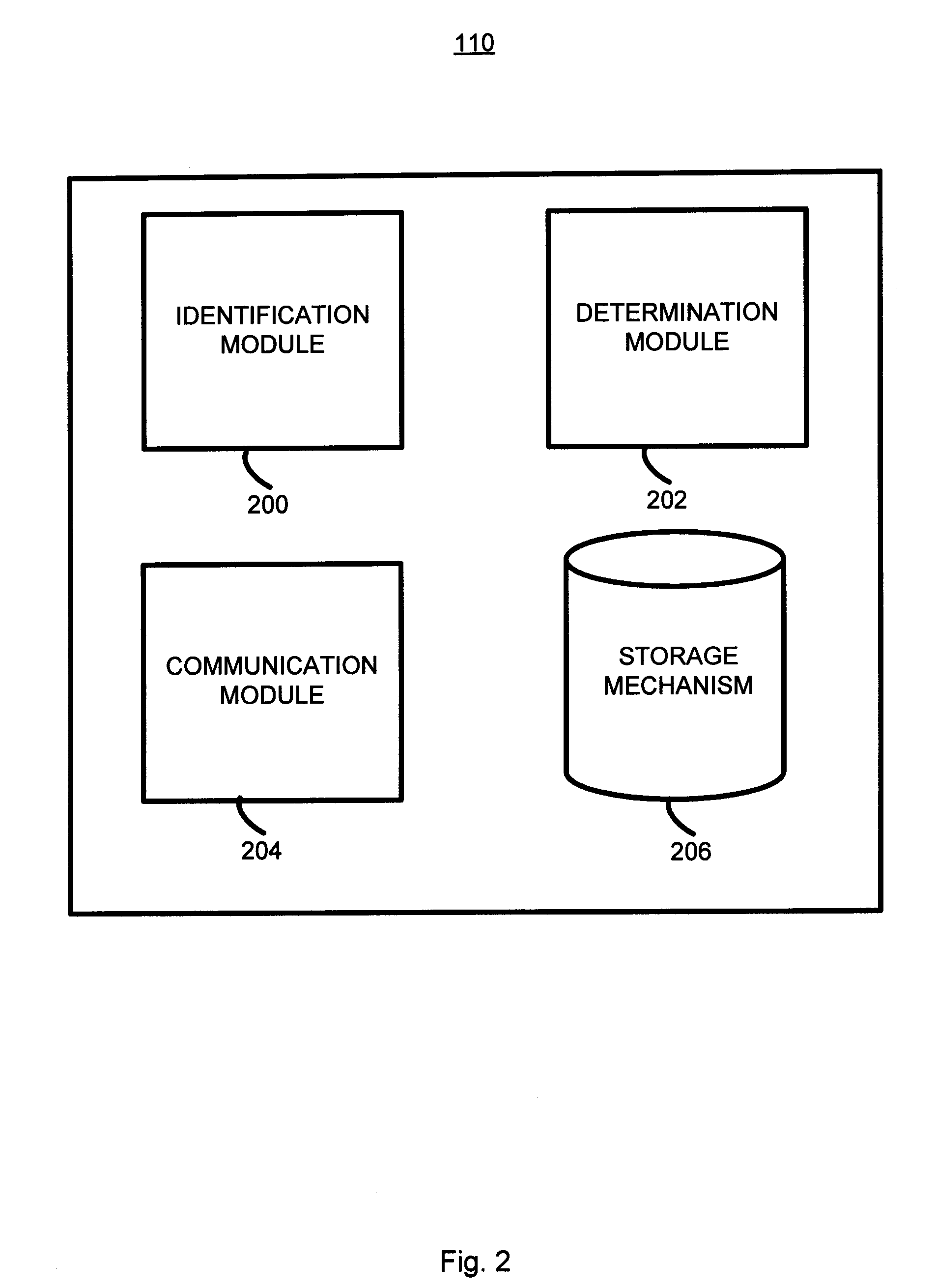
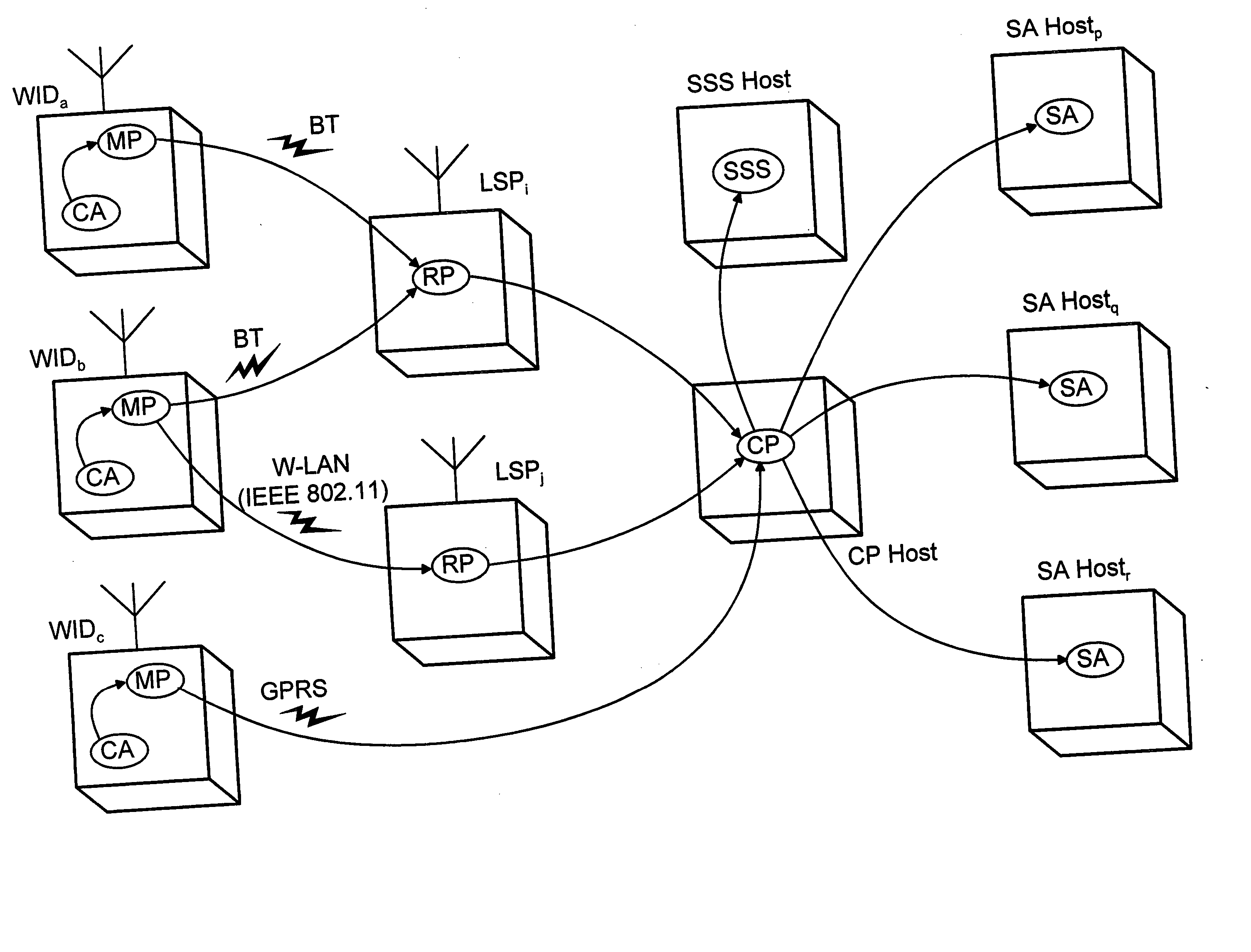
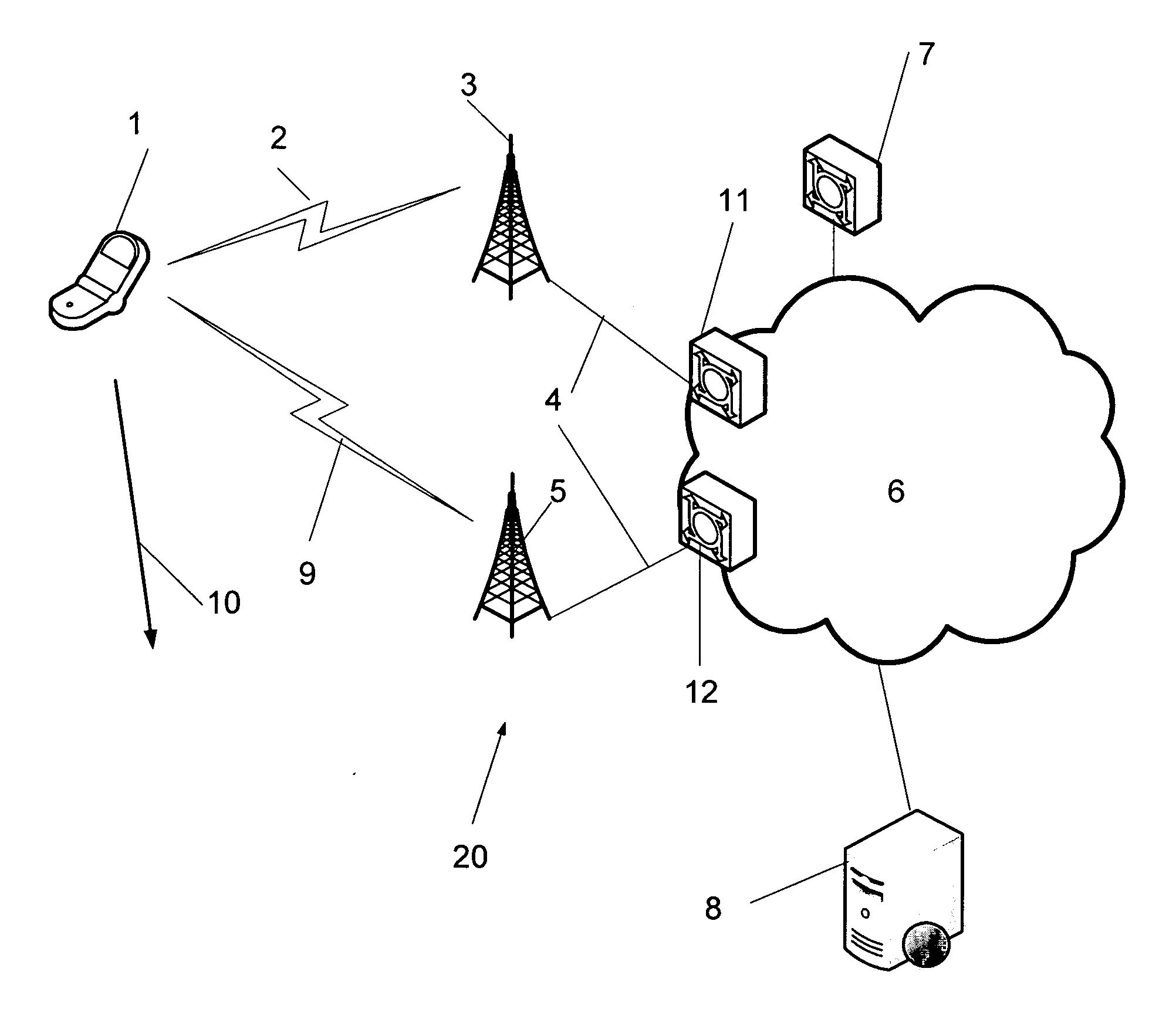
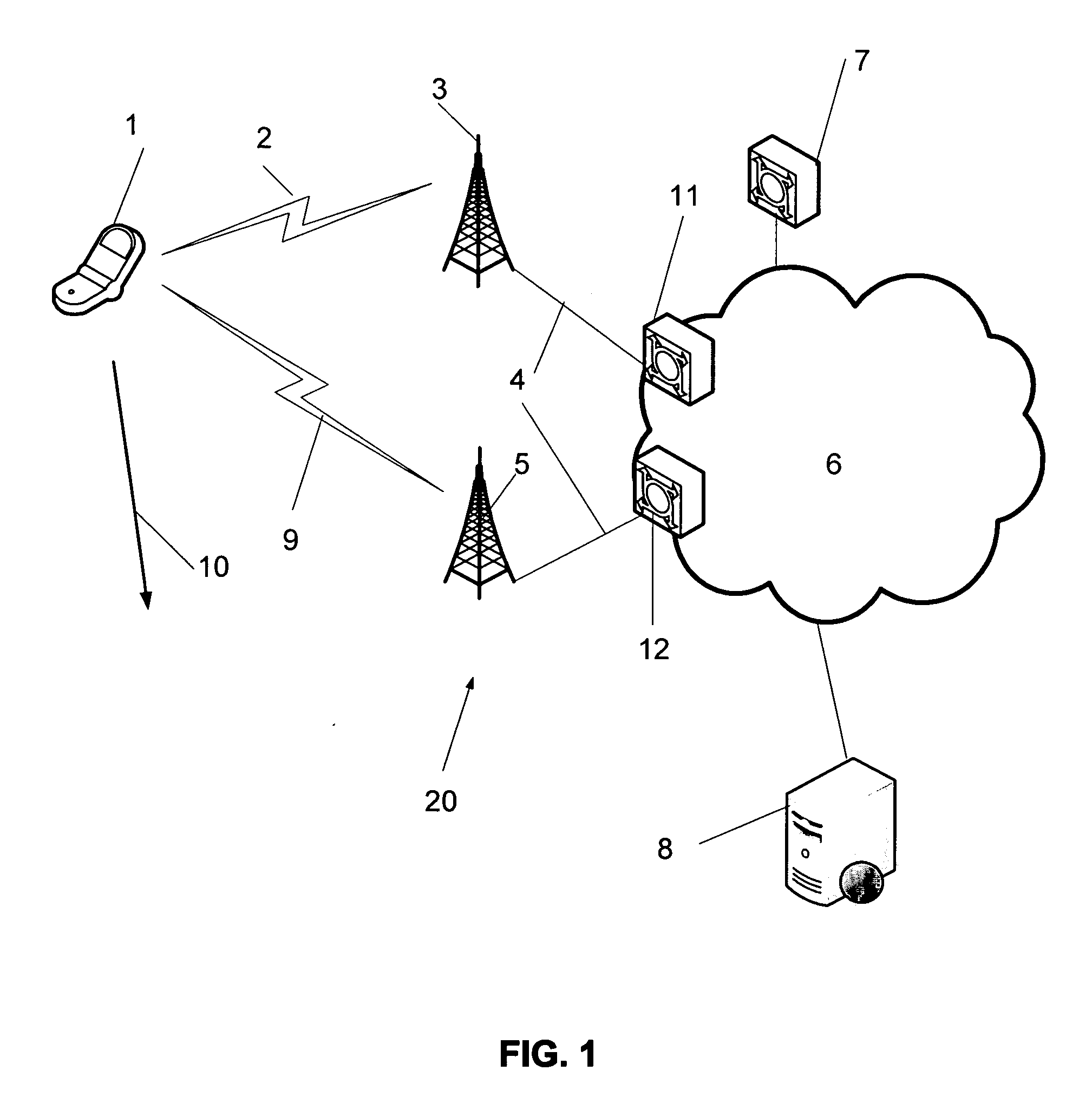
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
471 results about "Mobile agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
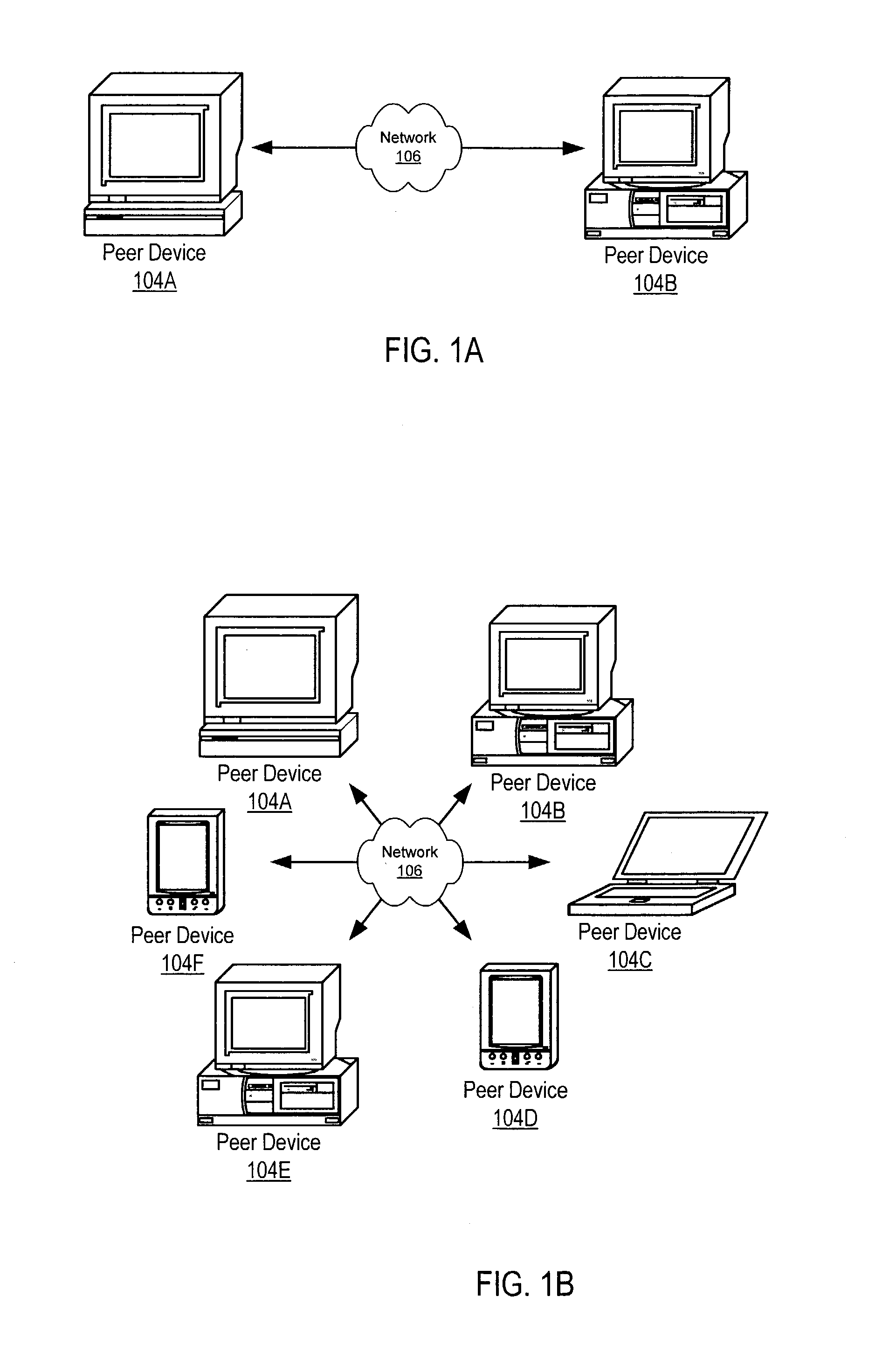
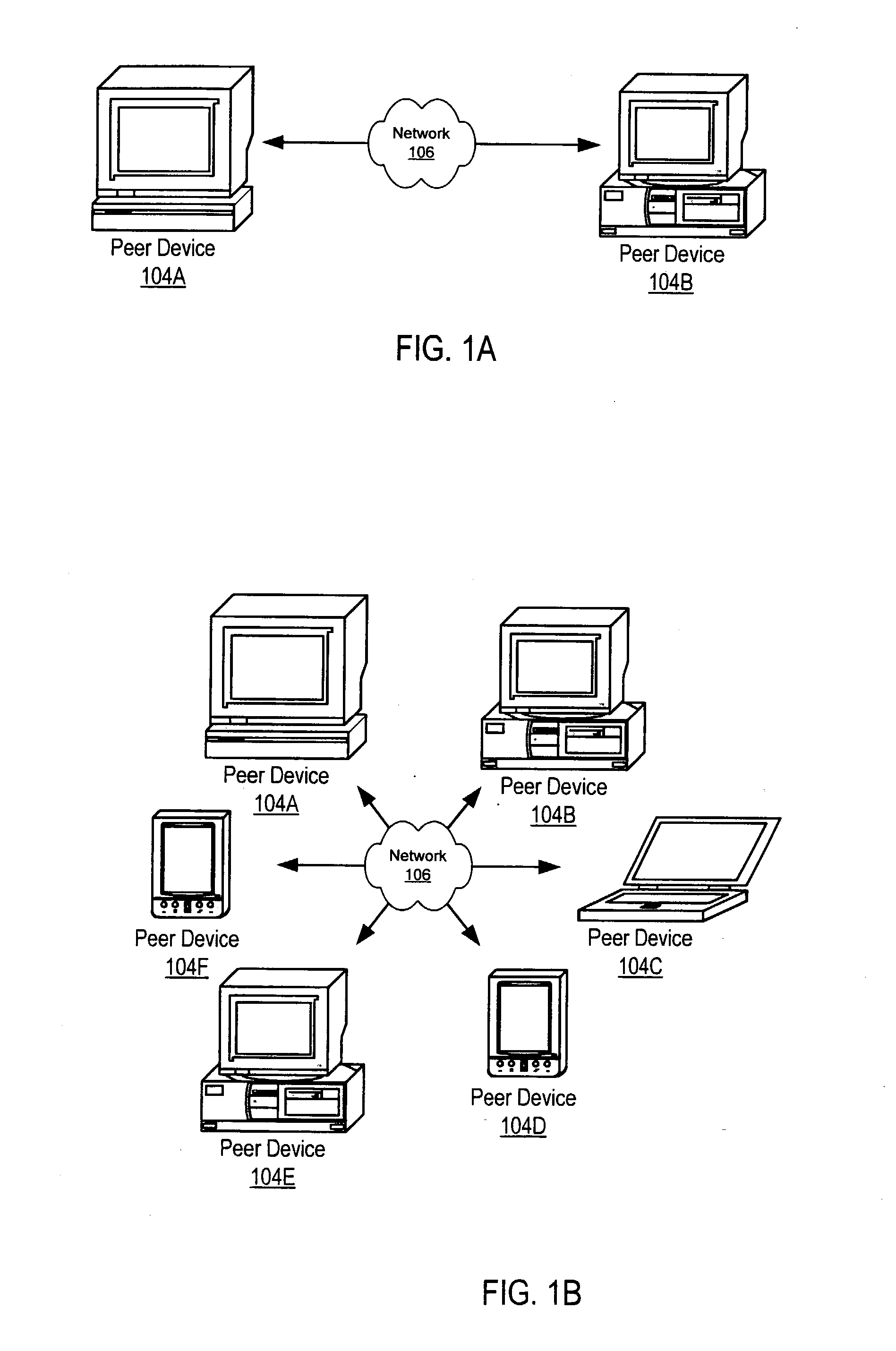
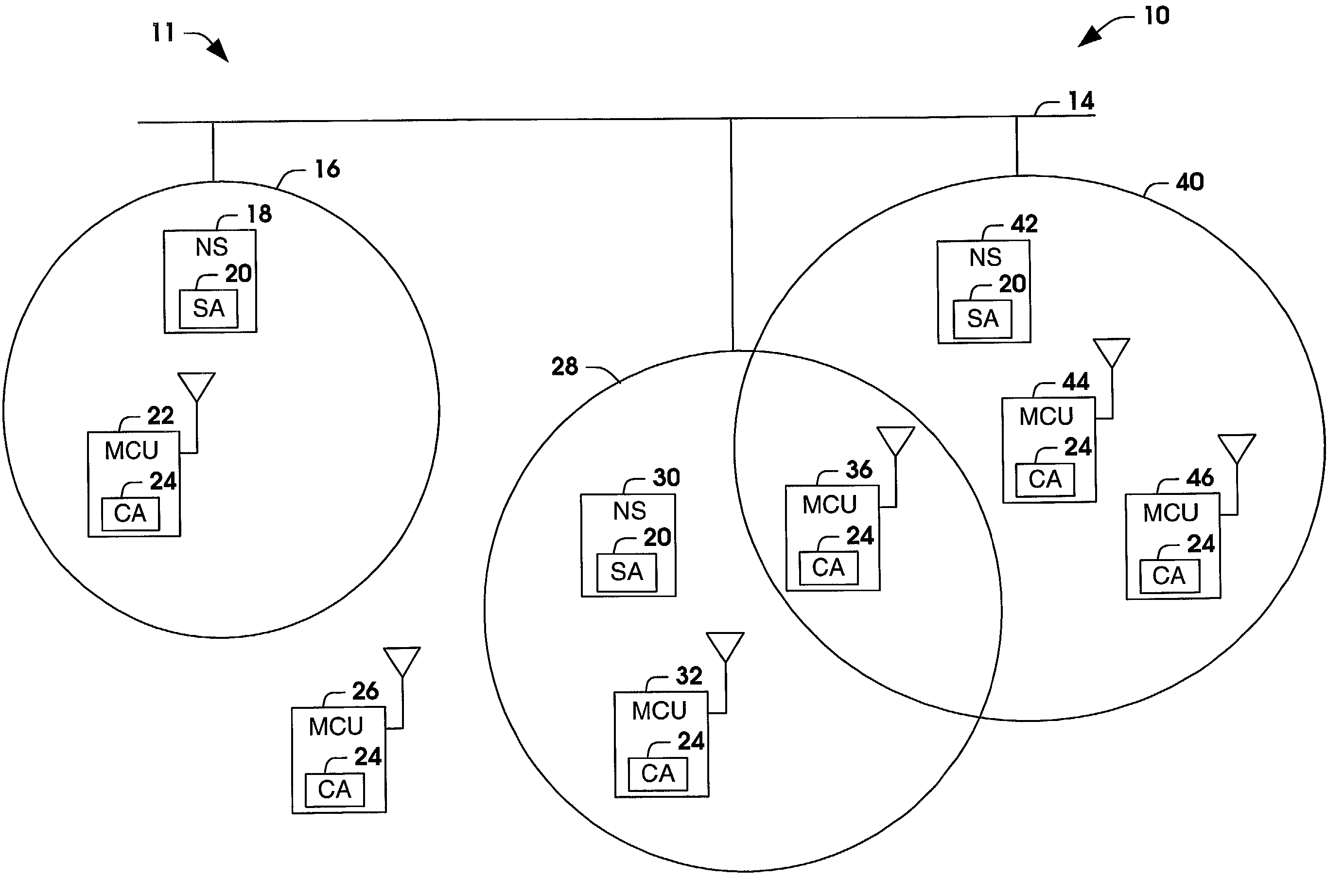
In computer science, a mobile agent is a composition of computer software and data which is able to migrate (move) from one computer to another autonomously and continue its execution on the destination computer. In reality, the mobile agent is the code/object on move which travels in its itinerary within the network of connected nodes.
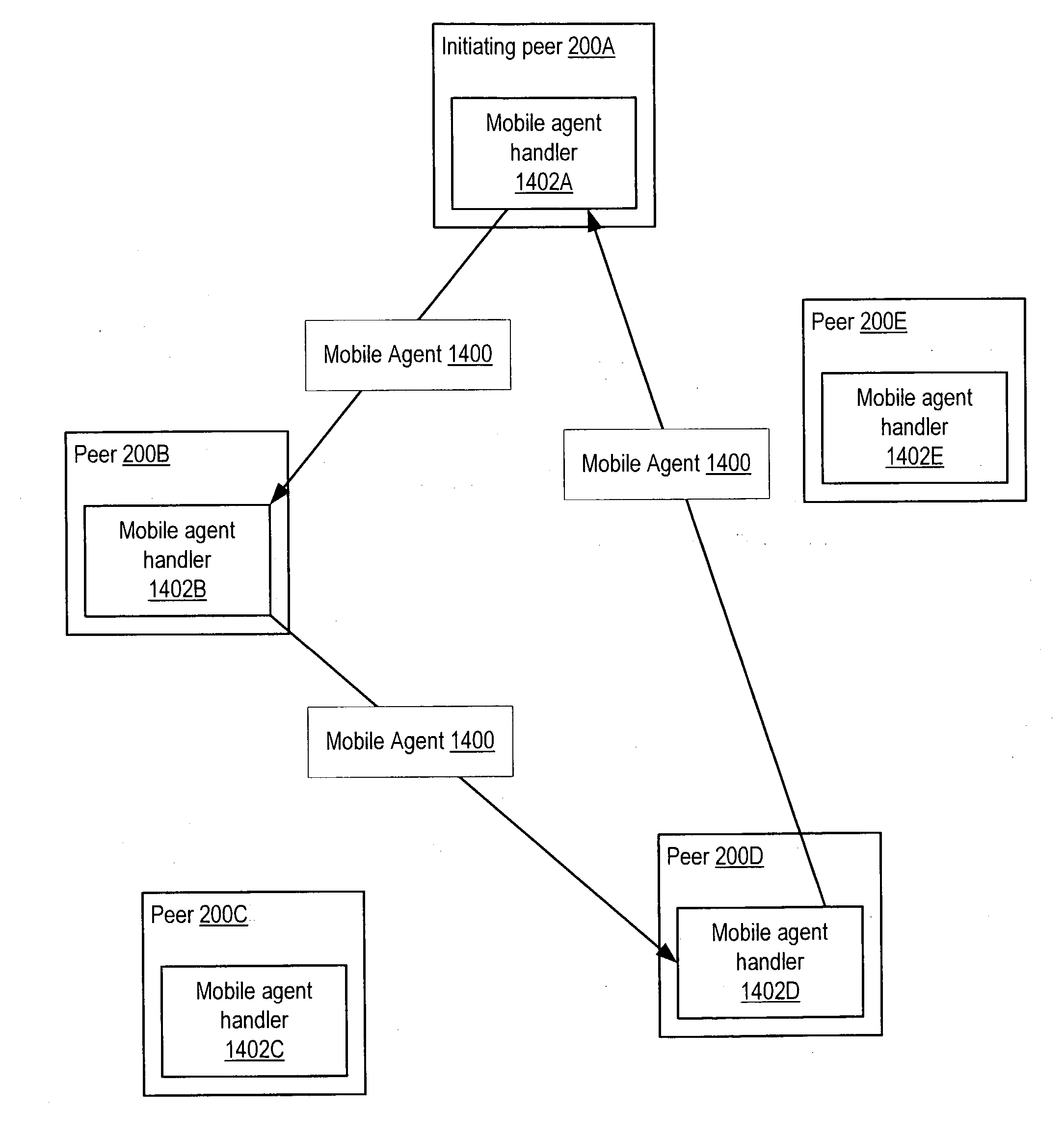
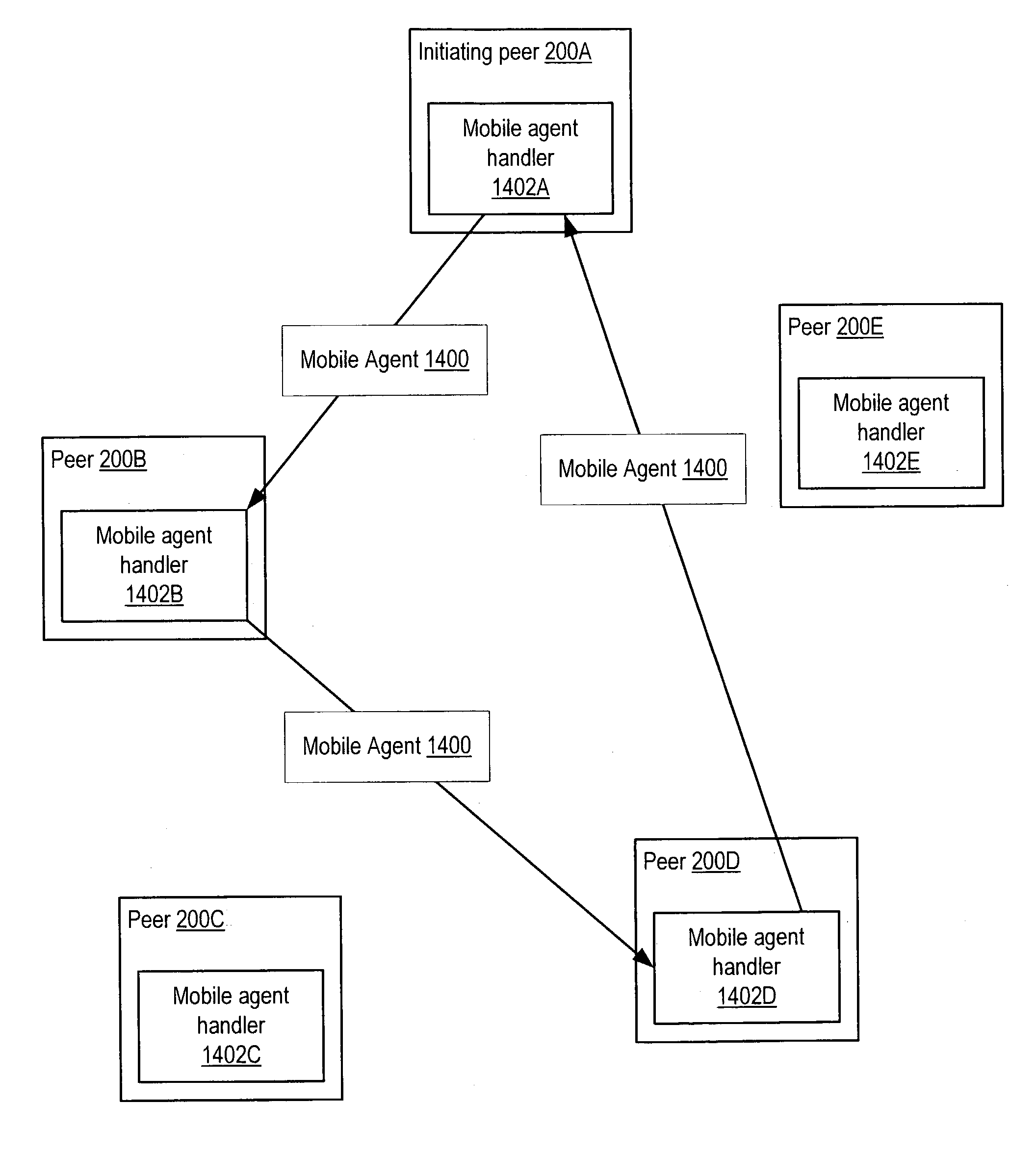
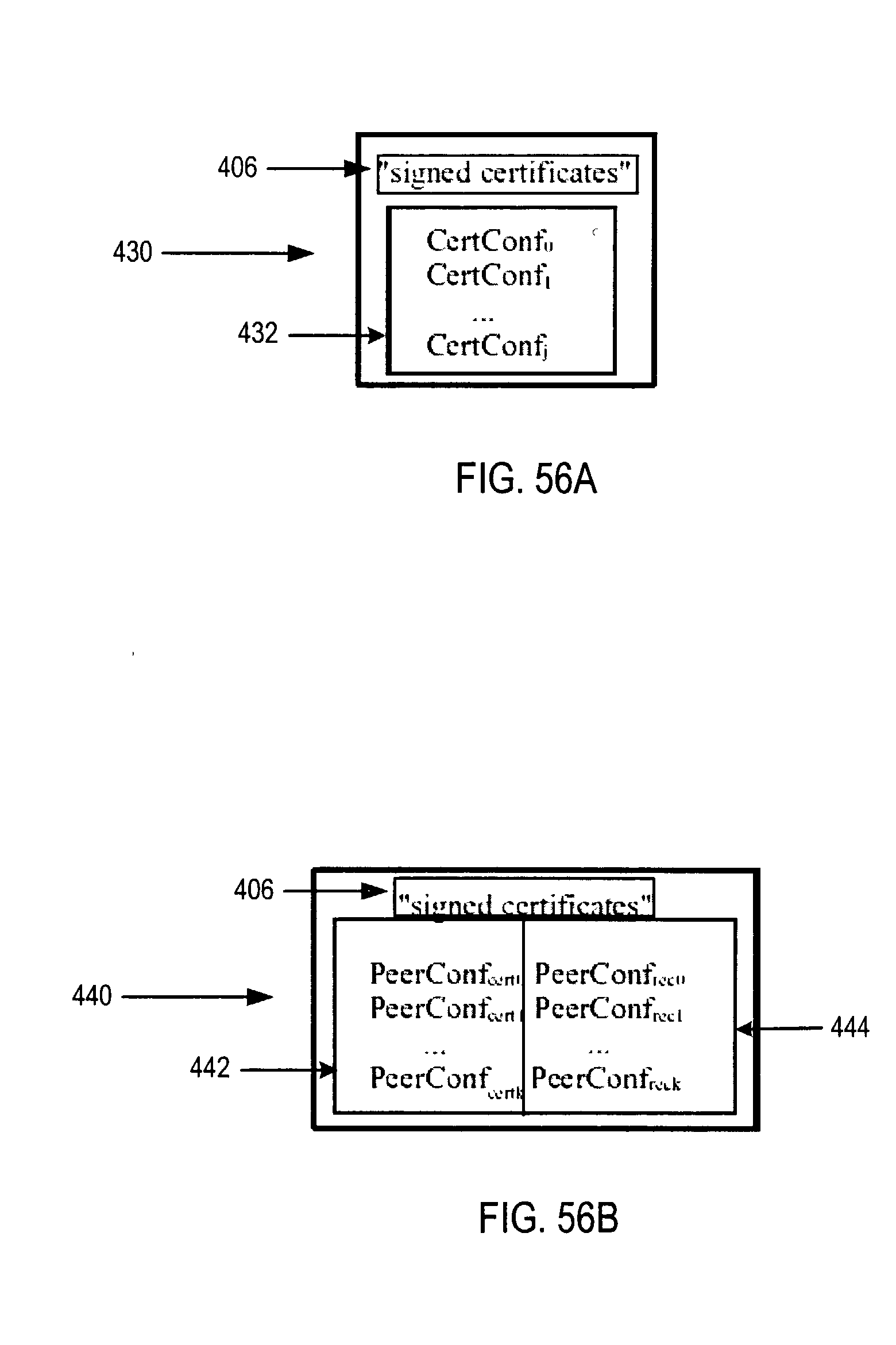
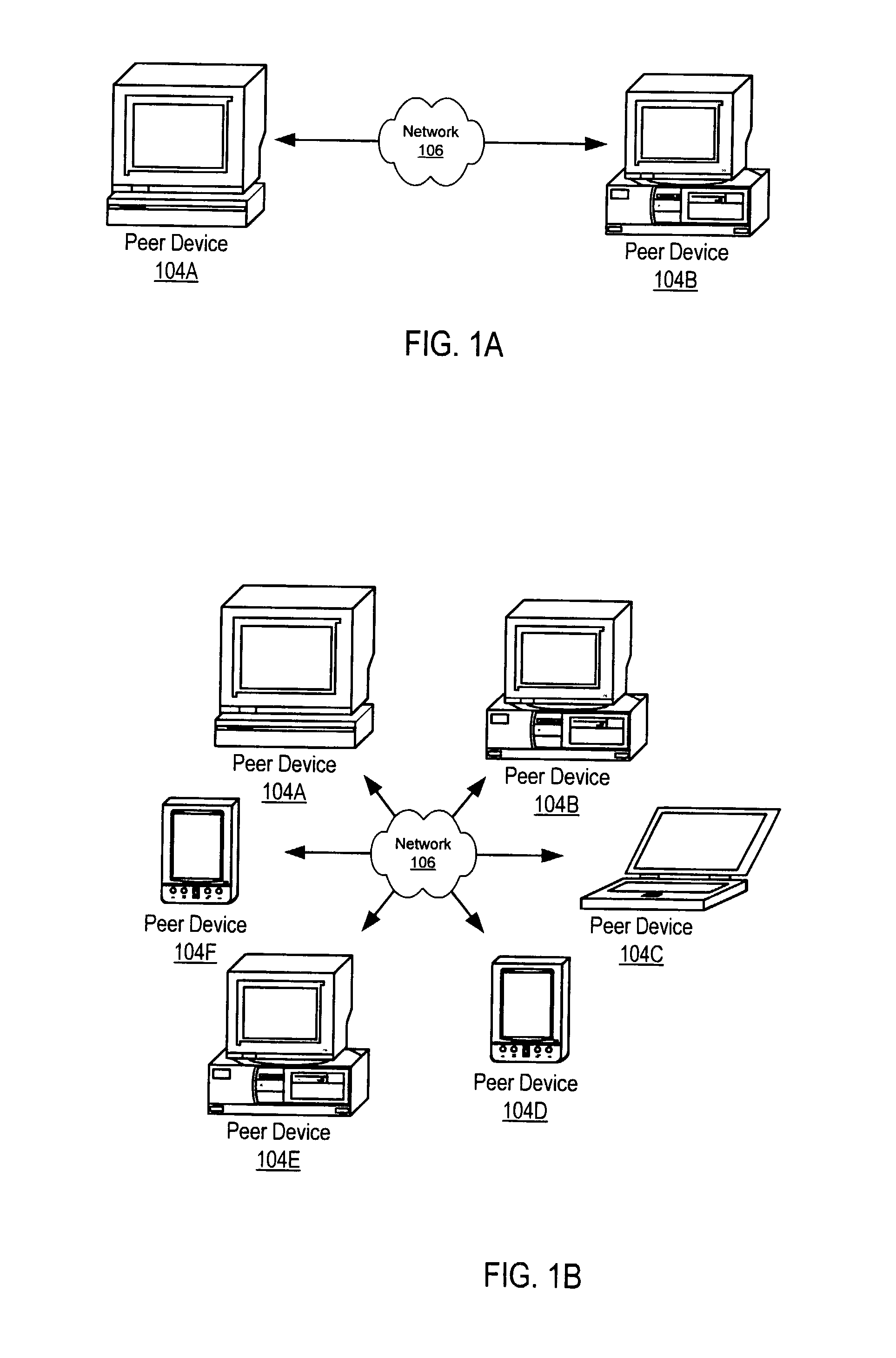
Managing distribution of content using mobile agents in peer-topeer networks
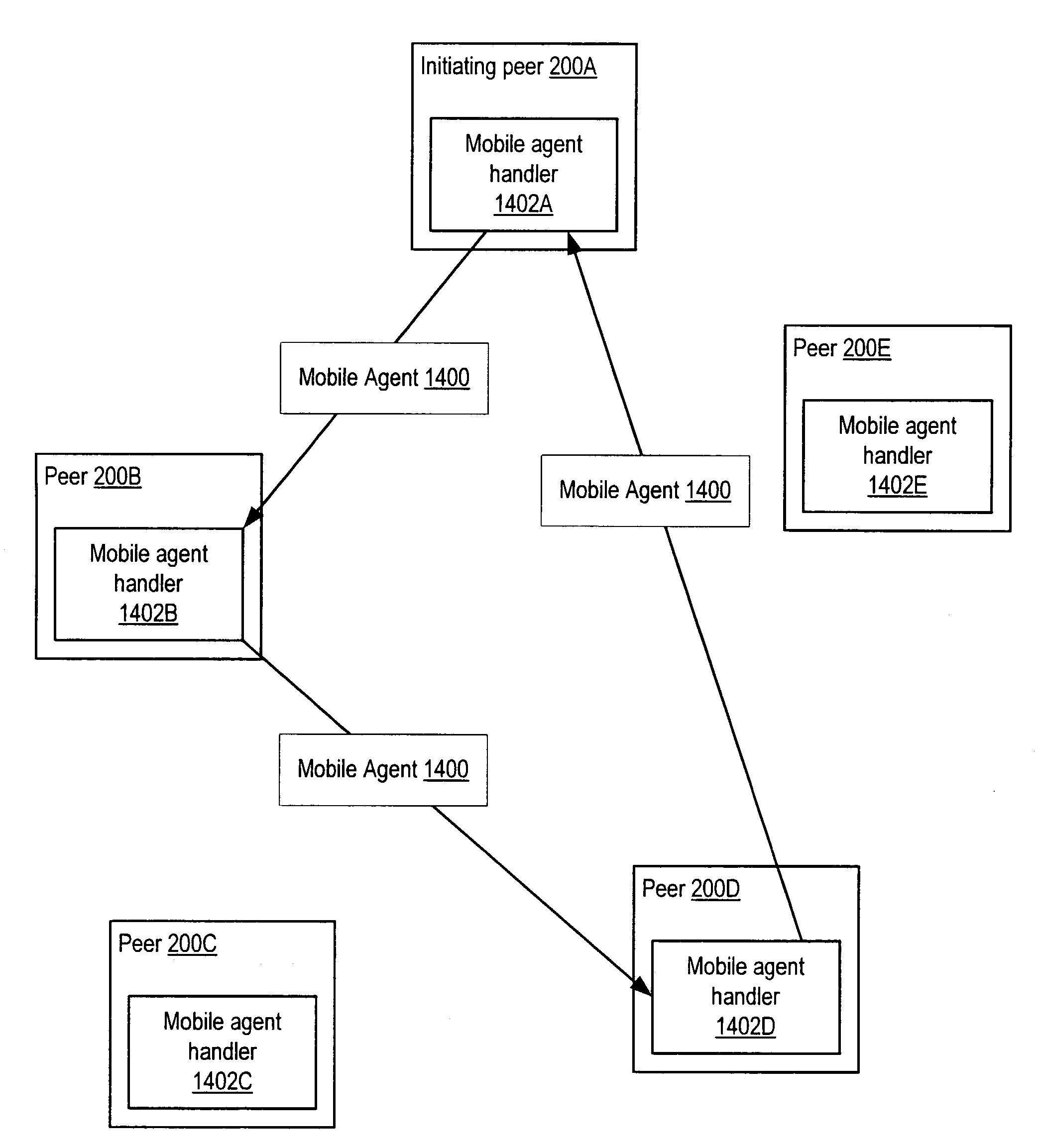
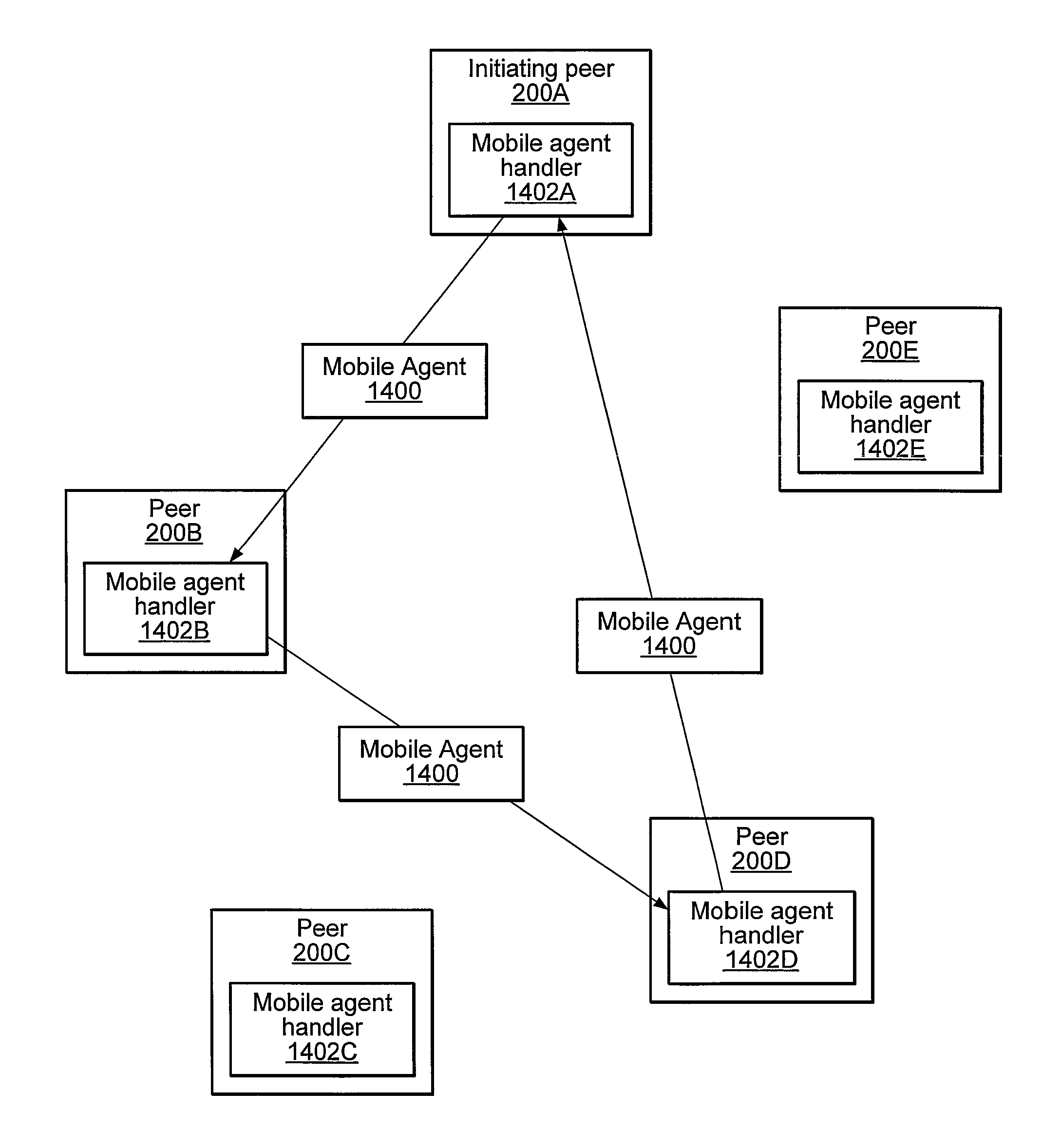
Embodiments of a system and method for using mobile agents for managing distribution of content in peer-to-peer networks. An initiating peer node may launch a mobile agent including an itinerary of a group of peer nodes configured to receive and share content from a distributor. The mobile agent may visit the peer nodes on the itinerary to search for and collect information on distributor content stored on the visited peer nodes. The mobile agent may return the payload to the initiating peer node after completing the itinerary. In one embodiment, the mobile agent may include authentication information, and each visited peer node may access the authentication information to verify the mobile agent as authorized by the distributor. The initiating peer node may examine the information provided by the mobile agent to detect unauthorized copies of the distributor content.
Owner:ORACLE INT CORP
Managing distribution of content using mobile agents in peer-topeer networks
Embodiments of a system and method for using mobile agents for managing distribution of content in peer-to-peer networks. An initiating peer node may launch a mobile agent including an itinerary of a group of peer nodes configured to receive and share content from a distributor. The mobile agent may visit the peer nodes on the itinerary to search for and collect information on distributor content stored on the visited peer nodes. The mobile agent may return the payload to the initiating peer node after completing the itinerary. In one embodiment, the mobile agent may include authentication information, and each visited peer node may access the authentication information to verify the mobile agent as authorized by the distributor. The initiating peer node may examine the information provided by the mobile agent to detect unauthorized copies of the distributor content.
Owner:ORACLE INT CORP
Collaborative content coherence using mobile agents in peer-to-peer networks
ActiveUS20040088646A1Data processing applicationsMultiple digital computer combinationsDocumentationDistributed computing
Embodiments of a system and method for using mobile agents for collaborative content control in peer-to-peer networks. A peer may launch a mobile agent including an itinerary of peers to be visited and indications of one or more documents that the peers are collaboratively editing. The mobile agent may visit peers indicated by the itinerary to collect version information for the document(s). The mobile agent may return the version information to the initiating peer, which may coordinate each of the document(s) on the peer to a most recent version in accordance with the version information provided by the mobile agent. Visited peers may use the payload to determine if their version of the document(s) are up to date and, if not, may add a version update request to the payload. The initiating peer may send the most recent version information to peers that added version update requests to the payload.
Owner:ORACLE INT CORP
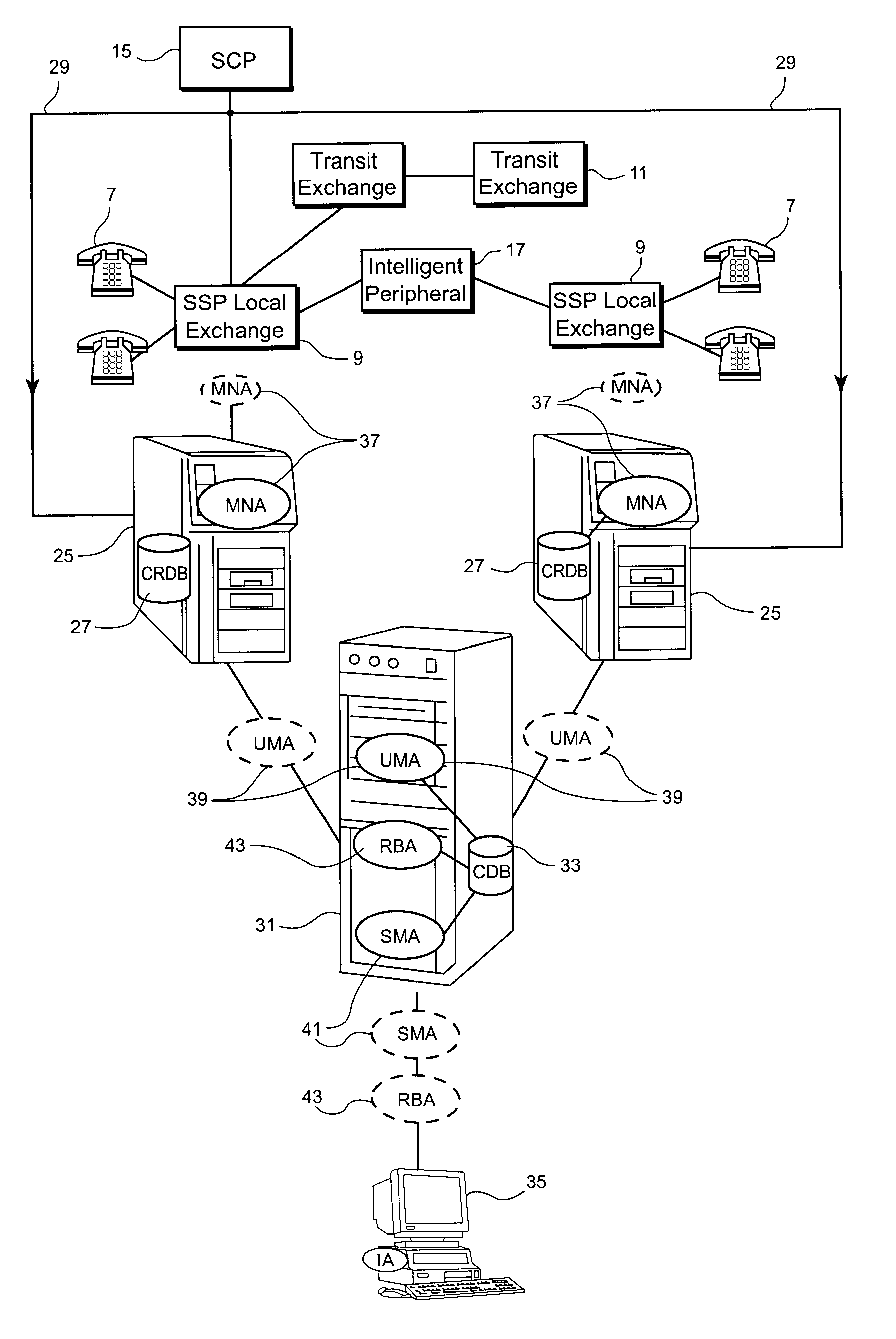
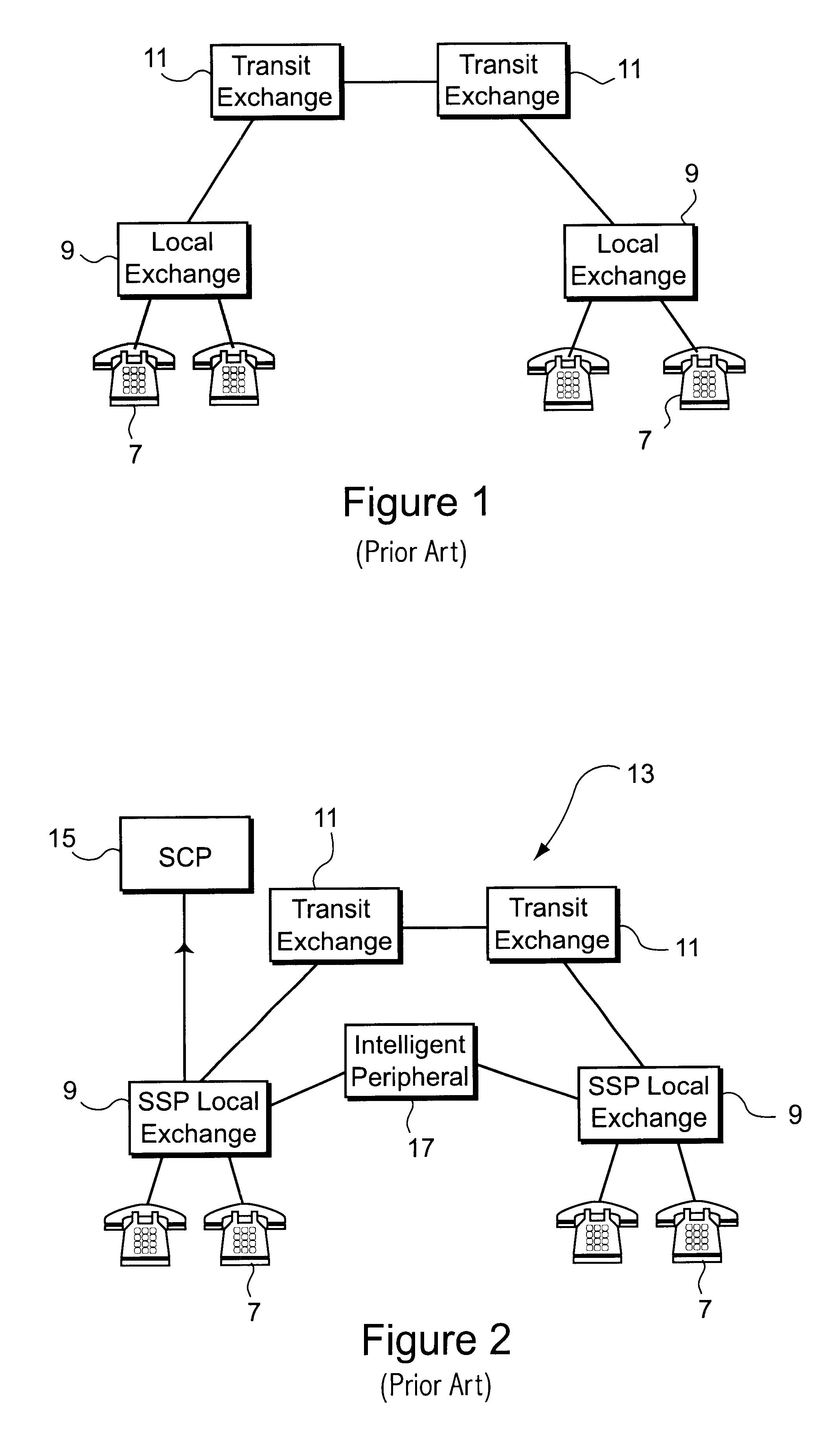
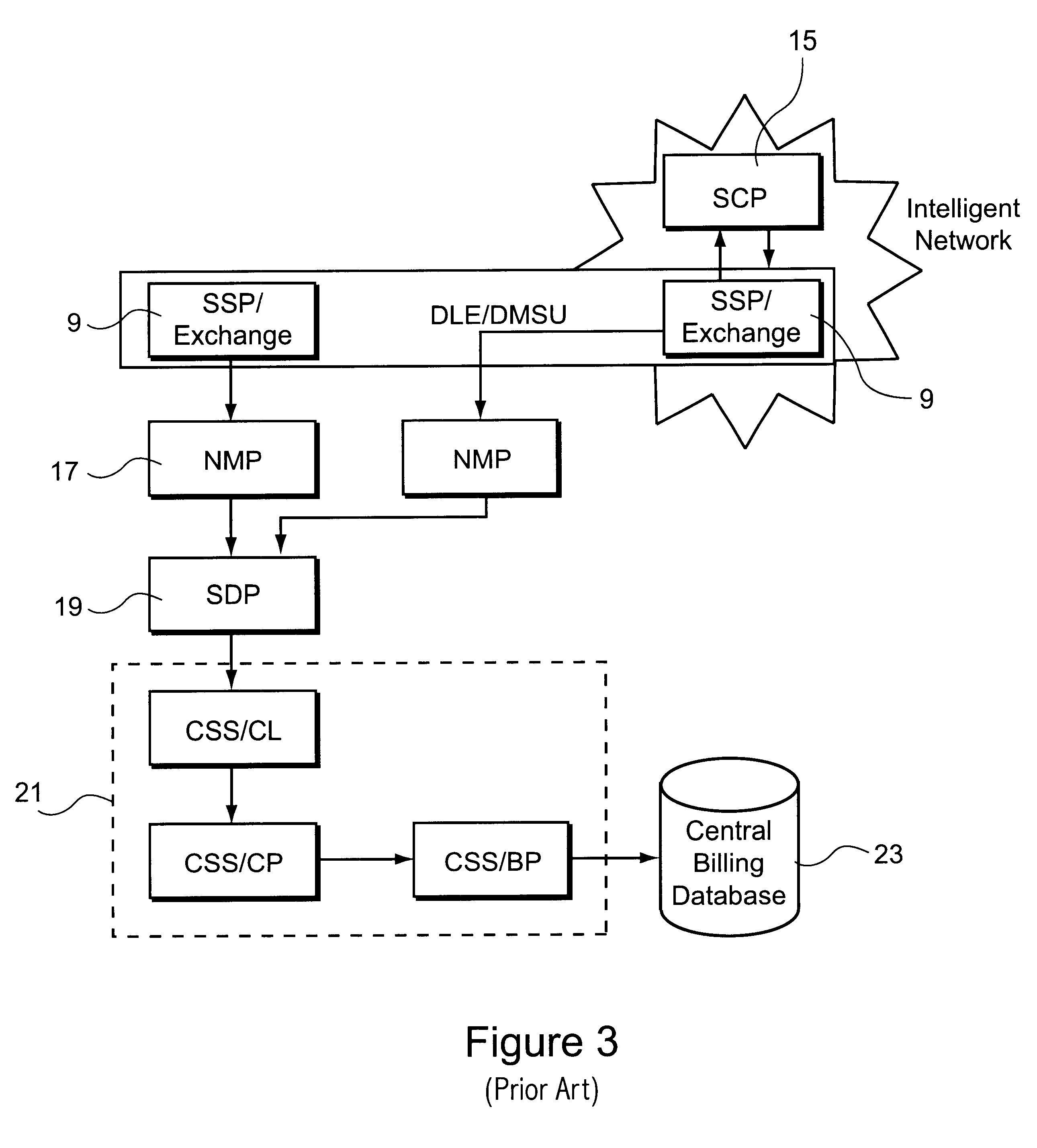
Billing system
A billing system for a telecommunications network uses a monitoring software agent to monitor messages, indicative of individual calls on the network, passing between a service switching point and a service control point. Call record information is extracted and is stored in a local call record database. Information from each call record database is then passed on to a central database, using updating mobile agents, the central database being accessible to such agents and report building agents which can extract billing information as requested by an operator. By monitoring the messages as they pass, the system can provide real time billing information without needing to poll the switch at the service switching point.
Owner:BRITISH TELECOMM PLC
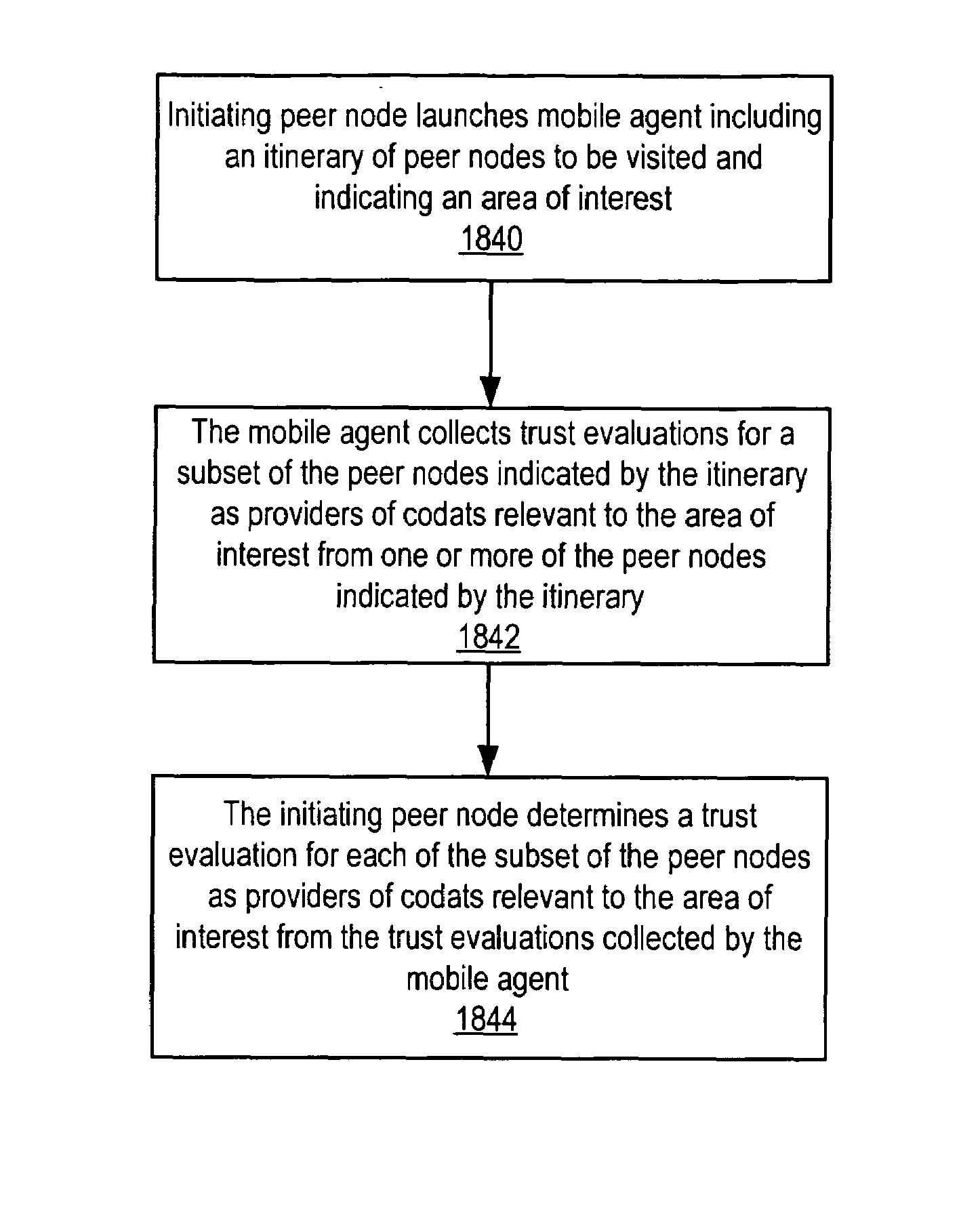
Peer trust evaluation using mobile agents in peer-to-peer networks
ActiveUS20040088369A1Digital data processing detailsMultiple digital computer combinationsPeer-to-peerRegion of interest
Embodiments of a system and method for using mobile agents to gather trust information for evaluating trust in peer-to-peer networks. A peer node may launch a mobile agent on a network including an itinerary of peer nodes to be visited by the mobile agent and an indication of an area of interest. The mobile agent may determine if a visited peer node stores trust evaluations for other peer nodes as providers of codats relevant to the area of interest and, if so, the trust evaluations may be stored as payload data in the mobile agent. After completing the itinerary, the mobile agent may return the payload to the initiating peer node. The initiating peer node may use the trust evaluations collected by the mobile agent in determining or adjusting trust evaluations for peer nodes as providers of codats relevant to the area of interest.
Owner:ORACLE INT CORP
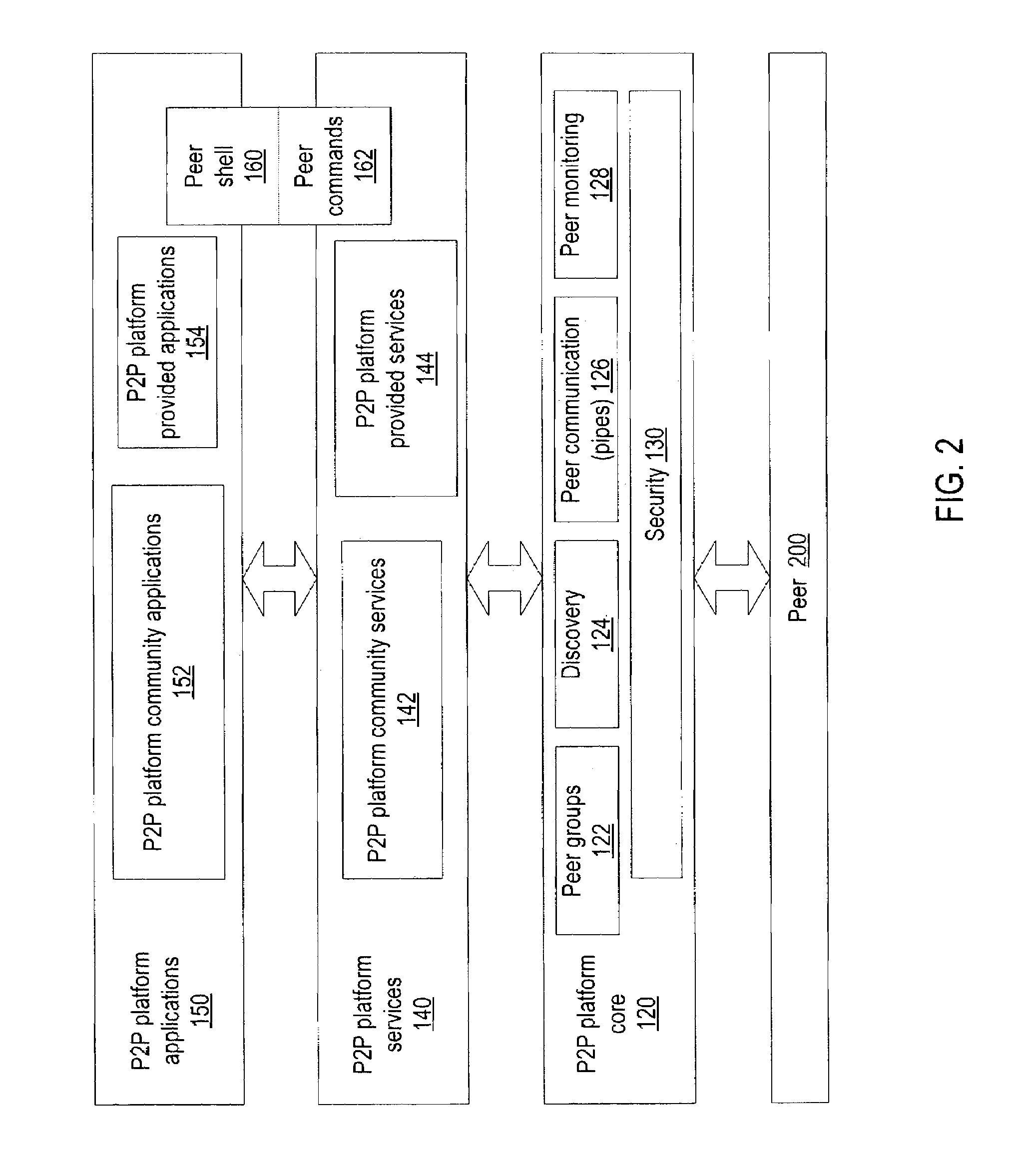
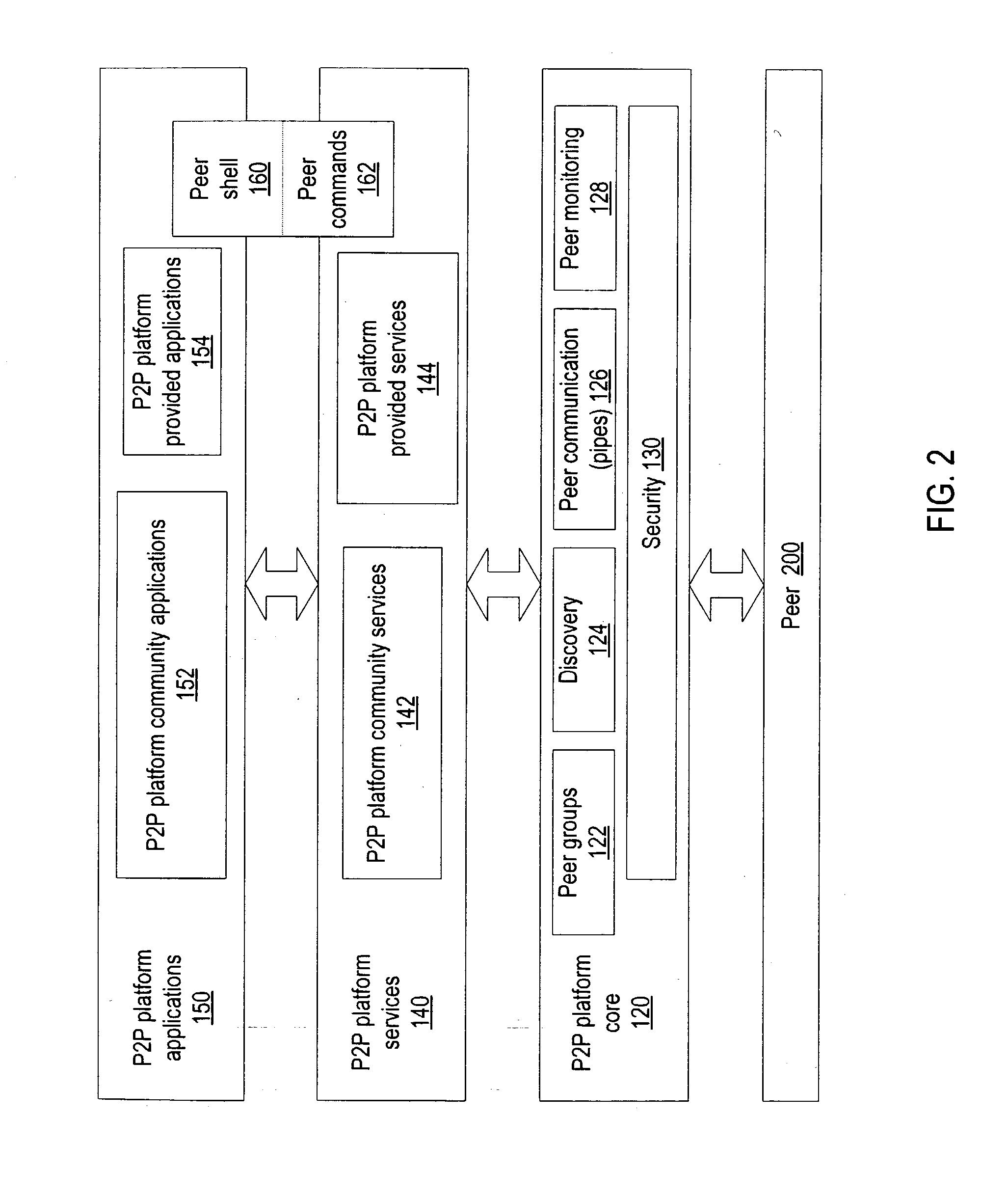
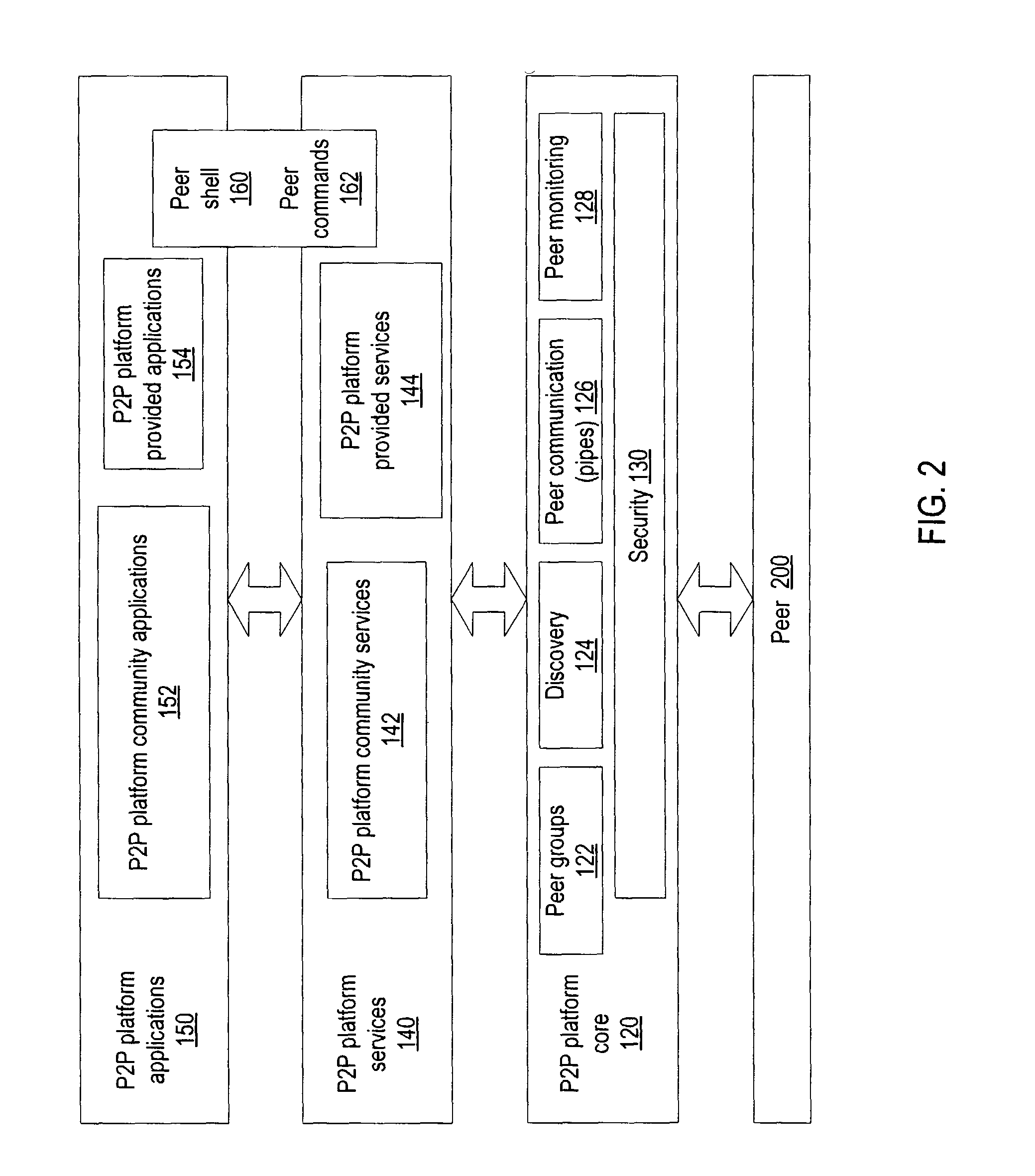
Mobile agents in peer-to-peer networks
ActiveUS20040088347A1Multiple digital computer combinationsTransmissionPeer-to-peerVirtual communication
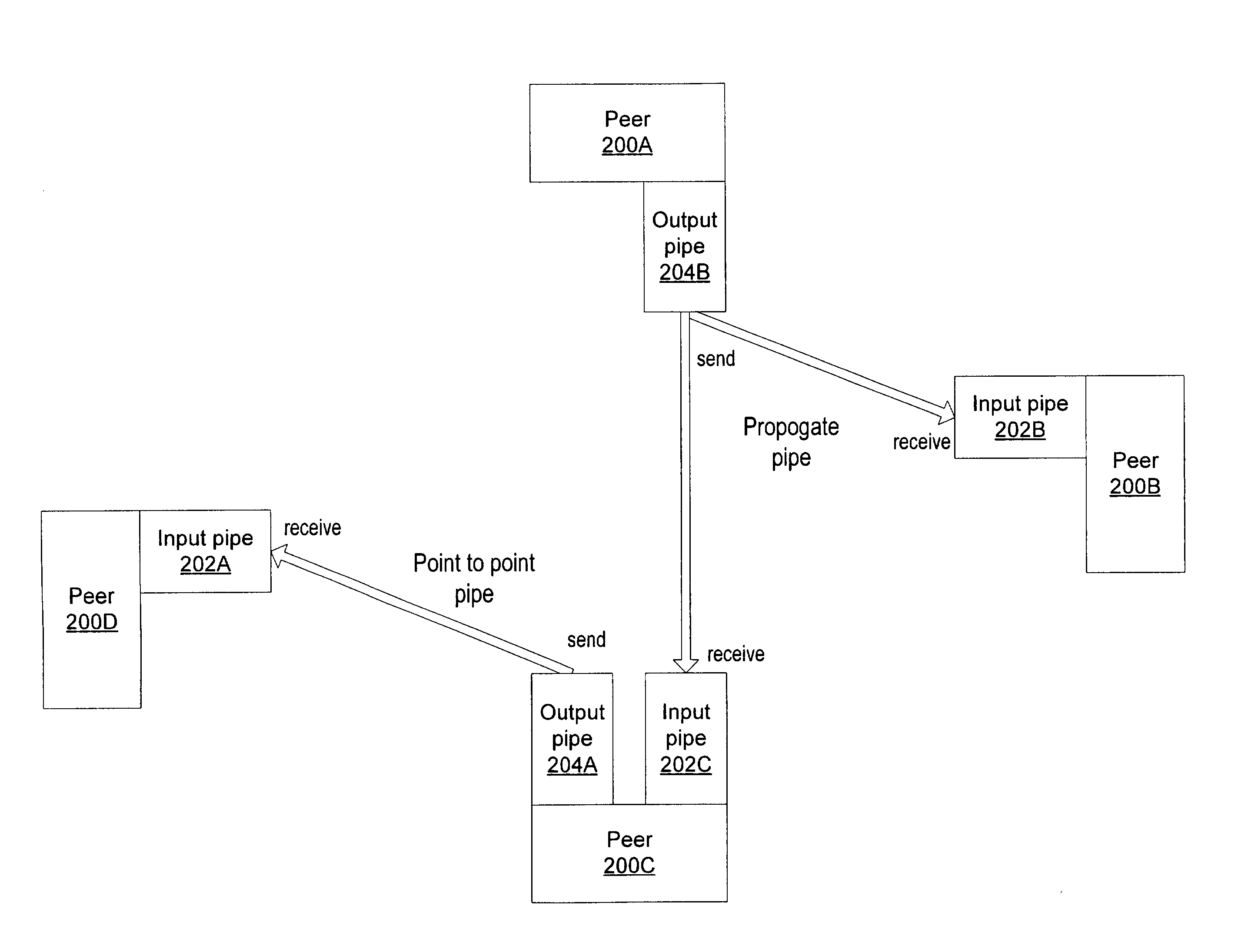
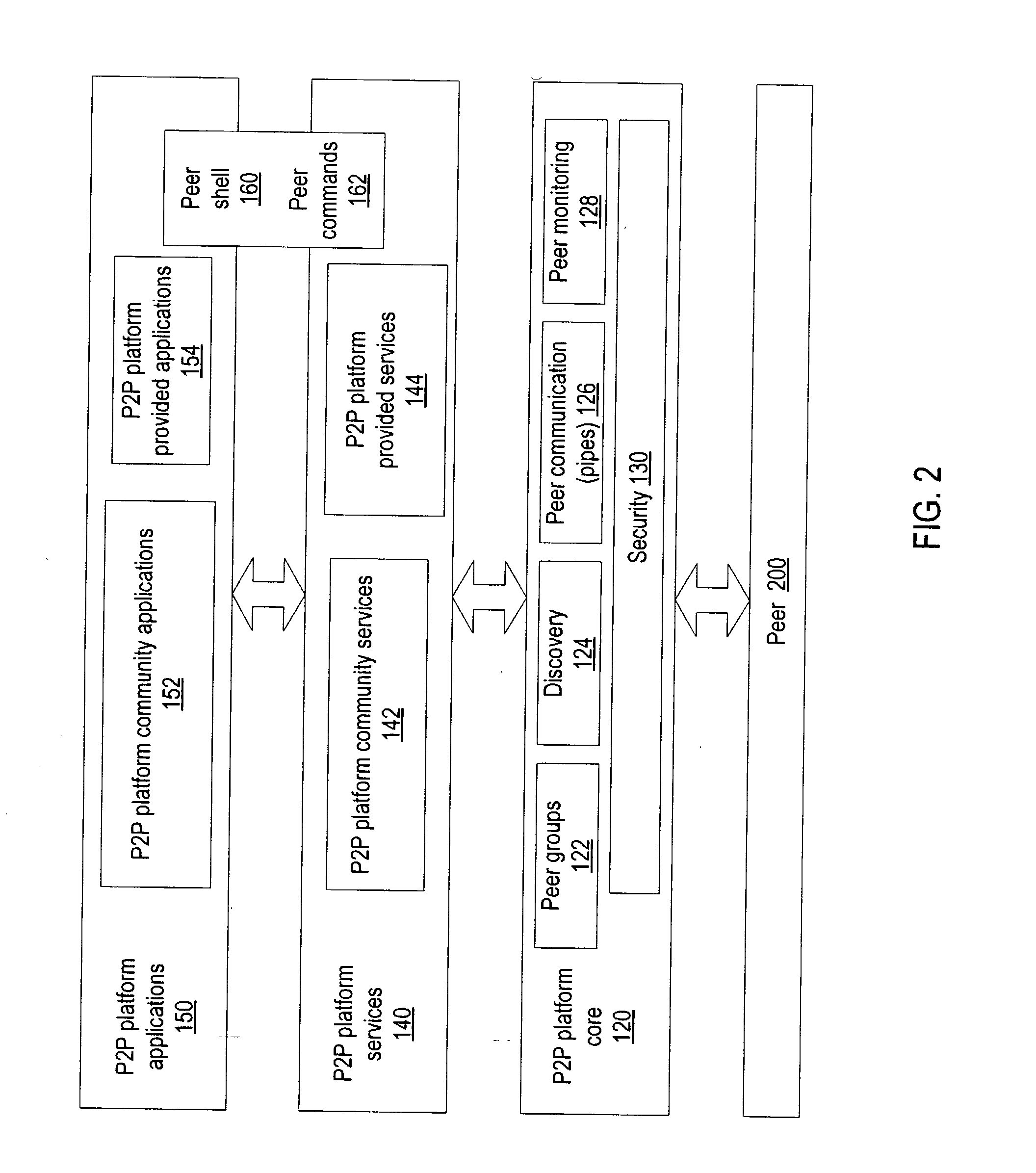
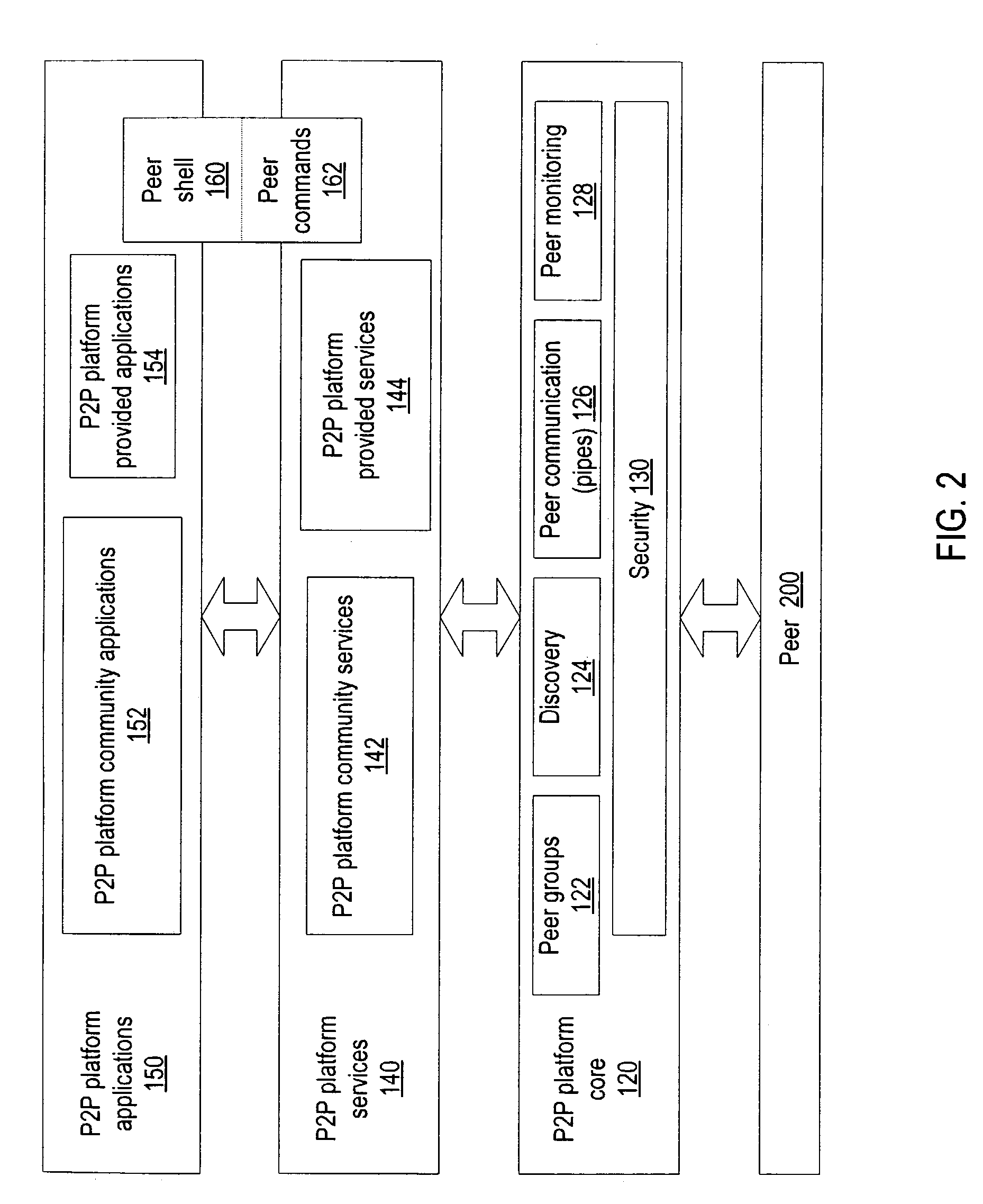
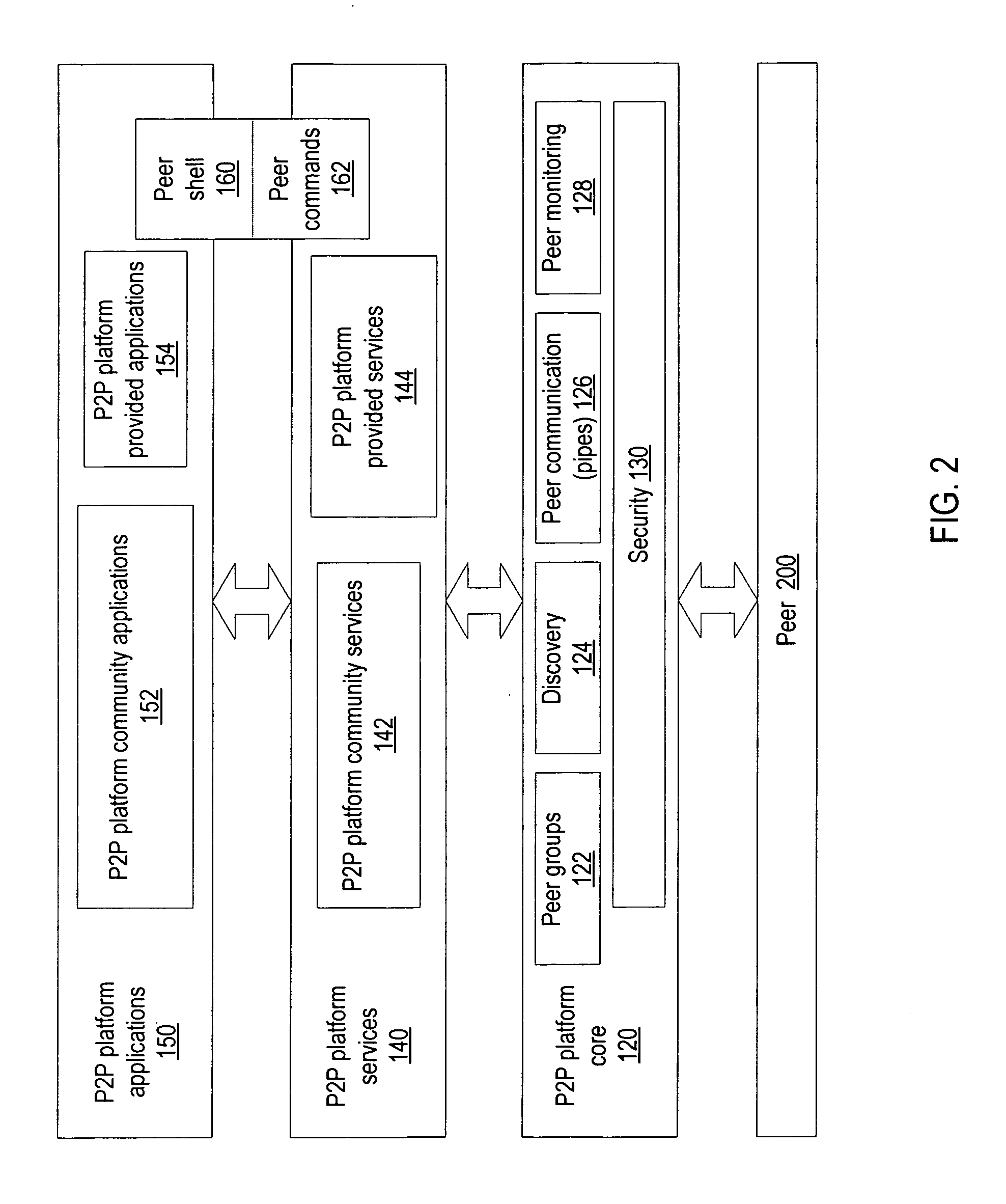
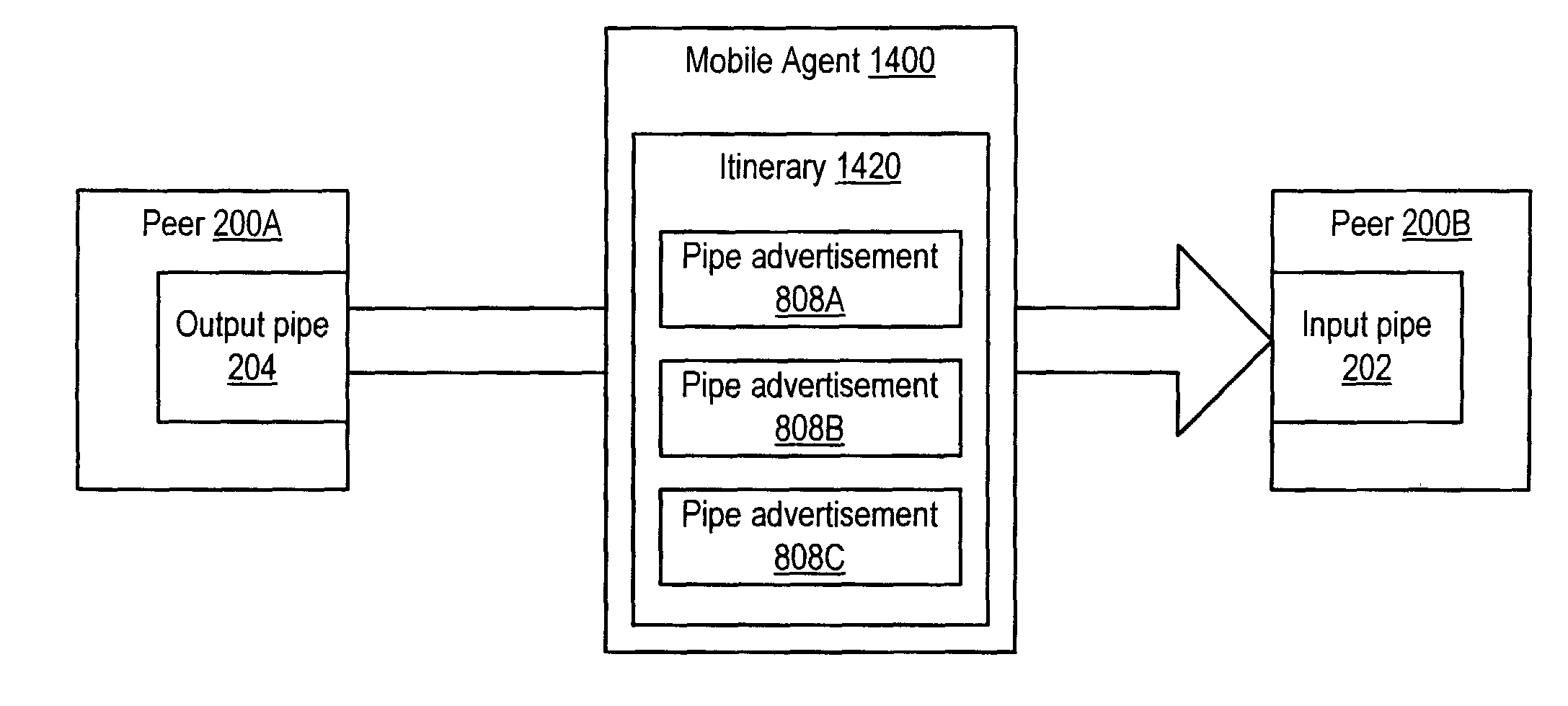
Embodiments of a mechanism for implementing mobile agents in peer-to-peer networks. An initiating peer may generate a mobile agent to perform one or more tasks on or gather information from other peers in the peer-to-peer network. The mobile agent may include an itinerary of peers that the mobile agent may visit. The mobile agent may be transmitted on communications channels in the peer-to-peer network to each peer on the itinerary in turn, and return to the initiating peer after visiting or attempting to visit each peer on the itinerary. In one embodiment, the mobile agent may traverse its itinerary via virtual communication channels (pipes) implemented according to a peer-to-peer platform. A mobile agent may include information identifying input pipes for each peer on its itinerary. Peers may generate and advertise input pipes for use by mobile agents.
Owner:ORACLE INT CORP
Collaborative content coherence using mobile agents in peer-to-peer networks
ActiveUS7328243B2Data processing applicationsMultiple digital computer combinationsDocumentationDistributed computing
A mobile agent may be provided for collaborative content control in peer-to-peer networks. A peer may launch a mobile agent including an itinerary of peers to be visited and indications of one or more documents that the peers are collaboratively editing. The mobile agent may visit peers indicated by the itinerary to collect version information for the document(s). The mobile agent may return the version information to the initiating peer, which may coordinate each of the document(s) on the peer to a most recent version in accordance with the version information provided by the mobile agent. Visited peers may use the payload to determine if their version of the document(s) are up to date and, if not, may add a version update request to the payload. The initiating peer may send the most recent version information to peers that added version update requests to the payload.
Owner:ORACLE INT CORP
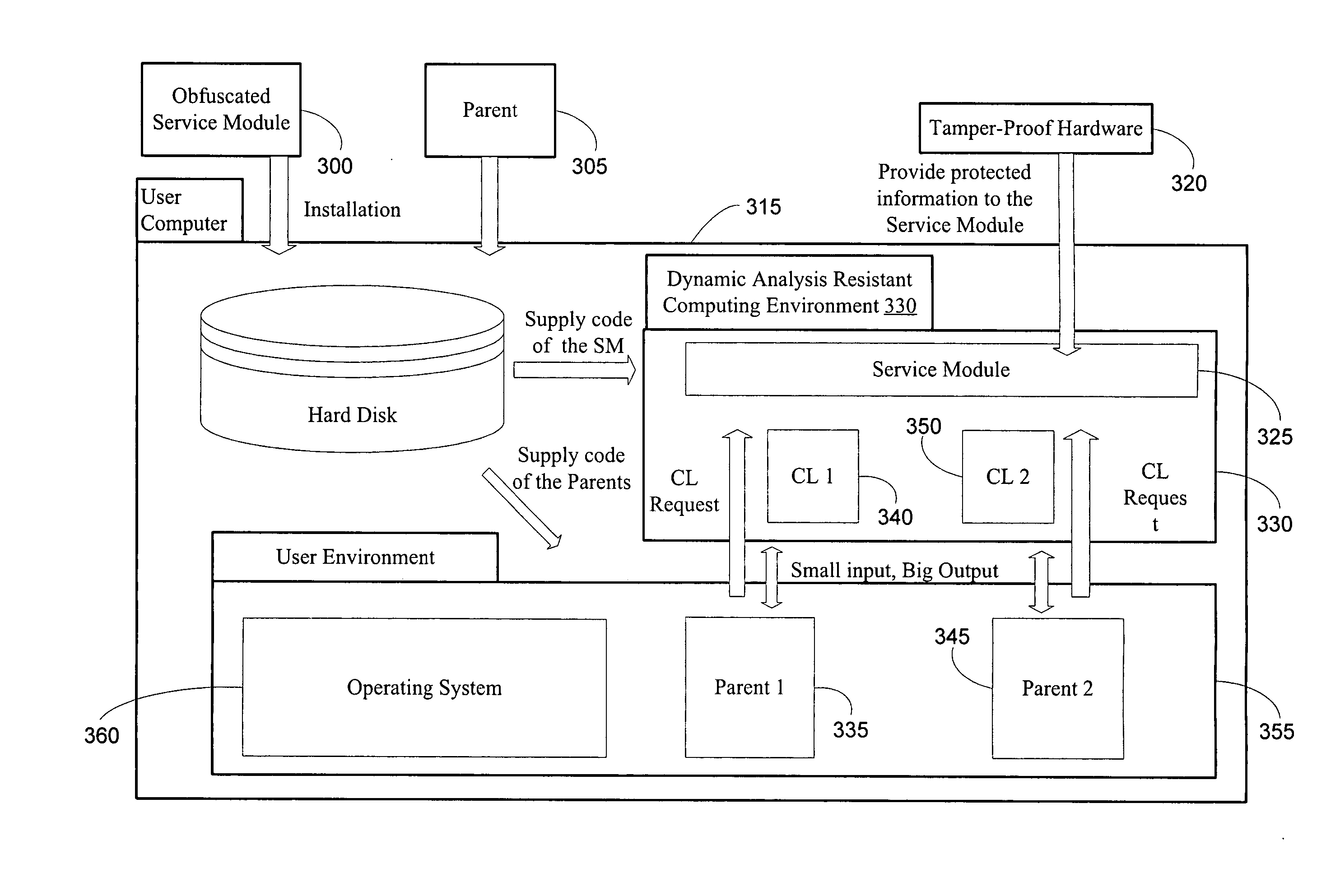
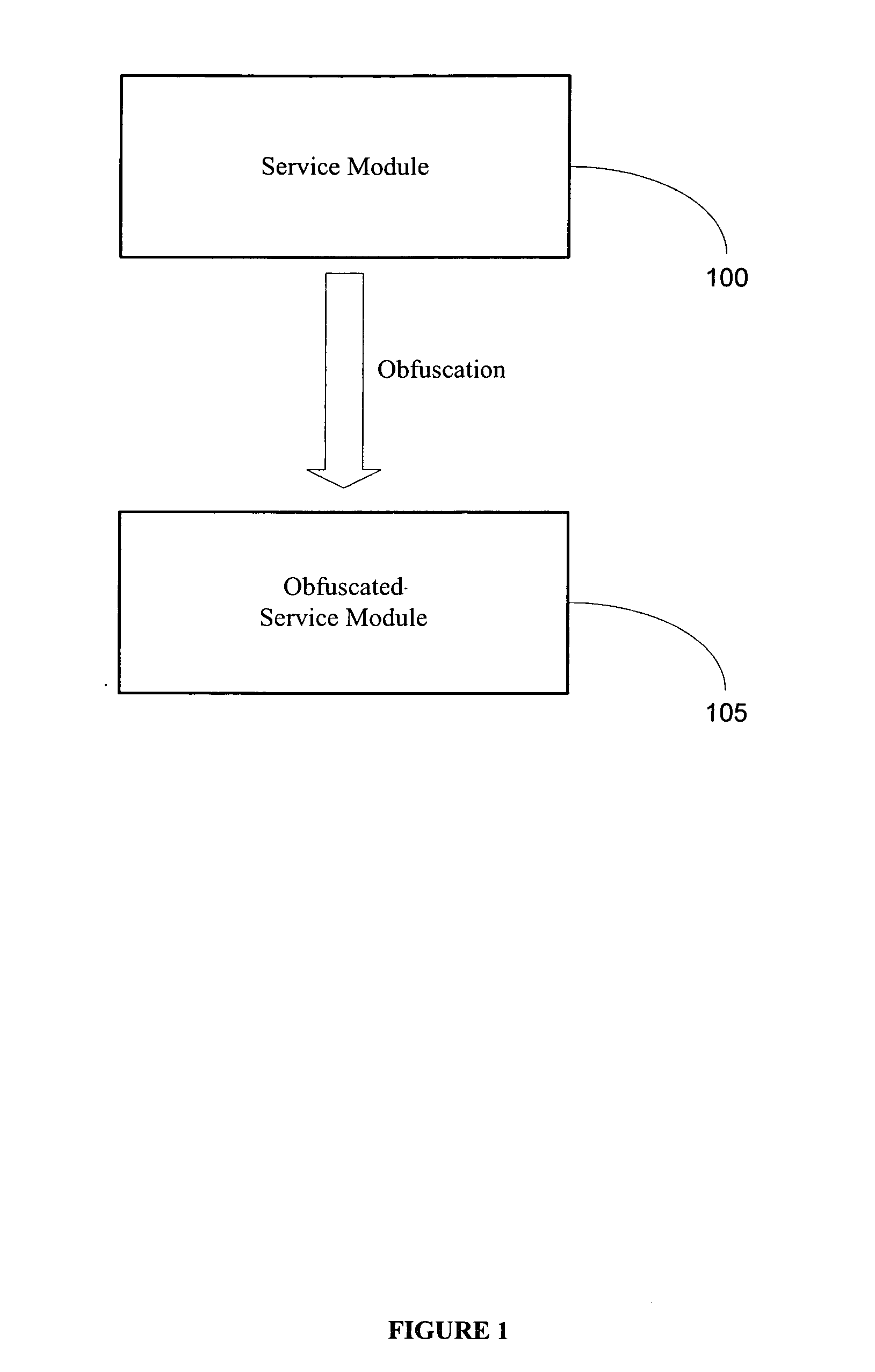
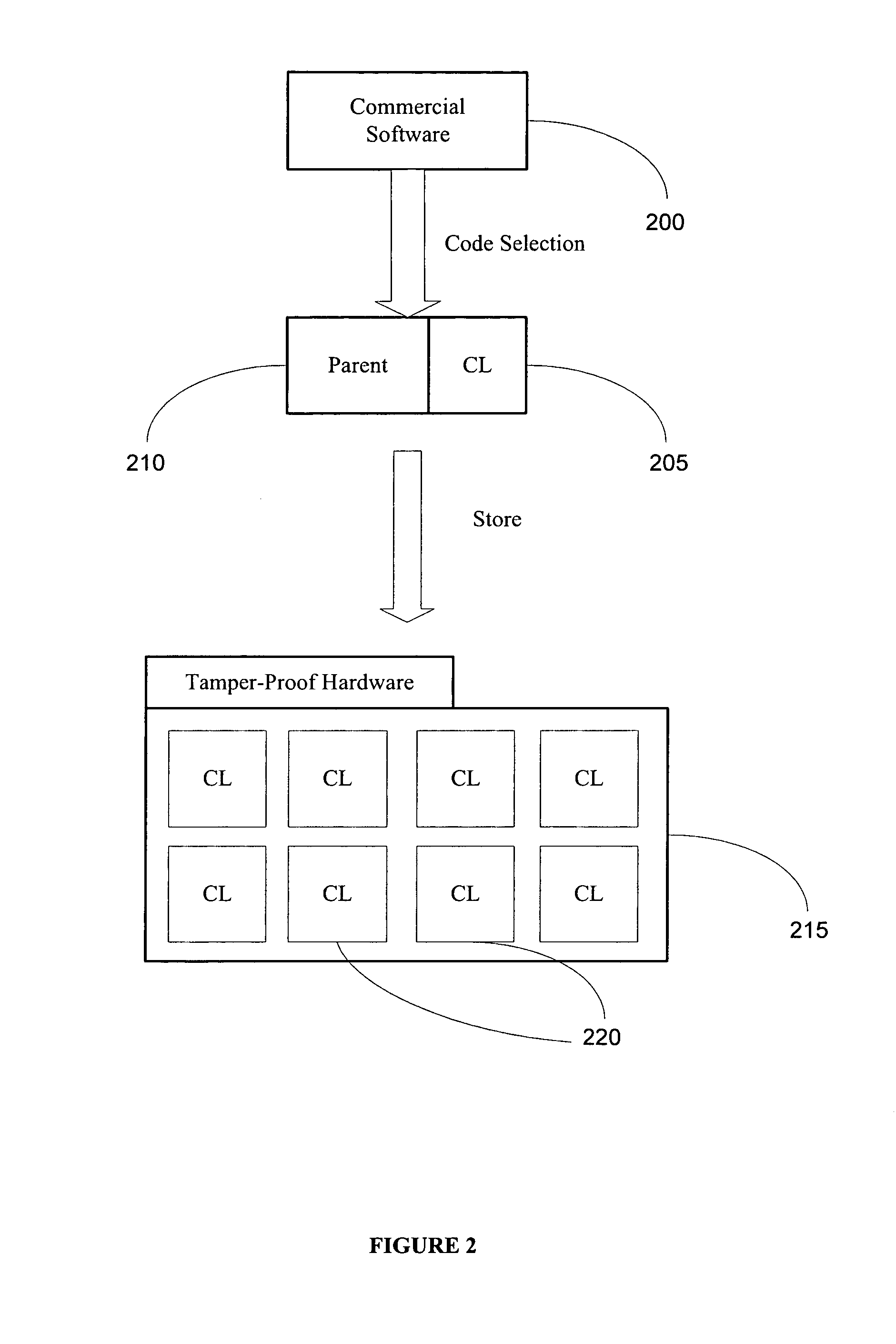
Method and system for providing tamper-resistant software
InactiveUS20060048223A1Performance penaltyImprove tamper resistanceMemory loss protectionDetecting faulty computer hardwareTamper resistanceObfuscation
A method and system for protecting only a portion of the software to be protected against tampering is described. Such a portion may be stored in a tamper-resistant physical device, with optional encryption, for downloading when needed for execution. Several layers of tamper resistance are provided without excessively impacting performance of the protected software. For instance, obfuscation is applied to the code for the service module to minimize the large expense associated with obfuscation. The invention includes embodiments that deliver critical logic, policy information and other similar information with the help of mobile agents, which may be hosted by a server in a smart card.
Owner:THE UNIVERSITY OF HONG KONG
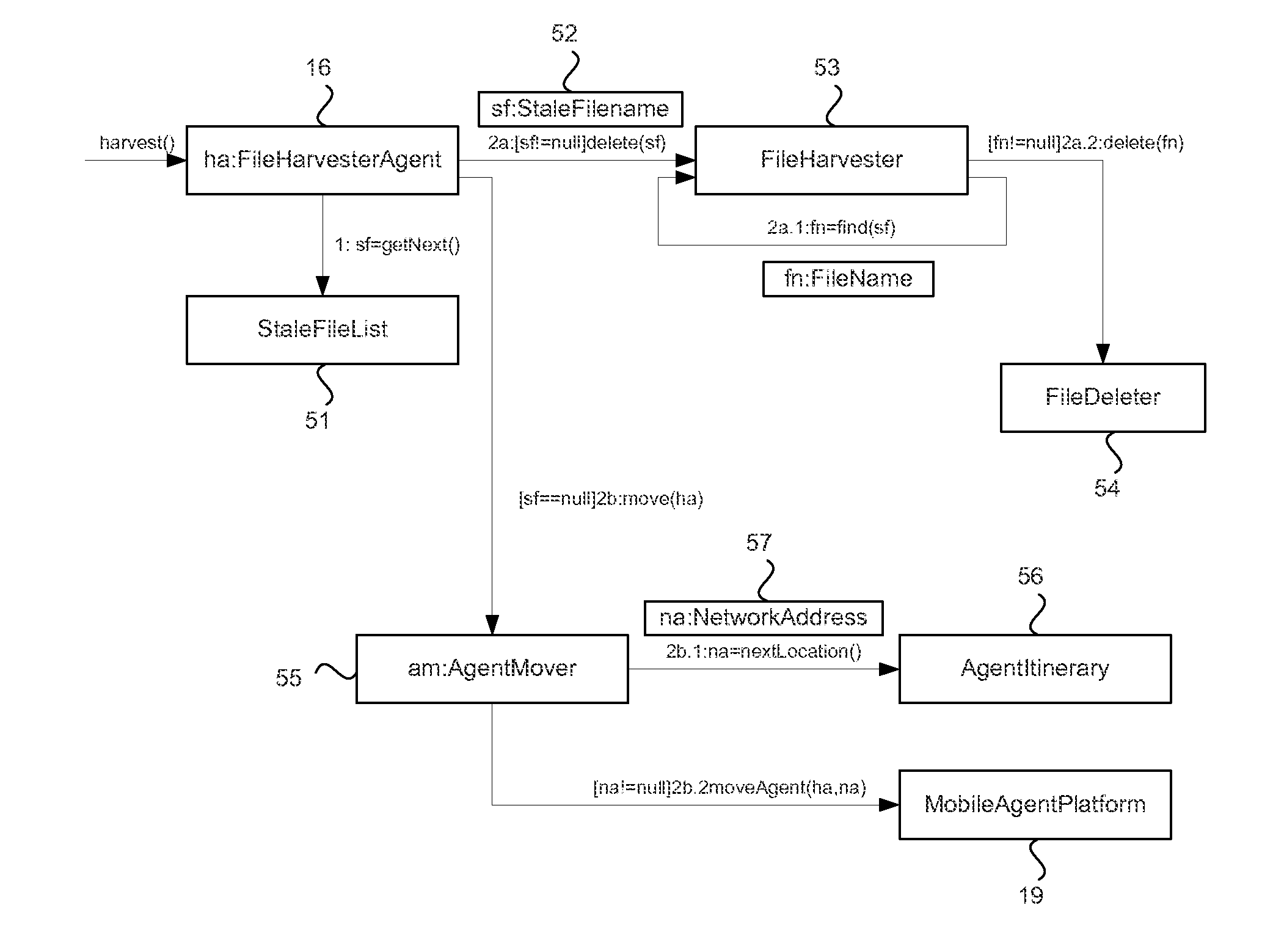
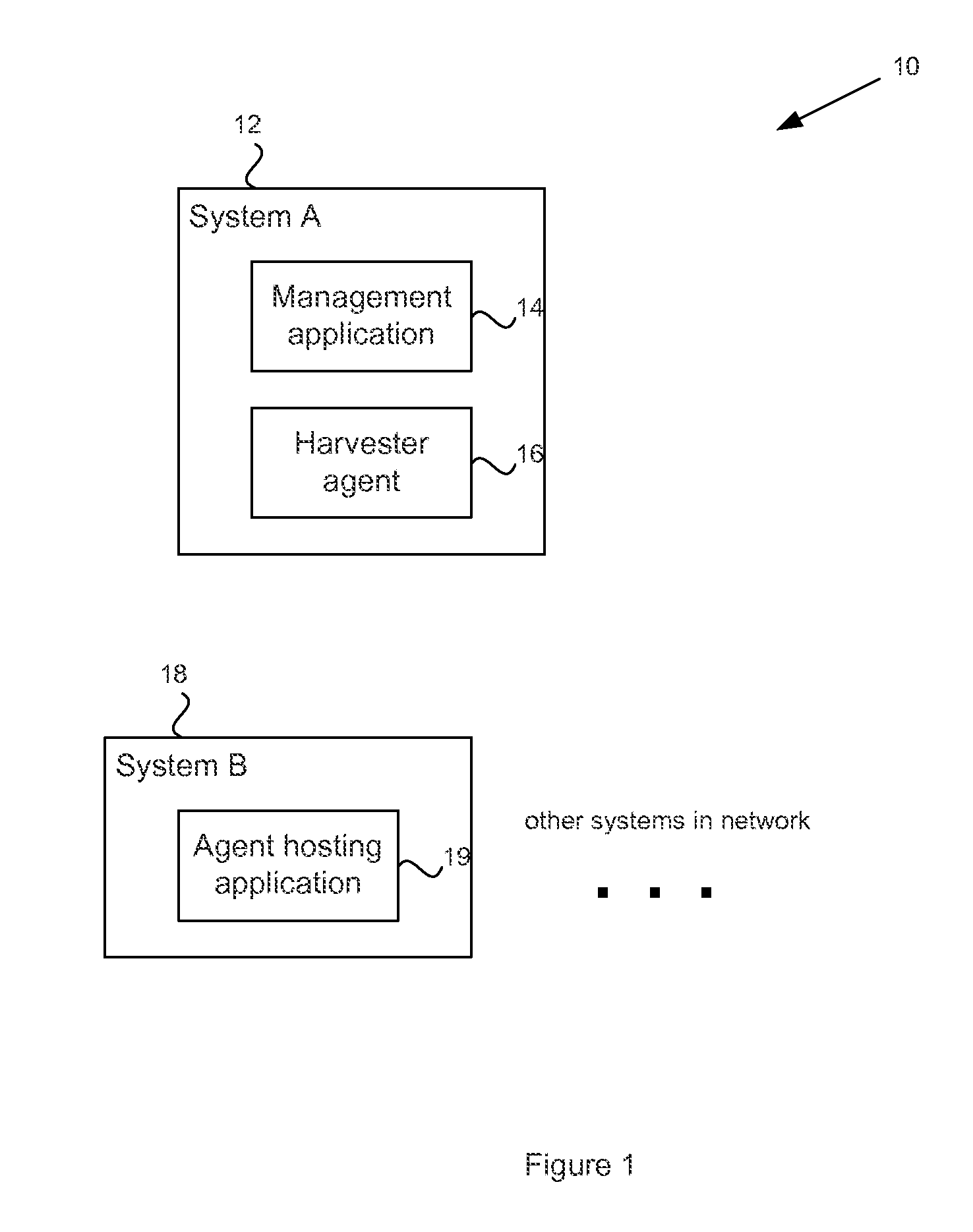
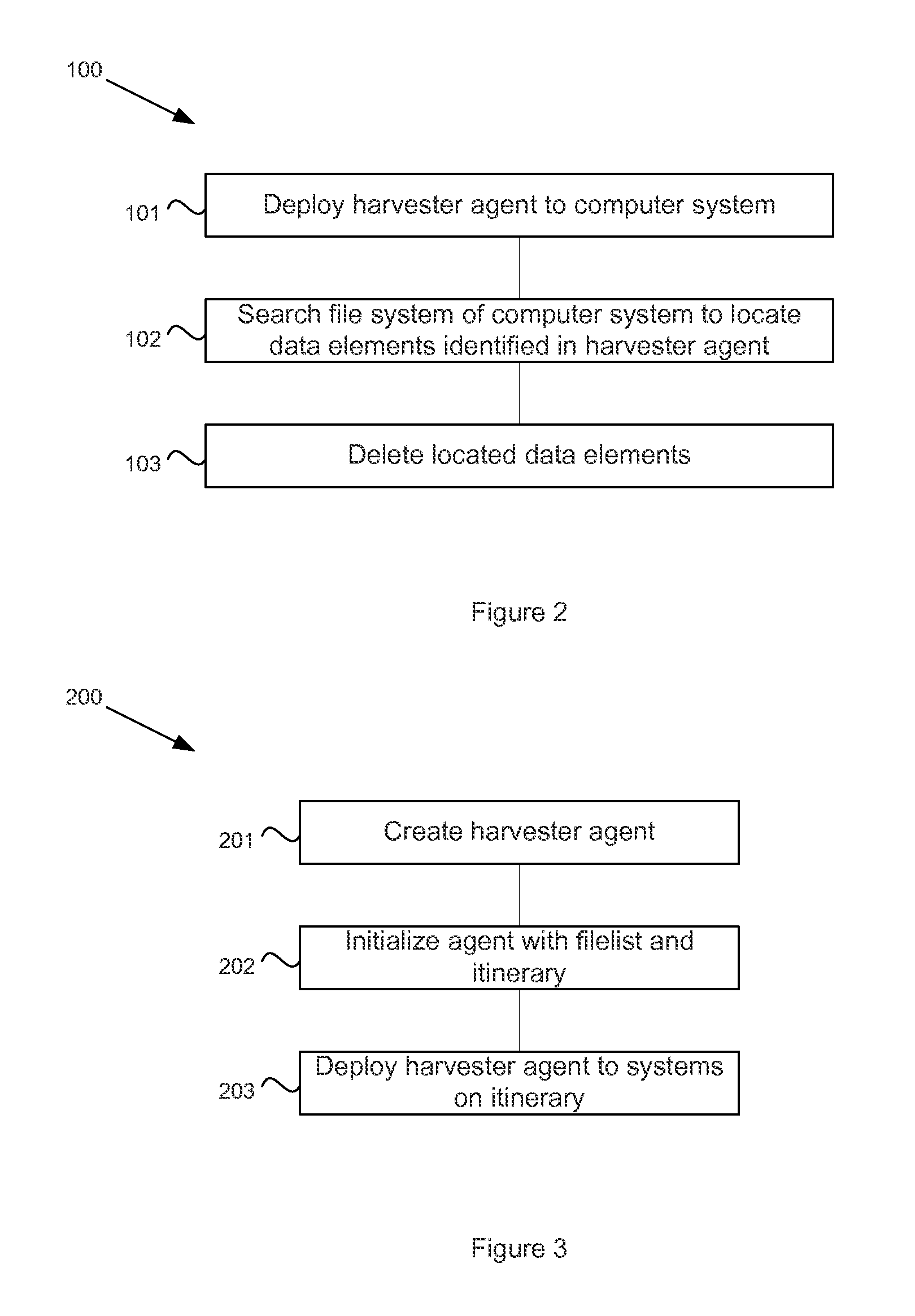
System and method for managing sensitive data using intelligent mobile agents on a network
ActiveUS20120254129A1Digital data processing detailsSpecial data processing applicationsFile systemData file
In order to manage stale data on a network of computer systems, a file harvester agent may be configured with a list of stale data files to be deleted. The file harvester agent may be deployed to the computer systems of a network. When executed in a computer system, the file harvester agent searches the file system of the computer system to locate any files or data indicated in the file list. Any located data files are deleted. Once the agent has finished processing the file list on a computer system, the agent can copy or replicate itself to other computer systems of the network in accordance with a pre-configured itinerary.
Owner:OPEN INVENTION NEWTORK LLC
Method and apparatus for breaking down computing tasks across a network of heterogeneous computer for parallel execution by utilizing autonomous mobile agents
InactiveUS7082604B2Ease of parallel processingProgram initiation/switchingResource allocationApplication softwareLarge applications
A method and apparatus is provided for breaking down computing tasks within a larger application and distributing such tasks across a network of heterogeneous computers for simultaneous execution. The heterogeneous computers may be connected across a wide or local area network. The invention supports mobile agents that are self-migrating and can transport state information and stack trace information as they move from one host to another, continuing execution where the mobile agents may have left off. The invention includes a server component for providing an execution environment for the agents, in addition to sub-components which handle real-time collaboration between the mobile agents as well as facilities monitoring during execution. Additional components provide realistic thread migration for the mobile agents. Real-time stack trace information is stored as the computing tasks are executed, and if over-utilization of the computing host occurs, execution of the computing task can be halted and the computing task can be transferred to another computing hosts where execution can be seamlessly resumed using the stored, real-time state information and stack trace information.
Owner:MOBILE AGENT TECH
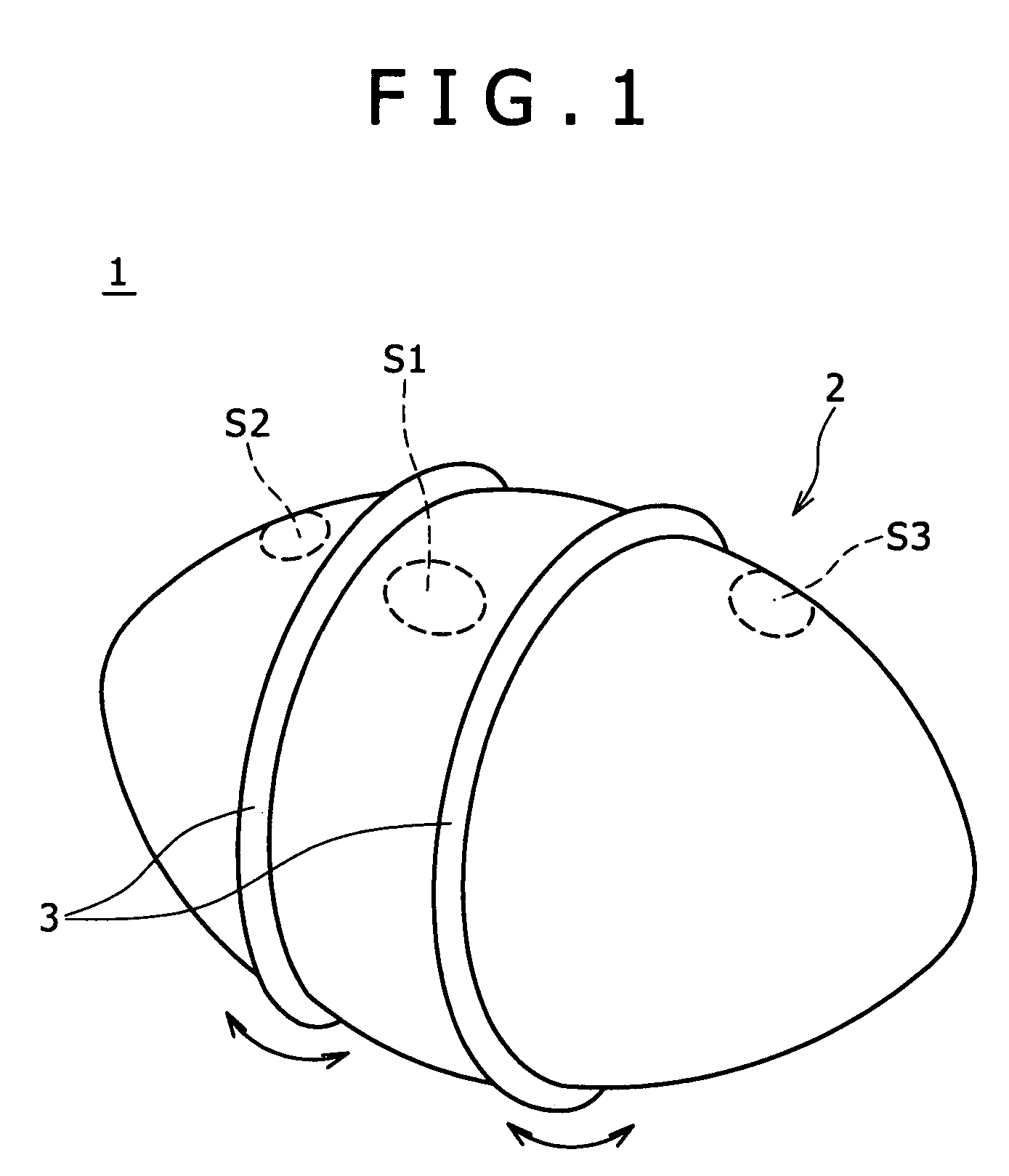
Moving subject recognizing system for automotive vehicle
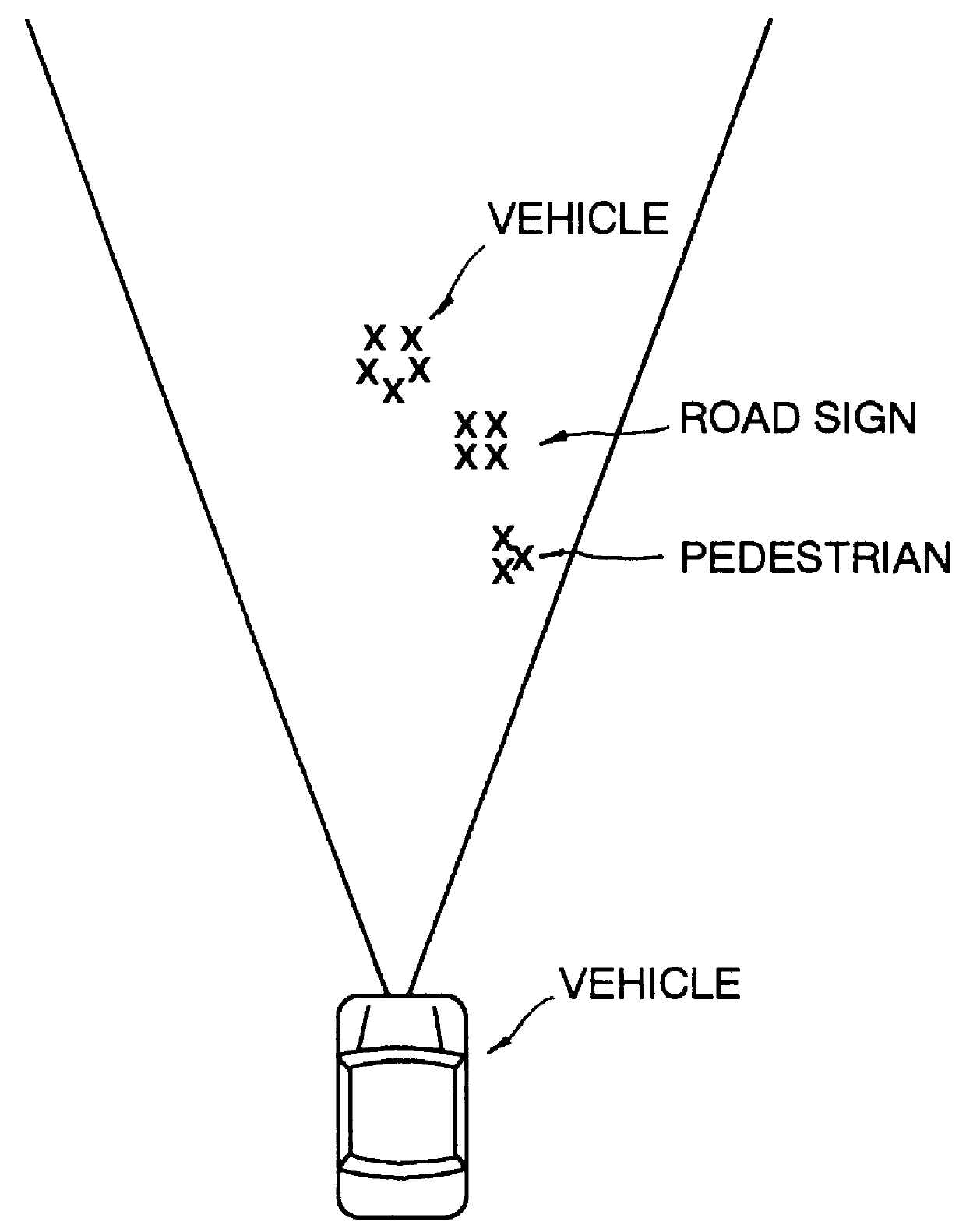
InactiveUS6035053AReduce probabilityEasy to identifyControlling traffic signalsTelevision system detailsEngineeringPedestrian
A moving subject recognizing system for recognizing a subject, such as a pedestrian, moving toward a forward path of a vehicle to avoid a collision against the subject scans a field ahead the vehicle to detect a transverse velocity of a subject moving in a transverse direction and a longitudinal distance of the subject in a direction of the traveling path which are compared with a first and a second threshold value, respectively, and recognize that the subject is in danger of entering the traveling path and hit by the vehicle when the transverse velocity is greater than the first threshold value and the variation of the longitudinal distance is smaller than the second threshold value.
Owner:MAZDA MOTOR CORP
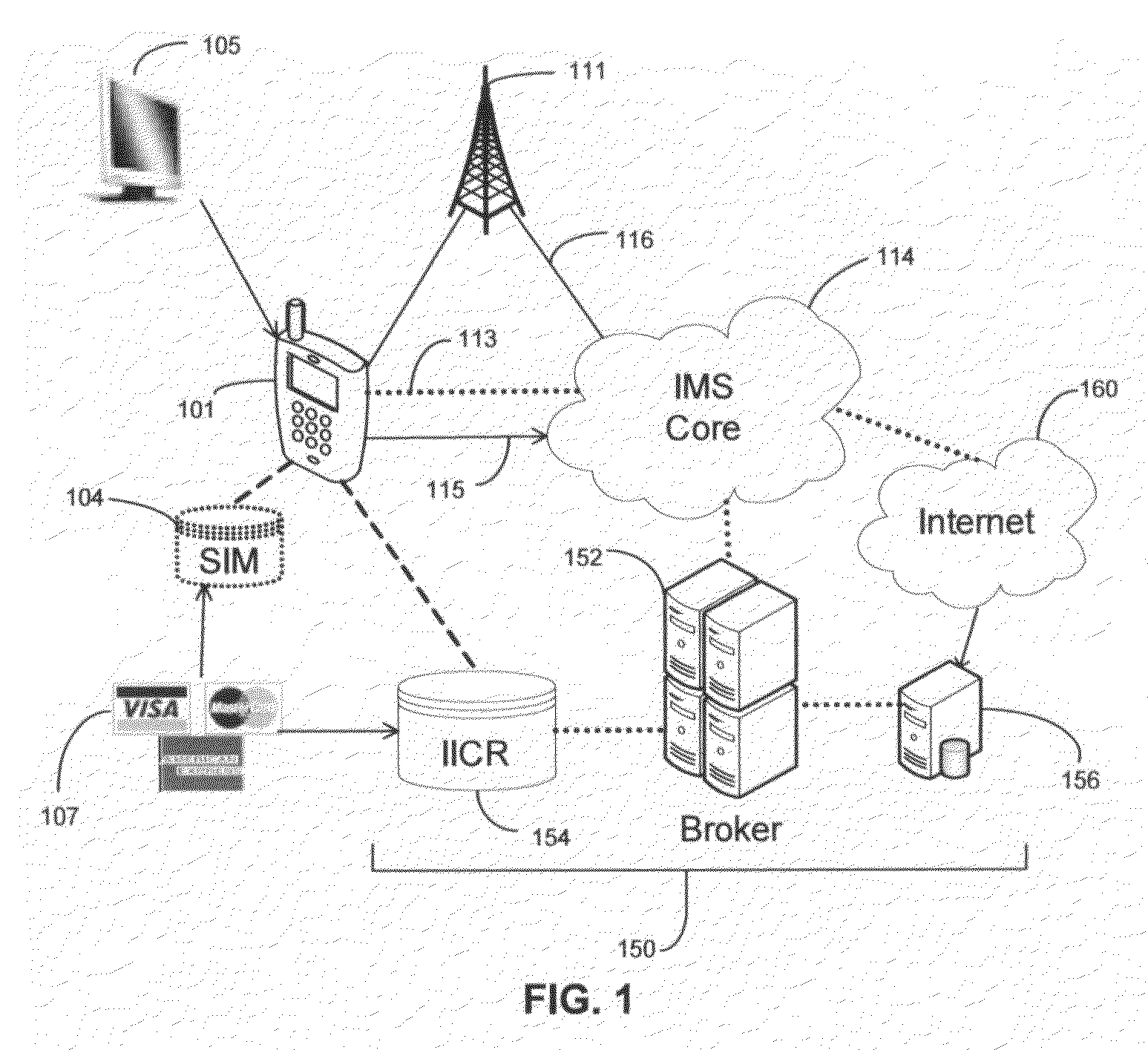
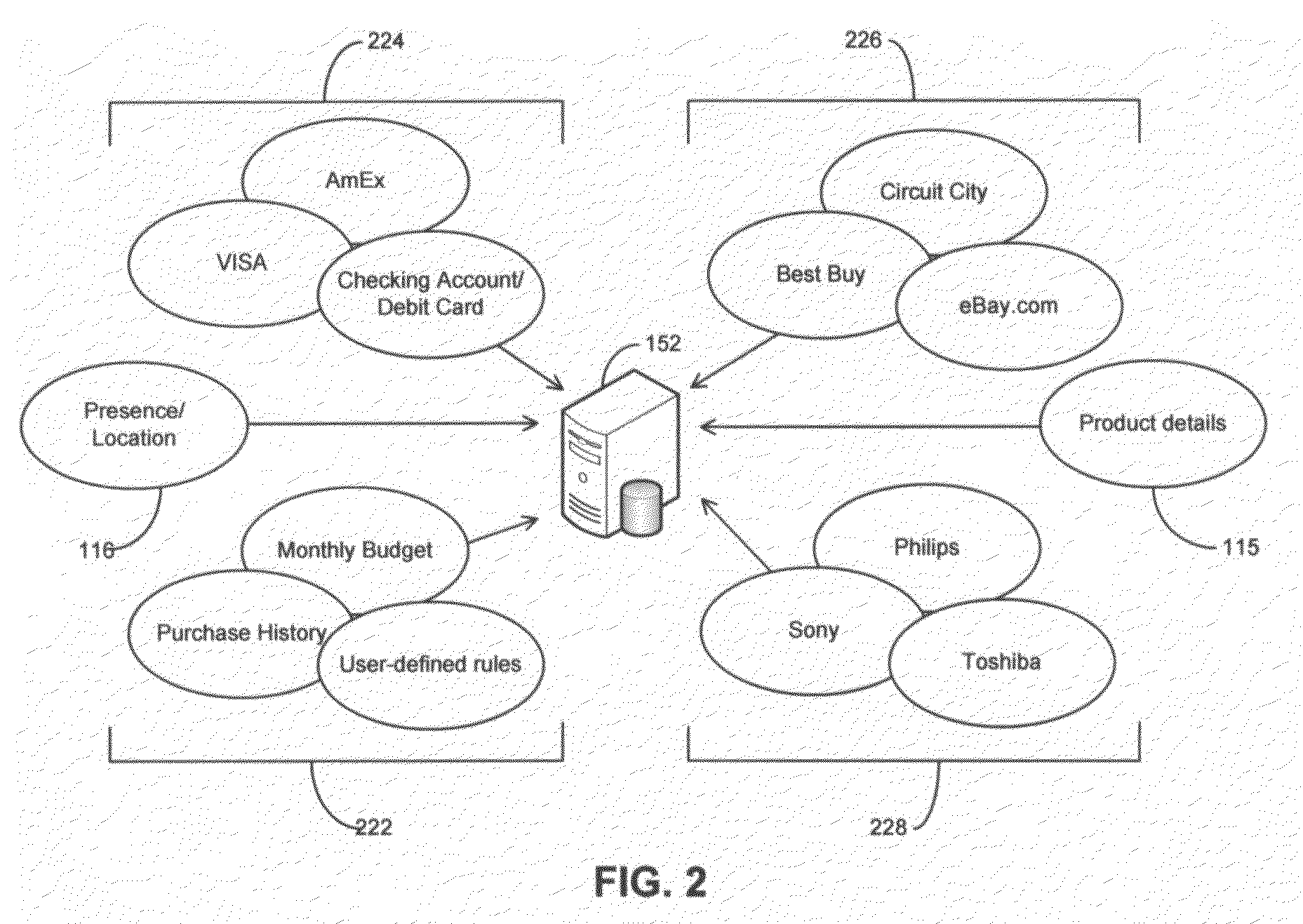
Systems and methods for profile-based mobile commerce
ActiveUS20080242274A1Minimize lagGreat dealFinanceSpecial service for subscribersSystems analysisFinancial transaction
The invention discloses systems and methods for integrating Mobile Commerce applications with dynamically generated user profiles. A profiling engine collects and stores information regarding a mobile subscriber's usage of Mobile Banking, Mobile Payment, and Mobile Brokerage, and stores the information in a profile. A Dynamic Event Server Subsystem comprising a Mobile Broker analyzes patterns in the subscriber's usage of these applications. The mobile broker can thus provide intelligent feedback regarding purchases and financial transactions back to the applications and to the subscriber. This feedback is provided in real time.
Owner:CINGULAR WIRELESS II LLC
Peer trust evaluation using mobile agents in peer-to-peer networks
ActiveUS7213047B2Digital data processing detailsMultiple digital computer combinationsPeer-to-peerRegion of interest
Embodiments of a system and method for using mobile agents to gather trust information for evaluating trust in peer-to-peer networks. A peer node may launch a mobile agent on a network including an itinerary of peer nodes to be visited by the mobile agent and an indication of an area of interest. The mobile agent may determine if a visited peer node stores trust evaluations for other peer nodes as providers of codats relevant to the area of interest and, if so, the trust evaluations may be stored as payload data in the mobile agent. After completing the itinerary, the mobile agent may return the payload to the initiating peer node. The initiating peer node may use the trust evaluations collected by the mobile agent in determining or adjusting trust evaluations for peer nodes as providers of codats relevant to the area of interest.
Owner:ORACLE INT CORP
Vehicle routing and path planning
InactiveUS20050216182A1Sufficient flexibilityEfficient and reliableInstruments for road network navigationNavigational calculation instrumentsMulti objective optimization algorithmPath generation
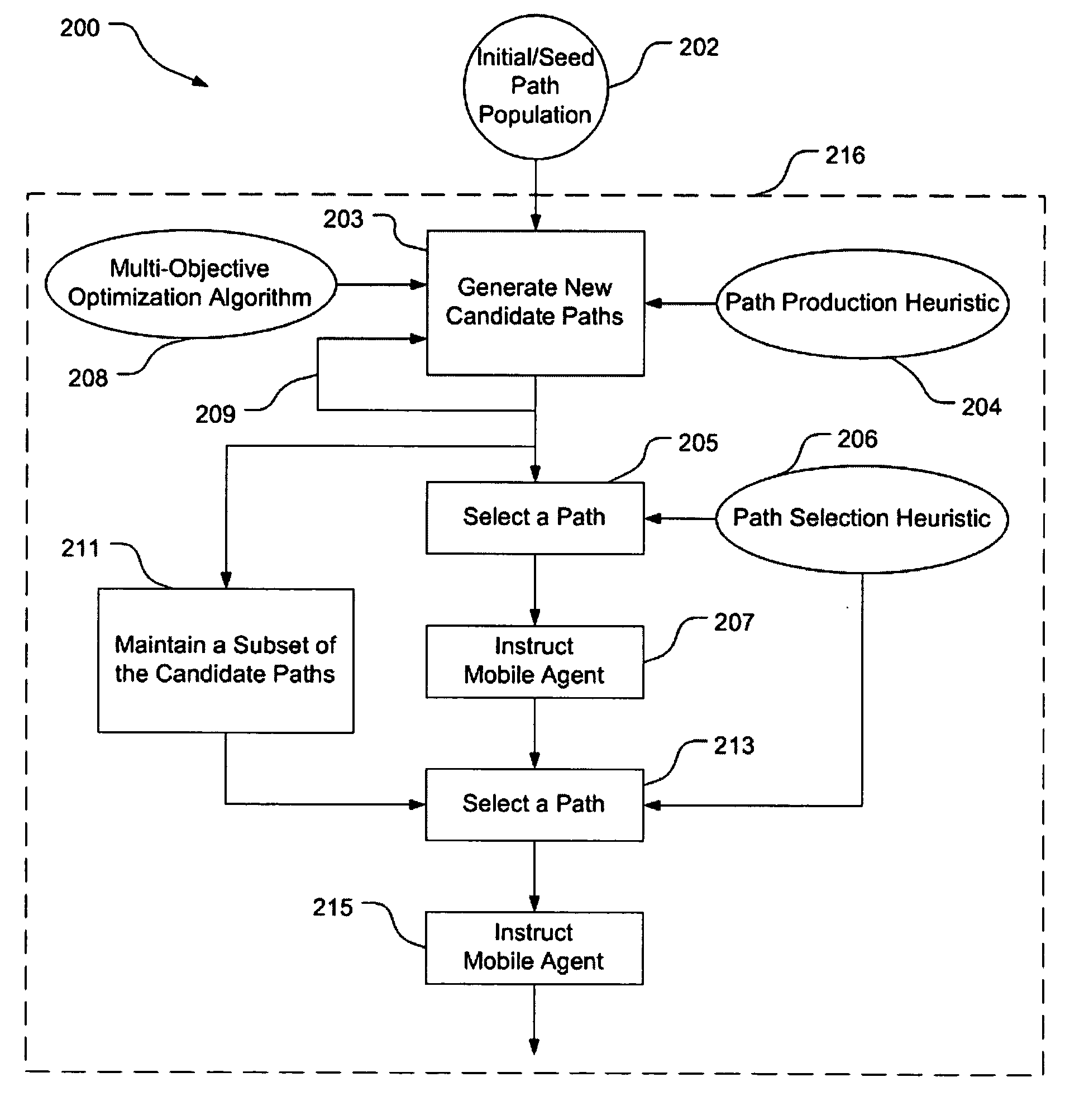
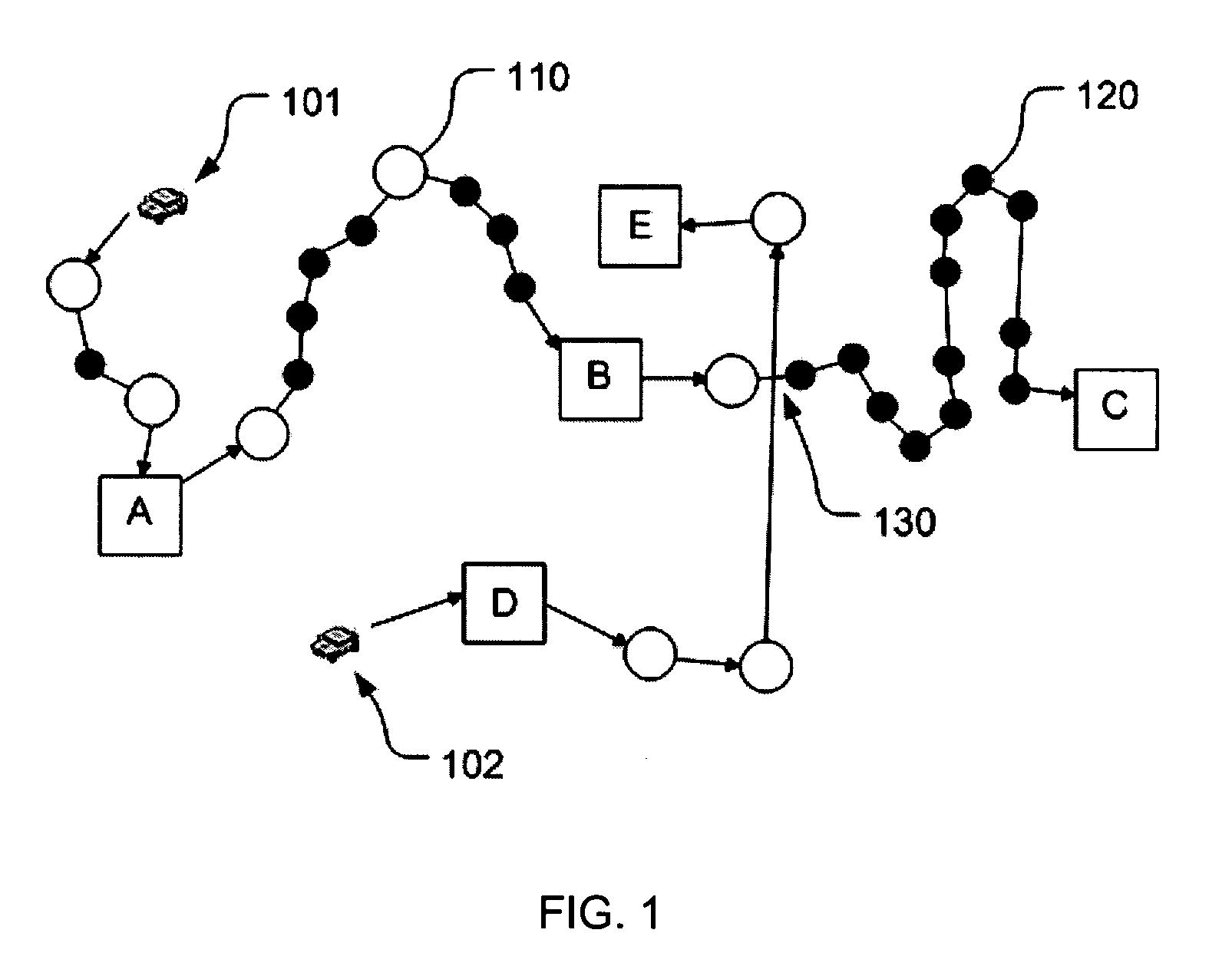
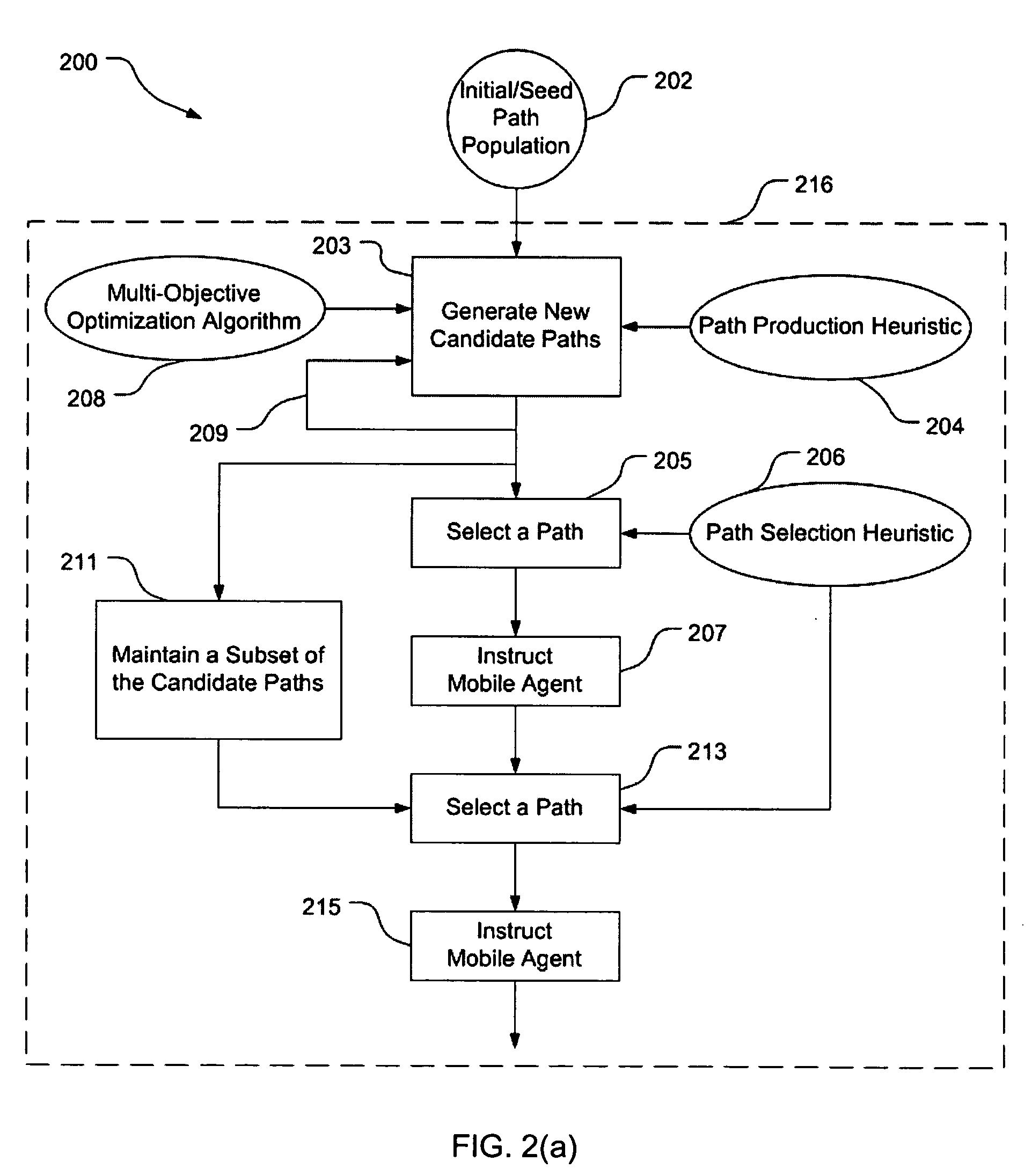
A method of determining a path having an ordered set of waypoints to be visited by a mobile agent to accomplish a mission includes: producing candidate paths using a multi-objective optimization algorithm, subject to a path production heuristic; selecting a path from the candidate paths, subject to a path selection heuristic; instructing the mobile agent to move according to the selected path; modifying a maintained subset of the candidate paths to produce a new candidate path using the algorithm and subject to the path production heuristic; designating either the currently-selected path or the new candidate path as the newly-selected path, subject to the path selection heuristic; and instructing the mobile agent to move according to the newly-selected path. The method may further include iterating production of new candidate paths, either randomly or based on modifications of previous candidate paths, to continually update an operation plan for the mobile agent.
Owner:BBN TECHNOLOGIES CORP
Computer method for delivery of financial services
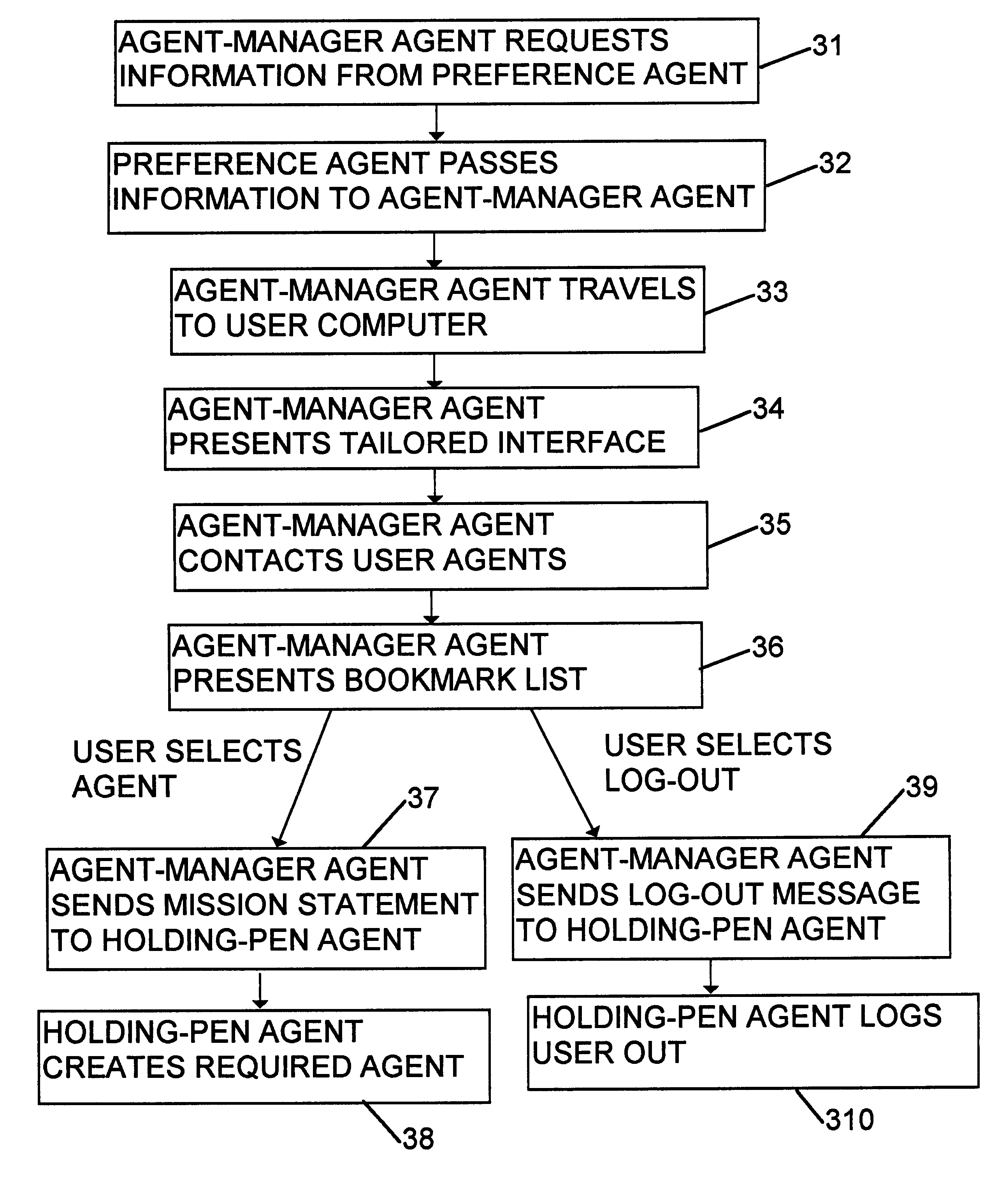
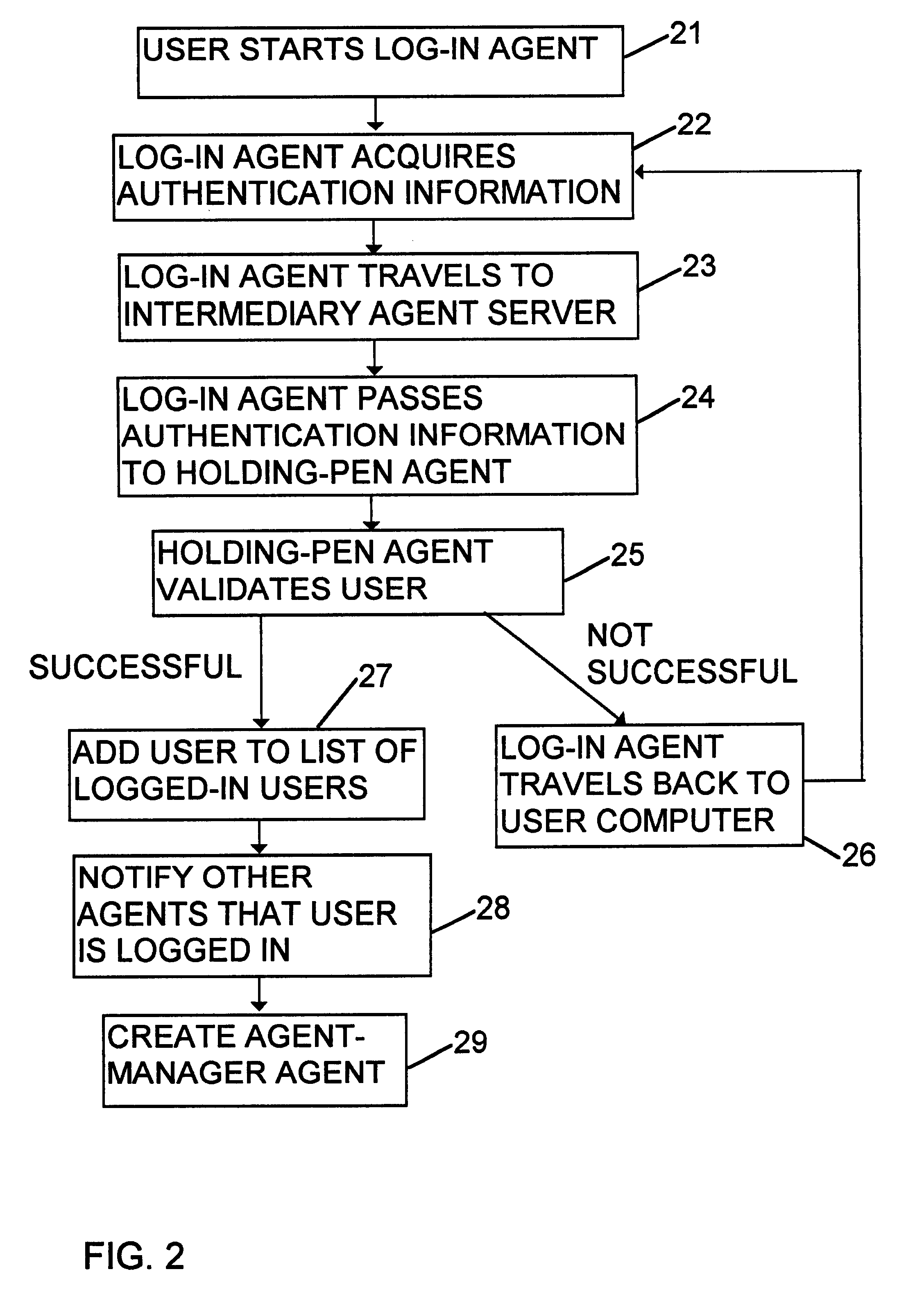
A computer system is provided for delivery of financial services, such as banking, general insurance, life assurance, pensions and investments, loans and mortgages, and financial planning and advisory services. The system comprises a number of user computers connected to a plurality of server computers by way of a network, such as the Internet. The system creates at least one mobile agent which obtains details of a user's requirements, obtains financial information from the server computers on behalf of the user in the light of the user's requirements, and then transports itself to the user's computer to deliver the financial information to the user.
Owner:INT COMP LTD
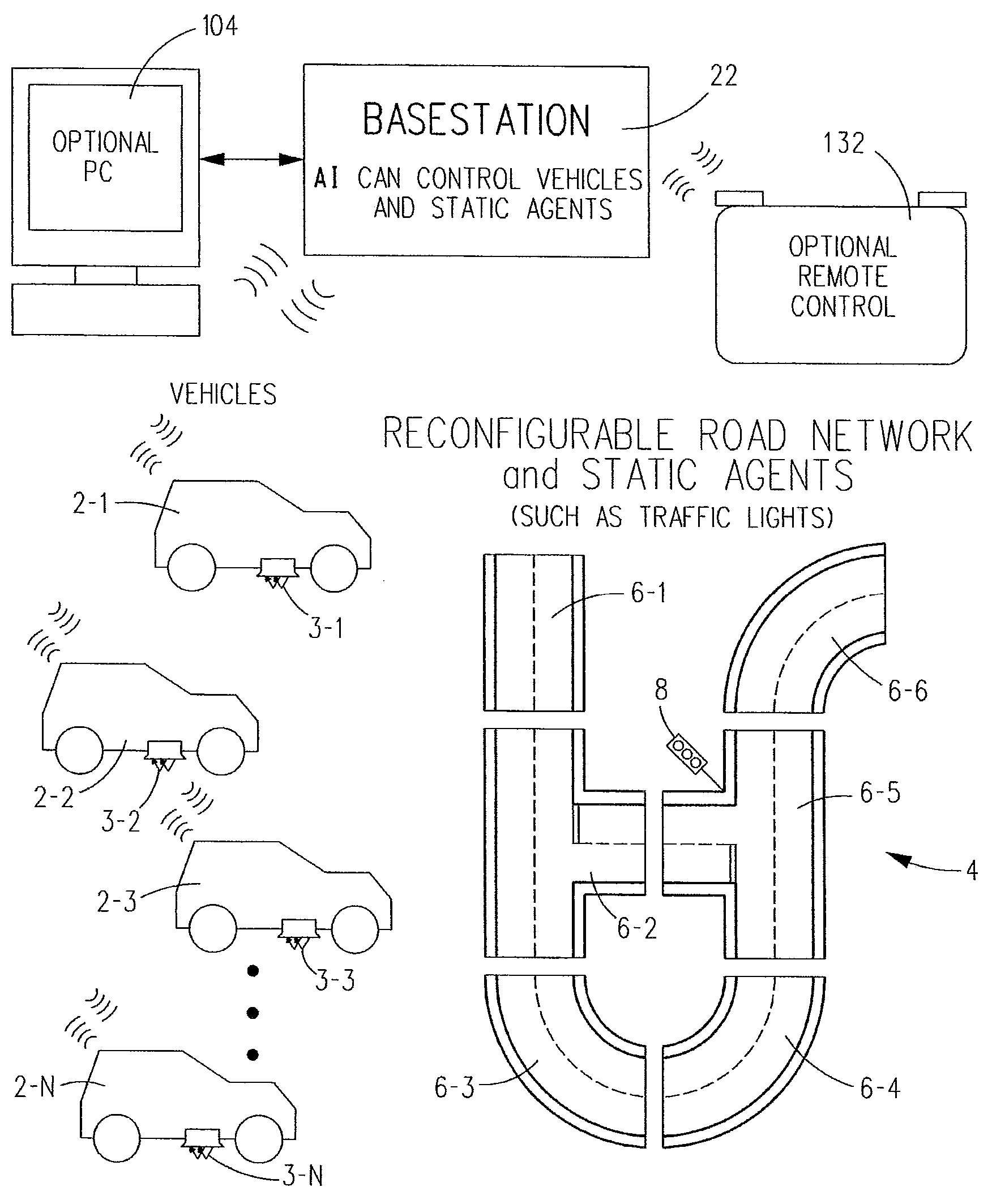
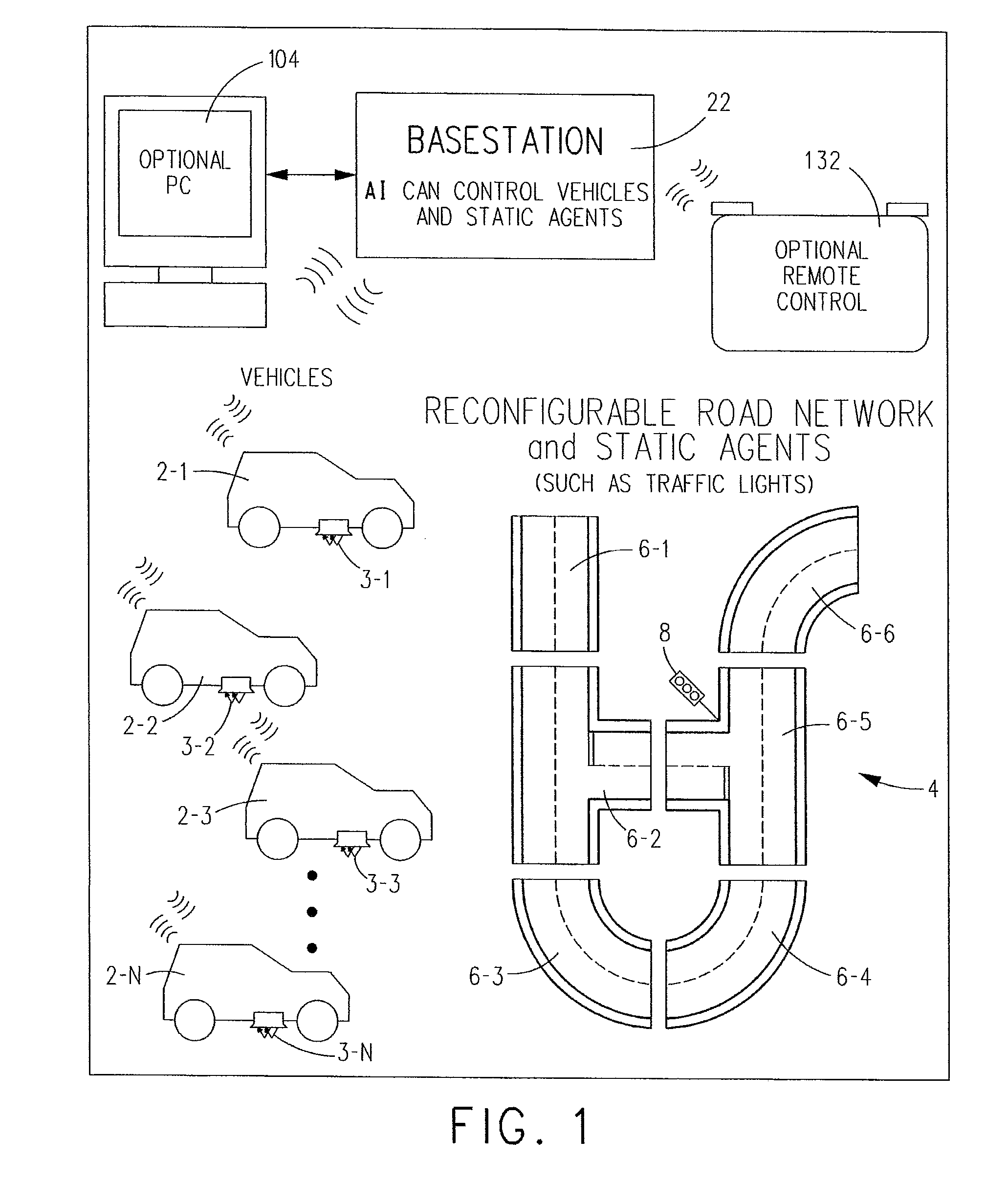
Distributed System of Autonomously Controlled Toy Vehicles
A toy system includes a drivable surface that includes location encoding markings. A toy vehicle or mobile agent is provided that includes a drive motor, an imaging system for taking images of the markings, a vehicle wireless transceiver, and a microcontroller operatively coupled to the motor, the imaging system, and the vehicle wireless transceiver. A basestation is provided that includes a controller operatively coupled to a basestation wireless transceiver. Via wireless communication between the wireless transceivers of the toy vehicle and the basestation, an action to be implemented by the toy vehicle can be determined by the basestation and communicated to the toy vehicle, whereupon the microcontroller of the toy vehicle controls detailed movement of the toy vehicle on the drivable surface based on images taken of the markings of the drivable surface by the imaging system to cause the toy vehicle to implement the action on the drivable surface.
Owner:DIGITAL DREAM LABS INC
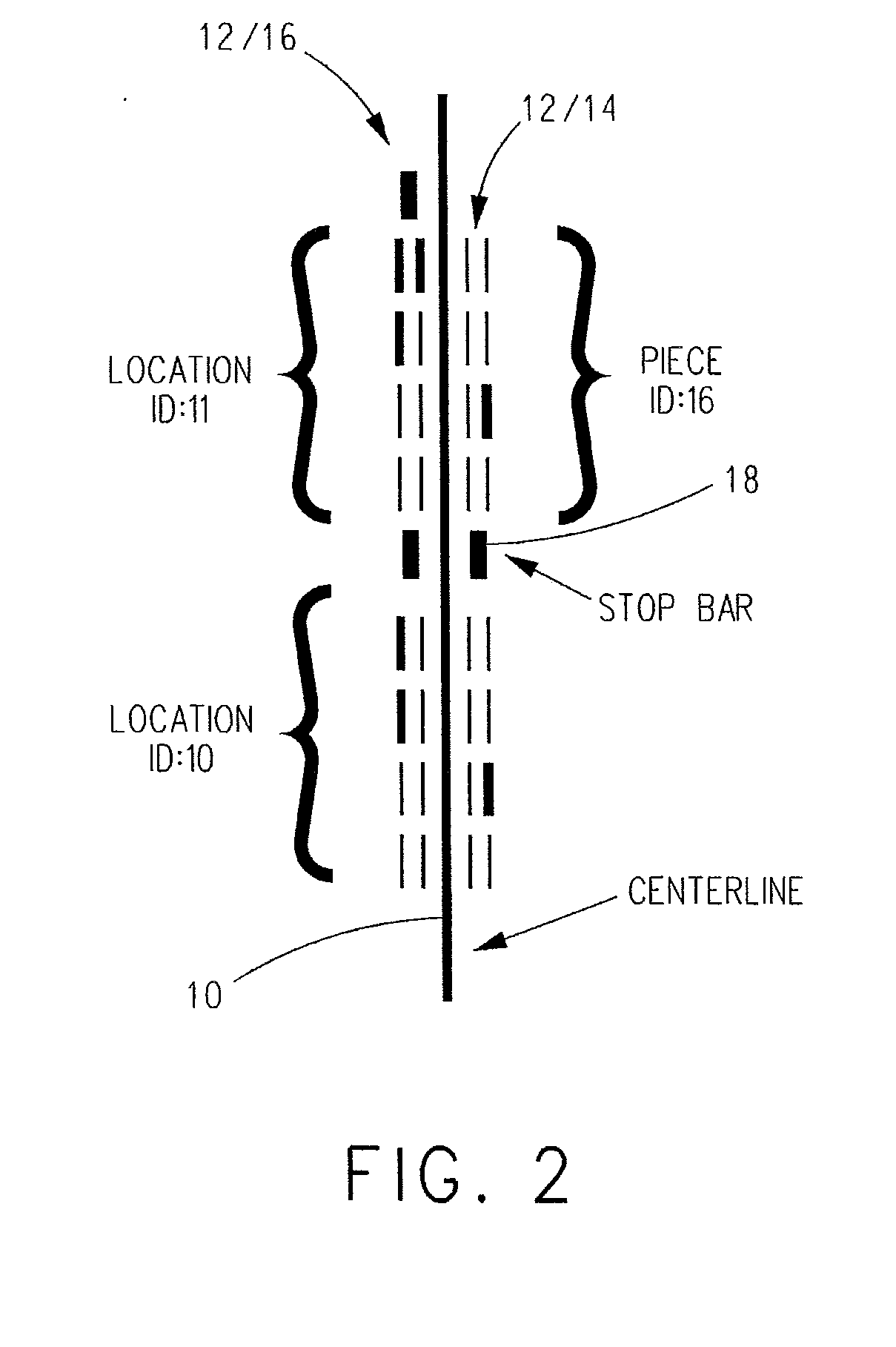
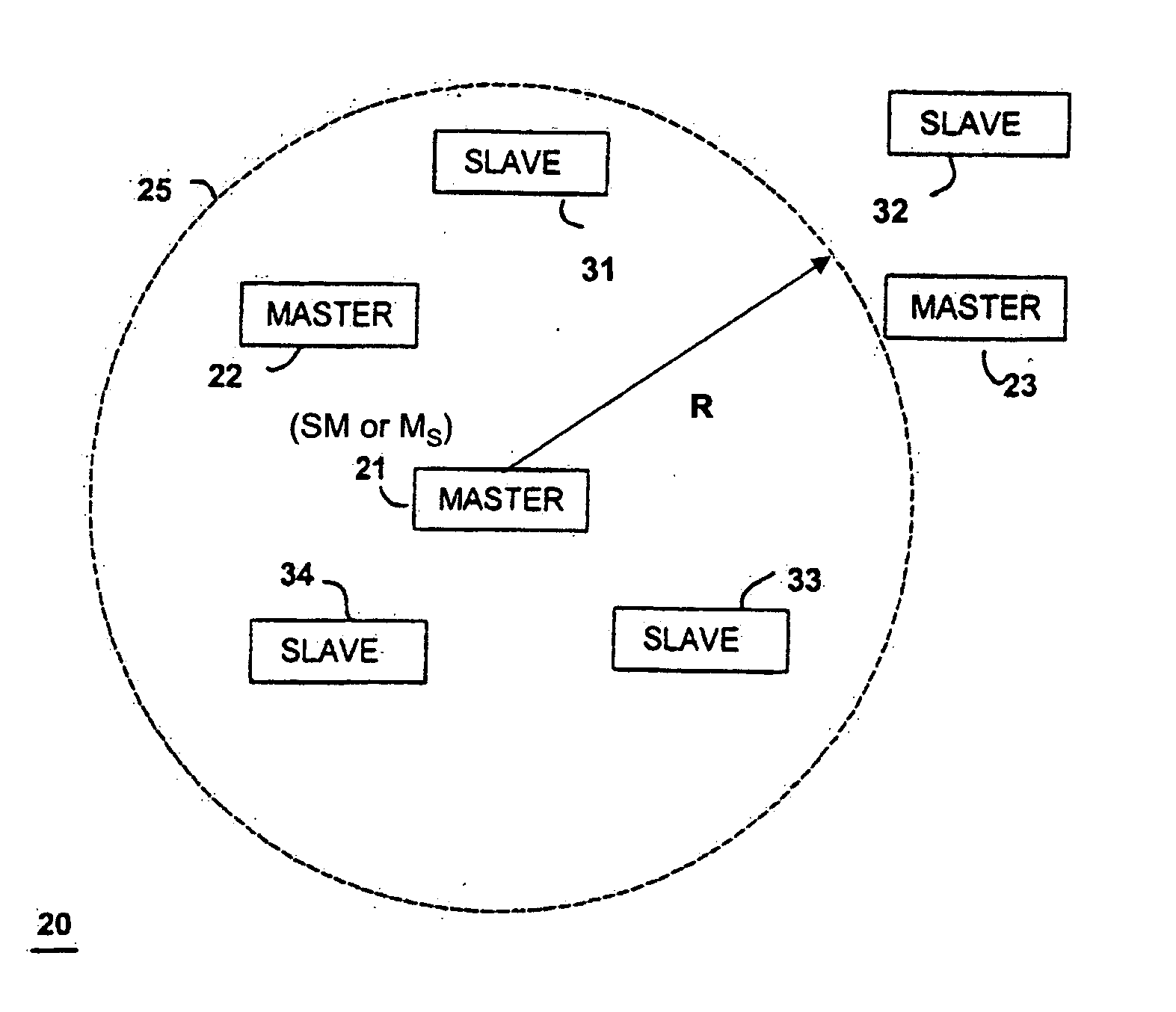
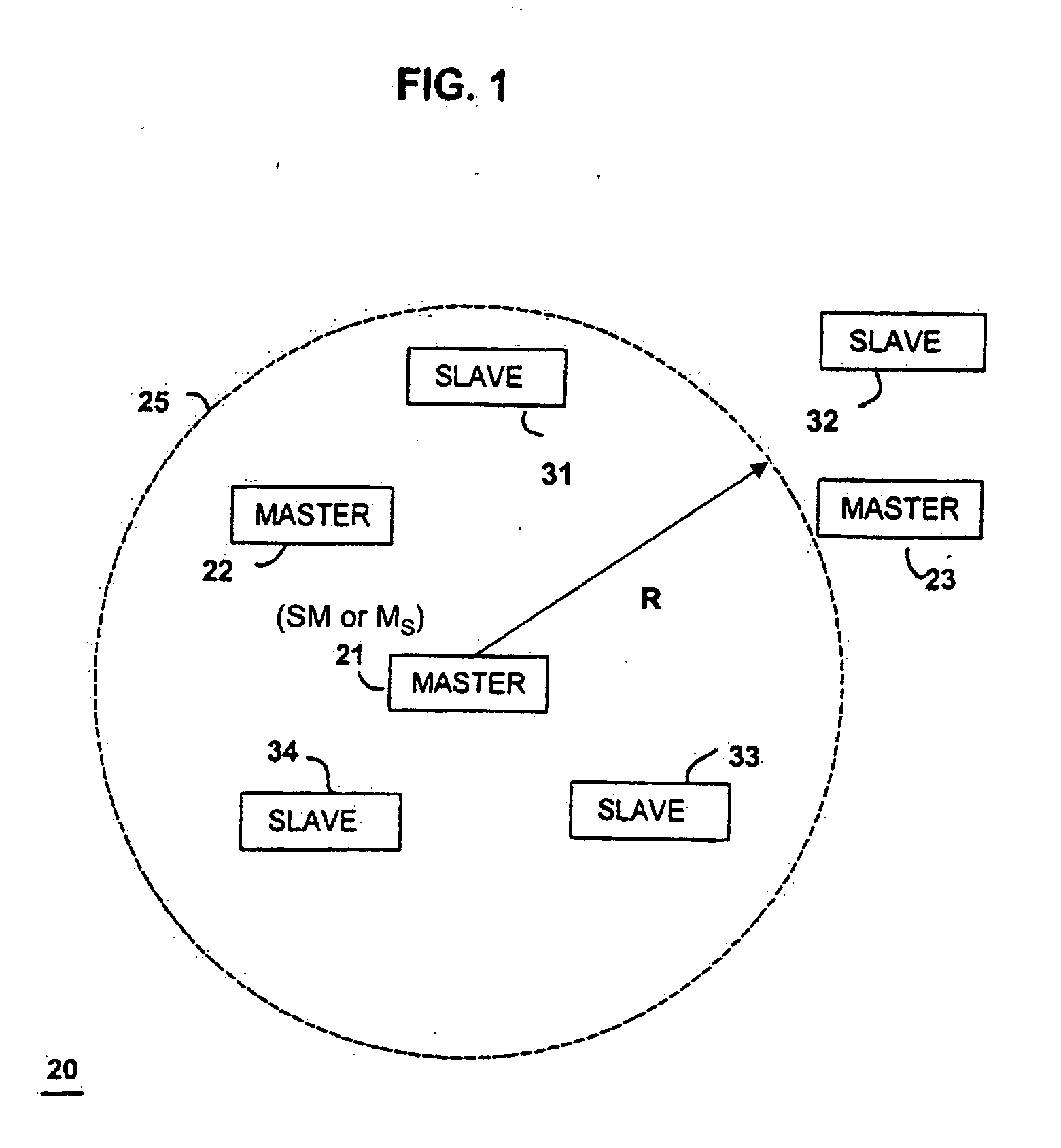
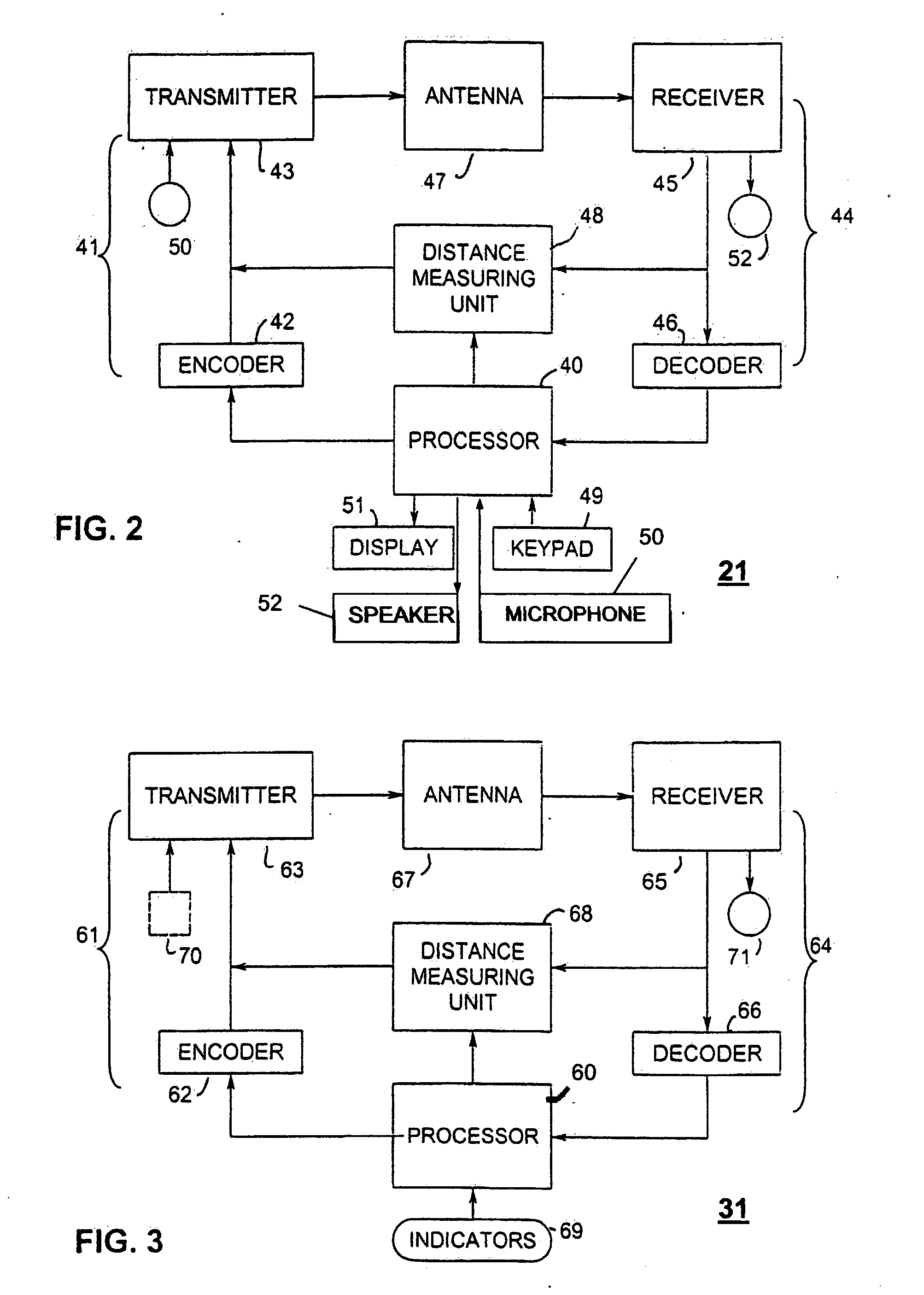
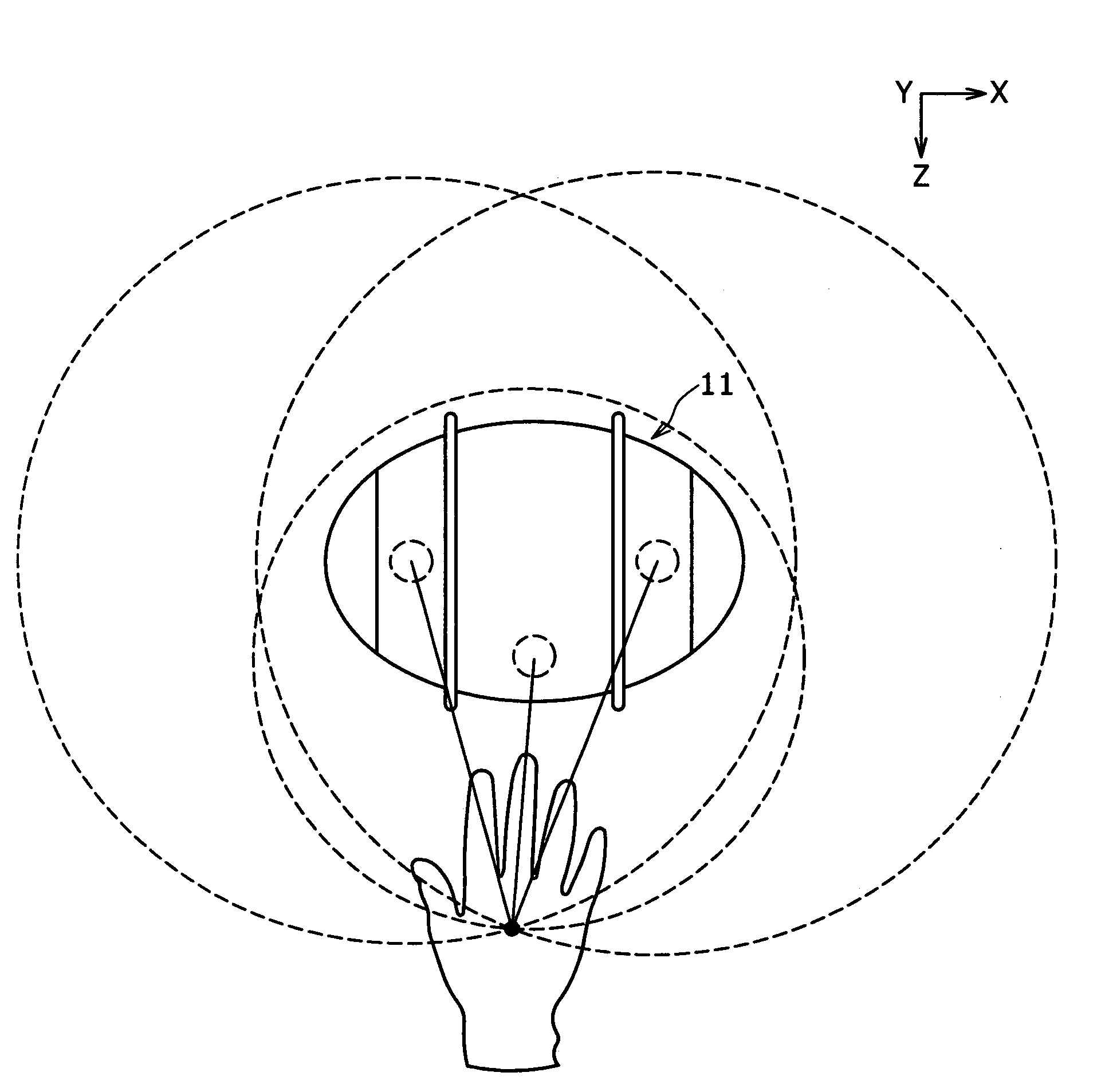
Method and system for finding
ActiveUS20060012476A1Simplified triangulationUser-device interaction is minimized—eliminatingElectric signalling detailsBurglar alarm by hand-portable articles removalUser deviceTransceiver
A wireless system and method for determining the location of a fixed or mobile subject or object includes a transponder disposed on the target, a transceiver for monitoring the location of the target, a wireless communication system operating on at least one Radio Frequency (RF) band configured to allow communication between the transponder and the transceiver, and a processor configured to find the target by virtual triangulation based on values of position information received from the transponder and the transceiver. The processor is configured to determine virtual triangulation based on successive values of the position information using at least three points P1, P2 and P3 of the transponder respective of the transceiver. The processor can include a means for position ambiguity reduction (PAR) configured to find the target by correcting the direction to the location of the target T based on the values of the position information. The processor can also determine the position of the target based on the average speed of the motion of the user of the transponder respective of the transceiver. Furthermore, the processor can determine virtual triangulation based on successive values of the position information from user input on the transceiver. The method finding the target T (“finder” techniques) based on one or more position determination principles including determining the position of the target using virtual triangulation between the master or monitoring unit and at least one target T, whereby the monitoring device Ms measures the distance between it and the slave unit and, alternatively, in addition to measuring the distance between itself and the slave unit, between itself and another monitoring unit, or the monitoring device Ms measures the distance between its own successive locations. The present invention also discloses methods for finding with virtual triangulation by: (1) finding with virtual triangulation by generating position information in real-time, in the case of (i) stationary and moving target, and or (ii) in the case of the presence of obstacles; (2) finding with virtual triangulation relating to the average speed of the motion of operator; and or (3) finding with simplified virtual triangulation, whereby the user-device interaction is minimized—eliminating the need for monitoring device Ms to measure the distance between its own successive locations as well as the user's signaling to the monitoring or master unit when in motion or during stops.
Owner:QUALCOMM TECHNOLOGIES INC
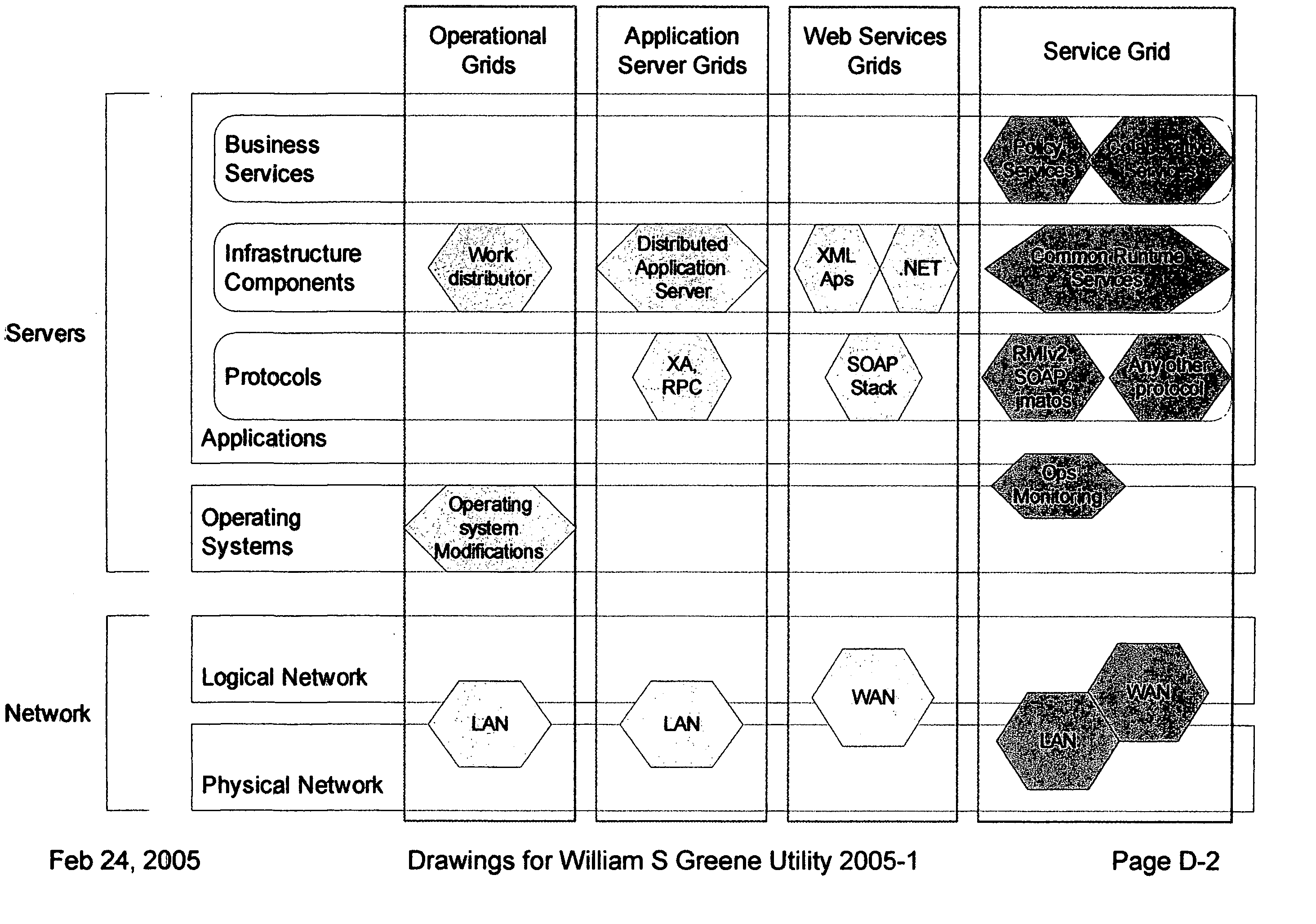
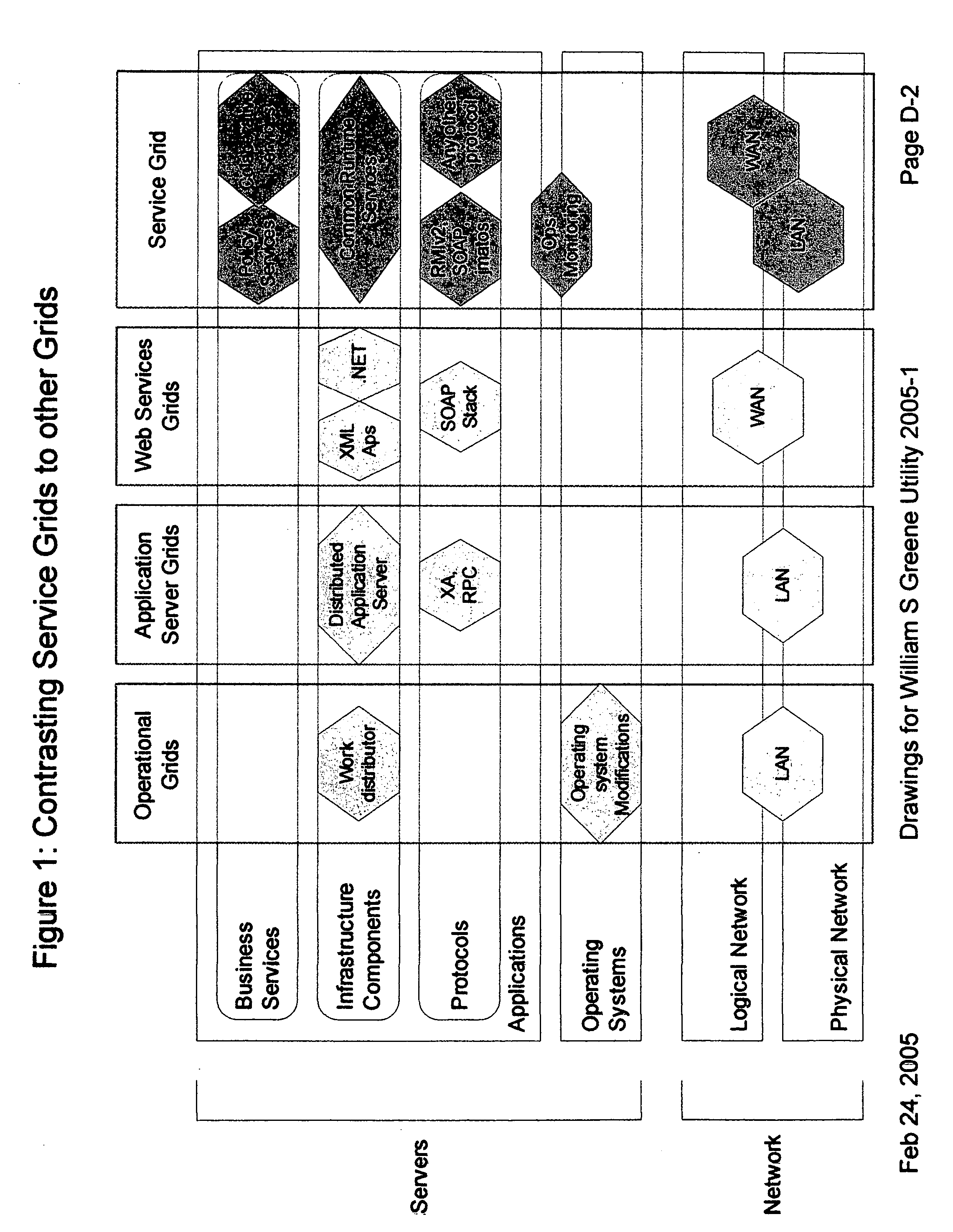
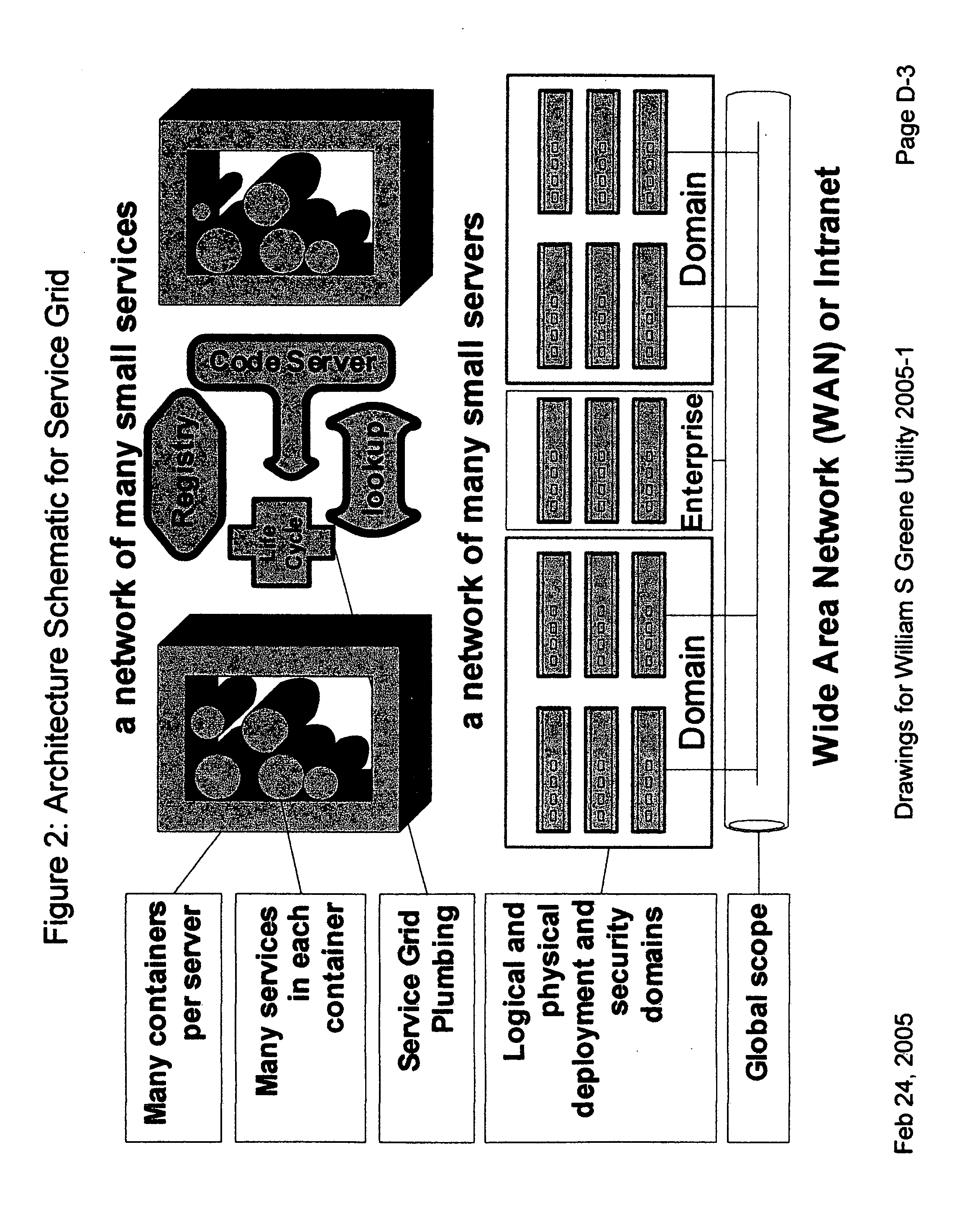
Providing secure data and policy exchange between domains in a multi-domain grid by use of a service ecosystem facilitating uses such as supply-chain integration with RIFD tagged items and barcodes
InactiveUS20050193222A1Simple methodImprove securityDigital data processing detailsMultiple digital computer combinationsSecurity domainRadio frequency
A system, method, and software implemented system of services provides enhanced security and management to multiple domain grids and allows intercommunications between the different grid domains providing for secure data exchange, policy exchange, and agent exchange between grids or grid domains. Via the exemplary example, utilizing the unique characteristics of the Service Grid and mobile agents, this is extended to provide enhanced security and management to supply chains: providing data exchange, policy exchange, and agent exchange between supply chain nodes and supply chain partners—facilitating enhanced methods of supply chain automation when using barcodes and Radio Frequency Identity (RFID) tags to identify and track goods through supply chains and consumer uses. Agents transport data and policy between supply-chain partners over an extranet, migrating across corporate boundaries and security domains, locating near where items are identified to provide local control, environmentally responsive policy, and ongoing permanent data capture & history.
Owner:GREENE WILLIAM SPROTT
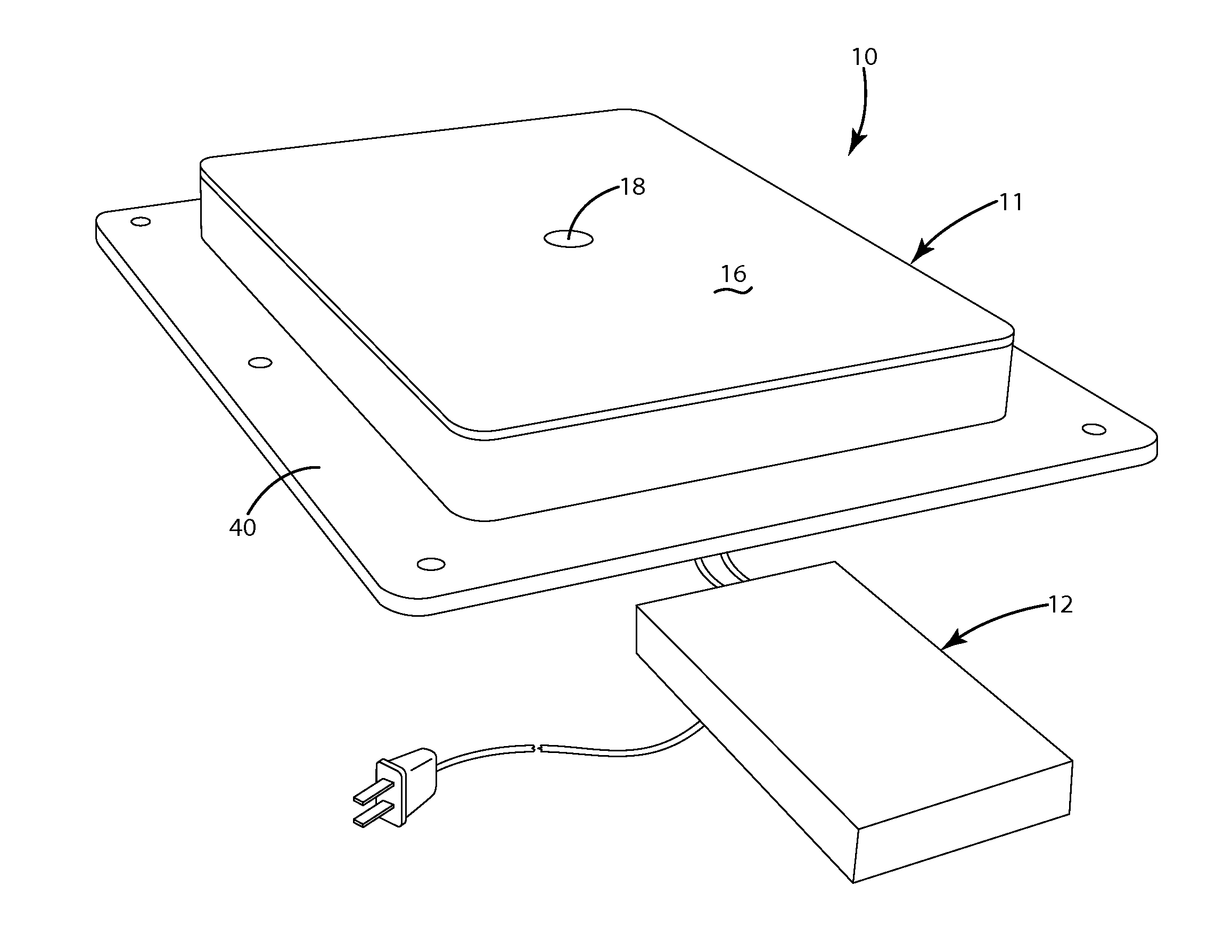
Inductive power supply
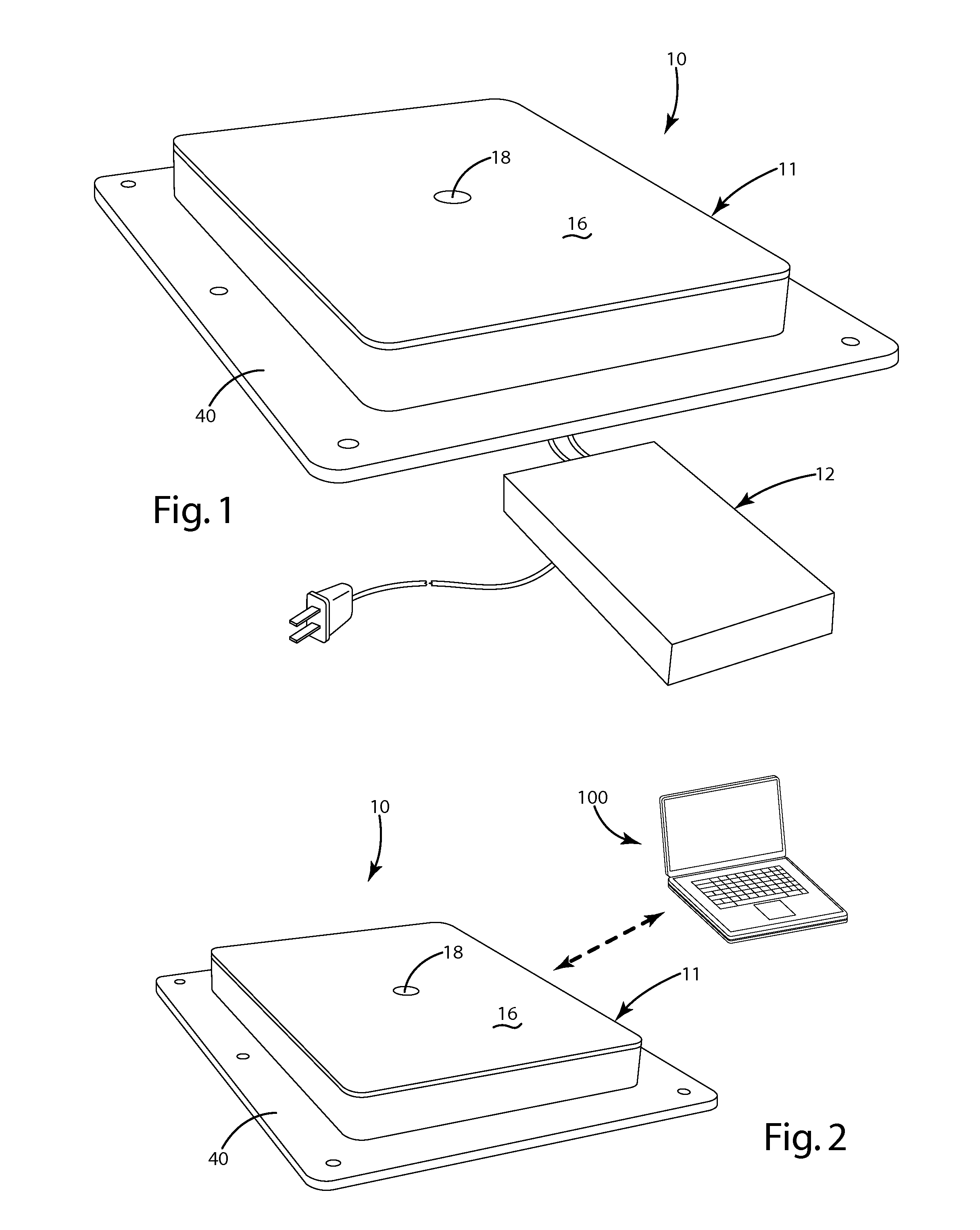
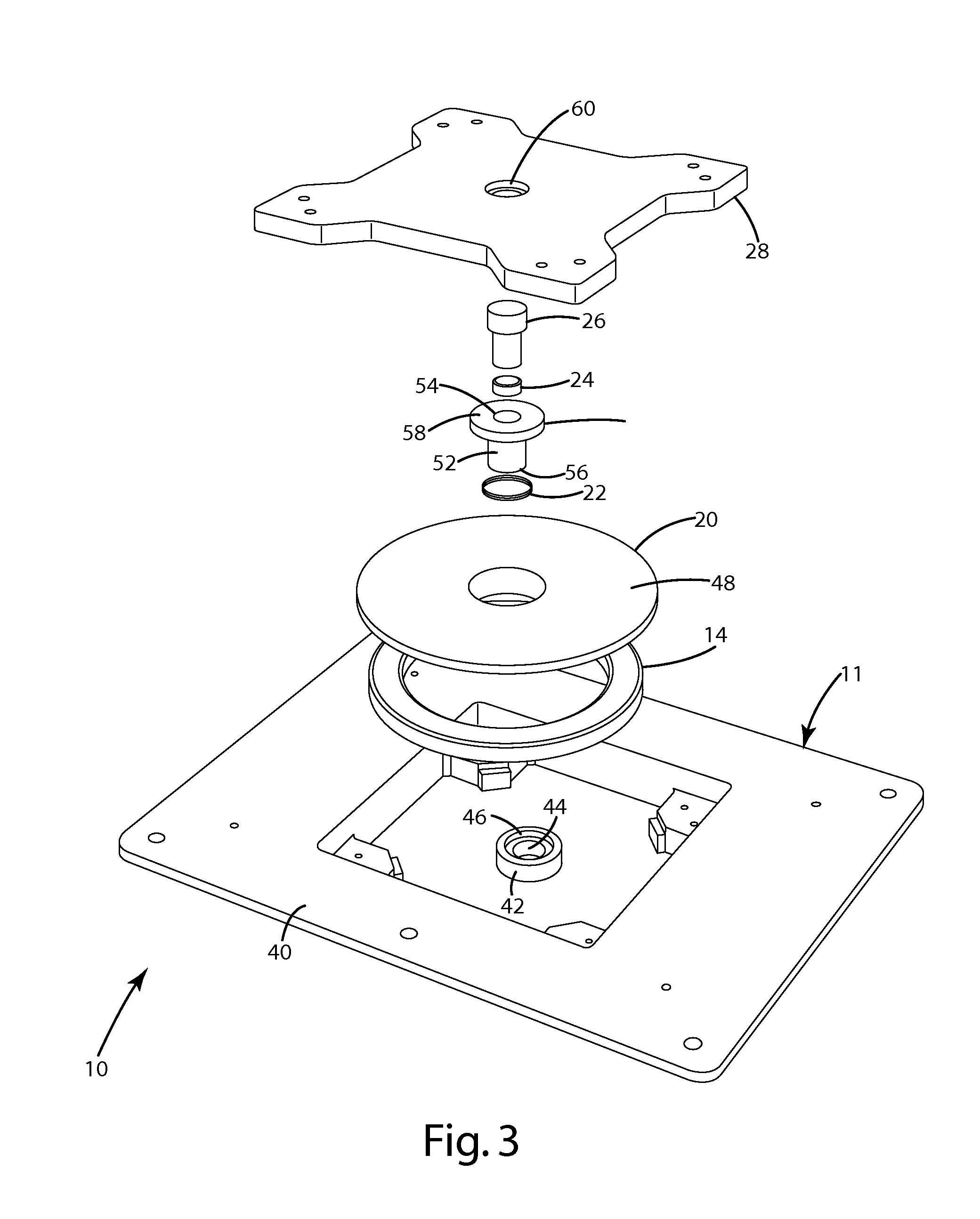
ActiveUS8373310B2Reduced footprintSimple mechanical structureBatteries circuit arrangementsElectromagnetic wave systemCharging stationMajor and minor
In one aspect, the present invention provides a wireless power supply having a plunger for mechanically interconnecting a remote device with the power supply. The plunger may be extendable / retractable to interfit with the remote device. In a second aspect, the present invention provides a wireless power supply with a movable primary that allows for close alignment between the primary and the secondary when the remote device is disposed within a range of different positions with respect to the charging surface. The movable primary may, for example, be coupled to the remote device by a peg, a plunger or a magnet. Alternatively, the position of the movable primary may be adjusted manually. In a third aspect, the present invention provides a charging bowl having a plurality of charging stations disposed about a common axis. Each charging station may include a movable primary that permits some freedom in positioning of the remote device on the charging surface. In a fourth aspect, the present invention provides a wireless power supply having a manually movable primary.
Owner:PHILIPS IP VENTURES BV
Method and system for providing location-based information to a group of mobile user agents
ActiveUS20100159943A1Broadcast service distributionLocation information based serviceLocation based informationUser agent
A method and system for providing location-based information to a group of mobile user agents. A group of mobile user agents may be identified based at least in part on agent information for each of the mobile user agents in the group. The location information may indicate a location for the mobile user agents, which may be determined using GPS information or GPS assistance information. Location-based information may be determined for the group and provided to the group by broadcasting or multicasting. The mobile user agents may be configured to receive and process the location-based information. The location-based information may comprise GPS assistance information.
Owner:VERIZON PATENT & LICENSING INC
Method for reducing data transport volume in data networks
InactiveUS20050117558A1Shorten the timeSolve large capacityDigital data information retrievalRadio/inductive link selection arrangementsClient-sideData transmission
Formed in a proxy server (CP) from the data output by a server application (SA) in response to a client (CA) inquiry is a message digest (MD) which is checked in said proxy server by comparison as to whether an identical message digest is already cached in the proxy server for said client. If so, a brief response message (HIT) is communicated by the proxy server to said client (CA) signalizing that the content can be found in the cache of a mobile proxy (MP) assigned to said client. If not, the complete content including the message digest serving as a key is communicated to the proxy of said client (CA) for caching there. Application in mobile data services requiring data transport via wireless networks.
Owner:DEUTSCHES ZENTRUM FUER LUFT & RAUMFAHRT EV
Topology Hiding Of Mobile Agents
InactiveUS20090313379A1Multiple digital computer combinationsWireless network protocolsSession managementTopology information
A method, infrastructure node (11, 12, 202), and mobile node (1) arranged to hide topology information from the user and mobile node by translating topology information to non-topology related address information and using session management messages of a first communication protocol as bearer for Internet Protocol mobility messages relating to a second communication protocol.
Owner:TELEFON AB LM ERICSSON (PUBL)
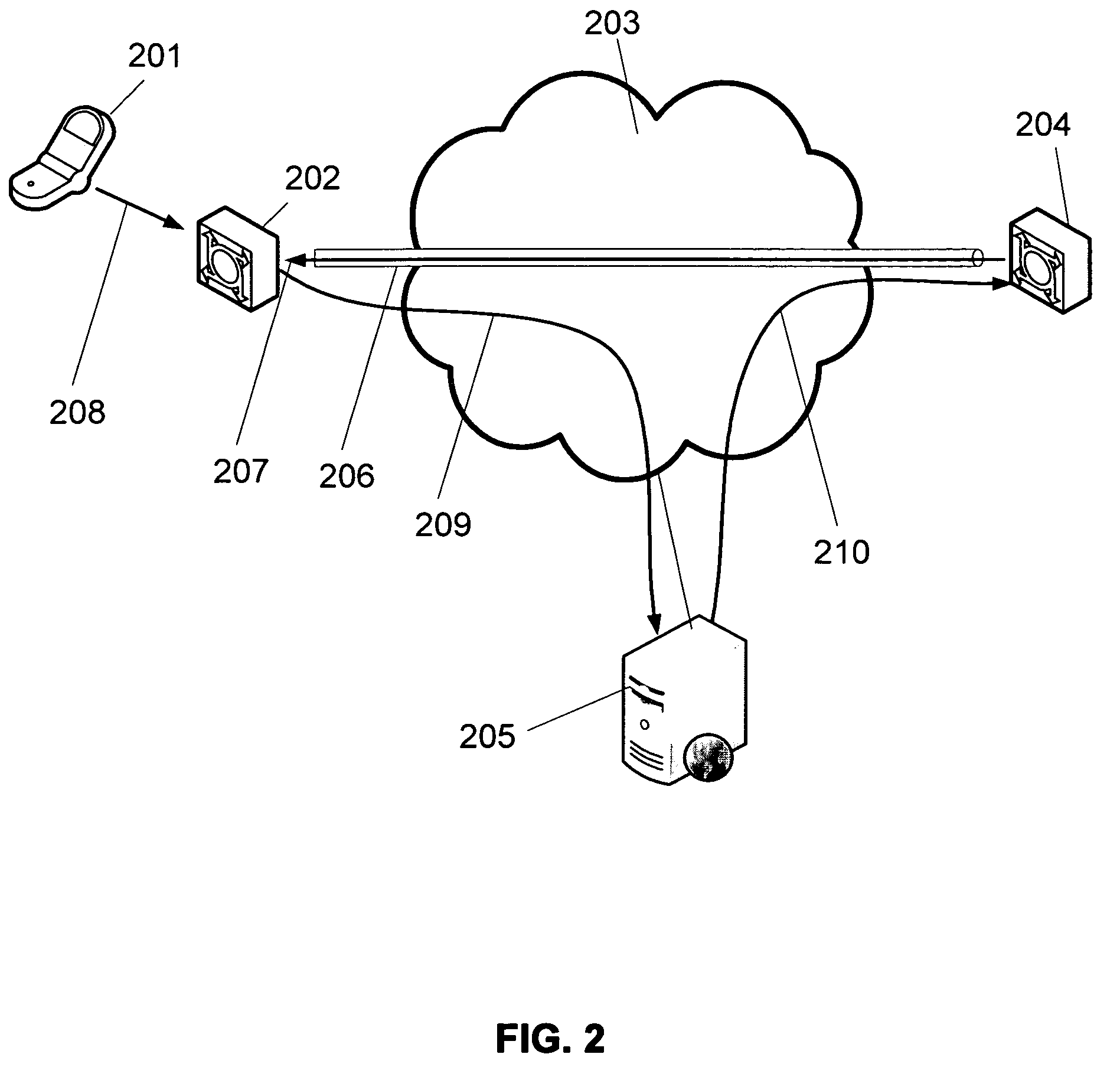
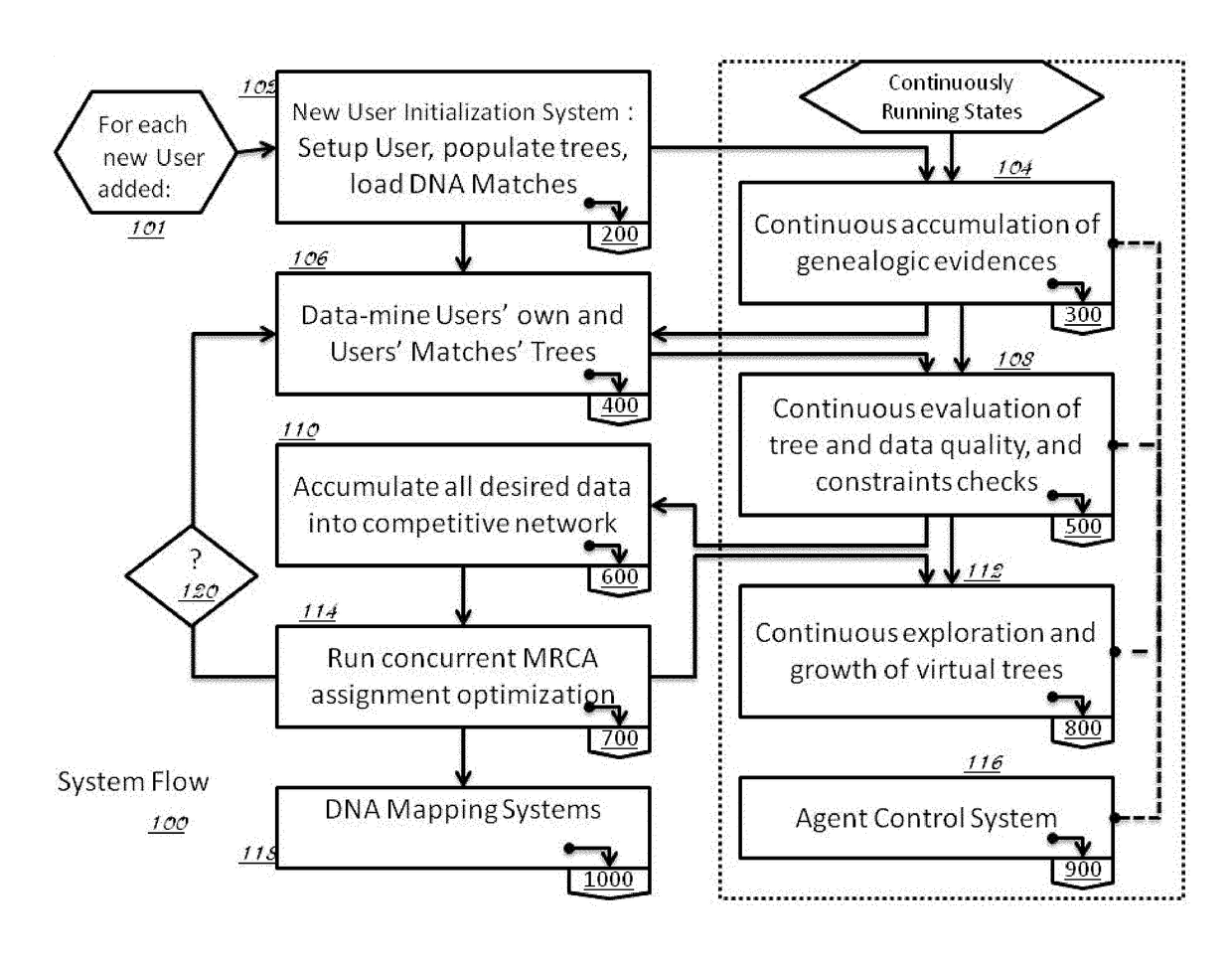
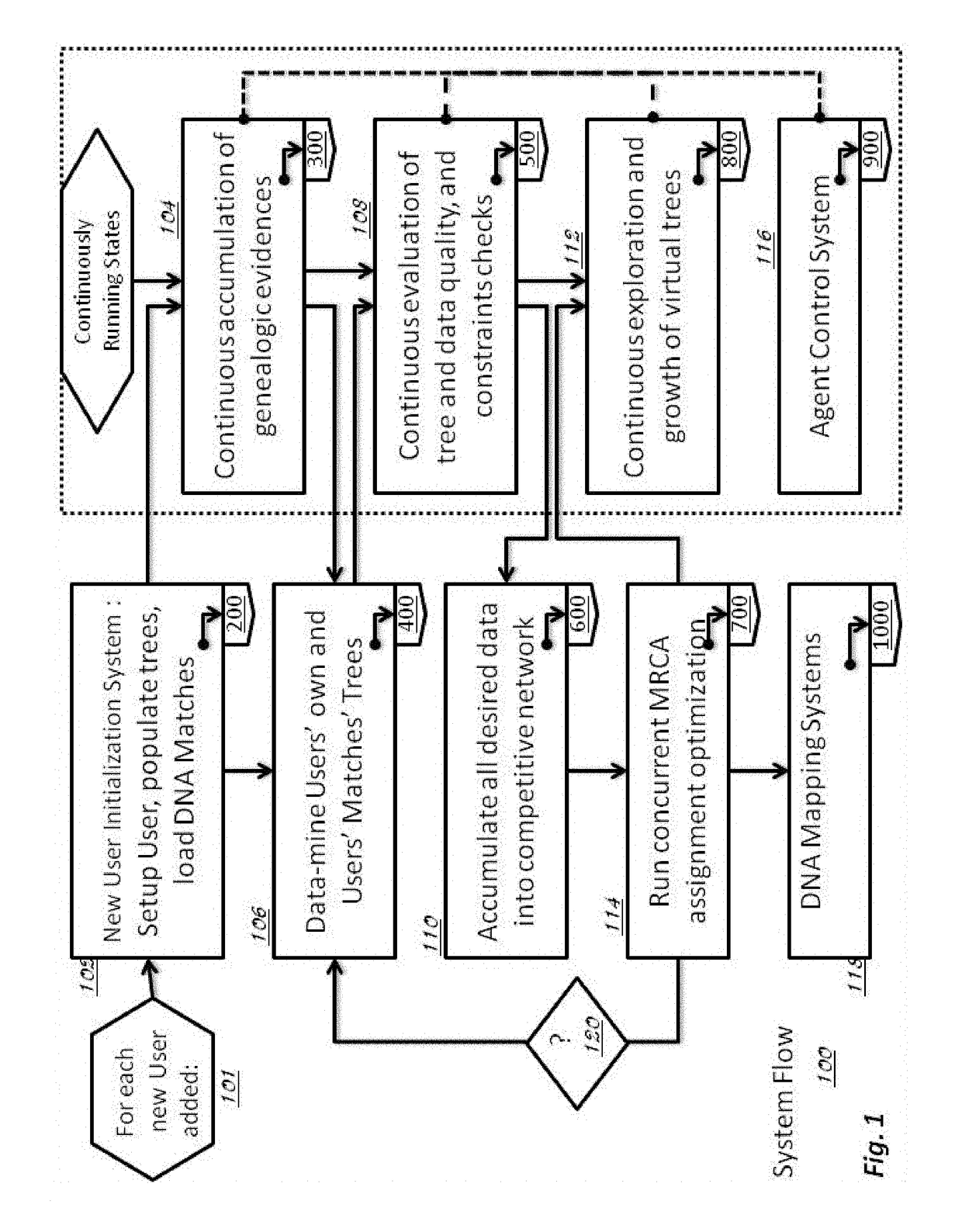
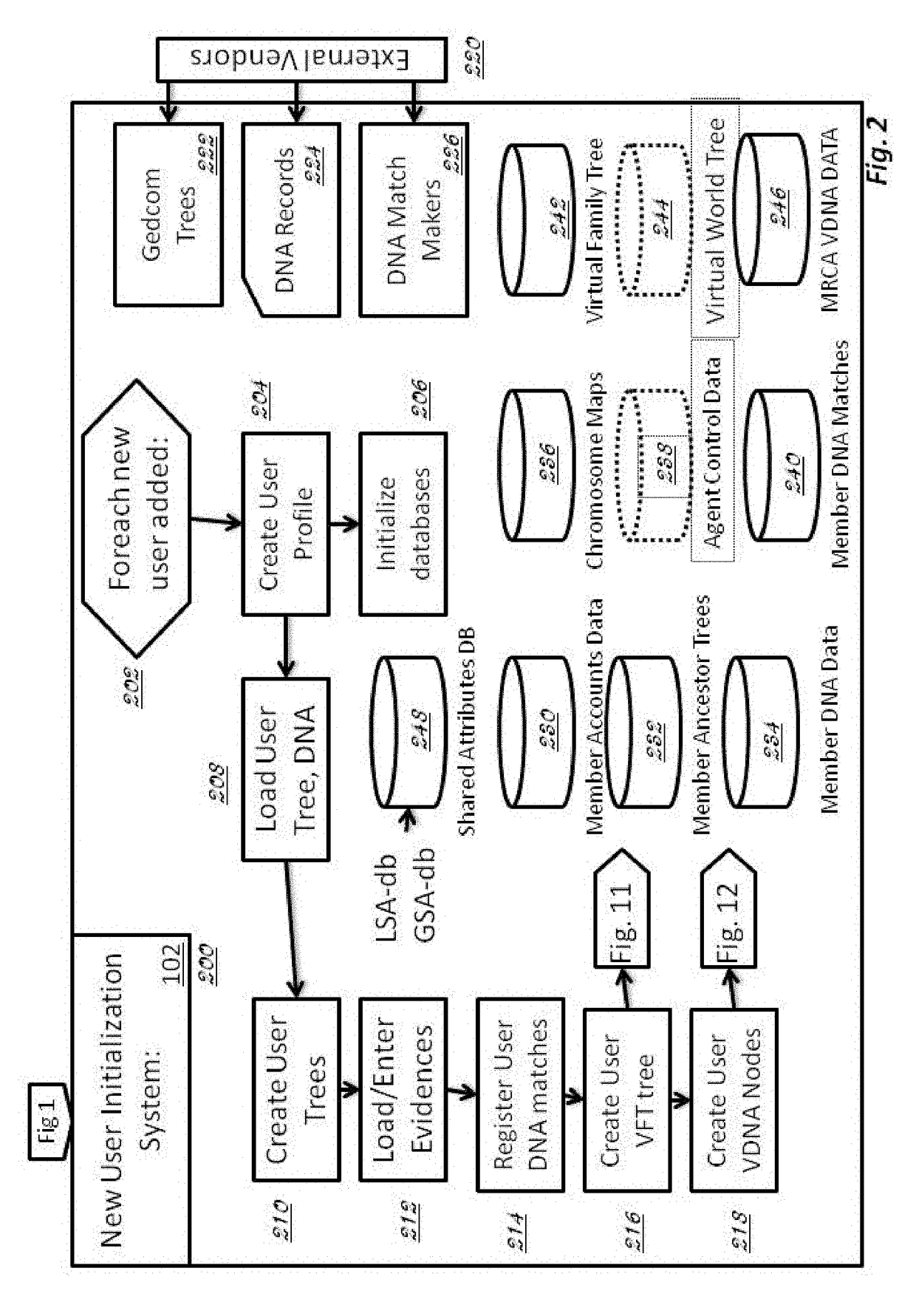
Method and System for Discovering Ancestors using Genomic and Genealogic Data
InactiveUS20170213127A1Reduced travel tendencyReduce in quantityData visualisationBiostatisticsCommon ancestryGenotype
Described invention and its embodiments, in part, facilitate discovery of ‘Most Recent Common Ancestors’ in the family trees between a massive plurality of individuals who have been predicted to be related according to amount of deoxyribonucleic acids (DNA) shared as determined from a plurality of 3rd party genome sequencing and matching systems. This facilitation is enabled through a holistic set of distributed software Agents running, in part, a plurality of cooperating Machine Learning systems, such as smart evolutionary algorithms, custom classification algorithms, cluster analysis and geo-temporal proximity analysis, which in part, enable and rely on a system of Knowledge Management applied to manually input and data-mined evidences and hierarchical clusters, quality metrics, fuzzy logic constraints and Bayesian network inspired inference sharing spanning across and between all data available on personal family trees or system created virtual trees, and employing all available data regarding the genome-matching results of Users associated to those trees, and all available historical data influencing the subjects in the trees, which are represented in a form of Competitive Learning network. Derivative results of this system include, in part, automated clustering and association of phenotypes to genotypes, automated recreation of ancestor partial genomes from accumulated DNA from triangulations and the traits correlated to that DNA, and a system of cognitive computing based on distributed neural networks with mobile Agents mediating activation according to connection weights.
Owner:DUNCAN MATTHEW CHARLES
Presence detection using mobile agents in peer-to-peer networks
ActiveUS8037202B2Resource allocationMultiple digital computer combinationsDistributed computingPeer-to-peer
Embodiments of a system and method for using mobile agents in peer-to-peer networks to gather presence information for determining active peers in groups of peers. In one embodiment, a mobile agent may be launched by an initiating peer in a peer group to attempt to visit each member peer in a peer group. The itinerary of the mobile agent may include information for accessing each member peer of the peer group. The mobile agent may return to its initiating peer with a payload indicating which of the member peers it was successful in contacting and visiting. When the mobile agent returns to the originating peer, the originating peer may update presence information indicating presence of member peer nodes in the group in accordance with the indications provided by the mobile agent.
Owner:ORACLE INT CORP
Mobile agents in peer-to-peer networks
ActiveUS8108455B2Multiple digital computer combinationsTransmissionPeer-to-peerVirtual communication
Embodiments of a mechanism for implementing mobile agents in peer-to-peer networks. An initiating peer may generate a mobile agent to perform one or more tasks on or gather information from other peers in the peer-to-peer network. The mobile agent may include an itinerary of peers that the mobile agent may visit. The mobile agent may be transmitted on communications channels in the peer-to-peer network to each peer on the itinerary in turn, and return to the initiating peer after visiting or attempting to visit each peer on the itinerary. In one embodiment, the mobile agent may traverse its itinerary via virtual communication channels (pipes) implemented according to a peer-to-peer platform. A mobile agent may include information identifying input pipes for each peer on its itinerary. Peers may generate and advertise input pipes for use by mobile agents.
Owner:ORACLE INT CORP
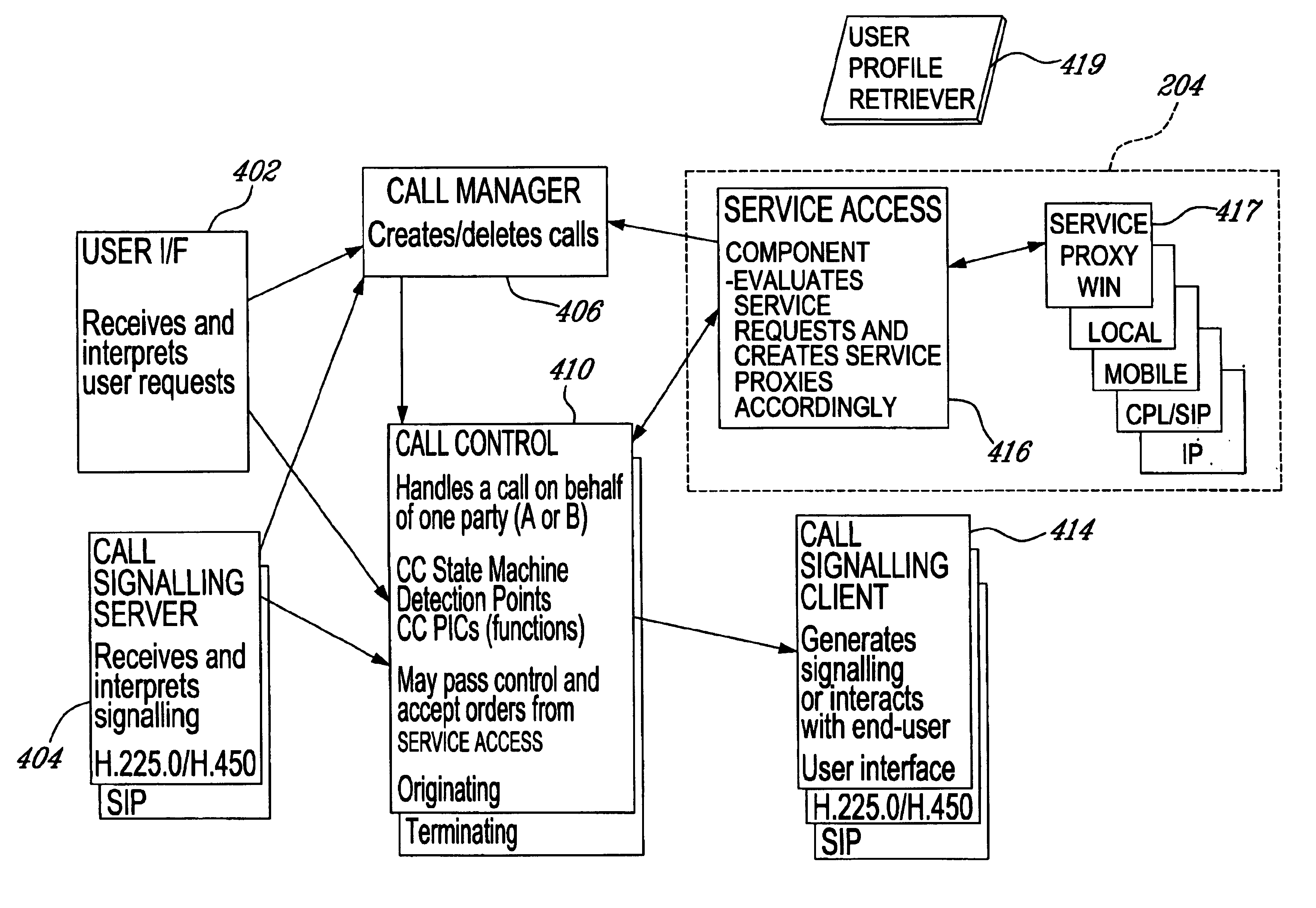
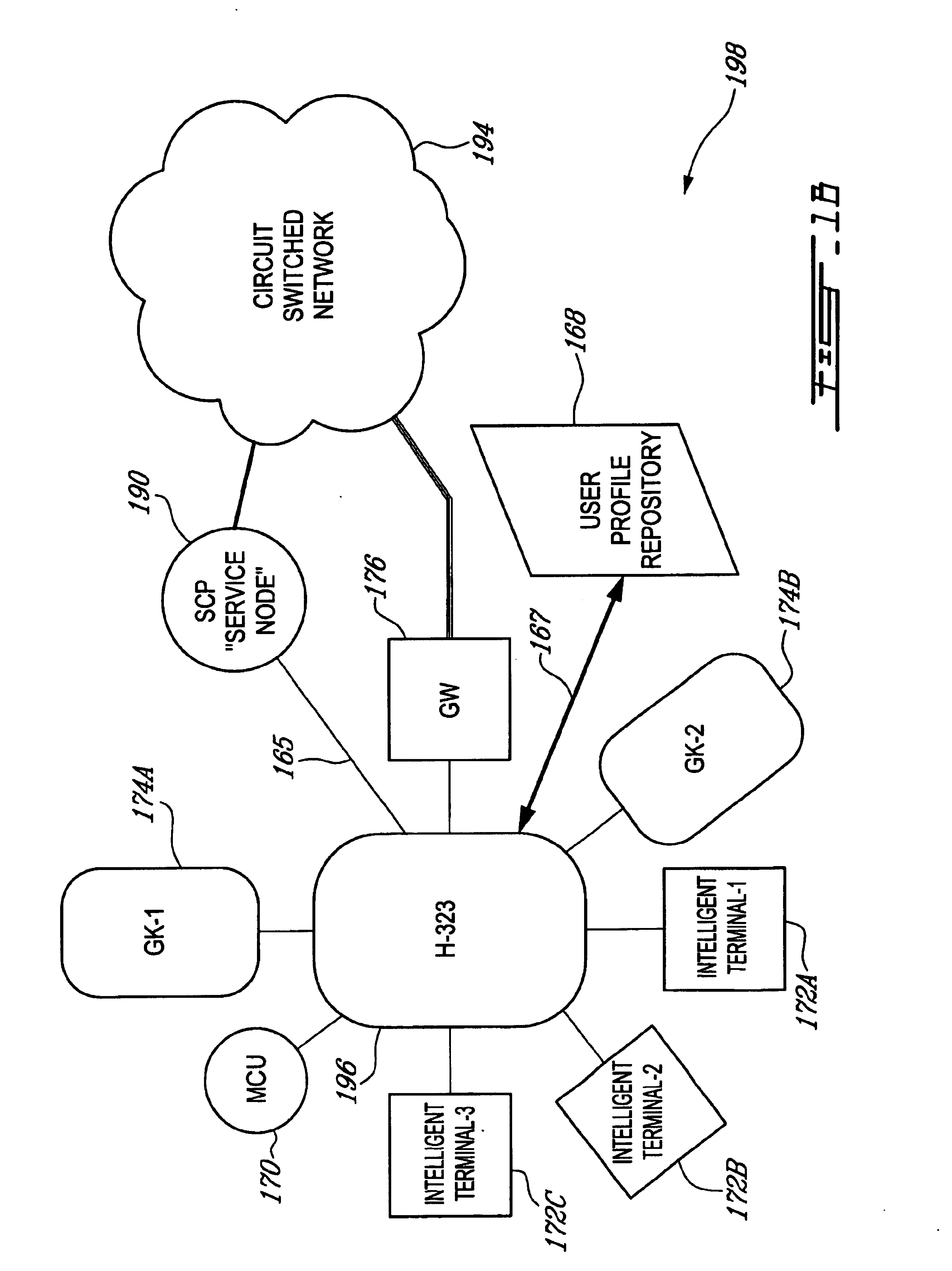
System and method for providing access to service nodes from entities disposed in an integrated telecommunications network
InactiveUS6940847B1Interconnection arrangementsTime-division multiplexTelecommunications networkComputer module
A system and method of accessing services from end terminals disposed in an integrated telecommunications network having a packet-switched network (PSN) portion such as, for example, a network portion using the Internet Protocol (IP) and a circuit-switched network (CSN) portion such as, for example, a wireless telephony network portion. A generalized service invocation and realization architecture includes one or more call control modules modified to include service-related Detection Points (DPs), a Service Access component or instance that is created when a new DP is encountered, and one or several service proxies which invoke services on behalf of the Service Access component and mediate between the call control modules and services. A common Service Logic Environment is implemented for local services, mobile agent services, and remote services. The PSN portion is preferably realized as a Voice-over-IP (VoIP) network having a gateway connected to the CSN portion.
Owner:OPTIS WIRELESS TECH LLC
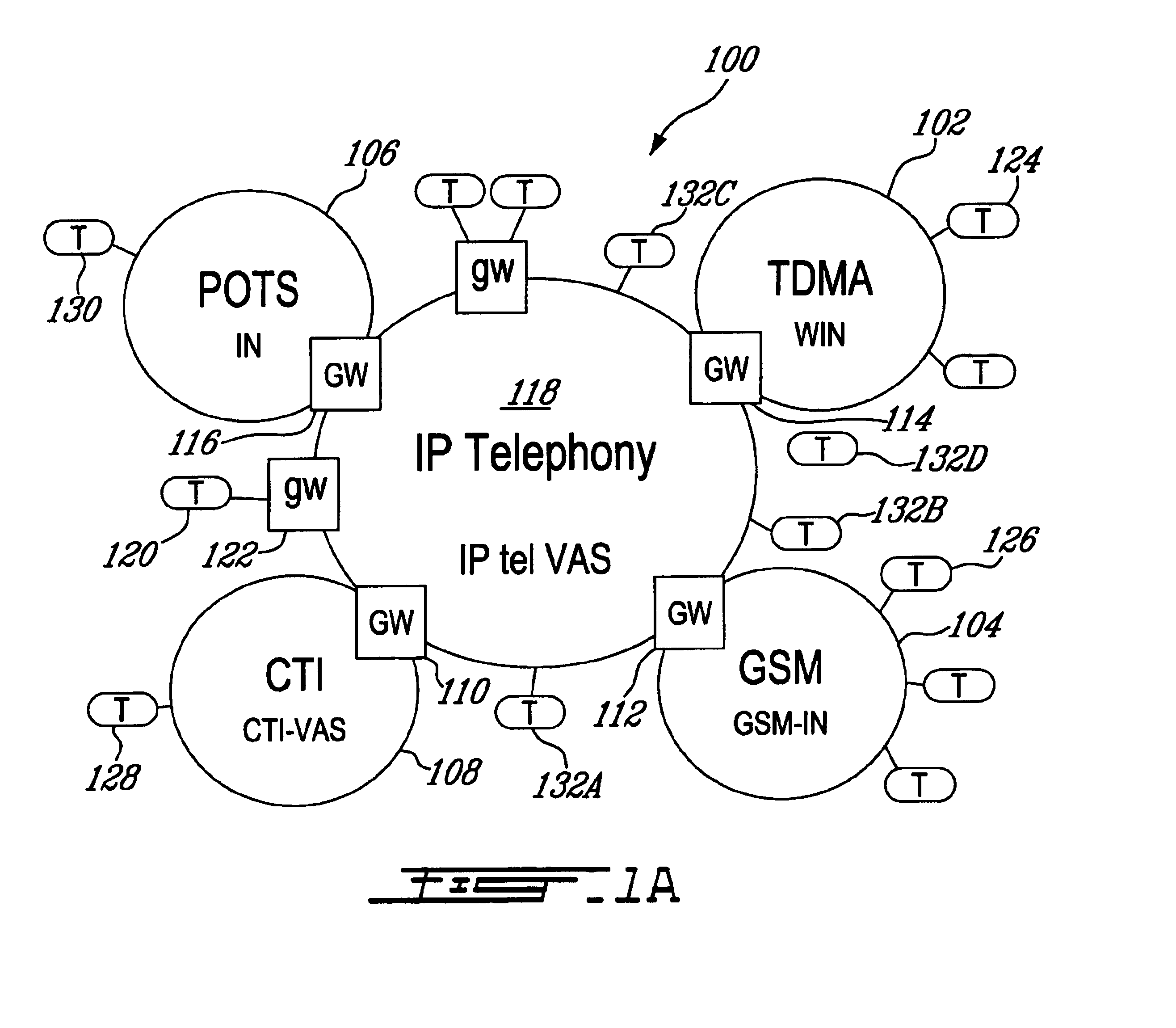
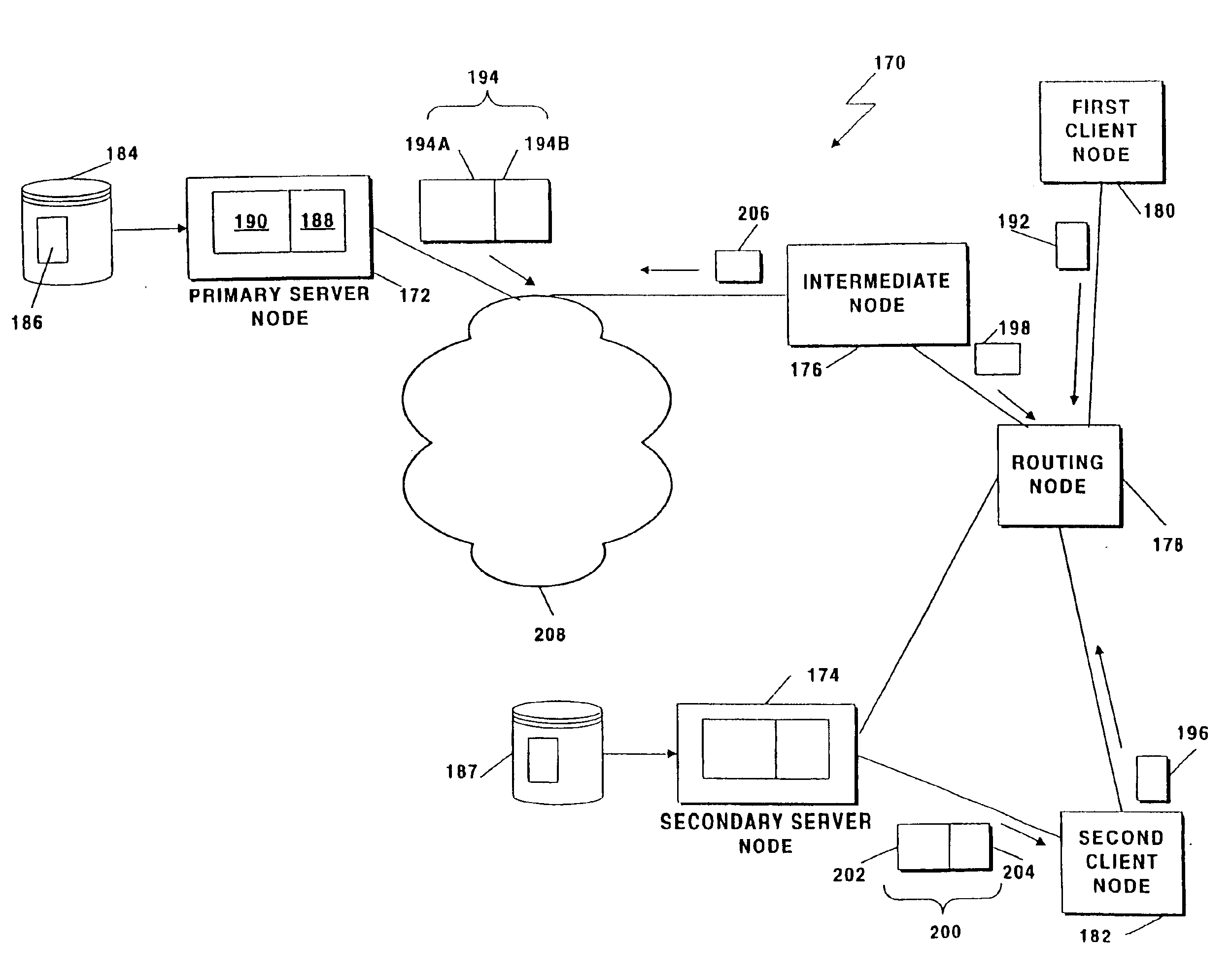
Extending network services using mobile agents
InactiveUS6892218B2Less network traffic is createdFast response timeResource allocationData switching by path configurationEngineeringNetwork service
A technique fulfills service requests in a system of computers that communicate as nodes within a network. The technique involves sending, in response to an initial service request that requests a service provided by a primary server node, a mobile agent from the primary server node to an intermediate node. The mobile agent indicates to the intermediate node that a secondary server node is capable of providing the service. The technique further involves intercepting, at the intermediate node, a subsequent service request sent from a client node to the primary server node, the subsequent service request requesting the service, and sending an instruction from the intermediate node to the secondary server node. The instruction instructs the secondary server node to provide the service. The technique further includes providing, in response to the instruction, the service from the secondary server node to the client node.
Owner:ARRAY NETWORKS
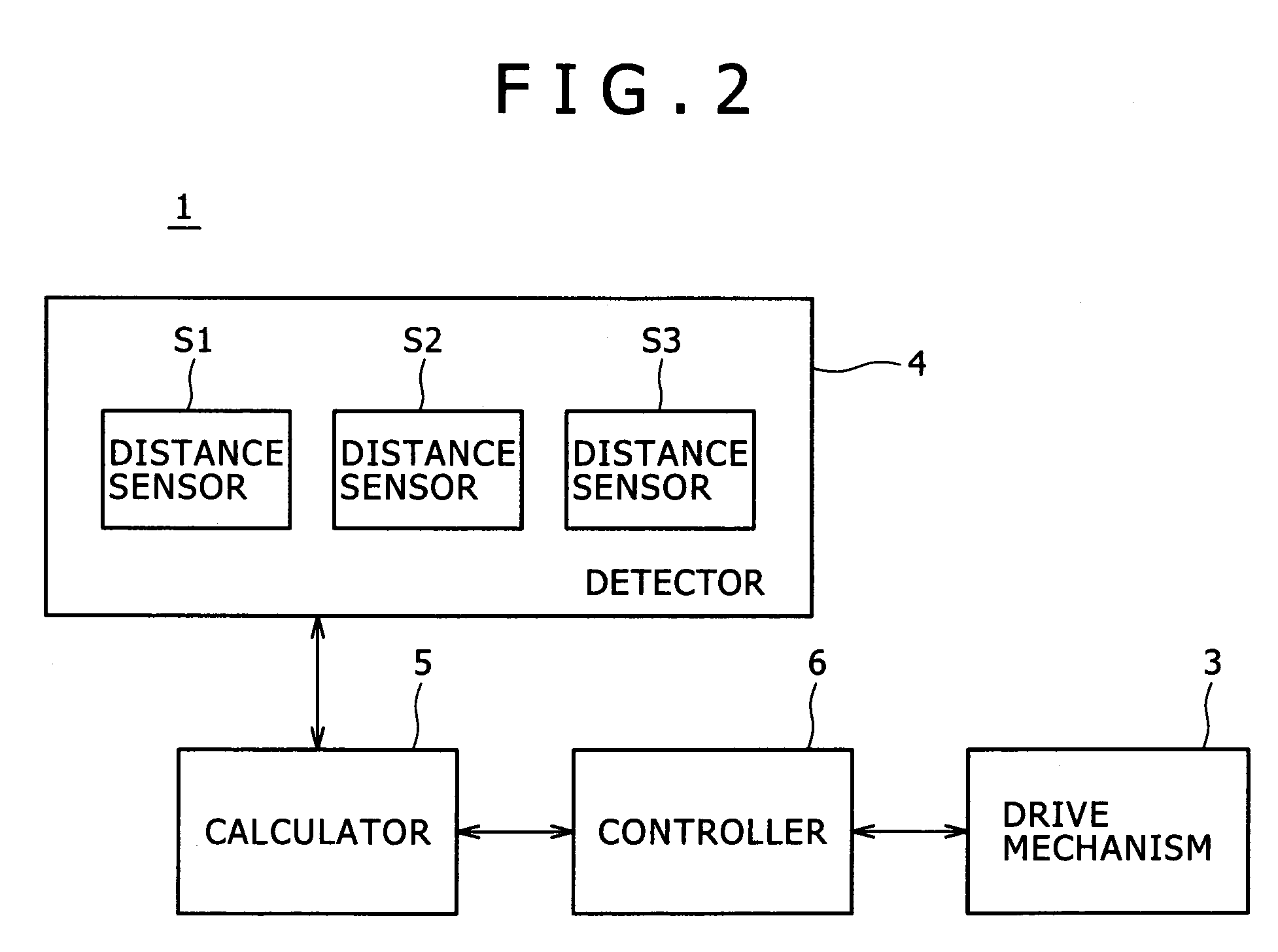
Electronic device and method of controlling same
InactiveUS7432718B2Easy to useElectrophonic musical instrumentsCosmonautic condition simulationsEngineeringCalculator
An electronic device includes a main body, a drive mechanism configured to move the main body, a detector having a plurality of sensors mounted in the main body for detecting distances to an object which is present in a space around the main body, a calculator configured to calculate a direction of the object relative to the main body based on the detected distances, and a controller configured to control the drive mechanism to change an orientation of the main body dependent on the calculated direction.
Owner:SONY CORP
Internet protocol collaborative mobility
ActiveUS20040202120A1Minimal disruptionEnhances standard domain namingError preventionTransmission systemsCommunication unitClient-side
Systems and methods are provided for maintaining communications with mobile users within organizational logical network groups when transitioning between logical groups. A client mobility agent resides as part of a mobile communication unit and monitors link metrics to determine if a transition to another logical network group is desired. The client mobility agents and a server mobility agent collaborate to reassign or re-home a mobile communication unit to a new home logical network group, and provide the mobile communication unit with a new group address upon entering a new logical network. The server mobility agent collaborates with a server mobility agent of the previous logical group that the mobile communication unit was a member to transfer sessions and services associated with the mobile communication unit to the new logical network.
Owner:NORTHROP GRUMMAN SYST CORP
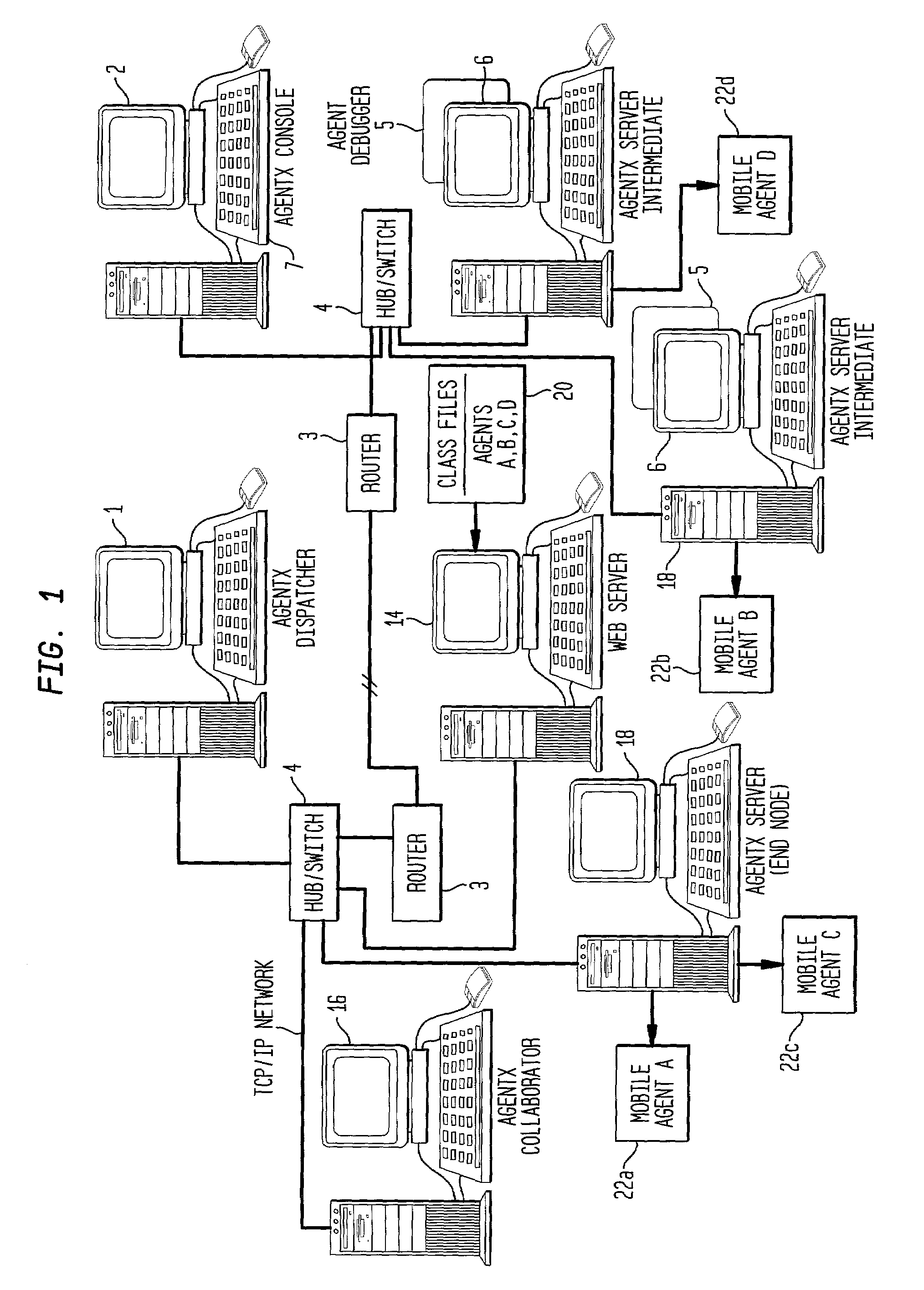
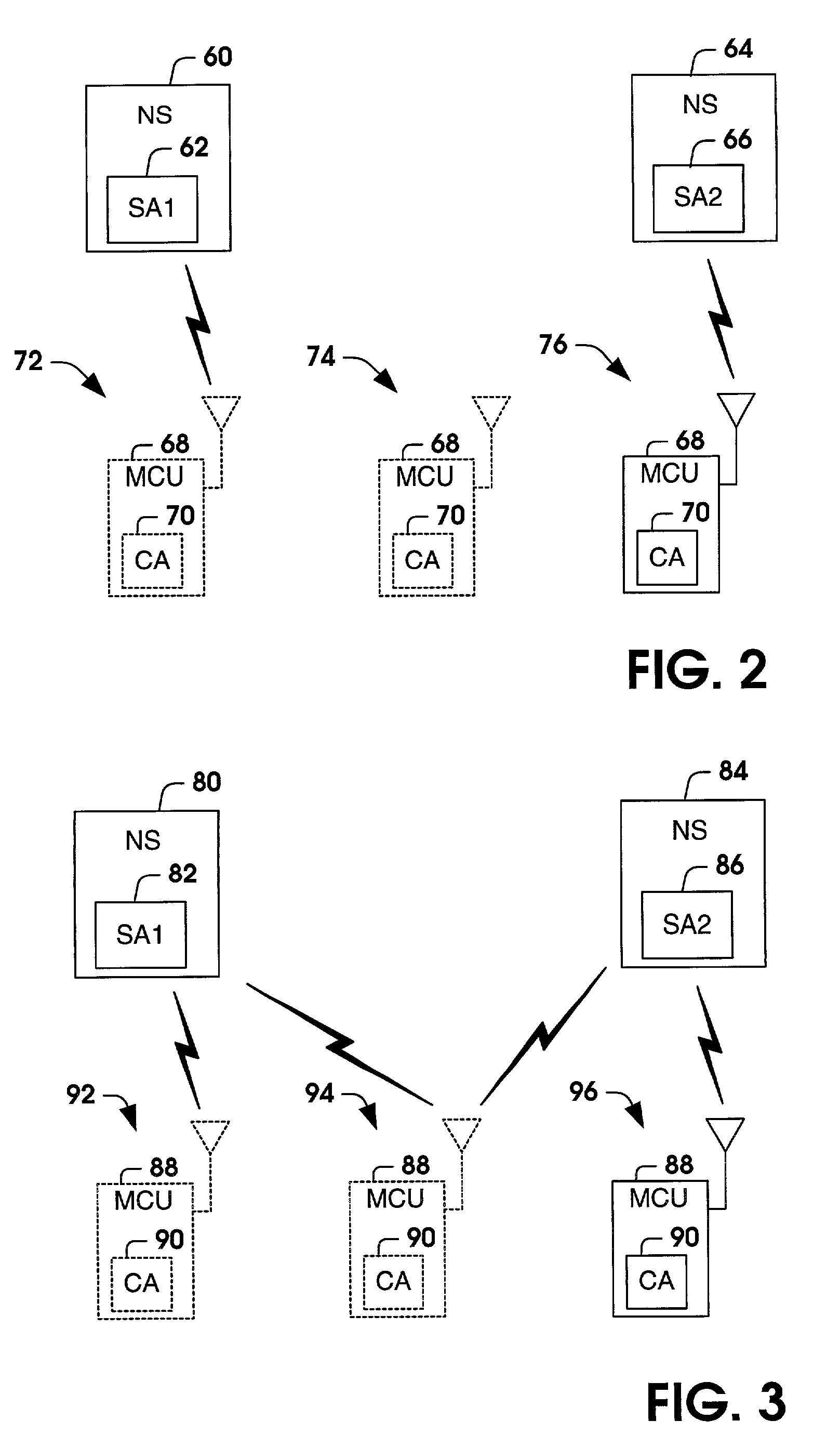
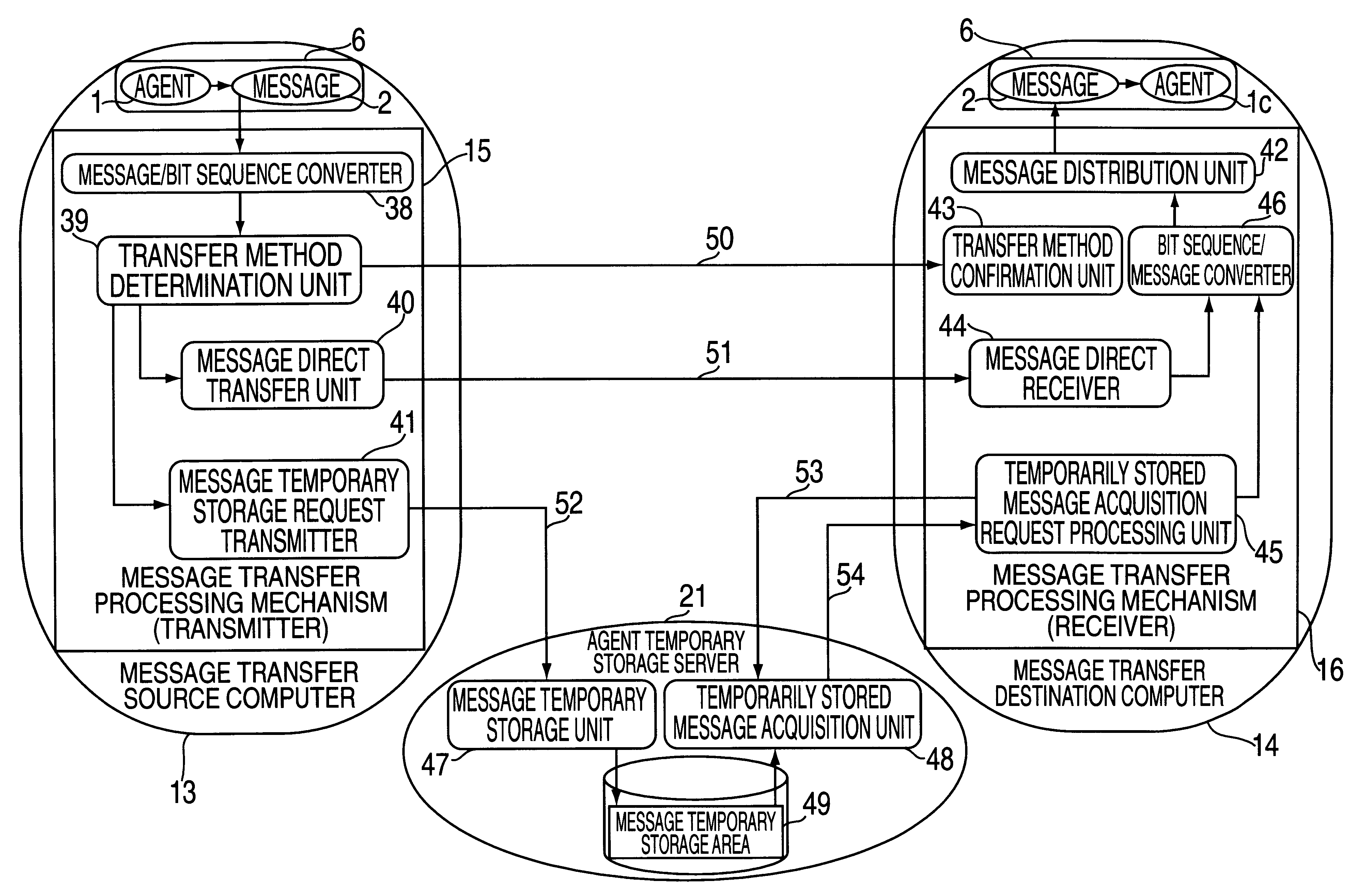
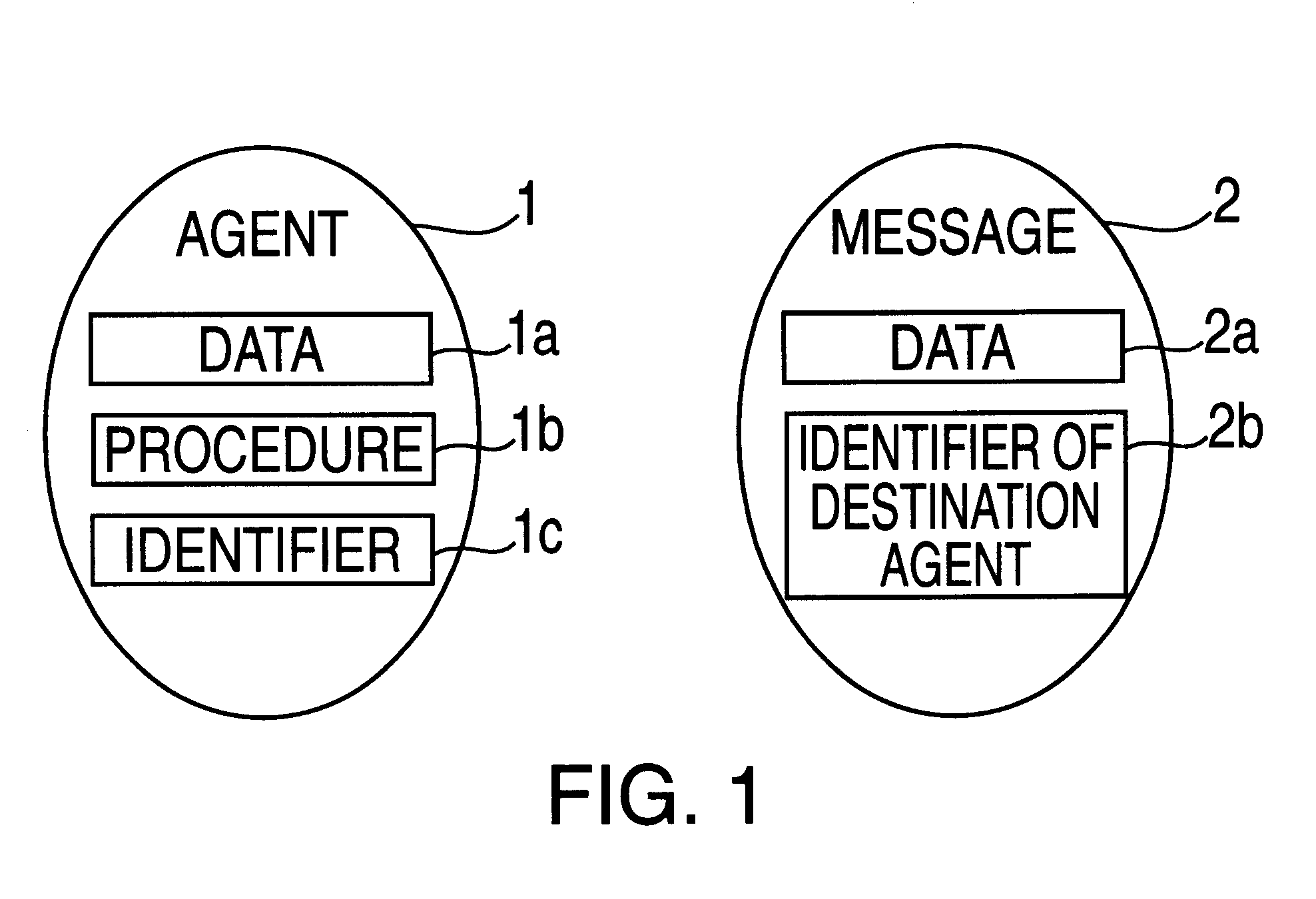
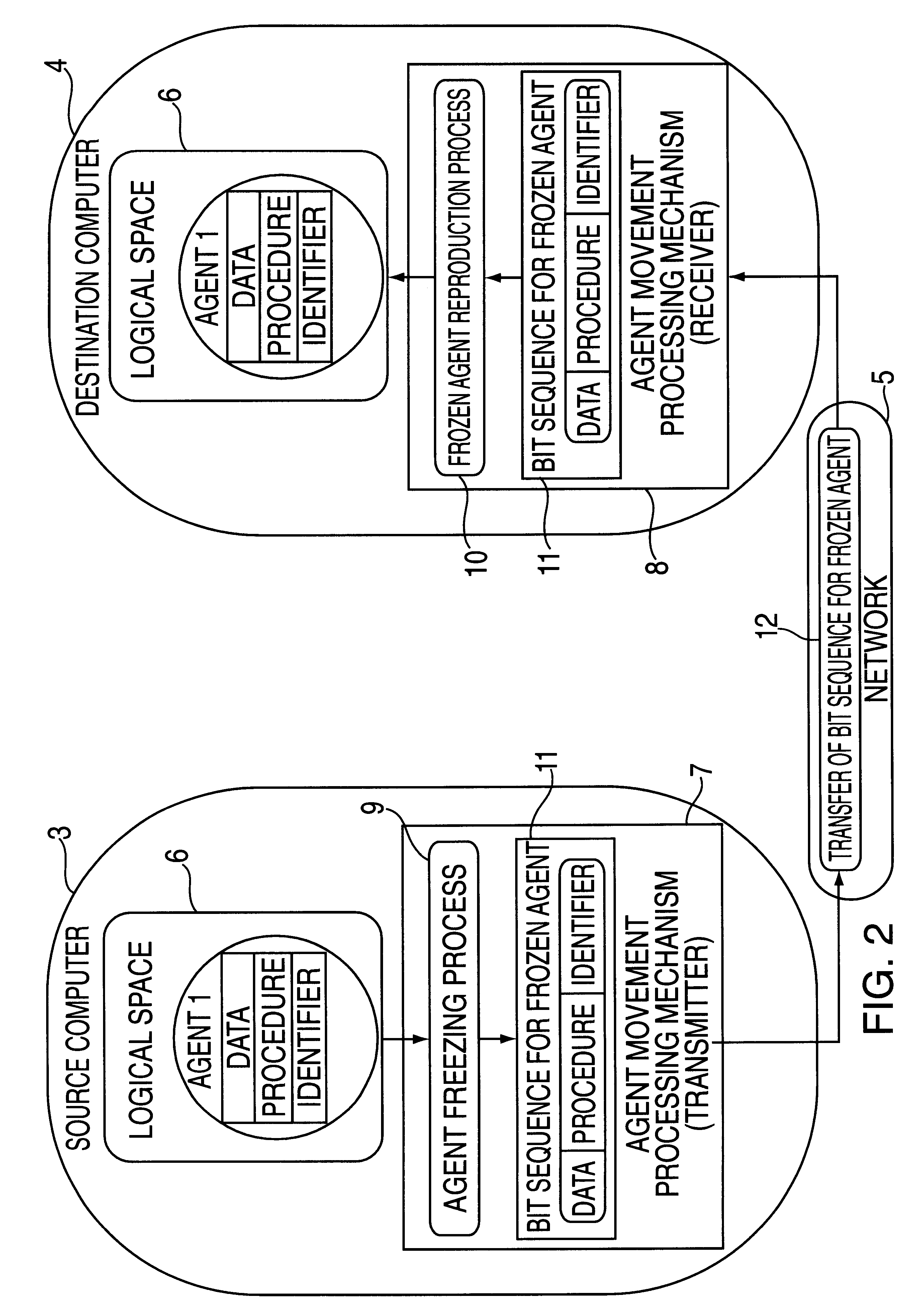
Agent moving method, message transmission method, agent transmission method, agent acquisition method, message acquisition method and agent list acquisition method, and computer
InactiveUS6282563B1Software engineeringMultiprogramming arrangementsComputer scienceTemporary storage
The present invention is directed to a mobile agent technique, and in particular to a method for moving / transmitting to a desired computer, an agent and a message that the agent issues. According to the present invention, a temporary storage area (a computer having a storage device) for a destination computer of a mobile agent and a message is provided. When a mobile agent or a message can not move directly to a destination computer, the mobile agent and the message are temporarily stored in the temporary storage area. At an appropriate time, the destination computer extracts from the temporary storage area the agent and the message addressed to it. Since the temporary storage area is provided, the movement of the agent and the transmission of the message are ensured. Also because the temporary storage device is provided, the destination computer can accept a mobile agent and a message in accordance with the situation and the condition of the destination computer.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com