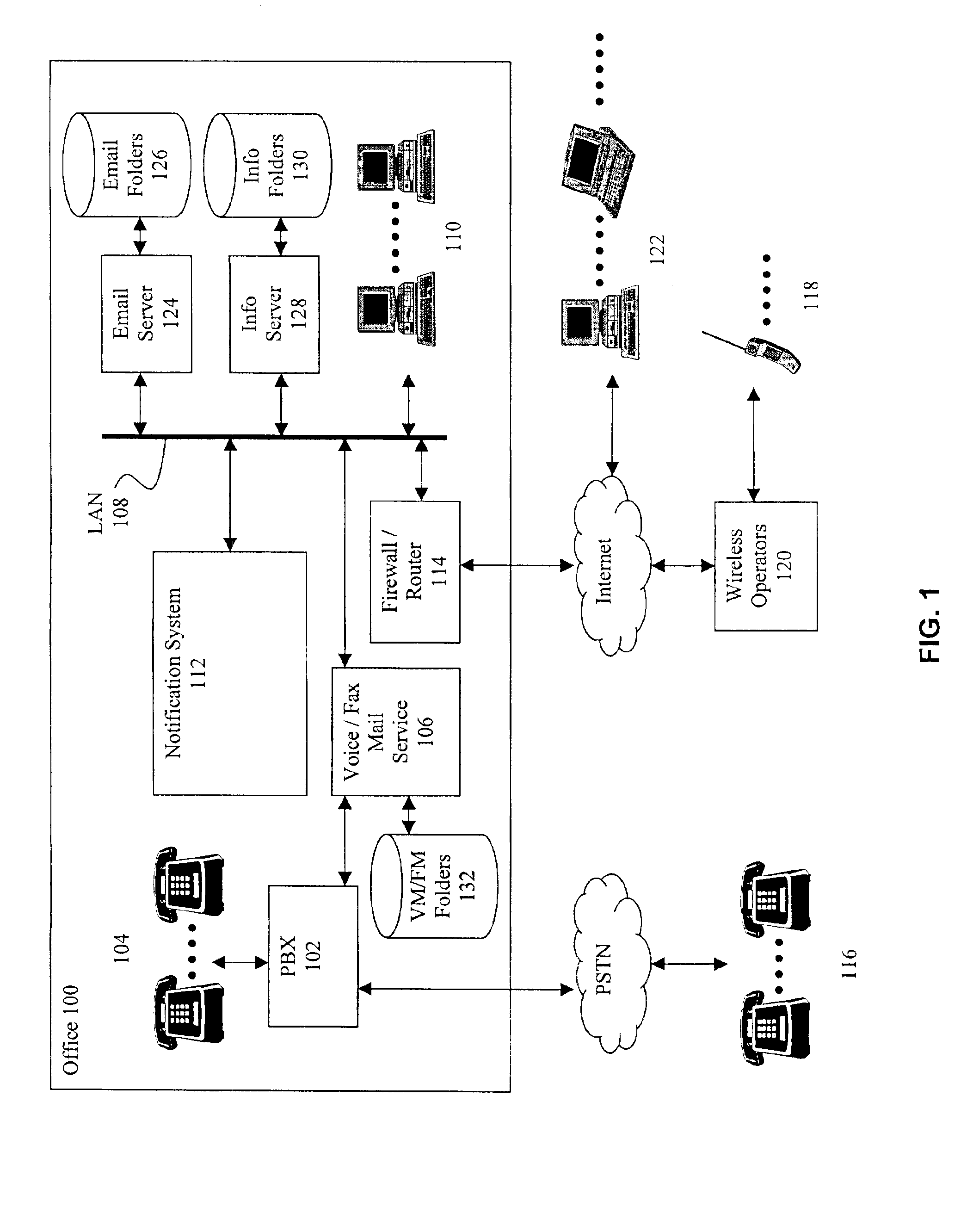
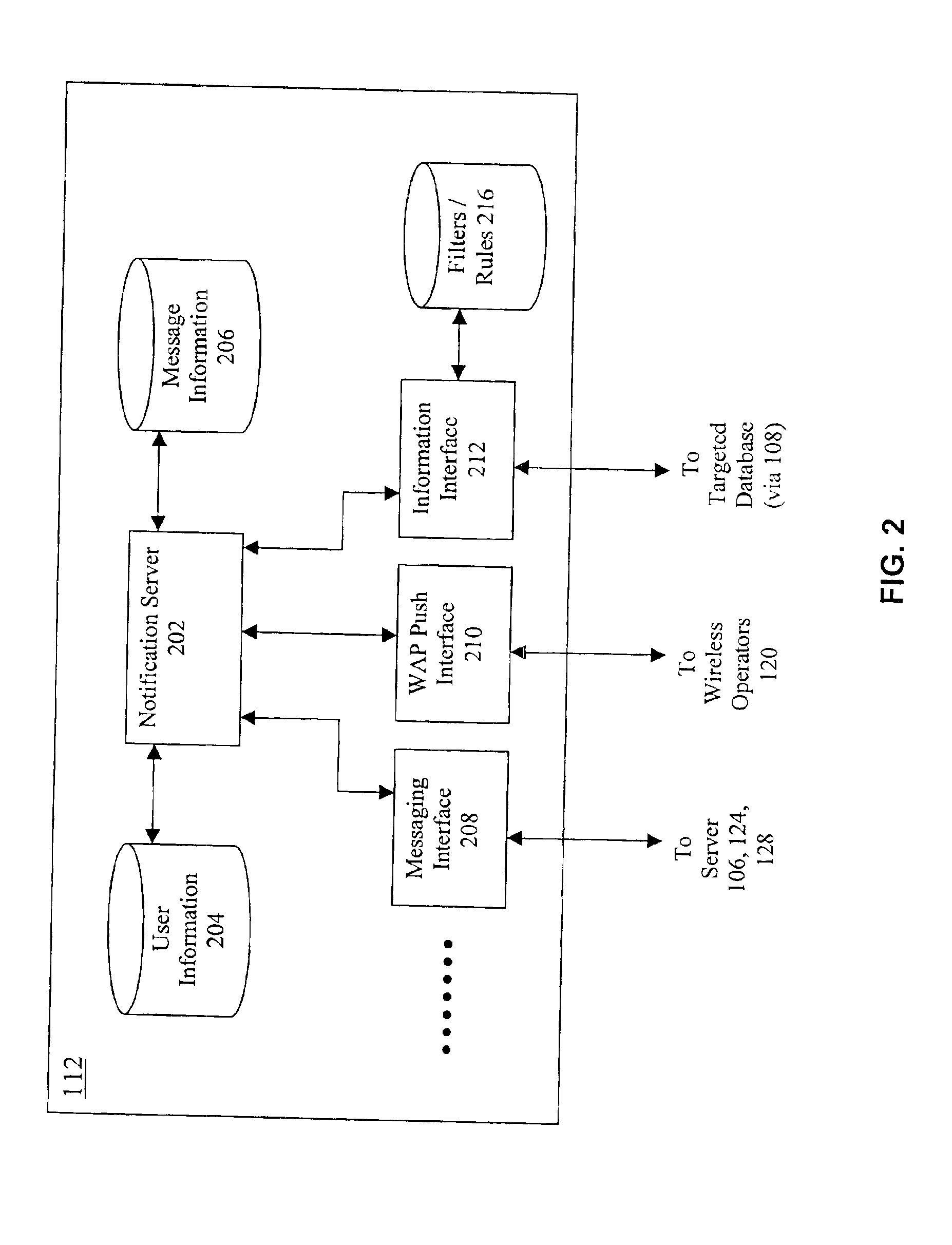
A notification system is coupled to a plurality of message services including a voice mail server, an email server and an information server in an office. Messages left for a user (e.g. voice mail, email, CRM event, etc.) are deposited in folders maintained by the messaging services. The notification system detects additions to the user's folders and when a new message arrives, the notification system sends an alert to a Wireless Access Protocol (WAP) enabled device (e.g. cell phone) configured for the user. The alert includes the total number of messages of each type received for the user, along with an indication of the most recently received message. The notification system may further monitor an information source for new information that may be of interest to the user (e.g. stock or product price quotes), and provide these in the alert notification if certain conditions are met (e.g. stock price exceeds a threshold).
Owner:MALIKIE INNOVATIONS LTD
Systems and methods of using the refresh button to determine freshness policy
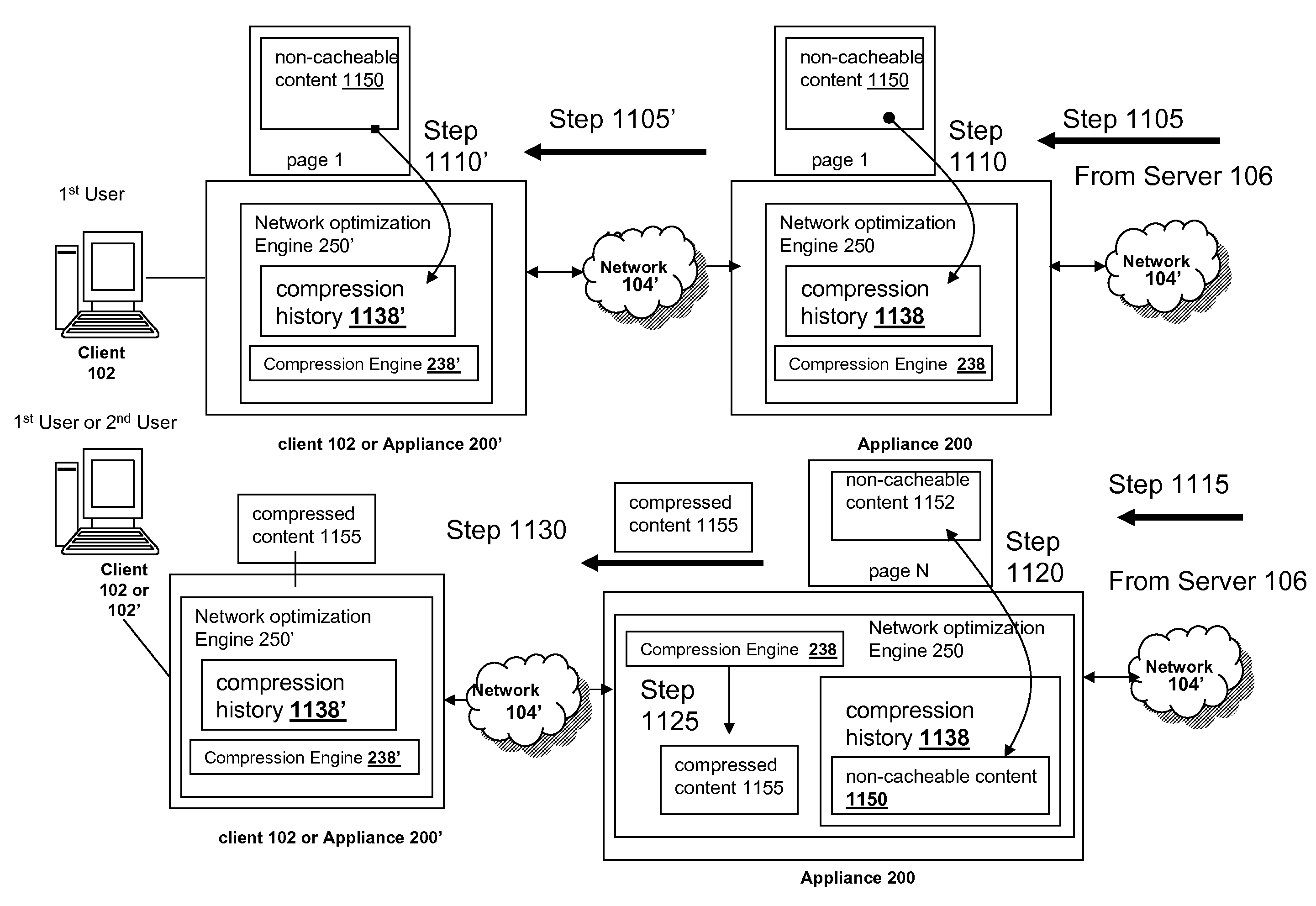
ActiveUS20080229025A1Improve efficiencyMore resolutionMemory architecture accessing/allocationMemory adressing/allocation/relocationClient agentDomain name
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
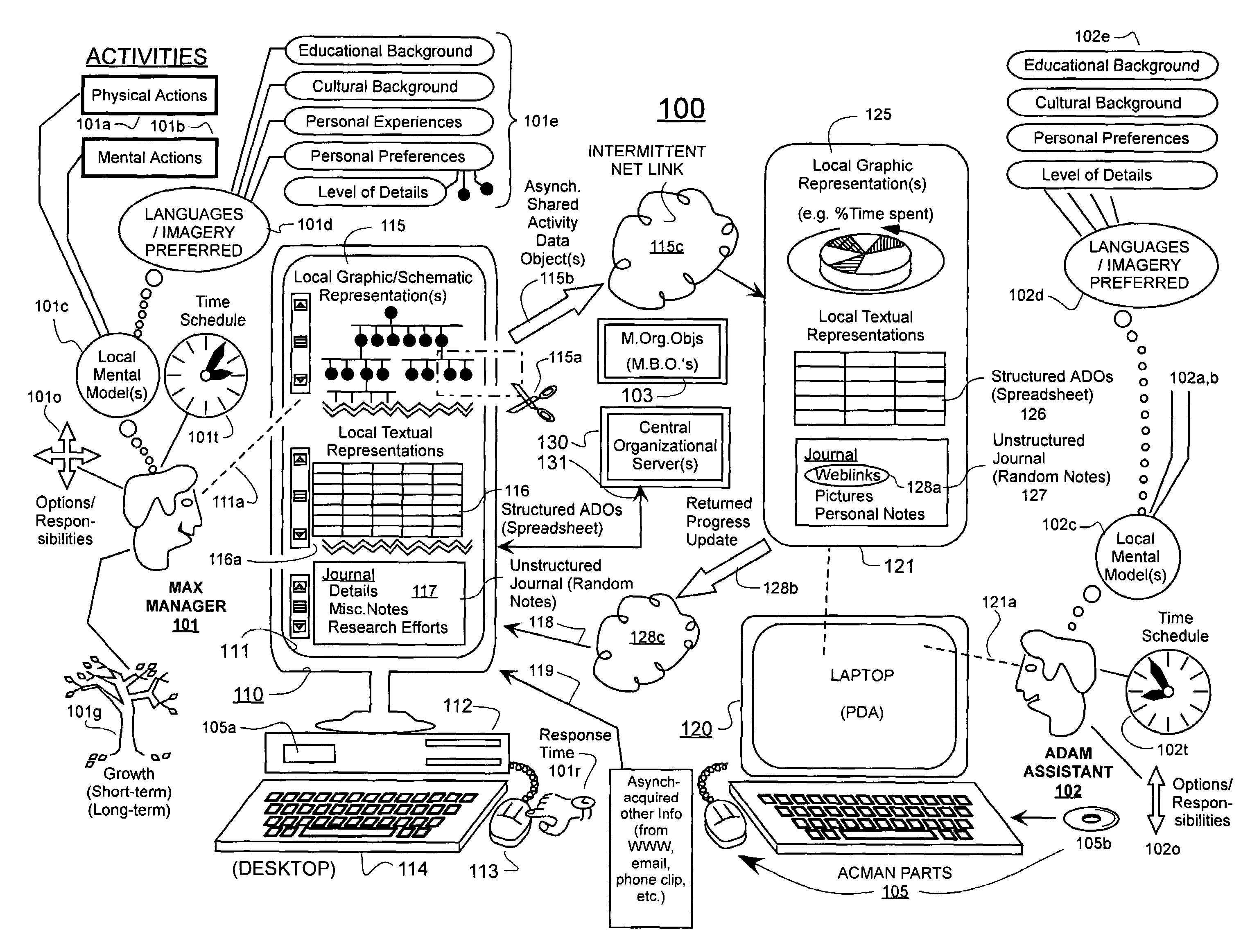
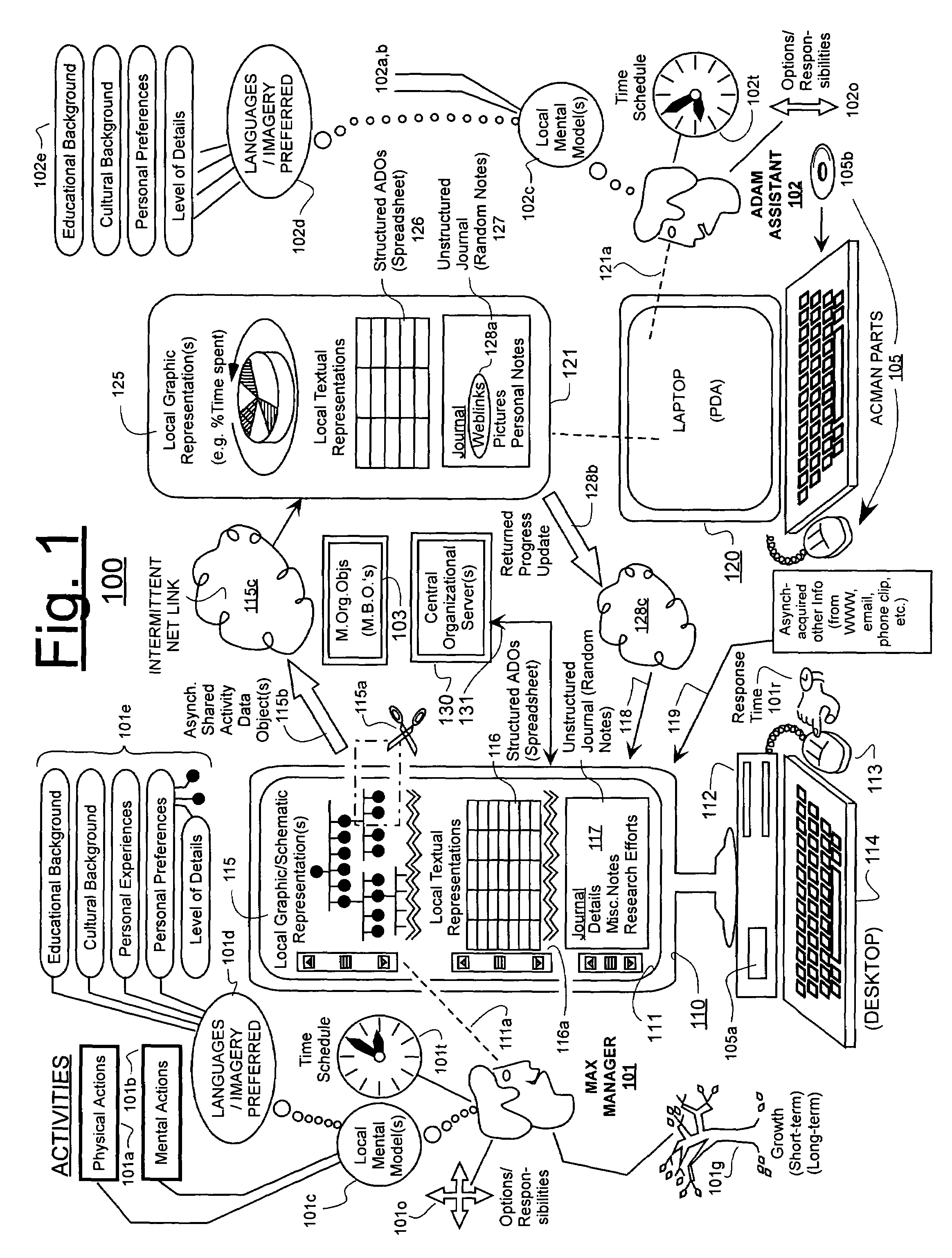
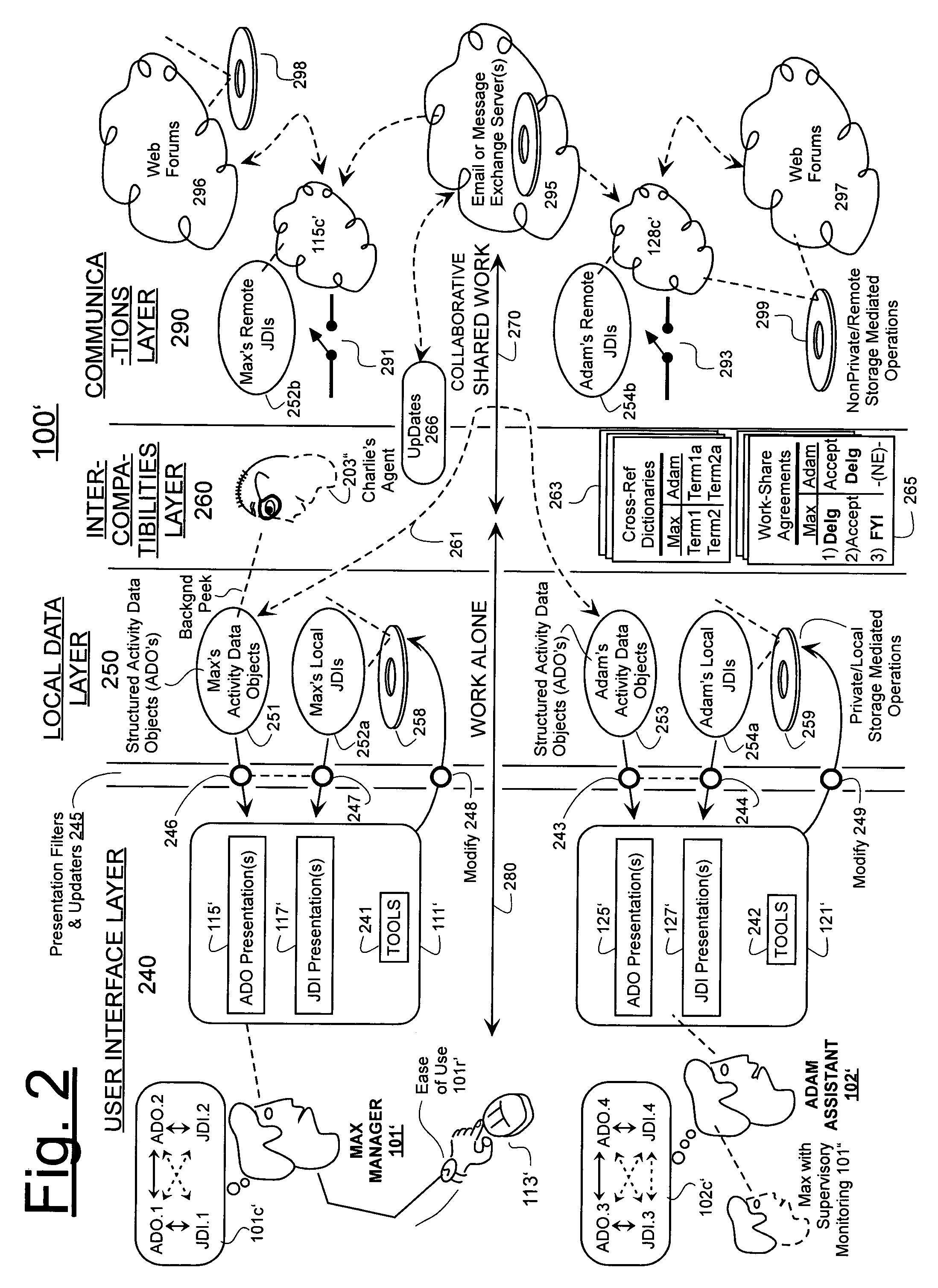
Machine-implemented activity management system using asynchronously shared activity data objects and journal data items
ActiveUS7197502B2ExchangeEasy to collectDigital data processing detailsOffice automationJob sharingInformation sharing
Machine-assisted methods and apparatus are disclosed for allowing individual users to develop and organize respective activity descriptions and supporting journal items according to their respective preferences. Cross-referencing mappings may be created between activity descriptions and journal items in order to find, filter and organize disparate data. Cross-referencing mappings may also be created between the developed activity descriptions of different users so they can better understand each others perspectives and possibly overlapping goals. Different users' activity descriptions can be presented to a user even while the user may be disconnected from communication networks. Hierarchical relationships between activity descriptions may be provided. Machine-assisted means may be provided for creating work-sharing, work-delegating and / or informational sharing agreements between different users. Further machine-implemented means may be provided for automatically and asynchronously updating users on shared activities by other users even though all users are not necessarily connected to one or more respective communication networks at same time.
Owner:CALLAHAN CELLULAR L L C
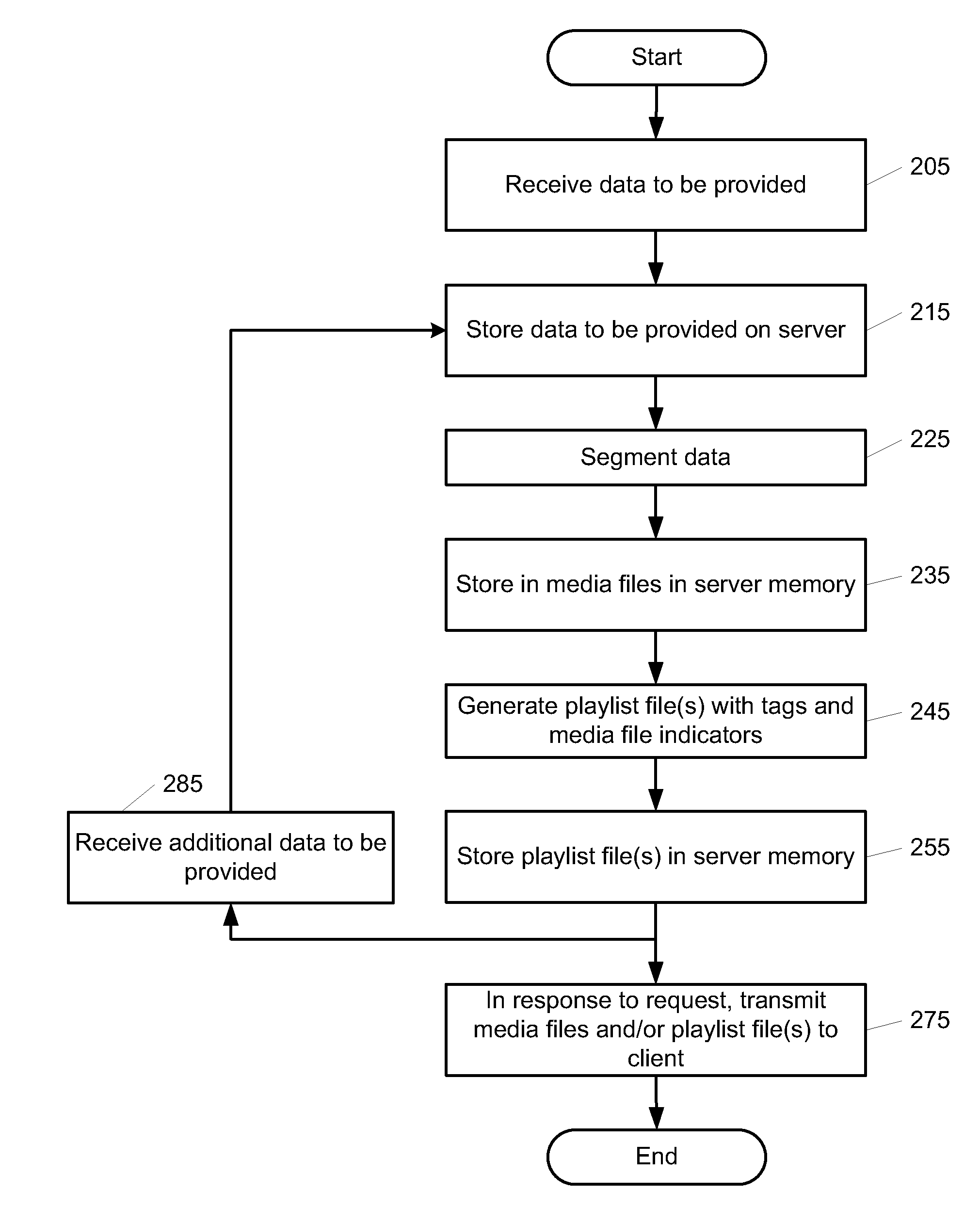
Playlists for real-time or near real-time streaming
InactiveUS20100169303A1Easy retrievalFacilitate a client in presenting the segmented user dataDigital data processing detailsTelevision systemsData streamClient-side
Methods and apparatuses for real-time or near real-time streaming of content using transfer protocols such as an HTTP compliant protocol. In one embodiment, a method includes dividing a stream of data, representing the contiguous time based content of a program (e.g. a live video broadcast), into a plurality of distinct media files, and generating a playlist file having a plurality of tags and Universal Resource Indicators (URIs) indicating an order of presentation of the plurality of distinct media files. The plurality of media files and the playlist file can be made available for transmission to a client device which can retrieve the media files using the playlist file.
Owner:APPLE INC
Method and apparatus to discover services and negotiate capabilities
ActiveUS6970869B1Data processing applicationsResource allocationDistributed Computing EnvironmentService provision
A service discovery protocol may allow clients in a distributed computing environment to search for services. Service providers (or a listener agent) may respond to search requests by publishing or providing corresponding service advertisements or URIs to corresponding service advertisements. When a service provider responds to a discovery search request (either directly or through a listener agent), the provider may choose to publish a protected or an un-protected (complete) advertisement. A protected advertisement may include the set of information necessary to obtain a complete advertisement. Publishing a protected advertisement may force the client to obtain a valid credential from an authentication service before receiving the complete un-protected advertisement from the service provider. A complete un-protected advertisement is needed to create a message endpoint for accessing the service. Forcing clients to obtain a valid credential before receiving an advertisement may provide an additional level of security for the service provider. The security credential that may need to be obtained to receive the complete advertisement may also be used to construct a message gate to communicate with the service where the gate embeds the security credential in each message to the service.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com