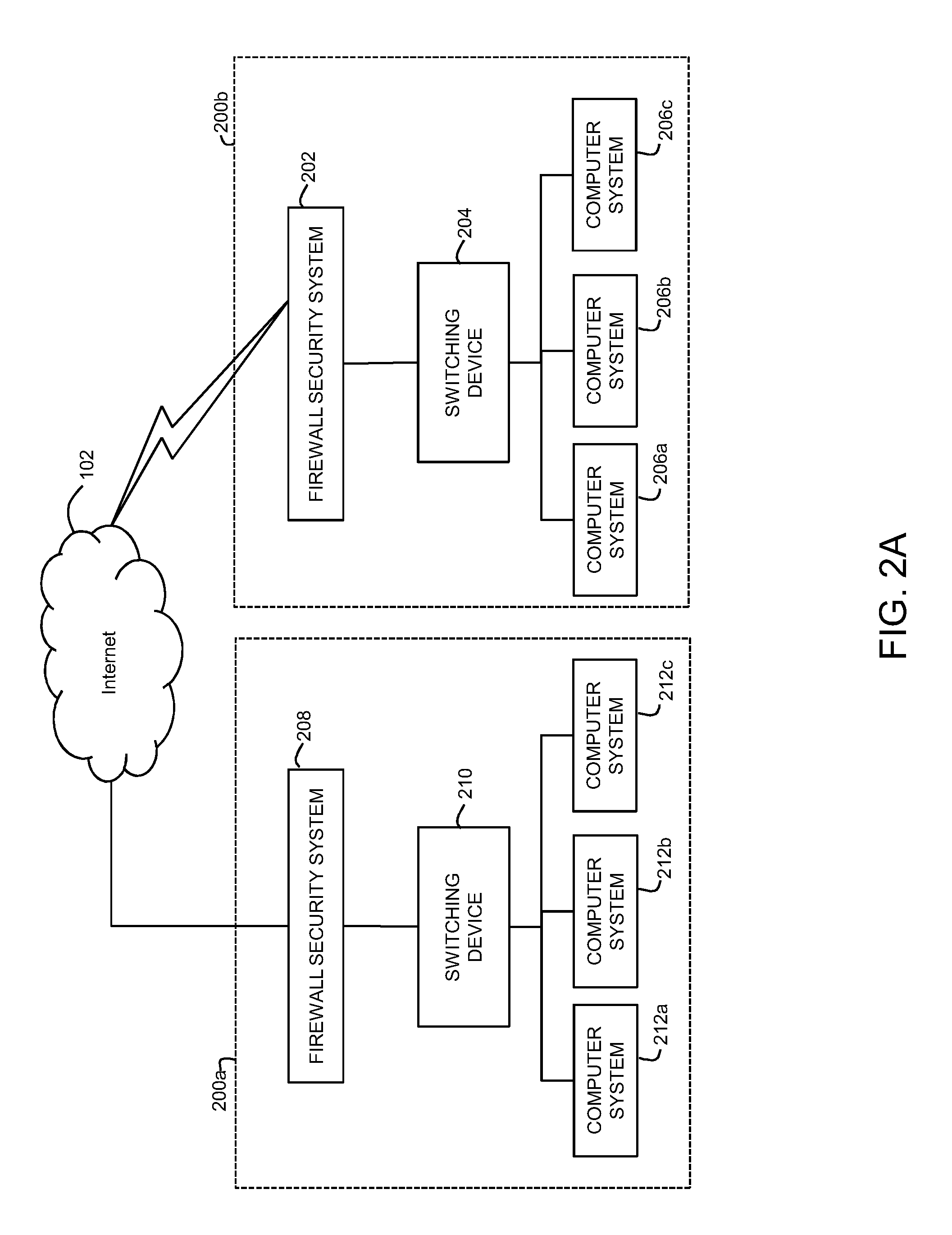
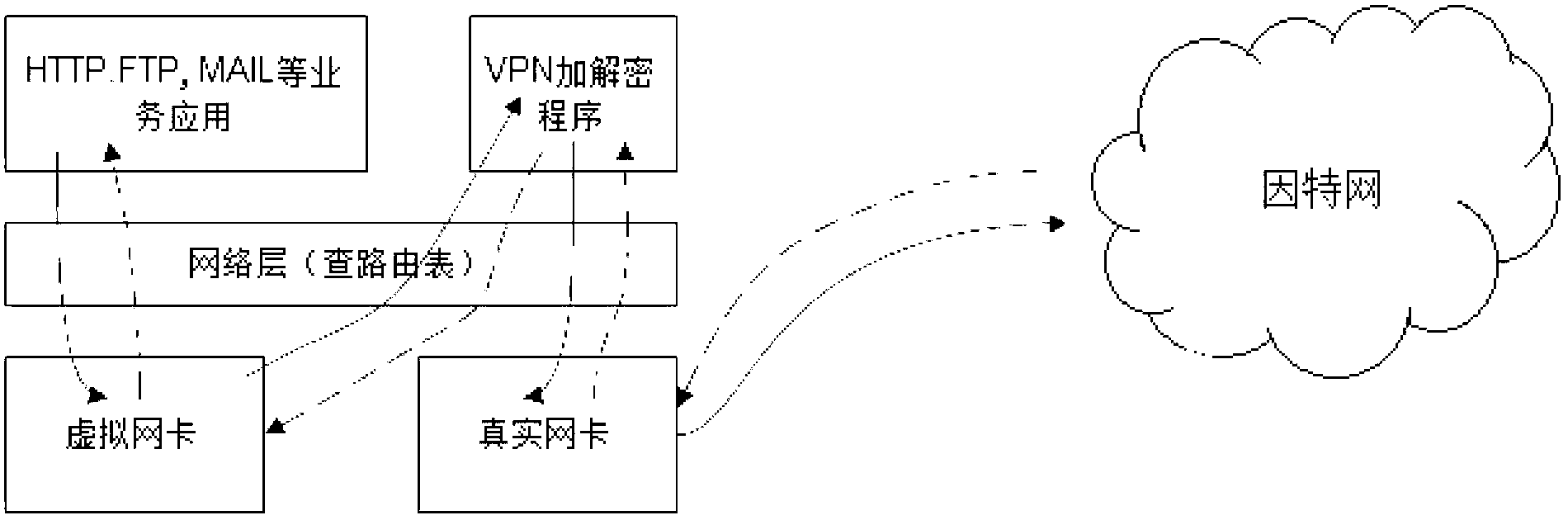
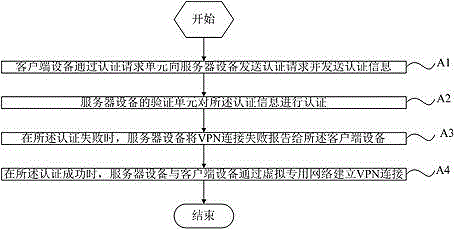
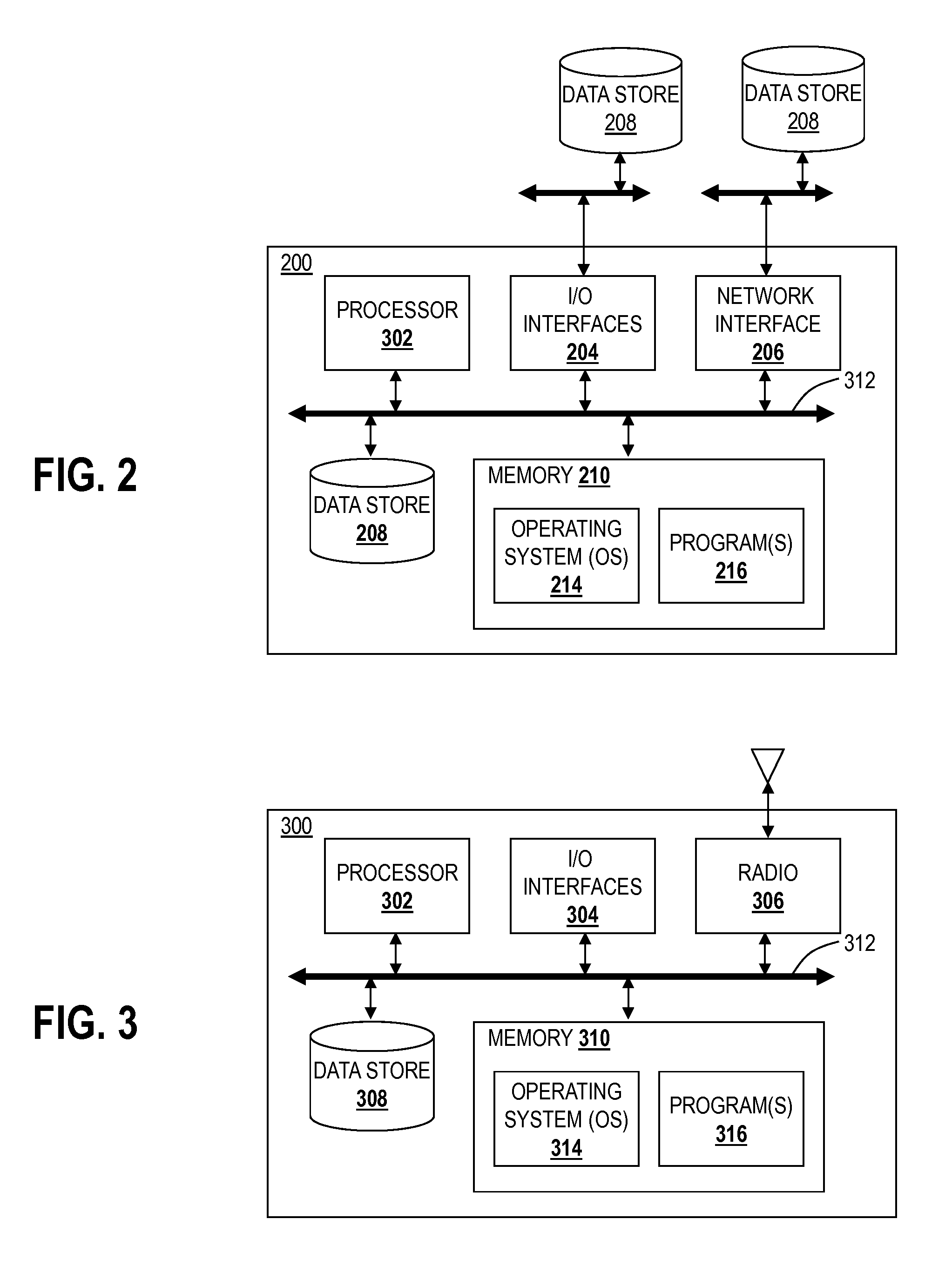
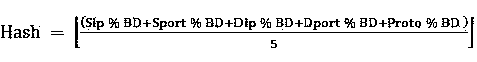Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
156 results about "Mobile virtual private network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A mobile virtual private network (mobile VPN or mVPN) is a VPN which is capable of persisting during sessions across changes in physical connectivity, point of network attachment, and IP address. The "mobile" in the name refers to the fact that the VPN can change points of network attachment, not necessarily that the mVPN client is a mobile phone or that it is running on a wireless network.
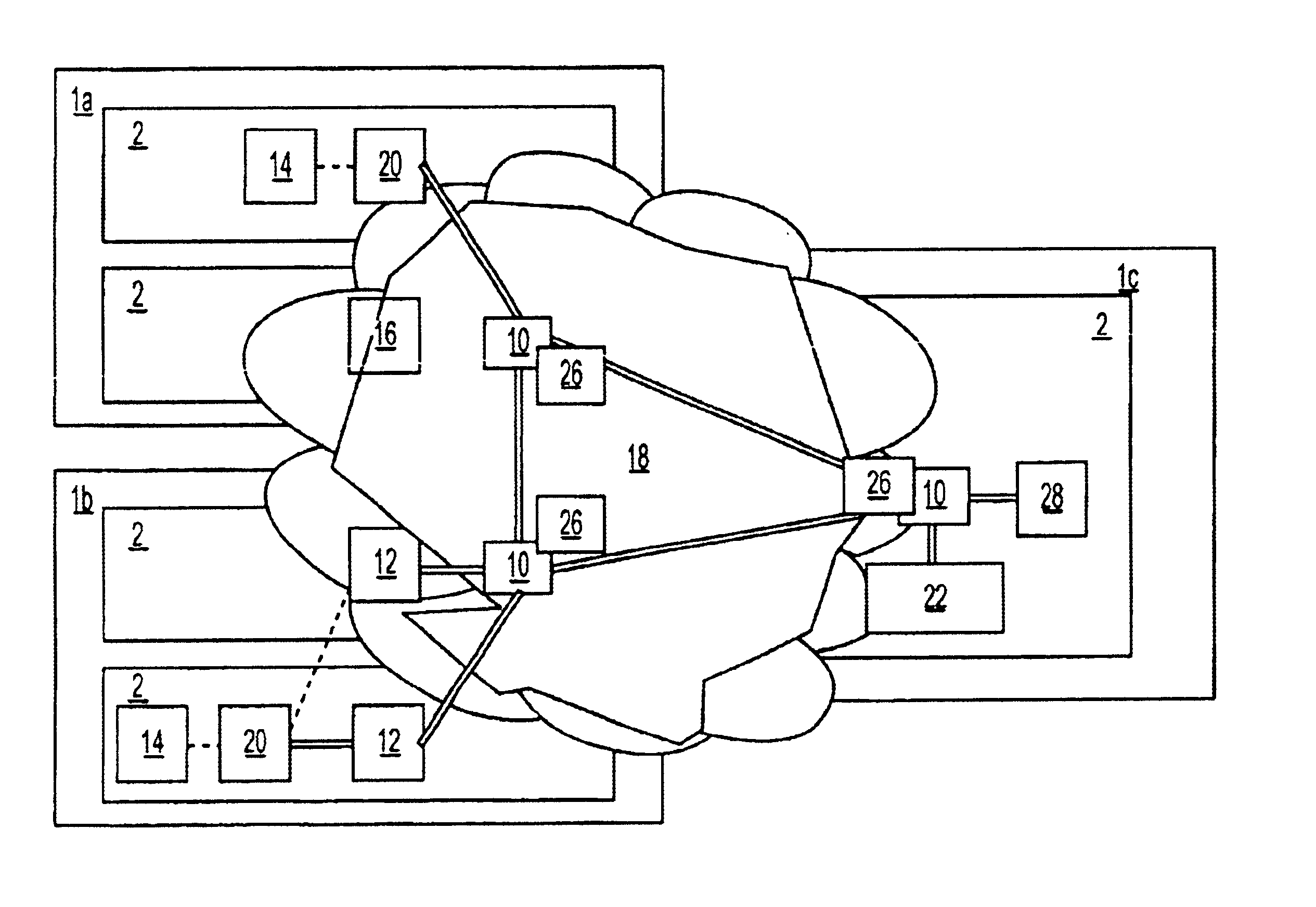
Network-based mobile workgroup system
InactiveUS6954790B2Multiple digital computer combinationsWireless network protocolsClient-sideAccess technology
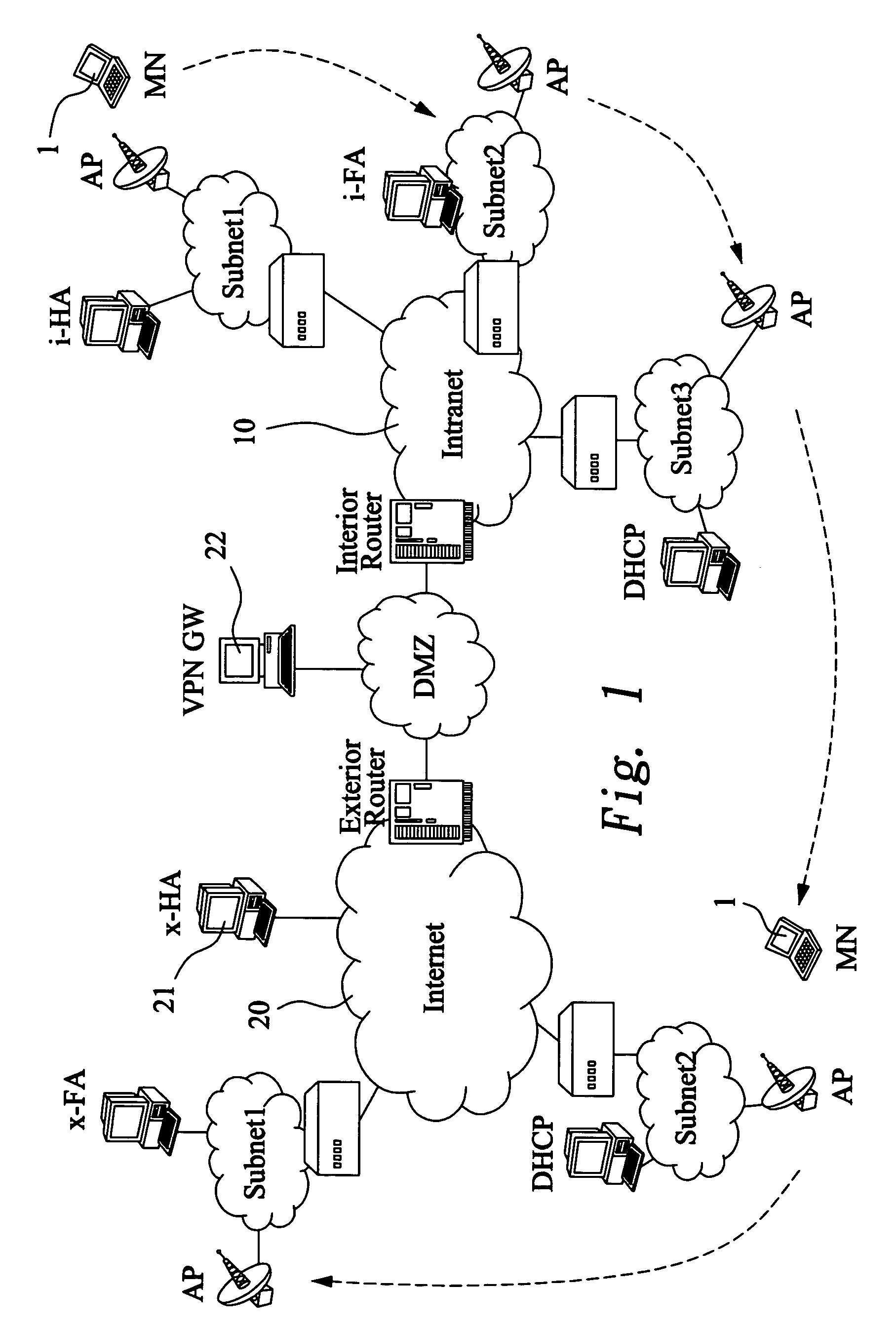
A network-based mobile workgroup system has considerably wider appeal and application than normal virtual private networks in that it provides seamless mobility across a number of access technologies at the same time as it offers a granular security separation down to workgroup level. The mobile workgroup system is an access management system for mobile users with VPN and firewall functionality inbuilt. The mobile user can access the mobile workgroup system over a set of access technologies and select server resources and correspondent nodes to access pending their workgroup membership approvals. All workgroup policy rules are defined in a mobile service manager and pushed down to one or more mobile service routers for policy enforcement. The mobile service router closest to the mobile client, and being part of the mobile virtual private network, performs regular authentication checks of the mobile client during service execution. At the same time it performs traffic filtering based on the mobile user's workgroup memberships. Together, these two components constitute an unprecedented security lock, effectively isolating a distributed workgroup into a mobile virtual private network.
Owner:LONGHORN HD LLC
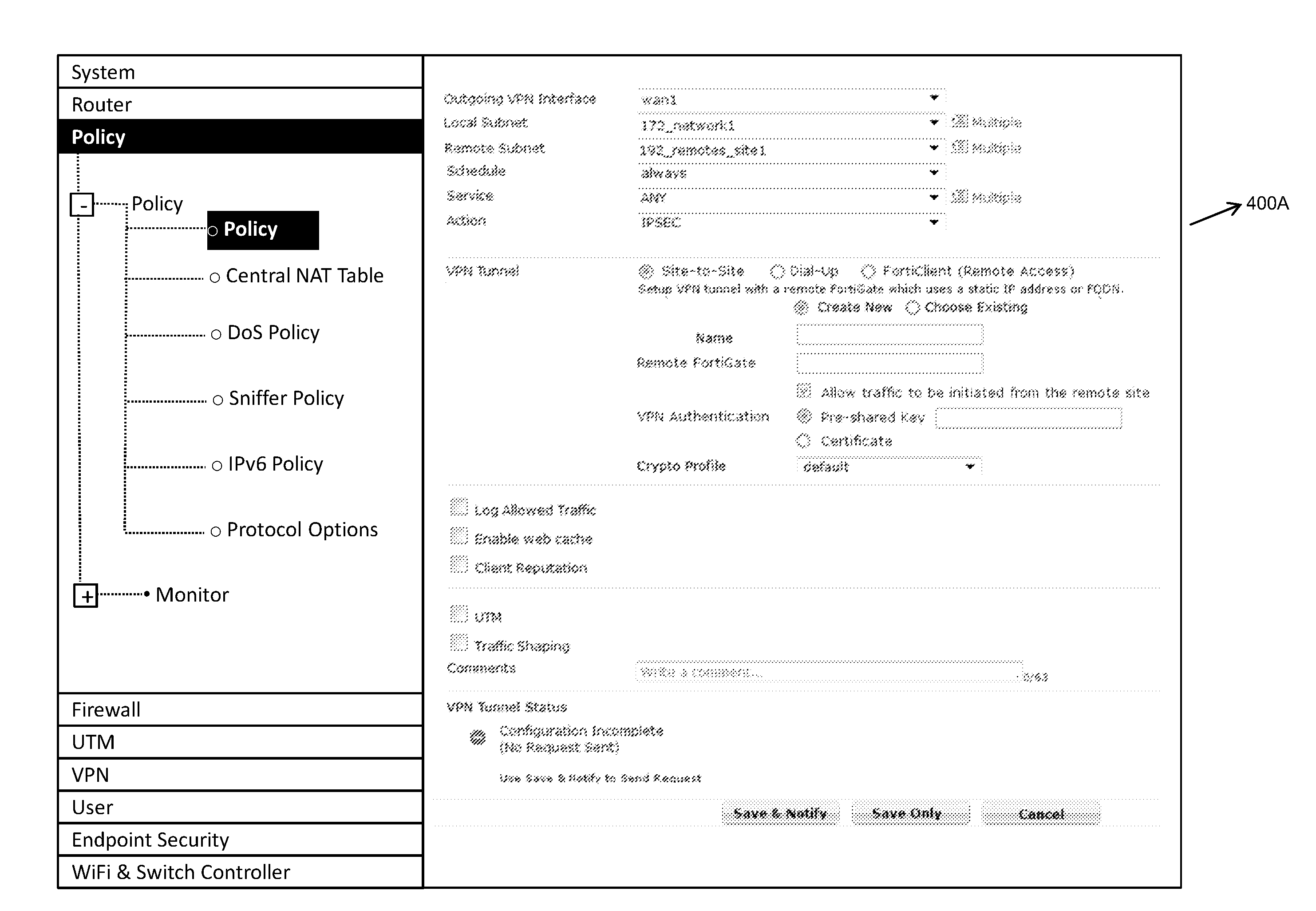
Policy-based configuration of internet protocol security for a virtual private network
ActiveUS20130298182A1Computer security arrangementsData switching networksInternet protocol suiteIPsec
A method for performing policy-based configuration of Internet Protocol Security (IPSec) for a Virtual Private Network (VPN) is provided. According to one embodiment, a browser-based interface of a network device displays a policy page through which multiple settings may be configured for a VPN connection. The settings include a type of IPSec tunnel to be established between the network device and a peer. One or more parameter values corresponding to one or more of the settings are received and responsive thereto a policy file is created or modified corresponding to the VPN connection. The policy file has contained therein multiple parameter values corresponding to the settings. Establishment of the VPN connection between the network device and the peer is requested based on the parameter values contained within the policy file by sending a notification request, including the policy file, from the network device to the peer.
Owner:FORTINET
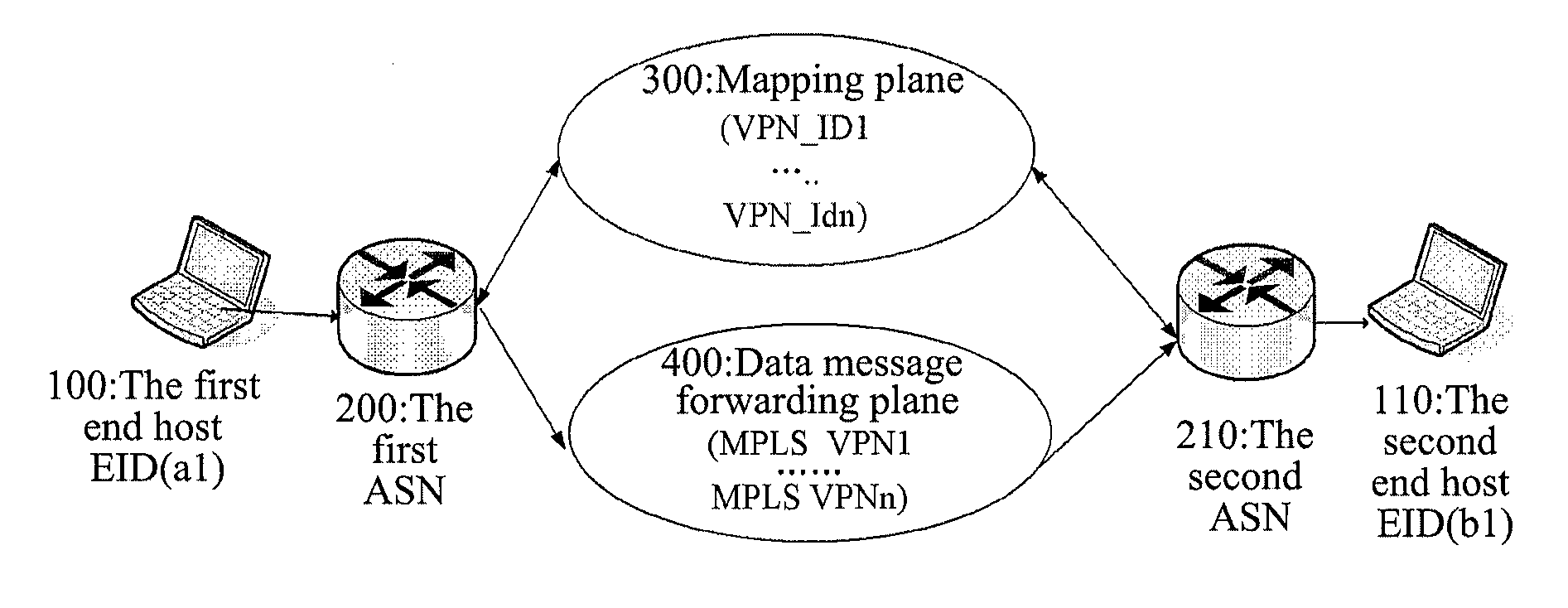
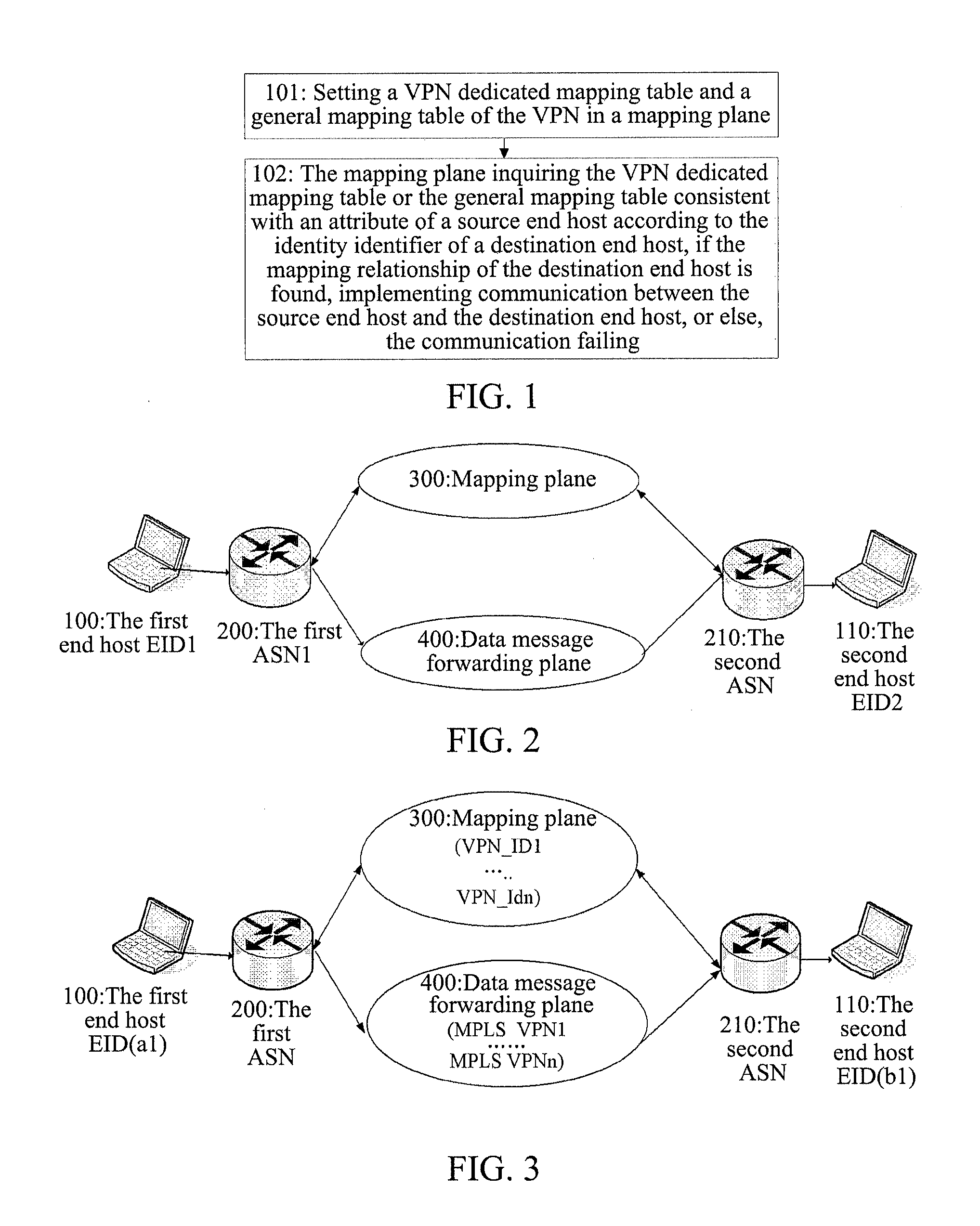
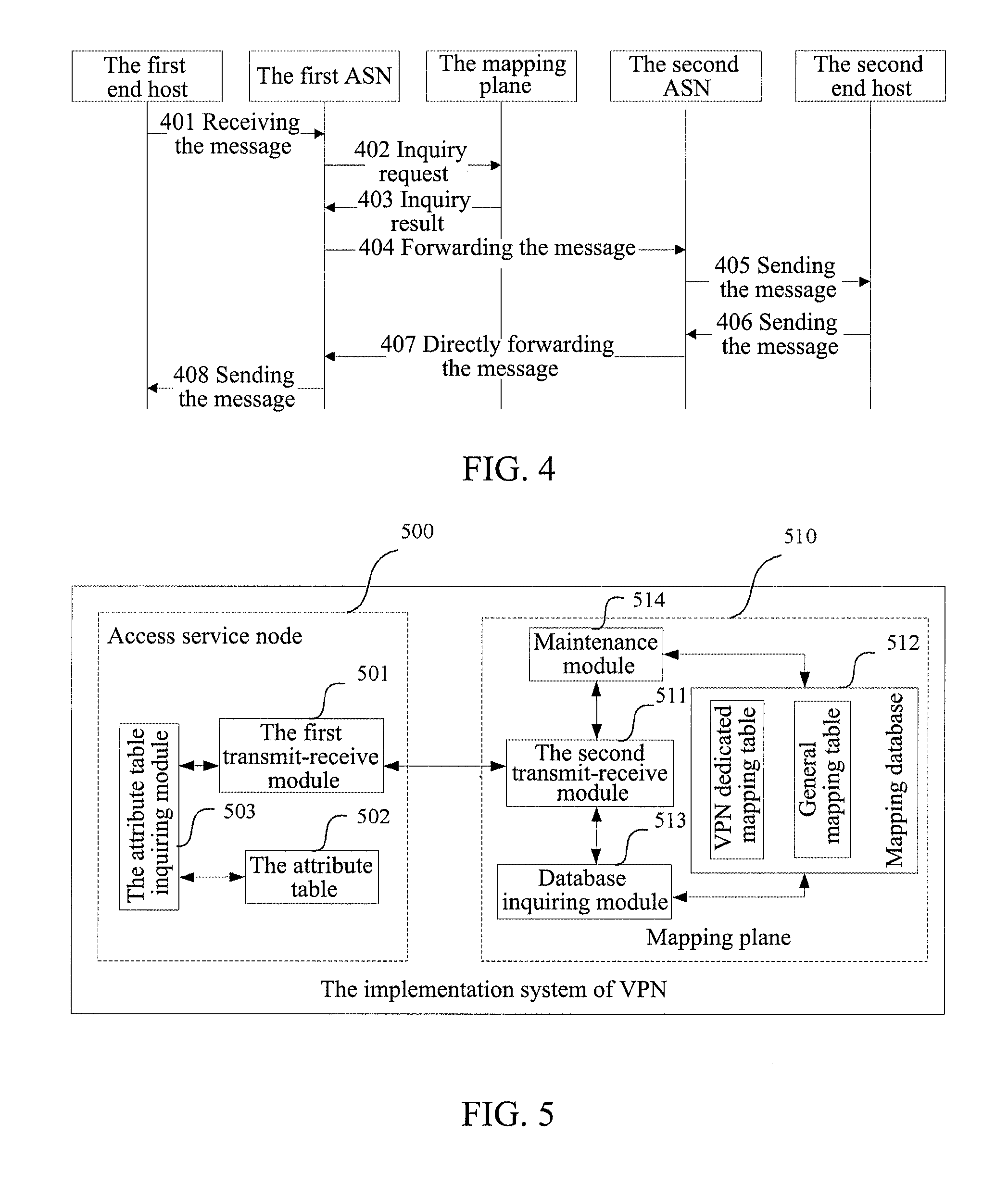
Implementation method and system of virtual private network
ActiveUS20120180122A1Computer security arrangementsData switching by path configurationSoftware engineeringComputer science
An implementation method and system of a virtual private network (VPN) are provided in the invention, wherein, the VPN dedicated mapping table of the VPN is stored in the mapping plane in the identity and location separation network, and it is determined whether to achieve the communication between the VPN end host users in the VPN or not according to the VPN dedicated mapping table, thereby the VPN is efficiently achieved in the identity and location separation network, meeting the user requirements for the VPN, eliminating the influence of the identity and location separation technical solution on the traditional VPN service, and reducing the changes on the existing devices and software tools due to the implementation of VPN.
Owner:ZTE CORP
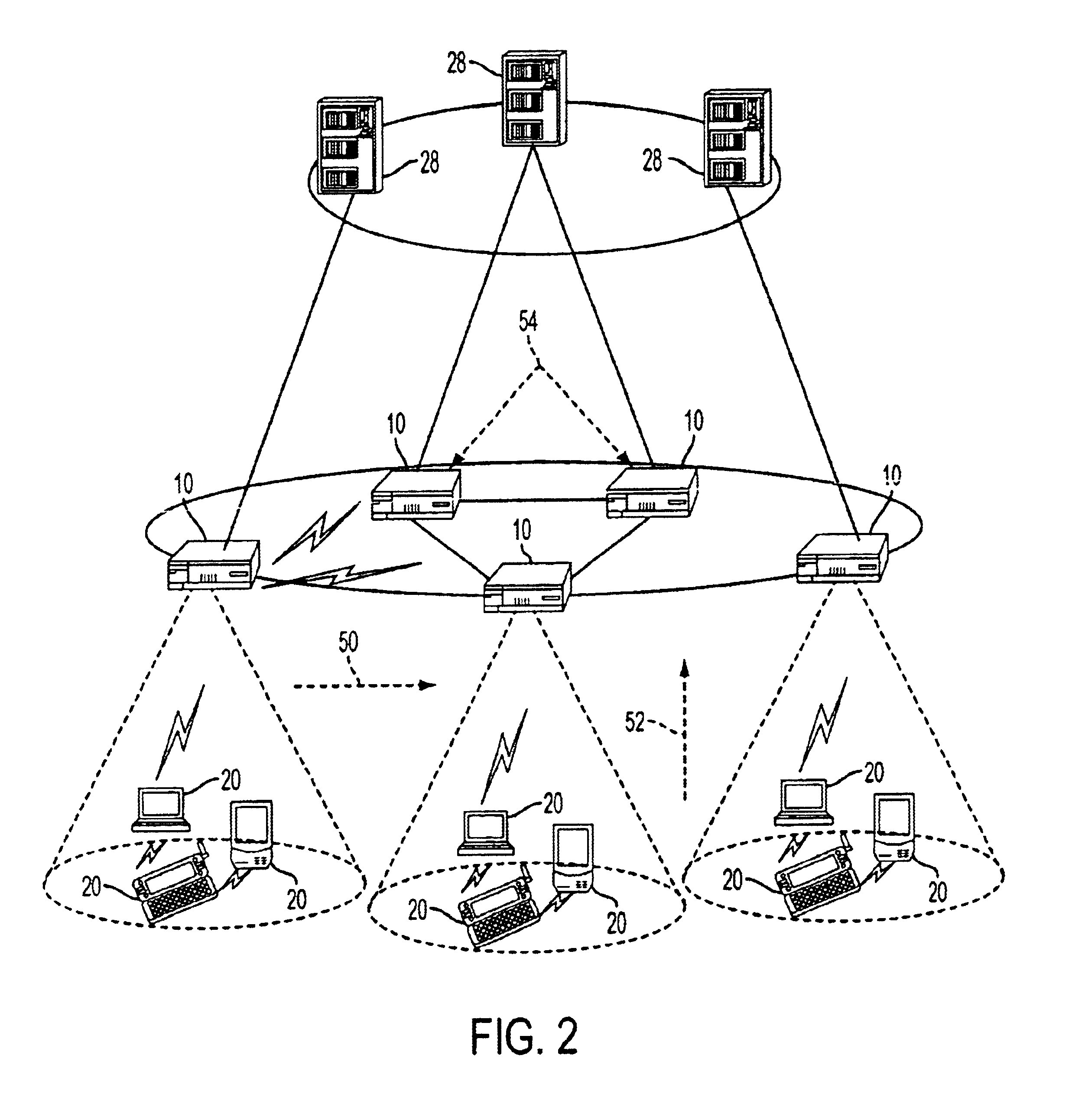
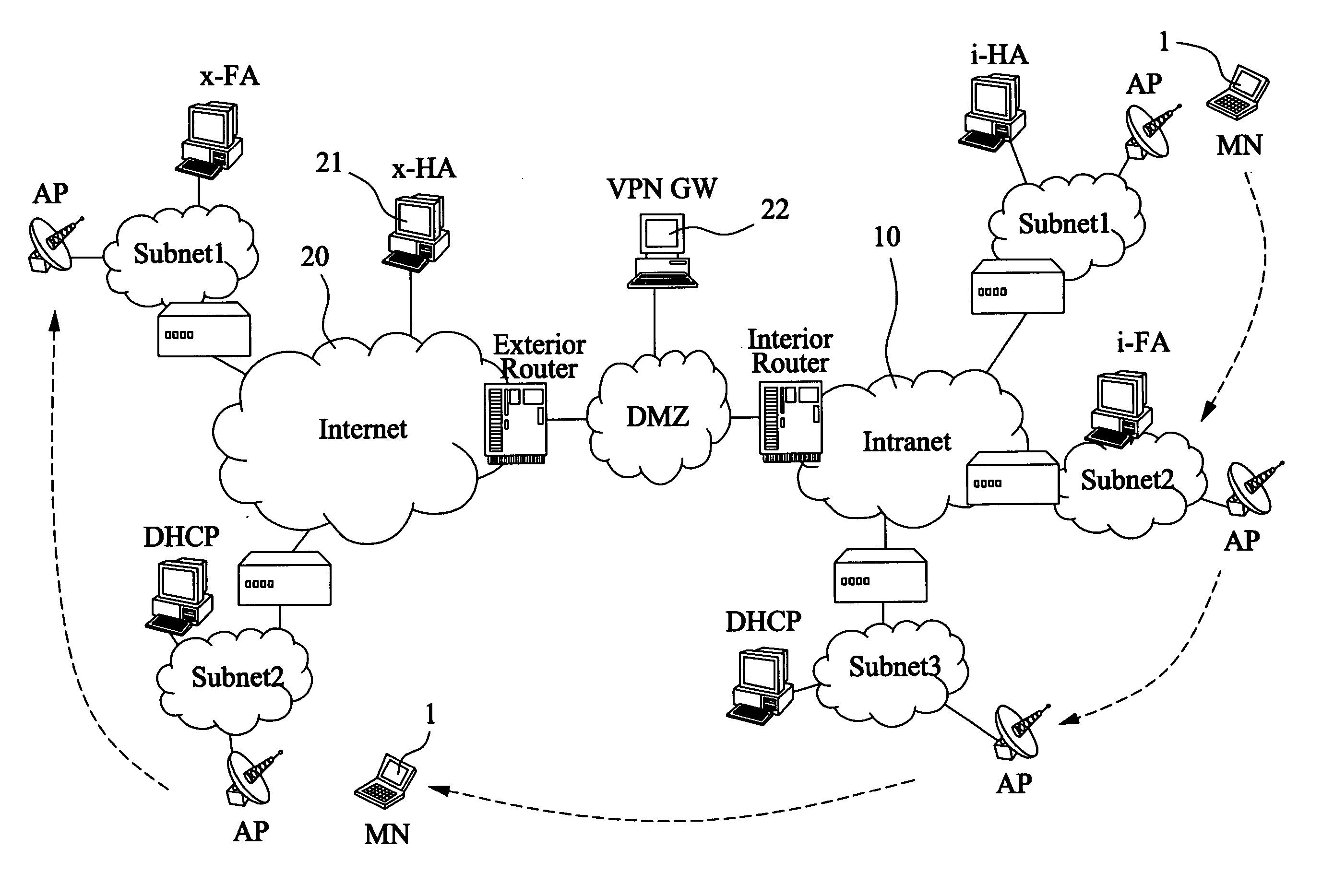
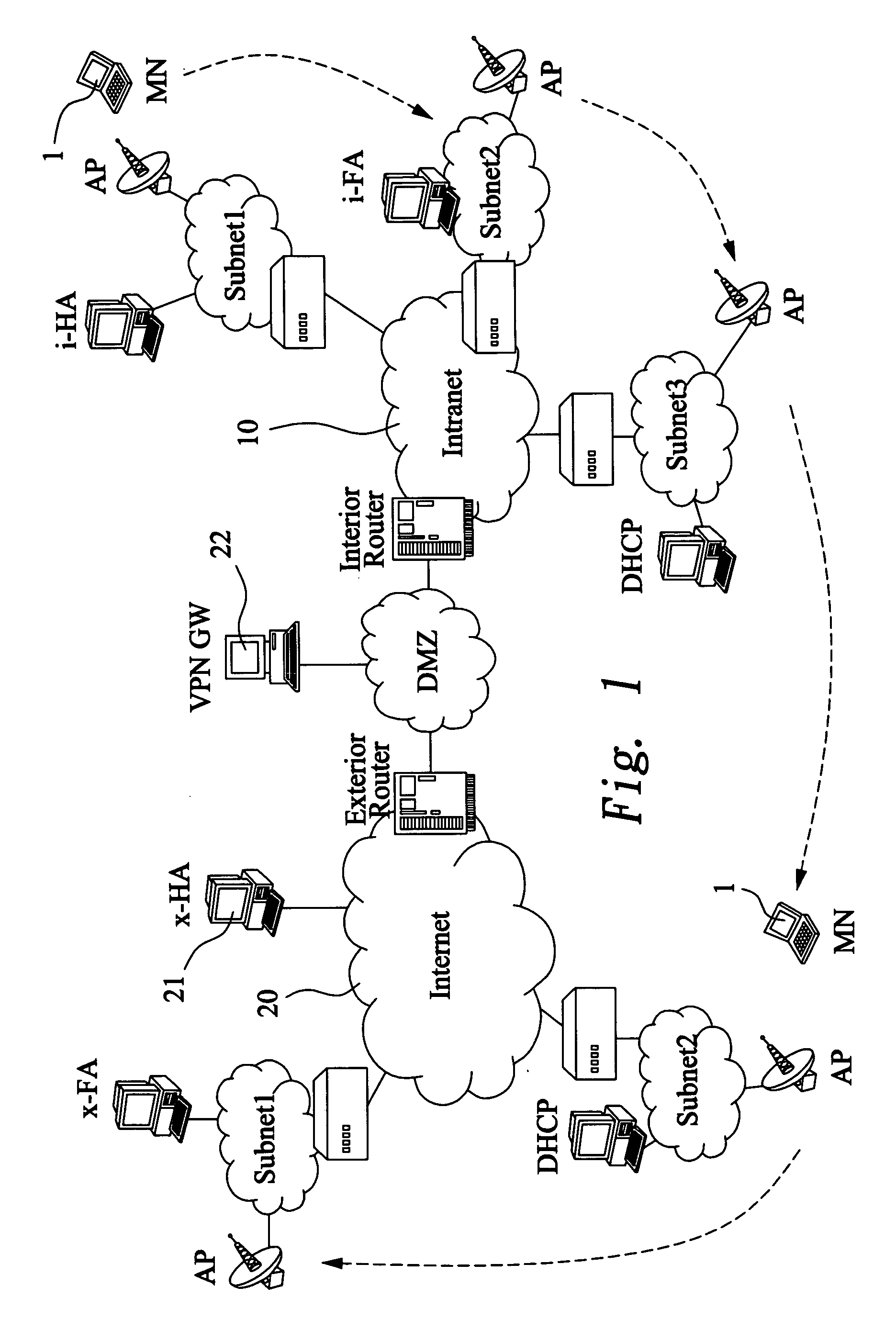
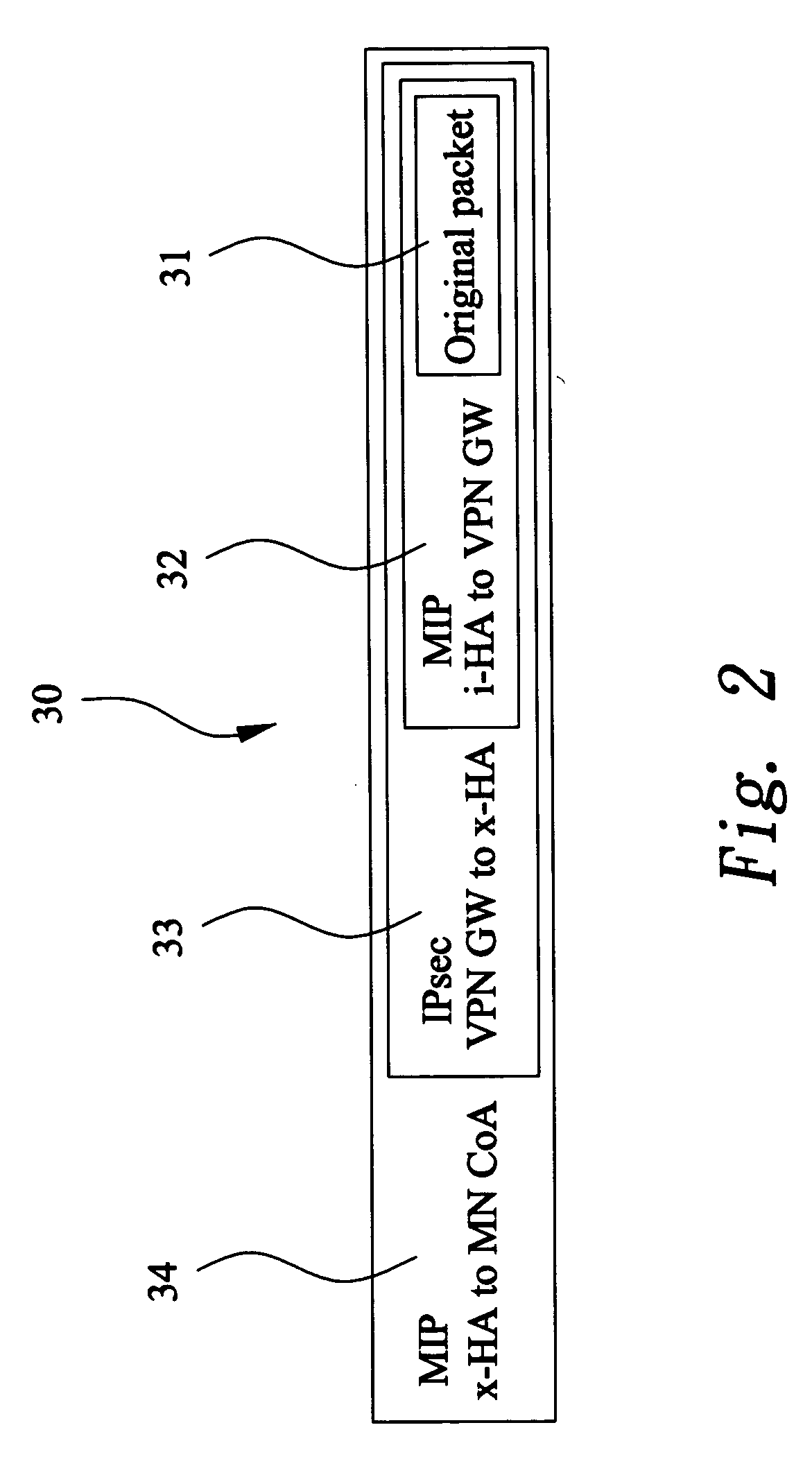
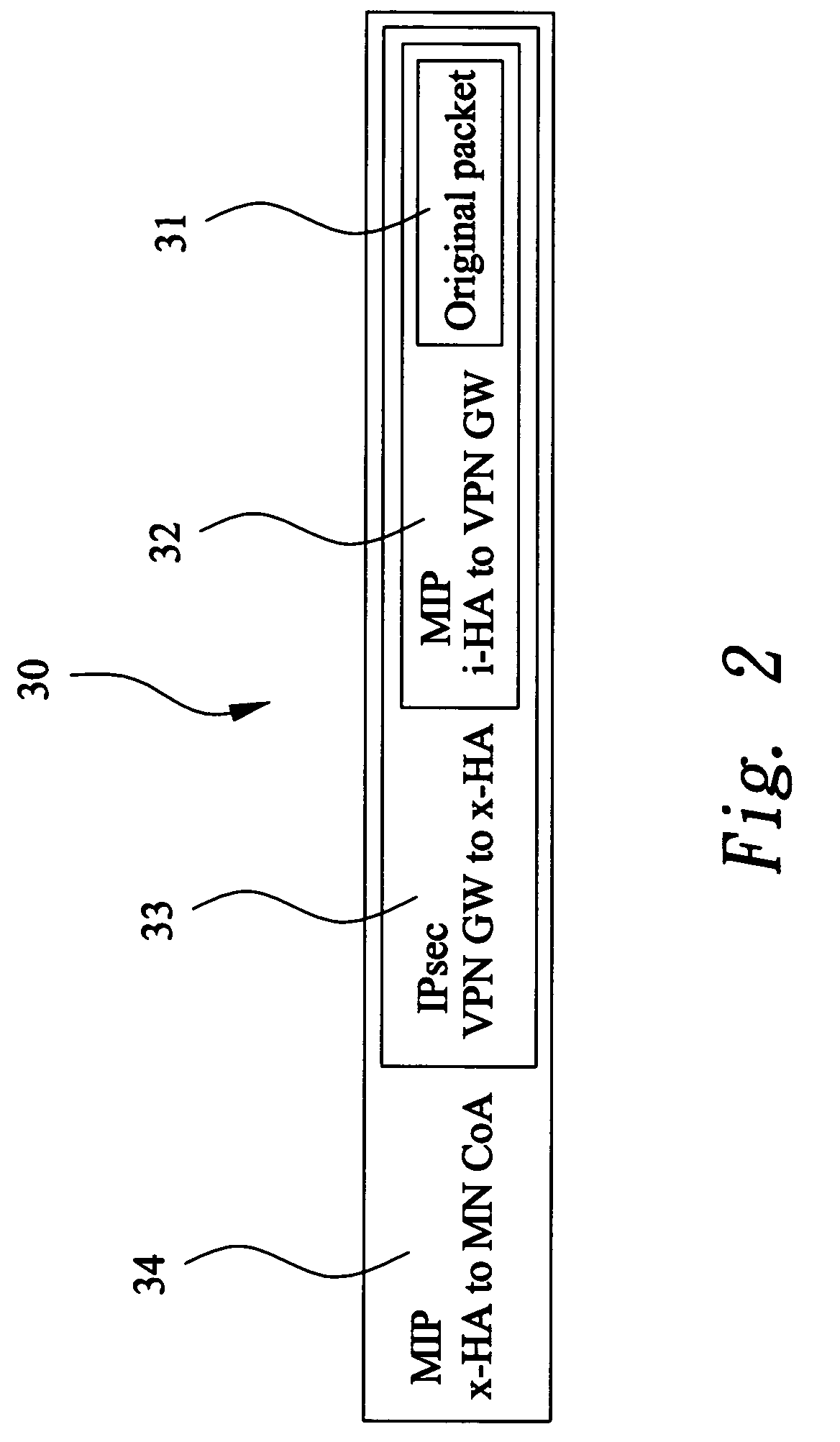
Device to facilitate the deployment of mobile virtual private networks for medium/large corporate networks
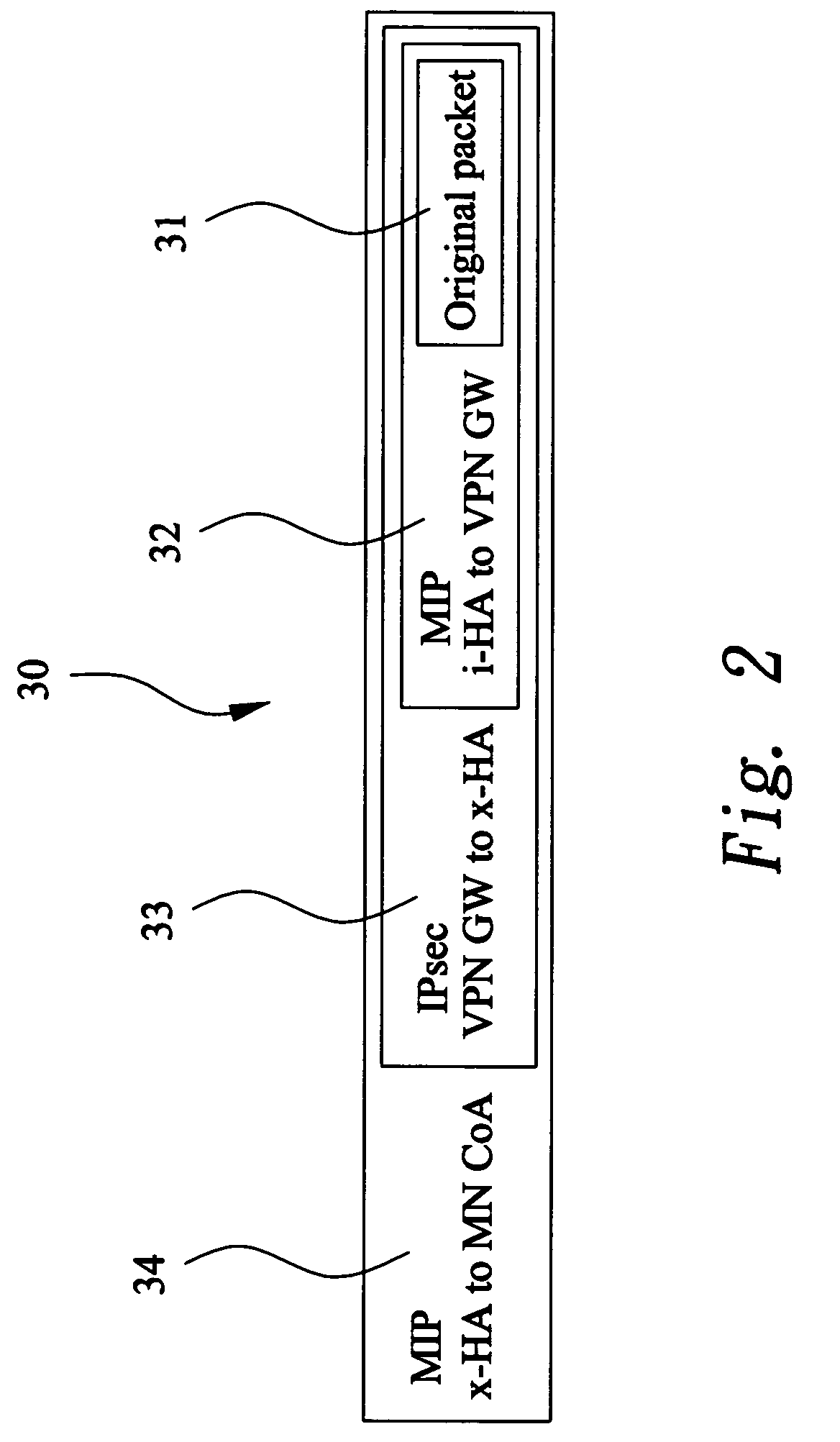
InactiveUS20070008924A1Substantial tunneling overheadFacilitating optimal traffic flowWireless network protocolsRadio/inductive link selection arrangementsIPsecUser authentication
A mobile agent device in a Mobile Virtual Private Network, said device comprising: termination of Mobile IP tunnel (6) from a remotely connecting Mobile Node (1); termination of an IPSec VPN tunnel (7) from the remotely connecting Mobile Node; dynamic Selection of Internal Mobile IP Home Agent based on user Authentication; tunneling of traffic to and / or from the assigned Internal Mobile Home Agent for this Mobile Node; and, provision of extended authentication, after Mobile IP connection establishment, and during the VPN negotiation phase, based on extra user credentials, one-time-password mechanism or similar.
Owner:RADIO IP SOFTWARE
Apparatus of dynamically assigning external home agent for mobile virtual private networks and method for the same
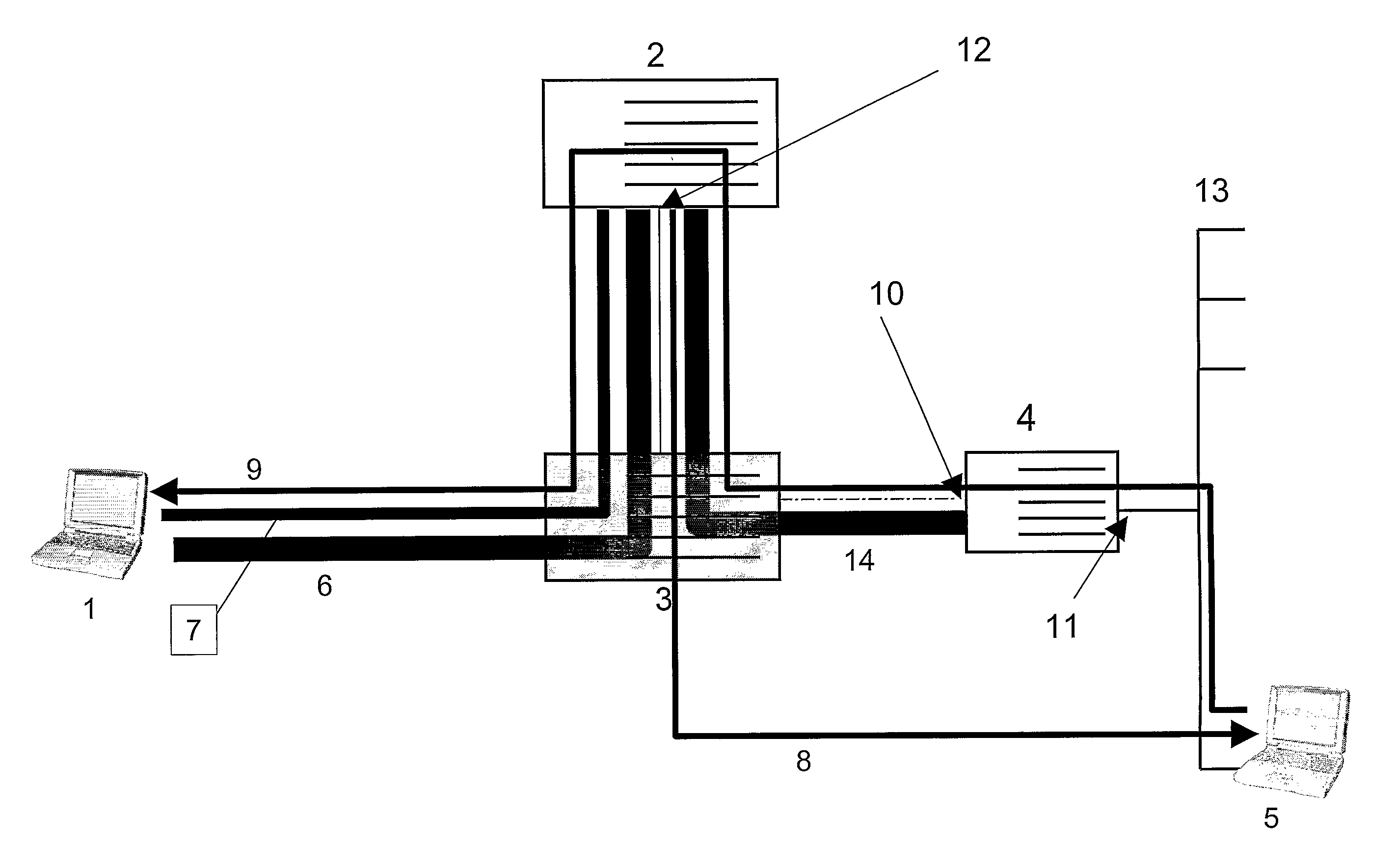
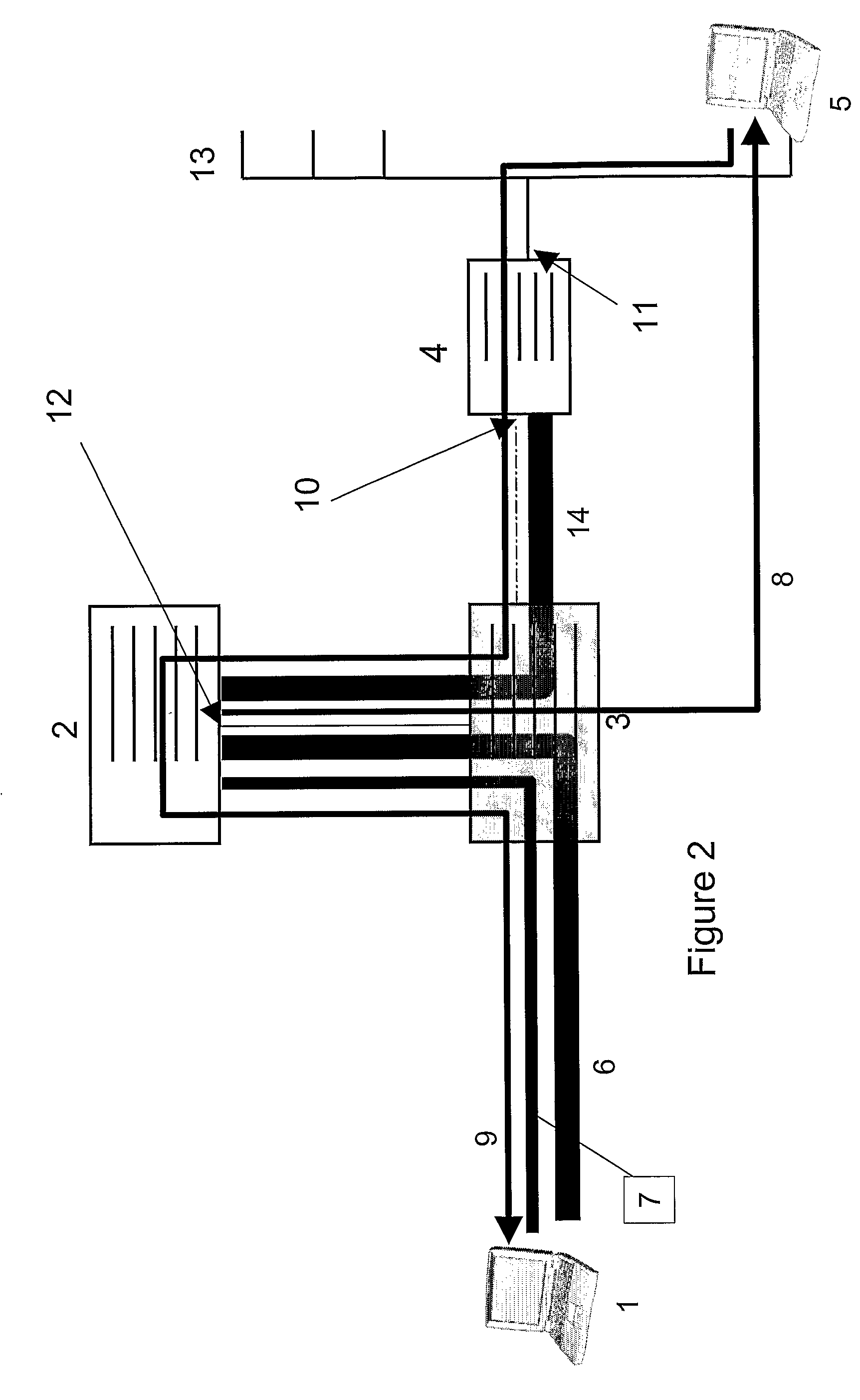
InactiveUS20060067271A1Reduce switching delayData switching by path configurationMultiple digital computer combinationsIPsecMobility management
An apparatus dynamically assigns external home agent (HA) for VPNs and a method for the same is proposed. The apparatus establishes VPN between an internal network and at least one external network, whereby a mobile node (MN) can roam in the external network with security. The external HA closest to the MN in the visited external network is selected for mobility management of the MN. The MN only needs to register with the same external HA when roaming in the same external network. The handoff latency and end-to-end latency for a roaming MN, therefore, could be reduced significantly. It will also not reestablish the IPsec tunnel within the same external network.
Owner:ZYXEL
Method and system for extended use of quantum keys in IPSec VPN (internet protocol security-virtual private network)
ActiveCN104660603ANovel structureIncrease update frequencyKey distribution for secure communicationData switching networksSession keyKey management
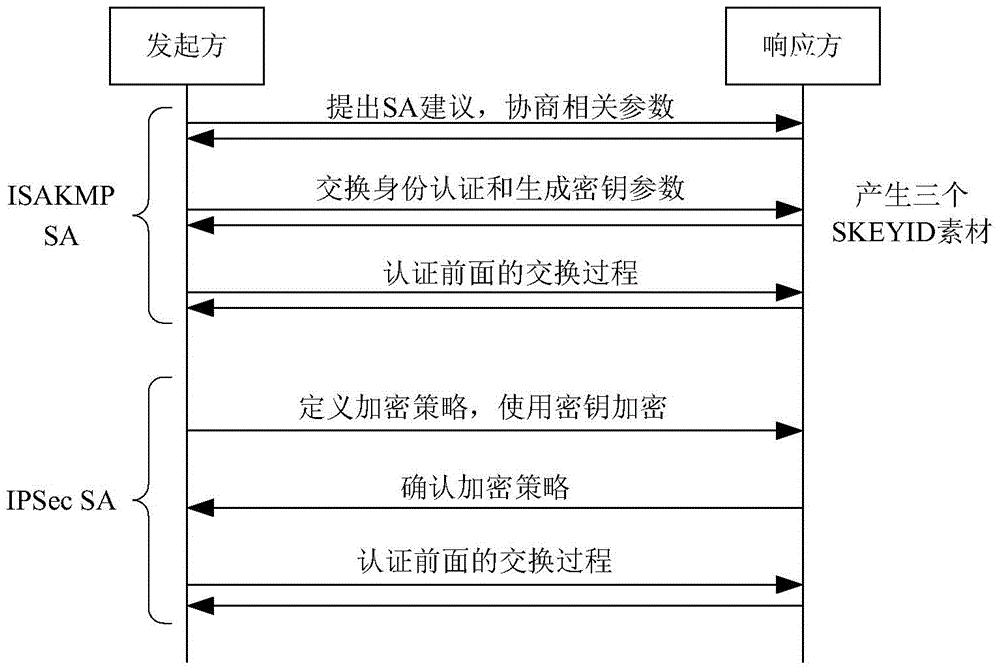
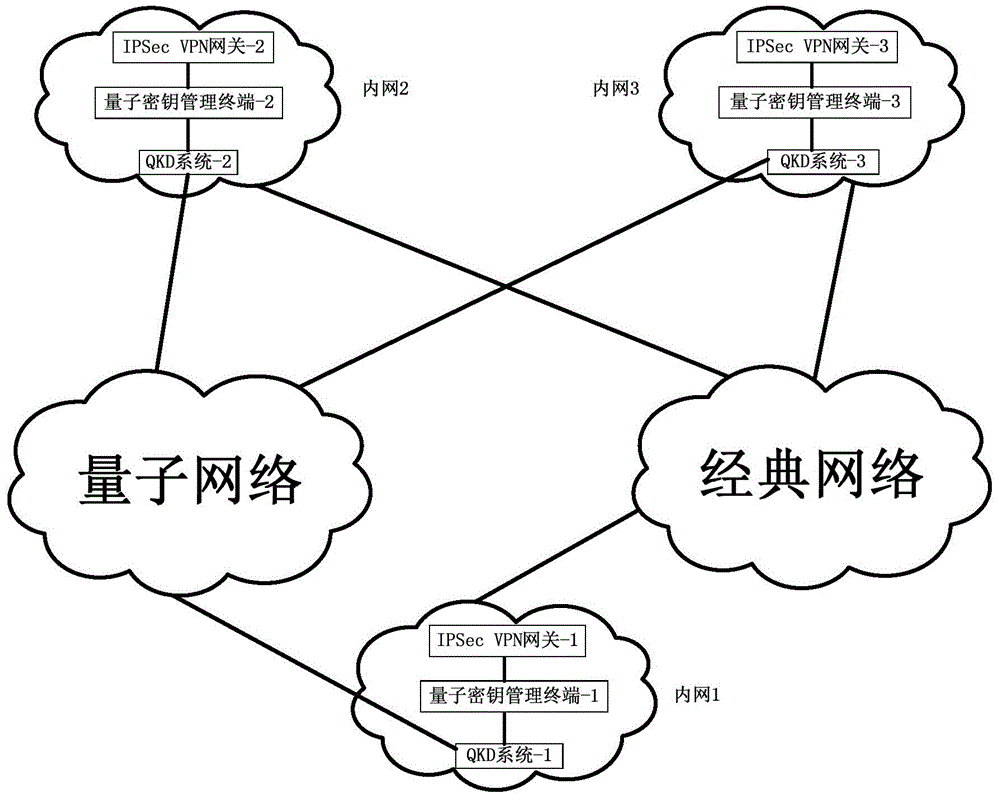
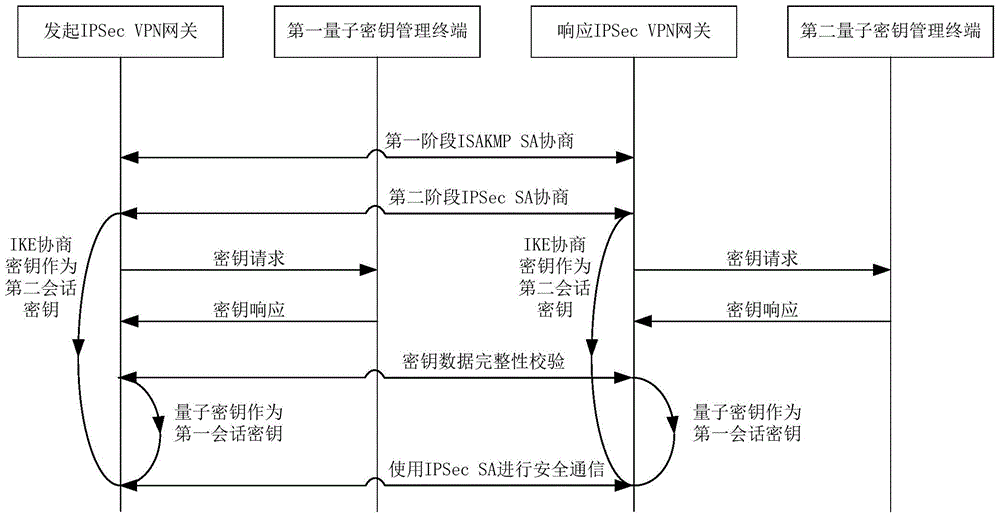
The invention discloses a method and a system for extended use of quantum keys in an IPSec VPN (internet protocol security-virtual private network) system. The IPSec VPN system comprises at least two IPSec VPN gateways including an initiating IPSec VPN gateway and a responding IPSec VPN gateway as well as corresponding quantum key management terminals. The method comprises steps as follows: through parallel processing of negotiation of the quantum keys and IKE (internet key exchange) negotiated keys, the quantum keys are taken as first session keys for preferential use, and the IKE negotiated keys are taken as second session keys for safety communication. Besides, the invention further provides the corresponding IPSec VPN gateway, the quantum key management terminals and the IPSec VPN system. The quantum keys are taken as the session keys through extended use, so that the session key updating frequency is greatly increased and the safety communication performance of conventional IPSec VPN is guaranteed under the condition that an original IPSec VPN is compatible.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +1
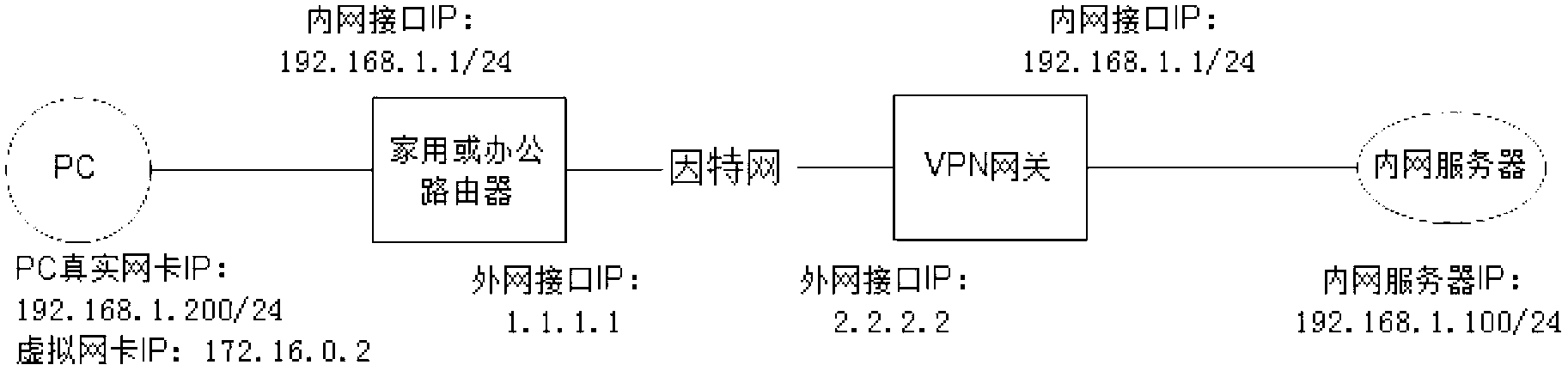
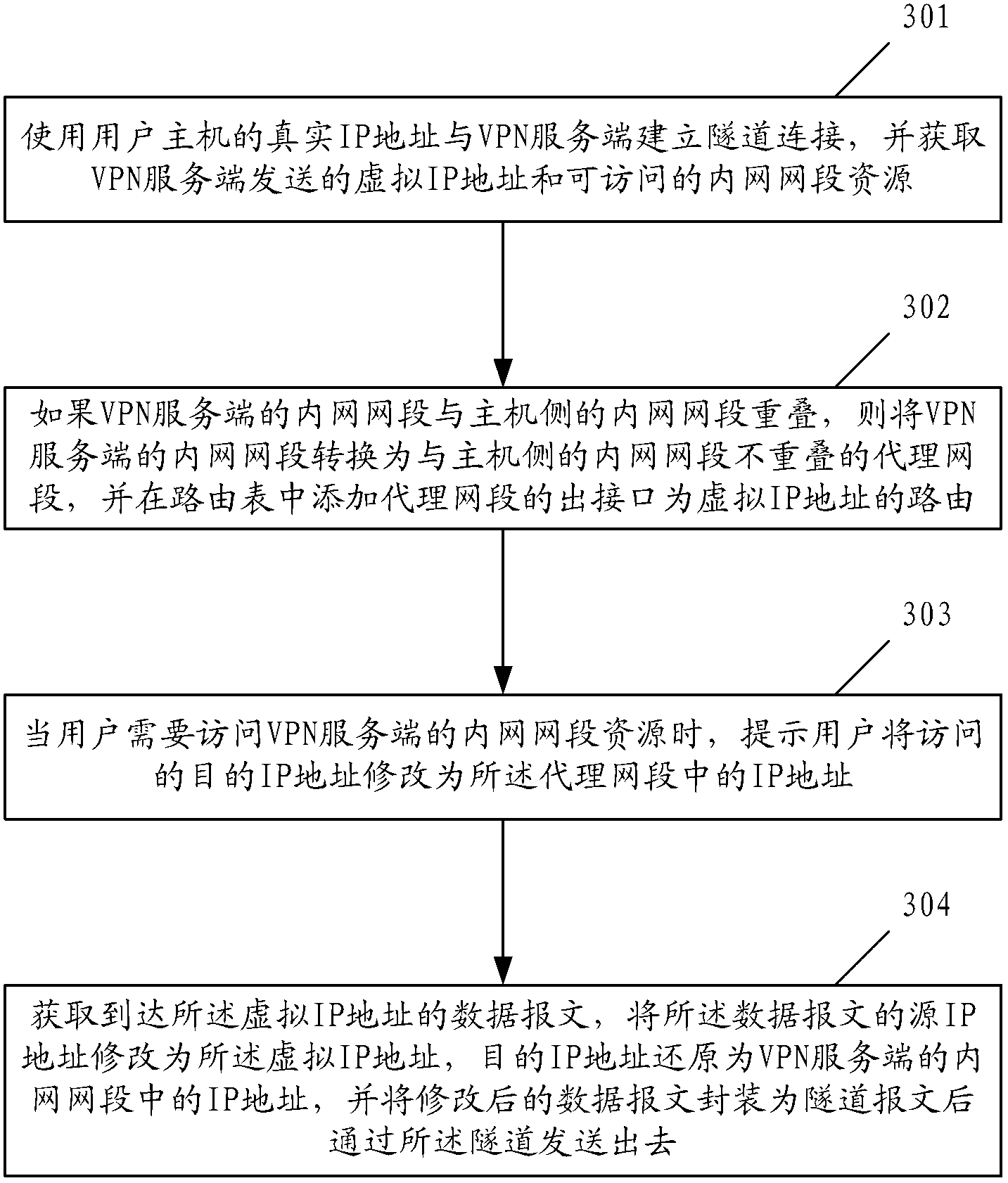
Method and device for accessing intranet resource of virtual private network (VPN) server
The invention provides a method and device for accessing an intranet resource of a virtual private network (VPN) server. The method includes that a real internet protocol (IP) address is used for building tunnel connection with the VPN server, and a virtual IP address sent by the VPN server and an accessible intranet section resource are obtained; an intranet section of the VPN server is overlapped with an intranet section of a host side, the intranet section of the VPN server is changed into a proxy network section which is not overlapped with the intranet section of the host side, and an output interface of the proxy network section is added into a routing table and used as a virtual IP route; if addresses are overlapped, users are prompted to revise an accessed target IP address into an IP address in the proxy network section; and a datagram reaching a virtual network interface card is obtained, the target IP address is restored into the IP address in the intranet section of the VPN server, and the datagram is packaged into a tunnel datagram and sent out through a tunnel. By means of the method and device, the problem that a user host can not access the intranet resource of the VPN server normally due to address overlapping can be solved.
Owner:杭州迪普信息技术有限公司
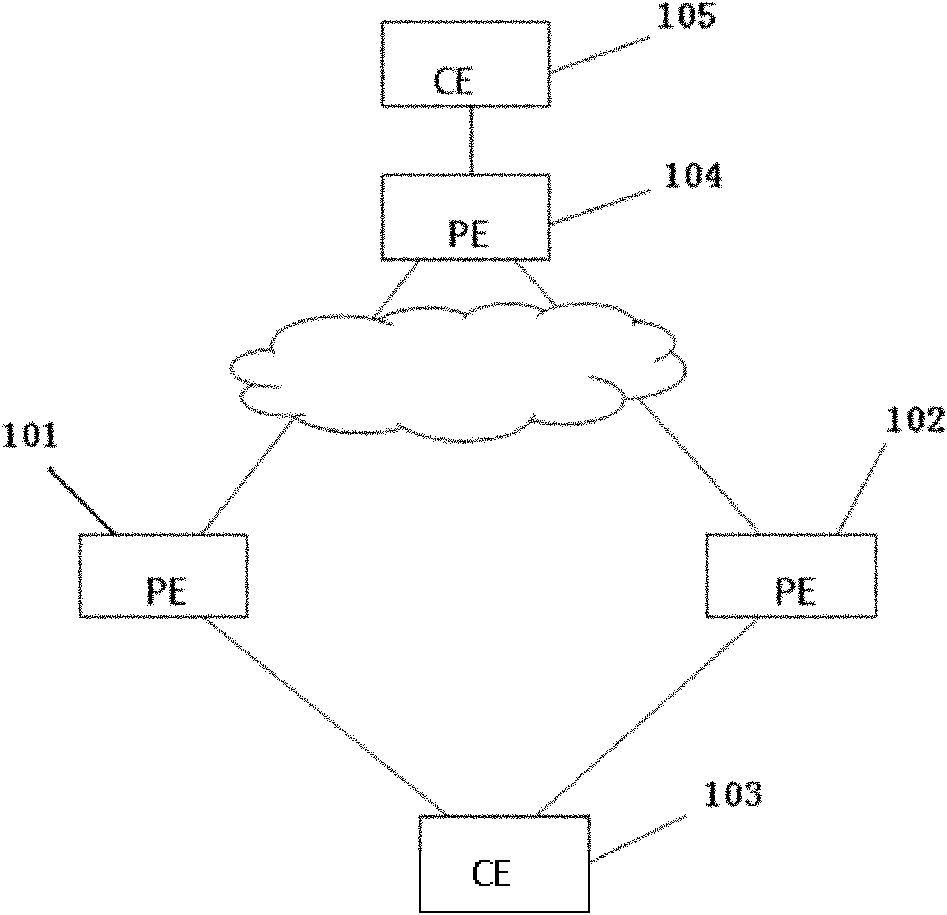
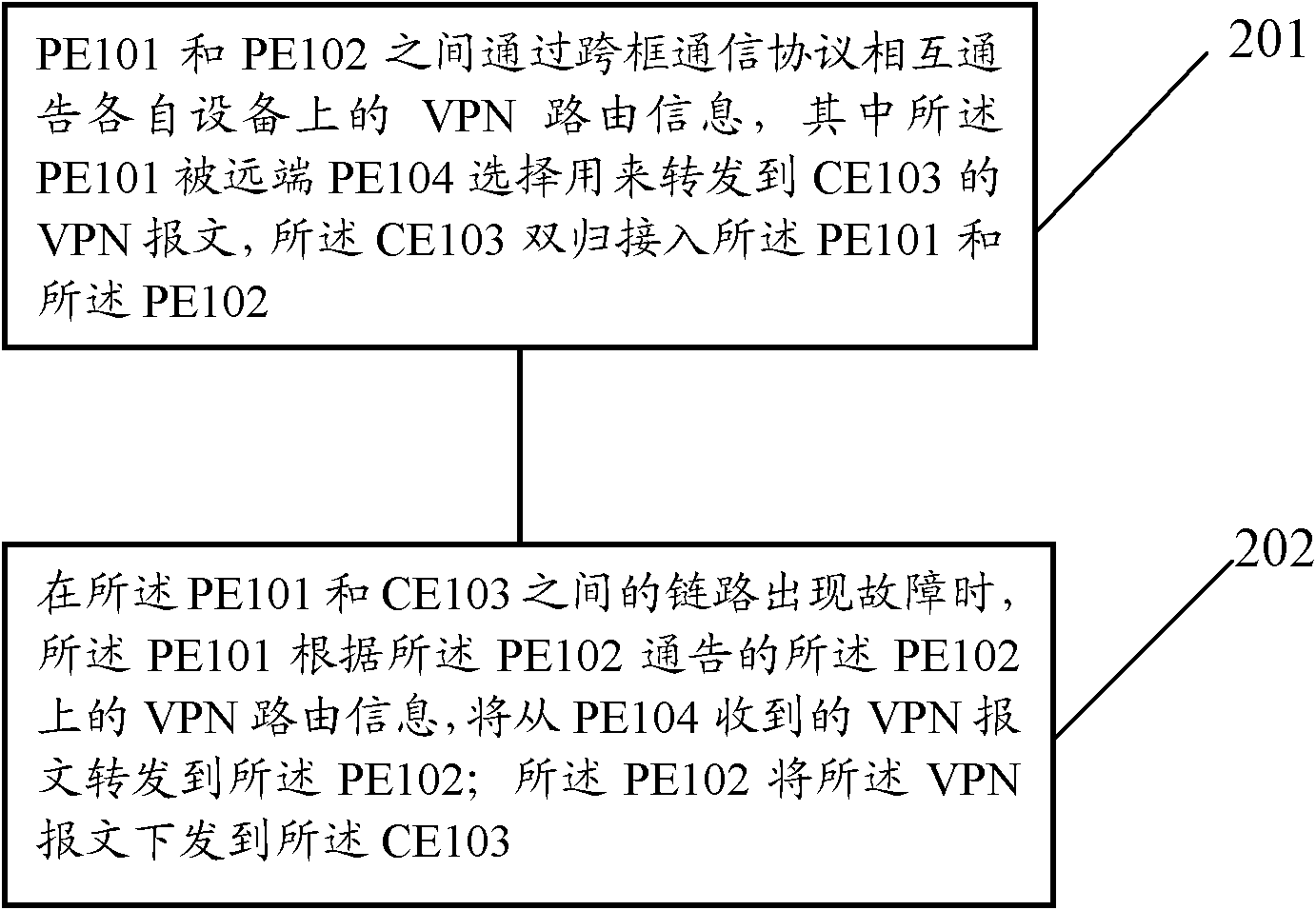
Method and equipment for real-time recovery of virtual private network (VPN) message forwarding in L3VPN
ActiveCN101977150AReduce loss rateNetworks interconnectionNetwork Communication ProtocolsProtocol for Carrying Authentication for Network Access
The embodiment of the invention provides a method for the real-time recovery of VPN message forwarding in three-layer virtual private network (L3VPN), which comprises the following steps: the VPN routing information of the respective equipment is mutually announced between first operator edge equipment PE and second PE through a cross-frame communication protocol; the first PE is selected by far-end PE to be used for forwarding the VPN message of user edge equipment CE; the CE is accessed to the first PE and the second PE in a double return mode; the first PE forwards the VPN message received from the far-end PE to the second PE according to the VPN routing information on the second PE announced by the second PE when a link between the first PE and the CE malfunctions; and the second PE transmits the VPN message to the CE. When the access side breaks down, the normal forwarding of the VPN message can be realized in the L3VPN network so as to reduce the loss probability of the VPN when malfunctions appear by adopting the technical scheme provided by the embodiment of the invention.
Owner:HUAWEI TECH CO LTD
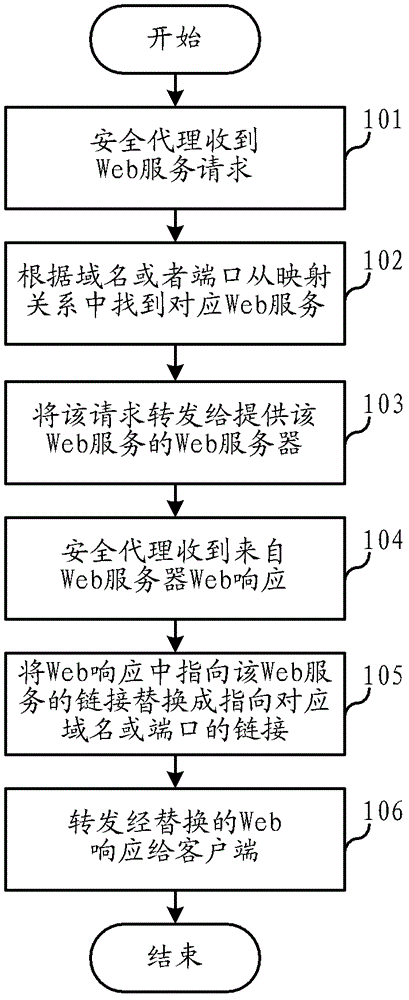
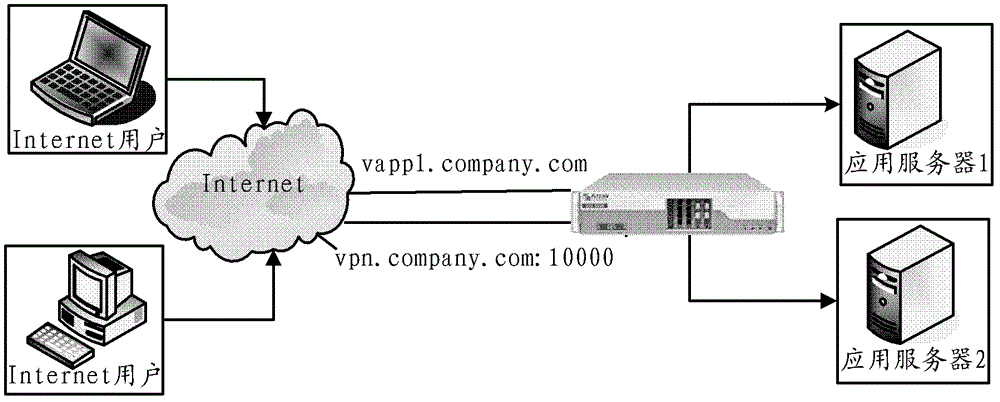
Web service mapping method and system of security agent in virtual private network (VPN)
The invention relates to the field of communications, and discloses a web service mapping method and a system of a security agent in a virtual private network (VPN). Web response analysis and rewriting processes are simplified, achieving is easy, and stability and efficiency are high. In the web service mapping method and the system of the security agent in the VPN, the mapping relation of a domain name or a port which supplies web services and security agents is preset by the security agent in the VPN, wherein different web services correspond to different domain names or different ports. When the security agent receives a web service request from a client terminal, a corresponding web service is found from the mapping relation according to the domain name in the request or the port which receives the request, and the request is forwarded to a web server which supplies the web service. When the security agent receives a web response from the web server, according to the mapping relation, chaining which points to the web service in the web response is replaced by chaining which points to a corresponding domain name or a corresponding port of the security agent, and then the replaced web response is forwarded to the client terminal.
Owner:ARRAY NETWORKS BEIJING
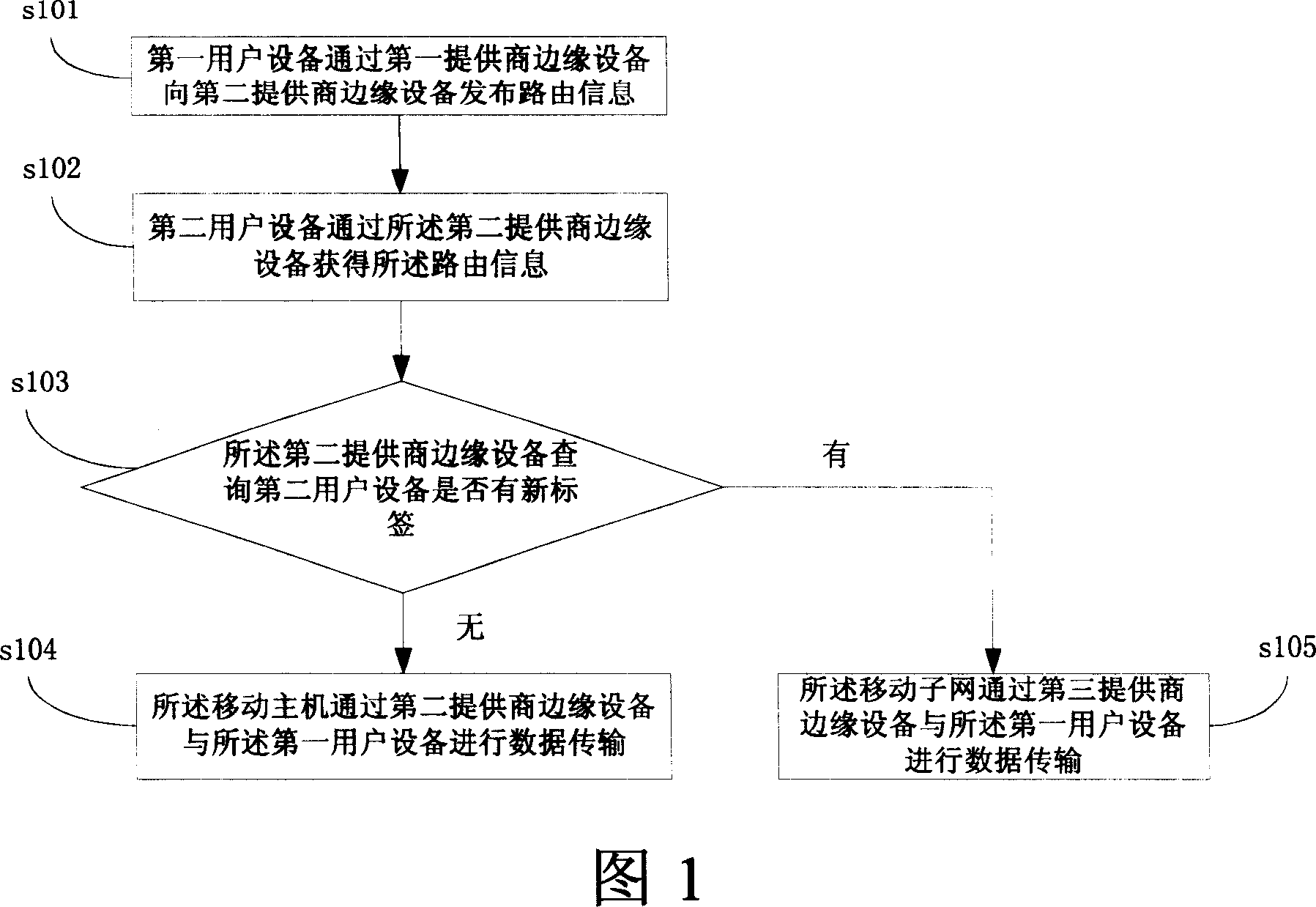
Realizing method and system for movable virtual special net
InactiveCN101052207ASolve the defect that it cannot support virtual private network mobilityFeel free to contactRadio/inductive link selection arrangementsWireless commuication servicesData transmissionUser equipment
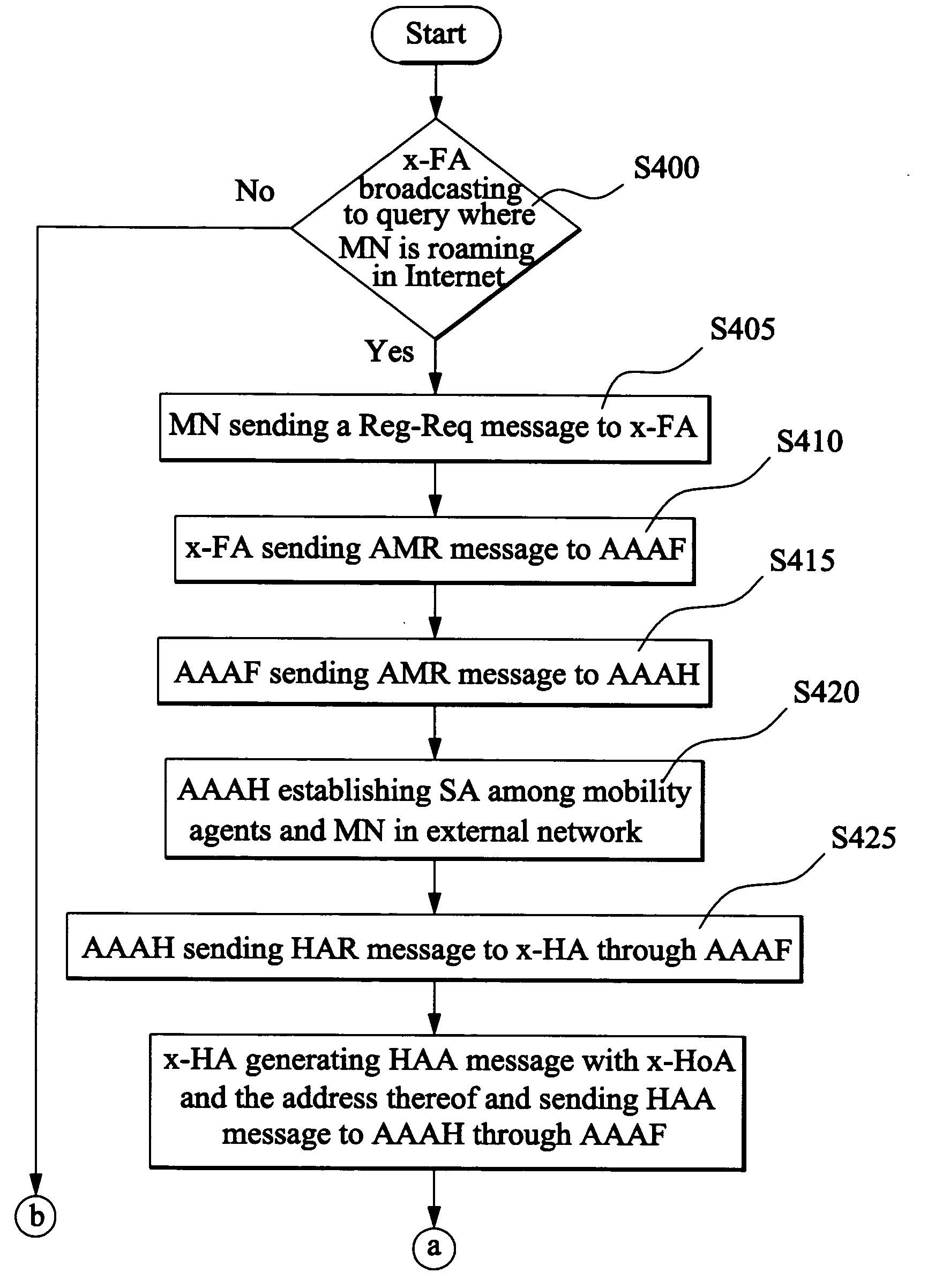
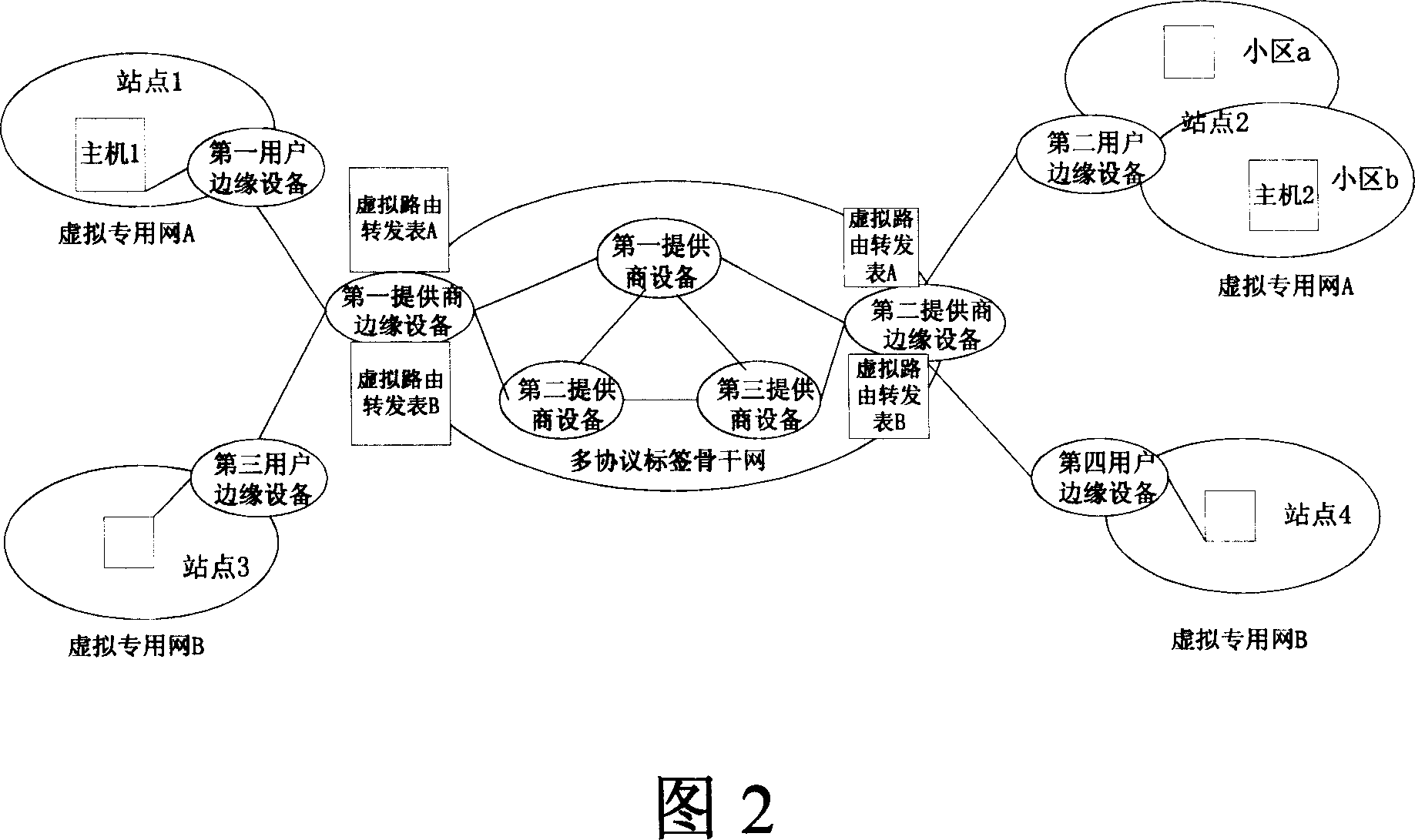
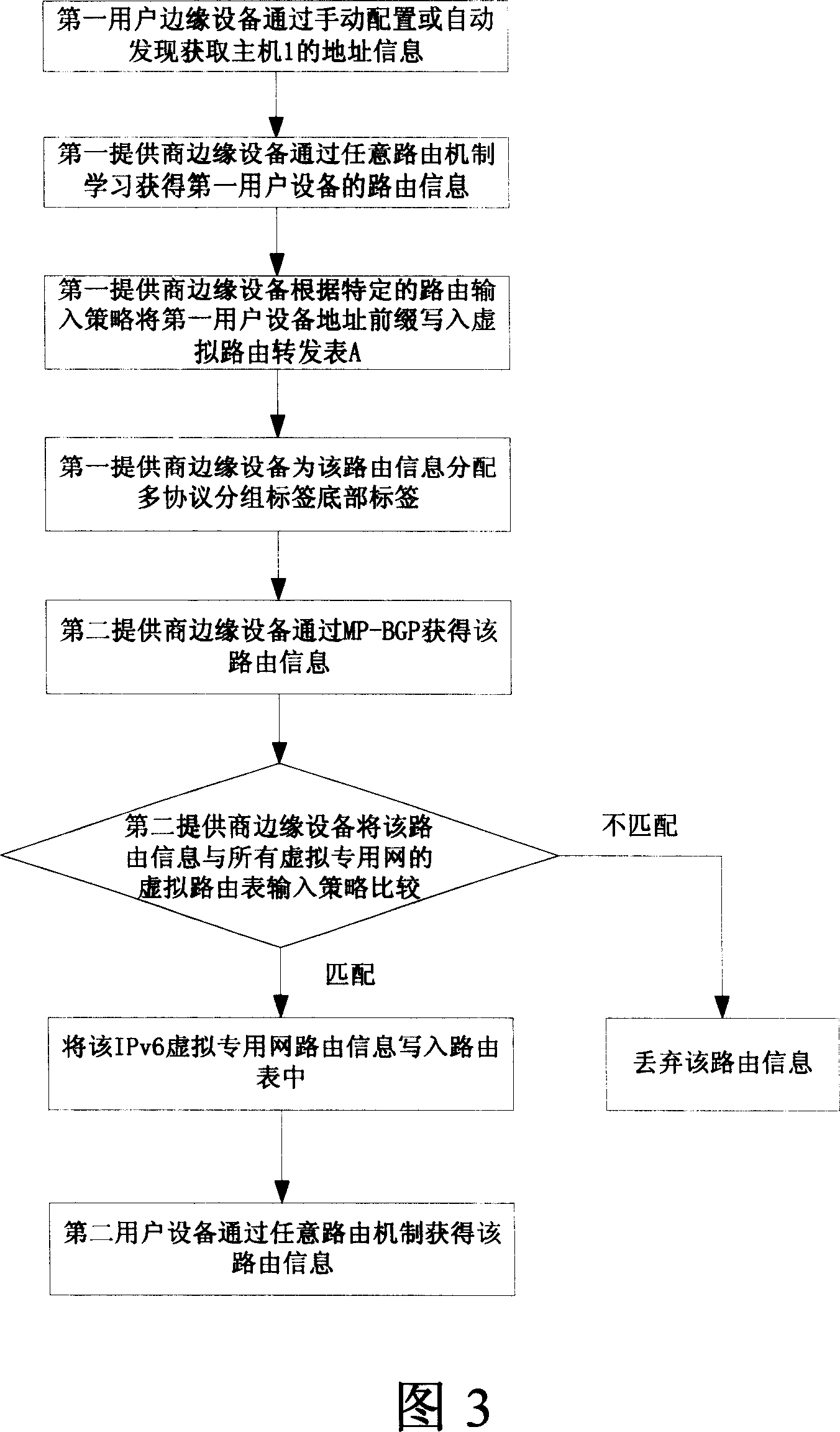
The method comprises: first user's device releases the route message to the edge router of second service provider through the edge router of the first service provider; the second user's device gets the route message through the second service provider; the edge router second service provider enquires if the second user's device has a new label; if yes, it indicates that the second user's device is a mobile sub-network; the mobile sub-network makes data transmission with the first user's device through a third service provider; otherwise, it indicates the second user's device is a mobile host machine; the mobile host machine makes communication with said first user's device through the edge router of the second service provider. The invention also reveals a mobile virtual private network.
Owner:HUAWEI TECH CO LTD +1
Virtual private network communication system, connection method and data packet transmission method
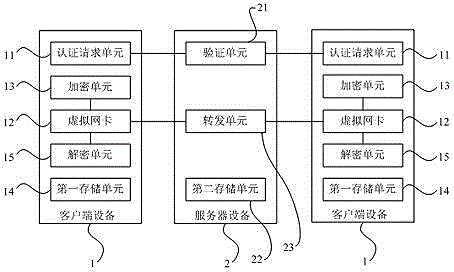
The invention discloses a virtual private network communication system. The virtual private network communication system comprises a plurality of client apparatuses and a server apparatus which establishes VPN connection with the client apparatuses through a virtual private network by using a preset protocol, wherein each of the client apparatuses comprises an authentication request unit, a first storage unit, a virtual network interface card and an encryption unit; the authentication request units are used for sending authentication information to the server apparatus to authenticate; the first storage units are used for storing the MAC address linked list of opposite-end client and the IP address of the server apparatus; the virtual network interface cards are provided with virtual IP addresses belonging to the virtual private network; the encryption units correspond to the virtual network interface cards and are used for encrypting the data packets which need to be sent from the virtual network interface cards. The invention also discloses a virtual private network connection method and a data packet transmission method. According to the virtual private network communication system, the virtual private network connection method and the data packet transmission method, an N2N structure is used for realizing the VPN network so as to ensure that the privacies of both sides of the communication are not revealed, the structure is concise and clear and simplicity and simplification are realized.
Owner:PHICOMM (SHANGHAI) CO LTD
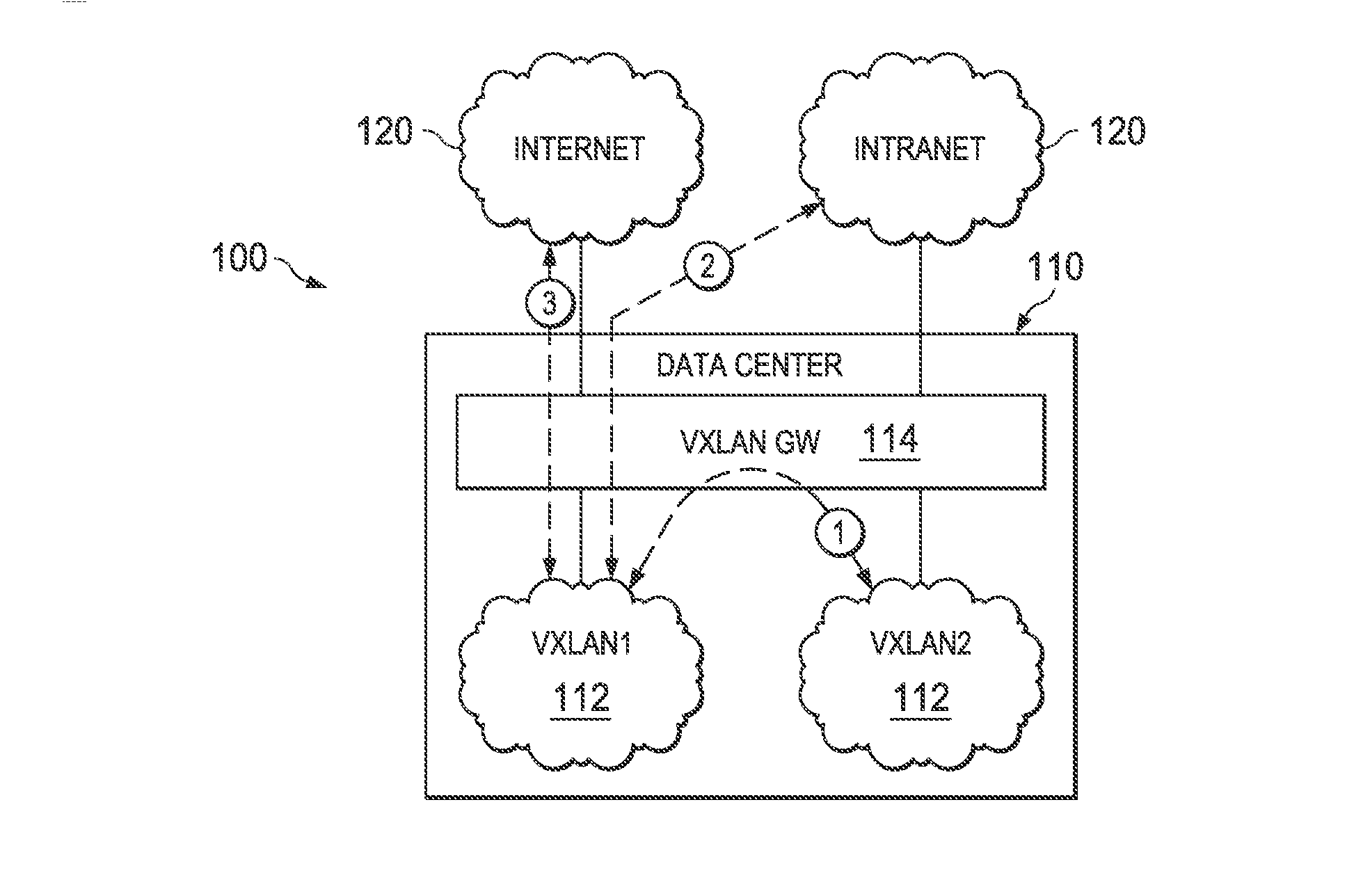
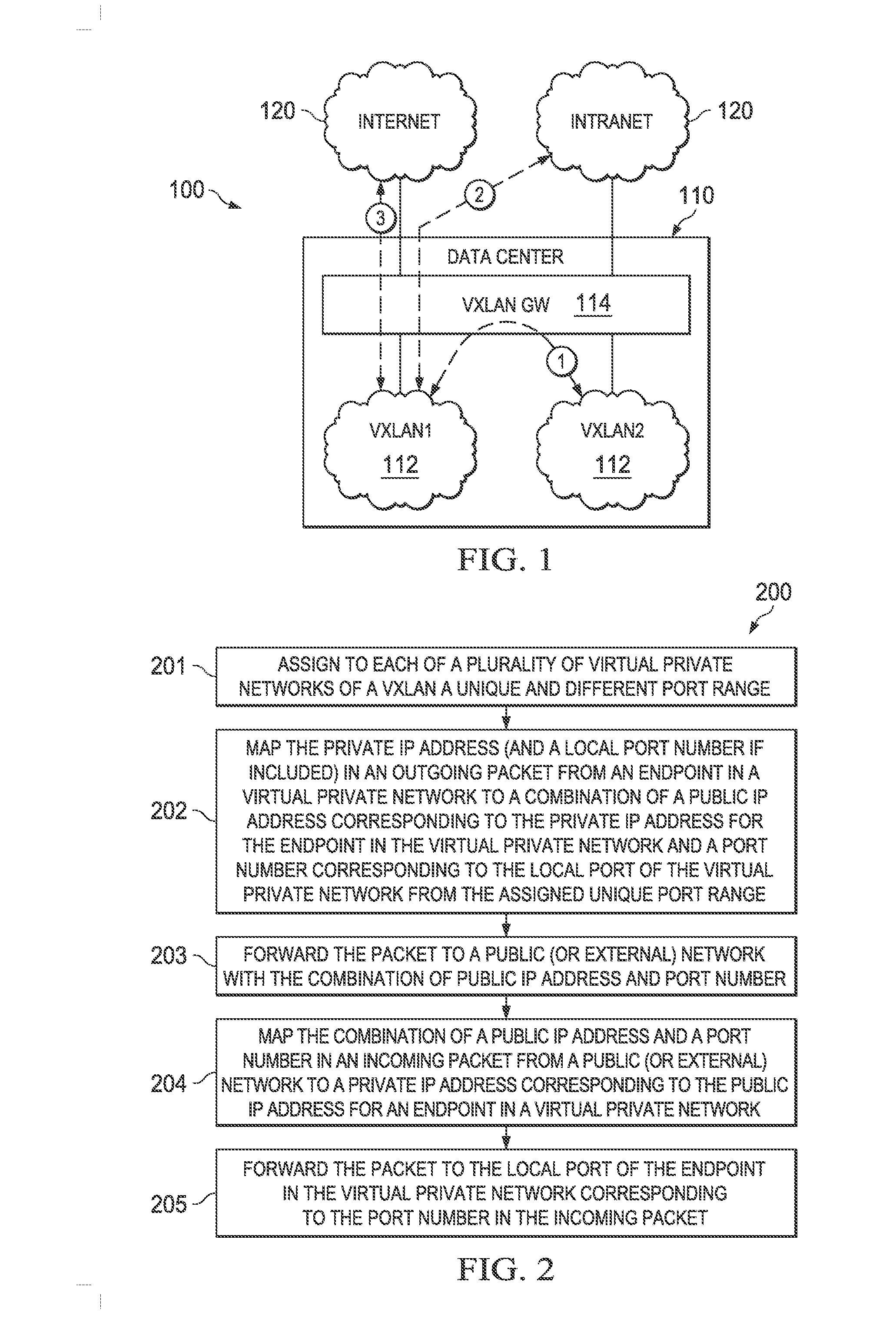
Supporting IP Address Overlapping Among Different Virtual Networks
System and method embodiments are disclosed here to resolve Internet Protocol (IP) address overlap of Virtual eXtensible Local Area Network (VXLAN) endpoints in packets forwarded between the VXLAN and an external or public network. An embodiment method includes assigning different port number ranges to different virtual private networks of the VXLAN, mapping private IP addresses for endpoints at the virtual private networks to corresponding public IP addresses known to a public network, and mapping local ports of the endpoints to corresponding port numbers from the port number ranges assigned to the virtual private networks, wherein each of the endpoints at the virtual private networks is assigned to a unique combination of public IP address and port number. The mapping can be done at a VXLAN gateway or at the endpoints on physical servers of the virtual private networks.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Link protection method and system for virtual private network
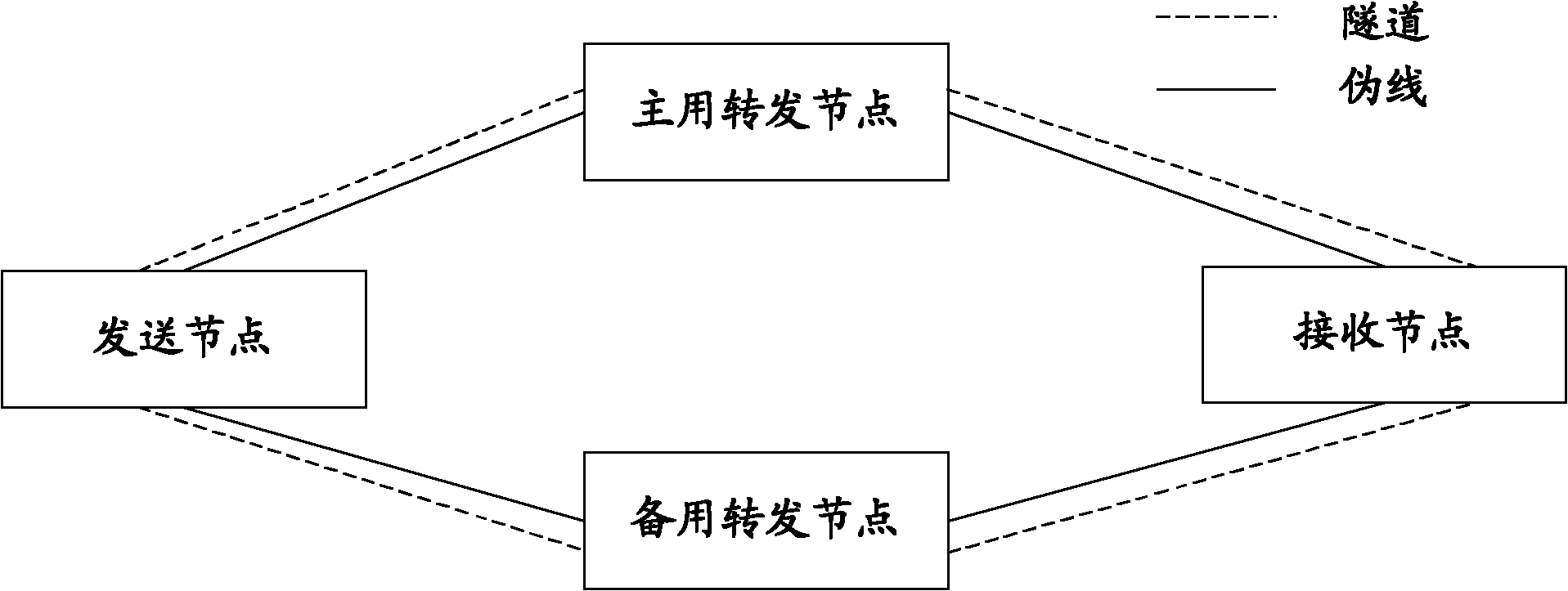
ActiveCN102035681AAchieving partial protectionProcessing content lessNetworks interconnectionPseudo-wireMobile virtual private network
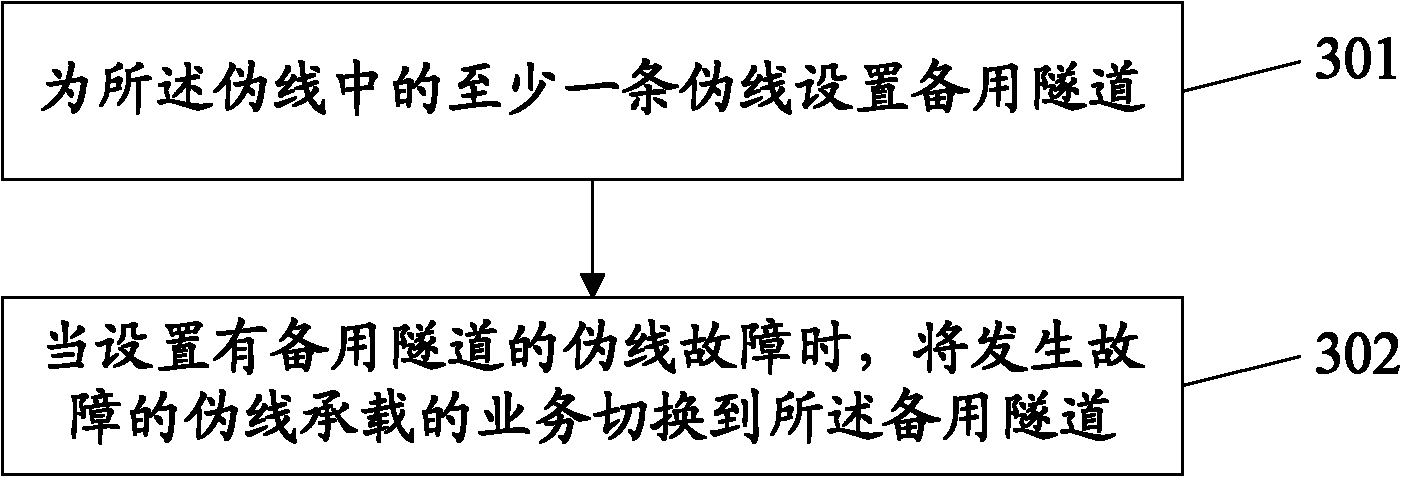
The invention provides a link protection method and a link protection system for a virtual private network and relates to the field of communication. Transmitting nodes and receiving nodes in the virtual private network are connected with main forwarding nodes and standby forwarding nodes through pseudowires. The method comprises the following steps of: setting a standby tunnel for at least one pseudowire in the pseudowires; and when the pseudowire provided with the standby tunnel breaks down, switching failed pseudowire-born service to the standby tunnel. The provided technical scheme can be applied to link protection management of a double-layer virtual private network.
Owner:ZTE CORP
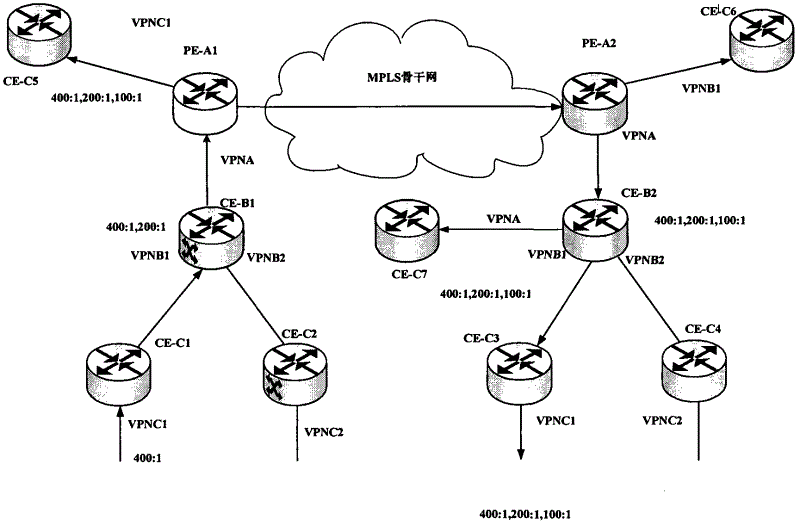
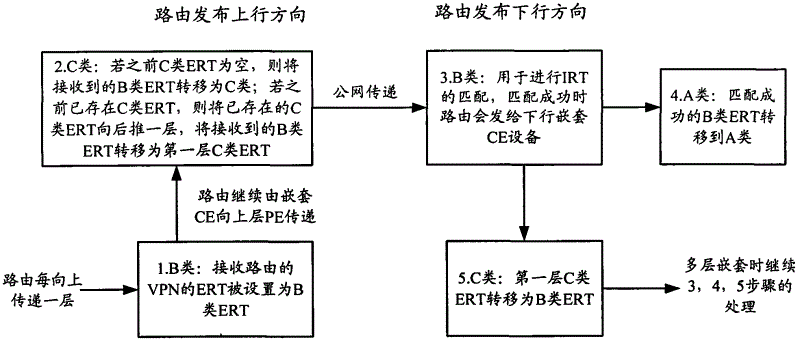
Virtual private network (VPN) routing information publication method and equipment
ActiveCN102624623AImprove securityNetworks interconnectionRouting tableMobile virtual private network
The invention discloses a virtual private network (VPN) routing information publication method and VPN routing information publication equipment, and is applied to a multi-protocol label switch layer-three virtual private network (MPLS L3VPN). The method comprises the following steps that: a customer edge receives a routing publication message from an uplink customer edge or an opposite-end customer edge, wherein the routing publication message carries nested VPN routing information and VPN attribute information; and the customer edge matches an import route target (IRT) of a local VPN and an export route target (ERT) of a VPN of a specified type in the VPN attribute information carried by the message, updates a local routing table according to the VPN routing information if the IRT of the local VPN is matched with the ERT of the VPN of the specified type, changes the specified type into the next-layer nested ERT of the ERT of the conventional specified type in the VPN attribute information, and transmits the routing publication message carrying the nested VPN routing information and the VPN attribute information to a corresponding VPN according to the matched IRT of the local VPN. The security of nested VPN routing publication can be improved.
Owner:XINHUASAN INFORMATION TECH CO LTD
Implementation method of VPN (virtual private network) on basis of SDN (software defined network)
The invention provides an implementation method of a VPN (virtual private network) on basis of an SDN (software defined network). The method comprises steps as follows: a user uses a northbound interface provided through an SDN controller to send a service request for establishing the VPN; the SDN controller receives the service request which comes from the user and is used for establishing the VPN, and the service request comprises a service type and service parameters; the SDN controller performs packaging processing on a data packet from a local area network host according to the service type and the service parameters, and the data packet is sent to a designated foreign network through an OpenFlow exchanger; after an SDN controller of the foreign network receives the data packet, corresponding de-encapsulation processing is performed, and the network data packet of a sender is recognized; finally, the VPN is established between networks of two places. According to the method, the VPN is partitioned in an SDN service deployment manner; the problems of single configuration manner, complicated configuration and management and difficulty in maintenance of conventional VPN configuration are solved.
Owner:NANJING ZHAOSHICHANG NETWORK TECH
Intelligent, cloud-based global virtual private network systems and methods
ActiveUS9350710B2Multiple digital computer combinationsProgram controlClient-sideDistributed computing
A method includes connecting to a client at a Virtual Private Network (VPN) device in a cloud system; forwarding requests from the client for the Internet or public clouds accordingly; and, for requests for an enterprise associated with the client, contacting a topology controller to fetch a topology of the enterprise, causing a tunnel to be established from the enterprise to the VPN device, and forwarding the requests for the enterprise through the tunnel. A cloud system and VPN system are also described. Advantageously, connections between the cloud and on-premises proxy are dynamic, on-demand and orchestrated by the cloud. Security is provided at the edge—there is no need to punch any holes in the existing on-premises firewalls.
Owner:ZSCALER INC
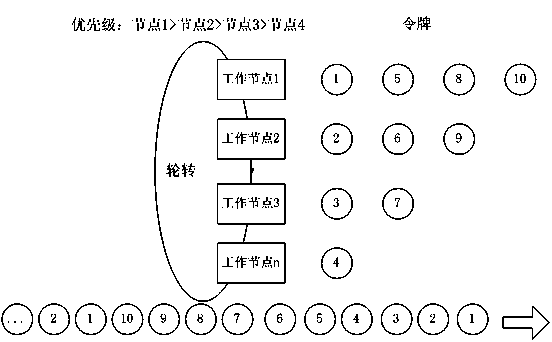
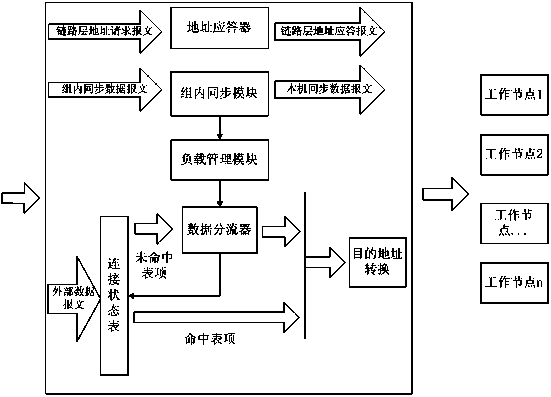
Balanced load SSL VPN (security socket layer, virtual private network) device cluster system and operating method thereof
The invention provides a balanced load SSL VPN (security socket layer, virtual private network) device cluster system and an operating method thereof. The balanced load SSL VPN device cluster system comprises an SSL VPN device serving as a master control node and a plurality of SSL VPN devices serving as worker nodes. An intra-group synchronous module is disposed in each of the SSL VPN devices. The SSL VPN device serving as the master control node is further internally provided with a load management module, an address transponder and a data divider. A cluster centrally provides a globally set virtual IP (internet protocol) address to the outside; the virtual IP address is used as a DNS (domain name server) resolution address for a virtual single SSL VPN device; the whole SSL VPN device cluster is connected with a network node and a server. The balanced load SSL VPN device cluster system and the operating method thereof have the advantages that the operating IP address of the SSL VPN cluster of different SSL VPN devices is unique, load balance and redundant backup are effective, the cost is lowered, and reliability is high.
Owner:中电科网络安全科技股份有限公司
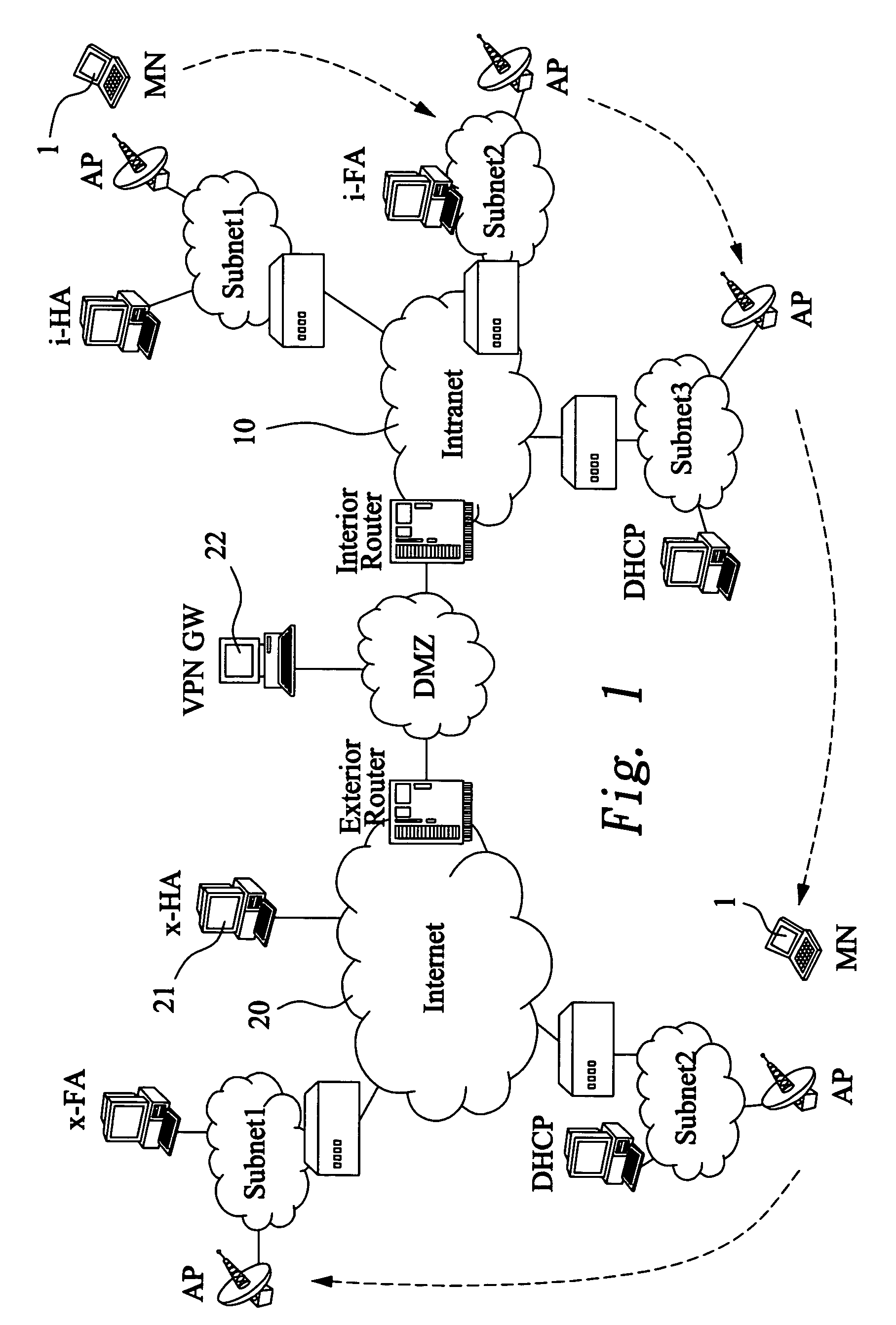
Apparatus of dynamically assigning external home agent for mobile virtual private networks and method for the same
InactiveUS20060067265A1Reduce switching delayWireless network protocolsRadio/inductive link selection arrangementsIPsecMobility management
An apparatus dynamically assigns external home agent (HA) for VPNs and a method for the same is proposed. The apparatus establishes VPN between an internal network and at least one external network, whereby a mobile node (MN) can roam in the external network with security. The external HA closest to the MN in the visited external network is selected for mobility management of the MN. The MN only needs to register with the same external HA when roaming in the same external network. The handoff latency and end-to-end latency for a roaming MN, therefore, could be reduced significantly. It will also not reestablish the IPsec tunnel within the same external network.
Owner:ZYXEL
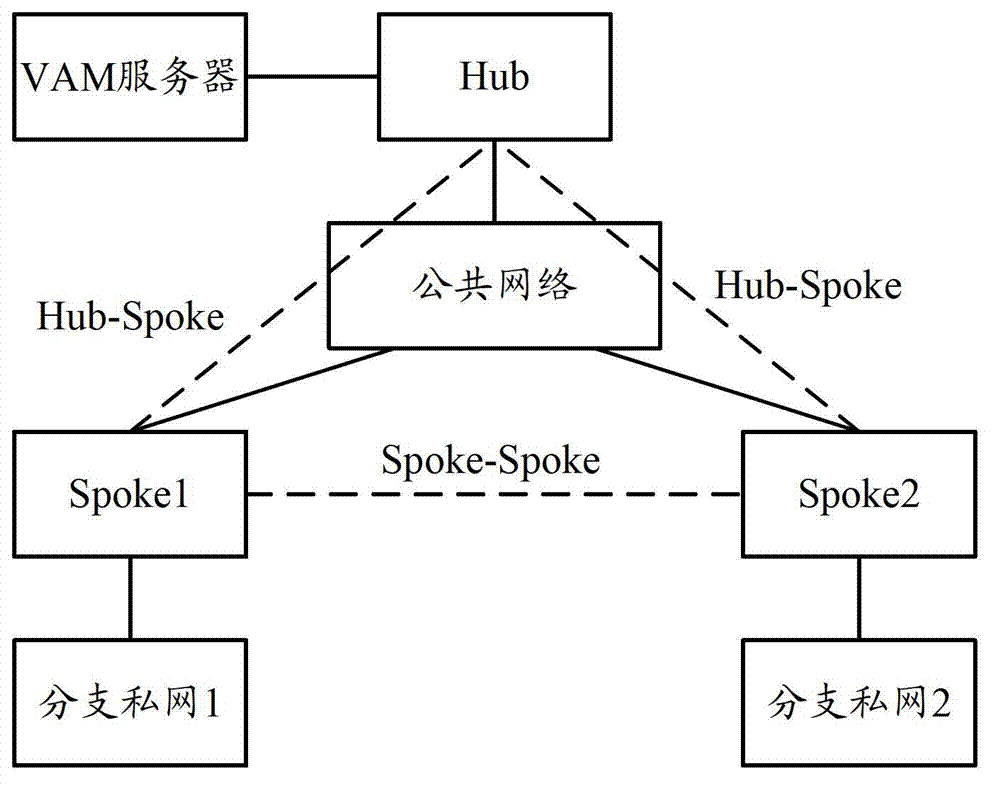
Dynamic virtual private network (DVPN)-based route generation method and equipment
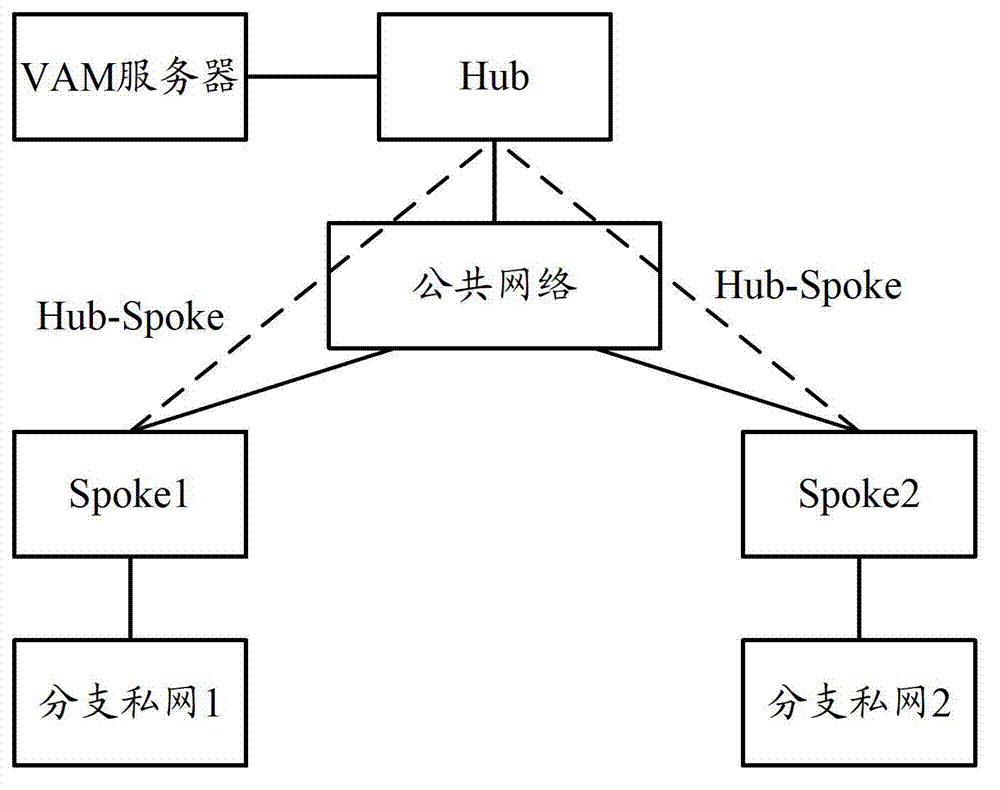
ActiveCN103209108ASimplify the configuration processReduce resource consumptionNetworks interconnectionPublic networkDynamic Multipoint Virtual Private Network
The invention discloses a dynamic virtual private network (DVPN)-based route generation method and DVPN-based route generation equipment. The method comprises the following steps that Hub and Spokes send login request messages to a virtual private network (VPN) address management (VAM) server, wherein a public network address, a private network address and a sub-network network segment which correspond to the Hub are carried in the login request message sent by the Hub, and public network addresses, private network addresses and sub-network network segments which correspond to the Spokes are carried in the login request messages sent by the Spokes; the Spokes and the Hub receive login success response messages from the VAM server respectively; after receiving the login success response messages, the Spokes send tunnel establishing request messages to the Hub, wherein the sub-network network segments corresponding to the Spokes are carried in the tunnel establishing request messages; Hub generates a route by utilizing the sub-network network segments corresponding to the Spokes; the Spokes receive a tunnel establishing success response message of the Hub, wherein the sub-network network segment corresponding to the Hub is carried in the tunnel establishing success response message; and the Spokes generate routes by utilizing the sub-network network segment corresponding to the Hub. By the embodiment of the invention, the consumption of system resources for routing computation on the Hub and the Spokes can be reduced.
Owner:XINHUASAN INFORMATION TECH CO LTD
Data transmission method and network device
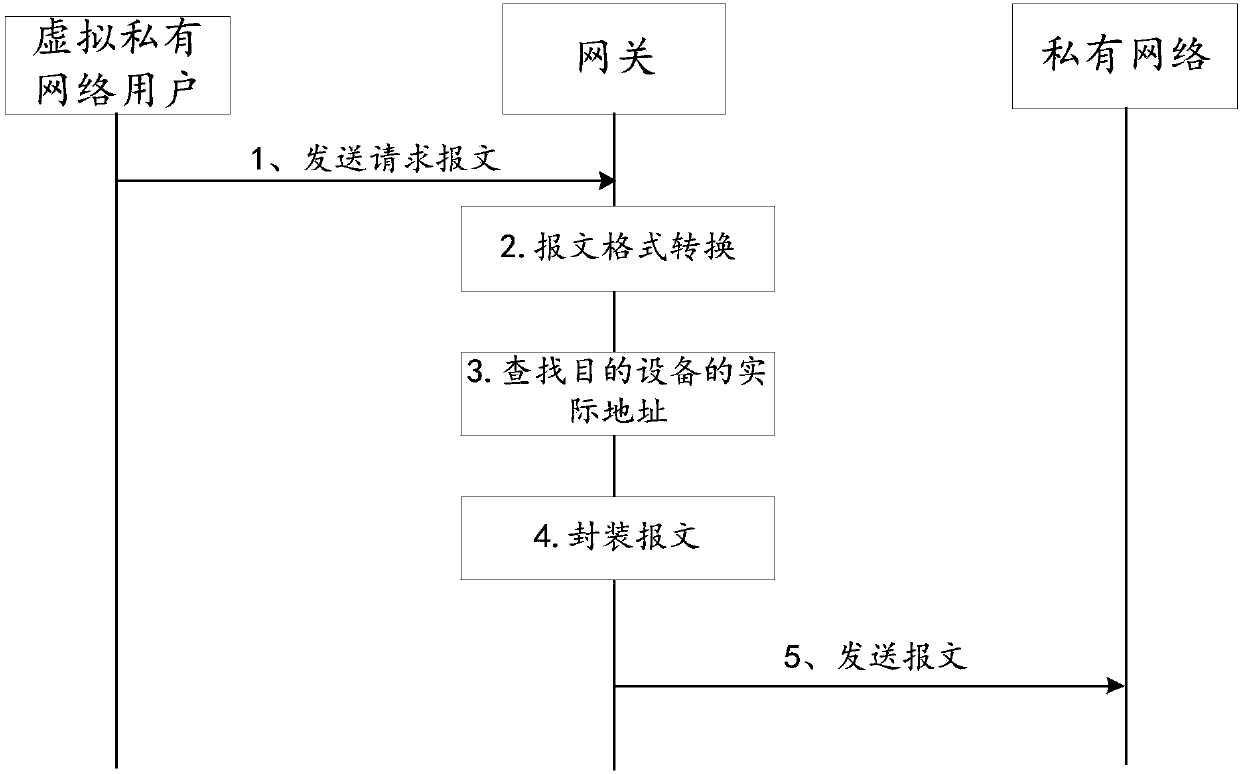
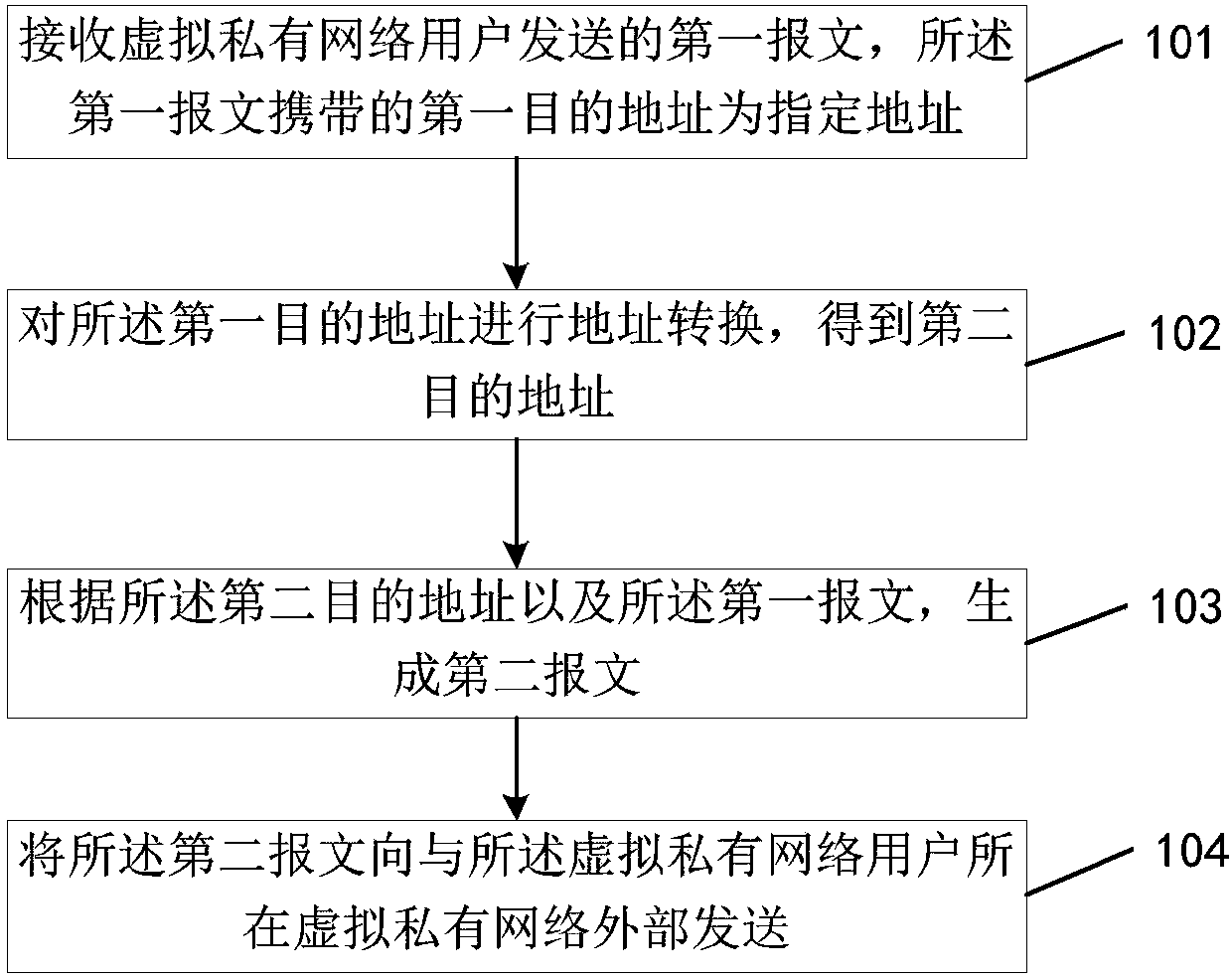
ActiveCN107872542AReduce trafficNetworks interconnectionNetwork connectionsData transmissionMobile virtual private network
An embodiment of the invention provides a data transmission method applied to the field of communication technology. According to the invention, specific setting is performed on the addresses of server providing services, so that a user in a virtual private network can acquire services provided by the corresponding servers only with the private network capable of providing services and the user inthe virtual private network does not need to acquires services through accessing other network except the private network. Therefore, traffic is saved for the user.
Owner:ALIBABA GRP HLDG LTD
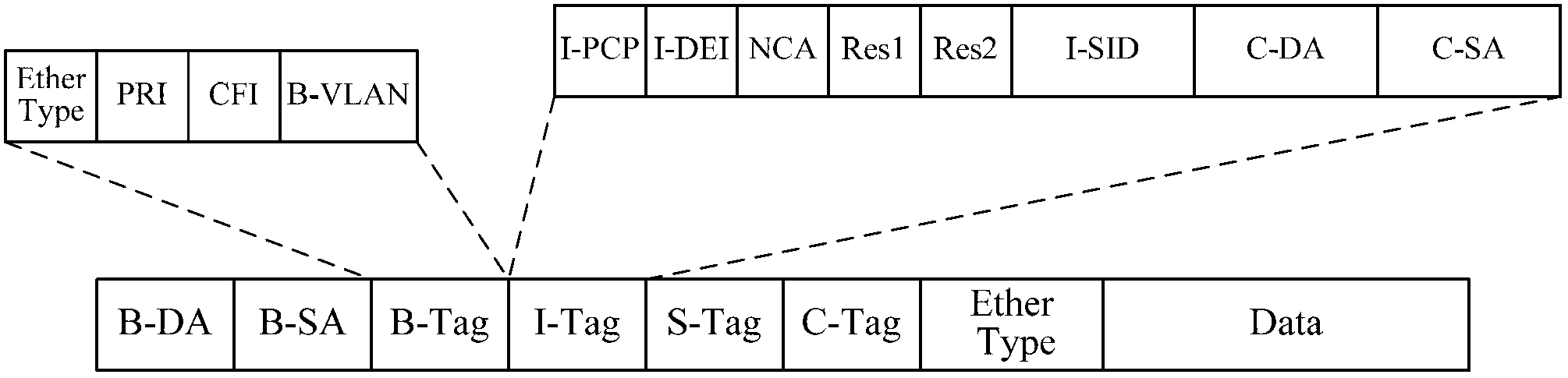
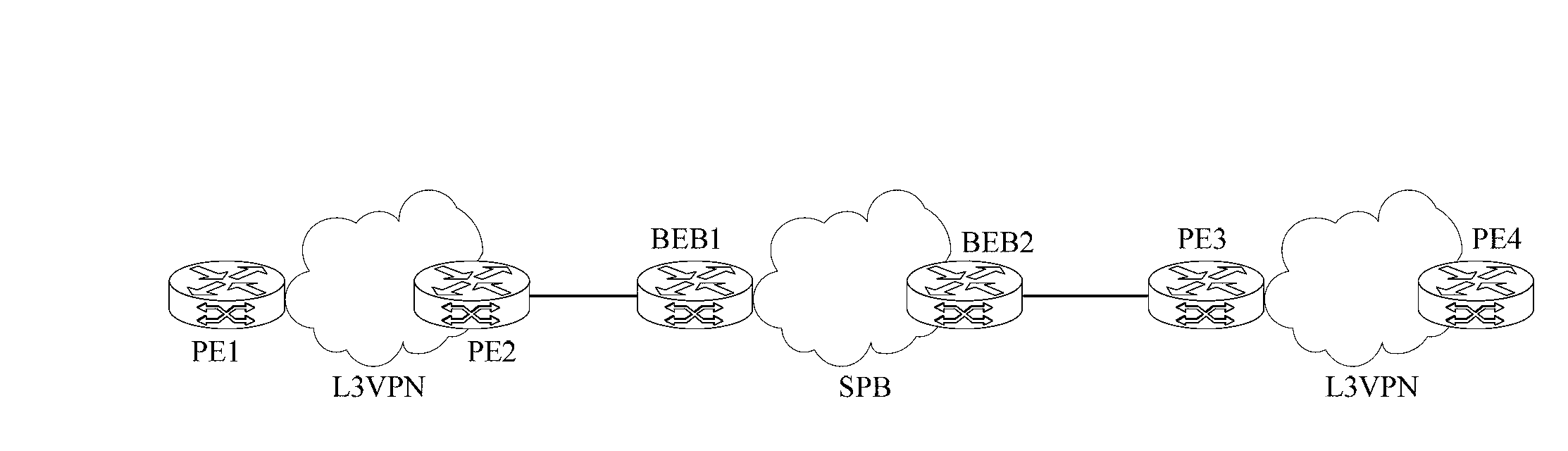
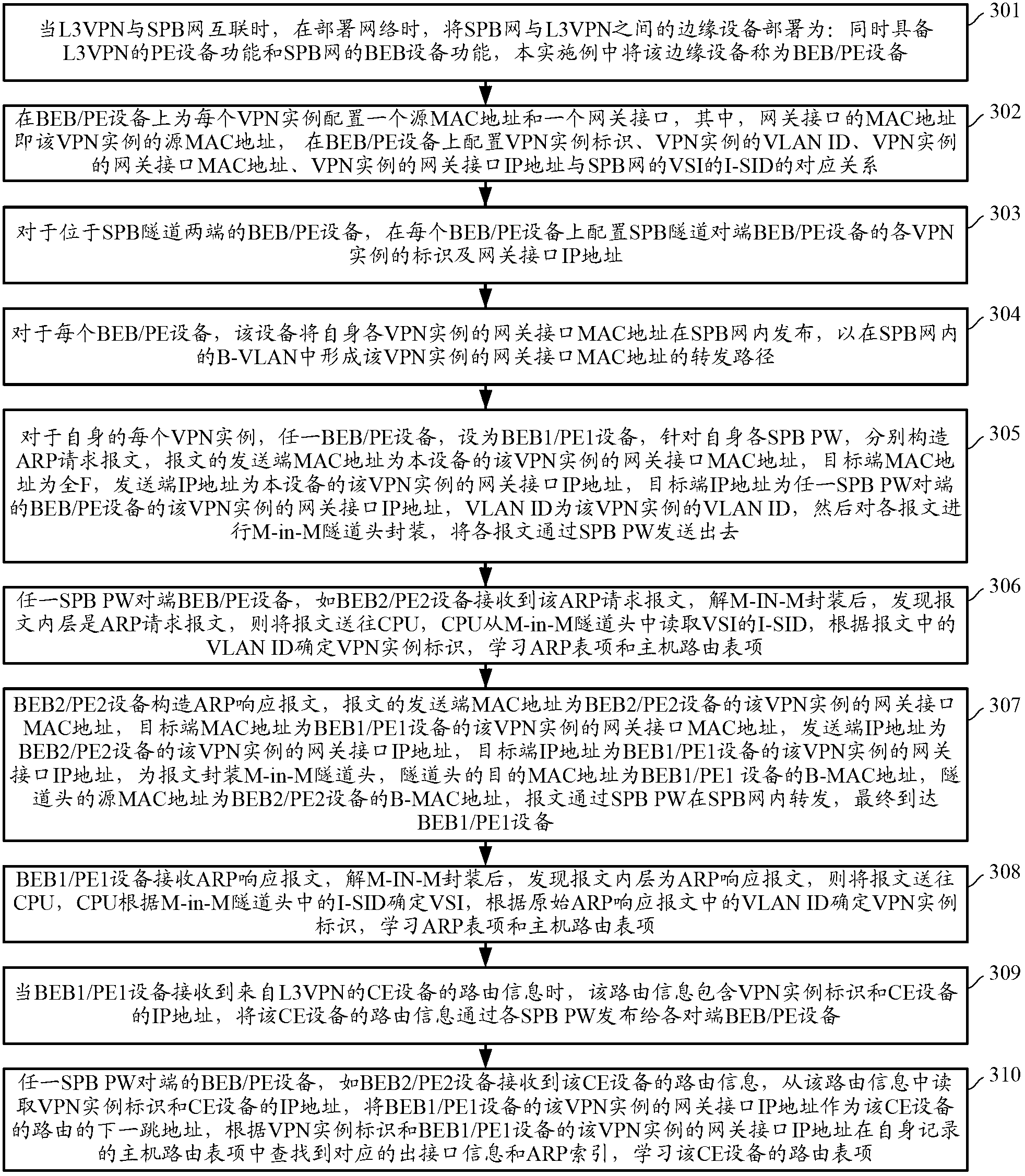
Intercommunication method of shortest path bridging network and Layer 3 virtual private network and common edge equipment
ActiveCN103227745ARealize direct exchange of visitsSave resourcesNetworks interconnectionRouting tableAddress resolution
The invention discloses an intercommunication method of a shortest path bridging (SPB) network and a Layer 3 virtual private network (L3VPN), and common edge equipment. The method comprises the steps that the SPB network is connected with the L3VPN by the common edge equipment; the edge equipment serves as BEB (backbone edge bridge) equipment of the SPB network and PE (provider edge) equipment of the L3VPN simultaneously; association relationships between VPN instances and VSIs (virtual service instances) of the SPB network are configured on the edge equipment; each VPN instance is provided with a gateway interface; MAC (media access control) addresses of the gateway interfaces of the different VPN instances are different; for each VPN instance, the common edge equipment learns an IP (internet protocol) address resolution table entry and a host routing table entry of the common edge equipment at an SPB PW opposite end, learns a VPN routing table entry in the VPN instance of the common edge equipment at the opposite end according to the learned host routing table entry, and forwards a message from the VPN to the SPB network, or a message from the SPB network to the VPN according to the learned table entries. The equipment cost for the intercommunication of the SPB network and the L3VPN is lowered.
Owner:XINHUASAN INFORMATION TECH CO LTD
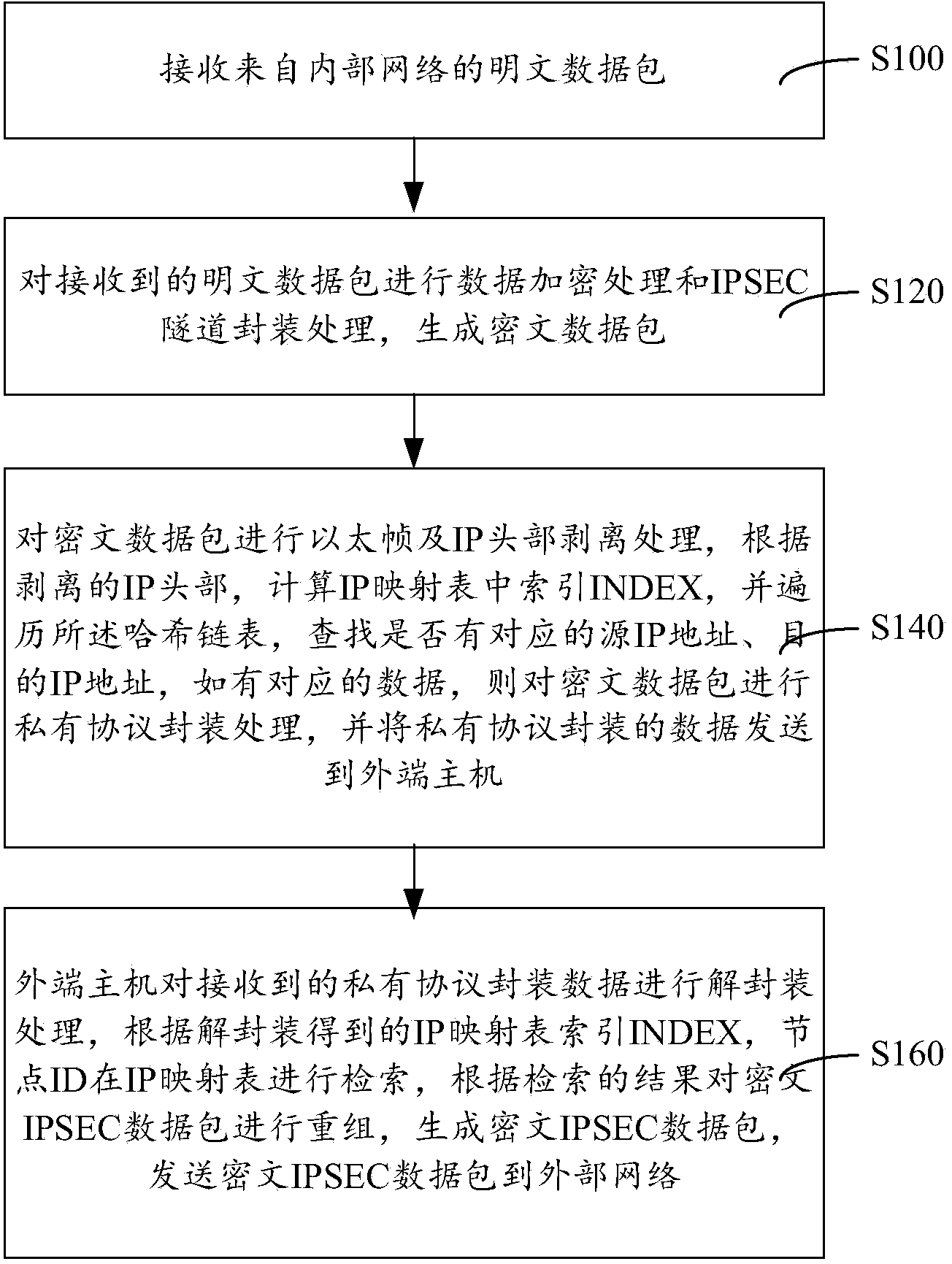
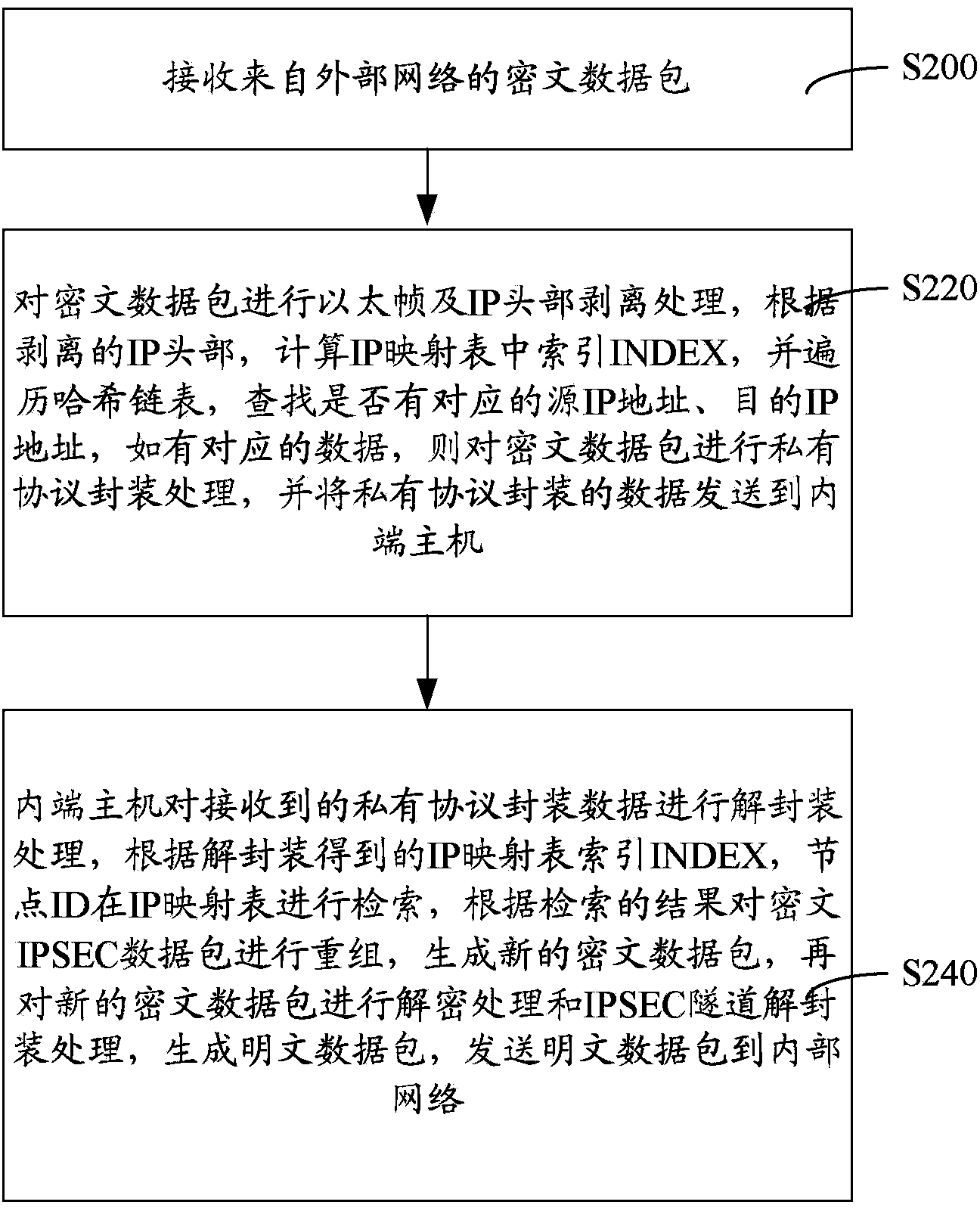
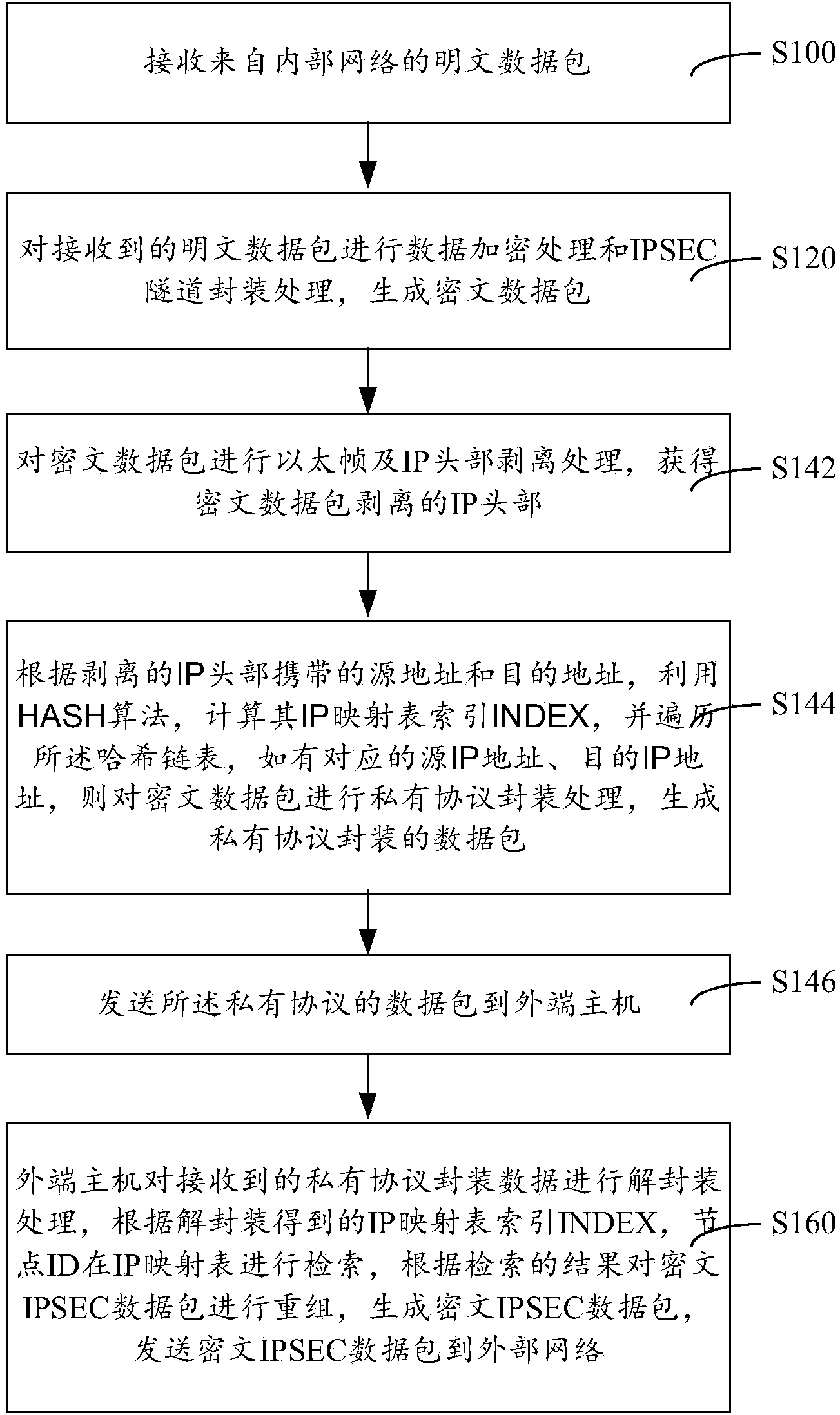
IPSEC (internet protocol security) VPN (virtual private network) device, isolation method thereof and isolation system thereof
ActiveCN103812861AAchieve security isolationPrevent intrusionTransmissionInternet protocol suiteNetwork packet
The invention provides an IPSEC (internet protocol security) VPN (virtual private network) device, an isolation method thereof and an isolation system thereof. The device comprises an inner end host, an outer end host and a non-network isolation card, the inner end host and the outer end host respectively maintain the same IP (internet protocol) mapping table, each table entry defines information such as a primary address, a destination address and IP mapping ID (identity), a data packet realizes network isolation by modes such as IP head stripping and recombination, IP mapping table search and filtering, private protocol capsulation and decapsulation and non-network isolation card transmission, an IPSEC VPN network data packet is encrypted and decrypted on an internal network host by the data packet, the device can resist malicious attack behaviors and transmission of viruses, Trojans and malicious plug-ins, security isolation in connection of an internal network and an external network is really achieved, higher-strength security protection for the internal network, the IPSEC VPN device and the network service data packet is realized, and the IPSEC VPN isolation device is high in security degree.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
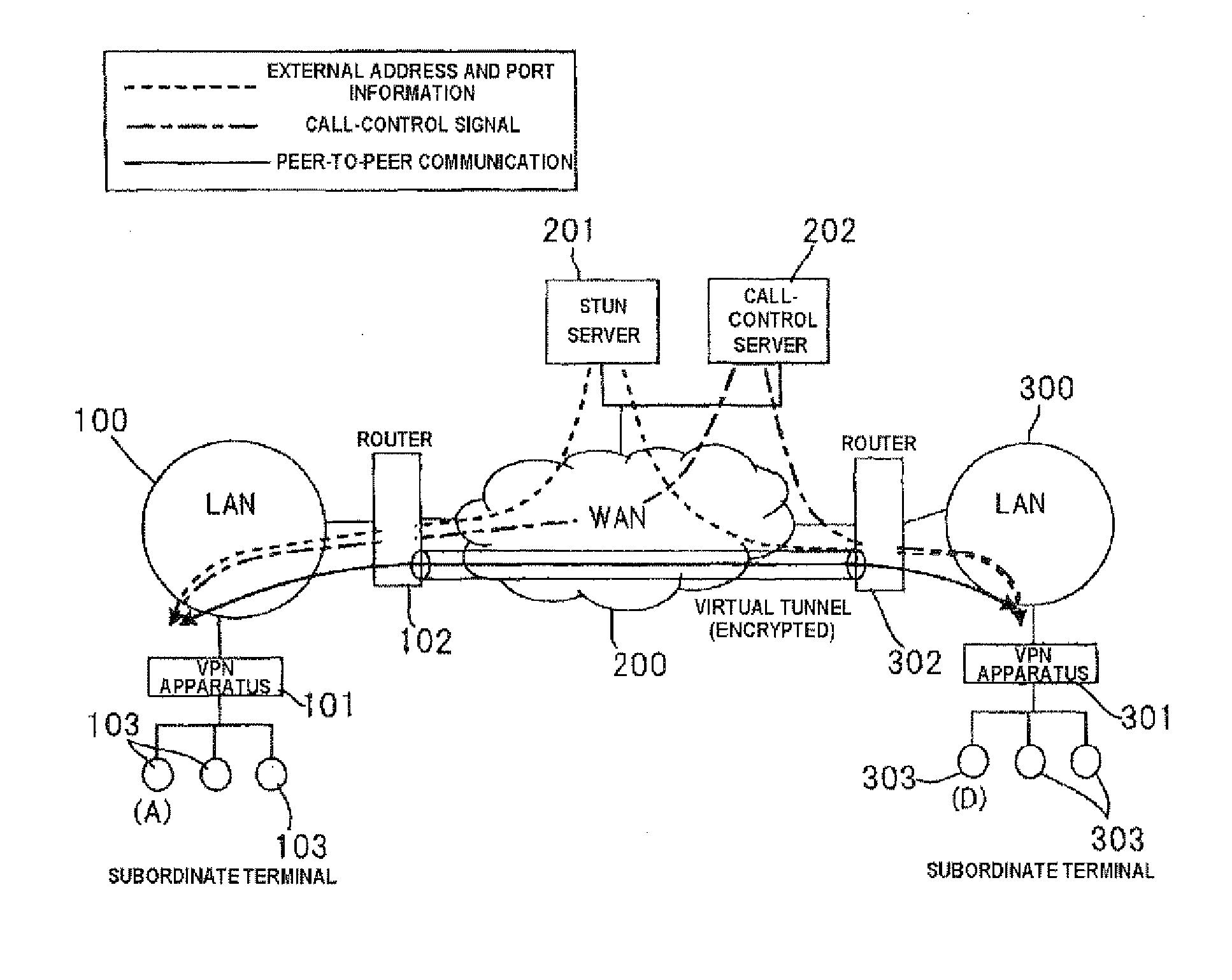
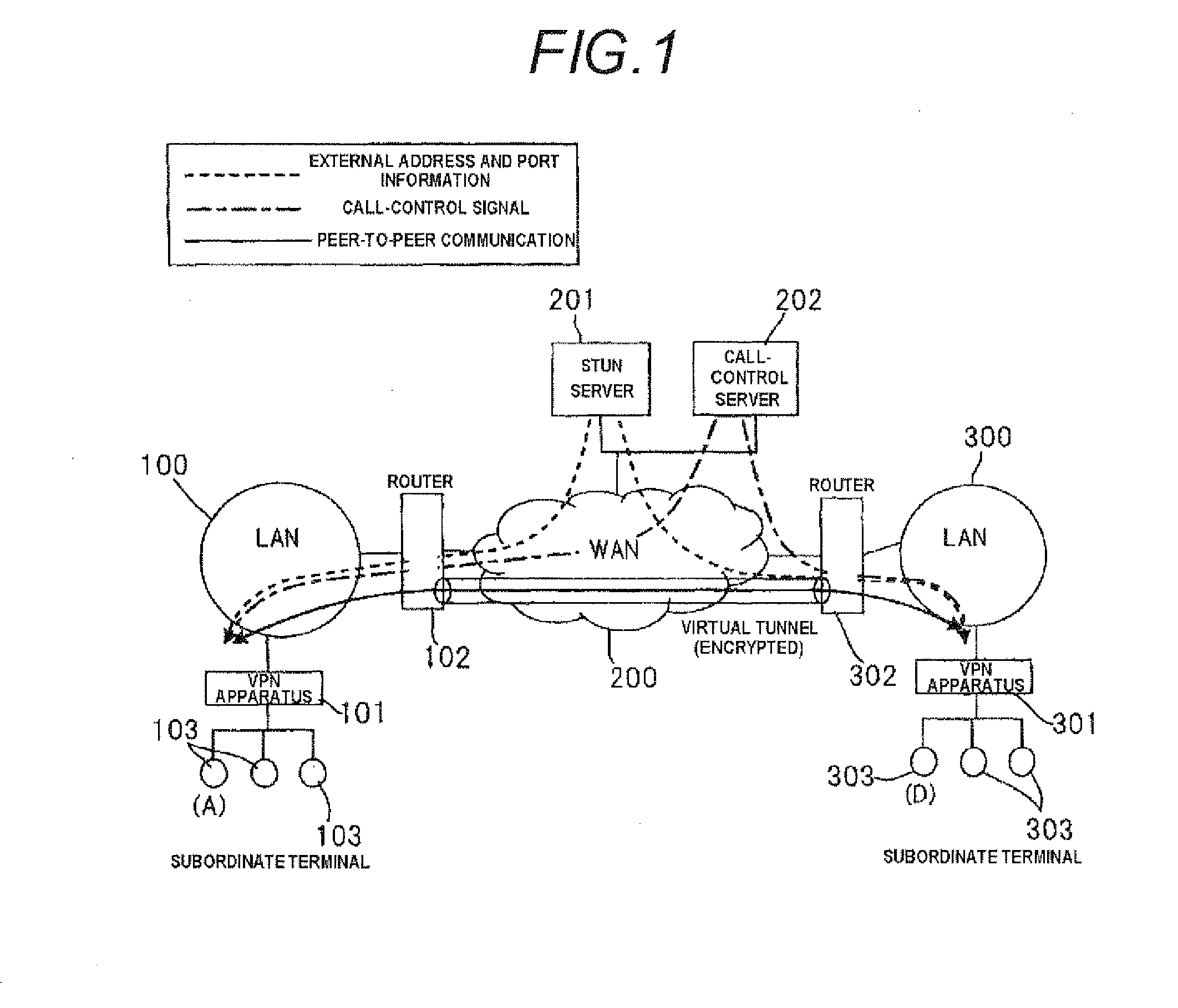
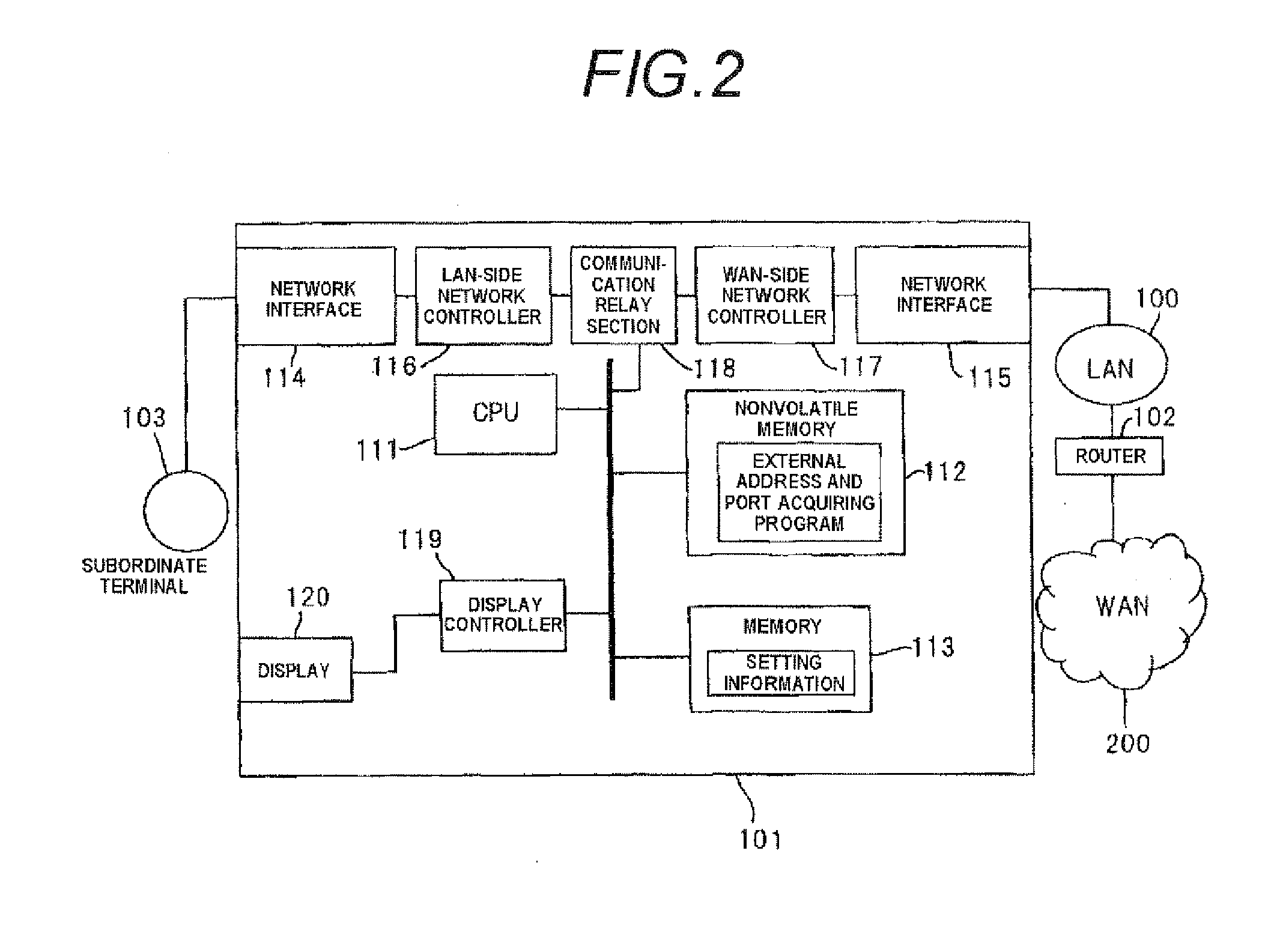
Networking method of communication apparatus, communication apparatus and storage medium
InactiveUS20110145426A1Multiple digital computer combinationsNetworks interconnectionProtocol for Carrying Authentication for Network AccessData transmission
In a networking method of a communication apparatus in which global address information and port information are acquired on a network, a virtual private network is established with another communication apparatus using the global address information and the port information to perform the communication, the networking method includes determining whether communication data that is transmitted from the communication apparatus is a first protocol or a second protocol, and starting a data transmission through the network before the virtual private network is established when the communication apparatus determines that the communication data is the first protocol, and starting a data transmission after the virtual private network is established when the communication apparatus determines that the communication data is the second protocol.
Owner:PANASONIC CORP
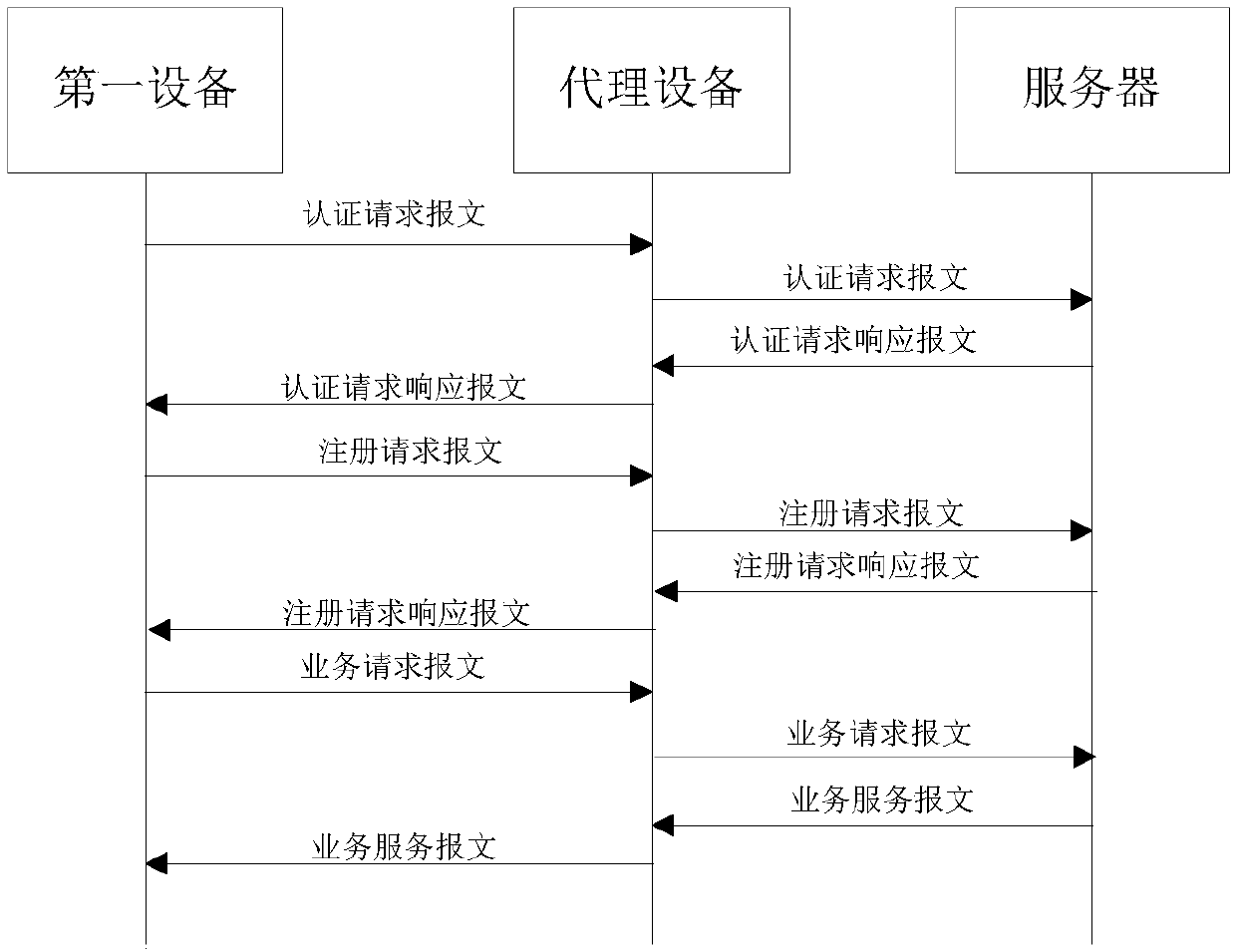
Communication method and apparatus of device and server in virtual private network VPN
The invention discloses a communication method and apparatus of a device and a server in a virtual private network VPN. The method comprises the following steps: providing authentication and registration services for a first device in the virtual private network VPN, and obtaining the authentication and registration information of the first device, wherein the authentication and registration information comprises a device identification number and a VPN identifier of the VPN where the device is located; receiving a business request message sent by the first device, and sending the business request message to the server according to a VPN identifier of the VPN where the first device is located and the authentication and registration information. According to the communication method and apparatus disclosed by the embodiment of the invention, a proxy device is arranged between the first device in the virtual private network VPN and the server in the Internet, so that the device in the virtual private network VPN can still communicate with the server without accessing the Internet, thereby ensuring the security of the device in the virtual private network VPN.
Owner:NEW H3C TECH CO LTD
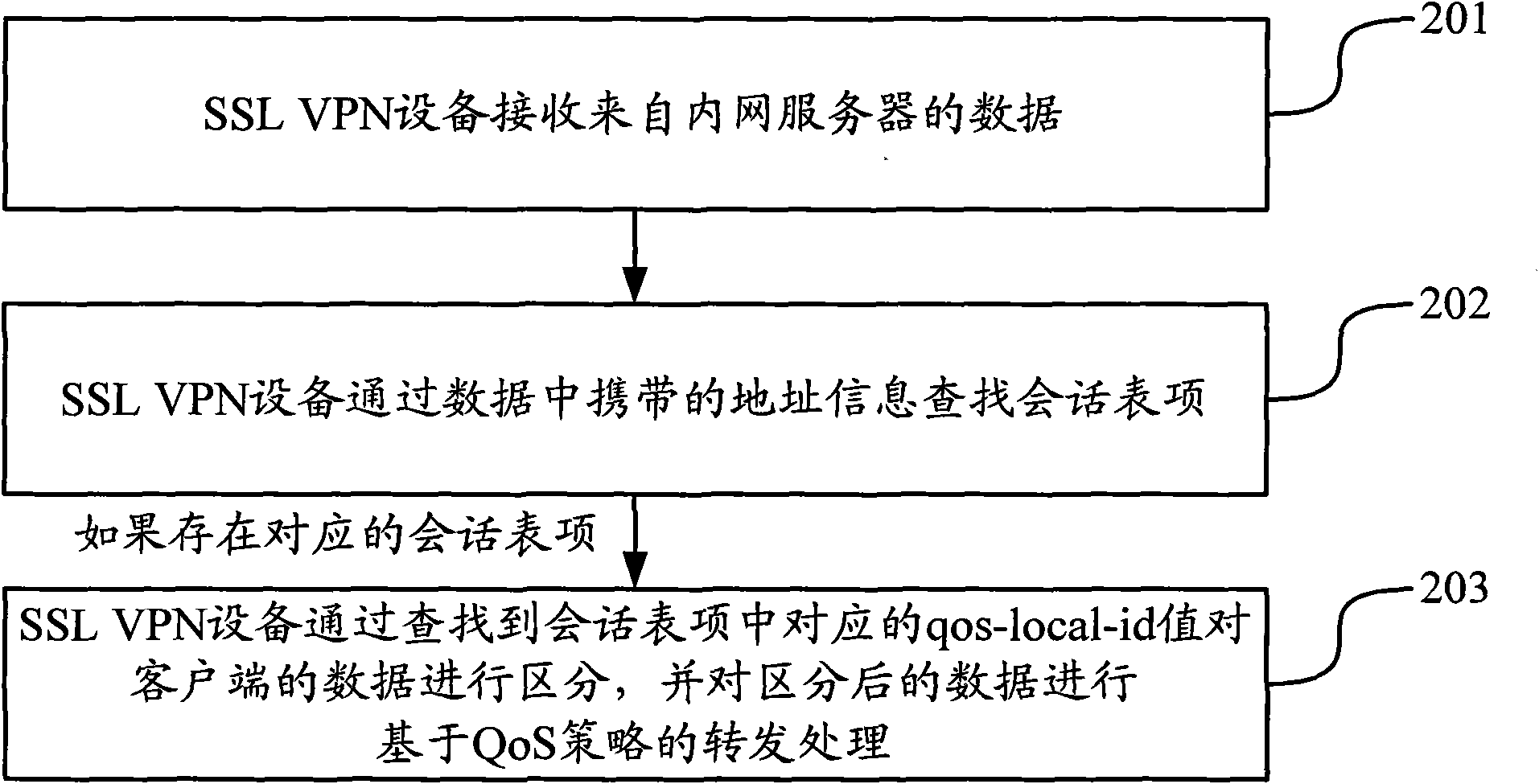
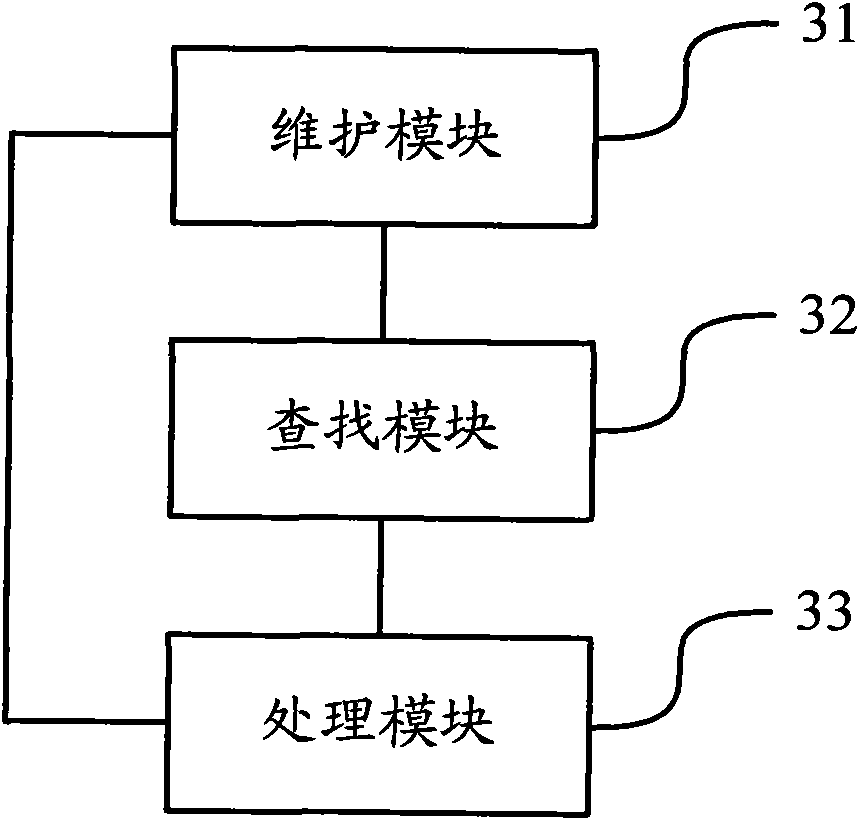
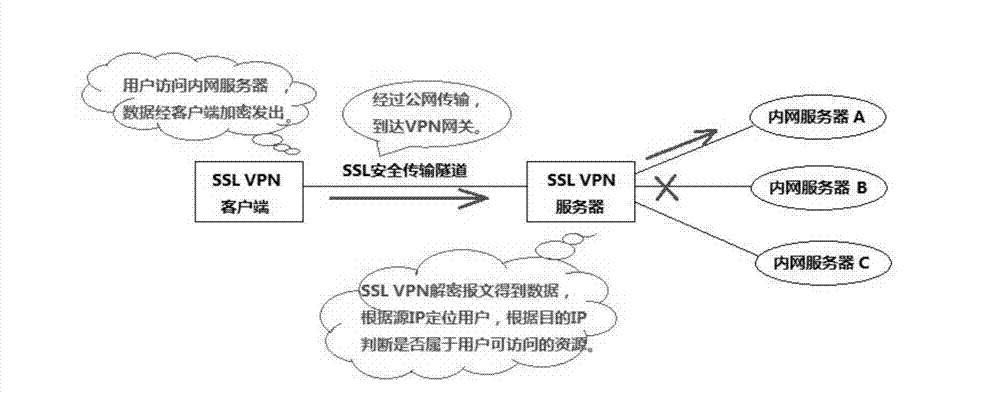
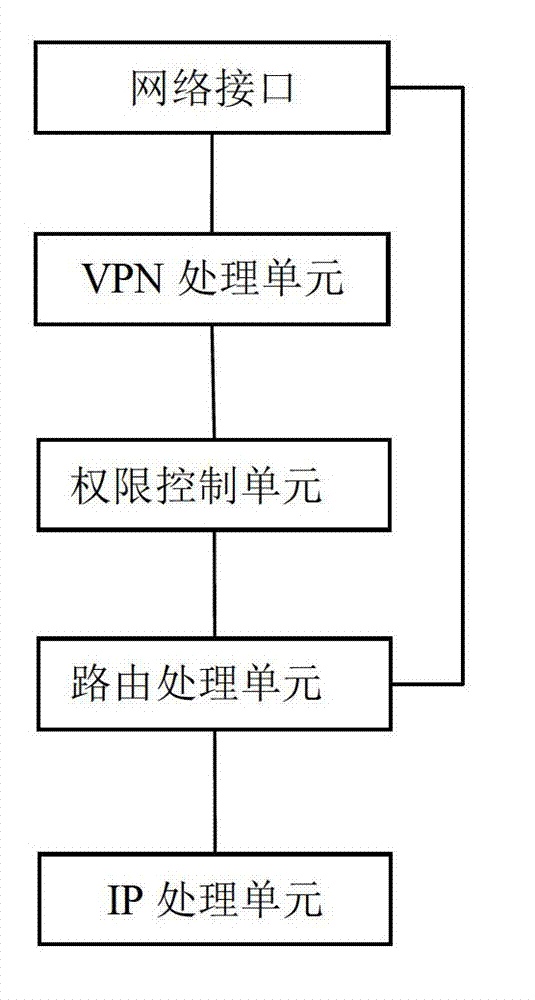
Method and equipment for forwarding data based on security socket layer (SSL) virtual private network (VPN)
ActiveCN102143088AGuaranteed not to loseBandwidth is not occupiedNetworks interconnectionQuality of serviceClient-side
The invention discloses a method and equipment for forwarding data based on a security socket layer (SSL) virtual private network (VPN). The method comprises: when SSL VPN equipment receives the data sent from an intranet server to a client, the SSL VPN equipment inquires a session table item through address information carried in the data, distinguishes the data of the client through inquiring the corresponding quality of service (QoS) identification information in the conversation table item and forwards the distinguished data based on a QoS strategy. In the invention, the bandwidth of a network can be reliably utilized, and the safety of the equipment is improved.
Owner:XINHUASAN INFORMATION TECH CO LTD
VPN (virtual private network) authority control method and device
InactiveCN102904867AAvoid consumptionReduce consumptionNetworks interconnectionTelecommunicationsAuthority control
The invention provides a VPN (virtual private network) authority control method which is applied to a subscriber's main station and includes A, establishing tunnel connection with a service terminal; B, acquiring an intranet IP(internet protocol) address from the VPN service terminal through a tunnel; C, acquiring an authority control list from the VPN service terminal through the tunnel; D, judging whether to allow a user message to pass or not according to the authority control list, if so, then allowing the user message to pass, and if not, then discarding the user message; and E, packaging the user message as a tunnel message, sending the tunnel message to the VPN service terminal through the tunnel, or receiving the tunnel message from the VPN service terminal and then restoring the same into the user message. By the VPN authority control method, processing resources of the subscriber's main station are utilized effectively, and excessive consumption of the resources for tunnel processing and authority control is avoided for the service terminal.
Owner:HANGZHOU DPTECH TECH
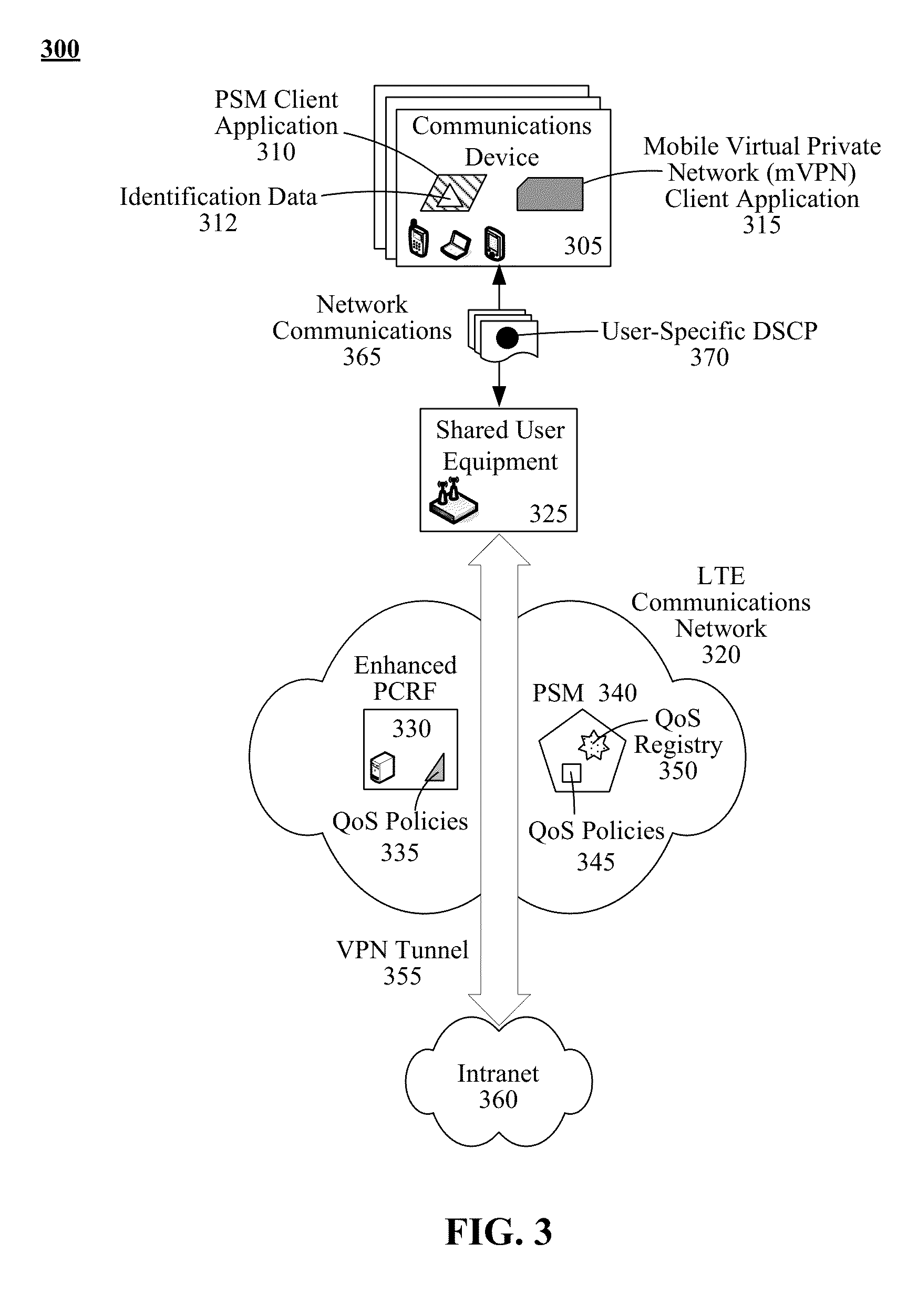
Method, Apparatus, and System for Mobile Virtual Private Network Communication
ActiveUS20120079113A1Improve maintenance efficiencyError detection/correctionNetwork topologiesNetwork addressingNetwork address
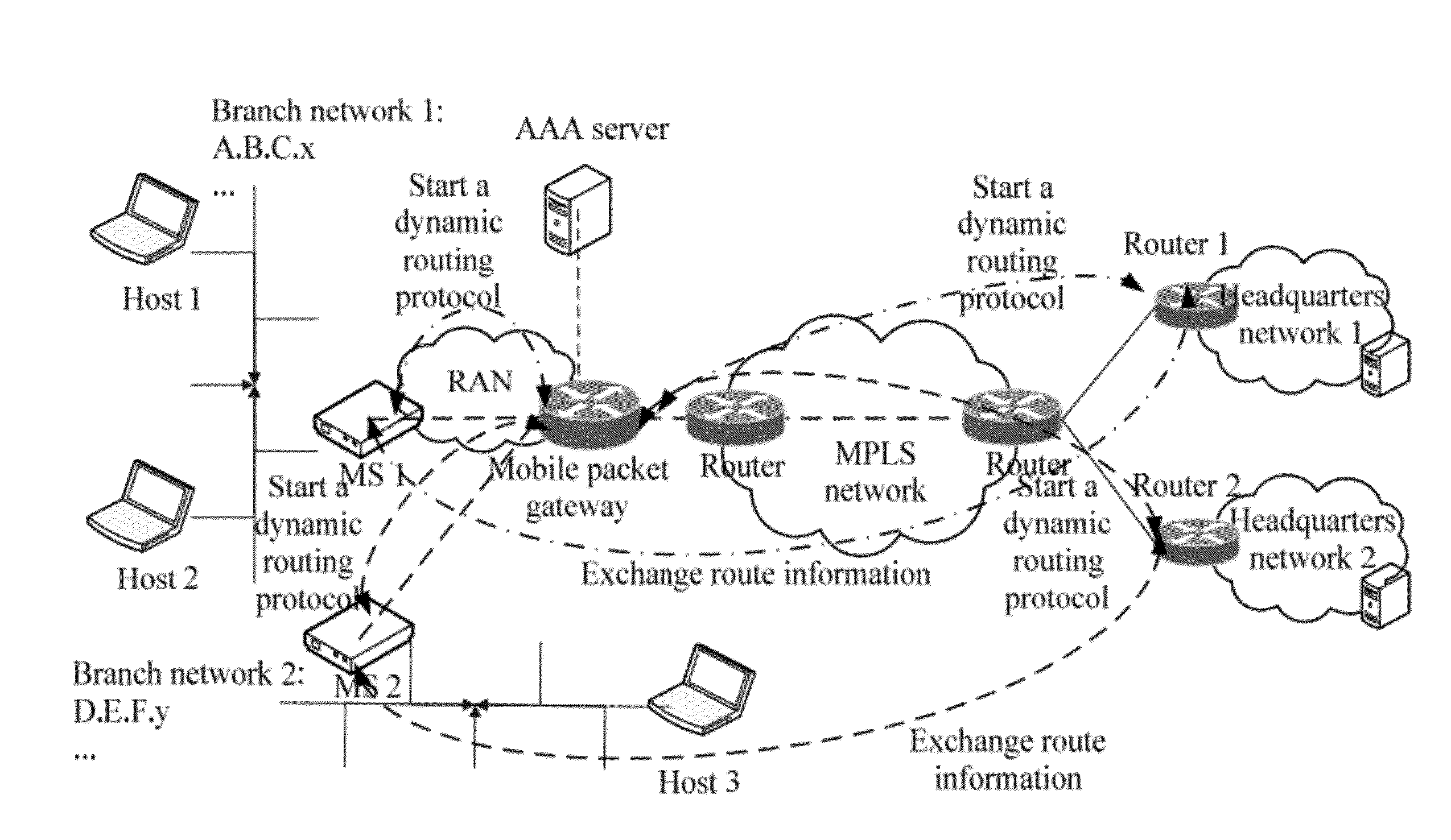
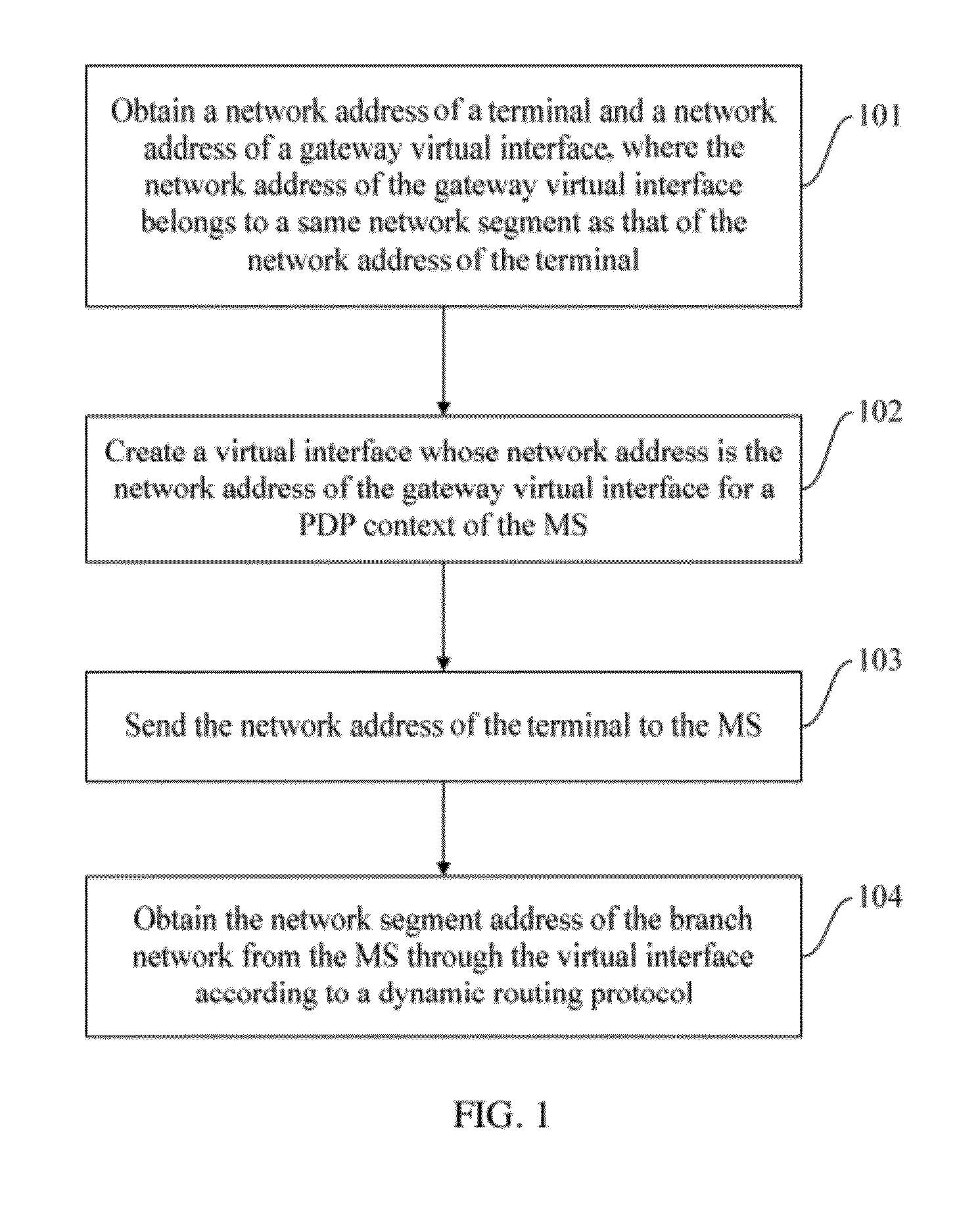
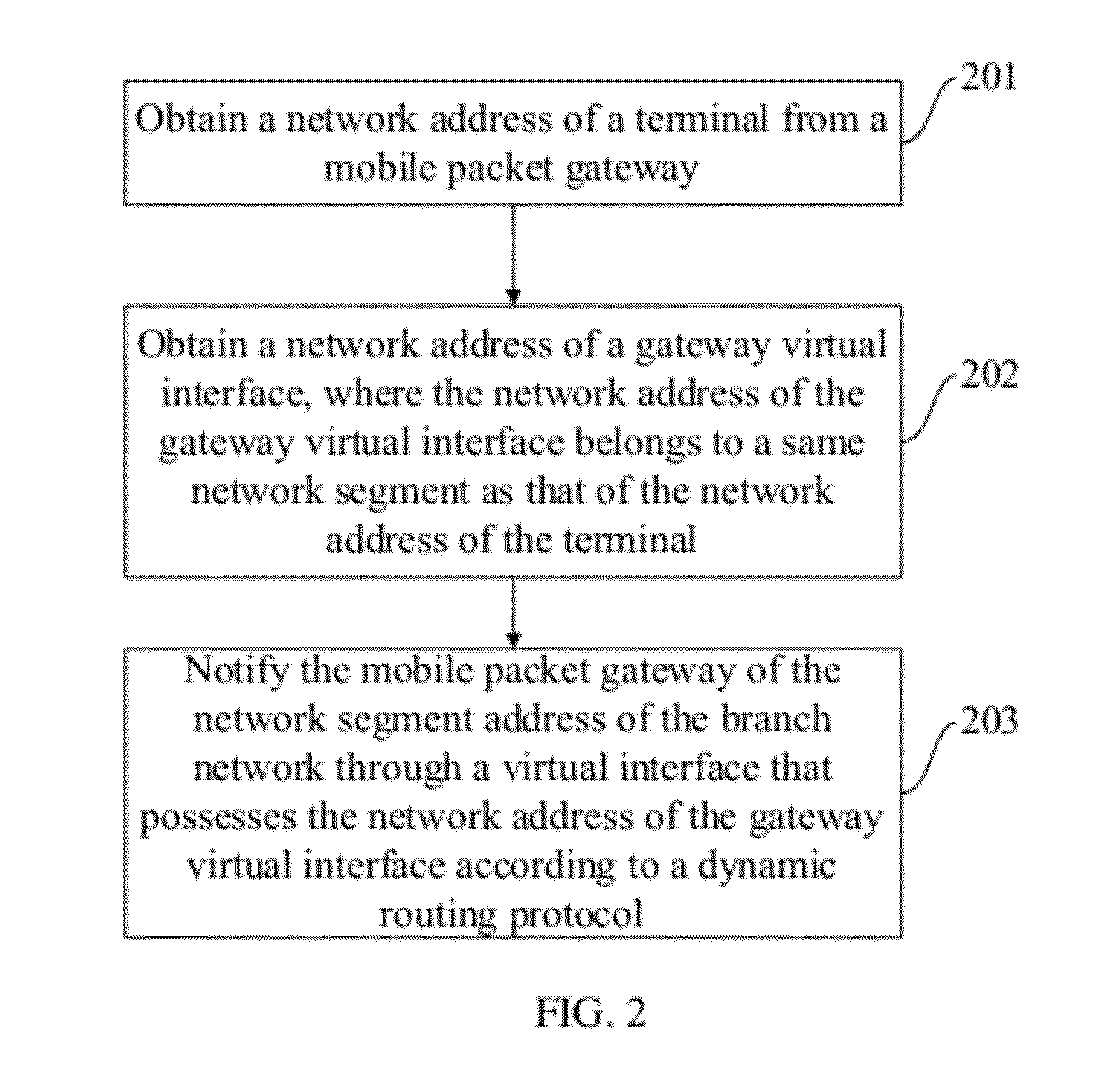
A mobile packet gateway obtains a network address of the terminal and a network address of a gateway virtual interface. The network address of the gateway virtual interface and the network address of the terminal belong to a same network segment. A virtual interface is created for a Packet Data Protocol Context (PDP context) of the MS according to the network address of the gateway virtual interface. A network segment address of a branch network served by the MS is obtained from the MS through the virtual interface according to a dynamic routing protocol.
Owner:HUAWEI TECH CO LTD
Determination of connection links to configure a virtual private network
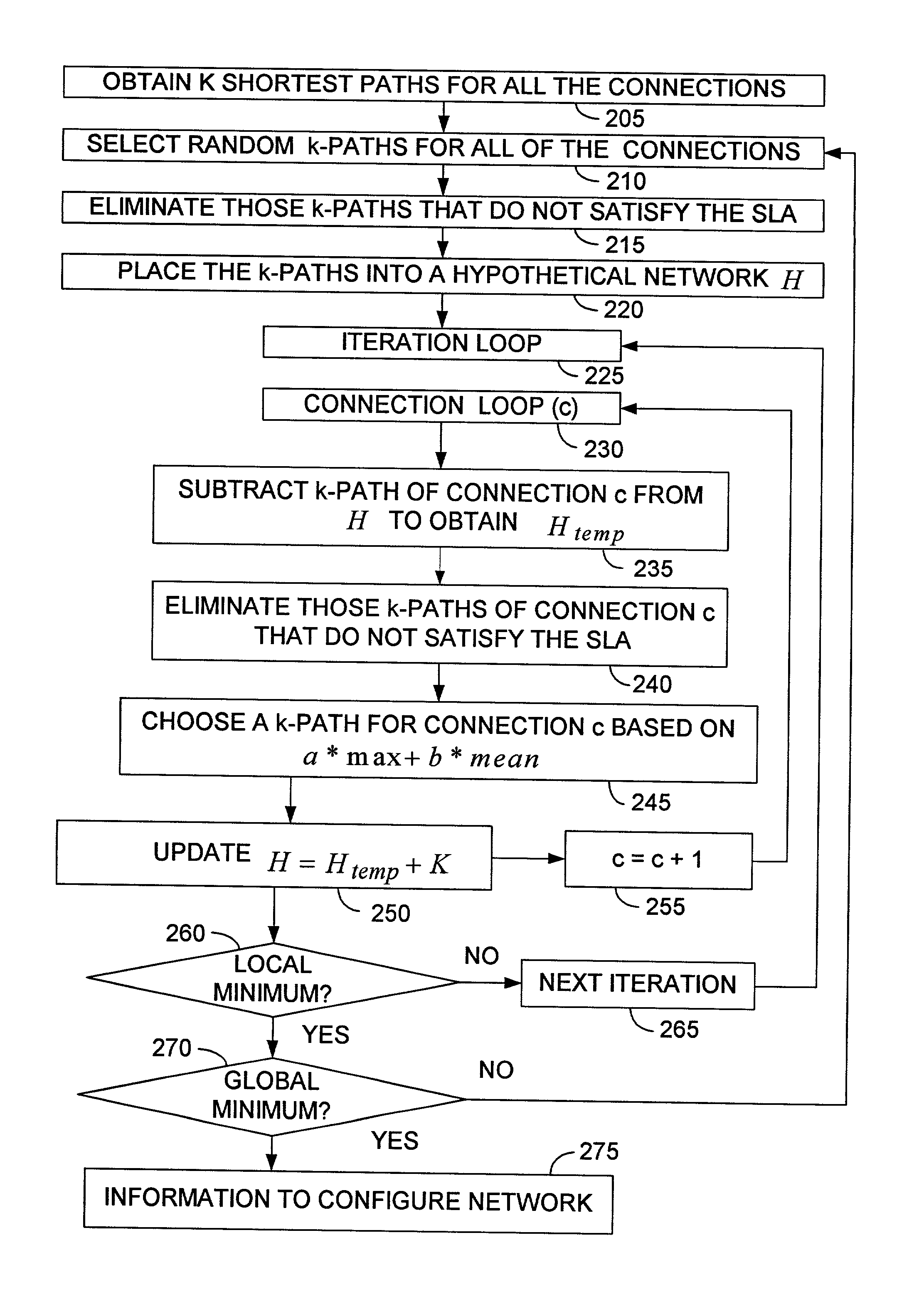
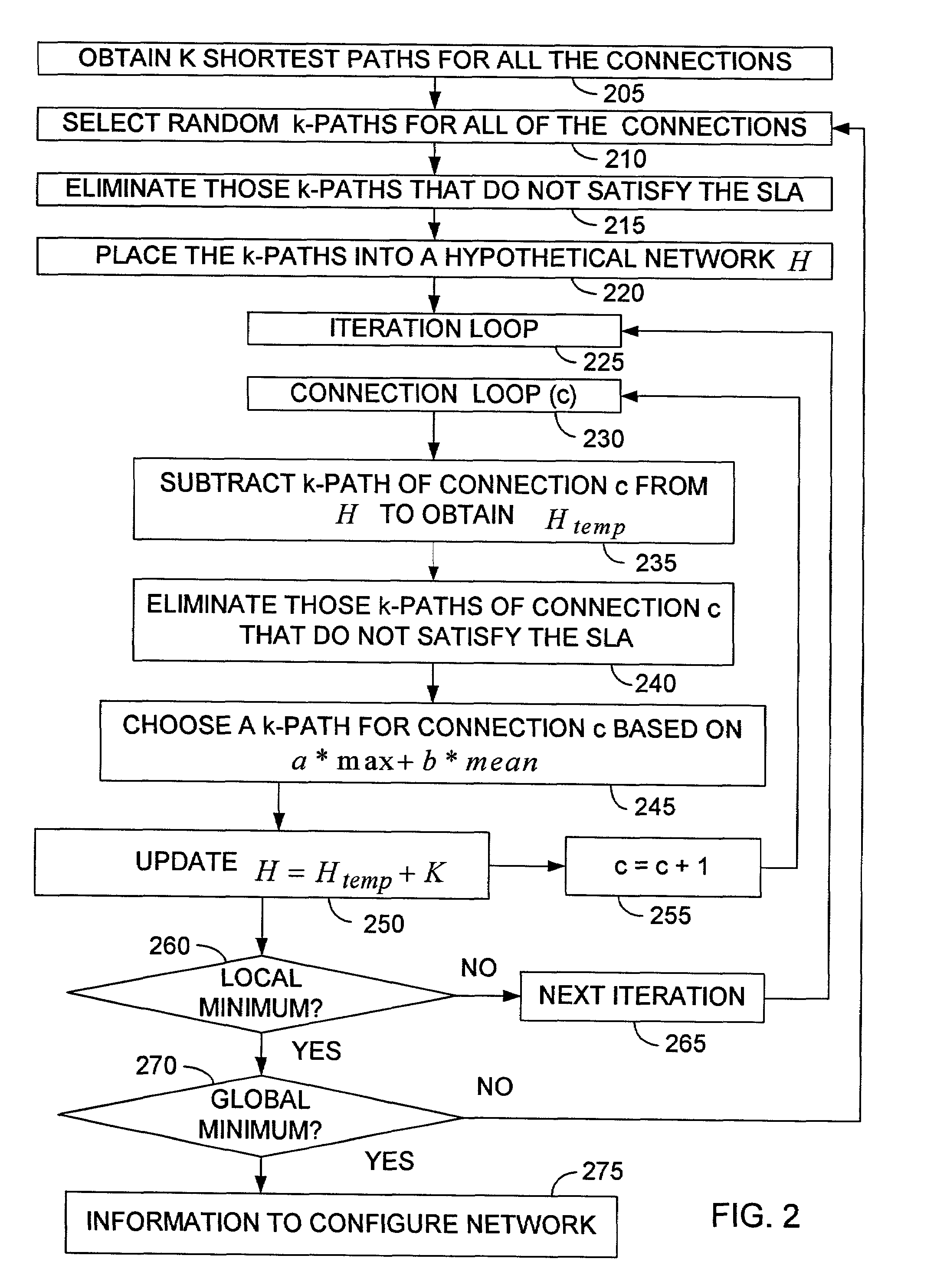
InactiveUS7035938B2Efficiently determinedMultiple digital computer combinationsNetworks interconnectionService-level agreementInterconnection
Owner:TELCORDIA TECHNOLOGIES INC
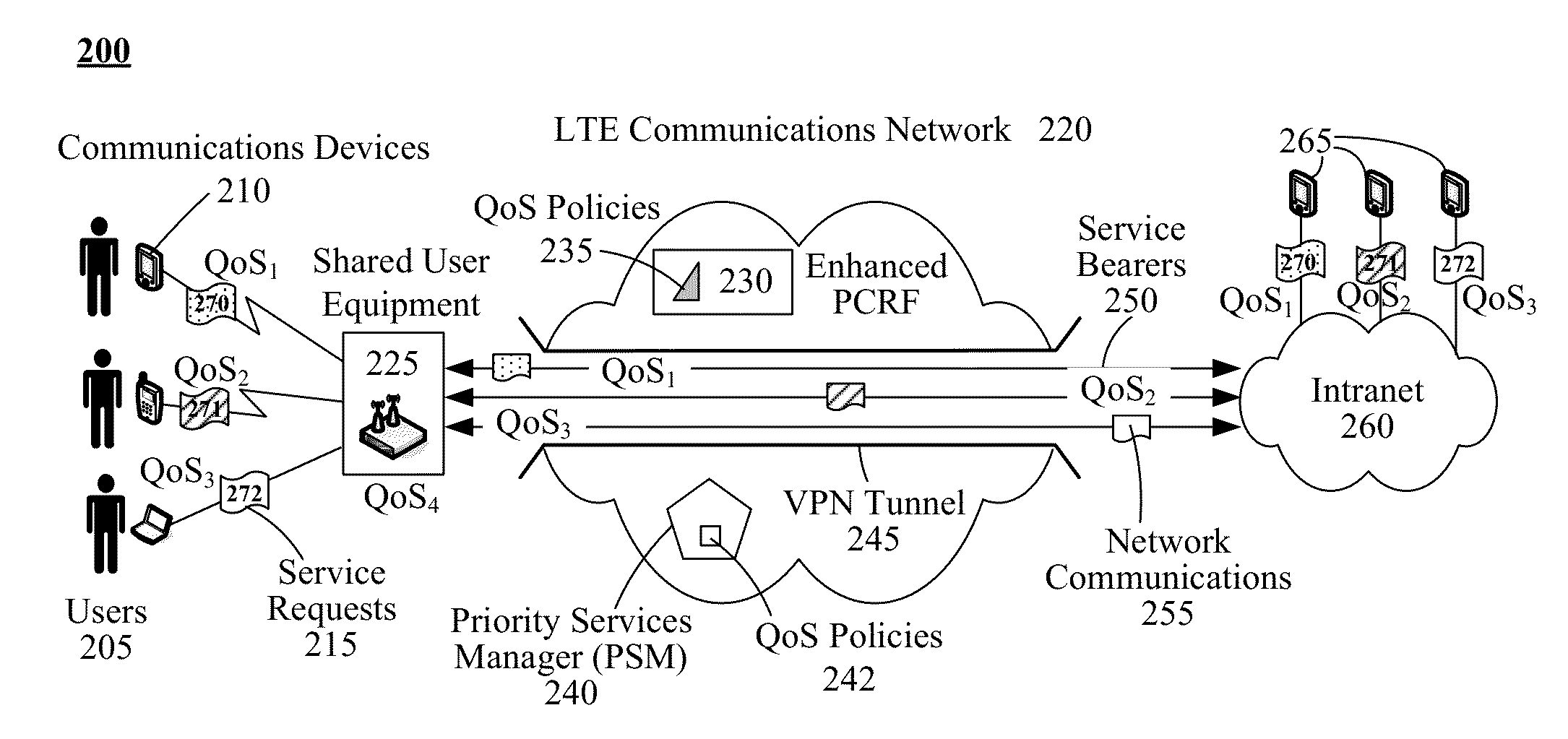
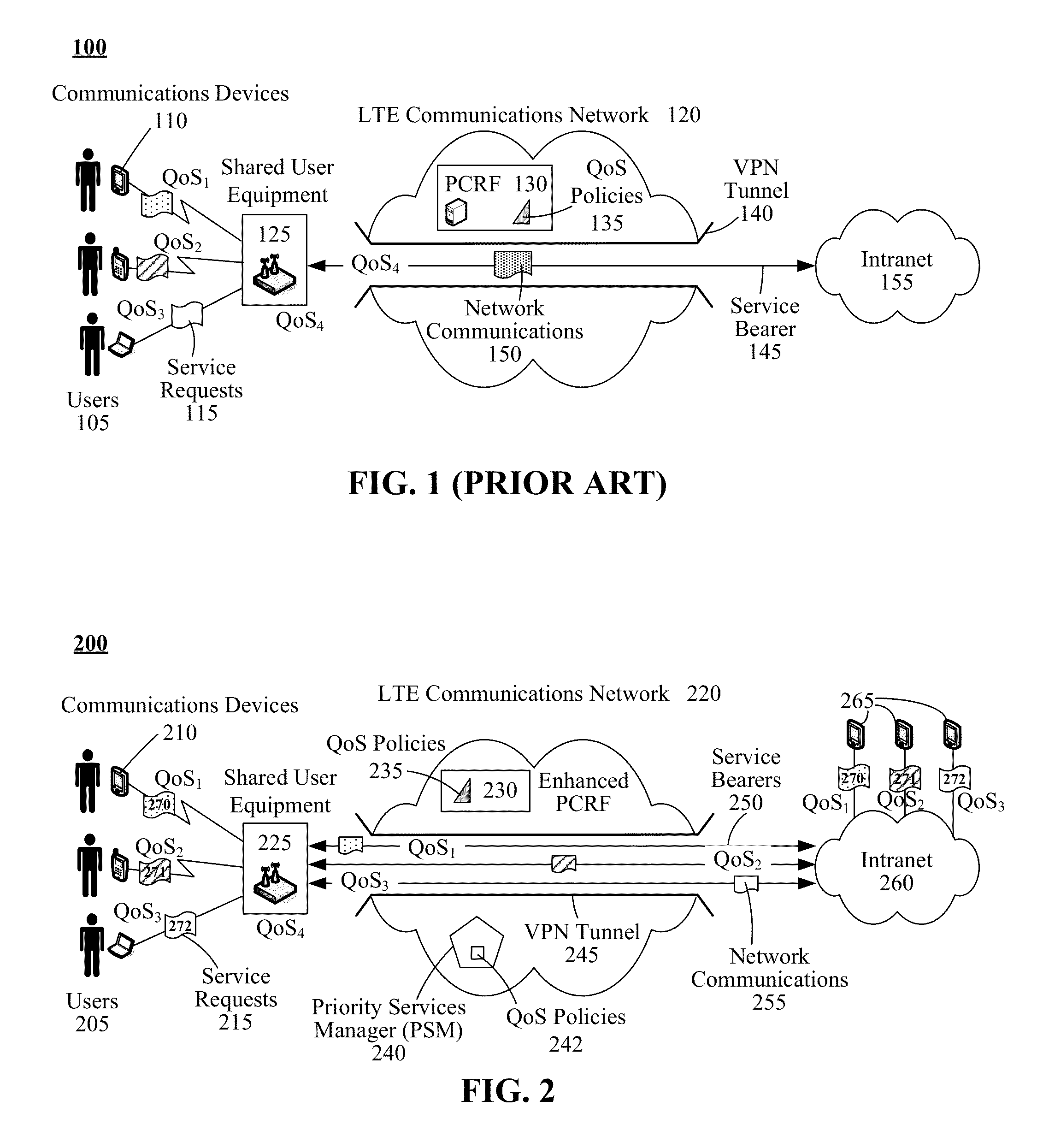
Preserving user-differentiated quality of service for mobile virtual private network communications made using a shared connection point
A set of different communication flows (270-272) can be established between a set of end-user devices (210) and remote devices (265) through an intermediary node (225). For each communication flow (270-272), a flow-specific bearer (250) can be generated between the intermediary node (225) and a corresponding one of the remote devices (265). Each bearer (250) can have quality of service attributes that correspond to flow-specific quality of service attributes of the flow (270-272) to which the flow-specific bearer (250) corresponds. Communication can occur between each of the proximate end-user devices (210) and the remote devices (265) in accordance with the flow-specific quality of service attributes. The intermediate node (225) can direct the exchanged data between unique local communication links and corresponding ones of the flow-specific bearers (250).
Owner:MOTOROLA SOLUTIONS INC
Apparatus of dynamically assigning external home agent for mobile virtual private networks and method for the same
InactiveUS7486951B2Data switching by path configurationMultiple digital computer combinationsIPsecMobility management
An apparatus dynamically assigns external home agent (HA) for VPNs and a method for the same is proposed. The apparatus establishes VPN between an internal network and at least one external network, whereby a mobile node (MN) can roam in the external network with security. The external HA closest to the MN in the visited external network is selected for mobility management of the MN. The MN only needs to register with the same external HA when roaming in the same external network. The handoff latency and end-to-end latency for a roaming MN, therefore, could be reduced significantly. It will also not reestablish the IPsec tunnel within the same external network.
Owner:ZYXEL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com