Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
457 results about "Policy enforcement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
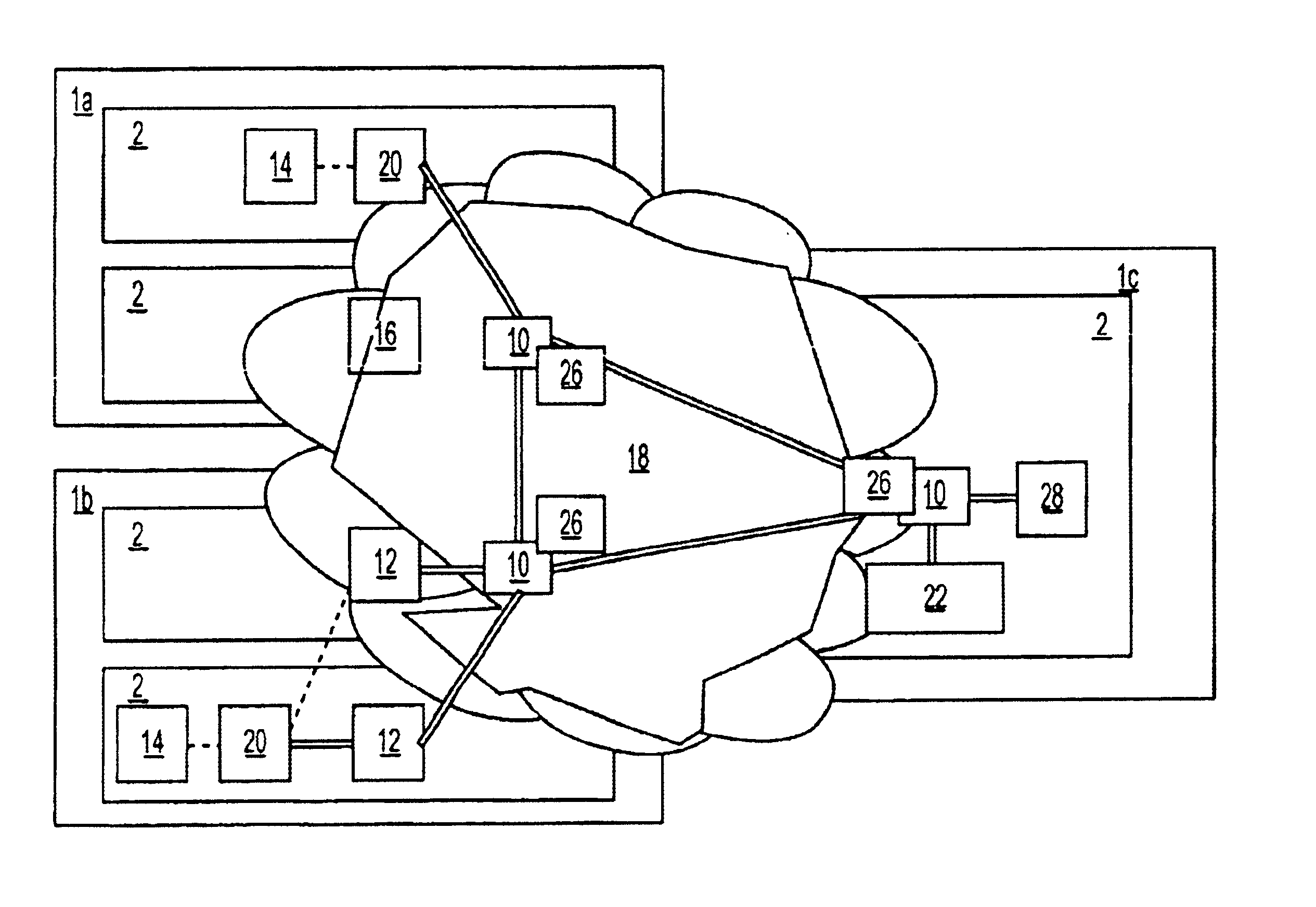
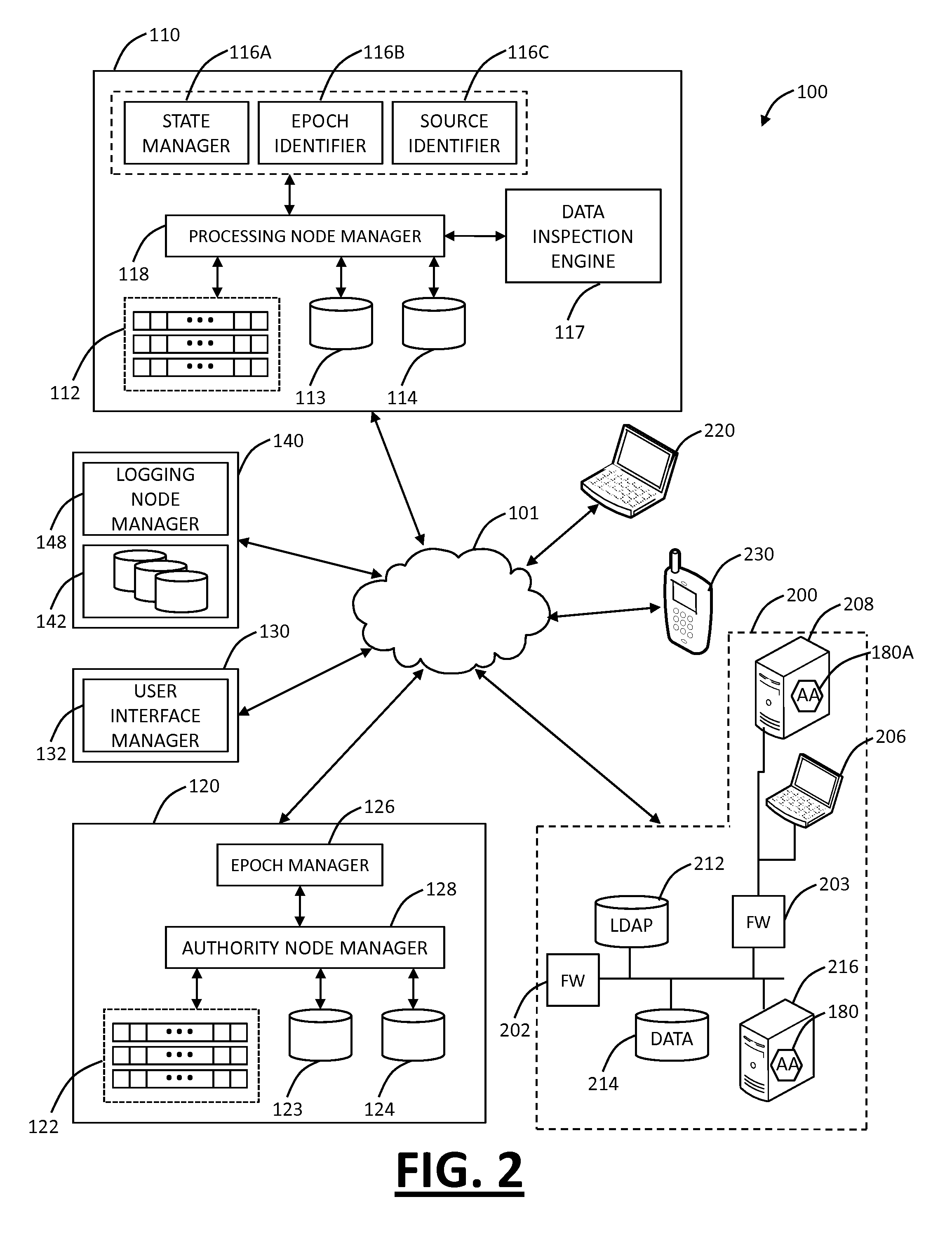
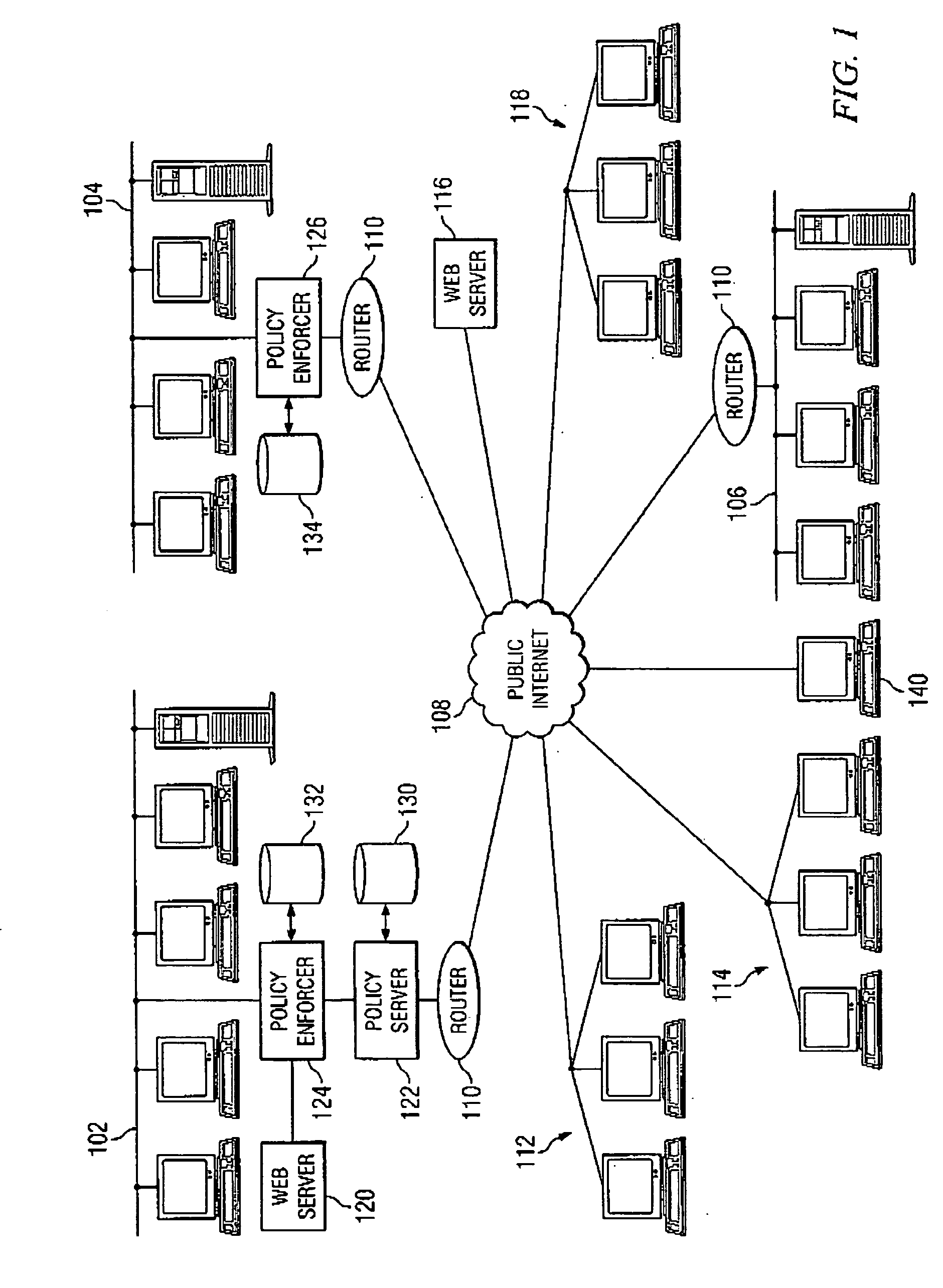
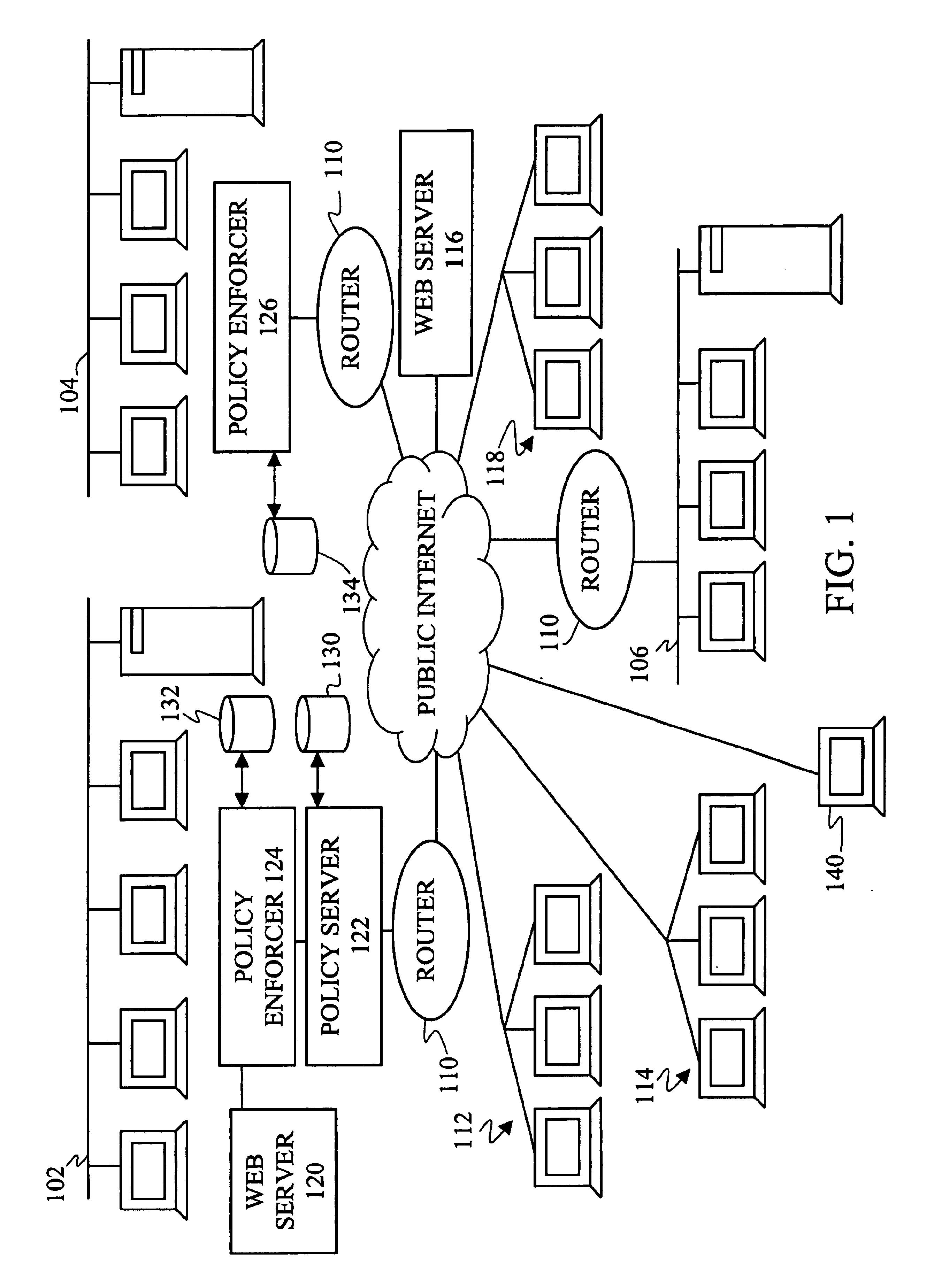
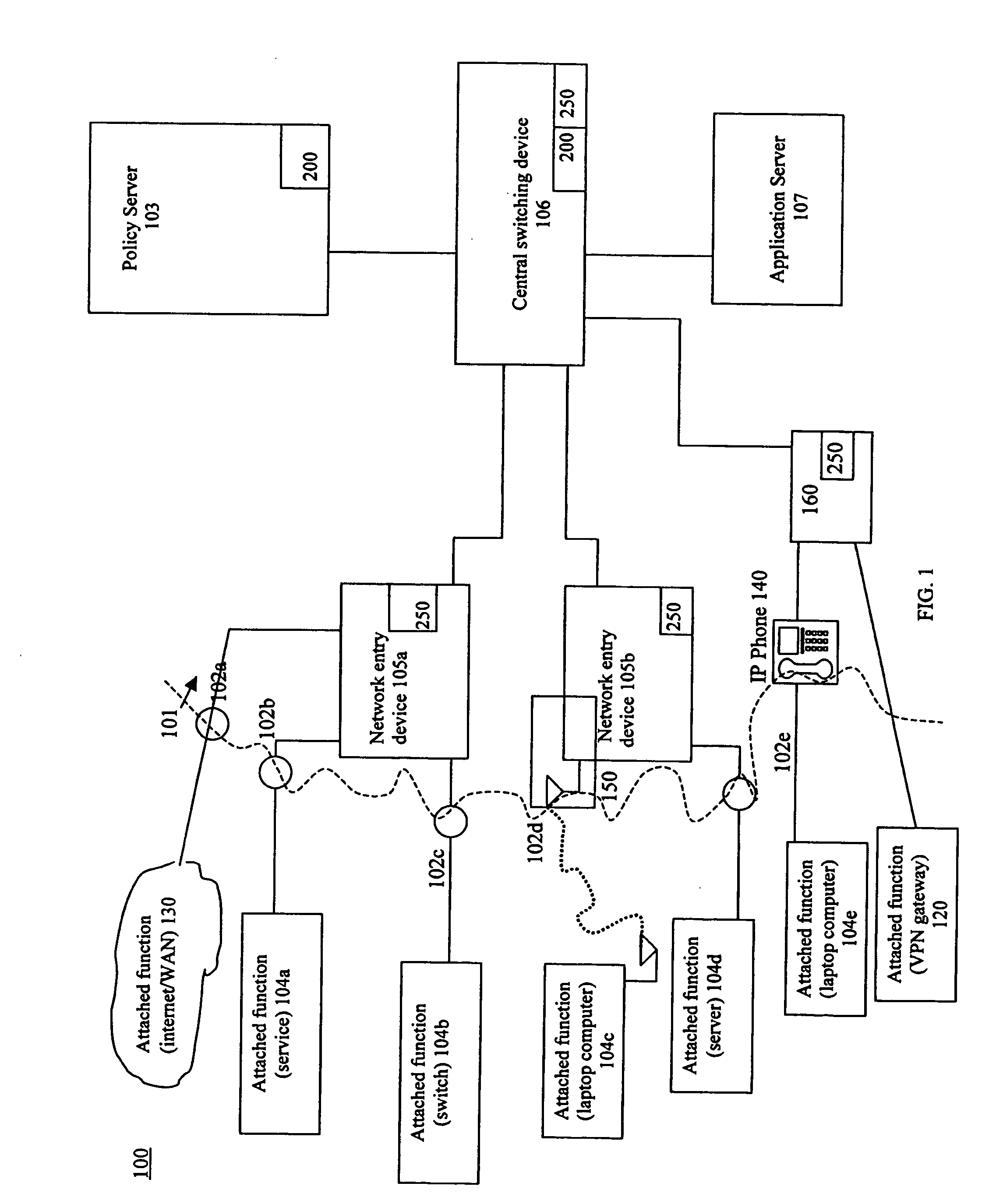
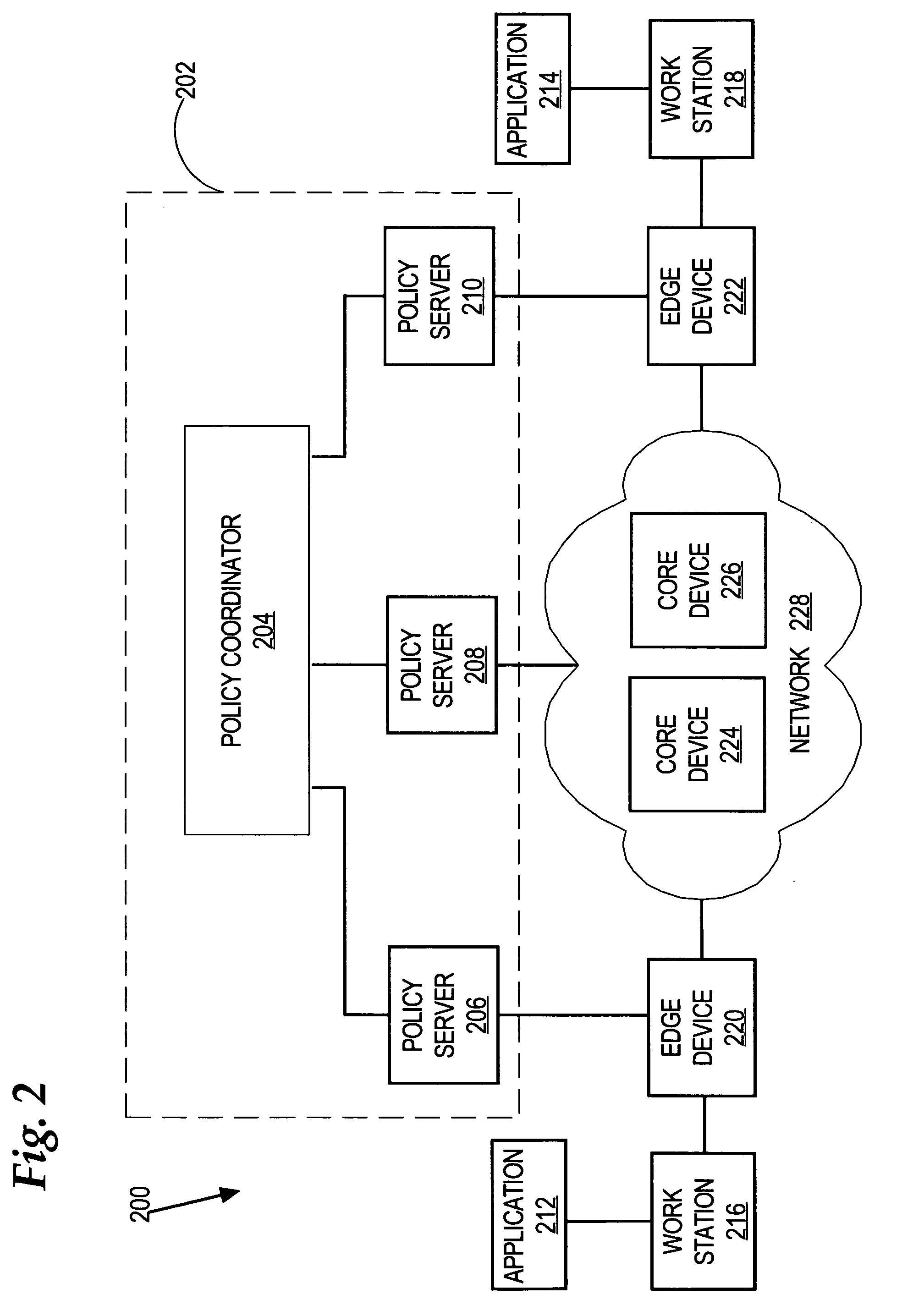
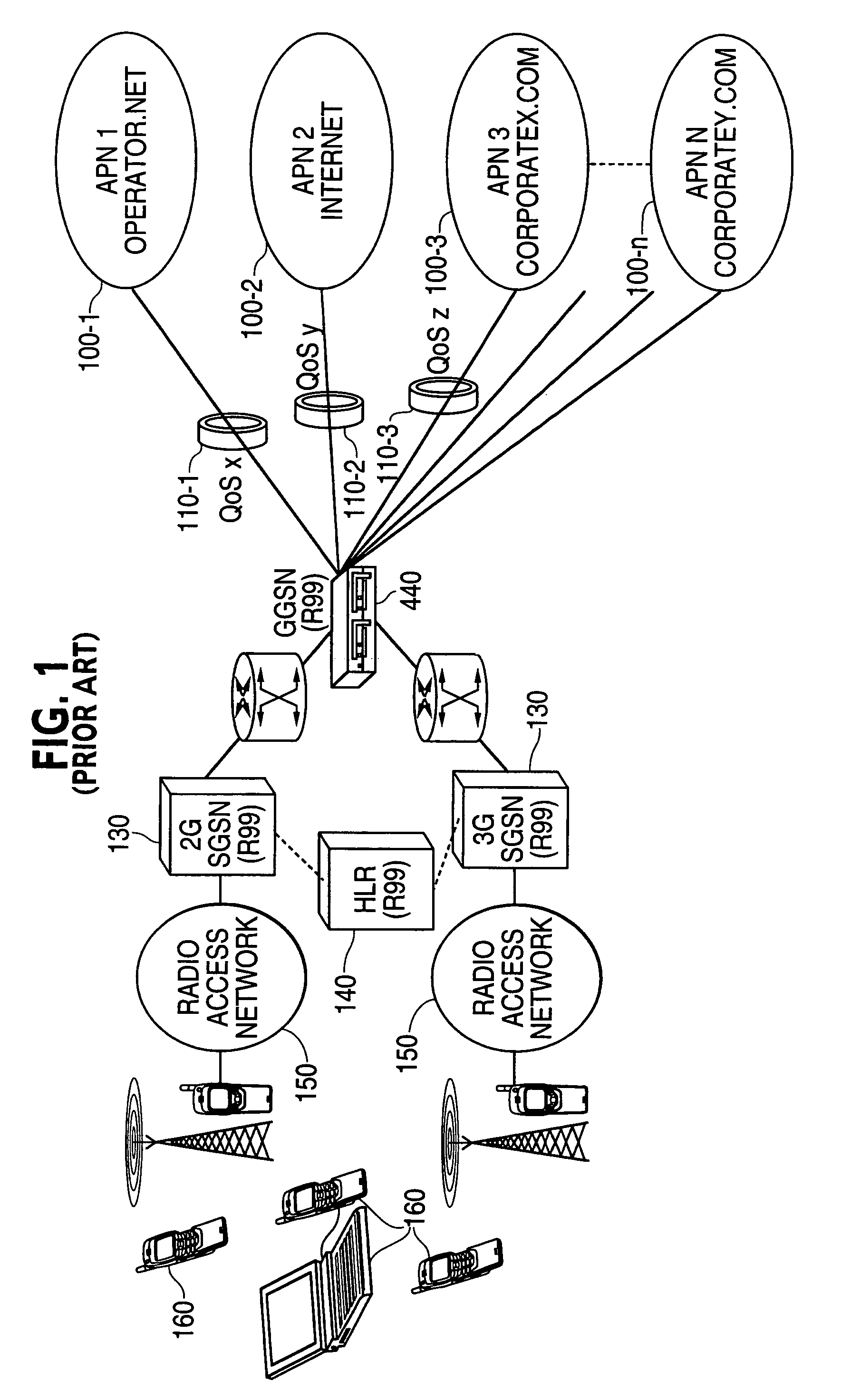
Network-based mobile workgroup system
InactiveUS6954790B2Multiple digital computer combinationsWireless network protocolsClient-sideAccess technology
A network-based mobile workgroup system has considerably wider appeal and application than normal virtual private networks in that it provides seamless mobility across a number of access technologies at the same time as it offers a granular security separation down to workgroup level. The mobile workgroup system is an access management system for mobile users with VPN and firewall functionality inbuilt. The mobile user can access the mobile workgroup system over a set of access technologies and select server resources and correspondent nodes to access pending their workgroup membership approvals. All workgroup policy rules are defined in a mobile service manager and pushed down to one or more mobile service routers for policy enforcement. The mobile service router closest to the mobile client, and being part of the mobile virtual private network, performs regular authentication checks of the mobile client during service execution. At the same time it performs traffic filtering based on the mobile user's workgroup memberships. Together, these two components constitute an unprecedented security lock, effectively isolating a distributed workgroup into a mobile virtual private network.
Owner:LONGHORN HD LLC
Cloud based mobile device security and policy enforcement
ActiveUS20120240183A1Computer security arrangementsMobile application execution environmentsTablet computerOperational system
The present disclosure relates to cloud based mobile device security and policy systems and methods to use the “cloud” to pervasively enforce security and policy on mobile devices. The cloud based mobile device security and policy systems and methods provide uniformity in securing mobile devices for small to large organizations. The cloud based mobile device security and policy systems and methods may enforce one or more policies for users wherever and whenever the users are connected across a plurality of different devices including mobile devices. This solution ensures protection across different types, brands, operating systems, etc. for smartphones, tablets, netbooks, mobile computers, and the like.
Owner:ZSCALER INC
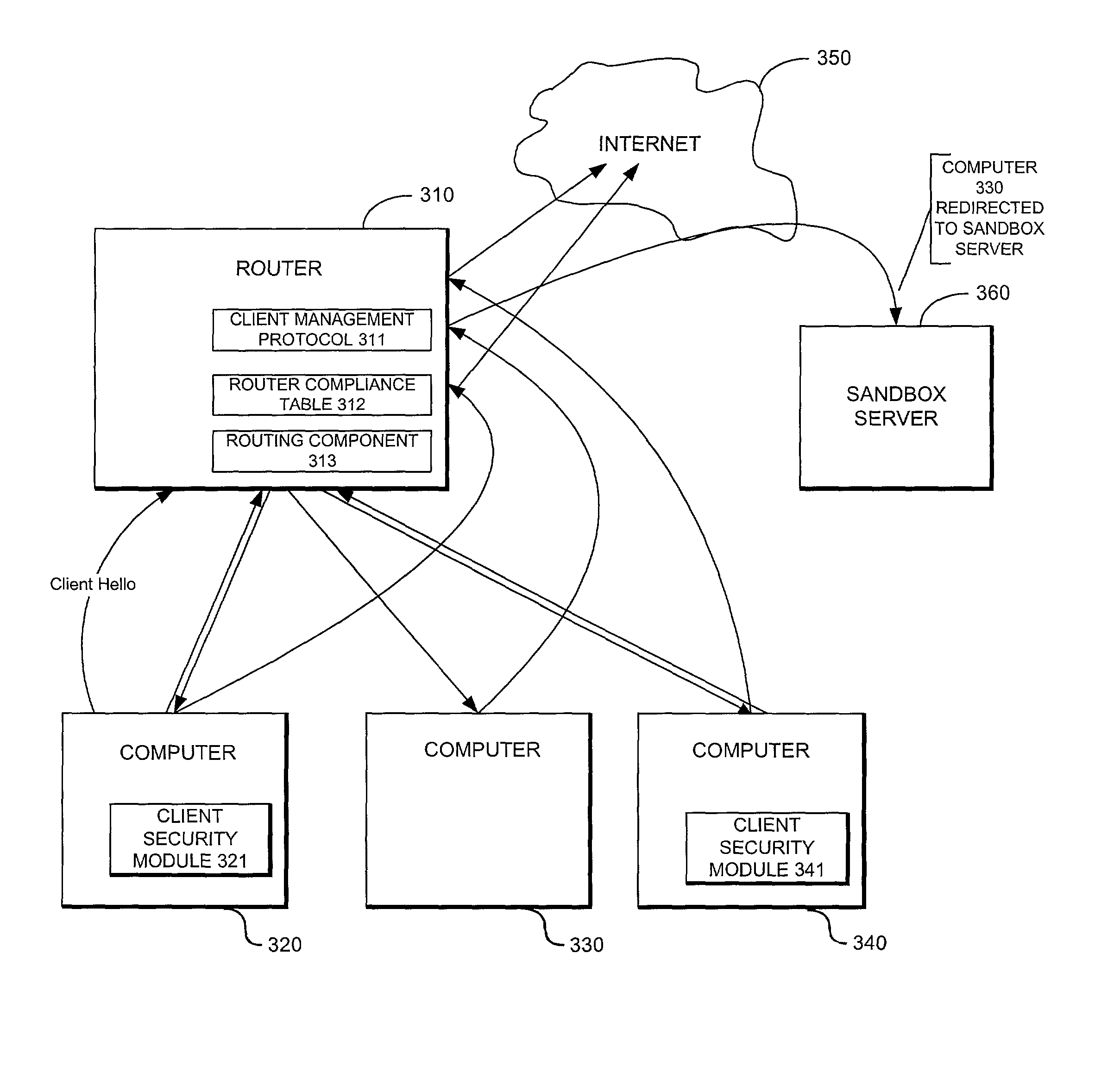
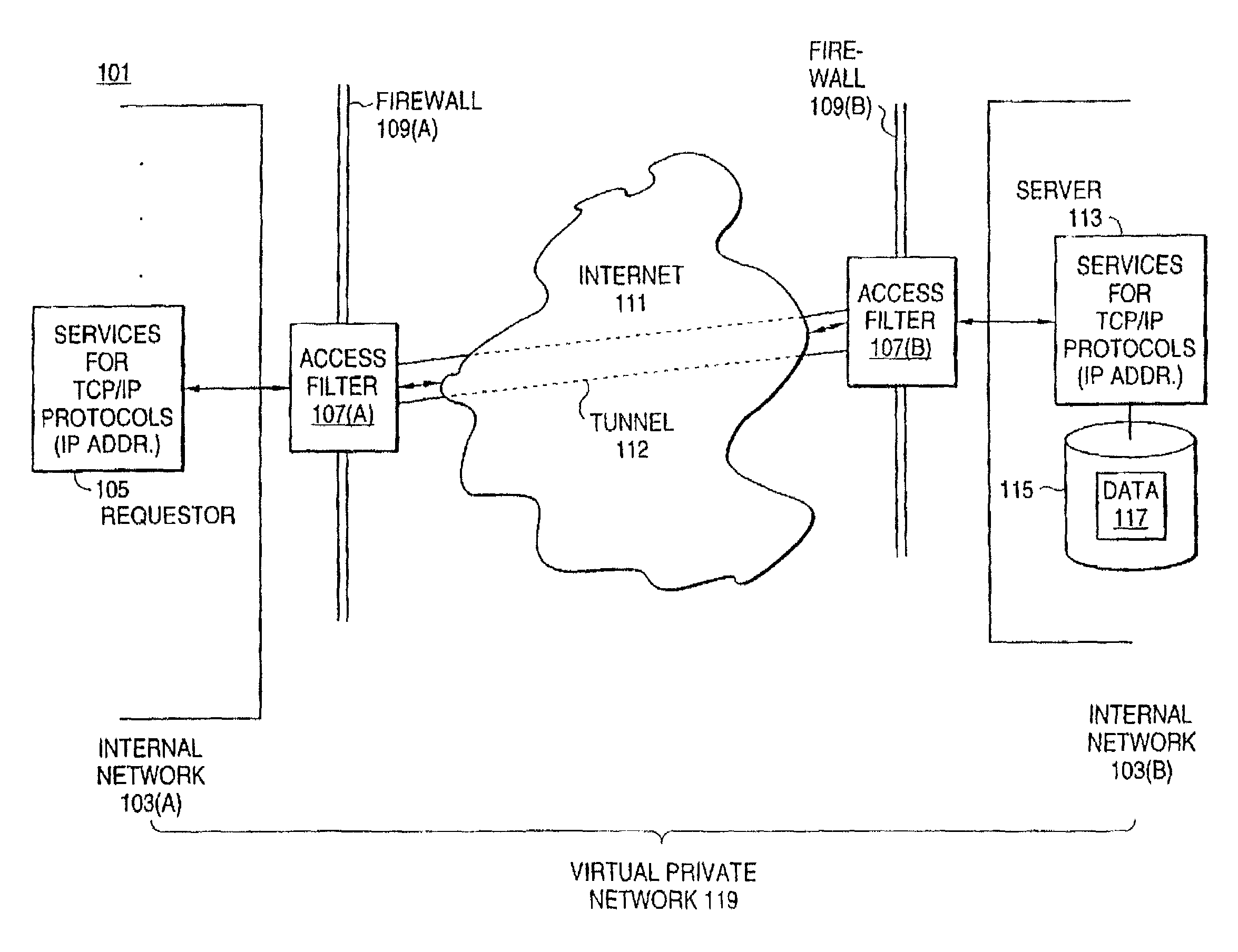
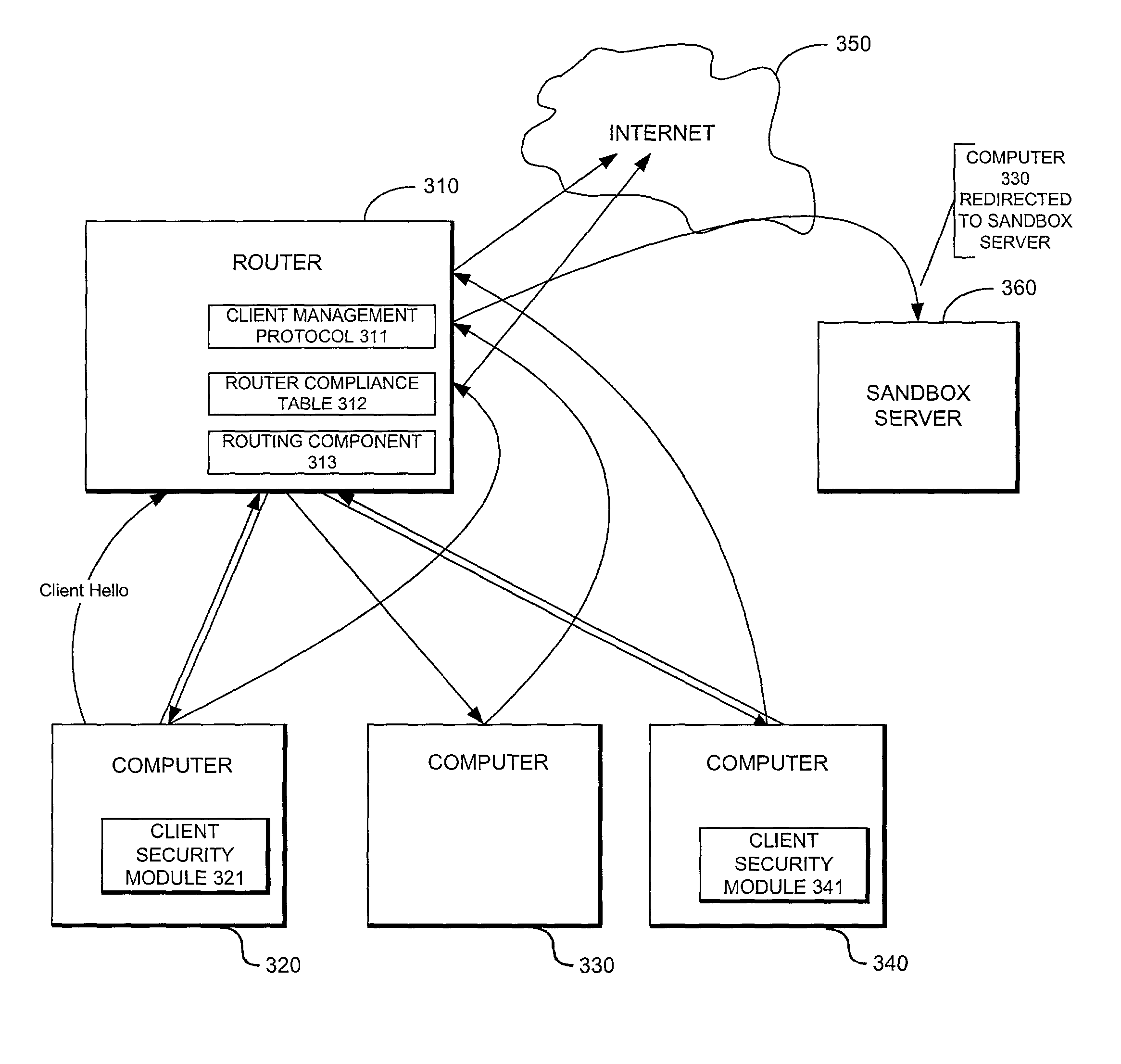
System providing internet access management with router-based policy enforcement
ActiveUS20030055962A1Multiple digital computer combinationsTransmissionInternet accessApplication software
A computing environment with methods for monitoring access to an open network such as the Internet, is described. The system includes one or more client computers, each operating applications (e.g., Netscape Navigator or Microsoft Internet Explorer) requiring access to an open network, such as a WAN or the Internet, and a router or other equipment that serves a routing function (e.g., a cable modem) for the client computers. A centralized security enforcement module on the router maintains access rules for the client computers and verifies the existence and proper operation of a client-based security module on each client computer. The router-side security module periodically sends out a router challenge via Internet broadcast to the local computers on the network. If the client-side security module is installed and properly operating, the client-side security module responds to the router challenge. The responses received by the router-side security module are maintained in a table. Each time the router receives a request from a client computer to connect to the Internet, the router-side security module reviews the table and analyzes whether or not the computer requesting a connection to the Internet properly responded to the most recent router challenge. If it determines that the computer has properly responded to the router challenge, then it permits the computer to connect to the Internet. If a computer has not properly responded or if a computer has not answered the router challenge, then the computer is not allowed to connect to the Internet as requested.
Owner:CHECK POINT SOFTWARE TECH INC
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protocol) gateways simultaneously
ActiveUS7039037B2Time-division multiplexData switching by path configurationCyber operationsComputer network
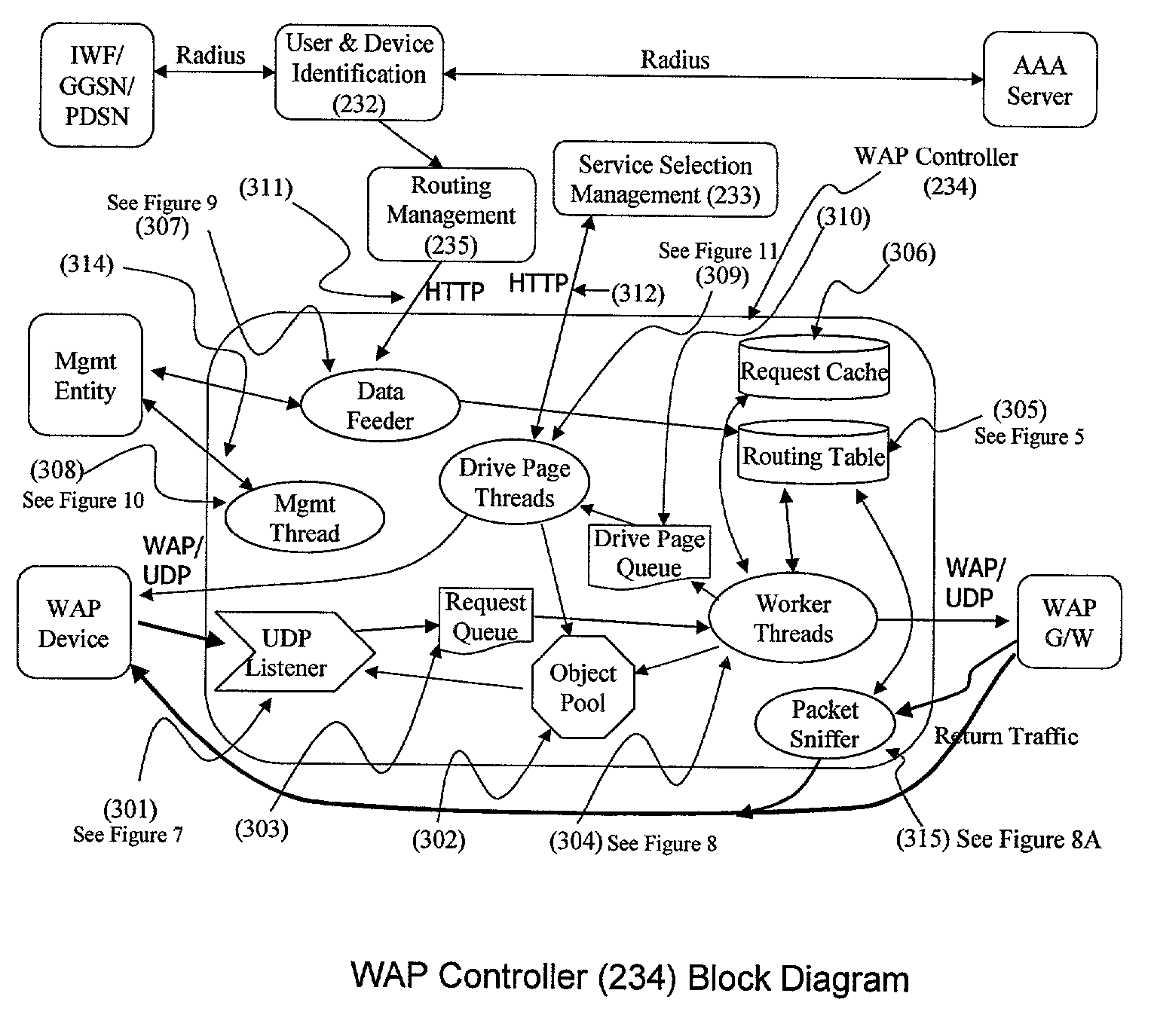
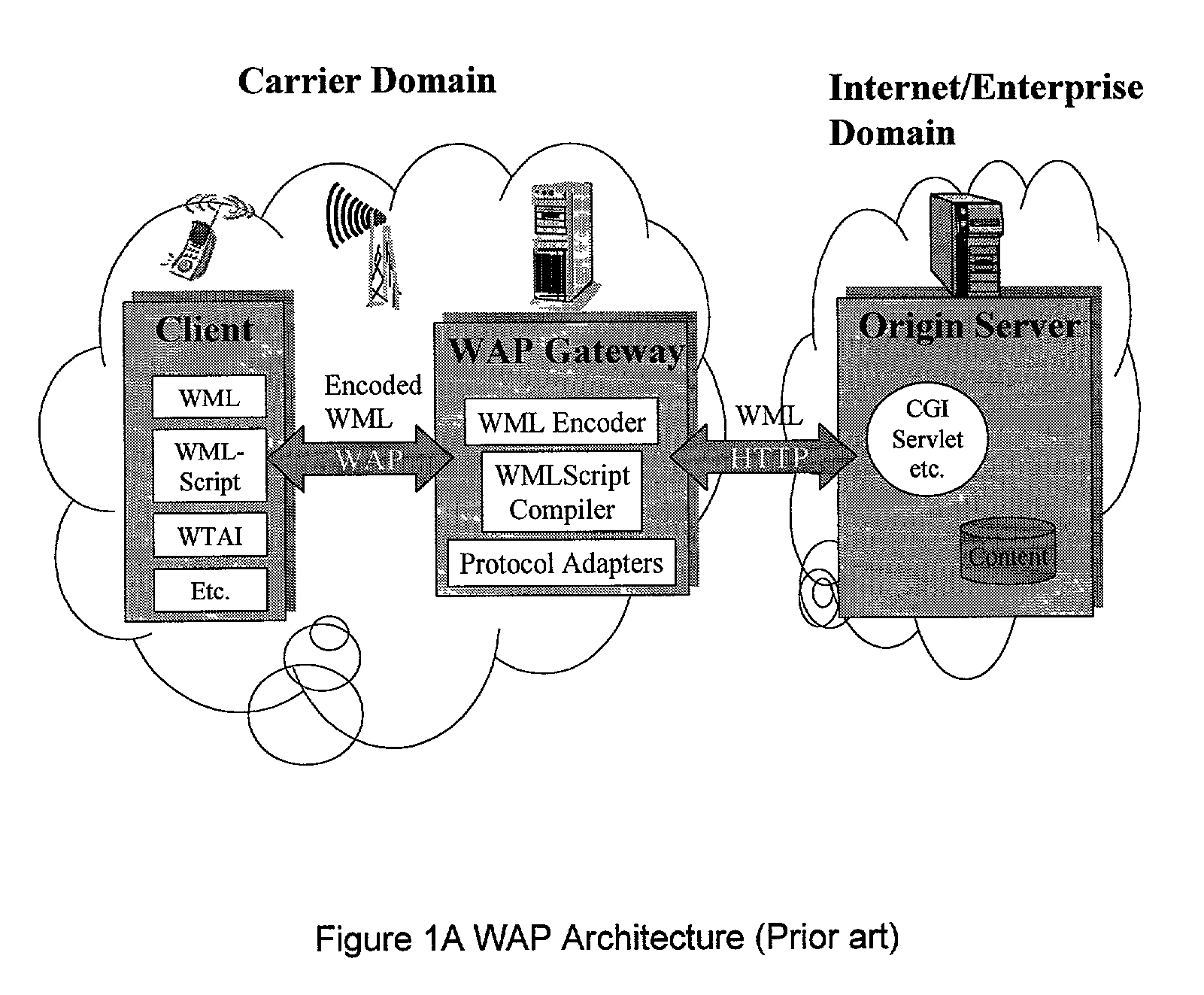
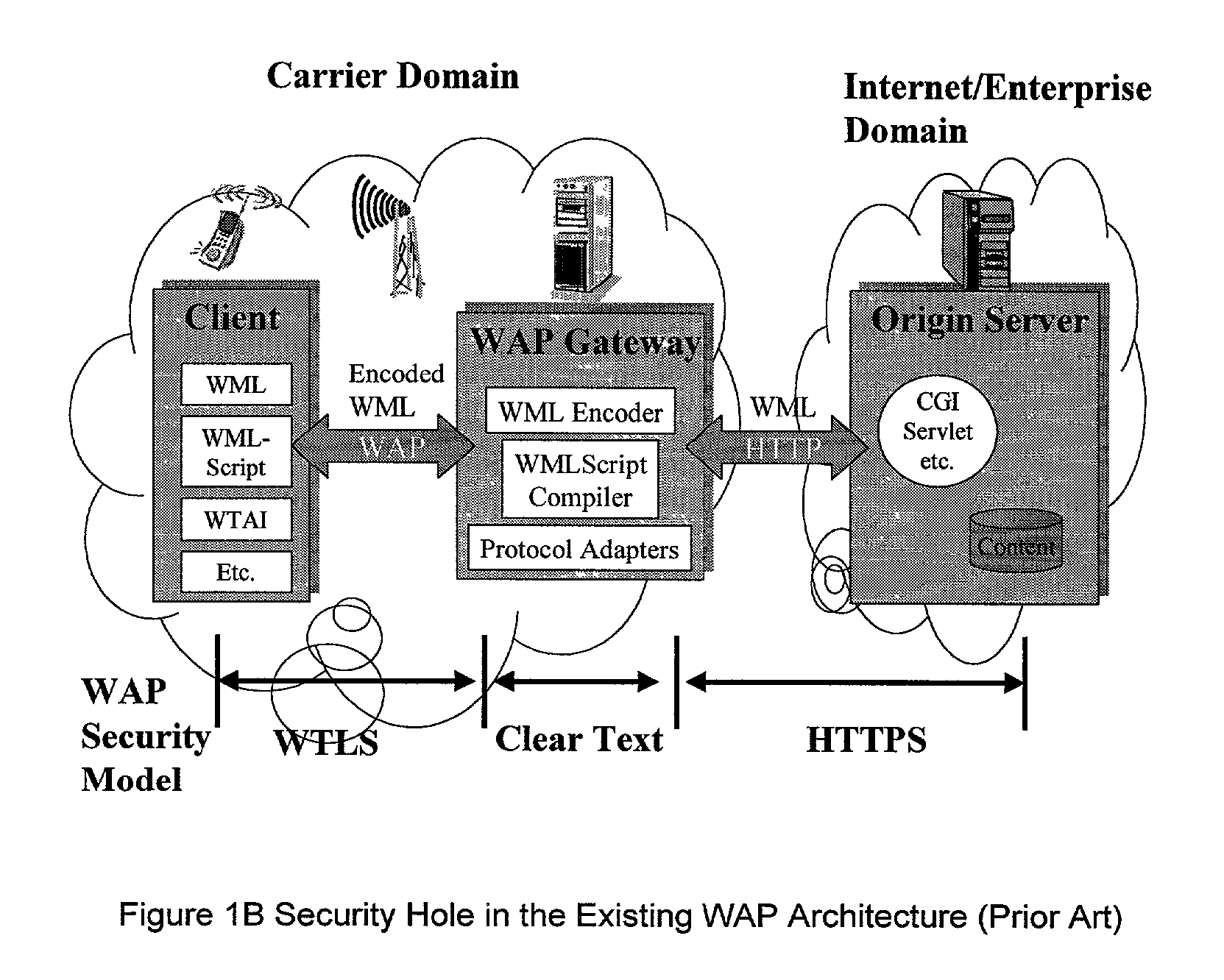
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYST INC
Consumer configurable mobile communication web filtering solution
InactiveUS7516219B2Multiple digital computer combinationsWireless network protocolsMobile deviceMobile Web
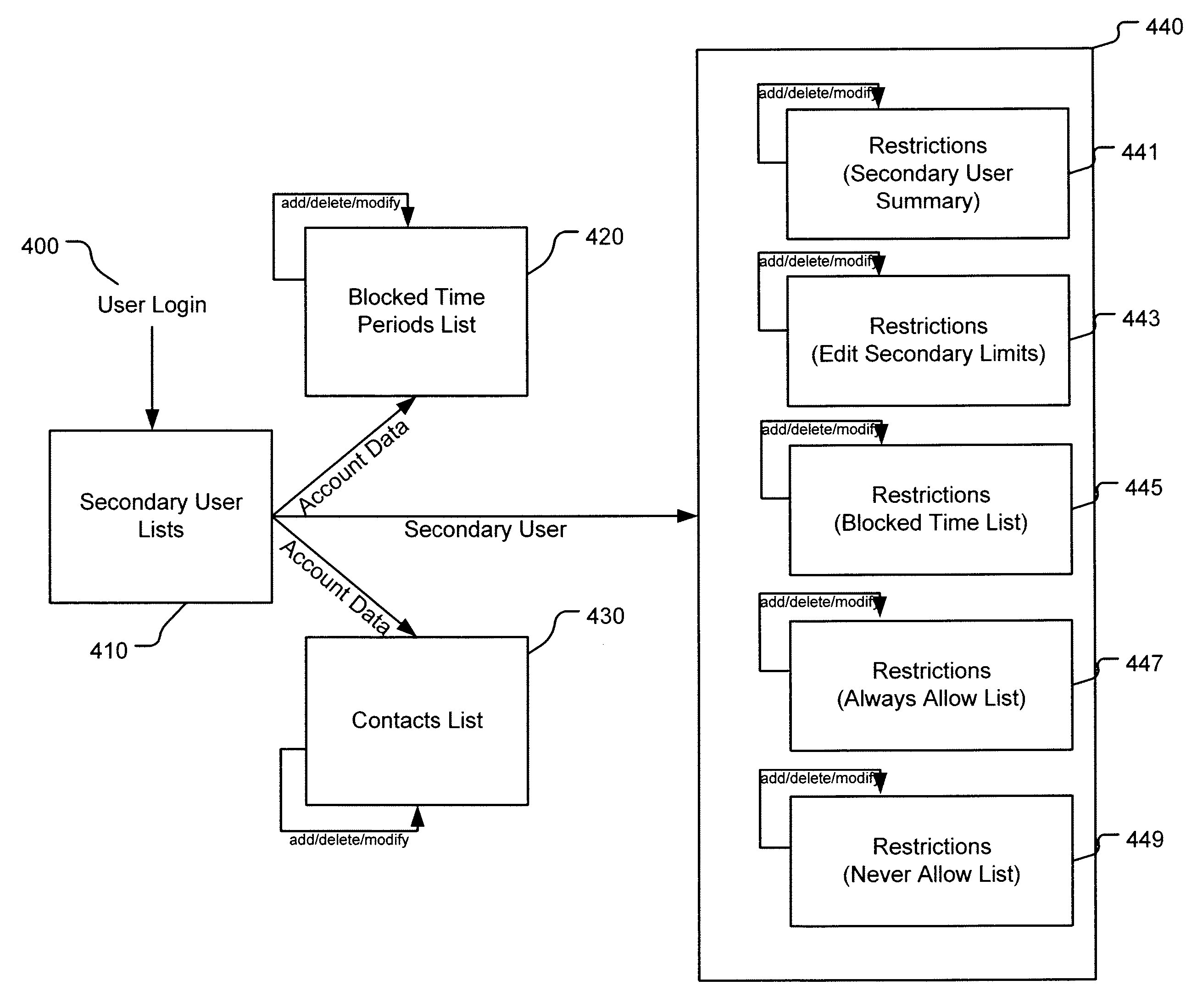
Consumer configurable mobile communications solution enabling web filtering based on policy-enforcement services allowing authorized users to define, manage and enforce restrictions for mobile web data and services of a secondary mobile device.
Owner:VENTRAQ CORP
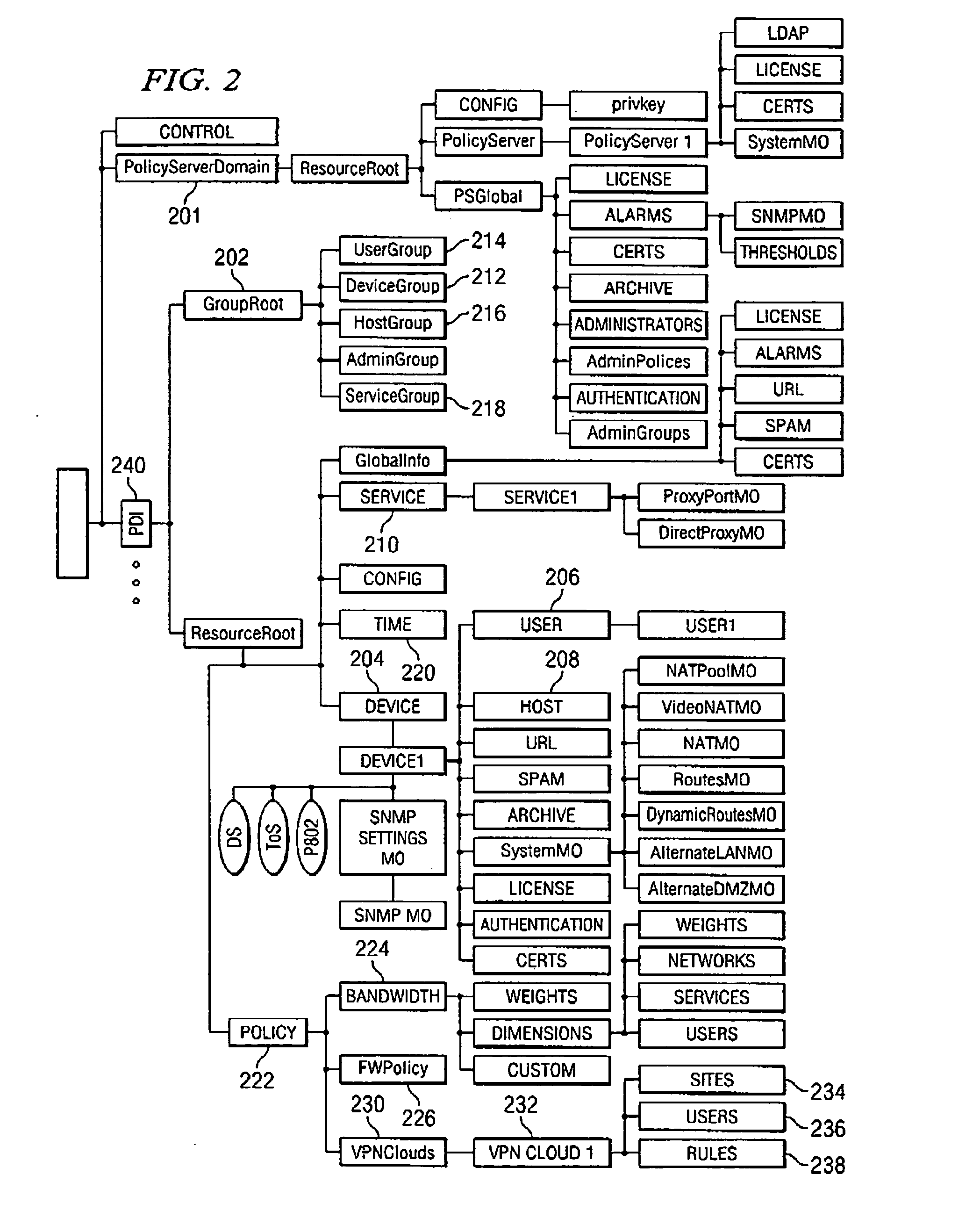
Generalized policy server
InactiveUS7272625B1Easy to handleMultiple digital computer combinationsTransmissionPolicy decisionTrust level
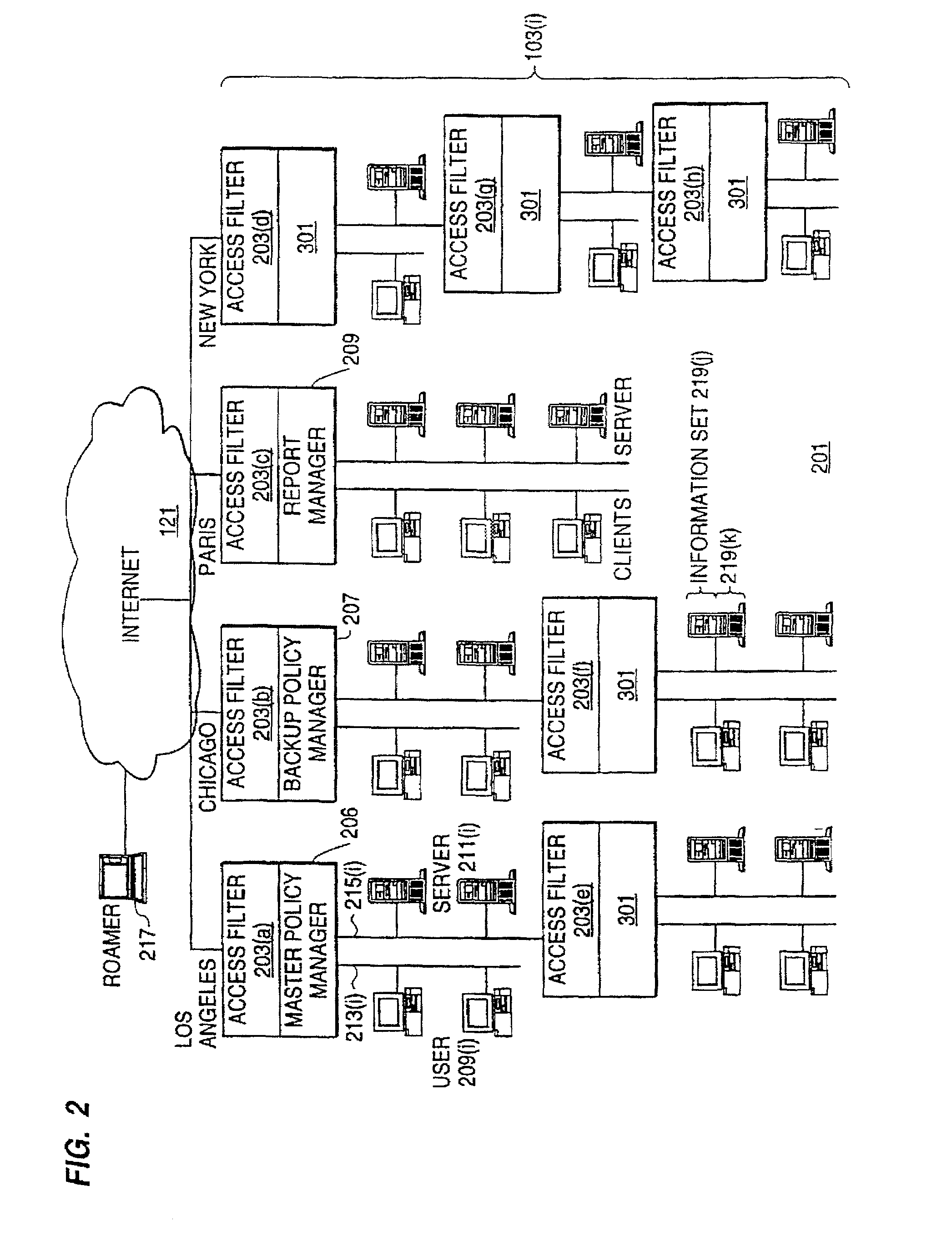
A policy system includes the policy server (2617); a policy database (2619) which located at policy decision point (2723); the access / response entity (2603); resource server (2711); policy message (2725) and policy enforcement point (2721). System connected through public network (2702) or internal network (103). The access filter (107, 203, 403) control access by use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Access is permitted or denied according to of access policies (307) which define access in terms of the user groups (FIGS. 9-12) and information sets (FIGS. 13A-18). The rights of administrators are similarly determined by administrative policies (FIGS. 23A-C). Access is further permitted only if the trust levels of the network by which is made by the sufficient access (FIGS. 25-29). A policy server component of the access filter has been separated from the access filter and the policies have been generalized to permit administrators of the policy server to define new types of actions and new types of entities. Policies may now further have specifications for time intervals during which the policies are in force and the entities may be associated with attributes that specify how the entity is to be used when the policy applies.
Owner:MARSHMAN RES +1
Multi-domain authorization and authentication
ActiveUS20030023880A1Special data processing applicationsSecuring communicationPolicy decisionAuthorization
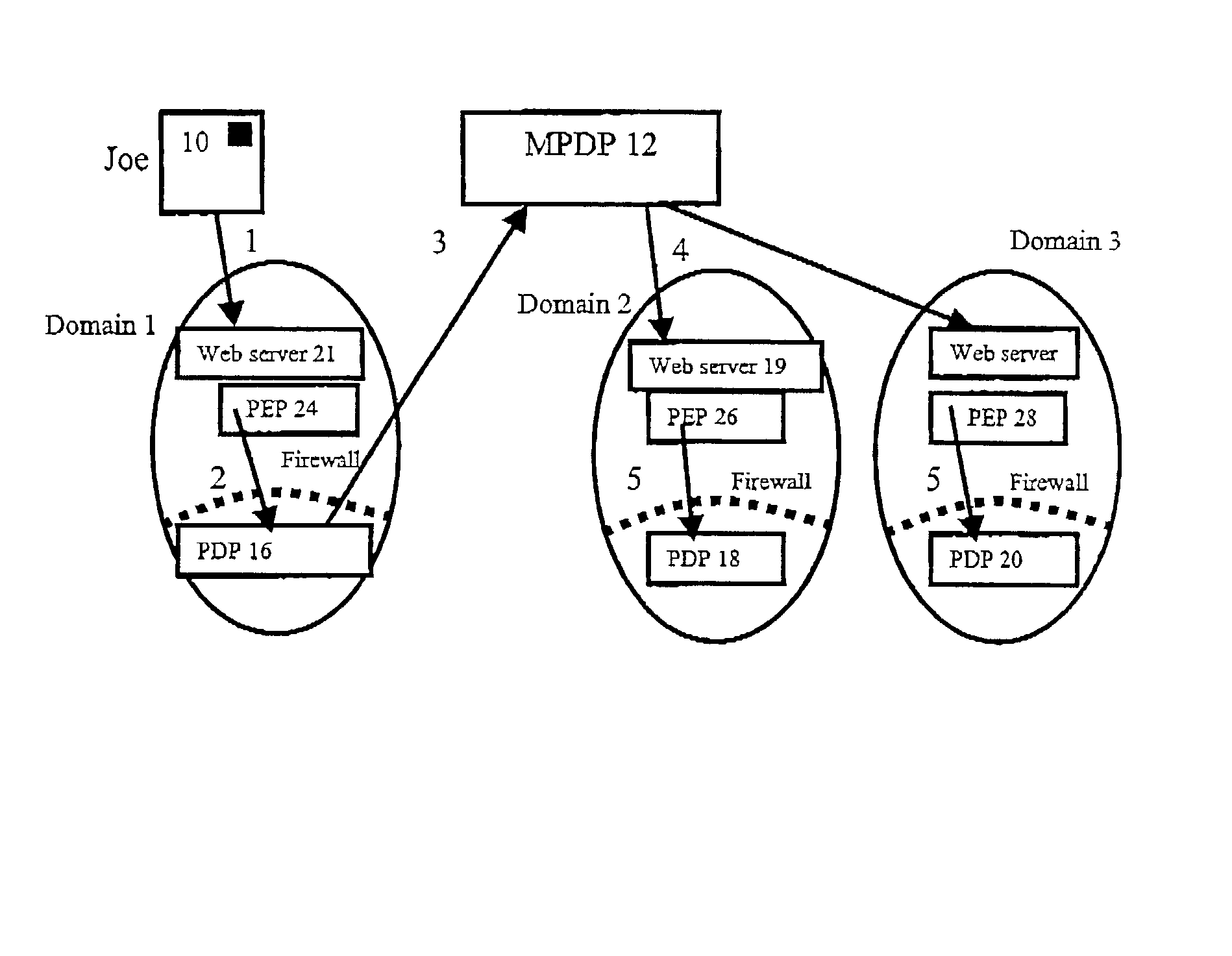
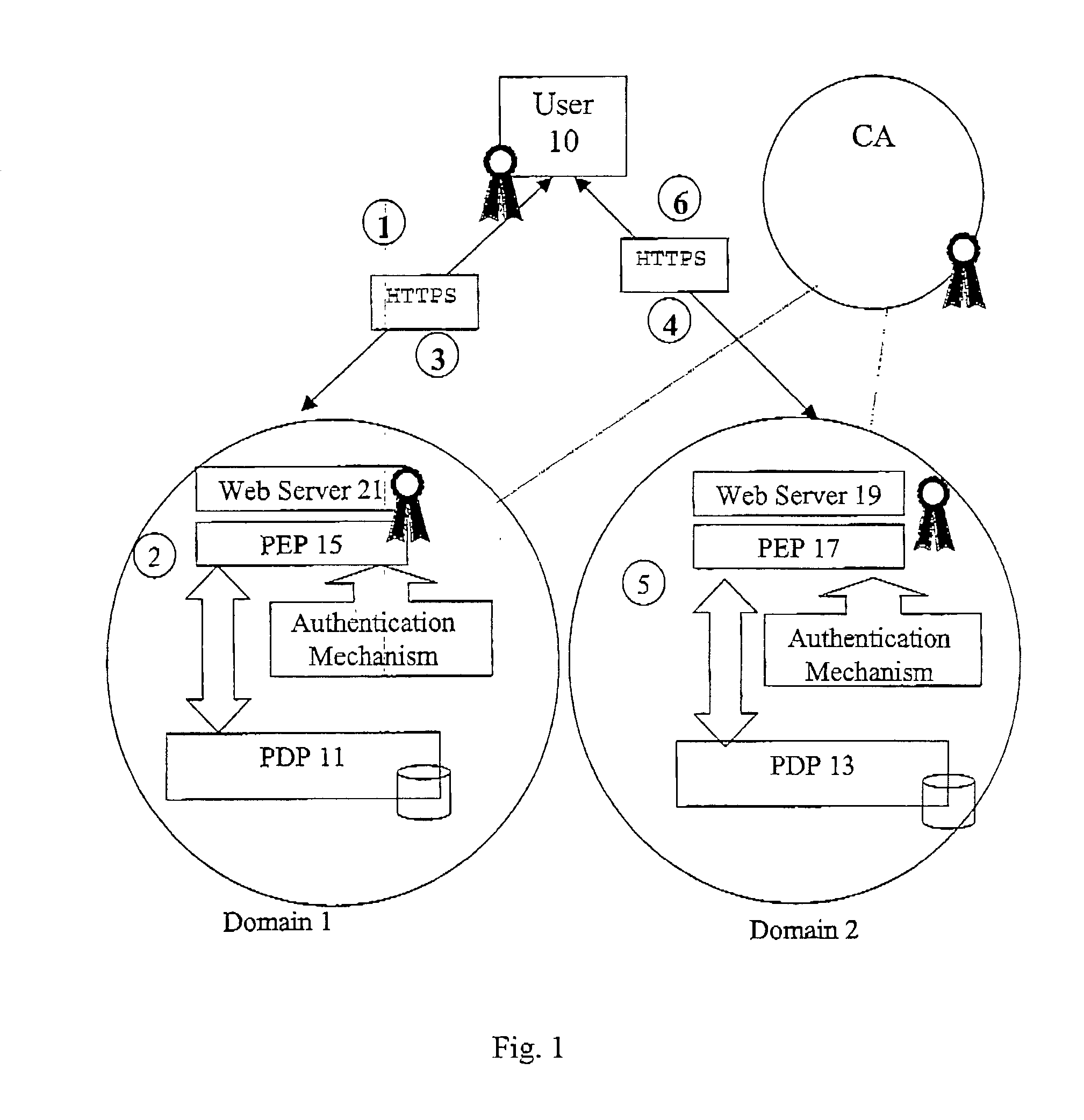
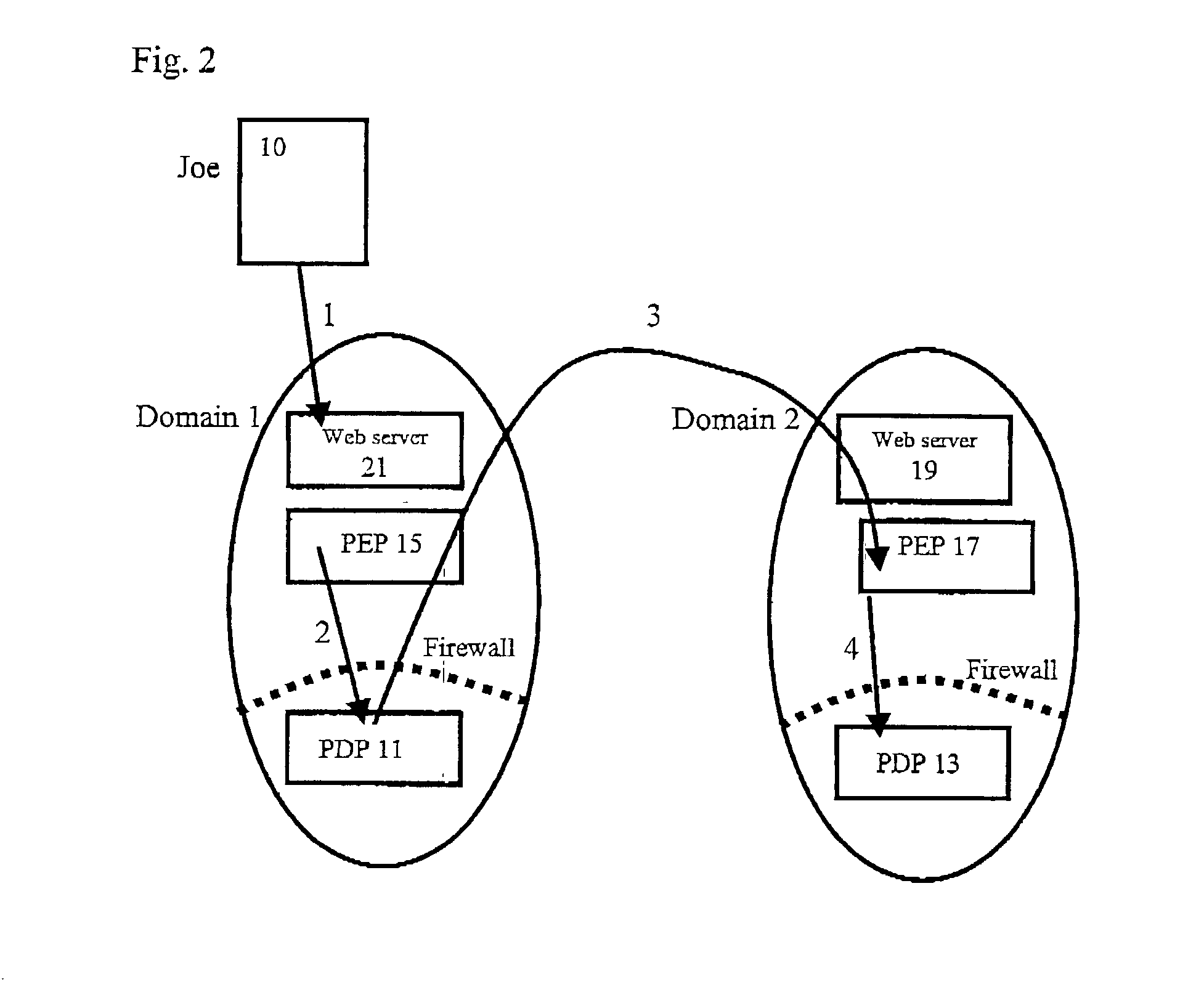
A method of multi-domain authorisation / authentication on a computer network comprises: a user making a request to a policy enforcement point of a computer for access to information on the computer; providing a location address for a user's authorisation and / or authentication information, a policy decision point of the service on the computer network then verifying the authorisation / authentication information; and the user being given access by the PEP to the information or the service requested, if the request is accepted, wherein the user's authorisation / authentication and / or further information is located on a meta policy decision point (MPDP).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Methods and systems for managing security policies
InactiveUS20040193912A1Data taking preventionDigital data processing detailsPolicy decisionSystems management
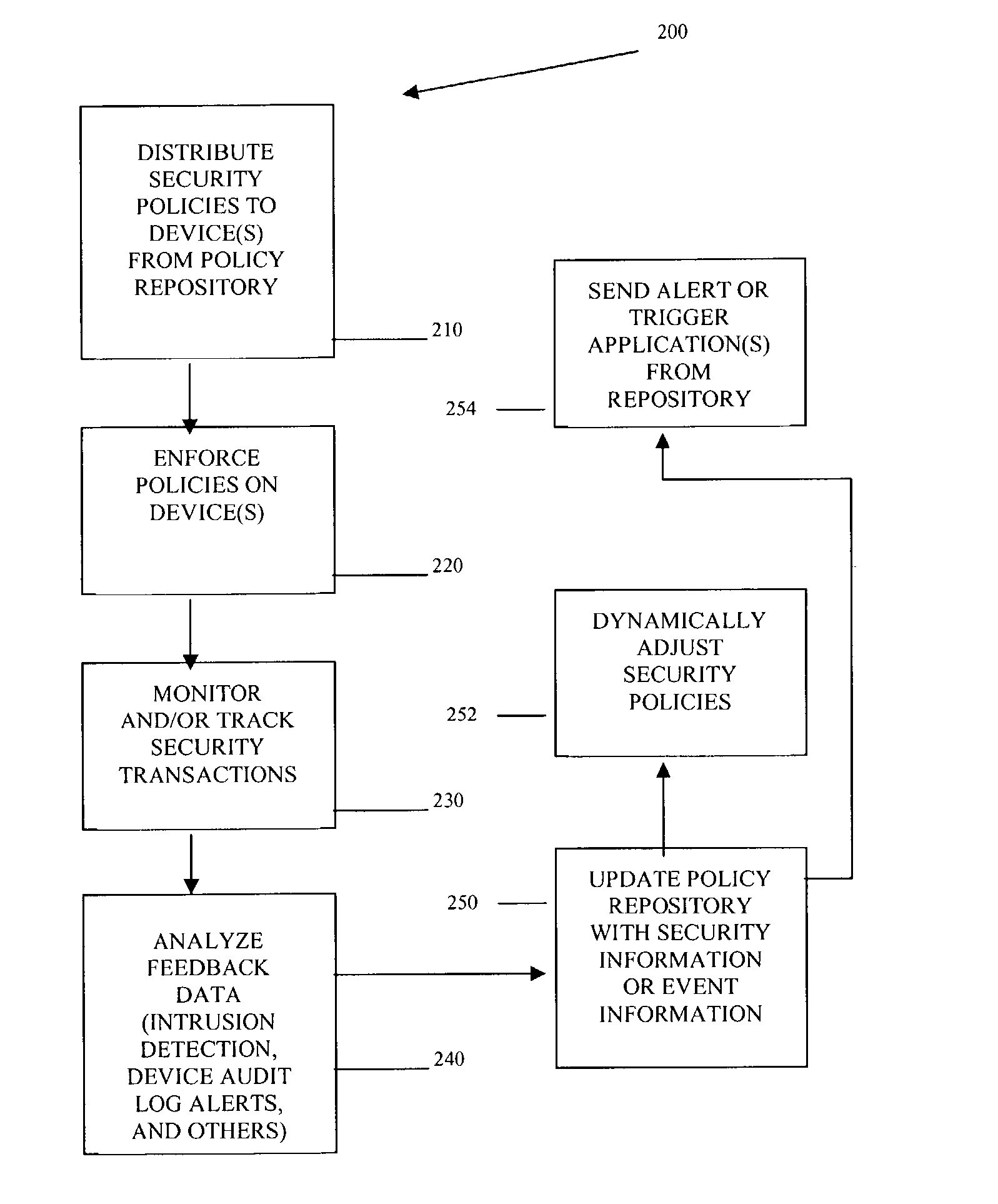
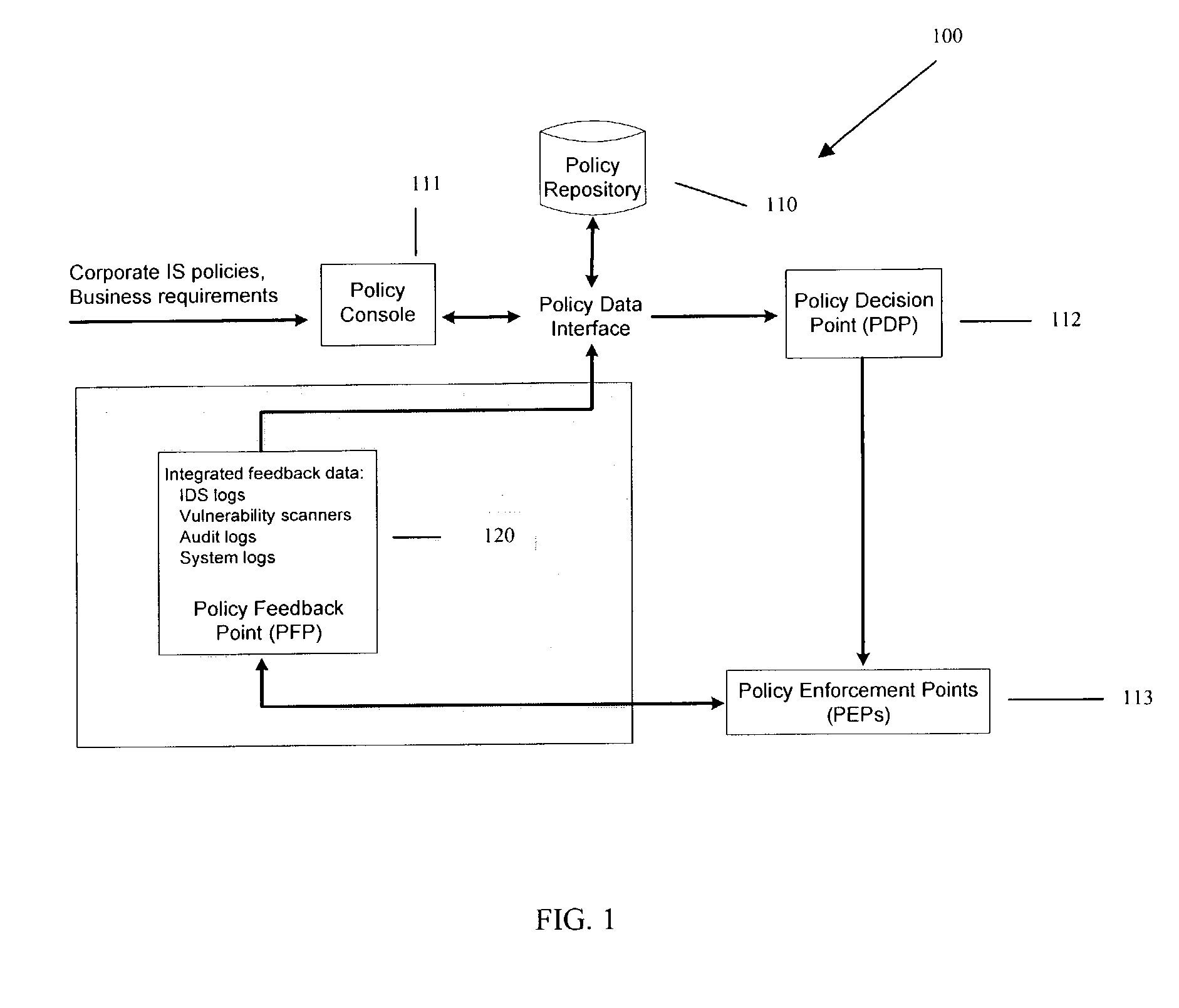
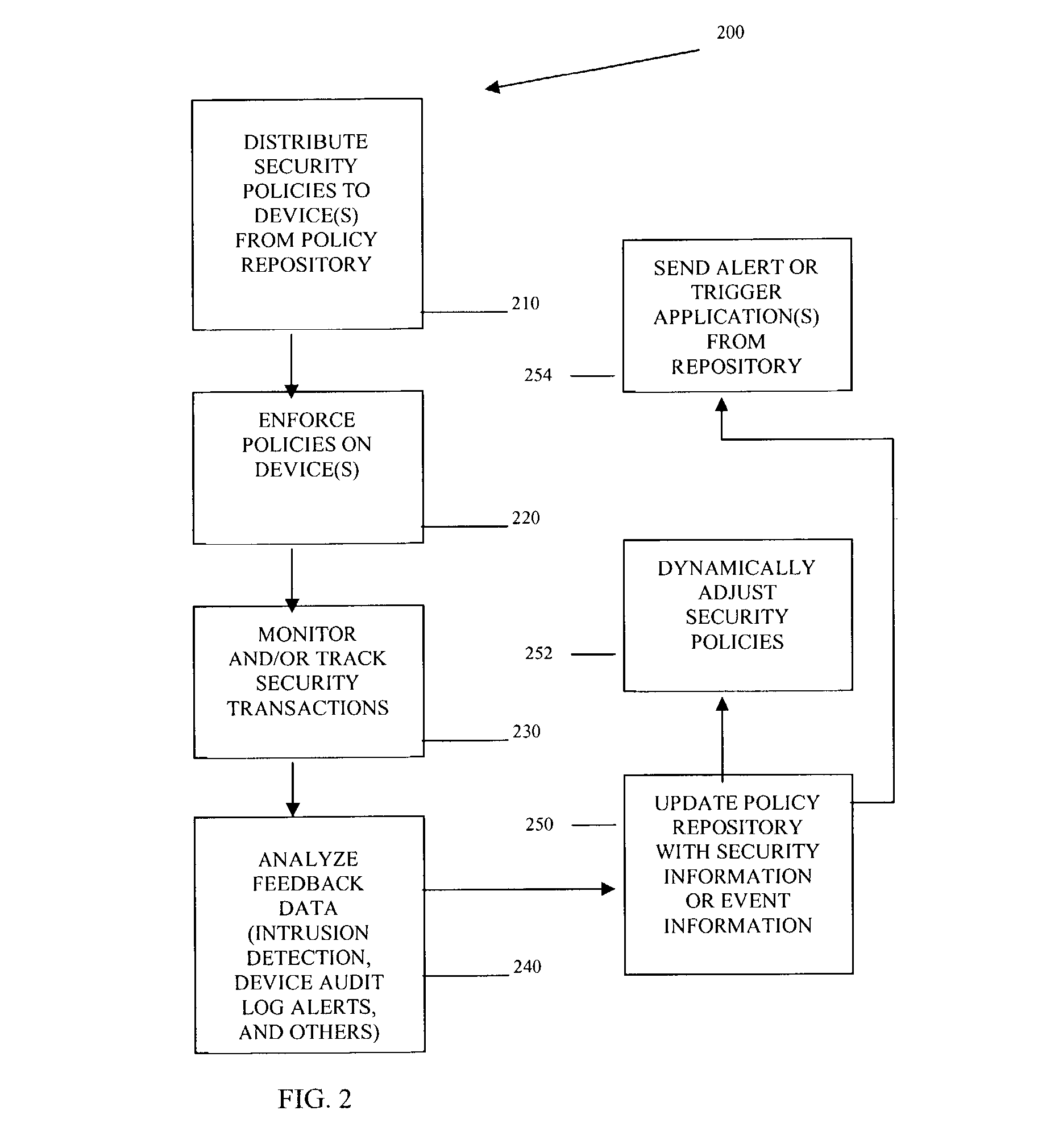
Methods, machines, and systems manage security policies of heterogeneous infrastructure and computing devices of a network. Security policy repository houses security policies that are pushed over the network by a policy decision point PDP to appropriate security-enabled devices (policy enforcement points (PEPs)) for enforcement. Using a closed feedback loop, a policy feedback point (PFP) collects and processes data from intrusions, alerts, violations, and other abnormal behaviors from a variety of PEPs or logs produced from PEPs. This data is sent as feedback to the policy repository. The PDP detects the data and analyzes it to determine if policy updates (which can be dynamic and automatic) need to be adaptively made and dynamically pushed to PEPs. The PDP can also send console messages or alerts to consoles or administrators.
Owner:INTEL CORP
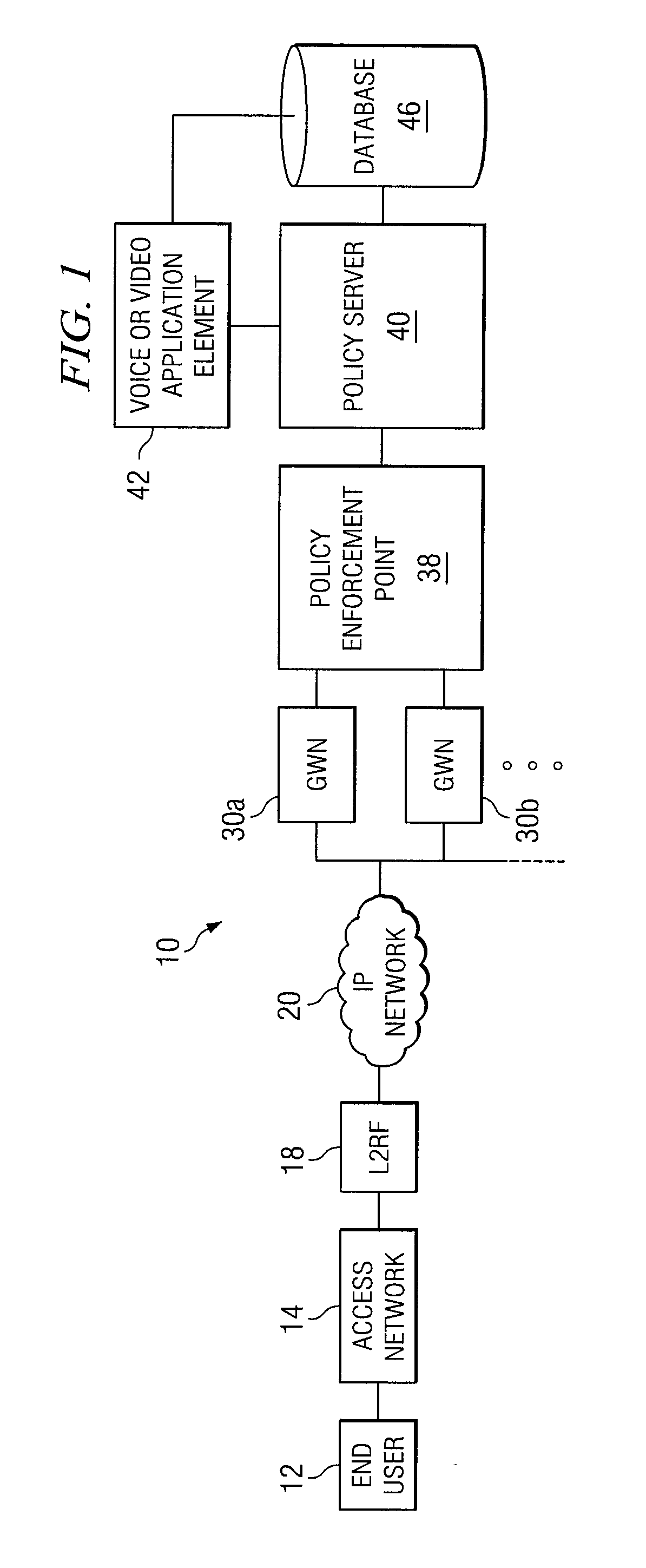
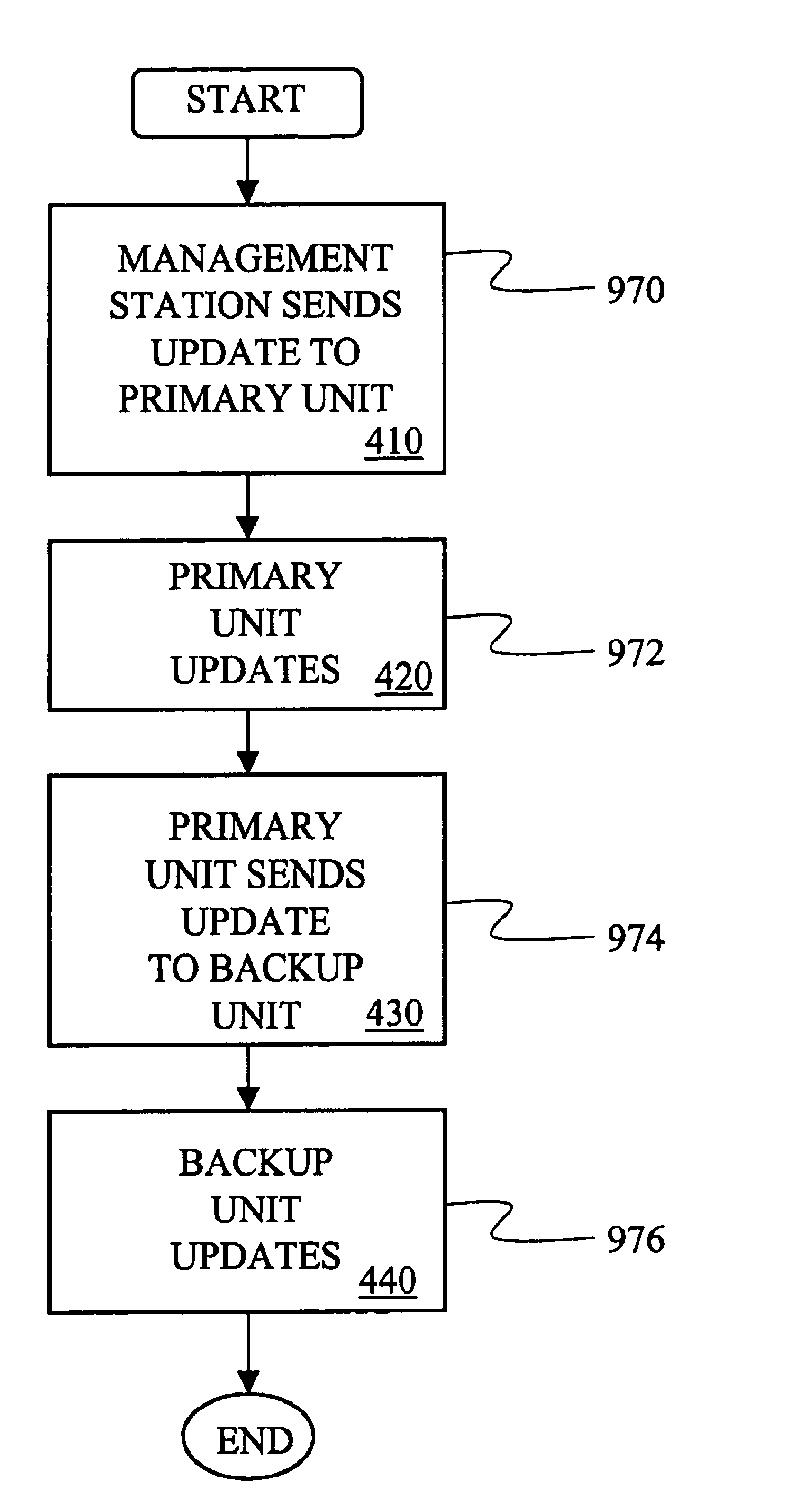
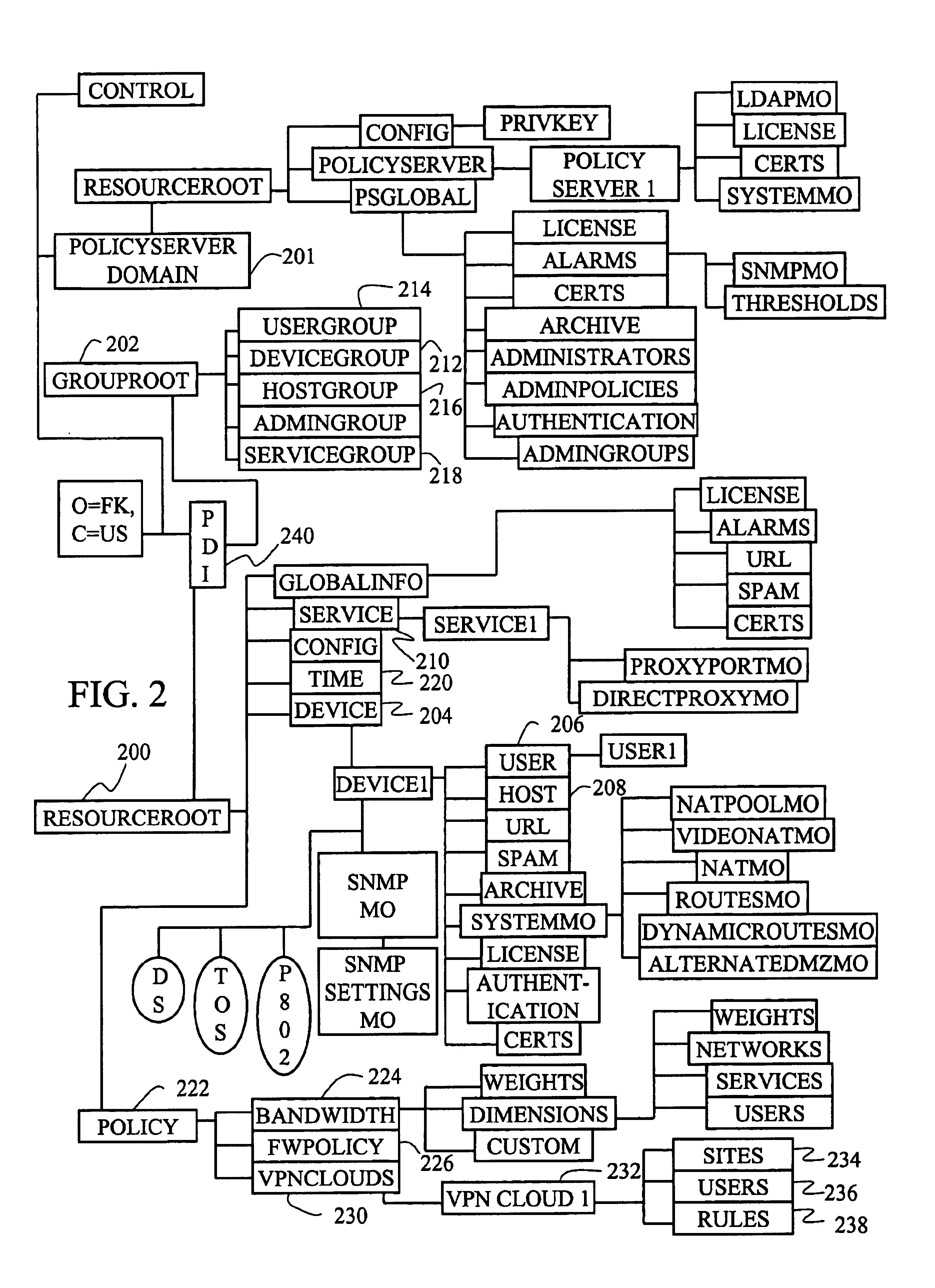
Virtual private network having automatic reachability updating
InactiveUS20050138204A1Easy to createCommunication securityEnergy efficient ICTDigital data protectionPrivate networkReachability
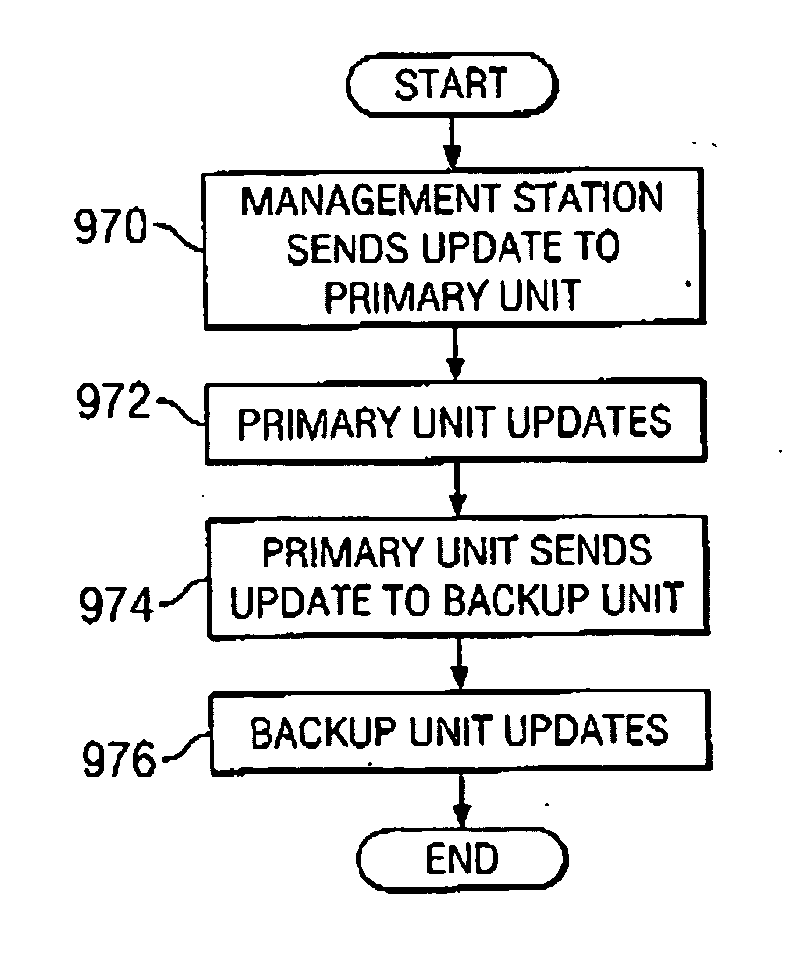
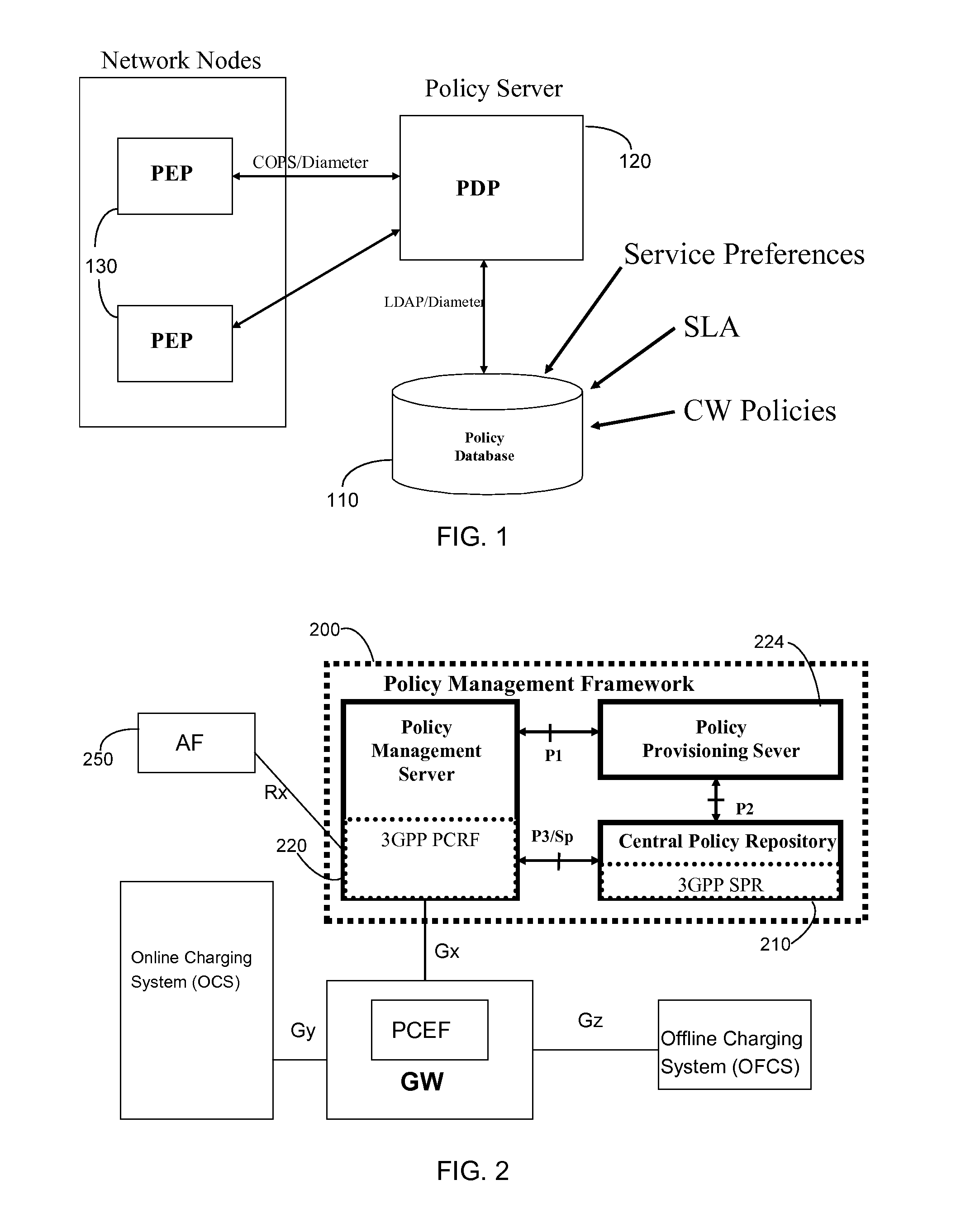
A unified policy management system for an organization including a central policy server and remotely situated policy enforcers. A central database and policy enforcer databases storing policy settings are configured as LDAP databases adhering to a hierarchical object oriented structure. Such structure allows the policy settings to be defined in an intuitive and extensible fashion. Changes in the policy settings made at the central policy server are automatically transferred to the policy enforcers for updating their respective databases. Each policy enforcer collects and transmits health and status information in a predefined log format and transmits it to the policy server for efficient monitoring by the policy server. For further efficiencies, the policy enforcement functionalities of the policy enforcers are effectively partitioned so as to be readily implemented in hardware. The system also provides for dynamically routed VPNs where VPN membership lists are automatically created and shared with the member policy enforcers. Updates to such membership lists are also automatically transferred to remote VPN clients. The system further provides for fine grain access control of the traffic in the VPN by allowing definition of firewall rules within the VPN. In addition, policy server and policy enforcers may be configured for high availability by maintaining a backup unit in addition to a primary unit. The backup unit become active upon failure of the primary unit.
Owner:IYER SHANKER V +3
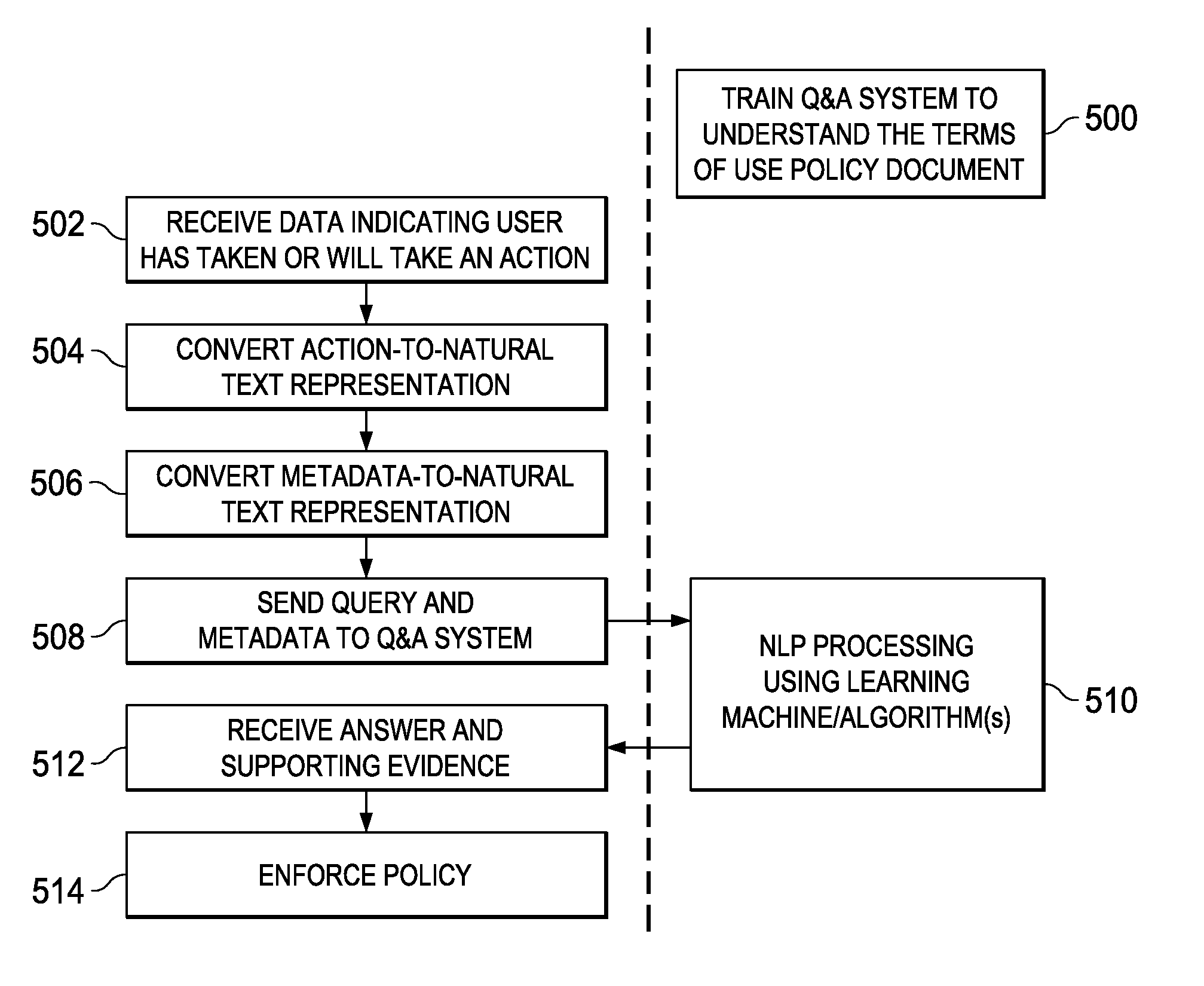
Policy enforcement using natural language processing
InactiveUS9369488B2TransmissionSpecial data processing applicationsState dependentOperational transformation
Owner:GLOBALFOUNDRIES INC
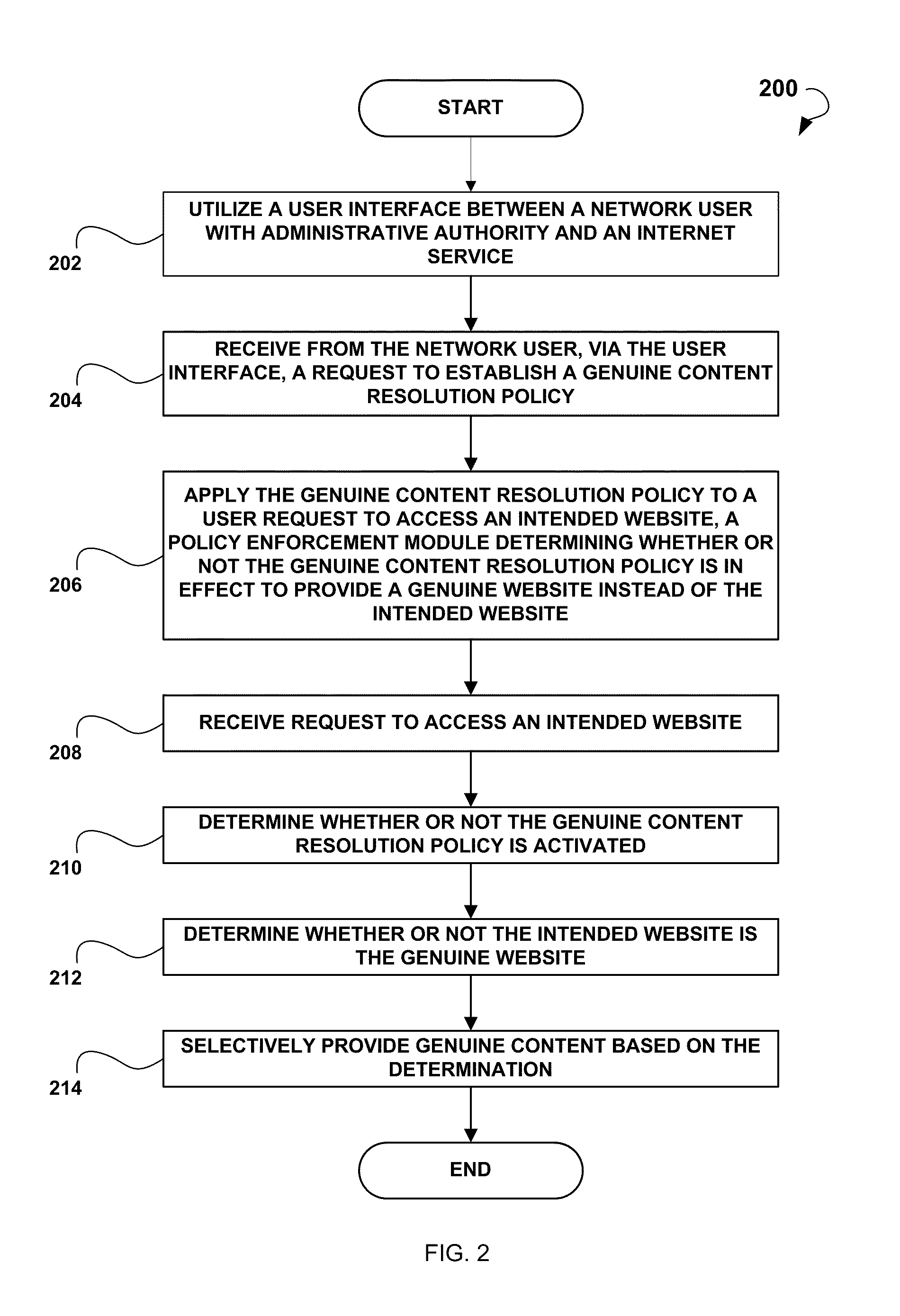
Systems and methods for redirection of online queries to genuine content
A system for redirection of online queries to a genuine content includes a user interface module to provide a user interface between a network user with administrative authority and an Internet service, a communication module to receive a request to establish a genuine content resolution policy for a network, a policy generating module to establish the genuine content resolution policy for the network, and a policy enforcement module to apply the genuine content resolution policy to a user request to access an intended website. The policy enforcement module may determine whether or not the genuine content resolution policy is activated, determine whether or not that the intended website is the genuine website, and based on the determination, selectively redirect the user to the genuine website.
Owner:NOMINUM
Secure enterprise network
ActiveUS8166554B2Digital data processing detailsDigital computer detailsUser authenticationApplication software
What is proposed is a method of implementing a security system (Packet Sentry) addressing the internal security problem of enterprises having a generalized approach for inferential determination and enforcement of network policy with directory service based group correlation with transparent authentication of the connected customer and the policy enforcement inside the network. The security system enables the network to analyze and enforce policy using any bit or bits in a stream or a packet, conduct Flow Vector analysis on the data traffic, provide Application Monitoring, Normalization and user authentication validation. The system enables the network to implement Group relationship Analysis and correlation using combination of Network inferences and Directory service data resulting in generation of Group norms using statistically significant relationships. These will provide a more secure enterprise environment where data security levels can be enforced and the usage monitored effectively in the infrastructure.
Owner:VMWARE INC
Method and apparatus for providing service selection, redirection and managing of subscriber access to multiple WAP (Wireless Application Protecol) geteways simultaneously
ActiveUS20030035409A1Time-division multiplexData switching by path configurationCyber operationsTraffic capacity
A method (FIG. 5) and apparatus (FIG. 3) to provide control and policy enforcement of WAP (Wireless Application Protocol) services in a wireless data networks is taught herein. WAP traffic is inspected with efficient algorithms to intercept un-registered WAP access and intercept dynamic change of user service selection. The intercepted WAP requests are modified with value-added parameters (such as QoS and subscriber identifiers) as per user and service provider agreement and table data. A series of strategies are described to blend wireless intelligence, user preference and service subscription, network operator requirements and service provider or enterprise preferences into routing and drive page generation. The means to dynamically provision users' service choices to wireless network elements are also presented without having to break the session within the system. This enables innovative data services such as pay-per-use, smart routing, and enterprise secured WAP services unlike any current conventional system.
Owner:MAVENIR SYSTEMS
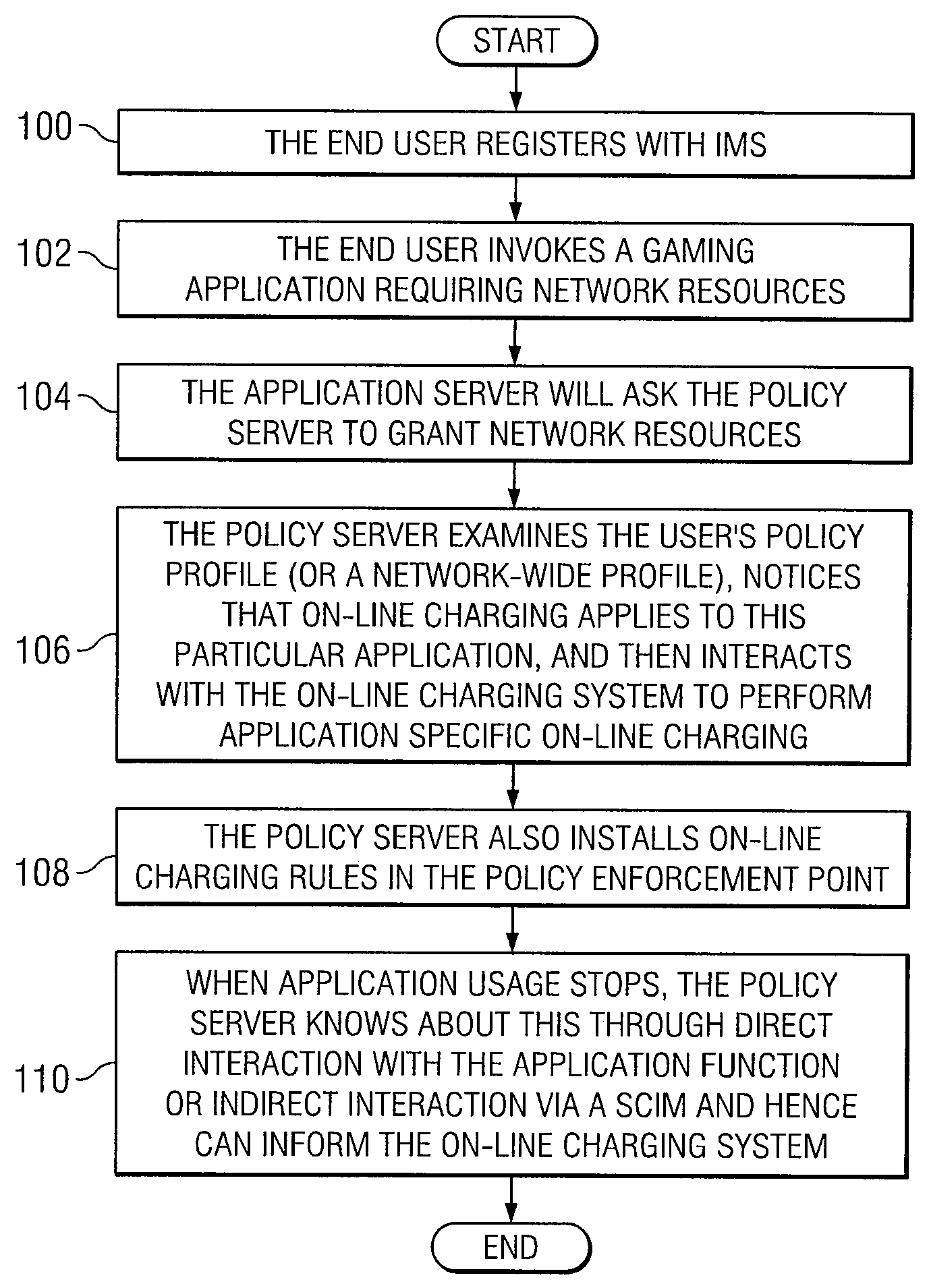
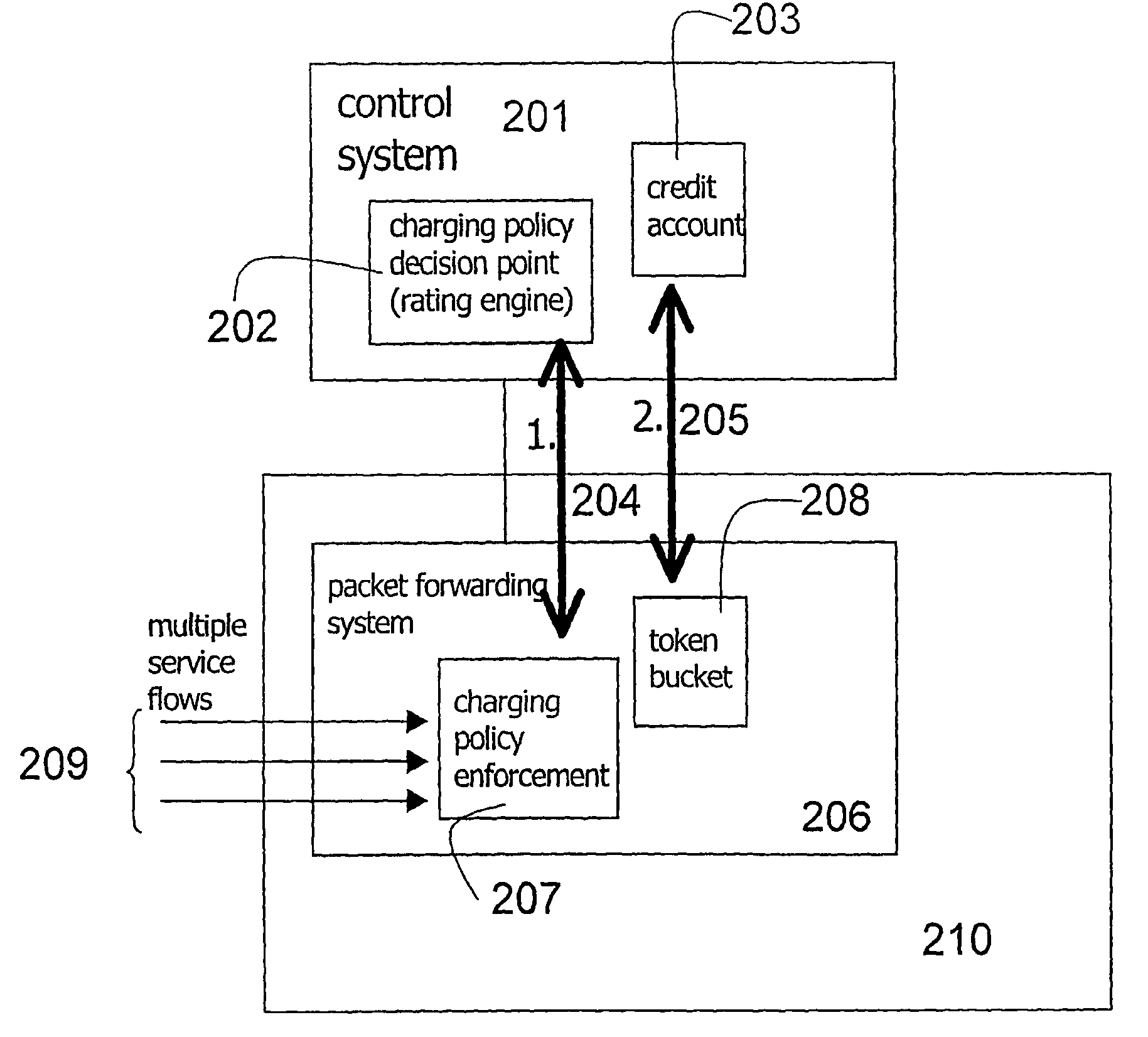
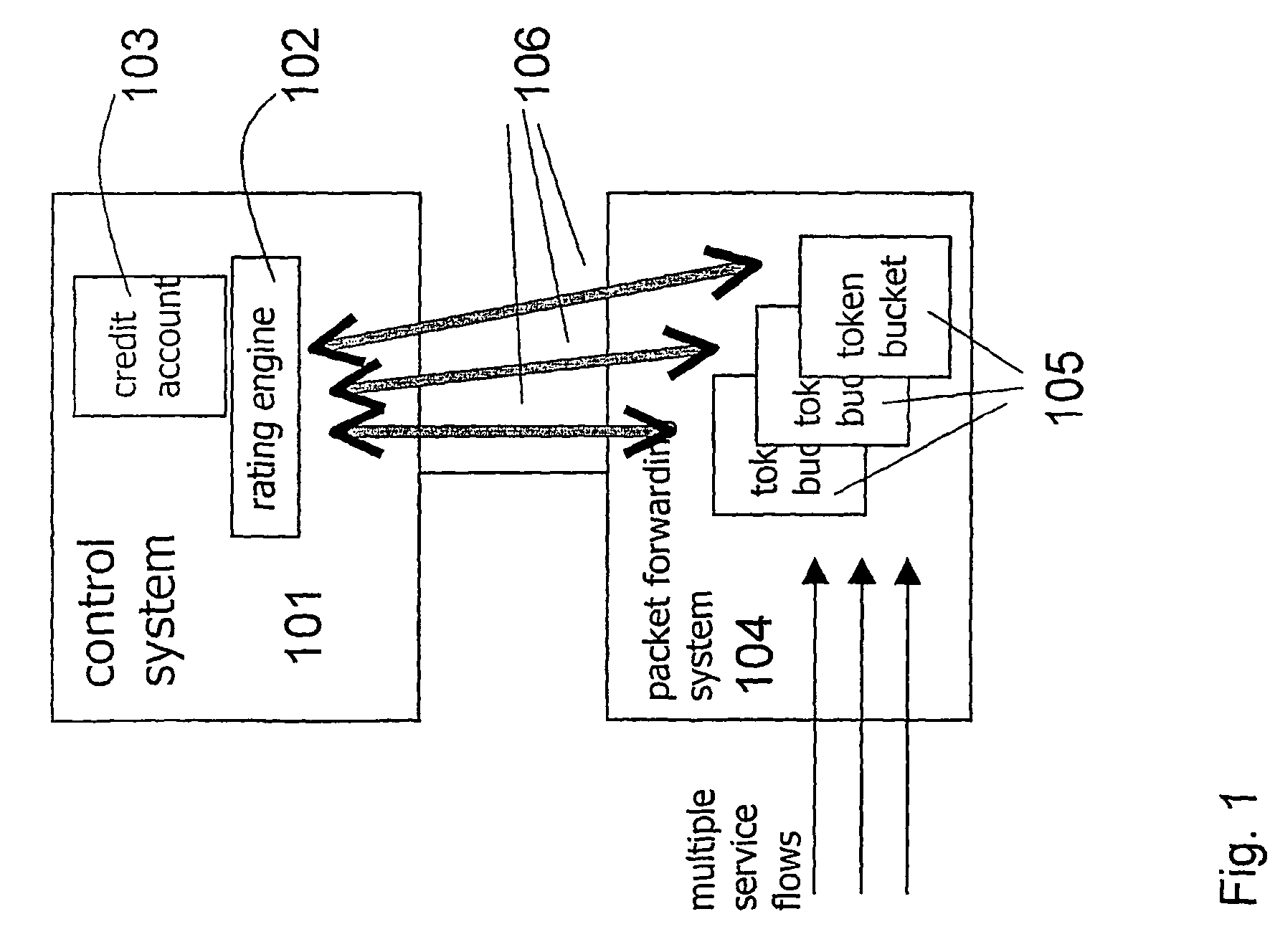
System and Method for Providing Application-Specific On-Line Charging in a Communications Environment
ActiveUS20080189760A1Optimal application configurationAccurate chargesDigital data processing detailsUser identity/authority verificationComputer networkApplication specific
An architecture for A method for providing on-line charging in a network environment is provided that includes interacting with an application that is selected by an end user, and with a policy enforcement point to install corresponding policies that are inclusive of charging rules. The method also includes performing, via a policy server, on-line charging interactions on behalf of the selected application itself such that application-specific on-line charging for the application is enabled. In more particular embodiments, the policy server understands which application is interacting with it by use of application tokens, source, or service identifiers. Also, the application element can query the policy server indirectly to grant network resources and the policy server examines an end user's policy profile or a network-wide profile (or both) and recognizes that on-line charging applies to the selected application.
Owner:CISCO TECH INC
Object model for network policy management
InactiveUS6944183B1Simplified managementEnergy efficient ICTDigital computer detailsNetwork managementAdaptive routing
Owner:ALCATEL-LUCENT USA INC
System for providing flexible charging in a network
ActiveUS7450591B2Reduce signaling loadReduce reservationMetering/charging/biilling arrangementsData switching by path configurationService flowPolicy decision
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for role-based security policy management
ActiveUS20050257244A1User identity/authority verificationUnauthorized memory use protectionConfigfsSecurity policy management
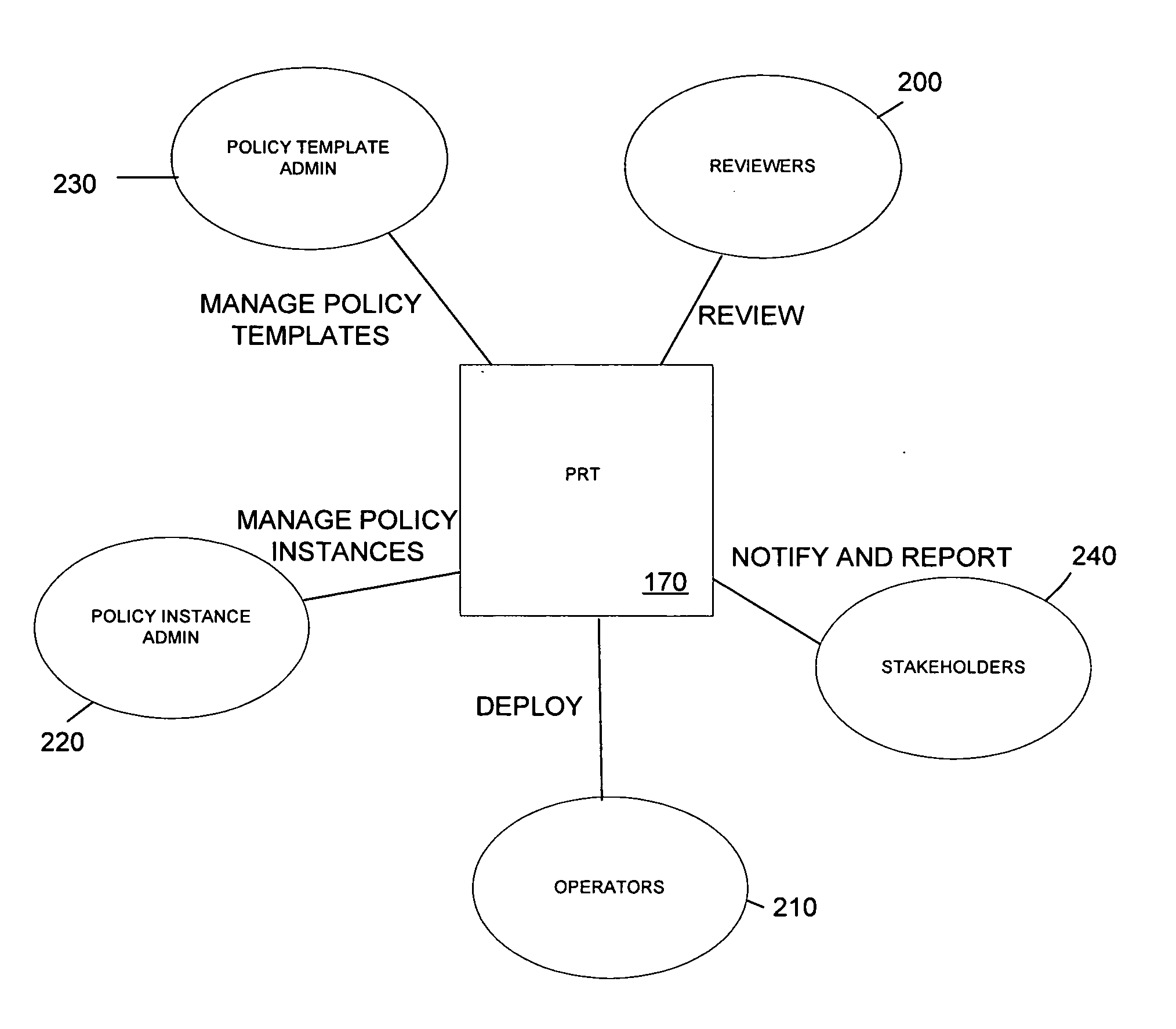
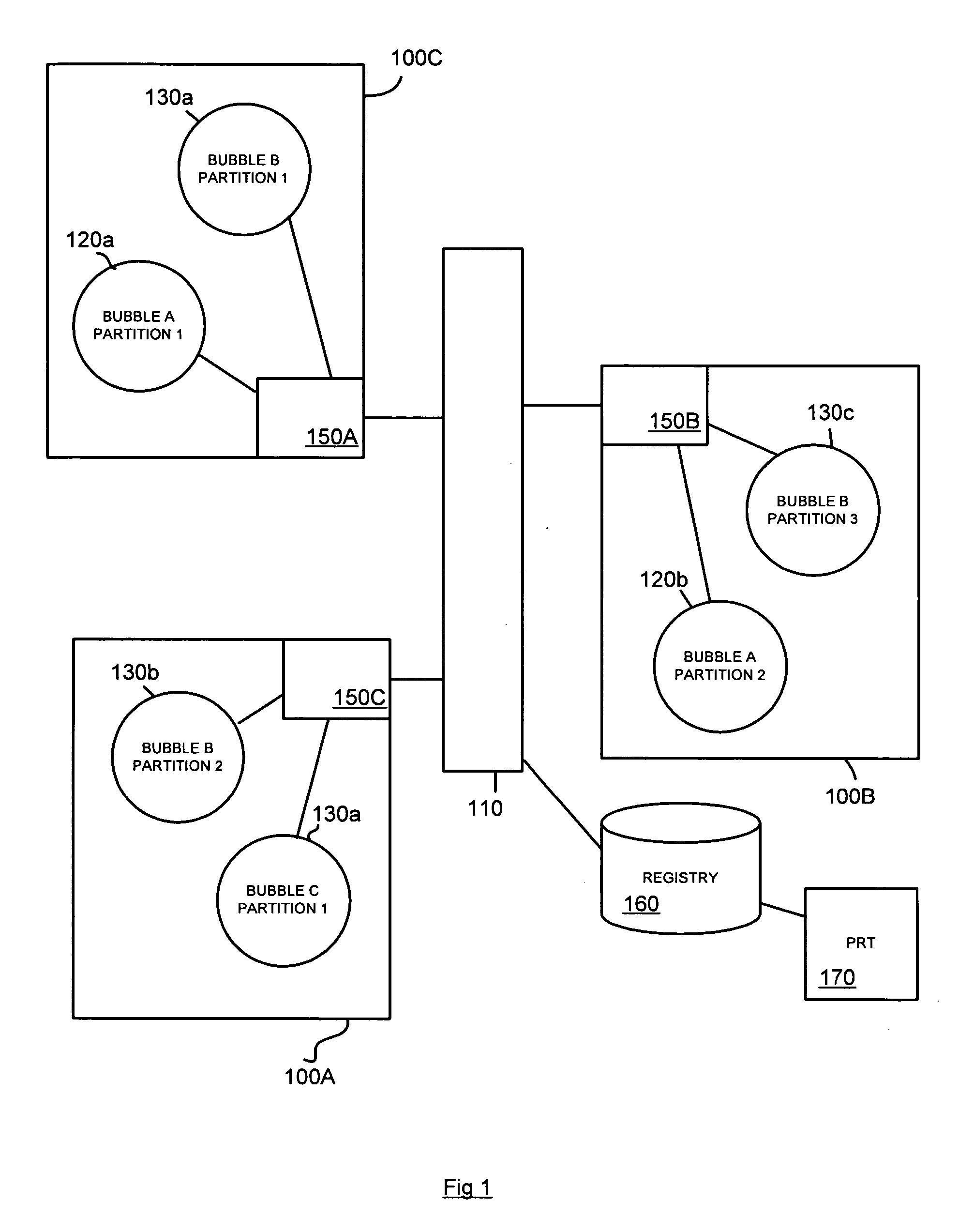
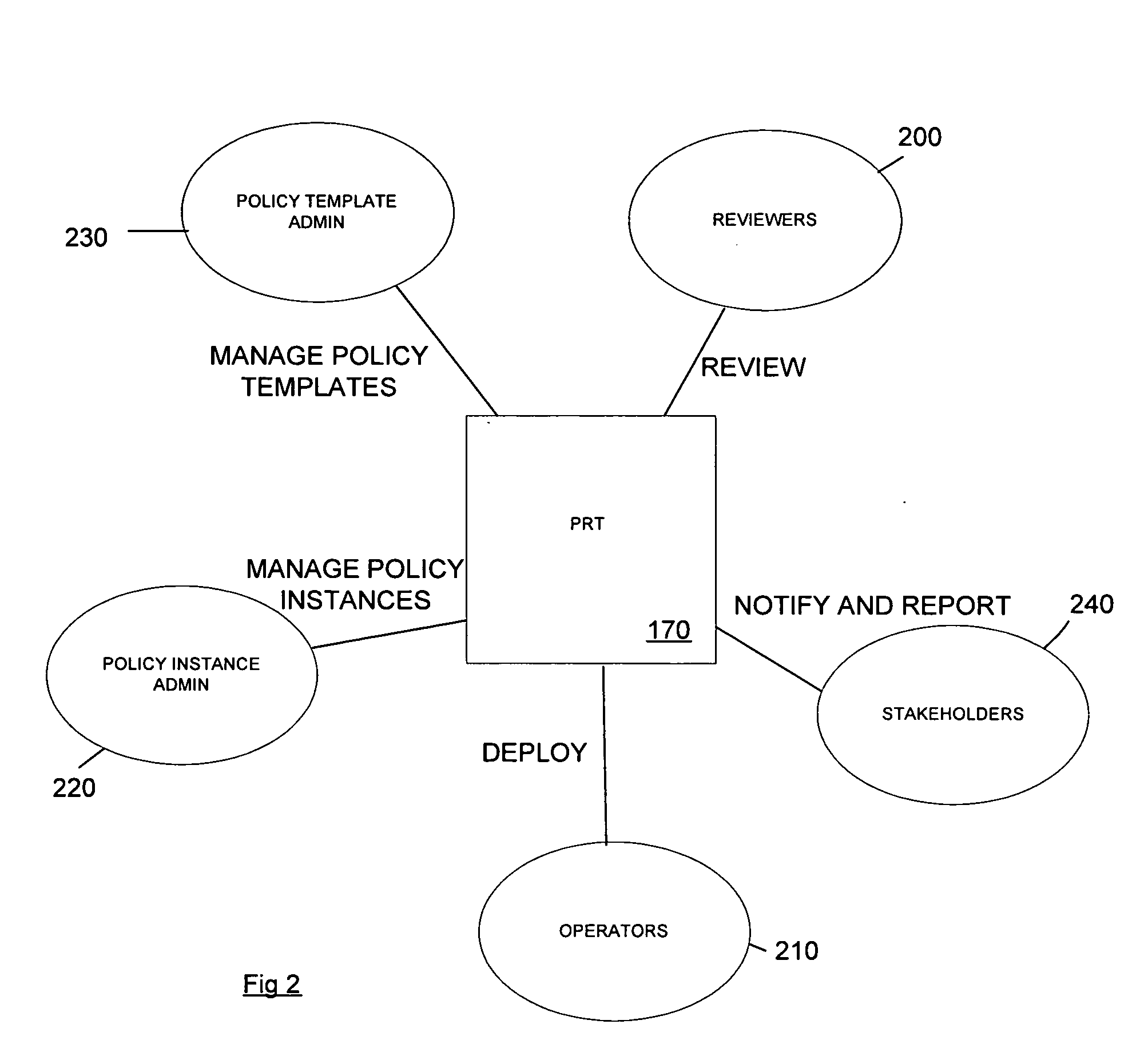
A method and corresponding tool are described for security policy management in a network comprising a plurality of hosts and at least one configurable policy enforcement point. The method, comprises creating one or more policy templates representing classes of usage control models within the network that are enforceable by configuration of the policy enforcement points; creating one or more policy instances, each based on one of the templates and instantiating the template for identified sets of hosts within the network to which the usage control model is to be applied, deploying the policy instances by generating and providing one or more configuration files for provisioning corresponding policy enforcement points within the network. Access to the templates and policy instances is controlled so that the policy templates are only modifiable by a first predeterminable user group, the policy instances are only modifiable by the first or a second predeterminable user group and the policy instances are only deployable by a third predeterminable user group.
Owner:VALTRUS INNOVATIONS LTD +1
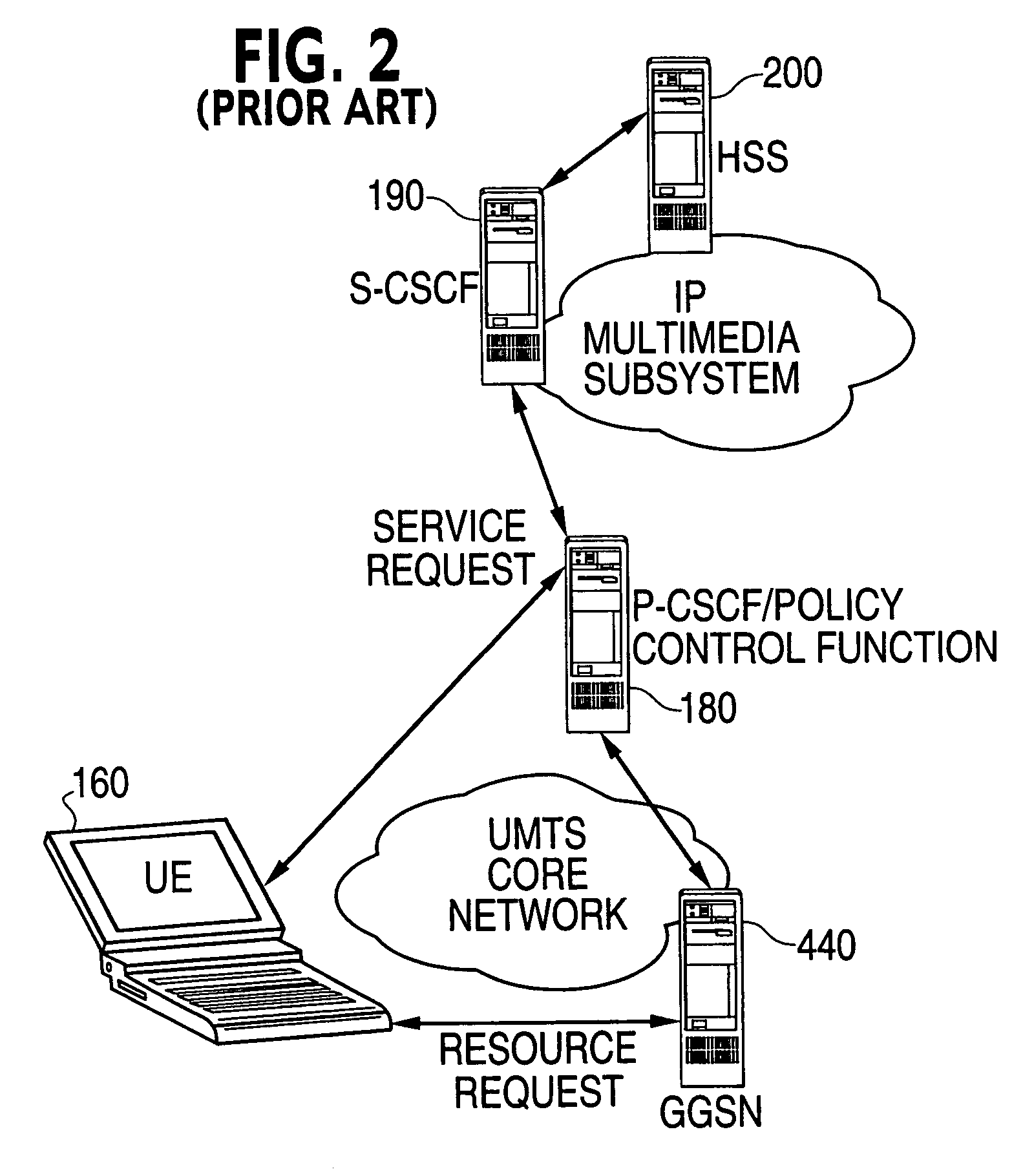
Multimedia next generation network architecture for IP services delivery based on network and user policy
InactiveUS7984130B2Network traffic/resource managementDigital computer detailsPolicy decisionService control
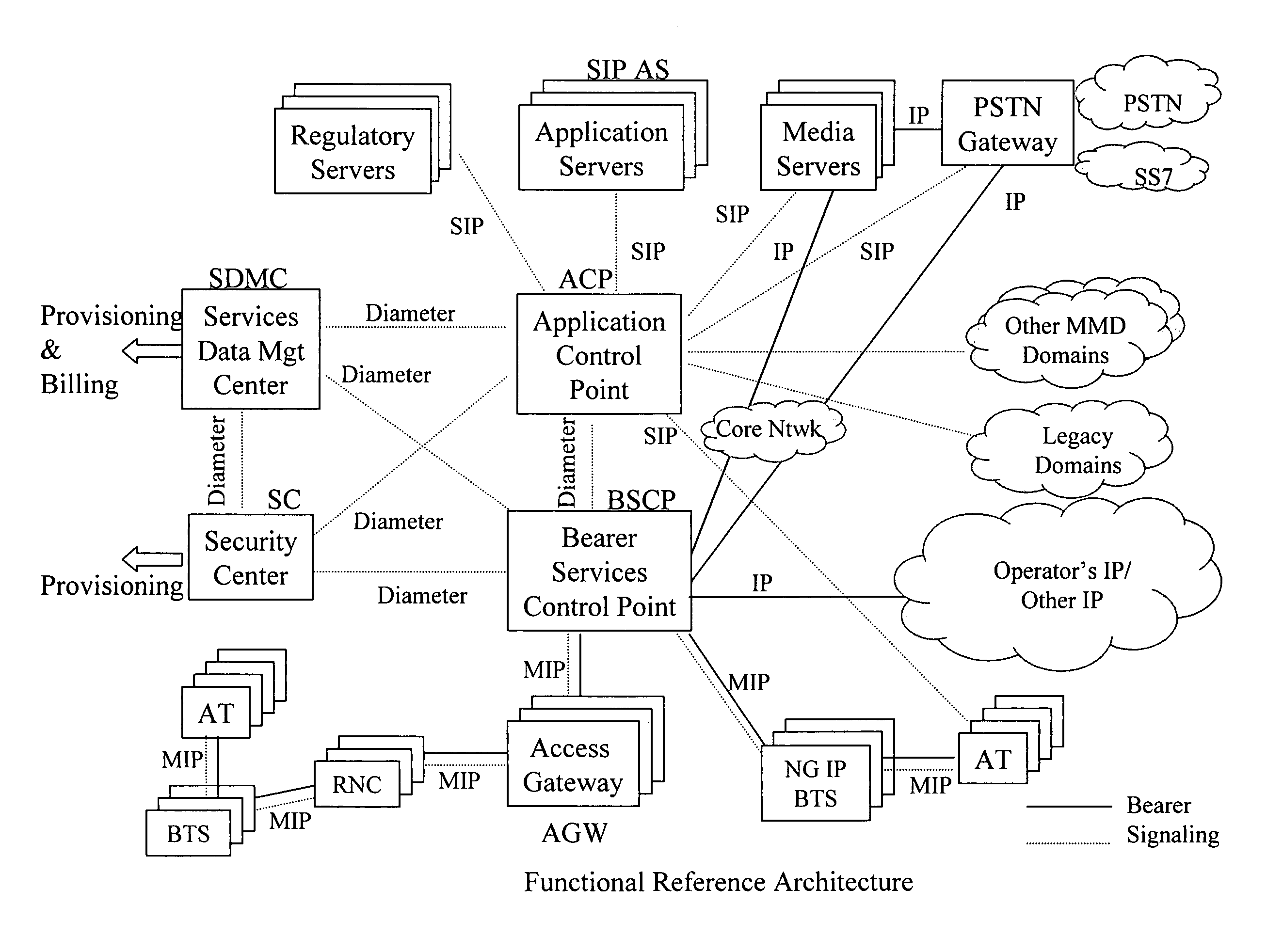
The exemplary Multimedia Next Generation Network architecture disclosed herein covers the entire next generation system, e.g. for wireless communication services, including application, signaling and bearer functionalities. The architecture addresses unification of subscriber databases for both SIP services and non-SIP services in a Services Data Management Center (SDMC). A Security Center (SC) provides a central repository for all security related databases and functions. An Application Control Point (ACP) provides a single point of services control for all active SIP services for all subscribers via state information and services interaction management. Policy decisions are made at the packet layer, for example in an Advanced Bearer Control Point (ABCP) clustered with other functions to form a Bearer Services Control Point (BSCP). Policy enforcement is implemented at various nodes at the network or packet layer (L3) and above, e.g. including the BSCP and ACP.
Owner:CELLCO PARTNERSHIP INC
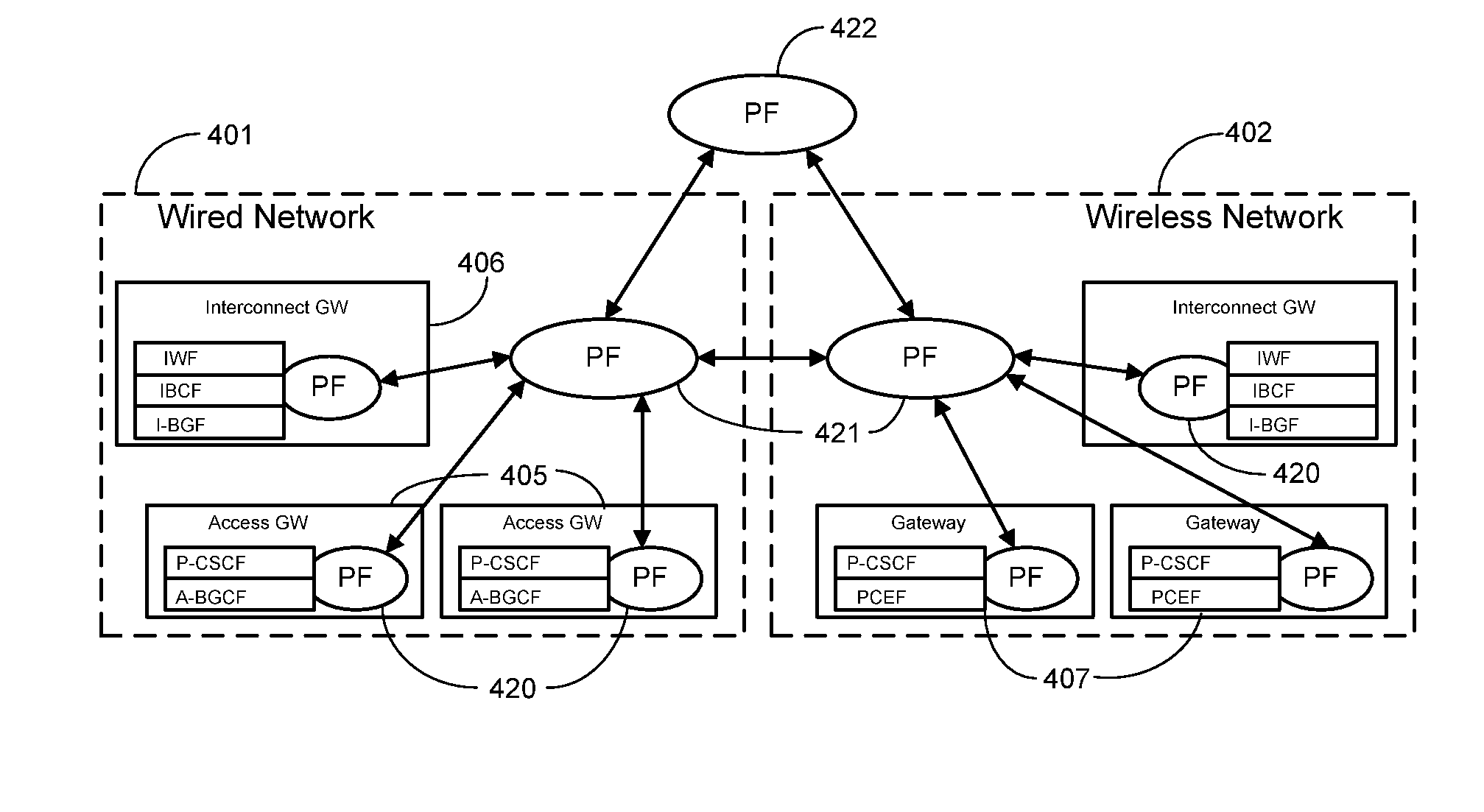
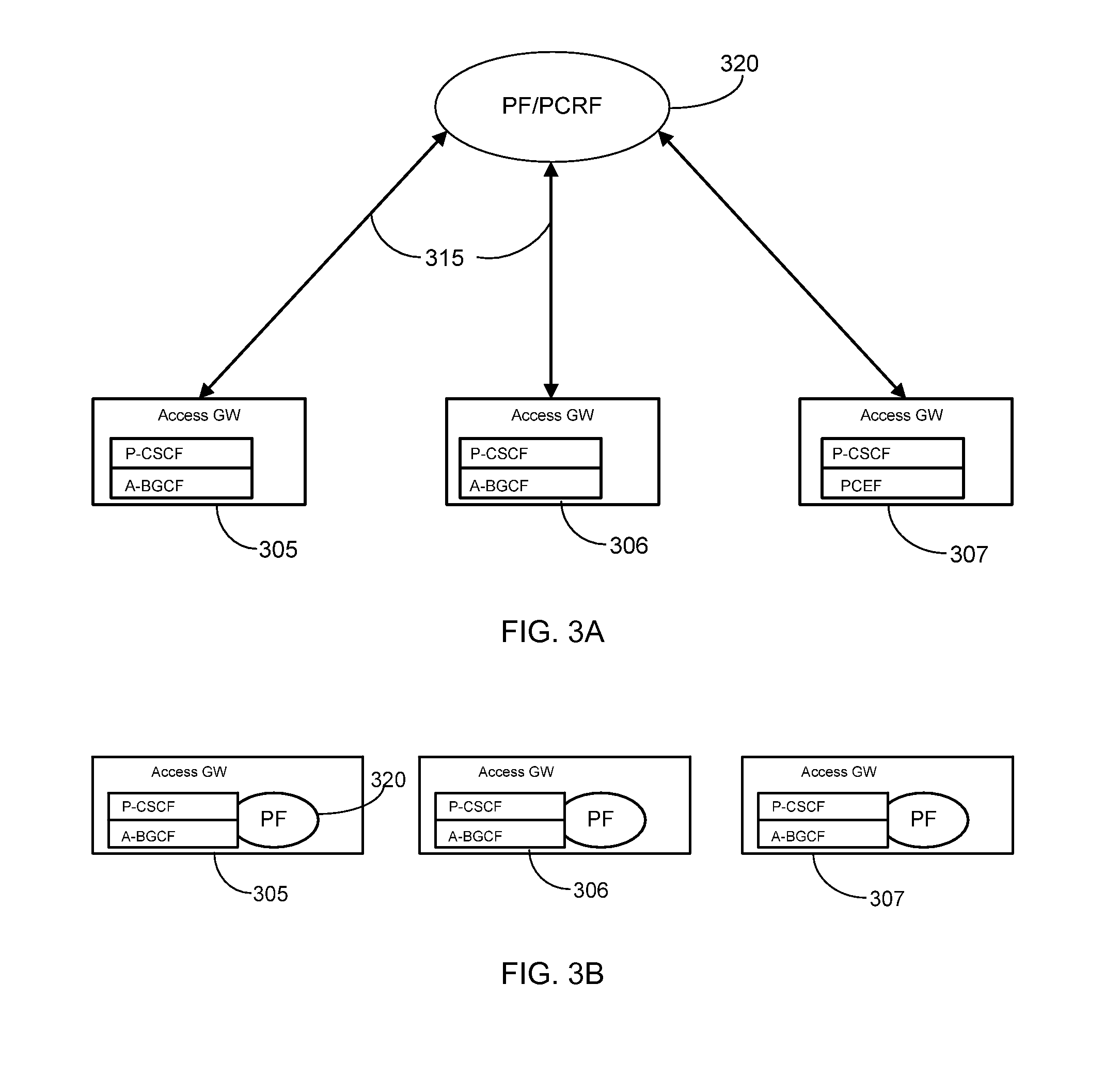
Cascading Policy Management Deployment Architecture
InactiveUS20090113514A1Improve performanceLimitation is enforcedError preventionTransmission systemsPolicy decisionWireless mesh network
Systems and methods are provided to implement a dynamic and efficient cascading policy management framework architecture for both wired and wireless networks. A plurality of Policy Functions (PFs) are assigned to a plurality of Policy Enforcement Points (PEP). The PFs make decisions regarding local policy control at the specific PEP. The PFs then delegate the policy requests or IP flows to a separate PEP that is more conducive to enforcing that policy request. Thus, policy decisions are made at the point where the most information is available, leading to fewer policy requests traversing back and forth across a network. Additionally, this cascading Policy Management Framework Architecture allows for unified policy management across multiple types of networks, including wired (Internet) and wireless (UMTS).
Owner:AT&T MOBILITY II LLC
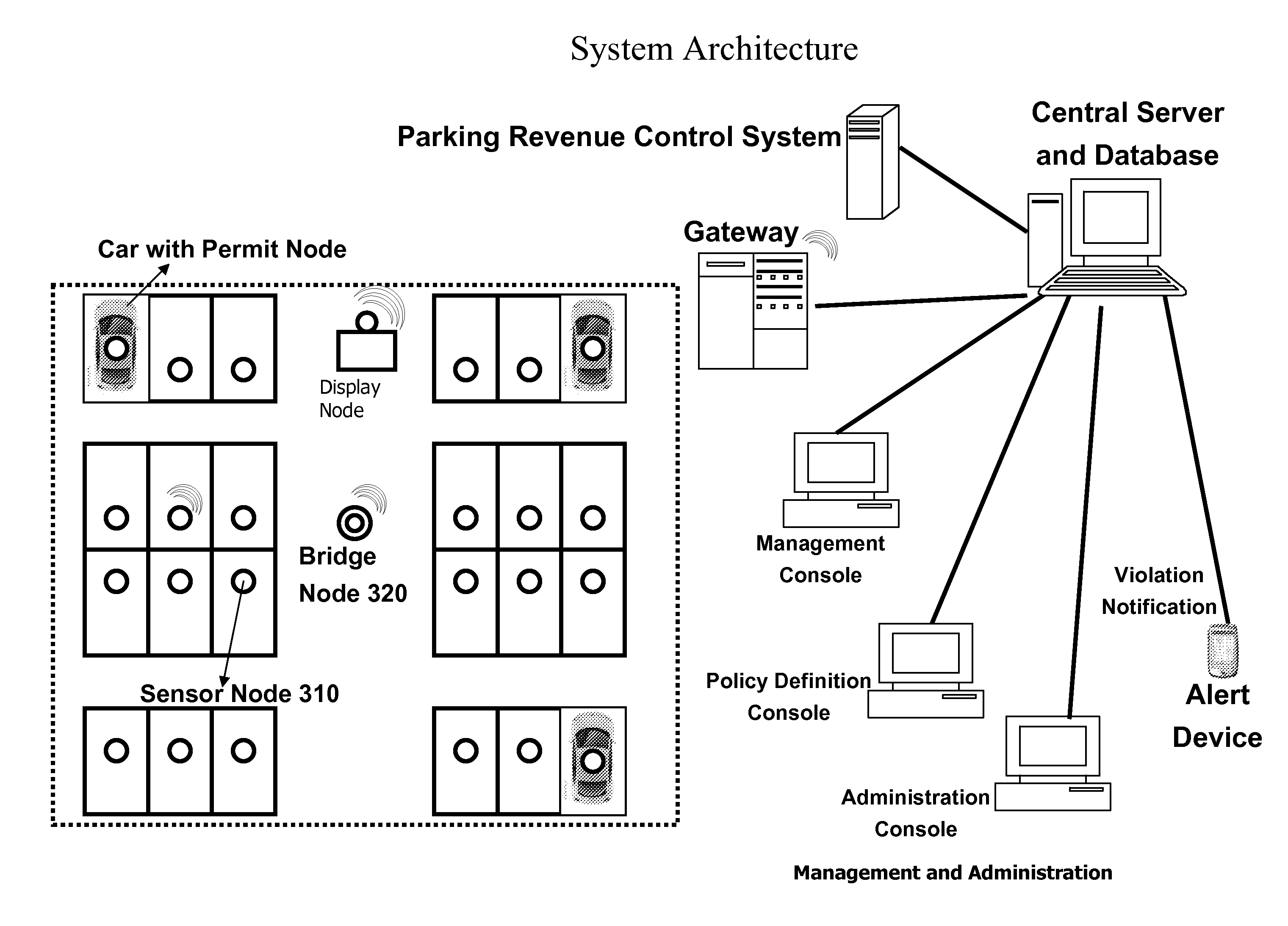
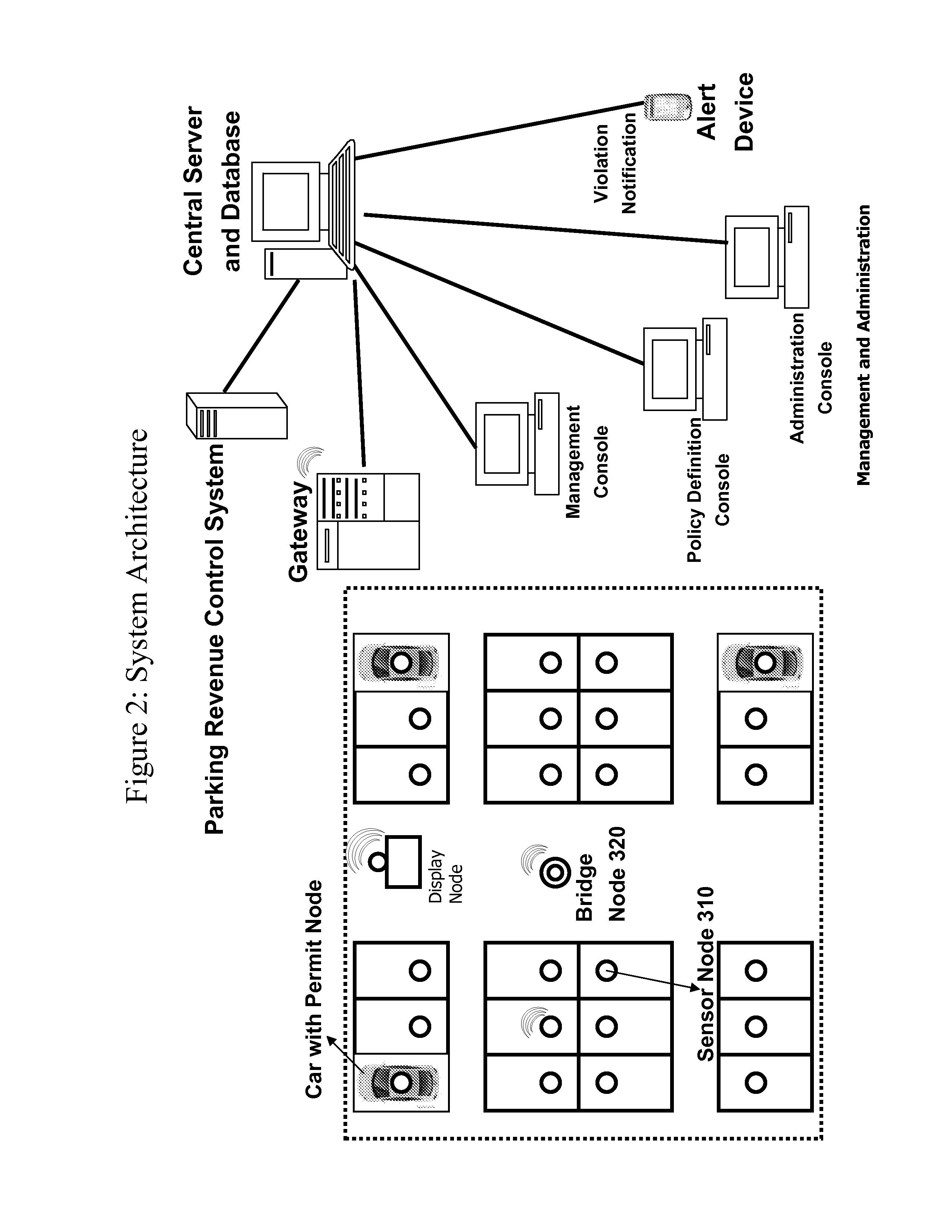
Automated Parking Policy Enforcement System
InactiveUS20110099126A1Optimally enforceUniformity in useTicket-issuing apparatusIndication of parksing free spacesDashboardParking area
A parking policy management system helps identify and enforce parking violations in real-time. By monitoring sensors distributed in a parking area, the system will determine whether one or more parking policies have been violated. The types of parking policies the system can monitor include duration, time of day, unauthorized vehicle, special permit parking, and paid parking. When a violation of a policy is detected, a notification may be delivered to enforcement personnel through the Internet, personal digital assistants (PDAs), cell phones, in-vehicle dashboards, and other means.
Owner:SENSACT APPL
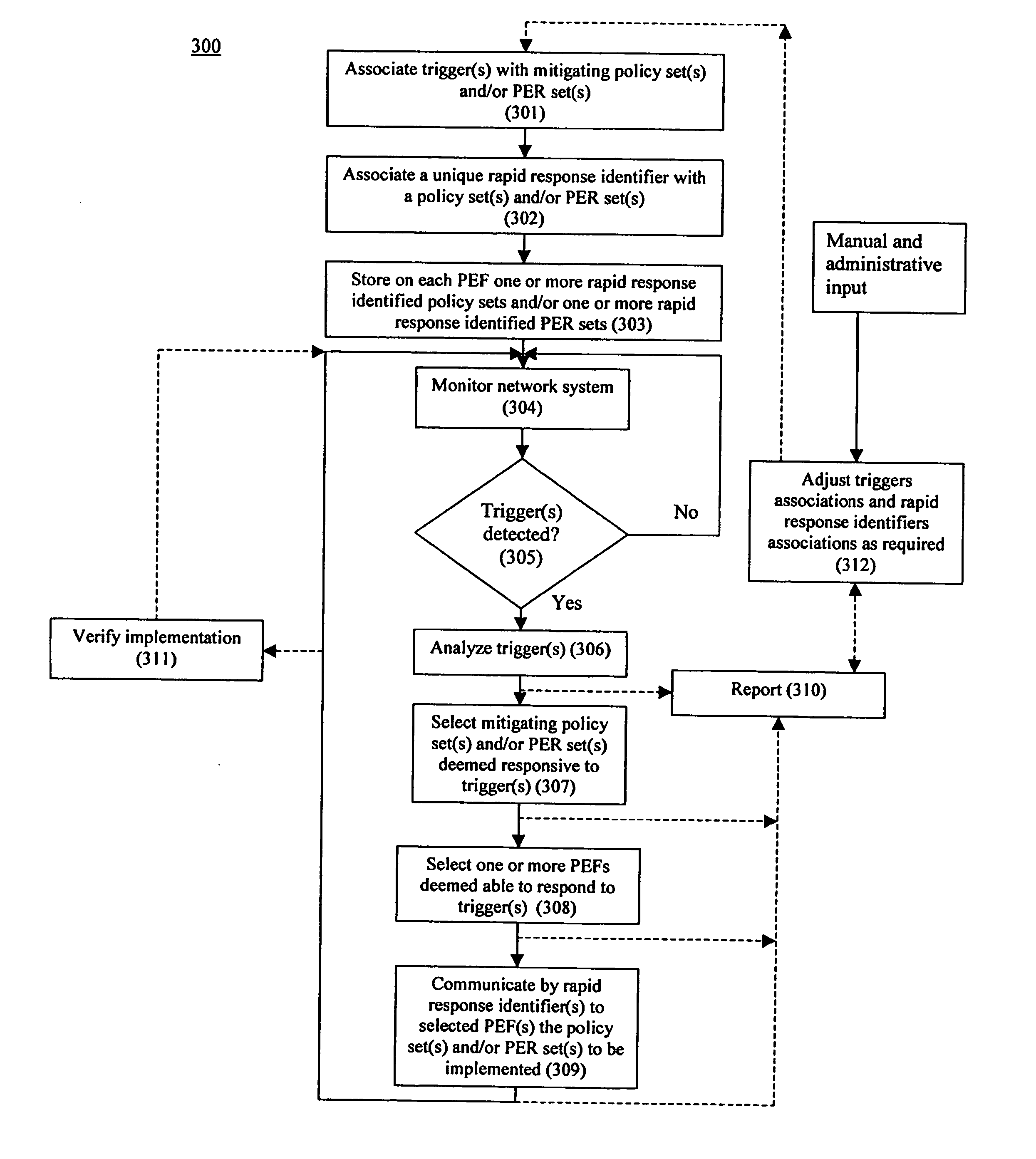
System and method for rapid response network policy implementation
A system and method for rapidly responding to triggering events or activities in a network system. The system includes a policy enforcement function, a policy manager function, and one or more network devices of the network system. The policy enforcement function includes one or more installed policy sets and / or policy enforcement rule sets suitably responsive to triggering events or activities. Upon detection of a trigger, the policy manager function analyzes the trigger and selects one or more appropriate policy sets and / or policy enforcement rule sets deemed to be responsive to the trigger. Each set has a unique rapid response identifier. The policy manager function signals for implementation of the one or more policy and / or rule sets, based on one or more rapid response identifiers, which are enforced through the policy enforcement function. The policy enforcement function may be a part of one or more of the one or more network infrastructure devices for implementing the policy change. The system and method enable rapid response to a detected trigger (which might be a manual input) by pre-installing responsive policy and / or rule sets first and then generating and transmitting the unique rapid response identifier(s) corresponding to one or more selected policy and / or rule sets for implementation. That is, the network device is already configured with a response through the pre-installed policy and / or rule sets. Responses may be implemented and / or removed gradually, and different network devices may be instructed to implement different policies in response to the same trigger and the same policy may be implemented with different policy enforcement rules on different devices, ports, or interfaces.
Owner:ENTERASYS NETWORKS
System and method of network access security policy management for multimodal device
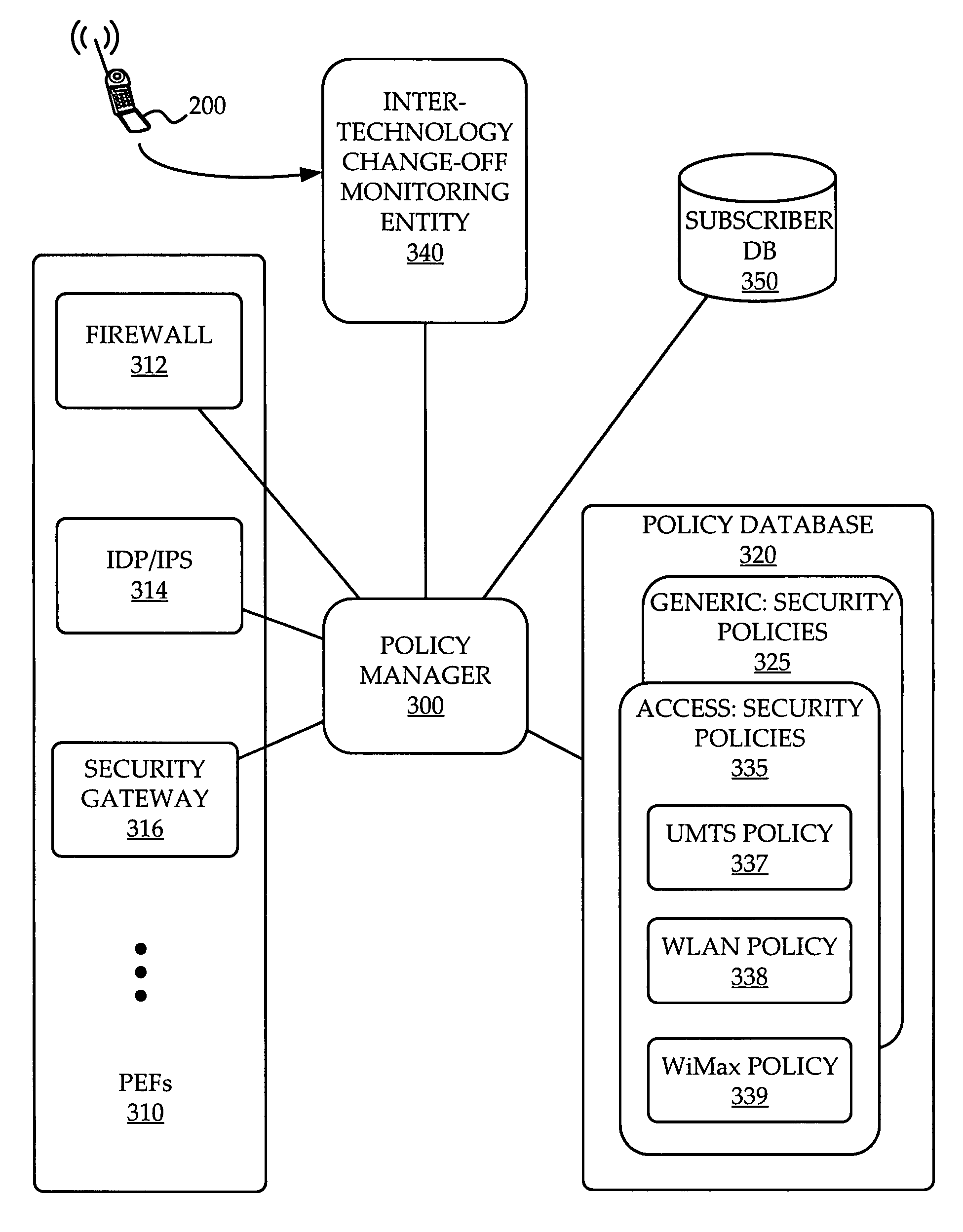
A system and method are provided for management of access security for access by a multimodal device to a converged fixed / mobile network. An inter-technology change-off monitoring entity (ICME) is provided to monitor an inter-technology change-off of the multimodal device and to notify a policy manager of the inter-technology change-off. The policy manager looks up in a policy database, security policies applicable to the user of the multimodal device and the particular technology being used by the multimodal device. The policy manager conveys to various policy enforcement points throughout the converged fixed / mobile network the applicable security policies which take into account the user's identity and the access technology being used.
Owner:WSOU INVESTMENTS LLC
Computer network security system and method having unilateral enforceable security policy provision
InactiveUS7174563B1Digital data processing detailsUser identity/authority verificationDigital signaturePassword
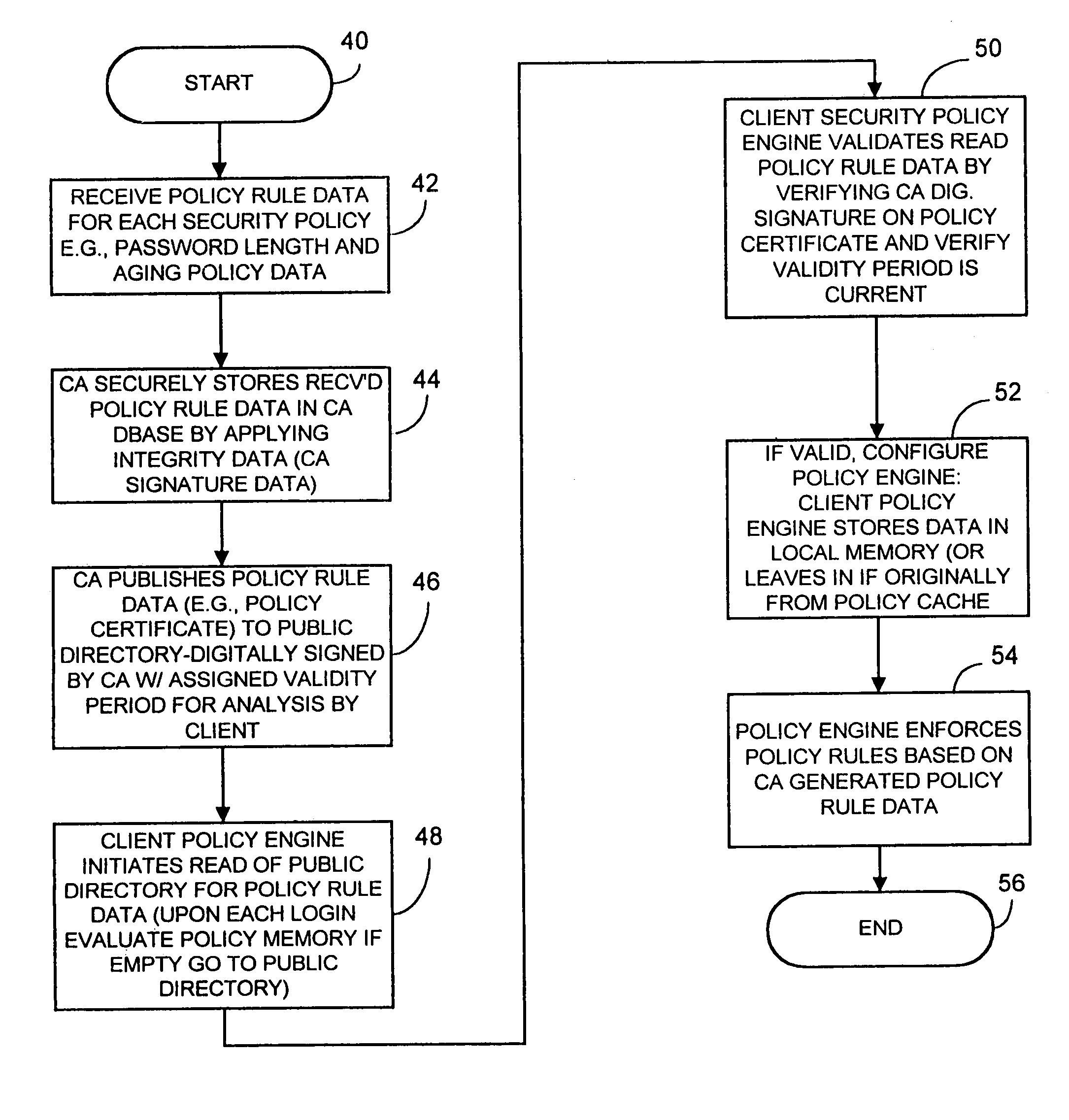
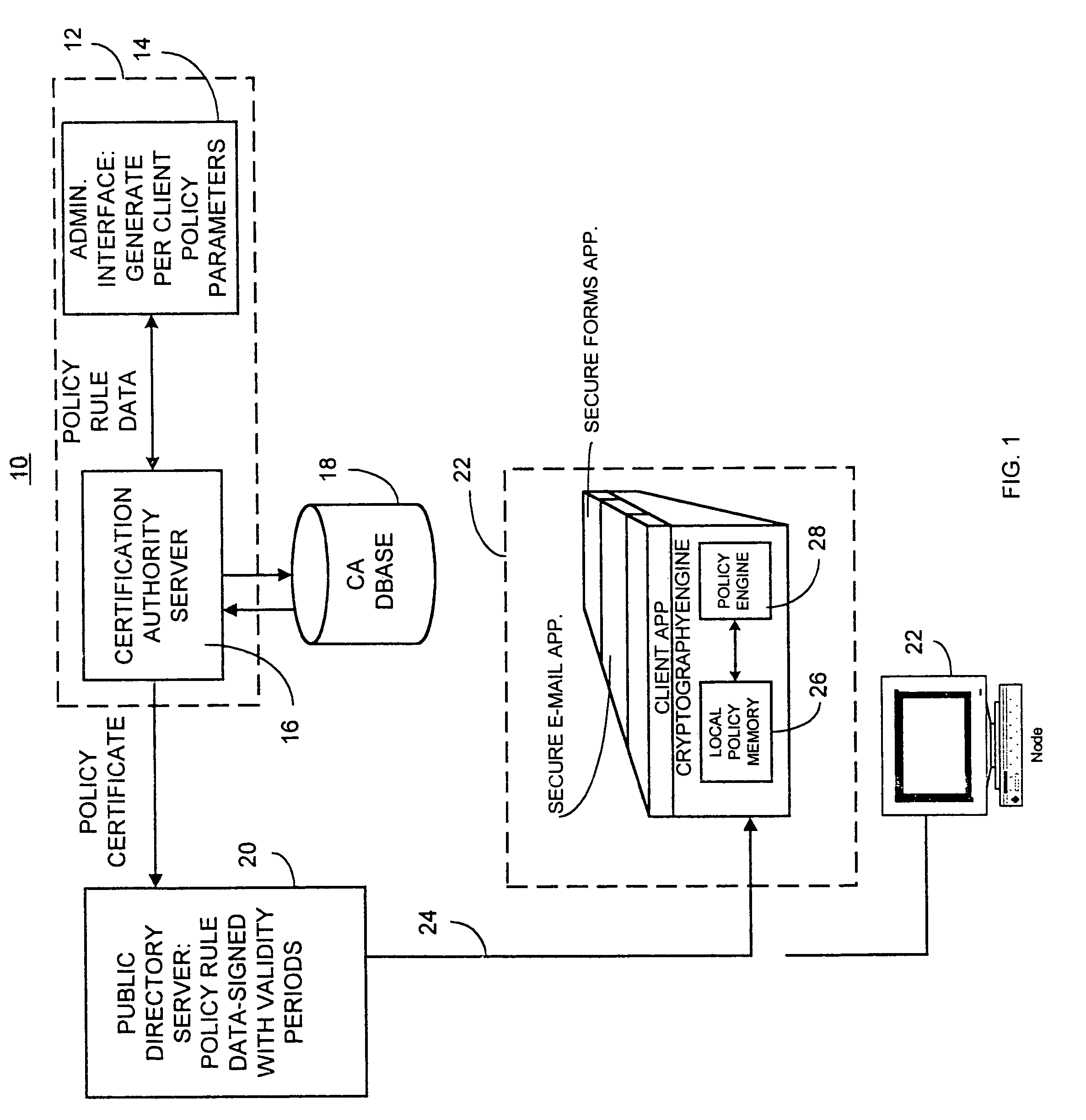
A computer network security system and method utilizes digitally signed and centrally assigned policy data, such as password length rules, that is unilaterally enforced at network nodes by node policy enforcement engines. The policy data may be variable on a per client or network node basis through a centralized authority, such as a certification authority. The computer network security system provides variable security policy rule data for distribution to at least one network node through a central security policy rule data distribution source, such as the certification authority. The central security policy rule data distribution source associates a digital signature to the variable security policy rule data to ensure the integrity of the policies in the system. Each network node uses a policy rule data engine and policy rule table to decode policy rule data and enforce the policy rules as selectively determined through the central authority.
Owner:ENTRUST
Cryptographic policy enforcement
ActiveUS20050166066A1User identity/authority verificationUnauthorized memory use protectionPassword policyData stream
Owner:MCAFEE LLC
Secure interprocess communications binding system and methods
InactiveUS20050182966A1Inhibit exchangeFlexible performanceDigital data processing detailsMultiple digital computer combinationsTrust relationshipInter-process communication
The secure trust relationship between communicating programs is established at any policy defined level down to individual program instances. Policy enforcement modules installed on host computer systems support qualified encrypted communications channels between discretely selected program instances. Program instances are qualified to establish communication channels, each defined by a unique session encryption key, based on an evaluation of security data including the individual process execution contexts, user authorizations, and access attributes of the program instances. A security appliance server performs the policy-based qualification based on a mutually interdependent evaluation of the security data for both the communications channel source and target program instances.
Owner:PHAM DUC +3
Method and apparatus for communicating network quality of service policy information to a plurality of policy enforcement points
A method is disclosed for communicating network quality of service policy information to a plurality of policy enforcement points. Active QoS configuration information is created and stored at a policy enforcement point, such as a router in a network. New configuration information is received and stored as an inactive configuration of the policy enforcement point. The policy enforcement point determines whether the inactive configuration information is properly functional in combination with the active QoS configuration information. The new configuration information is made active in place of the active QoS configuration information only in response to receiving an activation message. An inactive configuration may be signaled by a COPS protocol decision message from the policy decision point that identifies the configuration information as an inactive configuration by a specified flag bit in a message type value in a Context object that forms part of the decision message. Using the method, network quality of service policy information may be communicated to a plurality of policy enforcement points, with assurance that all receiving policy enforcement points can successfully deploy the configuration information. As a result, new QoS policy configuration information can be deployed to an entire network or to a large plurality of devices with assurance that all such information is received and deployed without adverse effects on the network or enforcement of policy information.
Owner:CISCO TECH INC
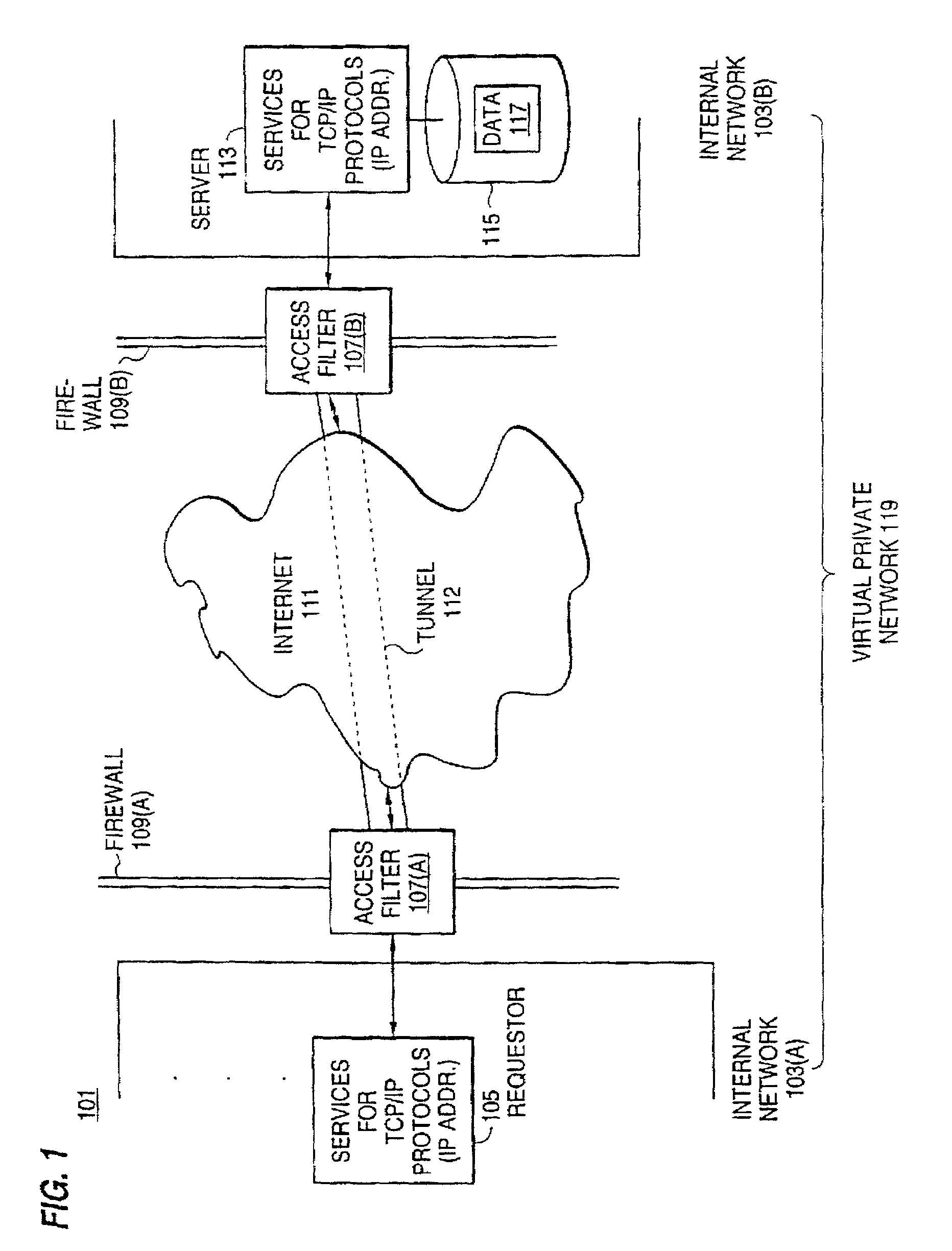
System providing internet access management with router-based policy enforcement
ActiveUS8200818B2Multiple digital computer combinationsTransmissionInternet accessApplication software
A computing environment with methods for monitoring access to an open network such as the Internet, is described. The system includes one or more client computers, each operating applications (e.g., Netscape Navigator or Microsoft Internet Explorer) requiring access to an open network, such as a WAN or the Internet, and a router or other equipment that serves a routing function (e.g., a cable modem) for the client computers. A centralized security enforcement module on the router maintains access rules for the client computers and verifies the existence and proper operation of a client-based security module on each client computer. The router-side security module periodically sends out a router challenge via Internet broadcast to the local computers on the network. If the client-side security module is installed and properly operating, the client-side security module responds to the router challenge. The responses received by the router-side security module are maintained in a table. Each time the router receives a request from a client computer to connect to the Internet, the router-side security module reviews the table and analyzes whether or not the computer requesting a connection to the Internet properly responded to the most recent router challenge. If it determines that the computer has properly responded to the router challenge, then it permits the computer to connect to the Internet. If a computer has not properly responded or if a computer has not answered the router challenge, then the computer is not allowed to connect to the Internet as requested.
Owner:CHECK POINT SOFTWARE TECH INC
Network access control system and method for devices connecting to network using remote access control methods
ActiveUS20090307753A1Digital data processing detailsMultiple digital computer combinationsControl systemUser authentication
A system and method for network access control (NAC) of remotely connected devices is disclosed. In embodiments, agents support role mapping and policy-based scanning. Embodiments automatically perform authentication, assessment, authorization, provisioning, and remediation. Capabilities include user authentication, role-based authorization, endpoint compliance, alarms and alerts, audit logs, location-based rules, and policy enforcement. Processes collect information about the user as well as the host being used from sources including, but not limited to, LDAP, the remote access device, and the agent. Once this data has been obtained, embodiments construct a comprehensive model of the host. This model is subsequently used to govern the actual host's network access when it connects to the network. Passive monitoring includes vulnerability scanning to control access rights throughout the duration of the connection.
Owner:FORTINET
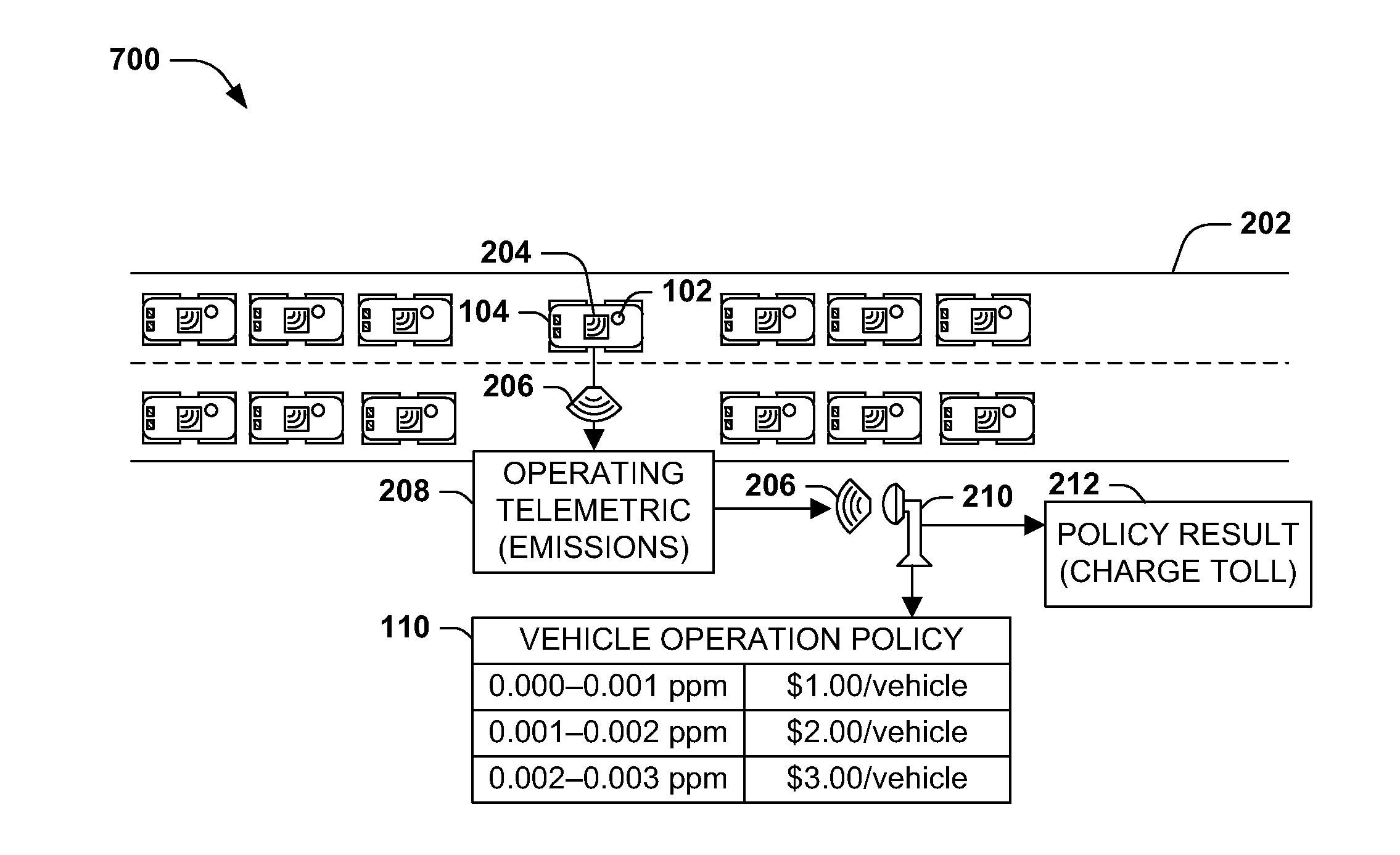
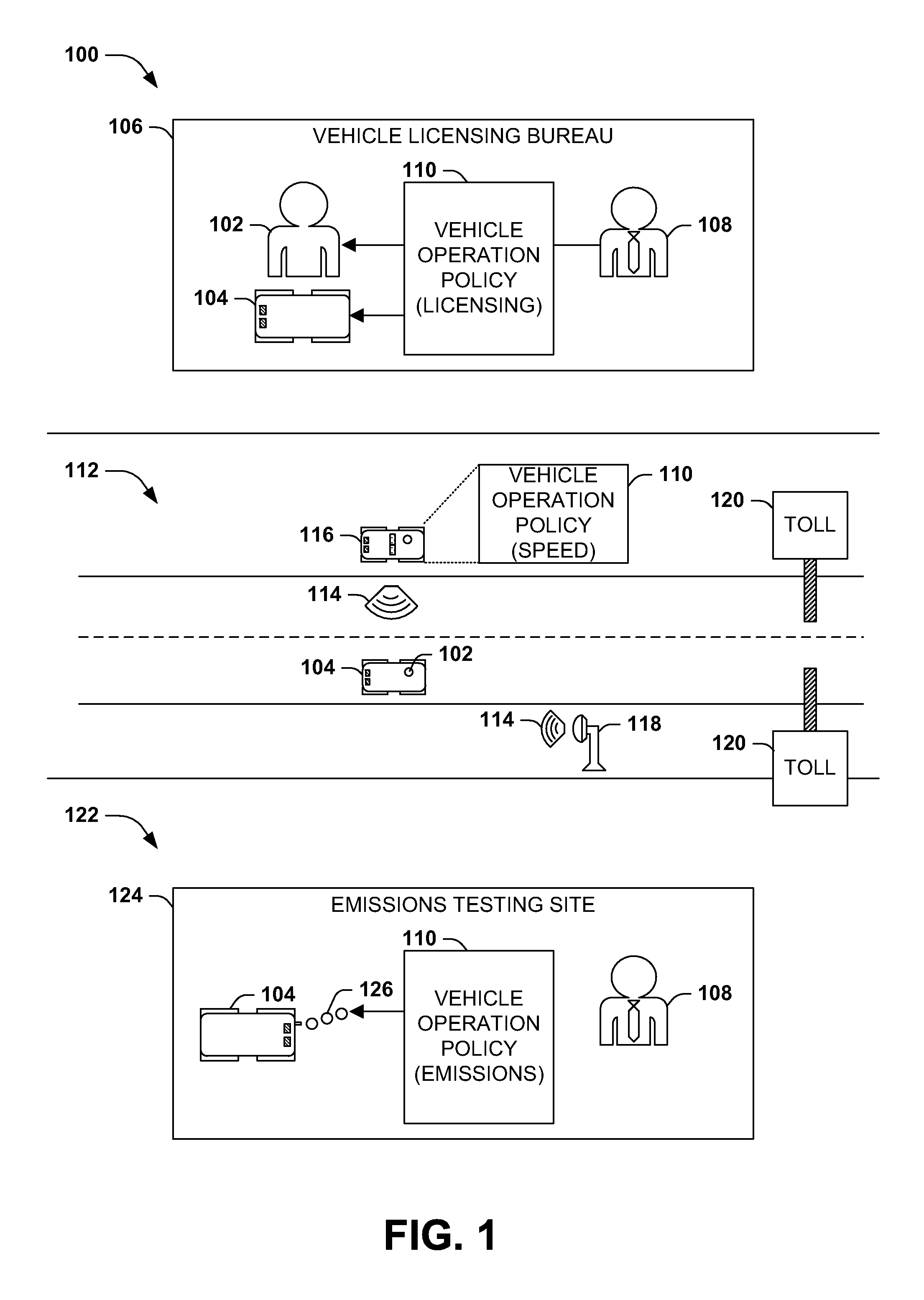
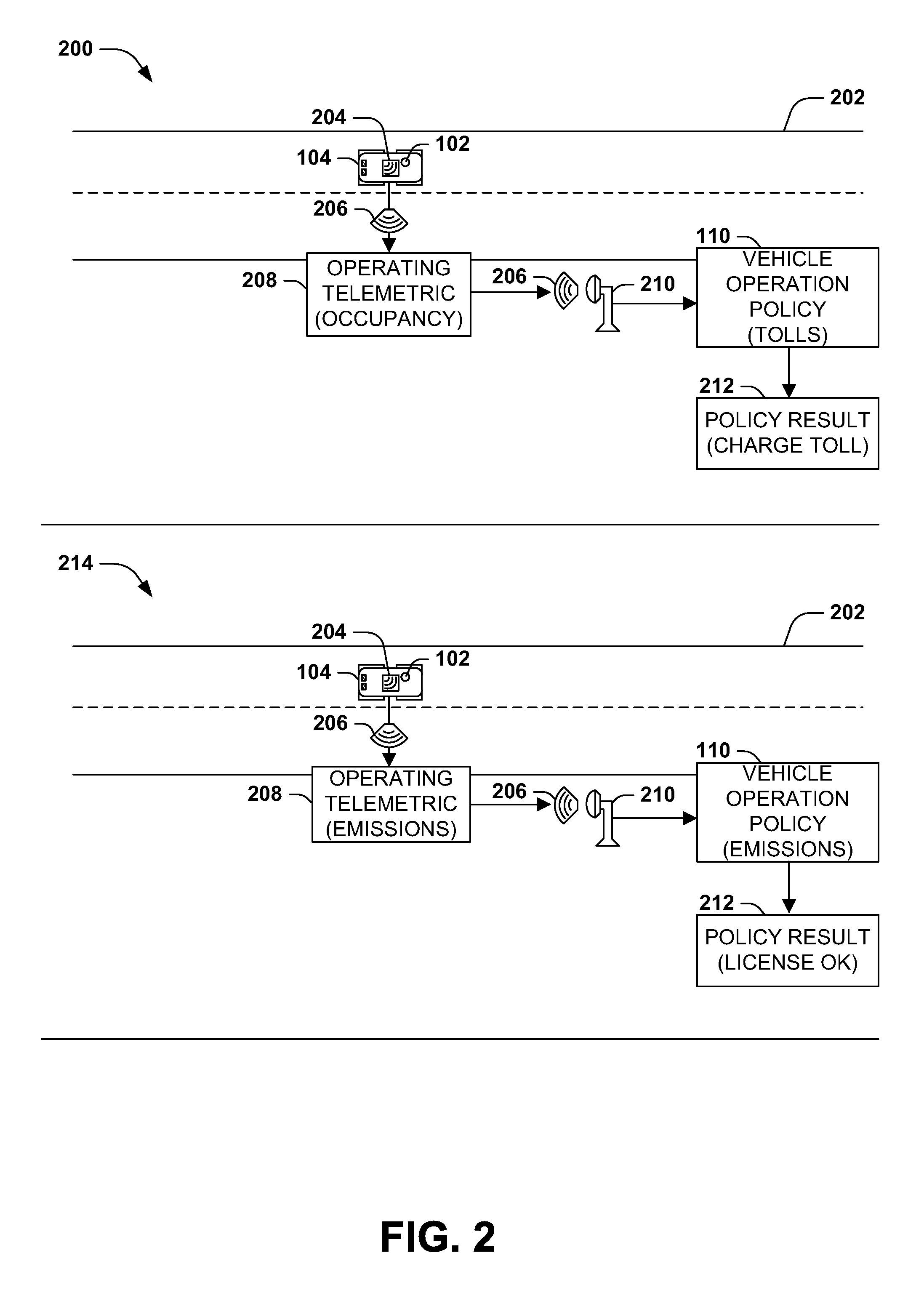
Telemetry-based vehicle policy enforcement
InactiveUS20140278840A1Analogue computers for vehiclesTicket-issuing apparatusParking spaceTraffic congestion
Vehicles operation is often regulated by vehicle operation policies, such as operator and vehicle licensing, safe operation rules, and emissions testing, as well as advisory policies (e.g., safety tips) and infrastructure policies (e.g., traffic congestion reduction). However, enforcement of vehicle operation policies may be infrequent, costly, inaccurate, and / or ineffective for particular types of problems. Presented herein are techniques for enforcing vehicle operation policies using vehicle telemetrics detected by a vehicle telemetry sensor and reported to telemetric monitoring components during operation of the vehicles. For example, in-car emissions sensors may regularly report emissions data to roadside monitors, enabling continuous monitoring, early detection of emissions problems, and accurate measurements during road travel. Additional telemetric exchange may promote the persuasion of advisory vehicle operation policies, such as safety tips, and the transmission of travel information of interest to other vehicles and individuals, such as road hazards, traffic congestion, and available parking spots.
Owner:INRIX
Enhanced QoS control
ActiveUS7209458B2Easy to controlNetwork traffic/resource managementData switching by path configurationPolicy decisionService information
The invention is a method and a system for the providing of service to user equipment (UE). A method of providing services to user equipment in accordance with the invention includes providing from a database (420) to a policy decision entity (405) subscriber information regarding permitted conditions for the users to obtain the services; providing service information from at least one network or server (100), regarding service offered by the at least one network or server to the user equipment, forming policy rules at the policy decision entity based upon the subscriber information and the service information. A requesting user equipment transmits a request for service to the communications network which is processed by the policy decision entity in accordance with the policy rules to determine if the service is to be allowed and if the service is allowed characteristics of the service to be provided to the requesting user equipment and the policy enforcement entity enforces at least one characteristic of an allowed service upon the communication network to insure that the allowed service obtained by the requesting user equipment has the at least one characteristic of the allowed service.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com